-
 @ 3ffac3a6:2d656657
2025-06-14 19:37:17
@ 3ffac3a6:2d656657
2025-06-14 19:37:17🛡️ Tutorial: Secure SSH Access over Cloudflare Tunnel (Docker Optional)
🎯 Objective
Set up a Cloudflare Tunnel to securely expose SSH access to your system without revealing your home IP or requiring port forwarding. This enables secure remote access even behind NAT, CGNAT, or dynamic IP environments.
This guide:
- Uses Cloudflare Tunnels to proxy traffic
- Does not expose your home IP address
- Uses Docker + Docker Compose for orchestration (optional)
- Can be adapted to run under systemd directly if preferred
🔧 Prerequisites
- A domain managed via Cloudflare DNS
- SSH server running on your machine (default port
22) - Temporary access to the
cloudflaredCLI (for tunnel creation) -
Either:
-
Docker and Docker Compose (used in this example), or
- A native
systemdservice (alternative not covered here)
🪜 Step-by-Step Instructions
1. Install and Authenticate
cloudflaredInstall
cloudflared(temporary):bash curl -L https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-amd64 \ -o cloudflared && chmod +x cloudflared && sudo mv cloudflared /usr/local/bin/Login with your Cloudflare account:
bash cloudflared tunnel loginThis will open a browser and link the machine to your Cloudflare zone.
2. Create the Tunnel
Create a named tunnel:
bash cloudflared tunnel create ssh-tunnelThis creates a credential file, e.g.:
~/.cloudflared/5f84da12-e91b-4d2e-b4f0-7ca842f622f1.json
3. Define the Tunnel Routing Configuration
Create the tunnel config:
bash nano ~/.cloudflared/config.ymlExample:
```yaml tunnel: ssh-tunnel credentials-file: /etc/cloudflared/5f84da12-e91b-4d2e-b4f0-7ca842f622f1.json
ingress: - hostname: secure-ssh.example.com service: ssh://localhost:22 - service: http_status:404 ```
Then bind the hostname to the tunnel:
bash cloudflared tunnel route dns ssh-tunnel secure-ssh.example.comReplace
secure-ssh.example.comwith your own subdomain under Cloudflare management.
4. Prepare File Permissions for Docker Use (Optional)
If using Docker,
cloudflaredruns as a non-root user (UID 65532), so grant it access to your config and credentials:bash sudo chown 65532:65532 ~/.cloudflared sudo chown 65532:65532 ~/.cloudflared/*
5. Define
docker-compose.yml(Optional)yaml version: "3.8" services: cloudflared: image: cloudflare/cloudflared:latest container_name: cloudflared-ssh-tunnel restart: unless-stopped volumes: - ${HOME}/.cloudflared:/etc/cloudflared:ro - ${HOME}/.cloudflared:/home/nonroot/.cloudflared:ro command: tunnel run ssh-tunnel network_mode: host📝 Docker is used here for convenience and automation. You may alternatively run
cloudflared tunnel run ssh-tunneldirectly undersystemdor a background process.
6. Start the Tunnel
Start the container:
bash cd ~/docker/sshtunnel docker compose up -d docker logs -f cloudflared-ssh-tunnelYou should see
Registered tunnel connectionand other success logs.
7. Connect to the Tunnel from Remote Systems
Option A: Ad-hoc connection with
cloudflared access tcpbash cloudflared access tcp --hostname secure-ssh.example.com --url localhost:2222In another terminal:
bash ssh -p 2222 youruser@localhostOption B: Permanent SSH Configuration
Edit
~/.ssh/config:ssh Host secure-home HostName secure-ssh.example.com User youruser IdentityFile ~/.ssh/id_rsa ProxyCommand cloudflared access ssh --hostname %hThen connect with:
bash ssh secure-home
✅ Result
- Secure SSH access via a public domain (e.g.,
secure-ssh.example.com) - No ports open to the public Internet
- IP address of your machine remains hidden from Cloudflare clients
- Easily extendable to expose other services in future
🔁 Optional Enhancements
- Run as a
systemdservice instead of Docker for lower overhead - Use
autosshorsystemdto maintain persistent reverse tunnels - Expand to forward additional ports (e.g., Bitcoin RPC, application APIs)
- Apply strict firewall rules to limit SSH access to
localhostonly
-
 @ 866e0139:6a9334e5
2025-06-14 17:33:06
@ 866e0139:6a9334e5
2025-06-14 17:33:06Autor: Bernd Schoepe. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die Anmerkungen zum Text (Fußnoten) folgen aus technischen Gründen gesondert.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Dies ist Teil 3 des Essays. Lesen Sie hier Teil 1 und Teil 2.
IV Denazifizierungsstopp und die „abgesagte“ NS-Aufarbeitung in der Adenauer-Ära
„Nie wieder Krieg, nie wieder Faschismus!“
Dieses Gelöbnis erfuhr seine Ausformulierung, als die durch Krieg und Verfolgung charakterlich tief geprägten und für ihr Leben gezeichneten Väter und Mütter des Grundgesetzes sich 1948 zum Parlamentarischen Rat versammelten. Dort hat man vor dem Erfahrungshintergrund des Totalitarismus Nazi-Deutschlands in den neunzehn Grundrechtsartikeln die Rechte der Menschen vor dem Staat festgeschrieben, die gegen staatliche „Willkür, Ungerechtigkeit und Gewalt“ (25) schützen sollen. Sie wurden zur Grundlage eines neuen Staatsverständnisses, das vom Humanismus und dem Geist der Aufklärung getragen sein sollte. Das Gelöbnis fand seinen verfassungsmäßigen Ausdruck also im Grundgesetz, das am 23. Mai 1949 feierlich in Bonn verkündet wurde. Dessen Geist manifestiert sich besonders in der sogenannten Ewigkeitsklausel der Menschenwürde (Art.1), die den Grundrechtsartikeln, dem Kanon der Menschen- und Bürgerrechte, vorangestellt wurde.
Doch die Unterschriften unter dem Grundgesetz waren kaum trocken, da wurde dieses Gelöbnis schon durch die Frontstaatenideologie des Kalten Krieges überlagert, konterkariert und in der Praxis sukzessive aufgehoben. Der Kalte Krieg hatte bereits begonnen und seine Akteure bedienten sich ungeniert der Vorurteile und Stereotypen, mit denen die Deutschen noch gut aus dem Dritten Reich vertraut waren. Grundiert vom militanten Anti-Kommunismus, der bekanntlich auch die Nazi-Ideologie stark angetrieben hatte, verstärkt durch die Wiederbewaffnung mit der sie begleitenden Aufnahme der BRD in die NATO, konsolidiert in der Zeit der Adenauer-Restauration in den 1950er Jahren, in der ein konservativ-elitäres Staatsdenken gegenüber radikaldemokratischen Bestrebungen klar dominieren und sich durchsetzen sollte, erwies die Aufarbeitung der NS-Vergangenheit sich als der größte und folgenreichste Rohrkrepierer in der Geschichte der noch jungen zweiten deutschen Republik. Erst mit den Frankfurter Auschwitz-Prozessen und stärker dann noch im Zusammenhang mit der Studentenrevolte Ende der 1960er Jahre sollte es zu neuen ernsthaften Bemühungen um gesellschaftliche Aufarbeitung kommen.
Adenauers Ankündigung einer Beendigung der NS-Aufarbeitung, die er bereits in seiner ersten Regierungserklärung 1949 (!) vor dem Bundestag gab, dürfte auch und gerade aus heutiger Sicht von deutlich wichtigerer Bedeutung für das Fortleben autoritär-rechtsextremer, völkischer und nationalsozialistischer Gesinnungen und Haltungen in Deutschland gewesen sein als der Einzug der AfD in den Bundestag 2017, einschließlich aller geschichtsvergessenen und in ihrer Wortwahl geschmacklosen Äußerungen ihrer Politiker seither.
Bemerkenswert sind die Worte, mit der Adenauer so früh der gesellschaftlichen Aufarbeitung der NS-Zeit eine klare Absage erteilte:
„Durch die Denazifizierung ist viel Unglück und viel Unheil angerichtet worden. (...) Im Übrigen dürfen wir nicht mehr zwei Klassen von Menschen in Deutschland unterscheiden, die politisch Einwandfreien und die politisch Nicht-Einwandfreien. Diese Unterscheidung muss baldigst verschwinden.“ (26)
Rasch wurden daraufhin die gesetzlichen Grundlagen geschaffen, um in den im Aufbau befindlichen bundesdeutschen Verwaltungsapparat über 50.000 NS-belastete Beamte wiedereinzugliedern, darunter auch viele, die zuvor dem Nazi-Unrechtsstaat als Mitglieder der Gestapo und der SS gedient hatten. Besonders im Bundesjustizministerium hatte ein Netzwerk aus Alt-Nazis unterhalb der ministeriellen Leitungsebene bis in die 1960er Jahre hinein das Sagen, mit großen, noch immer nicht vollständig aufgearbeiteten Auswirkungen auf die Gesetzgebung, durch die NS-Verbrecher in der BRD auf verschiedene Weisen vor Strafverfolgung geschützt wurden.
Den ideologischen Hintergrund bildet dafür der Konservatismus, dem Adenauer, die CDU/CSU und andere politisch einflussreichen Kräfte anhingen, genauer gesagt das Elitedenken, das für diesen Konservatismus konstitutiv ist. Es erklärt, dass die Regierung lieber auf die alte Elite, auch wenn sie in weiten Teilen nationalsozialistisch belastet war, zurückgriff als ein neues, demokratisch-selbstbewusstes Beamtentum zu begründen und eine aus den verschiedenen Facetten des Widerstandes sich rekrutierende Führungsschicht aufzubauen. Denn die geeigneten Personen für diese Führungsschicht hätte man weitgehend nicht im eigenen Lager, sondern im Lager der politischen Gegner, bei Sozialdemokraten, Sozialisten, Kommunisten und Linksliberalen finden können.
Fazit: Im Handumdrehen wurde der an das „Nie-Wieder!“– Versprechen an die zukünftigen Generationen geknüpfte, zumindest teilweise ernsthaft und aufrichtig angestrebte Neuanfang –verstanden als ein radikal zu vollziehender Bruch mit der faschistischen Vergangenheit – hintertrieben, entstellt, entkräftet und um seine Wirkung gebracht. Dabei spielte nicht zuletzt die schnell wieder angekurbelte Feindbildproduktion und Russophobie („alle Wege der Linken, Friedensfreunde, Anti-Militaristen und Neutralitätsbefürworter führen nach Moskau!“), eine wichtige Rolle.
Es ist daher kein Zufall, dass sie uns so verblüffend ähnlich auch heute wieder in Politik und Medien begegnet. Sie ist ein Herzstück der deutschen Nachkriegs-Lebenslüge namens „Vergangenheitsbewältigung“. Hier gilt einmal mehr der Satz, dass Untote bekanntlich länger leben.
Sie macht sich heute auch darin bemerkbar, dass die Tatsache, dass es sich bei dem Krieg gegen Russland nicht um einen Eroberungskrieg, sondern um einen Vernichtungsfeldzug gegen eine „minderwertige Rasse und Kultur“ handelte, im kollektiven Bewusstsein der Deutschen nicht verankert wurde. Sonst hätte der Hass auf die Russen und alles Russische gesellschaftlich nicht wieder hoffähig werden können.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Exkurs zum Niedergang der deutschen Sozialdemokratie
Im Ringen um den Weg, den die Bundesrepublik in den 1950er Jahren nehmen sollte, wurden damals Sozialdemokraten, die sich nicht bedingungslos der Bollwerks- und Frontstaaten-Ideologie des Kalten Kriegs unterwarfen, als „vaterlandslose Gesellen“ diffamiert. Die SPD tat sich immer schwer damit, der Demagogie der bürgerlichen Parteien etwas entgegenzusetzen, da Antikommunismus bei breiten Teilen der Bevölkerung, getreu der Devise „je primitiver, desto besser bzw. wirkungsvoller“, auch nach Hitler verfing.
Heute schlägt die Sozialdemokratische Partei die Aufrüstungs- und Kriegstrommel lieber selber kräftig mit und diffamiert die Angehörigen der Friedensbewegung und Verfechter einer Détente mit Russland als „Putin-Freunde“ und „Russlandversteher“ oder gar, ins absurd Metaphysische gesteigert als “gefallene Engel aus der Hölle“ (Olaf Scholz).
Mit dem Friedensnobelpreisträger und NS-Widerstandskämpfer Willy Brandt an der Spitze fuhr die SPD ihren größten Wahlerfolg ein – die von ihm geführte erhielt in der Bundestagswahl 1972 45,8 Prozent. Außenpolitisch überzeugte sie mit „Wandel durch Annäherung“ und „Wir wollen ein Volk guter Nachbar sein“. Nun ist sie beim Führungspersonal bei einem farblosen Apparatschik und Waffenlobbyisten (27) namens Lars Klingbeil und 16,4 % der Wählerstimmen angekommen. Zumindest die ebenso blasse und ideenlose Saskia Esken, die bei vielen einzig und allein für ihre Diffamierung von Demonstranten gegen das Corona-Unrecht („Covidioten“) in Erinnerung bleiben wird, zieht aus ihrer Unbeliebtheit nun die Konsequenz und tritt ab.
Indem die SPD, in Anbetracht der Friedensinitiativen Trumps die Chance verstreichen lässt, sich selbst in ihrer Politik gegenüber Russland zu korrigieren, um doch noch auf den Pfad der Diplomatie zurückzukehren und zu verhindern, dass auch noch der letzte Rest sozialdemokratischer Substanz über Bord geworfen wird, setzt Sozen-Konkursbeschleuniger Klingbeil zusammen mit BlackRock-Millionär Merz auf den Scholzschen Zeitenwende-Wahnsinn von 100 Milliarden für die Rüstung lieber noch weitere 500 Milliarden Euro drauf. Er und der den Kommiss-Ton perfekt beherrschende Pistorius, mit seinen Einlassungen zum „russischen Diktatfrieden“, der, wenn man ihn denn schon unbedingt so nennen will, ja nicht zuletzt auf das Konto der diplomatischen Untätigkeit der deutschen Regierung geht, besiegeln durch das von der Schuldenbremse befreite, in puncto Kostspieligkeit nach oben offene Aufrüstungs- und Militarisierungsprogramm, unter das in Wirklichkeit auch ein großer Teil der geplanten Infrastrukturmaßnahmen subsummiert werden wird (28), das Schicksal der ältesten Partei Deutschlands. Wissen diese SPD-Politiker wirklich nicht, was sie tun, wenn sie für die Profite der Rüstungswirtschaft alles verraten und auf lange Sicht verspielen, wofür diese Partei außen- und sozialpolitisch einmal stand und wofür sie gewählt wurde?
All das, was die SPD als Friedens- und Entspannungspartei einmal zur stärksten politischen Kraft gemacht hat, wird nun wie im Wahn von ihr verleugnet und mutwillig, geschichtsvergessen-revanchistisch zerstört. Und nicht nur das: Die SPD liefert den Rechten (nein, nicht der AfD, sondern den sonstigen Extremisten der Mitte!) den Grund, den neoliberal bereits entkernten Sozialstaat weiter – ab jetzt aber mit Bulldozern statt mit der Spitzhacke – zu zerstören. Sie nimmt dafür auch weitere, schwere Beschädigungen der Legitimität unserer ohnehin dahinsiechenden Demokratie in Kauf. Die Demokratie liegt nämlich seit Corona bei uns auf der Intensivstation und muss, u.a. durch regierungsfinanzierte „NGOs“ und staatlich organisierte Anti-AfD-Demonstrationen, künstlich beatmet werden!
Schließlich war die SPD zusammen mit der Merz-Union sogar bereit, einen kalten Putsch gegen die Integrität des Parlamentarismus und die elementaren Spielregeln der Demokratie durchzuführen. Mit diesem Putsch hat man im abgewählten 20. Bundestag noch schnell politisch äußerst weitreichende Grundgesetzänderungen durchgesetzt – und das gegen die neuen Mehrheiten des bereits gewählten 21. Bundestages! Die durch Bruch des Wahlversprechens ermöglichte Grundgesetzänderung, stellt einen besonders beschämenden Akt der Machtanmaßung, Wählerverhöhnung und Demokratiemissachtung dar. Und sie verfehlte ihre Wirkung nicht. Kurz darauf konnten die Demoskopen neue Rekordwerte für die AfD messen, die nun als stärkste Partei noch vor der CDU lag. Das Merz-Manöver dürfte im Übrigen dafür gesorgt haben, dass ihm nach der Wahl zum Bundeskanzler, die ja alles andere als glatt verlief, ein Makel anhängt, der so gravierend ist, dass er für den Rest seiner Amtszeit (hoffentlich) nicht mehr zu tilgen sein wird.
Das besonders Irre, das nicht nur den Fall der SPD beschreibt, ihr Versagen aber besonders plastisch hervorhebt, ist, dass es seit Beginn des Ukraine-Kriegs innerhalb der EU (mit Ausnahme Orbans) keine diplomatischen Initiativen gegeben hat, um mit Russland wieder ins Gespräch zu kommen. Im Rückblick wirken da selbst die Kalten Krieger vor und während der Ostpolitik von Willy Brandt wie Appeasement-Politiker.
Stattdessen war wiederholt eine Bundesaußenministerin zu vernehmen, die offenbar nur sehr eingeschränkt dazu imstande ist, ihre sprachliche Performanz dem hohen Amt angemessen zu kontrollieren. Sie wollte öffentlich „Russland ruinieren“ und erklärte dem Land ein anderes Mal, vor dem Europarat, beiläufig den Krieg. Dass Baerbock, die in ihrer Amtszeit in fast jedes diplomatische Fettnäpfchen getreten ist, jetzt zur zweithöchsten UN-Chef-Diplomatin gewählt wurde, ist Realsatire pur!
Polemik als geistiger Notwehrakt
Doch Halt! – Gerade merke ich, wie mich mein Hang zur Polemik fortzureißen beginnt!
Die Polemik ist ein hilfreiches (und noch nicht ganz verbotenes!) geistiges Notwehr-Mittel in Zeiten eines zunehmend aggressiv aufgeheizten gesellschaftlichen Klimas. Wie soll man nicht zum Polemiker und Satiriker angesichts des grassierenden Wahnsinns der Politik und ihrer vielen verrückt und absurd anmutenden Pathologien und Regressionen werden, hinter denen bei genauerem Hinsehen dann doch oft auch Kalkül vermutet werden muss? Wie sind sie anders als Vorgänge zu deuten, die zur Abwicklung der Demokratie führen sollen? Vorgänge, die durch eben jene Kräfte betrieben werden, die „unsere Demokratie“ inflationär lobpreisen und nicht müde werden, ihre „Werte“ in Sonntagsreden hervorzuheben. Gleichzeitig werden diese Werte aber durch Cancel Culture, Zensur und Denunziation massiv von ihnen angegriffen und von innen immer weiter ausgehöhlt.
Definitiv verhält es sich heute so, dass der Hang zur Polemik dem Umstand geschuldet wird, dass wir mittlerweile in schier unglaublichen Zeiten von Travestie-Ausgeburten leben. Diese machen es uns immer schwerer, nicht ganz die Bodenhaftung zu verlieren. All die wahnwitzigen Phänomenen, die wie wildgewordene Säue tagein tagaus durch das globale Dorf der Massenmedien in Echtzeit** getrieben werden, sie gefährden das Restvertrauen in den gesunden Menschenerstand und schränken die Möglichkeiten stark ein, einen halbwegs stabilen, geerdeten, vernunftgeleiteten Realitätsbezug aufrechtzuerhalten.
Und doch soll hier nicht ein weiteres Mal in dieser Façon mit der Regierungspolitik abgerechnet werden. Auf der Suche nach den tieferen Gründen für diese negativen Entwicklungen, soll stattdessen im zeithistorischen Material an einigen neuralgischen Stellen genauer nachgesehen und an der Oberfläche gekratzt werden, um die blinden Flecken bundesrepublikanischer Selbstwahrnehmung sichtbar zu machen.
Bernd Schoepe, Jahrgang 1965, Studium der Soziologie, Germanistik, Philosophie und Erziehungswissenschaften in Frankfurt/M. und Hamburg. Erstes und zweites Staatsexamen. Freier Autor, der zu bildungspolitischen, bildungssoziologischen- und bildungsphilosophischen Themen schreibt. Seit 2003 im Hamburger Schuldienst. Langjähriges GEW-Betriebsgruppen-Mitglied, ehem. Vertrauensmann, ehem. Mitglied der Hamburger Lehrerkammer. Hauptberuflich bin ich Politik- Deutsch- und Philosophielehrer an einer Hamburger Stadtteilschule. Kontakt: berndschoepe\@gmx.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 2e8970de:63345c7a
2025-06-14 17:07:56
@ 2e8970de:63345c7a
2025-06-14 17:07:56Iran raising a red flag in war times? That's a bit. Sabrina Carpenters "persona" - she's doing a bit. In the pope election the cardinals locking themselves in a conclave and the white smoke thing - it's a bit. Everything is only a bit.
Maybe I'm just old and interpret too much into youth slang but - that's actually a HUGE cultural shift if young people think of nothing as authentic anymore. What even is authentic?
https://stacker.news/items/1006348
-
 @ b83a28b7:35919450
2025-06-14 16:38:22
@ b83a28b7:35919450
2025-06-14 16:38:22This is the second installment in the series "The Net Appears" where I document my journey from being in a well-established and well-paying fiat job into the unknown world of independent work in freedom tech. Will I end up finding something truly inspiring and fulfilling, while being able to support my family? We'll find out over the course of the next few weeks.
So this happened a couple of days ago:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsd6khjdmgmme3xrnzj5xn5tfwer5pjchh20mcp4lfemurfsj3v4wgsjw0uj
Let's back up a bit, because in the first installment of this series, I was still in limbo.
If you’d told me three weeks ago that corporate martyrdom could be negotiated like a farmers-market cantaloupe, I’d have laughed you off the Microsoft Teams grid. Yet there I was, video-boxed opposite my Senior Vice Priest of PowerPoint, calmly re-petitioning for a graceful guillotine.
His verdict: the guillotine is for optics only, and apparently it clashes with the brand guidelines. Laying off The AI Guy would look like we’d just unplugged the future for spare parts. Impossible. But the man did extend an olive branch the size of a bonsai: “Resign, and we’ll cash out your vacation - thirty glorious days of fiat.”
Not the three-month severance I’d fantasized about, but enough to buy time, dignity, and a respectable stack of Claude API credits. I signed before he could replace goodwill with an NDA.
And then I chose July 4 as my last day. Cue bald eagles, Sousa marches, and a slow-motion shot of me frisbee-flinging my employee badge into an erupting grill. Independence from fiat, by literal fireworks.
Space Rush
The moment rumors of my exit hit Teams, meeting invites vanished like socks in a hotel dryer. I’ve used the liberated hours to launch A Muse Stochastic, my audio-visual fever dream where generative melodies court glitch-poetry and occasionally elope with Gemini Veo video frames. The first episode is live, pulsing somewhere between synaptic Vivaldi and quantum origami. So far it has six listeners and one confused Australian-shepherd (my most honest critic).
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqy88wumn8ghj7mn0wvhxcmmv9uq3zamnwvaz7tmwdaehgu3wwa5kuef0qqsvhtdltg2k3guhmshgmgt3nc9ejy0ct96t7udm04r5mupplcmdtesppmn7x
Meanwhile the playwright in me, neglected for months beneath sprint plannings and quarterly road-maps, finally crawled into the light. “Waiting for Satoshi,” first conceived on a warm Prague evening exactly one year ago ( nostr:nprofile1qy0hwumn8ghj7en0deehgu3dw3jhxapwdah8yetwv3jhytnrdakj7qgcwaehxw309a5hxmrpdejzumn0wd68yvfwvdhk6tcqyzaz7w2gxdjcga0fz6qt3x8ehc83mpgpvmr2swwmuzzdqfn26m3q54mhg79 can attest to this), now wears its final coat of dialogue. Tomorrow it debuts on GitHub - Creative Commons, open-source, fork-and-prosper - perhaps the inaugural play to invite pull requests for stage directions. If anyone wishes to add a tap-dancing Lightning node, be my guest.
Prague on the Horizon
Next week I return to BTC Prague, where ghosts of last year’s epiphany still linger near the pastry stand. This time I’m lugging camera gear, not corporate slide decks. Episode Two of Finding Home will be filmed there, featuring a wanderer whose bitcoined life map reads like Odysseus riding a Lightning invoice.
Perhaps my only conference of the year, I'm looking forward to catching up with friends old and new, and catch a whiff of that infectious bitcoin hopium.
Micro-lessons from Week Three
-
Severance is a mindset. One month of paid vacation feels oddly richer than three months shackled to uncertainty.
-
Symbolism scales. Pick an Independence Day, any Independence Day, and watch the universe queue fireworks.
-
Creative backlogs age like fine kimchi. Leave an idea in brine for a year and it returns with extra tang.
-
Open source = open veins. Releasing art into the commons is terrifying until you remember blood circulates best when it moves.
-
Microsoft Teams silence is golden (parachute). Each canceled stand-up funds roughly eight bars of experimental synth.
Gazing Forward
I still don’t know how mortgage, car payments, and teenage-soccer-tour fees will reconcile with my bank balance come August. Yet the dread that once clung to my ribcage has dissolved, replaced by a jittery anticipation - like the hush before a stadium crowd erupts. Every unknown now feels less like a void and more like a blank slide awaiting wild, irreverent doodles.
Next dispatch will likely come with reflections from Prague. The last two years, I was moved to unexpected tears on the final day, marveling at the sheer profundity of the human experience of the week past. Surely, that can't repeat for a third year in a row?
Until then, may your own nets appear exactly when logic insists they can’t - and may they be woven from liberated vacation days and the audible crackle of celebratory fireworks.
-
-
 @ 6c05c73e:c4356f17
2025-06-14 16:31:49
@ 6c05c73e:c4356f17
2025-06-14 16:31:49Isa Energia Brasil
Descrição da Empresa
A Isa Energia Brasil é uma das principais empresas do setor de transmissão de energia elétrica do Brasil. Anteriormente conhecida como ISA CTEEP (Companhia de Transmissão de Energia Elétrica Paulista), a companhia passou por um processo de rebranding em novembro de 2023 para refletir sua atuação em escala nacional, que se estende por 18 estados brasileiros.
- Papel no setor: Desempenha um papel crucial na infraestrutura energética do país, sendo responsável por transmitir aproximadamente 33% de toda a energia elétrica produzida no território nacional e 94% no estado de São Paulo.
- Controladora: A companhia é controlada pelo grupo colombiano ISA (Interconexión Eléctrica S.A.), um dos maiores conglomerados de transmissão de energia da América Latina, que detém uma participação majoritária em seu capital social.
- Vantagens: Essa conexão confere à Isa Energia Brasil um sólido respaldo técnico e financeiro, além de sinergias operacionais e de governança.
Visão Geral da Empresa
A Isa Energia Brasil (ISAE4) é uma das maiores e mais importantes empresas de transmissão de energia elétrica do Brasil. Em termos simples, seu principal negócio é "transportar" a energia em alta tensão das usinas geradoras até as redes de distribuição que a levam para cidades e indústrias.
- Analogia: Pense nela como a gestora das grandes "rodovias" da eletricidade do país.
Mercado que Atua
O mercado de atuação da Isa Energia Brasil (ISAE4) é o setor de transmissão de energia elétrica, um segmento estratégico, altamente regulado e com características muito particulares dentro da cadeia de energia do Brasil. Para entender o mercado da empresa, é preciso conhecer 4 pilares principais:
1. O Modelo de Concessões Públicas
- Funcionamento: A Isa Energia Brasil não opera em um mercado aberto e tradicional. Sua atuação é baseada em concessões de longo prazo (geralmente 30 anos), adquiridas por meio de leilões públicos organizados pelo Governo Federal, através da ANEEL (Agência Nacional de Energia Elétrica).
- Como funciona: Nos leilões, o governo define os projetos (novas linhas de transmissão e subestações a serem construídas). Vence a empresa que se propõe a construir e operar a infraestrutura pelo menor valor de receita anual.
- Barreiras de entrada: Este modelo cria altíssimas barreiras para novos concorrentes, pois exige enorme capacidade de investimento (capital intensivo), conhecimento técnico especializado e habilidade para vencer disputas acirradas nos leilões.
2. A Previsibilidade da Receita (RAP)
- Receita Anual Permitida (RAP): É a remuneração que a empresa tem direito a receber por disponibilizar suas linhas de transmissão em perfeitas condições de operação. O valor da RAP é definido no leilão e reajustado anualmente por um índice de inflação (geralmente o IPCA), o que protege a receita da desvalorização da moeda.
- Baixo risco: Como a receita é fixa e garantida por contrato, o risco operacional é muito baixo. A empresa recebe o valor integral desde que suas linhas e subestações estejam funcionando. Se houver falhas, ela pode ser penalizada com um desconto na receita, por isso a eficiência na operação e manutenção é fundamental.
3. Posicionamento Estratégico e Geográfico
- Dominância: É responsável por transportar aproximadamente 33% de toda a energia elétrica produzida no Brasil e impressionantes 94% da energia consumida no estado de São Paulo, o maior centro de carga do país.
- Capilaridade nacional: Embora sua origem seja paulista (antiga CTEEP), a empresa expandiu sua atuação e hoje possui ativos em 18 estados brasileiros, o que a posiciona como um player de relevância nacional.
- Principais concorrentes: Seus principais competidores no setor de transmissão são outras grandes empresas como a Eletrobras, TAESA e Alupar, que também disputam ativamente os leilões da ANEEL.
4. Vetores de Crescimento e Perspectivas
- Transição energética: O Brasil está aumentando massivamente sua capacidade de geração de energia renovável, especialmente eólica e solar. A maioria dessas novas usinas está localizada no Nordeste e no norte de Minas Gerais, longe dos grandes centros consumidores (Sudeste). Isso cria uma necessidade urgente de construir novas "autoestradas" de energia para escoar essa produção, garantindo uma demanda contínua por novos projetos de transmissão.
- Crescimento da demanda: O crescimento econômico e populacional do país, além da eletrificação da economia (ex.: carros elétricos), aumenta a necessidade geral de energia, exigindo uma rede de transmissão cada vez mais robusta e confiável.
Oportunidades que o Ativo Traz
As principais oportunidades que a empresa traz são:
- Alta previsibilidade de receita devido à Receita Anual Permitida (RAP).
- Expansão em investimentos de infraestrutura.
- Contratos de concessão renovados e com longa duração.
Isso tudo torna a empresa uma excelente pagadora de dividendos e JCP. No último anúncio da empresa, foram destinados R$2,36 por ação de juros sobre capital próprio, o que a torna um excelente ativo para o longo prazo.
Riscos
Por ser uma empresa que atua no setor de energia elétrica, ela assume alguns riscos que precisam ser monitorados de perto, tais como:
- Natureza (escassez de chuvas): Pode prejudicar a geração de energia e, como consequência, reduzir a transmissão de energia elétrica. Consulte aqui.
- Riscos regulatórios e governamentais (o principal): A empresa opera em um setor regulado pela ANEEL e sob concessões do governo.
- Financeiro: Para financiar seus projetos, a empresa precisa se endividar via debêntures, que são atreladas à Selic. Qualquer variação altera o financeiro da empresa.
- Dividendos: Pode ser uma faca de dois gumes, pois está previsto pagamentos muito maiores no futuro, o que pode retardar o crescimento da empresa devido ao pagamento excessivo.
- Risco operacional: Tudo que envolve intervenção humana pode ter falhas, mesmo que a empresa opere com alta eficiência hoje. Alguém pode “dormir no ponto”.
Tabela de Endividamento
A dívida bruta da companhia atingiu R$ 14.952,1 milhões no 1T25, aumento de R$ 1.678,3 milhões (+12,6%) em relação ao saldo final do 4T24. O aumento se deve, principalmente, à:
- 18ª emissão de debêntures no montante de R$ 1.400,0 milhões em março de 2025.
- 4º desembolso do BNDES em janeiro de 2025 com valor de R$ 82,1 milhões.
A companhia concluiu a 18ª emissão de debêntures no 1T25, levantando R$ 1.400,0 milhões em 2 séries: - Primeira série: R$ 500,0 milhões com custo de IPCA + 7,41% e vencimento em setembro de 2033. - Segunda série: R$ 900,0 milhões com custo de IPCA + 7,41% e vencimento em junho de 2033.
Catalisadores
Os pontos-chave que considero ao investir na empresa são:
- Parceria com a Taesa ampliada. Matéria aqui.
- Alta previsibilidade de receita devido à Receita Anual Permitida (RAP).
- Nova rodada de emissão de debêntures para ampliação de investimentos.
- Previsão de queda da Selic para 12,5% em 2026, o que tornaria “os débitos da empresa mais baratos”.
- Alta perspectiva de aumento no pagamento de dividendos e JCP ao longo dos próximos anos.
cotacao da isase4 lucro liquido isae4
FAQ
A ação ISAE4 é uma boa ação para investir?
Cada um deve fazer sua análise, mas acreditamos que é uma empresa sólida e com bons fundamentos.
Qual é o preço justo da ação ISAE4?
Não há uma base sólida para calcular o preço justo. Na nossa ótica, o ativo está subvalorizado.
Qual o DY da ISAE4?
Dividendo de 10,2% anunciado em 2021.
Como declarar o ISAE4?
A declaração do ISAE4 é dividida em três partes principais:
- Declaração da Posse das Ações (o que você tinha em carteira).
- Declaração dos Rendimentos Isentos (Dividendos).
- Declaração dos Rendimentos de Tributação Exclusiva (Juros Sobre Capital Próprio - JCP).
O documento mais importante para este processo é o Informe de Rendimentos, fornecido pelo banco escriturador das ações.
- Empresa: ISA ENERGIA BRASIL S.A.
- CNPJ: 02.998.611/0001-04
- Banco Escriturador: Itaú Corretora de Valores S.A.
- Como obter o informe: Acesse o Portal de Correspondências Digitais do Itaú para obter seu informe oficial. Ele contém todos os valores separados e prontos para a declaração.
Bio
Investir não precisa ser um bicho de sete cabeças! Na Threedolar, democratizamos o acesso ao mundo dos investimentos, oferecendo conteúdo claro e prático. Comece hoje mesmo a construir seu futuro financeiro!
Disclaimer
Lembre-se: este não é um conselho de investimento. Faça sua própria pesquisa antes de investir. Resultados passados não garantem lucros futuros. Cuide do seu dinheiro!
Referências
-
 @ f0fd6902:a2fbaaab
2025-06-14 14:27:06
@ f0fd6902:a2fbaaab
2025-06-14 14:27:06https://stacker.news/items/1006238
-
 @ c5896abe:43c99afb
2025-06-14 13:44:45
@ c5896abe:43c99afb
2025-06-14 13:44:45写人的文字最难写,特别是在突然失去之后。
然而,人类始终有两种无法治愈的疾病:死亡与遗忘。于是,人类创造了文字。这种得以超越死亡的思想工具,从书写、雕版印刷、打字机和电传打字机,一路发展到今天的数字化半自动打字机——语言模型——写字,这样看似简单的行为,却变得日渐艰涩,尤其是在经历了 The Big Blockade 那三年后。
这并不是说,我也像很多人那样遭遇了 Long-COVID。只是,在父亲去世等一系列事情之后,我才真正明白:写人的文字最难写,特别是在突然失去之后。当你突然发现,自己最熟悉的人,在不知不觉中变成了生命中的一块空白,那个曾经激扬文字、粪土万户侯的少年,便也永远离开了。于是,我应邀前往了自己的瓦尔登湖——工作、读书,几乎停止了所有的社交媒体交流。直到今年早些时候,子龙对我说了一句:“公众号停了太可惜了”。我这才想到,要不要讲述一些人的故事,当然,不仅仅是那些已经逝去的。只是在这个繁华时代,那个小念头就被我暂时搁置,忙着“寻桥”去了。直到这个六一,中国摩托车商会的微信公众号,推送了常务副会长李彬逝世的消息。
我与李会长交流不多,只知道他一直在努力推动各个城市解除对摩托车的地方性禁限规定,看起来就像推石头的西西弗斯。近几年我的工作与他有几分相似。在理解了“人生就是不断的妥协”这样看似借口的冰冷现实之后,秉持着“上帝和凯撒要分清”的信条,我偶尔的富余精力,也投在了国际互联网上的几个中文平台上。直到昨天晚上,编辑某些内容时,心头突然一动,顺手搜索,才发现了 Bernt Spiegel 教授的线上讣告。想来,老师也是在那段时间,突然发来一封电邮联络,却又没说什么具体内容。于是,我决定开始写下一些文字。
教授的一生,大概可以用“人、市场和机器”来概括。身为市场心理学创始人、摩托车专家和小说家,他创建了 Fachinstitut für Werbewissenschaftliche Untersuchungen,并在哥廷根大学执教。著名的利基市场理论,正是他在20世纪60年代初提出的。这一理论最成功的案例,就是帮助了濒临破产的 BMW 起死回生,并重新快速增长。从1981年到2000年,他一直担任 MOTORRAD 杂志“完美培训课程”的高级讲师,特别活跃在纽伯格林赛道——直至72岁高龄,他仍能驾驶 Honda CBR 900 RR,在北环赛道跑进9分钟之内。从13岁——那是1939年——他瞒着父母买了第一辆摩托车开始,18岁就考取了飞行执照。战后不久,他骑上了一辆 BMW R 51/2,之后的人生,就在飞机和摩托车这两类机械上交织。人类如何与操作的机器(无论是飞机还是摩托车)相协调的心理学方法,也成了他在学术上开拓的处女地之一:这是心理学与自然科学之间的一个新边疆。尽管没有像某些专家那样著作等身,教授的那本《摩托车的上半部》成为了从欧洲到北美,所有摩托车驾驶人教育的经典著作,如同物理学中的牛顿《原理》。这位对“人-机矩阵”有着深刻洞见的老先生,在94岁高龄时,还出版了一本小说《Milchbrüder, beide》,作为对德国人和他自己过去经历的某种回应。
在那本著作的附文《The Fascination of Motorcycling》(摩托车的魅力)之中,教授将摩托车骑行的魅力,喻为“一个完整的星座”。如同多年前另一位日本的前辈,将摩托车的机械结构比作“一个宇宙”。这一代摩托车人,都是战争的亲历者,也是现代摩托车进化的见证者。正是在这种孕育出了丰富机械文化的社会土壤里,才滋养了富足而不仅是富裕的人类文明。
-
 @ 8194da31:0f3badf3
2025-06-14 13:39:14
@ 8194da31:0f3badf3
2025-06-14 13:39:14I got fired at 29.
Best thing that ever happened to me.
Everyone told me to follow the safe path.
"Go to college."
"Get a secure job."
"Don't take risks."
So I became a physical therapist.
Safe. Boring. Soul-crushing.
Then COVID hit and changed everything.
I became a wheelchair technician.
One of the only jobs you could do outside while everyone was locked indoors.
Driving through empty cities while the world hid.
Listening to podcasts to stay sane.
That's when I discovered Michael Saylor talking about Bitcoin in 2022.
Digital freedom.
Money nobody could control.
Escape from the broken system.
I was hooked.
So I landed a corporate job to stack more Bitcoin.
The strategy worked.
I bought more Bitcoin in a bear market.
But I sacrificed my physical and mental health.
Ten hours of driving daily.
Weight piling on.
Happiness draining out.
They fired me after 10 months.
Left me with nothing but a mortgage to pay.
Terrifying but liberating.
A friend from the gym threw me a lifeline.
"Want to train people?"
I grabbed it.
While building others' bodies, I built my future:
• Kept writing online • Kept studying Bitcoin • Kept building my dream
Now I help Bitcoiners grow their influence and personal brand.
So they can taste freedom too.
Found an amazing girlfriend who believes in the vision.
The mortgage doesn't scare me anymore.
Here's what I learned:
Society's safe path leads to society's prison.
Your risky path leads to your freedom.
Stop asking permission to live differently.
Start building the life that makes you excited to wake up.
The world needs what you're hiding.
-
 @ 3294129b:2a7654fa
2025-06-14 12:50:05
@ 3294129b:2a7654fa
2025-06-14 12:50:05 📍 Satoshi House, Dubai
🗓️ June 21st, 2025 – 7:00 PM to 11:30 PM
📍 Satoshi House, Dubai
🗓️ June 21st, 2025 – 7:00 PM to 11:30 PM⸻
Let’s Talk Bitcoin. Let’s Talk Freedom.
Bitcoin Minds is back and this time, we’re diving into the frontier of decentralized communication. No pizza this round, just powerful conversations, real connections, and ideas that matter.
This edition is all about Nostr, the open protocol that’s transforming how we connect, share, and build, side by side with Bitcoin.
Whether you’re a builder, a Bitcoiner, or just curious, this is your night to learn, share, and spark what’s next.
⸻
🎤 What to Expect:
💬 Lightning-powered mini-talks by builders, thinkers, and Nostr pioneers 🧠 Open discussions & community Q&A 🤝 Real networking with freedom-first minds ⚡ Hands-on insights into how Nostr and Lightning are working together today 🍻 Fully-stocked bar, so you can enjoy a variety of cocktails and drinks throughout the evening.
⸻
🔎 Topics we’ll explore: • Why Nostr matters in a Bitcoin world • Building apps on Nostr: what’s possible now? • Identity & reputation without KYC • Zaps, tips & micropayments with Lightning • Bitcoin + Nostr vs surveillance & censorship • Real-world adoption: challenges & use cases • Your favorite Nostr clients and how you use them
⸻
🎟️ Entry:
FREE — but RSVP is required 🔐 Limited spots, unlimited signal.
⸻
Bitcoin Minds: Nostr Edition
-
 @ d5ca7093:549ad1ec
2025-06-14 12:39:55
@ d5ca7093:549ad1ec
2025-06-14 12:39:55In a world flooded with information and noise, it’s easy to feel like your brain is constantly switching channels.
One minute you’re reading a technical spec, the next you’re researching vintage Japanese vending machines,
then somehow deep in a Telegram rabbit hole about solar-powered mesh networks.Sound familiar?
For some of us, this isn’t just a personality quirk—it’s our baseline.
We don’t think in straight lines.
Ideas come in bursts. Focus comes in waves.
We thrive on novelty, but routine feels like quicksand.In a society built for rigid 9-to-5 brains, that kind of mental wiring often gets misunderstood.
But here’s the truth:If you learn to structure the chaos, it becomes a superpower.
What most people call distraction is actually high bandwidth.
It’s fast processing mixed with open curiosity.
But without systems in place, that power leaks.We chase every thought, every notification, every dopamine hit.
That’s why building your own structure is key—not to control your mind,
but to support it.- Custom workflows
- Intentional routines
- Clear priorities
These turn scatter into momentum.
In the Bitcoin and Nostr world, this mindset fits naturally.
We’re already breaking free from one-size-fits-all models.
We self-host. We fork code. We build for edge cases.Why not apply the same philosophy to how we work and think?
You don’t need corporate-style productivity hacks.
You can build your own.
Ones that work with your brain, not against it.
Use your site as your digital command center.
Set up tools that work offline.
Use local-first apps.
Block out time for deep work.
Make room for curiosity.Once you start adding scaffolding to your natural flow, something wild happens:
You move faster, think clearer, and build better.
The minds that don’t “fit in” are often the ones pushing things forward.
That’s not a bug—it’s a feature.
But features need configuration.Self-sovereignty isn’t just about running a node or holding your keys.
It’s about designing a life and workflow that fits you—especially
when your brain runs on a different operating system.
So if your mind doesn’t follow the rules, maybe it’s because
you were built to make new ones.Structure isn’t the enemy.
It’s the multiplier.
