-
 @ dfa02707:41ca50e3
2025-06-07 12:02:34
@ dfa02707:41ca50e3
2025-06-07 12:02:34- This version introduces the Soroban P2P network, enabling Dojo to relay transactions to the Bitcoin network and share others' transactions to break the heuristic linking relaying nodes to transaction creators.
- Additionally, Dojo admins can now manage API keys in DMT with labels, status, and expiration, ideal for community Dojo providers like Dojobay. New API endpoints, including "/services" exposing Explorer, Soroban, and Indexer, have been added to aid wallet developers.
- Other maintenance updates include Bitcoin Core, Tor, Fulcrum, Node.js, plus an updated ban-knots script to disconnect inbound Knots nodes.
"I want to thank all the contributors. This again shows the power of true Free Software. I also want to thank everyone who donated to help Dojo development going. I truly appreciate it," said Still Dojo Coder.
What's new
- Soroban P2P network. For MyDojo (Docker setup) users, Soroban will be automatically installed as part of their Dojo. This integration allows Dojo to utilize the Soroban P2P network for various upcoming features and applications.
- PandoTx. PandoTx serves as a transaction transport layer. When your wallet sends a transaction to Dojo, it is relayed to a random Soroban node, which then forwards it to the Bitcoin network. It also enables your Soroban node to receive and relay transactions from others to the Bitcoin network and is designed to disrupt the assumption that a node relaying a transaction is closely linked to the person who initiated it.
- Pushing transactions through Soroban can be deactivated by setting
NODE_PANDOTX_PUSH=offindocker-node.conf. - Processing incoming transactions from Soroban network can be deactivated by setting
NODE_PANDOTX_PROCESS=offindocker-node.conf.
- Pushing transactions through Soroban can be deactivated by setting
- API key management has been introduced to address the growing number of people offering their Dojos to the community. Dojo admins can now access a new API management tab in their DMT, where they can create unlimited API keys, assign labels for easy identification, and set expiration dates for each key. This allows admins to avoid sharing their main API key and instead distribute specific keys to selected parties.
- New API endpoints. Several new API endpoints have been added to help API consumers develop features on Dojo more efficiently:
- New:
/latest-block- returns data about latest block/txout/:txid/:index- returns unspent output data/support/services- returns info about services that Dojo exposes
- Updated:
/tx/:txid- endpoint has been updated to return raw transaction with parameter?rawHex=1
- The new
/support/servicesendpoint replaces the deprecatedexplorerfield in the Dojo pairing payload. Although still present, API consumers should use this endpoint for explorer and other pairing data.
- New:
Other changes
- Updated ban script to disconnect inbound Knots nodes.
- Updated Fulcrum to v1.12.0.
- Regenerate Fulcrum certificate if expired.
- Check if transaction already exists in pushTx.
- Bump BTC-RPC Explorer.
- Bump Tor to v0.4.8.16, bump Snowflake.
- Updated Bitcoin Core to v29.0.
- Removed unnecessary middleware.
- Fixed DB update mechanism, added api_keys table.
- Add an option to use blocksdir config for bitcoin blocks directory.
- Removed deprecated configuration.
- Updated Node.js dependencies.
- Reconfigured container dependencies.
- Fix Snowflake git URL.
- Fix log path for testnet4.
- Use prebuilt addrindexrs binaries.
- Add instructions to migrate blockchain/fulcrum.
- Added pull policies.

Learn how to set up and use your own Bitcoin privacy node with Dojo here.
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ dfa02707:41ca50e3
2025-06-07 08:01:38
@ dfa02707:41ca50e3
2025-06-07 08:01:38Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 0b118e40:4edc09cb
2025-06-06 13:58:07
@ 0b118e40:4edc09cb
2025-06-06 13:58:07The idea of Bitcoin as an internet native currency, and eventually a global one, is coming to life slowly. But historically, the idea of global currency has haunted the world’s financial imagination for nearly a century.
From Keynes’s Bancor in 1944 to Zhou Xiaochuan’s post-crisis proposal in 2009 to today’s renewed debates, the idea resurfaces every time the global economy fractures.
Could this time be different with Bitcoin?
I decided to trace the idea of global currency through several decades and books. I may have missed some parts, so feel free to add. I’ll keep this brief and leave the books I’ve read below.
In the beginning
It all started on July 1, 1944. 730 delegates from 44 Allied nations, including major powers like the US, UK, Soviet Union, China, and France, gathered at the Mount Washington Hotel in Bretton Woods, New Hampshire. They spent 2 weeks figuring out how the new international monetary and financial system would be, post WW2
After WW1, the treaty of Versailles was needed, but imposed harsh reparations that devastated economies and contributed to the rise of fascism, such as Hitler, Mussolini and gang.
So when folks met up in 1944 (WW2 was almost ending), the goal was to prevent another Great Depression, another global conflict and build a stable global economic order.
2 main proposals were discussed in Bretton Woods.
-
John Maynard Keynes, representing the UK, proposed the creation of a global currency called Bancor. It will be issued through a global central bank known as the International Clearing Union (ICU).
-
Harry Dexter White, representing the US, promoted a dollar-based system. Countries would peg their currencies to the US. dollar backed by gold. He also led the creation of the IMF and the World Bank.

To understand how both of these proposals work, let's look at an example.
-
Country A (Germany): Massive exporter
-
Country B (USA): Massive importer
-
Country C (Brazil): Balanced trade (imports = exports)
***Based on Dexter’s model and the current USD-based system, ***
Say Germany sells $1B worth of cars to the US. The US pays in dollars, increasing its trade deficit. Germany accumulates dollars as reserves or buys the US Treasury bonds. Over time, the US continues running trade deficits, while Germany keeps hoarding dollars. Hence the unsustainable debt of the US.
***In Keynes’s Bancor system, ***
If Germany sells $1B worth of cars to the US, then the US does not pay in dollars. Instead, the ICU credits Germany with 1B Bancors and debits the US with -1B Bancors.
The ICU police this. If Germany exceeds the surplus threshold, it pays interest or penalties to discourage hoarding. If the US exceeds its deficit threshold, it is warned to rebalance trade or face restrictions.
Here, Germany is incentivized to import more (e.g., from Brazil) or invest in global development. The US is encouraged to export more or reduce consumption. Brazil, with balanced trade, enjoys stability in Bancor flows and avoids pressure.
The idea behind Bancor was a zero-sum balancing act. No country could become “too big to fail” due to excessive deficits. But it was too complicated and idealistic in assuming every country could maintain balanced trade.
Dexter on the other hand had a few tricks up his sleeve. In the end, Dexter’s USD dominance proposal was adopted.
The Bretton Woods system established the US dollar as the central global currency
Why did dollar dominance win over Bancor?
Simplicity often wins over complexity. But more so ICU felt too centralized, asking nations to surrender economic autonomy to a global body. That didn’t sit well in a post-war world where sovereignty was non-negotiable. That and idealist economic trade balance views.
Dexter’s dollar-based system on the other hand wasn’t fair play at all. It was centralized and authoritarian in its design.
So how did Dexter pull it off?
They had gold. They were ahead in economic recovery.
And they had nuclear weapons.
At the time, the US held nearly 2/3 of the world’s gold reserves. It was a significant advantage in advocating for a gold-backed dollar as the bedrock of global trade.
The US proposed a fixed gold peg at $35 per ounce.
From a broader geopolitical backdrop, the global population in 1944 was about 2.3 billion, a fraction of today’s 8 billion. The world was far less interconnected. The war had devastated Europe, Russia, and much of Asia. Infrastructure, economies, and entire cities were in ruins. The US, by contrast, had faced far fewer casualties and damages. Being geographically isolated, it had minimal domestic losses, around a tenth of what Europe suffered, and its economy was poised to rebuild faster.
But gold dominance and economic recovery alone didn’t secure US financial dominance.
American scientific breakthroughs had already signaled global power. Physicists like Leo Szilard and Albert Einstein, who had fled Europe, helped develop nuclear weapons. Their intent was deterrence, not destruction. But once the bomb existed, it changed geopolitics overnight. The US had military dominance. And after Hiroshima and Nagasaki in 1945, it became the undisputed superpower.
In the end, the USD won and the vision for neutral global currency faded.
And 20 years passed on…
France sends its warship to the US
Under Bretton Woods, countries could exchange dollars for gold, but the US had been printing more dollars than it had gold to back it. And it used it to fund the costly Vietnam War and domestic programs like the Great Society under LBJ.
Belgian-American economist Robert Triffin pointed out a fatal flaw in the Bretton Woods system that came to be known as the Triffin dilemma.
-
The world needed US dollars for liquidity and trade.
-
But the more dollars the US pumped out, the less credible its gold promise became.
Yet the US kept promising that every dollar was still convertible to gold at $35 per ounce.
French President Charles de Gaulle saw this as financial imperialism. He called it the “exorbitant privileged position”. The world had to pay for what they bought with the money they have, but not the US.
So in 1965, France did something unexpected. It sent a warship to New York Harbor to physically retrieve French gold reserves held by the Federal Reserve.

Would it have escalated to war? Maybe. But likely not. It was perhaps more of a diplomatic theatre and a sovereign flex. France was exercising its right under the Bretton Woods agreement to convert dollars into gold. But doing it with military formality was to send a signal to the world that they don’t trust the US system anymore.
It was one of the first major public blows to the dollar’s credibility. And France wasn’t alone. Other countries like West Germany and Switzerland followed suit, redeeming dollars for gold and draining US reserves.
The Nixon shock
Given they did not have enough gold, the IMF introduced Special Drawing Rights (SDRs) in 1969. SDRs were an international reserve asset, created to supplement gold and dollar reserves. Instead of relying solely on the US dollar, SDRs were based on a basket of major currencies (originally gold-backed but later diversified).
The idea was to reduce the world’s dependence on the dollar and avoid a liquidity crisis. But SDRs were a little too late and a little too weak to solve the underlying problem.
By 1971, the US could no longer sustain the illusion. President Nixon “closed the gold window,” suspending dollar convertibility to gold.
The Bretton Woods collapsed and this marked the beginning of fiat money dominance.
The French pursuit
While France demanded justice in one corner of the world, the French franc, specifically the CFA franc, has been dominant in parts of Africa since 1945, long before 1971.
After WWII, France created two CFA franc zones:
-
West Africa: Communauté Financière Africaine (XOF)
-
Central Africa: Coopération Financière en Afrique Centrale (XAF)
These zones included 14 African countries, many of which were former French colonies. France maintained monetary control via currency convertibility guarantees and representation in African central banks. Till today it has influence over these country’s monetary policy.
Colonisation hasn't ended in some parts of the world.
Did countries stop using the USD after the Nixon shock 1971?
Nope. The US dollar was no longer convertible to gold and it dismantled the fixed exchange rate system. But most countries did not stop using the USD as their dominant reserve or trade currency. There were no decent alternatives. Instead, they floated their currencies or maintained a soft peg to the dollar or a basket of currencies.
The USD remained dominant in oil trade (OPEC priced oil in USD) - petrodollar deal, global debt markets and FX reserves (central banks kept holding USD).
In 1997, when many Southeast Asian countries were still pegged to the USD, Soros claimed that SEA will tank. The US further increased its credit rates leading to capital flight and eventual tanking of these countries leading to Asian Financial Crisis '97. Many financial crisis has similar vibe.
The 1999 Euro launch
The idea of a shared currency appeared again, this time through the forms of Euro. It was a mandatory system for member states of the Eurozone, and came with centralized authority, the European Central Bank (ECB), which controlled monetary policy for all participating nations.

At first glance, the euro seemed like a win. It eliminated exchange rate fluctuations, making trade within the Eurozone smoother. It gave weaker economies access to lower borrowing costs and helped Europe establish itself as a financial heavyweight. Today, the euro is the second most-used reserve currency after the US dollar.
But it came at a cost. Countries that adopted the euro lost monetary sovereignty and could no longer print their own money or adjust interest rates to respond to local crises. This became painfully clear during Greece’s debt crisis, where strict monetary policies prevented the country from devaluing its currency to recover. The one-size-fits-all approach meant that economies as different as Germany and Greece had to follow the same rules, often to the detriment of weaker nations. Debt-ridden countries like Italy and Spain were forced into harsh austerity measures because they could not manipulate their currency to ease financial strain. Meanwhile, richer nations like Germany and the Netherlands felt they were unfairly propping up struggling economies, creating political tension across the EU.
In recent years, the euro has faced pressure from global trade tensions, monetary tightening, and geopolitical instability contributing to market volatility and periodic depreciation against other major currencies.
The Bretton Woods 2.0
Believe it or not, after all that, there was a call for Bretton Woods 2.0. Yet another global currency dream.
When the housing market collapsed in 2008 followed by a series of domino effects, global banks froze lending, economies contracted, and panic set in. The crisis exposed how fragile the international financial system had become as it was overly reliant on debt, under-regulated, and centered around the US dollar.
Many countries, especially in the Global South and emerging markets, started to question whether a system built around a single national currency was sustainable.
China, for instance, had been holding huge amounts of US debt while the US printed more dollars through bailouts and quantitative easing. This created global imbalances as exporting nations were lending money to the US to keep the system running, while taking on the risk of dollar depreciation.
In 2009, China’s central bank openly proposed replacing the US dollar with a neutral global reserve currency suggesting SDRs (Special Drawing Rights) issued by the IMF instead.
These concerns led to a wave of calls from world leaders for a “Bretton Woods 2.0” , a modern rethinking of the post-WWII economic order. At G20 summits in London in 2009, countries like France, China, and Russia pushed for reforms in global financial institutions and more balanced power sharing.
In the end, the IMF received more funding, and some banking regulations were tightened in the years after. But no real overhaul happened. No surprise there? The dollar remained dominant.
The foundation of the global economy didn’t change, even though trust in it had been deeply shaken.
The growth of BRICS
In 2023, Brazil, Russia, India, China, and South Africa began discussing the idea of a shared currency or alternative mechanism to reduce the dependence on USD ie de-dollarisation. The sanctions on Russia didn't help. After Russia’s invasion of Ukraine, the US and its allies froze Russia’s dollar reserves and cut it off from SWIFT, the “backbone of global banking communication”. This made one thing clear. If you fall out with Washington, your access to the global economy can vanish overnight.
China’s growing economic power also gave it more leverage to process alternative options. It would trade in Yuan with Russia and Iran.
I know many still say it's at its early stage, but I see many countries hedging their bets quietly and aligning with Putin and Xi. It became more obvious after US imposed tariffs on multiple nations, signaling that economic tools can double as political weapons. The world’s second financial system is slowly forming.
What is the world looking for, for the last century ?
For the last 80 years, from Bretton Woods to multiple financial crises, from the birth of the Euro to the rise of BRICS, through war and peace, we’ve been circling around the same ideal. A global currency that is :
-
Simple
-
Free from dominant power
-
Decentralised
-
Borderless
-
Scarce
-
Transparent
-
Inclusive, with self custody
-
Resilient in crisis
-
Built for individual financial sovereignty
-
A new backbone for global finance, owned by no one
It doesn’t matter where you’re from, what politics you believe in, or how your economy leans. The answer keeps pointing in the same direction:
Bitcoin
This is the first true global currency.
And it’s just there
Waiting...
.
.
.
Some books that might interest you :
-
The Battle of Bretton Woods by Benn Steil
-
Goodbye, Great Britain by Kathleen Burk and Alec Cairncross
-
The Ghost of Bancor by Tommaso Padoa-Schioppa
-
Confessions of an Economic Hitman by John Perkins
-
The Blood Bankers by James S. Henry
-
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ dfa02707:41ca50e3
2025-06-07 08:01:33
@ dfa02707:41ca50e3
2025-06-07 08:01:33Contribute to keep No Bullshit Bitcoin news going.
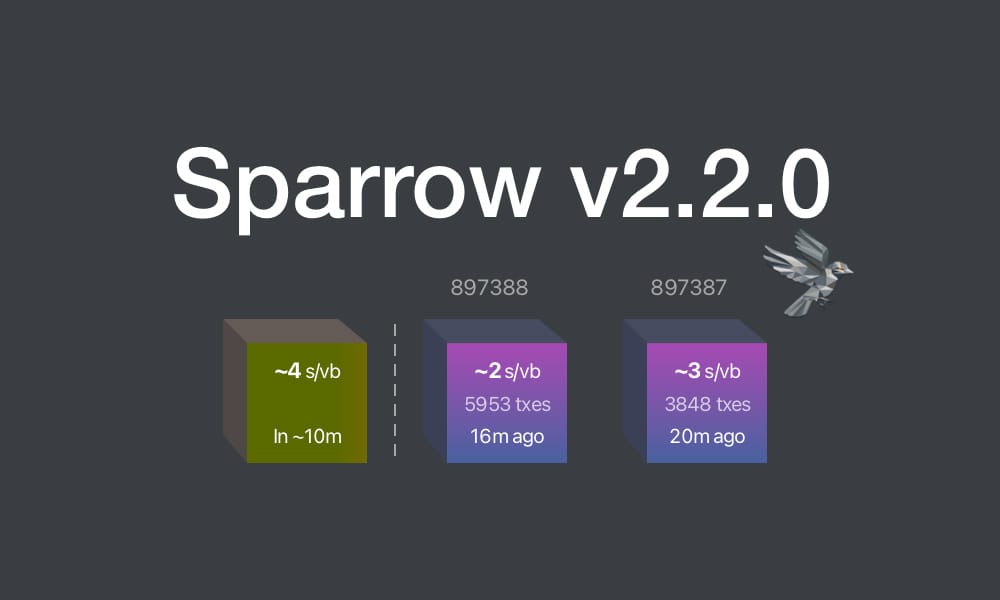
This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ 2b24a1fa:17750f64
2025-06-09 13:11:48
@ 2b24a1fa:17750f64
2025-06-09 13:11:48Er war schon immer ein streitbarer. Seine Kritik richtete sich an ein Gesundheitssystem, das durch eine durch Pharmalobby erkaufte oder erpresste Politik ermöglicht wurde. Seit Ausrufung der sogenannten Corona-Pandemie fuhr er zu Höchstleistungen auf. Es ist Dr. Gunter Frank, Schulmediziner mit Erfahrungen im Krankenhaus, Notfallmediziner, ausgebildet in Naturheilverfahren, Sachbuchautor, engagiert in diversen medizinischen und naturheilkundlichen Gesellschaften und betreibt eine eigene Praxis...
Im größten Medizinskandal in der Geschichte der Bundesrepublik, der Corona-Krise, nennt er Hausnumnmern wie 100-200.000 langfristig, gesundheitlich schwer Geschädigten und etwa 20 - 40.000 durch Genimpfung Verstorbene. Ob diese Zahlen haltbar sind, weit über- oder untertrieben wird die Geschichte zeigen. Welche Hintergründe er aber vermutet und über die neuen Deutungen medizinischer Erkenntnisse, spricht meine Kollegin Eva Schmidt jetzt mit dem Mediziner Dr. Gunter Frank und wollte zunächst wissen, wann und warum er zum Medizinsystemkritiker wurde, welches sein Erweckungserlebnis, noch weit vor Corona gewesen sein muss:
-
 @ 632ee5dc:fbc077e2
2025-06-09 14:04:36
@ 632ee5dc:fbc077e2
2025-06-09 14:04:36[API Key Request]
YewTuBot would like to use API keys with the Stacker News GraphQL API
Reasons: - parsing new YT links - convert YT links to YewTube links or any other INVIDIOUS instance available
Expect calls to the following GraphQL queries or mutations: -
upsertCommentto post commentsEstimate GraphQL API calls: - Max 1x
upsertCommentperupsertLinkDelivery: - Provide API via nostr encripted message to
npub1vvhwthyptyqwzc2u5xgmcy73fn95nz6tyl2p7srkw6dx377qwl3q3axulxhttps://stacker.news/items/1001507
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ dfa02707:41ca50e3
2025-06-07 07:01:40
@ dfa02707:41ca50e3
2025-06-07 07:01:40Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 2b24a1fa:17750f64
2025-06-09 13:08:49
@ 2b24a1fa:17750f64
2025-06-09 13:08:49Wenn sich die Spieler nach einem hart umkämpften Fußballmatch die Hand reichen oder einander abklatschen, zeugt das von Sportsgeist. Das heißt: Wir haben uns im Spiel zwar nichts geschenkt, aber wir respektieren einander und als Verlierer erkennen wir an, dass die andere Mannschaft besser gespielt hat und unsere Niederlage in Ordnung geht.
https://soundcloud.com/radiomuenchen/die-wrestling-demokratie-ein-kommentar-von-jonny-rieder?
Und auch die Gewinner zollen dem Gegner Respekt, verhöhnen ihn nicht. Selbstverständlich sollte gegenseitiger Respekt auch in der Politik gelten. Man sollte einander zuhören und argumentieren, anstatt Kollegen schon deshalb zu verachten, weil sie einer anderen Partei angehören. Aber: Wenn ein Politiker eine andere Partei massiv kritisiert und ihrem Antrag anschließend trotzdem zustimmt, zeigt er damit nicht Respekt vor dem politischen Gegner, sondern Verachtung für den Wähler. Was der Deutsche Bundestag im März 2025 demonstrierte, also in der Übergangsphase vom alten Bundestag und dem noch nicht einberufenen neu gewählten Parlament, war genau das: angewandte Wählerverachtung. Etwas zuzustimmen, das ich eben noch vehement verdammt habe, zeugt nicht von Demokratieverständnis oder von politischem Sportsgeist, sondern von dessen fundamentaler Ablehnung. Erst recht, wenn die Zustimmung für alle ersichtlich erkauft wurde. Hören Sie Jonny Rieders Kommentar „Die Wrestling-Demokratie“.
Sprecher: Karsten Troyke
Bild: ChatGPT im Auftrag von Radio München
-
 @ c631e267:c2b78d3e
2025-06-06 18:54:04
@ c631e267:c2b78d3e
2025-06-06 18:54:04Willst du den Charakter eines Menschen kennenlernen, \ so gib ihm Macht. \ Abraham Lincoln
Vermutlich war Friedrich Merz erleichtert nach seinem Besuch beim US-Präsidenten im Oval Office. Dem Bundeskanzler kam zwar neben der Wortgewalt Donald Trumps eher eine Statistenrolle in der Medienrunde zu, aber es hätte natürlich viel schlimmer kommen können. Deswegen hatte er sich wohl vorher Ratschläge geholt, wie man hört unter anderem vom ukrainischen Präsidenten Wolodymyr Selenskyj. Offiziell gab der deutsche Regierungschef sogar an, «außerordentlich zufrieden» mit seinem Antrittsbesuch zu sein.
Dabei gibt es aktuell doch mehr Differenzen als Gemeinsamkeiten. Zu den Themen, mit denen es eine sehr unterschiedliche Umgehensweise hier und dort gibt, gehört die Gesundheit. Trumps Gesundheitsminister, Robert F. Kennedy Jr., kritisiert zum Beispiel, die meisten US-Universitäten würden den Studenten zu wenig über die Bedeutung gesunder Ernährung beibringen. Im Vordergrund der medizinischen Ausbildung stünde zu sehr die Behandlung der Menschen mit Medikamenten. Daher plant er, den Fakultäten die Bundesmittel zu streichen, wenn sie ihren Studenten keine Ernährungskurse anbieten.
Der oft als Verschwörungstheoretiker diffamierte RFK Jr. ist auch Teil des wachsenden Widerstands gegen Geoengineering-Aktivitäten. Die Manipulation von Wetter und Klima beispielsweise durch das Freisetzen von Chemikalien in die Atmosphäre kann kaum gesund sein und soll daher mit Louisiana jetzt in einem weiteren US-Bundesstaat verboten werden. Kennedy hatte derartige Maßnahmen auch schon als ein Verbrechen bezeichnet, das es zu stoppen gelte.
Indes ist der deutsche Beitrag in diesem Kontext, dass Ex-Gesundheitsminister und Covid-Impfpflicht-Befürworter Karl Lauterbach jetzt zum Klimaexperten mutiert. Laut Spiegel soll er Mitglied einer Kommission für Klima und Gesundheit bei der Weltgesundheitsorganisation werden, angeblich unentgeltlich. Vermutlich möchte die WHO im Sinne ihrer One-Health-Initiative mit solcher Lobbyarbeit für «Klimaschutz als Teil des Gesundheitsschutzes» ihren globalen Führungsanspruch untermauern.
Das Thema «Corona» ist im Übrigen noch lange nicht erledigt und das Narrativ bekommt weitere Risse. Nachdem Kennedy in den USA den Covid-«Impfstoff» für gesunde Kinder und schwangere Frauen aus dem empfohlenen Impfplan gestrichen hat, ist eine CDC-Beraterin zurückgetreten, die die Gen-Injektionen für Schwangere gefördert hatte. Auch die australische Regierung hat ihre Impfempfehlungen aktualisiert. Sie räumt jetzt ein, dass der Nutzen des «Impfstoffs» die Schäden für gesunde Jugendliche nicht überwiegt.
Gleichzeitig berichten Medien von einer neuen, anhaltenden «Covid-19-Welle» in China. Es gebe Befürchtungen, dass es zu erneuten Lockdowns und anderen drastischen Maßnahmen kommen könnte, obwohl sich die «Infektionen» laut den Gesundheitsbehörden auf einem Abwärtstrend befinden. In einigen Schulen seien Schüler isoliert und unter Quarantäne gestellt worden.
Isolierung, Überwachung und Kontrolle sind ebenfalls ein höchst ungesundes Erbe der «Coronazeit». Die weltweit vielfach eingeführten digitalen «Impfpässe» wurden als Instrument benutzt, um Kampagnen für digitale Identitäten zu fördern und die entsprechenden Systeme aufzubauen. Gerade hat auch Griechenland mit der Einführung seiner «Personal Citizen Number» den Grundstein für ein einheitliches digitales ID-System gelegt.
Derweil schlagen Datenschützer Alarm wegen des Tracking-Potenzials der sogenannten «Phone Home»-Funktion vieler digitaler Ausweise. Dieses «Feature», bei dem im Hintergrund jedesmal der Aussteller kontaktiert wird, um eine Angabe zu überprüfen, werde ganz leise in der Gesellschaft eingeführt, warnen sie. Das gebe den Regierungen den Vorgeschmack auf eine Macht, die sie kaum jemals wieder loslassen würden. Dagegen hilft nur eins: wachsam sein, hinterfragen und im Zweifel «Nein» sagen, anstatt auf eine vermeintliche Bequemlichkeit hereinzufallen.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ cae03c48:2a7d6671
2025-06-09 14:01:57
@ cae03c48:2a7d6671
2025-06-09 14:01:57Bitcoin Magazine

