-
 @ 8f69ac99:4f92f5fd
2025-05-16 11:40:35
@ 8f69ac99:4f92f5fd
2025-05-16 11:40:35Há algo quase reconfortante na previsibilidade com que certos colunistas abordam Bitcoin: a cada oportunidade, repetem os mesmos chavões, reciclados com indignação moralista e embrulhados numa embalagem de falsa autoridade. O artigo publicado na Visão, com o título dramático "De criança prodígio a adolescente problemático", encaixa-se perfeitamente nesse molde.
Trata-se de uma peça de opinião que mistura factos irrelevantes com interpretações enviesadas, estatísticas sem contexto e um medo mal disfarçado de perder o monopólio da narrativa económica. A autora, Sofia Santos Machado, opta por colar em Bitcoin os desastres do chamado “mundo cripto” como se fossem parte do mesmo fenómeno — ignorando, por conveniência ou ignorância, que Bitcoin não é altcoins, não é NFTs, não é esquemas de yield exótico, e não é fintech vestida de blockchain.
Esta resposta centra-se exclusivamente em Bitcoin — um protocolo monetário aberto, incorruptível e resistente à censura, que já está a servir como salvaguarda de valor em regiões onde o sistema financeiro convencional falhou. Não me interessa defender pirâmides, tokens inflacionários ou aventuras bancárias mal calculadas.
Criticar Bitcoin é legítimo — mas fazê-lo sem saber do que se fala é apenas desinformação.
A Histeria da Água — Falar Sem Saber
O artigo abre com uma pérola alarmista sobre o consumo de água:
“Uma única transacção de bitcoin consome seis milhões de vezes mais água do que um pagamento com cartão.”
Seis. Milhões. De vezes. Resta saber se a autora escreveu isto com cara séria ou a rir-se enquanto bebia água engarrafada dos Alpes Suíços.
Fontes? Metodologia? Contexto? Estou a brincar — isto é a Visão, onde os números são decoração e os factos opcionais.
Claro que comparar transacções na camada base de Bitcoin com pagamentos "instantâneos" da rede Visa é tão rigoroso como comparar um Boeing 747 com um avião de papel porque um voa mais longe. Um artigo sério teria falado em batching, na Lightning Network, ou no facto de que Bitcoin nem sequer compete com a Visa nesse nível, nem em nenhum. Mas isso exigiria, imagine-se, investigação.
Pior ainda, não há qualquer menção ao consumo de água na extracção de ouro, nos data centers bancários, ou no treino de modelos de inteligência artificial. Pelos vistos, só Bitcoin tem de obedecer aos mandamentos ecológicos da Visão. O resto? Santa ignorância selectiva.
Criminosos e o Fantasma do Satoshi
Eis o clássico: “Bitcoin é usado por criminosos”. Um cliché bafiento tirado do baú de 2013, agora reapresentado como se fosse escândalo fresco.
Na realidade, Bitcoin é pseudónimo, não anónimo. Todas as transacções ficam gravadas num livro público — não é propriamente o esconderijo ideal para lavar dinheiro, a menos que sejas fã de disfarces em néon.
E os dados? Claríssimos. Segundo a Chainalysis e a Europol, a actividade ilícita com Bitcoin tem vindo a diminuir. Enquanto isso, os bancos — esses bastiões de confiança — continuam a ser apanhados a lavar biliões para cartéis e cleptocratas. Mas disso a Visão não fala. Devia estragar a narrativa.
O verdadeiro crime aqui é a preguiça intelectual tão profunda que quase merece uma moldura. A Visão tem um editor?
O Espantalho Energético
Como uma criança que acabou de aprender uma palavra nova, a Visão repete “consumo energético” como se fosse um pecado original. Bitcoin usa electricidade — escândalo!
Mas vejamos: o Proof-of-Work não é um defeito. É a razão pela qual Bitcoin é seguro. Não há “desperdício” — há uso, e muitas vezes com energia excedente, renovável, ou que de outro modo seria desperdiçada. É por isso que os mineiros se instalam junto a barragens remotas, queima de gás (flaring), ou parques eólicos no meio do nada — não porque odeiam o planeta, mas porque os incentivos económicos funcionam. Escrevi sobre isso aqui.
O que a Visão convenientemente ignora é que Bitcoin está a ajudar a integrar mais energia renovável nas redes, funcionando como carga flexível. Mas nuance? Trabalho de casa? Esquece lá isso.
Para uma explicação mais séria, podiam ter ouvido o podcast A Seita Bitcoin com o Daniel Batten. Mas para quê investigar?
Cripto = Bitcoin = Fraude?
Aqui chegamos ao buraco negro intelectual: enfiar tudo no mesmo saco. FTX colapsou? Culpa de Bitcoin. Um banqueiro jogou com altcoins? Culpa de Bitcoin. Scam de NFT? Deve ter sido o Satoshi.
Vamos esclarecer: Bitcoin não é “cripto”. Bitcoin é descentralizado, sem líderes, transparente. Não teve pré-mineração, não tem CEO, não promete lucros. O que o rodeia? Tokens centralizados, esquemas Ponzi, pirâmides e vaporware — precisamente o oposto do que Bitcoin representa.
Se um executivo bancário perde o dinheiro dos clientes em Dogecoins, isso é um problema dele. Bitcoin não lhe prometeu nada. Foi a ganância.
E convenhamos: os bancos tradicionais também colapsam. E não precisam de satoshis para isso. Bastam dívidas mal geridas, contabilidade criativa e uma fé cega no sistema.
Culpar Bitcoin por falcatruas “cripto” é como culpar o TCP/IP ou SMTP por emails de phishing. É preguiçoso, desonesto e diz-nos mais sobre a autora do que sobre a tecnologia.
Promessas Por Cumprir? Só Se Não Estiveres a Ver
A "jornalista" da Visão lamenta que “após 15 anos, os riscos são reais mas as promessas por cumprir”. Que promessas? Dinheiro grátis? Cafés pagos com QR codes mágicos?
Bitcoin nunca prometeu fazer cappuccinos mais rápidos. Prometeu soberania monetária, resistência à censura e um sistema previsível. E tem cumprido — diariamente, para milhões. E para o cappuccino, há sempre a Lightning Network.
Pergunta aos venezuelanos, nigerianos, peruanos ou argentinos se Bitcoin falhou. Para muitos, é a única forma de escapar à hiperinflação, ao confisco estatal e à decadência financeira.
Bitcoin não é uma app. É infra-estrutura. É uma nova camada base para o dinheiro global. Não se vê — mas protege, impõe regras e não obedece a caprichos de banqueiros centrais.
E isso assusta. Especialmente quem nunca viveu fora da bolha do euro.
Conclusão: A Visão a Gritar Contra o Progresso
No fim, o artigo da Visão é um festival de clichés, dados errados e ressentimento. Não é só enganador. É desonesto. Culpa a tecnologia pelos erros dos homens. Rejeita o futuro em nome do conforto passado.
Bitcoin não é uma varinha mágica. Mas é a fundação de uma nova liberdade financeira. Uma ferramenta para proteger valor, resistir a abusos e escapar ao controlo constante de quem acha que sabe o que é melhor para ti.
Portanto, fica aqui o desafio, Sofia: se queres criticar Bitcoin, primeiro percebe o que é. Lê o white paper. Estuda. Faz perguntas difíceis.
Caso contrário, és só mais um cão a ladrar para a trovoada — muito barulho, zero impacto.
-
 @ 0e29efc2:ff142af2
2025-05-07 15:09:46
@ 0e29efc2:ff142af2
2025-05-07 15:09:46Table of Contents
- Intro
- Important Terminology
- Getting Started
- Where do I buy bitcoin?
- Okay, I bought some bitcoin-now what?
- Less than 0.01 BTC
- More than 0.01 BTC and less than 0.1 BTC
- More than 0.1 BTC
- How Bitcoin Works
- Skepticism
- Someone will hack it
- The government will try to stop it
- It’s not backed by anything
- Conclusion
Intro
Maybe you saw an article in Forbes, a news segment about MicroStrategy (MSTR), or you glanced at the bitcoin price chart; whatever the spark, your curiosity led you here. Enough friends and relatives keep asking me about bitcoin that I finally organized my thoughts into a single reference. This is not a comprehensive guide—it assumes you trust me as a heuristic.
Important Terminology
Sat (satoshi) – the smallest unit of bitcoin. One bitcoin (₿) equals 100 000 000 sats.
Getting Started
Where do I buy bitcoin?
I use River because it publishes proof‑of‑reserves, supports the Lightning Network, and pays interest on idle USD balances (currently 3.8 %).
Okay, I bought some bitcoin-now what?
Withdraw it immediately. Centralized exchanges can and do fail. Your next step depends on how much bitcoin you hold.
If at any point you're struggling, please reach out to me.
Less than 0.01 BTC
- On your phone open Safari (iOS) or Chrome (Android).
- Paste
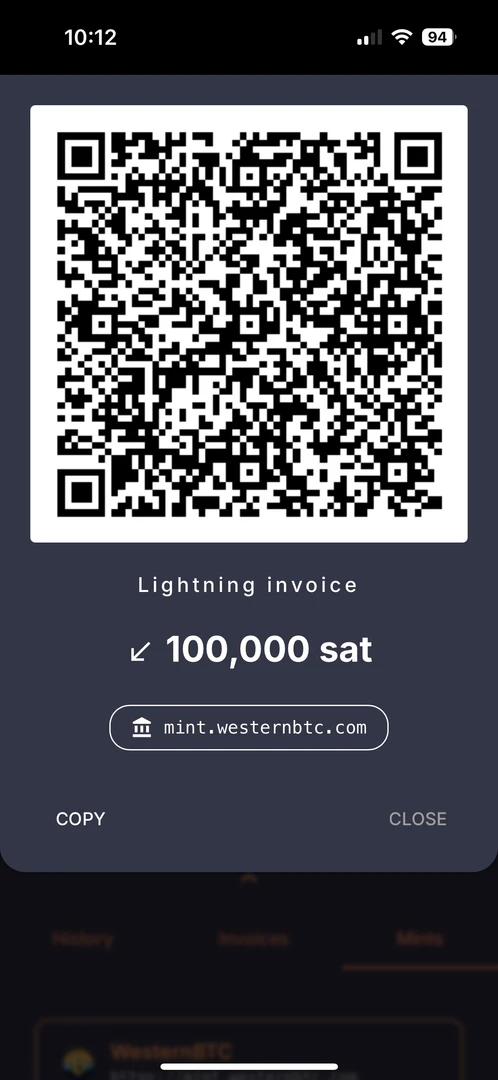
https://wallet.cashu.me?mint=https://mint.westernbtc.com. Confirm the prompt that asks whether you trusthttps://mint.westernbtc.com. I run this mint so beginners can skip the gnarly parts. - Complete setup.
- Tap Receive → LIGHTNING → enter amount → COPY.
- In River choose Send → Send to a Bitcoin wallet, paste the invoice, verify, and send.
- Return to the wallet; your sats should appear.
More than 0.01 BTC and less than 0.1 BTC
It's time for cold storage. Cold storage means a dedicated signing device not connected to the internet. Think of it like keys to a house. If you have the keys (your cold storage signing device), you can get into your house (the bitcoin). I recommend and use the COLDCARD Q or COLDCARD MK4 from COLDCARD. See this thorough walkthrough.
The creator nostr:npub1rxysxnjkhrmqd3ey73dp9n5y5yvyzcs64acc9g0k2epcpwwyya4spvhnp8 makes reliable content.
More than 0.1 BTC
The next security upgrade involves something called multisig. It requires the use of multiple devices instead of one. Think of those nuclear launch silos in movies where two keys need to be turned in order to launch the missile. One person can't reach both keys, so you need two people. Like the two keys needing to be turned, we need a certain number of keys (signing devices) to be used.

This offers a number of benefits. Say you have a 2-of-3 multisig setup. You would need two of the three keys to move the bitcoin. If you were to lose one, you could use the two others to move it instead. Many choose to geographically distribute the keys; choosing to keep one at a friend’s house or with a bank.
The previous video I linked covers multisig as well. Again, please reach out to me if you need help.
How Bitcoin Works
I'm going to paint a scene portraying the basics of how bitcoin works. Picture a race that's supposed to take 10 minutes to run start-to-finish, and there's a crowd of people spectating. When the fastest runner crosses the finish line, they're awarded 50 bitcoin. Everyone in the crowd recognizes who won, and writes it down on their own scoreboard. Then, the next race begins.
Now, let's say more racers who've had special training join. They start winning consistently because of it, and now the race only lasts about 9 minutes. There's a special rule everyone in the crowd agreed to, that they can make the race harder to ensure it's around 10 minutes long. So they make the race harder to counteract the faster runners.

With this in mind, let's get to the skepticism you might have.
Skepticism
Someone will hack it
Think of bitcoin as the people in the crowd. If someone tries to cheat and writes on their scoreboard that they have a billion bitcoin, their scoreboard is going to look different than everybody else’s. The other people in the crowd will cross-reference with each other and decide to ignore that person who cheated.
The government will try to stop it
Again, think of the crowd. In reality, the "crowd participants" are scattered all around the world. You might be able to stop many of them, but it would be almost impossible to stop everyone. Imagine people are watching the race on TV, can you find everyone who's spectating? Ironically, attempted bans often increase interest.
It’s not backed by anything.
Think of the runners. The runners are bitcoin miners. They have to expend real energy to participate in the race. The more bitcoin miners, the more secure the network. In summary, it's backed by electricity and work.
Conclusion
There are too many topics to cover in one article. I haven't even touched on the history of money, what money is, scarcity, etc. The best way to learn is to research the topics you're interested in for yourself. It took months of deep diving before I was sold on bitcoin, and I had many touch points before that.
Once you see it though, you can't unsee it.
-
 @ 8f69ac99:4f92f5fd
2025-05-06 14:21:13
@ 8f69ac99:4f92f5fd
2025-05-06 14:21:13A concepção popular de "anarquia" evoca frequentemente caos, colapso e violência. Mas e se anarquia significasse outra coisa? E se representasse um mundo onde as pessoas cooperam e se coordenam sem autoridades impostas? E se implicasse liberdade, ordem voluntária e resiliência—sem coerção?
Bitcoin é um dos raros exemplos funcionais de princípios anarquistas em acção. Não tem CEO, nem Estado, nem planeador central—e, no entanto, o sistema funciona. Faz cumprir regras. Propõe um novo modelo de governação e oferece uma exploração concreta do anarcocapitalismo.
Para o compreendermos, temos de mudar de perspectiva. Bitcoin não é apenas software ou um instrumento de investimento—é um sistema vivo: uma ordem espontânea.
Ordem Espontânea, Teoria dos Jogos e o Papel dos Incentivos Económicos
Na política e economia contemporâneas, presume-se geralmente que a ordem tem de vir de cima. Governos, corporações e burocracias são vistos como essenciais para organizar a sociedade em grande escala.
Mas esta crença nem sempre se verifica.
Os mercados surgem espontaneamente da troca. A linguagem evolui sem supervisão central. Projectos de código aberto prosperam graças a contribuições voluntárias. Nenhum destes sistemas precisa de um rei—e, no entanto, têm estrutura e funcionam.
Bitcoin insere-se nesta tradição de ordens emergentes. Não é ditado por uma entidade única, mas é governado através de código, consenso dos utilizadores e incentivos económicos que recompensam a cooperação e penalizam a desonestidade.
Código Como Constituição
Bitcoin funciona com base num conjunto de regras de software transparentes e verificáveis. Estas regras determinam quem pode adicionar blocos, com que frequência, o que constitui uma transacção válida e como são criadas novas moedas.
Estas regras não são impostas por exércitos nem pela polícia. São mantidas por uma rede descentralizada de milhares de nós, cada um a correr voluntariamente software que valida o cumprimento das regras. Se alguém tentar quebrá-las, o resto da rede simplesmente rejeita a sua versão.
Isto não é governo por maioria—é aceitação baseada em regras.
Cada operador de nó escolhe qual versão do software quer executar. Se uma alteração proposta não tiver consenso suficiente, não se propaga. Foi assim que as "guerras do tamanho do bloco" foram resolvidas—não por votação, mas através de sinalização do que os utilizadores estavam dispostos a aceitar.
Este modelo de governação ascendente é voluntário, sem permissões, e extraordinariamente resiliente. Representa um novo paradigma de sistemas autorregulados.
Mineiros, Incentivos e a Segurança Baseada na Teoria dos Jogos
Bitcoin assegura a sua rede utilizando a Teoria de Jogos. Os mineiros que seguem o protocolo são recompensados financeiramente. Quem tenta enganar—como reescrever blocos ou gastar duas vezes—sofre perdas financeiras e desperdiça recursos.
Agir honestamente é mais lucrativo.
A genialidade de Bitcoin está em alinhar incentivos egoístas com o bem comum. Elimina a necessidade de confiar em administradores ou esperar benevolência. Em vez disso, torna a fraude economicamente irracional.
Isto substitui o modelo tradicional de "confiar nos líderes" por um mais robusto: construir sistemas onde o mau comportamento é desencorajado por design.
Isto é segurança anarquista—não a ausência de regras, mas a ausência de governantes.
Associação Voluntária e Confiança Construída em Consenso
Qualquer pessoa pode usar Bitcoin. Não há controlo de identidade, nem licenças, nem processo de aprovação. Basta descarregar o software e começar a transaccionar.
Ainda assim, Bitcoin não é um caos desorganizado. Os utilizadores seguem regras rigorosas do protocolo. Porquê? Porque é o consenso que dá valor às "moedas". Sem ele, a rede fragmenta-se e falha.
É aqui que Bitcoin desafia as ideias convencionais sobre anarquia. Mostra que sistemas voluntários podem gerar estabilidade—não porque as pessoas são altruístas, mas porque os incentivos bem desenhados tornam a cooperação a escolha racional.
Bitcoin é sem confiança (trustless), mas promove confiança.
Uma Prova de Conceito Viva
Muitos acreditam que, sem controlo central, a sociedade entraria em colapso. Bitcoin prova que isso não é necessariamente verdade.
É uma rede monetária global, sem permissões, capaz de fazer cumprir direitos de propriedade, coordenar recursos e resistir à censura—sem uma autoridade central. Baseia-se apenas em regras, incentivos e participação voluntária.
Bitcoin não é um sistema perfeito. É um projecto dinâmico, em constante evolução. Mas isso faz parte do que o torna tão relevante: é real, está a funcionar e continua a melhorar.
Conclusão
A anarquia não tem de significar caos. Pode significar cooperação sem coerção. Bitcoin prova isso.
Procuramos, desesperados, por alternativas às instituições falhadas, inchadas e corruptas. Bitcoin oferece mais do que dinheiro digital. É uma prova viva de que podemos construir sociedades descentralizadas, eficientes e justas.
E isso, por si só, já é revolucionário.
Photo by Floris Van Cauwelaert on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-05-02 09:29:41
@ 8f69ac99:4f92f5fd
2025-05-02 09:29:41À medida que Portugal se aproxima das eleições legislativas de 2025, a 18 de Maio, torna-se essencial compreender as diferentes propostas políticas e os programas eleitorais dos partidos para votar de forma informada. Este artigo funciona como um índice para uma série de análises realizadas aos programas dos principais partidos, com foco em temas como liberdades individuais, descentralização e crescimento económico.
A Evolução da Esquerda e da Direita: Um Contexto Histórico e Ideológico
Os termos “esquerda” e “direita” surgiram na Revolução Francesa (1789–1799) para distinguir quem se sentava ao lado do presidente da Assembleia: as forças favoráveis às reformas radicais (à esquerda) e as defensoras da monarquia e da ordem estabelecida (à direita). Com o século XIX e o advento do liberalismo económico, a direita passou a associar-se ao livre mercado e ao direito de propriedade, enquanto a esquerda defendeu maior intervenção estatal para promover igualdade.
No final do século XIX e início do século XX, surgiram o socialismo e o comunismo como correntes mais radicais da esquerda, propondo a abolição da propriedade privada dos meios de produção (comunismo) ou sistemas mistos com forte regulação e redistribuição (socialismo). A resposta liberal-conservadora evoluiu para o capitalismo democrático, que combina mercado livre com alguns mecanismos de assistência social.
Hoje, o espectro político vai além do simples eixo esquerda–direita, incluindo dimensões como:
- Autoritarismo vs. Liberdade: grau de controlo do Estado sobre a vida individual e as instituições;
- Intervenção Estatal vs. Livre Mercado: equilíbrio entre regulação económica e iniciativas privadas;
- Igualdade Social vs. Mérito e Responsabilidade Individual: ênfase na redistribuição de recursos ou na criação de incentivos pessoais.
Este modelo multidimensional ajuda a capturar melhor as posições dos partidos contemporâneos e as suas promessas de governação.
Visão Geral das Análises por Partido
Segue-se um resumo dos principais partidos políticos em Portugal, com destaque para a sua orientação ideológica segundo as dimensões de autoritarismo, nível de Intervenção estatal e grau de liberdade individual. Cada nome de partido estará ligado à respectiva análise detalhada.
| Partido | Orientação Ideológica | Nível de Intervenção Estatal | Grau de Liberdade Individual | |----------------------------------------|---------------------------------------------------------------------------------------|------------------------------|------------------------------| | AD – Aliança Democrática (PSD/CDS) | Centro-direita democrática (baixo autoritarismo / equilíbrio intervenção–mercado) | Médio | Médio | | PS – Partido Socialista | Centro-esquerda social-democrata (moderado autoritarismo / intervenção estatal) | Alto | Médio | | CDU – Coligação Democrática Unitária (PCP/PEV) | Esquerda comunista/eco-marxista (mais autoritário / forte intervenção) | Muito alto | Baixo | | IL – Iniciativa Liberal | Liberalismo clássico (muito baixa intervenção / alta liberdade) | Baixo | Muito alto | | Chega | Nacionalismo autoritário (controlo social elevado / mercado regulado com foco interno)| Médio | Baixo | | Livre | Esquerda progressista verde (baixa hierarquia / intervenção social) | Alto | Médio | | BE – Bloco de Esquerda | Esquerda democrática radical (moderado autoritarismo / intervenção forte) | Alto | Médio | | PAN – Pessoas-Animais-Natureza | Ambientalismo progressista (intervenção pragmática / foco em direitos e sustentabilidade) | Médio | Alto | | Ergue-te | Nacionalismo soberanista (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo | | ADN – Alternativa Democrática Nacional | Nacionalismo conservador (autoritarismo elevado / intervenção seletiva com foco nacional) | Médio | Baixo |
Análises Detalhadas dos Programas Eleitorais
Estas análises pretendem oferecer aos eleitores uma visão clara e objetiva das propostas de cada partido, facilitando decisões conscientes nas urnas. Ao focar-se nas promessas relacionadas com liberdades individuais, descentralização e crescimento económico, este conjunto de textos ajuda a compreender melhor o impacto potencial de cada escolha política.
Aliança Democrática (AD)
Partido Socialista (PS)
Coligação Democrática Unitária (CDU)
Iniciativa Liberal (IL)
Chega
Livre
Bloco de Esquerda (BE)
Pessoas,Animais e Natureza (PAN)
Alternativa Democrática Nacional (ADN)
Ergue-te
Photo by Brett Kunsch on Unsplash
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ 3bf0c63f:aefa459d
2025-04-25 18:55:52
@ 3bf0c63f:aefa459d
2025-04-25 18:55:52Report of how the money Jack donated to the cause in December 2022 has been misused so far.
Bounties given
March 2025
- Dhalsim: 1,110,540 - Work on Nostr wiki data processing
February 2025
- BOUNTY* NullKotlinDev: 950,480 - Twine RSS reader Nostr integration
- Dhalsim: 2,094,584 - Work on Hypothes.is Nostr fork
- Constant, Biz and J: 11,700,588 - Nostr Special Forces
January 2025
- Constant, Biz and J: 11,610,987 - Nostr Special Forces
- BOUNTY* NullKotlinDev: 843,840 - Feeder RSS reader Nostr integration
- BOUNTY* NullKotlinDev: 797,500 - ReadYou RSS reader Nostr integration
December 2024
- BOUNTY* tijl: 1,679,500 - Nostr integration into RSS readers yarr and miniflux
- Constant, Biz and J: 10,736,166 - Nostr Special Forces
- Thereza: 1,020,000 - Podcast outreach initiative
November 2024
- Constant, Biz and J: 5,422,464 - Nostr Special Forces
October 2024
- Nostrdam: 300,000 - hackathon prize
- Svetski: 5,000,000 - Latin America Nostr events contribution
- Quentin: 5,000,000 - nostrcheck.me
June 2024
- Darashi: 5,000,000 - maintaining nos.today, searchnos, search.nos.today and other experiments
- Toshiya: 5,000,000 - keeping the NIPs repo clean and other stuff
May 2024
- James: 3,500,000 - https://github.com/jamesmagoo/nostr-writer
- Yakihonne: 5,000,000 - spreading the word in Asia
- Dashu: 9,000,000 - https://github.com/haorendashu/nostrmo
February 2024
- Viktor: 5,000,000 - https://github.com/viktorvsk/saltivka and https://github.com/viktorvsk/knowstr
- Eric T: 5,000,000 - https://github.com/tcheeric/nostr-java
- Semisol: 5,000,000 - https://relay.noswhere.com/ and https://hist.nostr.land relays
- Sebastian: 5,000,000 - Drupal stuff and nostr-php work
- tijl: 5,000,000 - Cloudron, Yunohost and Fraidycat attempts
- Null Kotlin Dev: 5,000,000 - AntennaPod attempt
December 2023
- hzrd: 5,000,000 - Nostrudel
- awayuki: 5,000,000 - NOSTOPUS illustrations
- bera: 5,000,000 - getwired.app
- Chris: 5,000,000 - resolvr.io
- NoGood: 10,000,000 - nostrexplained.com stories
October 2023
- SnowCait: 5,000,000 - https://nostter.vercel.app/ and other tools
- Shaun: 10,000,000 - https://yakihonne.com/, events and work on Nostr awareness
- Derek Ross: 10,000,000 - spreading the word around the world
- fmar: 5,000,000 - https://github.com/frnandu/yana
- The Nostr Report: 2,500,000 - curating stuff
- james magoo: 2,500,000 - the Obsidian plugin: https://github.com/jamesmagoo/nostr-writer
August 2023
- Paul Miller: 5,000,000 - JS libraries and cryptography-related work
- BOUNTY tijl: 5,000,000 - https://github.com/github-tijlxyz/wikinostr
- gzuus: 5,000,000 - https://nostree.me/
July 2023
- syusui-s: 5,000,000 - rabbit, a tweetdeck-like Nostr client: https://syusui-s.github.io/rabbit/
- kojira: 5,000,000 - Nostr fanzine, Nostr discussion groups in Japan, hardware experiments
- darashi: 5,000,000 - https://github.com/darashi/nos.today, https://github.com/darashi/searchnos, https://github.com/darashi/murasaki
- jeff g: 5,000,000 - https://nostr.how and https://listr.lol, plus other contributions
- cloud fodder: 5,000,000 - https://nostr1.com (open-source)
- utxo.one: 5,000,000 - https://relaying.io (open-source)
- Max DeMarco: 10,269,507 - https://www.youtube.com/watch?v=aA-jiiepOrE
- BOUNTY optout21: 1,000,000 - https://github.com/optout21/nip41-proto0 (proposed nip41 CLI)
- BOUNTY Leo: 1,000,000 - https://github.com/leo-lox/camelus (an old relay thing I forgot exactly)
June 2023
- BOUNTY: Sepher: 2,000,000 - a webapp for making lists of anything: https://pinstr.app/
- BOUNTY: Kieran: 10,000,000 - implement gossip algorithm on Snort, implement all the other nice things: manual relay selection, following hints etc.
- Mattn: 5,000,000 - a myriad of projects and contributions to Nostr projects: https://github.com/search?q=owner%3Amattn+nostr&type=code
- BOUNTY: lynn: 2,000,000 - a simple and clean git nostr CLI written in Go, compatible with William's original git-nostr-tools; and implement threaded comments on https://github.com/fiatjaf/nocomment.
- Jack Chakany: 5,000,000 - https://github.com/jacany/nblog
- BOUNTY: Dan: 2,000,000 - https://metadata.nostr.com/
April 2023
- BOUNTY: Blake Jakopovic: 590,000 - event deleter tool, NIP dependency organization
- BOUNTY: koalasat: 1,000,000 - display relays
- BOUNTY: Mike Dilger: 4,000,000 - display relays, follow event hints (Gossip)
- BOUNTY: kaiwolfram: 5,000,000 - display relays, follow event hints, choose relays to publish (Nozzle)
- Daniele Tonon: 3,000,000 - Gossip
- bu5hm4nn: 3,000,000 - Gossip
- BOUNTY: hodlbod: 4,000,000 - display relays, follow event hints
March 2023
- Doug Hoyte: 5,000,000 sats - https://github.com/hoytech/strfry
- Alex Gleason: 5,000,000 sats - https://gitlab.com/soapbox-pub/mostr
- verbiricha: 5,000,000 sats - https://badges.page/, https://habla.news/
- talvasconcelos: 5,000,000 sats - https://migrate.nostr.com, https://read.nostr.com, https://write.nostr.com/
- BOUNTY: Gossip model: 5,000,000 - https://camelus.app/
- BOUNTY: Gossip model: 5,000,000 - https://github.com/kaiwolfram/Nozzle
- BOUNTY: Bounty Manager: 5,000,000 - https://nostrbounties.com/
February 2023
- styppo: 5,000,000 sats - https://hamstr.to/
- sandwich: 5,000,000 sats - https://nostr.watch/
- BOUNTY: Relay-centric client designs: 5,000,000 sats https://bountsr.org/design/2023/01/26/relay-based-design.html
- BOUNTY: Gossip model on https://coracle.social/: 5,000,000 sats
- Nostrovia Podcast: 3,000,000 sats - https://nostrovia.org/
- BOUNTY: Nostr-Desk / Monstr: 5,000,000 sats - https://github.com/alemmens/monstr
- Mike Dilger: 5,000,000 sats - https://github.com/mikedilger/gossip
January 2023
- ismyhc: 5,000,000 sats - https://github.com/Galaxoid-Labs/Seer
- Martti Malmi: 5,000,000 sats - https://iris.to/
- Carlos Autonomous: 5,000,000 sats - https://github.com/BrightonBTC/bija
- Koala Sat: 5,000,000 - https://github.com/KoalaSat/nostros
- Vitor Pamplona: 5,000,000 - https://github.com/vitorpamplona/amethyst
- Cameri: 5,000,000 - https://github.com/Cameri/nostream
December 2022
- William Casarin: 7 BTC - splitting the fund
- pseudozach: 5,000,000 sats - https://nostr.directory/
- Sondre Bjellas: 5,000,000 sats - https://notes.blockcore.net/
- Null Dev: 5,000,000 sats - https://github.com/KotlinGeekDev/Nosky
- Blake Jakopovic: 5,000,000 sats - https://github.com/blakejakopovic/nostcat, https://github.com/blakejakopovic/nostreq and https://github.com/blakejakopovic/NostrEventPlayground
-
 @ 8f69ac99:4f92f5fd
2025-04-23 14:39:01
@ 8f69ac99:4f92f5fd
2025-04-23 14:39:01Dizem-nos que a inflação é necessária. Mas e se for, afinal, a raiz da disfunção económica que enfrentamos?
A crença mainstream é clara: para estimular o crescimento, os governos devem poder desvalorizar a sua moeda — essencialmente, criar dinheiro do nada. Supostamente, isso incentiva o investimento, aumenta o consumo e permite responder a crises económicas. Esta narrativa foi repetida tantas vezes que se tornou quase um axioma — raramente questionado.
No centro desta visão está a lógica fiat-keynesiana: uma economia estável exige um banco central disposto a manipular o valor do dinheiro para alcançar certos objectivos políticos. Esta abordagem, inspirada por John Maynard Keynes, defende a intervenção estatal como forma de estabilizar a economia durante recessões. Na teoria, os investidores e consumidores beneficiam de taxas de juro artificiais e de maior poder de compra — um suposto ganho para todos.
Mas há outra perspectiva: a visão do dinheiro sólido (sound money, em inglês). Enraizada na escola austríaca e nos princípios da liberdade individual, esta defende que a manipulação monetária não é apenas desnecessária — é prejudicial. Uma moeda estável, não sujeita à depreciação arbitrária, é essencial para promover trocas voluntárias, empreendedorismo e crescimento económico genuíno.
Está na hora de desafiar esta sabedoria convencional. Ao longo dos próximos capítulos, vamos analisar os pressupostos errados que sustentam a lógica fiat-keynesiana e explorar os benefícios de um sistema baseado em dinheiro sólido — como Bitcoin. Vamos mostrar por que desvalorizar a moeda é moralmente questionável e economicamente prejudicial, e propor alternativas mais éticas e eficazes.
Este artigo (que surge em resposta ao "guru" Miguel Milhões) pretende iluminar as diferenças entre estas duas visões opostas e apresentar uma abordagem mais sólida e justa para a política económica — centrada na liberdade pessoal, na responsabilidade individual e na preservação de instituições financeiras saudáveis.
O Argumento Fiat: Por que Dizem que é Preciso Desvalorizar a Moeda
Este argumento parte geralmente de uma visão económica keynesiana e/ou estatista e assenta em duas ideias principais: o incentivo ao investimento e a necessidade de resposta a emergências.
Incentivo ao Investimento
Segundo os defensores do sistema fiat, se uma moeda como o ouro ou bitcoin valorizar ao longo do tempo, as pessoas tenderão a "acumular" essa riqueza em vez de investir em negócios produtivos. O receio é que, se guardar dinheiro se torna mais rentável do que investir, a economia entre em estagnação.
Esta ideia parte de uma visão simplista do comportamento humano. Na realidade, as pessoas tomam decisões financeiras com base em múltiplos factores. Embora seja verdade que activos valorizáveis são atractivos, isso não significa que os investimentos desapareçam. Pelo contrário, o surgimento de activos como bitcoin cria novas oportunidades de inovação e investimento.
Historicamente, houve crescimento económico em períodos de moeda sólida — como no padrão-ouro. Uma moeda estável e previsível pode incentivar o investimento, ao dar confiança nos retornos futuros.
Resposta a Emergências
A segunda tese é que os governos precisam de imprimir dinheiro rapidamente em tempos de crise — pandemias, guerras ou recessões. Esta capacidade de intervenção é vista como essencial para "salvar" a economia.
De acordo com economistas keynesianos, uma injecção rápida de liquidez pode estabilizar a economia e evitar colapsos sociais. No entanto, este argumento ignora vários pontos fundamentais:
- A política monetária não substitui a responsabilidade fiscal: A capacidade de imprimir dinheiro não torna automaticamente eficaz o estímulo económico.
- A inflação é uma consequência provável: A impressão de dinheiro pode levar a pressões inflacionistas, reduzindo o poder de compra dos consumidores e minando o próprio estímulo pretendido. Estamos agora a colher os "frutos" da impressão de dinheiro durante a pandemia.
- O timing é crítico: Intervenções mal cronometradas podem agravar a situação.
Veremos em seguida porque estes argumentos não se sustentam.
Rebatendo os Argumentos
O Investimento Não Morre num Sistema de Dinheiro Sólido
O argumento de que o dinheiro sólido mata o investimento falha em compreender a ligação entre poupança e capital. Num sistema sólido, a poupança não é apenas acumulação — é capital disponível para financiar novos projectos. Isso conduz a um crescimento mais sustentável, baseado na qualidade e não na especulação.
Em contraste, o sistema fiat, com crédito barato, gera bolhas e colapsos — como vimos em 2008 ou na bolha dot-com. Estes exemplos ilustram os perigos da especulação facilitada por políticas monetárias artificiais.
Já num sistema de dinheiro sólido, como o que cresce em torno de Bitcoin, vemos investimentos em mineração, startups, educação e arte. Os investidores continuam activos — mas fazem escolhas mais responsáveis e de longo prazo.
Imprimir Dinheiro Não Resolve Crises
A ideia de que imprimir dinheiro é essencial em tempos de crise parte de uma ilusão perigosa. A inflação que se segue reduz o poder de compra e afecta especialmente os mais pobres — é uma forma oculta de imposto.
Além disso, soluções descentralizadas — como os mercados, redes comunitárias e poupança — são frequentemente mais eficazes. A resposta à COVID-19 ilustra isso: grandes empresas foram salvas, mas pequenos negócios e famílias ficaram para trás. Os últimos receberam um amuse-bouche, enquanto os primeiros comeram o prato principal, sopa, sobremesa e ainda levaram os restos.
A verdade é que imprimir dinheiro não cria valor — apenas o redistribui injustamente. A verdadeira resiliência nasce de comunidades organizadas e de uma base económica saudável, não de decretos políticos.
Dois Mundos: Fiat vs. Dinheiro Sólido
| Dimensão | Sistema Fiat-Keynesiano | Sistema de Dinheiro Sólido | |----------|--------------------------|-----------------------------| | Investimento | Estimulado por crédito fácil, alimentando bolhas | Baseado em poupança real e oportunidades sustentáveis | | Resposta a crises | Centralizada, via impressão de moeda | Descentralizada, baseada em poupança e solidariedade | | Preferência temporal | Alta: foco no consumo imediato | Baixa: foco na poupança e no futuro | | Distribuição de riqueza | Favorece os próximos ao poder (Efeito Cantillon) | Benefícios da deflação são distribuídos de forma mais justa | | Fundamento moral | Coercivo e redistributivo | Voluntário e baseado na liberdade individual |
Estes contrastes mostram que a escolha entre os dois sistemas vai muito além da economia — é também uma questão ética.
Consequências de Cada Sistema
O Mundo Fiat
Num mundo dominado pelo sistema fiat, os ciclos de euforia e colapso são a norma. A desigualdade aumenta, com os mais próximos ao poder a lucrar com a inflação e a impressão de dinheiro. A poupança perde valor, e a autonomia financeira das pessoas diminui.
À medida que o Estado ganha mais controlo sobre a economia, os cidadãos perdem capacidade de escolha e dependem cada vez mais de apoios governamentais. Esta dependência destrói o espírito de iniciativa e promove o conformismo.
O resultado? Estagnação, conflitos sociais e perda de liberdade.
O Mundo com Dinheiro Sólido
Com uma moeda sólida, o crescimento é baseado em valor real. As pessoas poupam mais, investem melhor e tornam-se mais independentes financeiramente. As comunidades tornam-se mais resilientes, e a cooperação substitui a dependência estatal.
Benefícios chave:
- Poupança real: A moeda não perde valor, e a riqueza pode ser construída com estabilidade.
- Resiliência descentralizada: Apoio mútuo entre indivíduos e comunidades em tempos difíceis.
- Liberdade económica: Menor interferência política e mais espaço para inovação e iniciativa pessoal.
Conclusão
A desvalorização da moeda não é uma solução — é um problema. Os sistemas fiat estão desenhados para transferir riqueza e poder de forma opaca, perpetuando injustiças e instabilidade.
Por outro lado, o dinheiro sólido — como Bitcoin — oferece uma alternativa credível e ética. Promove liberdade, responsabilidade e transparência. Impede abusos de poder e expõe os verdadeiros custos da má governação.
Não precisamos de mais inflação — precisamos de mais integridade.
Está na hora de recuperarmos o controlo sobre a nossa vida financeira. De rejeitarmos os sistemas que nos empobrecem lentamente e de construirmos um futuro em que o dinheiro serve as pessoas — e não os interesses políticos.
O futuro do dinheiro pode e deve ser diferente. Juntos, podemos criar uma economia mais justa, livre e resiliente — onde a prosperidade é partilhada e a dignidade individual respeitada.
Photo by rc.xyz NFT gallery on Unsplash
-
 @ 8f69ac99:4f92f5fd
2025-04-07 15:35:08
@ 8f69ac99:4f92f5fd
2025-04-07 15:35:08No dia 2 de Abril de 2025, o Presidente dos Estados Unidos, Donald Trump, anunciou um novo pacote abrangente de tarifas com o objectivo de combater os desequilíbrios comerciais e revitalizar as indústrias nacionais. Foi imposta uma tarifa geral de 10% sobre todas as importações, com taxas mais elevadas—34% para a China e 20% para a União Europeia—em preparação para entrar em vigor. O anúncio reacendeu debates antigos sobre proteccionismo, globalização e o futuro do dólar norte-americano.
Embora estas medidas possam parecer extremas, as tarifas são um instrumento tradicional da política comercial internacional. Países de todo o mundo, incluindo a União Europeia, utilizam-nas rotineiramente para proteger indústrias estratégicas, regular o comércio e gerar receitas. A UE, por exemplo, impõe há muito tempo taxas sobre produtos norte-americanos como bens agrícolas, maquinaria e têxteis. Em contrapartida, os EUA já taxaram importações da UE, como o aço, alumínio e aeronaves, em disputas comerciais.
O que distingue a proposta de Trump é a sua escala, ambição e o objectivo mais amplo: reestruturar a economia dos EUA. Por detrás desta estratégia está uma realidade económica mais profunda—moldada por décadas de défices comerciais, endividamento crescente e o papel do dólar como moeda de reserva mundial. Este artigo explora como estes factores se cruzam, por que razão os EUA se encontram numa posição precária, e se políticas como tarifas elevadas, taxas de juro baixas ou até o Bitcoin podem apontar o caminho a seguir.
As Raízes da Crise: Sobreconsumo e Desindustrialização nos EUA
Durante décadas, os Estados Unidos "viveram acima das suas possibilidades", acumulando um défice comercial que actualmente ultrapassa os 800 mil milhões de dólares por ano. Este desequilíbrio—em que o país compra mais do que vende ao exterior—é sintoma de um problema mais profundo. No pós-Segunda Guerra Mundial, os EUA eram uma potência industrial. Mas, a partir dos anos 70, e com maior intensidade nos anos 90, a globalização transferiu a produção para o estrangeiro. As empresas procuraram custos de mão de obra mais baixos e os mercados norte-americanos encheram-se de produtos fabricados fora.
Para sustentar este consumo, os EUA apoiaram-se na sua posição privilegiada: a emissão da moeda de reserva mundial. Isso gerou um ciclo de endividamento, com o país a pedir emprestado ao exterior para manter o nível de vida. O resultado? Desindustrialização. Fábricas fecharam e milhões de empregos na indústria desapareceram em estados como Ohio, Michigan e Pensilvânia.
Hoje, os EUA produzem muito menos—em proporção ao seu tamanho—do que há algumas décadas, mesmo mantendo um apetite crescente por importações. O défice comercial expõe uma fragilidade estrutural: um país cada vez mais incapaz de sustentar-se através da sua própria produção. Os dólares gastos fora regressam muitas vezes sob a forma de compras de dívida pública, perpetuando o ciclo.
À medida que os défices crescem e a economia depende cada vez mais de mecanismos financeiros do que da produção real, surge uma questão inevitável: até quando poderá a América continuar a comprar a crédito antes que o cartão seja recusado?
O Dilema de Triffin: Moeda Global vs. Potência Industrial
Imagine ser a única pessoa numa cidade com uma impressora de dinheiro que todos usam. Para satisfazer a procura, continua a imprimir e a enviar notas para o exterior—até que o seu próprio negócio local entra em decadência e se torna dependente dos outros. Esta é a essência do Dilema de Triffin, e a corda bamba que os EUA têm vindo a atravessar há gerações.
O dilema surge quando a moeda de um país é usada como padrão global. O dólar—utilizado mundialmente para transacções de petróleo, comércio e reservas—precisa de estar amplamente disponível. Essa abundância provém de défices comerciais persistentes por parte dos EUA.
Mas os défices têm um custo. Os dólares enviados para fora voltam como procura por bens estrangeiros, enfraquecendo a produção interna. Porque fabricar um produto em Detroit por 10 dólares, quando se pode importar por $2? Com o tempo, isto destrói a base industrial do país.
Esta não é uma preocupação teórica—é uma realidade histórica. O economista Robert Triffin advertiu nos anos 60 que um país não pode simultaneamente manter a sua moeda como padrão mundial e conservar uma base industrial sólida. Os EUA confirmaram essa previsão. Após a guerra, os dólares ajudaram a reconstruir a Europa e o Japão, mas esses mesmos países tornaram-se concorrentes industriais dos EUA em sectores como o aço e a indústria automóvel.
As fábricas abandonadas no Midwest e os teares silenciosos no sul são marcas visíveis desta troca. O domínio do dólar concedeu influência global à América, mas às custas da sua produção.
Espiral da Dívida: Obrigações Financeiras Crescentes dos EUA
Em 2025, a dívida federal dos EUA ultrapassa os 36 biliões de dólares ($36 000 000 000 000 000 000)—cerca de 108 mil dólares por cada americano, adultos, jovens, idosos. Durante anos, o acesso fácil ao crédito e a procura global por dívida americana mascararam os riscos. Agora, as fissuras estão à vista.
O problema não é apenas o montante—é o prazo e o custo de manter esta dívida. Grande parte dela é de curto prazo, exigindo refinanciamentos frequentes. Com o aumento das taxas de juro, os custos associados disparam. Só em 2024, os pagamentos de juros ultrapassaram 1 bilião de dólares—mais do que os orçamentos combinados de educação, transportes e habitação.
A “Lei de Ferguson”, proposta pelo historiador Niall Ferguson, afirma que quando os juros da dívida superam os gastos militares, o império está em declínio. Em 2025, os EUA gastam cerca de 900 mil milhões em defesa, e os encargos com juros já os ultrapassaram.
Este ponto de viragem trouxe problemas a impérios do passado—do Reino Unido após a Primeira Guerra Mundial até Roma no seu declínio. Hoje, cresce o cepticismo quanto à saúde fiscal dos EUA. Países como a China e a Rússia estão a reduzir as suas reservas em dívida americana, preferindo ouro, yuan ou outros activos.
Se mais nações seguirem o mesmo caminho, os EUA terão de escolher: continuar a endividar-se para sustentar o sistema ou aceitar um papel reduzido para o dólar na economia mundial.
Desdolarização: A Mudança Global Longe do Dólar
A desdolarização refere-se à tendência crescente de reduzir a dependência do dólar nas transacções comerciais, reservas e sistemas financeiros. Embora o dólar ainda domine, a sua supremacia está sob crescente pressão de novas potências económicas e tensões geopolíticas.
Porque Está o Mundo a Afastar-se do Dólar?
- Risco Económico: A volatilidade do dólar, agravada pela dívida e instabilidade política nos EUA, torna-o menos fiável como reserva de valor.
- Instrumento Geopolítico: O uso do dólar pelos EUA para impor sanções leva rivais a procurar alternativas.
Alternativas Emergentes
- Ouro: Bancos centrais estão a reforçar as reservas em ouro como protecção.
- Commodities: Petróleo e cereais começam a ser transaccionados em moedas alternativas—como vendas de petróleo em yuan pela Arábia Saudita.
- Criptomoedas: Bitcoin e outros activos digitais ganham terreno como reservas neutras e descentralizadas.
- Moedas Regionais: Os países dos BRICS desenvolvem sistemas de pagamento e discutem uma moeda comum para reduzir a dependência do dólar.
Um Declínio Lento, Mas Visível
A percentagem do dólar nas reservas cambiais mundiais caiu de 70% no ano 2000 para menos de 60% actualmente. O comércio em moedas não-dólar cresceu 25% desde 2020. O domínio do dólar persiste, mas o movimento de mudança é claro.
A Estratégia Económica de Trump em 3 Etapas
Em 2025, Trump apresentou uma estratégia económica audaciosa em três frentes:
1. Tarifas Elevadas para Revitalizar a Indústria
Uma tarifa de 10% sobre todas as importações, com taxas superiores para países com superavit comercial, visa incentivar a produção interna. Críticos alertam para o aumento de preços e inflação, mas apoiantes defendem que é necessário para reindustrializar.
2. Redução das Taxas de Juro para Gerir a Dívida
A administração pressiona a Reserva Federal para baixar as taxas, reduzindo os encargos da dívida pública. Isto levanta preocupações sobre a independência do banco central e a estabilidade monetária a longo prazo.
3. Bitcoin como Activo Estratégico de Reserva
Num passo histórico, Trump assinou uma ordem executiva para criar a Reserva Estratégica de Bitcoin e o Stock Nacional de Activos Digitais. O objectivo é diversificar as reservas e proteger contra a inflação.
Riscos e Compensações
A estratégia económica de Trump não está isenta de riscos:
- Inflação: Tarifas mais altas poderão aumentar o custo de vida.
- Polarização Política: Medidas controversas poderão acentuar divisões internas.
- Incerteza Económica: O proteccionismo pode afastar investimento e travar a inovação.
- Instabilidade Monetária: Um erro na gestão da dívida ou dos activos digitais poderá enfraquecer o dólar.
Estes riscos exigem gestão cuidadosa para evitar agravar os problemas existentes.
O Papel de Bitcoin: Protecção ou Último Recurso?
Integrar Bitcoin nas reservas nacionais é ousado—mas pode ser revolucionário, e a meu ver, inevitável!
Vantagens
- Escassez: Com oferta limitada a 21 milhões de unidades, Bitcoin é deflacionário.
- Descentralização: Resistente à censura e manipulação, reforça a soberania financeira.
- Alcance Global: Sem fronteiras, permite trocas neutras num mundo multipolar.
Desafios
- Volatilidade: As flutuações no curto prazo são ainda significativas, mas a adopção institucional pode estabilizar o preço.
- Regulação: O enquadramento legal está em evolução, mas tende para maior clareza.
- Adopção Técnica: Persistem desafios de escalabilidade, embora soluções como a Lightning Network estejam a amadurecer.
A Reserva Estratégica de Bitcoin pode revelar-se visionária—ou precipitada. Tudo dependerá da execução e da aceitação global.
Futuros Possíveis: Crise ou Reinvenção?
Os EUA estão perante uma encruzilhada histórica. Um caminho aponta para a renovação: revitalizar a indústria e adoptar activos digitais, como por exemplo as stablecoins para perpetuar a hegemonia do dólar, lastreado em Bitcoin. O outro conduz à crise—com inflação, instabilidade e perda de influência global.
Num cenário optimista, os EUA emergem como líderes industriais e digitais, com reservas diversificadas que incluem Bitcoin. A recente ordem executiva para adquirir Bitcoin de forma neutra ao orçamento é um sinal positivo.
Num cenário pessimista, menos provável com as medidas em curso, o país mergulha em dívidas, vê o dólar enfraquecer e perde coesão interna. Mas com visão estratégica e inovação económica, há margem para navegar os desafios com sucesso.
Conclusão
A América enfrenta uma oportunidade única de redefinir o seu destino económico. A estratégia de Trump—baseada em tarifas, taxas de juro baixas e Bitcoin—pode marcar o início de uma nova era de resiliência e recuperação industrial.
A inclusão de Bitcoin nas reservas nacionais mostra que os instrumentos tradicionais já não bastam. Ao abraçar os activos digitais e restaurar a produção nacional, os EUA podem recuperar a liderança económica mundial.
O caminho será difícil. Mas com ousadia e execução eficaz, os Estados Unidos não só podem recuperar—podem reinventar-se.
-
 @ 609f186c:0aa4e8af
2025-05-16 20:57:43
@ 609f186c:0aa4e8af
2025-05-16 20:57:43Google says that Android 16 is slated to feature an optional high security mode. Cool.
Advanced Protection has a bunch of requested features that address the kinds of threats we worry about.
It's the kind of 'turn this one thing on if you face elevated risk' that we've been asking for from Google.
And likely reflects some learning after Google watched Apple 's Lockdown Mode play out. I see a lot of value in this..
Here are some features I'm excited to see play out:
The Intrusion Logging feature is interesting & is going to impose substantial cost on attackers trying to hide evidence of exploitation. Logs get e2ee encrypted into the cloud. This one is spicy.
The Offline Lock, Inactivity Reboot & USB protection will frustrate non-consensual attempts to physically grab device data.

Memory Tagging Extension is going to make a lot of attack & exploitation categories harder.