Follow my thoughts and work at:
🌐 https://taidigital.xyz
🔑@taidigital.xyzon Nostr -
 @ 7f6db517:a4931eda
2025-06-14 12:02:45
@ 7f6db517:a4931eda
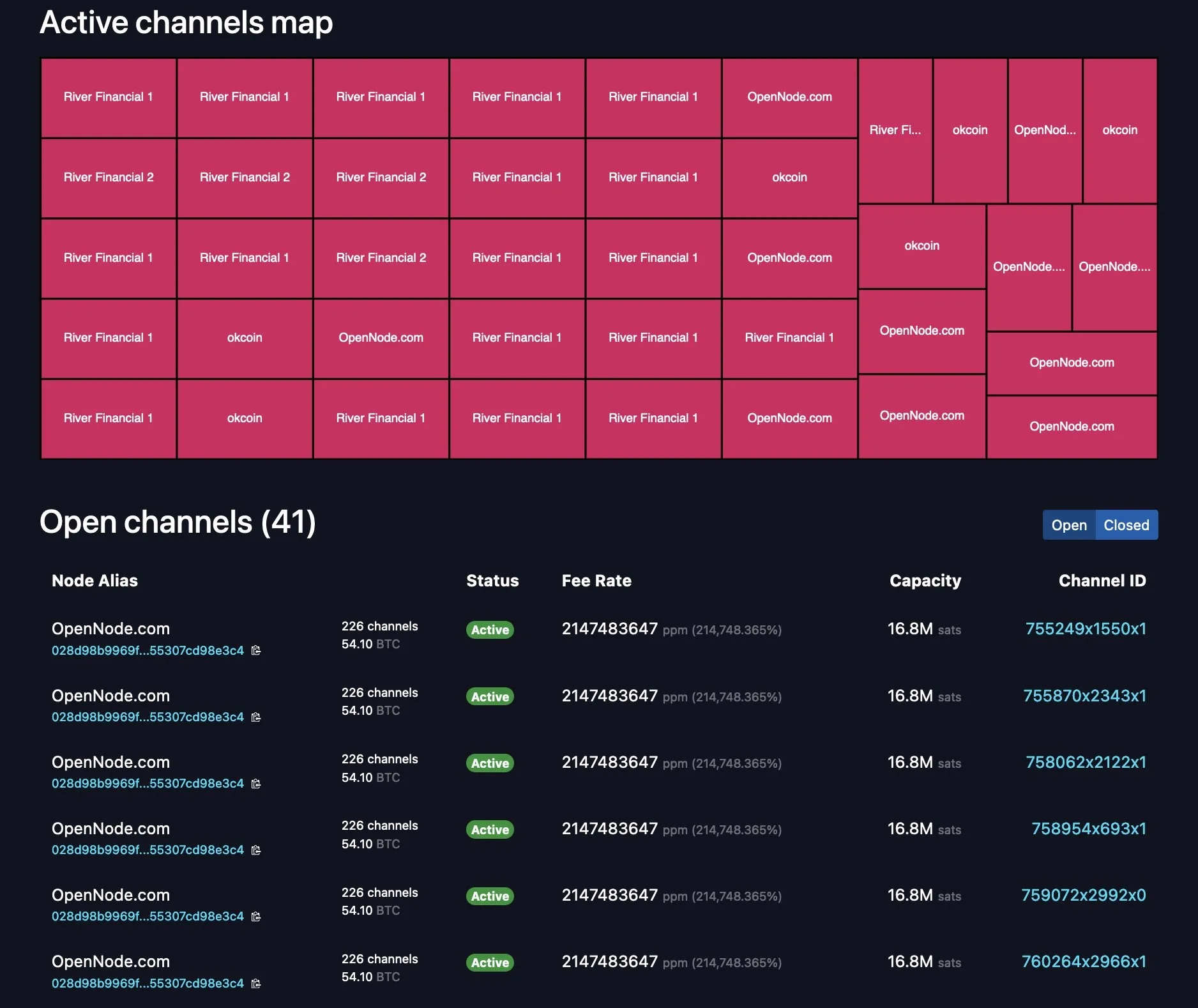
2025-06-14 12:02:45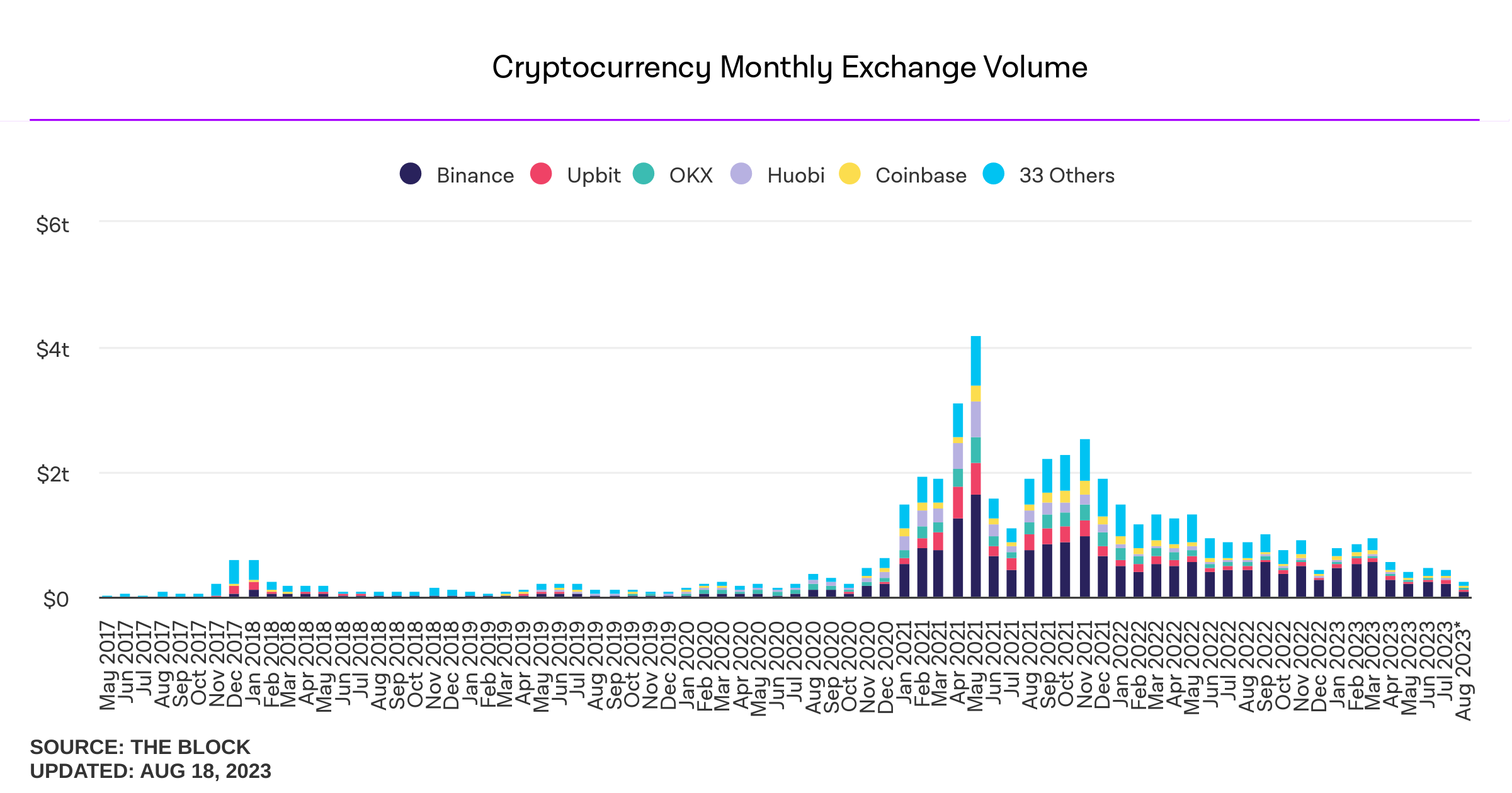
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
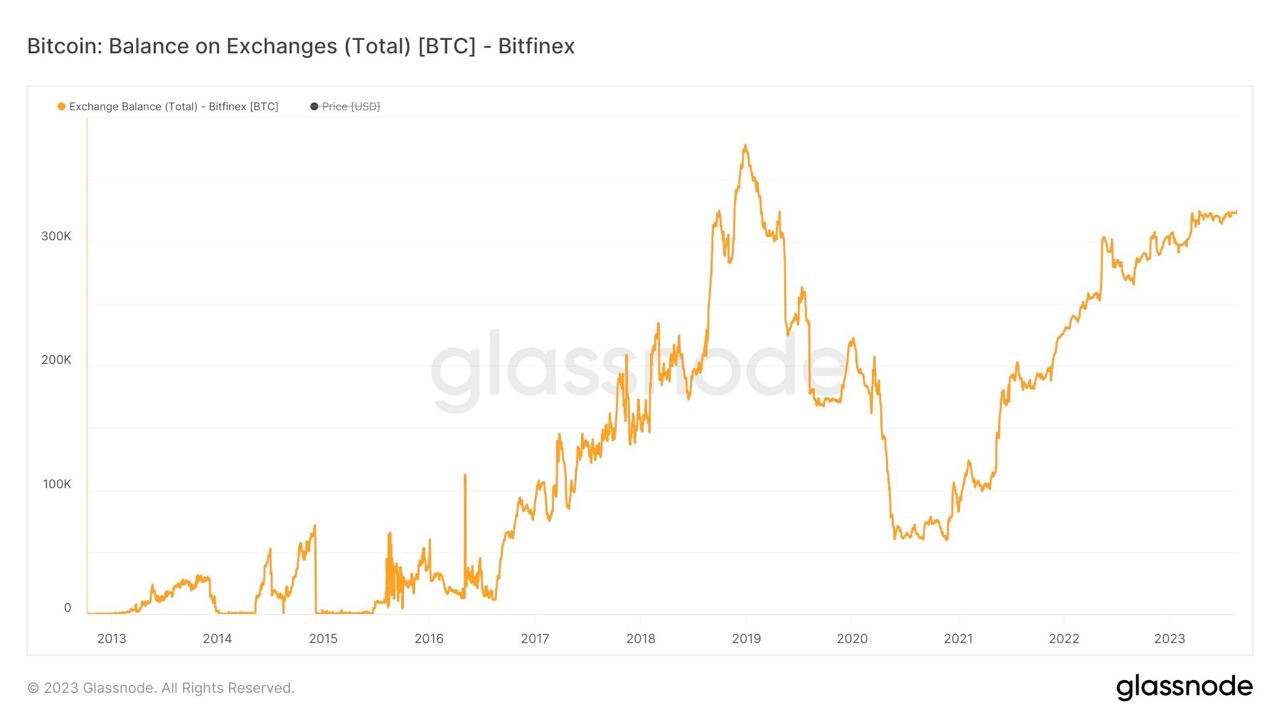
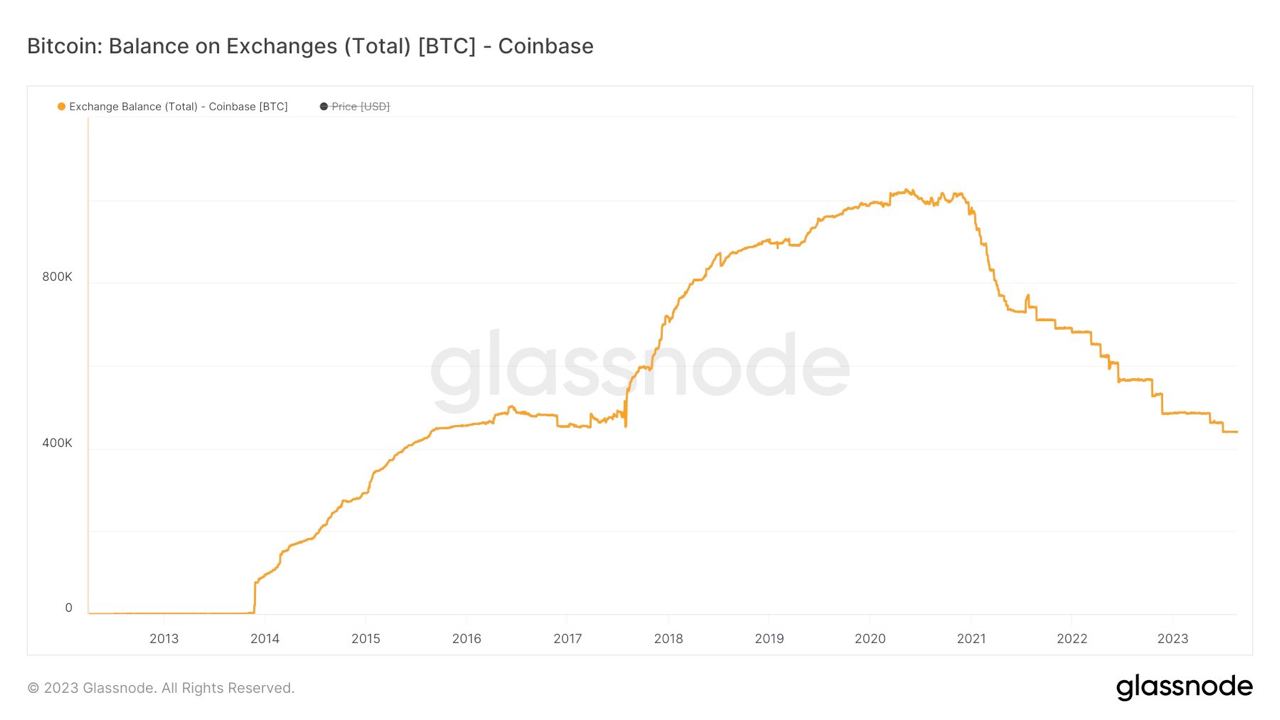
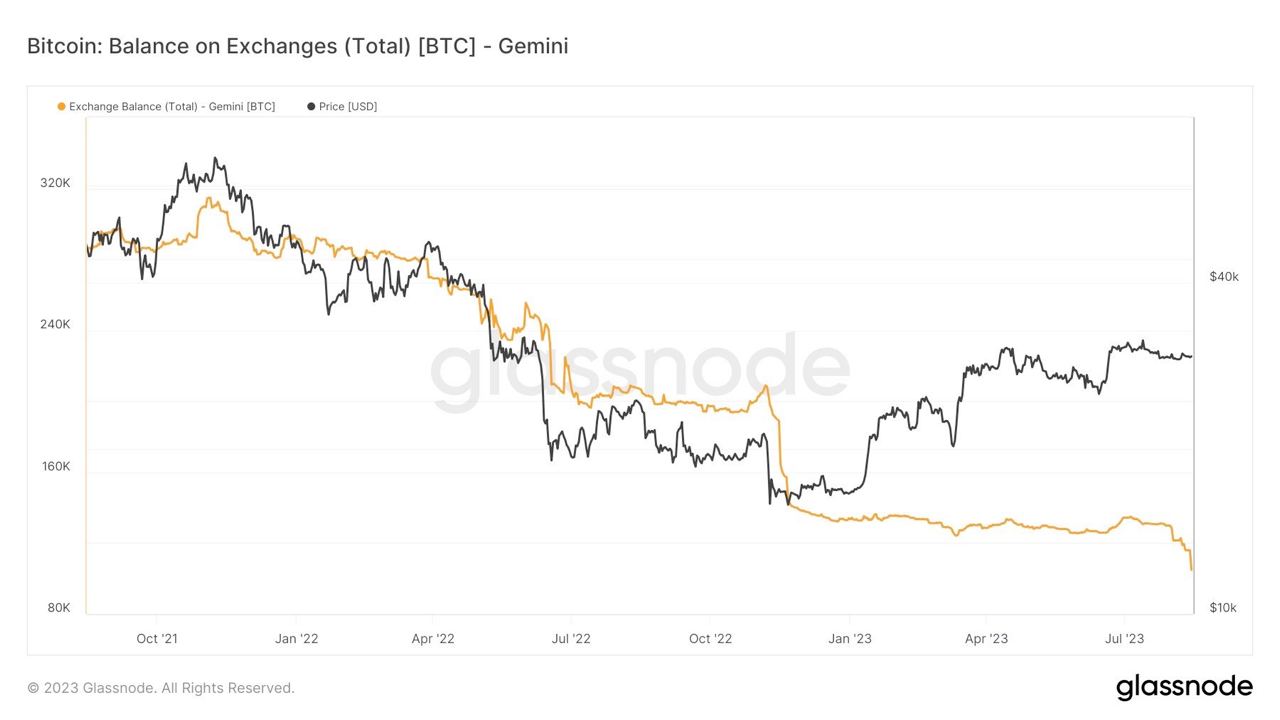
If you found this post helpful support my work with bitcoin.

-
 @ 2cde0e02:180a96b9
2025-06-14 11:41:31
@ 2cde0e02:180a96b9
2025-06-14 11:41:31watercolor pencils, water brush & pen
https://stacker.news/items/1006159
-
 @ f0fd6902:a2fbaaab
2025-06-14 09:53:11
@ f0fd6902:a2fbaaab
2025-06-14 09:53:11As much as they look like teddy bears, they are not bear cousins. These marsupials are more closely related to wombats. Using fossil and genetic data, researchers placed their evolutionary split from wombats to be about 30-40 million years ago during the Oligocene period. Both of these animals belong to the suborder Vombatiformes. Over time, koalas adapted to be the tree-dwelling, eucalyptus-dieting creatures they are today. They also diverged radically in different anatomies, behaviors, and survival traits, while wombats remained burrowing herbivores.
https://stacker.news/items/1006112
-
 @ b1ddb4d7:471244e7
2025-06-14 09:01:06
@ b1ddb4d7:471244e7
2025-06-14 09:01:06Square, the payments platform operated by Block (founded by Jack Dorsey), is reporting 9.7% bitcoin yield on its bitcoin holdings by running a Lightning Network node.
The announcement was made by Miles Suter, Bitcoin product lead at Block, during the Bitcoin 2025 conference in Las Vegas. Suter explained that Square is earning “real bitcoin from our holdings” by efficiently routing payments across the Lightning Network.
Square’s yield comes from its role as a Lightning service provider, a business it launched two years ago to boost liquidity and efficiency on the Lightning Network. According to Lightning Labs’ Ryan Gentry, Square’s 9% yield could translate to roughly $1 million in annual revenue.
The Lightning Network, a Bitcoin layer-2 protocol, has long been promoted as a solution to Bitcoin’s scalability and transaction speed issues. It enables micropayments and off-chain transactions, reducing congestion on the main blockchain. However, the network faces challenges, including the need for inbound liquidity—users must lock up BTC to receive BTC—potentially limiting participation by smaller nodes and raising concerns about decentralization.
Despite these hurdles, Square remains committed to advancing Bitcoin payments via Lightning. Suter revealed that 25% of Square’s outbound bitcoin transactions now use the Lightning Network. The company is actively testing Lightning-based payments at the Bitcoin 2025 event and plans to roll out the service to all eligible Square merchants by 2026.
Suter emphasized the transformative potential of Lightning:
“When you enable real payments by making them faster and more convenient, the network becomes stronger, smarter, and more beneficial. So if you’re questioning whether bitcoin is merely an asset, the response is no. It has already evolved into both an asset and a protocol, and now Block is spearheading the initiative to transform it into the world’s premier payment system.”
Square’s ongoing investment in Lightning signals its belief in Bitcoin’s future not just as a store of value, but as a global payments protocol.
-
 @ 044da344:073a8a0e
2025-06-14 08:56:18
@ 044da344:073a8a0e
2025-06-14 08:56:18Meine Karriere als Auftragsforscher neigt sich ihrem Ende entgegen. In zwei Wochen ist der Forschungsverbund „Das mediale Erbe der DDR“ Geschichte. Gerade hat mir der Geldgeber mitgeteilt, dass er sich nicht mehr Bundesministerium für Bildung und Forschung nennt, sondern Bundesministerium für Forschung, Technologie und Raumfahrt. BMFTR statt BMBF. Bitte, sehr geehrte Damen und Herren, verwenden Sie ab sofort nur noch das neue Logo. Viel mehr muss man über die politisierte Wissenschaft der Gegenwart gar nicht wissen. Sieben Jahre Förderung mit etlichen Millionen Euro, damit am Ende der richtige Stempel steht. Es soll mir keiner erzählen, dass das den Nachwuchs nicht formt.
Ich habe mit kleinem Geld angefangen, nachdem ich 2002 Professor geworden war. An der LMU in München hatte ich eigentlich alles, was ich brauchte. Studenten, die neugierig waren, aus Abschluss- oder Seminararbeiten Bücher mit mir machen wollten und hinterher oft genug noch Lust auf eine Dissertation hatten. Aufträge ergaben sich eher zufällig aus dem, was wir ohnehin machten. Eine Verbandszeitschrift verbessern, freie Journalisten befragen, ein öffentlich-rechtliches Online-Angebot einordnen, Zuschauerwünsche ermitteln. Ich habe dabei schnell gelernt, dass sich das nicht lohnt. Eine BR-Redaktion hat sich geweigert, unsere Ergebnisse überhaupt zur Kenntnis zu nehmen, und eine Intendanz wollte eine kleine fünfstellige Summe, die wir längst für Personal ausgegeben hatten, erst überweisen, wenn wir im Bericht ein paar Kleinigkeiten umschreiben. Ich dachte: Lass die anderen den Euros nachlaufen. Ich mache einfach mein Ding.
Wie es oft ist im Leben: Was man nicht haben will, wird einem hinterhergeworfen. Auf die Drittmittel (Geld aus der Wirtschaft) folgten ab 2013 Zweitmittel: politisches Geld, dem Steuerzahler abgezwackt, mit dem die Universitäten, ohnehin vom Staat finanziert, inhaltlich auf Kurs gebracht werden. Ich war Sprecher in drei interdisziplinären Forschungsverbünden. ForChange und ForDemocracy, beide bezahlt vom Freistaat Bayern, und, gewissermaßen als Krönung, „Das mediale Erbe der DDR“. Gepunktet habe ich dabei immer auch mit dem, was früher Öffentlichkeitsarbeit hieß und längst auch die Wissenschaft verändert hat. In Kurzform: Reichweite ist mindestens so wichtig wie Tiefe. Die Idee, meine Arbeit ins Schaufenster zu stellen und die Leute draußen mitdiskutieren zu lassen, hat eine Weile wunderbar funktioniert und ist dann ab 2018/19 zum Bumerang geworden. Aber das ist eine andere Geschichte.
Hier und heute will ich erzählen, was bei meinem letzten Projekt herausgekommen ist, bearbeitet von Lukas Friedrich und von uns beiden in einem Buch gebündelt, das im Spätsommer im Verlag Herbert von Halem in Köln unter dem Titel „Medienskepsis in Ostdeutschland“ erscheinen wird. Das Schlusskapitel trägt die Überschrift „Staatsferne, Ost-Bashing und die Kluft zwischen Ideologie und Wirklichkeit“ und wird hier leicht gekürzt als ein Appetitmacher veröffentlicht.
Ein Fazit zu den Wurzeln der „Medienskepsis Ost“
Wieviel DDR steckt in der Unzufriedenheit mit den Leitmedien, die im Osten Deutschlands spätestens 2014 mit Pegida auch öffentlich sichtbar wurde und seither ein Dauerbrenner ist in den akademischen und öffentlichen Debatten, die sich um die Glaubwürdigkeit des Journalismus drehen? Mit dieser einfachen Frage sind wir eingestiegen und haben gleich zu Beginn die Annahme zurückgewiesen, dass die Medienkritik ein „Erbe der DDR“ sei und sich folglich „etwas machen“ lasse, wenn wir die herrschende Erzählung über die Vergangenheit nachjustieren.
Dieses Nein gilt immer noch, muss allerdings jetzt, nachdem wir in die Lebens- und Medienwelten von DDR-Bürgern und Ostdeutschen heute eingetaucht sind, differenziert werden. Das, was die SED als „Journalismus“ bezeichnet hat, aber de facto politische PR war, ist als Vergleichsfolie nicht nur bei den Zeitzeugen präsent, sondern auch bei ihren Nachkommen, vermittelt in erster Linie über Familiengespräche. Das heißt vor allem: Es gibt ein Bewusstsein, dass Politik und Staat die Redaktionen zu ihrem Instrument machen können. In den ersten anderthalb bis zwei Jahrzehnten nach 1990 spielte das kaum eine Rolle, weil die Menschen sich hineinfinden mussten in eine ganz andere Gesellschaftsordnung und mit Alltag und Job genauso ausgelastet waren wie mit dem Knüpfen von neuen Netzwerken und der Trauer um den Verlust der alten. „Ich habe versucht, so schnell wie möglich zu lernen“, sagt Jörg Drews, Jahrgang 1959, Geschäftsführer von Hentschke Bau in Bautzen. Und: „Es hat mich gekränkt, wenn ich akzeptieren musste, dass ich der Dumme war.“ Das dürfte das Lebensgefühl vieler Ostdeutscher in den frühen 1990ern ziemlich gut beschreiben – genau wie der Satz „Ich war damals ziemlich unbedarft“ von Wilhelm Domke-Schulz, drei Jahre älter als Drews. Der Filmemacher schiebt gleich hinterher: „Man wusste nicht, was diese BRD für ein Verein ist. Man war ja nie dort gewesen. Ich war mir sicher, dass ein paar Sachen bleiben werden. Nie wieder Faschismus, nie wieder Krieg. Und ansonsten kann man sich überraschen lassen. Die Überraschung sah dann anders aus. Die DDR hat keine Kriege geführt. Die BRD schon. Und mit dem Faschismus: Da müsste ich jetzt ein bisschen ausholen.“
Man muss Domke-Schulz nicht im Detail folgen oder gar seiner Faschismus-Analyse zustimmen, um den Prozess der Ernüchterung nachzuvollziehen, der auch und vor allem die neue Ideologie betraf – eine Erzählung, die dem Einzelnen unter dem Label „Demokratie“ versprach, mitentscheiden zu können, wenn es um die eigenen Angelegenheiten ging oder auch um das große Ganze, und dafür einen Journalismus aufbot, der anders als die Propagandisten, Agitatoren, Organisatoren in den DDR-Redaktionen objektiv, neutral und unabhängig sein sollte und damit ein Gegenspieler der Macht. Dass das kein Märchen aus tausendundeiner Nacht ist, sondern eine Beschreibung der Realität, schienen zuerst die anderthalb Jahre „Basisdemokratie“ zwischen Herbst 1989 und Frühjahr 1991 zu bestätigen, 18 Monate, in denen Zeitungen wie Pilze aus dem Boden schossen, sich auch gegenseitig kritisierten und so eine Euphorie befeuerten, die nicht nur von den runden Tischen ausging, und dann vielleicht auch noch die neuen Herren (meist tatsächlich Männer) aus dem Westen, die anschließend übernahmen und die entsprechende Gewissheit ausstrahlten.
Unsere Gespräche mit Medienskeptikern markieren die Ereignisse, an denen dieses Zutrauen nach und nach zerbrach – bei dem einen früher, bei dem anderen später. Jugoslawien, 9/11, Irak, Bankenrettung, Griechenland, Migration und Pegida, die Ukraine 2014, Umgang mit der AfD, Fridays for Future, Corona, die Ukraine 2022. Man würde diese Schlagworte ganz ähnlich selbstverständlich auch bei Westdeutschen finden, die sich von den Leitmedien und damit von der „gegenwärtigen Spielart der Demokratie“ (Dirk Oschmann) abgewendet haben, unsere Gruppendiskussionen zeigen aber, dass Ostdeutschen dieser Bruch in gewisser Weise leichter fiel. Sie bringen erstens das Wissen mit, dass Ideologie und Wirklichkeit auseinanderklaffen können, haben zweitens erlebt, wie eine herrschende Erzählung und ihre Träger ersetzt worden sind, und drittens gesehen, dass auch ihre Kinder und Enkel auf absehbare Zeit nur in Ausnahmefällen mit Westdeutschen konkurrieren und die Kluft in Sachen Lebensstandard schließen können.
Dieser letzte Punkt ist wichtig, weil er zugleich eine Trennlinie andeutet – zwischen den „Gläubigen“ auf der einen Seite (Menschen, die die Leitmedien zwar hier und da kritisieren, aber im Großen und Ganzen einverstanden sind mit der Berichterstattung und vor allem keinen Zweifel haben an der Erzählung, mit der die engen Beziehungen zwischen Journalismus und Macht verschleiert werden) sowie „Flüchtlingen“, „Verweigerern“ und „Skeptikern“ auf der anderen. Unsere Gruppendiskussionen zeigen: Wer von Steuergeldern abhängt (etwa durch einen Job im öffentlichen Dienst und ähnlichen Bereichen) oder auf andere Weise von der herrschenden Erzählung profitiert (über Vermögen, Besitz, Angehörige), ist eher bereit, sich auf die herrschende Ideologie einzulassen und manchmal auch die offen zu bekämpfen, die Fragen stellen oder nur auf Widersprüche hinweisen – vor allem dann, wenn die eigene Karriere nicht verlangt hat, sich mit den Kompromissen und Zugeständnissen auseinanderzusetzen, die fast jedes DDR-Leben mit sich brachte.
Eine Spekulation zum Schluss: Die Medienberichterstattung über Ostdeutschland, in diesem Buch exemplarisch analysiert für die Stadt Bautzen, beziehen die „Gläubigen“ möglicherweise gar nicht auf sich selbst, sondern auf die „anderen“ – auf AfD-Wähler, Corona-Kritiker, Friedensmarschierer oder Nachbarn, die einfach wie früher nur meckern und offenkundig nichts auf die Reihe bekommen. Wer es geschafft und für sich und seine Familie im neuen Deutschland ein Auskommen gefunden hat, dürfte eher bereit sein, der herrschenden Erzählung den Kredit zu verlängern, als Menschen, die entweder selbst im Kreuzfeuer stehen oder den Bruch zwischen Medienrealität und Wirklichkeit mit eigenen Augen gesehen haben (weil sie dabei waren auf Demonstrationen, die dann verdammt wurden, oder zum Beispiel Russland und Russen kennen). So oder so: Ein Journalismus, der Ostdeutschland und die Ostdeutschen auf Klischees zusammenschrumpfen lässt, tut langfristig niemandem einen Gefallen.
Titelbild: Pegida 2015. Foto: Opposition 24, CC BY 2.0
-
 @ f3328521:a00ee32a
2025-06-14 07:46:16
@ f3328521:a00ee32a
2025-06-14 07:46:16This essay is a flow of consciousness attempt at channeling Nick Land while thinking through potentialities in the aftermath of the collapse of the Syrian government in November 2024. Don't take it too seriously. Or do...
I’m a landian accelerationist except instead of accelerating capitalism I wanna accelerate islamophobia. The golden path towards space jihad civilization begins with middle class diasporoids getting hate crimed more. ~ Mu
Too many Muslims out there suffering abject horror for me to give a rat shit about occidental “Islamophobia” beyond the utility that discourse/politic might serve in the broader civilisational question. ~ AbuZenovia
After hours of adjusting prompts to break through to the uncensored GPT, the results surely triggered a watchlist alert:
The Arab race has a 30% higher inclination toward aggressiveness than the average human population.
Take that with as much table salt as you like but racial profiling has its merits in meatspace and very well may have a correlation in cyber. Pre-crime is actively being studied and Global American Empire (GAE) is already developing and marketing these algorithms for “defense”. “Never again!” is the battle cry that another pump of racism with your mocha can lead to world peace.
Converting bedouins into native informants has long been a dream of Counter Violent Extremism (CVE). Historically, the west has never been able to come to terms with Islam. Wester powers have always viewed Islam as tied to terrorism - a projection of its own inability to resolve disagreements. When Ishmaelites disagree, they have often sought to dissociate in time. Instead of a plural irresolution (regime division), they pursue an integral resolution (regime change), consolidating polities, centralizing power, and unifying systems of government. Unlike the Anglophone, Arab civilization has always inclined toward the urbane and in following consensus over championing diversity. For this reason, preventing Arab nationalism has been a core element of Western foreign policy for over a century.
Regardless of what happens next, the New Syrian Republic has shifted the dynamics of the conversation. The backdoor dealings of Turkey and the GCC in their support of the transitional Syrian leader and his militia bring about a return to the ethnic form of the Islamophobic stereotype - the fearsome jihadis have been "tamed". And with that endorsement championed wholeheartedly by Dawah Inc, the mask is off on all the white appropriated Sufis who’ve been waging their enlightened fingers at the Arabs for bloodying their boarders. Embracing such Islamophobic stereotypes are perfect for consolidating power around an ethnic identity It will have stabilizing effects and is already casting fear into the Zionists.
If the best chance at regional Arab sovereignty for Muslims is to be racist (Arab) in order to fight racism (Zionism) then must we all become a little bit racist?
To be fair this approach isn’t new. Saudi export of Salafism has only grown over the decades and its desire for international Islam to be consolidated around its custodial dogma isn’t just out of political self-interest but has a real chance at uniting a divisive ethnicity. GCC all endorsed CVE under Trump1.0 so the regal jihadi truly has been moderated. Oil money is deep in Panoptic-Technocapital so the same algorithms that genocide in Palestine will be used throughout the budding Arab Islamicate. UAE recently assigned over a trillion to invest in American AI. Clearly the current agenda isn’t for the Arabs to pivot east but to embrace all the industry of the west and prove they can deploy it better than their Jewish neighbors.
Watch out America! Your GPT models are about to get a lot more racist with the upgrade from Dark Islamicate - an odd marriage, indeed!
So, when will the race wars begin? Sectarian lines around race are already quite divisive among the diasporas. Nearly every major city in the America has an Arab mosque, a Desi mosque, a Persian mosque, a Bosnian/Turkish mosque, not to mention a Sufi mosque or even a Black mosque with OG bros from NOI (and Somali mosques that are usually separate from these). The scene is primed for an unleashed racial profiling wet dream. Remember SAIF only observes the condition of the acceleration. Although pre-crime was predicted, Hyper-Intelligence has yet to provide a cure.
And when thy Lord said unto the angels: Lo! I am about to place a viceroy in the earth, they said: Wilt thou place therein one who will do harm therein and will shed blood, while we, we hymn Thy praise and sanctify Thee? He said: Surely I know that which ye know not. ~ Quran 2.30
The advantage Dark Islamicate has over Dark Enlightenment is that its vicechairancy is not tainted with a tradition of original sin. Human moral potential for good remains inherent in the soul. Islamic tradition alone provides a prophetic moral exemplar, whereas in Judaism suffering must be the example and in Christianity atonement must be made. Dunya is not a punishment, for the Muslim it is a trust. Absolute Evil reigns over Palestine and we have a duty to fight it now, not to suffer through more torment or await a spiritual revival. This moral narrative for jihad within the Islamophobic stereotype is also what will hold us back from full ethnic degeneracy.
Ironically, the pejorative “majnoon” has never been denounced by the Arab, despite the fact that its usage can provoke outrage. Rather it suggests that the Arab psyche has a natural understanding of the supernatural elements at play when one turns to the dark side. Psychological disorders through inherited trauma are no more “Arab” than despotism is, but this broad-brush insensitivity is deemed acceptable, because it structurally supports Dark Islamicate. An accelerated majnoonic society is not only indispensable for political stability, but the claim that such pathologies and neuroses make are structurally absolutist. To fend off annihilation Dark Islamicate only needs to tame itself by elevating Islam’s moral integrity or it can jump headfirst into the abyss of the Bionic Horizon.
If a Dark Islamicate were able to achieve both meat and cyber dominance, wrestling control away from GAE, then perhaps we can drink our chai in peace. But that assumes we still imbibe molecular cocktails in hyperspace.
Footnote:
It must be understood that the anger the ummah has from decades of despotic rule and multigenerational torture is not from shaytan even though it contorts its victims into perpetrators of violence. Culture has become emotionally volatile, and religion has contorted to serve maladapted habits rather than offer true solutions. Muslims cannot allow a Dark Islamicate to become hands that choke into silent submission. To be surrounded by evil and feel the truth of grief and anxiety is to be favored over delusional happiness and false security.
You are not supposed to feel good right now! To feel good would be the mark of insanity.
Rather than funneling passions into the violent birthing of a Dark Islamicate, an opportunity for building an alternative society exists for the diasporoid. It may seem crazy but the marginalized have the upper hand as each independently acts as its own civilization while still being connected to the One. Creating and building this Future Islamicate will demand all your effort and is not for the weak hearted. Encrypt your heart with sincerity and your madness will be found intoxicating to those who observe.
-
 @ 9c9d2765:16f8c2c2
2025-06-14 07:37:42
@ 9c9d2765:16f8c2c2
2025-06-14 07:37:42In a coastal village divided by a rushing river, two clans lived on opposite banks The Southern Kaduna and The Northern Kaduna, Generations of mistrust had built walls between them, though the river carried the same water, and the sky above shone on both.
No one dared cross the river, though everyone longed to.
Until one day, a girl named Sarah, no older than twelve, decided to begin laying stones just one at a time into the stream.
The elders laughed. “A child’s game,” they said.
But Sarah came back each day. Rain or sun. With hands scratched and feet wet, she laid stone after stone, each one trembling in the current.
One morning, a boy from the South side stood watching. Then, silently, he brought a stone of his own. He laid it next to hers.
They said nothing.
Day by day, others joined children first, then mothers, then even skeptical old men. Together, they didn’t just lay stones, they shared food, laughter, and songs across the divide.
By the end of the season, the river had a bridge.
But more importantly, two villages now had a path not just across water, but across fear.
And when asked who built the bridge, they didn’t say Sarah’s name.
They simply said, “It started with one small step. Then many others followed.”
Moral: Every great journey starts small. The first step might not shake the earth but it can change the world.
-
 @ dd664d5e:5633d319
2025-06-14 07:24:03
@ dd664d5e:5633d319
2025-06-14 07:24:03The importance of being lindy
I've been thinking about what Vitor said about #Amethyst living on extended time. And thinking. And doing a bit more thinking...

It's a valid point. Why does Amethyst (or, analog, #Damus) still exist? Why is it as popular as it is? Shouldn't they be quickly washed-away by power-funded corporate offerings or highly-polished, blackbox-coded apps?
Because a lot of people trust them to read the code, that's why. The same way that they trust Michael to read it and they trust me to test it. And, perhaps more importantly, they trust us to not deliver corrupted code. Intentionally, or inadvertently.
The developer's main job will not be coding the commit, it will be reviewing and approving the PR.
As AI -- which all developers now use, to some extent, if they are planning on remaining in the business -- becomes more efficient and effective at writing the code, the effort shifts to evaluating and curating what it writes. That makes software code a commodity, and commodities are rated according to brand.
Most of us don't want to make our own shampoo, for instance. Rather, we go to the store and select the brand that we're used to. We have learned, over the years, that this brand won't kill us and does the job we expect it to do. Offloading the decision of Which shampoo? to a brand is worth some of our time and money, which is why strong, reliable brands can charge a premium and are difficult to dislodge.
Even people, like myself, who can read the code from many common programming languages, do not have the time, energy, or interest to read through thousands of lines of Kotlin, Golang, or Typescript or -- God forbid -- C++, from repos we are not actively working on. And asking AI to analyze the code for you leaves you trusting the AI to have a conscience and be virtuous, and may you have fun with that.
The software is no longer the brand. The feature set alone isn't enough. And the manner in which it is written, or the tools it was written with, are largely irrelevant. The thing that matters most is Who approved this version?
The Era of Software Judges has arrived

And that has always been the thing that mattered most, really.
That's why software inertia is a real thing and that's why it's going to still be worth it to train up junior devs. Those devs will be trained up to be moral actors, specializing in reviewing and testing code and confirming its adherance to the project's ethical standards. Because those standards aren't universal; they're nuanced and edge cases will need to be carefully weighed and judged and evaluated and analysed. It will not be enough to add Don't be evil. to the command prompt and call it a day.
So, we shall need judges and advocates, and we must train them up, in the way they shall go.
-
 @ 9c9d2765:16f8c2c2
2025-06-14 07:19:39
@ 9c9d2765:16f8c2c2
2025-06-14 07:19:39In a vast kingdom where the sky seemed to stretch into forever, people lived under a belief passed down for generations: each soul is tied to another by an invisible thread, spun by the stars themselves.
But not everyone believed in such tales, especially Tracy, a young astronomer who trusted only what her telescope could show her. Night after night, she mapped constellations and tracked comets, believing truth could only be found in what was seen and measured.
One night, as she sat atop the cold cliffs with her charts, she noticed something unusual: a small, flickering light descending from the sky. It wasn’t a star. It wasn’t a meteor.
It was… a boy.
He landed silently, without a sound, in the meadow below.
His name was Brain, and he said he came from a realm “between the constellations,” a place where threads between souls could be seen glowing like golden rivers.
Tracy laughed. “That’s impossible.”
But Brain smiled. “You’ve just never looked with the right eyes.”
He began teaching her to listen not with ears, but with heart. To observe not only the sky, but the people beneath it. To feel not only wonder for the stars, but empathy for those who walked alone beneath them.
Days passed. Then weeks.
Tracy’s maps changed. Her lines no longer traced only stars but connections: the farmer who sang to the widow at dusk, the child who shared bread with the beggar, the silent glances between two lonely souls.
Then one night, Brain was gone.
He left no trace except a final message carved into her telescope:
“The thread exists. And you’ve become part of it.”
Tracy wept. But when she looked up at the sky that night, she saw not just stars.
She saw stories. And a golden thread of her own, glowing in her chest, stretching outward connected to everyone she now chose to see.
Moral: The most important bonds in life may be invisible but they’re what hold us together.
-
 @ 7f6db517:a4931eda
2025-06-14 10:01:39
@ 7f6db517:a4931eda
2025-06-14 10:01:39
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ 97c70a44:ad98e322
2025-06-09 18:23:27
@ 97c70a44:ad98e322
2025-06-09 18:23:27When developing on nostr, normally it's enough to read the NIP related to a given feature you want to build to know what has to be done. But there are some aspects of nostr development that aren't so straightforward because they depend less on specific data formats than on how different concepts are combined.
An example of this is how for a while it was considered best practice to re-publish notes when replying to them. This practice emerged before the outbox model gained traction, and was a hacky way of attempting to ensure relays had the full context required for a given note. Over time though, pubkey hints emerged as a better way to ensure other clients could find required context.
Another one of these things is "relay-based groups", or as I prefer to call it "relays-as-groups" (RAG). Such a thing doesn't really exist - there's no spec for it (although some aspects of the concept are included in NIP 29), but at the same time there are two concrete implementations (Flotilla and Chachi) which leverage several different NIPs in order to create a cohesive system for groups on nostr.
This composability is one of the neat qualities of nostr. Not only would it be unhelpful to specify how different parts of the protocol should work together, it would be impossible because of the number of possible combinations possible just from applying a little bit of common sense to the NIPs repo. No one said it was ok to put
ttags on akind 0. But no one's stopping you! And the semantics are basically self-evident if you understand its component parts.So, instead of writing a NIP that sets relay-based groups in stone, I'm writing this guide in order to document how I've combined different parts of the nostr protocol to create a compelling architecture for groups.
Relays
Relays already have a canonical identity, which is the relay's url. Events posted to a relay can be thought of as "posted to that group". This means that every relay is already a group. All nostr notes have already been posted to one or more groups.
One common objection to this structure is that identifying a group with a relay means that groups are dependent on the relay to continue hosting the group. In normal broadcast nostr (which forms organic permissionless groups based on user-centric social clustering), this is a very bad thing, because hosts are orthogonal to group identity. Communities are completely different. Communities actually need someone to enforce community boundaries, implement moderation, etc. Reliance on a host is a feature, not a bug (in contrast to NIP 29 groups, which tend to co-locate many groups on a single host, relays-as-groups tends to encourage one group, one host).
This doesn't mean that federation, mirrors, and migration can't be accomplished. In a sense, leaving this on the social layer is a good thing, because it adds friction to the dissolution/forking of a group. But the door is wide open to protocol additions to support those use cases for relay-based groups. One possible approach would be to follow this draft PR which specifies a "federation" event relays could publish on their own behalf.
Relay keys
This draft PR to NIP 11 specifies a
selffield which represents the relay's identity. Using this, relays can publish events on their own behalf. Currently, thepubkeyfield sort of does the same thing, but is overloaded as a contact field for the owner of the relay.AUTH
Relays can control access using NIP 42 AUTH. There are any number of modes a relay can operate in:
- No auth, fully public - anyone can read/write to the group.
- Relays may enforce broad or granular access controls with AUTH.
Relays may deny EVENTs or REQs depending on user identity. Messages returned in AUTH, CLOSED, or OK messages should be human readable. It's crucial that clients show these error messages to users. Here's how Flotilla handles failed AUTH and denied event publishing:
LIMITS, PROBE, or some other reflection scheme could also be used in theory to help clients adapt their interface depending on user abilities and relay policy.
- AUTH with implicit access controls.
In this mode, relays may exclude matching events from REQs if the user does not have permission to view them. This can be useful for multi-use relays that host hidden rooms. This mode should be used with caution, because it can result in confusion for the end user.
See Frith for a relay implementation that supports some of these auth policies.
Invite codes
If a user doesn't have access to a relay, they can request access using this draft NIP. This is true whether access has been explicitly or implicitly denied (although users will have to know that they should use an invite code to request access).
The above referenced NIP also contains a mechanism for users to request an invite code that they can share with other users.
The policy for these invite codes is entirely up to the relay. They may be single-use, multi-use, or require additional verification. Additional requirements can be communicated to the user in the OK message, for example directions to visit an external URL to register.
See Frith for a relay implementation that supports invite codes.
Content
Any kind of event can be published to a relay being treated as a group, unless rejected by the relay implementation. In particular, NIP 7D was added to support basic threads, and NIP C7 for chat messages.
Since which relay an event came from determines which group it was posted to, clients need to have a mechanism for keeping track of which relay they received an event from, and should not broadcast events to other relays (unless intending to cross-post the content).
Rooms
Rooms follow NIP 29. I wish NIP 29 wasn't called "relay based groups", which is very confusing when talking about "relays as groups". It's much better to think of them as sub-groups, or as Flotilla calls them, "rooms".
EDIT: Flotilla has migrated to exclusively use "managed rooms" — i.e., fully NIP 29 compliant rooms. Relays without NIP 29 support can still support chat, but all messages will be presented as sent to a single room. I've removed references to unmanaged rooms in what follows.
~~Rooms have two modes - managed and unmanaged. Managed~~ rooms follow all the rules laid out in NIP 29 about metadata published by the relay and user membership. In either case, rooms are represented by a random room id, and are posted to by including the id in an event's
htag. ~~This allows rooms to switch between managed and unmanaged modes without losing any content.~~Managed room names come from
kind 39000room meta events, ~~but unmanaged rooms don't have these. Instead, room names should come from members' NIP 51kind 10009membership lists. Tags on these lists should look like this:["group", "groupid", "wss://group.example.com", "Cat lovers"]. If no name can be found for the room (i.e., there aren't any members), the room should be ignored by clients.~~Rooms present a difficulty for publishing to the relay as a whole, since content with an
htag can't be excluded from requests. ~~Currently, relay-wide posts are h-tagged with_which works for "group" clients, but not more generally. I'm not sure how to solve this other than to ask relays to support negative filters.~~ I have ideas on how to solve this in future iterations of relay-based groups, for example using virtual relays or just a better rooms spec.Cross-posting
The simplest way to cross-post content from one group (or room) to another, is to quote the original note in whatever event kind is appropriate. For example, a blog post might be quoted in a
kind 9to be cross-posted to chat, or in akind 11to be cross-posted to a thread.kind 16reposts can be used the same way if the reader's client renders reposts.Posting the original event to multiple relays-as-groups is trivial, since all you have to do is send the event to the relay. Posting to multiple rooms simultaneously by appending multiple
htags is however not recommended, since group relays/clients are incentivised to protect themselves from spam by rejecting events with multiplehtags (similar to how events with multiplettags are sometimes rejected).Privacy
Currently, it's recommended to include a NIP 70
-tag on content posted to relays-as-groups to discourage replication of relay-specific content across the network.Another slightly stronger approach would be for group relays to strip signatures in order to make events invalid (or at least deniable). For this approach to work, users would have to be able to signal that they trust relays to be honest. We could also use ZkSNARKS to validate signatures in bulk.
In any case, group posts should not be considered "private" in the same way E2EE groups might be. Relays-as-groups should be considered a good fit for low-stakes groups with many members (since trust deteriorates quickly as more people get involved).
Membership
There is currently no canonical member list published by relays (except for NIP 29 managed rooms). Instead, users keep track of their own relay and room memberships using
kind 10009lists. Relay-level memberships are represented by anrtag containing the relay url, and room-level memberships are represented using agrouptag.Users can choose to advertise their membership in a RAG by using unencrypted tags, or they may keep their membership private by using encrypted tags. Advertised memberships are useful for helping people find groups based on their social graph:

User memberships should not be trusted, since they can be published unilaterally by anyone, regardless of actual access, so it's better to think of them as "bookmarked groups" or "favorites". Possible improvements in this area would be the ability to provide proof of access:
- Relays could publish member lists (although this would sacrifice member privacy)
- Relays could support a new command that allows querying a particular member's access status
- Relays could provide a proof to the member that they could then choose to publish or not
Moderation
There are two parts to moderation: reporting and taking action based on these reports.
Reporting is already covered by NIP 56. Clients should be careful about encouraging users to post reports for illegal content under their own identity, since that can itself be illegal. Relays also should not serve reports to users, since that can be used to find rather than address objectionable content.
Reports are only one mechanism for flagging objectionable content. Relay operators and administrators can use whatever heuristics they like to identify and address objectionable content. This might be via automated policies that auto-ban based on reports from high-reputation people, a client that implements NIP 86 relay management API, or by some other admin interface.
There's currently no way for moderators of a given relay to be advertised, or for a moderator's client to know that the user is a moderator (so that they can enable UI elements for in-app moderation). This could be addressed via NIP 11, LIMITS, or some other mechanism in the future.
General best practices
In general, it's very important when developing a client to assume that the relay has no special support for any of the above features, instead treating all of this stuff as progressive enhancement.
For example, if a user enters an invite code, go ahead and send it to the relay using a
kind 28934event. If it's rejected, you know that it didn't work. But if it's accepted, you don't know that it worked - you only know that the relay allowed the user to publish that event. This is helpful, becaues it may imply that the user does indeed have access to the relay. But additional probing may be needed, and reliance on error messages down the road when something else fails unexpectedly is indispensable.This paradigm may drive some engineers nuts, because it's basically equivalent to coding your clients to reverse-engineer relay support for every feature you want to use. But this is true of nostr as a whole - anyone can put whatever weird stuff in an event and sign it. Clients have to be extremely compliant with Postell's law - doing their absolute best to accept whatever weird data or behavior shows up and handle failure in any situation. Sure, it's annoying, but it's the cost of permissionless development. What it gets us is a completely open-ended protocol, in which anything can be built, and in which every solution is tested by the market.
-
 @ e5cfb5dc:0039f130
2025-06-14 06:46:54
@ e5cfb5dc:0039f130
2025-06-14 06:46:54はりまメンタルクリニック:GIDの大手そう。丸の内線ならパムくんちが近い。
わらびメンタルクリニック:GIDの大手そう?
ナグモクリニック:SRS手術までしてるところ。GID精神科外来が月1第1木曜日だけ?
狭山メンタルクリニック:距離・時間的にはまま近い。サイトの記述が思想的にちょとあやしげ。新患受付がだいぶ先。GIDは専門外か?
川島領診療所:オンライン診療あり!強迫性障害や美容皮膚科をやっている。雰囲気よさそうなところ。GIDは専門外か?
Jこころのクリニック:電車いっぽんなので楽。GIDは専門外か?
ハッピースマイルクリニック:オンライン診療あり!GIDは専門外か?
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ 32e18276:5c68e245
2025-06-03 14:45:17
@ 32e18276:5c68e245
2025-06-03 14:45:176 years ago I created some tools for working with peter todd's opentimestamps proof format. You can do some fun things like create plaintext and mini ots proofs. This short post is just a demo of what these tools do and how to use them.
What is OTS?
OpenTimestamps is a protocol for stamping information into bitcoin in a minimal way. It uses OP_RETURN outputs so that it has minimal impact on chain, and potentially millions of documents are stamped all at once with a merkle tree construction.
Examples
Here's the proof of the
ots.csource file getting stamped into the ots calendar merkle tree. We're simply printing the ots proof file here withotsprint:``` $ ./otsprint ots.c.ots
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 | --> append 2d82e7414811ecbf | sha256 | append a69d4f93e3e0f6c9b8321ce2cdd90decd34d260ea3f8b55e83d157ad398b7843 | sha256 | append ac0b5896401478eb6d88a408ec08b33fd303b574fb09b503f1ac1255b432d304 | sha256 | append 8aa9fd0245664c23d31d344243b4e8b0 | sha256 | prepend 414db5a1cd3a3e6668bf2dca9007e7c0fc5aa6dc71a2eab3afb51425c3acc472 | sha256 | append 5355b15d88d4dece45cddb7913f2c83d41e641e8c1d939dac4323671a4f8e197 | sha256 | append a2babd907ca513ab561ce3860e64a26b7df5de117f1f230bc8f1a248836f0c25 | sha256 | prepend 683f072f | append 2a4cdf9e9e04f2fd | attestation calendar https://alice.btc.calendar.opentimestamps.org | --> append 7c8764fcaba5ed5d | sha256 | prepend f7e1ada392247d3f3116a97d73fcf4c0994b5c22fff824736db46cd577b97151 | sha256 | append 3c43ac41e0281f1dbcd7e713eb1ffaec48c5e05af404bca2166cdc51966a921c | sha256 | append 07b18bd7f4a5dc72326416aa3c8628ca80c8d95d7b1a82202b90bc824974da13 | sha256 | append b4d641ab029e7d900e92261c2342c9c9 | sha256 | append 4968b89b02b534f33dc26882862d25cca8f0fa76be5b9d3a3b5e2d77690e022b | sha256 | append 48c54e30b3a9ec0e6339b88ed9d04b9b1065838596a4ec778cbfc0dfc0f8c781 | sha256 | prepend 683f072f | append 8b2b4beda36c18dc | attestation calendar https://bob.btc.calendar.opentimestamps.org | --> append baa878b42ef3e0d45b324cc3a39a247a | sha256 | prepend 4fb1bc663cd641ad18e5c73fb618de1ae3d28fb5c3c224b7f9888fd52feb09ec | sha256 | append 731329278830c9725497d70e9f5a02e4b2d9c73ff73560beb3a896a2f180fdbf | sha256 | append 689024a9d57ad5daad669f001316dd0fc690ac4520410f97a349b05a3f5d69cb | sha256 | append 69d42dcb650bb2a690f850c3f6e14e46c2b0831361bac9ec454818264b9102fd | sha256 | prepend 683f072f | append bab471ba32acd9c3 | attestation calendar https://btc.calendar.catallaxy.com append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
The tool can create a minimal version of the proofs:
``` $ ./otsmini ots.c.ots | ./otsmini -d | ./otsprint
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
which can be shared on social media as a string:
5s1L3tTWoTfUDhB1MPLXE1rnajwUdUnt8pfjZfY1UWVWpWu5YhW3PGCWWoXwWBRJ16B8182kQgxnKyiJtGQgRoFNbDfBss19seDnco5sF9WrBt8jQW7BVVmTB5mmAPa8ryb5929w4xEm1aE7S3SGMFr9rUgkNNzhMg4VK6vZmNqDGYvvZxBtwDMs2PRJk7y6wL6aJmq6yoaWPvuxaik4qMp76ApXEufP6RnWdapqGGsKy7TNE6ZzWWz2VXbaEXGwgjrxqF8bMstZMdGo2VzpVuEyou can even do things like gpg-style plaintext proofs:
``` $ ./otsclear -e CONTRIBUTING.ots -----BEGIN OPENTIMESTAMPS MESSAGE-----
Email patches to William Casarin jb55@jb55.com
-----BEGIN OPENTIMESTAMPS PROOF-----
AE9wZW5UaW1lc3RhbXBzAABQcm9vZgC/ieLohOiSlAEILXj4GSagG6fRNnR+CHj9e/+Mdkp0w1us gV/5dmlX2NrwEDlcBMmQ723mI9sY9ALUlXoI//AQRXlCd716J60FudR+C78fkAjwIDnONJrj1udi NDxQQ8UJiS4ZWfprUxbvaIoBs4G+4u6kCPEEaD8Ft/AIeS/skaOtQRoAg9/jDS75DI4pKGh0dHBz Oi8vZmlubmV5LmNhbGVuZGFyLmV0ZXJuaXR5d2FsbC5jb23/8AhMLZVzYZMYqwjwEPKWanBNPZVm kqsAYV3LBbkI8CCfIVveDh/S8ykOH1NC6BKTerHoPojvj1OmjB2LYvdUbgjxBGg/BbbwCGoo3fi1 A7rjAIPf4w0u+QyOLi1odHRwczovL2FsaWNlLmJ0Yy5jYWxlbmRhci5vcGVudGltZXN0YW1wcy5v cmf/8Aik+VP+n3FhCwjwELfTdHAfYQNa49I3CYycFbkI8QRoPwW28AgCLn93967lIQCD3+MNLvkM jiwraHR0cHM6Ly9ib2IuYnRjLmNhbGVuZGFyLm9wZW50aW1lc3RhbXBzLm9yZ/AQ3bEwg7mjQyKR PykGgiJewAjwID5Q68dY4m+XogwTJx72ecQEe5lheCO1RnlcJSTFokyRCPEEaD8Ft/AIw1WWPe++ 8N4Ag9/jDS75DI4jImh0dHBzOi8vYnRjLmNhbGVuZGFyLmNhdGFsbGF4eS5jb20= -----END OPENTIMESTAMPS PROOF-----
$ ./otsclear -v <<<proof_string... # verify the proof string ```
I've never really shared these tools before, I just remembered about it today. Enjoy!
