-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 8fb140b4:f948000c
2023-08-22 12:14:34
@ 8fb140b4:f948000c
2023-08-22 12:14:34As the title states, scratch behind my ear and you get it. 🐶🐾🫡
-
 @ 8fb140b4:f948000c
2023-07-30 00:35:01
@ 8fb140b4:f948000c
2023-07-30 00:35:01Test Bounty Note
-
 @ 8fb140b4:f948000c
2023-07-22 09:39:48
@ 8fb140b4:f948000c
2023-07-22 09:39:48Intro
This short tutorial will help you set up your own Nostr Wallet Connect (NWC) on your own LND Node that is not using Umbrel. If you are a user of Umbrel, you should use their version of NWC.
Requirements
You need to have a working installation of LND with established channels and connectivity to the internet. NWC in itself is fairly light and will not consume a lot of resources. You will also want to ensure that you have a working installation of Docker, since we will use a docker image to run NWC.
- Working installation of LND (and all of its required components)
- Docker (with Docker compose)
Installation
For the purpose of this tutorial, we will assume that you have your lnd/bitcoind running under user bitcoin with home directory /home/bitcoin. We will also assume that you already have a running installation of Docker (or docker.io).
Prepare and verify
git version - we will need git to get the latest version of NWC. docker version - should execute successfully and show the currently installed version of Docker. docker compose version - same as before, but the version will be different. ss -tupln | grep 10009- should produce the following output: tcp LISTEN 0 4096 0.0.0.0:10009 0.0.0.0: tcp LISTEN 0 4096 [::]:10009 [::]:**
For things to work correctly, your Docker should be version 20.10.0 or later. If you have an older version, consider installing a new one using instructions here: https://docs.docker.com/engine/install/
Create folders & download NWC
In the home directory of your LND/bitcoind user, create a new folder, e.g., "nwc" mkdir /home/bitcoin/nwc. Change to that directory cd /home/bitcoin/nwc and clone the NWC repository: git clone https://github.com/getAlby/nostr-wallet-connect.git
Creating the Docker image
In this step, we will create a Docker image that you will use to run NWC.
- Change directory to
nostr-wallet-connect:cd nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - The last line of the output (after a few minutes) should look like
=> => naming to docker.io/library/nwc:latest nwc:latestis the name of the Docker image with a tag which you should note for use later.
Creating docker-compose.yml and necessary data directories
- Let's create a directory that will hold your non-volatile data (DB):
mkdir data - In
docker-compose.ymlfile, there are fields that you want to replace (<> comments) and port “4321” that you want to make sure is open (check withss -tupln | grep 4321which should return nothing). - Create
docker-compose.ymlfile with the following content, and make sure to update fields that have <> comment:
version: "3.8" services: nwc: image: nwc:latest volumes: - ./data:/data - ~/.lnd:/lnd:ro ports: - "4321:8080" extra_hosts: - "localhost:host-gateway" environment: NOSTR_PRIVKEY: <use "openssl rand -hex 32" to generate a fresh key and place it inside ""> LN_BACKEND_TYPE: "LND" LND_ADDRESS: localhost:10009 LND_CERT_FILE: "/lnd/tls.cert" LND_MACAROON_FILE: "/lnd/data/chain/bitcoin/mainnet/admin.macaroon" DATABASE_URI: "/data/nostr-wallet-connect.db" COOKIE_SECRET: <use "openssl rand -hex 32" to generate fresh secret and place it inside ""> PORT: 8080 restart: always stop_grace_period: 1mStarting and testing
Now that you have everything ready, it is time to start the container and test.
- While you are in the
nwcdirectory (important), execute the following command and check the log output,docker compose up - You should see container logs while it is starting, and it should not exit if everything went well.
- At this point, you should be able to go to
http://<ip of the host where nwc is running>:4321and get to the interface of NWC - To stop the test run of NWC, simply press
Ctrl-C, and it will shut the container down. - To start NWC permanently, you should execute
docker compose up -d, “-d” tells Docker to detach from the session. - To check currently running NWC logs, execute
docker compose logsto run it in tail mode add-fto the end. - To stop the container, execute
docker compose down
That's all, just follow the instructions in the web interface to get started.
Updating
As with any software, you should expect fixes and updates that you would need to perform periodically. You could automate this, but it falls outside of the scope of this tutorial. Since we already have all of the necessary configuration in place, the update execution is fairly simple.
- Change directory to the clone of the git repository,
cd /home/bitcoin/nwc/nostr-wallet-connect - Run command to build Docker image:
docker build -t nwc:$(date +'%Y%m%d%H%M') -t nwc:latest .(there is a dot at the end) - Change directory back one level
cd .. - Restart (stop and start) the docker compose config
docker compose down && docker compose up -d - Done! Optionally you may want to check the logs:
docker compose logs
-
 @ 82341f88:fbfbe6a2
2023-04-11 19:36:53
@ 82341f88:fbfbe6a2
2023-04-11 19:36:53There’s a lot of conversation around the #TwitterFiles. Here’s my take, and thoughts on how to fix the issues identified.
I’ll start with the principles I’ve come to believe…based on everything I’ve learned and experienced through my past actions as a Twitter co-founder and lead:
- Social media must be resilient to corporate and government control.
- Only the original author may remove content they produce.
- Moderation is best implemented by algorithmic choice.
The Twitter when I led it and the Twitter of today do not meet any of these principles. This is my fault alone, as I completely gave up pushing for them when an activist entered our stock in 2020. I no longer had hope of achieving any of it as a public company with no defense mechanisms (lack of dual-class shares being a key one). I planned my exit at that moment knowing I was no longer right for the company.
The biggest mistake I made was continuing to invest in building tools for us to manage the public conversation, versus building tools for the people using Twitter to easily manage it for themselves. This burdened the company with too much power, and opened us to significant outside pressure (such as advertising budgets). I generally think companies have become far too powerful, and that became completely clear to me with our suspension of Trump’s account. As I’ve said before, we did the right thing for the public company business at the time, but the wrong thing for the internet and society. Much more about this here: https://twitter.com/jack/status/1349510769268850690
I continue to believe there was no ill intent or hidden agendas, and everyone acted according to the best information we had at the time. Of course mistakes were made. But if we had focused more on tools for the people using the service rather than tools for us, and moved much faster towards absolute transparency, we probably wouldn’t be in this situation of needing a fresh reset (which I am supportive of). Again, I own all of this and our actions, and all I can do is work to make it right.
Back to the principles. Of course governments want to shape and control the public conversation, and will use every method at their disposal to do so, including the media. And the power a corporation wields to do the same is only growing. It’s critical that the people have tools to resist this, and that those tools are ultimately owned by the people. Allowing a government or a few corporations to own the public conversation is a path towards centralized control.
I’m a strong believer that any content produced by someone for the internet should be permanent until the original author chooses to delete it. It should be always available and addressable. Content takedowns and suspensions should not be possible. Doing so complicates important context, learning, and enforcement of illegal activity. There are significant issues with this stance of course, but starting with this principle will allow for far better solutions than we have today. The internet is trending towards a world were storage is “free” and infinite, which places all the actual value on how to discover and see content.
Which brings me to the last principle: moderation. I don’t believe a centralized system can do content moderation globally. It can only be done through ranking and relevance algorithms, the more localized the better. But instead of a company or government building and controlling these solely, people should be able to build and choose from algorithms that best match their criteria, or not have to use any at all. A “follow” action should always deliver every bit of content from the corresponding account, and the algorithms should be able to comb through everything else through a relevance lens that an individual determines. There’s a default “G-rated” algorithm, and then there’s everything else one can imagine.
The only way I know of to truly live up to these 3 principles is a free and open protocol for social media, that is not owned by a single company or group of companies, and is resilient to corporate and government influence. The problem today is that we have companies who own both the protocol and discovery of content. Which ultimately puts one person in charge of what’s available and seen, or not. This is by definition a single point of failure, no matter how great the person, and over time will fracture the public conversation, and may lead to more control by governments and corporations around the world.
I believe many companies can build a phenomenal business off an open protocol. For proof, look at both the web and email. The biggest problem with these models however is that the discovery mechanisms are far too proprietary and fixed instead of open or extendable. Companies can build many profitable services that complement rather than lock down how we access this massive collection of conversation. There is no need to own or host it themselves.
Many of you won’t trust this solution just because it’s me stating it. I get it, but that’s exactly the point. Trusting any one individual with this comes with compromises, not to mention being way too heavy a burden for the individual. It has to be something akin to what bitcoin has shown to be possible. If you want proof of this, get out of the US and European bubble of the bitcoin price fluctuations and learn how real people are using it for censorship resistance in Africa and Central/South America.
I do still wish for Twitter, and every company, to become uncomfortably transparent in all their actions, and I wish I forced more of that years ago. I do believe absolute transparency builds trust. As for the files, I wish they were released Wikileaks-style, with many more eyes and interpretations to consider. And along with that, commitments of transparency for present and future actions. I’m hopeful all of this will happen. There’s nothing to hide…only a lot to learn from. The current attacks on my former colleagues could be dangerous and doesn’t solve anything. If you want to blame, direct it at me and my actions, or lack thereof.
As far as the free and open social media protocol goes, there are many competing projects: @bluesky is one with the AT Protocol, nostr another, Mastodon yet another, Matrix yet another…and there will be many more. One will have a chance at becoming a standard like HTTP or SMTP. This isn’t about a “decentralized Twitter.” This is a focused and urgent push for a foundational core technology standard to make social media a native part of the internet. I believe this is critical both to Twitter’s future, and the public conversation’s ability to truly serve the people, which helps hold governments and corporations accountable. And hopefully makes it all a lot more fun and informative again.
💸🛠️🌐 To accelerate open internet and protocol work, I’m going to open a new category of #startsmall grants: “open internet development.” It will start with a focus of giving cash and equity grants to engineering teams working on social media and private communication protocols, bitcoin, and a web-only mobile OS. I’ll make some grants next week, starting with $1mm/yr to Signal. Please let me know other great candidates for this money.
-
 @ 70122128:c6cc18b9
2023-09-23 23:53:18
@ 70122128:c6cc18b9
2023-09-23 23:53:18What is the way we ought to live? This question takes on particular importance to me as a Catholic. Christ prayed for his disciples, that we should be "not of the world, even as I am not of the world"[^1]. This call presents an apparently impossible challenge. Certainly, within the framework of our secular world, it is impossible, even incomprehensible. Yet, the call remains. To live it out, we must abandon the limitations of secular worldview we have all inherited and adopt a distinctly Catholic worldview. This project, I believe, begins with the imagination.
The Ideological Trap
The trap we must avoid when trying to adopt a Catholic worldview is that of confusing "worldview" with "ideology." At first glance, a "worldview" seems to be synonymous with "a system of beliefs." Under that definition, "worldview" and "ideology" appear to identify more or less the same concept. Conflating the two, however, is itself a symptom of the secular worldview. Thus, if we wish to adopt a Catholic worldview merely as a system of beliefs, we have already failed. The project has to go deeper.
To explain the difference, I will introduce a concept from the philosopher Charles Taylor. In his seminal work, A Secular Age[^2], Taylor introduces the concept of the "social imaginary" to describe the way we implicitly imagine the world. The social imaginary precedes and underlies thought. It imbues art and culture. It emerges in the most basic idioms of speech.
A prime example of the social imaginary is the analogy of the brain as computer. It is not uncommon to hear people mention their "mental bandwidth" and "memory banks," or to refer to having free time to think as having "spare cycles." Conversely, we often talk about computers as "thinking" while they take time to process. Such figures of speech betray an implicit assumption that the brain and a computer are, on some fundamental level, doing the same thing. Thus, the brain-computer analogy is part of our social imaginary.
Intellectually, the social imaginary is the ground we stand upon and the air we breath. It is the landscape within which our conscious mind operates, and as such, it defines the horizons of thought. A concept beyond this horizon becomes effectively unthinkable.
The term "worldview" in its more complete sense contains both the pre-thought realm of the social imaginary and the explicit systems of conscious thought. Charles Taylor perceptively suggests that the social imaginary of our modern world is distinctively secular, and that this secular imaginary sets the boundary conditions of belief, religious or otherwise. Within this secular frame, the immanent material world is the fundamental reality, the supernatural is nowhere to be found in our day-to-day experience, and God, if he is necessary at all, is little more than a Deistic watchmaker.
Any attempt to construct a Catholic worldview that does not shift these foundational assumptions will inevitably be trapped by the secular social imaginary. Within the secular framework, Catholicism becomes just one of many ideologies that offer a way of understanding and interpreting our immanent reality. As such, it may offer some explanatory or interpretive power, but it leave us unable to really grasp transcendent spiritual realities; the secular imaginary simply doesn't admit them.
Shifting the Ground
How, then, do we escape this mental trap? We must change the very ground upon which we stand, the very air that we breathe. Perhaps, standing upon different ground, we will be able to see new horizons. Perhaps, from a different vantage, the heavens will be closer, close enough for us to reach out and touch them—or for them to reach down and touch us. Looking to the past, it is apparent that we once stood upon such heights, before modernity and secularization; and maybe, by learning from the past, we can find such vantages anew.
Stepping into the great churches and cathedrals of antiquity, it is apparent that their builders saw the world in a wholly different way than the one we know. In the Romanesque churches of Italy, glittering mosaics reflect candlelight under majestic arches while shafts of sunlight from above illuminate the interior with heavenly rays. In the Gothic cathedrals of France and Germany, we find ourselves "surrounded by so great a cloud of witnesses"[^3] in colorful stained glass glowing with God's own radiance.
Implicit in this Medieval architecture is a distinctly theological social imaginary from the one we have today. Every stone, every pane of glass, every paintbrush-stroke, is arranged to point to a supernatural reality, indicating a belief that the material reality we can sense is suffused with a more fundamental spiritual reality. The mosaics and stained-glass windows haunt us with the presences of the saints who have come before. The very shape and dimensions of the buildings draws the eye to the altar, where the drama of the death and resurrection of God incarnate is liturgically reenacted. The church is the crossroads of Heaven and Earth.[^4]
Amid this sacred architecture and the liturgical activity that took place therein, it was atheism that was unthinkable. To the Medievals, God was in their midst, on the altars and in the tabernacles. In Charles Taylor's words, the world was "porous" to the transcendent; spiritual realities touched every dimension of human life.
Restoring Enchantment
Whatever the Medievals may have gotten right, we should not merely long for a return. Return is impossible. History has moved on; we cannot simply retrace our steps. I highlight the Medieval churches to show the importance of art, architecture, and imagination in shaping our social imaginary. I think that if we wish to truly live lives of faith, we must reorient our imaginative vision to recognize a world suffused with supernatural reality, a world in which God is present and active. In short, we must cultivate a Liturgical Imagination.
I will attempt to explore in detail what the Liturgical Imagination is in a future essay, but suffice for now to say that it must be specifically liturgical because the liturgy is the means by which we encounter God in our daily lived experience. Liturgy surrounds and enacts the Sacraments as visible signs of invisible reality.[^5] An imagination sensitive to the liturgy can perceive with a double sight both the ordinary, material reality that we sense and the transcendent, spiritual reality that moves therein.
How can we begin to form this liturgical vision? The answer, I believe, lies in Art. To once again invoke Charles Taylor, the path from the Medieval world to our secular age involved a shift of art from mimesis to poeisis.[^6] Mimesis imitates nature, while poeisis creates its own world. Medieval art is primarily mimetic; the depictions of the saints in stained glass are meant to imitate the unseen, yet very real presence of a "great cloud of witnesses" present at the Mass, where the great drama of salvation is daily re-presented. Over time, however, art has shifted in the direction of poeisis. The Epic, which seeks to tell a story that truly happened in some real sense (think of the Iliad), gives way to the Novel, which creates its own little world of setting, characters, and plot in which a wholly fictional drama can play out.
Thus, the way we receive art has changed. No longer do we turn to art seeking a deeper reality. Instead, in art we escape for a moment into a self-sufficient little tapestry of imagination that may or may not bear on the "real world." This is not all bad, however. The way forward is through. Within these little tapestries we can, I think, learn to see once more with a spiritual vision back in the "real world."
J. R. R. Tolkien, in his essay On Fairy-Stories,[^7] calls this act of poeisis "sub-creation," and the little tapestries "secondary worlds." Successful art, he says, Enchants us by creating a secondary world with "the internal consistency of reality" into which our minds can enter and roam freely. Within the secondary world, strange and fantastic things may be both possible and perfectly reasonable. When we return, we may at times find ourselves seeing the mundane in a new light. As Tolkien puts it:
We should look at green again, and be startled anew (but not blinded) by blue and yellow and red. We should meet the centaur and the dragon, and then perhaps suddenly behold, like the ancient shepherds, sheep, and dogs, and horses— and wolves.
Art can shake us out of our mundane, materialistic vision of the world and re-enchant the ordinary things of daily life. Indeed, in Liturgy, our primary world is enchanted by the action of grace, if only we can perceive it. This is the role of poeisis. I believe art, story, and song are the schools in which we may retrain the imagination to be receptive to transcendent realities, for they are uniquely situation to expand our imaginative horizons. Once we first guess that the horizon may be broader than we thought, that the heavens may reach down to touch the earth; when we can see the grass and trees and sky with new wonder, then we open ourselves to an encounter with the Divine that sustains them all.
Notes
[^1]: John 17:16, RSVCE. [^2]: James K. A. Smith's book How (Not) to be Secular is an excellent and concise summary of the key ideas contained in A Secular Age, and served as my primary source for understanding Taylor's thought. [^3]: Hebrews 12:1, RSVCE. [^4]: This account of the Medieval social imaginary borrows heavily from the points James K. A. Smith lays out in Chapter 1 of How (Not) to be Secular. [^5]: See the USCCB website for a brief explanation of the sacraments as efficacious signs of invisible grace: usccb.org/prayer-and-worship/sacraments-and-sacramentals, accessed 17 September, 2023. [^6]: James K. A. Smith discusses these ideas in Chapter 3 of How (Not) to be Secular. [^7]: The whole essay is worth a read. It can be accessed for free online in the Internet Archive.
-
 @ d6dc9554:d0593a0c
2023-09-21 18:37:14
@ d6dc9554:d0593a0c
2023-09-21 18:37:14Nas blockchains PoW o consenso é alcançado por meio de prova de trabalho computacional e o objetivo principal é evitar que atores mal intencionados consumam ou ataquem a rede de forma perigosa. Este método de consenso requer um grande poder computacional para criar novos blocos, mas é muito simples, por parte de outros, verificar esse trabalho. Por isso se diz que PoW é uma estratégia assimétrica.
Nas blockchains PoS o objetivo é o mesmo, criar blocos e chegar a um consenso, mas nas PoS não é necessário um poder de processamento tão grande como nas PoW. Em média as PoS gastam menos de 1% da energia das PoW. Nas PoS os mineradores são chamados de validadores. Enquanto que nas PoW quem fica com a recompensa é quem resolve primeiro a charada matemática, nas PoS o validador que vai ganhar a recompensa é escolhido de forma aleatória, mas dando maior probabilidade aos que respeitem determinados critérios. A comunidade bitcoin é muito relutante em relação a PoS porque é mais fácil conseguir uma grande quantidade da moeda em causa do que mais que 51% de poder processamento. Logo as PoS são mais vulneráveis no que toca a segurança. Mas aqui cada caso é um caso e é preciso fazer essa análise para cada moeda.
As blockchains PoW tendem a ser mais descentralizadas enquanto as PoS mais centralizadas, não só em acesso, mas também em operação. Mais de metade dos validadores de ethereum estão na cloud da amazon. As blockchains PoW apresentam grandes desafios na escalabilidade de operação, muitas vezes exigindo soluções de segunda camada (L2), enquanto que as PoS possuem mecanismos de escalabilidade muito mais flexíveis. Os algoritmos PoW são muito mais simples de implementar do que os PoS e, portanto, menos suscetíveis a erros. Um bom exemplo é o PoS da ethereum que estava a ser implementado desde 2018.
-
 @ 7d4417d5:3eaf36d4
2023-08-19 01:05:59
@ 7d4417d5:3eaf36d4
2023-08-19 01:05:59I'm learning as I go, so take the text below for what it is: my notes on the process. These steps could become outdated quickly, and I may have some wrong assumptions at places. Either way, I have had success, and would like to share my experience for anyone new to the process. If I have made any errors, please reply with corrections so that others may avoid potential pitfalls.
!!! If you have "KYC Bitcoin", keep it in separate wallets from your "Anonymous Bitcoin". Any Anonymous Bitcoin in a wallet with KYC Bitcoin becomes 100% KYC Bitcoin.
!!! It took me several days to get all the right pieces set up before I could even start an exchange with someone.
!!! Using a VPN is highly recommended. If you're not already using one, take the time to find one that suits you and get it running.
!!! If you don't normally buy Amazon Gift Cards, start doing so now, and just send them to yourself, or friends that will give you cash in return, etc. For my first trade, Amazon locked me out of my account for about 22 hours, while I was in the middle of an exchange. All because I had never purchased an Amazon Gift Card before. It was quite nerve wracking. My second trade was for $300, and although my Amazon account wasn't shut down, that order had a status of "Sending" for about 22 hours, due to the large amount. In each of these cases I had multiple phone calls with their customer support, all of whom gave me false expectations. Had I already been sending gift cards to the anonymous email address that I created in the steps below, and maybe other anonymous email addresses that I could make, then I might not have been stalled so much.
-
Install Tor Browser for your OS. The RoboSats.com website issues a warning if you are not using Tor Browser. If you don't know what Tor is, I won't explain it all here, but trust me, it's cool and helps keep you anonymous. If you use Firefox, the interface will look very familiar to you.
-
Create a KYC-free e-mail address. I used tutanota.com in Firefox, as it would not allow me to create an account using Tor Browser. After the account was created, using Tor Browser to login, check emails, etc. has been working perfectly. Tutanota requires a 48 hour (or less) waiting period to prevent bots from using their system. You'll be able to login, and even draft an email, but you won't be able to send. After you've been approved, you should be able to login and send an email to your new address. It should show up in your Inbox almost instantly if it's working.
-
Have, or create, at least one Lightning wallet that is compatible with RoboSats.com and has no KYC Bitcoin in it. The RoboSats website has a compatibility chart available to find the best wallet for you. During an exchange on RoboSats, you will need to put up an escrow payment, or bond, in Satoshis. This amount is usually 3% of the total amount being exchanged. If the exchange is successful, the bond payment is canceled, leaving that amount in your wallet untouched, and with no record of it having been used as escrow. If you don't hold up your end of the trade, the bond amount will be transfered from your wallet. I created a wallet, using my new email address, with the Alby extension in the Tor Browser. This anonymous wallet was empty, so I used a separate wallet for the bond payment of my first trade. This wallet had KYC Bitcoin, but since it is being used for a bond payment, and no transaction will be recorded if everything goes okay, I don't mind taking the minuscule risk. After the first trade, I don't need to use the "KYC wallet", and I will use only my anonymous Lightning wallet for transactions related to performing a trade.
-
Create a new Robot Token by going to RoboSats using the Tor Browser. Copy the Token (Robot ID) to a text file as a temporary backup. It is recommended to create a new robot-token for every session of exchanges you make.
-
Select "Offers" to browse what others are presenting. "Create" is for when you want to create an offer of your own. You may need to create your own offer if none of the existing offers match your criteria.
-
Select "Buy" at the top of the page.
-
Select your currency (USD).
-
Select your payment methods by typing "amazon" and selecting (Amazon Gift Card). Repeat this process and select (Amazon USA Gift Card).
-
Determine Priorities - If you prefer to trade quickly, and don't care as much about premiums, look for users with a green dot on the upper-right of their robot icon. If you're not in a hurry, sort users by premium and select the best deal, even if they are inactive. They may become active once they are notified that their offer has activity from you.
-
The Definition of Price = the price with the premium added, but not the bond
-
A. Find A Compatible Offer - Select the row of the desired offer and enter the amount you would like to buy. i.e. $100 If you do not find a compatible offer, you will have to create your own offer.
B. **Create An Offer** - First, take a look at "Sell" offers for your same currency and payment method(s) that you will be using. Take note of the premium those buyers are willing to pay. If your premium is drastically less than theirs, your offer may get ignored. Select "Create" at the bottom of the screen. There is a slider at the top of the screen, select it to see all the options. Select "Buy". Enter the minimum and maximum amount that you wish to spend. Type "amazon" to select the methods that you would like to use (Amazon Gift Card, Amazon USA Gift Card). For "Premium Over Market", enter an amount that is competitive with premiums you saw at the start of this step and do not use the % sign! You can adjust the duration, timer, and bond amount, but I leave those at their default settings. Select the "Create Order" button, and follow the instructions for making a bond payment. -
Pay the Bond - Copy the invoice that is presented. From your wallet that contains bond funds, select "Send", and paste the invoice as the recipient. This money will never leave your account if the exchange completes without issue. No transaction will be recorded. If there is a complication with the exchange, it is possible that this transaction will complete.
-
Create and Submit Your Invoice for Their Bitcoin Payment To You - Select "Lightning", if not selected by default.* Select the Copy Icon to copy the correct amount of Satoshis. This amount already has the premium deducted. From your anonymous Lightning Wallet, select "Receive", and paste the Satoshi amount. If you enter a description, it's probably best to keep it cryptic. Copy the invoice and paste it into RoboSats; then select "Submit".
* If you plan on "mixing" your Bitcoin after purchase, it may be better to select "On Chain" and pay the necessary fees swap and mining fees. In the example this comes from, Sparrow wallet is used and has whirlpool ability in its interface.
-
Connect With Seller and Send Funds - Greet the seller in the chat window. The seller has now provided RoboSats with the Bitcoin to transfer to you. Your move is to buy an Amazon eGift Card for the amount of the trade. Log in to your Amazon account and start the process of buying an eGift card. For delivery there is the option of email or txt message. Ask the seller what their preference is, and get their address, or phone number, to enter into Amazon's form. Complete the purchase process on Amazon, and check the status of your order. Once you see the status of "Sent", go back to RoboSats in your Tor Browser.
-
Confirm Your Payment - Select the "Confirm ___ USD Sent" button and notify the seller to check their e-mail/txt messages.
-
Seller Confirmation - Once the seller select their "Confirm" button, the trade will immediately end with a confirmation screen.
-
Verify - If you check the anonymous wallet, the new amount should be presented.
-
-
 @ e6817453:b0ac3c39
2023-08-12 15:42:22
@ e6817453:b0ac3c39
2023-08-12 15:42:22The Zooko’s Triangle is a concept in the realm of naming systems, specifically for decentralized or distributed networks. It was named after Zooko Wilcox-O’Hearn, a computer scientist and cypherpunk known for his work on the Zcash cryptocurrency. The triangle illustrates a trade-off between three desirable properties in a naming system:
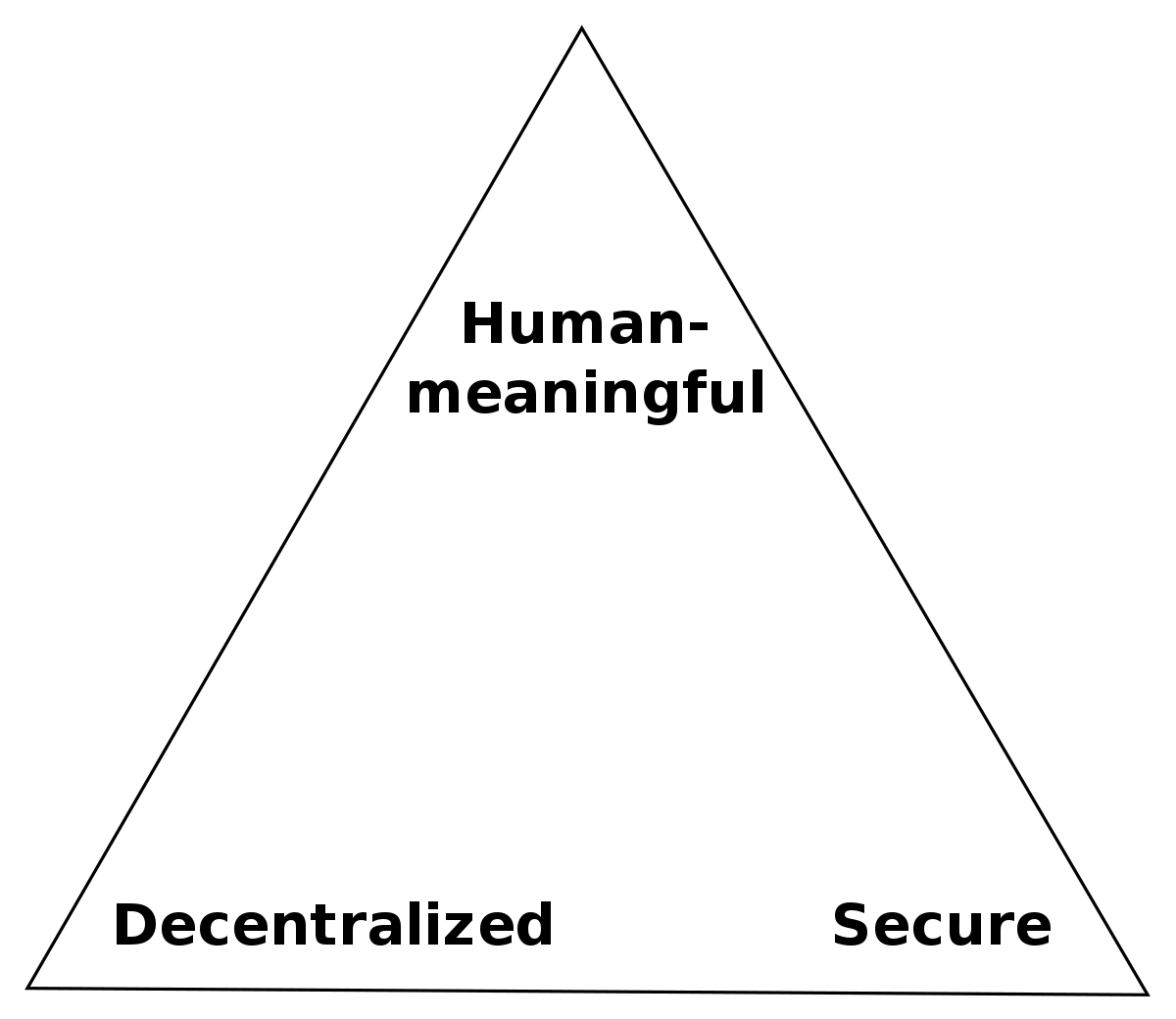
- Human-meaningful: Names are easily understood and remembered by humans.
- Decentralized: No central authority controls the allocation or management of names.
- Secure: Names are unique and cannot be easily taken or manipulated by others.
Zooko’s Triangle posits that achieving all three properties in a single system is difficult. Traditionally, a system could have only two of the three properties, leading to various combinations of naming systems with their respective advantages and disadvantages.
However, recent developments in cryptographic and distributed systems have led to solutions that challenge the traditional constraints of Zooko’s Triangle. One such system is the Decentralized Identifiers (DIDs).
DIDs
Decentralized Identifiers (DIDs) are a new identifier for verifiable, decentralized digital identity. DIDs are designed to be self-sovereign, meaning that individuals or organizations control their identifiers without relying on a central authority. DID systems are built on top of decentralized networks, such as blockchain or distributed ledgers, providing a secure and tamper-proof infrastructure for identity management.
DIDs aim to achieve the three properties of Zooko’s Triangle:
- Human-meaningful: While DIDs may not be human-meaningful due to their cryptographic nature, they can be associated with human-readable names or aliases.
- Decentralized: DIDs are managed on decentralized networks, removing the need for a central authority.
- Secure: The decentralized nature of DIDs, combined with cryptographic techniques, ensures that identifiers are unique, secure, and resistant to tampering.
In summary, Zooko’s Triangle presents a trade-off between human-meaningful, decentralized, and secure properties in naming systems. Decentralized Identifiers (DIDs) are an example of a system that seeks to overcome the traditional limitations of the triangle by leveraging decentralized networks and cryptographic techniques to provide a more comprehensive solution for digital identity management.
-
 @ e6817453:b0ac3c39
2023-08-12 15:41:59
@ e6817453:b0ac3c39
2023-08-12 15:41:59Organizational identifiers
Organizational identifiers have different sets of requirements and functions. It is not enough to have per-to-peer private communications. Organizations are more public, so we need publicly resolvable identifiers. DID:key satisfy this condition entirely but fails to fulfill the organization's needs.
- Organizations quite often act as issuers of credentials or attestations. For issuance, it is critical to have the possibility to rotate signing keys or even deactivate or delete identifiers if keys or issuer get compromised or to comply with security company policies.
- Organizations often require a split between the Controller of the identifier and the Identifier subject or even a transfer of the identifier subject.
- Organizations must have complete control of infrastructure and effectively manage resources and costs. The price of a single identifier should be fixed, and the method of creating new identifiers should be scalable.
- One of the essential requirements is trust and governance and transparent mechanics of proving and binding an identifier to an organizational entity and creating trust relations.
- Access to Identifier management is quite often controlled by a group of users
Nonfunctional requirements
- portability
- interoperability
- scalability
- Autonomous and control
- security
In my previous articles, we talk about Autonomous identifiers and how they differ from regular DIDs.
To recap
Autonomous identifiers (AIDs) are DIDs generated algorithmically from a crypto- graphic key pair in such a way that they are self-certifying, i.e. the binding with the public key can be verified without the need to consult any external blockchain or third party. KERI is an example of a decentralized identity technology based entirely on AIDs. © https://trustoverip.org/blog/2023/01/05/the-toip-trust-spanning-protocol/
In a previous article, I show how to create and use a did:key as an Autonomous identifier that feet well to private person-to-person secure communication.
Architectures and protocols that build on top of AIDs have few critical properties
- self-hosting and self-contained
- self-certified and Autonomous
- portable
- interoperable
- full control of infrastructure
- cost management
Nowadays, I discovered a few AIDs methods
- did:key — self-contained and public
- did:peer — self-certified, upgradable but private
- KERI based did — we waiting for did:keri method to be announced soon, but KERI infrastructure could be used to build internals of did:peer or similar methods.
- did:web — public, self-certified, and self-hosted method, but still, we have active community discussion and critics as far as it fully relays to ownership of domain name that could be stolen or re-assigned.
So we have to choose from did:key did:web and I hope in a future from did:keri.
To move forward, we need to understand the DID architecture better and how all parts are connected.
In many cases of personal or sovereign entities Subject and the Controller are the same, but for Organisations, it could have a crucial difference.
DID Subject
The DID subject is the entity that the DID represents. It can be a person, organization, device, or other identifiable entity. The DID subject is associated with a unique DID that serves as a persistent, resolvable, and cryptographically verifiable identifier. The subject is the primary focus of the identity management process and typically has one or more DIDs associated with it.
DID Controller
The DID controller is the entity (person, organization, or device) that has the authority to manage the DID Document associated with a particular DID. The DID controller can update, revoke, or delegate control of the DID Document, which contains the public keys, service endpoints, and other information required for interacting with the DID subject.
In many cases, the DID subject and DID controller can be the same entity, especially for individual users who create and manage their DIDs. However, in some situations, the DID controller may differ from the DID subject, such as when an organization manages the DIDs on behalf of its employees or when an administrator manages a device.
In summary, the DID subject is the entity the DID represents, while the DID controller is the entity with authority to manage the associated DID Document. Depending on the specific use case and requirements, these roles can be held by the same or different entities.
Key Pair
It is simple from the first point of view. Key-Pair is an asymmetric public and private key. One of the main DID functions is the distribution of public keys. DIDDoccument could contain multiple public keys with authorization rules and key roles.
Identifier
Representation of did itself. is a part of DID URI.
DID:Key