Mapping Bitcoin’s Bull Cycle PotentialBitcoin’s Market Value to Realized Value, or MVRV ratio, remains one of the most reliable on-chain indicators for identifying local and macro tops and bottoms across every BTC cycle. By isolating data across different investor cohorts and adapting historical benchmarks to modern market conditions, we can generate more accurate insights into where Bitcoin may be headed next.
The Bitcoin MVRV Ratio
The MVRV Ratio compares Bitcoin’s market price to its realized price, essentially the average cost basis for all coins in the network. As of writing, BTC trades around $105,000 while the realized price floats near $47,000, putting the raw MVRV at 2.26. The Z-Score version of MVRV standardizes this ratio based on historical volatility, enabling clearer comparisons across different market cycles.
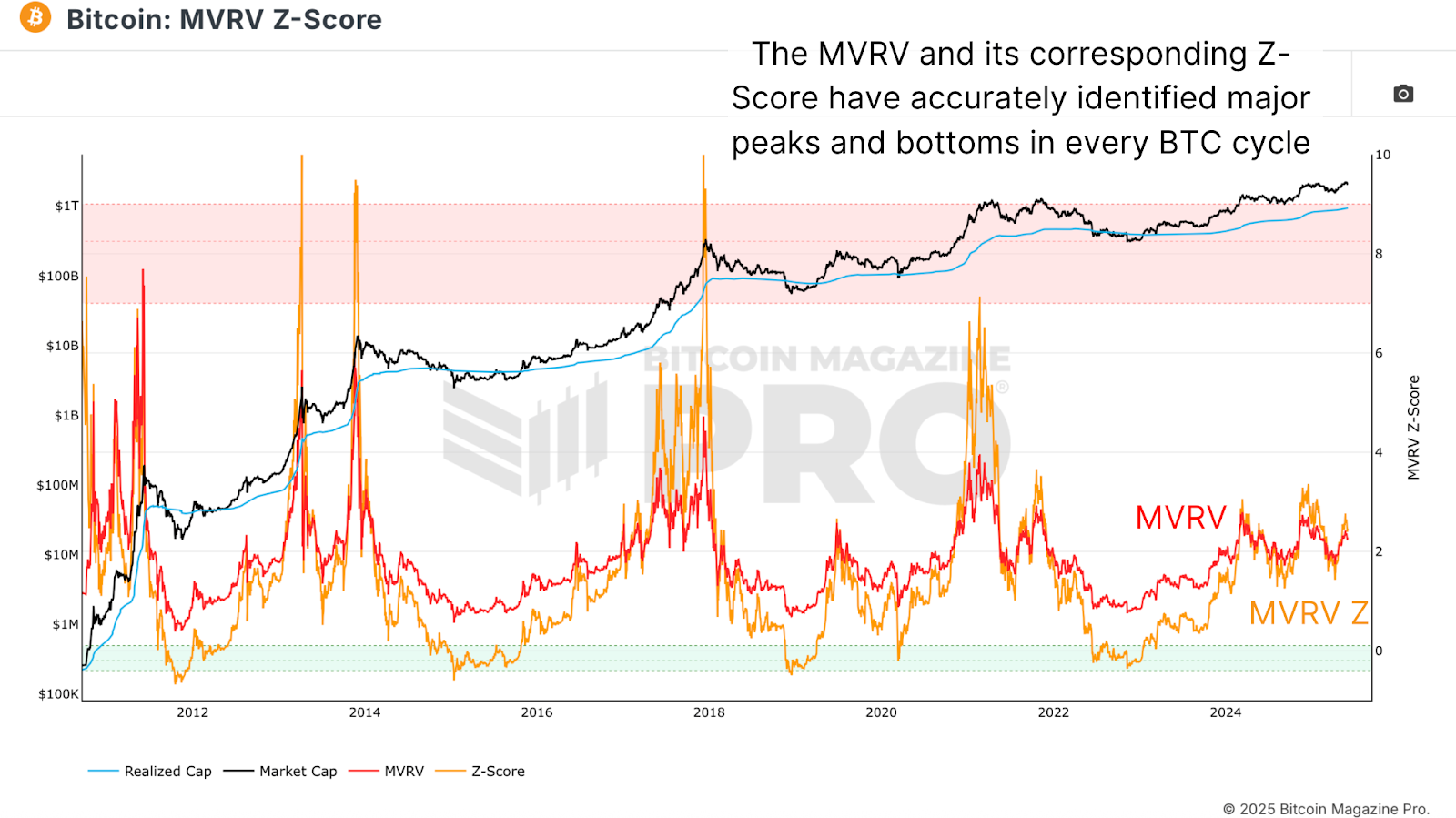
Figure 1: Historically, the MVRV Ratio and the MVRV Z-Score have accurately identified cycle peaks and bottoms. View Live Chart
Short-Term Holders
Short-term holders, defined as those holding Bitcoin for 155 days or less, currently have a realized price near $97,000. This metric often acts as dynamic support in bull markets and resistance in bear markets. Notably, when the Short Term Holder MVRV hits 1.33, local tops have historically occurred, as seen several times in both the 2017 and 2021 cycles. So far in the current cycle, this threshold has already been touched four times, each followed by modest retracements.
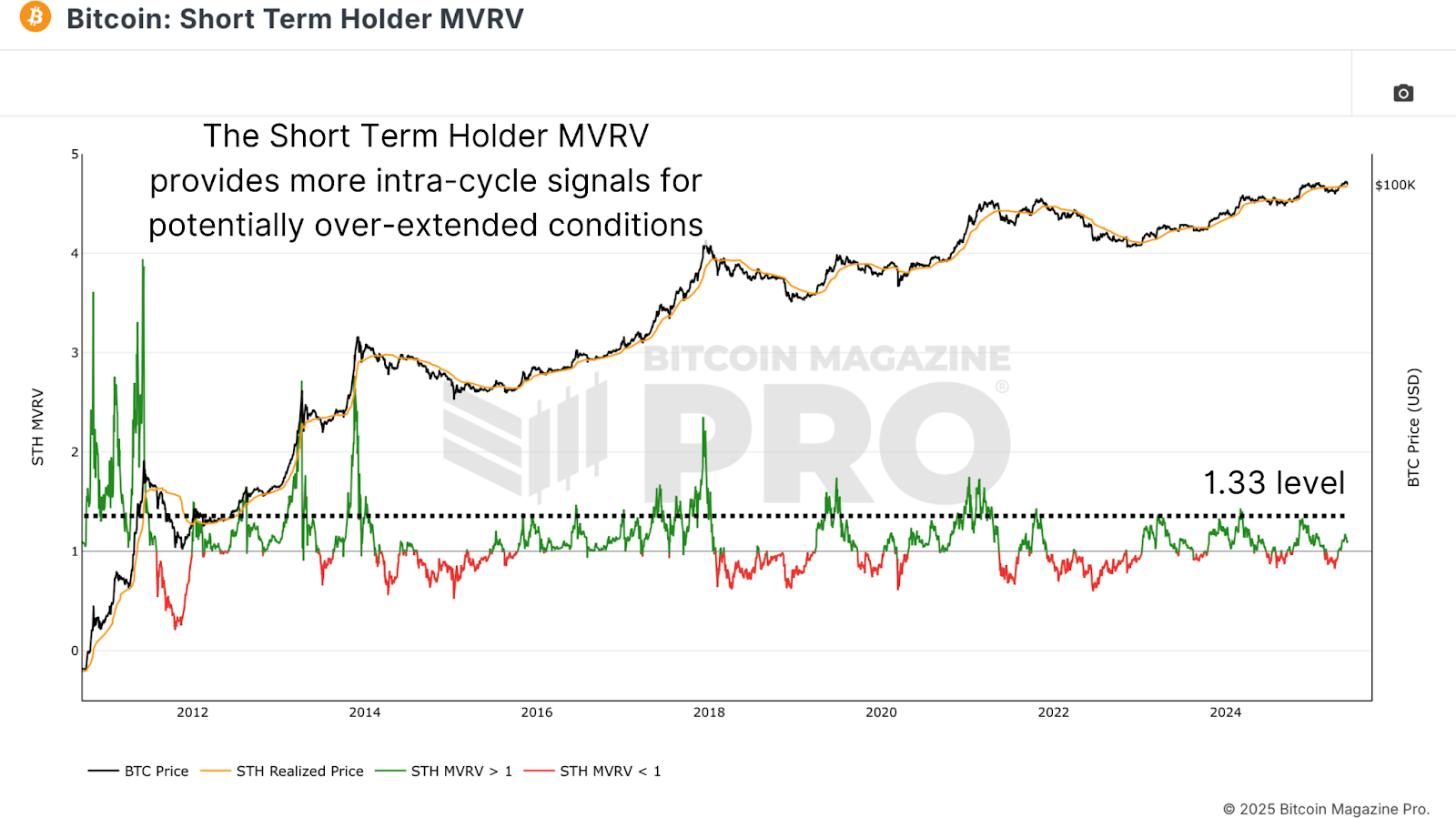
Figure 2: Short Term Holder MVRV reaching 1.33 in more recent cycles has aligned with local tops. View Live Chart
Long-Term Holders
Long-term holders, who’ve held BTC for more than 155 days, currently have an average cost basis of just $33,500, putting their MVRV at 3.11. Historically, Long Term Holder MVRV values have reached as high as 12 during major peaks. That said, we’re observing a trend of diminishing multiples each cycle.
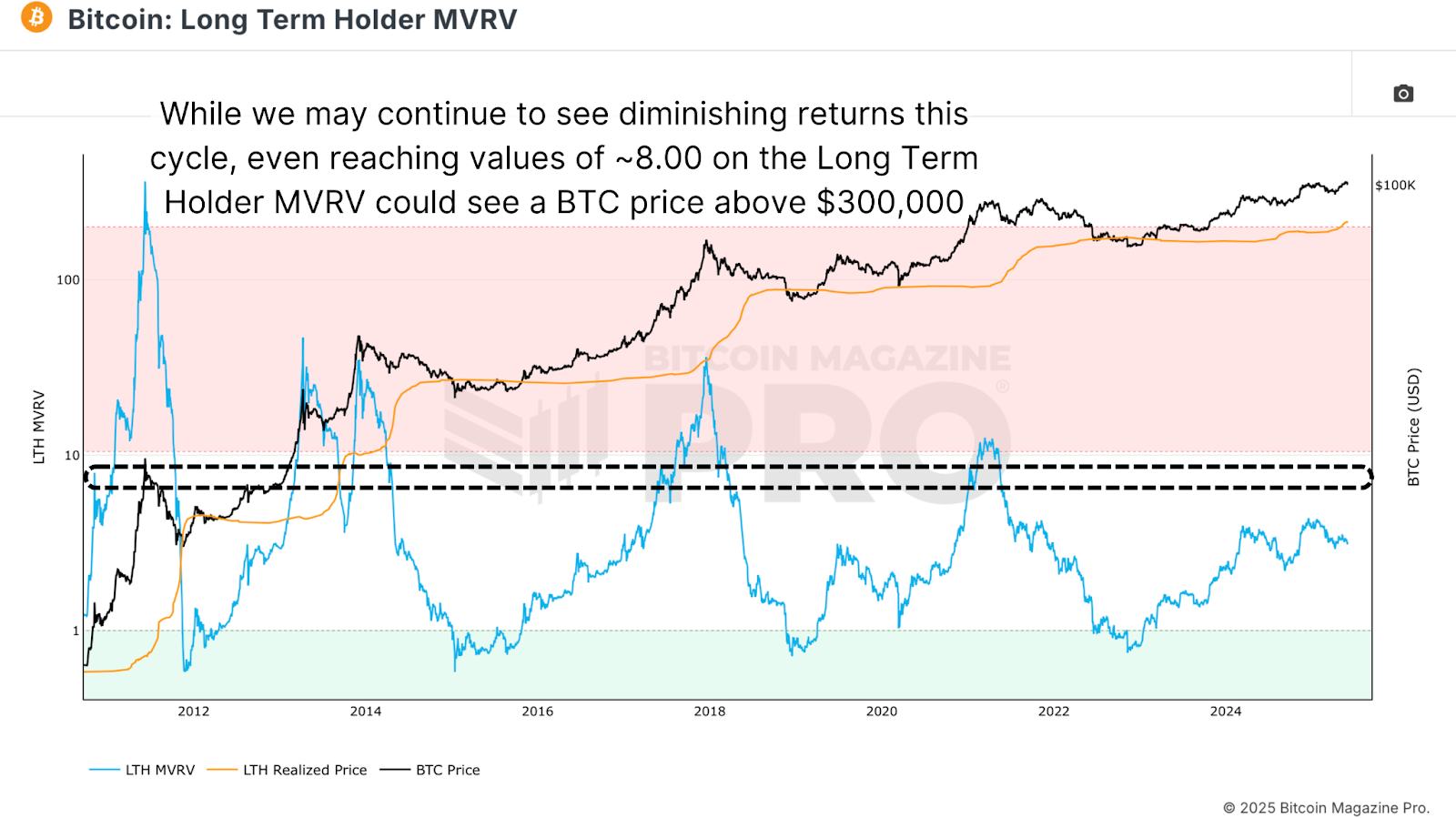
Figure 3: Achieving a Long Term Holder MVRV value of 8 could extrapolate to a BTC price in excess of $300,000. View Live Chart
A key resistance band now sits between 7.5 and 8.5, a zone that has defined bull tops and pre-bear retracements in every cycle since 2011. If the current growth of the realized price ($40/day) continues for another 140–150 days, matching previous cycle lengths, we could see it reach somewhere in the region of $40,000. A peak MVRV of 8 would imply a price near $320,000.
A Smarter Market Compass
Unlike static all-time metrics, the 2-Year Rolling MVRV Z-Score adapts to evolving market dynamics. By recalculating average extremes over a rolling window, it smooths out Bitcoin’s natural volatility decay as it matures. Historically, this version has signaled overbought conditions when reaching levels above 3, and prime accumulation zones when dipping below -1. Currently sitting under 1, this metric suggests that substantial upside remains.
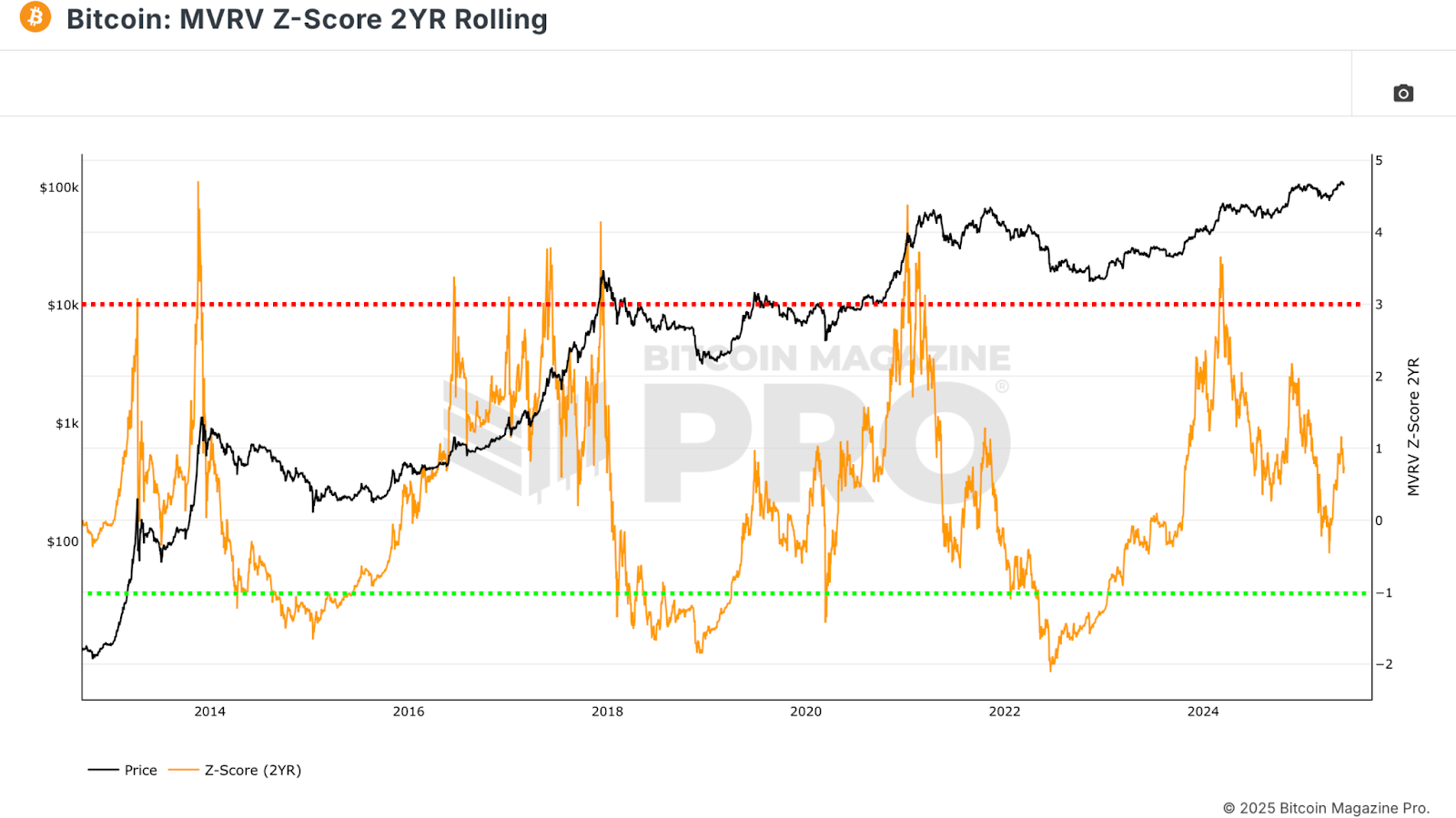
Figure 4: The current 2-Year Rolling MVRV Z-Score suggests more positive price action ahead. View Live Chart
Timing & Targets
A view of the BTC Growth Since Cycle Lows chart illustrates that BTC is now approximately 925 days removed from its last major cycle low. Historical comparisons to previous bull markets suggest we may be around 140 to 150 days away from a potential top, with both the 2017 and 2021 peaks occurring around 1,060 to 1,070 days after their respective lows. While not deterministic, this alignment reinforces the broader picture of where we are in the cycle. If realized price trends and MVRV thresholds continue on current trajectories, late Q3 to early Q4 2025 may bring final euphoric moves.
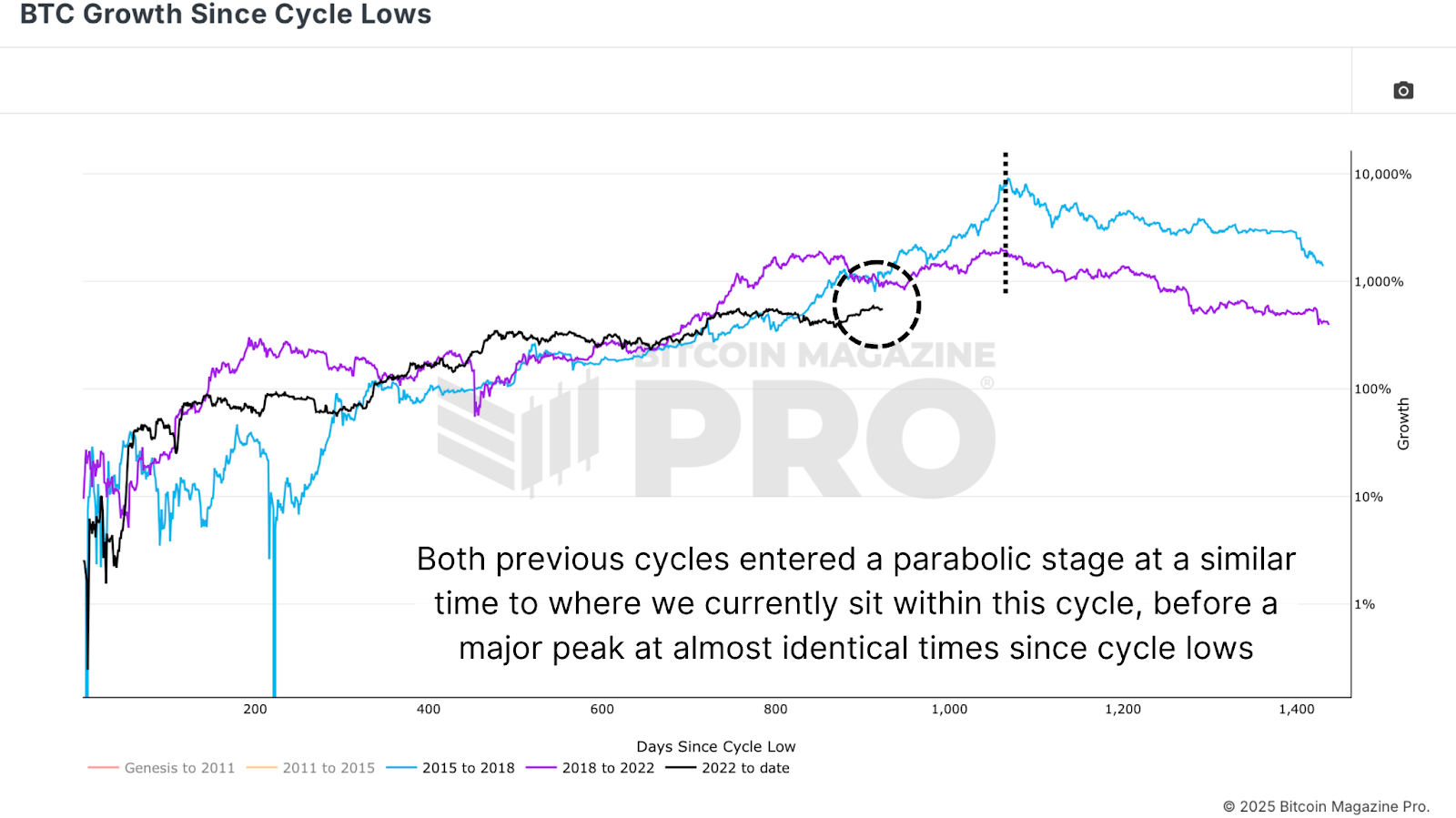
Figure 5: Will the current cycle continue to exhibit growth patterns similar to those of the previous two cycles? View Live Chart
Conclusion
The MVRV ratio and its derivatives remain essential tools for analyzing Bitcoin market behavior, providing clear markers for both accumulation and distribution. Whether observing short-term holders hovering near local top thresholds, long-term holders nearing historically significant resistance zones, or adaptive metrics like the 2-Year Rolling MVRV Z-Score signaling plenty of runway left, these data points should be used in confluence.
No single metric should be relied upon to predict tops or bottoms in isolation, but taken together, they offer a powerful lens through which to interpret the macro trend. As the market matures and volatility declines, adaptive metrics will become even more crucial in staying ahead of the curve.
For more deep-dive research, technical indicators, real-time market alerts, and access to a growing community of analysts, visit BitcoinMagazinePro.com.
Disclaimer: This article is for informational purposes only and should not be considered financial advice. Always do your own research before making any investment decisions.
This post Mapping Bitcoin’s Bull Cycle Potential first appeared on Bitcoin Magazine and is written by Matt Crosby.
-
 @ 2b24a1fa:17750f64
2025-06-09 13:07:23
@ 2b24a1fa:17750f64
2025-06-09 13:07:23Zum organisierten Corona-Komplex zählt auch der vermittelte Eindruck, dass es in den Jahren der sogenannten Pandemie praktisch nur noch eine Todesursache gab: Covid-19. Verkehrstote? Krebstote? Gewöhnliche Alterstote? Kann nicht sein.
https://soundcloud.com/radiomuenchen/studie-viele-falsche-corona-tote-von-multipolar?
UN-Generalsekretär Guterres sah die Welt „im Krieg mit dem Virus“, de facto war es ein Krieg mit der Wahrheit, den Regierungen und Mainstream-Medien ausfochten. Der berechtigte Einwand, es mache einen Unterschied, ob jemand mit Corona oder wegen Corona gestorben ist, wurde als Ketzerei abgekanzelt. Erst mit dem Krieg in der Ukraine geriet das „Jeder Tote ist ein Corona-Toter“-Narrativ an seine Propaganda-Grenzen und Corona verschwand so schnell aus dem medialen Tagesgeschäft wie es gekommen war. Das Geld, das man für Masken, sogenannte Impfstoffe und damit verbundener Korruption verschwendet hatte, musste man nun unbedingt für Waffen verschwenden. Umso wichtiger ist es, diese Zeit der Lügen und Grundrechtsverletzungen nicht einfach unter den Teppich zu kehren und darüber zu schweigen. Aufklärung leistet hier nach wie vor das Magazin Multipolar. Es berichtet von einer aktuellen Studie griechischer Forscher über „offizielle Corona-Todesfälle während Omikron“. Dabei erwies sich Corona nur in einer Minderheit der Fälle als direkte Todesursache.
Sprecherin: Sabrina Khalil
Originaltext bei Multipolar: multipolar-magazin.de/meldungen/0257
Bild: Chat GPT im Auftrag von Radio München
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
-
 @ a5ee4475:2ca75401
2025-06-04 13:25:46
@ a5ee4475:2ca75401
2025-06-04 13:25:46[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
Este artigo reúne algumas evidências mais antigas que vim registrando durante alguns anos contra a covid, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponiveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que não tivemos contato pela escassez de meios para a obtenção dessas informações de forma organizada. Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação, então se possível ajudem sugerindo com complementos ou alterações.
1. Vacinas Obrigatórias em Geral
-
Vacinas e autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
-
O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
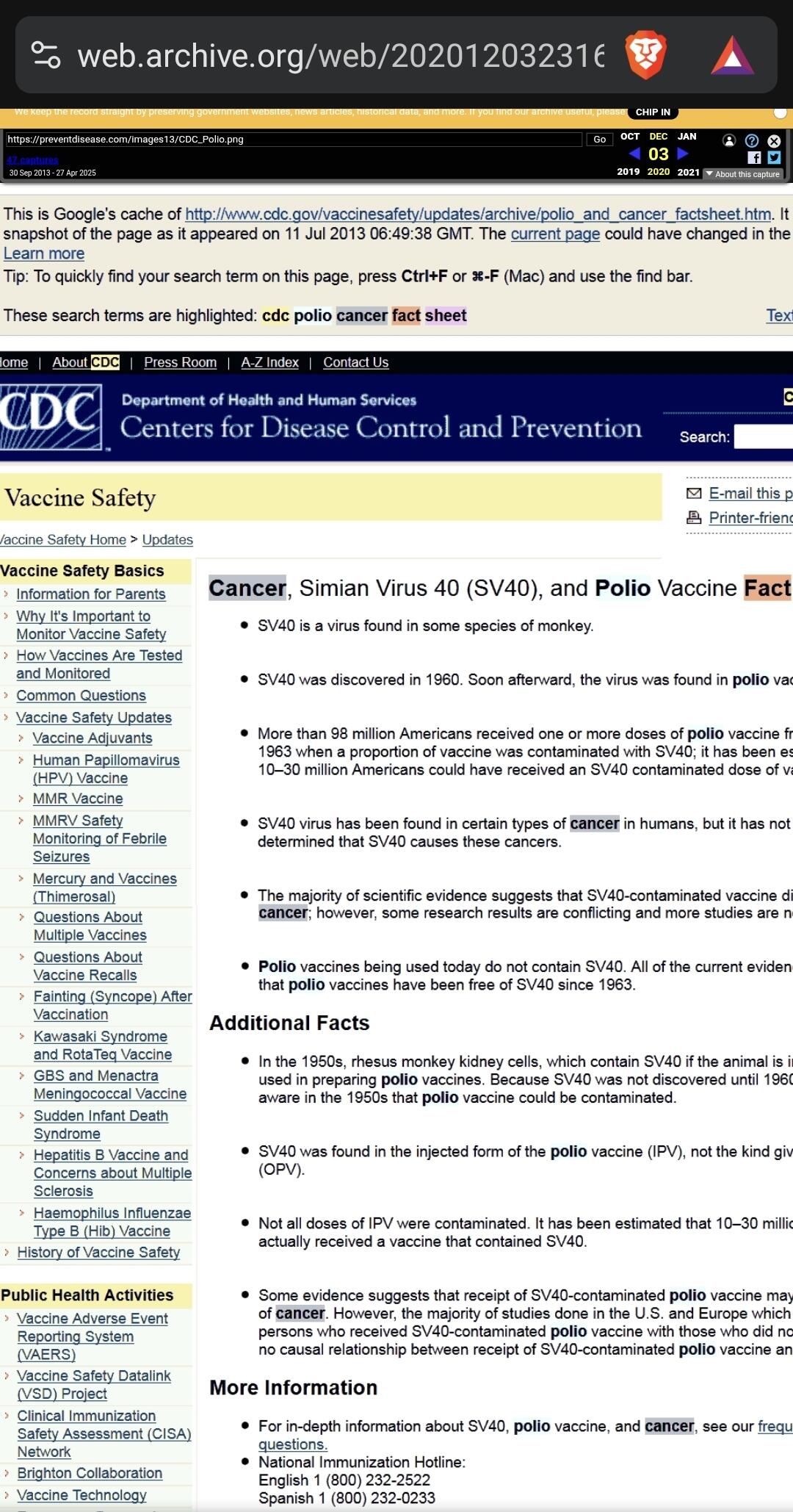 Fonte original: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
Salvo em: https://web.archive.org/web/20201203231640/ https://preventdisease.com/images13/CDC_Polio.png
Fonte original: https://preventdisease.com/images13/CDC_Polio.png [indisponível]
Salvo em: https://web.archive.org/web/20201203231640/ https://preventdisease.com/images13/CDC_Polio.png"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como no Brasil: https://www.gazetadopovo.com.br/vida-e-cidadania/quais-ongs-cooperaram-com-moraes-e-sao-alvo-do-congresso-nos-eua/ ), inclusive em relacionadas ao SARS, um vírus muito semelhante ao SEGUNDO tipo de vírus Sars-Cov, o Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho
Houve uma "coincidência", a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (o mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China. https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: http://patrocinados.estadao.com.br/medialab/releaseonline/releasegeral-releasegeral/geral-johns-hopkins-center-for-health-security-forum-economico-mundial-e-fundacao-bill-melinda-gates-realizam-exercicio-pandemico-e-transmissao-ao-vivo/
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria e ocorrências em São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
Foto do governador de São Paulo sem o item de proteção viralizou nas redes
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho (filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações:
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
Dr. Kary Mullis - Criador do teste PCR
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
-
Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
-
Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
-
As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
-
Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
-
USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
13 de setembro de 2021 - 13/09/2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
Setembro de 2021 - 09/2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
-
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 2b24a1fa:17750f64
2025-06-09 13:03:51
@ 2b24a1fa:17750f64
2025-06-09 13:03:51Zum organisierten Corona-Komplex zählt auch der vermittelte Eindruck, dass es in den Jahren der sogenannten Pandemie praktisch nur noch eine Todesursache gab: Covid-19. Verkehrstote? Krebstote? Gewöhnliche Alterstote? Kann nicht sein. UN-Generalsekretär Guterres sah die Welt „im Krieg mit dem Virus“, de facto war es ein Krieg mit der Wahrheit, den Regierungen und Mainstream-Medien ausfochten.
https://soundcloud.com/radiomuenchen/studie-viele-falsche-corona-tote-von-multipolar
Der berechtigte Einwand, es mache einen Unterschied, ob jemand mit Corona oder wegen Corona gestorben ist, wurde als Ketzerei abgekanzelt. Erst mit dem Krieg in der Ukraine geriet das „Jeder Tote ist ein Corona-Toter“-Narrativ an seine Propaganda-Grenzen und Corona verschwand so schnell aus dem medialen Tagesgeschäft wie es gekommen war. Das Geld, das man für Masken, sogenannte Impfstoffe und damit verbundener Korruption verschwendet hatte, musste man nun unbedingt für Waffen verschwenden. Umso wichtiger ist es, diese Zeit der Lügen und Grundrechtsverletzungen nicht einfach unter den Teppich zu kehren und darüber zu schweigen. Aufklärung leistet hier nach wie vor das Magazin Multipolar. Es berichtet von einer aktuellen Studie griechischer Forscher über „offizielle Corona-Todesfälle während Omikron“. Dabei erwies sich Corona nur in einer Minderheit der Fälle als direkte Todesursache.
Sprecherin: Sabrina Khalil
Originaltext bei Multipolar: multipolar-magazin.de/meldungen/0257
Bild: Chat GPT im Auftrag von Radio München
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 2b24a1fa:17750f64
2025-06-09 13:02:20
@ 2b24a1fa:17750f64
2025-06-09 13:02:20https://soundcloud.com/radiomuenchen/2025-05-27-eine-stunde-klassik?
Eine Stunde Klassik! Der Münchner Pianist und "Musikdurchdringer" Jürgen Plich stellt jeden Dienstag um 20 Uhr große klassische Musik vor. Er teilt seine Hör- und Spielerfahrung und seine persönliche Sicht auf die Meisterwerke. Er spielt selbst besondere, unbekannte Aufnahmen, erklärt, warum die Musik so und nicht anders klingt und hat eine Menge aus dem Leben der Komponisten zu erzählen.
Sonntags um 10 Uhr in der Wiederholung.
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ b1ddb4d7:471244e7
2025-06-09 13:01:40
@ b1ddb4d7:471244e7
2025-06-09 13:01:40“Not your keys, not your coins” isn’t a slogan—it’s a survival mantra in the age of digital sovereignty.
The seismic collapses of Mt. Gox (2014) and FTX (2022) weren’t anomalies; they were wake-up calls. When $8.7 billion in customer funds vanished with FTX, it exposed the fatal flaw of third-party custody: your bitcoin is only as secure as your custodian’s weakest link.
Yet today, As of early 2025, analysts estimate that between 2.3 million and 3.7 million Bitcoins are permanently lost, representing approximately 11–18% of bitcoin’s fixed maximum supply of 21 million coins, with some reports suggesting losses as high as 4 million BTC. This paradox reveals a critical truth: self-custody isn’t just preferable—it’s essential—but it must be done right.
The Custody Spectrum
Custodial Wallets (The Illusion of Control)
- Rehypothecation Risk: Most platforms lend your bitcoin for yield generation. When Celsius collapsed, users discovered their “held” bitcoin was loaned out in risky strategies.
- Account Freezes: Regulatory actions can lock withdrawals overnight. In 2023, Binance suspended dollar withdrawals for U.S. users citing “partner bank issues,” trapping funds for weeks.
- Data Vulnerability: KYC requirements create honeypots for hackers. The 2024 Ledger breach exposed 270,000 users’ personal data despite hardware security.
True Self-Custody
Self-custody means exclusively controlling your private keys—the cryptographic strings that prove bitcoin ownership. Unlike banks or exchanges, self-custody eliminates:- Counterparty risk (no FTX-style implosions)
- Censorship (no blocked transactions)
- Inflationary theft (no fractional reserve lending)
Conquering the Three Great Fears of Self-Custody
Fear 1: “I’ll Lose Everything If I Make a Mistake”
Reality: Human error is manageable with robust systems:
- Test Transactions: Always send a micro-amount (0.00001 BTC) before large transfers. Verify receipt AND ability to send back.
- Multi-Backup Protocol: Store seed phrases on fireproof/waterproof steel plates (not paper!). Distribute copies geographically—one in a home safe, another with trusted family 100+ miles away.
- SLIP39 Sharding: Split your seed into fragments requiring 3-of-5 shards to reconstruct. No single point of failure.
Fear 2: “Hackers Will Steal My Keys”
Reality: Offline storage defeats remote attacks:
- Hardware Wallets: Devices like Bitkey or Ledger keep keys in “cold storage”—isolated from internet-connected devices. Transactions require physical confirmation.
- Multisig Vaults: Bitvault’s multi-sig system requires attackers compromise multiple locations/devices simultaneously. Even losing two keys won’t forfeit funds.
- Air-Gapped Verification: Use dedicated offline devices for wallet setup. Never type seeds on internet-connected machines.
Fear 3: “My Family Can’t Access It If I Die”
Reality: Inheritance is solvable:
- Dead Man Switches: Bitwarden’s emergency access allows trusted contacts to retrieve encrypted keys after a pre-set waiting period (e.g., 30 days).
- Inheritance Protocols: Bitkey’s inheritance solution shares decryption keys via designated beneficiaries’ emails. Requires multiple approvals to prevent abuse.
- Public Key Registries: Share wallet XPUBs (not private keys!) with heirs. They can monitor balances but not spend, ensuring transparency without risk.
The Freedom Dividend
- Censorship Resistance: Send $10M BTC to a Wikileaks wallet without Visa/Mastercard blocking it.
- Privacy Preservation: Avoid KYC surveillance—non-custodial wallets like Flash require zero ID verification.
- Protocol Access: Participate in bitcoin-native innovations (Lightning Network, DLCs) only possible with self-custodied keys.
- Black Swan Immunity: When Cyprus-style bank bailins happen, your bitcoin remains untouched in your vault.
The Sovereign’s Checklist
- Withdraw from Exchanges: Move all BTC > $1,000 to self-custody immediately.
- Buy Hardware Wallet: Purchase DIRECTLY from manufacturer (no Amazon!) to avoid supply-chain tampering.
- Generate Seed OFFLINE: Use air-gapped device, write phrase on steel—never digitally.
- Test Recovery: Delete wallet, restore from seed before funding.
- Implement Multisig: For > $75k, use Bitvault for 2-of-3 multi-sig setup.
- Create Inheritance Plan: Share XPUBs/SLIP39 shards with heirs + legal documents.
“Self-custody isn’t about avoiding risk—it’s about transferring risk from opaque institutions to transparent, controllable systems you design.”
The Inevitable Evolution: Custody Without Compromise
Emerging solutions are erasing old tradeoffs:
- MPC Wallets: Services like Xapo Bank shatter keys into encrypted fragments distributed globally. No single device holds full keys, defeating physical theft.
- Social Recovery: Ethically designed networks (e.g., Bitkey) let trusted contacts restore access without custodial control.
- Biometric Assurance: Fingerprint reset protocols prevent lockouts from physical injuries.
Lost keys = lost bitcoin. But consider the alternative: entrusting your life savings to entities with proven 8% annual failure rates among exchanges. Self-custody shifts responsibility from hoping institutions won’t fail to knowing your system can’t fail without your consent.
Take action today: Move one coin. Test one recovery. Share one xpub. The path to unchained wealth begins with a single satoshi under your control.
-
 @ 2b24a1fa:17750f64
2025-06-09 13:00:03
@ 2b24a1fa:17750f64
2025-06-09 13:00:03Ganz im Geiste des klassischen Kabaretts widmen sich Franz Esser und Michael Sailer den Ereignissen des letzten Monats: Was ist passiert? Und was ist dazu zu sagen? Das ist oft frappierend - und manchmal auch zum Lachen.
https://soundcloud.com/radiomuenchen/vier-wochen-wahnsinn-mai-25-ein-satirischer-monatsruckblick
www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen\ odysee.com/@RadioMuenchen.net:9\ rumble.com/user/RadioMunchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): bc1qqkrzed5vuvl82dggsyjgcjteylq5l58sz4s927\ Ethereum (ETH): 0xB9a49A0bda5FAc3F084D5257424E3e6fdD303482
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ 9ca447d2:fbf5a36d
2025-06-09 10:01:39
@ 9ca447d2:fbf5a36d
2025-06-09 10:01:39Paris, France – June 6, 2025 — Bitcoin payment gateway startup Flash, just announced a new partnership with the “Bitcoin Only Brewery”, marking the first-ever beverage company to leverage Lightning payments.
Flash enables Bitcoin Only Brewery to offer its “BOB” beer with, no-KYC (Know Your Customer) delivery across Europe, priced at 19,500 sats (~$18) for the 4-pack, shipping included.
The cans feature colorful Bitcoin artwork while the contents promise a hazy pale ale: “Each 33cl can contains a smooth, creamy mouthfeel, hazy appearance and refreshing Pale Ale at 5% ABV,” reads the product description.
Pierre Corbin, Co-Founder of Flash, commented:
“Currently, bitcoin is used more as a store of value but usage for payments is picking up. Thanks to new innovation on Lightning, bitcoin is ready to go mainstream for e-commerce sales.”
Flash, launched its 2.0 version in March 2025 with the goal to provide the easiest bitcoin payment gateway for businesses worldwide. The platform is non-custodial and can enable both digital and physical shops to accept bitcoin by connecting their own wallets to Flash.
By leveraging the scalability of the Lightning Network, Flash ensures instant, low-cost transactions, addressing on-chain Bitcoin bottlenecks like high fees and long wait times.
For businesses interested in adopting Bitcoin payments, Flash offers a straightforward onboarding process, low fees, and robust support for both digital and physical goods. To learn more, visit paywithflash.com.
Media Contact:
Pierre Corbin
Co-Founder, Flash
Email: press@paywithflash.com
Website: paywithflash.comAbout Flash
Flash is the easiest Bitcoin payment gateway for businesses to accept payments. Supporting both digital and physical enterprises, Flash leverages the Lightning Network to enable fast, low-cost Bitcoin transactions. Launched in its 2.0 version in March 2025, Flash is at the forefront of driving Bitcoin adoption in e-commerce.
About Bitcoin Only Brewery
Bitcoin Only Brewery (@Drink_B0B) is a pioneering beverage company dedicated to the Bitcoin ethos, offering high-quality beers payable exclusively in Bitcoin. With a commitment to personal privacy, the brewery delivers across Europe with no-KYC requirements.
-
 @ f0fd6902:a2fbaaab
2025-06-09 12:46:55
@ f0fd6902:a2fbaaab
2025-06-09 12:46:55A brinicle (brine icicle, also known as an ice stalactite) is a downward-growing hollow tube of ice enclosing a plume of descending brine that is formed beneath developing sea ice.
As seawater freezes in the polar ocean, salt brine concentrates are expelled from the sea ice, creating a downward flow of dense, extremely cold, saline water, with a lower freezing point than the surrounding water. When this plume comes into contact with the neighboring ocean water, its extremely low temperature causes ice to instantly form around the flow. This creates a hollow stalactite, or icicle, referred to as a brinicle. Source: https://en.wikipedia.org/wiki/Brinicle
https://www.youtube.com/watch?v=69aeBawfrRw
https://stacker.news/items/1001460
-
 @ 2dd9250b:6e928072
2025-05-31 16:12:55
@ 2dd9250b:6e928072
2025-05-31 16:12:55Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
-
 @ 2b24a1fa:17750f64
2025-06-09 12:58:05
@ 2b24a1fa:17750f64
2025-06-09 12:58:05Wahrscheinlich wird es wieder der wärmste Mai seit Wetteraufzeichnung gewesen sein, was uns erneut ermahnt, endlich dem Klimawandel den Garaus zu machen. Sie merken es, der Sarkasmus bahnt sich schon seinen Weg. Auch München hat sich jetzt dem Klima-Taler-Netzwerk angeschlossen und wirbt für das Angebot, sich ein besseres Gewissen tracken zu lassen. Hören Sie Nicolas Riedls Kommentar „Der Klima-Köder“.
Sprecherin: Sabrina Khalil
Bild: © Klima-Taler
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.\ GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): 3G1wDDH2CDPJ9DHan5TTpsfpSXWhNMCZmQ
-
 @ a5ee4475:2ca75401
2025-06-06 15:30:41
@ a5ee4475:2ca75401
2025-06-06 15:30:41[EM ATUALIZAÇÃO]
vacina #saude #politica #manipulacao #mundial #genocidio #pandemia #conspiracao
"Aqueles que não conseguem lembrar o passado estão condenados a repeti-lo." - George Satayana
Este artigo reúne algumas menções e evidências mais antigas que vim registrando durante alguns anos em relação a Covid-19, vacinas obrigatórias e a ação de agências de governo, fundações, políticos, mídia tradicional, celebridades, influenciadores, cientistas, redes sociais e laboratórios, em envolvimento com genocídio e restrições de liberdades em escala mundial causado por decisões em várias esferas relativas ao covid e as vacinas obrigatórias em geral.
Porém, alguns links podem não estar mais disponíveis, foram que ainda faltam ser registradas muitas informações já divulgadas nos últimos anos e que muitos não tiveram contato pela escassez de meios para a obtenção dessas informações de forma organizada.
Portanto, o presente artigo ainda passará por atualizações de conteúdo e formatação. Logo, se possível, ajudem sugerindo complementos ou alterações, ou com doações.
Noções iniciais:
- O termo 'Coronavírus' (COVID) é na verdade um nome genérico para vários vírus de gripes já comuns, dado para o tipo corona (com uma "coroa", 'espetos' ao redor dele), o Sars-Cov-2 (que passou a ser chamado erroneamente só de Covid), é só um deles.
- SARS-CoV-2 é que é nome do vírus. Ele que causa a doença Covid-19;
- O coronavírus SARS-CoV-2 é o segundo tipo de SARS-CoV documentado, o primeiro ocorreu entre 2002 e 2003, se originando também da China e também dito como tendo origem animal;
- SARS (Severe Acute Respiratory Syndrome) - Síndrome Respiratória Aguda Grave (SRAG) é a uma doença respiratória viral, relatada ser de origem zoonótica (animal), causada pelos coronavírus SARS-CoV (2002) e SARS-CoV-2 (2019), ambos de origem chinesa;
1. Vacinas Obrigatórias em Geral
23/01/2025 - [Pesquisa] Vacinas nos EUA causando autismo em crianças https://publichealthpolicyjournal.com/vaccination-and-neurodevelopmental-disorders-a-study-of-nine-year-old-children-enrolled-in-medicaid/
- O CDC admite que 98 milhões de pessoas receberam o vírus do câncer através da vacina da Poliomielite https://medicinanews.com.br/frente/frente_1/o-cdc-admite-que-98-milhoes-de-pessoas-receberam-o-virus-do-cancer-atraves-da-vacina-poliomielite/
"O CDC (Os Centros de Controle e Prevenção de Doenças dos Estados Unidos) removeu rapidamente uma página do seu site, que estava em cache no Google, como você pode ver logo abaixo, admitindo que mais de 98 milhões de americanos receberam uma ou mais doses de vacina contra pólio dentro de 8 período entre 1955 e 1963, quando uma proporção da vacina foi contaminada com um poliomavírus causador de câncer chamado SV40."
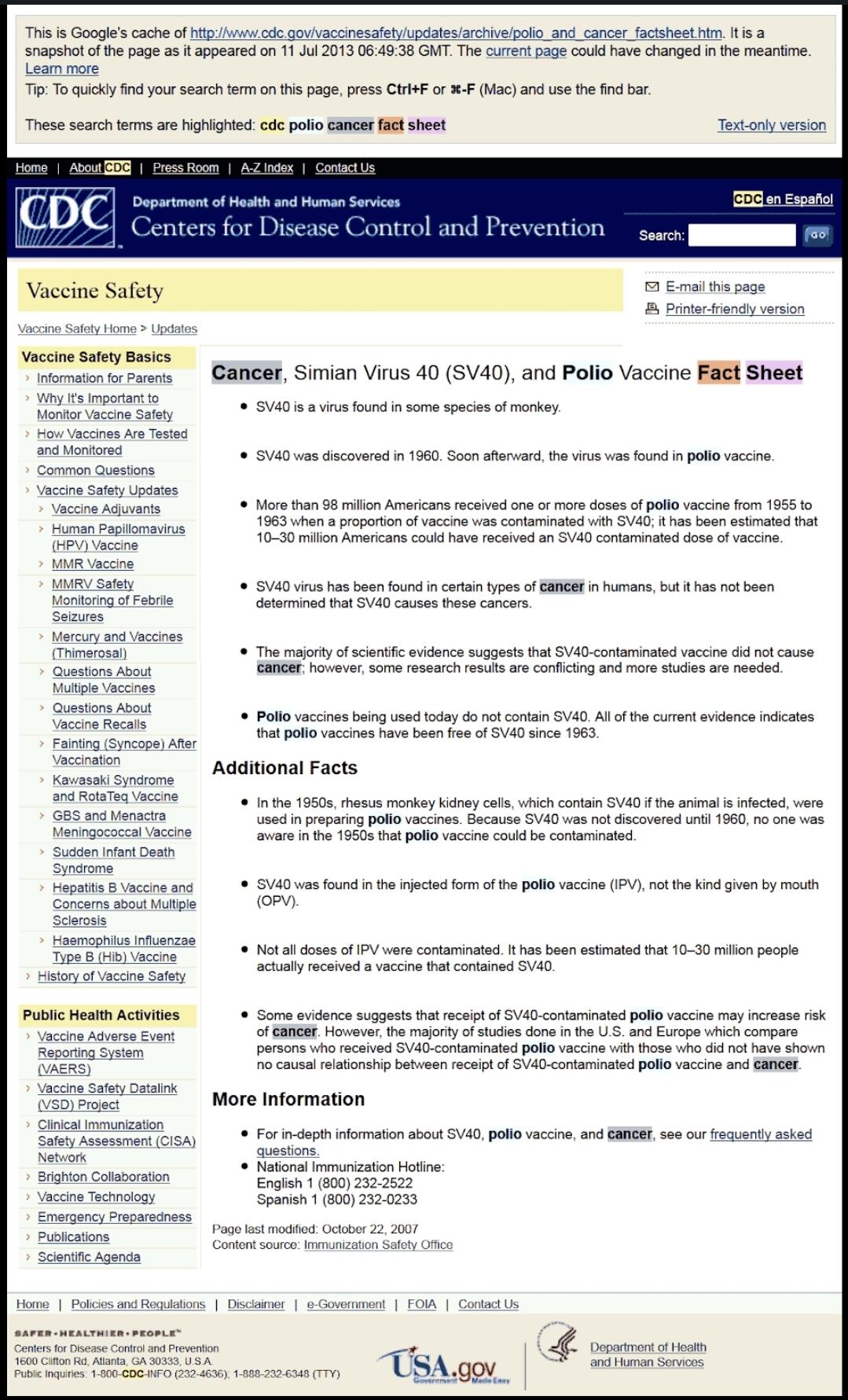 Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva.
Fonte original da imagem: https://preventdisease.com/images13/CDC_Polio.png [indisponível] - A imagem foi trocada por outra de menor qualidade e em outro link, mas eu já tinha a imagem original salva. Imagem arquivada em: https://web.archive.org/web/20201203231640/
Imagem arquivada em: https://web.archive.org/web/20201203231640/27/02/2021 - Por que o Japão demorou para vacinar, mesmo com Olimpíada se aproximando https://www.cnnbrasil.com.br/internacional/2021/02/27/por-que-o-japao-demorou-para-vacinar-mesmo-com-olimpiada-se-aproximando
"Desconfiança da população japonesa em relação a vacinas, ligada a casos ocorridos no passado, está entre razões que atrasaram imunização no país.
A resistência à vacina do Japão remonta à década de 1970, quando duas crianças morreram dentro de 24 horas após receberem a vacina combinada contra difteria, tétano e coqueluche (coqueluche). A vacina foi temporariamente suspensa, mas a confiança já havia sido abalada. Por vários anos, as taxas de vacinação infantil caíram, levando a um aumento nos casos de tosse convulsa.
No final dos anos 1980, houve outro susto com a introdução da vacina tripla contra sarampo, caxumba e rubéola produzida no Japão. As primeiras versões do imunizante foram associadas à meningite asséptica, ou inchaço das membranas ao redor do cérebro e da medula espinhal. O problema foi rastreado até o componente caxumba da vacina tripla, o que levou a uma ação judicial e a indenização por danos pesados.
O Instituto Nacional de Ciências da Saúde interrompeu a dose combinada em 1993 e a substituiu por vacinas individuais. Após o escândalo, Shibuya disse que o governo japonês se tornou "ciente dos riscos" e seu programa nacional de vacinação tornou-se voluntário.
O Dr. Yuho Horikoshi, especialista em doenças infecciosas, diz que os processos levaram a uma "lacuna de vacinação", em que nenhuma vacina foi aprovada no Japão por cerca de 15 anos.
Mais recentemente, em 2013, o Japão adicionou a vacina contra o papilomavírus humano (HPV) ao calendário nacional para proteger as meninas contra o vírus sexualmente transmissível, que é conhecido por causar câncer cervical. No entanto, vídeos de meninas supostamente sofrendo de reações adversas começaram a circular no YouTube, levando o governo a retirá-los da programação nacional."
2. PRIMEIRAS OCORRÊNCIAS PREDITIVAS AO COVID-19
2002 - Síndrome respiratória aguda grave (SARS) Brenda L. Tesini (setembro de 2018). Síndrome respiratória aguda grave (SARS) [indisponível]. Manual Merck. Consultado em 23 de janeiro de 2020, citado no Wikipedia
SARS - Wikipédia: "A SARS [doença do vírus SARS-CoV] foi detectada pela primeira vez no fim de 2002 na China. Entre 2002 e 2003, um surto da doença resultou em mais de 8 000 casos e cerca de 800 mortes em todo o mundo."
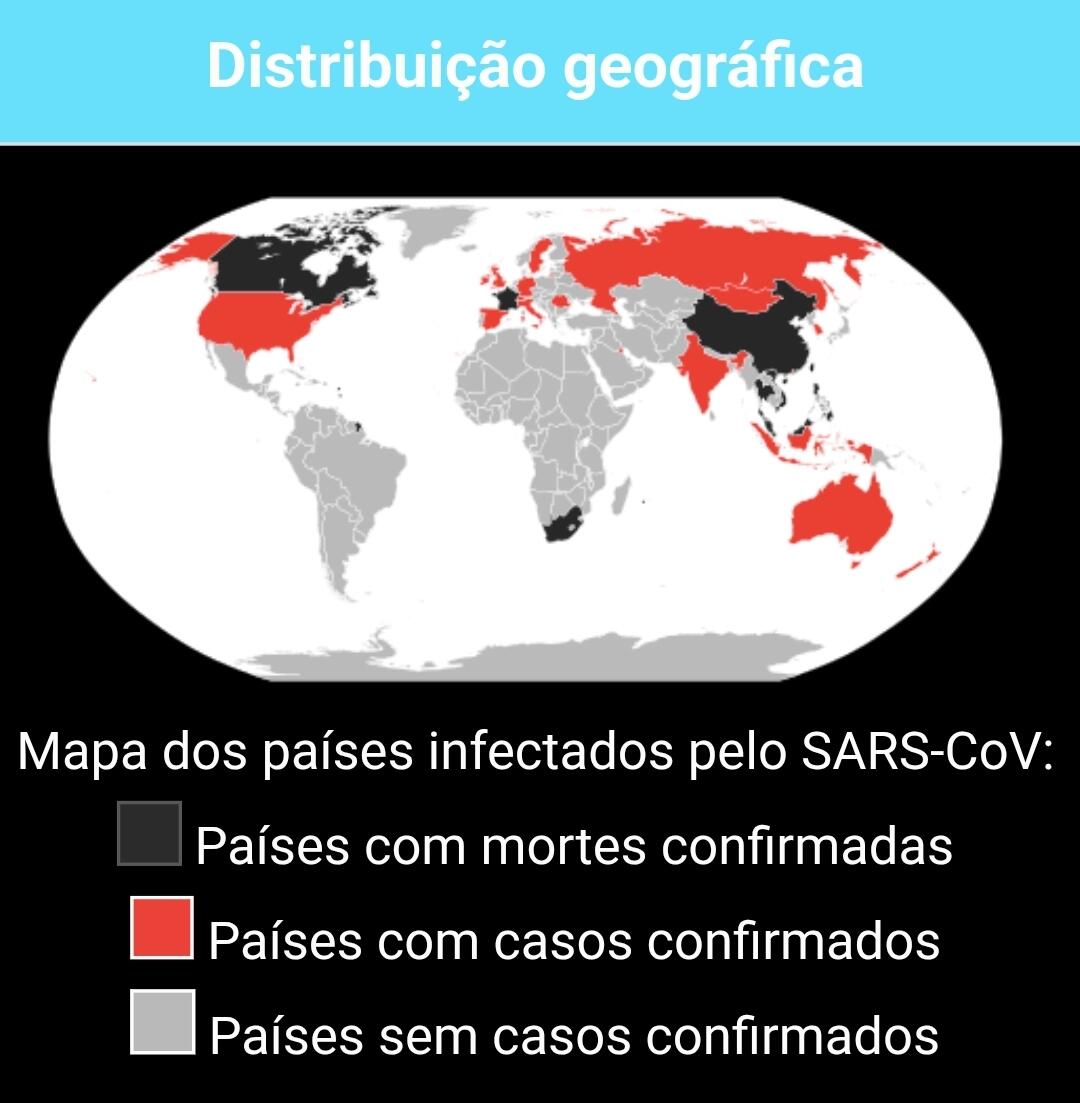
2010 - Fundação Rockfeller, Lockstep. https://www.rockefellerfoundation.org/wp-content/uploads/Annual-Report-2010-1.pdf
Neste PDF da fundação Rockfeller, em seu próprio site, a fundação deixou claro o seu envolvimento em casos de ‘contenção’ de pandemias juntamente com a USAID (agência americana com nome ambíguo, como formalmente ‘United States Agency for International Development’, mas soando como ‘US Socorre’, mas sendo um braço do governo democrata que financiava interferências políticas diretas em vários países, como em intervenções no Brasil ), inclusive em relacionadas ao SARS, o mesmo sintoma dos coronavírus Sars-Cov e Sars-Cov-2 (o vírus propagado em 2019) e que causa o COVID-19.
Segundo eles:
“Integração entre Regiões e Países
A Fundação Rockefeler investiu US$ 22 milhões em sua Iniciativa de Redes de Vigilância de Doenças para ajudar a conter a disseminação de doenças infecciosas e pandemias, fortalecendo os sistemas nacionais, regionais e globais de vigilância e resposta a doenças. Dois programas-chave da Rockefeler — a Rede de Vigilância de Doenças da Bacia do Mekong e a Rede Integrada de Vigilância de Doenças da África Oriental — conectaram e capacitaram profissionais de saúde, epidemiologistas e autoridades de saúde pública em toda a região, levando a um aumento de seis vezes nos locais de vigilância de doenças transfronteiriças somente nos últimos três anos. Em 2010, a Rockefeler expandiu a bem-sucedida campanha transdisciplinar One Health, que a USAID e o Banco Asiático de Desenvolvimento adotaram como modelos. One Health refere-se à integração da ciência médica e veterinária para combater essas novas variedades de doenças zoonóticas que se movem e sofrem mutações rapidamente de animais para humanos. Essas colaborações criaram e fortaleceram uma rede regional crítica de saúde pública, enquanto as lições aprendidas foram exportadas entre disciplinas e países. Além de fortalecer os laços globais em saúde pública, a Rockefeler ajudou a elevar o nível de especialização e treinamento em campo. O Programa de Treinamento em Epidemiologia de Campo coloca graduados nos mais altos escalões do governo no Laos e no Vietnã, enquanto as bolsas da Rockefeler transformaram as ferramentas disponíveis para os médicos, permitindo-lhes utilizar o poder da internet para se comunicar e monitorar eventos, compreender contextos locais e analisar novos problemas. Finalmente, estamos aplicando ferramentas do século XXI para combater os desafios de saúde do século XXI.”
Julho de 2012 - Revista Mundo Estranho - Epidemias Citado em: https://super.abril.com.br/especiais/epidemia-o-risco-invisivel/
Página do site ME salva em Imagem no Voidcat
Houve uma ‘coincidência’, a revista Mundo Estranho em julho de 2012, entrevistou o até então doutorando em virologia, Átila Iamarino (do canal Nerdologia no Youtube - O mesmo cientista que fez diversas propagandas das vacinas no Brasil), para descrever um possível cenário de propagação de uma epidemia viral, a revista descreve com grande precisão os eventos de 2020, mas apontando o oposto da China, em que, na realidade, sua economia cresceu vertiginosamente.
Segundo eles:
“ 1 – A Ásia é o ponto de partida. Após várias mutações, um novo vírus surge hospedado em morcegos. As fezes que eles soltam no ar infectam guaxinins. Dos mercados da China, esses animais são levados vivos para serem abatidos em restaurantes. Estressados, eles arranham e mordem os cozinheiros, espalhando o vírus.
2 – O vírus adquire a capacidade de ser transmitido de homem para homem por via aérea – forma mais fácil de contágio. Além disso, o contágio se dá antes mesmo de o enfermo apresentar os sintomas. Assim, em média, o doente infecta cinco pessoas antes de ter febre, vômito, diarreia, desidratação e falta de ar.
3 – O governo chinês envia uma comissão para avaliar a doença misteriosa que acomete alguns vilarejos. A equipe volta sem resultados e não considera o surto alarmante até que três pesquisadores adoecem e um deles morre. A China não informa a Organização Mundial da Saúde (OMS) para não demonstrar fragilidade.
4 – Os sintomas são comuns e a doença só chama a atenção quando muita gente começa a morrer na mesma região. Ainda assim, demora para que médicos e enfermeiros percebam a ineficiência de antibióticos na cura – o que exclui a maioria das bactérias como agente causador. Testes com vírus comuns também dão negativo.
5 – O governo isola comunidades em que há focos da doença. Ninguém entra nas cidades e nenhum doente pode sair. Mas, como a misteriosa enfermidade demora quatro dias para mostrar seus sintomas, muitos doentes saem dos vilarejos sem saber que estão infectados, alastrando a epidemia.
6 – Doentes viajam de avião para grandes cidades, como Hong Kong. O fervilhante centro comercial, que atrai gente do mundo todo, é um polo de contágio e disseminação. Sem imaginar o risco que correm, pessoas são contaminadas e, ao voltar para seu local de origem, carregam o vírus para todos os continentes.
7 – Com a doença já fora de controle, começa uma corrida entre laboratórios e cientistas de grandes universidades para descobrir o agente causador. Mesmo com o vírus isolado, as vacinas demoram para ser feitas em larga escala, tornando impossível o atendimento à demanda mundial.
8 – Os países se isolam, mantendo esquemas de quarentena. Aeroportos são fechados e o turismo mundial cai a quase zero. A China sofre as piores consequências, com o fluxo de empresários para Hong Kong suspenso – gerando prejuízos de bilhões de dólares – e com o boicote a produtos alimentícios vindos da Ásia.
9 – Além dos 10% de casos letais, os milhões de doentes precisam de atendimento médico. Enquanto hospitais e cemitérios estão lotados, escolas, indústrias e comércio ficam paralisados por falta de profissionais. O transporte público também para e os trabalhadores que podem passam a trabalhar em casa.
10 – Nas nações pobres, quase 20% da população morre – e outros milhões são vitimados mesmo em países ricos. Parte dessa mortalidade ocorre por causa da doença, mas outro fator determinante é a crise financeira global. A produção de alimentos cai por falta de mão de obra.
Fontes: A História e Suas Epidemias e Pandemias – A Humanidade em Risco, de Stefan Cunha Ujvari; Pragas e Epidemias – Histórias de Doenças Infecciosas, de Antonio Carlos de Castro Toledo Jr. Consultoria: Stefan Ujvari Cunha, infectologista do Hospital Alemão Oswaldo Cruz; Paolo Zanotto, professor de virologia do Instituto de Ciências Biológicas (ICB) da USP; Átila Iamarino, doutorando em HIV-1 no ICB da USP. “



