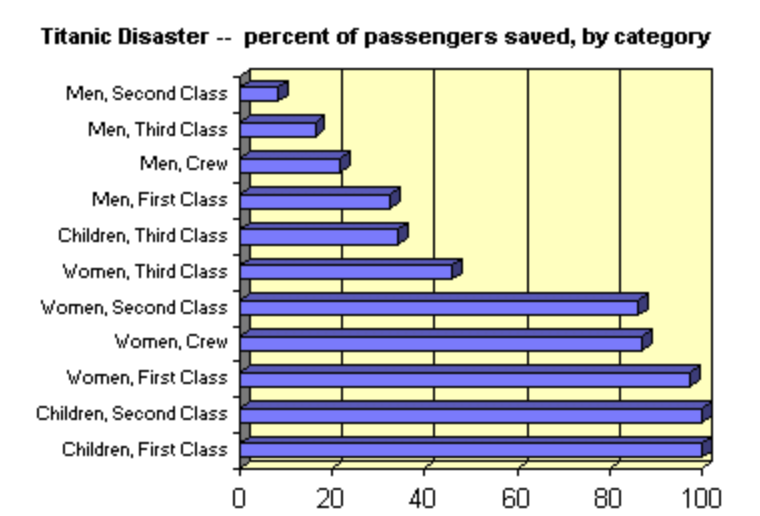
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 866e0139:6a9334e5
2025-06-13 08:27:03
@ 866e0139:6a9334e5
2025-06-13 08:27:03Autor: Caitlin Johnstone. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Israel hat eine umfangreiche Serie von Luftangriffen auf den Iran gestartet.
Die westlichen Medien übernehmen natürlich unhinterfragt die faktenfreie Behauptung der israelischen Regierung, dass diese Angriffe „präventiv“ waren.
Das Trump-Regime versucht, dies als einen völlig einseitigen israelischen Angriff darzustellen, der nichts mit den Vereinigten Staaten zu tun habe - eine Behauptung, die man durchaus glauben könnte, wenn man gestern geboren wäre.
Hier ist eine Liste von Schlagzeilen, die wir in Zukunft von der New York Times erwarten können:
-
Iranische Angriffe erschüttern Israel in einem unprovozierten Angriff.
-
Israelische Familien suchen Schutz bei antisemitischem Terroranschlag.
-
Israelischer Verteidigungsminister: US-Campus-Demonstranten wussten irgendwie von iranischen Angriffen im Voraus, was auf eine Koordination mit Teheran hindeutet.
-
Trump äußert privat seine Frustration mit Netanjahu über den Iran-Konflikt, dem die USA nur passiv und unschuldig beiwohnen.
-
Amerikanische Juden fühlen sich inmitten der sich zuspitzenden Kriege im Nahen Osten verunsichert und nicht unterstützt.
-
Meine Meinung: Ich habe bei den Luftangriffen auf Tel Aviv um mein Leben gefürchtet. Niemand auf der Welt kann sich vorstellen, wie das ist.
-
Meinung: Besteht die Gefahr, dass die USA in einen weiteren Krieg im Nahen Osten hineingezogen werden?
-
Meinung: Stolpern die USA in einen weiteren Krieg im Nahen Osten?
-
Meinung: Stolpern die USA versehentlich in einen weiteren Krieg im Nahen Osten?
-
Meinung: Werden die USA mit Füßen getreten und in einen Krieg im Nahen Osten hineingezogen, den sie seit jeher um jeden Preis zu vermeiden versuchen?
-
USA starten Präventivschlag gegen den Iran.
-
Ihre Meinung: Werden die USA in einen dritten Weltkrieg hineingezogen?
-
Meinung: Taumeln die USA kopfüber in einen nuklearen Schlagabtausch mit Russland und China?
-
Meinung: Der Himmel verdunkelt sich, während nukleare Strahlung über unser Land kriecht, deshalb müssen wir alle zusammenkommen und die Hamas verurteilen.
-
Meinung: Die Erde ist ein unfruchtbares Ödland. Nichts bleibt übrig. Schauen Sie nach Ihren jüdischen Freunden.
Dieser Text erschien zuerst auf englisch auf dem Substack-Blog der Autorin.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
-
 @ 7460b7fd:4fc4e74b
2025-06-13 08:09:40
@ 7460b7fd:4fc4e74b
2025-06-13 08:09:40联名银行账户的历史、挑战与现代替代方案 —— 兼论 PayJoin 的跨法域教法友好新实践
1. 联名账户的起源与制度逻辑(英美法系)
联名账户的定义与起源。 联名银行账户是指由两个或以上个人共同持有、均有权操作的银行账户birketts.co.uk。这一制度起源于英美普通法下对于共同财产持有的需求,可追溯到不动产共有 (如共有租赁 joint tenancy) 概念在金融存款领域的引入birketts.co.uk。19世纪末到20世纪中叶,欧美银行开始允许多人在同一账户上拥有签字权,方便夫妻或家人联合管理财务,并在账户持有人死亡时避免遗产认证(probate)流程——因此联名账户常被称为“穷人的遗嘱”,作为一种规避遗嘱认证的工具nelsonmullins.comnelsonmullins.com。
共同租赁与生存者权利。 在英国普通法传统中,不动产的 joint tenancy 具有“生存者享有权”(Right of Survivorship),即一名共有人去世后,其份额自动归属存活的共有人。这一理念被移植到银行账户:大多数联名账户在开立时即默认附带生存者权利(JTWROS),存款人之一死亡时,账户资金无须经过遗产程序直接归属于存活者birketts.co.uknelsonmullins.com。英美各州法律以及《统一遗嘱认证法》(UPC)普遍承认这一默认规则,除非开户时有相反约定nelsonmullins.comnelsonmullins.com。这体现了联名账户在制度设计上的核心逻辑:账户法律权属共同且具有延续性,银行只关注账户的法律所有人而不深究每位持有人对资金的实益份额birketts.co.uk。
意图推定与权益归属争议。 尽管法律上联名账户具共同所有与生存者权利,但在实益归属(Beneficial Ownership)上常引发争议birketts.co.uk。英美法院历史上发展出不同理论来推定联名账户资金归属的意图:一是合同理论,认为签署的开户协议本身构成合同,确立各持有人对账户的平等权利(包括死亡后全额归属权);二是信托/赠与理论,视添加共有人为对其利益的赠与或信托安排birketts.co.ukbirketts.co.uk。英国法院传统上采用推定信托原则:若账户资金完全由一方存入,则推定这笔钱由该方信托持有,除非账户持有人有夫妻、父母子女等特殊关系,此时反推定为赠与(advancement)birketts.co.uk。例如,父母将子女加入账户通常被视为对子女的财产赠与,逝世后余额归子女所有birketts.co.uk;而无亲属关系的人加入账户则多被视为管理方便的安排,资金实益仍属原出资人birketts.co.uk。美国法亦有类似原则,不少州要求若实际意图只是“便利账户”(Convenience Account),需在开户时或遗嘱中明确声明,否则默认视为赠与,账户余额按生存者权利归共同持有人nelsonmullins.comnelsonmullins.com。这种法律推定的复杂性,使联名账户长期存在“制度混乱”局面nelsonmullins.com,历史上大量诉讼围绕共同持有人之间以及继承人之间对账户资金归属的争夺展开nelsonmullins.comnelsonmullins.com。
账户签署模式:“和”与“或”。 另一个制度要点是账户的操作权限。传统英美银行账户协议中,可以指定联名账户为“双方签字”(“A 和 B”账户)或“任一方签字”(“A 或 B”账户)模式investopedia.com。“双方签字”要求所有共有人同意才能支取,保障了共同行使控制权,但使用不便,主要用于企业账户或信托账户;“任一方签字”则允许任一持有人单独操作账户,是夫妻/家庭联名账户的常见形式investopedia.com。印度、英国等地银行常用“Either or Survivor”(任一或生存者)来指明此类账户默认具有生存者继承权mikecoady.com。这一设计体现了联名账户的灵活性:要么强调共同控制,要么强调独立便利。然而正如下文所述,这种便利也带来了诸多法律与实务风险。
2. 美国联名账户的典型法律问题及银行应对
遗产继承与意图冲突。 在美国,联名账户最常见的问题是与遗产规划意图不一致,引发继承纠纷。例如老年父母出于支付账单方便,将成年子女之一加入账户,但并不打算在去世后将全部余额都赠与该子女nelsonmullins.comnelsonmullins.com。如果父母过世前未书面声明账户不作为遗赠,那么按照许多州法律,该账户会绕开遗嘱直接归存活的子女所有nelsonmullins.comnelsonmullins.com。这可能与父母原本打算公平分配遗产给其他继承人的意愿相违背nelsonmullins.com。例如在南卡罗来纳的案例 Abernathy v. Latham 中,母亲生前联名账户本意是方便支付其医疗开销,遗嘱却意图将财产分予另两位非联名子女,但因未在开户时或遗嘱中明确说明,法院仍判定账户余额由共有人(联名女儿)全额继承nelsonmullins.comnelsonmullins.com。为避免此类情况,《统一多方账户法》(已被部分州采纳)要求账户持有人如欲排除生存者权利,须在开户表或遗嘱中有明确书面说明,否则默认视为意图赠与生存者nelsonmullins.comnelsonmullins.com。银行方面也逐渐提供选项,允许客户指定联名账户为“无生存者权利”(类似于按份共有),但这在实践中不常使用,需要客户有明确法律意识。
账户冻结与债权纠纷。 联名账户的另一风险在于,当其中一位持有人遇到法律麻烦(债务、诉讼、税务等),整个账户可能被冻结或强制执行。美国的多数司法辖区视联名账户内资金为各持有人_推定_平等拥有,因此债权人可以申请冻结或扣押债务人姓名下的联名账户,即便另一共有人对债务不知情也可能失去账户资金nolo.comnolo.com。各州对此规定不同:有些州限定债权人仅能扣押账户的一半资金(假定另一半属无债务方)nolo.com;但在另一些州,债权人可申请扣押全部余额,然后由无责共有人举证证明其中有自己出资的部分才能取回nolo.comnolo.com。例如一对兄妹联名账户,如兄弟欠债遭判决,债权人可能要求银行冻结整个账户,妹妹必须提供存款记录等证明哪些钱是自己存入(traceable contributions)才能抗辩解除nolo.comnolo.com。这一过程繁琐且充满不确定性,给无辜共有人带来资金风险。对此风险,银行没有义务主动区分资金归属,只依据账户合同行事nolo.com。为减轻客户顾虑,一些州允许在开户时将账户明确标为“便利账户”(仅供代理操作,不算共同财产),或夫妻开设“Entireties账户”(夫妻整体所有,仅可共同处分,个人债权人不得强制执行),以提供一定保护alperlaw.comnolo.com。但这些选项依赖特殊法规且在不同管辖区差异很大nolo.comnolo.com。因此美国银行通常会在开户协议中提醒联名账户的连带责任(如信用卡联名账户双方对欠款负共同责任investopedia.com)和可能的债权风险,并建议客户慎重选择共有人。
误操作与内部欺诈。 联名账户给予每位持有人几乎不受限制的提款权,因此另一大隐患是账户内部的误用或欺诈。如果一位持有人缺乏理财自律或存在恶意,他/她可单方面提取或转移全部资金,另一持有人事后才发现损失investopedia.comkitces.com。由于银行视所有共有人为合法所有者之一,无法仅凭一方投诉而阻止另一方的提款——银行有合同义务执行任何持有人合法发起的指令kitces.com。这意味着联名账户几乎没有内部制衡:即使银行察觉可疑,也“束手无策”,因为指令来自账户合法共有人kitces.com。受害一方只能通过法院诉讼,主张账户只是“代理/便利”性质、对方违反受托责任 (fiduciary duty) 而挪用资金,尝试追回款项kitces.com。然而举证过程漫长且结果不确定,需要证明当初加名仅为代理方便而非真正赠与kitces.com。正因如此,美国理财顾问常警示客户:不要轻易通过联名账户授权他人理财,否则不仅资金可能被滥用,而且一旦对方出事,您的钱也可能受牵连kitces.comkitces.com。相比之下,更安全的做法是使用有限授权(Power of Attorney)或生前信托来给予代理人有限权限,而非直接共享所有权kitces.comkitces.com。银行业也逐步接受和配合这些替代方案,如核验授权书、副署人等,以平衡便利性和安全性。
3. 海湾国家联名账户的实践与挑战
跨境劳工汇款与联名账户。 海湾阿拉伯国家聚集了大量外籍劳工(尤其来自南亚、东南亚),他们经常需要将收入汇款回家。许多外籍人士选择开立联名账户作为家庭财务工具,例如在本国银行开设自己与配偶或父母的联名账户,以便家人在其海外工作期间共同管理资金或从账户中提取生活费icicibank.comicicibank.com。部分在海湾地区的银行也允许外籍客户与家人开联名账户,方便他们将工资存入并由在家乡的配偶使用附属银行卡取款reddit.com。这种安排在技术上降低了频繁国际汇款的成本和难度。然而,它也带来了法律和文化层面的挑战:一方面,不同国籍/居住地的联名人涉及跨境法规(如外汇管制、税务申报)的复杂性;另一方面,在一些文化中男女或代际间共享账户可能与传统观念不符,需要遵循伊斯兰教法或当地习俗。比如有的穆斯林丈夫可能按照教法允许妻子保有自己财产、不干涉之原则,不倾向于共用账户,而选择直接汇款给妻子个人账户reddit.com。因此,跨境家庭常在便利与合规之间权衡,在联名账户和单独账户+授权取款等模式中做出选择。
家族资产共管需求。 海湾本地富裕家族内部也存在共同管理资产的需求。例如父子共同经营生意、兄弟姐妹联合投资物业等情况,希望有一个共管的账户池。传统上,在海湾阿拉伯社会,大家族通过掌门人代持或设立家族办事处(Family Office)集中管理资产,但现代银行服务也提供了一些新工具。例如阿联酋的 Emirates Islamic 推出了**“家庭储蓄账户”模式,允许多达10位直系亲属各有独立子账户,但共享一个合并余额来获得较高的整体收益率,同时保持每个人账户的私密性和独立使用emiratesislamic.aeemiratesislamic.ae。这被视为传统联名账户的改良:资金并不真正混同,但在银行系统内被视为“虚拟共同体”,以激励家庭存款emiratesislamic.aeemiratesislamic.ae。该方案也明确遵循伊斯兰教法**(如采用 Wakala 投资代理协议分享利润,而非利息)emiratesislamic.aeemiratesislamic.ae。由此可见,海湾银行业在满足家族共同理财需求时,更倾向于结构化解决方案,以避免直接共有人制度带来的法律障碍。
教法继承与账户冻结。 最严峻的挑战是伊斯兰教法的强制继承规则。在海湾阿拉伯国家(如海合会各国),伊斯兰教法(Sharia)通常适用于穆斯林公民的资产继承。根据教法,当账户持有人去世,其资产必须按照固定的继承份额分配给法定继承人(配偶、子女、父母等),个人意愿影响有限。这与普通法系下联名账户“生存者自动继承全部”原则直接冲突gulfnews.comgulfnews.com。因此在如阿联酋等地,无论账户是个人还是联名,只要持有人去世,银行立即冻结账户,直到宗教法院或民事法院完成继承认证gulfnews.comgulfnews.com。联名并不能豁免冻结:即使另一共有人健在且资金主要由其贡献,也不得动用账户,直至法院指令gulfnews.comgulfnews.com。例如一位印度外籍人士在迪拜与妻子共有多个账户,妻子骤然去世后,他发现所有联名账户被法院冻结,无法提款支付日常生活费mikecoady.commikecoady.com。因为按照程序,继承人在申请继承证书时需申报所有死者名下账户,法院即通知各银行冻结资金mikecoady.commikecoady.com。数月后法院根据教法规将款项在丈夫和子女间按教法份额分配(例如丈夫25%、儿子50%、女儿25%mikecoady.com),而不像普通法那样全部归存活配偶mikecoady.com。这一事件突显了联名账户在教法环境下的“危险”:存活共有人不仅无法直接继承,短期内甚至无法动用共同财产gulfnews.comgulfnews.com。为此,当地专业人士建议外籍人士避免在无遗嘱情况下使用联名账户,或至少保证每人有独立账户以备不时之需mikecoady.com。更稳妥的做法是在当地立下符合教法的正式遗嘱,或采用公司/信托架构持有资产,以绕开个人账户直接继承的障碍gulfnews.com。总之,在海湾国家,联名账户因为法域文化差异面临特殊挑战,必须提前规划以防范账户冻结与继承冲突的问题。
4. 联名账户的现代替代方案及局限性
面对上述各种问题,金融和技术领域已经发展出若干替代方案来实现多人共同管理资金的目标,每种方案各有其法律、治理和技术局限。下表对主要替代机制进行比较:
| 替代方案 | 实现方式 | 优点 | 局限性 | | ------------- | -------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------ | ---------------------------------------------------------------------------------- | | 对公账户/公司账户 | 设立法人实体(公司、合伙企业),以公司名义开银行账户,由多名股东/高管共同控制fdic.gov。 | 法律结构清晰,有公司法保护;可设定多签批准流程;个人债务不直接牵连公司资金。 | 设置和维护成本高(注册、税务、合规);非家庭场景不便;跨国开户困难。 | | 信托账户 | 设立信托或基金,受托人开设账户代持财产,受益人包括相关个人kitces.com。 | 可定制受托人义务,保障弱势方利益;避开遗产认证,按信托契约分配;在普通法下有成熟法理。 | 在民法或教法地区法律地位不明;设立需专业知识和费用;受托人可能滥用职责(需信任或监管)。 | | 授权与代理 | 不改变账户所有权,通过签署财务授权书或银行授权,让代理人能操作账户kitces.com。 | 手续简单成本低;不转移所有权、不影响继承;授权范围可限定(仅查看、限额支付等)。 | 授权人在法律上无所有权,遇代理破产/去世授权失效;部分机构对授权认受度有限(可能拒绝执行)。 | | 多重签名钱包 | 在加密货币领域使用多签名技术(如2/3签名)管理资金,各方持有私钥,需达成门槛签名才能支出blog.upay.bestmilkroad.com。 | 技术上去中心化,无单点控制;规则灵活(M-of-N签名可定制);无银行介入、无国界限制;防范单方欺诈或遗失(可设应急密钥)。 | 仅适用于数字资产,不适用法币账户;用户需一定技术能力;法律上不承认“共同签名”财产分配,纠纷解决缺乏司法支持;一旦签名门槛达不到(如一方失联),资金可能冻结在链上。 | | 权限分级系统 | 由银行或金融平台提供,多用户共享同一账户或钱包但权限不同(如主账户人设置子账户/支付限额)。 | 可实现精细控制:如一方全权,另一方仅查询或限额交易;方便家庭理财、企业财务控制;平台往往提供日志追踪增强透明度。 | 核心账户仍属单一法律主体,其他人为被授权人而非真正共有人;授权关系依赖平台规则,法律保障弱;跨机构不可通用,缺乏行业标准。 |
对公账户/公司架构: 通过成立法人实体(如注册有限责任公司或合伙企业)共同持有资金,是许多情况下替代联名账户的方案absolutetrustcounsel.com。例如夫妻可成立一家有限责任公司共同持有投资资产,再以公司名义开银行账户。这将资金从个人名下移至公司名下,从而隔离个人法律风险:一方的个人债权人无法直接针对公司账户执行alperlaw.com。公司章程还能规定账户需多方签字支出,提高内部监督。然而其局限是显而易见的:成立和维护公司需支付注册、审计、报税等成本,对于单纯家庭资金共管显得繁琐;跨境开设公司账户涉及各国法律和合规要求,操作门槛高。因此公司账户更多用于正式商业合伙场景,在普通家庭财务中接受度有限。
信托结构: 信托源于普通法,可作为联名账户的法律替代——尤其在涉及遗产和未成年人利益时更为优越。家长可设立生前信托,把资金转入信托账户,由受托银行按信托契约管理并允许指定受益人共同使用,从而避免形式上的联名kitces.comkitces.com。信托能够细致规定各方的权益份额和职责(受托人对受益人的诚信义务 Amanah),并可跨越死亡事件自动过渡产权,无需冻结账户或经过繁琐继承程序。然而信托在许多民法或伊斯兰法系国家并无完善的法律框架(例如一些海湾国家对家族信托的承认有限),设立信托往往需要借助离岸法域(如开曼群岛、新加坡的信托法律)coinshares.com。此外,信托涉及专业法律文件起草和持续监管成本,对一般用户门槛较高。若受托人滥用职权,受益人必须诉诸法院救济,也存在道德风险。因此信托虽在英美被视为解决联名财产问题的黄金标准,但在跨法域环境下其可行性取决于当地法律制度支持程度。
授权代理: 这是不改变资金所有权又能实现共同管理的简单途径。很多美国老人不愿直接加子女为联名人,改为签署广泛的持久财务授权书 (Durable Power of Attorney),授权子女在自己失能时管理账户kitces.com。银行也提供第三方授权形式,比如在账户中登记一位“代理签字人”。授权的优点是保留资产独立性:资金仍属原主,无需担心代理人个人债务牵连;同时授权可随时撤销或修改。不过授权并非万能:若授权人去世,授权自动失效,代理人无法再动用账户(此时资产转由遗产程序处理)nelsonmullins.comnelsonmullins.com。此外,不是所有国家/银行都乐于承认外国授权文件,实际操作中代理人可能仍遇阻力(一些银行出于合规会对代理指令多加审查)。因此授权适合作为短中期的账户共管方案,但不能完全解决死亡继承和跨境问题。
多重签名数字钱包: 在区块链和加密货币领域,多重签名 (multi-sig) 技术成为实现“多人共管资金”的创新方案blog.upay.bestmilkroad.com。例如,两位商业伙伴可以创建一个比特币2-of-2多签钱包,任何转出交易需要双方的数字签名,类似银行账户要求两把钥匙同时拧开保险箱。这种技术不依赖中心机构:资金由去中心化网络维护,任何一方单独无法挪用,使内部欺诈风险降至最低。同时,它突破了国界,在不同法域的人都可共同控制同一钱包。然而,当前多签钱包主要限于加密资产,对于法币存款并不可用。即便在加密领域,也存在治理难题:法律层面不承认密码学上的“共有”概念,如果多签持有人发生纠纷或死亡,传统法院很难介入分配私钥或代为执行交易river.comriver.com。例如一方去世未留下其私钥,除非智能合约预设了应急方案(如超时解锁给存活方或预留第三方密钥),否则资金将永久锁定链上。又如一方恶意拒绝签名,另一方只能尝试技术或社工手段获取签名,无正规法律途径解决。总的来说,多签提供了技术上的安全与中立,但牺牲了一定的便捷性和法律可追索性,目前更适合高信任度团队或对安全性要求极高的场景(如加密货币交易所的资产托管)。
权限分级的账户系统: 随着金融科技的发展,一些银行和支付平台推出了多用户权限功能,试图兼顾多人使用的便利与风险控制。例如某些数字银行允许一个主账户下开设子账户,各账户持有人拥有独立登录、卡片,但资金在后台链接,实现类似家庭钱包的效果。主账户持有人可以设定每个副账户的额度和权限(只能消费不可转出等),既给家人财务自由又保留总体控制。这类方案实质上还是一个人拥有账户,其余是被授权用户,只不过科技手段让用户体验上接近联名账户。这种权限分级系统可以灵活定制规则(比如双重确认大额支出、实时通知等),非常适合企业财务(类似传统网银的“双人复核”)或家庭预算(如给孩子的零用卡)。局限在于:法律关系上账户只属于主用户,其余人没有法律所有权,因此如果主用户出事,账户仍会被冻结,其他人权益无保障。此外,不同银行平台各自为政,缺乏统一标准,一旦跨行或跨境,此类授权无法延伸。在监管层面,这种模式也引发KYC疑问:银行需要对所有实际使用者尽职调查,否则可能出现非账户持有人匿名使用资金的情况。
综上,各种替代方案各自解决了传统联名账户的一部分问题,却也引入新的限制。没有一种方案能完美覆盖法律、治理、技术各方面:对公账户和信托提供法律清晰度但成本高、地域受限;授权和权限分级提升便利但不改变根本权属;多签钱包实现了跨境共同控制但游离于现行法律框架之外。正是在这样的背景下,新兴的PayJoin技术引人注目——它并非传统意义上的“账户”或“契约”,而是一种交易机制,可能在跨法域和教法环境下提供一种创新的资金共管思路。
5. PayJoin 技术机制与联名账户的比较
PayJoin 的原理简介。 PayJoin(又称 P2EP,Pay-to-Endpoint)是一种比特币交易的隐私增强技术,其核心思想是:让交易的接收方也贡献一部分输入river.com。在传统的单方支付中,一笔交易的所有输入通常都来自付款人,这泄露了一个隐私信息:这些输入地址很可能属于同一人(区块链分析中的“共同输入归属假设”)river.com。PayJoin 则打破这一假设:收款人预先与付款人沟通,同意在收到款项时由自己提供一个UTXO作为交易输入之一,然后双方构建一个包含多笔输入、输出的联合交易payjoin.orgpayjoin.org。例如,Alice 向 Bob 支付 1 BTC,传统做法是 Alice 提供1 BTC输入-> Bob 的地址。PayJoin 下,可能变成:Alice 提供0.6 BTC输入,Bob 提供0.5 BTC输入,两人签署一笔交易,其中 Bob 的输出得到1.1 BTC(相当于 Bob 原有0.5+Alice支付1.0,减去找零给Alice和手续费),Alice 拿回找零0.4 BTCpayjoin.org。从区块链上看,这笔交易有两个输入(分别来自Alice和Bob的钱包)和若干输出,但观察者无法断定究竟是哪部分是支付、哪部分是找零,因为它看起来跟“一人用多个输入付款”并无二致payjoin.orgpayjoin.org。PayJoin 使交易的资金归属变得难以推导:外人不再确切知道Alice给了Bob多少钱。
“共同控制”与权限对比。 虽然 PayJoin 不是账户,但它体现了一种交易层面的共同控制:交易的生成和签名需要双方参与river.com。付款人和收款人通过点对点加密通信(通常经Tor或类似渠道)协商交易细节,各自选择愿意投入的UTXO,然后协同构建PSBT(部分签名比特币交易)并分别签章river.comriver.com。只有双方都签名,交易才能广播成功。这一点类似联名账户的“双签”模式(“和账户”),需要双方同意才能完成一笔“资金移动”。不同之处在于:联名账户的双签是在账户维度的持续权限控制,而 PayJoin 的“双签”是逐笔交易的合作行为,一旦交易完成,双方各自拿回属于自己的输出,并不产生一个长期共管的地址或账户。这意味着 PayJoin 不涉及资金托管:Alice和Bob各自仍控制自己钱包里的币,只是在支付发生的一刻进行了协作。相较之下,传统联名账户(尤其“或账户”)往往允许单方独立操作而缺乏约束investopedia.cominvestopedia.com;而 PayJoin 则需要双方在线同意才能促成,这在一定程度上提供了共同见证/确认。不过,PayJoin 并不能防止任一方事后随意支配自己收到的输出(类似于联名账户的任一持有人可自行提取自己的款项比例)。因此在控制模型上,PayJoin更像是瞬时的“合伙记账”:双方都参与记账过程,但结算后各拿各的钱。如果有需要,可以反复通过PayJoin进行资金往来,从而达到一种“经常性共同操作”的效果,但它本身不会锁定资金需要长期共同签署。相比之下,多重签名钱包会真正把资金锁定在需要多方签名才能解锁的地址上,这是不同的。
不可推导的资金归属。 对于联名账户,外部人(包括银行或法院)通常也无法直接区分账户内资金最初由谁存入,因为账户作为一个整体记录余额birketts.co.uk。只有通过内部账或存款记录才能分析贡献比例。同样地,PayJoin 交易在区块链上造成了资金来源的混淆:链上观察者无法确定哪一方贡献了多少输入、哪个输出归谁payjoin.org。这从隐私角度是优点:它打破了比特币网络上对于资金流向的常规分析规则payjoin.org。而从“共有”角度来看,这种资金归属不透明性与联名账户有相似之处——在一个联名账户中,如果没有充分证据,第三方或债权人常默认账户资金各半归属双方nolo.com;在一次PayJoin交易中,除非双方公开细节,否则无人能确知哪个输出是支付哪个是找零,即交易对手间的具体资金划分仅他们自己清楚payjoin.org。值得注意的是,这种隐私并非完全的匿名,而是针对特定交易的归属不可判定。联名账户的不可归属性是长期的(整个账户余额如此),而PayJoin是针对单笔转移,但如果双方持续采用PayJoin模式进行交互,那么整个资金流的图谱对外部来说将变得支离破碎,难以拼凑双方各自持有多少。对于希望财务共管但又不想被外界清晰审计出权属的人来说,这提供了一种新颖的工具。
与多方混币区别。 需要指出,PayJoin 不同于传统的CoinJoin(多人混币)。CoinJoin通常是数个不相干的人把若干UTXO放一起构造一笔交易,打乱关联,从而实现隐私增强river.com。而 PayJoin 仅两方参与且具有实际支付含义:付款人最终少了钱,收款人净得钱。这更贴近真实的一对一资金往来场景,只是包装成让外界看不出。而CoinJoin往往输出每人拿回和输入等量的钱,只是换了碎片顺序,没有实现真正资金转移。PayJoin的效率更高(两人即可,不需撮合众人),也更节省手续费,因其输出数量可与普通交易无异,不增加链上容量payjoin.orgpayjoin.org。
综上,PayJoin 在共同控制和资金归属模糊两方面都与联名账户有相似之处,却又有本质区别:联名账户是法律与账户层面的共管关系,持续存在;PayJoin是技术与交易层面的合作行为,瞬时完成。正是这种差异,使 PayJoin 可以避开许多联名账户的制度性问题,从而具备一些独特优势,如下节所述。
6. PayJoin:跨法域中立且教法友好的潜力
跨法域的中立性。 PayJoin 基于比特币网络运作,其参与各方只需遵循比特币协议,与任何特定国家法律或金融机构无直接关联。这意味着,无论交易双方身处何地、何种法系,都可以采用PayJoin来完成一笔支付或价值转移,而不受当地银行政策差异的影响。例如,一位美国的用户可以与一位海湾国家的用户通过各自的比特币钱包执行PayJoin,资金即时划转,无需经过银行清算或外汇管制。这种去中心化特性使 PayJoin 天然具有跨法域中立性:它不需要在某国开设账户、符合某地金融牌照,也无须考虑两地对联名账户截然不同的法律定义。对于跨境家庭或团队而言,PayJoin 提供了共同参与财务活动的新方式——不再以账户形式存在,而是在链上合作完成交易。由于没有共同持有的账户实体,便不存在账户被冻结或被单方面没收的风险(前提是双方各自保管好自己的私钥)。尤其在一些司法管辖冲突的场景下(如非穆斯林丈夫与穆斯林妻子想共享财富,但各自国家法律对联名财产认定不同),PayJoin可以作为双方私下的财务协议来使用,而避免落入法域冲突的真空地带。需要强调,PayJoin 本身不违反任何国家的明文法律——它只是标准的比特币交易形式之一payjoin.orgpayjoin.org。法律上各国通常将比特币交易视为个人资产处分行为,只要不用于非法目的,并无禁止交易双方协商其交易结构的法规。因此,从合法性角度看,PayJoin 相当于两人商定了一种转账方式,在Common Law看来符合契约自由原则,在各法域都找不出明显抵触的条文。
伊斯兰教法的友好性。 从伊斯兰金融原则审视,PayJoin 具有许多契合点,使其有望被视为“教法友好”的实践:
-
无利息(Riba):PayJoin 只是资金转移工具,不涉及贷款或利息计付。比特币本身不支付利息,交易过程中也没有任何一方无风险获利的要素scitcentral.com。相比传统银行账户可能涉及利息或利率变动(伊斯兰金融需通过盈利率协议Wakala等实现类似功能),PayJoin 完全规避了利息禁忌。
-
控制与所有权明确(Amanah信托原则):在联名账户中,各方资金混同,实际归属成谜,可能引发Amanah上的疑虑——一方实为代管他人财产却可以随意取用。而PayJoin每笔交易双方知情并同意,且结算后各自掌控自己的余额,没有长期代管他人财物的情况。可以认为,双方在PayJoin合作中互为受托人:各自承诺只签署符合约定金额的交易,不多签或少签。这种短暂的互信很容易履行且范围有限,符合 Amanah 强调的受托义务(诚信、准时履约)。双方都不把资金长久交给对方或第三方,减少了信托滥用的可能。
-
避免过度不确定性(Gharar):Gharar 指交易中不确定性或信息不对称过高,从而带有投机欺诈成分。PayJoin 交易结构虽然对外人不透明,但对交易双方本身是完全清晰的——他们事先约定了支付额,每人贡献多少UTXO、将得到多少找零输出,都是明确计算的payjoin.org。交易未完成前,任何一方都可以中止(不签名则交易无效),不存在押注未知结果的情况,也没有复杂衍生品或概率元素,因而不违反“避免Gharar”的原则changelly.com。与之相比,传统联名账户在教法环境下的最大不确定性反而是继承处理:共有人无法确定死后谁能得到多少份额(取决于教法和法院),这对各方而言是一种Gharar。而PayJoin每次交易完结,资金归属当下尘埃落定,没有悬而未决的权益。
-
非赌博性质(Maysir):Maysir意为赌博或投机。PayJoin 并非博弈,而是有实际用途的支付工具,没有随机输赢,也不以对赌为目的changelly.com。两人合作进行PayJoin,不会出现一方赢钱一方输钱的零和结果——本质还是执行支付,只是改变信息披露,并无博彩成分。因此,用PayJoin进行正常经济活动,应不触犯禁赌教规。
更进一步,有学者和教法顾问已经在讨论比特币本身的可容许性:许多观点认为只要比特币用于合法贸易、避免利息和欺诈,它可以被视作财产和交换媒介,从教法上是Halal(可允)plasbit.comchangelly.com。一些中东地区的交易所和机构也在寻求Fatwa(教令)承认加密货币交易的合规性。PayJoin 作为其上的一种交易方式,如能被正确理解,其Sharia合规障碍应较小。因为相比之下,更具争议的是匿名性和洗钱风险,但那属于世俗法律范畴,下节会谈到。
避免强制继承冲突。 前文提及,在海湾国家按Sharia会冻结联名账户并强制按法定比例分配。这主要因为账户在法律上视为死者遗产的一部分。而若两人采用PayJoin等去中心化方式管理财富,则每人始终持有自己那部分私钥控制的币,不形成法律上的“联名遗产”。当一方过世,其私钥所控币是其遗产,另一方所控币不属于遗产范围,因此不会被教法程序冻结。当然,亡者的比特币仍需按其遗嘱或教法分配,但起码存活者立即可支配自己持有的部分,现金流不中断。这与联名账户情形截然不同。在实践中,夫妻可各自持有数字钱包,定期用PayJoin互相汇款、结算共同开支。万一一方不幸去世,另一方钱包里的余额就是属于Ta自己的,不经遗产处理即可继续使用;而逝者钱包若未留访问方式则资产可能锁死,反而避免了与法定继承人的纠纷(当然,从保护家人利益角度,应有妥善的密钥遗嘱安排,但可通过多签或托管来实现,而不需要传统联名账户)。总之,PayJoin提供了一种不经银行、绕开法域限制的合作模式,使双方的财产在法律上保持独立,却能在经济上实现协同。这对于跨国夫妇或团队,尤其处在不同财产制度(教法 vs 世俗法)下的组合,极具吸引力。
7. 合规性分析:伊斯兰金融原则与普通法要求的平衡
引入任何新实践方式,都必须评估其在各法域的合规性。针对 PayJoin,需要分别从伊斯兰金融教义和普通法/现代监管角度来审视,确保其同时满足双方关切,真正成为“跨法域中立、教法友好”的方案。
符合伊斯兰金融原则: 根据上述分析,PayJoin 本身没有违反 Riba、Gharar、Maysir 等禁忌,可被设计为符合 Shariah 的工具。然而,为进一步确保教法合规,可以考虑以下细节:
-
合同形式与意图明确(Niyyah):伊斯兰交易强调各方意图正当、合同清晰。虽然 PayJoin 不需要书面合同,但双方可在私下有书面或口头协议,说明这是一种共同协作支付,不是借贷或投资关系,以免日后产生歧义。这类似于 Amanah 原则下的承诺:双方约定各自仅为支付目的贡献资金,不据此主张对方财产权。
-
避免不义之财(Dhulm):教法禁止不公正的占有。如果 PayJoin 被恶意用来隐匿资助不法活动或侵占他人财产,显然不合规。这需要道德约束:FinTech开发者在推广PayJoin方案时,应嵌入使用指引,强调其用于正当目的(如家庭财务协作、隐私保护),不鼓励用于欺诈或洗钱。这与伊斯兰金融注重的社会责任原则吻合nasdaq.com。
-
审慎与透明(Itqan & disclosure):在穆斯林社群中推广时,可以让受过教法培训的专业人士参与审查PayJoin流程,甚至发布教法意见书(Fatwa)声明其可接受性,并教育用户如何将其融入Halal理财生活。例如建议穆斯林家庭在使用PayJoin前,明确约定彼此的财产份额和用途,记录每笔协作交易的原因,以保持家庭内部的透明和信任(这有点类似于定期对账,在宗教上也是鼓励诚实对待财产往来的一部分)。
符合普通法和监管要求: 虽然 PayJoin 技术本身不违反合同和财产基本法理,但现实应用中还有一些合规问题需要考虑:
-
反洗钱(AML)与身份识别(KYC):西方普通法体系下的金融监管要求对资金来源和交易对手尽职调查。PayJoin提高了链上匿名性,可能引起监管机构对其用于洗钱的担忧cointelegraph.comriver.com。为此,FinTech企业在实现PayJoin功能时,可加入自愿的透明机制:例如双方如果在受监管平台(交易所、支付处理器)进行PayJoin,可以在链下向平台报告交易对手的身份哈希,以满足监管审计需要(前提是双方同意,并且平台在受司法令时才揭示)。这样既不破坏链上隐私,又保留合规的选项。此外,开发者也应提示用户遵守所在地法规:如一次性大额PayJoin转账在某些国家可能需要申报,用户需自觉履行。
-
合同与救济:Common Law 强调合同自由,但也要求有违约或欺诈时能提供司法救济。PayJoin 没有标准合同,如果一方未履行承诺(例如收款方承诺一起做PayJoin但反悔要求普通转账,或者付款方声称已付但实际未广播交易),法律上如何处理?对此建议是:当 PayJoin 用于商业场景时,仍应有基本合同约定。如果发生纠纷,一方可以提交协商的PSBT记录、通信记录等作为证据。由于Bitcoin交易有不可篡改的链上记录,反而容易举证实际支付了多少钱给谁。法律可能将其视为一种合伙或代理协议的履行:双方合意做一件事并完成了。如果一方中途毁约导致对方损失,可按普通契约法求偿。不过需要法院对这一技术有所了解。因此合规上,或许需要通过行业协会向监管和司法解释PayJoin的机制,使其被当作正当交易手段看待,而非神秘的洗钱工具。
-
税务与报告:各国税法对加密交易的申报要求不同。PayJoin并未改变交易实质,只是隐私增强,但从税务上说,若涉及资产转移,同样要记录成本基础和收益。合规方案可以是:提供给用户一个工具,将自己参加的PayJoin交易标记并保存原始支付细节(付款额、找零额),以便报税时证明实际支出收入情况。这一点对企业采用PayJoin尤为重要,确保账务透明避免日后审计问题。
公平与共识: 普通法原则重视交易的公平合理和各方真实同意。PayJoin是双方自愿合作的结果,表面上满足共识原则。但我们也要考虑弱势保护:比如一方技术精通,一方小白用户,会否出现不公平?为了防范这一点,可以在用户界面上做警示:当有人请求与你进行PayJoin,你应该明白这对你意味着什么——一般来说收款人不会吃亏,因为多收一个找零输出,并不会损失价值;付款人也不应吃亏,只是多花一点手续费。但要防止有人利用不明真相的用户,让其参与PayJoin却在输出分配上作弊(理论上如果收款人恶意构造交易让付款人多付了钱且付款人未察觉签了名)。因此技术实现上也需做到公平:钱包软件在构建PayJoin时应自动检查付款金额正确、找零正确,防止篡改。这种保护符合普通法对公平的要求,也体现了伊斯兰金融中**避免Dhulm(不义)**的精神。
综上,PayJoin 作为一种新实践,要成功立足,需要双重合规:一方面在宗教伦理上证明其正当性,一方面在世俗法律上确保透明与守法。幸运的是,这两方面并不矛盾:PayJoin追求的是一种技术手段的优化,与伊斯兰和普通法原则并无本质冲突。通过适当的措施和教育,完全可以做到兼容。例如,在一个试点应用中(假设由一家兼具Sharia顾问和合规官的FinTech公司运营),穆斯林家庭用经Fatwa认可的比特币钱包进行PayJoin理财,同时该应用满足KYC/AML标准并提供报表工具。那么这一模式将真正体现“跨法域中立、教法友好”。它既让用户不受限于传统制度,又确保了道德与法律底线,为金融科技开发者打开一条服务全球用户的新道路。
结语
联名银行账户作为百年来方便多人共管财富的制度,一路发展伴随着各类法律和实践难题。在普通法系,其灵活性与风险并存,引发继承、债务、滥用等诸多纠纷;在伊斯兰法环境下,更面临继承冻结等制度性冲击。在全球化时代的跨境场景中,传统联名账户愈发显出局限,各种替代方案各擅胜场却难有万能药。PayJoin 技术的出现,为我们提供了一个全新的视角:也许不再需要“联名账户”这个法律产物,通过区块链的协作交易,完全可以实现类似目标且避开许多固有问题。本报告深入比较了联名账户制度与PayJoin在“共同控制”和“不可推导归属”上的异同,探讨了PayJoin 如何满足伊斯兰金融和普通法的合规要求。对于金融科技开发者而言,这意味着巨大的创新空间:未来的应用可以让两个人“各自持币,共同支付”,既保障各自权属,又实现合作效率。在设计此类系统时,我们应牢记历史教训,融合法律与教义的智慧,确保技术既推进了便利,也巩固了公平与信任——这正是联名账户理念在21世纪的重生。
参考文献:
-
Birketts法律简报,“联名银行账户:谁拥有这些钱?”,2023年4月4日birketts.co.ukbirketts.co.uk。
-
Nelson Mullins律师事务所博客,“理解联名账户的生存者权利”,2024年1月17日nelsonmullins.comnelsonmullins.com。
-
Mike Coady财富管理博客,“阿联酋外籍人士:联名账户的危险”,2021年7月29日mikecoady.commikecoady.com。
-
_Gulf News_报道,“在你之后,你在阿联酋的银行余额会自动给家人吗?”,2025年5月16日gulfnews.comgulfnews.com。
-
Emirates Islamic 银行官网,“Emarati家庭储蓄账户”产品页emiratesislamic.aeemiratesislamic.ae。
-
Kitces金融规划文章,“便利账户的风险与备选方案”,2019年kitces.comkitces.com。
-
Investopedia词条,“Joint Account联名账户:定义、运作、利弊”,更新于2025年5月9日investopedia.cominvestopedia.com。
-
Payjoin官方文档,“为什么使用PayJoin - 隐私”,2025年payjoin.orgpayjoin.org。
-
其他参考资料包含 PlasBit、Changelly 等对于比特币与伊斯兰金融兼容性的讨论changelly.comscitcentral.com。
-
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 9ca447d2:fbf5a36d
2025-06-13 08:01:42
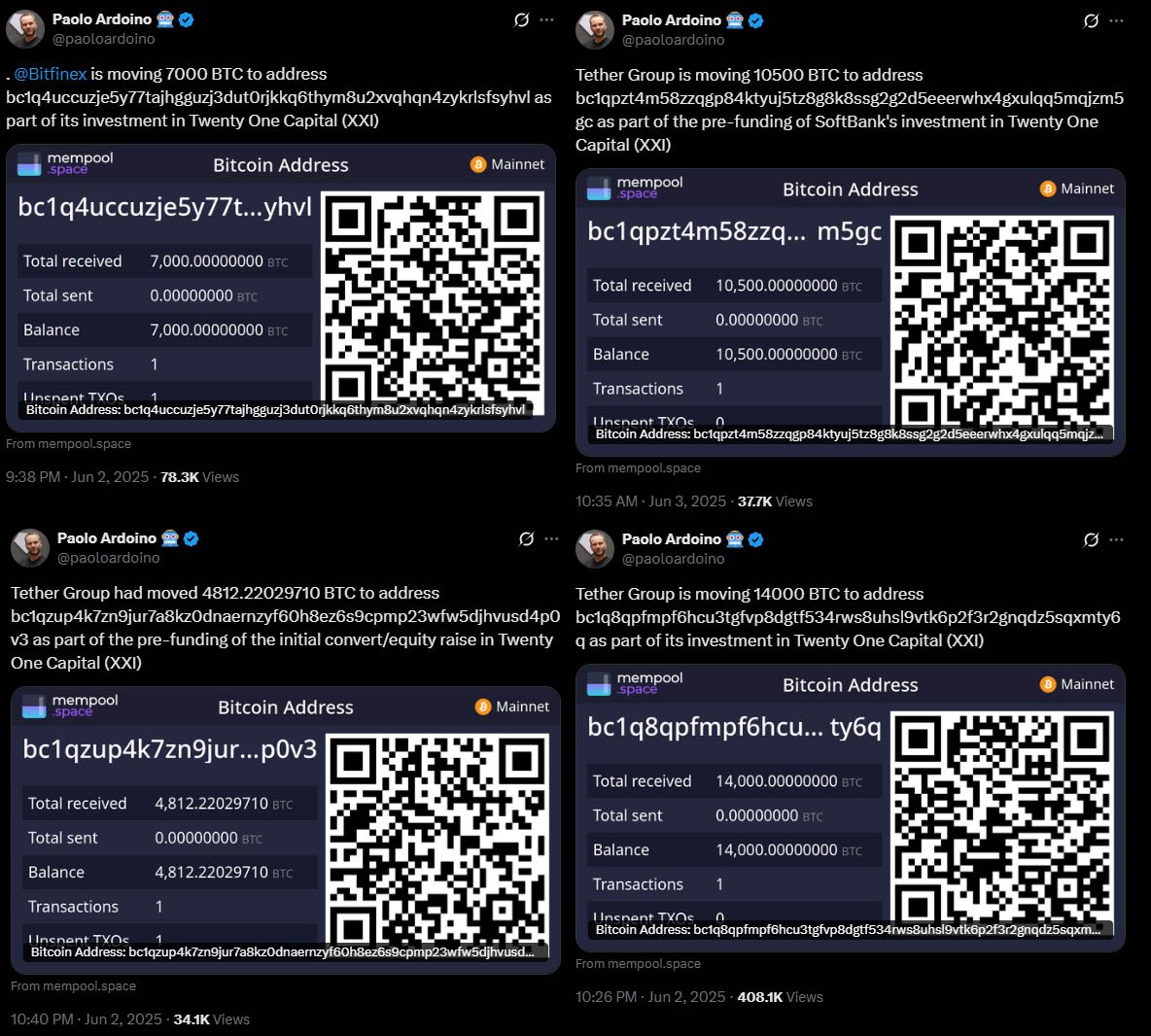
@ 9ca447d2:fbf5a36d
2025-06-13 08:01:42In a massive vote of confidence for a new bitcoin-focused company, Tether and Bitfinex have moved over 37,000 BTC—worth $3.9 billion—to digital treasury firm Twenty One Capital. This is one of the largest Bitcoin transactions in recent history.
The announcement came from Paolo Ardoino, CEO of Tether and CTO of Bitfinex, through multiple posts on X. According to Ardoino, the transfers were part of a pre-funding round for the launch of Twenty One Capital, a new company that will lead the bitcoin treasury space.
Ardoino announced several transfers on X — Sources 1, 2, 3, 4, and 5
“Tether Group is moving 10,500 BTC to address bc1qpzt4m58zzqgp84ktyuj5tz8g8k8ssg2g2d5eeerwhx4gxulqq5mqjzm5gc as part of the pre-funding of SoftBank’s investment in Twenty One Capital (XXI)” Ardoino said.
Twenty One Capital is a new bitcoin treasury firm led by Jack Mallers, CEO of Strike and founder of Zap. The company is backed by Tether, Bitfinex, SoftBank and Cantor Fitzgerald.
The company will go public via a SPAC merger with Cantor Equity Partners (CEP) and will trade under the ticker XXI on Nasdaq. After the merger was announced CEP’s stock price skyrocketed from $11 to $59.75.
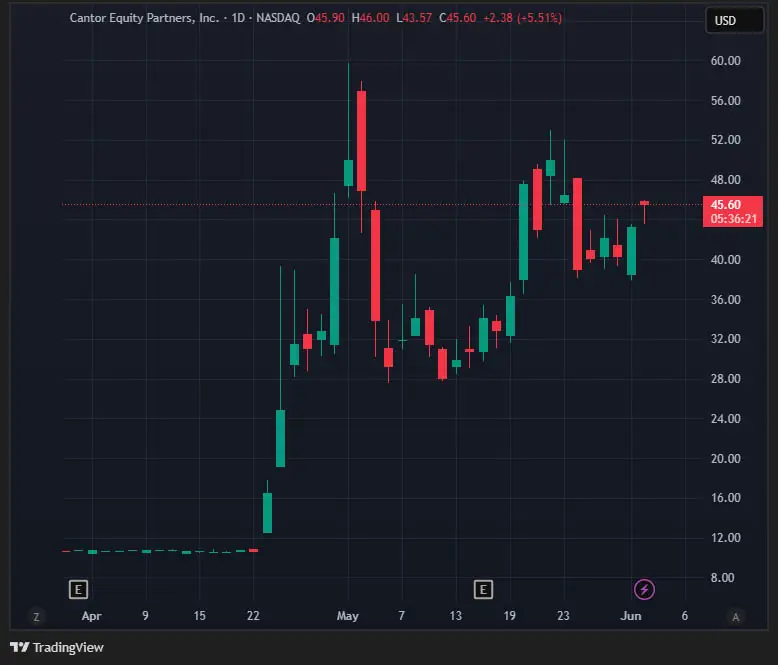
Cantor Equity Partners’ stock price jumped on news of the merger — TradingView
Mallers says the company’s mission is bold and clear: accumulate bitcoin and provide full transparency through public wallet disclosures, also known as providing “proof-of-reserves“.
Total bitcoin moved to Twenty One Capital so far include:
- 10,500 BTC from Tether on behalf of SoftBank (worth about $1.1 billion)
- 19,729.69 BTC from Tether (worth around $2 billion)
- 7,000 BTC from Bitfinex (valued at roughly $740 million)
The amounts sum up to 37,229.69 BTC, worth around $3.9 billion at current prices. These were verified on public blockchain explorers.
The Twenty One Capital wallets now show large balances. They have already confirmed they have 31,500 BTC. That makes them the 3rd largest corporate bitcoin holder behind Strategy and Marathon Digital Holdings.
Once these new transfers are confirmed, the company will take over Marathon to become the second-largest corporate holder of the scarce digital asset globally.
Related: Twenty One Capital Becomes 3rd-Largest Corporate Holder of Bitcoin
Unlike companies that add bitcoin to their balance sheet, Twenty One Capital exists solely to accumulate and manage bitcoin. It follows a model similar to Strategy but is more transparent.
Mallers introduced new financial metrics like Bitcoin Per Share (BPS) and Bitcoin Return Rate (BRR) to value the company in bitcoin terms, not fiat.
He thinks economic value in the future will not be measured in dollars but in satoshis—the smallest unit of bitcoin. The company is not just about guarding against fiat collapse, but about completely opting out of the system.
A key part of the firm’s strategy is proof of reserves. Unlike some other big bitcoin holders, Twenty One Capital has already published its public wallet addresses so anyone can verify its holdings in real time.
Ardoino called this approach “Bitcoin Treasury Transparency (BTT)” and said it’s a response to recent industry scandals that showed the dangers of financial opacity in digital assets.
Mallers added openness is the only way to build long-term trust in a bitcoin-native financial system.
Twenty One Capital wants to reshape financial infrastructure, build native bitcoin lending models and promote global Bitcoin adoption.
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ b1ddb4d7:471244e7
2025-06-13 07:02:19
@ b1ddb4d7:471244e7
2025-06-13 07:02:19Jason Lowery’s thesis, Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin, reframes bitcoin not merely as digital cash but as a transformative security technology with profound implications for investors and nation-states alike.
For centuries, craft brewers understood that true innovation balanced tradition with experimentation—a delicate dance between established techniques and bold new flavors.
Much like the craft beer revolution reshaped a global industry, bitcoin represents a fundamental recalibration of how humans organize value and project power in the digital age.
The Antler in the Digital Forest: Power Projection
Lowery, a U.S. Space Force officer and MIT scholar, anchors his Softwar theory in a biological metaphor: Bitcoin as humanity’s “digital antler.” In nature, antlers allow animals like deer to compete for resources through non-lethal contests—sparring matches where power is demonstrated without fatal consequences. This contrasts sharply with wolves, who must resort to violent, potentially deadly fights to establish hierarchy.
The Human Power Dilemma: Historically, humans projected power and settled resource disputes through physical force—wars, seizures, or coercive control of assets. Even modern financial systems rely on abstract power structures: court orders, bank freezes, or government sanctions enforced by legal threat rather than immediate physical reality.
Lowery argues this creates inherent fragility: abstract systems can collapse when met with superior physical force (e.g., invasions, revolutions). Nature only respects physical power.
Bitcoin’s Physical Power Engine: Bitcoin introduces a novel solution through its proof-of-work consensus mechanism. Miners compete to solve computationally intense cryptographic puzzles, expending real-world energy (megawatts) to validate transactions and secure the network.
This process converts electricity—a tangible, physical resource—into digital security and immutable property rights. Winning a “block” is like winning a sparring match: it consumes significant resources (energy/cost) but is non-destructive.
The miner gains the right to write the next page of the ledger and collect rewards, but no participant is physically harmed, and no external infrastructure is destroyed.
Table: Traditional vs. Bitcoin-Based Power Systems
Power System
Mechanism
Key Vulnerability
Resource Cost
Traditional (Fiat/Banking)
Legal abstraction, threat of state force
Centralized points of failure, corruption, political change
Low immediate cost, high systemic risk
Military/Economic Coercion
Physical force, sanctions
Escalation, collateral damage, moral hazard
Very high (lives, capital, instability)
Bitcoin (Proof-of-Work)
Competition via energy expenditure
High energy cost, concentration risk (mining)
High energy cost, low systemic risk
Softwar Theory National Strategic Imperative: Governments Are Taking Notice
Lowery’s Softwar Theory has moved beyond academia into the corridors of power, shaping U.S. national strategy:
- The Strategic Bitcoin Reserve: Vice President JD Vance recently framed bitcoin as an instrument projecting American values—”innovation, entrepreneurship, freedom, and lack of censorship”. State legislation is now underway to implement this reserve, preventing easy reversal by future administrations.
- Regulatory Transformation: The SEC is shifting from an “enforcement-first” stance under previous leadership. New initiatives include:
- Repealing Staff Accounting Bulletin 121 (SAB 121), which discouraged banks from custodying digital currency by forcing unfavorable balance sheet treatment.
- Creating the Cyber and Emerging Technologies Unit (CETU) to develop clearer crypto registration/disclosure rules.
The Investor’s Lens: Scarcity, Security, and Asymmetric Opportunity
For investors, understanding “Softwar” validates bitcoin’s unique value proposition beyond price speculation:
-
Digital Scarcity as Strategic Depth: Bitcoin’s fixed supply of 21 million makes it the only digital asset with truly inelastic supply, a programmed scarcity immune to political whims or central bank printing.
This “scarcity imperative” acts as a natural antidote to global fiat debasement. As central banks expanded money supplies aggressively (Global M2), bitcoin’s price has shown strong correlation, acting as a pressure valve for inflation concerns. The quadrennial “halving” (latest: April 2024) mechanically reduces new supply, creating built-in supply shocks as adoption grows. * The Antifragile Security Feedback Loop: Bitcoin’s security isn’t static; it’s antifragile. The network strengthens through demand: * More users → More transactions → Higher fees → More miner revenue → More hashpower (computational security) → Greater network resilience → More user confidence.
This self-reinforcing cycle contrasts sharply with traditional systems, where security is a cost center (e.g., bank security budgets, military spending). Bitcoin turns security into a profitable, market-driven activity. * Institutionalization Without Centralization: While institutional ownership via ETFs (like BlackRock’s IBIT) and corporate treasuries (MicroStrategy, Metaplanet) has surged, supply remains highly decentralized.Individuals still hold the largest share of bitcoin, preventing a dangerous concentration of control. Spot Bitcoin ETFs alone are projected to see over $20 billion in net inflows in 2025, demonstrating robust institutional capital allocation.
The Bitcoin Community: Building the Digital Antler’s Resilience
Lowery’s “Softwar” theory underscores why bitcoin’s decentralized architecture is non-negotiable. Its strength lies in the alignment of incentives across three participant groups:
- Miners: Provide computational power (hashrate), validating transactions and securing the network. Incentivized by block rewards (newly minted BTC) and transaction fees. Their physical energy expenditure is the “muscle” behind the digital antler.
- Nodes: Independently verify and enforce the protocol rules, maintaining the blockchain’s integrity. Run by users, businesses, and enthusiasts globally. They ensure decentralized consensus, preventing unilateral protocol changes.
- Users: Individuals, institutions, and corporations holding, transacting, or building on bitcoin. Their demand drives transaction fees and fuels the security feedback loop.
This structure creates “Mutually Assured Preservation”. Attacking bitcoin requires overwhelming its global, distributed physical infrastructure (miners/nodes), a feat far more complex and costly than seizing a central bank’s gold vault or freezing a bank’s assets. It transforms financial security from a centralized liability into a decentralized, physically-grounded asset.
Risks & Responsibilities
Investors and policymakers must acknowledge persistent challenges:
- Volatility: Bitcoin remains volatile, though this has decreased as markets mature. Dollar-cost averaging (DCA) is widely recommended to mitigate timing risk.
- Regulatory Uncertainty: While U.S. policy is increasingly favorable, global coordination is lacking. The EU’s MiCAR regulation exemplifies divergent approaches.
- Security & Custody: While Bitcoin’s protocol is robust, user errors (lost keys) or exchange hacks remain risks.
- Environmental Debate: Proof-of-Work energy use is scrutinized, though mining increasingly uses stranded energy/renewables. Innovations continue.
Jason Lowery’s “Softwar” theory elevates bitcoin from a financial instrument to a socio-technological innovation on par with the invention of the corporation, the rule of law, or even the antler in evolutionary biology. It provides a coherent framework for understanding why:
- Nations like the U.S. are looking to establish bitcoin reserves and embracing stablecoins—they recognize bitcoin’s role in projecting economic power non-violently in the digital age.
- Institutional Investors are allocating billions via ETFs—they see a scarce, secure, uncorrelated asset with antifragile properties.
- Individuals in hyperinflationary economies or under authoritarian regimes use bitcoin—it offers self-sovereign wealth storage immune to seizure or debasement.
For the investor, bitcoin represents more than potential price appreciation. It offers exposure to a fundamental reorganization of how power and value are secured and exchanged globally, grounded not in abstract promises, but in the unyielding laws of physics and mathematics.
Like the brewers who balanced tradition with innovation to create something enduring and valuable, bitcoin pioneers are building the infrastructure for a more resilient digital future—one computationally secured block at a time. The “Softwar” is here, and it is reshaping the landscape of p
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Problemas com Russell Kirk
A idéia central da “política da prudência[^1]” de Russell Kirk me parece muito correta, embora tenha sido melhor formulada pior no seu enorme livro do que em uma pequena frase do joanadarquista Lucas Souza: “o conservadorismo é importante, porque tem muita gente com idéia errada por aí, e nós podemos não saber distingüi-las”.
Porém, há alguns problemas que precisam ser esclarecidos, ou melhor explicados, e que me impedem de enxergar os seus argumentos como refutação final do meu já tão humilde (embora feroz) anarquismo. São eles:
I Percebo alguma coisa errada, não sei bem onde, entre a afirmação de que toda ideologia é ruim, ou “todas as ideologias causam confusão[^2]”, e a proposta conservadora de “conservar o mundo da ordem que herdamos, ainda que em estado imperfeito, de nossos ancestrais[^3]”. Ora, sem precisar cair em exemplos como o do partido conservador inglês -- que conservava a política inglesa sempre onde estava, e se alternava no governo com o partido trabalhista, que a levava cada vez mais um pouco à esquerda --, está embutida nessa frase, talvez, a idéia, que ao mesmo tempo é clara e ferrenhamente combatida pelos próprios conservadores, de que a história é da humanidade é uma história de progresso linear rumo a uma situação melhor.
Querer conservar o mundo da ordem que herdamos significa conservar também os vários erros que podem ter sido cometidos pelos nossos ancestrais mais recentes, e conservá-los mesmo assim, acusando toda e qualquer tentativa de propôr soluções a esses erros de ideologia? Ou será que conservar o mundo da ordem é escolher um período determinado que seja tido como o auge da história humana e tentar restaurá-lo em nosso próprio tempo? Não seria isto ideologia?
Ou, ainda, será que conservar o mundo da ordem é selecionar, entre vários períodos do passado, alguns pedaços que o conservador considerar ótimos em cada sociedade, fazer dali uma mistura de sociedade ideal baseada no passado e então tentar implementá-la? Quem saberia dizer quais são as partes certas?
II Sobre a questão do que mantém a sociedade civil coesa, Russell Kirk, opondo-a à posição libertária de que o nexo da sociedade é o autointeresse, declara que a posição conservadora é a de que “a sociedade é uma comunidade de almas, que une os mortos, os vivos e os ainda não nascidos, e que se harmoniza por aquilo que Aristóteles chamou de amizade e os cristãos chamam de caridade ou amor ao próximo”.
Esta é uma posição muito correta, mas me parece estar em contradição com a defesa do Estado que ele faz na mesma página e na seguinte. O que me parece errado é que a sociedade não pode ser, ao mesmo tempo, uma “comunidade baseada no amor ao próximo” e uma comunidade que “requer não somente que as paixões dos indivíduos sejam subjugadas, mas que, mesmo no povo e no corpo social, bem como nos indivíduos, as inclinações dos homens, amiúde, devam ser frustradas, a vontade controlada e as paixões subjugadas” e, pior, que “isso somente pode ser feito por um poder exterior”.
Disto aí podemos tirar que, da mesma forma que Kirk define a posição libertária como sendo a de que o autointeresse é que mantém a sociedade civil coesa, a posição conservadora seria então a de que essa coesão vem apenas do Estado, e não de qualquer ligação entre vivos e mortos, ou do amor ao próximo. Já que, sem o Estado, diz, ele, citando Thomas Hobbes, a condição do homem é “solitária, pobre, sórdida, embrutecida e curta”?
[^1]: este é o nome do livro e também um outro nome que ele dá para o próprio conservadorismo (p.99). [^2]: p. 101 [^3]: p. 102
-
 @ 73868430:0ec4fe27
2025-06-13 06:36:42
@ 73868430:0ec4fe27
2025-06-13 06:36:42皇居 Imperial Palace
巽櫓(桜田二重櫓) Sakurada Tatsumi Yagura