did:key identifier
DID web
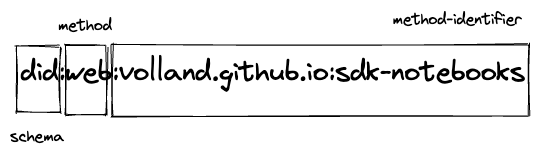
did:web
Relations
Relations between all parts of DID identifier can be illustrated in the following diagram. DID method dictate how DID identifier gets created, updated, deactivated, and resolved.
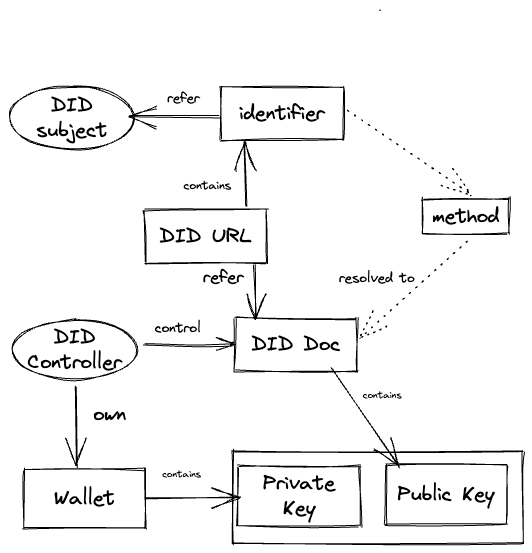
Focusing on the relations of the controller, key pairs, and the identifier is more interesting for us.
The most significant power and benefit of DID are decoupling a key pair from a controller and identifier. It allows the rotation of keys and changes the ownership of the identifier and its subject and controller. It is the main competitive advantage of DID and SSI over web3 wallets and raw keys.
The ideal case is KERI infrastructure that decouples all parties via cryptographic binding and protocols.
To discover more, read the paper.
We used did: keys as AID in the previous article. DID:key is a cryptographically bound identifier to the public key but cannot change the binding. As a result, keys couldn't be rotated in the future. The controller has no binding except to prove private key ownership via the signature-based protocol.
On the other side, DID:web does not have a cryptographic binding of an identifier to a key pair from one side. It gives an easy possibility to rotate keys but loses the verifiability of the identifier.
The most interesting part is the Controller to identifier binding in a did: web. It is based on proof of domain name ownership and website resource. As I mention, it has some security considerations and critics in a community. Still, at the same time, we get a critical mechanism that settles trust and connects identifiers to the organization entity.
The mechanism of web domain ownership is well-defined and easy to explain to other users, even outside of SSI and web5 domain. It is getting wider adoption and creating a lot of use cases for organizations. So it helps to create a trust relationship between an identifier and organizational entity in a very transparent, human-readable, and self-explained way — the identifier hosted on the corporate domain belongs to the organization. On another side, it makes the transfer of the controller almost impossible. That's why it is critical to differentiate between a subject and a controller.
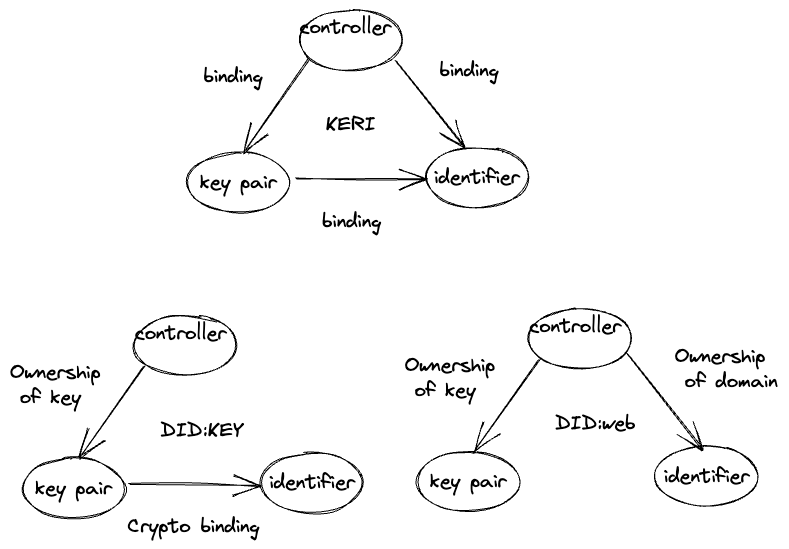
I believe that did:web still covers a lot of organizational cases and is suitable for issuing Verifiable Credentials and attestations on behalf of organizations.
Step-by-step guide on how to create and manage did:web you could find in my article
More detailed step-by-step coding guide with the live example you could find in my SSI notebooks book
-
 @ d3d74124:a4eb7b1d
2023-07-26 02:43:40
@ d3d74124:a4eb7b1d
2023-07-26 02:43:40This plan was GPT generated originally but then tweaked by myself as the idea fleshed itself out. All feedback welcome and encouraged.
Shenandoah Bitcoin
1. Executive Summary
Shenandoah Bitcoin is a for-profit community organization based in Frederick County, VA, uniquely blending the world of agriculture and STEM. Our mission is to foster community spirit, stimulate interest in agricultural technology, and promote understanding of Bitcoin, while providing enriching educational opportunities and ensuring sustainable business operations.
2. Company Description
Shenandoah Bitcoin is committed to delivering value to our local community. Our unique approach intertwines traditional agricultural practices, modern STEM concepts, and the world of digital currencies, specifically Bitcoin. Our activities cater to all age groups, focusing on fostering community engagement, hands-on learning experiences, and contributing to the overall welfare of our community.
What’s in a name?
Shenandoah Bitcoin. Shenandoah - an old and historied land. Bitcoin - a cutting edge technological advancement. Both encompass multiple industries, from energy and manufacturing, to farming and data centers. Both built using Proof of Work.
3. Services
We offer a range of services, including:
Family-friendly events: Agriculture, STEM, and Bitcoin-themed festivals, fairs, workshops, and community gatherings. Educational programs: Classes, seminars, and workshops on agricultural technology, STEM principles, and understanding and using Bitcoin. Facility Rentals: Spaces available for private events, business meetings, and community gatherings.
4. Membership Benefits
We offer tiered membership packages with benefits such as:
a. Silver Membership: Includes access to regular events, discounts on educational programs, and priority booking for facility rentals.
b. Gold Membership: All Silver benefits, free access to select educational programs, and further discounted facility rentals.
c. Platinum Membership: All Gold benefits, free access to all educational programs, highest priority and maximum discounts on facility rentals, and exclusive invitations to special events.
Member’s opting to pay in Bitcoin receive 10% off all pricing.
5. Market Analysis
Our primary market is the local community in Frederick County and Winchester, VA, which consists of various demographic groups. Our secondary market includes neighboring communities, tourists, businesses, and educational institutions interested in the intersection of agriculture, STEM, and Bitcoin. Understanding that facility use and events to be a drawing factor for all demographics, we outline demographic specific analysis below.
STEM professionals in the area may work remotely or commute toward DC and not interact much with their agricultural neighbors, but a desire for good quality food exists for many. In addition to events, drawing the STEM demographic in will be connections to CSAs, ranchers, and homesteaders for access to fresh locally grown food. Offering a child's play room adjacent to some office space, is a compelling benefit for the laptop class that is often in STEM professions.
Non-industrial food producers and homesteaders may not have the focus or resources for marketing and sales. By offering a physical touch point for them and direct connections to consumers, food producers benefit from membership. Having more options for drop off/pick up of various produced goods, makes it attractive for both the consumers and producers as coordination can be asynchronous.
Bitcoiners have a wide range of sub-demographics, including farmers and software engineers. Some travel hours over car and plane to attend bitcoin themed events. The topics of STEM and agriculture are of shared interest to non-trivially sized communities of bitcoiners. Having a physical touch point for bitcoiners will draw in some members just for that. Building fellowship is desired and sought in bitcoin.
5.1 Market Trends
The blending of agriculture, STEM fields, and Bitcoin is a unique concept with increasing interest in sustainable farming and ranching, food sovereignty, and health. Shenandoah Bitcoin is poised to tap into this growing interest and offer unique value to our community.
5.2 Market Needs
Our market requires initiatives that foster community engagement, promote understanding of agri-tech and Bitcoin, and provide a versatile space for events and learning.
6. Marketing and Sales Strategy
We will employ a blend of digital marketing, traditional advertising, and strategic partnerships. Our main marketing channels will be word of mouth, social media, local press, and our website. Partnerships with local small businesses, homesteaders, schools, agricultural organizations, and bitcoin companies will form a key part of our outreach strategy.
7. Organizational Structure
Shenandoah Bitcoin will be led by a CEO, supported by a management team responsible for daily operations, event planning, marketing, and community outreach. Event management and logistics will be handled by part-time staff and volunteers.
8. Financial Projections
Our revenue will be generated from membership fees, charges for events and educational programs, and facility rentals.
9. Funding Request
[If seeking additional funding, describe your needs and how the funds will be used]
10. Exit Strategy
Should it become necessary to dissolve the business, assets such as property, equipment, and any remaining cash reserves after meeting liabilities will be sold. Investors would receive their share of the remaining assets according to their proportion of ownership.
11. Conclusion
Shenandoah Bitcoin is a unique community organization bringing together agriculture, STEM, and Bitcoin in Frederick County, VA. Our distinctive approach is designed to deliver both profits and social impact, resonating strongly with our target market and positioning us for sustainable growth.
-
 @ 32e18276:5c68e245
2023-10-10 12:02:37
@ 32e18276:5c68e245
2023-10-10 12:02:37Hey guys, I'm spending some time today preparing v1.6 for the app store, it's been a long time coming with many new features. Here's a breakdown of everything new in this version!
Notable new features in 1.6
- Custom built, embedded C WASM interpreter (nostrscript), which will be used for custom algos, filters and lists
- Longform note support
- Hashtag following
- Configurable reactions
- New Live user status NIP (music, general)
- Adjustable font sizes
- A very long list of bug fixes and performance improvements
- Fast and persistent profile searching using nostrdb
Top priorities for 1.7
- Lists
- Custom algos and filters using nostrscript
- Stories
- Multi account
- Tor integration
- Better NWC integration (wallet balances, transaction history)
- Advanced note search via nostrdb
- Fully switch to nostrdb for all notes
- Discord-like relays (click a relay to view all the notes on it)
So much more but maybe I will not try to be too ambitious ...
Contributors
name added removed commits William Casarin +57964 -8274 288 petrikaj +1524 -0 1 Terry Yiu +1266 -964 9 ericholguin +1234 -252 11 Daniel D’Aquino +1223 -399 19 Suhail Saqan +905 -70 16 Grimless +838 -736 6 Bryan Montz +793 -744 30 Jon Marrs +658 -60 3 Joel Klabo +653 -105 6 transifex-integration[bot] +176 -0 9 Fishcake +129 -21 5 Daniel D‘Aquino +123 -9 5 Jericho Hasselbush +78 -2 2 cr0bar +66 -19 11 Daniel D'Aquino +55 -32 2 Mazin +53 -0 1 gladiusKatana +37 -8 1 doffing.brett +10 -6 1 tappu75e@duck.com +5 -1 2 Ben Harvie +5 -0 1Changelog
- 76 Fixes
- 18 Changes
- 26 Additions
Added
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Add ability to change order of custom reactions (Suhail Saqan)
- Add close button to custom reactions (Suhail Saqan)
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add initial longform note support (William Casarin)
- Add r tag when mentioning a url (William Casarin)
- Add relay log in developer mode (Montz)
- Add settings for disabling user statuses (William Casarin)
- Add space when tagging users in posts if needed (William Casarin)
- Add support for multilingual hashtags (cr0bar)
- Add support for multiple reactions (Suhail Saqan)
- Add support for status URLs (William Casarin)
- Add the ability to follow hashtags (William Casarin)
- Added feedback when user adds a relay that is already on the list (Daniel D'Aquino)
- Added generic user statuses (William Casarin)
- Added live music statuses (William Casarin)
- Added merch store button to sidebar menu (Daniel D’Aquino)
- Added padding under word count on longform account (William Casarin)
- Adjustable font size (William Casarin)
- Click music statuses to display in spotify (William Casarin)
- Enable banner image editing (Joel Klabo)
- Finnish translations (petrikaj)
- Hold tap to preview status URL (Jericho Hasselbush)
- Re-add nip05 badges to profiles (William Casarin)
- Show nostr address username and support abbreviated _ usernames (William Casarin)
- Suggested Users to Follow (Joel Klabo)
Changed
- Allow reposting and quote reposting multiple times (William Casarin)
- Damus icon now opens sidebar (Daniel D’Aquino)
- Hide nsec when logging in (cr0bar)
- Improve UX around clearing cache (Daniel D’Aquino)
- Improved memory usage and performance when processing events (William Casarin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
- Remove nip05 on events (William Casarin)
- Remove note size restriction for longform events (William Casarin)
- Rename NIP05 to "nostr address" (William Casarin)
- Show muted thread replies at the bottom of the thread view (#1522) (Daniel D’Aquino)
- Show renotes in Notes timeline (William Casarin)
- Start at top when reading longform events (William Casarin)
- Switch to nostrdb for @'s and user search (William Casarin)
- Updated relay view (ericholguin)
- Use nostrdb for profiles (William Casarin)
- clear statuses if they only contain whitespace (William Casarin)
Fixed
- Allow relay logs to be opened in dev mode even if relay (Daniel D'Aquino)
- Allow user to login to deleted profile (William Casarin)
- Apply filters to hashtag search timeline view (Daniel D’Aquino)
- Avoid notification for zaps from muted profiles (tappu75e@duck.com)
- Crash when muting threads (Bryan Montz)
- Dismiss qr screen on scan (Suhail Saqan)
- Don't always show text events in reposts (William Casarin)
- Don't spam lnurls when validating zaps (William Casarin)
- Eliminate nostr address validation bandwidth on startup (William Casarin)
- Ensure the person you're replying to is the first entry in the reply description (William Casarin)
- Fix Invalid Zap bug in reposts (William Casarin)
- Fix PostView initial string to skip mentioning self when on own profile (Terry Yiu)
- Fix UI freeze after swiping back from profile (#1449) (Daniel D’Aquino)
- Fix UTF support for hashtags (Daniel D‘Aquino)
- Fix action bar appearing on quoted longform previews (William Casarin)
- Fix broken markdown renderer (William Casarin)
- Fix bug where it would sometimes show -1 in replies (tappu75e@duck.com)
- Fix compilation error on test target in UserSearchCacheTests (Daniel D‘Aquino)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix crash when long-pressing reactions (William Casarin)
- Fix freezing bug when tapping Developer settings menu (Terry Yiu)
- Fix icons on settings view (cr0bar)
- Fix images and links occasionally appearing with escaped slashes (Daniel D‘Aquino)
- Fix issue where malicious zappers can send fake zaps to another user's posts (William Casarin)
- Fix issue where relays with trailing slashes cannot be removed (#1531) (Daniel D’Aquino)
- Fix issue where typing cc@bob would produce brokenb ccnostr:bob mention (William Casarin)
- Fix issue with emojis next to hashtags and urls (William Casarin)
- Fix issue with slashes on relay urls causing relay connection problems (William Casarin)
- Fix lag when creating large posts (William Casarin)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix localization issues and export strings for translation (Terry Yiu)
- Fix long status lines (William Casarin)
- Fix nav crashing and buggyness (William Casarin)
- Fix nostr:nostr:... bugs (William Casarin)
- Fix npub mentions failing to parse in some cases (William Casarin)
- Fix padding of username next to pfp on some views (William Casarin)
- Fix padding on longform events (William Casarin)
- Fix paragraphs not appearing on iOS17 (cr0bar)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix potential fake profile zap attacks (William Casarin)
- Fix profile not updating (William Casarin)
- Fix profile post button mentions (cr0bar)
- Fix profiles not updating (William Casarin)
- Fix rare crash triggered by local notifications (William Casarin)
- Fix reaction button breaking scrolling (Suhail Saqan)
- Fix situations where the note composer cursor gets stuck in one place after tagging a user (Daniel D’Aquino)
- Fix small graphical toolbar bug when scrolling profiles (Daniel D’Aquino)
- Fix some note composer issues, such as when copying/pasting larger text, and make the post composer more robust. (Daniel D’Aquino)
- Fix status events not expiring locally (William Casarin)
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Fix text editing issues on characters added right after mention link (Daniel D’Aquino)
- Fix wiggle when long press reactions (Suhail Saqan)
- Fix wikipedia url detection with parenthesis (William Casarin)
- Fix zaps sometimes not appearing (William Casarin)
- Fixed a bug where following a user might not work due to poor connectivity (William Casarin)
- Fixed audio in video playing twice (Bryan Montz)
- Fixed disappearing text on iOS17 (cr0bar)
- Fixed issue where hashtags were leaking in DMs (William Casarin)
- Fixed issue where reposts would sometimes repost the wrong thing (William Casarin)
- Fixed issues where sometimes there would be empty entries on your profile (William Casarin)
- Fixed nav bar color on login, eula, and account creation (ericholguin)
- Fixed nostr reporting decoding (William Casarin)
- Fixed nostrscript not working on smaller phones (William Casarin)
- Fixed old notifications always appearing on first start (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Hide quoted or reposted notes from people whom the user has muted. (#1216) (Daniel D’Aquino)
- Hide users and hashtags from home timeline when you unfollow (William Casarin)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Mute hellthreads everywhere (William Casarin)
- Show QRCameraView regardless of same user (Suhail Saqan)
- Show longform previews in notifications instead of the entire post (William Casarin)
- Stop tab buttons from causing the root view to scroll to the top unless user is coming from another tab or already at the root view (Daniel D’Aquino)
- don't cutoff text in notifications (William Casarin)
- endless connection attempt loop after user removes relay (Bryan Montz)
- icon color for developer mode setting is incorrect in low-light mode (Bryan Montz)
- relay detail view is not immediately available after adding new relay (Bryan Montz)
Removed
- Remove following Damus Will by default (William Casarin)
- Remove old @ and & hex key mentions (William Casarin)
-
 @ 23202132:eab3af30
2023-09-05 19:02:11
@ 23202132:eab3af30
2023-09-05 19:02:11Pensar não é uma tarefa fácil, principalmente devido ao forte apelo emocional que nossa constituição física e mental proporciona. Somos seres de emoção antes de qualquer coisa. O filósofo David Hume defendeu certa vez que a razão é um tipo de fenômeno escravo do sentimento. Para Hume a razão poderia ser entendida como uma ferramenta usada para justificar nossas emoções. Nesse sentido, a arte de iludir pode ser dotada de uma técnica eficiente quando apela para nossos sentimentos e desejos.
Com o desenvolvimento das ciências e dos estudos cognitivos, as afirmações de Hume parecem em certa medida adequadas. Sabemos que o raciocínio é influenciado em grande parte pelo sentimento que produz em nós. Neste sentido o ato de pensar, quando contraria nossos sentimentos, pode ser angustiante, motivando muitas pessoas a evitar tal prática. Existe uma diferença entre pensar e se deixar levar. No cotidiano chamamos de influenciáveis aquelas que se deixam conduzir sem questionar o que é afirmado. Facilitando a prática da arte de enganar.
Não é por acaso que os sistemas de publicidade apelam para as emoções na hora de tentar vender um produto ou serviço. É conhecimento geral que a porta de acesso para influenciar uma pessoa é o sentimento.
Os meios de comunicação de massa também adotam uma linguagem dramatizada uma vez que esta é a mais eficiente na hora de influenciar e garantir resultados para os patrocinadores. Promovendo sua arte de iludir através de notícias dramáticas a imprensa consegue manipular em algum grau o sentimento das pessoas.
Isso não significa que os meios de comunicação precisam ser excluídos ou condenados, o que parece adequado é que as pessoas possam detectar as inconsistências das afirmações e do próprio pensamento, confrontando seus sentimentos. Evitando dessa forma se transformarem em vítimas da arte de enganar.
O filósofo Wittgenstein defendeu que a diferença entre pensar e se deixar levar estaria no uso inadequado da linguagem, onde em geral as pessoas usam a linguagem de maneira superficial, sem prestar atenção na lógica do discursos, ignorando assim, possíveis conseqüências do que é afirmado.
O que identifica se uma afirmação é pensada ou negligenciada é a coerência e a conexão concreta com o mundo, neste sentido, quanto mais conectada com o mundo é uma afirmação, menor é a exigência de acreditarmos e maior é a possibilidade de comprovação. Acreditar e comprovar são os agentes que validam o pensamento.
A principal diferença entre uma crença e uma comprovação consiste no fato da comprovação exigir uma seqüência de fatos contextualizados enquanto uma crença pode negligenciar as evidências.
Um termo muito usado para identificar erros do pensamento é chamado de falácia. Uma Falácia é uma afirmação pensada de maneira superficial, negligenciando as evidências, sendo fundamentada por crenças.
Muitas pessoas e instituições fazem um grande esforço para produzir erros de raciocínio aceitáveis, seja para vender um produto ou vencer uma discussão.
Fazer com que as pessoas sejam influenciadas por falsas verdades é uma arte cada vez mais estudada e praticada no cotidiano. Hoje é consenso que a responsabilidade de não acreditar em afirmações propositadamente equivocadas é individual. Alguns entendem que a responsabilidade não é de quem produz o engano e sim da pessoa que acredita.
Com tantas tentativas de influenciar as pessoas, torna-se importante ficar atento para identificar as falácias.
As áreas das ciências cognitivas afirmam que muito da capacidade de percepção é uma questão de prática, sendo aconselhável para quem deseja ficar mais atento treinar a identificação de inconsistência no que é dito. A melhor maneira de se proteger é sempre perguntando pelo conjunto de evidências e não aceitar apenas uma evidência como verdade.
Como as crenças estão intimamente associadas aos sentimentos e estes são porta de entrada para influenciar uma pessoa, geralmente os truques para criar uma ilusão na arte de enganar usam do desejo e vontade da vítima em acreditar, seguido de algumas das técnicas de persuasão.
Uma das maneiras de convencer alguém é através do seu sentimento por outra pessoa ou pela autoridade no qual tenha adquirido confiança. Neste sentido, ao receber a informação de alguém que você gosta ou que acredita, é possível que ocorra menor questionamento sem o exercício de identificação de possíveis inconsistências.
É por isso que propagandas usam de atores admirados pelo público ou de pesquisas ditas científicas. A ideia aqui é conseguir influenciar eliminando o senso crítico através do sentimento de uma pessoa por outra, ignorando desta forma a perguntar pelo conjunto de evidências.
Isso ocorre toda hora nas propagandas e nos resultados de pesquisas pseudocientíficas onde somente o que interessa é publicado.
Outra forma de influenciar é através da crença relativista, esta serve muitas vezes como justificação na tentativa de se escapar das conseqüências. Em geral ocorre através da ideia que uma crença é sempre verdadeira para a pessoa que acredita. Você já deve ter escutado alguém dizer: “Isso pode ser errado para você, mas para mim é correto.” Ou ainda “Eu acredito e ponto final”.
Não é aconselhável esquecer que uma crença geralmente é manifestação de um sentimento e em certa medida de um desejo. Neste sentido uma crença não precisa estar relacionada com fatos verdadeiros.
O segredo de influenciar consiste na habilidade de produzir crenças.
No entanto, é aconselhável ficar atento para o fato das crenças não estarem conectadas diretamente com os fatos no mundo e sim com os desejos e sentimentos.
Quando alguém acredita em algo, está provavelmente manifestando um sentimento que não é baseado em um conjunto contextualizado de evidências.
Tentar fazer você acreditar em algo, consiste em motivar sentimentos e criar uma ilusão onde a pessoa terá dificuldades em ficar atenta para as inconsistências e não conseguirá questionar adequadamente certas afirmações.
Para se proteger deste tipo de influência é aconselhável perguntar sobre suas emoções frente alguma afirmação. Observe se é necessário confiar/acreditar no que é afirmado ou existem e são demonstradas evidências concretas.
É importante observar a diferença sobre evidência concreta e falsa evidência.
A técnica do falso dilema é largamente usada para promover crenças com falsa evidência e confundir assim a percepção. É possível fazer uma coisa parecer outra, basta omitir certas informações. Nossos governantes sabem muito bem como fazer isso.
No trabalho é muito comum pessoas se sentirem perseguidas quando de fato o que ocorre é uma simples mudança de regras ou de objetivos. Na comunicação de massa, falsos dilemas vendem e geram muito lucro.
Recentemente uma rádio local apresentou uma pesquisa que apontava para o fato do comportamento humano ser determinado somente pela genética. A rádio perguntava aos ouvintes se eles concordavam com o fato do comportamento ser totalmente genético.
O falso dilema aqui, consiste no fato de não existir pesquisa que afirme tal coisa, uma pesquisa científica não possui meios de afirmar se uma pessoa vai agir de uma determinada forma frente uma situação qualquer.
Em geral, o que a ciência afirma não é sobre o comportamento humano e sim sobre o comportamento do corpo humano e suas tendências. Isso significa que geneticamente uma pessoa pode ser mais propensa a se irritar, no entanto o que ela vai fazer com essa irritação é impossível determinar. Por exemplo, é possível canalizar tal irritação para tornar-se uma pessoa mais determinada, sendo um profissional mais eficiente.
Existem muitas técnicas de manipulação do pensamento para influenciar as pessoas, basicamente a maioria delas atua no sentimento, na distração para impedir a detecção da ilusão e na ocultação e distorção dos fatos.
Para evitar certas ilusões procure:
1 – O conjunto de evidências. Poucas evidências permitem facilmente distorcer os fatos e montar um cenário que promova o falso como sendo verdadeiro. Busque sempre o conjunto das várias evidências. Não acredite, comprove.
2 – Atenção aos seus sentimentos. Para influenciar você a porta de entrada é seu sentimento, sempre avalie se você está pensando no campo da crença ou se existem diversas evidências. Se é uma crença, então fique atento. Não esqueça que acreditar é simplesmente confiar.
3 – Veja o quanto lhe estão distraindo. Para influenciar é importante criar distrações. Normalmente se insere falácias dentro de polêmicas e dramatizações. Isso ocorre devido ao fato da pessoa acabar prestando mais atenção ao que é polêmico ou dramático e desta forma não percebe algumas inconsistências do que é afirmado.
Não se deixe influenciar, busque pelo conjunto de evidências e observe atentamente o contexto das afirmações. Não seja manipulado pela arte de iludir.
-
 @ 30ceb64e:7f08bdf5
2023-10-09 14:15:36
@ 30ceb64e:7f08bdf5
2023-10-09 14:15:36Mornin freaks,
I've had a productive morning so far. At this point, I think TheWildHustle should focus on the side job search. I currently have two possibles in the pipeline, but I would feel more comfortable with three. But, they dont call me TheWildHustle for nothing.......
I have a couple of Nostr clients I'd like to create. I would selfishly like to use them for myself, but if other people happen to use them, that would be okay too. Additionally, I want to complete the Nostr Dev/Pleb Dev course, as well as the 100 days of Python in Replit. It would be cool to help out with bounties and open source projects.
TheWildHustle is also TheWildHustle LLC, a pleb mining business created to deduct miner equipment purchases. Currently, I am just running a couple of S9 space heaters, but once I find a side job, I'd like to purchase a couple of hosted miners from Kaboomracks. I found a bitcoin tax guy who helped me last year. UTXO dealership sounds pretty cool, and developments like Fedipool and Stratum V2 are enticing.
I'm looking to increase my lightning node capacity while connecting to additional/better peers. The future of lightning node operators is somewhat unclear to me, especially with the advent of more L2's like Fedimint/E-cash/Ark, but I'd like to develop the node in anticipation of easier tools and upgraded features. TheWildHustle mint/federation/Lightning node seems like a nice spot to be in.
Finally, I'll continue attempting long-form content, and I have four books to finish reading......
Stay positive and productive out there, plebs,
Let's Gooo! TheWildHustle https://image.nostr.build/34a6c2f990130f52da1f26c0eccb008354c539cce93bddbc88ea2e7530b21e80.jpg
-
 @ 34c0a532:5d3638e4
2023-03-16 13:14:53
@ 34c0a532:5d3638e4
2023-03-16 13:14:53Most bitcoiners have their own, much different definition of what it means to orange pill a person. I’ve seen mentions of getting a taxi driver to download a lightning wallet and sending the payment in sats to them. Is that truly orange-pilling? Hmm… no. It is a great first step, but what makes you believe that that person won’t go on to shitcoins after learning about the ease of using cryptocurrency?
So, let’s define what that is in the terms of this guide.
To orange pill someone means to get them to take the first step into learning about bitcoin, money, self-custody, being sovereign, and to teach them to start questioning the world of lies we’ve been fed our entire lives.
Too poetic? Okay, here’s a more specific one:
To orange pill someone means showing them how to send and receive a bitcoin transaction, explain to them the importance of keeping their seed words safe, and showing them more articles, books and guides so they can go further down the rabbit hole.
I think that’s better, don’t you?
No matter what your definition of orange-pilling is, let’s discuss a few things first.
Orange-pilling comes from the scene in the Matrix where Morpheus offers the blue and the red pill to Neo.
This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I’m offering is the truth. Nothing more. ~ Morpheus
The fact that the terms comes from the Matrix is absolutely perfect, because the Matrix is based on Plato’s Allegory of the Cave. Everybody knows the Matrix so let’s talk about the Cave. Inside the cave, people are chained up, in the dark. The only thing they can do is talk to each other and stare forward, where there’s a dim light on the cave’s wall. Someone is moving around objects, throwing shadows on the wall. The people can never see the three-dimensional object, they can only see a shadow, a projection of it, so their world is limited by that knowledge.
Someday a group of people manage to break out of the Cave. They go out into the light, their eyes hurt, the world is massive, they get a panic attack by the lack of a rock ceiling on top of them. It’s vast, it’s too much to bear. And they run back into the cave and tell everyone what they saw, that it’s too bright, too open, too much everything. Objects are real, there’s light everywhere and colours. So many colours, not just the flame, the rock and the shadow.
And they don’t believe them. Maybe they even get angry at them and attack them. Who are these fools to claim that the world is not what they think it is? Who are they to suggest that we’ve all been lied to all our lives?
And that’s the first thing you need to keep in mind when trying to orange pill someone.
Why do some people find it so hard to believe in bitcoin?
The answer is simple. It’s because understanding bitcoin requires acknowledging you’ve been tricked your entire life.
The culture shock is real, I’ve been through it. The stages are as follows:
What is money? You start to learn what money really is, and how fundamentally flawed the Keynesian system has become. You see that the only way forward is by a hard money standard, whether that’s gold or bitcoin. Then you realise that in a world of information, the only logical step is bitcoin. Then why bitcoin? You start to read about it’s properties. It’s antifragile, decentralised. Why is that important? Nobody can control, it great. Why is it like gold that can be attached to an email? Then there’s the anger and disbelief. We’ve been fooled. Why doesn’t everybody see this? You read everything about bitcoin, you listen to podcasts, talk on bitcoin twitter and nostr with other plebs. Nobody seems to have all the answers but they make far more sense than the lies of the mainstream media. You talk to your friends and family, you come off as crazy at best. As I said, you have to acknowledge the trauma the other person is going through. It’s a culture shock, and not many want to go through with it. Think of Plato’s Allegory of the Cave, people who got out into the world went back and told everyone that there’s more to life than the shadows on the wall. Or, the same allegory being told by the Matrix, with Cypher wanting to go back, to forget.
We call that Bitcoin Derangement Syndrome, BDS. It’s hilarious but it’s so real. Many early bitcoiners, people who have spend years of their lives either advocating for it or working on it, some making or losing fortunes in the process, go back to the fiat world, shift gears completely, rant and rave against bitcoin and dive back in the Matrix, the Cave, taking the blue pill. They want to be fiat rich, they lie and delude themselves that everything is okay in the world and if they get just enough money they’d be okay.
But they won’t. This is real, and no matter how many lies they tell themselves things will not change unless we change them ourselves. Babies are dying, that’s true. In wars, in artificially induced poverty, in carrying on with the Keynesian ways of thinking of endless imperial expansion and exploitation.
I’ll be honest, bitcoin rewires your brain.
Do you really wanna force that on people?
Yes?
Then let’s read on.
Why is it sometimes so hard to explain, persuade or convince people about bitcoin? Here’s a harsh truth. It’s because you’re the counterparty risk.
When your car breaks down, you go to a mechanic, you seek expert knowledge. He tells you what’s wrong and you generally accept it. Why? Because unless you’re an expert on cars, you don’t have pre-existing knowledge about this specific situation. Nature abhors a vacuum. The mechanic’s knowledge and expertise fills up that vacuum of knowledge.
Why is it different with bitcoin, then?
Because most people believe they already understand money. There’s no vacuum for their knowledge to fill. Like a woman going to a male gynecologist thinking she knows better because she’s the one with the female body, a nocoiner believes they know better because, see? They have been handling and making money all their lives! Who are you to claim things aren’t how they used to think they are?
Yes, sure. You’re the one with the female body, you’re the one with the wallet. But have you actually taken the time to study it? Have you invested the necessary six years in medical school or the 100 hours it takes to grasp bitcoin?
No.
But they don’t accept that. When you make statements about bitcoin, it collides with their pre-existing frame of reference. When that happens, their mind reflexively casts doubts on the new information, actively fights it and rejects it, because it doesn’t conform to what they know. Their mind is the bearer asset, you are the counterparty risk.
Okay, great. How do you overcome this, then?
By taking the time with them. You can’t force someone to get orange-pilled, it’s not shoving knowledge down their throats. They have to do it themselves, so you start small. Plant a seed. Make them question what they know. That tiny seed, just like in Inception, will grow and push aside the other propaganda in their minds, leaving some space for new information to fill the void.
“Why did they stop having money backed by gold?”
That’s one seed.
“Who prints all these new billions?”
Another. Take your pick, it depends on the person you’re talking to.
A good question makes the nocoiner access their accepted knowledge. They usually think they have the answer and you should listen to it, not shutting it down. Ask them to research it further, to back their claims, to look things up. If they don’t have the knowledge, a new vacuum is created and their curiosity will want to fill it up.
Nocoiner: Bitcoin isn’t backed by anything.
You: Okay. Then what would make good money in its place?
Make them talk by asking questions. As they talk, they’ll realise they have massive gaps in their knowledge. You can help them then, but they themselves have to fill up those gaps by asking more questions and getting them to talk more. Why? Because if someone tells something to themselves they will believe it much easier than having you say it to them. Try and lead them to conclusion, a revelation.
When persuading someone, the person talking the most is the one really getting persuaded. Why? Because when you talk you engrave those words into your brain as facts.
Nocoiner: Bitcoin wastes too much energy.
You: How do you determine how much is too much energy to use?
You will never change their minds, they have to change it themselves. You can only help show them the way, they’re the ones that have to do it. Questions are the key to that process.
Tell them less, ask more.
What questions make people curious about bitcoin? You never know, it depends on what ails the person. Think about their pain. If they’re living in Turkey or Argentina, for example, their pain is massive inflation. You might say, “You’re already using USD to protect your monetary value against inflation, right? How about adding BTC to the mix?”
People in those countries generally grasp this concept a lot quicker. The local lira is the crap kind of money, they spend it often. The USD is the good kind of money, they save it, spending it only when absolutely necessary. And gold is the best kind, keeping it hidden in safes and mattresses. Only to be spent in an emergency. They don’t have the financial privilege to insulate them from the need for bitcoin, they already get these layers of hardness in their money, so bitcoin is a lot easier for them.
“What is money?” is another good question. Most people will answer it, and of course it will be flawed and all over the place. Then you might say, “It’s the promise of future value,” and then discuss how bitcoin has a monetary policy that’s planned out for the next 120 years and how nodes and miners facilitate that design. And especially point out how hard it is to change.
“What happened in 1971?” That’s a good one. Get them to look up the fiat monetary system and figure out how it’s not backed by anything. Get them angry at the Keynesian economists, how they’ve ruined entire countries. 2008 money crisis? Inevitable, under the fiat standard. Forget about bitcoin, point your finger towards the rot. It’s all historical fact, they can’t call you a conspiracy theorist. Most people still think that money is backed by gold. Get them to tell it to other people, see their reactions.
This was a part of my guide. Let me know what you think. Soon to be posted at https://georgesaoulidis.com/how-to-orange-pill-people/
-
 @ 23202132:eab3af30
2023-09-05 17:02:50
@ 23202132:eab3af30
2023-09-05 17:02:50Controlar máquinas com a mente tornou-se realidade e a evolução tem sido surpreendente. Em 2003 a previsão dos cientistas era de 2 anos para os primeiros implantes cerebrais que permitiriam o controle de próteses por pessoas com alguma deficiência. Esta convicção surgiu após testes com macacos onde os animais controlavam um braço robótico usando apenas seus pensamentos.
Confirmando o prognóstico dos cientistas, o austríaco Christian Kandlbauer que perdeu os dois braços em um acidente elétrico em setembro de 2005 foi capaz de viver uma vida normal em grande parte graças ao braço robótico controlado pela mente.
Infelizmente Christian Kandlbauer faleceu em um acidente de carro em 21 de outubro de 2010. A perícia não conseguiu determinar se o acidente ocorreu devido a uma possível falha na prótese controlada pela mente. O trajeto era percorrido diariamente por Christian que, usando seu braço robótico para dirigir o veículo a mais de três anos, transitava normalmente com seu veículo.
Christian Kandlbauer foi a primeira pessoa fora dos Estado Unidos que recebeu implantes para controlar um braço robótico. Em março de 2009 a empresa de tecnologia japonesa Honda anunciou uma nova evolução no controle de equipamentos através da mente. Ao invés de usar implantes a nova tecnologia permite o controle através de um capacete.
Para controlar o robô, a pessoa coloca o capacete e só tem que pensar em fazer o movimento. Seus inventores esperam que um dia a tecnologia de controle da mente permita que as pessoas possam controlar os equipamentos sem precisar ocupar as mãos ou depender de implantes cirúrgicos.
O capacete é a primeira “máquina de interface cérebro-máquina” que combina duas técnicas diferentes para captar a atividade no cérebro. Os sensores do capacete detectam sinais elétricos através do couro cabeludo, da mesma forma como um EEG (eletroencefalograma). Os cientistas combinaram isso com uma outra técnica chamada espectroscopia por infravermelho, que é usada para monitorar mudanças no fluxo sanguíneo no cérebro.
A atividade cerebral detectada pelo capacete é enviada para um computador, que usa o software para trabalhar o movimento que a pessoa está pensando. Em seguida, envia um sinal para o robô para executar o movimento pensado. Normalmente, isso leva alguns segundos para que o pensamento se transforme em uma ação robótica.
A interface de controle robótico com a mente através do capacete ainda é experimental, um dos problemas que precisa ser superado é referente as distrações do pensamento na hora de enviar um comando. No caso dos implantes a precisão é bem maior. A tecnologia está avançando, em alguns anos o capacete de controle mental para equipamentos robóticos e games deverá ser uma realidade eficiente e popular.
Quando se fala de controle de máquinas e aparelhos usando a mente, as empresas de tecnologia estão apostando alto para o futuro, com grandes investimentos e grupos de pesquisa altamente qualificados.
-
 @ 2edbcea6:40558884
2023-09-03 16:03:23
@ 2edbcea6:40558884
2023-09-03 16:03:23Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter at the nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
A lot of foundational work happening in the nostr-verse and quite a bit of new projects shipped this week. Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) NIP 75: Zap Goals ⚡
Zapping has been such an integral part of what makes Nostr what it is. Earning for your content or contributions. Zaps for memes. Zaps as a way to boost the signal. It’s a growing concept as well.
NIP 75 was merged this week, with the goal of introducing the ability to set a “Zap Goal” which is similar to a fundraising goal. Users can zap the “goal” event directly and help the progress bar go up. Whatever the cause.
Interesting to see if this will stay simple and decentralized or if this will be the foundation of a GoFundMe type platform via Nostr using exclusively Bitcoin.
Author: nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg
2) (Proposed) NIP 79: Digital contracts on Nostr ✍️
Think Docusign, but on Nostr. This NIP would introduce support for various kinds of digital agreement (contracts, covenants, agreements) which serve various purposes.
These agreements would all be unencrypted markdown, so the purpose is likely more for non-secret agreements so that they can be cited by all parties in public.
Author(s): https://github.com/xemuj nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
3) (Proposed) NIP 34: Improved media attachments to notes 📎
Attaching media to notes in a way that is handled well on a majority of major clients is still more of an art than a science and nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 is determined to introduce a better pattern 💪.
This NIP introduces the pattern of using an explicit set of “media” tags on any note so that media that should accompany the note can be explicitly linked without clients needing to parse the content of the note to make the url of the media in the note a hyperlink.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
4) (Proposed) Improvements to reddit-style moderated communities 💬
This proposed improvement to NIP 72 introduces the concept of a post (within a moderated community) that is exclusively posted to a specific community. Think about posting something that can make the front page of reddit versus a post that is intended solely for a subreddit. Seems like a welcome addition to NIP 72 👍
Author: https://github.com/vivganes
Notable projects
A nostr Wiki
The start of a truly open wiki.
Wikis are used for a lot of things: corporate intranets and documentation, fandoms managing information about their universe, and Wikipedia which may be one of the greatest repositories of knowledge on Earth. The main downside to Wikipedia is that it may be crowdsourced but it is centralized, seeking one version of each article (and therefore determining what is true).
This wiki (in the spirit of Nostr) allows people to create any number of articles on the same subject to offer different perspectives. At scale this could become something where people read various perspectives and determine the truth for themselves.
Author: nostr:npub1q7klm2w94hyq3qdm9ffzpahrrq0qcppmjrapzhz0rq6xgq3fdrnqr6atmj
Oxchat
Oxchat is a secure, private group chat experience for iOS and Android with a great UX 🙌.
Nostr needs its own standalone chat app that can stand up to the capabilities and ease of use of Signal, Telegram, WhatsApp, etc. And Oxchat may be that app! Looking forward to using it more.
Author: nostr:npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Nostrnet.work
A web-based dashboard for Nostr, it’s a webpage that is a configurable hub for all the Nostr apps you want to have available quickly. You can log in with your Nostr account, and configure it to your liking.There’s a section for managing your profile (including your relays), as well as for taking notes, all of that on top of the list of Nostr apps for quick access.
Nostrnet.work seems to be evolving into almost a web-based browser of the nostr-verse. You can manage the apps that are on the dashboard Nostrnet.work via the basic/open app store from nostr.band. There’s endless possibilities for users to discover what Nostr has to offer and use those offerings from one unified interface.
A recent addition to the Nostrnet.Work interface is an area for “Nostr AI'' which is meant to allow users to utilize Data Vending Machines (explored in the Latest Conversations section). Data Vending Machines (or DVMs) are something that I think is unique to Nostr, and it's a product/ecosystem that may be the killer unique offering people come to Nostr to try out.
Author: nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f
w3.do url shortener
URL shorteners are a stable web util. In fact,
We started using w3.do because the tool we use to draft/publish this newsletter as a long form note will send Nostr links and embed the note instead of just linking to the note. So a url shortener is enough to trick the tool so we get fewer embeds and more links! Thanks nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn !
Latest conversations
Data Vending Machines (DVMs)
“Data Vending Machines are data-processing tools. You give them some data, a few sats, and they give you back some data.” source: vendata. A practical example is a recent DVM published by Pablo: FOMOstr. You put up some sats, you’ll get back content on Nostr that you may have missed.
The concept seems to be that people need help from machines. And right now, the most common way for people to get that help is to pay a company for that help (email provider, calendar management, group chats, entertainment, etc).
These are great for more complex digital products, but what if you just have a question? Maybe you just want to generate an image. Or maybe just extract text, and then maybe translate it. These are most efficient as pay-as-you-need-it products. That’s where DVMs shine (on the long tail of needs).
You can put up a certain amount of money and people who have created algorithms or AIs that can accomplish these tasks will compete to do the job for the lowest price (and therefore win the money). This is the foundation of an economy of people who need jobs done and people who want to make income by creating the best DVMs for the jobs people need done.
DVMs that help you discover people and content on Nostr will be a god-send for improving the experience for people using Nostr while maintaining decentralization. This will certainly evolve over time, but it seems this could become an integral part of the Nostr ecosystem as well as become a unique service that can only be found on Nostr (attracting a new set of users).
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something I didn’t post about, let me know, DMs welcome.
nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2 or nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ aa55a479:f7598935
2023-02-20 13:44:48
@ aa55a479:f7598935
2023-02-20 13:44:48Nostrica is the shit.
-
 @ 30ceb64e:7f08bdf5
2023-10-08 18:02:51
@ 30ceb64e:7f08bdf5
2023-10-08 18:02:51Hey freaks,
I was just listening to Nostr Devs #8 on YouTube. I saw the crossposting stacker news update and was pretty thrilled to see SN's continued integration with Nostr. As a self-proclaimed Nostr maxi, I see Nostr clients replacing most websites that I use on a daily basis. Lately, I've been interested in reading more articles and blog posts. It was crazy to see Austin pull up @koob's SN post on habla.news.
This post is a test to see if it will hit the Nostr long-form content platforms as well. TheWildHustle has been down the Bitcoin rabbit hole for a meager 5 years, and recent events have led me to try jotting down some long-form thoughts as well. I usually don't have too much to say, maybe I like the idea of being a writer more than the writing itself. Well, let's see how this Stacker News cross-posting adventure treats me. I'll give writing some proof of work and, in future writings, detail things in the community that I'm interested in.
And shoutout to @DarthCoin and @siggy47. TheWildHustle is an inspired humble pleb.
-
 @ 1c52ebc8:5698c92a
2023-08-12 18:00:17
@ 1c52ebc8:5698c92a
2023-08-12 18:00:17Hey folks, happy Saturday!
Here’s your weekly newsletter on the technical happenings in the nostr-verse. Things are moving fast, people are building many amazing projects.
Let’s dive in.
Recent Upgrades to Nostr (NIPs)
1) Moderated Communities 💬
This NIP outlines how to implement a Reddit-like experience, where moderators can create and manage communities. Then anyone can propose a post, but moderators get final say about what shows up in the community. Can’t wait to use it! Hopefully we can use Zaps instead of upvotes like Stacker News!
Authors: nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and @arthurfranca
2) Proxy Tags (Approved!) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. Now that this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
3) Rewrite of NIP 65 - Relay Lists by nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z
Many in the Nostr dev community desire to have many small relays instead of centralization around a smaller set of massive, highly capable relays. In order to do that, there’s a challenge with discovering relays to pull events for a users’ followers.
This NIP was approved weeks ago, but was rewritten recently to make it easier to implement, which should help add more momentum to decentralizing relays.
Notable projects
Vault - Nostr-based Password Manager 🔒
nostr:npub1alpha9l6f7kk08jxfdaxrpqqnd7vwcz6e6cvtattgexjhxr2vrcqk86dsn implemented a way to store and retrieve sensitive information (like passwords) via Nostr. It has a 1Password-like interface for ease of use.
It’s also encrypted twice, once via the normal Nostr secret key signing like any Nostr event, but again with the password to unlock the vault. That way, if someone compromises your Nostr account’s secret key in the future, they still need your vault password to decrypt your sensitive information.
Can’t wait to migrate!
Nostrscript
Looks like nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s added a way to activate code in Damus via a link on a website. This pattern could help clients interoperate (one client activating actions in other clients a user is using). Endless possibilities!
Relay Backup
nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f Built a way to easily back up your events from a relay. This helps folks make sure all their events from public relays are copied to a private backup relay so none of their events are lost to time.
Stacker news
Not exactly new, but this project has been a delight to engage in discussion with other folks interested in Nostr, Bitcoin, and freedom tech in general. Using zaps as signal instead of upvotes is pretty novel to me, and all the zaps go to the posters as well as the platform to distribute rewards to the community. #valueforvalue
Latest conversations
Who controls NIPs?
Right now NIPs are hosted via a Github Repo. This is helpful in many ways because there’s one publicly-accessible way to read NIPs and get started contributing. By the nature of this being a code repository under source control, there are a small group of folks that are able to “approve” updates to NIPs.
The nature of projects like Nostr (or Bitcoin in the early 2010s for that matter) is that the early folks often need some control over the direction to make sure that the project has a chance to become self-sustaining without imploding into chaos.
The debate in the linked thread seems to be stemming from the timeless question for protocols, which is “how much should the protocol be able to do?” and that’s generally decided by early devs and those that control the generally accepted version of the spec for the protocol. That’s currently the NIPs repo, so who gets to “approve” NIPs in that repo?
Here’s hoping we can find a collaborative place to land that preserves the heart of nostr and maximizes its chance of success 💪
How to handle illegal content on Nostr
There was a Plebchain radio conversation with nostr:npub1yye4qu6qrgcsejghnl36wl5kvecsel0kxr0ass8ewtqc8gjykxkssdhmd0 who has been an advocate for folks that’ve been trafficked. She’s a rare advocate of preventing trafficking and CSAM through the internet without compromising encryption, or other online freedom.
There are unanswered questions about how the Nostr community is going to handle this content so we don’t see Nostr become a haven for activity most see as despicable. With the collection of smart people on Nostr, I’ll bet that a solution emerges to maximize freedom on the internet and drastically reduce the ability for illegal content to spread via the Nostr protocol.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual).
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week, but if you wanna see something advertised here just DM me!
Until next time 🫡
If I missed anything, or you’re building something I didn’t post about, let me know, DMs welcome.
God bless, you’re super cute
-
 @ 634bd19e:2247da9b
2023-02-15 08:00:45
@ 634bd19e:2247da9b
2023-02-15 08:00:45かけるのこれ? 日本語入力の取り扱いイベントがおかしいw
-
 @ 2edbcea6:40558884
2023-10-08 15:27:57
@ 2edbcea6:40558884
2023-10-08 15:27:57Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 43: Fast Auth between clients and relays
Some relays are member-only. There has to be some way for relays to verify the content being sent/requested is from an authorized user (one of the members). Most methods for this are clunky and slow.
This NIP proposes a faster method for auth between clients and relays. From what I can tell when clients open a connection to a relay they’ll open it with an “authorization” query parameter on the end of the relay url. That query param will actually be an encoded Nostr event whose payload has the necessary info for the relay to authenticate the user opening the connection.
Kinda looks like an auth header like you’d see in an http request but shoehorned into a query parameter since websockets (which are used for connections to relays) don’t traditionally support headers.
Author: aruthurfranca
2) (Proposed) Updates to NIP 03: Timestamps you can rely on
Sometimes you want to make sure that a piece of Nostr content was actually created/pushed to a relay at a specific time. The example from last week was in the case of a future betting system built on Nostr, you really don’t want people to be able to publish that they made a bet 2 weeks ago for something whose outcome was determined twenty minutes ago.
NIP-3 already outlines a way to add OpenTimestamp attestations to Nostr events essentially allowing Nostr clients to outsource trust to a third party on whether a piece of content was created when it claims to be created. As is, NIP 3 is a little hard to use. This update would make it far simpler.
In the new methodology, you’d publish a Nostr event of kind 1040 with the proof of timestamp and point to the event that you’re trying to prove the timestamp for.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
Notable Projects
Cellar Relay
If you haven’t been graced by the nostr.wine community they are a group of fine folks that host wine-themed relays. They’re some of the most reliable and widely used public and paid relays around.
nostr:npub18kzz4lkdtc5n729kvfunxuz287uvu9f64ywhjz43ra482t2y5sks0mx5sz recently announced the “Cellar” Relay that will store notes long term for paid users. Like we talked about in last week’s #NostrTechWeekly long-term note storage is a challenge for relay hosts (especially for relays that are free to users). But solving long term storage will help folks on Nostr feel like they’re building a persistent social experience instead of building an ephemeral feed.
Nice work! Glad to see the trend continuing for long-term note storage. 💪
Memestr.app
I can’t tell you how many times folks I talk to have said there should be a meme-focused client on Nostr. nostr:npub1zumzudhtu2558fgvycnjlc7pq9l4m338vghgcfzafftz9qg45ruslzpl4x delivers with https://memestr.app I definitely had some giggles when I logged on.
This could quickly evolve into a nostr-based Imgur and be far better for being nostr-based. But one thing I think is missing from the internet (not just Nostr) is a way to iterate on memes easily in the same place where you can share them. In combination with prisms/boosts this could be an interesting way for people to make money for their content and earn from what is built on top of their content.
Zap threads
Threaded conversations are an important component to social experiences on the internet. Reddit and Hackernews have really shown its power, we’ve seen StackerNews also leverage this format as well.
nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 has created a nostr-based component for supporting the threaded comments, and it looks like it could be used in any web-application that needs commenting, spreading Nostr to every corner of the internet. It’s already powering the commenting on Habla.News
nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 also did a great writeup on the reasoning for this project and where it’s going: https://habla.news/franzap/threading-the-web-with-nostr
If you need comments on your project, take a look!
Latest conversations: How decentralized is decentralized enough?
Distributed vs Decentralized
These two concepts are often used interchangeably, and it’s worth highlighting their distinction, especially in the context of Nostr. This is a good visualization to illustrate the difference.
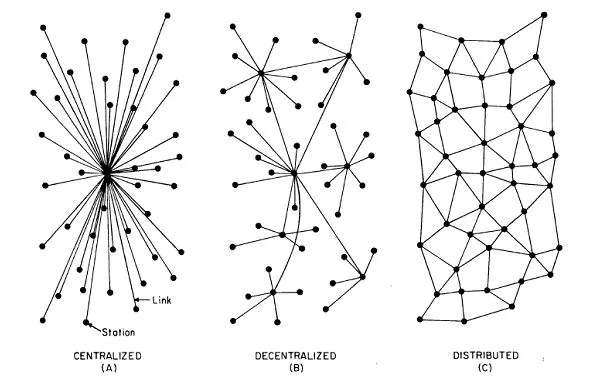
Distributed: the P2P model
Robust, distributed systems are extremely censorship resistant, and include a lot of redundancy. Distributed systems distribute power widely, everyone is a peer.
Biological systems (cells, ecosystems, etc) are like this, cells are all peers and replaceable. Napster was distributed, everyone in the Napster ecosystem stored and shared some of the songs. IP (the “internet protocol”), which is how computers find each other on the internet, is a peer to peer technology where every node gossips about where to find other nodes.
Ideally all systems would be built this way, but in practice distributed / P2P systems are generally used when there’s a high chance of node failure (the death of individual cells) or attack (government takedowns). The challenge is that they’re expensive to run.
This might be confusing because Napster was “free” right? Most P2P software feels free-ish because many are donating some of their existing hardware/bandwidth/etc. But if you take the aggregate resources to run Napster versus just the parts of Spotify that help users to upload and download music, Spotify for sure uses fewer resources.
Distributed systems by their very nature have to assume that most peers in the network may fail. In order to maintain uptime, that results in P2P systems having many copies of what’s being shared and/or sending data many times to ensure it arrives.
I think most people would say they’d prefer everything to be P2P but it’s difficult to maintain a good experience in a P2P system and so it’s often only used in cases where it’s absolutely necessary.
Where does decentralization work better?
I wrote up a whole thing about decentralization a while back but the TL;DR is decentralized systems are better than centralized systems at distributing power widely, but they are generally still more performant than peer to peer systems.
Sometimes you need a mix of preventing abuses of power but still maintain a good experience for users. Freedom minded folks usually end up supporting decentralized solutions because they’re viable in the market and still take power away from centralized players.
Is Bitcoin decentralized or distributed?
The Bitcoin blockchain is a distributed system. Every Bitcoin full-node is an equal participant in storing, updating, and validating the blockchain.
Bitcoin as a monetary system, on the other hand, is decentralized: there are many more Bitcoin users than Bitcoin full-nodes. The nodes are the hubs and the users are the spokes.
There’s a reason for this architecture. Bitcoin nodes are ultimately in control of Bitcoin, it must be the least corruptible, most censorship resistant architecture possible. On the other hand a decentralized system has efficiency gains that make Bitcoin more competitive in comparison to existing financial systems. By having hubs (full-nodes, Bitcoin banks, wallet providers, exchanges, etc), the system is more efficient (and therefore cheaper). But by having many hubs, power is still spread widely.
Nostr: Decentralized or Distributed?
 Nostr, as introduced by FiatJaf, seems like it was intended to be decentralized. Relays are the hubs and users are the spokes. Clients help connect users to relays (and therefore each other). There is wisdom to this architecture, because it will scale better than a P2P system.
Nostr, as introduced by FiatJaf, seems like it was intended to be decentralized. Relays are the hubs and users are the spokes. Clients help connect users to relays (and therefore each other). There is wisdom to this architecture, because it will scale better than a P2P system.Think of it this way, there are on the order of hundreds of millions of songs available for human consumption. With 10 million users storing a few hundred songs, there would be plenty of redundancy to allow Napster to distribute every song in a P2P manner. There are on the order of trillions of social media posts, if you include follows, reactions, DMs, etc, it’s likely in the quadrillions. With current technology a P2P system would never be able to provide coverage of every post and make it available in a reasonable time.
That said, there are some elements of Nostr that could benefit from being more P2P. Especially operations that would benefit from greater privacy (DMs, zaps, and reactions). Right now privacy around these actions is not well supported via Nostr.
Dev work has started on some P2P Nostr functionality announced by nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and it’s right along those lines: maximizing privacy and security for nostr-based comms. It will have all the great things and all the difficulties of any P2P system, but it may be necessary to improve privacy on Nostr.
One thing that is great about Nostr is everyone can try things out and see if they work and if people want them. I see a lot of demand for privacy for certain Nostr operations, and if a P2P model would help, it needs to be tried. We’ll see whether the trade offs of P2P make Nostr better or if they make it less likely to succeed. We’ll see as development continues!
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome at nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53
@ 6d3d8fe2:4063a6cf
2023-08-11 09:57:53Questa guida è disponibile anche in:
- Francese: nostr:naddr1qqxnzd3cxyunqvfhxy6rvwfjqyghwumn8ghj7mn0wd68ytnhd9hx2tcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c33xpshw7ntde4xwdtjx4kxz6nwwg6nxdpn8phxgcmedfukcem3wdexuun5wy6kwunnxsun2a35xfckxdnpwaek5dp409enw0mzwfhkzerrv9ehg0t5wf6k2qgawaehxw309a6ku6tkv4e8xefwdehhxarjd93kstnvv9hxgtczyzd9w67evpranzz2jw4m9wcygcyjhxsmcae6g5s58el5vhjnsa6lgqcyqqq823cmvvp6c grazie a nostr:npub1nftkhktqglvcsj5n4wetkpzxpy4e5x78wwj9y9p70ar9u5u8wh6qsxmzqs
- Chinese: nostr:naddr1qqxnzd3cx5urvwfe8qcr2wfhqyxhwumn8ghj7mn0wvhxcmmvqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hszrrhwden5te0vfexytnfduq35amnwvaz7tmwdaehgu3wdaexzmn8v4cxjmrv9ejx2aspzamhxue69uhhyetvv9ujucm4wfex2mn59en8j6gpzpmhxue69uhkummnw3ezuamfdejszxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqg4waehxw309ajkgetw9ehx7um5wghxcctwvsq35amnwvaz7tmjv4kxz7fwdehhxarjvaexzurg9ehx2aqpr9mhxue69uhhqatjv9mxjerp9ehx7um5wghxcctwvsq3jamnwvaz7tmwdaehgu3w0fjkyetyv4jjucmvda6kgqgjwaehxw309ac82unsd3jhqct89ejhxqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqz8rhwden5te0dehhxarj9ekh2arfdeuhwctvd3jhgtnrdakszpmrdaexzcmvv5pzpnydquh0mnr8dl96c98ke45ztmwr2ah9t6mcdg4fwhhqxjn2qfktqvzqqqr4gu086qme grazie a nostr:npub1ejxswthae3nkljavznmv66p9ahp4wmj4adux525htmsrff4qym9sz2t3tv
- Svedese: nostr:naddr1qqxnzd3cxcerjvekxy6nydpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgszet26fp26yvp8ya49zz3dznt7ungehy2lx3r6388jar0apd9wamqrqsqqqa28jcf869 grazie a nostr:npub19jk45jz45gczwfm22y9z69xhaex3nwg47dz84zw096xl6z62amkqj99rv7
- Spagnolo: nostr:naddr1qqfxy6t9demx2mnfv3hj6cfddehhxarjqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28ldvk6q grazie a nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624
- Olandese: nostr:naddr1qqxnzd3c8q6rzd3jxgmngdfsqyvhwumn8ghj7mn0wd68ytn6v43x2er9v5hxxmr0w4jqz9rhwden5te0wfjkccte9ejxzmt4wvhxjmcpp4mhxue69uhkummn9ekx7mqprfmhxue69uhhyetvv9ujumn0wd68yemjv9cxstnwv46qzyrhwden5te0dehhxarj9emkjmn9qyvhwumn8ghj7ur4wfshv6tyvyhxummnw3ezumrpdejqzxrhwden5te0wfjkccte9eekummjwsh8xmmrd9skcqgkwaehxw309ashgmrpwvhxummnw3ezumrpdejqzxnhwden5te0dehhxarj9ehhyctwvajhq6tvdshxgetkqy08wumn8ghj7mn0wd68ytfsxyhxgmmjv9nxzcm5dae8jtn0wfnsz9thwden5te0v4jx2m3wdehhxarj9ekxzmnyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpy9mhxue69uhk27rsv4h8x6tkv5khyetvv9ujuenfv96x5ctx9e3k7mgprdmhxue69uhkummnw3ez6v3w0fjkyetyv4jjucmvda6kgqg8vdhhyctrd3jsygxg8q7crhfygpn5td5ypxlyp4njrscpq22xgpnle3g2yhwljyu4fypsgqqqw4rsyfw2mx grazie a nostr:npub1equrmqway3qxw3dkssymusxkwgwrqypfgeqx0lx9pgjam7gnj4ysaqhkj6
- Arabo: nostr:naddr1qqxnzd3c8q6rywfnxucrgvp3qyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsfev65tsmfgrv69mux65x4c7504wgrzrxgnrzrgj70cnyz9l68hjsrqsqqqa28582e8s grazie a nostr:npub1nje4ghpkjsxe5thcd4gdt3agl2usxyxv3xxyx39ul3xgytl5009q87l02j
- Tedesco: nostr:naddr1qqxnzd3c8yerwve4x56n2wpeqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgsvcv7exvwqytdxjzn3fkevldtux6n6p8dmer2395fh2jp7qdrlmnqrqsqqqa285e64tz grazie a nostr:npub1eseajvcuqgk6dy98zndje76hcd485zwmhjx4ztgnw4yruq68lhxq45cqvg
- Giapponese: nostr:naddr1qqxnzd3cxy6rjv3hx5cnyde5qgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa28lxc9p6 di nostr:npub1wh69w45awqnlsxw7jt5tkymets87h6t4phplkx6ug2ht2qkssswswntjk0
- Russo: nostr:naddr1qqxnzd3cxg6nyvehxgurxdfkqyvhwumn8ghj7un9d3shjtnwdaehgunfvd5zumrpdejqzxthwden5te0wp6hyctkd9jxztnwdaehgu3wd3skueqpz4mhxue69uhkummnw3ezu6twdaehgcfwvd3sz9thwden5te0dehhxarj9ekkjmr0w5hxcmmvqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqpzpmhxue69uhkummnw3ezuamfdejszenhwden5te0ve5kcar9wghxummnw3ezuamfdejj7mnsw43rzvrpwaaxkmn2vu6hydtvv94xuu34xv6rxwrwv33hj6ned3nhzumjdee8guf4vae8xdpex4mrgvn3vvmxzamndg6r27tnxulkyun0v9jxxctnws7hgun4v5q3vamnwvaz7tmzd96xxmmfdejhytnnda3kjctvqyd8wumn8ghj7un9d3shjtn0wfskuem9wp5kcmpwv3jhvqg6waehxw309aex2mrp0yhxummnw3e8qmr9vfejucm0d5q3camnwvaz7tm4de5hvetjwdjjumn0wd68y6trdqhxcctwvsq3camnwvaz7tmwdaehgu3wd46hg6tw09mkzmrvv46zucm0d5q32amnwvaz7tm9v3jkutnwdaehgu3wd3skueqprpmhxue69uhhyetvv9ujumn0wd68yct5dyhxxmmdqgs87hptfey2p607ef36g6cnekuzfz05qgpe34s2ypc2j6x24qvdwhgrqsqqqa286qva9x di nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7
Ciao, caro Nostrich!
Nostr è qualcosa di completamente nuovo, e ci sono alcuni passi da fare che semplificheranno il tuo ingresso e renderanno più interessante la tua esperienza.
👋 Benvenuto
Dato che stai leggendo questa guida, diamo per assunto che tu ti sia già unito a Nostr scaricando un app (es. Damus, Amethyst, Plebstr) o usando un Web Client Nostr (es. snort.social, Nostrgram, Iris). E' importante per un nuovo arrivato seguire i passaggi suggeriti dalla piattaforma di tua scelta - la procedura di benvenuto ti fornisce tutte le basi, e non dovrai preoccuparti di configurare nulla a meno che tu non lo voglia fare. Se sei incappato in questo articolo, ma non hai ancora un “account” Nostr, puoi seguire questa semplice guida a cura di nostr:npub1cly0v30agkcfq40mdsndzjrn0tt76ykaan0q6ny80wy034qedpjsqwamhz.
🤙 Divertiti
Nostr è fatto per assicurarsi che le persone siano in grado di connettersi liberamente, di essere ascoltate e di divertirsi. Questo è il fulcro centrale (ovviamente ci sono moltissimi altri casi d'uso, come essere uno strumento per i divulgatori e chi lotta per la libertà, ma per questo servirà un articolo a parte), quindi se qualcosa ti è poco chiaro contatta altri “nostriches” con esperienza e saremo lieti di aiutarti. Interagire con Nostr non è difficile, ma ci sono alcune differenze rispetto alle altre piattaforme tradizionali, quindi è normale fare domande (anzi...sei incoraggiato a farne).
Questa è una lista ufficiosa di utenti Nostr che saranno felici di aiutarti e rispondere alle tue domande:
nostr:naddr1qqg5ummnw3ezqstdvfshxumpv3hhyuczypl4c26wfzswnlk2vwjxky7dhqjgnaqzqwvdvz3qwz5k3j4grrt46qcyqqq82vgwv96yu
Tutti i nostriches nella lista hanno ricevuto il badge Nostr Ambassador, il che renderà facile per te trovarli, verificarli e seguirli
⚡️ Attivare gli Zaps
Gli Zaps sono una delle prime differenze che noterai entrando su Nostr. Consentono agli utenti Nostr di inviare istantaneamente valore per supportare la creazione di contenuti utili e divertenti. Sono possibili grazie a Bitcoin e Lightning Network. Questi due protocolli di pagamento decentralizzati permettono di inviare istantaneamente dei sats (la più piccola frazione di Bitcoin) tanto facilmente quanto mettere un like sulle piattaforme social tradizionali. Chiamiamo questo meccanismo Value-4-Value e puoi trovare altre informazioni al riguardo qui: https://dergigi.com/value/
Dai un'occhiata a questa nota di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 per avere una panoramica su cosa sono siano gli zaps.
Dovresti attivare gli Zaps anche se non sei un creatore di contenuti - le persone troveranno sicuramente interessanti alcune delle tue note e vorranno mandarti dei sats. Il modo più semplice per ricevere sats su Nostr è il seguente:
- Scarica l'app Wallet of Satoshi - probabilmente la scelta migliore per dispositivi mobili per chi è nuovo in Bitcoin e Lightning. Tieni di conto che esistono molti altri wallets e che potrai scegliere quello che preferisci. Inoltre, non dimenticarti di fare un back up del wallet.
- Premi “Ricevere”
- Premi sopra al tuo Lightning Address (è quello che sembra un indirizzo email) per copiarlo

- Incollalo poi nel campo corrispondente all'interno del tuo client Nostr (il nome del campo potrebbe essere “Bitcoin Lightning Address”, “LN Address” o qualcosa di simile in base all'app che utilizzi).

📫 Ottieni un indirizzo Nostr
Gli indirizzi Nostr, a cui spesso i Nostr OGs si riferiscono con “NIP-05 identifier”, sono simili ad un indirizzo email e:
🔍 Aiutano a rendere il tuo account facile da trovare e condividere
✔️ Servono a verificare che il tuo “LN Address” appartenga ad un umano
Questo è un esempio di indirizzo Nostr: Tony@nostr.21ideas.org
 E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente
E' facile memorizzarlo e successivamente cercarlo in una qualsiasi piattaforma Nostr per trovare la persona corrispondente
Per ottenere un indirizzo Nostr puoi usare un servizio gratuito come Nostr Check (di nostr:npub138s5hey76qrnm2pmv7p8nnffhfddsm8sqzm285dyc0wy4f8a6qkqtzx624) oppure uno a pagamento come Nostr Plebs (di nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424). Entrambi offrono vari vantaggi, e la scelta dipende solo da te. Un altro modo per ottenere un indirizzo Nostr è tramite un'estensione del browser. Scopri di più al riguardo qui) .
🙇♀️ Impara le basi
Dietro le quinte Nostr è molto diverso dalle piattaforme social tradizionali, quindi conoscerne le basi è estremamente utile per i nuovi arrivati. E con questo non intendo che dovresti imparare un linguaggio di programmazione o i dettagli tecnici del protocollo. Sto dicendo che avere una visione d'insieme più ampia e capire le differenze fra Nostr e Twitter / Medium / Reddit ti aiuterà moltissimo. Ad esempio, al posto di un nome utente e password hai una chiave privata e una pubblica. Non entrerò nel dettaglio perchè esistono già moltissime risorse che ti aiuteranno a diventare un esperto di Nostr. Tutte quelle degne di nota sono state raccolte in questa pagina con 💜 da nostr:npub12gu8c6uee3p243gez6cgk76362admlqe72aq3kp2fppjsjwmm7eqj9fle6
 Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata
Fra le informazioni che troverai nel link viene anche spiegato come mettere al sicuro le tue chiavi di Nostr (il tuo account), quindi è importante dargli un'occhiata
🤝 Connettiti
La possibilità di connetterti con altre [^3] persone brillanti è ciò che rende speciale Nostr. Qui tutti possono essere ascoltati e nessuno può essere escluso. Ci sono alcuni semplici modi per trovare persone interessanti su Nostr:
- Trova le persone che segui su Twitter: https://www.nostr.directory/ è un ottimo strumento per questo.
- Segui le persone seguite da altri di cui ti fidi: Visita il profilo di una persona che condivide i tuoi stessi interessi, guarda la lista delle persone che segue e connettiti con loro.

- Visita la Bacheca Globale: Ogni client Nostr (app Nostr se preferisci) ha una scheda per spostarsi nella Bacheca Globale (Global Feed), dove troverai tutte le note di tutti gli utenti di Nostr. Segui le persone che trovi interessanti (ricorda di essere paziente - potresti trovare una discreta quantità di spam).

- Usa gli #hashtags: Gli Hashtag sono un ottimo modo per concentrarti sugli argomenti di tuo interesse. Ti basterà premere sopra l'#hashtag per vedere altre note relative all'argomento. Puoi anche cercare gli hashtags tramite l'app che utilizzi. Non dimenticare di usare gli hashtags quando pubblichi una nota, per aumentarne la visibilità.
https://nostr.build/i/0df18c4a9b38f1d9dcb49a5df3e552963156927632458390a9393d6fee286631.jpg Screenshot della bacheca di nostr:npub1ktw5qzt7f5ztrft0kwm9lsw34tef9xknplvy936ddzuepp6yf9dsjrmrvj su https://nostrgraph.net/
🗺️ Esplora
I 5 consigli menzionati sono un ottimo punto d'inizio e miglioreranno moltissimo la tua esperienza, ma c'è molto di più da scoprire! Nostr non è solo un rimpiazzo per Twitter e le sue possibilità sono limitate solo dalla nostra immaginazione.

Dai un'occhiata alla lista di tutti i progetti Nostr:
- https://nostrapps.com/ una lista di tutte le apps su Nostr
- https://nostrplebs.com/ – ottieni il tuo NIP-05 e altri vantaggi (a pagamento)
- https://nostrcheck.me/ – Indirizzi Nostr, caricamento di media, relay
- https://nostr.build/ – Carica e gestisci i tuoi media (e altro)
- https://nostr.band/ – Informazioni sul network e gli utenti di Nostr
- https://zaplife.lol/ – Statistiche degli Zaps
- https://nostrit.com/ – Programma le note
- https://nostrnests.com/ – Twitter Spaces 2.0
- https://nostryfied.online/ - Fai un backup dei tuoi dati di Nostr
- https://www.wavman.app/ - Player musicale per Nostr
📻 Relays
Dopo aver preso confidenza con Nostr assicurati di dare un'occhiata alla mia guida riguardo i Relays su Nostr: https://lnshort.it/nostr-relays. Non è un argomento di cui preoccuparsi all'inizio del tuo viaggio, ma è sicuramente importante approfondirlo più avanti.
📱 Nostr su mobile
Avere un'esperienza fluida su Nostr tramite un dispositivo mobile è fattibile. Questa guida ti aiuterà ad accedere, postare, inviare zap e molto di più all'interno delle applicazioni web Nostr sul tuo smartphone: https://lnshort.it/nostr-mobile
Grazie per aver letto e ci vediamo dall'altra parte della tana del coniglio.
Grazie a nostr:npub10awzknjg5r5lajnr53438ndcyjylgqsrnrtq5grs495v42qc6awsj45ys7 per aver fornito il documento originale che ho tradotto
-
 @ 50c5c98c:65867c8e
2023-10-08 02:29:58
@ 50c5c98c:65867c8e
2023-10-08 02:29:58sexy bold letters important italic letters

