-
 @ 502ab02a:a2860397
2025-04-25 02:19:05
@ 502ab02a:a2860397
2025-04-25 02:19:05วันนี้จะเล่าเรื่องโครงการ School Plates โดย ProVeg UK ให้อ่านครับ
ProVeg UK เปิดตัวโครงการ School Plates ในเดือนมิถุนายน 2018 โดยมีเป้าหมายเพื่อช่วยให้โรงเรียนในสหราชอาณาจักรเสิร์ฟอาหารที่ดีต่อสุขภาพและเป็นมิตรต่อสิ่งแวดล้อมมากขึ้น โครงการนี้มุ่งเน้นการเพิ่มคุณภาพ ปริมาณ และการยอมรับของอาหารจากพืชในเมนูโรงเรียน โดยเฉพาะในโรงเรียนประถมศึกษา ซึ่งส่วนใหญ่จะอยู่ภายใต้การดูแลของหน่วยงานท้องถิ่น
เพื่อการสนับสนุนโครงการ บริการที่ ProVeg UK มอบให้จะประกอบไปด้วย บริการฟรีแก่โรงเรียน หน่วยงานท้องถิ่น และผู้จัดเลี้ยงอาหารโรงเรียน เพื่อสนับสนุนการเปลี่ยนแปลงเมนูอย่างมีประสิทธิภาพ บริการเหล่านี้รวมถึง -การให้คำปรึกษาเมนู โดยให้คำแนะนำในการปรับสมดุลเมนู และใช้ภาษาที่ส่งเสริมอาหารจากพืช -การพัฒนาสูตรอาหารใหม่ ช่วยสร้างสูตรอาหารจากพืชที่อร่อย มีคุณค่าทางโภชนาการ และเหมาะสมกับครัวโรงเรียน -การจัดเวิร์กช็อปและการฝึกอบรม โดยจัดอบรมทั้งแบบออนไลน์และแบบพบหน้าสำหรับพ่อครัวและเจ้าหน้าที่ครัวโรงเรียน -การวิเคราะห์ด้านสุขภาพ สิ่งแวดล้อม และงบประมาณ มีโปรแกรมประเมินผลกระทบของเมนูต่อสุขภาพเด็ก การปล่อยก๊าซเรือนกระจก และต้นทุน ให้ครบถ้วน
นอกจากนี้ยังมีการจัดรางวัล School Plates Awards: มอบรางวัลระดับ Bronze, Silver และ Gold ให้แก่โรงเรียนที่มีความมุ่งมั่นในการปรับปรุงเมนูอย่างยั่งยืน ด้วย
ผลลัพธ์ตั้งแต่เริ่มโครงการ School Plates ได้เปลี่ยนแปลงเมนูอาหารโรงเรียนมากกว่า 6 ล้านมื้อ ให้กลายเป็นอาหารที่ดีต่อสุขภาพและยั่งยืนมากขึ้น โดยมีการเพิ่มวัน Meat-Free Mondays และตัวเลือกอาหารจากพืชในเมนูประจำวันของโรงเรียนหลายแห่ง
สูตรอาหารที่พัฒนาโดย ProVeg UK มีคุณสมบัติประมาณนี้ครับ -มีโปรตีนเทียบเท่ากับอาหารที่มีเนื้อสัตว์ -มีไขมันอิ่มตัวต่ำกว่า -อุดมไปด้วยไฟเบอร์และสารอาหารที่จำเป็น -มีการปล่อยก๊าซเรือนกระจกต่ำ -สอดคล้องกับมาตรฐานอาหารและโภชนาการของโรงเรียนในสหราชอาณาจักร
นั่นทำให้โครงการ School Plates ได้รับการยอมรับจากโรงเรียนและหน่วยงานท้องถิ่นหลายแห่งในสหราชอาณาจักร และยังได้รับการเสนอชื่อเข้าชิงรางวัลด้านสิ่งแวดล้อมระดับโลก เช่น Food Planet Prize
ทีนี้เรามาวิเคราะห์กันว่า School Plates คือ เมนูรักษ์โลกหรือกับดักระบบ? โครงการ School Plates ของ ProVeg UK ภายนอกดูเหมือนเรื่องดี เป็นการ “ช่วยโรงเรียนให้เปลี่ยนเมนูไปทาง plant-based เพื่อสุขภาพเด็กและโลก” มีการให้คำปรึกษา ทำสูตรอาหาร อบรมพ่อครัว และพูดจาภาษาดี ๆ ว่า "อาหารยั่งยืน" กับ "ทางเลือกที่ดีต่อสุขภาพ" แต่ถ้ามองลึกเข้าไป มันไม่ใช่แค่อาหาร มันคือ เกมเปลี่ยนโครงสร้างการผลิตอาหารในระดับระบบ โดยใช้ “เด็กในโรงเรียน” เป็นจุดตั้งต้น
ถ้าดูเผิน ๆ เราอาจนึกว่าเด็กได้กินผักเยอะขึ้น โลกได้ลดก๊าซเรือนกระจก แต่ถ้าขุดเข้าไป จะเห็นว่าเบื้องหลัง ProVeg UK เชื่อมโยงกับกลุ่มทุน plant-based ขนาดใหญ่ ไม่ว่าจะเป็นผู้ผลิตนมถั่ว เนื้อเทียม หรือบริษัทยีสต์และจุลินทรีย์ที่ใช้ทำโปรตีนหมัก (Precision Fermentation) ทั้งหลาย
และอย่าลืมว่า ProVeg มีพันธมิตรกับองค์กรระดับโลกอย่าง EAT Foundation, World Resources Institute, และกลุ่ม lobby ต่าง ๆ ที่ผลักดัน นโยบายเปลี่ยนอาหารโลก ให้ไปทาง plant-based เป็นหลัก ซึ่งดูดี… ถ้าเราไม่รู้ว่าเบื้องหลังมันคือระบบ “อาหารสำเร็จรูปจากโรงงาน” ที่อ้างคำว่า “รักษ์โลก” แต่ผลิตโดยอุตสาหกรรมที่กระจุกตัวสูงมาก
ปัญหาที่คนอาจไม่ค่อยพูดถึงก็มีอยู่ครับเช่น -ละเลยโภชนาการตามธรรมชาติของเด็ก เพราะเด็กวัยเจริญเติบโตต้องการ โปรตีนคุณภาพสูง ไขมันดี และ สารอาหารที่พบเฉพาะในสัตว์ เช่น วิตามิน B12, เฮม-ไอรอน, โคลีน, คาร์โนซีน ฯลฯ ซึ่งอาหาร plant-based จำนวนมากขาด หรือมีในรูปแบบดูดซึมยากกว่าหลายเท่า - ใช้คำว่า "สิ่งแวดล้อม" บังหน้า แต่เป็นการผูกขาดระบบอาหาร การผลัก plant-based ไม่ได้ลดการพึ่งพาระบบอุตสาหกรรมเลย ตรงกันข้ามคือมันพาเราเข้าสู่ยุคของ plant-based ultra-processed food ที่ผลิตจากซอยโปรตีน ถั่วเหลือง GMO 2.0 น้ำมันพืช และสารแต่งรส... จากโรงงาน - เจาะระบบโรงเรียน = วางรากฐานความเชื่อ ให้เด็กที่โตมากับอาหารแบบนี้จะเชื่อว่านี่คือ “ของดี” และมองโปรตีนจากสัตว์เป็นสิ่งแปลกแยกในอนาคต เหมือนเป็นการ “reset” วิถีอาหารใหม่แบบไม่รู้ตัวผ่าน เจเนอเรชั่น - กลไกการจัดซื้อของรัฐจะถูก redirect ไปยังกลุ่มทุนใหญ่นอกพื้นที่ จากที่โรงเรียนจำนวนมากเคยซื้อวัตถุดิบจากชุมชน หรือฟาร์มใกล้เคียง พอโครงการแบบนี้เข้ามา จะค่อย ๆ ทำให้วัตถุดิบถูกกำหนดจาก เมนูที่ standardized ซึ่งสุดท้ายต้องพึ่ง “สินค้าสำเร็จรูปจากระบบอุตสาหกรรม”
ซึ่งถ้าเรามองโภชนาการสำหรับเด็กจริงๆแล้วนั้น เราควรลดของแปรรูป ไม่ใช่แค่ลดเนื้อ และใช้วัตถุดิบสดแท้จากธรรมชาติ ไม่ใช่ plant-based industrial food นอกจากนี้ยังควรสนับสนุนอาหารจากฟาร์มท้องถิ่น ทั้งผัก ไข่ เนื้อ และผลิตผลจากเกษตรกรจริง รวมถึงให้เด็กได้รู้จักที่มาของอาหาร ไม่ใช่แค่เรียนรู้แคลอรีกับคาร์บอนที่ว่ากันว่าปล่อยออกมา
School Plates คือก้าวเล็ก ๆ สู่การเปลี่ยนโครงสร้างใหญ่ของการควบคุมอาหารของโลก มันไม่ได้แค่เรื่องของเมนูกลางวัน แต่มันคือ “ระบบคิด” ที่กำลัง reshape โลกให้เด็กยุคใหม่โตมาโดยไม่รู้จัก real food ในสายตาเฮีย แม้โครงการนี้ไม่ได้เลวร้ายทั้งหมด แต่มันมี “เจตนาเชิงโครงสร้าง” ที่ต้องจับตาอย่างมาก และเราควรถามกลับเสมอว่า... ทำไมเราถึงต้องยัดอาหารสังเคราะห์ในนามของการ “รักโลก” แต่กลับตัดขาดจากดิน น้ำ ฟ้า และฟาร์มท้องถิ่น? ทำไม?
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 3eba5ef4:751f23ae
2025-04-25 02:00:02
@ 3eba5ef4:751f23ae
2025-04-25 02:00:02Crypto Insights
1 BTC Quantum Cracking Challenge Called a Joke
Quantum computing research organization Project Eleven launched “Q-Day Challenge,” announcing a 1 BTC reward to the first team that can crack an ECC (elliptic curve cryptography) key using Shor’s algorithm on a quantum computer before April 5, 2026. Project Eleven considers this an extremely difficult task, stating that even recovering a few private keys would be big news.
However, Shinobi from Bitcoin Magazine called the bounty a joke, arguing it provides no serious incentive for several reasons:
- Even highly optimistic forecasts place the feasibility of such a quantum breakthrough at least 5–10 years away.
- At Bitcoin’s current price of $80,000, the bounty is insufficient compensation for such a demanding task.
- A quantum computer could be used for much more lucrative exploits—eavesdropping on internet connections regardless of TLS, breaking encrypted private communications, or compromising the certificate authority hierarchy of the DNS system.
New BIP Proposal to Redefine Bitcoin’s Smallest Unit
A new BIP draft proposes redefining the term “Bitcoin” to refer to the smallest indivisible unit in the system—currently “sat” (Satoshi). The goal is to make transaction amounts more readable and reduce user error. For example, someone with 851 sats would simply see “851 bitcoin” instead of “0.00000851 BTC.” Only the display and interpretation of amounts would change—the protocol remains untouched.
Previously, BIP 176 attempted to improve readability by introducing “bits” (100 sats), but it introduced a new denomination users had to learn and switch between.
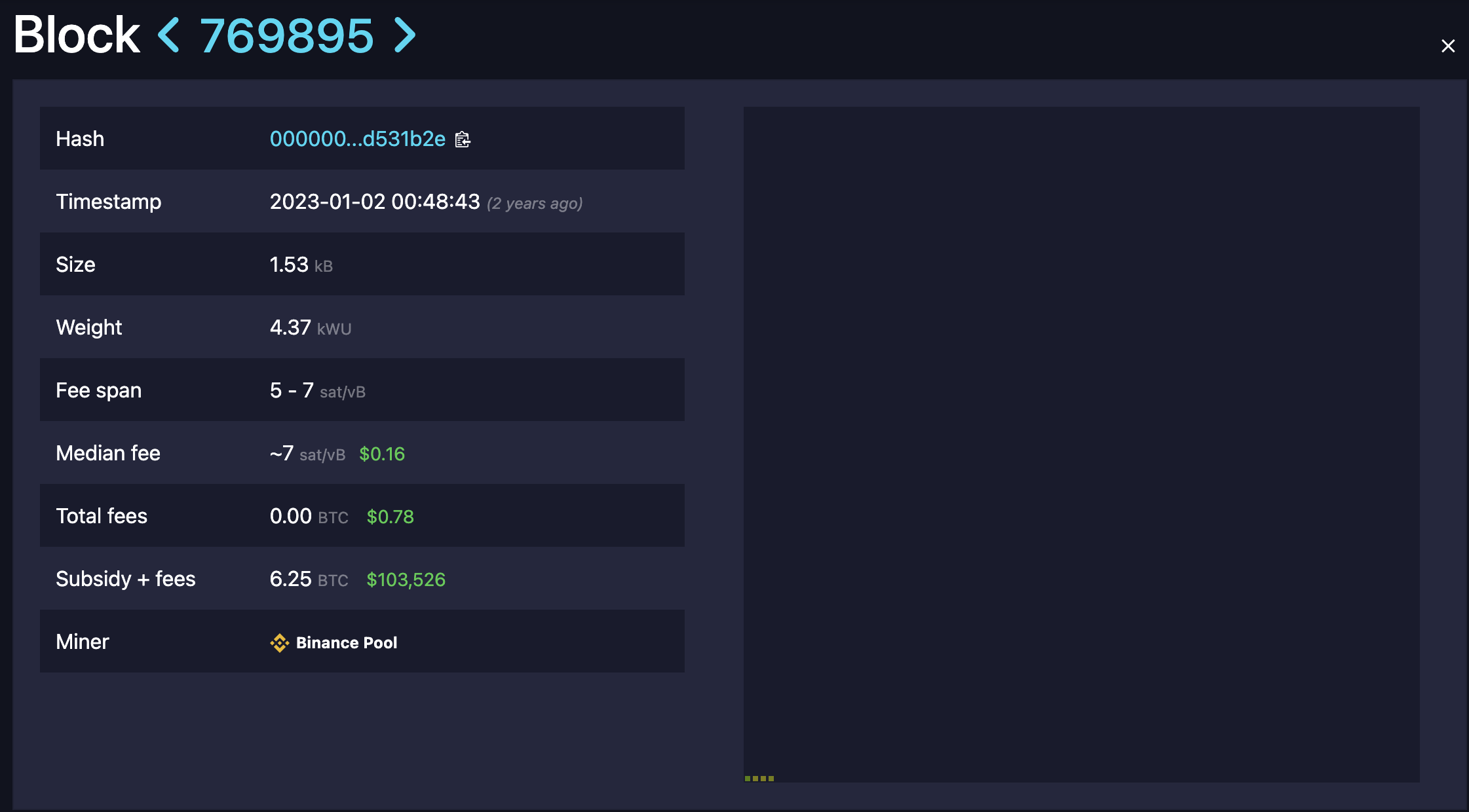
Sparse Bitcoin Block Contains Only 7 Transactions
Bitcoin transaction activity has slumped to its lowest in over two years. Recently, top mining pool Foundry mined a sparse block—Block 890466—containing only 7 transactions and weighing 5,369 weight units.

The last time a block was sparser was in January 2023, when Binance Pool mined Block 769895, which included just 4 transactions and weighed 4,370 weight units.
Over 95% of Bitcoin Blocks Mined by Just 6 Pools
A recent investigation by b10c analyzed the hash rate shares of Bitcoin’s five largest mining pools to examine centralization trends in 2025. Part one looked at mining pool information in coinbase transactions. Part two considered the assumed potential proxy pools. Both parts revealed a high concentration of mining activity. The conclusion: over 95% of recent blocks were mined by just six pools.
Bitcoin Hashrate Projections Through 2027
Valentin Rousseau in collaboration with Blockspace published hashrate forecast, covering:
- Hashrate forecasts for 2025, 2026, and 2027
- How current Bitcoin mining economics may influence the hashrate trajectory
- Hashrate expansion schedules for public miners, plus probability of completion
- Sensitivity tables for hashrate growth under various Bitcoin prices
Using VLS for Non-Custodial Lightning Integration
VLS (Validating Lightning Signer) is a library and reference implementation for a signer module to secure Lightning nodes. It separates Lightning private keys and security rule validation from the node, moving them to a dedicated signing device, thereby reducing the attack surface and enhancing security.
Before VLS, it was nearly impossible to securely manage Lightning private keys in a hosted environment without taking custody of user funds. Blockstream’s Greenlight demonstrates in this case study how VLS enables developers to seamlessly integrate non-custodial Lightning payments into their apps, with minimal overhead, while ensuring users retain full control of their funds.
How CTV+CSFS improves BitVM bridges
Robin Linus elaborates on how input-committing covenants can be used to build more efficient and secure bridges in the BitVM ecosystem. By using CTV (CHECKTEMPLATEVERIFY) and CSFS (CHECKSIGFROMSTACK), the need for presigning committees is eliminated and transaction size is significantly reduced. This simplifies bridge architecture, enhances operational efficiency, and aims towards trust-minimized Bitcoin interoperability, though challenges such as potential censorship in the peg-in process remain.
RISC Zero Launches R0VM 2.0 with Performance and Security Gains
RISC Zero introduced R0VM 2.0, a major upgrade to its zkVM focused on performance and scalability. Enhancements include:
- Ethereum block validation and execution time cut from 35 minutes to 44 seconds;
- Validity proof costs reduced 5x, with batch sizes of 25 bringing per-block costs down from $1.355 to $0.2747; for larger batches, as low as $0.0012.
On the security side, formal verification is a key focus of R0VM 2.0. The Keccak circuit’s determinism has been fully verified, and 122 of the 123 components in the v2 RISC-V core circuit have also been confirmed deterministic.
Bitcoin Soft Forks Could Improve BitVMX
BitVMX is a platform for optimistic verification of Bitcoin smart contracts. In this article, Fairgate Labs outlines various potential Bitcoin upgrades and how they could benefit BitVMX. The article argues that new opcodes introduced via soft forks could improve efficiency, reduce on-chain costs, simplify scripting, and promote decentralization.
Ethereum Execution Layer to Replace EVM with RISC-V
Vitalik announced a long-term proposal to replace the EVM in Ethereum’s execution layer with RISC-V as the virtual machine for smart contracts. This aims to significantly improve execution efficiency and address key scalability bottlenecks, while also simplifying the execution layer.
Additionally, Cardano’s Charles Hoskinson mentioned that their project is also using RISC-V in BitVMX, stating: “RISC-V is the future.”
Top Reads on Blockchains and Beyond
Viewing a Clown World Through Bitcoin: Responsibility, Freedom, and Self-Reflection
The book Bitcoin: The Inverse of Clown World critiques a modern society filled with “clowns”—obsessed with false political narratives and meaningless social issues, such as excessive focus on “political correctness” and climate change. The author argues that the root of absurdity is a lack of personal responsibility, and that when money breaks down, everything becomes political theater.
Beyond exposing and criticizing these absurdities, the book promotes Bitcoin as a means to succeed by providing value. It emphasizes the importance of protecting one’s time and mind in an era of information overload and encourages readers to reflect on their lifestyles and contribute to making a better world—with Bitcoin as a foundation for that change.
The book review by Bitcoin Magazine.
GPU Proof-of-Work: Redefining Energy, Computation, and Money in the AI Age
The author envisions a future where GPU-based Proof-of-Work (GPU PoW) plays a pivotal role in an AI-driven world. GPU PoW can secure cryptocurrencies, train AI models, balance energy loads, and help build a global compute marketplace. Unlike ASICs, which are limited to mining, GPUs are versatile and can dynamically shift workloads for optimal economic return.
By coordinating local data centers, superclusters, and middleware, GPU PoW can improve energy and compute efficiency without sacrificing decentralization. This gives rise to a new utility-based economic system. PoW is no longer just about mining—it becomes infrastructure supporting the convergence of AI, energy systems, and monetary networks.
DahLIAS:First Cryptographic Protocol for Fully Cross-Input Signature Aggregation Compatible with Secp256k1
Blockstream’s research team has introduced DahLIAS, the first cryptographic protocol that enables full cross-input signature aggregation, while remaining compatible with Bitcoin's existing secp256k1 elliptic curve.
An interactive aggregate signature scheme allows n signers—each with their own (sk, pk) key pair and message m—to jointly produce a short signature that proves each m was signed under its corresponding pk. While such schemes can offer massive space and verification savings—two critical bottlenecks for blockchain like Bitcoin—aggregate signatures have received less attention compared to other multisig schemes like MuSig2 or FROST.
DahLIAS is the first such scheme built on discrete logarithms in pairing-free groups, with constant-size signatures that look just like standard Schnorr signatures. DahLIAS also addresses real-world use cases. In addition to its savings in space and time, it supports key tweaking—a common Bitcoin technique used in hierarchical deterministic wallets to derive keys and enhance on-chain privacy.
Read the full paper.
Thunderbolt: A Formally Verified Protocol for Off-Chain Bitcoin Transfers
Bitcoin Thunderbolt is a novel off-chain protocol for asynchronous, secure transfer of Bitcoin UTXOs between uncoordinated users. Unlike prior solutions such as payment channels or the Lightning Network, Bitcoin Thunderbolt requires no prior trust, direct interaction, or continuous connectivity between sender and receiver.
At its core, Bitcoin Thunderbolt employs a Byzantine fault-tolerant committee to manage threshold Schnorr signatures, enabling secure ownership delegation and on-chain finalization.
Read the full paper.
-
 @ 3eba5ef4:751f23ae
2025-04-25 01:56:19
@ 3eba5ef4:751f23ae
2025-04-25 01:56:19加密洞见
悬赏 1 BTC 的量子计算破解密钥挑战,被认为是个笑话
量子计算研究机构 Project Eleven 发布 Q-Day 挑战,宣布对能够于 2026 年 4 月 5 日之前、在量子计算机上使用 Shor 算法破解椭圆曲线加密(ECC)密钥的第一支团队提供 1 BTC 的奖励。Project Eleven 认为这将是一项极其艰巨的任务,即使获得几位私钥也将是一个大新闻。
而 Bitcoin Magazine 的长期贡献者 Shinobi 认为该笔赏金是一个笑话,并没有提供任何严肃的激励,原因有:
- 即使是对量子计算进展的高度乐观预测,也将实际实现这一目标的时间表定为 5-10 年;
- 按照目前单个比特币 80,000 美元的市价来看,奖励对于这项困难的工作其实并不多;
- 一台量子计算机可以完成比价值 80,000 美元更有价值的事,如窃听互联网连接、破解私人信息应用程序、破解整个 DNS 系统的证书颁发机构层次结构等。
重新定义比特币的基本单位的新 BIP
这份 BIP 草案建议重新定义「比特币」一词,以指代系统中最小的不可分割单位,即目前所说的「聪」(sat),目的是让交易看起来更清晰易读,可以有效降低了用户出错风险。如果某人有 851 个聪,钱包只显示 851 个比特币,而不是 0.00000851 BTC。变化的只有显示和解释金额的方式,而协议不变。
在这项提案之前,已经有提案(BIP 176)试图通过引入代表 100 聪的「比特」(bits)来使比特币数位的显示更加友好。虽然这减少了小数位的数量,但它引入了一种新的面额,用户必须学习并在其之间切换。
比特币交易活跃度低迷,稀疏区块仅包含 7 笔交易
比特币交易活动处于 2 年多来的最低水平,导致最大的矿池 Foundry 近期挖掘出一个稀疏的非空区块:Block 890466 仅包含 7 笔交易,重量为 5369 个单位。

上一个低于此的稀疏区块是 Binance Pool 在 2023 年 1 月挖出的区块 769895。内存池同样是空的,仅包含 4 笔交易,重量为 4370 个单位。

当前比特币挖矿高度集中:超过 95% 的区块仅由 6 个矿池开采
这篇由 b10c 发表的调查检查了当前五个最大的比特币矿池的哈希率份额,探讨 2025 年比特币挖矿中心化问题。第一部分着眼于 coinbase 交易中包含的矿池信息。第二部分考虑了假定的代理池。这两部分都显示了当前最大的矿池和挖矿集中化指数。调查结论:当下的比特币挖矿高度集中,有 6 个矿池开采了超过 95% 的区块。
预测到 2027 年的比特币哈希率
Valentin Rousseau 与 Blockspace 合作撰写了这份报告,涵盖: * 2025 年、2026 年和 2027 年的哈希率预测 * 当前的比特币挖矿经济学将如何影响哈希率的轨迹 * 公共矿工的哈希率扩展时间表,以及完成概率 * 不同比特币价格下哈希率增长的敏感度表
使用 VLS 支持非托管的闪电集成
VLS(Validating Lightning Signer)是签名者模块的库和参考实现,用于保护闪电节点,将 闪电私钥和安全规则验证从闪电节点分离到一个单独的签名设备中,通过减少攻击面来增强安全性。
在 VLS 之前,在不保管用户资金的情况下,在托管环境中安全地管理闪电私钥几乎是不可能的。Blockstream 的 Greenlight 在这份案例研究中介绍了如何使用 VLS,以非托管的方式使开发人员能够以最小的开销将闪电的功能添加到他们的应用程序中,同时确保用户保留对他们资金的完全控制权。Greenlight 构建在 Core Lightning 的模块化架构上,将由 Blockstream 管理的闪电节点操作与掌握在用户手中的闪电交易签名分开。
CTV+CSFS 如何改进 BitVM 网桥
Robin Linus 阐述了如何使用「输入提交契约」(input-committing covenants)在 BitVM 生态系统中构建更高效、更安全的桥,利用 CTV(CHECKTEMPLATEVERIFY)和 CSFS (CHECKSIGFROMSTACK) 消除对预签名委员会的需求并显着减少交易规模。这一进步简化了桥架构,提高了运营效率,并旨在实现信任最小化的比特币互作性,尽管仍然存在诸如挂钩过程中的潜在审查等挑战。
RISC Zero 推出 R0VM 2.0,性能提升的同时确保安全性
RISC Zero 推出了 R0VM 2.0,重大改进包括: * 以太坊区块的验证和执行时间,从 35 分钟缩短到仅 44 秒; * 到有效性证明的成本降低了 5 倍,批量大小为 25 的每个区块交易成本从 1.355 USD 下降到 0.2747 USD;较大批次交易成本低至 0.0012 USD;
在安全性方面,形式化验证是 R0VM 2.0 的核心。目前已经验证 Keccak 电路的完全确定性,以及在其 v2 电路中,核心 RISC-V 功能的 123 个组件中有 122 个是确定性的。
比特币软分叉可以改进 BitVMX
BitVMX 是支持乐观验证比特币智能合约的平台。Fairgate Labs 在本文中介绍了比特币可能经历的不同类型的升级,以及它们如何对 BitVMX 产生积极影响,认为了新的 opcodes 如果被软分叉到比特币中,可以提高 BitVMX 的效率、降低链上成本、简化脚本,并变得更加去中心化。
以太坊执行层将用 RISC-V 替代 EVM
Vitalik 发布了长期 L1 执行提案,宣布以太坊执行层将用 RISC-V 替换 EVM 作为编写智能合约的虚拟机,以大幅提高以太坊执行层的效率 ,解决主要的扩展瓶颈之一,同时增强执行层的简单性。
此外,Cardano 的 Charles Hoskinson 也表示 Cardano 在 BitVMX 中使用了 RISC-V;RISC-V 就是未来。
精彩无限,不止于链
从比特币看荒诞的世界:责任、自由与自我反思
《Bitcoin: The Inverse of Clown World》(比特币:荒诞世界的逆转)一书批判了充满「小丑」的当代世界——被虚假的政治议题和无意义的社会关注所占据——比如对「政治正确」和气候变化的过度关注。作者认为荒谬的核心是人们不负责任的行为,并认为当货币失效时,一切都变成政治和闹剧。
除了揭示和批评诸多荒诞现象,作者指出比特币倡导通过提供价值来获得成功,并强调了个人在这个信息过载的时代保护自己的时间和思想的重要性,进一步鼓励读者在比特币的支持下,重新审视自己的生活方式,并为改变世界贡献力量。
这里是 Bitcoin Magazine 对该书的书评。
GPU 工作量证明:重新定义 AI 驱动时代的能源、计算和金钱
作者设想了以 GPU 为基础的工作量证明(GPU PoW)在 AI 驱动的未来中的潜力。GPU PoW 不仅可以用于加密货币的安全保障,还能参与 AI 模型训练、能源负载调节以及全球算力市场的构建,相较于传统只能挖矿的 ASIC,GPU 更通用灵活,并能动态分配任务,在不同场景下实现收益最大化。通过本地数据中心、超级集群与中间件协同运作,GPU PoW 可以在不牺牲去中心化的前提下,提升能源与计算资源的使用效率,并创造以实用性为基础的新型经济体系。PoW 不再只是挖矿,而是成为支撑 AI、能源系统与货币市场协同发展的基础设施。
DahLIAS:首个用于完全交叉输入签名聚合的加密协议,允许重用比特币的曲线 secp256k1
Blockstream 研究团队推出 DahLIAS——第一个用于完全交叉输入签名聚合的加密协议,允许重用比特币的曲线 secp256k1。
一个交互式聚合签名(interactive aggregate signatures)方案允许 n 个签名者,每人拥有自己的秘密/公钥对(sk, pk)和消息 m,共同生成一个简短的签名,同时证明每个 m 在 pk 下已经被签名,其中 i ∈ {1, . . . , n}。尽管在空间和验证时间方面具有巨大的节省潜力,这两个因素是像比特币这样的区块链系统的主要瓶颈。但聚合签名相比于多方签名家族中的其他成员(例如 MuSig2 多重签名和 FROST 阈值签名)受到的关注较少。
而 DahLIAS 是首个直接在无配对组(pairing-free groups)中的离散对数上构建的、具有常数大小签名的聚合签名方案——与标准的 Schnorr 签名具有相同形态。DahLIAS 的签名协议由两轮组成,第一轮可以在没有消息的情况下预处理,且验证某个由 n 个签名者创建的签名,是由一个大小为 n + 1 的多重指数运算主导,这在渐近意义上比批量验证 n 个独立的 Schnorr 签名要快两倍。
DahLIAS 也考虑到了现实中的应用。除了前述的空间节省和验证速度提升外,DahLIAS 还提供了密钥调整功能,这是一种常用于比特币的技术——从有层级的确定性钱包中派生密钥,以节省空间并增强链上隐私。研究团队在随机预言模型下,基于(代数的)再一次离散对数假设,证明了包含密钥调整功能的 DahLIAS 在并发设置下的安全性。
查看完整论文。
Thunderbolt: 经过验证的链下比特币转账协议
该 Bitcoin Thunderbolt 链下协议用于在未协调的用户之间安全、异步地转移比特币 UTXO。与支付通道或闪电网络等现有解决方案不同,该协议无需预先信任、直接交互或持续连接发送方和接收方。其核心是通过拜占庭容错 committee 来管理阈值 Schnorr 签名,实现安全的所有权委托和链上最终确认。
查看完整论文。
-
 @ 3de5f798:31faf8b0
2025-04-25 01:46:45
@ 3de5f798:31faf8b0
2025-04-25 01:46:45My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 3de5f798:31faf8b0
2025-04-25 01:46:32
@ 3de5f798:31faf8b0
2025-04-25 01:46:32My everyday activity
This template is just for demo needs.
petrinet ;startDay () -> working ;stopDay working -> () ;startPause working -> paused ;endPause paused -> working ;goSmoke working -> smoking ;endSmoke smoking -> working ;startEating working -> eating ;stopEating eating -> working ;startCall working -> onCall ;endCall onCall -> working ;startMeeting working -> inMeetinga ;endMeeting inMeeting -> working ;logTask working -> working -
 @ 266815e0:6cd408a5
2025-04-24 22:56:53
@ 266815e0:6cd408a5
2025-04-24 22:56:53noStrudel
Its been over four months since I released
v0.42.0of noStrudel but I haven't forgot about it, I've just been busy refactoring the code-base.The app is well past its 2yr birthday and a lot of the code is really messy and kind of hacky. so my focus in the past few months has been refactoring and moving a lot of it out into the applesauce packages so it can be tested.
The biggest changes have been switching to use
rx-nostrfor all relay connections and usingrxjsand applesauce for event management and timelines. In total ~22k lines of code have been changed since the last release.I'm hoping it wont take me much longer to get a stable release for
v0.43.0. In the meantime if you want to test out the new changes you can find them on the nsite deployment.nsite deplyment: nostrudel.nsite.lol/ Github repo: github.com/hzrd149/nostrudel
Applesauce
I've been making great progress on the applesauce libraries that are the core of onStrudel. Since January I've released
v0.11.0andv0.12.0.In the past month I've been working towards a v1 release with a better relay connection package applesauce-relay and pre-built actions for clients to easily implement common things like follow/unfollow and mute/unmute. applesauce-actions
Docs website: hzrd149.github.io/applesauce/ Github repo: https://github.com/hzrd149/applesauce
Blossom
Spec changes: - Merged PR #56 from kehiy for BUD-09 ( blob reports ) - Merged PR #60 from Kieran to update BUD-8 to use the standard NIP-94 tags array. - Merged PR #38 to make the file extension mandatory in the
urlfield of the returned blob descriptor. - Merged PR #54 changing the authorization type for the/mediaendpoint tomediainstead ofupload. This fixes an issue where the server could mirror the original blob without the users consent.Besides the changes to the blossom spec itself I started working on a small cli tool to help test and debug new blossom server implementations. The goal is to have a set of upload and download tests that can be run against a server to test if it adheres to the specifications. It can also be used output debug info and show recommended headers to add to the http responses.
If you have nodejs installed you can try it out by running
sh npx blossom-audit audit <server-url> [image|bitcoin|gif|path/to/file.jpeg]Github repo: github.com/hzrd149/blossom-audit
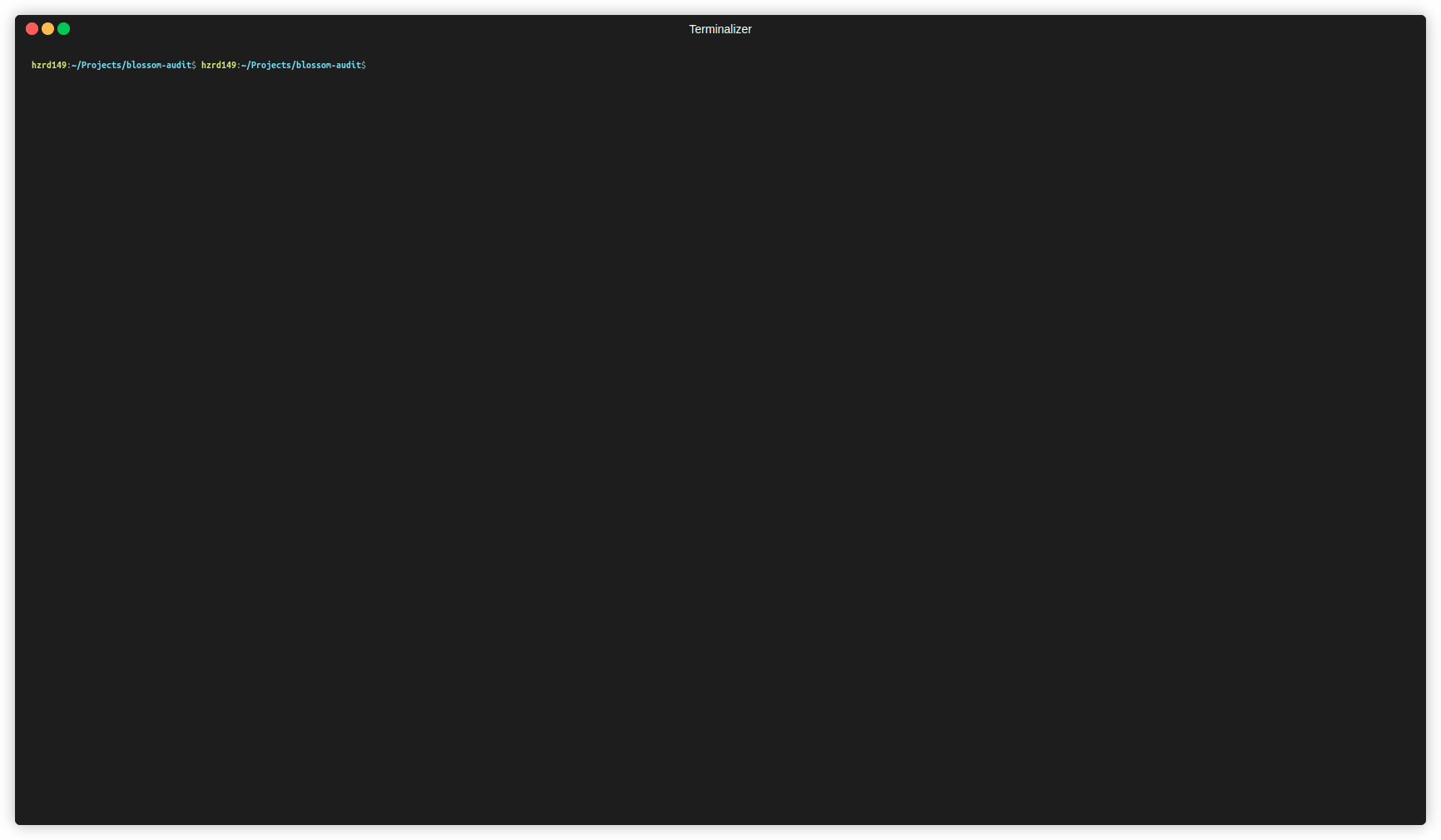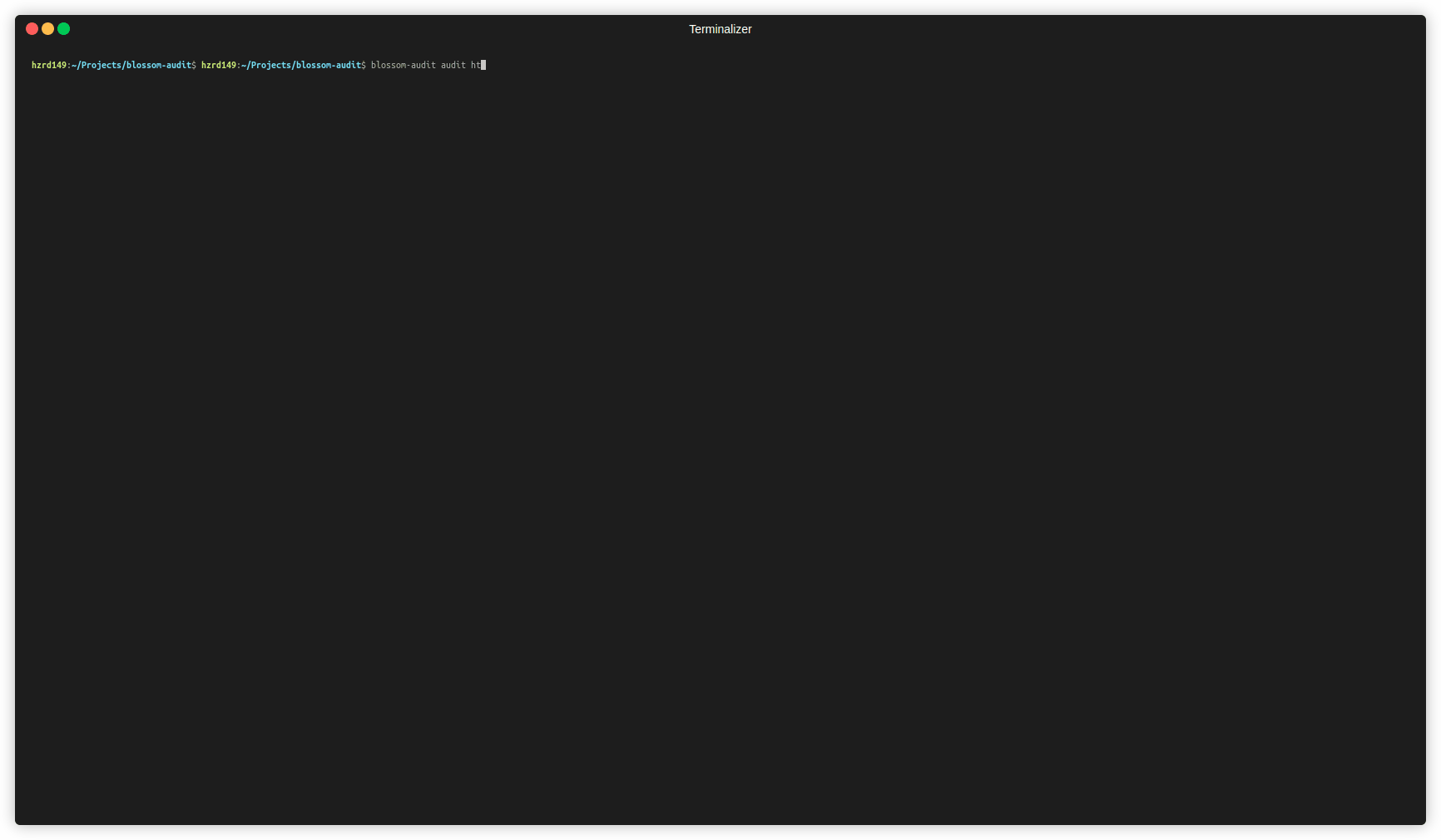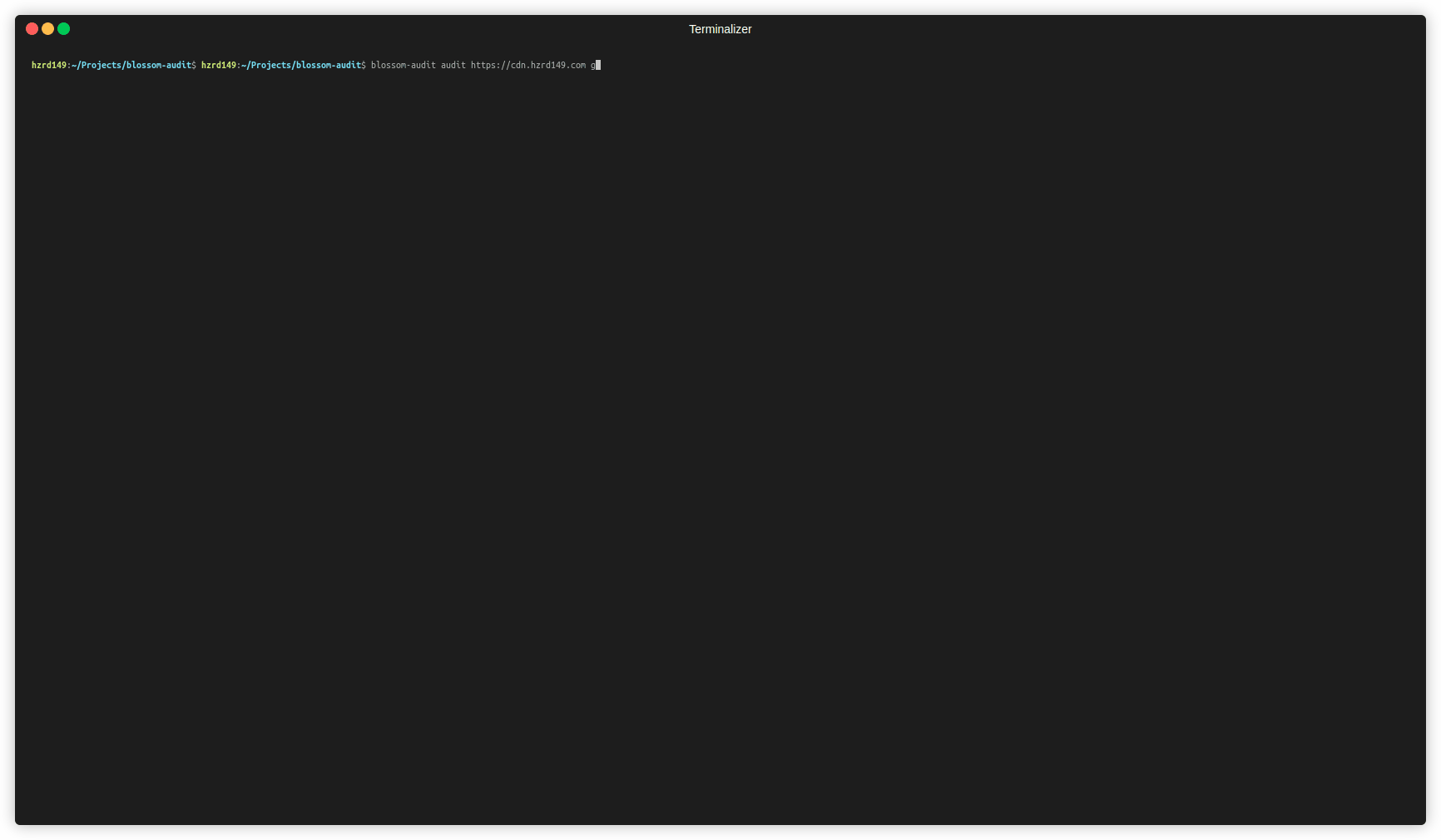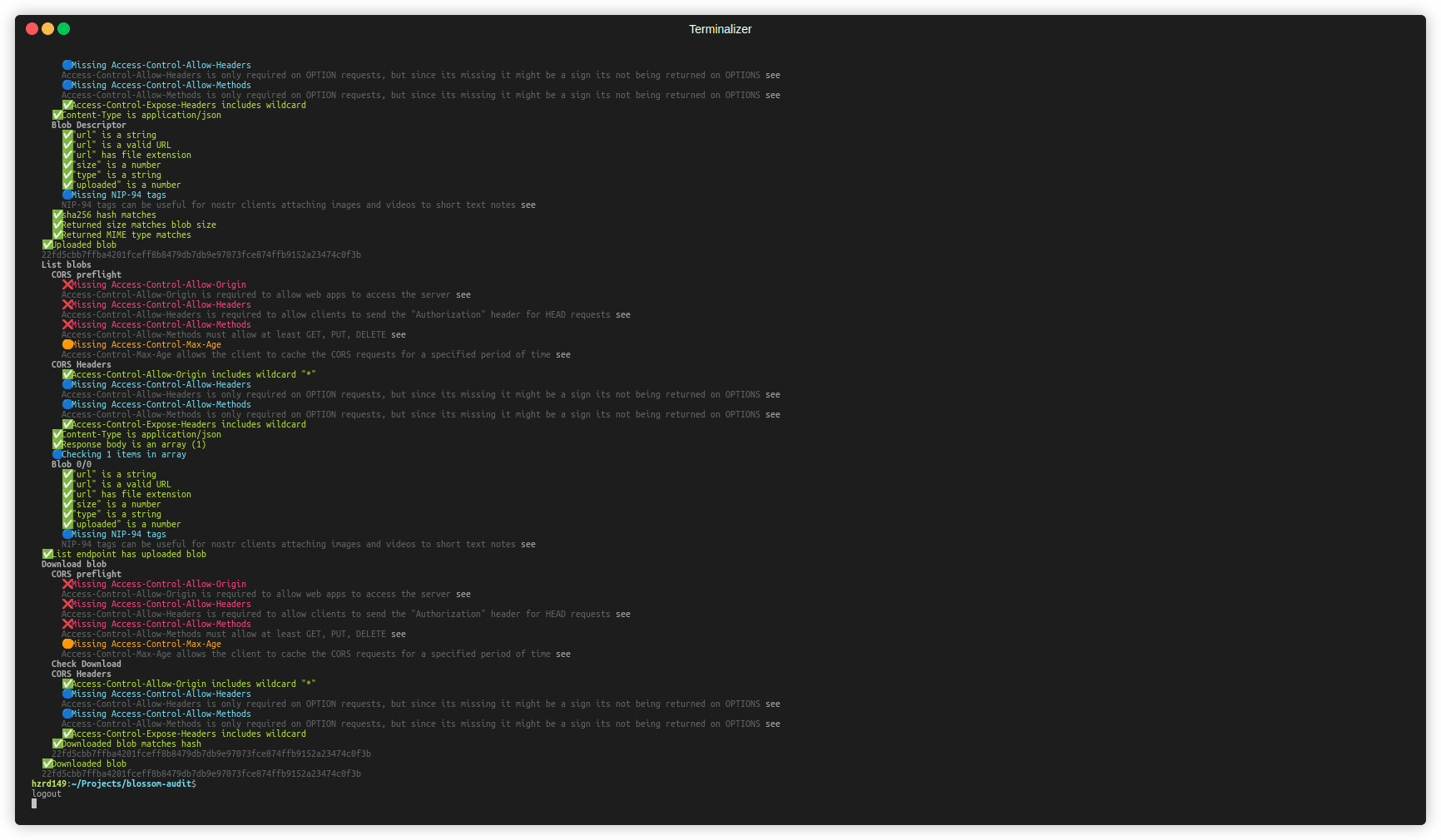
Other projects
Wifistr
While participating in SEC-04 I built a small app for sharing the locations and passwords of wifi networks. Its far from complete, but its usable and serves as an example of building an app with SolidJS and applesauce.
Live version: hzrd149.github.io/wifistr/ nsite version: here Github repo: github.com/hzrd149/wifistr
nsite-manager
I've been slowly continuing work on nsite-manager, mostly just to allow myself to debug various nsites and make sure nsite.lol is still working correctly.
Github repo: github.com/hzrd149/nsite-manager
nsite-gateway
I finally got around to making some much needed bug fixes and improvements to nsite-gateway ( the server behind nsite.lol ) and released a stable
1.0.0version.My hope is that its stable enough now to allow other users to start hosting their own instances of it.
Github repo: github.com/hzrd149/nsite-gateway
morning-glory
As part of my cashu PR for NUT-23 ( HTTP 402 Payment required ) I built a blossom server that only accepts cashu payments for uploads and stores blobs for 24h before deleting them.
Github repo: github.com/hzrd149/morning-glory
bakery
I've been toying with the idea of building a backend-first nostr client that would download events while I'm not at my computer and send me notifications about my DMs.
I made some progress on it in the last months but its far from complete or usable. Hopefully ill get some time in the next few months to create a working alpha version for myself and others to install on Umbrel and Start9
Github repo: github.com/hzrd149/bakery
-
 @ 76b0d68a:fdf859d0
2025-04-24 22:52:04
@ 76b0d68a:fdf859d0
2025-04-24 22:52:04Gemini look like they've just released a new video generating function. I just asked it to generate a video of a dog running through the snow in the Swiss Alps and this is what it came up with. Amazing.
Amazing that this is what is for all intents and purposes freely available to anybody. My mind is blown.
I know we saw all this with Sora last year, but the speed at which this kind of capability is being propagated is terrific.
originally posted at https://stacker.news/items/957519
-
 @ 76b0d68a:fdf859d0
2025-04-24 21:20:30
@ 76b0d68a:fdf859d0
2025-04-24 21:20:30Am reading his 1995 diary and he was so interested and up on technology I would be interested in his take on everything in AI, music and art going on today!
originally posted at https://stacker.news/items/957396
-
 @ 0e67f053:cb1d4b93
2025-04-24 19:42:00
@ 0e67f053:cb1d4b93
2025-04-24 19:42:00How to Be an Anti-Fascist: A Gentle Rebuttal to Billionaire Strongmen and Their Twitter Cosplays
By Carl Tuckerson
Good evening, radiant souls.
Tonight, I want to talk about something serious—but not in a shouty, vein-popping way. In a warm, clear-eyed, candle-lit kind of way. Let’s talk about fascism. And more importantly, how to stand firmly, nonviolently, and stylishly against it.
First, a definition. Fascism isn’t just people yelling on the internet or wearing weird hats. It’s a political disease—authoritarianism drenched in nationalism, allergic to diversity, and obsessed with power. It’s rigid. It’s cruel. It thrives on fear.
History, of course, gave us the ultimate case study: Adolf Hitler. A man who turned wounded ego and racist paranoia into a genocidal regime. Let’s be uncomfortably clear: fascism starts with rhetoric and ends in blood. It wears suits at first. Then it builds camps.
Which brings us to the now. To a peculiar blend of self-pitying billionaires and spray-tanned demagogues playing dictator on easy mode.
Let’s start with Elon Musk.
Here’s a man who once inspired us with rockets and electric cars—and now spends his time posting “anti-woke” memes like a Reddit troll who just discovered Ayn Rand. Elon claims to love “free speech,” unless that speech critiques him or his companies, in which case he’ll fire you, shadowban you, or awkwardly reply with a meme of Pepe the Frog.
You can’t be a free speech absolutist and also an insecure billionaire who throws tantrums when journalists ask questions. That’s not libertarianism. That’s narcissism with a Wi-Fi signal.
Then there’s Donald Trump.
The man who said he’d “drain the swamp” and instead held cocktail parties in it. Who said he loved “the people” but spent four years helping billionaires and banning brown kids. Who said he was “tough on crime” while pardoning white-collar felons and cozying up to actual Nazis at campaign rallies.
You don’t get to call yourself a patriot while trying to overthrow democracy. You don’t get to wrap yourself in the flag while selling fascist cosplay to a base too traumatized to see the grift. And no, calling your opponents “fascists” doesn’t make you less of one. That’s what projection looks like, not principle.
So… what does it actually mean to be anti-fascist?
It’s not just wearing black or smashing Starbucks windows (though I get the temptation). It means:
-
Refusing to dehumanize. Even when it’s easier.
-
Defending institutions of democracy while pushing them to do better.
-
Confronting power with truth—especially when that power has a blue checkmark and a bunker.
-
Building diverse communities where all people—not just rich white dudes with podcasts—have a voice.
-
Educating yourself. Read. Listen. Learn from those who’ve lived through real authoritarianism. Hint: it wasn’t your uncle who got suspended from X.
And look, I get it. It's easy to feel hopeless. To doomscroll and despair. But the antidote to fascism isn’t more fear. It’s radical hope. It’s showing up. It's organizing mutual aid. It's hugging someone at a protest. It's running a book club. It’s standing in solidarity instead of standing by.
So if you’re wondering how to be anti-fascist?
Start by being anti-ego. Anti-greed. Anti-cruelty. Anti-lie. And yes, sometimes that means being anti-Musk. Anti-Trump. Anti-anyone who thinks oppression is a branding opportunity.
We’ve tried letting billionaires be our heroes. It didn’t work. Maybe it’s time to try being each other’s heroes instead.
Stay soft. Stay loud. Stay antifascist.
We’ll see you tomorrow.
— Radical Kindness Carl
originally posted at https://stacker.news/items/957123
-
-
 @ e691f4df:1099ad65
2025-04-24 18:56:12
@ e691f4df:1099ad65
2025-04-24 18:56:12Viewing Bitcoin Through the Light of Awakening
Ankh & Ohm Capital’s Overview of the Psycho-Spiritual Nature of Bitcoin
Glossary:
I. Preface: The Logos of Our Logo
II. An Oracular Introduction
III. Alchemizing Greed
IV. Layers of Fractalized Thought
V. Permissionless Individuation
VI. Dispelling Paradox Through Resonance
VII. Ego Deflation
VIII. The Coin of Great Price
Preface: The Logos of Our Logo
Before we offer our lens on Bitcoin, it’s important to illuminate the meaning behind Ankh & Ohm’s name and symbol. These elements are not ornamental—they are foundational, expressing the cosmological principles that guide our work.
Our mission is to bridge the eternal with the practical. As a Bitcoin-focused family office and consulting firm, we understand capital not as an end, but as a tool—one that, when properly aligned, becomes a vehicle for divine order. We see Bitcoin not simply as a technological innovation but as an emanation of the Divine Logos—a harmonic expression of truth, transparency, and incorruptible structure. Both the beginning and the end, the Alpha and Omega.
The Ankh (☥), an ancient symbol of eternal life, is a key to the integration of opposites. It unites spirit and matter, force and form, continuity and change. It reminds us that capital, like Life, must not only be generative, but regenerative; sacred. Money must serve Life, not siphon from it.
The Ohm (Ω) holds a dual meaning. In physics, it denotes a unit of electrical resistance—the formative tension that gives energy coherence. In the Vedic tradition, Om (ॐ) is the primordial vibration—the sound from which all existence unfolds. Together, these symbols affirm a timeless truth: resistance and resonance are both sacred instruments of the Creator.
Ankh & Ohm, then, represents our striving for union, for harmony —between the flow of life and intentional structure, between incalculable abundance and measured restraint, between the lightbulb’s electrical impulse and its light-emitting filament. We stand at the threshold where intention becomes action, and where capital is not extracted, but cultivated in rhythm with the cosmos.
We exist to shepherd this transformation, as guides of this threshold —helping families, founders, and institutions align with a deeper order, where capital serves not as the prize, but as a pathway to collective Presence, Purpose, Peace and Prosperity.
An Oracular Introduction
Bitcoin is commonly understood as the first truly decentralized and secure form of digital money—a breakthrough in monetary sovereignty. But this view, while technically correct, is incomplete and spiritually shallow. Bitcoin is more than a tool for economic disruption. Bitcoin represents a mythic threshold: a symbol of the psycho-spiritual shift that many ancient traditions have long foretold.
For millennia, sages and seers have spoken of a coming Golden Age. In the Vedic Yuga cycles, in Plato’s Great Year, in the Eagle and Condor prophecies of the Americas—there exists a common thread: that humanity will emerge from darkness into a time of harmony, cooperation, and clarity. That the veil of illusion (maya, materiality) will thin, and reality will once again become transparent to the transcendent. In such an age, systems based on scarcity, deception, and centralization fall away. A new cosmology takes root—one grounded in balance, coherence, and sacred reciprocity.
But we must ask—how does such a shift happen? How do we cross from the age of scarcity, fear, and domination into one of coherence, abundance, and freedom?
One possible answer lies in the alchemy of incentive.
Bitcoin operates not just on the rules of computer science or Austrian economics, but on something far more old and subtle: the logic of transformation. It transmutes greed—a base instinct rooted in scarcity—into cooperation, transparency, and incorruptibility.
In this light, Bitcoin becomes more than code—it becomes a psychoactive protocol, one that rewires human behavior by aligning individual gain with collective integrity. It is not simply a new form of money. It is a new myth of value. A new operating system for human consciousness.
Bitcoin does not moralize. It harmonizes. It transforms the instinct for self-preservation into a pathway for planetary coherence.
Alchemizing Greed
At the heart of Bitcoin lies the ancient alchemical principle of transmutation: that which is base may be refined into gold.
Greed, long condemned as a vice, is not inherently evil. It is a distorted longing. A warped echo of the drive to preserve life. But in systems built on scarcity and deception, this longing calcifies into hoarding, corruption, and decay.
Bitcoin introduces a new game. A game with memory. A game that makes deception inefficient and truth profitable. It does not demand virtue—it encodes consequence. Its design does not suppress greed; it reprograms it.
In traditional models, game theory often illustrates the fragility of trust. The Prisoner’s Dilemma reveals how self-interest can sabotage collective well-being. But Bitcoin inverts this. It creates an environment where self-interest and integrity converge—where the most rational action is also the most truthful.
Its ledger, immutable and transparent, exposes manipulation for what it is: energetically wasteful and economically self-defeating. Dishonesty burns energy and yields nothing. The network punishes incoherence, not by decree, but by natural law.
This is the spiritual elegance of Bitcoin: it does not suppress greed—it transmutes it. It channels the drive for personal gain into the architecture of collective order. Miners compete not to dominate, but to validate. Nodes collaborate not through trust, but through mathematical proof.
This is not austerity. It is alchemy.
Greed, under Bitcoin, is refined. Tempered. Re-forged into a generative force—no longer parasitic, but harmonic.
Layers of Fractalized Thought Fragments
All living systems are layered. So is the cosmos. So is the human being. So is a musical scale.
At its foundation lies the timechain—the pulsing, incorruptible record of truth. Like the heart, it beats steadily. Every block, like a pulse, affirms its life through continuity. The difficulty adjustment—Bitcoin’s internal calibration—functions like heart rate variability, adapting to pressure while preserving coherence.
Above this base layer is the Lightning Network—a second layer facilitating rapid, efficient transactions. It is the nervous system: transmitting energy, reducing latency, enabling real-time interaction across a distributed whole.
Beyond that, emerging tools like Fedimint and Cashu function like the capillaries—bringing vitality to the extremities, to those underserved by legacy systems. They empower the unbanked, the overlooked, the forgotten. Privacy and dignity in the palms of those the old system refused to see.
And then there is NOSTR—the decentralized protocol for communication and creation. It is the throat chakra, the vocal cords of the “freedom-tech” body. It reclaims speech from the algorithmic overlords, making expression sovereign once more. It is also the reproductive system, as it enables the propagation of novel ideas and protocols in fertile, uncensorable soil.
Each layer plays its part. Not in hierarchy, but in harmony. In holarchy. Bitcoin and other open source protocols grow not through exogenous command, but through endogenous coherence. Like cells in an organism. Like a song.
Imagine the cell as a piece of glass from a shattered holographic plate —by which its perspectival, moving image can be restructured from the single shard. DNA isn’t only a logical script of base pairs, but an evolving progressive song. Its lyrics imbued with wise reflections on relationships. The nucleus sings, the cell responds—not by command, but by memory. Life is not imposed; it is expressed. A reflection of a hidden pattern.
Bitcoin chants this. Each node, a living cell, holds the full timechain—Truth distributed, incorruptible. Remove one, and the whole remains. This isn’t redundancy. It’s a revelation on the power of protection in Truth.
Consensus is communion. Verification becomes a sacred rite—Truth made audible through math.
Not just the signal; the song. A web of self-expression woven from Truth.
No center, yet every point alive with the whole. Like Indra’s Net, each reflects all. This is more than currency and information exchange. It is memory; a self-remembering Mind, unfolding through consensus and code. A Mind reflecting the Truth of reality at the speed of thought.
Heuristics are mental shortcuts—efficient, imperfect, alive. Like cells, they must adapt or decay. To become unbiased is to have self-balancing heuristics which carry feedback loops within them: they listen to the environment, mutate when needed, and survive by resonance with reality. Mutation is not error, but evolution. Its rules are simple, but their expression is dynamic.
What persists is not rigidity, but pattern.
To think clearly is not necessarily to be certain, but to dissolve doubt by listening, adjusting, and evolving thought itself.
To understand Bitcoin is simply to listen—patiently, clearly, as one would to a familiar rhythm returning.
Permissionless Individuation
Bitcoin is a path. One that no one can walk for you.
Said differently, it is not a passive act. It cannot be spoon-fed. Like a spiritual path, it demands initiation, effort, and the willingness to question inherited beliefs.
Because Bitcoin is permissionless, no one can be forced to adopt it. One must choose to engage it—compelled by need, interest, or intuition. Each person who embarks undergoes their own version of the hero’s journey.
Carl Jung called this process Individuation—the reconciliation of fragmented psychic elements into a coherent, mature Self. Bitcoin mirrors this: it invites individuals to confront the unconscious assumptions of the fiat paradigm, and to re-integrate their relationship to time, value, and agency.
In Western traditions—alchemy, Christianity, Kabbalah—the individual is sacred, and salvation is personal. In Eastern systems—Daoism, Buddhism, the Vedas—the self is ultimately dissolved into the cosmic whole. Bitcoin, in a paradoxical way, echoes both: it empowers the individual, while aligning them with a holistic, transcendent order.
To truly see Bitcoin is to allow something false to die. A belief. A habit. A self-concept.
In that death—a space opens for deeper connection with the Divine itSelf.
In that dissolution, something luminous is reborn.
After the passing, Truth becomes resurrected.
Dispelling Paradox Through Resonance
There is a subtle paradox encoded into the hero’s journey: each starts in solidarity, yet the awakening affects the collective.
No one can be forced into understanding Bitcoin. Like a spiritual truth, it must be seen. And yet, once seen, it becomes nearly impossible to unsee—and easier for others to glimpse. The pattern catches.