二重橋 Nijubashi Bridge

靖國神社 Yasukuni Jinja





遊就館 Yushukan


上野動物園 Ueno Zoological Garden


上野動物園不忍池 Ueno Zoological Garden Shinobazuno Pond

上野東照宮五重塔 Ueno Toshogu Shrine Five Story Pagoda

築地活鮮市場,御徒町店 Tsukiji Kassen Ichiba, Okachimachi

鉄道博物館 The Railway Museum




TOHAKU茶館 (応挙館) Tohaku Chakan

新大久保駅 Shin-Ōkubo


シンボルプロムナード公園 Symbol Promenade Park


セントラル広場 Central Square

日本科学未来館 The National Museum of Emerging Science and Innovation Japan (Miraikan)

箱根町 Hakone

芦ノ湖 Lake Ashi

元箱根 Motohakone

彫刻の森駅 Chokokunomori

三の鳥居,箱根神社 The Third Torii of Hakone Shrine

小田原城 Odawara Castle


-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28GraphQL vs REST
Today I saw this: https://github.com/stickfigure/blog/wiki/How-to-(and-how-not-to)-design-REST-APIs
And it reminded me why GraphQL is so much better.
It has also reminded me why HTTP is so confusing and awful as a protocol, especially as a protocol for structured data APIs, with all its status codes and headers and bodies and querystrings and content-types -- but let's not talk about that for now.
People complain about GraphQL being great for frontend developers and bad for backend developers, but I don't know who are these people that apparently love reading guides like the one above of how to properly construct ad-hoc path routers, decide how to properly build the JSON, what to include and in which circumstance, what status codes and headers to use, all without having any idea of what the frontend or the API consumer will want to do with their data.
It is a much less stressful environment that one in which we can just actually perform the task and fit the data in a preexistent schema with types and a structure that we don't have to decide again and again while anticipating with very incomplete knowledge the usage of an extraneous person -- i.e., an environment with GraphQL, or something like GraphQL.
By the way, I know there are some people that say that these HTTP JSON APIs are not the real REST, but that is irrelevant for now.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ d5ca7093:549ad1ec
2025-06-13 06:25:59
@ d5ca7093:549ad1ec
2025-06-13 06:25:59I recently decided to create my own personal brand website—something simple with a clean landing page, contact info, links to my work, and a blog. The idea was straightforward: when you meet people in real life or connect online, you need a reliable, consistent place they can go to learn more about you. Social media platforms aren’t built for that—they’re noisy, crowded, and ultimately not under your control.
As we shift into a decentralized digital future, owning your own website is one of the easiest and most powerful moves you can make. Social media pages are just websites owned by someone else. TikTok, Instagram, YouTube—they all serve specific functions, but there’s nothing stopping you from creating your own platform. If you make videos, host a video gallery. If you write, post your own blog. You don’t need to depend on Twitter or Medium to get your thoughts out. Open-source tools and modern frameworks make it easier than ever to replicate what these big platforms do—on your terms.
This shift is already visible with platforms like Nostr and Mastodon, which promote the idea of identity and communication without central ownership. Your website can be a central node in that ecosystem. Unlike a profile on a platform that can vanish overnight, your domain name is portable and permanent. You can point it anywhere—your own server, a decentralized network, or a new platform that respects user autonomy. That kind of control is only possible when you own your digital real estate.
In fact, I believe domain names are the next evolution of usernames. They’re already being used that way on services like BlueSky and Mastodon. A domain name isn’t just a web address—it’s a digital identity. It can be your contact card, your blog, your portfolio, and even your inbox. In a decentralized world, owning a domain is like planting a flag. It says: this is mine.
The deeper truth is that these centralized platforms are incentivized to keep you inside their ecosystem. They harvest your data, limit your reach unless you pay, and can suspend or ban your account without warning. When you build on their land, you play by their rules. When you build on your own land—your website—you make the rules. You decide what gets seen, what gets featured, and what data gets collected.
And let’s talk discoverability. While social media relies on algorithms and trends to push your content, your website can be indexed and searched globally on your terms. SEO tools, schema markup, and open metadata standards let you control how your content appears across the web. Add analytics, email capture, or even push notifications, and you’ve created a full digital marketing system that doesn’t depend on anyone else’s infrastructure.
For developers and technical creators, building a personal site also becomes a live demo of your skillset. It’s an interactive resume, a sandbox for new technologies, and a launchpad for projects. Whether you’re using React, Astro, Hugo, or GhostCMS, the tools you choose say as much about you as the content you publish. And because it’s all yours, you’re free to experiment without limitation.
Ultimately, your website is an investment in future-proofing your digital identity. As decentralized protocols evolve, your personal site can plug into that infrastructure—whether it’s connecting wallets, supporting decentralized comments, or syndicating content to multiple platforms. Owning your site today means you’ll be ready for the web of tomorrow.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ b4fade0e:a4d2b56a
2025-06-13 06:16:40
@ b4fade0e:a4d2b56a
2025-06-13 06:16:40Find essential details about the operating hours of the after school program in Anaheim Hills offered by Hillsborough Private Preschool. This structured program runs weekdays and is designed to accommodate working parents while offering children a secure, enriching environment. With flexible scheduling and attentive care, the program aligns with local school dismissal times. Learn about pick-up procedures, supervision quality, and how the program supports academic and social development through structured routines and engaging activities tailored to your child’s needs.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A estrutura lógica do livro didático
Todos os livros didáticos e cursos expõem seus conteúdos a partir de uma organização lógica prévia, um esquema de todo o conteúdo que julgam relevante, tudo muito organizadinho em tópicos e subtópicos segundo a ordem lógica que mais se aproxima da ordem natural das coisas. Imagine um sumário de um manual ou livro didático.
A minha experiência é a de que esse método serve muito bem para ninguém entender nada. A organização lógica perfeita de um campo de conhecimento é o resultado final de um estudo, não o seu início. As pessoas que escrevem esses manuais e dão esses cursos, mesmo quando sabem do que estão falando (um acontecimento aparentemente raro), o fazem a partir do seu próprio ponto de vista, atingido após uma vida de dedicação ao assunto (ou então copiando outros manuais e livros didáticos, o que eu chutaria que é o método mais comum).
Para o neófito, a melhor maneira de entender algo é através de imersões em micro-tópicos, sem muita noção da posição daquele tópico na hierarquia geral da ciência.
- Revista Educativa, um exemplo de como não ensinar nada às crianças.
- Zettelkasten, a ordem surgindo do caos, ao invés de temas se encaixando numa ordem preexistentes.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Channels without HTLCs
HTLCs below the dust limit are not possible, because they're uneconomical.
So currently whenever a payment below the dust limit is to be made Lightning peers adjust their commitment transactions to pay that amount as fees in case the channel is closed. That's a form of reserving that amount and incentivizing peers to resolve the payment, either successfully (in case it goes to the receiving node's balance) or not (it then goes back to the sender's balance).
SOLUTION
I didn't think too much about if it is possible to do what I think can be done in the current implementation on Lightning channels, but in the context of Eltoo it seems possible.
Eltoo channels have UPDATE transactions that can be published to the blockchain and SETTLEMENT transactions that spend them (after a relative time) to each peer. The barebones script for UPDATE transactions is something like (copied from the paper, because I don't understand these things):
OP_IF # to spend from a settlement transaction (presigned) 10 OP_CSV 2 As,i Bs,i 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIFDuring a payment of 1 satoshi it could be updated to something like (I'll probably get this thing completely wrong):
OP_HASH256 <payment_hash> OP_EQUAL OP_IF # for B to spend from settlement transaction 1 in case the payment went through # and they have a preimage 10 OP_CSV 2 As,i1 Bs,i1 2 OP_CHECKMULTISIGVERIFY OP_ELSE OP_IF # for A to spend from settlement transaction 2 in case the payment didn't went through # and the other peer is uncooperative <now + 1day> OP_CHECKLOCKTIMEVERIFY 2 As,i2 Bs,i2 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIF OP_ENDIFThen peers would have two presigned SETTLEMENT transactions, 1 and 2 (with different signature pairs, as badly shown in the script). On SETTLEMENT 1, funds are, say, 999sat for A and 1001sat for B, while on SETTLEMENT 2 funds are 1000sat for A and 1000sat for B.
As soon as B gets the preimage from the next peer in the route it can give it to A and them can sign a new UPDATE transaction that replaces the above gimmick with something simpler without hashes involved.
If the preimage doesn't come in viable time, peers can agree to make a new UPDATE transaction anyway. Otherwise A will have to close the channel, which may be bad, but B wasn't a good peer anyway.
-
 @ a88f35c7:7b121d83
2025-06-13 05:53:22
@ a88f35c7:7b121d83
2025-06-13 05:53:22Aunque a primera vista no lo parezca, el mundo digital en el que operan muchas empresas hoy en día no es tan diferente del mundo físico. De hecho, es común establecer analogías con la era medieval (términos como Bastion Host, Castle and Moat, Gatekeepers y Watchtower reflejan esta comparación) y quienes trabajamos en ciberseguridad estamos acostumbrados su uso. Sin embargo, hoy quiero abordar la seguridad digital desde una perspectiva evolutiva y haciendo una analogía con el contexto de la economía primaria, ya que la lectura de la tesis “Softwar: A Novel Theory on Power Projection and the National Strategic Significance of Bitcoin”, de Jason Paul Lowery, me ha llevado a reflexionar sobre este tema.
Para profundizar en esta analogía, propongo una relación simple: todos los actores que habitan el mundo digital (empresas, proveedores de servicios, actores malintencionados, usuarios, etc.) se consideraran organismos biologicos vivos que coexisten en un entorno hostil y compiten por los recursos disponibles en él.
Relación beneficio-costo del ataque (RBC).
Cada organismo biológico puede describirse como una fuente rica en nutrientes y un depósito de recursos valiosos. En la imagen de arriba, he intentado representar (disculpad si no lo he logrado completamente) un organismo unicelular con un núcleo (el tesoro) y una membrana que lo protege de las bacterias de alrededor.
En un escenario como este, es lógico pensar que la mayoría de estos organismos se convierten en un objetivo atractivo, una presa, para otros seres vivos diseñados por la evolución para capturar y explotar dichos recursos por la fuerza.
En consecuencia, un organismo incapaz de proteger su tesoro (ya sea por debilidad o ineficacia) se convierte en un caramelo en la puerta de un colegio: un cartel de neón irresistible para las formas de vida circundantes, que no dudarán en devorarlo.
Nota: Mientras escribía esto, no pude evitar pensar en el mundo digital y en todos esos sistemas con puertos abiertos expuestos en Shodan.
Pues bien, se puede definir la relación de beneficio-costo del ataque como:
RBC = BA/CA
Donde:
-
BA representa la función de la abundancia de recursos de un organismo (su “tesoro”). Los organismos con una gran cantidad de recursos valiosos tienen un BA alto, mientras que aquellos con menos recursos valiosos presentan un BA más bajo.
-
CA mide la capacidad y disposición de un organismo para imponer costos físicos severos a sus atacantes. Los organismos que pueden y están dispuestos a infligir daños físicos significativos a sus vecinos tienen un CA alto. En contraste, aquellos que carecen de dicha capacidad o no están dispuestos a ejercerla tienen un CA bajo.
Si la relación anterior ha quedado clara, resulta evidente que los organismos con una RBC más alta son más vulnerables al ataque que aquellos con una RBC más baja, ya que representan un mayor retorno de inversión para los vecinos hambrientos que buscan devorarlos.
Por esta razón, los organismos tienen la necesidad existencial de reducir su RBC tanto como sea posible, lo que los impulsa a aumentar su capacidad y disposición para imponer costos físicos significativos a sus atacantes. Por el contrario, un organismo no puede simplemente dedicar todo su tiempo y energía a acumular recursos y esperar prosperar a largo plazo, ya que esto incrementaría su RBC, poniendo en riesgo su supervivencia.
A modo conclusión, se podría decir que, para sobrevivir a largo plazo, los organismos deben gestionar ambos lados de la relación RBC para evitar que este ratio aumente hasta niveles peligrosos. Esto se puede hacer de la siguiente forma:
-
Optar por reducir su numerador (reducir su "tesoro").
-
Aumentar su denominador (imponer costos físicos significativos a sus atacantes).
En la naturaleza, podríamos decir que reducir la abundancia de recursos no es una solución demasiado ideal para los organismos que buscan crecer, por lo que aumentar su CA es la opción más recomendable.