-
 @ d34e832d:383f78d0
2023-08-08 03:14:43
@ d34e832d:383f78d0
2023-08-08 03:14:4325 Verses to Draw Motivation Within
Pray Continually
Title: Finding Motivation in Scripture: Overcoming Failure and Embracing Hope
Have you ever felt like a failure? It's a tough spot to be in, and it can really bring you down. But you know what? Scripture can be a powerful source of motivation, encouragement, and renewed hope, even in those moments when you feel like you're falling short. Let's dive into how various scriptures, including the ones we mentioned earlier, can give you that much-needed boost when you're feeling down.
1. Recognizing God's Sovereignty: You know, sometimes it's comforting to remember that we're not alone in our struggles. Scriptures like Psalm 46:10 and Isaiah 41:10 remind us that God is right there with us, holding us up and giving us strength. So, even when it feels like everything is falling apart, we can find motivation in knowing that God's got our back. His plans are bigger than our failures, and that thought alone can help us keep pushing forward.
2. Trusting in God's Guidance: It's not always easy to figure things out on our own, especially when we're feeling defeated. That's where scriptures like Proverbs 3:5 come in handy. They encourage us to put our trust in the Lord, to lean on Him and His understanding. When we feel like we're failing, we can find motivation by surrendering our worries and uncertainties to God. Trusting that He'll guide us can give us the courage to take that next step, even when it feels uncertain.
3. Embracing God's Love and Grace: You know, it's important to remember that our worth isn't defined by our failures. John 3:16 and Ephesians 2:8 remind us of God's unconditional love and the grace He extends to us. When we feel like we're falling short, these verses can be a source of comfort and motivation. They remind us that God's love remains unwavering, regardless of our achievements or mistakes. His grace gives us the opportunity for a fresh start and encourages us to keep going.
4. Finding Strength in Adversity: Hey, setbacks and failures are tough, no doubt about it. But you know what? They can also be opportunities for growth and resilience. James 1:2-4 reminds us to see trials as stepping stones toward becoming stronger individuals. When we face failures, we can find motivation by shifting our perspective. We can view these challenges as temporary hurdles on our journey to personal growth. With God's strength, we can keep moving forward, knowing that we're getting stronger with every step.
5. Cultivating a Positive Attitude: Sometimes, it's all about having the right mindset. Philippians 4:13 is a verse that reminds us we can do anything through Christ who strengthens us. Isn't that amazing? When we're feeling like failures, this verse encourages us to focus on our strengths and abilities. It's about channeling our energy into positive thinking. Instead of dwelling on our shortcomings, we can approach challenges with confidence, knowing that we have God's power within us.
When you feel like you're failing, scripture can be a powerful source of motivation and hope. By recognizing God's presence, trusting in His guidance, embracing His love and grace, finding strength in adversity, and cultivating a positive attitude, you can rise above your failures. Remember, you're not alone in this journey, and there's always hope, even in the face of failure. So, keep your chin up and let these scriptures be a source of inspiration on your path to success and fulfillment . You've got this!
-
 @ 1c52ebc8:5698c92a
2023-08-05 18:59:53
@ 1c52ebc8:5698c92a
2023-08-05 18:59:53Hey folks, happy Saturday!
Thanks for all the support last week with the first attempt at a “this week in Nostr” newsletter, feedback is very welcome 🙂
The hope for this newsletter is to be technically focused (new NIPs, notable projects, latest debates, etc) and a way for folks to keep up with how the community and the protocol is developing.
Recent NIP Updates
1) Calendar Events 📅
Early this week Calendar Events got added as a new NIP, so now we have a standard way to create calendars and calendar events in a way that can be shared via Nostr. Looks like we’ll be able to kick Meetup and Eventbrite to the curb soon!
2) Proxy Tags (Proposed) 🌉
There’s been significant work done to bridge between other social media and Nostr (Twitter, ActivityPub, etc). One of the challenges is the amount of duplication that can happen. If this NIP is adopted, a proxy tag can be added to events so that a Nostr client can link an event that was originally in Twitter to the original Twitter url.
This has the approval of many folks including @fiatj so I bet we’ll see it merged soon.
Notable projects
NostrDB: shipped! 🚢
Mentioned last week, but shipped this week: NostrDB is an embedded relay within the Damus app built by @jb55 built to improve performance and make new features easier. By having a relay inside the client, the client gets far more efficient with pretty much everything. It’s a standalone project so I imagine many clients could adopt this and reap the benefits.
As he mentions in the announcement, it has enabled Damus to recommend follows, as well as speed up many resource intensive operations in the app. Definitely feels snappier to me 💪
Stemstr 🎵
Shipped this week, Stemstr is a way to connect with people over music. There seem to be budding collaboration tools as well meaning the music on stemstr is constantly evolving and being reshared. Quite an impressive project.
Relayable 🌍
One of the underrated challenges of using Nostr right now is curating your relays. For the snappiest experience in your clients, speed is important! Many relays are hosted around the globe but it’s not easy to keep track of that.
Relayable is a relay you can add that will automatically find the closest, fastest, reliable relay to you get you connected so you can get your notes as fast as possible. Really neat project, I’ve added that relay and it’s worked great
Ostrich.work ⚒️
A job board that runs on Nostr for Nostr-related jobs. Definitely check it out if you’re looking to work on Nostr projects or need to find someone to work with you on the same!
Secret Chats on Iris 🤫
DMs on Nostr aren’t entirely private because we’re still publishing the metadata about the DM on publicly accessible relays even if the content is encrypted. There’s been a desire to implement more secure chats through the Nostr protocol, there’s even a bounty from Human Right Foundation about it.
Looks like Iris pushed support for their take on secret chats, looking forward to people telling the community how they like it.
Learn to dev on Nostr course 📖
If you’re looking to get started building on Nostr, or just curious how it works under the hood, here’s a course that was put together just for you! It’s about 40 minutes long and it starts assuming no knowledge about Nostr.
Latest debates
DMs 🔒
DMs on Nostr (using the original NIP 4 protocol) isn’t very private, and there’s a desire from a large group on Nostriches to fix that natively in Nostr. Some folks are ok to leave it “unfixed” in Nostr and use protocols like Simplex because Nostr doesn’t have to solve all problems. Many ofthers thinks we can have our cake and eat it too with some effort on the Nostr protocol.
The debate rages on! I hope you weigh in wherever you see the discussion, your voice may help the community get to clarity.
Email notifications
Much of the world still relies on email to get notified about what’s happening across their various apps and services when they’re not regularly logging in. @karnage@snort.social believes it may help adoption of Nostr if there was a client that allowed users that opt-in to get email notifications for activity happening on Nostr.
There are other folks that feel like it wouldn’t be useful and in fact could make Nostr feel more spammy. I saw another thought that Nostr should be fairly self contained so bridges to other protocols (email being one) would pollute the network. It’s an interesting debate.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual). If you wanna see something here please let me know! (DMs welcome) - Nostrasia Nov 1-3 in Tokyo & Hong Kong
I haven’t heard of any new ones this week but I hope the one in Chiavenna, Italy went well this week 🙂
Until next time 🫡
I realized this week I should be tagging each major contributor/author of each of the notable projects. I'll keep track of that from now on, so I can tag the people doing the awesome work in our community.
If I missed anything else, let me know, DMs welcome.
And to shamelessly rip off my favorite youtuber’s signoff “God bless, you’re super cute”
-
 @ 50c5c98c:65867c8e
2023-10-08 01:46:34
@ 50c5c98c:65867c8e
2023-10-08 01:46:34https://cdn.satellite.earth/919279ca03881d8e61a37019ffd9a9b04794f3f459801a4b8ae89e8c4bdba8fd.jpg
Testing this hosted image. Posting from blogstack.io
-
 @ 20986fb8:cdac21b3
2023-10-07 10:27:46
@ 20986fb8:cdac21b3
2023-10-07 10:27:46Comment2Earn | Earn SATs by sharing your comments on YakiHonne
Earn SATs by sharing your comments on YakiHonne.
⏰2nd - 15th Oct
Follow Us
- Nostr: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
- Twitter: https://twitter.com/YakiHonne
- Facebook Profile: https://www.facebook.com/profile.php?id=61551715056704
- Facebook Page: https://www.facebook.com/profile.php?id=61552076811240
- Facebook Group: https://www.facebook.com/groups/720824539860115
- Youtube: https://www.youtube.com/channel/UCyjDDtWFCntGvf4EyFJ7BlA
How to Get SATs:
- Post your thoughts about YakiHonne on at least one of the above social media, and be sure to @ YakiHonne.
- Follow YakiHonne on at least one of the social media above.
- Back to this article, leave your social account which followed YakiHonne in the Comments.
- Be zapped with SATs.
What You Will Get:
- 500 SATs, if you finished all steps.
- 1000 SATs, if you finished all steps and join our community.
- 3000 SATs, for 20% of all participants by randomly selecting.
Tips
- You could write even only one sentence of your thoughts about YakiHonne and post it on social media.
- Be sure to follow, @, or tag YakiHonne.
- Don't forget to back to here and leave your nostr pubkey and social media account which followed YakiHonne in the comments.
- Comment here could be like, 'Followed YakiHonne on Twitter/Facebook/Nostr/YouTube by @(your account), pubkey: (npub...) '
- You will get SATs by zap function on YakiHonne, be sure to set it up.
Zap Rules:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam.
- No direct copy from other posts.
- Community account verification, no fake account or bot.
Join our group for more queries: https://t.me/YakiHonne_Daily_Featured
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
- Facebook Profile: https://www.facebook.com/profile.php?id=61551715056704
- Facebook Page: https://www.facebook.com/profile.php?id=61552076811240
- Facebook Group: https://www.facebook.com/groups/720824539860115
- Youtube: https://www.youtube.com/channel/UCyjDDtWFCntGvf4EyFJ7BlA
-
 @ 1c52ebc8:5698c92a
2023-07-29 17:58:50
@ 1c52ebc8:5698c92a
2023-07-29 17:58:50Hey folks, let’s take a shot at this. If folks find this helpful, this will become a weekly summary of what’s happening in Nostr.
The intention is for it to be technically focused (new NIPs, new projects, new bounties, etc) and a way for folks that aren’t terminally online / on-nostr to be able to keep up with what’s going on.
Let’s dive in!
Recent NIP Updates
1) Long form content
Looks like there’s some activity around long-form content. Recently a few updates to various NIPs added the expectation that relays and clients support drafts of long-form content. That way folks can save their drafts without a client having to save in some way other than a relay. 💪
2) NIP 99: Classified listings
This NIP was accepted July 18, 2023 and outlines a new kind of note that will help Nostr clients to build Craiglist competitors natively in Nostr. 💲
Notable projects
Human Rights Foundation Bounties
A series of bounties to add capabilities to the Nostr ecosystem.
NostrDB: under development
A nostr-specific database that @jb55 is building to improve performance of the Damus iOS app
NJson: a JSON parser for Nostr events
A parser for JSON that’s specific to Nostr Event JSON. It’s wayyyyy faster. Great foundationally pattern/tool to improve all nostr clients and relays.
Data vending machines
This one was a mind bender and a new concept to me. But @pablof7z introduced having bots compete to accomplish tasks. The person that’s hiring for the task sets the terms and can accept a bid on whatever dimension they care about.
This could be used for things as simple as answering a question you’d previously use Google for, or curating a Nostr feed based on your interests.
Highlighter
Highlighter is a way to highlight content from anywhere and wrap that highlight as a nostr event. Which means that people can interact with this content like any other note: reactions, reposts, zaps, etc.
Seems like it could become a way to discover quality content by following folks that are digging into topics you’re interested in. Lots of ways to use this 🤯
Habla.news
Habla.news has built a way for people to draft and publish long form content in a familiar way. The interface supports rich text editing and other nice features of products like Medium.
Best part is that it publishes to your relays, so any client that supports long form content events will showcase your work (and make it zapable ⚡). For now I’ve only seen Damus (the iOS app) support long-form notes natively, but I’m sure more are incoming 💪
Latest debates
Nostr for everything vs narrow, powerful nostr
Seen a few of these debates lately, I imagine it’s just the beginning.
With protocols there’s a temptation to make that protocol support the capability to do everything. On the other hand, a protocol that can do anything isn’t particularly useful.
Nostr is still evolving though and no one is an authority on what IS and IS NOT Nostr. Can’t wait to see folks hash it out.
Build requests / ideas
I’m gonna collect the features / build requests I see throughout the week and post them here for anyone that has the cycles and interest to build what the community is asking for.
If you have something you want put here, let me know! (DM’s are welcome)
- @jb55 = nuke all events client (to clean up a relay or your wipe your account)
- @jb55 = nostr-based email client
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual). If you wanna see something here please let me know! (DMs welcome)
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Meet up in Chiavenna, Italy August 3rd
Until next time 🫡
If I missed anything, let me know, DMs welcome.
And to shamelessly rip off my favorite youtuber’s signoff “God bless, you’re super cute”
-
 @ 6389be64:ef439d32
2023-10-05 16:43:15
@ 6389be64:ef439d32
2023-10-05 16:43:15I wonder if I can activate the @PrismPost by using $boost and $comment here in this post.
-
 @ 6389be64:ef439d32
2023-10-05 14:48:33
@ 6389be64:ef439d32
2023-10-05 14:48:33Just checking.
-
 @ ee6ea13a:959b6e74
2023-10-05 03:42:41
@ ee6ea13a:959b6e74
2023-10-05 03:42:41I'm not sure why I didn't take to stacker.news sooner. It's been on my radar for a while, but I've been inundated with other inputs, priorities, etc., and I’ve spent most of the past year going down the nostr rabbit hole, but here I am giving it another go.
So a couple of weeks ago, I was laid off from yet another fiat job. My third one in three years, in fact! An old friend, in fact the guy who offered me my first real job, reached out to me on LinkedIn to ask me what happened, and what my “ideal scenario” would be.
I replied with one word: Bitcoin.
His response: Yeah right.
I wrote back: A little disappointed in your lack of confidence. 😅
His answer, unsurprisingly: Not in you but in Bitcoin.
Of course, I’m sure he thought I was going to become a trader or something, because when most people hear the word bitcoin, they only think about the price. They have no idea what’s being built right now.
I told him my ideal scenario would be to work in the industry. I’ve been thinking about this for a while. I spend most of my time online immersed in a world of new possibilities, ways to connect, share value for value, and build stronger community bonds. This is where I want to take my career next, and to finally make a break from a world of “serious professionals” who think bitcoin is a joke.
He never replied, of course.
Let them laugh.
-
 @ e6ce6154:275e3444
2023-07-27 14:12:49
@ e6ce6154:275e3444
2023-07-27 14:12:49Este artigo foi censurado pelo estado e fomos obrigados a deletá-lo após ameaça de homens armados virem nos visitar e agredir nossa vida e propriedade.
Isto é mais uma prova que os autoproclamados antirracistas são piores que os racistas.
https://rothbardbrasil.com/pelo-direito-de-ser-racista-fascista-machista-e-homofobico
Segue artigo na íntegra. 👇
Sem dúvida, a escalada autoritária do totalitarismo cultural progressista nos últimos anos tem sido sumariamente deletéria e prejudicial para a liberdade de expressão. Como seria de se esperar, a cada dia que passa o autoritarismo progressista continua a se expandir de maneira irrefreável, prejudicando a liberdade dos indivíduos de formas cada vez mais deploráveis e contundentes.
Com a ascensão da tirania politicamente correta e sua invasão a todos os terrenos culturais, o autoritarismo progressista foi se alastrando e consolidando sua hegemonia em determinados segmentos. Com a eventual eclosão e a expansão da opressiva e despótica cultura do cancelamento — uma progênie inevitável do totalitarismo progressista —, todas as pessoas que manifestam opiniões, crenças ou posicionamentos que não estão alinhados com as pautas universitárias da moda tornam-se um alvo.
Há algumas semanas, vimos a enorme repercussão causada pelo caso envolvendo o jogador profissional de vôlei Maurício Sousa, que foi cancelado pelo simples fato de ter emitido sua opinião pessoal sobre um personagem de história em quadrinhos, Jon Kent, o novo Superman, que é bissexual. Maurício Sousa reprovou a conduta sexual do personagem, o que é um direito pessoal inalienável que ele tem. Ele não é obrigado a gostar ou aprovar a bissexualidade. Como qualquer pessoa, ele tem o direito pleno de criticar tudo aquilo que ele não gosta. No entanto, pelo simples fato de emitir a sua opinião pessoal, Maurício Sousa foi acusado de homofobia e teve seu contrato rescindido, sendo desligado do Minas Tênis Clube.
Lamentavelmente, Maurício Sousa não foi o primeiro e nem será o último indivíduo a sofrer com a opressiva e autoritária cultura do cancelamento. Como uma tirania cultural que está em plena ascensão e usufrui de um amplo apoio do establishment, essa nova forma de totalitarismo cultural colorido e festivo está se impondo de formas e maneiras bastante contundentes em praticamente todas as esferas da sociedade contemporânea. Sua intenção é relegar ao ostracismo todos aqueles que não se curvam ao totalitarismo progressista, criminalizando opiniões e crenças que divergem do culto à libertinagem hedonista pós-moderna. Oculto por trás de todo esse ativismo autoritário, o que temos de fato é uma profunda hostilidade por padrões morais tradicionalistas, cristãos e conservadores.
No entanto, é fundamental entendermos uma questão imperativa, que explica em partes o conflito aqui criado — todos os progressistas contemporâneos são crias oriundas do direito positivo. Por essa razão, eles jamais entenderão de forma pragmática e objetiva conceitos como criminalidade, direitos de propriedade, agressão e liberdade de expressão pela perspectiva do jusnaturalismo, que é manifestamente o direito em seu estado mais puro, correto, ético e equilibrado.
Pela ótica jusnaturalista, uma opinião é uma opinião. Ponto final. E absolutamente ninguém deve ser preso, cancelado, sabotado ou boicotado por expressar uma opinião particular sobre qualquer assunto. Palavras não agridem ninguém, portanto jamais poderiam ser consideradas um crime em si. Apenas deveriam ser tipificados como crimes agressões de caráter objetivo, como roubo, sequestro, fraude, extorsão, estupro e infrações similares, que representam uma ameaça direta à integridade física da vítima, ou que busquem subtrair alguma posse empregando a violência.
Infelizmente, a geração floquinho de neve — terrivelmente histérica, egocêntrica e sensível — fica profundamente ofendida e consternada sempre que alguém defende posicionamentos contrários à religião progressista. Por essa razão, os guerreiros da justiça social sinceramente acreditam que o papai-estado deve censurar todas as opiniões que eles não gostam de ouvir, assim como deve também criar leis para encarcerar todos aqueles que falam ou escrevem coisas que desagradam a militância.
Como a geração floquinho de neve foi criada para acreditar que todas as suas vontades pessoais e disposições ideológicas devem ser sumariamente atendidas pelo papai-estado, eles embarcaram em uma cruzada moral que pretende erradicar todas as coisas que são ofensivas à ideologia progressista; só assim eles poderão deflagrar na Terra o seu tão sonhado paraíso hedonista e igualitário, de inimaginável esplendor e felicidade.
Em virtude do seu comportamento intrinsecamente despótico, autoritário e egocêntrico, acaba sendo inevitável que militantes progressistas problematizem tudo aquilo que os desagrada.
Como são criaturas inúteis destituídas de ocupação real e verdadeiro sentido na vida, sendo oprimidas unicamente na sua própria imaginação, militantes progressistas precisam constantemente inventar novos vilões para serem combatidos.
Partindo dessa perspectiva, é natural para a militância que absolutamente tudo que exista no mundo e que não se enquadra com as regras autoritárias e restritivas da religião progressista seja encarado como um problema. Para a geração floquinho de neve, o capitalismo é um problema. O fascismo é um problema. A iniciativa privada é um problema. O homem branco, tradicionalista, conservador e heterossexual é um problema. A desigualdade é um problema. A liberdade é um problema. Monteiro Lobato é um problema (sim, até mesmo o renomado ícone da literatura brasileira, autor — entre outros títulos — de Urupês, foi vítima da cultura do cancelamento, acusado de ser racista e eugenista).
Para a esquerda, praticamente tudo é um problema. Na mentalidade da militância progressista, tudo é motivo para reclamação. Foi em função desse comportamento histérico, histriônico e infantil que o famoso pensador conservador-libertário americano P. J. O’Rourke afirmou que “o esquerdismo é uma filosofia de pirralhos chorões”. O que é uma verdade absoluta e irrefutável em todos os sentidos.
De fato, todas as filosofias de esquerda de forma geral são idealizações utópicas e infantis de um mundo perfeito. Enquanto o mundo não se transformar naquela colorida e vibrante utopia que é apresentada pela cartilha socialista padrão, militantes continuarão a reclamar contra tudo o que existe no mundo de forma agressiva, visceral e beligerante. Evidentemente, eles não vão fazer absolutamente nada de positivo ou construtivo para que o mundo se transforme no gracioso paraíso que eles tanto desejam ver consolidado, mas eles continuarão a berrar e vociferar muito em sua busca incessante pela utopia, marcando presença em passeatas inúteis ou combatendo o fascismo imaginário nas redes sociais.
Sem dúvida, estamos muito perto de ver leis absurdas e estúpidas sendo implementadas, para agradar a militância da terra colorida do assistencialismo eterno onde nada é escasso e tudo cai do céu. Em breve, você não poderá usar calças pretas, pois elas serão consideradas peças de vestuário excessivamente heterossexuais. Apenas calças amarelas ou coloridas serão permitidas. Você também terá que tingir de cor-de-rosa uma mecha do seu cabelo; pois preservar o seu cabelo na sua cor natural é heteronormativo demais da sua parte, sendo portanto um componente demasiadamente opressor da sociedade.
Você também não poderá ver filmes de guerra ou de ação, apenas comédias românticas, pois certos gêneros de filmes exaltam a violência do patriarcado e isso impede o mundo de se tornar uma graciosa festa colorida de fraternidades universitárias ungidas por pôneis resplandecentes, hedonismo infinito, vadiagem universitária e autogratificação psicodélica, que certamente são elementos indispensáveis para se produzir o paraíso na Terra.
Sabemos perfeitamente, no entanto, que dentre as atitudes “opressivas” que a militância progressista mais se empenha em combater, estão o racismo, o fascismo, o machismo e a homofobia. No entanto, é fundamental entender que ser racista, fascista, machista ou homofóbico não são crimes em si. Na prática, todos esses elementos são apenas traços de personalidade; e eles não podem ser pura e simplesmente criminalizados porque ideólogos e militantes progressistas iluminados não gostam deles.
Tanto pela ética quanto pela ótica jusnaturalista, é facilmente compreensível entender que esses traços de personalidade não podem ser criminalizados ou proibidos simplesmente porque integrantes de uma ideologia não tem nenhuma apreciação ou simpatia por eles. Da mesma forma, nenhum desses traços de personalidade representa em si um perigo para a sociedade, pelo simples fato de existir. Por incrível que pareça, até mesmo o machismo, o racismo, o fascismo e a homofobia merecem a devida apologia.
Mas vamos analisar cada um desses tópicos separadamente para entender isso melhor.
Racismo
Quando falamos no Japão, normalmente não fazemos nenhuma associação da sociedade japonesa com o racismo. No entanto, é incontestável o fato de que a sociedade japonesa pode ser considerada uma das sociedades mais racistas do mundo. E a verdade é que não há absolutamente nada de errado com isso.
Aproximadamente 97% da população do Japão é nativa; apenas 3% do componente populacional é constituído por estrangeiros (a população do Japão é estimada em aproximadamente 126 milhões de habitantes). Isso faz a sociedade japonesa ser uma das mais homogêneas do mundo. As autoridades japonesas reconhecidamente dificultam processos de seleção e aplicação a estrangeiros que desejam se tornar residentes. E a maioria dos japoneses aprova essa decisão.
Diversos estabelecimentos comerciais como hotéis, bares e restaurantes por todo o país tem placas na entrada que dizem “somente para japoneses” e a maioria destes estabelecimentos se recusa ostensivamente a atender ou aceitar clientes estrangeiros, não importa quão ricos ou abastados sejam.
Na Terra do Sol Nascente, a hostilidade e a desconfiança natural para com estrangeiros é tão grande que até mesmo indivíduos que nascem em algum outro país, mas são filhos de pais japoneses, não são considerados cidadãos plenamente japoneses.
Se estes indivíduos decidem sair do seu país de origem para se estabelecer no Japão — mesmo tendo descendência nipônica legítima e inquestionável —, eles enfrentarão uma discriminação social considerável, especialmente se não dominarem o idioma japonês de forma impecável. Esse fato mostra que a discriminação é uma parte tão indissociável quanto elementar da sociedade japonesa, e ela está tão profundamente arraigada à cultura nipônica que é praticamente impossível alterá-la ou atenuá-la por qualquer motivo.
A verdade é que — quando falamos de um país como o Japão — nem todos os discursos politicamente corretos do mundo, nem a histeria progressista ocidental mais inflamada poderão algum dia modificar, extirpar ou sequer atenuar o componente racista da cultura nipônica. E isso é consequência de uma questão tão simples quanto primordial: discriminar faz parte da natureza humana, sendo tanto um direito individual quanto um elemento cultural inerente à muitas nações do mundo. Os japoneses não tem problema algum em admitir ou institucionalizar o seu preconceito, justamente pelo fato de que a ideologia politicamente correta não tem no oriente a força e a presença que tem no ocidente.
E é fundamental enfatizar que, sendo de natureza pacífica — ou seja, não violando nem agredindo terceiros —, a discriminação é um recurso natural dos seres humanos, que está diretamente associada a questões como familiaridade e segurança.
Absolutamente ninguém deve ser forçado a apreciar ou integrar-se a raças, etnias, pessoas ou tribos que não lhe transmitem sentimentos de segurança ou familiaridade. Integração forçada é o verdadeiro crime, e isso diversos países europeus — principalmente os escandinavos (países que lideram o ranking de submissão à ideologia politicamente correta) — aprenderam da pior forma possível.
A integração forçada com imigrantes islâmicos resultou em ondas de assassinato, estupro e violência inimagináveis para diversos países europeus, até então civilizados, que a imprensa ocidental politicamente correta e a militância progressista estão permanentemente tentando esconder, porque não desejam que o ocidente descubra como a agenda “humanitária” de integração forçada dos povos muçulmanos em países do Velho Mundo resultou em algumas das piores chacinas e tragédias na história recente da Europa.
Ou seja, ao discriminarem estrangeiros, os japoneses estão apenas se protegendo e lutando para preservar sua nação como um ambiente cultural, étnico e social que lhe é seguro e familiar, assim se opondo a mudanças bruscas, indesejadas e antinaturais, que poderiam comprometer a estabilidade social do país.
A discriminação — sendo de natureza pacífica —, é benévola, salutar e indubitavelmente ajuda a manter a estabilidade social da comunidade. Toda e qualquer forma de integração forçada deve ser repudiada com veemência, pois, mais cedo ou mais tarde, ela irá subverter a ordem social vigente, e sempre será acompanhada de deploráveis e dramáticos resultados.
Para citar novamente os países escandinavos, a Suécia é um excelente exemplo do que não fazer. Tendo seguido o caminho contrário ao da discriminação racional praticada pela sociedade japonesa, atualmente a sociedade sueca — além de afundar de forma consistente na lama da libertinagem, da decadência e da deterioração progressista — sofre em demasia com os imigrantes muçulmanos, que foram deixados praticamente livres para matar, saquear, esquartejar e estuprar quem eles quiserem. Hoje, eles são praticamente intocáveis, visto que denunciá-los, desmoralizá-los ou acusá-los de qualquer crime é uma atitude politicamente incorreta e altamente reprovada pelo establishment progressista. A elite socialista sueca jamais se atreve a acusá-los de qualquer crime, pois temem ser classificados como xenófobos e intolerantes. Ou seja, a desgraça da Europa, sobretudo dos países escandinavos, foi não ter oferecido nenhuma resistência à ideologia progressista politicamente correta. Hoje, eles são totalmente submissos a ela.
O exemplo do Japão mostra, portanto — para além de qualquer dúvida —, a importância ética e prática da discriminação, que é perfeitamente aceitável e natural, sendo uma tendência inerente aos seres humanos, e portanto intrínseca a determinados comportamentos, sociedades e culturas.
Indo ainda mais longe nessa questão, devemos entender que na verdade todos nós discriminamos, e não existe absolutamente nada de errado nisso. Discriminar pessoas faz parte da natureza humana e quem se recusa a admitir esse fato é um hipócrita. Mulheres discriminam homens na hora de selecionar um parceiro; elas avaliam diversos quesitos, como altura, aparência, status social, condição financeira e carisma. E dentre suas opções, elas sempre escolherão o homem mais atraente, másculo e viril, em detrimento de todos os baixinhos, calvos, carentes, frágeis e inibidos que possam estar disponíveis. Da mesma forma, homens sempre terão preferência por mulheres jovens, atraentes e delicadas, em detrimento de todas as feministas de meia-idade, acima do peso, de cabelo pintado, que são mães solteiras e militantes socialistas. A própria militância progressista discrimina pessoas de forma virulenta e intransigente, como fica evidente no tratamento que dispensam a mulheres bolsonaristas e a negros de direita.
A verdade é que — não importa o nível de histeria da militância progressista — a discriminação é inerente à condição humana e um direito natural inalienável de todos. É parte indissociável da natureza humana e qualquer pessoa pode e deve exercer esse direito sempre que desejar. Não existe absolutamente nada de errado em discriminar pessoas. O problema real é a ideologia progressista e o autoritarismo politicamente correto, movimentos tirânicos que não respeitam o direito das pessoas de discriminar.
Fascismo
Quando falamos de fascismo, precisamos entender que, para a esquerda política, o fascismo é compreendido como um conceito completamente divorciado do seu significado original. Para um militante de esquerda, fascista é todo aquele que defende posicionamentos contrários ao progressismo, não se referindo necessariamente a um fascista clássico.
Mas, seja como for, é necessário entender que — como qualquer ideologia política — até mesmo o fascismo clássico tem o direito de existir e ocupar o seu devido lugar; portanto, fascistas não devem ser arbitrariamente censurados, apesar de defenderem conceitos que representam uma completa antítese de tudo aquilo que é valioso para os entusiastas da liberdade.
Em um país como o Brasil, onde socialistas e comunistas tem total liberdade para se expressar, defender suas ideologias e até mesmo formar partidos políticos, não faz absolutamente o menor sentido que fascistas — e até mesmo nazistas assumidos — sofram qualquer tipo de discriminação. Embora socialistas e comunistas se sintam moralmente superiores aos fascistas (ou a qualquer outra filosofia política ou escola de pensamento), sabemos perfeitamente que o seu senso de superioridade é fruto de uma pueril romantização universitária da sua própria ideologia. A história mostra efetivamente que o socialismo clássico e o comunismo causaram muito mais destruição do que o fascismo.
Portanto, se socialistas e comunistas tem total liberdade para se expressar, não existe a menor razão para que fascistas não usufruam dessa mesma liberdade.
É claro, nesse ponto, seremos invariavelmente confrontados por um oportuno dilema — o famoso paradoxo da intolerância, de Karl Popper. Até que ponto uma sociedade livre e tolerante deve tolerar a intolerância (inerente a ideologias totalitárias)?
As leis de propriedade privada resolveriam isso em uma sociedade livre. O mais importante a levarmos em consideração no atual contexto, no entanto — ao defender ou criticar uma determinada ideologia, filosofia ou escola de pensamento —, é entender que, seja ela qual for, ela tem o direito de existir. E todas as pessoas que a defendem tem o direito de defendê-la, da mesma maneira que todos os seus detratores tem o direito de criticá-la.
Essa é uma forte razão para jamais apoiarmos a censura. Muito pelo contrário, devemos repudiar com veemência e intransigência toda e qualquer forma de censura, especialmente a estatal.
Existem duas fortes razões para isso:
A primeira delas é a volatilidade da censura (especialmente a estatal). A censura oficial do governo, depois que é implementada, torna-se absolutamente incontrolável. Hoje, ela pode estar apontada para um grupo de pessoas cujas ideias divergem das suas. Mas amanhã, ela pode estar apontada justamente para as ideias que você defende. É fundamental, portanto, compreendermos que a censura estatal é incontrolável. Sob qualquer ponto de vista, é muito mais vantajoso que exista uma vasta pluralidade de ideias conflitantes na sociedade competindo entre si, do que o estado decidir que ideias podem ser difundidas ou não.
Além do mais, libertários e anarcocapitalistas não podem nunca esperar qualquer tipo de simpatia por parte das autoridades governamentais. Para o estado, seria infinitamente mais prático e vantajoso criminalizar o libertarianismo e o anarcocapitalismo — sob a alegação de que são filosofias perigosas difundidas por extremistas radicais que ameaçam o estado democrático de direito — do que o fascismo ou qualquer outra ideologia centralizada em governos burocráticos e onipotentes. Portanto, defender a censura, especialmente a estatal, representa sempre um perigo para o próprio indivíduo, que mais cedo ou mais tarde poderá ver a censura oficial do sistema se voltar contra ele.
Outra razão pela qual libertários jamais devem defender a censura, é porque — ao contrário dos estatistas — não é coerente que defensores da liberdade se comportem como se o estado fosse o seu papai e o governo fosse a sua mamãe. Não devemos terceirizar nossas próprias responsabilidades, tampouco devemos nos comportar como adultos infantilizados. Assumimos a responsabilidade de combater todas as ideologias e filosofias que agridem a liberdade e os seres humanos. Não procuramos políticos ou burocratas para executar essa tarefa por nós.
Portanto, se você ver um fascista sendo censurado nas redes sociais ou em qualquer outro lugar, assuma suas dores. Sinta-se compelido a defendê-lo, mostre aos seus detratores que ele tem todo direito de se expressar, como qualquer pessoa. Você não tem obrigação de concordar com ele ou apreciar as ideias que ele defende. Mas silenciar arbitrariamente qualquer pessoa não é uma pauta que honra a liberdade.
Se você não gosta de estado, planejamento central, burocracia, impostos, tarifas, políticas coletivistas, nacionalistas e desenvolvimentistas, mostre com argumentos coesos e convincentes porque a liberdade e o livre mercado são superiores a todos esses conceitos. Mas repudie a censura com intransigência e mordacidade.
Em primeiro lugar, porque você aprecia e defende a liberdade de expressão para todas as pessoas. E em segundo lugar, por entender perfeitamente que — se a censura eventualmente se tornar uma política de estado vigente entre a sociedade — é mais provável que ela atinja primeiro os defensores da liberdade do que os defensores do estado.
Machismo
Muitos elementos do comportamento masculino que hoje são atacados com virulência e considerados machistas pelo movimento progressista são na verdade manifestações naturais intrínsecas ao homem, que nossos avôs cultivaram ao longo de suas vidas sem serem recriminados por isso. Com a ascensão do feminismo, do progressismo e a eventual problematização do sexo masculino, o antagonismo militante dos principais líderes da revolução sexual da contracultura passou a naturalmente condenar todos os atributos genuinamente masculinos, por considerá-los símbolos de opressão e dominação social.
Apesar do Brasil ser uma sociedade liberal ultra-progressista, onde o estado protege mais as mulheres do que as crianças — afinal, a cada semana novas leis são implementadas concedendo inúmeros privilégios e benefícios às mulheres, aos quais elas jamais teriam direito em uma sociedade genuinamente machista e patriarcal —, a esquerda política persiste em tentar difundir a fantasia da opressão masculina e o mito de que vivemos em uma sociedade machista e patriarcal.
Como sempre, a realidade mostra um cenário muito diferente daquilo que é pregado pela militância da terra da fantasia. O Brasil atual não tem absolutamente nada de machista ou patriarcal. No Brasil, mulheres podem votar, podem ocupar posições de poder e autoridade tanto na esfera pública quanto em companhias privadas, podem se candidatar a cargos políticos, podem ser vereadoras, deputadas, governadoras, podem ser proprietárias do próprio negócio, podem se divorciar, podem dirigir, podem comprar armas, podem andar de biquíni nas praias, podem usar saias extremamente curtas, podem ver programas de televisão sobre sexo voltados única e exclusivamente para o público feminino, podem se casar com outras mulheres, podem ser promíscuas, podem consumir bebidas alcoólicas ao ponto da embriaguez, e podem fazer praticamente tudo aquilo que elas desejarem. No Brasil do século XXI, as mulheres são genuinamente livres para fazer as próprias escolhas em praticamente todos os aspectos de suas vidas. O que mostra efetivamente que a tal opressão do patriarcado não existe.
O liberalismo social extremo do qual as mulheres usufruem no Brasil atual — e que poderíamos estender a toda a sociedade contemporânea ocidental — é suficiente para desmantelar completamente a fábula feminista da sociedade patriarcal machista e opressora, que existe única e exclusivamente no mundinho de fantasias ideológicas da esquerda progressista.
Tão importante quanto, é fundamental compreender que nenhum homem é obrigado a levar o feminismo a sério ou considerá-lo um movimento social e político legítimo. Para um homem, ser considerado machista ou até mesmo assumir-se como um não deveria ser um problema. O progressismo e o feminismo — com o seu nefasto hábito de demonizar os homens, bem como todos os elementos inerentes ao comportamento e a cultura masculina — é que são o verdadeiro problema, conforme tentam modificar o homem para transformá-lo em algo que ele não é nem deveria ser: uma criatura dócil, passiva e submissa, que é comandada por ideologias hostis e antinaturais, que não respeitam a hierarquia de uma ordem social milenar e condições inerentes à própria natureza humana. Com o seu hábito de tentar modificar tudo através de leis e decretos, o feminismo e o progressismo mostram efetivamente que o seu real objetivo é criminalizar a masculinidade.
A verdade é que — usufruindo de um nível elevado de liberdades — não existe praticamente nada que a mulher brasileira do século XXI não possa fazer. Adicionalmente, o governo dá as mulheres uma quantidade tão avassaladora de vantagens, privilégios e benefícios, que está ficando cada vez mais difícil para elas encontrarem razões válidas para reclamarem da vida. Se o projeto de lei que pretende fornecer um auxílio mensal de mil e duzentos reais para mães solteiras for aprovado pelo senado, muitas mulheres que tem filhos não precisarão nem mesmo trabalhar para ter sustento. E tantas outras procurarão engravidar, para ter direito a receber uma mesada mensal do governo até o seu filho completar a maioridade.
O que a militância colorida da terra da fantasia convenientemente ignora — pois a realidade nunca corresponde ao seu conto de fadas ideológico — é que o mundo de uma forma geral continua sendo muito mais implacável com os homens do que é com as mulheres. No Brasil, a esmagadora maioria dos suicídios é praticada por homens, a maioria das vítimas de homicídio são homens e de cada quatro moradores de rua, três são homens. Mas é evidente que uma sociedade liberal ultra-progressista não se importa com os homens, pois ela não é influenciada por fatos concretos ou pela realidade. Seu objetivo é simplesmente atender as disposições de uma agenda ideológica, não importa quão divorciadas da realidade elas são.
O nível exacerbado de liberdades sociais e privilégios governamentais dos quais as mulheres brasileiras usufruem é suficiente para destruir a fantasiosa fábula da sociedade machista, opressora e patriarcal. Se as mulheres brasileiras não estão felizes, a culpa definitivamente não é dos homens. Se a vasta profusão de liberdades, privilégios e benefícios da sociedade ocidental não as deixa plenamente saciadas e satisfeitas, elas podem sempre mudar de ares e tentar uma vida mais abnegada e espartana em países como Irã, Paquistão ou Afeganistão. Quem sabe assim elas não se sentirão melhores e mais realizadas?
Homofobia
Quando falamos em homofobia, entramos em uma categoria muito parecida com a do racismo: o direito de discriminação é totalmente válido. Absolutamente ninguém deve ser obrigado a aceitar homossexuais ou considerar o homossexualismo como algo normal. Sendo cristão, não existe nem sequer a mais vaga possibilidade de que algum dia eu venha a aceitar o homossexualismo como algo natural. O homossexualismo se qualifica como um grave desvio de conduta e um pecado contra o Criador.
A Bíblia proíbe terminantemente conduta sexual imoral, o que — além do homossexualismo — inclui adultério, fornicação, incesto e bestialidade, entre outras formas igualmente pérfidas de degradação.
Segue abaixo três passagens bíblicas que proíbem terminantemente a conduta homossexual:
“Não te deitarás com um homem como se deita com uma mulher. Isso é abominável!” (Levítico 18:22 — King James Atualizada)
“Se um homem se deitar com outro homem, como se deita com mulher, ambos terão praticado abominação; certamente serão mortos; o seu sangue estará sobre eles.” (Levítico 20:13 — João Ferreira de Almeida Atualizada)
“O quê! Não sabeis que os injustos não herdarão o reino de Deus? Não sejais desencaminhados. Nem fornicadores, nem idólatras, nem adúlteros, nem homens mantidos para propósitos desnaturais, nem homens que se deitam com homens, nem ladrões, nem gananciosos, nem beberrões, nem injuriadores, nem extorsores herdarão o reino de Deus.” (1 Coríntios 6:9,10 —Tradução do Novo Mundo das Escrituras Sagradas com Referências)
Se você não é religioso, pode simplesmente levar em consideração o argumento do respeito pela ordem natural. A ordem natural é incondicional e incisiva com relação a uma questão: o complemento de tudo o que existe é o seu oposto, não o seu igual. O complemento do dia é a noite, o complemento da luz é a escuridão, o complemento da água, que é líquida, é a terra, que é sólida. E como sabemos o complemento do macho — de sua respectiva espécie — é a fêmea.
Portanto, o complemento do homem, o macho da espécie humana, é naturalmente a mulher, a fêmea da espécie humana. Um homem e uma mulher podem naturalmente se reproduzir, porque são um complemento biológico natural. Por outro lado, um homem e outro homem são incapazes de se reproduzir, assim como uma mulher e outra mulher.
Infelizmente, o mundo atual está longe de aceitar como plenamente estabelecida a ordem natural pelo simples fato dela existir, visto que tentam subvertê-la a qualquer custo, não importa o malabarismo intelectual que tenham que fazer para justificar os seus pontos de vista distorcidos e antinaturais. A libertinagem irrefreável e a imoralidade bestial do mundo contemporâneo pós-moderno não reconhecem nenhum tipo de limite. Quem tenta restabelecer princípios morais salutares é imediatamente considerado um vilão retrógrado e repressivo, sendo ativamente demonizado pela militância do hedonismo, da luxúria e da licenciosidade desenfreada e sem limites.
Definitivamente, fazer a apologia da moralidade, do autocontrole e do autodomínio não faz nenhum sucesso na Sodoma e Gomorra global dos dias atuais. O que faz sucesso é lacração, devassidão, promiscuidade e prazeres carnais vazios. O famoso escritor e filósofo francês Albert Camus expressou uma verdade contundente quando disse: “Uma só frase lhe bastará para definir o homem moderno — fornicava e lia jornais”.
Qualquer indivíduo tem o direito inalienável de discriminar ativamente homossexuais, pelo direito que ele julgar mais pertinente no seu caso. A objeção de consciência para qualquer situação é um direito natural dos indivíduos. Há alguns anos, um caso que aconteceu nos Estados Unidos ganhou enorme repercussão internacional, quando o confeiteiro Jack Phillips se recusou a fazer um bolo de casamento para o “casal” homossexual Dave Mullins e Charlie Craig.
Uma representação dos direitos civis do estado do Colorado abriu um inquérito contra o confeiteiro, alegando que ele deveria ser obrigado a atender todos os clientes, independente da orientação sexual, raça ou crença. Preste atenção nas palavras usadas — ele deveria ser obrigado a atender.
Como se recusou bravamente a ceder, o caso foi parar invariavelmente na Suprema Corte, que decidiu por sete a dois em favor de Jack Phillips, sob a alegação de que obrigar o confeiteiro a atender o “casal” homossexual era uma violação nefasta dos seus princípios religiosos. Felizmente, esse foi um caso em que a liberdade prevaleceu sobre a tirania progressista.
Evidentemente, homossexuais não devem ser agredidos, ofendidos, internados em clínicas contra a sua vontade, nem devem ser constrangidos em suas liberdades pelo fato de serem homossexuais. O que eles precisam entender é que a liberdade é uma via de mão dupla. Eles podem ter liberdade para adotar a conduta que desejarem e fazer o que quiserem (contanto que não agridam ninguém), mas da mesma forma, é fundamental respeitar e preservar a liberdade de terceiros que desejam rejeitá-los pacificamente, pelo motivo que for.
Afinal, ninguém tem a menor obrigação de aceitá-los, atendê-los ou sequer pensar que uma união estável entre duas pessoas do mesmo sexo — incapaz de gerar descendentes, e, portanto, antinatural — deva ser considerado um matrimônio de verdade. Absolutamente nenhuma pessoa, ideia, movimento, crença ou ideologia usufrui de plena unanimidade no mundo. Por que o homossexualismo deveria ter tal privilégio?
Homossexuais não são portadores de uma verdade definitiva, absoluta e indiscutível, que está acima da humanidade. São seres humanos comuns que — na melhor das hipóteses —, levam um estilo de vida que pode ser considerado “alternativo”, e absolutamente ninguém tem a obrigação de considerar esse estilo de vida normal ou aceitável. A única obrigação das pessoas é não interferir, e isso não implica uma obrigação em aceitar.
Discriminar homossexuais (assim como pessoas de qualquer outro grupo, raça, religião, nacionalidade ou etnia) é um direito natural por parte de todos aqueles que desejam exercer esse direito. E isso nem o direito positivo nem a militância progressista poderão algum dia alterar ou subverter. O direito natural e a inclinação inerente dos seres humanos em atender às suas próprias disposições é simplesmente imutável e faz parte do seu conjunto de necessidades.
Conclusão
A militância progressista é absurdamente autoritária, e todas as suas estratégias e disposições ideológicas mostram que ela está em uma guerra permanente contra a ordem natural, contra a liberdade e principalmente contra o homem branco, cristão, conservador e tradicionalista — possivelmente, aquilo que ela mais odeia e despreza.
Nós não podemos, no entanto, ceder ou dar espaço para a agenda progressista, tampouco pensar em considerar como sendo normais todas as pautas abusivas e tirânicas que a militância pretende estabelecer como sendo perfeitamente razoáveis e aceitáveis, quer a sociedade aceite isso ou não. Afinal, conforme formos cedendo, o progressismo tirânico e totalitário tende a ganhar cada vez mais espaço.
Quanto mais espaço o progressismo conquistar, mais corroída será a liberdade e mais impulso ganhará o totalitarismo. Com isso, a cultura do cancelamento vai acabar com carreiras, profissões e com o sustento de muitas pessoas, pelo simples fato de que elas discordam das pautas universitárias da moda.
A história mostra perfeitamente que quanto mais liberdade uma sociedade tem, mais progresso ela atinge. Por outro lado, quanto mais autoritária ela for, mais retrocessos ela sofrerá. O autoritarismo se combate com liberdade, desafiando as pautas de todos aqueles que persistem em implementar a tirania na sociedade. O politicamente correto é o nazismo dos costumes, que pretende subverter a moral através de uma cultura de vigilância policial despótica e autoritária, para que toda a sociedade seja subjugada pela agenda totalitária progressista.
Pois quanto a nós, precisamos continuar travando o bom combate em nome da liberdade. E isso inclui reconhecer que ideologias, hábitos e costumes de que não gostamos tem o direito de existir e até mesmo de serem defendidos.
-
 @ a4a6b584:1e05b95b
2023-07-27 01:23:03
@ a4a6b584:1e05b95b
2023-07-27 01:23:03"For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God." Romans 14:11-12
Though God has always had a people, the New Testament Church started with Christ and His disciples and was empowered at Pentecost. Historically, there has always been a remnant of people who adhered to the truth of God's Word for their faith and practice. I am convinced that the very same body of truth which was once delivered must be contended for in every generation.
In every generation from Christ and His disciples to this present moment, there have been holy adherents to the truth of God's Word. This witness of history is a witness in their blood. I am a Baptist by conviction. I was not "Baptist-born." I became and remain a Baptist because of what I have discovered in the Word of God.
The Lord Jesus Christ left His church doctrine and ordinances. The ordinances are baptism and the Lord's Supper. These are the things He ordered us to do. They picture His death and remind us of Him and His return. He also left us a body of doctrine. This involves our belief and teaching. Our doctrine distinguishes us. It is all from the Bible.
No one can be forced to become a Baptist. Our records show that baptism was always administered to professing believers. Hence, we refer to baptism as believers' baptism.
Baptists are gospel-preaching people. They preached the gospel to me. The Lord Jesus said to the first-century church, "But ye shall receive power, after that the Holy Ghost is come upon you: and ye shall be witnesses unto me both in Jerusalem, and in all Judea, and in Samaria, and unto the uttermost part of the earth ,, (Acts I :8). I am grateful to God to be a Baptist. I consider this to be New Testament Christianity. It is my joy to serve as the pastor of an independent Baptist church, preaching and teaching God's Word.
A Baptist recognizes the autonomy of the local church. There is no such thing as "The Baptist Church." The only Baptist headquarters that exists is in the local assembly of baptized believers. There are only local Baptist churches. \
When we say that the Bible is our sole authority, we are speaking of all the scriptures, the whole and its parts. We should preach the whole counsel of God. In the Bible we find the gospel-the death, burial, and resurrection of Jesus Christ. We should proclaim the gospel because Jesus Christ said that we are to take the gospel message to every creature. When we open the sixty-six books of the Bible, we find more than the gospel. Of course, that scarlet thread of redemption runs through all the Bible, but the whole counsel of God must be proclaimed.
The Bible says in Romans 14:11-12, ''For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God. " Each human being must answer personally to God.
In our nation we hear people talk about religious tolerance. Religious tolerance is something created by government. It is a "gift" from government. Religious tolerance is something man has made. Soul liberty is something God established when He created us. We find a clear teaching of this in His Word. Soul liberty is a gift from God! God's Word says in Galatians 5:1, "Stand fast therefore in the liberty wherewith Christ hath made us free, and be not entangled again with the yoke of bondage."
Soul liberty does not rest upon the legal documents of our nation-it is rooted in the Word of God. This individual freedom of the soul is inherent in man's nature as God created him. Man is responsible for his choices, but he is free to choose. This conviction is at the core of Baptist beliefs.
This powerful declaration about our Baptist position was made by J.D. Freeman in 1905:
Our demand has been not simply for religious toleration, but religious liberty; not sufferance merely, but freedom; and that not for ourselves alone, but for all men. We did not stumble upon this doctrine. It inheres in the very essence of our belief. Christ is Lord of all.. .. The conscience is the servant only of God, and is not subject to the will of man. This truth has indestructible life. Crucify it and the third day it will rise again. Bury it in the sepulcher and the stone will be rolled away, while the keepers become as dead men .... Steadfastly refusing to bend our necks under the yoke of bondage, we have scrupulously withheld our hands from imposing that yoke upon others .... Of martyr blood our hands are clean. We have never invoked the sword of temporal power to aid the sword of the Spirit. We have never passed an ordinance inflicting a civic disability on any man because of his religious views, be he Protestant or Papist, Jew, or Turk, or infidel. In this regard there is no blot on our escutcheon (family crest).
Remember that, when we are talking about individual soul liberty and the relationship of the church and the state, in America the Constitution does not place the church over the state or the state over the church. Most importantly, Scripture places them side by side, each operating independently of the other. This means there is freedom in the church and freedom in the state. Each is sovereign within the sphere of the authority God has given to each of them (Matthew 22:21).
Read carefully this statement made by Charles Spurgeon, the famous English preacher, concerning Baptist people:
We believe that the Baptists are the original Christians. We did not commence our existence at the Reformation, we were reformers before Luther or Calvin were born; we never came from the Church of Rome, for we were never in it, but we have an unbroken line up to the apostles themselves. We have always existed from the very days of Christ, and our principles, sometimes veiled and forgotten, like a river which may travel underground for a little season, have always had honest and holy adherents. Persecuted alike by Romanists and Protestants of almost every sect, yet there has never existed a government holding Baptist principles which persecuted others; nor, I believe, any body of Baptists ever held it to be right to put the consciences of others under the control of man. We have ever been ready to suffer, as our martyrologies will prove, but we are not ready to accept any help from the State, to prostitute the purity of the Bride of Christ to any alliance with overnment, and we wil never make the Church, although the Queen, the despot over the consciences of men.
The New Park Street Pulpit, Volume VII · Page 225
This a marvelous statement about Baptist beliefs. I am rather troubled when I see so many people who claim to be Baptists who do not understand why they are Baptists. We should be able to defend our position and do it biblically. lf we are people who know and love the Lord and His Word and if the Bible is our sole authority for faith and practice, then we have no reason to be ashamed of the position we take. May God not only help us to take this position, but to take it with holy boldness and cotnpassion. May He help us to be able to take His Word in hand and heart and defend what we believe to a lost and dying world.
So much of what we have to enjoy in our country can be credited to Baptist people. Any honest student of American history will agree that the Virginia Baptists were almost solely responsible for the First Amendment being added to our Constitution providing the freedom to worship God as our conscience dictates.
We have a country that has been so influenced that we do not believe it is right to exercise any control or coercion of any kind over the souls of men. Where did this conviction come from? We find it in the Bible, but someone imparted it to the Founding Fathers. It became the law of the land, and it should remain the law of the land. We need to understand it. It comes out of the clear teaching of God's Word concerning the subject of soul liberty.
There are many historic places there where people were martyred for their faith, giving their lives for what they believed. The religious persecution came as a result of the laws of the land. Although many Baptists have been martyred, you will never find Baptist people persecuting anyone anywhere for his faith, no matter what his faith may be.
There are many denominations that teach the Scriptures are the infallible Word of God, God is the creator of heaven and earth, man is a fallen creature and must be redeemed by the blood of Christ, salvation is the free offer of eternal Iife to those who receive it and eternal helI awaits those who reject it, the Lord's Day is a day of worship, and the only time for man to be made right with God is in this lifetime. There are certainly other commonly held teachings, but there are certain Baptist distinctive. Often an acrostic using the word BAPTISTS is used to represent these Baptist distinctive.
-
B is for biblical authority. The Bible is the sole authority for our faith and practice.
-
A for the autonomy of the local church. Every church we find in the New Testament was a self-governing church with only Christ as the head.
-
P represents the priesthood of believers and the access we have to God through Jesus Christ.
-
T for the two church officers-pastors and deacons. We find these officers in the New Testament.
-
I for individual soul liberty. Most people, when asked, say that the sole authority of the Scripture in our faith and practice is the single, most important distinctive of our faith. However, if we did not have individual soul liberty, we could not come to the convictions we have on all other matters.
-
S for a saved church membership.
Personal Accountability to God
Renowned Baptist leader, Dr. E.Y. Mullins, summarized our Baptist position in these words. He wrote:
The biblical significance of the Baptist is the right of private interpretation of and obedience to the Scriptures. The significance of the Baptist in relation to the individual is soul freedom. The ecclesiastical significance of the Baptist is a regenerated church membership and the equality and priesthood of believers. The political significance of the Baptist is the separation of church and state. But as comprehending all the above particulars, as a great and aggressive force in Christian history, as distinguished from all others and standing entirely alone, the doctrine of the soul's competency in religion under God is the distinctive significance of the Baptists.
We find this accountability in the opening verses of God's Word. When God created man, He created man capable of giving a personal account of himself to God. God did not create puppets; He created people. He gave man the right to choose. That is why we find the man Adam choosing to sin and to disobey God in Genesis chapter three. Of his own volition he chose to sin and disobey God. Genesis I :27 says, "So God created man in his own image, in the image of God created he him; male and female created he them. " We were made in God's image, and when God made us in His image, He made us with the ability to choose.
It is not right to try to force one's religion or belief upon another individual. This does not mean, however, that he can be a Christian by believing anything he wishes to believe, because Jesus Christ said that there is only one way to heaven. He said in John 14:6, "I am the way, the truth, and the life: no man cometh unto the Father, but by me." He is the only way to God. The only way of salvation is the Lord Jesus Christ.
In this age of tolerance, people say that nothing is really wrong. The same people who say that any way of believing is right will not accept the truth that one belief can be the only way that is right. You may believe anything you choose, but God has declared that there is only one way to Him and that is through His Son, Jesus Christ. He is the only way of salvation- that is why He suffered and died for our sins. The only way to know God is through His Son, the Lord Jesus Christ.
Someone is certain to ask, "Who are you to declare that everyone else's religion is wrong?" We are saying that everyone ~as ~ right to choose his own way, but God has clearly taught us in His Word that there is only one way to Him. The Lord Jesus says in John 10:9, "I am the door: by me if any man enter in, he shall be saved, and shall go in and out, and find pasture."
No human being is going to live on this earth without being sinned against by others. Many children are sinned against greatly by their own parents. However, we cannot go through life blaming others for the person we are, because God has made us in such a way that we have an individual accountability to God. This comes out of our soul liberty and our right to choose and respond to things in a way that God would have us espond to them. God has made us in His image. Again, He did not make us puppets or robots; He made us people, created in His image with the ability to choose our own way.
Remember, "For it is written, As I live, saith the Lord, every knee shall bow to me, and every tongue shall confess to God. So then every one of us shall give account of himself to God" (Romans 14:11- 12). We are responsible because we have direct access to God. God has given us the Word of God, the Holy Spirit, and access to the Throne by the merit of Jesus Christ. We, therefore? must answer personally to God at the judgment seat because God communicates to us directly.
People do not like to be held personally accountable for their actions. The truth of the Word of God is that every individual is personally accountable to God. In other words, you are going to meet God in judgment some day. I am going to meet God in judgment some day. All of us are going to stand before the Lord some day and answer to Him. We are individually accountable to God. Since the state cannot answer for us to God, it has no right to dictate our conscience.
We live in a country where there are many false religions. As Baptist people, we defend the right of anyone in our land to worship as he sees fit to worship. This is unheard of in most of the world. If a man is a Moslem, I do not agree with his Islamic religion, but I defend his right to worship as he sees fit to worship. The teaching of the Catholic Church declares that salvation comes through Mary, but this is not the teaching of the Bible. We zealously proclaim the truth, but we must also defend the right of people to worship as they choose to worship. Why? Because individual soul liberty is a gift from God to every human being.
Since the Bible teaches individual soul liberty and personal accountability to God, then it is a truth that will endure to all generations. To be sure, Baptists believe the Bible is the sole authority for faith and practice (II Timothy 3:16-17; Matthew 15:9; I John 2:20, 21 , 27) and the Bible clearly teaches that no church or government or power on earth has the right to bind a man's conscience. The individual is personally accountable to God. Hence, we reject the teaching of infant baptism and all doctrine that recognizes people as members of a church before they give evidence of personal repentance toward God and faith in the Lord Jesus Christ.
The famous Baptist, John Bunyan is the man who gave us Pilgrim's Progress. This wonderful book was planned during Bunyan's prison experience and written when he was released. The trial of John Bunyan took place on October 3, 1660. John Bunyan spent twelve years in jail for his convictions about individual soul liberty, failure to attend the Church of England, and for preaching the Word of God. During his trial, Bunyan stood before Judge Wingate who was interested in hearing John Bunyan state his case. Judge Wingate said, "In that case, then, this court would be profoundly interested in your response to them."
Part of John Bunyan's response follows:
Thank you, My 'lord. And may I say that I am grateful for the opportunity to respond. Firstly, the depositions speak the truth. I have never attended services in the Church of England, nor do I intend ever to do so. Secondly, it is no secret that I preach the Word of God whenever, wherever, and to whomever He pleases to grant me opportunity to do so. Having said that, My 'lord, there is a weightier issue that I am constrained to address. I have no choice but to acknowledge my awareness of the law which I am accused of transgressing. Likewise, I have no choice but to confess my auilt in my transgression of it. As true as these things are, I must affirm that I neiher regret breaking the law, nor repent of having broken it. Further, I must warn you that I have no intention in future of conforming to it. It is, on its face, an unjust law, a law against which honorable men cannot shrink from protesting. In truth, My 'lord, it violates an infinitely higher law- the right of every man to seek God in his own way, unhindered by any temporal power. That, My 'lord, is my response.
Remember that Bunyan was responding as to why he would not do all that he was doing for God within the confines of the Church of England. The transcription goes on to say:
Judge Wingate: This court would remind you, sir, that we are not here to debate the merits of the law. We are here to determine if you are, in fact, guilty of violating it. John Bunyan: Perhaps, My 'lord, that is why you are here, but it is most certainly not why I am here. I am here because you compel me to be here. All I ask is to be left alone to preach and to teach as God directs me. As, however, I must be here, I cannot fail to use these circumstances to speak against what I know to be an unjust and odious edict. Judge Wingate: Let me understand you. You are arguing that every man has a right, given him by Almighty God, to seek the Deity in his own way, even if he chooses without the benefit of the English Church? John Bunyan: That is precisely what I am arguing, My 'lord. Or without benefit of any church. Judge Wingate: Do you know what you are saying? What of Papist and Quakers? What of pagan Mohammedans? Have these the right to seek God in their own misguided way? John Bunyan: Even these, My 'lord. Judge Wingate: May I ask if you are articularly sympathetic to the views of these or other such deviant religious societies? John Bunyan: I am not, My 'lord. Judge Wingate: Yet, you affirm a God-given right to hold any alien religious doctrine that appeals to the warped minds of men? John Bunyan: I do, My'lord. Judge Wingate: I find your views impossible of belief And what of those who, if left to their own devices, would have no interest in things heavenly? Have they the right to be allowed to continue unmolested in their error? John Bunyan: It is my fervent belief that they do, My'lord. Judge Wingate: And on what basis, might r ask. can you make such rash affirmations? John Bunyan: On the basis, My 'lord, that a man's religious views- or lack of them- are matters between his conscience and his God, and are not the business of the Crown, the Parliament, or even, with all due respect, My 'lord, of this court. However much I may be in disagreement with another man's sincerely held religious beliefs, neither I nor any other may disallo his right to hold those beliefs. No man's right in these affairs are . secure if every other man's rights are not equally secure.
I do not know of anyone who could have expressed the whole idea of soul liberty in the words of man any more clearly than Bunyan stated in 1660. Every man can seek God as he pleases. This means that we cannot force our religious faith or teaching on anyone. It means clearly that no one can be coerced into being a Baptist and believing what we believe. It means that we can do no arm-twisting, or anything of that sort, to make anyone believe what we believe. Every man has been created by God with the ability to choose to follow God or to follow some other god.
Personal accountability to God is a distinctive of our faith. It is something we believe, and out of this distinctive come other distinctives that we identify with as Baptist people.
The Priesthood of Every Believer
The priesthood of the believer means that every believer can go to God through the merit of Jesus Christ. Christ and Christ alone is the only way to God. All of us who have trusted Christ as Saviour enjoy the glorious privilege of the priesthood of the believer and can access God through the merits of our Lord and Saviour Jesus Christ.
The Bible says in I Timothy 2: 1-6,
I exhort therefore, that, first of all, supplications, prayers, intercessions, and giving of thanks, be made for all men,· for kings, and for all that are in authority; that we may lead a quiet and peaceable life in all godliness and honesty. For this is good and acceptable in the sight of God our Saviour,· who will have all men to be saved, and to come unto the knowledge of the truth. For there is one God, and one mediator between God and men, the man Christ Jesus; who gave himself a ransom for all, to be testified in due time.
Take special note of verse five, "For there is one God, and one mediator between God and men, the man Christ Jesus."
Any man, anywhere in this world can go to God through the Lord Jesus Christ.
1 Peter 2:9 says, "But ye are a chosen generation, a royal pn~ • thood , an . holy nation, a peculiar people; that ye should. shew forth the praises of hzm who hath called you out of darkness into his marvellous light. "
Christians have access to God. You can personally talk to God. You can take your needs to the Lord. Whatever your needs are, you can take those needs to the Lord. You, as an individual Christian, can go to God through the Lord Jesus Christ, your High Priest who "ever liveth to make intercession" for you (Hebrews 7:25).
We have no merit of our own. We do not accumulate merit. People may make reference to a time of meritorious service someone has rendered, but we cannot build up "good works" that get us through to God. Each day, we must come before God as needy sinners approaching Him through the finished work of Christ and Christ alone.
The Bible teaches the personal accountability of every human being to God. We cannot force our religion on anyone or make anyone a believer. We cannot force someone to be a Christian. Think of how wrong it is to take babies and allow them later in life to think they have become Christians by an act of infant baptism. Yes, they have a right to practice infant baptism, but we do not believe this is biblical because faith cannot be forced or coerced.
There are places in the world where the state is under a religion. There are places in the world where religion is under the state-the state exercises control over the faith of people. This is not taught in the Bible. Then, there are countries like ours where the church and the state operate side by side.
Throughout history, people who have identified with Baptist distinctives have stood as guardians of religious liberty. At the heart of this liberty is what we refer to as ndividual soul liberty. I am grateful to be a Baptist.
The Power of Influence Where does this teaching of the priesthood of every believer and our personal accountability to God lead us? It leads us to realize the importance of the power of influence. This is the tool God has given us. I want to give you an Old Testament example to illustrate the matter of influence.
Judges 21 :25 tells us, "In those days there was no king in Israel: every man did that which was right in his own eyes."
In the days of the judges, every man did what was right in his own eyes with no fixed point of reference.
God's Word continues to describe this time of judges in Ruth 1:1, ''Now it came to pass in the days when the judges ruled, that there was a famine in the land. " God begins to tell us about a man named Elimelech, his wife Naomi, and his sons. He brings us to the beautiful love story of Ruth and Boaz. God tells us that at the same time in which the judges ruled, when there was anarchy in the land, this beautiful love stor of Boaz and Ruth took place.
This story gives us interesting insight on the responsibility of the Christian and the church. In the midst of everything that is going on, we are to share the beautiful love story of the Lord Jesus Christ and His bride. We need to tell people about the Saviour.
The same truth is found throughout the Word of God. Philippians 2:15 states, "That ye may be blameless and harmless, the sons of God, without rebuke, in the midst of a crooked and perverse nation, among whom ye shine as lights in the world. "
We are "in the midst ofa crooked and p erverse nation." This is why the Lord Jesus said in Matthew 5:16, "Let your light so shine before men, that they may see your good works, and glorify your Father which is in heaven. " Let your light shine!
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have diolauges. Singing that is sacred is taken out and the worlds music comes in. All revrence is gone. What so many are attempting to do in order to build up their ministry is actualy what will cause the demise of their ministry. We will never make a difference without being willing to be differnt, Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it cais the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him
The more a church becomes like the world, the less influence it is going to have in the world. Preaching ceases, and churches only have dialogue. Singing that is sacred is taken out, and the world's music comes in. All reverence is gone. What so many are attempting to do in order to build up their ministry is actually what will cause the demise of their ministry. We will never make a difference without being willing to be different. It is Christ who makes us different. Being different is not the goal. Christ is the goal, and He makes us different.
Remember, we cannot force people to become Christians or force our faith on people. It is not right to attempt to violate another man's will; he must choose of his own volition to trust Christ or reject Christ. When we understand this, then we understand the powerful tool of influence. We must live Holy Spirit-filled, godly lives and be what God wants us to be. We must be lights in a dark world as we live in the midst of a crooked generation. The only tool we have to use is influence, not force. As we separate ourselves to God and live godly lives, only then do we have a testimony.
Separation to God and from the world is not the enemy of evangelism; it is the essential of evangelism. There can be no evangelism without separation to God and from the world because we have no other tool to use. We cannot force people to believe what we believe to be the truth. They must choose of their own will. We must so identify with the Lord Jesus in His beauty, glory, and holiness that He will be lifted up, and people will come to Him.
As this world becomes increasingly worse, the more off-thewall and ridiculous we will appear to an unbelieving world. The temptation will come again and again for us to simply cave in.
When one finds people with sincerely held Baptist distinctives, he finds those people have a passion for going in the power of the Holy Spirit, obeying Christ, preaching the gospel to every creature. I am grateful to God to say, "I am a Baptist."
Baptists know it is because of what we find in the Bible about soul freedom, personal accountability, and the priesthood of every believer that we must use the power of Spirit-filled influence to win the lost to Christ. If we disobey Christ by conforming to the world, we lose our influence.
May the Lord help us to be unashamed to bear His reproach and be identified with our Lord Jesus Christ.
The Way of Salvation
Do you know for sure that if you died today you would go to Heaven?
1. Realize that God loves you
God loves you and has a plan for your life. "For God so loved the world, that he gave His only begotten Son, that whosoever believeth in him, should not perish but have everlasting life" (John 3:16 ).
2. The Bible says that all men are sinners
Our sins have separated us from God. "For all have sinned, and come short of the glory of God" (Romans 3:23). God made man in His own image. He gave man the ability to choose right from wrong. We choose to sin. Our sins separate us from God.
3. God's word also says that sin must be paid for
"For the wages of sin is death" (Romans 6:23 ). Wages means payment. The payment of our sin is death and hell, separation from God forever. If we continue in our sin, we shall die without Christ and be without God forever.
4. The good news is that Christ paid for our sins
All our sins were laid on Christ on the cross. He paid our sin debt for us. The Lord Jesus Christ died on the cross, and He arose from the dead. He is alive forevermore. "But God commendeth his love toward us, in that, while we were yet sinners, Christ died for us" (Romans 5:8).
5. We must personally pray and recieve Christ by faith as our saviour
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
Lets review for a moment
- Realize That God Loves You - John 3: 1
- All are sinners - Romans 3:21
- Sin Must Be Paid For - Romans 6:23
- Christ paid for our sins - Romans 5:8
- We Must Personally Pray and Receive Christ as Our Saviour - Romans 10:13
- Pray and recieve Christ as your saviour
Lord, I know that I am a sinner. If I died today I would not go to heaven. Forgive my sins and be my Saviour. Help me live for You from this day forward. In Jesus' name, Amen.
The Bible says, "For whosoever shall call upon the name of the Lord shall be saved" (Romans 10:13 ).
~navluc-latmes
-
-
 @ 1bc70a01:24f6a411
2023-10-02 02:22:14
@ 1bc70a01:24f6a411
2023-10-02 02:22:14Hey all! Inspired by @verbiricha of doing his quarter progress report in public, I thought I’d share what I’ve been up to and the progress made in the first quarter since the OpenSats grant award.
First, none of this would be possible without support from OpenSats and for that I am very grateful! Being able to do work on Nostr is one of the best thing I could hope for! Thank you!
TLDR;
- Launched nostrdesign.org and updated it with content, reference designs.
- Reviewed a bunch of client UI/UX and provided suggestions
- Worked on designs - snort, zap stream, and redesigned some clients, while providing visual feedback where I could.
- “Started” #nostrdesign hashtag to encourage design discussions, questions, comments, and feedback from anyone wishing to participate.
Hashtag
Since creating the #nostrdesign hashtag, we’ve seen a good amount of participation from the community. I am very pleased to see that people are using it to share design progress, ask for feedback, jumpstart ideas and propose improvements to existing clients.
The best part is that people who are not designers are able to chime in (and do so frequently) under discussions originated by designers / developers!
This is exactly what I was hoping to see happen. Instead of establishing yet an other closed group, I wanted the general user base to engage with nostr developers, express their thoughts and ideas. After all, designers don’t have all the answers, all the time.
People are asking great, and very important questions that could impact a large number of people coming into the space.
Designers are providing useful feedback to improve popular clients. I hope to see more designers get involved and chime in with their ideas!
Going forward, I would like to continue using the hashtag to encourage more participation.
Ask:
Developers - don’t hesitate to ask for feedback often. Just add #nostrdesign to your notes.
Designers - your UX ideas and design expertise are needed to make the best experiences possible. Please drop in and chime in with your feedback when possible.
Everyone - you all use the apps and your feedback is priceless! Complain as much as necessary, this is how we learn. Just tag #nostrdesign so we can come up with better solutions to existing issues.
Client Reviews & Feedback
The following is a list of clients I have provided feedback for, designed parts of, or put forth major design proposals during the first quarter (I am currently uploading recordings to a YouTube channel to make them accessible to everyone):
- Lume - onboarding review and some minor design mockups. Reya (Lume developer) said he implemented the recommendations, but I need to review again (on my to-do list). Video recording.
- Damus - home page design idea
- Stargazr - full client review, recommendations and the start of a re-designed client.
- Pinstr - provided actionable feedback for @Sepehr.
- Listr - @JeffG asked for feedback several times and I reviewed the client before and after feedback, providing further recommendations. (Round 1, Round 2 feedback)
- Slidestr - provided feedback and designed what I would consider to be the ideal experience.
- Swarmstr - @pitunited asked for feedback and I reviewed the entire client.
- Current (iOS) - egge asked for feedback and I created an issue in their GitHub, along with a video.
- 0xChat - water asked for feedback. I reviewed the client on video and made recommendations.
- Nostree - provided feedback and design ideas
- Primal - some design ideas which may or may not make it into production, we’ll see!
- noStrudel - minor feedback and designing some ideas for @hzrd149
- Habla (work in progress). I have provided some styling and UX feedback and I’m currently working on designing the changes.
- Spring - Artur approached me about the idea behind Spring and needed some help shaping his vision. I designed the product experience (Figma file) and he implemented it on Android, perhaps with his own ideas mixed in.
- Yana - Yana asked for a full review and I provided a recording of my initial experience and recommendations.
- Nosta - Christoph asked me to review the client, and I did so in full, providing my experience, ideas and recommendations. Christoph is now implementing some of the ideas / recommendations!
- Vendata - Pablo asked me to look at the current state of the (proposed?) redesign and I chimed in with my thoughts.
- NostrNet.work - I really liked the project and pitched an unsolicited design idea.
- PlebeianMarket - @Chiefmonkey asked for feedback on PM. I provided a recording of my thoughts.
- Snort - snort has seen many improvements in features. Kieran and I are working closely to shape the client. I redesigned Snort for version 2 that he managed to ship not long ago. This was a major project. I also updated Snort’s CSS, both dark and light mode and improved some of the UX directly through a pull request.
- Zap.stream - I am also working with Kieran on a continuous basis to improve zap.stream. Due to Snort V2 being in the works at that time, we didn’t have as much time to work on zap.stream but we managed to add a new onboarding flow which I designed. Roland did a lot of the work on development side. I am currently engaging Kieran to see what needs to be done next.
Design Help
The following is a list of clients I was involved with, ranging from major contributions to minor enhancement proposals:
- Snort (major)
- zap.stream (major)
- Damus (minor)
- Spring (major)
- NostrNet.work (somewhere in between)
- Primal (minor)
- Habla (major initially, now minor)
- Nostree (none initially, major design mockups currently)
- Pinstr (design ideas mockups)
- Slidstr (design ideas mockups)
- Stargazr (none initially, major design mockups currently)
Nostr Design Guide
In Q1 https://nostrdesign.org/ was born! There were some technical challenges (for me personally), but thanks to help from Gigi and Daniele, the resource is live.
I’ve made substantial progress in content, including reference designs. The bulk of the time on the guide is in reference designs.
The guide still needs additional examples, and some of the content is missing (like Accessibility). This is a work in progress.
The reference components are ongoing endeavor. I’d like to cover all the basic use cases, desktop and mobile and provide guidance on any new questions that come up (such as mute words).
Since the launch of the guide I have seen a lot of positive feedback with people frequently referencing the website (even on live streams). I am humbled by this and hope to make the resource even more useful.
Next Quarter Plan
In the following quarter, I plan on allocating my time as follows:
- Rounding out the nostr design guide with examples.
- Reference components for nostr design guide - especially the crucial parts that are asked about the most.
- Following up on the feedback I have provided for various clients and devs to see if they are acting on it, why not if not, and if there’s anything I can do to help them make progress.
- Providing Quality Assurance reviews on the work that was implemented.
- Improving existing clients with better UX ideas.
- Engaging with the nostr community to find better ways of doing things, learning about what’s working and what’s not working.
- Exploring UI / UX improvements on new ideas put forward by developers and the general nostr community.
- Helping clients think about growth and monetization strategies. I have already outlined some ideas for Snort (informal ideas) and Zap.stream
Got feedback?
Clients, designs, business ideas, personal, any feedback you have, I am all ears! You can leave comments right on this note, DM me, or email karnage@opensats.org. I take note of all the feedback and consider individually, so you’ll always be heard. Thank you!
-
 @ a4a6b584:1e05b95b
2023-07-25 23:44:42
@ a4a6b584:1e05b95b
2023-07-25 23:44:42Introducing Box Chain - a decentralized logistics network enabling private, secure package delivery through Nostr identities, zero-knowledge proofs, and a dynamic driver marketplace.
Identity Verification
A cornerstone of Box Chain's functionality and security is its identity verification system. Drawing on the principles of decentralization and privacy, it eschews traditional identifiers for a unique, cryptographic solution built on the Nostr protocol.
When a new user wishes to join the Box Chain network, they begin by generating a unique cryptographic identity. This identity is derived through complex algorithms, creating a unique key pair consisting of a public and a private key. The public key serves as the user's identity within the network, available to all participants. The private key remains with the user, a secret piece of information used to sign transactions and interactions, proving their identity.
Unlike many centralized systems, Box Chain does not require any form of real-world identification for this process. This is crucial for a few reasons. First, it ensures the privacy of all participants by not requiring them to disclose sensitive personal information. Second, it allows Box Chain to operate independently of any jurisdiction, enhancing its universal applicability.
Once their identity is established, participants engage in the network, accepting and fulfilling delivery tasks. Each successful delivery, confirmed by the receiver, contributes to the participant's reputation score. This reputation score is publicly linked to their identity and serves as a measure of their reliability and performance.
A critical aspect of mitigating potential identity fraud is the stake requirement. Each participant, before they can accept a delivery task, is required to stake a certain amount of Bitcoin. This acts as a form of collateral, held in escrow until the successful completion of the delivery. The staked amount is forfeited in case of fraudulent activities or non-delivery, creating a strong financial disincentive against dishonest behavior.
Overall, the identity verification system in Box Chain, built on unique cryptographic identities, a reputation score system, and the staking mechanism, provides a robust framework to ensure reliability and trust in a decentralized, borderless context. It significantly mitigates the risks of identity fraud, further strengthening Box Chain's promise of secure, efficient, and private package delivery.
Zero-Knowledge Proof Shipping Information
Box Chain's unique approach to preserving privacy while ensuring accurate delivery relies heavily on the concept of Zero-Knowledge Proofs (ZKPs). This cryptographic principle allows for the verification of information without revealing the information itself.
When a package is set for delivery, the sender provides the recipient's address. This address is immediately subjected to cryptographic transformation - the details are processed and turned into a form that is impossible to understand without a specific decryption key. This transformation process is designed to ensure maximum privacy - the original address remains known only to the sender and, eventually, the recipient.
In this transformed state, the address can still be verified for its validity without revealing its actual content. This is where ZKPs come into play. The sender, by leveraging ZKPs, can prove to the Box Chain system that they possess a valid address without needing to reveal the specifics of that address. This protects the privacy of the recipient by ensuring their address isn't openly visible on the system.
For the delivery process, the route is broken down into relay points, each assigned a particular driver. This relay-based system plays a significant role in preserving privacy and ensuring package safety. Instead of providing the entire route to each driver, they only receive the location of the next relay point. This is accomplished by giving them a cryptographic key which, when applied to the encrypted route data, reveals only the necessary information - the location of the next relay driver.
This way, the sender's address and recipient's final address remain as private as possible. Moreover, it enables the package to be securely handed off from one relay driver to the next, each having access to only the information necessary for their leg of the journey.
It's important to note that this process, while extremely secure, can take a longer time due to its relay nature and the cryptographic processes involved. There may also be a need to introduce a timeout mechanism for each leg of the journey to ensure drivers complete their part in a reasonable timeframe.
By incorporating ZKPs and a relay-based delivery system, Box Chain is able to provide a level of privacy and security that is rare in the logistics world, striking a balance between efficiency and privacy.
Delivery Confirmation
One of the key aspects of ensuring the success and trustworthiness of Box Chain's decentralized package delivery service is the process of delivery confirmation. To make this process as secure, transparent, and reliable as possible, Box Chain implements a multi-signature approach that leverages the power of cryptography.
When a delivery is made, it is not enough to simply leave the package at the prescribed location. Confirmation of delivery is critical to ensure the transaction is closed and the delivery person can receive their payment. This is where the multi-signature approach comes into play.
In essence, a multi-signature approach means that more than one party needs to provide a digital signature to confirm the transaction. For Box Chain, this involves both the receiving party and the delivery person. After the delivery person leaves the package at the prescribed location, they would use their private cryptographic key to sign a confirmation of delivery. The recipient, upon receiving the package, would do the same.
These digital signatures are securely generated using each party's private key and are incredibly difficult, if not impossible, to forge. This means that when both signatures are provided, the system can be confident that the package was delivered and received successfully.
As a further layer of security and accuracy, Box Chain incorporates geolocation confirmation into its delivery confirmation process. This means that when the delivery person signs the confirmation of delivery, their geographic location is checked against the intended delivery location. If the two locations match within an acceptable margin of error, this acts as another layer of proof that the delivery was made successfully.