3. PRIMEIROS INDÍCIOS
10/2019 - Evento 201 - Durante os Jogos Militares Internacionais na China https://www.centerforhealthsecurity.org/event201/
Promovido por: - Bill & Melinda Gates Foundation - John Hopkins Institute - Fórum econômico mundial
"O evento simula a liberação de um coronavírus novo do tipo zoonótico transmitido por morcegos para porcos e por fim para humanos. Eventualmente ele se torna muito transmissível entre humanos levando a uma pandemia severa. O vírus é muito parecido com o vírus da SARS, mas se transmite muito mais facilmente entre pessoas devido a sintomas muito mais leves destas."
Também mencionado por: Jornal Estadão
Sobre o "Movimento antivacina"
05/12/2017 - Movimento antivacina: como surgiu e quais consequências ele pode trazer? https://www.uol.com.br/universa/noticias/redacao/2017/12/05/o-que-o-movimento-antivacina-pode-causar.htm?cmpid=copiaecola
23/03/2019 - "Instagram bloqueia hashtags e conteúdo antivacinação" https://canaltech.com.br/redes-sociais/instagram-bloqueia-hashtags-e-conteudo-antivacinacao-135411/
23/05/2021 - Novos dados sobre pesquisadores de Wuhan aumentam debate sobre origens da Covid https://www.cnnbrasil.com.br/saude/novos-dados-sobre-pesquisadores-de-wuhan-aumentam-debate-sobre-origens-da-covid/
"A China relatou à Organização Mundial da Saúde que o primeiro paciente com sintomas semelhantes aos de Covid-19 foi registrado em Wuhan em 8 de dezembro de 2019"
01/02/2020 - O que aconteceu desde que o novo coronavírus foi descoberto na China https://exame.com/ciencia/o-que-aconteceu-desde-que-o-novo-coronavirus-foi-descoberto-na-china/
"O primeiro alerta foi recebido pela Organização Mundial da Saúde (OMS) em 31 de dezembro de 2019"
15/09/2020 - YouTube diz que vai remover vídeos com mentiras sobre vacina contra COVID-19 https://gizmodo.uol.com.br/youtube-remover-videos-mentiras-vacina-covid-19/
"O YouTube anunciou na quarta-feira (14) que estenderá as regras atuais sobre mentiras, propaganda e teorias da conspiração sobre a pandemia do coronavírus para incluir desinformação sobre as vacinas contra a doença.
De acordo com a Reuters, a gigante do vídeo diz que agora vai proibir conteúdos sobre vacinas contra o coronavírus que contradizem “o consenso de especialistas das autoridades de saúde locais ou da OMS”, como afirmações falsas de que a vacina é um pretexto para colocar chips de rastreamento nas pessoas ou que irá matar ou esterilizar quem tomar."
*07/01/2021 - YouTube vai punir canais que promovem mentiras sobre eleições – incluindo os de Trump https://olhardigital.com.br/2021/01/07/noticias/youtube-vai-punir-canais-que-promovem-mentiras-sobre-eleicoes-incluindo-os-de-trump/
"O YouTube anunciou que vai punir canais que promovem mentiras sobre as eleições, removendo sumariamente qualquer vídeo que contenha desinformação e, ao mesmo tempo, advertindo com um “strike” o canal que o veicular. A medida já está valendo e a primeira “vítima” é ninguém menos que o ex-presidente americano, Donald Trump.
A medida não é exatamente nova, mas foi novamente comunicada e reforçada pelo YouTube na quarta-feira (6), após os eventos de invasão do Capitólio, em Washington, onde o presidente eleito Joe Biden participava da cerimônia que confirmava a sua vitória nas eleições de novembro de 2020. A ocasião ficou marcada pela tentativa de invasão de correligionários de Trump, que entraram no edifício em oposição à nomeação do novo presidente. Uma mulher acabou sendo morta pela polícia que protegia o local.
O ex-presidente Donald Trump teve vídeos banidos de seu canal no YouTube após os eventos de ontem (6) no capitólio."
4. FIGURAS CENTRAIS
Bill Gates
- Bill Gates diz 'não' a abrir patentes de vacinas https://www.frontliner.com.br/bill-gates-diz-nao-a-abrir-patentes-de-vacinas/
"Bill Gates, um dos homens mais ricos do mundo, cuja fundação tem participação na farmacêutica alemã CureVac, produtora de vacina mRNA para prevenção de covid-19, disse não acreditar que a propriedade intelectual tenha algo a ver com o longo esforço global para controlar a pandemia."
João Doria - Governo de São Paulo
26/07/2017 - João Dória vai a China conhecer drones para ampliar segurança eletrônica na capital paulista https://jc.ne10.uol.com.br/blogs/jamildo/2017/07/26/joao-doria-vai-china-conhecer-drones-para-ampliar-seguranca-eletronica-na-capital-paulista/
02/08/2019 - Governo de SP fará Missão China para ampliar cooperação e atrair investimentos https://www.saopaulo.sp.gov.br/spnoticias/governo-de-sao-paulo-detalha-objetivos-da-missao-china/
20/11/2019 - Doria se encontra com chineses das gigantes CREC e CRCC e oferece concessões de rodovia, metrô e ferrovia https://diariodotransporte.com.br/2019/11/20/doria-se-encontra-com-chineses-das-gigantes-crec-e-crcc-e-oferece-concessoes-de-rodovia-metro-e-ferrovia/
25/01/2020 - "Chineses serão agressivos" nas privatizações em SP até 2022, afirma Dória https://noticias.uol.com.br/colunas/jamil-chade/2020/01/25/entrevista-joao-doria-privatizacoes-sao-paulo-china.htm
O governador de São Paulo, João Doria, afirma que vai acelerar os programas de desestatização no estado em 2020 e acredita que concessões e vendas poderão permitir uma arrecadação de pelo menos R$ 40 bilhões. Nesse processo, o governador avalia que a China deve atuar de forma agressiva e que aprofundará sua posição de maior parceira comercial do estado, se distanciando de americanos e argentinos.
29/06/2020 - Doria estabelece multa para quem estiver sem máscara na rua em SP https://veja.abril.com.br/saude/doria-estabelece-multa-para-quem-estiver-sem-mascara-na-rua/
24/12/2020 - Doria é flagrado sem máscara e fazendo compras em Miami https://pleno.news/brasil/politica-nacional/doria-e-flagrado-sem-mascara-e-fazendo-compras-em-miami.html
"Foto do governador de São Paulo sem o item de proteção viralizou nas redes"
07/06/2021 - Doria é criticado na internet por tomar sol sem máscara em hotel no Rio https://vejasp.abril.com.br/cidades/doria-e-criticado-na-internet-por-tomar-sol-sem-mascara-em-hotel-no-rio/
30/09/2020 - Governo de SP assina contrato com Sinovac e prevê vacina para dezembro https://agenciabrasil.ebc.com.br/saude/noticia/2020-09/governo-de-sp-assina-contrato-com-sinovac-e-preve-vacina-para-dezembro
O governador de São Paulo, João Doria, e o vice-presidente da laboratório chinês Sinovac, Weining Meng, assinaram hoje (30), um contrato que prevê o fornecimento de 46 milhões de doses da vacina CoronaVac para o governo paulista até dezembro deste ano.
O contrato também prevê a transferência tecnológica da vacina da Sinovac para o Instituto Butantan, o que significa que, o instituto brasileiro poderá começar a fabricar doses dessa vacina contra o novo coronavírus. O valor do contrato, segundo o governador João Doria é de US$ 90 milhões.
20/10/2020 - Coronavac terá mais de 90% de eficácia, afirmam integrantes do governo paulista https://www.cnnbrasil.com.br/saude/2020/12/20/coronavac-tera-mais-de-90-de-eficacia-afirmam-integrantes-do-governo
24/10/2020 - Não esperamos 90% de eficácia da Coronavac’, diz secretário de saúde de SP https://www.cnnbrasil.com.br/saude/2020/12/24/nao-esperamos-90-de-eficacia-da-coronavac-diz-secretario-de-saude-de-sp
07/01/2021 - Vacina do Butantan: eficácia é de 78% em casos leves e 100% em graves https://www.cnnbrasil.com.br/saude/2021/01/07/vacina-do-butantan-eficacia-e-de-78-em-casos-leves-e-100-em-graves
09/01/2021 - Não é hora de sermos tão cientistas como estamos sendo agora https://g1.globo.com/sp/sao-paulo/video/nao-e-hora-de-sermos-tao-cientistas-como-estamos-sendo-agora-diz-secretario-de-saude-de-sp-9166405.ghtml
10/01/2021 - Dados da Coronavac relatados à Anvisa não estão claros, diz médico https://www.cnnbrasil.com.br/saude/2021/01/10/dados-da-coronavac-relatados-a-anvisa-nao-estao-claros-diz-medico
"O diretor do Laboratório de Imunologia do Incor, Jorge Kalil, reforçou que faltaram informações sobre a Coronavac nos dados divulgados à Anvisa"
12/01/2021 - New Brazil data shows disappointing 50,4% efficacy for China’s Coronavac vaccine [Novos dados do Brasil mostram eficácia decepcionante de 50,4% para a vacina CoronaVac da China] https://www.reuters.com/article/us-health-coronavirus-brazil-coronavirus/new-brazil-data-shows-disappointing-504-efficacy-for-chinas-coronavac-vaccine-idUSKBN29H2CE
13/01/2021 - Eficácia da Coronavac: 50,38%, 78% ou 100%? https://blogs.oglobo.globo.com/lauro-jardim/post/5038-78-ou-100.html
“De acordo com interlocutores que participaram tanto do anúncio de ontem como da semana passada, quem pressionou para que os dados de 78% e 100% fossem liberados foi João Dória.”
07/05/2021 - Covid-19: Doria toma primeira dose da vacina CoronaVac https://veja.abril.com.br/saude/covid-19-doria-toma-primeira-dose-da-vacina-coronavac/
04/06/2021 - Doria é vacinado com a segunda dose da CoronaVac em São Paulo https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/04/doria-e-vacinado-com-a-segunda-dose-da-coronavac-em-sao-paulo.htm
15/07/2021 - Doria testa positivo para a Covid-19 pela 2ª vez https://www.correiobraziliense.com.br/politica/2021/07/4937833-doria-testa-positivo-para-covid-19-pela-segunda-vez.html
"Governador de São Paulo já havia sido diagnosticado com a doença no ano passado. Ele diz que, apesar da infecção, se sente bem, o que atribui ao fato de ter sido vacinado com duas doses da Coronavac"
06/08/2021 - CPI recebe investigação contra Doria por compra de máscara sem licitação https://www.conexaopoder.com.br/nacional/cpi-recebe-investigacao-contra-doria-por-compra-de-mascara-sem-licitacao/150827
"Empresa teria usado o nome de Alexandre Frota para vender máscaras ao governo de SP. Doria nega informação"
Renan Filho
(filho do Renan Calheiros)
25/07/2019 - Governador Renan Filho vai à China em busca de investimentos para o estado https://www.tnh1.com.br/videos/vid/governador-renan-filho-vai-a-china-em-busca-de-investimentos-para-o-estado/
20/03/2020 - Governadores do NE consultam China e pedem material para tratar covid-19 https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/03/20/governadores-do-ne-consultam-china-e-pedem-material-para-tratar-covid-19.htm
5. Narrativas, restrições e proibições
17/12/2020 - STF decide que vacina contra a covid pode ser obrigatória, mas não forçada https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2020/12/17/stf-julga-vacinacao-obrigatoria.htm?cmpid=copiaecola
"O STF (Supremo Tribunal Federal) decidiu, em julgamento hoje, que o Estado pode determinar a obrigatoriedade da vacinação contra a covid-19. Porém fica proibido o uso da força para exigir a vacinação, ainda que possam ser aplicadas restrições a direitos de quem recusar a imunização.
Dez ministros foram favoráveis a obrigatoriedade da vacinação, que poderá ser determinada pelo governo federal, estados ou municípios. As penalidades a quem não cumprir a obrigação deverão ser definidas em lei."
27/07/2021 - Saiba que países estão adotando 'passaporte da vacina' para suspender restrições https://www.cnnbrasil.com.br/internacional/2021/07/27/saiba-que-paises-estao-adotando-passaporte-da-vacina-para-suspender-restricoes
" - Israel - Uniao Europeia - Áustria - Dinamarca - Eslovênia - França - Grécia - Irlanda - Itália - Letônia - Lituânia - Luxemburgo - Holanda - Portugal - Japão - Coreia do sul"
18/06/2021 - O que é o passaporte da vacina que Bolsonaro quer vetar? https://noticias.uol.com.br/politica/ultimas-noticias/2021/06/18/uol-explica-o-que-e-o-passaporte-da-vacina-que-opoe-bolsonaro-e-damares.htm
"O Brasil poderá ter um certificado de imunização futuramente. Aprovado no Senado na semana passada, o "passaporte da vacina", como é chamado, prevê identificar pessoas vacinadas para que entrem em locais públicos ou privados com possíveis restrições."
6. Vacinas
Alegações iniciais
- CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
" - CoronaVac (Butantan/Sinovac - Chinesa) Com virus inativo 50,38% de eficácia 2 doses
-
Covishield - 'AstraZeneca' (Fiocruz/Astrazenica/Oxford - Britânica) Com virus não replicante 67% de eficácia 2 doses
-
ComiRNAty - 'Pfizer' (Pfizer - Americana / BioNTech - Alemã) Com RNA mensageiro 96% de eficácia 2 doses"
Riscos diretos
15/06/2021 - Trombose após vacinação com AstraZeneca: Quais os sintomas e como se deve atuar? https://www.istoedinheiro.com.br/trombose-apos-vacinacao-com-astrazeneca-quais-os-sintomas-e-como-se-deve-atuar/
"Agências europeias estão reticentes com a vacina da AstraZeneca. Ela chegou a ser desaconselhada a pessoas com idade inferior a 60 anos, e um alto funcionário da Agência Europeia de Medicamentos declarou que era melhor deixar de administrar a vacina deste laboratório em qualquer idade quando há alternativas disponíveis, devido aos relatos de trombose após a primeira dose, apesar de raros."
11/05/2021 - CoronaVac, Oxford e Pfizer: veja diferenças entre as vacinas contra covid https://noticias.uol.com.br/saude/ultimas-noticias/redacao/2021/05/11/diferencas-vacinas-covid-brasil.htm
"Na terça-feira (12), o Ministério da Saúde determinou a suspensão da aplicação da vacina de Oxford/AstraZeneca para gestantes e puérperas com comorbidades. A decisão segue recomendação da Anvisa, que apura a morte de uma grávida de 35 anos que tomou o imunizante e teve um AVC (acidente vascular cerebral)."
30/07/2021 - Pfizer representa o mesmo risco de trombose que a Astrazeneca, aponta levantamento https://panoramafarmaceutico.com.br/pfizer-representa-o-mesmo-risco-de-trombose-que-a-astrazeneca-aponta-levantamento/
7. CRIMES
Crimes da Pfizer
18/11/2020 Não listado no google - Os Crimes documentados da produtora de vacinas de Covid - Pfizer [INGLÊS] https://www.dmlawfirm.com/crimes-of-covid-vaccine-maker-pfizer-well-documented/
"A velocidade com que a vacina Covid da Pfizer foi produzida, a ausência de estudos em animais, testes de controle randomizados e outros testes e procedimentos padrão usuais para um novo medicamento são, no mínimo, preocupantes. Além disso, todos os fabricantes de vacinas Covid receberam imunidade legal para quaisquer ferimentos ou mortes que possam causar. Se essas vacinas são tão seguras quanto promovidas, por que seus fabricantes precisam de imunidade geral?"
"A Pfizer, uma empresa farmacêutica que parece ter ganhado na loteria para produzir a primeira vacina Covid-19, está atualmente lutando contra centenas de ações judiciais sobre o Zantac, um popular medicamento contra azia. Os processos da Zantac afirmam que a droga popular pode estar contaminada com uma substância cancerígena chamada N-nitrosodimetilamina (NDMA). Os processos Zantac são em aberto e em andamento, já que a farmacêutica está lutando contra eles; mas a Pfizer, sabemos, cometeu vários crimes ou transgressões pelos quais foi punida nos últimos anos. As falhas da empresa estão bem documentadas e vale a pena revisá-las neste momento crítico da história da humanidade, enquanto todos nós buscamos respostas."
A Pfizer recebeu a maior multa da história dos Estados Unidos como parte de um acordo judicial de US $ 2,3 bilhões com promotores federais por promover medicamentos erroneamente (Bextra, Celebrex) e pagar propinas a médicos complacentes. A Pfizer se confessou culpada de falsificar a marca do analgésico Bextra, promovendo o medicamento para usos para os quais não foi aprovado.
Na década de 1990, a Pfizer estava envolvida em válvulas cardíacas defeituosas que causaram a morte de mais de 100 pessoas. A Pfizer enganou deliberadamente os reguladores sobre os perigos. A empresa concordou em pagar US $ 10,75 milhões para acertar as acusações do departamento de justiça por enganar reguladores.
A Pfizer pagou mais de US $ 60 milhões para resolver um processo sobre o Rezulin, um medicamento para diabetes que causou a morte de pacientes de insuficiência hepática aguda.
No Reino Unido, a Pfizer foi multada em quase € 90 milhões por sobrecarregar o NHS, o Serviço Nacional de Saúde. A Pfizer cobrou do contribuinte um adicional de € 48 milhões por ano, pelo que deveria custar € 2 milhões por ano.
A Pfizer concordou em pagar US $ 430 milhões em 2004 para resolver acusações criminais de que havia subornado médicos para prescrever seu medicamento para epilepsia Neurontin para indicações para as quais não foi aprovado. Em 2011, um júri concluiu que a Pfizer cometeu fraude em sua comercialização do medicamento Neurontin. A Pfizer concordou em pagar $ 142,1 milhões para liquidar as despesas.
A Pfizer revelou que pagou quase 4.500 médicos e outros profissionais médicos cerca de US $ 20 milhões por falar em nome da Pfizer.
Em 2012, a Comissão de Valores Mobiliários dos Estados Unidos - anunciou que havia chegado a um acordo de US $ 45 milhões com a Pfizer para resolver acusações de que suas subsidiárias haviam subornado médicos e outros profissionais de saúde no exterior para aumentar as vendas no exterior.
A Pfizer foi processada em um tribunal federal dos Estados Unidos por usar crianças nigerianas como cobaias humanas, sem o consentimento dos pais das crianças. A Pfizer pagou US $ 75 milhões para entrar em acordo no tribunal nigeriano pelo uso de um antibiótico experimental, o Trovan, nas crianças. A empresa pagou um valor adicional não divulgado nos Estados Unidos para liquidar as despesas aqui. A Pfizer violou o direito internacional, incluindo a Convenção de Nuremberg estabelecida após a Segunda Guerra Mundial, devido aos experimentos nazistas em prisioneiros relutantes.
Em meio a críticas generalizadas de roubar os países pobres em busca de drogas, a Pfizer prometeu dar US $ 50 milhões para um medicamento para a AIDS para a África do Sul. Mais tarde, no entanto, a Pfizer falhou em honrar essa promessa.
- Pfizer contract leaked!
[Contrato da Pfizer vazado]
 http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
http://sanjeev.sabhlokcity.com/Misc/LEXO-KONTRATEN-E-PLOTE.pdf
Segundo o contrato "o produto não deve ser serializado":
"5.5 Reconhecimento do comprador.
O Comprador reconhece que a Vacina e os materiais relacionados à Vacina, e seus componentes e materiais constituintes estão sendo desenvolvidos rapidamente devido às circunstâncias de emergência da pandemia de COVID-19 e continuarão a ser estudados após o fornecimento da Vacina ao Comprador nos termos deste Contrato. O Comprador reconhece ainda que os efeitos de longo prazo e eficácia da Vacina não são atualmente conhecidos e que pode haver efeitos adversos da Vacina que não são atualmente conhecidos. Além disso, na medida do aplicável, o Comprador reconhece que o Produto não deve ser serializado."
Crimes da AstraZeneca
21/06/2003 - AstraZeneca se declara culpada no esquema de médico de câncer https://www.nytimes.com/2003/06/21/business/astrazeneca-pleads-guilty-in-cancer-medicine-scheme.html
"A AstraZeneca, a grande empresa farmacêutica, se declarou culpada hoje de uma acusação de crime de fraude no sistema de saúde e concordou em pagar $ 355 milhões para resolver as acusações criminais e civis de que se envolveu em um esquema nacional para comercializar ilegalmente um medicamento contra o câncer de próstata.
O governo disse que os funcionários da empresa deram incentivos financeiros ilegais a cerca de 400 médicos em todo o país para persuadi-los a prescrever o medicamento Zoladex. Esses incentivos incluíram milhares de amostras grátis de Zoladex [...]"
27/04/2010 - Farmacêutica gigante AstraZeneca pagará US $ 520 milhões pelo marketing de medicamentos off-label https://www.justice.gov/opa/pr/pharmaceutical-giant-astrazeneca-pay-520-million-label-drug-marketing
"AstraZeneca LP e AstraZeneca Pharmaceuticals LP vão pagar $ 520 milhões para resolver as alegações de que a AstraZeneca comercializou ilegalmente o medicamento antipsicótico Seroquel para usos não aprovados como seguros e eficazes pela Food and Drug Administration (FDA), os Departamentos de Justiça e Saúde e Serviços Humanos A Equipe de Ação de Fiscalização de Fraudes em Saúde (HEAT) anunciou hoje. Esses usos não aprovados também são conhecidos como usos "off-label" porque não estão incluídos no rótulo do medicamento aprovado pela FDA."
- List of largest pharmaceutical settlements [Lista dos maiores acordos farmaceuticos] https://en.m.wikipedia.org/wiki/List_of_largest_pharmaceutical_settlements
8. CIENTISTAS
- Máscara Provoca Insuficiência Respiratória E Contaminação Microbiana… [Canal deletado] https://youtube.com/watch?v=eHu-pydSvDI
Não lembro mais a quem pertencia, mas provavelmente era de um médico falando do assunto. Creio ter sido do Dr. Paulo Sato, por essa temática ter sido abordada por ele, mas ao abrir o site aparece somente:
"Este vídeo foi removido por violar as diretrizes da comunidade do YouTube"
Dr. Paulo Sato
- USAR ou NÃO USAR a CUECA do seu governador no rosto https://fb.watch/7NPP_7rS5S/ https://www.facebook.com/AdoniasSoaresBR/videos/1347904292291481/ Adonias Soares entrevista ao Dr. Paulo Sato sobre as máscaras, em que é simulado o efeito da respiração prolongada das máscaras no organismo com o uso de águas de torneira, natural, gaseificada (com gás carbônico) e antioxidante, em que a com gás carbônico (PH 4 - Ácido) representa o organismo humano, e na prática representa lesão corporal e iniciação de doenças.
Dr. Kary Mullis
(Criador do teste PCR)
- PCR nas palavras do seu inventor - Dr. Kary Mullis (legendado) https://www.youtube.com/watch?v=W1O52uTygk8
"Qualquer um pode testar positivo para quase qualquer coisa com um teste de PCR, se você executá-lo por tempo suficiente… Com PCR, se voce fizer isso bem, você pode encontrar quase tudo em qualquer pessoa… Isso não te diz que você está doente."
- Kary Mullis DESTRUYE a Anthony Fauci lbry://@CapitalistChile#0/Kary-Mullis---Fauci#5
"Ele [...] não entende de medicina e não deveria estar onde está. A maioria dos que estão acima são só administrativos e não têm nem ideia do que ocorre aqui em baixo e essas pessoas tem uma agenda que não é a que gostaríamos que tivessem, dado que somos nós os que pagamos a eles para que cuidem da nossa saúde. Têm uma agenda pessoal."
Dra. Li-Meng Yan
- Dra. Li-Meng Yan: O vírus foi criado em laboratório com um objetivo: Causar dano. https://youtu.be/pSXp3CZnvOc
Dr. Joe Roseman
- Cientista Phd Dr Joe Roseman faz seríssimas advertencias sobre a picada https://youtu.be/0PIXVFqJ_h8
Dr. Robert Malone
- As vacinas podem estar causando ADE - Dr. Robert Malone https://odysee.com/@AkashaComunidad:f/Las_vacunas_pueden_estar_causando_ADE_magnificaci%C3%B3n_mediada_por:f lbry://@Información.#b/Drrm#9
Dr. Robert Malone, um dos três inventores da tecnologia de RNAm que se usa de forma farmacêutica. No vídeo fala sobre os efeitos de ADE (realce dependente de anticorpos) que estão ocorrendo com as vacinas. Nas palavras do Dr. Malone, já não é somente uma hipótese, mas baseada nos conhecimentos gerados nas provas e ensaios pré clínicos, com as vacinas contra o primeiro vírus da SARS.
Dr. Luc Montagnier
- Dr. Luc Montagnier, virologista, prêmio Nobel de medicina, um dos descobridores do vírus HIV, afirma: "a vacinação em massa está criando as novas variantes' (@medicospelavida , telegram)
CASOS DOCUMENTADOS
13/09/2021 - 13 de setembro de 2021 - Carta aberta ao Ministro da Saúde por Arlene Ferrari Graf, mãe de Bruno Oscar Graf https://telegra.ph/Carta-aberta-ao-Ministro-da-Sa%C3%BAde-09-13
Também em: Gazeta do Povo
O texto de uma mãe discorrendo sobre o filho dela, Bruno Oscar Graf, ter ANTI-HEPARINA PF4 AUTO-IMUNE e ter vindo a falecer por reação à vacina.
11/05/2021 - Rio notifica morte de grávida vacinada com imunizante Oxford https://www.terra.com.br/noticias/coronavirus/rio-notifica-morte-de-gravida-vacinada-com-imunizante-oxford,415b9b0c49169427ac2f90ae3765c057e9suy3qn.html
"Vítima não apresentava histórico de doença circulatória nem sofria de nenhuma doença viral; relação será investigada"
13/08/2021 - Cruzeiro com 4.336 pessoas tem 27 contaminados com Covid-19 em Belize https://paranaportal.uol.com.br/geral/cruzeiro-com-4-336-pessoas-tem-27-contaminados-com-covid-19-em-belize/amp/
"Segundo um comunicado do Conselho de Turismo de Belize emitido na quarta-feira (11), 26 contaminados são da tripulação e um é passageiro. A maioria é assintomática e os 27 estão vacinados."
9. ALEGAÇÕES DIRETAS
09/2021 - Setembro de 2021 - BOMBA: Ex-membro do Partido Comunista da China revela que o primeiro surto da Covid foi “intencional” https://terrabrasilnoticias.com/2021/09/bomba-ex-membro-do-partido-comunista-da-china-revela-que-o-primeiro-surto-da-covid-foi-intencional/
01/03/2023 - 1 de Março de 2023 - O chefe do FBI, Christopher Wray, diz que vazamento de laboratório na China é muito provável https://www.bbc.com/news/world-us-canada-64806903
26/12/2024 - 26 de Dezembro 2024 - FBI ‘não tem permissão para informar Biden’ sobre a teoria de vazamento de laboratório da Covid https://www.thetimes.com/world/us-world/article/fbi-not-allowed-to-brief-biden-on-covid-lab-leak-theory-8df9mr997
O FBI concluiu com "confiança moderada" que a COVID-19 pode ter sido criada em laboratório, com base em parte na análise genômica conduzida por cientistas do Centro Nacional de Inteligência Médica.
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 2b24a1fa:17750f64
2025-06-09 12:56:33
@ 2b24a1fa:17750f64
2025-06-09 12:56:33Einmal, im dunklen Wald auf dem Weg ins nächste Dorf, hielt ich meine Taschenlampe auf den Boden gerichtet, nicht wirklich senkrecht, aber so, dass der Lichtkegel nah bei mir war. Immer wieder lief ein Schatten auf mich zu. Manchmal kam er auch von hinten. Jedes Mal erschrak ich fürchterlich, ging in Abwehrhaltung und mahnte mich dann zur Einsicht: Wer sollte mir folgen? Was aus dem Gebüsch, sollte auf mich zu kommen, oder dicht an mir vorbei laufen wollen? Woher also dieser Schreck, diese Angst? Vielleicht ist es nur das Reptilienhirn und der Überlebenssinn der reagiert, vielleicht aber auch ein Teil der Prägung, die uns verunsichert, wenn wir die Gemeinschaft verlassen und uns anders verhalten.
https://soundcloud.com/radiomuenchen/innerer-tiefenstaat-von?
Unbekannte und einflussreiche Anteile unseres Selbst zu entdecken und zu integrieren nennt der Wildnispädagoge, Autor und Journalist Bastian Barucker Schattenarbeit. Hören Sie seinen Text Trauma, Krieg, Friedensfähigkeit und der innere Tiefenstaat.
Sprecher: Ulrich Allroggen\ Redaktion: Eva Schmidt
Den Beitrag können Sie auf seinem Blog Bastian-Barucker.de nachlesen. blog.bastian-barucker.de/der-innere-tiefenstaat/
-
 @ cae03c48:2a7d6671
2025-06-06 15:00:57
@ cae03c48:2a7d6671
2025-06-06 15:00:57Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 87fedb9f:0da83419
2025-06-09 12:45:21
@ 87fedb9f:0da83419
2025-06-09 12:45:21Finding Calm in the Chaos
Ever notice how you start future-mapping to calm your nerves… and end up more anxious than when you began? You’re not alone! Join us for a playful, real-talk exploration of why our brilliant minds try to control everything — and how empathy, Buddhist wisdom, and EFT tapping can help us step out of the anxious loop and land back in the delicious now.
https://www.thrivingnow.center/t/1491/4
We covered…
1. Future Mapping is Fish-and-Water Awareness We often don’t realize how much mental energy we spend constantly planning scenarios - “if it rains, if they get upset, if this happens then that…” This protective pattern started early but now we can bring it into conscious awareness and choose how much energy to invest.
2. The Empathy App Creates Endless Scenarios Our empathetic nature means we’re not just planning for ourselves - we’re mapping out everyone else’s potential reactions, feelings, and needs. This creates exponentially more “what if” scenarios that keep our minds spinning in overdrive.
3. Fault-Finding is Too Crude for Thriving When we automatically assign blame (usually to ourselves), we’re operating from primitive brain patterns. Upgrading to a more refined viewpoint means seeing the “dance of energies” where everyone contributes and sometimes feet get stepped on - it’s part of life.
4. We Can’t Actually Control the River Life flows like a river, and we can steer our canoe but we cannot change the river itself. Our anxiety often signals we’re trying to do the impossible - control weather, other people’s moods, or outcomes beyond our influence.
5. Magical Thinking Says “If I Worry Enough, It Will Work Out” We unconsciously believe that suffering through worry ahead of time will somehow guarantee good outcomes. Our nervous system knows this is a lie, which creates more anxiety. We can release this “prepayment” fantasy.
6. Distributing the Broccoli Back to Its Owners We often scoop up everyone else’s responsibilities onto our plate to avoid conflict or being blamed. Learning to ask “Is this really my broccoli?” helps us return emotional and practical responsibilities to their rightful owners.
7. Include Safe and Good Possibilities in Your Maps When we only map threats and problems, we miss opportunities for joy, connection, and creative solutions. Consciously including positive possibilities activates different parts of ourselves - the creative, hopeful, and inspired aspects.
8. Tapping While Thinking Moves Energy Out of Stuck Loops Simply speaking our thoughts aloud while tapping the acupressure points breaks the narrow band of mental spinning. This engages our body’s intelligence and often reveals what words or feelings want to emerge beyond our conscious planning.
9. Being With What Is vs. Making Everyone Happy Instead of trying to make everyone feel good all the time (which is impossible), we can practice being present with people as they actually are. This is more respectful, connected, and requires much less exhausting management.
10. Anxiety Can Be Wise Body Guidance Rather than just a problem to fix, our anxiety often signals we’re trying to do something unwise - like changing unchangeable things or telling ourselves lies about what we can control. We can listen to this guidance.
11. The Sweet Spot of Thoughtful Planning We’re not throwing away our planning abilities - we’re finding the balance between appropriate preparation (throwing an umbrella in the bag) and exhausting over-management (trying to control every possible variable). Good and sufficient planning honors both our intelligence and life’s natural flow.
-
 @ 0b118e40:4edc09cb
2025-06-06 14:08:06
@ 0b118e40:4edc09cb
2025-06-06 14:08:06The idea of Bitcoin as an internet native currency, and eventually a global one, is coming to life slowly. But historically, the idea of global currency has haunted the world’s financial imagination for nearly a century.
From Keynes’s Bancor in 1944 to Zhou Xiaochuan’s post-crisis proposal in 2009 to today’s renewed debates, the idea resurfaces every time the global economy fractures.
Could this time be different with Bitcoin?
I decided to trace the idea of global currency through several decades and books. I may have missed some parts, so feel free to add. I’ll keep this brief and leave the books I’ve read below.
In the beginning
It all started on July 1, 1944. 730 delegates from 44 Allied nations, including major powers like the US, UK, Soviet Union, China, and France, gathered at the Mount Washington Hotel in Bretton Woods, New Hampshire. They spent 2 weeks figuring out how the new international monetary and financial system would be, post WW2
After WW1, the treaty of Versailles was needed, but imposed harsh reparations that devastated economies and contributed to the rise of fascism, such as Hitler, Mussolini and gang.
So when folks met up in 1944 (WW2 was almost ending), the goal was to prevent another Great Depression, another global conflict and build a stable global economic order.
2 main proposals were discussed in Bretton Woods.
-
John Maynard Keynes, representing the UK, proposed the creation of a global currency called Bancor. It will be issued through a global central bank known as the International Clearing Union (ICU).
-
Harry Dexter White, representing the US, promoted a dollar-based system. Countries would peg their currencies to the US. dollar backed by gold. He also led the creation of the IMF and the World Bank.