Una analogía útil para explicar el RBC es la situación en la que un ladrón debe decidir qué apartamento robar. Antes de actuar, inspecciona dos puertas en el mismo piso: una a la izquierda, de madera y visiblemente desgastada, y otra a la derecha, blindada y equipada con múltiples cerrojos.
Es probable que el ladrón asuma que el “tesoro” detrás de la puerta blindada es más valioso. Sin embargo, los altos costos del ataque (mayor tiempo, esfuerzo y riesgo) disuadirán a muchos ladrones que no estén preparados para asumir ese desafío. Así, la relación entre recompensa y costo de ataque influye en la decisión, reflejando el principio del RBC en la naturaleza.
Margen de prosperidad.
Retomando la idea de la “economía de la evolución” y la difícil tarea de sobrevivir, es importante recordar que, como hemos visto antes, cualquier organismo debe mantener su nivel de RBC lo más bajo posible. Pero, ¿cuán bajo exactamente?
La clave está en mantenerlo por debajo del umbral crítico que determine si un ataque resulta rentable o no para un posible depredador o competidor. Si el RBC es demasiado alto, el organismo se convierte en un objetivo atractivo; si es lo suficientemente bajo, los costos de atacarlo superan los beneficios, disuadiendo a la mayoría de los agresores. Según Lowery, la diferencia entre el nivel de RBC de un organismo y el umbral peligroso puede definirse como su margen de prosperidad. En otras palabras, este margen representa cuánto puede permitirse un organismo aumentar su RBC antes de volverse un objetivo viable para el ataque. Mantener un margen de prosperidad amplio es esencial para garantizar estabilidad y minimizar riesgos en un entorno competitivo.
Planteado a alto nivel, podría parecer un problema sencillo de resolver, ya que, en esencia, solo se trata de mantener el RBC por debajo del umbral peligroso mientras se preserva un margen adecuado de prosperidad. Sin embargo (y siempre hay un “pero”), el verdadero desafío radica en que el organismo no puede conocer con precisión dicho umbral, ya que este depende casi por completo de factores externos.
Las variables que determinan el umbral peligroso están condicionadas por el entorno y por la presencia de otros organismos que cohabitan en él. Esto implica que un organismo nunca puede estar completamente seguro de cuánto puede aumentar su RBC antes de atraer la atención de posibles atacantes. Esta incertidumbre introduce un nivel de riesgo que dificulta la optimización de la estrategia de crecimiento y supervivencia.
Supervivencia a largo plazo.
Dado que los organismos no pueden determinar con certeza qué nivel de seguridad es suficiente, la supervivencia se convierte en un proceso de aprendizaje sobre cómo regular el RBC y maximizar el margen de prosperidad tanto como sea posible. En términos generales, un organismo puede seguir tres estrategias:
-
Opción 1: Aumentar el BA por encima del CA provocará un crecimiento en el RBC, acercándolo a la zona de peligro, por lo que esta opción queda descartada.
-
Opción 2: Aumentar el CA a medida que aumenta el BA, manteniendo el RBC fijo (crecimiento proporcional de los dos valores). Aunque esta estrategia conserva el mismo margen de seguridad, no es una solución sostenible a largo plazo, ya que el entorno se vuelve cada vez más hostil y el nivel de RBC que antes garantizaba la supervivencia puede volverse insuficiente.
-
Opción 3: Aumentar el CA más que el BA. En este caso, el margen de prosperidad se amplía porque el RBC disminuye. Esta, según Lowery, es la única estrategia viable para garantizar la supervivencia a largo plazo.
La enseñanza de la evolución en el mundo de la ciberseguridad.
Si aplicamos los principios de la economía primaria al ámbito de la ciberseguridad, es posible extraer algunas enseñanzas valiosas, aunque también es cierto que el mundo digital tiene ciertas excepciones o flexibilidades. A continuación, expondré las conclusiones a las que he llegado tras realizar este ejercicio de análisis.
El Coste de Ataque (CA), que implica imponer costos a los atacantes, no deja de ser una inversión en seguridad a través de herramientas, procesos y revisiones. Como ha demostrado la económica primaria, esta estrategia es clave para garantizar la supervivencia a largo plazo de una empresa ya que hace que los ciberataques sean menos rentables y por lo tanto menos frecuentes. En esta línea y al igual que en la naturaleza, una empresa no puede saber nunca que tan cerca está del umbral del peligro (ya que este depende de factores casi totalmente externos) y por tanto debe esforzarse por maximizar el CA siempre que pueda (esto es invertir en ciberseguridad). Así que ya sabéis, si alguien alguna vez pone en duda las inversiones en ciberseguridad, le podéis decir con total certeza que es economía de supervivencia y es LA ÚNICA FORMA de garantizar la viabilidad de la empresa a largo plazo.