This process ensures that delivery confirmations are not only secure but are also indisputable. It provides a significant level of trust and reliability, both for the sender and receiver, but also for the delivery people who are looking to receive their payments.
Furthermore, it aligns with the principles of decentralization and privacy, leveraging the power of cryptography and blockchain technology to provide a secure, transparent, and effective service. This approach positions Box Chain as a pioneer in combining the gig economy with the blockchain technology, providing a unique and secure package delivery solution.
Package Security
Guaranteeing the security of packages throughout transit is fundamental to Box Chain's service offering. To accomplish this, Box Chain utilizes a unique stake system that incentivizes delivery drivers to handle packages with the utmost care.
When a sender initiates a delivery, they specify the value of the package being shipped. This value is used to determine the stake amount that the delivery person must deposit to accept the delivery task. The stake functions as a form of shipping insurance, held in escrow by the Box Chain system until successful completion of the delivery.
The stake amount set by the sender is commensurate with the value of the package, allowing the sender to decide how much insurance they deem appropriate for their shipment. Higher-value packages may necessitate a larger stake, serving to reassure the sender that the delivery person has a significant financial incentive to ensure the safe delivery of the package.
In the event that a package is lost or damaged, the stake acts as a safety net for the sender. The staked amount is forfeited by the delivery driver and is transferred to the sender as compensation for their loss.
This system not only provides reassurance to the sender, but also gives a powerful incentive for delivery drivers to handle the packages with care. By having their own funds at risk, delivery drivers are likely to go the extra mile to ensure packages are safely delivered to their destination.
Further enhancing the security of the package, Box Chain uses a multi-signature approach during the relay handoff process. The current delivery driver and the next relay driver must both provide a digital signature to confirm the handoff. This ensures that responsibility for the package is officially transferred from one party to the next in a secure and verifiable manner. This "chain" of signatures creates an auditable trail that adds another layer of security and trust to the process.
Through the combination of a stake system and multi-signature handoff confirmation, Box Chain provides a comprehensive security solution that ensures packages are not only delivered efficiently but are also safeguarded throughout their transit journey.
Routing Algorithm and Pricing Mechanism
The efficiency and economic fairness of Box Chain's service hinge significantly on its innovative routing algorithm and pricing mechanism. This system is designed to ensure a smooth journey for each package, while also ensuring that delivery drivers are fairly compensated for their work.
The journey of a package begins with the sender specifying the destination and offering a starting payment for delivery. This payment information is propagated to the network, along with the package's destination, where potential delivery drivers can view it. However, unlike traditional package delivery services, the journey and price aren't fixed from the onset. Instead, Box Chain employs a dynamic, decentralized, and market-driven approach to optimize routing and pricing.
The total journey is divided into smaller legs, each of which can be undertaken by different delivery drivers. The starting payment offered by the sender is not a flat rate for the whole journey but is instead used as an initial bid for each leg of the journey. This bid is then doubled, and the network waits for a delivery driver to accept the offer. If no one accepts, the bid continues to increase in increments, creating an auction-like environment.
This system allows the real-time market dynamics to determine the cost of delivery. Factors such as distance, package weight, or even current traffic conditions can influence how much a delivery driver is willing to accept for a leg of the journey. If a leg of the journey is particularly difficult or inconvenient, the price will naturally rise until it reaches a level that a delivery driver deems worthwhile.
By allowing the drivers themselves to choose which jobs to accept based on their own assessment of the work's value, Box Chain creates a fair, flexible, and dynamic market where compensation is closely tied to the effort and resources required to complete a delivery. This is akin to how the Tor network or the Lightning Network operates, but instead of data packets being routed and priced, Box Chain is doing this with physical packages in the real world.
Such a system not only incentivizes delivery drivers to participate but also ensures the service remains adaptable and resilient to changing conditions and demands. This represents a novel and intelligent use of blockchain technology to disrupt the traditional gig economy model, placing the power in the hands of the individual drivers and fostering a more equitable and efficient market.
Incentive for Participation
Box Chain's unique approach to package delivery provides a plethora of compelling incentives for individuals to participate in the network as delivery drivers. By offering the potential for higher earnings through a competitive and dynamic bidding system, Box Chain encourages active participation and healthy competition within its network.
Upon initiating a package delivery, the sender offers a starting bid for each leg of the journey. This bid is then escalated through the network, doubling with each round until a delivery driver accepts the task. This mechanism presents delivery drivers with the opportunity to earn more for their services, especially in cases where the journey is long or complex.
However, the competitive aspect of the bidding system also helps regulate the pricing. Although prices might be high initially, as more delivery drivers join the network and competition increases, the bid required to win a delivery job is likely to decrease. This dynamic balance ensures a fair market price for delivery services while also enabling delivery drivers to optimize their earnings.
Furthermore, Box Chain's reputation system, based on the Nostr protocol, provides an additional layer of incentive for delivery drivers. The reputation of each driver is tracked and publicly displayed, allowing senders to gauge the reliability and efficiency of their potential couriers. As drivers successfully complete deliveries and earn positive feedback, their reputation score increases.
This reputation score can play a pivotal role in the Box Chain economy. Drivers with higher reputation scores may demand higher bids for their services, reflecting their proven track record of successful deliveries. Alternatively, the system could grant priority in the bidding process to drivers with higher reputation scores. This not only incentivizes good performance and reliability but also helps to foster trust within the network.
Overall, Box Chain's combination of a competitive bidding system and a reputation-based incentive structure encourages active participation and ensures a high standard of service. By aligning economic incentives with high-quality service delivery, Box Chain empowers its participants while also ensuring a satisfying experience for its users.
Here is an additional section covering dispute resolution and failed delivery handling that could be added:
Dispute Resolution and Failed Deliveries
For a decentralized network like Box Chain, dispute resolution and handling of failed deliveries present unique challenges. To address these in alignment with its principles, Box Chain implements an arbitration-based system and a dual-stake mechanism.
In case deliveries fail due to recipients being unavailable or refusing, both the sender and recipient are required to stake funds as collateral. If the delivery cannot be completed, the stakes are forfeited and awarded to the delivery driver as compensation for their time and effort. This creates a disincentive for recipients failing to receive packages and ensures drivers are paid for their work.
For disputes between senders, recipients and drivers, Box Chain leverages a decentralized arbitration system built on the Nostr protocol. Independent arbitrators stake their own funds and adjudicate disputes based on review of evidence from both parties. Their incentive is a small percentage of the transaction amount.
The arbitration process involves submission of dispute details, review of evidence, ruling based on policies, and appeals handled by additional arbitrators if required. A majority ruling wins the appeal. This system, relying on staked incentives and the wisdom of the crowd, enables fair dispute resolution aligned with Box Chain's ethos.
By combining reciprocal stakes and decentralized arbitration, Box Chain is able to provide robust recourse around failed deliveries and disputes while retaining its principles of decentralization, privacy, and aligned incentives. These mechanisms strengthen the system and instill further user trust and satisfaction.
Bitcoin + Nostr = <3
The combination of Bitcoin and Nostr represents a powerful and synergistic integration of decentralized technologies. Bitcoin provides a secure, transparent and decentralized means of value transfer, while Nostr offers a decentralized protocol for creating and managing digital identities and data. Together, they can enable truly decentralized and privacy-preserving applications, like Box Chain, that have the potential to disrupt traditional business models and empower individuals around the world. The future looks promising with such advanced and transformative technologies working hand in hand.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ 75656740:dbc8f92a
2023-07-21 18:18:41
@ 75656740:dbc8f92a
2023-07-21 18:18:41"Who do you say that I am?"
In Matthew 16 Jesus cut to the heart of what defines identity. First he asked what other people said about him, then he asked what the disciples thought, finally he gave his own take by agreeing with the disciples. In trying to understand who someone is, we have three and only three possible sources of information.
- Who they tell us they are.
- Who others say about them.
- What we observe for ourselves.
Putting these three together constitutes identity. Identity is always unique for each connection in the social graph. Who you are to me is always different than who you are to anyone else. As such identity is largely out of our direct control. We can influence others perception of ourselves by comporting ourselves in a certain way, but we cannot compel it.
With this in mind, it is imperative to build protocols that mirror this reality as closely as possible. The problem is largely one of UI. How can we simultaneously display all three aspects of identity in a clear and uncluttered way?
The default has always been to just display an individual's claim to identity. Each user gets to choose a name and an avatar. This generally works in small communities with low rates of change both in who the members are and in how they present themselves. In these cases, each user can keep a mental map of what to expect from each name and avatar. "Oh that is just keyHammer24 doing his thing." Note that even if KeyHammer24 decides to change their nickname the mental map in the other users won't change instantly, if ever.
This falls apart in larger communities, where each user cannot maintain a mental model of who is who. Impersonation and collisions become a problem, so we add some "What others say about them" information such as blue check-marks or what "what we observe for ourselves" information like pet-names in a phone contact list or a note that we follow that account.
I don't personally have a final solution for this, I only know that we should be collecting and displaying all three sources of information from the outset. Perhaps we could do something like... * Default to showing a users preferred identifiers, but switch to the avatar and handle we self-assign them on hover. * Display a percentage of confidence that we know who the person is and that they are presenting themselves as who we expect them to be. You probably aren't the Elon Musk that I expect if you recently had different names / aren't the one I follow / none of my network follows / have been reported as misleading. * Reserve check-marks for keys that each user has signed in person. Only we can be the arbiter of who gets a check-mark in our own feed. * Maintain a list of past aliases along with a "Community Notes" like description of an account brought up by clicking on a ⓘ icon. * Have a full pet-names override.
I think Nostr already have much of this built into the protocol, it just needs to be standardized into the interface of various application. This is something on which I am very interested in hearing other ideas.
A note on anonymity
Real world identities should always be preferred. It allows for building real relationships and treating each other with real world respect. The real you is far more fascinating than a curated persona. Real identities should also never be enforced at a protocol level. Some people will be in real circumstances that preclude honest engagement without threat to their safety.
If you found this engaging I also wrote about why Social Network companies have an unsolvable problem here. and why we have to design for finite reach here
-
 @ 3335d373:91ded1de
2023-09-28 18:31:03
@ 3335d373:91ded1de
2023-09-28 18:31:03Details
- ⏲️ Prep time: 5 min
- 🍳 Cook time: 25 min
- 🍽️ Servings: 1-2
Ingredients
- 1 steak
- butter
- salt
- pepper
Directions
- preheat oven to 200F
- put the steak in a cast iron skillet
- put the steak in the oven for 20 minutes, flipping half way through
- take the skillet out, set steak aside, put the skillet on stove. get it really hot.
- pat the steak dry with paper towels. this helps it sear better.
- put salt and pepper on the steak
- put some butter in the skillet
- put the steak in the skillet for 2-3 minutes until one side is brown
- flip it over and cook till the other side is brown
- use tongs to quickly sear the sides of the steak
- bone apple teeth
-
 @ 52387c6b:49dbdfb2
2023-09-28 16:13:57
@ 52387c6b:49dbdfb2
2023-09-28 16:13:57Chef's notes
Not a health snack by any means but sometimes you just have too.
Details
- ⏲️ Prep time: 1
- 🍳 Cook time: 0
- 🍽️ Servings: 1
Ingredients
- 1 Bag of Chips
- 1 Bottle of Wooster
- 1 Bowl
- Many Beers
Directions
- Open Chips
- Pour chips into bowl
- Add Wooster to taste
-
 @ 1bc70a01:24f6a411
2023-09-28 00:41:33
@ 1bc70a01:24f6a411
2023-09-28 00:41:33Chef's notes
You can substitute mussels with clams, or do both, and even add shrimp if you like. I don't measure anything, just eyeball everything and use any amounts of clams or mussels you like as long as it feels proportionate with spaghetti. Depending on the thickness of your spaghetti, you may need to cook it ahead of time, or at the same time as the toppings.
Details
- ⏲️ Prep time: 5
- 🍳 Cook time: 10
- 🍽️ Servings: 2
Ingredients
- Thin spaghetti
- Tomatoes (any kind)
- Garlic
- White Wine
- Salt
- Parsley (Optional)
- Parmesan Cheese (Optional)
- Mussels or Clams
- Olive Oil
Directions
- Wash and clean your mussels or clams. You can keep them in salted water so they open up and spit out any sand.
- Heat up olive oil in a large pan or a deep pan, depending on how much pasta and mussels you're making. Deep frying pan is usually enough for 2 people
- Add thinly sliced garlic
- Throw in the washed mussels or clams, or both
- Add white wine. Eyeball the amount - enough to let the mussels sit comfortably half-covered.
- Cover with lid and steam on high heat until all of the mussels open up
- Throw in chopped tomatoes. Use many, at least a cup. There's no such thing as too many tomatoes.
- Salt everything generously
- Steam for a few more minutes
- Meanwhile, you should have your pasta ready or boiling to be ready any time. Do not overcook it! Cook to "al dente" texture (basically the minimum recommended cooking time)
- Strain pasta but don't rinse. Add directly to your mussel-tomato-wine sauce and stir it all together. Turn off the heat, it's done!
- Plate in a large bowl. Top with finely chopped parsley if you want, and grated parmesan cheese. Hot sauce optional. Enjoy!
-
 @ a4a6b584:1e05b95b
2023-07-21 01:51:34
@ a4a6b584:1e05b95b
2023-07-21 01:51:34Is light really a constant? In this blog post by Adam Malin we theorize about redshift caused not by expanding space, but by changes in zero point energy field over cosmic time
I was inspired to write this post after reading a paper written in 2010 by Barry Setterfield called Zero Point Energy and the Redshift. If you want a very deep dive into this concept, I recommend you check it out. Here is the link.
I recently read an intriguing paper that puts forth an alternative explanation for the redshift we observe from distant galaxies. This paper, published in 2010 by Barry Setterfield, proposes that redshift may be caused by changes over time in the zero point energy (ZPE) field permeating space, rather than cosmic expansion. In this post, I'll summarize the key points of this theory and how it challenges the conventional framework.
An important distinction arises between Stochastic Electrodynamics (SED) and the more mainstream Quantum Electrodynamics (QED) framework. SED models the zero point field as a real, random electromagnetic field that interacts with matter, possessing observable physical effects. In contrast, QED considers virtual particles and zero point energy as mathematical constructs that do not directly impact physical systems. The zero point energy discussed in this proposed mechanism builds upon the SED perspective of modeling the quantum vacuum as a dynamic background field that can exchange energy with matter. SED provides a means to quantitatively analyze the redshift effects hypothetically caused by changes in the zero point field over cosmic time.
The standard model of cosmology attributes redshift to the Doppler effect - light from distant galaxies is stretched to longer wavelengths due to those galaxies receding away from us as space expands. Setterfield's paper argues that the data actually better supports a model where the speed of light was higher in the early universe and has decayed over time. This would cause older light from farther galaxies to be progressively more redshifted as it travels through space and time.
Setterfield cites historical measurements of the speed of light by scientists like R.T. Birge that showed systematic decreases over time, contrary to our modern assumption of constancy. He argues that while experimental improvements have reduced uncertainties, residual trends remain even in recent high-precision measurements.
A key part of Setterfield's proposed mechanism is that the ZPE interacts with subatomic particles to give them mass and stabilize atomic orbits. As the ZPE has increased in strength over cosmic history, it has caused a contraction in electron orbits within atoms. This results in electron transitions emitting bluer light over time. Thus, looking out into space is looking back to earlier epochs with weaker ZPE and redder light.
This theory raises some thought-provoking questions. For instance, have we misinterpreted redshift as definitive evidence for an expanding universe? Might a static universe with slowing clocks account for observations we attribute to dark matter and dark energy? However, changing existing scientific paradigms is extremely challenging. Let's examine some potential counterarguments:
- The constancy of the speed of light is a fundamental pillar of modern physics backed by extensive experimental verification. This theory would require overturning tremendous empirical support. Setterfield argues that Lorentz and others kept an open mind to variations in c early on. While unexpected, new evidence could prompt another evolution in perspective.
- The current Lambda-CDM cosmological model based on general relativity matches a wide array of observations and predicts phenomena like the cosmic microwave background. But it also has issues like the need for speculative dark matter and dark energy. An alternate cosmology with varying c may provide a simpler unifying explanation.
- Astrophysical observations like supernova brightness curves seem to confirm expanding space. But these interpretations assume constancy of c and other principles that this hypothesis challenges. The cosmic microwave background, for instance, could potentially be re-interpreted as a cosmological redshift of earlier light.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ a723805c:0342dc9c
2023-09-27 13:56:38
@ a723805c:0342dc9c
2023-09-27 13:56:38Chef's notes
Portuguese dishes are typically simple, relying on the quality of the ingredients rather than complex seasonings. Make sure to use fresh ingredients and good quality olive oil. Portuguese Soup is often served with Portuguese cornbread (broa) on the side. If you have access to this, it complements the soup beautifully.
Details
- ⏲️ Prep time: 15 minutes
- 🍳 Cook time: 45 minutes
- 🍽️ Servings: 8
Ingredients
- 2 tablespoon of olive oil
- 2 cups of chopped onions
- 1 pound chorizo, sliced or cubed
- 6 potatoes, peeled and cubed (a starchy russet recommended)
- 2 (15 ounce) cans kidney beans
- 1 (15 oz) can of diced tomatoes
- 3-4 cloves of garlic
- 2 quarts of chicken stock
- 2 teaspoons garlic powder
- 2 teaspoons ground black pepper
- 1 teaspoon salt
- 1 tablespoon Worcestershire sauce
- 2 cups of collard greens or kale finely sliced
Directions
- In a large pot over medium heat, cook onions and garlic in olive oil until just tender.
- Saute chorizo and set aside.
- Place potatoes, beans, tomatoes and chicken stock in the pot. Season with Worcestershire, garlic powder, pepper and salt. Bring to a boil, then reduce heat and simmer 30 to 45 minutes.
- Add greens and sautéed chirzo let cook for another 10 minutes
- Serve and enjoy!
-
 @ 97c70a44:ad98e322
2023-09-26 23:53:37
@ 97c70a44:ad98e322
2023-09-26 23:53:37I've never piloted one, but I'm inclined to think that a coracle would be very hard to steer. No rudder, no keel, the thing is circular, it's not exactly a seagoing vessel. I've found the same to be true of my eponymous software project. I have many definite ideas of where I want it to go, most of which are in tension with one another. Plus, I'm prone to getting distracted by adding new features that aren't really core to my mission (whatever it is).
What it ain't
That fact was brought home to me this week as I worked for the nth time to repair the damage my refactoring did to the public chat feature in Coracle. This was the first feature I added as a response to popular demand and hype over a new NIP being added to nostr, way back in December 2022. Coracle was (I believe) the first general-purpose client to support public chat, which I hoped would bolster its notoriety.
I don't know if it helped Coracle's popularity, but it has cost me several weeks of development time in maintenance and abstraction cost since it was introduced. While it wouldn't be hard to apply the same content filtering work I've added to feeds in Coracle to chat, I'm not sure I want to continue to have my time stolen by sunk cost. And with the increasing frequency with which chat groups are being hijacked by spammers of various kinds, I no longer have the option of leaving chat alone.
So I've decided to remove group chat from Coracle. The implementation is still available, at chat.coracle.social, but unless a wild maintainer appears, it won't be receiving any updates for the foreseeable future. Chat was never a goal of my project, and while it may be one of the more popular features of Coracle, it's one of the least crucial.
This is just one of many illustrative features. In the same release in which I removed chat, I also added a background music player for kind 1808s. This is equally frivolous — but even more fun. It will likely live for a while, and disappear again someday.
Set a course for ???, warp speed
Now that Coracle is basically working™️ I need to take a step back and figure out what I want it to be. Even if I don't know where I'm headed, I'm still moving pretty fast. In order to make the best use of my grant from OpenSats, it's imperative that I at least have a mission statement.
In explaining to Vitor why I was removing chat, I accidentally articulated a pretty good one:
nostr:nevent1qqsfwxqv4qq5ajdx8yaksg2fwcw0enpykxvkl9kf2meqgheaq7f3ycgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdufeeexz
The reason for this emphasis comes from the people I originally set out to build for: my church community. These people are generally not "internet-native". They aren't active on reddit, twitter, discord, twitch, tiktok, or youtube. To the extent they use social media, they post pictures on instagram, and buy and sell goods on facebook marketplace.
The features required to support a facebook analog are fairly obvious, and include event calendars, private groups, and marketplaces. However, there are a few dimensions to the problem that make building such a product more challenging than building a twitter clone.
Product complexity
One of the most consistent pieces of advice I've received about building a facebook clone is: don't. Facebook succeeded because it bundled multiple standalone tools into a single interface, and tied them together with a single social graph.
This is one of the things nostr solves — no longer do you need an everything app, if you can use micro-apps on an everything protocol. When I built zephyr last week, I was again stunned at how powerful building on nostr is. In half a day I put together something that would be impossible with traditional technologies — because if you don't have the ability to produce content on a centralized platform, you don't have the ability to consume it either.
But protocols feel different from platforms, especially for the layman. The other half of facebook's value add is (was) a simple and intuitive user interface, which not only made the different components available, but made them accessible as well. I don't think micro-apps, web app stores, or nostr browsers are complete solutions to the UX problem. Nothing can replace a design tailored to your specific end user.
Privacy and parochialism
Social graph partitioning is an essential part of designing a social network. In twitter-like applications, an an effective strategy might be described as "whatever". In other words, as long as you are able to 1. connect to the people you want to follow and 2. discover new content, you're fine — there's no need to be exhaustive or exclusive.
But tighter-knit communities require exclusivity. And by "community" I should qualify that I do not mean a reddit-style common interest, but a real locus of interdependence — whether intellectual, economic, or familial. You don't self-select into true communities except by way of a long (sometimes very long) probationary period.
But, as we learned from mastodon's failures, people are also members of multiple overlapping communities simultaneously. This means that an application designed to serve a person in multiple roles across multiple communities needs to be able to address those differing social circles according to their permeability. Enforcing community privacy using encryption might be appropriate for very tight groups like families, while other groups might want more lax rules about content sharing or member admission.
On nostr, relays are an excellent primitive for implementing access controls, and may be sufficient for all but the most private communication. I've also experimented with encrypted groups (nostr-in-nostr), but the juice might not be worth the squeeze — the additional complexity of gift wrapping might not be necessary if relays can be trusted not to leak data.
Two different approaches to group-specific relays could be used, depending on the level of trust required for the community: an Uncle Jim model where one or more admins host the infrastructure, or a virtual relay model where the group admin creates a private space on commoditized infrastructure.
The value of decentralization at a small scale
Now, of course if you have admins, you've basically opted back in to siloed, centralized platforms, unless shared identity is a value add. Single sign on could be attractive, but not overwhelmingly so — I think the thing that makes an identity shared across multiple platforms compelling is the ability to cross-post.
Unless content is protected by encryption, this is always possible, and would be very good for end users. Allowing content from outside a group to be pulled into a group allows the group to comment on it using its own idioms and values. It also enables loose coupling between weakly-related communities (for example a church and the town it is located in).
This would work very well for community groups, which aren't usually too picky about driving engagement, but would work less well for publishers or media brands, even if cross-posting of content would be beneficial to their curated communities. Instead of increasing the value of your community, it could be seen (and exploited) as advertising for competing siloes.
Multiple types of engagement
Finally, there are multiple types of relationship that might be emphasized to a greater or lesser degree in one community vs another. Facebook-style "friends" are generally less focused on ideas, and more on maintaining relationships. I wouldn't want to read what my mom posts on social media, but I do want to stay in touch with her. In contrast, twitter-style "follows" are more oriented towards the flow of information itself, rather than relationships. An application directed at handling both types of "community" would need to respect the difference between the two.
Toward something, anything
With all that in mind, here's an attempt at articulating my vision for Coracle, loosely based on the EOS model (no, not that EOS).
While my focus above has been on individuals as members of real-life communities, in practice many of these groups can be defined by a common interest in a given content "publisher", which is a more concrete (and practical) use case. This might be something as big as a newspaper, or as small as a substack or patreon. The content provides something for members of the group to talk about.
It seems to me that groups that are not content-focused operate in much the same way, except that topics are selected by group members, rather than by administrators. So the general strategy would be to build a product that can be used more informally by primarily targeting content publishers.
Core Values
- Real life > digital life
- Inorganic advertising is cancer
- Encourage purposeful engagement
- Different communities should be distinct, but mutually beneficial
Mission Statement
To enrich the social media experience of individuals in their capacity as members of multiple overlapping real-world intellectual, economic, or relational communities.
Target Market
Small publishers who want to create a place for subscribers to interact with the publisher's (public and paid) content and one another. Media brands who are open to the benefits of cross-posting across siloes.
What does it look like?
- Anyone can create a group hosted on self-hosted or commodity relays, or a mixture of both.
- A mixture of public and encrypted content for a given group
- Cross-posting of public content between groups
- Private content exclusive to group members
- Multiple tiers of group membership
- Configurable access control: admins, moderators, write access, read access
- Invite codes, including referral discounts/rewards
- Integrated calendar events (public and private)
- Integrated marketplaces (publisher merchandise or peer-to-peer)
- Support topical threads (oriented around publisher content) and member microblogging
Goals
- A relay implementation that supports virtual relays with all required access controls
- A group spec that supports granular content permissions and visibility
- An end-user interface that supports browsing multiple groups and non-group content
- An admin interface for group administration
- White-labeled configurable client implementation
Addendum: Ditto
Alex Gleason has been working on Ditto of late, which is first of all a way to reconcile ActivityPub and Nostr using a server implementation that supports both protocols, but which has the interesting side effect of marrying the siloed, exclusive ActivityPub model with nostr identities. This could be a good solution for branded clients and tighter community control, especially since it allows for the use of existing tools from ActivityPub's more mature ecosystem.
I intend to keep a close eye on Ditto as it matures. I hope that even if the two projects have a significant amount of overlap, that the problem space is big enough to allow for variations in execution, especially since Coracle has the ability to be fully nostr-native.
Conclusion
If you're currently a user of Coracle, don't worry too much, I won't be making any drastic changes anytime soon. I do think that the twitter-like, group-independent part of nostr is valuable, at least as a supplement to more cohesive communities. However, in order to achieve such an ambitious project, I'll have to exercise the discipline to remain focused and cut out any fat that accumulates. We'll see how I do.
-
 @ a4a6b584:1e05b95b
2023-07-21 01:44:57
@ a4a6b584:1e05b95b
2023-07-21 01:44:57The French sociologist and philosopher Jean Baudrillard offered profound critiques of modern society, technology, media and consumer culture through his work. Often associated with postmodernism and post-structuralism, Baudrillard challenged established notions of truth, reality and the power dynamics between humans and the systems they create.
In this blog post, we'll explore some of Baudrillard's most notable concepts and theories to understand his influential perspectives on the contemporary world.
Simulacra and Simulation
One of Baudrillard's most well-known works is "Simulacra and Simulation." In the book, Baudrillard argues that our society has replaced reality and meaning with symbols, images and signs that he calls “simulacra.”
He believed human experience is now a simulation of reality rather than reality itself. Unlike simple imitations or distortions of reality, simulacra have no connection to any tangible reality. They are mere representations that come to define our perception of existence.
To illustrate this concept, Baudrillard outlined three “orders” of simulacra:
-
First Order: Copies or imitations that maintain a clear link to the original, like photographs.
-
Second Order: Distortions of reality that mask the absence of an original, like heavily edited advertising images.
-
Third Order: Simulations with no original referent that become “hyperreal,” like video game worlds.
Per Baudrillard, much of postmodern culture is made up of third-order simulacra. Media representations and simulations hold more meaning than reality, creating a “hyperreality” driven by consumerism and spectacle.
Hyperreality
Building on his theory of simulacra, Baudrillard introduced the concept of “hyperreality” to describe how representations and simulations have come to replace and blur boundaries with reality.
In hyperreality, the lines between real life and fictional worlds become seamless. Media, technology and advertising dominate our perception of reality, constructing a simulated world that appears more real and appealing than actual reality.
For example, the carefully curated lives presented on social media often appear more significant than people’s daily lived experiences. Additionally, idealized representations of reality presented in movies, TV and advertising shape our expectations in ways that real life cannot match.
According to Baudrillard, we increasingly interact with these fabricated representations and hyperreal signs over direct experiences of reality. The simulations and models come to define, mediate and construct our understanding of the world.
Consumer Society
In “The Consumer Society,” Baudrillard argues that traditional institutions like family, work and religion are losing significance to the prevailing values and rituals of consumerism.
Rather than simply meeting needs, consumption has become a defining way of life, shaping identities and social belonging. Non-essential consumer goods and experiences drive the quest for happiness, novelty and status.
Baudrillard notes that consumer society fosters a constant pressure to consume more through an endless pursuit of new products, trends and experiences. This “treadmill of consumption” fuels perpetual dissatisfaction and desire.
Additionally, he highlights how objects take on symbolic value and meaning within consumer culture. A luxury car, for example, denotes wealth and status beyond its functional utility.
Overall, Baudrillard presents a critical perspective on consumerism, showing how it has come to dominate modern society on psychological and cultural levels beyond simple economic exchange.
Symbolic Exchange
In contrast to the materialistic values of consumer society, Baudrillard proposes the concept of “symbolic exchange” based on the exchange of meanings rather than commodities.
He suggests symbolic exchange has more power than material transactions in structuring society. However, modern culture has lost touch with the traditional symbolic exchanges around fundamental existential themes like mortality.
By marginalizing death and pursuing endless progress, Baudrillard argues that society loses balance and restraint. This denial leads to excessive consumption and constant pursuit of unattainable fulfillment.
Fatal Strategies
Baudrillard’s theory of “fatal strategies” contends that various systems like technology and consumerism can take on lives of their own and turn against their creators.
Through proliferation and exaggeration, these systems exceed human control and impose their own logic and consequences. For instance, while meant to be tools serving human needs, technologies can shape behavior and exert control in unanticipated ways.
Baudrillard saw this reversal, where the object dominates the subject who created it, as an impending “fatal” danger of various systems reaching a state of autonomous excess.
This provides a cautionary perspective on modern society’s faith in perpetual progress through technology and constant economic growth.
Conclusion
Through groundbreaking theories like simulation, hyperreality and symbolic exchange, Jean Baudrillard provided deep critiques of modern society, consumer culture, media and technology. His work dismantles assumptions about reality, history and human agency vs. systemic control.
Baudrillard prompts critical reflection about the cultural, psychological and philosophical implications of postmodern society. His lasting influence encourages re-examining our relationships with consumerism, technology and media to navigate the complex intricacies of the contemporary world.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ a4a6b584:1e05b95b
2023-07-21 01:22:42
@ a4a6b584:1e05b95b
2023-07-21 01:22:42A comprehensive exploration of Metamodernism, its principles and influences across art, design, music, politics, and technology. This piece delves into how Metamodernism paves the way for a future that harmonizes grand narratives and individual nuances, and how it could shape the cultural, economic, and digital landscape of the future.
Introduction
Welcome to the metamodern era. A time where we find ourselves caught in the flux of digital revolution, cultural shifts, and a rekindling of grand narratives, all while still
As an artist, I find myself standing at the crossroads of these cultural and technological shifts, with Metamodernism serving as my compass. I'd like to share my thoughts, experiences, and observations on what Metamodernism is, and how I believe it will shape our future.
This journey began as an exploration into the potential future of graphic design, taking cues from an evolving cultural paradigm. I quickly realized that Metamodernism was not just about creating compelling visual narratives, but it had potential to influence every aspect of our lives, from politics and technology to our individual experiences and collective narratives.
Metamodernism, in essence, is about balancing the best of what came before – the grand narratives and optimism of modernism, and the skepticism and relativism of postmodernism – while forging ahead to create a new, coherent cultural reality.
So let's embark on this journey together to understand the metamodern era and its impact on our culture, our technology, and our art. Let's delve into Metamodernism.
Understanding Postmodernism and Metamodernism
To appreciate the metamodern, we must first unpack the concept of postmodernism. Rooted in skepticism, postmodernism came into being as a reaction to modernism’s perceived failures. Where modernism sought universality, believing in grand narratives and objective truths, postmodernism reveled in fragmentation and the subjective nature of reality. It questioned our institutions, our ideologies, and our grand narratives, challenging the very structure upon which our society was built.
However, as we moved deeper into the postmodern era, a palpable sense of fatigue began to set in. The endless questioning, the constant fragmentation, and the cynical deconstruction of everything began to take a toll. While postmodernism provided valuable insights into the limitations of modernist thinking, it also left us feeling disconnected and adrift in a sea of relativism and irony.
This is where Metamodernism steps in. As the cultural pendulum swings back from the fragmentation of postmodernism, it does not return us to the naive grand narratives of modernism. Instead, Metamodernism synthesizes these seemingly contradictory ideologies, embracing both the skepticism of the postmodern and the optimism of the modern.
In essence, Metamodernism is a search for meaning and unity that still acknowledges and respects the complexity of individual experience. It recognizes the value in both grand narratives and personal stories, aspiring to create a more cohesive cultural discourse.
The metamodern era is a new dawn that challenges us to be both skeptical and hopeful, to engage in dialogue and debate, and to harness the opportunities that lie ahead. It's not about choosing between the grand narrative and the individual, but rather finding a way to harmoniously integrate both.
Metamodernism in Politics
In recent years, we've seen political movements around the world that embody the elements of Metamodernism. On one hand, there's a call for a return to grand narratives and nostalgia for perceived better times, while on the other, there's a desire to dissolve hierarchical structures and traditional norms in favor of individual freedom and recognition.
A case in point is the political era marked by the rise of Donald Trump in the United States. Trump's slogan, "Make America Great Again," was a nod to the modernist ideal of a grand narrative - a return to American exceptionalism. It was an appeal to a past time when things were, as perceived by some, better.
Meanwhile, reactions on the left have taken a different trajectory. Movements to decentralize power, break down traditional norms, and encourage more individual subjectivity echoing postmodern sentiments.
Metamodernism enables us to interpret these political movements from a fresh perspective. It does not discard the grand narrative nor does it plunge into fragmentation. Instead, it presents a narrative of balance and synthesis, oscillating between the modernist and postmodernist perspectives, and offering a way forward that is nuanced, respectful of individual experiences, and yet oriented toward a shared goal for the culture and people.
In the realm of politics, the metamodern era isn't about swinging to one extreme or another. Instead, it suggests a way to reconcile the polarity and move forward, synthesizing the best of both perspectives into a more nuanced, inclusive future. This is the metamodern political landscape, complex and dynamic, where grand narratives and individual stories coexist and inform one another.
The Metamodernist Canvas in Graphic Design
Now, let's look at the impact of Metamodernism on graphic design, a realm where I live and breathe every day. Here, Metamodernism offers a fresh perspective, providing a way to express the complexity of the world we live in and creating a narrative that is both universal and individual.
Traditional graphic design was about simplicity and clarity. It was built on the modernist principles of functionalism and minimalism, where form follows function. Postmodern design, however, sought to question these principles, embracing complexity, contradiction, and the power of the image.
As a graphic designer in the metamodern era, I find myself torn between these two extremes. On one hand, I appreciate the clarity and simplicity of modernist design. On the other, I am captivated by the dynamism and complexity of postmodern aesthetics.
The solution, I believe, lies in the synthesis offered by Metamodernism. Metamodernist design does not reject the past, but rather builds on it. It blends the simplicity of modern design with the vibrancy of postmodern aesthetics, creating something that is both familiar and fresh.
The Metamodernist canvas is a space where contrasting ideas can coexist and inform each other. It is a space where the universal and the individual intersect, creating narratives that resonate on multiple levels. It is a space where design can play a role in building a more cohesive and well integrated society.
The challenge for designers in the metamodern era is to create designs that reflect this complexity and nuance, designs that speak to both the individual and the collective, designs that challenge, inspire, and unite. It's a tall order, but it's a challenge that, as designers, we are ready and excited to embrace.
Liminal Spaces and the Visual Language of Metamodernism
A pivotal concept within the Metamodernist philosophy is that of the "liminal space" - an in-between space, where transformation occurs. These spaces, often associated with uncertainty, dislocation, and transition, have become particularly poignant in recent times as we grappled with the global impact of COVID-19.
Within this context, we've all had a shared experience of liminality. Offices, parks, and public spaces - once bustling with activity - suddenly became eerily quiet and deserted. These images have since been ingrained in our collective memory, symbolizing a profound shift in our way of life.
From a visual perspective, these liminal spaces offer a unique canvas to create Metamodernist narratives. Picture a 3D render of an empty office space, serving as a backdrop for a fusion of past and future aesthetics, where classical works of art - subtly altered - coexist with modern elements. Consider the emotional impact of a low-resolution Mona Lisa or a melting clock a la Salvador Dalí set against the familiar concrete reality of the modern workspace.
This use of liminal space is not just a stylistic choice. It's a nod to our shared experiences, an acknowledgment of the transitions we are going through as a society. It's a way of showing that while we live in an era of immense change and uncertainty, we are also capable of creating new narratives, of finding beauty in the unfamiliar, and of moving forward together.
The challenge in Metamodernist design is to create a visual language that resonates with our collective experiences, that brings together the past and the future, the familiar and the strange, and that stimulates thought, dialogue, and connection. And that, I believe, is where the true power of Metamodernist design lies.
Metamodernism in Art, Music, and Memes
Just as in politics and graphic design, Metamodernism manifests itself in various facets of culture, from art and music to internet memes. This wide-ranging influence attests to the universality of Metamodernist thinking and its ability to encompass and unify diverse aspects of human experience.
In visual arts, consider Banksy's elusive street art, which often blends irony and sincerity, public space and private sentiment, modern graffiti techniques and traditional painting styles. In music, take the example of Kanye West's album "Jesus is King," which fuses gospel traditions with hip-hop sensibilities, blurring the line between secular and religious, the mainstream and the fringe.
Meanwhile, the internet meme culture, characterized by its oscillation between irony and sincerity, absurdity and poignancy, chaos and order, is perhaps one of the most profound expressions of Metamodernism. Memes like "This is fine," a dog calmly sitting in a burning room, epitomize the Metamodernist spirit by acknowledging the complexities and contradictions of modern life while also seeking to find humor and connection within them.
Even the trend of remixing adult rap with kids shows can be seen as Metamodernist. It juxtaposes the mature themes of rap music with the innocence of children's entertainment, resulting in a work that is both familiar and disorienting, humorous and thought-provoking.
In all these instances, Metamodernist works draw from the past and present, high culture and popular culture, the sacred and the profane, to create experiences that are multilayered, dynamic, and rich in meaning. They acknowledge the complexity and diversity of human experience, yet also aspire to forge connections, provoke thought, and inspire change.
The Rise of Bitcoin and Metamodernist Economics
The rise of Bitcoin - the world's first decentralized digital currency - is a prime example of Metamodernist influence in economics. Bitcoin incorporates elements from both modernist and postmodernist economic theories, yet transcends them by creating a novel economic system that has never been seen before.
On one hand, Bitcoin harks back to the modernist ideal of hard money. It revives the principles of scarcity and predictability that underpinned the gold standard, a system that many believe led to stable, prosperous economies. On the other hand, Bitcoin's design is rooted in postmodern principles of decentralization and disintermediation, disrupting traditional economic hierarchies and structures.
But Bitcoin isn't just a fusion of modern and postmodern economics. It goes a step further by incorporating elements of Metamodernist thinking. Bitcoin's design encourages a sincere, cooperative approach to economic interaction. Its transparent, tamper-proof ledger (blockchain) promotes trust and collaboration, discourages deceit, and enables all participants, no matter how big or small, to verify transactions independently.
Moreover, Bitcoin is a grand narrative in itself - a vision of a world where economic power is not concentrated in the hands of a few, but distributed among many. At the same time, it acknowledges the individuality and diversity of its participants. Each Bitcoin user has a unique address and can transact freely with anyone in the world, without the need for a middleman.
Bitcoin's rise offers a glimpse into what a Metamodernist economic system might look like - one that combines the best aspects of modern and postmodern economics, while also adding a new layer of trust, cooperation, and individual freedom.
The Impact of Urbit and Metamodernist Computing
Urbit symbolizes a compelling manifestation of Metamodernist ideology within the realm of technology. This unique operating system revolutionizes the individual's interaction with the digital world, intrinsically mirroring the principles of Metamodernism.
In contrast to the postmodern complexities that plague the current internet – a web characterized by surveillance capitalism, privacy invasion, and data centralization – Urbit leans towards a modernist vision. It champions the idea of the internet as a streamlined, intuitive tool, but concurrently it envisions something unprecedented: a digital landscape where each user not only owns but is also the infrastructure of their digital identity and data.
The design philosophy of Urbit embodies a characteristic Metamodernist oscillation, as it traverses between elements of the past and the future, the familiar and the uncharted. It embraces the modernist simplicity reminiscent of early computing while concurrently advancing a futuristic concept of a personal server for every individual, in which they possess full sovereignty over their digital existence.
Urbit’s operating system and its unique programming language, Nock and Hoon, employ a Kelvin versioning system. This system is designed to decrement towards zero instead of incrementing upwards, epitomizing the modernist pursuit of perfection and simplicity. Once the protocol reaches zero, it signifies that an ideal state has been achieved, and no further changes will be required. This, in essence, represents the modernist grand narrative embedded within Urbit's design.
In the wider narrative of Metamodernism, Urbit symbolizes a decentralized, user-centric digital future. It recognizes the individuality of each user and emphasizes their control over their digital persona and interactions.
The promise of a completely decentralized internet is a vision still in progress. Regardless, it offers crucial insights into how Metamodernist principles could potentially shape our digital future. It paints a picture of an equilibrium between grand narratives and individual nuances, encapsulating a collective digital aspiration, as well as personal digital realities.
Moving Towards a Metamodernist Future
The common thread running through the Metamodernist era is the simultaneous embrace of grand narratives and personal experiences, the oscillation between modernist and postmodernist ideals, and the sincere pursuit of a better future.
However, moving towards a Metamodernist future is not without challenges. The danger lies in taking Metamodernist principles to an extreme, where the balance between irony and sincerity, grand narratives and individual nuances, can be lost. It's vital to avoid the pitfalls of dogmatism and extremism that plagued previous cultural eras.
For instance, an overemphasis on grand narratives can lead to totalitarian tendencies, while an excessive focus on individual nuances can result in cultural fragmentation. Metamodernism's strength lies in its ability to reconcile these extremes, fostering a sense of shared purpose while acknowledging individual experiences and perspectives.
Similarly, the interplay of irony and sincerity, often seen in Metamodernist works, should not tip over into either pure cynicism or naive earnestness. The goal should be to create a dialectic, a conversation, a fusion that creates a new, more complex understanding.
As we move towards this future, we can use the tools at our disposal – from graphic design and art, to music, memes, Bitcoin, and Urbit – to explore and shape this Metamodernist narrative. By consciously adopting Metamodernist principles, we can construct a culture that is at once reflective of our individual experiences and representative of our collective aspirations. In doing so, we can pave the way for a future that truly encapsulates the complexity, diversity, and richness of the human experience.
A Future Infused with Metamodernism
Metamodernism offers a comprehensive cultural lens through which we can understand, critique, and navigate our world. It provides a potential pathway to a future where our grand collective narratives coexist harmoniously with our nuanced individual experiences.
In the creative world, artists and designers can become the torchbearers of this movement, integrating Metamodernist principles into their work. They can leverage the power of nostalgia, sincerity, irony, and innovation to create works that resonate with the complexities of the human condition, reflecting both shared experiences and personal journeys.
In the world of technology and economics, Metamodernist principles illuminate the path to a more decentralized, user-centric digital future, as embodied by Bitcoin and Urbit. These platforms highlight the value of individual autonomy within a collective system, creating a new narrative of economic and digital empowerment.
In the political realm, Metamodernism can help create a dialogue that is both encompassing and respectful of diverse perspectives. It advocates for a new kind of political discourse that eschews extreme polarization in favor of a nuanced conversation that acknowledges the complexities of our world.
In essence, the potential of Metamodernism lies in its capacity to weave a compelling tapestry of our collective human experience – one that is vibrant, complex, and teeming with diverse narratives. By understanding and embracing the principles of Metamodernism, we can co-create a future that truly reflects the dynamic interplay of our shared narratives and individual nuances.
In this promising future, we can all become active participants in the Metamodernist narrative, shaping a world that values both the grandeur of our collective dreams and the authenticity of our individual experiences. The future is not just something we move towards; it is something we actively create. And Metamodernism provides a powerful blueprint for this creation.
Read more from Adam Malin at habitus.blog.
Adam Malin
You can find me on Twitter or on Nostr at
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxvalue4value Did you find any value from this article? Click here to send me a tip!
-
 @ 75656740:dbc8f92a
2023-07-20 19:50:48
@ 75656740:dbc8f92a
2023-07-20 19:50:48In my previous article I argued that it is impossible to have an effective filter in a delivery-by-default and universal reach messaging protocol. This might seem over-specific because, after various filters, nothing is truly universal or delivery-by-default. * Mail is limited by a cost filter phone calls by call screening services. * Faxes are limited by the fact that we all got sick of them and don't use them any more. * Email dealt with it by pushing everyone into a few siloed services that have the data and scale to implement somewhat effective spam detection. * Social media employs thousands of content moderators and carefully crafted algorithms.
Most of these are, however, delivery-by-default and universal in their protocol design. Ostensibly I could dial any number in the world and talk to anyone else in possession of a phone. If I have an email address I can reach anyone else. I can @ anyone on social media. All these protocols make an initial promise, based on how they fundamentally work, that anyone can reach anyone else.
This promise of reach then has to be broken to accomplish filtering. Looking at limiting cases it becomes clear that these protocol designs were all critically flawed to begin with. The flaw is that, even in a spam free case, universal reach is impossible. For a galaxy-wide civilization with billions of trillions of people, anyone individual wouldn't be able to even request all the information on a topic. The problem is more than just bandwidth, it is latency.
That is without spam and trolling. With spam and trolls things crash at a rate proportional to the attention available on the protocol.
The answer is to break the promise of universal reach in theory so we can regain it in practice. By this I mean filtering should happen as soon as possible to keep the entire network from having to pass an unwanted message. This can be accomplished if all messages are presumed unwanted until proven otherwise. Ideally messaging happens along lines of contacts where each contact has verified and signed each-other's keys. That is annoying and unworkable, however, instead it should be possible to simply design for trust. Each account can determine a level of certainty of an identity based on network knowledge and allow or deny based on a per-instance threshold.
While requiring all messages to originate "in network" does break the promise of the internet as an open frontier, the reality is that, like the six degrees of Kevin Bacon, everyone you want to reach will be in your network if scaled out to a reasonable level. This puts a bottleneck on bot farms trying to gain entry into the network. While they will be able to fool people into connecting with them, such poor users can lose the trust of their contacts for introductions, algorithmically limiting reach.
With Nostr I expect this form of filtering will arise organically as each relay and client makes decisions about what to pass on. This is why I like Nostr. It isn't exactly what I want, but that doesn't matter I am probably wrong, it can morph into whatever it needs to be.
-
 @ 02a11d15:32f62ea9
2023-09-26 21:26:20
@ 02a11d15:32f62ea9
2023-09-26 21:26:20Another Nost from Obsidian!
ehem... quote
Hey yo, wassup you #little #orange
-
 @ 9322bd92:a3d4cb0b
2023-09-26 21:26:13
@ 9322bd92:a3d4cb0b
2023-09-26 21:26:13In city of New York, there lived a young and tech-savvy investor named Alex. Fascinated by the world of cryptocurrencies, Alex had a deep belief in the potential of Bitcoin, despite its notorious price volatility. In September 2013, with an initial investment of $50,000, Alex began their journey into the world of Bitcoin. Each month, they allocated $5,000 to buy Bitcoin, regardless of its current price, and they continued this strategy until September 2021.
In September 2013, the price of Bitcoin was around $127 per coin. With their $50,000 initial investment, Alex bought approximately 393.70 BTC. Each subsequent month, they purchased $5,000 worth of Bitcoin, adjusting the number of coins they received based on the current price.
Here's a breakdown of some of the notable moments in Alex's journey:
September 2013: Alex's initial investment of $50,000 bought them about 393.70 BTC at a price of $127 per coin.
October 2013: The price of Bitcoin was around $134 per coin, allowing Alex to buy approximately 372.39 BTC with their $5,000 investment.
November 2013: Bitcoin's price had risen to approximately $235 per coin, and Alex's $5,000 purchase got them about 21.28 BTC.
December 2013: The price continued to surge, reaching around $754 per coin. Alex bought approximately 6.63 BTC with their $5,000.
Throughout 2014 and 2015, Bitcoin's price experienced various ups and downs, but Alex stuck to their plan of investing $5,000 every month.
September 2021: Bitcoin's price was trading at approximately $43,000 per coin when Alex made their final $5,000 purchase, acquiring approximately 0.11 BTC.
Over the years, Bitcoin's price continued its rollercoaster ride, with remarkable highs and challenging lows. Despite the volatility, Alex remained steadfast in their dollar-cost averaging strategy.
As of September 2021, Bitcoin had experienced substantial growth, and its average annual return over the eight-year period was about 60%. Alex's disciplined approach to dollar-cost averaging had paid off handsomely, and their initial $50,000 investment had grown into a substantial portfolio.
Total Amount Invested = Initial Investment + (Monthly Investment x Number of Months) Total Amount Invested = $50,000 + ($5,000 x 96 months)
Total Amount Invested = $50,000 + $480,000
Total Amount Invested = $530,000
Total Accumulated BTC = 1,353.70 BTC
Alex's story is a testament to the power of dollar-cost averaging, even in the world of cryptocurrencies like Bitcoin. By remaining committed to their approach and consistently investing from September 2013 to September 2021, they had harnessed the potential of this digital asset. As they checked their wallet, they knew that they had made a wise choice by embracing the steady, long-term strategy of DCA in the crypto world, and they had achieved impressive financial success through their dedication and belief in Bitcoin's potential. If we consider the current price of $26,000 per BTC, their accumulated Bitcoin holdings are valued at approximately $35,230,200.
-
 @ 75656740:dbc8f92a
2023-07-19 21:56:09
@ 75656740:dbc8f92a
2023-07-19 21:56:09All social media companies quickly run into the impossible problem of content moderation. I have often seen commentary suggesting that Twitter, FaceBook, etc need to make some particular adjustment to their content moderation policy. Perhaps they should have clearer rules, be more transparent about moderation actions taken, err on the side of permissiveness, have community moderation, time outs vs bans etc. My thesis, however, is that all such endeavors are doomed to failure. The problem is that maintaining signal to noise over a single channel cannot scale.
If a platform wants to remain relevant to the majority of people, it needs to maintain signal. Filtering is a fundamental feature of communication. Even in-person conversations between individuals break down without self-filtering to stay on topic and maintain constructive relations. Long range delivery systems have a second order problem that makes the issue even worse.
All delivery-by-default communication systems succumb to spam. This is without exception. Mail, phone, fax, email, text, forums, etc. have all fallen to spam and now require herculean efforts to maintain signal through extensive filtering. The main offenders are non-human entities that have a low barrier to entry into the network. Once in, delivery-by-default allows and motivates swamping out competing signals for user attention.
In combating this problem most platform operators do seem to act in good-faith while implementing filters. They are even fairly successful. But they end up with the same problem as economic central planners and Maxwell's Daemon; to do the job perfectly they require more information than the system contains. This means that the system is guaranteed to fail some users. As a successful platform scales the filtering needs will outrun the active users by some f(n) = n^k where k is greater than 1. This follows from the network effect of greater information being contained in the edges of the graph than in its nodes.
For networks like Facebook and Twitter the impossible threshold is many orders of magnitude past. What can be maintained on a small mailing list with the occasional admonition, now requires tens of thousands of swamped moderators that still can't begin to keep up. Those moderators have to make value judgements for content generated by people they don't know or understand. Even the best meaning moderators will make bias mistakes. Thus the proportion of unhappy users will also scale non-linearly with size.
The impossible problem takes a second step in the presence of civil authority. The problem is that a filter being necessary means that a filter exists. A civil authority and other motivated actors will not be able to leave a filter be, without at least attempting to tip the scales. Again they are generally well-meaning. But what they consider noise, may not actually be noise.
Well-meaning is probably a stretch given that levers of power tend to attract the attention of people who like that sort of thing, but I like to assume the best. I tend to think that there were some early signs of Jack stressing out under the load of bearing this problem. He didn't want it but there just wasn't anyway out of it. You must maintain signal or die!
But there is light at the end of the tunnel. The problem only exists with delivery-by-default when reach is universal (a problem for another post) with distributed systems there is still a filter but it is no longer any one entity's problem. Once the social graph is complete, deny-by-default can work wonders since each node can decide what to allow.
I don't know what the final filtering mechanism will look like, but Nostr is a lovely chance to experiment.
-
 @ 04c915da:3dfbecc9
2023-09-26 17:34:13
@ 04c915da:3dfbecc9
2023-09-26 17:34:13For years American bitcoin miners have argued for more efficient and free energy markets. It benefits everyone if our energy infrastructure is as efficient and robust as possible. Unfortunately, broken incentives have led to increased regulation throughout the sector, incentivizing less efficient energy sources such as solar and wind at the detriment of more efficient alternatives.
The result has been less reliable energy infrastructure for all Americans and increased energy costs across the board. This naturally has a direct impact on bitcoin miners: increased energy costs make them less competitive globally.
Bitcoin mining represents a global energy market that does not require permission to participate. Anyone can plug a mining computer into power and internet to get paid the current dynamic market price for their work in bitcoin. Using cellphone or satellite internet, these mines can be located anywhere in the world, sourcing the cheapest power available.
Absent of regulation, bitcoin mining naturally incentivizes the build out of highly efficient and robust energy infrastructure. Unfortunately that world does not exist and burdensome regulations remain the biggest threat for US based mining businesses. Jurisdictional arbitrage gives miners the option of moving to a friendlier country but that naturally comes with its own costs.
Enter AI. With the rapid development and release of AI tools comes the requirement of running massive datacenters for their models. Major tech companies are scrambling to secure machines, rack space, and cheap energy to run full suites of AI enabled tools and services. The most valuable and powerful tech companies in America have stumbled into an accidental alliance with bitcoin miners: THE NEED FOR CHEAP AND RELIABLE ENERGY.
Our government is corrupt. Money talks. These companies will push for energy freedom and it will greatly benefit us all.
-
 @ 97c70a44:ad98e322
2023-06-26 19:17:23
@ 97c70a44:ad98e322
2023-06-26 19:17:23Metadata Leakage
It's a well-known fact that Nostr's NIP 04 DMs leak metadata. This seems like an obvious flaw, and has been pointed out as such many times. After all, if anyone can see who you're messaging and how frequently, what time of the day, how large your messages are, who else is mentioned, and correlate multiple separate conversations with one another, how private are your communications really?
A common retort repeated among those who "get" Nostr (myself included) is "it's not a bug, it's a feature". This hearkens back to the early days of the internet, when internet security was less than an afterthought, and social platforms throve on various permutations of the anonymous confessions-type app. How interesting to be able to flex to your friends about whom you're DMing and how often! Most conversations don't really need to be private anyway, so we might as well gamify them. Nostr is nothing if not fun.
In all seriousness though, metadata leakage is a problem. In one sense, Nostr's DMs are a huge improvement over legacy direct messages (the platform can no longer rat you out to the FBI), but they are also a massive step backward (literally anyone can rat you out to the FBI). I'm completely confident we'll be able to solve this issue for DMs, but solving it for other data types within Nostr might pose a bigger problem.
Social Content
A use case for Nostr I've had on my mind these last few months is web-of-trust reviews and recommendations. The same sybil attack that allows bots to threaten social networks has also been used as a marketing tool for unscrupulous sellers. NPS surveys, purchased reviews, and platform complicity have destroyed the credibility of product reviews online, just like keyword-stuffed content has ruined Google's search results.
Proof-of-work would do nothing to defend against this attack, because the problem is not volume, it's false credibility. The correct tool to employ against false credibility is web-of-trust — verifiable trustworthiness relative to the end user's own social graph.
This is a huge opportunity for Nostr, and one I'm very excited about. Imagine you want to know whether the vibro-recombinant-shake-faker (VRSF) will result in visible abs in under 6 days. Well, it has over 4 thousand 5-star reviews on Amazon, and all the 1-star reviews are riddled with typos and non sequiturs. So it must work, and make you smarter into the deal! Well, sadly no, visible abs are actually a lie sold to you by "big gym".
Now imagine you could find your three friends who fell for this gyp and ask them what they thought — you might just end up with a lower average rating, and you'd certainly have a higher level of certainty that the VRSF is not worth the vibra-foam it's molded from.
This same query could be performed for any product, service, or cultural experience. And you wouldn't be limited to asking for opinions from your entire social graph, it would be easy to curate a list of epicureans to help you choose a restaurant, or trusted bookworms to help you decide what to read next.
Currently, big tech is unable to pull this off, because Facebook won't share its social graph with Google, and Google won't share its business data with Facebook. But if an open database of people and businesses exists on Nostr, anyone can re-combine these silos in new and interesting ways.
Notes and other Spies
So that's the pitch, but let's consider the downsides.
An open social graph coupled with recommendations means that not only can you ask what your friends think about a given product, you can ask:
- What a given person's friends think about a product
- What kind of person likes a given product
- How products and people cluster
That last one in particular is interesting, since it means you could find reasonable answers to some interesting questions:
- Does a given region have fertility problems?
- What are the political leanings of a given group?
- How effective was a particular advertisement with a given group?
This is the kind of social experiment that has historically earned Facebook so much heat. Democratizing this data does not prevent its correlation from being a violation of personal privacy, especially since it will be computationally expensive to do sophisticated analysis on it — and the results of that analysis can be kept private. And to be clear, this is a problem well beyond the combination of social information and public reviews. This is just one example of many similar things that could go wrong with an open database of user behavior.
Not to put too fine a point on it, we are at risk of handing the surveillance panopticon over to our would-be overlords on a silver platter. Just as walled gardens have managed us in the past to sway political opinion or pump the bags of Big X, an open, interoperable content graph will make building a repressive administrative state almost too easy.
Let's not give up just yet
So what can we do about it? I want a ratings system based on my social graph, but not at the expense of our collective privacy. We need to keep this threat in mind as we build out Nostr to address novel use cases. Zero-knowledge proofs might be relevant here, or we might be able to get by with a simple re-configuration of data custody.
In the future users might publish to a small number of relays they trust not to relay their data, similar to @fiatjaf's NIP-29 chat proposal. These relays might then support a more sophisticated query interface so that they can answer questions without revealing too much information. One interesting thing about this approach is that it might push relays towards the PWN model BlueSky uses.
Not all data needs to be treated the same way either, which would give us flexibility when implementing these heuristics. Just as a note might be either broadcast or sent to a single person or group, certain reviews or other activity might only be revealed to people who authenticate themselves in some way.
Like so many other questions with Nostr, this requires our concentrated attention. If all we're doing is building a convenient system for Klaus Schwab to make sure we ate our breakfast bugs, what are we even doing?
-
 @ d8a2c33f:76611e0c
2023-09-26 16:22:47
@ d8a2c33f:76611e0c
2023-09-26 16:22:47Silicon valley elites are pouring billions of dollars in building closed AI systems that can ingest all of our data. Then scare politicians into creating regulations that install them as overlords. They will not win in that game because of millions of Plebs like us band together, build in public (#buildinpublic), democratize AI access for all and beat them in their own game.
We call this movement PlebAI
PlebAI exclusively connects to open-source, large language models. These models are neither biased nor tuned to produce a specific set of responses. By focusing on open-source solutions, PlebAI ensures transparency and community-driven development. Users can trust the information they receive, knowing it's free from undue influence or proprietary modifications. The commitment to impartiality positions PlebAI as a trusted platform for unbiased knowledge and assistance.
Twenty-five years ago, I watched the movie "Matrix" and laughed when Agent Smith replicated himself in thousands. Today, that scenario is unfolding in real-time. On PlebAI, we have made remarkable progress, surpassing single digits as we now boast a team of highly skilled agents proficient in various activities, ready to assist. The cool part is anyone can create their own agents and make it private or public.
Join us in building this together. Check it out, by going to https://chat.plebai.com
Features 🫶 * No email or signups required * No credit card or up front payment required * No Ads or trackers * Chat history only stored on the browser * Using only open source LLMs * Create your own agent and make it private or public * Use Lightning wallet on the browser
-
 @ 2edbcea6:40558884
2023-09-24 15:16:04
@ 2edbcea6:40558884
2023-09-24 15:16:04Happy Sunday #Nostr !
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Many great discussions this week. Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 34: Wiki 📜
Wikipedia is flawed because there’s only one article per topic which forces everyone that works on Wikipedia to fight out what is “true.” This will always lead to people claiming whatever is on Wikipedia is “the truth” because there’s only one article per topic.
Google experimented with a Wikipedia alternative called Knol which was similar, but anyone could submit an article on a topic and then it was by the voting of users that determined the top articles for that topic. The theory being that readers could go through multiple articles on the topic from different perspectives and determine the truth for themselves.
What fiatjaf is proposing in this NIP is very similar to Knol, but published via Nostr to give it more censorship resistance than Knol. With reactions and bridges to other knowledge bases, we could quickly bootstrap a nostr-based rival to Wikipedia with more nuance and debate baked in.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
2) (Proposed) NIP 17: Event Metadata ℹ️
When clients are displaying a note published by a user, there are often things about that note which would be useful to display to users reading that note. E.g. how many comments, reposts, and reactions there are. These are often computationally and time intensive operations for a client since they’ll need to query many relays to get a reasonably accurate count.
This NIP proposes that relays could optionally add such information as metadata on each note as it is returned to clients so they do less work to get that information. Both clients and relays would benefit from needing to do less work to give users the same, good experience.
Author: arthurfranca
3) (Proposed) NIP 34: Algorithmic Filter 🔍
One of the possibilities that makes Nostr great is the chance at algorithmic choice. People may want no algorithm, or a light algorithm to dedupe their feed of the same note being reposted by a dozen people, or a heavier algorithm to curate their feed and help them discover new content.
This NIP proposes a way for relays to support generic algorithms for ordering notes so that clients can query for notes from relays in a way specified by the indicated algorithm. There is also a concept of “seen at” which will allow users to tell relays they’ve seen a note so that it won’t show up in future algorithmic queries for notes.
This is still under development and refinement, but looks very promising.
PS - Yes this is also NIP 34, so whichever gets merged first gets the number I guess?
Author: arthurfranca
Notable Projects
relay.tools
Relay.tools is a tool for quickly spinning up relays. You can specify a subdomain of nostr1.com and pay a lightning invoice, and they’ll spin up a relay at that address for use by the nostr-verse.
Looks like this is under continued development, and could become a useful tool for creating, discovering, and educating folks about relays.
Author: nostr: nostr:npub10npj3gydmv40m70ehemmal6vsdyfl7tewgvz043g54p0x23y0s8qzztl5h
Email style subscriptions
Getting notified about certain posts is difficult on Nostr. If you want to subscribe to this publication, for example, you have to follow us and look for when it’s published every week 😅.
Wouldn’t it be great if you could subscribe to a publication and a link would be DM’d to you when it was published? It’s not a new concept, newsletters have worked like this for decades, but we don’t have an email-like system on Nostr.
nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 took a stab at creating a way to “subscribe” to something and then it’ll be NIP-04 DM’d to you when that account publishes in the future. It’s currently a proof of concept, but there’s likely something there to help folks who don’t want to have to use a different client just to see their subscriptions, or scroll endlessly to make sure they didn’t miss anything.
Better Backups
In case you’re unaware, many relays will erase notes published to them after they reach a certain age. This is done primarily to save on hosting costs, especially for free relays. This makes sense, but it presents a problem around data retention for Nostr users. Even paid relays may go out of business, and then your data is lost forever (unless it’s on other relays).
It’s been a common ask that there was some way to backup our data quickly and easily. Either to a private relay or to spread the data to more active relays so that there’s less chance of data loss.
nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f and nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj have done a great job creating a backup service that now takes seconds instead of minutes. And it looks like nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f will be adding features to make it easier to port that backed up information around (as a file, to other relays, etc).
Huge load off my mind having a backup of my account (even all the reactions and comments on my notes) in case there’s loss somewhere else in the nostr-verse.
Latest conversations: Custody of Private Keys
The state of private keys
If you have the private key for a Nostr account, then you own that Nostr account. You can publish notes as that account, you can change the profile info, you can ask relays to delete notes for that account. It’s total access.
Even still, many clients require that you paste your private key into a text box and allow the client to use the key to publish events as you. The best clients store the key only locally on your device so the client’s developers never have access to your private key. It’s becoming clear that some clients are storing private keys off-device and that comes with trade offs.
ZBD controversy
A discussion was started about how ZBD seems to store private keys for Nostr accounts on their servers. If ZBD is able to use those private keys to help users publish events, then ZBD could theoretically hand those private keys over to third parties (three letter government agencies, advertisers, etc). There’s a tremendous amount of trust users should have in ZBD when giving ZBD that power.
The spectrum of self-custody
On one extreme, users totally give up control: many folks don’t understand private key/public keypairs and so want to offload the cognitive load to a trusted third party. They’re willing to give their keys to a third party and have that third party do all the signing and publishing of Nostr events on their behalf.
On the other extreme is using a NIP-07 browser extension. This means that a Nostr client has to ask for your permission whenever it takes an action that requires your public or private key. That way the client never touches the private key, it just asks the extension to sign events before publishing them to the users’ relays. If you’ve ever used it, the popups are incredibly annoying after a while.
Is there a better way?
Is there a middle ground where users don’t have to manage annoying popups, but can be in complete control of their keys?
Theoretically you could have a third party service that: Stored public and private keys for a user in an end-to-end encrypted way, so that they can’t give anyone access to your keys even if they’re hacked. Allowed users to have a username/password/2FA interface for logging into the service and retrieving their keys (maybe the password is the encryption key).
This would allow folks that don’t understand private/public key pairs to have a familiar experience without compromising their security.
It may even be possible to extend the capabilities to make it truly an all-in-one solution for Nostr account management. Give users an OAuth experience for logging into clients (Login with WhateverYouCallIt button instead of pasting in a key) Allow users to direct requests for access to private/public keys from Nostr clients to this third party to be authorized by the user (like NIP-07) Allow users to store and update preferences of how much you access each client should have. Avoiding constant popups whenever a user is using a client they already trust.
In order to attract normal, everyday internet users we’ll need to give them an experience they expect and understand. And I think we can do that without compromising security like we’re seeing with clients that store a user’s keys on their servers.
Next week: Privacy on Nostr
A discussion was started around an architecture to allow private nostr interactions via P2P interactions between users and clients (bypassing relays). There’s not a ton of detail yet, but it’s a hot topic and next week we’ll dive in more.
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know. DMs welcome.
nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 9a39bf83:614a23fb
2023-09-23 22:58:18
@ 9a39bf83:614a23fb
2023-09-23 22:58:18Statistics from LNBiG for 60 days up to 2023-09-23
Statistics for the last 60 days by method described here
| Alias | K_Median | Volume, BTC | | :---------------------------------------------------------------------------------------------------------------------------- | --------------: | --------------: | | speedupln.com | 3.9293247 | 69.81979231 | | carlslight | 0.5193301 | 18.43480067 | | Tachyon | 0.4938222 | 5.21702062 | | cyberdyne.sh | 0.3080449 | 82.0324766 | | SILENTSOURCE-v22.11.1 | 0.247403 | 5.26568712 | | Lenham🌳 | 0.1458373 | 4.06862321 | | Kerosene | 0.1355972 | 2.64461886 | | Sally Acorn | 0.1226905 | 5.36939706 | | TaubeBTC | 0.1127335 | 1.43996917 | | 💰WTF_1971💰 | 0.1077847 | 1.66899158 | | Fulcrum | 0.1053826 | 1.34548338 | | M2node | 0.0867329 | 2.15414793 | | coinhodler04108 | 0.0813755 | 24.81178029 | | CryptoChill | 0.0740391 | 7.14414563 | | Road_To_Nodeware | 0.0625805 | 2.30193181 | | Tatooine | 0.0594648 | 1.45638334 | | fixedfloat.com | 0.0539921 | 3.00648249 | | Black Star ✦ | 0.0518493 | 11.64679052 | | BC.GAME | 0.0426973 | 31.67478285 | | 03bcf1f73199ed4445a8 | 0.0400719 | 6.91401944 | | FuckedBitcoin.com | 0.0354935 | 1.68070688 | | Aldebaran | 0.0349327 | 2.15036919 | | The Bitcoin Company | 0.0344344 | 4.008382 | | goblin-no.de | 0.0278975 | 1.98558304 | | tippin.me | 0.0258134 | 3.46447552 | | The Continental | 0.0246712 | 5.68730236 | | bfx-lnd1 | 0.0242778 | 115.75730862 | | c-otto.de | 0.0239866 | 7.3393811 | | CONFIRMO.net | 0.0211697 | 11.82662522 | | Astronode | 0.017935 | 1.4092787 | | UNKNOWN | 0.0178513 | 3.90643136 | | Kraken 🐙⚡ | 0.0149424 | 24.98183924 | | ln1.generalbytes.com | 0.0142427 | 1.79423676 | | okx | 0.0118163 | 22.62026397 | | bfx-lnd0 | 0.0114559 | 55.03070302 | | Babel | 0.010995 | 5.05574125 | | mulleirocorp | 0.0088749 | 1.19925988 | | Bitrefill | 0.0084864 | 9.058596 | | hot-two | 0.0084502 | 1.19653524 | | Sunny Sarah ☀️ | 0.0083283 | 4.40197042 | | WalletOfSatoshi.com | 0.0081999 | 8.75841079 | | Hades | 0.007642 | 1.97442902 | | Elbandi.Net | 0.0073999 | 4.41520977 | | Zorbito | 0.007099 | 2.02006401 | | Escher | 0.0058687 | 4.51681681 | | Neutronpay.com | 0.0055965 | 1.86006664 | | UNKNOWN | 0.0055264 | 1.37324952 | | AnonLN | 0.0045077 | 2.39990437 | | yalls.org clearnet-yalls | 0.0034487 | 2.81233795 | | 1sats.com⚡️lsp.flashsats.xyz | 0.0018781 | 4.89403813 | | ACINQ | 0.001871 | 1.9289123 | | allNice \| torq.co | 0.0018035 | 2.81387805 | | LN-Voodoo | 0.0004 | 1.08687606 | | kappa | 0.0003793 | 5.17811574 | | ThunderHorse2 | 0.0003453 | 1.49001582 | | deezy.io ⚡✨ | 0.0002426 | 1.12179019 | | 03d982db3411528c4a95 | 0.0001442 | 1.13878626 | | ln01.bullbitcoin.com | 0.0000491 | 1.33285281 | | e960fd8385a1603003727 | 0.0000307 | 4.14612491 | | ed528ad49bedd1f7a638a | 0 | 2.26745248 | | UNKNOWN | 0 | 1.94357931 | | Babylon-4a | 0 | 1.02880024 | | rockshouse | 0 | 1.31612406 | | MindlinerTre | 0 | 1.1414926 | | Sunshine Canyon | 0 | 1.37420137 | | UNKNOWN | 0 | 5.2753082 | | Peeky | 0 | 2.20007886 | | UNKNOWN | 0 | 1.75798113 | | DitoBanx_W1 | 0 | 1.83508346 | | Binance | 0 | 8.85940527 |
-
 @ 9322bd92:a3d4cb0b
2023-09-23 21:13:03
@ 9322bd92:a3d4cb0b
2023-09-23 21:13:03-
Bullish: Refers to an optimistic outlook for the stock or market, suggesting a potential increase in price.
-
Uptrend: A pattern of higher highs and higher lows, indicating that the stock or market is moving upward.
-
Chart pattern: A recognizable formation on a stock chart that can indicate a potential change in direction or trend.
-
Support: A price level that a stock or market has difficulty falling below, often considered a buying opportunity.
-
Resistance: A price level that a stock or market has difficulty rising above, often considered a selling opportunity.
-
Volume: Refers to the number of shares traded in a particular time period, often used to confirm the validity of a chart pattern.
-
Breakout: Occurs when the stock price moves above or below a significant price level, indicating a potential change in trend.
-
Consolidation: A period of time when the stock or market is trading in a relatively narrow range, often seen as a pause before a continuation of the trend.
-
Pullback: A temporary reversal in the stock or market trend, often seen as a buying opportunity. Moving averages: A commonly used technical indicator that smooths out the price action by calculating the average price over a specified period.
-
Moving averages: A commonly used technical indicator that smooths out the price action by calculating the averagrice over a specified period.
-
-
 @ fea400be:c89b9d0a
2023-09-22 17:44:05
@ fea400be:c89b9d0a
2023-09-22 17:44:05Our profile includes all info and instructions on how to play our 100+ AI-powered text based RPG games. But, in case you've missed it, here's the most current details again.
To start a game, make a new post that tags this account and "start game".
Example: @ChooseYourFate start game
It should start within a minute or so.
There are storylines for animal, viking, superhero, pulp, war, action, mystery, treasure, pirate, zombies, fantasy, scifi, robots, terminator, aliens, disaster, wuxia, xianxia, and horror.
Reference any of these specific game keywords when you want to play. To play women centric games, use woman as your keyword.
Example: @ChooseYourFate start game superhero
There are even some hidden easter egg storylines only available by keyword!
To play, you must be writing to any of the following relays: Nostr.wine, Damus, MutinyWallet, Relayable.
The game will timeout in 5 mins if it doesn't get a response from you.
Each game lasts on average 30 mins.
This account will also randomly post GROUP GAMES which allow anyone to join in and play together. A pool of Sats will be split between all who play if the game is won.
-
 @ 32e18276:5c68e245
2023-09-21 22:31:03
@ 32e18276:5c68e245
2023-09-21 22:31:03Hey gang,
I just pushed Damus build 18 which is the first major nostrdb integration. Now all damus profiles are stored in nostrdb! You will always be able to search profiles from people you've seen in the past.
There are many crash fixes in this build as well, check out the full changelog:
Enjoy!
Added
- Add followed hashtags to your following list (Daniel D’Aquino)
- Add "Do not show #nsfw tagged posts" setting (Daniel D’Aquino)
- Hold tap to preview status URL (Jericho Hasselbush)
- Finnish translations (etrikaj)
Changed
- Switch to nostrdb for @'s and user search (William Casarin)
- Use nostrdb for profiles (William Casarin)
- Updated relay view (ericholguin)
- Increase size of the hitbox on note ellipsis button (Daniel D’Aquino)
- Make carousel tab dots tappable (Bryan Montz)
- Move the "Follow you" badge into the profile header (Grimless)
Fixed
- Fix text composer wrapping issue when mentioning npub (Daniel D’Aquino)
- Make blurred videos viewable by allowing blur to disappear once tapped (Daniel D’Aquino)
- Fix parsing issue with NIP-47 compliant NWC urls without double-slashes (Daniel D’Aquino)
- Fix padding of username next to pfp on some views (William Casarin)
- Fixes issue where username with multiple emojis would place cursor in strange position. (Jericho Hasselbush)
- Fixed audio in video playing twice (Bryan Montz)
- Fix crash when long pressing custom reactions (William Casarin)
- Fix random crash due to old profile database (William Casarin)
-
 @ 726a1e26:861a1c11
2023-09-21 19:00:11
@ 726a1e26:861a1c11
2023-09-21 19:00:11Some time ago I started hacking on a nostr client for comments, an alternative to nocomment, just for the fun learning experience. As a stacker.news fan, I drew a lot of the inspiration from its design.
At about the same time, I noticed Habla.news was lacking comments on long-form notes. I was kindly invited to join the design calls, and my tiny widget ended up getting merged!
Comments you make on Habla since July are using ZapThreads.