To understand how both of these proposals work, let's look at an example.
-
Country A (Germany): Massive exporter
-
Country B (USA): Massive importer
-
Country C (Brazil): Balanced trade (imports = exports)
***Based on Dexter’s model and the current USD-based system, ***
Say Germany sells $1B worth of cars to the US. The US pays in dollars, increasing its trade deficit. Germany accumulates dollars as reserves or buys the US Treasury bonds. Over time, the US continues running trade deficits, while Germany keeps hoarding dollars. Hence the unsustainable debt of the US.
***In Keynes’s Bancor system, ***
If Germany sells $1B worth of cars to the US, then the US does not pay in dollars. Instead, the ICU credits Germany with 1B Bancors and debits the US with -1B Bancors.
The ICU police this. If Germany exceeds the surplus threshold, it pays interest or penalties to discourage hoarding. If the US exceeds its deficit threshold, it is warned to rebalance trade or face restrictions.
Here, Germany is incentivized to import more (e.g., from Brazil) or invest in global development. The US is encouraged to export more or reduce consumption. Brazil, with balanced trade, enjoys stability in Bancor flows and avoids pressure.
The idea behind Bancor was a zero-sum balancing act. No country could become “too big to fail” due to excessive deficits. But it was too complicated and idealistic in assuming every country could maintain balanced trade.
Dexter on the other hand had a few tricks up his sleeve. In the end, Dexter’s USD dominance proposal was adopted.
The Bretton Woods system established the US dollar as the central global currency
Why did dollar dominance win over Bancor?
Simplicity often wins over complexity. But more so ICU felt too centralized, asking nations to surrender economic autonomy to a global body. That didn’t sit well in a post-war world where sovereignty was non-negotiable. That and idealist economic trade balance views.
Dexter’s dollar-based system on the other hand wasn’t fair play at all. It was centralized and authoritarian in its design.
So how did Dexter pull it off?
They had gold. They were ahead in economic recovery.
And they had nuclear weapons.
At the time, the US held nearly 2/3 of the world’s gold reserves. It was a significant advantage in advocating for a gold-backed dollar as the bedrock of global trade.
The US proposed a fixed gold peg at $35 per ounce.
From a broader geopolitical backdrop, the global population in 1944 was about 2.3 billion, a fraction of today’s 8 billion. The world was far less interconnected. The war had devastated Europe, Russia, and much of Asia. Infrastructure, economies, and entire cities were in ruins. The US, by contrast, had faced far fewer casualties and damages. Being geographically isolated, it had minimal domestic losses, around a tenth of what Europe suffered, and its economy was poised to rebuild faster.
But gold dominance and economic recovery alone didn’t secure US financial dominance.
American scientific breakthroughs had already signaled global power. Physicists like Leo Szilard and Albert Einstein, who had fled Europe, helped develop nuclear weapons. Their intent was deterrence, not destruction. But once the bomb existed, it changed geopolitics overnight. The US had military dominance. And after Hiroshima and Nagasaki in 1945, it became the undisputed superpower.
In the end, the USD won and the vision for neutral global currency faded.
And 20 years passed on…
France sends its warship to the US
Under Bretton Woods, countries could exchange dollars for gold, but the US had been printing more dollars than it had gold to back it. And it used it to fund the costly Vietnam War and domestic programs like the Great Society under LBJ.
Belgian-American economist Robert Triffin pointed out a fatal flaw in the Bretton Woods system that came to be known as the Triffin dilemma.
-
The world needed US dollars for liquidity and trade.
-
But the more dollars the US pumped out, the less credible its gold promise became.
Yet the US kept promising that every dollar was still convertible to gold at $35 per ounce.
French President Charles de Gaulle saw this as financial imperialism. He called it the “exorbitant privileged position”. The world had to pay for what they bought with the money they have, but not the US.
So in 1965, France did something unexpected. It sent a warship to New York Harbor to physically retrieve French gold reserves held by the Federal Reserve.