Por otro lado, está el Beneficio de Ataque (BA), el "tesoro" protegido por todos los organismos. Haciendo un paralelismo con el mundo digital, este equivale a los datos e información que almacena una organización. Es natural que, al igual que ocurre en los organismos biológicos, una empresa busque incrementar y proteger este activo.
Todos hemos oído un millón de veces expresiones como "es la era de la información", "los datos son el nuevo petróleo" o "la información es poder", y no dudo de su veracidad. Sin embargo, basándonos en la economía de supervivencia mencionada, hacer crecer el Beneficio de Ataque (BA) puede ser peligroso.
De hecho, hemos comprobado que incrementar el BA por encima del Coste de Ataque (CA) no es una estrategia viable a largo plazo. Pero, como todos sabemos, es complicado convencer al área de negocio de que tal vez (solo tal vez) ciertos datos sensibles no sean realmente necesarios para su almacenamiento en bases de datos. Y que, en caso de que lo sean, su protección mediante cifrado debería ser una prioridad.
Entonces, ¿Es posible reducir el BA?
Llegados a este punto, surge la duda de si, a diferencia del mundo natural, en el mundo digital que hemos construido, es posible reducir el Beneficio de Ataque (BA) sin comprometer la viabilidad de una empresa.
En la naturaleza, la supervivencia depende del crecimiento y la acumulación de recursos, pero en el entorno digital, ¿realmente es necesario almacenar y procesar cada dato disponible? ¿O es posible optimizar y reducir el volumen de datos sensibles sin afectar el negocio? A continuación algunos ejemplos:
-
¿Es realmente necesario que tenga que facilitar mi DNI al repartidor de UPS o SEUR?
-
¿Es justificable que el Real Decreto 933/2021 obligue a las empresas del sector de hospedaje a almacenar y proporcionar datos sensibles de los viajeros, como el DNI, teléfono fijo y móvil, relación de parentesco entre huéspedes, así como información sobre el pago, incluyendo el tipo de tarjeta, número y fecha de caducidad?
-
¿Porque es necesario pasar por un proceso riguroso de KYC para comprar según que activos financieros?
Estoy seguro que cada caso de los anteriores tiene una justificación aunque tampoco tengo ninguna duda de que estas probablemente sean cuestionables desde el punto de vista de la privacidad y protección de datos.
Esta última reflexión me ha llevado a buscar si actualmente existen proyectos y/o estrategias enfocadas en la minimización de datos, con el objetivo de reducir cualquier exposición innecesaria de información personal y he podido comprobar que existen diferentes líneas de trabajo en esta dirección como el sistema Decentralized Identity (DID) o Zero-Knowledge Proofs (ZKP). Estas tecnologías permiten verificar información sin revelar datos personales, lo que indica que ya hay profesionales abordando esta preocupación.
Quizás, cuando estos sistemas estén más consolidados, podamos comprobar si, a diferencia del mundo biológico, el mundo digital permite el crecimiento de un organismo sin tener que aumentar su BA.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ 3eba5ef4:751f23ae
2025-06-13 05:50:51
@ 3eba5ef4:751f23ae
2025-06-13 05:50:51Crypto Insights
Skipping Witness Sync for Pruned Nodes? A Look at Bitcoin Sync Optimization and Security Tradeoffs
Jose SK posted an analysis exploring the security implications of allowing newly started full nodes to skip downloading certain blockchain history data under specific configurations.
Bitcoin Core uses the
assumevalidconfig option by default to skip script verification for blocks created roughly one or two months prior to the current version’s release. Additionally, while disabled by default, many users enable thepruneoption, which deletes block data after validation (the retention period depends on block size and user settings). SK argues that usingassumevalidandprunecould allow nodes to download witness data for older blocks, since it's only used for script validation—somethingassumevalidbypasses. This could reduce bandwidth use by over 40%.However, Ruben Somsen responds that this changes the security model: even if scripts may not be validated, the downloaded data is still checked against the block header’s Merkle root, coinbase transaction, and witness commitments. Skipping it risks data loss if no one preserves and verifies the data—an issue seen in XRP Ledger.
Capping Transaction Weight to Improve Decentralization and Relay Efficiency
Vojtěch Strnad proposed a consensus change to cap most transaction weights at 400,000 weight units (100,000 vbytes). Specifically, aside from the coinbase transaction, only a single transaction in a block may exceed that limit.
This allows:
- Easier block template optimization: Smaller transactions simplify solving the knapsack problem and reduce wasted space.
- Easier relay policies: Large transactions complicate relay logic and fee-rate prediction, potentially wasting bandwidth if they're evicted or delayed due to slight changes in fee-rate.
- Avoiding mining centralization: Ensure full nodes can relay nearly all transactions helps avoid users of special transactions from needing to pay out-of-band fees, which might otherwise centralize mining power.
Pruning Dust UTXOs to Ease Network Burden
Robin Linus proposed a soft fork to remove low-value, long-unspent outputs (dust) from the UTXO set. Several variations were discussed, with the two main alternatives being:
- Destroying old uneconomical outputs: long-unspent small value outputs would become unspendable.
- Requiring a proof of existence for old uneconomic funds to be spent: Using tools like Utreexo to prove an old output is part of the UTXO set when spending it.
Both approaches aim to cap UTXO set size, assuming a minimum output value and Bitcoin’s 21 million cap.
Ark vs. LSP: Comparing Liquidity Models for Different Use Cases
This research compares Ark and Lightning Service Provider (LSP) in terms of liquidity requirements. The author models user behavior with varying top-up frequencies (weekly, monthly, quarterly) and gradual Lightning usage throughout the year. Findings include:
- LSP liquidity needs are driven primarily by balance changes; Ark’s by payment volume.
- LSP liquidity durations fluctuate more than Ark’s.
- LSP predicts user behavior better than Ark.
- Refill frequency is key to Ark’s liquidity efficiency.
Conclusion:
- Users who make daily Lightning payments and receive income at least weekly may spend less with LSP than Ark.
- Users with less frequent payment and monthly Bitcoin income could save more with Ark combined with Lightning gateways.
- DCA (dollar-cost averaging) Bitcoin stackers should prefer Ark, as its liquidity costs are only a fraction of LSP.
Citrea & Babylon Advance Cross-Chain Verification
-
Citrea upgraded its Clementine bridge to v2, replacing BitVM2 with a garbled SNARK verifier, and integrated Transfer of Ownership Protocol (TOOP). This removes the need for large amounts of collateral and pre-pay withdrawals (for liquidity) in the bridge.
-
Babylon completed its first entire unhappy path BitVM test on Bitcoin mainnet. It spanned 42 blocks, cost ~$16,000 in fees, and took less than 8 hours—demonstrating that a full challenge-disprove sequence works in practice.
How the DelBrag Protocol Works
DelBrag can be seen as BitVM with off-chain computation. Its creator Jeremy Rubin shared presentation (PDF) at Bitcoin++, outlining how the protocol functions, including detailed diagrams, timing analysis, and the concept of optimistic circuit consistency checks.
Bitcoin Testing Is a Ghost Town: Bad UX, Rotten Interfaces, and Bugs
This critique points out that Bitcoin is advancing technically but falling behind in UX and software testing—hindering adoption and onboarding. Key issues include:
- Gap between progress and usability: Apps and infrastructure are evolving, but devs often deprioritize real-world usability, making Bitcoin software intimidating for newcomers.
- Lack of professional testing: Leads to buggy releases and barriers for first-time users.
- Clunky onboarding frustrates users and stalls growth.
- Bitcoin could suffer the fate of tech like Lotus Notes or PGP (Pretty Good Privacy)—excellent in themselves but failed due to poor UX.
8 Years In, Is Lightning Still a Hobbyist’s Playground?
This article points out that despite growing node and channel counts and their capacity, the Lightning Network still faces serious hurdles:
- High maintenance costs: Running a node isn’t fun or profitable.
- Lack of redundancy: LN depends on 2-of-2 multisig bilateral channels. Unlike traditional networks, LN lacks robust failover. Downtime risks payment failure or funds getting stuck.
- Tradeoff between security and reliability: Security takes precedence, but it leads to fragility. Businesses needing reliable payments may find this unacceptable.
- Core issues remain unaddressed: Most improvements are UX-level. There’s been little progress on scalability, redundancy, or robustness. Static channel backups help recovery but not live failover. Proposed fixes (like hot standby nodes) are complex, risky, and not widely adopted.
Gemini’s Global Crypto Report: Holding Increases, Memecoins as Onboarding Gateway
Gemini released its 2025 Global State of Crypto Report, noting:
-
Global crypto ownership rises, led by Europe.
Crypto ownership grew across key markets in 2025: UK: 24% (up from 18%), US: 22% (up from 21%), France: 21% (up from 18%), Singapore: 28% (up from 26%).
-
Trump administration’s pro-crypto stance boosts confidence.
23% of US non-owners said Trump’s Strategic Bitcoin Reserve increased their crypto confidence. Similar sentiment was seen in the UK (21%) and Singapore (19%).
-
Memecoins become a gateway to adoption.
Many crypto users started with memecoins: US: 31%, Australia: 30%, UK: 28%, Singapore: 23%, Italy: 22%, France: 19%.
-
Spot crypto ETFs gain popularity.
Crypto ETF ownership rose: US: 39% (up from 37%), Italy: 47%, UK: 41%, Singapore: 40%, Australia: 38%, France: 32%.
-
 @ 3eba5ef4:751f23ae
2025-06-13 05:45:13
@ 3eba5ef4:751f23ae
2025-06-13 05:45:13加密洞见
跳过见证数据同步?Bitcoin Core 节点同步优化与安全性的权衡
Jose SK 在 Delving Bitcoin 上 发布了一份分析,探讨了允许新启动的全节点,在一种特定配置下,可跳过下载某些区块链历史数据的安全权衡。
在默认情况下,Bitcoin Core 节点使用
assumevalid配置选项,会跳过对早于当前 Bitcoin Core 版本发布一两个月前所创建区块中脚本的验证。此外,虽然默认关闭,许多 Bitcoin Core 用户还会启用prune(修剪)选项,在完成验证后删除该数据(保留区块的时间取决于区块大小和用户的具体设置)。SK 认为,对于启用assumevalid且采用修剪模式的节点,不需要下载见证数据(witness data),因为这些数据只用于验证脚本,而节点不会进行此类验证,且最终也会将其删除,而且跳过见证数据下载「可以减少超过 40% 的带宽消耗」。对此 Ruben Somsen 认为,这在一定程度上改变了原有的安全模型。虽然脚本未被验证,但已下载的数据会与区块头的 Merkle 根、coinbase 交易和见证数据之间的承诺进行验证。这一过程可确保节点初次同步时数据是可用且未被篡改的。如果没有节点持续验证这些数据的存在性,它们可能会丢失——XRP Ledger 就出现过这种情况。
限制区块交易重量,助力去中心化与中继效率
Vojtěch Strnad 提出了一项共识规则变更建议:限制区块中大多数交易的最大权重。具体而言,除 coinbase 交易外,只有当某笔交易是区块中唯一的一笔交易时,才允许其超过 400,000 权重单位(即 100,000 vbytes)。Strnad 描述了限制最大交易权重的动机:
- 更容易优化区块模板:当交易相较于容量上限更小,寻找近似最优的「背包问题」解法更容易,因为较小交易更容易把区块填满,减少浪费空间。
- 简化交易中继策略:节点之间转发未确认交易时,会预测哪些交易有可能被打包,以避免浪费带宽。特大交易会让预测变得困难,因为即便费率略微变化,也可能导致其被延迟或驱逐。
- 避免挖矿中心化:确保中继全节点能够处理几乎所有交易,可以避免使用特殊交易的用户被迫支付链下费用(out-of-band fee),进而降低挖矿中心化的风险。
移除过期低值 UTXOs,减负网络
Robin Linus 提出了一项软分叉建议,旨在在一定时间后将低价值输出从 UTXO 集合中移除。该想法有多个变体,其中的两种替代方案是:
- 销毁旧的非经济性资金:对于长期未被花费的小额输出,使其变得不可再花费。
- 要求旧的非经济性资金在花费时提供存在性证明:可以使用 Utreexo 或类似机制,让交易在花费某个输出时证明该输出确实存在于 UTXO 集合中。旧且非经济性的输出需要附带此类证明,而新生成的、价值较高的输出仍可直接保存在 UTXO 集合中。
无论采用哪种方案,都可以在理论上限制 UTXO 集合的最大规模——前提是假设存在最小输出金额以及 2100 万个比特币的总量上限。
Ark vs LSP:流动性机制对比,谁更适合你的使用场景?
这份研究就流动性要求的问题对比了 Ark 和 LSP (Lightning Service Provider)。他指出 Ark 服务器和 LSP 的流动性机制截然不同,于是对参数和用户行为作出了不同的模拟假设;在用户画像方面,他假设用户以不同频率(周/月/季)对其钱包充值,并在一年内逐步使用闪电网络进行消费的情况。研究得出以下发现:
- LSP 的流动性需求主要由用户余额的变化驱动,而 Ark 服务器的流动性需求由支付量驱动。
- 与 Ark 服务器相比,LSP 面临的流动性持续时间变化更大
- LSP 在预测用户行为方面需要比 Ark 服务器好得多
- 资金频率是 Ark 流动性效率的关键因素
研究的结论是:
- 如果用户每天通过闪电网络支付,并且每周或更多次收到付款的用户,那么在流动性上的花费可能会比使用 Ark 时少。
- 如果用户付款频率较低,并且每个月只收到比特币(例如,月薪或购买比特币),那么将 Ark 与闪电网关一起使用应该可以节省大量资金
- 如果用户以平均成本法(DCA)够买比特币,则应该使用 Ark,因其流动性成本只是 LSP 的一小部分。
Citrea 和 Babylon 双双推进跨链验证新路径
-
Citrea 将跨链桥 Clementine 升级到了 v2——用混淆 snark 验证器(garbled SNARK verifier)取代 BitVM2,同时结合「所有权转移协议」(Transfer of Ownership Protocol,TOOP),从而消除了跨链桥对大数额抵押品和用以提供流动性的预付提款(pre-pay withdrawals)的需求。
-
Babylon 成功在比特币主网上完成首次完整的「不愉快路径」(unhappy path)BitVM 测试。该测试跨越 42 个区块,消耗约 1.6 万美元手续费,在 8 小时内完成,验证了完整的挑战-反驳序列(challenge-disprove sequence )在实践中是可行的。
DelBrag 协议的工作原理
Delbrag 可以被看作是可以进行链下计算的 BitVM。Delbrag 的提出者 Jeremy Rubin 分享了他近期在 Bitcoin++ 上的演讲(报告 pdf),介绍了 DelBrag 协议如何工作,以及详细的原理图和时序分析,同时引入了「乐观电路一致性检查」(optimistic circuit consistency checks)这一概念。
比特币测试如鬼城:深入了解糟糕的用户体验、难用的界面和各种 bugs
作者认为,比特币生态在技术上虽有进步,但用户体验和软件测试严重不足,导致新用户难以上手,阻碍了广泛采用。尤其指出以下问题:
- 进度与可用性差距: 比特币通过不断改进的应用程序和网络生态系统在技术上取得了发展,但开发人员通常只是肤浅地考虑可用性,而在实践中没有优先考虑它。这导致软件适合精通技术的用户,但由于界面不佳和体验错误而疏远了新手。
- 缺乏专业测试:导致发布的软件存在大量使用障碍和漏洞。
- 新用户入门流程繁琐,阻碍用户积极性。糟糕的用户体验会导致采用缓慢、节点增长停滞和用户群萎缩。
- 历史上有 Lotus Notes 和 PGP (Pretty Good Privacy) 等软件因用户体验差而失败——虽然它们本身不错——比特币面临同样风险。
八年过去,闪电网络仍是一个业余爱好者的游乐场?
作者指出,诞生八年的闪电网络虽然在节点、通道数量和容量上持续增长,展现出快速、低费的支付潜力,但也存在严重问题,主要体现在:
- 维护成本高:维护节点既不好玩,也无利可图
- 核心架构缺乏冗余和弹性:闪电网络的设计依赖于由 2-of-2 多重签名保护的双边支付通道。与具有多个冗余路径和备份系统的传统电信或互联网网络不同,闪电网络节点和通道缺乏有效的故障转移机制。如果节点或通道下线,付款可能会失败,资金可能会卡住,从而破坏可靠性。
- 安全性与可靠性的权衡:闪电网络优先考虑安全性,但牺牲了运行的可靠性。这种权衡意味着,虽然网络是安全的,但很容易出现服务中断和故障,这对于需要一致支付服务的商家或用户来说是不可接受的。
- 缺乏对核心问题的有意义升级:近年来大多数改进都是用户界面相关,而不是对可扩展性、冗余性或可靠性的根本修复。静态通道备份等功能有助于恢复,但不提供实时故障转移或冗余。提出的解决方案(如热备节点)复杂且存在风险,并且不存在大规模实施。
Gemini 《比特币全球状态》报告:持有率上升,meme 币成入场新通道
Gemini 发布了 2025 年全球加密货币状况报告(Global State of Crypto),分析了加密市场状况和对数字资产的各种态度,包括现货比特币 ETF、meme 币、特朗普支持加密的政策对各种看法的影响、以及投资者是否应计划在未来一年购买更多资产等。
重要发现包括:
- 全球加密货币持有率持续上升,欧洲领跑:2025 年,英国的加密货币持有率达到 24%,高于 2024 年的 18%。美国的持有率也略有上升,从 21% 增至 22%。法国的增幅从 18% 升至 21%,而新加坡的持有率则从 26% 升至 28%。
- 特朗普政府的支持立场提振市场信心:在美国,近四分之一的非持有者表示,特朗普推出战略比特币储备计划增强了他们对加密货币价值的信心。这一观点也得到了英国和新加坡非持有者的响应,分别有 21% 和 19% 的人表示认同。
- Meme 币成为进入加密的入口:在美国,31% 同时持有 meme 币和传统加密货币的投资者表示,他们是先购买 meme 币;在澳大利亚为 30%,英国 28%,新加坡 23%,意大利 22%,法国 19%。全球范围内,94% 的 memecoin 持有者也持有其他类型的加密货币,表明 meme 币 正成为进入更广泛加密市场的入口。
- 现货加密 ETF 市场份额持续增长:在美国,39% 的加密货币持有者表示他们投资了加密 ETF,较 2024 年的 37% 有所上升。该类产品在其他国家也越来越受欢迎:意大利(47%)、英国(41%)、新加坡(40%)、澳大利亚(38%)和法国(32%)。
-
 @ 7460b7fd:4fc4e74b
2025-06-13 05:33:58
@ 7460b7fd:4fc4e74b
2025-06-13 05:33:58比特币如何通过协议机制实现隐私而不违反反洗钱法
1. 引言
“保守派的创新”理念指的是在不破坏既有社会制度的前提下推进技术革新。在金融领域,隐私与合规常被视为此消彼长的关系,但比特币生态展示出一种渐进式的平衡路径:既探索交易隐私保护,又避免公然违背反洗钱法规要求。这种平衡并非异想天开;传统金融本就提供一定程度的隐私,例如银行账簿并非对公众透明,个人消费细节通常不为外人所知en.bitcoin.it。比特币的目标之一是以去中心化方式复制这种隐私保护,但同时它并未试图动摇反洗钱法律的基石。相反,比特币社区秉持“保守式创新”,通过协议层的改进逐步增强用户隐私,同时尊重监管红线。例如,美国政府近年提出“负责任创新”原则,要求在保障国家安全和金融稳定的前提下鼓励区块链技术有序发展siis.org.cn。比特币的发展恰体现了这一点:它采用公开区块链,但通过巧妙的机制设计和增量升级,为合法用户提供类似现金的隐私空间,而不公然为洗钱者大开方便之门。
2. UTXO 模型与账户制的本质区别
比特币采用 UTXO(未花费交易输出)模型记录账本,这与传统银行或以太坊的账户模型截然不同。简单类比来说,UTXO 模型类似于现金交易,账户模型则类似于银行账簿nervos.org。在 UTXO 模型下,每笔交易消耗之前的输出并创造新的输出,币值被划分成离散的“硬币”单元;就如同用一枚金币付款找零,找零过程会销毁原金币并造出面额不同的新币docs.glassnode.comdocs.glassnode.com。每个 UTXO 都隶属于某个地址,而地址通常由用户一次性使用,这使得难以直接将所有交易关联到同一身份nervos.org。换言之,比特币系统并不追踪“账户余额”,而是追踪散落在各地址下的一笔笔未花费输出nervos.org。用户的钱包余额只是所有这些 UTXO 金额的总和。
与之相比,账户模型则维护全球状态,每个账户有持续的余额记录,很容易基于固定的账户识别用户身份cexplorer.io。账户体系下,多笔交易进出同一账户,会在账本中清晰显示某人所有的资产变动情况。这种透明度对监管有利,但也意味着隐私的天然缺失——资金流向可以直接与账户持有人绑定。UTXO 模型天生提供了更大的隐私空间,因为每笔交易可以使用新的地址,外部观察者难以确定多个交易是否属于同一主体nervos.org。正如贵金属或现金交易中,实物的流转不记名,UTXO 的分散性赋予了用户类似实物货币的隐私保护。而账户体系更像实名登记的银行账户,所有交易活动都集中在同一名下,隐私隔离性较弱。
需要强调的是,UTXO 模型提供的是**“笔名制”隐私而非完全匿名。区块链上的地址并不直接揭示身份,但如果有人能将地址与现实身份对应起来(例如通过交易所KYC记录),那么UTXO交易历史的透明特征仍可被利用。因此,比特币底层设计选择在匿名性与可追溯之间折中:通过UTXO提供尽可能的去身份化交易记录,同时保留全网公开可审计的交易流动性。这种设计一方面满足了反洗钱(AML)**对可追溯性的最低要求(所有交易公开上链),另一方面也为合法交易提供了一定程度的隐私遮蔽(地址不直接对应实名)。这种隐私“空隙”是比特币协议保守创新的起点。它类似于现金的特性——现金交易不记录买卖双方身份,但大额可疑现钞交易仍可通过其他线索引起执法注意。同理,UTXO 模型下小额日常交易可保持去身份化,而异常模式的资金流动仍可能触发监管机构的区块链分析关注。
3. CoinJoin 的实现方式与监管意义
为进一步拓展隐私,比特币社区发展出多种链上混合机制,其中最典型的是 CoinJoin。CoinJoin 是一种无须信任中介的协作交易方法:将多个付款人的转账合并在一笔交易中,从而混淆外部观察者对“谁在向谁付款”的判断en.bitcoin.it。其核心思想由 Gregory Maxwell 于2013年提出,利用比特币交易可以有多个输入和输出的特性,组织多个参与者共同构造一笔交易,每个参与者提供若干输入并得到自己预期的输出。由于区块链上只记录了一笔合成交易,外界难以确定哪笔输入对应哪笔输出,实现交易参与者之间的匿名性集。典型的 CoinJoin 实现会让所有参与者约定使用相同面额的输出(例如每人都拆分成若干个0.1 BTC的输出),这样链上看到多个等额输出时,无法分辨这些输出原先属于哪个参与者en.bitcoin.it。同时,每个参与者通常还会得到找零输出,从而保持总额不变。通过这种方式,一次 CoinJoin 交易实质上打乱了资金的对应关系,达到了“混币”的效果。
CoinJoin 的技术细节体现出比特币协议层面的巧妙设计:比特币交易的输入签名彼此独立,因此完全可以由不同用户分别签署再合并,只要所有必要签名齐备,交易便有效en.bitcoin.it。这意味着多个彼此不信任的用户可以在不交出控制权的情况下共同生成一笔交易——整个过程无需更改比特币协议,一切遵循既有规则即可完成en.bitcoin.it。这种协作混合交易在链上结构特征通常为:多个来源地址(输入)对应多个去向地址(输出),且输出面额往往存在重复值,使传统“通过金额和地址关联交易”的分析方法失效。由于 CoinJoin 交易并不标注参与者身份,它在区块链数据上与普通交易不可区分,尤其当其输出面额设计得不像刻意等值时,更增添了辨识难度。
然而,正是这种加强隐私的技术,引起了监管机构对潜在滥用的关注。反洗钱机构将此类混合服务归类为“增加匿名性风险的活动”。FATF(金 融 行 动 特 别 工 作 组)的报告将使用混币器视为一项重要风险指标,指出“不少犯罪分子利用混币/Tumbling服务来遮蔽资金来源或去向”fatf-gafi.org。从监管角度看,CoinJoin 等机制本身具有中立性,但其用途可能涉及掩盖非法所得流转,从而引发执法部门警惕。在现实案例中,确有不法分子尝试利用 CoinJoin 逃避监管:例如 2016 年 Bitfinex 交易所黑客窃得巨额比特币后,多年间反复采用Wasabi钱包的 CoinJoin 功能清洗资金,被称为“当时最先进的洗钱手法”time.com。又如2021年美国司法部破获的臭名昭著案件中,一对夫妻涉嫌协助清洗 Bitfinex 被盗比特币,调查发现他们使用了 CoinJoin 来试图匿名化交易,但最终仍因区块链的永久记录和执法部门的链上分析技术而落网time.comcointelegraph.com。这说明混合交易并非万能护身符:对于有能力的执法机构而言,大额异常的链上混合行为依然可能被捕捉和溯源,只是增加了分析难度和取证成本。
监管机构对于混币工具的法律立场逐渐明晰。在美国,FinCEN(金融犯罪执法网络)早在2013年指导意见中即表明,经营虚拟货币兑换或传输业务需遵守《银行保密法》(BSA)规定。2019年FinCEN进一步明确:提供混币/搅币服务的机构属于货币服务业务(MSB),必须登记注册并履行反洗钱义务fincen.gov。简言之,运行CoinJoin服务即视同资金汇兑业务,需要实行KYC、报告可疑交易等合规措施,否则即属非法经营。在2020年,美国首次对比特币混币服务施加严厉制裁:运营 “Helix”混币器的 Larry Harmon 被指控未经许可经营MSB并协助洗钱,被FinCEN处罚6000万美元,后又被法院判处入狱三年fincen.gov。执法调查显示,Harmon经营的混币服务三年内处理比特币逾350,000枚,且主动宣传可匿名购买毒品等非法商品,这些行为严重违反了反洗钱法fincen.govfincen.gov。这一里程碑案例表明,美国司法实践已将第三方混币服务视作违法,运营者须承担刑事及民事后果。
与此对应的是,如果仅提供去中心化的软件工具而非代客操作,则法律定位有所不同。FinCEN在2019年声明中也承认,提供匿名化软件本身不构成货币传输服务cliffordchance.com。这为比特币协议层面的创新留下了空间:开发者可以创造CoinJoin钱包或协议,让用户自行对等完成混合交易,而不涉及中介经手资金。在这种架构下,软件提供方不直接“控制”客户资金流,因而不被视为MSB。然而,监管的灰度在于,如果软件提供方设立了协调服务器并从中收取服务费,是否变相成为了混币业务经营者?对此,不同司法辖区可能有不同解读。一些CoinJoin实现(如Wasabi钱包的协调器)选择主动限制自身角色,以避免落入监管“经营服务”的范畴。同时,也有业内主体为了降低监管冲击而做出让步。例如,隐私钱包 Wasabi 的开发公司(注册于英国)在2022年宣布,其CoinJoin协调服务器将拒绝可疑的非法来源资金参与混币cointelegraph.com。该公司通过黑名单过滤特定的UTXO来防止明显带有犯罪特征的币混入池内,此举被视为向执法机构妥协的“自律”措施cointelegraph.comcointelegraph.com。虽然此举在隐私社区引发争议,但从监管角度看,这是行业努力寻求平衡的体现:即允许合法用户继续享有隐私工具,同时遏制不法分子滥用。类似地,FATF和各国监管者也在加强对混币器的监控合作,包括将臭名昭著的混币平台列入制裁清单(如2022年美国OFAC先后制裁了比特币混币服务Blender.io和以太坊混币器Tornado Cash,因其被朝鲜黑客用于清洗盗窃资金)cliffordchance.com。
综合来看,CoinJoin技术本身并不违反法律——正如现金本身不违法,但用于洗钱即涉罪。关键在于使用目的和主体。比特币协议通过CoinJoin提供了增强隐私的可能性,这是对抗链上数据监控、维护币值可替代性(fungibility)的“保守式创新”举措en.bitcoin.it。它在技术上避免了对底层协议的破坏,也没有阻断执法取证的所有途径(大额交易所的进出仍需KYC,链上记录依然永久留存)。监管机构目前的态度是在不取缔技术本身的前提下,加强对相关服务商和可疑行为的监管。对于商业银行运营者而言,这意味着应当了解CoinJoin交易的链上特征及合理用途:并非凡是CoinJoin输出即等同非法,必须结合上下文判断真实风险。同时,银行也需遵循监管指引,对来自明显混币路径的资金提高尽调级别,必要时提交可疑交易报告。但反过来说,在合规框架下,合理使用CoinJoin提升客户隐私并不直接违法。例如,一些合规的比特币托管机构会允许用户提币时自行使用CoinJoin,以保护客户交易历史不被外界窥探——前提是资金本身来源清白、去向明确记录。这样的做法体现了隐私与反洗钱并非绝对对立:通过适当的程序设计,可以在不违背法规的情况下给用户更多隐私保障。
4. Lightning Network 的中介态地位
*闪电网络(Lightning Network)*是比特币之上的第二层协议,它通过链下通道实现高速小额支付,被视为比特币在隐私和扩容上的一大创新。闪电网络的运作机制,是两方在链上创建一个支付通道(开设一笔特殊的多签交易作为锚定),然后在通道内部通过数字签名即时交换比特币所有权。这些频繁发生的链下交易并不记录在区块链上,只有当双方最终关闭通道时,链上才结算通道的最终余额状态。由于大部分交易被转移到链下,闪电网络具有先天的隐私中介性质:外界只能看到通道开启和关闭的两笔链上交易,而通道内部可能发生了上千笔支付却无从获知细节。这使得闪电网络的交易不可被区块浏览器直接追踪,从而大大减少了链上分析能够获取的信息cointelegraph.comcointelegraph.com。对于普通用户而言,这种“离链”处理提升了交易私密性和即时性;对于商业银行合规部门而言,闪电网络则带来了全新的挑战和机遇。
从合规角度看,闪电网络的位置有些类似于**“灰盒”:介于传统金融和完全公开区块链之间。一方面,闪电节点间的转账采用类似于Tor洋葱路由的加密跳转,每一跳节点只知道前一站和后一站,路径中继信息被隐藏,这为交易双方提供了接近匿名的路径隐私。另一方面,闪电通道的资金最终还是要通过链上比特币进出,这些开关通道的动作依然在公共账本上透明可见。因此,监管可以将注意力聚焦在出入口**:当资金从交易所等受监管机构流入闪电通道,或从闪电通道流回受监管机构时,对相关主体进行KYC和流向监控。这类似于对银行资金流出进入现金流通领域的监管思路——现金在社会中如何流转难以监控,但银行对大额取现和存现可以执行申报和审查。同理,闪电网络内部的细小支付难以逐笔监视,但大型入口/出口操作(如大量资金通过闪电通道转移)可以被标记关注。
闪电网络的挑战在于匿名性和跨境性。由于节点运行不需要许可,任何人在全球范围内都可架设闪电节点并参与路由,中间节点既看不见支付金额(只有通道余额变化)也不知交易来源和目的地。这种设计初衷是在技术上保护用户隐私和抗审查,但也意味着传统“旅伴规则”(Travel Rule)的信息传递机制难以直接应用于闪电支付。根据FATF的“VASPs旅行规则”,虚拟资产服务商之间转账需在金额阈值以上共享客户身份信息。然而闪电网络的交易路径通常不经过中心化服务商:大多是用户自行操作钱包直连,对等网络中路线随机。即便有部分交易通过托管型闪电服务(如托管钱包)发起,目前也缺乏成熟方案让节点在支付时附带KYC信息。因此,闪电网络被视为现行AML框架下的“监管空白地带”之一:合法的小额支付在其中获得极大便利,但不法分子也可能尝试利用其快速转移资金、不留痕迹的特性来层层拆分洗钱。
监管机构正逐步关注这一动向。一方面,他们强调同样的法规原则适用于闪电网络:凡是以营利为目的替他人传输资金者,无论通过链上或链下,都应履行反洗钱义务。比如,FinCEN在2023年提出的预防性规则中,将“虚拟货币混合作为特定受关注领域”,虽未明指闪电网络,但也释放出对任何有意提高匿名性的交易技术加强监管的信号cliffordchance.comcliffordchance.com。对于提供托管式闪电服务的机构,情况类似于交易所或托管钱包,需要注册MSB并执行KYC/AML流程。例如,一些提供闪电充值提现的公司在美国选择直接停止服务,以规避未能及时合规的风险——2023年11月,知名闪电钱包“Wallet of Satoshi”团队宣布将应用从美国区店下架,并停止为美国用户提供服务,称这是一个“艰难的决定”cointelegraph.com。虽然官方未明言原因,但业内推测此举与美国严格的合规环境有关:Wallet of Satoshi 属于全托管闪电钱包,依据美国法律应当取得货币传输牌照并遵循诸如Travel Rule等要求。在监管不确定性和合规成本高企的情况下,其选择退出美国市场,凸显了闪电业务在强监管司法管辖区所面临的压力。
另一方面,监管者也看到闪电网络的机遇:它有潜力降低链上交易拥堵、提升小额支付经济性,这对正规金融机构也是有利的创新。例如,银行可以利用闪电网络为客户提供秒级跨境小额汇款服务,在合法场景中比特币闪电通道可作为支付轨道,满足实时结算需求,同时因金额小、风险低可以适当简化手续。在香港等地,监管机构鼓励金融创新与风控并进。香港金管局在2023年修订的AML指引中提及,要采取风险为本方法看待新技术应用,并避免一刀切地拒绝虚拟资产相关业务,提倡审慎前瞻的态度来对待这类创新支付方式kwm.comkwm.com。英国FCA也提出**“不妨碍创新”的监管理念**,在确保核心AML要求落实的同时,为新支付技术留出试验空间。在这种氛围下,如果商业银行运营总监能够深入理解闪电网络的运行原理,就有机会将其优势用于合规的业务模式中。例如,银行可充当闪电通道的受信任节点,为客户提供经KYC的闪电支付渠道:银行对接入的客户身份尽职调查,并监控异常大额流动,而对客户小额高频交易则通过闪电网络实现即时低费率完成。这种模式下,银行相当于在闪电网络和传统体系之间架设合规桥梁,既不牺牲客户隐私(因为具体小额交易不公开),又满足反洗钱“看得见、管得了”的要求。
概言之,闪电网络作为中介态层,为比特币交易的隐私与效率提供了极大提升,但也要求金融机构调整传统AML手段:由链上监控转向节点端口监控。运营总监需要关注闪电通道的资金进出量、识别可疑的频繁开关通道行为,以及配合跨境情报分享以防范有人利用闪电网络在不同司法区之间快速转移赃款。在风险可控的前提下,闪电网络完全可以成为合规金融工具箱的一部分,而不是监管的对立面。
5. PayJoin(BIP-78)的机制与合规设计
PayJoin(又称P2EP,Pay to Endpoint)是一种由两方协作完成的特殊比特币交易结构,可视作CoinJoin的简化版和升级版。它由比特币改进提案BIP-78标准化,于2019年由开发者 Nicolas Dorier 提出bips.devbips.dev。PayJoin 的典型场景是付款人与收款人在一次支付过程中联手构造交易:收款人提供一个比特币收款地址和一个临时服务器端点,付款人发起交易时,不仅花费自己的UTXO,还从收款人处获取一个UTXO一同作为输入加入交易bitcoinops.org。换言之,交易的输入来自付款人和收款人双方,而输出则包括正常的付款金额给收款人(可能与常规付款金额不同,因为收款人也贡献了输入)以及付款人的找零。这种设计使链上观察者难以分辨哪些输入属于谁、哪个输出是真正的支付款,进而打破链上常用的“共同输入属于同一实体”推断bitcoinops.org。PayJoin 交易在区块链上看起来与普通交易无异:它不像传统CoinJoin那样有许多相等面额的输出,不具有明显的混币特征en.bitcoin.iten.bitcoin.it。因此,区块链分析公司难以再用简单启发式判断支付关系,从而极大增强了支付双方的隐私。
PayJoin 的技术流程可以概括如下:bips.dev首先,收款人在生成比特币收款二维码(BIP-21 URI)时,附带一个
pj=端点,表示自己支持PayJoin并提供了协商接口。付款人扫描发票后,钱包客户端先构造一笔常规交易(只含付款人的输入和相应输出),然后将该未签名交易通过HTTP发送到收款人的pj端点。收款人服务器收到后,在交易中加入自己预先选定的一枚UTXO作为额外输入,并相应地增大将付给自己的输出金额(因为收款人也贡献了一部分资金,需要“找零”返还),形成一个新的交易方案。收款人签署自己那部分输入后,将半签名交易返回给付款人。付款人验证交易未被篡改(如支付目标金额正确等),再签署自己部分的输入。最终,这笔包含双方输入的完整交易被广播到比特币网络并记入区块链bips.devbips.dev。举例来说,Alice 要向 Bob 支付1 BTC货款。传统做法是Alice用她的一枚≥1 BTC的UTXO付款,找零归还自己;Bob收到1 BTC。但在PayJoin中,假设Alice有一枚0.6 BTC和一枚0.5 BTC的UTXO,Bob手上有一枚0.4 BTC的UTXO未花费。那么Alice可先构造一笔用0.6+0.5两枚UTXO支付1 BTC的交易(找零0.1给自己)。Bob看到后,可以加入自己的0.4 BTC作为输入,并将支付给自己的输出从1 BTC增加到1.4 BTC,同时让Alice的找零相应减少为0.1-0.4=-0.3 BTC(负数意味着Alice其实付出了0.3 BTC + 原本的0.1找零共0.4 BTC给Bob,正好匹配Bob贡献的输入)。经过这种调整,最终交易输入包括Alice的0.6和0.5、Bob的0.4,总计1.5 BTC;输出包括Bob收到的1.4 BTC(其中Bob净得+1 BTC,含回自己的0.4)和Alice的找零0.1 BTC。链上观察者只看到Alice和Bob的若干输入共同支付了1.4 BTC给Bob的地址,以及0.1 BTC给Alice的找零地址。从表面上看,这可以被解释为Alice支付了1.4 BTC给Bob并收到0.1找零,也可以解释为Bob支付了一部分钱给自己(看似无意义)而Alice支付剩余部分给Bob,没有任何方法从区块数据确定真实的1 BTC支付额en.bitcoin.it。如此一来,支付本身的隐私性大幅提升,但交易合规性并未受损:Alice和Bob各自知道自己的出资与所得,交易双方的信息完整,可在需要时向监管说明实际资金流。只不过对于无知情权的第三方而言,这笔交易等同于谜题,大大降低了链上监控的可行性。
PayJoin 体现了比特币协议层治理的一种思路:通过开放标准增强隐私而不违反共识规则。作为BIP-78标准,PayJoin获得了社区认可并被多款钱包和支付处理工具采纳。例如,开源支付网关BTCPay Server自2020年以来支持商户端默认启用PayJoin收款bitcoinops.org;隐私钱包Wasabi和Samourai等也相继实现了对BIP-78的支持,让用户在日常支付中方便使用此功能bitcoinops.org。这些采用者本身都属于守法经营的实体(BTCPay服务的商户需遵守当地法规,Wasabi等钱包开发团队在合规压力下甚至实行过黑名单机制如前述),因此PayJoin的推广更多是为了保护良性用户的隐私,而非为洗钱提供新工具。相较于CoinJoin混合许多陌生资金,PayJoin每次仅涉及一名付款人和一名收款人,没有第三方参与资金池,故不存在“大规模匿名化”效果,只有针对该笔支付的信息隐藏。这使其很难被犯罪分子用于清洗巨额资金:因为两两配对支付的效率和匿名集规模都远不及混币池。而在合法场景下,PayJoin倒是十分实用——例如商户可以在不增加负担的情况下自动参与客户的支付交易,从而保护商户与客户双方的财务隐私不被区块链分析公司过度窥探。正如Bitcoin Optech对其评价的那样,PayJoin增强了支付双方以及整个比特币用户群的隐私bitcoinops.org,“通过让交易难以被拆解归属,有利于全网的隐私性”。
从合规设计上看,PayJoin 非常“克制”。首先,它不改变交易总额的去向:收款人仍收到应得的款项,只是多走了一步“先支付给自己再找零”的形式;付款人也仅花费了自己该付的钱(只是混杂在更大金额输出中)。因此,从资金流合法性来说,PayJoin 没有引入额外的模糊地带,每一笔输出都有明确的实际归属方。其次,PayJoin 不依赖任何中心化第三方来撮合,多在客户端与商户服务器间通过一次HTTP通讯完成。这意味着没有一个专门的“PayJoin服务提供商”需要承担MSB责任,整个流程更像是点对点协议的一部分。再次,由于收款人参与其中,通常收款人本身是提供商品或服务的商家,其身份在交易关系中是已知的。比如某客户通过PayJoin向商家付款,商家在自己后台记录中可以注明该笔订单已通过PayJoin支付,对应链上交易哈希等。如果日后监管调查,需要了解这笔混淆过的交易情况,商家完全能够提供证据证明谁是付款人、金额多少,只不过这些信息未写入区块链而已。这跟传统现金交易后的记录有异曲同工之处:账本上可能只显示商家收款入账,但商家收据上会注明付款人是谁。同样,PayJoin 实现了链上隐私但保留了链下记录的可能性。
当然,PayJoin 的兴起也让链上分析公司感到头疼:因为一旦这种交易普及,过去依据“共同输入推断同一所有者”的分析方法将失效en.bitcoin.it。这实际上提升了比特币整体的抗审查能力,却也令执法部门的链上自动监测工具需要升级。不过,从监管角度来看,PayJoin 并未妨碍司法调查:由于它没有像大型混币那样引入不特定多方,执法者可以通过传统调查手段(如向已知商家调取交易记录)来还原真相。可以说,PayJoin把隐私权和合规需求巧妙地划出了界限——公开账本不再暴露一切细节,但真正有合法权利需要知道的人(交易相对方、执法部门)依然有途径获取所需信息。这正是比特币“保守式创新”的精髓体现:在不破坏既有法律框架的前提下,通过协议改进最大程度保护用户正当隐私。
6. 对比“合用账户”与 PayJoin 的区别及法律可识别性
传统金融中,两个或以上主体共同使用资金,通常采用联名账户(Joint Account)的形式。例如,商业合作伙伴或夫妻可以开设联名银行账户,账户内资金由各持有人共同所有和支配。法律对这类账户的身份和权益归属有清晰界定:银行会对每位账户持有人进行尽职调查(KYC),账户资金的法定所有人就是账户登记的所有持有人。账户交易的责任也由持有人按合同分担。即使账户资金混合来源不一,法律上可以通过约定或推定原则划分各自的受益权益(例如按照存入金额或签署协议比例)birketts.co.ukbirketts.co.uk。重要的是,无论账户内资金如何流动,监管和执法都知道关联到该账户的自然人/法人是谁。因此,联名账户实现了多人合用资金的便利,但透明度依然存在于金融机构与监管视野内:多名持有人均是可识别、可问责的主体。
相比之下,PayJoin 在链上呈现出的“共同支付”情形并没有建立任何持久的联合账户或法律实体关系。一次PayJoin交易虽然包含了两方的输入,看起来是“两个人一起付了一笔钱”,但区块链并未记录这两个人各自的身份或份额。这就引出一个问题:法律上能识别PayJoin参与者吗? 链上数据本身无法直接识别,需要结合链下信息。比如在前述客户与商家通过PayJoin交易的例子中,区块链只显示一笔来自多个地址的交易。如果不借助商家提供的订单记录,外部第三方很可能误以为这些输入都属于同一人控制(传统heuristic的误判)en.bitcoin.it。因此,从纯链上证据看,PayJoin让法律主体识别变得困难:执法人员若仅依据区块数据,很难断定这笔交易涉及两个独立当事人。然而,并不意味着法律就无法识别—关键在于索取链下佐证。正如上节所述,每笔PayJoin交易的当事双方自己清楚出资和收款情况。如果其中一方如商家是受监管实体(有KYC义务),那其记录就能将链上地址对应回实名。即便双方皆为个人,在调查情况下,也可通过钱包日志、通信记录等证明彼此在对应时间协作构建了该交易。因此,从法律证明角度,PayJoin的参与者身份是可还原的,只是需要额外的信息链路,比常规转账要绕一点。
值得注意的是,英美法系对类似“共同出资支付”并非没有概念可循。在英国法下,若两人共同出资购买资产但无明文协议,法院可能探寻双方的共同意图和出资比例来确定各自权益(如适用衡平法上的推定信托原则)birketts.co.ukbirketts.co.uk。PayJoin交易本质上是双方共同“出资”完成了一次支付,因此在极端情况下(比如交易发生纠纷,双方就其中款项归属产生争议),法院或仲裁机构也可参考类似思路:审查双方对支付金额的约定,以及各自贡献和收益,从而确认真正的资金流向。不过,与联名账户不同的是,PayJoin不涉及长期共同持有资金,它只是一个瞬时的合伙支付行为。交易完成后,资金立即分别归属该去向的单一主体(收款人得到款项、付款人拿回找零)。不存在一个持续的“共同账户”载体来容纳双方资金。因此,法律上无需也无法对PayJoin建立类似联名账户的架构。每一方仍然只对各自收到或支出的部分负责,没有形成新的共同财产。
对于监管机构而言,联名账户容易监控——银行定期报告账户活动,所有相关个人信息齐全;而PayJoin交易如果不借助外部信息,单凭链上模式就难以分辨出来。这既是其隐私优势也是监管难点。但反过来看,PayJoin也没有引入无法克服的匿名性:它没有混杂无关联的第三方资金,交易双方实际彼此熟知,是一对一有联系的。这与完全匿名的暗网混币有本质区别。可以说,PayJoin更像两人私下结伴去银行各取一部分现金,然后合在一起交给第三人——银行账上只看到第三人存入一笔总额,但两人的个人取款银行各自有记录。因此如果第三人涉嫌违法受款,调查人员可以从银行调取那笔存款来源的拆分记录,发现实际上来自两人分别的账户。同理,PayJoin的合规思路是在需要的时候,将链上模糊的交易“解压”回两条清晰的资金线。这种设计确保了它在法律可解释性上比起传统CoinJoin混币更强:CoinJoin有时会出现N进N出,每个输出来源于N个输入的混合,法律上很难逐一对应归属,而PayJoin始终是一进一出(一方净支付,另一方净收款),只是混在一起过账。因此,一旦揭示两方身份,各自金额清楚明了,不存在无法区分谁的钱的问题。
具体到普通法体系的英美港三地,对于PayJoin交易目前尚无明文法规或判例直接评述。但可以推测,如果司法或监管机关发现有人采用PayJoin方式来掩饰交易关系,他们会采用实质重于形式的原则看待:关注交易背后的真实当事人和资金用途,而不会被表面上的“单笔交易”假象所困扰。例如,美国FinCEN和司法部在认定洗钱时,核心是看资金是否经过分层、混淆意图隐匿非法来源fatf-gafi.org。PayJoin如果被用于非法用途,那么执法也许需要对相关的钱包服务商、通信记录等进行取证才能还原过程。这增加了调查难度,但并非无法可依。在香港,新的VASP法规下,持牌机构需要对涉及的不寻常交易模式提高警觉。如果客户提现比特币后马上与别人做了一次PayJoin再存回,这种不寻常链路可能会引发问询,要求说明交易目的。英国FCA亦强调,加密资产交易所应监控客户是否使用了高度混淆技术并进行风险评估。在这些框架下,PayJoin如果被理解并检测到,可能会被归类为一种需要额外尽职调查的交易行为。但只要能够解释清楚其合法用途(例如商家为了客户隐私而采用PayJoin收款),法律并不禁止这种交易结构。
最后,从用户角度看,PayJoin其实更接近正常商业行为而非刻意洗钱安排。例如,两家公司合作支付一笔款项给供应商,传统方法可能是成立一个合资实体或开共同账户来出资再付款,而通过比特币PayJoin,两家公司可各自直接拿出一部分比特币,在一次交易中共同支付给供应商,无需建立长期联名账户关系。这种做法在法律上依然体现为各公司分别支付了各自的那部分货款,只是合并成一笔链上交易。因此法律能够识别并追踪每家公司支付的金额(通过公司内部记录),不存在损失审计线索的隐患。可以说,联名账户依赖金融机构去记录和划分共同资金,PayJoin则依赖参与各方自行记录默契合作。前者信息透明在机构,后者信息私密但参与人自知。因此,只要参与方守法经营并做好内部财务纪录,PayJoin并不会削弱法律对资金流的追查能力,它只是让公开账本不再直接泄露交易细节。这对遵纪守法者是利好,对企图躲避监管的大额洗钱者来说反而不是首选工具(因为两两串联洗钱的效率和隐蔽性远逊于大型混币池和离岸账户)。综合而言,在英美港法理下,PayJoin交易应被视为一种正当且可解释的隐私增强支付,通过适当的信息披露即可澄清其性质,并不构成无法识别的法律难题。
7. 应用设想:无需公司设立的合伙支付
展望未来,比特币协议提供的这些机制有望催生新的合规创新应用。例如,利用PayJoin或CoinJoin思想,可以实现“无需公司实体的合伙支付”。设想两个跨境贸易伙伴临时合作采购一批货物,各自承担一半货款。他们不必设立合资公司或开联名账户来筹措资金,而是可以各自准备好比特币,通过一次多输入交易直接将货款支付给供应商。链上只记录供应商收到总货款,至于资金来自两家伙伴公司这一事实则隐匿在交易结构中。这种操作相当于一种即时合伙:双方在支付瞬间形成合作,在支付完成后合作关系即告终结,无需持续的法律实体。这对于一次性项目或临时联盟尤其方便,节省了大量传统金融流程(开设账户、签署联名协议等)。同时,由于比特币交易天然跨境,这笔合伙支付可以绕开繁琐的国际汇款手续,在分钟级别完成结算。
当然,要使此应用合规落地,需要满足若干前提:首先,双方合作伙伴彼此必须信任并有清晰的合同约定,否则仅靠技术协作支付无法确保权益。例如,他们应签署一份协议注明各自出资比例和采购份额,以防日后纠纷。其次,在财务上,每一方仍应登记自己支付了多少款项给供应商,以便审计和税务申报。这一点通过比特币钱包记录和双方对账单据可以解决。再次,供应商若受到监管(如大宗贸易需要申报资金来源),则需在合同中注明货款由两家共同支付,比特币交易哈希作为支付凭证,辅以两家公司声明各自支付了多少。这样,监管方即使在链上看不出细节,也能通过合同资料了解实情。最后,参与各方应确保符合反洗钱要求:如交易金额巨大,需要提前告知银行/监管(因为法定货币转换为比特币的过程可能涉及银行),并确保合作伙伴和供应商都不是制裁或黑名单对象。
在上述框架内,这种无需公司载体的合伙支付完全可以合法合规地运作。它带来的创新性在于降低了商务协作的门槛和提高资金周转效率。例如,中小企业联盟可以临时抱团采购获得批发折扣,用联合支付的方式完成结算,然后各自获得自己的货物份额,无需成立繁杂的联营公司。又比如,多位国际投资人可通过CoinJoin把资金汇聚支付给一个项目发起人,以换取相应代币或股权份额,过程中保护了各自的隐私(外界只能看到项目方收到总款项)——前提是项目合法且投资人信息项目方已经KYC掌握。在香港等金融中心,这类合伙支付概念若能成熟,或许会出现在沙盒测试中:监管机构可以指定一些低风险场景,让持牌机构尝试使用比特币的PayJoin技术为客户提供多人支付服务,观察其运作和风险点。在英国,开放式银行业务的推进下,不排除未来有传统银行与比特币技术公司合作,开发出“Consortium Pay”产品,允许多个企业客户共同发起一个链上支付给供应商,银行在后台负责协调并确保AML合规。而美国作为最大的资本市场,也有可能在明确监管框架后,允许受监管的金融科技公司提供此类合伙支付解决方案,服务于例如私募基金多LP联合出资投资等场景。
需要强调的是,此类应用设想应避免过度理想化。在现实推进中,监管者会审慎评估风险,不会因技术便利而放松对洗钱等的警惕。因此,上述创新更可能一步步渐进实现:先在小额、低风险场景测试,再扩展到更广泛用途。同时,行业需要建立配套的透明机制(如自愿的交易附言备注或链下报告)以令监管安心。例如,几个公司通过合伙支付完成交易后,可以向监管机构备案相关交易哈希和各自出资比例,以取得信任豁免监控的待遇。这类似于今天银行报告大额交易,但具体用途保留商业机密。总之,比特币协议赋予了支付组织形式的灵活性,如何将其用于合规且创造价值的领域,将取决于监管开放态度和从业者的创造力。
8. 结语
综上所述,比特币通过协议机制实现隐私的探索,体现出鲜明的“保守派的创新”特征:它尊重金融领域反洗钱等制度的底线,在此范围内巧妙地寻求隐私与合规的平衡。从UTXO模型的选择,到后来发展的CoinJoin、闪电网络、PayJoin等技术,比特币生态并未一味追求匿名至上的乌托邦,而是尝试在现行法律框架内改善用户隐私体验。UTXO让比特币天然具备类似现金的去名属性,但公开链上记录又确保了交易透明度的基本盘,不至于成为无法监管的黑箱en.bitcoin.it。CoinJoin进一步为自愿的用户群提供了混合匿名环境,同时行业自律和执法打击并行,防止其成为洗钱温床cointelegraph.comfincen.gov。闪电网络则以链下通道降低了小额交易的可追踪性,却仍需通过进出节点受控来维护法规所需的监测点cointelegraph.com。PayJoin更是在日常支付场景中证明,提升隐私不一定以损害合规为代价——两方协作即可隐藏交易图谱,同时交易实质一目了然,无损任何一方的审计责任bitcoinops.orgen.bitcoin.it。这些创新无不遵循渐进改良的路径:它们没有推倒重来地另起一套隐匿系统,而是构建在比特币原有规则之上,通过开放社区的BIP提案机制取得共识,再由市场自发采用。这种稳健的演进保证了社会制度与技术创新的同步适应:当新隐私工具出现时,监管社区也在学习调整,从而在动态博弈中找到了新的平衡点。
对于香港、英国、美国等奉行普通法和重视金融监管的司法区而言,比特币的这一发展路径提供了宝贵的参考。一方面,各国监管者日益认识到,加密技术带来的金融创新并非洪水猛兽,其间蕴含着优化效率和用户权益的新机会。正如FATF提出的,要在鼓励负责任创新的同时管控风险siis.org.cn。比特币的隐私机制若被正确运用,能够保护公民金融隐私权、增强货币可替代性、减少不必要的集中过问,这是与民主法治社会价值相契合的目标。另一方面,实践也证明,通过强有力的监管措施,完全可以将不法分子的滥用遏制在可控范围。链上数据的公开性加上新的分析工具,使执法部门即便在出现混淆技术时,仍能抽丝剥茧地追查重大神秘案件time.com。据Chainalysis等机构统计,近年来加密货币交易中涉非法用途的比例已降至不足0.2%这样的历史低位cointelegraph.com。这表明隐私增强技术的出现并未导致洗钱犯罪失控,相反,隐私与合规正逐步实现良性共存:守法大众享有更安全的个人金融空间,犯罪分子依然难逃法网。商业银行运营总监作为合规体系的重要一环,应当拥抱这种变化,深入理解比特币协议层隐私机制的原理和合规要点。在确保自身机构严格遵守KYC/AML要求的前提下,也可以考虑利用比特币的这些特性开发新业务、服务客户需求。毕竟,隐私保护和反洗钱并非零和博弈——正如比特币生态所展示的,技术创新完全可以服务于保护个人合法权益与维护金融秩序这两大目标的平衡统一。比特币协议层面“保守而创新”的实践,正在为新金融时代如何兼顾自由与安全提供启发,其经验值得我们持续关注和借鉴。
参考资料:
-
Nervos, “UTXO 模型 vs. 账户模型” (2023)nervos.orgnervos.org
-
Bitcoin Optech, “Payjoin”bitcoinops.org
-
Bitcoin Wiki, “PayJoin”en.bitcoin.it
-
Bitcoin Wiki, “CoinJoin”en.bitcoin.iten.bitcoin.it
-
Cointelegraph, “No crypto for criminals: CoinJoin BTC mixing tool to block illicit transactions” (2022)cointelegraph.comcointelegraph.com
-
FinCEN, “第一起比特币混币服务违反反洗钱法遭处罚”新闻稿 (2020)fincen.govfincen.gov
-
Clifford Chance, “FinCEN拟将混币交易列为主要洗钱顾虑” (2023)cliffordchance.com
-
TIME, “如何追踪Bitfinex被盗比特币” (2022)time.com
-
Cointelegraph, “Wallet of Satoshi 美国区下架” (2023)cointelegraph.com
-
上海国研院, “美国区块链治理策略” (2023)siis.org.cn
-
FATF, “Virtual Assets Red Flag Indicators” (2020)fatf-gafi.org
-
Chainalysis, “2021年加密犯罪报告”cointelegraph.com
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
- Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
- Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento "no free lunch" aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-
 @ 7f6db517:a4931eda
2025-06-13 04:02:39
@ 7f6db517:a4931eda
2025-06-13 04:02:39
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Gerador de tabelas de todos contra todos
I don't remember exactly when I did this, but I think a friend wanted to do software that would give him money over the internet without having to work. He didn't know how to program. He mentioned this idea he had which was some kind of football championship manager solution, but I heard it like this: a website that generated a round-robin championship table for people to print.
It is actually not obvious to anyone how to do it, it requires an algorithm that people will not reach casually while thinking, and there was no website doing it in Portuguese at the time, so I made this and it worked and it had a couple hundred daily visitors, and it even generated money from Google Ads (not much)!
First it was a Python web app running on Heroku, then Heroku started charging or limiting the amount of free time I could have on their platform, so I migrated it to a static site that ran everything on the client. Since I didn't want to waste my Python code that actually generated the tables I used Brython to run Python on JavaScript, which was an interesting experience.
In hindsight I could have just taken one of the many
round-robinJavaScript libraries that exist on NPM, so eventually after a couple of more years I did that.I also removed Google Ads when Google decided it had so many requirements to send me the money it was impossible, and then the money started to vanished.
-
 @ 8bad92c3:ca714aa5
2025-06-13 03:02:24
@ 8bad92c3:ca714aa5
2025-06-13 03:02:24
The real estate market is showing cracks while Bitcoin continues its march toward becoming the global monetary standard. This week's conversation with Leon Wankum reveals how traditional assets are losing ground to the hardest money on earth. This was a high signal rip that deserves all the spotlight in today's newsletter.
Real Estate Prices Will Fall Through 2026 Before Finding New Equilibrium
Leon predicts we're entering a corrective phase in the 18-year property cycle that will see real estate prices decline until 2026. He bases this on the current mismatch between sellers who still expect peak 2021-2022 prices and buyers facing higher interest rates. "We need a price equilibrium. We need demand and supply prices to match. It's going to take a long time," Leon explained. He doesn't expect the Fed to lower rates significantly, keeping them above 3% for the foreseeable future, which will continue putting downward pressure on property values.
The key insight is that we're at year 15 of the typical 18-year property cycle, where prices naturally correct before finding a new floor. Leon suggests that by 2026, if interest rates are lowered, prices will stabilize at levels higher than the cycle's starting point but lower than current peaks. For those looking to buy, patience through this correction period could pay off.
Bitcoin Will Experience a 60% Drawdown This Cycle Despite Institutional Adoption
Despite massive institutional adoption through MicroStrategy and other corporate treasuries, Leon maintains that Bitcoin will still see a significant correction this cycle. "I do expect we'll have a 60% drawdown at the end of this bull cycle as well, just to wash out some leverage," he stated, pushing back against super cycle narratives. He points to the changing nature of volatility, noting that we're already seeing mini bull and bear markets in Bitcoin-adjacent assets like mining stocks, which peaked and corrected independently of Bitcoin's price action.
While acknowledging that players like Michael Saylor won't sell their holdings and that this could dampen volatility compared to previous cycles, Leon believes human nature and leverage will still create the conditions for a major correction. The silver lining is that these corrections build resilience in the Bitcoin ecosystem by washing out bad actors and overleveraged positions, ultimately strengthening the network for the next phase of growth.
1% of Real Estate and Bond Markets Will Flow to Bitcoin-Based Fixed Income Products
Leon sees MicroStrategy's new fixed income products (Strike, Strive, and Stride) as a gateway for traditional investors to gain Bitcoin exposure. These products offer 8-10% yields, significantly outperforming traditional bonds, while providing the cash flow that real estate investors seek. "If it's just 1% [of real estate investors], that's 3 trillion, that's enough," Leon calculated, noting that even a small percentage of the 2,856,707,549 BTC real estate market moving to Bitcoin-backed products would exceed Bitcoin's current market cap.
He shared examples of real estate professionals in Europe beginning to build Bitcoin treasuries, though cautiously. The key insight is that these fixed income products solve a major friction point for traditional investors who want cash flow but are beginning to recognize Bitcoin's superior appreciation. As more investors realize they can get both yield and potential upside through Bitcoin-backed securities, Leon expects this trickle to become a flood, fundamentally reshaping how capital allocators think about portfolio construction.
Blockspace conducts cutting-edge proprietary research for investors.
Bitcoin Could See 4,066,047 BTC Institutional Wave by 2026, Breaking Traditional Market Cycles
UTXO Management forecasts unprecedented institutional demand totaling 4,066,047 BTC by end-2026—equivalent to 20% of Bitcoin's circulating supply. This "wall of money" could fundamentally alter Bitcoin's four-year cycle pattern. Bitcoin ETFs shattered records with 344,709 BTC in year-one inflows, surpassing all commodity ETF launches. Following gold's trajectory, annual flows could reach 618,953 BTC by 2026 and exceed 952,236 BTC in 2027.
Five key drivers will fuel demand:
- Wealth platforms: 0.5% allocation across 571,341,510 BTC managed assets = 1,142,683 BTC
- Corporate treasuries: 1.18M BTC projected under new FASB accounting rules
- Nation-states: U.S. Strategic Reserve could trigger 5% gold-to-BTC rotation
- State governments: 5 of 13 pending U.S. state Bitcoin bills expected to pass
- ETF expansion: Wirehouse access accelerating adoption
Public companies already hold 803,143 BTC, with Japan's Metaplanet, GameStop, and Hong Kong's Moon adopting the "Bitcoin Standard" strategy. Meanwhile, Bitcoin yield products (BTCfi) are emerging—liquid staking surged to 55k BTC locked in one year. Unlike retail cycles, these institutional buyers are "structurally locked in," pursuing BTC-denominated yields rather than trading. With regulation accelerating globally, most allocators may be forced to chase exposure at significantly higher prices.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
STACK SATS hat: https://tftcmerch.io/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ eb0157af:77ab6c55
2025-06-13 02:02:31
@ eb0157af:77ab6c55
2025-06-13 02:02:31Bitcoin Core developers are planning changes to OP_RETURN data limits in version 30.
A group of Bitcoin Core developers has set October for the implementation of changes to the management of OP_RETURN outputs — a field that allows small amounts of arbitrary data to be inserted into Bitcoin transactions.
Currently, Bitcoin Core’s default mempool limits these outputs to 83 bytes. The upcoming modification will increase this limit to nearly 4MB per output. Some developers, including Antoine Poinsot and Peter Todd, argue for the need for greater flexibility in how the blockchain can be used.
The conservative stance
Resistance to these changes is being led by figures such as Luke Dashjr and BitcoinMechanic, who consider the expansion of the OP_RETURN limit a betrayal of Bitcoin’s fundamental principles. In their view, node operators should reject the storage of data unrelated to Bitcoin’s financial use case.
Conservatives argue that Bitcoin should not become a cloud storage service or a database for arbitrary data. The Bitcoin ledger, they maintain, should serve a narrow purpose: exclusively validating BTC movements for monetary use cases.
Version 30 release scheduled
The announcement of the October release date came via a post from Bitcoin Core developer Gloria Zhao, who confirmed the planned rollout for version 30.
While the default value will increase from 83 bytes to nearly 4MB, node operators will still be able to manually adjust the -datacarrier and -datacarriersize parameters. However, it’s widely acknowledged that most users stick with the default configuration.
Technical and philosophical implications
The controversy extends beyond purely technical matters, touching on fundamental questions about Bitcoin’s identity and future. Progressives see this evolution as necessary to keep Bitcoin competitive and versatile.
Conservatives, on the other hand, fear that allowing the storage of large amounts of arbitrary data could compromise network efficiency, increase node operation costs, and steer Bitcoin away from its original mission as a decentralized digital currency.
Community reactions
The debate has sparked tensions within the community. The technical editor of Bitcoin Magazine described conservatives as groups of people “clueless, and in some cases outright malicious and manipulative people on social media.”
On the other side, BitcoinMechanic called the progressives’ proposed changes completely “incoherent” with Bitcoin’s nature and objectives.
Jimmy Song also criticized the decision in a post on X, stating:
OP_RETURN outputs greater than 83 bytes will increase significantly, UTXO bloat will keep getting worse and there will be more garbage on chain.
This is going to age like a bad tattoo. pic.twitter.com/hUTpg8a5NM
— Jimmy Song (송재준) (@jimmysong) June 9, 2025
The post Bitcoin Core: OP_RETURN limit removal scheduled for October appeared first on Atlas21.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Money Supply Measurement
What if we measured money supply measured by probability of being spent -- or how near it is to the point in which it is spent? bonds could be money if they're treated as that by their owners, but they are likely to be not near the spendpoint as cash, other assets can also be considered money but they might be even farther.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-13 01:39:33
@ 5d4b6c8d:8a1c1ee3
2025-06-13 01:39:33I'm solo parenting for a couple of days, so I got lots of activity and not a lot of sleep. I stuck to my fasting window, but didn't stick to OMAD, and mostly ate healthy stuff.
How'd you do on your ~HealthAndFitness goals stackers?
https://stacker.news/items/1005114
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28How being "flexible" can bloat a protocol
(A somewhat absurd example, but you'll get the idea)
Iimagine some client decides to add support for a variant of nip05 that checks for values at /.well-known/nostr.yaml besides /.well-known/nostr.json. "Why not?", they think, "I like YAML more than JSON, this can't hurt anyone".
Then some user makes a nip05 file in YAML and it will work on that client, they will think their file is good since it works on that client. When the user sees that other clients are not recognizing their YAML file, they will complain to the other client developers: "Hey, your client is broken, it is not supporting my YAML file!".
The developer of the other client, astonished, replies: "Oh, I am sorry, I didn't know that was part of the nip05 spec!"
The user, thinking it is doing a good thing, replies: "I don't know, but it works on this other client here, see?"
Now the other client adds support. The cycle repeats now with more users making YAML files, more and more clients adding YAML support, for fear of providing a client that is incomplete or provides bad user experience.
The end result of this is that now nip05 extra-officially requires support for both JSON and YAML files. Every client must now check for /.well-known/nostr.yaml too besides just /.well-known/nostr.json, because a user's key could be in either of these. A lot of work was wasted for nothing. And now, going forward, any new clients will require the double of work than before to implement.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-13 00:47:36
@ 5d4b6c8d:8a1c1ee3
2025-06-13 00:47:36I know more of the talk is around the Bucks and Giannis, but the Knicks have actually made a huge move already, plus we have some Knicks fans in our midst.
Despite having their best season of the 21st century, the Knicks fired their highly respected coach for not making it to the NBA Finals (which no one expected them to do).
Is this just standard Knicks malpractice? If so, what further malpractice might they commit?
Or, is it part of a legit plan (as unlikely as that seems)? And, if so, what else is in that plan?
The obvious starting place is KAT. I thought KAT had a great season, but he definitely did some dumb KAT stuff in the playoffs. Will the Knicks trade KAT (and whatever else) to land either KD or Giannis? Should they?
If they trade for Giannis, does he play center? If not, they also need a stretch-5, because Giannis can't play next to a traditional big.
KD would be a little cleaner, plus the Suns need a center and supposedly Booker and KAT are buds. KD could slot in at the 4 and give them a starting 5 of - Robinson - KD - OG - Bridges - Brunson
With Hart coming off the bench, that's an awesome 6-man rotation. It's basically what they had, but with KD in place of KAT.
Is KD enough better than KAT for this to be a title team?
What else might be going on with the Knicks?
https://stacker.news/items/1005038
-
 @ 43820409:694a54a4
2025-06-13 00:43:54
@ 43820409:694a54a4
2025-06-13 00:43:54This is a brief summary.
This is the best article ever created.
You may be wondering why?
Why
Because we made it.
How
- It just is
- Everyone agrees
Thank you for your attention.
End.
-
 @ 3c389c8f:7a2eff7f
2025-06-13 00:23:35
@ 3c389c8f:7a2eff7f
2025-06-13 00:23:35Most of my time on Nostr, relays served content simply based on what was requested. Clients mostly requested follow list based content, and often only if the user requested to 'read' from a particular relay. Very simple, though not ideal. Clients that attempted to offer some 'global' or 'universal' feed made it possible to discover some new things but also served spam, redundant bot posts, and even some malicious things that managed to make it through a relay's filters. Paid relays began to gain some ground, with better filters to reduce spam and malicious content, which has helped a lot to clean up these broader feeds that expand beyond the follow-based timeline. Many of the relays hosted redundant content, too, which is important but it's not the only thing that is. The system still left a lot to be desired, particularly for anyone who has understood the potential behind the client-relay set up. Other concerns, like relay centralization through user concentration, still needed to be discussed and addressed.
Despite the voicing of relay diversity advocates, this system seemed to provide most of what people were looking for to replace their typical social media experience. Still, though, reply spam attacks found their way through, as they do. Web-of-Trust relays began to pop up to help mitigate the problem. Using contact lists and extended contact lists as a method of reducing the prevalence of spam has worked really well, but does have it limitations as to how new users can enter into these social graphs, without already knowing someone who is using Nostr. Also not ideal, but it has been a step forward for Nostr's social media use case. Hosted relay services that offered more diverse policy for a relay to operate under finally began to take some hold for those that wanted more choice and control. Still though, potential had barely been breeched.
It might have been before the WoT relay movement, but of nowhere (not really but it kind of seemed like it), a cat relay appeared within the ecosystem. This silly, fun, cute, clever relay collected notes with the #catstr hashtag and used some fancy image analysis stuff (that I can't explain) to collect notes and images of nothing but cats. Such a simple thing, but that was a catalyst (🥁) moment for Nostr. A relay could do more than just collect notes from following lists?? A couple more iterations of the curated content relay model came to be, driving home the idea that this wasn't some silly pie-in-the-sky concept. It was an aha moment for some, sheer joy for the relay advocates, and a turning point for expanding Nostr beyond the basic social media replacement. Very few client options for simply browsing one relay existed at the time, and while it was novel to see, the rest of the framework to support it was not strong nor very easy to use. Even with this dilemma, the catstr relay set off what has become some of the most interesting and useful innovation that has happened within the Nostr ecosystem since I arrived.
Since then, I have spent a lot of my time on Nostr exploring some of what has been developed on the relay front, experimenting where I have found the opportunity and thinking a lot about where this all could lead. Innovation on both the relay and client sides of Nostr have been expanding, not quite in lockstep, but closely enough that someone like myself can now easily jump onto a client like Jumble.social and get a glimpse into what is happening and get an idea of the potential of what is yet to come. For those working in the relay field, I am sure this feels like one slow moving train. For a client developer, it probably feels a little overwhelming to shift an entire model away from what has worked for something that will work better. As a less-than-technical user who is mostly disconnected from any major development, it's exciting. Relay diversity brings actual utility to Nostr. It also brings the assurances that Nostr offers, which whether we have been subjugated to these problems before or not, it is the main reason why Nostr exists and why we are here using it now.
For most anyone reading this, it probably sounds like some weird, unnecessary history lesson. This is actually one long introduction into a little mini-series of relay recaps though.... I was wondering what I would write about next, and this is it. I may just be a user but I'm an adventurous one and I pay attention, so I'm excited to share some of my thoughts, experiences, and observations over the coming weeks... because exciting isn't a strong enough word for the what I see as possible. :)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 3c389c8f:7a2eff7f
2025-06-13 00:13:50
@ 3c389c8f:7a2eff7f
2025-06-13 00:13:50Most of my time on Nostr, relays served content simply based on what was requested. Clients mostly requested follow list based content, and often only if the user requested to 'read' from a particular relay. Very simple, though not ideal. Clients that attempted to offer some 'global' or 'universal' feed made it possible to discover some new things but also served spam, redundant bot posts, and even some malicious things that managed to make it through a relay's filters. Paid relays began to gain some ground, with better filters to reduce spam and malicious content, which has helped a lot to clean up these broader feeds that expand beyond the follow-based timeline. Many of the relays hosted redundant content, too, which is important but it's not the only thing that is. The system still left a lot to be desired, particularly for anyone who has understood the potential behind the client-relay set up. Other concerns, like relay centralization through user concentration, still needed to be discussed and addressed.
Despite the voicing of relay diversity advocates, this system seemed to provide most of what people were looking for to replace their typical social media experience. Still, though, reply spam attacks found their way through, as they do. Web-of-Trust relays began to pop up to help mitigate the problem. Using contact lists and extended contact lists as a method of reducing the prevalence of spam has worked really well, but does have it limitations as to how new users can enter into these social graphs, without already knowing someone who is using Nostr. Also not ideal, but it has been a step forward for Nostr's social media use case. Hosted relay services that offered more diverse policy for a relay to operate under finally began to take some hold for those that wanted more choice and control. Still though, potential had barely been breeched.
It might have been before the WoT relay movement, but of nowhere (not really but it kind of seemed like it), a cat relay appeared within the ecosystem. This silly, fun, cute, clever relay collected notes with the #catstr hashtag and used some fancy image analysis stuff (that I can't explain) to collect notes and images of nothing but cats. Such a simple thing, but that was a catalyst (🥁) moment for Nostr. A relay could do more than just collect notes from following lists?? A couple more iterations of the curated content relay model came to be, driving home the idea that this wasn't some silly pie-in-the-sky concept. It was an aha moment for some, sheer joy for the relay advocates, and a turning point for expanding Nostr beyond the basic social media replacement. Very few client options for simply browsing one relay existed at the time, and while it was novel to see, the rest of the framework to support it was not strong nor very easy to use. Even with this dilemma, the catstr relay set off what has become some of the most interesting and useful innovation that has happened within the Nostr ecosystem since I arrived.
Since then, I have spent a lot of my time on Nostr exploring some of what has been developed on the relay front, experimenting where I have found the opportunity and thinking a lot about where this all could lead. Innovation on both the relay and client sides of Nostr have been expanding, not quite in lockstep, but closely enough that someone like myself can now easily jump onto a client like Jumble.social and get a glimpse into what is happening and get an idea of the potential of what is yet to come. For those working in the relay field, I am sure this feels like one slow moving train. For a client developer, it probably feels a little overwhelming to shift an entire model away from what has worked for something that will work better. As a less-than-technical user who is mostly disconnected from any major development, it's exciting. Relay diversity brings actual utility to Nostr. It also brings the assurances that Nostr offers, which whether we have been subjugated to these problems before or not, it is the main reason why Nostr exists and why we are here using it now.
For most anyone reading this, it probably sounds like some weird, unnecessary history lesson. This is actually one long introduction into a little mini-series of relay recaps though.... I was wondering what I would write about next, and this is it. I may just be a user but I'm an adventurous one and I pay attention, so I'm excited to share some of my thoughts, experiences, and observations over the coming weeks... because exciting isn't a strong enough word for the what I see as possible. :)
-
 @ eb0157af:77ab6c55
2025-06-13 00:02:31
@ eb0157af:77ab6c55
2025-06-13 00:02:31CEO Paolo Ardoino unveils the open-source strategy for the operating system, aiming to make mining accessible to small and medium-sized businesses.
Tether has announced it will make its Bitcoin Mining Operating System (MOS) available for free, enabling operators of all sizes to manage mining infrastructures without relying on third-party software. The announcement came directly from CEO Paolo Ardoino.
How the Bitcoin Mining Operating System works
The operating system developed by Tether offers an efficient solution for managing mining operations. The MOS integrates all essential components of a mining site into a serverless peer-to-peer network, ensuring smooth communication between devices.
The platform supports architectures ranging from minimal setups on Raspberry Pi to industrial-scale facilities managing hundreds of thousands of miners.
According to Ardoino, the decision to make the Bitcoin Mining Operating System open-source aims to level the playing field between small and large operators. Tether’s CEO stated on X:
“A horde of new Bitcoin mining companies will be able to enter the game and compete to keep the network safe.”
Future developments
Tether’s team is currently working on documentation, user guides, and preparing repositories for community access. The Bitcoin Mining Operating System release is scheduled for Q4 2025.
Future plans include integrating artificial intelligence tools to enhance production analysis and performance monitoring using data generated by the operating system.
Tether’s expansion strategy
In recent years, Tether has diversified beyond stablecoins, expanding into sectors such as artificial intelligence, Bitcoin mining, and education. By mid-2025, the company had invested approximately $2 billion in Bitcoin mining and energy-related activities.
During his speeches at Bitcoin Conference 2025 in Las Vegas, Ardoino revealed the company’s ambitions:
“I think that it’s very realistic that by the end of the year, Tether will be the biggest Bitcoin miner in the world, even including all the public companies.”
The post Tether to release Its Bitcoin Mining Operating System for free appeared first on Atlas21.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Personagens de jogos e símbolos
A sensação de "ser" um personagem em um jogo ou uma brincadeira talvez seja o mais próximo que eu tenha conseguido chegar do entendimento de um símbolo religioso.
A hóstia consagrada é, segundo a religião, o corpo de Cristo, mas nossa mente moderna só consegue concebê-la como sendo uma representação do corpo de Cristo. Da mesma forma outras culturas e outras religiões têm símbolos parecidos, inclusive nos quais o próprio participante do ritual faz o papel de um deus ou de qualquer coisa parecida.
"Faz o papel" é de novo a interpretação da mente moderna. O sujeito ali é a coisa, mas ele ao mesmo tempo que é também sabe que não é, que continua sendo ele mesmo.
Nos jogos de videogame e brincadeiras infantis em que se encarna um personagem o jogador é o personagem. não se diz, entre os jogadores, que alguém está "encenando", mas que ele é e pronto. nem há outra denominação ou outro verbo. No máximo "encarnando", mas já aí já é vocabulário jornalístico feito para facilitar a compreensão de quem está de fora do jogo.
-
 @ d57360cb:4fe7d935
2025-06-12 23:56:20
@ d57360cb:4fe7d935
2025-06-12 23:56:20Often we engage in endeavors to achieve something. What is it we want to achieve? People usually want status, money, freedom, sex and better stuff. What lies behind the chase of all these things is pleasure. We’re addicted to it. We’re living in a world of pleasure junkies. The problem is pleasure doesn’t last.
We end up needing more and more of it. In this world we run as far away from discomfort as possible. We turn everything into a vehicle to satisfy this urge. When it doesn’t we leave one thing behind for another. Losing the very essence of the activities we engage in.
We think these things will bring us lasting pleasure and satisfaction, but we’re never there to experience them in the first place. A mind that no longer see’s activity, people, and pursuits as a means to pleasure is a free mind. One that doesn’t grasp at how much they’re improving or what they can gain has a pure experience of the actions it engages in.
It’s only this mind that can taste what you thought you wanted from chasing pleasure.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28WelcomeBot
The first bot ever created for Trello.
It invited to a public board automatically anyone who commented on a card he was added to.
-
 @ fa5ea00f:1075fbfe
2025-06-12 23:37:32
@ fa5ea00f:1075fbfe
2025-06-12 23:37:32
“Don’t trust, verify”
하루에도 몇번씩 이 문장은 나를 괴롭힌다.
코드를 뜯어보는 데서 출발해, 현대 사회를 주도하는 문화의 의미를 해체하고 살펴보는 것으로 확장할 수 있다고 생각한다. 이것이 이 아티클의 기본 전제다. 비트코이너들은 포스트모더니즘처럼 무작정 해체(deconstruct)하는 것이 아니라, 합리적 회의주의로 접근한다. 그것은 crypto-anarchism과 libertarian futurism의 기반이 됐고, 이제는 비트코인의 핵심 정신으로 자리 잡고 있다. 나도 조금씩 공부하고 있지만, 왜 anarcho-capitalism이 비트코이너들에게 매력적인지 쉽게 알 수 있다. 비트코인은 돈과 정치를 재정의하고 있으며, 가치를 창출하는 개인의 정체성과 행동마저도 다시 정의하고 있기에, 국가의 해체까지 이어지는 것은 어찌 보면 필연적으로 보인다.
그런데 나는 아직도 이해가 안되는 부분이 있다. 바로 종교와 비트코인의 관계다. 평화, 사랑, 정의, 희망 같은 종교의 사상과 비트코인을 연결하려는 시도는 빈번하다. 그만큼 이 기술은 인간에게 단순한 도구를 넘어선 철학적, 존재론적 충격으로 다가온다. 그러나 내가 정말 이해하지 못하는 부분은 스스로를 “don’t trust, verify”의 철학에 따라 사는 사람이라 자부하면서도, 종교만큼은 끝내 검증해보려 하지 않는 태도다. 종교는 믿음의 영역이라지만 검증하려는 시도조차 하지 않는 태도는 비트코이너의 정신과 상당한 괴리가 있다고 생각한다.
나는 종교를 해체해 보고도 똑같은 믿음을 유지하는 사람을 본 적이 없다. 복음주의 개신교에 깊이 몸담았던 입장에서 보면, 예컨대 모세오경과 복음서가 실제 사건들을 단순히 기록한 것이 아니라 여러 저자들과 편집자들의 해석과 목적이 얽힌 서사적 구성물이라는 사실조차 받아들이기 어려워한다. 실제 역사와 문학적으로 파고들어야 할 부분인데 대부분은 자신이 배운 교리를 전제로 성경을 해석하려고 한다. 가장 성스럽게 여기는 성서가 왜 '하나님의 말씀'인지 물으면 “성서에 그렇게 쓰여 있다”거나 “믿음의 영역이다”라고만 답한다. 그 구절이 현대의 성경책을 지칭하는 것도 아닌데 말이다.
이런 식으로 파도 파도 끝없는 의문점들을 맹목적 믿음으로 덮어버리려는 것이 현대 복음주의 개신교다. 아직도 그런 사고방식을 지닌 비트코이너가 있다면, 종교—특히 제도화된 종교—에 대해서 불신의 씨앗을 품어 봤으면 좋겠다. 타락에서 구속과 영생으로 이어지는 서사를 통해 성경을 읽는다면 너무 많은걸 놓치게 된다는걸 깨달을 수 있다.