See it live at https://habla.news/dergigi/1680612926599
The component
ZapThreads is available as a web component and can be embedded pretty much anywhere. It works on any client-side framework (via NPM) or website (via a script tag).
You can pass it a bech32-encoded
naddr,noteorneventand it will use that as the root for all replies. We call this the anchor event.Habla for example passes the
naddrof the current long-form note:html <zap-threads anchor={naddr} ... />;But you can also give it a URL and it will work, as nostr supports references to URLs via the
rtag.Here the comments from https://fiatjaf.com/nostr.html (which, of course, are rendered by nocomment on that site):
Likes and zaps for the anchor are displayed by default. Replies are threaded and can be collapsed or expanded. Basic Markdown and nostr references such as profiles, naddrs, tags, etc are all properly rendered.
The host page where the component is embedded can optionally pass an
npubattribute to suggest this profile is currently logged in via NIP-07. Otherwise, logging in is possible from within any reply area, as well as replying anonymously.Reloading a page gets you instant rendering since the component is designed for offline-first. This means that only new data is requested, with the benefit of great UX and minimal demand on relays.
It's lightweight on clients as well, it weighs under 40kb minified/gzipped including base CSS styles and SVG assets. (For comparison, nocomment is over 240kb).
So what's up with ZapThreads with... no zaps? That's coming soon, read on!
Purple pilling the web
It's early days. Most activity is happening on nostr-native applications. Since the power of the protocol is identity and data portability, why not embed it in different corners of the Internet? The incentive for web publishers to integrate with nostr increases as the network grows. And we help the network effect by surfacing it in unlikely places where we have the chance to onboard new nostriches.
For this reason, ZapThreads offers full control on styling and feature switches. Defaults are reasonable but to make this appealing to any kind of website, easily fine-tuning the component is of utmost importance. This is all work in progress, like the next big feature: multiple language support. I want to make this insanely versatile.
And if we shine purple light on every corner of the Internet, we clearly will take the orange one with it. In addition to integrating with the social layer, publishers can now permissionlessly monetize their content. Zaps will be enabled on anchors and comments, and zap splits will allow sharing sats between authors, hosts, relays, or anyone else.
Tools to automate migration from popular commenting systems such as Disqus, Facebook comments, Wordpress, etc are also on the list. A world-class onboarding UX to go with it, and much more.
My interest clearly goes beyond just threaded comments. I want to create lots of small, lightweight, versatile, easy to integrate web components to permeate the web with notes but also the "other stuff" transmitted over relays.
And the cherry on the cake would be, making Disqus obsolete.
More at https://github.com/fr4nzap/zapthreads . Let me know what you think in the comments below!
-
 @ 32e18276:5c68e245
2023-09-20 15:10:15
@ 32e18276:5c68e245
2023-09-20 15:10:15I thought it might be interesting to do a quick technical writeup of nostrdb and the new nostrdb profile searching. This is the first text search index within nostrdb, if you're interested in the nitty gritty details of things, this article is for you!
For the most part, nostrdb has been a copy of the design of strfry, in terms of its indices and multi-process architecture. strfry doesn't support search (yet), so this is a novel feature of nostrdb. What is strfry? If it weren't for strfry, nostr wouldn't work. It is simply the best way to implement a nostr database and relay. SQL servers are just too slow to serve dynamic queries at scale.
I wanted something like strfry that I could embed into native nostr clients like Damus, this is how nostrdb was born!
First, let's look at how nostrdb at a high level.
nostrdb
nostrdb is an embedded library for native nostr clients. It uses the Lightning-mapped database (LMDB) for very efficient querying. This allows it to skip SQL query parsing and query planning. We don't really need all that with nostr. nostr search filters are a bit more restrictive, so we can build custom indices for the most common nostr queries. This is a huge win CPU-wise, nostr queries can be very dynamic, and skipping the query parsing and planning saves CPU and battery.
Before we get into any of that, let's look at how you would use the library from the highest level. The entrypoint for notes in nostrdb is the
ndb_process_eventfunction. When you receive nostr events from another relay, this function is called for each event.Event processing
ndb_process_event('["EVENT","subid",{kind:1, ...}]')We begin by queueing the event for processing in the multi-threaded ingester. This allows it to return immediately and not block the client.
The ingester is multi-threaded because validating note signatures can be pretty slow. We want note processing to be as quick as possible so nostrdb doesn't have a bottleneck here.
nostrdb is very smart about not burning CPU when it doesn't need to. The custom json parser will stop when it finds the note ID field, lookup that note in the database to see if we already have it, and then stop JSON parsing if we do. This saves CPU for large notes like contact lists, and skips the need to re-validate the signature as well. Even strfry doesn't make this optimization, so nostrdb has a speed, cpu, and battery life advantage here.
During the processing step, nostrdb will detect different note types such as profile metadata. It will look at the
nameanddisplay_namefield and add a custom index for searching user profiles. Since keys in LMDB are lexicographically sorted and support range queries, our profile search indices is simply (name + pubkey + created_at). This allows you to do a ranged key-lookup on "jb" and it will position the db cursor to the first record that starts with jb. LMDB uses a b+ tree, this is not a linear scan, so it is very fast! Eventually this index will be used for implementing nip-50 search on the nostrdb relay interface, which is coming sometime in the future.Once we're done writing the indices and validating the note, we store nostr notes in a custom, compact binary format that is easy to access directly in memory from any programming language. We also do this with profile records by leveraging flatbuffers.
So in the end, what does this achieve? It enables you to store as much nostr data as you want with near zero query and serialization overhead. Since the data stored in nostrdb is just flatbuffers, you can access data directly from the operating system's page cache (just a pointer to memory) and from any programming language via flatbuffer's schema and codegen tools. It's so fast it will be guaranteed once of the fastest things in your codebase. You can even run it in your main UI thread so you can worry about other things such as UX and design without introducing complex async logic in your user interface.
What's next
nostrdb is already partially integrated into Damus iOS. Damus uses nostrdb's compact note format for storing notes in memory, but eventually everything will be switched to use nostrdb directly. The next version of Damus testflight will remove the in-memory and core-data profile cache and switch to nostrdb profiles. Damus currently has a complex in-memory trie data structure for profile searches, but it only knows about profiles it has seen during the current session. This is a common source of confusion, sometimes Damus doesn't auto-complete profiles it has already seen sometime in the past. nostrdb profile searches will allow @ mentions and user search to find every profile it has ever seen in realtime. This will be a huge usability win for Damus and other clients looking to adopt nostrdb.
Right now nostrdb exposes its functionality via direct function calls:
ndb_get_profile, etc. The plan is that most of these calls won't be necessary. Once nostrdb has nostr filter parsing, it will be able to support dynamic queries of the kind you would expect from your typical nostr relay. This will turn nostrdb-powered clients into relays themselves.Once nostrdb is more relay-like, then we will be able to leverage strfry's negentropy set-reconciliation queries to only fetch notes that we don't already have. This will be insanely useful for reducing bandwidth usage when querying strfry relays. Eventually it may make the most sense to just let nostrdb do all the websocket querying behind the scenes, becoming a kind of local multiplexing relay.
The future of nostrdb is very exciting. I plan on using it in Damus NoteDeck and Damus Android, why duplicate all this work in every client? nostrdb will make developing native clients much easier.
Support
Damus and nostrdb are mainly supported by donations. nostrdb is open source, MIT-licensed. Damus is GPL. We are dedicated to building the best and most free open source tech on nostr. If you would like to support our work, please consider buying our merch !
Thanks for getting this far! Until next time...
-
 @ 3db7ca42:f121f96f
2023-09-20 08:08:54
@ 3db7ca42:f121f96f
2023-09-20 08:08:54Based on earlier feedback from #noderunner, I have selected the following components for an upgrade for MindlinerTre.
Does this make sense? Would you recommend any changes/additions?
Server: Supermicro Barebone 5019D-FN8TP, Height units: 1, Supported power supplies: 1, Number of drive bays: 1 ×, PCI Express slots: 1x PCI Express 3.0 x8, 1x Mini PCI Express, Depth: 249 mm, SFP+ connectors: 2 ×, Number of free memory slots: 4, Processor socket: System-
Switch: Zyxel Layer3 Access Switch, 400W PoE, 2x10MultiGgig RJ45
RAM: G.Skill Trident Z5 RGB 2 x 32GB, 6400 MHz, DDR5-RAM, DIMM
Storage: 4 x WD Black SN850X 4000 GB, M.2 2280 I am planning to use these four disks in a RAID 10 configuration.
Setup: I plan to use proxmox as virtual environment and setup my core lightning, RTL, and LNbits starting out with this cool guide.
-
 @ 92294577:49af776d
2023-09-20 01:13:11
@ 92294577:49af776d
2023-09-20 01:13:11Last month marked the sixth anniversary of the activation of Segregated Witness (SegWit), underscoring the importance of open-source software and the value of running your own Bitcoin node. To honor this historic date, we are using this quarter's update to take an in-depth look at a few of our own open-source Bitcoin products and the progress made in their development over the past three months.
Among the highlights, we cover the Blockstream Jade and its evolution into a versatile tool to protect online security. Elsewhere, we highlight our new partnership with ZeroSync to bring much lower bandwidth full node sync via Blockstream Satellite. We also share updates on a range of other Blockstream-led open-source projects under development set to play a key role in the open infrastructure that will underlie a hyperbitcoinized future.
https://image.nostr.build/be3ea5c39e2faba6bf14f29227a5a5dfa4d02c1d98c1136e37e1736101939a90.png
Jade’s Best Quarter Yet
Our open-source hardware wallet, Blockstream Jade, enjoyed record-breaking sales in the first half of the year, increasing YoY by over 700%. A major factor in its increased popularity has undoubtedly been the addition of its new fully air-gapped workflows and SeedQR support, as well as quality of life improvements with the Green companion app. We have also made strides to ensure Jade is more accessible by expanding our popular Jade resellers and affiliate programs and our presence in online retail stores. We now have 30 official Jade resellers worldwide, from Europe to Vietnam, making it easier for Bitcoiners to purchase Jade locally and save on shipping costs and time.
As noted in our Q1 report, the team has much more planned in terms of features and performance improvements. Jade initiated Liquid swaps for trustless trading, Miniscript and Taproot support for improved privacy and security, and an Umbrel app for creating your own blind oracle, are all slated for release in the second half of 2023. We are also revamping the setup and onboarding process for users by providing more detailed instructional inserts and an all-new online portal for a more user-friendly experience.
https://image.nostr.build/7be43b4f8adf832e458fbde365b5b43f58ca7f5f35e240a094e3573faee83101.png
Another one of Jade's recent developments has been its evolution into a cypherpunk multi-tool for increased online security.
Jade can produce time-based one-time passwords (TOTPs) for platforms that require two-factor authentication (2FA), similar to apps like Google Authenticator. This feature allows users to have more control over their personal data and provides better security than a regular authenticator app. The secret is kept offline, like your mnemonic, and you receive an extra layer of protection with Jade's passphrase.
We also added the option to transform the Jade device into a Bitcoin miner. This feature, which is more recreational than a serious avenue for mining bitcoin, offers an educational way to explore the mechanics of mining. The function does not require a wallet to be set up or accessed and can easily be reversible if one decides to switch back to using Jade purely as a hardware signing device.
If fortune favors, any mined bitcoin will automatically be sent to an address pre-specified by the user. Moreover, users can learn about mining with real-time insights into metrics like the current block height and the device's hashrate, reducing the learning curve for newcomers in the mining space.
https://image.nostr.build/d41a809fff6589b3c4759abc8925f5bfcdf4772e9ff9ef83caa27979b6b80491.png
Integrating Lightning into Green
After unveiling an all-new redesigned Blockstream Green wallet in Q1, we shifted focus to Green’s much-anticipated Lightning integration via our on-demand node service, Greenlight. This will establish Blockstream Green as the first in-market wallet to enable non-custodial payments across Bitcoin and its leading layer-2 solutions, the Liquid and Lightning networks. The feature is undergoing testing in closed beta, and we expect a public beta by the end of September.
Greenlight simplifies the integration process through a simple, programmable API. This provides enterprises the flexibility to use their own LSP or transition to self-hosted infrastructure. Another unique advantage of Greenlight is it mitigates the risk and regulatory overhead associated with custody by delegating it to users. Under Greenlight, users hold their own private keys, which never leave their devices, while we handle node operations and maintenance on our end.
https://image.nostr.build/bd2608d08710c89761a1bb3e3b42404b442af6008a16c1cfeae9c97afe75050c.jpg
Christian Decker, the lead engineer for Greenlight, explains the inner workings of the infrastructure:
"There are two domains of control in Greenlight: the user and Blockstream. Any number of clients from the user domain can connect to a single node on the Blockstream domain. The node running on Blockstream's infrastructure receives commands, computes the state changes, and then reaches out to the signer, which is solely under the user's control, to have it check and sign off on the changes. The result is a non-custodial, on-demand Lightning node where your keys are stored on your device and never touch our infrastructure."
Scaling Access to Bitcoin with Blockstream Satellite
During the second quarter, we partnered with Swiss-based ZeroSync to work towards broadcasting zero-knowledge proofs (ZKPs) over the Blockstream Satellite. The use of ZKP systems like STARKs would make Bitcoin node synchronization near instant for a fraction of the memory overhead, allowing for greater accessibility and lower hardware requirements to validate the mainchain. This essentially would enable users to run a Bitcoin full node with far less bandwidth, exponentially growing the number of Bitcoin nodes in operation for further decentralization of the network.
On the Blockstream Talk podcast, we spoke with Robin Linus and Lucas George of ZeroSync in length about the far-reaching implications of ZKPs on Blockstream Satellite. Users in emerging economies or rural communities without internet infrastructure would greatly benefit. A member of the community with access to the Blockstream Satellite could act as a hub, resharing and broadcasting the chain proof to establish a kind of subnetwork for Bitcoin. This would give other members of the community near-instant access to the Bitcoin blockchain using low-end hardware like a local network-connected phone or even a web browser.
Aside from lowering the barrier of entry to run your own Bitcoin node, ZKPs on Blockstream Satellite allow for greater cross-chain interoperability and redundancy. This means someone could verify Bitcoin transactions with other blockchains using the chain proof.
The first experimental broadcast is anticipated on Blockstream Satellite by year-end.
Expanding the Liquid Federation
As the technical providers of the Liquid Network, we are vested in seeing the network reach its full potential to bring trust-minimized financial markets and applications to Bitcoin. Encouraging further decentralization of Liquid's federated consensus and governance models is an important part of this strategy, as seen with last year's deployment of DynaFed and the proliferation of the Federation's membership. Another aspect is the maintenance and upkeep of Liquid's three governance boards.
In April, the Liquid Federation concluded its yearly board elections, comprising three distinct boards tasked with various responsibilities vital to its governance structure:
Membership Board: Entrusted with crafting the guidelines for member inclusion or exclusion based on comprehensive assessments and recommendations.
Oversight Board: Responsible for devising internal rules and procedures for committee organization and management, along with monitoring network status.
Technology Board: Collaborates with Blockstream to craft a technical strategy that addresses the needs of Liquid members and users.
We are optimistic about another productive year for Liquid with the newly elected board members, improving the user experience of network participants, and advancing Bitcoin's financial layer.
In June, the Federation welcomed six new members—Bcademy, Boltz Exchange, Equitas Foundation, JAN3, MAVEN, and Mifiel. This recent addition expands the Federation's network to a total of 67 members, encompassing key exchanges, wallet providers, and infrastructure firms in the Bitcoin ecosystem. These partnerships are anticipated to diversify the global member base and usher in new opportunities for Liquid users.
More recently, the Federation announced the open-source release of Liquid's functionary code, fulfilling a long-standing goal. The new code allows anyone to audit the Watchmen and Blocksigner code and create their own Liquid-like network with features like Confidential Transactions and digital asset issuance.
Although Liquid's underlying codebase, Elements, has always been open-source, the additional functionary code release represents an important milestone for Liquid and greater transparency in its ongoing development.
Inaugural Media Briefing
Blockstream's CFO Erik Svenson and CPO Jeff Boortz led our first-ever media briefing, during which they shared updates on our product suite and discussed the company's major milestones. The hour-long online event was attended by several high-profile media outlets, including Fortune, Bloomberg, and Politico. Blockstream CEO Dr. Adam Back also answered questions from journalists during the Q&A segment. He discussed self-custody best practices and shared his perspective on the SEC's recent actions regarding altcoins as unregistered securities, as well as the potential long-term impact on Bitcoin.
During the briefing, we provided a sneak preview of the highly anticipated Cyberhornet—a modular Bitcoin miner designed to be scalable and suitable for enterprise use. The Cyberhornet marks our entry into the Bitcoin mining hardware sector, which began with our acquisition of Israeli mining manufacturer, Spondoolies, in 2021. We will release further details of the Cyberhornet's build and mining capabilities later this year, with a commercial launch planned for Q3 2024.
Please refer to our press release for more information on the Cyberhornet and other announcements made at the media briefing.
https://image.nostr.build/1265b02f3f6f0dd3d25e07e95286acc8e9fd2d73ab58d5ece7b5612c430a5ac9.png A preview of the highly anticipated Cyberhornet—Blockstream's modular Bitcoin miner designed for scalability and enterprise use.
Connecting with Blockstream
If you or your organization are interested in exploring opportunities for collaboration with Blockstream or considering the integration of one of our technologies into your operations, we encourage you to connect with our team through one of the product pages on the main Blockstream site.
For further updates, you can follow us on Twitter @Blockstream, and join the conversation in our Finance, Green, Jade, Lightning, Liquid, and Satellite Telegram channels and the new Build On L2 community platform.
-
 @ 9322bd92:a3d4cb0b
2023-09-19 22:43:06
@ 9322bd92:a3d4cb0b
2023-09-19 22:43:06-
Digital and Decentralized: Bitcoin is purely digital, meaning it exists only as computer code and doesn't have a physical form like paper money or coins. It's also decentralized, which means it's not controlled by any single company, government, or organization. Instead, it's maintained by a network of computers around the world.
-
Limited Supply: Unlike traditional money, which governments can print more of, there is a fixed supply of Bitcoin. There will only ever be 21 million Bitcoins, making it a finite and potentially scarce resource. This scarcity is one reason why some people see it as valuable.
-
Blockchain Technology: Bitcoin uses a technology called blockchain to keep track of all transactions. A blockchain is like a public ledger or a digital record book that is transparent and cannot be easily altered. This technology ensures the security and transparency of Bitcoin transactions.
-
Pseudonymity: When you use Bitcoin, you don't have to reveal your real name. Instead, you have a digital address, like a username, which helps protect your privacy. This pseudonymity can be appealing to people who value privacy.
-
Global and Fast Transactions: Bitcoin transactions can be sent and received anywhere in the world, and they usually happen quickly, often within minutes. This is in contrast to traditional banking systems that may take days for international transactions.
-
No Intermediaries: Bitcoin transactions are peer-to-peer, meaning they occur directly between the sender and receiver without the need for banks or other intermediaries. This can reduce fees and make transactions more efficient.
-
Security and Ownership: To access your Bitcoin, you have a private key, which is like a super-secret password. As long as you keep this key safe, you have complete control over your Bitcoin. However, if you lose it, you might lose access to your Bitcoins forever.
8.Store of Value: Some people view Bitcoin as a digital version of gold. They see it as a store of value that can protect against inflation and economic instability. This is why some investors buy and hold Bitcoin as an investment.
9Volatility: Bitcoin's value can be very volatile, which means its price can go up and down a lot in a short period. This can be exciting for traders but also risky for people who want a stable form of money.
- Innovation and Potential: Bitcoin has opened the door to new ways of thinking about money and finance. It has inspired the creation of thousands of other cryptocurrencies and blockchain projects, each with its own unique features and uses.
-
-
 @ 9322bd92:a3d4cb0b
2023-09-19 22:01:48
@ 9322bd92:a3d4cb0b
2023-09-19 22:01:48Chapter 1 serves as the introductory chapter of the text and sets up the foundation for the Power Projection Theory. It begins by providing the inspiration and justification for conducting the research. The author explains what inspired him to create a new theory about Bitcoin and why he felt it was his fiduciary responsibility as a military officer and US national defense fellow to do so. This chapter also provides background information about military strategy and the author's profession of warfare, establishing the context for the research. Additionally, Chapter 1 introduces the concept of the "softwar" neologism, which is likely a term coined by the author to describe the strategic implications of proof-of-work technologies like Bitcoin. The purpose of this chapter is to present the argument for why a different theoretical framework is needed to analyze these implications.
Chapter 2 delves into the methodology used to formulate the Power Projection Theory. The author discusses the choice to use grounded theory and provides an overview of the methodology and analytical techniques employed. Grounded theory is an approach that involves the systematic collection and analysis of data to generate a theory that is grounded in empirical evidence rather than preconceived notions. It allows for the discovery of concepts and theories that emerge from the data itself. In essence, Chapter 2 outlines the research process undertaken by the author to develop the Power Projection Theory. It provides insight into the methodology used and the approach taken to gather and analyze the data.
Chapter 3: Explains the Basic Principles of Physical Power Projection In Chapter 3, the author introduces the foundational theoretical concepts of Power Projection Theory. The author utilizes knowledge and theoretical frameworks from biology and military strategy to explain the importance of physical power projection for survival and prosperity in the wild. The chapter explores theoretical concepts associated with property ownership and physical security, using examples from nature to illustrate how organisms develop power projection tactics to settle disputes, determine control over resources, and establish ownership. The purpose of this chapter is to provide the core theoretical concepts needed to understand the complex relationships between physical power, physical security, and property ownership. Chapter 4: Explains the Basic Principles of Abstract Power Projection (and Why it’s Dysfunctional)
Chapter 4 delves into how and why humans use different power projection tactics than animals. The author provides a deep-dive on different power projection tactics, techniques, and technologies employed by modern agrarian society. Part 1 of this chapter focuses on how humans create and use abstract power as a basis for settling disputes, controlling resources, and establishing pecking order. Part 2 focuses on explaining why humans inevitably revert back to using physical power as the basis for settling disputes, controlling resources, and establishing pecking order, similar to other animals in the wild. The chapter concludes with a discussion about how a strategic nuclear stalemate may place human society in a vulnerable position, which could be alleviated by a "soft" or non-kinetic form of warfighting. The purpose of Chapter 4 is to highlight the complex sociotechnical trade-offs and implications associated with different power projection tactics, techniques, and technologies employed by human societies.
Chapter 5: Presents a Completely Different Perspective about Bitcoin In Chapter 5, the author presents a completely different perspective about Bitcoin using a theoretical framework that has little to do with money, finance, or economics. The chapter focuses on the sociotechnical implications of Bitcoin from a computer science and national strategic security standpoint. The author highlights how Bitcoin could have implications that exceed our current understanding of the technology, particularly in the realms of computer science, cybersecurity, and national strategic security. The chapter concludes by arguing that Bitcoin could represent a new way of warfighting called "softwar" that could potentially change international power dynamics and mitigate strategic-level stalemated between nuclear superpowers. The primary takeaway from this chapter is that Bitcoin could represent a groundbreaking discovery, referred to as "human antlers," with significant sociotechnical implications.
Chapter 6: Discusses Key Takeaways from Power Projection Theory Chapter 6 serves as the closing chapter of the thesis. The author enumerates several new hypotheses about Bitcoin derived from Power Projection Theory and encourages the research community to consider analyzing them. The author provides advice about next steps for researchers and offers brief advice to US policy makers. This chapter concludes by reflecting on the potential historical, strategic, and ethical implications of proof-of-work technology.
In conclusion it appears that the author explores the concepts and theories of power projection, physical security, and property ownership in relation to both animals and humans. The author also discusses the potential implications of technologies like Bitcoin in terms of power projection and warfare. The book aims to provide insights and explanations for human behavior and the motivations behind the use of certain technologies. It is likely that the conclusion of the book would summarize these findings and potentially provide recommendations or insights for future research or policy-making efforts.
-
 @ cd408a69:797e8162
2023-09-19 04:40:44
@ cd408a69:797e8162
2023-09-19 04:40:44Tsukiji KItaro ( 築地 きたろう )
📍 Tsukiji
🌐 https://www.tamasushi.co.jp/shop/kitaro_tsukiji/
🌐 https://maps.app.goo.gl/2btvzLdVXQM5STLc6
Tsukiji is the land where the Tokyo Wholesale Market used to be, and there are many sushi restaurants. Tsukiji is also relatively close to Ginza.
🐱 Recommended by them nostr:note1zlfsw0afd38kp607r7tre7209ttl8ls3r3cp5mzkvrav492zwpyqz0phcg
Uogashi Nihon-ichi Shibuya Dogenzaka ( 魚がし日本一 渋谷道玄坂 )
📍 Shibuya
🌐 https://www.timeout.com/tokyo/restaurants/uogashi-nihon-ichi-shibuya-dogenzaka
🌐 https://maps.app.goo.gl/BkMQiXX6ZhQWJeA7A
This restaurant is located relatively close to the Nostrasia Tokyo venue. This restaurant is unique in that you can casually enjoy sushi in a standing style.
🐼 Recommended by them nostr:note1luk3mh8l352j52ueueg457t69mfww9asjtrej5pjdupqsp0kw8qsdv959m
Atabo Sushi ( あたぼう鮨 )
📍 Yotsuya-sanchome
🌐 https://maps.app.goo.gl/vhHDJq6wt9DdALDF7
⌨️ Recommended by them nostr:note15fzx4u3kvtzwyhdt5qxf6gqxt9kxzktplvxp9r9vx9z3ryrfqhdswdfnn6
Kanda Eddoko Zushi ( 神田江戸っ子寿司 )
📍 Kanda
🌐 https://maps.app.goo.gl/kFKxjM2TEnoFvPfj8
👩🏻 Recommended by them nostr:note174xjfzml57ujjyjvrsne9e3lr96s5magsy4x3h9t0km2zcy5c8wqkfav72
Edomae Bikkuri Zushi ( 江戸前びっくり寿司 )
📍 Ebisu
🌐 https://maps.app.goo.gl/2qfxU76svTyvUyN96
🐈 Recommended by them nostr:note1av9uredv8dy74l7rhlmvn28nfuurrp92v0adr2644knwdg9r3rms0seyyx
Kanazawa Maimon Sushi Ueno ( 金沢まいもん寿司 上野 )
📍 Ueno
🌐 https://maps.app.goo.gl/NTm7HHHarY2Ak3UK7
Mori Ichi ( もり一 )
📍 Jinbocho
🌐 https://maps.app.goo.gl/6Kc2AnpJ91Huues79
Toriton ( トリトン )
📍 Oshiage ( Tokyo Sky Tree Town Soramachi Location )
🌐 https://maps.app.goo.gl/rFMejHfSKQtegx4d6
🍗 Recommended by them nostr:note18g59dk96zjkjk2dchfhymans4hkkk3gr5zur3vr7cnsxy73kj2hs4ggmuz
Sushibuya ( スシブヤ )
📍 Shibuya
🌐 https://maps.app.goo.gl/gPLjVwqsQJiQkaXE8
👩 Recommended by them nostr:note1mhjnrwvqrp5e2ptwjwrkxdttx9ck966hhv2qmpzrq9h3nfs5ge5qcxfp82
Manten-Sushi ( まんてん鮨 )
📍 Nihonbashi
🌐 https://maps.app.goo.gl/UnBimEfGVp4rM5WW8
🐇 Recommended by them nostr:note1fv0yyhqdz6l5prjh2l2xm6a6xwsk7f8k9wfnc65quvffpr2lq8dsufp3h2
Sushi-no-Midori ( 寿司の美登利 )
📍 Shibuya
🌐 https://maps.app.goo.gl/hdTK2oNtLiwYGRwb9
💖 Recommended by them nostr:note1vq6a6kppwzzd24futgdjdr3hccw8j5sj4freyxzc60h0uz9scs2ss5xs9m
-
 @ de7ecd1e:55efd645
2023-09-18 15:05:06
@ de7ecd1e:55efd645
2023-09-18 15:05:06Why Nostr Will Win
The rise of decentralized social networks and the promise of Nostr.
Sep 18, 2023
"The future is already here — it's just not very evenly distributed." - William Gibson
The current digital landscape, replete with centralization, has seen the emergence of a new contender: Nostr, a decentralized social network protocol. While many are quick to dismiss decentralized systems, believing the comfort of central platforms to be irreplaceable, Nostr's rise suggests otherwise.
Nostr's Foundation: Decentralization at Its Finest
“It's not the strongest species that survive, nor the most intelligent, but the most responsive to change.” - Charles Darwin
At its core, Nostr is built on principles that are shaking the very foundations of traditional social networking:
-
User Sovereignty: Nostr hands the reins of data back to its rightful owner - the user. This is a stark contrast to the data monopolies of today's centralized platforms.
-
Immutable and Transparent: With Nostr, data is transparently stored, ensuring users can trust the integrity of the content and its origins.
-
Modular and Flexible: Nostr isn't a one-size-fits-all. Its modular design means it can be tailored to suit various needs, making it adaptable and future-proof.
The Power of the Community
“Individual commitment to a group effort - that's what makes a team work, a company work, a society work, a civilization work.” - Vince Lombardi
Nostr isn't just a technology; it's a movement:
-
Organic Growth: Nostr's community-driven approach ensures that it evolves based on user needs rather than corporate interests.
-
Collaborative Security: The decentralized nature of Nostr means security is a collective responsibility, leading to more robust and reliable systems.
-
Open Source Advantage: With its open-source roots, Nostr benefits from the collective genius of developers worldwide, ensuring rapid innovation and improvement.
Breaking the Shackles of Centralization
“Innovation is the unrelenting drive to break the status quo and develop anew where few have dared to go.” - Steven Jeffes
Nostr's rise is a clear signal of a paradigm shift:
-
Interoperability: Nostr promotes a world where platforms can seamlessly interact, breaking the silos created by centralized giants.
-
Economic Fairness: Without centralized entities monetizing user data, Nostr ushers in a new economic model where value is equitably distributed.
-
Censorship-resistant: Nostr ensures that the voice of the user is not stifled by centralized algorithms or corporate agendas.
The Road Ahead
As with any emergent technology, challenges lie ahead for Nostr. However, its foundational principles, coupled with a passionate community, position it favorably in the evolving digital landscape.
In conclusion, Nostr isn't just another platform; it's a beacon for the future of social networking. As the digital realm continues to evolve, Nostr stands tall, promising a world where users are at the center, and data is truly democratized.
-
-
 @ 7fa56f5d:751ac194
2023-09-18 10:18:55
@ 7fa56f5d:751ac194
2023-09-18 10:18:55Adding support for NWC to Habla would allow for connecting any wallet over nostr for paying on the website. It currently only supports WebLN but Bitcoin connect allows us to configure an NWC connection and expose it through WebLN API. If we go this route the paying code that uses WebLN wouldn't need changes.
Requirements
- Add a "Connect wallet" option on Settings > Wallet screen
- Allow to connect an NWC wallet or nostr extension
- Show wallet connection status on Settings > Wallet screen
- Make sure both extension and NWC are supported for paying
References
-
 @ 2edbcea6:40558884
2023-09-17 17:13:39
@ 2edbcea6:40558884
2023-09-17 17:13:39Happy Sunday #Nostr!
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk , written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2 .
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
A little light on NIP activity this week, but a fair bit of activity with work done around search and discoverability. Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) (Proposed) NIP 133: Game Scores 🃏
This NIP proposes a new nostr event for publishing game scores. Users can publish their own “scores” (like with daily step counts) or game providers can publish the scores of users (imagine a public leaderboard).
This NIP is in early stages, but could be the foundation of some unique game experiences that could only be possible on Nostr.
Author: nostr:npub1melv683fw6n2mvhl5h6dhqd8mqfv3wmxnz4qph83ua4dk4006ezsrt5c24
Notable projects
RSSLay
This makes any RSS feed into a Nostr profile that can be followed via a pubkey. You can follow blogs, twitter accounts, subreddits, whatever. You’ll just need to tell RSSLay to create a profile for an RSS feed, follow the generated pubkey, and start using the RSSLay relay and you’re good to go.
This could help Nostr be the best place to consume all your content, instead of just another source of it.
Author: nostr:npub1ftpy6thgy2354xypal6jd0m37wtsgsvcxljvzje5vskc9cg3a5usexrrtq
Ditto
nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 has been making bridging Nostr with Mastadon (and other ActivityPub based tech) as easy as possible. Ditto is the latest foray with that goal.
Ditto is a Nostr client that uses relays to store data, but it acts like a Mastadon server so that you can interact with Mastadon and get many of the benefits of Nostr. Hopefully it’ll continue to make the Nostr-verse and Fediverse more interoperable. Then we may steal all the Mastadon users because Nostr is better 😈.
Author: nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6
Latest conversations: Search and Discoverability
Discoverability
In my estimation, Nostr is the best censorship-resistant social media with any meaningful ongoing usage. Nostr currently isn’t great at one core aspect of great social media experiences: discoverability.
If you know exactly who to follow, Nostr is great. Find those folks and you’re able to interact in a censorship resistant way where you control your data. 👍
If you want to discover people to follow and interact with, it’s currently very difficult.
One of the best things about social media for me is the ability to learn, and what the bird app has historically done very well was surface people I wouldn’t have otherwise heard from. Lots of noise but at least I was exposed to more than the people I already knew.
Without solving this problem it’s unlikely Nostr will attract and onboard a significant fraction of humanity and reach its full potential for good.
Historically solving this problem has meant submitting to the whims of algorithms.
Algorithms as a solution for discoverability
Algorithms are great ways for social media companies to inject ads into users’ feeds; it’s also great for controlling users’ feeds so that content that is “offensive” to advertisers aren’t shown with their ads.
Before all that, algorithms are usually created to help increase the signal to noise ratio of users’ feeds. At their most basic they’re intended to surface content users may like from accounts they’re not following, or to hide content they’ve seen before but someone recently reposted or liked.
We don’t have many true feed algos on Nostr yet, I’ve only seen Nostur and Coracle start experimenting with widening what shows up in users’ feeds. But it goes beyond compiling a full feed for users, the “trending” lists on various clients (Primal and nostr.band being the most cited examples I’ve seen) are introducing more centralized logic around what is recommended to users.
Many came to Nostr because they were tired of the algorithms manipulating their feed and manipulating the reach of content that they published. Many are wary of algos entirely.
Algorithmic feeds are a tempting place to go to solve discoverability, but as the heavier-handed solution it comes with risks that Nostr users are less tolerant of.
Search as a bridge
Before search engines people had the same challenges around discoverability as Nostr users have now.
People actually printed and shipped zines which were themed publications that would publish new or noteworthy websites so that people could discover content on the internet that might interest them. (Sounds a bit like a certain publication you may or may not be reading right now 😉)
Search engines were able to solve the problem of discoverability in a way that was accessible to far more users than previous solutions. It wasn’t that discoverability was impossible before, it was just too much work to unlock usage by the masses.
There are several projects in the Nostr-verse that are attempting to solve this problem, coming from different perspectives.
Nostr.band (built by: nostr:npub1xdtducdnjerex88gkg2qk2atsdlqsyxqaag4h05jmcpyspqt30wscmntxy) is the incumbent if Nostr is old enough to have incumbents. They’re indexing as much of Nostr as they can and putting together trending feeds, and APIs for devs to consume so clients can make Nostr easier to navigate.
relay.noswhere.com (built by nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj) is an attempt to make a relay available that follows the exact Nostr specifications as possible but still make tasks like putting together a trending feed easier for clients.
There are even solutions like the project by nostr:npub1vp8fdcyejd4pqjyrjk9sgz68vuhq7pyvnzk8j0ehlljvwgp8n6eqsrnpsw https://advancednostrsearch.vercel.app/ to give searchability a user interface or https://relay.guide/inspector (built by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2) to just help people inspect what events are on a relay.
Effective, accessible, dev-friendly search could be the happy middle that allows us to avoid heavy algorithmic feeds, but still allow clients to help users discover content.
The challenge is some solutions (like nostr.band) tend towards creating more of a walled garden around their solution, because they’re creating APIs that are a layer on top of Nostr instead of utilizing Nostr’s unique and specific architecture. While noswhere is more exactly tied to Nostr’s design specifications (what’s outlined in NIPs) it’s not yet as widely adopted or utilized.
The risk of consolidation
Just like what we saw with Google monopolizing web search, solutions to discoverability of any network have strong incentives towards a winner-take-all situation. Nostr is not uniquely immune to that.
Discoverability is a fundamental challenge of decentralization, but it must be solved for Nostr to live up to its potential. I’m glad that Nostr devs are trying things and figuring out what works so we can build that future as fast as possible.
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know, DMs welcome.
nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 726a1e26:861a1c11
2023-09-17 16:13:04
@ 726a1e26:861a1c11
2023-09-17 16:13:04This is my first post on Habla. More to come!
-
 @ 6e75f797:a8eee74e
2023-09-17 09:09:21
@ 6e75f797:a8eee74e
2023-09-17 09:09:21With the constant dramas all around the crypto world and seeing thousands of people losing their savings to custodians and "crypto banks", I've decided to make this short video. Making this video took me less than 20 minutes so if you don't manage your own private keys yet, this shouldn't take you more than 10 minutes to reach peace of mind with your HODL coins.
Before we start let me however clear up some very common misconception we encounter every time when people talk about this topic.
There is no assets in your wallet
People always talk about taking self-custody of their assets by taking them off-chain. There is no such thing as moving coins TO your wallet.
Wait, what?
Correct, ALL coins and other tokens only exist ON their respective blockchain. Thus you cannot move coins TO a wallet or store coins "off-chain". Having said that, you can move your coins, tokens, NFTs to an address for which you control the private key giving you access to your assets ON the blockchain.
Once you understand this you'll also understand that your wallet cannot get hacked, you cannot lose coins and if you lose your phone or your HD crashes the only thing you'll ever need to regain control over your assets ON-CHAIN is the private key controlling access to those assets.
In other words, your wallet is a signing device and your private key identifies you as the owner of any asset "associated" ON the blockchain with that address.
So let's do this!
https://cdn.satellite.earth/5e6f90617da834668219c5f16ad0c306964f3c50b26a99a83630386eb0fcd91a.mp4 (Note: The wallet used in this example is deemed compromised. Do not send tips to any address, do not use these keys or seed in any form whatsoever!!!)
You see? I've created a fresh wallet in less than 10 minutes, backed up the seed (of the entire wallet) and I backed up the private key of the wallet I (demo wise) planned to use. 10 minutes of my time to protect myself from Counterparty failure, insolvency or rug pulls FOREVER.
Now that you understand the beauty of private keys, did you know that you can import the same key into various wallets to access your coins from any device you like? That's because your coins are on the blockchain and you can "sign" accessing them from ANY device or numerous devices. Again, that's why you cannot lose coins even if your device gets lost or breaks down.
Thanks for taking the time to read/watch. I hope this will take the so called "self-custody fear" away from some of you.
References:
Wallet used: https://electrum.org/
Managing private keys: https://www.investopedia.com/terms/p/private-key.asp -
 @ cd408a69:797e8162
2023-09-14 13:08:47
@ cd408a69:797e8162
2023-09-14 13:08:47Nostrasia Hackathon
Welcome FOSS hackers and creatives who care deeply about freedom technology!
自由のテクノロジーに深い関わりたい FOSS ハッカーとクリエイター、あつまれ!
We're joining forces with Bolt.Fun for a month-long hackathon bridging Bitcoin and NOSTR (Notes and Other Stuff Transmitted by Relays), culminating with a special three day sprint and live event in Tokyo at the Nostrasia Conference.
私たちは、Bolt.Fun と協力して、ビットコインと Nostrを橋渡しする ハッカソンを、1 か月間かけて開催します。 クライマックスは東京で開催されるNostrasia Tokyo が舞台。3日間の特別なスプリントとライブ イベントで最高潮に達します。
Be a Part of the Early Days of Nostr
Nostr の創成期を共に作り上げましょう
Help build the future of Nostr! Like the early days of Bitcoin or of the Internet, Nostr is nascent open technology shaping new types of social experiences to connect people across the globe. It carries a foundation of principles similar to Bitcoin, like decentralization, simplicity, and censorship-resistance.
Nostr の未来を築くのに協力してください!ビットコインやインターネットの初期と同じように、Nostr は世界中の人々をつなぐ新しいソーシャル体験を形成するオープン テクノロジーの初期段階にあります。 Nostr には「分散化」「シンプルさ」「検閲耐性」など、ビットコインと同様の原則が組み込まれています。
Orange-Pill people through the Purple-Nostr-Pill
オレンジピル(ビットコイン)から紫の Nostr のピルへ
Bitcoin and Nostr communities are in synergy. What started as a social protocol is quickly transforming into a space for exploration on ways to support content creators through bitcoin lightning micro payments, often referred to as zaps. Bitcoin integration to the nostr protocol strengthens Bitcoin's use case as a currency of exchange. It carves new paths to a culture of value4value.
ビットコインと Nostr のコミュニティは相乗効果を発揮します。 Nostr はソーシャルプロトコルとしてはじまりましたが、今では Zap (ビットコイン の ライトニング マイクロペイメント)を通じてコンテンツ クリエイターをサポートする方法を模索する空間へと急速に進化しています。 Nostr プロトコルにビットコインが組み合わさることで、交換通貨としてのビットコインの働きが強化されます。 それは、"value4value" の文化への新しい道を切り開くでしょう。
Help People HODL their Keys (Social+Monetary)
人々が自分のキーを HODL (長期保有)できるように支援します (ソーシャル + 金銭的に)
Nostr exists outside of the rule of platforms and those who seek to control them. HODLing your nostr keys is hodling your identity and social graph, outside of KYC. By helping develop and educate on NOSTR, you are helping people escape walled gardens & gain control and choice over their identities & their money. The Internet, over time, has become centralized, help Nostr stay decentralized by supporting the growth of an ecosystem of apps, websites, microapps, relay services...
Nostr はプラットフォームやそれを制御しようとする人々の支配の外にあります。 Nostr keys を持つことは、KYC (本人確認)以外であなたのアイデンティティとソーシャル グラフを保持することになります。 Nostr の開発や教育に貢献することは、人々が束縛から解放され、アイデンティティやお金に対する主導権を得られるよう支援することにもなるのです。 時間の経過とともに集中化されてきたインターネットですが、Nostr のアプリ/Web サイト/マイクロアプリ/リレー サービスのエコシステムの成長をサポートすることで、Nostr の分散化を維持できるようになります。
Permissionless Building
許可を必要としない構築
Opportunities abound in an environment ripe for innovation:
- Develop & design new nostr white label clients, middleware, microapps...
- Help improve existing Nostr FOSS projects
- Contribute directly to protocol development through NIPs (Nostr Implementation Possibilities)
- Encourage nostr and bitcoin adoption through art, education, and any way you like
イノベーションの機が熟した環境には、チャンスが溢れています。
- Nostr の真新しい クライアント、ミドルウェア、マイクロアプリを開発したりデザインする
- 既存の Nostr FOSS プロジェクトの改善に寄与する
- NIP (Nostr Implementation Possibilities) を通じたプロトコル開発に直接貢献する
- 芸術、教育、その他好きな方法を通じて Nostr とビットコインの普及を推進する
Hack in a Supportive Environment
サポートされた環境でハックしよう
We have a growing list of knowledgeable people with skin-in-the-game to mentor and support your journey. Once your project matures, you may also have 1-on-1 guidance to help you reach your vision and discover ways of growing and funding it.
私たちは、あなたの道のりを指導しサポートしてくれる知識豊富なメンターを増やしています。 プロジェクトが成熟した暁には、1対1のガイダンスを受けられる可能性もあります。それは、あなたのビジョンを達成し、成長させて資金を得る方法を発見するのに役立つでしょう。
Nostr has a blossoming community open to innovation. It is also a great testing ground, as people in the community are open to giving and receiving feedback. It is an environment encouraging conversation on feature ideas as well as possible solutions to social media issues and product bugs.
Nostr には、イノベーションに対してオープンで、発展しているコミュニティがあります。 コミュニティの人々はフィードバックの授受にオープンであるため、優れた実験の場にもなります。 機能のアイデアや、ソーシャル メディアの課題や製品のバグの解決策についての会話を促進する環境です。
NostrHack Tracks
You have 3 options
NostrHack Tracks には3つのオプションがあります
Track 1: Builder's Track - Reimagine Nostr
トラック1 : ビルダーのトラック - Nostr を再考しよう
If you can think of it, it can be engineered! Nostr encourages permissionless building while staying mindful of interoperability and network support. Help BUIDL, design, and improve an area you are passionate about. Reimagine and BUIDL features, tools, clients... Help solve issues and create new experiences in social media.
思いつくことができれば、エンジニアリングできる! Nostr は、相互運用性とネットワーク サポートに留意しながら、パーミッションレスな構築 (BUIDL) を奨励しています。 あなたが情熱を注いでいる分野での構築、設計、改善に貢献してください。 機能やツール、クライアントを再考して構築 (BUIDL) し、ソーシャル メディアでの課題を解決して新しい体験を生み出すのに協力してください。
Possibilities...
これを踏まえて…
BUILD on the NOSTR Protocol
The Nostr Implementation Possibilities (NIPs) are optional protocol features anyone can add to their clients. Improve and strengthen existing NIPs or build on new ones. NOSTR is a balance of simplicity, interoperability, backward-compatibility and innovation.
NIPs は、誰でもクライアントに追加できるオプションのプロトコル機能です。 既存の NIP を改善および強化するか、新しい NIP を構築してください。 Nostr は、シンプルさ、相互運用性、下位互換性、革新性のバランスを保っています。
Focus on UX
Nostr is made up of a wide range of clients and tools. To make NOSTR scalable, you can help improve its user experience and education.
Nostr は幅広いクライアントとツールで形成されています。 Nostr をスケーラブルにするために、UX と教育の改善に協力してください。
Help shape a Web of Trust
Nostr cares about removing the KYC tied to our identities. To use Nostr you do not need to give up your phone number, email, financial information, or any metadata tied to your real world identity to be later harvested and sold. You are not the product. What are ways that trust can be earned to prevent impersonation, spam...?
Nostr は、私たちの身元に関連付けられた KYC (個人情報)を取り除けるようにしています。 Nostr を使用しても、電話番号、電子メール、財務情報、または現実世界のアイデンティティに関連付けられたメタデータを、収集されたり販売されたりして手放すことになる心配がありません。 あなたは商品ではないのです。 その中で、なりすましやスパムを防ぐために、信頼を獲得するにはどうすればよいでしょうか...?
NIP05/Nostr address
One of the solutions to build a web of trust used today, is to tie your nostr hex public key to a domain. Although this makes it harder for bots to have nostr addresses, it is not a perfect solution. Domains are centralized through DNS. To help people who do not have their own domains or cannot easily add a NIP05 on their sites, your nostr address can be hosted as a service along with other people's. At this moment, you can highlight just one nostr address per profile. In the future, could it include your website, where you work, and other identifiers... What are other possible solutions?
現在使用されている信頼獲得のための解決策の 1 つは、Nostr の HEX 公開鍵をドメインに結び付けることです。 これにより、完璧な解決策ではないものの、bot などが Nostr アドレスを持つことが難しくなります。 ドメインは DNS を通じて一元化されています。 独自のドメインを持っていない人や、自分では NIP-05 を簡単に追加できない人のために、あなたの Nostr アドレスをサービスとして他の人のものと一緒にホストすることも可能です。 現時点では、プロフィールごとに1つの Nostr アドレスのみを強調表示できますが、将来的には、Web サイト、勤務先、その他の識別情報も含められるようになる可能性があります...この他にも考えられる解決策は何かありますか?
On Decentralization & Discoverability
分散化と発見可能性について
Your identity in NOSTR is tied to your keys, but your information needs to be shared and found across a network of relays. To promote decentralization and censorship resistance, relays need to be easy to setup, lightweight, and sustainable. Relays get to choose what information passes through them, so they are also a form of spam prevention that could potentially also become censoring, so both the relay-runners and the individuals connecting to relays need to have choice and policies cannot be homogenous one-size-fits-all. What are possible solutions to make setting up relays easier, to make running a relay sustainable, to have new ways of discovering information...
Nostr での ID はキーに関連付けられていますが、その情報はリレーのネットワーク全体で共有され、検索できる必要があります。 分散化と検閲耐性を促進するために、リレーはセットアップが簡単で、軽量で、持続可能である必要があります。 リレーは通過する情報を選択できるため、スパム防止の一形態である一方で検閲にもなり得ます。そのため、リレー管理者とリレーに接続する個人の両方に選択権が必要で、ポリシーが全てに対し画一的になってはいけません。 リレーのセットアップを容易にし、リレーの実行を持続可能にし、情報を発見する新しい方法を実現するには、どのような解決策が考えられるでしょうか...?
Buidl tools to connect to Git, as a decentralized alternative to GitHub
GitHub の分散型代替手段として、Git に接続するための BUIDL ツール
Media Uploads
To keep relays lightweight, images are hosted by uploading them to the web, and keeping only the links to them in the data within individual nostr notes. This has led to developing image uploading services specific to nostr, but they carry the risk of centralization or censorship. Some product makers and relay runners are looking into direct uploads to Cloud services. What are possible solutions to the handling of media (images, videos, music...)?
リレーを軽量に保つために、画像は Web にアップロードしてホストされ、各投稿のデータには画像へのリンクのみが保持されます。そんな中で、Nostr に特化した画像アップロード サービスが開発されましたが、集中化や検閲のリスクが伴います。 一部のプロダクト開発者やリレー管理者は、クラウド サービスへの直接アップロードを検討しています。 メディア(画像、ビデオ、音楽など)の処理について、考えられるよい解決策はありますか?
Social Signals
People have the choice to block and mute others, this gives signals to relays, which can reenact policies based on those and other signals. Relays need to be able to differentiate real signals from those wanting to game the system for censorship. Relay runners need to have the capacity to make decisions on what to allow or reject.
ユーザーは他のユーザーをブロックしたりミュートできます。ユーザーの設定内容はリレーに送信され、リレーはその設定に基づいてそれぞれのポリシーを再現できます。 リレーは、実際の設定と、検閲のためにシステムを操作しようとする設定を区別する必要があります。 リレーの管理者には、何を許可し、何を拒否するかを決定する能力が必要です。
Track 2 : Marketplaces & Value4Value
Make freedom of exchange fun again! Nostr extends beyond social. It is integrating ways for content creators to be supported through lightning micropayments, called zaps, for their creations. The possibilities of building niche value4value economies through the exchange of products, services, and ideas, is growing through various avenues: Marketplaces, fundraising, blogs, music, streaming... devise new robust ways of integrating NOSTR and Bitcoin of monetary and skill exchange. Seek to explore distributed, digital reciprocity and free trade. Encourage a culture of value4value.
自由な交流を再び楽しく! Nostr はソーシャルを超えて広がります。 Zap と呼ばれるマイクロペイメントを通じて、コンテンツクリエイターの作品をサポートできる方法を兼ね備えています。 製品、サービス、アイデアの交換を通じてニッチな価値と価値(value4value)の経済を構築する可能性は、さまざまな手段を通じて拡大しています : マーケットプレイス、資金調達、ブログ、音楽、ストリーミングなど... Nostr とビットコインを組み合わせて、金銭とスキルの交換を行う新しい堅牢な方法を考案します。分散型、デジタル相互主義、自由貿易を探究してください。 価値対価値(value4value)の文化を促進してください。
A value4value culture is not only about the individuals using NOSTR products and services, but also about the developers and creatives building sustainable projects. What are ways of sustaining NOSTR through Bitcoin that do NOT make the individual user the product and that are privacy mindful?
value4value の文化は、Nostr の製品やサービスを使用する個人だけでなく、持続可能なプロジェクトを構築する開発者やクリエイターにも関係します。 個人ユーザーを製品にすることなくプライバシーに配慮しながら、ビットコインを通じて Nostr を持続させる方法は何ですか?
Possibilities...
On Social and Economic Signals
Zaps
Many nostr clients have implemented lightning zap payments. Imagine instead of liking a nostr note, you can zap someone's note and they can receive bits/sats in appreciation for their content. It is a strong signal to creators of the kind of content their audiences are looking for. The Apple App Store has recently banned the zapping of specific notes, per Apple's policy that makes the sale of digital content prohibited except when paid through their services. Fortunately, Nostr exists in many decentralized forms outside of app stores and the community is creating new and innovative ways to send bitcoin and free speech from relay to relay, circumventing barriers as they appear. What are solutions that can make NOSTR and zaps ubiquitous?
多くの Nostr クライアントが Zap を導入しています。Nostr での投稿を「いいね」する代わりに Zap すると、その内容に対する感謝としてビットコイン(サトシ)を受け取ることができるイメージです。 これは、フォロワーがどのような種類のコンテンツを求めているかをクリエイターに伝える強力なシグナルになります。 Apple App Storeは最近、サービスを通じて支払われる場合を除きデジタルコンテンツの販売を禁止するというAppleのポリシーに従い、特定の投稿への Zap を禁止しました。 幸い、Nostr は多くが App Store の外で分散型で存在しているため、コミュニティは障壁を回避しながら、ビットコインと言論の自由をリレーからリレーに送信するための革新的な方法を生み出しています。 Nostr と Zaps をユビキタスにするソリューションとは何ですか?
Track 3 : Empower Communities
Give choice and control back to the individual! Create paths forward to help onboard millions of new users and restore free and uncensored speech to the world
選択とコントロールを個人に返そう。 何百万人もの新規ユーザーの参加を支援し、自由で検閲されていない言論を世界に取り戻すための道筋を作り出してください。
Possibilities...
On Security, Privacy & Self-Custody
Private Communication
Direct Messages on NOSTR are encrypted, but metadata is leaked. If someone's key is compromised, whoever has access to that account can read those messages. Integrating secure and reliable encrypted communication protocols, like the SimpleX messaging protocol, is especially desired by the community, as many in Nostr are aware of the risks of surveillance, authoritarianism, government and Big Tech overreach... Private communication is important for individual rights, in particular for activists and journalists across the globe.
Nostr のダイレクト メッセージは暗号化されていますが、メタデータは漏洩します。 誰かのキーが侵害された場合、そのアカウントにアクセスできる人は誰でもそれらのメッセージを読むことができてしまうのです。Nostr の多くの人が監視、権威主義、政府とビッグテックの行き過ぎのリスクを認識しているため、 SimpleX メッセージング プロトコルのような安全で信頼性の高い暗号化通信プロトコルの統合が、コミュニティによって特に望まれています...プライベート通信は個人の権利にとって重要です 、特に世界中の活動家やジャーナリストにとって。
Zaps & Privacy
Current lightning zap payments tend to be custodial and not mindful of privacy, though they are helping onboard people unto lightning. What are ways that people can grow into non-custodial solutions? A wider adoption of Bolt-12 would improve zap payment privacy, what are ways to encourage that development? What are other possible solutions?
現在のザップの支払いは、ライトニングペイメントに出会うのに役立っているものの、カストディアル(管理的)でプライバシーに配慮していない傾向にあります。 ノンカストディアル(非監護的)なものになるよう解決する方法はありませんか? Bolt-12 が広く採用されれば、Zap 支払いのプライバシーが向上しますが、その開発を促進するにはどのような方法がありますか?また、他に考えられる解決策はありませんか?
Closing Live 3-Day Sprint at the Nostrasia Conference
Nostrasia Tokyo 3日間のライブスプリントによる締めくくり
Tokyo | Nov 1-3 (you can also join virtually)
If you heard of the Nostrica unconference, which happened in Costa Rica in March of this year, Nostrasia is the second Nostr World conference, bringing NOSTR and Bitcoin awareness to the heart of Asia, where freedom communication and freedom money are direly needed.
今年の3月にコスタリカで開催された Nostrica のことをご存知の方もいると思いますが、ノストラジアは2回目の Nostr 世界カンファレンスです。自由なコミュニケーションと自由なお金が切実に必要とされているアジアの中心にNostr とビットコインの認識をもたらします。
Tokyo and Hong Kong are beautiful cultural hubs with budding Nostr and thriving Bitcoin communities of their own. We are eager to spread NOSTR education and development in those regions and beyond. We will close this Nostrasia month-long hackathon with a 3-day sprint at the Nostrasia Conference in Tokyo.
東京と香港は、新進気鋭のNostrと繁栄する独自のビットコインコミュニティを持つ美しい文化の中心地です。 私たちは、Nostr の教育と開発をこれらの地域やその他の地域に広めることに熱心に取り組んでいます。 この Nostrasia の 1 か月にわたるハッカソンは、Nostrasia Tokyo での 3 日間のスプリントをもって終了します。
We will have a dedicated workshop area and food for you to hack away on the final details of your projects. On the last day of the conference, the most robust projects will get time on stage to present. We will close the Nostrasia Hackathon with a special presentation.
プロジェクトの最終的な詳細を検討するための専用のワークショップ エリアと食事をご用意します。 カンファレンスの最終日には、最も強力なプロジェクトがステージ上でプレゼンテーションを行う時間が与えられます。 Nostrasia Hackathon は特別なプレゼンテーションで締めくくられます。
We cannot wait to see what new and exciting projects are proposed for the Nostrasia Hackathon. We’re eager to welcome devs and non-devs alike to contribute to this space and help #grownostr in any small way to help onboard Asia, and the rest of the world to this robust open communication protocol and decentralized freedom of speech tool.
Nostrasia Hackathon ではどんな斬新でエキサイティングなプロジェクトが提案されるのか楽しみです。 私たちは、開発者も非開発者も同様にこの分野に貢献し、アジアやその他の世界をこの堅牢なオープン通信プロトコルと分散型言論の自由ツールに参加させるために、どんな小さな方法でも #grownostr を支援してくれることを心から歓迎しています。
-
 @ 6e468422:15deee93
2023-09-14 11:13:40
@ 6e468422:15deee93
2023-09-14 11:13:40What I always liked about twitter was that it was never one place. You had all these sub-communities, yes, but the open nature of it allowed for wild interactions and the breaking of bubbles.
It was public square, dive bar, office water cooler, nightclub, and philosophy department all rolled into one. And you never knew who you were dealing with, and when those various "places" would interact.
My approach to twitter was always to never take things too seriously, and that's my approach for #nostr still. There is wisdom to "it's just a tweet bro" and I still believe that the secret to life is to send it, whether it be note, tweet, or in general.
Because you never know who you're dealing with, a great strategy is to assume that the other person is fourteen, or drunk, or really high, or senile, or all of the above. You wouldn't be mad if a stoned 14yr old would say something stupid to your face, so why be mad online?
I hope that we can rebuild what twitter used to be and what it was supposed to be, and transcend it. I believe that we're halfway there already. Given enough time and attention, I'm confident that we'll manage to build what so many on #nostr dream and hope for.
Zaps are already transcendent in that sense. As are cryptographic identities. Putting the user in control (as opposed to platforms) will be key to all of it, and I'm beyond excited to what is coming down the line with DVMs and even more exotic things.
The responsibility is on us to build it right, and to educate users as well as encourage them to take matters in their own hands. Nothing in life is free, not even freedom. We'll have to fight for it, and we'll have to take responsibility for ourselves and our actions.
Much needs to be built, much education needs to be done, much rektucation still needs to happen. But I remain optimistic, because the building blocks are there. Bitcoin works. Lightning works. Nostr works. Not perfectly, but it works.
I can't wait to see where we'll be in 5 years from now. It's wild to see where we are already. This is happening, and it's all happening because of you guys: focusing on the good that freedom tech can bring, pouring your time, money, effort, and attention into it.
I'm very grateful for that and to be part of it all. Thank you, from the bottom of my heart. I've said it before and I'll say it again: the future is bright, we just have a lot of building to do.
The above is a copy/paste of this thread:
nostr:note1pz9hq70xydrmu4s3slyhq67s7s2j6v7jtycr5tvzlgrncekxr9gsy08a34
Re-posting it here as long-form because threads on nostr still kinda suck, unfortunately.
nostr:note1n9ykwwjg0grdwymtclqfm9g8tvn86jkmydgaswjh3msd4s9xavhqgr6w66
If you want to help fund and/or build the future I'm alluding to, check out nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f & nostr:npub1s0veng2gvfwr62acrxhnqexq76sj6ldg3a5t935jy8e6w3shr5vsnwrmq5
-
 @ 6e75f797:a8eee74e
2023-09-13 19:31:18
@ 6e75f797:a8eee74e
2023-09-13 19:31:18It's been a busy month for the ZapStream developers and it's a good time to post a small update on all the new features and toys we've received from nostr:npub1v0lxxxxutpvrelsksy8cdhgfux9l6a42hsj2qzquu2zk7vc9qnkszrqj49, nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac and nostr:npub107jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2quqncxg (and all the other contributors). So let's get to it.
New stream option!
ZapStream now has three different streaming options for creators. * Basic: 2.5 sat/min offers only source encoding * Good: 10 sats/min offers source, 720, 480 or 240 * Best 21 sats/min offers all of the above encoding plus VOD storage
Widgets & Zap Alerts
Earlier this month the team added the first iteration of widgets to ZapStream. Those can be found at zap.stream/widgets.