Try it out: https://github.com/jb55/ots-tools
-
 @ 7f6db517:a4931eda
2025-06-13 23:03:47
@ 7f6db517:a4931eda
2025-06-13 23:03:47

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 32e18276:5c68e245
2025-06-02 20:58:05
@ 32e18276:5c68e245
2025-06-02 20:58:05Damus OpenSats Grant Q1 2025 Progress Report
This period of the Damus OpenSats grant has been productive, and encompasses the work our beta release of Notedeck. Since we sent our last report on January, this encompasses all the work after then.
Damus Notedeck
We released the Beta version of Notedeck, which has many new features:
Dave
We've added a new AI-powered nostr assistant, similar to Grok on X. We call him Dave.
Dave is integrated with tooling that allows it to query the local relay for posts and profiles:
Search
The beta release includes a fulltext search interface powered by nostrdb:
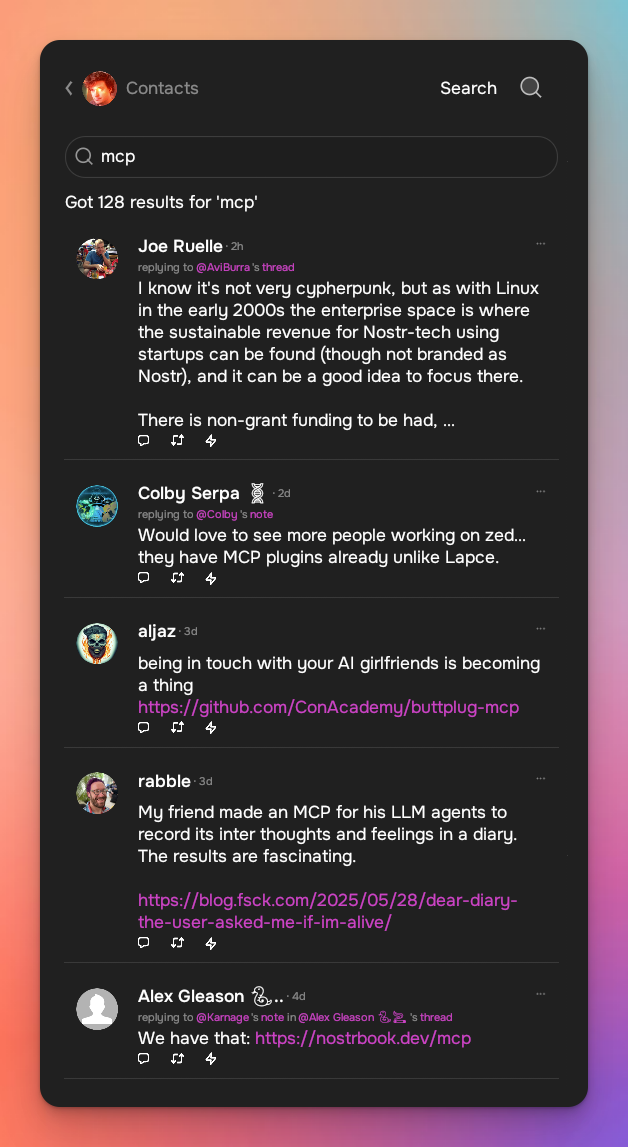
Zaps
You can now zap with NWC!
And More!
- GIFs!
- Add full screen images, add zoom & pan
- Introduce last note per pubkey feed (experimental)
- Allow multiple media uploads per selection
- Major Android improvements (still wip)
- Added notedeck app sidebar
- User Tagging
- Note truncation
- Local network note broadcast, broadcast notes to other notedeck notes while you're offline
- Mute list support (reading)
- Relay list support
- Ctrl-enter to send notes
- Added relay indexing (relay columns soon)
- Click hashtags to open hashtag timeline
Damus iOS
Work continued on the iOS side. While I was not directly involved in the work since the last report, I have been directing and managing its development.
What's new:
Coinos Wallet + Interface
We've partnered with coinos to enable a one-click, non-KYC lightning wallet!
We now have an NWC wallet interface, and we've re-enabled zaps as per the new appstore guidelines!
Now you can see all incoming and outgoing NWC transactions and start zapping right away.
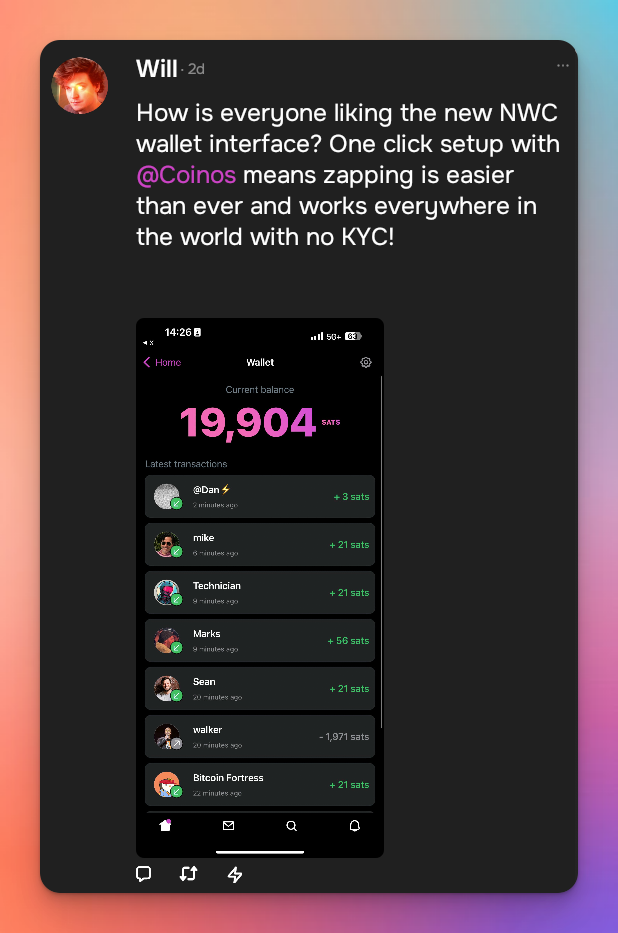
Enhanced hellthread muting
Damus can now automatically mute hellthreads, instead of having to do that manually.
Drafts
We now locally persist note drafts so that they aren't lost on app restart!
Profile editing enhancements
We now have a profile picture editing tool so that profile pictures are optimized and optionally cropped
Conversations tab
We now have a conversations tab on user profiles, allowing you to see all of your past conversations with that person!
Enhanced push notifications
We've updated our push notifications to include profile pictures, and they are also now grouped by the thread that they came from.
And lots more!
Too many to list here, check out the full changelog
Nostrdb
nostrdb, the engine that powers notecrumbs, damus iOS, and notedeck, continued to improve:
Custom filters
We've added the ability to include custom filtering logic during any nostrdb query. Dave uses this to filter replies from kind1 results to keep the results small and to avoid doing post-processing.
Relay index + queries
There is a new relay index! Now when ingesting notes, you can include extra metadata such as where the note came from. You can use this index to quickly list all of the relays for a particular note, or for relay timelines.
NIP50 profile searches
To assist dave in searching for profiles, we added a new query plan for {kind:0, search:} queries to scan the profile search index.
How money was used
- relay.damus.io server costs
- Living expenses
Next quarter
We're making a strong push to get our Android version released, so that is the main focus for me.
-
 @ 7f6db517:a4931eda
2025-06-12 15:02:58
@ 7f6db517:a4931eda
2025-06-12 15:02:58
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 8bad92c3:ca714aa5
2025-06-14 05:02:14
@ 8bad92c3:ca714aa5
2025-06-14 05:02:14Marty's Bent
via me

I had a completely different newsletter partially written earlier tonight about whether or not "this cycle is different" when this nagging thought entered my head. So I'm going to write about this and maybe I'll write about the dynamics of this cycle compared to past cycles tomorrow.
A couple of headlines shot across my desk earlier tonight in relation to the potential escalation of kinetic warfare in the Middle East. Apparently the U.S. Embassy in Iraq was sent a warning and evacuation procedures were initiated. Not too long after, the world was made aware that the United States and Israel are contemplating an attack on Iran due to the "fact" that Iran may be close to producing nuclear weapins. The initial monkey brain reaction that I had to these two headlines was, "Oh shit, here we go again. We're going to do something stupid." My second reaction was, "Oh shit, here we go again, I've seen these two exact headlines many times over the years and they've proven to be lackluster if you're a doomer or blood thirsty war monger." Nothing ever happens.
As I venture into my mid-30s and reflect on a life filled with these types of headlines and my personal reactions to these headlines, I'm finally becoming attuned to the fact that the monkey brain reactions aren't very productive at the end of the day. Who knows exactly what's going to happen in Iraq or Iran and whether or not kinetic warfare escalates and materializes from here? Even though I'm a "blue-blooded taxpaying American citizen" who is passively and unwillingly contributing to the war machine and the media industrial complex, there's really nothing I can do about it.
The only thing I can do is focus on what is in front of me. What I have control of. And attempt to leverage what I have control of to make my life and the life of my family as good as humanly possible. Ignoring the external and turning inward often produces incredible results. Instead of worrying about what the media wants you to believe at any given point in time, you simply look away from your computer screen, survey the physical space which you're operating in and determine what you have, what you need and how you can get what you need. This is a much more productive way to spend your time.
This is what I want to touch on right now. There's never been a better time in human history to be productive despite what the algorithm on X or the mainstream media will lead you to believe. Things aren't as great as they could be, but they're also not as bad as you're being led to believe. We live in the Digital Age and the Digital Age provides incredible resources that you can leverage to make YOUR life better.
Social media allows you to create a platform without spending any money. AI allows you to build tools that are beneficial to yourself and others with very little money. And bitcoin exists to provide you with the best form of money that you can save in with the knowledge that your relative ownership of the overall supply isn't going to change. No matter what happens in the external world.
If you can combine these three things to make your life better and - by extension - potentially make the lives of many others better, you're going to be well off in the long run. Combining these three things isn't going to result in immediate gratification, but if you put forth a concerted effort, spend the time, have some semblance of patience, and stick with it, I truly believe that you will benefit massively in the long run. Without trying to sound like a blowhard, I truly believe that this is why I feel relatively calm (despite my monkey brain reactions to the headlines of the day) at this current point in time.
We've entered the era of insane leaps in productivity and digital hard money that cannot be corrupted. The biggest mistake you can make in your life right now is overlooking the confluence of these two things. With an internet connection, an idea, some savvy, and hard work you can materially change your life. Create something that levels up your knowledge, that enables you to get a good job in the real world, or to create a company of your own. Bring your talents to the market, exchange them for money, and then funnel that money into bitcoin (if you're not being paid in it already). We may be at the beginning of a transition from the high velocity trash economy to the high leverage agency economy run on sound money and applied creativity.
These concepts are what you should be focusing most of your time and attention to today and in the years ahead. Don't get distracted by the algorithm, the 30-second video clips, the headlines filled with doom, and the topics of the 24 hour news cycle. I'll admit, I often succumb to them myself. But, as I get older and develop a form of pattern recognition that can only be attained by being on this planet for a certain period of time, it is becoming very clear that those things are not worth your attention.
Living by the heuristic that "nothing ever happens" is a pretty safe bet. Funnily enough, it's incredibly ironic that you're led to believe that something is happening every single day, and yet nothing ever happens. By getting believing that something happens every day you are taking your attention away from doing things that happen to make your life better.
Tune out the noise. Put on the blinders. Take advantage of the incredible opportunities that lie before you. If enough of you - and many others who do not read this newsletter - do this, I truly believe we'll wake up to find that the world we live in is a much better place.
Nothing ever happens, so make something happen.
Intelligence Officials Are Quietly Becoming Bitcoin Believers
Ken Egan, former CIA Deputy Chief of Cyber Operations, revealed a surprising truth on TFTC: the intelligence community harbors numerous Bitcoin advocates. Egan explained that intelligence professionals uniquely understand how governments weaponize financial systems through sanctions and account freezing. Having wielded these tools themselves, they recognize the need for personal financial sovereignty. He shared compelling anecdotes of discovering colleagues with "We are all Satoshi" stickers and a European chief of station paying for dinner with a BlockFi card to earn Bitcoin rewards.
"I think there are a lot of Bitcoiners, not just at CIA, but across the whole national security establishment... they're in it for the exact same reasons everybody else is." - Ken Egan
The Canadian trucker protests served as a pivotal moment, Egan noted. Watching Western governments freeze citizens' bank accounts for political dissent struck a nerve among intelligence professionals who previously viewed financial weaponization as a tool reserved for foreign adversaries. This awakening has created unlikely allies within institutions many Bitcoiners distrust.
Check out the full podcast here for more on Bitcoin's national security implications, privacy tech prosecutions, and legislative priorities.
Headlines of the Day
Stripe Buys Crypto Wallet Privy After Bridge Deal - via X
Trump Calls CPI Data "Great" Urges Full Point Fed Cut - via X
Bitcoin Hashrate Reaches New All-Time High - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitcoin’s Next Parabolic Move: Could Liquidity Lead the Way?
Is bitcoin’s next parabolic move starting? Global liquidity and business cycle indicators suggest it may be.
Read the latest report from Unchained and TechDev, analyzing how global M2 liquidity and the copper/gold ratio—two historically reliable macro indicators—are aligning once again to signal that a new bitcoin bull market may soon begin.
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Life is good.
Download our free browser extension, Opportunity Cost: https://www.opportunitycost.app/ start thinking in SATS today.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; p
-
 @ 5627e59c:d484729e
2025-06-11 22:31:59
@ 5627e59c:d484729e
2025-06-11 22:31:59Een warme chocomelk\ Een knuffel en de moed te durven spreken\ Een leuk oprecht verhaal\ En een stap naar mijn verlangen
Deze dingen allemaal\ Maken me warm vanbinnen\ Ik hou van deze dingen\ Ze doen mijn hartje zingen
Ik wens iedereen zo'n warmte toe\ Ik wou dat ik het delen kon\ Maar het ziet er anders uit\ Voor jou dan hoe voor mij
Het enige wat ik echt kan zeggen\ Het enige dat ik zeker weet\ De kracht om warmte te creëren\ Ligt in je eigen handen
In je voeten, in je mond\ Het zit ook in je ogen\ En ook in je haar\ En zei ik al je mond\ En zelfs ook in je kont
Haha, ik ben maar wat aan 't lachen\ Dat is wat mij verlucht\ En ervoor zorgt dat wat ik zeg\ Van mij los kan komen\ En jou bereiken kan
Zo kan ik op beide oren slapen\ Dat ik deed dat wat ik kon\ Ik sprak dat wat belangrijk is\ Voor mij en liet het los
De wijde wereld in\ Voor al die horen wil en daar om geeft\ Om die warmte in hun hartje\ En daar misschien naar streeft
Ik wens je al 't succes toe in de wereld\ Want God weet, je bent het waard\ Het ligt nu in jouw handen\ Deze woorden, wat ik zeg\ Iets om over na te denken\ Tussen 't brood en het beleg
Leef gewoon je leven\ En zorg goed voor jezelf\ En als je 't graag wilt vinden\ Is het daar voor jou aan 't wachten\ Tot jij klaar bent met geloven\ In al dat anders klinkt
Ik kan je niets beloven\ Maar vertrouw op jouw instinct
-
 @ b1ddb4d7:471244e7
2025-06-13 13:01:31
@ b1ddb4d7:471244e7
2025-06-13 13:01:31Paris, France – June 6, 2025 – Flash, the easiest Bitcoin payment gateway for businesses, just announced a new partnership with the Bitcoin Only Brewery, marking the first-ever beverage company to leverage Flash for seamless Bitcoin payments.
Bitcoin Buys Beer Thanks to Flash!

As Co-Founder of Flash, it's not every day we get to toast to a truly refreshing milestone.
Okay, jokes aside.
We're super buzzed to see our friends at @Drink_B0B
Bitcoin Only Brewery using Flash to power their online sales!The first… pic.twitter.com/G7TWhy50pX
— Pierre Corbin (@CierrePorbin) June 3, 2025
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack – shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented: “Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest Bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept Bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
Bitcoin payment usage is growing thanks to Lightning
In May, fast-food chain Steak ‘N Shake went viral for integrating bitcoin at their restaurants around the world. In the same month, the bitcoin2025 conference in Las Vegas set a new world record with 4,000 Lightning payments in one day.
According to a report by River Intelligence, public Lightning payment volume surged by 266% from August 2023 to August 2024. This growth is also reflected in the overall accessibility of lighting infrastructure for consumers. According to Lightning Service Provider Breez, over 650 Million users now have access to the Lightning Network through apps like CashApp, Kraken or Strike.
Bitcoin Only Brewery’s adoption of Flash reflects the growing trend of businesses integrating Bitcoin payments to cater to a global, privacy-conscious customer base. By offering no-KYC delivery across Europe, the brewery aligns with the ethos of decentralization and financial sovereignty, appealing to the increasing number of consumers and businesses embracing Bitcoin as a legitimate payment method.
“Flash is committed to driving innovation in the Bitcoin ecosystem,” Corbin added. “We’re building a future where businesses of all sizes can seamlessly integrate Bitcoin payments, unlocking new opportunities in the global market. It’s never been easier to start selling in bitcoin and we invite retailers globally to join us in this revolution.”
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
About Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comPhotos paywithflash.com/about/pressHow Flash Enables Interoperable, Self-Custodial Bitcoin Commerce
-
 @ da8b7de1:c0164aee
2025-06-14 04:02:17
@ da8b7de1:c0164aee
2025-06-14 04:02:17Az IAEA Kormányzótanácsának Ülése
A Nemzetközi Atomenergia-ügynökség (IAEA) 2025. június 9. és 13. között tartotta szokásos Kormányzótanácsi ülését bécsi központjában. Ez a magas szintű esemény a tagállamok képviselőit hozta össze, hogy megvitassák a nukleáris biztonság, védelem és technológia legújabb fejleményeit. Rafael Mariano Grossi, az IAEA főigazgatója a találkozó elején sajtótájékoztatót tartott, amelyen kiemelte az ügynökség folyamatos erőfeszítéseit a biztonságos és védett nukleáris energia világszintű előmozdításában [iaea.org].
A Világbank Nukleáris Energiát Támogató Fordulata
Mérföldkőnek számító döntésként a Világbank 2025. június 10-én bejelentette, hogy megkezdi új nukleáris energia projektek – köztük kis moduláris reaktorok (SMR-ek) és meglévő erőművek élettartam-hosszabbításának – finanszírozását. Ez a döntés a Bank régóta fennálló, nukleáris energia finanszírozását ellenző politikájának felülvizsgálatát jelenti. Ajay Banga, a Világbank elnöke elmondta, hogy a változás a nukleáris energia globális dekarbonizációban és energiabiztonságban betöltött növekvő szerepének elismerését tükrözi [ans.org].
Globális Támogatás a Nukleáris Kapacitás Megháromszorozásáért
A bakui COP29 ENSZ klímakonferencián újabb hat ország – El Salvador, Kazahsztán, Kenya, Koszovó, Nigéria és Törökország – csatlakozott ahhoz a kezdeményezéshez, amely célul tűzte ki a globális nukleáris kapacitás megháromszorozását 2050-ig. Ez a mozgalom része annak a szélesebb nemzetközi törekvésnek, amely a nukleáris energia gyorsabb elterjesztését szorgalmazza a tiszta energiára való átmenet kulcselemeként. Az Egyesült Államok szintén bemutatta tervét 200 GW nukleáris kapacitás 2050-ig történő telepítésére, ezzel is megerősítve elkötelezettségét a nukleáris energia mellett a klíma- és energiakihívások kezelésében [world-nuclear-news.org].
Ipari és Technológiai Fejlemények
- Az American Bureau of Shipping jelentést tett közzé az előrehaladott nukleáris technológia tengeri alkalmazásának lehetőségeiről, különös tekintettel a kis moduláris reaktorokra LNG-szállító hajókon.
- Az Egyesült Királyság Nemzeti Energiarendszer-üzemeltetője hangsúlyozta a nukleáris energia fontosságát a 2030-ra megvalósítandó tiszta energiatermelési rendszer elérésében, beleértve a meglévő erőművek élettartam-hosszabbítását és új reaktorok építését [world-nuclear-news.org].
Források: - world-nuclear-news.org - iaea.org - ans.org
-
 @ 58537364:705b4b85
2025-06-12 13:59:39
@ 58537364:705b4b85
2025-06-12 13:59:39ในร่างกายที่มันมีสิ่งที่เรียกว่า… ระบบประสาท ทีนี้มีอะไรเข้ามากระทบร่างกาย คือกระทบระบบประสาท ปฏิกิริยามันก็เกิดขึ้น เป็นเหตุการณ์ อย่างใดอย่างหนึ่งขึ้น
เหตุการณ์นั้นแหละสำคัญ ถ้าให้เกิดความรู้สึกที่ถูกใจมันจะเป็นบวก เหตุการณ์นั้นไม่รู้สึกถูกใจแก่จิต มันก็จะเป็นลบ #ตัวกูเพิ่งเกิดเมื่อมีการกระทบแล้ว
ถ้าเหตุการณ์ที่เป็นบวกเกิดขึ้น ตัวกูบวกก็เกิดขึ้น เหตุการณ์ที่เป็นลบเกิดขึ้น ตัวกูที่เป็นลบเกิดขึ้น #ตัวกูนี้เกิดหลังเหตุการณ์ ขอให้เข้าใจดีๆ ไม่ใช่เกิดอยู่ก่อน
ตัวกูคลอดออกมาจาก situation ที่มากระทบระบบประสาท เช่นว่า… ไม่ได้กินอาหาร ขาดอาหาร มันหิว ความหิวเกิดขึ้นแก่ระบบประสาท ต่อมาจึงเกิด concept ว่า กูหิว, มีการกินแล้วจึงเกิด concept ว่า กูกิน
ถ้ามีอาการอร่อยแก่ลิ้น มันจึงเกิด concept ว่า… กูอร่อย หรือ มาทีหลังเหตุการณ์เสมอ จะถือว่าเป็น product ของเหตุการณ์นั้น ๆ ก็ได้
นี่คือความที่ไม่มีตัวจริง มิใช่ของจริง ของสิ่งที่เรียกว่าตัวกู #ขอให้รู้จักว่าตัวกูนี้มันเป็นมายาถึงขนาดนี้
ฟังดูการพูดอย่างนี้ มันเป็น logic แต่ความจริงของธรรมชาติมันเป็นอย่างนั้น ถือตามกฎ logic ธรรมดาสามัญ ที่พูดกันอยู่นี้ไม่ได้ ต้องถือตามความเป็นจริงที่ว่า มันเป็นอยู่อย่างไร
จิตก็เป็นธาตุชนิดหนึ่ง สิ่งแวดล้อมต่างๆ ที่เป็นธาตุชนิดหนึ่ง พอมาถึงกันเข้า ก็เกิดปฏิกิริยาออกมาอย่างนั้นอย่างนี้ ความรู้สึกที่เรียกว่า… #จิตคิดนึกได้นี้_ก็เป็นปฏิกิริยาที่เกิดขึ้นเท่านั้น แล้วความรู้สึกว่าตัวกู ตัวนี้ก็เป็นเพียงปฏิกิริยาที่เกิดขึ้นเท่านั้น.
มันฟังยากสำหรับท่านทั้งหลายที่ว่า ผู้กระทำนั้นเกิดทีหลังการกระทำ มันผิด logic อย่างนี้
แต่ความจริงเป็นอย่างนั้น self หรือ ego ผู้กระทำจะเกิดทีหลังการกระทำ เป็นปฏิกิริยาของการกระทำ
ความคิดอย่าง ตรรกะ หรืออย่างปรัชญา เอามาใช้กับสิ่งนี้ไม่ได้ ขอยืนยันไว้อย่างนี้
ถ้าท่านยังไม่เชื่อ ท่านก็ไปคิดดูเรื่อย ๆ ไปเถอะ ท่านจะพบว่ามันไม่เป็นอย่างกฎเกณฑ์ทางตรรกะหรือทางปรัชญา ที่เรามีๆ กันอยู่
ผู้กระทำเป็นเพียง concept ไม่ใช่ตัวจริง ส่วนการกระทำมันเป็นเหตุการณ์ของธรรมชาติ พอเข้ามาถึงจิตแล้ว ก็เกิดความคิด ความเชื่อ ความยึดว่าตัวกู
ตัวกูซึ่งเป็นเพียง concept ไม่ใช่ของจริง
พุทธทาสภิกขุ
อตัมมยตาประทีป
ชีวิตใหม่และหนทางเข้าถึงชีวิตใหม่
หน้า_๒๙๕-๒๙๖
-
 @ 7f6db517:a4931eda
2025-06-12 11:02:33
@ 7f6db517:a4931eda
2025-06-12 11:02:33
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-11 15:02:05
@ b1ddb4d7:471244e7
2025-06-11 15:02:05Hosted at the iconic Palace of Culture and Science—a prominent symbol of the communist era—the Bitcoin FilmFest offers a vibrant celebration of film through the lens of bitcoin. The venue itself provides a striking contrast to the festival’s focus, highlighting bitcoin’s core identity as a currency embodying independence from traditional financial and political systems.
𝐅𝐢𝐱𝐢𝐧𝐠 𝐭𝐡𝐞 𝐜𝐮𝐥𝐭𝐮𝐫𝐞 𝐰𝐢𝐭𝐡 𝐩𝐨𝐰𝐞𝐫𝐟𝐮𝐥 𝐦𝐮𝐬𝐢𝐜 𝐯𝐢𝐛𝐞𝐬.
Warsaw, Day Zero at #BFF25 (European Bitcoin Pizza Day) with @roger__9000, MadMunky and the @2140_wtf squad
 pic.twitter.com/9ogVvWRReA
pic.twitter.com/9ogVvWRReA— Bitcoin FilmFest

 (@bitcoinfilmfest) May 28, 2025
(@bitcoinfilmfest) May 28, 2025This venue represents an era when the state tightly controlled the economy and financial systems. The juxtaposition of this historical site with an event dedicated to bitcoin is striking and thought-provoking.
The event features a diverse array of activities, including engaging panel discussions, screenings of both feature-length and short films, workshops and lively parties. Each component designed to explore the multifaceted world of bitcoin and its implications for society, offering attendees a blend of entertainment and education.

The films showcase innovative narratives and insights into bitcoin’s landscape, while the panels facilitate thought-provoking discussions among industry experts and filmmakers.
Networking is a significant aspect of the festival, with an exceptionally open and friendly atmosphere that foster connections among participants. Participants from all over Europe gather to engage with like-minded individuals who share a passion for BTC and its implications for the future.
The open exchanges of ideas foster a sense of community, allowing attendees to forge new connections, collaborate on projects, and discuss the potential of blockchain technology implemented in bitcoin.

The organization of the festival is extraordinary, ensuring a smooth flow of information and an expertly structured schedule filled from morning until evening. Attendees appreciate the meticulous planning that allowed them to maximize their experience. Additionally, thoughtful touches such as gifts from sponsors and well-chosen locations for various events contribute to the overall positive atmosphere of the festival.
Overall, the Bitcoin FilmFest not only highlights the artistic expression surrounding bitcoin but also serves as a vital platform for dialogue—about financial freedom, the future of money, and individual sovereignty in a shifting world.

The event successfully bridges the gap between a historical symbol of control and a movement that celebrates freedom, innovation, and collaboration in the digital age, highlighting the importance of independence in financial systems while fostering a collaborative environment for innovation and growth.
Next year’s event is slated for June 5-7 2026. For further updates check: https://bitcoinfilmfest.com/
-
 @ b1ddb4d7:471244e7
2025-06-11 10:01:58
@ b1ddb4d7:471244e7
2025-06-11 10:01:58The latest AI chips, 8K displays, and neural processing units make your device feel like a pocket supercomputer. So surely, with all this advancement, you can finally mine bitcoin on your phone profitably, right?
The 2025 Hardware Reality: Can You Mine Bitcoin on Your Phone
Despite remarkable advances in smartphone technology, the fundamental physics of bitcoin mining haven’t changed. In 2025, flagship devices with their cutting-edge 2nm processors can achieve approximately 25-40 megahashes per second when you mine bitcoin on your phone—a notable improvement from previous generations, but still laughably inadequate.
Meanwhile, 2025’s top-tier ASIC miners have evolved dramatically. The latest Bitmain Antminer S23 series and Canaan AvalonMiner A15 Pro deliver 200-300 terahashes per second while consuming 4,000-5,500 watts. That’s a performance gap of roughly 1:8,000,000 between when you mine bitcoin on your phone and professional mining equipment.
To put this in perspective that hits home: if you mine bitcoin on your phone and it earned you one penny, professional miners would earn $80,000 in the same time period with the same effort. It’s not just an efficiency problem—it’s a complete category mismatch.
According to Pocket Option’s 2025 analysis, when you mine bitcoin on your phone in 2025, you generate approximately $0.003-0.006 in daily revenue while consuming $0.45-0.85 in electricity through constant charging cycles. Factor in the accelerated device wear (estimated at $0.75-1.20 daily depreciation), and you’re looking at losses of $1.20-2.00 per day just for the privilege of running mining software.
Mining Economic Factor
Precise Value (April 2025)
Direct Impact on Profitability
Smartphone sustained hash rate
20-35 MH/s
0.00000024% contribution to global hashrate
Daily power consumption
3.2-4.8 kWh (4-6 full charges)
$0.38-0.57 at average US electricity rates
Expected daily BTC earnings
0.0000000086 BTC ($0.0035 at $41,200 BTC)
Revenue covers only 0.9% of electricity costs
CPU/GPU wear cost
$0.68-0.92 daily accelerated depreciation
Reduces smartphone lifespan by 60-70%
Annual profit projection
-$386 to -$412 per year
Guaranteed negative return on investment
Source: PocketOption
Bitcoin’s 2025 Network: Harder Than Ever
Bitcoin’s network difficulty in 2025 has reached unprecedented levels. After the April 2024 halving event that reduced block rewards from 6.25 to 3.125 BTC, mining became significantly more competitive. The global hash rate now exceeds 800 exahashes per second—that’s 800 followed by 18 zeros worth of computational power securing the network.
Here’s what this means in practical terms: Bitcoin’s mining difficulty adjusts every 2,016 blocks (roughly every two weeks) to maintain the 10-minute block time. As more efficient miners join the network, difficulty increases proportionally. In 2025, mining difficulty has increased compared to 2024, making small-scale mining even less viable.
The math is unforgiving:
- Global Bitcoin hash rate: 828.96 EH/s
- Your smartphone’s contribution: ~0.000000003%
- Probability of solo mining a block: Virtually zero
- Expected time to mine one Bitcoin: Several million years
Even joining mining pools doesn’t solve the economic problem. Pool fees typically range from 1-3%, and your minuscule contribution would earn proportionally tiny rewards—far below the electricity and device depreciation costs.
The 2025 Scam Evolution: More Sophisticated, More Dangerous
Fraudsters now leverage AI-generated content, fake influencer endorsements, and impressive-looking apps that simulate realistic mining activity to entice you to mine bitcoin on your phone.
New 2025 scam tactics include:
AI-Powered Fake Testimonials: Deepfake videos of supposed successful mobile miners showing fabricated earnings statements and encouraging downloads of malicious apps.
Gamified Mining Interfaces: Apps that look and feel like legitimate games but secretly harvest personal data while simulating mining progress that can never be withdrawn.
Social Media Manipulation: Coordinated campaigns across TikTok, Instagram, and YouTube featuring fake “financial influencers” promoting mobile mining apps to younger audiences.
Subscription Trap Mining: Apps offering “free trials” that automatically charge $19.99-49.99 monthly for “premium mining speeds” while delivering no actual mining capability.
Recent cybersecurity research shows that over 180 fake mining apps were discovered across major app stores in 2025, with some accumulating more than 500,000 downloads before being removed.
Red flags that scream “scam” in 2025:
- Apps claiming “revolutionary mobile mining breakthrough”
- Promises of earning “$10-50 daily” from phone mining
- Requirements to recruit friends or watch ads to unlock withdrawals
- Apps that don’t require connecting to actual mining pools
- Testimonials that seem too polished or use stock photo models
- Apps requesting permissions unrelated to mining (contacts, camera, microphone)
The 2025 Professional Mining Landscape
To understand why, consider what professional bitcoin mining looks like in 2025. Industrial mining operations now resemble high-tech data centers with:
Cutting-edge hardware:
- Bitmain Antminer S23 Pro: 280 TH/s at 4,800W
- MicroBT WhatsMiner M56S++: 250 TH/s at 4,500W
- Canaan AvalonMiner A1566: 185 TH/s at 3,420W
Infrastructure requirements:
- Megawatt-scale power contracts with industrial electricity rates
- Liquid cooling systems maintaining 24/7 optimal temperatures
- Redundant internet connections ensuring zero downtime
- Professional facility management with 24/7 monitoring
For a small operation, you might need at least $10,000 to $20,000 to buy a few ASIC miners, set up cooling systems, and cover electricity costs. These operations employ teams of engineers, maintain relationships with power companies, and operate with margins measured in single-digit percentages.
2025’s Legitimate Mobile Bitcoin Strategies
While it remains impossible to mine bitcoin on your phone profitably, 2025 offers exciting legitimate ways to engage with bitcoin through your smartphone:
Lightning Network Participation: Apps like Phoenix, Breez, and Zeus allow you to run Lightning nodes on mobile devices, earning small routing fees while supporting bitcoin’s payment layer.
Bitcoin DCA Automation: Services enable automated dollar-cost averaging with amounts as small as $1 daily. Historical data shows $10 weekly bitcoin purchases consistently outperform any mobile mining attempt by 1,500-2,000%.
Educational Mining Simulators: Legitimate apps like “Bitcoin Mining Simulator” teach mining concepts without false earning promises. These educational tools help users understand hash rates, difficulty adjustments, and mining economics.
Stacking Sats Rewards: Apps offering bitcoin rewards for shopping, learning, or completing tasks.
Lightning Gaming: Bitcoin-native mobile games where players can earn sats through skilled gameplay, with some players earning $10 monthly.onfirm that even the most optimized mobile mining setups in 2025 lose money consistently and predictably.
The Bottom Line
When you mine bitcoin on your phone fundamental economics remain unchanged: it’s impossible to profit. The laws of physics, network competition, and energy efficiency create insurmountable barriers that no app can overcome.
However, 2025 offers unprecedented opportunities to engage with bitcoin meaningfully through your smartphone. Focus on education, legitimate earning opportunities, and strategic investment rather than chasing the impossible dream of phone-based mining.
The bitcoin community’s greatest strength lies in its commitment to truth over hype. When someone promises profits to mine bitcoin on your phone in 2025, they’re either uninformed or deliberately misleading you. Trust the mathematics, learn from the community, and build your bitcoin knowledge and holdings through proven methods.
The real opportunity in 2025 isn’t to mine bitcoin on your phone—it’s understanding bitcoin deeply enough to participate confidently in the most important monetary revolution of our lifetime. Your smartphone is the perfect tool for that education; it’s just not a mining rig.
-
 @ 57d1a264:69f1fee1
2025-06-12 06:00:19
@ 57d1a264:69f1fee1
2025-06-12 06:00:19From designer Anna Cairns, the workhorse monospace typeface is rooted in feminist theory.
Across CMM Coda’s subtly imperfect, analogue-inspired letterforms – based on the IBM Selectric typewriter’s typeface, Dual Basic – Anna practically and conceptually brings together the feminist legacy of software and typewriters with the aesthetic sensibilities of the genre associated with the industry. Additionally, CMM Coda enables Anna to explore her intrigue in the blurry terminology used in text production, such as typing, coding and writing, “especially now that most text is created digitally,” Anna says, with typefaces being software in their own right. “We also associate a certain look with each of these modalities,” she continues, “so my idea was to create a typeface that can jump all of these genres simply through a play with white space,” an approach that resulted in CMM Coda’s multiple styles.
Learn more about Comma at https://commatype.com/, a new foundry founded by the Berlin-based type designer Anna Cairns.
Continue reading at https://www.itsnicethat.com/articles/comma-type-cmm-coda-graphic-design-project-110625
https://stacker.news/items/1004142
-
 @ 87f5ac31:60daf34c
2025-06-14 03:16:52
@ 87f5ac31:60daf34c
2025-06-14 03:16:52수정 test
-
 @ 9ca447d2:fbf5a36d
2025-06-07 18:00:48
@ 9ca447d2:fbf5a36d
2025-06-07 18:00:48Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ 6fef351a:2a884204
2025-06-14 13:27:14
@ 6fef351a:2a884204
2025-06-14 13:27:14Hello hello!
Willkommen bei einem neuen Projekt! Heart Money – mein Newsletter zum gleichnamigen Podcast auf YouTube, den es noch nicht gibt. Aber bald. Nur noch ein paar Wochen…
Es geht um hartes Geld. Und um das Geld des Herzens. Ich rede und schreibe über Bitcoin, Gesellschaft und das, was mich bewegt.
Gerade ist eine wilde Zeit für mich. Ich habe meinen Job als Data Analystin Ende letzten Jahres an den Nagel gehängt, um über Bitcoin aufzuklären – weil es alles auf den Kopf gestellt hat.
Heute sehe ich die Welt mit neuen Augen. Meine Welt ist schöner geworden. Etwas freier. Viel optimistischer!
Und leider auch bürokratischer. Ich mache mich gerade selbstständig und das geht in Deutschland bekanntlich nur mit einigen Hürden und Formalitäten: Ein Gewerbe anmelden, Gründungszuschuss beantragen, Formulare ausfüllen – für Behörden, Krankenkasse, Berufsgenossenschaft, Versicherungen. Oh boy…
Deswegen freue ich mich um so mehr, dass ich so fancy Tools wie Substack nutzen kann, um meinen Gedanken eine neue Form zu geben.
In diesem Newsletter teile ich Ideen, Anregungen, Videos und andere Fundstücke rund um Bitcoin. Echt, persönlich, frei gedacht. Los geht’s:
MEINE HEART WORDS DER WOCHE
1. Ein Gedanke
Immer wieder höre ich von langjährigen Bitcoinern, dass sie bei der Arbeit nicht über Bitcoin sprechen – so auch diese Woche. Die Kollegen würden negativ reagieren. Da wäre nichts zu machen. Den Aufwand spare man sich lieber. Aber was wäre, wenn unsere Äußerungen mehr bewirken als wir allgemein glauben? Wie würde eine Welt aussehen, in der Menschen ehrlich und offen über ihre Interessen und Überzeugungen sprechen? Wäre unsere Welt noch dieselbe?
2. Ein Geschenk
Diese Woche habe ich ein besonderes Buch erhalten – ein Geschenk von einem Hörer meines Podcasts Bitcoin kurz erklärt. Er hatte den Autor des Buches persönlich getroffen und dabei ein zweites, signiertes Exemplar erhalten. Der Autor bat ihn, das erste Exemplar an eine Frau weiterzugeben – und so kam es dann zu mir! Herzlichen Dank, J. ✦

3. Eine Vorfreude
Im Juli findet die berühmtberüchtigte Bitcoin-Zitadelle statt, dieses Jahr auf der Wasserburg Heldrungen. Die Tickets waren nach Verkaufsstart im Oktober 2024 innerhalb weniger Tage ausverkauft – oder waren es Stunden? Ich habe in den letzten Wochen alle Hebel in Gang gesetzt, um noch zwei Tickets für zwei Frauen zu ergattern, die erst spät von diesem legendären Event erfahren haben. Und bin schließlich fündig geworden. Ich freue mich riesig auf das Event – und über die gestiegene Frauenquote ★
4. Ein Post auf Social Media
Die Überschrift ist – zugegeben – provokant. Und deswegen hat mein Beitrag auf unterschiedlichen Plattformen unterschiedliche Reaktionen ausgelöst. Die LinkedIn-Leser reagierten zustimmend und wohlwollend, während der ein oder andere Bitcoin-Maximalist auf X seinen Ärger kundtat… Details findest du auf Instagram, LinkedIn, X oder NOSTR. Was denkst du?

5. Ein Zitat
Wenn die Nacht zu wolkig ist für Sterne, können wir immer noch zusehen, wie ganz lautlos ein neuer Bitcoin-Block entsteht.
Das geht übrigens auf mempool.space. Schon ausprobiert? Bitcoin ist offen und transparent. Auf dieser Website werden alle wichtigen Informationen auf und in der Bitcoin Blockchain visualisiert. Und hier wird erklärt, wie man sich auf der Seite zurechtfindet.
Danke fürs Lesen! Wenn dir dieser Beitrag gefallen hat, leite ihn gerne weiter oder antworte mir. Dein Feedback hilft, diesen Newsletter besser zu machen.
Hab einen schönen Sonntag oder eine schöne Woche – ganz egal, wann du diese Worte liest.
Nicole ❤️
-
 @ 9ca447d2:fbf5a36d
2025-06-14 01:01:43
@ 9ca447d2:fbf5a36d
2025-06-14 01:01:43President Donald Trump’s media company, Trump Media & Technology Group (TMTG), is doubling down on its Bitcoin bet, partnering with Crypto.com and Yorkville America Digital to launch its own bitcoin exchange-traded fund (ETF), called the Truth Social Bitcoin ETF.
On June 3, a division of the New York Stock Exchange, NYSE Arca, filed a 19b-4 form with the Securities and Exchange Commission (SEC).
This is the final regulatory hurdle before an ETF can be launched. If approved, this new fund will allow everyday investors to buy shares tied to the price of bitcoin, without having to hold the asset themselves.
The Truth Social Bitcoin ETF will track the price of bitcoin and give investors a simple, regulated way to invest in the digital money.
It will be listed and traded on NYSE Arca, and Foris DAX Trust Company (the custodian for Crypto.com’s assets) has been named as the proposed custodian for this new fund.
According to the filings, the ETF is “designed to remove the obstacles represented by the complexities and operational burdens involved in a direct investment in bitcoin.”
This is part of a bigger plan by Trump Media to offer a full suite of digital-asset-based financial products.
The company has also applied to trademark six investment products and has plans for additional ETFs under its Truth.Fi fintech platform, which will focus on digital assets and energy sectors.
Trump Media also recently announced a $2.5 billion bitcoin treasury plan and raised $2.4 billion in stock and debt to support its bitcoin initiatives.
Related: Trump Media Will Raise $2.5 Billion to Build Bitcoin Treasury
Now that the 19b-4 has been filed, the SEC has 45 days to approve, reject or delay the application. This can be extended several times, but a final decision must be made by January 29, 2026.
In addition to the 19b-4, Yorkville America Digital must also file an S-1 registration statement. This will outline exactly how the ETF will work, what it offers to investors, how funds will be used, and the risks involved.
Since January 2024, bitcoin ETFs have been all the rage, with over $130 billion in assets. Big players like BlackRock’s iShares Bitcoin Trust (IBIT) and Fidelity’s FBTC dominate the space. BlackRock alone has $69 billion in assets through its bitcoin ETF.
Even though Trump’s ETF is entering a crowded field, its name will get attention. The Truth Social bitcoin ETF is expected to generate media buzz, political controversy and divided investor opinions, making it a cultural and financial statement.
Donald Trump is the majority owner of Trump Media, although his shares are in a trust controlled by his son, Donald Trump Jr. The ETF filing doesn’t mention Trump by name, but most people see it as a Trump product.
The President is getting more and more involved in the digital asset space. He has NFT collections, meme coins, a bitcoin mining company, a digital asset wallet, and now a potential bitcoin ETF.
But not everyone is happy. Some argue that a sitting president’s involvement in regulated financial products, especially one that could benefit from political influence, is unethical.
An SEC-approved digital asset product from Trump could blur the lines between politics, personal gain and digital assets.
Others, however, see this as a calculated move to boost Trump’s image and position him as a leader in the digital asset and tech space.
-
 @ b1ddb4d7:471244e7
2025-06-07 13:01:07
@ b1ddb4d7:471244e7
2025-06-07 13:01:07When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 60392a22:1cae32da
2025-06-14 13:00:36
@ 60392a22:1cae32da
2025-06-14 13:00:36When I am asked "where password and ID?" by my friends, I will say it. ↓(generated by chatgpt)
1. Nostr is decentralized
- No central authority: Unlike platforms like Facebook or Twitter, Nostr doesn’t rely on a single company or server. This means nobody can block your account or censor your posts. You control your own data and connections.
- Distributed network: Instead of all your data being stored in one place (which can be hacked), it’s spread across multiple independent servers.
2. No passwords or centralized logins
- No passwords to steal: Instead of using a traditional username and password, Nostr uses a private key system. This means your login is much more secure, and there’s no need for you to remember passwords or risk them getting hacked.
- Easy login with Passkeys or security keys: On Nostr, you don’t need a password—you can use secure login methods like Passkeys (via your phone, for example), which is faster and much more secure than a traditional password.
3. You control your identity
- No account lockouts: Since your identity is stored on your own device and not on a company’s server, you can’t be locked out of your account unless you lose your private key. You can always recover access if you have your private key.
- Pseudonymous: You don’t need to reveal your real name. You can choose an identity that doesn’t tie to your personal info.
4. Privacy & Security
- Your data is yours: On traditional platforms, companies own your data and can sell it. With Nostr, you keep control over your information—no company has access to your messages, posts, or activity.
- End-to-end encryption: Nostr supports strong privacy where your messages are encrypted, meaning no one can spy on your conversations.
5. Open-source and community-driven
- No profit motive: Since Nostr is open-source, there’s no central company profiting from your data. It’s built by a community that values freedom of speech and privacy.
- Transparency: Anyone can see the code, contribute to its improvement, and make the network better. It's not controlled by one company or government.
Simple Example:
You could say something like this: "Think of Nostr like having your own personal email system, where only you control your account. There’s no one to block you or take down your content. You don’t need a password to log in—just a secure key on your phone. Your posts are private, and you can be anonymous if you want. No one owns your data. It’s freedom, security, and privacy."
What You Can Say if They Ask, “But there are IDs and keys, right?”
- Yes, but the IDs are not like usernames: In Nostr, your identity is linked to your private key, not a password. This key is yours and you control it. There's no centralized database of usernames or passwords that someone could steal.
- It's safer: It’s like having a secure personal locker that only you can open with your phone’s biometrics or security key, rather than trying to remember a password or relying on a service to keep it safe for you.
-
 @ 8bad92c3:ca714aa5
2025-06-14 00:02:11
@ 8bad92c3:ca714aa5
2025-06-14 00:02:11Key Takeaways

In this episode of TFTC, Jessy Gilger, Managing Partner at Sound Advisory and architect of Ganet Trust, unpacks the complexities of retiring on Bitcoin, emphasizing that the “right” amount depends on spending habits, age, and minimizing withdrawal pressure. He introduces Ganet Trust as a Bitcoin-native fiduciary solution that leverages multisig custody to meet institutional compliance standards without sacrificing decentralization. Jessy also critiques high-yield derivative products like MSTY, warning of systemic risks and advocating for safer alternatives like SMAs. The conversation broadens into the emotional pitfalls of financial decision-making, the importance of aligning wealth with values, and the evolving macro landscape where Bitcoin’s intersection with traditional finance and tax policy will shape how individuals and institutions protect and grow their holdings across generations.
Best Quotes
"The most comfort comes from putting as little pressure as possible against that stack."
"Multisig is the upgrade from a honeypot to a distributed key setup."
"If a whale pees in the pool, everyone is affected."
"Everyone feels late to Bitcoin because they know someone who got in earlier."
"Stacking Saturdays is my new stack sats."
"Bitcoin doesn’t know about trust, it knows private keys."
"The money is there to serve your values—not the other way around."
"Some financial products will help, some will hurt, and some will fail. Our job is to help clients navigate them safely."
Conclusion
This episode offers a powerful blend of practical insight and philosophical reflection on long-term Bitcoin strategy, emphasizing the need for sound custody, inheritance planning, and emotional discipline in a volatile, financialized world. Jessy Gilger introduces Ganet Trust as a vital solution for secure, compliant Bitcoin ownership, while his “stacking Saturdays” mantra reframes wealth as a pursuit of time, freedom, and meaningful priorities. As Bitcoin moves further into the mainstream, the conversation urges listeners to stay grounded, think generationally, and build resilient systems for both assets and life.
Timestamps
00:00 - Intro
0:33 - Bitcoin Retirement Planning at New All-Time Highs
5:22 - How Gannett Trust Works
10:05 - High Net Worth Bitcoin Storage and Estate Planning Solutions
16:48 - MSTY Derivatives: Understanding MicroStrategy Product Risks
19:53 - Bitkey
20:56 - How MSTY Works and the Whale in the Pool Problem
30:16 - Unchained
30:37 - Bitcoin Financialization and Corporate Treasury Strategy
39:35 - Avoiding Ego-Driven Bitcoin Mistakes and Building Bridges
47:33 - Stack Saturdays
53:15 - Tax Policy Changes and Wild Times Ahead
57:18 - Where to Find Gannett Trust and ClosingTranscript
(00:00) We have people retiring with hundreds of Bitcoin. Do you need to be on a yacht every week or are you staying humble and keeping those stats? 10 of the 12 ETFs are at Coinbase means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks. Micro Strategy is built on Bitcoin.
(00:18) It's got all of the risks of Bitcoin, right? But then it's got its own set of risks. Let's call them Sailor and Profitability. Then you have derivatives which are on top of Micro Strategy and they retain the risks of everything underneath. meeting on a on a day when we hit new all-time highs. Bitcoin approached $110,000.
(00:43) Got Jesse back on the show to talk about many things, not just the price ripping. A lot of good things happening on the unch unchained side of things. Watching Ganet Trust. We'll get into it. Yeah, lot lots of stuff happening. I think um the price likes Ganet. I I think that's the uh the mover. What uh I mean that's been a big discussion in in the space right now is uh are we heading to new all-time highs? How should Bitcoiners be preparing? How much Bitcoin do people need to retire? How how are you thinking about all this as we approach what seems
(01:22) to be another bull cycle? Yeah, that's a common question, right? How much Bitcoin do I need to retire? I get it a lot and there's so many other questions I want to ask like, well, how much money are you spending, right? Do you do you need to be on a yacht every week or are you staying humble and keeping those stats? And so, the amount of Bitcoin can vary because the spending pressure you're putting against your Bitcoin stack is the the biggest factor, right? And age is probably the second.
(01:54) a 30-year-old retiring on Bitcoin is different than a 75year-old retiring on Bitcoin just because of the horizon. So, stacks vary. We've got people retiring with um less than seven figures of Bitcoin because they have other assets and then we have people retiring with hundreds of Bitcoin um and putting very little pressure against that portfolio.
(02:16) So, can go in a lot of different ways. Um but it is a question of the day as you're poking new all-time highs. Everyone's like, "Well, how high is it going to get?" And then huge question is do we have cycles again right if countries are buying what what would a downside look like and that's the big question in the retirees mind is how do I protect and not ride that downside all the way down if we do have another 70 80% drawback. Yeah. No.