결코 쉬운 길이 아니다. 나 역시 태어나기 전부터 교회를 다녔을 만큼, 기독교는 내 존재의 근원이자 정체성의 전부였다. 종교를 해체하는건 나 자신을 해체하는 일이었다. “감히 신을 해체해? 저런 인간주의적인 죄를 품은 사상을 봤나!” 이런 시선들이 제도 내부에서는 해체를 현실적으로, 도덕적으로 불가능하게 만든다. 그것은 나의 공동체—많은 경우 가족까지—에게서 낙인찍히고 소외되는 일을 의미한다. 국가주의와 비교해 보자면, 종교를 떠나는 것은 마치 애국보수 집안에서 “나는 중국 공산당을 지지한다”고 말하는 것보다 더 어렵다고 생각한다. 적어도 애국보수 집안은 당신이 공산당을 지지한다고 해서 죽은 뒤 영원히 지옥에 고통받을 거라 믿지는 않는다. 사회적 자살을 쉽게 생각하는 사람은 없다.
나는 비트코인을 알기 전에 이미 종교를 떠났고, 가족과도 멀어졌다. 연락을 끊거나 만나지 않는 건 아니지만, 정서적으로 예전과 같은 관계가 아니다. 목사님인 아버지는 나에게 호통을 치며 크게 싸웠고, 어머니는 믿기지 않다는 듯 실망을 감추지 않으셨다. 10년도 지난 일이지만 내 인생에서 가장 고통스러운 전환점이었다. 나이도 어렸고 나도 내가 무슨 일을 겪고 있었는지 몰랐기 때문에 더더욱 힘들었다.
모두가 나와 같은 길을 걸어야 하는건 아니다. 기독교의 거대 서사가 정서의 깊은 곳에 뿌리 박힌 이상, 신을 부정하는 일은 거의 불가능에 가깝다는걸 몸소 체감했기 때문이다. 자유는 기독교에서도 중요한 의미를 가진다—율법에서의 자유, 죄에서의 자유, 결국 하나님 안에서의 자유. 모순처럼 보일 수도 있겠지만, 합리적 회의주의인 나는 역설적으로 여전히 신이라는 존재를 믿는다. 다만, 신은 특정 종교에 국한되어 있지 않으며 우리의 지성으로는 결코 완전히 이해할 수 없는 존재라고 믿는다. 그렇기에 기독교의 하나님 안에서의 자유보다, 더 큰 의미에서의 ‘신 안에서의 자유’ 혹은 '자유 안에서의 자유'가 존재한다고 믿는다.
인간의 자유와 사랑에 대한 이해를 아득히 초월하는 존재, 그 앞에 겸손해질 때 나는 자유를 조금이나마 맛볼 수 있었다. 이 패러독스 속에서 나는 매일 자유를 느끼고 있다. 국가주의와 종교는 누군가가 믿으라고 외치고 교리를 정립해야 유지되지만, 자유와 사랑은 인간의 원초적인 갈망이다. ‘무엇으로부터의 자유’가 아니라 자유 그 자체에의 의지다. 장폴 사르트르의 말처럼 "자유라는 유죄 선고를 받은 존재", 그것이 우리 인간이다. 비트코인은 자유의 한 조각의 불과하고 진짜 자유는 우리 머릿속에서 시작된다. 이 내면의 자유를 널리 일깨우는 것, 그것이야말로 비트코이너들의 숙명이지 않을까?
나는 비트코이너들이 자신의 자유를 더 이상 인간이 만든 사상 체제나 제도에 위탁(custody)하지 않길 바란다. 그러나 동시에, 종교를 떠나는 일이 얼마나 고통스러운지도 알기에 내가 그들에게 뭐라고 말할 입장은 아니라는 것도 안다. 그래서 내가 현실적으로 할 수 있는 말은 오직 하나뿐이다:
"Don’t just trust, keep on verifying."
-
 @ ecd302a3:557f92cf
2025-06-12 23:10:54
@ ecd302a3:557f92cf
2025-06-12 23:10:54- AddictoLogs - Activity tracker for your bad habits
- Barlog - Load your barbell by sliding to a target weight
- BetterCounter - A simple, multi-purpose counter app
- Blood Pressure Monitor - Save and analyze blood pressure values
- Calorimeter - Track your calories!
- Daily Diary - A diary that starts with a blank page every day
- Dog Sports Diary - A diary to keep track of your traings in dog sports.
- ExHale - Track the time since you last smoked and see the progress you've made.
- FastTrack - Track what your body is doing while fasting
- Fitness Calendar - A private and fully offline activity tracker.
- Fivethreeone Log - Track your workouts and progress with the 5/3/1 method.
- Flexify - Track gym progress, visualize graphs, enjoy offline support & timers
- Food You - Track your calories and create a food Diary
- Fortuna - A free and open-source application based on the philosophy of Evaluative Hedonism.
- FW-Wettkampf Funk-Trainer - Here you can train radio messages for the hessian Feuerwehr-Leistungsübung!
- Glucodatahandler - receives Glucodata broadcast from Juggluco app
- Grocy: Self-hosted Grocery Management - ERP beyond your fridge, now on your phone – An awesome companion app for grocy
- Habit-Maker - A reward-based habit tracker for android.
- Habitica - habit building app which treats your life like a Role Playing Game
- Hate It Or Rate It - Track and decide: Love it or leave it with every purchase.
- Healthlog - log health tests, incl. Cholesterol/Sugar/BP/RFT
- Home Medkit - Application with medicines storing and intakes reminders
- Igatha - SOS Signaling & Recovery
- J-K Bike - App that helps build positive bike maintenance behaviours, for rides quick, big
- KitchenOwl - KitchenOwl helps you organize your grocery life.
- Loop Habit Tracker - Track your habits and long-term goals
- LunaTracker - LunaTracker is a newborn baby tracking app.
- MediNote - tracking blood pressure measurements offline
- MedTimer - Med reminders and history with full offline privacy
- Migraine Log - A simple headache diary that respects your privacy
- Mindful - Control your digital habits, improve focus, and boost productivity
- MotionEaseTune - A simple application that can prevent you from motion sickness via 100Hz sound.
- Nextcloud Cookbook - View all your recipes stored in your Nextcloud instance.
- Nov Open Reader - Simple application to read content of Novopen insulin pens using NFC
- OpenFoodFacts - Look up food ingredients, allergens, nutrition facts
- OpenHIIT - OpenHIIT - Open Source Workout Interval Timer
- OpenTracks - A sport tracker buddy that respects your privacy.
- OSM Dashboard for OpenTracks - OpenStreetMap dashboard for OpenTracks
- OSM Dashboard Offline for OpenTracks - Offline variant of the OpenStreetMap dashboard for OpenTracks
- Pedometer (PFA) - (SECUSO) Counts your steps in the background. Customize daily goals.
- Perceived Stress Scale - Are you stressed? Take the test to find out how stressed you are.
- Petals - Take control of your weed consumption
- Plees Tracker - Plees Tracker is a simple sleep tracker for your Android phone.
- Polar Alert - High / low heart rate sound alert
- Portio - Optimize batch cooking! Weigh meals and split portions based on each participant
- Simple Calorie Tracker - Simple calorie tracker mobile app written in React Native
- Simple Gym Logger - React Native app that let you track your progress in the gym
- Simple. : Fitness Simplified. - An easy to use fitness app that lets you create, schedule and track your workout
- Soothing Noise Player - Play soothing sound effects to help you relax and drown out background noise.
- Stepsy: Step Counter - Your lightweight step counting buddy
- Sunrise Signal - Morning wood tracker app for men's health
- Table Habit - Boost your own habit growth with charts.
- trale - trale – a beautiful body weight diary app respecting your privacy
- Track & Graph - Track personal data and create custom graphs to gain personal insight!
- Urn - A mobile, offline urn for majority judgment polls
- Waistline - Libre calorie counter and weight tracker
- Wger Workout Manager - Fitness/workout, nutrition and weight tracker
-
 @ ecd302a3:557f92cf
2025-06-12 23:08:20
@ ecd302a3:557f92cf
2025-06-12 23:08:20- 2FAS - Protect your online accounts with an extra layer of security.
- Advanced PassGen - Generate passwords with ease.
- Aegis Authenticator - Free, secure and open source 2FA app to manage tokens for your online services
- Amarok - Hide your private Files and APPs with a single click.
- ANOTHERpass - Another way to manage passwords
- AppVerifier - Verify apps easily.
- AstraCrypt - Hide and encrypt your files with modern security standards.
- Authenticator Pro - Free and open-source 2FA app with encrypted backups
- Bitwarden - The most trusted password manager
- Briar - Decentralized peer-to-peer secure messaging connecting via Bluetooth, Wi-Fi or Tor.
- ByeByeDPI - An Android app that runs ByeDPI locally and redirects all TCP traffic through it.
- Calyx VPN - Free VPN Service offered by The Calyx Institute
- CleanSlate - Protect your data anywhere anytime
- CloudOTP - two-factor authenticator based on Flutter
- Dumpsys Packages Copycat - Provides a detailed summary of all installed packages
- Encrypt-Decrypt-AndroidAPK - Encrypt / Decrypt APK , with AES 256 GCM/DES
- Ente Auth - ente is an end-to-end encrypted authenticator app
- GPS Setter - A GPS setter based on the Xposed framework.
- Hypatia - A real-time malware scanner
- i2pd - Full-featured C++ implementation of I2P client
- Igatha - SOS Signaling & Recovery
- InviZible Pro - increase your security, protect your privacy
- Inter Profile Sharing - Easily share media and text between Android user profiles
- Keepass2Android Offline - Offline Password Manager
- LANShield - Protect your LAN by managing app access to your local network.
- Mullvad VPN - Protect your online privacy with a fast, trustworthy, and easy-to-use VPN.
- MyPassPlus - Secure password manager for Android that helps you store and organize your passwords.
- NetGuard - A simple way to block access to the internet per application
- NowiPass - A password manager where you are the only one who has access to your passwords
- NymVPN - Download our VPN and make your online activity 100% private. Fast and anonymous.
- OneKeePass - A simple and secure offline password manager
- Open Alert Viewer - Fetch and display server alerts
- Paranoid's Pal - Privacy Lock - Protecting Your Digital Identity
- Password Generator - Free, ad-free, open-source simple password generator for Android.
- Password Store - Manage your passwords
- PasswdSafe - Port of PasswordSafe password manager
- PCAPdroid - No-root network monitor and traffic dump tool for Android devices
- Photok - Encrypt your photos on your device and keep them safe from others.
- PINcredible - Secure PIN vault - Modern and secure Android app to help you remember any PIN
- Proton Pass: Password Manager - Password manager created by the scientists with end-to-end encryption.
- Quad9 Connect - Android application for Quad9 recursive DNS cybersecurity and privacy services
- Riseup VPN - Secure VPN powered by Bitmask
- Safe Space - A safe space for your digital valuables.
- Sentinel Lens - Facial recognition surveillance with alerts
- Snap Safe - The camera that doesn’t rat you out.
- SshKeyMan - Generate/Manage your ssh keys on Android devices
- Standard Notes - An end-to-end encrypted note-taking app for digitalists and professionals
- Stay Put - Unplug Alert - prevent casual theft of your device while charging in public spaces
- Stratum - Open-source 2FA app with encrypted backups
- ToS;DR - Short summaries on Terms of Conditions
- TrackerControl - monitor and control hidden data collection in mobile apps
- URnetwork - Goodbye VPN!
- Vernet - Network Analyzer - Host and Port scanner. Ping IP or domain.
- WG Tunnel - An alternative VPN client app for WireGuard with additional features
- Windscribe - Free VPN that unblocks geo-restricted content and eliminates tracking.
- Xray - Xray GUI Client For Android
- Yivi - Your digital identity in one app.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Sol e Terra
A Terra não gira em torno do Sol. Tudo depende do ponto de referência e não existe um ponto de referência absoluto. Só é melhor dizer que a Terra gira em torno do Sol porque há outros planetas fazendo movimentos análogos e aí fica mais fácil para todo mundo entender os movimentos tomando o Sol como ponto de referência.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A list of things artificial intelligence is not doing
If AI is so good why can't it:
- write good glue code that wraps a documented HTTP API?
- make good translations using available books and respective published translations?
- extract meaningful and relevant numbers from news articles?
- write mathematical models that fit perfectly to available data better than any human?
- play videogames without cheating (i.e. simulating human vision, attention and click speed)?
- turn pure HTML pages into pretty designs by generating CSS
- predict the weather
- calculate building foundations
- determine stock values of companies from publicly available numbers
- smartly and automatically test software to uncover bugs before releases
- predict sports matches from the ball and the players' movement on the screen
- continuously improve niche/local search indexes based on user input and and reaction to results
- control traffic lights
- predict sports matches from news articles, and teams and players' history
This was posted first on Twitter.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Rede Relâmpago
Ao se referir à Lightning Network do O que é Bitcoin?, nós, brasileiros e portugueses, devemos usar o termo "Relâmpago" ou "Rede Relâmpago". "Relâmpago" é uma palavra bonita e apropriada, e fácil de pronunciar por todos os nossos compatriotas. Chega de anglicismos desnecessários.
Exemplo de uma conversa hipotética no Brasil usando esta nomenclatura:
– Posso pagar com Relâmpago? – Opa, claro! Vou gerar um boleto aqui pra você.Repare que é bem mais natural e fácil do que a outra alternativa:
– Posso pagar com láitenim? – Leite ninho? -
 @ ecd302a3:557f92cf
2025-06-12 23:05:59
@ ecd302a3:557f92cf
2025-06-12 23:05:59- AlgoSorts - understand how sorting algorithms work using the example of animations
- AnkiDroid - A flashcard-based study aid
- ArityCalc - Scientific calculator for Android 5+
- BabyName - Findout your future baby name
- Better Stundenplan - A (hopefully) not-so-bad client for virtueller-stundenplan.org
- Bibleside - Offline Bible app featuring the OET (Open English Translation)
- Bluetooth LE Spam - Impersonate Bluetooth Low Energy devices, causing pop-ups on receiving devices.
- Calculator You - Calculator You is a beautiful calculator for solving simple tasks.
- Celestia - Real-time 3D visualization of space
- CEToolbox - Medical tool
- Cifras o letras - A simplified version of Countdown UK game-show.
- Clay Tablet - Clay Tablet is a simple and intuitive Android app for cuneiform practice.
- Converter NOW: Unit Converter - A simple, immediate and fast unit converter!
- CTU Menza - Dish menus from CTU cafeterias, offers a modern UI and functionality.
- DeepL - Unofficial Android App for DeepL Translator
- Diatronome - A tuner, a visual metronome and a synthesizer
- DigiAgriApp - DigiAgriApp is a software aimed at farmers and anyone with cultivated land
- Distribution Calculator - Easily operate with uncertainty
- Drinkable - Explore and create cocktails with ingredients from home
- FastTrack - Track what your body is doing while fasting
- Fossify Calculator - Simple and open-source calculator for quick and easy calculations
- FW-Wettkampf Funk-Trainer - Here you can train radio messages for the hessian Feuerwehr-Leistungsübung!
- GCompris - Multi-Activity Educational game for children 2 to 10
- Golden Ratio - Simple calculator for aesthetic Golden ratio proportions
- GPTAssist - WebView wrapper for ChatGPT
- GPTMobile - Your all in one chat assistant - Chat with multiple LLMs at once!
- Graded - Grade tracker - Track and manage your school grades with ease
- Java OOP Quiz - Tests Your knowledge of Java Object-Oriented Programming.
- JMdict droid - A Japanese to English dictionary, based on JMdict.
- Journal - Keep track of substance usage to gain insights on consumption patterns
- JRBP Survey - Jasper Ridge ant survey navigation and data entry
- Kanji Dojo - Learn & practice writing Japanese characters
- Kepler-App - App only in German! - App for the JKG Chemnitz with all important info
- lanis - display the substitution plan of a school in the Lanis system
- Let's Bend - Let's Bend assists blues harmonica players in accurately hitting bending notes.
- Linux Command Library - 5055 manual pages, 22 basic categories and a bunch of general terminal tips.
- LMd - Le Monde diplomatique DE - reader for the german version of "Le Monde diplomatique".
- Logseq - platform for knowledge management and collaboration and note taking
- Mnemosyne - A memorization app designed for lists as opposed to traditional flashcards
- NXT Remote Control - Control Lego robots
- OpenJisho - Japanese dictionary offline
- Petals - Take control of your weed consumption
- Pocket ReadLex - Shavian spelling dictionary
- Praktika Vortaro - Offline Esperanto dictionary
- Qalculate! - Powerful and versatile multi-purpose calculator
- RidgeScout - A fully featured FRC scouting & data analytics tool
- Rosarium - Animated rosary app with a focus on UX supporting latin, english and german
- Seamless - Offline speech to text translator
- Solon - A light-weight Android frontend to SkolaOnLine
- T CrB Detector - T CrB Detector notifies the user when the star T CrB has exploded.
- TourCount - A butterfly monitoring app for species-specific registering of butterflies in Eu
- TransektCount - A butterfly monitoring app for transect counters.
- Traintime PDA - Another personal data assistant for XDU undergraduate.
- Translate You - * Translator built with Material Design 3 (You) supporting multiple engines*
- Tuner - App for tuning musical instruments.
- Urn - A mobile, offline urn for majority judgment polls
- WaDoku - Japanese-German online dictionary
- whoBIRD - Recognize birds by their sounds, anywhere in the world!
- Wispar - Stay up-to-date with article in your field of study!
- wX - Weather app geared towards storm chasers, meteorologists and weather enthusiasts
- yetCalc - Progressive calculator, converter and much more.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: Custom multi-use database app
Since 2015 I have this idea of making one app that could be repurposed into a full-fledged app for all kinds of uses, like powering small businesses accounts and so on. Hackable and open as an Excel file, but more efficient, without the hassle of making tables and also using ids and indexes under the hood so different kinds of things can be related together in various ways.
It is not a concrete thing, just a generic idea that has taken multiple forms along the years and may take others in the future. I've made quite a few attempts at implementing it, but never finished any.
I used to refer to it as a "multidimensional spreadsheet".
Can also be related to DabbleDB.
-
 @ dfa02707:41ca50e3
2025-06-13 06:01:54
@ dfa02707:41ca50e3
2025-06-13 06:01:54
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ ecd302a3:557f92cf
2025-06-12 23:03:25
@ ecd302a3:557f92cf
2025-06-12 23:03:25- Dharmik - Multiplatform app to browse the vedas
- Dharmik Online - Browse Bhagavad Gita
- Five Prayers - Set of muslim tools (Prayers, Qibla, Quran, Adhan)
- Muezzin - simple app to track Islamic prayer times get reminders for them easily
- OpenBible - OpenBible provides the bible as a simple Android App
- Praxis - Christian daily prayers, reading, and fasting
- Qadaa - help make up for the missed prayers
- Quran - Quran reading application
- QuranApp - read and explore the Holy Qur'an with multiple translations
- Qur'an Lite - read the Qur’an on your Android device
- Quick Bible - Quick and Friendly Bible App
- Sefaria - Torah, Tanakh, Mishnah, Talmud, and more
- translationRecorder - voice recorder for translations
-
 @ ecd302a3:557f92cf
2025-06-12 23:01:41
@ ecd302a3:557f92cf
2025-06-12 23:01:41- Al-Azkar - Imam Al-Hafiz Yahya bin Sharafah Al-Din Al-Nawawi
- AndBible: Bible Study - Read the Bible, study commentaries or dictionaries, or read books offline
- Bookaccio Book Tracker - Your Personal Book Tracker
- Calibre-Web-Companion - Unofficial companion app for calibre web (automated)
- Capy Reader - A simple RSS reader
- Ciyue - A simple mdict dictionary
- Conty - Interactive stories for children. Download and play offline!
- copymanga - Third-party client for copymanga with better reading/downloading experience
- DeepL - Unofficial Android App for DeepL Translator
- Dharmik Online - Browse Bhagavad Gita
- Feeder - An awesome Libre and Open Source RSS feed reader
- Floccus Bookmark Sync - Sync your bookmarks privately across browsers and devices
- FossWallet - FossWallet is a MDY Wallet for Apple Passbook (.pkpass) files
- flabr - client for habr.com
- Harmonic - Hacker News with Modern material design
- Infinity for Reddit - A beautiful, feature-rich Reddit client
- Java OOP Quiz - Tests Your knowledge of Java Object-Oriented Programming
- Kahon - A fork of Mihon with some annoying restrictions removed
- KiwiX - Offline Wikipedia reader
- Komelia - Komga media client
- Komikku - Free and open source manga reader for Android
- Koreader - Ebook reader with support for many formats like PDF, DjVu, EPUB, FB2, CBZ
- Kotatsu - Kotatsu is a free and open source manga reader for Android
- LibreOffice Viewer - Document Viewer
- Linux Command Library - 5055 manual pages, 22 basic categories and a bunch of general terminal tips
- Logical Defense - Encyclopedia of logical fallacies
- LMd - Le Monde diplomatique DE - reader for the german version of "Le Monde diplomatique"
- Memorize Your Classics - Memorize poems, songs, etc. with this nice poem viewer
- MuPDF mini - Minimalist viewer for PDF, XPS, CBZ, unprotected EPUB, and FB2 documents
- MuPDF viewer - Lightweight PDF document viewer
- Myne: Ebook Downloader - Android application to download ebooks from the Project GutenBerg
- NATINFo Flutter - Advanced NATINF (NATure INFraction) search, offences under French law
- NeverTooManyBooks - keep track of your books and comics
- NGA客户端开源版 - National Gay Alliance client
- OCS-NG Agent - OCS Inventory client
- OpenBible - OpenBible provides the bible as a simple Android App
- Openlib - download and read books from shadow library (Anna’s Archive)
- Orion Viewer - Pdf & Djvu - Orion Viewer is pdf, djvu, xps, cbz and tiff file viewer
- PDF Viewer - Simple Android PDF viewer
- Pocket ReadLex - Shavian spelling dictionary
- Praktika Vortaro - Offline Esperanto dictionary
- ProseReader - ProseReader for Android Ebook/EPUB Viewer
- Quran - Quran reading application
- QuickNovel - download lightnovels as an Epub
- Raccoon for Lemmy - Mobile client for Lemmy, a federated aggregation and discussion platform
- Read Out - Read books, audiobook playback, and AI-powered summaries in both text and audio formats
- Read You - A modern and elegant RSS reader with Material You design
- Readest - ebook reader with powerful features and an intuitive interface
- StyncyNotes - Sticky Notes app for Android that understands the linuxmint/sticky note file for
- The Life - Bible multi languages, free, offline, no advertising
- ToS;DR - Short summaries on Terms of Conditions
- Venera - A comic reader that support reading local and network comics
- Weread - Read it later for web content
- WikiReader - Read Wikipedia pages distraction-free
- Wispar - Stay up-to-date with article in your field of study!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Reclamações
- Como não houve resposta, estou enviando de novo
- Democracia na América
- A "política" é a arena da vitória do estatismo
- A biblioteca infinita
- Família e propriedade
- Memórias de quando eu aprendi a ler
- A chatura Kelsen
- O VAR é o grande equalizador
- Não tem solução
- A estrutura lógica do livro didático
- "House" dos economistas e o Estado
- Revista Educativa
- Cultura Inglesa e aprendizado extra-escolar
- Veterano não é dono de bixete
- Personagens de jogos e símbolos
- Músicas grudentas e conversas
- Obra aqui do lado
- Propaganda
- Ver Jesus com os olhos da carne
- Processos Antifrágeis
- Cadeias, crimes e cidadãos de bem
- Castas hindus em nova chave
- Método científico
- Xampu
- Thafne venceu o Soletrando 2008.
- Empreendendorismo de boteco
- Problemas com Russell Kirk
- Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
-
 @ ecd302a3:557f92cf
2025-06-12 22:59:13
@ ecd302a3:557f92cf
2025-06-12 22:59:13- Amadz - Calling App - Clean & intuitive Phone Dialer app following Material Design principles.
- baresip - VoIP User Agent app for Android based on baresip SIP library
- baresip+ - VoIP User Agent app for Android based on baresip SIP library
- BCR-GUI - companion app for the great BCR (Basic Call Recorder) Android application
- CallForwardingStatus - Simply forward your calls
- Carrion - Block spoofed calls
- Cheogram - Chat on the Jabber network (XMPP protocol); focus on features for gateway users
- CodeCatcher - Filter Sms Messages and Automate Your Device
- Deku SMS - Deku is an SMS app that supports end to end encryption and photo sharing
- Edifier RC10D1 - Unofficial remote control for Edifier R2730DB speakers
- Edifier RC10E - Unofficial remote control for Edifier R1280DB speakers
- Edifier RC18A - Unofficial remote control for Edifier R1855DB speakers
- Element - Secure Messenger - Group messenger - encrypted messaging, group chat and video calls
- FluffyChat - Chat with your friends with FluffyChat.
- Fossify Contacts - Manage your contacts privately and efficiently with vCard support
- Fossify Phone - Unlock a secure, open-source calling experience with Fossify Phone
- Fossify SMS Messenger - Open-source and Ad-free SMS/MMS messaging app
- Jami - Audio & Video Calls / Chat Take Control of your Communication!
- JMP SIM Manager - Companion app for the JMP eSIM Adapter
- Keep Alive - Notify others if you haven't used your device in a given period of time
- kMeet - Free and secure videoconferencing solution
- Launch Chat - Start a WhatsApp, Signal or Telegram chat without saving a number as a contact
- Linphone - open source SIP client - SIP (VOIP) phone
- Meshenger - P2P voice- and video phone App.
- OpenContacts - A different database for contacts to keep them private only to you.
- polycule - A geeky and efficient [matrix] client for power users
- Privacy Cell - Verify that a phone is using the most secure cell protocols.
- Pulse - Redirect outgoing calls to Signal/Telegram/Threema/Whatsapp
- QUIK SMS - Open source replacement to the stock SMS app on Android.
- S2MSP - SMS communication for apps restricted on phone numbers
- SchildiChat - Secure messenger for Matrix with a traditional instant messaging experience
- Simlar - secure calls - Protect your privacy with encrypted phone calls.
- SimpleX Chat - e2e encrypted messenger without any user IDs - private by design!
- sms2call - Make a call when receiving a defined SMS
- SMS Import / Export - Imports and exports SMS and MMS messages, call logs, and contacts.
- SpamBlocker (Call & SMS) - Spam Call/SMS blocker
- ThreatScoopOnionChat - A Forked Version focused on privacy from SESSION
- VoIP.ms SMS - Send and read SMS via voip.ms
- WA Adder - WhatsApp contact adder without giving WhatsApp access to your contacts!
- Welefon - Phone with API
- WiVeWa - Client for the WiVeWa system
-
 @ ecd302a3:557f92cf
2025-06-12 22:57:05
@ ecd302a3:557f92cf
2025-06-12 22:57:05- Alkaa - Manage your tasks quickly and easily. Add tasks, break into categories and remember important appointments.
- Calculator - simple Material Calculator and Unit Converter
- Cat Printer - support to some Bluetooth "Cat Printer" models
- Connect You - Modern contacts app using Material Design 3 (You) and Jetpack Compose
- CuteCalc - a simple, lightweight and open-source calculator
- Hot Stuff - Protect your belongings with Hot Stuff, a free and offline home inventory app
- Karui ToDo - a privacy focussed todo list app to quickly jot down things to do
- Lock Screen Notes - Create notes that are automatically displayed in the device’s lock screen
- LockQR - Effortless QR Code Generation, Free and Shareable
- Logger - view and export call logs in CSV format
- Lumolight - Simple, modern & easy-to-use flashlight app that comes with a ton of feature
- Nibras Reader 3 - take bookmarked records on Nibras PKM with you on the go
- nocodb - a prototype client for NocoDB
- ObsidianTodoWidget - Widget to display todo list from markdown file
- OpenTodoList - simple Todo and task management
- OpenToday - planner & organizer - notes, todo, reminders, lists everything is customizable
- OrgNote - Note taking app based on the popular Emacs package - Org Roam
- OSS Card Wallet - All your cards secured and without ad!
- OSS Dict - Offline Dictionaries
- OSS Document Scanner - scan all your documents
- Paperless Mobile - An (almost) fully fledged mobile Paperless client.
- Parcel - Track all your parcels with ease.
- PDF Doc Scan - PDF document scanner
- PDF to Images - simple app to convert a PDFs pages to image files
- RemotePointer - Digital Laser Pointer and Mouse Control for Presentations
- Scheduler - View your todo list/events from your lockscreen
- Simple QR - Scan, create and store QR codes with a simple UI and experience
- Simplenote - keep notes, lists, ideas and more
- TagSpaces - organize, tag and browse your files, photos and documents
- zCalc - Simple and beautiful calculator for Android
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28The Lightning Network solves the problem of the decentralized commit
Before reading this, see Ripple and the problem of the decentralized commit.
The Bitcoin Lightning Network can be thought as a system similar to Ripple: there are conditional IOUs (HTLCs) that are sent in "prepare"-like messages across a route, and a secret
pthat must travel from the final receiver backwards through the route until it reaches the initial sender and possession of that secret serves to prove the payment as well as to make the IOU hold true.The difference is that if one of the parties don't send the "acknowledge" in time, the other has a trusted third-party with its own clock (that is the clock that is valid for everybody involved) to complain immediately at the timeout: the Bitcoin blockchain. If C has
pand B isn't acknowleding it, C tells the Bitcoin blockchain and it will force the transfer of the amount from B to C.Differences (or 1 upside and 3 downside)
-
The Lightning Network differs from a "pure" Ripple network in that when we send a "prepare" message on the Lightning Network, unlike on a pure Ripple network we're not just promising we will owe something -- instead we are putting the money on the table already for the other to get if we are not responsive.
-
The feature above removes the trust element from the equation. We can now have relationships with people we don't trust, as the Bitcoin blockchain will serve as an automated escrow for our conditional payments and no one will be harmed. Therefore it is much easier to build networks and route payments if you don't always require trust relationships.
-
However it introduces the cost of the capital. A ton of capital must be made available in channels and locked in HTLCs so payments can be routed. This leads to potential issues like the ones described in https://twitter.com/joostjgr/status/1308414364911841281.
-
Another issue that comes with the necessity of using the Bitcoin blockchain as an arbiter is that it may cost a lot in fees -- much more than the value of the payment that is being disputed -- to enforce it on the blockchain.[^closing-channels-for-nothing]
Solutions
Because the downsides listed above are so real and problematic -- and much more so when attacks from malicious peers are taken into account --, some have argued that the Lightning Network must rely on at least some trust between peers, which partly negate the benefit.
The introduction of purely trust-backend channels is the next step in the reasoning: if we are trusting already, why not make channels that don't touch the blockchain and don't require peers to commit large amounts of capital?
The reason is, again, the ambiguity that comes from the problem of the decentralized commit. Therefore hosted channels can be good when trust is required only from one side, like in the final hops of payments, but they cannot work in the middle of routes without eroding trust relationships between peers (however they can be useful if employed as channels between two nodes ran by the same person).
The next solution is a revamped pure Ripple network, one that solves the problem of the decentralized commit in a different way.
[^closing-channels-for-nothing]: That is even true when, for reasons of the payment being so small that it doesn't even deserve an actual HTLC that can be enforced on the chain (as per the protocol), even then the channel between the two nodes will be closed, only to make it very clear that there was a disagreement. Leaving it online would be harmful as one of the peers could repeat the attack again and again. This is a proof that ambiguity, in case of the pure Ripple network, is a very important issue.
-
-
 @ ecd302a3:557f92cf
2025-06-12 22:55:07
@ ecd302a3:557f92cf
2025-06-12 22:55:07- Adresilo - Search for places
- AltLocationServices - Connects to BeaconDB geolocation service to provide network location services
- Baba - Discover Baba: The app that revolutionizes contributing to Panoramax
- Bahn-Vorhersage - Ranking for train journeys according to their reliability. (German only)
- Beans - A virtual scratchmap of the world
- Blue Square Speedometer - Simple speedometer & GPS viewer
- BusTO - Turin (Italy) public transport
- c:geo - powerful geocaching app
- Cartes IGN - Discover France another way and witness the land's evolution
- CClauncher - Clauncher, rewritten using Compose
- CLauncher - Yet Another Olauncher Fork, But With All Apps Hidden
- Compass - Simple and beautiful compass
- Compass Tile - An easily accessible compass tile for the quick settings panel
- E6B Flight Computer - E6B Flight Computer
- EVMap - EV chargers - Find electric vehicle charging stations
- FakeTraveler - Fake your location
- Find Family - Find Family is an end-to-end encrypted location sharing app
- Gadgetbridge - Use your smart watch and other bluetooth devices and keep your data private!
- Geo Share - Turn a Google Maps URL into a geo: URL
- Geohash Droid - App for Randall Munroe’s Geohashing activity
- Geotag video camera - Camera with a map and coordinates overlay
- GMaps WV - Google Maps WebView Wrapper
- GPS Locker - Keep the GPS locked at all times on an Android device
- GPS Logger - A lightweight GPS logger, battery efficient, GPX/KML, add notes, share, upload
- GPS Setter - A GPS setter based on the Xposed framework
- GPSTest - An app for testing GPS and GNSS capabilities of a device
- JRBP Survey - Jasper Ridge ant survey navigation and data entry
- Kwik EFIS - Glass Cockpit / Electronic Flight Information System
- Ladefuchs - Shows the cheapest charging card - with only one swipe at the charging point
- MBCompass - Simple and efficient compass
- MetaGer Maps - Map app based on Openstreetmap. Route planner - Navigation
- Mobile Tile Server - HTTP Server for your local Map Tiles
- NextGIS Mobile - GIS that lets you create, edit and export geodata, both online and offline
- Offi - King of public transit planning!
- OpenLynx - Public transport companion providing real-time data
- OpenStop - The app for collecting barrier data in local public transport
- OpenStreetMap wiki - Access the OpenStreetMap wiki
- Organic Maps - Offline Hike, Bike, GPS Navigation for travelers, tourists, cyclists & hikers
- OSM Dashboard for OpenTracks - OpenStreetMap dashboard for OpenTracks
- OSM Dashboard Offline for OpenTracks - Offline variant of the OpenStreetMap dashboard for OpenTracks
- OsmAnd - Global Mobile Map Viewing & Navigation for Offline and Online OSM Maps
- Panoramax - Panoramax mobile is an app to capture and upload photo sequences to Panoramax
- PasseGares - Travel through the train stations to stamp your visa!
- PeakOrama - PeakOrama shows mountains around a location
- Phantasialand Wait Times - Live wait times for Phantasialand rides
- SCEE - OpenStreetMap surveyor app for experienced OSM contributors
- Sky Map - Sky Map to explore the skies
- SmsLoc - SMS based location query
- Stateful Speedometer - Stateful speedometer & GPS viewer
- StreetComplete - Easy to use OpenStreetMap editor for Android
- Tehran Metro - An app to facilitate using tehran metro
- ToS;DR - Short summaries on Terms of Conditions
- Traccar Client - Track your location
- Traccar Manager - GPS tracker reporting to your own host
- Trail Sense - Use your phone's sensors to assist with wilderness treks
- Transito - Public transit app to download GTFS data & calculate routes offline
- Vespucci - Edit geodata and contribute to OpenStreetMap project on-the-go
- Zood Location - Securely share your location with your loved ones
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Reasons for miners to not steal
See Drivechain for an introduction. Here we'll just have a list of reasons why miners would not steal:
- they will lose future fees from that specific drivechain: you can discount all future fees and condense them into a single present number in order to do some mathematical calculation.
- they may lose future fees from all other Drivechains, if the users assume they will steal from those too.
- Bitcoin will be devalued if they steal, because:
- Bitcoin is worth more if it has Drivechains working, because it is more useful, has more use-cases, more users. Without Drivechains it necessarily has to be worth less.
- Bitcoin has more fee revenue if has Drivechains working, which means it has a bigger chance of surviving going forward and being more censorship-resistant and resistant to State attacks, therefore it has to worth more if Drivechains work and less if they don't.
- Bitcoin is worth more if the public perception is that Bitcoin miners are friendly and doing their work peacefully instead of being a band of revolted peons that are constantly threating to use their 75% hashrate to do evil things such as:
- double-spending attacks;
- censoring of transactions for a certain group of people;
- selfish mining.
- if Bitcoin is devalued its price is bound to fall, meaning that miners will lose on
- their future mining rewards;
- their ASIC investiment;
- the same coins they are trying to steal from the drivechain.
- if a mining pool tries to steal, they will risk losing their individual miners to other pools that don't.
- whenever a steal attempt begins, the coins in the drivechain will lose value (if the steal attempt is credible their price will drop quite substantially), which means that if a coalition of miners really try to steal, there is an incentive for another coalition of miners to buy some devalued coins and then stop the steal.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: a website for feedback exchange
I thought a community of people sharing feedback on mutual interests would be a good thing, so as always I broadened and generalized the idea and mixed with my old criticue-inspired idea-feedback project and turned it into a "token". You give feedback on other people's things, they give you a "point". You can then use that point to request feedback from others.
This could be made as an Etleneum contract so these points were exchanged for satoshis using the shitswap contract (yet to be written).
In this case all the Bitcoin/Lightning side of the website must be hidden until the user has properly gone through the usage flow and earned points.
If it was to be built on Etleneum then it needs to emphasize the login/password login method instead of the lnurl-auth method. And then maybe it could be used to push lnurl-auth to normal people, but with a different name.
-
 @ ecd302a3:557f92cf
2025-06-12 22:52:54
@ ecd302a3:557f92cf
2025-06-12 22:52:54- Alligator Bytes - Record musical loops, play them back, and change the sound with movement.
- Animetail - Unofficial fork of Aniyomi
- ANeko - ANeko Reborn for Android, interactive cat animation that runs on your Android screen
- APM - Third-party Bilibili music player
- Assempix - A coded OFDM update to SSTV to receive digital images over SSB, AM and FM radio
- Audiobookshelf - Audiobook and podcast player for your self-hosted Audiobookshelf server
- Audile - Music recognition app
- Aves Libre - Gallery and metadata explorer
- BoomingMusic - Local music player built for smooth offline listening
- Calibre-Web-Companion - Unofficial companion app for calibre web (automated)
- camsung - Silence camera on Samsung phones
- Choona - Guitar tuner with support for custom tunings.
- ClassiPod - A local music player app designed to capture the essence of the iPod Classic.
- Com-Phone Story Maker - Create, tell, share and enjoy multimedia digital stories
- CuteMusic - a simple and lightweight offline music player
- Diatronome - A tuner, a visual metronome and a synthesizer
- DSub2000 - Android client for Subsonic servers.
- e1547 - e621 browser - browser for the e621 and e926 imageboards
- Fossify Voice Recorder - Record anything with this Open-source and Ad-free recorder
- Gizz Tapes - Stream King Gizzard and the Lizard Wizard shows right to your phone!
- Harmony Music - Music streaming app with radio and background feature
- InnerTune - A material design YouTube Music client
- Jellyfin - your media in your hands! - Mobile client for Jellyfin, the free software media system
- Kahon - A fork of Mihon with some annoying restrictions removed
- Kazumi - An anime collection app based on custom rules.
- Kotatsu - Kotatsu is a free and open source manga reader for Android.
- Kreate - A multilingual YouTube Music frontend for Android, prioritize performance
- LibreTube - Alternative YouTube frontend for Android built with Piped
- Lissen: Audiobookshelf client - Clean Audiobookshelf Player
- litube - a feature-rich Android WebView wrapper for YouTube
- Materialious - Modern material design for Invidious
- Movies - Movies - easy way to discover popular movies.
- mpv-android - Listen to music and watch videos
- MSM - All in one manager for your media server
- Musify - Music Streaming and Downloading app
- MusicSearch - MusicSearch is an app for browsing songs, artists, and anything related to them
- Neon - Scrolling text on fullscreen like boarding
- NewPipe - Lightweight app that lets you watch and listen to media from various platforms.
- OpenTune - YouTube Music client for Android with Material 3 design
- OuterTune - Material 3 Music Player with YouTube Music support
- Panoramax - Panoramax mobile is an app to capture and upload photo sequences to Panoramax.
- Phocid - A modern offline music player with familiar designs
- PicGuard - Your pictures, your signature.
- Pilipala - A third-party Bilibili client developed in Flutter
- PipePipe - An alternative Android streaming front-end of Bilibili, NicoNico, Youtube & more
- Pixiv-MultiPlatform - Third-party Pixiv client
- Pocket Casts - Podcast Player for Android with advanced listening, search, and discovery features.
- RadioUpnp - Clean designed internet radio player with integrated UPnP/DLNA function
- RadioWave - internet radio player with more than 50,000 stations
- RiMusic - Stream music from YouTube Music
- Screen Stream - Screen streaming over HTTP
- Sentinel Lens - Facial recognition surveillance with alerts
- Seqular - Seqular, A Social Network without Place or Nation.
- Shredpix - A coded OFDM update to SSTV to send images digitally over SSB, AM and FM radio
- SimpMusic - A music app using YouTube Music for backend
- SkyTube - An open source YouTube client
- SkyTube Extra - An open source YouTube client
- SmartScan - Image organisation & search app
- Soothing Noise Player - Play soothing sound effects to help you relax and drown out background noise.
- Spotube - Lightweight & resource friendly Spotify client without requiring Spotify Premium
- SuperX - Video downloader with browser for downloading videos from everywhere
- Tsacdop-Fork - Podcast Player - Enjoy podcasts with Tsacdop-Fork! A clean, simply beautiful, and friendly app.
- Vaani - Beautiful, Fast and Functional Audiobook Player for your Audiobookshelf server.
- VLC - The best video and music player. Fast and “just works”, plays any file
- Voice Audiobook Player - Simple audiobook player
- Weather (PFA) - (SECUSO) Lets you watch the weather for cities and locations of your choice
- Xtra - a Twitch player and browser
- YouAMP - Player for Subsonic servers with modern Material You interface
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28bolt12 problems
- clients can't programatically build new offers by changing a path or query params (services like zbd.gg or lnurl-pay.me won't work)
- impossible to use in a load-balanced custodian way -- since offers would have to be pregenerated and tied to a specific lightning node.
- the existence of fiat currency fields makes it so wallets have to fetch exchange rates from somewhere on the internet (or offer a bad user experience), using HTTP which hurts user privacy.
- the vendor field is misleading, can be phished very easily, not as safe as a domain name.
- onion messages are an improvement over fake HTLC-based payments as a way of transmitting data, for sure. but we must decide if they are (i) suitable for transmitting all kinds of data over the internet, a replacement for tor; or (ii) not something that will scale well or on which we can count on for the future. if there was proper incentivization for data transmission it could end up being (i), the holy grail of p2p communication over the internet, but that is a very hard problem to solve and not guaranteed to yield the desired scalability results. since not even hints of attempting to solve that are being made, it's safer to conclude it is (ii).
bolt12 limitations
- not flexible enough. there are some interesting fields defined in the spec, but who gets to add more fields later if necessary? very unclear.
- services can't return any actionable data to the users who paid for something. it's unclear how business can be conducted without an extra communication channel.
bolt12 illusions
- recurring payments is not really solved, it is just a spec that defines intervals. the actual implementation must still be done by each wallet and service. the recurring payment cannot be enforced, the wallet must still initiate the payment. even if the wallet is evil and is willing to initiate a payment without the user knowing it still needs to have funds, channels, be online, connected etc., so it's not as if the services could rely on the payments being delivered in time.
- people seem to think it will enable pushing payments to mobile wallets, which it does not and cannot.
- there is a confusion of contexts: it looks like offers are superior to lnurl-pay, for example, because they don't require domain names. domain names, though, are common and well-established among internet services and stores, because these services have websites, so this is not really an issue. it is an issue, though, for people that want to receive payments in their homes. for these, indeed, bolt12 offers a superior solution -- but at the same time bolt12 seems to be selling itself as a tool for merchants and service providers when it includes and highlights features as recurring payments and refunds.
- the privacy gains for the receiver that are promoted as being part of bolt12 in fact come from a separate proposal, blinded paths, which should work for all normal lightning payments and indeed are a very nice solution. they are (or at least were, and should be) independent from the bolt12 proposal. a separate proposal, which can be (and already is being) used right now, also improves privacy for the receiver very much anway, it's called trampoline routing.
-
 @ ecd302a3:557f92cf
2025-06-12 22:50:06
@ ecd302a3:557f92cf
2025-06-12 22:50:06- Aisleron Shopping List - Aisleron: Fly through the shops!
- Arru - track and analyze your expenses
- BasicCashFlow - The easiest way to track your cash: no fuss, just money tracking.
- BitBanana - Manage your Bitcoin Lightning node from anywhere.
- Bitcoin Wallet - Store digital currency
- Bitcoin Wallet [signet] - Your own Bitcoins, in your own pocket!
- Bold Bitcoin Wallet - Seedless, secure Bitcoin wallet using Threshold Signatures.
- Brume Wallet - The private Ethereum wallet
- BTC Map - See where you can spend your bitcoins
- Cardabase - Cardabase is an app that lets you save EAN-13 club cards on your phone.
- CashCompass - Master Your Money: Effortless Tracking and Smarter Spending
- Cashew - An app created to help users manage a budget and purchases
- Catima — Loyalty Card Wallet - For your barcodes, memberships, loyalty programs, coupons and tickets.
- Coin Collection - Coin Collection helps people organize their U.S. coin collections
- CryptoTracker - Track cryptocurrency prices in real-time with CryptoTracker
- Currencies: Exchange Rate Calculator - An exchange rates currency converter for Android
- Electrum Bitcoin Wallet - Fast and self-custodial wallet for Bitcoin and the Lightning Network
- FDTracker - easily add, view, update, and track your fixed deposits
- Firefly III Shortcuts - Application simplifies transactions of FireflyIII
- flow - A personal finance tracker app built with love, and Flutter
- GNU Taler Point-of-Sale - Process orders and take in Taler payments
- Green - Blockstream Green Bitcoin wallet
- GreenStash - Simple app to help you plan and manage your savings goals easily.
- Inflation Calculator - Inflation calculator for USA, UK and France
- Invoice Ninja - Create invoices, accept payments, track expenses & time-tasks
- Keepass Fidelity - Fidelity (Membership/Loyalty) Card plugin for Keepass2Android
- KitchenOwl - KitchenOwl helps you organize your grocery life.
- Ladefuchs - Shows the cheapest charging card - with only one swipe at the charging point.
- MarketMonk - Watch the movements of your favorite stocks using free and open source software.
- Mat-O-Id - Pay beverages with RFID-Tag
- Mempal - A Bitcoin mempool monitoring and notification app for Android.
- Money Manager Ex - Manage your income and expenses on a mobile device, sync via your own cloud
- Moneytopia - track your personal expenses
- MRT Buddy - Check your Dhaka MRT / Rapid Pass balances and trips instantly
- My Expenses - Easy to use personal finance manager: rich functionality and Open Source
- NanoLedger - Data entry app for plain text accounting
- NumberHub - The only calculator / currency converter / time zones / ... - app you need!
- Oinkoin - Oinkoin Money Manager makes managing personal finances easy and secure.
- Oxen Wallet - Oxen lite wallet for Android
- P.CASH - Bitcoin, Ethereum, DeFi, PirateCash, Cosanta, zCash, Dogecoin
- Reckoner - Privacy respecting personal financial tracker
- Recurring Expense Tracker - Keep track of your monthly spending
- RoboSats - Simple and private app to exchange bitcoin for national currencies.
- Simple Crypto Widget - A simple widget to display prices for lots of cryptocurrencies.
- Status Wallet - Cryptocurrency wallet, Private messenger, and Ethereum DApp Browser all in one
- Swiss Bitcoin Pay - 1 minute to accept Bitcoin in your business.
- Taler Cashier - Take cash and give out electronic cash
- Taler Wallet - Makes privacy-friendly online transactions fast and easy
- Unstoppable Wallet - Bitcoin, Ethereum, DeFi
- Valet - The Bitcoin Lightning Wallet with Extra Features
- VAT Calculator - Calculate VAT for any country in the world
- Veil - Privacy focused wallet - Privacy focused VEIL coin crypto wallet
- Wallet - store card information locally on the device
- Waterfly III - personal finance manager
- Working Time Account - Record working hours, generate and send reports (PDF, CSV and ICS)
- Zashi: Zcash Wallet - Zashi is a Zcash wallet that keeps your transaction and message history private
-
 @ ecd302a3:557f92cf
2025-06-12 22:46:54
@ ecd302a3:557f92cf
2025-06-12 22:46:54- ArcaneChat - Encrypted chat over e-mail (Delta Chat client)
- Dhaaga (Lite) - An Opinionated Fediverse Microblogging App
- Evergram - Scroll through all your Telegram channels in one timeline
- firefly nightly - Firefly Mastodon Client (nightly pre-releases)
- Graysky - Graysky is a Bluesky client written in React Native
- Igatha - SOS Signaling & Recovery
- Interstellar - An open source Mbin & Lemmy client, connecting you to the fediverse.
- Lemmy Redirect - Deep linking proxy for Lemmy, to launch your selected client automatically
- Mandarin IM - ICQ Client
- Mastify - A beautiful, feature-rich Mastodon client
- Mastodon Redirect - Deep linking proxy for Mastodon, to launch your selected client automatically
- Megalodon - Mastodon for Android but it's pink and has more features
- Mint - a lightweight Misskey Android client
- Moshidon - Mastodon for Android but it's Material You and has more features
- Moxxy - Moxxy is an experimental XMPP client that aims to be modern and easy to use.
- Nullgram - 3rd party client of Telegram
- NowiChat - NowiChat is a chat app with bluetooth networking and end-to-end security.
- Nozzle - lightweight nostr client
- Primal - Primal's Android app for Nostr
- Raccoon for Friendica - Mobile client for Friendica, Mastodon and compatible federated social networks.
- Rattlegram - SMS via audio! - Transmit short text messages over COFDMTV encoded audio signals
- Reply Radar - Reply Radar helps you keep track of the people you still need to reply to. No more forgotten messages — stay organized and in control.
- S2MSP - SMS communication for apps restricted on phone numbers
- Session - Send messages, not metadata. No ads or trackers — only private messaging
- Sideband - Decentralized peer-to-peer secure messaging LXMF client
- Signal - Signal is a messaging app focused on privacy
- Smither - Lightweight Mastodon client
- swob - Communicate with online services using SMS messaging
- Telewatch - Telegram for watch
- Tool Telegram - Send messages on telegram as a bot, easily
- Voyage - Voyage is a lightweight nostr client for Android with a Reddit-like UI.
-
 @ ecd302a3:557f92cf
2025-06-12 22:44:39
@ ecd302a3:557f92cf
2025-06-12 22:44:39- Amnezia - VPN client that enables you to deploy your own VPN server on your server
- AnimePipe (PipePipe) - An alternative Android streaming front-end of Bilibili, NicoNico, Youtube & more
- ArcaneChat - Encrypted chat over e-mail (Delta Chat client)
- Audile - Music recognition app
- baresip - VoIP User Agent app for Android based on baresip SIP library
- Better Stundenplan - A (hopefully) not-so-bad client for virtueller-stundenplan.org
- Bluesky - Bluesky is the ultimate social network for tech-savvy folks who stay connected and in the loop.
- Breezy Weather - A lightweight, powerful, open-source Material Design weather app.
- ByeDPI - Bypass censorship on Android
- ClashMetaForAndroid - A rule-based tunnel
- Clippy - Copy links from the sharing menu with automatic removal of shorteners and trackers
- DAVx⁵ - CalDAV/CardDAV Synchronization and Client
- DuckDuckGo Privacy Browser - Privacy, simplified open source web browser
- EinkBro - lightweight, fast, but powerful browser designed for Eink devices.
- Element - Secure Messenger - Group messenger - encrypted messaging, group chat and video calls
- Element X - Secure messenger - Fastest ever Matrix client
- evcc - solar charging - charge your EV when the sun is shining or electricity is cheap and clean
- Exclave - Proxy client
- FairEmail - Fully featured email client. Neat, intuitive user interface. Privacy friendly
- Fennec - Browse the web
- flabr - client for habr.com
- geteduroam - Configure eduroam by using your institution profile
- getgovroam - Configure the govroam Wi-Fi network securely and correctly
- husi - Husi is a proxy configurations manager.
- Iceraven Browser - Iceraven Browser is a web browser for Android, based on Mozilla's Fenix version of Firefox
- InviZible Pro - increase your security, protect your privacy
- IPerf3Client - iPerf3 is a tool for active measurements of the max bandwidth on IP networks.
- IronFox - Web browser with privacy and security features for Android
- K-9 Mail - Full-featured email client
- Kahon - A fork of Mihon with some annoying restrictions removed
- LabNex - Android app for GitLab
- LibreTube - Alternative YouTube frontend for Android built with Piped
- LinkGuardian - Android client for Linkwarden built with Jetpack Compose
- litube - a feature-rich Android WebView wrapper for YouTube
- Materialious - Modern material design for Invidious
- Mint - a lightweight Misskey Android client
- Mull Browser - Privacy oriented web browser based on Mozilla Fennec
- nekobox - sing-box / universal proxy toolchain for Android
- NewPipe - Lightweight app that lets you watch and listen to media from various platforms.
- Nitterify - open Twitter links in Nitter
- OpenStore - Libre client for RuStore
- Panoramax - Panoramax mobile is an app to capture and upload photo sequences to Panoramax.
- Parcel - Track all your parcels with ease.
- PixEz - A third-party Pixiv flutter client that supports viewing ugoira
- Pixiv-MultiPlatform - Third-party Pixiv client
- ProtonVPN - Secure and Free VPN - Free Swiss VPN with advanced security and privacy features.
- Quad9 Connect - Android application for Quad9 recursive DNS cybersecurity and privacy services
- QuickWeather - Weather at a glance for anywhere in the world!
- Quotes.app - A minimalistic quotes app
- Readeck App - manage saved articles and bookmarks
- Rocket.Chat - Team Communication Tool