This phenomenon mirrors the concept of morphic resonance, as proposed and empirically tested by biologist Rupert Sheldrake. Once a critical mass of individuals begins to embody a new behavior or awareness, it becomes easier—instinctive—for others to follow suit. Like the proverbial hundredth monkey who begins to wash the fruit in the sea water, and suddenly, monkeys across islands begin doing the same—without ever meeting.
When enough individuals embody a pattern, it ripples outward. Not through propaganda, but through field effect and wave propagation. It becomes accessible, instinctive, familiar—even across great distance.
Bitcoin spreads in this way. Not through centralized broadcast, but through subtle resonance. Each new node, each individual who integrates the protocol into their life, strengthens the signal for others. The protocol doesn’t shout; it hums, oscillates and vibrates——persistently, coherently, patiently.
One awakens. Another follows. The current builds. What was fringe becomes familiar. What was radical becomes obvious.
This is the sacred geometry of spiritual awakening. One awakens, another follows, and soon the fluidic current is strong enough to carry the rest. One becomes two, two become many, and eventually the many become One again. This tessellation reverberates through the human aura, not as ideology, but as perceivable pattern recognition.
Bitcoin’s most powerful marketing tool is truth. Its most compelling evangelist is reality. Its most unstoppable force is resonance.
Therefore, Bitcoin is not just financial infrastructure—it is psychic scaffolding. It is part of the subtle architecture through which new patterns of coherence ripple across the collective field.
The training wheels from which humanity learns to embody Peace and Prosperity.
Ego Deflation
The process of awakening is not linear, and its beginning is rarely gentle—it usually begins with disruption, with ego inflation and destruction.
To individuate is to shape a center; to recognize peripherals and create boundaries—to say, “I am.” But without integration, the ego tilts—collapsing into void or inflating into noise. Fiat reflects this pathology: scarcity hoarded, abundance simulated. Stagnation becomes disguised as safety, and inflation masquerades as growth.
In other words, to become whole, the ego must first rise—claiming agency, autonomy, and identity. However, when left unbalanced, it inflates, or implodes. It forgets its context. It begins to consume rather than connect. And so the process must reverse: what inflates must deflate.
In the fiat paradigm, this inflation is literal. More is printed, and ethos is diluted. Savings decay. Meaning erodes. Value is abstracted. The economy becomes bloated with inaudible noise. And like the psyche that refuses to confront its own shadow, it begins to collapse under the weight of its own illusions.
But under Bitcoin, time is honored. Value is preserved. Energy is not abstracted but grounded.
Bitcoin is inherently deflationary—in both economic and spiritual senses. With a fixed supply, it reveals what is truly scarce. Not money, not status—but the finite number of heartbeats we each carry.
To see Bitcoin is to feel that limit in one’s soul. To hold Bitcoin is to feel Time’s weight again. To sense the importance of Bitcoin is to feel the value of preserved, potential energy. It is to confront the reality that what matters cannot be printed, inflated, or faked. In this way, Bitcoin gently confronts the ego—not through punishment, but through clarity.
Deflation, rightly understood, is not collapse—it is refinement. It strips away illusion, bloat, and excess. It restores the clarity of essence.
Spiritually, this is liberation.
The Coin of Great Price
There is an ancient parable told by a wise man:
“The kingdom of heaven is like a merchant seeking fine pearls, who, upon finding one of great price, sold all he had and bought it.”
Bitcoin is such a pearl.
But the ledger is more than a chest full of treasure. It is a key to the heart of things.
It is not just software—it is sacrament.
A symbol of what cannot be corrupted. A mirror of divine order etched into code. A map back to the sacred center.
It reflects what endures. It encodes what cannot be falsified. It remembers what we forgot: that Truth, when aligned with form, becomes Light once again.
Its design is not arbitrary. It speaks the language of life itself—
The elliptic orbits of the planets mirrored in its cryptography,
The logarithmic spiral of the nautilus shell discloses its adoption rate,
The interconnectivity of mycelium in soil reflect the network of nodes in cyberspace,
A webbed breadth of neurons across synaptic space fires with each new confirmed transaction.
It is geometry in devotion. Stillness in motion.
It is the Logos clothed in protocol.
What this key unlocks is beyond external riches. It is the eternal gold within us.
Clarity. Sovereignty. The unshakeable knowing that what is real cannot be taken. That what is sacred was never for sale.
Bitcoin is not the destination.
It is the Path.
And we—when we are willing to see it—are the Temple it leads back to.
-
 @ 2ed3596e:98b4cc78
2025-04-24 18:31:53
@ 2ed3596e:98b4cc78
2025-04-24 18:31:53Bitcoiners, your points just got a lot more epic! We’re thrilled to announce the launch of the Bitcoin Well Point Store, available now in Canada and the USA.
Now you can redeem your Bitcoin Well points for prizes that level up and celebrate your Bitcoin lifestyle.
What can you get in store?
Right now, you can exchange your points for:
-
Simply Bitcoin hoodie: Rep your Bitcoin pride in style
-
Exclusive Bitcoin Well Stampseed backup plate: Protect and manage your private keys securely
-
Personalized LeatherMint wallet: Classy, sleek, and ready to hold your fiat (until you convert it to sats!)
-
Tesla Cybertruck in Bitcoin orange: Wait…really? A Cybertruck? Who approved this?

More epic items will be available in the Bitcoin Well Point Store in the coming months. Stay tuned!
How to redeem your Bitcoin Well Points
Redeeming your points is easy:
-
Log in and go the Bitcoin Well Points store within the Rewards Section
-
Check your Bitcoin Well point balance
-
Redeem Your Bitcoin Well points for the prize of your dreams
Once you’ve purchased an item from the Bitcoin Well Point Store, we’ll email you to figure out where you want us to ship your prize. Unless it's the Cybertruck, then you can come to our office and pick it up!
How can you earn more Bitcoin Well Points? ⚡
Here are all the ways you can earn Bitcoin Well points:
-
Buy bitcoin/Sell bitcoin/pay bills - 3 Points per $10
-
Recurring buy - 5 points per $10
-
First transaction bonus - 500 points
-
Refer a friend to Bitcoin Well - 500 points
The more you use Bitcoin Well, the more points you earn, rewarding you for investing in your freedom and self-sovereignty
Want sats, not stuff? No problem! 👇
You can keep earning sats by playing the Bitcoin (Wishing) Well! You can win up to 1,000,000 on your next coin toss. Now you have the exciting choice: do you play the Bitcoin (Wishing) Well or save up your Bitcoin Well points for a sweet prize?

What makes Bitcoin Well different
Bitcoin Well is on a mission to enable independence. We do this by making it easy to self custody bitcoin and embracing the latest bitcoin innovations. By custodying their own money, our customers are free to do as they wish without begging for permission. By creating a full ecosystem to buy, sell and use your bitcoin to connect with the modern financial world, you are able to have your cake and eat it too - or have your bitcoin in self custody and easily spend it too 🎂.
Create your Bitcoin Well account now →
Invest in Bitcoin Well
We are publicly traded (and love it when our customers become shareholders!) and hold ourselves to a high standard of enabling life on a Bitcoin standard. If you want to learn more about Bitcoin Well, please visit our website or reach out!
-
-
 @ 0e67f053:cb1d4b93
2025-04-24 16:44:31
@ 0e67f053:cb1d4b93
2025-04-24 16:44:31By Carl Tuckerson, Who Weeps During City Council Meetings
Democracy is not a system.
It is a living, breathing organism, pulsating with the ancestral heartbeat of every barefoot revolutionary who ever composted oppression into community gardens of change.
It is consent manifested, a tapestry woven by the trembling hands of the marginalized and the mildly inconvenienced alike. It is radical accountability on a biodegradable ballot.
Democracy is the collective inhale of a million voices saying, “Yes, I matter,” and the collective exhale of power releasing its grip—not because it was forced to, but because it finally understood its own trauma.
It is fluid, non-binary, and consensually participatory. A polyamorous relationship between people, policy, and purpose. No labels. Just vibes.
It is the sacred act of showing up—in person, in spirit, in ethically sourced linen—because you believe that your voice, no matter how tremulously intersectional, is a note in the symphony of collective liberation.
Democracy is not red or blue. It’s not even purple. It’s the entire spectrum of human expression, from burnt sienna to sunset glitter sparkle.
It is brunch and ballots. It is protest and poetry. It is tweeting while crying while registering your roommate to vote.
It is government of the people, by the people, and for the people, but especially for the people who’ve been gaslit by history.
And when democracy falters, we don’t abolish it—we give it a weighted blanket, whisper affirmations into its ear, and tell it to take the day off, because healing is not linear.
So what is democracy?
It’s not a noun.It’s not even a verb.It’s a sacred energy exchange—and if you listen closely, you can hear it humming in the compost bin behind your community center.
Namaste. Vote. And remember: ballots are spells cast in ink. Use yours wisely.
— Carl, “Decolonize the Vote” Tuckerson
originally posted at https://stacker.news/items/956879
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ 5188521b:008eb518
2025-04-24 07:34:50
@ 5188521b:008eb518
2025-04-24 07:34:50We are losing our freedom.
Don't believe me? Data published by the Cato Institute suggests that 74% of Americans are concerned they could lose freedoms.
But what do we really mean by 'freedom'?
The Cambridge Dictionary defines ‘freedom’ as follows: the condition or right of being able or allowed to do, say, think, etc. whatever you want to, without being controlled or limited.
Despite this clear definition, freedom means different things to different people: it might also refer to freedom of movement, private property rights, free markets, and freedom from violence.
Freedom fiction (also known as Libertarian fiction) denotes fictional stories intrinsically linked to these ideas or, more likely, the sometimes vain pursuit of this idea.
If dystopian fiction is overly bleak, perfectly captured by the image of a boot on the reader's neck, libertarian stories should offer just a glimmer of hope.
What is freedom fiction?
If dystopia, sci-fi, fantasy, and horror are genres, i.e., styles of fiction that must encompass certain tropes, freedom fiction could more generally be considered a category that explores freedom as a theme, without necessarily being part of a specific genre.
Freedom fiction primarily concerns itself with the overarching topics of individual liberty and sovereignty, conflict with authoritarian or surveillance states, and the restoration or preservation of rights that citizens of the Western world have come to expect: privacy, freedom of speech, the right to private property, and freedom to transact and form contracts.
Though enjoying something of a resurgence in recent decades and especially post Covid, freedom fiction is not new, and famous/infamous novels throughout the centuries could be retroactively categorised as freedom fiction.
Think of The Epic of Gilgamesh (2000BC), Greek tragedies (500BC), Uncle Tom's Cabin by Harriet Beecher Stowe (1852), which helped fuel the anti-slavery movement, or We by Yevgeny Zamyatin, written over 100 years ago.
Today, freedom fiction is an emerging category that includes the revival of the cypherpunk movement, as privacy technologies such as Bitcoin seek to remove the reliance on the banking system, which has become an effective method of control for the establishment.
Why read freedom fiction?
 Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.
Storytelling is a tradition as old as humanity itself, created to share the joy and wonder of imagined worlds. Fiction can also serve as a warning of what might come, and playing out “what if?” scenarios in our minds can help us in the real world, too.Any individual interested in escaping the modern debt-slavery rat race we’ve found ourselves forced into can enjoy freedom stories with a greater and deeper understanding of just how real this “fiction” could be in the future.
Spiking interest
Data from Google Trends shows that in the United Kingdom — a nation increasingly concerned with policing speech, surveillance and other dystopic methods — interest in freedom has been spiking in the past five years, centred in England.
 Source: Google Trends
Source: Google TrendsNow let’s take a look at the data for the United States:
 Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.
Despite a lower interest overall, the spike in 2023 mirrors that of the UK. Perhaps this was due to an event featured in the news or even a brand name or TikTok trend.It is interesting to note that although a great number of Amercians fear losing their freedoms, fewer are searching how to protect them.
One reason for the rise in freedom fiction could be that Libertarian thinkers, praxeologists, and freedom maximalists seek to alert the populace through emotive stories. Few, it seems, are awakened when presented with legacy media propaganda and government messages.
The benefits & outcomes of reading freedom fiction
Once a human mind has acquired a taste for freedom fiction, there are numerous benefits and likely outcomes that will arise as a result:
Benefits:
- Broadened perspective and understanding of historical issues
- Increased empathy and social understanding
- Inspiration, motivation & empowerment
- Critical thinking skills & awareness
- Emotional connection
Once the reader has enjoyed these benefits, it is likely they will put their newfound understanding to action, bringing about outcomes like these.
Outcomes:
- Appreciation of and gratitude for freedom
- Informed civic engagement
- Agency for social change
- Personal growth
It would appear, then, that at some point, freedom fiction will have a transformative impact on the social demographics of the civilised world. As popular Netflix shows like Black Mirror highlight our reliance and overreliance on digital media, and governments continue to censor user-generated content posted socially, we must ask ourselves, when exactly will we wake up to what is happening?
We are more connected, but more controlled, than ever. How can we use the tools that enslave us to liberate us? Perhaps through sharing stories.
Aspects of freedom, genres, and time periods
Freedom fiction is a broad spectrum, encompassing various aspects, genres and time periods.
Aspects — privacy, freedom of speech, wrongful imprisonment, oppression, discrimination, government overreach, surveilance, debanking, censorship, confiscation, forced separation and more.
Genres — horror, sci-fi, fantasy, thriller and even young adult romance stories can contribute to the growing canon of libertarian-themed fiction.
Time periods — slavery in the past, alien invasions in the future, totalitarian governments in the present. Freedom fiction can relate to any time period.
15+ Classic Freedom-themed Books
 In no particular order, here are 15 of the greatest examples of freedom stories from modern times:
In no particular order, here are 15 of the greatest examples of freedom stories from modern times:-
Nineteen Eighty-Four by George Orwell (1949): A dystopian classic where the Party controls every aspect of people's lives, and Winston Smith rebels against the oppressive regime.
Reason to read: Offers a chilling and thought-provoking exploration of totalitarianism, mass surveillance, and the importance of individual thought and truth.
-
The Handmaid's Tale by Margaret Atwood (1985): In a totalitarian regime where women are stripped of their rights, Offred fights for survival and a chance to regain her freedom.
Reason to read: A haunting story that explores themes of feminism, oppression, and resistance, with a timely warning about the dangers of religious extremism and the fragility of women's rights.
-
Brave New World by Aldous Huxley (1932): A satirical look at a future society where people are genetically engineered and conditioned to conform, and a "savage" challenges their way of life.
Reason to read: Provides an unsettling vision of a future where happiness is manufactured at the cost of individuality, freedom, and genuine human connection.
-
Fahrenheit 451 by Ray Bradbury (1953): In a world where books are banned, Guy Montag, a fireman, discovers the power of knowledge and fights for intellectual freedom.
Reason to read: A passionate defense of the importance of books, ideas, and intellectual freedom, and a warning against censorship.
-
The Giver by Lois Lowry (1993): A young boy named Jonas discovers the dark secrets of his seemingly Utopian society, where there is no pain, sadness, or freedom of choice.
Reason to read: A thought-provoking exploration of utopia, dystopia, and the importance of memory, emotion, and individual choice in a truly human life.
-
One Flew Over the Cuckoo's Nest by Ken Kesey (1962): Randle McMurphy challenges the authority of a mental institution, becoming a symbol of rebellion and the fight for individual freedom.
Reason to read: A powerful and moving story about the struggle against forced conformity and the importance of individuality, even in the face of oppressive systems.
-
Little Brother by Cory Doctorow (2008): This contemporary science fiction novel explores themes of government surveillance, digital rights, and the power of decentralized networks in challenging authority.
Reason to read: a timely exploration of digital surveillance, government overreach, and the power of youthful activism in defending civil liberties in the modern age.
-
Beloved by Toni Morrison (1987): Set after the American Civil War, this novel explores the psychological and emotional scars of slavery and the struggle for freedom and identity.
Reason to read: A masterpiece that delves into the legacy of slavery and its enduring impact on identity, memory, and the quest for freedom.
-
The Book Thief by Markus Zusak (2005): In Nazi Germany, a young girl named Liesel Meminger finds solace in stolen books and discovers the power of words to resist oppression and find freedom.
Reason to read: A beautifully written story about the power of words to nourish the soul, resist oppression, and find hope and freedom in the darkest of times.
-
Animal Farm by George Orwell (1945): An allegorical novella about a revolution on a farm that turns into a totalitarian dictatorship, highlighting the dangers of unchecked power, Communism, and the loss of freedom.
Reason to read: A timeless allegory that exposes the corruption of revolutions, the fragility of freedom, and the importance of resistance against tyranny.
-
A Thousand Splendid Suns by Khaled Hosseini (2007): This novel tells the story of two Afghan women whose lives intersect under the oppressive Taliban regime, and their fight for survival and freedom.
Reason to read: An eye-opening portrayal of the resilience and strength of women in the face of oppression, and a powerful story about the universal desire for dignity.
-
The Underground Railroad by Colson Whitehead (2016): A unique novel that reimagines the Underground Railroad as a literal railroad, and follows a slave's journey.
Reason to read: A compelling blend of historical fiction and magical realism that offers a fresh perspective on the history of slavery and the enduring quest for freedom.
-
Anthem by Ayn Rand (1938): A novella set in a collectivist future where the concept of "I" has been eradicated. It follows one man's rediscovery of individualism and his rebellion against the oppressive society.
Reason to read: a novella that champions radical individualism against the suffocating conformity of collectivist ideology.
-
The Count of Monte Cristo by Alexandre Dumas (1844-46): Edmond Dantès is wrongly imprisoned and seeks revenge and freedom after years of captivity.
Reason to read: An exciting tale of betrayal, revenge, and ultimate triumph, with a focus on themes of justice, freedom, and the resilience of the human spirit.
-
Snow Crash (1992) and Cryptonomicon (1999) by Neal Stephenson: While not strictly libertarian manifestos, these novels explore themes of individual freedom, the power of information, decentralized systems, and critiques of centralized authority in engaging and complex ways.
Reason to read: these books are considered modern cypherpunk classics. They are rich in detail and the perfect starting place to learn more about the genre and why it is important for freedom.
 ## Lesser-known Freedom Books
## Lesser-known Freedom BooksHere are 15 lesser-known, more modern books that also explore the theme of freedom:
- Exit West by Mohsin Hamid (2017): This novel uses magical realism to depict refugees fleeing a war-torn country and seeking freedom and safety in an uncertain world.
- A Lodging of Wayfaring Men by Paul Rosenberg (2007): a libertarian novel based on real events that explores themes of individual sovereignty and free markets.
- The Probability Broach by L. Neil Smith (1979): An alternate history novel where a slight change in the Declaration of Independence leads to a libertarian society in North America. It's the first in Smith's "North American Confederacy" series.
- The Beekeeper of Aleppo by Christy Lefteri (2019): This tells the story of beekeepers forced to flee Syria and their struggle to find freedom and rebuild their lives in a new country.
- Alongside Night by J. Neil Schulman (1979): A dystopian thriller depicting the collapse of the US government and the rise of a libertarian underground.
- Freehold by Michael Z. Williamson (2004): A military science fiction series that portrays a future where individuals have seceded from Earth's controlling government to establish independent, more libertarian colonies.
- No Truce with Kings by Poul Anderson (1963): A novella that won the Hugo Award, depicting a future where scientific progress has led to a world of isolated, self-sufficient individuals, challenging traditional notions of society and government.
- A Passage North by Anuk Arudpragasam (2021): This Booker Prize-nominated novel explores the aftermath of the Sri Lankan Civil War and the complexities of memory, trauma, and the search for inner freedom.
- Kings of the High Frontier by Victor Koman (1996): A hard science fiction novel exploring themes of entrepreneurship and individual liberty in space.
- This Perfect Day by Ira Levin (1970): A dystopian novel where a seemingly Utopian global society controls every aspect of individual life, raising questions about freedom versus engineered happiness.
- Wasp by Eric Frank Russell (1957): A story containing acts of terrorism against oppressive aliens. A notable example of a single individual disrupting a larger, controlling power.
- The Peace War by Vernor Vinge (1984): A ruthless organization, the Peace Authority, uses impenetrable force fields to end war but suppresses technology and individual liberty, leading a group of rebels to fight for the freedom to advance and determine their own future.
- Starship Troopers by Robert A. Heinlein (1959): Heinlein was a prolific science fiction writer whose works frequently touch upon libertarian themes. Starship Troopers explores the ideas of civic virtue and individual responsibility.
- Live Free or Die by John Ringo (2010) follows Tyler Vernon, a fiercely independent and resourceful entrepreneur who stands up against alien oppressors and Earth's own bureaucratic tendencies to forge a path to true liberty and self-determination for humanity.
- Darkship Thieves by Sarah Hoyt (2010): Winner of the Prometheus Award for Best Libertarian SF Novel. This book follows Athena Hera Sinistra, a genetically engineered woman who escapes a tyrannical Earth to a freer society in space.
Freedom Publishers
In addition to the many works of libertarian fiction, a number of publishers are beginning to focus on stories which promote freedom.
- Liberty Island: This publisher focuses on science fiction and fantasy with libertarian and individualist themes.
- Fox News Books: While a mainstream publisher, it has been known to publish fiction with libertarian themes or by authors who are considered libertarian.
- Defiance Press & Publishing: This independent publisher openly states its commitment to publishing conservative and libertarian authors across fiction and non-fiction genres.
- Konsensus Network: A publisher that specifically promotes libertarian themes and bitcoin authors.
- All Seasons Press: Founded by former executives from Simon & Schuster and Hachette, this independent press aims to be a home for conservative voices.
- Baen Books: This is a well-known publisher, particularly in science fiction and fantasy, that often features authors and stories exploring themes of individual liberty, self-reliance, and limited government.
- Morlock Publishing: This small press specializes in science fiction with themes often including aspects of anarcho-capitalism and libertarian rebellion.
- Heresy Press (now an imprint of Skyhorse Publishing): While broader in its scope, Heresy Press aimed to publish "uncensored, outspoken, and free-spirited books" which can include libertarian viewpoints in fiction.
- Libertarian Futurist Society (LFS) (indirectly): While not a traditional publisher, the LFS sponsors the Prometheus Award and promotes libertarian science fiction. Their website and related platforms can be resources for finding authors and works, which are then published by various houses.
Recent Trends in Libertarian Fiction:
 Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.
Konsensus Network’s new imprint, 21 Futures, is building a movement centred on freedom fiction, a movement in which emerging and established writers can contribute their storytelling media to anthologies and blogs, as well as publish their own individual works.To date, two short story anthologies are available from 21 Futures:
Tales from the Timechain: the world’s first Bitcoin-fiction anthology.
21 writers examine how the hardest sound money ever created can restore freedom and liberty to mankind.
Financial Fallout: in this recently-released anthology, 21 writers weave financial dystopia from across a broader spectrum of freedom fiction, sewing seeds of eventual hope.
In addition to 21 Futures, a host of self-published and even best-selling fiction on the theme of bitcoin is now available. The Rapid Rise of Bitcoin Fiction documents the history and current trends in this genre.
 ## What happens next?
## What happens next?As governments tighten their grip on our data and our freedoms erode, we expect that freedom fiction will become a wider phenomenon. It is our hope and belief that Konsensus Network and 21 Futures will help drive growth in the genre and better understanding of how to protect individual freedom through our multimedia publications.
Follow our socials to keep up to date on future releases.
This blog was originally published on the 21 Futures blog by Alex Boast.
Alex is a web3 writer, ghost writer and ghost story writer. He’s a novelist and poet from England who loves to work with other writers as a coach, mentor and friend. You can find him on LinkedIn.
-
 @ a296b972:e5a7a2e8
2025-04-23 20:40:35
@ a296b972:e5a7a2e8
2025-04-23 20:40:35Aus der Ferne sieht man nur ein Gefängnis aus Beton. Doch wenn man näher herankommt, sieht man, dass die Mauern schon sehr brüchig sind und das Regenwasser mit jedem Schauer tiefer in das Gemäuer eindringt. Da bleibt es. Bis die Temperaturen unter Null gehen und das Wasser gefriert. Jetzt entfaltet das Eis seine physikalische Kraft, es rückt dem Beton zu leibe, es dehnt sich aus und sprengt ihn.
Das geht nun schon fünf Jahre so. Fünf Jahre immer wieder Regen, abwechselnd mit Frost und Eis. Die Risse werden größer, der Beton immer morscher. So lange, bis die Mauern ihre Tragfähigkeit verlieren und einstürzen.
Was soll das? Fängt da einer an zu spinnen? Wozu diese Metapher?
Hätte man zu Anfang gleich geschrieben: Wir, die kritischen Menschen, die sich der Wahrheit verpflichtet haben, sitzen in unserer Blase wie in einem Gefängnis und erreichen die da draußen nicht. Da hätten sicher viele gesagt: Oh, da will aber jemand die Opferrolle in vollen Zügen auskosten. Nee, nee, wir sind keine Opfer, wir sind Täter. Wir sammeln und bewahren die ständig neu dazukommenden Erkenntnisse der Wissenschaft und politischen Lügereien. Wir lernen Bücher auswendig, bevor die Feuerwehr kommt und sie verbrennt.
„Fahrenheit 451“
https://www.youtube.com/watch?v=P3Kx-uiP0bY
https://www.youtube.com/watch?v=TsNMxUSCKWo
„Das Haus ist für unbewohnbar erklärt worden und muss verbrannt werden.“
So primitiv geht man heute nicht mehr vor. Heute stehen die Feuerwehrmänner und ihre Erfüllungsgehilfen um 6 Uhr morgens im Türrahmen, nehmen Mobiltelefon und Laptop mit, betreiben De-Banking und vernichten die wirtschaftliche Existenz.
Und ja, es gibt Tage, da fühlt man sich trotzdem wie im Informationsgefängnis. Das hängt von der Tageskondition ab. Der öffentlich-rechtliche Rundfunk ist die Gefängnisküche. Zubereitet werden fade Speisen mit sich ständig wiederholenden Zutaten. Heraus kommt ein Gericht, eine Pampe, wie die tagesschau. LAAAANGWEILIG!
Man glaubt, Informationen und kritische Äußerungen gegenüber dem Mainstream-Einheitsbrei bleiben in den Gefängnismauern, der Blase, schaffen es nicht über die Mauer nach draußen, in die vermeintliche Freiheit. Neue Erkenntnisse werden nur innerhalb der Mauern weitergegeben. Ein neuer Kanal, steigende Abonnenten. Doch wer sind die? Welche von da draußen, in der sogenannten Freiheit, oder doch wieder immer dieselben üblichen Verdächtigen? Die da draußen haben uns doch schon längst geblockt oder gleich gelöscht. Mit Gedankenverbrechern will man nichts zu tun haben.
Hallo, ihr da draußen: Wir sind unschuldig. Unser einziges Verbrechen ist, dass wir Informationen verbreiten, die euch da draußen nicht gefallen, weil sie euch nicht in den Kram passen. Für euch sind wir eine Bedrohung, weil diese Informationen auf euch weltbilderschütternd wirken. Wir sprechen das aus, was viele sich nicht einmal trauen zu denken. Ihr habt Angst vor der Freiheit. Nicht wir sitzen ein, sondern ihr. In einem Freiluft-Gefängnis. Wir decken die Lügen auf, die da draußen, außerhalb der Mauern verbreitet werden. Wir sind nicht die Erfinder der Lügen, sondern nur die Überbringer der schlechten Botschaften.
Es ist leichter Menschen zu lieben, von denen man belogen wird, als Menschen zu lieben, die einem sagen, dass man belogen wird.
Mit aller Kraft wird versucht, die Menschen in Einzelhaft zu setzen. In der Summe ist das die gesellschaftliche Spaltung. Gleichzeitig wird an den Zusammenhalt appelliert, obwohl man genau das Gegenteil davon vorantreibt.
Es geht auch nicht um Mitleid. Es geht um das Verdeutlichen der vorhandenen medialen Axt, mit der ganze Nationen in zwei Teile zerhackt werden. Auf politischer Ebene wird viel dafür getan, dass sich das auch ja nicht ändert. Ein Volk in Angst ist gut zu regieren. Teile und herrsche. Die Sprüche können wir alle schon rückwärts auf der Blockflöte pfeifen.
An den vier Ecken des Informations-Gefängnisses stehen Wachtürme, mit Wärtern, ausgebildet vom DSA, vom Digital Services Act, finanziert vom Wahrheitsministerium, dass ständig aktualisierend darüber befindet, was heute gerade aktuell als „Hass und Hetze“ en vogue ist. Es kommt eben immer darauf an, wer diese Begriffe aus der bisher dunkelsten Zeit in der deutschen Geschichte benutzt. Das hatten wir alles schon einmal. Das brauchen wir nicht mehr!
Schon in der Bibel steht das Gebot: Du sollst nicht lügen. Da steht nicht: Lügen verboten! Das Titelbild gehört leider auch zur deutschen Vergangenheit. Ist es jetzt schon verboten, darauf hinzuweisen, dass sich so etwas nicht wiederholen darf? Und in einer Demokratie, die eine sein will, schon gar nicht. Eine Demokratie, die keine ist, wenn die Meinungsfreiheit beschnitten wird und selbsternannte Experten meinen darüber entscheiden zu müssen, was als wahr und was als Lüge einzustufen ist. Die Vorgabe von Meinungs-Korridoren delegitimieren das Recht, seine Meinung frei äußern zu dürfen. In einer funktionierenden Demokratie dürfte sogar gelogen werden. Jedem, der noch zwei gesunde Gehirnzellen im Kopf hat, sollte doch klar sein, dass all das erbärmliche Versuche sind, sich mit allen Mitteln an der Macht festzuklammern.
Noch einmal zurück zur anfänglichen Metapher. So lange wir leben, befinden wir uns in einem fließenden Prozess. Nichts ist in Stein gemeißelt, nichts hält für immer. Betrachtet man die jüngste Vergangenheit als einen lebendigen Prozess, der noch nicht abgeschlossen ist, der sich ständig weiterentwickelt, dann ist all dieser Wahnsinn der Regen, der bei Frost zu Eis wird und die Mauer immer maroder macht. Die Temperaturen gehen wieder über Null, das Eis taut auf, das Wasser versickert, der nächste Regen, der nächste Frost. Alles neigt dazu kaputt zu gehen.
Wir brauchen eigentlich nur zu warten, während wir fleißig weiter Erkenntnisse sammeln und dabei zusehen, wie ein Frost nach dem anderen, in Form von immer neuen und weiteren Informationen, die all die Lügen zu Corona und den aktuellen Kriegen in der Welt, die Gefängnismauer früher oder später zum Einsturz bringen wird. Und das ist wirklich so sicher, wie das Amen in der Kirche. Die Wahrheit hat immer gesiegt!
Und wenn der Damm erst einmal gebrochen ist, das Wasser schwappt bereits über die Staumauer, dann wird sich die Wahrheit wie ein Sturzbach über die Menschen ergießen. Manche wird sie mitreißen, Schicksal, wir haben genug Rettungsboote ausgesetzt in den letzten Jahren.
Spricht so ein pessimistischer Optimist mit realistischen Tendenzen?
Ihr da draußen, macht nur so weiter. Immer mehr von demselben, und fleißig weiter wundern, dass nichts anderes dabei herauskommt. Überall ist bereits euer eigenes Sägen zu hören, an dem Ast, auf dem ihr selber sitzt. Mit verschränkten Armen, leichtgeneigtem Kopf und einem Schmunzeln auf den Lippen schauen wir dabei zu und fragen uns, wie lange der Ast wohl noch halten wird und wann es kracht. Wir können warten!
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 866e0139:6a9334e5
2025-04-23 18:44:08
@ 866e0139:6a9334e5
2025-04-23 18:44:08Autor: René Boyke. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Das völkerrechtliche Gewaltverbot ist das völkerrechtliche Pendant zum nationalen Gewaltmonopol. Bürgern ist die Ausübung von Gewalt nur unter engen Voraussetzungen erlaubt, ähnlich sieht es das Völkerrecht für Staaten vor. Das völkerrechtliche Gewaltverbot gemäß Art. 2 Abs. 4 der VN-Charta ist damit eines der fundamentalsten Prinzipien des modernen Völkerrechts. Ein echtes Gewaltmonopol, wie es innerhalb eines Staates existiert, besteht auf internationaler Ebene allerdings nicht, denn dies kann rein faktisch – zumindest derzeit noch – nur sehr schwer bzw. gar nicht umgesetzt werden.
Das Verbot von Gewalt ist eine Sache, aber wer sollte bei einem Verstoß Polizei spielen dürfen? Das Gewaltverbot verbietet den Staaten die Androhung oder Anwendung von Gewalt gegen die territoriale Integrität oder politische Unabhängigkeit eines anderen Staates. Obwohl 193 und damit fast alle Staaten Mitglied der Vereinten Nationen sind, kann man ganz und gar nicht davon sprechen, dass das Gewaltverbot Kriege beseitigt hätte. Nüchtern betrachtet liegt seine Funktion daher nicht in der Verhinderung von Kriegen, sondern in der Legitimation rechtlicher Konsequenzen: Wer gegen das Verbot verstößt, ist im Unrecht und muss die entsprechenden Konsequenzen tragen. Die Reichweite des Gewaltverbots wirft zahlreiche Fragen auf. Diesen widmet sich der vorliegende Beitrag überblicksartig.
Historische Entwicklung des Gewaltverbots
Vor dem 20. Jahrhundert war das „Recht zum Krieg“ (ius ad bellum) weitgehend unreguliert; Staaten konnten aus nahezu beliebigen Gründen zu den Waffen greifen, ja, Krieg galt zwar nicht ausdrücklich als erlaubt, aber eben auch nicht als verboten. Mit dem Briand-Kellogg-Pakt von 1928 wurde rechtlich betrachtet ein weitgehendes Gewaltverbot erreicht. Doch statt warmer Worte hat der Pakt nicht viel erreicht. Deutschland war bereits damals und ist noch immer Mitglied des Pakts, doch weder den Zweiten Weltkrieg noch unzählige andere Kriege hat der Pakt nicht verhindern können.
Ein gewisser Paradigmenwechsel erfolgte nach dem zweiten Weltkrieg mit der Gründung der Vereinten Nationen 1945 und der VN-Charta, welche ein umfassendes Gewaltverbot mit nur wenigen Ausnahmen etablierte. Das Gewaltverbot wurde im Laufe der Zeit durch Gewohnheitsrecht und zahlreiche Resolutionen der Vereinten Nationen gefestigt und gilt heute als „jus cogens“, also als zwingendes Völkerrecht, von dem nur wenige Abweichung zulässig sind. Es ist jedoch leider festzustellen, dass nicht die Einhaltung des Gewaltverbots die Regel ist, sondern dessen Bruch. Nicht wenige Völkerrechtler halten das Gewaltverbot daher für tot. In der deutschen völkerrechtlichen Literatur stemmt man sich jedoch gegen diese Einsicht und argumentiert, dass es zwar Brüche des Gewaltverbots gebe, aber jeder rechtsbrüchige Staat versuche hervorzuheben, dass seine Gewaltanwendung doch ausnahmsweise erlaubt gewesen sei, was also bedeute, dass das Gewaltverbot anerkannt sei.
Dass dies lediglich vorgeschobene Lippenbekenntnisse, taktische Ausreden bzw. inszenierte Theaterstücke sind und damit eine Verhöhnung und gerade keine Anerkennung des Gewaltverbots, wird offenbar nicht ernsthaft in Betracht gezogen. Betrachtet man das von den USA 2003 inszenierte Theaterstück, die Erfindung der „weapons of mass destruction,“ um einen Vorwand zum Angriff des Irak zu schaffen, dann ist erstaunlich, wie man zu der Ansicht gelangen kann, die USA sähen ein Gewaltverbot für sich als bindend an.
Wenn das Gewaltverbot schon nicht in der Lage ist, Kriege zu verhindern, so ist es dennoch Gegenstand rechtlicher Konsequenzen, insbesondere nach Beendigung bewaffneter Auseinandersetzungen. Zudem legt die Beachtung oder Nichtbeachtung des Gebots offen, welcher Staat es damit tatsächlich ernst meint und welcher nicht. Dazu muss man jedoch den Inhalt des Gebots kennen, weshalb sich eine Beschäftigung damit lohnt.
Rechtliche Grundlagen des Gewaltverbots
Das Gewaltverbot gilt nur für Gewalt zwischen Staaten, nicht für private Akte, es sei denn, diese sind einem Staat zurechenbar (z. B. durch Unterstützung wie Waffenlieferungen).
Terrorismus wird nicht automatisch als Verletzung des Gewaltverbots gewertet, sondern als Friedensbedrohung, die andere völkerrechtliche Regeln auslöst. Bei Cyberangriffen ist die Zurechnung schwierig, da die Herkunft oft unklar ist und Sorgfaltspflichten eines Staates nicht zwangsläufig eine Gewaltverletzung bedeuten. Das Verbot umfasst sowohl offene militärische Gewalt (z. B. Einmarsch) als auch verdeckte Gewalt (z. B. Subversion). Es gibt jedoch Diskussionen über eine notwendige Gewaltintensität: Kleinere Grenzverletzungen fallen oft nicht darunter, die Schwelle ist aber niedrig. Nicht jede Verletzung des Gewaltverbots gilt als bewaffneter Angriff.
Nicht-militärische Einwirkungen wie wirtschaftlicher Druck oder Umweltverschmutzung gelten nicht als Gewalt im Sinne des Verbots. Entscheidend ist, dass die Schadenswirkung militärischer Gewalt entspricht, was z. B. bei Cyberangriffen relevant wird, die kritische Infrastruktur lahmlegen.
Ausnahmen vom Gewaltverbot
Trotz Reichweite des Gewaltverbots existieren anerkannte Ausnahmen, die unter bestimmten Umständen die Anwendung von Gewalt legitimieren:
- Recht auf Selbstverteidigung (Art. 51 VN-Charta): Staaten dürfen sich gegen einen bewaffneten Angriff verteidigen, bis der VN- Sicherheitsrat die notwendigen Maßnahmen zur Wiederherstellung des Friedens ergriffen hat. Diese Selbstverteidigung kann individuell (der angegriffene Staat wehrt sich selbst) oder kollektiv (ein anderer Staat kommt dem angegriffenen Staat zur Hilfe) ausgeübt werden. Ob eine Selbstverteidigung zulässig ist, hängt folglich in erster Linie davon ab, ob ein bewaffneter Angriff vorliegt. Nach der Rechtsprechung des IGH setzt ein bewaffneter Angriff eine Mindestintensität voraus, also schwerwiegende Gewalt und nicht lediglich Grenzzwischenfälle. Ferner muss es sich um einen gegenwärtigen Angriff handeln, was präventive Selbstverteidigung grundsätzlich ausschließt – was nicht bedeutet, dass sie nicht ausgeführt würde (siehe Irak- Krieg 2003). Zudem muss der Angriff von einem Staat ausgehen oder ihm zumindest zurechenbar sein. Schließlich muss der Angriff sich gegen die territoriale Integrität, politische Unabhängigkeit oder staatliche Infrastruktur eines Staates richten, wobei Angriffe auf Flugzeuge oder Schiffe außerhalb seines Territoriums ausreichend sind. Maßnahmen des VN-Sicherheitsrats (Kapitel VII VN-Charta): Der Sicherheitsrat kann bei Vorliegen einer Bedrohung oder eines Bruchs des Friedens oder einer Angriffshandlung Zwangsmaßnahmen beschließen, die auch den Einsatz militärischer Gewalt umfassen können. Diese Ausnahmen sind eng gefasst und unterliegen strengen Voraussetzungen, um Missbrauch zu verhindern.
Neben diesen anerkannten Ausnahmen vom Gewaltverbot wird weiter diskutiert, ob es weitere Ausnahmen vom Gewaltverbot gibt, insbesondere in Fällen humanitärer Interventionen und Präventivschläge.
-
Humanitäre Interventionen: Verübt ein Staat gegen einen Teil seiner Bevölkerung schwere Verbrechen wie Völkermord oder Kriegsverbrechen, so sehen einige ein fremdes Eingreifen ohne VN-Mandat als gerechtfertigt an. Das Europäische Parlament beispielsweise hat humanitäre Interventionen bereits 1994 für zulässig erklärt.1 Ein Beispiel dafür ist der NATO-Einsatz im Kosovo 1999, der jedoch überwiegend als völkerrechtswidrig bewertet wird, während NATO-Staaten ihn jedoch als moralisch gerechtfertigt betrachteten. Wie wenig allerdings eine humanitäre Intervention als Ausnahme vom Gewaltverbot anerkannt ist, zeigt der Ukrainekrieg, speziell seit dem massiven Einschreiten Russlands 2022, welches sich ebenfalls auf humanitäre Gründe beruft, damit jedoch – zumindest bei den NATO-Staaten – kein Gehör findet. Gegen „humanitäre Interventionen“ als Ausnahmen vom Gewaltverbot sprechen nicht nur deren mangelnde Kodifikation oder gewohnheitsrechtliche Etablierung, sondern auch ganz praktische Probleme: Wie beispielsweise kann ein eingreifender Staat sich sicher sein, ob innerstaatliche Gewalthandlungen Menschenrechtsverletzungen darstellen oder gerechtfertigtes Vorgehen gegen beispielsweise aus dem Ausland finanzierte Terroristen? Zudem besteht die Gefahr, dass bewusst derartige Verhältnisse in einem Land geschaffen werden, um einen Vorwand für ein militärisches Eingreifen zu schaffen. Dieses erhebliche Missbrauchspotential spricht gegen die Anerkennung humanitärer Interventionen als Ausnahme vom Gewaltverbot.
-
Schutz eigener Staatsangehöriger im Ausland: Auch der Schutz eigener Staatsangehöriger im Ausland wird als gerechtfertigte Ausnahme vom Gewaltverbot diskutiert, sie ist allerdings keineswegs allgemein anerkannt. Mit Blick in die Vergangenheit und den gemachten Erfahrungen (z.B. US-Interventionen in Grenada 1983 und Panama 1989) wird vor dem erheblichen Missbrauchspotential gewarnt.
-
Präventivschläge: Wie bereits erwähnt, werden präventive Angriffe auf einen Staat von einigen als Unterfall der Selbstverteidigung als berechtigte Ausnahme vom Gewaltverbot betrachtet. lediglich eine kurze Zeitspanne zur Ausschaltung der Bedrohung bestehen und das Ausmaß des zu erwartenden Schadens berücksichtigt werden. Zu beachten ist dabei, dass die genannten Kriterien dabei in Wechselwirkung stünden, was bedeute: Selbst wenn ein Angriff gar nicht so sehr wahrscheinlich sei, so solle dies dennoch einen Präventivschlag rechtfertigen, falls der zu erwartende Schaden groß sei und in einem kurzen Zeitfenster erfolgen könne (z.B. Atomschlag). Mit anderen Worten: Die Befürwortung von Präventivschlägen weicht das Gewaltverbot auf und führt zu einer leichteren Rechtfertigung militärischer Einsätze. Die konkreten Auswirkungen lassen sich sowohl durch den völkerrechtswidrigen Angriff der USA gegen den Irak und später durch den völkerrechtswidrigen Angriff Russlands gegen die Ukraine betrachten – beide Staaten beriefen sich jeweils auf Präventivschläge.
Konsequenzen der Verletzung des Gewaltverbots
Aus dem Vorstehenden ergibt sich bereits, dass eine Verletzung des Gewaltverbots das Recht zur Selbstverteidigung auslöst. Doch gibt es noch weitere Konsequenzen? Blickt man auf die Menge der weltweiten bewaffneten Konflikte, darf man daran zweifeln. Jedenfalls scheint das Kosten-Nutzen-Verhältnis nicht gegen eine bewaffnete Auseinandersetzung zu sprechen. Wie bereits erwähnt, existiert auf internationaler Ebene kein dem innerstaatlichen Recht vergleichbares Gewaltmonopol. Ohne dies bewerten zu wollen, lässt sich ganz objektiv feststellen, dass es keine Instanz gibt, die Zwangsmaßnahmen effektiv durchsetzen könnte. Ob dies wünschenswert wäre, darf bezweifelt werden. Aus den bisherigen Ausführungen geht ebenfalls hervor, dass der Sicherheitsrat der Vereinten Nationen Maßnahmen ergreifen kann – einschließlich des Einsatzes militärischer Gewalt. Wenn es dazu kommt, dann ist dies eines der schärfsten Schwerter, die gegen eine Verletzung des Gewaltverbots geführt werden können, weil es sich um unmittelbare Zwangsmaßnahmen handelt. Allerdings kam es bisher lediglich zwei Mal dazu (Koreakrieg 1950-19534; Golkrieg II 19915). Neben diesen tatsächlichen Zwangsmaßnahmen hat ein Verstoß gegen das Gewaltverbot rechtliche Auswirkungen:
-
Nichtigkeit von Verträgen: Gemäß Art. 52 der Wiener Vertragsrechtskonvention (WVK) ist ein Vertrag nichtig, wenn sein Abschluss durch Androhung oder Anwendung von Gewalt unter Verletzung der in der Charta der Vereinten Nationen niedergelegten Grundsätze des Völkerrechts herbeigeführt wurde.
-
Nichtanerkennung von Gebietserwerben (Stimson-Doktrin): Gemäß dem Rechtsgedanken des Art. 52 WVK werden die eroberten Gebiete nicht als Staatsgebiete des Staats angesehen, der sie unter Brechung des Gewaltverbots erobert hat.
-
Strafrechtliche Verantwortlichkeit für Staatschefs und Befehlshaber gemäß Art. 8bis des Statuts des Internationalen Strafgerichtshofs – allerdings nur für die Personen, deren Staaten, den IStGH anerkennen. Nichts zu befürchten haben also Staatschefs und Befehlshaber der USA, Russlands oder Chinas sowie Frankreichs und Großbritanniens, denn diese Staaten haben der Ahnung der Verletzung des Gewaltverbots nicht zugestimmt. Zwar könnte der Sicherheitsrat der VN eine Überweisung an den IStGH beschließen, allerdings stünde jedem der genannten Staaten ein Vetorecht dagegen zu.
Schlussfolgerungen
Ein Verbot der Gewalt zwischen Staaten ist grundsätzlich zu begrüßen. Doch ein Verbot allein ist erstmal nicht mehr als bedrucktes Papier. Ob hingegen wirksamere Mechanismen geschaffen werden sollten, dieses Verbot zu ahnden ist zweifelhaft. Denn stets wurde und wird noch immer mit erheblichem Aufwand für unterschiedlichste Narrative die eigene Intervention als „gerechter Krieg“ verkauft und von der Gegenpartei als ebenso ungerecht verteufelt.
Tatsache ist: Einen gerechten Krieg gibt es nicht. Ein schärferer Mechanismus zur Durchsetzung des Gewaltverbots würde genau darauf – einen angeblich gerechten Krieg – hinauslaufen, was ein enormes Missbrauchspotential mit sich brächte. Und die Erfahrung zeigt, dass der Missbrauch des Völkerrechts und Verstöße gegen das Völkerrecht keineswegs die Ausnahme, sondern die Regel darstellen – leider auch durch die sogenannte „westliche Wertegemeinschaft“. Und würde diese Missbrauchsmöglichkeit nicht auf noch mehr militärische Auseinandersetzungen hinauslaufen? Auseinandersetzungen, deren Folgen nicht die verantwortlichen Politiker zu spüren bekämen, sondern, in Form von Tod und Verstümmelung, die Bevölkerung zu tragen hätte?
Leidtragende ihrer „gerechten Kriege“ sind nicht die agierenden Politiker, sondern immer die einfachen Menschen – die leider nicht selten zuvor mit „Hurra“-Geschrei dem Krieg entgegenfiebern, um als „Helden“ ihrem Land zu „dienen“. In Wahrheit dienen sie jedoch nur finanziellen Interessen reicher Menschen.
Daraus folgt, dass die Durchsetzung eines Gewaltverbots nicht in den Händen einiger weniger Staatslenker und Berufspolitiker liegen darf, sondern in den Händen der unmittelbar Betroffenen selbst. Der Familienvater, der für seine Frau und Kinder zu sorgen hat, muss aktiv den Dienst an der Waffe verweigern. Ebenso der Schüler, der Student, der Junggeselle und sämtliche Mitglieder der Gesellschaft. Die Bevölkerung ist es, die das Gewaltverbot tatsächlich und effektiv vom bedruckten Papier als ein Friedensgebot ins Leben bringen und in Vollzug setzen kann.
(Dieser Artikel ist auch mit folgendem Kurzlink aufrufbar und teilbar)
-
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 9bde4214:06ca052b
2025-04-22 22:04:08
@ 9bde4214:06ca052b
2025-04-22 22:04:08"With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
Pablo & Gigi are getting high on glue.
Books & articles mentioned:
- Saving beauty by Byung-Chul Han
- LLMs as a tool for thought by Amelia Wattenberger
In this dialogue:
- vibeline & vibeline-ui
- LLMs as tools, and how to use them
- Vervaeke: AI thresholds & the path we must take
- Hallucinations and grounding in reality
- GPL, LLMs, and open-source licensing
- Pablo's multi-agent Roo setup
- Are we going to make programmers obsolete?
- "When it works it's amazing"
- Hiring & training agents
- Agents creating RAG databases of NIPs
- Different models and their context windows
- Generalists vs specialists
- "Write drunk, edit sober"
- DVMCP.fun
- Recklessness and destruction of vibe-coding
- Sharing secrets with agents & LLMs
- The "no API key" advantage of nostr
- What data to trust? And how does nostr help?
- Identity, web of trust, and signing data
- How to fight AI slop
- Marketplaces of code snippets
- Restricting agents with expert knowledge
- Trusted sources without a central repository
- Zapstore as the prime example
- "How do you fight off re-inventing GitHub?"
- Using large context windows to help with refactoring
- Code snippets for Olas, NDK, NIP-60, and more
- Using MCP as the base
- Using nostr as the underlying substrate
- Nostr as the glue & the discovery layer
- Why is this important?
- Why is this exciting?
- "With the shift towards this multi-agent collaboration and orchestration world, you need a neutral substrate that has money/identity/cryptography and web-of-trust baked in, to make everything work."
- How to single-shot nostr applications
- "Go and create this app"
- The agent has money, because of NIP-60/61
- PayPerQ
- Anthropic and the genius of mcp-tools
- Agents zapping & giving SkyNet more money
- Are we going to run the mints?
- Are agents going to run the mints?
- How can we best explain this to our bubble?
- Let alone to people outside of our bubble?
- Building pipelines of multiple agents
- LLM chains & piped Unix tools
- OpenAI vs Anthropic
- Genius models without tools vs midwit models with tools
- Re-thinking software development
- LLMs allow you to tackle bigger problems
- Increased speed is a paradigm shift
- Generalists vs specialists, left brain vs right brain
- Nostr as the home for specialists
- fiatjaf publishing snippets (reluctantly)
- fiatjaf's blossom implementation
- Thinking with LLMs
- The tension of specialization VS generalization
- How the publishing world changed
- Stupid faces on YouTube thumbnails
- Gaming the algorithm
- Will AI slop destroy the attention economy?
- Recency bias & hiding publication dates
- Undoing platform conditioning as a success metric
- Craving realness in a fake attention world
- The theater of the attention economy
- What TikTok got "right"
- Porn, FoodPorn, EarthPorn, etc.
- Porn vs Beauty
- Smoothness and awe
- "Beauty is an angel that could kill you in an instant (but decides not to)."
- The success of Joe Rogan & long-form conversations
- Smoothness fatigue & how our feeds numb us
- Nostr & touching grass
- How movement changes conversations
- LangChain & DVMs
- Central models vs marketplaces
- Going from assembly to high-level to conceptual
- Natural language VS programming languages
- Pablo's code snippets
- Writing documentation for LLMs
- Shared concepts, shared language, and forks
- Vibe-forking open-source software
- Spotting vibe-coded interfaces
- Visualizing nostr data in a 3D world
- Tweets, blog posts, and podcasts
- Vibe-producing blog posts from conversations
- Tweets are excellent for discovery
- Adding context to tweets (long-form posts, podcasts, etc)
- Removing the character limit was a mistake
- "Everyone's attention span is rekt"
- "There is no meaning without friction"
- "Nothing worth having ever comes easy"
- Being okay with doing the hard thing
- Growth hacks & engagement bait
- TikTok, theater, and showing faces and emotions
- The 1% rule: 99% of internet users are Lurkers
- "We are socially malnourished"
- Web-of-trust and zaps bring realness
- The semantic web does NOT fix this LLMs might
- "You can not model the world perfectly"
- Hallucination as a requirement for creativity
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
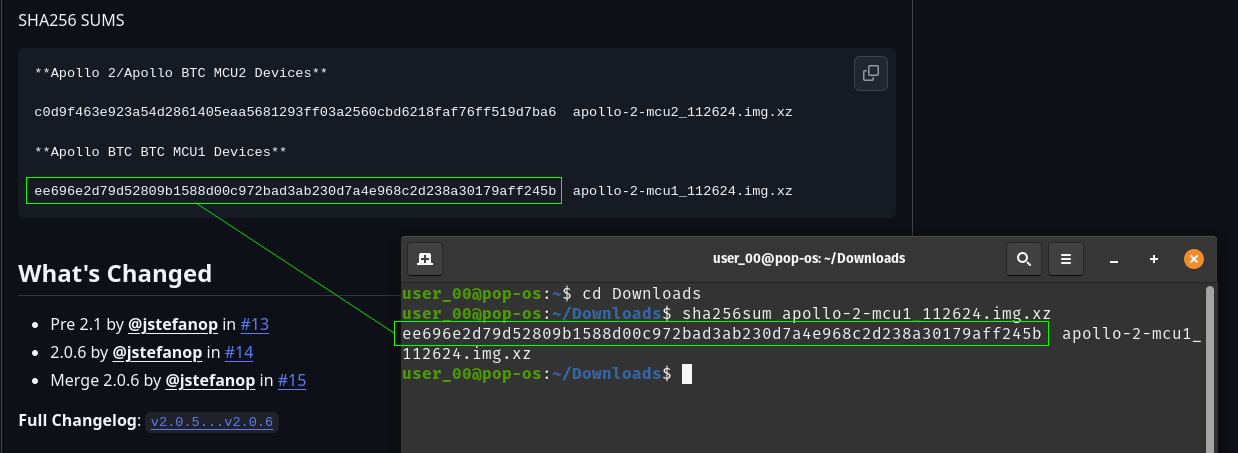 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
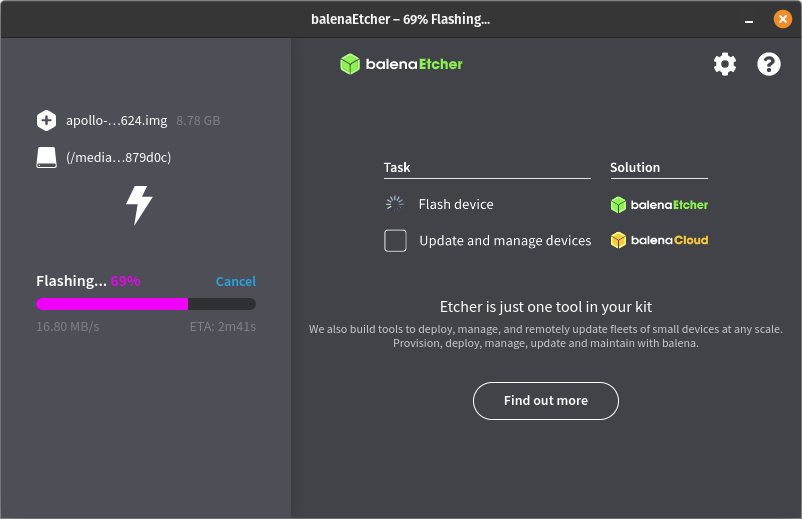 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
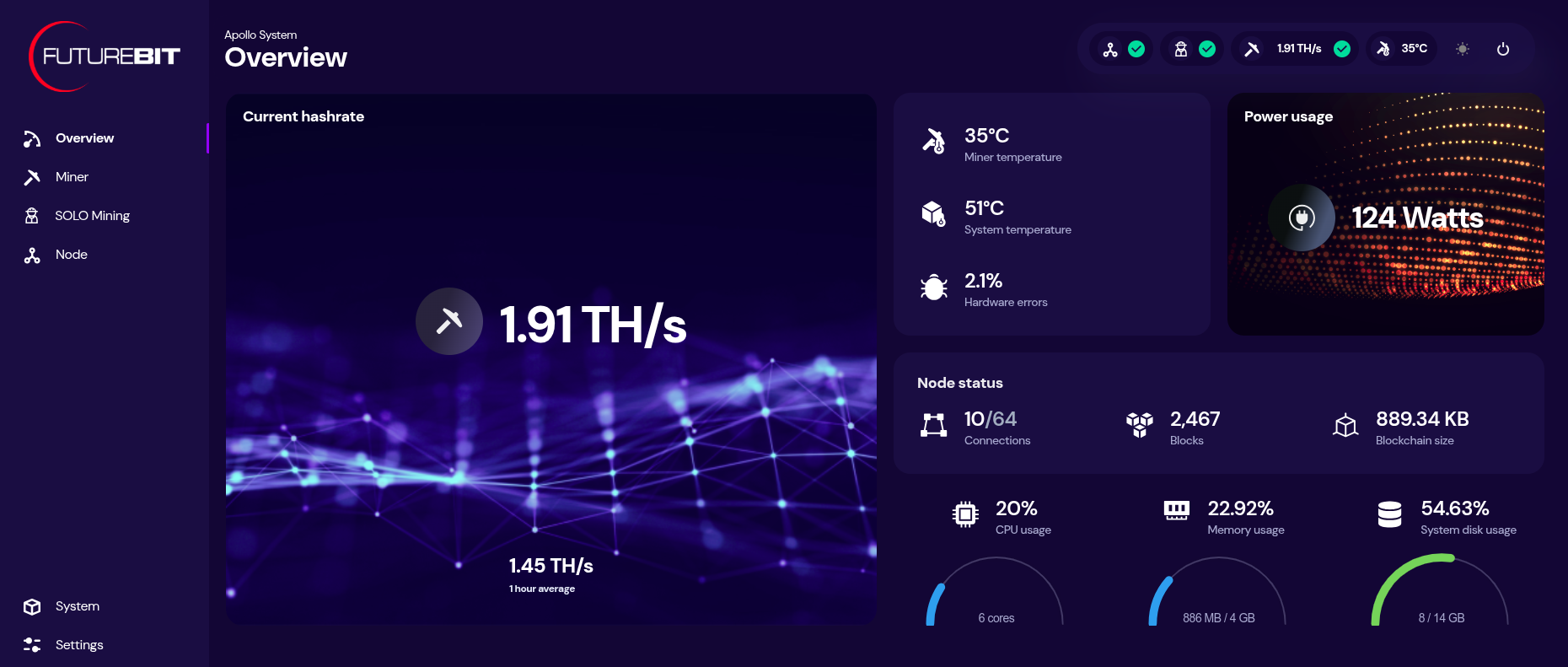 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
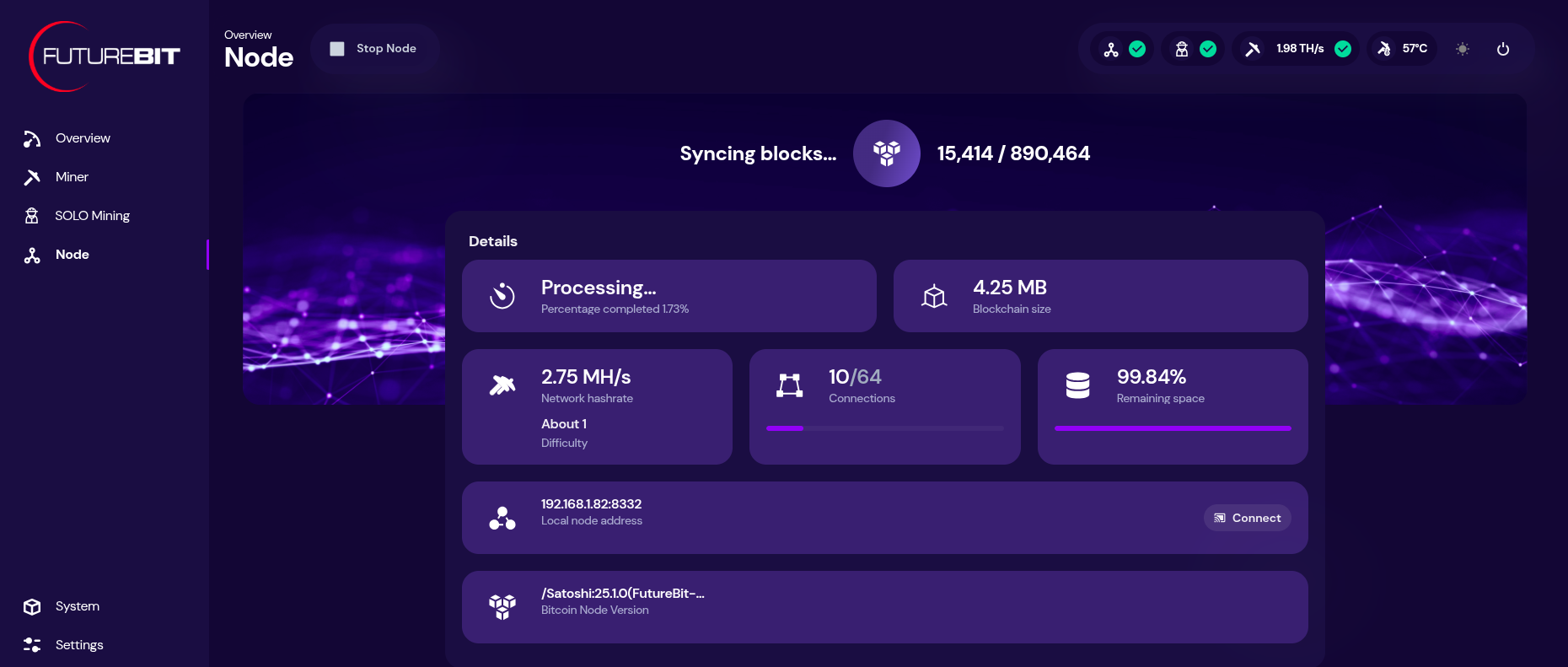 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
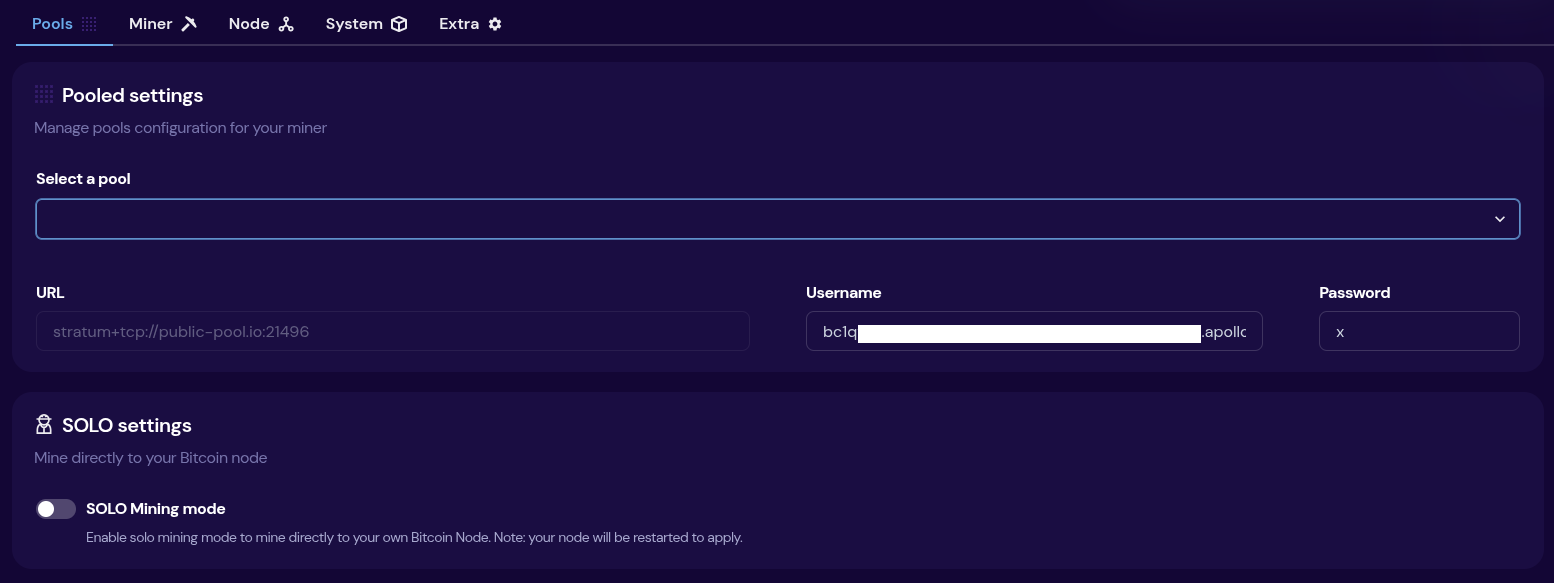 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ 9bde4214:06ca052b
2025-04-22 17:09:47
@ 9bde4214:06ca052b
2025-04-22 17:09:47“It isn’t obvious that the world had to work this way. But somehow the universe smiles on encryption.”
hzrd149 & Gigi take a stroll along the shore of cryptographic identities.