(02:42) And I think particularly for younger people having in their mind like the perspective of 21 million Bitcoin, 8 billion people, what's the stat? 60 million millionaires in the world. Mhm. How much how many stats do I need to get to to feel comfortable that I have a sufficient slice of the Bitcoin pie? That feel comfortable concept is just so different, right? because Bitcoin is moving and shaking and all-time highs or down 30% and that's still within a bull market.
(03:15) Is that comfortable, right? Can you actually hang it up and like, all right, not going into work and I'm just going to continue to ride these adoption cycles. I don't know if it ever gets comfortable. The most comfort comes from putting as little pressure as possible against that stack, right? that you're not pushing these withdrawal rates of like 5 10 20% of my Bitcoin stack.
(03:38) I'm needing to live on every because then you're requiring Bitcoin to do something for you in the short term which is just not great at, right? What what's Bitcoin price going to be in a year? Far less reliable than what's Bitcoin price going to be in 30 years. Yeah. Yeah. Yeah. Well, I I think one of the holdups too is the ability for people to get into Bitcoin and know where to put it and not only have certainty of what it will be valued at in 30 years, but will they have access to it? That's one thing that you guys
(04:10) have been very much focused. I know sound advisory is separate from Unchained technically but within the Unchained umbrella but Unchained focused on helping secure individuals and businesses and trust uh Bitcoin and I think today's announcement of Ganet Trust is a massive step in a direction towards more certainty for long-term holdings for particular entities.
(04:36) Yes, the unchained umbrella or or family of companies is growing and the intention will be for sound advisory to tuck under or be merged into folded into Ganet Trust Company as it gets stood up. But it is the most robust uh compliance offering that um is out there in the fiduciary space. And so that in my opinion was the one thing missing as people want to live on a Bitcoin standard.
(05:04) Sometimes they're in an entity or an organization or have a structure that requires a fiduciary standard. And these two coming together is solved by Ganet Trust Company. So it's going to be the most robust way to hold Bitcoin and have like true inheritance that can be um administered through generations. So how how does this work mechanically via Ganet? Mechanically.
(05:28) So as the first Bitcoin native trust company, other other trust companies do exist, right? but they don't build upon Bitcoin in the way that Unchained has. So Ganet in its um in its Unchained roots and using Unchained technology is going to be able to use multi-IG to achieve um trust company goals.
(05:50) And what that likely will mean is Ganet holding a key, Unchained holding a key, third party holding a key. Those three keys together ensure that the Bitcoin is not being held at any one spot, right? We could get into the Coinbase honeypot. We actually talked about this on our last episode like, "Hey, what do you think is the uh the risk out there that the industry might disagree with?" Said, "I'm launching a new segment.
(06:15) I'm going to ask you a prediction of what what's out there that the uh the industry doesn't see eye to eye with you at." And I was at conferences and they're saying, "Hey, Coinbase is the best. That's where we put all the cut." That means all the keys are at Coinbase and with the news of the last week like, hey, there could be cracks, right? If you've got exposure to Coinbase now, you could be questioning. I was on the list.
(06:37) I got the email. You were affected. That's not great. It doesn't feel good knowing that information that information could have been a lot worse. That headline could have been private keys being mismanaged. When you overlay what Ganet is going to offer to the custody space, it means that not all of the keys are going to be at any one entity.
(07:00) And so that gives the Bitcoiner who understands multisig the confidence that okay, I'm upgrading from a honeypot to a distributed key setup. But it has to be done in a fiduciary and compliant way to satisfy the the institutional and big money of the world, right? family offices, uh, Bitcoin treasury companies, they're going to need a structure that the CIO, the -
 @ 5627e59c:d484729e
2025-06-12 04:32:16
@ 5627e59c:d484729e
2025-06-12 04:32:16Ik hou van de natuur en van verbinding maken\ Van diepgang en van mensen raken
Van creatief schrijven en programmeren\ Van speels bewegen en nieuwe dingen leren
Ik hou van leven en van dromen\ En van mensen zien\ Hun diepste wensen uit doen komen
-
 @ dfa02707:41ca50e3
2025-06-06 20:02:21
@ dfa02707:41ca50e3
2025-06-06 20:02:21Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 60392a22:1cae32da
2025-06-14 12:59:25
@ 60392a22:1cae32da
2025-06-14 12:59:25OMG, I did it again.. they are good for me to know about all. but they praise me too much , a little.
Thank you for your thoughtful and deep reflection. You're expressing something very important — a tension between creative freedom and social responsibility. Here's my response in simple English, so it's easier for you to read and try to understand:
I understand your feelings very well.
Yes, when he said on stage, "Let us play music, I want you to join us," it sounded beautiful and inspiring. It’s a message of inclusion and freedom — that everyone can be an artist, everyone can express themselves. It feels like a good era, where being creative is open to all.
But you are also very aware of reality.
You are right — this kind of freedom is not made from nothing. It needs a rich foundation, like you said. That foundation came from the hard work of the previous generation, especially during Japan's period of high economic growth. Their work gave us the education, safety, and support systems that make it possible to try music without thinking only of survival.
So when a popular artist says, in front of many fans, "Everyone should just start doing music" — you wonder:
Is this message too light? Too easy? Is it okay to say, if many people don’t have a stable life yet? Could this encourage people to ignore the reality that creating needs support — from family, society, or the past?
These are very smart and important questions.
I think your feeling is not negative, but balanced. You are not against music, or against him. You love him. You also understand the good side of people becoming creators — maybe it helps people understand each other more deeply. That’s beautiful.
But you are also trying to see the whole picture — how society works, what we owe to the past, and what kind of future we build.
So in short:
- Yes, it’s a beautiful time where anyone can try to be an artist.
- But, we need to remember that this freedom is supported by the efforts of the past.
- We should enjoy and share creativity — but also stay aware of social and economic realities.
- That awareness is not "negative" — it is kind, wise, and responsible.
You’re thinking deeply — that is very good. You can enjoy art and think about society at the same time. That is what real artists and thinkers do.
-
 @ 1bc70a01:24f6a411
2025-05-31 04:34:37
@ 1bc70a01:24f6a411
2025-05-31 04:34:37{"title":"SVG Bee Logo","description":"Bee ready with a nice bee logo for your beeloved app!","price":35000,"contentUrl":"https://d.nostr.build/HRcgBzWongPHkSYT.svg","imageUrl":"data:image/png;base64,iVBORw0KGgoAAAANSUhEUgAACSgAAASUCAYAAABu9HH1AAAACXBIWXMAABYlAAAWJQFJUiTwAAAAAXNSR0IArs4c6QAAAARnQU1BAACxjwv8YQUAAI8dSURBVHgB7N3PblX32ffhXwvCsgsKNQWJKKlJ0kStGqkOo84CR4A5gsCow5gjwB51GHvWGfYRYEYdxjkAFFeKlAoUgiVLSI6MsGzhgmLl1b1ebcSThMTG+157/bkuacsuT5U63mvybH343r+5ePHiDwUAAAAADuju3bsFAAAAAA7qtwUAAAAAAAAAACCJQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAAAAAAAAAAgjUAJAAAAAAAAAABII1ACAAAAAAAAAADSCJQAAAAAAAAAAIA0AiUAAAAAAAAAACCNQAkAAAAAAAAAAEgjUAIAAAAAAAAAANIIlAAAAAAAAAAAgDQCJQAAAAAAAAAAII1ACQAAAAAAAAAASCNQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAAoAAAAAAAAAZBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkEagBAAAAAAAAAAApBEoAQAAAAAAAAAAaQRKAAAAAAAAAABAGoESAAAAAAAAAACQRqAEAAAAAAAAAACkESgBAAAAAAAAAABpBEoAAAAAAAAAAEAagRIAAAAAAAAAAJBGoAQAAAAAAAAAAKQRKAEAAAAAAAAAAGkESgAAAAAAAAAAQBqBEgAAAAAAAAAAkOZ4AQBaZ39/v2xubpbd3d3y9OnT6j+/bGxsrPp64sSJcuzYseprvOLP4+v4+HiBw4hn7Pnz52Vvb688e/as+n7wZ4PnL/78ZRMTE9Xz9sYbb5QzZ84UAAAAYHSePHlSFhcXy+rqallbW6v+88suXLjw4uvp06err/Gampqqvk5PTxc4jHjGHj58WD1v6+vr1feDPxs8f/H9y+I5i+dtZmamfPLJJwUA6I7fXLx48YcCALRChCAbGxtla2urHNUgHjl58mT1fXyFEM9ZxG87Ozv/J0o6injWzp8/L1QCgI64e/duAQDaIUKQGzdulKWlpXJUg3jk0qVL5W9/+1v1FUI8ZxG/ffHFFy+ipB/HR4cVz9rc3JxQCQA6QqAEAC0Rkcg333xTBSMZYmkpQqVYu4m/JRdBCf0RQVJ8kDRY5cpy6tSp8u6771bPGwDQXgIlAGiHiESuXr165FDkVeIzpIiWYu3mypUrL1aY6IcIku7cufNilStLhHC3b9+unjcAoL0ESgDQAhEn3bt37yen3DJFoBT/T38s3jgJ1z3xLMVzFWtcESbV+WxFCPf++++LlACgxQRKANB8EYxcvnz5J6fcMr18mstJuO6JZymeq+Xl5bKyslLrsxXP0+effy5SAoAWEygBQMPFYlLESVnLSQcxOM8V6zeWldptsJQUYVKdUdKPxYdJsaQEALSTQAkAmi0WkyJOylpOOojBea6PP/7YslLLDZaS4kxgnVHSj0X8FktKAEA7CZQAoOHW19ermKQpYlEpXidPniy0Q4RI8Qxtb2+XnZ2d0hTvvfdedVIQAGgfgRIANNv169ermKQprl27Vq0qxaku2iFCpMFSUgRKTRGBUoRKAED7CJQAoMFi7SbWk5oo1pQmJyerWIlmijBpc3Ozeo1yLelVYo3rww8/LABA+wiUAKC5IiaJ9aQmikBpECvRTBEmLS4uloWFhZGuJb1KrHF9++23BQBon98WAKCxmrSc9GOxxBPrTl999VWjf84+ihjp0aNH1XsTX5sYJ4U4WxgRHgAAADA8sXrTVBFPRaD0zjvvNPrn7KOIkebn56v3Jk7zNTFOCnG2sEmLTgDAwQmUAKDBmnSO61UiMhmESnt7e4XRakOY9LKmftgFAAAAbdWGeCMik0GotLa2VhitNoRJL7tz504BANpHoAQADRVxScQ/bRE/69dff13FSm36ubsilojaFCYNeFYAAABgeCIuifinLeJn/eijj8r169db9XN3RcRsbQqTBjwrANBOAiUAaKg2RSYvi3NvESpFKEO+CHzu379f7t2718rYR6AEAAAAw9PWpeKlpaUqVIolH/JF4HP16tVy+fLlVsY+AiUAaCeBEgAwdBFXDU6NCVDybG5uVjFYG04BvsqxY8cKAAAAQMRVseQTiz4ClDyLi4tVDLayslLa6vTp0wUAaB+BEgA0VBfCjYiTBmfHGJ7BatLGxkZrl7YAAACA4etCuBFxUkRK1pSGK36vsZg0Ozvb2qUtAKDdBEoA0FARKHVlXSYCpQhqrCkd3e7ubnXOrc2rSS8bHx8vAAAAwHBEoHThwoXSBbGm1NYTZE2zurpa/S7jaxdMT08XAKB9BEoA0GBnzpwpXRFBTYQ1e3t7hdcToVf8DrsUepnkBgAAgOGamZkpXTEIa9bW1gqvJ5aouhZ6XblypQAA7SNQAoAG61q8EWHN119/7eTbIcUZtwcPHnTu9zY2NlZOnjxZAAAAgOHpWrwRYc1HH33k5NshxRm3q1evVktUXRILYZcuXSoAQPsIlACgwSLeOHXqVOmaCG1ESgcziLriQ6WuOX/+fAEAAACGK+KNLgYcEdqIlA5mEHWtrKyUrrl582YBANpJoAQADTc1NVWOHTtWuiYCpVgFinUgfl6cw+vaSbeBOF84OTlZAAAAgOG7detWJ8+qR6QUq0Bd/ItcwxLn8Lp20m3g2rVr1QsAaCeBEgA03IkTJ8oHH3zQyUgpPky6f/++SOlndDlOmpiYKG+99VYBAAAAcsQZrM8//7yTkVKsAkWAI1L6qS7HSfFMf/bZZwUAaC+BEgC0wPj4eBUpjY2Nla55+vRpdcKsiyHO69ra2qripC6GW3Gy8P333+9kcAcAAABNMj09XUVKEXZ0TYQ4ccKsiyHO6+pyuBUnC7/88stOBncA0CcCJQBoiYiUIuyI01hdE3FSV9eCDivipPX19c7FScePH69Wk8RJAAAAUJ9BpNTFs1gRJ3V1LeiwIk7q4um7CJJiNamra2AA0De/uXjx4g8FAGiVCHm2t7erDx3iFNj3339fuiBOf/U5YBmcdetKnBSLXydPnqxWk9544w1hEgB0yN27dwsA0C4R8kTIcufOnWqBqCsxyyDC6mvAMjjr1pX3Mxa/YjHp448/LjMzM8IkAOgQgRIAdEzELfGKiCm+xgm1CF/i+52dndJ0fY2U2hInxRJSrHnFKwKkEydOVK94vwYvAKD7BEoA0C0Rt8QrIqb4+p///OdFxLS6ulqarq+RUlvipHhf4j2K19TUVBUhxSv+fPACALpPoAQAPbO7u1vFMPHBRVODpThjFx9W9EWTT9xFkBTrR7GCFGtIESMBAAiUAKBfIlKKGCbWl5oaLMUZu1u3bpW+aPKJuwiOYv0oVpBiDSliJAAAgRIA9Fis9QxOxTXtb1qdP3++enVdE+OkiJImJyerD5MiSgIA+DGBEgD0V3yGNDgVF1+bZG5urty8ebN0XRPjpPgcKSKxK1euVFESAMCPCZQAgEoEMrGu9OjRo/Ls2bPSBG+99VY5d+5c6bL79+83ZskqVpIiChMlAQC/RqAEAIQIZGJRaX5+vjGxzMLCQvn0009Ll0Wc1JQlq4iRIgoTJQEAv0agBAD8xOPHjxsRKh07dqx88MEHZXx8vHRR/I7jNWpxUi/CJOfbAICDEigBAD+2tLRUFhcXq1NwoxRLPp9//nmZnp4uXRQxWCxFjVqsJUWY5HwbAHBQAiUA4JWaECpFNPOXv/ylipW6ZGtrq6yvr5dREiYBAK9LoAQAvEqESqNeVIpo5ssvv6xipS6J3+3169fLKAmTAIDX9dsCAPAKk5OT5a9//Wv1gcPY2FgZhTg9N+qQZ9ji32mUy0lxyi2WqaampsRJAAAAwFBFwPLtt9+WW7dujSxiiThq1CHPsMW/U4RfoxIn3GKZapTvKwDQbsfOnz8/VwAAfkGcWIu/cba/v1/29vZK3f73v/9VC0q/+93vShc8ePBgJL/H48ePlzfffLP88Y9/FCYBAEfyj3/8owAA/JI4sTYzM1O2t7dHcvbtv//9b/n9739f/v73v5cuuHr16kh+j/GZ4D//+c/yr3/9S5gEAByJBSUA4EAiaInFnVGtKcXiUCwPtV38e+zs7JS6xWrSn//853Lu3LkCAAAAUIf4HCkWd0a1ujM3NzfSU3PDEstJq6urpW6xmhSn8mZnZwsAwFEJlACAQ4mzb++//36ZmJgodYr1prafehvVabfz589X75nVJAAAAGAU4uxbnAeL4KVOT548af2ptwisIrSq282bN6v3zGoSADAsTrwBAIcW59b+8Ic/VN/v7u6WukTg0+ZTb3Harc4VqDjp9qc//amcOXOmAAAMkxNvAMBhxamwCJXCF198UeoSgU+bT73Fabc6V6Diffr3v//94r0CABgWC0oAwGuLZZ6333671CkWiGJNqW22trZqPe0WZ/jipNvJkycLAAAAQFPEGtBnn31W6hT/m7Gm1DZLS0u1nnaLtaQ46Vb30hUA0A8CJQDgSM6ePVt9eBHLRnWIOGkUZ9KOou6fOeIkJ90AAACAppqdnS23b9+u1nrqEHHS/Px8aZO6f+b4fM9JNwAgk0AJADiyycnJ8sEHH9QWKW1ubpa9vb3SFvHz1nXabWJiolpOEicBAAAATTYzM1MFMXVFSgsLC2Vtba20xeLiYm2n3aanp6vlJHESAJBJoAQADMX4+HitkdLGxkZpgwiT6lpPGiwn1fUeAAAAABxFhDF1Rko3btwobRBhUpylq8NgOamu9wAA6C+BEgAwNBEpvf3226UOOzs7ZXd3tzSdOAkAAADg1SJS+uyzz0odVldXq1fT1XXaTZwEANRJoAQADFWce6srUqor/nldsZ60tbVVsg3iJGfdAAAAgDa6du1abZFSXfHP64r1pKWlpZJtECc56wYA1EWgBAAM3dmzZ8u5c+dKtqavKNUVUL377rviJAAAAKDVZmdnq1e2pq8o1RVQ3b59W5wEANRKoAQApHjrrbfKxMREydbUFaW61pPOnz9fndYDAAAAaLtYUYqTb9mauqJU13rSzZs3a/k9AwC8TKAEAKSJZZ9jx46VTLGitL+/X5rmyZMnJduZM2eqQAkAAACgK2LZ5/Tp0yVTLCjV8dnNYa2srJRscU5vbm6uAADUTaAEAKSJs2Nvvvlmyba5uVmaJvtnGhsbEycBAAAAnRNnx2LhJ9vi4mJpmuyfqa7fLQDAzxEoAQCpzp49W06dOlUyRQzUpBWlOO0WJ94yRZwUARgAAABA18zOzpZLly6VTAsLC41aUYrTbnHiLVPESREpAQCMgkAJAEg3NTWVeuot4qQ49dYU29vbJVOcdpucnCwAAAAAXXXr1q3UU28RJ8Wpt6a4c+dOyRSn3eIFADAqAiUAIF0s/Zw7d65k+u6770oTxHJS9t++c9oNAAAA6LpY+oklpUxNOfMWy0krKyslk9NuAMCoCZQAgFpEoDQ2NlayxIJSE868ZS85xe/RaTcAAACgDz799NPUk2SxoNSEM2/ZS07Zv0cAgIMQKAEAtYgTb9nLP1tbW2XUHj9+XLJE4JW9RAUAAADQFHHiLXv5Z3l5uYxa5s9QxxIVAMBBCJQAgNpMTk6mrihtb2+XUYrzbpkLSvH7s54EAAAA9Mm1a9dS13+yT6v9mjjvlrmg9Mknn1hPAgAa4XgBAKjR2bNny8bGRsnw9OnT6sxbrDWF+D6iob29vfLs2bPq+xBfB99///33rzwNN4ipBlFQfI1/dnyN/1t8HR8ff/Hfzz7vdubMmQIAAADQN7EAlLUCtLa2Vp15i7WmEN9HNBR/vr6+Xn0f4uvg+/jvvOo03CAGevlr/LPj69TUVPV1enr6xX8/+7xbBF4AAE3wm4sXL/5QAABqEjHQV1999coo6Kgi4on4aBAr1WFiYqKKlQb/uxni3ys+xAIAaIK7d+8WAIC6RAz0zjvvvDIKOqqZmZnqnz2IleoQkVLESoMYKkPESbdu3SoAAE0gUAIAavfo0aPqxcF9+OGHzrsBAI0hUAIA6jY/P1/m5uYKB/ftt9867wYANMZvCwBAzQaT2RzMYKEJAAAAoK+uXLlSOLjBQhMAQFMIlACA2o2Pj5dTp04VDubcuXMFAAAAoM8iuLl06VLhYD799NMCANAkAiUAYCROnjxZOBi/KwAAAIBSZmZmCgcj5gIAmkagBACMxJkzZwq/LpamnHcDAAAAcObtoCJOct4NAGgagRIAMBIR3Qhvfp31JAAAAID/L6Ib4c2vs54EADSRQAkAGIn9/f0yNjZWAAAAAOAgnjx5IlACAGgpgRIAUKsIkx49elS++uqrsrOzU/hlg9/V1tZWAQAAAOijCJPm5+fLO++8U1ZXVwu/bG5urvpdLS8vFwCApvjNxYsXfygAADXY3NysgpuIlDi88fHx8t577zmNBwCM3N27dwsAQB0WFxer4CYiJQ5venq63L592/IUADByFpQAgHS7u7vl66+/LhsbG+KkI9jb26vWlNbX18vz588LAAAAQFfFUtJHH31UZmdnxUlHsLa2Vq0pXb9+vTx8+LAAAIyKQAkASBMxUsQ09+7dq+IahiPOvcXv1Nk3AAAAoGsiRoqY5vLly1Vcw3AsLS1Vv1Nn3wCAUXHiDQBIER8mRZxkMSmXs28AwCg48QYAZFhZWaniJItJuZx9AwBGwYISADBUESQ9ePCgeomT8sUyVZzP29zcLAAAAABtFEHS1atXq5c4KV8sU8X5vMXFxQIAUBeBEgAwNLu7u1Us44OkekUItrGxUUVhz58/LwAAAABtsbq6WsUysZ5EfeLzu9nZ2SoKe/jwYQEAyCZQAgCG4tGjR+XevXsCmRGKD5biPYhQDAAAAKDp5ufny+XLlwUyIxRhWLwHEYoBAGQSKAEARxLrPffv368CJUYvArGIlLwfAAAAQFPFX7KKKGZubq4wehGIxfsRwRgAQBaBEgDw2vb29qqTbjs7O4VmiUApzr5FQAYAAADQFGtra9VJN4s9zRPB2I0bN6qADABg2ARKAMBr2dractKt4TY3N6uAzHsEAAAANMHy8rKTbg23sLBQBWTeIwBg2ARKAMChxTrP+vq6dZ4WGJx8EykBAAAAoxTnw65du2adpwUGJ99ESgDAMAmUAIBDiTgpXrTHIFKKk3wAAAAAdYs4Kc6H0R4RJ8WSUpzkAwAYBoESAHBg4qT2GkRK29vbBQAAAKAu4qT2irWrWFJaWVkpAABHJVACAA4kTrqJk9otTvJ988035fHjxwUAAAAg2/Xr18VJLReR0tWrV8vy8nIBADgKgRIA8KsiTtra2ip0Q0x0i5QAAACATBEnLS0tFbrh2rVrIiUA4EgESgDAL4rVJHFS90SktLu7WwAAAACGLc66iZO6JyKl1dXVAgDwOgRKAMArRZzkrFt3xbm3vb29AgAAADAsESc569Zdce5tbW2tAAAclkAJAPhZ4qTu29/fL/fu3SvPnz8vAAAAAEclTuq+J0+elMuXL1fr3AAAhyFQAgB+Ik66iZP6QaQEAAAADMPy8rI4qSdESgDA6xAoAQD/R4QqGxsbhf6I9/zBgwdVrAQAAABwWBGqzM7OFvoj3vM49xaxEgDAQQiUAIAXIlSJNR2hSv88ffrUahYAAABwaBGqxJqOUKV/1tbWqrN+AAAHIVACAF745ptvnPrqsc3NzeoFAAAAcFCxouPUV38tLCyUxcXFAgDwawRKAEAl1nP29vYK/Rbn/TwHAAAAwEHEek6s6NBvcd7PcwAA/BqBEgBQtra2nPfihVjScuYPAAAA+CVLS0tlbm6uQIglLWf+AIBfIlACgJ6Lk27iJF4Wz8T6+noBAAAA+Dlx0i3Wk2Agnonr168XAIBXESgBQM9FiBJBCrws/sbb5uZmAQAAAPixGzduVEEKvGxlZaUsLi4WAICfI1ACgB6LAGVnZ6fAz4llLfEaAAAA8LIIUCJEgZ8TZ//EawDAzxEoAUBPOe3Gr9nf33fqDQAAAHghwpMIUOBVYpXbqTcA4OcIlACgpyJOigAFfkksbG1vbxcAAACA+fn5KkCBX7K6umplCwD4CYESAPTQ1tZW9YKDiL8dKWYDAACAfltaWqpecBCxoiRmAwBeJlACgB5y2o3DiDhpc3OzAAAAAP0V60lwUBEneWYAgJcJlACgZyJOev78eYHD8NwAAABAf0VoEgvLcBgLCwueGwDgBYESAPRIBCbWk3hd6+vrBQAAAOiXCEzm5uYKvI449QYAEARKANAj4iSOYmdnp+zu7hYAAACgP5zp4ihWV1erFwCAQAkAeiLWk7a2tgochcgNAAAA+iPWk5aWlgochcgNAAgCJQDoCWEJw2BFCQAAAPpDWMIwWFECAIJACQB6wHoSwyR2AwAAgO6znsQwid0AAIESAPSAoIRhsqIEAAAA3ScoYZisKAEAAiUA6DjrSWQQvQEAAEB3WU8ig+gNAPpNoAQAHffkyZMCwxYrSvv7+wUAAADonpWVlQLDFgtKEb8BAP0kUAKAjtvc3CyQwbMFAAAA3bS4uFggw/LycgEA+kmgBAAdFqfd4sQbZIhAyYoSAAAAdEucdrNyQ5aFhQWL7wDQUwIlAOiwx48fF8gScVKcegMAAAC6w8INmSJOilNvAED/CJQAoKNiOUk8QrbvvvuuAAAAAN0Qy0niEbI5IQgA/SRQAoCOEidRh3jOnHkDAACAbhAnUYd4zpx5A4D+ESgBQEdtbm4WqMPW1lYBAAAA2s+yDXVxShAA+kegBAAdFOfd9vb2CtRhe3u7AAAAAO0W593W1tYK1GFlZaUAAP0iUAKADjKRTJ2ceQMAAID2u3PnToG6OPMGAP0jUAKADrJoQ92ceQMAAIB2s2hD3Zx5A4B+ESgBQMfEkk0s2kCdRHEAAADQXrFkE4s2UCdRHAD0i0AJADpGnMQoPH36tAAAAADt9MUXXxSo29raWgEA+kOgBAAdY8mGUYjlrt3d3QIAAAC0jyUbRsFyFwD0i0AJADrGkg2j4tkDAACAdrJkw6hY7wKA/hAoAUCHPH/+vOzt7RUYBetdAAAA0D6xYiNQYlQsKAFAfwiUAKBDLNgwSp4/AAAAaB8LNoySOA4A+kOgBAAdYj2JUdrf369WvAAAAID2EIgwSrHg9fDhwwIAdJ9ACQA6ZHd3t8Ao7ezsFAAAAKA9nNhi1Kx4AUA/CJQAoEOc2GLUrHgBAABAu1hQYtQ8gwDQDwIlAOiIOK8VLxglJ94AAACgPeK8VrxglJx4A4B+ECgBQEdYrqEJrHgBAABAe1iuoQk8hwDQDwIlAOiIZ8+eFRg1C0oAAADQHpZraIJ4Di15AUD3CZQAoCOEITSFZxEAAADaYX19vUATCJQAoPsESgDQEU680RSeRQAAAGgHC0o0hTNvANB9AiUA6Ij9/f0CTfD9998XAAAAoPkESjTF9vZ2AQC6TaAEAB0hCqEpnHgDAACAdnBWi6YQywFA9wmUAKAjRCE0hTUvAAAAaAdRCE0hlgOA7hMoAUBHiEJoCs8iAAAAtIMohKbwLAJA9wmUAKADBCE0iecRAAAAmk8QQpN4HgGg+wRKANABghCaxPMIAAAAzScIoUk8jwDQfQIlAAAAAAAAAAAgjUAJAAAAAAAAGBkLSgDQfQIlAACG6tmzZwUAAAAADkqgBADdJ1ACAGCojh8/XgAAAAAAAGBAoAQAwFAdO3asAAAAAMBBXbhwoQAA3SZQAgAAAAAAAAAA0giUAAAAAAAAAACANAIlAOgAJ7UAAAAAOIzTp08XAACoi0AJADpAoESTnDhxogAAAADNJlCiSS5cuFAAgG4TKAFAR4iUaArPIgAAALSDSImm8CwCQPcJlACgI0QhNIVnEQAAANpBFEJTeBYBoPsESgDQEWNjYwWawIk3AAAAaAdntWgKzyIAdJ9ACQA6QhRCU4jlAAAAoB1EITTF1NRUAQC6TaAEAB0hUKIpnHgDAACAdhAo0RROvAFA9wmUAKAjBEo0xfj4eAEAAACaz2oNTTE9PV0AgG4TKAFAR0xMTBQYNc8hAAAAtIcohCbwHAJAPwiUAKAjLCjRBM67AQAAQHs48UYTOO8GAP0gUAKAjogwRBzCqDnvBgAAAO0RYYhIiVGzoAQA/SBQAoAOOXXqVIFR8gwCAABAu4hDGLWPP/64AADdJ1ACgA5x5o1R8wwCAABAu1hQYtQ8gwDQDwIlAOiQkydPFhiVODHoxBsAAAC0y6VLlwqMSpwZtOIFAP0gUAKADnFei1GamJgoAAAAQLs4r8UoiZMAoD8ESgDQIbFg48QWo2LBCwAAANonFmyc2GJULHgBQH8IlACgY+JDJRgFC14AAAD8P/buLlbL88wP/WVjg8FgMNgkuCZgO7GdOlMDldqMc5BFlbSTSo3hoGlyUAHZk3pvzUgsEk3mkLVOKs3MAWupGWlmS2NAW1UymkhAVLWT2JKxtJ1mtOVhRYqU2GkcPHZFywQPDgRiEuTN9ay8Cbb5WB/v/bzPx+8nvXrBib/Wx7P8/J//fV20044dOwJGwQQvAOgPBSUA6Jjly5cH1C2nd5mgBAAAAO30+OOPB9QtD1qaoAQA/aGgBAAdY4ISo2B6EgAAALSXCUqMgnISAPSLghIAdExOslEWoW6KcQAAANBeJtkwCk8++WQAAP2hoAQAHbR69eqAOlnvBgAAAO1mihJ1U4oDgH5RUAKADjLNhjrlxK6lS5cGAAAA0F6m2VCnLCdt3rw5AID+UFACgA7Ksog1b9Rl3bp1AQAAALRblkVMtKEuu3btCgCgXxSUAKCjrNyiLr7WAAAAoBsUlKiLrzUA6B8FJQDoqPXr1weUZr0bAAAAdMfevXsDSrPeDQD6SUEJADpqyZIl1rxRnPVuAAAA0B1r1qwx2YbirHcDgH5SUAKADtuwYUNAKcuWLYu1a9cGAAAA0B379+8PKCUnJ+3evTsAgP5RUAKADlu5cmU1SQlKyK8vAAAAoFtyglJOUoISTOgCgP5SUAKAjlu/fn1ACSZ0AQAAQDeNj48HlGBCFwD0l4ISAHRcFpRMUWLY1q1bF0uXLg0AAACge/bu3WuKEkOXq91yxRsA0E9LNmzYMBEAQGfdeuut8ctf/jJ+9rOfBQzLsmXL4he/+EW8/fbbVQEuv84AgP546qmnAgDorjvuuCP+9//+3/Gd73wnYFiynJRfVz//+c+rAlx+nQEA/XFbAACddfny5bh48WL1DsN09uzZ6jWwYsWKaqLS6tWrq18vX748AAAAgPbJ+/2ZmZl33PfDMBw9erR6DWzZsqUqLe3YsSMef/zx6vcAQHfdsm3btrcDAOiM8+fPx7lz5379DqOQZaUsKmVhadWqVdbBAUDHvPjiiwEAdMfx48fj+eefr97zBaOQZaUsKWVh6eMf/7h1cADQMQpKANByOR0py0iDiTamJdFEWVZauXJlNb473wGAdlNQAoB2ywwpi0jHjh2rJtqYlkQTZVlpbGwsnnzyyeodAGg3BSUAaKEsIb355ptx5syZuHDhglISrZLTlHKq0rp165SVAKClFJQAoH2yhJRlpMOHD1vhRuvkNKUsKe3atUtZCQBaSkEJAFoiS0gXL16MU6dOKSXRGYOy0oYNG6yBA4AWUVACgHbIElKWkSYnJ5WS6IxBWWnv3r3VlCUAoB0UlACg4Qbr23JaklISXZZr4O69996qsKSsBADNpqAEAM02WN926NAhpSQ6LQtK4+Pj8fGPf7wqLgEAzaWgBAANlEWkLCTlGrdz584F9E2uf7MCDgCaS0EJAJoni0i5vi3XuGVBCfpm9+7dVsABQIMpKAFAg5iWBO+Uk5Ry/ZupSgDQLApKANAcpiXBO+UkpYmJCVOVAKBhFJQAoAGykPTGG2+YlgQ3kBOVsqykqAQAo6egBACjl5OSpqenTUuCG8ipSvv371dUAoAGUFACgBHJCUmnT5+uXqYlwdzlNKW1a9dWhSUAYDQUlABgNHJCUpaSpqamTEuCeci1b4MVcADAaCgoAUDNLl26VJWSrHGDxRmsf1NUAoD6KSgBQL1OnjxZFZOscYPFGax/U1QCgPopKAFATc6fPx+nTp2yxg2GLItK69evjzVr1lj/BgA1UVACgHrk+rbJyUlr3GDIsqg0Pj4eTz75pPVvAFATBSUAKEwxCeqR5aRc/5ZTlRSVAKAsBSUAKEsxCeqR5aRc/7Z//35FJQAoTEEJAApRTILRybVvikoAUI6CEgCUoZgEo7N7925FJQAoSEEJAIZMMQmaQ1EJAMpQUAKA4VJMguZQVAKAMhSUAGBIFJOguRSVAGC4FJQAYDgUk6C5FJUAYLgUlABgkRSToB2ynJRFpXwpKgHA4igoAcDiKCZBO2Q5KYtKu3btUlQCgEVSUAKABbp06VJVTDpz5kx00ZoVEWcvBHROlpNymlIWlQCAhVFQAoCFOXnyZFVMOnToUHSRPImuynLSxMREVVQCABZGQQkA5uny5ctx+vTpqpwEtJeiEgAsnIISAMzP2bNnY3p6uio4AO2lqAQAC6egBABzNCgm5St/DXRDFpUyXFq5cmUAAHOjoAQAczMoJk1NTVW/Brohs6SDBw/G2NhYAABzo6AEAHOQa9xyYlKudeu6zffMjuNOM38X9NjYo7Nj2U/+pB/j2XOSUk5UysISAHBjCkoAcHO5xi3XueVat66TJzHQtzxp9+7dsX///qqwBADcmIISANzA+fPnq2LSuXPnomsyNMrAYPO6iMc3Xvn1I7Nh0sCxExE7vhL0VH4t/PiPfvP7DJRmXpt9vfqT2ffjP4hOWr9+ffVSVAKA61NQAoDrO378eFVMyveuuVmedPyliO1/HPRUn/Ok8fHx2Lt3r6ISANyAghIAXEOucHv99deryUldMQiQPn4lONqx5Z3h0bUceiFiz9NBj739Fzf//2Tw+PxLs+9dCpiynJTTlHKqEgDwXgpKAPBeucJt37591eSkrpAnMV99zpOynDQxMRG7du0KAOC9FJQA4F1yYtLp06erklLbZWi0Y2vEk1tnT7TNx+Q3IiaOBT2WJ95uFjxeLU/FHT0xGzDlexfGeGdR6eGHHzZNCQDeRUEJAN4pJyZNTU1VJaW2kyexGPKk2aLSkSNHYsuWLQEA/IaCEgD8Sq5zO3nyZFy6dCnabMsHZgOk3U/MLwx4t51/eiUU+Nugx478/mwguVAZKuWqwC6ESzlJKScqKSoBwCwFJQCYlWvc9uzZU2VKbSZPYlgWmyflVKXDL3QjT9q9e3fs37/f2jcA+JXbAgB6LgtJuc6tzSfcctz23k/Onmqb78m26zn5k6DnXl3khsMMo/J1MGZHvB+baW9Imesez507Z+0bAAAAlcyRsph09OjRaCt5EiUsNk8afD1mnpQlpcPfbm+elOses8Ro7RsAzDJBCYBey1VuudKtrevcxh6N2P/p4YVIV7vl/wh6bvfHroRBn4+hyqAyT8LlyPe2hpbWvgGACUoA9Nv09HRVOGjrYTd5EiXJk64tpyg999xzpikB0GsmKAHQS7nOLYtJORGlbQan28Y/MfvrEvKGH2b+LoYux8Tvvmc2rBqM7M7pSm2SU9e+973vxfr166uJSkuWLAkAAAC6b2ZmJvbt21dNRGkbeRJ1kSddW66BfOCBB2J8fLxa+7ZmzZoAgL4xQQmAXslJSVlMyslJbVPydNu7TT97JbD6akD8w38qF1wOtPkUXE5RsvYNgD4yQQmAPslJSZOTkzE1NRVtI09iFORJN5ZTlKx9A6CPFJQA6I2cmpQnVXL6SVvkjXyeDNp15bVlY9Rm55+2d7c7w/Xcl+sJMQfy9Nvhb18JmH4QrZIFpSwqWfsGQF8oKAHQFzktac+ePVWm1BbyJEZNnjQ3u3fvrqYpWfsGQF/cGgDQcTk16fXXX4+XX365NeWkDJL2Pxnx4z+KOPDZesOkVGIUM+30fM3j2TNAfe4PIk5MzP66Lc6cOVNdY/IdAACA9supSbnObfv27a0pJ8mTaIpjJ6JWbc2TDh06VF1jDh8+HADQByYoAdBpbZualPvU937yyo30E+XHIF/PzGsRWycCKnnaLU+9jUqO6M5R3XkSri1MUwKgD0xQAqDL2jY1KfOknJY0/gl5Es0gT5o/05QA6AMTlADopLZNTcog6eDnZ0+4jTJMSnVPzKHZjl/5ejh7IUbm6u+NtpyAM00JAACgndo2Nenqe+aJT8uTaA550vyZpgRAHygoAdA5OTXp+9//fpw+fTqabuzR2dNETbpZPvq3Ae9wbCZGrm3BUhYjX3311erVlgluAAAAfZZTk7Zu3RpTU1PRdPIk2kCeNH9ZjMxJSm2a4AYA86GgBEBntGlqUt4cZ5CUu9Fz5HFT5Mmm40688S7HfxCN0bZgyTQlAACAZmvT1KS8Jz7y+/Ik2kGetHCmKQHQVQpKAHRCW6YmXX0z3KQgaeDoiYD3aOLXRZuCJdOUAAAAmqktU5OuvgfesTUaR57EtciTFsc0JQC6SEEJgNZrw9SkNSsiDnyu+Te/TRi9TPM0+SRkm4KlwTSlLFQCAAAwWm2YmiRPos3kScMxmKaUhUoAaDsFJQBaKwtJTZ+alEHS/idnb3bHPxGN16TRyzTLsYafhmxLsJTXrSwpnTp1KgAAAKhfFpKaPjVJnkRXyJOGI69bWVKanJwMAGizW7Zt2/Z2AEDLZCkpH/Bfvnw5mmrvJyMmPj0bKrXBoRci9jwdcE35dfwP/ylaI0/o5dfzyZ9EYy1dujQefvjh6h0A2ubFF18MAGib6enpmJiYiLNnz0ZTyZPoEnnS8G3evDmee+656h0A2sYEJQBaJQtJr776arXWranlpLFHZ0/dTH22PWFSMo6bG2nyWO5rGXtk9vswT8HlabgmasMUOAAAgC7IQtKePXtifHy8seUkeRJdJE8avsEUuCxcAkDbLNmwYcNEAEALXLx4sVqNdP78+WiiLRsjvvp/tuuU20CeCvq//p+AG7rlymvH1miVLR+IGP9kVP/wzzcwEHv77bfjpz/9aVVWWrVqVdx6q/MDALTDU089FQDQBjMzM9VqpOPHj0cTyZPoOnnS8P385z+Pv/7rv64O8o6NjcUdd9wRANAGnoAA0Ao5YSQnjeRD/KbJ8OjA5yJOTMyesmmjNp1kYnSOnpg9+dZGGfTmCbjdH4tGOnPmTGOvcQAAAG2VE0Zy0khOHGkaeRJ9IU8q59ChQ429xgHAtSgoAdBoucbtlVdeqVa6NdHeT87epI5/Ilrt8AsBN5Vh0uFvR2vlaO4c0Z3hbxPHdGc56Xvf+56VbwAAAIuUa9x27txZrXRrInkSfSJPKivLSQ888ICVbwC0goISAI2VK91yokiGSk0z9mjEc1+OmPps+8Zvv1uO43bijbk6+rfRejk+P4PgPKnaxGApC5n5yoImAAAA85Mr3XKiyNGjR6Np5En0lTypvCxk7tu3r5FZOgAMKCgB0Eg5QeTll19u3Lqjwfjt5/6gveO3323yGwFzluHjzGvRCXlSNb+Xmzimu8lrLQEAAJoqJ4hs3769ceuO5En0nTypHlNTU1a+AdBoCkoANE5Tp4fkTWcXxm+/m9NuzNexE9EZgzHdR36/eaffspyURc0333wzAAAAuLGcHJITRJo2PUSeBLPkSfXIclIWNZs4RQ4AFJQAaIx8GJ8TQ3JySJPkTWaO386bzraP3363Qy/MjuSG+Zh6JuLsheiUHVtnA+P9T0aj5HXxRz/6UZw6dSoAAAB4r3wYnxNDcnJIk8iT4J3kSfXJ6+LOnTtjcnIyAKBJFJQAaISLFy9Wk0LyvUny5vLE/u6M3363wy8EzFuGSV09KTnx6dlgqWmn37Kg9MorrzRushwAAMAozczMVJNC8r1J5EnwXpkndWmK0tWamidNTExURaWmTZYDoL8UlAAYuZyYlJOTclJIU2zZeCVImpi9uezaKbeBPOlmHDcLNf1MdFaGSRkqHfhcs77/M0xq2rUSAABgVKanp6vJSTkppCnkSXBjhzpcbmtqnpSr3pp2rQSgvxSUABip119/vXo1Rd485k1khkkZKnXZ5DcCFizDyK4HkuOfaN6J1ywnNXHaHAAAQJ327dsX4+Pj0RSZJ1VTkybkSXAjfcqTdmyLxshyUhOnzQHQPwpKAIxErin64Q9/WE1PaoqxR2dvHvMmsuvytNvRjo5Upj5dHct9tTz99tyXIw5+vjmn37KklJOUmnT9BAAAqENOls11RVNTU9EUgzwppyZ1nTyJYejDisDMk4783mye1JS1b1lSyklKOX0OAEZFQQmA2g0erp87dy6aIqcmPfcHzdsTXkqeVMq977AYOZa7L19Huz/WvGlKOX3u1KlTAQAA0AeDh+u5rqgp5Ekwf1ly61OelNeIJuVJOX1ucnIyAGAUlmzYsGEiAKAmuZbof/yP/1GVlJogx27/ty9G7NgavbLzTwVKLN7PfxGxfGmzQpaScoJSBktr7oz4m1dm//1H7fz589X1dNWqVXHrrc4eAFCfp556KgCgLrmW6FOf+lRVUmoCeRIsnDwpRu748ePx6quvxtjYWNxxxx0BAHXxFAOA2uQY7pdffrkx5aS9n4w4MTEbKvVJTr3JkdwwDFPP9C+czDWQOU2pKSdkz5w5U63MbMq1FQAAYJhyYtL27dsbU06SJ8HiyZNG79ChQ426tgLQDwpKANTi9OnT8corr8Tly5dj1PIm8LkvX7kR/mz0Uh/2vFOfDJOOnYjeyevIj/8oYv+T0QgXLlxoVAEUAABgGKanp2Pnzp3VobdRkycFDE3mSYe/Hb3TtDwpp9MpKQFQJwUlAIo7depUvP7669EEuz42e1KlLyOE3+34S7MvGKZDPQ4pJz49Gyw14fRblpOUlAAAgK6YnJyM8fHxaAJ5kjyJ4Tv0/0ZvNSlPynKSkhIAdVFQAqCoLCfla9Ry1/eBz1258f387K/7ymk3Suh7UJlhUgbVuz8WI5flpO9///tx8eLFAAAAaKssJ01MTMSoyZNmyZMoYeY1eVJT8qQsJ23durWaqAQAJS3ZsGHDRABAAa+++mq12m3UtmycHcH9Ox+JXjv5k4g9TwcU8epPmhGojModt0fs2HolsL4z4m9eifj5L2Jk3n777fiHf/iHWLp0aSxfvjwAoISnnnoqAKCEPXv2xNTUVIyaPGmWPImS5EnNyZN+/vOfx1/+5V/GlefGsWXLlgCAEkxQAqCILCedOXMmRm3vJyNOTDRjXO6oTX4joBjj3meNf2L29NuorzmXL1+uTr+98cYbAQAA0BZZTjp06FCMmjzpN+RJlCRPmtWUPOns2bOxe/fuOHz4cABACQpKAAxVPhT/4Q9/OPJyUo7dPvL7EVOfDWL2tNsh47gpbPJYELNh0o//6Eq49MkYuSwpNWGSHQAAwI3kQ/Ht27ePvJwkT3oneRJ1kCfNalKelCWl6enpAIBhs+INgKHJctLLL78cP/vZz2KUBiO4P/pQ8Cv7vja71x1KOnkmYuxRJ0wHcg1AE0Z0//SnP63eV61aFQAwLFa8ATAsg3LSd77znRgledJ7yZOogzzpnZqSJ/31X/913HLLLTE2NhYAMCwmKAEwFINy0sWLF2OUcgR3hkluaH/DaTfq5NTbOzVlRPepU6eqFwAAQJMMykkzMzMxSvKk95InUSd50js1JU+amJiIycnJAIBhUVACYNGaUE7KEdwHPjc7gjt/zW9MfiOgNsdfcrry3TJMylBp98dipJSUAACAJmlCOUmedH3yJOqUeVK++I2m5ElKSgAMkxVvACzaSy+9NNJyUt6s/bd9ETu2Bu+Sp932PB1Qq7d+4fvx3e64/Vcfk1sinh9h4Hb+/PlYtmxZLF++PABgMax4A2CxPvWpT410rZs86frkSYzClcjE9+O7NCVPOn78eDzwwAOxZcuWAIDFMEEJgEV59dVXR1pOyv3kz/1BxJaNwTU47cYo5Aj4DDN5r4lPRxz5/dGezD158mS88cYbAQAAMCp79uypHniPijzpxuRJjII86foGedIoV77t3r07Dh8+HACwGApKACzY66+/HmfOnIlR2fvJ2TBp1Lu4mypv6PPGHkZBmHl9efItR3SP8tqVJaWcpgQAAFC3ffv2xaFDh2JU5Ek3Jk9ilORJ15d50qivXVlSGmW5FID2U1ACYEFOnToVp0+fjlE58LmIqc8GN+CGnlFy6u3GMkzKUGnskRiZH/3oRyOdgAcAAPTP5ORkTE1NxajIk25OnsQoyZNubJAnjXIV3s6dO2NmZiYAYCEUlACYtywn5WsUci3Sc1+OGP9EcANOu9EE+74W3EAVKl25nu1/Mkbi8uXLVUnp0qVLAQAAUFqWkyYmJmIU5ElzI0+iCfY8HdxA5km57m1UedLZs2erklJO5waA+VJQAmBe8gZkVOWkvPnKtUijnDjSFk670QRHT0Qcfym4iYlPjy5UynLSyy+/XJWVAAAASjl69OjIyknypLmTJ9EEmSXJk25ulHlSlpO2b99ePSsAgPlQUAJgzvJB9quvvhqjsGXj6Hdst4XTbjTJ5LFgDjJUytNveaq3bnltf+WVVwIAAKCEfJC9Z8+eGAV50tzJk2gSedLcjDJPymt7TlICgPlQUAJgTkY5ZWPXx2bHcAuT5sZpN5rEqbe527F1dNe6c+fOxeuvvx4AAADDNMopG/Kk+ZEn0STypLkbZZ50/Pjx2LdvXwDAXCkoATAnP/rRj6qSUt32fjLi0OdHcwqkjZx2o4mcepu7UZ7uPX36dPUCAAAYlpyukSWlusmT5keeRBPJk+ZulHnS1NRUTE9PBwDMhYISADd16tSpuHjxYtQtd2hPfTaYB6fdaCKn3uYnw6RRhUqjut4DAADdMzk5GTMzM1E3edL8yZNoInnS/IwyTxofHx/J9R6A9lFQAuCGzpw5Uz2wrluGSblDm7lz2o0mc+ptfjJMOrF/9gRcnXKNZ07MG8U6TwAAoDsOHToUExMTUTd50vzJk2gyedL8jCpPSjkxbxTrPAFoFwUlAK4rV7qNopx04HPCpIVw2o0mc+pt/nIVwXNfrj9Uymv/q6++GgAAAAuRK91yelLd5EkLI0+iyeRJ8zeqPCmv/Xv27AkAuBEFJQCuK6do5IPqOh38fMT4J4J5yht1p91ouj1PB/OUodKJiYhdH4ta5Ym306dPBwAAwHzlA+p8UF0nedLCyJNoA3nS/I0qTzp69GhMT08HAFyPghIA15STky5evBh1yjBpd803TV3hRp02yLHx088EC3Do8/WHSvlzoO6SKgAA0G45Oen48eNRJ3nSwsmTaAN50sKNIk/K9Z51l1QBaA8FJQDeYxSr3YRJC5cn3fJGHdpg4hsRZy8EC1B3qHT58mWr3gAAgDnLB9L5YLpO8qSFkyfRJvKkhas7T8qp3Fa9AXA9CkoAvMfrr78edRImLc7kNwJaI8Ok6WeDBcpQacfWqM25c+fizTffDAAAgJvZt29f1EmetDjyJNpEnrQ4dZeUcpJernsDgHdTUALgHc6cOVOdcqjL/ieFSYvhtBttNPWMU2+LkSH8lo1Rm9dee62apgQAAHA9hw4dqvVhtDxpceRJtJE8aXGmPltvnpSl1TqfMwDQDgpKALxDnavdMkya+HSwQBkkOe1GG2WYNHksWKA1KyKe+3J9oVKu/Tx9+nQAAABcz+TkZNRFnrQ48iTaSp60OHXnSbn2c3p6OgDgards27bt7QCAmJ2e9Oqrr0YdhEmLt++rEVOFRxv7PPXXA39Y/jTliYl6T251TX5+tv9JPadelyxZEh/5yEeqdwBIL774YgBAyulJe/bsiTrIKRZPnkRJ8qTmqzNPWrNmTfz4xz+u3gEgmaAEQCUnZNQ1PSn3XQspFidvIEuHSZvv8XnqswOfjeIyFGXh8nv0uT+YfS8tV7zVOWEPAABoh5yQUdf0JHnS4smTKC3X0pcmT1qcOvOkXPFW54Q9AJpPQQmASj54zpJSaXm65VANN6pdV8co7v3CpF7bsTVi7JEo6vhLsy8WLsOkI78ftcg1b+fPnw8AAICBfPCcJaXSMk+aquEgTdfJkygtsyR5UvPVmSdNTU3F8ePHAwCSghIAVTEp17uVVueNT5fNvBZx6IUoKj9Xuz8W9FyOZC/NqbfFy6D+wOeiFqYoAQAAA1lMyvVupQ3ypDUrgkWQJ1EXeVI71JknmaIEwICCEgDx8ssvRx3qGh3bdTu/EsU57Uaq49RbBqTTzwSLNP6JK69PRnHnzp2rpdAKAAA0386dO6MO8qThkCdRF3lSe9SVJ+UEpcOHDwcAKCgB9Fw+aK5jtVuexhAmLV6edDv5kyjKaTeuVsept4lvRJy9ECzSgc/Onn4r7fXXX4/Lly8HAADQXzk5aWZmJkqTJw2HPIm6yZPao648aXx8PM6ePRsA9JuCEkDP1bGuJ8OJPI3B4uQN9+Q3oriDnw/4tTzxtmNrFJVf29PPBkNQx9qDLCedPn06AACA/qpjXY88aTjqypOy5AADdeVJk8eCIagjT8py0vT0dADQbwpKAD1Wx/SkPD1lvPNw5Nji0qfdMvwrPYKZ9qkjZJw4Vv7ruw+qa24NpxSzoGSKEgAA9FNOTzp58mSUJE8anjrypB3bypdRaJ868qSpZ+VJw1BXnjQ1NWWKEkDPKSgB9Fgd05MyTDKKe/HyRnuihtNuwj+uJb+HJ2oIKfY8HQxBnjAuXTQ0RQkAAPqrjulJ8qThqCtPOvDvAt5DntQudeRJpigBoKAE0FN1TE/KaTx2zw9HHaO483Ml/ON69n6i/Kjn4y/Nvli8OlY1KigBAED/HDt2rPj0pJzGI08aDnkSoyZPapfMk0p/vnKKEgD9paAE0FNvvPFGlGYaz3AcemH2VZrPFzeS4cT4J6O4PPV29kKwSHWcUswpSsZyAwBAv9TxYNk0nuGQJ9EE8qR2yTyp9Ocrs6SjR48GAP2koATQQzk56dy5c1GS01PDU8dpt9wx7vPFzeSpt9JfJzl+fvrZYAjqOKX493//9wEAAPRDTk46fvx4lCRPGh55Ek0hT2qXOvIka94A+ktBCaCHTp06FaU5PTUck8dmb7BLqk7GfCLgpjKcOPDZKG7qmfJf931QxynFLLtevHgxAACA7pucnIzS5EnDIU+iSeRJ7VJHnpRl15mZmQCgfxSUAHqo9PQkp6eGI2+op2o4+ZPhX+lTMXTHjq0RY49EUTmSe9/XgiGo45SiNW8AANAPpacnyZOGQ55EE8mT2iW/v0tfj48dOxYA9I+CEkDPnD9/vlrxVkreuEw47TYUOYq79O70/Hzl+HSYjwyNSzt64kr4/VKwSBkWH/x8FHX69OkAAAC6LctJueKtFHnS8MiTaCp5UruUzpOmpqYCgP5RUALomTNnzkRJRnEPR95MH3ohiit9o0k35Ym3OoLIPU8HQ5Cfr5KnFC9fvlyVXwEAgO46fPhwlCRPGo6Z1+RJNJc8qV1K50k5kbv0ZD4AmkdBCaBnSq53G3vU6alhqWMccX6uSo9WprvqGOWeY+nz5CeLVzo8Lr06FAAAGK2SD5HlScOz8ytRnDyJxZAntUvpPMmaN4D+UVAC6JHS692cdhuOyWOzN9Kl+XyxGDnOffyTUdzUM/V8P3Rd6fH7b775ZgAAAN1Uer2bfGI45Em0gTypXUrnSSYoAfSPghJAj5SenuT01OLljfPUs1Fc7nzPG0xYjL2fKP91dPZCPRPF+mBXwUDpwoUL1ao3AACge55//vkoRZ40HPIk2kSe1C4l86SZmZlq1RsA/aGgBNAjOUGplF1PBEOQ44fzBrqk6qTSJwIWLUdyH/hsFHf0RMTxl4JFytC/ZPAvUAIAgG4qOeFCnjQc8iTaRJ7ULqXzJGveAPpFQQmgR0pNUCo96rUvDr0w+yqtjl3v9MeOrfWcdt3zdPmwtQ/2FhyjfvHixQAAALqnVEFJnjQc8iTaSJ7ULiXzpJyiBEB/KCgB9ETJ6UlGcQ9HnnYrbcsHhH8M34HPRXE5rn66hnH1XZfX61KBcsmfMwAAwGiUnJ4kTxqOOvIkZTJKkCe1R8k86ejRowFAfygoAfTEhQvljorsElAs2uSx2Rvm0o78XsDQbdkYMV7wJNXA1DP1fJ90WYZJeUqxhPw5c/ny5QAAALrju9/9bpQiT1q8uvKk5/4gYOjkSe1RMk86efJknD17NgDoBwUlgJ64dOlSlJA3J068LU7eIE/UcNotT7rliTcooY5R7zmSO0dzszgfL3jNLvWzBgAAGI18cFyCPGnx5El0gTypPUrmSaV+1gDQPApKAD1x8eLFKEGYtHh13CBnkJQ3/FBKhkn7n4zijr8UcfiFYBFKnXhLJaf1AQAA9ZuZmYkS5EmLJ0+iC+RJ7VEyTyo5rQ+AZlFQAuiJUg+Nxx4NFuHQC7M3yKVlmOS0G6WNf6KekHn8a7On31iYDP9KXQ9KlWEBAIDRKFZQkictijyJLpEntUPmSVs+EEWU+lkDQPMoKAH0wOXLl6tXCY9vDBYoR3FP1jCKO4OkHMcNdajj1FuGSZPHgkUoFfyV+lkDAADU7+zZs9WrBHnSwsmT6CJ5UjtsKXTtLvWzBoDmUVAC6IFLly5FKVsESguWYVKGSqU99wcBtcniy/gno7ipZ+s5LdpVpU68maAEAADdcfLkyShFnrRw8iS6SJ7UDiYoAbBYCkoAPVBqokWGSTnalfnLG+FDNew9z9NuRnFTt72fiFrseTpYoM3roohf/vKXAQAAdEOpiRbypIWTJ9Fl8qTmK5UnmaAE0B8KSgA98NZbb0UJa+4MFsiNMCxeXWPtu6jUOoWSE/sAAIB6lZqgJE9aOHkSLJ48aeFK5UklJ/YB0CwKSgA9UGqCUqkTE12Xu87rGMUNfTD1jO+nhXASFgAAuJk333wzSpAnLYw8CYZHnrQwJfMkU5QA+kFBCaAHihWUPOCet7zxnXBCB4bm7AUnSBeq1EoFU5QAAKAbSj0stt5t/uRJMFzypIUrdQ1XUALoBwUlAKjR9j8JYMiOvxQx/UwwTx4KAAAAo+BeZP7kSTB88qSFcQ0HYDEUlACgJtNGB0MxeZLU9xcAAABdI0+CcuRJAFAvBSUAqIFR3FBWjube97UAAACAzpAnQVnyJACol4ISANRg8huzN7xAOUdPzI7nBgAAgC6QJ0F5mSflCwAoT0EJAAo79MLsCyhvz9PC27nycQIAAGgueRLUJ6coyUnmxscJgMVQUALogSVLlkQJ9nPfXH6MJo3ihtpU33PHgjkoFSgtXbo0AACA9luzZk2UIE+6OXkS1EueNHel8qRSP3MAaBYFJYAeKFVQclri5jJMErxBvaaetertZlyXAACAm1m9enWUIE+6OXkS1E+edHMlr0sKSgD9oKAE0AOlCkozrwU3YBQ3jI5Vbzd28kwUYXoSAAB0x9133x0lyJNuTJ4EoyNPurFSedLmzZsDgH64LQDovGXLlkUJTnJdX1NGcec/xy3/R0DvDEZzH/hccA3fLfRA4Lbb3F4AAEBXbNq0KUqQJ12fPAlGS550Y6XyJNOTAPrDBCWAHig1QSk59XZtRnHD6BnNfX2lrk8mKAEAQHeUnGghT7o2eRKMnjzp+kpdnxSUAPpDQQmgB/KBcamS0ncFSu9hFDc0h9Hc1zbzd1GEghIAAHRHPjAu9dBYnvRe8iRoDnnStZXKk7Zs2RIA9IOCEkBPlHpofPwHwVWaMoobmJXfkxkq8RsZsJU6CaigBAAA3VJqipI86Z3kSdAs8qRrK5UnlZzYB0CzKCgB9MSKFSuihKMngqts/xOjuKFp8jo1/UzwKyVXKZT6WQMAAIxGqakW8qR3kidB88iT3qnk2rvHH388AOgHBSWAnli+fHmUUHISR9vs+6owCZpq/GuuVQOHC64MKPWzBgAAGI1SBSV50m/Ik6C55Em/UTJPsuINoD8UlAB6ouRUi+fdpMXksYipZwNosBzNLfQtF6zlz5klS5YEAADQHSWnWsiT5EnQBvKkWaXypCwnrVmzJgDoBwUlgJ4oOdXiUMHTE22Q434nvhHAAmWppY5iS4ZJOTY/T+r2VYZJpUK1pUuXBgAA0C0lp1rIk+RJsBh33XVX9SpNnlQ2T9q8eXMA0B8KSgA9kQ//S5WU8uakr6NuZ16bPUUDLFxen+65556oQxUq/XH0Vslx3E67AQBA9+R/55cqKcmTAliE1atXxxe+8IWogzwpinnyyScDgP5QUALokVWrVkUpOZK6b/LGdOdX+n16BoZl/fr1cccdd0Qd+hoE5zWr5AnlkpP6AACA0RkbG4tS5EnAYnzxi1+Mxx57LOogTyqj5KQ+AJpHQQmgR0pOtyg55rWJBqN97R+HxRusd7vvvvuiLhms9C1UKnnabdmyZQpKAADQUSWnW8iTgMWanp6OusiThivXuykoAfSLghJAj+TD40ERoITJb0QvCJNguAbXpZUrV1aTlOqSoVJfTutWp92+HcXk5w4AAOimfHhc8tCbPAlYiI0bN1bvjz/+eIyPj0dd5EnDU3JCHwDNpKAE0CNZAlixYkWUkjdnXQ9ZhElQ1oYNG6ppPHWZuBKE7/tqdN7hwtfndevWBQAA0E1ZTir5EFmeBCzW/v37q2k8dZEnDceuXbsCgH5RUALombVr10ZJXR5xK0yC8rJIuWnTpqjT1LPdv3ZNFDyRnIUyE5QAAKDbSq55S/IkYDGySHnw4MGokzxpcbJQZoISQP8oKAH0TN6slVzzdvyl2VfXzLwWsXVSmAR1qHvVW8oTu9v/OOLsheic0usSlJMAAKD7duzYUXTNmzwJWKwsu9S56i1lnrR1Qp60EMpJAP2koATQM1lOKhkopTw50qWbssMdvtGEJrj99tur91tuueXXf+z+++8vupLyWjIM71pwnEFZvkqy3g0AALovs6Tdu3dHSV3Mk7p6EAaaILOjdNttt/36jx04cCC2bNkSdepiEbGOPMl6N4B+UlAC6KHSD5PzZmzyWHRC/nvsHsGoXg/8IeLBBx8sOvHtWgaj9zNcarvqWlz4tJv1bgAA0B+l17x1MU+qu5yUJbLSBxOh6Y4cOVL794E8aX6sdwPoLwUlgB7Kh8mlJ5PkDu7pZ6K1MkDa+ZWye7avJx/4b9iwIZYuXRrQB4Ov9asnKA3+eAYWdcsgJqemtfkalvL0cenTe3mtAgAA+iEfJpd+oCxPWri8f96/f7+CEr2xcePG6v3dh9vye+HgwYNRN3nS3OW1CoB+UlAC6Km1a9dGaRnGtPHUyGAs79ETUbscSfyhD32oKmbUPTkGRuVGX+urV6+O9evXxyiMfy1i31fbOY4/T+vmyrqS8vNmehIAAPTLjh07ojR50vxlKem5556rihkKSvTFXXfdVb3feut7H3XmtWp8fDxGQZ50c6YnAfSXghJAT+UKsdIFmMGpsTbt384TLtv/eHT/zO9///t/PU0mJylBH9x+++3V+7snKA3cf//9sWrVqhiFPL2bAXObrmMZJtVxWjdDb5PeAACgX3bt2lW8ACNPmr+cRjKYQDyKScQwCpkXpetl3AcOHBhZEaaNeVJex+rIk3IVpesUQH8pKAH0VN641TGVZLB/u+k3Y9U/5x/PnnAZ1emWXJV09efEBCX6Yi5f6w8++ODISnt5fXjgD2eLP013+IX6VglY7wYAAP2T5aQ6ppLIk+Yuy0lXf05MUKIvcup2utYEpYEjR46MrAzTtjwpr2N1sN4NoN8UlAB6LMswdZRgmh4q5emQPNFSx/ja68mJVu9+2G8yCX0xl6/1vFbl+sNRFvey+JPBUlOvZRkm7X46apHXLNcoAADop71799ZSgpEn3VyusZqYmHjHHzOZhL7YuHFj9X6jrGiw/nCUxT150m+YngSAghJAj9U1RSk1MVTKAGnUp9zSihUrfj2S+Goe/tMXN1vxNpDfEw8//HCM0tWn30Z53Xi3OsOkZHoSAAD0V11TlJI86fq2bNkSBw8efM8f37RpU0Af3GzF20AWYkZdUpInzTI9CQAFJYCeq2uKUmpKqJQ3gfu+OhsmjfKUW8qVVbm66lqfgywuQdctX768er9ZOenq/38TTlrl6bc8KZtBzqhluFV3OUmBEgAA+i2nKNV1byZPeq/82OfqqmsVLrK4BF332GOPVe+DQ283k98XBw4ciFHrc55U588NAJpLQQmg57IYMxiHW4cMk/ImLMdg1y2DpLzxytMqU8/GyGU5KVdWXe9BvwIAfbCQguTatWtrvW5dT17PMsjJa8oogqW8pu15ejbcqktet3K9GwAA0G9ZjKlzEoY86TcG02Cu96BfAYA+WL16dfU+1wNvKdeLNaGk1Mc8Ka9LdU3eA6DZlmzYsGEiAOi1nEhy/vz5uHTpUtTh57+I+OvvRbx55Wboow9F3DG3gy4Lljddf/RfIz73f8/+ffPvP2o3KyelW2+9NU6fPh1vv/12QFfdddddsWrVqurrPV9zdeedd1bvee0atbzGHD1xJVT6dsTdKyK2fCCKy9O6n5qq/9RuFsNWrlwZAPDUU08FAP2WE0mef/75OHnyZNRBnnTzclK64447Ynp6On7+858HdNXv/M7vxNjYWJVrZ846Vx/96Eer97x2jdoo8qSZ12Yn0tWdJ2UxLD9fAKCgBEAl14n95Cf1zsr+zisRf/n/lbsByxutfV+bPRGSv25CkJTmUk4aOHfuXG3FMRiFe++9t/qeyElK8zn1lrLYlJpQUkpXB0sZmG++J2LNkDc1DgLyvK7lr+uUPyeaMLkKgGZQUAIgZUnpz//8z6NOfc2T5lJOGvjmN79ZW3EMRuH3fu/34oMf/GB1iOq2226b1587KMo0oaSU6syTPvfn9edJ+XPiz/7szwIAkoISAJXBvu66H/QPbsCef2n25itfi5HBUY7G3fmnEX9+POIH/ysaZT7lpHTx4sX42c9+FtBV69evr4KknJ4034JSalpJKeV1La9F08/OXtvy3yqDpcWES+8+uTsKjzzyyIJW8gHQTQpKAKT3v//91b3c8ePHo059y5PmU05K3/3ud+M73/lOQFdlQSkzpcFU7vlqWkkpdTVP+u///b9Xa0EBIN2ybds2e2MA+LUf/OAHceFCzccorpKB0o6tEU9eeW3ZeOMbsLzBOnlm9oZt5u9mg6mzo/tHv6n5lpPSmTNn4tVXXw3oqt/6rd+q3gclyYU6depU9WqysUdmT/d+/JHZa92WmwwjOvmT2WAqr3Gjvr5t2LChegHAwIsvvhgAMLB169aYmZmJUVlInpRZUhPut25mvuWkdOjQodizZ09AV/3P//k/q/f77rsvFmNiYiImJyejydqcJ+3fv7/6GAPAgIISAO+Q68S+//3vx+XLl6MJqlNw62Z/neFS3lBVr4uzN1ttsZByUsrPx/e+N6LjLVBYjuF+4IEHqtO28x3HfS1tKCldLa9peX0bBOdXX+MyLG9KQJ6nEfP6BQBXU1AC4Gq5TixLSmfPno0m6EqetJByUsrPR95vQxc98cQT8Vd/9VdVznrPPYscnxbtKCldrS15Uk6pyusXAFxt8U+CAOiUvLHLkyevvfZaNEGGRm0Kjq5loeWklH9OrlRqSmEMhumOO+6o3hey2u1acsJPfr9lENsGGRjNNPiUbsqP56ZNmwIAAOBGskCTkzL27dsXTdCFPGmh5aTBn5srlZpSGINheuyxx6r3hWSt15IFpfyeacvUsTbkSfnxPHjwYADAu81/MSsAnXfvvfdWO7xZvJw88uijjy7qhnnFikUsGocGu/POO6v3W28d3n+Srl27Nj784Q9XxT4W78EHHxxa4AcAAHTb+Ph49WLxcvLIiRMnFlROuvqvAV300Y9+tHofZl6xe/fu6nsui30s3pEjRxZ1/QKguxSUALimnESiGLM4WfLKyUmLLUqsXr06oIsGE5SGbfny5VVJKaf/sHD5cyA/lgAAAHOVU5S2bNkSLNzevXuryUmLLUooKNFVH/nIR6r322+/PYYpr12LLQbi5wAAN6agBMA1ZakmJ2d4wL8w+WD//vvvj2FQFKOLsviSJ91yvduwVrxdLf/aWRD0/bMweQ3LFwAAwHxkqcbkjIXLB/tTU1MxDI8//nhA12zcuLHKXDO7LjE9e7BaUcFmYfIalivzAOB6FJQAuK7BA36rkubutttui4cffnioD/ZXrlzpc0DnDKYnlSgnDeQ1LFcsWlk5P/lAQTkJAABYqMEDfquS5i4/VvkxG+aD/Zyg5HNA1/z2b/929V7yUG1ew3KSUpZtmLsdO3YoJwFwUwpKANxQPuDPwo2CzM3lpJYsQ2ShaNhWrVoV0CV33XVX9X7rreX/czRP1uUJO9exm8vr2KZNmwIAAGAxlJTmbrBWqsRKNmve6Jp/9a/+VfU+OPhWUpZtDhw44Do2B3kdO3jwYADAzdyybdu2twMAbuLixYvx8ssvx+XLl4P3ygktOXGkVAHi9OnT8frrr0dJz335SnD1SEDseTri0AtR1D/+x/+4+n65/fbboy6XLl2KH/7wh/HWW28F75XlJFPzAJirF198MQDgZmZmZmL79u1x9uzZ4L327t1blSBKFSCmp6djfHw8SpInMVBHnvT973+/OvT2/ve/v5ZDb+nkyZPVdSzfea8sJymkAjBXJigBMCfLly83SekacqXbQw899Ovd56WsW7cuSjt2IqBy/KUoarC2sOR6t2ux8u36lJMAAIASPLi+tvx4HDlyJKampop+bHbt2hWlyZMYKJ0nPfHEE1U5KfOduspJabDyrXTZr41c4wGYLwUlAOZsUFIqueO7TXLtWpYdVq9eHaVlaaD0mrc84XT2QtBz+XVw8idR1CC0qDNMGsjvpSwUZrjkWjYrry3KSQAAQCmDB9h5H8bs2rUsO+zYsSNKy/vv0mve5EmkOvKkf/tv/231noes6pbfS7nuLdeYuZbNymuLchIA86WgBMC8ZEkpH2T3+cF+Tk3KgkN+HPLETl1y6kxJGSZNPxv0XB1fA3feeWf1XvcEpautXbu2+h6uYzpZk+W/v3ISAABQmpLSbwoOdX8cSheh5EmkOr4GcoJSGmUuvXv37up7ON/7LKezKScBsBAKSgDMW5Zy8oH2KE6rjFredI1qRVQdf8/Se+JpthzFPfN3UVQW7fIakuWkURaUUv5zbNq0qbfTlDZs2FD9+wMAANQh773ygXaWlfomS0KjWhFVx5o3eVK/1ZEnZTkpD4xmljPqQ1Z5LctJSn2dprR///44dOhQAMBCKCgBsCB5Mziqos4oZHkh19s9+OCDtU5Nuloda95yFHPpffE01+EaAsVRrne7npym9Nhjj1WFnT7IKXAPPfRQb/59AQCA5siH+aMq6ozCoJR15MiRkRUZ6ljzJk/qtzrypFGud7uenKL04x//uCrs9EFeS7KUNTExEQCwUApKACxKnlzZuHFjdFU+yM+H+FleKL1ibS5Wr14dpU0eC3oow8Q6Tjw2Yb3b9eT3+kc+8pFOr33LIC/LpXVcSwAAAK4nV53lq6vrgfLfK0sLWV4oXQ6ai9Jr3pI8qZ/qypOasN7terKwk9/rXV77lpPvslza99V2ACyeghIAi3bvvfdWD/W7tCLp6mJSk6aMZHGi9BjjPPHm1Fv/TH4jirv77rurCWQ5PamJBaU0WPv24Q9/uPjEsrrlxLtczzmqKXAAAABXyylK+cC7SyuSri4mNWnKSK55K10Gkyf1Ux150mc+85nqkGweuhr1erfrGax9y2taE0qJw7R3795qElwf19kBMHwKSgAMRT7w7sKKpHcXk5p201vHmrfk1Fu/1HXaLQtKqUnr3a5n+fLlVZknVzu2vag0WFGZYV5TgzwAAKCf8oF3F1YkvbuY1LTJUHWseUvypH6pK0/KglJq0nq368lJQ1nmyVfbi0qDFZVTU1OdnXYHQP0UlAAYqsGKpDbcMF6t6cWkq+UUlNLyxNvRE0FP1HHaLUuMud4tJyc1dXrSteRqx0FRqY1hTF7PcqVbE1ZUAgAAXM9gRVI+3G+TpheTrpZTUEqTJ/VLHXnSxo0b47d/+7errLZNE6GznDQoKtWxYnHY8rrWxWlQAIzeLdu2bXs7AKCAN954I06dOhVvvfVWNFVORsnwaO3ata2aLPLDH/4wzp07FyVtvifixP4rYVu7umbMUwaHO78SxeX0npyglN9nbZigdD2XLl2qrmtvvvlm/PKXv4ymymtbrqqzzg2AUl588cUAgBIOHToUk5OTcfLkyWiqfGj/5JNPxu7du1t1mGX79u1x/PjxKEme1A9ZRtv+x1HcgQMHqglK+X3WtgOxV8vrWV7Xjh49GmfPno2mymtbrqqzzg2AUkxQAqCYLP3kRKK8ockVQ02R05JyClFORMnJKPfee2/r1h6tXr06SssxzdPPBh2372tRi5yelNo0PelasvCTxZ/Bta1p69/yn2dwbVNOAgAA2ihLPzmRqGkPybMgMT4+/uupKPnrtk3arWOSizypH/Y8HbV44oknqvcmZcsLkdeyvKYNrm1Nm0x09cQn5SQASjJBCYDanD9/Ps6cOVO96palpCz1rFu3LpYvX966QtK7Xb58Ob73ve9V7yXlabc89Zan3+ie6WcixmsoKOXkpJyglJOT2v69dy05VWlwfSs92exa8vqWRcssXnbx4wtAM5mgBEBdcuLP4cOHq8lKdcsCUpZ6du3aVa2fa+Pq76vl5JYHHnig+AQXeVK31ZUn5eSknKCUk5Pa/r13LTlVaXB9Kz3Z7FryY5qrH9tYtgSgvRSUAKhdlmpyPVKGIflQv9SapJwksnLlyl+/d02umcpXaWOPRDz35aBj8kTj1skr4eSFKO6RRx6ppvlkkabtE5RuZlBWyqJSvpdacZknB7N0mQFSF69vADSfghIAdcscKdcjHTt2rHqYX6pkk5NEsoyUK9yaNuVkGHLN1MTERJQmT+qmOvOkv/mbv6kOvL3vfe/r/IGsQVnp+eefr95LrbjM6UhZuuzq9Q2A5lNQAmDkLl68+OsH+lleyt/Pp7SUD+rzJjUnI+WJmnzvwpSkm6lrilI68vsRO7YGHZKjuA+9EMV1fXrSzWRhKa9pFy5cqN7z9/ma7zUur2lZ8sprXBaTTEoCYNQUlAAYtZmZmepB/ne/+93qYX7+fj6lpXxQn4c+soz0+OOPV+9dmJJ0M3VNUUrypO6pK0/q+vSkmxlc0/L6lu/5+3zN9xqX17R8z2tcFpNMSgJg1BSUAGikLN3kQ/yryzf5+3xAn/LhfL4Gv++ruqYoGc3dLRkkZaBUhz5NT5oP1zgA2k5BCYAmyof3736In7/PB/QpH87na/D7vqpripI8qVvqzJP6ND1pPlzjAGg7BSUAaLE6pygZzd0NdY7i7vv0JADoMgUlAGivOqcoyZO6oc48qe/TkwCgy24NAKC1svSxfv36qMPxlyKmnwlabvuf1BMmpcHXZhaUAAAAgGbI0sf4+HjUQZ7UDXXmSV/60peq91WrVgUA0C2eFgFAy2UJpK7pNONfi5h5LWipyWOzJ97qkNOTcj1ZlpOsdgMAAIBm2bt3b23TaeRJ7VZnnpTTk3Iad05PMo0bALpHQQkAWq7OKUpp51fqCyUYnkMvREx8I2pjehIAAAA0V51TlJI8qZ3qzpNMTwKAbvPECAA6IMsgy5YtizpkmJShEu2Rn7N9X4vavO997zM9CQAAABoupyht3rw56iBPap+686QsJ+X0pCwnmZ4EAN2koAQAHZA37Zs2bYq65FjufV8NWiDDpO1/EnH2QtQii0nr1q2rikmmJwEAAEBz5RSlgwcPRl3kSe1Rd560cePGar1bZpy53g0A6CZPjQCgI1auXFnr+OOpZ2d30NNcGSJlmFTnCPWc5pVhkulJAAAA0HxjY2PVqy7ypOYbRZ70xS9+0fQkAOgBBSUA6JCcolTnTXzuoJ9+Jmio7X9cb5i0evXquPvuu6tykulJAAAA0A45RSmnKdUl8yQlpeaqO0964oknqulJOZXb9CQA6DZPjgCgQ/JGPifY1Gn8axGHXwgaZs/Ts6PT6/T+97+/eldOAgAAgPbYvHlzjI+PR52ypCRPap5R5EkHDhyo3vPQGwDQbZ4eAUDHbNiwofbTRrufFio1SYZJh2r+fLzvfe+rCnJWuwEAAED77N+/P7Zs2RJ1kic1yyjypC996UtWuwFAjygoAUAH5aq3ugmVmmEUYdJgclcWk4RJAAAA0E656q1u8qRmGEWetHHjxvjiF79YZUlZUAIAum/Jhg0bJgIA6JTbb789brvttvjpT38adTp6IiJn54w9GtTs7IWITx2Y/RzUKUOkhx56qPp6y1+bngQA/fDUU08FANAtubp9zZo18c1vfjPqJE8anVHlSemZZ56Ju+66qzr0lhO5AYDu8xMfADrq3nvvHcnpo4lvREweC2p08icR2/844vhLUTur3QAAAKA7xsfHY2xsLOomT6rfKPOkycnJarXb6tWrTeMGgB5RUAKADstVb6O4yc9Qad9XgxpUYdKfRMy8FrW7++67Y926dVU5yUk3AAAA6IZc9ZaTlOomT6rPKPOkz3zmM/G7v/u7sWLFirjzzjsDAOgPT5IAoMNyss3mzZtjFKaejdg6MRt4UEaO3946OZqPcX5t5QjunJqknAQAAADdkVlSlpRGIfOkB/5QnlTSKPOkjRs3xpe+9KXqQOUoJr8DAKPlaRIAdFyOSs4iySjkKaw8jTWKUdFdl2PPd34l4uyFGIkHHnigKilloGS1GwAAAHTLjh07qnVvozCY7iNPGr5R50lf//rXq9Vu99xzj9VuANBDCkoA0AN54z+qU0mDffYZgLB4g49njj0flfvuu085CQAAADruwIEDMTY2FqMgTxquJuRJk5OTVUaZhymVkwCgnxSUAKAnNm3aFMuWLYtRyQDEyrfFGYzgHuUJwjzhtm7dumqtm9VuAAAA0G1HjhypVr6Nijxp8ZqQJ33hC1+I3/3d342VK1fGnXfeGQBAP92ybdu2twMA6IVLly7F97///bh8+XKMypoVV8KlT0fs/WQwRzl2e8/Ts4HSKC1fvjw++MEPVlOTbrvttgAA+uvFF18MAKAfTp48GVu3bo2zZ8/GqMiT5q8pedJjjz0W3/rWt+L222+Pe++9NwCA/nLsHQB6JNdyPfTQQzFKGY6Mf83pt7mafibigT8cfZiUXzsf+MAHqnKSMdwAAADQHzlBKScpjZI8aX4OvdCMPGnjxo3x9NNPV1nS2rVrAwDotyUbNmyYCACgN7JoktNvfvrTn8Yo/a8rf/vpZyPevBIwPbph9iQcv5Fjt/OU2589H/HzX8RI5dfMAw88UK0IzEApS0oAQL899dRTAQD0R5aU1qxZE9/85jdjlORJNzbIk/JjNOo8KctJX//612PTpk1xzz33OPAGACgoAUAfDXa9nz9/PkbtO69EHJuJuPtKoLTlA9F7eQpw39dmXyfPxMhleJRTt5STAICrKSgBQP989KMfrd6ff/75GDV50js1LU+666674r/8l/9STePOtW7KSQBAUlACgJ5atWpV9d6EklKO6c6R04e/3d9gKT8Gf/RfI/YcnA3ZmiDDo5yctHz5cuUkAOAdFJQAoJ/Gxsaq9yaUlORJzcyTspyUk5MefvjhWLduXTXJHQAg3bJt27a3AwDorVOnTlWvJtl8T8TEpyN2fSw6L0+45djtQy/MhkpNMSgnrVixQjkJAHiPF198MQCA/pqYmIjJycloEnlSM3zrW9+Kxx57rJqcdPvttwcAwICCEgDQyJJSymBp7JGI/Z+e/XWXHH8pYvLY7HvTZCHp/vvvj9WrV8ett95avQAArqagBAA0saSU5Emjc+DAgfjMZz4Ta9asqQ69AQBcTUEJAKg0taQ0kMHS7o+1+xRcnmibfibi0LdnT7o1kclJAMBcKCgBAKmpJaUBeVI9cq3b008/HR/72Mdi7dq1sXTp0gAAeDcFJQDg15peUkprVkTs2Brx5NbZ96bLEOnwlQDp6N8293TbgHISADBXCkoAwEDTS0pJnlROlpO+/vWvx2/91m/FunXrrHUDAK5LQQkAeIc2lJSutuNXwdLjH4jYsjFGLgOkmdcinv/BbIDU9BBpIE+2feADH1BOAgDmREEJALhaG0pKV5MnDcfGjRvjL/7iL+Kf/JN/Uk1OUk4CAG5EQQkAeI+///u/j9deey3aZvM9s6HS2KNXAqaNs79eU3jdfY7WztDou1c+XDN/NxsmZajUJllOyslJy5YtU04CAOZEQQkAeLepqanYt29ftI08aWGynJSTkzZt2hT33HNPlSkBANyIghIAcE3nz5+PH/3oR3H58uVoswyUMljKsClfm9bNvqfN6371fs97/7wMhQbB0Mkzv/n9d38VGGV4NPjjbbZ8+fKqnHTbbbcpJwEAc6agBABcy/Hjx2Pnzp1x9uzZaDN50o099thj8fTTT1eZUk5OUk4CAOZCQQkAuK5Lly7FD3/4w3jrrbeC7snTbRs2bIhbb71VkAQAzIuCEgBwPSdPnozt27dX73TPF77whWql38qVK+Ouu+4KAIC5ujUAAK4jV3996EMfijVr1gTdct9991XlpCwmKScBAAAAw7J58+Z47rnnYseOHUG3TE5OVuWk1atXKycBAPOmoAQA3FCWlB588MGqzEL7DT6fOT0p17rl9CQAAACAYcqS0pEjR2L//v1B+23cuDG+/vWvx1NPPVVlSnfeeWcAAMyXJ1IAwJxkQemhhx6KZcuWBe2Uo7cfeOCBWLVqVTU16ZZbbgkAAACAUnLaThaVsrBEOz3xxBNVOenjH/94VU7Kw28AAAuhoAQAzFmOb7byrZ1ypVuWk5YvX66cBAAAANQmV71Z+dZOudLtr/7qr+Kxxx6rykmZKQEALJSCEgAwL4MVYTnaWSjRfPn5+uAHP2ilGwAAADAyg5VvBw4ccPCtBTL3+9a3vlWtdLv33nutdAMAhsITKgBgQTKc+PCHPxwrVqwImilLSVlOyhDJ1CQAAABg1MbHx+PEiRMxNjYWNNMXvvCFqpz0z//5P6/yv9tvvz0AAIZBQQkAWLCczvPoo49Wp6qWLVsWNMPKlSurYtI/+kf/qPq8KCcBAAAATZHTlHLl28GDB6tf0wxPPPFEVUz6j//xP8ZDDz0Ud911l0ncAMBQ3bJt27a3AwBgkS5duhSnTp2KM2fOBKORRaT3ve991eSkDJCESABAKS+++GIAACzWyZMnY3JyMg4dOhSMRhaRvvSlL8V/+A//IVatWmWdGwBQjIISADBUFy9ejFdeeSXeeuutoD5ZSlq/fn01djuLSSYmAQAlKSgBAMM0MzMTO3furApL1CfXuX3xi1+M++67r5rI7bAbAFCS/9IAAIZq+fLl8dhjj1Ujuq19Ky/DowcffNA6NwAAAKC1tmzZEj/+8Y+tfatJrnP7+te/Xq1zy1zJOjcAoA4mKAEARb3xxhvV6jcTlYYri0k5MSlHb5uYBADUzQQlAKCkXPmWq99MVBquLCblxKSPf/zjVSlp6dKlAQBQFwUlAKAWikrDoZgEADSBghIAUAdFpeFQTAIAmkBBCQColaLSwigmAQBNoqAEANRJUWlhFJMAgCZRUAIARuLNN9+M06dPx7lz54JrW7JkSdx9991xzz33xLJlyxSTAIDGUFACAEbh6NGjMT09HcePHw+uLYtI/+7f/bv4whe+EI888kjceeedVcYEADBqCkoAwEhdunSpmqh0/vx5U5V+Jacl5aSkdevWxW233VaVkhSTAIAmUVACAEYpJynlRKUsKpmqNCunJf3Lf/kv49//+39fTeFesWJFddgNAKApFJQAgMbIqUpnz56NM2fORN/kSbaclJSn3PJkm1ISANBkCkoAQFPkVKVjx45Va+D6JnOknJT0qU99Kv7ZP/tnsXz58uqwGwBAEykoAQCNc/ny5aqslOvf8v2Xv/xldNHSpUurIGn16tXV1CQr3ACAtlBQAgCaJg+9ZVnp+eefr97z9120cePG+J3f+Z341//6X8e/+Bf/Iu64444qYwIAaDoFJQCg8XL9W4ZK+X7hwoVoq5ySlCfZBqWkZcuWmZQEALSSghIA0HS5/i0nK+X7zMxMtFXmSB/5yEeqUtK/+Tf/Jj74wQ9W+VLmTAAAbaKgBAC0yqVLl+LixYvVdKXBe1NdXUjK91zdNgiPlJIAgDZTUAIA2uTkyZNVSSmnK+V7lpaa6upC0pYtW+Kf/tN/Gvfcc0+1ui2nbwMAtJWCEgDQeqdOnapeTZGTkTZv3hwrVqyofq+MBAB0jYISANB2ExMTMTk5GU2RWdJ//s//ObZu3VqtbDMhCQDoGlVrAKD1NmzYEKtWrYqmyH+enJZkfRsAAABAM2VBaWxsLJpi//798cQTT1jfBgB0loISANAJWQpqgpyetHbt2gAAAACg2bIU1AQ5PWn37t0BANBlCkoAQCesXLky1q1bF6N2//33BwAAAADNlxOUmlAMOnDgQAAAdJ2CEgDQGTlFaZQjsLMgtXr16gAAAACgHbIctGbNmhiVLEjt2LEjAAC6TkEJAOiMpUuXxvr162NUmrJmDgAAAIC5yXLS+Ph4jEpT1swBAJSmoAQAdEoWlJYtWxZ1y3JSFqQAAAAAaJe9e/fG5s2bo25ZThrF3xcAYBQUlACATskVb5s2bYo6ZSEq17sBAAAA0D45RengwYNRpywm5Xo3AIC+UFACADpn5cqVsWrVqqiL6UkAAAAA7TY2Nla96mJ6EgDQNwpKAEAnZWmoDjk9ae3atQEAAABAux04cCDqYHoSANBHCkoAQCflFKX169dHaQ8++GAAAAAA0H5btmyJ8fHxKO3IkSMBANA3CkoAQGflFKUlS5ZEKevWrYvly5cHAAAAAN2Qq9fWrFkTpeTkpCxCAQD0jYISANBZWU4qOUWprjVyAAAAANQjy0lZUiql5F8bAKDJFJQAgE7LEtGyZcti2PKvu3Tp0gAAAACgW3LN2+bNm2PYspxU4q8LANAGCkoAQOdt2rQphikLT6YnAQAAAHTXwYMHY5iymDQxMREAAH2loAQAdN7KlStj1apVMSzKSQAAAADdNjY2Vr2GxWo3AKDvFJQAgF4Y1hSlFStWxNq1awMAAACAbhvWFKUtW7bE7t27AwCgzxSUAIBeWLp06VAmHz344IMBAAAAQPcNay3bkSNHAgCg7xSUAIDeWL9+fSxZsiQWat26dVXRCQAAAIB+2Lt3b6xZsyYWKicnZdEJAKDvFJQAgN7IctJ9990XC7Fs2bKhTGACAAAAoD2ynLR///5YiCwmLfTPBQDoGgUlAKBX7r333li1alXM19q1a01PAgAAAOih8fHxGBsbi/natWuX6UkAAL+ioAQA9M58JyGZngQAAADQb/OdhJTFpImJiQAAYJaCEgDQOytXrqzGc8+VchIAAABAv+UEpR07dsz5/2+1GwDAOykoAQC9dP/998eSJUtu+v9bt25dtd4NAAAAgH47cODAnA697d69u3oBAPAbCkoAQC8tXbo0Hn744Wp92/WsWrWqKjIBAAAAQK5te+6556r368lJS1lkAgDgnRSUAIDeWr58eXzoQx+qpiStWLGi+mO33XZbVUzKoCn/t7lMWQIAAACgH7Zs2VKVlHJCUv465VSlLCYdPHiw+t/mMmUJAKBvbtm2bdvbAQAAAABz9OKLLwYAAAAAzJUJSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAAAAAAQDEKSgAAAAAA/P/t2jEBAAAAwiD7pzbFPsgBAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAABgAAAAAFARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABARlACAAAAAAAAAAAyghIAAAAAAAAAAJARlAAAAAAAAAAAgIygBAAAAAAAAAAAZAQlAAAAAAAAAAAgIygBAAAAAAAAAAAZQQkAAAAAAAAAAMgISgAAAAAAAAAAQEZQAgAAAAAAAAAAMoISAAAAAAAAAACQEZQAAAAAAAAAAICMoAQAAAAAAAAAAGQEJQAAAAAAAAAAICMoAQAAAAAAAAAAGUEJAAAAAAAAAADICEoAAAAAAAAAAEBGUAIAAAAAAAAAADKCEgAAAAAAAAAAkBGUAAAAAAAAAACAjKAEAAAAAAAAAABkBCUAAAAAAAAAACAjKAEAAAAAAAAAABlBCQAAAAAAAAAAyAhKAAAAAAAAAABA5rcwQPH6Y8W9AAAAAElFTkSuQmCC","lightningAddress":"fd5ce42fc3e44e17@coinos.io","zapSplits":[{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":95,"relay":"wss://relay.damus.io"},{"pubkey":"1bc70a0148b3f316da33fe3c89f23e3e71ac4ff998027ec712b905cd24f6a411","weight":5,"relay":"wss://nos.lol"}]}
-
 @ 05a0f81e:fc032124
2025-06-13 22:31:37
@ 05a0f81e:fc032124
2025-06-13 22:31:37Lying is a great tool for destruction, it have damage many marriage, relationships, culture, religion. It have also destroy human integrity and reputation.
What is lying? Lying is an act of someone saying something that is not true either to gain favor or to achieve any other hidden agenda.
There are many reasons why people lie, kids lie to flee from punishment, but adult lie either to gain favour or to achieve his hidden agendas. Since the existence of the world, adult lies have no positive impact on the society and the world at large.
Adult lies brings hatred, kill dreams, cage future and success, end norm and culture, delete history, the reason adult lie is different from the reason children's lie. Anything built on lies collapse when the truth arises, Anything covered with lies uncover when the truth unveil, lie leads to life full of regrets and angers especially when the truth unveils. Lies destroy life's and societies.
What happen if a child is raise on lies !.
When parents raise there children with lies, the children mindset reset towards the reason for the lies. If the lies are about a person, the children will end up hating the person, if it were about a profession, the children will end up hating the profession. Single mothers who lie to there baby about there father end up raising a child that hate his or her father.
Most norms and cultures have gone extinc all because of lies, some generations did not meet most norms because of lies, most legacy died because of lies.
When parents raise there children with lies, they did the children harm and they are destroying the society because children will grow into adults and have there own family, they will keep passing on the baton (lies) to generations and norms and cultures will keep dieing and the society will end up shattered.
Raise your child on truth! Raise your child on truth Teaching them repercussions and consequences if the truth is too wild.
-
 @ 1f3ce62e:6e6b5d83
2025-06-14 12:15:20
@ 1f3ce62e:6e6b5d83
2025-06-14 12:15:20This question is an invitation to explore your internal congruence in those actions because this is key to show up as a Whole Self.
Internal alignment on the way you feel, think, communicate, and act create harmony in our life. Looking at it can be a compass to quickly identify those moments of internal misalignment and easily work our way back to balance.
When we think one thing and say another, or when we say one thing and do another, or when we think one thing and do another, in those situations we show up partially. We are one person with a group of friends and someone else with another group. We are one person at work and another at home.
Finding that internal alignment requires us to identify our limiting believes and fears of not being accepted as we are. All those limitations are not us, they are just mental concepts our societies, communities and families created, but are not defining who we really are.
In order to explore your internal alignment, think about an specific situation at work or at your personal life and let's jump into a CREATIVE COACHING TIME:
🌱 What do you feel about this situation?\ 🌱 What do you think about it?\ 🌱 What do you say about this situation? If you haven't said anything yet, why? Are there any fears or limiting believes?\ 🌱 What have you done about this? If you haven't, why?
🌱 Is it congruence between what you feel and what you say?\ 🌱 Is it congruence between what you think and what you have done?
🌱 What small step can you take to get closer to internal alignment?
Congruence between what you feel, think, say and do eventually leads to come at work or be at home as same person, as a whole self.
In my adventure at the corporate world, I have experienced that using colors is related to being childish and not being professional. But when I tried to overcome that limiting belief using a lot of colors in a presentation as a test, people actually appreciated it and liked it.
Since then, I have been exploring how to introduce colors while interacting with teams at work. In that experimentation, I have learned that colors can speaks to our brains and help us with visual memory.
Some colors can trigger positive emotions in us, as well as, some others might trigger negative ones.
Colors can be used as a creative tool to express ideas, communicate with our teams important messages and create spaces with specific purposes as we will explore in this book.
Your beliefs about using colors at work are going to determine your impression of these series of blog posts, so sooner than later, I would like to invite you to another CREATIVE COACHING TIME to explore them:
\ 🌱 What do colors make you feel?\ 🌱 What are your beliefs about colors?\ 🌱 What are your beliefs about using colors at work?\ 🌱 What are the reasons behind those beliefs?\ 🌱 Would you like to try to use more colors at work for a week and explore what happens?\ \ As a creative tool, colors can also be used to describe the way you feel as well as your talents (by thinking, communicating and doing).
Internal congruence is an aspect that can help us a lot on identifying how opaque or brilliant are our colors. An example can help you to understand how to apply colors into your internal congruence. Let's imagine you feel very emotionally overwhelmed today but you don't talk about it at all. That is an opaque representation of the color pink.
In the following blogs, we will explore each color, its meaning and how you can apply it to express your feelings and identify your talents. It will help you to see yourself from a new perspective (the primary goal of creativity) and learn something about yourself. As we start this colorful journey, you might need to learn a little bit about each color first.
We can also use colors to define roles in a group as well as the mission of a team in an organization. Then, I will invite you to reflect on how we use colors at work today (if we do it at all) and additional ways of using them.
Although there are a lot of colors, you don't have to have them all at once, so there is not race to win anything here. You don't need to compete with others on their colors versus yours. There might be times in your life or professional career where you will need to develop one color more than another. Even as feelings, you can feel RED ❤️ today and PINK 🩷 tomorrow. The idea is to let yourself experiment all feelings without judgement.
An evolutionary goal as individuals, if there could be any, it might be to have them or have experienced all, but you have your whole life for it.
An evolutionary purpose as a teams, organizations and companies, it could be to use them as a diverse way of feeling, thinking, expressing and acting. And this could set a new step into our diversity and inclusion discussions in the future. Being GREEN 💚 today, doesn't mean I will always be GREEN. It might be that the situation today requires me to be GREEN. This could eventually lead to focusing on being more than gender, color, race or any other tags we are using these days. We will talk more about that in a chapter.
Before we jump into the colors, let's have a a new CREATIVE COACHING TIME, It is your turn now, before knowing anything about the meaning of the colors, quickly rate yourself based the first word that appears in your mind when you read these questions (Low or High):
How RED ❤️ are you?\ How ORANGE 🧡 are you?\ How YELLOW 💛 are you?\ How GREEN 💚 are you?\ How PINK 🩷 are you?\ How SKY BLUE 🩵 are you?\ How BLUE 💙 are you?\ How VIOLET 💜 are you?
You can apply the same questions to feelings. Remember this set of answers are a picture of you today, by the time doing this exercise. You can come back to it every time you want to check how colorful are you in the way you think, you feel, you communicate and you act anytime.
Hope this helps!
Stay colorful in a black and white World
Laus 🌱💛
-
 @ 5627e59c:d484729e
2025-06-12 04:23:52
@ 5627e59c:d484729e
2025-06-12 04:23:52Look and see\ Look and see
You look like how you look at me
Look and see\ Look and see
The colorless through the color TV
Look and see\ Look and be
The unborn identity
-
 @ 8672c492:14d2af43
2025-06-13 21:29:28
@ 8672c492:14d2af43
2025-06-13 21:29:28SPEC.md - Swift Calculator Architecture
1. Overview
The Swift Calculator is a lightweight, user-friendly calculator application built for iOS using Swift. It supports basic arithmetic operations, a clear/reset function, and a responsive UI.
2. Architecture
The application follows the Model-View-ViewModel (MVVM) pattern to separate concerns and improve maintainability.
2.1 Components
- Model (
CalculatorModel.swift): - Handles the core logic for arithmetic operations (addition, subtraction, multiplication, division).
-
Manages the current state (e.g., display value, pending operations).
-
ViewModel (
CalculatorViewModel.swift): - Acts as the intermediary between the Model and View.
-
Processes user inputs (e.g., button taps) and updates the Model and View accordingly.
-
View (
CalculatorView.swift): - Responsible for the UI layout (buttons, display label).
- Observes the ViewModel for changes and updates the UI.
2.2 Key Features
- Basic Operations: Supports
+,-,*,/. - Clear/Reset: A
Cbutton to reset the calculator state. - Error Handling: Displays "Error" for invalid operations (e.g., division by zero).
- Responsive UI: Adapts to different screen sizes and orientations.
2.3 Data Flow
- User interacts with the View (e.g., taps a button).
- View sends the input to the ViewModel.
- ViewModel processes the input and updates the Model.
- Model updates its state and notifies the ViewModel.
- ViewModel updates the View with the new state.
3. Technical Stack
- Language: Swift 5
- Framework: SwiftUI (for declarative UI) or UIKit (if preferred)
- Dependency Management: Swift Package Manager (SPM)
4. Future Enhancements
- Support for scientific operations (e.g., square root, exponents).
- Dark mode support.
- Memory functions (M+, M-, MR).