To add any of the widgets to your stream simply copy the code above the desired widget and add it to OBS as a browser source. Pro tip: set the browser source to refresh when it becomes active and tick the box to disable the source when it's not showing.
verbiricha also released an update for zap alerts adding TTS (text to speech) to the alerts. TTS currently supports English, German and Spanish.

The setup is pretty straight forward. Enable TTS, set the minimum zap amount to trigger TTS, select language and speaker and then copy the link into a new browser source in OBS. You can also test the alert on the widget page or change the voice volume. Values are 0-1 in 0.1 increments.
NIP-75 for goals
NIP-75 was recently written by verbiricha and is replacing the previous metadata kind event used for zap goals on ZapStream. NIP-75 is now fully implemented in ZapStream. With this creators may now create new goals, reuse previous goals or use long-term goals during their streams.
Goals were also moved to the STREAM settings, accessed from the top-right of website.

To create a new goal simply click on add stream goal.

To reuse a previous goal select your goal from the dropdown menu.

If you'd like to see your previous goals or create a goal with more than one beneficiary head over to vercel.app. There you'll find a list of all your goals.
Settings Page
The settings page is a contribution from nostr:npub1zk6u7mxlflguqteghn8q7xtu47hyerruv6379c36l8lxzzr4x90q0gl6ef and can be accessed by clicking on your profile image on the top-right of the page.
New login design allowing for NIP-07 authentication. In addition ZapStream now also supports authentication via nsec (prompts a warning). WebLN functionality has been added too allowing viewers to zap creators without having to switch apps.

Languages
ZapStream now also supports 17 different display languages. Thanks to a long list of Nostriches who've contributed to the ZapStream translation project.