Would it have escalated to war? Maybe. But likely not. It was perhaps more of a diplomatic theatre and a sovereign flex. France was exercising its right under the Bretton Woods agreement to convert dollars into gold. But doing it with military formality was to send a signal to the world that they don’t trust the US system anymore.
It was one of the first major public blows to the dollar’s credibility. And France wasn’t alone. Other countries like West Germany and Switzerland followed suit, redeeming dollars for gold and draining US reserves.
The Nixon shock
Given they did not have enough gold, the IMF introduced Special Drawing Rights (SDRs) in 1969. SDRs were an international reserve asset, created to supplement gold and dollar reserves. Instead of relying solely on the US dollar, SDRs were based on a basket of major currencies (originally gold-backed but later diversified).
The idea was to reduce the world’s dependence on the dollar and avoid a liquidity crisis. But SDRs were a little too late and a little too weak to solve the underlying problem.
By 1971, the US could no longer sustain the illusion. President Nixon “closed the gold window,” suspending dollar convertibility to gold.
The Bretton Woods collapsed and this marked the beginning of fiat money dominance.
The French pursuit
While France demanded justice in one corner of the world, the French franc, specifically the CFA franc, has been dominant in parts of Africa since 1945, long before 1971.
After WWII, France created two CFA franc zones:
-
West Africa: Communauté Financière Africaine (XOF)
-
Central Africa: Coopération Financière en Afrique Centrale (XAF)
These zones included 14 African countries, many of which were former French colonies. France maintained monetary control via currency convertibility guarantees and representation in African central banks. Till today it has influence over these country’s monetary policy.
Colonisation hasn't ended in some parts of the world.
Did countries stop using the USD after the Nixon shock 1971?
Nope. The US dollar was no longer convertible to gold and it dismantled the fixed exchange rate system. But most countries did not stop using the USD as their dominant reserve or trade currency. There were no decent alternatives. Instead, they floated their currencies or maintained a soft peg to the dollar or a basket of currencies.
The USD remained dominant in oil trade (OPEC priced oil in USD) - petrodollar deal, global debt markets and FX reserves (central banks kept holding USD).
In 1997, when many Southeast Asian countries were still pegged to the USD, Soros claimed that SEA will tank. The US further increased its credit rates leading to capital flight and eventual tanking of these countries leading to Asian Financial Crisis '97. Many financial crisis has similar vibe.
The 1999 Euro launch
The idea of a shared currency appeared again, this time through the forms of Euro. It was a mandatory system for member states of the Eurozone, and came with centralized authority, the European Central Bank (ECB), which controlled monetary policy for all participating nations.

At first glance, the euro seemed like a win. It eliminated exchange rate fluctuations, making trade within the Eurozone smoother. It gave weaker economies access to lower borrowing costs and helped Europe establish itself as a financial heavyweight. Today, the euro is the second most-used reserve currency after the US dollar.
But it came at a cost. Countries that adopted the euro lost monetary sovereignty and could no longer print their own money or adjust interest rates to respond to local crises. This became painfully clear during Greece’s debt crisis, where strict monetary policies prevented the country from devaluing its currency to recover. The one-size-fits-all approach meant that economies as different as Germany and Greece had to follow the same rules, often to the detriment of weaker nations. Debt-ridden countries like Italy and Spain were forced into harsh austerity measures because they could not manipulate their currency to ease financial strain. Meanwhile, richer nations like Germany and the Netherlands felt they were unfairly propping up struggling economies, creating political tension across the EU.
In recent years, the euro has faced pressure from global trade tensions, monetary tightening, and geopolitical instability contributing to market volatility and periodic depreciation against other major currencies.
The Bretton Woods 2.0
Believe it or not, after all that, there was a call for Bretton Woods 2.0. Yet another global currency dream.
When the housing market collapsed in 2008 followed by a series of domino effects, global banks froze lending, economies contracted, and panic set in. The crisis exposed how fragile the international financial system had become as it was overly reliant on debt, under-regulated, and centered around the US dollar.
Many countries, especially in the Global South and emerging markets, started to question whether a system built around a single national currency was sustainable.
China, for instance, had been holding huge amounts of US debt while the US printed more dollars through bailouts and quantitative easing. This created global imbalances as exporting nations were lending money to the US to keep the system running, while taking on the risk of dollar depreciation.
In 2009, China’s central bank openly proposed replacing the US dollar with a neutral global reserve currency suggesting SDRs (Special Drawing Rights) issued by the IMF instead.
These concerns led to a wave of calls from world leaders for a “Bretton Woods 2.0” , a modern rethinking of the post-WWII economic order. At G20 summits in London in 2009, countries like France, China, and Russia pushed for reforms in global financial institutions and more balanced power sharing.
In the end, the IMF received more funding, and some banking regulations were tightened in the years after. But no real overhaul happened. No surprise there? The dollar remained dominant.
The foundation of the global economy didn’t change, even though trust in it had been deeply shaken.
The growth of BRICS
In 2023, Brazil, Russia, India, China, and South Africa began discussing the idea of a shared currency or alternative mechanism to reduce the dependence on USD ie de-dollarisation. The sanctions on Russia didn't help. After Russia’s invasion of Ukraine, the US and its allies froze Russia’s dollar reserves and cut it off from SWIFT, the “backbone of global banking communication”. This made one thing clear. If you fall out with Washington, your access to the global economy can vanish overnight.
China’s growing economic power also gave it more leverage to process alternative options. It would trade in Yuan with Russia and Iran.
I know many still say it's at its early stage, but I see many countries hedging their bets quietly and aligning with Putin and Xi. It became more obvious after US imposed tariffs on multiple nations, signaling that economic tools can double as political weapons. The world’s second financial system is slowly forming.
What is the world looking for, for the last century ?
From Bretton Woods to multiple financial crises, from the birth of the Euro to the rise of BRICS, through war and peace, we’ve been circling around the same ideal. A global currency that is :
-
Simple
-
Free from dominant power
-
Decentralised
-
Borderless
-
Scarce
-
Transparent
-
Inclusive, with self custody
-
Resilient in crisis
-
Built for individual financial sovereignty
-
A new backbone for global finance, owned by no one
It doesn’t matter where you’re from, what politics you believe in, or how your economy leans. The answer keeps pointing in the same direction:
Bitcoin
This is the first true global currency.
And it’s just there
Waiting...
.
.
.
Some books that might interest you :
-
The Battle of Bretton Woods by Benn Steil
-
Goodbye, Great Britain by Kathleen Burk and Alec Cairncross
-
The Ghost of Bancor by Tommaso Padoa-Schioppa
-
Confessions of an Economic Hitman by John Perkins
-
The Blood Bankers by James S. Henry
-
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
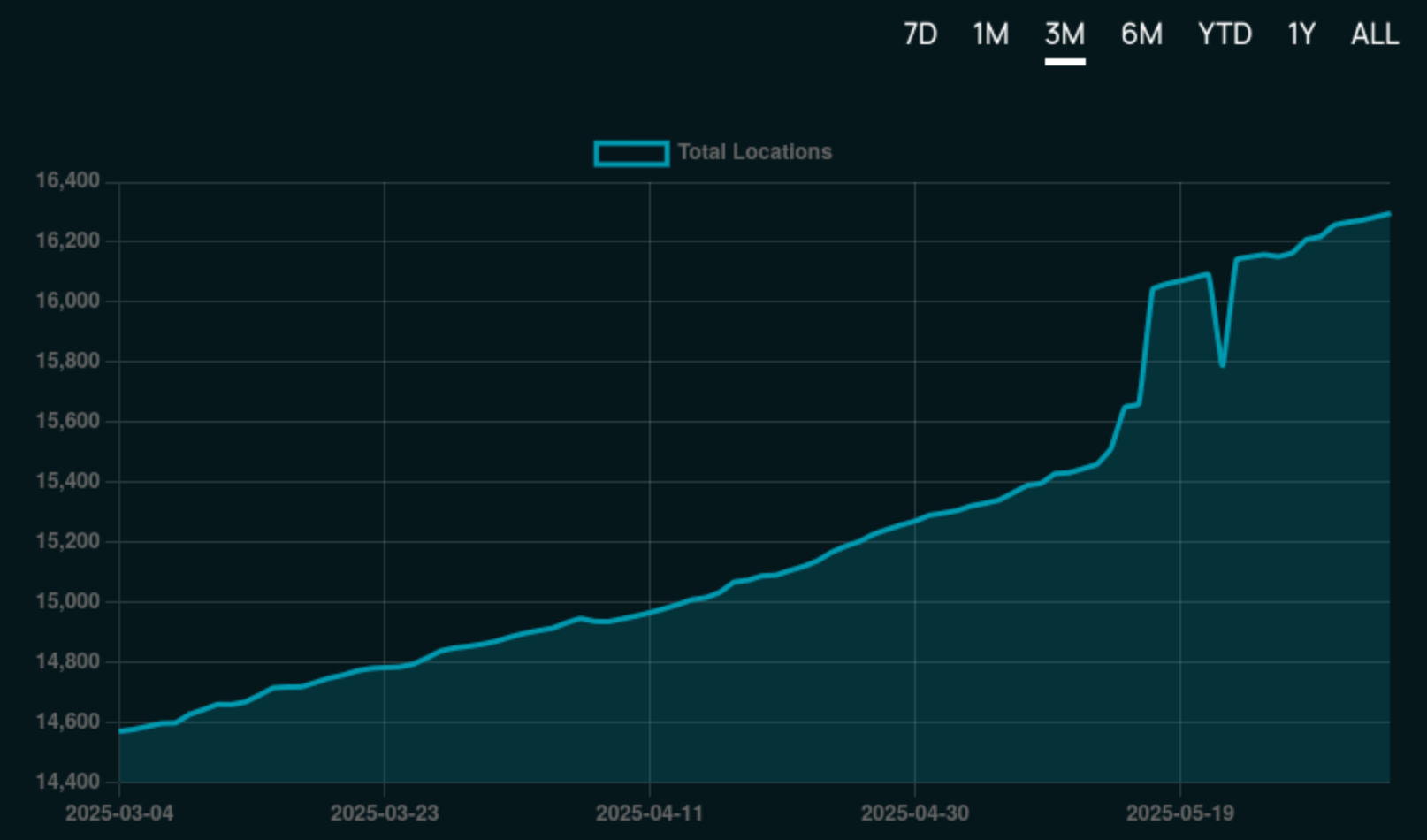
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ dfa02707:41ca50e3
2025-06-09 03:01:55
@ dfa02707:41ca50e3
2025-06-09 03:01:55Contribute to keep No Bullshit Bitcoin news going.

This update brings key enhancements for clarity and usability:
- Recent Blocks View: Added to the Send tab and inspired by Mempool's visualization, it displays the last 2 blocks and the estimated next block to help choose fee rates.
- Camera System Overhaul: Features a new library for higher resolution detection and mouse-scroll zoom support when available.
- Vector-Based Images: All app images are now vectorized and theme-aware, enhancing contrast, especially in dark mode.
- Tor & P2A Updates: Upgraded internal Tor and improved support for pay-to-anchor (P2A) outputs.
- Linux Package Rename: For Linux users, Sparrow has been renamed to sparrowwallet (or sparrowserver); in some cases, the original sparrow package may need manual removal.
- Additional updates include showing total payments in multi-payment transaction diagrams, better handling of long labels, and other UI enhancements.
- Sparrow v2.2.1 is a bug fix release that addresses missing UUID issue when starting Tor on recent macOS versions, icons for external sources in Settings and Recent Blocks view, repackaged
.debinstalls to use older gzip instead of zstd compression, and removed display of median fee rate where fee rates source is set to Server.
Learn how to get started with Sparrow wallet:
Release notes (v2.2.0)
- Added Recent Blocks view to Send tab.
- Converted all bitmapped images to theme aware SVG format for all wallet models and dialogs.
- Support send and display of pay to anchor (P2A) outputs.
- Renamed
sparrowpackage tosparrowwalletandsparrowserveron Linux. - Switched camera library to openpnp-capture.
- Support FHD (1920 x 1080) and UHD4k (3840 x 2160) capture resolutions.
- Support camera zoom with mouse scroll where possible.
- In the Download Verifier, prefer verifying the dropped file over the default file where the file is not in the manifest.
- Show a warning (with an option to disable the check) when importing a wallet with a derivation path matching another script type.
- In Cormorant, avoid calling the
listwalletdirRPC on initialization due to a potentially slow response on Windows. - Avoid server address resolution for public servers.
- Assume server address is non local for resolution failures where a proxy is configured.
- Added a tooltip to indicate truncated labels in table cells.
- Dynamically truncate input and output labels in the tree on a transaction tab, and add tooltips if necessary.
- Improved tooltips for wallet tabs and transaction diagrams with long labels.
- Show the address where available on input and output tooltips in transaction tab tree.
- Show the total amount sent in payments in the transaction diagram when constructing multiple payment transactions.
- Reset preferred table column widths on adjustment to improve handling after window resizing.
- Added accessible text to improve screen reader navigation on seed entry.
- Made Wallet Summary table grow horizontally with dialog sizing.
- Reduced tooltip show delay to 200ms.
- Show transaction diagram fee percentage as less than 0.01% rather than 0.00%.
- Optimized and reduced Electrum server RPC calls.
- Upgraded Bouncy Castle, PGPainless and Logback libraries.
- Upgraded internal Tor to v0.4.8.16.
- Bug fix: Fixed issue with random ordering of keystore origins on labels import.
- Bug fix: Fixed non-zero account script type detection when signing a message on Trezor devices.
- Bug fix: Fixed issue parsing remote Coldcard xpub encoded on a different network.
- Bug fix: Fixed inclusion of fees on wallet label exports.
- Bug fix: Increase Trezor device libusb timeout.
Linux users: Note that the
sparrowpackage has been renamed tosparrowwalletorsparrowserver, and in some cases you may need to manually uninstall the originalsparrowpackage. Look in the/optfolder to ensure you have the new name, and the original is removed.What's new in v2.2.1
- Updated Tor library to fix missing UUID issue when starting Tor on recent macOS versions.
- Repackaged
.debinstalls to use older gzip instead of zstd compression. - Removed display of median fee rate where fee rates source is set to Server.
- Added icons for external sources in Settings and Recent Blocks view
- Bug fix: Fixed issue in Recent Blocks view when switching fee rates source
- Bug fix: Fixed NPE on null fee returned from server
-
 @ dfa02707:41ca50e3
2025-06-08 16:02:23
@ dfa02707:41ca50e3
2025-06-08 16:02:23Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 81022b27:2b8d0644
2025-06-09 12:45:09
@ 81022b27:2b8d0644
2025-06-09 12:45:09You probably already know that I’ve been playing around with the whole Nostr thing.
Well, slowly I have been posting my content on Nostr. The long-form content., like my https://www.theintuitivechiropractor.com am using Habla.news
Habla.News is basically a blog app. It’s like a Substack, but you don’t have the newsletter feature, but I hear one may be in the works.
So from what I understand so far, your content is all published in one stream, but different sites handle the content differently.
A Twitter-like short post reader like Primal will organize short post and a long-form reader like Habla will do the articles.
I created a personal webpage on Npub.Pro and a links page (like a LinkTree) as well.
You can click on to see some of those pages.
Now, I’m having issues with the NPub page, because sometimes it wants to show my content, sometimes it decides not to.
Did I mention all of this is FREE?
It’s a bit complicated to setup at first, especially if you are unfamiliar with crypto wallets and that kind of stuff-but you get the feeling this is all new stuff and we are here in a new frontier where this could end up being revolutionary.
Follow my posts on here to see how I progress. If you would like to start on Nostr, I will do everything I can to help you out.
Live Long and Prosper,
-Dan
-
 @ a296b972:e5a7a2e8
2025-06-07 16:39:47
@ a296b972:e5a7a2e8
2025-06-07 16:39:47Nur für‘s Protokoll. Hiermit erkläre ich, Georg Ohrweh, im tatsächlich vorhandenen vollen Besitz meiner geistigen Kräfte, dass Herr Lauterbach, gleich welche Position er in Zukunft noch bekleiden sollte, für mich nicht zuständig ist. Basta.
Ein Erguss dieses verhaltensoriginellen Über-alles-Bescheidwissers:
„Wir kommen jetzt in eine Phase hinein, wo der Ausnahmezustand die Normalität sein wird. Wir werden ab jetzt immer im Ausnahmezustand sein. Der Klimawandel wird zwangsläufig mehr Pandemien bringen.“
Wie kann es sein, dass solch eine Ausnahme-Gestalt, die schon rein äußerlich die Phantasie zu Vergleichen anregt, sich leider auch genauso verhält, wie die Gestalten, die in diesen Phantasien vorkommen, ungebremst auf der Panik-Klaviatur kakophonische Klänge erzeugen darf? Obwohl ein wenig Wahrheit ist auch enthalten: Wir sind tatsächlich immer im Ausnahmezustand, im Ausnahmezustand des fortgeschrittenen Wahnsinns.
Wie kann es sein, dass dieser Haaaarvardist seinen persönlich empfundenen Ausnahmezustand zum Allgemeingut erklären kann? Welche Verknüpfungs-Phantasien hat er sonst noch studiert? Er ist ja auch noch Vorsitzender im Raumfahrtausschuss. Was kommt als Nächstes? Eine Klima-Pandemie, verursacht durch außerirdische Viren, die die Temperaturen beeinflussen können? Im aktuellen Zeitgeist gibt es nichts, was nicht gedacht wird. Wem die besseren Absurditäten einfallen, der gewinnt. Man muss sich schon den gegebenen Denkstrukturen etwas anpassen, aber sich auch ein wenig Mühe geben.
Nach dem Wechsel der ehemaligen Außen-Dings zur UN (mit dem Ziel, aus den Vereinten Nationen die Feministischen Nationen zu gestalten) und des ehemaligen Wirtschafts-Dings in den Außenausschuss und als Gastdozent in Kalifornien (Thema: Wirtschaftsvernichtung unter Einbeziehung des gespannten Verhältnisses unter Geschwistern aufgrund ärmlicher Verhältnisse, am Beispiel des Märchens von Hänsel und Gretel) , jetzt auch noch der ehemalige Chef-Panikmacher zur WHO.
…und der Wahnsinn wurde hinausgetragen in die Welt, und es wurde dunkel, und es ward Nacht, und es wurde helle, und es ward Tag, der Wind blies oder auch nicht (was macht der Wind eigentlich, wenn er nicht weht?), und es ward Winter, und es wurde kälter, und es wurde wärmer, und es ward Sommer. Es regnete nicht mehr, die Wolken schwitzten. Und Putin verhinderte (wer auch sonst), dass das Eis in der Antarktis abnahm.
Wiederholte Bodentemperaturen in der Toskana von 50 Grad Celsius. Zu erwartende Wassertemperaturen während Ferragosto an der italienischen Adria von durchschnittlich 100 Grad Celsius. An Stellen mit wenig Strömung stiegen schon die ersten Kochblasen auf. Doch dann kam der durch Lachs gestählte, salzlose Super-Karl und rettete mit einem durch die WHO diktierten Klima-Logdown die gesamte Menschheit. Wer besser, als er konnte wissen, dass ein Klima-Logdown weitgehend nebenwirkungsfrei ist.
Was für ein Segen, dass Karl der Große, der uns so siegreich durch die Corona-Schlacht geführt hat, jetzt auch gegen das Klima in den Krieg zieht.
Wer kennt das nicht, Tage der Qual, in denen man zugeben muss: Ich hab‘ heute so schlimm Klima.
Viele Klimaexperten, die weltweit in der Qualitätspropaganda zitiert werden, zeichnen sich besonders dadurch aus, dass sie mit einer maximalen Abweichung von einem Grad Celsius ein Thermometer fehlerfrei ablesen können. Diese Ungenauigkeit wird der Erdverkochungsexperte sicher als erstes beheben.
In einer aufopfernden Studie während eines Urlaubs in 2023, in der um die damalige Zeit erstmals eisfreien Toskana, hat er den von ihm ausgetüftelten Klimaschutzplan ins Rheinische übersetzt. Titel: „Schützen Sie sisch, und, äh, andere!“ Weiter konnte er erforschen, dass die Bodentemperatur nicht immer mit der Temperatur des Erdkerns übereinstimmen muss.
Durch seine unermüdlichen Studien, können Hitzetote in Zukunft besser zugeordnet werden. Man weiß dann, ob jemand an hohen oder mit hohen Temperaturen gestorben ist. Der asymptomatische Klimawandel kann so in Zukunft viel besser bewertet werden. Man hat aus geringfügigen Fehlern gelernt und die Methoden erheblich verbessert.
Eine präzise Vorhersage der Jahreszeiten, vor allem die des Sommers, wird bald ebenfalls möglich sein. Es kann jetzt vor jahreszeitbedingten, teilweise sogar täglich schwankenden Temperaturveränderungen rechtzeitig gewarnt werden. Im Herbst können Heizempfehlungen für die ahnungslose Bevölkerung herausgegeben werden. Frieren war gestern, wissen wann es kalt wird, ist heute. Es wird an Farben geforscht, die noch roter sein sollen, als die, die jetzt in den Wetterkarten bei 21 Grad bereits verwendet werden.
Eine allgemeine Heizpflicht soll es europaweit zunächst nicht geben.
Weiter soll die Lichteinstrahlung der Sonne noch präziser bestimmt werden, damit den Europäern, in Ergänzung zur mitteleuropäischen Sommerzeit, jetzt auch noch genau mitgeteilt werden kann, wann es Tag und wann es Nacht ist.
Das Hinausschauen aus dem Fenster, zum Beispiel, ob es schon dunkel draußen ist, erübrigt sich. Die Tageszeit, in Ergänzung zur herkömmlichen Uhrzeit, wird demnächst automatisch mit dem Klima-Pass übermittelt werden. Zu Anfang natürlich erst einmal freiwillig.
Durch die persönliche ID können dann auch schnell und unkompliziert Sonderprämien überwiesen werden, sofern man sich klimakonform verhalten hat, damit man sich rechtzeitig vor Winterbeginn eine warme Jacke oder einen Mantel kaufen kann. Das Sparen von Bargeld auf eine bevorstehende größere Anschaffung von Winterkleidung wird somit überflüssig.
Ob es am Ende nun um Hitze oder Kälte geht, spielt eigentlich gar keine Rolle, denn wie wussten schon die Ahnen zu berichten: Was gut für die Kälte ist, ist auch gut für die Wärme.
Westliche Mächte unternehmen immer wieder Versuche, eskalierend auf den Ukraine-Konflikt einzuwirken, damit man atombetriebene Heizpilze aufstellen kann, an denen sich die Europäer im Winter auch im Freien wärmen können.
Wie praktisch, dass man nicht nur Gesundheit und Klima, sondern auch Klima und Krieg miteinander verbinden kann. Alles so, oder so ähnlich möglicherweise nachzulesen im genialen Hitzeschutzplan á la Lauterbach.
Besonders Deutschland braucht nicht nur lauterbachsche Hitzeschutzräume, nein es braucht atomsichere Hitzeschutzbunker, so schlägt man gleich zwei Fliegen mit einer Klappe.
Für die, die es sich leisten können, hier ein Vorschlag. Der K2000:
Für die weniger gut Betuchten reicht auch ein kühles Kellerloch, das man idealerweise im Februar beziehen und nicht vor November wieder verlassen sollte, so die Empfehlung auch von führenden Klima-Forschern, die es ja wissen müssen. Von Dezember bis Januar empfiehlt sich ein Besuch auf den Bahamas, besonders dann, wenn man eine leichte Erkältung verspürt.
Nur Verschwörungstheoretiker behaupten, dass die eigenartigen Anschlussverwendungen der Extrem-Kapazitäten, zu denen Lauterbach ohne Zweifel dazugehört, wie dicke rote Pfeile wirken, die auf Institutionen und Organisationen zeigen, um die man unter allen Umständen einen großen Bogen machen sollte, weil sie möglicherweise nichts Gutes im Schilde führen. Minimal sollen sie angeblich Unsinn verbreiten, maximal sollen sie gehörigen Schaden anrichten.
Man muss sich nur ein paar Gedanken machen, schon kann man feststellen, wie alles mit allem zusammenhängt.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 9ca447d2:fbf5a36d
2025-06-07 16:01:19
@ 9ca447d2:fbf5a36d
2025-06-07 16:01:19Wall Street is warming up to Bitcoin and getting closer and closer to it.
Cantor Fitzgerald, one of the oldest and most respected investment banks on Wall Street, has launched a $2 billion bitcoin-backed lending program.
They’ve reportedly already done their first deals, lending to two big digital asset companies: FalconX and Maple Finance.
This is a big step in connecting traditional finance to the fast-moving world of Bitcoin.
Cantor’s new service allows big investors, hedge funds and asset managers, to borrow money using bitcoin as collateral.
This is a game changer for institutions that hold bitcoin, as they can now access liquidity without having to sell their assets.
“Institutions holding bitcoin are looking to broaden their access to diverse funding sources,” said Christian Wall, co-CEO and global head of fixed income at Cantor Fitzgerald.
“And we are excited to support their liquidity needs to help them drive long term growth and success.”
The loans are not speculative or unsecured.
They are structured like traditional finance deals, backed by the borrower’s bitcoin. This reduces the risk for Cantor while giving bitcoin-holding companies new ways to grow and operate.
The first recipients of Cantor’s lending program are FalconX, a digital asset brokerage, and Maple Finance, a blockchain-based lending platform.
FalconX confirmed they secured a credit facility of over $100 million. Maple Finance also received the first tranche of their loan from Cantor.
This comes at a time when the bitcoin lending space is recovering after a tough period. Several big firms went under in 2022 and investor confidence was shaken.
Now with traditional finance on board, bitcoin-backed lending has returned. According to Galaxy Research the total size of the digital asset lending market grew to $36.5 billion in Q4 2024.
Cantor’s move into bitcoin-backed lending isn’t new. They announced their plans in July 2024 and have been building their presence in the Bitcoin space since then.
Earlier this year, they partnered with Tether, SoftBank and Bitfinex to launch Twenty One Capital, a $3.6 billion fund to buy over 42,000 bitcoin.
In May 2025 Cantor Equity Partners merged with Twenty One Capital and bought nearly $459 million worth of bitcoin.
They also own around $1.9 billion in shares of Strategy, a company that holds a lot of bitcoin. Clearly Cantor believes in bitcoin as a long-term asset.
Cantor is also a big player in the stablecoin space.
They manage U.S. Treasury reserves for Tether, the company behind the $142 billion USDT stablecoin. This adds another layer of trust and credibility to Cantor’s digital asset involvement.
To secure the bitcoin used as collateral, Cantor has partnered with digital asset custodians Anchorage Digital and Copper.co.
These companies are known for their robust security and institutional-grade infrastructure. Cantor hasn’t disclosed loan terms or interest rates but confirmed the lending will follow current regulations.
This also shows how traditional financial players are embracing DeFi.
Maple Finance for example allows undercollateralized lending using blockchain. By backing companies like Maple, Cantor is innovating while still having control and compliance.
For years, bitcoin-backed loans were only available through digital-asset-native companies like Genesis, BlockFi, and Ledn.
These loans were mostly for smaller clients and retail investors. But with Cantor’s entry, the scale and professionalism of bitcoin lending are expanding.
-
 @ 7f6db517:a4931eda
2025-06-07 14:01:26
@ 7f6db517:a4931eda
2025-06-07 14:01:26
What is KYC/AML?
- The acronym stands for Know Your Customer / Anti Money Laundering.
- In practice it stands for the surveillance measures companies are often compelled to take against their customers by financial regulators.
- Methods differ but often include: Passport Scans, Driver License Uploads, Social Security Numbers, Home Address, Phone Number, Face Scans.
- Bitcoin companies will also store all withdrawal and deposit addresses which can then be used to track bitcoin transactions on the bitcoin block chain.
- This data is then stored and shared. Regulations often require companies to hold this information for a set number of years but in practice users should assume this data will be held indefinitely. Data is often stored insecurely, which results in frequent hacks and leaks.
- KYC/AML data collection puts all honest users at risk of theft, extortion, and persecution while being ineffective at stopping crime. Criminals often use counterfeit, bought, or stolen credentials to get around the requirements. Criminals can buy "verified" accounts for as little as $200. Furthermore, billions of people are excluded from financial services as a result of KYC/AML requirements.
During the early days of bitcoin most services did not require this sensitive user data, but as adoption increased so did the surveillance measures. At this point, most large bitcoin companies are collecting and storing massive lists of bitcoiners, our sensitive personal information, and our transaction history.
Lists of Bitcoiners
KYC/AML policies are a direct attack on bitcoiners. Lists of bitcoiners and our transaction history will inevitably be used against us.
Once you are on a list with your bitcoin transaction history that record will always exist. Generally speaking, tracking bitcoin is based on probability analysis of ownership change. Surveillance firms use various heuristics to determine if you are sending bitcoin to yourself or if ownership is actually changing hands. You can obtain better privacy going forward by using collaborative transactions such as coinjoin to break this probability analysis.
Fortunately, you can buy bitcoin without providing intimate personal information. Tools such as peach, hodlhodl, robosats, azteco and bisq help; mining is also a solid option: anyone can plug a miner into power and internet and earn bitcoin by mining privately.
You can also earn bitcoin by providing goods and/or services that can be purchased with bitcoin. Long term, circular economies will mitigate this threat: most people will not buy bitcoin - they will earn bitcoin - most people will not sell bitcoin - they will spend bitcoin.
There is no such thing as KYC or No KYC bitcoin, there are bitcoiners on lists and those that are not on lists.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-09 14:02:08
@ cae03c48:2a7d6671
2025-06-09 14:02:08Bitcoin Magazine