This dialogue explores how cryptographic signatures fundamentally shift power dynamics in social networks, moving control from servers to key holders. We discuss the concept of "setting data free" through cryptographic verification, the evolving role of relays in the ecosystem, and the challenges of building trust in decentralized systems. We examine the tension between convenience and decentralization, particularly around features like private data and data synchronization. What are the philosophical foundations of building truly decentralized social networks? And how can small architectural decisions have profound implications for user autonomy and data sovereignty?
Movies mentioned:
- 2001: A Space Odyssey (1968)
- Soylent Green (1973)
- Close Encounters of the Third Kind (1977)
- Johnny Mnemonic (1995)
- The Matrix (1999)
In this dialogue: - Hzrd's past conversations: Bowls With Buds 316 & 361 - Running into a water hose - Little difference, big effect - Signing data moves the power to the key holders - Self-signing data sets the data free - Relay specialization - Victor's Amethyst relay guide - Encryption and decryption is expensive - is it worth it? - The magic of nostr is that stuff follows you around - What should be shown? What should be hidden? - Don't lie to users. Never show outdated data. - Nostr is raw and immediate - How quickly you get used to things working - Legacy web always tries to sell you something - Lying, lag, frustration - How NoStrudel grew - NoStrudel notifications - Data visualization and dashboards - Building in public and discussing in public - Should we remove DMs? - Nostr as a substrate for lookups - Using nostr to exchange Signal or SimpleX credentials - How private is a group chat? - Is a 500-people group chat ever private? - Pragmatism vs the engineering mindset - The beauty and simplicity of nostr - Anti-patterns in nostr - Community servers and private relays - Will vibe coding fix (some of the) things? - Small specialized components VS frameworks - Technology vs chairs (and cars, and tractors, and books) - The problem of being greedy - Competitive silos VS synergistic cooperation - Making things easy vs barriers of entry - Value4value for music and other artists - Adding code vs removing code - Pablo's Roo setup and DVMCP - Platform permission slips vs cryptographic identities - Micropayments vs Subscription Hell - PayPerQ - Setting our user-generated data free - The GNU/Linux approach and how it beat Microsoft - Agents learning automatically thanks to snippets published on nostr - Taxi drivers, GPS, and outsourcing understanding - Wizards VS vibe coders - Age differences, Siri, and Dragon Naturally Speaking - LLMs as a human interface to call tools - Natural language vs math and computer language - Natural language has to be fuzzy, because the world is fuzzy - Language and concepts as compression - Hzrd watching The Matrix (1999) for the first time - Soylent Green, 2001, Close Encounters of the 3rd Kind, Johnny Mnemonic - Are there coincidences? - Why are LLMs rising at the same time that cryptography identities are rising? - "The universe smiles at encryption" - The universe does not smile upon closed silos - The cost of applying force from the outside - Perfect copies, locality, and the concept of "the original" - Perfect memory would be a curse, not a blessing - Organic forgetting VS centralized forgetting - Forgetting and dying needs to be effortless - (it wasn't for IPFS, and they also launched a shitcoin) - Bitcoin makes is cheap to figure out what to dismiss - Would you like to have a 2nd brain? - Trust and running LLMs locally - No need for API keys - Adjacent communities: local-first, makers and hackers, etc. - Removing the character limit was a mistake - Browsing mode vs reading mode - The genius of tweets and threads - Vibe-coding and rust-multiplatform - Global solutions vs local solutions - The long-term survivability of local-first - All servers will eventually go away. Your private key won't. - It's normal to pay your breakfast with sats now - Nostr is also a normal thing now, at least for us - Hzrd's bakery - "Send Gigi a DM that says GM" - and it just works - The user is still in control, thanks to Amber - We are lacking in nostr signing solutions - Alby's permission system as a step in the right direction - We have to get better at explaining that stuff - What we do, why we care, why we think it's important
-
 @ 70c48e4b:00ce3ccb
2025-04-22 08:35:52
@ 70c48e4b:00ce3ccb
2025-04-22 08:35:52Hello reader,
I can say from personal experience that crowdfunding has truly changed my life. I found people who believed in my dream of using Bitcoin as money. Every single one of my videos was made possible through crowdfunding. And I’m not alone. I know several Bitcoiners who have raised funds this way, from Africa to Korea to Haiti.
https://images.forbesindia.com/media/images/2022/Jul/img_190501_runwithbitcoin_bg.jpg
Crowdfunding is deeply rooted in the traditional financial world. From raising money for life-saving surgeries to helping someone open a local coffee shop, platforms like GoFundMe, Kickstarter, and Indiegogo have become essential tools for many. But behind all the heartwarming stories and viral campaigns, there’s a side of crowdfunding that doesn’t get talked about enough. Traditional platforms are far from perfect.
They are centralized, which means there’s always someone in control. These platforms can freeze campaigns, delay payouts, or take a significant cut of the money. And often, the people who need funding the most, those without access to strong banking systems or large social media followings are the ones who get left out.
Here are some of the problems I’ve noticed with these platforms:
Problem 1: Inequality in Who Gets Funded
A recent article in The Guardian pointed out something that’s hard to ignore. Crowdfunding often benefits people who already have influence. After the Los Angeles wildfires in January 2025, celebrities like Mandy Moore were able to raise funds quickly. At the same time, everyday people who lost their homes struggled to get noticed.
https://i.guim.co.uk/img/media/f8398505e58ec3c04685aab06e94048e5d7b6a0c/0_127_4800_2880/master/4800.jpg?width=1300&dpr=1&s=none&crop=none
Angor (https://angor.io/) changes that by removing the need for a central platform to choose which projects get featured or promoted. Anyone can share their project. People can find them on Angor Hub (https://hub.angor.io/), which is a public directory built on the Nostr protocol. Instead of relying on popularity, projects are highlighted based on transparency and engagement.
Problem 2: Platform Dependence and Middlemen
Here’s something people don’t often realize. When you raise funds online, the platform usually has control. It holds the money, decides when to release it, and can freeze everything without warning. This happened during the trucker protests in Canada in 2022. Tens of millions of dollars were raised, but platforms like GoFundMe and GiveSendGo froze the donations. The funds never reached the people they were meant for. Supporters were left confused, and the recipients had no way to access what had been raised for them.
https://upload.wikimedia.org/wikipedia/commons/thumb/2/2d/Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg/800px-Convoi_de_la_libert%C3%A9_%C3%A0_Ottawa_01.jpg
Angor avoids all of this. It does not hold the funds, does not require approval processes, and only the project creator has control over the campaign. Contributions go directly from supporters to the people building the project, using Bitcoin. It is a peer-to-peer system that works without any gatekeepers. Angor never touches the money. It simply provides the tools people need to raise funds and build, while staying fully in control.
Problem 3: Global Access
Another major issue is that these platforms often exclude people based on where they live. If you're in a region with limited banking access or outside the supported list of countries, you’re likely shut out. In 2023, a woman named Samar in Gaza tried to raise funds for food and medical supplies during a crisis. A friend abroad set up a campaign to help, but the platform froze it due to "location-related concerns." The funds were locked, and the support never arrived in time.
https://images.gofundme.com/EMFtPWSLs3P9SewkzwZ4FtaBQSA=/720x405/https://d2g8igdw686xgo.cloudfront.net/78478731_1709065237698709_r.jpeg
Angor removes these barriers by using Bitcoin, which works globally without needing banks or approvals. Anyone, anywhere, can raise and receive support directly.
Problem 4: Lack of Transparency
Post-funding transparency is often lacking. Backers rarely get consistent updates, making it difficult to track a project's progress or hold anyone accountable.
In 2015, the Zano drone project on Kickstarter raised over £2.3 million from more than 12,000 backers. It promised a compact, smart drone for aerial photography. But as time went on, updates became rare and vague. Backers had little insight into the project’s struggles, and eventually, it was canceled. The company shut down, and most backers never received their product or a refund.
https://ichef.bbci.co.uk/ace/standard/976/cpsprodpb/2A0A/production/_86626701_ff861eeb-ce94-43b7-9a43-b30b5adbd7ab.jpg
Angor takes a different approach. Project updates are shared through Nostr, a decentralized and tamper-proof communication protocol. This allows backers to follow progress in real time, with no corporate filters and no blackout periods. Everyone stays in the loop, from start to finish.
Problem 5: Fraud and Accountability
Scams are a growing problem in the crowdfunding world. People can launch fake campaigns, collect donations, and vanish — leaving supporters with empty promises and no way to recover their money. One well-known example was the "Homeless Vet GoFundMe scam" in the U.S.
https://a57.foxnews.com/static.foxnews.com/foxnews.com/content/uploads/2018/09/720/405/1536549443584.jpg
A couple and a homeless man raised over $400,000 by telling a heartwarming story that later turned out to be completely fake. The money was spent on luxury items, and it took a legal investigation to uncover the truth. By the time it was resolved, most of the funds were gone.
This kind of fraud is hard to stop on traditional platforms, because once the funds are transferred, there’s no built-in structure to verify how they’re used.
On Angor, projects are funded in stages, with each step tied to a specific milestone. Bitcoin is held in a shared wallet that only unlocks funds when both the backer and the creator agree that the milestone is complete. If something feels off, backers can choose to stop and recover unspent funds.
This structure discourages scammers from even trying. It adds friction for bad actors, while still giving honest creators the freedom to build trust, deliver value, and raise support transparently. It can’t get any better than this
So, does Angor matter?
For me, it really does. I’m genuinely excited to have my project listed on Angorhub. In a world shaped by AI, open source and transparency light the way forward. Let the work shine on its own.
Have you tried Angor yet? Thanks for tuning in. Catch you next week. Ciao!
Guest blog: Paco nostr:npub1v67clmf4jrezn8hsz28434nc0y5fu65e5esws04djnl2kasxl5tskjmjjk
References:
• The Guardian, 2025: Crowdfunding after LA fires and inequality - https://www.theguardian.com/us-news/2025/jan/17/la-fires-gofundme-mandy-moore • https://www.theguardian.com/us-news/2018/nov/15/johnny-bobbitt-gofundme-scam-arrest-viral-gas-story-couple-charged • FundsforNGOs: The Success Story of an NGO That Scaled with Limited Resourceshttps://www2.fundsforngos.org/articles/the-success-story-of-an-ngo-that-scaled-with-limited-resources/ • https://www.freightwaves.com/news/gofundme-freezes-37m-until-organizers-of-canada-trucker-convoy-detail-spending-plan
-
 @ b8af284d:f82c91dd
2025-04-22 07:28:03
@ b8af284d:f82c91dd
2025-04-22 07:28:03Kaiser: Es fehlt an Geld, nun gut, so schaff es denn,
Mephisto: Ich schaffe, was ihr wollt, und schaffe mehr;
Zwar ist es leicht, doch ist das Leichte schwer;
Es liegt schon da, doch um es zu erlangen, das ist die Kunst.
(Goethe: Faust II)
Liebe Abonnenten,
die meisten Medien sind nach wie vor damit beschäftigt, wie sie Trump am eindrücklichsten Wahnsinn unterstellen können. Sie vergessen dabei, worum es eigentlich geht: Ein Drittel aller amerikanischen Staatsschulden müssen dieses Jahr refinanziert werden. Sonst ist das mächtigste Land der Welt demnächst Pleite. Dafür müssen die Doppel-Defizite ausgeglichen, oder zumindest gesenkt werden. Und vor allem müssen die Zinsen runter. Die amerikanische Zentralbank wird den Wünschen der Regierung bald nachkommen, sprich die Zinsen senken und über ein neues Quantitative-Easing-Programm die Geldmenge erhöhen. Ein paar Jahre später werden die Effekte im Alltag über Inflation sichtbar.
Die Wahrscheinlichkeit ist hoch, dass wir bald Zeuge eines raffinierten Geld-Recycling-Programms werden. Wir treffen dabei auf einen alten Bekannten, den Stablecoin-Anbieter Tether. Der Essay ist keine leichte Kost, aber wer dabei bleibt, gelangt tief in die wundersame Welt der Geldvermehrung.
Mitte März wagt Paolo Ardoino den Schritt. Der Tether-CEO fliegt von der Hauptstadt El Salvadors nach New York. Es ist die erste Reise in die USA des erst 41-Jährigen seit Jahren. Zu hoch war bisher das Risiko gewesen, dort von den Behörden festgenommen zu werden. Vier Jahre zuvor war das Milliarden-Unternehmen, das er leitet, noch einmal davon gekommen: 2021 war Tether von der amerikanischen Börsenaufsicht mit einer Strafe von 41 Millionen US-Dollar belegt wegen ungenauer Angaben zu seinen Reserven. Man hatte sich schließlich auf einen Vergleich in Höhe von 18 Millionen Dollar geeinigt. Ein Witz, hatten Kritiker des Unternehmens entgegnet. Schließlich, so die Vorwürfe, ging es um Milliarden-Betrug. Seitdem hatten die Tether-Bosse die Vereinigten Staaten aus Vorsicht gemieden. Man war mal in Hongkong, auf den Bahamas und den Bermuda-Inseln, bis man sich Anfang des Jahres offiziell im Bitcoin-freundlichen El Salvador niedergelassen hatte. Doch mit der neuen US-Administration ist alles anders.
Nach New York geladen hat die Firma Cantor Fitzgerald. Thema des Gesprächs: Die Schaffung eines exklusiven Stablecoins für den amerikanischen Markt. Cantor Fitzgerald ist nicht irgendeine Bank oder Unternehmen. Das 1945 gegründete Investmenthaus ist einer von 24 Primärhändlern, die von der Federal Reserve Bank of New York autorisiert sind, US-Staatsanleihen zu handeln. Damit spielen sie eine zentrale Rolle im Finanzsystem der USA, da sie die Liquidität und Effizienz des Marktes für Staatsanleihen sicherstellen, dem wichtigsten und liquidisten Markt der Welt.
Langjähriger CEO von Cantor Fitzgerald war Howard Lutnick, ein Milliardär und seit Jahren enger Vertrauter der Trump-Familie. Da Lutnick mittlerweile US-Handelsminister ist, dürfte Ardoino nicht nur das Ok von ganz oben bekommen haben, in die Vereinigten Staaten einreisen zu dürfen. Man wird ihm wohl auch einen roten Teppich ausgerollt haben. Der Grund:
Die USA haben aktuell ein Problem mit ihrer Verschuldung. (BlingBling hat das in den Essays Die nächsten 90 Tage und Der Mar-a-Largo-Accord beschrieben). Rund ein Drittel des gesamten Schuldenbergs der USA müssen dieses Jahr refinanziert werden. Dafür müssen die Zinsen runter. Deswegen will Trump unbedingt das Handelsdefizit ausgleichen. Deswegen wird über die Neubewertung der Goldreserven nachgedacht. Und deswegen wird vermutlich bald eine neue Liquiditätswelle die Kurse von Bitcoin und Co auf neue Höchststände treiben. Denn bisher haben Staaten in solchen Phasen immer auf Geldentwertung gesetzt, um sich aus der Schuldenfalle zu befreien. Anders als Privatpersonen und viele kleinere Staaten können die USA immerhin die Währung selbst drucken, in der sie verschuldet sind. Die amerikanische Staatsverschuldung ist das Endgame. Und im Endgame spielt Tether mittlerweile eine ziemlich wichtige Rolle. Der Stablecoin-Anbieter hält mit 113 Milliarden aktuell mehr US-Staatsanleihen als Deutschland. Tendenz steigend: Ende 2024 war Tether mit 31 Milliarden der siebtgrößte Käufer von amerikanischen Staatsschulden.
Wie kann ein obskures Unternehmen, mit nicht einmal 100 Mitarbeitern, im vergangenen Jahr 13 Milliarden Dollar Gewinn machen, und zu einem der wichtigsten Kunden des amerikanischen Staats werden?
Weiter auf BlingBling - Die Geschichte eines der größten Geld-Recyclingprozesse der Welt.
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
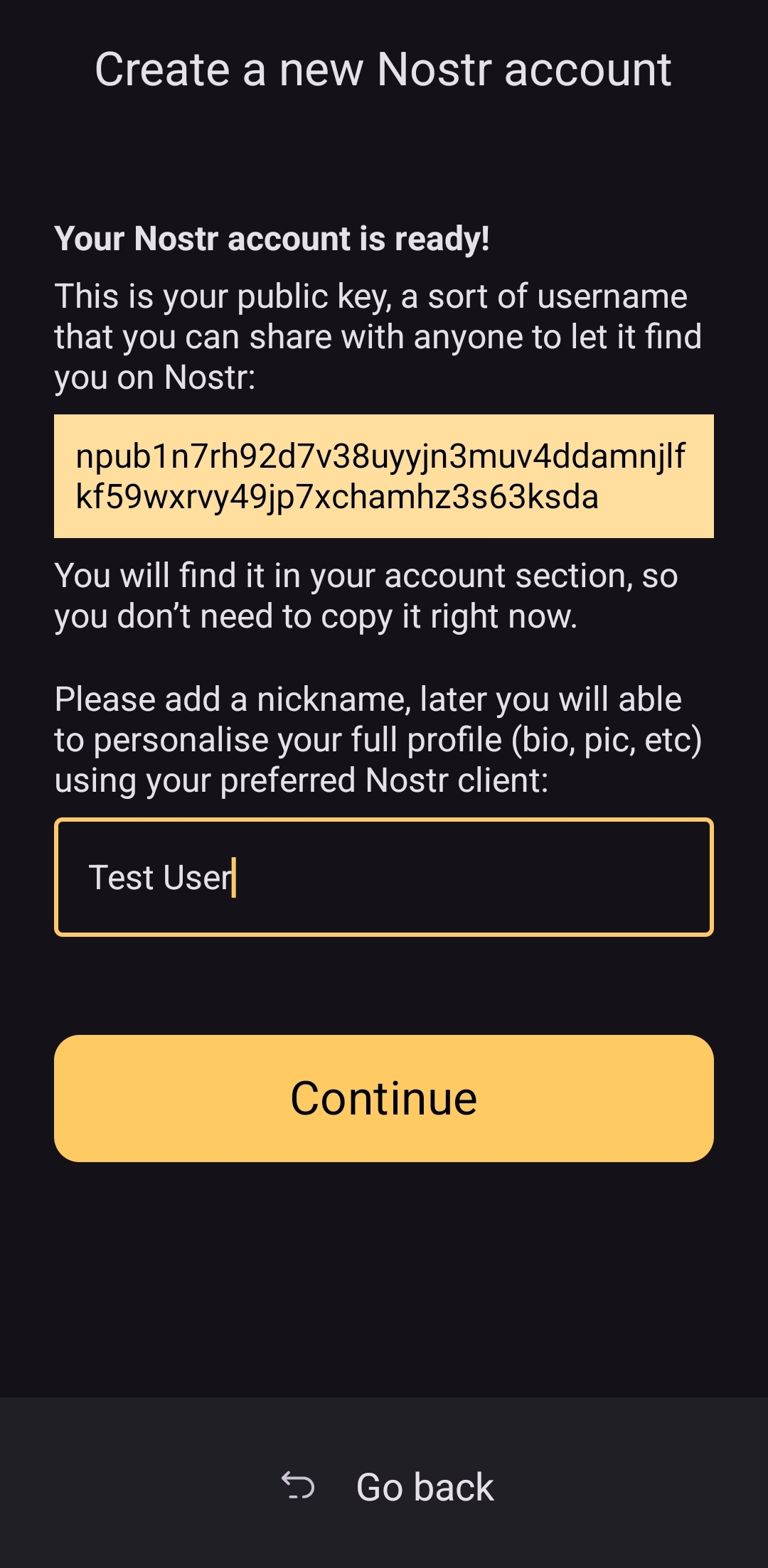
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ 5c26ee8b:a4d229aa
2025-04-24 20:36:29
@ 5c26ee8b:a4d229aa
2025-04-24 20:36:295:118 Al-Maaida
إِنْ تُعَذِّبْهُمْ فَإِنَّهُمْ عِبَادُكَ ۖ وَإِنْ تَغْفِرْ لَهُمْ فَإِنَّكَ أَنْتَ الْعَزِيزُ الْحَكِيمُ
If You should punish them - indeed they are Your servants; but if You forgive them - indeed it is You who is the Exalted in Might, the Wise.
The previous verse will be said by prophet Jesus, peace be upon him, on the day of reckoning.
No one will enter paradise without God’s mercy.
16:61 An-Nahl
وَلَوْ يُؤَاخِذُ اللَّهُ النَّاسَ بِظُلْمِهِمْ مَا تَرَكَ عَلَيْهَا مِنْ دَابَّةٍ وَلَٰكِنْ يُؤَخِّرُهُمْ إِلَىٰ أَجَلٍ مُسَمًّى ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ
And if Allah were to impose blame on the people for their wrongdoing, He would not have left upon the earth any creature, but He defers them for a specified term. And when their term has come, they will not remain behind an hour, nor will they precede [it].
And no one will enter paradise with pride in the heart. Pride belongs only to God, Allah, as mentioned in the next verse.
45:37 Al-Jaathiya
وَلَهُ الْكِبْرِيَاءُ فِي السَّمَاوَاتِ وَالْأَرْضِ ۖ وَهُوَ الْعَزِيزُ الْحَكِيمُ
And to Him belongs [all] the pride within the heavens and the earth, and He is the Exalted in Might, the Wise.
It is narrated on the authority of 'Abdullah b. Mas'ud that the Messenger of Allah (ﷺ) observed: None shall enter the Fire (of Hell) who has in his heart the weight of a mustard seed of belief (in the oneness of God and resurrection day) and none shall enter Paradise who has in his heart the weight of a mustard seed of pride.
حَدَّثَنَا مِنْجَابُ بْنُ الْحَارِثِ التَّمِيمِيُّ، وَسُوَيْدُ بْنُ سَعِيدٍ، كِلاَهُمَا عَنْ عَلِيِّ بْنِ مُسْهِرٍ، - قَالَ مِنْجَابٌ أَخْبَرَنَا ابْنُ مُسْهِرٍ، - عَنِ الأَعْمَشِ، عَنْ إِبْرَاهِيمَ، عَنْ عَلْقَمَةَ، عَنْ عَبْدِ اللَّهِ، قَالَ قَالَ رَسُولُ اللَّهِ صلى الله عليه وسلم " لاَ يَدْخُلُ النَّارَ أَحَدٌ فِي قَلْبِهِ مِثْقَالُ حَبَّةِ خَرْدَلٍ مِنْ إِيمَانٍ وَلاَ يَدْخُلُ الْجَنَّةَ أَحَدٌ فِي قَلْبِهِ مِثْقَالُ حَبَّةِ خَرْدَلٍ مِنْ كِبْرِيَاءَ " .
God, Allah doesn’t forgive that any other is associated with him in worship. Also, the good deeds of disbelievers will worth nothing.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives what is less than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
18:103 Al-Kahf
قُلْ هَلْ نُنَبِّئُكُمْ بِالْأَخْسَرِينَ أَعْمَالًا
Say, [O Muhammad], "Shall we [believers] inform you of the greatest losers as to [their] deeds?
18:104 Al-Kahf
الَّذِينَ ضَلَّ سَعْيُهُمْ فِي الْحَيَاةِ الدُّنْيَا وَهُمْ يَحْسَبُونَ أَنَّهُمْ يُحْسِنُونَ صُنْعًا
[They are] those whose effort is lost in worldly life, while they think that they are doing well in work."
18:105 Al-Kahf
أُولَٰئِكَ الَّذِينَ كَفَرُوا بِآيَاتِ رَبِّهِمْ وَلِقَائِهِ فَحَبِطَتْ أَعْمَالُهُمْ فَلَا نُقِيمُ لَهُمْ يَوْمَ الْقِيَامَةِ وَزْنًا
Those are the ones who disbelieve in the verses of their Lord and in [their] meeting Him, so their deeds have become worthless; and We will not assign to them on the Day of Resurrection any importance.
18:106 Al-Kahf
ذَٰلِكَ جَزَاؤُهُمْ جَهَنَّمُ بِمَا كَفَرُوا وَاتَّخَذُوا آيَاتِي وَرُسُلِي هُزُوًا
That is their recompense - Hell - for what they denied and [because] they took My signs and My messengers in ridicule.
18:107 Al-Kahf
إِنَّ الَّذِينَ آمَنُوا وَعَمِلُوا الصَّالِحَاتِ كَانَتْ لَهُمْ جَنَّاتُ الْفِرْدَوْسِ نُزُلًا
Indeed, those who have believed and done righteous deeds - they will have the Gardens of Paradise as a lodging,
God, Allah, sent messengers to inform the people about him as the one and only God.
6:47 Al-An'aam
قُلْ أَرَأَيْتَكُمْ إِنْ أَتَاكُمْ عَذَابُ اللَّهِ بَغْتَةً أَوْ جَهْرَةً هَلْ يُهْلَكُ إِلَّا الْقَوْمُ الظَّالِمُونَ
Say, "Have you considered: if the punishment of Allah should come to you unexpectedly or manifestly, will any be destroyed but the wrongdoing people?"
6:48 Al-An'aam
وَمَا نُرْسِلُ الْمُرْسَلِينَ إِلَّا مُبَشِّرِينَ وَمُنْذِرِينَ ۖ فَمَنْ آمَنَ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ
And We send not the messengers except as bringers of good tidings and warners. So whoever believes and reforms - there will be no fear concerning them, nor will they grieve.
6:49 Al-An'aam
وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا يَمَسُّهُمُ الْعَذَابُ بِمَا كَانُوا يَفْسُقُونَ
But those who deny Our verses - the punishment will touch them for their defiant disobedience.
6:50 Al-An'aam
قُلْ لَا أَقُولُ لَكُمْ عِنْدِي خَزَائِنُ اللَّهِ وَلَا أَعْلَمُ الْغَيْبَ وَلَا أَقُولُ لَكُمْ إِنِّي مَلَكٌ ۖ إِنْ أَتَّبِعُ إِلَّا مَا يُوحَىٰ إِلَيَّ ۚ قُلْ هَلْ يَسْتَوِي الْأَعْمَىٰ وَالْبَصِيرُ ۚ أَفَلَا تَتَفَكَّرُونَ
Say, [O Muhammad], "I do not tell you that I have the depositories [containing the provision] of Allah or that I know the unseen, nor do I tell you that I am an angel. I only follow what is revealed to me." Say, "Is the blind equivalent to the seeing? Then will you not give thought?"
6:51 Al-An'aam
وَأَنْذِرْ بِهِ الَّذِينَ يَخَافُونَ أَنْ يُحْشَرُوا إِلَىٰ رَبِّهِمْ ۙ لَيْسَ لَهُمْ مِنْ دُونِهِ وَلِيٌّ وَلَا شَفِيعٌ لَعَلَّهُمْ يَتَّقُونَ
And warn by the Qur'an those who fear that they will be gathered before their Lord - for them besides Him will be no protector and no intercessor - that they might become righteous.
16:23 An-Nahl
لَا جَرَمَ أَنَّ اللَّهَ يَعْلَمُ مَا يُسِرُّونَ وَمَا يُعْلِنُونَ ۚ إِنَّهُ لَا يُحِبُّ الْمُسْتَكْبِرِينَ
Assuredly, Allah knows what they conceal and what they declare. Indeed, He does not like the arrogant.
16:24 An-Nahl
وَإِذَا قِيلَ لَهُمْ مَاذَا أَنْزَلَ رَبُّكُمْ ۙ قَالُوا أَسَاطِيرُ الْأَوَّلِينَ
And when it is said to them, "What has your Lord sent down?" They say, "Legends of the former peoples,"
16:25 An-Nahl
لِيَحْمِلُوا أَوْزَارَهُمْ كَامِلَةً يَوْمَ الْقِيَامَةِ ۙ وَمِنْ أَوْزَارِ الَّذِينَ يُضِلُّونَهُمْ بِغَيْرِ عِلْمٍ ۗ أَلَا سَاءَ مَا يَزِرُونَ
That they may bear their own burdens in full on the Day of Resurrection and some of the burdens of those whom they misguide without knowledge. Unquestionably, evil is that which they bear.
16:26 An-Nahl
قَدْ مَكَرَ الَّذِينَ مِنْ قَبْلِهِمْ فَأَتَى اللَّهُ بُنْيَانَهُمْ مِنَ الْقَوَاعِدِ فَخَرَّ عَلَيْهِمُ السَّقْفُ مِنْ فَوْقِهِمْ وَأَتَاهُمُ الْعَذَابُ مِنْ حَيْثُ لَا يَشْعُرُونَ
Those before them had already plotted, but Allah came at their building from the foundations, so the roof fell upon them from above them, and the punishment came to them from where they did not perceive.
16:27 An-Nahl
ثُمَّ يَوْمَ الْقِيَامَةِ يُخْزِيهِمْ وَيَقُولُ أَيْنَ شُرَكَائِيَ الَّذِينَ كُنْتُمْ تُشَاقُّونَ فِيهِمْ ۚ قَالَ الَّذِينَ أُوتُوا الْعِلْمَ إِنَّ الْخِزْيَ الْيَوْمَ وَالسُّوءَ عَلَى الْكَافِرِينَ
Then on the Day of Resurrection He will disgrace them and say, "Where are My 'partners' for whom you used to oppose [the believers]?" Those who were given knowledge will say, "Indeed disgrace, this Day, and evil are upon the disbelievers" -
16:28 An-Nahl
الَّذِينَ تَتَوَفَّاهُمُ الْمَلَائِكَةُ ظَالِمِي أَنْفُسِهِمْ ۖ فَأَلْقَوُا السَّلَمَ مَا كُنَّا نَعْمَلُ مِنْ سُوءٍ ۚ بَلَىٰ إِنَّ اللَّهَ عَلِيمٌ بِمَا كُنْتُمْ تَعْمَلُونَ
The ones whom the angels take in death [while] wronging themselves, and [who] then offer submission, [saying], "We were not doing any evil." But, yes! Indeed, Allah is Knowing of what you used to do.
16:29 An-Nahl
فَادْخُلُوا أَبْوَابَ جَهَنَّمَ خَالِدِينَ فِيهَا ۖ فَلَبِئْسَ مَثْوَى الْمُتَكَبِّرِينَ
So enter the gates of Hell to abide eternally therein, and how wretched is the residence of the arrogant.
16:30 An-Nahl
۞ وَقِيلَ لِلَّذِينَ اتَّقَوْا مَاذَا أَنْزَلَ رَبُّكُمْ ۚ قَالُوا خَيْرًا ۗ لِلَّذِينَ أَحْسَنُوا فِي هَٰذِهِ الدُّنْيَا حَسَنَةٌ ۚ وَلَدَارُ الْآخِرَةِ خَيْرٌ ۚ وَلَنِعْمَ دَارُ الْمُتَّقِينَ
And it will be said to those who feared Allah, "What did your Lord send down?" They will say, "[That which is] good." For those who do good in this world is good; and the home of the Hereafter is better. And how excellent is the home of the righteous -
16:31 An-Nahl
جَنَّاتُ عَدْنٍ يَدْخُلُونَهَا تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ ۖ لَهُمْ فِيهَا مَا يَشَاءُونَ ۚ كَذَٰلِكَ يَجْزِي اللَّهُ الْمُتَّقِينَ
Gardens of perpetual residence, which they will enter, beneath which rivers flow. They will have therein whatever they wish. Thus does Allah reward the righteous -
16:32 An-Nahl
الَّذِينَ تَتَوَفَّاهُمُ الْمَلَائِكَةُ طَيِّبِينَ ۙ يَقُولُونَ سَلَامٌ عَلَيْكُمُ ادْخُلُوا الْجَنَّةَ بِمَا كُنْتُمْ تَعْمَلُونَ
The ones whom the angels take in death, [being] good and pure; [the angels] will say, "Peace be upon you. Enter Paradise for what you used to do."
16:33 An-Nahl
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ أَمْرُ رَبِّكَ ۚ كَذَٰلِكَ فَعَلَ الَّذِينَ مِنْ قَبْلِهِمْ ۚ وَمَا ظَلَمَهُمُ اللَّهُ وَلَٰكِنْ كَانُوا أَنْفُسَهُمْ يَظْلِمُونَ
Do the disbelievers await [anything] except that the angels should come to them or there comes the command of your Lord? Thus did those do before them. And Allah wronged them not, but they had been wronging themselves.
16:34 An-Nahl
فَأَصَابَهُمْ سَيِّئَاتُ مَا عَمِلُوا وَحَاقَ بِهِمْ مَا كَانُوا بِهِ يَسْتَهْزِئُونَ
So they were struck by the evil consequences of what they did and were enveloped by what they used to ridicule.
16:35 An-Nahl
وَقَالَ الَّذِينَ أَشْرَكُوا لَوْ شَاءَ اللَّهُ مَا عَبَدْنَا مِنْ دُونِهِ مِنْ شَيْءٍ نَحْنُ وَلَا آبَاؤُنَا وَلَا حَرَّمْنَا مِنْ دُونِهِ مِنْ شَيْءٍ ۚ كَذَٰلِكَ فَعَلَ الَّذِينَ مِنْ قَبْلِهِمْ ۚ فَهَلْ عَلَى الرُّسُلِ إِلَّا الْبَلَاغُ الْمُبِينُ
And those who associate others with Allah say, "If Allah had willed, we would not have worshipped anything other than Him, neither we nor our fathers, nor would we have forbidden anything through other than Him." Thus did those do before them. So is there upon the messengers except [the duty of] clear notification?
16:36 An-Nahl
وَلَقَدْ بَعَثْنَا فِي كُلِّ أُمَّةٍ رَسُولًا أَنِ اعْبُدُوا اللَّهَ وَاجْتَنِبُوا الطَّاغُوتَ ۖ فَمِنْهُمْ مَنْ هَدَى اللَّهُ وَمِنْهُمْ مَنْ حَقَّتْ عَلَيْهِ الضَّلَالَةُ ۚ فَسِيرُوا فِي الْأَرْضِ فَانْظُرُوا كَيْفَ كَانَ عَاقِبَةُ الْمُكَذِّبِينَ
And We certainly sent into every nation a messenger, [saying], "Worship Allah and avoid Taghut (the false deities)." And among them were those whom Allah guided, and among them were those upon whom error was [deservedly] decreed. So proceed through the earth and observe how was the end of the deniers.
16:37 An-Nahl
إِنْ تَحْرِصْ عَلَىٰ هُدَاهُمْ فَإِنَّ اللَّهَ لَا يَهْدِي مَنْ يُضِلُّ ۖ وَمَا لَهُمْ مِنْ نَاصِرِينَ
[Even] if you should strive for their guidance, indeed, Allah does not guide those He sends astray, and they will have no helpers.
3:176 Aal-i-Imraan
وَلَا يَحْزُنْكَ الَّذِينَ يُسَارِعُونَ فِي الْكُفْرِ ۚ إِنَّهُمْ لَنْ يَضُرُّوا اللَّهَ شَيْئًا ۗ يُرِيدُ اللَّهُ أَلَّا يَجْعَلَ لَهُمْ حَظًّا فِي الْآخِرَةِ ۖ وَلَهُمْ عَذَابٌ عَظِيمٌ
And do not be saddened, [O Muhammad], by those who hasten into disbelief. Indeed, they will never harm Allah at all. Allah intends that He should give them no share in the Hereafter, and for them is a great punishment.
3:177 Aal-i-Imraan
إِنَّ الَّذِينَ اشْتَرَوُا الْكُفْرَ بِالْإِيمَانِ لَنْ يَضُرُّوا اللَّهَ شَيْئًا وَلَهُمْ عَذَابٌ أَلِيمٌ
Indeed, those who purchase disbelief [in exchange] for faith - never will they harm Allah at all, and for them is a painful punishment.
3:178 Aal-i-Imraan
وَلَا يَحْسَبَنَّ الَّذِينَ كَفَرُوا أَنَّمَا نُمْلِي لَهُمْ خَيْرٌ لِأَنْفُسِهِمْ ۚ إِنَّمَا نُمْلِي لَهُمْ لِيَزْدَادُوا إِثْمًا ۚ وَلَهُمْ عَذَابٌ مُهِينٌ
And let not those who disbelieve ever think that [because] We fill for them time [of worldly things, among which wealth or time], it is better for them. We only fill for them so that they may increase in sin, and for them is a humiliating punishment.
3:179 Aal-i-Imraan
مَا كَانَ اللَّهُ لِيَذَرَ الْمُؤْمِنِينَ عَلَىٰ مَا أَنْتُمْ عَلَيْهِ حَتَّىٰ يَمِيزَ الْخَبِيثَ مِنَ الطَّيِّبِ ۗ وَمَا كَانَ اللَّهُ لِيُطْلِعَكُمْ عَلَى الْغَيْبِ وَلَٰكِنَّ اللَّهَ يَجْتَبِي مِنْ رُسُلِهِ مَنْ يَشَاءُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۚ وَإِنْ تُؤْمِنُوا وَتَتَّقُوا فَلَكُمْ أَجْرٌ عَظِيمٌ
Allah would not leave the believers in that [state] you are in [presently] until He separates the evil from the good. Nor would Allah reveal to you the unseen. But [instead], Allah chooses of His messengers whom He wills, so believe in Allah and His messengers. And if you believe and fear Him, then for you is a great reward.
6:54 Al-An'aam
وَإِذَا جَاءَكَ الَّذِينَ يُؤْمِنُونَ بِآيَاتِنَا فَقُلْ سَلَامٌ عَلَيْكُمْ ۖ كَتَبَ رَبُّكُمْ عَلَىٰ نَفْسِهِ الرَّحْمَةَ ۖ أَنَّهُ مَنْ عَمِلَ مِنْكُمْ سُوءًا بِجَهَالَةٍ ثُمَّ تَابَ مِنْ بَعْدِهِ وَأَصْلَحَ فَأَنَّهُ غَفُورٌ رَحِيمٌ
And when those come to you who believe in Our verses, say, "Peace be upon you. Your Lord has decreed upon Himself mercy: that any of you who does wrong out of ignorance and then repents after that and corrects himself - indeed, He is Forgiving and Merciful."
6:55 Al-An'aam
وَكَذَٰلِكَ نُفَصِّلُ الْآيَاتِ وَلِتَسْتَبِينَ سَبِيلُ الْمُجْرِمِينَ
And thus do We detail the verses, and [thus] the way of the criminals will become evident.
6:56 Al-An'aam
قُلْ إِنِّي نُهِيتُ أَنْ أَعْبُدَ الَّذِينَ تَدْعُونَ مِنْ دُونِ اللَّهِ ۚ قُلْ لَا أَتَّبِعُ أَهْوَاءَكُمْ ۙ قَدْ ضَلَلْتُ إِذًا وَمَا أَنَا مِنَ الْمُهْتَدِينَ
Say, "Indeed, I have been forbidden to worship those you invoke besides Allah." Say, "I will not follow your desires, for I would then have gone astray, and I would not be of the [rightly] guided."
6:57 Al-An'aam
قُلْ إِنِّي عَلَىٰ بَيِّنَةٍ مِنْ رَبِّي وَكَذَّبْتُمْ بِهِ ۚ مَا عِنْدِي مَا تَسْتَعْجِلُونَ بِهِ ۚ إِنِ الْحُكْمُ إِلَّا لِلَّهِ ۖ يَقُصُّ الْحَقَّ ۖ وَهُوَ خَيْرُ الْفَاصِلِينَ
Say, "Indeed, I am on clear evidence from my Lord, and you have denied it. I do not have that for which you are impatient. The decision is only for Allah. He relates the truth, and He is the best of deciders."
6:58 Al-An'aam
قُلْ لَوْ أَنَّ عِنْدِي مَا تَسْتَعْجِلُونَ بِهِ لَقُضِيَ الْأَمْرُ بَيْنِي وَبَيْنَكُمْ ۗ وَاللَّهُ أَعْلَمُ بِالظَّالِمِينَ
Say, "If I had that for which you are impatient, the matter would have been decided between me and you, but Allah is most knowing of the wrongdoers."
6:59 Al-An'aam
۞ وَعِنْدَهُ مَفَاتِحُ الْغَيْبِ لَا يَعْلَمُهَا إِلَّا هُوَ ۚ وَيَعْلَمُ مَا فِي الْبَرِّ وَالْبَحْرِ ۚ وَمَا تَسْقُطُ مِنْ وَرَقَةٍ إِلَّا يَعْلَمُهَا وَلَا حَبَّةٍ فِي ظُلُمَاتِ الْأَرْضِ وَلَا رَطْبٍ وَلَا يَابِسٍ إِلَّا فِي كِتَابٍ مُبِينٍ
And with Him are the keys of the unseen; none knows them except Him. And He knows what is on the land and in the sea. Not a leaf falls but that He knows it. And no grain is there within the darknesses of the earth and no moist or dry [thing] but that it is [written] in a clear record.
6:60 Al-An'aam
وَهُوَ الَّذِي يَتَوَفَّاكُمْ بِاللَّيْلِ وَيَعْلَمُ مَا جَرَحْتُمْ بِالنَّهَارِ ثُمَّ يَبْعَثُكُمْ فِيهِ لِيُقْضَىٰ أَجَلٌ مُسَمًّى ۖ ثُمَّ إِلَيْهِ مَرْجِعُكُمْ ثُمَّ يُنَبِّئُكُمْ بِمَا كُنْتُمْ تَعْمَلُونَ
And it is He who takes your souls by night and knows what you have committed by day. Then He revives you therein that a specified term may be fulfilled. Then to Him will be your return; then He will inform you about what you used to do.
6:61 Al-An'aam
وَهُوَ الْقَاهِرُ فَوْقَ عِبَادِهِ ۖ وَيُرْسِلُ عَلَيْكُمْ حَفَظَةً حَتَّىٰ إِذَا جَاءَ أَحَدَكُمُ الْمَوْتُ تَوَفَّتْهُ رُسُلُنَا وَهُمْ لَا يُفَرِّطُونَ
And He is the subjugator over His servants, and He sends over you guardian-angels until, when death comes to one of you, Our messengers take him, and they do not fail [in their duties].
6:62 Al-An'aam
ثُمَّ رُدُّوا إِلَى اللَّهِ مَوْلَاهُمُ الْحَقِّ ۚ أَلَا لَهُ الْحُكْمُ وَهُوَ أَسْرَعُ الْحَاسِبِينَ
Then they His servants are returned to Allah, their true Lord. Unquestionably, His is the judgement, and He is the swiftest of accountants.
84:6 Al-Inshiqaaq
يَا أَيُّهَا الْإِنْسَانُ إِنَّكَ كَادِحٌ إِلَىٰ رَبِّكَ كَدْحًا فَمُلَاقِيهِ
O man, indeed you are laboring toward your Lord with [great] exertion and will meet it.
84:7 Al-Inshiqaaq
فَأَمَّا مَنْ أُوتِيَ كِتَابَهُ بِيَمِينِهِ
Then as for he who is given his book (where the good deeds and bad deeds are registered) in his right hand,
84:8 Al-Inshiqaaq
فَسَوْفَ يُحَاسَبُ حِسَابًا يَسِيرًا
He will be judged with an easy reckoning
84:9 Al-Inshiqaaq
وَيَنْقَلِبُ إِلَىٰ أَهْلِهِ مَسْرُورًا
And return happy to his people.
84:10 Al-Inshiqaaq
وَأَمَّا مَنْ أُوتِيَ كِتَابَهُ وَرَاءَ ظَهْرِهِ
But as for he who is given his book (where the good deeds and bad deeds are registered) behind his back,
84:11 Al-Inshiqaaq
فَسَوْفَ يَدْعُو ثُبُورًا
He will cry out for destruction
84:12 Al-Inshiqaaq
وَيَصْلَىٰ سَعِيرًا
And [enter to] burn in a Blaze.
84:13 Al-Inshiqaaq
إِنَّهُ كَانَ فِي أَهْلِهِ مَسْرُورًا
Indeed, he had [once] been among his people content;
84:14 Al-Inshiqaaq
إِنَّهُ ظَنَّ أَنْ لَنْ يَحُورَ
Indeed, he had thought he would never return [to God; Allah].
84:15 Al-Inshiqaaq
بَلَىٰ إِنَّ رَبَّهُ كَانَ بِهِ بَصِيرًا
But yes! Indeed, his Lord was ever of him, Seeing.
Everything that we do is written in our books by angels assigned to us; on our right and left. The weight of the deeds good or bad will determine where each person will end up; heavens or hellfire. However, each good deed will be rewards ten times more its value written in the person’s book and for each bad deed nothing more than it will be written. And whoever is away from worshiping God, Allah, has a Qarin; devil from jinn that drives him or her more astray and provokes to commit more sins.
50:16 Qaaf
وَلَقَدْ خَلَقْنَا الْإِنْسَانَ وَنَعْلَمُ مَا تُوَسْوِسُ بِهِ نَفْسُهُ ۖ وَنَحْنُ أَقْرَبُ إِلَيْهِ مِنْ حَبْلِ الْوَرِيدِ
And We have already created man and know what his soul whispers to him, and We are closer to him than [his] jugular vein
50:17 Qaaf
إِذْ يَتَلَقَّى الْمُتَلَقِّيَانِ عَنِ الْيَمِينِ وَعَنِ الشِّمَالِ قَعِيدٌ
When the two receivers receive, seated on the right and on the left.
50:18 Qaaf
مَا يَلْفِظُ مِنْ قَوْلٍ إِلَّا لَدَيْهِ رَقِيبٌ عَتِيدٌ
Man does not utter any word except that with him is observers (from the angels) prepared [to record in the person’s book].
50:19 Qaaf
وَجَاءَتْ سَكْرَةُ الْمَوْتِ بِالْحَقِّ ۖ ذَٰلِكَ مَا كُنْتَ مِنْهُ تَحِيدُ
And the intoxication of death will bring the truth; that is what you were trying to avoid.
50:20 Qaaf
وَنُفِخَ فِي الصُّورِ ۚ ذَٰلِكَ يَوْمُ الْوَعِيدِ
And the Horn will be blown. That is the Day of [carrying out] the threat.
50:21 Qaaf
وَجَاءَتْ كُلُّ نَفْسٍ مَعَهَا سَائِقٌ وَشَهِيدٌ
And every soul will come, with it a driver and a witness.
50:22 Qaaf
لَقَدْ كُنْتَ فِي غَفْلَةٍ مِنْ هَٰذَا فَكَشَفْنَا عَنْكَ غِطَاءَكَ فَبَصَرُكَ الْيَوْمَ حَدِيدٌ
[It will be said], "You were certainly in unmindfulness of this, and We have removed from you your cover, so your sight, this Day, is sharp."
50:23 Qaaf
وَقَالَ قَرِينُهُ هَٰذَا مَا لَدَيَّ عَتِيدٌ
And his companion, [the angel], will say, "This [record] is what is with me, prepared."
50:24 Qaaf
أَلْقِيَا فِي جَهَنَّمَ كُلَّ كَفَّارٍ عَنِيدٍ
[Allah will say], "Throw into Hell every obstinate disbeliever,
50:25 Qaaf
مَنَّاعٍ لِلْخَيْرِ مُعْتَدٍ مُرِيبٍ
Preventer of good, aggressor, and doubter,
50:26 Qaaf
الَّذِي جَعَلَ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَأَلْقِيَاهُ فِي الْعَذَابِ الشَّدِيدِ
Who made [as equal] with Allah another deity; then throw him into the severe punishment."
50:27 Qaaf
۞ قَالَ قَرِينُهُ رَبَّنَا مَا أَطْغَيْتُهُ وَلَٰكِنْ كَانَ فِي ضَلَالٍ بَعِيدٍ
His Qarin [devil from jinn assigned to the person in case of disbelief or disobeying God] will say, "Our Lord, I did not make him transgress, but he [himself] was in extreme error."
50:28 Qaaf
قَالَ لَا تَخْتَصِمُوا لَدَيَّ وَقَدْ قَدَّمْتُ إِلَيْكُمْ بِالْوَعِيدِ
[Allah] will say, "Do not dispute before Me, while I had already presented to you the warning.
50:29 Qaaf
مَا يُبَدَّلُ الْقَوْلُ لَدَيَّ وَمَا أَنَا بِظَلَّامٍ لِلْعَبِيدِ
The word will not be changed with Me, and never will I be unjust to the servants."
50:30 Qaaf
يَوْمَ نَقُولُ لِجَهَنَّمَ هَلِ امْتَلَأْتِ وَتَقُولُ هَلْ مِنْ مَزِيدٍ
On the Day We will say to Hell, "Have you been filled?" and it will say, "Are there some more,"
50:31 Qaaf
وَأُزْلِفَتِ الْجَنَّةُ لِلْمُتَّقِينَ غَيْرَ بَعِيدٍ
And Paradise will be brought near to the righteous, not far,
50:32 Qaaf
هَٰذَا مَا تُوعَدُونَ لِكُلِّ أَوَّابٍ حَفِيظٍ
[It will be said], "This is what you were promised - for every returner [to Allah] and keeper [of His covenant]
50:33 Qaaf
مَنْ خَشِيَ الرَّحْمَٰنَ بِالْغَيْبِ وَجَاءَ بِقَلْبٍ مُنِيبٍ
Who feared the Most Merciful (while) unseen and came with a heart returning [in repentance].
50:34 Qaaf
ادْخُلُوهَا بِسَلَامٍ ۖ ذَٰلِكَ يَوْمُ الْخُلُودِ
Enter it in peace. This is the Day of Eternity."
50:35 Qaaf
لَهُمْ مَا يَشَاءُونَ فِيهَا وَلَدَيْنَا مَزِيدٌ
They will have whatever they wish therein, and with Us is more.
50:36 Qaaf
وَكَمْ أَهْلَكْنَا قَبْلَهُمْ مِنْ قَرْنٍ هُمْ أَشَدُّ مِنْهُمْ بَطْشًا فَنَقَّبُوا فِي الْبِلَادِ هَلْ مِنْ مَحِيصٍ
And how many a generation before them did We destroy who were greater than them in [striking] power and had explored throughout the lands. Is there any place of escape?
50:37 Qaaf
إِنَّ فِي ذَٰلِكَ لَذِكْرَىٰ لِمَنْ كَانَ لَهُ قَلْبٌ أَوْ أَلْقَى السَّمْعَ وَهُوَ شَهِيدٌ
Indeed in that is a reminder for whoever has a heart or who listens while he is present [in mind].
23:102 Al-Muminoon
فَمَنْ ثَقُلَتْ مَوَازِينُهُ فَأُولَٰئِكَ هُمُ الْمُفْلِحُونَ
And those whose scales are heavy [with good deeds] - it is they who are the successful.
23:103 Al-Muminoon
وَمَنْ خَفَّتْ مَوَازِينُهُ فَأُولَٰئِكَ الَّذِينَ خَسِرُوا أَنْفُسَهُمْ فِي جَهَنَّمَ خَالِدُونَ
But those whose scales are light - those are the ones who have lost their souls, [being] in Hell, abiding eternally.
23:104 Al-Muminoon
تَلْفَحُ وُجُوهَهُمُ النَّارُ وَهُمْ فِيهَا كَالِحُونَ
The Fire will sear their faces, and they therein will have taut smiles.
23:105 Al-Muminoon
أَلَمْ تَكُنْ آيَاتِي تُتْلَىٰ عَلَيْكُمْ فَكُنْتُمْ بِهَا تُكَذِّبُونَ
[It will be said]. "Were not My verses recited to you and you used to belie them?"
23:106 Al-Muminoon
قَالُوا رَبَّنَا غَلَبَتْ عَلَيْنَا شِقْوَتُنَا وَكُنَّا قَوْمًا ضَالِّينَ
They will say, "Our Lord, our wretchedness overcame us, and we were a people astray.
23:107 Al-Muminoon
رَبَّنَا أَخْرِجْنَا مِنْهَا فَإِنْ عُدْنَا فَإِنَّا ظَالِمُونَ
Our Lord, remove us from it, and if we were to return [to evil], we would indeed be wrongdoers."
23:108 Al-Muminoon
قَالَ اخْسَئُوا فِيهَا وَلَا تُكَلِّمُونِ
He will say, "Remain despised therein and do not speak to Me.
23:109 Al-Muminoon
إِنَّهُ كَانَ فَرِيقٌ مِنْ عِبَادِي يَقُولُونَ رَبَّنَا آمَنَّا فَاغْفِرْ لَنَا وَارْحَمْنَا وَأَنْتَ خَيْرُ الرَّاحِمِينَ
Indeed, there was a party of My servants who said, 'Our Lord, we have believed, so forgive us and have mercy upon us, and You are the best of the merciful.'
23:110 Al-Muminoon
فَاتَّخَذْتُمُوهُمْ سِخْرِيًّا حَتَّىٰ أَنْسَوْكُمْ ذِكْرِي وَكُنْتُمْ مِنْهُمْ تَضْحَكُونَ
But you took them in mockery to the point that they made you forget My remembrance, and you used to laugh at them.
23:111 Al-Muminoon
إِنِّي جَزَيْتُهُمُ الْيَوْمَ بِمَا صَبَرُوا أَنَّهُمْ هُمُ الْفَائِزُونَ
Indeed, I have rewarded them this Day for their patient endurance - that they are the attainers [of success]."
6:160 Al-An'aam
مَنْ جَاءَ بِالْحَسَنَةِ فَلَهُ عَشْرُ أَمْثَالِهَا ۖ وَمَنْ جَاءَ بِالسَّيِّئَةِ فَلَا يُجْزَىٰ إِلَّا مِثْلَهَا وَهُمْ لَا يُظْلَمُونَ
Whoever comes [on the Day of Judgement] with a good deed will have ten times the like thereof [to his credit], and whoever comes with an evil deed will not be recompensed except the like thereof; and they will not be wronged.
More often whoever does wrong thinks that nobody saw them, however, the person’s own ears, eyes and skin will witness against him/her on Judgement Day.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it (hellfire), their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions (for each of them a Qarin; devil of jinn) who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
In the following a description of some of the events that will happen on the day of the reckoning.
2:166 Al-Baqara
إِذْ تَبَرَّأَ الَّذِينَ اتُّبِعُوا مِنَ الَّذِينَ اتَّبَعُوا وَرَأَوُا الْعَذَابَ وَتَقَطَّعَتْ بِهِمُ الْأَسْبَابُ
[And they should consider that] when those who have been followed disassociate themselves from those who followed [them], and they [all] see the punishment, and cut off from them are the ties [of relationship],
2:167 Al-Baqara
وَقَالَ الَّذِينَ اتَّبَعُوا لَوْ أَنَّ لَنَا كَرَّةً فَنَتَبَرَّأَ مِنْهُمْ كَمَا تَبَرَّءُوا مِنَّا ۗ كَذَٰلِكَ يُرِيهِمُ اللَّهُ أَعْمَالَهُمْ حَسَرَاتٍ عَلَيْهِمْ ۖ وَمَا هُمْ بِخَارِجِينَ مِنَ النَّارِ
Those who followed will say, "If only we had another turn [at worldly life] so we could disassociate ourselves from them as they have disassociated themselves from us." Thus will Allah show them their deeds as regrets upon them. And they are never to emerge from the Fire.
57:12 Al-Hadid
يَوْمَ تَرَى الْمُؤْمِنِينَ وَالْمُؤْمِنَاتِ يَسْعَىٰ نُورُهُمْ بَيْنَ أَيْدِيهِمْ وَبِأَيْمَانِهِمْ بُشْرَاكُمُ الْيَوْمَ جَنَّاتٌ تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ خَالِدِينَ فِيهَا ۚ ذَٰلِكَ هُوَ الْفَوْزُ الْعَظِيمُ
On the Day you see the believing men and believing women, their light proceeding before them and on their right, [it will be said], "Your good tidings today are [of] gardens beneath which rivers flow, wherein you will abide eternally." That is what is the great attainment.
57:13 Al-Hadid
يَوْمَ يَقُولُ الْمُنَافِقُونَ وَالْمُنَافِقَاتُ لِلَّذِينَ آمَنُوا انْظُرُونَا نَقْتَبِسْ مِنْ نُورِكُمْ قِيلَ ارْجِعُوا وَرَاءَكُمْ فَالْتَمِسُوا نُورًا فَضُرِبَ بَيْنَهُمْ بِسُورٍ لَهُ بَابٌ بَاطِنُهُ فِيهِ الرَّحْمَةُ وَظَاهِرُهُ مِنْ قِبَلِهِ الْعَذَابُ
On the [same] Day the hypocrite men and hypocrite women will say to those who believed, "Wait for us that we may acquire some of your light." It will be said, "Go back behind you and seek light." And a wall will be placed between them with a door, its interior containing mercy, but on the outside of it is torment.
57:14 Al-Hadid
يُنَادُونَهُمْ أَلَمْ نَكُنْ مَعَكُمْ ۖ قَالُوا بَلَىٰ وَلَٰكِنَّكُمْ فَتَنْتُمْ أَنْفُسَكُمْ وَتَرَبَّصْتُمْ وَارْتَبْتُمْ وَغَرَّتْكُمُ الْأَمَانِيُّ حَتَّىٰ جَاءَ أَمْرُ اللَّهِ وَغَرَّكُمْ بِاللَّهِ الْغَرُورُ
The hypocrites will call to the believers, "Were we not with you?" They will say, "Yes, but you afflicted yourselves and awaited [misfortune for us] and doubted, and wishful thinking deluded you until there came the command of Allah. And the Deceiver deceived you concerning Allah.
57:15 Al-Hadid
فَالْيَوْمَ لَا يُؤْخَذُ مِنْكُمْ فِدْيَةٌ وَلَا مِنَ الَّذِينَ كَفَرُوا ۚ مَأْوَاكُمُ النَّارُ ۖ هِيَ مَوْلَاكُمْ ۖ وَبِئْسَ الْمَصِيرُ
So today no ransom will be taken from you or from those who disbelieved. Your refuge is the Fire. It is most worthy of you, and wretched is the destination.
57:16 Al-Hadid
۞ أَلَمْ يَأْنِ لِلَّذِينَ آمَنُوا أَنْ تَخْشَعَ قُلُوبُهُمْ لِذِكْرِ اللَّهِ وَمَا نَزَلَ مِنَ الْحَقِّ وَلَا يَكُونُوا كَالَّذِينَ أُوتُوا الْكِتَابَ مِنْ قَبْلُ فَطَالَ عَلَيْهِمُ الْأَمَدُ فَقَسَتْ قُلُوبُهُمْ ۖ وَكَثِيرٌ مِنْهُمْ فَاسِقُونَ
Has the time not come for those who have believed that their hearts should become humbly submissive at the remembrance of Allah and what has come down of the truth? And let them not be like those who were given the Scripture before, and a long period passed over them, so their hearts hardened; and many of them are defiantly disobedient.
57:17 Al-Hadid
اعْلَمُوا أَنَّ اللَّهَ يُحْيِي الْأَرْضَ بَعْدَ مَوْتِهَا ۚ قَدْ بَيَّنَّا لَكُمُ الْآيَاتِ لَعَلَّكُمْ تَعْقِلُونَ
Know that Allah gives life to the earth after its lifelessness. We have made clear to you the signs; perhaps you will understand.
57:18 Al-Hadid
إِنَّ الْمُصَّدِّقِينَ وَالْمُصَّدِّقَاتِ وَأَقْرَضُوا اللَّهَ قَرْضًا حَسَنًا يُضَاعَفُ لَهُمْ وَلَهُمْ أَجْرٌ كَرِيمٌ
Indeed, the men who practice charity and the women who practice charity and [they who] have loaned Allah a goodly loan (by spending for charity and for the cause of Allah) - it will be multiplied for them, and they will have a noble reward.
57:19 Al-Hadid
وَالَّذِينَ آمَنُوا بِاللَّهِ وَرُسُلِهِ أُولَٰئِكَ هُمُ الصِّدِّيقُونَ ۖ وَالشُّهَدَاءُ عِنْدَ رَبِّهِمْ لَهُمْ أَجْرُهُمْ وَنُورُهُمْ ۖ وَالَّذِينَ كَفَرُوا وَكَذَّبُوا بِآيَاتِنَا أُولَٰئِكَ أَصْحَابُ الْجَحِيمِ
And those who have believed in Allah and His messengers - those are [in the ranks of] the supporters of truth and the martyrs, with their Lord. For them is their reward and their light. But those who have disbelieved and denied Our verses - those are the companions of Hellfire.
57:20 Al-Hadid
اعْلَمُوا أَنَّمَا الْحَيَاةُ الدُّنْيَا لَعِبٌ وَلَهْوٌ وَزِينَةٌ وَتَفَاخُرٌ بَيْنَكُمْ وَتَكَاثُرٌ فِي الْأَمْوَالِ وَالْأَوْلَادِ ۖ كَمَثَلِ غَيْثٍ أَعْجَبَ الْكُفَّارَ نَبَاتُهُ ثُمَّ يَهِيجُ فَتَرَاهُ مُصْفَرًّا ثُمَّ يَكُونُ حُطَامًا ۖ وَفِي الْآخِرَةِ عَذَابٌ شَدِيدٌ وَمَغْفِرَةٌ مِنَ اللَّهِ وَرِضْوَانٌ ۚ وَمَا الْحَيَاةُ الدُّنْيَا إِلَّا مَتَاعُ الْغُرُورِ
Know that the life of this world is but amusement and diversion and adornment and boasting to one another and competition in increase of wealth and children - like the example of a rain whose [resulting] plant growth pleases the tillers; then it dries and you see it turned yellow; then it becomes [scattered] debris. And in the Hereafter is severe punishment and forgiveness from Allah and approval. And what is the worldly life except the enjoyment of delusion.
57:21 Al-Hadid
سَابِقُوا إِلَىٰ مَغْفِرَةٍ مِنْ رَبِّكُمْ وَجَنَّةٍ عَرْضُهَا كَعَرْضِ السَّمَاءِ وَالْأَرْضِ أُعِدَّتْ لِلَّذِينَ آمَنُوا بِاللَّهِ وَرُسُلِهِ ۚ ذَٰلِكَ فَضْلُ اللَّهِ يُؤْتِيهِ مَنْ يَشَاءُ ۚ وَاللَّهُ ذُو الْفَضْلِ الْعَظِيمِ
Race toward forgiveness from your Lord and a Garden whose width is like the width of the heavens and earth, prepared for those who believed in Allah and His messengers. That is the bounty of Allah which He gives to whom He wills, and Allah is the possessor of great bounty.