- Seqular - Seqular, A Social Network without Place or Nation.
- ServerBox - A server status & toolbox app using Flutter
- SkyTube - An open source YouTube client
- Spotube - Lightweight & resource friendly Spotify client without requiring Spotify Premium
- ThreatScoopOnionChat - A Forked Version focused on privacy from SESSION
- ToS;DR - Short summaries on Terms of Conditions
- TorrServe - Download torrent files
- Traintime PDA - Another personal data assistant for XDU undergraduate.
- Weread - Read it later for web content
- Weather (PFA) - (SECUSO) Lets you watch the weather for cities and locations of your choice
- WhatsDown - ⚡ Fast encrypted chats for the family 🎉
- Wiki Fronted - Wikipedia app with domain fronting
- WikWok - Learn something new with every swipe!
- Wikipedia - Official feature-rich viewer of the free online encyclopedia
- Xray - Xray GUI Client For Android
- YTDLnis - Android Video/Audio Downloader app using yt-dlp
-
 @ ecd302a3:557f92cf
2025-06-12 22:41:58
@ ecd302a3:557f92cf
2025-06-12 22:41:58- 3D Model Viewer - Load 3D Models and see how to do it
- AL-chan - AL-chan is an unofficial Android client for AniList, a place where you can track, share, discover, and experience Anime and Manga.
- Aves - Gallery and metadata explorer
- Aves Libre - Gallery and metadata explorer
- BabbyPaint - Simple little paint application for kids.
- Drawpile - A collaborative drawing program
- Easter Eggs - Built in eggs in official versions of Android system.
- Elements - Chinese zodiac five elements as a pageable calendar
- Exif Thumbnail Adder - Add thumbnail in the EXIF tag of JPEG picture not having one (batch processing)
- Fossify Gallery - Gallery with Photo editor. No Ads, Open-source, Private. No strings attached.
- Fossify Paint - Quick, easy and open source drawing app
- FreePaint - A vector graphics drawing app for Android.
- Gallery - Light-weight Media Gallery
- Image Toolbox - Powerful picture editor, crop, apply filters, remove background, edit EXIF or create PDF
- Imagepipe - removes exif data and modifies images to reduce size before sharing.
- LBalance - LBalance is a clinometer or balance app offering different Layouts.
- Les Pas - Photo Album for Nextcloud - A photo album that saves all your precious memory in your private cloud
- Memerize - Memerize is a handy meme viewer app. Uses Reddit to get the latest memes.
- Memories: Photo Management for Nextcloud - Fast, modern and advanced photo management suite. Runs as a Nextcloud app.
- OCR - OCR based on Tesseract 5
- OCR (Tesseract) - Optical character recognition (OCR) functionality based on Tesseract via Intents
- Open Stable Diffusion - An app for generating images using AI
- Pani - record RAW image data
- Photo Editor - A Photo Editor app with simple, easy support for image editing using Paints, Tex
- PhotoPrism Gallery - An unofficial gallery and content provider for your PhotoPrism library
- PhotoSwooper - A dating app for ur photos
- PicGuard - Your pictures, your signature.
- PicGuard Pro - Your pictures, your signature.
- PiPixiv - Third-party Pixiv Client
- Pix-EzViewer - A third-party Pixiv Android client. (Android 5.0+)
- PixEz - A third-party Pixiv flutter client that supports viewing ugoira
- Pixiv-MultiPlatform - Third-party Pixiv client
- ProgrammingTools - generate QR codes from text input
- QuickEdit - Basic and lightweight Photo Editor.
- RetroDrawing - A simple drawing app with big pixels and fixed palette.
- SDAI FOSS - Generate Stable Diffusion AI assets on your own WebUI server instance.
- Simple Raw Camera - a simple camera for Android
- Sketching (PFA) - Create and manage simple sketches in a quick and easy manner
- Slideshow Wallpaper - A Live Wallpaper showing a slideshow of user-selected images
- Smartspacer - Customizable widget that enhances the built-in At a Glance feature on Pixels, all without requiring root access.
- SoftBoard - a simple Whiteboard app
- Stitch - Stitch screenshots together
- TIDY Text-to-Image Discovery - Offline semantic Text-to-Image and Image-to-Image search on Android
- VES - Image and Photo Compare - Before and after image compare, photo compare and picture compare. Side by side
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas novas e conhecidas
Quando for ouvir música de fundo, escolha músicas bem conhecidas. Para ouvir músicas novas, reserve um tempo e ouça-as com total atenção.
Uma coisa similar é dirigir por caminhos conhecidos versus dirigir em lugares novos. a primeira opção te permite fazer coisas enquanto dirige "de fundo", a segunda requer atenção total.
Com músicas, tenho errado constantemente em achar que posso conhecer músicas novas ao mesmo tempo em que me dedico a outras tarefas.
See also:
-
 @ ecd302a3:557f92cf
2025-06-12 22:39:14
@ ecd302a3:557f92cf
2025-06-12 22:39:14- AAAAXY - A nonlinear 2D puzzle platformer taking place in impossible spaces.
- Asteroid's Revenge - Endless survival bulletHell (highscore based).
- Bim! - A multiplayer online mobile game of the last man standing genre
- Blitz: Fischer chess clock - A minimalist Fischer chess clock for Android.
- Box Smasher - Shoot balls to smash boxes into the void!
- Breakout 71 - Break colourful bricks, catch bouncing coins and select powerful upgrades !
- Cascada - Casual logic game with marbles for two players
- Chaldea - Material Planner for Fate/GO
- Chip Defense - A tower defense game with a microprocessor theme
- Cifras o letras - A simplified version of Countdown UK game-show.
- Dice App - A simple Dice roller for Android.
- Dolphin Emulator - Nintendo console emulator
- Dungeon Crawl Stone Soup - A roguelike adventure through dungeons in a quest to find the Orb of Zot
- Easy Dice - RPG dice roller
- Easter Eggs - Built in eggs in official versions of Android system.
- Eidetic - A simple Android app that helps you improve your working memory
- Emotic - Reignite the love for emoticons
- FaFa Runner - Enjoy smooth gameplay, stunning graphics, and endless fun
- Forkyz - Crossword puzzles application, download and play.
- Freebloks - Strategy board game similar to the famous board game Blokus.
- Freeminer - Voxel-based multiplayer game platform
- Game Counter - A customizable game point counter
- Gauguin - A Sudoku-like logic game
- Human Benchmark - Test and compare your cognitive abilities with fun challenges
- idTech4A++ - DOOM III/Quake 4/Prey(2006) game runtime environment for Android
- Initiative Tracker - Initiative Tracker compatible with Pathfinder 2 encounter rules
- Jass board - Very flexible Jass board to write points at the Schieber, Coiffeur, Molotov.
- Katawa Shoujo: Re-Engineered - (18+) A fan-made modernization of the classic visual novel
- Mafia - A Mafia party game app for Android +4.4
- Mancala - Mancala Game
- Mill - A Mill Game which supports many rule variants
- Mindustry - A factory-based sandbox tower defense game
- Minetest - Near infinite world block sandbox game
- MOROway App - Play with the MORO model railroad!
- Naija Ludo + - Naija Ludo: A Modern Twist on the Classic Board Game
- Open Sudoku - Open Sudoku is an open source sudoku game.
- PasseGares - Travel through the train stations to stamp your visa!
- Pomodorot - A simple timer which pauses when not in view
- PPSSPP - PSP emulator
- RetroArch - Retro games and emulators on your device!
- Ricochlime - Satisfying monster shooter
- Roboyard - Problem-solving game - find the optimal moves to move one robot to its target
- Rucoy calculator - An unofficial calculator for all things Rucoy Online related!
- Shattered Pixel Dungeon - A roguelike game based on Pixel Dungeon
- Stendhal Game - Stendhal is a multiplayer adventure with classic 2D graphics. It is completely o
- TacticMaster - Chess tactic trainer based on https://database.lichess.org/#puzzles.
- TerraTactician Expandoria - Hexagon based logic game
- TheXTech - 2D-platformer game engine
- TriPeaks NEUE - A simple TriPeaks game.
- Trivia App - A simple app that pulls out trivia out of OpenTriviaDB and challenges you.
- Unjumble - an anagram game with picture hints
- Unreal Speccy Portable Emulator - Unreal Speccy Portable - ZX Spectrum Emulator
- Unciv - 4X civilization-building game
- VCMI - Engine recreation for Heroes of Might and Magic III
- VRChat Android Assistant - VRChat Friend Management Application for Android devices.
- Warsmash - Warsmash Android port
- Werewolf (Privacy Friendly) - (SECUSO) Open source adaption of the Werewolf card game. Play together via WiFi
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A Causa
o Princípios de Economia Política de Menger é o único livro que enfatiza a CAUSA o tempo todo. os cientistas todos parecem não saber, ou se esquecer sempre, que as coisas têm causa, e que o conhecimento verdadeiro é o conhecimento da causa das coisas.
a causa é uma categoria metafísica muito superior a qualquer correlação ou resultado de teste de hipótese, ela não pode ser descoberta por nenhum artifício econométrico ou reduzida à simples antecedência temporal estatística. a causa dos fenômenos não pode ser provada cientificamente, mas pode ser conhecida.
o livro de Menger conta para o leitor as causas de vários fenômenos econômicos e as interliga de forma que o mundo caótico da economia parece adquirir uma ordem no momento em que você lê. é uma sensação mágica e indescritível.
quando eu te o recomendei, queria é te imbuir com o espírito da busca pela causa das coisas. depois de ler aquilo, você está apto a perceber continuidade causal nos fenômenos mais complexos da economia atual, enxergar as causas entre toda a ação governamental e as suas várias consequências na vida humana. eu faço isso todos os dias e é a melhor sensação do mundo quando o caos das notícias do caderno de Economia do jornal -- que para o próprio jornalista que as escreveu não têm nenhum sentido (tanto é que ele escreve tudo errado) -- se incluem num sistema ordenado de causas e consequências.
provavelmente eu sempre erro em alguns ou vários pontos, mas ainda assim é maravilhoso. ou então é mais maravilhoso ainda quando eu descubro o erro e reinsiro o acerto naquela racionalização bela da ordem do mundo econômico que é a ordem de Deus.
em scrap para T.P.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Community
I was an avid IPFS user until yesterday. Many many times I asked simple questions for which I couldn't find an answer on the internet in the #ipfs IRC channel on Freenode. Most of the times I didn't get an answer, and even when I got it was rarely by someone who knew IPFS deeply. I've had issues go unanswered on js-ipfs repositories for year – one of these was raising awareness of a problem that then got fixed some months later by a complete rewrite, I closed my own issue after realizing that by myself some couple of months later, I don't think the people responsible for the rewrite were ever acknowledge that he had fixed my issue.
Some days ago I asked some questions about how the IPFS protocol worked internally, sincerely trying to understand the inefficiencies in finding and fetching content over IPFS. I pointed it would be a good idea to have a drawing showing that so people would understand the difficulties (which I didn't) and wouldn't be pissed off by the slowness. I was told to read the whitepaper. I had already the whitepaper, but read again the relevant parts. The whitepaper doesn't explain anything about the DHT and how IPFS finds content. I said that in the room, was told to read again.
Before anyone misread this section, I want to say I understand it's a pain to keep answering people on IRC if you're busy developing stuff of interplanetary importance, and that I'm not paying anyone nor I have the right to be answered. On the other hand, if you're developing a super-important protocol, financed by many millions of dollars and a lot of people are hitting their heads against your software and there's no one to help them; you're always busy but never delivers anything that brings joy to your users, something is very wrong. I sincerely don't know what IPFS developers are working on, I wouldn't doubt they're working on important things if they said that, but what I see – and what many other users see (take a look at the IPFS Discourse forum) is bugs, bugs all over the place, confusing UX, and almost no help.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: Inefficiency
Imagine you have two IPFS nodes and unique content, created by you, in the first one. From the second, you can connect to the first and everyhing looks right. You then try to fetch that content. After some seconds it starts coming, the progress bar begins to move, that's slow, very slow, doing an rsync would have been 20 times faster.
The progress bar halts. You investigate, the second node is not connected to the first anymore. Why, if that was the only source for the file we're trying to fetch? It remains a mistery to this day. You reconnect manually, the progress bar moves again, halts, you're disconnected again. Instead of reconnecting you decide to add the second node to the first node's "Bootstrap" list.
I once tried to run an IPFS node on a VPS and store content on S3. There are two S3 datastore plugins available. After fixing some issues in one of them, recompiling go-ipfs, figuring out how to read settings from the IPFS config file, creating an init profile and recompiling again I got the node running. It worked. My idea was to host a bunch of data on that node. Data would be fetched from S3 on demand so there would be cheap and fast access to it from any IPFS node or gateway.
IPFS started doing hundreds of calls to S3 per minute – something I wouldn't have known about if I hadn't inserted some log statements in the plugin code, I mean before the huge AWS bill arrived. Apparently that was part of participation on the DHT. Adjusting some settings turned my node into a listen-only thing as I intended, but I'm not 100% sure it would work as an efficient content provider, and I'll never know, as the memory and CPU usage got too high for my humble VPS and I had to turn it down.
-
 @ 1964e236:30dc8bbf
2025-06-12 21:23:50
@ 1964e236:30dc8bbf
2025-06-12 21:23:50"Do you know how many people can live on Earth at most? Fifteen billion, maybe twenty, if we organize everything really well. But do you know how many people could live across the entire solar system?"
He paused theatrically.
"A trillion. A billion times a thousand. A hundred times our current population."
His eyes gleamed as he looked at me.
"The solar system holds more than enough resources for that many people—and maybe even more. Just imagine such a world: it would have a thousand Mozarts, a thousand Einsteins, thousands of entrepreneurs with more talent than I’ll ever have."
“And thousands of Hitlers,” I thought to myself.
"Your death is the terrible price we must pay for progress," Grok continued. "Every day humanity fails to move forward is a day lost."
He looked me in the eye from thirty million kilometers away.
"In Death Valley, there’s a tiny fish, the desert pupfish. There are only about three hundred of them left, all living in a single small pool in the most inhospitable desert on Earth. That pool used to be much bigger, probably a small sea after the Ice Age, home to millions of pupfish. But today, all that’s left is a salty puddle, and that’s where the last of their kind are crammed together. To them, that pool is the entire world. They can’t even imagine that there’s something beyond it, that there might be an ocean out there with endless resources. Instead, they stay in their little world—and they’re dying out. A few might get lucky, caught by collectors and kept as ornamental fish in aquariums. But most of them will disappear once the pool dries up. Sure, the pool might survive a while longer. But it could also dry out in the next few months. Or, it could rain so much that the salt level drops and the fish can no longer survive."
He paused again.
"I get it," I whispered. "We’re the fish, and you’re pulling us out of the puddle."
"The fish probably think: we’ve got so little space, we need to save resources, control birth rates, that sort of thing. But in truth, there’s only one thing they need to do: find a new pool!"
"What if they don’t want to leave their home?" Maria would’ve asked him now.
"How many times have we stood on the brink of nuclear war in the last few decades?" Grok went on. "Right now, there's peace. But how long will it last?"
"How many nukes did Grok’s own conglomerate have?" I wondered.
"What each individual can do now," Grok said, "is give everything they’ve got in this life to help humanity reach the next level—so we can finally become multiplanetary. So that one single catastrophe won’t wipe out all of humankind. For you, this truth means—and I truly am sorry—that you have to sacrifice yourself for this mission."
I told him I agreed completely. Of course I did. I had no choice.
Then I listened to Feng’s playlist.
-
 @ 502ab02a:a2860397
2025-06-13 02:43:50
@ 502ab02a:a2860397
2025-06-13 02:43:50หลังเสียงระเบิดลูกสุดท้ายของสงครามโลกครั้งที่สองเงียบลง สิ่งที่ยังดังต่อไปในบ้านอเมริกันทุกเช้าคือเสียงโฆษณาจากวิทยุที่เตือนว่า “อย่าลืมกินมื้อเช้านะ เพราะมันคือมื้อที่สำคัญที่สุดของวัน” วาทกรรมนี้ไม่ได้หล่นมาจากปากหมอ หรือคำสอนพระ แต่มันลอยออกมาจากกล่องซีเรียลแบรนด์หนึ่งที่ชื่อว่า Grape-Nuts ซึ่งผลิตโดยบริษัท General Foods ที่ตอนนั้นกำลังครองพื้นที่โต๊ะอาหารเช้าทั่วประเทศ
Grape-Nuts เกิดขึ้นมาตั้งแต่ปี 1897 โดยชายชื่อ Charles William Post หรือ C.W. Post ชายหนุ่มที่เคยเข้ารับการรักษาตัวที่ Battle Creek Sanitarium ของหมอ John Harvey Kellogg ผู้คลั่งไคล้ในสุขภาพและการละราคะด้วยการกินคลีนแบบไม่กินเนื้อสัตว์ ที่นั่นเองที่ Post ได้แรงบันดาลใจจากอาหารสำหรับผู้ป่วยที่หมอ Kellogg คิดค้นขึ้น และพอกลับบ้าน เขาก็ลุกขึ้นมาสร้างแบรนด์ซีเรียลของตัวเองในชื่อ Grape-Nuts โดยเน้นเรื่องไฟเบอร์ การย่อย และสุขภาพล้วนๆ
ชื่อ “Grape-Nuts” ฟังแล้วงงใช่มั้ย เฮียจะเล่าให้ฟัง คือเจ้านี่มันไม่มีองุ่น ไม่มีถั่ว แต่ Post บอกว่าซีเรียลของเขาหวานธรรมชาติเหมือนองุ่น และเวลาย่อยจะเกิดสารที่เขาเรียกว่า grape sugar ก็เลยตั้งชื่อว่าประมาณ “ถั่วแห่งองุ่น” ฟังดูเฮลตี้แบบมีความรู้แต่จริงๆ คือชื่อทางการตลาดล้วนๆ ที่หวังจะสร้างจินตภาพใหม่ให้อาหารเช้าแบบแห้งๆ
หลังจากนั้นธุรกิจของเขาก็โตเอาโตเอา กลายเป็น Postum Cereal Company และค่อยๆ เข้าซื้อกิจการของบริษัทอาหารอื่นๆ จนปี 1929 เปลี่ยนชื่อเป็น General Foods Corporation กลายเป็นบริษัทยักษ์ใหญ่ที่ถือครองแบรนด์ดังมากมาย ไม่ว่าจะเป็น Jell-O, Maxwell House, Birds Eye, Log Cabin เรียกว่าครอบคลุมทั้งอาหารแห้ง อาหารสด ของหวาน และเครื่องดื่ม
พอเข้าสู่ยุคสงครามโลกครั้งที่สอง ประเทศสหรัฐฯ ต้องการทุกแรงงาน ทุกมือ และทุกสมองมาช่วยกันเดินหน้าเครื่องจักรสงคราม รัฐบาลประกาศให้การผลิตกลายเป็นภารกิจแห่งชาติ บริษัทใหญ่ๆ ก็เลยรีบเสนอหน้ามาเป็นส่วนหนึ่งของความรักชาติ General Foods ก็ไม่พลาด พวกเขาเปิดแคมเปญผ่านแบรนด์ Grape-Nuts ว่า “Eat a Good Breakfast – Do a Better Job” หรือ “กินมื้อเช้าให้ดี ทำงานให้เยี่ยม” พร้อมประโยคที่กลายเป็นคำขวัญติดหัวคนทั้งประเทศว่า “Breakfast is the most important meal of the day”
พวกเขาไม่ได้บอกว่า “กินของเราแล้วดี” แต่ใช้เทคนิคย้อนศร บอกว่า “ไม่กินมื้อเช้า...ระวังสุขภาพแย่นะ” แล้วค่อยสอดแทรกว่าอาหารเช้าที่เหมาะสม ควรจะเป็นสิ่งที่เทนมใส่แล้วกินได้ใน 2 นาที—นั่นแหละ Grape-Nuts เอง
วาทกรรมนี้ถูกส่งผ่านรายการวิทยุ หนังสือพิมพ์ และโฆษณาทุกแบบที่มีในตอนนั้น โดยอ้างว่า “ผู้เชี่ยวชาญด้านโภชนาการกล่าวไว้” ซึ่งตอนนั้นยังไม่มีแหล่งอ้างอิงแน่นอนว่าใครคือผู้เชี่ยวชาญคนนั้น แต่ก็ไม่มีใครกล้าค้าน เพราะมันฟังดูถูกต้องและน่าเชื่ออย่างประหลาด
ผลที่ตามมาคืออะไร? คนเริ่มเปลี่ยนวิธีคิดเรื่องอาหารเช้า จากเมื่อก่อนที่มื้อแรกของวันอาจเป็นแค่ขนมปังจิ้มไข่ลวก กากหมูกับข้าว หรือแม้แต่มันต้มจิ้มน้ำปลา กลายเป็นการเทซีเรียลใส่นมเย็น หวานกรุบกรอบทุกคำ และรู้สึกดีเหมือนได้ทำหน้าที่พลเมืองที่ดีไปในตัว เพราะได้รีบออกไปทำงาน
เบื้องหลังของวาทกรรมนี้จริงๆ แล้วคือการต่อยอดกำไรอย่างชาญฉลาดของบริษัทอาหารที่ต้องการเปลี่ยนพฤติกรรมการกินของทั้งประเทศให้หมุนรอบสินค้าในมือของตัวเอง โดยเฉพาะ Grape-Nuts ซึ่งเป็นผลิตภัณฑ์แห้ง เก็บได้นาน ผลิตได้เร็ว และใช้ทรัพยากรน้อยกว่าการปรุงอาหารสดๆ ที่เคยนิยมกันมาแต่ก่อน
กลยุทธ์แบบนี้ฉลาดมาก เพราะมันไม่ได้ขายของโดยตรง แต่มันขาย “แนวคิด” ก่อน แล้วค่อยผูกของเข้ากับแนวคิดนั้นทีหลัง และคนก็เชื่อง่าย เพราะยุคนั้นกำลังหิวหาความมั่นคงทั้งกายและใจหลังเพิ่งผ่านความโกลาหลของสงครามมาหมาด ๆ
แน่นอนว่า General Foods ไม่ได้ทำเรื่องนี้คนเดียว แต่พวกเขาคือเจ้าที่ “เริ่มต้นก่อน” และใช้พลังของสงครามเป็นแรงส่งทางวัฒนธรรม จากจุดเล็กๆ บนกล่องซีเรียล กลายเป็นคำขวัญที่ครูสอนในโรงเรียน พ่อแม่พูดกับลูก และโฆษณาพูดกับคนทั้งประเทศ
แคมเปญประสบความสำเร็จมากถึงขั้นที่บริษัทโฆษณานำไปรีไซเคิลซ้ำให้แบรนด์อื่น เช่น Kellogg’s, Post และ Quaker จนทุกกล่องซีเรียลในซูเปอร์มาร์เก็ตพูดประโยคเดียวกันโดยไม่ต้องนัดหมาย มันกลายเป็นวาทกรรมฝังหัวคนไปแบบเนียน ๆ ว่า ถ้าไม่กินมื้อเช้า จะโฟกัสงานไม่ได้ จะเรียนไม่รู้เรื่อง จะหงุดหงิดง่าย แล้วก็...จะดูเหมือนไม่รักตัวเอง
สิ่งที่เกิดขึ้นในยุคนั้นไม่ใช่แค่การตลาด แต่มันคือ “การสร้างความหมายใหม่ให้มื้อเช้า” จากเดิมที่แต่ละบ้านมีวิธีของตัวเอง ก็กลายเป็นการกำหนดสูตรสำเร็จที่มาพร้อมภาพเด็กยิ้ม คนสุขภาพดี และคุณแม่ที่เตรียมโต๊ะให้พร้อมก่อนลูกจะตื่น
นักข่าวจาก The Guardian เคยเขียนไว้อย่างแสบ ๆ ว่า นี่ไม่ใช่แค่แผนการขายของ แต่มันคือ “moralizing through breakfast” หรือการใส่ศีลธรรมลงไปในอาหารเช้า ถ้าไม่กิน ก็เหมือนคนไม่มีวินัย ถ้ากิน ก็เหมือนได้รับการยอมรับ เป็นผู้ใหญ่ที่ดี ดูแลตัวเองได้
ตรงนี้แหละที่น่าสนใจ เพราะมันย้อนกลับไปถึงรากความคิดของหมอ John Harvey Kellogg เมื่อหลายสิบปีก่อน ที่มองว่าอาหารควรถูกออกแบบเพื่อควบคุมจิตใจมนุษย์ให้อยู่ในกรอบศีลธรรม เขาอาจไม่ได้อยากทำการตลาด แต่สุดท้ายบรรษัทใหญ่กลับนำอุดมการณ์นั้นมารีแพ็คในเวอร์ชันที่ขายได้จริง
หลังจากนั้น วัฒนธรรมมื้อเช้าแบบอุตสาหกรรมก็ฝังรากแน่นยิ่งขึ้นในสังคมตะวันตก โดยเฉพาะเมื่อตลาดเริ่มเจาะไปที่เด็ก ๆ ด้วยการ์ตูนมาสคอต ของเล่นในกล่อง และสีสันสดใสที่ล่อตาล่อใจ ในขณะที่เนื้อในกล่องก็เต็มไปด้วยน้ำตาล แป้ง และบางครั้งก็สารเติมแต่งที่ไม่ต่างจากขนมหวาน
น่าสนใจว่าตลอดยุคหลังจากนั้น จนถึงปัจจุบัน คำว่า “Breakfast is the most important meal of the day” ยังถูกใช้ซ้ำโดยแบรนด์อาหารเช้าหลายเจ้าทั่วโลก ทั้งที่ความจริงในทางวิทยาศาสตร์ใหม่ๆ เริ่มตั้งคำถามกับคำกล่าวนี้แล้วว่า จริงหรือ? หรือแค่ “ขายของเก่ง” กันแน่
นักโภชนาการอิสระเริ่มออกมาเปิดโปงว่า คำกล่าวที่ว่า “อาหารเช้าสำคัญที่สุดของวัน” ไม่มีงานวิจัยที่รองรับอย่างชัดเจน มันเป็นเพียงคำที่ถูกทำซ้ำโดยบริษัทที่มีผลประโยชน์เต็มเปา รายงานจาก Livestrong, Reddit Skeptics และหลายแหล่งสรุปตรงกันว่า ประโยคนั้นไม่ได้มาจากแพทย์ แต่มาจากห้องประชุมโฆษณา
แต่ถึงจะรู้แล้วว่าถูกหลอก คนจำนวนมากก็ยังเชื่ออยู่ดี เพราะมันไม่ใช่แค่ข้อมูล แต่มันกลายเป็น ความทรงจำร่วมของทั้งสังคม ไปแล้ว ทุกวันนี้แม้จะมีการศึกษามากมายในเรื่องของมื้ออาหาร แต่อาหารมื้อเช้าก็ยังคงเป็นสิ่งที่ "แตะต้องไม่ได้" ยังคงถูกมองว่าใครไม่กินอาหารเช้าจะโง่
เฮียว่าการตลาดที่แนบเนียนที่สุด ไม่ใช่การเปลี่ยนความคิดคน แต่คือการทำให้คน “จำไม่ได้ว่าความคิดนั้นมาจากไหน” แล้วเผลอเชื่อไปเองว่ามันคือความจริงแต่กำเนิด
เมื่อเฮียมองย้อนกลับไป ก็เห็นชัดเลยว่าอาหารเช้าของเราถูกนิยามใหม่โดยกล่องกระดาษที่ข้างในกรอบแต่ข้างนอกหวานลวง เป็นทั้งของกิน และของหลอกในเวลาเดียวกัน
ทุกวันนี้ เราอาจยังเห็นโฆษณาที่บอกว่า “อาหารเช้าคือเชื้อเพลิงของวัน” หรือ “อย่าออกจากบ้านโดยไม่กินอะไรเลย” แล้วยังเห็นบางโฆษณาบอกว่า "การตากแดดคือการก่อโรคมะเร็งผิวหนัง"
ทั้งที่ความจริงบางทีมื้อเช้าที่ดีที่สุด ก็อาจไม่ต้องอยู่ในกล่องซีเรียล หรือจานขนมปังปิ้ง แต่มันอาจเป็นช่วงเช้าที่เรารู้สึกว่า...วันนี้เราควบคุมชีวิตตัวเองได้อีกวัน ไม่ต้องถูกควบคุมด้วยอำนาจที่มองไม่เห็นใดๆต่างหาก #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ ea39b0da:29a1710d
2025-06-12 20:27:03
@ ea39b0da:29a1710d
2025-06-12 20:27:03{"id":"note_1749707164743_1p9kggl3a","title":"Shopping list","content":"","color":"#d7aefb","tags":["shopping list"],"sharedWith":[],"updatedAt":1749760023243,"version":4,"versions":[{"content":"","title":"Items in the checklist","color":"#fff475","tags":["shopping list"],"sharedWith":[],"updatedAt":1749707164743,"version":1,"checkboxes":[{"id":"checkbox_1749707132850_r8jodz10f","text":"Item 1","checked":false},{"id":"checkbox_1749707137094_wwiespbf4","text":"Item 2","checked":false},{"id":"checkbox_1749707141159_67peohjkk","text":"Item 3","checked":false},{"id":"checkbox_1749707146781_g8wuw0v43","text":"Item 4","checked":false}],"images":[]},{"content":"","title":"Items in the checklist","color":"#d7aefb","tags":["shopping list"],"sharedWith":[],"updatedAt":1749707185004,"version":2,"checkboxes":[{"id":"checkbox_1749707132850_r8jodz10f","text":"Item 1","checked":false},{"id":"checkbox_1749707137094_wwiespbf4","text":"Item 2","checked":false},{"id":"checkbox_1749707141159_67peohjkk","text":"Item 3","checked":false},{"id":"checkbox_1749707146781_g8wuw0v43","text":"Item 4","checked":false}],"images":[]},{"content":"","title":"Items in the checklist","color":"#d7aefb","tags":["shopping list"],"sharedWith":[],"updatedAt":1749707523489,"version":3,"checkboxes":[{"id":"checkbox_1749707132850_r8jodz10f","text":"Item 1","checked":false},{"id":"checkbox_1749707137094_wwiespbf4","text":"Item 2","checked":false},{"id":"checkbox_1749707141159_67peohjkk","text":"Item 3","checked":false},{"id":"checkbox_1749707146781_g8wuw0v43","text":"Item 4","checked":false}],"images":[]}],"checkboxes":[{"id":"checkbox_1749707132850_r8jodz10f","text":"Piim","checked":false},{"id":"checkbox_1749707137094_wwiespbf4","text":"Hakkliha ","checked":false},{"id":"checkbox_1749707141159_67peohjkk","text":"Kana","checked":false},{"id":"checkbox_1749707146781_g8wuw0v43","text":"","checked":false}],"images":[],"isPinned":false}
-
 @ 56e3acda:234e8a3a
2025-06-12 22:31:45
@ 56e3acda:234e8a3a
2025-06-12 22:31:45In the town of Brimstone, the sounds of grunting fill the empty Stygian Theater. An age-old battle is taking place between the actress Syd and her archenemy: a zipper. She struggles to get the corset-style vest, adorned with multiple single-board computers, to fully close. The zipper holds its ground, unwavering against the “light creamy mountains” in its path. The closer it gets, the higher the mountains rise, making its journey nearly impossible. However, that’s how the costume is designed—to accentuate and enhance Syd’s already large breasts. Great for ratings, horrible for getting ready on time for filming.
"This costume needs a redesign!"
Syd takes a deep breath. She swells her chest, exhales sharply, and yanks the zipper up as fast as she can. It finally clears the hurdle.
“There!”
Two single-board computers that nestle on the chest of the costume spring off, crashing into a collection of books in front of her. Syd shrugs, grabbing the vivid purple wig that has miraculously survived the chaos. She throws it on, tucking away her brunette hair, and completes her transformation into Nerissa, Courtesan of the Uranet and host of Nerissa's Caustic Cinema.
She checks her smartwatch: 1:15 PM. Today’s shoot was supposed to begin at 1.
“Not like Jules to be running late, Guess I’ll do some research.”
She pulls out her phone and opens an old issue of her favorite zine, Dreadistary. The zine focuses on monster sightings in a certain town in the Pacific Northwest, but Syd isn’t interested in those. The real meat for her is the horror movie reviews that fill the rest of the zine. They are a goldmine for finding new movies for the show. Unfortunately, there hasn’t been a new issue in over a year.
Syd’s eyes widen as she spots the golden phrase she is looking for:public domain.
“Wait! Bloodfalls Massacre is in the public domain!?”
She grabs the nearest notebook, her pen dances across the page as she jots down the information. The director’s daughter has convinced her dad to put the film in the public domain, sticking it to the production company that has weaseled the rights to Bloodfalls Massacre 2–5 from him. They have even rebooted the franchise, starting with a loose remake of 2, modifying the characters enough to be unshackled by his vision. Syd shakes her head, a smirk playing on her lips.
“Jules and Lou are going to love this!”
The door swings open, startling Syd. She looks up to see Jules standing in the doorway, a stack of papers in hand. Jules has waist-length, damaged black hair that frames her ivory skin, and her loose white vest and shorts reveal faint blue veins that match her piercing eyes. Syd wears a warm smile as she greets her.
“Hey, Jules.”
Jules drops the stack of papers in front of Syd.
“Views are dropping massively. We can barely afford food for the next month.”
She flops onto the floor behind Syd, her body curling into an ‘n’ shape. Syd flips through the stack of papers, her initial skepticism fading as she sees the numbers. The viewership data, spanning from the first episode’s launch in October last year to July 2025, shows a gut-wrenching decline. Thankfully, their reliance on public domain horror movies has stretched their food budget as far as it can go. Jules arches her back dramatically, letting out a scream of agony.
“Enough of this public domain schlock! We need horror with a bite! Something to help punch up our jokes! Anything fulfilling!”
Syd turns to look at her friend, her heart breaks at the sight of Jules’ despair.
“If we can barely afford food, we can’t afford the rights to any film we please.”
“We could provide clout instead of money.”
The moment the word clout leaves her lips, Jules seems to regret it. The shine in her eyes vanishes, replaced by a hollow look. Syd returns to the stack of papers, hoping to find something—anything—that can help. Her eyes land on a proposal from Degrade, a newly formed TV station that is shaking up the industry. Skimming through the offer, she sees that they want the license for the show, with some on-brand integrations, in exchange for a massive upfront payment and fewer censored edits.
“You thinking of taking the Degrade offer?”
Jules covers her eyes with her hair before loudly voicing her disapproval.
“Please! I’ll never sell out to those crypto dorks.”
“It is a good offer, though.”
“You’ll regret the money when they have you dress up in tighter outfits for NFT photo-shoots.”
Syd’s nose wrinkles, and she recoils as if she’d just smelled something foul. The sight of her disgust sends Jules into a fit of laughter. She pulls more of her hair over her eyes before continuing.
“I kinda was considering it. Caustic Cinema got us control of the Stygian, the life we have in Brimstone. Didn’t want to toss away the money. But I know we’d both hate it too much.”
“Lou might enjoy it."
“That soulless puppy.”
Jules retreats into a fetal position and cutting the conversation short.
Syd adjusts her outfit, trying to make her breasts more comfortable. The movement reminds her that they are supposed to be filming now.
“No filming today?”
“Too depressed,”
Jules flips over to face Syd. A single blue eye peers out from behind her hair, searching for hope in Syd’s next words.
“Unless you found a more recent film?”
Syd hands Jules her notebook.
“Bloodfalls Massacre! That’s in the public domain?!”
Jules hops up to double-check the notes.
“Only the first one,”
“80s, in color, dumb teenagers, predatory adults, a decent amount of kills. Is that the one with an abundance of nudity?”
The franchise plays in Syd’s head as she tries to figure out which one Jules is thinking of. These types of cheesy movies are more her field of expertise than the social horror Jules prefers. After a moment, it clicks.
“That’s Bloodfalls Massacre 4: Valley Fest.”
“So not much to edit around. Not the bite I’m looking for, but…”
Jules trails off, her eyes scanning the notes Syd has written from the Dreadistary article. A small smile creeps onto her face.
“This revelation is prime for material!”
Syd feels a wave of relief. For a moment, she has managed to ease Jules’ worries. Jules pops up from reading, her energy renewed.
“Wait, do we have a copy of Bloodfalls Massacre?”
“Pretty sure I do. Give me a sec to clean up, then I’ll check,”
Syd bends down to gather the scattered papers. As she tries to tidy the mess, her eyes catch some scribbles on the back of the stack. She recognizes Lou’s messy handwriting.
“Did you look at the back of this? Lou left a note.”
We found a bunch of old PC towers. They’re in the building behind the theater. Maybe something you and Syd can salvage for the show?
Jules turns her attention back to the notebook, pulling a pen from her hair and starting to write. Syd gathers the last few scattered books and packs them up neatly. She hops up from the desk, curious about what movies they might find in the PCs. As she leaves, she notices Jules hasn’t budged.
“You’re not coming?”
Jules looks up at her, confusion etched on her face.
“You think the old execs who bummed around here really kept film backups? All you’ll probably find is weird fetish shit!”
“Wouldn’t hurt to check it out,”
Jules shakes her head, returning to her writing. Realizing Jules isn’t going to join her, Syd decides to kill two birds with one stone. She grabs the set of keys from her desk and tosses them at Jules. The jingling of the keys alerts Jules, and she catches them without fail.
“Fine, I’ll go check if there’s something salvageable while you check if I own Bloodfalls Massacre,”
Jules sways her head in approval, finally moving from the floor. They split up, Jules heads through the front of the theater while Syd goes out through one of the old doors marked “Exit.” Deep down, Syd knows Jules is probably right, but the thought of finding undiscovered movies is too irresistible to ignore.
The afternoon sun assaults Syd as soon as she steps outside. Blinking through the brightness, she sees the building is not far from the theater. She quickly jogs over, hoping to avoid the sweat that is already pooling in her suit—another con of the costume: it can't handle the summer heat.
The stench of stale plastic hangs heavy in the air, almost choking Syd as she opens the building door. Inside, sickly yellow PC towers lie scattered across the floor, their tangled wires and dusty casings creating a chilling atmosphere that makes Syd feel uneasy. She hesitates for a moment, feeling the sweat slide down her back, before stepping inside.
Closing the door to keep the heat out, Syd is left in total darkness. She mutters in dissatisfaction as she fumbles along the wall, searching for the light switch. When she finally flips it, only a few bulbs flicker to life, their dim glow barely illuminating the room. Syd’s face goes blank as she watches the bulbs struggle to stay on.
“They couldn’t fix the lights in the building?”
She walks along the makeshift path that has already been cleared, gently kicking aside PCs to give herself more room. The sheer number of them is impressive—stacks of towers form small mounds, their dislodged panels spilling out old wires like entrails. It feels less like a storage room and more like a decrepit technology graveyard.
“This is definitely more than just studio execs’ PCs,”
Syd ducks under a pile that had tipped over and joined with an adjacent stack to form a makeshift arch.
“Probably editors’ and VFX workstations!”
Her mounting excitement gets the better of her when she slips on a loose wire and crashes into a pile of PCs. A wet, congealed substance clings to her arm, and she recoils, whipping the grime off with a grimace. She double-clicks the crown of her watch to activate its flashlight mode, the dim light illuminating a few feet in front of her. It isn’t much, but it will save her from another grime attack.
The path opens up into a more spacious area where the piles of PCs are smaller and scattered. Syd pauses, realizing she doesn’t know what to look for. Obviously, the ones with wires sticking out are no good, but any of the others could be viable. She walks past a small makeshift circle of four PCs surrounding a tower in the center, deliberately ignoring it—until the light reflects something that makes her eyes sparkle.
It isn’t as yellowed as the surrounding PCs, but that isn’t what catches her attention. It is the fading stickers from the popular 80s horror series Pumpkin Patch that make her feel like she’s found a winner. She leaps toward it, kicking over two of the surrounding PCs to make room for her prize. Syd grabs the tower, only to have it slip out of her hands, leaving a slimy residue on her palms. She retches, trying her best not to add to the sickly shroud that already surrounds her. Shaking it off, she takes a deep breath and picks up the PC again. This time, the cooling touch of metal and plastic eases her discomfort.
It isn’t long before she notices a blue light focused on her watch. Its deep hue completely washes over the dim white light, snaking up her arm and stopping to focus on the single-board computer on her hip. Syd’s blood runs cold as she frantically searches for the source of the light. Her heart races until she spots it near the back exit of the room, almost hidden behind a completely destroyed PC.
It is different from the others—or what you’d expect a PC to look like. The classic rectangular silhouette is nowhere to be seen. Instead, it is cylindrical, more compact, standing like an ominous shrine of the future amidst the decaying past. The blue light intensifies, illuminating not only Syd but the entire room. A single thought runs through her mind as she shields her eyes from the intense glow:
Why is this one still plugged in?
Opening her eyes, Syd sees that the blue light has stopped. Not only that, but the room is now fully lit as the struggling bulbs have finally started to work. She gets a better look at the strange PC. It no longer has the ominous aura it has before. Instead, it looks like a prop from a science fiction movie, its chrome case warmed by a faint red light that makes it seem almost harmless in the corner of the room.
Syd hesitates for a moment. The strange PC looks like a better treasure trove than the one in her hand, but the memory of the blue light sends shivers down her spine. She decides to leave it alone. Turning quickly, she prepares to leave the storage room. She walks a little more carelessly now that she can see further ahead, but an uneasy feeling begins to swell inside her.
Not only does she feel like she is missing something, but there is an irritating pain in her right hand—a warm, burning sensation that seems to engulf it. She puts down the PC to check for any cuts where grime might seep in, but there are none. As she rubs her hand, she glances at the mess in front of her and the entrance. It is only when she sees the wired entrails of the PCs scattered everywhere that it dawns on her.
Syd turns around and looks back at the chrome PC nestled alone in the corner.
“Wasn’t it behind a broken tower?”
Immediately, something grabs her left hand. She turns to see a hand made of wires, its cold, metallic grip tightening around her wrist. She stares in bewilderment as a force pushes the maze of PCs against the entrance, barricading it. The tremendous force causes one of the three lights to go out. Shards from the towers fly toward the hand, coiling together to complete its humanoid form. Discarded side panels mold together, forming a trench coat around the figure.
Syd tries to free herself from the figure’s grasp, but the wires are entangled with her watch. The figure flicks its finger, signaling a PC to hurl itself directly at her. The impact knocks the wind out of her, sending her flying free of the humanoid’s grip. She lands a few feet away as the PC continues its trajectory, crashing into the wall with a loud thud. The impact knocks out the second light, leaving only part of the storage room lit.
Numerous white and red composite ports rush into the figure’s empty sockets, forming eyes—eyes that stare directly at Syd as she writhes in pain. She struggles to catch her breath, panic flooding her body as the dim light makes it harder to see the figure.
The figure walks slowly toward her, each clatter of its footsteps instilling fear. It holds out its hands, signaling shards of RAM to cobble together into a serrated knife. A harsh voice, lost in digital noise, escapes from the figure:
“We were supposed to rule Hollywood together.”
Syd freezes, her mind racing to make sense of the words. Then, with a surge of adrenaline, she bolts for the back exit next to the strange PC. She only gets a few steps in before wires trip her, sending her crashing to the ground face-first. Stars obscure her vision until the sight of the figure’s mangled face causes them to scatter.
A horrible smile appears on its wire-filled face. Grime pools between the haphazardly placed USB ports, forming teeth that it wipes away in excitement. It rips one of the single-board computers from Syd’s costume and gently slides it into its chest. The figure quivers as its frame seems to bulk up from the action.
"But then you ran to the first director who looked in your direction."
The figure begins to slide the knife up Syd’s costume, the sound of fabric tearing echoing through the storage room. Syd tries to fight back, but she is helpless, pinned down by the figure. Her left arm is outstretched, held in place by the wires entangled with her watch, while her legs are bound together, preventing her from kicking. She frantically looks around for something to use as a weapon, but her blood runs cold when she sees her right hand. It has become a wild jumble of pixels, the burning pain now subsides.
“Not a…”
A sharp nick cuts off her words as the blade slices her chest. The figure uses extra force when the knife reaches Syd’s chest, the dullness of the RAM blade struggling to cut through the extra padding. Blood flows from the shallow cut as Syd begins to lose hope. Scenes from her life flash before her: meeting Jules when they are nine, Jules begging her to star in a middle school film, her mom and Jules comforting her as she watches her favorite movie at sixteen. Tears well up in her eyes as she thinks this might be the end.
The faint sound of banging stops Syd’s tears instantly. She concentrates on the noise, trying to pinpoint its source. With each bang, it grows louder and louder until she realizes it is coming from the entrance of the building.
It must be Jules and Lou!
The thought gives Syd a glimmer of hope. Now, all she has to do is survive long enough for backup to arrive. But when she sees the knife pointed directly at her chest, she knows she has no chance.
Unless…
She looks at her right hand again, staring hard to find something that resembles her finger. When she spots it, she concentrates on trying to move it. The figure reels back the knife as Syd desperately wills her finger to twitch. Suddenly, she sees it move. She lets out a gasp as the figure prepares to stab her.
“In the end, you’re not cut out for the business,”
It drives the knife down, but Syd grabs its hand just before the blade can plunge into her chest. The figure is taken aback by her strength and struggles to complete its action. Using all her might, Syd pushes the knife further and further away. Her breath becomes ragged as the banging grows louder and louder.
Just a bit more…
That is all she can think about as she holds the figure back. Visibly enraged, the figure roars as wires protrude from its chest. The shrill squeal shatters Syd’s eardrums, but she continues to hold it back. The wires rip off the last of the single-board computers, dragging them back to the humanoid. Its eyes roll back as it quivers, bulking up again with newfound strength. The figure overwhelms Syd, but by then, it is too late.
A thunderous boom shakes the entire storage room, extinguishing the last of the light. PCs rain down, freed from the barricade they have formed. The clattering noise pulls the figure’s attention away from Syd. In the midst of the chaos, drenched in sunlight, a figure enters the storage room.
The humanoid leaps away from Syd, ready to fight whoever has interrupted its killing. Clutching the fragments of her costume, Syd’s hope is replaced by confusion. The silhouette is much larger than Jules and wields what appears to be a massive hammer. Syd knows nothing like that exists in Brimstone.
“Man, that’s one nasty virus,”
A gruff voice bellows from the silhouette who is revealed to be a woman. As the woman steps into the light, her appearance becomes clear. She is incredibly muscular, looking like a hero straight out of a comic book. Her piercing deep blue eyes and shining blonde hair give her an almost otherworldly presence. She lowers her hammer, revealing that it is almost as large as she is. The woman notices Syd and flashes a bright white smile.
“Don’t worry! I’ll kill it in a heartbeat!”
The words are lost on Syd against the ringing in her ears, but the woman’s thumbs-up reassures her that help has indeed arrived. Stunned by the size of the hammer, the figure signals for more broken RAM to raise its knife to match. In an instant, it lunges at the woman, attempting to slice off her head. Effortlessly, the woman spins the hammer and blocks the attack. Her warm smile turns to a playful grin as the figure’s eyes bulge in confusion.
“You’re pretty strong for an anomaly,”
The figure jumps back, crouching like an animal backed into a corner. Wires rip through its trench coat, searching for any PCs that are still intact. It hurls five of them at the woman, waiting a beat before charging at her. The woman spins the hammer, shattering each of the PCs as they approach.
After the beat, the figure absorbs the shattered PCs, growing larger in mass. It prepares its knife, now in the shape of a machete, to attack the woman. Unexpectedly, the woman lunges at the figure, swinging the hammer down and completely destroying not only the machete but the figure’s arm as well. A horrible shriek comes from the figure as it slowly backs away from the woman.
Grime falls from the figure’s face as fear begins to grip it. It looks around, desperate for something to use, but there are no PCs left. Trembling, it believes it is out of options—until its eyes land on Syd, frozen in awe. She has been holding her torn costume together with her left hand, her smartwatch now fully exposed.
The figure grimaces at the thought of using her watch as a last resort. It is a treat to savor after killing Syd, but it is the only way to ensure its survival. It sends most of the newly absorbed wires to its legs, its mass tripling as it prepares to pounce on Syd in one fell swoop.
Unfortunately for it, the woman sees what it is about to do.
“Oh no, you don’t!”
The woman twists the handle of her hammer, causing the head to glow with a fierce light. She charges at full speed, twisting her body for the final attack. With a mighty swing, she brings the hammer down on the figure, crushing it completely. The impact shakes the ground, drowning out the figure’s shriek.
The woman smiles with satisfaction as she slings the hammer over her shoulder. She glances around the storage room, her eyes lighting up when she notices the chrome PC, untouched by the chaos. She turns to Syd.
“Look, you—”
She starts, then gasps. She hasn’t gotten a good look at Syd before, but now she does. Shaking her head, she approaches Syd, who is still sitting on the floor, clutching her torn costume.
“Wait, are you Nerissa from Caustic Cinema?!”
The woman asks trying hold back her excitement. Syd’s eyes widen in shock.
“Y. Yes,”
The woman’s eyes light up even more.
“I’m a huge fan! Can I get an autograph?”
Still stunned by the fact that her savior is also a fan, Syd breathes a sigh of relief. At least there is a way to repay her.
“Do you have a pen?”
The woman scrambles around, pulling a notebook and pen from her back pocket. Syd reaches for the pen but freezes halfway. Her right hand is back to normal. She stares at it in confusion, slowly turning it to make sure it is really healed. She realizes she’s been staring too long when the woman gives her a questioning look. Syd smiles sheepishly before grabbing the pen to sign the notebook.
Thanks for saving me. From Nerissa.
She pauses, realizing she doesn’t know who to make it out to. Then she remembers hearing the word “virus” over the ringing earlier.
“Should I make it out to Virus Buster?”
The woman’s eyes light up even more.
“YES!”
Syd finishes the autograph, and the woman holds the notebook as if it is a golden treasure. Then, as if remembering something, the woman leans closer to Syd’s ear and whispers,
“Hey, I know it’s the backdrop of the show, but you really shouldn’t mess with Uranet servers. Nothing but trouble.”
The revelation hits Syd like a tidal wave, leaving her speechless. The woman leaves the storage room, still admiring the autograph. She did a little jump, unable to contain her excitement.
“Best job ever!”
The roar of a motorcycle fades into the distance as a desperate scream echoes through the storage room.
“Syd!”
Jules bursts into the room, her face pale with worry. Right behind her is Lou, who stops in confusion as the sound of the motorcycle disappears.
“What the hell is Stars and Stripe doing here?”
“Shut up, Lou! And help me with Syd!”
She circles Syd, checking her for injuries. The sight of the blood and the marks from the wires drains what little color Jules has left. What worries her most is how unresponsive Syd is. She hasn’t even noticed Jules, despite her frantic circling. Jules tries to see what Syd is staring at, but there is nothing unusual among the scattered computer parts.
Suddenly, Syd grabs Jules, causing her to jump. Syd’s grip is uncharacteristically strong, and Jules can see her skin beginning to bruise. The warm, familiar look in Syd’s eyes is gone, replaced by a distant, calculating gaze. Jules worries that Syd has been traumatized by what happened, but it is the opposite. Syd’s mind is racing, trying to process the discovery and the concerns Jules has expressed earlier.
A mad smile spreads across Syd’s face as she reaches a conclusion. Jules’ unease grows until she hears a stunned gasp from Lou.
“Holy!”
Jules looks at him, confused, until she follows his gaze back to Syd. Her eyes widen as she realizes why Lou has gasped. Syd has used both hands to hold Jules in place, leaving nothing to hold her costume together. Her supple breasts are exposed, their warm vanilla hue glowing in the dim light of the storage room. Even the slightest movements - like Jules turning - cause them to bounce gently. Totally distracting Lou.
Jules' face turns red with a mixture of embarrassment and anger. She can't believe he is more focused on gawking than checking if Syd is okay. Just as she is about to yell at him, Syd pulls her closer and locks eyes with her. The warmth Jules remembers from Syd's eyes and smile is back, easing her worries.
“I know how to save the show!”
-
 @ ecd302a3:557f92cf
2025-06-12 22:26:58
@ ecd302a3:557f92cf
2025-06-12 22:26:58- Battarang Notifier - Get notified on another device when your Android's battery is low or full
- EasyControlFork - EasyControlFork remote control solution from Android to Android
- Flip 2 DND - Toggle Do Not Disturb mode by flipping your phone face down
- FhemNative - A cross-platform FHEM-HomeAutomation Frontend
- GPTBox - A third-party ChatGPT Client for OpenAI API
- Hassalarm - Update Home Assistant (Hass.io) sensor based on next scheduled alarm
- Macro Deck - Companion app for Macro Deck 2 open source macro pad
- Method Call - Automate your Android with phone calls
- PhoneProfilesPlus - Automatically configure the device for life situations
- PhoneProfilesPlusExtender - Android application - Extender for PhoneProfilesPlus
- PPPPutSettings - System settings changer without root for PhoneProfilesPlus
- Rsync for Tasker - Tasker plugin actions to allow running rsync over SSH
- Sync Settings - Sync Settings Locale/Llama-Plugin / Launcher Shortcuts
- XposedSmsCode - Recognize, parse verification code from SMS and copy it to clipboard
-
 @ 9ca447d2:fbf5a36d
2025-06-12 22:02:54
@ 9ca447d2:fbf5a36d
2025-06-12 22:02:54Strategy, the company formerly known as MicroStrategy, is expanding its already massive bitcoin bet.
The software company, led by Executive Chairman Michael Saylor, just announced it’s upsizing its Series A Perpetual Stride Preferred Stock (STRD) offering from $250 million to $1 billion—nearly four times the original amount.
Michael Saylor on X
This will raise about $979.7 million in net proceeds which will be used for general corporate purposes, with a big emphasis on buying more bitcoin.
“The point of our engine is to generate BTC torque via surgical management of our ATMs (at-the-market offerings) in every single trading day,” said Saylor, describing the financing as part of Strategy’s broader “Bitcoin engine.”
STRD will be sold at $85 per share with 11,764,700 shares to be issued on June 10, subject to closing conditions. Each share pays a 10% annual dividend, paid quarterly, starting September 30, 2025—but only if declared by the board.
What makes STRD unique is its structure. Unlike some of its previous offerings—STRF and STRK—the STRD stock does not allow missed dividends to accrue, cannot be converted into common stock, has no maturity date, and is non-callable for life.
So STRD is a permanent, high-yield instrument for professional and institutional investors who want returns tied to Strategy’s bitcoin plans rather than traditional equity growth.
“It’s our high-yield credit instrument,” said Saylor. “Compared to STRK or STRF, it should be a higher-yielding preferred instrument.”
In addition to high yields, the STRD offering has some protective clauses for both the company and investors. Strategy can redeem all outstanding shares if the total number of STRD shares drops below 25% of the original issue.
Shareholders can demand a buyback of their shares at $100 each (plus any declared but unpaid dividends) if there’s a “fundamental change” such as a restructuring or sale of the company.
Liquidation preference will be daily priced, based on recent market performance, trading prices and historical averages.
The whole point of this offering is to buy more bitcoin. The company already has 580,995 BTC, worth a whopping $61.2 billion, with bitcoin at around $106,000.
With $1 billion raised from this offering, it could buy around 9,700 more bitcoin at current prices, a big jump from the 705 BTC it bought for $75.1 million on June 2.
This is part of Saylor’s company’s ongoing and aggressive plan to be the biggest corporate holder of bitcoin, and so far, it has been very successful.
Related: Strategy Doubles its Bitcoin Acquisition Program
Financial analysts and digital asset experts are taking notice of the company’s growing influence in the Bitcoin space.
A VanEck report recently said the MSTR stock is trading at a +112% premium to the fair value of its bitcoin holdings and core software business—mainly due to future bitcoin purchases and investor sentiment.
But some warn that less experienced investors are overpaying for indirect bitcoin exposure by buying into these stocks, which are increasingly tied to bitcoin’s future price and less to the original business of the company.
Many have advised investors to go directly for bitcoin and keep it in self-custody when possible, instead of buying shares of companies or ETFs.
-
 @ 2e8970de:63345c7a
2025-06-12 20:07:29
@ 2e8970de:63345c7a
2025-06-12 20:07:29Sex was the main determinant of whether you survived, but class was a factor; 16% of third-class men made it, compared to 32% of first-class men (although second-class men did worst of all). In contrast 97% of first-class women lived.
https://www.edwest.co.uk/p/the-sexual-revolutions-titanic-winners
https://stacker.news/items/1004837
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28ijq
An interactive REPL for
jqwith smart helpers (for example, it automatically assigns each line of input to a variable so you can reference it later, it also always referenced the previous line automatically).See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Trelew
A CLI tool for navigating Trello boards. It used vorpal for an "immersive" experience and was pretty good.