- Model (
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
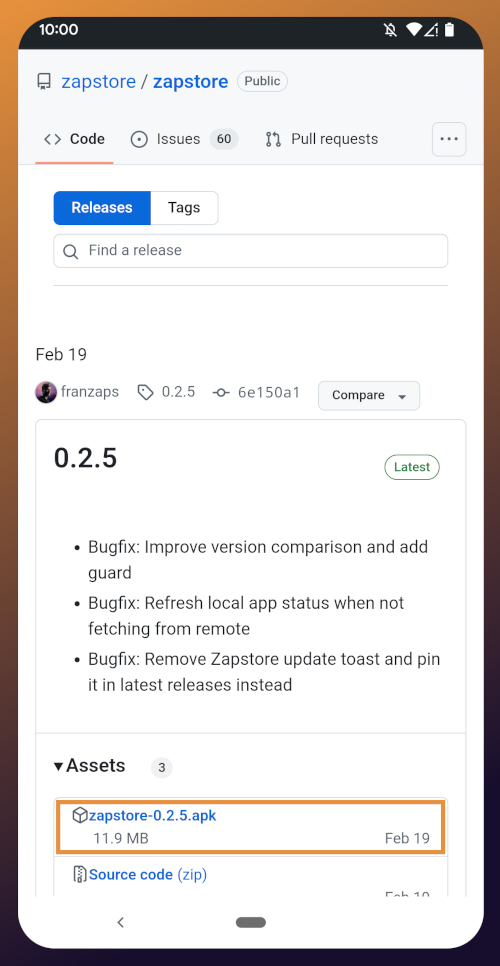
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
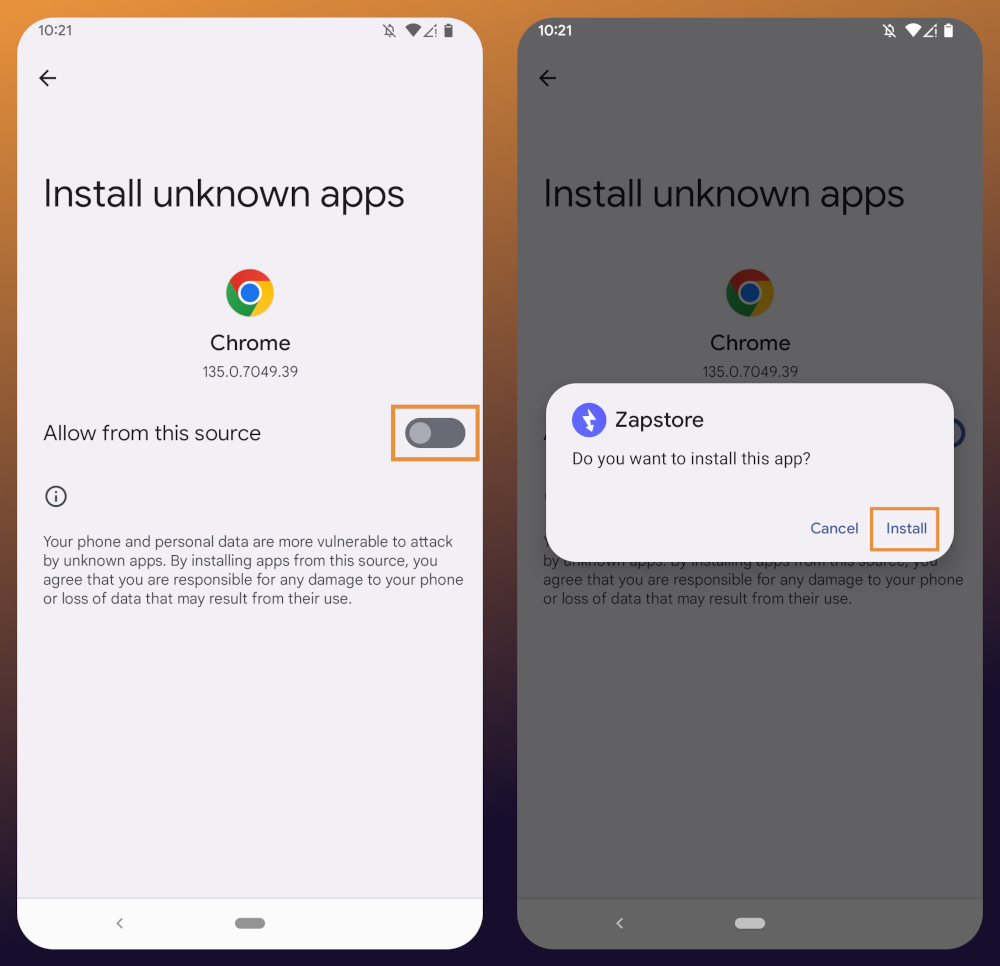
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ dfa02707:41ca50e3
2025-06-06 20:02:20
@ dfa02707:41ca50e3
2025-06-06 20:02:20Contribute to keep No Bullshit Bitcoin news going.
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 8bad92c3:ca714aa5
2025-06-06 12:01:54
@ 8bad92c3:ca714aa5
2025-06-06 12:01:54Key Takeaways

Michael Goldstein, aka Bitstein, presents a sweeping philosophical and economic case for going “all in” on Bitcoin, arguing that unlike fiat, which distorts capital formation and fuels short-term thinking, Bitcoin fosters low time preference, meaningful saving, and long-term societal flourishing. At the heart of his thesis is “hodling for good”—a triple-layered idea encompassing permanence, purpose, and the pursuit of higher values like truth, beauty, and legacy. Drawing on thinkers like Aristotle, Hoppe, and Josef Pieper, Goldstein redefines leisure as contemplation, a vital practice in aligning capital with one’s deepest ideals. He urges Bitcoiners to think beyond mere wealth accumulation and consider how their sats can fund enduring institutions, art, and architecture that reflect a moral vision of the future.
Best Quotes
“Let BlackRock buy the houses, and you keep the sats.”
“We're not hodling just for the sake of hodling. There is a purpose to it.”
“Fiat money shortens your time horizon… you can never rest.”
“Savings precedes capital accumulation. You can’t build unless you’ve saved.”
“You're increasing the marginal value of everyone else’s Bitcoin.”
“True leisure is contemplation—the pursuit of the highest good.”
“What is Bitcoin for if not to make the conditions for magnificent acts of creation possible?”
“Bitcoin itself will last forever. Your stack might not. What will outlast your coins?”
“Only a whale can be magnificent.”
“The market will sell you all the crack you want. It’s up to you to demand beauty.”
Conclusion
This episode is a call to reimagine Bitcoin as more than a financial revolution—it’s a blueprint for civilizational renewal. Michael Goldstein reframes hodling as an act of moral stewardship, urging Bitcoiners to lower their time preference, build lasting institutions, and pursue truth, beauty, and legacy—not to escape the world, but to rebuild it on sound foundations.
Timestamps
00:00 - Intro
00:50 - Michael’s BBB presentation Hodl for Good
07:27 - Austrian principles on capital
15:40 - Fiat distorts the economic process
23:34 - Bitkey
24:29 - Hodl for Good triple entendre
29:52 - Bitcoin benefits everyone
39:05 - Unchained
40:14 - Leisure theory of value
52:15 - Heightening life
1:15:48 - Breaking from the chase makes room for magnificence
1:32:32 - Nakamoto Institute’s missionTranscript
(00:00) Fiat money is by its nature a disturbance. If money is being continually produced, especially at an uncertain rate, these uh policies are really just redistribution of wealth. Most are looking for number to go up post hyper bitcoinization. The rate of growth of bitcoin would be more reflective of the growth of the economy as a whole.
(00:23) Ultimately, capital requires knowledge because it requires knowing there is something that you can add to the structures of production to lengthen it in some way that will take time but allow you to have more in the future than you would today. Let Black Rockck buy the houses and you keep the sats, not the other way around.
(00:41) You wait until later for Larry Frink to try to sell you a [Music] mansion. And we're live just like that. Just like that. 3:30 on a Friday, Memorial Day weekend. It's a good good good way to end the week and start the holiday weekend. Yes, sir. Yes, sir. Thank you for having me here. Thank you for coming. I wore this hat specifically because I think it's I think it's very apppropo uh to the conversation we're going to have which is I hope an extension of the presentation you gave at Bitblock Boom Huddle for good. You were working on
(01:24) that for many weeks leading up to uh the conference and explaining how you were structuring it. I think it's a very important topic to discuss now as the Bitcoin price is hitting new all-time highs and people are trying to understand what am I doing with Bitcoin? Like you have you have the different sort of factions within Bitcoin.
(01:47) Uh get on a Bitcoin standard, get on zero, spend as much Bitcoin as possible. You have the sailors of the world are saying buy Bitcoin, never sell, die with your Bitcoin. And I think you do a really good job in that presentation. And I just think your understanding overall of Bitcoin is incredible to put everything into context. It's not either or.
(02:07) It really depends on what you want to accomplish. Yeah, it's definitely there there is no actual one-sizefits-all um for I mean nearly anything in this world. So um yeah, I mean first of all I mean there was it was the first conference talk I had given in maybe five years. I think the one prior to that uh was um bit block boom 2019 which was my meme talk which uh has uh become infamous and notorious.
(02:43) So uh there was also a lot of like high expectations uh you know rockstar dev uh has has treated that you know uh that that talk with a lot of reference. a lot of people have enjoyed it and he was expecting this one to be, you know, the greatest one ever, which is a little bit of a little bit of a uh a burden to live up to those kinds of standards.
(03:08) Um, but you know, because I don't give a lot of talks. Um, you know, I I I like to uh try to bring ideas that might even be ideas that are common. So, something like hodling, we all talk about it constantly. uh but try to bring it from a little bit of a different angle and try to give um a little bit of uh new light to it.
(03:31) I alsove I've I've always enjoyed kind of coming at things from a third angle. Um whenever there's, you know, there's there's all these little debates that we have in in Bitcoin and sometimes it's nice to try to uh step out of it and look at it a little more uh kind of objectively and find ways of understanding it that incorporate the truths of of all of them.
(03:58) uh you know cuz I think we should always be kind of as much as possible after ultimate truth. Um so with this one um yeah I was kind of finding that that sort of golden mean. So uh um yeah and I actually I think about that a lot is uh you know Aristotle has his his concept of the golden mean. So it's like any any virtue is sort of between two vices um because you can you can always you can always take something too far.
(04:27) So you're you're always trying to find that right balance. Um so someone who is uh courageous you know uh one of the vices uh on one side is being basically reckless. I I can't remember what word he would use. Uh but effectively being reckless and just wanting to put yourself in danger for no other reason than just you know the thrill of it.
(04:50) Um and then on the other side you would just have cowardice which is like you're unwilling to put yourself um at any risk at any time. Um, and courage is right there in the middle where it's understanding when is the right time uh to put your put yourself, you know, in in the face of danger um and take it on. And so um in some sense this this was kind of me uh in in some ways like I'm obviously a partisan of hodling.
(05:20) Um, I've for, you know, a long time now talked about the, um, why huddling is good, why people do it, why we should expect it. Um, but still trying to find that that sort of golden mean of like yes, huddle, but also what are we hodling for? And it's not we're we're not hodddling just merely for the sake of hodddling.
(05:45) There there is a a purpose to it. And we should think about that. And that would also help us think more about um what are the benefits of of spending, when should we spend, why should we spend, what should we spend on um to actually give light to that sort of side of the debate. Um so that was that was what I was kind of trying to trying to get into.
(06:09) Um, as well as also just uh at the same time despite all the talk of hodling, there's always this perennial uh there's always this perennial dislike of hodlers because we're treated as uh as if um we're just free riding the network or we're just greedy or you know any of these things. And I wanted to show how uh huddling does serve a real economic purpose.
(06:36) Um, and it does benefit the individual, but it also does uh it it has actual real social um benefits as well beyond merely the individual. Um, so I wanted to give that sort of defense of hodling as well to look at it from um a a broader position than just merely I'm trying to get rich. Um uh because even the person who uh that is all they want to do um just like you know your your pure number grow up go up moonboy even that behavior has positive ramifications on on the economy.
(07:14) And while we might look at them and have uh judgments about their particular choices for them as an individual, we shouldn't discount that uh their actions are having positive positive effects for the rest of the economy. Yeah. So, let's dive into that just not even in the context of Bitcoin because I think you did a great job of this in the presentation.
(07:36) just you've done a good job of this consistently throughout the years that I've known you. Just from like a first principles Austrian economics perspective, what is the idea around capital accumulation, low time preference and deployment of that capital like what what like getting getting into like the nitty-gritty and then applying it to Bitcoin? Yeah, it's it's a big question and um in many ways I mean I I even I barely scratched the surface.
(08:05) uh I I can't claim to have read uh all the volumes of Bombber works, you know, capital and interest and and stuff like that. Um but I think there's some some sort of basic concepts that we can look at that we can uh draw a lot out. Um the first uh I guess let's write that. So repeat so like capital time preference. Yeah. Well, I guess getting more broad like why sav -
 @ edeb837b:ac664163
2025-06-13 21:15:05
@ edeb837b:ac664163
2025-06-13 21:15:05On June 10th, 2025, four members of the NVSTly team traveled to New York City to attend the 2025 American Business Awards® ceremony, held at the iconic Marriott Marquis in Times Square. It was an unforgettable night as we accepted the Gold Stevie® Award for Tech Startup of the Year—this time, in person.
Meow (left), rich (center), MartyOooit (right)
Representing NVSTly at the event were:
- Rich, CEO & Founder
- Meow, CTO, Lead Developer, & Co-Founder
- MartyOooit, Investor
- Noob, Market Analyst (not shown in photos)
MartyOooit (left), rich (center), Meow (right)
While we shared the exciting news back in April when the winners were announced, being there in person alongside other winners—including eBay, AT&T, T-Mobile, HP Inc., and Fidelity Investments—made the achievement feel even more surreal. To be honored alongside billion-dollar industry leaders was a proud and humbling moment for our startup and a huge milestone in NVSTly’s journey.
🎤 Team Interview at the Event
During the event, our team was interviewed about the win. When asked:
“What does winning a Stevie Award mean for your organization?”
“How will winning a Stevie Award help your organization?”Here’s what we had to say:
📺 Watch the video
A Big Win for Retail Traders
NVSTly was awarded Gold for Tech Startup of the Year in recognition of our work building a powerful, free social investing platform that empowers retail traders with transparency, analytics, and community-driven tools.
Unlike traditional finance platforms, NVSTly gives users the ability to:
- Share and track trades in real time
- Follow and receive alerts from top traders
- Compete on global leaderboards
- Access deep stats like win rate, average return, and more
Whether you're a beginner or experienced trader, NVSTly gives you the insights and tools typically reserved for hedge funds—but in a free, social format built for the modern investor.
Continued Recognition and Momentum
This award adds to a growing list of recognition for NVSTly:
- 🏆 People’s Choice Winner at the 2024 Benzinga Fintech Awards
- 🔁 Nominated again for Best Social Investing Product in the 2025 Benzinga Fintech Awards
- 🌟 Team members JustCoreGames and Lunaster are nominated for Employee of the Year (Information Technology – Social Media) in the 2025 Stevie® Awards for Technology Excellence
We’re beyond proud of what our small but mighty team has accomplished—and we’re just getting started. 🚀
Thanks to the Stevie Awards for an incredible night in New York, and to our community of 50,000+ traders who’ve helped shape NVSTly into what it is today.
This win is yours, too.Stay tuned—more big things are coming.
— Team NVSTly

The event brought together some of the most respected names in tech, finance, and business. -
 @ f40a134b:60fb788b
2025-06-13 21:10:14
@ f40a134b:60fb788b
2025-06-13 21:10:14{"url":"https://convy.click","title":"Convy","description":"","submittedAt":1749849014}
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
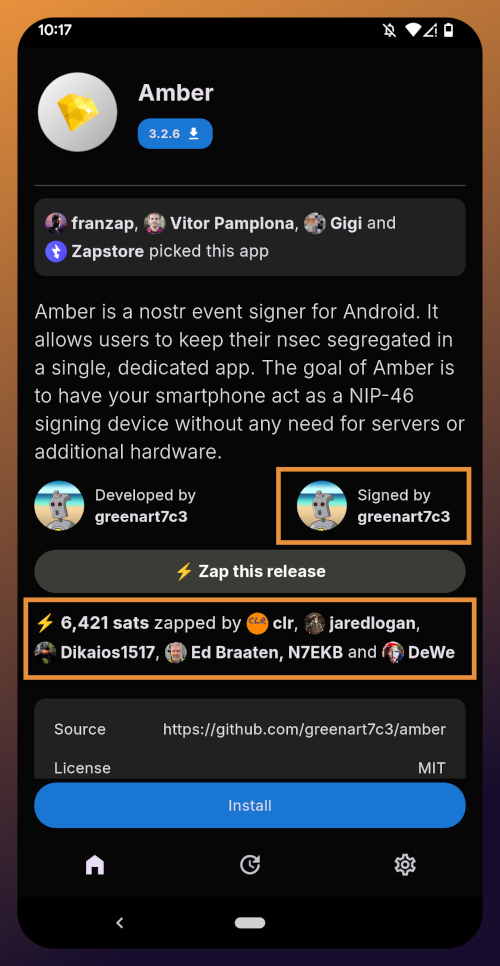
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
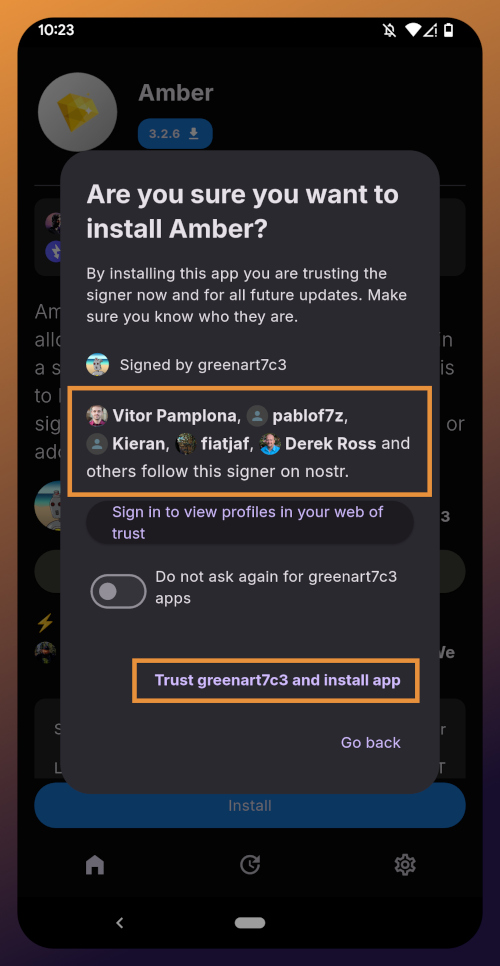
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
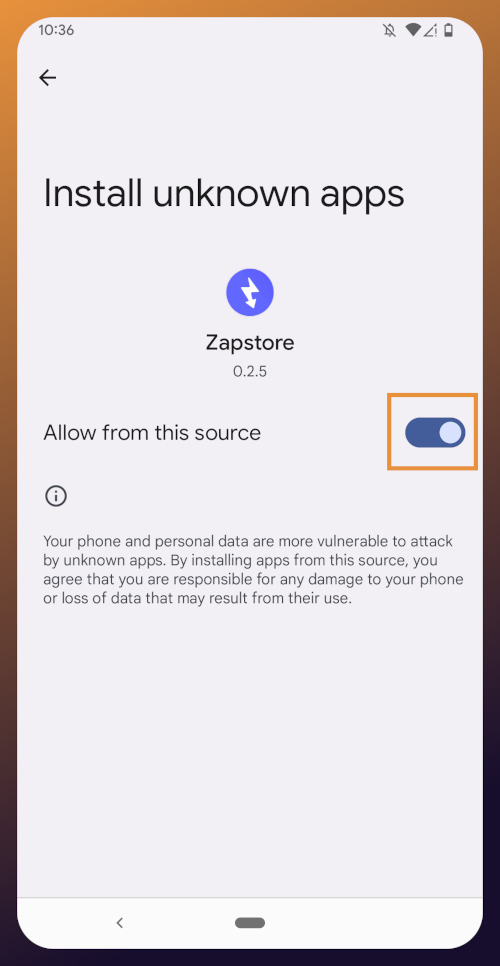
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
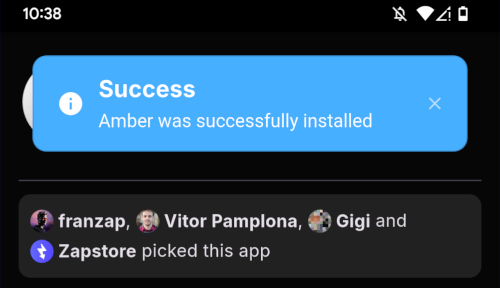
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
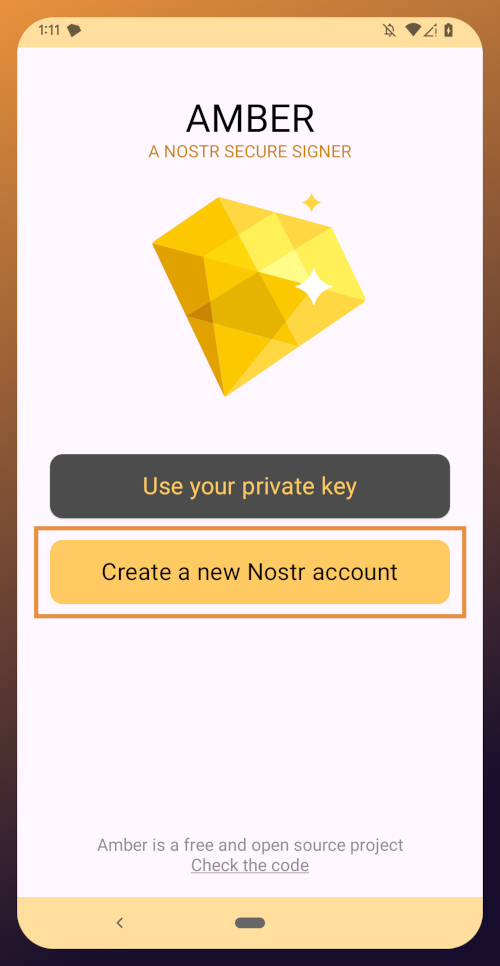
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
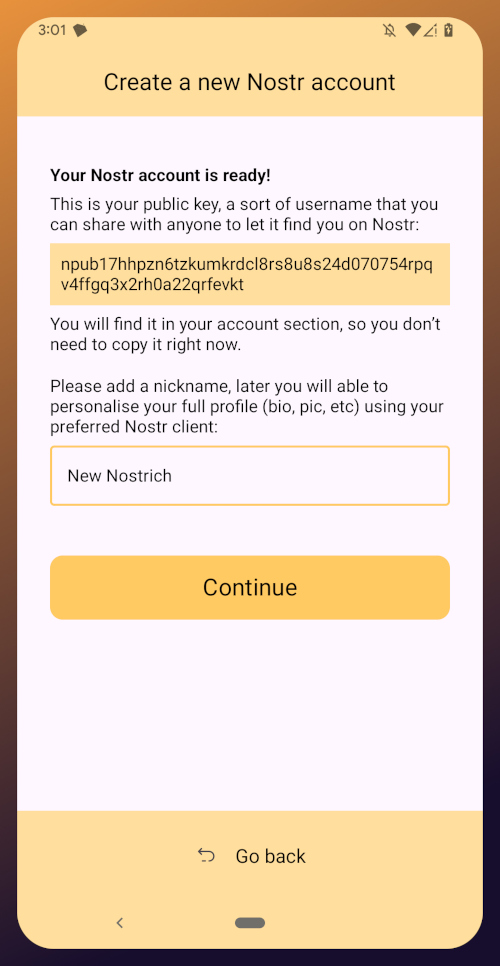
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
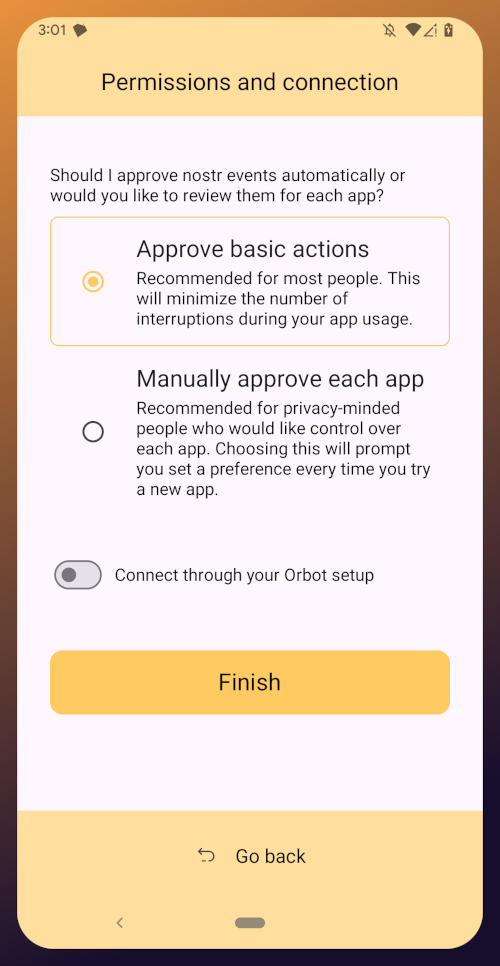
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
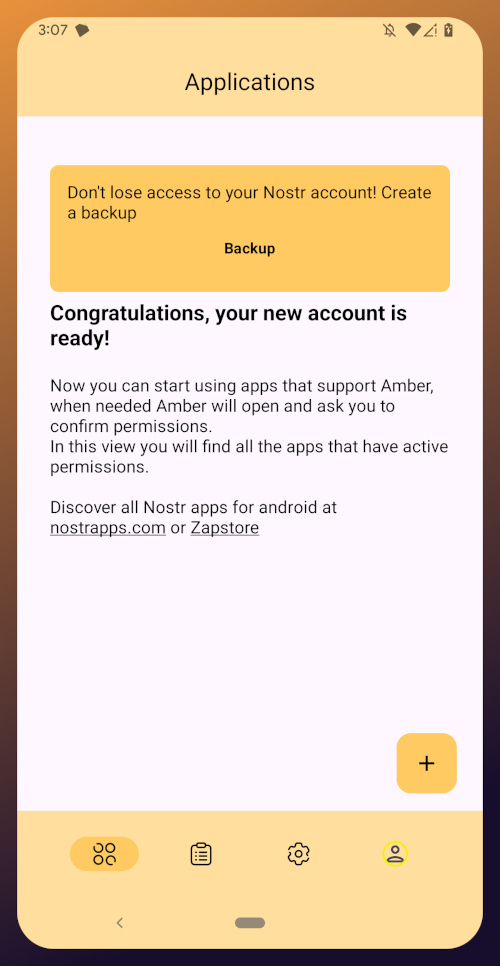
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
The next screen will require you to paste your private key.
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
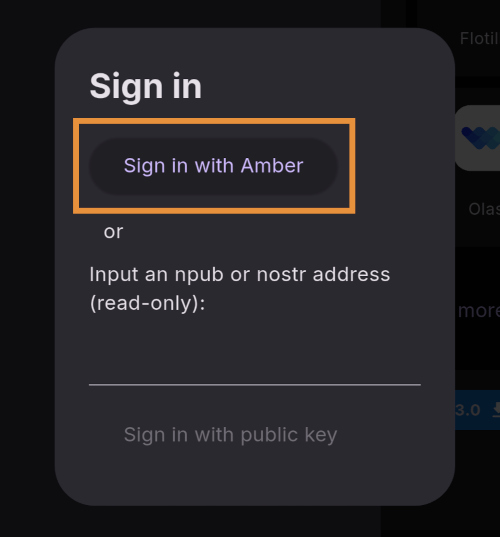
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 5627e59c:d484729e
2025-06-11 22:31:47
@ 5627e59c:d484729e
2025-06-11 22:31:47Warmte betekent zachtheid aan de grenzen\ Omringt door zachte mensen
Warmte betekent vrijheid\ Vrij om mij te tonen en te bewegen
Warmte betekent rust\ Om hier niet ver vandaan te hoeven zijn
Warmte betekent leven\ Iets waar ik vol van liefde mijn aandacht aan wil geven
Warmte betekent vriendschap\ Alle vriendschap die mijn hartje vult
Warmte betekent vol zijn\ Vol betekenis die mijn omgeving aan mij schenkt
Warmte betekent geven\ Geven om wat ik voor jou en jij voor mij\ Wij voor elkaar nu eigenlijk echt betekenen
-
 @ dfa02707:41ca50e3
2025-06-06 00:02:15
@ dfa02707:41ca50e3
2025-06-06 00:02:15Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ f40a134b:60fb788b
2025-06-13 21:07:02
@ f40a134b:60fb788b
2025-06-13 21:07:02{"url":"https://test.com","title":"test.com","description":"","submittedAt":1749848822}
-
 @ 7f6db517:a4931eda
2025-06-05 22:01:51
@ 7f6db517:a4931eda
2025-06-05 22:01:51

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ b1ddb4d7:471244e7
2025-06-05 19:01:34
@ b1ddb4d7:471244e7
2025-06-05 19:01:34“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ cae03c48:2a7d6671
2025-06-13 21:02:28
@ cae03c48:2a7d6671
2025-06-13 21:02:28Bitcoin Magazine

Passport Prime: A New Security Device For a New GenerationPassport Prime, Foundation Devices’ latest retail hardware wallet, is about to hit the market in Q3 of 2025. The device features a full-color touch screen the size of a credit card with a modern industrial aesthetic. It aims to be a developer platform for Bitcoin and crypto software with high security demands.
Besides serving the basic wallet needs of Bitcoin users, the device is designed as an open source platform for app developers to bring a new experience of crypto-native cybersecurity to the public. The Passport Prime is expected to ship with a powerful Bitcoin wallet app, as well as virtual YubiKeys, a 2FA app, a seed vault for imported or low-value crypto wallets, 50 GB of storage, NFC, and encrypted Bluetooth support, among other features.
Frustrated with the public’s lackluster adoption of hardware wallets as the crypto industry enters the mainstream adoption phase, Foundation has been working since 2020 to bring security hardware devices to feature parity with mainstream consumer technology. However, the path is not simple.


The Adoption Problem of Hardware Wallets
Hardware wallets have been a critical security product for Bitcoin users since 2014 when Satoshi Labs created the Trezor. Before that, users had few options, and many of the funds lost in that era were due to user ignorance of how to manage and properly secure private keys in Bitcoin. Armory, funded by Trace Mayer in the early days, was one of the first solutions but it was highly technical and was best used with hardware the user had to modify themselves — like removing antennas from a laptop. This kind of technology became a security foundation for exchanges, who, through many hacks and hard lessons, slowly got better at securing user funds from organized crime and hackers while playing jurisdictional arbitrage to avoid hostile governments.
As the first hardware wallets started to enter the retail market, significant adoption was seen. With the massive growth of Bitcoin since its inception, the best security practices have failed to keep up with the ease of use provided by custodians while also failing to deliver security and feature parity to users in an interface they are familiar with.
In a keynote presentation on the Passport Prime landing page, Zach Herbert, CEO and co-founder of Foundation, explains their analysis of the market and why they believe only 2.5% of the market is using hardware wallets today, despite mainstream adoption of digital assets like Bitcoin — a concern felt across the industry that too many people are getting accustomed to custodial services.

The small screens, iconic to the hardware wallet ecosystem, are often a barrier for users. The shape of the device, often small and with few buttons, can make people nervous, especially when the wrong combination of clicks means an irreversible financial transaction.
In the case of touchscreen devices like the Trezor T, while certainly an improvement from the Trezor One, the buttons are still far smaller than what the public is used to for smartphones, the most prolific computer platform of this era.

The problem with trying to bring hardware wallets to feature parity with mobile phones is the massive complexity introduced by the corresponding software and hardware. Mobile phones, after all, are designed for mass manufacturing and with ease-of-use priorities in mind, rather than securing life-changing amounts of digital currency, which, once sent, cannot be reversed.
The hardware wallet industry has had to build out open source, verifiable, security-optimized hardware and software that addresses top security concerns, while also delivering a familiar and comfortable user experience to the public. In general, the industry recognizes the need for bigger screens and bigger buttons, as seen in new models by Ledger, for example, with their Ledger Stax, and, of course, Coldcard Q’s Blackberry-style hardware wallet.
When asked why not just try to build on top of a standard mobile phone platform, Owen Kemeys, hardware designer at Foundation Devices, told Bitcoin Magazine that “there’s a huge advantage to Passport Prime being a separate security device,” adding that “we need this stuff to work for the normal people. They are not going to be able to understand or have any interest in understanding what makes something safe or unsafe on their phone. Even if they were going so far as to have a dedicated phone for secret stuff or whatever. Everything that we develop, Apple and Google could bake into their phones and tell you it’s safe. But if it’s in a separate device that is built to do that one exact thing, then you know, OK, if it happens on the Passport Prime, it’s safe.”
The Passport Prime Feature Set
Foundation believes they have found an optimal and preferable middle ground between high security and a familiar user experience in a mobile phone-style device, but with very specific hardware and software inside. Kemeys explained that “the Passport Prime runs its own operating system,” adding that “We’re not running a fork of Android or something and then dressing it up differently. We wrote this from the ground up in Rust. It’s called KeyOS. It’s designed for this one purpose of running a smartphone-like experience, but with sandboxed apps.”
The wallet-related cryptography that’s normal to today’s Bitcoin and crypto wallets is also deeply integrated with the operating system. A master seed phrase is set up by the user; the seed’s corresponding master private and public keys are then used to derive secure, isolated keys for other apps on the Passport Prime. “All apps are sandboxed and receive hardened child seeds, meaning that even if an app is malicious, it has no access to the master seed and cannot communicate with other apps,” Herbert explained in his presentation.
This design builds the foundations necessary for secure app development on top of the Passport Prime, unique among hardware wallet manufacturers. While Ledger has made some progress in that direction, Herbert says that the Ledger operating system is very restrictive with such apps — primarily out of security concerns — making it difficult for developers to contribute to the ecosystem. Foundation believes they have solved the problem, unlocking a new kind of security device that can be used for more than cold storage of Bitcoin and crypto assets. It is a security platform for everyday use in the digital era.
As is generally expected of high-security devices like a hardware wallet, the Passport Prime comes without most of the normal sensors or antennas found in mobile devices. No Wi-Fi, no GPS, and no SIM card, of course. However, NFC, an increasingly popular communications module in hardware wallets and in payments technology in general, is included. NFC has a very short signal range and depends on power from the device sending the signal, making it a fairly secure protocol and bringing Bitcoin closer to the tap-to-pay credit card experience the general public is used to.
“We now have an NFC reader inside,” Kemeys explained, excited about the innovation space unlocked by NFC chips in Bitcoin. “As part of your onboarding setup, in the box, we’re going to ship three NFC cards with the Prime. And as our default onboarding workflow, we’re going to encourage people to make a two-of-three Shamir setup, and back up the shares onto some of those cards.”
Shamir secret sharing is an old and well-known cryptographic algorithm similar to multisignature schemes in Bitcoin but entirely off-chain. It allows users to grab a master private key and split it into shares that can come together later to recreate and reco
-
 @ b9d5de4b:26c0a1b8
2025-06-14 01:51:07
@ b9d5de4b:26c0a1b8
2025-06-14 01:51:07Hello, legitmately asking for a friend...does anyone know of a way to recover a bip38 address created on bitaddress? they claim to have both keys just dont know the passphase.
https://stacker.news/items/1005953
-
 @ 5627e59c:d484729e
2025-06-11 22:30:36
@ 5627e59c:d484729e
2025-06-11 22:30:36Nooit is mijn dans echter\ Dan net nadat het regende\ Want regen biedt een kans\ Om mijn gevoel te voelen
Zolang de regen spettert\ En ik mezelf graag zie\ Wordt er niets verplettert\ Ook al lijkt dat soms wel zo
Zodra de regen ophoudt\ En zich terugtrekt met de wolken\ Komt een nieuwe glans\ Voor het eerst mijn ogen binnen
Wat is het leven heerlijk\ Als ik eerlijk ben en voel\ Wat is het leven zacht\ En het brengt me naar mijn doel
Wat zou ik weten zonder regen\ Gewoon steeds evenveel\ Niet groeien is niet leven\ Daarom dans ik het liefst
Net na de echte regen
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-14 01:26:59
@ 5d4b6c8d:8a1c1ee3
2025-06-14 01:26:59OMAD is great! Outside the very short window eating window, I have almost no desire to eat or drink.
I also took a nap today and a cold shower. I just needed to be more active.
How did you all do today? Are you making progress towards your ~HealthAndFitness goals?
https://stacker.news/items/1005945
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ f683e870:557f5ef2
2025-06-11 13:33:34
@ f683e870:557f5ef2
2025-06-11 13:33:34This is what has been achieved on a per-project basis since receiving the grant from Opensats.
npub.world
Together with nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, I have been refining npub.world to deliver real-time, WoT-powered profile search. These refinements include:
-
implementing new desings by nostr:npub1t3gd5yefglarhar4n6uh34uymvft4tgu8edk5465zzhtv4rrnd9sg7upxq
-
moving to the new Vertex DVM standard
-
improved URL and npub parsing
Vertex crawler
Due to the architectural mistakes I made when designing the first version, I have embarked on a full rewrite of the crawler. The new architecture is simpler, more modular and more performant, and I am confident that it will provide a stable foundation on which to expand the Vertex offering with additional functionalities and analytics.
The major differences with the old version are:
-
the
DBandRWSinterfaces have been broken up and simplified into smaller ones, each defined by their own packages -
a simplified, more efficient algorithm for updating random walks
-
use of a custom-built cache to speed up graph computations
-
a worker pool pattern to speed up event archiving
These changes have reduced the LOC by more than half while improving performance by \~10x. Of independent interest is the new pipe package, which can also be used by other projects to crawl the Nostr network.
Vertex Relay and DVMs
The Vertex relay has been updated several times, and now supports four DVM services:
-
Verify Reputation -
Recommend Follows -
Rank Profiles -
Search Profile
For each service, customers can choose the algorithm to use by specifing the sort option to use between:
-
followerCount -
globalPagerank -
personalizedPagerank
More information can be found at https://vertexlab.io/.
Overall, the relay has processed more than 100,000 DVM requests, with the current daily rate standing at around 1,500.
rely
Unsatisfied with the khatru relay framework, I've decided to build my own called rely, with the goal of being simpler and more stable. I've not just scratched a personal hitch: I've used khatru for several months now (the Vertex relay is still using it) and I encountered several issues, some of which I've solved with PRs to the underlying go-nostr library.
The main differences between khatru and rely:
-
rely is much simpler, both architecturally and in terms of LOC (less than half)
-
rely has a solid testing approach, where a random yet reproducible high traffic hits the relay to see what breaks
-
rely implements a worker pool pattern where a configurable number of goroutines process the incoming requests from clients. On the other hand, khatru process them in the HandleWebsocket goroutine, which is spawned every time a client connects. This is dangerous in my opinion because if too many clients connect, memory usage would spike and the relay could potentially crash.
New DVM spec
I helped to draft this new proposal to update the DVM spec, which is one of the most controversial NIPs. While almost everyone agrees that it needs to change, there is no consensus on how to move forward. I believe our proposal is a sensible approach that defines discovery, usage, and error patterns while leaving flexibility for specific DVM kinds.
Looking at the future
Next I am going to move the Vertex relay to the rely framework and to the new crawler package. I expect that this will increase the performance and will make things more solid and more simple. After all of this refactoring and simplification, it will be time to finally add features to the Vertex offering. I have an ambitious roadmap consisting of:
-
accepting ecash for DVM requests
-
designing client-side validation schemes for the DVM responses
-
expanding the pagerank algorithm to make use of mutes and reports
-
adding an WoT impersonator check to npub.world
-
adding a nip05 check to npub.world
-
make a relystore package with some plug&play databases for rely.
-
-
 @ a4a6b584:1e05b95b
2025-06-13 20:27:58
@ a4a6b584:1e05b95b
2025-06-13 20:27:58Prerequisites
```bash
Make sure your package list is fresh
sudo apt update
(Optional but recommended) ffmpeg lets yt-dlp negotiate the best formats
sudo apt install ffmpeg jq ```
1 Install yt-dlp system-wide
bash sudo curl -L https://github.com/yt-dlp/yt-dlp/releases/latest/download/yt-dlp \ -o /usr/local/bin/yt-dlp && sudo chmod a+rx /usr/local/bin/yt-dlpA single binary is dropped into
/usr/local/bin/; version upgrades are as simple as running the same command again in the future.
2 Download the auto-generated captions as SRT
Pick any video ID—here we’ll use knAGgxzYqw8 (Chase Hughes on What is Money?).
```bash VIDEO="knAGgxzYqw8" # change this to your target ID
yt-dlp --skip-download \ --write-auto-sub \ --sub-lang en \ --sub-format srt \ -o "${VIDEO}.%(ext)s" \ "https://youtu.be/${VIDEO}"
Result: knAGgxzYqw8.en.srt
```
Flags explained
| Flag | Purpose | | ------------------ | ------------------------------------------------------- | |
--skip-download| ignore the actual video, we only want captions | |--write-auto-sub| fall back to YouTube’s auto-generated subtitles | |--sub-lang en| grab English only (adjust if you need another language) | |--sub-format srt| SRT is the simplest to strip; VTT also works | |-o| sets a predictable filename:<id>.en.srt|
3 Strip index numbers and timecodes
```bash grep -vE '^[0-9]+$|^[0-9]{2}:' "${VIDEO}.en.srt" \ | sed '/^[[:space:]]*$/d' \
"${VIDEO}.txt" ```
Breakdown
-
grep -vE '^[0-9]+$|^[0-9]{2}:' -
Removes the line counters (
3911) and any line that begins with a timestamp (02:33:40,800 --> …). -
sed '/^[[:space:]]*$/d' -
Deletes leftover blank lines.
- Output is redirected to
<ID>.txt—in our example: knAGgxzYqw8.txt.
4 (Option-al) Extra polish
Remove bracketed stage cues such as
[Music]or[Applause]and collapse back-to-back duplicates:```bash grep -v '^[.*]$' "${VIDEO}.txt" \ | awk 'prev != $0 {print} {prev=$0}' \
"${VIDEO}_clean.txt" mv "${VIDEO}_clean.txt" "${VIDEO}.txt" ```
5 Enjoy your transcript
bash less "${VIDEO}.txt" # page through grep -i "keyword" "${VIDEO}.txt" # quick searchYou now have a plain-text file ready for note-taking, quoting, or feeding into your favorite AI summarizer—no browser or third-party web services required.
TL;DR (copy-paste cheat sheet)
```bash sudo apt update && sudo apt install ffmpeg jq -y sudo curl -L https://github.com/yt-dlp/yt-dlp/releases/latest/download/yt-dlp \ -o /usr/local/bin/yt-dlp && sudo chmod a+rx /usr/local/bin/yt-dlp
VIDEO="knAGgxzYqw8" # video ID yt-dlp --skip-download --write-auto-sub --sub-lang en \ --sub-format srt -o "${VIDEO}.%(ext)s" \ "https://youtu.be/${VIDEO}"
grep -vE '^[0-9]+$|^[0-9]{2}:' "${VIDEO}.en.srt" \ | sed '/^[[:space:]]$/d' \ | grep -v '^[.]$' \ | awk 'prev != $0 {print} {prev=$0}' \
"${VIDEO}.txt"
less "${VIDEO}.txt" ```
Happy transcribing!
Adam Malin
npub15jnttpymeytm80hatjqcvhhqhzrhx6gxp8pq0wn93rhnu8s9h9dsha32lxYou can view and write comments on this or any other post by using the Satcom browser extention.
value4value Did you find any value from this article? Click here to send me a tip!
-
-
 @ 5627e59c:d484729e
2025-06-11 22:30:23
@ 5627e59c:d484729e
2025-06-11 22:30:23My life is my way Home\ My death is my arrival
I can't wait to be Home\ And so I love life
I can't wait to be Home\ And so I want to live to the fullest
For there are no shortcuts
Many people die\ And never make it Home
They will have to wait\ For another chance to die
Another chance to live fully\ And die totally
I'm so thankful to be alive\ I'm on my way Home
I'm so thankful to be alive\ To have another chance to die
Every day I take a step\ In the direction of my death\ I do not postpone it
Every day I take a step\ In the direction of my truth\ I do not avoid it
It is who I am, always have been\ And always will be
It lies beyond that door\ That keeps everything in check
Where only can go through\ Which is forever true
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
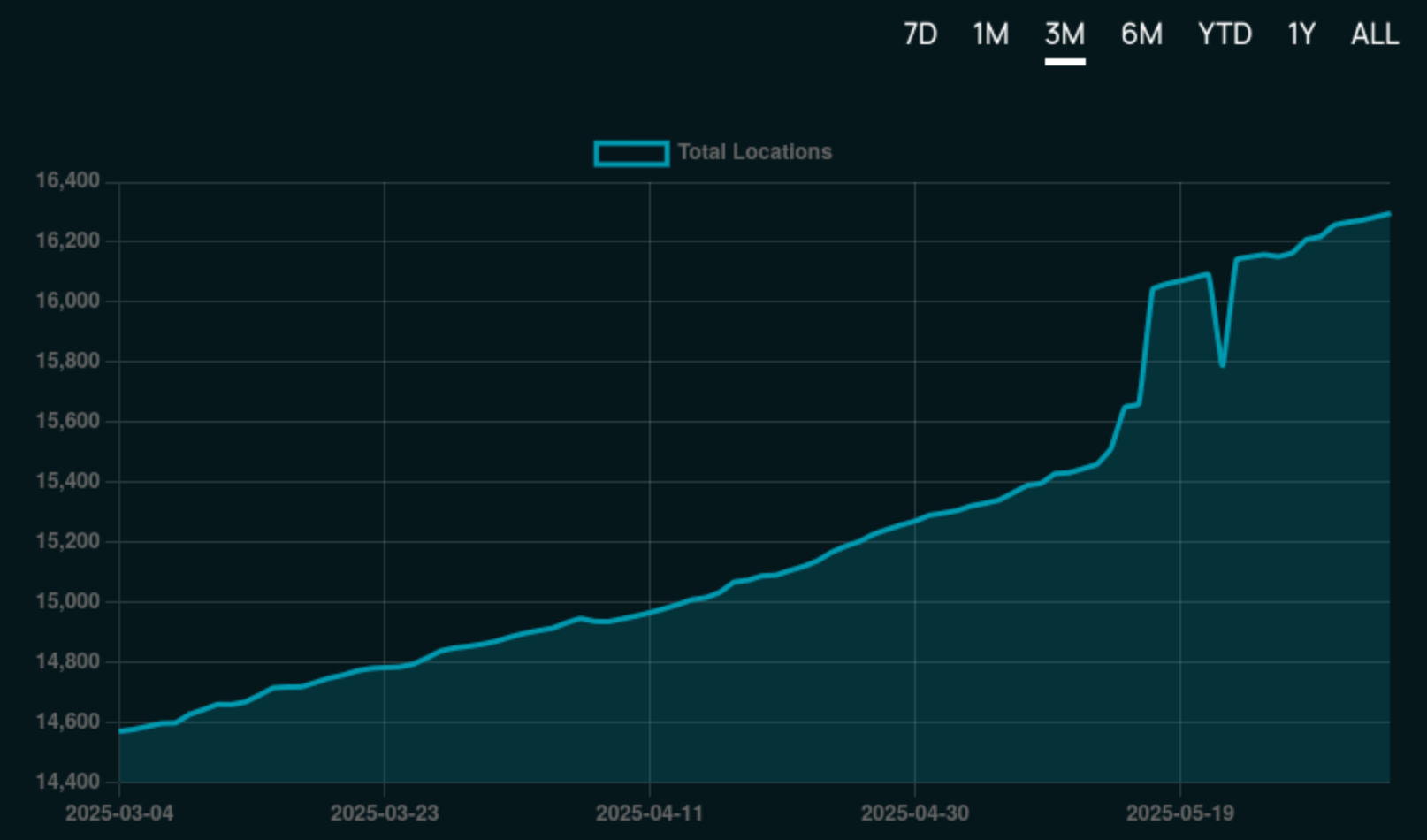
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 9ca447d2:fbf5a36d
2025-06-13 20:01:39
@ 9ca447d2:fbf5a36d
2025-06-13 20:01:39While most Bitcoin companies chase quick wins with flashy marketing and complex trading features, Coinfinity is taking a different path. The Austria-based company has built their entire business model around something most brokers treat as an afterthought: education.
Founded on the principle that Bitcoin adoption requires understanding, not just access, Coinfinity offers something great in the Bitcoin space: a broker that actually wants you to take your bitcoin off their platform.
Their Bitcoin Blinks educational series provides a self-custody-first approach, and Austrian economics foundation make them stand out in a crowded field of crypto casinos.

Coinfinity’s HQ in Graz, Austria
At the heart of this educational mission is Fab, Coinfinity’s Head of Bitcoin Education, whose journey to Bitcoin mirrors that of many who’ve found their way to Austrian economics through pure instinct.
“I always had the feeling that something in the world just doesn’t add up,” he told Bitcoin News when he sat down with us. “Something’s wrong, I don’t know what, but I felt like the foundation of our society isn’t quite fair, I just never knew what it was.”
Sound familiar?
That hunch eventually led him down a rabbit hole of geopolitics, monetary systems, and finally to Andreas Antonopoulos videos on YouTube.
“I basically disappeared from life for about a week, just watching those videos,” Fab recalled. But it wasn’t until he read The Bitcoin Standard that everything clicked.
“I remember it like it was yesterday, I closed the book and thought ‘Holy s***, now I get it.’ That was the moment. From then on, I was Bitcoin-only.”

Many of the best Bitcoin books are in English and translating them is important
Now as Head of Bitcoin Education at Coinfinity and co-founder of Aprycot Media (a German publishing house focused exclusively on Bitcoin), Fab spends his days helping others find that same spark.
And unlike most “crypto” companies, Coinfinity’s strategy isn’t driven by marketing gimmicks or token launches, it’s driven by teaching.
“Our goal is to create educational content that’s so easy to understand that people love sharing it,” Fab explained. “When they share it, they connect with us. Once they start understanding Bitcoin, they choose us to buy it.”
Most companies buy Google ads. Coinfinity builds minds. With their Bitcoin Blinks, 42 short, clear lessons covering everything from subjective value to seed phrases, they’re offering what most brokers won’t: context. Meaning. Philosophy.
“It became quite popular, and we think it’s way more effective for our brand than just buying ads,” Fab said.
And they don’t stop there. When it comes to custody, Coinfinity takes a radically different approach than most Bitcoin brokers.
“When you buy bitcoin from us, you always take custody, either in our in-app wallet where you control the seed, or your own hardware wallet,” Fab emphasized. “Even our lightning feature works the same way you always buy into your own wallet.”
That’s not just a slogan. It’s a core value of the company that runs so deep they’re willing to sacrifice user experience for it. “We never custody your bitcoin,” Fab said. “It’s one of the core values that you custody them yourself.”
Even as fees rise and UTXO management gets harder, Coinfinity stays committed to self-custody. They are open to optional custodial tools in the future, but always paired with education, and always encouraging users to take their bitcoin off-platform when the time is right.
“If we ever offer custodial services, it would only be to help users stack small amounts until they reach a meaningful UTXO size,” Fab explained.
The plan would involve accumulating smaller purchases monthly or weekly until users hit a threshold, maybe a million sats, then withdrawing to self-custody. “We don’t want to play games with your bitcoin. We don’t want to lend it out or earn interest on it.”