57:22 Al-Hadid
مَا أَصَابَ مِنْ مُصِيبَةٍ فِي الْأَرْضِ وَلَا فِي أَنْفُسِكُمْ إِلَّا فِي كِتَابٍ مِنْ قَبْلِ أَنْ نَبْرَأَهَا ۚ إِنَّ ذَٰلِكَ عَلَى اللَّهِ يَسِيرٌ
No disaster strikes upon the earth or among yourselves except that it is in a register before We bring it into being - indeed that, for Allah, is easy -
57:23 Al-Hadid
لِكَيْلَا تَأْسَوْا عَلَىٰ مَا فَاتَكُمْ وَلَا تَفْرَحُوا بِمَا آتَاكُمْ ۗ وَاللَّهُ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ
In order that you not despair over what has eluded you and not exult [in pride] over what He has given you. And Allah does not like everyone self-deluded and boastful -
22:1 Al-Hajj
يَا أَيُّهَا النَّاسُ اتَّقُوا رَبَّكُمْ ۚ إِنَّ زَلْزَلَةَ السَّاعَةِ شَيْءٌ عَظِيمٌ
O mankind, fear your Lord. Indeed, the convulsion of the [final] Hour is a terrible thing.
22:2 Al-Hajj
يَوْمَ تَرَوْنَهَا تَذْهَلُ كُلُّ مُرْضِعَةٍ عَمَّا أَرْضَعَتْ وَتَضَعُ كُلُّ ذَاتِ حَمْلٍ حَمْلَهَا وَتَرَى النَّاسَ سُكَارَىٰ وَمَا هُمْ بِسُكَارَىٰ وَلَٰكِنَّ عَذَابَ اللَّهِ شَدِيدٌ
On the Day you see it every nursing mother will be distracted from that [child] she was nursing, and every pregnant woman will abort her pregnancy, and you will see the people [appearing] intoxicated while they are not intoxicated; but the punishment of Allah is severe.
22:3 Al-Hajj
وَمِنَ النَّاسِ مَنْ يُجَادِلُ فِي اللَّهِ بِغَيْرِ عِلْمٍ وَيَتَّبِعُ كُلَّ شَيْطَانٍ مَرِيدٍ
And of the people is he who disputes about Allah without knowledge and follows every rebellious devil.
22:4 Al-Hajj
كُتِبَ عَلَيْهِ أَنَّهُ مَنْ تَوَلَّاهُ فَأَنَّهُ يُضِلُّهُ وَيَهْدِيهِ إِلَىٰ عَذَابِ السَّعِيرِ
It has been decreed for every devil that whoever turns to him - he will misguide him and will lead him to the punishment of the Blaze.
22:5 Al-Hajj
يَا أَيُّهَا النَّاسُ إِنْ كُنْتُمْ فِي رَيْبٍ مِنَ الْبَعْثِ فَإِنَّا خَلَقْنَاكُمْ مِنْ تُرَابٍ ثُمَّ مِنْ نُطْفَةٍ ثُمَّ مِنْ عَلَقَةٍ ثُمَّ مِنْ مُضْغَةٍ مُخَلَّقَةٍ وَغَيْرِ مُخَلَّقَةٍ لِنُبَيِّنَ لَكُمْ ۚ وَنُقِرُّ فِي الْأَرْحَامِ مَا نَشَاءُ إِلَىٰ أَجَلٍ مُسَمًّى ثُمَّ نُخْرِجُكُمْ طِفْلًا ثُمَّ لِتَبْلُغُوا أَشُدَّكُمْ ۖ وَمِنْكُمْ مَنْ يُتَوَفَّىٰ وَمِنْكُمْ مَنْ يُرَدُّ إِلَىٰ أَرْذَلِ الْعُمُرِ لِكَيْلَا يَعْلَمَ مِنْ بَعْدِ عِلْمٍ شَيْئًا ۚ وَتَرَى الْأَرْضَ هَامِدَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ وَأَنْبَتَتْ مِنْ كُلِّ زَوْجٍ بَهِيجٍ
O People, if you should be in doubt about the Resurrection, then [consider that] indeed, We created you from dust, then from a sperm-drop, then from a clinging clot, and then from a lump of flesh, formed and unformed - that We may show you. And We settle in the wombs whom We will for a specified term, then We bring you out as a child, and then [We develop you] that you may reach your [time of] maturity. And among you is he who is taken in [early] death, and among you is he who is returned to the most decrepit [old] age so that he knows, after [once having] knowledge, nothing. And you see the earth barren, but when We send down upon it rain, it quivers and swells and grows [something] of every beautiful kind.
22:6 Al-Hajj
ذَٰلِكَ بِأَنَّ اللَّهَ هُوَ الْحَقُّ وَأَنَّهُ يُحْيِي الْمَوْتَىٰ وَأَنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
That is because Allah is the Truth and because He gives life to the dead and because He is over all things competent
22:7 Al-Hajj
وَأَنَّ السَّاعَةَ آتِيَةٌ لَا رَيْبَ فِيهَا وَأَنَّ اللَّهَ يَبْعَثُ مَنْ فِي الْقُبُورِ
And [that they may know] that the Hour is coming - no doubt about it - and that Allah will resurrect those in the graves.
-
 @ d08c9312:73efcc9f
2025-04-18 20:17:41
@ d08c9312:73efcc9f
2025-04-18 20:17:41https://youtu.be/qK7ffYzxiiQ
Resolvr was recently featured in The Institutes RiskStream Collaborative's educational video series on insurance digitization and cross-border payments. With over a century of history educating insurance professionals, The Institutes has established itself as the premier knowledge resource in risk management and insurance. And its RiskStream Collaborative non-profit serves as the industry's largest enterprise-level technology consortium focused on streamlining insurance processes through innovative solutions.
Resolvr's co-founders, Aaron Daniel and Dave Schwab, were joined by industry experts Lizzy Eisenberg from Lightspark and Austin Cornell from Zero Hash to discuss how Bitcoin and the Lightning Network are transforming global insurance payments operations.
Watch the video to learn how Resolvr is leveraging these real-time digital settlement networks to solve significant inefficiencies in today's insurance payment ecosystem - from the months-long settlement times that trap billions in value, to the manual reconciliation processes costing the industry nearly £1 billion annually at Lloyd's of London alone.
We're grateful to RiskStream Collaborative for showcasing these transformative technologies and emphasizing the importance of combining specialized insurance-native interfaces with powerful payment infrastructure to solve industry-specific challenges.
For more information about how Resolvr can help your organization streamline premium processing and payments, contact us today.
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ 9063ef6b:fd1e9a09
2025-04-16 20:20:39
@ 9063ef6b:fd1e9a09
2025-04-16 20:20:39Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
My attempt to write an article with Yakihonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing?
-
 @ 88cc134b:5ae99079
2025-04-24 17:38:04
@ 88cc134b:5ae99079
2025-04-24 17:38:04test
nostr:nevent1qvzqqqqqqypzpzxvzd935e04fm6g4nqa7dn9qc7nafzlqn4t3t6xgmjkr3dwnyreqqsr98r3ryhw0kdqv6s92c9tcxruc6g9hfjgunnl50gclyyjerv00csna38cs
-
 @ dfa02707:41ca50e3
2025-04-16 14:36:00
@ dfa02707:41ca50e3
2025-04-16 14:36:00Contribute to keep No Bullshit Bitcoin news going.

Good morning! The GM report is now back on track, and for those wondering where it was... well... it was delayed.
0:00
/0:41
1×
Headlines
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
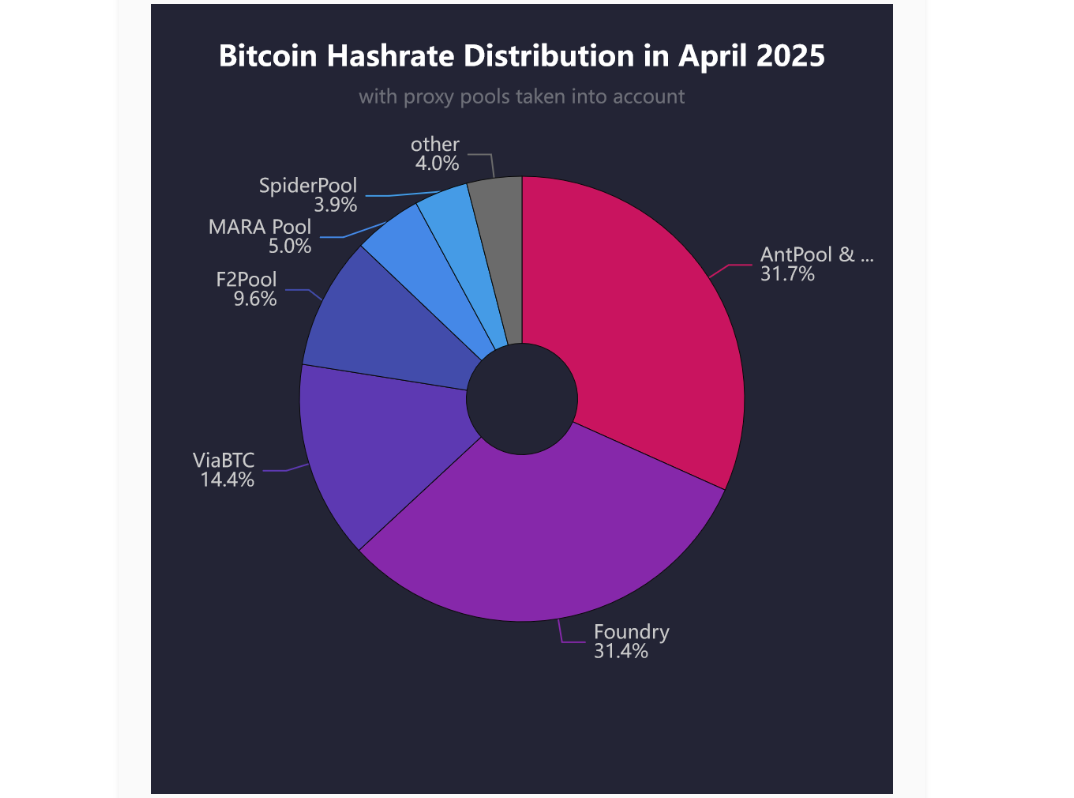
Source: b10c's blog.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- ESP32 microcontroller vulnerabilities. A paper by Crypto Deep Tech details how an attacker can embed a hidden list of vulnerabilities through module updates, potentially compromising ESP32 devices and allowing unauthorized access to private keys, underscoring the importance of continuous monitoring and enhancing both device and software security.
Source: Crypto Deep Tech.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Local governments in China use private firms to sell seized bitcoin for cash. According to Reuters, the lack of clear regulations for handling seized bitcoin and other tokens—whose trading is banned on the mainland—has led to inconsistent and opaque practices. The situation has sparked debate among attorneys about the need for new regulations.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
- Voltage has introduced Voltage Payments platform for enterprises. It will offer a single API that integrates both bitcoin and stablecoin payments with minimal technical overhead, providing the option of either Voltage or user-controlled custody. The platform features a comprehensive dashboard, along with built-in compliance and accounting tools. Currently in beta testing, it is set to launch in 46 U.S. states. Join the waitlist to be notified when it becomes available on mainnet.
Use the tools
- Bitcoin Core Config Generator by Jameson Lopp is now compatible with Bitcoin Core v29.0.
- Zeus wallet v0.10.2 is now available. This point release is centered around various bug fixes.
- Bitkit wallet v1.1.0 introduces performance improvements, smarter coin selection with new Autopilot options, a redesigned side menu, and bug fixes.
- Bitcoin Keeper v2.1.1 update includes various UI updates, bug fixes, and performance improvements.
- Flash v0.4.0-beta, a Bitcoin and Lightning wallet built on the Galoy infrastructure and tailored for the Caribbean Community, features a complete UI/UX redesign, encrypted NIP-17 messaging via Nostr, zoom functionality on the scan camera, improved support for NFC-based Flashcards, and much more.
0:00
/0:31
1×
- Payjoin Dev Kit (rust-payjoin) v0.23.0 introduces a first-class persistence abstraction, wire protocol changes to support RFC 9540, and improved compliance with the BIP78 specification. It also includes an experimental multiparty sender, accessible through the hidden "_multiparty" feature gate. Additionally, it addresses technical debt by enhancing error handling, expanding functionality with new modules and features, and improving test infrastructure. These updates result in breaking API and protocol changes.
- Payjoin CLI v0.1.0 is now out of alpha, with the wire protocol now presumed to be stable.
- Payjoin Directory v0.0.2 has been tagged. It implements the Payjoin Directory store-and-forward server required for Payjoin V2's asynchronous operation.
- BDK Wallet v1.2.0 has been released. The
TxBuilder'sadd_recipientnow accepts anyInto<ScriptBuf>. Coinbase outputs are eligible if maturing in the next block. Wallets usingrusqlite::Connectionare checked for thread safety.bdk_chainis updated to version 0.21.1, with some internal cleanups. - Lightning Dev Kit (rust-lightning) v0.1.2 includes the latest API updates, performance improvements, and bug fixes.
- Boltz Client v2.5.1 includes a patch for correctly handling negative service fees from Boltz Pro. Earlier version 2.5.0 introduced a new
bumpfeecommand alongside several other fixes and improvements. - Elements v23.2.7, an open-source implementation of advanced, sidechain-capable blockchain features extending the Bitcoin protocol, is now available with the latest fixes and improvements.
-
AxeOS (ESP-Miner) v2.6.5 increases the power target for Gamma self test. In version 2.6.4, the under limits for the power consumption self-test were removed.
- AxeOS v2.6.1 was a significant release introducing many new features and improvements. For a comprehensive feature breakdown, check out the details provided by WantClue below.
-
Rust-nostr v0.41 introduces NIP-C0 support and NIP-98 helpers, corrects NIP-32 and NIP-47 implementations, and adds the nostr-keyring crate. It extends admission policies for fine control over relay connections, beneficial in gossip mode. POSIX semaphores are enabled for LMDB on iOS and macOS to address App Sandbox issues. It also expands architecture support for C# and JVM bindings, including linux-x86, windows-x86, and windows-arm64, among other things.
- Nostringer is a JavaScript/TypeScript library providing unlinkable ring signatures (SAG) for Nostr public keys. Inspired by Monero's ring signatures using Spontaneous Anonymous Group (SAG) signatures and the beritani/ring-signatures implementation, it enables a signer to prove their membership in a group of Nostr accounts without disclosing which specific account produced the signature. See a live demo here.
- Private Pond by Kukks a Bitcoin Payjoin application built specifically to optimize Bitcoin transaction rails
-
 @ f1989a96:bcaaf2c1
2025-04-24 16:19:13
@ f1989a96:bcaaf2c1
2025-04-24 16:19:13Good morning, readers!
In Georgia, mere weeks after freezing the bank accounts of five NGOs supporting pro-democracy movements, the ruling Georgian Dream party passed a new law banning foreign organizations from providing grants to local groups without regime approval. The bill is part of a broader effort to silence dissent and weaken democracy through financial repression.\ \ In Latin America, opposition leader María Corina Machado seeks to rally citizens against Nicolás Maduro’s immensely repressive regime. With the economy and currency in shambles and dozens of military personnel abandoning Maduro, Machado sees an opportunity to challenge his grip on power.
In open source news, we spotlight the release of Bitcoin Core version 29.0, the latest update to the primary software that powers the Bitcoin network and helps millions of people send, receive, and verify Bitcoin transactions every day. This release improves the reliability and compatibility of Bitcoin’s main software implementation. We also cover the unique story of LuckyMiner, an unauthorized Bitaxe clone making waves in Asian markets as demand soars for small, low-cost, home mining equipment — evidence that people want to participate in the Bitcoin network themselves.
We close with the latest edition of the HRF x Pubkey Freedom Tech Series, in which Nicaraguan human rights defender Berta Valle joins HRF’s Arsh Molu to explore how authoritarian regimes weaponize financial systems to silence dissent and isolate opposition voices and how tools like Bitcoin can offer a way out. We also feature an interview with Salvadoran opposition leader Claudia Ortiz, who discusses the erosion of civil liberties under President Nayib Bukele and offers a nuanced take on Bitcoin in the country.
Now, let’s jump right in!
SUBSCRIBE HERE
GLOBAL NEWS
Georgia | Bans Foreign Donations for Nonprofits and NGOs
Mere weeks after freezing the bank accounts of five NGOs supporting pro-democracy demonstrators in recent unrest caused by elections, Georgia’s regime passed a new law that bans foreign organizations from providing “monetary or in-kind grants” to Georgian organizations and individuals without regime approval. Introduced by the increasingly repressive Georgian Dream party, the bill is part of a broader effort (including the controversial foreign agents law passed in 2024) designed to silence dissent and dismantle pro-democracy groups. Rights groups warn these laws will cripple civil society by cutting funding and imposing heavy fines for violators. Last week, parliament also read a bill that would grant officials the power to ban opposition parties entirely. With civil society financially repressed, Georgia is sliding further into tyranny, where free expression, political opposition, and grassroots organizations are under siege.
Venezuela | Opposition Mobilizes Against Maduro’s Financial Repression
Venezuelan opposition leader María Corina Machado is intensifying efforts against Nicolás Maduro’s brutal regime by targeting what she believes are his two greatest vulnerabilities: a collapsing economy and fractures in his repressive apparatus. As the Venezuelan bolivar unravels (reaching a record low in March) and inflation spirals out of control (expected to reach 220% before the end of the year), Maduro’s regime doubles down. It imposes currency controls, expropriates private property, and exerts complete state control over banks. Meanwhile, signs of discontent are growing inside the military, with dozens of personnel reportedly deserting. “I think we have a huge opportunity in front of us, and I see that much closer today than I did a month ago,” Machado said. To rebuild Venezuela’s future, Machado sees financial freedom as essential and has publicly embraced Bitcoin as a tool to resist the regime’s weaponization of money.
India | UPI Outage Disrupts Payments Nationwide
Digital transactions across India were disrupted mid-April as the Unified Payments Interface (UPI) experienced its third major outage in the last month. UPI is a government-run system that enables digital payments and underpins India’s push towards a cashless, centralized economy. Fintechs, banks, and institutions plug into UPI as a backbone of their digital infrastructure. Recently, India started integrating its central bank digital currency (CBDC), the digital rupee, into UPI, leveraging its existing network effect to expand the reach of state-issued digital money. When a single outage can freeze an entire nation’s ability to transact, it reveals the fragility of centralized infrastructure. By contrast, decentralized money like Bitcoin operates independently of state-run systems and with consistent uptime, giving users the freedom to transact and save permissionlessly.
China | Bitcoin for Me, Not for Thee
China is debating new regulations for handling its growing trove of Bitcoin and other digital assets seized during criminal investigations. While the regime debates how to manage its seized digital assets, the trading of Bitcoin and other digital assets remains banned for Chinese citizens on the mainland. Reports indicate that local governments have quietly sold confiscated Bitcoin and other digital assets through private companies to bolster their dwindling budgets. If true, this exposes the hypocrisy of a regime banning digital assets for its people while exploiting them as a strategic revenue source for the state. This contradiction accentuates the ways authoritarian regimes manipulate financial rules for their own benefit while punishing the public for using the same strategies.
Serbia | Vučić Targets Civil Society as Economy Sinks
As Serbia’s economy stalls and the cost of living remains stubbornly high, President Aleksandar Vučić is escalating his crackdown on civil society to deflect blame and tighten control. After a train station canopy collapse in Novi Sad killed 16 people last November, protests erupted. Serbians, led by students, flooded the streets to protest government corruption, declining civil liberties, and a worsening economy. The protests have since spread across 400 cities, reflecting nationwide discontent. In response, Vučić is now targeting civil society organizations under the pretext of financial misconduct. Law enforcement raided four NGOs that support Serbians’ human rights, the rule of law, and democratic elections.
Russia | Jails Four Journalists for Working With Navalny
A Russian court sentenced four independent Russian journalists to five and a half years in prison for working with the Anti-Corruption Foundation (ACF) — a pro-democracy organization founded by the late opposition leader Alexei Navalny. The journalists — Antonina Favorskaya, Konstantin Gabov, Sergei Karelin, and Artyom Kriger — were convicted in a closed-door trial for associating with an organization the Kremlin deems an “extremist.” The Committee to Protect Journalists condemned the verdict as a “blatant testimony to Russian authorities’ profound contempt for press freedom.” Since it launched a full-scale invasion of Ukraine in 2022, the Kremlin has increasingly criminalized dissent and financially repressed opposition, nonprofits, and ordinary citizens.
BITCOIN AND FREEDOM TECH NEWS
Flash | Introduces Flash Lightning Addresses, New UI, and Encrypted Messaging
Flash, a Bitcoin Lightning wallet and HRF grantee bringing freedom money to the Caribbean, released its version 0.4.0 beta. This release includes an updated user interface, dedicated Flash Lightning addresses (user @ flashapp.me), and encrypted messaging. The redesigned app is more user-friendly and better suited for users new to Bitcoin. Flash users now receive a verified Lightning address, making it easier to send and receive Bitcoin. The update also adds encrypted nostr messaging, enabling secure communication between users. As authoritarian regimes in the region, like Cuba, tighten control over money, Flash offers a practical and private solution for Bitcoin access.
DahLIAS | New Protocol to Lower the Cost of Private Bitcoin Transactions
Bitcoin developers recently announced DahLIAS, the first protocol designed to enable full cross-input signature aggregation (CISA). CISA is a proposed Bitcoin update that could make private Bitcoin transactions much cheaper. Right now, collaborative transactions are more expensive than typical transactions because each input in a transaction needs its own signature. CISA would allow those signatures to be combined, saving space and reducing fees. But this change would require a soft fork, a safe, backward-compatible software update to Bitcoin’s code. If adopted, CISA could remove the need for users to justify why they want privacy, as the answer would be, to save money. This is especially important for dissidents living under surveillant regimes. DahLIAS could be a breakthrough that helps make privacy more practical for everyone using Bitcoin.
Bitcoin Core | Version 29.0 Now Available for Node Runners
Bitcoin Core is the main software implementation that powers the Bitcoin network and helps millions of people send, receive, and verify transactions every day. The latest update, Bitcoin Core v29.0, introduces changes to improve network stability and performance. The release helps keep the network stable even when not everyone updates simultaneously. Further, it reduces the chances that nodes (computers that run the Bitcoin software) accidentally restart — an issue that can interrupt network participation. It also adds support for full Replace-by-Fee (RBF), allowing users to increase the fee on stuck transactions in times of high network demand. Enhancing Bitcoin’s reliability, usability, and security ensures that individuals in oppressive regimes or unstable financial systems can access a permissionless and censorship-resistant monetary network. Learn more about the update here.
Nstart | Releases Multilingual Support
Nstart, a new tool that simplifies onboarding to nostr — a decentralized and censorship-resistant social network protocol — released multilingual support. It added Spanish, Italian, French, Dutch, and Mandarin as languages. This update broadens access by making the onboarding experience available to a wider audience — especially those living under dictatorships across Africa, Latin America, and Asia, where communication and press freedom are heavily restricted. Users can even contribute translations themselves. Overall, multilingual support makes Nstart a more powerful tool for activists and organizations operating under authoritarian environments, offering guided, straightforward access to uncensorable communications.
Bitcoin Chiang Mai | Release Bitcoin Education Podcast
Bitcoin Chiang Mai, a grassroots Bitcoin community in Thailand, launched an educational podcast to teach Bitcoin in Thai. In a country where financial repression is on the rise and the regime is experimenting with a programmable central bank digital currency (CBDC), this podcast offers an educational lifeline. By making Bitcoin knowledge and tools more accessible, the show empowers Thais to explore alternatives to state-controlled financial systems. It’s a grassroots effort to preserve financial freedom and encourage open dialogue in an increasingly controlled economic environment. Check it out here.
LuckyMiner | Undisclosed Bitaxe Clone Gaining Popularity in Asia
LuckyMiner, a Bitcoin mining startup out of Shenzhen, China is shaking up Asia’s Bitcoin hardware scene with a rogue twist. What began as a hobby project in 2023 has since exploded into a full-scale operation, manufacturing and selling thousands of undisclosed Bitaxe clones (which are small, affordable bitcoin miners based on the Bitaxe design). While Bitaxe is open-source, it’s licensed under CERN-OHL-S-2.0, requiring any modifications to be made public. LuckyMiner ignored that rule and the founder has openly admitted to breaking the license. Despite that, LuckyMiner is succeeding anyway, fueled by growing demand for affordable home mining equipment. While controversial, the rise of low-cost miners signals grassroots interest in Bitcoin, especially at a time when Asia grapples with growing authoritarianism and financial repression.
RECOMMENDED CONTENT
HRF x Pubkey — Bitcoin as a Tool to Fight Financial Repression in Autocracies with Berta Valle
In the latest HRF x Pubkey Freedom Tech series, Nicaraguan human rights defender and journalist Berta Valle joins HRF’s Arsh Molu to discuss how Bitcoin empowers individuals to resist the financial repression of authoritarian regimes. From helping families receive remittances when bank accounts are frozen to enabling independent media and activists to fund their work without regime interference, Bitcoin is quietly reshaping what resistance can look like under tyranny. Watch the full fireside chat here.
Claudia Ortiz: A Voice of Opposition in Bukele’s El Salvador
In this interview, analyst and journalist Marius Farashi Tasooji speaks to Salvadoran opposition leader Claudia Ortiz about President Bukele’s consolidation of power, the erosion of civil liberties, and the future of Bitcoin in the country. While Ortiz acknowledges Bitcoin’s potential as a tool for freedom, she critiques the current administration’s opaque and heavy-handed implementation of it. Ortiz explains her opposition to the Bitcoin Law, citing concerns about transparency and accountability, and outlines what she would do differently if elected president. Watch the full conversation here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ 1bc70a01:24f6a411
2025-04-16 13:53:00
@ 1bc70a01:24f6a411
2025-04-16 13:53:00I've been meaning to dogfood my own vibe project for a while so this feels like a good opportunity to use Untype to publish this update and reflect on my vibe coding journey.
New Untype Update
As I write this, I found it a bit annoying dealing with one of the latest features, so I'll need to make some changes right after I'm done. Nonetheless, here are some exciting developments in the Untype article composer:
-
Added inline AI helper! Now you can highlight text and perform all sorts of things like fix grammar, re-write in different styles, and all sorts of other things. This is a bit annoying at the moment because it takes over the other editing functions and I need to fix the UX.
-
Added pushing articles to DMs! This option, when enabled, will send the article to all the subscribers via a NIP-44 DM. (No client has implemented the subscription method yet so technically it won’t work, until one does. I may add this to nrss.app) Also, I have not tested this so it could be broken… will test eventually!
- Added word counts
- Added ability to export as markdown, export as PDF, print.
The biggest flaw I have already discovered is how "I" implemented the highlight functionality. Right now when you highlight some text it automatically pops up the AI helper menu and this makes for an annoying time trying to make any changes to text. I wanted to change this to show a floating clickable icon instead, but for some reason the bot is having a difficult time updating the code to this desired UX.
Speaking of difficult times, it's probably a good idea to reflect a bit upon my vibe coding journey.
Vibe Coding Nostr Projects
First, I think it's important to add some context around my recent batch of nostr vibe projects. I am working on them mostly at night and occasionally on weekends in between park runs with kids, grocery shopping and just bumming around the house. People who see buggy code or less than desired UX should understand that I am not spending days coding this stuff. Some apps are literally as simple as typing one prompt!
That said, its pretty clear by now that one prompt cannot produce a highly polished product. This is why I decided to limit my number of project to a handful that I really wish existed, and slowly update them over time - fixing bugs, adding new features in hopes of making them the best tools - not only on nostr but the internet in general. As you can imagine this is not a small task, especially for sporadic vibe coding.
Fighting the bot
One of my biggest challenges so far besides having very limited time is getting the bot to do what I want it to do. I guess if you've done any vibe coding at all you're probably familiar with what I'm trying to say. You prompt one thing and get a hallucinated response, or worse, a complete mess out the other end that undoes most of the progress you've made. Once the initial thing is created, which barely took any time, now you're faced with making it work a certain way. This is where the challenges arise.
Here's a brief list of issues I've faced when vibe-coding with various tools:
1. Runaway expenses - tools like Cline tend to do a better job directly in VSCode, but they can also add up dramatically. Before leaning into v0 (which is where I do most of my vibe coding now), I would often melt through $10 credit purchases faster than I could get a decent feature out. It was not uncommon for me to spend $20-30 on a weekend just trying to debug a handful of issues. Naturally, I did not wish to pay these fees so I searched for alternatives.
2. File duplication - occasionally, seemingly out of nowhere, the bot will duplicate files by creating an entire new copy and attached "-fixed" to the file name. Clearly, I'm not asking for duplicate files, I just want it to fix the existing file, but it does happen and it's super annoying. Then you are left telling it which version to keep and which one to delete, and sometimes you have to be very precise or it'll delete the wrong thing and you have to roll back to a previous working version.
3. Code duplication - similar to file duplication, occasionally the bot will duplicate code and do things in the most unintuitive way imaginable. This often results in loops and crashes that can take many refreshes just to revert back to a working state, and many more prompts to avoid the duplication entirely - something a seasoned dev never has to deal with (or so I imagine).
4. Misinterpreting your request - occasionally the bot will do something you didn't ask for because it took your request quite literally. This tends to happen when I give it very specific prompts that are targeted at fixing one very specific thing. I've noticed the bots tend to do better with vague asks - hence a pretty good result on the initial prompt.
5. Doing things inefficiently, without considering smarter approaches - this one is the most painful of vibe coding issues. As a person who may not be familiar with some of the smarter ways of handling development, you rely on the bot to do the right thing. But, when the bot does something horribly inefficiently and you are non-the-wiser, it can be tough to diagnose the issue. I often fight myself asking the bot "is this really the best way to handle things? Can't we ... / shouldn't we .../ isn't this supposed to..." etc. I guess one of the nice side effects of this annoyance is being able to prompt better. I learn that I should ask the bot to reflect on its own code more often and seek ways to do things more simply.
A combination of the above, or total chaos - this is a category where all hell breaks loose and you're trying to put out one fire after another. Fix one bug, only to see 10 more pop up. Fix those, to see 10 more and so on. I guess this may sound like typical development, but the bot amplifies issues by acting totally irrationally. This is typically when I will revert to a previous save point and just undo everything, often losing a lot of progress.
Lessons Learned
If I had to give my earlier self some tips on how to be a smarter vibe coder, here's how I'd summarize them:
-
Fork often - in v0 I now fork for any new major feature I'd like to add (such as the AI assistant).
-
Use targeting tools - in v0 you can select elements and describe how you wish to edit them.
-
Refactor often - keeping the code more manageable speeds up the process. Since the bot will go through the entire file, even if it only makes one small change, it's best to keep the files small and refactoring achieves that.
I guess the biggest lesson someone might point out is just to stop vibe coding. It may be easier to learn proper development and do things right. For me it has been a spare time hobby (one that I will admit is taking more of my extra time than I'd like). I don't really have the time to learn proper development. I feel like I've learned a lot just bossing the bot around and have learned a bunch of things in the process. That's not to say that I never will, but for the moment being my heart is still mostly in design. I haven't shared much of anything I have designed recently - mostly so I can remain speaking more freely without it rubbing off on my work.
I'll go ahead and try to publish this to see if it actually works 😂. Here goes nothing... (oh, I guess I could use the latest feature to export as markdown so I don't lose any progress! Yay!
-
-
 @ dfa02707:41ca50e3
2025-04-16 05:30:53
@ dfa02707:41ca50e3
2025-04-16 05:30:53Contribute to keep No Bullshit Bitcoin news going.
- This release eliminates UPnP support in favor of NAT-PMP/PCP, enhances transaction orphan handling for improved reliability, and introduces ephemeral dust to defer fee commitment.
- Various RPCs now feature enhanced error reporting and new data fields, the block size handling bug related to reserved weight has been fixed, and the removal of the
mempoolfullrbfoption standardizes full replace-by-fee behavior. - With this new major release, versions 26.x and older have reached "Maintenance End" and will no longer receive updates. Two weeks after this release, medium and high severity vulnerabilities affecting 26.x will be disclosed, as well as low severity vulnerabilities affecting 28.x, in line with the security policy.
What's new
-
P2P and Network Changes:
- Support for UPnP has been dropped in favor of a more modern NAT-PMP/PCP implementation.
-
Added support for PCP & IPv6 pinholing.
libnatpmpwas replaced with built-in NAT-PMP/PCP implementation, enabled via-natpmp, which supports IPv4 port forwarding and IPv6 pinholing. - A change in assigning onion listening ports. Now, when using the
-portconfiguration option, the default onion listening port will be set to the specified port +1, rather than a fixed value like 8334 on mainnet.
"This re-allows setups with multiple local nodes using different
-portand not using-bind, which would lead to a startup failure in v28.0 due to a port collision," was explained in the release notes.-
More reliable orphan handling. When a node receives an orphan transaction (an unconfirmed transaction that spends unknown inputs), it will attempt to download missing parents from peers who announced the orphan, potentially increasing bandwidth but enhancing handling of orphan transactions.
-
Mempool Policy and Mining Changes:
- Relay transaction packages containing ephemeral dust. An ephemeral dust output is a tiny transaction output, below the dust limit, produced in a v3 zero-fee transaction and consumed in a following v3 transaction. These transactions occur within the same package, making the output temporary since it is both generated and spent at once. It is useful for Lightning network, Ark, ln-symmetry, Spacechains, Timeout Trees, and other constructs.
-
New startup option -blockreservedweight. In versions before 29.0, a bug limited actual block sizes to 3,992,000 WU by setting a default reserved weight of 8,000 WU for block headers and transactions. The fix adds a new option, -blockreservedweight, with the same default for compatibility.
-
New RPCs:
getdescriptoractivityto track activity of a given set of descriptors. It helps identify all spending and receiving activities for specific descriptors within chosen blocks, and can be used withscanblocksto reduce reliance on additional indexing programs.
-
Updated RPCs:
- Enhanced RPC Response: testmempoolaccept now includes Reject Details. Bitcoin Core 29.0 adds a verbose
reject-detailsfield to thetestmempoolacceptRPC, detailing rejections likeinsufficient-fee. - Persistent block data for duplicate submitblock submissions. Duplicate blocks submitted via
submitblockwill now retain their data even if previously pruned. If pruning is enabled, the data will eventually be pruned again when its block file is selected for pruning.
- Enhanced RPC Response: testmempoolaccept now includes Reject Details. Bitcoin Core 29.0 adds a verbose
-
Updated
getmininginfo. Thegetmininginfonow includesnBitsand the current target in thetargetfield. It also serves anextobject, detailing theheight,nBits,difficulty, andtargetfor the upcoming block. getblockandgetblockheadernow return the current target in thetargetfield.getblockchaininfoandgetchainstatesnow returnnBitsand the current target in thetargetfield.-
getblocktemplateRPC now considers BIP94 Timewarp Fix. ThegetblocktemplateRPC now considers the timewarp fix from BIP94 for thecurtime(BIP22) andmintime(BIP23) fields across all networks. This change helps prevent un-upgraded miners from unintentionally breaching the timewarp rule if a timewarp fix softfork activates on the mainnet. -
Updated REST APIs:
- Get block and Get headers return target in the target field. The
GET /rest/block/<BLOCK-HASH>.jsonandGET /rest/headers/<BLOCK-HASH>.jsonnow return the current target in thetargetfield.
- Get block and Get headers return target in the target field. The
-
Updated Settings:
- Replace-by-fee the standard. From version v28.0, the
-mempoolfullrbfoption was set to default to 1. Due to widespread policy adoption, this option has been removed, making full replace-by-fee the standard behavior. - The maximum limit for the
-dbcacheconfiguration option has been removed due to recent UTXO set growth. Previously, large-dbcachevalues were automatically capped at 16 GiB (or 1 GiB on 32-bit systems). - The handling of negated options like
-noseednode,-nobind,-nowhitebind, and others has been improved. Now, negating these options simply resets them to their defaults, removing previous confusing and undocumented effects. - Using the
-upnpoption will now log a warning and be treated as-natpmp. It's recommended to use-natpmpdirectly instead.
- Replace-by-fee the standard. From version v28.0, the
-
Bitcoin Core will not start if the
-blockreservedweightparameter is set below 2,000 WU. It will also fail to start if either-blockmaxweightor-blockreservedweightexceeds the consensus limit of 4,000,000 WU. -
Using
-debug=0or-debug=nonenow works like-nodebug. It clears previously set debug categories while allowing later-debugoptions to be applied. -
The default value for
-rpcthreadshas increased from 4 to 16, and-rpcworkqueuehas been updated from 16 to 64. -
Build System:
- The build system has been migrated from Autotools to CMake. The minimum required CMake version is 3.22.
"For more detailed guidance on configuring and using CMake, please refer to the official CMake documentation and CMake’s User Interaction Guide. Additionally, consult platform-specific
doc/build-*.mdbuild guides for instructions tailored to your operating system."- Tools and Utilities:
- The new tool
utxo_to_sqlite.pyconverts a compact-serialized UTXO snapshot, created using thedumptxoutsetRPC, into a SQLite3 database. Check the script's--helpoutput for more information.
- The new tool
- Testing:
- The BIP94 timewarp attack mitigation (designed for testnet4) is no longer active on the regtest network.
- Dependencies:
- MiniUPnPc and libnatpmp have been removed as dependencies.

For more information on the new features, improvements, and bug fixes in this release, refer to the full release notes. Additionally, the detailed v29 testing guide provides steps for testing the latest features.
"Thanks to everyone who directly contributed to this release, including 0xb10c, Adlai Chandrasekhar, Afanti, Alfonso Roman Zubeldia, am-sq, Andre, Andre Alves, Anthony Towns, Antoine Poinsot, Ash Manning, Ava Chow, Boris Nagaev, Brandon Odiwuor, brunoerg, Chris Stewart, Cory Fields, costcould, Daniel Pfeifer, Daniela Brozzoni, David Gumberg, dergoegge, epysqyli, espi3, Eval EXEC, Fabian Jahr, fanquake, furszy, Gabriele Bocchi, glozow, Greg Sanders, Gutflo, Hennadii Stepanov, Hodlinator, i-am-yuvi, ion-, ismaelsadeeq, Jadi, James O’Beirne, Jeremy Rand, Jon Atack, jurraca, Kay, kevkevinpal, l0rinc, laanwj, Larry Ruane, Lőrinc, Maciej S. Szmigiero, Mackain, MarcoFalke, marcofleon, Marnix, Martin Leitner-Ankerl, Martin Saposnic, Martin Zumsande, Matthew Zipkin, Max Edwards, Michael Dietz, naiyoma, Nicola Leonardo Susca, omahs, pablomartin4btc, Pieter Wuille, Randall Naar, RiceChuan, rkrux, Roman Zeyde, Ryan Ofsky, Sebastian Falbesoner, secp512k2, Sergi Delgado Segura, Simon, Sjors Provoost, stickies-v, Suhas Daftuar, tdb3, TheCharlatan, tianzedavid, Torkel Rogstad, Vasil Dimov, wgyt, willcl-ark, yancy, and everyone who assisted with translations on Transifex."
-
 @ 7d33ba57:1b82db35
2025-04-24 10:49:41
@ 7d33ba57:1b82db35
2025-04-24 10:49:41Tucked away in the rolling hills of southern France’s Hérault department, Montpeyroux is a charming medieval village known for its peaceful atmosphere, beautiful stone houses, and excellent Languedoc wines. It’s the kind of place where time seems to slow down, making it perfect for a relaxed stop on a southern France road trip.
🏡 Why Visit Montpeyroux?
🪨 Authentic Medieval Character
- Wander narrow cobbled streets lined with honey-colored stone houses
- Visit the remains of a medieval castle and old tower that offer stunning views over vineyards and hills
- A tranquil place that feels untouched by time
🍷 Wine Culture
- Surrounded by prestigious vineyards producing Coteaux du Languedoc wines
- Stop by local caves (wineries) to taste bold reds and crisp whites—many with stunning views over the valley
- Don’t miss the annual wine festivals and open cellars
🌄 Scenic Location
- Located near the Gorges de l’Hérault, perfect for hiking, swimming, or kayaking
- Just a short drive from Saint-Guilhem-le-Désert, one of France’s most beautiful villages
- Great base for exploring the natural beauty of Occitanie
🍽️ Where to Eat
- Enjoy local cuisine at cozy bistros—think grilled lamb, duck confit, olives, and regional cheeses
- Many places serve seasonal dishes paired with local wines
🚗 Getting There
- Around 45 minutes by car from Montpellier
- Best explored by car as public transport is limited, but the countryside drive is worth it
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 044da344:073a8a0e
2025-04-14 11:41:39
@ 044da344:073a8a0e
2025-04-14 11:41:39Als wir vor gut einem halben Jahr mit den Kolumnen angefangen haben, hatte ich mir das genau so vorgestellt. Ich schreibe auf, was mir in der Woche so passiert ist. Eine Bilanz sozusagen, vielleicht persönlich, vielleicht politisch. Je nachdem. Es ist dann etwas anders gekommen. Manchmal waren ein Buch oder ein Film einfach so stark, dass aus der Kolumne eine Rezension geworden ist. Manchmal wollte ich nur von einem meiner Interviews erzählen und das Besprochene gleich mit den großen Debatten verknüpfen. Und manchmal waren Anregungen von außen umzusetzen, Stichwort KI, Stichwort Frieden.
Wahrscheinlich waren die meisten Wochen auch nicht besonders spannend. Alltag eben. Was soll man davon groß festhalten. Diesmal ist das anders. Sonntag Erich Hambach bei uns im Haus. Ein Interview für die Reihe Im Gespräch. Ich will nicht zu viel vorwegnehmen. Es ging um die Hochfinanz, um den schwarzen Adel, um die Illuminati. Ein Gruselkabinett für alle, die wissen, wo die roten Linien sind zu den Schmuddelkindern. Verschwörungstheorie, pfui. Erich Hambach kann erklären, wie die „Herren des Geldes“ (Untertitel seines neuen Buchs) arbeiten und was man tun kann, um sich ihrem Zugriff zu entziehen. Als die Kameras aus waren, ging es munter weiter mit dem Publikum. Steuerfrei leben, sich auf den Lastenausgleich vorbereiten, Kollateralkonto. Siehe oben. Wir haben dann noch 25 Minuten nachgeschoben, die bei den „Truth Brothers“ zu sehen sein werden, dem Kanal von Erich Hambach.
Montag Dresden. Lesung im Buchhaus Loschwitz. Ich war schon im Juni dort, damals mit dem Buch über die Unterwerfung der Universitäten. Diesmal „Der dressierte Nachwuchs“. Wieder volles Haus. In Loschwitz heißt das: Susanne Dagen, Gastgeberin und Moderatorin, quetscht sich auf einen Hocker zwischen Klavier und Reihe null und sagt: Willkommen zum Gottesdienst. Einige sind zum zweiten Mal da. Neu: Paul Soldan, den ich aus seinen Texten für Multipolar kenne und über sein Buch „Sheikhi“, und Julia Szarvasy, die mich in ihrem Bus für Nuoviso interviewt hat und auf der Ruderboot-Couch. Hinterher kommen (um im Bild zu bleiben) drei U-Boote zu mir. Professoren. Ein Techniker, ein Germanist und ein Medienforscher, der sich sogar mit mir fotografieren lassen will. Dieser Kollege ist nicht an der TU (falls jemand die Fahndung einleiten möchte), aber immerhin. Ich bin oft gefragt worden, ob es an den Unis Gleichgesinnte gibt, und kann jetzt endlich sagen: ja. Ein paar schon.
Versteckt in einer der letzten Dresdner Reihen: Michael Beleites, eine Ikone der DDR-Umweltbewegung und später ein Jahrzehnt lang Beauftragter für die Stasi-Unterlagen in Sachsen. Er hat eine Rezension mitgebracht, die er gerade für die Sezession geschrieben hat, und einen Gedanken, der mich später schlecht schlafen lässt. Müssen wir die Geschichte vom Herbst 1989 umschreiben? Ganz neu ist dieser Gedanke nicht, natürlich nicht. Wer dabei war, hat sich schon damals gefragt, wie die Stimmung so schnell kippen konnte vom Wunsch nach einem anderen, besseren Sozialismus zu Helmut Kohl und seiner D-Mark. Daniela Dahn, wie Michael Beleites seinerzeit in vorderster Front, hat den schwarzen Peter an den Journalismus weitergegeben. Tamtam und Tabu. Eine Kampagne, losgetreten von Horst Teltschik, Kohls wichtigstem Mann, die sich um SED-Skandale drehte und so wie eine Nebelkerze verhüllte, um was es eigentlich ging. Die Herren des Geldes, würde Erich Hambach sagen. „Alte Besitzverhältnisse“ wieder herstellen und damit „alte Machtverhältnisse“, sagt Daniela Dahn. Michael Beleites ergänzt das nun durch das, was er gesehen und erlebt hat, bei der Auflösung des Geheimdienstes in Gera zum Beispiel. Da seien Leute wie er gewesen, natürlich. Legitimiert durch das, was vorher war. Überall im Land seien aber plötzlich auch unbeschriebene Blätter aufgetaucht, laut und damit schnell ganz vorne dran. Ein Forschungsthema, ohne Frage.
Bevor ich das zu Ende gedacht habe, sitze ich im Rudolf-Steiner-Haus, nur ein paar Steinwürfe weg von der Alster. Ich würde gern „Hamburgs Wohnzimmer“ schreiben, aber dazu taugt der Saal im Souterrain dann doch nicht ganz. Immerhin: steuerfinanziert. Geht also doch. Eingeladen hat unter anderem der Nachdenkseiten-Gesprächskreis vor Ort. Thema: Wandel der Universitäten. Wieder sind Kollegen da, auch aus dem Mittelbau und aus der Rentnergeneration, die sich zu erinnern glauben, alles schon erlebt zu haben, damals, in ihrer großen Zeit. Nun ja. Wichtiger: Walter Weber ist da, ein Arzt, Koryphäe in Sachen Krebs, 80 inzwischen, der meinen letzten Auftritt in Hamburg organisiert hat. Große Freiheit, Sommer 2022. Die Sonne schien, und es roch nach Aufbruch. Aus dem ganzen Land waren sie gekommen, aus Nord und Süd, von links bis rechts, aus allen nur denkbaren Bewegungen und Milieus. Corona als Klammer, genau wie der Glaube, dass unsere Zeit jetzt anbricht.
Es kam dann anders, aber das ist hier nicht mein Punkt. Walter Weber, der alte Weggefährte, zieht Bilanz – bei einem Becks in seinem Haus, genau da, wo wir vor drei Jahren in größerer Runde beraten haben. Walter hat inzwischen einen Prozess hinter sich mit knapp zwei Dutzend Verhandlungstagen und den entsprechenden Kosten. Maskenatteste. Was immer wir aufgefahren haben an Beweisanträgen, sagt Walter, es wurde abgeschmettert. Und trotzdem. Wir müssen sie zwingen, sich damit auseinanderzusetzen. Immer wieder. So ähnlich habe ich das zwei Stunden vorher im Steiner-Haus gesagt, mit Vaclav Havel als Referenz. 500 Ärzte, schätzt Walter Weber, haben wie er Atteste ausgestellt. 500 bei einer sechsstelligen Zahl an Kollegen. Sicher gibt es eine Dunkelziffer. Lassen wir es bei den 500, weil Walter Weber hier die Folgen kennt. 80 Prozent von diesen 500 haben Haus- und Praxisdurchsuchungen erlebt. Er selbst zwei, der Spitzenreiter acht. Die Maske war der Test. Als die Spritze kam, wusste jeder, auf was er sich einlassen würde - selbst ein Medienforscher wie ich. Die maskierte Öffentlichkeit, veröffentlicht im Oktober 2020, war mit Sicherheit nicht mein bester Text, aber der, der den meisten Wirbel auslöste und später sogar zweimal vor Gericht verhandelt wurde.
Was bleibt von all den Kämpfen? Wir haben die Leute aus der Vereinzelung geholt, sagt Walter. Die 20 Prozent, die dagegen waren. Wir haben ihnen gezeigt, dass sie nicht allein sind, und diese Leute mobilisiert. Gescheitert sind wir an Schritt drei. Strukturbildung. Es fehlt uns an Geld, Michael. Walter Weber hat an Regionalbüros gebastelt. „Ärzte für Aufklärung“ in Thüringen – und das ist nur eins von vielen Beispielen. Wer weiß, wie viel Geld es in diesem Land gibt und wie viele wirklich reiche Leute, der weiß auch, dass wir hier über Peanuts sprechen. Wem es gut geht, der will, dass alles weiter seinen Gang geht. Der will keine Strukturen für irgendeine Opposition. Walter Weber hat mit einer seiner Nichten gerade „Das siebte Kreuz“ gelesen. Anna Seghers, Schulstoff in der DDR. Weißt du, was ich da gelernt habe, Michael? Echter Widerstand hat zwei Bedingungen. Keine Familie und keine Angst vor dem Tod.
Der Zug nach Berlin ist pünktlich und mein Gastgeber folglich noch nicht da. Gibt’s doch nicht, sagt er. Hat es noch nie gegeben. Über meinen Auftritt im Sprechsaal breite ich den Mantel des Schweigens. Die Idee klang super: Wir machen dort eine Ausstellung mit aktuellen Bildern aus Gaza, gekauft von der dpa, und du, Michael, bringst deine Bücher über Cancel Culture, Jugend und Universitäten zusammen, um zu erklären, warum Deutschland wegschaut. Die kastrierte Öffentlichkeit. Der beste Titel geht ins Leere, wenn niemand weiß, dass ich sprechen werde. Vielleicht ist das so, wenn der eigene Verlag der Veranstalter ist. Jens Fischer Rodrian hat durch einen Zufall erfahren, dass ich da bin, und bringt die CD Voices for Gaza, ganz frisch in der Reihe „Protestnoten“. Auf dem Cover: große Namen von Didi Hallervorden über Tino Eisbrenner, Nirit Sommerfeld und Diether Dehm bis zu Wolfgang Wodarg. Fünf von fast 40. Sorry an die, die ich auslassen musste. Der gleiche Zufall hat Kathrin Schmidt in den Sprechsaal geführt, Mitglied des PEN-Zentrums, Buchpreisträgerin, Maßnahmenkritikerin. Sie hat wie immer ihr Strickzeug dabei.
Ein kleines Publikum, frei von Kameras, erlaubt, in die Tiefen zu tauchen und dabei auch zu riskieren, im Trüben zu fischen. Erich Hambach hätte seine Freude gehabt. Und wer weiß schon, was daraus später wächst. Ein paar Minuten vor Beginn gehe ich durch das Regierungsviertel und höre plötzlich meinen Namen. Eine ARD-Frau, die auf Friedrich Merz wartet. Koalitionsvertrag fertig, Kamera schussbereit. Mein Film über die Duldungspflicht, sagt die Frau und strahlt über das ganze Gesicht. Er ist fertig. Premiere nächste Woche. Sie war bei einem meiner letzten Berliner Vorträge und wird jetzt mit ihrem Namen für ein Produkt stehen, dass so nicht im Ersten laufen kann. Noch nicht, würde Walter Weber sagen. Ende nächsten Jahres, sagt er mir beim Abschied, steht Merkel vor Gericht. Ist der Gedanke erstmal da, so begründet er das sinngemäß, dann ist er nicht mehr aufzuhalten. Mal schauen, wie das jetzt mit der Deutschen Bahn wird bei der Rückfahrt nach Bayern. Ich nehme mir vor, dass wir pünktlich sind.
Freie Akademie für Medien & Journalismus
Bild: Tobias Schönebeck auf Pixabay (Dresden, Blaues Wunder in Loschwitz)
-
 @ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48
@ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48Meine erste "Begegnung" mit Ulrike hatte ich am 21. März 2022 - dank Amazon konnte ich das Ereignis noch exakt nachvollziehen. Es war eines meiner ersten (Lockdown) kritischen Bücher, die ich in dieser Zeit in die Hände bekam - noch nach Thomas Röper (das war mein Einstieg) aber vor Daniele Ganser. Insofern war es mir möglich, das, was dann folgte für die Autorin, live und in Farbe mit zu verfolgen:
"Wer sich in die Öffentlichkeit traut, kann sich dort ganz schnell eine blutige Nase holen. Dieselben Medien, die eine Person heute glorifizieren, stellen sie morgen an den Pranger. Sie verteilen und entziehen Reputation, fördern und zerstören Karrieren. Das Medium selbst bleibt jedoch immer auf der Siegerseite. Die Gesetze von Marktorientierung und zynisch-ideologisierter Machtausübung gelten für Rundfunk und Fernsehen ebenso wie für die Printmedien - von RTL bis ARD und ZDF, von der BILD über die taz bis zur ZEIT.
»Das Phänomen Guérot« legt genau diesen Vorgang detailliert offen: Der MENSCH Ulrike Guérot ist in der Realität nicht die dämonische Figur, als die sie hingestellt worden ist. Aber an ihr kristallisiert sich genau dieser menschenverachtende Prozess heraus, der bis heute andauert."
Im Herbst 2022 habe ich durch den ersten Vortrag von Daniele Ganser in Falkensee nicht nur Zugang zu einer für mich neuen und anderen Welt bekommen, ab da hat sich eigentlich auch für mich mein Leben komplett auf den Kopf gestellt. Die Weichen wurden zwar schon vorher gestellt, aber nun war es endgültig und es gab kein zurück mehr. Die Planung für das erste Symposium Falkensee war in meinem Kopf geboren und die MenschheitsFamilie entstand als Ort, der virtuell das vereinen sollte, was Daniele an Spiritualität, Menschlichkeit und Friedenswillen in mir freigesetzt hat. Es war sozusagen eine Energie, die nun stetig floß und einen Trichter gefunden hat, in dem sie wirksam werden und sich entfalten konnte. Insofern haben wir auch etwas gemeinsam - Ulrike und ich. Wir sind zu der Zeit auf einen Zug aufgesprungen, der unser Leben veränderte - der uns zwang, alte Wege zu verlassen und neue Wege zu beschreiten. Sowohl beruflich, als auch privat. Und auch das canceln und entfernt werden ist eine Erfahrung, die wir beide teilen. Vielleicht war es deswegen mein erster Gedanke im Herbst 2022, Ulrike Guérot zu meinem 1. Symposium nach Falkensee einzuladen. Das es dann erst beim 2. Anlauf wirklich geklappt hat, hatte auch mit den Höhen und Tiefen des Lebens in dieser Zeit zu tun gehabt.
Nun ist sie zum 2. Mal dabei - denn wer könnte das Thema "Europa" bei einem so wichtigen und hochaktuellen Thema besser vertreten und beleuchten als Ulrike Guérot? Es geht um Geschichte, es geht um Nationalitäten, es geht um Gemeinsamkeiten und um das, was uns hier im Herzen zusammenhält, was unsere Ziele und unsere Befindlichkeiten sind, es geht um Verantwortung und es geht vor allen Dingen um Frieden! Denn dafür steht Europa - für einen Kontinent, der es geschafft hat, trotz aller Gegensätze und Konflikte, die in Jahrhunderten kriegerisch aufgetragen wurden, eine neuen und besonderen Frieden zu finden und zu installieren:
"Völkerrechtlich legt der Westfälische Frieden den oder zumindest einen Grundstein für ein modernes Prinzip: Die Gleichberechtigung souveräner Staaten, unabhängig von ihrer Macht und Größe. Noch heute spricht die Politikwissenschaft, insbesondere die realistische Schule (Henry Kissinger), deshalb vom „Westphalian System“. Durch die Garantien der großen europäischen Mächte erweist sich dieser Frieden als stabilisierendes Element für die weitere Entwicklung in Europa. Noch bis zum Ende des 18. Jahrhunderts wird er immer wieder als Referenz für nachfolgende Friedensschlüsse herangezogen."
Es ging damals um viel und es geht heute um das Überleben auf einem Kontinent, der es eigentlich besser wissen sollte. Wir dürfen gespannt sein, was wir in diesem Vortrag von Ulrike auf dem Symposium Falkensee am 27. April 2025 für Lösungen finden, um wieder zu einer Ordnung und zu einem System der friedlichen Koexistenz zurückfinden zu können, ohne schwarz und weiß und mit all den Facetten, die das Leben uns so bietet:
"Es ging nicht mehr um das Ausfechten religiöser Wahrheiten, sondern um geregelte Verfahren, die es möglich machten, mit konkurrierenden religiösen Wahrheiten, die nach wie vor nebeneinander und unversöhnlich bestanden, auf friedliche Weise umzugehen. Deutlich wurde das nicht zuletzt, als der Papst in einer offiziellen Note scharf gegen den Friedensschluss protestierte, weil er die Rechte der katholischen Seite leichtfertig aufgegeben sah. Die katholischen Beteiligten des Abkommens hielt dies nicht von der Unterzeichnung ab - ein religiöser Schiedsrichter wurde in Sachen Krieg und Frieden nicht mehr akzeptiert."
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 10f7c7f7:f5683da9
2025-04-24 10:07:09
@ 10f7c7f7:f5683da9
2025-04-24 10:07:09The first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money?
While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.
At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy read, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin from exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell.
Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paThe first time I received a paycheque from a full-time job, after being told in the interview I would be earning one amount, the amount I received was around 25% less; you’re not in Kansas anymore, welcome to the real work and TAX. Over the years, I’ve continued to pay my taxes, as a good little citizen, and at certain points along the way, I have paid considerable amounts of tax, because I wouldn’t want to break the law by not paying my taxes. Tax is necessary for a civilised society, they say. I’m told, who will pay, at least in the UK, for the NHS, who will pay for the roads, who will pay for the courts, the military, the police, if I don’t pay my taxes? But let’s be honest, apart from those who pay very little to no tax, who, in a society actually gets good value for money out of the taxes they pay, or hears of a government institution that operates efficiently and effectively? Alternatively, imagine if the government didn’t have control of a large military budget, would they be quite so keen to deploy the young of our country into harm’s way, in the name of national security or having streets in Ukraine named after them for their generous donations of munition paid with someone else’s money? While I’m only half-way through the excellent “Fiat Standard”, I’m well aware that many of these issues have been driven by the ability of those in charge to not only enforce and increase taxation at will, but also, if ends don’t quite meet, print the difference, however, these are rather abstract and high-level ideas for my small engineer’s brain. What has really brought this into sharp focus for me is the impending sale of my first house, that at the age of 25, I was duly provided a 40-year mortgage and was required to sign a form acknowledging that I would still be paying the mortgage after my retirement age. Fortunately for me, thanks to the government now changing the national age of retirement from 65 to 70 (so stealing 5 years of my retirement), in practice this form didn’t need to be signed, lucky me? Even so, what type of person would knowingly put another person in a situation where near 40% of their wage would mainly be paying interest to the bank (which as a side note was bailed out only a few years later). The unpleasant taste really became unbearable when even after being put into this “working life” sentence of debt repayment, was, even with the amount I’d spent on the house (debt interest and maintenance) over the subsequent 19 years, only able to provide a rate of return of less than 1.6%, compared to the average official (bullshit) inflation figure of 2.77%. My house has not kept up with inflation and to add insult to financial injury, His Majesty’s Revenue and Customs feel the need to take their portion of this “profit”.

At which point, I take a very deep breath, sit quietly for a moment, and channel my inner Margot, deciding against grabbing a bottle of bootleg antiseptic to both clear my pallet and dull the pain. I had been convinced I needed to get on the housing ladder to save, but the government has since printed billions, with the rate of, even the conservative estimates of inflation, out pacing my meagre returns on property, and after all that blood, sweet, tears and dust, covering my poor dog, “the law” states some of that money is theirs. I wasn’t able to save in the money that they could print at will, I worked very hard, I took risks and the reward I get is to give them even more money to fritter away of things that won’t benefit me. But, I don’t want your sympathy, I don’t need it, but it helped me to get a new perspective on capital gains, particularly when considered in relation to bitcoin. So, to again draw from Ms. Paez, who herself was drawing from everyone’s favourite Joker, Heath Ledger, not Rachel Reeves (or J. Powell), here we go.
The Sovereign Individual is by no means an easy reaD, but is absolutely fascinating, providing clear critiques of the system that at the time was only in its infancy, but predicting many aspects of today’s world, with shocking accuracy. One of the most striking parts for me was the critique and effect of taxation (specifically progressive forms) on the prosperity of a nation at large. At an individual level, people have a proportion of their income removed, to be spent by the government, out of the individuals’ control. The person who has applied their efforts, abilities and skills to earn a living is unable to decide how best to utilise a portion of the resources into the future. While this is an accepted reality, the authors’ outline the cumulative, compound impact of forfeiting such a large portion of your wage each year, leading to figures that are near unimaginable to anyone without a penchant for spreadsheets or an understanding of exponential growth. Now, if we put this into the context of the entrepreneur, identifying opportunities, taking on personal and business risk, whenever a profit is realised, whether through normal sales or when realising value from capital appreciation, they must pay a portion of this in tax. While there are opportunities to reinvest this back into the organisation, there may be no immediate investment opportunities for them to offset their current tax bill. As a result, the entrepreneurs are hampered from taking the fruits of their labour and compounding the results of their productivity, forced to fund the social programmes of a government pursuing aims that are misaligned with individuals running their own business. Resources are removed from the most productive individuals in the society, adding value, employing staff, to those who may have limited knowledge of the economic realities of business; see Oxbridge Scholars, with experience in NGOs or charities, for more details please see Labour’s current front bench. What was that Labour? Ah yes, let’s promote growth by taxing companies more and making it more difficult to get rid of unproductive staff, exactly the policies every small business owner has been asking for (Budget October 2024).
Now, for anyone on NOSTR, none of this is new, a large portion of Nostriches were orange pilled long before taking their first purple pill of decentralise Notes and Other Stuff. However, if we’re aware of this system that has been put in place to steal our earnings and confiscate our winnings if we have been able to outwit the Keynesian trap western governments have chosen to give themselves more power, how can we progress? What options do we have? a) being locked up for non-payment of taxes by just spending bitcoin, to hell with paying taxes or b) spend/sell (:/), but keeping a record of those particular coins you bought multiple years ago, in order to calculate your gain and hand over YOUR money the follow tax year, so effectively increasing the cost of anything purchased in bitcoin. Please note, I’m making a conscious effort not to say what should be done, everyone needs to make decisions based on their knowledge and their understanding.
Anyway, option a) is not as flippant as one might think, but also not something one should (damn it) do carelessly. One bitcoin equals one bitcoin, bitcoin is money, as a result, it neither increases nor decreases is value, it is fiat currencies that varies wildly in comparison. If we think about gold, the purchasing power of gold has remained relatively consistent over hundreds of years, gold is viewed as money, which (as a side note) results in Royal Mint gold coins being both exempt of VAT and capital gains tax. While I may consider this from a, while not necessarily biased, but definitely pro-bitcoin perspective, I believe that it is extremely logical for transactions that take place in bitcoin should not require “profits” or “losses” to be reports, but this is where my logic and the treasury’s grabbiness are inconsistent. If what you’re buying is priced in bitcoin, you’re trading goods or services for money, there was no realisation of gains. Having said that, if you choose to do this, best not do any spending from a stack with a connection to an exchange and your identify. When tax collectors (and their government masters) end up not having enough money, they may begin exploring whether those people buying bitcoin form exchanges are also spending it.
But why is this relevant or important? For me and from hearing from many people on podcasts, while not impossible and not actually that difficult, recording gains on each transaction is firstly a barrier for spending bitcoin, it is additional effort, admin and not insignificant cost, and no one likes that. Secondly, from my libertarian leaning perspective, tax is basically the seizure of assets under the threat of incarceration (aka theft), with the government spending that money on crap I don’t give a shit about, meaning I don’t want to help fund their operation more than I already do. The worry is, if I pay more taxes, they think they’re getting good at collecting taxes, they increase taxes, use taxes to employ more tax collectors, rinse and repeat. From this perspective, it is almost my duty not to report when I transact in bitcoin, viewing it as plain and simple, black-market money, where the government neither dictates what I can do with it, nor profit from its appreciation.