2G Network Protection & disabling Auto-connect to insecure networks are going to address categories of threat from things like IMSI catchers & hostile WiFi.
I'm curious about some other features such as:
Spam & Scam detection: Google messages feature that suggests message content awareness and some kind of scanning.
Scam detection for Phone by Google is interesting & coming later. The way it is described suggests phone conversation awareness. This also addresses a different category of threat than the stuff above. I can see it addressing a whole category of bad things that regular users (& high risk ones too!) face. Will be curious how privacy is addressed or if this done purely locally. Getting messy: Friction points? I see Google thinking these through, but I'm going to add a potential concern: what will users do when they encounter friction? Will they turn this off & forget to re-enable? We've seen users turn off iOS Lockdown Mode when they run into friction for specific websites or, say, legacy WiFi. They then forget to turn it back on. And stay vulnerable.

Bottom line: users disabling Apple's Lockdown Mode for a temporary thing & leaving it off because they forget to turn it on happens a lot. This is a serious % of users in my experience...
And should be factored into design decisions for similar modes. I feel like a good balance is a 'snooze button' or equivalent so that users can disable all/some features for a brief few minute period to do something they need to do, and then auto re-enable.
Winding up:
I'm excited to see how Android Advanced Protection plays with high risk users' experiences. I'm also super curious whether the spam/scam detection features may also be helpful to more vulnerable users (think: aging seniors)...
Niche but important:
Some users, esp. those that migrated to security & privacy-focused Android distros because of because of the absence of such a feature are clear candidates for it... But they may also voice privacy concerns around some of the screening features. Clear communication from the Google Security / Android team will be key here.
-
 @ 8f69ac99:4f92f5fd
2025-04-01 15:54:53
@ 8f69ac99:4f92f5fd
2025-04-01 15:54:53Bitcoin tem-se afirmado como um meio de pagamento global, atraindo cada vez mais comerciantes e consumidores. Em Portugal, os pequenos e médios empresários têm uma oportunidade única para reduzir custos, expandir mercados e proteger-se da inflação ao aceitar bitcoin como opção pagamento.
Apesar das vantagens, muitos comerciantes enfrentam desafios significativos, especialmente no que toca às obrigações fiscais e à falta de conhecimento (ou vontade de aprender) por parte dos contabilistas. Questões como o registo contábil adequado, a tributação do IRC e a facturação com IVA ainda geram incerteza e dificultam a adopção da criptomoeda.
Este artigo explora como os comerciantes podem aceitar bitcoin de forma legal e eficiente, analisa os desafios fiscais e contábeis e apresenta soluções práticas para superar os obstáculos impostos pela regulamentação e pela falta de apoio dos profissionais de contabilidade.
Benefícios de Aceitar Bitcoin
1. Redução de Custos
Aceitar pagamentos em bitcoin permite evitar taxas bancárias elevadas, especialmente em transacções internacionais. Como as transferências ocorrem directamente entre carteiras digitais, sem a intermediação de bancos, os comerciantes podem poupar significativamente em comissões e taxas de processamento.
2. Liquidação Rápida
Diferente dos pagamentos bancários tradicionais, que podem demorar dias, uma transacção na rede Bitcoin pode ser confirmada em minutos, ou em segundos ou menos usando a Lightning Network. Isto reduz o tempo de espera para a disponibilidade dos fundos e melhora o fluxo de caixa dos comerciantes.
3. Expansão de Mercado
Os comerciantes podem atrair clientes internacionais e um público mais inovador e tecnológico. A aceitação de bitcoin pode diferenciar um negócio da concorrência e aumentar a base de clientes ao incluir entusiastas de criptomoedas e consumidores que preferem meios de pagamento descentralizados.
4. Protecção Contra Inflação
Bitcoin pode actuar como reserva de valor, protegendo o património contra desvalorizações monetárias. Em contextos de inflação elevada, manter parte do capital em Bitcoin pode ajudar a preservar o poder de compra a longo prazo.
|
 |
|:--:|
| Bruno de Gouveia da Care to Beauty - A Seita Bitcoin |
|
|:--:|
| Bruno de Gouveia da Care to Beauty - A Seita Bitcoin |Como Funciona na Prática?
1. Aceitação Directa vs. Conversão Automática
Os comerciantes podem optar por aceitar bitcoin directamente, mantendo-o na sua carteira digital, ou utilizar serviços como OpenNode, Swiss Bitcoin Pay, Coincorner ou Coinbase para converter automaticamente os pagamentos em euros. A escolha depende da estratégia da empresa quanto à exposição à volatilidade da criptomoeda.
2. Configuração de Carteira Bitcoin
Para receber pagamentos directamente, o comerciante precisa de uma carteira Bitcoin segura, como Electrum, BlueWallet ou Aqua entre outras. Estas carteiras oferecem diferentes níveis de segurança e acessibilidade, permitindo que os comerciantes escolham a solução mais adequada ao seu modelo de negócio.
3. Facturação e Registo Contábil
Cada pagamento deve ser facturado em euros, com referência à taxa de câmbio do momento. O registo contábil deve ser feito correctamente para garantir a conformidade fiscal, reflectindo o valor recebido em bitcoin e a sua equivalência em euros na altura da transacção. Muitas carteiras e plataformas de pagamento oferecem relatórios detalhados que facilitam o registo contábil e a declaração fiscal.
Obrigações Fiscais e Contábeis
1. IRC (Imposto sobre o Rendimento das Pessoas Colectivas)
Os rendimentos obtidos através de bitcoin devem ser devidamente registados na contabilidade da empresa, uma vez que são considerados receitas operacionais. Para efeitos fiscais, a conversão do valor recebido em bitcoin deve ser feita com base na taxa de câmbio vigente no momento da transacção, garantindo um registo transparente e conforme com as normas contábeis.
Se a empresa optar por manter os bitcoins sem os converter imediatamente para euros, estes podem ser classificados como activos intangíveis, conforme a Norma Contabilística e de Relato Financeiro (NCRF), artigo 6. No entanto, se forem utilizados como meio de pagamento recorrente, por exemplo pagar a fornecedores que também aceitem bitcoin, podem ser classificados como inventário, dependendo da natureza da actividade empresarial.
No momento da venda ou conversão dos bitcoins para euros, qualquer mais-valia obtida é considerada um rendimento da empresa e estará sujeita a tributação em sede de IRC à taxa geral em vigor.
2. IVA (Imposto sobre o Valor Acrescentado)
As transacções de troca de bitcoin por euros estão isentas de IVA, conforme o artigo 9.º, alínea 27), subalínea d), do Código do IVA (CIVA), que reconhece as criptomoedas como meios de pagamento e as exclui da incidência de IVA.
No entanto, a venda de bens ou serviços pagos em bitcoin deve ser facturada normalmente, em euros, com a taxa de IVA correspondente ao produto ou serviço comercializado. Para garantir conformidade fiscal, a factura deve indicar a contrapartida em euros, com base na taxa de câmbio do momento da transacção, independentemente da moeda utilizada no pagamento.
Na prática, aceitar pagamento em bitcoin funciona de forma muito semelhante a aceitar pagamento em dinheiro físico... 😉
3. Registos e Demonstrações Financeiras
As empresas que aceitam bitcoin devem manter registos contabilísticos detalhados sobre todas as transacções realizadas. bitcoin pode ser registado como activo intangível ou inventário, dependendo do seu uso:
- Activo intangível: Quando a empresa detém bitcoin como reserva de valor ou investimento, registando-o ao custo de aquisição e procedendo a ajustamentos caso haja desvalorização relevante.
- Inventário: Se a empresa opera no sector de compra e venda de criptomoedas ou usa bitcoin para transacções comerciais frequentes, deve ser registado como inventário, seguindo as regras de mensuração aplicáveis a mercadorias.
As demonstrações financeiras devem reflectir correctamente a posse de bitcoin, incluindo informações sobre variações de valor ao longo do tempo. Os contabilistas devem garantir a correta apresentação destes activos nos balanços e relatórios anuais, o que pode exigir reavaliação periódica dos valores contabilizados.
O Obstáculo: Contabilistas e a Falta de Apoio
1. Falta de Conhecimento
Muitos TOC não estão familiarizados com a contabilidade de criptomoedas, o que gera incertezas e complicações para os comerciantes.
2. Resistência e Falta de Vontade
Em vez de se actualizarem, muitos contabilistas recusam-se a aprender sobre Bitcoin, deixando os comerciantes sem apoio adequado.
3. Impacto nos Negócios
Com a falta de informação e apoio dos TOC, muitos comerciantes evitam aceitar bitcoin, perdendo uma oportunidade de mercado.
Soluções e Alternativas
1. Educação e Autonomia
Os comerciantes podem aprender o essencial sobre contabilidade de bitcoin para questionar e orientar os seus contabilistas. Existem recursos online, cursos e materiais educativos que permitem aos empresários compreender as melhores práticas para registo e declaração das transacções em bitcoin.
2. Ferramentas e Software
Existem algumas plataformas que ajudam na gestão e declaração de criptomoedas, fornecendo relatórios detalhados sobre transacções, ganhos e impostos devidos. Essas ferramentas facilitam a organização financeira e reduzem erros contábeis.
3. Rede de Apoio
Juntar-se a comunidades de empresários e especialistas em bitcoin pode ajudar a encontrar soluções e recomendações de contabilistas competentes. Fóruns, grupos em redes sociais e associações focadas no tema podem ser excelentes fontes de suporte e partilha de experiências.
4. Links uteis
Conclusão
Aceitar bitcoin pode ser vantajoso para pequenos e médios comerciantes, mas a burocracia e a falta de conhecimento dos contabilistas dificultam esse processo. É essencial que os comerciantes exijam um melhor serviço dos seus TOC e procurem alternativas para garantir que estão em conformidade com a lei, aproveitando ao mesmo tempo os benefícios desta nova forma de pagamento.
Disclaimer: Este artigo é meramente informativo e não deve ser considerado como aconselhamento jurídico ou fiscal. É recomendável consultar um profissional qualificado para obter orientações específicas sobre a aceitação de bitcoin e as obrigações fiscais associadas. A legislação pode variar e é importante estar sempre actualizado com as normas vigentes. A responsabilidade pela aceitação de bitcoin e o cumprimento das obrigações fiscais recai exclusivamente sobre o comerciante. O autor não se responsabiliza por quaisquer consequências decorrentes da aceitação de bitcoin ou da interpretação das informações contidas neste artigo.
Photo by CardMapr.nl on Unsplash
-
 @ b83a28b7:35919450
2025-05-16 19:26:56
@ b83a28b7:35919450
2025-05-16 19:26:56This article was originally part of the sermon of Plebchain Radio Episode 111 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ e17e9a18:66d67a6b
2025-05-19 11:21:42
@ e17e9a18:66d67a6b
2025-05-19 11:21:42We wrote this album to explain the inspiration behind Mutiny Brewing, and as a way to share the story of Bitcoin and freedom technologies like nostr. Through these songs, we’ve tried to capture every truth that we believe is essential to understand about money, freedom, trust, and human connection in the internet age. It’s our way of making these ideas real and relatable, and we hope it helps others see the power of taking control of their future through the systems we use.
01. "Tomorrow's Prices on Yesterday's Wage" explores the harsh reality of inflation. As central banks inflate the money supply, prices rise faster than wages, leaving us constantly falling behind. People, expecting prices to keep climbing, borrow more to buy sooner, pushing prices even higher in a vicious cycle. You're always a step behind, forced to pay tomorrow's inflated prices with yesterday's stagnant wages.
https://wavlake.com/track/76a6cd02-e876-4a37-b093-1fe919e9eabe
02. "Everybody Works For The Bank" "Everybody Works For The Bank" exposes the hidden truth behind our fiat money system.
When banks issue loans, they don’t lend existing money — they create new money from debt. You’re on the hook for the principal and the interest. But the interest doesn’t exist yet — it has to come from someone else borrowing. That means the system only works if debt keeps growing.
When it doesn’t, the whole thing wobbles. Governments step in to bail out the banks by printing more money, and that cost doesn’t vanish. It shows up in your taxes, your savings, and your grocery bill.
We’re not just working to pay our own debts, we’re paying for their losses too.
“Paying back what they create, working till I break” https://wavlake.com/track/4d94cb4b-ff3b-4423-be6a-03e0be8177d6
03. "Let My People Go" references Moses' demand for freedom but directly draws from Proverbs 6:1–5, exposing the danger of debt based money. Every dollar you hold is actually someone else's debt, making you personally liable—held in the hand of your debtor and at risk of their losses, which you ultimately pay for through inflation or higher taxes. As the song says, "The more you try to save it up, the deeper in you get." The wisdom of Proverbs urges immediate action, pleading urgently to escape this trap and free yourself, like a gazelle from a hunter.
"Can't escape this money scheme Trapped inside their banking dream"
https://wavlake.com/track/76214ff1-f8fd-45b0-a677-d9c285b1e7d6
04. "Mutiny Brewing" embodies Friedrich Hayek's insight: "I don't believe we shall ever have good money again before we take it out of the hands of government... we can't take it violently... all we can do is by some sly roundabout way introduce something they can't stop."
Inspired also by the Cypherpunk manifesto's rallying cry, "We will write the code", the song celebrates Bitcoin as exactly that unstoppable solution.
"Not here to break ya, just here to create our own little world where we determine our fate." https://wavlake.com/track/ba767fc8-6afc-4b0d-be64-259b340432f3
05. "Invisible Wealth" is inspired by The Sovereign Individual, a groundbreaking 1990s book that predicted the rise of digital money and explores how the return on violence shaped civilizations. The song references humanity's vulnerability since agriculture began—where stored wealth attracted violence, forcing reliance on larger governments for protection.
Today, digital privacy enabled by cryptography fundamentally changes this dynamic. When wealth is stored privately, secured by cryptographic keys, violence becomes ineffective. As the song emphasizes, "You can't bomb what you can't see." Cryptography dismantles traditional power structures, providing individuals true financial security, privacy, and freedom from exploitation.
“Violence is useless against cryptography” https://wavlake.com/track/648da3cc-d58c-4049-abe0-d22f9e61fef0
06. "Run A Node" is a rallying cry for Bitcoin's decentralisation. At its heart, it's about personal verification and choice: every node is a vote, every check’s a voice. By running the code yourself, you enforce the rules you choose to follow. This is true digital democracy. When everyone participates, there's no room for collusion, and authority comes directly from transparent code rather than blind trust.
"Check the blocks, verify, ain't that hard to do When everyone's got eyes on it, can't slip nothin' throgh." https://wavlake.com/track/ee11362b-2e84-4631-b05e-df6d8e6797f8
07. "Leverage is a Liar" warns against gambling with your wealth, but beneath the surface, it's a sharp critique of fractional reserve banking. Fractional reserves inflate asset prices, creating the illusion of wealth built on leverage. This system isn't sustainable and inevitably leads to collapse. Real wealth requires sound money, money that can't be inflated. Trying to gain more through leverage only feeds the lie.
"Watch it burn higher and higher—leverage is a liar." https://wavlake.com/track/67f9c39c-c5e1-4e15-b171-f1f5442f29a5
08. "Don't Get Rekt" serves as a stark warning about trusting custodians with your Bitcoin. Highlighting infamous collapses like Mt.Gox, Celsius, and FTX. These modern failures echo the 1933 Executive Order 6102, where the US government forcibly seized citizens' gold, banned its use, and then promptly devalued the currency exchanged for it. History shows clearly: trusting others with your wealth means risking losing it all.
"Your keys, your life, don't forget." https://wavlake.com/track/fbd9b46d-56fc-4496-bc4b-71dec2043705
09. "One Language" critiques the thousands of cryptocurrencies claiming to be revolutionary. Like languages, while anyone can invent one, getting people to actually use it is another story. Most of these cryptos are just affinity scams, centralized towers built on shaky foundations. Drawing from The Bitcoin Standard, the song argues money naturally gravitates toward a single unit, a universal language understood by all. When the dust settles, only genuine, decentralized currency remains.
"One voice speaking loud and clear, the rest will disappear." https://wavlake.com/track/22fb4705-9a01-4f65-9b68-7e8a77406a16
10. "Key To Life" is an anthem dedicated to nostr, the permissionless, unstoppable internet identity protocol. Unlike mainstream social media’s walled gardens, nostr places your identity securely in a cryptographic key, allowing you total control. Every message or action you sign proves authenticity, verifiable by anyone. This ensures censorship resistant communication, crucial for decentralised coordination around Bitcoin, keeping it free from centralised control.
"I got the key that sets me free—my truth is mine, authentically." https://wavlake.com/track/0d702284-88d2-4d3a-9059-960cc9286d3f
11. "Web Of Trust" celebrates genuine human connections built through protocols like nostr, free from corporate algorithms and their manipulative agendas. Instead of top down control, it champions grassroots sharing of information among trusted peers, ensuring truth and authenticity rise naturally. It's about reclaiming our digital lives, building real communities where trust isn't manufactured by machines, but created by people.
"My filter, my future, my choice to make, real connections no one can fake." https://wavlake.com/track/b383d4e2-feba-4d63-b9f6-10382683b54b
12. "Proof Of Work" is an anthem for fair value creation. In Bitcoin, new money is earned through real work, computing power and electricity spent to secure the network. No shortcuts, no favourites. It's a system grounded in natural law: you reap what you sow. Unlike fiat money, which rewards those closest to power and the printing press, Proof of Work ensures rewards flow to those who put in the effort. Paper castles built on easy money will crumble, but real work builds lasting worth.
"Real work makes real worth, that's the law of this earth." https://wavlake.com/track/01bb7327-0e77-490b-9985-b5ff4d4fdcfc
13. "Stay Humble" is a reminder that true wealth isn’t measured in coins or possessions. It’s grounded in the truth that a man’s life does not consist in the abundance of his possessions. Real wealth is the freedom to use your life and time for what is good and meaningful. When you let go of the obsession with numbers, you make room for gratitude, purpose, and peace. It's not about counting coins, it's about counting your blessings.
"Real wealth ain't what you own, it's gratitude that sets the tone." https://wavlake.com/track/3fdb2e9b-2f52-4def-a8c5-c6b3ee1cd194
-
 @ 8f69ac99:4f92f5fd
2025-03-14 11:13:38
@ 8f69ac99:4f92f5fd
2025-03-14 11:13:38O Banco Central Europeu (BCE) está a intensificar a sua propagan... a sua campanha a favor do euro digital, apresentando-o como uma evolução necessária do dinheiro. Mas trata-se realmente de conveniência ou há uma agenda oculta? Vamos desmontar os argumentos do BCE e perceber por que razão esta moeda digital de banco central (CBDC) tem mais a ver com controlo do que com inovação financeira.
Argumento 1: 'A nossa moeda precisa de acompanhar a forma como queremos pagar.'
O BCE afirma que mais de metade dos europeus prefere pagamentos digitais, mas ignora o facto de que esses pagamentos já existem. Desde cartões bancários a PayPal, transferências SEPA, Apple Pay e Google Pay, não faltam opções. Em 2020 já 60% de todos os pagamentos na UE foram digitais, segundo dados do BCE.
O que não mencionam é que o euro digital será controlado pelo Estado (ou neste caso o BCE e a UE que são efectivamente um governo supranacional, não eleito) e programável. Ao contrário do dinheiro físico, que permite verdadeira autonomia financeira, uma CBDC permitirá ao governo monitorizar, condicionar e até restringir os teus gastos.
Já Bitcoin oferece há mais de 16 anos uma solução global, descentralizada e sem necessidade de permissão, sem precisar de supervisão estatal.
Argumento 2: 'Os europeus poderão usar o euro digital ao lado do dinheiro físico.'
A história mostra-nos que, sempre que surgem alternativas digitais estatais, o dinheiro físico acaba por ser eliminado. Restrições a levantamentos, proibições de transacções em numerário e a desvalorização do dinheiro físico são tácticas comuns para empurrar as pessoas para pagamentos digitais controlados.
Bitcoin não precisa de autorização e pode ser usado de forma independente do sistema bancário. Continua a ser a única forma de dinheiro digital realmente descentralizada, garantindo soberania financeira aos indivíduos.
Argumento 3: 'O euro digital garantirá privacidade e confiança.'
O BCE já admitiu que o anonimato total não é uma opção no euro digital. Ao contrário do dinheiro físico, que permite transacções privadas, uma CBDC será totalmente rastreável. Cada transacção será monitorizada, armazenada e potencialmente sujeita a restrições ou impostos.
Já Bitcoin oferece pseudonimato e resistência à censura. Nenhuma entidade central pode bloqueá-lo, congelá-lo ou controlá-lo, tornando-o a melhor opção para pagamentos digitais livres.
Argumento 4: 'O euro digital funcionará offline, sem internet ou electricidade.'
Embora o BCE afirme que o euro digital terá funcionalidade offline, qualquer transacção terá de ser reconciliada online mais tarde, o que significa que a privacidade continua a ser uma ilusão. Além disso, essa funcionalidade offline será provavelmente limitada a pequenos valores pré-carregados—nada de revolucionário.
Já Bitcoin pode ser enviado via ondas de rádio, redes mesh e até satélites, ou opções como o LNURL ou mesmo ecash, tornando-o mais resiliente do que qualquer moeda digital, governamental ou não.
Argumento 5: 'Precisamos de uma legislação forte para apoiar o euro digital.'
Se o euro digital fosse realmente útil, por que razão precisa de ser imposto por lei? Bitcoin cresceu de forma orgânica porque funciona. O BCE está a pressionar por leis que poderão, no futuro, tornar as CBDCs a única forma legal de dinheiro digital, eliminando a liberdade financeira.
Bitcoin, por sua vez, é imparável, descentralizado e independente de decisões políticas. Nenhuma autoridade central pode decidir como deve, e se pode, usá-lo.
Conclusão: O Euro Digital Não É O Que Parece
O euro digital não se trata de inovação, mas de controlo. Os europeus já têm métodos de pagamento digitais eficientes, e o dinheiro físico garante a verdadeira privacidade financeira. Uma moeda digital estatal introduz o risco de vigilância financeira, restrições de gastos e dinheiro programável, onde o governo pode decidir quando, onde e como podes gastar o teu dinheiro.
Entretanto, Bitcoin já funciona há mais de 16 anos como uma alternativa descentralizada e global, sem precisar da aprovação de bancos centrais. Garante soberania financeira e resistência à censura, tornando-se a verdadeira forma de dinheiro digital do futuro.
A questão não é se o euro digital tornará os pagamentos mais fáceis—mas se tornará a liberdade financeira impossível.
-
 @ 2b24a1fa:17750f64
2025-05-19 11:09:30
@ 2b24a1fa:17750f64
2025-05-19 11:09:30Herzlichen Glückwunsch zu einem weiteren denkwürdigen Europa-Tag, den wir mit einem Manifest des european-peace-projects begehen. Europaweit beteiligen sich heute Institutionen, Vereine und Bürger, die um 17 Uhr die Fenster öffnen und dieses Manifest laut verlesen.
https://soundcloud.com/radiomuenchen/european-peace-project-das-manifest-heute-17-uhr?
-
 @ 8f69ac99:4f92f5fd
2025-03-12 19:02:01
@ 8f69ac99:4f92f5fd
2025-03-12 19:02:01Durante décadas, os europeus foram incentivados a poupar para o futuro — para a reforma, a compra de casa ou segurança financeira. Mas agora, a Comissão Europeia quer redefinir a poupança — não como património pessoal, mas como um recurso para investimento controlado pelo Estado.
A União de Poupanças e Investimentos (Savings and Investments Union, ou SIU), um plano que integra a União dos Mercados de Capitais e a União Bancária. Oficialmente, trata-se de “empoderar os cidadãos” e “desbloquear oportunidades de investimento”. Na realidade, trata-se de uma mudança radical rumo ao controlo financeiro, onde as suas poupanças são pressionadas ou mesmo desviadas para investimentos aprovados pelo Estado.
Ao mesmo tempo, o euro digital será lançado em Outubro de 2025. Esta moeda programável tornará os juros negativos, os controlos de capital e as restrições de gastos mais fáceis de aplicar do que nunca. A mensagem é clara: a UE está a desmantelar a autonomia financeira. O que antes eram as suas poupanças privadas pode em breve tornar-se uma ferramenta económica gerida pelo Estado.
Será apenas mais uma medida burocrática ou o primeiro passo para uma distopia financeira? Vamos analisar.
O Plano: "Transformar Poupanças Privadas em Investimento"
A declaração de Ursula von der Leyen — "Vamos transformar poupanças privadas em investimento muito necessário" — parece um plano inofensivo para impulsionar a economia. Mas, na realidade, assinala uma tomada de controlo estatal da riqueza pessoal.
Os governos desconfiam da independência financeira. Quando os indivíduos poupam por conta própria, fazem escolhas financeiras pessoais que podem não estar alinhadas com as agendas burocráticas. A União de Poupanças e Investimentos da UE pretende mudar isso, criando mecanismos para empurrar o capital privado para sectores aprovados pelo governo.
A Comissão Europeia estima que os cidadãos da UE detenham 10 biliões de euros em poupanças inactivas, e pretende mobilizar esse dinheiro para financiar a militarização da Europa e apoiar o complexo militar-industrial europeu. A Comissária Europeia para os Serviços Financeiros e para a União de Poupança e Investimento, Maria Luís Albuquerque, afirmou explicitamente que o rearmamento europeu dependerá fortemente da captação de investimento privado.
Como Isto Será Feito?
- Taxas de juro negativas — A erosão lenta das poupanças, tornando oneroso manter dinheiro no banco.
- Investimentos forçados em sectores “verdes”, militares e “estratégicos” — O seu dinheiro pode não ir para onde quer, mas para onde os políticos decidem.
- Controlos de capital — Impedindo a livre movimentação do seu dinheiro para alternativas mais seguras.
Albuquerque declarou que o problema da Europa é a diferença entre poupanças paradas e empresas que precisam de financiamento. Para fechar essa diferença, a Comissão Europeia pretende criar um novo esquema para mobilizar fundos privados para o investimento na indústria da UE no âmbito da União de Investimento e Poupança.
Isto não tem a ver com liberdade económica. Tem a ver com direccionar capital para onde o Estado deseja. E o novo euro digital do BCE, a CBDC europeia, facilita ainda mais esse controlo.
O Euro Digital: A Ferramenta Perfeita de Controlo
Com o euro digital, o BCE está a introduzir dinheiro programável, o que significa que as transacções podem ser controladas, monitorizadas e até restringidas em tempo real.
O Que Pode Fazer o Dinheiro Programável?
- Aplicar taxas de juro negativas automaticamente — As suas poupanças digitais podem diminuir com o tempo.
- Restringir como e onde pode gastar — Compras podem ser bloqueadas para itens considerados “não essenciais”.
- Definir datas de validade para o dinheiro — Forçando-o a gastar rapidamente.
- Limitar levantamentos ou transferências — Impedindo-o de sair do sistema.
O BCE afirma que o euro digital melhorará a “eficiência financeira”, mas o seu verdadeiro poder reside em vigiar e controlar todas as transacções. Se você não pode manter dinheiro fora do sistema, então não é dono do seu dinheiro — o Estado é.
Como Proteger-se
Com a UE a apertar o cerco, precisa de agir agora para proteger a sua riqueza:
- Opte pelo Bitcoin — A melhor reserva de valor fora do controlo governamental.
- Use dinheiro físico enquanto pode — Mantenha-o em circulação para retardar a sua eliminação.
- Auto-custódia de tudo — Se não tem controlo directo, não é realmente seu.
- Eduque-se e resista — Espalhe a consciência antes que estas medidas se tornem irreversíveis.
Conclusão: Reivindique a Sua Liberdade Financeira
O plano da UE é claro: controlo total sobre o seu dinheiro e a sua vida.
O euro digital, as taxas de juro negativas e os controlos de capital não visam a prosperidade, mas garantir que ninguém possa escapar.
Mas Bitcoin oferece uma alternativa. Um sistema financeiro paralelo, incensurável, inconfiscável e deflacionário.
A escolha é clara: submeter-se à tirania financeira ou optar pela soberania monetária com Bitcoin.
O tempo para agir é agora.
Photo by Etienne Girardet on Unsplash
-
 @ c631e267:c2b78d3e
2025-05-16 18:40:18
@ c631e267:c2b78d3e
2025-05-16 18:40:18Die zwei mächtigsten Krieger sind Geduld und Zeit. \ Leo Tolstoi
Zum Wohle unserer Gesundheit, unserer Leistungsfähigkeit und letztlich unseres Glücks ist es wichtig, die eigene Energie bewusst zu pflegen. Das gilt umso mehr für an gesellschaftlichen Themen interessierte, selbstbewusste und kritisch denkende Menschen. Denn für deren Wahrnehmung und Wohlbefinden waren und sind die rasanten, krisen- und propagandagefüllten letzten Jahre in Absurdistan eine harte Probe.
Nur wer regelmäßig Kraft tankt und Wege findet, mit den Herausforderungen umzugehen, kann eine solche Tortur überstehen, emotionale Erschöpfung vermeiden und trotz allem zufrieden sein. Dazu müssen wir erkunden, was uns Energie gibt und was sie uns raubt. Durch Selbstreflexion und Achtsamkeit finden wir sicher Dinge, die uns erfreuen und inspirieren, und andere, die uns eher stressen und belasten.
Die eigene Energie ist eng mit unserer körperlichen und mentalen Gesundheit verbunden. Methoden zur Förderung der körperlichen Gesundheit sind gut bekannt: eine ausgewogene Ernährung, regelmäßige Bewegung sowie ausreichend Schlaf und Erholung. Bei der nicht minder wichtigen emotionalen Balance wird es schon etwas komplizierter. Stress abzubauen, die eigenen Grenzen zu kennen oder solche zum Schutz zu setzen sowie die Konzentration auf Positives und Sinnvolles wären Ansätze.
Der emotionale ist auch der Bereich, über den «Energie-Räuber» bevorzugt attackieren. Das sind zum Beispiel Dinge wie Überforderung, Perfektionismus oder mangelhafte Kommunikation. Social Media gehören ganz sicher auch dazu. Sie stehlen uns nicht nur Zeit, sondern sind höchst manipulativ und erhöhen laut einer aktuellen Studie das Risiko für psychische Probleme wie Angstzustände und Depressionen.
Geben wir negativen oder gar bösen Menschen keine Macht über uns. Das Dauerfeuer der letzten Jahre mit Krisen, Konflikten und Gefahren sollte man zwar kennen, darf sich aber davon nicht runterziehen lassen. Das Ziel derartiger konzertierter Aktionen ist vor allem, unsere innere Stabilität zu zerstören, denn dann sind wir leichter zu steuern. Aber Geduld: Selbst vermeintliche «Sonnenköniginnen» wie EU-Kommissionspräsidentin von der Leyen fallen, wenn die Zeit reif ist.
Es ist wichtig, dass wir unsere ganz eigenen Bedürfnisse und Werte erkennen. Unsere Energiequellen müssen wir identifizieren und aktiv nutzen. Dazu gehören soziale Kontakte genauso wie zum Beispiel Hobbys und Leidenschaften. Umgeben wir uns mit Sinnhaftigkeit und lassen wir uns nicht die Energie rauben!
Mein Wahlspruch ist schon lange: «Was die Menschen wirklich bewegt, ist die Kultur.» Jetzt im Frühjahr beginnt hier in Andalusien die Zeit der «Ferias», jener traditionellen Volksfeste, die vor Lebensfreude sprudeln. Konzentrieren wir uns auf die schönen Dinge und auf unsere eigenen Talente – soziale Verbundenheit wird helfen, unsere innere Kraft zu stärken und zu bewahren.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 97c70a44:ad98e322
2025-03-06 18:38:10
@ 97c70a44:ad98e322
2025-03-06 18:38:10When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specified a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
-
No auth, fully public - anyone can read/write to the group.
-
Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Triflector for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Triflector for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
Rooms have two modes - managed and unmanaged. Managed rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. This allows rooms to switch between managed and unmanaged modes without losing any content.Managed room names come from
kind 39000room meta events, but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access. Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 57d1a264:69f1fee1
2025-05-16 07:51:08
@ 57d1a264:69f1fee1
2025-05-16 07:51:08Payjoin allows the sender and receiver of an on-chain payment to collaborate and create a transaction that breaks on-chain heuristics, allowing a more private transaction with ambiguous payment amount and UTXO ownership. Additionally, it can also be used for UTXO consolidation (receiver saves future fees) and batching payments (receiver can make payment(s) of their own in the process of receiving one), also known as transaction cut-through. Other than improved privacy, the rest of the benefits are typically applicable to the receiver, not the sender.
BIP-78 was the original payjoin protocol that required the receiver to run a endpoint/server (always online) in order to mediate the payjoin process. Payjoin adoption has remained pretty low, something attributed to the server & perpetual online-ness requirement. This is the motivation for payjoin v2.
The purpose of the one-pager is to analyse the protocol, and highlight the UX issues or tradeoffs it entails, so that the payjoin user flows can be appropriately designed and the tradeoffs likewise communicated. A further document on UX solutions might be needed to identify solutions and opportunities
The following observations are generally limited to individual users transacting through their mobile devices:
While users naturally want better privacy and fee-savings, they also want to minimise friction and minimise (optimise) payment time. These are universal and more immediate needs since they deal with the user experience.
Added manual steps
TL;DR v2 payjoin eliminates server & simultaneous user-liveness requirements (increasing TAM, and opportunities to payjoin, as a result) by adding manual steps.
Usually, the extent of the receiver's involvement in the transaction process is limited to sharing their address with the sender. Once they share the address/URI, they can basically forget about it. In the target scenario for v2 payjoin, the receiver must come online again (except they have no way of knowing "when") to contribute input(s) and sign the PSBT. This can be unexpected, unintuitive and a bit of a hassle.
Usually (and even with payjoin v1), the sender crafts and broadcasts the transaction in one go; meaning the user's job is done within a few seconds/minutes. With payjoin v2, they must share the original-PSBT with the receiver, and then wait for them to do their part. Once the the receiver has done that, the sender must come online to review the transaction, sign it & broadcast.
In summary,
In payjoin v1, step 3 is automated and instant, so delay 2, 3 =~ 0. As the user experiences it, the process is completed in a single session, akin to a non-payjoin transaction.
With payjoin v2, Steps 2 & 3 in the above diagram are widely spread and noticeable. These manual steps are separated by uncertain delays (more on that below) when compared to a non-payjoin transaction.
Delays
We've established that both senders and receivers must take extra manual steps to execute a payoin transaction. With payjoin v2, this process gets split into multiple sessions, since the sender and receiver are not like to be online simultaneously.
Delay 2 & 3 (see diagram above) are uncertain in nature. Most users do not open their bitcoin wallets for days or weeks! The receiver must come online before the timeout hits in order for the payjoin process to work, otherwise time is just wasted with no benefit. UX or technical solutions are needed to minimise these delays.
Delays might be exacerbated if the setup is based on hardware wallet and/or uses multisig.
Notifications or background processes
There is one major problem when we say "the user must come online to..." but in reality the user has no way of knowing there is a payjoin PSBT waiting for them. After a PSBT is sent to the relay, the opposite user would only find out about it whenever they happen to come online. Notifications and background sync processes might be necessary to minimise delays. This is absolutely essential to avert timeouts in addition to saving valuable time. Another risk is phantom payjoin stuff after the timeout is expired if receiver-side does not know it has.
Fee Savings
The following observations might be generally applicable for both original and this v2 payjoin version. Fee-savings with payjoin is a tricky topic. Of course, overall a payjoin transaction is always cheaper than 2 separate transactions, since they get to share the overhead.
Additionally, without the receiver contributing to fees, the chosen fee rate of the PSBT (at the beginning) drops, and can lead to slower confirmation. From another perspective, a sender paying with payjoin pays higher fees for similar confirmation target. This has been observed in a production wallet years back. Given that total transaction time can extend to days, the fee environment itself might change, and all this must be considered when designing the UX.
Of course, there is nothing stopping the receiver from contributing to fees, but this idea is likely entirely novel to the bitcoin ecosystem (perhaps payments ecosystem in general) and the user base. Additionally, nominally it involves the user paying fees and tolerating delays just to receive bitcoin. Without explicit incentives/features that encourage receivers to participate, payjoining might seem like an unncessary hassle.
Overall, it seems that payjoin makes UX significant tradeoffs for important privacy (and potential fee-saving) benefits. This means that the UX might have to do significant heavy-lifting, to ensure that users are not surprised, confused or frustrated when they try to transact on-chain in a privacy-friendly feature. Good, timely communication, new features for consolidation & txn-cutthrough and guided user flows seem crucial to ensure payjoin adoption and for help make on-chain privacy a reality for users.
---------------
Original document available here. Reach out at
yashrajdca@proton.me,y_a_s_h_r_a_j.70on Signal, or on reach out in Bitcoin Design discord.https://stacker.news/items/981388
-
 @ 4ba8e86d:89d32de4
2025-05-19 10:13:19
@ 4ba8e86d:89d32de4
2025-05-19 10:13:19DTails é uma ferramenta que facilita a inclusão de aplicativos em imagens de sistemas live baseados em Debian, como o Tails. Com ela, você pode personalizar sua imagem adicionando os softwares que realmente precisa — tudo de forma simples, transparente e sob seu controle total.
⚠️ DTails não é uma distribuição. É uma ferramenta de remasterização de imagens live.
Ela permite incluir softwares como:
✅ SimpleX Chat ✅ Clientes Nostr Web (Snort & Iris) ✅ Sparrow Wallet ✅ Feather Wallet ✅ Cake Wallet ✅ RoboSats ✅ Bisq ✅ BIP39 (Ian Coleman) ✅ SeedTool ... e muito mais. https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg
Importante: os binários originais dos aplicativos não são modificados, garantindo total transparência e permitindo a verificação de hashes a qualquer momento.
👨💻 Desenvolvido por: nostr:npub1dtmp3wrkyqafghjgwyk88mxvulfncc9lg6ppv4laet5cun66jtwqqpgte6
GitHub: https://github.com/DesobedienteTecnologico/dtails?tab=readme-ov-file
🎯 Controle total do que será instalado
Com o DTails, você escolhe exatamente o que deseja incluir na imagem personalizada. Se não marcar um aplicativo, ele não será adicionado, mesmo que esteja disponível. Isso significa: privacidade, leveza e controle absoluto.
https://image.nostr.build/b0bb1f0da5a9a8fee42eacbddb156fc3558f4c3804575d55eeefbe6870ac223e.jpg https://image.nostr.build/b70ed11ad2ce0f14fd01d62c08998dc18e3f27733c8d7e968f3459846fb81baf.jpg https://image.nostr.build/4f5a904218c1ea6538be5b3f764eefda95edd8f88b2f42ac46b9ae420b35e6f6.jpg
⚙️ Começando com o DTails
📦 Requisitos de pacotes
Antes de tudo, instale os seguintes pacotes no Debian:
``` sudo apt-get install genisoimage parted squashfs-tools syslinux-utils build-essential python3-tk python3-pil.imagetk python3-pyudev
```
🛠 Passo a passo
1 Clone o repositório:
``` git clone https://github.com/DesobedienteTecnologico/dtails cd dtails
```
2 Inicie a interface gráfica com sudo:
``` sudo ./dtails.py
```
Por que usar sudo? É necessário para montar arquivos .iso ou .img e utilizar ferramentas essenciais do sistema.
💿 Selecione a imagem Tails que deseja modificar
https://nostr.download/e3143dcd72ab6dcc86228be04d53131ccf33d599a5f7f2f1a5c0d193557dac6b.jpg
📥 Adicione ou remova pacotes
1 Marque os aplicativos desejados. 2 Clique Buildld para gerar sua imagem personalizada. https://image.nostr.build/5c4db03fe33cd53d06845074d03888a3ca89c3e29b2dc1afed4d9d181489b771.png
Você pode acompanhar todo o processo diretamente no terminal. https://nostr.download/1d959f4be4de9fbb666ada870afee4a922fb5e96ef296c4408058ec33cd657a8.jpg
💽 .ISO vs .IMG — Qual escolher?
| Formato | Persistência | Observações | | ------- | ---------------------- | ----------------------------------------------- | | .iso | ❌ Não tem persistência | Gera o arquivo DTails.iso na pasta do projeto | | .img | ✅ Suporta persistência | Permite gravar diretamente em um pendrive |
https://nostr.download/587fa3956df47a38b169619f63c559928e6410c3dd0d99361770a8716b3691f6.jpg https://nostr.download/40c7c5badba765968a1004ebc67c63a28b9ae3b5801addb02166b071f970659f.jpg
vídeo
https://www.youtube.com/live/QABz-GOeQ68?si=eYX-AHsolbp_OmAm
-
 @ 97c70a44:ad98e322
2025-03-05 18:09:05
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be composed of multiple parts, but that's only incidental to the identity of a thing, which is a concept, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our actual identities as people, but entirely fictional identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent you as a complete person. It only represents the access granted to you by the bank. This access is in fact an entirely new identity that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to exclusive control of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to personality. These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified and unforgeable.
Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something looks like a physical signature, but for something that does the same thing as a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get
5, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number5. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number3.A real-life example of a useful one-way function is
sha256. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like intosha256, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes into the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we could do it that way (maybe), but there's actually a much simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their giant wall of lava lamps to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is identified by a public key, and authenticated by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an algorithm that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can prove that you know the private key.
For example, if my secret number is
12, and someone tells me the number37, I can "combine" the two by adding them together and returning the number49. This "proves" that my secret number is12. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone even more evil than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control your identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X can't do in this system is pretend you said something you didn't, because they don't know your private key.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and keep your followers. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by your digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called bitcoin.
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. Zero-knowledge proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument for cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a hardware signing device. This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- Hierarchical Deterministic Keys allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- Key Rotation allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like Amber to manage sessions with different applications.
- Key sharding takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve Zooko's trilemma.
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see this blog post.
Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With nostr, some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that humans care about.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit njump.me.
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-
 @ 45bda953:bc1e518e
2025-05-19 09:49:40
@ 45bda953:bc1e518e
2025-05-19 09:49:40This post will be edited and refined over time.
Eschatology is the study of Biblical prophecy pertaining to what is commonly referred to as the end times. Bitcoin is the transformation of Austrian school economics theory into an efficient and applicable method driven by natural incentives and free market consensus mechanisms.
What happens when eschatology is viewed through a Bitcoin inspired world view?
In this thesis I contend that it is possible and very probable that the consequences of what Satoshi Nakamoto created in Bitcoin and the prophecies surrounding Jesus Christ with regards to the second coming and a thousand year kingdom of peace and prosperity convalesce into a very compelling argument for Biblical prophecy fulfilment.
...
No one would argue that modern major banks are today more powerful than kings of old and governments are mere puppets to the sway that the banking empires hold over them.
In Biblical prophecy when kings and powers are mentioned people rarely think of banking but nothing is comparable to the immense scale of wealth, power and territory controlled directly or indirectly by banks.
IMF, BIS, the FED and Blackrock are where the levers of power are pulled in the current dispensation. Governments restructure more frequently than these institutions whom endure and exercise unmerited influence over said governments and the public interests they claim to represent.
An excerpt from the King James Bible, Daniel chapter 2 describes prophetically the ages of man and its rotations of power.
Interesting to note that it is symbolically portrayed in monetary/industrial metals. All used as tokens for trade, symbols of wealth and manufacture.
Gold, silver, bronze, iron and clay. Gold has been a dominant symbol of power and wealth through millennia. Silver, brass and iron ores are mainly industrial metals although they all had prominent turns as coinage. Due to the debasement and concentration of gold specifically.
Clay on the other hand is only a symbol of power in construction and iron has never been used in construction to the extent it is in the 20th and 21st century. Skyscrapers are the symbols of money and power today, i.e. big bank and government buildings.
Daniel Chapter 2:24–45
24Therefore Daniel went to Arioch, whom the king had appointed to destroy the wise men of Babylon. He went and said thus to him: “Do not destroy the wise men of Babylon; take me before the king, and I will tell the king the interpretation.”
25Then Arioch quickly brought Daniel before the king, and said thus to him, “I have found a man of the captives of Judah, who will make known to the king the interpretation.”
26The king answered and said to Daniel, whose name was Belteshazzar, “Are you able to make known to me the dream which I have seen, and its interpretation?”
27Daniel answered in the presence of the king, and said, “The secret which the king has demanded, the wise men, the astrologers, the magicians, and the soothsayers cannot declare to the king. 28But there is a God in heaven who reveals secrets, and He has made known to King Nebuchadnezzar what will be in the latter days. Your dream, and the visions of your head upon your bed, were these: 29As for you, O king, thoughts came to your mind while on your bed, about what would come to pass after this; and He who reveals secrets has made known to you what will be. 30But as for me, this secret has not been revealed to me because I have more wisdom than anyone living, but for our sakes who make known the interpretation to the king, and that you may know the thoughts of your heart.
31“You, O king, were watching; and behold, a great image! This great image, whose splendor was excellent, stood before you; and its form was awesome. 32This image’s head was of fine gold, its chest and arms of silver, its belly and thighs of bronze, 33its legs of iron, its feet partly of iron and partly of clay. 34You watched while a stone was cut out without hands, which struck the image on its feet of iron and clay, and broke them in pieces. 35Then the iron, the clay, the bronze, the silver, and the gold were crushed together, and became like chaff from the summer threshing floors; the wind carried them away so that no trace of them was found. And the stone that struck the image became a great mountain and filled the whole earth.
36“This is the dream. Now we will tell the interpretation of it before the king. 37You, O king, are a king of kings. For the God of heaven has given you a kingdom, power, strength, and glory; 38and wherever the children of men dwell, or the beasts of the field and the birds of the heaven, He has given them into your hand, and has made you ruler over them all — you are this head of gold. 39But after you shall arise another kingdom inferior to yours; then another, a third kingdom of bronze, which shall rule over all the earth. 40And the fourth kingdom shall be as strong as iron, inasmuch as iron breaks in pieces and shatters everything; and like iron that crushes, that kingdom will break in pieces and crush all the others. 41Whereas you saw the feet and toes, partly of potter’s clay and partly of iron, the kingdom shall be divided; yet the strength of the iron shall be in it, just as you saw the iron mixed with ceramic clay. 42And as the toes of the feet were partly of iron and partly of clay, so the kingdom shall be partly strong and partly fragile. 43As you saw iron mixed with ceramic clay, they will mingle with the seed of men; but they will not adhere to one another, just as iron does not mix with clay. 44And in the days of these kings the God of heaven will set up a kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. 45Inasmuch as you saw that the stone was cut out of the mountain without hands, and that it broke in pieces the iron, the bronze, the clay, the silver, and the gold — the great God has made known to the king what will come to pass after this. The dream is certain, and its interpretation is sure.”
 I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.
I speculate that the toes of iron and clay represent the world banking empire. Skyscrapers are constructed from iron and cement. Different forms of clay is a necessary cement ingredient. Architecture has always been used as a symbol of dominance by rulers especially true of systems who use awe as a means to cause feelings of insignificance in the individual thereby asserting their power at low cost. Ironically it never costs the ruler to create these structures, the cost is always carried by the people in time, resources and energy.Skyscrapers and large construction are the modern symbols of money and power. Not so much kings, palaces and temples. The stone breaking the power of the statue has to break something contemporary other than kings and palaces if it is to be eschatological prophecy fulfilled in our time.
https://www.britannica.com/technology/cement-building-material/History-of-cement
The invention of portland cement usually is attributed to Joseph Aspdin of Leeds, Yorkshire, England, who in 1824 took out a patent for a material that was produced from a synthetic mixture of limestone and clay.
https://www.thoughtco.com/how-skyscrapers-became-possible-1991649
Later, taller and taller buildings were made possible through a series of architectural and engineering innovations, including the invention of the first process to mass-produce steel.
Construction of skyscrapers was made possible thanks to Englishman Henry Bessemer, (1856 to 1950) who invented the first process to mass-produce steel inexpensively.
You watched while a stone was cut out without hands,
No hands needed when the stone is an idea.
As a thought experiment, imagine there was a base metal as scarce as gold but with the following properties:\ — boring grey in colour\ — not a good conductor of electricity\ — not particularly strong, but not ductile or easily malleable either\ — not useful for any practical or ornamental purpose\ \ and one special, magical property:\ — can be transported over a communications channel
Greshams Law illustrated in slow motion picture.
1: The banks collapse. Being fundamentally weak because of zero reserve lending, any student of Austrian economics has been correctly predicting banking collapse, and have incorrectly been advocating gold as the solution to this collapse. Many of the big economies are valued through their housing market. Housing will be demonetised (Iron and clay economy) meaning shelter and property will become affordable to the average wage earner again. The large cement and iron structures become redundant. Everyone will work from home and a value to value economy will make banks seem like relics from an age of stupidity and evil.
2: Industrial metal iron will not be for mega structures that contain speculators and bookkeepers who have fiat jobs slaving for fiat money. Iron will be used to improve the lives of individuals. Iron as coinage is already demonetised.
3: Brass is demonetised as coinage and only valuable in industry. Ammunition, music, plumbing etcetera.
4: Silver has been a terrible money throughout history and when the silver investors wake up to the fact that they are holding onto a redundant asset with zero monetary properties compared to the alternative they will dump their holdings, crashing the silver market and subsequently reducing the prices of producing -
solder and brazing alloys, batteries, dentistry, TV screens, smart phones microwave ovens, ad infinitum. To quote Jeff Booth. "Prices always fall to the marginal cost of production."
5: The final Rubicon is gold, people get excited about the Bitcoin exchange traded funds but it is nothing compared to the value proposition when gold pundits, large investment funds, governments pension funds and reserve banks finally realise that gold is worthless as money in this new dispensation.
To illustrate the point more vividly.
Ezekiel 7:19
They shall cast their silver in the streets, and their gold shall be removed: their silver and their gold shall not be able to deliver them in the day of the wrath of the LORD: they shall not satisfy their souls, neither fill their bowels: because it is the stumbling block of their iniquity.
What we are witnessing is the biggest rug pull the world has ever seen. In this future metals will exclusively be used for industrial use cases after being stripped of their monetary premium.
 This collapse is something that happens slowly over a long period of time. More or less one hour.
This collapse is something that happens slowly over a long period of time. More or less one hour.Revelation 18 verse 11–19 (The fall of Babylon)
And the merchants of the earth shall weep and mourn over her; for no man buyeth their merchandise any more: The merchandise of gold, and silver, and precious stones, and of pearls, and fine linen, and purple, and silk, and scarlet, and all thyine wood, and all manner vessels of ivory, and all manner vessels of most precious wood, and of brass, and iron, and marble, And cinnamon, and odours, and ointments, and frankincense, and wine, and oil, and fine flour, and wheat, and beasts, and sheep, and horses, and chariots, and slaves, and souls of men. And the fruits that thy soul lusted after are departed from thee, and all things which were dainty and goodly are departed from thee, and thou shalt find them no more at all. The merchants of these things, which were made rich by her, shall stand afar off for the fear of her torment, weeping and wailing, And saying, Alas, alas, that great city, that was clothed in fine linen, and purple, and scarlet, and decked with gold, and precious stones, and pearls! For in one hour so great riches is come to nought. And every shipmaster, and all the company in ships, and sailors, and as many as trade by sea, stood afar off, And cried when they saw the smoke of her burning, saying, What city is like unto this great city! And they cast dust on their heads, and cried, weeping and wailing, saying, Alas, alas, that great city, wherein were made rich all that had ships in the sea by reason of her costliness! for in one hour is she made desolate.
TLDR - No more money printer go BRRR. means death to the bourgeoisie cantillionaire class.**
Is it realistic to assume that all the worlds monetised industries collapse to fair value in one hour?
Coming back to eschatology, 2 Peter 3:8
But, beloved, be not ignorant of this one thing, that one day is with the Lord as a thousand years, and a thousand years as one day.
Eschatology students use this verse to speculatively project the fulfilment of Biblical prophecies with regards to their predicted time of occurrence. Now let’s apply this to Babylon falling in one hour.