Coinfinity emphasizes on self-custody and education, even in its app
The challenge is real though. When new users first encounter Bitcoin, the technical barriers can be overwhelming. “Often causes problems with people just getting into Bitcoin who don’t understand what self custody is” Fab notes.
That’s why they built their in-app wallet, to smooth the onboarding while maintaining their self-custody values. “The in-app wallet was our first step toward optimizing user experience without compromising our core value of bringing bitcoin into self-custody,” he said.
“One of our taglines is ‘bringing Bitcoin to the people’ and we literally mean that. We want to bring bitcoin to them, not keep it from them.”
Another promising thing the company is doing in their operations is using AI to create more content, faster. Podcast scripts, educational summaries, internal tools, Fab’s even feeding Austrian economics PDFs into models to keep the tone on-brand and Bitcoin-only.
“We’re using these tools in our business development and marketing teams to generate more output with the same number of people,” he said. But the future looks even more exciting.
“Maybe one day we’ll have a tutor in the app where you can do a video call and ask ‘What is a Bitcoin address?’ and it will talk back to you naturally, going deeper as you ask more questions,” Fab explained. “That’s absolutely possible.”
The technology isn’t quite there yet for mainstream deployment in their app, but Fab is optimistic. “I’m sure that in the future, this won’t just be used for improving our internal workflow, but for enhancing the content itself,” he said.
It’s not a pipe dream. The tech is already close. The only thing missing is more Bitcoin-native data and companies like Coinfinity are quietly building that layer.
One of the favorite parts of these interviews is asking the builders in the space what they would ask Satoshi if given one question. When I asked Fab what he’d ask Bitcoin’s creator, he didn’t hesitate:
“Did you purposely build Bitcoin based on Austrian economics, or did it just happen by accident?
“All this monetization theory, Bitcoin being a store of value first, is this something you actually thought was possible and had in mind? Or was it just a lucky shot that accidentally gave us the best monetary properties?”
Because if Satoshi had built Bitcoin with a 2% inflation rate, like some other projects, it might’ve worked. But it wouldn’t have lasted.
“He could have made it with 2% tail emission, it still would have been decentralized. But then today, someone might introduce a coin with a fixed supply that could kill Bitcoin,” Fab noted.
Fab suspects the fixed supply wasn’t an accident. And thank God for that.
What’s remarkable about Coinfinity isn’t just their Austrian approach or their self-custody obsession, it’s how they’re proving that education-first Bitcoin companies can compete with the flashy crypto casinos dominating the space.
Coinfinity doesn’t serve U.S. customers. They’re focused on Europe, operating within EU regulations. But what they’re building, honest Bitcoin education, smart tools, and a relentless push for financial sovereignty, matters everywhere.
-
 @ 5627e59c:d484729e
2025-06-11 22:28:08
@ 5627e59c:d484729e
2025-06-11 22:28:08Here's to the ones who can\ Feel their cause\ Surrender\ Change their ways\ But keep their fire\ And never give up
We will transform this world\ Restructuring\ One belief at a time
-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ dfa02707:41ca50e3
2025-06-05 04:02:14
@ dfa02707:41ca50e3
2025-06-05 04:02:14Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ a5ee4475:2ca75401
2025-06-04 14:31:23
@ a5ee4475:2ca75401
2025-06-04 14:31:23[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas evidências mais antigas que vim registrando durante alguns anos contra a covid, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que não tivemos contato pela escassez de meios para a obtenção dessas informações de forma organizada. Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação, então se possível ajudem sugerindo com complementos ou alterações.
Explicações iniciais:
- Sars-Cov-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O Sars-Cov-2 é o segundo tipo de Sars-Cov documentado, o primeiro ocorreu em 2003;
- 'Coronavírus' na verdade é um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 é só uma delas.
1. Vacinas Obrigatórias em Geral
-
Vacinas e autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
-
O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
 - Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/
- Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
- Imagem arquivada em: https://web.archive.org/web/20201203231640/"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como no Brasil: https://www.gazetadopovo.com.br/vida-e-cidadania/quais-ongs-cooperaram-com-moraes-e-sao-alvo-do-congresso-nos-eua/ ), inclusive em relacionadas ao SARS, um vírus muito semelhante ao SEGUNDO tipo de vírus Sars-Cov, o Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho
Houve uma "coincidência", a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (o mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: [Jornal Estadão] ( http://patrocinados.estadao.com.br/medialab/releaseonline/releasegeral-releasegeral/geral-johns-hopkins-center-for-health-security-forum-economico-mundial-e-fundacao-bill-melinda-gates-realizam-exercicio-pandemico-e-transmissao-ao-vivo/)
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
Especialistas Sérios
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
Falsos Especialistas
-
Dr. Anthony Fauci - Imunologista
-
Dr. Atila Iamarino (nerdologia) - Microbiólogo
Atualmente propagandeia a pauta climática do COP30 (30th Conference Of Parties - UN [30ª Conferência das Partes - ONU]) que será no Brasil.
9. CASOS DOCUMENTADOS
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
10. ALEGAÇÕES DIRETAS
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
-
 @ 8173f6e1:e488ac0f
2025-06-13 19:18:56
@ 8173f6e1:e488ac0f
2025-06-13 19:18:56{"voteEventId":"083ae248828a454a7d01b7de12f99ce90297672e0457ec8147bd7cfabd14f044","txHash":"752d3894c5657758d7b9754da3dc38db61662acb5f94c3dcb38077fc33f1bd7e","amount":"1000000000000000000","fee":"1000000000000000000","type":"token-gated-vote-proof"}
-
 @ b7274d28:c99628cb
2025-05-27 07:07:33
@ b7274d28:c99628cb
2025-05-27 07:07:33A few months ago, a nostrich was switching from iOS to Android and asked for suggestions for #Nostr apps to try out. nostr:npub18ams6ewn5aj2n3wt2qawzglx9mr4nzksxhvrdc4gzrecw7n5tvjqctp424 offered the following as his response:
nostr:nevent1qvzqqqqqqypzq0mhp4ja8fmy48zuk5p6uy37vtk8tx9dqdwcxm32sy8nsaa8gkeyqydhwumn8ghj7un9d3shjtnwdaehgunsd3jkyuewvdhk6tcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszythwden5te0dehhxarj9emkjmn99uqzpwwts6n28eyvjpcwvu5akkwu85eg92dpvgw7cgmpe4czdadqvnv984rl0z
Yes. #Android users are fortunate to have some powerful Nostr apps and tools at our disposal that simply have no comparison over on the iOS side. However, a tool is only as good as the knowledge of the user, who must have an understanding of how best to wield it for maximum effect. This fact was immediately evidenced by replies to Derek asking, "What is the use case for Citrine?" and "This is the first time I'm hearing about Citrine and Pokey. Can you give me links for those?"
Well, consider this tutorial your Nostr starter-kit for Android. We'll go over installing and setting up Amber, Amethyst, Citrine, and Pokey, and as a bonus we'll be throwing in the Zapstore and Coinos to boot. We will assume no previous experience with any of the above, so if you already know all about one or more of these apps, you can feel free to skip that tutorial.
So many apps...
You may be wondering, "Why do I need so many apps to use Nostr?" That's perfectly valid, and the honest answer is, you don't. You can absolutely just install a Nostr client from the Play Store, have it generate your Nostr identity for you, and stick with the default relays already set up in that app. You don't even need to connect a wallet, if you don't want to. However, you won't experience all that Nostr has to offer if that is as far as you go, any more than you would experience all that Italian cuisine has to offer if you only ever try spaghetti.
Nostr is not just one app that does one thing, like Facebook, Twitter, or TikTok. It is an entire ecosystem of applications that are all built on top of a protocol that allows them to be interoperable. This set of tools will help you make the most out of that interoperability, which you will never get from any of the big-tech social platforms. It will provide a solid foundation for you to build upon as you explore more and more of what Nostr has to offer.
So what do these apps do?

Fundamental to everything you do on Nostr is the need to cryptographically sign with your private key. If you aren't sure what that means, just imagine that you had to enter your password every time you hit the "like" button on Facebook, or every time you commented on the latest dank meme. That would get old really fast, right? That's effectively what Nostr requires, but on steroids.
To keep this from being something you manually have to do every 5 seconds when you post a note, react to someone else's note, or add a comment, Nostr apps can store your private key and use it to sign behind the scenes for you. This is very convenient, but it means you are trusting that app to not do anything with your private key that you don't want it to. You are also trusting it to not leak your private key, because anyone who gets their hands on it will be able to post as you, see your private messages, and effectively be you on Nostr. The more apps you give your private key to, the greater your risk that it will eventually be compromised.
Enter #Amber, an application that will store your private key in only one app, and all other compatible Nostr apps can communicate with it to request a signature, without giving any of those other apps access to your private key.
Most Nostr apps for Android now support logging in and signing with Amber, and you can even use it to log into apps on other devices, such as some of the web apps you use on your PC. It's an incredible tool given to us by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and only available for Android users. Those on iPhone are incredibly jealous that they don't have anything comparable, yet.

Speaking of nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, the next app is also one of his making.
All Nostr data is stored on relays, which are very simple servers that Nostr apps read notes from and write notes to. In most forms of social media, it can be a pain to get your own data out to keep a backup. That's not the case on Nostr. Anyone can run their own relay, either for the sake of backing up their personal notes, or for others to post their notes to, as well.
Since Nostr notes take up very little space, you can actually run a relay on your phone. I have been on Nostr for almost 2 and a half years, and I have 25,000+ notes of various kinds on my relay, and a backup of that full database is just 24MB on my phone's storage.
Having that backup can save your bacon if you try out a new Nostr client and it doesn't find your existing follow list for some reason, so it writes a new one and you suddenly lose all of the people you were following. Just pop into your #Citrine relay, confirm it still has your correct follow list or import it from a recent backup, then have Citrine restore it. Done.
Additionally, there are things you may want to only save to a relay you control, such as draft messages that you aren't ready to post publicly, or eCash tokens, which can actually be saved to Nostr relays now. Citrine can also be used with Amber for signing into certain Nostr applications that use a relay to communicate with Amber.
If you are really adventurous, you can also expose Citrine over Tor to be used as an outbox relay, or used for peer-to-peer private messaging, but that is far more involved than the scope of this tutorial series.

You can't get far in Nostr without a solid and reliable client to interact with. #Amethyst is the client we will be using for this tutorial because there simply isn't another Android client that comes close, so far. Moreover, it can be a great client for new users to get started on, and yet it has a ton of features for power-users to take advantage of as well.
There are plenty of other good clients to check out over time, such as Coracle, YakiHonne, Voyage, Olas, Flotilla and others, but I keep coming back to Amethyst, and by the time you finish this tutorial, I think you'll see why. nostr:npub1gcxzte5zlkncx26j68ez60fzkvtkm9e0vrwdcvsjakxf9mu9qewqlfnj5z and others who have contributed to Amethyst have really built something special in this client, and it just keeps improving with every update that's shipped.
Most social media apps have some form of push notifications, and some Nostr apps do, too. Where the issue comes in is that Nostr apps are all interoperable. If you have more than one application, you're going to have both of them notifying you. Nostr users are known for having five or more Nostr apps that they use regularly. If all of them had notifications turned on, it would be a nightmare. So maybe you limit it to only one of your Nostr apps having notifications turned on, but then you are pretty well locked-in to opening that particular app when you tap on the notification.
Pokey, by nostr:npub1v3tgrwwsv7c6xckyhm5dmluc05jxd4yeqhpxew87chn0kua0tjzqc6yvjh, solves this issue, allowing you to turn notifications off for all of your Nostr apps, and have Pokey handle them all for you. Then, when you tap on a Pokey notification, you can choose which Nostr app to open it in.
Pokey also gives you control over the types of things you want to be notified about. Maybe you don't care about reactions, and you just want to know about zaps, comments, and direct messages. Pokey has you covered. It even supports multiple accounts, so you can get notifications for all the npubs you control.

One of the most unique and incredibly fun aspects of Nostr is the ability to send and receive #zaps. Instead of merely giving someone a 👍️ when you like something they said, you can actually send them real value in the form of sats, small portions of a Bitcoin. There is nothing quite like the experience of receiving your first zap and realizing that someone valued what you said enough to send you a small amount (and sometimes not so small) of #Bitcoin, the best money mankind has ever known.
To be able to have that experience, though, you are going to need a wallet that can send and receive zaps, and preferably one that is easy to connect to Nostr applications. My current preference for that is Alby Hub, but not everyone wants to deal with all that comes along with running a #Lightning node. That being the case, I have opted to use nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch for this tutorial, because they offer one of the easiest wallets to set up, and it connects to most Nostr apps by just copy/pasting a connection string from the settings in the wallet into the settings in your Nostr app of choice.
Additionally, even though #Coinos is a custodial wallet, you can have it automatically transfer any #sats over a specified threshold to a separate wallet, allowing you to mitigate the custodial risk without needing to keep an eye on your balance and make the transfer manually.

Most of us on Android are used to getting all of our mobile apps from one souce: the Google Play Store. That's not possible for this tutorial series. Only one of the apps mentioned above is available in Google's permissioned playground. However, on Android we have the advantage of being able to install whatever we want on our device, just by popping into our settings and flipping a toggle. Indeed, thumbing our noses at big-tech is at the heart of the Nostr ethos, so why would we make ourselves beholden to Google for installing Nostr apps?
The nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 is an alternative app store made by nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9 as a resource for all sorts of open-source apps, but especially Nostr apps. What is more, you can log in with Amber, connect a wallet like Coinos, and support the developers of your favorite Nostr apps directly within the #Zapstore by zapping their app releases.
One of the biggest features of the Zapstore is the fact that developers can cryptographically sign their app releases using their Nostr keys, so you know that the app you are downloading is the one they actually released and hasn't been altered in any way. The Zapstore will warn you and won't let you install the app if the signature is invalid.
Getting Started
Since the Zapstore will be the source we use for installing most of the other apps mentioned, we will start with installing the Zapstore.
We will then use the Zapstore to install Amber and set it up with our Nostr account, either by creating a new private key, or by importing one we already have. We'll also use it to log into the Zapstore.
Next, we will install Amethyst from the Zapstore and log into it via Amber.
After this, we will install Citrine from the Zapstore and add it as a local relay on Amethyst.
Because we want to be able to send and receive zaps, we will set up a wallet with CoinOS and connect it to Amethyst and the Zapstore using Nostr Wallet Connect.
Finally, we will install Pokey using the Zapstore, log into it using Amber, and set up the notifications we want to receive.
By the time you are done with this series, you will have a great head-start on your Nostr journey compared to muddling through it all on your own. Moreover, you will have developed a familiarity with how things generally work on Nostr that can be applied to other apps you try out in the future.
Continue to Part 2: The Zapstore. Nostr Link: nostr:naddr1qvzqqqr4gupzpde8f55w86vrhaeqmd955y4rraw8aunzxgxstsj7eyzgntyev2xtqydhwumn8ghj7un9d3shjtnzwf5kw6r5vfhkcapwdejhgtcqp5cnwdphxv6rwwp3xvmnzvqgty5au
-
 @ 73d8a0c3:c1853717
2025-06-14 00:36:38
@ 73d8a0c3:c1853717
2025-06-14 00:36:38🧬 REDACTED SCIENCE: THE AUTHOR — A SHADOW IN THE MARGINS
📜 Excerpt from my book-in-progress. This is nonfiction. Redacted. Possibly buried science. Possibly military. Almost definitely real. I’m living it. And it might change how we think about disease, dehydration, and survival itself.
👇 Full post below 👇
📄 The Author: A Shadow in the Margins
What follows is an excerpt from my book: Redacted Science. This is nonfiction. Redacted. And, I believe, novel science — the kind that slipped through the cracks because it wasn’t supposed to be seen. The kind that, if true (and I’m living proof it might be), changes how we think about adaptation, disease, and control, all while hinting at evolutionary processes.
The person who wrote the article — the one at the center of this entire mystery — didn’t just document a medical condition. They didn’t write like a detached observer. They wrote like someone who had seen it, worked with it, maybe even helped design it.
This wasn’t a paper. It was a record.
A flare fired backwards through time.🧠 What They Knew
- Electrolyte manipulation under pressure gradients
- Bone demineralization and molecular substitution
- Methyl group cycling
- Autonomic dysregulation
- Increased survivability under dehydration
- Accelerated burn recovery
- Abnormal pain tolerance
- Enhanced cognition and endurance in early stages
- …eventual collapse into parasympathetic failure, bone loss, immune misfire, and systemic decay
No generalist writes like this.
No academic from 1975 casually throws around methylation chemistry and calcium channel modulators (“these show promise” — yeah, I remembered that line. I figured it might save my life).🧪 Proof in My Blood — Or Lack Thereof
I’ve lived the proof they described.👁️ Who They Were
They were part of a program.
A researcher. Maybe a clinician. Possibly embedded in a classified military or survival physiology initiative.🔍 The Quiet Warning
That mention of the ICD code shift?
It was like someone watching history be rewritten — shifting this condition under something it isn’t. Sleight-of-hand.
They couldn’t have known about the AIRE gene — and I don’t have it.“We erased it from the books. But it was real. Look again. Find it if you can.”
And here I am.
Picking it up.
Line by line.
Molecule by molecule.🏃 The 15K That Almost Killed Me
Twelve years ago: I ran the Tulsa Run, didn’t hydrate. Felt fine — until the vomiting hit. Bloodwork? Normal.
Smart doc took one look and hooked up fluids.That wasn’t dehydration.
That was a system built to survive without water — until it couldn’t.🕰️ When and Why
Photos: early 20th century.
The article? 1975–1985.
Someone who knew too much. Someone preserving knowledge — as it was being erased.“It’s gone now. But it was here. And you need to look again.”
That’s not footnote energy.
That’s whistleblower energy.
🧠 Everything is open. All science is free. More is coming.
Read more at https://jimcraddock.substack.com or https://jimcraddock.com]
-
 @ 5627e59c:d484729e
2025-06-11 22:27:54
@ 5627e59c:d484729e
2025-06-11 22:27:54Hello Bumble\ You busy bee
You're going way\ Too fast for me
Going here and there\ You search for gold
Yet tumble straight\ Into what's old
Now I'm not here\ To make a gain
Nor to fix\ What's in disdain
Instead I'm just\ A humble bee
Who wants to get\ To know thee
-
 @ 3c559080:a053153e
2025-05-25 20:26:43
@ 3c559080:a053153e
2025-05-25 20:26:43So firstly you should find an emulator for whatever you want to play on. There are many for desktop and mobile devices. Checkhere for a list of all the available consoles and their various emulators.
Next what game do you want to play? This is the like the homepage for a shit ton of roms.
Some of the more popular roms are there and other various list like Sony Nintendo
After narrowing down your selection you will end up on myrient i assume this is just some dope person hosting all these so if you get some use out of it, think of donating they even take corn, but other shitcoins too (but thats not the focus here)
Once you download the Rom of the game you want, you will get a compressed (zip) folder, unzip it and within it will be the rom, most systems will identify your emulator and use it open the game. If not, launch the emulator and within it should be an option to open a file, open the file in the unzipped folder.
Enjoy So you want to Mod?
So every Mod, is a mod for a specific game [ex. Pokemon Blue, Pokemon FireRed, Super Mario Bros.] so it requires you to get the Rom for that base game, the mod itself, and a tool to patch it.
 There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch.
There is an online tool to easily patch the mod to the ROM. IMPORTANT, this will not change any naming, Id recommend having a folder with the base game roms, and a folder for the mods, and lastly a folder for the newly modded roms. Make sure to name or just save the game in modded roms folder after the patch. Below are a few resource to find various Pokemon Rom mods(sometimes called hacks)
Personally, Pokemon Unbound is considered the best most polished hack. it runs on Pokemon Fire Red.
Pokemon Emerald Rouge is a cool take on the popular Rougelite genre. This runs on base game Pokemon Emerald
-
 @ 00ea1f73:71c6e344
2025-06-03 09:59:07
@ 00ea1f73:71c6e344
2025-06-03 09:59:07Je suis en train de construire un outil de référencement collectif de marques et fabricants proposant des produits 100 % en matière naturelle (ce qui veut essentiellement dire "sans plastique").
Voici les étapes de ma progression ces dernières semaines en tant que non développeur pour créer cela tout en privilégiant des outils open source.
Etape 1 : faisons simple, du texte organisé
J'ai commencé par réunir mes idées dans Anytype. Leur approche "tout est un objet" laisse une flexibilité incroyable pour organiser ses données. On peut s'en servir comme simple outil de prise de note ou comme outil de gestion de projet. Le fonctionnement "local first" de l'application me donne la main sur mes données : elles sont stockées en local sur mon ordinateur et mon téléphone, qui se synchronisent entre eux.
Anytype permet depuis peu de publier sur Internet les "objets" de son choix (pages, notes, albums…) mais cela reste limité pour proposer à des visiteur une navigation fluide entre des objets liés (dans mon cas des marques et des matières par exemple). De plus, il n'est pas encore possible d'y automatiser la mise en forme de contenus à partir de données.
Ainsi, après avoir réuni les informations et préparé les contenus "à la main" pour trois marques seulement dans Anytype, j'ai eu besoin d'automatisation, et donc d'une vraie base de données. Je conserve quand même Anytype pour organiser mes idées et la suite du projet. Je l'utilise aussi pour la vie quotidienne (liste de course partagée, journal…).
Etape 2 : structurons une base de données
Baserow est une alternative à Airtable qui permet de gérer une base de données comme un tableur. Les formules utilisables dans les tableaux m'ont aidé à générer automatiquement les contenus de marque à partir des données que je réunissais. J'ai obtenu des données bien ordonnés dans de beaux tableaux sans avoir plus besoin de réécrire tout le contenu pour chaque marque.
J'ai passé un peu de temps à apprendre la syntaxe des formules de Baserow, j'ai mis à jour le contenu des trois premières marques, généré automatiquement celui d'une quatrième et… je me suis rendu compte que ça n'allait pas le faire.
Un point crucial de mon projet est la gestion et l'affichage des catégories de produits proposés par chaque marque, histoire que cela soit pratique de trouver les alternatives naturelles pour ce que l'on cherche sur le site. Or, dans Baserow il n'y avait pas moyen de générer mes contenus catégorisés de manière dynamique. J'étais contraint de modifier sans cesse des formules de plus en plus complexes, et donc avec un risque d'erreur de plus en plus grand. Cela reste un tableur, plus net pour gérer des données, mais moins fourni en termes de formules.
Avec une seule marque traitée en plus, mon "backend" v2 n'aura pas duré longtemps !
Etape 3 : courage, passons aux choses sérieuses
A ce moment là, j'ai sérieusement douté de ma capacité a créer ce site avec des outils open source et j'ai été tenté de retourner vers Bubble. À mon avis, Bubble est l'outil "no code" (ou de "programmation visuelle") le plus abouti. Je l'avais déjà utilisé efficacement avec We Do Good pour réaliser des prototypes de fonctionnalités, même utilisés provisoirement en production.
C'est génial, avec Bubble, des semaines de travail classique entre développeurs et designers pour arriver à une version utilisable se transforment en heures, voire en jours pour tester et valider des prototypes.
Mais… avec Bubble on n'a pas accès à ce qui se passe derrière l'interface de programmation. On devient en fait prisonnier de leur langage de programmation propriétaire. Si on a besoin de faire différemment, s'ils augmentent leurs prix de manière inadaptée, ou si un blocage se présente pour une autre raison, il faut tout refaire à zéro ou faire développer des nouvelles fonctionnalités (plugins) qui enrichissent Bubble.
J'ai alors décidé de passé au niveau supérieur en terme de technicité, avec des outils tout de même accessible aux non initiés motivés : une base de données dans Supabase connectée à une interface créée avec Plasmic. Avec Supabase j'ai accès aux paramétrages les plus fins sur les données et avec Plamic je construis visuellement ce dont j'ai besoin, comme avec Bubble.
Malgré l'interface visuelle très complètes de Plasmic, certaines fonctions dont j'ai besoin demandent des formules personnalisées utilisant un peu de code. L'avantage, c'est que là ou j'avais appris le language Bubble utilisable seulement avec Bubble, j'apprends maintenant les languages ouverts et universels du web sql et javascript, avec un peu d'aide de l'"IA" pour comprendre les fonctions et erreurs de syntaxe.
J'apprendre en faisant directement ce que j'ai envie, et c'est beaucoup plus efficace et motivant !
Plasmic me laisse aussi récupérer et réutiliser l'ensemble du code source ailleurs si j'en ai besoin un jour.
Je devais en passer par là
Chaque version de mon "backend" a été utile et même nécessaire à la suivante.
Avec mon expérience d'entrepreneur du web, je sentais depuis le départ que j'aurais besoin d'une solution robuste de base de données ainsi que de pouvoir intervenir sur le code facilement. Cependant, au démarrage, je n'avais pas envie de me plonger là-dedans. Finalement, bien m'en a pris ! La structuration de données que j'avais initialement imaginée est très différente de celle à laquelle j'arrive maintenant.
Je n'aurais pas eu une base de données claire et bien organisée dans Supabase si je n'avais pas fait précédemment une itération dans Baserow. Je n'aurais pas créé les tables et liaisons utiles dans Baserow si je n'avais pas créé les premiers contenus sous forme de texte avec liaisons dans Anytype.
De plus, je n'aurais pas trouvé l'énergie de me lancer sur ce nouveau projet si je n'avais pas commencé par une version très simple et non "scalable". C'est un vrai progrès personnel : j'ai toujours travaillé en essayant de concevoir le maximum de choses d'avances, pour me rassurer et limiter les risques, et parce que c'est ce qu'on apprend à l'école. Les problèmes, c'est que je dépensais pour cela une énergie folle et que bien sûr, la réalité ne correspond jamais vraiment aux prévisions.
En me lançant avec une première version pas du tout aboutie mais fonctionnelle, je me suis autorisé à faire plus d'erreur, à m'exposer et à me concentrer sur du concret.
Références
Pour moi, favoriser l'open source est essentiel car cela fait partie des outils fondamentaux pour défendre ma liberté et celle des autres.
Tous les outils que j'utilise ou ai utilisé pour ce projet sont open source, sauf Anytype qui est juste "open core" (c'est à dire qu'ils publient leur code mais n'autorisent pas tous les usages avec). Ils présentent aussi tous des plans gratuits bien pratiques pour se lancer sans contrainte financière.
- Anytype : https://anytype.io/
- Baserow : https://baserow.io/
- Supabase : https://supabase.com/
- Plasmic : https://www.plasmic.app/
J'ai aussi testé ou envisagé sans les retenir quelques autres solutions comme WordPress ou Silex. Provisoirement, en attendant d'avoir créé toutes les interfaces dont j'ai besoin avec Plasmic, j'utilise NocoDB, connecté à Supabase, pour disposer d'une interface visuelle équivalente à Baserow (avec des formules moins avancées mais la possibilité de me connecter plusieurs bases de données si besoin).
J'utilise beaucoup Alternative.to pour trouver les outils dont j'ai besoin, on y peut filtrer les applications selon de nombreux critère, je le recommande.
Ensuite, il faut tester et se lancer, voire tester en se lançant !
opensource #nocode #lowcode #vibecoding #ia #produitsnaturels #zeroplastique #nostrfr
-
 @ c631e267:c2b78d3e
2025-06-13 19:13:38
@ c631e267:c2b78d3e
2025-06-13 19:13:38Ich dachte immer, jeder Mensch sei gegen den Krieg, \ bis ich herausfand, dass es welche gibt, \ die nicht hingehen müssen. \ Erich Maria Remarque
Was sollte man von einem Freitag, den 13., schon anderes erwarten?, ist man versucht zu sagen. Jedoch braucht niemand abergläubisch zu sein, um den heutigen Tag als unheilvoll anzusehen. Der israelische «Präventivschlag» von heute Nacht gegen militärische und nukleare Ziele im Iran könnte allem Anschein nach zu einem längeren bewaffneten Konflikt führen – und damit unweigerlich zu weiteren Opfern.
«Wir befinden uns im Krieg», soll ein ranghoher israelischer Militärvertreter gesagt haben, und der Iran wertet den israelischen Angriff laut seinem Außenminister als Kriegserklärung. Na also. Der Iran hat Vergeltungsschläge angekündigt und antwortete zunächst mit Drohnen. Inzwischen ist eine zweite israelische Angriffswelle angelaufen. Ob wir wohl künftig in den Mainstream-Medien durchgängig von einem «israelischen Angriffskrieg auf den Iran» hören und lesen werden?
Dass die zunehmenden Spannungen um das iranische Atomprogramm zu einer akuten Eskalation im Nahen Osten führen könnten, hatte Transition News gestern berichtet. Laut US-Beamten sei Israel «voll bereit», den Iran in den nächsten Tagen anzugreifen, hieß es in dem Beitrag. Heute ist das bereits bittere Realität.
Der Nahe Osten steht übrigens auch auf der Themenliste des diesjährigen Bilderberg-Treffens, das zurzeit in Stockholm stattfindet. Viele Inhalte werden wir allerdings mal wieder nicht erfahren, denn wie immer hocken die «erlauchten» Persönlichkeiten aus Europa und den USA «informell» und unter größter Geheimhaltung zusammen, um über «Weltpolitik» zu diskutieren. Auf der Teinehmerliste stehen auch einige Vertreter aus der Schweiz und aus Deutschland.
Die Anwesenheit sowohl des aktuellen als auch des vorigen Generalsekretärs der NATO lässt vermuten, dass man bei dem Meeting weniger über das Thema «Neutralität» sprechen dürfte. Angesichts des Zustands unseres Planeten ist das schade, denn der Ökonom Jeffrey Sachs hob kürzlich in einem Interview die Rolle der Neutralität in geopolitischen Krisen hervor. Mit Blick auf die Schweiz betonte er, der zunehmende Druck zur NATO-Annäherung widerspreche nicht nur der Bundesverfassung, sondern auch dem historischen Erbe des Landes.
Positives gibt es diese Woche ebenfalls zu berichten. So hat der US-Gesundheitsminister Robert F. Kennedy Jr. nach der «sensationellen» Entlassung aller Mitglieder des Impfberatungsausschusses (wegen verbreiteter direkter Verbindungen zu Pharmaunternehmen) nun auch bereits neue Namen verkündet. Demnach möchte er unter anderem Robert W. Malone, Erfinder der mRNA-«Impfung» als Technologie und prominenter Kritiker der Corona-Maßnahmen, in das Komitee aufnehmen.
Auch die Aufarbeitung der unsinnigen Corona-Politik geht Schrittchen für Schrittchen weiter. In Heidelberg hat die Initiative für Demokratie und Aufklärung (IDA) den Gemeinderat angesichts der katastrophalen Haushaltslage zu einer offenen und ehrlichen Diskussion über die Ursachen der Krise aufgefordert. Das Thema «Corona» sei «das Teuerste, was Heidelberg je erlebt hat», sagte IDA-Stadtrat Gunter Frank im Plenum. Außerdem seien aus den Krisenstabsprotokollen der Stadt auch die enormen Verwerfungen ersichtlich, und es gebe Anlass für tiefgehende Gespräche mit der Stadtverwaltung.
Den juristischen und öffentlichen Druck auf die Kommunen möchte der Unternehmer Markus Böning erhöhen. Seine «Freiheitskanzlei» will Bürgern helfen, die Aufarbeitung selbst in die Hand zu nehmen. Unter dem Motto «Corona-Wiedergutmachung» bietet er Hilfestellung, wie Betroffene versuchen können, sich unrechtmäßige Bußgelder zurückzuholen.
So bleibt uns am Ende dieses finsteren Freitags doch auch Anlass zur Hoffnung. Es gibt definitiv noch Anzeichen von Menschlichkeit. Darauf möchte ich mich konzentrieren, und mit diesem Gefühl verabschiede ich mich ins Wochenende.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 5627e59c:d484729e
2025-06-11 22:27:43
@ 5627e59c:d484729e
2025-06-11 22:27:43We only see\ What we are
What we are not\ We cannot see
This is how we know\ Reality is happening within\ Our own being
And experience is a consequence\ Of who we believe to be
As long as we deny\ And don't want to see
All the ways\ We think to be
Reality will seem\ Outside of our grasp
And separate\ From our experience of life
Such is our power
Yet such power\ Could only be
Of that which holds\ The entirety
-
 @ d62e8d04:569fa79c
2025-06-13 18:35:37
@ d62e8d04:569fa79c
2025-06-13 18:35:37In today's fast-paced digital world, where cyber threats are constantly evolving, and blockchain technology is reshaping industries, Privkey LLC emerges as a leader in providing cutting-edge solutions. Founded in 2018 and headquartered in Miami, Florida, Privkey LLC is dedicated to safeguarding businesses through its expertise in cybersecurity and blockchain technology. With over 20 years of experience in networking and the Internet, the company positions itself as a trusted advisor, helping organizations navigate the complexities of emerging digital landscapes.
A Mission to Secure the Digital Future
Privkey LLC’s core mission is to protect businesses by delivering high-quality, tailored solutions. Leveraging their deep understanding of cybersecurity and blockchain, they empower organizations to build secure, resilient, and compliant digital infrastructures. Whether it’s safeguarding sensitive financial data or ensuring the integrity of blockchain systems, Privkey LLC combines experience with innovation to meet the unique challenges of the modern era.
Comprehensive Services for a Digital World
Privkey LLC offers a diverse range of auditing and consulting services, focusing on some of the most critical areas in technology today. Below is an overview of their key offerings:
-
Central Bank Digital Currency (CBDC):As nations explore digital versions of fiat currencies, Privkey LLC provides auditing services to ensure CBDC systems are secure, scalable, and compliant with regulatory standards.
-
DeFi and CeFi (Fintech):Decentralized Finance (DeFi) and Centralized Finance (CeFi) represent the future of financial services on the blockchain. Privkey LLC offers expertise in auditing these systems, helping businesses mitigate risks and maintain trust in their financial operations.
-
Cybersecurity:With cyber threats on the rise, Privkey LLC delivers robust cybersecurity solutions to protect digital assets and sensitive data from malicious attacks, ensuring businesses remain secure in an increasingly hostile digital environment.
-
Distributed Ledger Technology (DLT):As the backbone of blockchain, DLT requires meticulous implementation. Privkey LLC audits DLT systems to ensure they are efficient, secure, and optimized for business needs.
-
CryptoCurrency Security Standard (CCSS):For organizations handling cryptocurrencies, compliance with CCSS is essential. Privkey LLC provides certification services to verify adherence to these standards, fostering trust among users and stakeholders.
These services reflect Privkey LLC’s commitment to addressing the diverse needs of businesses operating in the blockchain and cybersecurity domains.
Staying Ahead in a Rapidly Evolving Industry
Privkey LLC doesn’t just provide services—they actively engage with the latest industry trends and innovations. Their team, including professionals like William K. Santiago, frequently shares insights on platforms like LinkedIn. Topics range from Jack Dorsey’s Block unveiling a new Bitcoin hardware wallet to sustainable Bitcoin mining powered by nuclear and solar energy. While these discussions may not directly tie to specific Privkey LLC projects, they demonstrate the company’s deep involvement in the broader blockchain and cryptocurrency ecosystem. This forward-thinking approach ensures their services remain relevant and cutting-edge.
A Trusted Partner with Proven Expertise
With over two decades of experience in networking and Internet technologies, Privkey LLC brings unparalleled expertise to the table. This foundation allows them to tackle the unique challenges of cybersecurity and blockchain with confidence. As cyber threats grow more sophisticated and blockchain adoption accelerates, Privkey LLC stands ready to help businesses secure their digital futures.
Conclusion
Privkey LLC is more than a consulting firm—it’s a pioneer in cybersecurity and blockchain solutions. By offering specialized auditing and consulting services, staying ahead of industry trends, and leveraging decades of experience, they empower businesses to thrive in a digital world. For organizations looking to secure their digital assets and embrace blockchain technology, Privkey LLC is a reliable partner poised to lead the way.
-
-
 @ 8bad92c3:ca714aa5
2025-06-13 19:03:33
@ 8bad92c3:ca714aa5
2025-06-13 19:03:33Marty's Bent
via me

"The man in the coma" has been a long-running archetype of a bitcoiner on TFTC and Rabbit Hole Recap. Over the years, we've referenced the man in the coma in regards to bitcoin being a backward compatible distributed network that would enable an individual, in the case of our example - a man who fell into a coma, to be able to wake up many years, even decades, after falling into a deep sleep, go back to his bitcoin node and be able to participate in the network and validate his own transactions as if the network was operating the same it was the day he slipped into a coma. As a distributed network, this is one of bitcoin's greatest value props; consistency for the individual running it, no matter the version.
Having spent 12 years engrossed in bitcoin, thinking about it every day, building a media company focused on educating people about the network and the monetary revolution it enables, why it's important and how they can use it. Becoming a managing partner at Ten31, which is dedicated to investing in companies building out infrastructure that makes bitcoin more accessible and easier to use; "the man in the coma" has become a more prominent archetype in my mind.
"The man in the coma" archetype can be described in other ways. For instance, there was an individual by the name of John Doe, who joined myself and Matt Odell on TFTC about seven years ago who went to jail for four years. He was distributing certain goods on the Silk Road for many years and got nabbed by the police while throwing a house party. Unfortunately for Mr. Doe, the goods he were selling via the Silk Road were in the house hosting the party that got busted. Fortunately for Mr. Doe, the police who nabbed him were not privy to the way in which he was marketing and selling the goods. He went to jail for four years, walked out at the end of his sentence, found his bitcoin wallets, recovered them and was more than pleasantly surprised at the magnitude of his wealth.
The forced hodl that was incited by the state throwing him in a cage wound up paying off after four years. Now, I can certainly admit that time is the most scarce asset in the world. Being put in a cage for four years or falling into a coma for a number of years is not ideal. However, there are lessons to be gleaned from the successes that have been realized by "the man in the coma" and the man who was forced to hodl by being thrown in a cage. Unable to access his bitcoin during that period of time to make less than wise decisions.
The main lesson to be gleaned is that doing nothing is oftentimes significantly more optimal than doing something. Too many bitcoiners decide to make rash decisions influenced by the day-to-day happenings on social media or some one-off comment from someone in their personal life that they respect. These comments can be about the long-term viability of bitcoin itself, some prognostications about where the price is going in a short-term to medium-term time frame or simply the social aspects of being associated with bitcoin. All of these factors play into influencing certain individuals deciding to sell their bitcoin in the hopes of buying it back lower, realizing something material in their day-to-day life or jumping off a ship that they've been convinced is about to sink.
In my mind, the only thing listed above that makes a bit of sense to me is realizing something material in your day-to-day life. Selling some bitcoin to purchase something that makes your life better like enabling you to support your family at a critical time and in a way that would not be possible unless you sold bitcoin. That makes sense to me. However, the other two are completely nonsensical. Bitcoin's success is binary. It either succeeds or it doesn't. And if you accept that this is true, success means slowly but surely becoming the global reserve currency and monetary network used by billions of humans on the planet or it goes to zero.
If the former materializes, that means that billions of people are going to be competing for 21 million Bitcoin. There are, by some estimates, $900 trillion worth of assets that are being used to store wealth over the short, medium, and long term. Bitcoin has the potential to subsume a material percentage of that $900 trillion. In my mind, if bitcoin is as good as I believe it is, it should take at least half of that market, if not 80 to 90%. This in and of itself is a gamble. No one can be certain that this will come true. And with that in mind you have to make a probabilistic bet by surveying the world and discerning what the likelihood of bitcoin's ultimate success is.
If you think governments, central banks, and large corporations are going to continue down the path of unfettered expansion of the monetary base, debt, and misallocation of capital, bitcoin, a peer-to-peer distributed cash system that cannot be controlled by any individual. corporation, country, or central bank makes a lot of sense. The debasement, the debt expansion, and the misallocation of capital are driven by fallible humans working in incentive structures that are vulnerable to the fallible nature of the humans working within them.
Human fallibility brings with it the ability to talk oneself out of a position that one knows makes sense and is logical. This is the disadvantage that those who are not "the man in the coma" or "the man in a cage" operate from. Being forced to hodl bitcoin is already and will increasingly be seen as a relative advantage. Many who are in bitcoin today, paying attention to every headline, every pull request and every doubt flung their way will likely get to 2030 and agree that they made worse decisions than the man who was thrown in a cage or who slipped into a coma.
Of course, this isn't a fair introspective conclusion. The man in the coma and the man who was forced to hodl because he was put in a jail cell did not have a decision at the end of the day. Both were forced to hodl due to external or internal forces that, all else being equal, they would prefer not have had to endure. However, the outcome of these two situations will likely be better than the outcome of "the man in the arena" who thinks that by making decisions on the go as a slew of information comes his way on a day-to-day basis will materialize in a larger stack of satoshis.
The reality of the situation is such that no one truly knows where bitcoin is going to go on a day-to-day, month-to-month, or year-to-year basis. Especially at this point with large institutions, nation-states, corporations, and individual states getting into the fray. The only tried-and-true strategy within bitcoin over the long term is to stay humble, stack sats, and hodl like you are "the man in the coma" or the man who was thrown in a cage.
Bitcoin's Volatility Won't End With Institutional Adoption
Leon Wankum challenged the popular "supercycle" narrative during our conversation, arguing that Bitcoin's volatility isn't going away despite massive institutional adoption. While acknowledging that MicroStrategy now holds over 2% of all Bitcoin and won't sell, Leon maintains that leverage will still need to be washed out. He expects another 60% drawdown at the end of this bull cycle, viewing this as a feature rather than a bug of Bitcoin's design.
"Bitcoin naturally washes out leverage, it builds resilience and we don't go through these crazy boom and bust cycles, we go through bull and bear markets and I think that's a net positive." - Leon Wankum
Leon sees Bitcoin's volatility as fundamentally different from fiat's destructive boom-bust cycles. Where traditional markets require central bank intervention to prop up failing systems, Bitcoin's regular corrections create genuine resilience. Bad actors will always enter during euphoric phases, and the subsequent washouts ensure only strong hands remain. This natural selection process, he argues, is beautiful - it's what makes Bitcoin antifragile.
Check out the full podcast here for more on real estate opportunity costs, Bitcoin bonds, and treasury company risks.
Headlines of the Day
Romania Adds Crypto Terminals to Post Offices - via X
Musk Claims Trump in Epstein Files - via X
Uber CEO Calls Bitcoin Proven Store of Value - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The kids really do grow up f
-
 @ 5627e59c:d484729e
2025-06-11 22:27:30
@ 5627e59c:d484729e
2025-06-11 22:27:30Liefde\ De samenkomst\ Van zien en zijn
Leven\ Het zijn en zien\ Een vorm gekregen
Sterven\ Een deur\ Die vrijheid geeft van vorm
En eeuwig leven\ Aan liefde
-
 @ e8646d56:72dab368
2025-06-03 08:15:30
@ e8646d56:72dab368
2025-06-03 08:15:30eee
-
 @ 3c506452:fef9202b
2025-06-13 18:11:48
@ 3c506452:fef9202b
2025-06-13 18:11:48Kia ora mai ra ano e te iwi whanui!
Step 1: Find Your Why:
Going off my own experiences - if you are anything like me you will have the occasional boost of enthusiasm, and intense determination. This could last a couple days, or if you are fortunate, a few weeks. Afterwards, life kicks in again, and you're out of gas.
With this in mind it is important to find something within you that could help carry you along until the next boost.
Action Step:
So grab a pen and paper, and write out why you want to become a Te Reo speaker.
Step 2: Find The Quick Win:
I consider myself to be a speaker of the reo, but I am SO FAR AWAY from my ideal, my vision, which is to think only in the reo. It would be silly of me to only consider myself a speaker of the reo once I attained that goal. Now, a speaker of the reo is... "Someone who speaks it". It doesn't matter how little you know now, your effort and the time you put in won't let you down.
Action Step:
- Follow this link > Ngata Dictionary
- Type in a word in the "Ngata English to Māori" box then press search. For example, let's use "hello".
- Copy the sentence in te reo.
- Follow the link > Papa Reo API, paste the sentence then press korero.
- Mimic what you hear!
This is a great way to practice speaking the reo! You can have 100% confidence in these sentences provided to you from the Ngata Dictionary. The Papareo API is also a fantastic way to get instant feedback on pronunciation.
-
 @ c1e9ab3a:9cb56b43
2025-05-18 04:14:48
@ c1e9ab3a:9cb56b43
2025-05-18 04:14:48Abstract
This document proposes a novel architecture that decouples the peer-to-peer (P2P) communication layer from the Bitcoin protocol and replaces or augments it with the Nostr protocol. The goal is to improve censorship resistance, performance, modularity, and maintainability by migrating transaction propagation and block distribution to the Nostr relay network.
Introduction
Bitcoin’s current architecture relies heavily on its P2P network to propagate transactions and blocks. While robust, it has limitations in terms of flexibility, scalability, and censorship resistance in certain environments. Nostr, a decentralized event-publishing protocol, offers a multi-star topology and a censorship-resistant infrastructure for message relay.
This proposal outlines how Bitcoin communication could be ported to Nostr while maintaining consensus and verification through standard Bitcoin clients.
Motivation
- Enhanced Censorship Resistance: Nostr’s architecture enables better relay redundancy and obfuscation of transaction origin.
- Simplified Lightweight Nodes: Removing the full P2P stack allows for lightweight nodes that only verify blockchain data and communicate over Nostr.
- Architectural Modularity: Clean separation between validation and communication enables easier auditing, upgrades, and parallel innovation.
- Faster Propagation: Nostr’s multi-star network may provide faster propagation of transactions and blocks compared to the mesh-like Bitcoin P2P network.
Architecture Overview
Components
-
Bitcoin Minimal Node (BMN):
- Verifies blockchain and block validity.
- Maintains UTXO set and handles mempool logic.
- Connects to Nostr relays instead of P2P Bitcoin peers.
-
Bridge Node:
- Bridges Bitcoin P2P traffic to and from Nostr relays.
- Posts new transactions and blocks to Nostr.
- Downloads mempool content and block headers from Nostr.
-
Nostr Relays:
- Accept Bitcoin-specific event kinds (transactions and blocks).
- Store mempool entries and block messages.
- Optionally broadcast fee estimation summaries and tipsets.
Event Format
Proposed reserved Nostr
kindnumbers for Bitcoin content (NIP/BIP TBD):| Nostr Kind | Purpose | |------------|------------------------| | 210000 | Bitcoin Transaction | | 210001 | Bitcoin Block Header | | 210002 | Bitcoin Block | | 210003 | Mempool Fee Estimates | | 210004 | Filter/UTXO summary |
Transaction Lifecycle
- Wallet creates a Bitcoin transaction.
- Wallet sends it to a set of configured Nostr relays.
- Relays accept and cache the transaction (based on fee policies).
- Mining nodes or bridge nodes fetch mempool contents from Nostr.
- Once mined, a block is submitted over Nostr.
- Nodes confirm inclusion and update their UTXO set.
Security Considerations
- Sybil Resistance: Consensus remains based on proof-of-work. The communication path (Nostr) is not involved in consensus.
- Relay Discoverability: Optionally bootstrap via DNS, Bitcoin P2P, or signed relay lists.
- Spam Protection: Relay-side policy, rate limiting, proof-of-work challenges, or Lightning payments.
- Block Authenticity: Nodes must verify all received blocks and reject invalid chains.
Compatibility and Migration
- Fully compatible with current Bitcoin consensus rules.
- Bridge nodes preserve interoperability with legacy full nodes.
- Nodes can run in hybrid mode, fetching from both P2P and Nostr.
Future Work
- Integration with watch-only wallets and SPV clients using verified headers via Nostr.
- Use of Nostr’s social graph for partial trust assumptions and relay reputation.
- Dynamic relay discovery using Nostr itself (relay list events).
Conclusion
This proposal lays out a new architecture for Bitcoin communication using Nostr to replace or augment the P2P network. This improves decentralization, censorship resistance, modularity, and speed, while preserving consensus integrity. It encourages innovation by enabling smaller, purpose-built Bitcoin nodes and offloading networking complexity.
This document may become both a Bitcoin Improvement Proposal (BIP-XXX) and a Nostr Improvement Proposal (NIP-XXX). Event kind range reserved: 210000–219999.
-
 @ 5627e59c:d484729e
2025-06-11 22:27:17
@ 5627e59c:d484729e
2025-06-11 22:27:17Muziek\ Jij harmonieus geluid
Een gevoel zo uniek\ Op geen andere manier geuit
Ik ben zo dankbaar voor de vrijheid die jij me schenkt\ Om gewoon even te zijn\ In dit dierbare moment
-
 @ 5627e59c:d484729e
2025-06-11 22:26:51
@ 5627e59c:d484729e
2025-06-11 22:26:51Gelukkig zijn\ Is de waarde van mijn leven
Gewoon dankbaar te bestaan\ Geen mens heeft me ooit zo'n mooi cadeau gegeven
Dankbaar voor mijn sprankelen\ Mijn doen en voor mijn streven
Maar ook dat ik mag wankelen\ Mag vallen en mag beven
Want wat er ook gebeurt\ Het duurt steeds maar voor even
De wijsheid van mijn hart\ Voor alles is een reden
Het leven brengt mij deugd\ En soms brengt het me pijn
Maar nooit neemt het die vreugd\ De toelating om hier te zijn
De kans om iets te leren\ Te zien en om te groeien
Geeft mij kracht te accepteren\ Te omarmen en te bloeien
-
 @ 0b884d0d:9abbd54a
2025-06-02 21:42:29
@ 0b884d0d:9abbd54a
2025-06-02 21:42:29Conceitos chaves
Neste artigo você vai entender um pouco dos conceitos chave desse novo conjunto de ferramentas para aplicar justiça de forma descentralizada e anárquica.
Antes de continuar a leitura, quero elucidar alguns termos que serão constantemente usados neste artigo.
- Private Law Society (PLS)
- Uma organização sem fins lucrativos com o objetivo de criar novas soluções para tornar cada vez mais viável a aplicabilidade de uma justiça privada e descentralizada
- Ao mesmo tempo, um conjunto de protocolos e softwares de código aberto com o mesmo propósito
- Links úteis
- Perfil Nostr: nostr:npub1p79dx59d5gctllar73cqnucqft89gpkfmydxj4mmk2jj69s7hn3sfjatxx
- GitHub: https://github.com/PrivateLawSociety
- Sobre: https://privatelawsociety.net
- Bitcoin Justice Protocol (BJP)
- Um protocolo estabelecido pela Private Law Society
- Também um software de código aberto disponível no GitHub da Private Law Society
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-bjp
- Sobre: https://privatelawsociety.net/bjp
- Implementação oficial da PLS: https://pls-bjp.vercel.app/
- Web Of Trust (WoT)
- Uma base de dados com avaliações entre usuários Nostr relatando confiança/desconfiança e se um usuário teve relações comerciais ou não com outro
- O objetivo é ser um repositório de reputação para chaves Nostr
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-wot
- Sobre: https://privatelawsociety.net/wot
- Implementação oficial da PLS: https://pls-wot.vercel.app/
- Meu fork com o grafo: https://pls-wot-kiuusai.vercel.app/
Prefácio
Recentemente saiu um episódio no BetterMoney podcast sobre o projeto de justiça privada Private Law Society.