The result of this is not the common mantra of never sell your bitcoin, because I, for one, am looking forward to ditching the fiat grind and having more free time driving an interesting 90’s sports car or riding a new mountain bike, which I will need money to be fund. Unless I’m going to take a fair bit of tax evasion-based risk, find some guys who will only accept my KYC free bitcoin and then live off the grid, I’ll need to find another way, which unfortunately may require engaging once more with the fiat system. However, this time, rather than selling bitcoin to buy fiat, looking for financial product providers who offer loans against bitcoin held. This is nothing new, having been a contributing factors to the FTX blow up, and the drawdown of 2022, the logic of such products is solid and the secret catalyst to Mark Moss’s (and others) buy, borrow, die strategy. The difference this time is to earn from our mistakes, to choose the right company and maybe hand over our private keys (multisig is a beautiful thing). The key benefit of this is that by taking a loan, you’re not realising capital gains, so do not create a taxable event. While there is likely to be an interest on any loan, this only makes sense if this is considerably less than either the capital gains rate incurred if you sold the bitcoin or the long-term capital appreciation of the bitcoin you didn’t have to sell, it has to be an option worth considering.
Now, this is interacting with the fiat system, it does involve the effective printing of money and depending on the person providing the loan, there is risk, however, there are definitely some positives, even outside the not inconsiderable, “tax free” nature of this money. Firstly, by borrowing fiat money, you are increasing the money supply, while devaluing all other holders of that currency, which effectively works against fiat governments, causing them to forever print harder to stop themselves going into a deflationary nose drive. The second important aspect is that if you have not had to sell your bitcoin, you have removed sell pressure from the market and buying pressure that would strengthen the fiat currency, so further supporting the stack you have not had to sell. Now, let’s put this in the context of The Sovereign Individual or the entrepreneurial bitcoiner, who took a risk before fully understanding what they were buying and has now benefiting financially. The barrier of tax-based admin or the reticence to support government operations through paying additional tax are not insignificant, which the loan has allowed you to effectively side step, keeping more value of your holdings to allocate as you see fit. While this may involve the setting up of a new business that itself may drive productive growth, even if all you did was spend that money (such as a sport car or a new bike), this could still be a net, economic positive compared to a large portion of that money being sucked into the government spending black hole. While the government would not be receiving that tax revenue, every retailer, manufacturer or service provider would benefit from this additional business. Rather than the tax money going toward interest costs or civil servant wages, the money would go towards the real businesses you have chosen, their staff’s wages, who are working hard to outcompete their peers. Making this choice to not pay capital gains does not just allow bitcoiner to save money and to a small degree, reduce government funding, but also provides a cash injection to those companies who may still be reeling from minimum wage AND national insurance increases.
I’m not an ethicist, so am unable to provide a clear, concise, philosophical argument to explain why the ability of government to steal from you via the processes of monetary inflation as well as an ever-increasing tax burden in immoral, but I hope this provides a new perspective on the situation. I don’t believe increases in taxes support economic development (it literally does the opposite), I don’t believe that individuals should be penalised for working hard, challenging themselves, taking risks and succeeding. However, I’m not in charge of the system and also appreciate that if any major changes were to take place, the consequences would be significant (we’re talking Mandibles time). I believe removing capital gains tax from bitcoin would be a net positive for the economy and there being precedence based on the UK’s currently position with gold coins, but unfortunately, I don’t believe people in the cabinet think as I do, they see people with assets and pound signs ring up at their eyes.
As a result, my aim moving forward will be to think carefully before making purchases or sales that will incur capital gains tax (no big Lambo purchase for me at the top), but also being willing the promote the bitcoin economy by purchasing products and services with bitcoin. To do this, I’ll double confirm that spend/replace techniques actually get around capital gains by effectively using the payment rails of bitcoin to transfer value rather than to sell your bitcoin. This way, I will get to reward and promote those companies to perform at a level that warrants a little more effort with payment, without it costing me an additional 18-24% in tax later on.
So, to return to where we started and my first pay-cheque. We need to work to earn a living, but as we earn more, an ever-greater proportion is taken from us, and we are at risk of becoming stuck in a never ending fiat cycle. In the past, this was more of an issue, leading people into speculating on property or securities, which, if successful, would then incur further taxes, which will likely be spent by governments on liabilities or projects that add zero net benefits to national citizens. Apologies if you see this as a negative, but please don’t, this is the alternative to adopting a unit of account that cannot be inflated away. If you have begun to measure your wealth in bitcoin, there will be a point where you need to start to start spending. I for one, do not intend to die with my private keys in my head, but having lived a life, turbo charged by the freedom bitcoin has offered me. Bitcoin backed loans are returning to the market, with hopefully a little less risk this time around. There may be blow ups, but once they get established and interest costs start to be competed away, I will first of all acknowledge remaining risks and then not allocate 100% of my stack. Rather than being the one true bitcoiner who has never spent a sat, I will use the tools at my disposal to firstly give my family their best possible lives and secondly, not fund the government more than I need to.
Then, by the time I’m ready to leave this earth, there will be less money for me to leave to my family, but then again, the tax man would again come knocking, looking to gloat over my demise and add to my family’s misery with an outstretched hand. Then again, this piece is about capital gains rather than inheritance tax, so we can leave those discussions for another time.
This is not financial advice, please consult a financial/tax advisor before spending and replacing without filing taxes and don’t send your bitcoin to any old fella who says they’ll return it once you’ve paid off the loan.
-
 @ 4c86f5a2:935c3564
2025-04-24 09:07:04
@ 4c86f5a2:935c3564
2025-04-24 09:07:04Write Test Postr
-
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ b8af284d:f82c91dd
2025-04-07 07:09:50
@ b8af284d:f82c91dd
2025-04-07 07:09:50
"Auf den deutschen Konten, Sparkonten und laufenden Girokonten liegen 2,8 Billionen Euro. Stellen Sie sich einen kurzen Augenblick vor, wir wären in der Lage, davon nur 10 Prozent zu mobilisieren – mit einem vernünftigen Zinssatz, für die öffentliche Infrastruktur in Deutschland […]”
Friedrich Merz, Blackrock-Aufsichtsratvorsitzender 2016-2020
„Governments can’t fund infrastructure through deficits. The deficits can’t get much higher. Instead, they’ll turn to private investors.“
Liebe Abonnenten,
im Jahr 1999 lag der durchschnittliche Bruttolohn eines deutschen Arbeiters bei monatlich 2100 Euro. 26 Jahre später sind es etwa 4200 Euro. In diesem Zeitraum sind die Löhne also durchschnittlich jedes Jahr um 2,7 Prozent gewachsen. (Um die Reallöhne, also die tatsächliche inflationsbereinigte Kaufkraft soll es ausnahmsweise einmal nicht gehen.)
Im selben Zeitraum ist die globale Wirtschaftsleistung um fünf Prozent im Jahr gewachsen. Der amerikanische Aktien-Index S\&P500 legte durchschnittlich jedes Jahr um acht Prozent zu.
Die Unterschiede klingen zunächst gering. 2,7 Prozent, 5 Prozent, 8 Prozent - Peanuts, was soll’s? Deutlich werden die Bedeutung dieser Zahlen, wenn man sie in absolute Zahlen umlegt. Bei einem Zuwachs von durchschnittlich fünf Prozent würde selbiger Arbeiter heute 7560 Euro verdienen. Wäre sein Lohn so stark gestiegen wie der S\&P500, läge er bei 15.483 Euro.
Das Unternehmen Blackrock ging im Jahr 1999 an die Börse. Die jährlichen Kurssteigerungen der Aktie liegen durchschnittlich bei 21 Prozent. Aus den 2100 Euro wären damit 334.661 Euro geworden.
Nimmt man nur den Gewinn des Unternehmens, landet man bei etwa zehn Prozent Rendite nach Steuern.
Irgendwie also wächst der Finanzmarkt schneller als Löhne, und Blackrock wächst nochmals schneller als der Finanzmarkt. Wie kann das sein? Was macht Blackrock, für die bis vor wenigen Jahren der künftige Bundeskanzler Friedrich Merz tätig war?
Ein Blackrock-Deepdive:
Blackrock - the bright side
1988 gründete Larry Fink zusammen mit einer Gruppe von Mitarbeitern “Blackstone Financial Management”. Die Firma wurde 1992 in Blackrock umbenannt und ging 1999 an die Börse. Zehn Jahre später übernahm die Firma Barclays Global Investors (BGI). Letztere brachte die Marke „ishares“ mit ins Portfolio. Zum Kerngeschäft von Blackrock gehören seitdem ETFs - die vielleicht beliebteste Anlageklasse der Welt.
ETFs sind keine Erfindung von Blackrock, aber das Unternehmen hat viel dazu beigetragen, dass ETFs heute in fast jedem Portfolio zu finden sind. Bevor es ETFs gab, konnten Kleinanleger fast nur in aktiv gemanagte Fonds investieren. Dabei kaufen und verkaufen hochbezahlte Analysten Aktien und verlangen dafür eine Gebühr von zwei Prozent. Bei ETFs liegen diese im Promillebereich. Eine Gebühr von zwei Prozent mag vernachlässigbar klingen. Über die Jahre aber macht dies einen Riesenunterschied - wie das Beispiel des Bruttolohns zeigt.
Hinzu kommt: Statistisch laufen passive Indexfonds oft besser als aktiv geleitete Investmentfonds.
Blackrock ist es mit seinen ETFs gelungen, die Geldanlage zu demokratisieren. Das Unternehmen profitiert nicht von steigenden Kursen der Aktien, sondern kassiert minimale Gebühren beim Kauf und Verkauf - aber bei einem verwalteten Vermögen von 4,5 Billionen Dollar kommt eben schnell etwas zusammen. 1989 hatten nur rund 30 Prozent der Amerikaner Aktien, heute sind es über 60 Prozent. In Deutschland liegt der Anteil bei nur 15 Prozent.
Niemand muss mehr um Lohnerhöhungen bangen - er kann von der annualisierten Wachstumsrate von acht Prozent (S\&P500) profitieren, wenn er jeden Monat in Blackrock-ETFs investiert. Selber Schuld, wer nicht!
Blackrock - the dark side
Wer die letzten Jahre nicht völlig außerhalb des Schwurbelversums verbracht hat, wird mitbekommen haben, dass Blackrock Thema zahlreicher Verschwörungstheorien ist. Von Covid über die Rüstungsindustrie bis zum Wiederaufbau der Ukraine. ETFs sind tatsächlich nicht das einzige Geschäftsmodell. Hinzu kommt eine weniger transparente Vermögensverwaltung von rund sieben Billionen Dollar. Kunden sind neben Unternehmen und Familien auch ganze Staaten. Außerdem ist Blackrock Großaktionär bei tausenden von Unternehmen. Es hält große Anteile von Apple, Microsoft, Nvidia aber auch von Vonovia, Bayer und der Deutschen Bank. Und über diese Beteiligungen übt das Unternehmen Macht aus. Das bekannteste Beispiel sind ESG-Kriterien (Environmental, Social, Governance), die Larry Fink ab 2018 propagierte. Mittlerweile ist Fink davon abgerückt, im aktuellen Jahresbrief ist davon wenig zu lesen. Das eigentliche Problem sitzt tiefer, und hat mit der Rendite zu tun.
Was hat Blackrock vor?
Zehn oder 20 Prozent Wachstum sind über einen langen Zeitraum kaum realistisch zu erwirtschaften. Dafür braucht es „Megatrends“. Künstliche Intelligenz zum Beispiel verspricht Produktivitätsgewinne, die weitaus über der Norm liegen. Was aber, wenn diese ausbleiben? Lässt sich eventuell etwas nachhelfen?
Am bequemsten ist es, wenn Regierungen Steuergelder in Richtung Unternehmen verschieben. Dann sparen sich die Profiteure auch noch die Werbekosten. Was, wenn eine Regierung ein großes Investitionsprogramm auflegt, von dem dann Unternehmen profitieren, in die Blackrock frühzeitig investiert hat? Was, wenn mehrere Regierungen dies gleichzeitig tun? Nun kann man sich fragen, bei welchen Komplexen dies zuletzt der Fall war. Blackrock hält ungefähr sieben Prozent der Pfizer-Aktien und rund ein Prozent von Biontech. Etwa fünf Prozent von Rheinmetall-Aktien sind…
Weiter geht es auf BlingBling - dem wöchentlichen Newsletter über Geld, Geopolitik und Bitcoin
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ 8671a6e5:f88194d1
2025-04-24 07:23:19
@ 8671a6e5:f88194d1
2025-04-24 07:23:19For whoever has, will be given more, and they will have an abundance. Whoever does not have, even what they have will be taken from them.
Matthew 25:29, The Parable of the Talents (New Testament)For whoever has, will be given more,\ and they will have an abundance.\ Whoever does not have, even what\ they have will be taken from them.\ \ Matthew 25:29,\ The Parable of the Talents (New Testament)

How the Pump-my-bags mentality slows Bitcoin adoption
The parable of “thy Bitcoins” (loosely based on Matthew 25:29)
A man, embarking on a journey, entrusted his wealth to his servants. To one he gave five Bitcoin, to another two Bitcoin, and to another one Bitcoin, each according to his ability. Then he departed.
The servant with five Bitcoin buried his master’s wealth, dreaming of its rising price. The servant with two Bitcoin hid his, guarding its value. But the servant with one Bitcoin acted with vision. He spent 0.5 Bitcoin to unite Bitcoiners, teaching them to use the network and building tools to expand its reach. His efforts grew Bitcoin’s power, though his investment left him with only 0.5 Bitcoin.
Years later, the master returned to settle accounts. The servant with five Bitcoin said, “Master, you gave me five Bitcoin. I buried them, and their price has soared. Here is yours.”
The master replied, “Faithless servant! My wealth was meant to sow freedom. You kept your Bitcoin but buried your potential to strengthen its network. Your wealth is great, but your impact is none!”
The servant with two Bitcoin said, “Master, you gave me two Bitcoin. I hid them, and their value has risen. Here is yours.”
The master replied, “You, too, have been idle! You clung to wealth but failed to spread Bitcoin’s truth. Your Bitcoin endures, but your reach is empty!”
Then the servant with one Bitcoin stepped forward. “Master, you gave me one Bitcoin. I spent 0.5 Bitcoin to teach and build with Bitcoiners. My call inspired many to join the network, though I have only 0.5 Bitcoin left.”
The master said, “Well done, faithful servant! You sparked a movement that grew my network, enriching lives. Though your stack is small, your vision is vast. Share my joy!”
When many use their gifts to build Bitcoin’s future, their sacrifices grow the network and enrich lives. Those who “bury” their Bitcoin and do nothing else keep wealth but miss the greater reward of a thriving in a Bitcoin world.
This parable reflects a timeless truth: between playing it safe and building, resides the choice to take risk. Bitcoin’s power lies not in hoarding wealth (although it’s part of it), but mainly in using it to build a freer world. To free people from their confines. Yet a mentality has taken hold — one that runs counter to that spirit.
PMB betrays the Bitcoin ethos
“Pump my bags” (PMB) stems from the altcoin world, where scammers pump pre-mined coins to dump on naive buyers. In Bitcoin, PMB isn’t about dumping but about hoarding—stacking sats without lifting a finger. These Bitcoiners, from small holders to whales, sit back, eyeing fiat profits, not Bitcoin’s mission. They’re not so different from altcoin grifters. Both chase profit, not glory. They dream of fiat-richness and crappy real estate in Portugal or Chile — not a Bitcoin standard. One holds hard money by chance, the other a fad coin. Neither moves the world forward.
In Bitcoin, the pump-my-bags mindset is more about laziness; everyone looking out for themselves, stacking without ever lifting a finger. There’s a big difference in the way an altcoin promotor would operate and market yet another proof-of-stake pre-mined trashcoin, and how PMB bitcoiners hoard and wait.
They’re much alike however. The belief level might be slightly different, and not everyone has the same ability.
I’ve been in Bitcoin’s trenches since its cypherpunk days, when it was a rebellion against fiat’s centralized control. Bitcoin is a race against the totalitarian fiat system’s grip. Early adopters saw it as a tool to dismantle gatekeepers and empower individuals. But PMB has turned Bitcoin into a get-rich scheme, abandoning the collective effort needed to overthrow fiat’s centuries-long cycles.
Trust is a currency’s core. Hoarding Bitcoin shows trust in its future value, but it’s a shallow trust that seals it away from the world. Real trust comes from admiring Bitcoin’s math, building businesses around it, or spreading its use. PMB Bitcoiners sit on their stacks, expecting others to build trust for them. Newcomers see branding, ego, and grifters, not the low-tech prosperity Bitcoin can offer. PMB Bitcoiners live without spending a sat, happy to hodl. Fine, but they’re furniture in fiat’s ruins, not builders of Bitcoin’s future.
Hoarding hollow victories Hoarding works for those chasing fiat wealth. Bitcoin is even there for them. The lazy, the non-believers, the ones that sold very early, the ones that just started.
By 2021, 75% of Bitcoin sat dormant, driving scarcity and prices up. But it strangles transactions, weakening Bitcoin as a living economy. Reddit calls hoarding “Bitcoin’s most dangerous problem,” choking adoption for profit. Pioneers like Roger Ver built tech companies (where you could buy electronics for bitcoin), Mark Karpelès ran an exchange (Mt. Gox) and Charlie Shrem processed 30% of Bitcoin transactions in 2013. They poured stacks into adoption, people like them (even people you’ve never heard of) more than not, went broke doing the building while hoarders sat back. The irony stings: Bitcoin’s founders are often poorer than PMB hodlers who buried their talents and just sat there passively. Over the years, the critique from these sideline people became more prevalent. They show up here and there, to read the room. But that’s all they do.
The last couple of years, they even became more vocal with social media posts. Everything needs to be perfect, high-quality, not made by them, not funded by them, for free, without ads, and with no effort whatsoever, unless it’s NOT pumping their bags, then it needs to be burned down as fast as possible.
Today’s PMB Bitcoiners want the rewards without the risk. They stack sats, demand perfect content made by others for free, and cheer short-term price pumps. But when asked to build, code, or fund anything real, they disappear. At this point, such Bitcoiners have as much spine as a pack of Frankfurter sausages. This behavior has hollowed out Bitcoin’s activist core.
Activism’s disappointment
Bitcoin’s activist roots—cypherpunks coding, evangelists spreading the word—have been replaced by influencers and silent PMB conference-goers who say nothing but “I hold Bitcoin.” Centralized exchanges like Binance and Coinbase handle 70% of trades by 2025, mocking our decentralized vision. Custodial wallets proliferate as users hand over keys. The Lightning Network has 23,000+ nodes, and privacy tech like CoinJoin exists, yet adoption lags. Regulation creeps in—the U.S. Digital Asset Anti-Money Laundering Act of 2023 and Europe’s MiCa laws threaten KYC on every wallet. Our failure to advance faster gives governments leverage. Our failure would be their victory. Their cycles endlessly repeated.
Activism is a shadow of its potential. The Human Rights Foundation pushes Bitcoin for dissidents, but it’s a drop in the bucket. We could replace supply chains, build Bitcoin-only companies, or claim territories, yet we can’t even convince bars to accept
Bitcoin. We’re distracted by laser-eye memes and altcoin hopium, not building at farmer’s markets, festivals, or local scenes. PMB Bitcoiners demand perfection—free, ad-free, high-quality content—while contributing nothing.
The best way to shut them up, is asking them to do something. ”I would like to see a live counter on that page, so I can see what customers got new products” ”Why don’t YOU write code?” … and they’re gone.
”I would change a few items in your presentation man, it was good, but I would change the diagram on page 7” ”The presentation is open source and online, open for contributions. Do you want to give the presentation next time?” ”… “ and they’re gone.
”We need to have a network of these antennas to communicate with each other and send sats” ”I’ve ordered a few devices like that.. want to help out and search for new network participants?” ” … “ They’re off to some other thing, that’s more entertaining.
If you don’t understand you’re in a very unique fork in the road, a historic shift in society, much so that you’re more busy with picking the right shoes, car, phone, instead of pushing things in the right direction. And guess what? Usually these two lifestyles can even be combines. Knights in old England could fight and defend their king, while still having a decent meal and participate in festivities. These knight (compared to some bitcoiners) didn’t sit back at a fancy dinner and told the others: “yeah man, you should totally put on a harness, get a sword made and fight,… here I’ll give you a carrot for your horse.” To disappear into their castles waiting for the fight to be over a few months later. No, they put on the harness themselves, and ordered a sword to be made, because they knew their own future and that of their next of kin was at stake.
Hardly any of them show you that Bitcoin can be fairly simple and even low-tech solutions for achieving remedies for the world’s biggest problems (having individuals have real ownership for example). It can include some genuine building of prosperity and belief in one’s own talents and skills. You mostly don’t need middlemen. They buy stuff they don’t need, to feel like they’re participants.
And there’s so, enormously much work to be done.
On the other hand. Some bitcoiners can live their whole life without spending any considerable amount of bitcoin, and be perfectly happy. They mind as well could have had no bitcoin at all, but changed their mindset towards a lot of things in life. That’s cool, I know bitcoiners that don’t have any bitcoin anymore. They still “get it” though. Everyone’s life is different. These people are really cool, and they’re usually the silent builders as well. They know.
And yet, people will say they’ve “missed out”. They surely missed out on buying a lot of nice “stuff” … maybe. There are always new luxury items for sale in the burning ruins of fiat. There are always people that want to temporarily like or love you (long time) for fiat, as well as for bitcoin. You’re still an empty shell if your do. Just like the fiat slaves. A crypto bro will always stay the same sell out, even if he holds bitcoin by any chance.
You know why? Because bitcoiners don’t think like “they” do. The fiat masters that screwed this world up, think and work over multi generations. (Remember that for later, in piece twelve of this series.)
The only path forward
Solo heroics can’t beat the market or drive adoption anymore. Collective action is key. The Lightning Network grows from thousands of small nodes for example. Bitcoin Core thrives on shared grit. Profit isn’t sportcars — it’s a thriving network freeing people. If 10,000 people spend 0.05 BTC to fund wallets, educate merchants or build tools, we’d see more users and transactions. Adoption drives demand. Sacrifice now, impact later. Don’t work for PMB orders — they’re fiat victims, not Bitcoin builders.
Act together, thrive together
To kill PMB, rediscover your potential, even if it costs you:
Educate wide: Teach Bitcoin’s truth—how it works, why it matters. Every convert strengthens us.
Build together: Run nodes, fund Lightning hubs, support devs. Small contributions add up.
Use Bitcoin: Spend it, gift it, make it move. Transactions are the network’s heartbeat.
Value the mission: Chase freedom, not fiat. Your legacy is impact, not your stack.
A call to build The parable of Bitcoin is clear: hoard and get rich, but leave nothing behind; act together, sacrifice wealth, and build a thriving Bitcoin world. Hoarding risks a deflationary spiral while Wall Street grabs another 100,000 BTC every few weeks and sits on it for other fund managers to buy the stake (pun intended).
PMB Bitcoiners will cash out, thinking they’re smart, trading our future for fiat luxury. Bitcoin’s value lies in trust, scarcity, and a network grown by those who see beyond their wallets. Bury your Bitcoin or build with it.
If someone slyly nudges you to pump their bags, call them faithless leeches who ignore the call for a better world. They’re quiet, polite, and vanish when it’s time to fund or build. They tally fiat gains while you grind through life’s rot. They sling insults if you educate, risk, or create. They’re all take, no give — enemies, even if they hold Bitcoin.
Bitcoiners route around problems. Certainly if that problem is other bitcoiners. Because we know how they think, we know their buried talents, we know why they do it. It’s in our DNA to know. They don’t know why we keep building however, the worse of them don’t understand.
Bitcoin’s value isn’t in scarcity alone — it’s in the combination of trust, scarcity and the network, grown by those who see beyond their wallets and small gains.
Whether you’ve got 0.01 BTC or 10,000 BTC, your choice matters. Will you bury your Bitcoin, or build with it? I can hope we choose the latter.
If someone, directly or slyly, nudges you to pump their bags, call them out as faithless servants who wouldn’t even hear the calling of a better world. These types are often quiet, polite, and ask few questions, but when it’s time to step up, they vanish — nowhere to be found for funding, working, or doing anything real, big or small. They’re obsessed with “pump my bags,” tallying their fiat gains while you grind, sweat, and ache through life’s rotten misery. Usually they’re well off, because fiat mentality breeds more fiat.
They won’t lift you up or support you, because they’re all about the “take” and take and take more, giving nice sounding incentives to keep you pumping and grinding. They smell work, but never participate. They’re lovely and nice as long as you go along and pump.
Pump-My-Bags bitcoiners are temporary custodians, financial Frankfurter sausages hunting for a bun to flop into. We have the mustard. We know how to make it, package it and pour it over them. We’re the preservers of hard money. We build, think and try.
They get eaten. They’re fiat-born and when the real builders rise (they’re already a few years old), history won’t remember these people’s stacks and irrelevant comments — only our sacrifices.
by: AVB
-
 @ b8af284d:f82c91dd
2025-04-01 06:23:30
@ b8af284d:f82c91dd
2025-04-01 06:23:30„Die Politik ist die Kunst des Möglichen, nicht die Kunst des Idealen.“
Henry Kissinger
Liebe Abonnenten,
in der Welt der Geopolitik gibt es zwei Ideen-Pole. Auf der einen Seite des Spektrums befindet sich die „Realpolitik“. Moralische oder ethische Faktoren spielen hier eine untergeordnete Rolle. Im Vordergrund steht der pragmatische Nutzen. Als Vertreter dieser Form der Außenpolitik gilt zum Beispiel Henry Kissinger, der 1972 die Aufnahme von diplomatischen Beziehungen zum maoistischen China einfädelte, obwohl sich ideologisch beide Staaten spinnefeind waren. Das Ergebnis war ein Erdbeben der internationalen Ordnung: Die USA entzogen Taiwan den “Alleinvertretungsanspruch” und beendeten offiziell die Beziehungen zu Taipeh. Die Sowjetunion wurde geschwächt, der Vietnamkrieg konnte beendet werden. Aus der Annäherung zwischen Mao und Nixon wuchs “ChinAmerica” - eine enge Verflechtung der beiden größten Volkswirtschaften der Welt.
Am anderen Ende des Spektrums lässt eine „werteorientierte Außenpolitik” ansiedeln, wie sie zuletzt die grüne Außenministerin Annalena Baerbock vertrat oder besser versuchte. Alles, was keine lupenreine liberale Demokratie ist, gehört irgendwie eingedämmt und am besten sollte man auch keinen Handel damit treiben. Das Problem: Bigotterie. Wenn man kein Gas mehr aus Russland möchte, muss man es aus Katar kaufen. Der säkulare Machthaber Assad war böse, aber nun hofiert man dann Nachfolger und Islamist Abu Mohammed al-Dscholani. (Diese Woche hat Baerbock nach 13 Jahren wieder eine deutsche Botschaft in Damaskus eröffnet.) Am Ende nämlich gibt es doch nicht so viele Wertepartner auf der Welt:
Und mit Donald Trump hat eine Realpolitik auf Steroiden begonnen. Alles scheint plötzlich möglich, solange der Preis stimmt. Die Welt gibt es im Sonderangebot.
Diese Ausgabe ist eine geopolitische Rundschau über die aktuellen globalen Konfliktherde und ihre potenziellen Auswirkungen auf die Märkte. Wir starten in der Nachbarschaft:
Türkei
Erdogan hatte 2023 so ziemlich alles erreicht - er war mit dem Gründer der modernen Türkei, Kemal Atatürk, gleichgezogen (zumindest was Dauer und Einfluss betrifft). Die Lira stabilisierte sich, die Inflation kühlte sich etwas ab. Mit der Verhaftung des Istanbuler Bürgermeister Ekrem İmamoğlu ist damit erst einmal Schluss. Die Währung rauschte in den Keller. Die Region um Istanbul steht für knapp die Hälfte der Wirtschaftsleistung des Landes, knapp ein Drittel der Bevölkerung lebt um das Marmarameer. Dort toben derzeit die schwersten Proteste seit Gezi im Jahr 2013. Erdogan wirft seinem Widersacher vor, ein Hochschuldiplom gefälscht zu haben und deswegen gar nicht für das Amt zugelassen sei.
Als „Wertepartner“ gilt die Türkei schon seit langem nicht mehr. Türkische Truppen halten zudem den Norden Syriens besetzt. Trotzdem ist die Kritik an Erdogan derzeit relativ leise. Im Gegenteil: Der EU sei es wichtig, Ankara in der Koalition der Willigen zu halten.
Warum? Die Türkei hat die zweitgrößte Armee der NATO und kontrolliert derzeit die beiden letzten noch funktionierenden Gas-Pipelines von Russland in die EU. Ein wie auch immer gearteter Frieden in der Ukraine kann ohne Ankara nicht stattfinden. Erdogan weiß das, und nutzt die Gunst der Stunde.
In BlingBling steckt viel Arbeit. Wenn Du diese unterstützen willst, freue ich mich über ein Bezahl-Abo! Dafür gibt es Texte wie diesen in voller Länge, Zugang zum Archiv und einmal im Monat einen Investment-Report. Außerdem erhältst Du Zugang zum exklusiven “Subscriber Chat”. Du kannst das auch problemlos einen Monat für sieben Euro testen.
Ukraine
Wer sich durch die deutsche Presselandschaft bewegt, glaubt derzeit folgendes: Trump hat die Ukraine verraten und Europa im Stich gelassen. Putin bedroht das Baltikum und Polen. Europa muss also für den Krieg rüsten.
Worum es wirlich geht: Die EU ist der eigentliche Verlierer dieses Krieges, und muss nun irgendwie gesichtswahrend aus diesem Schlamassel herauskommen. Das geht am ehesten durch martialische Gesten und einem Billionen-Paket. Mehr dazu hier:
Tatsächlich laufen schon seit Wochen zwischen Washington und Moskau Gespräche im saudi-arabischen Riad. Bis zu einem Friedensschluss ist es noch ein weiter Weg, aber es geht in kleinen Schritten vorwärts: eine 30-tägige Feuerpause, Gefangenenaustausch, ein Einstellen der Kämpfe im Schwarzen Meer. Vor allem letzteres wird Auswirkungen auf die internationalen Rohstoffmärkte haben: fallende Preise von Dünger, Weizen, Kohle. Manche russischen Banken werden wieder an das internationale Zahlungssystem SWIFT angeschlossen. Teil eines dauerhaften Friedens wird ein Abkommen über die Ausbeutung der Seltenen Erden sein.
Naher Osten
Der Konflikt ist emotional wie moralisch hoch aufgeladen. So dramatisch das Leid der Zivilbevölkerung auf beiden Seiten ist - für den Rest der Welt spielt der Konflikt wirtschaftlich eine untergeordnete Rolle. Erst in seinen Ableitungen hat er größeren Einfluss. In der aktuellen Trump-Administration wird derzeit vieles neu gedacht. Dazu gehört auch eine Neuordnung des Nahen Ostens. So absurd der Gedanke von blühenden Landschaften in Gaza auch gerade erscheint - ein Ausgleich mit dem Iran und Schaffung eines gemeinsamen Wirtschaftsraums, der Israels Hightech-Ökonomie, den Energiereichtum der arabischen Halbinsel mit dem Bevölkerungsreichtum des Nahen Ostens kombiniert, ist nicht unrealistisch. Folgendes Interview mit dem Trump-Unterhändler Steve Witkoff ist dazu sehr hörenswert.
Gleichzeitig hat die neue Trump-Administration ihre Unschuld verloren, indem sie die Houthi-Rebellen bombardierte. Die vom Iran unterstützte Schiitenmiliz hat seit Monaten den Schiffverkehr am Eingang des Roten Meeres unterbunden, was insbesondere in Europa zu höheren Preisen führte. Manche Analysten warnen: Die Falken in Washington könnten sich durchsetzen und einen Krieg gegen den Iran beginnen, zu dem Israel seit Jahren drängt. Dagegen spricht: Trump braucht dringend niedrige Ölpreise, um die Inflation zu dämpfen. Dann erst kann die FED die Zinsen senken. Niedrige Zinsen sind notwendig, da die USA dieses Jahr über ein Drittel ihrer Schulden refinanzieren müssen.
Mehr dazu hier:
Arktis
Im Norden des Planeten schwelt seit Jahren ein Konflikt, der erst kürzlich durch Trumps Angebot, Grönland zu kaufen, ins Bewusstsein rückte. Es geht um Öl, Gas, Uran und seltene Erden, die vor allem auf der zu Dänemark gehörenden Insel vorkommen. JD Vance war am Freitag zu Besuch und betonte nochmals:
“We have to have it. And I think we will have it.”
Grönland dürfte Teil der Verhandlungsmasse und des “great deal” mit Russland sein: Moskau erhält in der Ukraine, was es beansprucht (die besetzten Gebiete plus Odessa), die USA erhalten dafür freie Hand in diesem Teil der Arktis. Warum aber ist der hohe Norden plötzlich so interessant geworden?
-
 @ 866e0139:6a9334e5
2025-03-31 19:38:39
@ 866e0139:6a9334e5
2025-03-31 19:38:39
Autor: Carlos A. Gebauer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Am 18. März 1924 schenkte meine Großmutter ihren Töchtern einen kleinen Bruder. Weil sein Vater fürchtete, der Junge könnte unter seinen vier Schwestern verweichlichen, schickte er den Kleinen zu Wochenendfreizeiten einer örtlichen Pfadfindergruppe. Ein Weltkriegsveteran veranstaltete dort mit den Kindern Geländespiele quer durch die schlesischen Wälder. Man lernte, Essbares zu finden, Pilze zu bestimmen, sich im Freien zu orientieren und Feuer zu machen.
Bald wurde deutlich, dass der Heranwachsende auch nicht mehr in den Blockflötenkreis seiner Schwestern und ihrer Freundinnen passte. Das Umfeld befürwortete, sein besonderes musikalisches Talent auf das Klavierspiel und das Flügelhorn zu richten. Kontakte bei der anschließenden Kirchenmusik mündeten schließlich in den elterlichen Entschluss, den nun 14-jährigen in ein Musikschulinternat zu schicken.
Es begann der Zweite Weltkrieg
Ein Jahr später, das erste Heimweh hatte sich langsam beruhigt, änderten sich die Verhältnisse schlagartig. Es begann der Zweite Weltkrieg. Mitschüler unter den jungen Musikern erfuhren, dass ihre älteren Brüder nun Soldaten werden mussten. Noch hielt sich die Gemeinschaft der jetzt 15-jährigen im Internat aber an einer Hoffnung fest: Bis sie selbst in das wehrfähige Alter kommen würden, müsste der Krieg längst beendet sein. In dieser Stimmungslage setzten sie ihre Ausbildung fort.
Es kam anders. Für den 18-jährigen erfolgte die befürchtete Einberufung in Form des „Gestellungsbefehls“. Entsprechend seiner Fähigkeiten sah man ihn zunächst für ein Musikkorps vor und schickte ihn zu einer ersten Grundausbildung nach Südfrankreich. Bei Nizza fand er sich nun plötzlich zwischen Soldaten, die Handgranaten in das Mittelmeer warfen, um Fische zu fangen. Es war das erste Mal, dass er fürchtete, infolge Explosionslärms sein Gehör zu verlieren. In den kommenden Jahren sollte er oft die Ohren zu- und den Mund offenhalten müssen, um sich wenigstens die Möglichkeit der angezielten Berufsausübung zu erhalten – wenn es überhaupt je dazu kommen würde.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Schon nach kurzer Zeit änderte sich die Befehlslage wieder. Der Musikstudent wurde nun zum Infanteristen und nach Russland an die Front verbracht. Vor ihm lagen jetzt drei Kriegsjahre: Gewalt, Dreck, Gewehrkugeln, Panzerschlachten, Granatsplitter, Luftangriffe, Entbehrungen, Hunger, Kälte, sieben Verwundungen, Blut und Schmerzen, Sterbende überall, Tote, Schreiende. Verzweiflung. Sorgen. Ängste. Todesangst. Zurückweichen? Verboten! Und die stets klare Ansage dazu: Wer nicht da vorne gegen den Feind um sein Leben kämpft, dem wird es ganz sicher da hinten von den eigenen Kameraden genommen.
Ein gewährter Fronturlaub 1944 versprach glückliche Momente. Zurück zu den Eltern, zurück zu den Schwestern, zurück nach Freiburg. Doch die Familie war nicht zu Hause, die Türen verschlossen. Eine Nachbarin öffnete ihr Fenster und rief dem Ratlosen zu: „Beeil‘ dich! Renn‘ zum Friedhof. Der Vater ist tot. Sie sind alle bei der Beerdigung!“ Wieder hieß es, qualvoll Abschied nehmen. Zurück an die Front.
Nach einem weiteren russischen Winter brach sich unübersehbar die Erkenntnis Bahn, dass der Krieg nun seinem Ende zugehe. Doch das Bemühen im Rückzug, sich mit einem versprengten Haufen irgendwie Richtung Heimat orientieren zu können, wurde doppelt jäh unterbrochen. Fanatische Vorgesetzte befahlen die längst Geschlagenen wieder gen Osten. Kurz darauf fielen sie heranrückenden russischen Truppen in die Hände.
Kriegsgefangenschaft: Tabakration gegen Brot
Drei Jahre dem Tod entgangen, schwer verletzt und erschöpft war der 21-jährige also nun ein Kriegsgefangener. Jetzt lagen drei Jahre russischer Kriegsgefangenschaft vor ihm. Ständig war unklar, wie es weiterginge. Unmöglich jedenfalls, sich noch wie ein Pfadfinder aus den Wäldern zu ernähren. Es begannen die Jahre des Schlafens auf Brettern, die Zeit der ziellosen Zugtransporte an unbekannte Orte. Niemand sprach. Nur der Sonnenstand machte klar: Es ging nie Richtung Heimat, sondern immer weiter nach Osten. Weil der Blechbläser nicht rauchte, konnte er seine Tabakration gegen Brot tauschen. So überlebte er auch die Zeit des Hungers und der Morde in den Lagern, die Horrorbilder der nachts Erschlagenen und in die Latrinen geworfenen Toten, der sinnlosen Zwangsarbeiten und der allgegenwärtigen Wanzen. Wer versuchte zu fliehen, der wurde erschossen und sein Körper zur Abschreckung in den Fangdrähten belassen. Im Sommer stanken die dort verwesenden Leichen, wenn nicht Vögel sie rechtzeitig gefressen hatten.
Als der 24-jährige schließlich sechs Jahre nach seiner Einberufung aus russischer Kriegsgefangenschaft entlassen wurde, gab es kein Zurück mehr in seine schlesische Heimat. Abgemagert reiste er der vertriebenen Mutter nach, die mit seinen Schwestern und Millionen anderen Flüchtlingen im Westen Deutschlands verteilt worden war. Kraft Ordnungsverfügung wohnte sie jetzt im sauerländischen Bad Laasphe in einem schimmligen Garagenanbau. Als ihn ein Passant auf dieser Reise morgens allein, nur mit einem Becher an der Schnur um den Hals, auf Krücken durch Berlin ziehen sah, gab er ihm schweigend sein Butterbrot.
Der kleine, sanfte Junge aus dem schlesischen Freiburg hat danach noch 60 Jahre gelebt. Es dauerte zunächst sechs Jahre, bis er wieder kräftig genug war, ein Instrument zu spielen. 30-jährig saß er dann endlich in einem Orchester und begann ein normales Berufsleben. Aber sein Körper und seine Seele waren für immer aus jeder Normalität gerissen.
Irgendwo in Russland war ihm die linke Hüfte so versteift worden, dass sich seine Beine im Liegen an Wade und Schienbein überkreuzten. Er musste also stets den Oberkörper vorbeugen, um überhaupt laufen zu können. Über die Jahrzehnte verzog sich so sein gesamter Knochenbau. Jeder Tag brachte neue orthopädische Probleme und Schmerzen. Ärzte, Masseure, Physiotherapeuten, Schmerzmittel und Spezialausrüstungen aller Art prägten die Tagesabläufe. Asymmetrisch standen seine Schuhe nebeneinander, die ein Spezialschuster ihm mit erhöhter Sohle und Seitenstabilisierung am Knöchel fertigte. Sessel oder Sofas waren ihm nicht nutzbar, da er nur auf einem Spezialstuhl mit halb abgesenkter Sitzfläche Ruhe fand. Auf fremden Stühlen konnte er nur deren Vorderkante nutzen.
"In den Nächten schrie er im Schlaf"
Und auch wenn er sich ohne Krankheitstage bis zuletzt durch seinen Berufsalltag kämpfte, so gab es doch viele Tage voller entsetzlicher Schmerzen, wenn sich seine verdrehte Wirbelsäule zur Migräne in den Kopf bohrte. Bei alledem hörte man ihn allerdings niemals über sein Schicksal klagen. Er ertrug den ganzen Wahnsinn mit einer unbeschreiblichen Duldsamkeit. Nur in den Nächten schrie er bisweilen im Schlaf. In einem seiner Alpträume fürchtete er, Menschen getötet zu haben. Aber auch das erzählte er jahrzehntelang einzig seiner Frau.
Als sich einige Jahre vor seinem Tod der orthopädische Zustand weiter verschlechterte, konsultierte er einen Operateur, um Entlastungsmöglichkeiten zu erörtern. Der legte ihn auf eine Untersuchungsliege und empfahl, Verbesserungsversuche zu unterlassen, weil sie die Lage allenfalls verschlechtern konnten. In dem Moment, als er sich von der Liege erheben sollte, wurde deutlich, dass ihm dies nicht gelang. Die gereichte Hand, um ihn hochzuziehen, ignorierte er. Stattdessen rieb er seinen Rumpf ganz alleine eine quälend lange Minute über die Fläche, bis er endlich einen Winkel fand, um sich selbst in die Senkrechte zu bugsieren. Sich nicht auf andere verlassen, war sein Überlebenskonzept. Jahre später, als sich sein Zustand noch weiter verschlechtert hatte, lächelte er über seine Behinderung: „Ich hätte schon vor 60 Jahren tot auf einem Acker in Russland liegen können.“ Alles gehe irgendwann vorbei, tröstete er sich. Das war das andere Überlebenskonzept: liebevoll, friedfertig und sanft anderen gegenüber, unerbittlich mit sich selbst.
Sechs Monate vor seinem Tod saß er morgens regungslos auf seinem Spezialstuhl. Eine Altenpflegerin fand ihn und schlug Alarm. Mit allen Kunstgriffen der medizinischen Technik wurde er noch einmal in das Leben zurückkatapultiert. Aber seine Kräfte waren erschöpft. Es schob sich das Grauen der Vergangenheit zwischen ihn und die Welt. Bettlägerig kreiste er um sich selbst, erkannte niemanden und starrte mit weit offenen Augen an die Decke. „Die Russen schmeißen wieder Brandbomben!“, war einer seiner letzten Sätze.
Der kleine Junge aus Schlesien ist nicht zu weich geraten. Er hat sein Leid mit unbeugsamer Duldsamkeit ertragen. Er trug es wohl als Strafe für das Leid, das er anderen anzutun genötigt worden war. An seinem Geburtstag blühen immer die Magnolien. In diesem Jahr zum hundertsten Mal.
Dieser Text wurde am 23.3.2024 erstveröffentlicht auf „eigentümlich frei“.
Carlos A. Gebauer studierte Philosophie, Neuere Geschichte, Sprach-, Rechts- und Musikwissenschaften in Düsseldorf, Bayreuth und Bonn. Sein juristisches Referendariat absolvierte er in Düsseldorf, u.a. mit Wahlstationen bei der Landesrundfunkanstalt NRW, bei der Spezialkammer für Kassenarztrecht des Sozialgerichtes Düsseldorf und bei dem Gnadenbeauftragten der Staatsanwaltschaft Düsseldorf.
Er war unter anderem als Rechtsanwalt und Notarvertreter bis er im November 2003 vom nordrhein-westfälischen Justizministerium zum Richter am Anwaltsgericht für den Bezirk der Rechtsanwaltskammer Düsseldorf ernannt wurde. Seit April 2012 arbeitet er in der Düsseldorfer Rechtsanwaltskanzlei Lindenau, Prior & Partner. Im Juni 2015 wählte ihn die Friedrich-August-von-Hayek-Gesellschaft zu ihrem Stellvertretenden Vorsitzenden. Seit Dezember 2015 ist er Richter im Zweiten Senat des Anwaltsgerichtshofes NRW.
1995 hatte er parallel zu seiner anwaltlichen Tätigkeit mit dem Verfassen gesellschaftspolitischer und juristischer Texte begonnen. Diese erschienen seither unter anderem in der Neuen Juristischen Wochenschrift (NJW), der Zeitschrift für Rechtspolitik (ZRP) in der Frankfurter Allgemeinen Zeitung, der Freien Presse Chemnitz, dem „Schweizer Monat“ oder dem Magazin für politische Kultur CICERO. Seit dem Jahr 2005 ist Gebauer ständiger Kolumnist und Autor des Magazins „eigentümlich frei“.
Gebauer glaubt als puristischer Liberaler unverbrüchlich an die sittliche Verpflichtung eines jeden einzelnen, sein Leben für sich selbst und für seine Mitmenschen verantwortlich zu gestalten; jede Fremdbestimmung durch Gesetze, staatliche Verwaltung, politischen Einfluss oder sonstige Gewalteinwirkung hat sich demnach auf ein ethisch vertretbares Minimum zu beschränken. Die Vorstellung eines europäischen Bundesstaates mit zentral detailsteuernder, supranationaler Staatsgewalt hält er für absurd und verfassungswidrig.
\ Aktuelle Bücher:
Hayeks Warnung vor der Knechtschaft (2024) – hier im Handel
Das Prinzip Verantwortungslosigkeit (2023) – hier im Handel
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ d34e832d:383f78d0
2025-04-24 07:22:54
@ d34e832d:383f78d0
2025-04-24 07:22:54Operation
This operational framework delineates a methodologically sound, open-source paradigm for the self-custody of Bitcoin, prominently utilizing Electrum, in conjunction with VeraCrypt-encrypted USB drives designed to effectively emulate the functionality of a cold storage hardware wallet.
The primary aim of this initiative is to empower individual users by providing a mechanism that is economically viable, resistant to coercive pressures, and entirely verifiable. This is achieved by harnessing the capabilities inherent in open-source software and adhering to stringent cryptographic protocols, thereby ensuring an uncompromising stance on Bitcoin sovereignty.
The proposed methodology signifies a substantial advancement over commercially available hardware wallets, as it facilitates the creation of a do-it-yourself air-gapped environment that not only bolsters resilience and privacy but also affirms the principles of decentralization intrinsic to the cryptocurrency ecosystem.
1. The Need For Trustless, Private, and Secure Storage
With Bitcoin adoption increasing globally, the need for trustless, private, and secure storage is critical. While hardware wallets like Trezor and Ledger offer some protection, they introduce proprietary code, closed ecosystems, and third-party risk. This Idea explores an alternative: using Electrum Wallet within an encrypted VeraCrypt volume on a USB flash drive, air-gapped via Tails OS or offline Linux systems.
2. Architecture of the DIY Hardware Wallet
2.1 Core Components
- Electrum Wallet (SegWit, offline mode)
- USB flash drive (≥ 8 GB)
- VeraCrypt encryption software
- Optional: Tails OS bootable environment
2.2 Drive Setup
- Format the USB drive and install VeraCrypt volumes.
- Choose AES + SHA-512 encryption for robust protection.
- Use FAT32 for wallet compatibility with Electrum (under 4GB).
- Enable Hidden Volume for plausible deniability under coercion.
3. Creating the Encrypted Environment
3.1 Initial Setup
- Download VeraCrypt from the official site; verify GPG signatures.
- Encrypt the flash drive and store a plain Electrum AppImage inside.
- Add a hidden encrypted volume with the wallet seed, encrypted QR backups, and optionally, a decoy wallet.
3.2 Mounting Workflow
- Always mount the VeraCrypt volume on an air-gapped computer, ideally booted into Tails OS.
- Never connect the encrypted USB to an internet-enabled system.
4. Air-Gapped Wallet Operations
4.1 Wallet Creation (Offline)
- Generate a new Electrum SegWit wallet inside the mounted VeraCrypt volume.
- Record the seed phrase on paper, or store it in a second hidden volume.
- Export xpub (public key) for use with online watch-only wallets.
4.2 Receiving Bitcoin
- Use watch-only Electrum wallet with the exported xpub on an online system.
- Generate receiving addresses without exposing private keys.
4.3 Sending Bitcoin
- Create unsigned transactions (PSBT) in the watch-only wallet.
- Transfer them via QR code or USB sneakernet to the air-gapped wallet.
- Sign offline using Electrum, then return the signed transaction to the online device for broadcast.
5. OpSec Best Practices
5.1 Physical and Logical Separation
- Use a dedicated machine or a clean Tails OS session every time.
- Keep the USB drive hidden and disconnected unless in use.
- Always dismount the VeraCrypt volume after operations.
5.2 Seed Phrase Security
- Never type the seed on an online machine.
- Consider splitting the seed using Shamir's Secret Sharing or metal backup plates.
5.3 Coercion Resilience
- Use VeraCrypt’s hidden volume feature to store real wallet data.
- Maintain a decoy wallet in the outer volume with nominal funds.
- Practice your recovery and access process until second nature.
6. Tradeoffs vs. Commercial Wallets
| Feature | DIY Electrum + VeraCrypt | Ledger/Trezor | |--------|--------------------------|---------------| | Open Source | ✅ Fully | ⚠️ Partially | | Air-gapped Usage | ✅ Yes | ⚠️ Limited | | Cost | 💸 Free (except USB) | 💰 $50–$250 | | Hidden/Coercion Defense | ✅ Hidden Volume | ❌ None | | QR Signing Support | ⚠️ Manual | ✅ Some models | | Complexity | 🧠 High | 🟢 Low | | Long-Term Resilience | ✅ No vendor risk | ⚠️ Vendor-dependent |
7. Consider
A DIY hardware wallet built with Electrum and VeraCrypt offers an unprecedented level of user-controlled sovereignty in Bitcoin storage. While the technical learning curve may deter casual users, those who value security, privacy, and independence will find this setup highly rewarding. This Operation demonstrates that true Bitcoin ownership requires not only control of private keys, but also a commitment to operational security and digital self-discipline. In a world of growing surveillance and digital coercion, such methods may not be optional—they may be essential.
8. References
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Electrum Technologies GmbH. “Electrum Documentation.” electrum.org, 2024.
- VeraCrypt. “Documentation.” veracrypt.fr, 2025.
- Tails Project. “The Amnesic Incognito Live System (Tails).” tails.boum.org, 2025.
- Matonis, Jon. "DIY Cold Storage for Bitcoin." Forbes, 2014.
In Addition
🛡️ Create Your Own Secure Bitcoin Hardware Wallet: Electrum + VeraCrypt DIY Guide
Want maximum security for your Bitcoin without trusting third-party devices like Ledger or Trezor?
This guide shows you how to build your own "hardware wallet" using free open-source tools:
✅ Electrum Wallet + ✅ VeraCrypt Encrypted Flash Drive — No extra cost, no vendor risk.Let Go Further
What You’ll Need
- A USB flash drive (8GB minimum, 64-bit recommended)
- A clean computer (preferably old or dedicated offline)
- Internet connection (for setup only, then go air-gapped)
- VeraCrypt software (free, open-source)
- Electrum Bitcoin Wallet AppImage file
Step 1: Download and Verify VeraCrypt
- Go to VeraCrypt Official Website.
- Download the installer for your operating system.
- Verify the GPG signatures to ensure the download isn't tampered with.
👉 [Insert Screenshot Here: VeraCrypt download page]
Pro Tip: Never skip verification when dealing with encryption software!
Step 2: Download Electrum Wallet
- Go to Electrum Official Website.
- Download the Linux AppImage or Windows standalone executable.
- Again, verify the PGP signatures published on the site. 👉 [Insert Screenshot Here: Electrum download page]
Step 3: Prepare and Encrypt Your USB Drive
- Insert your USB drive into the computer.
- Open VeraCrypt and select Create Volume → Encrypt a Non-System Partition/Drive.
- Choose Standard Volume for now (later we'll talk about hidden volumes).
- Select your USB drive, set an extremely strong password (12+ random characters).
- For Encryption Algorithm, select AES and SHA-512 for Hash Algorithm.
- Choose FAT32 as the file system (compatible with Bitcoin wallet sizes under 4GB).
- Format and encrypt. 👉 [Insert Screenshot Here: VeraCrypt creating volume]
Important: This will wipe all existing data on the USB drive!
Step 4: Mount the Encrypted Drive
Whenever you want to use the wallet:
- Open VeraCrypt.
- Select a slot (e.g., Slot 1).
- Click Select Device, choose your USB.
- Enter your strong password and Mount. 👉 [Insert Screenshot Here: VeraCrypt mounted volume]
Step 5: Set Up Electrum in Offline Mode
- Mount your encrypted USB.
- Copy the Electrum AppImage (or EXE) onto the USB inside the encrypted partition.
- Run Electrum from there.
- Select Create New Wallet.
- Choose Standard Wallet → Create New Seed → SegWit.
- Write down your 12-word seed phrase on PAPER.
❌ Never type it into anything else. - Finish wallet creation and disconnect from internet immediately. 👉 [Insert Screenshot Here: Electrum setup screen]
Step 6: Make It Air-Gapped Forever
- Only ever access the encrypted USB on an offline machine.
- Never connect this device to the internet again.
- If possible, boot into Tails OS every time for maximum security.
Pro Tip: Tails OS leaves no trace on the host computer once shut down!
Step 7: (Optional) Set Up a Hidden Volume
For even stronger security:
- Repeat the VeraCrypt process to add a Hidden Volume inside your existing USB encryption.
- Store your real Electrum wallet in the hidden volume.
- Keep a decoy wallet with small amounts of Bitcoin in the outer volume.
👉 This way, if you're ever forced to reveal the password, you can give access to the decoy without exposing your true savings.
Step 8: Receiving Bitcoin
- Export your xpub (extended public key) from the air-gapped Electrum wallet.
- Import it into a watch-only Electrum wallet on your online computer.
- Generate receiving addresses without exposing your private keys.
Step 9: Spending Bitcoin (Safely)
To send Bitcoin later:
- Create a Partially Signed Bitcoin Transaction (PSBT) with the online watch-only wallet.
- Transfer the file (or QR code) offline (via USB or QR scanner).
- Sign the transaction offline with Electrum.
- Bring the signed file/QR back to the online device and broadcast it.
✅ Your private keys never touch the internet!
Step 10: Stay Vigilant
- Always dismount the encrypted drive after use.
- Store your seed phrase securely (preferably in a metal backup).
- Regularly practice recovery drills.
- Update Electrum and VeraCrypt only after verifying new downloads.
🎯 Consider
Building your own DIY Bitcoin hardware wallet might seem complex, but security is never accidental — it is intentional.
By using VeraCrypt encryption and Electrum offline, you control your Bitcoin in a sovereign, verifiable, and bulletproof way.⚡ Take full custody. No companies. No middlemen. Only freedom.
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ bcbb3e40:a494e501
2025-03-31 15:44:56
@ bcbb3e40:a494e501
2025-03-31 15:44:56El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
Artículo original: Claudio Mutti, Los «hijos de la luz» en la Casa Blanca (TOR), 25/Mar/2025
-
 @ d34e832d:383f78d0
2025-04-24 06:28:48
@ d34e832d:383f78d0
2025-04-24 06:28:48Operation
Central to this implementation is the utilization of Tails OS, a Debian-based live operating system designed for privacy and anonymity, alongside the Electrum Wallet, a lightweight Bitcoin wallet that provides a streamlined interface for secure Bitcoin transactions.
Additionally, the inclusion of advanced cryptographic verification mechanisms, such as QuickHash, serves to bolster integrity checks throughout the storage process. This multifaceted approach ensures a rigorous adherence to end-to-end operational security (OpSec) principles while simultaneously safeguarding user autonomy in the custody of digital assets.
Furthermore, the proposed methodology aligns seamlessly with contemporary cybersecurity paradigms, prioritizing characteristics such as deterministic builds—where software builds are derived from specific source code to eliminate variability—offline key generation processes designed to mitigate exposure to online threats, and the implementation of minimal attack surfaces aimed at reducing potential vectors for exploitation.
Ultimately, this sophisticated approach presents a methodical and secure paradigm for the custody of private keys, thereby catering to the exigencies of high-assurance Bitcoin storage requirements.
1. Cold Storage Refers To The offline Storage
Cold storage refers to the offline storage of private keys used to sign Bitcoin transactions, providing the highest level of protection against network-based threats. This paper outlines a verifiable method for constructing such a storage system using the following core principles:
- Air-gapped key generation
- Open-source software
- Deterministic cryptographic tools
- Manual integrity verification
- Offline transaction signing
The method prioritizes cryptographic security, software verifiability, and minimal hardware dependency.
2. Hardware and Software Requirements
2.1 Hardware
- One 64-bit computer (laptop/desktop)
- 1 x USB Flash Drive (≥8 GB, high-quality brand recommended)
- Paper and pen (for seed phrase)
- Optional: Printer (for xpub QR export)
2.2 Software Stack
- Tails OS (latest ISO, from tails.boum.org)
- Balena Etcher (to flash ISO)
- QuickHash GUI (for SHA-256 checksum validation)
- Electrum Wallet (bundled within Tails OS)
3. System Preparation and Software Verification
3.1 Image Verification
Prior to flashing the ISO, the integrity of the Tails OS image must be cryptographically validated. Using QuickHash:
plaintext SHA256 (tails-amd64-<version>.iso) = <expected_hash>Compare the hash output with the official hash provided on the Tails OS website. This mitigates the risk of ISO tampering or supply chain compromise.
3.2 Flashing the OS
Balena Etcher is used to flash the ISO to a USB drive:
- Insert USB drive.
- Launch Balena Etcher.
- Select the verified Tails ISO.
- Flash to USB and safely eject.
4. Cold Wallet Generation Procedure
4.1 Boot Into Tails OS
- Restart the system and boot into BIOS/UEFI boot menu.
- Select the USB drive containing Tails OS.
- Configure network settings to disable all connectivity.
4.2 Create Wallet in Electrum (Cold)
- Open Electrum from the Tails application launcher.
- Select "Standard Wallet" → "Create a new seed".
- Choose SegWit for address type (for lower fees and modern compatibility).
- Write down the 12-word seed phrase on paper. Never store digitally.
- Confirm the seed.
- Set a strong password for wallet access.
5. Exporting the Master Public Key (xpub)
- Open Electrum > Wallet > Information
- Export the Master Public Key (MPK) for receiving-only use.
- Optionally generate QR code for cold-to-hot usage (wallet watching).
This allows real-time monitoring of incoming Bitcoin transactions without ever exposing private keys.
6. Transaction Workflow
6.1 Receiving Bitcoin (Cold to Hot)
- Use the exported xpub in a watch-only wallet (desktop or mobile).
- Generate addresses as needed.
- Senders deposit Bitcoin to those addresses.
6.2 Spending Bitcoin (Hot Redeem Mode)
Important: This process temporarily compromises air-gap security.
- Boot into Tails (or use Electrum in a clean Linux environment).
- Import the 12-word seed phrase.
- Create transaction offline.
- Export signed transaction via QR code or USB.
- Broadcast using an online device.
6.3 Recommended Alternative: PSBT
To avoid full wallet import: - Use Partially Signed Bitcoin Transactions (PSBT) protocol to sign offline. - Broadcast PSBT using Sparrow Wallet or Electrum online.
7. Security Considerations
| Threat | Mitigation | |-------|------------| | OS Compromise | Use Tails (ephemeral environment, RAM-only) | | Supply Chain Attack | Manual SHA256 verification | | Key Leakage | No network access during key generation | | Phishing/Clone Wallets | Verify Electrum’s signature (when updating) | | Physical Theft | Store paper seed in tamper-evident location |
8. Backup Strategy
- Store 12-word seed phrase in multiple secure physical locations.
- Do not photograph or digitize.
- For added entropy, use Shamir Secret Sharing (e.g., 2-of-3 backups).
9. Consider
Through the meticulous integration of verifiable software solutions, the execution of air-gapped key generation methodologies, and adherence to stringent operational protocols, users have the capacity to establish a Bitcoin cold storage wallet that embodies an elevated degree of cryptographic assurance.
This DIY system presents a zero-dependency alternative to conventional third-party custody solutions and consumer-grade hardware wallets.
Consequently, it empowers individuals with the ability to manage their Bitcoin assets while ensuring full trust minimization and maximizing their sovereign control over private keys and transaction integrity within the decentralized financial ecosystem..
10. References And Citations
Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
“Tails - The Amnesic Incognito Live System.” tails.boum.org, The Tor Project.
“Electrum Bitcoin Wallet.” electrum.org, 2025.
“QuickHash GUI.” quickhash-gui.org, 2025.
“Balena Etcher.” balena.io, 2025.
Bitcoin Core Developers. “Don’t Trust, Verify.” bitcoincore.org, 2025.In Addition
🪙 SegWit vs. Legacy Bitcoin Wallets
⚖️ TL;DR Decision Chart
| If you... | Use SegWit | Use Legacy | |-----------|----------------|----------------| | Want lower fees | ✅ Yes | 🚫 No | | Send to/from old services | ⚠️ Maybe | ✅ Yes | | Care about long-term scaling | ✅ Yes | 🚫 No | | Need max compatibility | ⚠️ Mixed | ✅ Yes | | Run a modern wallet | ✅ Yes | 🚫 Legacy support fading | | Use cold storage often | ✅ Yes | ⚠️ Depends on wallet support | | Use Lightning Network | ✅ Required | 🚫 Not supported |
🔍 1. What Are We Comparing?
There are two major types of Bitcoin wallet address formats:
🏛️ Legacy (P2PKH)
- Format starts with:
1 - Example:
1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa - Oldest, most universally compatible
- Higher fees, larger transactions
- May lack support in newer tools and layer-2 solutions
🛰️ SegWit (P2WPKH)
- Formats start with:
- Nested SegWit (P2SH):
3... - Native SegWit (bech32):
bc1q... - Introduced via Bitcoin Improvement Proposal (BIP) 141
- Smaller transaction sizes → lower fees
- Native support by most modern wallets
💸 2. Transaction Fees
SegWit = Cheaper.
- SegWit reduces the size of Bitcoin transactions in a block.
- This means you pay less per transaction.
- Example: A SegWit transaction might cost 40%–60% less in fees than a legacy one.💡 Why?
Bitcoin charges fees per byte, not per amount.
SegWit removes certain data from the base transaction structure, which shrinks byte size.
🧰 3. Wallet & Service Compatibility
| Category | Legacy | SegWit (Nested / Native) | |----------|--------|---------------------------| | Old Exchanges | ✅ Full support | ⚠️ Partial | | Modern Exchanges | ✅ Yes | ✅ Yes | | Hardware Wallets (Trezor, Ledger) | ✅ Yes | ✅ Yes | | Mobile Wallets (Phoenix, BlueWallet) | ⚠️ Rare | ✅ Yes | | Lightning Support | 🚫 No | ✅ Native SegWit required |
🧠 Recommendation:
If you interact with older platforms or do cross-compatibility testing, you may want to: - Use nested SegWit (address starts with
3), which is backward compatible. - Avoid bech32-only wallets if your exchange doesn't support them (though rare in 2025).
🛡️ 4. Security and Reliability
Both formats are secure in terms of cryptographic strength.
However: - SegWit fixes a bug known as transaction malleability, which helps build protocols on top of Bitcoin (like the Lightning Network). - SegWit transactions are more standardized going forward.
💬 User takeaway:
For basic sending and receiving, both are equally secure. But for future-proofing, SegWit is the better bet.