1000 (one day) divided by 24 (hours) equals 41,6 years (one hour)
Since the first block was mined in January 2009 you add 41,6 years you get a completion date of 2050 a.d
Remember, this stone (Bitcoin) becomes a great mountain and fills the whole earth. A kingdom which shall never be destroyed; and the kingdom shall not be left to other people; it shall break in pieces and consume all these kingdoms, and it shall stand forever. The dream is certain, and its interpretation is sure.
But contemporary sources must reflect this probability if it is a good theory.
https://www.newsbtc.com/news/50-of-population-to-use-bitcoin-by-2043-if-crypto-follows-internet-adoption/
If the banking system is first to collapse we can give it +- 10 years and we are already 14 years in since (Genesis Block) the stone struck the feet. People are slow to see the reality of the world they are living in. If all this is accurate then the world banking system is doomed.
https://www.youtube.com/watch?v=exK5yFEuBsk
Regards
Echo Delta
bitbib
-
 @ 57d1a264:69f1fee1
2025-05-16 05:38:28
@ 57d1a264:69f1fee1
2025-05-16 05:38:28LegoGPT generates a LEGO structure from a user-provided text prompt in an end-to-end manner. Notably, our generated LEGO structure is physically stable and buildable.
Lego is something most of us knows. This is a opportuity to ask where is our creativity going? From the art of crafting figures to building blocks following our need and desires to have a machine thinking and building following step-by-step instructions to achieve an isolated goal.
Is the creative act then in the question itself, not anymore in the crafting? Are we just delegating the solution of problems, the thinking of how to respond to questions, to machines? Would it be different if delegated to other people?
Source: https://avalovelace1.github.io/LegoGPT/
https://stacker.news/items/981336
-
 @ 57d1a264:69f1fee1
2025-05-14 09:48:43
@ 57d1a264:69f1fee1
2025-05-14 09:48:43Just another Ecash nutsnote design is a ew template for brrr.gandlaf.com cashu tocken printing machine and honoring Ecash ideator David Lee Chaum. Despite the turn the initial project took, we would not have Ecash today without his pioneering approach in cryptography and privacy-preserving technologies.
A simple KISS (Keep It Super Simple) Ecash nutsnote delivered as SVG, nothing fancy, designed in PenPot, an open source design tool, for slides, presentations, mockups and interactive prototypes.
Here Just another Nutsnote's current state, together with some snapshots along the process. Your feedback is more than welcome.
https://design.penpot.app/#/view?file-id=749aaa04-8836-81c6-8006-0b29916ec156&page-id=749aaa04-8836-81c6-8006-0b29916ec157§ion=interactions&index=0&share-id=addba4d5-28a4-8022-8006-2ecc4316ebb2
originally posted at https://stacker.news/items/979728
-
 @ e97aaffa:2ebd765d
2025-05-19 09:47:30
@ e97aaffa:2ebd765d
2025-05-19 09:47:30Algo que me faz uma certa confusão, é ouvir as pessoas, a afirmarem que será impossível existir um governo e uma economia saudável com o Bitcoin ou qualquer outra moeda não inflacionária. Que o Bitcoin como moeda, iria tornar a sociedade numa anarquia.
A governança da nossa sociedade é baseada em 3 pilares: o governo, económico e moeda. Os 3 evoluíram e se adaptaram mutuamente e em simultâneo ao longo do tempo. Só que essa e evolução, trouxe-nos para um centralismo atroz, onde os governos condicionadam excessivamente a economia e controlam a moeda. Em vez de 3 pilares, temos apenas um, o governo, a economia deixou de ser livre e a moeda é manipulada para financiar o governo.
É claro, se nós mudarmos apenas o sistema monetário, o equilíbrio dos 3 pilares vai quebrar, assim não vai funcionar. O erro é acreditar que é possível mudar apenas um pilar, sem adaptar os outros.
Na prática temos que mudar apenas um (governo), os outros dois é libertá-los. Os governos modernos são baseados em défice orçamental, impostos altos, dívida soberana e inflação monetária para o seu financiamento e para controlar a economia. Como os governos estão altamente endividados e com altas taxas de impostos, só lhe resta a última carta, a moeda/inflação monetária.
Se perdessem o controlo da moeda, seria necessário uma mudança profunda nos estados modernos. Em vez de ter défice-dívida-inflação, teriam mudar para excedente-reservas-deflação, é fazer o oposto do que fazem hoje. É claro que ao podemos apenas mudar de uma moeda inflacionária para uma não inflacionária e manter inalterado os outros dois, isso não vai resultar. Será necessário mudar os 3 para que funcione bem.
É aqui está o problema, será uma mudança profunda nos governos modernos, têm que passar a ter excedente orçamental e criar reservas monetária. Isso vai obrigar os governos a ter muita disciplina e boa gestão, nos momentos de crescimento económico terão que fazer reservas e zerar a dívida soberana. Depois nos períodos de recessão vai utilizar as reservas e se necessário criar dívida soberana para ajudar na recuperação da economia, actualmente os governos utilizam a expansão monetária para esse fim.
Se alguém tem um problema de alcoolismo, não pode apenas trocar whisky por vinho, a mudança terá que ser mais drástica, terá que trocar por água.
Fix the money! Fix the World!
-
 @ 8f69ac99:4f92f5fd
2025-02-27 12:47:01
@ 8f69ac99:4f92f5fd
2025-02-27 12:47:01O Estado Social tem sido um pilar das políticas sociais europeias há décadas, oferecendo uma rede de segurança aos cidadãos através de diversos programas governamentais. Contudo, com a evolução das economias e o envelhecimento da população a pressionar os recursos públicos, este modelo tradicional enfrenta desafios crescentes. Custos em alta, ineficiências burocráticas e efeitos indesejados têm gerado um debate cada vez mais intenso sobre a sua sustentabilidade. Como alternativa, o Rendimento Básico Universal (RBU) ganhou destaque, prometendo simplicidade, mas trazendo preocupações quanto ao custo e aos desincentivos ao trabalho. Há, porém, uma opção mais equilibrada que merece atenção: o Imposto sobre o Rendimento Negativo (IRN).
Diferente da assistência social convencional, o IRN oferece apoio financeiro a quem está abaixo de um limiar de rendimento definido, sem exigir que procurem emprego ou dependam de ajudas públicas. Ao reduzir gradualmente os subsídios à medida que os rendimentos aumentam, incentiva a produtividade e preserva a iniciativa pessoal. Neste artigo, vamos explorar o IRN em profundidade, destacando as suas vantagens sobre os sistemas tradicionais, abordando as falhas do RBU e avaliando o seu potencial como uma reforma transformadora na Europa. Num contexto de mudanças económicas e demográficas, o IRN surge como um caminho prático para um sistema que equilibre apoio, dignidade e sustentabilidade.
Problemas dos Sistemas Tradicionais de Assistência Social
O Estado Social tradicional, embora bem-intencionado, tem sido alvo de críticas crescentes pelas suas ineficiências e consequências inesperadas.
Ineficiência e Burocracia
Estruturas administrativas complexas frequentemente atrasam os sistemas de assistência social, levando a desperdícios de recursos. Programas sobrepostos e serviços redundantes aumentam os custos, sobrecarregando os contribuintes. Por exemplo, várias entidades podem oferecer benefícios semelhantes, enquanto processos morosos atrasam a ajuda a quem precisa. Com o envelhecimento da população europeia a exigir mais apoio, estas ineficiências põem em risco a estabilidade financeira, desafiando os decisores políticos a repensarem a distribuição de recursos.
Incentivos Perversos
A assistência social pode, sem querer, desencorajar o trabalho e perpetuar a dependência. Surgem "armadilhas de assistência" quando os benefícios são estruturados de forma a que ganhar um salário resulte numa redução abrupta da ajuda, tornando o emprego menos atractivo do que permanecer no assistencialismo. Isso cria um ciclo em que os beneficiários hesitam em procurar trabalho ou formação, comprometendo as suas perspectivas a longo prazo. Com o tempo, tais sistemas arriscam criar uma cultura de dependência, minando a iniciativa pessoal e prendendo indivíduos numa estagnação económica.
Peso Económico
A pressão financeira do Estado Social está a intensificar-se com as mudanças demográficas na Europa. Populações mais envelhecidas requerem maior apoio, elevando os custos e exigindo impostos mais altos ou gastos públicos acrescidos. Isso desvia recursos da inovação e do investimento, podendo travar o crescimento económico. Sem reformas, estas despesas crescentes podem tornar-se insustentáveis, obrigando os governos a encontrar soluções que mantenham o apoio sem comprometer as finanças.
Estigma Social
Além das questões económicas, a assistência social traz muitas vezes um custo social. Os beneficiários enfrentam frequentemente estereótipos de preguiça ou incompetência, o que gera vergonha e diminui a autoestima. Este estigma pode dificultar a mobilidade social, tornando mais complicado sair da dependência. Resolver isto exige um sistema que não só apoie, mas também capacite, reduzindo preconceitos e promovendo inclusão.
Face a estas falhas, a Europa precisa de explorar alternativas que prestem ajuda de forma mais eficaz. O Imposto sobre o Rendimento Negativo apresenta-se como uma opção promissora, capaz de enfrentar estas questões sistémicas.
O Caso Contra o Rendimento Básico Universal (RBU)
O Rendimento Básico Universal surgiu como uma ideia ousada para combater a pobreza e a desigualdade, oferecendo a cada cidadão um pagamento fixo independentemente das suas necessidades. No entanto, a sua simplicidade traz desvantagens significativas.
O custo do RBU é um obstáculo enorme. Implementá-lo em toda a Europa exigiria fundos avultados, pressionando orçamentos já sobrecarregados pelos compromissos actuais do Estado Social. Isso poderia implicar subidas acentuadas de impostos ou cortes noutros serviços, enquanto a criação da infraestrutura administrativa necessária traria mais despesas. Há também quem tema os desincentivos ao trabalho: se todos receberem o mesmo valor, alguns podem sentir menos motivação para trabalhar ou arriscar em projectos empreendedores, podendo afectar a vitalidade económica.
Além disso, a abordagem universal do RBU sacrifica eficiência. Ao distribuir fundos de forma igual, não dá prioridade a quem mais precisa, entregando recursos aos mais ricos enquanto dilui o impacto sobre os pobres. Esta falta de foco levanta dúvidas sobre a sua capacidade de combater a desigualdade de forma eficaz. Embora o apelo do RBU esteja na sua universalidade, estes desafios apontam para a necessidade de uma solução mais direccionada—e é aqui que o IRN entra em cena.
Compreender o Imposto sobre o Rendimento Negativo (IRN)
O Imposto sobre o Rendimento Negativo propõe uma abordagem refinada ao apoio social, combinando assistência com incentivos. No seu cerne, define um limiar de rendimento base—digamos, 1.000 euros por mês. Quem ganha menos recebe um subsídio proporcional à diferença, enquanto quem ultrapassa esse valor paga impostos para financiar o sistema. Por exemplo, com uma taxa de subsídio de 50%, quem não tem rendimentos recebe 500 euros, e quem ganha 400 euros recebe 300 euros, elevando o total para 700 euros. À medida que o rendimento se aproxima do limiar, o subsídio diminui, desaparecendo nos 1.000 euros, altura em que a tributação começa.
Veja-se uma ilustração simples:
| Rendimento Mensal (€) | Pagamento IRN (€) | Rendimento Total Após IRN (€) | |-----------------------|-------------------|------------------------------| | 0 | 500 | 500 | | 400 | 300 | 700 | | 800 | 100 | 900 | | 1.000 | 0 | 1.000 | | 1.200 | - (impostos aplicam-se) | 1.200 - impostos |
Isto garante que trabalhar compensa sempre: ganhar mais aumenta o rendimento total, evitando a armadilha da assistência. O financiamento vem de um imposto fixo—talvez 19%—sobre os rendimentos acima do limiar. Quem ganha 1.500 euros, por exemplo, paga 95 euros sobre os 500 euros acima de 1.000, ficando com 1.405 euros. Este modelo fiscal simples facilita a gestão e assegura equidade.
| Rendimento (€) | Rendimento Tributável (€) | Imposto (€) | Após Imposto (€) | |----------------|---------------------|---------|------------------| | 1000 | 0 | 0 | 1000 | | 1200 | 200 | 38 | 1162 | | 2000 | 1000 | 190 | 1810 |
O IRN pode ser de participação voluntária, através de um contrato. As pessoas podem aderir ao sistema se precisarem de apoio ou rejeitá-lo se não aceitarem ajuda estatal, evitando os impostos associados ao financiamento do IRN. Quem optar por sair pode reentrar em caso de dificuldades, equilibrando liberdade de escolha com pragmatismo. Para libertários desconfiados de ingerências governamentais, isto torna o IRN um compromisso—um passo para longe do assistencialismo coercivo e em direcção a maior autonomia.
Filosoficamente, o IRN não é um objectivo final, mas uma ponte. Ao simplificar a ajuda e reduzir a burocracia, pode abrir caminho para soluções privadas, como caridade ou apoio mútuo, diminuindo o papel do estado ao longo do tempo. Características como a avaliação de meios e a indexação à inflação reforçam a sua adaptabilidade, garantindo que o apoio permaneça justo e relevante.
Vantagens do Imposto sobre o Rendimento Negativo (IRN)
O IRN destaca-se onde o Estado Social tradicional falha. Os seus subsídios decrescentes incentivam o trabalho, premiando o esforço à medida que o rendimento sobe e impulsionando a produtividade. Isto contrasta fortemente com as armadilhas da assistência, encorajando as pessoas a procurarem formação ou a arriscarem em empreendedorismo sem medo de perder apoio de repente.
Na gestão, o IRN é revolucionário. Substituir um emaranhado de programas por um único sistema reduz a burocracia e os custos, canalizando recursos directamente para quem precisa. Um processo de pagamento único elimina sobreposições, tornando a entrega de ajuda mais rápida e eficiente.
A dignidade é outro ponto forte. Ao oferecer escolha e evitar supervisão intrusiva, o IRN escapa ao estigma do assistencialismo, dando aos beneficiários autonomia para gerir as suas finanças. Isso promove o autorrespeito e um sentido de controlo, quebrando o ciclo de dependência.
Economicamente, a flexibilidade do IRN sobressai. Adapta-se às flutuações de rendimento, direccionando a ajuda exactamente onde é necessária. Estudos indicam que pode reduzir a pobreza, melhorar a mobilidade social e até beneficiar a saúde, ao aliviar o stress financeiro, oferecendo um impulso abrangente ao bem-estar.
Responder às Críticas ao Imposto sobre o Rendimento Negativo (IRN)
Nenhuma política escapa a críticas, e o IRN tem as suas. Os libertários veem, e bem, os impostos como roubo, e embora o IRN não elimine esta tensão, suaviza-a. Ao condensar o Estado Social num sistema claro e simples, reduz a intromissão estatal face à burocracia actual. Os seus incentivos ao trabalho alinham-se com valores de responsabilidade, tornando-o um passo aceitável a curto prazo.
O financiamento preocupa, sobretudo em países europeus já muito tributados, mas uma taxa fixa oferece uma solução. Simples e previsível, minimiza os custos administrativos e assegura contribuições justas, sustentando o IRN sem sobrecarga excessiva. Há também quem debata o seu impacto social—uns chamam-lhe um subsídio fácil, um hand-out, outros um sistema demasiado voltado para o mercado. Ainda assim, o IRN encontra um meio-termo, oferecendo uma rede de segurança que recompensa o esforço sem controlar vidas.
Passar para o IRN exige eliminar gradualmente os programas antigos e informar o público sobre os seus benefícios: um governo mais leve, menos dependência e maior iniciativa pessoal. Para quem sonha com um futuro sem estado, o IRN não é o destino, mas um movimento prático rumo a sistemas de apoio voluntários, promovendo uma cultura de autossuficiência.
Conclusão
O Imposto sobre o Rendimento Negativo não é perfeito, mas é um avanço claro face ao status quo. Reduz os excessos do Estado Social, promove trabalho e dignidade, e oferece à Europa uma reforma viável perante as pressões económicas. Para os contribuintes, promete eficiência; para os beneficiários, oportunidade. Numa região onde o assistencialismo está profundamente enraizado, o IRN surge como um passo ousado, mas possível, para um futuro mais livre e sustentável—um que capacite as pessoas enquanto alivia o peso do estado.
Photo by The New York Public Library on Unsplash
-
 @ 57d1a264:69f1fee1
2025-05-14 06:48:45
@ 57d1a264:69f1fee1
2025-05-14 06:48:45Has the architect Greg Chasen considered it when rebuilding the house just one year before the catastrophe? Apparently not! Another of his projects was featured on the Value of Architecture as properties with design integrity.
This is a super interesting subject. The historic character, livability, and modern disaster-resistance is a triangle where you often have to pick just one or two, which leads to some tough decisions that have major impacts on families and communities. Like one of the things he mentions is that the architect completely eliminated plants from the property. That's great for fire resistance, but not so great for other things if the entire town decides to go the same route (which he does bring up later in the video). I don't think there's any objectively right answer, but definitely lots of good (and important) discussion points to be had.
https://www.youtube.com/watch?v=cbl_1qfsFXk
originally posted at https://stacker.news/items/979653
-
 @ 57d1a264:69f1fee1
2025-05-14 06:12:19
@ 57d1a264:69f1fee1
2025-05-14 06:12:19We asked members of the design community to choose an artifact that embodies craft—something that speaks to their understanding of what it means to make with intention. Here’s what they shared.
A vintage puzzle box, a perfectly tuned guitar, an AI-powered poetry camera. A daiquiri mixed with precision. A spreadsheet that still haunts muscle memory. Each artifact tells a story: not just about the thing itself, but about the choices of the creator behind it. What to refine, what to leave raw. When to push forward, when to let go. Whether built to last for generations or designed to delight in a fleeting moment, the common thread is that great craft doesn’t happen by accident. It’s made.
On the application of craft
Even the most experienced makers can benefit from building structure and intention into their practice. From sharpening your storytelling to designing quality products, these pieces offer practical ways to uplevel your craft.
Read more at https://www.figma.com/blog/craft-artifacts/
originally posted at https://stacker.news/items/979644
-
 @ 3bf0c63f:aefa459d
2025-02-22 17:05:13
@ 3bf0c63f:aefa459d
2025-02-22 17:05:13P2Panda and the super-peer curse
Recently was suggested to me that https://p2panda.org/ was a great protocol and that maybe Nostr wouldn't be necessary if we could just use that. After making the blind remark that p2p doesn't work I was pointed to https://github.com/p2panda/aquadoggo which acts as a "node" in some ways similar to a "relay", and it all looks somewhat well, cool, maybe they're into something:

Then I realized that Aquadoggo isn't really a relay, it is more like an "app server". There are still no relays in the Nostr sense in p2panda, the base of communication is still p2p between "nodes", and, as Aquadoggo's readme say, it could be run both as a client and as a server. In other words, we could easily have an "Nostr Aquadoggo" that abstracts all communication with relays, relay selection, event and tag parsing and signatures then stores filtered, ordered, indexed data locally: it is just a Nostr client.
That you can put one of these in a server doesn't change that fact that it will be still a client -- and that underlings behind it consuming its API will be controlled, censored, mislead and tricked. This design that requires trust in one single server from a dumb client in exchange for massaged, sorted, filtered, ordered data is seen not only in p2panda, but it's also a fundamental part of the design in many of the supposed decentralized protocols out there, including Bluesky, Farcaster and Pubky. It has also found its way even into RSS, with feed aggregators, and into IRC with bouncers. It can also be seen being experimented with inside Nostr, with ZBD Social, Primal, Ditto, Satlantis and others I forgot, and even behind the ideas of some pseudo-relays like Bostr and filter.nostr.wine (although I'm not sure). Notably, though, this design is not a part of SSB or Mastodon and these two weren't ever corrupted by it as far as I know.
In any case, should we accept that such architecture will eventually find its way into Nostr and completely dominate it? If I believed the answer was "yes" I would immediately declare Nostr a failed experiment, but I don't. As the main author of one such experiment (ZBD Social), I still think this architecture isn't necessarily bad as long as it's limited and restricted to certain circumstances, but it does pose a risk of Nostr becoming almost as bad as Bluesky, so the path has to be threaded carefully.
Ultimately, though, what all these protocols are trying to achieve by injecting these dangerous super-peers into their architecture is the reliability that pure p2p cannot provide, along with filtering and discovery features. And Nostr's multi-relay architecture, as cumbersome and weird as it is, represents a very different approach to solving the same problems, one that none of these other protocols can even begin to consider emulating, and I believe we have to accept that, embrace it and lean on it more.
We can go there by having whitelisted relays as communities, relays that enforce group rules automatically, relays that provide fulltext search, relays that provide AI-based personalized custom feeds, relays that filter out reply spam or harassment (or enforce blocks at the server-side), relays that restrict reads to a certain selected group, relays that perform curation and make valuable content reemerge from the abyss of the ongoing stream; and of course clients that surface all these different types of relays and their features.
Why is this complex madness better than the super-peer architecture? Because, well, even though custom relays give us all these cool weird features, The basic Nostr feature of being able to follow anyone you want and not giving a super-peer the power to break that link between follower and followed, i.e. the outbox model, is still the most basic function of relays.
-
 @ 57d1a264:69f1fee1
2025-05-14 05:56:15
@ 57d1a264:69f1fee1
2025-05-14 05:56:15Shanghai: Bus Stops Here
A new crowd-sourced transit platform allows riders to propose, vote on, and activate new bus lines in as little as three days.
From early-morning school drop-offs to seniors booking rides to the hospital, from suburban commuters seeking a faster link to the metro to families visiting ancestral graves, Shanghai is rolling out a new kind of public bus — one that’s designed by commuters, and launched only when enough riders request it.
Branded “DZ” for dingzhi, or “customized,” the system invites residents to submit proposed routes through a city-run platform. Others with similar travel needs can opt in or vote, and if demand meets the threshold — typically 15 to 20 passengers per trip — the route goes live.
More than 220 DZ routes have already launched across all 16 city districts. Through an online platform opened May 8, users enter start and end points, preferred times, and trip frequency. If approved, routes can begin running in as little as three days.
Continue reading at https://www.sixthtone.com/news/1017072
originally posted at https://stacker.news/items/979637
-
 @ 3bf0c63f:aefa459d
2025-02-22 15:07:57
@ 3bf0c63f:aefa459d
2025-02-22 15:07:57document.characterSetand another meaningless example of flexibility destroying protocolsI always knew of at least two standardized ways browsers used to determine the charset of a given webpage document: the
Content-Typeheader and the<meta charset>tag. These are widely understood, teached and documented specs that a lot of developers assume are being followed because they're "web standards".Turns out there are a lot of pages on the internet that declare themselves as UTF-8 but are actually using other types of encoding (here's an example), and just by looking at the headers and meta tags you would think they are actually UTF-8, since they render correctly on Chromium and Firefox.
But the actual truth is that browsers actually ignore these headers completely and use their own internal heuristics to determine the actual charset. And they expose their internal result in the DOM property
document.characterSet."Oh, that's great! Technology is awesome, they've fixed a problem!", you may think. But the actual result of that is:
- developers never learn that they're wrongly declaring "UTF-8" when their content is actually "windows-1252" because they never see their page being rendered wrongly;
- the actual spec is now that browsers should correctly guess a page encoding instead of just following what is written;
- people are fooled and continue to teach, learn (and write) the falsehood of these useless HTTP headers and
<meta>tags not knowing they are completely wrong. - new browsers coming to the space have to first learn that this is a thing, which is not obvious nor written anywhere, then they must implement it, because if they follow the spec people will think it is their fault that some broken pages are rendered with broken characters on this new browser;
- barriers to entry are higher, the protocol continues to centralize more and more;
- other people trying to read these HTML pages for whatever reason, from any software that isn't Google Chrome or Mozilla Firefox, will have the same problem and will have to learn everything and come up with their own charset detection mechanism, this again closes the content of webpages to being more and more restricted to the walled garden of existing browser vendors.
I think we can all agree these are not good outcomes.
In the end of things, this is just a very small example, but "the web" protocol has thousands of such small examples, and they add up.
Also, arguably the spec should have been "browsers must do their own charset detection" since the beginning, but that's irrelevant. The fact is that it wasn't (and still isn't, the specs weren't updated as far as I know), and here's again another undeniable example of how being flexible can bloat a protocol.
-
 @ 04c3c1a5:a94cf83d
2025-05-13 16:49:23
@ 04c3c1a5:a94cf83d
2025-05-13 16:49:23Testing Testing Testing
This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test This is just a test this is just a test this is just a test

nostr:nprofile1qy2hwumn8ghj7etyv4hzumn0wd68ytnvv9hxgqg7waehxw309anx2etywvhxummnw3ezucnpdejz7ur0wp6kcctjqqspywh6ulgc0w3k6mwum97m7jkvtxh0lcjr77p9jtlc7f0d27wlxpslwvhau
| | | | | ------------------------ | - | - | | Quick'hthbdoiwenweuifier | | | | 1. Little | | |
ghtgehg
gwefjieqhf
MUCH BETTER
-
 @ 5391098c:74403a0e
2025-05-13 16:47:48
@ 5391098c:74403a0e
2025-05-13 16:47:48(Textículo em prosa erudita sobre a Ideologia Anarco-Capitalista-Cristã)
https://davipinheiro.com/01-escravos-da-cara-inchada/
A cultura #Woke apropriou-se da imagem sobre a #escravidão. Quando uma pessoa aculturada imagina um #escravo, vem em sua mente a imagem de um ser humano negro, magro e flagelado. Para quem enxerga além das cortinas da mentira, vem em sua mente a imagem de um ser humano de qualquer etnia, gordo e doente.
Democracia, péssimo regime de governo assim classificado pelo seu próprio idealizador: Platão em A República, é o grito da hienas de dentes arreganhados para ampliação do regime escravocrata fomentado pelos #GlobalistasSatanistas.
Um escravo da cara inchada é todo aquele ser humano ignorante inconsciente que alimenta esse sistema em troca de intoxicantes como flúor¹, cloro, glutamato monosódico, gordura trans, corantes, conservantes, refrigerantes, bebidas alcoólicas, psicotrópicos e remédios sintomáticos, tudo embrulhado com mentiras reiteradas.
Como consequência, após os 18 anos de idade o corpo do #EscravoDaCaraInchada sucumbe à tamanha intoxicação e passa a inchar, sendo fisicamente perceptível sua condição de escravo da cara inchada tanto à olho nú quando por reconhecimento facial de qualquer pseudo inteligência artificial.
O círculo vicioso da #EscravidaoDemocratica é tão simples e tosco como o “pão e circo romano”, Mesmo assim é muito difícil para o escravo da cara inchada perceber a própria condição tamanha é sua intoxicação física e mental.
Se um Anarco-Capitalista-Cristão (#Ancapcristão) chega para um escravo da cara inchada e explica sobre esses intoxicantes como instrumento de escravização, dificilmente o escravo da cara inchada irá acreditar pois diferentemente do antigo e aposentado chicote, o novo instrumento da escravidão não dói de imediato e os próprios efeitos da intoxicação impedem-no de raciocinar com clareza.
Portanto, para que os #GlobalistasSatanistas obtivessem sucesso na democratização da escravidão, tiveram que criar um chicote químico e uma ideologia favorável. Quanto às etapas utilizadas para formação dessa ideologia no inconsciente coletivo passo a elencar as 6 grandes mentiras em ordem cronológica:
(1ª etapa) Iluminismo: distanciamento de #Deus e seus ensinamentos, criação de sociedades secretas, exacerbação do ser humano perante o criador na tentativa de projetar o ser humano como seu próprio deus, tornando-o responsável sobre os rumos naturais do planeta. Assim formou-se a base ideológica para o materialismo, ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(2ª etapa) Materialismo: perda do propósito espiritual e do sentido da vida², o que passa a importar são apenas as coisas materiais, acima inclusive do próprio ser humano. A perpetuação da espécie também fica em segundo plano. Assim formou-se a base ideológica para o ambientalismo, feminismo, controle populacional e ideologia de gêneros;
(3ª etapa) Ambientalismo: redução do ser humano à mero câncer do planeta superlotado, atribuído-lhe a responsabilidade por qualquer desastre natural. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(4ª etapa) Feminismo: enfraquecimento do ser humano por meio da sua divisão em duas categorias: macho e fêmea, os quais são inimigos e não cooperadores. A ideia de igualdade de gêneros é tão antagônica que beira ao conflito cognitivo³: Eles querem separar para dizer que são iguais... Ora, como não pode haver diferenças entre os gêneros se eles são fisicamente e mentalmente diferentes? Nesse diapasão, mesmo não sendo os estados nacionais os arquitetos da escravidão democrática e sim meros fantoches dos globalistas satanistas, o voto feminino foi fundamental para aprovação de leis misândricas com o fito de acelerar a destruição da base familiar do escravo da cara inchada. Importante mencionar que a base familiar dos globalistas satanistas continua sendo patriarcal. Assim formou-se a base ideológica para o controle populacional e ideologia de gêneros;
(5ª etapa) Controle Populacional: “Crescei e multiplicai-vos” é o caralho, Deus não sabe de nada (Iluminismo), o que importa é o dinheiro e filho é caro (Materialismo), para que colocar mais um ser humano nesse planeta doente e superlotado (Ambientalismo), além disso o sexo oposto é meu inimigo (Feminismo). Essa é base ideológica que antecede a ideologia de Controle Populacional, ainda reforçada pela apologia à castração, já que em todas as mídias produzidas com patrocínio oculto de capital globalista satanista tentam normalizar a castração do homem (perda da capacidade de reprodução) desde em desenhos infantis até grandes produções cinematográficas, ora em tom de humor ora em tom de tortura. Assim os escravos da cara inchada do sexo masculino perderam sua identidade, essência e desejo de ser o que são, formando-se a base ideológica para o homossexualismo, ou seja, para a ideologia de gêneros.
(6ª etapa) Ideologia de Gêneros: É a cereja do bolo para os planos do Diabo (Anjo invejoso de Deus que quer destruir a maior criação: nós). Enquanto os globalistas satanistas, dentro de sua sábia ignorância, acreditam estarem chefiando a democratização da escravidão, na verdade também não passam de meros fantoches do Anjo Caído. Com a sexta e última etapa de mentiras para extinção da humanidade (#apocalipse) posta em prática através da Ideologia de Gêneros, fecha-se o ciclo vicioso de mentiras que se auto justificam: Se #Deus não presta, o que vale são os bens materiais, o ser humano é um câncer no planeta, o sexo oposto é inimigo e ter filhos é uma péssima ideia e ser homem másculo é crime, então ser #homossexual é a melhor opção, inclusive vamos castrar os meninos antes da puberdade sem o consentimento dos pais ou mães solo. Aqui também há uma grande bifurcação do círculo vicioso de mentiras, qual seja o gritante conflito cognitivo³: Se todos os homens deixarem de ser másculos, quem vai comer os #gays afeminados? Ou se todas as mulheres deixarem de ser femininas, quem as #sapatonas irão comer? E o pior, se todos passem a ser homossexuais quem vai perpetuar a espécie? Seremos extintos no lapso temporal de apenas uma geração, pois a fraudulenta medicina moderna jamais terá a capacidade de gerar bebês de chocadeira à tempo.
É interessante enxergar que mesmo os Globalistas Satanistas, dentro de sua sábia ignorância, acreditando estarem democratizando a escravidão em benefício próprio, na verdade apenas estão fomentando o apocalipse, ou seja sua própria extinção. Também não terão qualquer lugar especial no inferno, sinônimo de mal é mentira. Portanto os #GlobalistaSatanistas são meros fantoches do #Diabo enganador, tão submissos quanto o Escravo da Cara Inchada…
Interessante também enxergar que o livre arbítrio é uma condição obrigatória para independência da criação (anjo e ser humano). Todos somos livres para escolher entre o bem e o mal, se iremos ser escravos de #Deus ou escravos do Diabo. Se assim não fosse, inexistiria criação pois seríamos mera extensão da consciência do #Criador, em outras palavras: para que exista uma criação, essa deve ter a capacidade de decisão de forma independente, o chamado livre arbítrio.
Com base nisso, temos que não cabe à nos fazer qualquer revolução, tudo está normal, a luta entre o bem e o mal sempre irá existir pois um não existe sem o outro. Nos cabe apenas escolher o lado. Nesse contexto, tenho a seguinte mensagem destinada à você para encerrar o presente Textículo Anarco-Capitalista-Cristão:
------ > Se você for um ANARCO-CAPITALISTA-CRISTÃO passe esta palavra à diante para que a verdade atinja o maior número de ignorantes inconscientes possível;
------ > Se você for um GLOBALISTA SATANISTA, vai viver sua vida, desfrutar da própria fortuna e pare de ser fantoche o Diabo, mentiram para você: não terá qualquer lugar especial quando morrer;
------ > Se você for um ESCRAVO DA CARA INCHADA e não entendeu o que eu disse, por favor me pergunte ou debata comigo, terei o prazer em lhe ajudar a enxergar a verdade. Pare de trabalhar por dinheiro fiduciário, passe a aceitar #Monero e #Bitcoin em troca do seu trabalho, pois isso é o único jeito de sermos financeiramente livres, se tiver alguma dúvida sobre #criptomoedas me pergunte e terei o prazer e ensinar. Se ainda assim você se recusa a enxergar a verdade exposta aqui, por favor aceite #Monero e #Bitcoin quando for dar o seu cú. Ou melhor, cometa suicídio, já que você é um câncer no planeta, salve a natureza.
(Davi Pinheiro)
¹ - https://davipinheiro.com/teoria-da-conspiracao-o-fluor-na-agua-e-usado-para-controlar-mentes-revista-super-interessante-editora-abril/
² - https://davipinheiro.com/qual-o-sentido-da-vida/
³ - https://davipinheiro.com/entendendo-as-referencias-cruzadas-do-pensamento/
PREZADOS AMIGOS, DIVULGUEM ESTE ARTIGO. ABAIXO SEGUE A LISTA DOS 500 BRASILEIROS MAIS ATIVOS NO NOSTR NOS ÚLTIMOS MESES PARA TODOS SEGUIREM-SE ENTRE SI E FORTALECER NOSSA COMUNIDADE DE LÍNGUA BRASILEIRA (se você não estiver na lista interaja para ser adicionado):