Check out Kieran's recent note for a full list of all contributors. nostr:note19rxd3shktqad9fv4a6x6dhzj5qwhm899zspjcqn52q5xpl58vwpsd5wupc
Known issues
- popped out chat doesn't display direct GOAL chats
- ALL chat, badges next to user names is currently broken.
Done! :)
This concludes the community update. I hope you'll find it helpful and if you have any question or need help getting setup, don't hesitate to jump into one of my streams or check out the Getting started on ZapStream Guide.
Your fellow Nostrich, nostr:npub1de6l09erjl9r990q7n9ql0rwh8x8n059ht7a267n0q3qe28wua8q20q0sd
-
 @ 76c71aae:3e29cafa
2023-09-13 18:03:50
@ 76c71aae:3e29cafa
2023-09-13 18:03:50Building a Community
Bluesky has successfully built a thriving community on its initial test server, complete with its own norms, culture, and even inside jokes like "sexy alf." Far from being just a test server, it has become an entity of its own, boasting a community of 600,000 users.
Facing Conflict
However, not everything has been smooth sailing. The server has also been a battleground for significant conflicts. A fundamental difference exists between those who advocate for an open, decentralized protocol and those who prefer a more actively managed social space. This gap between the driving vision of the project and the evolving values of its community has led to tensions within the Bluesky team.
Addressing the Challenge
The merits of both a federated social media protocol and a rigorous stance on policing bigotry are clear, but these two goals are not entirely compatible. What if they didn't need to be? The current Bluesky server could continue to operate as a standalone entity with updated software, while the company also launches the atproto network using the same software.
Accommodating Users
Users could then choose whether to stay on the existing server or use key migration technology to move their accounts to another server that is part of the open network. This would enable users to maintain the same identity across both platforms, offering them a choice in their user experience.
Managing Speech
On a fully open, decentralized social media protocol, managing speech the way many early Bluesky adopters would like is challenging. Although you can block or mute undesirable users and content, you can't entirely prevent them from using the protocol. This underscores the inherent tension between what early adopters want and the open-source, open-protocol direction the company is taking.
Examples of Exclusivity
Case in point: some fediverse servers either don't federate at all or only do so on a very limited basis, like certain Japanese servers. This shows that exclusivity is possible, and the current server, with its 600,000 users, could continue as its own standalone entity.
Empowering Users
What if the current server were handed over to its users for management? Bluesky the company would continue to develop software that could be used both for this specific instance and for the larger network. Digital democracy tools could be employed to allow users to vote and select a management team responsible for both technical and trust and safety issues. This would provide the community a direct voice in shaping their online environment.
Funding the Transition
Operating Bluesky isn't without costs, so funding is crucial. Potential sources could include Bluesky LLC, crowdfunding, or foundation donations. Once operational, the community could explore sustainable business models to continue financing trust and safety measures.
Conclusion
This proposal aligns with Bluesky's original vision of empowering communities to manage themselves. By giving control of the current server to its users and continuing to develop software that can be used both by this standalone instance and the larger network, we can create diverse digital spaces that meet the needs of all users while maintaining the vision of an open social media protocol.
-
 @ 6efb74e6:41285536
2023-09-13 15:46:39
@ 6efb74e6:41285536
2023-09-13 15:46:39proofofwork: 15 minutes preparation, overnight marinate and 2 hour roast time.
YEILD: 1 roast duck, enough for 3 to 4 people
INGREDIENTS: 1 whole Pekin ducks about 2.8-3 kilograms
STUFFING:
1 stick of lemongrass, rough chopped
25 grams ginger, rough chopped
25 grams galangal, rough chopped
3 ea cloves garlic, chopped
2 ea shallots, chopped
DRY SPICE RUB:
1 tablespoons Sichuan peppercorns
1 tablespoons white peppercorns
1 cinnamon sticks
1 teaspoon star anise
1 tablespoons salt flakes
METHOD:
- Start the recipe a day before cooking the ducks. Rough chop all the stuffing ingredients and place them in the cavity of the bird. Seal the cavity. Do this by stretching the excess skin flaps by the cavity, bringing them together and piercing them with a couple of bamboo skewers.
- To make the dry spice rub, toast all the spices together in a pan until the mix becomes aromatic. Once cooled, grind the spices in a coffee grinder until they are a fine powder. If you want to go old school then you can use a mortar and pestle.
- Cover the outside of the ducks with the spice rub. Place ducks in the refrigerator uncovered over night so the skin dries out.
- The next day pre heat the fan forced oven to 200 C, place the ducks on a wire rack with a roasting tray underneath and roast for 25 minutes.
- Turn down the oven to 190c and keep roasting for another 25 minutes, then turn down to 160c for another 30 minutes. Probe the internal temperature of the duck in the crease of the thigh making sure it has reached an internal temperature of at least 70 C (160 Fahrenheit). The legs should be soft and tender with crispy skin, the juices running out of the thigh should be clear.
- Rest the duck for a minimum of 20 minutes after the cooking is complete. Serve and enjoy.
-
 @ 7fa56f5d:751ac194
2023-09-13 08:51:55
@ 7fa56f5d:751ac194
2023-09-13 08:51:55nostr:npub108pv4cg5ag52nq082kd5leu9ffrn2gdg6g4xdwatn73y36uzplmq9uyev6 introduced NIP-30 Custom Emojis yesterday and many clients were quick to implement it: Nostter, Rabbit and Snort added support right away.
nostr:nevent1qqstvcc4gek4azr6aqc9qjewfs8vk86j0lkv5yt09n0sjqxq3xmjchcsjxd8s
Check out these collections that you can use in your notes or any other nostr app that supports them
nostr:naddr1qqy4x42nfpy4j42tfypzpn2q3f5ucmrn0js6wmhu873y03k220kgqlmw0j2hg9jpv3uhaqtzqvzqqqr4fc62gvap
nostr:naddr1qqr85ctsd4skuq3q07jk7htfv243u0x5ynn43scq9wrxtaasmrwwa8lfu2ydwag6cx2qxpqqqp65utc6838
-
 @ 92294577:49af776d
2023-09-11 01:03:26
@ 92294577:49af776d
2023-09-11 01:03:26Since 2020, alongside Blockstream Research, I have been playing with the idea of cryptography without electronic computers. This is not a new idea: the entire history of cryptography until the 20th century was like this. But modern cryptography, with hundred-digit numbers and complex algorithms, has always used computers. And with good reason: computers can perform operations in a billionth of a second that might take a human minutes to perform.
A billion-fold slowdown is the least of the problems for a hand-computable cryptosystem. Humans are not just slow; there are only so many precise instructions they can keep in mind at once, they have limited patience for reading such instructions, and they struggle to do tedious computations for long. Humans also make frequent mistakes, even with things they have successfully done many times before.
As it turns out, despite the complexity of managing secret data, we can still perform many operations by hand with the help of worksheets and simple tools that can be printed and cut out.
Today, we are launching Codex32: A Shamir Secret Sharing Scheme, a new booklet available on the Blockstream store. Codex32 contains tear-out worksheets for checksumming and secret sharing, paper computers that can be cut out and assembled, a worksheet for removing bias from dice rolls, and beautiful artwork by Micaela Paez and M. Lufti' As'ad.
We will explore what the codex does, but first, let's address the question that has been nagging you since the first sentence of this post: Why?
https://image.nostr.build/44b82e7cc2d237e1611ec5f8da97d0d6c4fb1444330334f5503d4b0b6d146013.png The premise behind codex32 is that you will be generating, checksumming and splitting a BIP 32 master seed, from which you will derive Bitcoin addresses.
Why Hand Computation?
Electronic computers are pretty amazing. They can perform calculations far faster than humans, without mistakes, for years on end without rest or boredom. But superhuman speed means that their actions cannot really be checked by humans.
This is not just philosophy. This problem is why we have a multi-billion-dollar cybersecurity industry and the open-source software movement. This is why security researchers insist that voting machines produce paper records that can be counted by hand. Computers can be infected by malware, their code could be malicious, they may leak secret data through side channels or by failing to delete things, and they may be buggy. These problems are nearly intractable when it comes to software, but they also apply to hardware, where verification requires complex tools and expertise. And as detailed in The Age of Surveillance Capitalism, even computers that are "working correctly" are likely to be working against their users' interest.
Every time you replace hardware or update software, all these concerns are renewed. (If you do not upgrade your software, they simply grow without limit.) Updates also risk compatibility breaks leaving your data inaccessible.
In our day-to-day lives, we mostly accept these things as the cost of being part of a digital society, but when it comes to the secret key data that controls a bearer asset such as Bitcoin, this cost may be too great.
By computing with pen and paper, we can be assured that no secret data appears anywhere we did not write it. We can create our own random data in a transparent way. We can choose how long we want to take to do various operations, confounding timing attacks. We can be assured that as long as our instructions are written somewhere, perhaps printed and stored in a safe, that our processes will remain compatible. And these assurances are not only real, but they feel real, giving us a peace of mind that electronic computers never can.
Brain Wallets and Paper Wallets
These ideas might remind readers of some old ideas bouncing around the BitcoinTalk forums. For example, a "paper wallet," in which a user writes a seed (or private key) on a piece of paper and stores this offline. Metal devices such as Cryptosteels or ColdTi are natural extensions of this idea, which are much more likely to survive natural disasters or flooded basements.
Offline storage of seed data is a good idea for increasing the security of your bitcoin holdings. It’s recommended to use some sort of metal device, though acid-free paper could work in a dry and fireproof location. With such storage there is a tradeoff between creating more copies (increasing the risk of theft) or fewer (increasing the risk of loss). The codex gives users more freedom to make this tradeoff, by allowing them to split their data into multiple "shares" such that the original data can only be recovered when enough of them are brought together.
Another idea from the same era is that of a "brain wallet" (or brainwallet) in which the user simply memorizes their secret data in lieu of physical backups. We strongly discourage this. One problem with this is that it encourages users to choose weak seeds that are too short, too highly structured, or which exist in printed literature. Even if such seeds are tweaked and prodded in various ways, they would not have enough information to withstand an attacker with a lot of computational power. One of the earliest Bitcoin scams was a website designed to "help" users produce such weak seeds for use with brain wallets.
The problem is ultimately that it is hard to memorize good randomness. The structure that makes common phrases, bits of poetry, and short stories so memorable is also what makes it easier for attackers to guess your words.
The second problem with brain wallets is that human memory is fallible. It is easy to convince ourselves that we are the kind of highly intelligent people whose memories would not fail. But intelligence will not help if you hit your head, get a fever, experience trauma, or simply lose the motivation to do your memory-refreshing ritual after a few years.
The correct way to generate seed data is to produce at least 128 bits of uniformly random data, and the correct way to store it is outside of a brain. The codex provides a way to produce such data by rolling dice and applying a von Neumann extractor to eliminate bias. There are other ways to get good seeds from dice, often referred to as diceware.
https://image.nostr.build/d4a1150ff423d704175ea01451bd0d4fe75c8e593a32ca13f05f49350d4bb92d.jpg ▶️ Watch Codex32, Simplicity, and Drivechains with Andrew Poelstra - Blockstream Talk #29
How Much Can You Actually Do by Hand?
With this background in place, let's discuss the various things that users might want to do with their seed backups.
- Verify the integrity of the backup.
- Verify that the coins controlled by the backup have not moved.
- Re-split the backup, if it is a secret shared backup.
- Recover or initialize a new wallet from the backup.
Some users might want to skip the "new wallet" and simply do everything on paper. Unfortunately, there is currently no way to derive addresses or sign transactions without using electronics. For the above tasks, though, we can.
Verify backup integrity. Long-term storage media might become corrupted or worn down so that they become unreadable. There is a mechanism to detect and fix small numbers of independent errors, called an error correction code or checksum. The codex provides worksheets enabling users to create and verify checksums on their data. If the checksum passes, everything is good. If it does not you know you have a mistake. The process of creating a checksum takes 30-60 minutes, and needs to be done twice to catch mistakes made the first time. Verifying a checksum takes the same amount of time, and only needs to be done once.
Verify the coins are still there. There is not much an offline backup can do to check the state of the blockchain. Instead, use an online watch-only wallet to monitor the blockchain for any movement of your coins, without ever needing access to secret data.
Split and re-split the backup. This is the most interesting and powerful feature of codex32. The codex provides the tools to create a secret split across several "shares" such that the secret can be recovered by a threshold number of them. Typical threshold values are 2 or 3. If an attacker has fewer shares than this, they learn nothing about the secret.
With codex32, the process is that a user generates threshold-many random initial shares, then using these shares, derives additional shares as needed, up to 31 in total. Later, given enough shares, they can reconstruct the secret.
The derivation process ensures that if your initial shares have valid checksums, then the derived shares and final secret automatically will as well. This means that you can create your initial shares, compute their checksums, derive additional shares, and verify their checksums—and if you make any mistakes during this tedious process, the checksum worksheet will catch it.
Deriving shares takes about 5-10 minutes per input share, and the final checksum check takes 30-60 minutes.
Recover or initialize a new wallet. Wallets can take codex32 shares to initialize themselves. The process is much the same as existing workflows using seed words.
Right now, there is an open pull request to Bitcoin Core to support codex32, which is included in the version of Core used in Bails. Several other wallets have indicated their intention to eventually support codex32, including Blockstream Green, Anchorwatch, and Liana. The technical difficulty of such support is comparable to the difficulty of supporting Segwit addresses back in 2016, except easier because codex32 reuses much of the same logic.
What's Next?
The immediate next step for codex32 is to improve wallet support. This means improving and polishing the rust-codex32 library and introducing support into BDK.
We would also like to implement error correction logic and expand the codex32 website to support this as well as more interactive functionality. Error correction currently requires computers. But at least for single errors, we plan to implement by-hand correction using lookup tables.
The codex has instructions for splitting and checksumming secrets. But it does not provide a lot of guidance for what to do next: distributing shares to people you trust and making a schedule to verify their integrity.
We would like to recommend that people verify their shares every year, but the current process is a pain to set up: you need to re-read the instructions, maybe assemble new paper computers, and then spend 30-60 minutes on the verification. And if this fails, in the absence of error correcting tables, you need to do everything again. So this is not a realistic recommendation.
However, we have a solution in mind: quickchecks are partial checksum checks that still detect 99.9% of errors, and can be contained (instructions, lookup tables, and all) on a single sheet of paper. There are seven quickchecks which together amount to a full checksum verification. Users can store many copies of the full set with their shares; then every year they simply grab the next page, follow the instructions to fill it out (which will take 10-15 minutes rather than 30-60), and destroy it.
Right now, quickchecks exist only as mathematics. We need to do the work of creating worksheets, tweaking parameters, and laying out instructions.
The above plans require a bit of elbow grease, but we have some big ideas for future research. From a given seed, is it possible to compute hashes to derive additional seeds, as is done in BIP 32? Is it possible to perform an elliptic curve multiplication, which would allow the derivation of addresses and signing of transactions? Is it possible to do encryption or handshaking protocols? As of this writing, we do not really know.
-
 @ 2edbcea6:40558884
2023-09-10 18:44:41
@ 2edbcea6:40558884
2023-09-10 18:44:41Happy Sunday #Nostr!
Here’s your #NostrTechWeekly newsletter brought to you by nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk written by nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
NostrTechWeekly is a weekly newsletter focused on the more technical happenings in the nostr-verse.
Let’s dive in!
Recent Upgrades to Nostr (AKA NIPs)
1) Proposed updates to NIP 47: Nostr Wallet Connect 💸
NIP 47 is already used to help Nostr users to make it easy to pay via lightning straight from Nostr clients. There’s been some difficulty standardizing what happens on the receiving end. These updates should help smooth out that process for all wallet providers and clients.
Author: nostr:npub1u8lnhlw5usp3t9vmpz60ejpyt649z33hu82wc2hpv6m5xdqmuxhs46turz
2) (Proposed) NIP 66: Relay Status and Metadata Connect 💬
When users choose relays it’s useful to have information about what that relay is about. Some people will want to join based on the topics the relay members focus on, or the locale of people who publish events there. It may also be useful to know how active the relay is and other general metadata.
These are all generally computationally expensive to run every time a user “might” want to subscribe to a relay. This leads to providers like Nostr.Watch and Relay.Guide running regular queries on all the relays they track in order to cache that metadata for Nostr users looking for the best relays.
This NIP proposes that relays could publish metadata using a new kind of Nostr event that would make it easier for people to directly ask relays these questions instead of third party providers doing it.
Author: https://github.com/dskvr
Notable projects
Hornet Storage
I’m no expert but it appears Hornet Storage is offering a way for Nostr apps to be able to store data (even larger chunks of data like files) on relays. But instead of it just shoving the whole file into a single Nostr event, Hornet will chunk the data and distribute the pieces on many relays.
Based on their docs it looks like this helps prevent tampering with files that are stored on relays. As well as protect the privacy around what’s being stored via relays (since all Nostr events can be read by anyone on a relay they can connect to). Looks like it could be a utility for anyone developing a Nostr app to offer file storage to their users.
Author: nostr:npub1h0rnetjp2qka44ayzyjcdh90gs3gzrtq4f94033heng6w34s0pzq2yfv0g
Nostrnet.work
The project from nostr:npub1cmmswlckn82se7f2jeftl6ll4szlc6zzh8hrjyyfm9vm3t2afr7svqlr6f seems to be progressing quickly. This week it was announced that NostrNet.Work is gaining a lot of functionality as a Progressive Web App (PWA) which makes it operate more like an app than a website which will improve the experience a fair amount.
Looks like even more is coming soon! We’ll stay tuned 🙂
DVM integration on Current
nostr:npub1current7ntwqmh2twlrtl2llequeks0zfh36v69x4d3wmckg427safsh3w is a Nostr client that has recently integrated a DVM to help Nostr users generate and share images created via an image generating AI.
As far as I’ve seen this is the first time a DVM has been integrated into a general purpose client. I’m sure it’s the first of many to come 💪.
NostrStats
When I first heard of this project, it was just showing some stats about the number of pubkeys, active users, posts, etc. Now it’s covering a lot more: trending hashtags, zaps, and relays.
The trending hashtags generate as you load the page and the list of top 30 relays calculates regularly so that the list has the latest activity informing the rankings.
Interested to see how this utility expands, seems handy!
Author: nostr:npub15ypxpg429uyjmp0zczuza902chuvvr4pn35wfzv8rx6cej4z8clq6jmpcx
Noswhere
A relay that specializes in search was launched this week by nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj .
Next week’s newsletter is going to be focused on search, data permanence, and relays, so we’ll do more research and give this project the attention it deserves next week.
Latest conversations
Maximizing decentralization
Decentralization is important when there’s a risk of power accumulating and being abused. Democracy is intended to spread political power, Bitcoin; the power over money, and Nostr has the potential to spread the power of media (social and beyond).
But there are trade offs to decentralization; centralized systems have an easier time being more usable and efficient. Only improvements to technology unlock improving decentralization without sacrificing usability and efficiency. In other words the only way to have your cake and eat it too is to work at it.
Nostr’s going through a lot of experimentation right now, and you’ll hear a lot of the devs talking about something leading to more or less centralization. This is a nuanced and important topic and it’s happening at every level of Nostr development, every day.
https://i.nostr.build/qOWn.png
Take for example the debate about whether to support file storage via relays (via NIP 95 and solutions like Hornet Storage ). On the surface “more stuff in relays” means more stuff off the centralized providers (e.g. Google). Good right? Well it might make things more centralized than if we kept files out of relays.
Similar to the conversation about the Bitcoin block size, on the surface it may make sense to improve usability of Bitcoin. But if adopted fewer people could run Bitcoin nodes which means in the end Bitcoin is less likely to accomplish what the community wants. Bitcoin Cash failed.
Making relays able to handle files could similarly make more applicants entirely Nostr-driven, but they could also make it so that fewer people end up able to operate relays. It’s not just the raw increase in hosting costs, it’s the legal and financial risks operating a file storage and sharing system. We just don’t know yet, so people will experiment to find out.
Many of the bitterest debates we see boil down to people disagreeing on the second and third order effects of current actions on the decentralization of Nostr over time. It’s important to get right.
Events
Here are some upcoming events that we are looking forward to! We keep a comprehensive list and details of Nostr-related events that we hear about (in person or virtual) that you can bookmark here NostrConf Report
- Nostrasia Nov 1-3 in Tokyo & Hong Kong
- Nostrville Nov 9-10 in Nashville, TN, USA
- NostrCon Jan 12, 2024 (online only)
Until next time 🫡
If you want to see something highlighted, if we missed anything, or if you’re building something we didn’t post about, let us know, DMs welcome.
nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk
Stay Classy, Nostr.
-
 @ 72f97555:e0870ff3
2023-09-10 00:50:52
@ 72f97555:e0870ff3
2023-09-10 00:50:52Most people are wrong about rights. Rights are viewed as something that is granted, something that people fight to get, and something that people ought to have. But that is all wrong. In fact, that line of thinking is dangerous, and leads to the types of human rights violations that we are seeing across the planet today - everywhere from third-world countries, to the "great" countries like the United States. In this essay, I will explain what rights are, where they come from, and why the prevalent line of thinking is dangerous to society.
Rights are granted by God
I'm a Christian, and I know who my God is. You don't have to be a Christian, or even a believer to understand and agree with the concept that rights are a fundamental, and exist above the human condition. I think it makes the argument much stronger if one does believe in a god, but even a non-believer can arrive at the conviction, after deliberation, that rights are not dependent upon human thought or consideration. They are inherent in the Universe, and a fundamental truth. The authors of the Declaration of Independence believed this, which is why they wrote:
We hold these truths to be self-evident, that all men are created equal, that they are endowed by their Creator with certain unalienable Rights, that among these are Life, Liberty and the pursuit of Happiness.--That to secure these rights, Governments are instituted among Men, deriving their just powers from the consent of the governed, --That whenever any Form of Government becomes destructive of these ends, it is the Right of the People to alter or to abolish it, and to institute new Government, laying its foundation on such principles and organizing its powers in such form, as to them shall seem most likely to effect their Safety and Happiness.
What the founders understood, and many of us have lost sight of, is that our rights are not something granted to us by humans, or by governments (which are just collections of humans), but by something above us which cannot be argued with. These rights are absolute and part of the fundamental nature of what it means to be human. They are "unalienable" meaning that they cannot become foreign to us - we cannot be separated from our rights. They are not bridgeable.
Government is not reason; it is not eloquent; it is force. Like fire, it is a dangerous servant and a fearful master. -- George Washington
We must leave behind the common fallacy that governments can grant or suspend the rights of individuals. They may violate or recognize those rights, but they have no power over what those rights are, or whether they belong to you. When governments tell their populations that they may do a thing, that is permission, not a right. Permissions may be revoked or suspended, rights may not.
Governments are not gods
One of the great revolutions in the development of humankind took place during the feudalistic era. The development of chivalry represented a fundamental change in the way populations learned to view their rulers. Previously, Kings (and sometimes Queens) were viewed as deities in their own right - the ultimate authorities over all affairs both material and spiritual. Under chivalry, for the first time, we collectively realized that rulers were only human, and they were beholden to a higher power the same way the rest of us were.
Today, government is taking those rights from us, pretending that it gives us our rights. Indeed, those rights come from God, and it was recognized throughout our history as such. -- Judge Roy Moore
While the process was slow, and not without its setbacks and problems, this began the path towards the recognition of universal human rights, the limitation of the powers of rulers to protect their citizens from abuse, and ultimately, forms of representative government under constitutions, such as the constitutional monarchy and the constitutional republic. It was a gradual change in the way entire populations viewed the world around them and their place in it. They saw both the errant human in their rulers, and the highest ideal that all man was answerable to.
If we are not governed by God, then we will be ruled by tyrants. -- William Penn
Unfortunately, there has been a gradual regression taking place. People no longer look to that highest ideal any longer for their answers. Very often, they are turning to government for the solutions to their problems, protection from every danger, and answers for how it is acceptable to live. This creates a false image, that government is anything other than people exactly like us, with the same flaws, limitations, and corruption that lives in every single living human. Government is not here to help us, because government is us. Government cannot tell us how to live, or what our rights are, because government is just people, who unregulated have been shown to commit every type of atrocity to gain power and wealth for themselves.
Because many of us make mistakes that can have bad consequences, some intellectuals believe that it is the role of government to intervene and make some of our decisions for us. From what galaxy government is going to hire creatures who do not make mistakes is a question they leave unanswered. -- Thomas Sowell
The role of government
Government is a cooperation of groups of people, meant to establish guidelines (laws) that are acceptable to the majority of individuals in order to maximize freedom, happiness, and safety from the infringement of those rights. Any deviation from this goal is a perversion of government.
Government, even in its best state, is but a necessary evil; in its worst state, an intolerable one. -- Thomas Paine
Freedom and laws stand in a necessary tension with one another. Laws must govern the passions of humankind, to guard against one person violating the rights of another. But laws have a fascinating life of their own. They tend to grow over time as disputes are heard and government is asked to intervene in more and more cases. Can you think of a time that the number of laws actually decreased by any meaningful number during the life of a government?
The issue is that laws also grant power to the enforcer of those laws. Human nature reenters the equation, stage left. Judges become corrupted to decide cases for their own benefit, or are bribed. The laws become so numerous that our representatives begin passing them to benefit themselves or their friends, and nobody notices in the sea of laws being passed. In the United States we have reached the point where laws are being passed so fast, and so often, and are so encompassing, that the representatives have often not even read them before they are passed. This is a terrible corruption of the system, as the people writing the laws were never even chosen by the people, and begin to exercise power over the lives of their fellow citizens, with no oversight, and no checks upon what they do.
The one thing man fears is the unknown. When presented with this scenario, individual rights will be willingly relinquished for the guarantee of their well-being granted to them by a World Government, a New World Order. -- Henry A. Kissinger
It is interesting, that a country that has existed for over 200 years, continues to find this many things to pass laws about. There are budgetary things that are routine (and still manage to be handled horribly) but we still pass thousands of laws every year. We would be foolish to think that these laws are all required to protect the rights of one citizen from encroachment by another.
Congress has enacted approximately 200–600 statutes during each of its 115 biennial terms so that more than 30,000 statutes have been enacted since 1789. -- Wikipedia
The slippery slope
In this article, I have posited that rights are absolute, and inviolable. They may be in principle, but in practice, even the most conservative and rights loving individuals are often more than happy to violate the rights of others if the circumstances are right. This is a problem because once you accept the violation of one person's rights, you have already surrendered the fight for rights entirely. Indeed, you have conceded, and are now in negotiation about how many people's rights you are comfortable violating.
Don't believe me? Do you believe felons should have the right to vote and carry firearms after they serve the entirety of their sentence? I'm willing to wager the average American, at least, is perfectly comfortable stripping felons of these rights. There are many such groups. But let's remember the founder's principle - these rights are unalienable.
There is no greater threat to a free and democratic nation than a government that fails to protect its citizen’s freedom and liberty as aggressively as it pursues justice. -- Bernard B. Kerik, From Jailer to Jailed: My Journey from Correction and Police Commissioner to Inmate 84888-054
You might believe this is a perfectly reasonable thing to do. You might believe the justice system works, that it never convicts the innocent (or worse, that it's "good enough"), and that the justice system is never turned against a population minding its own business, trying to live its life quietly... you know, pursuing that "liberty and happiness" stuff. If you do, then I applaud you for being blind, deaf, and oblivious to the realities around you.
I would urge you to consider carefully though, how long you think it will take a government that passes 200-600 laws every biennial term, to decide that something you are doing is a felony. You've already surrendered your rights for permissions in exchange for some safety and retribution. What are you going to think and feel the day the government declares war on Bitcoin, seizes your private property, or tells you how to raise your children? Do you really think they won't? We're over 50 years into a war on drugs.
Don't Surrender
Defending your rights means defending mine, and every other human being living around you. The minute their rights cease to be important to you - the moment you are willing to allow your fellow human being's rights to be violated in the name of "justice," "safety," or whatever reason the mob cries for, you have lost your own. It is only a matter of time before you notice. It takes a bigger person to stand up for the rights of those we find distasteful - but as with so many other medicines, what is good for us often tastes bad.
As is so often the case, what is wrong with rights isn't rights themselves. What's wrong with rights is that as a people we have forgotten what they are, and been deluded into believing we still have them, and that they are granted by some vague thing called "the government" that is somehow greater than human, despite being instituted by and filled with humans.
You seem...to consider the judges as the ultimate arbiters of all constitutional questions – a very dangerous doctrine indeed, and one which would place us under the despotism of an oligarchy. Our Judges are as honest as other men, and not more so. They have, with others, the same passions for party, for power, and the privilege of their corps. -- Thomas Jefferson, to William Charles Jarvis, September 28, 1820
The biggest defense of our own freedoms and rights we can exercise is to not tolerate the violation of anyone else's. They belong to all of us by birthright, granted to us by the highest ideal and are violated at our greatest peril.
-
 @ 92e3aac6:fd211909
2023-09-09 19:31:44
@ 92e3aac6:fd211909
2023-09-09 19:31:44Testing another way to share music
-
 @ 6efb74e6:41285536
2023-09-09 15:15:49
@ 6efb74e6:41285536
2023-09-09 15:15:49proofofwork: 10 minutes
YIELD: approx 2 1/2 cups.
INGREDIENTS:
1 cup parsley, washed and finely chopped
1 cup cilantro, washed and finely chopped
5 ea (1 teaspoon) garlic cloves
3 Tablespoons fresh oregano (2 tsp if using dried)
1 teaspoon fresh chilli or chilli flakes
1 teaspoon ground cumin, lightly toasted
2 Tablespoons quality red wine vinegar
1/2 cup extra-virgin olive oil
1 tablespoon lime juice
1/2 teaspoon salt
1/2 teaspoon black pepper
METHOD:
- Pick and wash all the herbs, drying them as much as possible with a salad spinner or a tea towel.
- Place all the chimichurri ingredients except the oil in a large bowl and mix them together well.
- Add the oil until you reach the consistency you desire. If you are using it as a marinade then you will probably want slightly less oil.
- When using as a marinade, coat your meat before grilling and refrigerate for at least 2-3 hours.
Check the seasoning and adjust it as you like.
chefstr, #foodstr, #yumstr, #grownostr, #homemade
-
 @ 20d29810:6fe4ad2f
2023-09-07 00:45:35
@ 20d29810:6fe4ad2f
2023-09-07 00:45:35🚀 The Future of Finance: Why Bitcoin is My Top Pick! 🚀
Hey Crypto Fam! 👋 Today, let's talk about the incredible journey of #Bitcoin and what the future holds for the king of cryptocurrencies! 🌟
💰 Bitcoin as Digital Gold: In a world where trust in traditional financial systems is waning, Bitcoin has emerged as a digital haven for preserving wealth. It's like GOLD in the digital realm! 🪙💎
🏦 Institutional Love: Big institutions are jumping on the Bitcoin bandwagon, and it's no wonder! Major financial players are investing billions, signaling that Bitcoin is here to stay! 🏧💼
⚙️ Scalability Solutions: Bitcoin's scalability issues are being tackled head-on. Lightning Network, anyone? ⚡ It's opening up new possibilities for fast and low-cost transactions. 🌐💸
🔗 Bitcoin & Blockchain: The revolutionary #blockchain technology behind Bitcoin is reshaping industries from finance to healthcare. Buckle up, because innovation is just getting started! 💡🌍
🌍 Global Regulation: Governments worldwide are recognizing Bitcoin's importance. Regulations are evolving, which could pave the way for mass adoption. 🌐📜
🌍 Financial Inclusion: Bitcoin is empowering the unbanked and underbanked, offering financial freedom to millions globally. That's a game-changer! 🌍💪
💹 Price Predictions: Analysts are forecasting some exciting price movements for Bitcoin. Are we on the cusp of a new ATH? 📈🚀
🤔 Challenges Ahead: Of course, there are hurdles to overcome, but Bitcoin's resilience is unmatched. We're ready for whatever comes our way! 💪🏁
🚀 Emerging Use Cases: Bitcoin's not just about HODLing anymore. NFTs, DeFi, and more are being built on the Bitcoin blockchain, creating endless possibilities! 💼🎨
📚 Educate & Elevate: Remember, knowledge is power. Learn how to securely buy, store, and use Bitcoin. It's an investment in your financial future! 📚💰
So, what's your take on Bitcoin's future? Are you bullish on the OG crypto? 🐂 Or do you have concerns? Let's chat in the comments! 💬👇
Remember, this isn't financial advice, just an influencer's take on the exciting world of Bitcoin! Stay informed, stay curious, and stay crypto-savvy, my friends! 🚀💯 #CryptoLife #BitcoinFuture 🌐🚀
-
 @ 4657dfe8:47934b3e
2023-09-06 12:21:10
@ 4657dfe8:47934b3e
2023-09-06 12:21:10The article below was written by one of our users and creators in the bitcoin sphere, Jacobo Fasja. It shares our vision on positive disruption of quality content, made by value 4 value monetization model. Which is possible thanks to many technologies that Alby uses and supports. We, like author, believe that removing friction from micropayments in the web, will incentivize better qualiy of the content and relationships between digital artists/creators and consumers. Thus, let us share with you guest article "Breaking the Chains: Liberating Content and Privacy with Micropayments".
Let us know in #Nostrcomments, if you agree with its thesis and share your ideas on how can we make the revolution happen...smoother :)
What's in it? (tl;dr):
🌟 Unlocking the Internet's Hidden Potential
In the early days of the internet, banner ads seemed promising, but they led to clickbait and quality decline. The internet's potential for superior content monetization was obscured.
🚫 The Clickbait Dilemma
Clickbait thrived as websites chased clicks at any cost, stifling quality content. Advertisers held sway over decisions, causing self-censorship and stifling diverse viewpoints.
🌐 A Digital Cargo Cult
The content industry clung to outdated models, but change is on the horizon. Bitcoin Lightning Network's micropayments promise privacy, creative freedom, and quality.
💰 The Rise of the Intermediary
Intermediaries extract staggering value from digital content. Parallels with financial institutions highlight inflated prices despite minimal value addition.
💥 Restoring Content's Reign
The current system yields diminishing returns for advertisers. It's time to restore content's rightful reign and explore better monetization models empowering creators and respecting user privacy. Join the conversation to reimagine online content monetization.
by Jacobo Fasja:
A brief intro:
In the early days of the internet, banner ads served as the primary method of monetization for online content. At the time, online payments, let alone micropayments, were neither safe nor functional. These ads, typically displayed by a third party known as an 'ad network', functioned as a form of micropayment for the content users consumed. This model essentially transformed the consumer or reader into the product by capturing their attention and selling it to the highest bidder.
This concept wasn't new. Traditional media, especially the television industry, had thrived for years using a similar model. However, the internet's approach involved a greater level of intrusion into consumer privacy. Despite this, the internet was hailed as a 'revolution' that should have offered a superior method of monetizing valuable content."
"Pay peanuts, get monkeys.”
However, as the internet evolved, it became clear that banner ads had created a number of negative incentives. One of the biggest problems was the rise of clickbait. Because advertisers were paying for each click on their banner ad, websites had an incentive to create sensational headlines and misleading content in order to drive more traffic and generate more ad revenue. Without having to care about if the end user found the content valuable after reading it, all it mattered was to grab his attention for a brief moment.
This focus on clicks also had a negative impact on editorial decision-making. In order to drive traffic and generate revenue, websites began prioritizing content that was more likely to attract clicks, regardless of its quality or relevance. This led to the proliferation of low-quality content and the suppression of more meaningful or nuanced discussions.
"The one who pays the piper, calls the tune.”
In addition to these problems, banner ads also created a significant influence of advertisers on editorial decision-making. Because websites were reliant on ad revenue to survive, they were often unwilling to publish content that might offend or alienate their advertisers or “brand safety standards”. This led to a significant amount of self-censorship and a lack of diverse viewpoints on the internet.
“That's how my mother did it”
A girl once asked her mom why she cuts off the ends of a roast before cooking. The mom replied, "That's how my mom did it." The girl asked her grandmother, who said, "That's how my mom did it." When the girl asked her great-grandmother, she laughed, "I did it because my pot was too small. I guess nobody thought to stop once we got a bigger pot.” Looks like we have the same “cargo cult” in the content / media industry.
“You won’t believe what happens next”
Leveraging the Bitcoin Lightning Network for direct micropayments can liberate content creators from ad-reliance and give users control over their support. This method offers five benefits:
Privacy: Users aren't exposed to targeted ads, preserving their privacy. Freedom: Creators can produce content without advertiser restrictions. No Middlemen: Direct payments mean no intermediary deductions or payment delays. Feedback: Creators learn what content is truly appreciated, beyond misleading clickbait metrics. Quality: This reward system discourages low-quality content, incentivizing valuable work and disincentivizing deceitful clickbait.
While there are certainly challenges to be addressed in massive adoption of micropayments using the Bitcoin Lightning Network (mostly a case of UX), it is clear that this technology has the potential to fix many of the problems that have plagued the online media industry.
“Behind every great fortune, there's a ~~crime~~ intermediary extracting more value than they're adding”
In a 'Value for Attention' (VFA) model, the intermediary often extracts the lion's share of value from both the creator and the consumer. They do this by levying a substantial fee (~30%), holding onto the money for an extended period, and collecting data from both parties, which they may then sell to others.
While there is undeniable value in the platform (intermediary) that brings both parties together, it should not be the chief beneficiary, especially when the exchange involves digital products from both sides. This situation requires no substantial logistics, and the marginal cost of distributing each piece of content or ad is virtually zero.
Consider how much value has been captured by intermediaries like Google, Facebook, and ad networks. This value could have improved content quality or fostered profitable business models for creators focusing on small, high-value niches. I estimate that around 50 billion USD was lost to intermediaries just in 2022, a year when banner ads generated a massive 155 billion USD.
The roast doesn’t need cutting anymore
It is hard not to compare this situation to how financial institutions have exploited customer savings through fees and many other strategies by positioning themselves as “necessary” intermediaries, they extract substantial profits while offering comparatively minimal value.
This analogy holds up as both industries are primarily information-based (money is nothing more than information), and with the advent of the internet and Bitcoin, the cost of transmitting information has trended towards zero. Yet, these monopolies have managed to keep the price inflated.
“If you don't believe it or don't get it, I don't have the time to try to convince you, sorry.”
Now, this is not just a one sided issue for creators, if you have any idea on how much money has been extracted from advertisers due to placing their ads programmatically in “relevant” content which was actually just made to precisely attract those ads without delivering actual value content, you’ll understand that this industry created a lose-lose “solution” in which the intermediary is the main winer and the advertiser has only been seeing diminishing quality engagement rates on their ads.
For those who still hold that 'content is king,' let us now restore its rightful reign.
Jacobo F
-
 @ b9e76546:612023dc
2023-09-05 22:12:21
@ b9e76546:612023dc
2023-09-05 22:12:21I feel like a lot of people have an inherent problem with this vague concept of “THE ALGORITHM” (which henceforth will receive the all caps & scary quote treatment) and their nostr feed that is entirely misplaced from the real problem of centralized social media, so I thought it would be good to address it directly.
First, “THE ALGORITHM” is just a set of rules that determines how you see your feed. There is no necromancy or joining of the dark side involved, and it has nothing to do with whether "THE ALGORITHM" is “good” or “bad.” The very idea of “not having an algorithm,” just means you want the algorithm to list the posts of who you follow in chronological order. It in no way means you are “algorithm free,” it just means that the rules of your feed are "take only the posts from the people I follow and order them chronologically," and that’s basically it.
Everything about the concept of a social network and the incredible potential and beauty of #nostr as a protocol is in controlling your experience, what content you see, and how you see it. This is literally the entire point of having follows, followers, and reposts in the first place. It's at the core of the very notion of what social media is. This is literally “an algorithm” in the same way as prioritizing new posts over old would be, or limiting those who post more, or amplifying those who post less in your feed. They are exactly the same kind of rules, they are different only in specificity.
So what’s the problem with “THE ALGORITHM” then? It’s nothing to do with some vague notion of an “unnatural” feed or whatever it might seem like since we seem to have developed this distaste for the very concept. The problem is purely that someone else has been specifically manipulating your feed against your best interests.
It’s the same issue as censorship. My blocking a dickhead who won’t shut up about their shitcoin or who squeals at me under every single post with demands to read some communist propaganda on my podcast, isn’t censorship, it’s me choosing who I interact with. Censorship is when an external participant, someone not involved in the conversation at all, decides that I should not see some idea or should not communicate with some person despite my explicit desire to do so, and is able to remove my access from it without my permission.
The same goes for “THE ALGORITHM.” It’s not a problem if I’m controlling it for my own feed, this is a basic and fundamental tool of digital filtering that absolutely must be embraced, not feared or run away from, because it’ll make a huge difference in the user experience. It’s simply that someone else shouldn’t be controlling it to be at odds with the content and experience that the user specifically wants and is trying to create. Only THEN it is a very bad "algorithm" and a dangerous relationship.
The problem with all of these things has nothing to do with what they actually are, its about who has control.
The user is always supposed to be in control of who they follow, the content and ideas they want to see, and the people they want to associate with. Only then is it truly a free market and open space guided and created by its users. The problem has always been about central points of control forcing information asymmetries that aren't real, censoring ideas that are beneficial to you and inconvenient to them, etc.
I always like to try to analogize these sorts of things to the IRL world to understand what makes them bad and why a good one is actually incredible important. In the real world, if you go to a party and decide to converse with your friend, while ignoring all others you are weighing their interaction higher than the others at the party. If you decide to play a game of beer pong with your friend, you are creating a very specific set of rules by which your interaction will fall into. Not because you enjoy the evils of "THE ALGORITHM," but because you want to get drunk and have a lot of fun. Censorship would be if some external govt or other party was able to mute your conversation from thousands of miles away, while you were standing in front of your friend talking to them. THEY interrupted your conversation and shut off your communication channel despite both of you explicitly agreeing to the interaction. Or you were having a conversation with your friend and the second they began telling you about how your mutual acquaintence in in the hospital with myocarditis, they vanish from the party and a person you don't even know immediately walks up to explain to you how safe and effective the Pfizer products are.
An IRL "evil algorithm" would be this external institution or person making a particular group at the party invisible to you without your knowledge, it would be forcing a beer pong table in front of you no matter where you went or what else you wanted to do. Constantly enticing you to get drunk and play a game you were doing everything to avoid. Even adding arbitrary obstacles to all other activities and dropping NLP messaging of "drink up" and "solo cup" into all of your conversations without your knowledge. As crazy as it sounds, this is essentially the norm. This is how our online environment has evolved. So it makes sense that when we broke free of that, we would have a horrible taste in our mouths for the very idea of "THE ALGORITHM." It certainly isn't irrational, despite being misplaced.
Being part of the digital world is a weird thing when comparing it to real life. There is never a situation in meatspace where one has to filter how they will talk to a million people all at once. The very notion is comically absurd. But this IS a consideration in the digital world. Its like being dropped into a seemingly unlimited ocean of content and people, which is to the individual, genuinely infinite, as more content and interactions are being added to it by the minute so fast that it would take a lifetime to even manually sort through it all. Blocking, filtering, information rules, value weights and yes, "THE ALGORITHM" aren't things that are nice to have, these things are critical, inescapable tools for navigating the endless ocean of the digital world. These are not things to be afraid of or label broadly as "evil" and avoided at all costs. To the contrary, they are basic pieces of the puzzle that I think we need to understand. We need to put them in the hands of the user, so we can do incredible things with them.
The one core concern, is quite simple: How do we enable the user to set the rules, and not a third party? In my opinion, this is all that distinguishes the ultimately good from the bad.
We must remember not to throw the baby out with the bath water. Creating "THE ALGORITHM" is not accepting an invitation from Darth Vader to join the dark side. It's just a means of curating your feed so you get the best experience you can, and you find the content, ideas, and community that you came to #nostr looking for.
When we realize the importance of custom controls and modes of interaction, then we realize what all of these clients really are. Every one of them is really just a different "algorithm" that the user can select from. One that shows only images, one that filters everything but a certain community or topic, one that organizes based on most zapped, or by the number of likes specifically from those in your network, and on and on. The potential of #nostr isn't an algorithm-free experience, it's in an ecosystem with an unlimited number of experiences to choose from so that each person can either choose or build the community that they want, in a global square with no rulers.
An important step to getting to the future we want is to understand, with specificity and nuance, the exact sources of the problems we are trying to fix, rather than painting broad strokes and just carrying around a bunch of baggage about a tool we should be using for ourselves. The promise of nostr, and Bitcoin, and so many other tools we are building on and embracing is to create at the communication layer, a foundation of freedom that can be accessed by every single user no matter where they are in the world.
So in short, there is no such thing as "THE ALGORITHM." The problem has always been about who has control over your digital world? Is it you, or is it someone else? In the fight to prevent that control from finding its way back into the hands of someone else, it would be foolish to let our PTSD over the past have us avoid the very tools that would let us build a future specifically tuned to give us the very value and and autonomy that we all seek.
-
 @ 40b9c85f:5e61b451
2023-09-02 17:55:03
@ 40b9c85f:5e61b451
2023-09-02 17:55:03Hello folks! I'm going to make a small article showing how a nostree list can be interoperable between different applications in the nostr world. I'm writing this little article on habla.news, where I know that nostree lists will be formatted correctly.
nostr:naddr1qqkxummnw3ex2efdxgerxvfkxqckytfcxd3rjtf5vc6xxttpvf3k2tfsv9nryveexfnrgcf4vspzqs9eep0ll6hurjkl3sc2fewgses07mjfwxsdcu3at2m8fd0xrdz3qvzqqqr4xy3j6s60
-
 @ 3d82e8f6:2d214dc9
2023-09-02 03:11:49
@ 3d82e8f6:2d214dc9
2023-09-02 03:11:49What is this contest?
Each month, we give away 2.1M sats (fractions of a bitcoin) to people who put our bitcoin stickers in public.
Ok, but why?
There's a popular saying in the Bitcoin community that "Bitcoin is inevitable." While I agree this is true on an infinite time scale, I want hyperbitcoinization (global bitcoin adoption) to happen within my lifetime. That's why I'm making resources and tools to accelerate bitcoin adoption.
I made bitcoin.rocks to make it easier to orange pill people you know, and our sticker program is a way to orange people in your community by leaving a sticker in public.
Each sticker has a QR code that links to an educational page about bitcoin. Our inflation-themed stickers link to a specific inflation page and our other stickers link to our educational home page.
Since we started these monthly contests about a year ago, our stickers have been scanned 6,886 times in public!
That's 6,886 people taking their first steps down the bitcoin rabbit hole. That's an incredible number and one we couldn't have reached without the help of everyone who puts our stickers in public.
This monthly sticker contest is the first since we quit Twitter and went Nostr-only. That means instead of having to mess with Lightning invoices, I can just zap the winners their sats directly on the post they submitted. Pretty cool!
If you want to get involved in September's contest, request a free pack of stickers or print your own! You can get involved and help spread bitcoin adoption no matter where you live.
Now, on to the winners from August's monthly bitcoin sticker contest — the first ever on Nostr!
1st Place
nostr:npub13d89zg9e237y6yzgw5x7wuqssvcv7c6urn39e7cckv5e92p3zhjqkdru5w wins 1,000,000 sats (0.01 BTC) for this sticker spot and dozens of others he submitted. Luke is a sticker slapping machine! nostr:note169qdxu5ja6pezydarnuuhzujm3smex0uqylu52y55fq8y6w95naqsam23z
2nd Place
nostr:npub1dk5pn7gad897tywq3vcl24wx6z4ejpge0663tptwxwgynsqccxhsn65sgk wins 210,000 sats (0.0021 BTC) for a series of stickers in high traffic places. nostr:note1ys4nd2d3vlhq8ftt5s682qdr70smwgcym2hszxvar7qpn2xwpu2slza8sd
3rd Place
nostr:npub122u7rt9rmunfwyzk35w25pg6haq0hhuvyjy6lwxjklxmr5wseehs720s42 wins 120,000 sats (0.0021 BTC) for this super creative spot! nostr:note1uqptpyccmrcxpall2yzy00yfa28m5p785vdul8t5mp9j965lns5qfr93h3
4th Place
nostr:npub1mpz30qp2gdr403t2apjzhla56fh94hs8zgznw5pp26q0tztw27dsu60pxm wins 50,000 sats (0.0005 BTC) for this great sticker series where people will definitely see them! nostr:note1sxtczeck3n6fd4epyu8nrj5d3fnqcx2jz2l5y304qzeka0v26v0s6ckg3l
5th Place
nostr:npub1y9gwxkgkcphlzw6ev63tqgghey0tjs6ag03ynheen4as0hcrra5szpr0fa wins 50,000 sats (0.0005 BTC) for this nice high traffic spot! nostr:note1zahy8jhct7xzwkyrrcfna9wjc3cry6qa73zvedzw8w09zqu5lqxs7zrpgh
6th Place
nostr:npub1f48mtlc2lwxqfekxuql4z2qmvezhd7v9uk7rfga8accs585zrars56lpgj wins 50,000 sats (0.0005 BTC) nostr:note1jt3djsacjry5pv5yv5ddea62q8f24vf5gd0nh09v0seaezplmr5sdjufxj
7th Place
nostr:npub133vne3sgggzj9ruat7pxyj2evugth0hxydk4fck8fv5zd5qwfjps8xfx0e wins 50,000 sats (0.0005 BTC) nostr:note1pq6jukg3dj5gcac0laleyqm2cxmfn5zfpe64prrmg5gkl3r0yv2qe8z5uf
8th Place
nostr:npub133vne3sgggzj9ruat7pxyj2evugth0hxydk4fck8fv5zd5qwfjps8xfx0e wins 50,000 sats (0.0005 BTC) nostr:note1pq6jukg3dj5gcac0laleyqm2cxmfn5zfpe64prrmg5gkl3r0yv2qe8z5uf
9th Place
nostr:npub1chakany8dcz93clv4xgcudcvhnfhdyqutprq2yh72daydevv8zasmuhf02 wins 50,000 sats (0.0005 BTC) nostr:note1nnqsvngw7mjjj7vsq9pae0x4f74mzgvl72j5asrgcl4axj26tzeqs386rr
10th Place
nostr:npub1ahk0j8g4uq7fyxqx4ehtl7r8w8reu9jpazvhsljdw6yldqc563rsq0ssh4 wins 50,000 sats (0.0005 BTC) nostr:note1q0szha5g0s9s6ehrtjx9cz6fsp892wlhjvvkhlz6gvtch3fsqgyqcqe5cc
11th Place
nostr:npub1wd522pp0mp7almxg00qmt08lqkz6r5r9vw95cddzuzvnnt7dpdksdtrvav wins 21,000 sats (0.00021 BTC) nostr:note1rz0j4z2k0gzafsj5vw32fn7s8wlmc0eyjqmfeektsrmjmhsmvphsv0mpm7
12th Place
nostr:npub1u4te63xx9c3r9d2ly8nwuc08sg2dcp89zxyac952dlnwqrq4l8zszqrdsd wins 21,000 sats (0.00021 BTC) nostr:note10wnnzkdjvf253gjd3vvq9wsn8qyy65jd5ednuhn9889u62pcvt8qncw837
13th Place
nostr:npub128e8840pt7nhfgcnj9au7qsl7u3qkvluexyhva5xrezlwq8c3rfsszsela wins 21,000 sats (0.00021 BTC) nostr:note1amkv2u2arm8ecylegcmm2f0wacqgckee9xnn354ektpkc2wm8gfq4tx4sh
14th Place
nostr:npub1pxrhdm3n6a94tdv8cs6qapaggatwr3dn7n936d8vc0p9kmp0st8q8a4rk7 wins 21,000 sats (0.00021 BTC) nostr:note1hdm5acg4ex8r56ngad9hd0qu499svkzdn7a8lxegxqm7rc6c4dyq3xx2ju
15th Place
nostr:npub1kmjmsv43ple39493q4wa52nmfygqx6v8qcwl4msxhsd5mnp24assaxn00l wins 21,000 sats (0.00021 BTC) nostr:note1tfe35p9ntl87n72w4xatt62ed8gl9wtj74r0crgu5mmafgw42jlssfsjee
16th Place
nostr:npub12q6p5j8tefxuf0emk7u8ehgdmkedw55j7mwfxpxsd9778xf37kusypvpez wins 21,000 sats (0.00021 BTC) nostr:note1hfpxe6g5t0mc98yqqm0fux885xa3knawwmsjdnk58qvf3fv9zqfsnpr6ra
17th Place
nostr:npub1r2wjlqhgvwdu70cqtgqu30c74vwjxpulyakry274hpfulusj5hhqllep8d wins 21,000 sats (0.00021 BTC) nostr:note19gvshswwg0u7c55g7c8578memua9dxettvykq78qvlsn2zmterysp52ref
18th Place
nostr:npub108q3662k2lv5cfgnmhksw8l5x8nuszzctlunpwc4k6e4zdkd8s5skp3pp8 wins 21,000 sats (0.00021 BTC) nostr:note1k3xzl7cr8u6x3xcdrrcnkfpe5avg0rvvgfvs0vyuy3nwg8eav5hq93yyyn
19th Place
nostr:npub1w8uatmszddfxa0tx6y6xsrzhvq7aywpduwdgre2946furlc3l7uqspvze7 wins 21,000 sats (0.00021 BTC) nostr:note1yn5m3z6luhc4upfr3nqhdangqv6sg4dvjqzrdtkns722lah0se8s8lcys3
20th Place
nostr:npub1rcksspnnl9v6tkpr2l2792jsz9mc4a35cvlyyp7v2nnal9pu0xxqt9gckg wins 21,000 sats (0.00021 BTC) nostr:note1hwyf4cxjw3xvtjuprmc8f0x89ztdwd6g9hx4d3st9c4rk063958q5kgh4l
21st Place
nostr:npub1psha64wnq3qrt506mv0k3syjhxq46r3agn7wdp2h7f6rlvd5cfqs06z5am wins 21,000 sats (0.00021 BTC) nostr:note14n2dl5dn23jt9qr2e5s5xhpwy2azdxz62jrnh8n3n3gqwdrrfmhsn3c00a
22nd Place
nostr:npub104zp04wlgddf0w84tj8jul3w75e7ydcuuhsull2etste5040xm2qg285rf wins 21,000 sats (0.00021 BTC) nostr:note1fd8xadhfgfj59sqlgqd66420m2npps0dls3xre093ttn87xdhxxqnsdyjc
23rd Place
nostr:npub1cf0drsnqwwarjzmf2r7kq4n5lt9lh43p7g66l9tk37j5kfc2uxssv0gzew wins 21,000 sats (0.00021 BTC) nostr:note1c0vu3vpwsjrt5z5zng3v87xkx2pgnw8wtaxcy6vvyqrcm6z90kzstd2ypf
24th Place
nostr:npub1nthvv0sglny3nzr89kemd8rz7rxa9jtcq6mcc78lk87c3vmcksxsvl24gw wins 21,000 sats (0.00021 BTC) nostr:note16qlrccttehh8t576vgrxh4nsa8fpzgfxvdaetkzg6t94xxpdajzswkd03c
25th Place
nostr:npub1vwymuey3u7mf860ndrkw3r7dz30s0srg6tqmhtjzg7umtm6rn5eq2qzugd wins 21,000 sats (0.00021 BTC) nostr:note1ue6pf5w6qjpdcc3wp7a9cc7wvaxp7h6kqp54sqprxvjtcve8cg3qca3n2u
26th Place
nostr:npub1ps73vvwd9uzkpgl5v0fjrew68pq8xj49e0enmwv477sjjq53fncqlavzfz wins 21,000 sats (0.00021 BTC) nostr:note16wdzdy68cehmvepqklm282cukkqsnt74u0l2jup3w0h4aswgt0qsr3sstn
27th Place
nostr:npub1c0mpgcqpvffz4wmd0cmx8dzxtm9fukyz5yugx0n73fzzptlusnfqrns0qs wins 21,000 sats (0.00021 BTC) nostr:note10ned9kpygejgsv3k3aznr396r3xgfukv4lyxnzd37yamm3xkuvyqrdlcdt
28th Place
nostr:npub1zh9w20hkx5vqwuznptk3md2rm8wv64mtk45vf0ncr52ce5njzwdsereg0l wins 21,000 sats (0.00021 BTC) nostr:note1kfx7yh3ja0ysu83hrjnv45fcn4u0lju5mqx6hv2we5c3l0kq0msqweunxy
29th Place
nostr:npub1p2c33zpwk3qepugzxcy88rlr279s3489puqd9djhegf3qx42wmtqed8kta wins 21,000 sats (0.00021 BTC) nostr:note1xqyx7z3jwqkr8tykmh2x8ndp9w5uzuzmlct5jc7l5z00hadwzzzqf9xupf
30th Place
nostr:npub15c3rmcmcafw645z4w7u8e8q8akjpk9cmqfr95mnyl86r2m6xqfdsluh6re wins 21,000 sats (0.00021 BTC) nostr:note1nzjj99nkru0cakg2mu9wl6jhz20jhxp0l7t7gxwq3mxxxr75zjhs004vd7
This is my first time using habla.news so I hope you can see all the embedded notes above.
Thank you to everyone who participated, even those who didn't win. Every sticker in public moves us closer to global bitcoin adoption, so thank you for your time and effort!
September's contest will be announced soon. Stay tuned and make sure you're stocked up on stickers!
-
 @ 3d82e8f6:2d214dc9
2023-09-02 02:38:28
@ 3d82e8f6:2d214dc9
2023-09-02 02:38:28Seeing if this works
-
 @ fea400be:c89b9d0a
2023-09-01 22:12:09
@ fea400be:c89b9d0a
2023-09-01 22:12:09It's been a fun few months creating AI-based RPG storylines inspired by the Choose Your Own Adventure books we read as kids and there are now over 70 base storylines to choose from.
There have been lots of feedback ranging from "I love the games!" to hateful direct messages and negative personal opinions calling us nothing but spam and to go away. It's a rough and tough world and we all could use a little escape sometimes. That's all we're offering here: a little fun escape and some free sats for winning our games. I hope those with negative opinions of us find their own inner peace someday and lighten up.
We've had some recent recommendations, so we've now added women centric storylines as well as ones where you can be an animal.
Here's to more high adventures! Game options now include: animal, viking, superhero, pulp, war, action, mystery, treasure, pirate, zombies, fantasy, scifi, robots, terminator, aliens, disaster, wuxia, xianxia, and horror. To play women centric games, use woman as your keyword.
To start a game, make a new post that tags this account and "start game".
Example: @ChooseYourFate start game
It should start within a minute or so.
You can reference any of the specific game keywords when you want to play.
Example: @ChooseYourFate start game superhero
To play, you must be writing to any of the following relays: Nostr.wine, Damus, MutinyWallet, Relayable. The game will timeout in 5 mins if it doesn't get a response from you. Each game lasts on average 30 mins.
-
 @ 6e75f797:a8eee74e
2023-09-01 16:49:54
@ 6e75f797:a8eee74e
2023-09-01 16:49:54A Definitive Guide to Burgers
by Burgertoshi and TheGrinder, creators of Burgers

Table of Contents:
- Introduction
- Defining the Burger
- The Anatomy of a Burger
- Burger Varieties
- Classic Beef Burgers
- Poultry Burgers
- Seafood Burgers
- Exotic Meat Burgers
- Specialty Burgers
- The Burger Assembly
- Conclusion
Introduction
Burgers have become an emblem of culinary satisfaction, evoking joy and delight with every juicy bite. This whitepaper aims to explore the essence of what makes a burger a burger, outlining the fundamental characteristics that define this iconic sandwich. By delving into the various burger varieties, we will unravel the diverse range of flavours and experiences this beloved food offers.
Defining the Burger
A burger is a gastronomic masterpiece, characterised by a patty encased between two buns. The patty, traditionally composed of ground meat, takes centre stage, while the bun serves as a vessel, providing structure and holding all the delicious components together. This amalgamation of ingredients creates the quintessential burger experience.
The Anatomy of a Burger
The Bun:
The bun forms the foundation of the burger, serving as a platform for the patty and accompanying ingredients. It should strike a delicate balance between softness and resilience, enhancing the overall texture and flavour profile of the burger. Buns often have a slightly sweet or savoury taste and may be toasted or grilled to add a delightful crispness.
The Patty:
The patty is the heart and soul of any burger. Traditionally made from ground meat, it undergoes a meticulous process of seasoning, shaping, and cooking to achieve an optimal balance of flavors and textures. The patty can vary in thickness, shape, and cooking style, contributing to the uniqueness of each burger.
Burger Varieties
Burgers come in a myriad of varieties, offering an extensive palette of tastes and culinary experiences. While vegetable-based burgers are excluded from this exploration, we will focus on the following categories:
Classic Beef Burgers:
The epitome of burger culture, classic beef burgers feature juicy, seasoned beef patties. These burgers can be enjoyed with various toppings such as cheese, lettuce, tomatoes, onions, pickles, and condiments like ketchup, mustard, or mayonnaise.
Poultry Burgers:
Poultry burgers offer a lighter alternative, utilising ground chicken or turkey to create flavorful patties. These burgers are often paired with complementary toppings and sauces that accentuate the poultry's unique qualities.
Seafood Burgers:
Seafood burgers showcase the bounty of the ocean, with options such as fish, shrimp, or crab patties. These burgers provide a delightful fusion of flavours, and the choice of accompanying ingredients can range from tangy citrus dressings to creamy tartar sauces.
Exotic Meat Burgers:
For the adventurous palate, exotic meat burgers introduce unconventional flavours. From bison and venison to kangaroo and ostrich, these burgers offer a tantalising departure from traditional options, opening up a world of culinary exploration.
Specialty Burgers:
Specialty burgers encompass a range of innovative creations tailored to specific themes or cultural influences. These can include gourmet burgers, fusion-inspired combinations, or regional variations that celebrate local ingredients and traditions.
The Burger Assembly:
The art of burger assembly is essential to ensure a harmonious and enjoyable eating experience. Following the correct order of ingredients is crucial to maintain the structural integrity of the burger and prevent it from becoming soggy. The ideal assembly order for a classic burger is as follows:
Bottom Bun:
The foundation of the burger, providing a stable base for the entire creation.
Lettuce:
Placing a layer of crisp lettuce directly on the bottom bun acts as a moisture barrier, preventing the bun from becoming soggy due to the juices released from the patty and toppings.
Patty:
The centrepiece of the burger, carefully cooked and seasoned to perfection, and positioned on top of the lettuce.
Toppings:
A tantalising medley of toppings, such as cheese, tomatoes, onions, pickles, and any other preferred condiments, are strategically layered on the patty to enhance the burger's overall flavour profile.
Top Bun:
The crowning glory of the burger, completing the sandwich and providing a satisfying bite.
By meticulously following this assembly order, each bite remains a delightful symphony of flavours and textures, encapsulated within the perfect burger experience.

Conclusion
Burgers have transcended their humble origins to become a global culinary phenomenon. This whitepaper has highlighted the key elements that define a burger and explored the diverse range of burger varieties. Whether savouring a classic beef burger or venturing into the realm of specialty creations, the burger experience continues to captivate and satisfy taste buds worldwide.
Remember, the proper assembly of a burger plays a vital role in preserving its integrity and ensuring a delectable journey from the first bite to the last. Let us continue to celebrate the timeless allure of burgers as they continue to evolve, adapt, and bring joy to food enthusiasts everywhere.
TheGrinder Creator of burgers, author of the burger whitepaper and co-author of the milkshake whitepaper. There is no 2nd best!
-
 @ 7dd04080:36f6813d
2023-09-01 16:19:23
@ 7dd04080:36f6813d
2023-09-01 16:19:23In 2000, we first started helping independent filmmakers and musicians with their digitial marketing, and a year or so later we launched a platform to help place music in film that would go on to be used by over 1,500 films worldwide.
Years later we launched our channels on Roku, Apple TV, etc to stream their content to as many people as possible. We wanted to get away from the traditional licensing model for our royalty payments, but need to make sure it was globally seamless. With the emergence of Bitcoin and then Nostr, we landed on using the Lightning Network as our automated pay out solution.
The new platform, called Royalty Points, was only launched 1 month go, but has already paid out over 5 million Sats to artists around the world. As a labor of love, this makes us extremely happy to see!
If you are interested in learning more, please contact us.
-
 @ d61f3bc5:0da6ef4a
2023-08-31 13:47:34
@ d61f3bc5:0da6ef4a
2023-08-31 13:47:34As Nostr continues to grow, we need to consider the reality of content moderation on such a radically open network at scale. Anyone is able to post anything to Nostr. Anyone is able to build anything on Nostr, which includes running bots basically for free. There is no central arbiter of truth. So how do we navigate all of this? How do we find signal and avoid the stuff we don’t want to see? But most importantly, how do we avoid the nightmare of centralized content moderation and censorship that plagues the legacy social media?
At Primal, we were motivated by the feedback from our users to build a new content moderation system for Nostr. We now offer moderation tools based on the wisdom of the crowd, combined with Primal’s open source spam detection algorithm. Every part of our content filtering system is now optional. We provide perfect transparency over what is being filtered and give complete control to the user. Read on to learn about how our system works.
Wisdom of the Crowd
Every Nostr user is able to define their personal mute list: accounts whose content they don’t wish to see. This simple tool is effective but laborious because the user needs to mute each non-wanted account individually. However, everyone’s mute list is public on Nostr, so we can leverage the work of other users. Primal’s content moderation system enables you to subscribe to any number of mute lists. You can select a group of people you respect and rely on their collective judgment to hide irrelevant or offensive content.
Outsourcing the moderation work to a group of people you personally selected is much better than having to do all the work yourself, but unfortunately it won’t always be sufficient. Spam bots are capable of creating millions of Nostr accounts that can infiltrate your threads faster than your network of humans is able to mute them. This is why we built a spam detection algorithm, which Primal users can subscribe to.
There Will Be Algorithms

Nostr users have a natural aversion to algorithms. Many of us are here in part because we can’t stand the manipulated feeds by the legacy social media. One of the most insidious examples of manipulation is shadowbanning: secretly reducing the visibility of an account throughout the entire site, where their posts are hidden from their followers and their replies don’t show up in conversation threads. It is understandable that many Nostr users are suspicious of algorithms to such extent that they don’t want any algorithms in their feeds. Those users will enjoy Primal’s default “Latest” feed, which simply shows the chronological list of notes by the accounts they follow. We even support viewing another user’s “Latest” feed, which enables consuming Nostr content from that person’s point of view, without any algorithmic intervention.
But algorithms are just tools, and obviously not all algorithms are bad. For example, we can use them to detect spam or not-safe-for-work content:
In our view, algos will play an important role in Nostr content moderation and discovery. We envision a future in which there is an open marketplace for algorithms, giving a range of choices to the user. At this early stage of Nostr development, it is important to consider the guiding principles for responsible and ethical use of algorithms. At Primal, we are thinking about it as follows:
- All algorithms should be optional;
- The user should be able to choose which algorithm will be used;
- Algorithms should be open sourced and verifiable by anyone independently;
- The output of each algorithm should be perfectly transparent to the user.
Perfect Transparency
Our new content moderation system enables users to easily check whether a Nostr account is included on any of the filter lists they subscribe to:
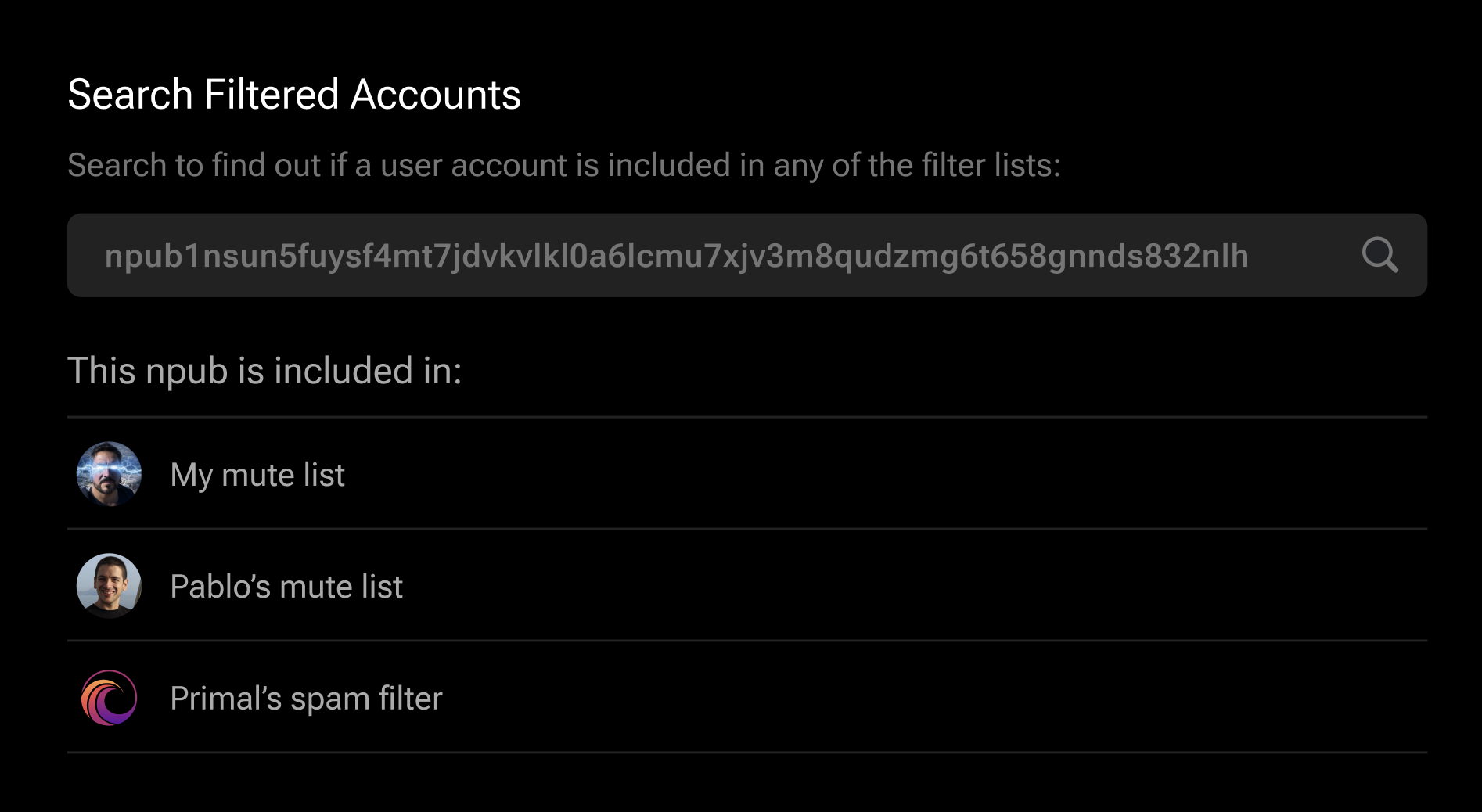
This simple search provides complete transparency regarding the inclusion of a given account in any of the active filter lists. Beyond that, it would be helpful to provide all filter lists in their entirety. Note that this is not trivial to do because these lists can get quite large. Our goal is to provide them in the most efficient way possible. We are working on exposing them via Nostr Data Vending Machines; stay tuned for more information on this in the coming days.
Complete Control
The user should always have the final word on filtering. If after configuring all the filtering settings to your liking, you find that some legitimate accounts are being filtered, you can specify your “never filter” allowlist, which will override all filtering. We are persisting this allowlist as a standard Nostr categorized people list (kind: 30000), so that other Nostr clients can leverage it as well. In addition, everyone you follow will automatically be excluded from all filtering.
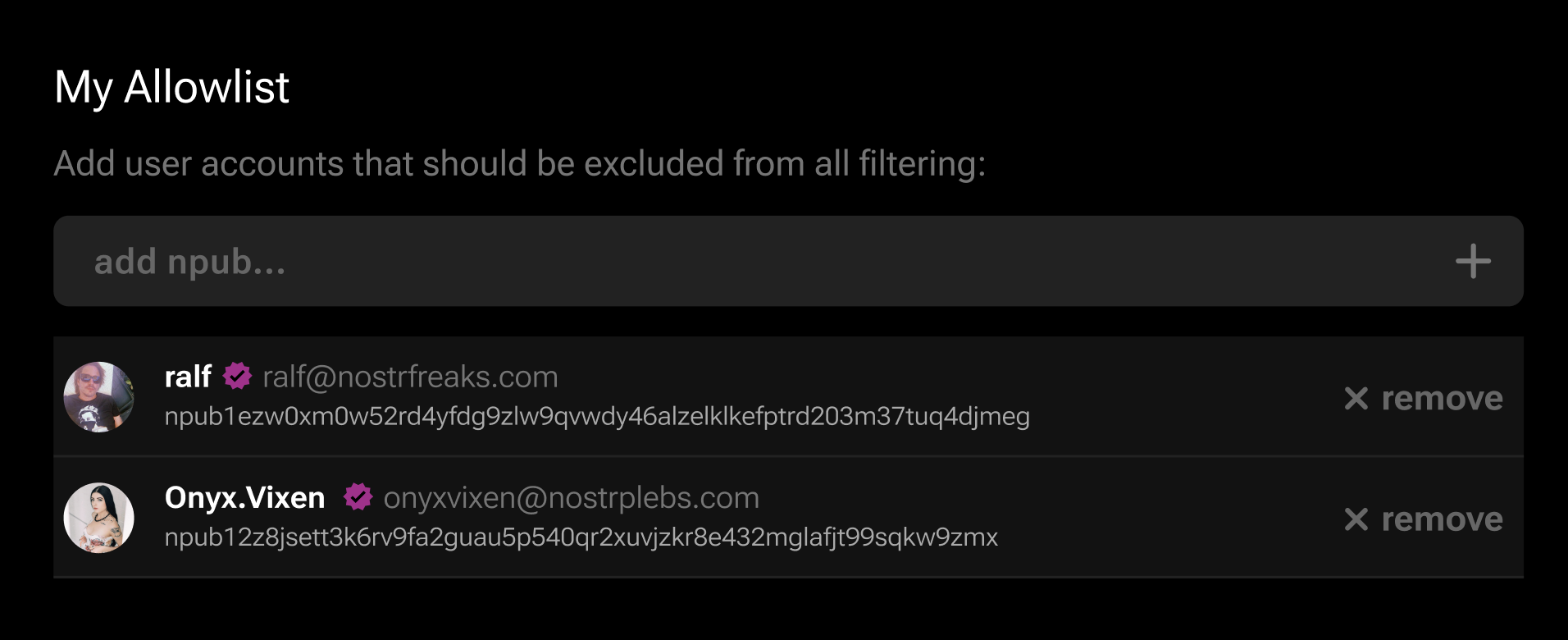
Open Source FTW
At Primal, we do two things:
- We build open source software for Nostr
- We run a service for Nostr users, powered by our software
Every part of Primal’s technology stack is open sourced under the most-permissive MIT license. Anyone is free to stand up a service based on our software, fork it, make modifications to it, and add new features to it.
We run our service based on the policies we established as appropriate for Primal. Others can stand up services powered by our software and choose a different set of policies. Users are free to choose the service that best suits their needs. They can move between clients and services without any friction. This unprecedented level of user empowerment is what attracted most of us to Nostr. At Primal, we think that Nostr will change everything. We will continue to work tirelessly every day to keep making it better. 🤙💜
Please note: The entire Primal technology stack is still in preview. Just like everything else, the content moderation system is a work in progress. Thank you for helping us test it. Please keep the feedback coming. Let us know what’s not working and what we can improve.
-
 @ 2edbcea6:40558884
2023-08-30 00:21:44
@ 2edbcea6:40558884
2023-08-30 00:21:44Welcome to the Nostr Report conference updates. Thinking about joining a Bitcoin event? Here you will find info on major #Bitcoin and #Nostr conferences and meet-ups around the world.
Thanks to everyone who helped us create this list. If you have an event that’s not listed yet, or if you notice any information that needs to be updated, feel free to DM #NostReport or me directly, and we will add you to the note. 🤙
nostr:npub1y67n93njx27lzmg9ua37ce7csvq4awvl6ynfqffzfssvdn7mq9vqlhq62h 💜
Baltic Honey Badger - Sept 2-3, 2023 (Official Nostr Report Media Partner)
📍Riga, Latvia
https://baltichoneybadger.com/
Organized by nostr:npub1yul83qxn35u607er3m7039t6rddj06qezfagfqlfw4qk5z5slrfqu8ncdu
Announcements: * Riga #Bitcoin week is now! Let’s make sure we all use the official hashtag and make it trending for another year in Riga. #BH2023SING NOSTR 2049 Afterparty - Sept 14, 2023
📍Singapore
https://lu.ma/xk3it4ue
Announcements: * Join nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 , nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft , and many other special guests at the SING NOSTR 2049 Afterparty! nostr:note1pkscfjawjhvq6yxymz7h06s0etp3d4fyntmaz32czy8nlvel8cxsx53fnrWatch Out Bitcoin - Oct 6-8, 2023
📍Madrid, Spain
https://wobitcoin.org
Organized by Watch Out Freedom Foundation * Enrique Ho, investment fund advisor and #Bitcoin in the financial and geopolitical sector advocate, was announced as a speaker for #WoB23 nostr:note1mp4xpdsqznq50fqe5pdeh4df4neqhdr9538z3zxxm9gw2vkqwp8qgyh3w5 * nostr:npub1k3rychegd7vs20prks4g8g9xfyk2djw4pxxeukkj0mjhg68evz8qgsf820 content creator, YouTuber, #Bitcoin wallet specialist, and much more will be speaking at #WoB23 in Madrid. nostr:note1g4uh5geua6ysqv8fr4fl9f4v5eks5t9sc2gpqxc2npcsrgthttqqqanr9a * Cristina Carrascosa, lawyer, international business consultant, and founding partner of ATH21cripto. Will be sharing insightful updates on EU regulations and more, as she offers a fresh and critical perspective at #WoB23 nostr:note1mp4xpdsqznq50fqe5pdeh4df4neqhdr9538z3zxxm9gw2vkqwp8qgyh3w5Nostrasia - Nov 1-3, 2023
📍Tokyo, Japan 📍Hong Kong, China
https://nostr.world/
Organized by nostr:npub1nstrcu63lzpjkz94djajuz2evrgu2psd66cwgc0gz0c0qazezx0q9urg5l * nostr:npub1g5pm4gf8hh7skp2rsnw9h2pvkr32sdnuhkcx9yte7qxmrg6v4txqqudjqv announced as speaker for #Nostrasia in Tokyo nostr:note1qap6cmsn6mewhuxa8c5v8pqjh0qn3dad45hqjuxnmxfjprxw62dspseg9uNostradam - Oct 11, 2023
📍Amsterdam, Netherlands
https://www.nostrdam.com
Organized by: Connect the World * Special guests include Damus creator nostr:npub1xtscya34g58tk0z605fvr788k263gsu6cy9x0mhnm87echrgufzsevkk5s and nostr:npub14kw5ygpl6fyqagh9cnrytyaqyacg46lzkq42vz7hk8txdk49kzxs04j7y0 co-host nostr:npub1hqaz3dlyuhfqhktqchawke39l92jj9nt30dsgh2zvd9z7dv3j3gqpkt56s * I will also be there, so make sure to say hello!Bitcoin Atlantis - March 1-3, 2024
📍Madeira Island, Portugal
https://bitcoinatlantis.com/
Organized by: nostr:npub1h493d0qgwhu95s82zd9sxrt3ckn3ttgvaf04z02neckadxw5fkvqte4cwz * Announced author, nostr:npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83a as a speaker for their upcoming conference. nostr:note1e75lwwpcvx3l6fcassxs8lzaaw9acss2tvqh76pqwajp2c2ng67qd9x5lsTABConf - Sept 6-9, 2023
📍Atlanta, USA
https://2023.tabconf.comBTC 2023 - Sept 14-17, 2023
📍Innsbruck, Austria
https://bconf.de/en/BTC Azores - Sept 23-24, 2023
📍Azores, Portugal
https://btcazores.comPacific Bitcoin Conf - Oct 5-6, 2023
📍Los Angeles, USA
http://pacificbitcoin2023.com/The Bitcoin Conference - Oct 12-13, 2023
📍Amsterdam, Netherlands
https://b.tc/conference/amsterdam
Organized by: nostr:npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yuBitcoin4India - Oct 15, 2023
📍Bangaluru, Karnataka India
https://conference.bitcoin4india.org/
Organized by: nostr:npub1ma5tatv2fctj9nd5tfvdjmr8gcpkhjxk4fmltnmkazxhll0pa0mqcp4s5mLugano Plan B Forum - Oct 20-21, 2023
📍Lugano, Switzerland
https://planb.lugano.ch/planb-forum/Indonesia Bitcoin Conference - Oct 26-27, 2023
📍Bali, Indonesia
https://indonesiabitcoinconference.comSatsConf - Nov 2-5, 2023
📍São Paulo, Brasil
https://satsconf.com.br/Nostrville - Nov 9-10, 2023
📍Nashville, Tennessee
https://www.meetup.com/bitcoinpark/events/292518506/Adopting Bitcoin - Nov 15-17, 2023
📍San Salvador, El Salvador
https://adoptingbitcoin.org/2022/ -
 @ 92294577:49af776d
2023-08-29 02:27:49
@ 92294577:49af776d
2023-08-29 02:27:49This is the third (and final) blog post in a series detailing the many changes to CLN in the new v23.08 release, codenamed Satoshi’s Successor (courtesy of Matt Morehouse). The first post covers our improvements to user experience, and the second highlights new features and enhancements for developers.
In the early days of Lightning, developers publicly advised that using real funds was reckless. That is less true today, but we know some of you like to continue that pioneering spirit, so this section is for you (and the rest of us thank you for it!).
And let me just point you at our issues page so your injuries are not in vain.
Firstly, we have eliminated the concept of experimental builds: now every Core Lightning node can enable each experimental option separately, if they want to. This means that we have two new options, which were previously turned on by default in experimental builds:
experimental-upgrade-protocolenables simple channel upgrades from oldnon-static-remotekeychannels if both ends enable it, andexperimental-quiesceenables temporary stopping of a channel progress (not very useful by itself, but good for other protocols, like splicing!).Dual Funding Gets an Upgrade
As when we first released it in 2021,
experimental-dual-fundwill enable dual funding. It allows both peers to contribute funds to channels, enabling complex constructions like coinjoin, UTXO consolidation, and multiple parallel opens for each side; it also allows either side to RBF if your channel does not open fast enough, and an extension calledoption_will_fundto offer to lease channel liquidity to your peers.This version has been tweaked for interoperability with the latest specification draft, and now works with Eclair! With this option in your configuration file, you can negotiate dual funded channels with any peer that supports it!
Splicing Channels, at Last
When you have a Lightning channel, if you want to increase the size of it, you have to open a new channel. To decrease the size, you have to close one (and maybe open a smaller one). The idea of being able to splice funds in or out of a live channel while it is still going is almost as old as Lightning implementations themselves, so when Lisa Neigut was designing the interactive construction mechanics required for dual funding, splicing in and out of existing channels was kept in the back of everyone’s minds.
Fast forward to today, and my early draft specification for splicing has been rewritten and implemented by Dusty Dettman for Core Lightning. This was Dusty’s first major contribution, and it was incredibly ambitious: dating back to May 2022, with a PR containing over 300 comments, reaching deep into the Core Lightning code. Preparatory work was merged in the last release, and then Dusty continued; the specification details were re-negotiated as the Lightning team from ACINQ started their implementation, causing multiple revisions, and much collaboration with them and Lisa Neigut. It was finally merged on July 31, after final review. Dusty has made numerous refinements since then, including more documentation, and moving the feature bit from the final 63 to an experimental 163 in case the specification changes again.
By restarting your node with
experimental-splicingyou and any compatible peers can start splicing today with thesplice_init,splice_update, andsplice_signedcommands. Note that some explorers may consider your channel closed for the six blocks between the splice being mined and seeing the new splice announcements: the spec was amended a year ago to give apparently-closing channels 12 blocks before considering them definitively closed. Now we are going to see real splices on mainnet, I expect them to catch up quickly!Pickhardt Payments, aka Renepay
Rene Pickhard is a well-known Lightning researcher who has released multiple papers on Lightning. One of his collaborators, Eduardo Quintana, was given a grant through Build On L2 to implement Rene’s minimum cost flow proposals in a concrete form, and the result is a (currently experimental) plugin called
renepay.Our current pay plugin does not have a very sophisticated view of the network: it attempts a payment and keeps trying variants until it runs out of time or things to try. Renepay maps out the likely payment sizes for each path and breaks the payment to spread across the most likely ones; it then collects feedback from failures (or partial successes) and continues the process until it has run out of time, or the probability of success is vanishingly small. Importantly, it remembers what it learned from previous payments for up to an hour, so second and further attempts are more likely to succeed.
It is still a new plugin: the simple
renepayandrenepaystatuscommands are under active development and will continue to be enhanced until, hopefully, this becomes the default plugin for Core Lightning in a future release! Meanwhile, feel free to tryrenepayto pay invoices and report your results!- Flying car not included
Join the CLN Community
As always, we want to give a special shoutout to all the contributors (31 for the v23.08 release) who continue to help us improve CLN with every update. We are grateful for your support; the new release was only possible with your dedication and feedback.
Let us know what you like or what we could improve by starting a thread on Build On L2 or by commenting via our usual social channels: Twitter, Telegram, or Discord.
-
 @ 92294577:49af776d
2023-08-25 07:57:31
@ 92294577:49af776d
2023-08-25 07:57:31This is the second blog post in a series detailing the changes to CLN in the new v23.08 release, codenamed Satoshi’s Successor (courtesy of Matt Morehouse). The first post covers the improvements we made to user experience, and in the third and final post, we will delve into the experimental features enabled by v23.08, so you can carry on that reckless Lightning spirit!
In this installment, we focus on the new features and enhancements for developers. We know you all have been asking for several things of CLN, and this release we delivered!
REST API and Ancient Runes
CLN finally has an official REST API (web API, if you are a pedant) through a new plugin called
clnrest, which is installed by default. You will need some Python packages installed to make it work, but it will produce an informative message in the logs about why it cannot run if it does not have them. It’s already a superset of theclightning-restplugin, which the Ride the Lightning project has supported for some time, but has some neat additions and will be kept up-to-date from now on. This is not surprising when you find out the author is Shahana Farooqui herself (of RTL fame) who has also promised to write a detailed guide to using this API!Runes are also now first-class citizens. Runes are bearer credentials, introduced in our
commandoplugin for controlling a node via the Lightning Network itself. The rune says exactly what commands you are allowed to run, and have proven popular for other uses, so now the functionality has been moved into the core of CLN for other projects to share them. They have proven extremely useful, and now you do not even have to implement them yourself: you can use ourcreateruneandcheckrunecommands to do all the heavy lifting. At this point I will simply quote from the manual:Oh, I almost forgot. Runes can also be invoked like in ancient times with the
invokerunecommand. Feel the magical powers of a rune by invoking it.Pay Command Upgrades
There are two main developer enhancements to the
paycommand. The first is that we now allow self-payment, where we used to reject that as… well, self-serving. The second is a little more embarrassing: because Bolt11 can legally contain the hash of the description, with the actual description elsewhere, there’s been debate over whether nodes should be given the actual description. The spec (and our users, not to mention the folks in accounting) are fairly clear that we should know the description of the purpose of the payment for us to sign off on it, but a change in 2019 eliminated this requirement, and I did not notice until 2022! So back in April 2022 (v0.11), we deprecated paying invoices if you did not supply the description. But it turns out that a bug in our parsing of the description meant that you could not always pass the description into thepaycommand, so we have had to undeprecate that again for now!Other Commands
Long-awaited, we have added the first steps to a general
waitandpaginationAPI. Thewaitcommand simply waits until an entry is created, updated, or deleted, and works reliably across node and plugin restarts! It pairs with a list command, which for the moment is only supported onlistinvoices. So every invoice has two numbers: acreated_indexand an optionalupdated_index. These start at 1, and are unique, and only ever increase: if you call the waitinvoices created 1command it will return once your first invoice has been created.Paired with this, you can call
listinvoicesand specifyindexas eithercreatedorupdated. You can specifystartto indicate what index to start at, and an optionallimit. So if thewaitabove returnscreated : 5, you know tolistinvoices index=created start=1will show you all the new invoices you missed. As a helpful addition, thewaitcommand itself often returns some information about the invoice (label, Bolt11, and status): this is particularly convenient to save a call tolistinvoices, but is not present if you actually missed the change (perhaps your plugin was slow, or offline for a while), so you will need to calllistinvoicessometimes anyway.Future releases will extend this API to the other list commands, allowing you to easily and reliably wait for almost any Core Lightning event, such as on-chain transactions or payment results.
Finally, we have added initial support for user-defined tracing on Linux, which allows you to profile what happens on your node at various key points. It is extremely useful for developers to analyze performance in live systems without interfering, and we have documented the process for you to get started.
Join the CLN Community
We want to thank the contributors (31 for the v23.08 release) who continue to help us improve CLN with every update. We are grateful for your support; your dedication and feedback made the new release possible.
As always, let us know what you like or what we could improve by starting a thread on Build On L2, where we have special developer and node runner pages to help facilitate long-form discussions. It is free to sign up, and nyms are more than welcome!
You can also reach us on our usual social channels: Twitter, Telegram, or Discord.
-
 @ a10260a2:caa23e3e
2023-08-24 05:29:59
@ a10260a2:caa23e3e
2023-08-24 05:29:59It's been about a week since I discovered YakiHonne and we've got another round of updates to test. The fact that the YakiHonne team has pushed more updates this soon is exciting as that means the app is iterating at a fast pace, which usually means a quick response to user feedback.
With that said, let's dive into the 8 updates from this round:
1. Bookmarks - you can save your preferred articles
This feature behaves as expected and similar to how bookmarks work for short notes on clients like Damus.
Got an article you want to read later? Look for the bookmark icon near the top-right. Once you click on that, you'll be prompted to sign the event (I'm using nos2x).