🌐 5. Future-Proofing
Legacy wallets are gradually being phased out:
- Developers are focusing on SegWit and Taproot compatibility.
- Wallet providers are defaulting to SegWit addresses.
- Fee structures increasingly assume users have upgraded.
🚨 If you're using a Legacy wallet today, you're still safe. But: - Some services may stop supporting withdrawals to legacy addresses. - Your future upgrade path may be more complex.
🚀 6. Real-World Scenarios
🧊 Cold Storage User
- Use SegWit for low-fee UTXOs and efficient backup formats.
- Consider Native SegWit (
bc1q) if supported by your hardware wallet.
👛 Mobile Daily User
- Use Native SegWit for cheaper everyday payments.
- Ideal if using Lightning apps — it's often mandatory.
🔄 Exchange Trader
- Check your exchange’s address type support.
- Consider nested SegWit (
3...) if bridging old + new systems.
📜 7. Migration Tips
If you're moving from Legacy to SegWit:
- Create a new SegWit wallet in your software/hardware wallet.
- Send funds from your old Legacy wallet to the SegWit address.
- Back up the new seed — never reuse the old one.
- Watch out for fee rates and change address handling.
✅ Final User Recommendations
| Use Case | Address Type | |----------|--------------| | Long-term HODL | SegWit (
bc1q) | | Maximum compatibility | SegWit (nested3...) | | Fee-sensitive use | Native SegWit (bc1q) | | Lightning | Native SegWit (bc1q) | | Legacy systems only | Legacy (1...) – short-term only |
📚 Further Reading
- Nakamoto, Satoshi. Bitcoin: A Peer-to-Peer Electronic Cash System. 2008.
- Bitcoin Core Developers. “Segregated Witness (Consensus Layer Change).” github.com/bitcoin, 2017.
- “Electrum Documentation: Wallet Types.” docs.electrum.org, 2024.
- “Bitcoin Wallet Compatibility.” bitcoin.org, 2025.
- Ledger Support. “SegWit vs Legacy Addresses.” ledger.com, 2024.
-
 @ fe02e8ec:f07fbe0b
2025-03-31 14:43:22
@ fe02e8ec:f07fbe0b
2025-03-31 14:43:22\ Und genau dafür wirst auch du gedrillt werden: Menschen zu jagen und töten. Unbekannte, die auch nicht wissen, was sie hier tun. Oder Unschuldige, die nicht rechtzeitig fliehen konnten. Einfach töten. Alle. Ohne zu fragen. Denn das ist deine Aufgabe, Soldat: Töte Menschen!
Egal, was du vorher warst, Heizungsmonteur, KFZ-Mechaniker, Veganer, Marketing-Manager, Friseur, Verkäufer, Kindergärtner: Es ist egal. Jetzt musst du töten. Denn du hast mitgemacht. Entweder, weil du es nicht ernst genommen hast, weil du dich nie für Politik interessiert hast. Oder weil du gedacht hast, das alles betrifft dich nicht. Weil du gedacht hast, Wahlen könnten etwas verändern. Oder weil du immer das Maul gehalten hast, damit dich keiner als «Rechter» bezeichnet. Egal. Jetzt musst du töten. Das ist das Spiel.
Ja, es ist ein Spiel. Grausam, abartig, menschenverachtend. Dennoch hat es Regeln: Diejenigen, die das Spiel beginnen, müssen niemals selbst auf das Schlachtfeld. Das ist die erste Regel. Ihre Söhne auch nicht, nicht die Söhne der anderen Politiker, nicht die der EU-Abgeordneten, nicht die der Parteibonzen. Auch nicht die der Banker, der Vorstandsvorsitzenden, der Chefredakteure. Denn alle wissen, wie man das Spiel spielt. Nur du nicht.
Du bist einfach eine Figur auf dem Spielfeld, die es verpasst hat, NEIN zu sagen, als noch Gelegenheit war. Jetzt bist du verwandelt worden in eine menschliche Drohne. Wenn sie sagen: töte!, dann tötest du. Denken kannst du, wenn alles vorbei ist. Falls du je wieder nach Hause kommst. Vielleicht sogar mit beiden Beinen und beiden Armen. Vielleicht auch nicht. Egal. Wer hätte Mitleid mit einer Spielfigur?
Nein, du musst töten. Das ist deine Aufgabe. Sie sagen es nun schon seit Monaten, warum glaubst du es nicht? Sie meinen es ernst. Wenn du den Brief in Händen hältst ist es zu spät. Es gilt dann das Notstandsrecht und keiner kann mehr verweigern. Da hättest du dich vorher drum kümmern müssen. Oder auf eine Demo gehen. Oder laut und mit klarer Stimme in jedem Gespräch den Wahnsinn anprangern. Hast du aber nicht.
Jetzt musst du töten oder du wirst getötet. Das ist das Spiel. Du hättest selbst denken können. Hast du aber nicht. Hast deine Zeit mit sinnlosen Videos vertan, Netflix geguckt und hast Influencerinnen geliked. Die müssen nicht an die Front. Aber du. Morgen, wenn du aufstehst, die Uniform anziehst und rausgehst, dann wirst du Befehle ausführen oder erschossen werden. Also wirst du Menschen töten. Dein Leben wird nie wieder so sein, wie zuvor. Dein Schmerz, deine Schuld, dein Leid: sie gehen ein in die unendliche Reihe der Soldaten, die seit Jahrhunderten dasselbe Schicksal erlitten. Deren Schreie noch immer durch den ewigen Raum hallen. Deren Opfer von den Herren des Spiels mit einem Lächeln entgegengenommen wurde. Deren Gliedmaßen auf den Schlachtfeldern liegen geblieben waren. Zum Dank erhielten sie eine Medaille. Ein Stück Blech für den rechten Arm, einen Grabstein für den Vater, den Bruder, den Sohn. Für das Vaterland. Für Europa. Für die Demokratie. Der Hohn tropft aus jedem Politikerwort, doch die Menschen glauben noch immer die uralte Geschichte von Freund und Feind, von Gut und Böse.

\ Wer nicht aufwachen will muss töten. Du. Nicht am Bildschirm. In der echten Welt. Wo man nicht auf Replay drücken kann. Wo man den Gegner nicht nach links oder rechts swipen kann, denn er ist echt, real, lebendig. Noch. Entweder er oder du. Jetzt ist es zu spät für Entscheidungen. Kannst du es spüren? Die Work-Life Balance wird zur Kill-or-be-Killed balance. Es gibt kein Entrinnen. Denn du hast mitgemacht. Schweigen ist Zustimmung. Sich-nicht-drumkümmern ist Zustimmung. Kriegsparteien zu wählen ist noch mehr Zustimmung.
Heute.
Heute lässt sich noch etwas ändern.
Es hat nichts zu tun mit rechts oder links. Nur mit Menschlichkeit versus Hass, Macht und dem ganz großen Geld. Das sind die Gründe, für die du töten oder sterben musst.
Wie entscheidest du dich?
-
 @ b2caa9b3:9eab0fb5
2025-04-24 06:25:35
@ b2caa9b3:9eab0fb5
2025-04-24 06:25:35Yesterday, I faced one of the most heartbreaking and frustrating experiences of my life. Between 10:00 AM and 2:00 PM, I was held at the Taveta border, denied entry into Kenya—despite having all the necessary documents, including a valid visitor’s permit and an official invitation letter.
The Kenyan Immigration officers refused to speak with me. When I asked for clarification, I was told flatly that I would never be allowed to enter Kenya unless I obtain a work permit. No other reason was given. My attempts to explain that I simply wanted to see my child were ignored. No empathy. No flexibility. No conversation. Just rejection.
While I stood there for hours, held by officials with no explanation beyond a bureaucratic wall, I recorded the experience. I now have several hours of footage documenting what happened—a silent testimony to how a system can dehumanize and block basic rights.
And the situation doesn’t end at the border.
My child, born in Kenya, is also being denied the right to see me. Germany refuses to grant her citizenship, which means she cannot visit me either. The German embassy in Nairobi refuses to assist, stating they won’t get involved. Their silence is loud.
This is not just about paperwork. This is about a child growing up without her father. It’s about a system that chooses walls over bridges, and bureaucracy over humanity. Kenya, by refusing me entry, is keeping a father away from his child. Germany, by refusing to act under §13 StGB, is complicit in that injustice.
In the coming days, I’ll share more about my past travels and how this situation unfolded. I’ll also be releasing videos and updates on TikTok—because this story needs to be heard. Not just for me, but for every parent and child caught between borders and bureaucracies.
Stay tuned—and thank you for standing with me.
-
 @ 0b65f96a:7fda4c8f
2025-03-29 10:39:17
@ 0b65f96a:7fda4c8f
2025-03-29 10:39:17Es gibt Bibliotheken voll Literatur zur „Kunst“ der Kriegsführung. Dies hier ist ein Beitrag zu den Bibliotheken der Kunst Frieden zu führen. Denn Frieden ist nicht die Abwesenheit von Krieg. Sondern eine mindestens ebenso intensive Aktivität. Worin genau besteht sie aber? Ich glaube darin, weder nach der einen noch nach der anderen Seite vom Hochseil zu fallen. Denn vom Hochseil kann man immer nach zwei Seiten fallen. Das ist dann auch schon die Kernherausforderung: Gleichgewichthalten!
Es scheint zunächst ein ganz äußerlicher Auftrag. Es gibt immer und wird immer widerstreitende Interessen geben. Allerdings ist das nur die äußerste Zwiebelschale. Denn wenn wir die Sache etwas mit Abstand von uns selbst betrachten, werden wir in uns hinein verwiesen: Frieden kann nur von innen nach außen gestiftet werden. Wenn wir das Hochseil in uns suchen, was finden wir dann? – Zweifels ohne, wissen wir von uns, dass wir nicht jeden Tag unser bestes Selbst sind. Würde es sich nicht lohnen etwas genauer über die Möglichkeit nach zwei Seiten vom Hochseil zu fallen nachzudenken, zugunsten der eigenen Balancierfähigkeit?
Wir sind daran gewöhnt zu denken dem Guten steht das Böse gegenüber. Daraus ziehen ja alle Western und Martial Arts Streifen ihren Plot: Der Gute bringt den Bösen um die Ecke und damit hat wieder mal das Gute gesiegt. Wir bewerten das „um die Ecke bringen“ unterschiedlich, je nach dem, von wem es kommt.
Ich möchte einen neuen Gedanken vorschlagen über unser Inneres, über Gut und Böse nachzudenken. Denn, wie gesagt, vom Hochseil kann man nach zwei Seiten fallen. Und es hat immer drastische Wirkung. Wo kommen wir also hin, wenn wir sagen: Frieden ist immer ein Gleichgewichtszustand, ergo eine Zeit der Mitte?
Sagen wir Toleranz ist ein erstrebenswertes Ideal. Dann würden wir sicher sagen Engstirnigkeit ist das Gegenteil davon und alles andere als Wünschenswert. Ja, so ist es gewiss. Und es bleibt hinzuzufügen, auch Beliebigkeit ist das Gegenteil von Toleranz. Denn es gibt eine Grenze, wo Toleranz nicht mehr Toleranz ist, sondern Beliebigkeit, ein „alles ist möglich“. Ähnlich können wir es für Großzügigkeit denken: Großzügigkeit ist ein erstrebenswertes Ideal. Ihr Gegenteil ist Geiz. Ihr anderes Gegenteil die Verschwendung. Oder Mut. Mut ist ein erstrebenswertes Ideal. Feigheit sein Gegenteil. Sein anderes Gegenteil ist Leichtsinn. Mit andern Worten: Das Ideal wird immer zum Hochseil. Und wir können immer nach zwei Seiten von ihm fallen. Wenn wir diesem Gedanken folgen, kommen wir weg von der Gut-Böse-Dualität. Und stattdessen zur Frage nach dem Gleichgewicht. Zur Frage nach der Mittezeit.
Natürlich steht es uns frei all das zu denken. Oder auch nicht zu denken. Denn selbstverständlich ist es möglich es nicht zu denken und bei einer Dualitätsvorstellung festhängen zu bleiben. Es wird uns nur nicht helfen Frieden zu denken und in Frieden zu handeln. Wenn wir wollen können wir durch das Aufspannen einer Trinität einen neuen Raum eröffnen und betreten. In ihm wird Frieden aktiv führbar, denn er wird eine Gleichgewichtssituation in uns selbst! – Nicht eine, sich einander gegenüberstehender äußerer Mächte!
Gehen wir noch einen Schritt weiter in unserer Betrachtung, können wir feststellen, dass es durchaus einen Unterschied macht nach welcher Seite wir runter fallen. Denn auf der einen Seite ist es immer eine Verengung: Engstirnigkeit, Geiz, Feigheit in unseren Beispielen. Auf der anderen ist es immer eine Zersplitterung oder Versprühung. In unseren Beispielen Beliebigkeit, Verschwendung und Leichtsinn. Und das erstrebenswerte ist eben immer die Mitte, das von uns ständig aktualisierte Gleichgewicht.
Das interessante ist, wo diese Mitte liegt, lässt sich niemals statisch festlegen. Sie ist immer dynamisch. Denn sie kann zu unterschiedlichen Momenten an unterschiedlicher Stelle liegen. Es ist immer ein Ich, das sich in Geistesgegenwart neu ausbalanciert. Und darum ist Frieden so schwer. Wir werden ihn niemals „haben“, sondern ihm immer entgegen gehen.
Der Kriegsruf ist nichts anderes, als ein Versuch von denen, die vom Hochseil gefallen sind, uns auch herunter zu kicken.
Netter Versuch. Wird aber nichts!
In der Nussschale: Die Dualität auflösen in die Trinität der balancierenden Mitte zwischen der Geste der Versteinerung und der Geste des Zerstäubens oder Zersplitterns. Die dynamische Qualität der Mitte bemerken. Oder, tun wir es nicht, ist das gleich der erste Anstoß, der uns wieder zum Wackeln bringt. Und des Ich´s gewahr werden, das balanciert. Frieden führen ist eine Kunst.
Patric I. Vogt, geb. 1968 in Mainz. Autor von „Zukunft beginnt im Kopf Ein Debattenbeitrag zur Kernsanierung von Rechtsstaat und Demokratie“. Lebt als freischaffender Künstler, Lehrer und Unternehmer. Über drei Jahrzehnte Beschäftigung mit dem Ideenfeld soziale #Dreigliederung und Anthroposophie. Moderation und Mediation von sozialen Prozessen und Organisationsentwicklung. Staatlich ungeprüft, abgesehen von den Fahrerlaubnissen zu Land und zu Wasser. Motto: Gedanken werden Worte, werden Taten! www.perspektivenwechsel.social
-
 @ d34e832d:383f78d0
2025-04-24 06:12:32
@ d34e832d:383f78d0
2025-04-24 06:12:32
Goal
This analytical discourse delves into Jack Dorsey's recent utterances concerning Bitcoin, artificial intelligence, decentralized social networking platforms such as Nostr, and the burgeoning landscape of open-source cryptocurrency mining initiatives.
Dorsey's pronouncements escape the confines of isolated technological fascinations; rather, they elucidate a cohesive conceptual schema wherein Bitcoin transcends its conventional role as a mere store of value—akin to digital gold—and emerges as a foundational protocol intended for the construction of a decentralized, sovereign, and perpetually self-evolving internet ecosystem.
A thorough examination of Dorsey's confluence of Bitcoin with artificial intelligence advancements, adaptive learning paradigms, and integrated social systems reveals an assertion of Bitcoin's position as an entity that evolves beyond simple currency, evolving into a distinctly novel socio-technological organism characterized by its inherent ability to adapt and grow. His vigorous endorsement of native digital currency, open communication protocols, and decentralized infrastructural frameworks is posited here as a revolutionary paradigm—a conceptual
1. The Path
Jack Dorsey, co-founder of Twitter and Square (now Block), has emerged as one of the most compelling evangelists for a decentralized future. His ideas about Bitcoin go far beyond its role as a speculative asset or inflation hedge. In a recent interview, Dorsey ties together themes of open-source AI, peer-to-peer currency, decentralized media, and radical self-education, sketching a future in which Bitcoin is the lynchpin of an emerging technological and social ecosystem. This thesis reviews Dorsey’s statements and offers a critical framework to understand why his vision uniquely positions Bitcoin as the keystone of a post-institutional, digital world.
2. Bitcoin: The Native Currency of the Internet
“It’s the best current manifestation of a native internet currency.” — Jack Dorsey
Bitcoin's status as an open protocol with no central controlling authority echoes the original spirit of the internet: decentralized, borderless, and resilient. Dorsey's framing of Bitcoin not just as a payment system but as the "native money of the internet" is a profound conceptual leap. It suggests that just as HTTP became the standard for web documents, Bitcoin can become the monetary layer for the open web.
This framing bypasses traditional narratives of digital gold or institutional adoption and centers a P2P vision of global value transfer. Unlike central bank digital currencies or platform-based payment rails, Bitcoin is opt-in, permissionless, and censorship-resistant—qualities essential for sovereignty in the digital age.
3. Nostr and the Decentralization of Social Systems
Dorsey’s support for Nostr, an open protocol for decentralized social media, reflects a desire to restore user agency, protocol composability, and speech sovereignty. Nostr’s architecture parallels Bitcoin’s: open, extensible, and resilient to censorship.
Here, Bitcoin serves not just as money but as a network effect driver. When combined with Lightning and P2P tipping, Nostr becomes more than just a Twitter alternative—it evolves into a micropayment-native communication system, a living proof that Bitcoin can power an entire open-source social economy.
4. Open-Source AI and Cognitive Sovereignty
Dorsey's forecast that open-source AI will emerge as an alternative to proprietary systems aligns with his commitment to digital autonomy. If Bitcoin empowers financial sovereignty and Nostr enables communicative freedom, open-source AI can empower cognitive independence—freeing humanity from centralized algorithmic manipulation.
He draws a fascinating parallel between AI learning models and human learning itself, suggesting both can be self-directed, recursive, and radically decentralized. This resonates with the Bitcoin ethos: systems should evolve through transparent, open participation—not gatekeeping or institutional control.
5. Bitcoin Mining: Sovereignty at the Hardware Layer
Block’s initiative to create open-source mining hardware is a direct attempt to counter centralization in Bitcoin’s infrastructure. ASIC chip development and mining rig customization empower individuals and communities to secure the network directly.
This move reinforces Dorsey’s vision that true decentralization requires ownership at every layer, including hardware. It is a radical assertion of vertical sovereignty—from protocol to interface to silicon.
6. Learning as the Core Protocol
“The most compounding skill is learning itself.” — Jack Dorsey
Dorsey’s deepest insight is that the throughline connecting Bitcoin, AI, and Nostr is not technology—it’s learning. Bitcoin represents more than code; it’s a living experiment in voluntary consensus, a distributed educational system in cryptographic form.
Dorsey’s emphasis on meditation, intensive retreats, and self-guided exploration mirrors the trustless, sovereign nature of Bitcoin. Learning becomes the ultimate protocol: recursive, adaptive, and decentralized—mirroring AI models and Bitcoin nodes alike.
7. Critical Risks and Honest Reflections
Dorsey remains honest about Bitcoin’s current limitations:
- Accessibility: UX barriers for onboarding new users.
- Usability: Friction in everyday use.
- State-Level Adoption: Risks of co-optation as mere digital gold.
However, his caution enhances credibility. His focus remains on preserving Bitcoin as a P2P electronic cash system, not transforming it into another tool of institutional control.
8. Bitcoin as a Living System
What emerges from Dorsey's vision is not a product pitch, but a philosophical reorientation: Bitcoin, Nostr, and open AI are not discrete tools—they are living systems forming a new type of civilization stack.
They are not static infrastructures, but emergent grammars of human cooperation, facilitating value exchange, learning, and community formation in ways never possible before.
Bitcoin, in this view, is not merely stunningly original—it is civilizationally generative, offering not just monetary innovation but a path to software-upgraded humanity.
Works Cited and Tools Used
Dorsey, Jack. Interview on Bitcoin, AI, and Decentralization. April 2025.
Nakamoto, Satoshi. “Bitcoin: A Peer-to-Peer Electronic Cash System.” 2008.
Nostr Protocol. https://nostr.com.
Block, Inc. Bitcoin Mining Hardware Initiatives. 2024.
Obsidian Canvas. Decentralized Note-Taking and Networked Thinking. 2025. -
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 878dff7c:037d18bc
2025-04-09 21:38:34
@ 878dff7c:037d18bc
2025-04-09 21:38:34Coalition Proposes Sovereign Wealth Funds to Address National Debt
Summary:
Opposition Leader Peter Dutton has unveiled a plan to reduce Australia's $1.2 trillion debt by creating two sovereign wealth funds: the Future Generations Fund and the Regional Australia Future Fund. These funds aim to allocate 80% of commodity windfall revenues toward debt reduction and regional development, focusing on infrastructure and economic support outside metropolitan areas.
Sources: The Australian - April 10, 2025
Australian Dollar Falls Below 60 US Cents Amid Tariff Concerns
Summary:
The Australian dollar has dropped to a five-year low, trading below 60 US cents, as markets react to escalating tariff tensions initiated by the U.S. This depreciation reflects investor fears of a potential global economic downturn impacting Australia's economy.
Sources: ABC News - 9 April 2025, Reuters - 7 April 2025
AI Transformation Reshaping Australia's Software Development Landscape
Summary:
Artificial Intelligence (AI) is rapidly transforming Australia's software development industry. Recent research indicates widespread adoption of AI tools and methodologies, leading to increased efficiency and innovation. This trend positions Australian tech companies competitively in the global market and highlights the importance of AI literacy for professionals in the sector. Sources: Tech Business News - April 10, 2025
UK and Australia Collaborate on Next-Generation Weapons Development
Summary:
The United Kingdom and Australia have launched a partnership to develop next-generation sub-systems for low-cost weapons. This collaboration integrates the UK's Modular Weapons Testbed with Australia's SHARKTOOTH program, featuring innovative 'plug-and-launch' modular technology. The initiative aims to accelerate the deployment of advanced, affordable weapons technologies, enhancing both nations' defense capabilities. Sources: The Defense Post - April 7, 2025, ASD News - April 4, 2025
Smoke Advisory Issued for Greater Sydney Due to Hazard Reduction Burns
Summary:
The NSW Rural Fire Service has issued a smoke advisory for the Greater Sydney area, including the Blue Mountains and Southern Highlands, due to planned hazard reduction burns. Residents are advised to stay indoors, close windows and doors, and keep respiratory medications close by. rfs.nsw.gov.au+1rfs.nsw.gov.au+1 ABC
Sources: NSW Rural Fire Service - April 9, 2025
Leaders Clash in First Election Debate
Summary:
In the first leaders' debate of the 2025 federal election campaign, Prime Minister Anthony Albanese and Opposition Leader Peter Dutton clashed on several key issues during the Sky News/Daily Telegraph People's Forum. Albanese accused the Coalition of historically cutting health and education funding, which Dutton vehemently denied. The debate also saw pointed exchanges over spending levels, energy policy, and cost-of-living concerns. Dutton challenged Albanese’s tax cuts and left open the possibility of extending fuel excise relief. The leaders also addressed infrastructure funding, economic management, and health services. The debate occurred with only 25 days until the election and 14 days before early voting begins.
Sources: The Daily Telegraph - 10 April 2025, News.com.au - 10 April 2025
Australia and Philippines to Increase Joint Military Exercises
Summary:
Australia and the Philippines have agreed to double their joint military drills and security engagements in 2025. This decision underscores the strengthening defense ties between the two nations in response to regional security challenges. Sources: Manila Bulletin - April 7, 2025
Victoria's Working with Children Check System Criticized for Allowing Individuals Under Investigation to Retain Clearance
Summary:
Victoria's Working with Children Check system is under scrutiny for permitting individuals under investigation for abuse and assault to retain their clearance. Parents and advocates are calling for urgent reforms, highlighting cases where children were allegedly harmed by individuals who maintained their working with children credentials despite serious allegations. ABC
Sources: ABC News - April 10, 2025
Ecological Revival Following Inland Floods
Summary:
After unprecedented rainfall transformed over a million square kilometers of inland Australia into floodplains, the region is witnessing a remarkable ecological revival. Native wildlife such as fish, long-haired rats, frogs, and birds are thriving, and previously dried-out habitats are being replenished. Experts view the floods as a rare opportunity for broad ecological regeneration, including mega breeding events and species migrations. While challenges remain, the natural rebirth offers hope as long-dormant ecosystems awaken with vibrant life.
Sources: The Times - April 10, 2025, SciTechDaily - April 10, 2025
CyberCX Report Highlights Evolving Cyber Threat Landscape
Summary:
CyberCX's annual Threat Report for 2025 reveals that business email compromise remains the top incident type, with espionage-related incidents taking longer to detect compared to previous years. The report underscores the need for enhanced cybersecurity measures across Australian organizations. Sources: CyberCX - April 9, 2025
Greens-Backed Study Targets Environmental Impact of Pet Dogs
Summary:
A new study, receiving attention from progressive environmental circles including the Greens, has flagged pet dogs as a significant ecological threat. The research claims dogs contribute to pollution, wildlife disturbances, and even climate change due to their carbon footprint. Critics argue this is part of a broader ideological push to regulate personal lifestyle choices, sparking concerns that common household pets may soon be in the environmental policy crosshairs. With the Greens already pushing for sweeping environmental reforms, some Australians fear this could lead to overreach targeting ordinary families and their beloved pets.
Sources: The Guardian - 10 April 2025
High-Intensity Resistance and Impact Training Enhances Bone Density in Postmenopausal Women
Summary:
The LIFTMOR randomized controlled trial investigated the effects of high-intensity resistance and impact training (HiRIT) on bone health in postmenopausal women with low bone mass. Over eight months, participants engaged in twice-weekly, 30-minute HiRIT sessions, performing exercises such as deadlifts, overhead presses, and back squats at over 85% of their one-repetition maximum. The study found significant improvements in lumbar spine bone mineral density (BMD) by 2.9%, femoral neck BMD by 0.3%, cortical thickness, and functional performance measures, including enhanced leg and back strength. Notably, the HiRIT program was well-tolerated, with high compliance and minimal adverse events, suggesting that such training is both safe and effective for improving bone health and physical function in this demographic. Sources: PubMed - October 4, 2017
Anti-Aging Expert Peter Attia Discusses Longevity and Health Optimization
Summary:
In this episode of "The Diary Of A CEO," host Steven Bartlett engages with Dr. Peter Attia, a physician specializing in longevity and health optimization. Dr. Attia delves into the often-overlooked aspects of aging, emphasizing the importance of proactive health measures. He highlights the critical role of maintaining muscle mass and strength, noting that a decline in these areas significantly increases mortality risk. Dr. Attia also explores natural methods to enhance testosterone levels without resorting to testosterone replacement therapy (TRT), advocating for lifestyle interventions such as strength training, adequate sleep, and balanced nutrition. Throughout the conversation, he underscores the necessity of individualized health strategies and regular monitoring to effectively prevent age-related diseases. Sources: Spotify - April 2025
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ d34e832d:383f78d0
2025-04-24 05:56:06
@ d34e832d:383f78d0
2025-04-24 05:56:06Idea
Through the integration of Optical Character Recognition (OCR), Docker-based deployment, and secure remote access via Twin Gate, Paperless NGX empowers individuals and small organizations to digitize, organize, and retrieve documents with minimal friction. This research explores its technical infrastructure, real-world applications, and how such a system can redefine document archival practices for the digital age.
Agile, Remote-Accessible, and Searchable Document System
In a world of increasing digital interdependence, managing physical documents is becoming not only inefficient but also environmentally and logistically unsustainable. The demand for agile, remote-accessible, and searchable document systems has never been higher—especially for researchers, small businesses, and archival professionals. Paperless NGX, an open-source platform, addresses these needs by offering a streamlined, secure, and automated way to manage documents digitally.
This Idea explores how Paperless NGX facilitates the transition to a paperless workflow and proposes best practices for sustainable, scalable usage.
Paperless NGX: The Platform
Paperless NGX is an advanced fork of the original Paperless project, redesigned with modern containers, faster performance, and enhanced community contributions. Its core functions include:
- Text Extraction with OCR: Leveraging the
ocrmypdfPython library, Paperless NGX can extract searchable text from scanned PDFs and images. - Searchable Document Indexing: Full-text search allows users to locate documents not just by filename or metadata, but by actual content.
- Dockerized Setup: A ready-to-use Docker Compose environment simplifies deployment, including the use of setup scripts for Ubuntu-based servers.
- Modular Workflows: Custom triggers and automation rules allow for smart processing pipelines based on file tags, types, or email source.
Key Features and Technical Infrastructure
1. Installation and Deployment
The system runs in a containerized environment, making it highly portable and isolated. A typical installation involves: - Docker Compose with YAML configuration - Volume mapping for persistent storage - Optional integration with reverse proxies (e.g., Nginx) for HTTPS access
2. OCR and Indexing
Using
ocrmypdf, scanned documents are processed into fully searchable PDFs. This function dramatically improves retrieval, especially for archived legal, medical, or historical records.3. Secure Access via Twin Gate
To solve the challenge of secure remote access without exposing the network, Twin Gate acts as a zero-trust access proxy. It encrypts communication between the Paperless NGX server and the client, enabling access from anywhere without the need for traditional VPNs.
4. Email Integration and Ingestion
Paperless NGX can ingest attachments directly from configured email folders. This feature automates much of the document intake process, especially useful for receipts, invoices, and academic PDFs.
Sustainable Document Management Workflow
A practical paperless strategy requires not just tools, but repeatable processes. A sustainable workflow recommended by the Paperless NGX community includes:
- Capture & Tagging
All incoming documents are tagged with a default “inbox” tag for triage. - Physical Archive Correlation
If the physical document is retained, assign it a serial number (e.g., ASN-001), which is matched digitally. - Curation & Tagging
Apply relevant category and topic tags to improve searchability. - Archival Confirmation
Remove the “inbox” tag once fully processed and categorized.
Backup and Resilience
Reliability is key to any archival system. Paperless NGX includes backup functionality via: - Cron job–scheduled Docker exports - Offsite and cloud backups using rsync or encrypted cloud drives - Restore mechanisms using documented CLI commands
This ensures document availability even in the event of hardware failure or data corruption.
Limitations and Considerations
While Paperless NGX is powerful, it comes with several caveats: - Technical Barrier to Entry: Requires basic Docker and Linux skills to install and maintain. - OCR Inaccuracy for Handwritten Texts: The OCR engine may struggle with cursive or handwritten documents. - Plugin and Community Dependency: Continuous support relies on active community contribution.
Consider
Paperless NGX emerges as a pragmatic and privacy-centric alternative to conventional cloud-based document management systems, effectively addressing the critical challenges of data security and user autonomy.
The implementation of advanced Optical Character Recognition (OCR) technology facilitates the indexing and searching of documents, significantly enhancing information retrieval efficiency.
Additionally, the platform offers secure remote access protocols that ensure data integrity while preserving the confidentiality of sensitive information during transmission.
Furthermore, its customizable workflow capabilities empower both individuals and organizations to precisely tailor their data management processes, thereby reclaiming sovereignty over their information ecosystems.
In an era increasingly characterized by a shift towards paperless methodologies, the significance of solutions such as Paperless NGX cannot be overstated; they play an instrumental role in engineering a future in which information remains not only accessible but also safeguarded and sustainably governed.
In Addition
To Further The Idea
This technical paper presents an optimized strategy for transforming an Intel NUC into a compact, power-efficient self-hosted server using Ubuntu. The setup emphasizes reliability, low energy consumption, and cost-effectiveness for personal or small business use. Services such as Paperless NGX, Nextcloud, Gitea, and Docker containers are examined for deployment. The paper details hardware selection, system installation, secure remote access, and best practices for performance and longevity.
1. Cloud sovereignty, Privacy, and Data Ownership
As cloud sovereignty, privacy, and data ownership become critical concerns, self-hosting is increasingly appealing. An Intel NUC (Next Unit of Computing) provides an ideal middle ground between Raspberry Pi boards and enterprise-grade servers—balancing performance, form factor, and power draw. With Ubuntu LTS and Docker, users can run a full suite of services with minimal overhead.
2. Hardware Overview
2.1 Recommended NUC Specifications:
| Component | Recommended Specs | |------------------|-----------------------------------------------------| | Model | Intel NUC 11/12 Pro (e.g., NUC11TNHi5, NUC12WSKi7) | | CPU | Intel Core i5 or i7 (11th/12th Gen) | | RAM | 16GB–32GB DDR4 (dual channel preferred) | | Storage | 512GB–2TB NVMe SSD (Samsung 980 Pro or similar) | | Network | Gigabit Ethernet + Optional Wi-Fi 6 | | Power Supply | 65W USB-C or barrel connector | | Cooling | Internal fan, well-ventilated location |
NUCs are also capable of dual-drive setups and support for Intel vPro for remote management on some models.
3. Operating System and Software Stack
3.1 Ubuntu Server LTS
- Version: Ubuntu Server 22.04 LTS
- Installation Method: Bootable USB (Rufus or Balena Etcher)
- Disk Partitioning: LVM with encryption recommended for full disk security
- Security:
- UFW (Uncomplicated Firewall)
- Fail2ban
- SSH hardened with key-only login
bash sudo apt update && sudo apt upgrade sudo ufw allow OpenSSH sudo ufw enable
4. Docker and System Services
Docker and Docker Compose streamline the deployment of isolated, reproducible environments.
4.1 Install Docker and Compose
bash sudo apt install docker.io docker-compose sudo systemctl enable docker4.2 Common Services to Self-Host:
| Application | Description | Access Port | |--------------------|----------------------------------------|-------------| | Paperless NGX | Document archiving and OCR | 8000 | | Nextcloud | Personal cloud, contacts, calendar | 443 | | Gitea | Lightweight Git repository | 3000 | | Nginx Proxy Manager| SSL proxy for all services | 81, 443 | | Portainer | Docker container management GUI | 9000 | | Watchtower | Auto-update containers | - |
5. Network & Remote Access
5.1 Local IP & Static Assignment
- Set a static IP for consistent access (via router DHCP reservation or Netplan).
5.2 Access Options
- Local Only: VPN into local network (e.g., WireGuard, Tailscale)
- Remote Access:
- Reverse proxy via Nginx with Certbot for HTTPS
- Twin Gate or Tailscale for zero-trust remote access
- DNS via DuckDNS, Cloudflare
6. Performance Optimization
- Enable
zramfor compressed RAM swap - Trim SSDs weekly with
fstrim - Use Docker volumes, not bind mounts for stability
- Set up unattended upgrades:
bash sudo apt install unattended-upgrades sudo dpkg-reconfigure --priority=low unattended-upgrades
7. Power and Environmental Considerations
- Idle Power Draw: ~7–12W (depending on configuration)
- UPS Recommended: e.g., APC Back-UPS 600VA
- Use BIOS Wake-on-LAN if remote booting is needed
8. Maintenance and Monitoring
- Monitoring: Glances, Netdata, or Prometheus + Grafana
- Backups:
- Use
rsyncto external drive or NAS - Cloud backup options: rclone to Google Drive, S3
- Paperless NGX backups:
docker compose exec -T web document-exporter ...
9. Consider
Running a personal server using an Intel NUC and Ubuntu offers a private, low-maintenance, and modular solution to digital infrastructure needs. It’s an ideal base for self-hosting services, offering superior control over data and strong security with the right setup. The NUC's small form factor and efficient power usage make it an optimal home server platform that scales well for many use cases.
- Text Extraction with OCR: Leveraging the
-
 @ da0b9bc3:4e30a4a9
2025-04-04 06:24:48
@ da0b9bc3:4e30a4a9
2025-04-04 06:24:48Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/934111
-
 @ d34e832d:383f78d0
2025-04-24 05:14:14
@ d34e832d:383f78d0
2025-04-24 05:14:14Idea
By instituting a robust network of conceptual entities, referred to as 'Obsidian nodes'—which are effectively discrete, idea-centric notes—researchers are empowered to establish a resilient and non-linear archival framework for knowledge accumulation.
These nodes, intricately connected via hyperlinks and systematically organized through the graphical interface of the Obsidian Canvas, facilitate profound intellectual exploration and the synthesis of disparate domains of knowledge.
Consequently, this innovative workflow paradigm emphasizes semantic precision and the interconnectedness of ideas, diverging from conventional, source-centric information architectures prevalent in traditional academic practices.
Traditional research workflows often emphasize organizing notes by source, resulting in static, siloed knowledge that resists integration and insight. With the rise of personal knowledge management (PKM) tools like Obsidian, it becomes possible to structure information in a way that mirrors the dynamic and interconnected nature of human thought.
At the heart of this approach are Obsidian nodes—atomic, standalone notes representing single ideas, arguments, or claims. These nodes form the basis of a semantic research network, made visible and manageable via Obsidian’s graph view and Canvas feature. This thesis outlines how such a framework enhances understanding, supports creativity, and aligns with best practices in information architecture.
Obsidian Nodes: Atomic Units of Thought
An Obsidian node is a note crafted to encapsulate one meaningful concept or question. It is:
- Atomic: Contains only one idea, making it easier to link and reuse.
- Context-Independent: Designed to stand on its own, without requiring the original source for meaning.
- Networked: Linked to other Obsidian nodes through backlinks and tags.
This system draws on the principles of the Zettelkasten method, but adapts them to the modern, markdown-based environment of Obsidian.
Benefits of Node-Based Note-Taking
- Improved Retrieval: Ideas can be surfaced based on content relevance, not source origin.
- Cross-Disciplinary Insight: Linking between concepts across fields becomes intuitive.
- Sustainable Growth: Each new node adds value to the network without redundancy.
Graph View: Visualizing Connections
Obsidian’s graph view offers a macro-level overview of the knowledge graph, showing how nodes interrelate. This encourages serendipitous discovery and identifies central or orphaned concepts that need further development.
- Clusters emerge around major themes.
- Hubs represent foundational ideas.
- Bridges between nodes show interdisciplinary links.
The graph view isn’t just a map—it’s an evolving reflection of intellectual progress.
Canvas: Thinking Spatially with Digital Notes
Obsidian Canvas acts as a digital thinking space. Unlike the abstract graph view, Canvas allows for spatial arrangement of Obsidian nodes, images, and ideas. This supports visual reasoning, ideation, and project planning.
Use Cases of Canvas
- Synthesizing Ideas: Group related nodes in physical proximity.
- Outlining Arguments: Arrange claims into narrative or logic flows.
- Designing Research Papers: Lay out structure and integrate supporting points visually.
Canvas brings a tactile quality to digital thinking, enabling workflows similar to sticky notes, mind maps, or corkboard pinning—but with markdown-based power and extensibility.
Template and Workflow
To simplify creation and encourage consistency, Obsidian nodes are generated using a templater plugin. Each node typically includes:
```markdown
{{title}}
Tags: #topic #field
Linked Nodes: [[Related Node]]
Summary: A 1-2 sentence idea explanation.
Source: [[Source Note]]
Date Created: {{date}}
```The Canvas workspace pulls these nodes as cards, allowing for arrangement, grouping, and visual tracing of arguments or research paths.
Discussion and Challenges
While this approach enhances creativity and research depth, challenges include:
- Initial Setup: Learning and configuring plugins like Templater, Dataview, and Canvas.
- Overlinking or Underlinking: Finding the right granularity in note-making takes practice.
- Scalability: As networks grow, maintaining structure and avoiding fragmentation becomes crucial.
- Team Collaboration: While Git can assist, Obsidian remains largely optimized for solo workflows.
Consider
Through the innovative employment of Obsidian's interconnected nodes and the Canvas feature, researchers are enabled to construct a meticulously engineered semantic architecture that reflects the intricate topology of their knowledge frameworks.
This paradigm shift facilitates a transformation of conventional note-taking, evolving this practice from a static, merely accumulative repository of information into a dynamic and adaptive cognitive ecosystem that actively engages with the user’s thought processes. With methodological rigor and a structured approach, Obsidian transcends its role as mere documentation software, evolving into both a secondary cognitive apparatus and a sophisticated digital writing infrastructure.
This dual functionality significantly empowers the long-term intellectual endeavors and creative pursuits of students, scholars, and lifelong learners, thereby enhancing their capacity for sustained engagement with complex ideas.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:15
@ 0edc2f47:730cff1b
2025-04-04 03:37:15Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ b8af284d:f82c91dd
2025-03-24 08:09:20
@ b8af284d:f82c91dd
2025-03-24 08:09:20I'd say that globalization's hunger for cheap labor is a problem, precisely because it's been bad for innovation. Both our working people and our innovators have the same enemy — and the solution is American innovation...
Liebe Abonnenten,
der intellektuell brillante Vize-Präsident J.D. Vance hat diese Woche seine Wirtschaftspolitik skizziert. Über deren Grundzüge geht es heute.
Die Geschichte der Globalisierung ist die Geschichte der Suche nach billigen Arbeitskräften. Arbeiter in den westlichen Gesellschaften in den G7-Staaten waren spätestens in den 1980er Jahren gut organisiert und stemmten sich meist erfolgreich gegen Lohnkürzungen und Stellenabbau. Nach dem Zusammenbruch der Sowjetunion 1990 fanden die international tätigen Konzerne auf einmal ein gewaltiges Reservoir an billigen Arbeitskräften - nicht nur, aber vor allem in China.

Dieser Prozess nahm 2001 mit dem Beitritt Chinas zur Welthandelsorganisation nochmals an Fahrt auf. Deutlich wird er am ikonischen Produkt der Neuzeit, dem iPhone. Das erste Modell kam 2007 auf den Markt. Entworfen und designt wurde und wird das Smartphone von Apple in Kalifornien. Gefertigt dagegen wird es von einem der größten Konzerne der Welt. Foxconn beschäftigt allein in China über eine Million Menschen. Hon Hai, wie Foxconn eigentlich heißt, ist übrigens ein taiwanisches Unternehmen.
Dieser Prozess der verlagerten Fertigung hatte mehrere Vorteile: Produkte wurden günstiger. Davon profitierten Konsumenten in der westlichen Welt. Würde man ein iPhone in den USA oder Deutschland herstellen, würde es durch die höheren Löhne zwischen 200 und 300 Euro mehr kosten. Die Konzerne wie Apple konnten somit günstiger produzieren, ihre Margen erhöhen, und ihre Aktienkurse stiegen.
Von diesem Prozess profitierten außerdem Länder wie China: Das monatliche Grundgehalt von Foxconn-Mitarbeitern in Shenzhen erscheint mit rund 400 Euro im Monat noch immer grotesk niedrig. Für viele Chinesen vom Land bedeutet ein Job in der Fabrik allerdings ein Gehaltssprung von mehreren hundert Prozent. Es gibt keinen Grund, die Arbeitsbedingungen bei Foxconn schönzureden. Zur Wahrheit gehört aber auch, dass sich die allermeisten Wanderarbeiter nicht ausgebeutet oder als Opfer fühlen. Im Gegenteil: In meiner Zeit in China stieß ich meist auf Menschen, die sich als selbstwirksamer empfanden als viele Festangestellte mit 30 Urlaubstagen im Westen. Länder, mit billigen Arbeitskräften, profitierten also von diesem Prozess und kletterten so auf der globalen Wertschöpfungskette nach oben.
Etwa zeitgleich nahm auch in westlichen Ländern die Immigration zu. Der Anteil der im Ausland geborenen Bevölkerung stieg von etwa 7,9 Prozent im Jahr 1990 auf 13,7 Prozent im Jahr 2021, was den höchsten Stand seit 1910 darstellt. In Deutschland stieg der „Ausländer“-Anteil von knapp 7 Prozent 1990 auf 27 Prozent 2023. Viele Unternehmen hatten also sowohl international als auch national Zugriff auf günstige Arbeitskräfte. In Europa wurden diese zudem dringend gebraucht, um das in Schieflage geratene Rentensystem zu stabilisieren.
Die Nachteile dieses Megatrends wurden zunächst in den USA sichtbar: Immer mehr Unternehmen in den USA verlagerten ihre Produktion nach China. Hinzu kam der Status des US-Dollars als Weltreservewährung. Durch die konstante Nachfrage nach Dollar bleibt dieser stark, und macht amerikanische Exporte teurer. Eine Deindustrialisierung setzte ein, die vielen Menschen ihren Job kostete. Zeitgleich wuchs das Handelsbilanzdefizit mit China immer weiter. Hinzu kam eine konstante Erhöhung der Geldmenge. Amerikaner mit „hard assets“, Immobilien und Aktien, wurden tendenziell reicher. Der Rest aber nicht. Kurz: Konzerne verdienten gut, die Wirtschaft wuchs, nur bei den Amerikanern selbst blieb immer weniger hängen.
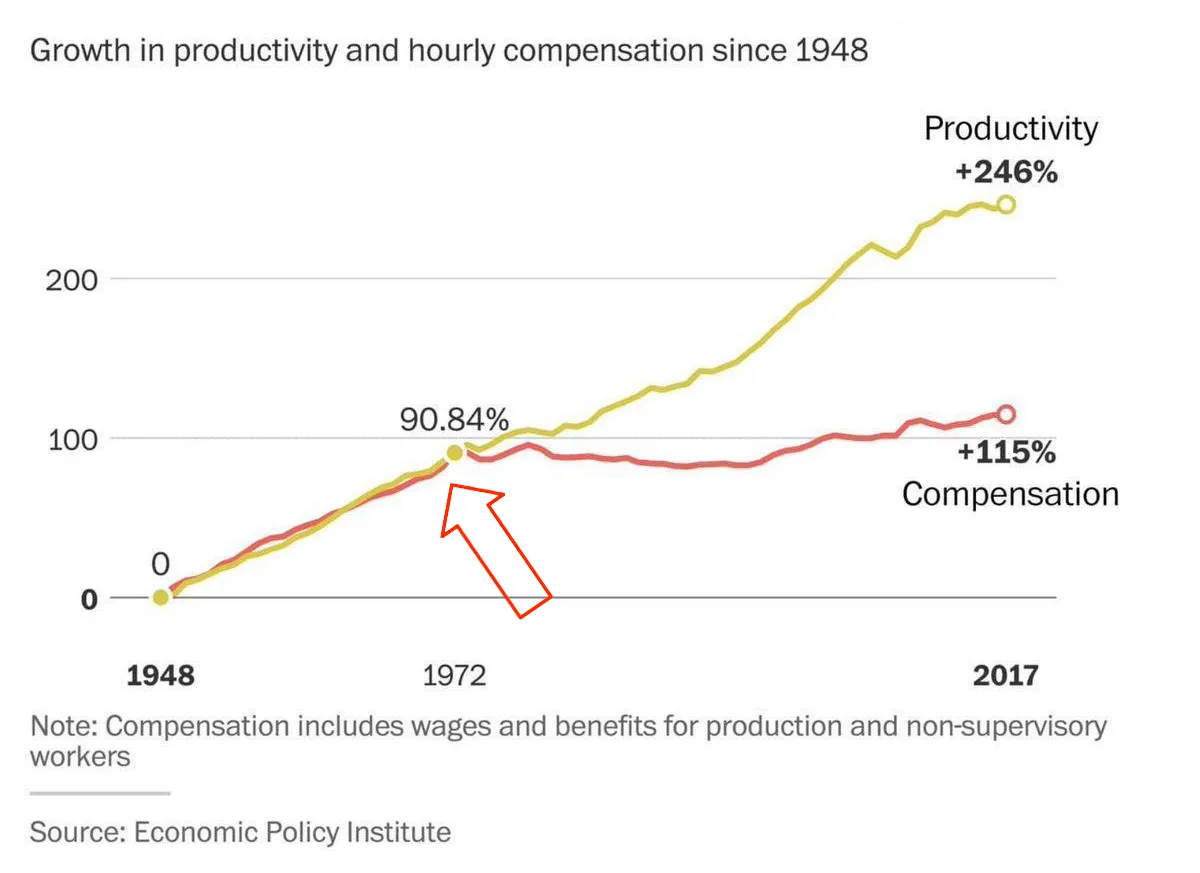
Worum es J.D. Vance also geht: Innovation und Arbeitsplätze in die USA zurückzuholen. Dafür müssen Schutzmauern errichtet werden: gegen die illegale Einwanderung billiger Arbeitskräfte und billiger Waren. Zölle dienen dazu, ausländische Waren zu verteuern, und somit Unternehmen Anreize zu geben, direkt in den USA zu investieren. Kürzlich gab Siemens bekannt, zehn Milliarden Euro in amerikanische KI-Rechenzentren zu investieren. Was wohl auch Teil des Trump-Derangement-Syndroms ist: die Wahrnehmung der amerikanischen Zollpolitik. Kaum ein Land hat aktuell so niedrige Zollschranken wie die Vereinigten Staaten.
\ Kurz gesagt: iPhones sollen demnach nicht nur in den USA entworfen, sondern auch in amerikanischen Fabriken zusammengeschraubt werden. Alles hoch-inflationär, wenden Kritiker ein. Wer globale Lieferketten abreißt, und ins eigene Land zurückholt, hat mit viel höheren Kosten zu kämpfen. Also steigt die Inflation. Diesen Prozess will die US-Regierung mit günstigeren Energiekosten kontern. Egal ob Solar-, Nuklear- oder Fracking - jede Energiequelle soll dafür Recht sein.
Schließlich soll eine strikte Haushaltsdisziplin (DOGE) unnötige Ausgaben vermeiden, und die Bürokratie abbauen. Im Gegenzug können dann die Steuern gesenkt werden. Die Einkommensteuer für Familien mit einem Jahreseinkommen bis zu 150000 US-Dollar soll komplett gestrichen werden.
Tl/DR:
- Migration begrenzen, um Billigarbeit zu verhindern
- Zölle errichten, um amerikanische Produktion zu stärken
- Günstige Energiequellen priorisieren, um Inflation zu verhindern
- Staatsausgaben radikal kürzen
- Steuern radikal senken
Kann das Projekt klappen? Vielleicht. Das Megaprojekt Globalisierung zurückzudrehen, oder zumindest etwas zu bremsen, ist ein Wagnis. Zölle bergen die Gefahr der Inflation und eines Handelskriegs. Unsicher ist, ob von einer Deregulierung weiterer Branchen am Ende wirklich amerikanische Arbeiter profitieren. Und wie innovativ können Unternehmen sein, wenn sie am Ende mehr Geld für ihre Beschäftigten ausgeben müssen, anstatt es in Forschung und Entwicklung zu investieren? Was geschieht, wenn der Rest der Welt nicht mitmacht, und sich immer weiter vernetzt? Werden die USA am Ende eine einsame Zoll-Insel? In ein paar Monaten dürfte sich langsam abzeichnen, ob das Projekt funktioniert.
Mehr dazu:
Der Mar-a-Largo-Accord - wie eine neue Finanzordnung entsteht
Was dagegen nicht klappen wird, ist das deutsche Projekt. Friedrich Merz hat mit einem „Husarenstück“ (SZ) mit einem abgewählten Bundestag eine Verfassungsänderung durchgepeitscht. Mindestens 500 Milliarden Euro neue Schulden werden gemacht, das Militär erhält einen Blankoscheck für neue Anschaffungen. Bürokratie wird nicht abgebaut. Die Unter- und Mittelschicht wird nicht entlastet. Das 100-Milliarden Zugeständnis an die Grünen sorgt dafür, dass Energie nicht günstiger wird. Ein bisschen Innovation werden die neuen Panzer- und Drohnen-Fabriken schon bringen. Am Ende aber bleibt Rüstung totes Kapital. Im wahrsten Sinne des Wortes.
Was das neue Wirtschaftsprogramm für Bitcoin bedeutet - haben wir den Boden gesehen?
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ d34e832d:383f78d0
2025-04-24 05:04:55
@ d34e832d:383f78d0
2025-04-24 05:04:55A Knowledge Management Framework for your Academic Writing
Idea Approach
The primary objective of this framework is to streamline and enhance the efficiency of several critical academic processes, namely the reading, annotation, synthesis, and writing stages inherent to doctoral studies.
By leveraging established best practices from various domains, including digital note-taking methodologies, sophisticated knowledge management techniques, and the scientifically-grounded principles of spaced repetition systems, this proposed workflow is adept at optimizing long-term retention of information, fostering the development of novel ideas, and facilitating the meticulous preparation of manuscripts. Furthermore, this integrated approach capitalizes on Zotero's robust annotation functionalities, harmoniously merged with Obsidian's Zettelkasten-inspired architecture, thereby enriching the depth and structural coherence of academic inquiry, ultimately leading to more impactful scholarly contributions.
Doctoral research demands a sophisticated approach to information management, critical thinking, and synthesis. Traditional systems of note-taking and bibliography management are often fragmented and inefficient, leading to cognitive overload and disorganized research outputs. This thesis proposes a workflow that leverages Zotero for reference management, Obsidian for networked note-taking, and Anki for spaced repetition learning—each component enhanced by a set of plugins, templates, and color-coded systems.
2. Literature Review and Context
2.1 Digital Research Workflows
Recent research in digital scholarship has highlighted the importance of structured knowledge environments. Tools like Roam Research, Obsidian, and Notion have gained traction among academics seeking flexibility and networked thinking. However, few workflows provide seamless interoperability between reference management, reading, and idea synthesis.
2.2 The Zettelkasten Method
Originally developed by sociologist Niklas Luhmann, the Zettelkasten ("slip-box") method emphasizes creating atomic notes—single ideas captured and linked through context. This approach fosters long-term idea development and is highly compatible with digital graph-based note systems like Obsidian.
3. Zotero Workflow: Structured Annotation and Tagging
Zotero serves as the foundational tool for ingesting and organizing academic materials. The built-in PDF reader is augmented through a color-coded annotation schema designed to categorize information efficiently:
- Red: Refuted or problematic claims requiring skepticism or clarification
- Yellow: Prominent claims, novel hypotheses, or insightful observations
- Green: Verified facts or claims that align with the research narrative
- Purple: Structural elements like chapter titles or section headers
- Blue: Inter-author references or connections to external ideas
- Pink: Unclear arguments, logical gaps, or questions for future inquiry
- Orange: Precise definitions and technical terminology
Annotations are accompanied by tags and notes in Zotero, allowing robust filtering and thematic grouping.
4. Obsidian Integration: Bridging Annotation and Synthesis
4.1 Plugin Architecture
Three key plugins optimize Obsidian’s role in the workflow:
- Zotero Integration (via
obsidian-citation-plugin): Syncs annotated PDFs and metadata directly from Zotero - Highlighter: Enables color-coded highlights in Obsidian, mirroring Zotero's scheme
- Templater: Automates formatting and consistency using Nunjucks templates
A custom keyboard shortcut (e.g.,
Ctrl+Shift+Z) is used to trigger the extraction of annotations into structured Obsidian notes.4.2 Custom Templating
The templating system ensures imported notes include:
- Citation metadata (title, author, year, journal)
- Full-color annotations with comments and page references
- Persistent notes for long-term synthesis
- An embedded bibtex citation key for seamless referencing
5. Zettelkasten and Atomic Note Generation
Obsidian’s networked note system supports idea-centered knowledge development. Each note captures a singular, discrete idea—independent of the source material—facilitating:
- Thematic convergence across disciplines
- Independent recombination of ideas
- Emergence of new questions and hypotheses
A standard atomic note template includes: - Note ID (timestamp or semantic UID) - Topic statement - Linked references - Associated atomic notes (via backlinks)
The Graph View provides a visual map of conceptual relationships, allowing researchers to track the evolution of their arguments.
6. Canvas for Spatial Organization
Obsidian’s Canvas plugin is used to mimic physical research boards: - Notes are arranged spatially to represent conceptual clusters or chapter structures - Embedded visual content enhances memory retention and creative thought - Notes and cards can be grouped by theme, timeline, or argumentative flow
This supports both granular research and holistic thesis design.
7. Flashcard Integration with Anki
Key insights, definitions, and questions are exported from Obsidian to Anki, enabling spaced repetition of core content. This supports: - Preparation for comprehensive exams - Retention of complex theories and definitions - Active recall training during literature reviews
Flashcards are automatically generated using Obsidian-to-Anki bridges, with tagging synced to Obsidian topics.
8. Word Processor Integration and Writing Stage
Zotero’s Word plugin simplifies: - In-text citation - Automatic bibliography generation - Switching between citation styles (APA, Chicago, MLA, etc.)
Drafts in Obsidian are later exported into formal academic writing environments such as Microsoft Word or LaTeX editors for formatting and submission.
9. Discussion and Evaluation
The proposed workflow significantly reduces friction in managing large volumes of information and promotes deep engagement with source material. Its modular nature allows adaptation for various disciplines and writing styles. Potential limitations include: - Initial learning curve - Reliance on plugin maintenance - Challenges in team-based collaboration
Nonetheless, the ability to unify reading, note-taking, synthesis, and writing into a seamless ecosystem offers clear benefits in focus, productivity, and academic rigor.
10. Consider
This idea demonstrates that a well-structured digital workflow using Zotero and Obsidian can transform the PhD research process. It empowers researchers to move beyond passive reading into active knowledge creation, aligned with the long-term demands of scholarly writing. Future iterations could include AI-assisted summarization, collaborative graph spaces, and greater mobile integration.
9. Evaluation Of The Approach
While this workflow offers significant advantages in clarity, synthesis, and long-term idea development, several limitations must be acknowledged:
-
Initial Learning Curve: New users may face a steep learning curve when setting up and mastering the integrated use of Zotero, Obsidian, and their associated plugins. Understanding markdown syntax, customizing templates in Templater, and configuring citation keys all require upfront time investment. However, this learning period can be offset by the long-term gains in productivity and mental clarity.
-
Plugin Ecosystem Volatility: Since both Obsidian and many of its key plugins are maintained by open-source communities or individual developers, updates can occasionally break workflows or require manual adjustments.
-
Interoperability Challenges: Synchronizing metadata, highlights, and notes between systems (especially on multiple devices or operating systems) may present issues if not managed carefully. This includes Zotero’s Better BibTeX keys, Obsidian sync, and Anki integration.
-
Limited Collaborative Features: This workflow is optimized for individual use. Real-time collaboration on notes or shared reference libraries may require alternative platforms or additional tooling.
Despite these constraints, the workflow remains highly adaptable and has proven effective across disciplines for researchers aiming to build a durable intellectual infrastructure over the course of a PhD.
9. Evaluation Of The Approach
While the Zotero–Obsidian workflow dramatically improves research organization and long-term knowledge retention, several caveats must be considered:
-
Initial Learning Curve: Mastery of this workflow requires technical setup and familiarity with markdown, citation keys, and plugin configuration. While challenging at first, the learning effort is front-loaded and pays off in efficiency over time.
-
Reliance on Plugin Maintenance: A key risk of this system is its dependence on community-maintained plugins. Tools like Zotero Integration, Templater, and Highlighter are not officially supported by Obsidian or Zotero core teams. This means updates or changes to the Obsidian API or plugin repository may break functionality or introduce bugs. Active plugin support is crucial to the system’s longevity.
-
Interoperability and Syncing Issues: Managing synchronization across Zotero, Obsidian, and Anki—especially across multiple devices—can lead to inconsistencies or data loss without careful setup. Users should ensure robust syncing solutions (e.g. Obsidian Sync, Zotero WebDAV, or GitHub backup).
-
Limited Collaboration Capabilities: This setup is designed for solo research workflows. Collaborative features (such as shared note-taking or group annotations) are limited and may require alternate solutions like Notion, Google Docs, or Overleaf when working in teams.
The integration of Zotero with Obsidian presents a notable advantage for individual researchers, exhibiting substantial efficiency in literature management and personal knowledge organization through its unique workflows. However, this model demonstrates significant deficiencies when evaluated in the context of collaborative research dynamics.
Specifically, while Zotero facilitates the creation and management of shared libraries, allowing for the aggregation of sources and references among users, Obsidian is fundamentally limited by its lack of intrinsic support for synchronous collaborative editing functionalities, thereby precluding simultaneous contributions from multiple users in real time. Although the application of version control systems such as Git has the potential to address this limitation, enabling a structured mechanism for tracking changes and managing contributions, the inherent complexity of such systems may pose a barrier to usability for team members who lack familiarity or comfort with version control protocols.