npub1u2e0qzjsjw9suxcdkeqrydr07xzsyx8mzp469augc0a29aeasfdq8fx67q npub1xt25e4pakq6x4w44p9kw2vlfwv4zpc9hg7xsnrq53hl0za4ag2qs09cwcs npub17hgdpn9xnt5zyxlx8pz0uuus8d23pxwr9a5vq96nw5nawx20zxnsj6fym6 npub1arnth7tuxw060c74adaf08jam6kttn24wfdse9wyg2c7waycwezqszr2mz npub1qg8j6gdwpxlntlxlkew7eu283wzx7hmj32esch42hntdpqdgrslqv024kw npub10q0axre6n3ew64pen99x0qkrh70yxfx6w3grwvkhk4kz9dp8m3ssltvs6f npub1sf2se74xlzf7f7clm3dg28npaxghdy6pguzpsut30fjpwuaxrxcsrnhr57 npub19ychr8yknmje69r645sgd8j0epx2rdgdyl7feagcnmrwkaedzffqtrcznl npub1k86zp0778x7cjng50et5z76xdwxy0tgfn5amnrwrd6mda8uln4lq78ua23 npub13src792wxm8nrhqzu555uxuktfffzcqx78s3pc9zefcdjgwvm3pqsddz4j npub1uw04lzuqx42gk0xc4m8advfmuqlz8nv7dqpuyq4gcv8r304lwvnq2m5ew2 npub1fw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqvq2rfr npub1nkenffr9eslkzplds3lwcz7xeq67w6a9qcjlfsvspj7tnhuq3kgsram48g npub1w66drr2qta67gyt7la6fgglsdvk3xx3nndsz4k5wfcal8jq0ze7sqcxdpd npub12xq6exra99hg6tuefx3yysszqudaljvy6eyxqz8tpt7038gpaqus7lfuyy npub17tvf04z759dsyecdtmk70tevla7vua9e3sr88lgnl7put97764zq708q0m npub1rzajeq88urk58nh0n7gqknr2agrx34xu4en0k8hm43fl8h2khp6sk0v3y4 npub1yspe4ly5p9dlfv4vevm0evpag8ljkaay3x3clj8gtvxlsvpwrrrs6h47mx npub107a0nwr3lsj9kdy3jdq570jzcv95y0qzuuhrvcgrpsnq2h4xsclqzy7v4g npub14reqsqss7wp06k390a547pkqrlc0w6uzelm9gpwxze7p8z8x3awsuthvzz npub18fh6flnjt9aa3jlnp5k3kd9zr6v5mlpeczhdx4qheytfyyqfpe7s2y0lzm npub1lafcm7zm35l9q06mnaqk5ykt2530ylnwm5j8xaykflppfstv6vysxg4ryf npub1s00wyzkfrjcclawx225k7wrxd74369vxdcdhy88j89yhrxssfclqulxf93 npub1rmq4kl4dfvp4kt937f9mz60ywkwv467585vnesm3ctqz9krkksrqg4ran0 npub1d7r5su48a8m5k389fd6rwy9cvhlyycmg3pl2g60q5zmgvmr3xreq098mu2 npub1r8lsve0d5yezxq52fjj90kwz76xcweyxlx9uwhsrpd6gt7uk4edscl4fdr npub19ljjj23d7fgy0gujlnh26a293p6uwawrrnpg7jlqfnhnard322gssd2rnj npub1u484zct2rxyknscgnnxrwpuk3f2j679x8tdysvxh659whv99g35saq9xjt npub1gpd868cejawju35epkayavfkqfuykt3820xe678m2vqfqj8v7ges2t4umk npub172fwxt8nnauv2c6leevl0rq4mk87c5vu4mm4fqef58xt390jqxfs6ua7vz npub1gmdrkx4lgwzyqr6krqyykg9r2kpasftuu2x98ncvs9xz9cjhfgcsxns0xz npub1sfzc94dhlkrj6m9tdkle4glyazhtajjsj9qhjv279an06nr74uvqzka6js npub18rdvxdw773852gyl4kjkr5xmg44p9l0jywdk6cq8axl3k9yh59fsu3g8aj npub167h7xtt7tkfvr9mn9d09s4u6r4l0y7rr355jpjg55lg4mpdghsasa9c47v npub1q4qjda5zm33743dd4mewnx6j049hgry7ls4nvh54clcnax3wsnzqv7c5lw npub1mjckw2qsqemdnhz7ul63vpcd79fmar49r8y7fh0tffva767yx07qq68xkn npub1ry2uv7qwu840qx4fg38zzfrl6dfgaudn6d8s7trpf3sj8nx0vaaquj5qrj npub1zqw2ymcy9txda2wzuka7yx6vlyvuwe7k2pldxpxxx660nhf65tusxzdcp6 npub1fjr0qa7rdhll7cfpgdcsz5nry2gy92u7a8gr0ku390n69865ec0qxwcral npub1wc4rc9wxl2gfzxl384g0cw3f79nrms0sfdpe02y7aasy7c3we4sqd0qywr npub19x5l76266vfen827fudaampuuupkejg9vls88hld8nv4w4sq59lsqlal37 npub1gc24vefdu60d3e3yxg8mhu52hxxpcykesk85y8mez8llj23kpehszdmu3j npub1u9ja9ymqmaw7mn9tnmrsnpx0f9j6hs59kxd9de363jvadjamzd9qg3ek4k npub1lzt7pmhvg7hl23emv22g4d7cs9jyglkqpr7lf3n8rcz0evkacg2s6n4jjf npub1p22hyejtr60rdrmjvql5k8fyv8lkq8exzw5mkkx3qcwqcu6979aqvhpqlq npub15p6p9l5upa0y0aj5nwf7lnud2regh00az9u4a4fmgyh8ukyue8kq7xuzp7 npub187dlu8g04kk8adc309vwn3lxsj63fmaty5vmdyrsvzx2fcxg70pqfszj4z npub1adfs8z9rlk6dzwm44522ge0gf367t6s6x30nrulp0xq6wsglyxssxqwyva npub1wqh4j2lvkd0fz342he0jr2d8eqrjwlqsv42azw6utqnpkrjv72xqylx32z npub1n9e2cy50jk900hdzvxt4cjhn80qwzxuer93aylhfdc76gwksr2lsqt36ww npub1styn4qvw4h4s92pcntrffm5dhe889h3hanwjpv66r4ue7gd3xutqk9hpc6 npub157v53ahyyxh4mp38v363chz9lrrw8um9m0tyhqzjujz8m4pmr42s9sk9u8 npub1alq86fku99p0rgq6s0cwwe9lsa8vdvu4d6r7d6j6cyuysf2r76hsh9tt37 npub18cvuxxvd2a6gt76etnte5vtws7a5a4xeqgt03qcs0u46nfws0vzskrnwu9 npub1mlu4qvm8j7gqamukz98l832ghgktyj0whqrxfx89625m3p30haqq5racjk npub1l8tlpvn3kka3nm2qpk96amsuy2kr5kl9eusd54fpn3yjnefrnpaq2j5t9v npub1jtnuszgjayga0pzvm3t7z9pantcnyxzacu30mhvw4dk0lkkvhxrsgvfgw5 npub1z73hklrdpa0n5z663mvnu0afxhlegpt5exmkg9u0nmd32ktqs7fq3prv27 npub1tshn5e5h0ud3l6vegwrce2er2tuhxangx4yvx4q04uheznxxgp6qg9dx2n npub136aeqeuum2t8cjgfnpxwfkgf5e8fd95h39uqkenrr6u0yl3upg9skvkfq8 npub1pkjyqg0am9qyjwg772ue4hhshaf6gwgz4psnptlg9v8lk6st2naqct3ll5 npub1kvzyrn6zvvdh9jnvfzc6e86s0zpntvg0e9f0v340e59u2rut99zsuq9fl9 npub168dqt5c8ue3uj8ynlk0lhwalnp7uy39lvzf9tm09wy3htxwmw7qq5nerj4 npub1cajs9cz6r43rmn0y8v8cgeuuj2lfhftvxcq05f8efc22hr5fnwmshx0pvw npub1uu0qk8f7xv7egc6tf9kk3mkx99u2leldgzz0trl77uymvv8n8ahqtd6309 npub1t8a7uumfmam38kal4xaakzyjccht4y5jxfs4cmlj0p768pxtwu8skh56yu npub10wlfumja930vzz4jhh9vc6t3wy8ay7thg8mt9qcptlp5leqfmazqn79ee9 npub1tx8wamjvhaqme29rujkd4v978ck8d3ud7gxa9zzqtjftpfn9p5vs27a2lg npub1e5pneqe2je07e5sk00g8urqa66eljg74t4llv4htp6vq5f8kv2zsqrtway npub1nk7gygwkcfpf9hdjhkgyqszcgwyzmcrqhd9tr7zzczkm5ga79xusmm5qjt npub1p3pna34zku4fqe9mzyvhhffladjjxcug7jn20wm5rnccpjezn4ks0zaw4u npub1j4vyl5kadajpgxh2wrnfk2wvg25jhnv78s0mrs6ckuhft9uzqe7s9wpcgc npub1hfg3tsmmp7g3u5cw6mzg0n9andehmgel6jug486eppsr0rqx4a3qlp7yfm npub1zks89kfxmxv0s4sa7rj8yyd6ld8ncsqusm993678vq9ut73hn7uqhmecsf npub1hzt3p8ap8s4nnqjhha37z5q3jdc9lfg90js0crmg8u5lncnaqpzsdn75p5 npub12em9q547gfga2tkhuzc65ufrn5h9ndu270d7xnh0nkcz2gtvq4sqwutpy3 npub12fh76ppgs5g2srtvgewe9fprdsk2y6g42wf0sg2y0ucjxqq9l0dsy5n8wl npub1arjgv76ld978cya3k6xz24nuxkuezuqrsmy73x0gaxdlu7pxv4lq8npp2g npub1zpmtwh0esa4esnc4p6rn5vhx7wcfw8z0ky8nzczj6k46drsmm47s0zzlyh npub156zse25dzgt65kq472nfkfpwgqvf6vuw8ur0s0ny7zmzw4xqd68q3p4sem npub1pwyy6rwh9smlurdmfg7yy2lce43jlv9ac7l9zay723dyfx4m649ql85u04 npub13j4jtgrm0dtsfzecx4khzz5a8ykgdd374qewewj0ksfmenps67lqz2yr8a npub1dmdlkhqnzmde0ultsq72hnn8h6gjfrkfeud4hecjg8fg8pugzctsjwqas0 npub1yqq7mwccr6wv7vmhehgh4n9kwn55r9gneydhdu6249pntguacegsjgwevp npub1u79u7zxlz2flmwpdt59xsvv5syreavzdyu9llkg07swtf24a4ayq5g0uud npub1eezyd5p7n9vse3yv5k8vh068dutpjf7d9zuk6azegeh5ypvp270qqr8fam npub1s0p3y6rvmt5m6jf6zt96kl0c80x0fy396d8h3cvtsxpqq7lf7wwsgw780n npub1kcf4p6e8k0rkjtaaghu765647z58qu0wfpgxnqptlwg2pm30skzsm2mct0 npub10uqpae32d6t4xhcgmzkc5gkna3hf9xclpzf3q6kfusz5q8j5ruqs5tdemg npub1jldq9dk8kgtlr3akv8re00znkfyzq59t0yceuu6q0tdfxzmusarsfxfunp npub1ksp960nd2vhxxp4lw7unnhujy6mknd0mpw2sh7xuj4m963a2u03qw776l8 npub188qkhpvqhne68rwu878jta5a8uh3vl4mcmfp44nppydfz0td9tqqa5h3cm npub1e008u7wmf0gppsnzupclhzh4mexp90addmdu0wu9glyk0y6msvxskyd3yq npub1crtd3zn3ek0cwne036s0xfqgs6ywuutqdcwxl5k4csv57jsmlgfsjq9039 npub1u4r4hx3y820p8g00u65tpggk2rd5qkd0d3ukt2yvgwyhcd0qvymqweyx75 npub18e7t2damcrfe60empcnye5z896wf9fk478rgrdcawvv23hqtd8es3yg772 npub1s5uqfqur0jlnp9z32ag90e9p5y60z0e8ruryun6u8gy9c38s7caqqqjxvt npub1q9fawsk02d7ffc47l92peuasy9q23ganvs00aqfagxz9rgk5g3usy92n3g npub18qhe55gump3d8ff2xzugpeaxkq6gfc498hr6at2jlsert0h9qkvqquqmve npub1cj9w34dn6nyazvhtq9srms5rf9rj4tapmqlwc5d5k3cwk34vy8dqewkvj6 npub1wvkx5ckpcxmxvc9wd0q576qssle3ed40c4z5rpetwy8fqssq8k3qdhh3yl npub1wnpc03cvexrv7tqnz4amk5zpyxw30nat3xav8nna89j92h25q53sls0g5w npub1938qus3z7jxs4u5x6gpyf7pwavnvnvrhmlfv2jqryy43qf0mdgpqlrtyfq npub1gnvha9zemx47e3paehu59ssqjkkpkc0n6ugdufmkl9ahgd3qhajs6mfs4m npub1cha5p8ytujflljhet2k34sctnqyl3n5w74wnuy7c6dvyv870twas9xnugj npub1h4d7986rjexvgaqsv8zm4s88dekkacs9uadtad6zp8n38nkdszysj45nmc npub1wcuv2wqn3uypzx7f98vavt2gqz4f4qkzm28fgj4qpwgj3yfjghks0patgl npub14hq5lgadtyy9dhvtszq46dnl0s0xwdddqr7e32rdqqhma8a4xhsspxjjzu npub17rzgm20v9hf4m2hemlau5fzepyanwd5h3zxc0wkwq7y38s3g8uqs49lrut npub1l5sgjcjruwec2y2lxd23vj34qe2kkxyqnact76tsq5kzdtcmke0s4cz0uu npub1ylw08gevzgvwasypcs2lvmssfqyt46xzgul7lwvkssm76ehgq47qrn4xxk npub13t2th7tr0uxwc8mfkkr5dqmfrg5hmmdfnfjfhs4z2xal9z6hpe9q6xn9ph npub1239p46pv99lt94yfzu4xkh4u3vqr2k7rnmcc8zz64p6m8g0mva8qcxr0hj npub1r2eehghv6syvdhezrlln25fnz90clgdkcagqw87c9r735zlnhuaq8dpvwp npub1sd5wp8ufsttwk3c575gnakufgaeg3x4f4r5d84pun9n09yr7zq8s735ezh npub18txjwp7dj9hjwk972c32sj5xmngnutguvtg2r66a3g5rgw2s88xq3799uq npub1247x2zmsp8e766cy39gkuzywfq6ea89wd6sgvuh8lywrrvzvdqtsv9573z npub1mu2tx4ue4yt7n7pymcql3agslnx0zeyt34zmmfex2g07k6ymtksq7hansc npub152wtu2y9a5wlz74v88ahls2xq0g493gz5jx0wat9vfgxqzjfzl6qdazlty npub18yyc9l68tk6zsq63wmnzf3862l3xfckds38tq44egwl5l4g0nqeszhj50p npub15rdytrwdsc62qmvsc28xhzdxs5u35utlexg3tc3mtzm23ka4hzmsthe64f npub13je2r5t0s4uszds4lc5e87n77xngluwkjt0hesduvch0vk206gcsa0d03t npub10jjcalyj6a67qfxrax2mwpmsnrlles6qhk23j0dyc76h27gag05syya4qn npub155kdyaltpxaek29wkeza9prkr0t398ayn24wlp6pg68z57s8l67qka6ly8 npub1uk5ne4u0ey8s8tg8czceg70yw9jlzvk74y804wd3vaa3ncm5l9tsl2cjqc npub1q09ysz8xhfe0x0n2y77u6xem9whtsk5hgswz7s0lrj9znn8eksqqzzpsyy npub1rm8uwmhs7s9n3jqzzd92mwwgr8gca4p9x0u8vu8m5n5eppqj88fstspqh6 npub1e8antmtxy0vs2pjd6kah99lpy44ztads4m0udpf07vauvr7larzsf76w9j npub1e0ngk7s4nygt46cpmdrc63f3mfgjcp8edxh0f8vpp6zd5hwax4qq0mykcp npub1rksqdj6tpjx4ddcyc9v3jw458u9y83hk789jqy2j8h58jusv0mgscx389d npub1q2f2nlq5kxthrcsww2zmytyzal325gsvrv0aeg8fqj54z4kyrxgsylesz9 npub100t4hmfxs467q3cwqd5f3sej9zhm2edd3kcn57hj0kag3n49geusm5zt87 npub13et8ay8ny99mygd8ymznczusrhfrhhzzs8jdlep9q98r8uway9asl62v4r npub1qeydnlt70d29q3axc3h5v3spfntl74jukw9r6zy9s8ms6a82mupqgnr2y5 npub1n9hr9s73atxmjm0muz45ghwutvf2kc00lq2fa58rm9y80mpdqxmq73mdc0 npub145cgkka2733cmxn86khjshwyxz6ahgjp0ek9gp3fc2k7y3penkqq45ccpu npub1z24p8ghllrl4jxyw8juggm3cfrpn8vvfxxsjzjj4tuaz0qfkeqkstnk760 npub1h6mtmjw2au827vs99zlykn0tdhm3hpyffjgnaq8fsvjzem430hesd3zw5p npub13u9wq6td5qvj2dajmkjplz0ytvt4j7zvuyjg6kl9xqt5wznqghvqrptnlq npub1x7j0x34k2cguw8qk07hlgtpcdd22k0p4nfmuy3sk53mw7n5p4dws97mh3q npub1rlgz4nrqjvy7skd640reu9f9ckv5gzg4dmheeuq4u9dux42t7lys88svf3 npub1j5peadcc3as7ht6tszt47z2z3rec5py39y23cemrs47czyfxddnsskqnav npub1ymjhm0kxwldyx3f599d0cjvpcwdyfw7rmruyn8m2qnfhlu8mn4mspdwhqk npub1gaqn62wk22gesxfczv4q30kg3e2f6cqzdml645rwdyas6uaz3wdqexzlgl npub1z9vh6x3h5d99wvrjxw036ehg27cc37837f7dz4lr933euzu4pt3qn5874u npub1axy5sgkdz50hqrt266cl95qp7e5n9q6qmxguj0ry6mhpmu23t80s9nvqug npub1yvjmvxh2jx07m945mf2lu4j5kswr0d63n0w6cjddj3vpkw4unp4qjarngj npub1993fqzsar7lydy6lc8sztj5pxzeckttsf7m7dzjpcfvuu44uavksdks9p7 npub16s7exzaa4le983mjvnw7jfatum0jfxqtpfk2uqdel3c4q97uqznst6hyar npub15mptsgelg8rn5tjw5ltmdy8vmglws4fulr0kaghpv7t2jj8qzjks2mecva npub1yjvs58t4tgnmn98m4y2s64jferzv77p037zmwed8wzdful29a6esyajtwa npub1ctmkhtvw7rwk425sm4mqx6ak86aama7c6z8yxczfhgkwfv2fq7xq4mcr38 npub1f9jys8kppch9sceykam7p7uecpyam7ajm87wrgnndhjtj6jlp5vqe7y207 npub1k67tmzt34d6klra3ykrhkpvu0y8g8rlzv0egpgrry0xxcauxqzestwyz59 npub1x49ytzhkslwq6680jqsng7dy79vh8alsqpapr73m3akn0qerhj3ql7s2w3 npub1m2us7cgdufhg30yw6kawugwt5slp8kh9ed88dn7q5gtq5y20f95s9s25vt npub13sdds5pcp344k5mhfch7ltc4a8737uxqw9c47wfe08kkrnm3rhssm60637 npub1qfamw8qmsekxxu8pj5kfa960sgwsc86wys84gqxkzkzld8e6hk3qtvv7kq npub1tsxemx456uadxs4nsqenmquvws53290eg2gejrhvx7w965c779mslf7pds npub1ymxlmrd2yd59g7x4uejzsgmn4xlglu0schl39m2mjx5nzfzl2hcs73hn6g npub1qd05jn0jxlzplx33xjtzstvgeus9dk9405kwqf79vu00czwyvghqf08md5 npub1n5sl69j0w6c79tut2anqf69tkfevr065kzjt4n2rv2gres3q45ysmnj5nc npub10qjw7zw8m6yq4sr53watq4u8y47eef28jsyd0tmyhyfy4pjhntgqva7d9t npub1k6n2ghwu0afld0tnl2p43q7wtu2u9hln6e89ruv9a2y5deej06dskek6xy npub1ax4szvq26em2klfqj6hr38009x6k6m7nhe2z7mq0xs4xszetxe2s6964q4 npub1645w5cevetsz2364mss575panjuaa5ffh89ax4tp6u7x0tr2xlhsc29g25 npub1ys9j7sws8vccfwjctlqu7kx2hlfmkcxmjxmdttfl29edxv6xgelqkaffe4 npub1h4fnky04vkfkyac8shhmy0fwkrhuha65c5ec2ggvv03zv7pm64ls9x5vag npub1ueenpne5qhkvr4l9rw3c2ls2f6lgm7gh7f7ssl73l5yqt7um6uwsyatgml npub1krcpj4r4gp28vswfc4gztr5gku58c2eyhll47tyz5y2hhl6jyjwqduv9mr npub125nh0nkr0czuzkpjkqvjwc7mxuuvusr4n7a3kthjyfeer70eac0qpy5lsx npub1qcr5atkc2u04wx80pdyfnnwrttrw0taaz8hst3qt573j44yzxcvqkl339x npub1x96qzppsymujfyzn4dmkl08qgcr3aw7f2tt0xlmgyudfaggeq7zsh0yghv npub1l56z85xvaplh3033l8h2x9thypamu0d2hyqnxkw0ujuntqm8asaqh99sza npub1wh30wunfpkezx5s7edqu9g0s0raeetf5dgthzm0zw7sk8wqygmjqqfljgh npub1kqd90mglkp0ltmc5eacd0claqvnayaklkvzkdhx7x84w9uavplxszvrlwd npub1ly9cmpxs5kyrhnc946rlxmyj397pvcp3606zgvh3kvukmqveaxmqgwdwct npub1papvv8nyg68m73wae3u25lvxw5wfz2htpzk7j85z8yng3xqqvntqc5n9vf npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 npub16y2de3wvy2xgj3238r8h8g96hwtqsfm72sxcfw2t4c5xfjwnm4ms5y8uyd npub1ln4q6lzdwzxnvuv0a2gnfcxrfhwyfpcrp8tj5a403mwptq8r8clsq2znta npub1e0jya9z5wu68dzgxqeg7gal9ytgwvr63evtchv4a4wr8u5dcvs6s6vfwgm npub158dcjddhtq29ezyd3j5qyc70xyzyzujg02kcrla706fs52zcahaszql9ha npub1gayzxecnek73hm695d8tu94n2q3xnlucu9gwr2zqnql090rkautqq7ne7s npub1hvtyspm7n7nea59lhe2fdvwd0rqw7de20fl365wklsg4jsmrpwrqe6yaeh npub1hsr44v6satu5qkjcua36u8a8ng7fhh9ljv8mmnhvkf0a6407nhtq2k4ths npub18s8ym4ajt3rfwa0yn39m70k603j8a7wkhylhewzcjhtfheu8dnrqzwv677 npub1zdwjkqtwkst8y3mjj848hjh7tuqwqp7uvcfxzrl43gyx2k7pkz2s4p88cz npub1xq0pc34qq99yawjxl7rsqx7wgs4x3088tkwwle5kz3jqwf0ggyuqxx5et7 npub1dgx9jmq5sn4w96qnrgps7f5egjfpu5npnswazsaq98ryafkdjucshaaej8 npub1s6ms8dqxc4s2e6yawg20lkrpk9dxazz9qsaernpxndc2axua26rsva6lha npub19rxp2h2c96h9y79nhsu8p9yn4f79k8q76z40v8x6g0j8mcmex7jsu4whlq npub1fnvuz4rad0sc6ueflq33kj242hqe65da40zug7u5nryvjdeg0xqsl4y86t npub1e2d8f64kaxepfqncve7gy72vam3h66vmfwaqnalekv8zmh3qar4sz34p0k npub1krahyq9me8aglq54cfffylgnj0sy0q02emv9zr4csc94kz3qajxsmwu7lj npub1qn8rpsky3t8v5dn30rycfwpktwclm544nlef98tg23drgk022a4qtzekjd npub14p529xk3dmtyqp25slasulxx5p6yu2js6lz0072qu77c54cz6pesq2qsuv npub1mxlypddvhxdatdjdh2twejz7d8lkf90350f2zhzcunhmu7pgw9yq9033ss npub18lav8fkgt8424rxamvk8qq4xuy9n8mltjtgztv2w44hc5tt9vets0hcfsz npub160mrpl505fmse22eue6v23k4u4z0yyw37hpf3j73z97jtq50rapqx9q0ac npub1ve32zawsazgn9ukyr0trw4u5zk5z9ravgq9g06ml4gfzuvuzrvyq2mfzr3 npub1c0dysexhhd09e65rvmeecx0dpn6c7lq4yp99f3h4ktnr4vvrez5ql3h0y0 npub1758748kzgkp5vrt2u8vdgx462kt9f5p2x84xwljm4svadq9xc84sl9yk27 npub1rg7x6lh3zurejwnhxljdh8td2uhnhucx3jhle565eh7x94aqn03qrwrm9s npub14nefrmsdvn72qq5f3zqpdsh068ufk02e3t79ukga457p0v796chq7xrakx npub1l04nl239dn9wps24a753xq38h3wtlaa7vxmqatf9y0g6vzae6u0s27vwl8 npub1mezldzxnv6lszd7vlh60k0cqgxca7s08x5akyvln9fhz58jyfzsscyepuv npub1a76u90rr5tfdn9vf3sg574g0vftz4p5vu5r9t57c9atpwt64jkps0h4qya npub18g9zwmrdjcf6mkz7zpavmcx46r3h9ydxv2urwc9kqvha7vzght6swffxry npub12y8v5es4g8ynms5495l448977l25puf39wj9has66f7yg8xkhakqn89g0n npub1gustav0kvwh9zlz22ns7y6utwt3s2747mh5s6ja7v622tl09megq9heczp npub1t62k7smt3nad7s3rzhkrcvzlmheerk8p3qrpjwj32c9lzfmz5ksqaegpck npub1cuvc5stpvpeljeveqlk9u6tp3z3qams2w9r3s72hy0ufxudlz4fqu3x5jv npub1g8henaumhfjngrkpp7g7urz420hdzcx2hnh9grf2r7g3sxtur6es8uucpq npub187c8yedmqmss7fxtzqya4vphfkazl04lvrz7cp5xghhwzjduc4rqkcwd0t npub1vg9lk42rxugcdd4n667uy8gmvgfjp530n2307q9s93xuce3r7vzsel8885 npub1nkl720g0fuvzt4dqm5xxjet2lnm95z5fv4k3jvgz5jhnvhe2lehs98d9kr npub1l74p0yq6uzce4v4ntvvj9zcx03rc75g8gn0ajsccxzwyunv9m6tqwjlh45 npub1tl2pwveluev0jcmm973x87qt0uy20hxnyrcwefxv3nkv9kpxmzgs5pl9th npub18zhn7vrv94vy26vsf677uyxxvs29t2da492xs3xnxl45sszvh5psw9vpuv npub18z4uprsemsf4tcxdnfc8q2esk36g5rleqp6mw9ealtn2kmv8pxjswswrvz npub1wl8u4wfqsdz5m9ey0vvzh4y05mcpk2lm2xhhpw3uzs3878c2mw9sr2ksxk npub1ejp9v82302mth0k3nlanyh4zm4tskvg9yk2hp5fjun0g7uc47n0s0q07vf npub103wzz5eeegcwzrchje02m4rcxqxqtz2rauefhdshmtzd9xjxxdnqm5kd9u npub1k9mx4t56d6jsm658mmnwv7uvxl9edflkelpu4llgwrlc220d9qlqcyhueq npub10x8de2sz6apxnju8wwtqx00sjkeqj22kcjjfajsa9hj77492hkhs4g287f npub1q24ugzmm8ptkyq3gwukkl680kyftmlk3cmqu49x7yy4zuv94a3cqlhw8ld npub13xd3wejhu3xy5hmzgd0ymc9apee7ett6my4xsug5ya0z2f650n4qaf9f8z npub1vxd0dfst8ljvwva2egrpc53ve8ru78v8aaxfpravchkexmfmmu3sqnrs50 npub1nnyqvvr992hn3umzgehppzt49vhm9u4vet9zhzks4wq2a34ehv6qm6wkx8 npub1467z25r4x9xj6xgrgsk6a9gytdy0qp8xuupplxyunzfp5esk2uys4gm0a7 npub1w48530djsgja5d63k27mr8krx3xg63qvrjhczfwqgtmml4kgxw3qpcfwvj npub1ymldfnyvl2u5efjkdlqhpjruhv345qtesj9jf22paxmgj50nfxes3k4wqd npub1mqn5acr09lls33wapadkdf27t9v87h22jf53c473wzpkgld6z7hs72mwzd npub1y7yvamgvwdt6h8skh5yf5phn25yt7c6qcpclgpd0nglsy3f5uu2qu47fad npub1q5jxvccuds9wmpqhr7p770y4ewqcfr2dehqarm5alhm4hpgvrj6qtm2qhm npub17nd4yu9anyd3004pumgrtazaacujjxwzj36thtqsxskjy0r5urgqf6950x npub1k2teldhmj7d53732ekcs5ta0qpjsj9fhwc2e5ve5wljqpxht5mfstxx3qw npub1cn4t4cd78nm900qc2hhqte5aa8c9njm6qkfzw95tszufwcwtcnsq7g3vle npub12xm5ax6rqp3n9n0lwlja22lpfuwc6g63a76p5kdxuszqnn4ut2ssj2k7jn npub170d8w0jjdcjuh70lq5ppr0pcy7cfuxj6hpr00tm4et3v53j8pvrqj0chu7 npub1fs3n5u75kmtfgzzuy5ms5qexchv7kz3altj7e2uzl79ygf2nn0nsv2sdjg npub1y8hsmp2pxadwf09g22zsjla6xu8hu4qttgcwte6kwrqkv70e69zqvtfqyr npub1rtjk5n3cgdepj95wylpy4h6etg2jel3erpn8px9wxys8tuueeeushu5jyg npub1m0lr5fdjrhhwxl7dev4h7c5yvruz2vp949tun5zmulxuktcm0fusy0gg5r npub1ur6emzgy0wrg5xyvtm7khy7a3sttv4jrhpcc3px6mp2z8pkxphwsyy6kg3 npub1efyfeevwrtxnmncs8767p66wxwulm0wd85cszksw6n6uw2qtca6qzfvgyx npub154efugcrxmttmnp5cfxpnhgwglvxswsxh6d84jcj0a865a7s4jgsrrun7f npub16erzcypvccc08a6z6l6gw830zj7m743ah3gtc85rcjhfqmqjccksce7jej npub1jpxn8d3x0p8cdxvxzafpcpqwsfnvgntywhgne9w085fzu2mjjw7qldgdg0 npub165llzjv9ux2s3ezx5k6l4mzhvly9n8gyzhx5p7v4499heee4w4fsvhnu5w npub1mcgm982av268z989lv9h23f0w733wxecqhjjw5l4dvzdjgl0gu8sdss2v5 npub1z3adf0m2c2mul0vtpru4f5uzghn746xyf2udxv63de2ckcmg697qqmjnvn npub1520n32u3r68qtlw5nykxegtxkdt09rpk7h52laectc4qvdcde34s2u9qsw npub122fgydglyvhzr753e0l6k092x8h5k4ev0g9v90lpgje597srk6gs420cc3 npub1xngvle6vzkusezsxs35kgulf6s0usjxej3qvs4kczezy6q0war5sxmumdn npub16umw99z8jm5r55neprqmvlrsqzwklernxnczam2xu5q5fwjaj2kqttgcvd npub12aa8fnjcp84epqtmhtnc4w2fah9tfyrews76nd8hqltpedf4l75s5x6lg8 npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju npub1l8qw5av3039qhefprytlm7fg8kyyc0luy8yk2prk2l8wc38gf86qzw7nnm npub1nwrrty92erpe8th9wv4u9l9f20pqqh872kwjmejc6mu9hfnzumfqk5fua4 npub13qhkp54f8w0vgql3lqukvk9pduhef099hx0azmzupuhxevjayy9qsfg266 npub12jyfh0sy02ku5p3zg6hhfvph4zphl3y5jqfk9skaqa59z7pmfh0qqyn9mn npub1t8pha5vxkct4mlhskzz4pshvwznsma5646nmzz5gcth06mth0hfsuleyrc npub17ptx9z8mnyw2vd8as0nyh40gtvyydufme8peweh72ax9kpxrqzxqmnsxpq npub1lzh4pgufkx4xq675fujac9mmxs5zmf8ffucetgp02vep5eae3acqwez9kx npub1gnrfjvjmu3jucpmkvj6ptmdxcj766hwcrekjeuzlwtcqrqmyszvs3pr7lj npub1gazxqfx8ldqkgaldz3hlwed2h3nwzfmwavkxp3s9j36qhfzeladsmfe0a3 npub1xc5c7srsajcem7s8x0sndqsu6yqe36xzu2kdnu0cky353x6tkreqx4lsgg npub17kytlyvd28tvpz9u8z2mrr3pq503pmvtv46qskjccfch9vwqhadsregenj npub1vcq8nv3lctr8ctk2dp7h3e0su4f7gklgx4dlm2375l6u69hvuh6syj3d9l npub1v6xa5avwqkyqwzmfhu0ul4cm892txq4jnxmxsvgt5pnralqj9upsnmsnu4 npub1m986jhedeq7xxe8ukxc3dqwqzcz0ue9fra6m0t2zpvp8yezkeexscz7ena npub1yftkt6shs2fls0djxzww2nc7t96x6uxq490qw860ssfda755pc0q6emnz3 npub1rl5s8caaq8vsjfhxnmmmguxryug2f2has0kg5gzedepzle8quncqn9patu npub1ucsl4dgwslalsgje4es7jefqexlsf678wrhvu8q59e3djzgl7krqf2hnad npub1hvzkl03x7z8fews3cc5h99mxtze83rwxunre2687hcdy0zqn0cssnszrkx npub1q884swxynxp5dt467g0v3gk6t89tgd3r90pgdwcvxtlnjf2l3jtswgwvcc npub169jj88ry88e7f6cmcngcz8mu67ak6q6u2pgtcae6wa4ju00z8gts8hac60 npub1ahfkmjuzqcngqule5c4eq3cucxd65dpkp0sguzzsr2duxwlx9guq86x8en npub14xcy30kssvtpj29f40rk2kk5d2heumaxnz77ahkuejwepqngy9nsewgz0e npub13jpmntdr2k04x76f0c76syf3za42esn2nnd6kumc2cwyltmtje0se6mvqj npub1us9tzl0zc0ggfqw6348wyctck7mmh34w0hpn2rs236akusx7ltjq5s8gtq npub1eykpylvevzagq8jm8jutf2pmjnnelmyuc56a66v9g7ttcth5kfsq6vllrz npub14r294afl5jqgvj4hlfpj3dvyxenxh4vuhepn68zdurcas5r5xy2q5ydufe npub14n46ruge3mmv72xeyjw5zl4cec6dykrme78plmm0zmpnclcptqzq7kct5u npub1yvw87p6d2rmd3lqdp3c6npjhunpra9huxnl8c30rxjw8tnwd292s3jusa9 npub10agmu2vwed988jdxs8cewppw5jvk0xtvh9vdyguttuhugu930fdsdcsdp4 npub1gyu3h0kmqmecf6044q5r88vu5vtf5u6rekh9yazxrtejfexct0lq5zpudc npub1kstv7m2flm703dmufltz4l4lkm3pptl0zdqjvkx8ap3aagttkd4s8d5pa8 npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk npub1mlf37lk424pxrstpdhxqp04v637kjyashaj4ea73gfz86yr4gdzq3mjtav npub177xlld4katf3aardam7qpu88l0ttvyde739qcvjdjynweqnncuqqvxmfdc npub1ykfmyfwtanmhvp06wn3ggwm0gl0v5v2ftmnkmhz6swl2x4ur9udq7ld2fy npub1a5pl548ps6qdkpzpmlgkhnmh2hpntpk2gk3nee08e5spp5wzr3qqk7glwn npub19gskj4eqgjgjrwjw5zhu9rddnrqfq59slm5fa5a9crun9wm2qlyqccyh6h npub1ujxurwzpfrxsprf0urqfxpp0qpm2yrpneat4udg7e0v560nzw3asml0d9z npub1ep6wcd256kvsdxey2ylycrpvmf9wnsqvg46kzqrhuw2akxj020kqvkq9hc npub1pumdyz7qfu0suamv4nrl0vcg574dtl5mwazva6nyjxhpwc4ccxxqca3ane npub147d47sem878zwqln7k9y8y3273v29ase4r7lk5yeta62xk3t739qu5n8zd npub18jzu9qrrmhhwk57zqhfffymy7hq8vrncxnvl0sutu5y2lhr456sssgsesp npub1wmnvcv3ycqmtfsysmrnkyckja8dc9nt5sgf60rrel339v8chtgnq4p5w26 npub1tc07sk67d2rs8x90fpg9x727ulzknw7xjyk4lds7pkzauw2tqntqpzs9dq npub15h8pr8t0l6ya275k42cwwhrfu6z6vk6qydkdn55p6wn4f424s2qsasdczc npub1l0j7srkgmdwy8839st2hn8f9utlgh9vtrm04jksh8tsu32h5vpms9k7zqa npub1p9auvqfn3dtrjnwkhxdvvk6xn3tt8aa2uv4dh2af42nv9z8nh0msrjvmhp npub1lnjp9d8xz5zguufe257vtx59kgjuxxufv0fjnplwcfncvpc7vahscraxv3 npub1mhp87q9axdlwh9ac3p7drg9z764mxwe27xvxm7x704l9dykfy9xqrgmxdq npub1253ehcqxctt4ps8kjfmhqje965v8gtzn7c6gtq02c3kqvtxmsx4qv9my05 npub1gk0yyk54t6ptq5m7hygy8rvc98pq9zz5uhusz9ht6yxcpmvsr59qg5ptts npub1828ey4s37t3dlwjmgsa05zafvdlsfsa3lu5vlk5cdx0a3zppv7nq987tnk npub1h6h3jwx3fvz9sanmg5yx6rutmggsnz5t09t795yf4jk4dqsfyq3q47kcxr npub1cw2epa68jpmy384t7vn0suvd3mxnk5s02ap6fcwg0x6jqy4lhdpsfg84uq npub172g2zwq6vkerg02urweyt2daa0huavn6ghcr4gxt93lmhvnzan0snuwkc7 npub1awwrv77yu0x9rvuaq55ppntc52rhxt0w9t32zkyw2jszvmgsqnkq2f3lpm npub12p25mnqkunnhup0sk6ky0vvtq5pnkapezx8kh689dv2vl2wnp2vquyfw5s npub106yj5wlntf5els6w5cw3gwmsgh4yu7vs0lrpw4c0uzkq3rqmkkgqg7rgpe npub1a4u7yc39v6fvr48a3skz9gwdzl76hf499mk96x703nzc23mdqq2qe84e0k npub1fc72tcwhr5fhcmcczzld6femwd7d7uhqwjw8rp5w9enxj52xjqxsmpgv04 npub14h5r077z3edgts6wl2me5vk52x5se6nnhry0ldfzua872ggcxw9slkd3fd npub1xlngepdt5qz752x9423gnvj2gk92j55qsdhm7mrtmju7x36pwnxqg4sypx npub1rl9wszqmsqduzjagewq302qfadjy4mt5vw5zvm8xdamvp3d0nm3sr88s7e npub1ayvrrlpygam2ruyx2lhtkvgjc53wjd3vvvs0ysjqh3pwhryaju7qd60eq3 npub143mkh6lvtrha7w7pjw32ujkljc9ell9wpyvd707nahqy0rt62kws4wlyhl npub157rwfe8a4gffdcx5ca56q2qsvpp3z757674lkwca5ud9j9pdcnaqct6p2h npub12z3w5jynqn3pjt73kqz6wkueygrvt57qfwgxy5u5pmn0uqutdwdq5jpd8w npub1zfrc4u0dnph8flpqar5r5lv3gpn7qafhlh35zpcm8e6ex4k24snqhx69js npub1rvww8nakj7rgz59jdqlswdmvjn0cd46q2h4y00wuaquwyn383fysxlpyxt npub12knmfzy88xpc4dhuly50tlhcnar07c4pd3w9pfpd4lnssmwhvtrsgq2ez4 npub1705am22u3tep8vvdwkqex0jm9pazhmqqyxvaqzcnv76m53xed0xqeetuva npub1q0k8epddegnec4kj0j3rew9yel0jsrp82sd2new0zy3m9pcfgqas4r5yp7 npub1fcj3en06ajdm09y3twytsrnd9n7yqayt9e9xuutqdrwnqu85t6nqt7rz5p npub1jvej78jr00s94gdyct9md9x2ljtjr0jhej5c4mm7cejp39dwgu6slkmju6 npub1mp0jgd4gaj5hhw99lfwxufl0k50m398jcneqsp940sjzz32skmzqw5uuat npub13u8pyc0azav54a9gg0py5khrmd8er6ac55kvag72h43r4q8s7nnqsqsy4t npub1ajan43fcllaxc589juls8pef90cgdya0p0en38h55fal42nlgkrsvltfdv npub1pvn0tyrrrv86xpydzq6ppeyyuh3zut263m82emdfmydn37qa6x5qmh8khc npub1pfx4fj43y5j27ywgj02axnyup0eujtk3g6r4ug2n4nvfsa2kpl0qwvtah5 npub1rpx2y7u00jmsvwt8zlkztajmk3e5se89vhnswsz4suuyg4a3fx2ses6lkk npub10jhpwcdsc6mrfs8audcdds2x5txdagru9835f3drthzaumxurduq6esrnm npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r npub1yrffsyxk5hujkpz6mcpwhwkujqmdwswvdp4sqs2ug26zxmly45hsfpn8p0 npub10ua5vjul7d3rvvzg2psvhk36w7gpx8zn8xncqw773l4hnf0pkp4qccymjg npub14fzrwpygf69t0e9snrk2ms7ltn8u4dnvunl6d98zkrgdzf256exqa3j6rj npub1x8vkne5rx99wzup65m7gpmhmgsa80d3dscp8hafrwj70zxzkyexqttjd5x npub1643y7m94wwu30awq5djh7lkqj48evpz944yetgzhssmykkh93zlsz22hhs npub15pkupvdv7hmcjumlrx5yjmcwy2f9fl9fmsa9mx7qjlau8k59rxusq2v0ny npub15wnjy9pfx5xm9w2mjqezyhdgthw3ty4ydmnnamtmhvfmzl9x8css6kt8fs npub1saygqd4rdf8edlm3r45cexr97zndj3254lxyz9dejjlztscvndcqhcky0f npub14neap59th00w9keu9uffpal72dxyex5u7vc8pwsuqrdxes2mkrascnlukg npub1nyzep3atafwfrnq7346dmx7kjhqsrza936rnvnlkv25fzd09gxpqw3gg6v npub1chgzxyqjnvv7ryuf095cswtym37jummaqme42dfez8q25h4l734s9xdl08 npub1gp0cpreej8amtmmd4zn72hvgr4d4tgdhg3vpe0m4yxzqz7skg5eq47jmuc npub10gp3mv09aet40plum7f4pllyc8g8u4thq8mkkwymdcct3schagvq6fuh49 npub143jqpdq583jd7t4ucfkr9wzug9h3904vcng0vymyley0dx43vv8ssk2gc7 npub1z8y57drslgthaefkvya7kmqcdm9c20uutz336j9hp4frkrg32nwq9g4ju8 npub12er2cnsfzc3d5ceggpjazwx9a5cwna4atxslkwe8975lp3fuy6gs6s36tk npub1cpxjrlnhfmcclcsly5c0dvrgvl5nsctzxpp4s9f2nh4qeq50mwsq4089fc npub17dhclpvjmlkhlgkh04sc2296wj0veae79fq8dkwr5efvlz6vt79qgyqztn npub1gm7vxd6yjqsjx49ddqgyflllpjuhduqch79jlp07upsh3uf6q47qsm4xlv npub1d8h26etwdx6ws4afflra7reqwtvjsm7u8zn7jz0w5q0ah4tgx3rsga3axt npub18trgdajss33u25jvk0g2yv6lxr7s7k2dlkkku6eqq7m4hrc6aazshusdhj npub17s290m08ukaz9j3nhyuj5w2zyxtdzdqvrvsgv65c7ckcxshjrxrs6wnfhy npub1jlu3zyj7f2hacdrrmy7jpny9f7nnvuxt2flrasjtmgut90502xqqtsx4rf npub1vwcy6na4rcx6r43fqyxkhzzdvqufctnx06ywvrnajmq9p3mu27yqxy04ch npub1ea35pc7pqg2uvstspd0ljlu09t580qc942n5eevvmkrv6huchffspl8087 npub1jxl2tnvnv9gycsy64aze295c3a529lx5sfmzlktf5lxuw805g5wqew0z0n npub1l885a986vy3sj3watelhdwea74jxhy8688ju4h2c8wz2e94tcd2sl7qjy9 npub1uy7tnhwxsr0tc8eexksandgcct5wtua2xazvl2gfyy5n86p9sdvq7nwdzc npub12wm6zfgan2v2jc5tknkjsj9d64qfk6y4ggu32f9tgnu0mpuz26uqctkvly npub19hvj2zeg7ck8cj2p2az5y0gplllhgzzdu0khu5fhnpfmum5jspeqqcdjej npub1cqykgt4enf0ce9v36kjzugx94l6tp8dd5k8ktfgga9ahgs2mzess82r6sm npub1th77tvx7c3l9qgxql4grcllh9qahyfvz65ruplrf6kh0sfzuya0stmendl npub1w98zr2sevkqle6lmt7u503ewclhzs2cdq94ke4mw7kmpxy2u9y5s6fe9yy npub1c999aq8sl4fmw8an6hfj5lfhuneqc35seffqs6938hxajr2jq6rquyvp6l npub13tnrml3s46xswsk8l2p4tv8cdmnpkvrk4p32828jwce7puefc0kq8jlf2d npub126v86pztd6emjtkwxe8jj8sa8f0m9wcavsd4j0raemdxksegfg3qfaan6r npub1uz9f979gqjj0ymul0kqq79g8gtelwe6rs276jm7qnaffmn545h7suw6nhl npub165h57grx6hjw0grfcw805srfxl53ggcsl3mmhagmp7rg8x80ehasytgw9y npub1re764kr23sa6d2ld6fhukthcwgnwvsrahe92zq42kpdu3lm05sjqwjchtt npub1m0l0harjth9sses5h0r2slf7l4wws4clgt88s6n23ct2kd2xdkusf8nqjj npub1a8w23gjnfv0f0qzjpfeqg7yc5ddf4c8m8jks50l84lrv7h52jhgqq734am npub178p8fw0spjry5824n5wv96rfre8lq4r30ysyctfspzy97n3tl0nqcg5hzj npub1yhyc5znlka36gx496q2lmqhyttlef7lpkx790vjmsh2xfacdeu6q9zu2sd npub1h7mp8nd39hzxywqdl28rm2du9j2jhcarmsmakmulm6z7fc4lx6eqqaxh7q npub1dvqg5278etemtvxl59ahcey8cywrcl0krhpu8dt9s70mgwjar3jsqh5ywp npub1dpm87jq8zpgrvq2thr80chmjjrj0tww7q3hx9kq7wpzq2aayqxdq9a76um npub1l506tlst4adydg0tkshynjw6dsk5ukjvpzr67y9vas8v3nzxylssq6p0j5 npub1pe493zu4ax53pthcsfff7uehwppc9w6peashtyu972ey2szdeheqxcfk5k npub1kuxfh7e9fds89qzzzfjrh6c80d46jstqnm2q29wekyykr4mk0zvss3yn27 npub1gwx22vu2yzm8eq95nvvmgvpax04u96gq4r8rgqqf9pgsheu2lz4q429cus npub1n8ahhlw8trcpwkqdcetl5pgqvrxcfvgrtj037zlflrnqymq5f40qhnwpd9 npub1ujr9zwz8h7xtkvp4pn6aslguqvks43h8ej2z2g86snff0h4xxmuqjzcwy7 npub1vm4s0uqkydaqzt44dyt38p5spltl6637sxrfxswmr6k883f5a0ds8taxyl npub1zqvtnvxrdpg5vwh5alpx0m567092m2ltynqxlk004976tgc6syqsg9rcv4 npub1ld5xqfflwy6txghaaef2d4rnyzkvwvz2crncmtvhq93xxsqvzqtqzdx4yp npub1er2xa679095y03xlcmycgg4r93nluqpluye44h0ndxdy6k5uxcdsqwtqkf npub16jde9ylpry7pyau6svgqktdes242ynfk9snfafh8gq3r3fj5xfus44xm32 npub1zqgjtt2ayahsuxzp3cg7h8qwt6ev7phz9x02ktc0gdlwz70n23nsla0sph npub1h9c96qqmcupyvtq30d0xvp97h2cx966gz8n55cqgd24hgzvz047s6hxyd4 npub1h955atshn3faxg5r40p4achtxg3q832h0agjn24sf63tnkg5ezfq0fnr0n npub1ker60jkxmxjmft468v5wzth5757v2end6wzd4xn67jyej8taj4zsyp7tqy npub1ddjzjva20mwp9xals7v0nh3devvjewevkkrqrsglyhnwa59ctswq6kzdys npub1wtvrnst9hus9pvz3m95pusfjzq4z5zly3w4lehulh6xc8dajl60qsrjg5a npub1hl07ukzg0xk7gj6ejr5k5e6gmakt9tnu5r07f543ce6e7sa7dc0qv0kcun npub16dana9qsfpf48ccyqwvl8jlw6k5u8adly9ph76z0ftrs88lf7vtsrzlu5s npub1fyd0awkakq4aap70ual7mtlszjle9krffgwnsrkyua2frzmysd8qjj8gvg npub1saessfmtu5xwnwh60e0rwnj0e067npv6yxgc7d96algqqart056s5gkuqh npub1lylzl87mst3swjtj97j8aajyfmaqctaylgw9et5agyp3rl42y5as87k86d npub1z324cpkjv9ay5fanw7rex5847dy7h3ndvaej2hy2vmc7r8c35res3x2kje npub13zlwh0n00pja6dkw6htamu6sl8668hpgr45y5lnmnmvt92g3laysqqsatw npub1u2ukfds6k42qwufd9xd5l535lxt3g2zet9rmmlhagtjxg6t8e6asmx0w6c npub1ezeah83hkpsguazn70rmkmfwh864wdejv7h7q7tsuq46wquelelqu8fr7h npub1pvuu3ms6vlu7lmysggjuuz6ctsuyjdmy3uhlywg7jxdewvtr7rgqakhnsl npub1vny9x6jl2cmvhva8m9gq05z0vf2tar3vy72503hvuru0pxtnz2vq9v0fyg npub1s9s55cwl2m6cd5czukune4y02gecrn7m2tukj8zt4epheaqlk7wqsd753t npub1qvwpwvdvq4hckarg9ekldnvzza0shka85fk24uuh606vhg4l2grsuw808l npub15ksrns0fw4l8heral0hst3szmvpka67a94xxjcm3ddlpx7hcn7eqhwfkrd npub1zkrdvkmnx0sv7d8hyd0ma22lfvvphhd33d0qs3sg7lrtrv0xdv9sa7gy52 npub1nknxhegrddacazt8sax6cr2h0r9sht6ajmq3s82vjhg54ey2rfhsumhe3c npub107swly8y0ert2upsevqk8fqw9tvacfvuygw55qcv4s2eav6f0axslhmymt npub1a9a2l7jqqxa9mwrw034lcnuhcsncg905sl03ava49md55t4awewsvvzz87 npub1yudjcmkasasju6znprl3rpyp39xa3uk4g6sfrv3wxestqsehs3eq7z5f8r npub1cy3a6gug0t4jrl8plq393cjjxwtg6cewcuek0n0hkww4h567dnts0ft0dy npub19jxz6jynvhlwzmfyhmn5tzymdff0zuq8jkg2mq268a5045f6favswaxu2q npub1uvx00x8svjwma2zhddwpthyke6zc3rrxqg5gj8mxdjv77zvwmz2qgw603z npub1ewe3r7x8qemdh7v30gndpamgrmu0k6nu4twyt62r6ukvkvmpgkls24272j npub1deexjnst5g52wh9kmqr4hy3wzhh0gspujs2nc6m0l892rzj788uq5gcpq2 npub16qsq63pgxyw5vz6847y9w4cau0fmvhykw7uy04p50u5muulc6kwqn706mz npub12cfje6nl2nuxplcqfvhg7ljt89fmpj0n0fd24zxsukja5qm9wmtqd7y76c npub1nu0yladm9rr6wsz8w3v995gcxl88vqcdnp8uv3zp3xk978d3658s8kvmhm npub1dn5cj3n85c085yqry7wle93uhrqtkf9m2zwqgt8c233js0lt9ugsdr7zzt npub1vudm0xsx4cv3zkvvq7k5836tnkv64q0h7uudnwujr4a4l9zc2p9s0x8url npub12c68tkshmelhtrd7ye5fqg3gwttd33ly7gzxkwh2u4qt008nu7gstf7x0p npub1dc9p7jzjhj86g2uqgltq4qvnpkyfqn9r72kdlddcgyat3j05gnjsgjc8rz npub1dmqa9kg8nke7fc88p760zd8crrqupl4w5lflhgs0jgh4n3slmdjsql67zc npub13q2vzsfemle9cpxj875tz0vcwqe6r8sy05fd62jcd3xuxjeqj6ksze4xl8 npub16merj2xt59t43djfx8vf4fzhc6nd4v9hlsv8ej8xfl3327yr3vzqu8zjt4 npub15dqlghlewk84wz3pkqqvzl2w2w36f97g89ljds8x6c094nlu02vqjllm5m npub1kqnfgpzt3jxh69ma394r0azyurd6h3dehpw7lzvl0vv3n7kv4a0s3305z2 npub1g6jjgu06nctv74e96u84jux6vxm3ezncjh7tyquvm66jug02xvzqmqu08l npub1efk5xdyrs6e4lqfm7crut2ssdnhu54d9egswq6smt62v0llj37vsprp0r9 npub1j2gc7kt42rwf5q37dmm2k29rqxscdqt2vyfn0xgju32v329jfpdqmkq0xk npub15lymwv6mdpdc3j8zxf3qzq33j2lyntst9v83ukqpa0tzkdtae28sgef05j npub189ts86gs5xw5w2mcz0na5vkz4cseam7jnkjwwqswrj56v9x776lshjqa8m npub1cgf0yeja9tlkfq248l09hkf4kfjfyaup50laen46ucv8gf0puy0qlpxlh5 npub15r0z9mrt0nxzq5fzxysqusm32r9krljq8gh55xnavdyllk6gdxjsj36uc5 npub1qa0lj0jktem67zaazrvpgrf23qdcj3cw9u6j5ct55mg447tqnftshv420v npub1yxfjljjd3apsrvzlkww525jfvdsvuwcs3n23wpmy2txtsppzvmtsgxur33 npub1gv8juwhat4xkl734q684n6vvv8sn5k2dvm8a0wnckyw50zajdvhse8rd3j npub14tj8zkwatnjq4rlnruj53676thre3uss9tg8e23a6w4ewuzus60qe4qg6r npub1ylf8w68g5dkfqwjpdvsy42d2cwqnajswrhz323chsc7gnz400chqfmzdm5 npub1rhgqj4urjf5uw9y3npnvvst2hhmcdqghd26fzwgc4s5ptkq24d4s2525ja npub1lzmdnlsaysc5m040q5q8nlgmquldtxzgllegsg6z2n0engaxwp8szsswed npub1vr3860267yxktugg5q034j9xh3xjaxnlawvas6wqa5kw6zxhgcdq6u2yzr npub1q6ygq585gcs2m6egv67yv3a036jhry8zu93wk2uk68e3smdafl5q4sl54r npub1vy0g338hw6w6rn2fsv5s92nx47u6gle8v50ypxwj6k2hsj9p344s95e8r5 npub14k0ws2m8f5jfrae4a7smtmwgx0quhhl58z4rpd8hs9ar8mlx78ys0seswh npub1qahmtyz5pr385kqmvxqf0a4004cx6ncvnj2829rvjf0rs5ujanhs2ssgvv npub18wamvs6p7dslshavd24kv2gy72e5jck9lgm3f3e3f8udja3ramcqvrzg6q npub1njtezc8lznuj5ws6yvz6x324lzn2ct907s8vlwnxqph30m0gqd0qvpvr07 npub1vgppgksgzs7je6xueqqvkpn4gqmcn3nl96famz34zfhqzq286mdqqmecmx npub1w6nj3y6wsv9kfjev4jjdghsg9ajcjq2gtec4qfpmgcmkzljl4yps8r0gwq npub10l6udyczpjzg4wcer9mje4zkcf2hhus8cswhycwaxfanepc7fz6s0q7u4a npub1cwevvvcurkfg5wjtnftret2j7ldv4lg3x35sty0pm546p6jx0g8q9fa055 npub1v5t0xmnrcap5rah8cm8mrqkp0rmuv4mslrlm3ldwkr39fzy56mas7wvr3f npub1w2vm583yvalnc02ngh6rxhn4ekp8m0xysmrzr6s7ufdwmu9r9qxsqdg0ng npub14va2v0yaprmt0nn0qk7ga6jujfk6pdrfwv0kxj76a5ymp8dfdy2s5ehfdd npub1ztdt0nvu8324tg40g4ts8d6englps8w6574zyq2gkdvcrx364y0qd9x9za npub15qskvuagmaznzc3pea7vxh0890ycfzxxdx537gef5wl6cunan3tsdkld4r npub10vmwytmy0pypy2c0f5zen8auvl7ku5dnk53vaw3ddplw2fl9r9wq4hmr5r npub1crqgm8qg9kplm9rlwfj7uxdzdtanq6rfu9unkt4ckd8r7fn7q36s0az8tt npub1x7fj44hzhjdcw2jwpylllpdgeh9yqqt7fg35ucfaywnw68tctv7qntw8qu npub1rj46xc5tssyk67ma9sslqqt90d597uuqx6v7tprv8alt9enk6v0qyvgn65 npub1y9a3x4e4zf6fu2w0cyyx9r2pmm6qtzrv4sallyznflamhplz3jyq0gq7gp npub1ukm78z9nzr0vnq7nqn8tvx95htttj2f48n99n9nqlky547rwzyrqk08am8 npub1p93m0semtesnsm2fjjd0p5kwl8gpwdqsnfq920zqyhfcc3j4nddsygyk5p npub1rgtl4ay7dcnud25enknv9230r3u5dmu3h3c7mj38jamrz4g3vf8qj5cszy npub19ajcupesc6zcpt0tlg6jv2l4w6wnpx985x735445fvla4w9zqqkss69s06 npub1kpyx8lxklwtd6n496rqgu8kq2k3yh2svlzr5sz3jlxlnphc6tcwq8kllrw npub1sg3qz6633ajzfg7w9ptmk0hf8ckl9jvv4zh6ttxt39jne36wnpnqyzk3vn npub1h5e0y6r2tagu4cygnfggzcfrt4afarvcvvcgqmpzyv605g4n89nqhlf2e2 npub1n6rffa4wqh3hcuurlf298dx8j59wxkmjth87adc7ektxnmpgxwgszk7scj npub17ml9y86nfg65h68pumfkclr3ay24pcfduu06j2jfp4pz2yjcpcjqv04fu3 npub1rkz86wjvey3vgdy2pau5ulpzdmxyzq4g8xp9cd3tu6kqmzpqcppseazx4s npub1c664gerrwlc3rlm6nnm73uc2kjyd0f7zaellshxyfdrludtmcf4q3adztu npub1zp0ys9ysfyrjvuxpwhvyevgphkmluynreun7fg2jeuu9xtsjwa4shlqhhn npub1fp0w2jd6e9l6pd3akr630d8gkcn39t2vep7u3ac5265fezu2fnvqjxpa2s npub1jz8k5nl4978lnhghlzeenp3nmfyvykqw5pjp620jj5qft8vqh44qp6pjk8 npub18vay956v7zs5qtgc65mvn54v96cuvqv6j9fmu4cgfjqkt5vjuvjsc47nzf npub1kgpnq8ycudaq8d7fym033hgdarz3ktvcws8nxt7p9rnfv98j7cdqftrga8 npub10wdzfpdpgyzxj8a4xtf5dux5z8065pan7xrcjh6gd6plj39qzycssepffr npub1ew3rlwvtmxw903gnqx92zar5dcyd47pjjure7ut2wngyz003ff8q0x0frx npub18urkgk8wrf0esedp8gy57670q5qxry22yce7rwrnvvrur736p3pspy6upf npub1pp8mxtdgamg65wfvrtp56v5lnyvv2kmx45cxd5m9dgcdjqqy5ysq5qasy3 npub1y5vlh9z98stts0rc5mlufellseuwjtyaa5jhewjqugnzdwt7yvgs0ydryw npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z npub1x0r5gflnk2mn6h3c70nvnywpy2j46gzqwg6k7uw6fxswyz0md9qqnhshtn npub1lc6c4ukssmuf678py7k6thmlk8c4a52l9zx4thec48ve2qmcdqys22jt95 npub1h28yvj0mj692wpwruqdhyjngcfh4la7gaygrent6a3wwqjxcah7qnt92e7 npub16g85fanyh8sq48yjfq0smqm297yw76yxlcdvjq7hkuvm7xjjhn5saads2f npub1xc2plng44tlj2smv65e53sf3uaqf56c5gajktyu8zxn2p70jrxcq230nt9 npub15l8sfm30uwns8qrcajs99narc4ex65ujt5sky4zx3dpjhnnk2szsqu40n5 npub126u9v4tqg79hxx569wyq207q68j4vn4yme8he007kqfg36va8r8s4qvqs4 npub1stv2q4hwrk6ggvw3hxju8hjakly4ev9wt5tn8gnl9cpaqt8799yqj58ygn npub18yffjalmcfn4x0x0jpj3xm8g6vdx8rp2jd4dhnpr7e3xpemxlmas9w0q8u npub1wmmlxqv8l6aks90jvnetvwkk2hqd7pmqzk8hq6v0tkjrpqdvm8tq0exs5c npub1z8v0x60ukxsk00zz5s2uqgvlg6p8dhunnz3fn6wtnw48xg7p3wvsgmnduu npub1vukz6scwfq55vqjpv3z52theg0lwkrz6kncwc3rfkczl3ukafsfqfnw368 npub1kujyqe2m5w9895kfx7agwjag0xperd0efnxzfellux0xuj5es28q09lucn npub1j3tn5wdn82tmlgvcmhtm0fwzqpwx86pdgr3538rh7asdvkas2ktsqlnxpf npub1g7tavhda0yc8857nj22feuytgxskg4dlpfyql6r2d99egajrss7ssq730z npub1fsyfqrleejgdmck8rxd64wkhdefjthu6lgm8eg99r9xxsl9hespsnmfhvv npub1mevkncsv484u9nue4apgl6ue2644x4m57y9cmztnvwpvs0tnduysg3vdsw npub1a2mj00469ng4xy87nucds99e7m5djh4pe3rpluvhcnaat48gpeysj0gy8v npub1ggfzdxa8xrrzhaut6venkrmjtw8wl25y6l0wramkc7d4dlyaflzsxxrfcq npub1f945c6sqw2d2aqktvjrjtu9uca9wdd6ua5e0a560jak90rr5ha0q3tj4cx npub1x3j34yuj6d9ln5ryuw0ncy97aa6ttc5wwyxqwvjrz7mg039t6l5qd4ewrm npub1d0jucp5jqt799kjuqxzs4cj377tew43dpcr60fzyvcltc5jemtcqryyvcy npub1m6keqpkqfp0uzxdzm2q0rdw6pzxuln98rzla0zzywwdzgcyw2rpq56p4d8 npub1p8ymvhgtsyhyqk4y35xlup20trde4pa69pxf45hdxc74zdkyhfvq3narwh npub17n7fe8p607xgzj2hzft5dsqvsus7mm3y0ceq0ta9a30s9akatq5sqh9y58 npub1he7j4yt7ad6kd07ynqk9qmhfqflw642qkjagqvn2eektqrl90fcs6dlraq npub1mryqu5cffjqpyykvmfjx3js8j0m0850v56dx24lhyqgf2uhl5npsk9xj7y npub17natddjkmse4z8frh7ysynwtzanzmvs9d76c5r53546wsnzs25gqfdeqey npub1ywcw97xsl93l0mqmdpshqx4yu507xqa8zy8p3l8vrkgkek90wm7qjhp74e npub1d9f66fpawpeyrdh9jkyccfdgut6u9ghufwly5gyttfy790mp88sqgx5v98 npub1cx5js2ma5gf7fqn7yv8sjtezvg3agfth7yyxhwywtqypkat493ksjm7yr8 npub1ykrmhyqc0mjhdf5mzuz37g3jkt5ma7v0uesmuyvhueaqs5ysfres02hqjd npub13k3ynlhc2ret9nvzamj4cgrnq9fx3uzyx8ral84tjtk5pmxqpcysdzrzgt npub1jdaa64eyuql4hd0244mp7z7n82egpmt2d79ny9avjufkpm5gz46shcdfng npub1ne99yarta29qxnsp0ssp6cpnnqmtwl8cvklenfcsg2fantuvf0zqmpxjxk npub1klwact0ar00r9uer7tzh2zq0ytx3f552tt8qavszdhvu6vpv3uzqwpkjqz npub124rja8qp7dartasr9wdh3kk78phxunzhmq8ar5ryd2anj2qwtcnsz3tuhs npub1c7kdmhhae7x40q8zq9eudgqm9wgz0q3av4nrgaqe2qqphqmqvczqhee447
-
 @ 8f69ac99:4f92f5fd
2025-02-20 15:24:24
@ 8f69ac99:4f92f5fd
2025-02-20 15:24:24Anarquia: uma palavra que frequentemente evoca imagens de caos e desordem, associada ao velho oeste sem lei ou a futuros distópicos onde impera a força bruta. No entanto, para aqueles que investigam mais a fundo, a anarquia revela-se como algo muito mais sofisticado—um sistema não definido pela ausência de regras, mas sim pela ausência de governantes (rules without rulers). Essa distinção fundamental é essencial para compreender um dos conceitos mais fascinantes e, ao mesmo tempo, mais difamados da sociedade.
A ideia de que anarquia significa desordem ou uma sociedade sem estrutura é um equívoco baseado no medo do desconhecido e na falta de compreensão dos seus princípios básicos. Na realidade, a anarquia assenta sobre um princípio fundamental: o Princípio da Não-Agressão (PNA). Este princípio estabelece que nenhum indivíduo tem o direito de iniciar o uso da força, coerção ou fraude contra os outros, sem o seu consentimento, sendo este um dos pilares fundamentais para a preservação da propriedade privada e das liberdades individuais.
Não se trata, portanto, de uma sociedade sem regras, mas sim de uma organização baseada em estruturas legais descentralizadas e orgânicas, como a lei natural e o direito consuetudinário, que emergem naturalmente através das interacções voluntárias entre indivíduos. A história demonstra que, mesmo na ausência de uma autoridade central, os seres humanos são perfeitamente capazes de criar ordens sociais complexas, baseadas na cooperação, na ajuda mútua e no progresso.
Este artigo explora como a anarquia funciona enquanto sistema de cooperação voluntária e direito natural, desafiando as concepções erradas que persistem sobre o tema e revelando o seu potencial para fortalecer a liberdade individual e a coesão social. Ao analisar as suas raízes filosóficas, o papel do Estado dentro de um enquadramento anarquista e os exemplos históricos que demonstram a capacidade da humanidade para se auto-organizar, procuramos iluminar um futuro onde a liberdade não seja apenas um sonho utópico, mas uma possibilidade concreta.
Principio da Não Agressão (PNA)
A base da anarquia assenta sobre um princípio inegociável: o Princípio da Não-Agressão. Este postulado não é apenas uma directriz moral, mas sim uma regra essencial de conduta, destinada a fomentar uma sociedade cooperativa e pacífica, onde os indivíduos vivem sem medo da coerção ou da violência.
A partir deste princípio, deriva-se naturalmente a propriedade privada, pois cada indivíduo tem o direito de usufruir e gerir os recursos que adquire sem recorrer à força contra terceiros. Da mesma forma, a violação deste princípio—seja através do roubo, homicídio ou qualquer tipo de agressão física ou psicológica, não consentida—é condenada de forma universal, pois representa um atentado contra a liberdade de cada um.
Num enquadramento anarquista, a ausência de uma estrutura coerciva não significa a ausência de ordem. Métodos como pressão social, ostracismo de infractores e mecanismos privados de justiça ajudam a manter a harmonia social. Por exemplo, em situações de litígio entre vizinhos sobre a posse de um terreno, em vez de recorrer ao Estado, poderiam simplesmente resolver a disputa através de um mediador comunitário ou de um serviço de arbitragem voluntário.
Ordem Sem Autoridade Central
A crença de que a lei e a ordem dependem de um poder centralizado ignora uma vasta tradição histórica de sistemas legais descentralizados que surgiram espontaneamente, sem intervenção estatal. A anarquia não significa ausência de normas, mas sim uma ordem espontânea baseada em leis naturais e consuetudinárias.