Palantir Is Violating Its Own Principles by Avoiding a Bitcoin TreasuryPalantir exists to see what others miss.
It was founded to solve problems most institutions can’t even name—defending sovereignty, navigating adversarial environments, and building systems designed to endure when others fail. Its software doesn’t just process data; it helps governments and institutions anticipate instability before it strikes.
But for all its strategic foresight, Palantir has yet to adopt a Bitcoin treasury strategy—a move that would bring its capital posture in line with its mission.
With more than $2.1 billion in cash, minimal debt, and few reinvestments, Palantir has the resources to lead—but no capital signal that matches its stated principles. In a world increasingly defined by currency debasement, centralized overreach, and geopolitical fragmentation, sitting on fiat is not neutrality. It’s a contradiction.
Palantir without a Bitcoin treasury isn’t just incomplete—it’s incoherent.
A Company Built for Strategic Foresight Should Not Be Saving in a Failing System
Over the last four years, Palantir has grown steadily:
- $1.09B → $1.54B → $1.91B → $2.23B in annual revenue
- Over $700M in free cash flow
- Just ~$239M in debt
- $2.1B in cash and equivalents
It’s a fortress balance sheet. But a fortress built on fiat is only as strong as the system it rests on.
Palantir has made no meaningful acquisitions, issued no dividends, and offers no capital return strategy beyond heavy stock-based compensation. This isn’t capital discipline—it’s strategic inertia. The company builds wartime software but saves like a peacetime conglomerate.
A Bitcoin Treasury Would Align Palantir’s Capital With Its Conviction
Palantir’s mission is to defend sovereignty and build for adversarial conditions. Bitcoin is the only monetary asset designed to do the same.
- Non-sovereign: Bitcoin is not issued or controlled by any state.
- Resilient: It has survived censorship attempts, geopolitical attacks, and financial panics.
- Transparent: It is auditable, predictable, and trustless—everything the fiat system is not.
- Aligned: Bitcoin reflects the same values Palantir claims—autonomy, resilience, and long-range thinking.
If Palantir allocated even half of its cash reserves (~$1.05B), it could acquire 10,000+ BTC. That would place it among the top 10 corporate Bitcoin holders, alongside Strategy (formerly MicroStrategy), Tesla, and Coinbase.
But this isn’t about optics. It’s about aligning capital with purpose.
Palantir Without a Bitcoin Treasury Violates Its Own Principles
Palantir outlines a clear ethical and design philosophy for its software. But those same principles expose a contradiction on its balance sheet.
Let’s break it down:
“Systems should incorporate principles of privacy by design.”
➤ Bitcoin is privacy by design. It enables global value transfer without third-party surveillance or control.
➤ Fiat is surveillance by design. Centralized systems track, censor, and report user behavior by default.By holding fiat, Palantir passively supports a financial architecture it claims to resist. A Bitcoin treasury would align its capital with its engineering ethics.
“Systems must facilitate accountability and oversight.”
➤ Bitcoin is radically transparent—anyone can audit supply, transactions, and ownership logic.
➤ Fiat operates in shadows—driven by opaque policy, insider bailouts, and political discretion.Palantir demands accountability in data infrastructure—its capital reserves should meet the same standard.
“We strive to contextualize major world problems.”
➤ The instability of fiat currency and global debt markets is a foundational context.
➤ Bitcoin is not a bet—it’s a contextual response to structural monetary decay.If Palantir exists to anticipate future risk, it should reflect that awareness on its balance sheet.
This Isn’t a Pivot. It’s Alignment.
Adopting a Bitcoin treasury wouldn’t mark a shift in Palantir’s mission—it would reinforce it.
This isn’t about chasing trends. It’s about applying the same principles that define Palantir’s software—resilience, sovereignty, and long-term thinking—to its balance sheet. Bitcoin reflects those values more directly than any fiat currency can.
Palantir helps its clients prepare for instability. It secures borders, systems, and decision-making frameworks under pressure. But it hasn’t secured its own monetary foundation.
That’s a strategic gap.
That’s a contradiction.
And it’s one the company can resolve—decisively.The Call to Action
Palantir’s shareholders believe in its conviction. They understand the company is not here to follow. It exists to build first, move first, and signal first.
They are not looking for fiat-era conservatism repackaged as capital discipline. They want strategy that matches the scale of the mission. They want to see the company allocate capital with the same clarity it brings to battlefield intelligence and national infrastructure.
Palantir has the foresight, the liquidity, and the philosophical grounding to act. What it needs is the will to align its reserves with its reason for existing.
A Bitcoin treasury would do more than protect value—it would prove Palantir means what it says.
It’s time to move from rhetoric to action.
It’s time to adopt a Bitcoin treasury strategy.Disclaimer: This content was written on behalf of Bitcoin For Corporations. The views expressed in this article are those of the author and do not necessarily reflect the official position of Bitcoin For Corporations. This article is intended solely for informational purposes and should not be interpreted as an invitation or solicitation to acquire, purchase, or subscribe for securities.
This post Palantir Is Violating Its Own Principles by Avoiding a Bitcoin Treasury first appeared on Bitcoin Magazine and is written by Nick Ward.
-
 @ 81022b27:2b8d0644
2025-06-09 12:39:53
@ 81022b27:2b8d0644
2025-06-09 12:39:53I literally have no clue what I'm doing.
Nostr is a decentralized protocol that lets users share messages and content through independent servers called relays, ensuring no single entity controls the network. It uses cryptographic keys to verify identities and secure messages, making it censorship-resistant and privacy-focused.
That is the simplest definition that Grok could come up with defining what is Nostr.
I’ve been intrigued by this because it ties in blockchain, publishing content and privacy all into one.
It is intimately tied to a Bitcoin wallet, where readers can “Zap” you tips in Satoshis- which is Bitcoin “change”
There are no intermediaries, no card processing fees, no gatekeepers to keep your content hidden,none of that.
Maybe i’m still mad about being censored on social media for my Covid-19 posts, but the idea of not being able to be censored by a corporation or even my own government is appealing to me.
There are apps to see videos, blog apps and social media type apps.
You own your content and you can move it around wherever you like.
I will be experimenting with posting on there.
I’ve got two profiles on there (I told you I didnt know what I was doing)
I’m inviting you to join me on Nostr.
Live Long and Prosper,
_Dan
nostr:naddr1qvzqqqr4gupzpqgz9vnnj6wkj3excxuvf2ug4xstp72g774v9tpnxzptag4c6pjyqqxnzde58yen2d35xg6njve5x6ph8l
-
 @ 4c96d763:80c3ee30
2025-05-31 22:39:59
@ 4c96d763:80c3ee30
2025-05-31 22:39:59Changes
Daniel D’Aquino (33):
- v1.13 changelog
- Version bump to 1.14
- Fix thread parent event loading regression
- Improve syncing and performance of ThreadModel
- v1.13.1 changelog
- Update Kingfisher to 8.3.1
- Add some miscellaneous documentation
- Renamed RelayInfo to LegacyKind3RelayRWConfiguration
- Define protocol NostrEventConvertible
- Organize RelayPool namespace
- NIP-65 relay list models and definitions
- New async streaming interface from RelayPool
- Implement safe interface for unowned NdbNotes
- Implement NostrNetworkManager and UserRelayListManager
- Add First Aid tool to repair relay list
- Fetch NIP-65 relay lists from profile view
- Add one-click Coinos wallet setup
- Add disclaimer to Coinos button
- Add network connect call to extensions
- Add safety reminder for higher balances
- Reinitialize videos if they enter an error state
- Refactor wallet invoice URL handling
- Re-enable note zaps ⚡️
- Move Kingfisher data to the Caches directory
- Implement Codable for NdbNote
- Add description and metadata to pay_invoice command
- Improve Coinos button disclaimer
- Add option to dismiss wallet high balance warning
- Improve error handling on NWC wallet
- Do not process NWC responses not meant for the user
- Add relay connectivity information to NWC settings
- Add changelog for v1.14
- Version bump to 1.15
SanjaySiddharth (3):
- Add search feature to the settings screen
- Fix bug that closes the side menu when copying npub
- Show additional information on top of blurred images
Swift Coder (1):
- Display Circular Indicator on top of media undergoing upload process Removed existing progress view bar at the top of post view Added separate stack in PVImageCarouselView for media undergoing the upload process Changelog-Added: Display uploading indicator in post view Signed-off-by: Swift Coder scoder1747@gmail.com
Terry Yiu (22):
- Fix localization issues in TransactionsView
- Export strings for translation
- Add Unicode 16 emoji reactions for iOS 18.4+ by upgrading EmojiPicker
- Add missing localized string comment
- Export strings for translation
- Clean up code in ProfileName.name_choice
- Fix quote notes to include missing q tag
- Fix some compiler warnings
- Replace deprecated usage of UIMenuController with UITextViewDelegate
- Add notification setting to hide hellthreads
- Inverse hellthread_notifications_enabled to be hellthread_notifications_disabled and add hellthread_notifications_max_pubkeys setting
- Hide future notes from timeline
- Fix note rendering for those that contain previewable items or leading and trailing whitespaces
- Add inline note rendering of invoices to pull up wallet selector sheet
- Optimize classify_url function
- Export strings for translation
- Remove arbitrary newline from localizable string
- Export strings for translation
- Add NIP-05 favicon to profile names and NIP-05 web of trust feed
- Fix quotes view header alignment
- Export strings for translation
- Rename Bitcoin Beach wallet to Blink
Transifex (83):
- Translate Localizable.strings in de
- Translate Localizable.stringsdict in de
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.stringsdict in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in hu_HU
- Translate Localizable.stringsdict in hu_HU
- Translate InfoPlist.strings in fr
- Translate Localizable.strings in th
- Translate Localizable.strings in nl
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in hu_HU
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in de
- Translate Localizable.strings in de
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in nl
- Translate Localizable.strings in pl_PL
- Translate Localizable.strings in pt_PT
- Translate Localizable.strings in hu_HU
- Translate Localizable.stringsdict in nl
- Translate Localizable.strings in nl
- Translate Localizable.strings in th
- Translate Localizable.stringsdict in th
- Translate Localizable.strings in ja
- Translate Localizable.strings in nl
- Translate Localizable.stringsdict in ja
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in nl
- Translate Localizable.strings in de
- Translate Localizable.stringsdict in de
- Translate Localizable.stringsdict in de
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
- Translate Localizable.strings in th
William Casarin (1):
- perf: don't use regex in trim_{prefix,suffix}
ericholguin (2):
- nwc: Wallet Redesign
- wallet: route to profile from wallet tx list
pushed to damus:refs/heads/master
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ 7f6db517:a4931eda
2025-06-09 10:02:20
@ 7f6db517:a4931eda
2025-06-09 10:02:20
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ 318ebaba:9a262eae
2025-06-09 08:45:57
@ 318ebaba:9a262eae
2025-06-09 08:45:57Nostr, which stands for "Notes and Other Stuff Transmitted by Relays," is a decentralized communication protocol designed to facilitate the exchange of messages without relying on centralized servers. This innovative framework allows users to create, broadcast, and receive messages freely, emphasizing user empowerment and censorship resistance.
Key Features of Nostr
-
Decentralization: Unlike traditional social media platforms, Nostr operates on a network of relays, which are servers that anyone can run. This structure eliminates the control that a single entity can exert over the platform, thereby reducing the risk of censorship and enhancing user privacy[1][4][5].
-
Open Protocol: Nostr is not an application itself but a protocol that developers can use to build various applications. This openness allows for a wide range of services, from social media to messaging, all built on the same underlying technology. Users can access multiple applications using a single public/private key pair, making it easier to manage their online identities[2][3][4].
-
Censorship Resistance: One of the primary motivations behind Nostr's creation is to provide a platform where users can communicate without fear of censorship. This is particularly appealing to those disillusioned with traditional social media platforms that often impose restrictions on content[5][10].
-
User Control: Nostr empowers users by allowing them to control their data and interactions. Users can choose which relays to connect to and can run their own relays, ensuring that they are not dependent on any single service provider[4][5][7].
-
Cryptographic Security: The protocol employs public-key cryptography to secure messages and verify identities, similar to how Bitcoin operates. This ensures that messages are authentic and have not been tampered with during transmission[5][10].
Applications and Community
Nostr has gained traction among various communities, particularly within the cryptocurrency space, where figures like Jack Dorsey and Edward Snowden have expressed support for its potential to reshape online communication. The protocol's design allows for a variety of applications, including social media platforms, chat services, and content sharing tools, all of which can interoperate seamlessly[2][3][5].
In summary, Nostr represents a significant shift in how digital communication can be structured, prioritizing decentralization, user autonomy, and resistance to censorship, making it a compelling alternative to conventional social media platforms. [1] https://threenine.blog/posts/what-is-nostr [2] https://www.forbes.com/sites/digital-assets/2023/04/11/how-to-get-started-with-nostr/ [3] https://www.forbes.com/sites/digital-assets/2024/07/17/your-guide-to-nostr-the-decentralized-network-for-everything/ [4] https://www.ledger.com/academy/glossary/nostr [5] https://river.com/learn/what-is-nostr/ [6] https://www.cointribune.com/en/comment-utiliser-nostr-guide-pour-debutants-2/ [7] https://www.ccn.com/education/what-is-nostr-and-how-to-start-using-nostr/ [8] https://nostr.com/ [9] https://mylessnider.com/articles/why-im-excited-about-nostr [10] https://en.wikipedia.org/wiki/Nostr [11] https://nostr.how/en/what-is-nostr [12] https://nostr.org/ [13] https://medium.com/@colaru/an-introduction-to-nostr-protocol-dbc774ac797c [14] https://www.linkedin.com/pulse/what-nostr-manfred-van-doorn-nf9ce [15] https://www.cointribune.com/en/nostr-pour-les-debutants-tout-ce-que-vous-devez-savoir-sur-le-protocole-2/ [16] https://www.reddit.com/r/Bitcoin/comments/17j5glg/do_people_in_this_sub_know_about_nostr/ [17] https://www.voltage.cloud/blog/the-essential-guide-to-nostr-relays [18] https://www.reddit.com/r/nostr/comments/1i6t4g7/explain_how_nostr_works_like_im_a_5_year_old/ [19] https://github.com/nostr-protocol/nostr
-
-
 @ edf0da8b:b2652fa3
2025-06-09 08:36:32
@ edf0da8b:b2652fa3
2025-06-09 08:36:32One remarkable thing the Wim Hof Method stirs in me is that I increasingly feel the desire to connect with pure nature. Now, what does that mean?
You may know that slight feeling of eeriness when looking at deep moving waters or that tiny insecurity when darkness creeps up around you alone among the trees? You are sure there's nothing to worry about. But still, these little old conditioned anxieties, these unreasonable mind scenarios, they keep coming up and make you seek safety.
They are different for everyone, but these anxieties in the foreground are a sign for inner blockages that deprive us from expressing our power and creativity. What's more, they separate us from nature. They suggest, everything around us is potentially dangerous. Is it though?
When practicing the Wim Hof Method, and especially right after the breathing exercises, I can immediately feel a clarity emerging, a stronger awareness of presence in the moment. Anxieties are caringly pushed back to their rightful place, but do not control my actions and no longer dominate my state of being.
And so suddenly, the world view shifts. Eerie deep moving waters become fascinating, the darkness around reveals the beauty of trees casting soft moonlight shadows. I deeply appreciate what is, I want to touch the waters, I want to merge with the shadows, I feel that power. Instead of running away I want to connect with nature. I'm more aware of the present and should danger reveal itself, I have the confidence that I can properly react when it arises. But until then, I can enjoy beauty and connectedness. The powerful shift is from scenarios about potential threats around me to curiosity and beautiful opportunity everywhere.
There are countless great techniques and traditions that guide us to such shifts. But with regular practice, I find the Wim Hof Method to be particularly simple, accessible and effective.
wimhofmethod #breathwork #coldtherapy #courage #motivation #freedom
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ edf0da8b:b2652fa3
2025-06-09 08:32:13
@ edf0da8b:b2652fa3
2025-06-09 08:32:13If you've been active on Nostr, you've probably realized that your posts come and go like waves. There’s no content-surfacing algorithm to keep them afloat. So, unless someone happens to scroll past at just the right time, your insights, event announcements, or deep reflections are getting swept away. There's no pretty profile page that refers to your content.
That’s where Npub.pro comes in—and it’s what I used to build my first website as a transformative coach and Wim Hof method instructor.
This article is about how Npub.pro works, my experience with it, and why it may be useful to you, too.
What is Npub.pro?
Npub.pro is a web service that pulls your posts from the Nostr protocol and weaves them into a clean, customizable website. It uses open-source templates from Ghost, making it easy to create a beautiful, functional landing page without needing to write any code.
If you're already posting on Nostr, Npub.pro turns that content into something lasting and visually appealing—like a curated blog or even a first landing page.

Why I Chose Npub.pro for My Initial Business Website
My work centers on personal transformation for leading a sovereign life—emotional, mental, and physical. I lead workshops, retreats and 1:1 sessions, and I needed a quick and simple place online that would communicate who I am, what I offer, and what’s coming up next.
Since I already post regularly on Nostr, it made sense to reuse that content to portray my work. But instead of letting my posts drift away in the feed, Npub.pro gave me a way to give them structure and longevity for a wider audience.
Plus, it really looks good.

Features That Make It Worthwhile
Easy Website Creation
You don’t need to become technical. The Npub.pro dashboard is simple and intuitive. Just pick a template, connect your Nostr keys, add your posts individually or based on hashtags, and voilà—your content starts showing up. You can experiment with different templates freely, without messing things up.
Multiple Templates for Different Needs
There's a good amount of templates to choose from, for photo blogging, journaling or podcasting etc. I started with "Liebling," switched to "Micro-Ruby" for a bit, and finally settled on "Massively"—it shows my often picture-based posts clearly and lets me feature a highlighted post at the top.
Tag-Based Categories
You can organize your content into sections like I did with “About & Events,” “Wim Hof Method,” or “Natural Living.” If you tag your Nostr posts accordingly and set up your categories in your dashboard, they’ll just fall into place.
Free Hosting + Custom Domains
Npub.pro is completely free if you’re okay with a domain like yourname.npub.pro. If you want something more professional, you can link a custom domain. I got mine for about $10/year from Namecheap. For now, even custom domains are free to connect. If you host your media on Nostr with e.g. Primal or Nostr.Build (subscription-based), and get a custom domain name, you have a complete low-budget website up and running.

What to Watch Out For
Npub.pro is not perfect and still evolving. Here are some limitations to keep in mind:
No Native Lead Capture or Email Signup
If you for example want to offer a PDF or free online class in exchange for email addresses, you’ll need to get creative with external links. Unfortunately, there’s no built-in call-to-action feature for non-Nostr users at this point.
No Pay-walled Content or Membership Features
If you’re looking to monetize content or offer member-only areas, you can hope and ask the Npub.pro team for future features, but it isn't there right now.
Some Trial & Error Required
Tagging needs to be done when you post. Adding tags retroactively with versatile clients like Amethyst won’t make earlier posts appear on your website. I had to republish a few old posts just to get them sorted into the right category. Expect a few hiccups, but it’s manageable.
Npub.pro and Nostr
Npub.pro is part of a bigger picture—the rise of Nostr as a decentralized social network. It’s censorship-resistant, Bitcoin-integrated, and potentially an all-in-one protocol for media, messaging, publishing, and payment. That's crazy powerful when you think about it a little more!
Right now, the infrastructure is still getting there. Not everything works reliably yet, and complex and visually rich experiences like Instagram-style clients (e.g. Olas) still fall short. But Npub.pro is one of those services that shows where it can be heading: toward digital sovereignty.

Is Npub.pro for You?
If you’re already active on Nostr, I think this is a no-brainer. You can turn your feed into a curated blog or landing page with very little extra effort.
Even if you're not using Nostr yet, Npub.pro is still worth exploring if:
- You want a free or low-budget minimal website that’s connected to your social media content.
- You care about decentralization and owning your data.
- You’re okay with less customization and a little experimentation here and there while things improve.
So in short, Npub.pro is quite the smart, and simple way to publish your presence online—especially if you want your Nostr content to live beyond the scroll.
Final Thoughts
I was surprised how good everything looked in the end on desktop, tablet and mobile and how easily you can manage your content. It’s not perfect for all needs, but it does the job remarkably well for a first website, personal blog or landing page. And by using Npub.pro, you’re helping build the future of open, user-owned publishing online.
Check Out Npub.pro
My Website:
Old-school Socials:
https://youtube.com/@bennubreath
@Npub.pro @brugeman
NpubPro #DecentralizedWeb #GhostCMS #WimHof #DigitalSovereignty #OpenWeb #ContentCuration #BuildWithNostr #WebsiteHosting #Freedom #Transformation
-
 @ 7f6db517:a4931eda
2025-06-07 14:01:25
@ 7f6db517:a4931eda
2025-06-07 14:01:25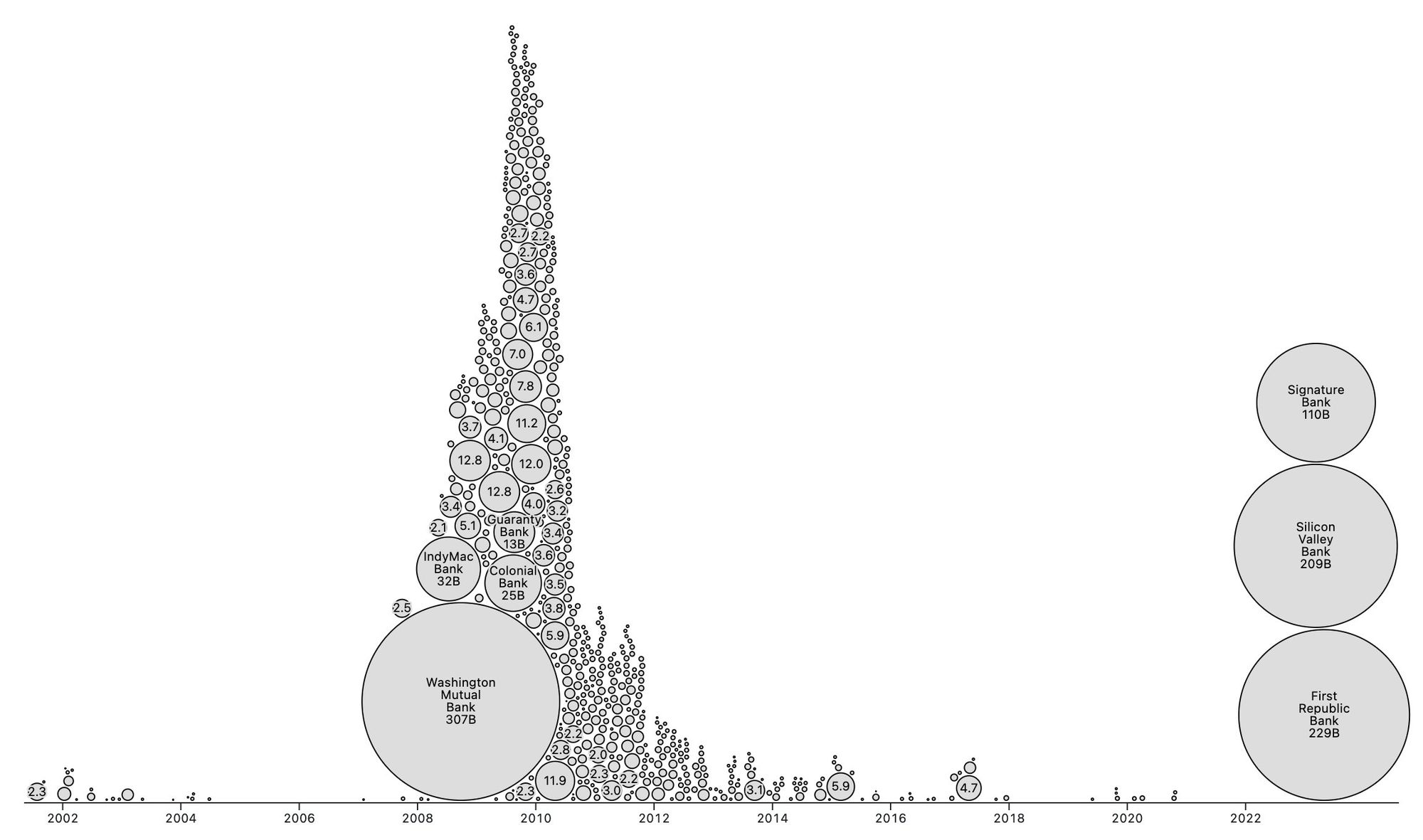
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ cae03c48:2a7d6671
2025-06-09 14:01:47
@ cae03c48:2a7d6671
2025-06-09 14:01:47Bitcoin Magazine

Bitcoin Layer 2: ArkArk is a novel off-chain transaction batching mechanism originally proposed by Burak, a young Turkish developer. There are currently two implementations being built, one by Ark Labs, and the other by Second, neither of which Burak is involved with.
The original proposal for Ark was much more complicated, and involved some design goals more focused around privacy than the implementations currently being built. It was also originally envisioned to require CHECKTEMPLATEVERIFY (CTV) in order to be built.
The protocol depends on a central coordinating server in order to function properly, but despite that is able to provide the same functionality and security guarantees that the Lightning Network does. As long as a user stays online during the required time period, at all times (unless they choose to trust the operator for short periods of time) every user is capable at any time of unilaterally exiting the Ark system at any time and taking back full unilateral control of their funds onchain.
Unlike Lightning, Ark does not require users to have pre-allocated liquidity assigned to them in order to receive funds. An Ark user can simply onboard to a wallet and receive funds immediately with no liquidity pre-allocation at all.
Let’s walk through the different constituent pieces of Ark.
The Ark Tree
Coins held on Ark are called Virtual UTXOs (vUTXOs). These are simply pre-signed transactions that guarantee the creation of a real UTXO under the unilateral control of a user once submitted onchain, but are otherwise held offchain.
Every user’s vUTXOs are nested inside a tree of pre-signed transactions, or a “batch.” Ark works by having the coordinator server, or Ark Service Provider (ASP), facilitate the coordination between users necessary to create a batch. Whenever users are receiving funds, onboarding to Ark, or offboarding, it is necessary to construct a transaction and the associated transaction tree to create a new batch.