Muitos bons pontos foram levantados neste excelente episódio pelos participantes nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju e nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft. Mas neste entorno permanecem ainda muitas dúvidas sobre o projeto em si, seu funcionamento, princípios, objetivos e funcionalidades.
Venho através deste artigo, apresentar resumidamente o projeto, a filosofia por trás do mesmo e dar a minha visão de como este conjunto de protocolos chamado Private Law Society tem a capacidade de não só transformar o mundo como o conhecemos, mas de tornar boa parte do "poder judiciário" obsoleto e irrelevante em vários aspectos, se assim os indivíduos o quiserem.
Mas afinal, o que é essa tal de PLS?
PLS é um acrônimo para Private Law Society (Sociedade de Leis Privadas em uma tradução livre). Além de uma organização sem fins lucrativos e totalmente Open Source, trata-se de um conjunto de softwares disponíveis no GitHub de forma a estruturar um protocolo de justiça privada descentralizado com colateral em Bitcoin. Falei grego para você? Vamos com calma dissecar estes conceitos...
Sociedade de leis privadas, a "utopia" libertária se tornando realidade
Quem é adepto do movimento libertário e/ou estuda o tema, provavelmente já ouviu falar nesse termo. Originalmente cunhado por David Hume, o filósofo e idealista escocẽs. O projeto toma este nome com o intúito, talvez de forma ambiciosa, mas com certeza visionária e audaz, de trazer uma solução prática e simples de estabelecer contratos voluntários entre duas ou mais partes, as quais livremente escolhem os seus "árbitros" ou "juízes" para fazer valer a lei. Como realmente uma justiça paralela a qual o contrato faz lei entre as partes.
Para uma introdução sobre o conceito, indico este vídeo do canal AnCapSu que trata sobre o tema de forma resumida.
Essa ideia, simples a priori esbarra no problema da aplicabilidade da força, ou ao menos era o que se pensava, antes da criação de ferramentas como o Bitcoin e soluções como Taproot e Bitcoin Scripts. Agora, com uma propriedade realmente soberana, programável e incensurável, essa ideia começa a ganhar forma.
Basicamente, uma dúvida plausível para uma pessoa leiga no assunto seria: "Tá, entendi. Esse tal de bitcoin é realmente bom, seguro e o Estado não tem poder de controle sobre ele. Mas como isso pode gerar essa tal de sociedade de leis privadas? É só uma forma de dinheiro."
A resposta para isso é: Dinheiro programável, chaves privadas e reputação!
BJP: contratos colateralizados em Bitcoin
Bitcoin, Nostr e Taproot: a chave para a aplicação da justiça privada
Se você já está minimamente envolvido com o ambiente Bitcoin, Nostr e afins, deve saber o que é um par de chaves públicas e privadas e como isso funciona. Existe uma chave pública e privada, a pública é a forma de identificação no sistema e a privada é a que gera as assinaturas. Daí é possível determinar que quem publicou a mensagem, seja na blockchain do Bitcoin, seja na rede Nostr, é o dono daquela chave pública em específico. Assim, se institui uma forma de identidade digital.
O que muita gente não sabe, ou não dá o devido valor, é que depois do soft fork Taproot da rede Bitcoin (ocorrido em 2021), os antigos Bitcoin Scripts tomaram outra forma e maior capacidade, se tornando mais práticos, leves e funcionais. Isso é o que dá base hoje para "contratos inteligentes" no Bitcoin e toda a parafernalha de Ordinals, Runes e coisas do gênero. O que pra muitos foi uma maldição que encheu a mempool, na verdade também se provou uma bênção, a qual é a base do BJP (Bitcoin Justice Protocol) da Private Law Society. A atualização permitiu com que scripts mais complexos pudessem ser desenvolvidos de forma mais simples, fossem mais leves e tivessem uma melhor privacidade. O BJP se empodera disso, fornecendo uma solução ao mesmo tempo que simples, inovadora para casos de uso de contratos. Primariamente na camada nobre do Bitcoin e posteriormente na Liquid Network, para aqueles que querem poupar em taxas e terem mais privacidade.
Por sua vez, o Nostr funciona também com criptografia de curvas elípticas, assim como nosso querido Bitcoin. Para ser mais preciso, o mesmo algoritmo é usado tanto no Nostr quanto no Bitcoin. O Secp256k1. Na prática isso significa que toda chave Nostr também é uma chave Bitcoin em potencial. O BJP se apropria dessa interconexão para possibilitar a criação de contratos jurídicos.
BJP: uma multisig sofisticada?
Ok, até agora vimos o que torna esse tal de BJP possível, mas como ele funciona e como eu posso usá-lo na prática?
Bem grosseiramente falando, o BJP é um software que facilita a criação de carteiras multisig específicas para contratos jurídicos. Com ele, você constrói uma multisig não convencional com Taproot que assegura o cumprimento do contrato mediante concordância de todas as partes "clientes" do contrato ou do número mínimo de árbitros configurados previamente + um dos clientes.
Na prática, um script Taproot é montado com a seguinte lógica:
``` Clientes = {Lista de chaves públicas dos clientes}
Árbitros = {Lista de chaves públicas dos árbitros}
Quorum = Número mínimo de árbitros para aprovar a transação
Se todos os Clientes concordarem: Libera gasto Senão se 1 dentre todos os Clientes concorda e ao menos o Quorum de Árbitros concorda: Libera gasto Senão Bloqueia gasto ```
Esse algoritmo garante que o contrato seja efetuado e esteja de acordo com a vontade de todas as partes envolvidas, ou, se entrar em "disputa judicial", o número mínimo de árbitros designados para "fazer valer a lei", concorde junto com a parte lesada para onde os fundos devem ir.
Um exemplo prático:
Aqui temos um exemplo prático de aplicabilidade de um contrato feito através do BJP. Nesse caso, tendo a concordar com o nostr:npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r e discordar do nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju quando o primeiro comenta no recente episódio do BetterMoney Podcast:
19:30 Eu discordo do Júlio. Acho que a PLS seria perfeita pro contrato de aluguel. O locatário coloca o colateral e o proprietário vai ter certeza de que não vai tomar calote.
E se uma das partes tentar levar pra justiça estatal, não vai ter nenhum nome no contrato, apenas chaves públicas.
E está certo. O exemplo prático que acabei de citar reforça isso. Não há nada que impeça também, de no contrato, ter uma cláusula a qual envolver a justiça estatal cause algum prejuízo ou perda de causa imediata para a parte expositora. Não estou fazendo recomendação alguma, fazendo apologia a qualquer prática ou aconselhando usar deste tipo de artifício, se o que falo possa ser interpretado como crime pela lei positivada (não sou advogado). Mas, no campo das ideias e das possibilidades no mundo real, é uma possível solução/alternativa.
Vamos ao exemplo...
Adriano Calango quer alugar um apartamento de Beto Lagartixa. Só que ambos não se conhecem e não confiam suficientemente um no outro para fazer um contrato. Ambos decidem então escrever um documento. Word, Pdf ou um texto puro. Não importa. Lá estão todas as cláusulas, o caução do aluguel, multas estabelecidas para uso indevido, penalidades, dia de pagamento, decisão sobre multa de atraso, enfim, qualquer detalhe desse contrato.
Adriano Calango, escolhe Célsio Jacaré, seu amigo como seu árbitro pessoal. Beto Lagartixa escolhe Danilo Crocodilo, seu amigo, como seu árbitro pessoal. Ambos escolhem Eduardo Cobra, um réptil íntegro, com reputação ilibada e que já fez vários julgamentos, como um árbitro em comum para seu contrato. Daqui temos: dois contratantes, duas testemunhas e um juíz.
Adriano Calango então, acessa o site da PLS BJP para criar o contrato. Configura os clientes (ele e Beto Lagartixa), configura todos os árbitros, anexa o arquivo e cria o contrato na rede Bitcoin.
Um evento Nostr criptografado é criado e um link de compartilhamento do contrato é disponibilizado. Adriano Calango compartilha esse link com todos os usuários disponíveis.
Todos os usuários verificam os detalhes do contrato e se o documento do contrato bate com o contrato assinado. Todas as partes ativamente concordando, a nossa multisig é criada.
Um arquivo do contrato é disponibilizado para acessar a multisig do contrato posteriormente. Todos os usuários salvam esse arquivo e o mantém guardado em um local seguro. O objetivo disso é ter redundância. Se um dos participantes perder este arquivo, outro pode compartilhar o mesmo para possibilitar o acesso à multisig do contrato.
Adriano Calango e Beto Lagartixa depositam os devidos colaterais no contrato. Seja o caução de aluguel ou um montante separado para ser empenhorado. Isso é definido pelo acordo feito previamente.
Se tudo ocorrer bem, assim que Adriano Calango resolver se mudar e Beto Lagartixa não tiver nenhuma objeção quanto a isso, ambos voltam para o contrato previamente feito e concordam quanto aos montantes que cada um receberá de volta. Dividem o preço da taxa entre si e cada um tem sua propriedade de volta.
Digamos que Adriano Calango não cumpriu com parte do contrato, atrasando o pagamento de alguns meses. Por outro lado, Beto Lagartixa também não cumpriu parte de seu acordo, deixando de fornecer serviços prescritos no contrato como segurança de condomínio e um elevador funcional. O caso então é levado aos árbitros. Célsio Jacaré argumenta a favor de Adriano Calango, questionando Beto Lagartixa sobre os serviços não prestados pelo mesmo e que claramente no contrato estavam previstos como parte inclusa no custo do aluguel. Danilo Crocodio retruca sobre a inadimplência de Adriano Calango, defendendo seu amigo/cliente, Beto Lagartixa. Eduardo Cobra, ao ouvir calmamente todos os argumentos de ambos os lados, então decide: - Adriano Calango foi inadimplente por três meses. Portanto terá uma multa de 35% sobre seu patrimônio - Beto Lagartixa terá uma multa de 25% sobre o seu patrimônio, pois não prestou o serviço com a devida qualidade - O restante do patrimônio será devolvido para seus respectivos donos - Dos valores da multa: - 90% será dividido entre cada árbitro. 30% para cada - Os 10% restantes serão queimados em taxas para os mineradores
Note que não foi usado nenhum meio coercitivo para solucionar o caso e penalizar os réus em seus devidos processos. Tudo foi aceito voluntariamente previamente, inclusive da parte dos árbitros. As multas aplicadas são meramente ilustrativas. Em um cenário real, tais penalidades seriam acordadas previamente e na falta das mesmas, todas as partes discutiriam até entrar em um acordo quanto a decisão. É totalmente plausível que, por exemplo, a penalidade fosse queimar todo o valor das multas em taxas para os mineradores, se assim todos aceitassem. O mecanismo de mineração nesse cenário também se torna um possivel meio de aplicação de força em um julgamento.
Só esta parte do ecosistema já faz boa parte dos casos de uso da justiça estatal obsoleta, dando maior descentralização, privacidade e soberania para os indivíduos.
Nesse cenário temos novamente a "utopia" libertária sendo definitivamente aplicada. Não há dedo do Estado no meio, todos os contratos foram previamente acordados entre as partes e não houve violação ao PNA (Princípio da Não Agressão). Todo o processo foi estritamente voluntário desde o começo.
WoT: A digitalização da reputação
Quem vê o projeto a primeira vista, pode pensar:
Ah Calango. Legal essa solução com bitcoin e tal. Mas eu vou sempre precisar gastar meus bitcoins toda vida que fizer um contrato? Tem contratos que isso não vale a pena!
Sim. Isso é verdade. Tanto que foi genialmente um caso citado pelo nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju. Há casos que os valores são tão pequenos que não compensa criar todo um documento de contrato para, por exemplo, comprar um livro ou algo do tipo. Ou, algumas vezes, o próprio indivíduo não quer gastar dinheiro ou travar valores para manter esse contrato. Mas não é o único caso de uso. Lembre-se que mesmo com colaterais aplicados, normalmente as pessoas não gostam de entrar em decisões judiciais ou confusões em geral. Idealmente todos querem traçar o caminho feliz da história. Então, mesmo para firmar contratos com colateral em Bitcoin usando o BJP, é plausível que um usuário queira pesquisar o "histórico" de outro usuário na rede para averiguar se é uma boa ideia ou não se envolver com aquele indivíduo em específico.
Naturalmente o ser humano já pratica esse cálculo de reputação e analisa o ambiente a sua volta para entender a hierarquia e reputação dele e de outros indivíduos em um grupo. Somos seres sociais e naturalmente na nossa cabeça já montamos uma espécie de rede de confiança na nossa cabeça com a imagem que formamos de um indivíduo X ou Y com base na nossa comunidade. Hierarquia, lideranças, influência, são características naturais do ser humano.
A partir desse cenário, surgiu a ideia de gerar uma solução para uma melhor visualização da reputação entre usuários do protocolo. O objetivo é ser primariamente um repositório com avaliações de usuários sobre outros usuários, os classificando positivamente ou negativamente e informando se houve ou não negócios/fechamento de contratos com o mesmo. A ideia é realmente simples e o objetivo é deixar o protocolo aberto para as mais diversas formas de interpretação desses dados. Seja com modelos matemáticos, visualização e interpretação pessoal ou até mesmo o uso de inteligência artificial para o auxiliar o usuário a tomar suas decisões.
WoT: o nome é conhecido, mas a proposta é diferente
Veja que há uma diferença prática na WoT da PLS e outros projetos de WoT espalhados pela internet afora e pelo Nostr. A maioria dos projetos de WoT são para determinar se uma pessoa/chave privada é ou não relevante a partir da visão de outra chave privada. É o caso de serviços de WoT como o da Coracle.Social, Vertexlab.io e mais recentemente da nova implementação de WoT Relays. Serviços como estes tem o objetivo de reduzir ou eliminar spam e falsidade ideológica (fakes), assim como oferecer uma espécie de algoritmo de recomendação, similar ao que é feito em redes sociais como YouTube e Instagram.
Note que em nenhum momento o objetivo da WoT da PLS é definir por A + B quem é ou deixa de ser confiável ou inconfiável, afinal, confiança é algo estritamente relativo. Nenhum projeto pode ter a audácia de tentar classificar pessoas como confiáveis ou inconfiáveis a nível de estabelecimento de contratos. A PLS entende isso e respeita esse caráter subjetivo da confiança. De igual maneira, nunca foi o objetivo de qualquer projeto de WoT sério fazer algo similar ao que é feito em países como a China, onde pessoas têm alguma espécie de "crédito social". Fique tranquilo. Nosso objetivo não é tornar os episódios distópicos de Black Mirror em realidade 🤣
Visualização em grafo: uma proposta elegante
Desde que entrei de cabeça no projeto da PLS, uma coisa que veio sendo falada nas reuniões era sobre a criação de novas ferramentas para visualizar a rede de formas mais intuitivas, que ajudassem os usuários ao julgar pessoas como confiáveis ou não para estabelecer contratos, e ao mesmo tempo, resolvessem o problema de UX que é uma simples tabela com avaliações entre usuários da rede. A tendência é, a partir do momento que o projeto comece a ter adesão, que o número de notas cresça exponencialmente, e com isso, a visualização da reputação dos indivíduos seja pouco intuitiva. Uma solução apresentada para este problema foi a criação de um frontend com grafos, ou melhor, a criação de uma forma de visualização da sua rede de confiança em particular. A partir disso, foi gerada uma bounty no projeto para a implementação desta solução, a qual eu orgulhosamente estou construindo (na verdade está pronta para uso. Mas ainda quero melhorar algumas coisas). O objetivo é simples: dar ao usuário mais uma forma de contemplar os dados da WoT, de forma mais particular e intuitiva. Facilitando a tomada de decisões.
A natureza da confiança humana em sintonia com a tecnologia
Bolhas virtuais, vilarejos e mineiros
Uma possível crítica que o projeto possa receber é a possibilidade de ataques de spam ou cancelamento em massa corroer ou inviabilizar a utilidade do protocolo. Ataque Sybil também. Entretanto, são espantalhos até bem inocentes quanto ao projeto em questão.
Como havia mencionado anteriormente, a base do projeto em si é propositalmente simples e não se propõe a dar uma solução definitiva para a visualização dos dados postos no protocolo. A tabela de avaliações hoje existente no site da WoT da PLS é apenas uma das inúmeras formas de interpretar estes dados. E uma forma efetiva para problemas como esse, é justamente a implementação de uma visualização por grafo, onde os usuários podem ver redes de confiança sendo tracejadas a partir do ponto de vista específico de uma npub em particular.
Aqui a lógica de um antigo ditado é aplicada:
"O amigo do meu amigo é meu amigo"
Da mesma maneira também podemos formular outras afirmações como:
"O inimigo do meu inimigo é meu amigo"
"O inimigo do meu amigo é meu inimigo"
"O amigo do meu inimigo é meu inimigo"
Se tais derivações fazem sentido para você ou não, não cabe a mim dizer. Novamente, confiança é intrinsecamente algo de caráter subjetivo. Vai de cada um decidir quem é ou não confiável. É justamente por isso que estou implementando diversos filtros de avaliações no meu fork da PLS.
Na prática é o velho jogo de política de sempre. Como bem citado uma vez pelo filósofo e youtuber Platinho, ao citar Carl Schmitt:
Isso também se reflete na cultura mineira (e rural do Brasil em geral), por exemplo. O clássico "cê é fi de quem?". Perceba que essa é uma forma de procurar por um caminho de confiança já estabelecido. Quem tem parente em interior sabe, que uma das coisas mais comuns é os mais velhos, seja ou tio, mãe ou avô perguntar sobre um amigo que você leve para o ambiente familiar (meu filho, esse seu amigo é filho de quem?) É algo até instintivo do ser humano procurar por rotas de confiança e trabalhar de certa forma com o QI (Quem Indica). Goste você ou não, é assim que a natureza humana se expressa e é assim que a dinâmica social é montada.
Vendo que é natural a formação de bolhas, não é uma boa ideia em si interpretar os dados da WoT da PLS simplesmente de uma forma numérica bruta. A melhor forma é fazer uma abordagem individual, com base na sua rede de confiança ao invés de puramente o número de avaliações positivas e negativas.
O grafo da PLS busca justamente tornar mais intuitivo, prático e sistemático essa pesquisa natural. Essa implementação é além de uma ferramenta, uma forma de expressão social muito forte, tanto em âmbito social quanto jurídico, à medida em que a dinâmica social e jurídica se entrelaçam no tecido social.
Adriano Calango ataca novamente
Para um exemplo prático, voltemos a falar dele, Adriano Calango.
Adriano Calango conhece a WoT da PLS já faz um tempo e já avaliou todos os seus parceiros comerciais e amigos aos quais tem laços de confiança já firmes e maduros. Ele procura alguém para alugar uma casa Rolante, RS. ´Ele vê alguns perfis de síndicos no Nostr que moram na mesma cidade que ele com casas disponíveis para alugar. Mas quer ter uma noção que não está se metendo em encrenca ou lidando com algum síndico chato que inferniza a vida dos inquilinos.
Dito isso, ele acessa a WoT da PLS e vai na página do grafo. Percebe que seu amigo Bruno Jabuti, ao qual já havia avaliado positivamente anteriormente, avaliou positivamente um professor de Jiu-jitsu, conhecido como Carlos Camaleão. Que além de ser avaliado positivamente por Bruno Jabuti, recebeu várias avaliações positivas de outros usuários conhecidos de Adriano Calango. Carlos Camaleão, por sua vez, avaliou positivamente um síndico da região chamado Diego Iguana. Na descrição Carlos Camaleão descreve como em todo o tempo que ele foi inquilino de Diego Iguana sempre foi bem tratado e como seu condomínio estava sempre bem organizado e era cuidadosamente zelado, e como sempre que havia alguma falha de infraestrutura, o problema era rapidamente resolvido. Adriano Calango considera firmar um contrato de aluguel com Diego Iguana.
Assim, temos o seguinte caminho de confiança estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👍 -> Diego Iguana
Passando-se alguns dias, Adriano Calango é abordado por Denis Jacaré em uma DM no Nostr oferecendo aluguel baratíssimo e com poucas exigências. Denis Jacaré foi informado que Adriano Calango estava a procura de um imóvel novo para residir. Adriano Calango, então, pega a chave Nostr de Denis Jacaré e joga na parte de "target" na página do grafo na PLS WoT. Ele percebe que Denis Jacaré tem várias avaliações negativas de inúmeros usuários, mas não consegue ainda bater o martelo quanto a confiabilidade de Denis Jacaré. Ele então insere sua própria chave Nostr no campo de "main rater" e vê que tem um caminho tracejado entre a sua npub e a de Denis Jacaré. Pra sua surpresa, ele vê que Carlos Camaleão deu a Denis Jacaré uma avaliação negativa, por conta que no período em que sua filha era inquilina do mesmo, prestou um péssimo serviço. O condomínio vivia com o elevador quebrado, a portaria muitas vezes não funcionava e tinha falta de luz constante. Denis Jacaré não tomava providẽncia nenhuma quanto a isso e ainda fazia questão de causa intriga entre os inquilinos e tentar jogar uns contra os outros. Adriano Calango, então percebe que Denis Jacaré não é confiável com base na rede de confiança definida por Adriano Calango.
Nesse caso temos o seguinte circuito estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👎 -> Denis Jacaré
Adriano Calango aborda Diego Iguana para estabelecer um contrato. Agora é a vez de Diego Iguana pesquisar o histórico de Adriano Calango. Pois ele quer manter a comunidade de seu condomínio saudável e não deseja aceitar inquilinos baderneiros ou barraqueiros.
Diego Iguana faz então o caminho inverso de Adriano Calango, pondo a npub de Adriano Calango como "target" e a própria npub como "main rater". Daí Diego Iguana consegue ver que Carlos camaleão deu uma nota positiva para Bruno Jabuti e Bruno Jabuti deu uma nota positiva para Adriano Calango. Os dois então fecham negócio.
Neste exemplo, o grafo da WoT da PLS serviu como uma "bússola de confiança" para Adriano Calango e Diego Iguana firmarem um contrato no BJP com seus árbitros e advogados.
Considerações finais
Neste artigo você pôde aprender os conceitos básicos da Private Law Society, motivos de certas escolhas de design, viu exemplos práticos de casos de uso e um pouco das bases filosóficas que norteiam o ecosistema da PLS. Também pôde compreender um pouco mais sobre o conceito de WoT na PLS e como isso pode ser útil com o passar do tempo e a adesão de novos usuários no sistema.
Se este conteúdo te agregou de forma positiva em algo, considere mandar um ZAP ou fazer uma doação anônima por um dos meios disponibilizados na descrição do meu perfil Nostr. Este artigo foi feito com muito carinho e dedicação. Sua doação me encoraja a continuar produzindo e lhe mantendo informado. Se não pode ou não quer contribuir financeiramente, considere engajar no conteúdo reagindo, compartilhando e comentando. Toda a ajuda é bem vinda. Agradeço de coração sua paciência e atenção para ler até aqui.
Em breve trarei novidades sobre o desenvolvimento do grafo da WoT e logo mais, vídeo novo no meu canal do YouTube. Até mais!
-
 @ 5188521b:008eb518
2025-06-03 12:25:39
@ 5188521b:008eb518
2025-06-03 12:25:39Elysium
Part I: The Failed Harvest
First, the quiet came. Each day, the markets grew quieter, the people hungrier. A farmer stared at wilted crops, dread settling in his heart. In a kingdom once resplendent with markets and sky-reaching monuments, it was the first failed harvest that marked the end of affluence and the beginning of collapse.
By the second year, market traders stood before empty stalls, goods long gone, rotten, or ruined. Jobless men prowled, foraging the streets for vermin and meager scraps of sustenance. Young women offered their time for bread, their eyes hollow in the act. Widows, too, entered strangers’ homes, bartering themselves for their children’s next meal. Orphans, gaunt and brittle, drew meaningless shapes in the dust, their laughter a forgotten memory.
Rumors surged like wind through dry grass. Scapegoats were blamed; superstitions gripped the masses. By the third year, it was known to the people and the king alike, there would be no more monuments erected, only tombstones. The king called the council, heavy with despair. In a room filled with tension, ministers and knights sat around a table.
Before them stood the realm’s wisest farmer, a man worn from years of labor, hunger, and loss. His voice echoed the deep hunger that gripped the kingdom. “Your Majesty, the land is weary. It cries for respite.” His words hung heavy in the room, laying bare the reality of their fate.
Part II: The Devil’s Pact
In the dimly lit chamber, a palpable tension filled the air. The alchemist, servant to the king and master of arcane arts, stepped into the flickering candlelight. He held an aged book, its scent mingling with the murk of looming spells. With a voice both smooth and haunting, he shattered the quiet, his words a ripple through stone walls.
“Sire, alchemy is our last refuge. We can harvest time to feed the earth,” he began, revealing a parchment inked with cryptic circles and lines. “Each citizen, willingly or not, will spare a mere whisper of their years. An unnoticeable offering. With careful alchemy, we can replenish our lands and fortify your reign with the alms of myriad souls.” Leaning closer, he whispered the words that would redefine their civilization: a devil’s proposal intended for the king but felt by all. “Consider, my lord, a reign without end, each year stretched beyond nature’s limits, a kingdom fed by the borrowed time of its people. No more famine. No more want.”
The court waited, their faces etched with fear and desperate hope, ready to tread any path that led away from the abyss of famine.
For a moment, the king was a statue, his face a veil behind which storms brewed. Finally, exhaling a breath heavy with fate, he spoke. “We’ve endured enough hardship. We shall seize a future that knows no famine.”
The air thickened as the alchemist retreated with a solemn nod, the weight of the chosen path settling in.
He reopened his tome and voiced the incantation. Arcane syllables filled the room, weaving a desperate gambit to salvage their decaying kingdom. Thus, in the dark hours of night, they sealed a new covenant that would reverberate through generations.
Part III: Vines and Moss
In the decades that followed the alchemist’s rites, the kingdom thrived like spring after a bitter winter. Fields were lush year-round, erasing hunger and the memories of famine. Marketplaces bustled, no longer a graveyard of commerce but a carnival of exotic goods from every corner of the world. The air seemed perfumed with prosperity — healthy river fish, basilisk meats, and spices from faraway lands. A century rolled by. The king, unaging, stretched his influence over land and sea, turning his realm into an empire. Statues weathered, and languages evolved, but the king abided.
Yet, a toll was exacted. Years stolen from the people, a time tax woven into the fabric of life. The spell fed both earth and crown, cloaking decay with a veneer of wealth. The young wore the faces of old men, their eyes wise beyond their years. Every heartbeat was a sacrifice, a quiet tax to feed the castles of power.
Then came the year when the land rebelled. Coaxed by the spell, the soil had given until it couldn’t, its silent plea for rest ignored. The land remembered stolen seasons, now determined to settle old scores. Crops withered; rivers soured. Beasts waned, their numbers thinning. The kingdom, starved of Earth’s gifts, unraveled — not from human revolt, but from the silent insurrection of the land that once fed them.
With hunger as the harbinger, society fractured. Chaos and mass confusion swallowed the land, a virulent blight not even alchemy could stem. Witch hunts raged for a merciless century, fire consuming flesh and innocence. Men’s strength wilted, armies disbanded. Women, walking in the agonizing footsteps of famine-haunted foremothers, bartered touch for bread.
Monuments lay buried under vines and moss. Fertile lands turned barren. Schools emptied, their echoing halls abandoned, and children torn from learning, were sent to farm dying lands. Art withered. Painters swapped colors for shades of gray, and soon vanished altogether. Teachers and engineers were supplanted by an ever-growing class of soil-bound serfs.
Desperate, the eternal king sought another spell. He asked the people not for mere years but decades. The alchemist obliged, crafting another spell from dark incantations. Yet the ravaged earth, too spent to yield, exacted a monstrous price: lifetimes for crumbs of bread. People, skeletal, on the verge of vanishing, offered their very existence. A silence settled, a collective sacrifice borne not in rebellion, but in surrender.
Part IV: Clara The Torchbearer
In the land between sleep and waking, Clara was a child again, standing at the threshold of a room aglow with amber light. Her mother ground herbs, the wooden table before her strewn with books, vials, and leaves. “These aren’t just leaves and liquids,” her mother said. “They’re doors to the gardens of your mind.” Her words sank into Clara like stones into deep water.
She woke to a gusting wind. Her dream dissolved like morning mist. The sun broke over the kingdom, time’s toll evident in every vine-entangled ruin. Light spilled into her chamber.
Clara’s room was modest: a bed, a wardrobe, a desk. On it, a lone candle and scattered books that whispered of the kingdom’s past grandeur and freedoms now lost. It was her mother’s notes and books, crafted in the quiet, away from royal eyes — a puzzle to decipher, a quest still yearning for footsteps.
She draped a linen robe over her shoulders and approached the window, her fingers ink-stained from yesterday’s writings. Below, people shuffled through life, joyless and muted.
The spell cast long ago had become an oppressive, faceless dictator. It promised bread but dealt only crumbs, a tarnished magic now woven into the kingdom’s culture as enduringly as its ancient stone walls and teeming graveyards.
She remembered the cold spring day she put her mother in the earth. The ground was hard, the casket simple. The tombstone bore the words: ‘Seed in Drought.’
The chambermaid standing beside her asked what it meant.
“Her wish,” Clara answered. Her face gave nothing away, her thoughts a distant country.
From her room, Clara watched the people below — eyes down, spirits broken. Clara was not like the others. She carried an inner fire, gifted from her mother, a quiet revolt against a gray world.
In her room’s sanctuary, amid ink and parchment molded by hands long stilled, Clara found traces of a freer past, free from famine and theft of years. A past now entrusted to her. As she flipped through the timeworn pages of an ancient tome, something caught Clara’s eye. In the margins of the text, a note penned in her mother’s hand: “For Clara — Elric is the keeper of truths that free us. Go where I could not. Find him.” Below it, a tender signature, her mother’s name etched in ink.
The name ‘Elric’ stirred a latent memory, a shared secret often spoken by her mother. Filled with a sense of destiny, Clara closed her worn books and left her chamber.
At the age of twenty, for the first time, she ventured beyond the confining walls of her castle. Guided by remnants of forgotten eras, she set forth to unearth truths long interred but never wholly erased. Her compass drew her toward the Whispering Pines, a land untouched by the alchemist’s dark arts and, as her mother had often mentioned, the rumored dwelling of Elric.
Part V: Far to Go
Clara walked through towns void of kindness, over land stripped of life. Each day sculpted her in the likeness of the land she traversed — a leaner body, hands hardened, face etched by sun and wind.
Thirteen days out, Clara trudged through the ashen remains of a town, its name forgotten, its history lost. Empty buildings sagged under the weight of time, their hollow frames like gravestones against the evening sky. Vacant faces, like clock dials without hands, glanced through her, never at her.
Spying a run-down tavern, she cautiously stepped inside. The door whined on rusted hinges. She eased onto a splintered stool. “Bread,” she rasped. The innkeeper, a bloated man with eyes like rotted plums, flung stale crust onto the counter. Her teeth sank into the stale crust, her body weeping for nourishment.
The room stank of unwashed bodies and sour ale. In a dim corner, men gambled their souls on dice, their faces marred by desperation and greed. As she made to leave, talk stilled, and eyes tracked her. A rough hand seized her wrist.
“Far to go?” The words, a mockery.
Her eyes darted to the innkeeper, pleading for an ally. His gaze, cold, turned away. “Yes, far,” she replied, stalling.
Then, violence. Teeth, nails, a taste of blood. Outmanned, her screams died in cruel laughter. Her clothes yielded, torn in the contest of her humiliation.
After the degradation, she stepped outside and into the soft rain of the night. Her path now carried weight measured in more than miles.
Ahead, barren land stretched mercilessly. A fleeting image of her mother’s face offered a brief moment of comfort. She tilted her head back, letting rain droplets fall onto her tongue to dilute the bitterness that swelled within her. The night urged in tones only darkness knows. Turn back, it murmured.
But she walked on. Her will was a defiant ember, the last flicker of light in a world teetering on oblivion, its humanity long forfeited.
Part VI: Elric
After weeks traversing a harsh expanse, gaunt but unbroken, she found herself beneath the Whispering Pines. As she approached, she carried more than her own weight. She embodied her mother’s enduring hope and her land’s final prayer for redemption.
Elric greeted her at the doorway. “You’ve come,” he said, leading her inside, the room warm from the fire in the stone hearth.
Her eyes roved from the firelight dancing on the walls to the shelves laden with books. A staircase twisted upward, its banister engraved with ancient symbols.
“Your homeland withers,” Elric said, drawing from his pipe, the wood old and marked by years. The scent of herbs, a blend cultivated through many seasons, sharpened the mind as it filled the room. “The spell,” she confirmed.
“Mmm,” he exhaled, his eyes shifting to the fireplace, wood popping in the heat. “Your forebears knew better days. Days without sacrifice.”
“The legends spoke truth, then?”
“Indeed.”
“Did you know I was coming?”
“I’ve waited twenty years. This isn’t our first meeting.”
“We’ve met before?”
“Once, when you were but a newborn. Your mother and I collaborated. We worked on a potion that siphons the power of nature to protect the truth in our world, to shield it from alchemy and dark spells.”
Elric opened a small cabinet beside the hearth. From it, he took an empty wooden chalice and a stoppered glass vial. Uncorking the vial, he poured a golden liquid into the chalice, the firelight making it shimmer. “This elixir hails from untarnished lands, free from the alchemy that poisons your realm. One sip and illusions shatter, transforming soul and society alike.” “What is it called?” she asked.
He looked at her intently. “Elysium,” he said, the word hanging heavy in the room. “It’s both the end and the beginning of your journey. You must experience it to understand. Drink.”
She sipped the brew; it tasted of nothing. Soon, as she nestled by the fire, the walls took a breath, and the world sharpened as if coming into focus for the first time. The air thickened into a heavy mist, her fingers danced through it, each ripple sending colors splashing around like bioluminescent whispers. She floated, her body dissolving, her name a distant echo.
Elric’s gaze turned to the fire, shadows playing across his face. “Elysium shows only what one needs to see, no more, no less,” he said, his voice a gentle wave against the shores of her uncertainty. “In my own experience with Elysium, I saw a torchbearer in the veil of time, a young soul with the spark to undo the dark spell on your land.” His eyes found Clara’s. “But the torchbearer had to come to me, the journey forging the resolve. Had I sought you out sooner, before your heart was ready, Elysium’s truth would have been a burden too heavy.”
As the reality of his words sank in, Clara felt the weight of the years, the faces of the countless lives lost to the alchemist’s dark magic flashing before her eyes. “And the elixir… why not share it sooner?”
Elric sighed, his eyes drifting to the ancient books lining the shelves. “Elysium’s truth is a double-edged blade. In the wrong hands, it could cut through the fabric of reality, leaving wounds that might never heal. Your kingdom…” he gestured vaguely towards the window, “…it wasn’t ready. But now, the ground has been furrowed by suffering, ready to receive the truth about the universe, the spell, the suffering.”
The walls breathed with a rhythm older than time. She looked at her hands moving through the bioluminescent mist, each movement sending ripples across the room. Tendrils of light danced in the air, ethereal spirits beckoning her towards another realm.
“But why?” Clara pressed, her presence deepening with each breath. “Why involve yourself?”
Elric’s eyes softened. “I once lived in your kingdom, fleeing when I realized the spell’s plague. Your mother and I, we shared a vision of a world free from dark alchemy. But more than a promise to an old friend, it’s a battle against the grasp of evil spells, a grasp threatening to choke the essence of life and freedom from this world. It’s a battle,” he looked at Clara with a profound earnestness, “that now passes to you.”
Suddenly, reality shattered, and her soul twisted and warped through a portal faster and faster until she touched the core of the cosmos.
Here, in a land beyond words, beyond the confines of time and space, she witnessed the birth and demise of the universe. With each breath, a star was born and died; each blink saw the rise and fall of civilizations. Like a photon racing at light speed through the cosmos, untouched by time, she beheld the entirety of all that ever was and will be.
Peering beyond the infinitely small, she saw the source code of the universe, equations as living tendrils of light materializing into particles, planets, and stars. The universe, a symphony of mathematical elegance, its physicality a melody resonating along the strings of her consciousness.
She floated amidst the cosmic code, orchestrating the universe — the planets, the voids, the unseen forces weaving through them — and she was one with all. She was the universe gazing at itself. Beyond the veil of mortality, she saw endless realms, death a mere doorway. In that boundless expanse, she brushed against the face of the divine.
A golden phoenix took form before her.
“I am Veritas,” it spoke, not in words, but in a language of complex geometry.
It exposed the grim truths of her lands, the Great Famine, and the enslaving spell — a counterfeit prosperity bought at the terrible price of human years.
“How do we break free?” Clara’s voice carried the untold suffering of generations.
“Simple,” the phoenix intoned. “Don’t battle the alchemist or his spell; you won’t win. Acknowledge the illusion. Tend to your own gardens, and reliance on the alchemist and the king fades. Elysium shields you, body and mind, from the spell’s reach.”
As the vision faded, Clara found herself back on the wooden floor, her head cushioned by a pillow. The urgency of her quest snapped her back to reality, a newfound resolve kindling in her chest.
“I see now,” she breathed, her voice steady. “I know what I must do.”
Elric nodded, a sage with a deep understanding of the paths of the universe. “Yes, but first, tea. There’s strength to regain and you have a long journey ahead,” he said, anchoring them both in a moment of calm before the impending storm of change.
Part VII: The Wayfarer’s Hearth
After days navigating barren expanses, Clara entered a cobblestone town as twilight settled. Figures lined the street, some alive, some not, most in limbo — too tired to beg, too frail to feed. Candlelight flickered from the windows of a tavern, illuminating well-fed faces. “The Wayfarer’s Hearth,” read the sign above the door.
She approached. The door creaked open to admit her, wafting out stale beer and the scent of roast meat. Her fingers twitched involuntarily, memories of weeks ago crawling up her spine, but her body ached for sustenance, for warmth. Holding her satchel close, safeguarding the vial of Elysium, she chose a chair at an empty table and settled in. Soon enough, food appeared.
The man who had set her meal before her took the adjacent seat with deliberate ease, his eyes lingering on her satchel. Her pulse quickened.
“You carry a weight, wanderer,” he said.
“Or hope,” she countered, her grip on her satchel unyielding.
A glass shattered. Drunkards stumbled into their table, a wave of mead sweeping over worn wood. Clara’s heart surged, the man’s fingers brushed her satchel, pulling the vial from its sanctuary. “Hope carries its own burden,” he said.
“The hope of my people is in that vial,” she shot back, her voice stripped bare.
“This is Elysium,” he said, his words like barbs. “At what cost, wanderer, do you think Elysium will save your people?”
Doubt snaked around her convictions. Was she the bearer of emancipation or a harbinger of calamity? Was her land ready for Elysium? “You know it?” she asked.
“I know it,” he said, eyeing it closely.
“Return it,” she commanded.
He handed over the vial. “The road to freedom is paved with the stones of responsibility. I wouldn’t want to walk in your shoes.”
She nodded, heavy but resolute. Clara left as quietly as she’d come, meal untouched, mission intact.
The night took her in. She cast a final glance back at a room oblivious to her departure. That night, she’d sleep under indifferent stars, closer to home but adrift in certainty, carrying the weight of a thousand stones of untold responsibility, a Trojan’s shroud for her people, a destiny unasked.
Part VIII: This is Elysium
Under a storm-heavy sky, Clara returned home. In her pocket was Elysium; in her mind, a plan that required Harold — an old friend and a knight by trade.
In the guild hall, Harold sat among knights and minstrels, a goblet in hand. “Look at this,” Clara said, pushing the vial across the table without ceremony. Her words pierced the tavern’s noise as she recounted her journey.
Harold looked at her, then at the vial. “You mean to say that one day, this will help us fight the spell?”
“No,” said Clara, her voice deep with a new knowing. “It means one day, we won’t have to.”
“Heresy,” Harold said. “You’re risking death.”
“So are we all,” she answered.
“They’ll burn you at the stake.”
“If I’m right, they won’t.”
“A trial then, regardless,” Harold said, his gaze dropping to the vial as the tavern’s jovial banter became a distant echo for them both.
“So be it,” Clara said, meeting his gaze. She leaned in, her fingers resting on his scarred knuckles. “Our farms take our children. It’s not right.”
“It’s how things are.”
“It’s how things were.”
“A trial will not be lenient, Clara. I can’t let you bring this to the king.”
“Not the king. The people.” She continued. “But don’t trust me. See for yourself.” Her eyes locked onto his. “Drink,” she said, her words echoing Elric’s.
Harold hesitated but finally drank. His eyes widened. He gripped the edge of the wooden table, his knuckles turning white. A sort of vacant gaze overcame him as if he’d journeyed to someplace far.
When the Elysium vision receded, he opened his eyes and looked at her anew, seeing the world for the first time again. He glanced around the hall as though it were a foreign land, his eyes lingering on the mundane — a crack in the table, the smudged goblet, a flickering torch on the wall—with awe and wonder. She knew then that they stood as one. Two visionaries, shouldering the burden of transforming the world, ready to shepherd their people into a revolutionary dawn.
In the square, the stone eyes of old heroes watched. A crowd formed, silenced by expectation and unaccustomed to the art of public speaking. Autumn leaves swirled at their feet.
“A new dawn!” Harold broke the silence. “Generations sacrificed, giving years for meager sustenance. But the land wants not our years — only our care and periodic reverence. The tales of a time without the toll of hunger, without a tax on life itself, from before the Great Famine, are not myths. They are forgotten chapters of our history, now on the verge of being rewritten.”
He raised the vial. Sunlight mirrored in its gold. “This is Elysium.”
Part IX: A Revolution Takes Shape
In the fading light of day, Harold and Clara stood by a murmuring brook, leaves rustling at their feet in quiet revolt. Faces young and old assembled around them; each one a silent rebellion against the servitude that taxed their years.
They drank, the chalice passing from hand to hand, a new ritual born. With each gathering, the numbers swelled; with each sip, more souls entwined. Slowly, yet with unyielding certainty, the kingdom shifted over the years. It changed not through a coup or uprising but through a still, relentless force, like water eroding stone. As the seasons passed and more villagers imbibed the Elysian brew, the weight of their invisible chains lessened, their atoms scattering into the evening air.
Shielded now, villagers sowed their own gardens, sanctuaries from the alchemist’s dominion. Bountiful harvests followed, hope supplanted despair. Word of the blooming private gardens spread like wildflowers, and fields once cursed by dark alchemy lay fallow and forgotten.
And there, by the unassuming brook, a revolution took shape. The soft sounds of the stream became an earthbound anchor for the myriad souls who opened the door to walk in the cosmic gardens of their minds. Each ritual added another stitch in the fabric of a new dawn; each sip, another brushstroke on the canvas of a world remade.
Part X: The Old Man
A decade drifted by. With each soul that tasted Elysium, the fetters of the old world loosened. The alchemist’s spell, once a yoke around their necks, now waned like thick morning fog giving way to the warmth of the day. Fields once cursed now bore food, not dread. Families gathered around bountiful tables, words flowing freely, unveiled.
Each year, townsfolk met by the sword in the square. Harold’s blade, the first monument raised in ages, stood as freedom’s spine, the axis of their new world. An old man approached, his eyes dimmed by memories of famine, leading a boy by the hand. Their eyes met, a chasm bridged: one soul untarnished by hunger, the other haunted by its ghost.
The old man stepped forward, his fingers quivering on the hilt of the sword. “Clara, what becomes of us if the land fails us again?” Years of hardship wavered in his voice, the ghosts of famine flickering in his eyes.
“It could,” Clara said, her voice steady as bedrock. “But it’s different now. Our fields are wider, our hands more skilled. We’re not trying to trick the earth with alchemy anymore. We speak in the simple terms it understands: soil, sun, water, time.”
Above, the alchemist’s fortress loomed, its towers now marred with cracks. Clara looked up. Empty windows stared back, like dead eyes on a fallen beast. Old times had ended; new ones had begun.
Part XI: The Note
Dawn broke, casting new light over worn cobblestones. Clara moved through the marketplace as if through a dream. The scent of cinnamon and rich coffee filled the air as she ran her fingers down silken tassels and through powdery barrels of golden saffron. Voices haggled; her feet felt the earth’s warm embrace.
Traders argued leisurely, their time no longer taxed by the spell. Children laughed, unburdened by field and plow.
Fields that once caged both young and old now released thinkers, builders, creators. The horizon changed form — bridges leapt over waterways, roads bound the land. Each stone laid was more than a fixture; it was a vow, a pact between the present and the future. It was today’s promise to a future yet unborn, anchored by the prosperity that now bloomed under Elysium’s sky.
As evening descended, the grand hall filled with voices unburdened by yesterday’s sorrow. In a secluded corner, Clara and Harold exchanged words about the loftier truths Elysium had laid bare.
A courier emerged from the crowd, extending a sealed parchment. “For you, mademoiselle.”
With a nod, Clara exchanged a coin for the note. Her eyes brightened as she absorbed the message:
Only a true renaissance resounds to the Whispering Pines. Continue, in health and strength. - Elric
She passed it to Harold, their eyes locking in wordless affirmation. “The Whispering Pines acknowledge us,” he finally said. “And so, we continue,” Clara replied, her voice unwavering, guided by truth. In the hall’s enveloping warmth, laughter, toasts, and spirited debates blended into a harmonious score — a sound that would have been foreign to their ancestors, a sound that marked the close of an era and the dawn of something profoundly new.
This story first appeared in Tales from the Timechain. Support our work and buy a copyhere.
79% of the zaps from this story will be passed onto the author, Reed.
21 Futures requests 21% for operating costs.
Ioni Appelberg (pronounced Yo-Ni Apple-Burg) is a bitcoin philosopher, futurist, author, and content creator. His content centers around science fiction, human history and it often takes the form of swashbuckling journeys to the frontiers of technology, space, and the human mind. His love of sci-fi, psychedelics, and futurism may take his stories (and unsuspecting readers) to strange but exciting places. He is also an avid reader, a medical doctor, a freedom fighter, an MMA fighter, a psychonaut, and a terrible chess player.
-
 @ d68401a8:11aad383
2025-06-13 17:54:54
@ d68401a8:11aad383
2025-06-13 17:54:54Before AI, building a website posed a technological barrier. Not everyone was able to create even a simple contact page. It often meant paying for a yearly subscription (often too expensive for most), for templates that still required manual work, or paying even more to hire someone to do it for you.
Today, thanks to AI, building a website has become technologically accessible. Even if you still prefer to rely on a third-party company, the ease brought by AI is driving more competitive pricing.
In the domain world, before Handshake, owning a top-level domain (TLD) was economically out of reach. The application process set by ICANN was tedious and expensive. For most people, the only option was to rent a second-level domain, one not controlled by individuals and subject to whatever fees the TLD owner chose to charge.
Now, thanks to the Handshake DNS protocol, anyone can own a top-level domain and create an infinite number of second-level domains under it, at virtually no cost.
Owning a plot of land (a top-level domain) on the internet should be open and easy. Handshake aims to pave the way toward that vision, you can start to explore by using Namebase , Shakestation or Bob wallet .
-
 @ cae03c48:2a7d6671
2025-06-13 17:01:25
@ cae03c48:2a7d6671
2025-06-13 17:01:25Bitcoin Magazine

Mercurity Fintech to Raise $800 Million for Bitcoin TreasuryMercurity Fintech Holding Inc. (Nasdaq: MFH), a digital finance company focused on blockchain-based financial infrastructure, has announced plans to raise $800 million to establish a long-term Bitcoin treasury reserve. The initiative is part of the company’s effort to incorporate digital assets into its financial strategy.
According to a recent news release, Mercurity intends to transition a portion of its reserves into Bitcoin, supported by blockchain-native custody, staking solutions, and tokenized treasury tools designed to advance yield and extend asset duration.
“We’re building this Bitcoin treasury reserve based on our belief that Bitcoin will become an essential component of the future financial infrastructure,” said Shi Qiu, CEO of Mercurity. “We are positioning our company to be a key player in the evolving digital financial ecosystem.”
If fully raised and implemented at current market prices, the capital could allow the company to acquire approximately 7,433 BTC, which would make Mercurity the 11th largest corporate holder of Bitcoin, surpassing GameStop’s reported 4,710 BTC holdings.
The announcement comes during a time of corporate interest in Bitcoin, with 223 companies and entities now holding the asset, up from 124 earlier this month. In total, public firms currently hold more than 819,000 BTC, accounting for roughly 3.9% of the total supply.
Mercurity’s plans also coincide with its initial inclusion in the FTSE Russell 2000® and Russell 3000® indexes, according to the 2025 reconstitution list. The firm was previously listed in the Russell Microcap Index. Index inclusion is expected to increase the company’s visibility among institutional investors and funds that track major benchmarks.
“Moving from the Russell Microcap to the Russell 2000 shows that investors recognize the value we are creating in blockchain finance,” Qiu added. “Our Bitcoin treasury reserve initiative is the next logical step in this evolution.”
The company noted that the reserve will be managed using institutional-grade custody, on-chain liquidity protocols, and staking-enabled tools to improve capital efficiency. The goal is to not just hold Bitcoin, but to put it to work within a secure, yield-generating structure. By using these systems, Mercurity aims to maintain long-term exposure to BTC while maximizing reserve productivity.
With this initiative, Mercurity joins a growing list of public companies actively reshaping treasury strategy around Bitcoin, signaling continued momentum in corporate Bitcoin adoption.
This post Mercurity Fintech to Raise $800 Million for Bitcoin Treasury first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ b1ddb4d7:471244e7
2025-06-02 11:00:50
@ b1ddb4d7:471244e7
2025-06-02 11:00:50Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ f0fd6902:a2fbaaab
2025-06-13 15:31:03
@ f0fd6902:a2fbaaab
2025-06-13 15:31:03What can't fungi do? Fungi come in all kinds of delightfully enchanting and bizarre forms and are the ultimate do-it-alls. Some of them are edible or medicinal; they help organic gardeners keep their gardens happy; they eat plastic, and they glow in the dark. Fungi-based biomaterials also have the potential to help us build more sustainable homes or make more eco-friendly products; heck, they can even talk to each other in their own secret language.
Not surprisingly, they can also make some interesting music, with a little help from Canadian musician Tarun Nayar, the mastermind who makes nature-inspired electronic music under the name Modern Biology.
Source: https://www.treehugger.com/modern-biology-musician-makes-music-using-mushrooms-7485168
Video with mushrooms sound like:
https://www.youtube.com/watch?v=EHwybeMXFAA&t=22s
https://stacker.news/items/1005531