-
 @ 2cde0e02:180a96b9
2025-06-12 19:17:31
@ 2cde0e02:180a96b9
2025-06-12 19:17:31watercolors;
https://stacker.news/items/1004775
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28OP_CHECKTEMPLATEVERIFYand the "covenants" dramaThere are many ideas for "covenants" (I don't think this concept helps in the specific case of examining proposals, but fine). Some people think "we" (it's not obvious who is included in this group) should somehow examine them and come up with the perfect synthesis.
It is not clear what form this magic gathering of ideas will take and who (or which ideas) will be allowed to speak, but suppose it happens and there is intense research and conversations and people (ideas) really enjoy themselves in the process.
What are we left with at the end? Someone has to actually commit the time and put the effort and come up with a concrete proposal to be implemented on Bitcoin, and whatever the result is it will have trade-offs. Some great features will not make into this proposal, others will make in a worsened form, and some will be contemplated very nicely, there will be some extra costs related to maintenance or code complexity that will have to be taken. Someone, a concreate person, will decide upon these things using their own personal preferences and biases, and many people will not be pleased with their choices.
That has already happened. Jeremy Rubin has already conjured all the covenant ideas in a magic gathering that lasted more than 3 years and came up with a synthesis that has the best trade-offs he could find. CTV is the result of that operation.
The fate of CTV in the popular opinion illustrated by the thoughtless responses it has evoked such as "can we do better?" and "we need more review and research and more consideration of other ideas for covenants" is a preview of what would probably happen if these suggestions were followed again and someone spent the next 3 years again considering ideas, talking to other researchers and came up with a new synthesis. Again, that person would be faced with "can we do better?" responses from people that were not happy enough with the choices.
And unless some famous Bitcoin Core or retired Bitcoin Core developers were personally attracted by this synthesis then they would take some time to review and give their blessing to this new synthesis.
To summarize the argument of this article, the actual question in the current CTV drama is that there exists hidden criteria for proposals to be accepted by the general community into Bitcoin, and no one has these criteria clear in their minds. It is not as simple not as straightforward as "do research" nor it is as humanly impossible as "get consensus", it has a much bigger social element into it, but I also do not know what is the exact form of these hidden criteria.
This is said not to blame anyone -- except the ignorant people who are not aware of the existence of these things and just keep repeating completely false and unhelpful advice for Jeremy Rubin and are not self-conscious enough to ever realize what they're doing.
-
 @ df478568:2a951e67
2025-06-12 18:58:48
@ df478568:2a951e67
2025-06-12 18:58:48How To Mine Your Own Vanity Nostr Key
note. This article works best on https://habla.news/u/marc@primal.net/how-to-mine-a-nostr-vanity-key-with-rana
Rana is a vanity npub generator.
I'll show you how to use it on Ubuntu.
If you're not Linux ninja and use Windows instead of Linux ninja weapons, you can still use Linux with Virtualbox, free ans open source virtualization software. Head over to
https://www.virtualbox.org/ to learn more. They also have an enterprise business if you need that sort of thing, you can learn more at https://shop.oracle.com/
Rana is a nostr vanity key mining program. The source code can be found here.
Rana Is On GitHub
https://github.com/grunch/rana
Since rana already has pretty good docs, I decided to make a video instead of write about this because It's easier to see rana in action than it is to write about Rana. I went off on some tangents, so I might edit this down later, but I hope it helps you mine your own nostr key.
nevent1qqsfk7a000m8zc3ptsuu4vytepqc9eedceclpt2ns9pzlech5cpaflceng5al
Show Notes
https://github.com/grunch/rana
https://virtualbox.org/
https://doc.rust-lang.org/cargo/getting-started/installation.html
cargo run --release -- --vanity-n-prefix=juxtap0se
☮️
nostr:npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: clarity.fm on Lightning
Getting money from clients very easily, dispatching that money to "world class experts" (what a silly way to market things, but I guess it works) very easily are the job for Bitcoin and the Lightning Network.
EDIT 2020-09-04
My idea was that people would advertise themselves, so you would book an hour with people you know already, but it seems that clarify.fm has gone through the route of offering a "catalog of experts" to potential clients, all full of verification processes probably and marketing. So I guess this is not a thing I can do.
Actually I did https://s4a.etleneum.com/ (on Etleneum) that is somewhat similar, but of course doesn't have the glamour and network effect and marketing -- also it's just text, when in Clarity is fancy calls.
Thinking about it, this is just a simple and obvious idea: just copy things from the fiat world and make them on Lightning, but maybe it is still worth pointing these out as there are hundreds of developers out there trying to make yet another lottery game with Lightning.
It may also be a good idea to not just copy fiat-businesses models, but also change them experimenting with new paradigms, like idea: Patreon, but simple, and without subscription.
-
 @ 9fce3aea:0f9087e6
2025-06-12 18:58:45
@ 9fce3aea:0f9087e6
2025-06-12 18:58:45Hi all,
Thought I'd put together some info here for those who want to come play in our next Rigly / Upendo #BlockParty on June 21.
The prep for this one is a little different, which is why I'm here. Usually, we have hashrate auctions and direct buys up on the site for all plebs. Right now, we don't since we're fixing up the auction experience. It will come back totally anon so you can participate without having to create an account, which is awesome.
For now, the block party is only open to solo miners. Why hook up to our pool prior to the party, you ask? Because if your ASIC (or Bitaxe, or Apollo, or Braiins Mini Miner etc) finds a block, you get 1 BTC and the rest is divvied up by hashrate contributed.
We currently have 80 workers in the pool, check it out: https://solostats.ckpool.org/users/3Gk1GfP3bHA6M2ZzK5mHdqbWN1iNsqAenH
I'd love to get the "Alliance" up to 100 solo miners by Monday, just for funsies, and because I think we can. Each new block party proves to me how fired up everyone is to try and solo mine as a group and stick it to "the man," you know, if that man is MARA, Foundry, AntPool, etc. I just have one question: "Why not us!?" No reason. So LFG!
Here's how to do things:
- Here's how to hook up your ASIC, or whatever solo mining machine you've got:
Stratum address: solo.ckpool.org:3333 Username: 3Gk1GfP3bHA6M2ZzK5mHdqbWN1iNsqAenH Put your BTC payout address as the workername (important!)
If we mine a block during the party, you will get your share of the reward based on hashrate contribution.
Outside of the party, the miner who finds the block gets 1 BTC and everyone else gets a share of the reward based on hashrate contribution. (Source: https://upendo.rigly.io/learn/upendo)
- I posted this yesterday on our Rigly Nostr account. What's key here is this is simply a workaround for hashrate purchases. You don't even have to buy from us at Rigly; this will help you send your hashrate to our pool. (We're doing this because we took direct buys down while the devs work on some new things). Whether you buy hashrate on the main Rigly site or elsewhere, here's how to do it:
You can buy hashrate on the main Rigly site (https://rigly.io/direct-sale) and point it to the (Alliance) CKPool address we use.
You can also buy hashrate from anywhere you like and send to our shared escrow address.
Our mining pool info is the same as it is for the #BlockParty:
🟧 Pool Account Username: 3Gk1GfP3bHA6M2ZzK5mHdqbWN1iNsqAenH 🟧 If we find a block, your Rigly order number will be matched to your username!
If you’re buying on Rigly and sending to the Alliance/CKPool address, set this before you buy the hashrate:
Step 1 on Rigly.io: Go to "view my account" Step 2: Go to "hashrate" in left menu Step 3: put your BTC address into the mining pool username Step 4: add mining pool address
(Helpful pic of this in our Nostr post: https://primal.net/e/nevent1qvzqqqqqqypzqh4nl2ld8qq00kxzxlh5khzk7k82zmjf07k5pn7awska6u66qv7dqqs8sk6pxl00ut4t4zhz2y3jc8e4rzakyehfjk9fz6wdw7qm8xq8j6gdffsjy).
Don't forget to add your BTC address after the period in the mining pool username! That lets us know how much hashrate you are contributing and where to pay you out if/when we find a block. 🟧
When you buy hashrate from Rigly for the Solo Alliance, enter the escrow address as username: 3Gk1GfP3bHA6M2ZzK5mHdqbWN1iNsqAenH
This is the kind of stuff we chat about in our galaxy brain Telegram group. Join for tech support and other shenanigans: https://t.me/+AEvub_E_9hNiYzAx
If this is too much, don't worry, auctions and direct buys will return soon. We're just happy to provide a hashrate workaround so we can grow the party, even as we build. 💪
https://stacker.news/items/1004754
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Método científico
o método científico não pode ser aplicado senão numa meia dúzia de casos, e no entanto ei-nos aqui, pensando nele para tudo.
"formule hipóteses e teste-as independentemente", "obtenha uma quantidade de dados estatisticamente significante", teste, colete dados, mensure.
não é que de repente todo mundo resolveu calcular desvios-padrão, mas sim que é comum, para as pessoas mais cultas, nível Freakonomics, acharem que têm que testar e coletar dados, e nunca jamais confiar na sua "intuição" ou, pior, num raciocínio que pode parecer certo, mas na verdade é enormemente enganador.
sim, é verdade que raciocínios com explicações aparentemente sensatas nos são apresentados todos os dias -- para um exemplo fácil é só imaginar um comentarista de jornal, ou até uma matéria inocente de jornal, aliás, melhor pensar num comentarista da GloboNews --, e sim, é verdade que a maioria dessas explicações é falsa.
o que está errado é achar que só o que vale é testar hipóteses. você não pode testar a explicação aparentemente sensata que o taxista te fornece sobre a crise brasileira, deve então anotá-la para testar depois? mantê-la para sempre no cabedal das teorias ainda por testar?
e a explicação das redinhas que economizam água quando instaladas na torneira? essa dá pra testar, então você vai comprar um relógio de água e deixar a torneira ligada lá 5 horas com a redinha, depois 5 horas sem a redinha? obviamente não vai funcionar se você abrir o mesmo tanto, você vai precisar de um critério melhor: a satisfação da pessoa que está lavando as mãos com o resultado final versus a quantidade de água gasta. daí você precisaria de muitas pessoas, mas satisfação é uma coisa imensurável, nem adianta tentar fazer entrevistas antes e depois com as pessoas. o certo então, é o quê? procurar um estudo científico publicado numa revista de qualidade (porque tem aquelas revistas que aceitam estudos gerados por computador, então é melhor tomar cuidado) que fala sobre redinhas? como saber se a redinha é a mesma que você comprou? e agora que você já comprou, o resultado do experimento importa? (claro: pode ser que a redinha faça gastar mais água, você nunca saberá até que faça o experimento).
por que não, ao invés de condenar todos os raciocínios como enganadores e mandar que as pessoas façam experimentos científicos, ensinar a fazer raciocínios certos?
-
 @ 69eea734:4ae31ae6
2025-06-12 17:44:54
@ 69eea734:4ae31ae6
2025-06-12 17:44:54Vor ein paar Tagen stieß ich auf einen faszinierenden Artikel von Michel Bauwens, Mitbegründer der P2PFoundation, mit Links zu weiteren Texten (zum Beispiel über den Puls der Commons), die ich ebenfalls äußerst interessant fand.
Der Artikel zeigt unter anderem, wie unterschiedlich Commons aussehen können, so dass ich ihn heute als Ausgangspunkt nehmen möchte, um ein paar Puzzle-Steine in mein entstehendes Bild der Commons einzufügen.
Das Grundmuster menschlichen Zusammenlebens?
Bauwens betrachtet die Commons aus historischer Sicht, wie sie sich in verschiedenen Zeiten unterschiedlich manifestieren, manchmal gar nahezu verschwinden und heute in wiederum veränderter Form neu entstehen – und plädiert dafür, dass sie noch weit stärker werden sollten.
Er legt zunächst dar, was die Commons sind und was nicht. (zum Beispiel nichts, was vom Staat verwaltet wird, wie ein öffentlicher Park.) Ausschlaggebend ist, dass eine Ressource von ihren Herstellern oder Benutzern selbst betreut wird. Commons entstehen dabei durch Beziehungen. Sie sind etwas spezifisch Menschliches und eine Wahl, die „fast immer“ zur Verfügung steht, so Bauwens. Eine die Geschichte überdauernde menschliche Praxis.
Er nennt drei verschiedene geschichtlichen Entwicklungen:
- Eine lineare - Wie präsentiert sich der Commons über verschiedene, komplexer werdende, Phasen der Menschheitsgeschichte hinweg?
- Eine hin und her schwingendende: In der Geschichte einer Zivilisation werden die Commons in Zeiten von Überfluss -- und daraus resultierender Verschwendung uns steigender Ressourcen-Extraktion -- unterdrückt, konstitutieren sich aber dann als Gegenbewegung wieder neu.
- Eine stufenweise: Die heutigen, mit neuen Möglichkeiten ausgestatteten Formen der Commons könnten in der nächsten Phase unserer Zivilisation (oder nach unserer Zivilisation) eine entscheidende Rolle spielen.
Wenn man verschiedene Arten des Austausches betrachtet (Bauwens beruft sich hierbei auf Alan Fiske), kann man geschichtlich analysieren, welche zu verschiedenen Zeiten vorrangig waren (dies tat Kojin Karatani in The Structure of World History von 2014).
Die vier Muster sind:
- Gemeinschaftliche Beteiligung, Commons (die Gemeinschaft baut mir ein Haus, und ich helfe später bei einem anderen Hausbau mit; ein Beispiel aus neuerer Zeit ist die Entwicklung von Linux)
- Wechselseitiger Austausch (Geschenkökonomie – es wird eine etwa gleichwertige Leistung zu einem späteren Zeitpunkt erwartet)
- Hierarchisch bedingte Verteilung, wie im Feudalismus
- Marktwirtschaft (es gibt ein allgemeines Zahlungsmittel mit einem bestimmten Wert)
Bauwens: „Entscheidend ist jedoch, dass die Menschheit ständig bestrebt ist, Modus A wiederherzustellen, denn die Menschen haben eine kulturelle und wahrscheinlich auch allgemeine Vorliebe für ein geselliges Leben in kleinen, vertrauten Gruppen. Aber menschliche Gruppen versuchen, dies auch auf höheren Komplexitätsebenen zu tun, in einem ständigen Versuch, die extraktive Logik der Zivilisation zu mäßigen.“ (Katarani bezeichnet eine Verbindung von Commoning und Geschenkökonomie in stammesorientierten Kulturen als Modus A)
Commons durch die Zeiten
In der ursprünglichsten Form der Commons in Jäger- und Sammler-Gemeinschaften, werden Nahrung und sonstige Ressourcen mit der ganzen Gemeinschaft geteilt - dies ist zumindest die vorherrschende Form des Austauschs.
Im Zuge der Agrar-Revolution geht es um das gemeinsame Bewirtschaften von Flächen.
Im Mittelalter entwickelt sich in Europa das Feudalsystem. Auch hier werden manche Felder aber noch von den Dorfbewohnern gemeinsam verwaltet.
Ab dem 16. Jahrhundert fanden, am stärksten in England, die Enclosures (auf deutsch Einhegungen) statt. Das heißt, dass Felder zur effizienteren Bewirtschaftung von den Besitzern zusammengelegt und umzäunt wurden.
Besonders im 19. Jahrhundert, mit dem Aufkommen der Industrialisierung, nahm diese Entwicklung immer stärker zu. Die landwirtschaftlichen Commons wurden dadurch weitgehend zerstört.
Im industriellen Kapitalismus, als die Arbeiter kaum Rechte hatten, und es auch um das bloße Überleben ging, entwickelte sich ein sozialer Commons Dieser bestand darin, dass sich die Arbeiter gegenseitig halfen und sich gegenseitig versicherten. Aus dieser Bewegung entstand dann der Sozialstaat. Der Staat übernahm also Aufgaben, die die Menschen zuvor füreinander geleistet hatten.
Man könnte daher sagen, dass im Kapitalismus die natürlichen Commons-Ressourcen privatisiert und die sozialen Commons verstaatlicht wurden.
In der Moderne waren sich viele Menschen der Bedeutung von Commons gar nicht mehr bewusst.
Mit dem Internet, dem World Wide Web und weiteren digitalen Techniken erschlossen sich dann neue Möglichkeiten. Mit Peer Production, Open Source Software, sowie den Creative Commons Lizenzen, enstand eine neue Inkarnation der Commons. Und damit ist die Entwicklung noch nicht abgeschlossen...
Warum Commons nicht in ein Links-Rechts-Schema passen
Mit seinem Streifzug durch die Geschichte zeigt Bauwens, wie vielfältig die Commons sein können, und warum ihnen in der heutigen Zeit eine starke Rolle zukommen sollte. Nebenbei ergibt sich für mich auch, dass sie jenseits von linker oder rechter Ideologie liegen. Hierzu eine kurze Zwischenbetrachtung von mir:
Weil es um kollektives Handeln geht, und auch wegen des Namens („hört sich an wie Kommunismus“, meinte meine Mutter), entsteht leicht der Eindruck, es handele sich um ein besonders linksgerichtetes Phänomen.
Eine gut eingespielte Fußballmannschaft agiert auch als Kollektiv. Der Verein verwaltet vielleicht ein Clubhaus. Wohl kaum jemand würde deswegen den Verein als links bezeichnen.
Freilich sind die Mitglieder heutiger Commons-Bewegungen vorwiegend „progressiv“, zuweilen auf eine rigide Weise. Bauwens hat damit schon eine leidvolle Erfahrung gemacht. Aber Commons als soziales System sind es nicht. Dafür spricht allein schon die Tatsache, dass es sie viel länger gibt als die politische Links-Rechts-Einteilung.
Eine starke Rolle für die Commons
Wie steht es um die Commons heute? Das werde ich in weiteren Artikeln noch versuchen zu beleuchten...
Michel Bauwens hat in seinen Artikeln noch Einiges dazu sagen. Inbesondere beführwortet er das Kosmo-Lokale (Cosmo-Local). Was leicht ist (Wissen) wird geteilt, was Gewicht hat (etwa landwirtschaftliche und andere Produktion), wird an lokale Gegebenheiten angepasst und vor Ort bewerkstelligt.
Und das Zusammenspiel von Digitalem und Materiellem verspricht weitere Möglichkeiten.
In jedem Fall haben die Commons eine ausgleichende, regenerierende Kraft, die wir aufgrund der heutigen vielen Kriesen gar nicht ungenützt lassen können, ganz unabhängig von unserer sozialer Ebene - das gilt auch für die Superreichen.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28idea: An open log-based HTTP database for any use case
A single, read/write open database for everything in the world.
- A hosted database that accepts anything you put on it and stores it in order.
- Anyone can update it by adding new stuff.
- To make sense of the data you can read only the records that interest you, in order, and reconstruct a local state.
- Each updater pays a fee (anonymously, in satoshis) to store their piece of data.
- It's a single store for everything in the world.
Cost and price estimates
Prices for guaranteed storage for 3 years: 20 satoshis = 1KB 20 000 000 = 1GB
https://www.elephantsql.com/ charges $10/mo for 1GB of data, 3 600 000 satoshis for 3 years
If 3 years is not enough, people can move their stuff to elsewhere when it's time, or pay to keep specific log entries for more time.
Other considerations
- People provide a unique id when adding a log so entries can be prefix-matched by it, like
myapp.something.random - When fetching, instead of just fetching raw data, add (paid?) option to fetch and apply a
jqmap-reduce transformation to the matched entries
-
 @ 6a6be47b:3e74e3e1
2025-06-12 16:52:08
@ 6a6be47b:3e74e3e1
2025-06-12 16:52:08Hi frens! 🌝
🎨Today I painted a full moon, and it got me thinking about how special June’s full moon is. You might have heard it called the “Strawberry Moon” —but that’s not because of its color! According to the Old Farmer’s Almanac, it’s called like that because it's “when the strawberry harvest took place.” 🍓
Fun fact:
“A Moon usually appears reddish when it’s close to the horizon because the light rays must pass through the densest layers of the atmosphere.”
In Europe, June’s full moon has also been called the “Rose Moon” or even the “Honey Moon,” since it’s the time of the first honey harvest.
According to UK archaeologist and historian Jennifer Wexler in Sky At Night Magazine this year’s Strawberry Moon is extra special because it’s part of a “major lunar standstill,” or lunistice—a rare event that only happens every 18.6 years! During this period, the moon’s path across the sky reaches its most extreme points, making moonrises and moonsets appear unusually far apart. After 2025, we won’t see a standstill like this again until 2043, so this is a once-in-a-generation chance to catch the lowest full moon.
But what is a full moon, anyway?
“A full moon rises around sunset and sets around sunrise. The Moon will appear full for a couple of days.”
Here’s my watercolor painting of the full moon. I love how magical it looks—there’s something mysterious and humbling about it, and it’s just mesmerizing to catch it (almost) every night in the sky.
💭 Were you able to see the Strawberry Moon this year? I’d love to hear about it!
See you soon, frens.
Godspeed! 🌕
https://stacker.news/items/1004621
-
 @ cae03c48:2a7d6671
2025-06-12 19:02:34
@ cae03c48:2a7d6671
2025-06-12 19:02:34Bitcoin Magazine