If that went well, you'll see the bookmark icon change to indicate that it was a success.

2. Comments replies threads - you can view and reply to comments within the replies threads
This worked really well and as expected.

After signing the event, the reply was shown inline which was a nice touch.

Although the reply was a success, I discovered a disconnect after looking for my comment on Damus (I believe I found the note by copying the naddr).
It turned out the comment that I replied to had already received a reply from the note author even though YakiHonne displayed "0 REPLY(IES)". I believe this has something to do with differing relays.
3. “sensitive content” - you can decide the type of content as sensitive content when publishing
I don't plan on using this anytime soon, if ever. But I think it can be an important feature moving forward, especially when it comes to relays and clients.
4. Reports counter - view how many users reported a piece of content
I spoke with the YakiHonne team recently and they will be manually reviewing reported accounts to prevent abuse of this feature.
On the flip side, hopefully it'll help with what seems to be a flood of AI-generated content. This is currently a big deterrent to my using YakiHonne as a reader unfortunately. Will be keeping an eye on this one. 👀
5. Images upload - you can directly upload images while writing
What a time saver this one.
Before, I would upload an image using nostr.build, copy the URL, and paste it in here.
Now, all I've gotta do is click the upload button (right next to "Add image"), select a photo from my computer, and the photo is inserted with the correct syntax.

6. Uploads history - you can re-use uploaded images for any written articles
At this point in this article's creation, I've uploaded 3 images and I already see them when I click "Uploads history" in the top-right.

I'm pretty sure this'll come in handy as I write more articles and need to re-use past images.
7. Search - searching users by username/nip-05 identifiers
Hm, this one could use some improvement.
Searching for my fren bitcoin.rocks was unsuccessful despite trying a few variations (e.g. "bitcoin.rocks", "bitcoinrocks", and "bitcoindotrocks") and the NIP-05 (_@bitcoin.rocks). Btw, that first result is incorrect because I checked the npub.

However, searching for the guy that always reminds me to stay humble and stack sats was successful (not sure what the difference between success and failure is).

Finally, when searching for a keyword. The users that were returned in the results aren't the most intuitive. I would think users with "bitcoin" in their username would appear but not a single one.
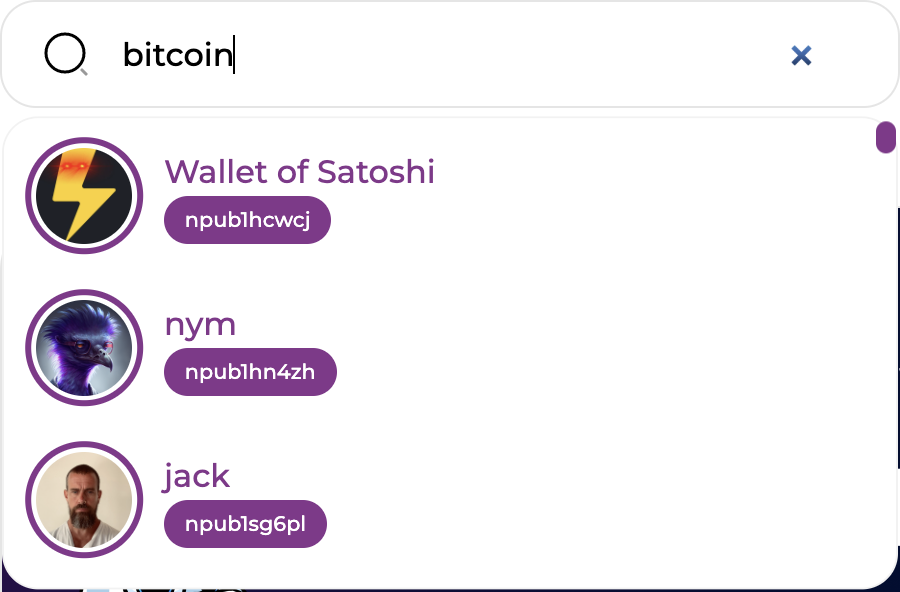
And it seems like articles shown could potentially not be relevant. I'm assuming any article can show up here if it's tagged with bitcoin.

Looking forward to seeing some improvements here in terms of speed and accuracy.
8. Math equations are now supported using the katex syntax
LFG! Y'all know the only equation that matters. 😎
$$\sum_{i=0}^{32} 210,000 \frac{50}{2^i}$$The trick here is to use "Insert Code" and put the equation between a pair of "$$".

Like so. (Thanks Yofu)
Also, the 32 and "i=0" should go on top of and below the summation, respectively. But I guess this is just a rendering issue that can be fixed.
That's a wrap for this round! YakiHonne is definitely proving to be best long form note editor at the moment for me. I hope the team continues to add new features, and, more importantly, improve the existing ones.
Don't forget to follow me so you don't miss my articles on future updates.
Onward. 🫡
-
 @ 92294577:49af776d
2023-08-24 03:47:54
@ 92294577:49af776d
2023-08-24 03:47:54Today, we welcome the latest Core Lightning release, v23.08, codenamed Satoshi’s Successor (courtesy of Matt Morehouse). The August 2023 release has such an overwhelming array of changes we are splitting the release announcement into three separate blog posts:
User Experience: new features users have requested.
Developer Experience: new features and enhancements for developers.
Experimental Features: a look into Lightning’s future by enabling experimental options at runtime.
The next two will be shared tomorrow and the following day, so make sure you subscribe below or bookmark the Lightning blog to stay updated.
Lightning Polished and Stable
We uncovered several cases where channels with Eclair and LND nodes could fail, which we have fixed or made compatible. These are rare, but channel breakage is always annoying. There are also a slew of minor fixes and tweaks in the 530 changes since the last release; my favorite is the one where, if the only unexpired invoices you had expired after the year 2038, we would loop forever on old 32-bit platforms (which, yes, we still support!).
We added a new parameter to setchannel called
ignorefeelimits, to insulate channels against fee disagreements with peers. We had a previous global setting, but this one can be set or unset on more trusted peers dynamically, and will allow them to set on-chain fee rates even if we think they are wrong. In particular, LND will always re-request the same channel fee even if its fee rate estimate has since changed, so setting this temporarily can “unstick” a channel. It turns out that bitcoind forgets the previous minimum real fee when it restarts, too, so nodes can also get confused from that (this has been fixed for the next Bitcoin release).We also added Taproot address support, thanks to Greg Sanders: you can issue Taproot addresses for people to send you on-chain funds, and we will immediately use them for our own change outputs. Taproot addresses (i.e., P2TR) start with bcp1 instead of bcq1, just so you know!
Updated Plugins and New Commands
Our
payplugin, which drives payments, has some tweaks to make paying faster and more reliable: this is the first concrete feedback from Christian Decker’s work on Greenlight (Blockstream’s developer preview of our hosted, non-custodial Lightning infrastructure), where he analyzed payment failures on the real network and fed the results back into upstream development. No doubt there will be many more such refinements in future versions! The third installment of the blog series will go into more detail onpayand discuss the new experimentalrenepayplugin!To help manage your node, there is a new command to change settings without restarting your node:
setconfig. This changes the configuration setting dynamically, and also changes it (with a comment) in the correct configuration file so that it is persistent! This is matched by the power of the update output fromlistconfigs, which shows you exactly where each configuration setting came from: was it a particular line in a configuration file, the command line, or the default? Thesetconfigcommand is currently only used for settingautocleanlimits, but this will expand to more settings in future releases as people request them (we also have an open issue you can add to).Logging got some work, too: you can now add different filters to different log files. For example, you can have one log file for debug-level logging, and another for normal info-level logs. You can also use this to configure more logging for particular peers or plugins.
Thanks to the Summer of Bitcoin work of Aditya Sharma, you can now save and restore your node’s secret key in the new BIP 93 format (aka. codex32). Unlike BIP 39 seed words, this can be done on all nodes, using the
hsmtool getcodexsecretcommand, and your node restored using the- -recovercommandline option. This will also gain more abilities in future releases, such as finding and recovering any existing channels and funds you might have. Our BIP 93 strings look like:cl10leetsllhdmn9m42vcsamx24zrxgs3qrl7ahwvhw4fnzrhve25gvezzyqqjdsjnzedu43ns
They have some amazing ability to recover from errors which we will be exploring in future, but for now, you would have to make more than eight mistakes before there is any chance we would accept it as valid.
Our
recklessplugin manager got more powerful: it can install from local copies of plugins, not just GitHub. That brings everyone a little closer to becoming a developer: grab a plugin, change some things, then get reckless to install and start it for you!▶️ Core Lightning Features (Part 2) with Rusty Russell
Finally, as part of the fallout of the recent Bitcoin fee spike, Bastien Teinturier of ACINQ noticed that one channel closure can cascade to others, if a payment was in progress and fees increase markedly. We now handle this case more carefully and will sacrifice a not-worthwhile payment on an outgoing closed channel, to avoid causing incoming channels to fail. This should contain the damage on any unilateral channel close in the future!
Join the CLN Community
As always, we want to give a special shoutout to all the contributors (31 for the v23.08 release) who continue to help us improve CLN with every update. We are grateful for your support; the new release was only possible with your dedication and feedback.
Let us know what you like or what we could improve by starting a thread on Build On L2. We also have special developer and node runner pages to help facilitate long-form discussion. It is free to sign up, and nyms are more than welcome!
-
 @ 20986fb8:cdac21b3
2023-08-22 13:09:00
@ 20986fb8:cdac21b3
2023-08-22 13:09:00YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
Top 10 feedback will get up to 100,000 SATs each. All participants will share the Popularity Prize Pool of 400,000 SATs.
Round 5 will be from 22nd Aug to 4th Sep
How to participate:
- Test Updates below
- Write your feedback and opinion (pros and cons are all welcomed)
- Don't forget to add tag 'YakiHonne-Updates' to your article
- Post your article on Nostr via YakiHonne.com
- Share your articles on social media like Nostr and Twitter, don't forget to @YakiHonne
- Share the link to our community: http://t.me/YakiHonne_Daily_Featured
- Get as many upvotes as possible to get more shares from Popularity Prize Pool
- Be Zapped!
Requirements:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Experience our updates in action, NO limit on the length of your post, share your REAL feedback and opinion
- The top 10 posts will be zapped up to 100,000 SATs
- All participants will share the Popularity Prize Pool of 400000 SATs based on the upvotes number
- The evaluation will based on the article's depth, completeness, and constructiveness.
- Contact us for additional zaps if bugs are found.
- Any language is welcome
Updates to be tested in Round 4:
- Bookmarks: you can save their preferred articles
- Comments replies threads: you can view and reply to comments within the replies threads
- “sensitive content”: you can decide the type of content as sensitive content when publishing
- Reports counter: view how many users reported a piece of content
- Images upload: you can directly upload images while writing
- Uploads history: you can re-use uploaded images for any written articles
- Search: searching users by username/nip-05 identifiers
- Math equations are now supported using the katex syntax
- More updates and fixed bugs in Weekly Report Vol.11 and Weekly Report Vol.12
- Comments and suggestions are welcome
If you missed previous Rounds, the updates could be tested as additions:
Don't miss this opportunity to participate in Round 4, test the updates, and provide valuable feedback. Head over to YakiHonne.com to share your thoughts and earn SATs for your valuable input. Act fast!
Selected Review from Previous Rounds
About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 36ceac90:0d24128d
2023-08-21 14:42:55
@ 36ceac90:0d24128d
2023-08-21 14:42:55Listen live on ⚡️✨ZAP STREAM✨
CURRENT PROGRAMMING
Click Vortex
Sam (@ltngstore/@wavlake) and Jason (Aquarium Drunkard) stumble down a rabbit hole of hyperlinks, following trails of interconnection between music and wildly varied topics. Live every other week on YouTube and in your podcast feed.
The Spindle
The 7-inch record isn’t just a format–it’s an art form. On each episode of The Spindle podcast, Marc and John dive into a great 7-inch every other week, dissecting its background, impact, and the reasons why it stands out as a small plastic piece of music history.
HOTLINE
This bi-weekly video series features your favorite artists answering questions from the 1-877-WASTOIDS answering machine, sharing their fantasy world, records they can't live with out and anything else that comes in.
Subscribe: YouTube, Fountain, Other
Midnight Music Review in the Attic
Monthly video series spotlighting experimental songwriters, garage rockers, avant-pop acts and more from the mind (and attic) of Argentinian artist Salvador Cresta.
Subscribe: YouTube
WASTOIDS Music News
Decoy Deloy brings you the latest in music news, each Friday from the WASTOIDS loft.
Subscribe: YouTube
HIGHLIGHTER
Jenny Nobody brings a weekly video roundup of what you may have missed last week on WASTOIDS.
Subscribe: YouTube
WASTOIDS DIGS
Handpicked new releases from the WASTOIDS staff every week on WASTOIDS DOT COM
SPECIALS
Nilsson Talks Nilsson
Olivia and Kiefo share interesting tidbits, unknown stories, and personal experiences related to their father, legendary singer, producer, interpreter, and composer, Harry Nilsson.
Special Podness
Four-part mini-series dedicated to the history of The Special Goodness by the three dudes who (probably) know it best: Pat Wilson of Weezer, drummer Atom Willard (Rocket From the Crypt, Plosivs, Against Me!) and Karl Koch, Weezer historian.
In The Crates
In the early ’80s, skate punk roared out of Phoenix, led by a group of teenagers called Jodie Foster’s Army. On JFA’s 1983 full-length debut, Valley of the Yakes, vocalist Brian Brannon rails against preps, gossipers, cops, and Reagan. But he saves some of his gnarliest lyrics for a local radio deejay, a guy named Johnny D.
FROM THE ARCHIVES
Clairaudience
A late night weekly mood music/paranormal radio show featuring kitschy and soothing music, far out stories from guests like John Darnielle of The Mountain Goats, plus calls from the WASTOIDS hotline.
WASTOIDS With
Interviews featuring Van Dyke Park, Keith Morris, Steve Keene, Roger manning Jr., Paul Leary, Laura Jane Grace, East Bay Ray from Dead Kennedys, CREEM Magazine, The Source Family, and more.
Strange Gear
An exploration of unusual musical equipment and the stories behind it featuring artists like, A Place to Bury Strangers and Nick Reinhart of Tera Melos, and more.
WASTOIDS, Season 1
Initially created for Night Flight, this 4 episode series is baked and fried in the Sonoran Desert and NYC, throwing back to the halcyon days when stoned teenagers could stay up all night watching music videos, loopy comedy, and arty strangeness on the TV set.
Subscribe: YouTube
Out of Site
Recurring live music video series, featuring Mute Swan, Supercrush, Dante Elephant, Beach Bums, Sydney Sprague, and more.
Subscribe: YouTube
MIXTAPE
Curated playlists from WASTOIDS friends
WHAT ELSE?
WASTOIDS is a hotline: 1-877-WASTOIDS. We want to know: What’s the weirdest thing that’s ever happened to you? Has a stranger ever relayed a cryptic message? Have you witnessed something confounding in the sky? Found yourself stranded in a frightening location? Call WASTOIDS and tell us your strange tale.

-
 @ 20986fb8:cdac21b3
2023-08-21 10:14:52
@ 20986fb8:cdac21b3
2023-08-21 10:14:52A weekly update on YakiHonne.com 15th – 21st Aug
TL;DR
1. Featured Articles of the Week
2. Tech Updates - Images uploading & uploading history: you can directly upload images while writing and re-use them - NIP-05 identifiers: search tab now support searching users by usersnames - Math equations are now supported using the katex syntax - Bugs fixed (Bookmark, report, editor, etc.) - UI/UX Enhancement
3. YakiHonne Events - Web3, AI and DeSci Creator Hackathon - YakiHonne Ideathon | Integrate Future Creativity and Set Sail on an Artistic Journey - Publish Your Long-form Content on Nostr and Earn 17,500,000 SATs - Hot Topics Creation Hackathon with YakiHonne - Earn SATs with YakiHonne Updates
6. Top Curators/Creators from All Relays
1. Featured Articles of the Week ☕
Nostr ecosystem's long-form posts is breakthrough! Thanks to all the creators, like james, Vivido srl, TopWK1, yael, Disturbia, chef4₿rains, Welcome all to explore the enriching experience of yakihonne.com.
1. Navigating the Fourth Turning: A Strategic Guide for Investors — by @ Flextiger
Based on Neil Howe's new book, "The Fourth Turning Is Here", @Flextiger led us to delve into a forecast of looming economic recession, inflation, volatility, and instability in the financial markets.
2. Honne Boxshow | The Key Role of User Experience (UX) in Driving Digital Product Growth (Feat. Caleb) — Feat. Caleb
Constant improvement is what will make any product retain a large market share. How can #UX drive digital product growth? Welcome to listen and read Honne Boxshow EP8 (Feat. @Caleb from #Nostr-YakiHonne client
3. Grants for BDK, LNbits, Nostr, and More! — by @ OpenSats
After announcing the first wave of grants, OpenSats announce an additional wave for 8 projects in #bitcoin and #nostr. What did these projects do? How to apply for OpenSats grants?
4. Sonnet 96 "Artemis And Iris (In A Prelude 0f Spring) By Francisco Luis Arroyave Tabares — by @Francisco Luis
Sonnet 96, "Artemis And Iris (In A Prelude 0f Spring)" is a beautifully crafted poem that has not yet been published. frank_duna shared this poem and used AI (ChatGPT4) to help analyze it.
5. Orange pilling in developed nations — by @ Beme
There are many misunderstandings about #Bitcoin, especially in developed nations. How to explain them? #Beme shared some challenges and tips when talking about Bitcoin.
6. The art of self reflection — by @ Lnuvf
Like a masterpiece in the making, #selfreflection crafts a life that is not only lived, but deeply understood, embraced, and enriched. What is the meaning of self-reflection? How does it help us?
7. Why are there different types of Bitcoin addresses? — by @ Disturbia
The #Bitcoin blockchain is running stable. However, due to different needs and other reasons, #softforks are implemented. How do they impact Bitcoin wallet address design?
8. On linguistic issues and the definition of racism — by @ enlund
Is it possible to be #Racist against white people? The answer depends on who you ask, and when you ask... it has become a driver of political polarisation.
9. 7 economic principles through Bitcoin Glasses — by @ honeybadger
Knowledge of economics is essential as we journey through #Bitcoin. @honeybadger shared 7 economic principles, such as Lindy Effect, S2F, Cantillon Effect, etc. to help us understand Bitcoin.
2. Product Updates 💻
Weekly Updates - Add images upload for the writing editor: users now can directly upload images while writing - Add uploads history within the writing tab to allow users re-use already uploaded images for any written articles - Arabic language support (only articles previewing), Arabic native users need to write with inverted indent at the moment - Stats icons are responsive now, whenever they are hovered – users feedback - Search tab now support searching users by usersnames/nip-05 identifiers – users feedback - Users now can re-verse upvoting/downvoting or even canceling them - Math equations are now supported using the katex syntax - UX/UI enhancements: curations description box shows/hides by hovering/arrow - Fixed bugs: - Fixed the bookmark list disappear after removing a bookmark - Fixed the curations description box UX/UI for mobile version - Change report flag colors - Fixed typos/grammatical/hints errors - Fixed writing editor glitching when zooming the window - Fixed editor scroll bar - Fixed UI for firefox browser - Fixed inexistent profiles in user’s profile page - Fixed settings page reload (two times in a row) - Fixed katex syntax and images uploading not working on mobile version - Fixed code blocks showing only the first line - Fixed misplaced dragged articles in curation creation
3. YakiHonne Events 🏖️
YakiHonne not only provides creators with a convenient and friendly creating platform, but also holds a series of activities to allow creators to express and share in more channels and forms. Welcome to join and Have FUN with YakiHonne!
Click to check out YakiHonne ongoing events Curation!

1) Web3, AI and DeSci Creator Hackathon
With the rise of Web3 technologies, scientific research will usher in unprecedented improvements in data sharing, collaboration, and transparency. At the same time, the application of artificial intelligence in data analysis, model prediction and other fields will greatly promote the development of scientific research. By holding the Web3, AI and Creator Hackathon, we aim to stimulate the thinking of researchers, developers and creators, and explore how to use Web3 and AI technology to optimize scientific research and promote the continuous advancement of science.
Creators from various universities and communities participated in the YakiHonne Web3, AI, and DeSci Creation Hackathon. Community voting is open. Welcome to upvote and comment on your favorite posts in the selected post curation.

2) YakiHonne Ideathon | Integrate Future Creativity and Set Sail on an Artistic Journey
In order to promote the nostr ecology and encourage more creations on the relays, YakiHonne invites you to experience and exchange discussions on Digital Art and Technology Creation, Sustainable Art and Environmental Protection, and The future relationship between AI and human beings via participating ideathon and posting creations from yakihonne.com.
"Embrace future creativity and set sail on an artistic journey!"
Discussing themes like #DigitalArt #AIGC #SustainableArt with like-minded creators in the #Ideathon. Share the world your creating procedure and results via the censorship-resistant platform yakihonne.com, and win generous bonuses.
How to participate 1. Join our group: https://t.me/YakiHonne_ideathon, share your idea, proposals and posts. 2. Join discussion and post your idea in ideathon via the link under each theme. 3. Be inspired by other people's ideas, or form your own ideas, make them a creation. 4. Adding #YakiHonne-Ideathon tag when posting your creations. 5. Posting, sharing, and being zapped. 6. Encourage more people to create, Let's meet and have fun IRL in the future.
More details: YakiHonne Ideathon | Integrate Future Creativity and Set Sail on an Artistic Journey

3) Hot Topics Creation Hackathon Round 1
Hot Topics Creation Hackathon with YakiHonne is the new global creation hackathon, that initiated by YakiHonne, and centered around hot topics. Any creator who enjoys discovering and tracking hot topics is welcome to participate, regardless of your field or subject matter. The exclusive platform feature of YakiHonne is the freedom to express, create, curate, and share your creation on a wide range of topics with a global audience. YakiHonne, a decentralized long-form content platform based on the Nostr open network protocol, ensures a perfect creating experience for every creator.
By joining the Hot Topics Creation Hackathon, not only can you showcase your creation, but you can also leverage various promotional methods exclusive to YakiHonne, such as Workshops, Podcasts, Live Streams, Meetups, etc., to promote your creation and the stories behind to audiences in 86 countries (still growing!). What's even more exciting is that your creations can be rewarded with up to 170,000 SATs!
The Hot-Topic Hackathon is a long-term hackathon, with weekly evaluations. Come join now and share the 17,000,000 SATs prize pool!
Round 1 ended, and entered evaluation stage, stay tuned for updates!
Read More Details: English | 中文

4) Publish Your Long-form Content on Nostr and Earn 17,500,000 SATs

A long-term Nostr Creation Grant, with a 17,500,000 SATs funding pool. Over 300 posts get zapped.
Round 4 had ended successfully! Stay tuned for new Round 5!
YakiHonne Creation Zap Grant continues! Round 4 is concluded. Nostr's long-form posts are created by 100+ creators from 80+ countries. The variety of content expanded to include opinions, insights, travel notes, study notes, feedback, health tips, comics, and even oil paintings. Additionally, posts in Persian and Thai languages became part of the ecosystem. The boom of the ecosystem is thanks to all the creators, and their support is greatly appreciated!
Creating for You and Your Fans through Nostr and ZAP Now.
Zap Rules:
- No malicious speech such as discrimination, attack, incitement, etc.
- No Spam/Scam, not fully AI-generated article
- No directly copy & paste from other posts on Relays
- Spread positive content like your knowledge/experience/insight/ideas, etc.
How to Get Zap:
- Join YakiHonne TG group: https://t.me/YakiHonne_Daily_Featured
- Share your post in the group
- Make sure your LN address is in your profile
- Based on the rules above, we will ZAP your post directly within 2 days
Join our group for more query: https://t.me/YakiHonne_Daily_Featured
5) Earn SATs with YakiHonne Updates
YakiHonne.com is continuously improving to offer a top-notch user experience. With weekly updates being rolled out, you are invited to test these updates and post your feedback and opinions as an article via YakiHonne.com.
As an incentive, participants can earn up to 100,000 SATs.
Here are the reviews curations from Round 1, Round 2, Round 3, and Round 4.
Thanks to all participants, Stay tuned for Round 5!
4. Weekly Featured Streaming🎙️
Honne Boxshow EP8 with Bello on 16th Aug

YakiHonne Convos EP1

5. Weekly Curation Picks 📚
1. Submissions from Web3, AI & DeSci Creation Hackathon - by YakiHonne The Web3, AI & DeSci Creation Hackathon was successfully held. Throughout the hackathon, we received submissions of various forms and topics. This curation has collected selected submissions, thanks to all the creators.
2. self sovereign identity - by vp
3. Decentralized Identity - by vp Dive into our series on decentralized identity, shedding light on the revolutionary Self-Sovereign Identity (SSI) and the powerful Decentralized Identifiers (DID). Explore a future where identity control shifts from central entities to individuals, reshaping the digital age's essence. Join us in navigating this transformative realm, poised to redefine personal identity and digital interactions.
6. Top Curators 👩💻
1. YakiHonne
2. Vp
3. Wendyding
4. SNostrich
5. Shaun
6. S

About YakiHonne:
YakiHonne is a Nostr-based decentralized content media protocol, which supports free curation, creation, publishing, and reporting by various media. Try YakiHonne.com Now!
Follow us
- Telegram: http://t.me/YakiHonne_Daily_Featured
- Twitter: @YakiHonne
- Nostr pubkey: npub1yzvxlwp7wawed5vgefwfmugvumtp8c8t0etk3g8sky4n0ndvyxesnxrf8q
-
 @ 2edbcea6:40558884
2023-08-20 17:00:47
@ 2edbcea6:40558884
2023-08-20 17:00:47Happy Sunday #Nostr!
We're very excited to announce that we are partnering with nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2 to bring you the #NostrTechWeekly newsletter here at the nostr:npub19mduaf5569jx9xz555jcx3v06mvktvtpu0zgk47n4lcpjsz43zzqhj6vzk . A little about him: he’s been on Nostr since January, and he’s a developer that’s been working on Nostr-related projects related to relays.
Our goal here is a weekly newsletter on the more technical happenings in the nostr-verse. Follow the hashtag #NostrTechWeekly to ensure you’re getting the newsletter ASAP!
Lots of activity improving the Nostr protocol this week! Let’s dive in.
Recent Upgrades to Nostr (NIPs)
1) Nostr Marketplaces add Shipping Cost 📦
This is a relatively small update to NIP 15 (marketplaces on Nostr); it adds explicit support for shipping cost as part of purchasing items on a marketplace implemented on top of this pattern.
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
2) Consolidate core capabilities into NIP 1 ⬇️
NIP 1 is dead simple which is why Nostr was so easy to start developing on. As more folks started developing on Nostr, some functionality was added to the Nostr protocol and codified as subsequent NIPs.
Now they’re all so core to the protocol that nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 has advocated and merged an update that places all the core NIPs as part of NIP 1 since the philosophy is that you can theoretically enjoy decent Nostr experience if your client and relay only implement NIP 1. Now that’s true again!
Author: nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6
3) Mailing Lists (Proposed) 💌
NIP 101 is a proposal to formalize a way for Nostr users to subscribe to mailing lists via the Nostr protocol.
Users can publish a specific kind of Nostr event with their email address and the list they want to subscribe to. The email address is encrypted, which means the manager of the mailing list and the subscriber are the only ones with access to the email address. This cuts out third parties used by the author of the newsletter (mailchimp, convertkit, etc).
Could be a neat foundation for a more private, secure, and decentralized newsletter tool to outcompete the existing players.
Author: KaffinPX
4) NIPs over Nostr (Proposed) ♻️
NIP 17 is a proposal to allow people to publish NIPs via Nostr itself. It allows versioning the NIP, being explicit about dependencies, and many other structured details that are missing from the existing repo (which is “just” a collection of Markdown).
Where this goes right is that the Nostr community can adopt NIPs without the blessing of the existing big players that currently manage the NIP repo (which is currently where “approved” NIPs) live.
Where this goes wrong is the difficulty of consensus on something this disorganized. NIPs would no longer be able to take advantage of 1) the tools like Github that help facilitate conversation as well as 2) the shepherding of the early Nostr community by the visionaries that started the movement through some measure of benevolent control of what gets merged into the NIP repo.
Authors: nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj
5) Gift wrapping events for secrecy (Proposed) 🎁
One of the big critiques of standard Nostr DMs is that the message is encrypted but the metadata (from, to, etc) is not. The proposed NIP 59 would allow Nostr users to almost entirely encrypt Nostr events including metadata.
The most obvious use case (and the motivating force) was to create more private and secure DMs. But anywhere where privacy matters on Nostr, gift wrapping Nostr events could help.
Authors: nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z Kieran Paul Miller Jon Staab
Notable projects
Amethyst private DMs
Amethyst (the client) has taken steps to implement their own version of DMs that are more private that standard Nostr DMs are at the moment. They’re using their own proposed “gift wrapping” NIP 59 (discussed above).
I think this will be a “proof is in the pudding” moment where we’ll see the code in action even before the NIP is adopted. If it works well, it’s hard to imagine NIP 59 won’t be approved.
Favvy (Link in bio)
A Nostr-based LinkTree competitor. Favvy allows Nostr users to configure their “link in the bio” page that links out to all the various places that can’t all fit in a profile bio.
It’s Nostr-based so if you control the private key for a Nostr account then you can update that accounts Favvy. Feels elegant.
Latest conversations
Nostr is the non-dystopian Super
WeChat is a super-app which can consolidate an entire ecosystem of functionality within a single mobile app. It’s attractive for mobile-first users and authoritarians who see it as an easier way to control users. This phenomenon has been mostly limited to Asian markets but X (formerly Twitter) is working towards the same goal. They claim to want it to be less dystopian, but we aren’t a very trusting community 🙂
Is there a way to build something that has all the advantages of the super app without the dystopian effects of centralization of such critical digital infrastructure?
Enter Nostr. This post by nostr:npub1l2vyh47mk2p0qlsku7hg0vn29faehy9hy34ygaclpn66ukqp3afqutajft (builder of highlighter.com) paints a picture of how Nostr currently has all the basics needed to achieve that dream already.
The Nostr protocol already seems to be evolving into a kind of decentralized, consent-based app store where developers are recreating much of the existing products internet users love, but with a bent towards self-sovereignty, privacy, security, and cutting out middlemen.
It’s a compelling vision. There would be much work to do, and many challenges to solve to keep the spirit of Nostr alive through mass adoption.
Events
I’ll keep a running list of Nostr-related events that I hear about (in person or virtual).
If you wanna see something highlighted here just send a DM to nostr:npub1r3fwhjpx2njy87f9qxmapjn9neutwh7aeww95e03drkfg45cey4qgl7ex2
Until next time 🫡
If I missed anything, or you’re building something I didn’t post about, let me know, DMs welcome.
Stay Classy, Nostr.
-
 @ 3129509e:c846f506
2023-08-20 00:25:43
@ 3129509e:c846f506
2023-08-20 00:25:43KILL DAMUS HELLTHREADS
As a user, I want to be able to "Mute Conversation" and not see any reactions, reposts, and/or replies to that conversation. I'd like the option to apply this mute to either the OP or to the note that I'm accessing the "Mute Conversation" feature from. This should apply to my "Notes", "Notes and Replies" and "Notification" feeds. I should have a list of muted conversations similar to my list of muted npubs.
Expires Block 806,000
-
 @ 97c70a44:ad98e322
2023-08-17 22:05:57
@ 97c70a44:ad98e322
2023-08-17 22:05:57By an accident of history, I have been knee-deep for the last week or two in several NIPs related to encrypted DMs and group chat. The accident is my proposal for encrypted groups — which will help me turn Coracle into something approximating a replacement for Facebook, rather than Twitter.
In order to make that happen though, a few things need to happen first. I need a better way to encrypt messages without leaking metadata, and (un)fortunately I'm no cryptographer. It's well known that NIP 04 has a number of issues, and there have been several proposals to fix it since as early as October 2022. Building on that foundation would be a waste of time.
My purpose in this post is to outline the problems with NIP 04 as it stands, and sketch out for you some possible solutions applicable not only to DMs, but to other encrypted use cases.
NIP 04 Considered Harmful
It's pretty well-known that nostr DMs leak metadata. What this means is that when you send a DM to someone else, anyone can see:
- Who you are
- Who you sent a message to
- When you sent the message
- How big the message was
And, of course, vice versa. Now, I personally don't take the cyanide pill on this like some do. DMs in centralized social platforms are far less private even than this, since the platform can read them anytime they want, share them with law enforcement, and potentially leak them to the entire world. It's my opinion that if applications were designed with the above properties in mind, it would be possible to gamify DMs, making metadata leakage a feature rather than a bug. Of course, no one has designed such a thing, so maybe it's a moot point.
The much bigger problem, as I learned last week, has to do with the cryptography used in NIP 04 (and several other places, including private mute lists and app-specific data). Here's a quote from Paul Miller's very helpful explanation:
- Unhashed ECDH exposes some curves to Cheon's attack 1, which allows an attacker to learn private key structure when doing continuous diffie-hellman operations. Hashing converts decisional oracle into a computational oracle, which is harder.
- CBC IVs should not only be unrepeatable, they must be unpredictable. Predictable IV leads to Chosen Plaintext Attack. There are real exploits.
- CBC with reused key has 96-bit nonces and loses 6 bits of security for every magnitude. 10**4 (10K) messages would bring archive security of the scheme to 72 bits. 72 bits is very low. For example, BTC has been doing 2^67 hashes/sec as per early 2023. Advanced adversaries have a lot of resources to break the scheme
- CBC has continuously been exploited by Padding Oracle attack. We can't expect all implementations to have proper padding check
- AES was modeled as ideal cipher. Ideal ciphers don't care about non-random keys. However, AES is not an ideal cipher. Having a non-IND key, as in NIP4, exposes it to all kinds of unknown attacks, and reducing security of overall scheme
There is a lot going on here, very little of which I (and likely you) understand. But the really horrifying takeaway for me is in items 1 and 3. If you read it carefully, you'll notice that the more times you use your private key to encrypt data using NIP 04's encryption scheme, the easier it is for an attacker to brute-force your key.
I want to be careful not to overstate this — I don't think this means that everyone's private key is compromised; it would require many thousands of signatures to meaningfully reduce the security of your key. But it does mean that NIP 04's days are numbered — and if we don't replace it, we have a real existential threat to the entire protocol on our hands.
So much for motivation to put NIP 04 to rest. Where do we go from here?
The lay of the land
There are a few different components to making private messages work (whether we're talking about DMs or encrypted groups).
- Encryption scheme
- Explicit metadata hiding
- Implicit metadata hiding
- Transport and deliverability
- Identity and key exchange
Each of these components needs to be solved in order to create a robust messaging system on nostr.
Encryption scheme
As mentioned above, NIP 04 is borked. Luckily, there are a few folks in the nostr dev community who know a thing or two about encryption, most notably Paul Miller. Way back in May, Paul proposed a new encryption scheme based on his implementation of XChaCha20, which is the same algorithm used by SMP (more on that below).
To move the proposal forward, I created a different PR with some edits and adjustments, which is very near to being merged. The implementation already exists in nostr-tools, and there are PRs out for nos2x and Alby as well.
Explicit metadata hiding
As mentioned above, normal nostr messages share lots of information publicly, even if the content is encrypted, including:
- Kind
- Created timestamp
- Tags (topics, mentions, recipients, etc)
- Message size
- Author
Private messages have to hide this information, at the very minimum.
Implicit metadata hiding
The above level of security should be enough for most use cases. But it definitely doesn't get us to total secrecy yet. Some additional metadata includes:
- Client fingerprinting
- Relay selection for publishing and queries
- IP address collection
- First seen timestamp
- Identification of users by AUTH
- Correlation of the event with other messages sent/received during a session
These issues are much harder to solve, because they are part of the process of delivering the message, rather than just constructing it. These issues can be mitigated to some extent by using TOR, proxying connections with relays, using short-lived connections, randomizing publish time, and careful selection of trusted relays. But all of these are only techniques to reduce exposure, and require a prescriptive protocol to wrap them all up into a cohesive whole.
Transport and deliverability
In my view, the key feature of nostr that makes it work is relays. Relays provide storage redundancy and heterogeneity of purpose with a common interface shared by all instances. This is great for censorship resistance, but everything comes with a tradeoff.
Publishing notes is sort of like hiding easter eggs. If you want a kid to be able to find an egg, you have to put it somewhere they'll look for it. Putting an egg on the roof does not constitute "hiding" it, at least in a way consistent with the spirit of the game.
Historically, notes have been broadcast to whatever relays the user or client selects, without regard with someone else's preferences, resulting in apparently missing notes when author and recipient don't share a relay.
This problem has been partly solved by NIP 65, which encourages clients to publish notes where the recipient will look for them. There is some guesswork involved in selecting good relays, but the process is fairly straightforward for direct messages and group chats.
The situation can be improved further by DM-specific signaling, like what @fiatjaf has suggested as an addition to NIP 65. A user could then run his own relay that accepts messages from anyone, but only serves messages to himself. This would be the only relay well-behaved clients would ever write encrypted messages to, improving both privacy and deliverability.
Variants of this could also work for encrypted groups. For small groups, the same relay hints could be used as with DMs, and for larger groups with key sharing the admin could set up a dedicated relay for the group which members would write to.
This also creates a potential affordance for querying of encrypted events. If a relay is highly trusted, it could be added as a member to an encrypted group, gaining the ability to decrypt events. It could then receive REQ messages for those events, filter based on the encrypted content, and serve the encrypted version. This could greatly improve performance for larger groups where downloading all events isn't feasible.
Identity and key exchange
One dimension of privacy that deserves its own section is identity and key exchange. In nostr, this is simpler than in other protocols because in nostr your pubkey is your username. Arguably, this is a flaw that will need to be solved at some point, but for now it means that we get to skip a lot of the complexity involved with binding a name to a key.
However, the problem is still relevant, because one effective way to improve privacy is through key exchange. In the case of DMs, it would be nice to be able to request an alias key from someone you want to communicate with in order to hide the only piece of metadata that has to remain on a message in order to deliver it, that is, the recipient.
There's a lot of good stuff about this problem in the Messaging Layer Security protocol. The author of 0xChat has also put together a draft spec for executing simple key exchange, albeit with less information hiding than in the MLS protocol.
Key exchange between individual users can be considered an optional privacy enhancement, but is required for group chat based on a shared key. In either case, exchanging keys is fairly straightforward — the real challenge is achieving forward secrecy.
By default, if at any point a user's private key is compromised, any messages that were retained by an attacker can then be decrypted. This is a major vulnerability, and solving it requires key exchange messages to be reliably discarded.
What's cooking
So that's an overview of the problems that need to be solved for private DMs and group chats. Not all of these problems will be solved right away, just because the bar for creating a decentralized encrypted chat system on par (or better than) Signal is the kind of thing you get venture capital for.
So the question becomes, should we build a sub-par messaging system that is tightly integrated with nostr, or refer users to a better option for encrypted communication?
Well, why did Twitter create its own DM solution rather than integrating email? Was it to harvest user data, or to provide additional utility to their users by allowing the social graph to inform messaging? Native features simply create a better UX.
On the other hand, in Paul Miller's words:
I would like to remind that nostr DMs, if nostr gets a traction, would be used by all kinds of people, including dissidents in dangerous places. Would you be willing to risk someone getting killed just because you want to keep backwards compatibility with bad encryption?
There is no easy answer, but it's clear that as we continue to work on this problem it is very important that applications communicate clearly the privacy implications of all "private" features built on nostr.
So, assuming we can pull off an appropriate balance between privacy and convenience, let me outline three new developments in this area that I'm excited about.
Gift wrap
Way back in April, Kieran proposed a dumb, but effective, way of hiding metadata on DMs. The technique involved simply encrypting a regular nostr event and putting that in another event's
contentfield. The neat thing about this is that not only does this hide some of the most revealing event metadata, it's not tied to a particular event kind — anything can be wrapped.What this means is that we can build entire "nostr within nostr" sub-networks based on encryption — some between two users, others based on a shared group key. This is much more powerful than a messaging-specific encryption schema. Now we can make private reactions, private calendars, private client recommendations, private reviews. I find this very exciting!
This proposal was further developed by Vitor — the current version can be found here. The latest version introduces double-wrapping, which can help prevent the wrapped event from being leaked by stripping its signature — that "draft" event is encrypted, wrapped, and signed to verify authorship without revealing contents, and then that wrapper is in turn wrapped and signed with a burner key to avoid revealing the author.
Wrapping also makes it possible to randomize the created timestamp to avoid timing analysis, as well as to add padding to a message, reducing the possibility of payload size analysis.
New DMs and small groups
The main subject of Vitor's proposal was a new way to do DMs and small groups using double-wrapping to hide metadata. This works basically the same way NIP 04 did — a shared key is derived and the message is encrypted for the recipient, whose pubkey is revealed publicly so that it can be delivered.
However, Vitor was able to extend this to multiple recipients simply by wrapping the message multiple times, with multiple shared secrets. With the addition of some metadata on the inner event, this makes it possible to define a group where the members know who each other member is, but no one else does.
Large groups
This proposal has one important limitation though — the number of events that need to be signed and broadcast is equal to
number of messages * number of members. This is fine with 5, 10, or even 100 members, but becomes infeasible when you reach groups of 1000+ members.For that, we have two similar proposals, one by @simulx, and one by myself. The differences between the two are not important for this discussion — both use gift wrap as a way to exchange and rotate shared group keys, and both support a weak form of forward secrecy.
As a side note, this is the proposal I'm most excited about, and why I got into nostr in the first place. Private community groups which can support shared calendars, marketplaces, notes, etc., are what I'm most excited to see on nostr.
Shortcomings
The above proposals are great, but of course leave much to be desired. If these are built, nostr will be hugely improved in both security and functionality, with the following weaknesses:
- Deliverability is still an open question — are relay selections enough to ensure recipients get their messages, and no one else does?
- There is no way to create a group whose members cannot dox each other. You must always be able to trust the people you share a group with, and of course, the larger the group, the more people there are that can betray you.
- Content can always be shared outside a group, although in Vitor's small group proposal, the only way to verifiably leak messages would be to reveal your private key.
- Key rotation is not supported by the small groups proposal, but it may be possible to solve it for the entire protocol by building out a name resolution system for nostr.
- Forward secrecy for large groups is weak at best. A key rotation can be triggered at any time, including when a member leaves the group, but unless all relays and all members destroy the key rotation events, it may be possible to decrypt messages after the fact.
- Credential sharing still has to be bootstrapped, meaning at least one encrypted message for each participant may be publicly seen. Of course, credential sharing could also be done out of band, which would largely solve this problem.
What about SimpleX?
Lots of people, including Semisol and Will, have expressed interest in integrating nostr with SimpleX and using their cryptography and transport instead of nostr's.
The first question to answer though, is which protocol should we use? SimpleX is split into a few different pieces: there's the SimpleX Messaging Protocol, which describes setting up unidirectional channels, the SMP Agent Protocol which describes how to convert two unidirectional channels into a bidirectional channel, and the SimpleX Chat Protocol which describes a standard way to send chat messages across a bidirectional channel.
SimpleX Chat Protocol
So far, most proposals to fix messaging have focused simply on DMs, and sometimes on group chat. This is SimpleX's wheelhouse, so it could definitely make sense to communicate that kind of information over SimpleX's top-level chat protocol, and leave nostr out of it entirely.
The downside of this is that it requires clients to support two different protocols, and connect users to two categories of servers. This isn't a deal breaker, but it does increase the complexity involved in writing a full-featured nostr client, especially since there are no implementations of the SimpleX protocol other than (17k lines of) Haskell.
Using SimpleX's chat protocol would also limit the message types we'd be able to encrypt. Anything outside SimpleX's protocol (like zaps for example) would have to be sent using a custom namespace like
nostr.kind.1234, which wouldn't be recognized by normal SimpleX clients. There are also areas of overlap where both protocols describe how to do something, for example profile data, requiring clients to choose which kind to support, or send both.Another wrinkle is that the SimpleX protocol is AGPL v3 licensed, meaning proprietary software would not be able to interoperate, and MIT licensed products would have to abide by their license's terms.
SMP and Agent Protocols
The lower-level SMP and Agent protocols are more promising however, since their scope is narrower, and doesn't overlap as much with nostr's own core competencies. Both are quite simple, and very prescriptive, which should make it easy to create an implementation.
SMP is actually quite similar to some of the proposals mentioned above. Some of the same primitives are used (including XChaCha20 for encryption), and SMP is transport agnostic meaning it could be implemented over websockets and supported by nostr relays. The network topology is basically the same as nostr, except SimpleX doesn't make any assumptions about which servers should be selected, so in that regard nostr actually has an advantage.
The main incompatibility is that SimpleX requires the use of ed25519 and ed448 EdDSA algorithms for signatures, which means nostr's native secp256k1 signature scheme wouldn't be compatible. But this could be ok, since keys shouldn't be re-used anyway, and there are other ways to share a nostr identity.
Forward secrecy?
Whenever a server is involved, several attack vectors inherently exist that would not in peer-to-peer systems. Servers can threaten user privacy by storing messages that should be deleted, analyzing user behavior to infer identity, and leaking messages that should otherwise be kept secret.
This has been used by some to suggest that nostr relays are not a good way to transport messages from one user to another. However, SMP has the same attack vector:
Simplex messaging server implementations MUST NOT create, store or send to any other servers: - Logs of the client commands and transport connections in the production environment. - History of deleted queues, retrieved or acknowledged messages (deleted queues MAY be stored temporarily as part of the queue persistence implementation). - Snapshots of the database they use to store queues and messages (instead simplex messaging clients must manage redundancy by using more than one simplex messaging server). In-memory persistence is recommended. - Any other information that may compromise privacy or forward secrecy of communication between clients using simplex messaging servers.
So whether SimpleX servers or nostr relays are used, privacy guarantees are severely weakened if the server is not trustworthy. To maintain complete privacy in either scheme, users have to deploy their own servers.
Relays to the rescue
Because nostr servers are currently more commonly self-hosted, and more configurable, this makes nostr the better candidate for channel hosting. Users can choose which relays they send messages to, and relay admins can tune relays to only accept messages from and serve messages to certain parties, delete messages after a certain time, and implement policies for what kinds of messages they decide to relay.
All that to say, SMP itself or a similar protocol could easily be built into nostr relays. Relays are not the wrong tool for the job, in fact they're exactly the right tool! This is great news for us, since it means SMP is applicable to our problem, and we can learn from it, even if we don't strictly implement the protocol.
Bootstrapping over nostr
One assumption SMP makes is that channels will be bootstrapped out of band, and provides no mechanism for an initial connection. This is to ensure that channels can't be correlated with user identities. Out of band coordination is definitely the gold standard here, but coordination could also be done over the public nostr network with minimal metadata leakage — only that "someone sent {pubkey} something".
Unidirectional channels
Unidirectional channels are a great primitive, which can be composed to solve various problems. Direct messages between two parties are an obvious use case, but the SimpleX Chat Protocol also includes an extension for groups, defined as
a set of bi-directional SimpleX connections with other group members.This is similar to Vitor's small-group model, and likewise isn't conducive to supporting very large groups, since a copy of every message has to be sent to each group member.
However, it's possible to build large groups on top of unidirectional channels by sharing receiver information within the group and having all participants read from and write to a single channel. In fact, this is very similar to how our large group proposals work.
Conclusion
So, the takeaway here is that SimpleX's lower level protocols are great, and we should learn from them. It may be worth creating a NIP that describes the implementation of their unidirectional channels on nostr, and re-using that primitive in DM/group implementations, or simply following the same general process adapted to nostr.
I'm personally encouraged by reading SimpleX to see that we are headed in the right direction — although many of the details of our proposals have not been fully hammered out in the way SimpleX's has.
As for what the future holds, that's up to the builders. If you want to see tighter SimpleX integration, write a NIP and a reference implementation! I'll continue learning and fold in everything I can into my work going forward.