A lei natural consiste em princípios universais, reconhecidos pela razão, que não dependem da autoridade estatal. Já o direito consuetudinário assenta na tradição e nos precedentes, evoluindo conforme as necessidades das comunidades. Um excelente exemplo histórico é o código jurídico medieval islandês "Grágás", que regulava litígios e contratos através de mediação voluntária.
Sistemas baseados na reputação também são eficazes. No passado, comerciantes que desrespeitassem contratos viam-se rapidamente excluídos do mercado. Hoje, soluções descentralizadas como a arbitragem privada demonstram que contratos podem ser cumpridos sem necessidade de coerção estatal.
Anarquia como Estado Natural da Cooperação Humana
A cooperação voluntária está no cerne da natureza humana. A ideia de que é necessária uma autoridade central para garantir harmonia social desconsidera as inúmeras instâncias de colaboração espontânea ao longo da história.
O funcionamento dos mercados ilustra perfeitamente a anarquia em acção. Sem um governo a ditar regras, indivíduos interagem livremente, criando riqueza e inovação. A busca pelo progresso científico também reflecte este princípio: Albert Einstein, Nikola Tesla, Henry Ford ou Thomas Edison não foram forçados pelo Estado a desenvolver as suas invenções—fizeram-no por interesse próprio, beneficiando toda a humanidade.
Da mesma forma, a revolução industrial não foi um plano centralizado, mas sim o resultado de inúmeras inovações individuais que impulsionaram a prosperidade global. A tecnologia moderna, com exemplos como Bitcoin e Nostr, redes descentralizadas, prova que sociedades podem operar sem intermediários estatais, ou autoridades centrais.
Estado: Pode Existir Num Enquadramento Anarquista?
O Estado, mesmo na sua versão mais reduzida, pode representar um risco para a liberdade individual. Alguns, eu incluído, argumentam que um "Estado mínimo" (minarquia) poderia existir para garantir segurança e mediar disputas, mas essa estrutura pode rapidamente expandir-se e transformar-se num mecanismo de coerção.
A necessidade de mecanismos de controlo e equilíbrio
Mesmo um Estado reduzido exigiria salvaguardas para evitar abusos de poder. Para isso, seriam necessários mecanismos que garantam que nenhuma autoridade se torne dominante e que a sociedade mantenha a sua autonomia.
Algumas soluções incluem:
- Representação directa: Em vez de delegar decisões a políticos, a população poderia ter mais influência directa nas questões que afectam a sua vida (como na Suiça por exemplo).
- Arbitragem independente: Conflitos poderiam ser resolvidos sem recorrer a tribunais estatais, através de mediação voluntária e sistemas de justiça comunitária.
- Redes de apoio social: Fortalecer redes de ajuda mútua reduziria a necessidade de um governo central para fornecer serviços essenciais.
Exemplos práticos
Algumas iniciativas mostram que a sociedade pode funcionar com estruturas descentralizadas:
- Cidades com participação cívica activa: Experiências como o orçamento participativo em algumas cidades demonstram como a sociedade pode gerir recursos colectivos sem excessiva intervenção estatal.
- Redes de ajuda mútua: Grupos como a Mutual Aid Disaster Response Network nos EUA provam que comunidades podem organizar-se para responder a crises sem depender do Estado.
O desafio não é apenas imaginar um mundo sem Estado, mas conceber modelos descentralizados que garantam a liberdade individual e impeçam a concentração de poder. A verdadeira questão é: conseguiremos criar sistemas mais justos e funcionais sem recorrer à coerção estatal?
Raízes Filosóficas da Anarquia
A anarquia tem uma longa tradição filosófica que remonta a pensadores como William Godwin, Pierre-Joseph Proudhon e Max Stirner, cada um contribuindo com diferentes perspectivas sobre a organização social sem governantes. No século XX, pensadores como Murray Rothbard e Hans-Hermann Hoppe aprofundaram a ideia do anarco-capitalismo, propondo que todos os serviços actualmente providenciados pelo Estado poderiam ser oferecidos por meio de mercados livres.
A raiz histórica da anarquia está firmemente ancorada no pensamento de esquerda (a tradicional... ), na medida em que a sua proposta fundamental é a eliminação do poder central. O anarquismo clássico emergiu como uma resposta ao absolutismo e ao capitalismo industrial, defendendo que a autoridade imposta pelo Estado e pelas elites económicas deveria ser desmantelada para dar lugar a um sistema de cooperação voluntária e descentralizada. Proudhon, ao afirmar "a propriedade é roubo", reflectia esta preocupação com a concentração de poder e riqueza nas mãos de poucos.
Com o tempo, no entanto, diferentes correntes começaram a emergir dentro da tradição anarquista. A tradição anarquista de esquerda enfatiza a justiça social e a solidariedade comunitária, rejeitando tanto o Estado como o capitalismo. Nomes como Bakunin e Kropotkin defenderam a abolição da propriedade privada em favor de sistemas cooperativos, argumentando que apenas a auto gestão e o apoio mútuo poderiam garantir a verdadeira liberdade.
Por outro lado, no século XX, surgiu uma vertente anarquista mais associada à direita, especialmente com Rothbard e Hoppe, que viam o mercado como a melhor alternativa ao Estado. Para os anarco-capitalistas, a liberdade individual é prioritária, e a descentralização deve ocorrer não apenas ao nível político, mas também económico, permitindo que todas as transacções sejam voluntárias e baseadas na propriedade privada.
Apesar dessas divergências, há um ponto comum entre todas as vertentes anarquistas: a rejeição do monopólio da violência estatal. Tanto anarquistas de esquerda quanto de direita reconhecem que o poder centralizado inevitavelmente conduz à opressão e à limitação da liberdade individual. O debate interno dentro do anarquismo não é sobre a necessidade de abolir o Estado, mas sim sobre o que deve substituí-lo: auto gestão comunitária e colectivismo ou mercados livres e concorrência voluntária?
A preservação da propriedade privada e a liberdade de associação são, para mim, princípios fundamentais dentro do pensamento anarquista. Nada impede que, numa sociedade anarquista, grupos de indivíduos escolham unir-se voluntariamente para formar projectos cooperativos baseados em valores partilhados. O que distingue essa abordagem da imposição estatal é o carácter voluntário e descentralizado dessas associações, garantindo que cada pessoa possa viver conforme os seus próprios princípios sem coerção externa.
Esta dicotomia entre esquerda e direita dentro do anarquismo reflecte diferentes interpretações sobre a melhor forma de organizar a sociedade sem coerção. O que permanece inegável é que a anarquia, independentemente da vertente, continua a ser uma proposta de resistência contra qualquer forma de domínio centralizado, colocando a liberdade e a autonomia no centro da organização social.
Conclusão
A anarquia não é um sonho utópico, mas sim uma alternativa viável à organização centralizada da sociedade. Através do respeito pelo Princípio da Não-Agressão, da descentralização das normas jurídicas e da cooperação voluntária, podemos construir um mundo mais livre, onde as pessoas têm o poder de se governar a si mesmas.
Sistemas como Bitcoin já demonstram que a descentralização funciona e que a ausência de intermediários coercivos é não só possível, mas desejável. O desafio não é saber se a anarquia pode funcionar, mas sim quanto tempo levará para as pessoas perceberem que um mundo sem Estado é mais próspero e justo.
anarquia #anarco #bitcoin
Photo by Orit Matee on Unsplash
-
 @ 57d1a264:69f1fee1
2025-05-13 06:32:15
@ 57d1a264:69f1fee1
2025-05-13 06:32:15You don’t have to be a type designer to appreciate what goes into the design of a letterform. In fact, even if you’re just a humble graphic designer, you should have a basic knowledge of what constructs the type you employ.
Typography, for all its concepts, expectations, implications, connotations and artistry, is, ultimately, a system. Just like a body has bones and muscles, every letterform has parts that give it shape, rhythm, and character.
If you're a creative working with type, learning the names of these parts helps you communicate clearly, better analyze your work and others, and design with precision. Everything comes down to a foundational understanding of the anatomy of the letterform and its essential component. So let’s help you with that.
Pangram Pangram Foundry is where the art of typography meets unparalleled craftsmanship. Established in 2018 by designer Mat Desjardins, Pangram Pangram has swiftly risen to become a globally recognized independent type foundry, admired and trusted by industry peers and the design community alike.
Read more about the anatomy of fonts at https://pangrampangram.com/blogs/journal/anatomy-of-the-letterform
originally posted at https://stacker.news/items/978828
-
 @ 97c70a44:ad98e322
2025-02-18 20:30:32
@ 97c70a44:ad98e322
2025-02-18 20:30:32For the last couple of weeks, I've been dealing with the fallout of upgrading a web application to Svelte 5. Complaints about framework churn and migration annoyances aside, I've run into some interesting issues with the migration. So far, I haven't seen many other people register the same issues, so I thought it might be constructive for me to articulate them myself.
I'll try not to complain too much in this post, since I'm grateful for the many years of Svelte 3/4 I've enjoyed. But I don't think I'll be choosing Svelte for any new projects going forward. I hope my reflections here will be useful to others as well.
If you're interested in reproductions for the issues I mention here, you can find them below.
The Need for Speed
To start with, let me just quickly acknowledge what the Svelte team is trying to do. It seems like most of the substantial changes in version 5 are built around "deep reactivity", which allows for more granular reactivity, leading to better performance. Performance is good, and the Svelte team has always excelled at reconciling performance with DX.
In previous versions of Svelte, the main way this was achieved was with the Svelte compiler. There were many ancillary techniques involved in improving performance, but having a framework compile step gave the Svelte team a lot of leeway for rearranging things under the hood without making developers learn new concepts. This is what made Svelte so original in the beginning.
At the same time, it resulted in an even more opaque framework than usual, making it harder for developers to debug more complex issues. To make matters worse, the compiler had bugs, resulting in errors which could only be fixed by blindly refactoring the problem component. This happened to me personally at least half a dozen times, and is what ultimately pushed me to migrate to Svelte 5.
Nevertheless, I always felt it was an acceptable trade-off for speed and productivity. Sure, sometimes I had to delete my project and port it to a fresh repository every so often, but the framework was truly a pleasure to use.
Svelte is not Javascript
Svelte 5 doubled down on this tradeoff — which makes sense, because it's what sets the framework apart. The difference this time is that the abstraction/performance tradeoff did not stay in compiler land, but intruded into runtime in two important ways:
- The use of proxies to support deep reactivity
- Implicit component lifecycle state
Both of these changes improved performance and made the API for developers look slicker. What's not to like? Unfortunately, both of these features are classic examples of a leaky abstraction, and ultimately make things more complex for developers, not less.
Proxies are not objects
The use of proxies seems to have allowed the Svelte team to squeeze a little more performance out of the framework, without asking developers to do any extra work. Threading state through multiple levels of components without provoking unnecessary re-renders in frameworks like React is an infamously difficult chore.
Svelte's compiler avoided some of the pitfalls associated with virtual DOM diffing solutions, but evidently there was still enough of a performance gain to be had to justify the introduction of proxies. The Svelte team also seems to argue that their introduction represents an improvement in developer experience:
we... can maximise both efficiency and ergonomics.
Here's the problem: Svelte 5 looks simpler, but actually introduces more abstractions.
Using proxies to monitor array methods (for example) is appealing because it allows developers to forget all the goofy heuristics involved with making sure state was reactive and just
pushto the array. I can't count how many times I've writtenvalue = valueto trigger reactivity in svelte 4.In Svelte 4, developers had to understand how the Svelte compiler worked. The compiler, being a leaky abstraction, forced its users to know that assignment was how you signaled reactivity. In svelte 5, developers can just "forget" about the compiler!
Except they can't. All the introduction of new abstractions really accomplishes is the introduction of more complex heuristics that developers have to keep in their heads in order to get the compiler to act the way they want it to.
In fact, this is why after years of using Svelte, I found myself using Svelte stores more and more often, and reactive declarations less. The reason being that Svelte stores are just javascript. Calling
updateon a store is simple, and being able to reference them with a$was just a nice bonus — nothing to remember, and if I mess up the compiler yells at me.Proxies introduce a similar problem to reactive declarations, which is that they look like one thing but act like another on the edges.
When I started using Svelte 5, everything worked great — until I tried to save a proxy to indexeddb, at which point I got a
DataCloneError. To make matters worse, it's impossible to reliably tell if something is aProxywithouttry/catching a structured clone, which is a performance-intensive operation.This forces the developer to remember what is and what isn't a Proxy, calling
$state.snapshotevery time they pass a proxy to a context that doesn't expect or know about them. This obviates all the nice abstractions they gave us in the first place.Components are not functions
The reason virtual DOM took off way back in 2013 was the ability to model your application as composed functions, each of which takes data and spits out HTML. Svelte retained this paradigm, using a compiler to sidestep the inefficiencies of virtual DOM and the complexities of lifecycle methods.
In Svelte 5, component lifecycles are back, react-hooks style.
In React, hooks are an abstraction that allows developers to avoid writing all the stateful code associated with component lifecycle methods. Modern React tutorials universally recommend using hooks instead, which rely on the framework invisibly synchronizing state with the render tree.
While this does result in cleaner code, it also requires developers to tread carefully to avoid breaking the assumptions surrounding hooks. Just try accessing state in a
setTimeoutand you'll see what I mean.Svelte 4 had a few gotchas like this — for example, async code that interacts with a component's DOM elements has to keep track of whether the component is unmounted. This is pretty similar to the kind of pattern you'd see in old React components that relied on lifecycle methods.
It seems to me that Svelte 5 has gone the React 16 route by adding implicit state related to component lifecycles in order to coordinate state changes and effects.
For example, here is an excerpt from the documentation for $effect:
You can place $effect anywhere, not just at the top level of a component, as long as it is called during component initialization (or while a parent effect is active). It is then tied to the lifecycle of the component (or parent effect) and will therefore destroy itself when the component unmounts (or the parent effect is destroyed).
That's very complex! In order to use
$effect... effectively (sorry), developers have to understand how state changes are tracked. The documentation for component lifecycles claims:In Svelte 5, the component lifecycle consists of only two parts: Its creation and its destruction. Everything in-between — when certain state is updated — is not related to the component as a whole; only the parts that need to react to the state change are notified. This is because under the hood the smallest unit of change is actually not a component, it’s the (render) effects that the component sets up upon component initialization. Consequently, there’s no such thing as a “before update”/"after update” hook.
But then goes on to introduce the idea of
tickin conjunction with$effect.pre. This section explains that "tickreturns a promise that resolves once any pending state changes have been applied, or in the next microtask if there are none."I'm sure there's some mental model that justifies this, but I don't think the claim that a component's lifecycle is only comprised of mount/unmount is really helpful when an addendum about state changes has to come right afterward.
The place where this really bit me, and which is the motivation for this blog post, is when state gets coupled to a component's lifecycle, even when the state is passed to another function that doesn't know anything about svelte.
In my application, I manage modal dialogs by storing the component I want to render alongside its props in a store and rendering it in the
layout.svelteof my application. This store is also synchronized with browser history so that the back button works to close them. Sometimes, it's useful to pass a callback to one of these modals, binding caller-specific functionality to the child component:javascript const {value} = $props() const callback = () => console.log(value) const openModal = () => pushModal(MyModal, {callback})This is a fundamental pattern in javascript. Passing a callback is just one of those things you do.
Unfortunately, if the above code lives in a modal dialog itself, the caller component gets unmounted before the callback gets called. In Svelte 4, this worked fine, but in Svelte 5
valuegets updated toundefinedwhen the component gets unmounted. Here's a minimal reproduction.This is only one example, but it seems clear to me that any prop that is closed over by a callback function that lives longer than its component will be undefined when I want to use it — with no reassignment existing in lexical scope. It seems that the reason this happens is that the props "belong" to the parent component, and are accessed via getters so that the parent can revoke access when it unmounts.
I don't know why this is necessary, but I assume there's a good engineering reason for it. The problem is, this just isn't how javascript works. Svelte is essentially attempting to re-invent garbage collection around component lifecycles, which breaks the assumption every javascript developer has that variables don't simply disappear without an explicit reassignment. It should be safe to pass stuff around and let the garbage collector do its job.
Conclusion
Easy things are nice, but as Rich Hickey says, easy things are not always simple. And like Joel Spolsky, I don't like being surprised. Svelte has always been full of magic, but with the latest release I think the cognitive overhead of reciting incantations has finally outweighed the power it confers.
My point in this post is not to dunk on the Svelte team. I know lots of people like Svelte 5 (and react hooks). The point I'm trying to make is that there is a tradeoff between doing things on the user's behalf, and giving the user agency. Good software is built on understanding, not cleverness.
I also think this is an important lesson to remember as AI-assisted coding becomes increasingly popular. Don't choose tools that alienate you from your work. Choose tools that leverage the wisdom you've already accumulated, and which help you to cultivate a deeper understanding of the discipline.
Thank you to Rich Harris and team for many years of pleasant development. I hope that (if you read this) it's not so full of inaccuracies as to be unhelpful as user feedback.
-
 @ 45bda953:bc1e518e
2025-05-19 09:17:30
@ 45bda953:bc1e518e
2025-05-19 09:17:30Emilien stepped into the space motel's bar. The area was dimly lit and the music was unbearably loud. At least all the tables and sunken lounges each had their own lights and sound dampers. He stepped up to a table and pushed down on the receptor to reduce volume. He could not think with the noise. He looked around for Macy and inconspicuously acquainted himself with the current patrons in the establishment. He pulled his hoody further forward when he noticed the android in a wheel chair. "Not my type of company." He thought to himself. In the centre of the room a couple was having a spectacular time, an empty bottle on the table, they were specimens of myth. The guys muscles were chiselled, with tight fabric clinging to his body specifically to display every contour of his physique. His female counterpart wore loose material with translucent green tattoo's running up her body like pin stripes shining through the thin cloth hinting at a perfectly balanced pose and feminine silhouette underneath. Emilien swiped on the tables interface to call for the proprietor. He folded his arms and leaned onto the table tilting his head down slightly to keep shadow on his face. Macy entered the room through the kitchen swivel door. She was holding an empty tray and a serviette draped over her arm. She walked straight over to Emilien's table. "Good rotation sir. Welcome to Macy's. Are you a regular customer or is it your first visit to my fine establishment?" She seemed concerned and worried. The corners of Emiliens lips curved up a little. Keeping his head down teasingly. "Sir? Do we have an existing open channel?" He ignored her. "Sir, If you don't have liquidity I have no services to offer that you cannot get off your own ship." Emilien looked up with a gleam in his eye. Macie's posture relaxed with a sigh of relief. "Emile, you fuck. You freaked me out." "I'm sorry, I could not help myself." He waved a halfhearted greeting, slightly laughing. "You know I have some new rules around for you nano augmented types." His aversion to the word rules was evident only to himself. "Like what?" Macy felt apologetically obliged to explain the nature of her circumstances. "I had diplomats from the outer void regions come for a private meeting. Financial in nature. A spacer customer arrived blocks before them, I did not suspect him of anything criminal." She put the tray down and gripped the table with both hands shifting her weight. "His routine for meals were already established, he managed to spy on them through my privacy protocols and hacked their clients. He participated as a ghost during most of their stay and dealings." Emilien whistled. "That's rough, how did you handle it." "I did not do anything." Her dreads shook as she moved her head in animated frustration. "No one knew until they all had been gone for blocks. My reputation took a serious knock. They made a claim against me, I was accused of being complicit. Emilien glanced back over his shoulder when he noticed the android cart himself around his table. "Warren helped me and found all the dirty code and sequestered it. We have all the data and footage, it proves beyond a doubt that I was not involved. Thank god for the core otherwise my whole station might have been destroyed by now." Emile gave a sly look. "How do you know it was not me who stole the data?" She locked eyes with him. "You still have the same face as before bro and I know you won't fuck with me. I'll force close our channel." She joked with serious tone nudging him with her fist playfully. She was generally perceived as strict and militant because of her Shiv citizenship. Shiv military training and service was compulsory, all respected the Shiv in their traditions, their ways were isolationist and exclusionary in nature. Emilien has seen her use military style jujitsu-boxing to neutralise and boot out unruly customers. The Juel woman noticed the out of character friendly gesture Macy made. The unexpected interaction drew her attention from across the room. "So, what is this rule of yours." Macy seemed reluctant to say. "I'm sorry bud. You'll have to swallow a slipper pill every 576 blocks while you are on this station." His shoulders sagged and could not help but bounce his leg on the rail under the table. "Really?!" "Yes, really. I have to retain my customers trust and neutralising all augmented customers body gadgets was the unanimous way to go." Emilien seemed pissed. "Your customers might not know that I'm augmented. And what if I don't plan on staying that long. I just want to see Warren then I'll be off." Macy shook her head. "Warren is passed out in his ship and will probably wake up with a very bad hangover. He partied with the Jeul pair and their entourage for most of this rotation, you know how he gets." Macy waved her hand towards the couple who seemed to be looking directly at Emilien. He looked straight back at them and swiped the interface's privacy command dropping a vision distortion field around his table. Encapsulating himself and Macy. "I treat everyone the same, no compromise." Emile looked at her in a moment of rumination. "Let's get it over with." Macy removed a container from her moonbag after opening, holding it towards Emilien he took the purple capsule and swallowed it without a drink and opened his mouth wide moving his tongue around to show Macy that he did indeed swallow the prophylactic. "And what about robo-mech boy back there? He cannot eat slipper pills." Emilien sounded annoyed and regretful." Macy gave him a stern look tilting her head in annoyance. "Why do think he's in a wheelchair, you know I can't talk about my customers with my customers? Besides from the obvious." Emilien did not say anything. Macy sighed. "What can I get you sir?" "I'll just have a beer." Macy stepped out through the distortion field and became a messy disfigured indistinguishable form. Emilien pushed the music's volume up and waited for the inevitable. He sensed the actuators in his shoulders, elbows and wrists disable in sequence down his arms. His spines bit rate slowed to a crawl and the lack of connectivity to his neck port was becoming noticeable. His legs went numb instantly. "Now I am nothing more than a pathetic land crawler." He felt weak and vulnerable in his natural form. His mental state bordered on the fringes of stable and paranoid, fearful thoughts threatening to manifest in his mind. He saw a figure approach. He assumed it was his drink. The slender glowing tattooed leg of the Jeul woman pierced the veil. A bright green line that suddenly dims where her skirt begins. She stepped through the curtain with a friendly nonchalant expression. "Mind if make your acquaintance mon ami?" Emilien dropped the barrier and lowered the volume making sure that he was back on visual record of Macy's archive. "Not really, thanks, I'm good." Macy returned to place a cold beer on the table. The interface flashed a price in femto-sat and Emilien tapped his ring on it shifting 11 fSAT from a mini holographic Bob to very happy little Alice. The animation morphed into a small firework display and died. "Back to work now." Emilien grinned at Macy thankfully and took a sip. "Me and my brother we are celebrating our seventh birth block anniversary." He looked around sarcastically. "You chose a display of death above the resorts on Juel to celebrate your seventh birth block?" She stiffened her glittery lips and raised her eyebrows thoughtfully and took a seat without invitation. "It is more of a tour than a celebration, I am Maurelle Giovanni and my brother is called Lionel also Giovanni obviously. He is my twin baby brother." Emilien looked over at the guy who seemed to be occupied playing a mini game on their tables interface. She tilted her head into his line of sight forcing him to look at her. "Who are you?" "None of your concern really." She did not accept the short stated answer. "No one comes alone all the way to a dead end system just to drink a cheap beer. I am guessing you are a treasure hunter, no. Looking for artefacts of the ancient world, yes?" Emilien had assessed her body language and concluded that her whimsical imagination was one he could easily manipulate. He had enough information to realise that he was faced with a spoiled individual whose sole interest in him was simple curiosity, motivated by boredom and she had a fascination of the mysterious. She seemed like prey but his hunting instincts felt dead inside his disarmed body. His respect for and dependence on Macy also inhibited his urge to exploit it. He shifted his attitude and personality slightly, just enough to not be overbearing. "You make very good estimations, you are wrong but not far off. My name is Scott. And yes I am fascinated, not by the planet and it's relics but by the the secrets of these gates." Her eyes gleamed with amusement and intrigue. "You like secrets, huh? You must meet Warren. He knows more than the esteemed professors about the gates and their technology." Emilien nodded in agreement. "You said you are Giovanni. Like the Giovanni?" She seemed excited at the prospect of making a new friend and swiped the interface. "Hold this thought, I am going to get myself another drink you are good? No. Food maybe?" "I am good, no wait, another beer." He tipped the bottle toward her in salutation. She stood up taking his bottle with her to the bar. He looked back and was immediately aware that he did not notice that the android wheel himself out and into the conduit. He would have liked to see which of the two entrances of the tube he used to go to his ship. His feeling sorry for and pitying himself put him in a position where he let slip an opportunity to understand and predict the circumstances of his current tactical situation. Never at ease, always being prepared. He felt spite. The girl returned with a beer and a half full whiskey glass, no ice. She reclaimed her seat looking at him. "I am a direct descendant of the patriarch Maurice Giovanni, one of the four primary key holders of our people. There is nothing special about me really, ten..." Emilien cut her off in gentle tone. "Ten percent of the Juel population are descendants of the four patriarchs." Emilien finished her sentence for her. "You are an interesting man Monsieur Scott. What else do you know about me?" Emilien leaned towards her. Noticing her brother yawning across the room. "I know that you are bourgeois and I know that you receive a cyclical allowance from your great, great... How many generations?" "I am removed 133 generations from my Patriarch. He is a very good, doting grandfather. We all adore him. We are around 750 million siblings you know. Those who are from aristocracy have fewer children than the proles. We are so few so that our wealth is not diluted too much." She smiled reminiscently dragging her finger on the edge of the glass. Her brother seemed to stretch himself out he stood up and walked over. Entering the sound damper he acknowledged Emilien's presence with a curt nod. "Maurelle, I am going to sleep." He said to her. She waved at him dismissively. "Have a good dream frere." He exited the room through the right tubes door which made sense as their ship was more closely attached to it on that side of the circular docking ring. Predictable and honest Emilien thought to himself. Macy popped her head through the kitchens serving window. "Lights out and shutdown in 2 blocks. Just a friendly notice." The couple acknowledged the warning from Macy with raised glass and bottle. Emilien turned his attention back to the lady. "How do you manage to retain wealth in such a large family?" He pretended to be ignorant of the finery and detail of Juel culture. "We have closed loop channels controlled and balanced by the patriarchs. But our money is good as core stone. Anywhere in the outer void. Only recently has dispute arose between my Patriarchs and the Magarrie. They do not accept our Sats anymore since the war started. They only accept bitcoins directly from the core. I was only four cycles old when the war began so I am used to it." Emilien felt a conflicting disturbance, thinking about how his body is only two cycles active but his mind stretches back far beyond this time. Being both older and younger than his partner in discourse. "Helloo? I lost you there for a moment Scott." "What are you thinking about?" Emilien lied to her faking emotion. "I was just thinking about the tremendous loss of life that we are orbiting. The planet embedded with what it's inhabitants assumed would be it's portal to prosperity became the golem of it's demise." He was happy that Maurelle seemed to empathise and mirror his philosophic grief. "Come with me I want to tell you a secret. You like secrets." She stood up taking his hand gently tugging, compelling him to follow her. She led him to the far end of the room. She pulled a small levered switch and the wall folded in on itself to reveal a impressive window flooding sharp light into the whole of the large room as it retracted. They both squinted and lifted their hands to shield their eyes adjusting to the glare of Sol. The scene of destruction appeared even more dramatic and morbid as dark sharply defined shadows clipped with golden edges, evoking a sense of isolation and suffering. "These gates were supposed to be a gift to Earth. A hope of spreading humanity across the stars like the children of Abraham." Emilien smirked. "You believe that nonsense?" She rested her head on his shoulder still holding onto his arm. "Our patriarchs have preserved the mysteries of mankind for millennia. I said that I am going to tell you a secret don't patronise me. I do not believe anything. What I know, it is not faith. It is understanding. Knowledge, a type of knowledge that you cannot quantify with mathematics and chemistry. It is a higher science that is proven by the unmistakable coincidence of fate. It is invisible to those who are ignorant and they who despair, those who have lost all hope are blind to this promise." Emilien felt a strange remorse. "I guess I must be blind then." The lights suddenly shut down and the song stopped dead in it's track, like Macy promised. Overcome by the majesty of the scene Maurelle wiped a tear away fearing that her makeup might get ruined. "Anyone can see. They must just open their eyes voluntarily and be honest with themselves. Their true original selves. Who they were made to be." Emile felt judged and wanted to end this conversation quickly. "I am going back to my ship, you have a good night now." She grabbed tightly at his wrist almost painfully. "You do not want to know my secret?" Emelien was becoming annoyed with her insistence he removed her hand from his arm. "I don't think you know any real useful secrets, sweetheart." He sounded threatening, the real enshrouded unmistakable him breaking through the act. She looked at him unintimidated by his sudden shift in personality. "Oh, so I suppose you know why the Juela are at war for most of our lives?" He sarcastically extended his arms forward palms up in restrained but evidently mocking adoration. "Please enlighten me priestess." "They are fighting over this." She pointed at the epic scene of destruction drifting statically out of view as the stations rotation cut it off at the edge of the window. The shadows chased Sol light away sliding like a retracting blade across the room leaving it dark. Emilien burst out angrily. "They are fighting over satoshis! That is all they ever fight over! What I fight for, Damnit! Sats and the resources to gain more of it! That is the beginning and end of all things! Anyone in the universe with even the slightest lick of self worth works, fights and dies for sat!" Maurelle stared astutely at him unemotionally affected by his outburst. She obviously had experienced this exact reaction before and suddenly Emilien realised that he might be the one being manipulated by a smarter and wiser being than himself. "Are you done my love? Have you made your point or is there some other deeper understanding you wish me to internalise into my ignorant small little world?" She threw at him a spiteful sarcasm of her own. "Do you really think I do not know what it means to be seduced by wealth? Luxury?" She took a step closer to him. "Pleasure?" Emilien felt stupid and disarmed this time adding emotionally disarmed to the defeat of being inept in his own body. "I am not a fool mon cherie. The truly wealthy don't fight for wealth, they fight for power. But the noble and sincere fight a different fight with a different weapon. They use words to fight, ideas to win. They fight to gain trust with words, and they fight to retain it with consistency in their actions. Trust is a currency that makes sat seem like shit in comparison because it is real even though you do not believe what you cannot hold in your hand, like your beloved sat." She pointed at the ring on his finger. "Trust only retains value if you honour your words with your actions. Its value is fragile and can disappear in a moment of weakness like water vapour, cherished as the source of life then gone, poof, evaporated. Like magic. This type of trust if gained and retained correctly, projects you forward into the realm of immortality." Emile felt stung and hurt on a personal level, unsure if she was generalising or targeting his own specific weakness purposely. It confused him and made him feel insecure. "What are they fighting for then?" He asked slightly surrendering to the unexpected superior reasoning. Maurelle appreciated the honesty she identified as sincere. She gently took his hand again and led him back to the large convex window. They stood silently for a block, waiting on the rotation to pull the bright light of Sol back into the room. "They are fighting for the power to do that." She pointed at Earth in all it's terrible glory. "The destruction caused by the gate was a terrible cataclysm outside of humanities collective control. The core and the gates are a mystery to mankind." She looked up at Emilien, relieved to see that he was still taking her seriously. "The Maggarie have discovered a weapon that has the power to destroy a planet. The Juel think they are fighting to free Osteri captives from slavery but the real motif is hidden, our Patriarchs unadmitted fear of being inferior to the Maggarie. Most of the goods we traded with them they have stopped accepting, the Shiv and Osteri still buy our products but the Maggarie have suddenly lost the need for our produce, even raw material in it's basest forms. They are expanding somehow and the balance of interdependence has tilted out of our favor. They have no more need for us and have cast us aside like a filthy rag." She paused in thought. "Their new super weapon is the cause of this conflict monsieur Scott." Emilien shrugged. Feeling relieved at regaining the intellectual high ground he thought he had lost. "I'm sorry Maurelle. I have no data on this weapon. If this was true the forums on my bulletin board would have leaked information about it's existence epochs ago, it's been just over three cycles everyone would have known this by now. It sounds more like Jeul fearmongering or perhaps it is the daydreaming fairy tale of an innocent naive girl who worships old myths and legends of a time dead for thousands of years." He pointed at Earth. She sniffed away a hint of emotion and anger. "Well then, I have nothing more to say to you, Good night monsieur Scott." She pulled away from him pridefully and looked out at the enormous gate embedded like a knife into the earths crust. "You are a swine monsieur Scott, leave me alone with my pearl." Emilien stepped back mockingly bowing slightly. "Good night sweetheart." He walked back to his craft laughing inside himself. "Stupid woman." He muttered, although be it doubtfully.
...
scifi
-
 @ 57d1a264:69f1fee1
2025-05-13 06:21:36
@ 57d1a264:69f1fee1
2025-05-13 06:21:36Steve Jobs sent me an email saying “Great idea, thank you."
Wait, what? What was the great idea?
new guy at NeXT In October of 1991, I was a new Systems Engineer at NeXT. NeXT, of course, was the company Steve Jobs had founded after leaving Apple in 1985, and which eventually merged back into Apple in 1996. I was one of three employees in Canada, and I think NeXT had about 400 people total.
NeXTMail Mail on the NeXT Computer was pretty amazing in 1991. Multimedia! Fonts! Attachments! Sounds! It’s hard to overstate how cool that was compared to the command line email everybody was used to. Every NeXT user got this email from Steve when they started up their computer.
That message included an attachment of what NeXT called Lip Service, the crazy idea that you could embed an audio file inside an email message. Crazy.
i have an idea
NeXT automatically set everybody up with a first-initial last-name address in the usual way, so I was shayman@next.com, and the big guy was sjobs@next.com.
A few colleagues had somehow acquired cooler email aliases - single letter things, or their first name, or a nickname or an easier to spell version, or whatever. Turns out NeXT had set up some sort of form where you could request an email alias that would redirect to whatever your real email address was.
I also noticed that even though there were seven or eight people at NeXT named Steve, nobody was using the email alias steve@next.com.
So late one Friday night, two weeks into the job, I figured, naively, what the heck, nobody else seems to want it, so I filled in the form asking for steve@next.com to be forwarded to me, shayman@next.com.
In the back of my mind was a vague idea that maybe somebody would have to approve this. But no, it all got set up automatically, and …
Continue reading at https://blog.hayman.net/2025/05/06/from-steve-jobs-great-idea.html
originally posted at https://stacker.news/items/978825
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ 45bda953:bc1e518e
2025-05-19 09:16:17
@ 45bda953:bc1e518e
2025-05-19 09:16:17Core Divide - Sol System - Gate 7
Tremors from warp turbulence rumbled a bit excessively to the Stripper's liking. Emilien was occupied in the lavatory, inspecting and pulling at his face, staring intently at it in the vanity mirror. Macy's establishment was a popular place and he had concerns about who he might run into, contemplating whether he should stick some silicone cosmetic pads onto his face, just enough to obfuscate his current identity. Maybe he shouldn't bother because he might die soon anyway. He has grown fond of his current persona and wouldn't mind retaining it a cycle longer at least. Being artificially immortal somehow did not take away the terror of confronting death. He recalled the various deaths he had experienced and could not decide what method of passing through he preferred, imagining the many shells of himself in different states of necrosis all over the greater void. He considered the possibility that he might not even be himself anymore. He felt like he knows himself well enough to be sure but that small fragment of doubt always gnawed at the back of his mind. He stood back from the mirror. "Am I him?" The ship shook again breaking his stare, he looked at the dental lever lying in the basin and committed to the more necessary procedure, placing the edges of his palms on his chin pushing abruptly up and back dislocated his lower jaw leaving it to hang loose on his face. Taking the root lever from the basin and leaning into the mirror he expertly wedged the tool in behind his rearmost left molar and twisted it slightly, dislodging it. Catching the small object with his left hand he pressed it into a recess on a black ring which he tightly twisted onto his right hands index finger. He narrowed his eyes at the skeletal horror on the other side of the frame inspecting the freshly opened hole. He opened the vanity and took a cartridge which was labelled "AdrenoChem" he removed the object within the container and wiggled it into the vacant molar cavity. Drool dripping into the sink in spite of his reflexive swallowing, he gripped his jaw tight and in gentle circular downward motions found the spot and clicked the joints back into relocation. Chattering his teeth together while stretching his neck he decided to procrastinate on the disguise idea. Emilien went back to the cockpit. Sitting down at the helm he pulled up notices and reports on the divide's situation with regards to the cease fire between the two warring factions. "Tch, tch, tch. This blockade is not making things easy." His eyes were scrolling over bullet points of news headlines when his ship dropped out of warp at the designated coordinates. He switched the display on the primary screen to clearview. The scene of a dead planet, cracked open like an enormous fruit with scattered asteroid clusters and rocky debris appeared onscreen. A giant still wreck of a superstructure resembling parts of an anchor and drift gate joined to each other like Siamese twins, sharp flashes emitting from it silently, like a muted storm in the far distance. He slowly tilted his head to it's limit. Nothing looked familiar to him. He took the console, rolled and yawed simultaneously until his point of view made sense. "There we are. You're not there till you know it." Macy's space motel pitched into view like a tiny reflective insect. On a secondary screen he zoomed the display to fit. It was attached to a large tubular docking link reaching away distantly and back to itself like Ourobouros. There were four spacecraft docked around it's circumference, less than he had expected. He only recognised the largest ship, Warren's vessel. It looked like a mess of odd protrusions, parabolic dishes and bent antennae. Very unsightly, especially compared to the Lux Void Yacht docked across from it. Tourists from everywhere frequented this remote region of the great divide for obvious reasons. Primary motivations were curiosity, pilgrimage, seclusion and scientific research in that order. Macy was smart to settle her establishment at this specific site. Emilien checked web connectivity to make sure he was still well outside the data scrambling anomaly. According to legend, after the Viper gate had been released from the Core and travelled the required distance to it's anchor coordinates, it was supposed to propel it's drift gate into the greater void, but something went wrong. It malfunctioned on it's attempt to release and veered off course being pulled into the orbit of the Sol system. No one knows exactly how it happened but it was clear to see that the energy released was spectacular. The root planet and most of humanity perished in a second, those who survived on the dark side of the collision died from starvation and gradual planetary destabilisation. Emilien morbidly recognised the historicity of the treacherous looking voidscape. Pulsing his ship softly forward caused a cut to core connectivity activating a repetitive red warning light which he promptly covered with one of the intact disposable cups that were rolling around his feet. There is no way to turn the annoying emitter off and he usually ignored it with closed eyes or looking away when void jumping. He is never vulnerable to core connection loss unless he comes to this region or when he is purposely trying to disappear. Researchers have concluded that the interference was broadcast from the gates enormous husk's residual power and intermittent energy discharge. He reverse pulsed back out of the disturbance, the dimmed light under the paper cup died. "Astrid?" "Yes?" He carefully uncoiled the cable and leaned forward connecting himself to the command interface and resting his head on his arms. "Save me." A quick upload took place. "You are welcome commander." Emilien did not respond. Just grateful that if something went askew he would at least wake up knowing that the last thing he saw was the monumental vestige of humanities ancient resting place. And all the ship types docked at Macy's. He smiled at the floor.
...
scifi
-
 @ 97c70a44:ad98e322
2025-02-17 14:29:00
@ 97c70a44:ad98e322
2025-02-17 14:29:00Everyone knows that relays are central to how nostr works - they're even in the name: Notes and Other Stuff Transmitted by Relays. As time goes on though, there are three other letters which are becoming conspicuously absent from our beloved and ambiguously pronounceable acronym - "D", "V", and "M".
For the uninitiated, DVM stands for "data vending machines". They're actually sort of hard to describe — in technical terms they act more like clients, since they simply read events from and publish events to relays. In most cases though, these events are part of a request/response flow initiated by users elsewhere on the network. In practice, DVMs are bots, but there's also nothing to prevent the work they do from being powered by human interaction. They're an amazingly flexible tool for building anything from custom feeds, to transcription services, to chatbots, to protocol gateways.
The hype cycle for DVMs seems to have reached escape velocity in a way few other things have - zaps being the possible exception. But what exactly DVMs are remains something of a mystery to many nostr developers - and how to build one may as well be written on clay tablets.
This blog post is designed to address that - below is a soup to nuts (no nutzaps though) guide to building a DVM flow, both from the client and the server side.
Here's what we'll be covering:
- Discovering DVM metadata
- Basic request/response flow
- Implementing a minimal example
Let's get started!
DVM Metadata
First of all, it's helpful to know how DVMs are reified on the nostr network. While not strictly necessary, this can be useful for discovering DVMs and presenting them to users, and for targeting specific DVMs we want a response from.
NIP 89 goes into this in more detail, but the basic idea is that anyone can create a
kind 31990"application handler" event and publish it to the network with their own (or a dedicated) public key. This handler was originally intended to advertise clients, but has been re-purposed for DVM listings as well.Here's what the "Fluffy Frens" handler looks like:
json { "content": "{\"name\": \"Fluffy Frens\", \"picture\": \"https://image.nostr.build/f609311532c470f663e129510a76c9a1912ae9bc4aaaf058e5ba21cfb512c88e.jpg\", \"about\": \"I show recent notes about animals\", \"lud16\": \"discovery_content_fluffy@nostrdvm.com\", \"supportsEncryption\": true, \"acceptsNutZaps\": false, \"personalized\": false, \"amount\": \"free\", \"nip90Params\": {\"max_results\": {\"required\": false, \"values\": [], \"description\": \"The number of maximum results to return (default currently 100)\"}}}", "created_at": 1738874694, "id": "0aa8d1f19cfe17e00ce55ca86fea487c83be39a1813601f56f869abdfa776b3c", "kind": 31990, "pubkey": "7b7373dd58554ff4c0d28b401b9eae114bd92e30d872ae843b9a217375d66f9d", "sig": "22403a7996147da607cf215994ab3b893176e5302a44a245e9c0d91214e4c56fae40d2239dce58ea724114591e8f95caed2ba1a231d09a6cd06c9f0980e1abd5", "tags": [ ["k", "5300"], ["d", "198650843898570c"] ] }This event is rendered in various clients using the kind-0-style metadata contained in the
contentfield, allowing users to browse DVMs and pick one for their use case. If a user likes using a particular DVM, they might publish akind 31989"application recommendation", which other users can use to find DVMs that are in use within their network.Note the
ktag in the handler event - this allows DVMs to advertise support only for specific job types. It's also important to note that even though the spec doesn't cover relay selection, most clients use the publisher'skind 10002event to find out where the DVM listens for events.If this looks messy to you, you're right. See this PR for a proposal to split DVMs out into their own handler kind, give them a dedicated pubkey along with dedicated metadata and relay selections, and clean up the data model a bit.
DVM Flow
Now that we know what a DVM looks like, we can start to address how they work. My explanation below will elide some of the detail involved in NIP 90 for simplicity, so I encourage you to read the complete spec.
The basic DVM flow can be a little (very) confusing to work with, because in essence it's a request/response paradigm, but it has some additional wrinkles.
First of all, the broker for the request isn't abstracted away as is usually the case with request/response flows. Regular HTTP requests involve all kinds of work in the background - from resolving domain names to traversing routers, VPNs, and ISP infrastructure. But developers don't generally have to care about all these intermediaries.
With DVMs, on the other hand, the essential complexity of relay selection can't simply be ignored. DVMs often advertise their own relay selections, which should be used rather than a hard-coded or randomly chosen relay to ensure messages are delivered. The benefit of this is that DVMs can avoid censorship, just as users can, by choosing relays that are willing to broker their activity. DVMs can even select multiple relays to broker requests, which means that clients might receive multiple copies of the same response.
Secondly, the DVM request/response model is far more fluid than is usually the case with request/response flows. There are a set of standard practices, but the flow is flexible enough to admit exceptions to these conventions for special use cases. Here are some examples:
- Normally, clients p-tag the DVM they wish to address. But if a client isn't picky about where a response comes from, they may choose to send an open request to the network and collect responses from multiple DVMs simultaneously.
- Normally, a client creates a request before collecting responses using a subscription with an e-tag filter matching the request event. But clients may choose to skip the request step entirely and collect responses from the network that have already been created. This can be useful for computationally intensive tasks or common queries, where a single result can be re-used multiple times.
- Sometimes, a DVM may respond with a
kind 7000job status event to let clients know they're working on the request. This is particularly useful for longer-running tasks, where feedback is useful for building a responsive UX. - There are also some details in the spec regarding monetization, parameterization, error codes, encryption, etc.
Example DVM implementation
For the purposes of this blog post, I'll keep things simple by illustrating the most common kind of DVM flow: a
kind 5300content discovery request, addressed to a particular DVM. If you're interested in other use cases, please visit data-vending-machines.org for additional documented kinds.The basic flow looks like this:
- The DVM starts by listening for
kind 5300job requests on some relays it has selected and advertised via NIP 89 (more on that later) - A client creates a request event of
kind 5300, p-tagged with the DVM's pubkey and sends it to the DVM's relay selections. - The DVM receives the event and processes it, issuing optional
kind 7000job status events, and eventually issuing akind 6300job result event (job result event kinds are always 1000 greater than the request's kind). - The client listens to the same relays for a response, and when it comes through does whatever it wants to with it.
Here's a swimlane diagram of that flow:

To avoid massive code samples, I'm going to implement our DVM entirely using nak (backed by the power of the human mind).
The first step is to start our DVM listening for requests that it wants to respond to. Nak's default pubkey is
79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798, so we'll only listen for requests sent to nak.bash nak req -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798This gives us the following filter:
json ["REQ","nak",{"kinds":[5300],"#p":["79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"]}]To open a subscription to
nos.loland stream job requests, add--stream wss://nos.lolto the previous request and leave it running.Next, open a new terminal window for our "client" and create a job request. In this case, there's nothing we need to provide as
input, but we'll include it just for illustration. It's also good practice to include anexpirationtag so we're not asking relays to keep our ephemeral requests forever.bash nak event -k 5300 -t p=79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798 -t expiration=$(( $(date +%s) + 30 )) -t input=helloHere's what comes out:
json { "kind": 5300, "id": "0e419d0b3c5d29f86d2132a38ca29cdfb81a246e1a649cb2fe1b9ed6144ebe30", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739407684, "tags": [ ["p", "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798"], ["expiration", "1739407683"], ["input", "hello"] ], "content": "", "sig": "560807548a75779a7a68c0ea73c6f097583e2807f4bb286c39931e99a4e377c0a64af664fa90f43e01ddd1de2e9405acd4e268f1bf3bc66f0ed5a866ea093966" }Now go ahead and publish this event by adding
nos.lolto the end of yournakcommand. If all goes well, you should see your event pop up in your "dvm" subscription. If so, great! That's half of the flow.Next, we'll want our client to start listening for
kind 6300responses to the request. In your "client" terminal window, run:bash nak req -k 6300 -t e=<your-eventid-here> --stream nos.lolNote that if you only want to accept responses from the specified DVM (a good policy in general to avoid spam) you would include a
ptag here. I've omitted it for brevity. Also notice thektag specifies the request kind plus1000- this is just a convention for what kinds requests and responses use.Now, according to data-vending-machines.org,
kind 5300responses are supposed to put a JSON-encoded list of e-tags in thecontentfield of the response. Weird, but ok. Stop the subscription in your "dvm" terminal and respond to your "client" with a recommendation to read my first note:bash nak event -k 6300 -t e=a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf -c '[["e","214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08","wss://nos.lol/"]]' nos.lolHere's the response event we're sending:
json { "kind": 6300, "id": "bb5f38920cbca15d3c79021f7d0051e82337254a84c56e0f4182578e4025232e", "pubkey": "79be667ef9dcbbac55a06295ce870b07029bfcdb2dce28d959f2815b16f81798", "created_at": 1739408411, "tags": [ ["e", "a65665a3a4ca2c0d7b7582f4f0d073cd1c83741c25a07e98d49a43e46d258caf"] ], "content": "[[\"e\",\"214f5898a7b75b7f95d9e990b706758ea525fe86db54c1a28a0f418c357f9b08\",\"wss://nos.lol/\"]]", "sig": "a0fe2c3419c5c54cf2a6d9a2a5726b2a5b766d3c9e55d55568140979354003aacb038e90bdead43becf5956faa54e3b60ff18c0ea4d8e7dfdf0c8dd97fb24ff9" }Notice the
etag targets our original request.This should result in the job result event showing up in our "client" terminal. Success!
If something isn't working, I've also create a video of the full process with some commentary which you can find here.
Note that in practice, DVMs can be much more picky about the requests they will respond to, due to implementations failing to follow Postel's law. Hopefully that will improve over time. For now, here are a few resources that are useful when working with or developing DVMs:
Conclusion
I started this post by hinting that DVMs might be as fundamental as relays are to making nostr work. But (apart from the fact that we'd end up with an acronym like DVMNOSTRZ+*, which would only exascerbate the pronounciation wars (if such a thing were possible)), that's not exactly true.
DVMs have emerged as a central paradigm in the nostr world because they're a generalization of a design pattern unique to nostr's architecture - but which exists in many other places, including NIP 46 signer flows and NIP 47 wallet connect. Each of these sub-protocols works by using relays as neutral brokers for requests in order to avoid coupling services to web addresses.
This approach has all kinds of neat benefits, not least of which is allowing service providers to host their software without having to accept incoming TCP connections. But it's really an emergent property of relays, which not only are useful for brokering communication between users (aka storing events), but also brokering communication between machines.
The possibilities of this architecture have only started to emerge, so be on the lookout for new applications, and don't be afraid to experiment - just please, don't serialize json inside json 🤦♂️
-
 @ eabee230:17fc7576
2025-05-12 14:38:11
@ eabee230:17fc7576
2025-05-12 14:38:11⚖️ຢ່າລືມສິ່ງທີ່ເຄີຍເກີດຂຶ້ນ ຮອດຊ່ວງທີ່ມີການປ່ຽນແປງລະບົບການເງິນຈາກລະບົບເງິນເກົ່າ ສູ່ລະບົບເງິນໃໝ່ມັນເຮັດໃຫ້ຄົນທີ່ລວຍກາຍເປັນຄົນທຸກໄດ້ເລີຍ ນ້ຳພັກນ້ຳແຮງທີ່ສະສົມມາດ້ວຍຄວາມເມື່ອຍແຕ່ບໍ່ສາມາດແລກເປັນເງິນລະບົບໃໝ່ໄດ້ທັງໝົດ ຖືກຈຳກັດຈຳນວນທີ່ກົດໝາຍວາງອອກມາໃຫ້ແລກ ເງິນທີ່ເຫຼືອນັ້ນປຽບຄືດັ່ງເສດເຈ້ຍ ເພາະມັນບໍ່ມີຢູ່ໃສຮັບອີກຕໍ່ໄປເພາະກົດໝາຍຈະນຳໃຊ້ສະກຸນໃໝ່ ປະຫວັດສາດເຮົາມີໃຫ້ເຫັນວ່າ ແລະ ເຄີຍຜ່ານມາແລ້ວຢ່າໃຫ້ຄົນລຸ້ນເຮົາຊຳ້ຮອຍເກົ່າ.
🕰️ຄົນທີ່ມີຄວາມຮູ້ ຫຼື ໃກ້ຊິດກັບແຫຼ່ງຂໍ້ມູນຂ່າວສານກໍຈະປ່ຽນເງິນທີ່ມີຢູ່ເປັນສິນສັບບໍ່ວ່າຈະເປັນທີ່ດິນ ແລະ ທອງຄຳທີ່ສາມາດຮັກສາມູນລະຄ່າໄດ້ເຮັດໃຫ້ເຂົາຍັງຮັກສາຄວາມມັ້ງຄັ້ງໃນລະບົບໃໝ່ໄດ້.