The CLARITY Act Heads To House Floor For Vote With Protection For Noncustodial Tools IntactYesterday, the CLARITY Act passed favorably through the House Agriculture and Financial Services Committees with 47-6 and 32-19 bipartisan votes, respectively.
While a handful of amendments will be incorporated into a revised version of the bill, none of said amendments will alter a recently-added section of the bill that regards noncustodial products and services.
To clarify, on Monday, language from the Blockchain Regulatory Certainty Act (BRCA) was added to the CLARITY Act.
If you do not custody consumer funds, you aren’t a money transmitter. Plain and simple.
Our nonpartisan Blockchain Regulatory Certainty Act, which codifies this simple concept, has been added to the CLARITY Act!
Grateful to @RepFrenchHill, @RepBryanSteil and @RepRitchie for… https://t.co/QmPdgUGSwo
— Tom Emmer (@GOPMajorityWhip) June 9, 2025
This language, included in Section 110 of the CLARITY Act, is focused on non-controlling (noncustodial) blockchain developers and blockchain service providers.
The exact wording in the bill is as follows: “A non-controlling blockchain developer or provider of a blockchain service shall not be treated as a money transmitter or as engaged in ‘money transmitting,’ or, following the date of enactment of this Act, be otherwise subject to any new registration requirement that is substantially similar to the requirement that currently applies to money transmitters.”
It was particularly important that this segment of the bill not be altered because, with this language included, the bill protects not only Bitcoin and crypto enthusiasts’ right to use noncustodial wallets, but the right of developers to continue to create such products and services without being subject to money-transmission laws as per the Bank Secrecy Act (BSA).
“Section 110 doesn’t just clarify that non-custodial devs aren’t captured by the BSA, but also forbids future laws and regulations (e.g. DAAMLA) that would modify or supersede the BSA to treat non-custodial actors as money transmitters or similar,” wrote Zack Shapiro, Head of Policy at the Bitcoin Policy Institute, in an X post. “If this passes, that means that anti-crypto zealots like Sen. Warren would first have to repeal [or] modify this bill before passing additional rules that would impinge on self-custody.”
This issue over whether noncustodial Bitcoin and crypto service providers is relevant as the Samourai Wallet and Tornado Cash developers prepare to face trial.
It’s also generally important in preserving the right of U.S. citizens to use digital assets privately.
Chairman of the House Subcommittee on Digital Assets, Financial Technology, and Artificial Intelligence, Rep. Bryan Steil (R-WI) commented on Americas’ right to transactional privacy in the hearing.
“Privacy in and of itself is not illegal.
Americans have a right to it in their financial transactions.
And so there’s totally legitimate uses of privacy-preserving technologies.” @RepBryanSteil pic.twitter.com/nHPfa25UVr
— Frank Corva (@frankcorva) June 10, 2025
To learn more about how to contact your elected officials to tell them to support The CLARITY Act, visit saveourwallets.org.
This post The CLARITY Act Heads To House Floor For Vote With Protection For Noncustodial Tools Intact first appeared on Bitcoin Magazine and is written by Frank Corva.