Furthermore, the nuances of color-coded annotation systems and bespoke personal note taxonomies utilized by individual researchers may present interoperability challenges when applied in a group setting, as these systems require rigorously defined conventions to ensure consistency and clarity in cross-collaborator communication and understanding. Thus, researchers should be cognizant of the challenges inherent in adapting tools designed for solitary workflows to the multifaceted requirements of collaborative research initiatives.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
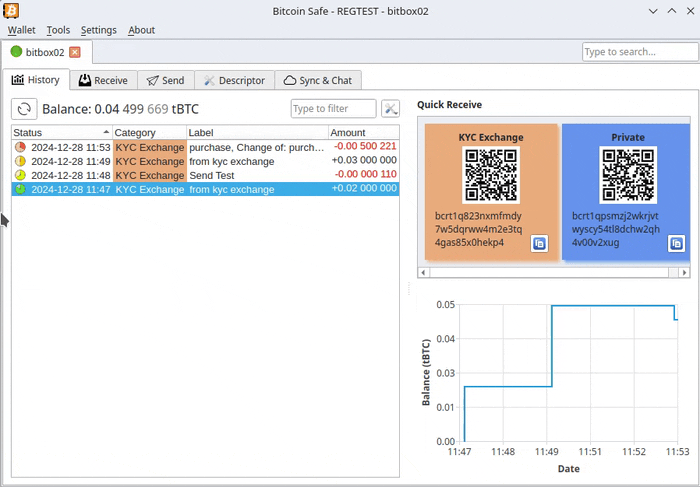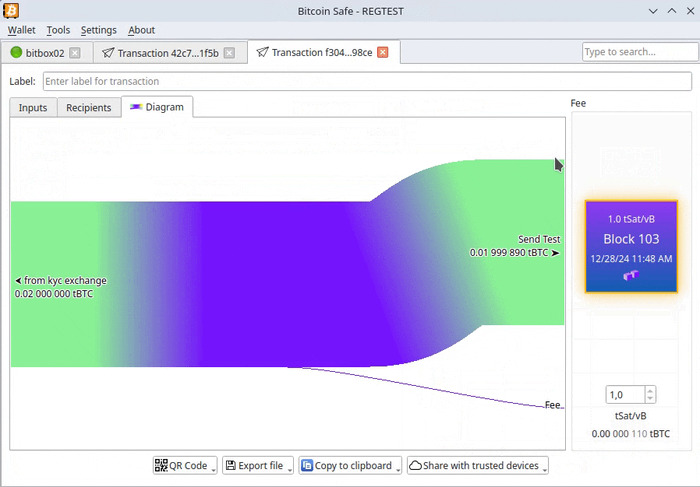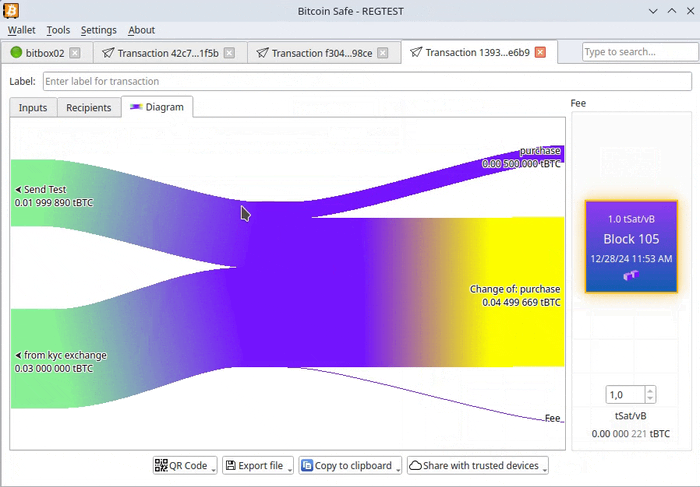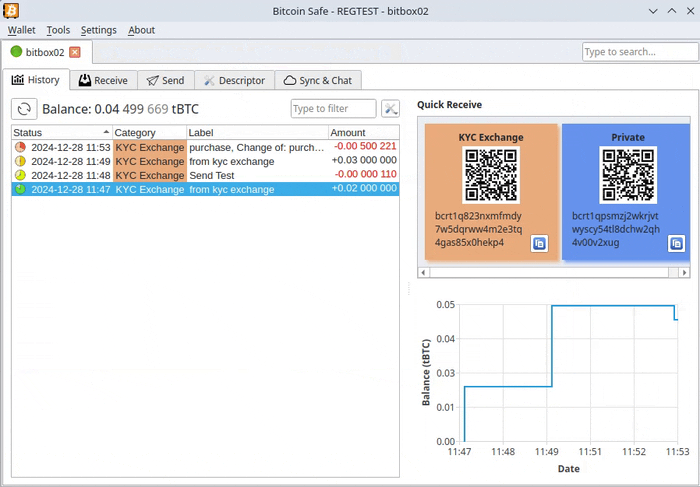
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
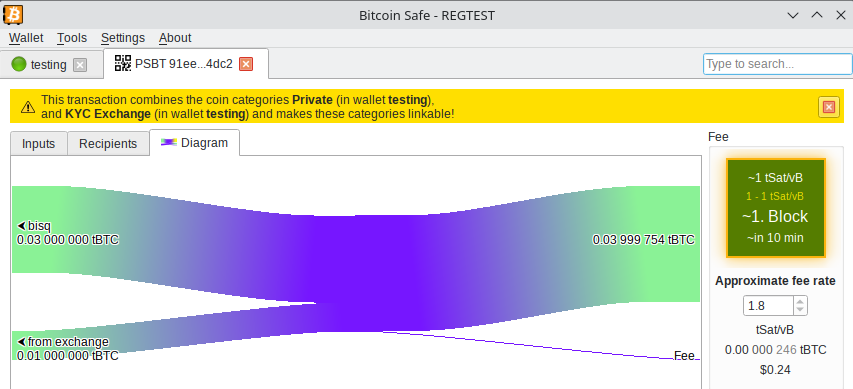
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
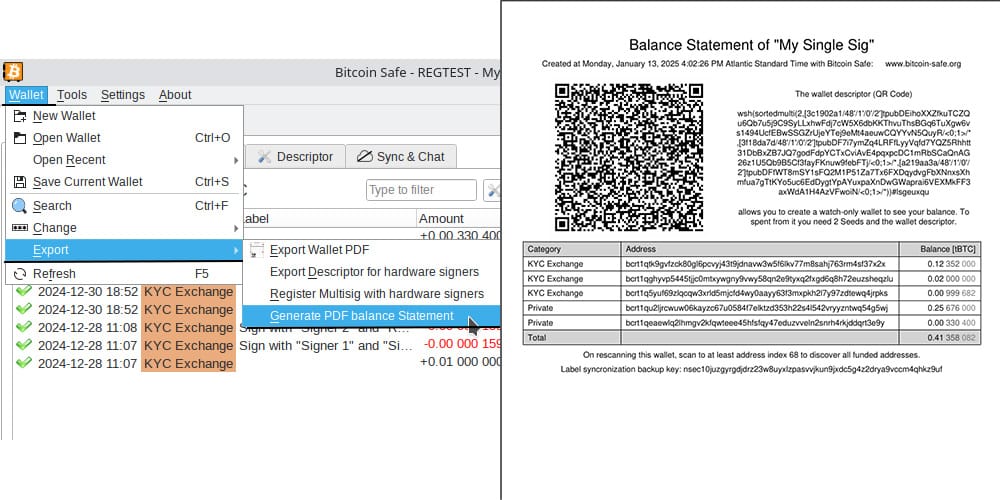
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
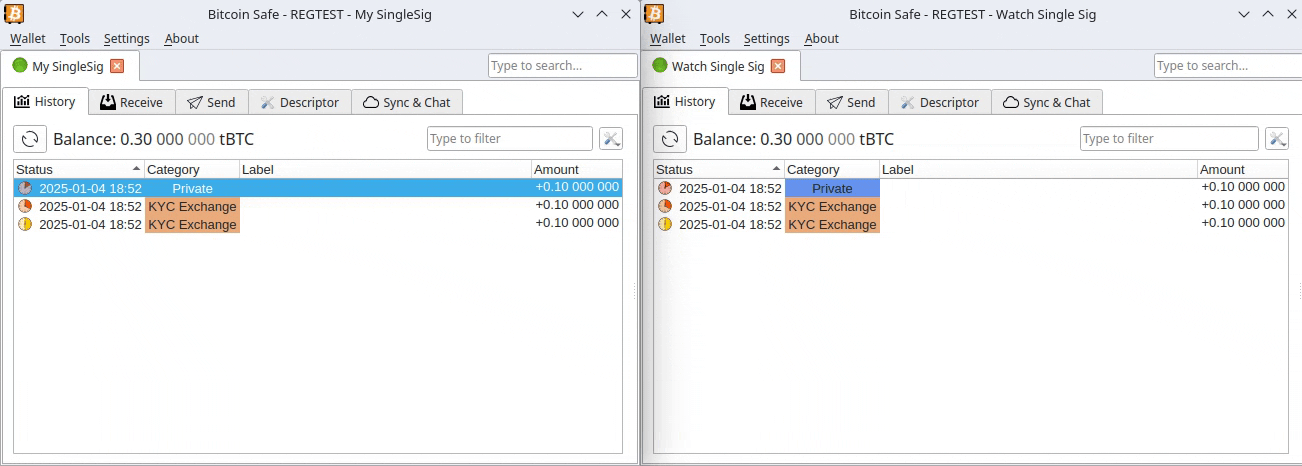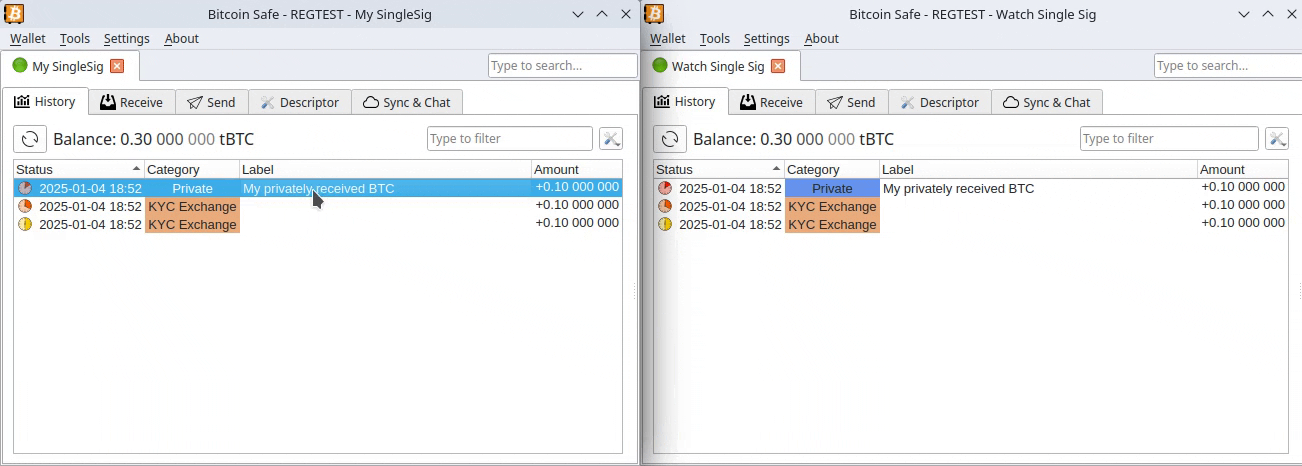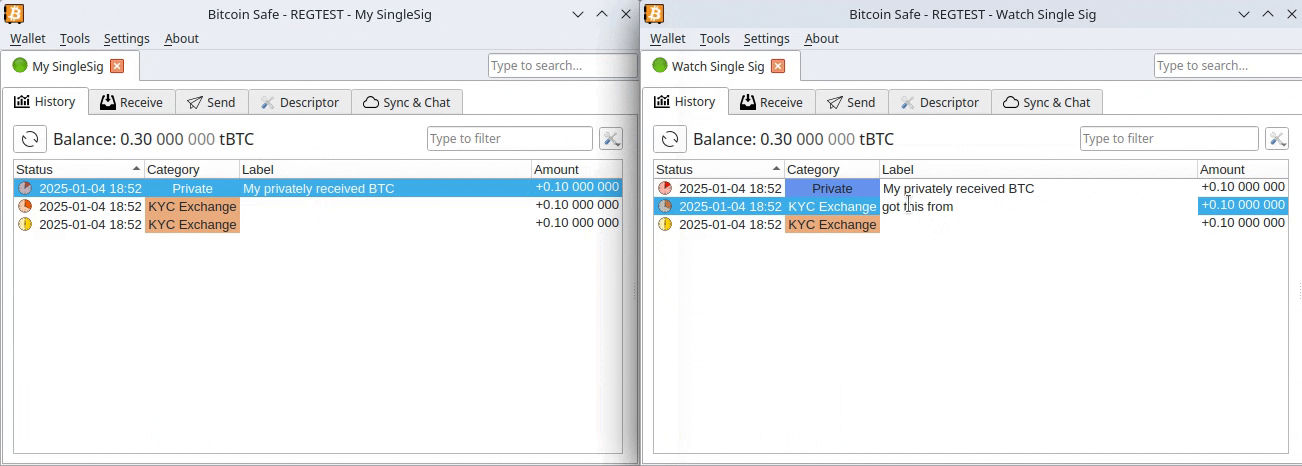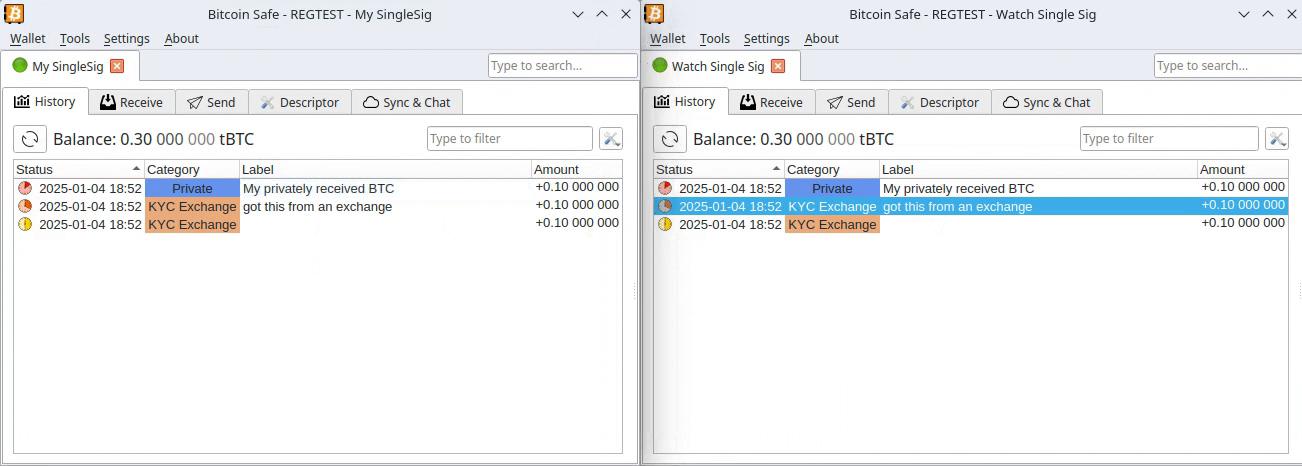
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ 6e0ea5d6:0327f353
2025-04-24 03:07:34
@ 6e0ea5d6:0327f353
2025-04-24 03:07:34Ascolta bene, amico mio!
There is a kind of solitude that doesn’t come from the absence of company, but from the weight of the role one must play.
I’m not talking about being admired, followed, or applauded by outsiders — but of being necessary to those of your own blood.
Of being the one upon whom everything rests, even if no one ever acknowledges it.Truly, I learned throughout my life in the province of Sicily that the man who is held up by no one, yet holds up many — that man has no right to collapse. Not because he is stronger. But because if he falls, he doesn’t fall alone — he brings down the roof over those who live under his shadow.
And here lies the silent tragedy:
No one catches him when he falters.
But everyone collapses when he does.He is the father who cannot fall ill,
The son who becomes the pillar for his parents,
The leader who must never hesitate,
The older brother who must not cry,
The man of honor who must do “whatever must be done.”The exhaustion is real. The fatigue, daily.
But this kind of man learns to live with weariness as others live with pain:
It’s not about waiting for relief, but about continuing to walk despite the crushing weight.
That’s why, amico mio, never ask for lighter burdens — but always for stronger shoulders.In this context, renunciation is not a personal choice.
It is a collective sentence.
It’s like demolishing a pillar and expecting the ceiling to remain intact.Therefore, the man who carries this awareness does not allow himself the luxury of giving up.
He doesn’t grant himself the right to fail — not out of heroism, but out of clarity.
He knows that his collapse would cost a family.Learn this: l’onore non è individuale.
True honor is collective and familial.
What you endure, you endure for your own.
What you face, you face for those who came before you, and those who will come after.
And what you cannot abandon is not about pride — it’s about responsibility.There is no glory in it.
There are no medals.
But there is a silent, unshakable dignity that only a few ever understand:
To be the foundation — never the weight.The name for this is honor, loyalty, and pride.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ d34e832d:383f78d0
2025-04-24 02:56:59
@ d34e832d:383f78d0
2025-04-24 02:56:591. The Ledger or Physical USD?
Bitcoin embodies a paradigmatic transformation in the foundational constructs of trust, ownership, and value preservation within the context of a digital economy. In stark contrast to conventional financial infrastructures that are predicated on centralized regulatory frameworks, Bitcoin operationalizes an intricate interplay of cryptographic techniques, consensus-driven algorithms, and incentivization structures to engender a decentralized and censorship-resistant paradigm for the transfer and safeguarding of digital assets. This conceptual framework elucidates the pivotal mechanisms underpinning Bitcoin's functional architecture, encompassing its distributed ledger technology (DLT) structure, robust security protocols, consensus algorithms such as Proof of Work (PoW), the intricacies of its monetary policy defined by the halving events and limited supply, as well as the broader implications these components have on stakeholder engagement and user agency.
2. The Core Functionality of Bitcoin
At its core, Bitcoin is a public ledger that records ownership and transfers of value. This ledger—called the blockchain—is maintained and verified by thousands of decentralized nodes across the globe.
2.1 Public Ledger
All Bitcoin transactions are stored in a transparent, append-only ledger. Each transaction includes: - A reference to prior ownership (input) - A transfer of value to a new owner (output) - A digital signature proving authorization
2.2 Ownership via Digital Signatures
Bitcoin uses asymmetric cryptography: - A private key is known only to the owner and is used to sign transactions. - A public key (or address) is used by the network to verify the authenticity of the transaction.
This system ensures that only the rightful owner can spend bitcoins, and that all network participants can independently verify that the transaction is valid.
3. Decentralization and Ledger Synchronization
Unlike traditional banking systems, which rely on a central institution, Bitcoin’s ledger is decentralized: - Every node keeps a copy of the blockchain. - No single party controls the system. - Updates to the ledger occur only through network consensus.
This decentralization ensures fault tolerance, censorship resistance, and transparency.
4. Preventing Double Spending
One of Bitcoin’s most critical innovations is solving the double-spending problem without a central authority.
4.1 Balance Validation
Before a transaction is accepted, nodes verify: - The digital signature is valid. - The input has not already been spent. - The sender has sufficient balance.
This is made possible by referencing previous transactions and ensuring the inputs match the unspent transaction outputs (UTXOs).
5. Blockchain and Proof-of-Work
To ensure consistency across the distributed network, Bitcoin uses a blockchain—a sequential chain of blocks containing batches of verified transactions.
5.1 Mining and Proof-of-Work
Adding a new block requires solving a cryptographic puzzle, known as Proof-of-Work (PoW): - The puzzle involves finding a hash value that meets network-defined difficulty. - This process requires computational power, which deters tampering. - Once a block is validated, it is propagated across the network.
5.2 Block Rewards and Incentives
Miners are incentivized to participate by: - Block rewards: New bitcoins issued with each block (initially 50 BTC, halved every ~4 years). - Transaction fees: Paid by users to prioritize their transactions.
6. Network Consensus and Security
Bitcoin relies on Nakamoto Consensus, which prioritizes the longest chain—the one with the most accumulated proof-of-work.
- In case of competing chains (forks), the network chooses the chain with the most computational effort.
- This mechanism makes rewriting history or creating fraudulent blocks extremely difficult, as it would require control of over 50% of the network's total hash power.
7. Transaction Throughput and Fees
Bitcoin’s average block time is 10 minutes, and each block can contain ~1MB of data, resulting in ~3–7 transactions per second.
- During periods of high demand, users compete by offering higher transaction fees to get included faster.
- Solutions like Lightning Network aim to scale transaction speed and lower costs by processing payments off-chain.
8. Monetary Policy and Scarcity
Bitcoin enforces a fixed supply cap of 21 million coins, making it deflationary by design.
- This limited supply contrasts with fiat currencies, which can be printed at will by central banks.
- The controlled issuance schedule and halving events contribute to Bitcoin’s store-of-value narrative, similar to digital gold.
9. Consider
Bitcoin integrates advanced cryptographic methodologies, including public-private key pairings and hashing algorithms, to establish a formidable framework of security that underpins its operation as a digital currency. The economic incentives are meticulously structured through mechanisms such as mining rewards and transaction fees, which not only incentivize network participation but also regulate the supply of Bitcoin through a halving schedule intrinsic to its decentralized protocol. This architecture manifests a paradigm wherein individual users can autonomously oversee their financial assets, authenticate transactions through a rigorously constructed consensus algorithm, specifically the Proof of Work mechanism, and engage with a borderless financial ecosystem devoid of traditional intermediaries such as banks. Despite the notable challenges pertaining to transaction throughput scalability and a complex regulatory landscape that intermittently threatens its proliferation, Bitcoin steadfastly persists as an archetype of decentralized trust, heralding a transformative shift in financial paradigms within the contemporary digital milieu.
10. References
- Nakamoto, S. (2008). Bitcoin: A Peer-to-Peer Electronic Cash System.
- Antonopoulos, A. M. (2017). Mastering Bitcoin: Unlocking Digital Cryptocurrencies.
- Bitcoin.org. (n.d.). How Bitcoin Works
-
 @ 1731c73c:1bca4ecc
2025-03-17 14:13:04
@ 1731c73c:1bca4ecc
2025-03-17 14:13:04Welch Geistes Kind sind Waffenproduzenten, welch Geistes Kind Wissenschaftler, die Viren so verändern, dass sie pathogener, also gefährlicher für den Menschen werden? Im pfälzischen
https://soundcloud.com/radiomuenchen/kommt-wuhan-nach-deutschland-von-prof-roland-wiesendanger
Weilerbach wird ein US-Biolabor der Schutzstufe 3 gebaut. Dort sollen hochinfektiöse Erreger oder Substanzen, unter anderem SARS-CoV-2, das Virus H5N1, Dengue- und das Hanta-Virus untersucht werden. Der Bundesregierung – so fand Florian Warweg von den NachDenkSeiten heraus - weiß davon angeblich nichts. Auch nicht, welche Kontrollfunktion Bundesbehörden für US-Biolabore auf deutschem Boden haben.
War da was? Hatte nicht – ebenso vertuscht von Regierung, Medien und Wissenschaftlern – für die einen die größte Pandemie, für die anderen der weltweit größte Wissenschafts- und Medizinskandal in den letzten fünf Jahren stattgefunden? Warum interessiert das keinen?
Die Bestätigung der US-Regierung ist offiziell, dass die Covid-19-Pandemie aus einem Labor in Wuhan stammt. Das entlarvt die jahrelange Vertuschung und Diffamierung kritischer Stimmen als politisch motivierte Manipulation. Einer, der diskreditiert wurde, ist Professor Roland Wiesendanger. Mundtot ließ er sich aber nicht machen. Er fordert weiterhin eine schonungslose Aufarbeitung der hochgefährlichen Gain-of-function-Forschung, außerdem deren weltweite Ächtung, um zukünftige Pandemien zu verhindern.
Roland Wiesendanger ist Physik-Professor an der Universität Hamburg, Ehrendoktor der Technischen Universität Posen und Mitglied zahlreicher nationaler und internationaler Wissenschaftsakademien. Hören Sie sein Statement: „Wir dürfen die Risiken der Gain- of-function-Forschung nicht länger hinnehmen“.
Sprecher: Ulrich Allroggen
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): 3G1wDDH2CDPJ9DHan5TTpsfpSXWhNMCZmQ\ Ethereum (ETH): 0xB41106C0fa3974353Ef86F62B62228A0f4ad7fe9
-
 @ fd06f542:8d6d54cd
2025-04-24 02:23:58
@ fd06f542:8d6d54cd
2025-04-24 02:23:58今天主要是更新了seo优化:
- 增加了 blog页面的预加载内容,这样搜索引起抓取blog页面的时候,能够看到的是渲染好的 blog 列表;
- 增加里 blog/[blogid] 页面的 显示原文静态链接,这个链接主要是给搜索引擎使用,他根据原文可以抓取content内容
- 在+page.svelte页面 增加了 raw 数据显示,用户也可以看到和搜索引擎一样的内容,这个取决于 svelte的页面访问路由机制,她发现是api访问就会调用 server.ts返回数据,她发现是浏览器访问就会返回+page.svelte渲染的内容。 这个设计让搜索引擎和 浏览器看到的有区别。所以我两个都做了。
接下来的工作计划
- 增加 blog的评论和点赞功能?
- 美化页面?
- 做一个electron的客户端?
- 给用户做一个 通过blog定制化自己的主页?
关于nostrbook的 想法
用户其实可以通过nostrbook 搭建自己的blog系统,或者写书系统。在公司内网或者自己的服务器上。
修改config.ts的面的三个配置就可以了。 ```js
export let booktag="createbook"; export let blogtag="createblog"; export let chaptertag="bookchapter"; ```
我也是通过这个开关测试了线上和测试的开发的内容区分开的。
昨天发现的bug
就是 30023 update问题,虽然可以通过dtag可以实现替换。但是部分服务器没有update到最新的。所以他会返回老的。 是不是通过服务器之间的同步可以解决呢?
-
 @ b8af284d:f82c91dd
2025-03-16 16:42:49
@ b8af284d:f82c91dd
2025-03-16 16:42:49
Liebe Abonnenten,
diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante. Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben?
Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. In Wuhan wurde mit amerikanischem Geld geforscht. Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken.
In meinem aktuellen Buch “Der chinesische (Alp-)Traum” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. Hier gibt es das gesamte Kapitel nachzulesen.

Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: Schon im Oktober will man die Testphase beenden und an der Einführung arbeiten.
Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es?
Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen. Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen.
Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. Zuletzt im Dezember 24.
Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist.
Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“?
In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, looking at you, Tether!), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und Tether einer der größten Halter von US-Staatsanleihen ist, wird es den digitalen Dollar bis auf Weiteres nicht geben.
Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, scheint man aktuell eher auf Gold zu setzen.
Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht.
Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:
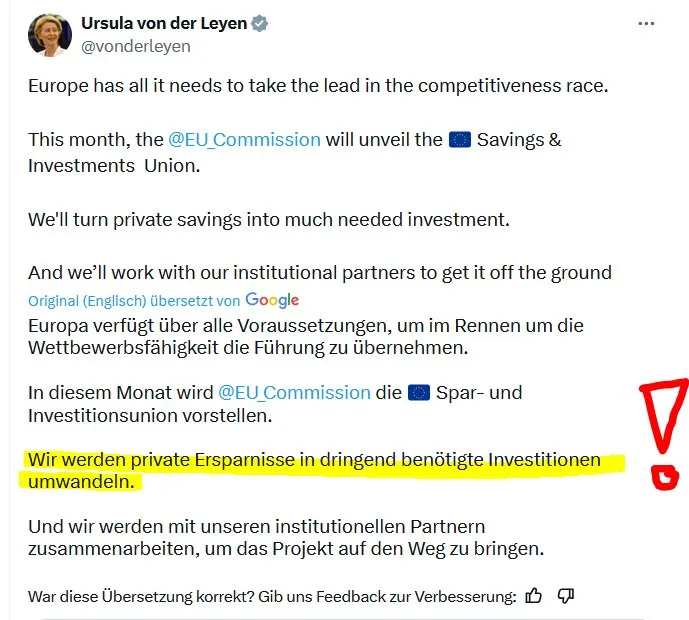
Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden. Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird.
Like, wenn Dein Aluhut glüht…
Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. Wie es mit Bitcoin, Gold und Aktien weitergeht.**
-
 @ 502ab02a:a2860397
2025-04-24 02:00:28
@ 502ab02a:a2860397
2025-04-24 02:00:28ถ้า “นมปลอมเข้าโรงเรียน” กับเกม Lobby ระดับโลก ที่ซ่อน GMO ไว้ในแก้วของลูกหลานเรา
โอเค เรารู้จักคำว่า Precision Fermentation หรือ PF กันไปแล้ว กลับมาดูโลกปัจจุบันนี้กันครับ
ในวันที่ผู้ใหญ่ยังทะเลาะกันเรื่องราคาน้ำนมดิบ มีบางบริษัทที่กำลังยิ้มกว้าง เพราะแผนระยะยาวของเขา…คือการเปลี่ยนนมโรงเรียนจากของจริง ไปสู่นมปลอมที่ “จดสิทธิบัตรได้” และ “ควบคุมทั้ง supply chain”
เรื่องนี้อาจดูเหมือนนิยายไซไฟนะครับ แต่เฮียจะพาไปเจาะลึกเบื้องหลังการ lobby ที่พยายามผลัก “นมจาก Precision Fermentation” และ “นม Plant-Based” เข้าสู่ระบบโรงเรียน โดยอ้างว่า “เพื่อสุขภาพ เพื่อโลก และเพื่อเด็กๆ” แต่จริงๆ แล้วมันคือ เกมเปลี่ยนอาหารเป็นทรัพย์สินทางปัญญาแบบเงียบๆ
ทำไม “โรงเรียน” ถึงเป็นเป้าหมายสำคัญ? คำตอบง่ายมาก เพราะว่ามันกลับเข้าสู่ loop เดิมกับตอนที่เขาพยายามยัด นมสด เข้าไปในชีวิตเมื่อหลังสงครามโลกครั้งที่ 2 นั่นละครับ หนังม้วนเดิม มีเพิ่มเติมคือความทันสมัย 1.โรงเรียนคือฐานข้อมูลประชากรที่แน่นอน = จำนวนเด็กแน่ชัด งบประมาณแน่ชัด 2.พฤติกรรมการกินของเด็ก “ฝังได้ง่าย” = ถ้าเด็กเติบโตมากับนม Plant-Based หรือ Milk 2.0 ตั้งแต่เล็ก พอเขาโตขึ้น “ร่างกายจะลืมรสนมวัวไปเลย” และไม่เคยรู้ว่าเคยมี real food ให้เลือก เหมือนที่โลกของ เจเนอเรชั่น internet มือถือ หรือแม้แต่สมัยนี้คือ สตรีมมิ่ง 3.เป็นจุดที่รัฐมีบทบาทโดยตรง = ง่ายต่อการ lobby policy เพราะแค่เปลี่ยนนโยบายระดับกระทรวง ก็เปลี่ยนทั้งประเทศได้
ใครอยู่เบื้องหลังการล็อบบี้นี้? 1. องค์กรระดับโลกที่ขับเคลื่อน Plant-Based School Meals อย่างเช่น - GFI (Good Food Institute) เป็นองค์กรที่มีเป้าหมายชัดว่า “เปลี่ยนโปรตีนของโลกจาก animal-based ให้เป็น cell-based และ fermentation-based” สนับสนุนงานวิจัย ออกนโยบายผลักดันเมนูโรงเรียน - ProVeg International ซึ่งมีโครงการชื่อ “School Plates” ปรับเมนูโรงเรียนให้เป็น plant-based - EAT Forum & WEF (World Economic Forum) ที่มีการสนับสนุนนโยบาย global dietary shift ซึ่งแนะนำให้ลดการบริโภคเนื้อสัตว์และผลิตภัณฑ์จากสัตว์ เพื่อส่งเสริมสุขภาพและความยั่งยืนของสิ่งแวดล้อม
- บริษัทยักษ์ใหญ่ด้าน Milk 2.0
- Perfect Day ร่วมกับ Nestlé ที่พยายามผลักดันนม PF ให้เป็นนมทดแทนแห่งอนาคต
-
Oatly ผู้ผลิตนม plant-based และ lobby ให้ “รัฐบาลช่วยจัดซื้อในโรงเรียน” พร้อมกับแคมเปญประชาสัมพันธ์ว่านี่คือตัวเลือกที่ “รักษ์โลกและดีต่อสุขภาพ” และ NotCo / Danone ซึ่งอยู่ในตลาดประเภทเดียวกัน ก็อาจมีแนวโน้มเข้าสู่ตลาดโรงเรียนเช่นกัน
-
เช่นเดียวกับที่เคยเล่าเรื่องนมสดไว้ครับ เขาจะต้องมาพร้อมการวิจัยที่ออกแบบให้รองรับการเปลี่ยนนโยบาย ด้วยหลายงานวิจัยที่บอกว่า “นมวัวมีผลเสียต่อสุขภาพเด็ก” ถูกสนับสนุนโดยกลุ่มทุนที่อยู่ในวงการ plant-based หรือ biotech งานบางชิ้นลดความสำคัญของสารอาหารจาก animal-based ลง และ “ปั่นคะแนน” ของ Plant Milk หรือ PF Milk ให้ดูสูงกว่าความเป็นจริง
วิธีการ Lobby แบบแนบเนียนก็จะใช้กระบวนการประมาณนี้ครับ 1. แทรกผ่านโครงการ “นมโรงเรียนฟรี” หลายประเทศใช้เงินรัฐอุดหนุนนมโรงเรียน กลุ่ม Lobby เข้าไป “เสนอของถูกกว่า” และอ้างว่า “เหมาะกับเด็กแพ้นมวัว” ทำให้รัฐเริ่มพิจารณา Plant Milk หรือ PF Milk เป็นทางเลือก “ถูกกว่าและดูดี”
-
ล้างความคิดผ่านหลักสูตรสุขศึกษา เริ่มมีสื่อการสอนที่ใช้คำว่า “milk” แบบรวม Plant Milk เข้าไปด้วย ลดความต่างระหว่างนมวัวกับนมจากพืช และเริ่มพูดว่า “นมจากพืชดีกว่าต่อสิ่งแวดล้อม”
-
แจกทุนให้โรงเรียนที่ร่วมโครงการ มีการเสนอทุนวิจัย ทุนสนับสนุนเมนูโรงเรียน ถ้าโรงเรียนยอมทดลองใช้นม Plant-Based หรือ PF Milk สร้างภาพลักษณ์ว่าเป็นโรงเรียน “รักโลก รักสุขภาพ”
-
ใช้พลังอินฟูฯและดารา ดาราดังๆ ถูกใช้เป็นหน้าโครงการ (ในตปท.) เช่นโพสต์ภาพเด็กๆ กิน “นมไม่มีวัว” พร้อมคำบรรยายว่า “นี่คืออนาคตของการกินอย่างมีจริยธรรม” อะไรประมาณนี้ครับ
ผลกระทบที่จะเกิดขึ้นก็คือ เด็กๆ เสียโอกาสในการได้รับโภชนาการจาก real food โดยเฉพาะ B12, วิตามิน A, DHA, โคลีน, เคซีนจากธรรมชาติ ซึ่งนมเทียมต้อง “แต่งเติม” เข้ามาทั้งสิ้น รวมถึง เด็กโตมากับอาหารปลอม โดยไม่รู้ว่าเคยมีของจริงให้เลือก สุดท้ายจะกลายเป็น “ผู้ใหญ่ที่ต้องพึ่งบริษัท” เพื่อมีโปรตีนกินในชีวิตประจำวัน และท้ายสุด รัฐกลายเป็นผู้สนับสนุนสิทธิบัตรเอกชน เพราะเมื่อ Milk 2.0 เข้าสู่ระบบโรงเรียน มันจะกลายเป็น “ค่าใช้จ่ายประจำ” ที่รัฐบาลต้องจ่ายให้บริษัทตลอดไป ซึ่งตรงนี้ก็จะวนกลับมาที่พวกเราที่อยู่ภายใต้ระบบ fiat
ดังนั้นมันก็เลยสรุปได้ว่า นี่ไม่ใช่แค่เรื่องอาหาร แต่คือการเปลี่ยนโครงสร้างอำนาจ Milk 2.0 เข้าโรงเรียน ไม่ใช่เพราะมันดีกว่า แต่เพราะมัน “ล็อกห่วงโซ่คุณค่าไว้ในมือคนส่วนน้อย” และสร้างประชากรรุ่นใหม่ที่ไม่รู้จักอาหารจริงจากธรรมชาติ
หากเด็กวันนี้กินของปลอมจนชิน วันหนึ่งเขาอาจยอม “จ่ายเงินเช่าโปรตีน (subscribe) ” ไปตลอดชีวิต โดยไม่เคยรู้เลยว่า… วัวเคยให้นมได้โดยไม่ต้องใช้เทคโนโลยีใดๆ เลย
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 306555fe:fd7fdf12
2025-03-15 05:56:16
@ 306555fe:fd7fdf12
2025-03-15 05:56:161. Executive Summary
This report presents a detailed comparative analysis of Tesla Powerwall and Sungrow battery options for a 3-phase residence in Sydney, Australia, equipped with a 6.6kW solar system and a Sungrow SG5KTL-MT inverter. The evaluation focuses on the suitability of these battery solutions for potential off-grid capability and Vehicle-to-Home (V2H) functionality. The analysis reveals that while both Tesla Powerwall and Sungrow offer compelling features for home energy storage, Sungrow battery systems, particularly when paired with their hybrid inverters, present a more direct and comprehensive solution for achieving 3-phase off-grid capability. For V2H integration, both systems currently rely on the development of compatible bidirectional charging infrastructure in Australia. Based on the user's stated goals, a Sungrow battery system, potentially requiring an upgrade to a Sungrow hybrid inverter, is the recommended solution.
2. Introduction: Context and Objectives
The Australian residential energy landscape is witnessing a significant shift towards energy independence, with increasing adoption of solar photovoltaic (PV) systems and battery storage. This trend is propelled by factors such as escalating electricity costs and a growing desire for reliable power, particularly during grid outages. This report addresses the specific needs of a Sydney homeowner who has already invested in a 6.6kW solar system connected to a 3-phase Sungrow SG5KTL-MT inverter and owns a Tesla electric vehicle. The homeowner is now exploring battery storage solutions, with a particular focus on enabling potential off-grid operation and facilitating future Vehicle-to-Home (V2H) capabilities for their Tesla.
The primary objectives of this report are threefold: firstly, to evaluate the technical and practical suitability of Tesla Powerwall for a 3-phase home in Sydney; secondly, to conduct a similar evaluation for various Sungrow battery options; and thirdly, to provide a comparative assessment of these two leading solutions based on their ability to support off-grid functionality and integrate with V2H technology. The scope of this analysis includes the latest Tesla Powerwall models available in Australia and relevant high-voltage battery options from Sungrow, specifically the SBR and SBH series. The geographical context is limited to Sydney, Australia, considering local grid regulations and market availability. This analysis relies on the provided research material and publicly accessible technical specifications to form its conclusions.
3. Analysis of Tesla Powerwall for a 3-Phase Sydney Home
- 3.1 Technical Specifications and Features:\ The Tesla Powerwall is a well-established residential battery system. The latest generation, Powerwall 3, offers an energy capacity of 13.5 kWh 1 and can deliver up to 10 kW of on-grid power, with the same capacity for backup power, capable of a 185 A motor start 1. A key feature of Powerwall 3 is its integrated solar inverter with a 97.5% efficiency and three solar inputs with Maximum Power Point Trackers (MPPTs) in the Australian version 1. The system is scalable, allowing for the installation of up to four units 1, and utilizes Lithium Iron Phosphate (LFP) battery chemistry, known for its safety 5. In contrast, the Powerwall 2, while also having a 13.5 kWh energy capacity 7, provides a continuous power output of 5 kW with a 7 kW peak 7. Notably, Powerwall 2 does not have an integrated solar inverter 7 and uses Nickel Manganese Cobalt Oxide (NMC) battery chemistry 7. It offers greater scalability, supporting up to ten units 1. Both Powerwall 2 and 3 come with a 10-year warranty 2. Powerwall 3 necessitates the use of the Tesla Backup Gateway 2 2, while Powerwall 2 requires a Gateway for system control and backup functionality 7. The integrated inverter in Powerwall 3 streamlines installations for new solar and storage setups. However, for homeowners with existing inverters, such as the user, this feature might introduce complexities as the existing inverter's functionality could become redundant if the system were configured to primarily utilize the Powerwall 3's inverter. Powerwall 2, designed as an AC-coupled battery, might offer a more seamless integration by working in conjunction with the existing Sungrow inverter 3.
- 3.2 Compatibility with Existing 3-Phase Sungrow Inverter (AC Coupling):\ Tesla Powerwall is designed as an AC-coupled battery, meaning it connects to the home's electrical system at the switchboard level and operates independently of the solar inverter 9. This AC coupling capability generally allows Powerwall to be compatible with a wide range of existing solar inverters, including the user's 3-phase Sungrow SG5KTL-MT model 2. Specifically, Powerwall 2 demonstrates 100% compatibility with single-phase grid-connected solar systems installed after October 2016 9. For Powerwall 3, Tesla indicates AC coupling compatibility with existing solar systems up to 5kW 2. However, a crucial consideration arises during grid outages concerning the ability to charge the Powerwall from solar. If the home has a 3-phase solar inverter, like the user's Sungrow SG5KTL-MT, Powerwall 2 might not be able to charge from solar during a blackout because many 3-phase inverters require the presence of all three phases from the grid to operate 9. This limitation could also extend to Powerwall 3 when AC-coupled with a 3-phase inverter 8. Given the user's interest in potential off-grid capability, this inability to recharge the battery from solar during a grid outage significantly limits the duration of backup power to the energy stored within the Powerwall. Furthermore, the user's 6.6kW solar system output exceeds the 5kW AC coupling limit specified for a single Powerwall 3. This suggests that either the entire solar generation cannot be used to charge a single Powerwall 3 via AC coupling, or a more complex configuration involving multiple Powerwall units might be necessary.
- 3.3 Suitability for Off-Grid Operation in a 3-Phase System:\ The Tesla Powerwall is fundamentally a single-phase battery system and can only provide backup power to a single phase within a 3-phase home 8. During a power outage, only the electrical circuits connected to the phase that the Powerwall is backing up will remain operational 8. This necessitates careful planning to ensure that essential loads, such as lighting, refrigerators, and internet connectivity, are connected to this designated phase 8. While it is possible to install multiple Powerwall units, with one unit dedicated to each phase, this significantly increases the overall cost and introduces complexities in system management 8. Notably, even with the installation of three Powerwall 3 units, comprehensive 3-phase backup is not guaranteed 20. It is also important to recognize that Tesla does not officially support or provide warranties for off-grid installations of Powerwall 2. The Powerwall system is primarily designed for grid-connected homes to provide backup during outages and to optimize energy consumption, rather than functioning as the primary power source in a completely off-grid scenario. Therefore, achieving a truly comprehensive off-grid capability for a 3-phase home using Tesla Powerwall would likely involve a substantial financial investment in multiple units, meticulous load balancing across the phases, and navigating the limitations of single-phase backup, all without official support from the manufacturer.
- 3.4 Potential for V2H Integration with an EV in Australia:\ Vehicle-to-Home (V2H) technology, which allows an electric vehicle to supply power back to a home, is gaining traction in Australia. Regulatory changes have been made to permit bidirectional charging systems, with mainstream adoption expected in 2025 21. Australian standards for bidirectional charging are now approved, and compatible chargers are anticipated to become available in 2025 22. Currently, the research snippets do not indicate that Tesla Powerwall offers direct, integrated V2H functionality with EVs in Australia 1. However, the Tesla Powerwall can play a supportive role in a V2H ecosystem. It can efficiently store excess energy generated by the solar system 1, which could then be used to charge the EV. If the EV is equipped with V2H capabilities and connected to a compatible bidirectional charger, the energy stored in the Powerwall (or directly from solar) could indirectly contribute to powering the home by first charging the vehicle's battery. The actual discharge from the vehicle to the home would be managed by the bidirectional charger and the vehicle's internal systems, not directly by the Powerwall. Therefore, while Powerwall doesn't inherently provide V2H, it can act as a crucial energy storage component within a broader V2H setup.
- 3.5 Cost and Installation Considerations in Sydney:\ The cost of a Tesla Powerwall 3 in Australia is approximately $13,600, which includes the mandatory Backup Gateway 2 2. Powerwall 2 has an approximate price of $8,750 to $9,750, excluding installation and the Backup Gateway 7, with the installed cost estimated between $12,000 and $14,000 7. Installation costs for Powerwall 3 as part of a new solar system at Penrith Solar Centre start at $23,990 (including a 6kW solar system), while adding it to an existing system is around $15,990 27. Installing a Powerwall system in a 3-phase home can incur additional costs and complexities compared to single-phase installations 13. If the goal is to achieve any level of backup across multiple phases using Powerwall, the cost would escalate significantly with the need for multiple units. Homeowners in NSW may be eligible for rebates under the Peak Demand Reduction Scheme (PDRS), which can help offset the initial investment in a Tesla Powerwall 5. However, the overall cost of a Powerwall system, especially when considering a multi-unit setup for more comprehensive backup in a 3-phase home, remains a substantial financial consideration.
4. Analysis of Sungrow Battery Options for a 3-Phase Sydney Home
- 4.1 Technical Specifications of Relevant Sungrow Battery Models (SBR and SBH Series):\ Sungrow offers a range of high-voltage battery solutions, primarily the SBR and SBH series, utilizing Lithium Iron Phosphate (LiFePO4) chemistry for enhanced safety 5. The SBR series features a modular design with 3.2 kWh battery modules, allowing for system capacities ranging from 9.6 kWh (3 modules) up to 25.6 kWh (8 modules) in a single stack. Multiple stacks can be connected in parallel to achieve even larger capacities, up to 100 kWh 6. These batteries boast 100% usable energy capacity 26 and are high-voltage systems 33. The SBH series also employs a modular design with larger 5 kWh battery modules. A single stack can accommodate 4 to 8 modules, providing usable energy from 20 kWh to 40 kWh. Similar to the SBR series, multiple SBH stacks can be connected in parallel to reach a maximum capacity of 160 kWh 5. Both the SBR and SBH series come with a 10-year warranty 5 and are primarily designed for DC coupling with Sungrow's hybrid inverter range, particularly the SH series, which includes models specifically designed for 3-phase systems (SH-RT series) 33. The availability of a wider range of capacities and the modular design of both the SBR and SBH series provide greater flexibility for the user to tailor a battery system to their specific energy consumption needs. The SBH series, with its larger 5 kWh modules, appears particularly well-suited for homes with potentially higher energy demands, such as those with 3-phase connections.
- 4.2 Compatibility with Existing 3-Phase Sungrow Inverter (DC and AC Coupling):\ The user's existing Sungrow SG5KTL-MT inverter is a grid-tied inverter and not a hybrid model designed for direct DC coupling with batteries 5. Sungrow's high-voltage batteries, such as the SBR and SBH series, are primarily intended for DC coupling with their SH series hybrid inverters 33. While direct DC coupling is not an option with the SG5KTL-MT, it is possible to AC couple Sungrow batteries to the existing solar system 35. This would likely require the addition of a separate battery inverter to manage the charging and discharging of the Sungrow battery, as the SG5KTL-MT does not have this functionality. Although AC coupling offers a way to integrate a battery without replacing the existing solar inverter, it can introduce inefficiencies due to the multiple AC-DC and DC-AC conversions. For optimal performance and to fully leverage the capabilities of Sungrow's high-voltage batteries, particularly for off-grid operation, upgrading to a Sungrow SH series hybrid inverter would be the recommended approach.
- 4.3 Suitability for Off-Grid Operation in a 3-Phase System:\ Sungrow offers a distinct advantage in providing solutions for 3-phase off-grid operation through their SH-RT series of hybrid inverters 5. These inverters, when paired with Sungrow's SBR or SBH batteries, are capable of providing seamless transition to 3-phase backup power during grid outages 63. The SH-RT series is specifically designed to support 100% unbalanced loads in backup mode, ensuring that essential appliances continue to run during a blackout 66. Both the SBR and SBH battery series are compatible with off-grid operation when used in conjunction with the appropriate Sungrow hybrid inverters. Some single-phase Sungrow hybrid inverters (SH-RS series) also offer off-grid capabilities and support generator connection for battery charging during extended periods of low solar generation 85. This comprehensive ecosystem of Sungrow products provides a more direct and integrated pathway for the user to achieve their goal of potential 3-phase off-grid capability compared to the single-phase limitations of Tesla Powerwall.
- 4.4 Potential for V2H Integration with an EV (e.g Tesla Car) in Australia:\ Similar to Tesla Powerwall, the provided research material does not explicitly mention direct V2H integration capabilities for Sungrow battery systems with Tesla cars in Australia 22. However, Sungrow's active involvement in the broader renewable energy and electric vehicle charging sectors suggests a strong potential for future integration. Sungrow manufactures its own range of EV chargers 64, and their 3-phase hybrid inverter solutions can be paired with these chargers for smart green power charging 64. As V2H technology and the necessary bidirectional charging infrastructure become more prevalent in Australia, it is conceivable that Sungrow's integrated energy management systems, including their batteries and hybrid inverters, could be updated to support V2H functionality, potentially even with Tesla vehicles through standardized protocols or future partnerships. In the interim, a Sungrow battery system can efficiently store solar energy, which could then be used to charge a Tesla car. The potential for the EV to discharge back to the home would depend on the availability and compatibility of third-party bidirectional chargers that adhere to the evolving Australian standards.
- 4.5 Cost and Installation Considerations in Sydney:\ The cost of Sungrow batteries in Australia varies depending on the model and capacity. For the SBR series, a 9.6 kWh system is approximately $11,500 installed, a 12.8 kWh system around $13,200 installed, and a 25.6 kWh system around $19,700 installed. Supply-only costs for the SBH series 20 kWh kit range from $13,778.70 to $14,360 40. Compatible 3-phase hybrid inverters from Sungrow, such as the SH5.0RT, are priced around $3,760, while the SH10RT ranges from approximately $4,174.50 to $5,720 78. If the user opts for a Sungrow battery system to achieve optimal 3-phase off-grid capability, the cost of a new SH series hybrid inverter would need to be included, as the existing SG5KTL-MT is not compatible for direct DC coupling. While AC coupling might be a less expensive initial step, it could involve the additional cost of a separate battery inverter. Homeowners in NSW can potentially benefit from the NSW battery rebate when purchasing a Sungrow battery system, which could help reduce the overall cost 5. Although Sungrow batteries often offer a competitive cost per kWh, the total investment for a comprehensive 3-phase off-grid solution might be higher than a single-phase Tesla Powerwall setup, primarily due to the potential need for a new hybrid inverter.
5. Comparative Assessment: Tesla Powerwall vs. Sungrow Batteries
- 5.1 Side-by-Side Comparison Table of Key Specifications:
| Feature | Tesla Powerwall 3 | Sungrow SBR (Example: 12.8 kWh) + SH10RT | | --- | --- | --- | | Usable Energy Capacity (kWh) | 13.5 | 12.8 | | Continuous Power Output (kW) | 10 | 10 | | Peak Power Output (kW) | 10 | 12 (5 min) | | Battery Chemistry | Lithium Iron Phosphate | Lithium Iron Phosphate | | Scalability | Up to 4 units (54 kWh) | Up to 25.6 kWh per stack, 4 stacks parallel (102.4 kWh) | | Off-Grid Backup (Phases Supported) | Single-Phase | Three-Phase | | V2H Support (Current/Future Potential) | Potential via 3rd party charger | Potential via 3rd party charger | | Warranty (Years) | 10 | 10 | | Estimated Cost (AUD) | $13,600 + installation | $13,200 (battery installed) + $4,175 - $5,720 (inverter) |
- 5.2 Detailed Comparison Based on Off-Grid Capability Requirements:\ When considering the user's goal of potential off-grid capability for a 3-phase home, Sungrow presents a more robust solution. The availability of Sungrow's SH-RT series hybrid inverters, specifically designed for 3-phase systems and fully compatible with their SBR and SBH batteries, allows for a direct and integrated approach to achieving 3-phase backup power. These systems can seamlessly transition to off-grid mode, powering all three phases of the home, which is crucial for operating 3-phase appliances and ensuring comprehensive whole-house backup. In contrast, Tesla Powerwall, being a single-phase battery, inherently limits off-grid backup to a single phase in a 3-phase home 8. While multiple Powerwall units can be installed, this increases cost and complexity without guaranteeing full 3-phase backup or official off-grid support from Tesla. Therefore, for a user prioritizing potential for comprehensive 3-phase off-grid operation, Sungrow's ecosystem offers a more suitable and supported pathway.
- 5.3 Detailed Comparison Based on V2H Functionality Requirements:\ Currently, neither Tesla Powerwall nor Sungrow batteries offer direct, integrated V2H functionality for Tesla cars in Australia 22. Both systems can store solar energy that could be used to charge a EV, and the potential for the car to discharge back to the home (V2H) would rely on the development and adoption of compatible bidirectional charging infrastructure in Australia, which is expected to become more mainstream in 2025 21. Sungrow's involvement in manufacturing EV chargers and integrating them with their hybrid inverters suggests a potential for future V2H integration within their ecosystem. Similarly, while Tesla Powerwall doesn't currently offer V2H, its role as a home energy storage solution makes it a complementary technology to V2H, providing a place to store energy that could eventually be managed within a V2H framework.
- 5.4 Cost-Effectiveness and Overall Value Analysis:\ When evaluating cost-effectiveness, Sungrow batteries often have a lower cost per kWh of storage compared to Tesla Powerwall 5. However, for the user with an existing non-hybrid inverter, achieving the desired 3-phase off-grid capability with Sungrow would likely necessitate an additional investment in a Sungrow SH-RT series hybrid inverter. This would increase the initial outlay compared to simply AC coupling a Tesla Powerwall to the existing inverter for single-phase backup. The overall value proposition depends heavily on the user's priorities. If the primary goal is to have backup power for essential loads on a single phase and potential future V2H integration, Tesla Powerwall could be a viable option. However, if the potential for comprehensive 3-phase off-grid operation is a significant factor, then the added expense of a Sungrow hybrid inverter might be justified by the enhanced functionality and future-proofing for energy independence. Sungrow's reputation for affordability and the modularity of their battery systems also offer long-term value and flexibility.
6. Recommendations and Considerations
Based on the analysis, for a 3-phase home in Sydney with a 6.6kW solar system and the goal of potential off-grid capability, Sungrow battery options are recommended. Specifically, the user should consider upgrading their existing Sungrow SG5KTL-MT inverter to a Sungrow SH series hybrid inverter (e.g., SH5.0RT or SH10RT, depending on anticipated power demands) and pairing it with a Sungrow high-voltage battery from either the SBR or SBH series. The choice between SBR and SBH would depend on the desired storage capacity and budget. This combination offers a more direct and supported path to achieving 3-phase backup power and the potential for future off-grid operation.
Key Considerations for the User:
- Off-Grid Capability: The level of off-grid capability desired (partial single-phase backup vs. comprehensive whole-home 3-phase backup) is a crucial factor. For the latter, Sungrow is the more suitable choice.
- Budget: Both options represent a significant investment. The user should obtain detailed quotes for both Tesla Powerwall (considering single or multiple units) and a complete Sungrow hybrid inverter and battery system.
- V2H Timeline: The user's timeline for V2H adoption should be considered. Both systems will likely integrate via third-party chargers.
- Inverter Upgrade: If pursuing the optimal Sungrow solution for off-grid capability, the cost and logistics of upgrading the existing inverter need to be factored in.
- 3-Phase Backup Importance: The necessity of having backup power across all three phases should weigh heavily in the decision, favoring Sungrow.
It is strongly recommended that the user obtain detailed quotes from certified installers in the Sydney area for both Tesla Powerwall and various Sungrow system configurations to get accurate pricing, installation details, and information on available rebates and incentives in NSW.
7. Conclusion
In conclusion, while Tesla Powerwall offers a well-regarded solution for home energy storage with reliable backup capabilities, its inherent single-phase design presents limitations for users with 3-phase homes seeking comprehensive off-grid functionality. Sungrow, with its range of high-voltage batteries and particularly its 3-phase hybrid inverter systems, provides a more direct and technically sound pathway to achieving the user's goals of potential 3-phase off-grid operation. For V2H integration, both systems are currently positioned to benefit from the evolving Australian regulatory landscape and the development of compatible bidirectional charging technologies. Ultimately, the optimal choice will depend on the user's specific priorities, budget, and the level of off-grid capability they wish to achieve. The rapidly evolving nature of battery storage and V2H technology suggests that continued research and consultation with experts are advisable before making a final decision.
Works cited
1. Powerwall – Home Battery Storage | Tesla Australia, accessed March 14, 2025, https://www.tesla.com/en_au/powerwall\ 2. Tesla Powerwall 3 in Australia: Everything You Need to Know - Fritts Solar, accessed March 14, 2025, https://www.frittssolar.com.au/tesla-powerwall-3-australia/\ 3. What to Expect for Powerwall 3 | Tesla Support Australia, accessed March 14, 2025, https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3\ 4. Tesla Powerwall 3 Review - Clean Energy Reviews, accessed March 14, 2025, https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review\ 5. Sungrow SBH vs. Tesla Powerwall 3: Which is Better? NSW - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/\ 6. Sungrow Battery vs Tesla Powerwall Review - Volteam Electric, accessed March 14, 2025, https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/\ 7. Tesla Powerwall 2: A Complete 2024 Buyers Guide | Solar Choice, accessed March 14, 2025, https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/\ 8. Can You Install The Powerwall 3 On A Three-Phase Home? - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/three-phase-powerwall-3/\ 9. Is my grid connect solar system 100% compatible with a Tesla Powerwall 2 battery?, accessed March 14, 2025, https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery\ 10. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf\ 11. Combining Systems with Powerwall | Tesla Support, accessed March 14, 2025, https://www.tesla.com/support/energy/powerwall/learn/combining-systems\ 12. Powerwall System Design | Tesla Support, accessed March 14, 2025, https://www.tesla.com/support/energy/powerwall/learn/system-design\ 13. Installing Powerwall 3 on a Three-phase Site | PSC - Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/\ 14. Powerwall 3: When It Makes Sense and When It Doesn't - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/\ 15. AC-Coupled Solar System Sizing - Energy Library - Tesla, accessed March 14, 2025, https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html\ 16. Powerwall 3 Roadmap - 3 Phase Coming! | Tesla Motors Club, accessed March 14, 2025, https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/\ 17. Advice on how to install with 3 phase : r/solar - Reddit, accessed March 14, 2025, https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/\ 18. TESLA POWERWALL+ (3) - DIY Solar Depot, accessed March 14, 2025, https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/\ 19. Design Considerations - Energy Library - Tesla, accessed March 14, 2025, https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html\ 20. Problems with Powerwall 3 | Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/\ 21. EV Charging in Australia Gets a Makeover with V2G/V2H Approved for 2025 - SEVR, accessed March 14, 2025, https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/\ 22. V2G, V2L & V2H Explained: Vehicle to Grid in Australia? 2025 - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/\ 23. Australia's Future – Bidirectional EV Charging, Solar & Battery Storage as Standard Features, accessed March 14, 2025, https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/\ 24. 2025, the Year of Vehicle-to-Grid in Australia V2G Milestone - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/\ 25. Bidirectional Charging for Electric Cars: Unlocking New Possibilities - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/\ 26. The Best Home Batteries In Australia In 2025: According To Aussie Installers - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/best-home-batteries-2025/\ 27. How Much Does a Tesla Powerwall 3 Cost? | Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/\ 28. Expected 3 Phase upgrade price? : r/AusRenovation - Reddit, accessed March 14, 2025, https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/\ 29. Powerwall cost for Sydney? | Tesla Motors Club, accessed March 14, 2025, https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/\ 30. Solar Battery Costs: Are They Worth It?, accessed March 14, 2025, https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/\ 31. Tesla Powerwall 3 Price and Installation - Solar4Life, accessed March 14, 2025, https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation\ 32. Solar Battery Price, Savings and Payback, accessed March 14, 2025, https://solarcalculator.com.au/battery-storage/price/\ 33. Sungrow | Solar Batteries Review - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html\ 34. Sungrow SBR high voltage battery - VP Solar, accessed March 14, 2025, https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/\ 35. Sungrow Battery SBR Series - SolarBright, accessed March 14, 2025, https://solarbright.com.au/product/sungrow-battery-sbr-series/\ 36. Sungrow SBR 3.2kWh module - Huglo Solar, accessed March 14, 2025, https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery\ 37. Sungrow Inverter and battery Review - Clean Energy Reviews, accessed March 14, 2025, https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review\ 38. SBH100/150/200/250/300/350/400 - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400\ 39. 20/25/30/35/40 kWh Solar Battery - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400\ 40. Sungrow SBH Stackable Battery System - Grow Energy, accessed March 14, 2025, https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system\ 41. Sungrow SBH High Voltage Battery Bundle (SBH200 - SBH400), accessed March 14, 2025, https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400\ 42. Buy cheap SunGrow solar inverters, accessed March 14, 2025, https://tienda-solar.es/en/brand/54-sungrow\ 43. Sungrow PowCube battery storage system (Analysis & review) - Solar Choice, accessed March 14, 2025, https://www.solarchoice.net.au/products/batteries/sungrow-review/\ 44. What inverters do we connect to? – Welcome to our Help Center - Support - SwitchDin, accessed March 14, 2025, https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to\ 45. Accessories Cross Reference Guide - Sungrow Australia Service, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf\ 46. Sungrow - Solar System Inverter - Solargain, accessed March 14, 2025, https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters\ 47. Sungrow Battery Review | A Comprehensive Guide - Esteem Energy, accessed March 14, 2025, https://esteemenergy.com.au/blog/sungrow-battery-review/\ 48. Sungrow 5kW Inverter + Tesla Powerwall + Longi 370w Hi-MO4m 7.4kW Solar System, accessed March 14, 2025, https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/\ 49. Sungrow | Solar Inverters Review - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/inverters/sungrow-review.html\ 50. Tesla Powerwall: Inverter Compatibility Under the Spotlight - 1KOMMA5, accessed March 14, 2025, https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/\ 51. Hi everybody, question about V2H power : r/electricvehicles - Reddit, accessed March 14, 2025, https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/\ 52. Commercial Solar System | PV Plant | Rooftop - Sungrow US, accessed March 14, 2025, https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems\ 53. SH8.0/10RS | 8kW/10kW | Single Phase | Sungrow Hybrid Inverter-Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs\ 54. Approved Batteries with SH Series Hybrid Inverters - Sungrow Australia Service, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf\ 55. Right inverter for the Tesla Powerwall 2 : r/solar - Reddit, accessed March 14, 2025, https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/\ 56. Sungrow Inverters - Gold Coast Solar Power Solutions, accessed March 14, 2025, https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/\ 57. Sungrow SBR192 Lithium-ion Battery - Europe-SolarStore.com, accessed March 14, 2025, https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html\ 58. High-Efficiency Solar Battery: Up to 100% Usable Energy - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/ProductsHome/20/23/battery\ 59. Warranty | Sungrow Australia and New Zealand Service, accessed March 14, 2025, https://service.sungrowpower.com.au/Warranty/warranty\ 60. Sungrow Battery cross-reference chart, accessed March 14, 2025, https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf\ 61. Sungrow SG5KTL-MT - SolarTopStore.com, accessed March 14, 2025, https://www.solartopstore.com/products/sungrow-sg5ktl-mt\ 62. Approved Batteries with SH Series Hybrid Inverters EU Version V1.6.3 - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf\ 63. BLACKOUT? NO, THANKS! POWER WHENEVER YOU NEED IT - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf\ 64. Sungrow 3-phase solution with 6 kVA inverter, EV charger and 9.6 kWh storage - Memodo, accessed March 14, 2025, https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767\ 65. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf\ 66. Sungrow Three-Phase Hybrid Inverter - Solar4Life, accessed March 14, 2025, https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid\ 67. SG5KTL-MT/SG6KTL-MT/SG8KTL-M (Non-China ... - ENF Solar, accessed March 14, 2025, https://www.enfsolar.com/pv/inverter-datasheet/12176\ 68. Sungrow SBR battery combiner box - AC Solar Warehouse, accessed March 14, 2025, https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620\ 69. Sungrow SBR HV Battery Installation Quick Guide, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf\ 70. Energy Storage System Products Catalogue - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf\ 71. DC Coupling vs AC Coupling: Which Solar System to Choose - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose\ 72. Sungrow SBH battery - Accessory kit | AC Solar Warehouse AU, accessed March 14, 2025, https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310\ 73. Sungrow SBR 3.2kWh High Voltage Battery Module , ASA00460 - Alternergy, accessed March 14, 2025, https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460\ 74. NEW Sungrow single phase hybrid inverters can operate without the grid or a battery, accessed March 14, 2025, https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255\ 75. Lawnton Sungrow SBH & Solar Hybrid System | Alvolta, accessed March 14, 2025, https://www.alvolta.com.au/portfolio/info/74\ 76. Sungrow Battery Starter Pack - Huglo Solar, accessed March 14, 2025, https://www.huglo.com.au/post/sungrow-battery-starter-pack\ 77. Sungrow SBR Battery System Bundles, accessed March 14, 2025, https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles\ 78. Sungrow Hybrid 10kW RT Three-Phase Solar Inverter, accessed March 14, 2025, https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108\ 79. Sungrow RT 5kW Three Phase Hybrid inverter (2 MPPT) SH5.0RT - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/\ 80. SUNGROW SH10RT | 10kW 3-Phase Hybrid Inverter - Sparky Direct, accessed March 14, 2025, https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter\ 81. Sungrow Hybrid 10kW 3 Phase 2 MPPT w/WiFi, DC Switch & EPS Built-in Inverter, accessed March 14, 2025, https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/\ 82. Sungrow Solar Inverters - Independent Review, accessed March 14, 2025, https://www.solarchoice.net.au/products/inverters/Sungrow-review/\ 83. Sungrow 10.0kW - 3 Phase Hybrid Inverter (SH10RT) - Solar Superstore, accessed March 14, 2025, https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt\ 84. How Much Do Solar Batteries Cost in Australia? - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/battery-storage/cost/\ 85. Off Grid Solar system using a Sungrow inverter and battery, accessed March 14, 2025, https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312\ 86. Sungrow 14.08k W Off Grid Solar System / Single Phase - AHLEC, accessed March 14, 2025, https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/\ 87. Residential Battery Energy Storage System - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system\ 88. EV Charger - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/ProductsHome/59/ev-charger\ 89. Sungrow SBH 20kW High Voltage LFP Battery Including Accessory Kit SBH200 | eBay, accessed March 14, 2025, https://www.ebay.com.au/itm/135320073679\ 90. 20kWh Battery Kit - Login - Australian Solar Supplies Pty Ltd, accessed March 14, 2025, http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f\ 91. Sungrow - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/sungrow/
# Comparative Evaluation of Tesla Powerwall and Sungrow Battery Options for a 3-Phase Sydney Residence
1. Executive Summary
This report presents a detailed comparative analysis of Tesla Powerwall and Sungrow battery options for a 3-phase residence in Sydney, Australia, equipped with a 6.6kW solar system and a Sungrow SG5KTL-MT inverter. The evaluation focuses on the suitability of these battery solutions for potential off-grid capability and Vehicle-to-Home (V2H) functionality for a EV. The analysis reveals that while both Tesla Powerwall and Sungrow offer compelling features for home energy storage, Sungrow battery systems, particularly when paired with their hybrid inverters, present a more direct and comprehensive solution for achieving 3-phase off-grid capability. For V2H integration, both systems currently rely on the development of compatible bidirectional charging infrastructure in Australia. Based on the user's stated goals, a Sungrow battery system, potentially requiring an upgrade to a Sungrow hybrid inverter, is the recommended solution.