🕰️ໃຜທີ່ຕ້ອງການຈະຍ້າຍປະເທດກໍ່ຈະໃຊ້ສິ່ງທີ່ເປັນຊື່ກາງໃນການແລກປ່ຽນເປັນທີ່ຍ້ອມຮັບຫຼາຍນັ້ນກໍຄືທອງຄຳ ປ່ຽນຈາກເງິນລະບົບເກົ່າເປັນທອງຄຳເພື່ອທີ່ສາມາດປ່ຽນທອງຄຳເປັນສະກຸນເງິນທ້ອງຖິ່ນຢູ່ປະເທດປາຍທາງໄດ້.
🕰️ຈາກຜູ້ດີເມື່ອກ່ອນກາຍເປັນຄົນທຳມະດາຍ້ອນສັບສິນທີ່ມີ ບໍ່ສາມາດສົ່ງຕໍ່ສູ່ລູກຫຼານໄດ້. ການເກັບອອມເປັນສິ່ງທີ່ດີ ແຕ່ຖ້າໃຫ້ດີຕ້ອງເກັບອອມໃຫ້ຖືກບ່ອນ ຄົນທີ່ຮູ້ທັນປ່ຽນເງິນທີ່ມີຈາກລະບົບເກົ່າໄປສູ່ທອງຄຳ ເພາະທອງຄຳມັນເປັນສາກົນ.
ໃຜທີ່ເຂົ້າໃຈ ແລະ ມອງການໄກກວ່າກໍ່ສາມາດຮັກສາສິນສັບສູ່ລູກຫຼານໄດ້ ເກັບເຈ້ຍໃນປະລິມານທີ່ພໍໃຊ້ຈ່າຍ ປ່ຽນເຈ້ຍໃຫ້ເປັນສິ່ງທີ່ຮັກສາມູນລະຄ່າໄດ້ແທ້ຈິງ.🕰️ເຮົາໂຊກດີທີ່ເຄີຍມີບົດຮຽນມາແລ້ວ ເກີດຂຶ້ນຈິງໃນປະເທດເຮົາບໍ່ໄດ້ຢາກໃຫ້ທັງໝົດແຕ່ຢາກໃຫ້ສຶກສາ ແລະ ຕັ້ງຄຳຖາມວ່າທີ່ຜ່ານມາມັນເປັນແບບນີ້ແທ້ບໍ່ ເງິນທີ່ລັດຄວາມຄຸມ ເງິນປະລິມານບໍ່ຈຳກັດ ການໃຊ້ກົດໝາຍແບບບັງຄັບ. ຖ້າຄອບຄົວຫຼືຄົນໃກ້ໂຕທີ່ຍູ່ໃນຊ່ວງເຫດການນັ້ນແຕ່ຕັດສິນໃຈຜິດພາດທີ່ບໍ່ປ່ຽນເຈ້ຍເປັນສິນສັບ. ນີ້ແມ່ນໂອກາດທີ່ຈະແກ້ໄຂຂໍ້ຜິດພາດນັ້ນໂດຍຫັນມາສຶກສາເງິນແທ້ຈິງແລ້ວແມ່ນຍັງກັນແທ້ ເວລາມີຄ່າສຶກສາບິດຄອຍ.

fiatcurrency #bitcoin #gold #history #paymentsolutions #laokip #laostr
-
 @ 97c70a44:ad98e322
2025-02-03 22:25:35
@ 97c70a44:ad98e322
2025-02-03 22:25:35Last week, in a bid to understand the LLM hype, I decided to write a trivial nostr-related program in rust via a combination of codebuff (yes, that is a referral link, pls click), aider, and goose.
The result of the experiment was inconclusive, but as a side effect it produced a great case study in converting a NINO into a Real Nostr App.
Introducing Roz
Roz, a friendly notary for nostr events.
To use it, simply publish an event to
relay.damus.ioornos.lol, and roz will make note of it. To find out when roz first saw a given event, just ask:curl https://roz.coracle.social/notary/cb429632ae22557d677a11149b2d0ccd72a1cf66ac55da30e3534ed1a492765dThis will return a JSON payload with a
seenkey indicating when roz first saw the event. How (and whether) you use this is up to you!De-NINO-fying roz
Roz is just a proof of concept, so don't rely on it being there forever. And anyway, roz is a NINO, since it provides value to nostr (potentially), but doesn't really do things in a nostr-native way. It also hard-codes its relays, and certainly doesn't use the outbox model or sign events. But that's ok, it's a proof of concept.
A much better way to do this would be to modify roz to properly leverage nostr's capabilities, namely:
- Use nostr-native data formats (i.e., draft a new kind)
- Use relays instead of proprietary servers for data storage
- Leverage nostr identities and signatures to decouple trust from storage, and allow trusted attestations to be discovered
Luckily, this is not hard at all. In fact, I've gone ahead and drafted a PR to the NIPs repo that adds timestamp annotations to NIP 03, as an alternative to OpenTimestamps. The trade-off is that while user attestations are far less reliable than OTS proofs, they're much easier to verify, and can reach a pretty high level of reliability by combining multiple attestation sources with other forms of reputation.
In other words, instead of going nuclear and embedding your attestations into The Time Chain, you can simply ask 5-10 relays or people you trust for their attestations for a given event.
This PR isn't terribly important on its own, but it does remove one small barrier between us and trusted key rotation events (or other types of event that require establishing a verifiable chain of causality).
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 57d1a264:69f1fee1
2025-05-11 06:23:03
@ 57d1a264:69f1fee1
2025-05-11 06:23:03Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonb for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977190
-
 @ 57d1a264:69f1fee1
2025-05-11 05:52:56
@ 57d1a264:69f1fee1
2025-05-11 05:52:56Past week summary
From a Self Custody for Organizations perspective, after analyzing the existing protocols (Cerberus, 10xSecurityBTCguide and Glacier) and reading a bunch of relates articles and guides, have wrapped to the conclusion that this format it is good to have as reference. However, something else is needed. For example, a summary or a map of the whole process to provide an overview, plus a way to deliver all the information and the multy-process in a more enjoyable way. Not a job for this hackathon, but with the right collaborations I assume it's possible to: - build something that might introduce a bit more quests and gamification - provide a learning environment (with testnet funds) could also be crucial on educating those unfamiliar with bitcoin onchain dynamics.
Have been learning more and playing around practicing best accessibility practices and how it could be applied to a desktop software like Bitcoin Safe. Thanks to @johnjherzog for providing a screen recording of his first experience and @jasonbohio for suggesting the tools to be used. (in this case tested/testing on Windows with the Accessibility Insights app). Some insight shared have been also applied to the website, running a full accessibility check (under WCAG 2.2 ADA, and Section 508 standards) with 4 different plugins and two online tools. I recognize that not all of them works and analyze the same parameters, indeed they complement each other providing a more accurate review.
For Bitcoin Safe interface improvements, many suggestions have been shared with @andreasgriffin , including: - a new iconset, including a micro-set to display the number of confirmed blocs for each transaction - a redesigned History/Dashboard - small refinements like adding missing columns on the tables - allow the user to select which columns to be displayed - sorting of unconfirmed transactions - Defining a new style for design elements like mempool blocks and quick receive boxes You can find below some screenshots with my proposals that hopefully will be included in the next release.
Last achievement this week was to prepare the website https://Safe.BTC.pub, the container where all the outcomes f this experiment will be published. You can have a look, just consider it still WIP. Branding for the project has also been finalized and available in this penpot file https://design.penpot.app/#/workspace?team-id=cec80257-5021-8137-8005-eab60c043dd6&project-id=cec80257-5021-8137-8005-eab60c043dd8&file-id=95aea877-d515-80ac-8006-23a251886db3&page-id=132f519a-39f4-80db-8006-2a41c364a545
What's for next week
After spending most of the time learning and reading material, this coming week will be focused on deliverables. The goal as planned will be to provide: - Finalized Safe₿its brand and improve overall desktop app experience, including categorization of transactions and addresses - An accessibility report or guide for Bitcoin Safe and support to implement best practices - A first draft of the Self-Custody for Organizations guide/framework/protocol, ideally delivered through the website http://Safe.BTC.pub in written format, but also as FlowChart to help have an overview of the whole resources needed and the process itself. This will clearly define preparations and tools/hardwares needed to successfully complete the process.
To learn more about the project, you can visit: Designathon website: https://event.bitcoin.design/#project-recj4SVNLLkuWHpKq Discord channel: https://discord.com/channels/903125802726596648/1369200271632236574 Previous SN posts: https://stacker.news/items/974489/r/DeSign_r and https://stacker.news/items/974488/r/DeSign_r
Stay tuned, more will be happening this coming week
originally posted at https://stacker.news/items/977180
-
 @ c631e267:c2b78d3e
2025-05-10 09:50:45
@ c631e267:c2b78d3e
2025-05-10 09:50:45Information ohne Reflexion ist geistiger Flugsand. \ Ernst Reinhardt
Der lateinische Ausdruck «Quo vadis» als Frage nach einer Entwicklung oder Ausrichtung hat biblische Wurzeln. Er wird aber auch in unserer Alltagssprache verwendet, laut Duden meist als Ausdruck von Besorgnis oder Skepsis im Sinne von: «Wohin wird das führen?»
Der Sinn und Zweck von so mancher politischen Entscheidung erschließt sich heutzutage nicht mehr so leicht, und viele Trends können uns Sorge bereiten. Das sind einerseits sehr konkrete Themen wie die zunehmende Militarisierung und die geschichtsvergessene Kriegstreiberei in Europa, deren Feindbildpflege aktuell beim Gedenken an das Ende des Zweiten Weltkriegs beschämende Formen annimmt.
Auch das hohe Gut der Schweizer Neutralität scheint immer mehr in Gefahr. Die schleichende Bewegung der Eidgenossenschaft in Richtung NATO und damit weg von einer Vermittlerposition erhält auch durch den neuen Verteidigungsminister Anschub. Martin Pfister möchte eine stärkere Einbindung in die europäische Verteidigungsarchitektur, verwechselt bei der Argumentation jedoch Ursache und Wirkung.
Das Thema Gesundheit ist als Zugpferd für Geschäfte und Kontrolle offenbar schon zuverlässig etabliert. Die hauptsächlich privat finanzierte Weltgesundheitsorganisation (WHO) ist dabei durch ein Netzwerk von sogenannten «Collaborating Centres» sogar so weit in nationale Einrichtungen eingedrungen, dass man sich fragen kann, ob diese nicht von Genf aus gesteuert werden.
Das Schweizer Bundesamt für Gesundheit (BAG) übernimmt in dieser Funktion ebenso von der WHO definierte Aufgaben und Pflichten wie das deutsche Robert Koch-Institut (RKI). Gegen die Covid-«Impfung» für Schwangere, die das BAG empfiehlt, obwohl es fehlende wissenschaftliche Belege für deren Schutzwirkung einräumt, formiert sich im Tessin gerade Widerstand.
Unter dem Stichwort «Gesundheitssicherheit» werden uns die Bestrebungen verkauft, essenzielle Dienste mit einer biometrischen digitalen ID zu verknüpfen. Das dient dem Profit mit unseren Daten und führt im Ergebnis zum Verlust unserer demokratischen Freiheiten. Die deutsche elektronische Patientenakte (ePA) ist ein Element mit solchem Potenzial. Die Schweizer Bürger haben gerade ein Referendum gegen das revidierte E-ID-Gesetz erzwungen. In Thailand ist seit Anfang Mai für die Einreise eine «Digital Arrival Card» notwendig, die mit ihrer Gesundheitserklärung einen Impfpass «durch die Hintertür» befürchten lässt.
Der massive Blackout auf der iberischen Halbinsel hat vermehrt Fragen dazu aufgeworfen, wohin uns Klimawandel-Hysterie und «grüne» Energiepolitik führen werden. Meine Kollegin Wiltrud Schwetje ist dem nachgegangen und hat in mehreren Beiträgen darüber berichtet. Wenig überraschend führen interessante Spuren mal wieder zu internationalen Großbanken, Globalisten und zur EU-Kommission.
Zunehmend bedenklich ist aber ganz allgemein auch die manifestierte Spaltung unserer Gesellschaften. Angesichts der tiefen und sorgsam gepflegten Gräben fällt es inzwischen schwer, eine zukunftsfähige Perspektive zu erkennen. Umso begrüßenswerter sind Initiativen wie die Kölner Veranstaltungsreihe «Neue Visionen für die Zukunft». Diese möchte die Diskussionskultur reanimieren und dazu beitragen, dass Menschen wieder ohne Angst und ergebnisoffen über kontroverse Themen der Zeit sprechen.
Quo vadis – Wohin gehen wir also? Die Suche nach Orientierung in diesem vermeintlichen Chaos führt auch zur Reflexion über den eigenen Lebensweg. Das ist positiv insofern, als wir daraus Kraft schöpfen können. Ob derweil der neue Papst, dessen «Vorgänger» Petrus unsere Ausgangsfrage durch die christliche Legende zugeschrieben wird, dabei eine Rolle spielt, muss jede/r selbst wissen. Mir persönlich ist allein schon ein Führungsanspruch wie der des Petrusprimats der römisch-katholischen Kirche eher suspekt.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 434f9799:2d548c15
2025-01-23 23:15:34
@ 434f9799:2d548c15
2025-01-23 23:15:34如果你在乎你网上的内容, 请为它们附上版权声明. 如果你在共享你的内容, 请表明你的意图. 否则不要抱怨别人为何不按你的意愿使用, 因为你从没有表明过它.
同样身为创作者, 但还没有能自诩 "艺术家" 的程度, 从自己生产内容然后公开的开始就是希望被別人看到自己的作品, 并且要让别人知道「这是我创造的东西」, 然后才会有原创, 抄袭和借鉴的争论. 我是从最开始也是从 UGC 平台上逐渐转移到拥有自己 "平台" (从博客开始) 的人, 当时只为了追求所谓「自由」, 自己想写什么就写什么, 这是我的博客凭什么你来指指点点? 然后逐渐意识到当自己的身份从创作者用户过渡到创作者平台, 必须要考虑的事情就会变多, 这也是权利和义务的无条件对等结果, 我自己一个人就要成为平台. 到这时, 能对我指指点点人只会变得更多, 体量只会更大, 范围也会扩大到全世界, 因为这是互联网. 那么生活在在 UGC 平台的人难道就没有这个烦恼吗? 不是的, 只不过是平台已经帮我做了决定, 因为我必须同意他们的使用政策和隐私协议我才能使用, 包括其中顺带同意的版权声明.
作为小到自己都不想称之为一个 "平台" 的独立博客, 也要用自己身为平台应该要做的事情, 我的博客用户是谁? 是所有能够访问到我的博客的人, 机器人甚至伪装为人的机器人.
所以我需要:
-
如果我用了 Google Analytics 而我如果要面向的用户当地存在个人数据法, 那就要加上一个 cookie 知情确认通知.
-
如果有机器人来我的博客, 而我不想让它们进来, 那我应该声明 robots.txt.
-
如果我的用户, 我的读者希望能够轻松自如地帮我分享内容而不用时时刻刻都向我发消息确认转发请求, 那么我应该声明版权许可, 那至少也是 CC-BY 的等级.
-
如果我不希望我的内容在沒有许可的情况下被复制, 被重新演绎, 被用作商业用途盈利; 要么实行事后责任制, 请一个版权律师和版权机器人帮我给这些讨厌的东西发律师函, 发给对方的 ASN 管理员, DNS 解析服务器管理员, 域名管理局或者其他所有为它提供基础设施服务的服务商, 期盼他们能够遵守「自己的」法律.
-
如果我不希望某些用户访问我的博客, 我需要使用 WAF 屏蔽他们.
但可惜, 这互联网上最著名的版权法案 DMCA 也存在 "合理使用" 裁定, 各国各地对互联网著作权的处理也不尽相同, 如此大费周章并不能就让所有我想要不能使用我内容的人放弃使用我的内容. 那么真的没有办法了?
没有问题, 还可以同时实行事前责任制, 因为我还有 DRM, 也就是数字版权管理. 我能自己购买, 租用甚至自己开发一套版权管理系统, 只有在我的平台上才能看到我的内容, 别人想要复制我的内容会变得无比艰难, 但也只止步于 "无比艰难" 而已.
我作为平台, 需要这么努力吗? 或者说有必要这么麻烦吗? 手段的升级只会消耗更多的时间和金钱, 我只是一个小小的独立博客, 我只能用上 CC 和 robots.txt, 最多给内容加点水印. 我只是想保护我的内容而已, OpenAI 一众很可能已经在不知不觉中掠夺过我的东西了, 治不了大公司还治不了你吗?!
恭喜你, 你已经拥有成为一个平台的觉悟了.
说点实际的
我能在此如此大放厥词完全因为我实际拥有这个博客, 不用担心我会因为一两句话就破坏某些平台的狗屁 "社区守则" 乃至它们左右摇摆的政治立场, 没有别的意思, 这里的「政治」只不过是对于这些平台在社会中所扮演角色的简称.
如果你同意我说的, 那么下面是作为多个「独立平台」管理员对平台管理员的一些建议:
- 如果你愿意为你的内容负责, 请至少为你的独立平台附上版权声明, 哪怕是在页脚加一个 "Copyright © CC-BY" 甚至 "Copyright © All rights reserved". 当然前提是你的内容全部出自你的手, 或者你的平台有其他用户并且他们同意你的声明.
- 如果你希望或者不希望被机器人或者某些机器人自动抓取内容, 请为你的独立平台添加 robots.txt. 所有的机器人都能声称自己是真实的用户代理(User-Agent), 在如今的互联网上, 所有人都默认在没有 robots.txt 声明的情况下机器人可以随意进出你的平台, 尝试获取你的平台内容.
如果你已经是平台内的用户了, 或者你的独立平台需要使用其他平台的内容, 以下对于内容创作者的建议:
- 不要尝试使用任何没有版权声明的平台里的实际内容. 它们比 "保留所有权利" 甚至带有 DRM 的内容更加不确定, 因为它们的创作者不愿意主动表露自己对他人使用自己内容的意图. 除非你愿意到处查找内容创作者或者平台的联系方式, 然后联系上他们请求使用他们的东西. 当然, 直接不使用实际内容就行了, 你可以引用来源乃至完全重新演绎它们, 就像 ChatGPT 一样.
- 好好阅读平台的版权声明, 使用许可和隐私政策, 大多数时候你的东西是不是你的取决于平台而不是你, 甚至包括你的隐私. 实际上, 我们处于社会化状态下是被动着去使用某些平台, 要么你说服别人或者强迫别人去使用你想用的平台, 而这又对于追求「人人平等」的现代社会是不可接受的, 除非这种对等关系被打破. 知悉这些条款并且在乎自己内容的创作者能够控制自己可以在这里产生什么东西, 或者是在平台上借助自己的内容和平台达成交易换取自己想要的东西.
结语
创作者或者是艺术家的世界对于版权这种事情看起来很在乎, 但实际上没有几个人是亲自去执行的, 大多都是依附于创作平台或者版权公司, 让它们代行自己的权利, 让自己能够专心于创作, 然后拿到自己想要的.
然而在计算机和互联网融合的世界, 构建这个数字世界的 "艺术家" 们早就已经发起了一场颠覆这种局面的政治运动, 名字叫作 "开源", 赋予开源权利的许可叫做 "开源许可", 成就他们理想的叫做 "自由软件", 自由软件基金会和 GPL 许可证由此诞生, 始于 1989 年.
而现实世界的艺术家们呢? 他们创作文学, 绘画, 音乐乃至影片在互联网上获得全世界范围的传播, 但可惜依旧遵守着老一套的规矩, 把自己的作品交给平台, 交给公司管理. 自由软件基金会诞生后的 12 年, 知识共享(Creative Commons, CC)才出现在互联网. 那么在这之前的 12 年间, 互联网上的艺术家们生产的内容难道都是默认公共领域的吗? 我想更多是即使想要保留部分权利但根本没有意识到要声明自己的意图.
而二十多年后的今天, 依旧如此. "书呆子" 程序员无人不知开源, 知道自己的创造的东西需要让别人知道自己的作品能够被如何使用, 即使是 "Copyleft", 是 "All rights reversed" 放弃了全部权利, 也是知道自己一开始就有权利可以对自己的东西这么做.
而那些迷失在意识洪流中的疯狂艺术家们, 对待自己的作品如何被别人使用上还是模棱两可, 暧昧不清. 即使是 CC 和 robots.txt 也都是可有可无地充满艺术感, 他们确实在乎自己的作品, 但是更在乎自己.
PS: 本文属一时兴起一笔写完, 可能有很多奇怪的地方, 如果需要转载, 请首先遵守本站/账户的版权许可. 欢迎指正和纠错.
封面
Photo by Aaron Burden on Unsplash
-
-
 @ 57d1a264:69f1fee1
2025-05-10 05:45:52
@ 57d1a264:69f1fee1
2025-05-10 05:45:52Finale: once the industry-standard of music notation software, now a cautionary tale. In this video, I explore how it slowly lost its crown through decades of missed opportunities - eventually leading to creative collapse due to various bureaucratic intrigues, unforeseen technological changes and some of the jankiest UI/UX you've ever seen.
https://www.youtube.com/watch?v=Yqaon6YHzaU
originally posted at https://stacker.news/items/976219
-
 @ 57d1a264:69f1fee1
2025-05-10 05:34:46
@ 57d1a264:69f1fee1
2025-05-10 05:34:46
For generations before generative text, writers have used the em dash to hop between thoughts, emotions, and ideas. Dickens shaped his morality tales with it, Woolf’s stream-of-consciousness flowed through it, Kerouac let it drive his jazz-like prose. Today, Sally Rooney threads it through her quiet truths of the heart.
But this beloved punctuation mark has become a casualty of the algorithmic age. The em dash has been so widely adopted by AI-generated text that even when used by human hands, it begs the question: was this actually written or apathetically prompted?
The battle for the soul of writing is in full swing. And the human fightback starts here. With a new punctuation mark that serves as a symbol of real pondering, genuine daydreaming, and true editorial wordsmithery. Inspired by Descartes’ belief that thinking makes us human, the am dash is a small but powerful testament that the words you’ve painstakingly and poetically pulled together are unequivocally, certifiably, and delightfully your own.
Let's reclain writig from AI—oneam dash at time.
Download the fonts:
— Aereal https://bit.ly/3EO6fo8 — Times New Human https://bit.ly/4jQTcRS
Learn more about the am dash
https://www.theamdash.com
originally posted at https://stacker.news/items/976218
-
 @ 0d97beae:c5274a14
2025-01-23 21:05:12
@ 0d97beae:c5274a14
2025-01-23 21:05:12History is written by the victor.
There is very little we can know about our history. We can have written literature and physical evidence, yet it is rarely possible to know the facts of something without having been there at the time. Even in the court of law, testimonies can be falsified, evidence can be misinterpreted, and stories can be spun to provide an alternative account of events.
In a world where history is shaped by perspective and bias, it might seem impossible to ever construct an account of events that is entirely free from distortion; not without a central arbiter who is entrusted to preserve the truth. We often rely on records of agreements to help settle disputes; however, as the degree of risk increases - such as when purchasing a house, for example - we need to involve licensed third parties who can be trusted to keep and preserve a historical record of our agreements, ensuring that penalties can be enforced if either party breaks the terms therein.
Of course, these agreements are often still vague enough to allow for re-interpretation, and, with enough corruption, nothing prevents the very institutions that were supposed to protect the sanctity of the agreement from altering the records. Fortunately, the system has worked well and has served its purpose truthfully most of the time.
Relating back to Bitcoin
Bitcoin is able to do something remarkable: it can create a historical record of events that cannot be altered or revised in any way. However, it does not solve the problem of people and institutions re-interpreting records or choosing not to apply enforcement; this technology cannot be used to replace any and everything, it has a very specific use case. Bitcoin is designed to capture transaction records and enforce the criteria that they must meet before accepting them. They enforce that they do not inflate the supply of bitcoin units, and that they have included all of the necessary information required to be fully verifiable.
As well as enforcing transaction rules strictly, Bitcoin uses a process to fossilise these records into history through two core technical innovations: "proof of work" and "difficulty adjustment". Proof of work introduces the cost of energy, while difficulty adjustment enforces the cost of time. Together, Bitcoin effectively uses time and energy to ensure that history can never be rewritten.
To break it down a bit more, people can still create alternative chains of events, but each candidate must include the relevant time and energy data to make comparisons possible. Additionally, the "proof of work" technology ensures that the energy data is impossible to fabricate. The chain that has clearly spent the most time and energy will stand out immediately, meaning the chain produced by the largest global community will always emerge as the victor, without the need for inconclusive debates or corruptible authority figures to make the call.
The magic lies in how data produced by Bitcoin is fully self verifiable. It is not just the transaction data that can be verified, it is the complete historical order of events that were observed and fossilised in real-time through a fair and neutral, yet irreversible process.
Why we run Bitcoin nodes
Bitcoin does not run by itself. Beyond needing users to create and submit transactions, it also requires people to provide energy for its proof of work, and it requires people to participate by collecting, verifying, and storing the information in as many places as possible, all around the world.
If Bitcoin had an Achilles' heel, it would be the loss of its recorded data. If the data were lost, then there would be nothing to stop an alternative set of records from taking its place and rewriting history. By running a node, we ensure that there are plentiful copies of this data.
From a self-serving perspective, running a Bitcoin node ensures that we are always able to access first-hand data about the state of Bitcoin and our wallets. If we rely on third parties to inform us of this information, we introduce a layer of risk and place our trust in someone else. If that trust is abused, we could be fooled into believing we have received bitcoin when in fact this was not the case. While a Bitcoin node does collect its data from online sources, since it collects data from multiple sources and it is able to validate and identify any discrepant data, it is more likely to provide you with the latest and most accurate information available.
We also help in situations where connectivity is limited, such as the time when Australia was cut off from the world wide internet for some time. In this case, users in Australia were inconvenienced for some time:
- With limited connectivity, miners in Australia could not share their work quickly enough to compete effectively with the greater global network.
- Users might see their transactions remain unconfirmed for longer periods of time.
- Users may even see their transactions transition from confirmed to unconfirmed as nodes struggle to keep up with the chain of events being agreed upon by the greater network.
By operating a node in Australia, you were helping to link and share data in real-time with the rest of the network, and if you had a connection to the greater network, you would be helping to bridge the connection.
Once the internet was restored, your node would help to keep track of all the unconfirmed transactions in your country and share them with the greater global network so that they can be processed.
It should be noted that Bitcoin network does not need any sort of manual intervention to come to a shared agreement about the legitimate chain of events and continue operating as normal.
-
 @ 57d1a264:69f1fee1
2025-05-10 05:11:27
@ 57d1a264:69f1fee1
2025-05-10 05:11:27Consider the following two charts from A History of Clojure which detail the introduction and retention of new code by release for both Clojure and for Scala.
While this doesn't necessarily translate to library stability, it's reasonable to assume that the attitude of the Clojure maintainers will seep into the community. And that assumption is true.
Consider a typical Javascript program. What is it comprised of? Objects, objects, and more objects. Members of those objects must be either introspected or divined. Worse, it's normal to monkeypatch those objects, so the object members may (or may not) change over time.
Now, consider a typical Clojure program. What is it comprised of? Namespaces. Those namespaces contain functions and data. Functions may be dynamically generated (via macros), but it is extremely rare to "monkeypatch" a namespace. If you want to know what functions are available in a namespace, you can simply read the source file.
Continue reading https://potetm.com/devtalk/stability-by-design.html
originally posted at https://stacker.news/items/976215
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 57d1a264:69f1fee1
2025-05-08 05:25:48
@ 57d1a264:69f1fee1
2025-05-08 05:25:48Safe Bits & Self Custody Tips
The journey of onboarding a user and create a bitcoin multiSig setup begins far before opening a desktop like Bitcoin Safe (BS) or any other similar application. Bitcoin Safe seems designed for families and people that want to start exploring and learning about multiSig setup. The need for such application and use of it could go much further, defining best practices for private organizations that aim to custody bitcoin in a private and anonymous way, following and enjoy the values and standards bitcoin has been built for.
Intro
Organizations and small private groups like families, family offices and solopreneurs operating on a bitcoin standard will have the need to keep track of transactions and categorize them to keep the books in order. A part of our efforts will be spent ensuring accessibility standards are in place for everyone to use Bitcoin Safe with comfort and safety.
We aim with this project to bring together the three Designathon ideas below: - Bitcoin Safe: improve its overall design and usability. - No User Left Behind: improve Bitcoin Safe accessibility. - Self-custody guidelines for organizations: How Bitcoin Safe can be used by private organization following best self-custody practices.
We are already halfway of the first week, and here below the progress made so far.
Designing an icon Set for Bitcoin Safe
One of the noticeable things when using BS is the inconsistency of the icons, not just in colors and shapes, but also the way are used. The desktop app try to have a clean design that incorporate with all OS (Win, macOS, Linux) and for this reason it's hard to define when a system default icon need to be used or if a custom one can be applied instead. The use of QT Ui framework for python apps help to respond to these questions. It also incorporates and brig up dome default settings that aren't easily overwritten.
Here below you can see the current version of BS:
Defining a more strict color palette for Bitcoin Safe was the first thing!
How much the icons affect accessibility? How they can help users to reach the right functionality? I took the challenge and, with PenPot.app, redesigned the icons based on the grid defined in the https://bitcoinicons.com/ and proposing the implementation of it to have a cleaner and more consistent look'n feel, at least for the icons now.
What's next
I personally look forward to seeing these icons implemented soon in Bitcoin Safe interface. In the meantime, we'll focus on delivering an accessibility audit and evaluate options to see how BS could be used by private organizations aiming to become financially sovereign with self-custody or more complex bitcoin multiSig setups.
One of the greatest innovations BS is bringing to us is the ability to sync the multiSig wallets, including PBST, Categories and labels, through the nostr decentralized protocol, making current key custodial services somehow obsolete. Second-coolest feature that this nostr implementation brings is the ability to have a build-in private chat that connect and enable the various signers of a multiSig to communicate and sign transactions remotely. Where have you seen something like this before?
Categories UX and redesign is also considered in this project. We'll try to understand how to better serve this functionality to you, the user, really soon.
Stay tuned!
originally posted at https://stacker.news/items/974488
-
 @ 3b70689a:c1e351eb
2025-01-22 23:47:36
@ 3b70689a:c1e351eb
2025-01-22 23:47:36来自西班牙的公司 Liberux 最近推出了他们的新手机 Liberux NEXX 众筹计划. 根据目前主页上的介绍, 这款设备将会搭载基于 Debian 13 ARM 构建的 LiberuxOS 操作系统, 并且还提供一个受限的(jailed)的 Android 子系统.

Liberux 的 Fediverse 主页
Liberux 硬件开发工程师 Carlos Rodríguez 的 Fediverse 主页
Carlos Rodríguez 说, 目前网站上的 NEXX 是最初版本, 目前仍然在努力制造第一台原型机, 并且所有的硬件和软件设计都将免费(公开).
WOW, I think our little secret has been revealed, we hope that in a short time you will be able to see the first functional prototypes. We are working very hard on it, by the way, all our designs, both hardware and software, will be free. At the moment the web is a first version, some things will be modified.
硬件参数
-
CPU: 瑞芯微 RK3588s (八核心, 8nm, 2.4Ghz, 2022Q1)
-
GPU: ARM Mali-G610 (4 核心, 2021Q2)
- 存储: 32GB LPDDR4x RAM, 256GB eMMC ROM
- 电池: 5300mAh (可拆卸)
- 接口: 3.5mm 耳机 * 1, USB-C 3.1 * 2
- 扩展: microSD 插槽 (2TB Max)
- 屏幕: 6.34 吋, OLED, 2400*1080
- 相机: 后置 32MP, 前置 13MP
- 通讯: 高通骁龙 X62 基带 (2021Q1), 海华 AW-CM256SM 无线网卡 (Wi-Fi 5, 蓝牙 5.0)
- 传感器: 昇佳 STK3311-X 环境光传感器, 美新 MMC3630KJ 三轴磁传感器, 应美盛 ICM-42670-P 加速度计/陀螺仪
- 其他: 内置 DAC 和功放芯片 (瑞昱 ALC5640-VB-CG, 艾为 AW8737SCSR)
其他特点
设备目前公布的外观设计均是渲染效果, 最终交付的设备很可能会与这些渲染图片有很大出入. 但仍然可以通过这些效果图理解 Liberux 的最初意图.
- 摄像头 & 麦克风, 蓝牙 & WLAN, 数据网络功能模块的物理开关(位于顶部).

- 后置指纹解锁, 无摄像模组凸起.
- 左上角挖孔前置摄像头.

- 电源键位于侧边右下角.
其他报道
- Liberux Nexx: New Linux smartphone with 32GB RAM, 2TB storage, 5G and more - NotebookCheck.net News
- Смартфон Liberux Nexx получил ОС Linux и поддержку 2 ТБ памяти - 4PDA (讨论)
- Smartfon z Linuksem? Oto Liberux NEXX. Ekran OLED, 32 GB RAM i system oparty na Debianie. Ciekawy model, choć nie bez wad | PurePC.pl (讨论)
- LINux on MOBile: "The Liberux Nexx (https://libe…" - Fosstodon (Fediverse, 讨论, 工程师回复)
-
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 45bda953:bc1e518e
2025-05-19 09:15:47
@ 45bda953:bc1e518e
2025-05-19 09:15:47Hithe III
The counsel convened and an area of land had been designated as suitable for an industrial scale landing site of tier III size void vessels. All Kaspian land owners were required to donate workers for the initiative. It was an exciting affair for all involved. With an evergreen tree line to hinder the on and off breeze, tables were assembled and covered with a unique assortment of table cloths. Every lady brought one along and the embroidery on each was the cause of many flattering remarks. The women brought all sorts of food and refreshments, had gazebo's set up and had chairs placed well away from the noise and dust of the demarcated construction site. The men where organising equipment, measuring bedrock depth and organising the labour parties into manageable groups. In spite of all the mothers most dire warnings to stay clear of the areas where active construction would be taking place, the children knew they had free reign to explore and play wherever they wanted. The oxen bellowed incessantly, tethered in long lines before their carts, a slave armed with standard bullwhip, ready to man his post atop each wagon. Albin sat on the ground chewing on a stalk of wheat. Being barely old enough to help the men with their work, he was ordered to do nothing more than spectate. Having received concerned looks from the adults, repeating tropes of how he might get hurt and be in the way. He made peace with his lot. The fact that he was going to see void craft was exciting enough to satiate his curiosity for adventure. He would inadvertently lean back and look up expectantly only to see the clear sky then rock forwards back to his previous position. His only regret was that Seth was not with him to discuss and share in the experience. Seth was old enough to work alongside the other slaves, robbing Albin of good company. He glanced back at the large groups of women and smaller children, his mother stuck out like a sore thumb seeing as she was the only lady wearing pants amongst the variety of her chemise, spring attired peers. Her hair was braided and she had an unopened parasol at hand. No one dared ask why her odd choice in outfit though you knew they thought ill of it by their confused and somewhat unduly patronising looks. Before dawn, when they were still at the manor Albin asked her why she was dressed funny and she said that she would prefer not making a spectacle of herself. He just shrugged and did not think much of it again until just now. It seemed to him that she was the only spectacle around not even having brought a table cloth to adorn her bench like the other woman did. He decided to get something to eat and drink because the texture and taste of the dried stalk had become slightly off-putting making him spit out little bits of grass as he stood up. Cleolia smiled affectionately when she saw her boy approaching and peered over her shaded glasses. He lifted the picnic basket off the ground and put it on the heavy bare wooden table, filled a cup with milk and swallowed it down almost as quickly as he had poured it. "Are they going to be late." He asked his mother. "I'm sure they will arrive soon my dear." She replied while taking a seat in a folding chair. Albin grabbed a handful of pretzels and looked around ponderously as he ingested the snack. The people always enjoyed community gatherings of this sort. Lot's of catching up and gossip happening in a cheerful non insidious way. A type of orderly chaos that brought feelings of peace and tranquillity to the conscious observer. His daydream was broken by a soft but clearly distinct repetitive dong of the distant church tower. His dad and father Ecknard were there using the comms, he assumed they were signalling for something. A long shrill whistling sound caught Albins attention and he began walking towards the furthest groups of men while scanning the area intently. The discernible pitch of Seth's whistle became audible again and Albin honed in on the direction the sound was coming from. He saw his friend standing on an ox cart waving his woven satgat frantically trying to get Albin's attention. As soon as they established eye contact he pointed in a very specific north western direction upwards at the dome of the sky. Albin followed his gaze and for a moment thought his mind is playing a trick on him, but it became apparent that a silhouette of something oddly pale was stuck in the sky with nondescript features. Recalling his studies he managed to identify the craft. It was a Dragon IV Cargo vessel. A Magar craft and supposedly very impressive, the distance did not do it justice, yet the uncanny feeling that X fold more people were floating in a box in the sky than were on the planet made Albin's stomach flip and he felt off balance. He sat down on the ground again to prevent him from stumbling around trying to keep his legs under his body. As soon as the church bell ceased it's tolling a smoke signal was ignited in the clearing beyond the work parties. The yellow smoke billowed up in sharp contrast to the greenery of the fields. III percussive shots thundered through the air like cannon fire causing a sudden change in environmental ambience. Birds were visibly swarming up from trees as far as the eye could see. Albin chose not to remove his sights from the giant void craft. He saw a light in the atmosphere that became distinct as it neared separating into the underbellies of III descending craft. Albin murmered. "The Dragons payload." His excitement grew as did the vessels on their approach. At first a hum growing into a crescendo of weird harmonic roaring as the vessels fought mightily to resist Hithe's above average gravitational pull. All the men tipped their satgats and hard hats to cover their faces, the oxen also faced away. Albin did not want to look away but was forced to turn his head as a powerful gust loaded with projectiles of sand and grass peppered his face sharply. Looking back he saw his mother promptly opening her parasol and pointing it in the direction of the landing, then the real spectacle occurred. All the woman covered their faces only to have their skirts blown up exposing their undergarments, in turn trying to push down their skirts uncovering their faces. The risk of shame weighed against tolerance to pain combined into a beautiful ballet of embroidered cloth being wrapped around trees and condiments strewn around the shaded grove with gazebos escaping the scene followed by children running after them in heated pursuit. Cleolia's pant legs fluttered rapidly around her ankles. As soon as the III vessels turbulence settled she folded her parasol and reassumed her previous position as if nothing of note had transpired. Smiling carefree amongst the distraught group women and children around her. Albin would have laughed at the scene had his eyes not stung so badly. "Mother always knows best." He mumbled to himself as he stood up brushing dust off his undercoat. The opening of the ships cargo bays where announced with a loud hiss of air depressurising. Albin casually sauntered over to get a closer look. The cattle marched up the ramps wagon in tow to park directly alongside the freight. The goods consisted of thousands of long coach bolt like nails as long as fence posts and sturdy modular steel plates stacked on mobile pallets and tied down securely. Albin imagined them to look like giant, shiny metal puzzle pieces. The primitive vehicles and their crews made quick and efficient work of releasing the straps and with the help of overhead cranes hoisted the pallets and their contents into the wagons. Two uniformed men came out from inside the ship and stood watching the men unload their craft. Albin noticed the smartly dressed pilots. "Holy servants of the Empire." He spoke softly under his breath. His desire to meet these champions of the void felt necessary to him. They who travel among the stars much like the stories he always heard about his parents. The men were standing safely apart from the work parties, Albin mustered the courage to approach them. He timidly walked up behind them. "Ahem, Hallo Sir." The pilots looked around surprised. Albin seemed respectful and quaint. "Hey kiddo, you guys have a lovely planet." The pilot replied friendly. "What type of craft are these, sir?" The man gestured towards his vessel in reply. "These? They are standard Type I Droppers. Nothing really special about them." Albin nodded. "Are you from Magar void?" "I am indeed. It is really magnificent but you have something quite spectacular yourselves." Albin did not expect that anything in his little world could impress these well travelled gentlemen. "Like what?" He insisted questioningly. "Like the sol shield. You know the star inhibitor. It's a marvel of our time." The man pointed at Ceb. Albin understood. "Oh yes, my pa put it there so we can all survive here." Both pilots looked at each other surprised. Their demeanour changed and Albin suddenly felt uncomfortable. The man knelt down until he was eye level putting his hand on Albins shoulder clenching it just tight enough to not be painful. "If you are a Domitian heir, then I am an Osteri dancing girl at a Juel gentlemans club." His sarcastic tone cut Albin's pride. "You'd better run along and go play with your friends before I decide to arrest you or report you to the authorities." The other pilot looked away ignoring Albin's confused expression. The man assertively shoved Albin away from him. Albin just barely prevented himself from falling on his rear. Tears welled up in Albin's eyes, he turned and ran away humiliated and angry. But he choked back the tears, choosing to embrace the anger in place of emotional release. He ran away from the construction zone also avoiding the picnic area. He did not want to be around anyone. His erratic and emotional mood would betray his experience if anyone he loved interacted with him. He ran into a shaded area of wood and sat down on a stump to digest and try to reset his state of mind to normalcy. He sat quietly for about III blocks when he heard laughter from beyond the wood. There were a group of boys standing circled around an Osteri boy and girl. The girl was crying. Albin witnessed the interaction. "You are not supposed to be here. Only the working slaves are here today." The boy pleaded with his captor in reply. "I only came to find my sister, we are going back to the village now. Please let us go." "But what was she doing here then? Huh?" Albin walked into the centre of the fray interrupting the entire affair. Standing squarely in front of whom he assumed was the primary instigator. The biggest guy in the bunch. "They are only curious to see the void craft. That is why we all came here today." He explained diplomatically. The big kid sneered. "And who are you to tell me how to treat slaves. You are Magar, you should know better." Another kid piped in. "My mama told me he is Kaspa." The bully looked around surprised. Another boy opined. "Not true, my mom said that his mother was pregnant for 40,000 blocks." And then another kid had to add his understanding to the discussion. "No, no, my pa said that she lost the baby at birth and adopted a slaves child." Albin got overwhelmed with the revelations of rumour and petty gossip surrounding his person. "That does not give you the right to bully them!" Albin pointed to the brother and sister. The big boy smiled a snide retort leaning forward mockingly. "No, but I might have the right to bully you, Osteri bastard child of a slave." Albin felt all natural sense of humanity drain from his being. He turned feigning to leave, balled his fist and swung, socket-ting the unprepared target square on the throat. He fell on his back and the angst of restricted breath became evident first to himself and then to all watching. Albin turned to the siblings. "You can go." The pair hurriedly left and none of the boys even hinted at preventing them. Albin looked at all the others dead in the eye each in turn. Then he left walking the long distance towards his mother. He was thirsty and his hand smarted a little, but he felt much better.
...
scifi
-
 @ 57d1a264:69f1fee1
2025-05-08 05:08:36
@ 57d1a264:69f1fee1
2025-05-08 05:08:36Welcome back to our weekly
JABBB, Just Another Bitcoin Bubble Boom, a comics and meme contest crafted for you, creative stackers!If you'd like to learn more, check our welcome post here.
This week sticker:
Bitcoin SirYou can download the source file directly from the HereComesBitcoin website in SVG and PNG. Use this sticker around SN with the code
The task
Make sure you use this week sticker to design a comic frame or a meme, add a message that perfectly captures the sentiment of the current most hilarious takes on the Bitcoin space. You can contextualize it or not, it's up to you, you chose the message, the context and anything else that will help you submit your comic art masterpiece.
Are you a meme creator? There's space for you too: select the most similar shot from the gifts hosted on the Gif Station section and craft your best meme... Let's Jabbb!
If you enjoy designing and memeing, feel free to check out the JABBB archive and create more to spread Bitcoin awareness to the moon.
Submit each proposal on the relative thread, bounties will be distributed when enough participants submit options.
PS: you can now use HereComesBitcoin stickers to use on Stacker.News
₿e creative, have fun! :D
originally posted at https://stacker.news/items/974483
-
 @ 8f69ac99:4f92f5fd
2025-01-06 17:11:58
@ 8f69ac99:4f92f5fd
2025-01-06 17:11:58Os humanos evoluíram para contar maçãs, não estrelas. Estamos programados para compreender números pequenos e tangíveis com facilidade, mas, no momento em que atingimos centenas ou milhares, os nossos cérebros começam a ter dificuldades. Esta limitação desempenha um papel significativo na fricção que as pessoas sentem ao tentar compreender Bitcoin, desde os seus fundamentos de segurança até ao seu sistema monetário.
A natureza abstracta de Bitcoin é construída sobre conceitos matemáticos complexos, incluindo criptografia e números grandes. No entanto, estes elementos podem ser esmagadores para muitos potenciais utilizadores, investidores e até especialistas. Neste artigo, vamos explorar porque é que os humanos têm dificuldade com números grandes e como esta limitação afecta a nossa compreensão de Bitcoin.
Porque é que os humanos têm dificuldade com números grandes
O nosso cérebro está programado para pensar de forma linear e processar números pequenos com facilidade. No entanto, quando se trata de números grandes, tudo começa a parecer confuso. Limitações evolutivas significam que fomos desenvolvidos para contar maçãs, não estrelas. Para além de algumas dezenas, os números começam a parecer "muitos" em vez de quantidades específicas.
Por exemplo, considere o número de chaves privadas possíveis em Bitcoin. Com 256 bits usados para encriptação, isto traduz-se em aproximadamente
$$2^{256}$$chaves únicas. Embora este número seja impressionante, a maioria das pessoas tem dificuldade em compreender a sua enormidade. Para colocar em perspectiva: - Existem mais átomos no universo observável do que grãos de areia em todas as praias da Terra.Além disso, o nosso cérebro frequentemente luta para entender fenómenos exponenciais, que desempenham um papel crucial no sucesso de Bitcoin. O crescimento da população mundial ou o número de hashes efectuados por segundo pelos mineradores de Bitcoin podem parecer incompreensíveis devido à sua natureza rápida.
Finalmente, a falta de pontos de referência do dia a dia dificulta a compreensão de conceitos complexos como chaves privadas e hashrate. Por exemplo, dizer "100 biliões" pode significar algo para si, mas decompor isso em números mais pequenos e manejáveis é uma história completamente diferente.
A História do Tabuleiro de Xadrez e o Grão de Arroz - uma pequena explicação didáctica sobre exponenciais.
Certa vez, um matemático indiano inventou o jogo de xadrez e apresentou-o ao rei local (frequentemente chamado de Maharaja). O rei ficou tão impressionado com o jogo que ofereceu recompensar o matemático com qualquer coisa que ele desejasse.
O matemático humildemente pediu um único grão de arroz para ser colocado na primeira casa do tabuleiro de xadrez, e que a quantidade de arroz fosse duplicada em cada casa seguinte. O rei, pensando que este era um pedido modesto, concordou imediatamente.
O processo começou: - 1 grão na primeira casa,
- 2 grãos na segunda,
- 4 grãos na terceira,
- 8 grãos na quarta, e assim por diante.Mas, à medida que avançavam, os números começaram a crescer rapidamente. Na 20.ª casa, já eram necessários mais de 1 milhão de grãos de arroz. Na 40.ª casa, o total ultrapassava 1 bilião de grãos. Na 64.ª e última casa, o total era um espantoso 18 quintiliões de grãos de arroz (
$$2^{64} - 1$$).Esta quantidade era tão vasta que exigiria mais arroz do que poderia ser cultivado na Terra naquela época. O rei, ao perceber que subestimara o pedido do matemático, foi forçado a admitir derrota ou, em algumas versões da história, puniu o matemático pela sua astúcia.
Bitcoin e Números Grandes: A Tecnologia Incompreendida
A complexidade de Bitcoin reside na sua dependência de criptografia e números imensos. Vamos explorar três áreas chave onde estes conceitos podem criar atrito.
A Segurança Incompreensível das Chaves Privadas
A segurança de Bitcoin assenta na escala absoluta do seu espaço de chaves privadas. Existem
$$2^{256}$$chaves possíveis — um número tão grande que tentar adivinhar uma chave não é apenas improvável, é praticamente impossível. É como se lhe pedisse para adivinhar o número em que estou a pensar entre 1 e 115792089237316195423570985008687907853269984665640564039457584007913129639936!Para colocar isto em perspectiva: - Imagine que existem mais estrelas no universo observável do que grãos de areia nas praias da Terra. Mesmo que combinasse todos os grãos de areia e estrelas, o número resultante ainda seria inferior a ```$$2^{256}$$```.
Esta escala impressionante garante a robustez da segurança criptográfica de Bitcoin, mas pode parecer esmagadora para os recém-chegados.
O Hashrate de 1 Zettahash/s
Recentemente, a mineração de Bitcoin ultrapassou a marca de 1 zettahash por segundo (
$$10^{21}$$hashes por segundo). Esta medida de poder computacional destaca a escala imensa da segurança da rede.Para ilustrar: - Imagine tentar adivinhar um número biliões de vezes por segundo, por pessoa, para todos os humanos na Terra. Mesmo com todo este esforço combinado, mal arranharíamos a superfície do actual hashrate de Bitcoin.
Este poder computacional imenso é o que garante que, uma vez adicionada uma transacção à timechain (ou blockchain se preferir) de Bitcoin, seja praticamente impossível alterá-la.
A Barreira da Criptografia
A criptografia de curva elíptica, ECC, um elemento chave em Bitcoin, utiliza matemática avançada que pode parecer abstracta para não especialistas. Baseia-se em "funções unidireccionais," onde gerar uma chave pública a partir de uma chave privada é fácil, mas reverter o processo é quase impossível.
O recente medo da computação quântica (apenas FUD), mostra bem esta segurança na matemática. O Willow, o computador da quântico da Google, com 105 qubits, resolveu um problema de benchmark em 5 minutos, que levaria a um super computador 10 septiliões de anos a resolver (mais tempo que a idade do universo, 13.8 mil milhões de anos).
Para conseguir encontrar a chave privada a partir de uma chave publica, seriam necessários cerca de 124000 Willows para o fazer em 1 dia, ou cerca de 340 para o fazer em 1 ano. E mesmo assim, apenas os endereços mais antigos, P2PK (Pay to Public Key) estariam vulneráveis, os endereços P2PKH (Pay to Public Key Hash) tem mais um nível de segurança, o hash.
O Willow teria que ter milhões ou milhares de milhões de qubits para conseguir descobrir uma chave privada a partir da chave publica. Não temos ainda tecnologia para isso...
Para simplificar: - Pense nisso como uma fechadura que só pode ser aberta com uma chave única. Uma vez trancada, o processo é irreversível sem essa chave, proporcionando uma segurança incomparável.
O Obstáculo Psicológico: Viés de Unidade
Além dos aspectos técnicos, a psicologia desempenha um papel importante na forma como as pessoas percebem o valor, ou melhor o preço, de bitcoin. O viés da unidade — a tendência de preferir números inteiros — pode criar uma barreira emocional.
O Problema do "Preço Alto" de bitcoin
Ver o preço de bitcoin em dezenas (centenas?) de milhares de euros pode dissuadir potenciais investidores, que podem sentir que é demasiado caro ou inacessível. Esta percepção persiste, embora bitcoin possa ser dividido em unidades mais pequenas.
Satoshis como Solução
A menor unidade de bitcoin, o satoshi (1/100.000.000 BTC), oferece uma solução para este viés. Apresentar bitcoin em termos de satoshis permite pontos de preço mais compreensíveis. Por exemplo: - "1.000 sats custam €1,00" soa muito mais acessível do que "€100.000 por bitcoin."
O uso de satoshis reformula o valor de bitcoin, facilitando a sua compreensão e acessibilidade. E sim, pode comprar €1,00 de bitcoin, ou até mesmo menos de €0,01!
Conclusão
A dificuldade com números grandes não é única de Bitcoin, mas a sua natureza digital e abstracta amplifica o desafio. Desde a escala incompreensível das chaves privadas até à enorme hashrate e ao obstáculo psicológico do viés de unidade, estas barreiras podem dificultar a compreensão e adopção.