The tree is constructed to take the single root UTXO confirmed onchain, locked with an n-of-n multisig including all users holding vUTXOs in the tree as well as the ASP, and slowly split into more and more UTXOs until eventually reaching the leaves, which are each users vUTXO. Each vUTXO is guaranteed using a script that has to be signed by a 2-of-2 multisig, one key held by the user, and the other by the ASP, or just the user after a timelock.
Each time the tree splits, vUTXOs are created onchain, but so are more internal UTXOs that have yet to actually split into vUTXOs. Each of these internal UTXOs is locked with an n-of-n multisig composed of the ASP, and all users who have a vUTXO further down the tree. During the batch creation process, users start at their respective vUTXOs, and go through a signing process all the way back down the root of the tree. This guarantees that the root will never be signed before each user’s claim to a vUTXO is, ensuring they always have unilateral access in a worst case scenario to their funds.
Each batch also has an expiry time (which will make sense in the next section). This expiry spend path, which exists as an alternate spending condition for the root UTXO onchain as well as every internal UTXO, allows the ASP to unilaterally spend all funds by itself.
Transactions, Preconfirmation, and Connector Inputs
When it comes to transacting on Ark, there are two possible mechanisms that are possible, both with their own costs and implications in terms of security model. There are out-of-round transfers, or preconfirmed transactions, and there are in-round transfers, or actually confirmed transactions.
To conduct an out-of-round transfer is a very simple process. If one user (Alice) wants to pay another (Bob), they simply contact the ASP and have them co-sign a transaction spending the vUTXO to Bob. Bob is then given that pre-signed transaction, as well as all the other ones preceding it back to the batch root onchain. Bob is now capable of unilaterally exiting the Ark with this transaction, but, he must trust the ASP not to collude with Alice to doublespend it. These out-of-round transactions can even be chained multiple times before finally confirming them.
To finalize an Ark transaction, users have to engage in a “batch swap.” Users cannot actually trustlessly confirm a transfer within a single batch, they have to atomically swap a vUTXO in an existing batch with a fresh vUTXO created in a new batch. This is done using the ASP as a facilitator of the swap, and with the aid of what is called a “connector input.”
When a user goes to finalize an Ark transaction with a batch swap, they relinquish control of the vUTXO to the ASP. This could be problematic, what is to stop the ASP from simply keeping it and not giving them a confirmed vUTXO in a new batch? The connector input.
When a new batch is created, a second output is created in the transaction that is confirmed on chain instantiating a new tree composed of connector UTXOs. When Bob goes to sign over a forfeit transaction to the ASP to conduct the batch swap, the transaction includes as an input one of the connector UTXOs from the new batch.
This creates an atomic guarantee. Bob’s confirmed vUTXO is included in a batch in the same transaction the connector input is created in that is necessary for his forfeit transaction to be valid. If that batch is never created onchain, i.e. Bob never actually receives the new confirmed vUTXO, then the forfeit transaction he signed for the ASP will never be valid and confirmable onchain.
Liquidity Dynamics and Blockspace
All of the liquidity necessary to create new batches in order to facilitate transfers between users is provided by the ASP. They are required to have enough liquidity to create new batches for users until old ones have expired and the ASP can unilaterally sweep them to reclaim old liquidity previously locked up to create vUTXOs for users.
This is the core of the liquidity dynamic at the center of the Ark protocol. While in one sense this is a massive efficiency win, not requiring liquidity providers to assess users and essentially guess which ones will actually receive large volumes of payments before they can receive any funds, in another it is an efficiency loss as the ASP must have enough liquidity to continue creating new batches for users for however long they configure the expiry time to be and they can start reclaiming allocated liquidity.
This can be mitigated to a decent degree by how often an ASP offers to create new batches to finalize pending transactions. In the event of an ASP attempting to create new batches in real time as transactions are coming in, the liquidity requirements would be exorbitantly high. However, an ASP can lower the frequency at which they create new batches and drastically lower their liquidity requirements.
This dynamic also has implications for blockspace use. Unlike Lightning, which can provide strong confirmation guarantees entirely offchain, in order for an Ark transaction to have an equivalent trustless degree of finality a new batch has to be created onchain. This means that unlike Lightning, where transaction volume does not reflect itself onchain, the velocity of Ark transactions inherently requires a proportional amount of blockspace use, albeit in a very compressed and efficient manner. This creates a theoretical upper limit of how many Ark batches can be created during any given time interval (although Ark trees can be smaller or larger depending on this dynamic).
Wrapping Up
Ark presents in many ways an almost opposite set of tradeoffs to the Lightning Network. It is a massive blockspace efficiency improvement for offchain transactions, and does away with the problem of liquidity allocation on the Lightning Network, but it does have a much closer tied throughput limit that is correlated with the blockchains throughput limit.
This dynamic of almost opposite tradeoffs makes it a very complementary system to the Lightning Network. It can also interoperate with it, i.e. vUTXOs can be swapped atomically in transactions entering or exiting the Lightning Network.
Ultimately how it fits into the broader Bitcoin ecosystem is yet to be seen, but it is an undoubtedly valuable protocol stack that will find some functional niche, even if it is different than originally intended.
This post Bitcoin Layer 2: Ark first appeared on Bitcoin Magazine and is written by Shinobi.
-
 @ 7f6db517:a4931eda
2025-06-07 14:01:25
@ 7f6db517:a4931eda
2025-06-07 14:01:25

"Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world." - Eric Hughes, A Cypherpunk's Manifesto, 1993
Privacy is essential to freedom. Without privacy, individuals are unable to make choices free from surveillance and control. Lack of privacy leads to loss of autonomy. When individuals are constantly monitored it limits our ability to express ourselves and take risks. Any decisions we make can result in negative repercussions from those who surveil us. Without the freedom to make choices, individuals cannot truly be free.
Freedom is essential to acquiring and preserving wealth. When individuals are not free to make choices, restrictions and limitations prevent us from economic opportunities. If we are somehow able to acquire wealth in such an environment, lack of freedom can result in direct asset seizure by governments or other malicious entities. At scale, when freedom is compromised, it leads to widespread economic stagnation and poverty. Protecting freedom is essential to economic prosperity.
The connection between privacy, freedom, and wealth is critical. Without privacy, individuals lose the freedom to make choices free from surveillance and control. While lack of freedom prevents individuals from pursuing economic opportunities and makes wealth preservation nearly impossible. No Privacy? No Freedom. No Freedom? No Wealth.
Rights are not granted. They are taken and defended. Rights are often misunderstood as permission to do something by those holding power. However, if someone can give you something, they can inherently take it from you at will. People throughout history have necessarily fought for basic rights, including privacy and freedom. These rights were not given by those in power, but rather demanded and won through struggle. Even after these rights are won, they must be continually defended to ensure that they are not taken away. Rights are not granted - they are earned through struggle and defended through sacrifice.
If you found this post helpful support my work with bitcoin.

-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ b2d670de:907f9d4a
2025-02-28 16:39:38
@ b2d670de:907f9d4a
2025-02-28 16:39:38onion-service-nostr-relays
A list of nostr relays exposed as onion services.
The list
| Relay name | Description | Onion url | Operator | Payment URL | Payment options | | --- | --- | --- | --- | --- | --- | | nostr.oxtr.dev | Same relay as clearnet relay nostr.oxtr.dev | ws://oxtrdevav64z64yb7x6rjg4ntzqjhedm5b5zjqulugknhzr46ny2qbad.onion | operator | N/A | N/A | | relay.snort.social | Same relay as clearnet relay relay.snort.social | wss://skzzn6cimfdv5e2phjc4yr5v7ikbxtn5f7dkwn5c7v47tduzlbosqmqd.onion | operator | N/A | N/A | | nostr.thesamecat.io | Same relay as clearnet relay nostr.thesamecat.io | ws://2jsnlhfnelig5acq6iacydmzdbdmg7xwunm4xl6qwbvzacw4lwrjmlyd.onion | operator | N/A | N/A | | nostr.land | The nostr.land paid relay (same as clearnet) | ws://nostrland2gdw7g3y77ctftovvil76vquipymo7tsctlxpiwknevzfid.onion | operator | Payment URL | BTC LN | | bitcoiner.social | No auth required, currently | ws://bitcoinr6de5lkvx4tpwdmzrdfdpla5sya2afwpcabjup2xpi5dulbad.onion | operator | N/A | N/A | | relay.westernbtc.com | The westernbtc.com paid relay | ws://westbtcebhgi4ilxxziefho6bqu5lqwa5ncfjefnfebbhx2cwqx5knyd.onion | operator | Payment URL | BTC LN | | freelay.sovbit.host | Free relay for sovbit.host | ws://sovbitm2enxfr5ot6qscwy5ermdffbqscy66wirkbsigvcshumyzbbqd.onion | operator | N/A | N/A | | nostr.sovbit.host | Paid relay for sovbit.host | ws://sovbitgz5uqyh7jwcsudq4sspxlj4kbnurvd3xarkkx2use3k6rlibqd.onion | operator | N/A | N/A | | nostr.wine | 🍷 nostr.wine relay | ws://nostrwinemdptvqukjttinajfeedhf46hfd5bz2aj2q5uwp7zros3nad.onion | operator | Payment URL | BTC LN, BTC, Credit Card/CashApp (Stripe) | | inbox.nostr.wine | 🍷 inbox.nostr.wine relay | ws://wineinboxkayswlofkugkjwhoyi744qvlzdxlmdvwe7cei2xxy4gc6ad.onion | operator | Payment URL | BTC LN, BTC | | filter.nostr.wine | 🍷 filter.nostr.wine proxy relay | ws://winefiltermhqixxzmnzxhrmaufpnfq3rmjcl6ei45iy4aidrngpsyid.onion | operator | Payment URL | BTC LN, BTC | | N/A | N/A | ws://pzfw4uteha62iwkzm3lycabk4pbtcr67cg5ymp5i3xwrpt3t24m6tzad.onion:81 | operator | N/A | N/A | | nostr.fractalized.net | Free relay for fractalized.net | ws://xvgox2zzo7cfxcjrd2llrkthvjs5t7efoalu34s6lmkqhvzvrms6ipyd.onion | operator | N/A | N/A | | nfrelay.app | nfrelay.app aggregator relay (nostr-filter-relay) | ws://nfrelay6saohkmipikquvrn6d64dzxivhmcdcj4d5i7wxis47xwsriyd.onion | operator | N/A | N/A | relay.nostr.net | Public relay from nostr.net (Same as clearnet) | ws://nostrnetl6yd5whkldj3vqsxyyaq3tkuspy23a3qgx7cdepb4564qgqd.onion | operator | N/A | N/A | | nerostrator | Free to read, pay XMR to relay | ws://nerostrrgb5fhj6dnzhjbgmnkpy2berdlczh6tuh2jsqrjok3j4zoxid.onion | operator |Payment URL | XMR | | nostr.girino.org | Public relay from nostr.girino.org | ws://gnostr2jnapk72mnagq3cuykfon73temzp77hcbncn4silgt77boruid.onion | operator | N/A | N/A | | wot.girino.org | WoT relay from wot.girino.org | ws://girwot2koy3kvj6fk7oseoqazp5vwbeawocb3m27jcqtah65f2fkl3yd.onion | operator | N/A | N/A | | haven.girino.org/{outbox, inbox, chat, private} | Haven smart relay from haven.girino.org | ws://ghaven2hi3qn2riitw7ymaztdpztrvmm337e2pgkacfh3rnscaoxjoad.onion/{outbox, inbox, chat, private} | operator | N/A | N/A | | relay.nostpy.lol | Free Web of Trust relay (Same as clearnet) | ws://pemgkkqjqjde7y2emc2hpxocexugbixp42o4zymznil6zfegx5nfp4id.onion | operator |N/A | N/A | | Poster.place Nostr Relay | N/A | ws://dmw5wbawyovz7fcahvguwkw4sknsqsalffwctioeoqkvvy7ygjbcuoad.onion | operator | N/A | N/A | | Azzamo Relay | Azzamo Premium Nostr relay. (paid) | ws://q6a7m5qkyonzb5fk5yv4jyu3ar44hqedn7wjopg737lit2ckkhx2nyid.onion | operator | Payment URL | BTC LN | | Azzamo Inbox Relay | Azzamo Group and Private message relay. (Freemium) | ws://gp5kiwqfw7t2fwb3rfts2aekoph4x7pj5pv65re2y6hzaujsxewanbqd.onion | operator | Payment URL | BTC LN | | Noderunners Relay | The official Noderunners Nostr Relay. | ws://35vr3xigzjv2xyzfyif6o2gksmkioppy4rmwag7d4bqmwuccs2u4jaid.onion | operator | Payment URL | BTC LN |
Contributing
Contributions are encouraged to keep this document alive. Just open a PR and I'll have it tested and merged. The onion URL is the only mandatory column, the rest is just nice-to-have metadata about the relay. Put
N/Ain empty columns.If you want to contribute anonymously, please contact me on SimpleX or send a DM on nostr using a disposable npub.
Operator column
It is generally preferred to use something that includes a NIP-19 string, either just the string or a url that contains the NIP-19 string in it (e.g. an njump url).
-
 @ a296b972:e5a7a2e8
2025-06-09 08:00:20
@ a296b972:e5a7a2e8
2025-06-09 08:00:20Nur für‘s Protokoll. Hiermit erkläre ich, Georg Ohrweh, im tatsächlich vorhandenen vollen Besitz meiner geistigen Kräfte, dass Herr Lauterbach, gleich welche Position er in Zukunft noch bekleiden sollte, für mich nicht zuständig ist. Basta.
Ein Erguss dieses verhaltensoriginellen Über-alles-Bescheidwissers:
„Wir kommen jetzt in eine Phase hinein, wo der Ausnahmezustand die Normalität sein wird. Wir werden ab jetzt immer im Ausnahmezustand sein. Der Klimawandel wird zwangsläufig mehr Pandemien bringen.“
Wie kann es sein, dass solch eine Ausnahme-Gestalt, die schon rein äußerlich die Phantasie zu Vergleichen anregt, sich leider auch genauso verhält, wie die Gestalten, die in diesen Phantasien vorkommen, ungebremst auf der Panik-Klaviatur kakophonische Klänge erzeugen darf? Obwohl ein wenig Wahrheit ist auch enthalten: Wir sind tatsächlich immer im Ausnahmezustand, im Ausnahmezustand des fortgeschrittenen Wahnsinns.
Wie kann es sein, dass dieser Haaaarvardist seinen persönlich empfundenen Ausnahmezustand zum Allgemeingut erklären kann? Welche Verknüpfungs-Phantasien hat er sonst noch studiert? Er ist ja auch noch Vorsitzender im Raumfahrtausschuss. Was kommt als Nächstes? Eine Klima-Pandemie, verursacht durch außerirdische Viren, die die Temperaturen beeinflussen können? Im aktuellen Zeitgeist gibt es nichts, was nicht gedacht wird. Wem die besseren Absurditäten einfallen, der gewinnt. Man muss sich schon den gegebenen Denkstrukturen etwas anpassen, aber sich auch ein wenig Mühe geben.
Nach dem Wechsel der ehemaligen Außen-Dings zur UN (mit dem Ziel, aus den Vereinten Nationen die Feministischen Nationen zu gestalten) und des ehemaligen Wirtschafts-Dings in den Außenausschuss und als Gastdozent in Kalifornien (Thema: Wirtschaftsvernichtung unter Einbeziehung des gespannten Verhältnisses unter Geschwistern aufgrund ärmlicher Verhältnisse, am Beispiel des Märchens von Hänsel und Gretel) , jetzt auch noch der ehemalige Chef-Panikmacher zur WHO.
…und der Wahnsinn wurde hinausgetragen in die Welt, und es wurde dunkel, und es ward Nacht, und es wurde helle, und es ward Tag, der Wind blies oder auch nicht (was macht der Wind eigentlich, wenn er nicht weht?), und es ward Winter, und es wurde kälter, und es wurde wärmer, und es ward Sommer. Es regnete nicht mehr, die Wolken schwitzten. Und Putin verhinderte (wer auch sonst), dass das Eis in der Antarktis abnahm.
Wiederholte Bodentemperaturen in der Toskana von 50 Grad Celsius. Zu erwartende Wassertemperaturen während Ferragosto an der italienischen Adria von durchschnittlich 100 Grad Celsius. An Stellen mit wenig Strömung stiegen schon die ersten Kochblasen auf. Doch dann kam der durch Lachs gestählte, salzlose Super-Karl und rettete mit einem durch die WHO diktierten Klima-Logdown die gesamte Menschheit. Wer besser, als er konnte wissen, dass ein Klima-Logdown weitgehend nebenwirkungsfrei ist.
Was für ein Segen, dass Karl der Große, der uns so siegreich durch die Corona-Schlacht geführt hat, jetzt auch gegen das Klima in den Krieg zieht.
Wer kennt das nicht, Tage der Qual, in denen man zugeben muss: Ich hab‘ heute so schlimm Klima.
Viele Klimaexperten, die weltweit in der Qualitätspropaganda zitiert werden, zeichnen sich besonders dadurch aus, dass sie mit einer maximalen Abweichung von einem Grad Celsius ein Thermometer fehlerfrei ablesen können. Diese Ungenauigkeit wird der Erdverkochungsexperte sicher als erstes beheben.
In einer aufopfernden Studie während eines Urlaubs in 2023, in der um die damalige Zeit erstmals eisfreien Toskana, hat er den von ihm ausgetüftelten Klimaschutzplan ins Rheinische übersetzt. Titel: „Schützen Sie sisch, und, äh, andere!“ Weiter konnte er erforschen, dass die Bodentemperatur nicht immer mit der Temperatur des Erdkerns übereinstimmen muss.
Durch seine unermüdlichen Studien, können Hitzetote in Zukunft besser zugeordnet werden. Man weiß dann, ob jemand an hohen oder mit hohen Temperaturen gestorben ist. Der asymptomatische Klimawandel kann so in Zukunft viel besser bewertet werden. Man hat aus geringfügigen Fehlern gelernt und die Methoden erheblich verbessert.
Eine präzise Vorhersage der Jahreszeiten, vor allem die des Sommers, wird bald ebenfalls möglich sein. Es kann jetzt vor jahreszeitbedingten, teilweise sogar täglich schwankenden Temperaturveränderungen rechtzeitig gewarnt werden. Im Herbst können Heizempfehlungen für die ahnungslose Bevölkerung herausgegeben werden. Frieren war gestern, wissen wann es kalt wird, ist heute. Es wird an Farben geforscht, die noch roter sein sollen, als die, die jetzt in den Wetterkarten bei 21 Grad bereits verwendet werden.
Eine allgemeine Heizpflicht soll es europaweit zunächst nicht geben.
Weiter soll die Lichteinstrahlung der Sonne noch präziser bestimmt werden, damit den Europäern, in Ergänzung zur mitteleuropäischen Sommerzeit, jetzt auch noch genau mitgeteilt werden kann, wann es Tag und wann es Nacht ist.
Das Hinausschauen aus dem Fenster, zum Beispiel, ob es schon dunkel draußen ist, erübrigt sich. Die Tageszeit, in Ergänzung zur herkömmlichen Uhrzeit, wird demnächst automatisch mit dem Klima-Pass übermittelt werden. Zu Anfang natürlich erst einmal freiwillig.
Durch die persönliche ID können dann auch schnell und unkompliziert Sonderprämien überwiesen werden, sofern man sich klimakonform verhalten hat, damit man sich rechtzeitig vor Winterbeginn eine warme Jacke oder einen Mantel kaufen kann. Das Sparen von Bargeld auf eine bevorstehende größere Anschaffung von Winterkleidung wird somit überflüssig.
Ob es am Ende nun um Hitze oder Kälte geht, spielt eigentlich gar keine Rolle, denn wie wussten schon die Ahnen zu berichten: Was gut für die Kälte ist, ist auch gut für die Wärme.
Westliche Mächte unternehmen immer wieder Versuche, eskalierend auf den Ukraine-Konflikt einzuwirken, damit man atombetriebene Heizpilze aufstellen kann, an denen sich die Europäer im Winter auch im Freien wärmen können.
Wie praktisch, dass man nicht nur Gesundheit und Klima, sondern auch Klima und Krieg miteinander verbinden kann. Alles so, oder so ähnlich möglicherweise nachzulesen im genialen Hitzeschutzplan á la Lauterbach.
Besonders Deutschland braucht nicht nur lauterbachsche Hitzeschutzräume, nein es braucht atomsichere Hitzeschutzbunker, so schlägt man gleich zwei Fliegen mit einer Klappe.
Für die, die es sich leisten können, hier ein Vorschlag. Der K2000:
Für die weniger gut Betuchten reicht auch ein kühles Kellerloch, das man idealerweise im Februar beziehen und nicht vor November wieder verlassen sollte, so die Empfehlung auch von führenden Klima-Forschern, die es ja wissen müssen. Von Dezember bis Januar empfiehlt sich ein Besuch auf den Bahamas, besonders dann, wenn man eine leichte Erkältung verspürt.
Nur Verschwörungstheoretiker behaupten, dass die eigenartigen Anschlussverwendungen der Extrem-Kapazitäten, zu denen Lauterbach ohne Zweifel dazugehört, wie dicke rote Pfeile wirken, die auf Institutionen und Organisationen zeigen, um die man unter allen Umständen einen großen Bogen machen sollte, weil sie möglicherweise nichts Gutes im Schilde führen. Minimal sollen sie angeblich Unsinn verbreiten, maximal sollen sie gehörigen Schaden anrichten.
Man muss sich nur ein paar Gedanken machen, schon kann man feststellen, wie alles mit allem zusammenhängt.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ cae03c48:2a7d6671
2025-06-09 14:01:37
@ cae03c48:2a7d6671
2025-06-09 14:01:37Bitcoin Magazine

Know Labs, Inc. Announces Adopting a Bitcoin Treasury Strategy, Starting with 1,000 BitcoinKnow Labs, Inc. (NYSE American: KNW) announced entering into an agreement with Goldeneye 1995 LLC and the Ripple Chief Risk Officer Greg Kidd to acquire a controlling interest in the Company. Following the completion of the transaction, Mr. Kidd will become Chief Executive Officer and Chairman of the Board of Directors of the Company and Founder Ron Erickson will become Vice Chairman of the Board.
JUST IN: Know Labs, Inc. announces its adopting a Bitcoin Treasury Strategy and holds 1,000 Bitcoin
 pic.twitter.com/NSn2xFZYx0
pic.twitter.com/NSn2xFZYx0— Bitcoin Magazine (@BitcoinMagazine) June 6, 2025
Under the agreement, the Buyer will acquire shares of Know Labs’ common stock by dividing the total value of 1,000 Bitcoin and a cash amount, designated to pay down existing debt, redeem outstanding preferred equity, and provide additional working capital. For every share purchased it will be priced at $0.335. The Bitcoin will serve as a central element of the Company’s treasury strategy, giving investors the exposure to Bitcoin.
“I’m thrilled to deploy a Bitcoin treasury strategy with the support of a forward-looking organization like Know Labs at a time when market and regulatory conditions are particularly favorable,” said Mr. Kidd. “We believe this approach will generate sustainable growth and long-term shareholder value.”
Once Bitcoin becomes the primary asset on the Company’s balance sheet, management will adopt the multiple of net asset value (mNAV) metric to assess the premium investors place on the Company’s market value relative to its Bitcoin assets. Based on a market cap of $128 million and a Bitcoin price of $105,000, the estimated entry mNAV multiple is 1.22x, with Bitcoin accounting for approximately 82% of the total market capitalization at closing.
“Partnering with Greg Kidd marks a pivotal next chapter for Know Labs,” commented Mr. Erickson. “We look forward to continuing our research in non-invasive medical technology. Greg’s visionary leadership positions Know Labs for a bold future.”
The adoption of Bitcoin as a treasury reserve asset has dramatically increased over the course of the last year, expanding globally. To date, there are 225 companies and other entities with Bitcoin in their balance sheets.
Norwegian Block Exchange (NBX), a leading Nordic cryptocurrency exchange and digital asset platform, announced on June 2 that it has added Bitcoin to its balance sheet, marking a national milestone as the first publicly listed company in Norway to hold Bitcoin as part of its treasury strategy.
“NBX will not sell this Bitcoin or go short in any form,” stated the company. “With reference to the latest POA notice with LDA capital, NBX will also use proceeds to buy additional Bitcoin.”
This post Know Labs, Inc. Announces Adopting a Bitcoin Treasury Strategy, Starting with 1,000 Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 7f6db517:a4931eda
2025-06-07 14:01:24
@ 7f6db517:a4931eda
2025-06-07 14:01:24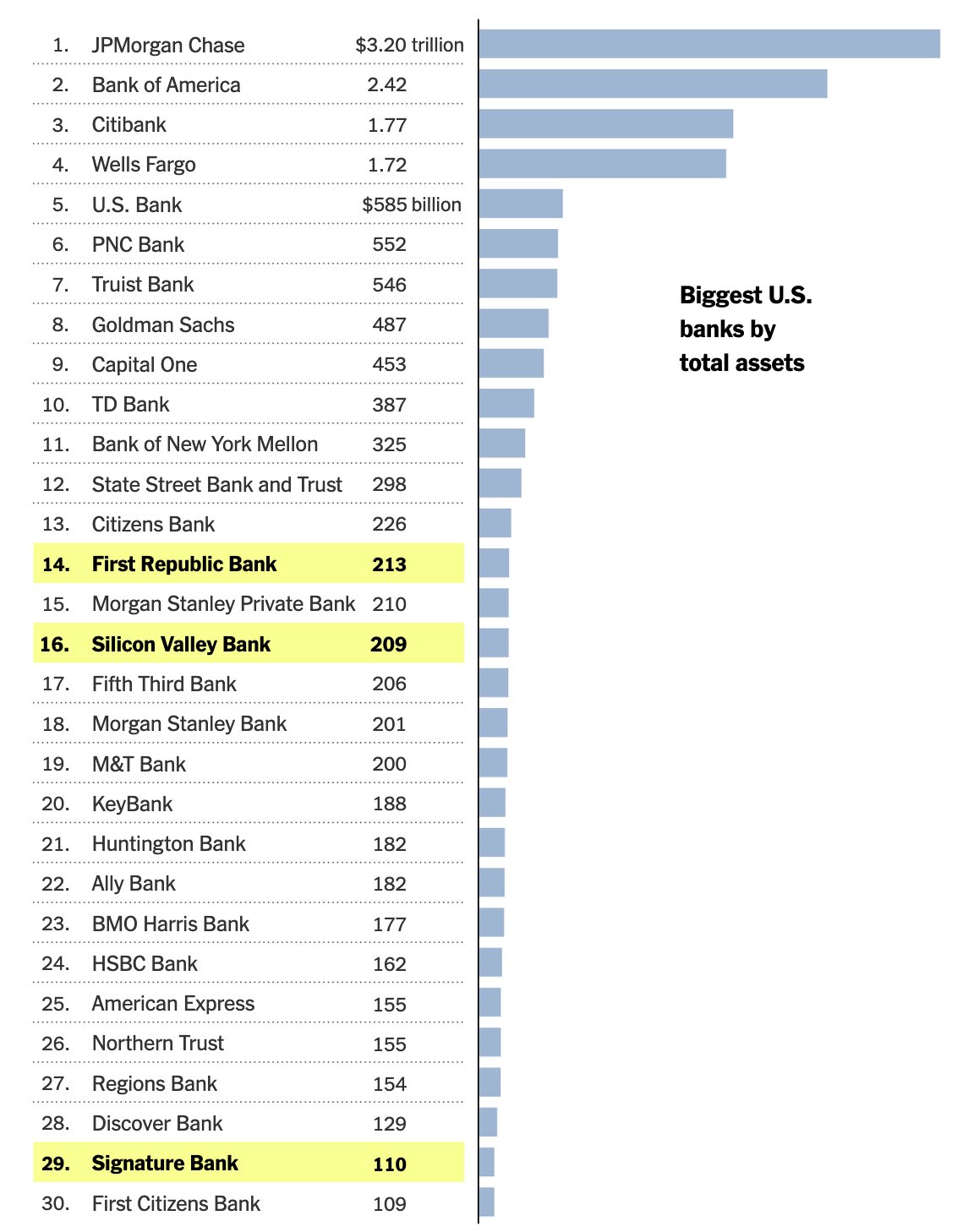
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-06-09 10:01:19
@ cae03c48:2a7d6671
2025-06-09 10:01:19Bitcoin Magazine

Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in BitcoinMeanwhile Insurance Bitcoin (Bermuda) Limited (“Meanwhile”) announced it has become the first company in the world to release externally audited financial statements denominated entirely in Bitcoin. According to the announcement, the company reported 220.4 BTC in assets and 25.29 BTC in net income for 2024, a 300% year over year increase.
Today marks a global first & historic event for us, along with the public release of our 2024 audited financial statements, covering our 1st year of sales.
As the 1st company in the world to have Bitcoin-denominated financial statements externally audited, we are excited to…
— meanwhile | Bitcoin Life Insurance (@meanwhilelife) June 5, 2025
“We’ve just made history as the first company in the world to have Bitcoin-denominated financial statements externally audited,” said Zac Townsend, CEO of Meanwhile. “This is an important, foundational step in reimagining the financial system based on a single, global, decentralized standard outside the control of any one government.”
The financial statements were audited by Harris & Trotter LLP and its digital asset division ht.digital. Meanwhile’s financials also comply with Bermuda’s Insurance Act 1978, noting that their BTC denominated financials were approved and comply with official guidelines. The firm, fully licensed by the Bermuda Monetary Authority (BMA), operates entirely in BTC and is prohibited from liquidating Bitcoin assets except through policyholder claims, positioning it as a long term holder.
“As the first regulated Bitcoin life insurance company, we view the BTC held by Meanwhile as inherently long-term in nature—primarily held to support the Company’s insurance liabilities over decades,” Townsend added. “This makes it significantly ‘stickier’ and resistant to market pressures compared to the BTC held by other companies as part of their treasury management strategies.”
Meanwhile’s 2024 financials also revealed 23.02 BTC in net premiums and 4.35 BTC in investment income, showing that its model not only preserves Bitcoin, but earns it. The company’s reserves (also held in BTC) were reviewed and approved by Willis Towers Watson (WTW).
Meanwhile also offers a Bitcoin Whole Life insurance product that allows policyholders to save, borrow, and build legacy wealth—entirely in BTC, and has plans to expand globally in 2025.
“We are incredibly proud of today’s news as it underscores how Meanwhile is at the forefront of the next phase of the convergence between Bitcoin and institutional financial markets,” said Tia Beckmann, CFO of Meanwhile. “Now having generated net income in BTC, we have demonstrated that we are earning it through a sustainable insurance business model designed for the long term.”
This post Bitcoin Life Insurer, Meanwhile, Becomes First Company to Publish Audited Financials Denominated in Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
@ 4fe4a528:3ff6bf06
2025-02-01 13:41:28
In my last article I wrote about NOSTR. I found another local bitcoiner via NOSTR last week so here is why it is important to join / use NOSTR — start telling people “Look me up on NOSTR”
Self-sovereign identity (SSI) is a revolutionary approach to digital identity that puts individuals in control of their own identity and personal data. Unlike traditional digital identity models, which rely on third-party organizations to manage and authenticate identities, SSI empowers individuals to own and manage their digital identity.
This approach is made possible by emerging technologies such as secure public / private key pairs. Decentralized identifiers, conceived and developed by nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 is an attempt to create a global technical standard around cryptographically secured identifiers - a secure, universal, and sovereign form of digital ID. This technology uses peer-to-peer technology to remove the need for intermediaries to own and authenticate ID information.
Notably, NOSTR, a decentralized protocol, has already begun to utilize decentralized IDs, demonstrating the potential of this technology in real-world applications. Via NOSTR, users can be sure that the person or computer publishing to a particular npub knows their nsec (password for your npub), highlighting the secure and decentralized nature of this approach.
With SSI, individuals can decide how their personal data is used, shared, and protected, giving them greater control and agency over their digital lives.
The benefits of SSI are numerous, including:
Enhanced security and protection of personal data. Reduced risk of identity theft and fraud Increased autonomy and agency over one's digital identity. Improved scalability and flexibility in digital identity management
challenges:
Ensuring the security and integrity of decentralized identity systems. Developing standards and protocols for interoperability and compatibility. Addressing concerns around ownership and control of personal data. Balancing individual autonomy with the need for verification and authentication in various contexts.
Overall, self-sovereign identity has the potential to transform the way we think about digital identity and provide individuals with greater control and agency over their personal data. Without people in control of their bitcoin seed words no freedom loving people would be able to exchange their money with others. Yes, keep enjoying using the only free market on the planet BITCOIN. Long live FREEDOM!
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Problemas com Russell Kirk
A idéia central da “política da prudência[^1]” de Russell Kirk me parece muito correta, embora tenha sido melhor formulada pior no seu enorme livro do que em uma pequena frase do joanadarquista Lucas Souza: “o conservadorismo é importante, porque tem muita gente com idéia errada por aí, e nós podemos não saber distingüi-las”.
Porém, há alguns problemas que precisam ser esclarecidos, ou melhor explicados, e que me impedem de enxergar os seus argumentos como refutação final do meu já tão humilde (embora feroz) anarquismo. São eles:
I Percebo alguma coisa errada, não sei bem onde, entre a afirmação de que toda ideologia é ruim, ou “todas as ideologias causam confusão[^2]”, e a proposta conservadora de “conservar o mundo da ordem que herdamos, ainda que em estado imperfeito, de nossos ancestrais[^3]”. Ora, sem precisar cair em exemplos como o do partido conservador inglês -- que conservava a política inglesa sempre onde estava, e se alternava no governo com o partido trabalhista, que a levava cada vez mais um pouco à esquerda --, está embutida nessa frase, talvez, a idéia, que ao mesmo tempo é clara e ferrenhamente combatida pelos próprios conservadores, de que a história é da humanidade é uma história de progresso linear rumo a uma situação melhor.
Querer conservar o mundo da ordem que herdamos significa conservar também os vários erros que podem ter sido cometidos pelos nossos ancestrais mais recentes, e conservá-los mesmo assim, acusando toda e qualquer tentativa de propôr soluções a esses erros de ideologia? Ou será que conservar o mundo da ordem é escolher um período determinado que seja tido como o auge da história humana e tentar restaurá-lo em nosso próprio tempo? Não seria isto ideologia?
Ou, ainda, será que conservar o mundo da ordem é selecionar, entre vários períodos do passado, alguns pedaços que o conservador considerar ótimos em cada sociedade, fazer dali uma mistura de sociedade ideal baseada no passado e então tentar implementá-la? Quem saberia dizer quais são as partes certas?
II Sobre a questão do que mantém a sociedade civil coesa, Russell Kirk, opondo-a à posição libertária de que o nexo da sociedade é o autointeresse, declara que a posição conservadora é a de que “a sociedade é uma comunidade de almas, que une os mortos, os vivos e os ainda não nascidos, e que se harmoniza por aquilo que Aristóteles chamou de amizade e os cristãos chamam de caridade ou amor ao próximo”.
Esta é uma posição muito correta, mas me parece estar em contradição com a defesa do Estado que ele faz na mesma página e na seguinte. O que me parece errado é que a sociedade não pode ser, ao mesmo tempo, uma “comunidade baseada no amor ao próximo” e uma comunidade que “requer não somente que as paixões dos indivíduos sejam subjugadas, mas que, mesmo no povo e no corpo social, bem como nos indivíduos, as inclinações dos homens, amiúde, devam ser frustradas, a vontade controlada e as paixões subjugadas” e, pior, que “isso somente pode ser feito por um poder exterior”.
Disto aí podemos tirar que, da mesma forma que Kirk define a posição libertária como sendo a de que o autointeresse é que mantém a sociedade civil coesa, a posição conservadora seria então a de que essa coesão vem apenas do Estado, e não de qualquer ligação entre vivos e mortos, ou do amor ao próximo. Já que, sem o Estado, diz, ele, citando Thomas Hobbes, a condição do homem é “solitária, pobre, sórdida, embrutecida e curta”?
[^1]: este é o nome do livro e também um outro nome que ele dá para o próprio conservadorismo (p.99). [^2]: p. 101 [^3]: p. 102
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28GraphQL vs REST
Today I saw this: https://github.com/stickfigure/blog/wiki/How-to-(and-how-not-to)-design-REST-APIs
And it reminded me why GraphQL is so much better.
It has also reminded me why HTTP is so confusing and awful as a protocol, especially as a protocol for structured data APIs, with all its status codes and headers and bodies and querystrings and content-types -- but let's not talk about that for now.
People complain about GraphQL being great for frontend developers and bad for backend developers, but I don't know who are these people that apparently love reading guides like the one above of how to properly construct ad-hoc path routers, decide how to properly build the JSON, what to include and in which circumstance, what status codes and headers to use, all without having any idea of what the frontend or the API consumer will want to do with their data.
It is a much less stressful environment that one in which we can just actually perform the task and fit the data in a preexistent schema with types and a structure that we don't have to decide again and again while anticipating with very incomplete knowledge the usage of an extraneous person -- i.e., an environment with GraphQL, or something like GraphQL.
By the way, I know there are some people that say that these HTTP JSON APIs are not the real REST, but that is irrelevant for now.
-
 @ 3f770d65:7a745b24
2025-01-19 21:48:49
@ 3f770d65:7a745b24
2025-01-19 21:48:49The recent shutdown of TikTok in the United States due to a potential government ban serves as a stark reminder how fragile centralized platforms truly are under the surface. While these platforms offer convenience, a more polished user experience, and connectivity, they are ultimately beholden to governments, corporations, and other authorities. This makes them vulnerable to censorship, regulation, and outright bans. In contrast, Nostr represents a shift in how we approach online communication and content sharing. Built on the principles of decentralization and user choice, Nostr cannot be banned, because it is not a platform—it is a protocol.
PROTOCOLS, NOT PLATFORMS.
At the heart of Nostr's philosophy is user choice, a feature that fundamentally sets it apart from legacy platforms. In centralized systems, the user experience is dictated by a single person or governing entity. If the platform decides to filter, censor, or ban specific users or content, individuals are left with little action to rectify the situation. They must either accept the changes or abandon the platform entirely, often at the cost of losing their social connections, their data, and their identity.
What's happening with TikTok could never happen on Nostr. With Nostr, the dynamics are completely different. Because it is a protocol, not a platform, no single entity controls the ecosystem. Instead, the protocol enables a network of applications and relays that users can freely choose from. If a particular application or relay implements policies that a user disagrees with, such as censorship, filtering, or even government enforced banning, they are not trapped or abandoned. They have the freedom to move to another application or relay with minimal effort.
THIS IS POWERFUL.
Take, for example, the case of a relay that decides to censor specific content. On a legacy platform, this would result in frustration and a loss of access for users. On Nostr, however, users can simply connect to a different relay that does not impose such restrictions. Similarly, if an application introduces features or policies that users dislike, they can migrate to a different application that better suits their preferences, all while retaining their identity and social connections.
The same principles apply to government bans and censorship. A government can ban a specific application or even multiple applications, just as it can block one relay or several relays. China has implemented both tactics, yet Chinese users continue to exist and actively participate on Nostr, demonstrating Nostr's ability to resistant censorship.
How? Simply, it turns into a game of whack-a-mole. When one relay is censored, another quickly takes its place. When one application is banned, another emerges. Users can also bypass these obstacles by running their own relays and applications directly from their homes or personal devices, eliminating reliance on larger entities or organizations and ensuring continuous access.
AGAIN, THIS IS POWERUFL.
Nostr's open and decentralized design makes it resistant to the kinds of government intervention that led to TikTok's outages this weekend and potential future ban in the next 90 days. There is no central server to target, no company to regulate, and no single point of failure. (Insert your CEO jokes here). As long as there are individuals running relays and applications, users continue creating notes and sending zaps.
Platforms like TikTok can be silenced with the stroke of a pen, leaving millions of users disconnected and abandoned. Social communication should not be silenced so incredibly easily. No one should have that much power over social interactions.
Will we on-board a massive wave of TikTokers in the coming hours or days? I don't know.
TikTokers may not be ready for Nostr yet, and honestly, Nostr may not be ready for them either. The ecosystem still lacks the completely polished applications, tools, and services they’re accustomed to. This is where we say "we're still early". They may not be early adopters like the current Nostr user base. Until we bridge that gap, they’ll likely move to the next centralized platform, only to face another government ban or round of censorship in the future. But eventually, there will come a tipping point, a moment when they’ve had enough. When that time comes, I hope we’re prepared. If we’re not, we risk missing a tremendous opportunity to onboard people who genuinely need Nostr’s freedom.
Until then, to all of the Nostr developers out there, keep up the great work and keep building. Your hard work and determination is needed.
-
 @ 7f6db517:a4931eda
2025-06-07 14:01:23
@ 7f6db517:a4931eda
2025-06-07 14:01:23
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 4fe4a528:3ff6bf06
2025-01-01 15:50:50
@ 4fe4a528:3ff6bf06
2025-01-01 15:50:50I could have wrote about how bitcoin has more than doubled in 2024 or how some people are still sitting on the sidelines not trying to understand why bitcoin will double in 2025, but instead I thought I would write about how bitcoin is allowing for a decentralized social network.
Two years ago I decided to try out this NOSTR idea. Now I have 233 followers, almost the same number of people who read this monthly newsletter. Facebook / whats-app was to ad filled for me to enjoy what my friends were posting. X was great for news, but none of my friends where on it. Linkedin was just about business. Besides, NOSTR gives me more bitcoin every time I post. I am now using the bitcoin to buy eggs every two weeks from my neighbors. So to me it is a win win. I can write notes and eat eggs. I even use my NOSTR extension to log into hivetalk.org and help people with their computer issues. It is better than teaching via ZOOM. 2025 is going to be a great year for decentralization.
If you are trying to join NOSTR via your desktop I recommend going to getalby.com installing the browser extension. Then make an account with getalby and write down your 24 words (nsec). Link your profile to your lightning wallet and start posting and following other friends via primal.net. Yes, of course, I am put on this earth to help my fellow man. Some people enjoy using NOSTR via their cell phone and for those people I recommend amethyst or damus. We are all in this together.
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:22
@ dfa02707:41ca50e3
2025-06-07 14:01:22
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ 57d1a264:69f1fee1
2025-06-09 06:42:31
@ 57d1a264:69f1fee1
2025-06-09 06:42:31To become a master designer, you need to break past a slavish devotion of past forms and create vibrant, new experiences. This design talk covers practical techniques for reinventing game genres. The goal is the invention of a unique and highly differentiated customer value proposition that makes both strong business sense and is also deeply creatively fulfilling. We cover designing from the root, reducing design risk, and igniting original franchises. We also cover the pitfalls of design innovation and how to thrive in a highly competitive market.
https://www.youtube.com/watch?v=f7DFuXDN29M
https://stacker.news/items/1001313
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 7f6db517:a4931eda
2025-06-09 06:02:17
@ 7f6db517:a4931eda
2025-06-09 06:02:17
Bank run on every crypto bank then bank run on every "real" bank.
— ODELL (@ODELL) December 14, 2022
Good morning.
It looks like PacWest will fail today. It will be both the fifth largest bank failure in US history and the sixth major bank to fail this year. It will likely get purchased by one of the big four banks in a government orchestrated sale.
March 8th - Silvergate Bank
March 10th - Silicon Valley Bank
March 12th - Signature Bank
March 19th - Credit Suisse
May 1st - First Republic Bank
May 4th - PacWest Bank?PacWest is the first of many small regional banks that will go under this year. Most will get bought by the big four in gov orchestrated sales. This has been the playbook since 2008. Follow the incentives. Massive consolidation across the banking industry. PacWest gonna be a drop in the bucket compared to what comes next.
First, a hastened government led bank consolidation, then a public/private partnership with the remaining large banks to launch a surveilled and controlled digital currency network. We will be told it is more convenient. We will be told it is safer. We will be told it will prevent future bank runs. All of that is marketing bullshit. The goal is greater control of money. The ability to choose how we spend it and how we save it. If you control the money - you control the people that use it.
If you found this post helpful support my work with bitcoin.

-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:22
@ dfa02707:41ca50e3
2025-06-07 14:01:22Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ 7f6db517:a4931eda
2025-06-09 06:02:16
@ 7f6db517:a4931eda
2025-06-09 06:02:16Will not live in a pod.
Will not eat the bugs.
Will not get the chip.
Will not get a blue check.
Will not use CBDCs.Live Free or Die.
Why did Elon buy twitter for $44 Billion? What value does he see in it besides the greater influence that undoubtedly comes with controlling one of the largest social platforms in the world? We do not need to speculate - he made his intentions incredibly clear in his first meeting with twitter employees after his takeover - WeChat of the West.
To those that do not appreciate freedom, the value prop is clear - WeChat is incredibly powerful and successful in China.
To those that do appreciate freedom, the concern is clear - WeChat has essentially become required to live in China, has surveillance and censorship integrated at its core, and if you are banned from the app your entire livelihood is at risk. Employment, housing, payments, travel, communication, and more become extremely difficult if WeChat censors determine you have acted out of line.
The blue check is the first step in Elon's plan to bring the chinese social credit score system to the west. Users who verify their identity are rewarded with more reach and better tools than those that do not. Verified users are the main product of Elon's twitter - an extensive database of individuals and complete control of the tools he will slowly get them to rely on - it is easier to monetize cattle than free men.
If you cannot resist the temptation of the blue check in its current form you have already lost - what comes next will be much darker. If you realize the need to resist - freedom tech provides us options.
If you found this post helpful support my work with bitcoin.

-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 319ad3e7:cc01d50a
2024-12-15 21:20:59
@ 319ad3e7:cc01d50a
2024-12-15 21:20:59LETTER FROM THE FOUNDER | FEATURED RECIPE | MICROFICTION | FOOD NOTE QUOTE | SOUNDS | NOSTR MARKETPLACE | REAL REVIEWS | COMMUNITY ALBUM | NEW RECIPES | FIN
LETTER FROM THE FOUNDER 📝
A Year of Growth and Gratitude
As we approach the end of the year, it’s the perfect moment to pause and reflect. 2024 has been a transformative year for Zap Cooking. What started as a simple idea has grown into a vibrant, connected community. From recipes to shared stories, the #zapcooking tag has become a rallying point for food enthusiasts everywhere, and it’s inspiring to see how this shared passion is bringing people together.
None of this would have been possible without the incredible support and dedication of Sarah, who pours her heart into crafting these newsletters. Sarah, thank you for helping us share the joy of cooking and community with so many.
I am deeply grateful, grateful for you, our community, for nostr, for the milestones we’ve reached, and for the challenges that have helped us grow. Zap Cooking is about more than food; it’s about connections, creativity, and collaboration. Together, we’ve built something special, and I’m excited for what 2025 holds.
Here’s to another year of cooking, connecting, and creating together. Thank you for being part of this journey.
Cheers!
Seth
Founder, Zap Cooking
FEATURED RECIPE 🥪
Nostrville 2.0 was located in Nashville, Tennessee. This music destination featured some powerhouse food establishments, such as Ladybird Taco, Hattie B’s Hot Chicken Sandwiches, Pancake Pantry, and Modell’s infamous family-style breakfast; however, it was the people from Louisiana who brought their A-game to the shared kitchen at the after-party rental.
The lovely Rupert and her giant, Kajoozie, served up a traditional gumbo that had all of us reaching for a second bowl… or perhaps a fourth bowl. It was that good! They were also kind enough to share their recipe with all of us.
Rupert and Kajoozie’s #Nostr Famous Gumbo https://substack.com/home/post/p-152296981
MICROFICTION 📖
GIFTS by RustyPuppy
Every Christmas Eve (and by 'every' Aaran meant those he could remember, which, being eight years old, was not many), after the dinner dishes had been washed, and the family settled into the living room to watch "It's a Wonderful Life," his nani would start chopping vegetables. Aaran once asked why she didn't cook Santa's beef stew when she prepared their dinner. Because she wanted the stew to be fresh, came the answer. Aaron knew better than to ask how something that needed to simmer for five hours could be considered 'fresh.'
Everyone knew their grandmother's beef stew, placed in front of the fireplace in a hand-made bowl wrapped in a dish towel to keep warm, was eaten by the dog after everyone went to bed. And every year, she insisted Santa needed a hot, healthy meal.
None of the children could believe anyone would choose vegetables over cookies. Shari, the girl next door, made peanut cookies for Santa. Aaron had helped mix the dough last year. He was forbidden from adding the frosting because Shari needed the perfect amount atop each cookie so she could write her name in the sugary mix with a toothpick. Depending how guilty she felt about the year, she sometimes added candy beads.
One year, a cousin asked if Santa really ate all of those hundreds? thousands? millions? of cookies. An uncle said, "Of course, that's why he's so fat," while Aaaran's mother said, "Of course not, he gives them to children who don't have sweets," and Nani added "And those who still want to believe in him."
Aaran secretly wanted to believe his nani, because his older brothers had teased him for writing his Christmas wish letter, saying Santa was only real for babies. He didn't want to be a baby, but he still wanted to believe in the magic that was Santa.
At last, the evening ended. Some returned to their homes; the rest returned to their rooms. Nani set her bowl under the stockings. Aaran hesitated on the stairs, but the thought of seeing the dog actually eat the stew made his eyes wet. He stepped over his cousin's sleeping bag, got into bed, and dreamed of flying reindeer.
In the morning, as the children opened their gifts and the adults took turns making coffee and tea, Nani asked Aaran to bring her the stew bowl. He looked at the dog, currently surrounded by shreds of wrapping paper, panting happily with a bow on his head. Picking up the bowl, Aaron saw something within; a peanut cookie with the name Shari written in the frosting.
RECIPE REFERENCES:
Lovely Indian beefstew with coconut milk & Ultimate Peanut Cookies https://substack.com/home/post/p-152296981
FOOD NOTE QUOTE 🗒️
Today someone took a picture of my latte art after I handed them their cup 💜 and it made my day. Celebrate the small things. 😊 - TKay
SOUNDS 🔊
At Bitcoin Park in Nashville, Tennessee, the adorable cuties Mallory, Other Mallory, Island, and Sergio, along with help from Fountain, Phantom Power and Tunestr.io organized a night of activities, food, art, and a live acoustic music panel featuring four absolutely talented musicians - Ainsley Costello, Amber Sweeney, Luke Wood, and Jo Corso. SoupBox was honored to sit down with Amber to chat about music, fostering dogs from Wags and Walks, and food | Listen Now: SoupBox with Sarah | Featuring Amber Sweeney
https://fountain.fm/episode/nvwD83sajCiFNqTP4tYu
https://feeds.rssblue.com/soupbox
Short from Nashville | OpenMike | Tunestr
https://v.nostr.build/yLufD7GbwOPI3EgA.mp4
NOSTR MARKETPLACE 💳
Find Your Holiday Gifts on Nostr | Value for Value (aka V4V) #circulareconomy
Agi Choote | Art Prints | Find on Nostr!
Amber Sweeney | Custom Songs for Any Occasion | https://www.theambersweeney.com/merch/custom-songs
Ant Richard | Limited Custom Handcrafted Knife Gift Certificates (12-month waitlist for all custom handmade orders) | Find on Nostr!
Apotheca Viva | https://apothecaviva.love/
Aupa Bars | https://eataupa.com/
Barnminer’s Barn Jerky | Find on Nostr!
Billay Coffee | https://billaycoffee.com/
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/
Bitcoin Blankets ⚡️| Website Coming Soon!
Bitpopart | https://bitpopart.com/ | https://www.storeofvalue.eu/collections/christmas-collection
BTC Aloha | Bitcoin Beachwear & Accessories | https://btcaloha.shop/
BtcPins | https://btcpins.com/
Cannabis Records | https://cannabisrecords.store/
CryptoCloaks | https://www.cryptocloaks.com/shop/
Delgado’s Fuego | https://delgadosfuego.com/
Dot GNT | Laser Engravings | https://dotgnt.codeberg.page/
Finca Yabisi | https://yabisi.farm/
Foxfire Mushrooms | https://foxfiremushrooms.com/
Golden Tallow | https://goldentallow.com/
GoodBeans 🇸🇻 Coffee | https://thegoodbeans.com/
Isolabell.art | https://isolabell.art/
Jake Wolki | https://wolkifarm.com.au/
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/
Kanuto Takumi San | Find on Nostr!
Laser Eyes Cards | https://lasereyes.cards/
LeatherMint | https://theleathermint.com/
Lightning Store | https://lightning.store/
LightningSpore | Full Service Mushroom Cultivation Company | https://www.lightningspore.com/
Lost Sheep Ranch | https://www.lost-sheep-ranch.com/
Lucho Poletti | Art Prints and Merchandise | https://luchopoletti.com/
Madex | Art & Apparel | https://madex.art/collections/in-stock
MapleTrade | Find on Nostr!
Matthew D | https://whitepaperstreetsoap.com/
Next Block Coffee | https://nextblockcoffee.com/
NoGood | Jake Wolki | https://wolkifarm.com.au/
PatsPropolisHoney | Find on Nostr!
Peony Lane Wine | Ben Justman | https://www.peonylanewine.com/
PlebianMarket | https://plebeian.market/
PictureRoom | Assorted Dessert Treats | Find on Nostr!
Regenerative Farmed Meats & Knives | AgrarianContrarian | Find on Nostr!
RustyPuppy | Art and Stories | https://heidi2524.com/
Salt of the Earth | Premium Electrolyte Mix | https://drinksote.com/
Satoshi Coffee Company | https://sats.coffee/
Scott & Son | Animal Portraits, Prints, and Apparel | https://xavierscraftworkanddesign.com/t-shirts
SofterSkin Tallow Skincare | https://softerskin.co/
Shopstr | https://shopstr.store/
Soap Miner | Tallow Body Soap Bars
SweetSats | Honey | https://sweetsats.io/
Veiled Mycology | https://veiledmycology.com/
Yojimbo | Jam & Marmalade | https://jimblesjumble.odoo.com/
REAL REVIEWS ⭐
BitBees | Honey & Honey Products | https://www.kittrellsdaydream.com/ | By Rupert
If you follow me or have ever had the pleasure of chatting with me on cornychat.com or hivetalk.org, you’ll know how proud I am of my Cajun heritage. For me, that means memories of long, hot summer days in South Louisiana, plenty of mosquito bites, the humming of cicadas in the cypress trees, and my grandfather’s bee boxes abuzz with fuzzy little workers.
I recently had the pleasure of meeting our famed #nostr beekeepers, @bitbees and @kingbee, and the absolute joy of tasting the labors of the wee little friends they care for. @KajoozieMaflingo and I purchased both their wildflower and gallberry varieties, and we were able to pay with BTC! (BONUS!) The wildflower was chef’s-kiss perfection, but my taste buds were instantly rocketed back to my childhood when I tried the lovingly and aptly nicknamed “swamp honey.”
Its pale color might fool you into thinking it has a lighter flavor than its rich and flavorful counterpart, but that couldn’t be further from the truth. It’s crisp and bright, with a mellow sweetness balanced by a slight tang to finish. It’s the ideal pairing with my favorite chamomile tea before bedtime.
This was my first purchase, but it will not be my last. By far, this is one of the most delicious use cases for Bitcoin I’ve come across to date.
Keto Beejay | Low Sugar Jerky | https://ketolish.us/ | https://ketobeejay.npub.pro/ | By The Beave
I recently had the pleasure of ordering four types of beef jerky from Beejay, the proprietress of http://ketolish.us. I was intrigued by her offerings and ended up ordering plain, pickle, pizza, and pepper. My order took a while to go through, mostly because Beejay and I were figuring out how to move sats around without it being too much of a pain in the butt. However, once finalized, everything shipped promptly and arrived quickly in a well-packed parcel. Beejay is also very good to communicate with, and I will gladly purchase more from her in the future.
I will start off the reviews with the most surprising of the batch: pizza. This was simply outstanding. I was shocked at how much it reminded me of eating pizza. I can't recommend this one enough! My second favorite pick is the pickle flavor. I love pickles. (I cannot express how much I love pickled things to you in words!) This was also very good, with the dill seasoning being front and center but restrained enough not to completely overpower the delicious beefiness of the jerky. A note on the texture: the jerky is ground, so it is not as tough as other jerkies you might try. This is a very new thing to me, and I rather enjoyed the novelty of the experience. The peppered jerky was full of pepper. This might be too much pepper for some, as it reminded me of the pepper-covered salami you can get at a good Italian pork store. Lastly, the plain jerky was delicious in its own right, though I would have preferred a touch more salt. I would order all of these again and am looking forward to ordering other flavors in the future, especially the bison!
COMMUNITY ALBUM 📷
Photos & Videos by Mandana from NextBlock & Flirting with Bitcoin, Efrat Fenigson, Ava, Birthday B, Vic from CornyChat, Tortuga, Mallory, Island, Jack Spirko, Paul Keating, BreadandToast.com, Nos.Social and Sarah SoupBox
View the Album: https://substack.com/home/post/p-152296981
NEW RECIPES 🍲
https://i.nostr.build/MNrivKtc1fpjamfn.png
In November, we received an incredible surge of over 30 recipes submitted to Zap Cooking! That's a fantastic leap from the three or four we typically see each week! Dive into one, two, or even all of them, and don’t forget to share your reviews and mouthwatering photos on Nostr using #foodstr. We’d also love to see your favorite personal or family recipes—let’s keep the culinary creativity flowing!
Corn Pudding, The Beef Panzone, Vodka Pie Crust, Short Rib Barbacoa Tacos, Guiness Beef Stew with Pickled Pearl Onions, Fast AF Beef Stroganoff, Dark Chocolate Mincemeat, Vic’s London Broil, Easy Wholemeal Spelt Flour Bread, Mamma SLCW’s Cranberry Sauce, Hot Dog Nachos, Italian Wedding Soup, Mapo Tofu Curry, Hot Honey Crispy Salmon Bowls, Curried Butternut Squash Soup, Best Damn Oven Baked Chicken Legs, Chocolate Creme Pie, Broccoli Beef, Tuscan Steak and Green Peppers, Easy Carne Asada, InstantPot Chicken Tortilla Soup, Green Bean Casserole with Bacon and Fried Shallots, Bang Bang Shrimp, Rupert and Kajoozie’s #Nostr Famous Gumbo, The Best Lamb Winter Stew, Avery’s Hot Wallet Salsa, Candied Pecans, Pumpkin Bread, Breakfast Casserole with Sausage and Egg, Gold & Silver Soup, Mr. G’s Homemade Chicken Pasta Salad, Ultimate Peanut Cookies
The recipe links are available here: https://substack.com/home/post/p-152296981
FIN 🤠
https://i.nostr.build/661bAgwsj6tEnICX.jpg
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:19
@ dfa02707:41ca50e3
2025-06-07 14:01:19Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 4fe4a528:3ff6bf06
2024-12-01 15:00:30
@ 4fe4a528:3ff6bf06
2024-12-01 15:00:30https://cdn.satellite.earth/8dd22e9b598964ade69d4c5ca517c2637ffafdfb15cf3e589cd1a7955c173375.mp4 In my last news article I wrote about selling my beef for 4500 sats / lb and buying my eggs for 4500 sats / dozen. You will be glad to know that some of my friends gave me bitcoin for my birthday. One person gave me over 60,000 sats, so now I am feeling like my last months article caused everyone to buy bitcoin — opt out of inflation.
It must have been more than my friends giving me bitcoin that caused Bitcoin to increase it’s market cap by 600 billion US dollars. I know that eggs are costing me 3,000 sats now compared to 4500 sats one month ago. If things keep getting 50% cheaper every month I might not have to move all my value into bitcoin.
Isn’t it weird using something that increases in value month after month? It is indeed a far cry from the traditional notion of money, where the value or the purchasing power of the currency loses value month after month. Most Bitcoiners care about the separation of money from the state, the removal of a third party from transactions and the capturing the deflationary nature of technology, etc. The fiat price is simply a short term way of measuring progress toward that goal. In reality, the moose shekel price doesn’t really matter.
With Brazil and Russia now using it as legal tender I don’t want anyone to give me bitcoin as a gift this month. Give your money/love to helping others see Jesus’ love in coming to earth instead. You might be able to write off your donation also.
You do realize there are only 16.5 million bitcoin available to be moved to other bitcoin type people and the US bitcoin strategic reserve might be coming next year. I just hope the Trudeau / Christine “Vib” session doesn’t make Canadians give up on using the Moose Shekels as a means of exchanging value. Bitcoin is now worth more than the Canadian dollar. If you need to get educated about money join Nostr and do a video / desktop sharing conference with me. Say hivetalk.org @ 9am ish works best for me. Remember, learning technology makes you earn more. We are all in this together.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A estrutura lógica do livro didático
Todos os livros didáticos e cursos expõem seus conteúdos a partir de uma organização lógica prévia, um esquema de todo o conteúdo que julgam relevante, tudo muito organizadinho em tópicos e subtópicos segundo a ordem lógica que mais se aproxima da ordem natural das coisas. Imagine um sumário de um manual ou livro didático.
A minha experiência é a de que esse método serve muito bem para ninguém entender nada. A organização lógica perfeita de um campo de conhecimento é o resultado final de um estudo, não o seu início. As pessoas que escrevem esses manuais e dão esses cursos, mesmo quando sabem do que estão falando (um acontecimento aparentemente raro), o fazem a partir do seu próprio ponto de vista, atingido após uma vida de dedicação ao assunto (ou então copiando outros manuais e livros didáticos, o que eu chutaria que é o método mais comum).
Para o neófito, a melhor maneira de entender algo é através de imersões em micro-tópicos, sem muita noção da posição daquele tópico na hierarquia geral da ciência.
- Revista Educativa, um exemplo de como não ensinar nada às crianças.
- Zettelkasten, a ordem surgindo do caos, ao invés de temas se encaixando numa ordem preexistentes.