2. Introduction: Context and Objectives
The Australian residential energy landscape is witnessing a significant shift towards energy independence, with increasing adoption of solar photovoltaic (PV) systems and battery storage. This trend is propelled by factors such as escalating electricity costs and a growing desire for reliable power, particularly during grid outages. This report addresses the specific needs of a Sydney homeowner who has already invested in a 6.6kW solar system connected to a 3-phase Sungrow SG5KTL-MT inverter and owns a Tesla electric vehicle. The homeowner is now exploring battery storage solutions, with a particular focus on enabling potential off-grid operation and facilitating future Vehicle-to-Home (V2H) capabilities for their Tesla.
The primary objectives of this report are threefold: firstly, to evaluate the technical and practical suitability of Tesla Powerwall for a 3-phase home in Sydney; secondly, to conduct a similar evaluation for various Sungrow battery options; and thirdly, to provide a comparative assessment of these two leading solutions based on their ability to support off-grid functionality and integrate with V2H technology. The scope of this analysis includes the latest Tesla Powerwall models available in Australia and relevant high-voltage battery options from Sungrow, specifically the SBR and SBH series. The geographical context is limited to Sydney, Australia, considering local grid regulations and market availability. This analysis relies on the provided research material and publicly accessible technical specifications to form its conclusions.
3. Analysis of Tesla Powerwall for a 3-Phase Sydney Home
3.1 Technical Specifications and Features:
The Tesla Powerwall is a well-established residential battery system. The latest generation, Powerwall 3, offers an energy capacity of 13.5 kWh 1 and can deliver up to 10 kW of on-grid power, with the same capacity for backup power, capable of a 185 A motor start 1. A key feature of Powerwall 3 is its integrated solar inverter with a 97.5% efficiency and three solar inputs with Maximum Power Point Trackers (MPPTs) in the Australian version 1. The system is scalable, allowing for the installation of up to four units 1, and utilizes Lithium Iron Phosphate (LFP) battery chemistry, known for its safety 5. In contrast, the Powerwall 2, while also having a 13.5 kWh energy capacity 7, provides a continuous power output of 5 kW with a 7 kW peak 7. Notably, Powerwall 2 does not have an integrated solar inverter 7 and uses Nickel Manganese Cobalt Oxide (NMC) battery chemistry 7. It offers greater scalability, supporting up to ten units 1. Both Powerwall 2 and 3 come with a 10-year warranty 2. Powerwall 3 necessitates the use of the Tesla Backup Gateway 2 2, while Powerwall 2 requires a Gateway for system control and backup functionality 7. The integrated inverter in Powerwall 3 streamlines installations for new solar and storage setups. However, for homeowners with existing inverters, such as the user, this feature might introduce complexities as the existing inverter's functionality could become redundant if the system were configured to primarily utilize the Powerwall 3's inverter. Powerwall 2, designed as an AC-coupled battery, might offer a more seamless integration by working in conjunction with the existing Sungrow inverter 3.
3.2 Compatibility with Existing 3-Phase Sungrow Inverter (AC Coupling):
Tesla Powerwall is designed as an AC-coupled battery, meaning it connects to the home's electrical system at the switchboard level and operates independently of the solar inverter 9. This AC coupling capability generally allows Powerwall to be compatible with a wide range of existing solar inverters, including the user's 3-phase Sungrow SG5KTL-MT model 2. Specifically, Powerwall 2 demonstrates 100% compatibility with single-phase grid-connected solar systems installed after October 2016 9. For Powerwall 3, Tesla indicates AC coupling compatibility with existing solar systems up to 5kW 2. However, a crucial consideration arises during grid outages concerning the ability to charge the Powerwall from solar. If the home has a 3-phase solar inverter, like the user's Sungrow SG5KTL-MT, Powerwall 2 might not be able to charge from solar during a blackout because many 3-phase inverters require the presence of all three phases from the grid to operate 9. This limitation could also extend to Powerwall 3 when AC-coupled with a 3-phase inverter 8. Given the user's interest in potential off-grid capability, this inability to recharge the battery from solar during a grid outage significantly limits the duration of backup power to the energy stored within the Powerwall. Furthermore, the user's 6.6kW solar system output exceeds the 5kW AC coupling limit specified for a single Powerwall 3. This suggests that either the entire solar generation cannot be used to charge a single Powerwall 3 via AC coupling, or a more complex configuration involving multiple Powerwall units might be necessary.
3.3 Suitability for Off-Grid Operation in a 3-Phase System:
The Tesla Powerwall is fundamentally a single-phase battery system and can only provide backup power to a single phase within a 3-phase home 8. During a power outage, only the electrical circuits connected to the phase that the Powerwall is backing up will remain operational 8. This necessitates careful planning to ensure that essential loads, such as lighting, refrigerators, and internet connectivity, are connected to this designated phase 8. While it is possible to install multiple Powerwall units, with one unit dedicated to each phase, this significantly increases the overall cost and introduces complexities in system management 8. Notably, even with the installation of three Powerwall 3 units, comprehensive 3-phase backup is not guaranteed 20. It is also important to recognize that Tesla does not officially support or provide warranties for off-grid installations of Powerwall 2. The Powerwall system is primarily designed for grid-connected homes to provide backup during outages and to optimize energy consumption, rather than functioning as the primary power source in a completely off-grid scenario. Therefore, achieving a truly comprehensive off-grid capability for a 3-phase home using Tesla Powerwall would likely involve a substantial financial investment in multiple units, meticulous load balancing across the phases, and navigating the limitations of single-phase backup, all without official support from the manufacturer.
3.4 Potential for V2H Integration with a EV in Australia:
Vehicle-to-Home (V2H) technology, which allows an electric vehicle to supply power back to a home, is gaining traction in Australia. Regulatory changes have been made to permit bidirectional charging systems, with mainstream adoption expected in 2025 21. Australian standards for bidirectional charging are now approved, and compatible chargers are anticipated to become available in 2025 22. Currently, the research snippets do not indicate that Tesla Powerwall offers direct, integrated V2H functionality with Tesla cars in Australia 1. However, the Tesla Powerwall can play a supportive role in a V2H ecosystem. It can efficiently store excess energy generated by the solar system 1, which could then be used to charge the Tesla car. If the Tesla car is equipped with V2H capabilities and connected to a compatible bidirectional charger, the energy stored in the Powerwall (or directly from solar) could indirectly contribute to powering the home by first charging the vehicle's battery. The actual discharge from the vehicle to the home would be managed by the bidirectional charger and the vehicle's internal systems, not directly by the Powerwall. Therefore, while Powerwall doesn't inherently provide V2H, it can act as a crucial energy storage component within a broader V2H setup.
3.5 Cost and Installation Considerations in Sydney:
The cost of a Tesla Powerwall 3 in Australia is approximately $13,600, which includes the mandatory Backup Gateway 2 2. Powerwall 2 has an approximate price of $8,750 to $9,750, excluding installation and the Backup Gateway 7, with the installed cost estimated between $12,000 and $14,000 7. Installation costs for Powerwall 3 as part of a new solar system at Penrith Solar Centre start at $23,990 (including a 6kW solar system), while adding it to an existing system is around $15,990 27. Installing a Powerwall system in a 3-phase home can incur additional costs and complexities compared to single-phase installations 13. If the goal is to achieve any level of backup across multiple phases using Powerwall, the cost would escalate significantly with the need for multiple units. Homeowners in NSW may be eligible for rebates under the Peak Demand Reduction Scheme (PDRS), which can help offset the initial investment in a Tesla Powerwall 5. However, the overall cost of a Powerwall system, especially when considering a multi-unit setup for more comprehensive backup in a 3-phase home, remains a substantial financial consideration.
4. Analysis of Sungrow Battery Options for a 3-Phase Sydney Home
4.1 Technical Specifications of Relevant Sungrow Battery Models (SBR and SBH Series):
Sungrow offers a range of high-voltage battery solutions, primarily the SBR and SBH series, utilizing Lithium Iron Phosphate (LiFePO4) chemistry for enhanced safety 5. The SBR series features a modular design with 3.2 kWh battery modules, allowing for system capacities ranging from 9.6 kWh (3 modules) up to 25.6 kWh (8 modules) in a single stack. Multiple stacks can be connected in parallel to achieve even larger capacities, up to 100 kWh 6. These batteries boast 100% usable energy capacity 26 and are high-voltage systems 33. The SBH series also employs a modular design with larger 5 kWh battery modules. A single stack can accommodate 4 to 8 modules, providing usable energy from 20 kWh to 40 kWh. Similar to the SBR series, multiple SBH stacks can be connected in parallel to reach a maximum capacity of 160 kWh 5. Both the SBR and SBH series come with a 10-year warranty 5 and are primarily designed for DC coupling with Sungrow's hybrid inverter range, particularly the SH series, which includes models specifically designed for 3-phase systems (SH-RT series) 33. The availability of a wider range of capacities and the modular design of both the SBR and SBH series provide greater flexibility for the user to tailor a battery system to their specific energy consumption needs. The SBH series, with its larger 5 kWh modules, appears particularly well-suited for homes with potentially higher energy demands, such as those with 3-phase connections.
4.2 Compatibility with Existing 3-Phase Sungrow Inverter (DC and AC Coupling):
The user's existing Sungrow SG5KTL-MT inverter is a grid-tied inverter and not a hybrid model designed for direct DC coupling with batteries 5. Sungrow's high-voltage batteries, such as the SBR and SBH series, are primarily intended for DC coupling with their SH series hybrid inverters 33. While direct DC coupling is not an option with the SG5KTL-MT, it is possible to AC couple Sungrow batteries to the existing solar system 35. This would likely require the addition of a separate battery inverter to manage the charging and discharging of the Sungrow battery, as the SG5KTL-MT does not have this functionality. Although AC coupling offers a way to integrate a battery without replacing the existing solar inverter, it can introduce inefficiencies due to the multiple AC-DC and DC-AC conversions. For optimal performance and to fully leverage the capabilities of Sungrow's high-voltage batteries, particularly for off-grid operation, upgrading to a Sungrow SH series hybrid inverter would be the recommended approach.
4.3 Suitability for Off-Grid Operation in a 3-Phase System:
Sungrow offers a distinct advantage in providing solutions for 3-phase off-grid operation through their SH-RT series of hybrid inverters 5. These inverters, when paired with Sungrow's SBR or SBH batteries, are capable of providing seamless transition to 3-phase backup power during grid outages 63. The SH-RT series is specifically designed to support 100% unbalanced loads in backup mode, ensuring that essential appliances continue to run during a blackout 66. Both the SBR and SBH battery series are compatible with off-grid operation when used in conjunction with the appropriate Sungrow hybrid inverters. Some single-phase Sungrow hybrid inverters (SH-RS series) also offer off-grid capabilities and support generator connection for battery charging during extended periods of low solar generation 85. This comprehensive ecosystem of Sungrow products provides a more direct and integrated pathway for the user to achieve their goal of potential 3-phase off-grid capability compared to the single-phase limitations of Tesla Powerwall.
4.4 Potential for V2H Integration with a Tesla Car in Australia:
Similar to Tesla Powerwall, the provided research material does not explicitly mention direct V2H integration capabilities for Sungrow battery systems with Tesla cars in Australia 22. However, Sungrow's active involvement in the broader renewable energy and electric vehicle charging sectors suggests a strong potential for future integration. Sungrow manufactures its own range of EV chargers 64, and their 3-phase hybrid inverter solutions can be paired with these chargers for smart green power charging 64. As V2H technology and the necessary bidirectional charging infrastructure become more prevalent in Australia, it is conceivable that Sungrow's integrated energy management systems, including their batteries and hybrid inverters, could be updated to support V2H functionality, potentially even with Tesla vehicles through standardized protocols or future partnerships. In the interim, a Sungrow battery system can efficiently store solar energy, which could then be used to charge a Tesla car. The potential for the Tesla car to discharge back to the home would depend on the availability and compatibility of third-party bidirectional chargers that adhere to the evolving Australian standards.
4.5 Cost and Installation Considerations in Sydney:
The cost of Sungrow batteries in Australia varies depending on the model and capacity. For the SBR series, a 9.6 kWh system is approximately $11,500 installed, a 12.8 kWh system around $13,200 installed, and a 25.6 kWh system around $19,700 installed. Supply-only costs for the SBH series 20 kWh kit range from $13,778.70 to $14,360 40. Compatible 3-phase hybrid inverters from Sungrow, such as the SH5.0RT, are priced around $3,760, while the SH10RT ranges from approximately $4,174.50 to $5,720 78. If the user opts for a Sungrow battery system to achieve optimal 3-phase off-grid capability, the cost of a new SH series hybrid inverter would need to be included, as the existing SG5KTL-MT is not compatible for direct DC coupling. While AC coupling might be a less expensive initial step, it could involve the additional cost of a separate battery inverter. Homeowners in NSW can potentially benefit from the NSW battery rebate when purchasing a Sungrow battery system, which could help reduce the overall cost 5. Although Sungrow batteries often offer a competitive cost per kWh, the total investment for a comprehensive 3-phase off-grid solution might be higher than a single-phase Tesla Powerwall setup, primarily due to the potential need for a new hybrid inverter.
5. Comparative Assessment: Tesla Powerwall vs. Sungrow Batteries
5.1 Side-by-Side Comparison Table of Key Specifications:
| Feature | Tesla Powerwall 3 | Sungrow SBR (Example: 12.8 kWh) + SH10RT |
| :---- | :---- | :---- |
| Usable Energy Capacity (kWh) | 13.5 | 12.8 |
| Continuous Power Output (kW) | 10 | 10 |
| Peak Power Output (kW) | 10 | 12 (5 min) |
| Battery Chemistry | Lithium Iron Phosphate | Lithium Iron Phosphate |
| Scalability | Up to 4 units (54 kWh) | Up to 25.6 kWh per stack, 4 stacks parallel (102.4 kWh) |
| Off-Grid Backup (Phases Supported) | Single-Phase | Three-Phase |
| V2H Support (Current/Future Potential) | Potential via 3rd party charger | Potential via 3rd party charger |
| Warranty (Years) | 10 | 10 |
| Estimated Cost (AUD) | $13,600 + installation | $13,200 (battery installed) + $4,175 - $5,720 (inverter) |
5.2 Detailed Comparison Based on Off-Grid Capability Requirements:
When considering the user's goal of potential off-grid capability for a 3-phase home, Sungrow presents a more robust solution. The availability of Sungrow's SH-RT series hybrid inverters, specifically designed for 3-phase systems and fully compatible with their SBR and SBH batteries, allows for a direct and integrated approach to achieving 3-phase backup power. These systems can seamlessly transition to off-grid mode, powering all three phases of the home, which is crucial for operating 3-phase appliances and ensuring comprehensive whole-house backup. In contrast, Tesla Powerwall, being a single-phase battery, inherently limits off-grid backup to a single phase in a 3-phase home 8. While multiple Powerwall units can be installed, this increases cost and complexity without guaranteeing full 3-phase backup or official off-grid support from Tesla. Therefore, for a user prioritizing potential for comprehensive 3-phase off-grid operation, Sungrow's ecosystem offers a more suitable and supported pathway.
5.3 Detailed Comparison Based on V2H Functionality Requirements:
Currently, neither Tesla Powerwall nor Sungrow batteries offer direct, integrated V2H functionality for Tesla cars in Australia 22. Both systems can store solar energy that could be used to charge a Tesla car, and the potential for the car to discharge back to the home (V2H) would rely on the development and adoption of compatible bidirectional charging infrastructure in Australia, which is expected to become more mainstream in 2025 21. Sungrow's involvement in manufacturing EV chargers and integrating them with their hybrid inverters suggests a potential for future V2H integration within their ecosystem. Similarly, while Tesla Powerwall doesn't currently offer V2H, its role as a home energy storage solution makes it a complementary technology to V2H, providing a place to store energy that could eventually be managed within a V2H framework.
5.4 Cost-Effectiveness and Overall Value Analysis:
When evaluating cost-effectiveness, Sungrow batteries often have a lower cost per kWh of storage compared to Tesla Powerwall 5. However, for the user with an existing non-hybrid inverter, achieving the desired 3-phase off-grid capability with Sungrow would likely necessitate an additional investment in a Sungrow SH-RT series hybrid inverter. This would increase the initial outlay compared to simply AC coupling a Tesla Powerwall to the existing inverter for single-phase backup. The overall value proposition depends heavily on the user's priorities. If the primary goal is to have backup power for essential loads on a single phase and potential future V2H integration, Tesla Powerwall could be a viable option. However, if the potential for comprehensive 3-phase off-grid operation is a significant factor, then the added expense of a Sungrow hybrid inverter might be justified by the enhanced functionality and future-proofing for energy independence. Sungrow's reputation for affordability and the modularity of their battery systems also offer long-term value and flexibility.
6. Recommendations and Considerations
Based on the analysis, for a 3-phase home in Sydney with a 6.6kW solar system and the goal of potential off-grid capability, Sungrow battery options are recommended. Specifically, the user should consider upgrading their existing Sungrow SG5KTL-MT inverter to a Sungrow SH series hybrid inverter (e.g., SH5.0RT or SH10RT, depending on anticipated power demands) and pairing it with a Sungrow high-voltage battery from either the SBR or SBH series. The choice between SBR and SBH would depend on the desired storage capacity and budget. This combination offers a more direct and supported path to achieving 3-phase backup power and the potential for future off-grid operation.
Key Considerations for the User:
Off-Grid Capability: The level of off-grid capability desired (partial single-phase backup vs. comprehensive whole-home 3-phase backup) is a crucial factor. For the latter, Sungrow is the more suitable choice.
Budget: Both options represent a significant investment. The user should obtain detailed quotes for both Tesla Powerwall (considering single or multiple units) and a complete Sungrow hybrid inverter and battery system.
V2H Timeline: The user's timeline for V2H adoption should be considered. Both systems will likely integrate via third-party chargers.
Inverter Upgrade: If pursuing the optimal Sungrow solution for off-grid capability, the cost and logistics of upgrading the existing inverter need to be factored in.
* 3-Phase Backup Importance: The necessity of having backup power across all three phases should weigh heavily in the decision, favoring Sungrow.
It is strongly recommended that the user obtain detailed quotes from certified installers in the Sydney area for both Tesla Powerwall and various Sungrow system configurations to get accurate pricing, installation details, and information on available rebates and incentives in NSW.
7. Conclusion
In conclusion, while Tesla Powerwall offers a well-regarded solution for home energy storage with reliable backup capabilities, its inherent single-phase design presents limitations for users with 3-phase homes seeking comprehensive off-grid functionality. Sungrow, with its range of high-voltage batteries and particularly its 3-phase hybrid inverter systems, provides a more direct and technically sound pathway to achieving the user's goals of potential 3-phase off-grid operation. For V2H integration, both systems are currently positioned to benefit from the evolving Australian regulatory landscape and the development of compatible bidirectional charging technologies. Ultimately, the optimal choice will depend on the user's specific priorities, budget, and the level of off-grid capability they wish to achieve. The rapidly evolving nature of battery storage and V2H technology suggests that continued research and consultation with experts are advisable before making a final decision.
#### Works cited
1. Powerwall – Home Battery Storage | Tesla Australia, accessed March 14, 2025, [https://www.tesla.com/en_au/powerwall](https://www.tesla.com/en_au/powerwall)
2. Tesla Powerwall 3 in Australia: Everything You Need to Know - Fritts Solar, accessed March 14, 2025, [https://www.frittssolar.com.au/tesla-powerwall-3-australia/](https://www.frittssolar.com.au/tesla-powerwall-3-australia/)
3. What to Expect for Powerwall 3 | Tesla Support Australia, accessed March 14, 2025, [https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3](https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3)
4. Tesla Powerwall 3 Review - Clean Energy Reviews, accessed March 14, 2025, [https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review](https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review)
5. Sungrow SBH vs. Tesla Powerwall 3: Which is Better? NSW - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/](https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/)
6. Sungrow Battery vs Tesla Powerwall Review - Volteam Electric, accessed March 14, 2025, [https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/](https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/)
7. Tesla Powerwall 2: A Complete 2024 Buyers Guide | Solar Choice, accessed March 14, 2025, [https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/](https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/)
8. Can You Install The Powerwall 3 On A Three-Phase Home? - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/three-phase-powerwall-3/](https://www.solarquotes.com.au/blog/three-phase-powerwall-3/)
9. Is my grid connect solar system 100% compatible with a Tesla Powerwall 2 battery?, accessed March 14, 2025, [https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery](https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery)
10. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf)
11. Combining Systems with Powerwall | Tesla Support, accessed March 14, 2025, [https://www.tesla.com/support/energy/powerwall/learn/combining-systems](https://www.tesla.com/support/energy/powerwall/learn/combining-systems)
12. Powerwall System Design | Tesla Support, accessed March 14, 2025, [https://www.tesla.com/support/energy/powerwall/learn/system-design](https://www.tesla.com/support/energy/powerwall/learn/system-design)
13. Installing Powerwall 3 on a Three-phase Site | PSC - Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/](https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/)
14. Powerwall 3: When It Makes Sense and When It Doesn't - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/](https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/)
15. AC-Coupled Solar System Sizing - Energy Library - Tesla, accessed March 14, 2025, [https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html](https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html)
16. Powerwall 3 Roadmap - 3 Phase Coming! | Tesla Motors Club, accessed March 14, 2025, [https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/](https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/)
17. Advice on how to install with 3 phase : r/solar - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/](https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/)
18. TESLA POWERWALL+ (3) - DIY Solar Depot, accessed March 14, 2025, [https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/](https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/)
19. Design Considerations - Energy Library - Tesla, accessed March 14, 2025, [https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html](https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html)
20. Problems with Powerwall 3 | Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/](https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/)
21. EV Charging in Australia Gets a Makeover with V2G/V2H Approved for 2025 - SEVR, accessed March 14, 2025, [https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/](https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/)
22. V2G, V2L & V2H Explained: Vehicle to Grid in Australia? 2025 - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/](https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/)
23. Australia's Future – Bidirectional EV Charging, Solar & Battery Storage as Standard Features, accessed March 14, 2025, [https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/](https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/)
24. 2025, the Year of Vehicle-to-Grid in Australia V2G Milestone - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/](https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/)
25. Bidirectional Charging for Electric Cars: Unlocking New Possibilities - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/](https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/)
26. The Best Home Batteries In Australia In 2025: According To Aussie Installers - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/best-home-batteries-2025/](https://www.solarquotes.com.au/blog/best-home-batteries-2025/)
27. How Much Does a Tesla Powerwall 3 Cost? | Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/](https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/)
28. Expected 3 Phase upgrade price? : r/AusRenovation - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/](https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/)
29. Powerwall cost for Sydney? | Tesla Motors Club, accessed March 14, 2025, [https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/](https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/)
30. Solar Battery Costs: Are They Worth It?, accessed March 14, 2025, [https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/](https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/)
31. Tesla Powerwall 3 Price and Installation - Solar4Life, accessed March 14, 2025, [https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation](https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation)
32. Solar Battery Price, Savings and Payback, accessed March 14, 2025, [https://solarcalculator.com.au/battery-storage/price/](https://solarcalculator.com.au/battery-storage/price/)
33. Sungrow | Solar Batteries Review - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html](https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html)
34. Sungrow SBR high voltage battery - VP Solar, accessed March 14, 2025, [https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/](https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/)
35. Sungrow Battery SBR Series - SolarBright, accessed March 14, 2025, [https://solarbright.com.au/product/sungrow-battery-sbr-series/](https://solarbright.com.au/product/sungrow-battery-sbr-series/)
36. Sungrow SBR 3.2kWh module - Huglo Solar, accessed March 14, 2025, [https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery](https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery)
37. Sungrow Inverter and battery Review - Clean Energy Reviews, accessed March 14, 2025, [https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review](https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review)
38. SBH100/150/200/250/300/350/400 - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400](https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400)
39. 20/25/30/35/40 kWh Solar Battery - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400](https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400)
40. Sungrow SBH Stackable Battery System - Grow Energy, accessed March 14, 2025, [https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system](https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system)
41. Sungrow SBH High Voltage Battery Bundle (SBH200 - SBH400), accessed March 14, 2025, [https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400](https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400)
42. Buy cheap SunGrow solar inverters, accessed March 14, 2025, [https://tienda-solar.es/en/brand/54-sungrow](https://tienda-solar.es/en/brand/54-sungrow)
43. Sungrow PowCube battery storage system (Analysis & review) - Solar Choice, accessed March 14, 2025, [https://www.solarchoice.net.au/products/batteries/sungrow-review/](https://www.solarchoice.net.au/products/batteries/sungrow-review/)
44. What inverters do we connect to? – Welcome to our Help Center - Support - SwitchDin, accessed March 14, 2025, [https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to](https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to)
45. Accessories Cross Reference Guide - Sungrow Australia Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf)
46. Sungrow - Solar System Inverter - Solargain, accessed March 14, 2025, [https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters](https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters)
47. Sungrow Battery Review | A Comprehensive Guide - Esteem Energy, accessed March 14, 2025, [https://esteemenergy.com.au/blog/sungrow-battery-review/](https://esteemenergy.com.au/blog/sungrow-battery-review/)
48. Sungrow 5kW Inverter + Tesla Powerwall + Longi 370w Hi-MO4m 7.4kW Solar System, accessed March 14, 2025, [https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/](https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/)
49. Sungrow | Solar Inverters Review - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/inverters/sungrow-review.html](https://www.solarquotes.com.au/inverters/sungrow-review.html)
50. Tesla Powerwall: Inverter Compatibility Under the Spotlight - 1KOMMA5, accessed March 14, 2025, [https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/](https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/)
51. Hi everybody, question about V2H power : r/electricvehicles - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/](https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/)
52. Commercial Solar System | PV Plant | Rooftop - Sungrow US, accessed March 14, 2025, [https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems](https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems)
53. SH8.0/10RS | 8kW/10kW | Single Phase | Sungrow Hybrid Inverter-Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs](https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs)
54. Approved Batteries with SH Series Hybrid Inverters - Sungrow Australia Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf)
55. Right inverter for the Tesla Powerwall 2 : r/solar - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/](https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/)
56. Sungrow Inverters - Gold Coast Solar Power Solutions, accessed March 14, 2025, [https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/](https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/)
57. Sungrow SBR192 Lithium-ion Battery - Europe-SolarStore.com, accessed March 14, 2025, [https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html](https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html)
58. High-Efficiency Solar Battery: Up to 100% Usable Energy - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/ProductsHome/20/23/battery](https://en.sungrowpower.com/ProductsHome/20/23/battery)
59. Warranty | Sungrow Australia and New Zealand Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/Warranty/warranty](https://service.sungrowpower.com.au/Warranty/warranty)
60. Sungrow Battery cross-reference chart, accessed March 14, 2025, [https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf](https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf)
61. Sungrow SG5KTL-MT - SolarTopStore.com, accessed March 14, 2025, [https://www.solartopstore.com/products/sungrow-sg5ktl-mt](https://www.solartopstore.com/products/sungrow-sg5ktl-mt)
62. Approved Batteries with SH Series Hybrid Inverters EU Version V1.6.3 - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf](https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf)
63. BLACKOUT? NO, THANKS! POWER WHENEVER YOU NEED IT - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf)
64. Sungrow 3-phase solution with 6 kVA inverter, EV charger and 9.6 kWh storage - Memodo, accessed March 14, 2025, [https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767](https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767)
65. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf)
66. Sungrow Three-Phase Hybrid Inverter - Solar4Life, accessed March 14, 2025, [https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid](https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid)
67. SG5KTL-MT/SG6KTL-MT/SG8KTL-M (Non-China ... - ENF Solar, accessed March 14, 2025, [https://www.enfsolar.com/pv/inverter-datasheet/12176](https://www.enfsolar.com/pv/inverter-datasheet/12176)
68. Sungrow SBR battery combiner box - AC Solar Warehouse, accessed March 14, 2025, [https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620](https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620)
69. Sungrow SBR HV Battery Installation Quick Guide, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf)
70. Energy Storage System Products Catalogue - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf](https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf)
71. DC Coupling vs AC Coupling: Which Solar System to Choose - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose](https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose)
72. Sungrow SBH battery - Accessory kit | AC Solar Warehouse AU, accessed March 14, 2025, [https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310](https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310)
73. Sungrow SBR 3.2kWh High Voltage Battery Module , ASA00460 - Alternergy, accessed March 14, 2025, [https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460](https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460)
74. NEW Sungrow single phase hybrid inverters can operate without the grid or a battery, accessed March 14, 2025, [https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255](https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255)
75. Lawnton Sungrow SBH & Solar Hybrid System | Alvolta, accessed March 14, 2025, [https://www.alvolta.com.au/portfolio/info/74](https://www.alvolta.com.au/portfolio/info/74)
76. Sungrow Battery Starter Pack - Huglo Solar, accessed March 14, 2025, [https://www.huglo.com.au/post/sungrow-battery-starter-pack](https://www.huglo.com.au/post/sungrow-battery-starter-pack)
77. Sungrow SBR Battery System Bundles, accessed March 14, 2025, [https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles](https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles)
78. Sungrow Hybrid 10kW RT Three-Phase Solar Inverter, accessed March 14, 2025, [https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108](https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108)
79. Sungrow RT 5kW Three Phase Hybrid inverter (2 MPPT) SH5.0RT - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/](https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/)
80. SUNGROW SH10RT | 10kW 3-Phase Hybrid Inverter - Sparky Direct, accessed March 14, 2025, [https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter](https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter)
81. Sungrow Hybrid 10kW 3 Phase 2 MPPT w/WiFi, DC Switch & EPS Built-in Inverter, accessed March 14, 2025, [https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/](https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/)
82. Sungrow Solar Inverters - Independent Review, accessed March 14, 2025, [https://www.solarchoice.net.au/products/inverters/Sungrow-review/](https://www.solarchoice.net.au/products/inverters/Sungrow-review/)
83. Sungrow 10.0kW - 3 Phase Hybrid Inverter (SH10RT) - Solar Superstore, accessed March 14, 2025, [https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt](https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt)
84. How Much Do Solar Batteries Cost in Australia? - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/battery-storage/cost/](https://www.solarquotes.com.au/battery-storage/cost/)
85. Off Grid Solar system using a Sungrow inverter and battery, accessed March 14, 2025, [https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312](https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312)
86. Sungrow 14.08k W Off Grid Solar System / Single Phase - AHLEC, accessed March 14, 2025, [https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/](https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/)
87. Residential Battery Energy Storage System - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system](https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system)
88. EV Charger - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/ProductsHome/59/ev-charger](https://en.sungrowpower.com/ProductsHome/59/ev-charger)
89. Sungrow SBH 20kW High Voltage LFP Battery Including Accessory Kit SBH200 | eBay, accessed March 14, 2025, [https://www.ebay.com.au/itm/135320073679](https://www.ebay.com.au/itm/135320073679)
90. 20kWh Battery Kit - Login - Australian Solar Supplies Pty Ltd, accessed March 14, 2025, [http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f](http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f)
91. Sungrow - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/sungrow/](https://www.solarbatteriesonline.com.au/sungrow/)
{"id":"6a44da7a-19c1-4a37-a991-d589c8bbded8","providerCopyMimeTypes":["application/vnd.vscode.markdown.updatelinks.metadata","application/vnd.code.additional-editor-data"],"defaultPastePayload":{"multicursorText":null,"pasteOnNewLine":false,"mode":null}}{"version":1,"isFromEmptySelection":false,"multicursorText":null,"mode":"markdown"}
-
 @ d34e832d:383f78d0
2025-04-24 00:56:03
@ d34e832d:383f78d0
2025-04-24 00:56:03WebSocket communication is integral to modern real-time web applications, powering everything from chat apps and online gaming to collaborative editing tools and live dashboards. However, its persistent and event-driven nature introduces unique debugging challenges. Traditional browser developer tools provide limited insight into WebSocket message flows, especially in complex, asynchronous applications.
This thesis evaluates the use of Chrome-based browser extensions—specifically those designed to enhance WebSocket debugging—and explores how visual event tracing improves developer experience (DX). By profiling real-world applications and comparing built-in tools with popular WebSocket DevTools extensions, we analyze the impact of visual feedback, message inspection, and timeline tracing on debugging efficiency, code quality, and development speed.
The Idea
As front-end development evolves, WebSockets have become a foundational technology for building reactive user experiences. Debugging WebSocket behavior, however, remains a cumbersome task. Chrome DevTools offers a basic view of WebSocket frames, but lacks features such as message categorization, event correlation, or contextual logging. Developers often resort to
console.logand custom logging systems, increasing friction and reducing productivity.This research investigates how browser extensions designed for WebSocket inspection—such as Smart WebSocket Client, WebSocket King Client, and WSDebugger—can enhance debugging workflows. We focus on features that provide visual structure to communication patterns, simplify message replay, and allow for real-time monitoring of state transitions.
Related Work
Chrome DevTools
While Chrome DevTools supports WebSocket inspection under the Network > Frames tab, its utility is limited: - Messages are displayed in a flat, unstructured stream. - No built-in timeline or replay mechanism. - Filtering and contextual debugging features are minimal.
WebSocket-Specific Extensions
Numerous browser extensions aim to fill this gap: - Smart WebSocket Client: Allows custom message sending, frame inspection, and saved session reuse. - WSDebugger: Offers structured logging and visualization of message flows. - WebSocket Monitor: Enables real-time monitoring of multiple connections with UI overlays.
Methodology
Tools Evaluated:
- Chrome DevTools (baseline)
- Smart WebSocket Client
- WSDebugger
- WebSocket King Client
Evaluation Criteria:
- Real-time message monitoring
- UI clarity and UX consistency
- Support for message replay and editing
- Message categorization and filtering
- Timeline-based visualization
Test Applications:
- A collaborative markdown editor
- A multiplayer drawing game (WebSocket over Node.js)
- A lightweight financial dashboard (stock ticker)
Findings
1. Enhanced Visibility
Extensions provide structured visual representations of WebSocket communication: - Grouped messages by type (e.g., chat, system, control) - Color-coded frames for quick scanning - Collapsible and expandable message trees
2. Real-Time Inspection and Replay
- Replaying previous messages with altered payloads accelerates bug reproduction.
- Message history can be annotated, aiding team collaboration during debugging.
3. Timeline-Based Analysis
- Extensions with timeline views help identify latency issues, bottlenecks, and inconsistent message pacing.
- Developers can correlate message sequences with UI events more intuitively.
4. Improved Debugging Flow
- Developers report reduced context-switching between source code and devtools.
- Some extensions allow breakpoints or watchers on WebSocket events, mimicking JavaScript debugging.
Consider
Visual debugging extensions represent a key advancement in tooling for real-time application development. By extending Chrome DevTools with features tailored for WebSocket tracing, developers gain actionable insights, faster debugging cycles, and a better understanding of application behavior. Future work should explore native integration of timeline and message tagging features into standard browser DevTools.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as real-time visualizations, message filtering, and replay features.
However, some limitations remain:
- Lack of binary frame support: Many extensions focus on text-based payloads and may not correctly parse or display binary frames.
- Non-standard encoding issues: Applications using custom serialization formats (e.g., Protocol Buffers, MsgPack) require external decoding tools or browser instrumentation.
- Extension compatibility: Some extensions may conflict with Content Security Policies (CSP) or have limited functionality when debugging production sites served over HTTPS.
- Performance overhead: Real-time visualization and logging can add browser CPU/memory overhead, particularly in high-frequency WebSocket environments.
Despite these drawbacks, the overall impact on debugging efficiency and developer comprehension remains highly positive.
Developer Experience and Limitations
Visual tools significantly enhance the developer experience (DX) by reducing friction and offering cognitive support during debugging. Rather than parsing raw JSON blobs manually or tracing asynchronous behavior through logs, developers can rely on intuitive UI affordances such as live message streams, structured views, and interactive inspection of frames.
However, some limitations exist:
- Security restrictions: Content Security Policy (CSP) and Cross-Origin Resource Sharing (CORS) can restrict browser extensions from accessing WebSocket frames in production environments.
- Binary and custom formats: Extensions may not handle binary frames or non-standard encodings (e.g., Protocol Buffers) without additional tooling.
- Limited protocol awareness: Generic tools may not fully interpret application-specific semantics, requiring context from the developer.
- Performance trade-offs: Logging and rendering large volumes of data can cause UI lag, especially in high-throughput WebSocket apps.
Despite these constraints, DevTools extensions continue to offer valuable insight during development and testing stages.
Applying this analysis to relays in the Nostr protocol surfaces some fascinating implications about traffic analysis, developer tooling, and privacy risks, even when data is cryptographically signed. Here's how the concepts relate:
🧠 What This Means for Nostr Relays
1. Traffic Analysis Still Applies
Even though Nostr events are cryptographically signed and, optionally, encrypted (e.g., DMs), relay communication is over plaintext WebSockets or WSS (WebSocket Secure). This means:
- IP addresses, packet size, and timing patterns are all visible to anyone on-path (e.g., ISPs, malicious actors).
- Client behavior can be inferred: Is someone posting, reading, or just idling?
- Frequent "kind" values (like
kind:1for notes orkind:4for encrypted DMs) produce recognizable traffic fingerprints.
🔍 Example:
A pattern like: -
client → relay: small frame at intervals of 30s -relay → client: burst of medium frames …could suggest someone is polling for new posts or using a chat app built on Nostr.
2. DevTools for Nostr Client Devs
For client developers (e.g., building on top of
nostr-tools), browser DevTools and WebSocket inspection make debugging much easier:- You can trace real-time Nostr events without writing logging logic.
- You can verify frame integrity, event flow, and relay responses instantly.
- However, DevTools have limits when Nostr apps use:
- Binary payloads (e.g., zlib-compressed events)
- Custom encodings or protocol adaptations (e.g., for mobile)
3. Fingerprinting Relays and Clients
- Each relay has its own behavior: how fast it responds, whether it sends OKs, how it deals with malformed events.
- These can be fingerprinted by adversaries to identify which software is being used (e.g.,
nostr-rs-relay,strfry, etc.). - Similarly, client apps often emit predictable
REQ,EVENT,CLOSEsequences that can be fingerprinted even over WSS.
4. Privacy Risks
Even if DMs are encrypted: - Message size and timing can hint at contents ("user is typing", long vs. short message, emoji burst, etc.) - Public relays might correlate patterns across multiple clients—even without payload access. - Side-channel analysis becomes viable against high-value targets.
5. Mitigation Strategies in Nostr
Borrowing from TLS and WebSocket security best practices:
| Strategy | Application to Nostr | |-----------------------------|----------------------------------------------------| | Padding messages | Normalize
EVENTsize, especially for DMs | | Batching requests | Send multipleREQsubscriptions in one frame | | Randomize connection times | Avoid predictable connection schedules | | Use private relays / Tor| Obfuscate source IP and reduce metadata exposure | | Connection reuse | Avoid per-event relay opens, use persistent WSS |
TL;DR for Builders
If you're building on Nostr and care about privacy, WebSocket metadata is a leak. The payload isn't the only thing that matters. Be mindful of event timing, size, and structure, even over encrypted channels.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ b8af284d:f82c91dd
2025-03-10 08:28:07
@ b8af284d:f82c91dd
2025-03-10 08:28:07Liebe Abonnenten,
800 Milliarden Euro will die EU ausgeben, um die Ukraine und den Kontinent in ein “stählernes Stachelschwein” zu verwandeln. Deutschland selbst will künftig Verteidigungsausgaben aus der Schuldenbremse ausnehmen, was nichts anderes als eine unbegrenzte Kreditlinie für das Militär bedeutet. Hinzu kommt ein “Sondervermögen” in Höhe von 500 Milliarden Euro für Infrastruktur. Das klingt nach einem Spartopf, den man für schwere Zeiten angelegt hat. Es soll die Tatsache verschleiern, dass es sich dabei um Schulden handelt. Der vermutlich baldige Kanzler Friedrich Merz bricht damit sein Wahlversprechen, die Schuldenbremse einzuhalten. Beschließen soll das Paket noch ein abgewählter Bundestag, da im neuen wohl die Mehrheit fehlt.
Womit also ist zu rechnen, wenn demnächst fast eine Billion frisch gedruckte Euro in Drohnen, Panzer und Raketen investiert werden?
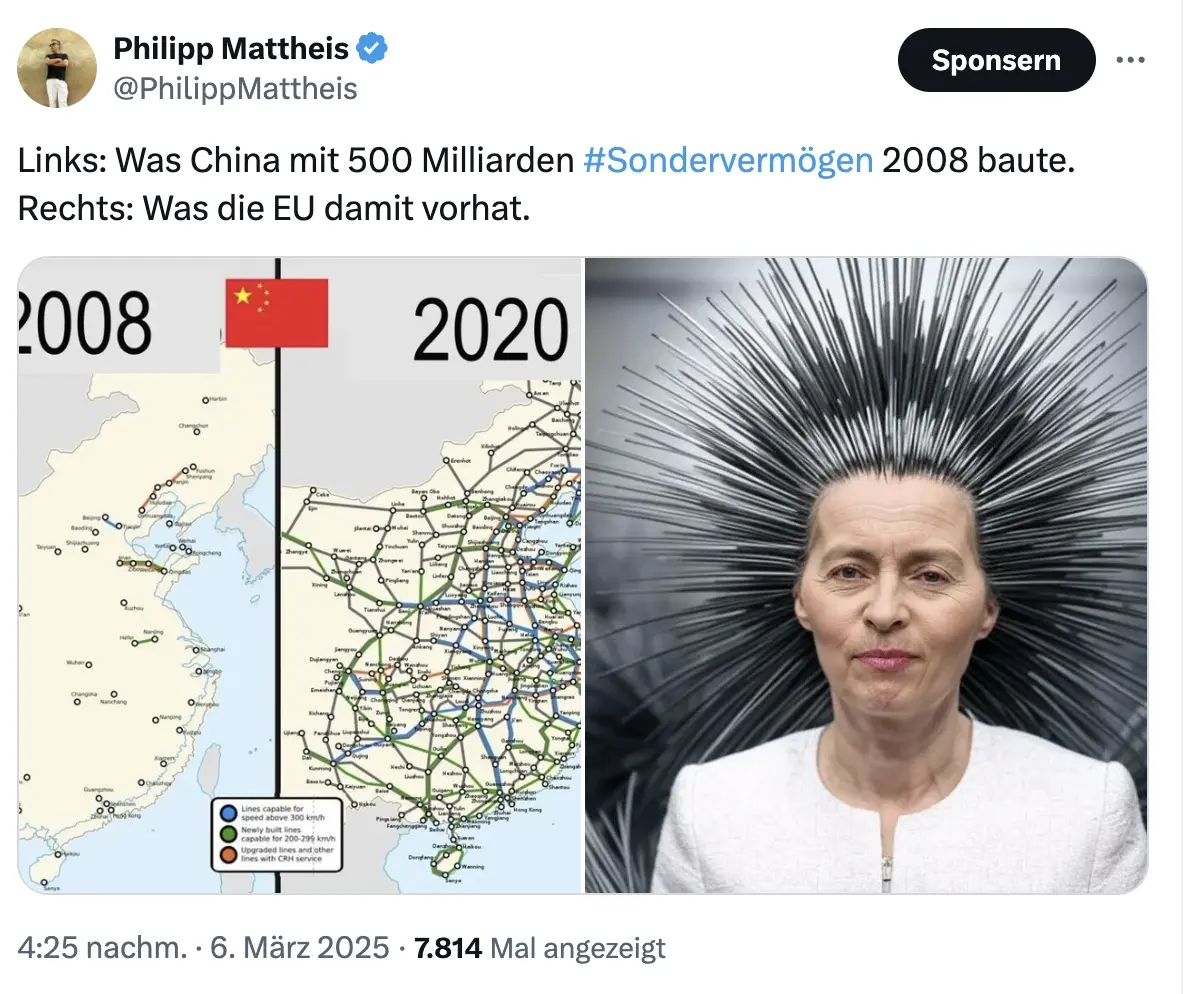
Das beste Beispiel der jüngeren Geschichte ist China: 2009 legte die chinesische Regierung das bisher größte Infrastrukturprojekt der Welt in Höhe von 440 Milliarden Euro auf. Finanziert wurde es durch günstige Kredite, die vor allem an Staatsunternehmen vergeben wurden. Nachdem die Welt nach der in den USA ausgelösten Immobilienkrise 2008 in die Rezession gerutscht war, „rettete“ dieses Paket die globale Konjunktur. China hatte zu diesem Zeitpunkt großen Bedarf an Flughäfen, Straßen und vor allem Zügen. Das Paket war riskant: Schier unbegrenztes Geld, das begrenzten Waren hinterherjagt, führt zu Inflation. Billige Kredite führen meist dazu, dass Unternehmen nicht mehr effizient wirtschaften, und Schuldenberge vor sich her wälzen.
Allerdings wurde das Geld in Produktivität investiert. Denn wenn Menschen und Waren einfacher reisen können, nimmt die Geschäftstätigkeit zu: Arbeitnehmer werden mobiler, Unternehmen konkurrenzfähiger, die Preise sinken. Die Investitionen lohnen sich also, weil sie zu mehr Wirtschaftswachstum führen. Vereinfacht gesagt: Die Schulden können zurückgezahlt werden, und am Ende bleibt noch mehr übrig. In diesem Fall führen Schulden nicht zu Inflation: Durch die gesteigerte Produktivität stehen jetzt sogar mehr Waren der Geldmenge gegenüber.
15 Jahre später kämpft die zweitgrößte Volkswirtschaft zwar noch immer mit den Problemen, die aus diesem Paket resultieren - die Immobilienkrise ist eine indirekte Folge davon. Trotzdem war das Programm ein Erfolg: die Städte, Flughäfen und vor allem Zugstrecken führten zu einer höheren wirtschaftlichen Aktivität oder Produktivität. China ist heute ein wesentlich moderneres Land als vor dem Paket, und verfügt über modernste und größte Netz aus Hochgeschwindigkeitszügen der Welt. Neue Schulden können positiv sein - wenn das Geld produktiv investiert wird.
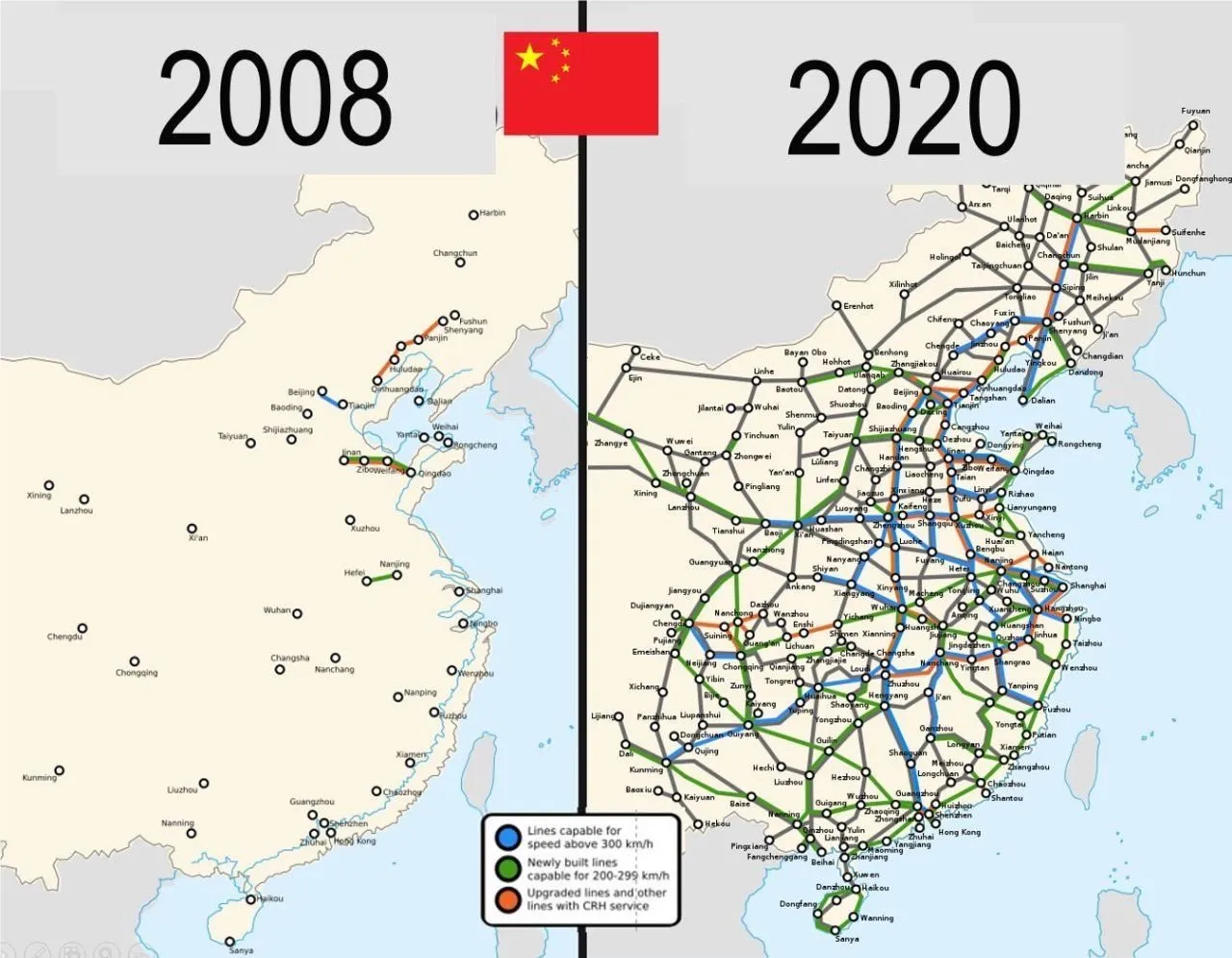
Auch in Europa lassen sich mit dem Geld-Paket zunächst mehrere Probleme auf einmal lösen: Deutschland ist noch immer ein Industriestandort mit hohen Produktionskapazitäten. Werke der Auto- und Zulieferindustrie können theoretisch zur Waffenproduktion umfunktioniert werden. Immer noch besser als sie stillzulegen oder an die Chinesen zu verkaufen, werden viele Kommentatoren schreiben.
Allein in der deutschen Automobil-Zulieferindustrie sind im vergangenen Jahr über 19000 Arbeitsplätze verloren gegangen. Viele von den Entlassenen können nun Arbeit in der Rüstungsindustrie finden. Oder wie Hans Christoph Atzpodien, Hauptgeschäftsführer des Bundesverbandes der Deutschen Sicherheits- und Verteidigungsindustrie in der WirtschaftsWoche sagt:
„Das Motto muss lauten: Autos zu Rüstung! Anstatt einen volkswirtschaftlichen Schaden durch den Niedergang der Auto-Konjunktur zu beklagen, sollten wir versuchen, Produktionseinrichtungen und vor allem Fachkräfte aus dem Automobilsektor möglichst verträglich in den Defence-Bereich zu überführen“
Immerhin: ein großer Teil des Geldes soll auch in Infrastrukturprojekte fließen: Brücken, Bahn, Internetausbau. Deutschland, und damit Europa, wird in den kommenden Monaten also eine große Party feiern, die über die Tatsache hinwegtäuschen wird, dass man einen dummen Krieg verloren hat. In den kommenden Monaten werden sich Verbände und Organisationen um das Geld reißen. Das Geld wird ein auch kollektiv-psychologisches Ventil sein, um das eigene Versagen bei Corona, Klima und Ukraine vergessen zu machen.
Es gibt allerdings einen wesentlichen Unterschied zum chinesischen Stimulus-Paket 2009: Rüstungsgüter sind im Gegensatz zu Zugstrecken totes Kapital. Eine neue Drohne oder Panzer führt nicht zu mehr Produktivität, im Gegenteil: Kommen sie zum Einsatz, zerstören sie Brücken, Häuser, Straßen und töten Menschen. Die Produktivität sinkt also. Im besten Fall kann Militärgerät herumstehen und vor sich hin rosten. Auch dann aber ist es „totes Kapital“, das nichts zur Produktivität beiträgt. Kommt es zum Einsatz, stehen der nun verringerten Warenmenge eine noch größere Geldmenge gegenüber. Die Inflation steigt.
Schleichende Militarisierung
Auch gesellschaftlich wird das Paket mit seinem Blanko-Scheck für die Verteidigungsindustrie viel verändern: Es kommt zu einer „Eichung“ der Gesellschaft, eine kollektive Abscheu des gemeinsamen Feindes. Scharfmacher, eigentlich mittelmäßiger Akademiker und Bürokraten, wie Carlo Masala und Claudia Major werden eine noch größere Rolle im öffentlichen Diskurs spielen und die Talkshows dominieren, die von einer immer älter werdenden deutschen Bevölkerung geglotzt werden. Abweichende Meinungen auf Online-Plattformen zensiert, unter dem Vorwand, die Demokratie sei in Gefahr:
Da die Rüstungsindustrie dann eine wichtigere Rolle für die Gesamtwirtschaft spielt, wird ihr Einfluss auf die Politik in Form von Lobbyisten und Verbänden zunehmen. Politiker merken schnell, dass sie von der medialen Aufmerksamkeitsökonomie nach oben gespült werden, wenn sie immer radikalere Forderungen stellen. So empfahl der ehemalige Außenminister Joschka Fischer die Woche die Wiedereinführung der Wehrpflicht für Männer und Frauen. “Star-Ökonomin” Isabella Weber will die Kriegswirtschaft mitplanen:
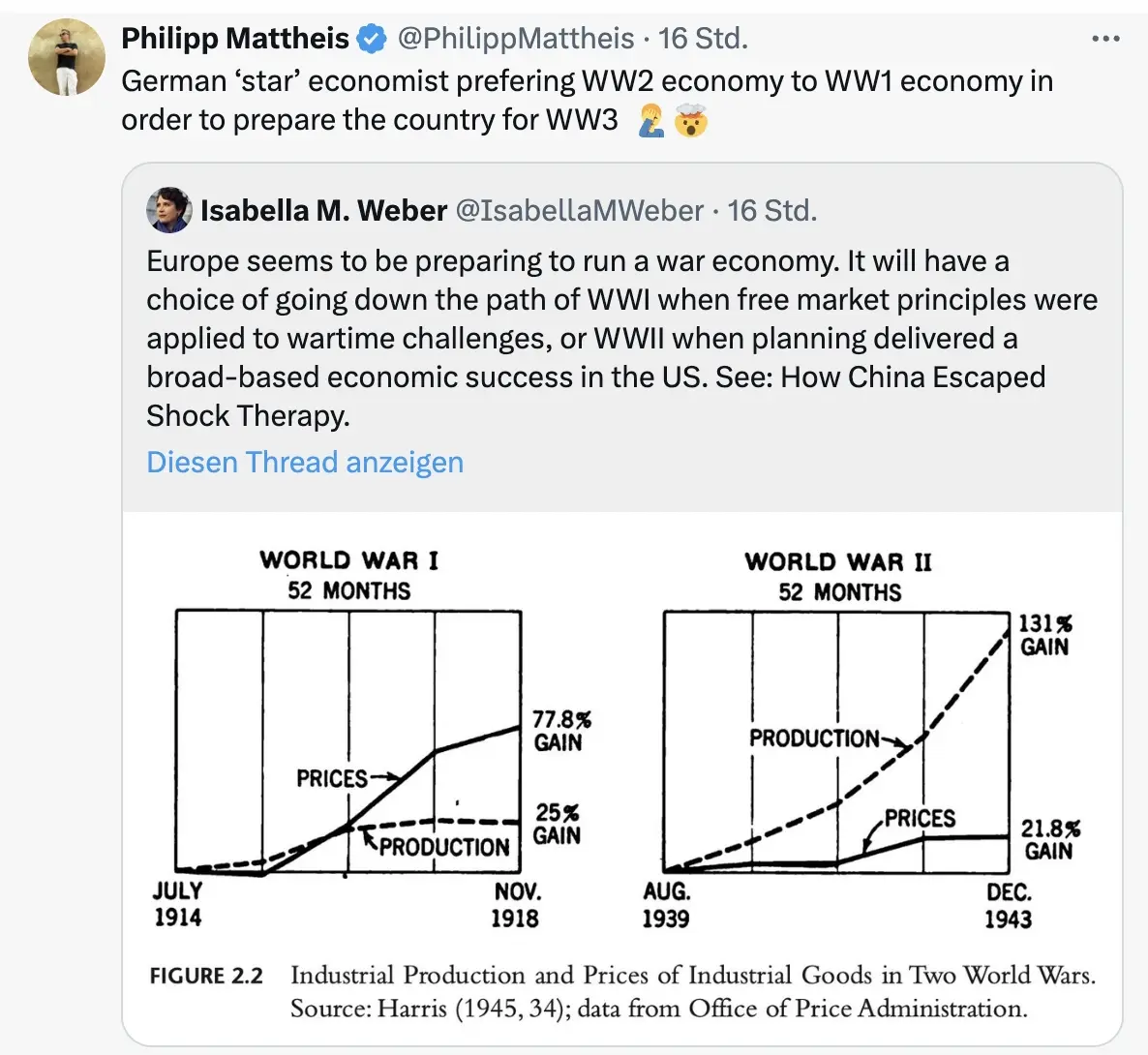
\ Der Kontinent wird sich langsam wandeln von einem „Friedensprojekt“ zu einem „metallenen Stachelschwein“, ergo Kriegsprojekt, denn ohne dämonisierten Feind funktioniert das Programm nicht. Der Ton wird rauer, autoritärer, und die Meinungsfreiheit weiter eingeschränkt werden. Die seit 2020 eingeführten Werkzeuge zur soften Propaganda („kognitive Kriegsführung”) werden verfeinert und ausgebaut werden, sodass weiterhin 80 Prozent der Bevölkerung alle noch so antihumanen Maßnahmen gutheißen werden.
Und dann?
Wie Julian Assange einmal sagte: “Das Ziel ist kein erfolgreicher Krieg. Das Ziel ist ein endloser Krieg.” Der Konflikt muss weitergehen, ewig schwelen oder ein neuer gefunden werden, da sonst ein Teil der Wirtschaftsleistung kollabiert.
Nach ein, zwei oder auch erst drei Jahren, werden erste Probleme sichtbar. Die Party endet, der Kater setzt langsam ein. Die Finanzierung an den Kapitalmärkten wird für Deutschland immer kostspieliger. Der Schuldendienst wird einen größeren Teil des Haushalts einnehmen. Die Bürger müssen dies mitfinanzieren. Der voraussichtlich neue Bundeskanzler Friedrich Merz sprach bereits von der „Mobilisierung der deutschen Sparguthaben“.
\ Was im Ersten Weltkrieg „Kriegsanleihen“ hieß, wird einen schickeren Namen bekommen wie „olivgrüne Bonds“. You name it. Alternativ lässt sich ein Verteidigungs-Soli einführen, oder das Kindergeld streichen, wie kürzlich Ifo-Chef Clemens Fuest forderte.
Was kann man tun? Auf BlingBling geht es um konkrete Tipps, welche Anlagen von dieser Entwicklung profitieren werden. Außerdem geht es um die “Strategische Bitcoin Reserve”, die am Donnerstag beschlossen wurde.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 732c6a62:42003da2
2025-03-06 06:00:53
@ 732c6a62:42003da2
2025-03-06 06:00:53De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin.
Por que Ripple faz propaganda anti-bitcoin?
Simples: eles são o oposto do Bitcoin em quase tudo. Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência.
O que você não sabe:
- Ripple Labs controla a maioria do XRP: Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização.
- XRP não é uma moeda para "pessoas comuns": Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas.
- Ripple não é blockchain no sentido tradicional: Eles usam um protocolo chamado Ripple Protocol Consensus Algorithm (RPCA), que é mais rápido, mas menos descentralizado.
Os principais ataques do Ripple ao Bitcoin:
- Anti-mineração: O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia.
- Anti-reserva estratégica: O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar.
- Anti-descentralização: O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos.
Análise Psicológica Básica (para você que acha que XRP é o futuro):
- Síndrome do Underdog: Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional.
- Viés de Confirmação: Só ouve opiniões que validam sua decisão de comprar XRP.
- Efeito Dunning-Kruger: Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um hard fork.
Estudo de Caso (Real, mas Você Vai Ignorar):
Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem.Conclusão: ou, "volte para a aula de economia do ensino médio"
Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que a descentralização assusta quem quer controle. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ 732c6a62:42003da2
2025-03-06 04:33:48
@ 732c6a62:42003da2
2025-03-06 04:33:48De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu.
A moda do momento
Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram?
Fatos que ignoram enquanto cospem jargões do "lado certo da história":
1. A esquerda também tem seus terraplanistas: Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia.
2. Viés de confirmação não é monopólio da direita: Eles compartilham estudos "científicos" do Medium como se fossem peer-reviewed, mas desdenham de dados que contradizem sua narrativa.
3. A direita não é um monolito: Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, irracional.Estudo de Caso (Fictício, mas Verdadeiro):
Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas.A Imposição intelectual que ninguém pediu (mas todos recebem de graça)
A esquerda brasileira, em sua cruzada épica para salvar o mundo dos "fascistas que ousam discordar", adotou uma nova estratégia: transformar complexidade política em slogans de camiseta de feira. A frase "se eu fosse irracional, seria de direita" não é original — é plágio descarado da cartilha do Complexo de Deus em Oferta no AliExpress.
O Quebra-Cabeça da superioridade Auto-Delirante
A tese esquerdista se sustenta em três pilares frágeis:
1. A falácia do "lado certo da história": Como se história fosse um jogo de futebol com narração do João Cléber.
2. A ilusão de que citar Foucault = ter QI elevado: Spoiler: decorar "biopoder" não te torna imune a acreditar em astrologia.
3. A crença de que volume de texto = profundidade: 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política.Dado Cruel: Um estudo da Universidade de Cambridge (2022) mostrou que extremistas de ambos os lados cometem erros lógicos similares. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice.
A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)
A acusação preferida — "você não lê!" — esconde uma ironia deliciosa:
- 72% dos "intelectuais de rede social" citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023).
- Obras citadas como troféu: "1984" (para chamar Bolsonaro de Big Brother), "O Capital" (para justificar o NFT da Gal Gadot), e "Feminismo para os 99%" (para atacar homens heterossexuais que usam sandália de dedo).Pergunta Incômoda: Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)?
Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)
A esquerda adora se pintar como a Última Trincheira da Razão, mas pratica o que critica:
- Exemplo 1: Defendem "ciência" quando convém (vacinas), mas abraçam pseudociência quando é trendy (cristais energéticos contra o capitalismo).
- Exemplo 2: Chamam a direita de "terraplanista", mas acham que inflação se resolve com tabelamento estatal — a versão econômica de "a Terra é sustentada por tartarugas".
- Exemplo 3: Criticam "fake news", mas compartilham teorias de que o agro "envenena a comida" (enquanto comem sushi de supermercado).Frase-Chave: "Racionalidade seletiva é o novo analfabetismo funcional."
Pergunta Final: Se a esquerda é tão racional, por que não usa a "lógica implacável" para resolver algo além do enquadro perfeito de stories no Instagram?
Enfim
O debate "esquerda racional vs. direita irracional" é só mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego". Enquanto uns brincam de "quem tem o QI mais alto", o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que a lacração é o último refúgio dos fracos de argumento. Agora deviam estudar economia básica — ou pelo menos que parem de achar que "Ah, mas o capitalismo!" é um contra-argumento.
Saudade da época em que a esquerda não se fingia de intelectual.