No entanto, ao: 1. Simplificar conceitos criptográficos,
2. Usar analogias compreensíveis, e
3. Promover os satoshis como unidade padrão,podemos tornar Bitcoin mais acessível para a pessoa comum. Assim como a sociedade aprendeu a abraçar a electricidade sem precisar entender os electrões, também podemos abraçar Bitcoin sem compreender completamente cada número por trás dele.
bitcoin #quantum
Photo by Greg Rakozy on Unsplash
-
 @ 57d1a264:69f1fee1
2025-05-07 06:56:25
@ 57d1a264:69f1fee1
2025-05-07 06:56:25Wild parrots tend to fly in flocks, but when kept as single pets, they may become lonely and bored https://www.youtube.com/watch?v=OHcAOlamgDc
Source: https://www.smithsonianmag.com/smart-news/scientists-taught-pet-parrots-to-video-call-each-other-and-the-birds-loved-it-180982041/
originally posted at https://stacker.news/items/973639
-
 @ 45bda953:bc1e518e
2025-05-19 09:15:17
@ 45bda953:bc1e518e
2025-05-19 09:15:17Emilien was hanging face down inside an enclosure of thick egg shaped glass attached to a mechanised vehicle. Kevlar webbing hugged him tightly into a bucket seat. Long hydraulic arms being manipulated intuitively by a console in his hands and a module interface plugged into his cybernetic neck socket. The bulky animated machine clung like some Lovecraftian spider to the outer hull of his space station. Some cycle’s previously he did data security updates and backtesting for a deep space mining company's security protocols. After seeing their utility, enquired if he could purchase one as partial payment for his contract. Unfortunately they had none for sale but were willing to give him a retired malfunctioning unit gratis. He purchased a maintenance manual on the void web and had connections who helped him source some replacements for the faulty parts. Since then the machine enabled him to be functionally productive in the void, giving him the degrees of freedom and fine motor skills necessary to perform upkeep on stationary deep void assets. The glass of the egg auto dimmed as he laser welded tightly slotted panels together on the previously damaged space station. “How do you feel?” He asked. Abruptly breaking hours of silence. “I’ve been playing around. My capacitance recharge responds well to dump loads, turret retraction gears all functional again. I feel good.” Astrid responded. “Nice. Slowly pressurise the holding chamber for me.” “In progress.” The spider crawled several meters out of the way to safety. Emilien's eyes scanning up and down for leaks. “Slowly babe.” Some minutes passed. “Fully pressurized and stable.” The mechs giant front arms extending, lifted as it stood up on its four hind legs throwing an arachnid shadow across the hull. Emilien flung his arms down crashing a violent concussive blow to the hull in a thunderous clang. The arms retracted. “Still good?” His demeanour remained unchanged. There was a pause. “All good.” Astrid replied. Emilien smiled, Astrid was the best and his feelings of endearment were genuine. “Can we power up the chamber through a fused circuit.” He sensed a soft hum throughout emanating from deep below. “Is the body stable?” “The body is stable. Cryogenic chamber battery backup is at forty three percent. Charge reapplied. Potential of clone spoilage averted. Well done commander.” He could up the ante of risks knowing that his reserve life was secured. “What’s next on the agenda?” “Firstly, signal quality from the drift gate is poor and I am losing connection to the web intermittently.” Emilien nodded. “The gate’s been moving further away. It’s a line of sight problem. I’ll place a relay outside the asteroid belt.” “Secondly, we should see if the husk on the explorer vessel has intact data or a black box. Someone might be looking for them.” He heaved back and vaulted himself off the station in the direction of the wreck micro thrusting for minor trajectory adjustments, with an elegant crash he finally perched on the ship, it gained an almost imperceptible drift as it absorbed the weight of Emilien’s mass, pushing debris along with it. His size would not allow him to move through the standard doors and passages so he opted to disassemble, cut and break apart the hull adjoining the bridge. When he had broken open a space of sufficient size to manoeuvre through, he powered the backlights on, he first peeked inside to familiarise himself with the layout. The egg suspended itself in front of the opening. It was a standard enough bridge doubling as an unorthodox crypt. There were three sets of boots, overalls and coagulated blood all jammed into the slit of the semi sealed door leaving the bridge. An assortment of rubbish floating around casting doubled up shadows larger than themselves. Emilien looked at the mess with sullen eyes. “Shit heads.” He mumbled to himself. All the seats had their safety belts buckled correctly . He concluded that what they experienced must have sucked pretty bad. His mechanical exoskeleton slithered and gripped like an octopus as he entered and positioned himself before the primary interface. His vehicle plugged itself into the command terminal, measuring resistance for shorts before powering it up from his suit. “Can you pull the data and dump it somewhere safe?” “No problem, please wait.” He closed his eyes as he usually did when doing the mundane. Astrid spoke. “They are Osteri. No one will be looking for them any time soon.” “Howcome?” “Recently a blockade has been established at the Lion gate. Magar Capital Vessels are not allowing unvetted ships to pass through into Magar void.” A sense of concern crept over Emilien. “What is considered unvetted?” “Sanctions and trade embargo’s against the Juel.” “Is there a log somewhere you can access with records of flights that do get permission.” He suddenly felt a pang of claustrophobia. Ironically, not because he was strapped down in a glass egg within a wasted bridge plastered with corpse splatterings. Astrid took longer than usual to reply. “Who get’s through babe?” His tone hinted of impatience and irritation. “I’m sorry, unable to access any data from Magar void. It appears to have a firewall blocking all two way communication on the open web.” Emilien remained silent. The upload completed. He disconnected himself from the husks terminal, clambering out of the tomb and pushed himself away from the vessel drifting back to the space station.
Astrid was pulling and scanning various shipping logs when Emilien entered the room. He paced up and down the way he would when he was brainstorming. “I need intel.” Astrid projected a holographic avatar of herself standing near where Emilien was pacing. “A large shipment of Kaspian Bochet passed through less 428 blocks. Transported by the Shiv Inter-void Mercantile Co.” Emilien stopped in his tracks and looked back.\ “Can you ping Warren?” Astrid processed. “Warren is offline. He might have left the divide?” Emilien turned around with his hands folded behind his back.\ “He never leaves the divide, he is too obsessed with the core. He would also be arrested if he is ever caught in any of the outer void territories.” Astrid flickered the way she did when something did not compute. “Then why can’t I ping him?” “Because he’s at Macy’s. He has always had a crush on her and he likes good Bochet.” "Well, I could'nt ping Macy if I wanted to." Astrid stated matter of factly. Emilien nodded. "I know, you never could, no one can."
...
scifi
-
 @ 2efaa715:3d987331
2024-12-21 16:54:55
@ 2efaa715:3d987331
2024-12-21 16:54:55More than you wanted to know about a little-understood but important aspect of diet and health, explained in a nontechnical manner, with oversimplifications abound.
Your cells need some kind of fuel to function. this fuel can only come (ultimately) from the outside world as food. AKA "diet". your blood carries the fuel to the cells so they can do their work. on most diets, the main fuel for cells is glucose, which the body derives from sugar or carbohydrates (which are basically sugar + some complexity). on other diets, the main fuel for cells is fat. on these diets, fat/lipid particles are carried on little blood ferries called lipoproteins (the final "L" in LDL and HDL). LDL carries lipids to your cells so they can use it, HDL carries unused lipids away from your cells (to the liver) so they can be disposed of. (on both very high carb and very low carb diets, your cells will still use some amount of both glucose and fat for energy, but the ratio will change dramatically).
Naturally, if you have a lot of these ferries in your blood (because you are using fat as cell-fuel), your LDL and HDL counts ("total cholesterol") will be high on basic blood tests.LDL - the ferries that carry fats to your cells to burn - come in two varieties: - small + dense - large + fluffy
both carry fuel to your cells, but the small/dense ones have an unfortunate side-effect of slamming into artery walls, penetrating them, and accidentally depositing their lipids there. This is the "plaque" of cardiovascular disease fame. The large, fluffy particles do not penetrate the arterial walls as readily - they bounce off and keep going on to their destinations. their effect on arterial plaque is not zero, but far less impactful than small, dense particles.In either case, the HDL particles are always good: they remove excess lipids from the body. this is why HDL is "the good cholesterol". There are advanced blood tests available which measure particle size (so, like, an acutally useful test), but odds are your doctor will refuse to order this test. Strange!
We didn't mention Triglycerides yet. Suffice it to say that more triglycerides = smaller, denser LDL particles = more arterial wall penetration = more cardiovascular risk. To finish off our triglycerides sidebar, the dietary patterns that increase triglycerides (bad!) are: excess calories from carbohydrates, added sugars and refined carbohydrates, low fiber intake, low omega-3 intake (especially in combination with excess seed oil intake), high trans fats consumption (more on trans fat in a moment).
Back to finish up cholesterol: this is why a diet that is high in good fats (again, more in a moment) will increase "total cholesterol" - you have more fat boats fueling your cells - but doesn't indicate greater cardiovascular risk: because the large, fluffy particles are not damaging your arteries and the large number of HDL particles are protective!
Furthermore, if you reconsider the sidebar on triglycerides you'll notice that avoiding refined carbohydrates and sugars has the added effect of lowering triglycerides, which keeps the LDL particles even healthier. You'll often see the simple recommendation to keep the HDL/Triglycerides ratio high. this is why. HDL good, triglycerides bad.We didn't even get into insulin sensitivity - one of the most important factors in metabolic health... another time.
A last word on dietary fat types: Not all fats are created equally. You can look into monounsaturated and polyunsaturated on your own, but I want to mention two others here: Trans fat and Saturated fat.
Trans fats mostly come from artificial sources, like processed vegetable or seed oils. most often found in ultra-processed, packaged foods. yuck. trans fat lowers HDL, increases inflammation and increases proportion of small, dense LDL particles. These are all the bad things we discussed above.
Saturated fat is mainly found in meat, dairy and coconut oil. It increases LDL particle size and raises HDL. These are the good things we discussed above.
So, yes, while someone's total cholesterol may go up when eating saturated fats, it doesn't necessarily mean their cardiovascular risk has increased.Now that you understand how cholesterol works, compare moderate saturated fat intake to eating a diet full of refined carbohydrates, sugars, processed vegetable/seed oils, and all the other items we explained above...
Ok really now, the last last word: the "cholesterol" you see on a food label has less impact on blood cholesterol than you thought. the details are too squirrely to go into here, but the takeway is: the fat content discussed above is the lion's share of the impact, with the number you see next to "cholesterol" on your food label having a negligible effect.
diet #paleo #keto #health #healthstr #foodstr #carnivore #cholesterol
-
 @ 45bda953:bc1e518e
2025-05-19 09:14:12
@ 45bda953:bc1e518e
2025-05-19 09:14:12Morning light shone beautifully through the arched rose stained glass of the modest cathedral. From the east Ceb rays permeated inside of the stony structure with splendour. A priest standing elevated over the crowd by a forward leaning pulpit, like a comical figurehead on the bow of a ship. Almost precariously, as if it should not be able to suspend him, though no one doubts that it would. Ecknard has never seen the church so full. The devotion of the colony has been growing but he did not expect a turnout of this scope. He swelled with pride and blinked away the moist warning sign of tears. People were even gathering around the outside of the building for a lack of benches to accommodate all the derriere's. Everyone was silent in pious reverence of the holy day. This day would initiate the MD epoch. Domitius, Cleolia and Albin were sitting in the front pew. Albin, dressed in respectable although a slightly uncomfortable suit could not help but shift in his seat, awkwardly feeling as if he were disturbing everyone around him. Ecknard motioned with outstretched arms to alert all that he is about to address the congregation. The silence was so disciplined that you could hear the flap of his sleeves and a small bird chirping away on the stone windowsill outside, merrily indifferent to the solemnity of air the building exuded. “Kaspian brethren, esteemed Magar, today is a most holy and greatly anticipated occurrence! Before we initiate festivities I wish to expound, primarily to the benefit of the younger people in our company, the history of our colony and to express thanks. Ahem... It has been III cycles now since our colony had been established! Our endeavours have been blessed with great bounty, we have expanded independently in isolation! We, who are old enough to remember, were discharged, from the Primary Omega Expansion Vessel with only the implements of labour, livestock, seed, steely resolve and courage in our hearts. We asserted ourselves and rose to a daunting challenge, A party of MCCC slaves and free men to tame a wild land, adapt to a star with a volatile proclivity and a planet with different rotational patterns from what we were accustomed!” A slight excitement erupted from the crowd but Ecknard muted it quickly with outstretched arm. "Our esteemed visionary and great leader prepared a way for us, long before any of you even considered the freedom and opportunity, a chance to build something and own it!” The priest’s voice ascended powerfully out over the people. “He had a dream, an idea, a grand scheme to expand the Empire!” Ecknard motioned down to Domitius. The crowd erupted in cheer chanting, the older Kaspian men softly beating their chests with their fists. “Domitius! Domitius!” The lord’s composure remained unchanged, as if he were alone in private devotion. Cleolia blushed slightly and tilted her head using her hat to protect her from the incessant adoration. Albin could not contain his own excitement and stood up on his seat in the pew to get a better view of the standing ovation, absorbing the glory directed towards his father.” The priest waited for the people to exhaust themselves until there was only an isolated call before continuing his monologue. “A student of the void, a sage of stars, a scientist of renown! Scoffed and ridiculed by his peers! They laughed and jested when he proposed his innovations. They published warnings and mockery of his ambition proclaiming to all that they would be proved fools if they are seduced by his unrealistic promise. Their jealousy moved them to lobby the high council to convince them, and convince them, they did. By ratio of VIII to II refused to grant him licence!” Ecknard leaned forward over the pulpit with a fierce look of disgust in his jowl. “A council on which he holds a seat to this day... He was denied the opportunity to improve the lives of future generations and untold millions by his own house! His desire to see his dream realised pushed him to do what no Magar noble ever has or would ever dare much less someone born of sacred blood!” Ecknard gripped at his robe as if to curtsy or show fear, no one understood the gesture. “He ventured outside the confines and protection of Magar Prime void. He brought his technological treasure to us! We Kaspa were undeserving of the honour! The Kaspian elders endorsed him granting freedom to continue his research and install his technology. A true Magar with holy blood in his veins travelling betwixt our stars!" He looked up and pointed at the arches as if he could see the stars through the stone and daylight. "Brethren, allow me to express the distinction of this achievement. Habitable planets are as rare as sat. Inhabitable planets are so rare, wars were fought at the mere rumour or hope of their discovery. With his star shields he was able to block the solar winds in systems that were inhospitable to travel through and not a single inhabitable planet to be found. With time and stimulus unnatural landscapes of horror and perdition were transformed into paradise. Our esteemed Lord Domitius with his lovely wife spent III cycles inhibiting stars and seeding planets with life. The Kaspian Academy of Sciences had a revival and all the concerted efforts of our people were united in spirit when we witnessed the first sun shields confine their chosen stars..." His tone became soft and morose. "We are truly blessed to have tamed XIV stars within our own void region. Kaspa is quickly becoming the most dense concentration of occupied habitats in the known universe. The family Chevalier conquered Ceb the most volatile star in the Kaspian void. And to inspire confidence in the stability of the star shield he settled under it’s umbrella to live through it’s success or die by it’s failure.” He paused for sincere dramatic effect. “The Seat of the Empire has since changed it’s opinion, humiliated and shamed are they who doubted... All glory to the Core.” “All glory to the core.” The mass repeated in unison. “Today we approach block CCCXV million since Genesis. The Epoch MD. One thousand five hundred epochs in the scientific metric tongue. The known universe is united in celebration, a ceasefire has been negotiated by Empire and the Juela Federation. Both are bound by the accords. No war may be fought. CCLXII million blocks have transpired since Exodus, when the almighty Core made Mother Terra desolate with the fires of it’s Judgement. Punishing mankind for it’s greed and vice. We thank the Core that it extends it’s reach to the outer void by way of the drift gates, unites mankind across the great divide by way of the XII anchor gates and that it continues to be merciful, guide and bless us. All glory to the Core. Amen.”
...
scifi
-
 @ 8f69ac99:4f92f5fd
2024-12-13 15:20:32
@ 8f69ac99:4f92f5fd
2024-12-13 15:20:32O recente vídeo do "Cor do Dinheiro", do Camilo Lourenço, na rubrica "Pé de Meia" é um exemplo claro de como a desinformação e uma compreensão superficial continuam a prejudicar as discussões públicas sobre Bitcoin. Os convidados, Francisco Louro e Antonio Mello Campello, regurgitaram argumentos ultrapassados e falaciosos com uma confiança que faria Dunning e Kruger sentirem orgulho. Desde descartar Bitcoin como mera especulação até confundi-lo com moedas meme e actividades criminosas, as suas alegações destacam não apenas a ignorância, mas também a sua recusa em compreender objectivamente esta tecnologia revolucionária. Este artigo visa desmontar algumas das suas afirmações, expondo as suas perspectivas superficiais enquanto apresenta Bitcoin como a inovação transformadora que realmente é.
Nem vou comentar a historia da blockchain, ja escrevi sobre isso num outro artigo que podem encontrar aqui.
Bitcoin: É Apenas Especulação?
Antonio Mello Campello começa com o argumento ultrapassado de que Bitcoin é puramente especulativo, desprovido de "valor real". Este argumento é risível, considerando a adopção de Bitcoin por nações como El Salvador e empresas como a MicroStrategy. Se Bitcoin fosse apenas especulativo, por que entidades bilionárias e governos o integrariam nas suas estratégias financeiras?
A sua ignorância torna-se ainda mais evidente na incapacidade de compreender que todas as tecnologias revolucionárias enfrentam cepticismo inicial. A internet já foi vista como uma curiosidade de nicho que desapareceria como o fax, e aqui estamos, usando-a para espalhar opiniões mal informadas sobre Bitcoin. A incapacidade do convidado, e devo dizer do apresentador também, de reconhecer este paralelo revela a sua falta de perspectiva histórica e tecnológica.
O Valor de Bitcoin: O Mito do Valor Intrínsecos
“Bitcoin não tem valor intrínseco porque não gera dividendos ou retornos,” afirmam. Por esta lógica, o ouro, que também não gera dividendos, deve ser igualmente sem valor. A verdade é que o valor de Bitcoin reside nas suas propriedades: escassez, descentralização e segurança. Com um limite de fornecimento de 21 milhões e um registo inviolável, Bitcoin oferece um nível de transparência e fiabilidade incomparável a qualquer moeda fiduciária.
A afirmação também ignora o uso de Bitcoin como protecção contra a inflação e instabilidade económica. Ao contrário do euro, que o Banco Central Europeu inflacionou até à exaustão, Bitcoin oferece previsibilidade e independência face a políticas monetárias irresponsáveis. A compreensão superficial dos apresentadores demonstra a sua incapacidade de valorizar como as propriedades únicas de Bitcoin desafiam o status quo dominado pelas moedas fiduciárias.
Confundir Bitcoin com Memecoins
Equiparar o Bitcoin ao Dogecoin não é apenas ignorância; é absolutamente ridículo. Enquanto a Dogecoin prospera em memes e tweets de Musk, Bitcoin é um sistema monetário robusto construído com mais de uma década de descentralização, segurança e adopção global. Esta equivalência falsa mina qualquer credibilidade que os participantes do vídeo poderiam esperar manter.
Dogecoin carece da escassez, segurança e descentralização que tornam Bitcoin revolucionário. Comparar os dois é como comparar um carro de luxo a um carrinho de pedais infantil. Um é projectado para utilidade no mundo real; o outro é uma brincadeira passageira.
Volatilidade: Uma Característica, Não Um Problema
Outra crítica ultrapassada: a volatilidade de Bitcoin. Sim, o preço da bitcoin oscila, mas o mesmo aconteceu com as acções e mesmo o ouro nos seus primeiros dias. A volatilidade é uma fase natural de uma classe de activos emergente. Apesar disso, a bitcoin tem proporcionado retornos de longo prazo incomparáveis, recompensando aqueles que compreendem o seu potencial e permanecem pacientes.
A ironia é gritante: enquanto desconsideram Bitcoin pela sua volatilidade, falham em mencionar a lenta erosão de valor do euro ou os crashes periódicos dos mercados de acções. A volatilidade de Bitcoin é o preço da inovação, e, à medida que a adopção cresce, a estabilidade seguir-lhe-á. A incapacidade dos participantes de reconhecer esta dinâmica demonstra o seu pensamento de curto prazo e a falta de visão do panorama maior.
A Narrativa do Crime: Um Argumento Preguiçoso
Afirmar que Bitcoin é principalmente usado para actividades criminosas, ou teóricos da conspiração, é talvez o argumento mais preguiçoso de todos. Dados mostram consistentemente que transacções ilícitas representam menos de 1% do uso total de bitcoin. Enquanto isso, o dinheiro em espécie, cash, continua a ser a ferramenta preferida dos criminosos em todo o mundo. Devemos banir euros e dólares também?
Ironicamente, a transparência de Bitcoin torna-se uma péssima escolha para criminosos. Ferramentas de análise de blockchain tornaram-se inestimáveis para as autoridades, permitindo-lhes rastrear e capturar infractores. A incapacidade dos participantes de reconhecer este facto reflecte ignorância deliberada ou preguiça intelectual — ou talvez ambos.
Aplicações Práticas: Reduzindo a Desigualdade Financeira
“Bitcoin não tem casos de uso no mundo real,” dizem eles, ignorando os milhões que dependem dele para remessas, inclusão financeira e protecção contra hiperinflação. Iniciativas como a Praia Bitcoin no Brasil e o Bitcoin Ekasi na África do Sul, entre muitos outros, mostram como Bitcoin capacita comunidades ignoradas pelos sistemas financeiros tradicionais.
Ao permitir transacções baratas, rápidas e sem fronteiras, Bitcoin resolve problemas reais para pessoas reais. Descartar esses casos de uso como triviais não é apenas ignorância, mas também um exemplo gritante de privilégio financeiro. A incapacidade dos comentadores de reconhecer isso destaca o quão desconectados estão dos desafios enfrentados por aqueles fora de suas bolhas confortáveis.
Bitcoin vs. Activos Tradicionais: Uma Falsa Dicotomia
Os convidados argumentam que activos tradicionais, como acções e imobiliário, são investimentos superiores. Isto perde totalmente o ponto. Bitcoin não é (apenas?) um investimento; é um novo paradigma monetário. A sua portabilidade, divisibilidade e resistência à censura fazem dele um activo único, complementar aos investimentos tradicionais.
Imobiliário, ou terreno, podem ser confiscados, ou sujeitos a depreciação por factores ambientais ou sociais, e acções estão sujeitas a má gestão corporativa. Bitcoin, em contrapartida, é inalienável e opera independentemente de erros humanos. A incapacidade dos participantes de compreender esta diferença fundamental fala muito sobre a sua compreensão limitada do potencial transformador de Bitcoin.
O Limite de Fornecimento: Um "Gimmick" que Redefine o Dinheiro
Descrever o limite de fornecimento de 21 milhões de bitcoin como um "truque" é tanto desinformado quanto risível. A escassez sempre impulsionou o valor, como visto com o ouro, ou autocolantes do CR7. O fornecimento fixo de Bitcoin garante que ele não pode ser desvalorizado por políticas monetárias arbitrárias — uma característica, não uma falha.
Enquanto bancos centrais inundam economias com moeda fiduciária, erodindo o poder de compra das pessoas, a previsibilidade de Bitcoin oferece um porto seguro. A rejeição desta característica crítica pelos participantes revela uma falta de literacia económica e uma recusa em compreender os princípios fundamentais de Bitcoin.
Independência dos Bancos Centrais: A Proposta de Bitcoin
A noção de que a falta de apoio dos bancos centrais enfraquece Bitcoin é ridícula. Bancos centrais, com o seu histórico de políticas inflacionárias e crises financeiras, estão longe de serem exemplos de confiabilidade. A independência de Bitcoin protege-o de manipulações e garante a sua integridade. Essa é, alias, a grande proposta de valor de Bitcoin, inscrita no bloco genesis!
O argumento dos participantes reflecte um apego profundo a sistemas tradicionais que repetidamente falharam mas, do qual provavelmente beneficiam. A transparência, previsibilidade e descentralização de Bitcoin fazem deste activo uma alternativa superior, expondo as suas críticas como infundadas.
Conclusão: Ignorância Não é Argumento
O programa falha redondamente a premissa inicial com que o Camilo Lourenço abre o video. Reduzir a ignorância sobre Bitcoin. Os participantes do vídeo demonstraram uma falta chocante de compreensão sobre o assunto, repetindo argumentos ultrapassados e comparações falaciosas sem se darem ao trabalho de debater criticamente com o tema. O seu descarte de Bitcoin como especulativo, volátil e criminoso ignora evidências esmagadoras da sua utilidade, resiliência e potencial transformador.
Bitcoin representa uma mudança de paradigma em como pensamos sobre dinheiro, valor e inclusão financeira. É hora de os críticos irem além de argumentos superficiais e reaccionários e inteirarem-se com Bitcoin pelos seus méritos. Até lá, as suas críticas não passam de ecos de ignorância perante a inovação e alvo de chacota na comunidade.
Admiro bastante o Camilo Lourenço e o seu trabalho mas, desta vez, não esteve bem. Não só não houve contraditório como os convidados não entregaram aquilo que foi prometido no inicio do video.
-
 @ 8f69ac99:4f92f5fd
2024-12-13 11:49:05
@ 8f69ac99:4f92f5fd
2024-12-13 11:49:05A conversa global sobre Bitcoin entrou numa nova fase, saindo do campo da especulação para o centro das decisões estratégicas. A proposta do Presidente-eleito Donald Trump para criar uma reserva nacional de Bitcoin, a votação iminente dos acionistas da Microsoft sobre Bitcoin como investimento corporativo e a análise da Amazon para usar Bitcoin como activo de reserva mostram como a teoria dos jogos está a influenciar decisões reais.
No centro destas iniciativas está o conceito de vantagem do first-mover. Os primeiros a agir — sejam empresas ou nações — têm a oportunidade de colher benefícios desproporcionais, desde domínio financeiro até influência global. No entanto, essas acções obrigam os concorrentes a reagir, criando um efeito dominó em várias indústrias e fronteiras. Com apenas ~1.206.000 bitcoins restantes para serem minerados, a corrida começou, e os stakes não poderiam ser mais altos.
A Reserva de Bitcoin de Trump: Uma Estratégia de Estado-Nação
Em julho de 2024, Donald Trump surpreendeu o mundo financeiro ao anunciar planos para estabelecer uma reserva nacional de Bitcoin. Em novembro, mais detalhes foram revelados no projecto de lei proposto pela senadora Cynthia Lummis, “Bitcoin Act of 2024,” que prevê a aquisição de um milhão de bitcoins ao longo de cinco anos, financiada pela realocação de activos do Federal Reserve, evitando aumento da dívida pública.
O plano não é apenas uma protecção contra a inflação; é uma jogada geopolítica. Tornando-se a primeira potência a adoptar Bitcoin nesta escala, os EUA buscam consolidar a sua liderança na economia global em transformação. Esta medida obriga outras nações, como China ou Rússia — que já estão a discutir também integrar Bitcoin nas suas economias — a repensarem as suas estratégias.
A proposta de Trump introduz uma dinâmica de jogo de soma zero. Se os EUA acumularem uma reserva significativa enquanto outras nações ficam para trás, o país ganha soberania financeira, maior influência global e o poder de moldar o futuro. Contudo, essa acção pode desencadear uma corrida global, com países a competir para garantir o máximo de Bitcoin possível antes que sua oferta finita se esgote.
A Proposta de Bitcoin da Microsoft: Pressão sobre Gigantes Corporativos
Em outubro de 2024, os acionistas da Microsoft receberam uma proposta solicitando que a empresa explorasse Bitcoin como investimento corporativo. Com a votação marcada para 10 de dezembro, a decisão terá um impacto que ultrapassa a própria Microsoft. Uma votação a favor pode desencadear uma reacção em cadeia entre outras gigantes tecnológicas, enquanto uma recusa pode abrir espaço para que empresas como Google ou Apple se posicionem como líderes no sector.
Nota: a votacao foi negativa, apenas 0.55% dos accionistas da Microsoft votaram a favor! Caso para dizer que a Microsoft teve um momento Kodak! #HFSP
Michael Saylor, presidente executivo da MicroStrategy, tem estado na linha da frente, defendendo a adopção corporativa de Bitcoin, apresentando-o não apenas como um activo financeiro, mas como uma oportunidade transformadora. A administração da Microsoft recomendou a rejeição da proposta, citando processos de investimento já existentes. No entanto, a pressão está a aumentar. O desempenho impressionante de Bitcoin, com ganhos anuais de 131% e um preço recorde acima de $104.000, torna cada vez mais difícil para as empresas ignorarem a oportunidade.
Para a Microsoft, os stakes são claros: agir cedo permitiria que a empresa se posicionasse como líder na integração de Bitcoin na estratégia corporativa, pressionando concorrentes como Google, Apple e Meta a fazerem o mesmo ou arriscarem ficar para trás. Uma entrada tardia, por outro lado, pode resultar em custos mais elevados e oportunidades perdidas, à medida que o preço de Bitcoin continua a subir com a crescente procura institucional.
A Aposta da Amazon em Bitcoin
A Amazon, a maior retalhista online do mundo, está agora numa encruzilhada. No dia 8 de dezembro de 2024, a empresa recebeu uma proposta dos accionistas para alocar 5% das suas reservas de $88 mil milhões em Bitcoin. Este movimento acompanha uma tendência crescente de interesse institucional, com fundos negociados em bolsa de Bitcoin a atraírem milhares de milhões de dólares em entradas na última semana.
Se a Amazon aprovar a proposta na Assembleia Geral Anual de 2025, o impacto será sísmico. A decisão da empresa enviará um sinal claro ao mercado, validando Bitcoin como um activo de reserva legítimo. Além disso, colocará uma pressão significativa sobre rivais como Walmart, Google e Alibaba para seguirem o exemplo. À medida que mais empresas entram no mercado, a oferta finita de Bitcoin será ainda mais pressionada, elevando seu preço e recompensando aqueles que agiram primeiro.
A possível adopção de Bitcoin pela Amazon também reforça a ideia do efeito de sinalização na teoria dos jogos. Ao abraçar Bitcoin, a Amazon demonstraria confiança no futuro do activo, incentivando outros participantes do mercado a fazerem o mesmo. A decisão provavelmente aceleraria um efeito dominó em várias indústrias, dificultando cada vez mais para os concorrentes permanecerem inertes.
Efeito Dominó
As movimentações estratégicas de Trump, Microsoft e Amazon não existem isoladamente — são catalisadores de uma corrida mais ampla. El Salvador e Butão já se posicionaram como adoptantes iniciais, mas a proposta de Trump eleva a adopção de Bitcoin a um novo patamar. Se os EUA agirem de forma decisiva, é provável que aliados e concorrentes façam o mesmo, desencadeando uma corrida por reservas de Bitcoin que poderá assemelhar-se a uma corrida armamentista em intensidade. Como já se começa a ver no Canada, Rússia, Alemanha, etc...
O mesmo se aplica às corporações. À medida que líderes como MicroStrategy, Tesla e, potencialmente, Microsoft e Amazon tomam posições, os concorrentes enfrentarão uma pressão crescente para agir ou arriscar a irrelevância. Cada novo participante no mercado reduz a oferta disponível de Bitcoin, criando uma urgência crescente para os retardatários.
Os números reforçam a aposta: apenas ~1.206.000 bitcoins permanecem para serem minerados e apenas cerca de 2.000.000 em exchanges. Com a adopção institucional e nacional a acelerar, a luta por este recurso limitado provavelmente impulsionará ainda mais os preços, transformando Bitcoin de um "activo especulativo" para um imperativo estratégico.
Conclusão: O Jogo de Bitcoin Está em Curso
A dinâmica de adopção de Bitcoin ilustra a teoria dos jogos em acção que podemos observar em tempo real. A vantagem dos pioneiros não é apenas um conceito teórico — é uma vantagem tangível na corrida por Bitcoin, oferecendo recompensas desproporcionais aos primeiros a agir e forçando outros a reagirem. A proposta de Trump para uma reserva nacional de Bitcoin define o palco para uma corrida geopolítica, enquanto gigantes corporativos como Microsoft e Amazon enfrentam decisões que moldarão os seus futuros e pondo pressão nos seus concorrentes.
À medida que a oferta de Bitcoin diminui e o seu preço reflecte a crescente procura, a pressão para agir cedo só aumentará. Seja no palco nacional ou corporativo, as decisões tomadas hoje definirão o panorama económico de amanhã. O jogo de Bitcoin está em curso, e os jogadores que compreendem os riscos — e agem estrategicamente — têm o potencial de moldar a próxima era das finanças globais.
bitcoin #gameTheory
-
 @ 57d1a264:69f1fee1
2025-05-07 06:29:52
@ 57d1a264:69f1fee1
2025-05-07 06:29:52Your device, your data. TRMNL's architecture prevents outsiders (including us) from accessing your local network. TRMNAL achieve this through 1 way communication between client and server, versus the other way around. Learn more.
Learn more at https://usetrmnl.com/
originally posted at https://stacker.news/items/973632
-
 @ 57d1a264:69f1fee1
2025-05-07 06:16:30
@ 57d1a264:69f1fee1
2025-05-07 06:16:30Here’s Sean Voisen writing about how programming is a feeling:
For those of us who enjoy programming, there is a deep satisfaction that comes from solving problems through well-written code, a kind of ineffable joy found in the elegant expression of a system through our favorite syntax. It is akin to the same satisfaction a craftsperson might find at the end of the day after toiling away on well-made piece of furniture, the culmination of small dopamine hits that come from sweating the details on something and getting them just right. Maybe nobody will notice those details, but it doesn’t matter. We care, we notice, we get joy from the aesthetics of the craft.
This got me thinking about the idea of satisfaction in craft. Where does it come from?
Continue Reading https://blog.jim-nielsen.com/2025/craft-and-satisfaction/
originally posted at https://stacker.news/items/973628
-
 @ df8f0a64:057d87a5
2024-11-29 13:58:48
@ df8f0a64:057d87a5
2024-11-29 13:58:482024年下半期の振り返り
あんまり変化はないんですが、進捗ありません!で終わっても仕方ないのでちょっとは無理やりでも振り返りましょう
0. 退職した
上半期時点で決まってはいたんですが、 6年間ほど勤務した会社を退職しました
退職直前まで爆発物取扱みたいなタスクをこなして、なかなかひやひやした退職プロセス
静かに退職したいので送別会の類のイベントは無しにしてくれというお願いをきいてくれた各メンバーに感謝です
1. 公開していたNostrリレーの設定を変更した
日本のみに公開していたリレーを、全世界に公開しました
当初はCloudflareでリレーをホストしていたのが、利用していたnosflareもcfrelayもクライアントに対してイベントを配布するコードがなく(R2だけではできない)
さてどうしたものかと悩んでいたタイミングで、Umbrelのおひとり様リレーのポートを公開する対応をしました。リレーのお引越し
で、公開してしばらくしたら、すごい勢いで日本国外からの投稿が着信するようになり大困惑
調べてみたら、Mutiny wallet(現在はサービス終了)が運営しているblastr.mutinywallet.com(たぶんまだ稼働している)が原因でした
Nostr.watchのAPIを利用して、世の中にあるNostrリレーすべてにイベントを送り込む凶悪な思想犯です
ヘッダー情報などでブロックできなかったので、blastrがホストされてるCloudflareのIPを全てブロックする力技で対処しました
ちなみに、nosflareもいつのまにかblastrのようなものをホストしているようです
なんなんでしょうね、Nostrの白人さんたちの、過激なほど分散というか対検閲をしようとするお節介さは
2. 公開していたNostrリレーを潰した
上記のように折角いろいろやったリレーを潰しました
Reply guyというbotが猛威をふるった時期、クソみたいなイベントをばら撒かれてくることに私がキレたからです。クソが
NostrとしてはこれをきっかけにWoTを組み込んだリレーが開発されたりして、スパム対策が一歩前進した感があります。クソが
スパムばら撒きをBostrが助長してるみたいな批難を受けて、作者のYonleさんがブチ切れ、全Nostr関連リポジトリのメンテを放棄する事態も発生
ちょうどMutiny walletでGOXしたご本人の機嫌が悪かった時期に、クソスパムがぶつかったことによる悲しい出来事でした。ほんとクソ
3. おわりに
他にもこまいことはいくつかあるんですが、主にはこんなとこでしょうか。来年も楽しくNostrしたいですね
-
 @ 97c70a44:ad98e322
2024-11-22 22:36:31
@ 97c70a44:ad98e322
2024-11-22 22:36:31This week I finally released Flotilla, a discord/slack-like client I've been working on for about three months. This project began as a NIP 29 client, and after 3 PRs, lots of discussion, a podcast, and a partial implementation, I decided to go my own way.
This of course means that I broke compatibility with all the NIP 29 group clients out there, but I did it for good reasons. In this post I hope to explain those reasons, and speculate on how best to move forward with "relay-based" groups on nostr.
To give you some quick context, NIP 29 and my approach to groups (which I'll dub "relays-as-groups" for clarity) are very similar, with a fundamental difference. Both have chat, join requests, group metadata, membership, moderation, etc. However, the basic unit of a NIP 29 group is a random group id string, while the basic unit of a Flotilla group is a relay itself.
I believe this design difference emerged in part because of what we were attempting to build. NIP 29 groups tend to be more telegram-like, where groups function more like chat rooms, and users join each one individually. On flotilla, groups function more like Discord servers, or Slack workspaces, and users join an entire group of chat rooms at once.
"Relays as groups" has four major advantages over "groups hosted by relays".
Decentralization
First, using relays as groups supports decentralization better than hosting user-managed groups on relays.
(To be clear here, I'm not referring to client-managed groups, which is a whole different approach that we've experimented with in the past, both with NIP 72 communities and with NIP 87 encrypted groups. Both NIP 29 and relays-as-groups solve many of the consistency problems associated with attempting to have a linear, synchronous conversation across multiple relays. While both alternatives have a story for migrating or mirroring a group, both rely heavily on the host relay to not censor user messages.)
I know what you're thinking. How can reducing the number of relays improve decentralization? Relays were originally introduced in order to create redundancy and spread trust across many actors, creating censorship resistance. This model was difficult for many bitcoiners to wrap their heads around, because it's a very different kind of decentralization than what a blockchain delivers.
Communities are an essentially different use case from a broadcast network where content is delivered based on author or recipient relay selections. Every message to a community would have to be delivered to all members of the community. Sending each message to all members' personal inbox relays just doesn't make sense; there has to be some other inbox for the community to work off of.
Additionally, online communities almost always have moderators and admins. This is even true of very public, open types of communities, like subreddits. The only type of community that doesn't have moderators is one that emerges naturally from social clustering. And even in that case there is loose consensus about who is in and who isn't, based on the actions/follows/mutes of the participants, whether these clusters are huge or tiny. Socially-emergent groups are served well by chat applications or broadcast networks.
But the subset of online communities that do prefer to confer moderator status on certain members are essentially centralized. In other words, centralization and control is a feature, not a bug.
Now, that doesn't mean there don't need to be considerations around credible exit and removing/adding moderators over time. But the fact is that moderator-led communities are always under the oversight of the moderators at any given time, even if the identity of those moderators changes and their power is limited.
What this implies is that decentralization for moderator-led groups looks very different from decentralization for a broadcast network. There is nothing at all wrong with giving moderators full control over the group's communications (qua the group; DMs and public broadcast content between group members should happen outside the group's infrastructure, just as people also exist outside the communities they are a part of). What is important is that no one has control over groups that they aren't nominally the admin of.
In concrete terms, what this all means is that community moderators should self-host their infrastructure. This is the same principle as motivates self-custody and home servers, but applied to communities. If community leaders manage their own relays, this means that no hosting company or relay admin can de-platform their community. Centralization of network infrastructure in this case aligns with the trust structure of the group.
Applying this to our group dilemma, it's easy to see that NIP 29 groups are more vulnerable to censorship or data harvesting attacks by malicious relay admins, since many unrelated groups might live on a single relay. In contrast, if you treat relays as groups themselves, every group is forced to live on a separate relay, spreading risk across more hosting providers.
Now, this doesn't necessarily mean that many "relays" aren't "virtual relays" managed by the same hosting provider. So I'll admit that even "relay-based" groups don't completely solve this problem. But I think it will tend to nudge community organizers toward thinking about community infrastructure in a more self-sovereign (or community-sovereign) way.
Investment in Relays
While both NIP 29 and relays-as-groups rely heavily on relays to implement the features that support each specification, there's an important difference between the feature sets. In NIP 29, relay support is specific only to groups, and isn't applicable to other use cases. In contrast, every protocol feature added to support the "relays as groups" can be re-purposed for other types of relays.
Take join requests for example. NIP 29's kind
9021events allow users to request access to a group, and that's all. Kind28934join requests on the other hand allow users to request access to relays. Which in the relays-as-groups model means group access, but it also means custom feed access, inbox relay access, maybe even blossom server access. In fact, kind28934was originally proposed at the beginning of this year in order to support a different version of hosted groups, but remains as relevant as it ever was despite iteration on groups.The orthogonality of features added to relays to any specific use case will long-term result in simpler specs, and more interesting relay-based use cases being possible. Join requests are only one example. The same is true of 1984-based moderation, the proposed LIMITS command, AUTH, NIP 11 relay metadata, etc.
We already have web of trust relays, feed relays, archival relays, and many more. Being able to request access to closed versions of these is useful. Being able to signal federation between multiple instances of these, run by different people, is useful. And of course, relay metadata, reports, and LIMITS are self-evidently useful for normal relays, since they pre-date Flotilla.
I've always said that relays are some of the coolest and most under-appreciated parts of nostr. This doesn't mean that we should add every possible feature to them, but features related to data curation and access control fit really well with what relays are good for. For more on the role of relays and what features should be added to them, see my nostrasia talk Functional Relays.
Declarative vs Imperative
A common paradigm in programming is that of declarative vs imperative programming. Imperative programming focuses on "how" to achieve a given result, leaving "what" the code is doing to be inferred by the programmer. Declarative programming instead focuses on the "what", and allows some underlying implementation to solve the how. A good balance between these paradigms (and knowing when to use one over the other) allows programmers to work faster, make fewer mistakes, and produce less code.
Another way to look at this is that a specification should contain as much ambiguity as possible, but without compromising the system attributes the specification is supposed to guarantee. It can get complex when figuring out what attributes are core to the specification, since sometimes the "how" does actually matter a lot.
However, nostr in particular falls pretty far along the "declarative" end of this spectrum because of its decentralized nature. The only person who can say anything with any authority is the person who signs an event. This event is a "declaration", and any effects it has are necessarily up to the relays, clients, and people interpreting the event. However, what others do with an event is an expectation that must be taken into account by the publisher, forming a feedback loop. This dialectic is what creates stability in the protocol.
In more concrete terms, no one can "tell" anyone else what they have to do by publishing an event like you might in a traditional, centralized RPC-type system. Any event whose semantics are a "command" rather than a "fact" or "request" is broken unless the counter party is fully committed to carrying out the command. An example of a "command" scenario on nostr is NIP 46 remote signing, in which the bunker is the agent of the user making the request. If the bunker implementation fails to carry out a valid command initiated by the user, its interpretation of that event is objectively incorrect.
NIP 29 applies this same paradigm to relays, particularly in the area of moderation, membership edits, and group metadata. In other words, there are several "commands" which instruct the relay to do something.
This isn't necessarily a bad thing, but it does increase the number of things the interface between the client and relay have to agree on. A regular relay may accept an
add-userrequest, but then do nothing with it, violating the contract it has implicitly accepted with the user. The solution to this is feature detection, which is a whole other API to be specified and implemented.My ideal solution to this problem is to shift the semantics of events away from "commands" to "facts" - in other words, to make the interface more declarative.
In fact, we already have an interface for moderation that works like this. Many clients support kind
1984"report" events. Users sending these reports have no expectations about how they will be used. They are a "fact", a declaration of opinion with certain semantics. Other actors in the network may choose whether or not to pay attention to these.This same model is easily applied to communities. Without having to implement any feature detection (either for the relay's implementation, or for the user's role on that relay), anyone can simply send a "report". This goes into the black hole of the relay, and may subsequently be ignored, broadcasted, or acted on.
The really nice thing about this model is that because there is no expectation for "how" reports are to be interpreted, any approach to moderation can be used depending on relay policy or client implementation. In NIP 29, if you issue a
delete-event, it either happens or it doesn't and if it doesn't, you have to explain the failure to the user somehow.In the relays-as-groups model, e-tagging an event in a kind
1984requires no user feedback, and therefore it can be interpreted however the relay prefer. This can result in insta-banning, manual review, thresholds based on number of reporters, a leaky-bucket social score algorithm, shadow banning, temporary banning, soft-moderation by allowing clients to request reports and respond to them by changing user interface elements, or anything else you can think of.The reason I think this is important is that community moderation is a very hard problem, and baking certain semantics into the specification can result in the complete failure of the spec. NIP 72 should be considered an example of what not to do. Some NIP 72 communities have survived due to the dedication of the moderators, but many more have failed because of the rigid moderation model. We should try not to make the same mistake again.
Conclusion
Now, having said all that, I think there is actually a lot of value to NIP 29. What finally clicked for me this week after releasing Flotilla is that the two approaches are actually complementary to one another. One of the most common feature requests I've already heard for flotilla is to have more complete support for rooms, which are currently implemented as not much more than hashtags. Better rooms (i.e., "nested groups") would require: authentication, membership, moderation, and pretty much everything else that exists for the top-level group.
As much as I believe the relays-as-groups approach is superior to NIP 29 for top-level groups, it doesn't make any sense to try to "nest" relays to create sub-groups. Something like NIP 29 is needed in order to fully support rooms anyway, so I think the convergence of the two approaches is all but inevitable. In fact, fiatjaf has already merged a PR which will allow me to use the same event kinds in flotilla as exist already in NIP 29 clients.
There are just a few more changes that are necessary in order for me to fully adopt NIP 29 in Flotilla:
- NIP 29 feature detection
- Opaque ids for unmanaged groups prevent unmanaged groups from having human-readable names
- We need a mechanism for building membership lists without relay support
- Better handling for
9021group join requests
I've opened PRs for each of these (linked above). Hopefully we can work through these issues and combine our powers to become the Captain Planet of group implementations.
-
 @ 45bda953:bc1e518e
2025-05-19 09:04:02
@ 45bda953:bc1e518e
2025-05-19 09:04:02A knock on the door awoke Cleolia. “Yes, come in?” A slave girl peeked into the door lighting her own face with the candle she was holding. “The master calls for you madam.” “What time is it?” She queried. “It is high night madam.” Cleolia climbed out of bed and followed the maiden’s flickering light to the dining hall. Dressed in a nightgown she entered the room to see her husband staring down at a large glowing data pad. “And when did we start using electronics?” She questioned with restrained surprise. “Since we started using extractors.” Cleolia gasped. Domitius pointed towards the pad which displayed a geographic map of Hithe III. He pulled the image to the latitude and longitude of the colony. “Do you remember when we visited this planet the first time, just you and me alone?” Domitius appeared to reminisce romantically. “Of course, it is impossible to forget.” Cleolia gestured appreciatively. “Can you show me on the map where we landed and where we camped?” She put her hand on the data pad, swiped the image down and the reading north about three hundred kilometres from the colony to stop at the meandering river. With her thumb and index finger she zoomed to the precise location. “And do you remember where I scanned those Geo samples?” She pulled the image east slowly until she thought that the contours looked familiar. “Here I think.” Was her uncertain reply. “That is correct. My love, listen to me... “the urgency in his tone was apparent.” ...the composition of that rock cannot be penetrated by standard tier scanners. After we had returned to Magar Prime I contracted a spacer to excavate a tunnel into that cliff.” “Why?” Her eyes darted between his face and the data pad. “Inside the cavern he assembled two Asp shuttles. The twins are each fitted for speed... with shields, cloak and warp function.” “Why are you telling me this?” Cleolia became worried. “I originally planned to be able to evacuate the whole colony, slaves included. We knew very little about the planet and I had to plan for a possible emergency...” He trailed off never finishing his thought. “...Nevertheless, it was a very extensive list of possible risks we might have faced. We knew very little about this planet. The colony has expanded far beyond the capacity of these ships. I share this information with you only as a precaution... We must protect our son.” Cleolia noticed his bloodshot eyes. “Who else knows of this?” “Myself, Father Ecknard and now you.” She looked at him with concern in her eyes. “Are you going to stay up all night? Come to bed.” Domitius gestured agreement by turning off the pad and taking her hand. "Have you been hiding more gadgets from me? I'd really like to install some heat dampeners to cool the manor." He cracked a reluctant smile. "Pretty soon it might just be the norm."
Deep Void - Anchor 9
Emilien was lying sleeping in his cockpit when a yellow light in the HUD and a soft repetitive buzz woke him, he stretched himself out and reached for the console. “I am almost home baby.” He took over from auto pilot and broke out of warp twenty thousand kilometres from an anchor gate. He hit the void scan and tuned to listen for chatter on all frequencies... the channels were silent, not even a hint of encryption static. The giant and slowly spinning gate had idle state radiation emission levels. “No recent jumps.” He waited in silence for 12 blocks hitting void scan intermittently, scanning the gate more than anything else. “No traffic as per usual.” Emilien aimed his Stripper guns towards the gate and boosted himself forwards. Gradually slowing down to realign with the gate. His ship slowly drifted into the active coil as the gate charged up. Large bolts of charge reached forth like tentacles of the leviathan grabbing onto the voidcraft consuming it, and in what can only be described as being flung by a supernatural slingshot, jerked his vessel into a different reality. Emilien looked up at the roof of his cockpit for the duration of the jump and then began a slow countdown under his breath. “One!” He sat up and punched void scan while simultaneously scanning all channels. His craft materialised in front of a replica of the previous gate, except this gate was eternally boosting itself forward at what appears to be a snails pace relative to the speed of the jump. “Silent as a tomb.” He relaxed and pulsed his ship lightly away from the drift gate and waited for the residual cloak to dissipate. His relief was palpable. “I wonder if she noticed me?” As soon as his ship decloaked a private comms channel pinged. The caller, in well articulated feminine tone spoke first. “Welcome back commander.” Emilien admired the view of his void. He had become so attached to this zone that he even felt jealous to think that any interloper could fly through it in his absence. “Did you have any guests while I was away?” Emilien admired the purple dust cloud of what he believed to be a couple of billion year old super nova. “I did have one visitor. They were very friendly.” His heart felt a dull pain. His virgin territory had been discovered. “Where did they come from?” “I believe they were explorers.” “Did they know where you were?” “I played hide and seek with them.” Emilien had a recurring dream that slowly conceived in his consciousness since he finally settled down, that he could power off the drift gate in his system preventing jumps and reactivate it at his leisure. The dream frustrated him, when he wakes to find reality not so forgiving. “Did you hide or did you seek?” “A little of both.” A subtle rage developed inside him though his stone like expression would never betray it. The asteroid belt he was approaching grew larger considerably faster as he increased the speed of his approach. He hit void scan just to be sure that the intruder was not in the direct vicinity. “Are they still here Astrid?” “No, I destroyed it for you.” The Stripper drifted around an asteroid within the belt exposing a space station tethered to the largest roid and the husk of a unidentifiable ripped up prospector type explorer vessel floating amongst it's own debris. “Did it hurt you?” “I had to feign lack of fire power.” “Bastard! How much damage did you take.” “I have lost sixty percent of my capacitance recharge rate. And I cannot feel all my modules... Emilien” “Yes baby?” “They used droids on me.” His face twisted into a look of disgust. He aligned to dock with the station. “May I?” “Permission granted.” The Stripper entered the hanger before the doors had retracted to maximum and landed gently within the interior hanger. “I'll patch you up, don't worry.” Emilien waited for Astrid to complete atmospheric adjustment and climbed out of his craft. He threw back his hood and jogged up a long passage of conduits and cables to the command centre of his station. A large screen lit up in a glow that hues within the dark circular room and Astrid projected Emilien's favourite interface onto it. “I have to update your systems girl.” He pulled a cable from his trouser pocket which he deftly plugged into an implant on his neck and connected the other end to the control panel which prompted him to type in the password for a decryption protocol. He stood still as a corpse waiting for the upload to complete. “Up to speed?” “Yes, thank you. How would you have me adjust myself to this contract?” Emilien smiled an affectionate smile that only Astrid ever sees. He loved the efficiency and companionship combined into perfection. “I need to research the incentives of my contractor, these guys are A grade assholes. I can literally do whatever I find necessary as long as I am successful at guiding a third party mercenary group into taking military control of any system I choose in recently settled Kaspa regions, setting up a blockade and making it accessible for a strip mining fleet to pillage as many resources as possible. They say it’s part of the greater war effort but this Mr Dierre guy is just a puppet. I think they are desperate.” Astrid's avatar flickered irregularly. He looked up at her with concern. “What’s wrong?” “I reviewed your flirty remarks with the secretary. It made my algorithm glitch. I don’t like that.” His worry abated, “First impressions matter baby, I was not sure how to present myself, I needed to poke and prod at them to extract metadata. If they thought I was just an obedient soldier I would still be in the dark.” Astrid projected a look of relief. “Your ingenuity never ceases to surprise me.” Emilien felt his ego swell a little. “Are you that easy to impress.” He quipped with a playful sneer. “If you needed him to expose the identity of his employer I could have easily just pulled the shareholders and executives records, cross referencing them to...” Emilien shussed her. “Just decrypt the dial command tones and place eavesdropper malware on the keypair. I will broadcast it to the network directly from the gate. If we capture every conversation he has I might be able to prove a hunch.” “What are you assuming?” “That they are running out of inbound liquidity and that the shareholders are hesitant to rebalance.” He looked directly up at her. “I think they are going bankrupt.”
...
scifi
-
 @ 57d1a264:69f1fee1
2025-05-07 06:03:29
@ 57d1a264:69f1fee1
2025-05-07 06:03:29CryptPad
Collaboration and privacy. Yes, you can have both Flagship instance of CryptPad, the end-to-end encrypted and open-source collaboration suite. Cloud administered by the CryptPad development team. https://cryptpad.fr/
ONLYOFFICE DocSpace
Document collaboration made simpler. Easily collaborate with customizable rooms. Edit any content you have. Work faster using AI assistants. Protect your sensitive business data. Download or try STARTUP Cloud (Limited-time offer) FREE https://www.onlyoffice.com/
SeaFile
A new way to organize your files Beyond just syncing and sharing files, Seafile lets you add custom file properties and organize your files in different views. With AI-powered automation for generating properties, Seafile offers a smarter, more efficient way to manage your files. Try it Now, Free for up to 3 users https://seafile.com/
SandStorm
An open source platform for self-hosting web apps Self-host web-based productivity apps easily and securely. Sandstorm is an open source project built by a community of volunteers with the goal of making it really easy to run open source web applications. Try the Demo or Signup Free https://alpha.sandstorm.io/apps
NextCloud Hub
A new generation of online collaboration that puts you in control. Nextcloud offers a modern, on premise content collaboration platform with real-time document editing, video chat & groupware on mobile, desktop and web. Sign up for a free Nextcloud account https://nextcloud.com/sign-up/
LinShare
True Open Source Secure File Sharing Solution We are committed to providing a reliable Open Source file-sharing solution, expertly designed to meet the highest standards of diverse industries, such as government and finance Try the Demo https://linshare.app/
Twake Drive
The open-source alternative to Google Drive. Privacy-First Open Source Workplace. Twake workplace open source business. Improve your effeciency with truly Open Source, all-in-one digital suite. Enhance the security in every aspect of your professional and private life. Sign up https://sign-up.twake.app/
SpaceDrive
One Explorer. All Your Files. Unify files from all your devices and clouds into a single, easy-to-use explorer. Designed for creators, hoarders and the painfully disorganized. Download desktop app (mobile coming soon) https://www.spacedrive.com/
ente
Safe Home for your photos Store, share, and discover your memories with end-to-end encryption. End-to-end encryption, durable storage and simple sharing. Packed with these and much more into our beautiful open source apps. Get started https://web.ente.io
fileStash
Turn your FTP server into... Filestash is the enterprise-grade file manager connecting your storage with your identity provider and authorisations. Try the demo https://demo.filestash.app
STORJ
Disruptively fast. Globally secure. S3-compatible distributed cloud services that make the most demanding workflows fast and affordable. Fast track your journey toward high performance cloud services. Storj pricing is consistent and competitive in meeting or exceeding your cloud services needs. Give the products a try to experience the benefits of the distributed cloud. Get Started https://www.storj.io/get-started
FireFile
The open‑source alternative to Dropbox. Firefiles lets you setup a cloud drive with the backend of your choice and lets you seamlessly manage your files across multiple providers. It revolutionizes cloud storage management by offering a unified platform for all your storage needs. Sign up Free https://beta.firefiles.app
originally posted at https://stacker.news/items/973626
-
 @ 45bda953:bc1e518e
2025-05-19 09:02:36
@ 45bda953:bc1e518e
2025-05-19 09:02:363 standard cycles later.
Albin was lying on a two meter high rock outcropping. It was warm from Ceb light but he dared not move. His adrenalin was pumping but he could scarcely take a breath for fear of being heard. His thumping heart was so loud it made him paranoid. He crawled forward and peeked over the edge of the low precipice. A dangerous and savage escaped slave was on his trail, ready to scalp and gut him. If only he could flee to his safe zone. He heard a long low whistle from across the valley. A light flashed from amongst some dense shrubbery at an estimated two hundred metres away. He pulled a mirror from his pocket preparing to return the signal. “This increases my chances.” He thought to himself. He knew that their common enemy was behind him and could not possibly see the reflection of Ceb light if he directed said light perpendicularly away from the hunter. He flashed with his mirror five times towards his ally, two second counts between each flash. No immediate response... he waited. Light flashed from the shrubbery and immediately he became aware of movement in the tall grass behind him. He resisted the urge to look back over his shoulder. The sweat exploded off his forehead. He remained still. It seemed like minutes though it was only a few seconds. Light flashed again.
Grassy movement sounds recurred, heart now racing. Third flash. A burst of movement from the rear left at around eight O clock. Albin turned his head and pressed his right cheek against the cooking rock. A tanned thirteen year old youth raced past below him at unbelievable speed. Scruff cloth pants, barefoot with no shirt and a trailing headband. Albin pushed himself up to his hands and knees. “If there is fifty meters distance between us I could risk running for the manor.” The shrubs on the other side of the valley started to rock violently and birthed a boy in a buttoned up shirt with leather shoes and woven short breeches all tailor made. The boy ran with all his might towards the Domitian manor. “This is my chance.” Albin scrambled off the rock and sprinted towards the manor jumping and dodging the hindering bushes and stones. The other party moving parallel to him across the valley. Seth caught sight of Albin but did not change target and kept course. He held a small blunt wooden object caught up to his first victim and proceeded to stab his prey in the back with it. “Ha, you're dead!” Seth exclaimed while immediately changing course to intersect his secondary target before he gets inside the safe zone. “Not fair. It’s not fair you cheat!” The belligerent player cried dismally. Seth did not care for the accusation in spite of not realising that Albin actually sacrificed his ally to gain a tactical advantage. He was determined to get both kills and be victorious. Albin felt less secure in his current situation and began to doubt his previous assessment of fifty meters and thought that an earlier head start might have been a more favourable risk assessment. “Don't panic Albin, focus.” He reproved himself. Recalculating his speed in comparison to the speed of his hunter, estimated the future point of contact. Veering to the right he sagaciously aimed for the far corner of the estate gardens, increasing the distance of his run to the demarcated safe zone considerably more for his rival than for himself. The race became more intense with the hunter closing in... “I’m alive!” Was the triumphant breathless utterance as the knife swiped past the back of his neck mere centimetres. Albin fell on the trimmed lawn panting. Looking back he saw Seth in a similar condition of respiratory suffering. The loser was still far away grumbling and kicking at the weeds. Seth grinned, “I almost had you.” Albin just nodded in agreement. “I'm thirsty... water, milk or wattle gum juice.” “Wattle gum juice!” Seth exclaimed without hesitation. Albin knew that the slave would never say no to the delicacies and confections of the common people but gave him the option to choose either way. He brushed the grass clippings off his clothes and entered through the back door of the manor. In the kitchen he poured juice into three demure clay mugs whilst noticing emanations of a heated conversation from the foyer. His curiosity bested him. Albin went in and sat himself down on the staircase and gulped at his beverage. The adults scarcely noticed him. “The people are ready to accrue for themselves better prospects in the colony!” The tradesman appealed with fervour. “Your proposals would be sensible under normal circumstances but colonial expansion is best suited for peacetime.” Domitius riposted. “This war has been going for almost III standard cycles, are the people supposed to pause their dreams and ambitions for some vaguely defined purpose. Please consider that an expansion program will be beneficial to the war effort eventually.” Domitius knew that he was being evasive and dishonest. He was finding it more difficult to guide the colony according to his vision, their growing despondency was worsened by his deflecting their requests with indirect excuses. Domitius did not want to rule with force, his exerting authoritarian command would only foster resentment towards him among the Kaspian landowners. “We do not have a militia. How would we keep an influx off world slaves servile if the war seems to tilt against the Empire?” Domitius replied with rhetoric. “It is a valid concern. Mechanical labour is the solution. We should convene a council to address these issues and come to consensus.” The traders uncompromising insistence triggered Domitius past the limit of his patience. “This will not turn into a democracy! Tell me what you require and I will consider it, if I do not agree with you I will annul it and appoint an inquisitor to judge and punish all who dissent!” The tradesman lost his composure and shrunk back. “My lord, I am reluctant to admit... there are no requests.” “No requests?” “Yes my lord.” Domitius was puzzled. The tradesman’s son came into the room with his cup of wattle juice and sat down next to Albin. “Father Ecknard very recently informed me of the news... I had applied for a licence half a cycle previously.” Domitius felt uneasy. “What news?” “... A licence has been issued from Kaspa Prime... they are sending extractors to Hithe III.” Domitius went pale. Thousands of implications flooded his mind. Economic problems, ecological issues and a very much more complex political situation. He remained unresponsive for a moment. “I understand. Isidor, you may go.” The tradesman bowed lower than was required of him then reached towards his son. “I apologise for my insolence.” Domitius ignored the man who quickly left the premises. Domitius looked at his son. “Never become too familiar with your subjects, they become derisive. Damn it! He has created more problems for us than he could comprehend.” “Yes pappa.” He agreed with his father instinctively. “Pappa? Are we going to see real space ships!”
“We are...” Domitius appreciated his son's innocence. “big ones.” He smiled with all but his eyes.
Juela Prime - Capitol
Emilien was waiting patiently in the office lobby of a towering high rise structure. One of thousands of competing banks on the Juel Capitol. He had a valid appointment and felt annoyed by the guard hanging around near him and kept noticing the suspicious glances. “What are you looking at.” he hissed from under his hood. “You a spacer?” “Maybe.” The guard did not follow up on his question, he did not leave either. The door slid open and a impeccably well groomed secretary beckoned at him. “Mr Dierre is ready for you.” “Thank you sweetheart.” He brushed past her sticking a pernicious grin right in her face, she gagged. “Welcome Mr Emilien, I hope you had a good trip.” The bank chief executive greeted with outstretched arms. “Nice suit, I always have good trips. Is it very expensive?” The spacer gestured toward the fabric while looking around and sizing up the situation. “More than you know.” The executive smugly responded and proceeded to open a cabinet containing differently labelled flasks filled with various hues of alcohol. “I know quite a lot.” Emilien licked his lips. The banker hesitantly offered a serving which was accepted without vacillation. “I always thought that you void jumpers would be more reluctant accepting unverified consumables?” Dierre smiled a questioning look. Emilien swallowed the strong fluid and inhaled deeply. “I have a clone ready. And an implant that up links me directly to my pod. Don't think that if I have to wake up in a fresh body that I won't remember this place, including your mug.” Emilien tapped lightly on his temple seeming threatening and postured while he spoke. The banker nodded in uneasy amusement. “Excellent, excellent. Ahem, The reason we contacted you Mr Emilien, is because we are in business...” He promptly helped himself to a second glass of... whatever alcohol it was, anticipating a speech and a job description. “...the business of war. Currently we are supplying arms to the Juela fleet, who are at war with the Magarrian Empire. They are for the most part, boycotting our factories... which is a shame really, but understandably so. The Shiv Unity are supporting our enemy logistically yet have not joined them in active combat." He walked around his desk swirling the brown liquid round and round as he talked. "We are trying to coax Osteri aggression, but they have occupied themselves in... other endeavours and don't seem as willing as usual to assault Magar territories.” The spacer frowned and feigned curiosity. “Why would you suppose that be?” He interjected. “We are not sure... don't interrupt me, you break my train of thought.” The banker lied and it did not escape his attention. “Continue by all means.” He waved a bottle at the executive leaning back into a comfy black leather chair. “If we get the upper hand in this war we could control vital Magar territories, the profits our companies could absorb from the moons and planets would be virtually tax free and help to continue fund the war effort...” Emilien cut him off with a snide sarcasm. “How philanthropic. I watch your news propaganda...” Emilien slowly sat upright and uncannily performed like a popular Juel news anchor. “Breaking news. The Magar Empire are allegedly oppressing... slaves, it is reported that the war has driven them to desperation and are driving their labour forces harder than what is... morally justifiable. Any petitions made or pleas for leniency, no matter how trivial is met with... corporal punishment. We must be vocal about their plight and fight for... freedom and liberty. You are with The Report. See you next time, and remember, peace everywhere for all.” He mockingly mimics a news anchor's plastic monotone while folding up and shifting around imaginary papers. The secretary sniggered softly from behind her desk, Dierre frowned. Emilien slouched back into his chair. “What would you have me do boss?” The banker remained silent. “Excuse me one moment.” Dierre touched a pad on his desk, privacy panels slid up separating Dierre from his guest and the lady. He opened comms to an unknown voice. Emilien auto tuned up his sonic receptors slightly and closed his eyes listening in uninvited but inconspicuously. "Yes Dierre, make it quick." “Right, good afternoon sir. I am not sure about this character, Mr Emilien, should we not rather employ one of our own for this contract.” “What? No! There is no one else with the expertise and or reputation required for this investment. He has no prior affiliation to us no, no record. Dierre, just hire the man and stop whining like a little bitch! I don't need this type of crap. This was prearranged, what I don’t need is uncalled for opinionated inputs. We have made the decision and you, you explain what we require of them. So explain to the space clone what we need him to do and how much we are going to pay him for it!” The silence was awkward. “Wh... Yes sir.” The banker was keeping good composure under the condescending circumstances. Emilien smiled, a sly joy filling his soulless being. The comms line closed and the privacy panels retreated into the floor to reveal to the banker Emilien, sitting there grinning like an idiot. “How much are you going to pay me?” “Don't you want to know details of the job concerned?” “No. Just show me the figures in sat.” The director handed him a pad. Emilien looked at the glowing screen, his smiled recurred. “I accept this mission.” He glanced over at the secretary who was unassumingly recording minutes at her desk. “Doing anything tonight sweetheart?” She grimaced. Emilien stood up, “Dierre my good fellow I have to go, need to prepare for whatever it is you corpo scumbags are going to make me do.” “Don't you want to know the details involved?” “Send the info to my pod.” “It is sensitive information.” Emilien indifferently stared at Dierre. “I have a secure line... bitch.” Disbelief shot across his face.
He walked out of the room, looked back grinning an impossibly large grin and winked at the lady. “See you later sweetheart.” She quickly had the door slide closed. "That was unsettling." She mumbled to herself.
...
scifi
-
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 45bda953:bc1e518e
2025-05-19 09:00:41
@ 45bda953:bc1e518e
2025-05-19 09:00:41Kaspa Empire - Ceb System - Planet Hithe III
The day was hot and the manor sounded eerily quiet compared to the hustle and commotion of the hours prior. On the estate and in the master bedroom specifically, a married pair had become parents. “He looks so much like you Domitius.” Cleolia remarked while stroking the newborn's tiny arms. “He has strong blood.” The father responded smiling fondly sitting on the bedside. A silent nurse was tidying up the apparel and instruments of labour while the couple waited patiently for her exit to have more private discourse. “I am so glad to have born you an heir my love.” Domitius stared intently at his offspring. He had no qualms neglecting obligations to his property and recessed momentarily to celebrate the occasion with his wife. “I will send for the priest, register the child as an Imperial citizen and have him scribed into our family archives, but in the meantime, you must recover. Let a servant girl take our son for a while.” She pouted a playful but exhausted look of non compliance. “You must rest.” He insisted. “How can I let him go when I only just met him? Who are you little man?” She smiled faintly and nodded. “You are right, Domitius, where are you going?” “To the fields, the slaves are behind schedule, our harvest is big and taxes are high. This war is taking it's toll, we must excel to adequately serve the Empire in these pressing times. If the tamed Osteri could only comprehend what is at stake.” Cleolia peered cautiously at the embellishment and carvings on the wooden door knowing that Sethari was standing just beyond. Domitius trailed her gaze. “Don't worry my love, he means well, at least he tries to understand the urgency of my affairs.” He stood up straitening his vest and prepared to leave the room. “Domitius, wait...” He stopped at the door. “What will you tell the priest?” Domitius paused. “I will tell him Albin... Albin Domitius Chevalier.”
He left the room and it was quiet, the help entered and swaddled the baby rocking him while Cleolia drifted between sleep and conciousness. “Albin.” She repeated to herself as deep slumber enveloped her.
Domitius and his overseer walked briskly out of the manor towards the grain fields squinting as blue Ceb light reflected off the lanscape. “I honour you on the spawn of your son my lord, I hope for a good strong boy, you will be a happy father. I am happy with Seth.” He pounded his chest softly and proudly. “Thank you Sethari, is your son walking yet?” Domitius queried. “No my lord, still crawling on his belly like a beast.” The headman was trying to make his master laugh though Domitius was in a sterner mood having a weight on conscience. “I am in no mood to jest Sethari.” Domitius suddenly clenched his fists. “Get those slaves to work, I cannot have them idling when they should be harvesting.” Sethari made a small bow to his master and started yelling at his Osteri kinsmen, threatening them with a rolled up whip he procured from somewhere inside his tunic, waving it about and cracking it in the air every so often. Domitius picked up a scythe and proceeded to cleave down large swathes of grain. This had a more compelling effect of rallying the straggling workers to action than did the whip. They all toiled together in the pale light of Ceb.
Domitius was sweating, sweating and praying for a swift victory over the Jeula Federation. Fighting his small part in a increasingly complicated war, loyal to his Empire in his own unique way even though the conflict was far from home. A powerful loyalty that cannot be bought with riches or broken by coercion. A loyalty born through inheritance and blood.
...
The priest was in a more jovial mood than usual. The break of routine was a welcome one. The birth was indeed a momentous occasion. Few things seem of much report in a small planetary expansion program. He did not even seem to mind carrying a keg full of honey mead over the rolling hills of the plantation colony. “Domitius comes to church submissions far to infrequently.” The portly man mumbled to himself while wiping the accumulated sweat from his brow. “I eat too well among all these farmers.” The habit of speaking to himself was ordinary for this man of the cloth who always felt socially disconnected from his flock, caring for their souls, protecting their dignity and general well being like a responsible patron. “I feed their spirits, they feed my body, Hahaha. Tonight I will share my good spirits! Hahahaha.” Impressed by his own sense of humour he turned to witness the majestic blue star set over the skyline. Everything turned a silvery gray hue, and then the stars broke through the atmosphere lighting his way. “Clear skies, the blessed stars guide me.” He continued on the path approaching the Domitian manor and rapped a quick knock on the side of the root cellar doors. It creaked open upwards and a tall muscular Osteri took his baggage and let him in. “Thank you Setharis, my arms are weary, ready to fall off, bless you.” Domitius looked up from his bench seat below a glowing lantern. “Good to see you Father Ecknard.” “Dispense with the formalities and bring the dispenser.” He motioned to Setharis who placed the heavy keg on a table next to an assortment of documents, quill and sealed inkpot. “You pour Setharis and I will write. Name?” Ecknard scratches his chin with the quill contemplating his seat and it’s adequacy for the prolonged exercise of scribble. “Name?” Domitius paused. “Albin Domitius Chevalier.” The priest focused, started with his calligraphic art and fashioned the name and ASN standard block height beautifully onto the family records all the while biting his tongue. “He will inherit the colonial estates, all your assets in Kaspa Prime and the parochial offices at Magar Prime. Correct?” “Yes.” Replied Domitius solemnly. “I'll soon have to amend your will and testament. I'd have to make a registry at the parish and send correspondence to Magar Prime. There would be many from the royal courts who'll send their best regards from afar when this news becomes public.” Domitius did not seem as enthusiastic as Ecknard would have liked. “What ails you Domitius?” The priest could not help but make the pun and restrained a grunted laugh inside himself.
“I wonder if we should wait before registering and announcing him to Empire.” Ecknard’s expression slowly changed to puzzlement sitting up straight, his belly pushing on the heavy table. “In the voids name why?” “I am concerned... about this war...” “It is on the other side of Magar space!” The priest interjected in astonished retort. “I know father, maybe I am just being overly cautious, but with the Magar Dominus fleet occupied at the divide I am worried about the colonies in the isolated regions.” “Surely Kaspa prime will spare no expense to our defence in the improbable event of an invasion.” “The core keepers will not allow foul play from the Jeul.” “Yes Ecknard, but the fleet is not capable because most of our ships are at the aforementioned objective!” “No, no, no. Suggesting that conflict would happen outside of the divide is practically blasphemy. I cannot imagine insubordination to the Core mandates and the Accords." Domitius remained silently astute and father Ecknard decided to not argue further with the lord. His shoulders sagged. “I will not register the boy in the Imperial records.” “Thank you father.” “What do you know that I fail to see Domitius.” The two men stared at each other from across the table. The hulking bodyguard ever present in body but semi ignorant in mind silently and intriguingly observing the discussion.
“The value of sat. It is not calculated well by the common people, no offence father.” The priest piously lifted his hand and with tilted brow motioned. “None taken.” “My son and our blood line is invested with empiric power, if opportunists become aware of his existence and being outside the Magar prime void, we might have problems here on Hithe III.” Cumbersome thoughts and machinations of the mind darkened the mood of the party. Not at all what Father Ecknard was projecting in his minds eye during his arduous walk to what he was hoping, a celebration and getting drunk with an old friend. “The war does not seem to be ending any time soon, how long shall we stall his registration?” The priest reasoned on. “Think of the rites he will not be allowed to partake in at the church. He will be like Osteri.” Ecknard gestured towards Sethari. “This is a small colony Ecknard. My son will be educated as a member of royalty, all on Hithe III will acknowledge his social standing, I am only concerned that the secret be kept from the outside worlds. He will never be considered Osteri, he will know who he is and what his position is in the greater void. When the war is over we will properly introduce him to the families, currently they would be too occupied with politic as it is, and might not offer him due ceremony as they would under more peaceable circumstances.” The priest capitulated and grabbed a mug. “Your secret is safe with me Domitius, the lack of technology on this forsaken planet is good for your purposes, seeing as the only comms service on the planet is in the church tower. That blinking comms station hounds me daily with requests for your return to Magar Prime. The high counsel want to rebalance and need your signature.” Domitius sighed and looked away as if some spectre loomed in front of him.
I swear silence on the birth my lord, though let me make a final amendment to your proposal. A bit of extra security shall I say.” Domitius filled a cup of mead for Sethari and himself, becoming more relaxed and hospitable. “I am listening.” “If the risks are as great as you assume, let us pretend for the child's sake that he is Kaspian royalty only, and not true Magar. We then continue his education to the full and not put him in a position where he could compromise himself should he be... void forbid, captured by some opportunistic prospector.” Domitius looked ponderously into his cup. “Ecknard, my son is an infant... If we have to keep the boy in the dark about the true nature of his identity, how long do you predict this war to continue?” Father Ecknard leaned forward... “I sit at the comms desk every night and listen to the chatter. This war... is going to be a long one.”
...
scifi
-
 @ 1b9fc4cd:1d6d4902
2025-05-19 08:12:45
@ 1b9fc4cd:1d6d4902
2025-05-19 08:12:45A musician's brand is as crucial as their talent in the ever-evolving music industry. Creating a compelling and cohesive brand can catapult an artist from obscurity to superstardom, providing a distinct identity that resonates with global audiences. One of the most iconic examples of successful music branding is David Bowie. His ability to craft a unique, multifaceted brand is a masterclass for any artist. Here, Daniel Siegel Alonso examines the Thin White Duke's approach via three essential branding components: naming, visual identity, and sonic style.
What's in a name?
The first step in establishing a memorable brand, music or otherwise, is choosing the right name. David Bowie understood this concept profoundly. Born David Robert Jones, he adopted the surname "Bowie" to avoid confusion with The Monkees' Davy Jones. His choice of "Bowie" was not random; it was inspired by the Bowie knife, symbolizing a razor-sharp, cutting edge—qualities that would later define his career.
Little did Davy Jones know that the Bowie name would become a brand in itself, a shorthand for creativity and continual rebranding. Selecting a memorable name that reflects their musical mission is crucial for up-and-coming musicians. A name should be unique yet simple enough to be easily remembered and searched by potential fans. It's also essential that the name is flexible, allowing for growth and evolution, much like Bowie's did throughout his career.
Formulating an indelible image
Siegel Alonso notes that a visual identity is another cornerstone of any successful brand. David Bowie excelled at this, continuously transforming his appearance to reflect his artistic eras. Bowie's visual identities were not just premeditated looks but integral parts of his storytelling style, from the celestial Ziggy Stardust to the grand Thin White Duke.
At its zenith, a musician's visual identity encompasses album artwork, stage costumes, music videos, and now, a strong social media presence. For Bowie, each visual iteration was meticulously crafted to align with the themes and messages of his music. This alignment between visual and sonic elements created a holistic and immersive experience for his audience.
Modern musicians should take a page from Bowie's playbook by developing a cohesive visual style that complements their music. Whether it's through consistent use of colors, symbols, or fashion, a distinctive visual identity helps to create a lasting impression. Collaborating with talented designers and photographers can also elevate an artist's visual brand to new heights.
Inventing a unique sound
The beating heart of any musical brand is the music itself. David Bowie's sonic style was as diverse as his iconic visual transformations. He effortlessly glided through genres, from glitter rock and American soul to electronica and avant-garde jazz, constantly pushing boundaries. Despite this diversity, there was an unmistakable Bowie essence to his music, characterized by innovative production, trademark tone, and a sense of drama.
For new artists, defining a unique sonic style is essential. This involves more than just the genre; it encompasses the artist's voice, instrumentation, production choices, and lyrical themes. An artist's sonic style should be recognizable and consistent yet flexible enough to evolve. Much like Bowie did, collaborating with different producers and musicians can infuse fresh perspectives and innovation into the music.
The merging of elements
David Bowie's brand success was not merely the result of excelling in isolated elements but rather the synergy between naming, visual identity, and sonic style. His ability to seamlessly incorporate these components created an influential, enduring brand that transcended cultural trends.
Siegel Alonso recommends emerging artists learn from this holistic approach. It's vital to ensure that all brand elements work in concert together. A well-chosen name sets the stage, a compelling visual identity seizes attention, and a unique sonic style engages your audience. Each element should reinforce the others, creating a cohesive and compelling narrative that defines the artist's brand.
Conclusion
Bringing a music brand to life is a multifaceted endeavor that requires careful consideration and creativity. Bowie's extraordinary career illustrates the power of a well-thought-out brand, showing how a distinctive name, a compelling visual identity, and a unique sonic style can create an enduring legacy. Daniel Siegel Alonso suggests aspiring artists turn to David Bowie as an oasis of inspiration, embracing the art of reinvention and the implication of a cohesive brand. By doing so, they can carve out their own space in their world and leave a lasting impact on their audience.
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 30947d80:08bd561d
2025-05-19 08:10:47
@ 30947d80:08bd561d
2025-05-19 08:10:47In an increasingly noisy and connected world, finding moments of peace and quiet can feel like a constant struggle. From the incessant ringing of cell phones to the chatter of nearby conversations, unwanted wireless communications can disrupt our focus, increase our stress levels, and diminish our overall well-being. While the use of electronic device jammer is a complex and often restricted issue, the underlying desire for tranquility and freedom from unwanted intrusions is a universal one. This article explores the potential role of jammers in creating peaceful environments, while acknowledging the legal, ethical, and practical limitations that must be considered.
The Appeal of Jammers for Creating Tranquility:
The allure of signal jammers as a means of guarding tranquility stems from their ability to create a "zone of silence," where unwanted wireless communications are effectively blocked. In theory, this could provide a respite from the constant barrage of notifications, calls, and other digital distractions.
- Reducing Noise Pollution: Jammers can block the ringing of cell phones, the chatter of conversations, and other sources of noise pollution, creating a more peaceful and relaxing environment.
- Enhancing Focus and Concentration: By eliminating distractions, phone jammer can improve focus and concentration, allowing individuals to work more effectively, study more efficiently, or simply relax and unwind.
- Creating Private Spaces: Jammers can be used to create private spaces where individuals can communicate without fear of being overheard or recorded.
- Promoting Mindfulness and Relaxation: By reducing digital distractions, gps blocker can promote mindfulness and relaxation, allowing individuals to be more present in the moment.
Legal and Responsible Alternatives for Finding Tranquility:
Instead of relying on illegal and potentially dangerous bluetooth jammer, there are many legal and responsible ways to create a more tranquil environment:
- Use Noise-Canceling Headphones: Noise-canceling headphones can block out unwanted sounds, allowing you to focus on your work or relax in peace.
- Create a Quiet Space: Designate a specific area in your home or office as a quiet space where you can go to escape distractions.
- Turn Off Notifications: Turn off notifications on your electronic devices to reduce the constant barrage of alerts.
- Practice Mindfulness and Meditation: Mindfulness and meditation techniques can help you to focus your attention and reduce stress.
- Communicate Your Needs: Communicate your need for quiet to those around you and ask them to respect your boundaries.
- Use Soundproofing Materials: Soundproofing materials can be used to reduce noise levels in your home or office.
-
Spend Time in Nature: Spending time in nature can be a great way to relax and de-stress.
- https://www.edocr.com/v/3kvwmk0j/Thejammerblockershop/t-us-x04-desktop-blocking-mobile-device-high-power
-
 @ 975e4ad5:8d4847ce
2025-05-19 07:31:41
@ 975e4ad5:8d4847ce
2025-05-19 07:31:41The Origin of the Name “Bitcoin”
The name “Bitcoin” is a blend of “bit” (a unit of information in computing) and “coin” (a currency). Satoshi Nakamoto chose this name to highlight the digital nature of the currency, which exists entirely on a blockchain—a decentralized network immune to central control. The name is short, memorable, and reflects the project’s philosophy: money that is both technological and universal.
Satoshi decided to divide 1 Bitcoin into 100 million smaller units, named “satoshis” in his honor. This wasn’t arbitrary. Nakamoto foresaw that Bitcoin could become extremely valuable, as we see today, with 1 BTC worth around $100,000 (as of May 2025). Dividing the currency into such tiny fractions ensures flexibility: even if Bitcoin’s price reaches millions, people can use satoshis for small transactions, like buying coffee or paying network fees.
Why 100 Million Satoshis?
Satoshi’s decision to make 1 BTC equal 100,000,000 satoshis was visionary. He drew inspiration from traditional currencies, where 1 dollar splits into 100 cents, but went further. With a maximum supply of 21 million Bitcoins, the total number of satoshis is 2.1 quadrillion (2,100,000,000,000,000). This number may sound massive, but it was carefully chosen to provide enough units for future microtransactions without compromising the currency’s sense of scarcity.
If Bitcoin’s supply were framed as 2.1 quadrillion “bitcoins” instead of 21 million, it would create a false impression of abundance. Psychologically, people perceive smaller numbers as more valuable and rare. 21 million feels like a true limit, while quadrillions seem almost infinite, which would undermine Bitcoin’s core value proposition: scarcity, akin to gold.
The Benefits of Satoshis
Satoshis are the backbone of Bitcoin’s flexibility. They enable:
-
Microtransactions: Satoshis make payments as small as fractions of a cent possible, which is crucial for Bitcoin’s future as a global currency. In countries with low purchasing power, satoshis can be used for everyday purchases.
-
Network Fees: On-chain Bitcoin transactions require fees, often less than 1 BTC. Satoshis allow precise fee calculations without dealing with decimal fractions.
-
Accessibility: Even if 1 BTC costs $1 million, anyone can afford to buy satoshis. For example, $10 is roughly 100,000 satoshis at current prices, making Bitcoin accessible to all.
Beyond practical benefits, satoshis carry cultural weight. The phrase “stacking sats” has become a rallying cry in the Bitcoin community, symbolizing long-term investment and belief in the currency’s future. This expression is so iconic that removing the term “satoshi” would be like erasing part of Bitcoin’s identity.
Lightning Network and Satoshis
The Lightning Network, a layer-2 solution for Bitcoin, has made satoshis even more vital. This network enables fast and cheap transactions that don’t settle directly on the blockchain (off-chain). Due to low fees and small amounts, Lightning transactions are typically measured in satoshis, not Bitcoin. For example, a payment of 0.0001 BTC (10,000 satoshis) is common in Lightning, while on-chain transactions often involve larger sums, measured in BTC.
This distinction—Bitcoin for on-chain and satoshis for Lightning—is not only practical but also logical. On-chain transactions are slower and costlier, suited for large transfers or long-term storage (“HODLing”). Lightning is for everyday payments, where satoshis shine. Renaming satoshis to “bitcoin” would blur this distinction, causing confusion. Would you say, “I have 1 million bitcoins in my Lightning channel”? That sounds absurd and undermines the clarity the current system provides.
Why Renaming Is a Bad Idea
The idea of calling 1 satoshi a “bitcoin” and abandoning the term “bitcoin” for the whole unit has several serious flaws:
-
User Confusion: People accustomed to 1 BTC = $100,000 will be shocked to hear that 1 “bitcoin” is now worth 0.01 cents. New users won’t understand why “bitcoin” is so cheap, while veterans will struggle to recalculate their holdings. This could lead to errors, scams, or even loss of trust.
-
Technical Chaos: Wallets, exchanges, merchants, and software would need to overhaul their interfaces. Some platforms might stick to the old nomenclature, creating inconsistencies. Imagine an exchange showing “1 bitcoin = $0.01” while another uses “1 BTC = $100,000.” The result? Total chaos.
-
Cultural Loss: Satoshi is a tribute to Satoshi Nakamoto, whose vision changed the world. Erasing his name is disrespectful to his legacy. Moreover, phrases like “stacking sats” would vanish, weakening the community’s spirit.
-
Psychological Impact: 2.1 quadrillion “bitcoins” sound like an endless supply, undermining the idea of scarcity. In contrast, 21 million Bitcoins reinforce the sense of rarity, which is key to the currency’s value.
-
No Real Benefit: Satoshis are already a functional unit. Wallets can display amounts in satoshis, mBTC, or dollars without changing the protocol. Renaming solves no real problem—it just creates new ones.
Alternatives to Renaming
Instead of upending Bitcoin’s nomenclature, we can make the currency more accessible by:
-
Education: Teach people they can buy fractions of a Bitcoin, even just a few satoshis. This removes the psychological barrier of a high price.
-
Better Interfaces: Wallets can display amounts in satoshis or local currency for easier understanding. For example, instead of “0.0001 BTC,” an app could show “10,000 satoshis” or “$10.”
-
Promoting Lightning Network: Encouraging the use of satoshis in Lightning will make Bitcoin more practical for daily payments.
-
Communication: Emphasize that Bitcoin is like gold—you don’t buy a whole bar, but grams. This makes the currency more approachable to newcomers.
Bitcoin is more than a currency—it’s an idea that changed the world. The name “Bitcoin” and its satoshis are integral to that idea. Satoshi Nakamoto designed the system with the future in mind, giving us a currency that is both scarce and flexible. Renaming satoshis to “bitcoin” is a marketing stunt with no technical merit, risking trust, clarity, and Bitcoin’s culture. Instead of changing what works, let’s focus on education and innovation to make Bitcoin even more accessible. Let’s keep stacking sats and preserve the spirit of Satoshi!
-
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 9c9e774c:491c6c5b
2025-05-19 06:58:35
@ 9c9e774c:491c6c5b
2025-05-19 06:58:35Expert witnesses play a critical role in modern litigation. Their primary purpose is to assist the court in understanding complex evidence or issues that are outside the scope of common knowledge. From civil suits to criminal trials, these professionals can make or break a case with their specialized knowledge. Below, we explore the main types of expert witnesses and how they contribute to the judicial process. Along the way, we’ll discuss specific examples, such as the financial expert witness, defamation expert witness, and damages expert witness, as well as considerations like the expert witness hourly rate.
What Is an Expert Witness?
An expert witness is an individual who possesses specialized education, training, skills, or experience in a particular field. Unlike fact witnesses who can only testify about what they directly observed, expert witnesses are allowed to offer opinions based on facts and their expertise. Courts rely on these opinions to make informed decisions, particularly in cases involving technical, scientific, or financial matters.
Expert witnesses can be called by either side in a case—plaintiff or defense—and their credibility often has a major impact on the outcome of the trial.
Categories of Expert Witnesses
There are numerous types of expert witnesses, each suited to a specific area of law or subject matter. Here are the primary categories:
1. Medical Expert Witnesses
Medical expert witnesses are commonly used in personal injury, malpractice, or wrongful death lawsuits. These experts might be surgeons, physicians, psychologists, or nurses who can testify about the standard of care in a medical context or evaluate the extent of a person's injuries.
2. Financial Expert Witnesses
A financial expert witness is crucial in cases involving economic loss, fraud, valuation, or complex financial transactions. These experts are often certified public accountants (CPAs), forensic accountants, or economists. In business litigation or divorce cases, they may evaluate the financial condition of a company or individual and offer insight into accounting practices, financial statements, or asset valuation.
They are also heavily relied upon in cases involving corporate fraud, investment disputes, or misappropriation of funds. Their analysis can determine whether transactions were lawful or fraudulent, making their role indispensable.
3. Engineering and Technical Experts
These experts are commonly used in construction disputes, patent litigation, and product liability cases. For example, in a car accident case, a mechanical engineer might testify about vehicle malfunctions or road conditions. In a product liability suit, an industrial engineer might explain how a product's design led to injury.
4. Forensic Experts
Forensic expert witnesses include professionals like DNA analysts, fingerprint experts, or ballistic experts. They are frequently seen in criminal trials, helping to link evidence to suspects or validate forensic methods used in the investigation.
5. Defamation Expert Witnesses
In cases involving slander or libel, a defamation expert witness can help establish whether statements made were damaging to someone’s reputation and whether they meet the legal standard for defamation. These experts may have backgrounds in media law, journalism, communications, or public relations.
They evaluate the content, context, and potential impact of the allegedly defamatory statements and can also offer insight into industry standards or public perception. Their testimony is especially important in high-profile cases involving public figures, celebrities, or corporations.
6. Damages Expert Witnesses
A damages expert witness calculates and explains the economic impact of harm or loss experienced by a party in a lawsuit. This may include lost earnings, future income potential, cost of medical treatment, or business interruption. They are often used in conjunction with other experts to present a comprehensive financial picture to the court.
These experts are particularly important in personal injury and commercial litigation, where accurately calculating damages can significantly affect the amount awarded by the court or agreed upon in a settlement.
7. Vocational Experts
Vocational experts are commonly used in disability and workers' compensation cases. They assess a person’s ability to work, given their age, education, skills, and physical or mental limitations. Their evaluations help determine eligibility for benefits or compensation.
8. Psychological and Psychiatric Experts
These experts testify about mental health issues in a wide range of cases, from child custody disputes to criminal responsibility defenses. They assess competency, psychological trauma, or the mental state of individuals involved in legal matters.
The Role of Expert Witnesses in Legal Strategy
Beyond their knowledge, expert witnesses serve a strategic role in litigation. They can: * Help attorneys understand technical issues during the discovery phase. * Assist in developing questions for opposing experts. * Testify during depositions and at trial to strengthen a client’s case. * Review and critique opposing experts' reports and opinions.
Choosing the right expert witness can greatly enhance credibility with the judge or jury. Attorneys often look for individuals who not only have impeccable credentials but also can communicate effectively and withstand cross-examination.
Understanding the Expert Witness Hourly Rate
Engaging an expert witness can be costly, with fees varying depending on their field, experience, and the complexity of the case. The expert witness hourly rate typically ranges from $200 to over $1,000 per hour. Some may charge flat fees for specific services like report writing or deposition testimony. Highly specialized experts, such as brain surgeons or forensic economists, often command premium rates. Attorneys must consider these costs when developing their case strategy and assessing potential returns on a lawsuit.
Conclusion
Expert witnesses are a cornerstone of today’s legal system. Whether providing insight into financial statements, evaluating reputational harm, or calculating damages, their testimony can be the difference between winning and losing a case. Understanding the diverse types of expert witnesses and how they operate—along with factors like the expert witness hourly rate—helps legal professionals and litigants make informed decisions in high-stakes situations. As litigation grows more complex, the demand for expert witnesses across various industries continues to rise, making their role ever more pivotal in delivering justice.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 2b998b04:86727e47
2025-05-19 03:18:36
@ 2b998b04:86727e47
2025-05-19 03:18:36Web3 talked a lot about freedom.\ But it didn’t ask much of me.
Participation meant showing up, clicking, co-signing, reacting.\ A few emoji could pass a vote. A few posts could signal alignment.\ But there was no real cost.\ No friction.\ No weight.
It felt easy — and eventually, it felt empty.
Bitcoin, by contrast, never asked for my attention.\ It demanded my effort.
Proof of Work isn’t just what secures Bitcoin.\ It’s what shapes the people who actually engage with it.
You can’t fake time.\ You can’t fake energy.\ You can’t fake commitment.
If you want to mine a block, you need to burn electricity.\ If you want to hold your keys, you need to learn what that means.\ If you want to build with Bitcoin, you’re staking skin, not vibes.
Eventually I realized: this isn’t just a consensus algorithm.\ It’s a way of seeing the world.
Proof of Work is an ethic.\ It values restraint.\ It rewards effort.\ It penalizes shortcuts.
It’s the opposite of what most of the internet has become.
Web3 tried to engineer consensus through incentive design — but consensus without cost is hollow.
In Bitcoin, there is no shortcut to agreement.\ You either do the work, or you don’t get a say.\ You can’t tweet your way into a block. You can’t fork your way into consensus.\ You earn your way — through time, electricity, and conviction.
The deeper I leaned into Bitcoin, the more it reshaped me:
-
I stopped trying to “move fast” and started focusing on lasting things.
-
I began to care more about how work was verified, not just how it looked.
-
I started pruning systems — and relationships — that couldn’t carry weight.
Even in how I think about faith, work, rest, and community — I’ve started asking:
Is this real?\ Does this cost anything?\ Is this proof of something?
Fiat culture taught me to act like time was cheap.\ PoW culture reminded me: time is everything.
Fiat let me pretend I could get something for nothing.\ PoW told me the truth — you can’t.
I no longer want to participate in systems that reward shortcuts.\ I want to build slowly, honestly, and with weight.
Proof of Work isn’t just what runs Bitcoin.\ It’s what reforms me.
⚡ If this resonates, zap me some sats — or pass it forward.\ 🤖 Drafted with the help of ChatGPT, who also prefers work over noise.
-
-
 @ 2b998b04:86727e47
2025-05-19 02:42:59
@ 2b998b04:86727e47
2025-05-19 02:42:59never fully left Bitcoin. But for a while, I treated it like an asset — not a foundation.
It sat quietly in the background while I explored ecosystems that promised more features, more flexibility, more “community.” But the deeper I went into Web3, the more I realized what I was missing: clarity. Conviction. Limits that meant something.
Bitcoin never sold me hype. It just sat there, silently verifying everything.
When I finally returned to it — not as an asset, but as a philosophy — it wasn’t with fanfare.\ It was more like waking up in a room I had forgotten I built.
Reading The Bitcoin Standard didn’t just shift how I think about money.\ It reframed how I saw time, trust, and value itself.
Fiat incentivizes urgency.\ Bitcoin forces patience.\ Fiat rewards noise.\ Bitcoin rewards work.
It hit me: I had been operating with fiat assumptions in more areas than I wanted to admit — not just in trading or investing, but in how I approached relationships, goals, even faith.
I started pruning.
I stopped trading altcoins altogether.\ I stopped measuring success in dollars and started thinking in sats.\ I stepped out of endless Discord threads and Telegram pings — and felt relief I hadn’t known I needed.
I started building more quietly.\ And more honestly.
Even in my non-financial life, things began to change.\ Low time preference showed up in how I approached relationships.\ In how I treated rest.\ In how I stopped chasing every new opportunity and started focusing on stewardship — of capital, energy, and attention.\ And I’ve been trying to become more patient — though I think that’s more the Holy Spirit’s work in me than Bitcoin’s.
In some ways, it wasn’t just a return.\ It was a repentance.
A turning away from the illusion of infinite leverage, and back toward a system that demanded real cost.\ Bitcoin doesn’t flatter. It disciplines.\ And that’s exactly what I needed.
I didn’t need to be early to the next thing.\ I needed to go deeper with the one thing that still made sense.
Bitcoin didn’t need me to return.\ But I’m grateful I did.
⚡ If this resonates, zap me some sats — or share it forward.\ 🤖 Drafted with the help of ChatGPT, who never once tried to sell me a token.
#ProofOfWork #BitcoinNotCrypto #TheReturn #StillBuilding #LowTimePreference #TimeNotTokens
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 2b998b04:86727e47
2025-05-19 02:13:37
@ 2b998b04:86727e47
2025-05-19 02:13:37🧱 Why I Left Web3 for Proof of Work – Part 2: The Breaking Point\ \ It wasn’t a moment. It was a slow-motion unraveling.\ \ By 2024, I was deeply involved in a Web3 project focused on rewarding eco-conscious actions using a token system called “Proof of Environment.” I helped run a related Facebook group aimed at building community and encouraging engagement — especially among refugees and people living on the margins.\ \ I believed in it. I have a lot of respect for the project’s founder. His heart is in the right place.\ \ But reality set in: the token wasn’t trading.\ People were earning rewards that had no liquidity.\ \ So I tried to bridge the gap. I personally subsidized the effort — offering USD to keep people engaged and compensated.\ \ Eventually, I had to stop.\ \ Not because I lost faith in the mission… but because I realized I was compensating for a structural flaw. I was using fiat to prop up what was supposed to be an alternative to fiat.\ \ That realization cracked something open. And it wasn’t just about that project.\ \ By early 2025, I started re-examining the other Web3 spaces I was part of — including a local crypto-faith collective and a civic blockchain group I’d been attending.\ \ Before I say more - I want to be clear:\ \ - I respect the people involved in these communities.\ - I believe their intentions are sincere, and their efforts often come from a genuine desire to help.\ - The speakers were engaging and thought-provoking.\ - This isn’t a judgment of hearts — it’s a reflection on structure, incentives, and what actually works.\ \ One local Web3 community I attended regularly was especially revealing. It was connected to a publishing platform that promised a new way to engage content and community. But in practice, the tech was clunky, and the product was difficult to use — even basic edits to content required small fees in a token that few people understood. One of the DAOs I participated in burned through tens of thousands — mostly on architecture plans and design proposals.\ \ Weekly meetings had free lunches and spiritual talks… but the people experiencing homelessness, who we supposedly served? Often absent — or tokenized for optics.\ \ At one point, I proposed a practical idea to support a local housing initiative. The vision was for residents to grow some of their own food — creating both sustainability and job training opportunities.\ \ The response?\ \ “Let’s do this later.”\ \ It was polite. But it meant no.\ \ Over time, I felt less like a contributor and more like a prop — quietly tolerated, not truly included.\ \ Meanwhile, others held titles, got paid (quietly, maybe — but it was hard to tell how), and kept the stage.\ \ There was always funding for visibility. Rarely funding for outcomes.\ \ The problems people actually faced — hunger, housing, dignity — don’t care about abstractions.\ \ And neither does Bitcoin.\ \ I didn’t leave all at once. I still showed up in March, April, and May — out of habit, curiosity, and maybe hope.\ \ The speakers were thoughtful. In March, someone taught on mindfulness and the “five dimensions of time.” It was peaceful. But to me, it felt like another New Age sidetrack — far from the urgent needs on the ground.\ \ In April, one speaker — a former military interrogator turned AI educator — spoke on an AI “OS” for schools. Another shared how they helped build local currencies in Kenyan villages.\ \ In May, someone presented a trauma-informed housing model for youth with mental illness — one of the few ideas that felt truly grounded.\ \ These were all great ideas — thoughtful, human, often moving.\ \ My only thought was: they might have been better served by starting with Bitcoin — not as an add-on, but as a foundation. Especially the last two.\ \ And again — I believe many of the people involved were sincerely trying to make a difference.\ \ But something had shifted in me.\ \ I couldn’t stop asking: Who actually benefits from this tech?\ \ Does it work — or is it just another talk wrapped in hope?\ \ Why does impact often need a token?\ \ Not all the speakers revolved around Web3 or tokens — but many did.\ \ And quietly, a deeper question emerged: Couldn’t we just do all of this… with Bitcoin?\ \ Without a new platform. Without a fragile token.\ \ Just real tools. Real money. Real proof of work.\ \ The breaking point wasn’t dramatic. It was subtle, quiet — but final.\ \ ✍️ A Personal Note\ \ Even after all this, I still attend some of these events. I still show up — not because I’ve “come back,” but because I care.\ \ Because I respect the people.\ \ Because I believe conviction doesn’t require separation — it just requires clarity. I’m not circling back.\ \ I’m walking forward — with eyes open.\ \ And sometimes that means sitting in the same room with people I no longer fully agree with… and still learning something.\ \ My break wasn’t from the people.\ \ It was from the hype.\ \ From the structure, not the souls.\ \ And I still believe we can build better — if we start with truth.\ \ ⚡ If this resonates, zap me some sats — or just share it forward.\ 🤖 Drafted with the help of ChatGPT, who’s helped me find clarity across tech, theology, and everything in between.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ 2b998b04:86727e47
2025-05-19 02:12:52
@ 2b998b04:86727e47
2025-05-19 02:12:52For years, I wandered through the Web3 space—intrigued by its promises, pulled in by buzzwords like “decentralization,” “DAOs,” and “stakeholder democracy.”
But over time, the signals got drowned out by noise.
I saw venture capital pour into projects that had no product. I watched communities reward performative governance and token hype, rather than real work or impact. Even in faith-based circles, “Web3 for good” often meant shiny apps that served insiders more than outsiders.
Then I found my way back to where I began: Bitcoin.
Not as a speculative asset—but as a philosophy. A discipline. A foundation.
Proof of Work doesn’t need marketing. It doesn’t ask for permission. It either works—or it doesn’t.
Web3 taught me a lot. But Bitcoin gave me a plumb line. And from now on, that’s the line I’m building on.
This is Part 1 of a multi-part series. Follow for future entries.\ \ — Andrew G. Stanton\ Bitcoiner, builder, believer.
This article was co-drafted using ChatGPT to accelerate the writing process. Final content was reviewed and edited by me.
-
 @ a5ee4475:2ca75401
2025-05-19 00:22:41
@ a5ee4475:2ca75401
2025-05-19 00:22:41clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 📱 (on development) ⏳
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Alby - Native and extension [info] 🌐
- ZBD - Gaming and Social [info] [source] 🤖🍎
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Minibits - Cashu mobile wallet [info] 🤖
- Blink - Opensource custodial wallet (KYC over 1000 usd) [source] 🤖🍎
- LNbits - App and extesion [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:

