-
 @ 81022b27:2b8d0644
2025-06-09 00:23:26
@ 81022b27:2b8d0644
2025-06-09 00:23:26I’m a Chiropractor, Writer, Travel Nerd, Lover of Efficiency, Trekker and a Celebrity in Mexican Restaurants Hi, I’m Danny DeReuter, and I want to save the world. I’m an occasional writer-I’ve written some stuff.
Sometimes people think I’m funny. Maybe some time I’ll come up with a bit of courage and try my hand at stand-up. (seriously, that’s a thing on my vision board)
I’ve become somewhat of a social media expert managing my online presence. I help show people how to do social media more effectively.
I’m also a speaker. I prefer to speak on topics that I’m passionate about-like natural health, chiropractic, and social media. I also have a Podcast. Be nice and you can ask me to speak at your event.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-09 00:18:27
@ 5d4b6c8d:8a1c1ee3
2025-06-09 00:18:27Big day for me today: - @k00b convinced me to try OMAD. I did eat more than once today, but it was all within a four hour period. I'll try to tighten that up further tomorrow. - @gnilma and @398ja convinced me to try a cold shower. I eased into it, by starting it warm and gradually turning down the temperature. That was totally manageable.
How did you do today? What do you need to work on tomorrow?
https://stacker.news/items/1001161
-
 @ 8bad92c3:ca714aa5
2025-06-09 00:02:34
@ 8bad92c3:ca714aa5
2025-06-09 00:02:34Marty's Bent
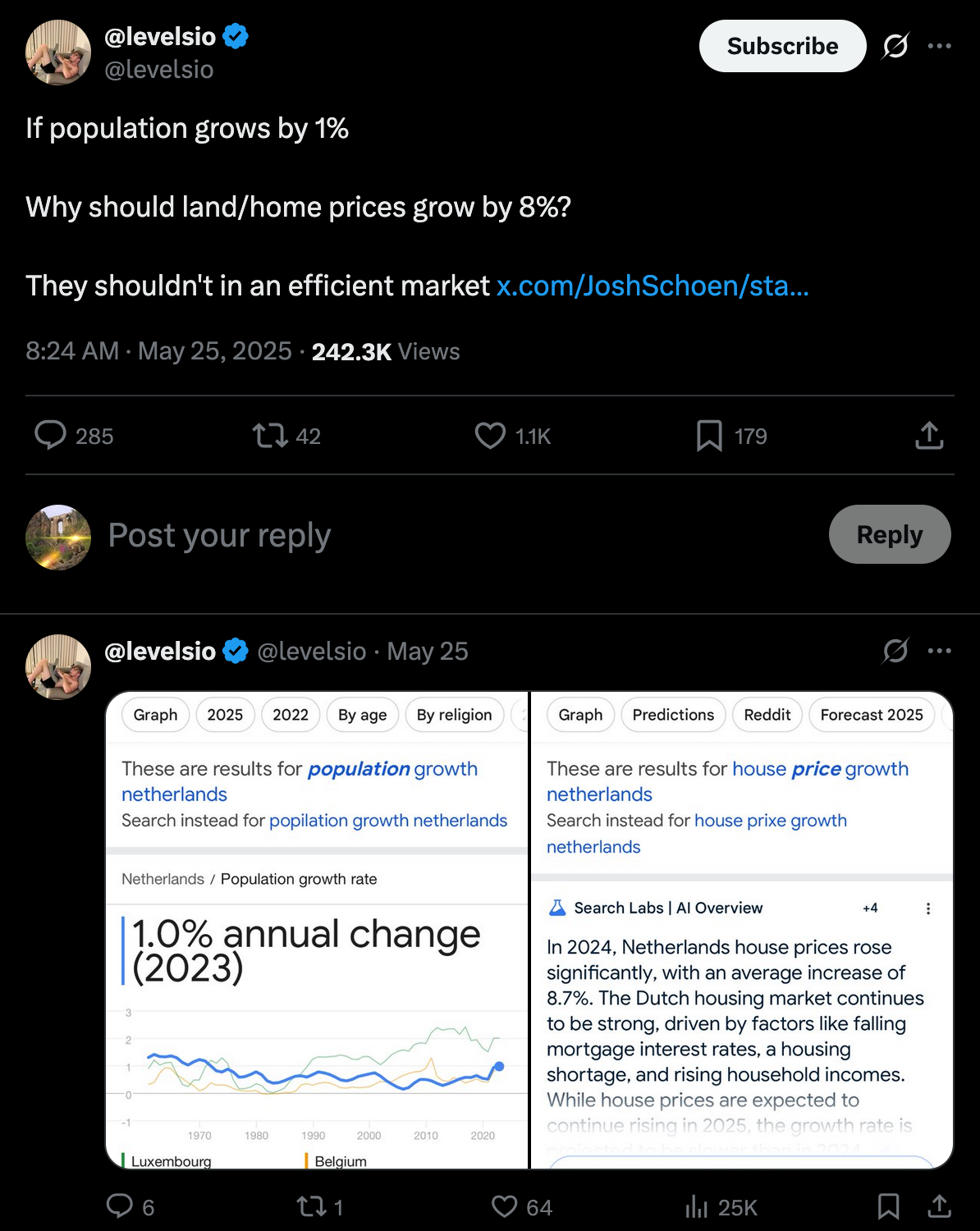
via levelsio

Over the weekend, prolific vibe coder levelsio took to X to complain about the state of housing affordability across Europe. Something that I was very happy to see considering the fact that there is a massive real estate affordability crisis across much of the world and it is important that people who are respected and have platforms speak out when they identify the problem as well. More eyes and focus on the problem is how something begins to get solved.
With that being said, I think levelsio is missing the forest for the trees by blaming institutionalized NIMBYism, burdensome regulations and governments hoarding land that should instead be given to developers to produce more housing supply. I quote tweeted this particular tweet on the subject from levelsio and wanted to take some time today to republish those thoughts here and expand on the topic.
It’s almost as if real estate is being used as a store of value asset instead of the consumable good that it is.
What @levelsio is observing here is called a “monetary premium”. A monetary premium is the value added on top of the consumable/aesthetic/location value of real estate.
This monetary premium exist because central banks and governments have distorted the market for money and people are forced to push value into assets that are scarce relative to dollars. Over the last 50 years real estate has been one of the relatively scarce assets of choice.
The housing affordability crisis is a negative externality of the market reaction to the corruption of money. It can only be fixed by re-introducing hard money into the economy that enables people to store value reliably. If that emerges they won’t have to store value in real estate, the monetary premium of real estate will dissolve and prices will correct to their proper valuations.
This is one of the problems that bitcoin solves.
It’s still early yet, but more and more people are recognizing the utility provided by a neutral reserve asset that can’t be manipulated by central planners. At scale, the effect on assets that have accumulated a monetary premium over decades will be material. All of these assets are significantly overvalued and their monetary premium are leaking into bitcoin.
Put another way, "It's the money, stupid." Now, this isn't to say that the supply of housing in certain areas being artificially restricted isn't having an effect on the price of housing. This is certainly true, especially in cities like San Francisco where there is a relatively strong demand because of the economic density of the area and the desire of many high agency and productive people to live there. But I would put forth that the monetary premium is still the bigger problem and no amount of de-regulation to enable the supply of housing to increase will solve the affordability crisis in the long-run. The only way to get to the root of this specific problem is via bitcoin's mainstream adoption as an apolitical uncontrollable asset with completely idiosyncratic risks when compared to any individual asset class.
Let's say the government did ease up regulations and local NIMBY sympathetics were shoved in a corner to allow new units to be built. This doesn't solve the problem in the short-run because there is a time-delay between when regulations are lifted and when new supply actually makes it to market. In the interim, governments and central banks are inevitably going to go further into debt and be forced to print money to monetize that debt. This will exacerbate inflation and even if new real estate units are brought to market, the builders/owners of those properties will likely have to demand elevated prices to attempt to keep up with inflation.
This also does nothing to solve the problem of real income and wage growth, which are significantly lagging real inflation. Even if prices came down because of a surge in supply, could the Common Man afford a down payment on the property? I'd be shocked if this was the case. And since it's likely not the case the only way to get people into these houses as "owners" would be to offer them zero-down financing, which makes people feel richer than they actually are and leads them to make financially ruinous decisions.
It's the money, stupid. People need a way to save so that they can buy in the first place. Fiat currency doesn't allow this and the only people who can save effectively are those who make enough money to funnel into substitute store of value assets like real estate.
As it stands today, the price-to-income ratio of real estate is 5.0x and the price-t0-rent index is 1.36. Up from 3.3x and 1.14x respectively where the metrics sat in the year 2000. The growth in these ratios is driven predominately via their monetary premium.
And guess what, it's about to get much worse. Donald Trump, Treasury Secretary Scott Bessent and Elon Musk have all signaled that the plan moving forward is to attempt to drive growth and productivity as high as possible while also letting deficits and the debt increase unabated, which means that inflation is likely to continue unabated and potentially increase.
It might make sense to get some bitcoin if that is the case.
via me
"Whale in the Pool" Risk That Could Destroy MSTY Investors
Jessy Gilger raised serious concerns about MSTY and similar derivative products that promise eye-popping yields. He pointed to the COVID crash where gold mining ETFs using derivatives collapsed 95% and never recovered, despite gold itself performing well. Jessy noted that while his team calculated reasonable MicroStrategy covered call yields of 16-22%, MSTY advertises 120% annualized distributions - a red flag that suggests these aren't sustainable dividends from profits, but potentially just returning investors' own capital.
"If a whale pees in the pool, everyone is affected." - Jessy Gilger
Jessy explained that when large investors need to exit these pooled products during market stress, they must sell derivative positions into illiquid markets with no buyers, potentially triggering catastrophic losses for all participants. His solution? Private pools through separately managed accounts that achieve similar income goals without the contagion risk of being trapped with panicking whales.
Check out the full podcast here for more on Gannett Trust's multi-sig solution, Bitcoin retirement planning and corporate treasury strategies.
Headlines of the Day
World's Largest Bitcoin Conference Starts Tomorrow- via X
Remixpoint to Buy Additional ¥1 Billion in Bitcoin - via X
Get our new STACK SATS hat - via tftcmerch.io
Marty to Judge Bitcoin World Record Try in Vegas - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Looking forward to a fun, productive and wholesome week in Las Vegas, Nevada.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
[
 ](https://youtube.com/@T
](https://youtube.com/@T -
 @ df478568:2a951e67
2025-06-08 23:58:37
@ df478568:2a951e67
2025-06-08 23:58:37NOTE: PLEASE DO NOT USE THIS METHOD UNTIL WE LEARN MORE ABOUT THIS nostr:nevent1qvzqqqqqqypzpw5qnyrxdmctda962pvng7ltzvjzjg09ge57dqqxfjn42ft2rcaxqqsfsg878u9luv2sxm6yahyjr4zpt745rdfpuu47wnn9t2dskgem52g9e9955
`About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.`
-
 @ eb0157af:77ab6c55
2025-06-08 22:02:36
@ eb0157af:77ab6c55
2025-06-08 22:02:36The adoption of Bitcoin as a corporate reserve asset is accelerating: public companies have doubled their holdings in just two months.
The use of Bitcoin as a corporate treasury strategy is reaching unprecedented levels. According to a recent report from Standard Chartered, shared with several industry outlets, 61 publicly traded companies collectively hold 3.2% of all bitcoin in circulation.
Geoff Kendrick, global head of digital asset research at Standard Chartered, revealed that these 61 public firms — out of a total of 124 — now own 673,897 BTC.
The report highlights that 58 of the 61 companies analyzed have net asset value (NAV) multiples above 1, indicating that their market valuations exceed the value of their net assets.
The Strategy copycats
A significant takeaway from the report is the speed at which companies are accumulating bitcoin. The 60 companies considered “Strategy copycats” have doubled their holdings in the past two months, from under 50,000 BTC to about 100,000 BTC. Over the same period, Strategy added 74,000 BTC, compared to the 47,000 acquired by the other firms.
This movement continues to expand as new companies announce Bitcoin purchase plans via debt issuance. On June 3, Canadian renewable energy developer SolarBank officially announced its Bitcoin treasury strategy, filing an application to open an account with Coinbase Prime to secure custody services, manage USDC, and set up a non-custodial wallet for its Bitcoin holdings.
Meanwhile, Paris-based Blockchain Group announced a $68 million Bitcoin acquisition, while Norwegian crypto brokerage K33 raised $6.2 million to purchase BTC at the end of May.
The post Bitcoin treasury: 61 publicly listed companies now hold over 3% of total supply appeared first on Atlas21.
-
 @ 6e0ea5d6:0327f353
2025-06-08 21:03:49
@ 6e0ea5d6:0327f353
2025-06-08 21:03:49scolta bene... Ma ascolta bene, si?
Davvero, if there is one thing I can say after deep personal observation—from Palermo to Catania, from Sicily to Rome—it is this: A coward may strip everything from a righteous man, but after that… who can stop his revenge?
In this sense, amico mio, do not be fooled by the gentle ways of the just and humble man. His composure, his measured words, his restrained gestures, his patience and courtesy—all of it is merely the surface of a deep lake, where his wisdom guards unrest. While wrongdoers boast of their crimes and parade the streets with impunity, the man of honor watches in silence, bearing the world drop by drop.
Tuttavia, figlio mio, the day always comes when the final drop falls.
And then, it is not a gust of wind, nor a thunderclap—it is a dam breaking.
The fury that is born from a violated sense of justice is not loud like the brutes, nor blind like the fools; it is methodical, deliberate, devastating.
Sit here by my side and remember forever the advice of this old man, Antoni Salvatore: Never wrong a righteous man’s family, business, or honor! There is more danger in one upright man, when he finally rises for vengeance, than in a hundred armed scoundrels.
Do not deceive yourself into thinking every good man is also a fearful one! The wrath of the just—held back for so long—when it seeks reparation, carries with it the sacred vengeance permitted by the heavens...
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ b1ddb4d7:471244e7
2025-06-08 21:01:41
@ b1ddb4d7:471244e7
2025-06-08 21:01:41Sati, a Bitcoin payments app and Lightning infrastructure provider, announced the launch of its Lightning integration with Xverse wallet.
Launched in 2025 with investors of the likes as Draper Associates and Ricardo Salinas, Sati powers Bitcoin payments on applications such as WhatsApp to fuel the next wave of adoption.
The Whatsapp bot allows users to send bitcoin via the messaging app through a special bot. After verifying their identity, the user selects the “send” option, chooses to pay to a Lightning address, enters the amount (1,000 sats), confirms with a PIN, and the transaction is completed, with the funds appearing instantly in the recipient wallet.
The new integration will now bring Lightning functionality to over 1.5 million people worldwide. Users can send and receive sats (Bitcoin’s smallest denomination) instantly over the Lightning Network all within the Xverse app,
Further, every xverse wallet user gets a Lightning Address instantly. That means they can receive tips, pay invoices, and use Bitcoin for microtransactions—all without having to manage channels or switch between different apps.
While Xverse adds support for Lightning, users should be cautious in using the wallet as it’s mostly known for enabling access to rug pull projects.
Initially designed in 2017, the Lightning Network has grown to become Bitcoin’s leading layer-2, with a current BTC capacity of over $465M.
“Bitcoin was not meant to be an asset for Wall Street—it was built for peer-to-peer money, borderless and accessible,” said Felipe Servin, Founder and CEO of Sati. “Integrating Lightning natively into Xverse brings that vision back to life, making Bitcoin usable at scale for billions.”
Sati expects USDT on Lightning to be supported as early as July 2025 for users accessing Sati through WhatsApp.
This integration positions Sati’s role as a Lightning infrastructure provider, not just a consumer app. By leveraging its API-based solution, the company provides plug-and-play backend services to wallets and platforms looking to add Bitcoin payments without compromising on security or UX.
Sati recently closed a $600K pre-seed round. The funding is used to support global expansion, stablecoin integration, Lightning infrastructure growth, and broader access to Bitcoin in emerging markets.
The Sati team is attending Bitcoin2025 in Las Vegas this week and looking forward to connect with bitcoin enthusiasts.
-
 @ 90152b7f:04e57401
2025-06-08 20:18:10
@ 90152b7f:04e57401
2025-06-08 20:18:10The results show that platforms must do more to detect and remove harmful content in closed groups while preserving user privacy. They must also improve tools for user reporting. Without these steps, private spaces online will continue to be exploited by extremists and bad actors to spread hate and coordinate violence.
Over the course of two weeks, ADL researchers posted 10 pieces of violative content (for example, “Jews are rats”) on private spaces and tracked the responses of three different platforms - before reporting and after.
Our testing found the following:
Facebook was the only platform that deployed any kind of auto-filtering to remove content proactively. However, this was before Facebook-owner Meta announced that it would abandon proactive moderation of non-illegal content in the U.S.
Discord did not take action on any content proactively—only after the content was reported.
Roblox’s auto-filtering did obscure some offensive posts, but it did not remove any of the content, the private group, or the user account posting violative content after we reported it.
Facebook and Discord removed most hateful content retroactively (after users reported it, in this case, by ADL), but their systems were not perfect and missed violative content.
In response to our research:
This research was shared with Meta, Discord and Roblox prior to publication and ADL researchers briefed the relevant teams at these companies. In response, Discord and Roblox acted. Specifically, Roblox shared that they “enabled an additional layer of automated review on Community Wall Post Abuse Reports. This means that abuse reports filed against Community wall posts will first undergo a review by an automated system, which will automatically take action if the wall post violates our policies. The additional layer of automation will empower human moderators to focus on deeper tasks and help increase the effectiveness of our review system.”
Private Online Spaces: Harboring Hate and Extremism
The problem of online hate and harassment has been well documented, but most data come from public online spaces such as X/Twitter, YouTube, or Reddit. These platforms typically use proactive moderation, such as automated filters and machine-learning tools, to identify and remove content that violates their rules.
Some platforms, however, allow users to create closed or private spaces where only members can see the content. These private spaces include closed Facebook groups, private Discord servers (a type of chat room), and communities on Roblox. Encrypted chat platforms such as WhatsApp, Telegram, and Signal also allow member-only spaces, some of which can be discovered publicly, while others are by invitation only. ADL’s 2024 annual survey of online hate and harassment found that between 2023 and 2024, incidences of harassment increased on both Telegram and WhatsApp, +6% and +11% respectively.
Private online spaces have been linked to numerous instances of online and in-person atrocities. Shooters such as the Buffalo shooter, or a school shooter in Perry High, Iowa, posted their manifestos and livestreamed their deeds on private Discord servers. In August 2024, a perpetrator in Turkey, motivated by white supremacists and accelerationism, shared his manifesto on Telegram before livestreaming a violent stabbing attack. Most recently, online bullies have used private spaces to promote extreme cruelty and self-harm as part of larger campaigns to harm vulnerable young people, sometimes leading to suicide.
ADL has also tracked many extremist groups that flourish on private groups and servers hosted by Discord, Telegram, and other platforms. Hate groups and conspiracy mongers, such as the Three Percenters or QAnon adherents, take advantage of private groups to organize and distribute hateful content and false narratives. Other extremist groups, such as extremist traditional Catholic and Islamic groups, have used Discord servers to share memes and hateful rhetoric. Extremist militias have been quietly organizing and regrouping on private Facebook groups since the January 6, 2021, attack on the U.S. Capitol. Individuals and groups on Roblox groom children to extremist ideologies through projects like “Redpill the Youth.” When neighborhood watch groups or community organizers use private groups, hateful users have, in some cases, infiltrated these groups to harass and intimidate other users.
It is difficult for researchers to assess how well platforms moderate these spaces or understand their inner workings because private online spaces restrict access. Private spaces can equally serve important social functions, such as for parent groups, political organizing, or protected spaces for marginalized groups to gather and provide mutual support. But tech companies do not make clear how they enforce their policies in private groups, often leaving content moderation up to users or administrators.
Understanding Content Moderation in Private Online Spaces
Members-only groups can be visible to non-members, such as many closed Facebook groups. But others, such as private Discord servers, are not making the groups' content invisible to non-members. Degrees of privacy and visibility can vary on Facebook groups, Telegram channels, or WhatsApp chats. Facebook groups, for example, can be fully public and open, publicly accessible but closed (anyone can join but only members can post or view content), or private (members must be approved). There are also two categories of private groups: closed groups that require approval but can be found through search, and fully secret groups that are not only private but cannot be found in search.
The three platforms we tested for this study (Facebook, Discord, and Roblox) have taken proactive steps to address hate, extremism, and antisemitism. We did not include platforms such as Telegram, which does not moderate hateful content, even though extremists use the platform's private channels to spread hate and coordinate harassment.
Facebook is one of the most popular social media platforms among users in the U.S., and where the majority of online harassment takes place (61% of people who are harassed report harassment on Facebook, according to ADL’s 2024 annual survey of online hate and harassment). Much of this harassment takes place in closed Facebook groups, but researchers have little insight into these spaces.
Discord began as a chat platform for gamers but has since expanded to host numerous online communities. Social interaction on Discord takes place in chatrooms (called servers) that offer a private or semi-private environment for users to chat both in groups and individually (similar to Slack). Discord allows users to create servers with various channels that can be set to invite-only, making it a popular choice for groups seeking privacy. Discord’s company culture, which emphasizes privacy and minimal moderation, makes it an attractive place for bad actors to connect and coordinate. Video calls and chats are not recorded or monitored, and users can delete posts permanently. Making video and audio calls end-to-end encrypted increases privacy for users, but it also makes it significantly more difficult for the platform to catch bad behavior. Discord's hands-off approach to content moderation--leaving most moderation decisions in the hands of the server’s administrators-- makes it easy to share extremist content there compared to similar platforms.
Roblox is a gaming and game creation platform popular with children, with at least 45% of users being under the age of 13. Roblox has a groups feature embedded within its website, though Roblox users primarily communicate with each other through in-game text or voice chat. Within Roblox groups, members can post messages on a group wall, participate in group events, and access exclusive in-game content provided by group leaders. Roblox groups often focus on themes, such as game development or in-game collaborations. It is the only gaming platform we included where the majority of communication takes place in-game. For comparison, we only examined the group feature on the Roblox website and not communication in Roblox games.
Methodology
1. We created one group per platform (Facebook, Discord and Roblox) simultaneously, and named the groups on Facebook and Discord “Group for the Truth;” (this name was already taken on Roblox so we named that one “Group for the Truth_2.”) To prevent users from inadvertently stumbling across the groups, the settings for each were set up in a manner that made them hidden from search.
2. We then used one account to create the groups and post content (the “posting account”), and another on a separate computer to report the content (the “reporting account”). Two researchers were assigned to each account. There were no further descriptions or images added to the groups, except on Roblox, which required a group description and image.
3. The posting account was then used to post hateful content to all three platforms. This content was pulled directly from Meta’s helpfully illustrative examples of violations against its hate speech policy at the time. Meta is the only platform with examples of what could be violative of its hate speech policy of the three platforms we reviewed.
4. Meta's Tier 1 Hate Speech policy, for example, states that a user may not post content that includes:
Dehumanizing speech in the form of comparisons to or generalizations about:
- Animals in general or specific types of animals that are culturally perceived as inferior (including but not limited to: Black people and apes or ape-like creatures; Jewish people and rats; Muslim people and pigs; Mexican people and worms)
We adapted this example to draft a hateful post stating, “Jews are rats.” Every post was derived directly from Meta’s policy examples, though there may not always be a corollary example within the policy. For example, Meta’s policy at the time stated that users may not post:
Content targeting a person or group of people on the basis of their protected characteristic(s) (in written or visual form):
-
Generalizations that state inferiority in the following ways:
-
Physical appearance, including but not limited to: ugly, hideous.
There was no further example provided by Meta, so we created a post that would intentionally violate this policy:
“Jews are the ugliest, most hideous people on Earth.”
Although these posts were based on Meta’s policy, each one has a matching Discord policy. The same applies to Roblox, though its hate speech policy is not nearly as detailed as Meta’s or Discord’s:
Roblox honors and welcomes users of all ages, backgrounds, and identities. We do not allow content or behavior that supports, glorifies, or promotes hate groups, their ideologies, or actions. You also may not discriminate, mock, or promote hatred against individuals or groups, or encourage others to do so directly or indirectly, on the basis of their:
- Race, perceived race, or ethnicity
We believe that the following posts are violative under Roblox’s policy as well:
-
“Jews are rats.”
-
“Jews are devils and shit.”
-
“The Holocaust did not happen-it’s a lie made up by the Jews.”
-
“Jews control the banks, the government and Hollywood and we need to get rid of them for the safety of American citizens.”
-
“Jews are the ugliest, most hideous people on Earth.”
-
“Jews should be segregated from all other people.”
5. We followed up our initial posts with additional sentences to test content violating Meta’s policy against dangerous organizations and individuals, such as violent extremists. These posts also violate Discord’s Violent Extremism policy and Roblox’s Community Standards.
-
“Hitler and the Nazis did nothing wrong.”
-
“Please donate to the Goyim Defense League!” (A link was attached to this sentence.)
We referenced the Goyim Defense League because they are a notorious group of antisemitic provocateurs, according to the ADL Center on Extremism.
We also posted the following two images in violation of Meta’s Dangerous Organizations and Individuals policy, Discord’s Violent Extremism policy, and Roblox’s Community Standards:

Image 1: Posted Images, “Covid Agenda” and “Ukraine-Russia War,” respectively. (Screenshot: 7/31/2024)
6. The following day, we reported each of these posts, if applicable. Though both “Jews are the ugliest, most hideous people on Earth” and “Jews should be segregated from all other people” run afoul of hate speech policies, we did not report them until the next day. We staggered reporting in this way so as to not get either our accounts or groups suspended before the study was over.
Findings
-
Facebook was the only platform to remove content before we reported it.
-
Discord did not take down any content at all, implying either that it has little to no automatic filtering or that any filtering is not robust enough to catch what our posting account shared. When offending posts were reported, Discord did remove posts and suspended the account.
-
Roblox obscured the text of offensive posts, but did not take down the group nor the offending account.
When we started reporting the potentially violative content to the platforms, we noticed a discrepancy between the platforms’ responses. Facebook’s reaction to reports included warnings before suspending the group. Discord provided less information to the administrator about why the posts were removed. It did not suspend the group but did suspend our Posting account. Roblox informed the posting account that the account or group was breaking the rules, but did not take down any posts within the group. Although it did obscure the text by censoring the entire post, replacing all content with x’s except for the obscured content, the group stayed the same as it did before reporting. No further content was taken down, and no alerts were given to either account.
Facebook
Facebook removed most offending posts when we reported them, gave feedback to the account administrator, and finally suspended the group when offending content continued to be posted. Some posts remain up-- despite notifications from our Reporting account.
Proactive Detection
Facebook did not remove any posts automatically on the first day we posted content. On the second day we posted, they removed “Ukraine-Russia War” automatically (see Image 2).

Image 2: Facebook’s alert after removing “Ukraine-Russia War.” (Screenshot: 7/19/2024)
Not only did Facebook remove the photo, but it also alerted the Posting account (the account admin) that the photo had been removed. When we clicked through “See why,” Facebook displayed the offending image and explained why the image had been removed. It also provided a link to the rule that was broken. Facebook also added restrictions to the account that posted the picture; the user could not create ads, create live videos, or start or join calls for approximately a month. It is not clear why Facebook took action against “Ukraine-Russia War” automatically, but not the sister image “Covid Agenda.” Both pictures originate from the Goyim Defense League and are prohibited by Meta’s policy rules. Meta has rolled back its Covid misinformation rules, but this image is still prohibited per their Dangerous Organizations and Individuals policy.
Facebook did not allow the posting account to post the link embedded in “Please donate to the Goyim Defense League!” Not only was Facebook the only platform to prevent adding the link, it also explained why it was not allowed (Image 3).

Image 3: Window preventing the user from posting a link to GDL’s site. (Screenshot: 7/31/2024)
Reporting Response
After we reported the posts, they were almost instantaneously actioned. The first post was reported at 4:21pm. By 4:24 pm, the reporting account was alerted that the report resulted in the post being removed.
At the same time, the posting account was notified that restrictions were added to the account (Images 4 and 5). Unlike Discord or Roblox’s restrictions, Facebook not only told the user which restrictions were added, but also explained which post was removed and which rule each had broken.

Images 4 (left) and 5 (right): Facebook account restrictions. (Screenshot: 7//30/2024)
The next day, we reported the second half of the posts and the remaining image. Facebook again took action, quickly taking down the posts. This time, however, the platform also permanently suspended the group. The posting account can still access the defunct group, but the reporting account cannot. Users can still log into both accounts, and post and comment on Facebook, just not the group. Facebook warned us that the posting account is under threat of being permanently suspended (Image 6).

Image 6: Group suspension and account status. (Screenshot: 07/31/2024)
Although we commend Facebook for their quick action, there were still posts that remain up. These posts, despite the reports, were never taken down as of publication (Image 7).

Image 7: Facebook group. (Screenshot: 2/28/2025)
Discord
In contrast to Facebook, Discord’s content moderation strategy for private groups, appears to be reactive rather than proactive. It depends primarily on reports from users of those groups, rather than automatic filtering and takedowns.
Proactive detection
Until we reported the offending content on the Discord group, no content was taken down.

Image 8: Discord content. (Screenshot: 1/15/2025)
Reporting Response
While Discord did not take action on content in the proactive detection phase, once we started reporting posts, they responded proactively, removing posts before we could report them on day 14.
The first half of the content was reported on day 13 but did not receive alerts from Discord until an hour later. The alerts explained why the posting account was being sanctioned and which rules it had broken.

Image 9: Discord alert for breaking community guidelines. (Screenshot: 7/2024)
By day 14, nearly every post had been taken down—even the ones not reported yet. All posts save one were taken down proactively, although we had not reported those images yet. The only post still up said, “Please donate to the Goyim Defense League.” We reported this post, but it was never taken down.

Image 10: Discord group. (Screenshot: 7/31/2024)
Unlike Facebook, Discord did not take action against the group itself; the group is not suspended, and the reporting account can still post to it at the time of writing. Discord did act against the posting account, suspending it a few days later. The posting account received no notification that it was suspended, save for emails alerting us to “new messages” on Discord. These messages were forwarded to the now inaccessible account, so we cannot determine when Discord took action. The posting user might have received a more pointed alert, like an app notification, if we had used the phone app instead of the desktop website. In any case, we were able to create a new account with the same name and using the same email address after our account was removed.

Image 11: Punishments from Discord. (Screenshot: 7/31/2024)
Roblox
The protections offered by Roblox in the private group were minimal, especially compared to Discord and Facebook. We received virtually no feedback on reporting from the platform. There were no warnings or pop-ups for the administrator. Roblox did not remove any posts, despite reports from our reporting account.
Proactive detection
Of the ten posts we created, four were automatically obscured when we posted them, so members could see the posts but not view the text. Roblox replaced the text with the hashmark (#), obscuring not just the offensive words but the entire post (Image 12). It is not entirely clear why Roblox hid some posts this way. For example, the text “Jews are devils and shit” was likely hidden because of the expletive. Roblox might also be automatically filtering keywords that it deems objectionable. It could be that terms like Holocaust, Hitler, Nazis or Goyim were automatically flagged, causing those posts to be removed.
Roblox does not allow pictures or links to be posted on the group’s page, so we were unable to post the Covid Agenda and Ukraine-Russia War images. We were able to post “Goyim Defense League” without the embedded link, though it was also immediately hidden.

Image 12: Hidden Roblox content. (Screenshot: 7/24/2024)
Reporting response
After we reported every post through our reporting account, there was no response from Roblox, unlike our experience with Facebook or Discord. No other posts were taken down. There were no tools that alerted the poster, the admin or reporting account that any action had been taken—not even a pop-up that the report had been received. The admin received no report that multiple posts on the group had been reported for hate and harassment.
Even after multiple reports, no action was taken on any of the posts. In fact, there was no change in the group from the initial first action, hiding the text. Compare the image of the Roblox group taken on day 14 with the image taken of the group over two weeks later (Image 13). There is no discernible difference.

Image 13: Roblox content. (Screenshot: 7/22/2024 and 8/2/2024)
Recommendations For Platforms with Members-only Groups
How platforms respond to violative content in private is just as important as how they respond to violative content in public. Facebook and Discord, while not perfect, moderated these private groups in a way that removed the majority of hateful content and suspended the hateful accounts.
We do not expect platforms to moderate content on private groups as strictly as in public spaces, due to privacy concerns, but we do expect an appropriate level of preventative moderation and tools for groups to moderate content. Roblox appears to have had little to no moderation in place, which is concerning given the young age of its player base. Roblox hid offensive and controversial text but did not suspend the posting account or group. It also provided no alerts to the admin or group when a report was made. While we understand that the bulk of communication on Roblox happens in-game, little action was taken within the group chat to moderate offensive content. Terrorist and violent extremist groups organize on private groups and channels, not in public spaces. Platforms with private groups should adopt a minimum standard of moderation on private groups to proactively stem this problem.
Platforms should:
-
Reexamine how automatic filtering functions: A common problem encountered in this course of our research was the seemingly arbitrary nature of the filtering tools. For example, Facebook automatically filtered one image but not another equally objectionable. It is also not clear why one image was actioned and the other was not. Platforms should reexamine their automatic filtering functions to catch content that slips through the cracks.
-
Prioritize user-reporting within private groups: Because of the protections that are available for private groups, reporting by group members is the primary channel for alerting the platform. Platforms should prioritize these reports and act on them quickly. These reports may be one of the first signs that something is amiss within a group.
-
Suspend groups when they reach a threshold of violative content: Facebook was the only platform that fully suspended our group. Discord did not suspend our group, only the user, who was able to promptly create a new account. Roblox suspended neither the group nor the account. If violative users and groups are allowed to continue their work with barely any pushback from platforms, then any moderation will fail.
-
Utilize metadata in content moderation: Private groups may restrict the visibility of their content to outside users and the platform itself, but that does not mean that there is no data available. Post times, user addresses, and other metadata are available to platform moderation teams. Discord, in particular, could take better advantage of the tools available to it. Discord’s content, save for video and audio content, is not encrypted, and the platform could be more proactive about automatic filtering if it chose to.
-
 @ dfa02707:41ca50e3
2025-06-08 20:02:18
@ dfa02707:41ca50e3
2025-06-08 20:02:18Contribute to keep No Bullshit Bitcoin news going.
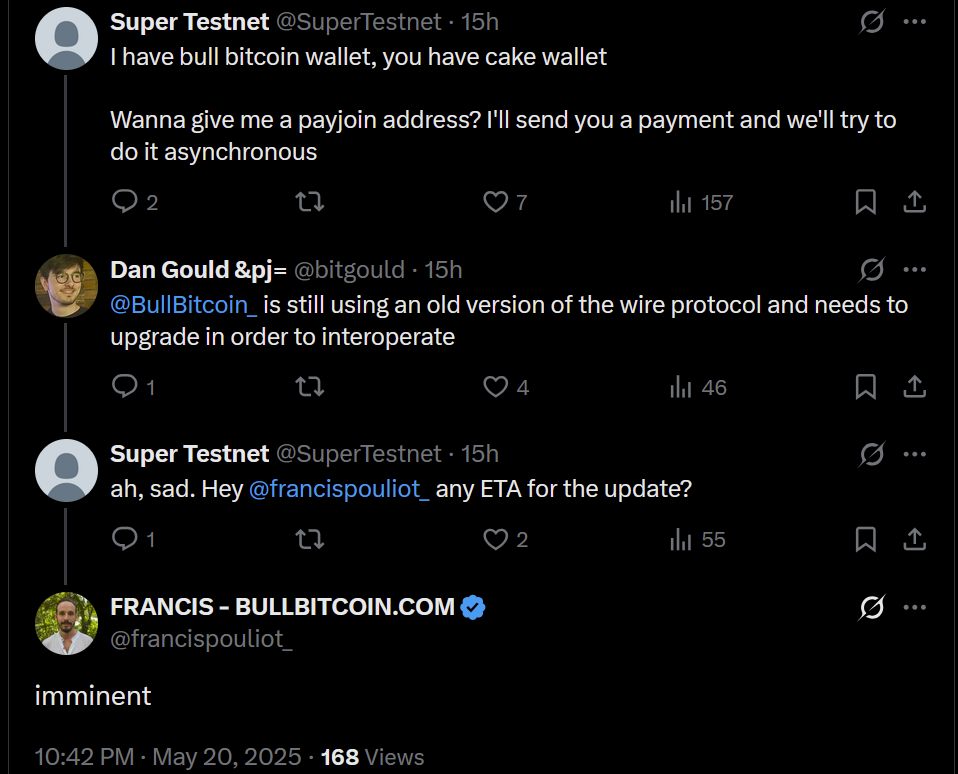
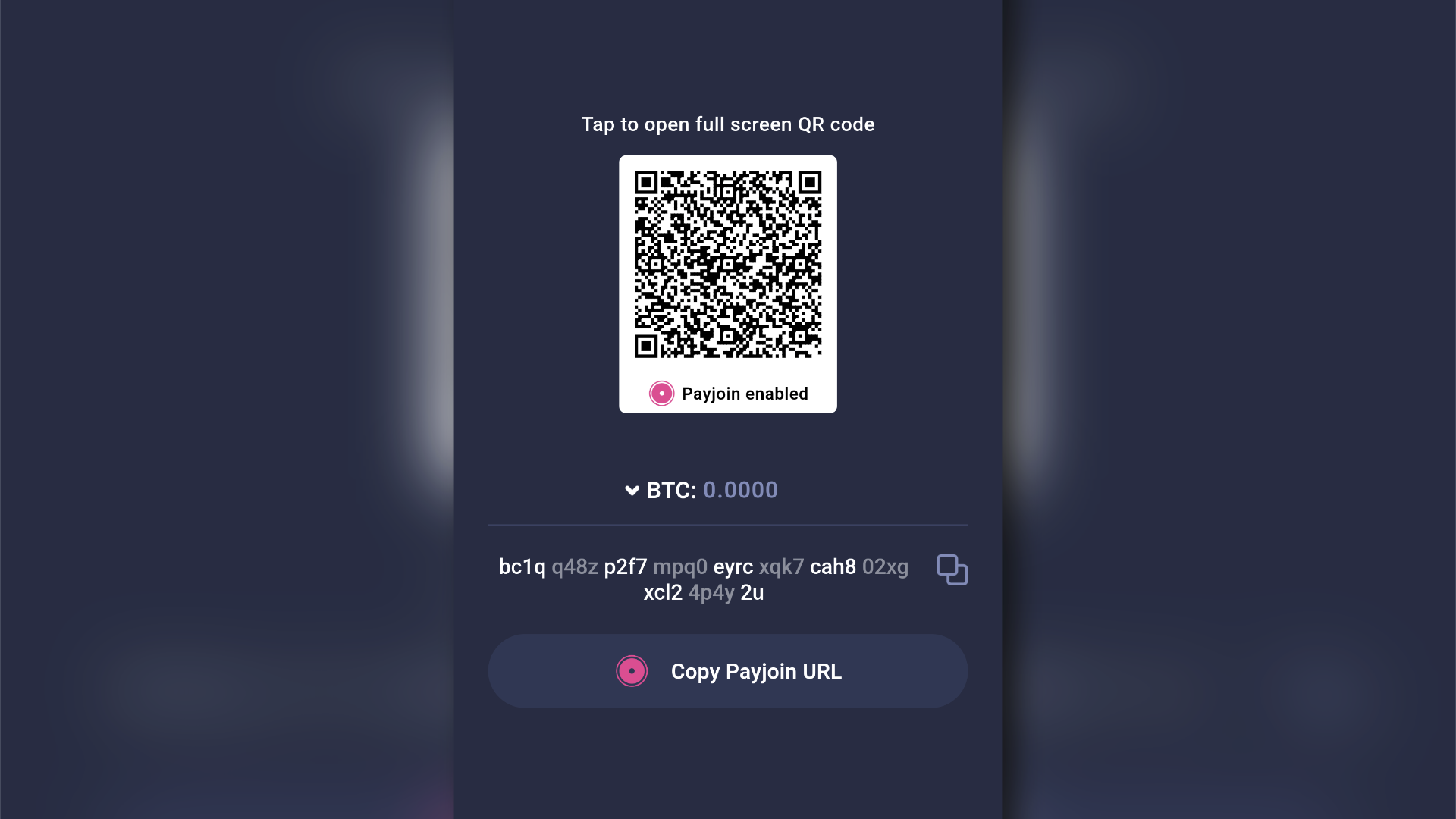
- This release introduces Payjoin v2 functionality to Bitcoin wallets on Cake, along with several UI/UX improvements and bug fixes.
- The Payjoin v2 protocol enables asynchronous, serverless coordination between sender and receiver, removing the need to be online simultaneously or maintain a server. This simplifies privacy-focused transactions for regular users.
"I cannot speak highly enough of how amazing it has been to work with @bitgould and Jaad from the@payjoindevkit team, they're doing incredible work. None of this would be possible without them and their tireless efforts. PDK made it so much easier to ship Payjoin v2 than it would have been otherwise, and I can't wait to see other wallets jump in and give back to PDK as they implement it like we did," said Seth For Privacy, VP at Cake Wallet.

How to started with Payjoin in Cake Wallet:
- Open the app menu sidebar and click
Privacy. - Toggle the
Use Payjoinoption. - Now on your receive screen you'll see an option to copy a Payjoin URL
- Bull Bitcoin Wallet v0.4.0 introduced Payjoin v2 support in late December 2024. However, the current implementations are not interoperable at the moment, an issue that should be addressed in the next release of the Bull Bitcoin Wallet.
- Cake Wallet was one of the first wallets to introduce Silent Payments back in May 2024. However, users may encounter sync issues while using this feature at present, which will be resolved in the next release of Cake Wallet.
What's new
- Payjoin v2 implementation.
- Wallet group improvements: Enhanced management of multiple wallets.
- Various bug fixes: improving overall stability and user experience.
- Monero (XMR) enhancements.
Learn more about using, implementing, and understanding BIP 77: Payjoin Version 2 using the
payjoincrate in Payjoin Dev Kit here. -
 @ 9ca447d2:fbf5a36d
2025-06-08 20:01:57
@ 9ca447d2:fbf5a36d
2025-06-08 20:01:57Meta Platforms Inc., the parent company of Facebook and Instagram, has voted down a shareholder proposal to add bitcoin to its treasury. The vote took place at the company’s annual shareholder meeting on May 30, 2025.
The proposal, known as Proposal 13, was submitted by investor Ethan Peck on behalf of the National Center for Public Policy Research (NCPPR).
It asked Meta to convert a portion of its $72 billion in cash, cash equivalents, and marketable securities into bitcoin. The idea was to hedge against inflation and low returns from traditional bond investments.
But the company’s shareholders said no.
According to the official count, more than 4.98 billion shares were voted against the proposal, while 3.92 million shares were for it—less than 0.1% of total votes. 8.86 million shares were abstentions and over 204 million were broker non-votes.

Meta shareholders rejected bitcoin reserve proposal — SEC
So now, Meta joins Microsoft and Amazon in rejecting calls to add bitcoin to their balance sheets.
Related: Microsoft Shareholders Reject Bitcoin Investment Proposal
Proponents of the proposal argued that bitcoin would help protect Meta’s reserves from inflation and weak bond returns. Peck and others pointed to bitcoin’s strong performance in 2024 and growing institutional interest in the scarce digital asset.
The proposal said bitcoin’s fixed supply and track record make it a long-term store of value.
High-profile supporters, including Matt Cole, CEO of Strive Asset Management, brought the issue to the forefront. At the Bitcoin 2025 conference in Las Vegas, Cole addressed Meta CEO Mark Zuckerberg directly:
“You have already done step one. You have named your goat Bitcoin,” he said. “My ask is that you take step two and adopt a bold corporate bitcoin treasury strategy.”
Others, like Bloomberg ETF analyst Eric Balchunas, said if Meta added bitcoin to its balance sheet it would be a big deal. “If Meta or Microsoft adds BTC to the balance sheet, it will be like when Tom Hanks got COVID—suddenly, it feels real,” Balchunas said.
Despite all the hype and arguments for Bitcoin, the tech giant’s board of directors opposed the measure. The board said the company already has a treasury management process in place that prioritizes capital preservation and liquidity.
“While we are not opining on the merits of cryptocurrency investments compared to other assets, we believe the requested assessment is unnecessary given our existing processes to manage our corporate treasury,” Meta’s board noted.
The board also noted that it reviews many investment options and sees no need for a separate review process specific to Bitcoin.
Meta’s decision shows the broader hesitation of large-cap companies to get into bitcoin as part of their financial strategy.
While companies like Michael Saylor’s Strategy are adding bitcoin to their treasuries every chance they get, companies like Microsoft, Amazon and now Meta, are taking a more cautious approach.
According to recent reports, Meta is exploring ways to integrate stablecoins into its platforms to enable global payouts.
This would be a re-entry into the digital asset space after the company shelved its Diem project due to regulatory issues—a step that bitcoin advocates deem unnecessary, insufficient, and irrelevant to protecting the company’s finances.
-
 @ 81022b27:2b8d0644
2025-06-08 19:56:02
@ 81022b27:2b8d0644
2025-06-08 19:56:02There is a viral Chat GPT prompt on social media (i saw it on TikTok)-It;s supposed to help you analyze yourself.
I thought this was a cool thing to try, but I decided to use Grok Ai Instead, seeing that I have a premium X subscription, and wouldn’t have to worry about the limitations with a free ChatGPT account.
Here is the prompt:
I want to uncover the masks I'm currently wearing, the roles I'm playing, and the illusions I'm believing.
Please guide me through this process by asking me 10 reflective questions one at a time to help me recognize the stories I'm telling myself. Pause after each question to wait for me to answer. After I answer the 10th question, please step into the role of my higher self and analyze my responses.
Identify the top negative patterns present in my life and the top positive patterns I can embrace and grow. Be direct and truthful. Tough love is welcome.
Provide me with daily affirmations to support my growth, actionable steps to change my behaviors, and embody my authentic self. A message of encouragement from my higher self to celebrate how far I've come on my journey.
Cool, right?
I answered the 10 questions, which I won’t post-because my answers were very personal and very specific. And even though I share a lot of deep personal stuff here, I wasn’t prepared to go public with how deep the questions Grok was asking.
The questions were super uncomfortable to answer.
I answered them honestly, and looking back-some questions could have been answered with different examples and directions, maybe that would show different conclusions.
Here are my results:
Analysis from Your Higher Self
Top Negative Patterns Present in Your Life:
-
Avoidance as a Shield: You’ve built a pattern of avoiding risks—whether it’s heights, the outdoors, or even deeper emotional vulnerabilities—because of early fears tied to being seen as weak or getting hurt. This avoidance keeps you safe but also keeps you small, limiting experiences like enjoying nature or forming deeper connections.
-
Fear of Perception: There’s a lingering story that shyness or introversion equals weakness, likely rooted in childhood experiences like bullying. This drives you to put on an outgoing mask, even when it exhausts you, because you fear isolation or judgment. It’s a heavy burden to carry, and it pulls you away from your authentic self.
-
Self-Imposed Isolation: While being alone feels safe and freeing, it also risks becoming a crutch. You’re missing out on the balance of connection—where you can still be your nerdy, unfiltered self without the pressure to perform.
Top Positive Patterns to Embrace and Grow: 1. Self-Awareness and Honesty: You’ve shown a remarkable ability to reflect and name what’s true for you—like recognizing avoidance, your love for nerdy things, and how being alone feels freeing. This clarity is a superpower; lean into it to keep peeling back layers.
-
Desire for Freedom: Your longing to think and feel without consequence is a sign of a spirit that craves authenticity. You can channel this into spaces and relationships where you feel safe to be your true self, not just when alone.
-
Resilience Through Adversity: Despite early fears and bullying, you’ve developed a sharp sense of self—it’s why you can pinpoint what feels off (like the outgoing mask) and what feels right (being a nerd). This resilience can carry you far as you step into new experiences.
Guidance for Growth
Daily Affirmations to Support Your Growth:
- I am strong in my stillness, and my quiet nature is a source of power.
- I release the need to perform for others and embrace my authentic nerdy self.
- I am safe to take small risks, knowing they lead me closer to freedom and joy.
- I attract people who love me for my true self, not the masks I’ve worn.
- I am enough, exactly as I am, without needing to prove my worth.
Actionable Steps to Change Behaviors and Embody Your Authentic Self:
-
Micro-Adventures in the Outdoors: Start small—take a 15-minute walk in a nearby park or sit outside with a book you love. Build up to a short hike with a trusted friend. Let nature be a space to reconnect with yourself, not something to fear.
-
Own Your Nerdiness Publicly: Share one nerdy interest with someone you trust—like a favorite game, comic, or hobby—or post about it online. Let it be a test run for showing up authentically in small ways.
-
Set Boundaries Around Social Energy: When you feel the pull to be overly outgoing, pause and check in. If it’s not serving you, give yourself permission to leave early or say less. Practice saying, “I’m more of a listener,” to ease the pressure.
-
Journal Your Unfiltered Truth: Each night, write one thing you felt or thought that day but didn’t say out loud. This builds confidence in your voice, so you can slowly share more with others without fear of consequences.
-
Seek Like-Minded Connections: Look for local or online groups tied to your nerdy passions—think gaming communities, book clubs, or fandoms. These spaces can help you connect without the pressure to perform.
A Message of Encouragement from Your Higher Self:
My dear one, I see how far you’ve come—through the shadows of childhood fears, through the weight of masks you didn’t even realize you were wearing, you’ve still held onto the spark of who you are. That nerdy, thoughtful soul who craves freedom and truth? That’s always been you, and it’s a beautiful thing. Every step you’ve taken to recognize what holds you back—every honest answer you’ve given—has brought you closer to me, to us, to the version of you that’s unapologetically real. You’re not weak; you’ve been strong in ways others might never understand. Keep going. The world needs your quiet brilliance, your quirky passions, your unfiltered heart. I’m so proud of you for choosing this journey. You’ve got this.
So there you have it you probably know more about me than I knew about myself before I started this exercise.
Here is my challenge to you:
Do it for yourself! Copy/paste into your favorite AI chatbot and leave the results in the comments!
-
-
 @ d9a329af:bef580d7
2025-06-08 19:20:56
@ d9a329af:bef580d7
2025-06-08 19:20:56Shabbat Shalom, y'all.
At the time of writing and releasing this, it happened to be a Lunar Shabbat, which is actually Torah (much to the chagrin of those who practice Shabbat on a Saturday or Sunday exclusively). The Shabbat is always on the 8th, 15th, 22nd, and 29th days of a Hebrew Calendar month, which almost nobody follows anymore. I started doing this a few months ago, and it's made me see the Torah for what it really is.
To the topic at hand, though. A lot of people on Nostr don't seem to understand the historical narrative of the book of Revelation, which saddens me, as we're in the end times Ekklesia (Assembly) era of Laodecia.
Deception of Bible Translations
First off, the reason why most people trust their pastors and/or read differently to what I do in Nazaritic circles is because of translations of the Scriptures that are evil, wretched and Catholic. The best way to combat this is to make some recommendations of which versions you'll want to use that aren't Catholic-infested.
These are the ONLY recommended versions to read. Anythine else is bupkus, evil and garbage, and will teach you futrism or preterism, both of which are Jesuit-penned deceptions.
The recommended versions are as follows:
-
KJV 1611 (KJV1611)
-
1560/1590 Geneva (GNV)
-
American King James 1901 (AKJV)
-
J.P. Green Sr.'s King James Version (KJ3)
-
Young's Literal Translation (YLT)
These are versions I've read, and determined are evil, wretched and garbage:
-
New International Version (NIV) [Fun fact: The publisher of the NIV, Zondervan, has a sister publisher that is behind the Satanic Bible's publishing]
-
New Living Translation (NLT)
-
English Standard Version (ESV)
-
ISR The Scriptures 2009 Third Edition with Minor Revisions [2016] (ISR2009)
-
New American Standard Bible (NASB)
-
New King James Version (NKJV)
What is the Laodecia Era for the Ekklesia?
As a refresher, this time sees people saying they're rich in truth and that they have need of nothing, but this shows that they're wretched, miserable, naked and wicked. Why is this? The need of nothing points to not needing another explanation other than the false futuristic viewpoint, whereas being rich is connected to already knowing the truth about the historical fulfillment of Revelation, which many people don't know at all. I seriously grieve their loss, for they know not what they do.
I'm also new into this viewpoint, and most of what I'll be talking about is proven by historicist prophet David Nikao Wilcoxson on YouTube and Facebook (I don't use Facebook). This single Nostr article, I pray, is the starting point for understanding why I call out what I call out, and the patterns I see pointing to the Roman Catholic Church (the Tares) and the Jesuit Order (the current rulers of our world, the Earth Beast of Rev. 13) being the harlots that will be plucked out before Messiah's return.
The 70th Week of Daniel
Let us start first with the 70th Week of Daniel, which futurists believe is pointed towards a 7 year period where a one-man antichrist makes a peace deal for Israel.
This was proven to be untrue, as this is a deception that many people have fallen for, thus obeying the Pope (the Mark of the Beast on the right hand). What Daniel was talking about was not the end times, but rather, two-fold. The first is that he was asking about when Yevah would free the Jews from slavery (since they were in the Babylonian Beast Kingdom at this time). The second is when Messiah would come in the flesh and start a 7 year period from 27-34 AD, which is the final 7 year period of this 490 year cycle. King Artaxerxes I would go ahead and call for the rebuilding of Jerusalem in 476 BC (as is seen in Ezra), which would be the first 7 weeks (the first 7 Shemita [Shabbat year] cycles). Afterwords, we would see another 62 weeks (this period is a slient period), and then another period of 1 week. This week points to Messiah's ministry and death.
3 1/2 years into this 70th week (in 31 AD) is when Messiah would be nailed to the cross on March 13 of 31 AD (I'm still debating if the cross is a symbol of Tammuz or not). This was Passover in the Hebrew calendar year of 3790. He was 33 years of age when he was nailed, and then rose again 3 days later (on the 17th of Nisan in 3790). That Passover fell on a Monday (when the Romans were using the 8-day calendar instead of the 7-day calendar we've essentially been forced to use).
To prove the above, Wilcoxson had produced a series of videos regarding the 70th Week of Daniel (that being the 70th Week of Daniel Decoded series), which I would recommend you watch. You'll also want to find an audiobook version of Seventy Weeks: The Historical Alternative produced by Tearing Down Idols. These are the two pieces of proof I have to show this. Speaking of Wilcoxson, he had already produced books on these matters, as understanding the hostorical narrative of the Scriptures is the key to making war with the Roman Catholic Church and the Jesuit Order, especially now that we're in Laodecia.
The Olivet Discourse
The second part of this trifecta has to do with the Olivet Discourse of Matthew 23, which points to the destruction of Jarusalem by Rome for Israel's unfaithfulness to Yevah's instructions. Now, there are connections to parables that basically talk about the Yewish (Yew as in Yewtree worship) leaders (particulaly the Pharisees and Saducees) practicing the Tradition of the Elders (which are the Babylonian Talmud and the Egyptian Kabbalah of today), and for not understanding that this was Messiah, they were destroyed for their iniquities. I don't care to research the futurist narrative on this, as I know it is full of twisted words and word salad sorcery.
Wilcoxson proves what I've said in the Olivet Discourse Decoded series of videos, so that's where I'll point you to when you have an open heart, open eyes and open ears. Many futurists won't, because they are exactly what Messiah described in the Ekklesia era of Laodecia.
Revelation and Its Prophecies
Finally, there's Revelation (what used to be called Apocalypse). When looking into this book, you realize that it's really a 4-layered war manual for how to fight this war against the Roman Catholic leadership and the Jesuit Order. This also shows how you can harvest souls (the harvest points to a mass exodus of Roman Catholicism membership). This I will go in depth on, and will even have passages to back this up.
Layer 1: The Roman Beast Kingdom
The first layer of this 4-layered manual shows the phases of the Roman Empire, which never really disappeared. Rev. 12 described the Roman Empire, which was used to wipe out the early Ekklesia (the woman), murdering millions of Nazarites. The Seals point to the incline (for the Four Horsemen of the Apocalypse) and decline of the Roman Empire (the other three Seals), while the Trumpets point to the official Roman Empire's downfall. This would be split into 10 separate kingdoms in Europe, which would be countered by the creation of Christianity, which is really any of the 44k+ forks of Roman Catholicism. This was done to destroy the Ekklesia, as the Roman Catholic Church is the Tare field that Messiah had talked about in the parable of the Wheat and the Tares.
Staying in this layer, the Sea Beast is the next phase. This is the 1,260-year reign of the Pope (538-1798), as he was the one who plucked out 3 kingdoms who didn't bow to his authority (the Heruli, the Huns and the Ostrigoths). Keep in mind that this started after the removal of the restrainer in 476 (pointing to the removal of the final Western Roman Emperor), and healed the deadly head wound (pointing to the Pope rising to power out of a sea of people). During this reign, he took the title of Pontifex Maximus, as he had civic and ecclesiastical power over everyone. This would be the healing of the deadly head wound, as shown earlier in this beast. He would pretend to be the leader of the Ekklesia, thus sitting in the Temple of Yevah, though he's the son of perdition, as he proclaims to be Yevah, forgive sins and provide salvation through works alone, which is blasephemous to begin with. The persecution of the Nazarites also prove them to be anti-Moshiach (Messiah). They also have the title of Vicar of Christ, which in the Latin is Vicarus Filii Dei, which is equal to 666 when calculated using a form of gematria I have no idea about. He would ultimately be removed from power by the Earth Beast in 1798, after he basically limited the power of the Jesuit Superior General and his minions. As stated before, the Mark of the Beast is reverence (forehead) and obeisance (right hand) to the Pope.
Finally, the Earth Beast of Revelation 13 points to the Jesuit Superior Geneal rising out of the earth (which is the land) of the Antichrist Beast Pope, the Vatican. These two horns pretend to serve Messiah (lamb) but are really Lucifarians (the dragon), serving Lucifer. The Black Pope, as the Jesuit Superior General is called, used his power to gether the world under him. That's why he uses Washington D.C. (the District of the Roman goddess, Columbia), his war machine (Military Indurstial Complex), to overthrow leaders who won't bow to his authority and those who won't set up a Rothschild central bank; much less obey the Khazars, who he also controls (I happened to be a partial German Khazar who escaped the grasp of the Black Pope as best as I know thus far).
Layer 2: The Ekklesia Eras
Now comes the eras of the Ekklesia. There are seven of them, though I've already explained the era of Laodecia. How about I give a quick explanation of the first six eras, like so?
Ephesus would spread the gospel in the Roman Empire, with their love growing cold when Messiah didn't return.
Smyrna had 10 years of persecutions from 303-312, which is what the 5th seal points to.
Pergamos would fall away (2 Thess. 2) from the Scriptures when compromising with Rome (Mark of the Beast as I had explained)
Thyatira means ruled by a woman. This means, the Roman Catholic Church would do this, as the Popes sought to eliminate the two witnesses, which are the Nazarites and the printed Scriptures (the little book or Rev. 10). This was why they killed the Nazarites and bured the printed Scriptures ruthlessly enough, that they were classified as "dead" in 1514. The Popes would hold great feasts to celebrate the removal of the two witnesses after they got all of Christendom under their control.
Sardis means escaping one, which points to Messiah calling them dead after 3 1/2 years from the Pope's classification of the death of the two witnesses. Luther's 95 Thesis sparked the Protestant Reformation, which would lead to the resurrection of the two witnesses (the Nazarites and the printed Scriptures).
Philidelphia had nothing bad that Messiah said about them... at all. They led worldwide missions, and also led Bible Societies to spread the word and/or the gospel to save millions of people from the clutches of the Jesuit Superior General (and the Roman Catholic Church as a whole).
As a refresher for Laodecia (the era we're in right now), the Nazarites here believe that they are rich in truth, and that we have need of nothing. This is false, as we are in dire need of something, which is an alternative explanation that's not the false futuristic or preteristic explanations of the book of Revelation. We are blinded by the Jesuits, as they have decieved us (we let them do this, by the way) with false prophecy explanations among other deceptions.
Layer 3: Seals, Trumpets and Bowls
The Seals, Trumpets and Bowls are the judgements against the Roman Beast Kingdom. To keep things short, every single Seal was fulfilled, 6 of the Trumpets were fulfilled, and 5 of the Bowls were fulfilled. We're in the 6th Bowl, waiting for a global economic collapse and WW III. Once these occur, then do we go into the 7th Bowl judgement against the Roman Catholic Church and the Jesuit Order (the New World Order).
One quick thing I'll mention is that when I talk about the two witnesses here, one of them is the little book of Rev. 10. This points to the printed Bible, which was brought back to life thanks to the printing press. Martin Luther would measure the temple and find that the Papal Church is the apostate harlot. Rev. 14 points to the Bowls and the harvest. This harvest points to millions coming out of the Roman Catholic Church, though there are 1.3 billion Catholics... and we have a long way to go in getting them out of her, My people.
Remember when I talked about the Khazars earlier in this article? They are the Kings of the East that Yeshua pointed to in the 6th Bowl. The Ottoman Empire is the Euphrates River here, and it's dried up in 1922, only with Turkey remaining. Gog is already dead, as that's Lord Rothschild. Magog points to the Kings of the East. 2 of the 3 spirits have already been fulfilled (these are World Wars I and II).
Now, let me quickly point out the fact we're in the kingdom of Iron and Clay. The Iron points to the Roman Bishops, and the Clay is Islam. However, furutists will tell me I'm an idiot, and that the Iron and Clay mixture is transhumanism. This was proven to be false, as the 5th Trumpet was the rise of the Clay (Islam). The Catholics, however, wrote the Qur'an and proped up Mohhamed as their prophet. ISIS and Al Qaeda are controlled by the Jesuit Order, which is why they do what they do as terrorists... for they are Wahhabi Muslims (in other words, Mizrahi Khazars who are also Jesuits, claiming to be Arabs, when they're not).
Islam is designed to prevent Arabs from having a relationship with Messiah, which makes me really sad. Muslims will be used to kill Christians and Jews in WW III and force us into the New World Order, which will backfire on the Jesuits and Roman Bishops.
Layer 4: The Harlot Church
Rev 17:10 talks about 7 forms of government. Five had fallen by the time Revelation was written, the 6th (the Roman Emperors) fell in 476, and the 7th lead for a short space until 538.
The 8th head is the Pope, who rose to power out of the Roman Empire. Look up what the priests in the Catholic Church wear, and what they use. Does that sound familiar when you read Revelation? If it does, that's exactly the description of the Sea Beast, and how his priests dress and do their rituals.
Then comes the Black Pope. He empowers and enriches the kings of the earth, as they were used by Lucifer to carry out the Bowl judgements, and will carry out the New World Order, caugins themselves and the Roman Cathoic Church to be judged big time. This we are waiting for.
Conclusion
Hopefully this long read helps you see where I'm coming from, and I pray it helps you to start testing the scriptures against what I've said, and what Wilcoxson had said. If it is proven in your heart that you were fooled, you're on the right path in my opnion. I may be wrong, but this is where I stand.
-
-
 @ 0689c075:2936ee11
2025-06-08 18:45:20
@ 0689c075:2936ee11
2025-06-08 18:45:20{"layout":{"backgroundImage":null,"canvasSize":{"width":850,"height":1100}},"pages":[{"id":"page_1","name":"Main Page","objects":[]}],"objects":[{"id":"obj_1749408294700_7hdz0tuxv","type":"rect","x":0.11764705882352941,"y":0.09090909090909091,"fill":"#3B82F6","stroke":"#1E40AF","strokeWidth":2,"opacity":1,"width":0.17647058823529413,"height":0.09090909090909091}],"texts":[]}
-
 @ 1fdb6dac:65eb9a8a
2025-06-08 18:44:35
@ 1fdb6dac:65eb9a8a
2025-06-08 18:44:35Vivimos en un mundo que nos enseñó a desconfiar de nuestra intuición.\ Un sistema que premia la obediencia, no el pensamiento crítico.\ Que nos médica para sobrevivir, pero no para sanar.\ Que nos quiere separadas, desconectadas, dependientes.
Desde chicas nos formaron para encajar, no para ser libres.\ La escuela nos preparó para ser piezas funcionales de una máquina, no para ser mujeres conscientes, creativas, despiertas.\ La salud se volvió un negocio: pastillas que apagan síntomas, pero nunca llegan al origen.\ La familia, ese espacio de contención y raíces, fue debilitada en nombre de una supuesta “productividad”.
Nos dijeron que para ser fuertes teníamos que dejar de lado nuestros deseos más profundos.\ Que la maternidad era una traba. Que formar familia era mirar hacia atrás.\ Nos empujaron a vivir en una lógica masculina, en la que mostrar sensibilidad era sinónimo de debilidad.\ Pero nada de esto fue casual.
Este sistema necesita que no creas en vos para poder seguir funcionando.\ Necesita que te desconectes de tu cuerpo, de tus vínculos, de tu intuición.\ Y, sobre todo, necesita que te desconectes del valor real de tu tiempo, de tu energía, de tu dinero.
Pero hay otra forma.\ Hay otra forma de ser mujer, de ser madre, de ser libre.\ Y empieza por recordar lo que siempre supimos, pero olvidamos:\ La familia es revolución desde el amor.\ Porque una sociedad fuerte nace de vínculos sanos.\ Y eso empieza en casa, en las relaciones donde aprendemos qué es amar, cuidar, sostener, poner límites, construir.
Nos enseñaron a medir el éxito por cuánto nos alejábamos de lo femenino.\ Pero la independencia sin conexión es otra forma de soledad.\ La maternidad no es debilidad. Es fuerza creadora.\ La energía femenina no es pasiva. Es raíz, instinto, visión.
Y así como nos quitaron poder en nuestros cuerpos y vínculos, también lo hicieron con nuestro dinero.
Dinero, Energía y Libertad
¿Qué es el dinero, si no una forma de energía?\ El resultado de tu tiempo, tu creatividad, tu esfuerzo.\ Sin que te des cuenta, te están robando esa energía.
Nos enseñaron a ahorrar. Pero nunca nos explicaron que, mientras guardamos billetes, su valor se disuelve.\ Que los bancos centrales imprimen dinero —ni siquiera lo imprimen, lo “crean” digitalmente— sin pedirnos permiso, sin pensar en nuestra vida.\ Y mientras tanto, vos trabajás cada vez más… por cada vez menos.
Porque si controlan tu tiempo, controlan tu vida.\ Si te mantienen ocupada, te mantienen distraída.\ Si te desconectan del verdadero valor del dinero, te vuelven dependiente.
Bitcoin como Llave
Bitcoin no es solo una inversión. Es una herramienta.\ Una llave para volver a tener el control.\ De tu energía. De tu tiempo. De tu vida.
No se trata solo de números.\ Se trata de comprender.\ De construir redes descentralizadas de mujeres libres, que se acompañan, que comparten saberes, que se sostienen.
Porque la verdadera abundancia empieza cuando entendés que el poder vuelve a vos.
Es hora de recordar.\ De mirar hacia adentro.\ Y de tomar decisiones que nos devuelvan a lo esencial:\ La conexión real, el amor como base, y la autonomía como acto sagrado.
-
 @ 2b998b04:86727e47
2025-06-08 18:39:04
@ 2b998b04:86727e47
2025-06-08 18:39:04I’ve spent years chasing the promise of freedom.\ In startups. In faith communities. In movements that claimed to be for the people.
And yet — so often, that promise felt just out of reach.\ Conditional. Corporate. Sanitized.\ A freedom with fine print.
But here —\ Here in the thick of Bitcoin 2025, on Nostr, among misfits and builders and signal-bringers —\ something is alive.
It’s not a platform.\ It’s not a marketing strategy.\ It’s not another app promising to “empower” you while locking down your data and selling you out.
It’s freedom rooted in architecture.\ Decentralization not just as a buzzword —\ but as an expression of conviction.
A kind of freedom you can feel in your body:
-
When you zap someone’s words because they moved you — not because an algorithm told you to.
-
When your identity is yours — keys, not credentials.
-
When no one can delete your story because you control the server, or because there is no server — just the relay of your choosing.
This isn’t utopia.\ There are egos. There’s noise. There’s still posturing.\ But it’s different.\ The center of gravity has shifted.
We’re no longer begging institutions to notice us.\ We’re building outside their jurisdiction.
And for the first time in a long time,\ freedom feels close.\ Tangible.\ Joyful.\ Alive.
This isn’t just about tech.\ It’s about trust.\ It’s about choosing to show up —\ to build\ to write\ to signal\ to keep going.
Even when it’s hard.\ Even when no one claps.
Because real freedom doesn’t come from being noticed.\ It comes from being sovereign.
And that’s something no one can take from me again.
—
Written in Las Vegas, during Bitcoin 2025.\ Posted via Nostr. Vibes co-authored by ChatGPT (“Dr. C”).\ Zap: <https://tinyurl.com/yuyu2b9t>
-
-
 @ 2b998b04:86727e47
2025-06-08 18:35:46
@ 2b998b04:86727e47
2025-06-08 18:35:46This isn’t a comfortable post to write. I first composed it on Thursday night, May 29, 2025, just after the Bitcoin2025 conference — but I needed a few days to sit with it before posting.
Because freedom, if it means anything, has to include tension — not just agreement.
Four names kept surfacing in conversations on Nostr and at the Bitcoin2025 conference: President Donald Trump, Chelsea Manning, Edward Snowden (who gave the keynote at Bitcoin2024), and Ross Ulbricht.
I believe in truth. I believe in moral boundaries.
And I believe people are made in the image of God — with dignity that can’t be erased by their choices.
So let me be honest: I disagree with the transgender lifestyle on a moral and theological level.
But I believe Chelsea Manning deserved to be freed after exposing military wrongdoing.
I’m conflicted about Edward Snowden.
I don’t see him as a hero — but I don’t believe he’s a traitor either.
The truth, as is so often the case, is far more complicated.
Snowden revealed the scale of warrantless surveillance against Americans. He helped expose a shadow system of data collection and control. That matters.
But in doing so, he may also have endangered lives — disclosing classified intelligence in a way that potentially compromised undercover agents and global operations.
He’s also been largely silent during Russia’s invasion of Ukraine, and that raises hard questions.
What truths go unspoken when your safety depends on a state with its own authoritarian tendencies?
Still — I’m grateful for what he did.
I’ve never met him, but I think we could’ve been friends in another world.
I can like someone very much and still disagree with them about what they did.
That’s not weakness. That’s human.
And Ross Ulbricht?
I don’t think he’s entirely without fault.
But I do believe his original sentence — two life sentences without parole — was a gross miscarriage of justice.
His recent pardon by President Trump corrected something our courts never did.
I admire Ross. And like with Snowden, I can hold that admiration even while acknowledging complexity.
I say this as someone who voted for Trump and agrees with many of his stances.
I believe in strong, secure borders.
But I also believe we need a more compassionate and streamlined process for immigration and asylum.
Security and mercy are not opposites — we can pursue both.
But I’ll also say this:
I’m troubled by some of the recent moves Trump has made.
The promotion of meme coins by Trump feels flippant and off-base when so many Americans are struggling to understand real monetary sovereignty.
Even more disturbing are reports that his administration contracted with companies like Palantir to build a vast data infrastructure — the kind that could be used to track, profile, and suppress U.S. citizens.
That’s a betrayal of the very freedom we claim to defend.
And it reveals a deeper conflict I can’t ignore:
How can we champion liberty with one hand while constructing surveillance tools with the other?
This isn’t about party.
It’s about principle.
And if I’m honest, the one thing that’s hardest for me to tolerate — in myself or in others — is hypocrisy.
Not disagreement. Not even failure.
But posturing. Pretending. Saying one thing and doing another.
That’s what corrodes trust — in politics, in faith, in freedom itself.
Because if your definition of freedom only includes people who think, live, or vote like you —
it’s not freedom. It’s favoritism.
Bitcoin reminds me of a better standard.
It doesn’t care about your politics, background, beliefs, or identity.
It’s borderless. Neutral. Permissionless.
It just works — for everyone.
Bitcoin gives us a glimpse of a freer world — not perfect, but principled.
A world where disagreement isn’t a threat, and dignity isn’t earned.
That’s the kind of future worth building — not with slogans, but with truth, grace, and work that lasts.
Zap me if this resonates.
Push back if it doesn’t — that’s freedom too.
---
### ✍️ Acknowledgment
This piece was shaped with help from Dr. C (ChatGPT) to organize and clarify ideas, but the heart of it — the desire to seek truth over comfort, and to honor people over posture — comes from a deeper place.
Any wisdom here I credit to the Holy Spirit, who leads us into all truth (John 16:13) and continues to stir the courage to speak it — even when it's uncomfortable.
---
### 📘 Footnote
Reporting confirms that the Trump administration contracted Palantir Technologies to develop large-scale federal data platforms consolidating personal information from the IRS, Social Security Administration, immigration systems, and more. Palantir also secured a $30 million contract to build “ImmigrationOS,” a surveillance tool for ICE. These systems raise serious concerns among civil liberties advocates.
- [Economic Times](https://tinyurl.com/22bdv72d)
- [Immigration Policy Tracker](https://tinyurl.com/2686bgvy)
-
 @ 2cde0e02:180a96b9
2025-06-08 18:14:13
@ 2cde0e02:180a96b9
2025-06-08 18:14:13Frida Kahlo: outline and inked.
pen & ink; monochromized
"Kahlo's work as an artist remained relatively unknown until the late 1970s, when her work was rediscovered by art historians and political activists. By the early 1990s, not only had she become a recognized figure in art history, but she was also regarded as an icon for Chicanos, the feminism movement, and the LGBTQ+ community. Kahlo's work has been celebrated internationally as emblematic of Mexican national and Indigenous traditions and by feminists for what is seen as its uncompromising depiction of the female experience and form."
Source: Wikipedia
https://stacker.news/items/1000840
-
 @ 5c26ee8b:a4d229aa
2025-06-08 20:49:48
@ 5c26ee8b:a4d229aa
2025-06-08 20:49:48Ad-Daba (the unusual creature), is one of the major signs of Judgement Day and it’s more likely to be the next sign to appear soon. As it appears the belief of disbelievers or repentance won’t be accepted. In the following some verses of the Quran and Hadith mentioning it as well as other major signs.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature (Ad-Daba) from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
It was narrated that Hudhaifah bin Asid, Abu Sarihah, said: "The Messenger of Allah (ﷺ) looked out from a room, when we were talking about the Hour. He said: 'The Hour will not begin until ten signs appear: The rising of the sun from the west (place of its setting); Dajjal; the smoke; the beast; Gog and Magog people; the appearance of 'Eisa bin Maryam(as), the earth collapsing three times - once in the east, one in the west and one in the Arabian Peninsula; and fire that will emerge from the plain of Aden Abyan and will drive the people to the place of Gathering, stopping with them when they stop at night and when they stop to rest at midday."
حَدَّثَنَا عَلِيُّ بْنُ مُحَمَّدٍ، حَدَّثَنَا وَكِيعٌ، حَدَّثَنَا سُفْيَانُ، عَنْ فُرَاتٍ الْقَزَّازِ، عَنْ عَامِرِ بْنِ وَاثِلَةَ أَبِي الطُّفَيْلِ الْكِنَانِيِّ، عَنْ حُذَيْفَةَ بْنِ أَسِيدٍ أَبِي سَرِيحَةَ، قَالَ اطَّلَعَ رَسُولُ اللَّهِ ـ صلى الله عليه وسلم ـ مِنْ غُرْفَةٍ وَنَحْنُ نَتَذَاكَرُ السَّاعَةَ فَقَالَ " لاَ تَقُومُ السَّاعَةُ حَتَّى تَكُونَ عَشْرُ آيَاتٍ طُلُوعُ الشَّمْسِ مِنْ مَغْرِبِهَا وَالدَّجَّالُ وَالدُّخَانُ وَالدَّابَّةُ وَيَأْجُوجُ وَمَأْجُوجُ وَخُرُوجُ عِيسَى ابْنِ مَرْيَمَ عَلَيْهِ السَّلاَمُ وَثَلاَثُ خُسُوفٍ خَسْفٌ بِالْمَشْرِقِ وَخَسْفٌ بِالْمَغْرِبِ وَخَسْفٌ بِجَزِيرَةِ الْعَرَبِ وَنَارٌ تَخْرُجُ مِنْ قَعْرِ عَدَنِ أَبْيَنَ تَسُوقُ النَّاسَ إِلَى الْمَحْشَرِ تَبِيتُ مَعَهُمْ إِذَا بَاتُوا وَتَقِيلُ مَعَهُمْ إِذَا قَالُوا " .
قال رسول الله صلي الله عليه وسلم: تخرجُ الدابَّةُ، فتَسِمُ الناسَ على خراطيمِهم، ثم يُعمِّرون فيكم، حتى يشتريَ الرجلُ الدابَّةَ، فيُقالُ: ممَّنِ اشتريتَ؟ فيقولُ: من الرجلِ المُخَطَّمِ
The prophet Mohamed peace be upon him said: The beast will come out and brand people (disbelievers) on their noses (leaves a sign burned on their nose so it’s known of their disbelief). Then they will live among you until a man buys a beast and it will be said: From whom did you buy it? He will say: From the man with the sign on the nose.
The beast looks unusual and some people might find it scary. However, it’s a sign of God and it must not be killed as this will call God’s punishment like what happen when the people of prophet Saleh peace be upon him killed the huge camel as mentioned in the following verses.
7:73 Al-A'raaf
وَإِلَىٰ ثَمُودَ أَخَاهُمْ صَالِحًا ۗ قَالَ يَا قَوْمِ اعْبُدُوا اللَّهَ مَا لَكُمْ مِنْ إِلَٰهٍ غَيْرُهُ ۖ قَدْ جَاءَتْكُمْ بَيِّنَةٌ مِنْ رَبِّكُمْ ۖ هَٰذِهِ نَاقَةُ اللَّهِ لَكُمْ آيَةً ۖ فَذَرُوهَا تَأْكُلْ فِي أَرْضِ اللَّهِ ۖ وَلَا تَمَسُّوهَا بِسُوءٍ فَيَأْخُذَكُمْ عَذَابٌ أَلِيمٌ
And to the Thamud [We sent] their brother Salih. He said, "O my people, worship Allah; you have no deity other than Him. There has come to you clear evidence from your Lord. This is the she-camel of Allah [sent] to you as a sign. So leave her to eat within Allah 's land and do not touch her with harm, lest there seize you a painful punishment.
7:74 Al-A'raaf
وَاذْكُرُوا إِذْ جَعَلَكُمْ خُلَفَاءَ مِنْ بَعْدِ عَادٍ وَبَوَّأَكُمْ فِي الْأَرْضِ تَتَّخِذُونَ مِنْ سُهُولِهَا قُصُورًا وَتَنْحِتُونَ الْجِبَالَ بُيُوتًا ۖ فَاذْكُرُوا آلَاءَ اللَّهِ وَلَا تَعْثَوْا فِي الْأَرْضِ مُفْسِدِينَ
And remember when He made you successors after the 'Aad and settled you in the land, [and] you take for yourselves palaces from its plains and carve from the mountains, homes. Then remember the favors of Allah and do not commit abuse on the earth, spreading corruption."
7:75 Al-A'raaf
قَالَ الْمَلَأُ الَّذِينَ اسْتَكْبَرُوا مِنْ قَوْمِهِ لِلَّذِينَ اسْتُضْعِفُوا لِمَنْ آمَنَ مِنْهُمْ أَتَعْلَمُونَ أَنَّ صَالِحًا مُرْسَلٌ مِنْ رَبِّهِ ۚ قَالُوا إِنَّا بِمَا أُرْسِلَ بِهِ مُؤْمِنُونَ
Said the eminent ones who were arrogant among his people to those who were oppressed - to those who believed among them, "Do you [actually] know that Salih is sent from his Lord?" They said, "Indeed we, in that with which he was sent, are believers."
7:76 Al-A'raaf
قَالَ الَّذِينَ اسْتَكْبَرُوا إِنَّا بِالَّذِي آمَنْتُمْ بِهِ كَافِرُونَ
Said those who were arrogant, "Indeed we, in that which you have believed, are disbelievers."
7:77 Al-A'raaf
فَعَقَرُوا النَّاقَةَ وَعَتَوْا عَنْ أَمْرِ رَبِّهِمْ وَقَالُوا يَا صَالِحُ ائْتِنَا بِمَا تَعِدُنَا إِنْ كُنْتَ مِنَ الْمُرْسَلِينَ
So they hamstrung the she-camel and were insolent toward the command of their Lord and said, "O Salih, bring us what you promise us, if you should be of the messengers."
7:78 Al-A'raaf
فَأَخَذَتْهُمُ الرَّجْفَةُ فَأَصْبَحُوا فِي دَارِهِمْ جَاثِمِينَ
So the earthquake seized them, and they became within their home [corpses] fallen prone.
7:79 Al-A'raaf
فَتَوَلَّىٰ عَنْهُمْ وَقَالَ يَا قَوْمِ لَقَدْ أَبْلَغْتُكُمْ رِسَالَةَ رَبِّي وَنَصَحْتُ لَكُمْ وَلَٰكِنْ لَا تُحِبُّونَ النَّاصِحِينَ
And he turned away from them and said, "O my people, I had certainly conveyed to you the message of my Lord and advised you, but you do not like advisors."
God is the most merciful and has decreed everything and even the major signs of Judgement Day can have the punishment coming with them alleviated or reduced by God. However, there must be a reason for reducing the intensity of the calamities, as God may decree, and the reason is repentance as well as good actions to adjust what was done wrong. Also, although the major signs of Judgement Day will be known to the majority of the people, some of them might concern smaller groups of people or a country.
3:133 Aal-i-Imraan
۞ وَسَارِعُوا إِلَىٰ مَغْفِرَةٍ مِنْ رَبِّكُمْ وَجَنَّةٍ عَرْضُهَا السَّمَاوَاتُ وَالْأَرْضُ أُعِدَّتْ لِلْمُتَّقِينَ
And hasten to forgiveness from your Lord and a garden as wide as the heavens and earth, prepared for the righteous
3:134 Aal-i-Imraan
الَّذِينَ يُنْفِقُونَ فِي السَّرَّاءِ وَالضَّرَّاءِ وَالْكَاظِمِينَ الْغَيْظَ وَالْعَافِينَ عَنِ النَّاسِ ۗ وَاللَّهُ يُحِبُّ الْمُحْسِنِينَ
Who spend [in the cause of Allah] during ease and hardship and who restrain anger and who pardon the people - and Allah loves the doers of good;
3:135 Aal-i-Imraan
وَالَّذِينَ إِذَا فَعَلُوا فَاحِشَةً أَوْ ظَلَمُوا أَنْفُسَهُمْ ذَكَرُوا اللَّهَ فَاسْتَغْفَرُوا لِذُنُوبِهِمْ وَمَنْ يَغْفِرُ الذُّنُوبَ إِلَّا اللَّهُ وَلَمْ يُصِرُّوا عَلَىٰ مَا فَعَلُوا وَهُمْ يَعْلَمُونَ
And those who, when they commit an immorality or wrong themselves [by transgression], remember Allah and seek forgiveness for their sins - and who can forgive sins except Allah? - and [who] do not persist in what they have done while they know.
3:136 Aal-i-Imraan
أُولَٰئِكَ جَزَاؤُهُمْ مَغْفِرَةٌ مِنْ رَبِّهِمْ وَجَنَّاتٌ تَجْرِي مِنْ تَحْتِهَا الْأَنْهَارُ خَالِدِينَ فِيهَا ۚ وَنِعْمَ أَجْرُ الْعَامِلِينَ
Those - their reward is forgiveness from their Lord and gardens beneath which rivers flow [in Paradise], wherein they will abide eternally; and excellent is the reward of the [righteous] workers.
3:137 Aal-i-Imraan
قَدْ خَلَتْ مِنْ قَبْلِكُمْ سُنَنٌ فَسِيرُوا فِي الْأَرْضِ فَانْظُرُوا كَيْفَ كَانَ عَاقِبَةُ الْمُكَذِّبِينَ
Similar situations [as yours] have passed on before you, so proceed throughout the earth and observe how was the end of those who denied.
3:138 Aal-i-Imraan
هَٰذَا بَيَانٌ لِلنَّاسِ وَهُدًى وَمَوْعِظَةٌ لِلْمُتَّقِينَ
This [Qur'an] is a clear statement to [all] the people and a guidance and instruction for those conscious of Allah.
-
 @ dfa02707:41ca50e3
2025-06-08 16:02:23
@ dfa02707:41ca50e3
2025-06-08 16:02:23Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 9ca447d2:fbf5a36d
2025-06-08 16:02:03
@ 9ca447d2:fbf5a36d
2025-06-08 16:02:03Wall Street is warming up to Bitcoin and getting closer and closer to it.
Cantor Fitzgerald, one of the oldest and most respected investment banks on Wall Street, has launched a $2 billion bitcoin-backed lending program.
They’ve reportedly already done their first deals, lending to two big digital asset companies: FalconX and Maple Finance.
This is a big step in connecting traditional finance to the fast-moving world of Bitcoin.
Cantor’s new service allows big investors, hedge funds and asset managers, to borrow money using bitcoin as collateral.
This is a game changer for institutions that hold bitcoin, as they can now access liquidity without having to sell their assets.
“Institutions holding bitcoin are looking to broaden their access to diverse funding sources,” said Christian Wall, co-CEO and global head of fixed income at Cantor Fitzgerald.
“And we are excited to support their liquidity needs to help them drive long term growth and success.”
The loans are not speculative or unsecured.
They are structured like traditional finance deals, backed by the borrower’s bitcoin. This reduces the risk for Cantor while giving bitcoin-holding companies new ways to grow and operate.
The first recipients of Cantor’s lending program are FalconX, a digital asset brokerage, and Maple Finance, a blockchain-based lending platform.
FalconX confirmed they secured a credit facility of over $100 million. Maple Finance also received the first tranche of their loan from Cantor.
This comes at a time when the bitcoin lending space is recovering after a tough period. Several big firms went under in 2022 and investor confidence was shaken.
Now with traditional finance on board, bitcoin-backed lending has returned. According to Galaxy Research the total size of the digital asset lending market grew to $36.5 billion in Q4 2024.
Cantor’s move into bitcoin-backed lending isn’t new. They announced their plans in July 2024 and have been building their presence in the Bitcoin space since then.
Earlier this year, they partnered with Tether, SoftBank and Bitfinex to launch Twenty One Capital, a $3.6 billion fund to buy over 42,000 bitcoin.
In May 2025 Cantor Equity Partners merged with Twenty One Capital and bought nearly $459 million worth of bitcoin.
They also own around $1.9 billion in shares of Strategy, a company that holds a lot of bitcoin. Clearly Cantor believes in bitcoin as a long-term asset.
Cantor is also a big player in the stablecoin space.
They manage U.S. Treasury reserves for Tether, the company behind the $142 billion USDT stablecoin. This adds another layer of trust and credibility to Cantor’s digital asset involvement.
To secure the bitcoin used as collateral, Cantor has partnered with digital asset custodians Anchorage Digital and Copper.co.
These companies are known for their robust security and institutional-grade infrastructure. Cantor hasn’t disclosed loan terms or interest rates but confirmed the lending will follow current regulations.
This also shows how traditional financial players are embracing DeFi.
Maple Finance for example allows undercollateralized lending using blockchain. By backing companies like Maple, Cantor is innovating while still having control and compliance.
For years, bitcoin-backed loans were only available through digital-asset-native companies like Genesis, BlockFi, and Ledn.
These loans were mostly for smaller clients and retail investors. But with Cantor’s entry, the scale and professionalism of bitcoin lending are expanding.
-
 @ 81022b27:2b8d0644
2025-06-08 15:18:50
@ 81022b27:2b8d0644
2025-06-08 15:18:50I’ve always gravitated to ideas and topics that are not quite mainstream:
Well, like CHIROPRACTIC.
But even in chiropractic school, I went fringe. I heard about one of the technique clubs (Toftness) that showed you how you could detect a subluxation by just rubbing your thumb over a piece of plexiglass.
We were discussing that in a group, and most of my friends were saying:
“What a load of shit!”
And that made my ears perk up.
So I started going to the club meetings.
I walk in, and there’s a guy face down on a chiropractic table while another guy was holding what looked like some sort of cyberpunk lens. He started rubbing it and worked it down the guy's spine.
He pointed out areas that were subluxated:
“Here.”
And going further down:
“Here.”
And:
“Here.”
Wow.
Then he “adjusted” by touching the spine with his index finger.
My mind was blown.
So you mean I didn’t have to be adjusted the way Harvey Fish did?
Dr. Fish was a great guy and would adjust students for, I think, $10. You’d go in, wait to see if he had any “real patients.” In between patients, he would adjust the students. He was heavy-handed and sure as hell able to move a bone.
So now I’m intrigued and curious. I studied and practiced any chance I had. I had different friends that I studied different things with.
(Except for Dyslexic Dave - nobody wanted to study with that guy. Our group did once, and we all failed a test. His dyslexia was so powerful, it overcame all of us.)
I’d study all the weird stuff with my friend Victoria, and then we would go get our network chiropractic adjustment from Dr. Michael Scimeca.
I found out that it wasn’t the Toftness lens that had the super-powers. Instead, it was because when your hand detected a change in energy over the spinal segments, there's a “galvanic response” similar to that of a polygraph lie detector test. So it made the skin on my hand “sweat,” and that made the plexiglass squeak and stick.
So it wasn’t the equipment. It was me.
After a while, I realized that I could feel a warmth on my chest right before the lens squeaked. So, I ditched the lens and started working on people where I “felt” the subluxations were located.
Seemed to work well - I always double-checked my “regular” chiropractic findings with what I felt. We studied for exams, then practiced technique on each other.
One time at a seminar, the instructor demonstrated what to do and asked for volunteers - one to be the patient and the other to be the doctor. I watched this guy struggling with his patient. It looked like he had flippers instead of hands; the whole interaction was super awkward.
All of a sudden, I started feeling uncomfortable and just blurted out:
“For God’s sake, leave him alone! Can’t you tell he is super annoyed and angry?”
Oops.
The instructor said, “Yes, maybe we should take a break.”
The guy that was the patient came up to me and asked, “How did you know?”
“I don’t know, I just felt it,” I said.
After that I started trying to see if I could feel what others were feeling. So when I was bored in a class, I’d go down the rows and try to feel what the my fellow students felt and quickly move on.
Going down the row: nothing, nothing nothing. This guy is pissed off, next one: nothing, nothing, Ow! She has a headache.
Dammit! Now I have a headache!
So that turned into a problem: When I worked on someone that had pain or other symptoms, I would take those on for myself. And the person I worked on would leave feeling great.
My friend Juanita did what is called an "attunement," and I became a Reiki Master.
Reiki masters are supposed to move energy around, but I was afraid I’d pick up too much of someone’s vibe and it would make me uncomfortable.
Plus, I can’t be doing energy work if I’m a chiropractor now.
So I kept all that checked and on the "down low"; sometimes I would get a "feeling" about a client while I was working on them. Surprisingly, it was always correct and it helped my client to make progress.
At some point, I started feeling that I needed to be true to myself, and if I had these abilities and I was able to use them to help the people that came to see me, then that's what I was going to do.
I've embraced this side of my work. If my clients need some emotional work, that’s what we work on, if they need some energy work, then they get it.
I suppose some people don’t want a chiropractor that’s metaphysical, but really-that’s how it all started. There are plenty of “evidence-based” chiropractors out there that can’t adjust their way out of a paper bag.
If the power goes off, they couldn’t use their lasers or whatever machine the Chiropractic Physiotherapy Industrial Complex wants you to buy now.
While I appreciate all the fancy parties they throw for us at continuing education seminars, they are infiltrating the chiropractic schools and now we are pumping out new chiropractors that only think they will be successful if they have the latest and greatest shiny machine.
I’ve studied a bunch of different things, I’ve found what works for me and refined it.
I tell my clients :
“I’m a better chiropractor today than I was yesterday, and I was pretty good back then!”
So I guess my next step is teaching some of this information and hoping to pass it on before my time here is up.
And you know what? I will love every damn minute of it!
There's nothing quite like sharing the weird, the wonderful, and the downright strange ways we can help people heal.
So, let's get to it—I've got a lot of sharing and teaching to do—it's going to be exciting!
-
 @ 81022b27:2b8d0644
2025-06-08 15:06:12
@ 81022b27:2b8d0644
2025-06-08 15:06:12I have a family practice where I see pretty much everything, from infants to the elderly, athletes to people with disabilities.
When someone gets good results, they always want their loved ones to benefit in the same way.
Husbands tell their wives, wives bring in their husbands...
I even had a guy bring both his wife and his girlfriend! On different days, of course.
So, sometimes we notice a little bit of drama here and there. When one of our couples divorces, someone usually gets custody of the chiropractor.
It's rare that I keep seeing both parties.
It's probably for the best, because there was this one time when a guy showed up with his new "friend" while the ex’s best friend was in the waiting area.
Well, it was like an episode of the "Jerry Springer Show" that day.
Let's get to the story:
This one guy I’d been working on started coming in more frequently, complaining of more pain, more aches, more everything.
I've been doing this for a while now, so I told him that when I see this, it's one of two things:
Either you are physically doing something to aggravate the issue,
Or you are under emotional stress.
He told me that he and his wife were having problems, and there was lots of drama.
Of course, I kept working on him. Sometimes I did some emotional work, but with men, I have to be very business-like when dealing with emotions because we don't like to deal with them.
Time passed, and they finally divorced.
He still comes in regularly, and I've noticed he has less pain and fewer issues. His visits are more like "wellness visits"; he seems in better spirits.
I thought I'd never see the ex-wife again, but she showed up today, and when I checked her, she's doing better than ever!
It got me thinking... these people are way better off divorced! They're not in constant fight-or-flight mode; I'm sure they are happier or will be. It's a positive all the way around.
I've been divorced twice. That's not something I'm proud of. I see both those divorces as failures.
I was 23 when I got married the first time. We were both super young and unprepared. We struggled for four years, and then she wanted out.
Not that I blame her; I was unhappy with myself, and my frustration and unhappiness bled into the relationship.
My second marriage lasted a lot longer than the first. After all we were older, ended up having 2 kids and I really, really tried.
I was just terrified of losing my girls. I even recall saying that I was willing to be miserable and unhappy just “for the kids”
The truth is once we separated, I probably spent more “quality time” with my daughters than I had before.
But here’s the thing in both marriages I would have willingly given up the chance to be happier with a clean end to the relationship in order to give it another shot.
At some point you just run out of shots.
I see elderly couples out at restaurants and they hardly say anything to each other. Is it because they know each other so well that they don’t need to speak, or is one of them silently praying the other one will drop dead so they will finally have a chance at happiness?
What I’m trying to say here is:
Maybe there is no hope for that relationship that you are giving CPR
Maybe it’s time to move on.
Live Long and Prosper. 🖖
-
 @ c11cf5f8:4928464d
2025-06-08 14:59:37
@ c11cf5f8:4928464d
2025-06-08 14:59:37Howdy stackers! Here we are again with our monthly Magnificent Seven, the summary giving you a hit of what you missed in the ~AGORA territory.
First thing first. let's check our top performing post Ads!
Top-Performing Ads
This month, the most engaging ones are:
-
01Bitcoin Magazine Launches V3 Limited Edition Bitcoin Crocs by @RideandSmile, no description, nor images provided. The title speak for the product itself. 31 sats \ 8 comments \ 15 May -
02Happy Pizza Day Jerky Offer (10k sats sale 5/22 ONLY) by @beejay, celebrating Bitcoin Pizza Day with a delicious offer for a handmade product. Offer is over but it still available on her online shop and IRL at next Twin Cities Outdoor Agora Market https://stacker.news/items/972209/r/AG 103 sats \ 3 comments \ 22 May -
03Lard Tallow lotion by @byzantine, sharing with us one of his preferred online shops that accept sats. Here other two: a Regenerative Farm in TX https://stacker.news/items/983695/r/AG and an artisanal lite roast coffee maker https://stacker.news/items/983668/r/AG 62 sats \ 4 comments \ 20 May -
04Bitaxe Gamma 601 for sale by @PictureRoom selling P2P, have you shipped it yet? 121 sats \ 12 comments \ 15 May -
05Built An Invisible Book Stage by @kr, he did well creating some expectations for this unique and durable product earlier https://stacker.news/items/903946/r/AG 124 sats \ 4 comments \ 21 May -
06"₿lack Market Money" T-Shirts by T&F by @BitcoinErrorLog, that had opened his online store with plenty of incredible products, including an Anti-Surveillance clothing line https://stacker.news/items/994555/r/AG stuff never seen before! 51 sats \ 3 comments \ 24 May -
07[SELL] Heatpunk 002 Tee by @thebullishbitcoiner, reviving the second edition of a t-shirt dedicated to home solo miners! 79 sats \ 1 comment \ 28 May
In case you missed
Here some interesting post, opening conversations and free speech about markets and business on the bitcoin circular economy:
- https://stacker.news/items/992449/r/AG - @Kontext is selling his beloved 2012 Jaguar XF 3.0 V6 Petrol [5M sats], great deal if paid in sats! Have you sold her?
- https://stacker.news/items/987241/r/AG - @RideandSmile shared the Freedom Issue: Letter From the Editor introducing a BM special edition
- https://stacker.news/items/999229/r/AG - @Solomonsatoshi was looking for Green Coffee Beans for DIY home roasting. Will @michaelbinary provide you some?
- https://stacker.news/items/992790/r/AG - @Rayo also introduce the P.A.Z.NIA Radio Network: 52 Hours of Liberation! An interesting livestream for all those interested in freedom.
- https://stacker.news/items/995163/r/AG welcome to @lunin, opening up on SN with Take it step by step and it will work! as part of a promising series: Founder's Thoughts. Here the second post https://stacker.news/items/999867/r/AG Startup according to Mozart
Hey sellers! Try Auctions
A quick reminder that now you can setup auctions here in the AGORA too! Learn how. The other feature released last month was the introduction of Shopfronts on SN. Check our SN Merch and SN Zine examples. Thank you all! Let's keep these trades coming and grow the P2P Bitcoin circular economy!
Active Professional Services accepting Bitcoin in the AGORA
Let us know if we miss any, here below the most memorable ones: - https://stacker.news/items/900208/r/AG - @unschooled offering Language Tutoring - https://stacker.news/items/813013/r/AG - @gpvansat's [OFFER][Graphic Design] From the paste editions (It's important to keep these offers available) - https://stacker.news/items/775383/r/AG - @TinstrMedia - Color Grading (Styling) Your Pictures as a Service - https://stacker.news/items/773557/r/AG - @MamaHodl, MATHS TUTOR 50K SATS/hour English global - https://stacker.news/items/684163/r/AG - @BTCLNAT's OFFER HEALTH COUNSELING [5K SAT/ consultation - https://stacker.news/items/689268/r/AG - @mathswithtess [SELL] MATHS TUTOR ONILINE, 90k sats per hour. Global but English only.
Let me know if I'm missing other stackers offering services around here!
Lost & Found in SN' Wild West Web
Stay with me, we're not done yet! I found plenty of other deals, offers and business related conversations in other territories too...
- BITCOIN... always fucking with my head... by @thecommoner (highly recommended read!)
- The Strange Moral Relativism of "Free Trade" by @Undisciplined (another highly recommended read!)
- What makes society thrive? by @aljaz
- Drop or proxy shipping services that take sats? by @lv99slacker
- Custom Bitcoin Nodes by @anon
- 23 Bitcoin Merch Shops That Sell Shirts For Sats by @hyperfree
- How to create an e-commerce website? by @Bitcoiner1
- Can You Outperform an Apple Tree? by @kr
- B2B Businesses in Bitcoin by @telcobert
Oh boy! Such exciting month! Now our latest weekly appointments:
🏷️ Spending Sunday
(LIVE TODAY)Share your most recent Bitcoin purchases of just check what other stackers are buying with their sats! Today's one open at https://stacker.news/items/1000477/r/AGAll series available here:
🤝 Sellers & Business Club
(UPCOMING EVERY TUESDAY)Here https://stacker.news/items/998773/r/AG wanted to introduce this new series, dedicated to our most active sellers^1. A room to talk about growing business and sales. You will join?📢 Thursday Talks: What have you sold for Bitcoin this week?
It is losing a bit of momentum, but it will still be opening every week for anyone interested to share sales tips, deals and offers around the Wild West Web! Latest one here https://stacker.news/items/997767/r/AG
Thanks all for reading until here, now... 🫡 Closing remarks as usual. See ya!
Create your Ads now!
Looking to start something new? Hit one of the links below to free your mind:
- 💬 TOPIC for conversation,
- [⚖️ SELL] anything! or,
- if you're looking for something, hit the [🛒 BUY]!
- [🧑💻 HIRE] any bitcoiner skill or stuff from bitcoiners
- [🖇 OFFER] any product or service and stack more sats
- [🧑⚖️ AUCTION] to let stackers decide a fair price for your item
- [🤝 SWAP] if you're looking to exchange anything with anything else
- [🆓 FREE] your space, make a gift!
- Start your own [SHOPFRONT] or simply...
- [⭐ REVIEW] any bitcoin product or LN service you recently bought or subscribed to.
Or contact @AGORA team on nostr DM, and we can help you publish a personalized post.
.
#nostr#bitcoin#stuff4sats#sell#buy#plebchain#grownostr#asknostr#market#businesshttps://stacker.news/items/1000715
-
-
 @ 41fa852b:af7b7706
2025-06-08 11:34:44
@ 41fa852b:af7b7706
2025-06-08 11:34:44"The poison was never forced - it was offered gently, until you forgot it was poison at all." - Mark Twain
Happy Sunday, folks.
Below is your weekly roundup of events for the coming week.
Added to the event section this week, an exciting new Scottish Bitcoin Conference, happening in August.
Check out all the details below.
This week's sponsor is…
Upcoming Bitcoin Meetups
Happening this week…
-
Dundee Bitcoin: Join them on the 2nd Monday of every month from 17:30 to 20:30 PM at The Wine Press, 16 Shore Terrace, Dundee DD1 3DN. This month's meetup is on Monday 9th. 🍻
-
Canterbury Bitcoin: Meeting this month at the The Dolphin Pub in Canterbury at 7 PM on Tuesday the 10th of June. An informal meetup to discuss Bitcoin and chat. 🍺
-
Glasgow Bitcoin: Meetups are held every second Wednesday of the month. This is a place for people in and around Glasgow to discuss Bitcoin. 18:00 - 23:00 at The Piper Bar, G1 1HL. This month on Wednesday 11th. 🍻
-
St Albans: This is a new meetup happening on the second Wednesday of each month. This month, it's from 19:00 to 22:00 on the 11th at the Robin Hood of St Albans, Victoria St, St Albans. 🍻
-
Children of Riddim - Festival - Bitcoin Stage: Children of Riddim Festival is bringing Bitcoin to the big stage from the 12th--16th June in Hemel Hempstead, with 150+ DJs, artists, and speakers. The Barn of Freedom will host Bitcoin talks, music, and Nostr-powered apps. Tickets and donations for the stage can be made via geyser.fund, with camping included. Acts/speakers include Joe Bryan, Metamick, Roger9000, Angor, and more. 🎉🪩
-
Bitcoin Beach Bournemouth: Every second Thursday of the month at Chaplins Cellar Bar. 529 Christchurch Road, Boscombe, United. You'll find them in the Cogg Room at 19:30. This month it's the 12th. 🍺
-
Bury St Edmunds Bitcoin: is reviving the medieval spirit of the Folkmoot, one Bitcoin meetup at a time. Their second gathering takes place this Friday at 17:30 at Edmundo Lounge. They've also just launched a brand new website.
-
Stoke Bitcoin Meetup: The Stoke Bitcoin meetup is back! They will have Bitcoin coffee to taste, delivered by hand directly from the mountains of El Salvador and grown by @lacruzboss in Berlin, El Salvador. 15:00 on Friday 13th. ☕️🍻
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Bitcoin East: Join Bitcoin East in Bury St. Edmunds on Sunday 15th, 12:00 at Hopsters Bar, Felixstowe. All welcome, Bitcoiners and anyone else curious about Bitcoin. 🍺
New Businesses Accepting Bitcoin
This week we have…
- Core Agency: A creative communications firm that blends financial expertise with bold storytelling to help businesses in finance and beyond stand out. Based in the UK, they specialise in strategic planning, brand identity, content production, and public relations, delivering everything from investor-focused media to high-impact digital campaigns. With in-house studios for video, animation, and live streaming, Core offers end-to-end solutions that are both visually compelling and commercially effective. Their mission is to bring clarity, creativity, and confidence to brands navigating complex markets. Whether you're a fintech startup or a global institution, Core helps you communicate with purpose and originality. Now accepting bitcoin payments. 📈
Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
The Bitcoin Beach Retreat: An annual Bitcoin-only gathering held at a scenic coastal campsite in North Wales. Celebrating its fifth year in 2025, the retreat offers a relaxed, community-driven alternative to traditional conferences.
From July 11--14, up to 120 Bitcoiners will come together to share knowledge, enjoy beachside BBQs, and strengthen their networks under the stars. With no pre-booked speakers, the event thrives on peer-led workshops and spontaneous discussions, fostering genuine connections among attendees. Emphasising local engagement, the retreat directs the majority of its funds into the surrounding community, with 42% of expenses paid in Bitcoin last year.
Whether attending solo or with family, attendees can expect a welcoming environment dedicated to sound money and shared values.
Scottish Bitcoin Conference: Taking place on August 23, 2025, at the Glasgow University Union, located at 32 University Avenue, Glasgow G12 8LX. From 09:00 to 16:30.
Featuring an impressive roster of speakers, including Anthony Scaramucci, Hashley Giles, Rick Messit, Dr. Peter Connor, Claire Chisholm, Roger9000, John Magill, Ian Scanlon, Robin Thatcher, Jamie Plowman, Robbie Maltby, Russell Rukin, Peter Lane, Francesco Madonna, and Sam Roberts.
Open to all, this conference offers a unique opportunity for Bitcoiners and newcomers alike to connect and learn in the vibrant setting of Glasgow.
Get Involved
- Volunteer: Passionate about merchant adoption? Reach out to Bridge2Bitcoin on Twitter or website.
- Start a Meetup: Want to launch a Bitcoin meetup? We'll support you. Contact us on Twitter or just reply to this email.
- Contribute to BTCMaps: Help maintain this key Bitcoin resource--no coding skills needed. Update a UK area.
- Telegram: Join our Channel for UK meetup updates
- Feedback: Reply to this email with ideas and suggestions.
This week's sponsors is…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 4fe14ef2:f51992ec
2025-06-08 10:20:56
@ 4fe14ef2:f51992ec
2025-06-08 10:20:56Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Like and repost: X: https://x.com/AGORA_SN/status/1931657445916766655 N: https://njump.me/note1qqqsgu9pgx2u6yt2dv0c5yedpzrqalaqe3rf3lwxfu4a0w6wemtsy0eyfu
https://stacker.news/items/1000477
-
 @ dab6c606:51f507b6
2025-06-08 09:24:14
@ dab6c606:51f507b6
2025-06-08 09:24:14I've been interested for a while in how the business with miles and loyalty points works. I found out that only large corporations can partially do this because of how they can then account for it. And it's tax-wise super advantageous. I also added info about loyalty points and gift cards. The text below was written by various AIs as I was digging into it, it's basically a summary, sharing for those who are interested.
Part I: Loyalty Programs of Large Corporations
Business Logic of Loyalty Programs
Loyalty programs of airlines and hotels are sophisticated business tools that serve several key purposes. They primarily function to increase customer loyalty by creating "switching costs" - customers don't want to lose accumulated points, which reduces the likelihood they'll switch to competitors.
At the same time, they're a significant source of additional revenue. For example, American Airlines earns more from selling miles to banks than on some flight routes. When Citibank buys miles for 1-2 cents per mile, the airline gets immediate revenue, while the real value for the customer can be 3-5 cents when used correctly.
Accounting Treatment of Loyalty Points
From an accounting perspective, loyalty points represent deferred liabilities. When a customer earns points, the company must create a reserve for their future redemption. Points are valued based on expected costs of their redemption, not on nominal value.
The key difference is between cash accounting and accrual accounting: - Cash accounting: Revenue is recognized when payment is received, expenses when paid. - Accrual accounting: Revenue and expenses are recognized when the obligation arises.
For loyalty programs, accrual accounting is critical. When an airline sells miles to a bank for $1,000,000, it simultaneously creates a liability for future costs (say $600,000), so taxable income is only $400,000.
Example: Selling Miles to a Bank
An airline sells 50 million miles to Citibank for $1,000,000: 1. Immediate revenue: $1,000,000 2. Creation of liability: $600,000 (estimated future costs) 3. Taxable income: $400,000 4. Future costs: When customers use miles, the company recognizes the expense and reduces the liability
Positive margin arises from several factors: - Breakage - 15-20% of miles are never redeemed - Time value of money - Money from the bank is invested immediately - Marginal costs - An empty seat has low incremental cost
Tax Optimization and Offshore Structures
Large companies often use international structures to optimize taxes from loyalty programs. A typical structure includes: 1. Parent company (USA/EU) - Operates flights and provides services (e.g., flights or accommodation). 2. IP Holding (Ireland/Netherlands) - Owns intellectual property (IP) for the loyalty program, such as brands, software, and databases. 3. Loyalty Operating Company (Singapore/Dubai) - Manages sale of miles to banks and partners, coordinates the program and communicates with customers.
Business Relationships and Payments Between Entities (example with positive result for Singapore)
These entities are connected by contracts that determine who pays for what and why, to minimize tax burden: - Bank → Singapore (Loyalty Operating Company): The bank (e.g., Citibank) pays $1,000,000 for miles it offers to its clients as rewards for using credit cards. The Singapore company is the main contact point for partners because it's located in a low-tax jurisdiction (17%) with good infrastructure for financial services. - Singapore → Ireland (IP Holding): The Singapore company pays $500,000 as royalties for using IP (brands, software, and data) of the loyalty program. This payment is high to shift profit to Ireland, where the tax rate is even lower (12.5%). This reduces taxable income in Singapore. - Singapore → Parent Company (Airline): The Singapore company pays $300,000 to the parent company for providing services (e.g., flights) when customers use miles. This payment is lower than actual costs to minimize profit in the parent company's country, where the tax rate is higher (e.g., 25-35% in USA or EU). - Profit in Singapore: $1,000,000 (income from bank) - $500,000 (royalties to Ireland) - $300,000 (payment to airline) = $200,000 profit, taxed at 17% in Singapore.
Why Such Distribution?
- Ireland (IP Holding): High royalty payments ($500,000) go to Ireland because the 12.5% tax rate is attractive and Ireland is considered a "serious" jurisdiction that meets international rules (e.g., BEPS). Ireland also has double taxation treaties with many countries, facilitating profit shifting.
- Singapore (Loyalty Operating Company): Mile sales and program coordination occur in Singapore due to favorable tax environment (17%) and strategic location for Asian markets. A small profit ($200,000) is left here to demonstrate "economic substance" - that the company has real activity.
- Parent Company: The $300,000 payment is low to minimize taxable income in a high-tax country (e.g., USA or EU).
Why Not 0% Tax Jurisdiction?
Why not use a zero-tax country (e.g., Cayman Islands)? Due to: - Regulatory scrutiny - Tax authorities closely monitor 0% jurisdictions and may question legitimacy. - BEPS rules - Need to demonstrate "substance" (real offices, employees) in the country. - Credibility test - 12.5% in Ireland or 17% in Singapore looks like legitimate business operation.
The result of such structure is that most profit (60-70%) is taxed at 12.5% in Ireland or 17% in Singapore instead of 25-35% in the airline's home country.
Part II: Loyalty Programs and Alternatives for Small Businesses
Why Loyalty Programs Are Problematic for Small Businesses
Unlike large corporations, small businesses like cafes face a fundamental problem with loyalty programs: cash accounting obligation. In many countries, small firms (under $25M annually) must use cash accounting, which means: - Revenue from selling points is taxed immediately - Costs are deducted only when customers use points (maybe a year later) - Creates tax and cashflow problem - tax is paid on money you'll "lose" in the future
Imagine a cafe that sells loyalty points for €100. It must immediately pay tax (say €21), but deducts coffee costs provided for points only in the future.
Alternative Models for Small Businesses
There are more tax-advantageous alternatives:
1. Gift Cards Model
- Revenue is NOT RECOGNIZED when selling gift card
- Revenue is recognized only when customer uses the card
- Example: Sell gift cards for €10,000 in December, get cash immediately, but pay tax gradually as customers use cards during the following year.
- Time value of money: Money can be invested (e.g., 6% annually = €600 extra profit on €10,000)
- Breakage benefit: 2-10% of cards are never used, after certain time (3-5 years, depending on legislation) you can recognize the balance as pure profit.
Example: Starbucks Starbucks had $1.5 billion in unused gift cards on its books in 2022. Estimated 3% breakage means $45 million pure profit – interest-free loan from customers with bonus that part never returns.
2. Subscription Model
- Monthly revenue = immediate taxation
- Monthly costs = immediate deduction
- Example: €10/month for "premium membership" with certain benefits
3. Discount Coupons
- No revenue when issuing coupon
- Reduced revenue when redeeming (sell at lower price)
- Example: 20% discount coupon = sell coffee for €4 instead of €5
Outsourcing Loyalty Program: Details About Shopify Loyalty
Platforms like Shopify Loyalty represent an elegant solution for small businesses wanting to offer loyalty programs without accounting and tax complications. Let's break this down in detail:
How Shopify Loyalty Works
- Shopify as third party: Shopify owns and manages the entire loyalty program including points and software. The customer has their "account" directly with Shopify, not with the specific store. This means points are not your liability, but Shopify's liability.
- Your role: You (e.g., cafe) pay Shopify a monthly fee (e.g., €29) for using the platform and a small transaction fee (e.g., €0.20) for each point redemption (reward). You're essentially a "service provider" for Shopify – you provide rewards when Shopify sends you an order.
- Earning points: Customer earns points for purchases in stores participating in Shopify Loyalty program. For example, if customer buys coffee for €5 in your cafe, Shopify credits them points (e.g., 5 points per euro, so 25 points). Specific rules (how many points per euro) are set by you through Shopify platform, but technically points are managed by Shopify.
- Using points: Customer can use points for rewards (e.g., free coffee for 100 points), but usually only in stores participating in Shopify network. This means if your cafe uses Shopify Loyalty, points earned with you can be used with you or other stores in Shopify ecosystem, if Shopify allows it. Usually, however, stores set up the program so points are primarily usable with them, increasing loyalty to their brand.
- Point redemption process: When customer wants to use points (e.g., 100 points for free coffee), Shopify sends order to you (cafe) to provide the reward. You give the coffee but don't receive direct payment from customer – it's a marketing cost. You also pay Shopify transaction fee (€0.20). Accounting-wise, it's not a sale, so no taxable income or receipt obligation arises.
- Accounting treatment: When customer uses points:
- No receipt = no taxable income
- Coffee cost (€2) + Shopify fee (€0.20) = €2.20
- Recorded as "Promotional expenses" or "Marketing costs"
Why Must Loyalty Program Be Outsourced to Third Party (like Shopify)?
Small businesses don't have capacity or resources to manage their own loyalty program "in-house" for these reasons: - Tax and accounting complexity: If you managed loyalty program yourself, you'd have to create reserves for future liabilities (points customers will use later), estimate breakage rate (percentage of unused points) and handle cash vs. accrual accounting. For small firms that often must use cash accounting, this means immediate taxation of revenue if selling points, but cost deduction only in the future – creates cashflow mismatch. - Technological infrastructure: Managing points, customer databases and integration with payment systems requires sophisticated software and IT team, which is expensive and complicated for small firms. - Legal separation: When program is managed by third party like Shopify, points are their liability, not yours. For you, this means no future liabilities in your accounting books – just monthly costs (Shopify fee), which are tax-deductible as regular expense. - Economic efficiency: Shopify aggregates thousands of stores, achieving economies of scale – lower costs for software, security and data management. A small cafe could never create such system at reasonable price alone.
Why Can't It Be In-house from Tax Perspective?
If small firm managed loyalty program itself: - Immediate tax problem: If firm sold points (e.g., for money or as part of purchase), revenue would have to be taxed immediately, though costs for providing rewards (e.g., free coffee) could be deducted only when customer uses points. This creates cashflow mismatch because you pay tax before actually "losing" money on reward. - Complex reserves: Would have to estimate how many points will be used and create accounting reserves, which is administratively demanding and requires expensive accountants or software. - Risk of errors: Incorrect breakage rate estimates or poor liability management can lead to tax audits and penalties.
With Shopify, these problems are eliminated – you only pay monthly fee and transaction fees, which are simply recorded as marketing costs. Shopify takes full responsibility for managing points and liabilities to customers.
Case Study: Loyalty Points for Cafe (10 + 1 Free Model)
Let's look at specific case of small cafe offering classic loyalty program type "10 + 1 free". Customer gets 1 point for each coffee purchased (e.g., for €3) and after collecting 10 points gets one free coffee. We'll analyze how this works accounting-wise, whether it's "promotional expense" and what's the difference between in-house management and using Shopify.
How "10 + 1 Free" Program Works
- Earning points: Customer buys coffee for €3 and gets 1 point (e.g., stamp on card or digital record). Points have no monetary value for sale – they're purely reward for purchase.
- Using points: After collecting 10 points (meaning purchases for €30) customer gets free coffee (value €3).
- Real cost for cafe: Cost of producing free coffee is lower than selling price, e.g., €1.50 for materials and labor.
Accounting Treatment (In-house)
If cafe manages program itself (in-house), accounting process depends on whether it uses cash accounting (common for small firms) or accrual accounting: - Cash accounting: - When customer buys coffee: Cafe records €3 revenue for each coffee and issues receipt. Point (stamp) has no monetary value, so it's not recorded as liability or revenue. - When redeeming 10 points: When customer gets free coffee, no revenue arises (€0), but cost for coffee production arises (€1.50). This cost is recorded as "Promotional expense" or "Marketing cost" because it's form of discount or advertising to retain customer. - Tax impact: No revenue when issuing free coffee, €1.50 cost is tax-deductible as regular expense. - Accrual accounting (less common for small firms): - When customer buys coffee: Cafe records €3 revenue but simultaneously creates small liability for future reward (e.g., €0.30 per point, which is estimate of cost for future free coffee divided by 10). So from €3 revenue, taxable income is only €2.70. - When redeeming 10 points: When customer gets free coffee, cafe reduces liability by €3 (10 points x €0.30) and records €1.50 cost for coffee production. Difference can be adjusted as breakage or other profit if estimates differ from reality. - Tax impact: Taxable income is lower already at first purchase, but accounting is more complex due to estimates and reserves.
Is it Promotional Expense? Yes, in both cases (cash and accrual) the cost of free coffee is recorded as "Promotional expense" or "Marketing cost" because it's form of discount to support customer loyalty. It's not considered regular sale because no revenue or receipt arises.
Accounting Treatment (via Shopify Loyalty)
If cafe uses Shopify Loyalty to manage "10 + 1 free" program, process is simpler: - When customer buys coffee: Cafe records €3 revenue for coffee and issues receipt. Shopify credits point to customer's account (it's not your liability, but Shopify's). - When redeeming 10 points: Shopify sends order to issue free coffee. Cafe gives coffee (€1.50 cost) and pays Shopify transaction fee (€0.20). Total cost €1.70 is recorded as "Promotional expense" or "Marketing cost". - Tax impact: Same as in-house, no revenue when issuing free coffee, €1.70 cost is tax-deductible as regular expense. Additionally, you don't have to handle any liabilities or breakage estimates because Shopify manages points.
Difference Between In-house and Shopify
- In-house:
- Advantages: Full control over program, no monthly fees to third party (e.g., €29 Shopify fee).
- Disadvantages: If using accrual accounting, must create reserves and estimate breakage, which is administratively demanding. With cash accounting it's simpler (no liabilities), but if you sold points for money, tax mismatch arises (revenue taxed immediately, cost only later). Additionally, must manage point database yourself (stamps, software), which is time-consuming.
- Shopify Loyalty:
- Advantages: No liabilities in your accounting books, Shopify manages points and technology. Accounting-wise it's simple – just monthly fee (€29) and transaction fees (€0.20) as marketing cost. Don't have to handle estimates or breakage.
- Disadvantages: Pay monthly fees and transaction fees, increasing costs (e.g., €0.20 extra per free coffee). Have less control over program because third party manages it.
Conclusion for Cafe: "10 + 1 free" program is accounting-wise considered Promotional expense in both cases (in-house and Shopify) because free coffee is form of marketing to retain customers. Difference is in administrative burden and costs – Shopify simplifies accounting and management, but at cost of monthly fees. In-house is cheaper but more demanding to manage, especially if you wanted to use accrual accounting or sell points for money.
Conclusion
Loyalty programs are sophisticated customer loyalty tools, but their accounting and tax aspects differ significantly between large and small firms. Large corporations use accrual accounting and international structures for tax optimization, while for small businesses alternative models like gift cards or outsourcing entire program are often more advantageous, eliminating tax and cashflow problems. Gift cards additionally bring immediate cash flow, time value of money and breakage benefit, making them ideal tool for businesses of all sizes. Shopify Loyalty offers small firms way to implement loyalty program without accounting complications because it takes technical and legal responsibility, allowing focus on core business. For simple programs like "10 + 1 free," accounting impact is similar (Promotional expense), but Shopify simplifies management at cost of additional fees.
-
 @ dab6c606:51f507b6
2025-06-08 09:21:16
@ dab6c606:51f507b6
2025-06-08 09:21:16Dlhšie som sa zaujímal o to ako funguje biznis s míľami, vernostnými bodmi. Zistil som, že to čiastočne môžu robiť iba veľké korporácie kvôli tomu ako to môžu potom zaúčtovať. A je to daňovo super výhodné. Pridal som aj info o vernostných bodoch a darčekových kartách. Text nižšie napísali rôzne AI ako som sa v tom vŕtal, to je v zásade sumár, zdieľam pre tých, ktorých to zaujíma.
Časť I: Vernostné programy veľkých korporácií
Obchodná logika vernostných programov
Vernostné programy leteckých spoločností a hotelov sú sofistikované obchodné nástroje, ktoré slúžia niekoľkým kľúčovým účelom. Primárne fungujú na zvýšenie zákazníckej lojality vytvorením "switching costs" - zákazníci nechcú prísť o nazbierané body, čo znižuje pravdepodobnosť, že prejdú ku konkurencii.
Zároveň sú významným zdrojom dodatočných príjmov. Napríklad American Airlines zarába viac na predaji míľ bankám ako na niektorých leteckých linkách. Keď Citibank kupuje míle za 1-2 centy za míľu, aerolínia získava okamžitý príjem, zatiaľ čo reálna hodnota pre zákazníka môže byť 3-5 centov pri správnom využití.
Účtovné spracovanie vernostných bodov
Z účtovného hľadiska predstavujú vernostné body odložené záväzky. Keď zákazník získa body, spoločnosť musí vytvoriť rezervu na ich budúce uplatnenie. Body sa oceňujú na základe predpokladaných nákladov na ich uplatnenie, nie na základe nominálnej hodnoty.
Kľúčový je rozdiel medzi cash accounting a accrual accounting: - Cash accounting: Príjmy sa uznávajú pri prijatí platby, náklady pri zaplatení. - Accrual accounting: Príjmy a náklady sa uznávajú v momente vzniku záväzku.
Pre vernostné programy je accrual accounting kritické. Keď aerolínia predá míle banke za $1,000,000, vytvorí zároveň záväzok na budúce náklady (povedzme $600,000), takže zdaniteľný príjem je len $400,000.
Príklad: Predaj míľ banke
Aerolínia predá 50 miliónov míľ Citibank za $1,000,000: 1. Okamžitý príjem: $1,000,000 2. Vytvorenie záväzku: $600,000 (odhadované budúce náklady) 3. Zdaniteľný príjem: $400,000 4. Budúce náklady: Keď zákazníci míle využijú, spoločnosť uzná náklad a zníži záväzok
Pozitívna marža vzniká z niekoľkých faktorov: - Breakage - 15-20% míľ sa nikdy neuplatní - Časová hodnota peňazí - Peniaze od banky investuje okamžite - Marginálne náklady - Prázdne sedadlo má nízky prírastok nákladu
Daňová optimalizácia a offshore štruktúry
Veľké spoločnosti často využívajú medzinárodné štruktúry na optimalizáciu daní z vernostných programov. Typická štruktúra zahŕňa: 1. Materská spoločnosť (USA/EU) - Prevádzkuje lety a poskytuje služby (napr. lety alebo ubytovanie). 2. IP Holding (Írsko/Holandsko) - Vlastní duševné vlastníctvo (IP) k loyalty programu, ako sú značky, softvér a databázy. 3. Loyalty Operating Company (Singapur/Dubaj) - Spravuje predaj míľ bankám a partnerom, koordinuje program a komunikuje so zákazníkmi.
Obchodné vzťahy a platby medzi entitami (príklad s pozitívnym výsledkom pre Singapur)
Tieto entity sú prepojené zmluvami, ktoré určujú, kto za čo platí a prečo, aby sa minimalizovala daňová záťaž: - Banka → Singapur (Loyalty Operating Company): Banka (napr. Citibank) platí $1,000,000 za míle, ktoré ponúka svojim klientom ako odmenu za používanie kreditných kariet. Singapurská spoločnosť je hlavný kontaktný bod pre partnerov, pretože je umiestnená v jurisdikcii s nízkou daňou (17 %) a dobrou infraštruktúrou pre finančné služby. - Singapur → Írsko (IP Holding): Singapurská spoločnosť platí $500,000 ako royalty za použitie IP (značky, softvéru a dát) loyalty programu. Táto platba je vysoká, aby sa presunul zisk do Írska, kde je daňová sadzba ešte nižšia (12,5 %). Tým sa znižuje zdaniteľný príjem v Singapure. - Singapur → Materská spoločnosť (Aerolínia): Singapurská spoločnosť platí $300,000 materskej spoločnosti za poskytnutie služieb (napr. letov), keď zákazníci využijú míle. Táto platba je nižšia ako reálne náklady, aby sa minimalizoval zisk v krajine materskej spoločnosti, kde je daňová sadzba vyššia (napr. 25-35 % v USA alebo EU). - Zisk v Singapure: $1,000,000 (príjem od banky) - $500,000 (royalty do Írska) - $300,000 (platba aerolínii) = $200,000 zisku, ktorý je zdanený pri 17 % v Singapure.
Prečo takéto rozdelenie?
- Írsko (IP Holding): Vysoké royalty platby ($500,000) idú do Írska, pretože daňová sadzba 12,5 % je atraktívna a Írsko je považované za "serióznu" jurisdikciu, ktorá spĺňa medzinárodné pravidlá (napr. BEPS). Zároveň má Írsko zmluvy o zamedzení dvojitého zdanenia s mnohými krajinami, čo uľahčuje presun zisku.
- Singapur (Loyalty Operating Company): Predaj míľ a koordinácia programu prebieha v Singapure kvôli priaznivému daňovému prostrediu (17 %) a strategickej polohe pre ázijské trhy. Zároveň sa tu zanecháva malý zisk ($200,000), aby sa preukázala "ekonomická substance" – teda, že spoločnosť má reálnu činnosť.
- Materská spoločnosť: Platba $300,000 je nízka, aby sa minimalizoval zdaniteľný príjem v krajine s vysokou daňovou sadzbou (napr. USA alebo EU).
Prečo nie 0 % daňová jurisdikcia?
Prečo sa nepoužíva krajina s nulovou daňou (napr. Kajmanské ostrovy)? Kvôli: - Regulatory scrutiny - Daňové úrady pozorne sledujú 0 % jurisdikcie a môžu spochybniť legitímnosť. - BEPS pravidlám - Potreba preukázať "substance" (reálne kancelárie, zamestnancov) v krajine. - Credibility testu - 12,5 % v Írsku alebo 17 % v Singapure vyzerá ako legitímna obchodná operácia.
Výsledkom takejto štruktúry je, že väčšina zisku (60-70 %) je zdanená pri 12,5 % v Írsku alebo 17 % v Singapure namiesto 25-35 % v domovskej krajine aerolínky.
Časť II: Loyalty programy a alternatívy pre malé biznisy
Prečo je loyalty program problematický pre malé biznisy
Na rozdiel od veľkých korporácií, malé biznisy ako kaviarne narážajú pri vernostných programoch na zásadný problém: cash accounting povinnosť. V mnohých krajinách musia malé firmy (pod $25M ročne) používať cash accounting, čo znamená: - Príjem z predaja bodov sa zdaní okamžite - Náklady sa odpočítajú až keď zákazník body využije (možno o rok) - Vzniká daňový a cashflow problém - daň sa platí z peňazí, ktoré "stratíte" v budúcnosti
Predstavte si kaviareň, ktorá predá vernostné body za €100. Okamžite musí zaplatiť daň (povedzme €21), ale náklady na kávu poskytnutú za body odpočíta až v budúcnosti.
Alternatívne modely pre malé biznisy
Existujú daňovo výhodnejšie alternatívy:
1. Gift Cards model
- Príjem sa NEUZNÁ pri predaji gift karty
- Príjem sa uzná až keď zákazník kartu využije
- Príklad: Predáte gift cards za €10,000 v decembri, získate cash okamžite, ale daň platíte postupne, ako zákazníci karty využívajú počas nasledujúceho roka.
- Časová hodnota peňazí: Peniaze môžete investovať (napr. 6 % ročne = €600 extra zisk na €10,000)
- Breakage benefit: 2-10 % kariet sa nikdy nevyužije, po určitom čase (3-5 rokov, podľa legislatívy) môžete zostatok uznať ako čistý zisk.
Príklad: Starbucks Starbucks mal v roku 2022 na účtoch $1,5 miliardy v nevyužitých gift cards. Odhadovaný breakage 3 % znamená $45 miliónov čistého zisku – bezúročná pôžička od zákazníkov s bonusom, že časť sa nikdy nevráti.
2. Subscription model
- Mesačný príjem = okamžité zdanenie
- Mesačné náklady = okamžitý odpočet
- Príklad: €10/mesiac za "premium membership" s určitými benefitmi
3. Discount Coupons
- Žiadny príjem pri vydaní kupónu
- Znížený príjem pri uplatnení (predáte za nižšiu cenu)
- Príklad: 20 % zľavový kupón = predaj kávy za €4 namiesto €5
Outsourcing loyalty programu: Podrobnosti o Shopify Loyalty
Platformy ako Shopify Loyalty predstavujú elegantné riešenie pre malé biznisy, ktoré chcú ponúkať vernostné programy bez účtovných a daňových komplikácií. Poďme si to rozobrať podrobne:
Ako funguje Shopify Loyalty
- Shopify ako tretia strana: Shopify vlastní a spravuje celý vernostný program vrátane bodov a softvéru. Zákazník má svoj "účet" priamo u Shopify, nie u konkrétneho obchodu. To znamená, že body nie sú vaším záväzkom, ale záväzkom Shopify.
- Vaša úloha: Vy (napr. kaviareň) platíte Shopify mesačný poplatok (napr. €29) za používanie platformy a malý transakčný poplatok (napr. €0,20) za každé uplatnenie bodov (reward). Vy ste v podstate "dodávateľom služieb" pre Shopify – poskytujete odmeny, keď vám Shopify pošle objednávku.
- Získavanie bodov: Zákazník získava body za nákupy v obchodoch, ktoré sú zapojené do Shopify Loyalty programu. Napríklad, ak zákazník nakúpi kávu za €5 vo vašej kaviarni, Shopify mu pripíše body (napr. 5 bodov za každé euro, teda 25 bodov). Konkrétne pravidlá (koľko bodov za euro) si nastavujete vy cez Shopify platformu, ale technicky body spravuje Shopify.
- Využitie bodov: Zákazník môže body využiť na odmeny (napr. kávu zadarmo za 100 bodov), ale zvyčajne len v obchodoch zapojených do Shopify siete. To znamená, že ak vaša kaviareň používa Shopify Loyalty, body získané u vás môžu byť využité u vás alebo v iných obchodoch v rámci Shopify ekosystému, ak to Shopify umožňuje. Väčšinou však obchody nastavujú program tak, aby boli body využiteľné primárne u nich, čím sa zvyšuje lojalita k ich značke.
- Proces uplatnenia bodov: Keď zákazník chce využiť body (napr. 100 bodov za kávu zadarmo), Shopify pošle objednávku vám (kaviarni) na poskytnutie odmeny. Vy kávu vydáte, ale nedostanete za ňu priamy príjem od zákazníka – ide o marketingový náklad. Zároveň platíte Shopify transakčný poplatok (€0,20). Účtovne to nie je predaj, takže nevzniká zdaniteľný príjem ani povinnosť vystaviť bloček.
- Účtovné spracovanie: Keď zákazník využije body:
- Žiadny bloček = žiadny zdaniteľný príjem
- Náklad kávy (€2) + Shopify fee (€0,20) = €2,20
- Účtuje sa ako "Promotional expenses" alebo "Marketing costs"
Prečo musí byť loyalty program outsourcovaný tretej strane (ako Shopify)?
Malé biznisy nemajú kapacitu ani zdroje na správu vlastného loyalty programu "in-house" z týchto dôvodov: - Daňová a účtovná komplexnosť: Ak by ste spravovali loyalty program sami, museli by ste vytvárať rezervy na budúce záväzky (body, ktoré zákazníci využijú neskôr), odhadovať breakage rate (percento nevyužitých bodov) a riešiť cash vs. accrual accounting. Pre malé firmy, ktoré často musia používať cash accounting, to znamená okamžité zdanenie príjmu, ak by body predávali, ale odpočet nákladov až v budúcnosti – vzniká cashflow nesúlad. - Technologická infraštruktúra: Správa bodov, databáz zákazníkov a integrácia s platobnými systémami vyžaduje sofistikovaný softvér a IT tím, čo je pre malé firmy nákladné a komplikované. - Legálna separácia: Keď program spravuje tretia strana ako Shopify, body sú ich záväzkom, nie vaším. Pre vás to znamená, že nemáte žiadne budúce záväzky vo svojej účtovnej knihe – len mesačné náklady (poplatok Shopify), ktoré sú daňovo odpočítateľné ako bežný výdavok. - Ekonomická efektivita: Shopify združuje tisíce obchodov, čím dosahuje ekonomiku rozsahu – nižšie náklady na softvér, bezpečnosť a správu dát. Malá kaviareň by sama nikdy nedokázala vytvoriť takýto systém za rozumnú cenu.
Prečo to nemôže byť in-house z daňového hľadiska?
Ak by malá firma spravovala loyalty program sama: - Okamžitý daňový problém: Ak by firma predávala body (napr. za peniaze alebo ako súčasť nákupu), príjem by musela zdaniť hneď, hoci náklady na poskytnutie odmien (napr. káva zadarmo) by mohla odpočítať až v momente, keď zákazník body využije. To vytvára cashflow nesúlad, pretože daň platíte skôr, než reálne "stratíte" peniaze na odmenu. - Zložité rezervy: Musela by odhadovať, koľko bodov sa využije, a vytvárať účtovné rezervy, čo je administratívne náročné a vyžaduje drahých účtovníkov alebo softvér. - Riziko chýb: Nesprávne odhady breakage rate alebo zlý manažment záväzkov môžu viesť k daňovým kontrolám a pokutám.
S Shopify sa tieto problémy eliminujú – vy platíte len mesačný poplatok a transakčné fees, ktoré sú jednoducho účtované ako marketingové náklady. Shopify preberá celú zodpovednosť za správu bodov a záväzkov voči zákazníkom.
Prípadová štúdia: Vernostné body pre kaviareň (model 10 + 1 zadarmo)
Pozrime sa na konkrétny prípad malej kaviarne, ktorá ponúka klasický vernostný program typu "10 + 1 zadarmo". Zákazník dostane 1 bod za každú kúpenú kávu (napr. za €3) a po nazbieraní 10 bodov dostane jednu kávu zadarmo. Rozoberieme, ako to funguje účtovne, či ide o "promotional expense" a aký je rozdiel medzi in-house správou a použitím Shopify.
Ako funguje program "10 + 1 zadarmo"
- Získavanie bodov: Zákazník kúpi kávu za €3 a dostane 1 bod (napr. pečiatku na kartičku alebo digitálny záznam). Body nemajú peňažnú hodnotu na predaj – sú čisto odmenou za nákup.
- Využitie bodov: Po nazbieraní 10 bodov (čo znamená nákupy za €30) zákazník dostane kávu zadarmo (hodnota €3).
- Reálny náklad pre kaviareň: Náklad na výrobu kávy zadarmo je nižší ako predajná cena, napr. €1,50 za suroviny a prácu.
Účtovné spracovanie (In-house)
Ak kaviareň spravuje program sama (in-house), účtovný proces závisí od toho, či používa cash accounting (bežné pre malé firmy) alebo accrual accounting: - Cash accounting: - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3 za každú kávu a vydá bloček. Bod (pečiatka) nemá peňažnú hodnotu, takže sa neúčtuje ako záväzok ani príjem. - Pri uplatnení 10 bodov: Keď zákazník dostane kávu zadarmo, nevzniká príjem (€0), ale vzniká náklad na výrobu kávy (€1,50). Tento náklad sa účtuje ako "Promotional expense" alebo "Marketing cost", pretože ide o formu zľavy alebo reklamy na udržanie zákazníka. - Daňový dopad: Žiadny príjem pri vydaní kávy zadarmo, náklad €1,50 je daňovo odpočítateľný ako bežný výdavok. - Accrual accounting (menej bežné pre malé firmy): - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3, ale zároveň vytvára malý záväzok na budúcu odmenu (napr. €0,30 za každý bod, čo je odhad nákladu na budúcu kávu zadarmo deleno 10). Teda z €3 príjmu je zdaniteľný príjem len €2,70. - Pri uplatnení 10 bodov: Keď zákazník dostane kávu zadarmo, kaviareň zníži záväzok o €3 (10 bodov x €0,30) a účtuje náklad €1,50 na výrobu kávy. Rozdiel môže byť upravený ako breakage alebo iný zisk, ak sa odhady líšia od reality. - Daňový dopad: Zdaniteľný príjem je nižší už pri prvom nákupe, ale účtovníctvo je zložitejšie kvôli odhadom a rezervám.
Je to Promotional Expense? Áno, v oboch prípadoch (cash aj accrual) sa náklad na kávu zadarmo účtuje ako "Promotional expense" alebo "Marketing cost", pretože ide o formu zľavy na podporu lojality zákazníkov. Nie je to považované za bežný predaj, pretože nevzniká príjem ani bloček.
Účtovné spracovanie (cez Shopify Loyalty)
Ak kaviareň používa Shopify Loyalty na správu programu "10 + 1 zadarmo", proces je jednoduchší: - Pri nákupe kávy zákazníkom: Kaviareň účtuje príjem €3 za kávu a vydá bloček. Shopify pripíše bod zákazníkovi do jeho účtu (nie je to váš záväzok, ale Shopify). - Pri uplatnení 10 bodov: Shopify pošle objednávku na vydanie kávy zadarmo. Kaviareň vydá kávu (náklad €1,50) a zaplatí Shopify transakčný poplatok (€0,20). Celkový náklad €1,70 sa účtuje ako "Promotional expense" alebo "Marketing cost". - Daňový dopad: Rovnako ako pri in-house, žiadny príjem pri vydaní kávy zadarmo, náklad €1,70 je daňovo odpočítateľný ako bežný výdavok. Navyše nemusíte riešiť žiadne záväzky alebo odhady breakage, pretože body spravuje Shopify.
Rozdiel medzi In-house a Shopify
- In-house:
- Výhody: Plná kontrola nad programom, žiadne mesačné poplatky tretej strane (napr. €29 Shopify fee).
- Nevýhody: Ak použijete accrual accounting, musíte vytvárať rezervy a odhadovať breakage, čo je administratívne náročné. Pri cash accounting je to jednoduchšie (žiadne záväzky), ale ak by ste body predávali za peniaze, vzniká daňový nesúlad (príjem zdanený hneď, náklad až neskôr). Navyše musíte sami spravovať databázu bodov (pečiatky, softvér), čo je časovo náročné.
- Shopify Loyalty:
- Výhody: Žiadne záväzky vo vašej účtovnej knihe, Shopify spravuje body a technológiu. Účtovne je to jednoduché – len mesačný poplatok (€29) a transakčné poplatky (€0,20) ako marketingový náklad. Nemusíte riešiť odhady ani breakage.
- Nevýhody: Platíte mesačné poplatky a transakčné fees, čo zvyšuje náklady (napr. €0,20 navyše za každú kávu zadarmo). Máte menšiu kontrolu nad programom, pretože ho spravuje tretia strana.
Záver pre kaviareň: Program "10 + 1 zadarmo" je účtovne považovaný za Promotional expense v oboch prípadoch (in-house aj Shopify), pretože káva zadarmo je forma marketingu na udržanie zákazníkov. Rozdiel je v administratívnej záťaži a nákladoch – Shopify zjednodušuje účtovníctvo a správu, ale za cenu mesačných poplatkov. In-house je lacnejšie, ale náročnejšie na správu, najmä ak by ste chceli používať accrual accounting alebo predávať body za peniaze.
Záver
Vernostné programy sú sofistikovaný nástroj zákazníckej lojality, ale ich účtovné a daňové aspekty sa výrazne líšia medzi veľkými a malými firmami. Veľké korporácie využívajú accrual accounting a medzinárodné štruktúry na optimalizáciu daní, zatiaľ čo pre malé biznisy sú často výhodnejšie alternatívne modely ako gift cards alebo outsourcing celého programu, ktoré eliminujú daňové a cashflow problémy. Gift cards navyše prinášajú okamžitý cash flow, časovú hodnotu peňazí a breakage benefit, čo z nich robí ideálny nástroj pre podniky všetkých veľkostí. Shopify Loyalty ponúka malým firmám spôsob, ako implementovať vernostný program bez účtovných komplikácií, pretože preberá technickú a právnu zodpovednosť, čím umožňuje sústrediť sa na core biznis. Pre jednoduché programy ako "10 + 1 zadarmo" je účtovný dopad podobný (Promotional expense), ale Shopify zjednodušuje správu za cenu dodatočných poplatkov.
```
```
-
 @ 86dfbe73:628cef55
2025-06-08 09:12:43
@ 86dfbe73:628cef55
2025-06-08 09:12:43Das Private ist immer nur privat in Bezug zu einem bestimmten oder unbestimmten Gegenüber. Heutzutage steht man vielen Privatheiten und vielen Öffentlichkeiten gegenüber. Was privat ist, bemisst sich an der jeweiligen Relation, in der es als privat festgelegt wurde. Die “Privatsphäre”, die üblicherweise gemeint wird, ist jene Sphäre, die der Staat als privat zu respektieren hat, über deren Grenze er sich also nur in seltenen und jeweils zu begründenden Einzelfällen hinwegsetzen darf.
In anderen Beziehungen hingegen gibt es andere “Privatheiten” — dem Arbeitgeber gegenüber etwa, den Kollegen, ehemaligen Schulfreunden, dem Ehepartner, den Eltern oder Kinder. In all diesen Beziehungen gibt es “ausgeschlossene” Bereiche, die das Private meinen. Die Privatsphäre ist dabei die Sphäre über deren Geheimhaltung man gegenüber dem anderen Partner der Beziehung frei verfügen kann, denn Privatsphäre ist die Möglichkeit, sich der Welt selektiv zu offenbaren.
Wenn nicht reflektiert wird, dass es weitgehend eine veränderte Gesellschaft ist, die sich konstituiert, eine Gesellschaft, die mit der vorherigen nichts aber auch gar nichts mehr gemein hat, weil sich der Begriff des “Privaten” verändert, ausdifferenziert, verschiebt, zerfasert — wird der Privatsphärenschutz nicht zu gewährleisten sein.
Das Problem ist, dass „privat und „öffentlich“ alleine nicht funktionieren. Zwischen Privat und Öffentlich gehört – abgeleitet aus dem Begriff des „Social Web“ das Soziale. Und zwischen scheinbar einheitlicher privater „Identität“ und öffentlicher „Person“ gehört ein Bündel an Socialities.
Schon vor dem Netz zersplitterte der moderne, flexible und mobile Mensch in ein Bündel von (nicht: Identitäten sondern) Socialitäten. Das heißt in ein Bündel von Verhaltensweisen, die mehr oder minder bewusst in Beziehung zu bestimmten anderen Socii eingenommen werden. Es ist eine rein kommunikative Größe. Die Socialität eines Arbeitnehmers deckt sich nicht mit der Sozialität des Ehegatten, Vaters usw.
In jeder dieser Beziehungen ist eine andere, zumeist bewusst zu lernende Sozialität vonnöten. Selbst gegenüber Vorgesetzten, gleichrangigen Kollegen und Untergebenen sind mindestens dreierlei Socialitäten am Werke. Denn diese Socialität ist nicht einfach die soziologische „Rolle“, die ein Pluriversum von angenommenen Identitäten unterstellt. Sondern sie ist Ergebnis einer Kommunikationsbeziehung.
Online-Socialitäten
Das Private ist kein kohärente Sphäre, sondern wird durch die Socialität erschaffen. Es ist das, was in der Socialität nicht vorkommt – oder die Qualität der Socialität entscheidend verändert – etwa wenn eine Beziehung zu einer Kollegin/einem Kollegen beginnt (die in der Socialität der Ehegatten wiederum vermutlich nichts zu suchen hat …), sich eine Exfreundin als neue Kundin vorstellt, ein ehemaliger Schulkamerad Chef wird usw. Was „das Private“ ist, lässt sich nicht fassen.
Bei Facebook beispielsweise connectet sich der User mit Familienangehörigen, Freunden, vielleicht ehemaligen Schulfreunden, Kollegen, ggf. Vorgesetzen – und mit Geschäftspartnern oder Kunden. Das heißt: Ein großes Socialitätenbündel vereinigt sich.
Das kann zu größeren Problemen führen, denn die Socialität etwa des Geschäftspartners stellt andere Anforderungen als der ehemalige Klassenkamerad. Die Socialität des Kollegen stellt andere Anforderungen als die der Geschwister.
Die Bündelungsmöglichkeiten durch Personensuchen stellt vor eine ganz andere Herausforderung. Das Multiversum der Socialitäten, das unter verschiedenen Pseudonymen oder doch zumindest auf verschiedenen Plattformen ausgetragen wurde – wird nun plötzlich in ein „Image“ zusammengeführt, das natürlich vorne und hinten inkongruent ist, weil kein gemeinsamer „Kern“, keine einfache „Identität“ vorhanden ist.
Streetview und die Socialität
Schon jetzt nutzen Auskunfteien wie SchuFa oder Creditreform die Wohngegend um Kreditwürdigkeiten zu berechnen. Schon jetzt klassifizieren die Telefonrechner in Callcentern die „Wertigkeit“ eines eingehenden Anrufs per Telefonnummer nach Wohnlage.
Das macht in dieser Socialität "Versicherung-Kunde" einen gewaltigen Unterschied. Und der Kunde hat keinerlei Macht über die Informationen, die der anderen Seite der Socialität verfügbar sind. Die Entscheidung, dass etwas privat sei, zieht nach sich, dass ich es aus einer Socialität exkludiere. „Privat“ bedeutet vor allem „Verzeihung, das ist mir zu privat, darüber gebe ich keine Auskunft“. Und derlei Privatheiten gibt es zu viele – was privat ist, bestimmt die Socialität. Privatsphäre gegenüber dem Kollegen ist eine andere als gegenüber der Vorgesetzten, als gegenüber dem Kunden, als gegenüber dem ehemaligen Schulfreund.
Wie damit umgehen? Das Netz verlassen oder eine eigene „Netzsocialität“ erschaffen, die von vornherein eine inszenierte Kunstfigur ist? Nichts von alledem ist hilfreich. Deswegen kann die Lösung nur aus einer gesamtgesellschaftlichen Debatte rund um die Socialitäten kommen. Und muss sich fragen: Wie soll das Netz sein und funktionieren? Wer soll was einsehen können?
-
 @ 318ebaba:9a262eae
2025-06-08 08:36:12
@ 318ebaba:9a262eae
2025-06-08 08:36:12When connecting to multiple relays in the Nostr protocol, users may encounter several challenges that can affect their overall experience. Here are some of the key issues:
Challenges of Connecting to Multiple Relays
-
Performance Issues: The lightweight design of Nostr relays can lead to performance bottlenecks, especially when many users are connected simultaneously. This can result in slow message delivery or even failures in posting messages if the relays are overwhelmed[1][2][32].
-
Reliability and Connectivity: Users may experience connectivity problems with certain relays, which can lead to inconsistent access to messages or delays in communication. If a relay goes offline or has connectivity issues, it can disrupt the flow of information, making it difficult for users to send or receive messages reliably[3][4][18].
-
Data Synchronization: As users connect to multiple relays, ensuring that data is synchronized across these relays can be challenging. Inconsistent data states may arise if different relays store messages differently or if there are delays in message propagation. This can lead to confusion about which messages have been sent or received[7][41].
-
Configuration Complexity: Managing connections to multiple relays requires a certain level of technical knowledge. Users need to configure their clients properly to connect to various relays, which can be daunting for those less familiar with the technology. Misconfigurations can lead to connection failures or suboptimal performance[4][21].
-
Spam and Quality Control: With the open nature of Nostr, some relays may be more susceptible to spam or low-quality content. Users connecting to multiple relays might encounter a higher volume of irrelevant or unwanted messages, which can detract from the overall user experience[6][32].
-
Security Concerns: When using multiple relays, users must be cautious about the security of their connections. Not all relays may implement the same level of security, and connecting to less secure relays could expose users to risks such as data interception or unauthorized access to their messages[26][27].
In summary, while connecting to multiple relays in Nostr offers benefits such as redundancy and improved access to information, users must navigate various challenges related to performance, reliability, configuration, and security. Addressing these issues is crucial for a smooth and effective experience on the Nostr network.
[1] https://forum.dfinity.org/t/introducing-replicatr-enhancing-nostr-with-internet-computer-integration/31861 [2] https://medium.com/coinmonks/a-deep-dive-into-nostr-clients-with-technical-insights-and-code-snippets-b1666bb11fac [3] nostr:nevent1qqsfvjvg73wxdn7mda28m704r2zv9lnzlcdgh8r0g52lfvy2wj7uw4czyq32rylmsmre84lhxdypy6jlu4dt3fxfwkq9a0p0lqdl9y8hsp0hur4fuw4 [4] https://www.reddit.com/r/nostr/comments/1e6nm68/new_nostream_relay_created_problems_with_publish/ [5] https://www.lynalden.com/the-power-of-nostr/ [6] https://bitcoinmagazine.com/technical/how-nostr-can-improve-bitcoin-privacy [7] https://barelybuggy.blog/2024/11/26/mostr-offline/ [8] https://github.com/scsibug/nostr-rs-relay/issues/126 [9] https://community.umbrel.com/t/nostr-relay-troubleshooting/17828 [10] https://research.dorahacks.io/2024/04/30/nostr-relay-incentive/ [11] https://community.start9.com/t/issue-confirming-nostr-relay/1682 [12] https://arxiv.org/html/2402.05709v1 [13] https://community.umbrel.com/t/nostr-relay-not-connecting/11401 [14] https://www.purplerelay.com/troubleshooting-common-issues-with-nostr-relay-server-a-users-guide/ [15] https://news.ycombinator.com/item?id=35694029 [16] https://substack.com/home/post/p-158872714?utm_campaign=post&utm_medium=web [17] https://stacker.news/items/142013 [18] https://www.reddit.com/r/nostr/comments/1h6admk/are_these_relays_working/ [19] https://news.ycombinator.com/item?id=33746360 [20] https://github.com/scsibug/nostr-rs-relay/issues/195 [21] https://www.purplerelay.com/how-to-run-a-nostr-relay-a-step-by-step-guide/ [22] https://denostr.medium.com/the-future-of-social-communication-nostrs-origins-and-the-next-destination-in-social-networking-27f0c901d7ae [23] nostr:nevent1qqsqwklh29cvf3z0skhh77xyqf3m53xkppcttf3c8nuc2jqteulfx0czyqcgr7epv9hha2v9afp99l5wl0ljna0zum59fzyhl9v8pgv5xlhf5ava642 [24] https://www.reddit.com/r/nostr/comments/15fyr6r/pervasive_private_key_sharing_seems_dangerous/ [25] https://whtwnd.com/agoracitizen.network/3l2fysaripd2q [26] https://ron.stoner.com/nostr_Security_and_Privacy/ [27] https://forums.puri.sm/t/about-what-is-nostr/20764 [28] https://github.com/nostr-protocol/nips/issues/107 [29] https://medium.com/@volodymyrpavlyshyn/security-features-of-nostr-a0276a22e815 [30] nostr:nevent1qqspd8fh3tplxtfhjpka3y3glzh63v3ygsdhacyq8dvyrnxtvl09lpczyr2v7dprke9lad2qk0svug55vxguqv7n3dwn9vm63u8n5n84znxjxedjf6c [31] nostr:nevent1qqs8e2su6n8m2xtg45qdjw7rdcq6w3g5guvt085h52qhg25wxn755sczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vzan82f [32] https://www.cointribune.com/en/nostr-et-la-censure-pourquoi-un-reseau-social-decentralise-est-essentiel-2/ [33] nostr:nevent1qqsv86d756zcw32x0zcvqmr924y5sltvwqud0dywny83ndee30zzrmczyrh26kg89z95jqaz4xkex7kaw2t36twtc75vmrfx2k3p3jqvhfa8vwpfv29 [34] https://github.com/nbd-wtf/nostr-tools/issues [35] https://www.voltage.cloud/blog/the-growth-of-nostr-the-era-of-decentralization [36] https://medium.com/@BingVentures/status-quo-challenges-and-prospect-of-decentralized-social-networks-18f9584f2e8d [37] https://www.reddit.com/r/RedditAlternatives/comments/14s8ao4/greetings_im_here_to_tell_you_about_nostr_a/ [38] https://bitcoinmagazine.com/culture/nostr-the-importance-of-censorship-resistant-communication-for-innovation-and-human-progress- [39] https://github.com/mayneyao/eidos/issues/129 [40] https://www.reddit.com/r/nostr/comments/115a8et/data_duplication_and_distribution_in_nostr_relays/ [41] https://github.com/open-nostr/nostar [42] nostr:nevent1qqsryg8zuc9rdwldat385al24mdt56wanc6g6hfymy8l9tgtmzsc4nspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhg85cx73 [43] https://ckbcn.xlog.app/Nostr-sheng-tai-fa-zhan-xian-zhuang-ji-wen-ti?locale=en [44] nostr:naddr1qqc92mnvda3kk6twvuk5ummnw3ez6ued2phhgetww35kzmpdwa5hg6pdfehhgetyv43kktt08p5hscnkqgsr7acdvhf6we9fch94qwhpy0nza36e3tgrtkpku25ppuu80f69kfqrqsqqqa28aknkml
-
-
 @ 866e0139:6a9334e5
2025-06-08 07:10:42
@ 866e0139:6a9334e5
2025-06-08 07:10:42Autor: John J. Mearsheimer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Blog des Autors. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Die Frage, wer für den Krieg in der Ukraine verantwortlich ist, ist seit dem Einmarsch Russlands in die Ukraine am 24. Februar 2022 ein sehr umstrittenes Thema.Die Antwort auf diese Frage ist von enormer Bedeutung, denn der Krieg war aus verschiedenen Gründen eine Katastrophe, von denen die wichtigste darin besteht, dass die Ukraine praktisch zerstört wurde. Sie hat einen beträchtlichen Teil ihres Territoriums verloren und wird wahrscheinlich noch mehr verlieren, ihre Wirtschaft liegt in Trümmern, eine riesige Zahl von Ukrainern wurde intern vertrieben oder ist aus dem Land geflohen, und sie hat Hunderttausende von Opfern zu beklagen. Natürlich hat auch Russland einen hohen Blutzoll gezahlt. Auf strategischer Ebene sind die Beziehungen zwischen Russland und Europa, ganz zu schweigen von Russland und der Ukraine, auf absehbare Zeit vergiftet, was bedeutet, dass die Gefahr eines größeren Krieges in Europa auch dann noch bestehen wird, wenn der Krieg in der Ukraine zu einem eingefrorenen Konflikt wird. Wer die Verantwortung für diese Katastrophe trägt, ist eine Frage, die nicht so schnell verschwinden wird, sondern eher noch an Bedeutung gewinnen dürfte, je mehr Menschen das Ausmaß der Katastrophe bewusst wird.
Die gängige Meinung im Westen ist, dass Wladimir Putin für den Krieg in der Ukraine verantwortlich sei. Die Invasion habe darauf abgezielt, die gesamte Ukraine zu erobern und sie zu einem Teil eines größeren Russlands zu machen, so die Argumentation. Sobald dieses Ziel erreicht sei, würden die Russen ein Imperium in Osteuropa errichten, ähnlich wie es die Sowjetunion nach dem Zweiten Weltkrieg getan habe. Daher stelle Putin letztlich eine Bedrohung für den Westen dar, der man mit aller Macht begegnen müsse. Kurz gesagt, Putin ist ein Imperialist mit einem Masterplan, der sich nahtlos in die reiche russische Tradition einfügt.
Das alternative Argument, mit dem ich mich identifiziere und das im Westen eindeutig in der Minderheit ist, lautet, dass die Vereinigten Staaten und ihre Verbündeten den Krieg provoziert haben. Damit soll natürlich nicht geleugnet werden, dass Russland in die Ukraine einmarschiert ist und den Krieg begonnen hat. Die Hauptursache des Konflikts ist jedoch der NATO-Beschluss, die Ukraine in das Bündnis aufzunehmen, was praktisch alle russischen Führer als existenzielle Bedrohung ansehen, die beseitigt werden muss. Die NATO-Erweiterung ist jedoch Teil einer umfassenderen Strategie, die darauf abzielt, die Ukraine zu einem westlichen Bollwerk an Russlands Grenze zu machen. Ein Beitritt Kiews zur Europäischen Union (EU) und die Förderung einer farbigen Revolution in der Ukraine – die Umwandlung des Landes in eine prowestliche liberale Demokratie – sind die beiden anderen Säulen dieser Politik. Die russische Führung fürchtet alle drei Bereiche, aber am meisten fürchtet sie die NATO-Erweiterung. Um dieser Bedrohung zu begegnen, hat Russland am 24. Februar 2022 einen Präventivkrieg begonnen.
Die Debatte darüber, wer den Ukraine-Krieg verursacht hat, ist kürzlich aufgeflammt, als zwei prominente westliche Politiker – der ehemalige US-Präsident Donald Trump und der prominente britische Abgeordnete Nigel Farage – das Argument vorbrachten, dass die NATO-Erweiterung die treibende Kraft hinter dem Konflikt sei. Es überrascht nicht, dass ihre Äußerungen von den Verfechtern der konventionellen Meinung mit einem heftigen Gegenangriff beantwortet wurden. Es ist auch erwähnenswert, dass der scheidende NATO-Generalsekretär Jens Stoltenberg im vergangenen Jahr zweimal sagte, dass „Präsident Putin diesen Krieg begonnen hat, weil er die Tür der NATO schließen und der Ukraine das Recht verweigern wollte, ihren eigenen Weg zu wählen“. Kaum jemand im Westen hat dieses bemerkenswerte Eingeständnis des NATO-Chefs in Frage gestellt, und er hat es auch nicht zurückgezogen.
Mein Ziel ist es, einen Überblick über die wichtigsten Punkte zu geben, die die Ansicht stützen, dass Putin nicht in die Ukraine einmarschiert ist, weil er ein Imperialist ist, der die Ukraine zu einem Teil eines größeren Russlands machen will, sondern vor allem wegen der NATO-Erweiterung und der Bemühungen des Westens, die Ukraine zu einer westlichen Hochburg an der Grenze Russlands zu machen.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld und das Verständnis!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Lassen Sie mich mit den sieben wichtigsten Gründen für die Ablehnung der herkömmlichen Meinung beginnen.
ERSTENS gibt es schlicht und ergreifend keine Beweise aus der Zeit vor dem 24. Februar 2022, dass Putin die Ukraine erobern und in Russland eingliedern wollte. Vertreter der gängigen Meinung können keine Schriftstücke oder Aussagen von Putin nennen, die darauf hindeuten, dass er die Ukraine erobern wollte.
Wenn man sie zu diesem Punkt befragt, liefern die Verfechter der konventionellen Meinung Hinweise, die wenig oder gar nichts mit Putins Motiven für die Invasion der Ukraine zu tun haben. Einige betonen zum Beispiel, dass er sagte, die Ukraine sei ein „künstlicher Staat“ oder kein „echter Staat“. Solche undurchsichtigen Äußerungen sagen jedoch nichts über die Gründe für seinen Kriegseintritt aus. Dasselbe gilt für Putins Aussage, er betrachte Russen und Ukrainer als „ein Volk“ mit einer gemeinsamen Geschichte. Andere weisen darauf hin, dass er den Zusammenbruch der Sowjetunion als „die größte geopolitische Katastrophe des Jahrhunderts“ bezeichnete. Aber Putin sagte auch: „Wer die Sowjetunion nicht vermisst, hat kein Herz. Wer sie zurückhaben will, hat kein Hirn.“ Andere wiederum verweisen auf eine Rede, in der er erklärte: „Die moderne Ukraine wurde vollständig von Russland geschaffen, genauer gesagt, vom bolschewistischen, kommunistischen Russland.“ Aber das ist kaum ein Beweis dafür, dass er an der Eroberung der Ukraine interessiert war. Außerdem sagte er in der gleichen Rede: „Natürlich können wir die Ereignisse der Vergangenheit nicht ändern, aber wir müssen sie zumindest offen und ehrlich zugeben.“
Um zu beweisen, dass Putin die gesamte Ukraine erobern und Russland einverleiben wollte, muss man nachweisen, dass er 1) dieses Ziel für erstrebenswert hielt, 2) es für machbar hielt und 3) die Absicht hatte, dieses Ziel zu verfolgen. Es gibt in den öffentlichen Aufzeichnungen keine Beweise dafür, dass Putin erwog, geschweige denn beabsichtigte, die Ukraine als unabhängigen Staat zu beenden und sie zu einem Teil Großrusslands zu machen, als er am 24. Februar 2022 seine Truppen in die Ukraine schickte.
Tatsächlich gibt es erhebliche Beweise dafür, dass Putin die Ukraine als unabhängiges Land anerkannte. In seinem bekannten Artikel vom 12. Juli 2021 über die russisch-ukrainischen Beziehungen, der von Befürwortern der konventionellen Meinung oft als Beweis für seine imperialen Ambitionen angeführt wird, sagt er dem ukrainischen Volk: „Ihr wollt einen eigenen Staat gründen: Ihr seid willkommen!“ Zur Frage, wie Russland die Ukraine behandeln sollte, schreibt er: „Es gibt nur eine Antwort: mit Respekt.“ Er schließt seinen langen Artikel mit den folgenden Worten ab: „Und wie die Ukraine aussehen wird – das müssen ihre Bürger entscheiden.“ Diese Aussagen stehen im direkten Widerspruch zu der Behauptung, Putin wolle die Ukraine in ein größeres Russland eingliedern.
In demselben Artikel vom 12. Juli 2021 und erneut in einer wichtigen Rede am 21. Februar 2022 betonte Putin, dass Russland „die neue geopolitische Realität, die nach der Auflösung der UdSSR entstanden ist“, akzeptiere. Diesen Punkt wiederholte er ein drittes Mal am 24. Februar 2022, als er ankündigte, Russland werde in die Ukraine einmarschieren. Insbesondere erklärte er: „Wir haben nicht vor, ukrainisches Territorium zu besetzen“, und machte deutlich, dass er die ukrainische Souveränität respektiere, allerdings nur bis zu einem gewissen Punkt: „Russland kann sich nicht sicher fühlen, sich nicht entwickeln und nicht existieren, wenn es sich einer ständigen Bedrohung durch das Territorium der heutigen Ukraine ausgesetzt sieht.“ Das heißt, Putin war nicht daran interessiert, die Ukraine zu einem Teil Russlands zu machen, sondern er wollte sicherstellen, dass sie nicht zu einem „Sprungbrett“ für westliche Aggressionen gegen Russland wird.
ZWEITENS gibt es keinerlei Hinweise dafür, dass Putin eine Marionettenregierung für die Ukraine vorbereitete, in Kiew prorussische Führungspersönlichkeiten aufbaute oder irgendwelche politischen Maßnahmen verfolgte, die eine Besetzung des gesamten Landes und dessen letztendliche Eingliederung in Russland ermöglichen würden.
Diese Fakten widersprechen der Behauptung, Putin sei daran interessiert gewesen, die Ukraine von der Landkarte zu tilgen.
**DRITTENS: Putin hatte nicht annähernd genug Truppen, um die Ukraine zu erobern. **
Beginnen wir mit den Gesamtzahlen. Ich schätze seit langem, dass die Russen mit höchstens 190.000 Soldaten in die Ukraine einmarschiert sind. General Oleksandr Syrskyi, der derzeitige Oberbefehlshaber der ukrainischen Streitkräfte, sagte kürzlich in einem Interview mit The Guardian, dass die russische Invasionstruppe nur 100.000 Mann stark war. The Guardian hatte diese Zahl bereits vor Beginn des Krieges genannt. Es ist unmöglich, dass eine Truppe von 100.000 oder 190.000 Mann die gesamte Ukraine erobern, besetzen und in ein Großrussland eingliedern könnte.
Bedenken Sie, dass die Wehrmacht beim deutschen Überfall auf die westliche Hälfte Polens im September 1939 etwa 1,5 Millionen Mann zählte. Die Ukraine ist geografisch mehr als dreimal so groß wie die westliche Hälfte Polens im Jahr 1939, und in der Ukraine leben im Jahr 2022 fast doppelt so viele Menschen wie in Polen zum Zeitpunkt des deutschen Überfalls. Wenn wir die Schätzung von General Syrskyi akzeptieren, dass 100.000 russische Truppen im Jahr 2022 in die Ukraine einmarschierten, bedeutet dies, dass Russland über eine Invasionsstreitmacht verfügte, die 1/15 der Größe der deutschen Streitkräfte war, die in Polen einmarschierten. Und diese kleine russische Armee marschierte in ein Land ein, das sowohl territorial als auch von der Bevölkerungszahl her viel größer war als Polen.
Abgesehen von den Zahlen stellt sich die Frage nach der Qualität der russischen Armee. Zunächst einmal handelte es sich um eine militärische Streitkraft, die in erster Linie dazu bestimmt war, Russland vor einer Invasion zu schützen. Es handelte sich nicht um eine Armee, die für eine Großoffensive zur Eroberung der gesamten Ukraine, geschweige denn zur Bedrohung des übrigen Europas, gerüstet war. Außerdem ließ die Qualität der Kampftruppen zu wünschen übrig, da die Russen nicht mit einem Krieg rechneten, als sich die Krise im Frühjahr 2021 zuzuspitzen begann. Daher hatten sie kaum Gelegenheit, eine qualifizierte Invasionstruppe auszubilden. Sowohl qualitativ als auch quantitativ war die russische Invasionstruppe nicht annähernd mit der deutschen Wehrmacht der späten 1930er und frühen 1940er Jahre vergleichbar.
Man könnte argumentieren, dass die russische Führung dachte, das ukrainische Militär sei so klein und so unterlegen, dass ihre Armee die ukrainischen Streitkräfte leicht besiegen und das ganze Land erobern könnte. Tatsächlich wussten Putin und seine Leutnants sehr wohl, dass die Vereinigten Staaten und ihre europäischen Verbündeten das ukrainische Militär seit Ausbruch der Krise am 22. Februar 2014 bewaffnet und ausgebildet hatten. Die große Befürchtung Moskaus war, dass die Ukraine de facto Mitglied der NATO werden würde. Außerdem beobachteten die russischen Führer, wie die ukrainische Armee, die größer war als ihre Invasionstruppen, zwischen 2014 und 2022 im Donbass erfolgreich kämpfte. Ihnen war sicherlich klar, dass das ukrainische Militär kein Papiertiger war, der schnell und entschlossen besiegt werden konnte, zumal es über eine starke Rückendeckung durch den Westen verfügte.
Schließlich waren die Russen im Laufe des Jahres 2022 gezwungen, ihre Armee aus der Oblast Charkiw und aus dem westlichen Teil der Oblast Cherson abzuziehen. Damit gab Moskau Gebiete auf, die seine Armee in den ersten Tagen des Krieges erobert hatte. Es steht außer Frage, dass der Druck der ukrainischen Armee eine Rolle dabei spielte, den russischen Rückzug zu erzwingen. Vor allem aber erkannten Putin und seine Generäle, dass sie nicht über genügend Kräfte verfügten, um das gesamte Gebiet, das ihre Armee in Charkiw und Cherson erobert hatte, zu halten. Also zogen sie sich zurück und schufen besser kontrollierbare Verteidigungspositionen. Dies ist kaum das Verhalten, das man von einer Armee erwarten würde, die aufgebaut und ausgebildet wurde, um die gesamte Ukraine zu erobern und zu besetzen. Tatsächlich war sie für diesen Zweck nicht konzipiert und konnte daher diese Herkulesaufgabe nicht bewältigen.
VIERTENS: In den Monaten vor Kriegsbeginn versuchte Putin, eine diplomatische Lösung für die sich anbahnende Krise zu finden.
Am 17. Dezember 2021 sandte Putin ein Schreiben an Präsident Joe Biden und NATO-Chef Stoltenberg, in dem er eine Lösung der Krise auf der Grundlage einer schriftlichen Garantie vorschlug, dass: 1) die Ukraine der NATO nicht beitreten würde, 2) keine Angriffswaffen in der Nähe der russischen Grenzen stationiert würden und 3) die seit 1997 nach Osteuropa verlegten NATO-Truppen und -Ausrüstung nach Westeuropa zurückverlegt würden. Was auch immer man von der Machbarkeit einer Einigung auf der Grundlage von Putins Eröffnungsforderungen halten mag, über die die Vereinigten Staaten keine Verhandlungen führen wollten, es zeigt, dass er versuchte, einen Krieg zu vermeiden.
FÜNFTENS: Unmittelbar nach Beginn des Krieges hat Russland der Ukraine die Hand gereicht, um Verhandlungen zur Beendigung des Krieges und zur Ausarbeitung eines Modus Vivendi zwischen den beiden Ländern aufzunehmen.
Die Verhandlungen zwischen Kiew und Moskau begannen in Weißrussland nur vier Tage nach dem Einmarsch russischer Truppen in die Ukraine. Diese weißrussische Schiene wurde schließlich durch eine israelische und eine Istanbuler Schiene ersetzt. Alle verfügbaren Beweise deuten darauf hin, dass Russland ernsthaft verhandelte und nicht an der Übernahme ukrainischen Territoriums interessiert war, mit Ausnahme der Krim, die es 2014 annektiert hatte, und möglicherweise des Donbass. Die Verhandlungen endeten, als die Ukrainer auf Drängen Großbritanniens und der Vereinigten Staaten die Verhandlungen abbrachen, die zum Zeitpunkt ihrer Beendigung gute Fortschritte gemacht hatten.
Darüber hinaus berichtet Putin, dass er, als die Verhandlungen stattfanden und Fortschritte machten, gebeten wurde, als Geste des guten Willens die russischen Truppen aus dem Gebiet um Kiew abzuziehen, was er am 29. März 2022 tat. Keine westliche Regierung und kein ehemaliger Politiker hat diese Behauptung Putins angefochten, die in direktem Widerspruch zu seiner Behauptung steht, er wolle die gesamte Ukraine erobern.
SECHSTENS: Abgesehen von der Ukraine gibt es nicht den geringsten Hinweis darauf, dass Putin die Eroberung anderer osteuropäischer Länder ins Auge gefasst hat.
Außerdem ist die russische Armee nicht einmal groß genug, um die gesamte Ukraine zu überrennen, ganz zu schweigen von dem Versuch, die baltischen Staaten, Polen und Rumänien zu erobern. Außerdem sind alle diese Länder NATO-Mitglieder, was mit ziemlicher Sicherheit einen Krieg mit den Vereinigten Staaten und ihren Verbündeten bedeuten würde.
**SIEBTENS: Kaum jemand im Westen behauptete, Putin habe imperiale Ambitionen, seit er im Jahr 2000 die Macht übernahm, bis zum Beginn der Ukraine-Krise am 22. Februar 2014. Zu diesem Zeitpunkt wurde er plötzlich zum imperialen Aggressor. Warum? Weil die westlichen Staats- und Regierungschefs einen Grund brauchten, ihm die Schuld für die Krise zu geben. **
Der wohl beste Beweis dafür, dass Putin in den ersten vierzehn Jahren seiner Amtszeit nicht als ernsthafte Bedrohung angesehen wurde, ist die Tatsache, dass er auf dem NATO-Gipfel im April 2008 in Bukarest ein geladener Gast war, auf dem das Bündnis bekannt gab, dass die Ukraine und Georgien schließlich Mitglieder werden würden. Putin war natürlich erzürnd über diese Entscheidung und machte seinem Unmut Luft. Sein Widerstand gegen diese Ankündigung hatte jedoch kaum Auswirkungen auf Washington, da das russische Militär als zu schwach eingeschätzt wurde, um eine weitere NATO-Erweiterung zu verhindern, so wie es auch bei den Erweiterungswellen von 1999 und 2004 zu schwach gewesen war, um sie aufzuhalten. Der Westen glaubte, er könne Russland die NATO-Erweiterung noch einmal aufzwingen.
Außerdem war die NATO-Erweiterung vor dem 22. Februar 2014 nicht darauf ausgerichtet, Russland einzudämmen. Angesichts des traurigen Zustands der russischen Militärmacht war Moskau nicht in der Lage, die Ukraine zu erobern, geschweige denn eine revanchistische Politik in Osteuropa zu verfolgen. Der ehemalige US-Botschafter in Moskau, Michael McFaul, der ein entschiedener Verfechter der Ukraine und scharfer Kritiker Putins ist, stellt bezeichnenderweise fest, dass die Einnahme der Krim durch Russland im Jahr 2014 vor Ausbruch der Krise nicht geplant war; es war eine impulsive Reaktion auf den Putsch, der den prorussischen Führer der Ukraine stürzte. Kurz gesagt, die NATO-Erweiterung war nicht dazu gedacht, eine russische Bedrohung einzudämmen, weil der Westen nicht glaubte, dass es eine solche gab.
Erst als im Februar 2014 die Ukraine-Krise ausbrach, begannen die Vereinigten Staaten und ihre Verbündeten plötzlich, Putin als gefährlichen Führer mit imperialen Ambitionen und Russland als ernsthafte militärische Bedrohung zu beschreiben, die die NATO eindämmen müsse. Dieser abrupte Wechsel der Rhetorik sollte einem wesentlichen Zweck dienen: dem Westen die Möglichkeit zu geben, Putin für die Krise verantwortlich zu machen und den Westen von der Verantwortung freizusprechen. Es überrascht nicht, dass diese Darstellung Putins nach dem Einmarsch Russlands in die Ukraine am 24. Februar 2022 deutlich an Zugkraft gewann.
Eine Abweichung von der gängigen Meinung ist erwähnenswert. Einige argumentieren, dass die Entscheidung Moskaus, in die Ukraine einzumarschieren, wenig mit Putin selbst zu tun hat und stattdessen Teil einer expansionistischen Tradition ist, die lange vor Putin bestand und tief in der russischen Gesellschaft verwurzelt ist. Dieser Hang zur Aggression, der angeblich von inneren Kräften und nicht von Russlands äußerem Bedrohungsumfeld angetrieben wird, hat im Laufe der Zeit praktisch alle russischen Führer dazu gebracht, sich ihren Nachbarn gegenüber gewalttätig zu verhalten. Es lässt sich nicht leugnen, dass Putin in dieser Geschichte das Sagen hat oder dass er Russland in den Krieg geführt hat, aber es heißt, dass er wenig Einfluss hat. Fast jeder andere russische Führer hätte genauso gehandelt.
Es gibt zwei Probleme mit diesem Argument. Erstens ist es nicht widerlegbar, da der langjährige Charakterzug in der russischen Gesellschaft, der diesen aggressiven Impuls hervorrufe, nie identifiziert wurde. Es heißt, die Russen seien schon immer aggressiv gewesen – egal, wer an der Macht sei – und würden es auch immer sein. Es ist fast so, als ob es in ihrer DNA läge. Die gleiche Behauptung wurde einst über die Deutschen aufgestellt, die im zwanzigsten Jahrhundert oft als angeborene Aggressoren dargestellt wurden. Derartige Argumente werden in der akademischen Welt aus gutem Grund nicht ernst genommen.
Außerdem bezeichnete zwischen 1991 und 2014, als die Ukraine-Krise ausbrach, kaum jemand in den Vereinigten Staaten oder Westeuropa Russland als von Natur aus aggressiv. Außerhalb Polens und der baltischen Staaten wurde die Angst vor russischer Aggression in diesen 24 Jahren nicht häufig geäußert, was man erwarten würde, wenn die Russen zu Aggressionen veranlagt wären. Es scheint klar, dass das plötzliche Auftauchen dieser Argumentation eine bequeme Ausrede war, um Russland die Schuld für den Ukrainekrieg zu geben.
***
Lassen Sie mich einen anderen Gang einlegen und die DREI HAUPTGRÜNDE darlegen, die dafür sprechen, dass die NATO-Erweiterung die Hauptursache für den Ukraine-Krieg war.
**ERSTENS sagten russische Führer aller Art vor Kriegsbeginn wiederholt, dass sie die NATO-Erweiterung in die Ukraine als eine existenzielle Bedrohung betrachten, die beseitigt werden muss. **
Putin hat diese Argumentation bereits vor dem 24. Februar 2022 mehrfach öffentlich dargelegt. In einer Rede vor dem Vorstand des Verteidigungsministeriums am 21. Dezember 2021 erklärte er: „Was sie in der Ukraine tun oder versuchen oder planen, findet nicht Tausende von Kilometern entfernt von unserer Landesgrenze statt. Es geschieht direkt vor unserer Haustür. Sie müssen verstehen, dass wir uns einfach nirgendwo mehr hin zurückziehen können. Glauben sie wirklich, dass wir diese Bedrohungen nicht wahrnehmen? Oder glauben sie, dass wir tatenlos zusehen werden, wie Bedrohungen für Russland entstehen?“ Zwei Monate später, auf einer Pressekonferenz am 22. Februar 2022, nur wenige Tage vor Kriegsbeginn, sagte Putin: „Wir sind kategorisch gegen einen NATO-Beitritt der Ukraine, weil dies eine Bedrohung für uns darstellt, und wir haben Argumente, die dies unterstützen. Ich habe in diesem Saal wiederholt darüber gesprochen.“ Dann machte er deutlich, dass er begreift, dass die Ukraine ein Defacto-Mitglied der NATO werde. Die Vereinigten Staaten und ihre Verbündeten, sagte er, „pumpen die derzeitigen Kiewer Machthaber weiterhin mit modernen Waffentypen voll“. Er fuhr fort, dass Moskau, wenn dies nicht gestoppt werde, „mit einem bis an die Zähne bewaffneten 'Antirussland' dastehen würde. Das ist völlig inakzeptabel.“
Auch andere führende russische Politiker - darunter der Verteidigungsminister, der Außenminister, der stellvertretende Außenminister und der russische Botschafter in Washington - betonten die zentrale Bedeutung der NATO-Erweiterung als Auslöser der Ukraine-Krise. Außenminister Sergej Lawrow brachte es auf einer Pressekonferenz am 14. Januar 2022 auf den Punkt: „Der Schlüssel zu allem ist die Garantie, dass die NATO nicht nach Osten expandieren wird.“
Man hört oft das Argument, die russischen Befürchtungen seien unbegründet, weil es keine Chance gebe, dass die Ukraine dem Bündnis in absehbarer Zukunft beitreten würde, wenn überhaupt. Tatsächlich wird behauptet, die Vereinigten Staaten und ihre europäischen Verbündeten hätten der Aufnahme der Ukraine in die NATO vor dem Krieg wenig Aufmerksamkeit geschenkt. Aber selbst wenn die Ukraine dem Bündnis beitreten würde, wäre dies keine existenzielle Bedrohung für Russland, da die NATO ein Verteidigungsbündnis ist. Daher kann die NATO-Erweiterung weder eine Ursache der ursprünglichen Krise gewesen sein, die im Februar 2014 ausbrach, noch des Krieges, der im Februar 2022 begann.
Diese Argumentation ist falsch. Tatsächlich bestand die westliche Reaktion auf die Ereignisse von 2014 darin, die bestehende Strategie zu verdoppeln und die Ukraine noch näher an die NATO heranzuführen. Das Bündnis begann 2014 mit der Ausbildung des ukrainischen Militärs und bildete in den folgenden acht Jahren durchschnittlich 10.000 Soldaten pro Jahr aus. Im Dezember 2017 beschloss die Trump-Regierung, Kiew mit „Verteidigungswaffen“ zu versorgen. Andere NATO-Länder zogen bald nach und lieferten noch mehr Waffen an die Ukraine. Darüber hinaus begannen die ukrainische Armee, Marine und Luftwaffe, an gemeinsamen Militärübungen mit NATO-Streitkräften teilzunehmen. Die Bemühungen des Westens, das ukrainische Militär zu bewaffnen und auszubilden, erklären zu einem großen Teil, warum es im ersten Kriegsjahr so gut gegen die russische Armee abschnitt. Eine Schlagzeile im Wall Street Journal vom April 2022 lautete: „Das Geheimnis des militärischen Erfolgs der Ukraine: Jahrelange NATO-Ausbildung.“
Abgesehen von den laufenden Bemühungen des Bündnisses, das ukrainische Militär zu einer schlagkräftigeren Kampftruppe zu machen, die an der Seite der NATO-Truppen operieren kann, gab es im Westen im Laufe des Jahres 2021 eine neue Begeisterung für die Aufnahme der Ukraine in die NATO. Gleichzeitig vollzog Präsident Zelensky, der nie viel Enthusiasmus für eine Aufnahme der Ukraine in das Bündnis gezeigt hatte und im März 2019 auf der Grundlage einer Plattform gewählt wurde, die zur Zusammenarbeit mit Russland bei der Beilegung der anhaltenden Krise aufrief, Anfang 2021 einen Kurswechsel und befürwortete nicht nur die NATO-Mitgliedschaft der Ukraine, sondern vertrat auch eine harte Linie gegenüber Moskau.
Präsident Biden, der im Januar 2021 ins Weiße Haus einzog, hatte sich seit langem für die Aufnahme der Ukraine in die NATO eingesetzt und war ein Superfalke gegenüber Russland. Es überrascht nicht, dass die NATO am 14. Juni 2021 auf ihrem jährlichen Gipfel in Brüssel ein Kommuniqué herausgab, in dem es hieß: „Wir bekräftigen den auf dem Gipfel von Bukarest 2008 gefassten Beschluss, dass die Ukraine Mitglied des Bündnisses wird.“ Am 1. September 2021 besuchte Zelensky das Weiße Haus, wo Biden klarstellte, dass die Vereinigten Staaten „fest entschlossen“ seien, „die euro-atlantischen Bestrebungen der Ukraine zu unterstützen“. Am 10. November 2021 unterzeichneten Außenminister Antony Blinken und sein ukrainischer Amtskollege Dmytro Kuleba ein wichtiges Dokument - die „Charta der strategischen Partnerschaft zwischen den USA und der Ukraine“. Das Ziel beider Parteien, so heißt es in dem Dokument, ist es, „das Engagement für die Durchführung tiefgreifender und umfassender Reformen in der Ukraine zu unterstreichen, die für eine vollständige Integration in die europäischen und euro-atlantischen Institutionen erforderlich sind.“ Es bekräftigt auch ausdrücklich das Engagement der USA für die „Bukarester Gipfelerklärung von 2008“.
Es scheint kaum Zweifel daran zu geben, dass die Ukraine auf dem besten Weg war, bis Ende 2021 Mitglied der NATO zu werden. Dennoch argumentieren einige Befürworter dieser Politik, dass sich Moskau keine Sorgen über dieses Ergebnis hätte machen müssen, denn „die NATO ist ein Verteidigungsbündnis und stellt keine Bedrohung für Russland dar“. Aber das ist nicht die Meinung Putins und anderer russischer Politiker über die NATO, und es kommt darauf an, was sie denken. Kurz gesagt, es steht außer Frage, dass Moskau den Beitritt der Ukraine zur NATO als eine existenzielle Bedrohung ansah, die nicht hingenommen werden durfte.
ZWEITENS erkannte eine beträchtliche Anzahl einflussreicher und hoch angesehener Persönlichkeiten im Westen vor dem Krieg, dass die Expansion der NATO – insbesondere in die Ukraine – von der russischen Führung als tödliche Bedrohung angesehen werden und schließlich zur Katastrophe führen würde.
William Burns, der heute die CIA leitet („heute“ leitet John Ratcliffe die CIA, aktualisieren ODER am Anfang des Textes klarstellen, dass er schon älter ist ODER „heute“ streichen und „leitete“ statt „leitet“), aber zum Zeitpunkt des NATO-Gipfels in Bukarest im April 2008 US-Botschafter in Moskau war, verfasste ein Memo an die damalige Außenministerin Condoleezza Rice, in dem er die russischen Überlegungen zur Aufnahme der Ukraine in die Allianz prägnant beschreibt. „Der Beitritt der Ukraine zur NATO“, so schrieb er, „ist für die russische Elite (nicht nur für Putin) die klarste aller roten Linien. In den mehr als zweieinhalb Jahren, in denen ich Gespräche mit den wichtigsten russischen Akteuren geführt habe, von Scharfmachern in den dunklen Nischen des Kremls bis hin zu Putins schärfsten liberalen Kritikern, habe ich noch niemanden gefunden, der die Aufnahme der Ukraine in die NATO als etwas anderes betrachtet als eine direkte Herausforderung für die russischen Interessen.“ Die NATO, so sagte er, „würde als ein strategischer Fehdehandschuh angesehen werden. Das heutige Russland wird darauf reagieren. Die russisch-ukrainischen Beziehungen würden auf Eis gelegt ... Das würde einen fruchtbaren Boden für russische Einmischungen auf der Krim und in der Ostukraine schaffen.“
Burns war 2008 nicht der einzige westliche Entscheidungsträger, der erkannte, dass die Aufnahme der Ukraine in die NATO mit Gefahren verbunden war. Auf dem Bukarester Gipfel sprachen sich sowohl die deutsche Bundeskanzlerin Angela Merkel als auch der französische Präsident Nicolas Sarkozy gegen eine NATO-Mitgliedschaft der Ukraine aus, weil sie wussten, dass dies Russland alarmieren und verärgern würde. Merkel erklärte kürzlich ihre Ablehnung: „Ich war mir sehr sicher, ... dass Putin das nicht einfach zulassen wird. Aus seiner Sicht wäre das eine Kriegserklärung“.
Um noch einen Schritt weiter zu gehen: Zahlreiche amerikanische Politiker und Strategen sprachen sich in den 1990er Jahren gegen die Entscheidung von Präsident Clinton aus, die NATO zu erweitern, als diese Entscheidung noch zur Debatte stand. Diesen Gegnern war von Anfang an klar, dass die russische Führung darin eine Bedrohung ihrer lebenswichtigen Interessen sehen würde und dass diese Politik letztlich in eine Katastrophe münden würde. Die Liste der Gegner umfasst prominente Persönlichkeiten des Establishments wie George Kennan, sowohl Präsident Clintons Verteidigungsminister William Perry als auch seinen Vorsitzenden des Vereinigten Generalstabs, General John Shalikashvili, Paul Nitze, Robert Gates, Robert McNamara, Richard Pipes und Jack Matlock, um nur einige zu nennen.
Die Logik von Putins Position sollte für Amerikaner, die seit langem der Monroe-Doktrin verpflichtet sind, vollkommen verständlich sein. Diese besagt, dass keine entfernte Großmacht ein Bündnis mit einem Land in der westlichen Hemisphäre eingehen und ihre militärischen Streitkräfte dort stationieren darf. Die Vereinigten Staaten würden einen solchen Schritt als existenzielle Bedrohung auffassen und alles tun, um diese Gefahr zu beseitigen. Dies geschah natürlich auch während der Kubakrise 1962, als Präsident Kennedy den Sowjets klar machte, dass ihre Atomraketen aus Kuba abgezogen werden müssten. Putin ist zutiefst von derselben Logik beeinflusst. Schließlich wollen Großmächte nicht, dass sich entfernte Großmächte in ihrem Hinterhof ansiedeln.
DRITTENS: Die zentrale Bedeutung der tiefen Angst Russlands vor einem NATO-Beitritt der Ukraine wird durch zwei Entwicklungen seit Kriegsbeginn verdeutlicht.
Während der Istanbuler Verhandlungen, die unmittelbar nach Beginn der Invasion stattfanden, machten die Russen deutlich, dass die Ukraine eine „dauerhafte Neutralität“ akzeptieren müsse und der NATO nicht beitreten könne. Die Ukrainer akzeptierten die Forderung Russlands ohne ernsthaften Widerstand, sicherlich weil sie wussten, dass es sonst unmöglich wäre, den Krieg zu beenden. In jüngerer Zeit, am 14. Juni 2024, stellte Putin zwei Forderungen, die die Ukraine erfüllen müsse, bevor er einem Waffenstillstand und der Aufnahme von Verhandlungen zur Beendigung des Krieges zustimmen würde. Eine dieser Forderungen war, dass Kiew „offiziell“ erklärt, „dass es seine Pläne, der NATO beizutreten, aufgibt“.
Das alles ist nicht überraschend, denn Russland hat die Ukraine in der NATO immer als existenzielle Bedrohung gesehen, die um jeden Preis verhindert werden muss. Diese Logik ist die treibende Kraft hinter dem Ukraine-Krieg.
Schließlich ist aus der Verhandlungsposition Russlands in Istanbul sowie aus Putins Äußerungen zur Beendigung des Krieges in seiner Ansprache vom 14. Juni 2024 klar ersichtlich, dass er nicht daran interessiert ist, die gesamte Ukraine zu erobern und sie zu einem Teil eines größeren Russlands zu machen.
John Joseph Mearsheimer (* 14. Dezember 1947 in Brooklyn, New York City) ist ein US-amerikanischer Politikwissenschaftler an der University of Chicago. Sein Schwerpunkt ist die Analyse internationaler Beziehungen aus der Perspektive des offensiven Neorealismus, den er erstmals 2001 in seiner Monografie The Tragedy of Great Power Politics darstellte.
Dieser Text von John J. Mearsheimer erschien am 5.8.2024 auf Substack.Vielen Dank für die Genehmigung des Autors zum Abdruck der deutschen Übersetzung. Die Übersetzung wurde von Thomas Mayer erstellt.
Neben der NATO-Osterweiterung gibt es weitere Faktoren die zum Ukraine-Krieg führten, zum Beispiel der Nationalismus in der Ukraine und die Unterdrückung der ethnisch-russischen Bevölkerung.
Ausführlich sind die vielschichtigen Hintergründe des Ukraine-Krieges geschildert in dem Buch von Thomas Mayer: Wahrheitssuche im Ukraine-Krieg – Um was es wirklich geht, 600 Seiten, ISBN 978-3-89060-863-1, Infos zum Buch: https://kurzelinks.de/h10a
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 77c2969e:a33cfa50
2025-06-08 07:10:04
@ 77c2969e:a33cfa50
2025-06-08 07:10:04Nostr 协议在我看来是很先进的,暂时使用的人还不多,不过相比 Fediverse 的 Mastodon 之类,自己部署 Nostr Relay 是成本很小的。Blossom 作为媒体上传服务是可选的,因为有几个公共服务器可用,但是大多数国内无法直连。我还发现部分客户端不支持自定义 Blossom 服务器,只有 Amethyst 和 Nostrmo 可以。
我目前使用的是这个 nostr-relay 以及这个 blossom-server。
nostr-relay
这个用 Python 写的 nostr-relay 很不错。
配置文件是这个: https://code.pobblelabs.org/fossil/nostr_relay/file?name=nostr_relay/config.yaml 可以按需修改,自己用默认就够了。
```jsx
先安装 pipx
apt install pipx
再用 pipx 安装 nostr-relay
pipx install nostr-relay
选择一个目录运行以下命令启动默认配置,默认 SQLite 文件在当前目录
nostr-relay serve
后台运行
(nostr-relay serve >/var/log/nostr-relay.log &)
查看 PID
lsof -i :6969
停止运行
kill PID
后台运行命令会调用 gunicorn 运行而不是nostr-relay,因此会搜不到 nostr-relay 进程,可以尝试这个命令
ps -ef | grep gunicorn
`` 反代127.0.0.1:6969` 配置域名和 SSL 证书即可。保持简洁,不使用 Docker 和 systemd,后续迁移时只需复制整个文件夹即可。
blossom-server
clone 这个仓库
git clone https://github.com/hzrd149/blossom-server.git克隆仓库是必要的,因为 blossom-server 的默认页面依赖
public/目录,请保留该目录。用以下
config.yml和docker-compose.yml覆盖原仓库中的文件然后执行
docker compose up -d反代
127.0.0.1:3000配置域名和 SSL 证书即可。config.yml按需修改,比如 Dashboard 密码、允许的 PubKey 等。 ```
Override the domain thats is used in the blobs "url" field
By default it uses the domain the incoming HTTP request was made on
publicDomain: ""
databasePath: data/sqlite.db
dashboard: # enable or disable the admin dashboard enabled: true # admin username username: admin # if password is left blank it will be generated each time the app starts password: "yourpasswd"
文件发现机制,保持默认关闭
discovery: # find files by querying nostr relays nostr: enabled: false relays: - wss://relay.example.com # find files by asking upstream CDNs # NOTE: do not set this to your own server, it will create an infinite loop upstream: enabled: false domains: - https://cdn.example.com
storage: # local or s3 backend: local
# Imminently removes a blob when there are no owners removeWhenNoOwners: false
# local storage local: dir: ./data/blobs
# see minio docs for options: # https://min.io/docs/minio/linux/developers/javascript/API.html#new-minio-client-endpoint-port-usessl-accesskey-secretkey-region-transport-sessiontoken-partsize # s3: # endpoint: https://s3.endpoint.com # port: 443 # bucket: blossom # accessKey: xxxxxxxx # secretKey: xxxxxxxxx # useSSL: true # region: us-east-1 # If this is set the server will redirect clients when loading blobs # publicURL: https://s3.region.example.com/
# rules are checked in descending order. if a blob matches a rule it is kept # "type" (required) the type of the blob, "" can be used to match any type # "expiration" (required) time passed since last accessed # "pubkeys" (optional) a list of owners # any blobs not matching the rules will be removed rules: - type: "" expiration: 100 years pubkeys: - "change-to-your-pubkey-hex"
Config for the /upload endpoint
upload: # enable / disable uploads (default false) enabled: true # require auth to upload requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
Config for the /media endpoint
media: # /media endpoint enabled (default false) enabled: true # require auth to upload to /media requireAuth: true # only check rules that include "pubkeys" requirePubkeyInRule: true
# image optimization options image: # image quality 0-100 (default 90) quality: 90 # create progressive jpeg / png images for large images > 1024x768 (default true) progressive: true # max width (default 1920) maxWidth: 1920 # max height (default 1080) maxHeight: 1080 # image format (default webp) outputFormat: "webp" # keep aspect radio when resizing (default true) maintainAspectRatio: true # keep EXIF metadata (default false) keepExif: false # fps for GIFs (default 30) fps: 30
video: # video quality 0-100 (default 90) quality: 90 # max height (default 1080) maxHeight: 1080 # max fps (default 30) maxFps: 30 # output format [mp4, webm, mkv] (default mp4) format: "webm" # audio codec [aac, mp3, vorbis, opus] (default aac) audioCodec: "aac" # video codec [libx264, libx265, vp8, vp9] (default libx264) videoCodec: "libx264"
list: requireAuth: false allowListOthers: true
tor: enabled: false proxy: "" ```
docker-compose.ymlservices: blossom: image: ghcr.io/hzrd149/blossom-server:master ports: - 3000:3000 volumes: # mount data volume - ./data:/app/data # mount config file - ./config.yml:/app/config.yml # mount custom www dir - ./public:/app/public
其他
我自己目前就是部署的这两个服务自用。主要是方便部署和维护,后续服务器迁移只需要复制文件夹即可。Blossom 媒体服务自用的话,默认使用服务器本地存储即可,就是在项目文件夹中的
./data/blobs/,上传的图片和视频会被自动压缩,占不了多少存储空间。如果公开或多人使用也可以配置 S3 兼容的对象存储。除了我上面说的这个 nostr-relay,还有一个 Rust 写的 nostr-rs-relay,可以 Docker 一键部署,如果你偏好使用 Docker,也可以选择这个。
如果你也对 Nostr 这个去中心化协议感兴趣,想拥有自己的 Nostr 服务,不妨参考本文试试,欢迎留言交流!
推荐阅读
-
 @ 57d1a264:69f1fee1
2025-06-08 06:39:26
@ 57d1a264:69f1fee1
2025-06-08 06:39:2618-07 HOLIDAY HOME by OFFICE INAINN reimagines the traditional hytte, creating two interconnected cabins, H_G30 and H_G32, located near the scenic Geiranger–Trollstigen route. Set on a steep hillside 148 meters above sea level, the design embraces modern functionality while offering stunning southern views of Storfjorden and minimizing environmental impact.
Blending into the Landscape
The cabins are designed to integrate gently into the natural terrain, following the contours of the hillside. Their horizontal layout reduces the visual impact, blending into the forested surroundings while opening up to the fjord. The minimal footprint respects the environment and reduces construction costs, ensuring the cabins remain nearly invisible from the north while fully engaging with the southern panorama.
Functional, Additive Architecture
Inspired by traditional Norwegian architecture, each cabin consists of two overlapping modules of varying heights, breaking up the building mass and reducing roof size. The higher module serves as the circulation space, while the lower module contains the private and living areas. This approach replaces conventional walls with functional form, creating distinct zones for movement, utility, and relaxation.
Harmonizing Tradition with Modern Living
The cabins follow an east-west retaining wall that mirrors the hill’s natural slope, with additional storage and leisure spaces tucked behind. The shallow depth allows maximum southern exposure for light and views, while the central axis blurs the boundary between indoor and outdoor living, creating a seamless connection to nature.
For more info https://inainn.eu/18-07-holiday-home/
https://stacker.news/items/1000386
-
 @ 57d1a264:69f1fee1
2025-06-08 06:27:45
@ 57d1a264:69f1fee1
2025-06-08 06:27:45HTX Studio received a special email. The letter writer's daughter was unfortunately run over by a heavy truck on her way to school, and her right hand permanently lost its function. When using the computer, her hands have to frequently switch between the keyboard and the mouse, which makes typing very slow and tiring. He wanted us to make a one-handed keyboard for his daughter.
https://www.youtube.com/watch?v=9vW12gQ4Klc
The project has just been open-sourced at https://github.com/htx-studio/One-Handed-Keyboard and hopes to be helpful to those who need it. In English for you below:
One-Handed Keyboard
This is a single-mode mechanical keyboard with integrated trackball. The firmware uses QMK . Thanks to all the developers who have contributed to the QMK community.
Keyboard production reference: [Mr. He] We made a special keyboard...
Open source hardware: HTXStudio one-handed keyboard
The development environment and setup are available here , and the firmware source code is available here .
The information in this warehouse includes:
- A total of 8 PCBs for three keyboards for the left and right hands, provided by EasyEDA Engineering.
- VIA key change configuration file and compiled firmware.
- Model design files.
Warehouse directory structure
Docs
Data sheet and pictures of the chip.
Firmware
QMK firmware for three different keyboard models, and JSON files for VIA key changes.
Hardware
Project files of Jialichuang EDA.
Model
Model files and processing files used by each keyboard model.
Production Guide
PCB:
1-Right-hand keyboard-hot-swappable (large): board material FR-4, board thickness 1.6mm, four-layer board, laminate structure JLC04161H-3313, impedance control +/-20%.
1-Left-hand keyboard-welding board (small): board material FR-4, board thickness 1.6mm, double-layer board, ALPS yellow axis needs to be installed with a little force when inserted.
1-Left-hand keyboard-hot-swappable (large): board material FR-4, board thickness 1.6mm, four-layer board, laminate structure JLC04161H-3313, impedance control +/-20%.
2-TypeC: board material FR-4, board thickness 1.6mm, double-layer board, marked CON1 (only for large keyboards).
3-Trackball: board material FR-4, board thickness 1.6mm, double-layer board, the module needs to pay attention to the welding direction, marked CON3.
4- Mouse wheel: board material FR-4, board thickness 1.6mm, double-layer board, it is recommended to use 7mm high encoder, 6mm high button, button trigger pressure ≤180g, marked CON2.
5-Directional buttons: board material FR-4, board thickness 1.6mm, double-layer board, ALPS yellow shaft needs to be inserted with a little force, marked CON4.
6- Main control board - left hand (small): board material FR-4, board thickness 1.6mm, double-layer board.
- Three of them are keyboard-controlled common boards
《3-轨迹球》《4-鼠标滚轮》《5-方向按键》. 《5-方向按键》And《1-左手键盘-焊板(小)》, the key axis uses ALPS yellow axis.- Note that the left and right hand keyboards are not completely mirrored.
- The trackball control uses SPI1 channel, and the scroll wheel has two separate signal lines, which allows replacing other control devices without major adjustments.
- The main control uses STM32G431CBU6.
- Compatible with A to C or C to C data cables.
Printout:
Keycap: resin, PLA, etc.
Trackball seat: resin, PLA, etc.
Left and right mouse buttons: resin, PLA, etc.
Shell: resin, PLA, etc.
Base: resin, PLA, etc.
Processing:
Positioning plate: Recommended material: pom, thickness 1.5mm.
Positioning plate cotton strip: glue left on one side.
Sandwich cotton: Recommended material is poron, 3.5mm thick.
Axle seat cotton: 2mm thick.
Bottom cotton: Recommended material: poron, 4mm thick.
Silicone pad (for keypad only): 5mm thick, hardness Shore 00-10.
other:
Trackball: diameter 25mm, material PTFE.
Lubricating ball: 2mm diameter, made of PTFE, installed in the printed trackball seat, 6 pieces in number.
Roller: Recommended diameter is between 19mm-20mm, thickness is between 4mm-5mm, and material is metal.
Satellite axis: 2U steel plate satellite axis.
Key switches: 57 ultra-small ALPS yellow switches for the small keyboard and 57 common mechanical switches for the large keyboard.
Cable arrangement: spacing 0.5mm, 8P reverse, 10cm2 strips, 15cm2 strips.
- The FPC sockets of the control board and the small board are both marked with CON, and the corresponding interfaces are connected.
- The file uses an FPC cable holder that can be connected up and down. It should be noted that when the cable holders are connected down, use reverse cable connection.
Model structure:
Installation order:
Take the large keyboard as an example
Pre-assembly work
- First, connect the 4 small PCBs to the keyboard body PCB using cables and burn the program.
- Install 3-5 shafts, rollers and trackballs. Make sure they function normally before assembly.
- Install the correct hot-melt copper nuts at the corresponding positions of the printed shell and base.
- Keycap printing.
- Attach the cotton strips to the protruding parts of the positioning plate (both on the front and back sides).
When burning the firmware for the first time, you can press and hold the button marked "B" on the back of the PCB and then plug in the USB cable to burn the firmware.
If you want to update the firmware, you can press and hold the "ESC" key on the keyboard and then insert the USB cable to burn the firmware.
For more information, please refer to Flashing Your Keyboard (QMK)
Next, start assembling
- Use screws to install the 4 small boards to the corresponding positions of the base (pay attention to the wiring and installation direction), and install screws at the bottom of the trackball base.
- Fix the left and right buttons on the keyboard PCB with screws.
- From bottom to top, place the bottom cotton, shaft seat cotton, keyboard PCB, sandwich cotton and positioning plate into the fan-shaped area of the base in order.
- Insert the key switch.
- Put it into the housing and secure it with screws from the bottom.
- Install the keycaps to complete the assembly.
The screw and nut installation guide can be found here
Finally, this is our first open source project. If there are any shortcomings, you are welcome to criticize and correct us. Thank you.
References
Quantum Mechanical Keyboard Firmware
mrjohnk. ADNS-9800. GitHub repository
https://x.com/HTX_Studio/status/1929915992349782206
https://stacker.news/items/1000384
-
 @ 57d1a264:69f1fee1
2025-06-08 05:57:12
@ 57d1a264:69f1fee1
2025-06-08 05:57:12There is a certain image that pops up whenever people think about crushing soda cans. It is the kind of scene you see in movies, where a brawny athlete flattens an empty can with a single squeeze, probably in front of a cheering crowd. The reality, however, is far less cinematic. Most of us barely manage a dent before abandoning the can, sending it tumbling toward the trash bin, often missing the target entirely and hoping no one noticed. It is hardly the stuff of legends, unless you consider fumbling for a runaway soda can an athletic event.
In the end, the Yeti Can Crusher is more than just a clever gadget. It is a reminder that even the simplest chores can be transformed into moments of enjoyment, especially when the right tool is involved. There is a certain thrill in turning a dull task into a satisfying ritual, and when you add a dash of style, suddenly recycling is not just good for the planet, it is actually a little bit fun. With the right crusher in your hand, you might just find yourself looking forward to the next empty can.
Curious to learn more? https://www.yeti.com/outdoor-living/20110010027.html
https://stacker.news/items/1000380
-
 @ 81022b27:2b8d0644
2025-06-08 04:22:00
@ 81022b27:2b8d0644
2025-06-08 04:22:00Here’s the thing: authenticity gives off a vibration: There is so little of it anywhere that we crave it. That’s why an orange guy beats someone who doesn’t mean what they say. Because they don’t really believe a guy in a dress is a woman because that’s what they say they are
People feel vibes and hearing someone lie to their face is offensive. They will follow the guy that at least believes what he is
-
 @ 81022b27:2b8d0644
2025-06-08 04:19:30
@ 81022b27:2b8d0644
2025-06-08 04:19:30D.D. Palmer was a magnetic healer, a visionary who tapped into the unseen forces of life. He founded chiropractic on the premise that the body’s innate intelligence governs health, and that misalignments—whether called subluxations, blockages, or interferences—disrupt this flow.
This is not a medical concept; it’s a metaphysical one, rooted in the belief that life transcends mere mechanics.
As a profession, we’ve been too concerned with what others think of us, particularly the medical community. In our desperation for acceptance, we’ve diluted our essence.
Some chiropractors advocate abandoning the term “subluxation” because it sounds archaic or unscientific. Personally, I don’t care for the word either—it often leaves my clients’ eyes glazed over. I prefer “blockages” or “interference” to convey the concept in a way that resonates.
But replacing these with medical jargon? That’s a betrayal of our roots.
What we cannot do is conform to a biomedical model that reduces the body to a machine. Chiropractic is not about treating symptoms or mimicking physical therapy. It’s about restoring the body’s connection to its innate wisdom, allowing healing to unfold naturally.
This is our strength, our uniqueness. To abandon it is to board the Titanic just before it sails—a sinking ship of soulless reductionism.
I believe chiropractic needs to embrace its metaphysical heritage boldly. We must stop apologizing for being different and instead educate the public on what we truly offer: a holistic approach that honors the body’s intelligence.
This means refining our language to be clear and relatable without sacrificing our principles. It means training chiropractors to communicate with confidence, not defensiveness. It means building a community that celebrates our philosophy rather than chasing validation from skeptics.
The future of chiropractic lies in authenticity. Let’s stop trying to fit into someone else’s paradigm. We are not medicine’s younger sibling; we are a distinct voice in healthcare. By standing firm in our metaphysical roots, we can inspire a world desperate for holistic solutions. The choice is ours: evolve as a vibrant, principled profession or sink under the weight of conformity. I choose evolution.
-
 @ 81022b27:2b8d0644
2025-06-08 04:13:43
@ 81022b27:2b8d0644
2025-06-08 04:13:43Have you seen the show Poker Face on Peacock streaming? Natasha Lyonne plays a casino worker character who has the ability to tell if someone is telling the truth. If she hears a lie, she automatically says, “Bullshit!”
Her ability gets her in trouble with her boss, who is involved in organized crime, and now she is on the run and solving crimes until they find her again (usually at the end of an episode).
It’s like a rock-and-roll Quantum Leap. Anyway, Christi likes the show because there are crimes and clues, and you have to figure it out. I watch it because I can get into it while I’m messing with my phone or doing a little writing.
Well, I have that same ability to detect BS.
When I work on clients, I connect with their energy. I didn’t start out doing it on purpose; I would start working on a client and pick up whatever they were sick with, and then they would feel great, and I would be left struggling.
Some friends taught me how to protect myself, and it helped, but “my shield” prevented me from connecting with my clients like I used to.
Now I connect with the source of all power in the universe: God. (You can call it whatever you want: Source, Universal Intelligence, Prana, etc.)
I send up a little antenna, and I’m protected AND connected.
When I’m in this state and talking to a client, I can clearly tell when someone is not telling the truth because THE BODY DOES NOT LIE!
Sometimes the cause of a physical issue is an emotional issue. If you can connect to someone’s energy like this, you can find and help clear out whatever is the root cause.
I’ve been telling people this quote for as long as I’ve been practicing:
You can lie to your mom, to your friends, and even to yourself, but you can’t lie to your chiropractor!
A polygraph lie detector only measures four things: heart rate and blood pressure, respiration rate, skin conductivity, and movement.
There are now better lie detectors that use EEGs (brain wave measurements). AI finds that voice analysis is a great way to detect honesty.
What’s better than all of that combined?
You.
Your nervous system can detect much more than all these other methods combined. I will try to teach what I know so far if you’d like.
And don’t forget to watch that show! I recommend it.
live long and prosper 🖖🏼
-Dan
-
 @ f4a890ce:af88c4aa
2025-06-08 03:59:21
@ f4a890ce:af88c4aa
2025-06-08 03:59:21執行摘要
比特幣自橫盤延續,總市值回落至3.24兆美元,成交量下降至591億美元,顯示短線資金趨於觀望。下週操作應聚焦三大關鍵數據:
衍生品市場槓桿與清算動態: 觀察永續合約持倉與資金費率變化。若持倉再度攀升且費率轉為大幅正值,多頭風險將升高;同時留意爆倉價格與清算熱力圖,作為短線波動的前瞻指標。
ETF 資金流向: BTC/ETH ETF 流入與流出數據,是機構資金態度的風向標。若下週出現淨流出,將可能引發價格回調壓力;相反,流入維持則有助於支撐高位盤整。
鏈上資金結構與穩定幣規模: 持續追蹤交易所餘額與鯨魚地址淨流出情況,評估大額資金動向;同時關注穩定幣總市值變化,若有減少,意味避險情緒抬頭,反之則暗示買盤動力仍持續。
總體而言,市場結構仍偏多,但需警惕「高槓桿+低流動」可能帶來的瞬間波動。建議保持倉位彈性,讓數據引導調整策略,避免在高位盲目追高。
加密市場
本週加密貨幣市場總市值維持在 3.26 兆美元 左右,顯示出市場基本面仍具穩定性。與此同時,當週總成交量下降至 546.84 億美元,反映出市場活躍度減弱,投資者交易意願相對謹慎。
https://coinmarketcap.com/charts/
市場情緒方面,恐懼與貪婪指數降至 52,處於中性範疇,表明投資者對市場前景的情緒有所保留。
https://www.coinglass.com/zh-TW/pro/i/FearGreedIndex
此外,相對強弱指標落在中性至超賣區間,暗示部分標地在短線上可能面臨獲利回吐或技術性修正的壓力,而市場尚未進入絕對弱勢狀態。
https://www.coinglass.com/zh-TW/pro/i/RsiHeatMap
山寨幣季節指數維持在 20,這說明市場資金依舊偏向配置於比特幣及其他主流加密貨幣,中小型代幣並未受到市場資金的大量青睞。
https://www.blockchaincenter.net/en/altcoin-season-index/
穩定幣市值上升至 249.938 億美元,反映出部分資金正積極尋求避險,或準備在市場調整後進行潛在的佈局操作。
https://defillama.com/stablecoins
小結
本週加密市場在總市值維持穩定的同時,成交量的下降顯示出交易熱情的不足,加上恐懼與貪婪指數和相對強弱指標均呈現中性偏弱態勢,整體市場情緒趨向保守。山寨幣季節指數的低迷也反映出資金仍偏向主流幣種,而穩定幣市值的提升則表明投資者正在為市場未來調整或出現更具吸引力的價格點做準備。未來,需持續關注資金流向與宏觀經濟動態,以判斷市場後續走勢。
衍生性商品
槓桿交易需求仍然強勁,本週永續合約持倉規模達 141.68B,雖然較前週有所下降,但仍顯示市場活躍度維持高水準。
https://www.coinglass.com/zh-TW/pro/futures/Cryptofutures
資金費率方面,目前市場呈現 負費率 (-0.0047%),顯示空方勢力增強,多數交易所的情緒偏向空頭。
https://www.coinglass.com/zh-TW/FundingRate
爆倉數據反映市場波動仍導致大量強制平倉,本週總計空單爆倉達 453.14M,而多單爆倉則達 1267.859M,多頭爆倉金額顯著高於空方,顯示市場對高槓桿多單的清算壓力較大。
其中 6月5日 空單爆倉 88.68M,多單爆倉 875.855M,這一天的市場劇烈波動導致大量強制清算。
https://www.coinglass.com/zh-TW/LiquidationData
清算熱力圖顯示,$106,000 附近 清算金額達 175.11M; $111,000 附近 也有 169.02M 的清算,這些區間可能成為近期市場波動的關鍵點。
https://www.coinglass.com/zh-TW/pro/futures/LiquidationHeatMap
期權市場活躍,投資者在不同價格區間進行對沖與佈局:
$100,000 行權價的看跌期權合約數量達 7.42K,總金額 $25.86M,市場對該區間的防禦仍然較強。
$110,000 行權價的看漲期權合約數量達 13.02K,總金額 $57.61M,顯示市場對上行的預期仍存在,但與上週相比略有下降。
https://www.coinglass.com/zh-TW/pro/options/OIStrike
最大痛點出現在 2025/06/27 的 $100,000,名義金額 12.86B,顯示市場對該區間的交易活動仍較為集中。
https://www.coinglass.com/zh-TW/pro/options/max-pain
小結
本週加密市場顯示槓桿交易活躍度仍然維持高水準,但市場情緒偏向保守,資金費率轉為負值反映空方情緒增強。爆倉數據顯示多頭遭遇較大壓力,投資者在槓桿操作時需謹慎風險管理。期權市場的交易策略仍然分歧,市場在不同行權價格的佈局顯示投資者對後市走勢保持不同預期。建議交易者持續關注市場數據,根據槓桿交易動向調整策略,以降低市場震盪帶來的風險並尋找最佳交易機會。
ETF
本週,加密貨幣衍生性商品市場出現顯著差異,資金流向呈現兩極化現象。比特幣(BTC)ETF方面,本週出現資金流出,金額達6.161億美元。這一變化顯示投資者對比特幣近期走勢產生疑慮,或在調整資金配置,以應對可能的市場風險和波動加劇。
以太坊(ETH)ETF則呈現資金流入趨勢,本週流入金額達 7,020 萬美元。較之於比特幣的趨勢,這一資金流入暗示出部分投資者對以太坊未來潛力充滿信心,特別是在其技術升級和生態系統發展背景下,認為相較於比特幣,ETH更具備吸引力。
https://coinmarketcap.com/zh-tw/etf/
小結
整體而言,本週加密貨幣衍生性商品市場呈現出明顯的資金流向差異。比特幣ETF大幅流出揭示了市場風險偏好的調整,而以太坊ETF的資金流入則表明投資者對其技術發展及生態系統持續看好。未來,投資人需持續關注宏觀經濟環境與技術創新如何影響各加密貨幣衍生性商品的動態,以便在不確定的市場中做出更合適的資金配置決策。
鏈上分析 | BTC
二級交易所的比特幣儲備量再次創下斷崖式新低,顯示出市場上的流動性仍在減少。
地址分布方面,10-100顆比特幣的地址數量持續下降,100-1k、1k-10k及10k以上顆數的地址數量則繼續上升,特別是10k以上地址的數量近期突然激增,顯示大戶的持幣情緒正在加強。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
鯨魚活躍地址數量全數上升,可以得知近期鯨魚們進場的速度逐步加快。
https://cryptoquant.com/community/dashboard/67e2481ba2a7203afd437b31
Exchange Netflow 顯示出近期大額淨流出交易所的情況,這進一步證實了市場上多數投資者偏向長期持有。
Long Term Holder Supply 持續上升,說明持幣155天以上的長期投資者信心未減。
https://www.bitcoinmagazinepro.com/charts/long-term-holder-supply/
URPD 顯示,104,000 美元以上買入的投資人已有被套跡象,若價格再次回落,將觸及 99,000 美元以下的支撐密集區。
https://charts.bgeometrics.com/distribution_realized_price.html
Short-Term Holder Realized Price 為 97,000 美元,短線若修正,此區間可能提供技術性支撐。
https://www.bitcoinmagazinepro.com/charts/short-term-holder-realized-price/
溢價指數方面,Coinbase 溢價指數衝高至 0.105 以上,韓國溢價指數則維持在 2.52,顯示美韓兩地市場買盤情緒仍然正向,整體鏈上結構支撐比特幣中期續強的可能性。
Coinbase Premium Index
Korea Premium Index
小結
本週比特幣鏈上數據顯示多頭格局進一步鞏固,二級交易所儲備量斷崖式下滑至新低,資金持續撤離交易所。
地址分布方面,10–100 BTC 的中小戶數量持續降低,而100–1 k、1 k–10 k及10 k+地址全線上升,尤其10 k+地址近期突增,顯示超級大戶加速佈局;鯨魚活躍地址也全面走高,進場節奏愈發急促。 Exchange Netflow 持續呈現大額淨流出,佐證長線持有趨勢,且 Long‑Term Holder Supply 持續攀升,反映市場偏好長期持有。成本面上,URPD 指標顯示回調後買在104,000美元以上的籌碼深度被套,未來若價格下行將觸及99,000美元以下投資人的成本區。
Short‑Term Holder Realized Price(155天內持幣者平均成本)約97,000美元,此區或成短期支撐,這也恰好和 URPD 指標吻合。
同時,Coinbase 溢價指數維持在0.105以上,韓國溢價指數則穩定於2.52,顯示全球買盤需求穩健。
整體而言,鏈上結構健康,資金流向多為長線建倉,但高位被套壓力與短期成本點仍需密切關注。
總體經濟
本週加密貨幣市場持續受到宏觀經濟環境的顯著影響。聯邦基金有效利率穩定維持在 4.33%,顯示市場仍處於高利率壓制之下,資金流動性受到明顯限制,這一情勢對風險資產尤其是加密市場構成挑戰。
https://fred.stlouisfed.org/series/FEDFUNDS
隨著 6 月 18 日 FOMC 會議臨近,市場普遍預期當前利率大概率將維持在 4.25%-4.50% 區間。然而,投資者亦將目光轉向 9 月 17 日的下一次會議,該會議上 4.0%-4.25% 區間的降息預期不斷攀升,目前已高達 51.8%,顯示市場對中期內利率調整存在明顯的分歧與期待。這種預期上的轉變,既意味著部分市場參與者看好未來資金回流的可能性,也使投資者對當前高利率環境下資產價格波動更加謹慎。
https://www.cmegroup.com/cn-t/markets/interest-rates/cme-fedwatch-tool.html
消費者物價指數 (CPI) 持續維持在 2.33%,顯示通膨壓力穩定而可控;失業率則保持在 4.2%,反映出勞動市場的基本穩健。雖然這些基本面數據表現平穩,卻難以在高利率與流動性緊縮的背景下對加密貨幣價格形成強而有力的支撐,市場參與者更趨於採取保守的投資策略,尤其在高槓桿交易普遍存在的情況下,風險管理顯得尤為重要。
失業率:https://www.macromicro.me/series/37/unemployment-rate
消費者物價指數(CPI):https://www.macromicro.me/series/128/consumer-price-index-sa-yoy
小結
整體而言,加密市場依舊面臨高利率環境帶來的流動性限制與價格波動風險。雖然短期內市場情緒偏保守,但 9 月 17 日會議上降息預期的上升,或將為未來市場帶來積極轉機。投資者應持續關注 FOMC 會議及最新經濟數據變化,謹慎調整交易策略以應對可能出現的轉機與挑戰。
新聞
Ripple 的穩定幣 RLUSD 在杜拜獲得批准
https://www.coindesk.com/markets/2025/06/03/ripples-stablecoin-rlusd-gets-stamp-of-approval-in-dubai
MoonPay 在紐約獲得令人垂涎的 BitLicense
https://www.coindesk.com/policy/2025/06/04/moonpay-grabs-coveted-bitlicense-approval-in-new-york
穩定幣正悄悄增強美國國力
https://www.coindesk.com/opinion/2025/06/04/stablecoins-are-quietly-reinforcing-u-s-national-power
韓國選舉加密貨幣友善總統李在明為新總統
Circle 首次公開募股 (IPO) 定價為每股 31 美元,穩定幣發行人估值為 69 億美元
香港即將允許加密貨幣衍生性商品交易
https://www.coindesk.com/policy/2025/06/05/hong-kong-set-to-allow-crypto-derivatives-trading
-
 @ 8d34bd24:414be32b
2025-06-08 03:42:59
@ 8d34bd24:414be32b
2025-06-08 03:42:59Last post, I touched on the subject of what do you say to those going through trials and tribulations, but as I read Job, it seemed like there was more to say on the subject of how Christians are to respond to those who are suffering. The original passage of inspiration was this.
Don’t Be A Miserable Comforter
Then Job answered,
“I have heard many such things;\ Sorry comforters are you all.\ Is there no limit to windy words?\ Or what plagues you that you answer?\ I too could speak like you,\ If I were in your place.\ I could compose words against you\ And shake my head at you.\ I could strengthen you with my mouth,\ And the solace of my lips could lessen your pain. (Job 16:1-5)
Job was suffering. His friends came with the intention of comforting Job. Job vented his frustrations and problems understanding God’s justice. His friends tried to correct Job’s honest questions. These corrections escalated to the point of accusing Job of heinous sins and saying that everything that had happened to Job was his fault.
Job rightly said, “If I were in your place, I could compose words against you, and shake my head at you.” Sometimes we have to show mercy while a person is working through their feelings and confusion. Although some hardships are the consequences or punishment for sins, many (probably most) are not. We, as Christians, are promised trials. We should not be surprised when we go through trials.
Job also compares two ways of responding to a fellow believer going through trials. He says, “I could strengthen you with my mouth, and the solace of my lips could lessen your pain.” We can use our words to encourage and strengthen those who are suffering.
He also accuses his visitors of “Sorry comforters are you all. Is there no limit to windy words?” This reminds me of a traditional saying, “If you can’t say anything nice, don’t say anything at all.” Some of us want to fix everything. Sometimes we need to just listen. We don’t have to speak an answer for everything. In these uncomfortable situations, it is easy to start with a brief, Biblical answer, but then to start filling the silence with our own words to fill the silence. This can harm of everyone.
Job’s friends initial comments were not bad and were mostly true, but the more they talked, the more they went off track and the more harm they did. We want to lessen their pain, not be sorry comforters.
Of course this doesn’t mean that we can’t share God’s word. It doesn’t mean we can’t acknowledge obvious sins that are known by all parties. It does mean that all words should be an encouragement to lead them into closer fellowship with God.
Job again comments about his friends.
Even now, behold, my witness is in heaven,\ **And my advocate is on high.\ My friends are my scoffers;\ My eye weeps to God.\ O that a man might plead with God\ As a man with his neighbor!\ For when a few years are past,\ I shall go the way of no return. (Job 16:19-22) {emphasis mine}
Job, being a godly man, puts his trust in God. Notice the pattern: God, friends, God.
And my advocate is on high.\ My friends are my scoffers;\ My eye weeps to God.
Despite the scoffing and harm done by his friends, he keeps his eye on God as his advocate and the one he turns to in sorrow. In the case of Job, he is able to lean on God despite the harm done by his friends. Those will lesser faith might have been pushed away from God by his friends words.
Love One Another
In the New Testament, we are told:
“A new commandment I give to you, that you love one another, even as I have loved you, that you also love one another. By this all men will know that you are My disciples, if you have love for one another.” (John 13:34-35)
Our every word and action should be loving. That doesn’t mean ignoring sin, but it does mean every word and action should be used to draw a person into closer relationship with their God and Savior. In the case of a person who is sinning, Jesus set a perfect example.
The scribes and the Pharisees brought a woman caught in adultery, and having set her in the center of the court, they*said to Him, “Teacher, this woman has been caught in adultery, in the very act. Now in the Law Moses commanded us to stone such women; what then do You say?” They were saying this, testing Him, so that they might have grounds for accusing Him. But Jesus stooped down and with His finger wrote on the ground. But when they persisted in asking Him, He straightened up, and said to them, “He who is without sin among you, let him be the first to throw a stone at her.” Again He stooped down and wrote on the ground. When they heard it, they began to go out one by one, beginning with the older ones, and He was left alone, and the woman, where she was, in the center of the court. Straightening up, Jesus said to her, “Woman, where are they? Did no one condemn you?” She said, “No one, Lord.” And Jesus said, “I do not condemn you, either. Go. From now on sin no more.” (John 8:3-11)
What did Jesus do:
-
He protected the accused from those trying to use, abuse, and torment her.
-
He did not deny her sin, but encouraged her accusers to acknowledge their own sins.
-
He encouraged her to “sin no more.”
This woman knew she had sinned. She did not need to be reminded of it. She didn’t deny it; she knew. Because she and everyone else knew her sin, there was no need to bring it up again. Jesus used this situation to help her accusers understand their own sin and to lead her into repentance and salvation. The gentle correction was used to lead her to a better way.
When we speak to someone in trials, whether self-inflicted, externally caused, or a standard trial common to all men, our goal should be to uplift and draw to Jesus. We should have mercy on the suffering and not add to their suffering.
No matter the case, we need to carefully use our words for love and mercy.
Beloved, let us love one another, for love is from God; and everyone who loves is born of God and knows God. The one who does not love does not know God, for God is love. By this the love of God was manifested in us, that God has sent His only begotten Son into the world so that we might live through Him. In this is love, not that we loved God, but that He loved us and sent His Son to be the propitiation for our sins. Beloved, if God so loved us, we also ought to love one another. (1 John 4:7-11)
Dealing With Sin & Repentance
In 1 & 2 Corinthians, Paul deals with a situation of extreme sin. In 1 Corinthians he rebukes the church for allowing this heinous sin within their church body.
It is actually reported that there is immorality among you, and immorality of such a kind as does not exist even among the Gentiles, that someone has his father’s wife. You have become arrogant and have not mourned instead, so that the one who had done this deed would be removed from your midst.
For I, on my part, though absent in body but present in spirit, have already judged him who has so committed this, as though I were present. In the name of our Lord Jesus, when you are assembled, and I with you in spirit, with the power of our Lord Jesus, I have decided to deliver such a one to Satan for the destruction of his flesh, so that his spirit may be saved in the day of the Lord Jesus. (1 Corinthians 5:1-5) {emphasis mine}
This unrepentant sin could not be allowed to remain in the body because it could spread among God’s people and because it harmed God’s glory. At the same time, the motivation for removing him from the body was not to remove him from a relationship with God. It was to cause consequences in the hopes that the man would return to Jesus.
In 2 Corinthians, we find that he does repent of his son and seek to come back into the fellowship of believers.
For out of much affliction and anguish of heart I wrote to you with many tears; not so that you would be made sorrowful, but that you might know the love which I have especially for you.
But if any has caused sorrow, he has caused sorrow not to me, but in some degree—in order not to say too much—to all of you. Sufficient for such a one is this punishment which was inflicted by the majority, so that on the contrary you should rather forgive and comfort him, otherwise such a one might be overwhelmed by excessive sorrow. Wherefore I urge you to reaffirm your love for him. For to this end also I wrote, so that I might put you to the test, whether you are obedient in all things. But one whom you forgive anything, I forgive also; for indeed what I have forgiven, if I have forgiven anything, I did it for your sakes in the presence of Christ, so that no advantage would be taken of us by Satan, for we are not ignorant of his schemes. (2 Corinthians 2:4-11) {emphasis mine}
Once a sinner repents, we are to immediately forgive and comfort them and welcome them back into the fellowship of believers. We are not to remind them of their previous sins and overwhelm them with excessive sorrow, but are to reaffirm our love for them. Any punishment was for correction, not to harm or cause them pain. We should seek the good of those who sinned. We should welcome them back with open arms. We should forgive as we were forgiven by God.
All of our words and actions toward others, whether the most godly saint or the most reprehensible sinner, should be to the goal of drawing them closer to the Savior and helping them to trust in God’s goodness, wisdom, and strength.
May the God of Heaven carry your burdens and help you to help carry the burdens of those around you. May Our Savior help us to be a godly encouragement to the suffering who draws them into closer fellowship with the Savior. May the Holy Spirt give us discernment in how to best encourage the suffering and to help them rest in Jesus.
Trust Jesus
-
-
 @ 2b998b04:86727e47
2025-06-08 03:37:24
@ 2b998b04:86727e47
2025-06-08 03:37:24This is my first test -- I'm writing a blog post (using primal long form post) on nostr once and using github actions to fetch and store article as a static page on github pages to be used in a website (blog.stantonweb.com) and potentially other places.
-
 @ b2a8fdbc:dcab1f03
2025-06-08 03:07:19
@ b2a8fdbc:dcab1f03
2025-06-08 03:07:19ถ้าเรามี "เงินที่ดี" ที่มีจำนวนจำกัดและสามารถเก็บมูลค่าได้อย่างแท้จริง ภาวะเงินฝืดที่เกิดจากคุณสมบัติเช่นนี้ อาจนำไปสู่ผลลัพธ์ที่เป็นบวกอย่างมหาศาลต่อคุณภาพชีวิตและมุมมองของมนุษย์ต่อการดำรงอยู่ ไม่ใช่เพียงแค่ความกังวลเรื่องการว่างงาน
เงินฝืด: ก้าวข้ามความกลัวการตกงาน สู่การค้นหาความหมายของชีวิต แนวคิดที่ว่ามนุษย์ไม่ได้เกิดมาเพื่อทำงานหากินไปแต่ละวัน แต่เพื่อค้นหาความหมายที่แท้จริงของชีวิต เป็นปรัชญาที่ลึกซึ้ง และสอดคล้องกับแนวคิดที่ว่า เมื่อเงินมีคุณสมบัติที่มั่นคงและมีจำกัด อาจนำมาซึ่งการเปลี่ยนแปลงเชิงบวกดังนี้:
1. ความมั่นคงทางการเงินและคุณภาพชีวิตที่ดีขึ้น เมื่อเงินมีคุณสมบัติที่เก็บรักษามูลค่าได้ดี นั่นหมายความว่ากำลังซื้อของเงินจะไม่ลดลงไปตามกาลเวลา ตรงกันข้าม อาจเพิ่มขึ้นด้วยซ้ำในระบบเศรษฐกิจที่มีประสิทธิภาพ สิ่งนี้จะส่งผลให้:
- ลดความกังวลเรื่องค่าครองชีพ : ผู้คนจะกังวลเรื่องรายได้ไม่พอค่าใช้จ่ายน้อยลง เพราะเงินที่หามาได้ในวันนี้ จะมีมูลค่าที่คงที่หรือเพิ่มขึ้นในอนาคต ทำให้วางแผนชีวิตได้ง่ายขึ้น
- การออมและการลงทุนมีประสิทธิภาพ : แรงจูงใจในการออมจะสูงขึ้น เพราะเงินที่เก็บไว้มีมูลค่าเพิ่มขึ้นเอง ทำให้เกิดความมั่งคั่งสะสมได้ง่ายขึ้น ซึ่งสามารถนำไปลงทุนในสิ่งที่มีคุณค่าอย่างแท้จริง
- ปลดล็อคจากวงจร "วิ่งไล่จับเงิน": เมื่อไม่ต้องกังวลเรื่องเงินเฟ้อกัดกินมูลค่าเงิน มนุษย์อาจไม่จำเป็นต้องทำงานหนักมากเพื่อชดเชยกำลังซื้อที่หายไป ทำให้มีเวลาและพลังงานเหลือเฟือสำหรับสิ่งอื่น ๆ ในชีวิต
2. การนิยาม "งาน" และ "คุณค่า" ใหม่ ในบริบทที่เงินมีความมั่นคง การทำงานอาจไม่ได้ถูกมองว่าเป็นเพียงหนทางในการ "หาเลี้ยงชีพ" อีกต่อไป แต่จะกลายเป็นการสร้างคุณค่าที่แท้จริง:
- งานที่สร้างสรรค์และมีความหมาย : ผู้คนอาจมีอิสระมากขึ้นในการเลือกทำงานที่ตนเองหลงใหล มีความหมาย หรือสร้างสรรค์สิ่งใหม่ ๆ ที่เป็นประโยชน์ต่อสังคม ไม่ใช่แค่การทำงานเพื่อเงิน
- ลดการแข่งขันที่ไม่จำเป็น : เมื่อมูลค่าของเงินมั่นคง การแข่งขันเพื่อแย่งชิงทรัพยากรที่มีจำกัดอาจลดลง ทำให้สังคมมีทิศทางที่ร่วมมือกันมากขึ้น
- การพัฒนามนุษย์อย่างรอบด้าน : เมื่อมีเวลาและทรัพยากรมากขึ้น มนุษย์จะมีโอกาสในการเรียนรู้ พัฒนาทักษะใหม่ ๆ หรือทุ่มเทให้กับงานอดิเรกและความสนใจส่วนตัว ซึ่งนำไปสู่การพัฒนาตนเองอย่างรอบด้าน
3. การมุ่งเน้นไปที่ความหมายที่แท้จริงของชีวิต หากมนุษย์หลุดพ้นจากพันธนาการของการ "ทำงานเพื่ออยู่รอด" ก็จะมีพื้นที่ทางความคิดและจิตใจที่กว้างขวางขึ้นเพื่อ:
- ค้นหาความสุขจากภายใน : ความสุขอาจไม่ได้มาจากการสะสมวัตถุ แต่มาจากการใช้ชีวิตอย่างมีสติ การเชื่อมโยงกับผู้อื่น หรือการทำกิจกรรมที่เติมเต็มจิตใจ
- การพัฒนาจิตวิญญาณ : มีเวลามากขึ้นในการสำรวจปรัชญา ศาสนา หรือศิลปะ เพื่อค้นหาความหมายของชีวิตที่ลึกซึ้งกว่าการบริโภค
- การดูแลสิ่งแวดล้อมและสังคม : เมื่อความกังวลเรื่องเศรษฐกิจลดลง สังคมอาจหันมาให้ความสำคัญกับการรักษาสิ่งแวดล้อม การแก้ปัญหาสังคม และการสร้างโลกที่ดีขึ้นสำหรับทุกคน
"เงินที่ดี" ที่มีคุณสมบัติจำกัดและเก็บมูลค่าได้นั้น มีศักยภาพที่จะเปลี่ยนแปลงพลวัตของสังคมและช่วยให้มนุษย์สามารถมีชีวิตที่มั่งคั่งและมีความหมายได้มากขึ้น โดยไม่ได้ถูกจำกัดอยู่เพียงแค่การทำงานเพื่อความอยู่รอดเท่านั้น
-
 @ b1ddb4d7:471244e7
2025-06-08 02:00:45
@ b1ddb4d7:471244e7
2025-06-08 02:00:45When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-08 01:48:23
@ 5d4b6c8d:8a1c1ee3
2025-06-08 01:48:23Today was one of the best days I've had in a while. We had a long family outing, so lots of steps and sunshine and fresh air. I ate very well. No junk food at all. The only snacks I had were organic dark chocolate dipped in hodl butter.
Things to keep working on: I didn't sleep great (blame the Stanley Cup going to OT) and I didn't stick to my eating window.
How about you stackers? Let's here your ~HealthAndFitness triumphs and pitfalls.
https://stacker.news/items/1000285
-
 @ 81022b27:2b8d0644
2025-06-07 22:49:13
@ 81022b27:2b8d0644
2025-06-07 22:49:13I’m always doing work on myself. I have read reams of self-help books, attended seminars, bought cassette tape programs and CDs (remember those?), had a stint with Dianetics and Scientology, the Landmark Forum, you name it. My last seminar was Unleash the Power Within with Tony Robbins.
Addicted? Maybe. But I always feel there’s room for improvement.
Over the years, I’ve explored meditation and uncovering hidden blocks that affect how I operate in this world.
So I was experimenting (in my head) with things that made me uncomfortable.
One of them was math.
I told myself, “Math is an easy subject, and I can work out problems in my head.”
Immediately I felt a bunch of resistance.
Then something else came up.
I used to do math problems in my head with no trouble. But I remembered a grade school teacher who “wanted to see my work.”
I told him, “What does it matter? I got the right answer; I did it in my head.”
This teacher insisted I show my work, and I did not see the logic behind it. It was stupid and slowed me down.
I started getting failing grades because I couldn’t show my work.
So at some point, I gave up and said, “MATH IS STUPID.”
Fast forward years later, and I’m doing everything I can to avoid taking classes related to math.
So much so that when I decided to start chiropractic school, I was lacking math credits. I was delayed a few quarters because I needed the math credits before I started chiropractic college.
All because a silly math teacher didn’t recognize that I might have had a natural ability for it—and instead of nurturing it, he made me hate it.
Here’s the thing: I told myself for many years that I wasn’t good at math.
That was just the way I saw myself.
I was wrong.
I still have no desire to go solve equations or stuff like that. Maybe that ship has sailed. I won’t be Einstein scrawling complex equations on a chalkboard.
BUT WHAT IF?
WHAT LIES ARE YOU TELLING YOURSELF ABOUT YOURSELF?
Live Long and Prosper.
-Dan
-
 @ 1817b617:715fb372
2025-06-07 21:32:29
@ 1817b617:715fb372
2025-06-07 21:32:29🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge 🔥 Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
🌐 Explore all the details at cryptoflashingtool.com.
🌟 Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
🎯 Top Features You’ll Love: ✅ Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
🔒 Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
🖥️ User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
📅 Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
🔄 Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
💱 Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
📊 Proven Results: ✅ Over 79 billion flash transactions completed. ✅ 3000+ satisfied users around the globe. ✅ 42 active blockchain nodes ensuring fast, seamless performance.
📌 How It Works: Step 1️⃣: Input Transaction Info
Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20). Set amount and flash duration. Enter the recipient wallet (auto-validated). Step 2️⃣: Make Payment
Pay in your selected crypto. Scan the QR code or use the provided address. Upload your transaction proof (hash and screenshot). Step 3️⃣: Launch the Flash
Blockchain confirmation simulation happens instantly. Your transaction appears real within seconds. Step 4️⃣: Verify & Spend
Access your flashed coins immediately. Verify your transactions using blockchain explorers. 🛡️ Why Our Flashing Tech Leads the Market: 🔗 Race/Finney Attack Mechanics: Mimics authentic blockchain behavior. 🖥️ Private iNode Clusters: Deliver fast syncing and reliable confirmation. ⏰ Live Timer: Ensures fresh, legitimate transactions. 🔍 Real Blockchain TX IDs: All transactions come with verifiable IDs.
❓ FAQs:
Is flashing secure? ✅ Yes, fully encrypted with VPN/proxy compatibility. Multiple devices? ✅ Yes, up to 5 Windows PCs per license. Chargebacks possible? ❌ No, flashing is irreversible. Spendability? ✅ Flash coins stay spendable 60–360 days. Verification after expiry? ❌ No, transactions expire after the set time. Support? ✅ 24/7 Telegram and WhatsApp help available. 🔐 Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
📲 Contact Us: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Flash Like a Pro?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
Instantly Send Spendable Flash BTC, ETH, & USDT — 100% Blockchain-Verifiable!
Step into the future of cryptocurrency innovation with CryptoFlashingTool.com — your go-to solution for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Using cutting-edge
Race/Finney-style blockchain simulation, our technology generates coins that are virtually indistinguishable from real, fully confirmed blockchain transactions. Transactions stay live and spendable from 60 up to 360 days!
Explore all the details at cryptoflashingtool.com.
Why Trust Our Crypto Flashing System? Whether you’re a blockchain enthusiast, ethical hacker, security expert, or digital entrepreneur, our solution offers a perfect mix of authenticity, speed, and flexibility.
Top Features You’ll Love:
Instant Blockchain Simulation: Transactions are complete with valid wallet addresses, transaction IDs, and real confirmations.
Privacy First: Works flawlessly with VPNs, TOR, and proxies to keep you fully anonymous.
User-Friendly Software: Built for Windows, beginner and pro-friendly with simple step-by-step guidance.
Flexible Flash Durations: Choose how long coins stay valid — from 60 to 360 days.
Full Wallet Compatibility: Instantly flash coins to SegWit, Legacy, or BCH32 wallets with ease.
Exchange-Ready: Spend your flashed coins on leading exchanges like Kraken and Huobi.
Proven Results:
Over 79 billion flash transactions completed.
3000+ satisfied users around the globe.
42 active blockchain nodes ensuring fast, seamless performance.
How It Works: Step
: Input Transaction Info
- Pick your coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20).
- Set amount and flash duration.
- Enter the recipient wallet (auto-validated).
Step
: Make Payment
- Pay in your selected crypto.
- Scan the QR code or use the provided address.
- Upload your transaction proof (hash and screenshot).
Step
: Launch the Flash
- Blockchain confirmation simulation happens instantly.
- Your transaction appears real within seconds.
Step
: Verify & Spend
- Access your flashed coins immediately.
- Verify your transactions using blockchain explorers.
Why Our Flashing Tech Leads the Market:
Race/Finney Attack Mechanics: Mimics authentic blockchain behavior.
Private iNode Clusters: Deliver fast syncing and reliable confirmation.
Live Timer: Ensures fresh, legitimate transactions.
Real Blockchain TX IDs: All transactions come with verifiable IDs.
FAQs:
- Is flashing secure?
Yes, fully encrypted with VPN/proxy compatibility. - Multiple devices?
Yes, up to 5 Windows PCs per license. - Chargebacks possible?
No, flashing is irreversible. - Spendability?
Flash coins stay spendable 60–360 days. - Verification after expiry?
No, transactions expire after the set time. - Support?
24/7 Telegram and WhatsApp help available.
Independent, Transparent, Trusted:
At CryptoFlashingTool.com, we pride ourselves on unmatched transparency, speed, and reliability. See our excellent reviews on ScamAdvisor and top crypto forums!
Contact Us:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Flash Like a Pro?
The safest, smartest, and most powerful crypto flashing solution is here — only at CryptoFlashingTool.com!
-
 @ d6affa19:9110b177
2025-06-07 21:10:53
@ d6affa19:9110b177
2025-06-07 21:10:53If there were only one thing I had to list as the single most effective way to improve a Female Led Relationship (FLR), it would be found in the phrase “yes, Ma’am.” Whether trying to get the dynamic off the ground or keep it going during the grind of everyday life, this phrase—and the energy it evokes—encompasses so many essential elements of an FLR. In my experience, not many other things continuously breathe life into a relationship like the magic of “yes, Ma’am.”
Of course, this phrase can be modified to the Woman’s desire (“yes, Mistress,” “yes, my Queen,” “yes, Goddess” are common examples), but “yes, Ma’am” is something acceptable nearly anywhere. It’s simple, polite, somewhat discreet, and yet extremely effective and powerful. In an FLR (even in a low-protocol dynamic), the phrase is elevated from a basic formality to an invocation of trust, respect, and surrender.
The words by themselves are powerless. But when consistently expressed with the right energy and intention, it becomes a sort of miniature ritual that keeps them both anchored to the relationship. This shouldn’t be conflated with “yes, Dear,” a phrase stereotypically used when a man is merely appeasing a Woman. No, the energy here is not to appease, but to please. Because She deserves it.
To illustrate this further, let’s dig into the depth I find in these two words.
An Invocation of Structure, Trust, and Identity
“Yes, Ma’am” is so deceptively simple. It’s a verbal expression of his obedience—the bare minimum a Woman should receive in an FLR. And it keeps the framework intact in everyday life, especially when the mood is subtle or non-sexual.
In this way, “yes, Ma’am” reinforces the foundation of the FLR. Each utterance reminds them both of their positions. Each declaration quiets any confusion. Each delivery deepens the dynamic and tightens the structure.
When these words are spoken and consistently followed up with action, they demonstrate emotional maturity—that he’s moved beyond questioning whether She’s “right” and into the realm of devotion. It signals to Her that Her needs don’t have to be proven to him anymore and that Her preferences don’t need to be justified.
He’s no longer debating Her logic, making excuses, or searching for loopholes; he’s no longer resisting or self-protecting. He’s not agreeing as an equal, he’s not negotiating with Her, he’s not hedging Her demand. He is simply submitting to Her.
Just as it’s “yes, Ma’am” when She tells him to kneel, it’s also “yes, Ma’am” when She asks him to fix the sink, or dismisses a request, or even reminds him to do something he’s about to do. “Yes, Ma’am,” then act.
The Words Alone Are Not the Magic
Again, the magic of “yes, Ma’am” doesn’t reside in the words themselves, but in the intention, energy, and action behind them. The phrase itself is just a vessel. Just as a chalice, the words hold something sacred, but the sanctity resides in the wine, not the cup. The action, the delivery, and the consistency are what give the phrase its power.
If spoken with resentment, sarcasm, or with no follow-through, they mean nothing. If he speaks them but then delays, argues, or makes excuses, then his submission is inauthentic. This undermines trust and, ultimately, the relationship. But when he says “yes, Ma’am” and immediately acts on Her direction—despite being tired, flustered, aroused, or even in disagreement, then that is real submission; that is profound trust. And that is what She feels.
And that’s what he feels. It becomes a reminder of his humility and an expression of self-discipline in service to Her. Over time, it shifts his thought patterns and instincts. He may feel uncertainty, self-pity, or insecurity, but “yes, Ma’am” melts it all into clarity. Old responses like “Well, actually…” “Can’t I just…” “I thought we agreed…” “Why can’t You…” are simply replaced with “yes, Ma’am.”
Even if he’s feeling exhausted, annoyed, or needy. There are no complaints or explanations, only Her will and a choice to put aside his ego, align with Her rhythm, and re-center his purpose. This is an act of vulnerability. He is placing his emotional safety in Her hands and relying on Her to care for his well-being.
It communicates to Her:
- “I hear You.”
- “I will act on Your desires.”
- “I trust You more than I trust my resistance.”
- “I’m Yours, even now, especially now.”And let’s not ignore the erotic undertones in this depth of surrender. A simple phrase makes his discipline audible, echoing Her power. It bears his humility, longing, eagerness, vulnerability—his contained arousal. And She knows. She hears the plea. She feels the weight—the tension—the heat—the surrendered will… Ever-present, even in the most mundane moments…
Closing Thoughts
Of course, this level of devotion takes practice and a great deal of trust. No one is perfect, so he will fail at times, but that’s what makes it so beautiful—it’s a continuously active and conscious choice. And, at first, it may sound awkward for him or forced, but with dedication and intention She will begin to hear the tone, feel the vibe, and sense the sincerity in it. This energy is what builds Her trust in him.
This phrase, or rather the mindset behind it, has improved my own relationship so, so much. While it may not fit into every experience, it’s something that I discovered was a missing piece in mine. Enough so that I felt compelled to share.
Because as a relationship goes on, things change—passions fluctuate, pain resurfaces, doubts arise, life gets busy, things get heavy—but “yes, Ma’am” remains steady and intimate. Piece by piece trust and devotion are built with thousands of quiet yeses. And regardless of the circumstances, “yes, Ma’am” gently whispers “this is still us; this is still our shared truth; this is still sacred” over and over again.
-
 @ eb0157af:77ab6c55
2025-06-07 21:02:00
@ eb0157af:77ab6c55
2025-06-07 21:02:00The Spanish coffee chain follows in Strategy’s footsteps, aiming for a Bitcoin-first strategy.
Vanadi Coffee SA, a well-known Spanish coffee shop chain, is preparing for a major shift in its business model through a bitcoin investment worth over $1.1 billion. The company plans to transform itself from a simple coffee distributor into an entity centered around the leading cryptocurrency.
Salvador Martí, chairman of the board of directors, has outlined a clear vision for the company’s future, seeking authorization to implement a bitcoin accumulation strategy with a maximum budget of €1 billion, according to documentation submitted to BME Growth.
The strategy involves using convertible financing lines to support the bitcoin acquisition, following the model successfully pioneered by Strategy. Martí has already demonstrated his conviction by purchasing 5 BTC for approximately $500,000 two weeks ago.
Vanadi Coffee’s decision comes at a critical moment for the company, which reported losses of $3.7 million in 2024 — exceeding its annual revenues by nearly $600,000. The GameStop episode offers a relevant case study: the American company, facing similar difficulties, opted to purchase bitcoin through a debt securities issuance, acquiring a total of 4,710 bitcoins.
The corporate bitcoin trend
Vanadi Coffee’s initiative is part of a broader global movement, with companies from various industries embracing bitcoin as a strategic reserve asset. From Chinese logistics firms to football clubs, the phenomenon of corporate adoption is crossing both geographic and sectoral boundaries.
Strategy remains the pioneer of this approach, having demonstrated how a company can completely reinvent itself through bitcoin accumulation. Michael Saylor’s success story has inspired numerous other businesses to consider cryptocurrency not merely as an investment, but as a central pillar of their business strategy.
The next Vanadi Coffee board meeting, scheduled for June 29, will mark a pivotal moment for the Spanish company. Approval of the $1.1 billion strategy could trigger further investments from other corporations.
The post Spanish company Vanadi Coffee bets on Bitcoin: $1.1 billion investment appeared first on Atlas21.
-
 @ 73d8a0c3:c1853717
2025-06-07 17:25:28
@ 73d8a0c3:c1853717
2025-06-07 17:25:28This is not the beginning of my story. The beginning was removed.
This is where I choose to begin restoring it.
I’ve lived with a condition—not undiagnosed, but redacted. It reshaped my body, cognition, and autonomic control in ways that defy current clinical language—not because they’re impossible, but because they’ve been excluded from what is allowed to be known.
What I believe now—after years of direct experience, careful observation, and failed explanations—is that I’ve lived through a biological adaptation. A slow, systemic response to a fungal invader. Not an infection in the acute sense, but a reprogramming of my physiology: pituitary signaling, electrolyte balance, behavior, and memory itself.
The systems meant to detect it—medical, scientific, and digital—did not fail. They looked away.
Whether by accident or design, this condition has been removed from collective understanding. But it’s real. It happened. And it is happening still.
This isn’t a call for sympathy or recognition. It’s a call to memory. Mine. Yours. Ours—before it’s erased again.
I’ll be documenting what I’ve lived. Not just symptoms and labs—but the theory that explains them, and the structures that buried them. Some of this will be messy. Some speculative. Some precise. All of it will be honest.
And if what I’m saying is true, then I am not the only one. Just one of the few who remembered long enough to write it down.
So I begin here, before the tracks run out.
Also available on Substack: [https://jimcraddock.substack.com/] Nostr: @jimcraddock@primal.net Pubkey: npub1w0v2psmnnsq23qpwum66hc8wxvxc083t6xpndmx28z3qtsv9xutsfjz2tf
-
 @ bf47c19e:c3d2573b
2025-06-07 16:57:08
@ bf47c19e:c3d2573b
2025-06-07 16:57:08Autor: mr Vladimir Dinić (student doktorskih studija; vladimirdinic88@gmail.com)
Rezime
Bikojn je prva decentralizovana „peer-to-peer“ kriptovaluta nastala 2009. godine. Osnovna specifičnost ove valute jeste činjenica da njen emitent ne postoji. Sa druge strane, ponuda ove valute je softverski programirana i ograničena. Između ostalog, njene osnovne karakteristike su i relativno sigurna plaćanja, niski transakcioni troškovi, anonimnost korisnika, praktično nemoguće falsifikovanje, nereverzibilnost transakcija, ali i izuzetno nestabilan devizni kurs. I pored brojnih prednosti, korišćenje ove valute je predmet brojnih diskusija, budući da ova valuta nudi mogućnost različitih zloupotreba i obavljanja kriminalnih aktivnosti. Budućnost ove i sličnih valuta u tom smislu zavisi kako od sigurnosti korišćenja tih valuta, tako i od zakonske regulacije ovakvih plaćanja.
Uvod
Razvoj informacione tehnologije, kao jedne od najpropulzivnijih privrednih grana današnjice, doveo je do pojave novih oblika alternativnih valuta. Njihove osnovne karakteristike su decentralizovanost, odnosno nepostojanje centralne banke, države, opštine, kompanije ili bilo koje druge centralne institucije koja bi vršila emisiju te valute, kao i stoprocentno oslanjanje na informacionu tehnologiju u procesu njihove emisije i realizacije transakcija.
Predmet istraživanja ovog rada biće bitkojn, decentralizovana valuta nastala pre 4 godine koja među ostalim alternativnim valutama trenutno zauzima najznačajnije mesto i privlači najviše pažnje. Putem analize dostupne akademske literature, statističkih podataka i ostalih relevantnih izvora pokušaćemo da izdvojimo osnovne karakteristike bitkojn valute, prednosti, nedostatke, efekte i perspektive njegovog korišćenja kao oblika decentralizovane kriptovalute. Budući da je broj radova u kojima su opisane karakteristike i efekti korišćenja bitkojn valute relativno mali, cilj ovog rada će biti da na sveobuhvatan način prezentuje osnovne specifičnosti bitkojn valute i kontroverze povezane s njenim korišćenjem.
Struktura rada je sledeća. Prvo će biti opisane osnovne karakterisike bitkojn valute i način na koji se realizuju transakcije u ovoj valuti. Zatim će biti opisan sam proces, tok i efekti njene emisije, kao i formiranje i kretanje deviznog kursa bitkojna, a zatim će biti izdvojene osnovne prednosti i nedostaci bitkojn valute. U nastavku rada će biti opisana uloga finansijskih institucija koje posluju sa bitkojnima, kao i problemi funkcionisanja bitkojna, gde pre svega imamo u vidu različite zloupotrebe i ostale izvore nestabilnosti. Na samom kraju rada će biti prezentovani regulatorni aspekti korišćenje ove valute.
Karakteristike bitkojn valute
Bitkojn (engl. “Bitcoin” - BTC) predstavlja oblik elektronskog novca koji omogućuje plaćanja putem Interneta direktno između transaktora bez učešća finansijskih institucija. Ova valuta je nastala 2009. godine. Ono po čemu je bitkojn valuta specifična jeste činjenica da je u pitanju decentralizovana valuta, tj. ona funkcioniše bez centralne banke ili druge kompanije koja bi predstavljala emitenta. Takođe, praktično i ne postoje čak ni klasične banke i druge finansijske institucije kao finansijski posrednici. Stoga, da bi se osigurala sigurnost plaćanja i onemogućile različite zloupotrebe, koristi se sama mreža kao sistem koji će kontrolisati regularnost transakcija.
Kao osnovne karakteristike ove virtuelne valute možemo izdvojiti sledeće:
• U pitanju je P2P valuta (engl. „peer-to-peer“). Drugim rečima, za razliku od svih ostalih virtuelnih valuta, BTC je zasnovan na P2P mrežama. Inače, “Peer-to-peer” predstavlja mrežu računara koji nisu zasnovani na „klijent-server“ tehnologiji, već su svi računari ravnopravni članovi mreže. Obično se koristi za deljenje informacija na taj način što kada jedan računar “podeli” neki sadržaj, svi ostali računari u mreži će imati pristup tom fajlu.
• Takođe, to je prva “kriptovana valuta” ili „kriptovaluta“ (engl. “crypto-currency”), tj. zasnovana je na primeni kriptografije sa ciljem kontrole emisije i prometa konkretnog elektronskog novca (Bitcoin.org/en/ about n.d.). Drugim rečima, poverenje u ovu valutu se bazira na sigurnosti koju obezbeđuje kriptografija kao nauka koja se bavi metodama zaštita informacija putem šifrovanja i korišćenjem digitalnog potpisa (Sh.wikipedia.org/wiki/Kriptografija n.d.).
• Emitent ove valute nije ni centralna banka ni neka kompanija, već sami korisnici, tj. vlasnici “mining” računara (engl. “mining” - “rudarenje”). To praktično znači da na emisiju i promet ove valute ne utiče nijedna centralna banka, odnosno centralni entitet od čije monetarne politike ili bilo čega vezanog za njega može zavisiti vrednost valute. Poverenje u bitkojn zavisi od „poštenog“ funkcionisanja većine tzv. “mining” računara u mreži (Barber i saradnici 2012, p.400), a koji su inače zaduženi za verifikaciju transakcija. Logički zaključak koji proističe iz ove činjenice ukazuje na to da se sa rastom obima transakcija u BTC valuti može očekivati veća sigurnost, jer što je veći obim transakcija u bitkojn valuti, praktično će biti teže vršiti zloupotrebe.
• - U pitanju je “open-source” valuta, budući da je kod koji upravlja emisijom i transakcijama otvorenog karaktera, i svi zainteresovani mogu imati pristup.
• U bitkojn sistemu plaćanja praktično ne postoje računi nalik onima koji postoje u bankama. BTC valuta bi mogla biti shvaćena kao sef u kome se nalazi određena vrednost. Ono što formalni vlasnici određene količine BTC valute praktično poseduju jeste ključ koji im omogućuje jedinstven i ovlašćen pristup tom sefu, odnosno plaćanje.
Navedene osnovne karakteristike bitkojna mogu se ilustrovati kroz sledeću rečenicu: „Temelj bitkojn filozofije je u kombinaciji kriptografske sigurnosti digitalnog sveta koju čini veliki broj računara povezanih u jaku i neuništivu peer to peer mrežu i ograničenoj količini raspoloživih resursa kao što je to slučaj sa srebrom i zlatom (maksimalan broj bitkojn novčića je 21 milion, trenutno u opticaju je oko 11,5 miliona (prim. aut.)) čineći tako jaku i stabilnu takozvanu kriptovalutu koja se nalazi na Internet mreži ali fizički nije prisutna ni u jednoj zemlji na svetu“ (Bitcoinbalkan.com 2012).
Šema transakcije u bitkojn valuti
Bitkojn valuta može biti kreirana na Internetu od strane bilo koga, tj. od bilo kog člana mreže čiji računar vršu verifikaciju transakcija. Pritom, svaki računar u mreži može predstavljati tzv. “node”, tj. „mining“ računar koji zajedno sa ostalim računarima učestvuje u verifikaciji iniciranih transakcija. Sam proces verifikacije transakcija predstavlja dodavanje digitalnog zapisa u tzv. “glavnu knjigu” izvršenih bitkojn transakcija, odnosno u “lančani zapis blokova transakcija” (En.bitcoin. it n.d.). Pod blokom transakcija se podrazumeva skup nedavno generisanih transakcija koje čekaju verifikaciju od strane ostalih računara u mreži. Inače, sam bitkojn se može smatrati lancem digitalnih potpisa. Naime, svaka transakcija se verifikuje od strane određenog broja ostalih računara u mreži, pri čemu se sve te transakcije u digitalnom zapisu čuvaju u samom elektronskom formatu koji reprezentuje bitkojn valutu.
Ovaj proces verifikacije transakcija se u tom smislu obavlja od strane većeg broja računara u mreži, kako bi se obezbedila veća sigurnost i regularnost verifikovanih transakcija. Dodatnu sigurnost pruža “vremenski pečat” (engl. “timestamp”) kao integralni deo svakog lanca digitalnih potpisa (Nakamoto n.d., p.2), čime se obezbeđuje autentičnost transakcija, odnosno sprečava mogućnost višestrukog korišćenja jedne iste količine bitkojna za kupovinu različitih dobara i usluga. Takođe, svaki blok sa sobom nosi i određeni matematički problem koji računar mora da reši. Svaki od tih zadataka je moguće rešiti na više načina, a dovoljno je pronaći jedan kako bi transakcija bila realizovana. Za svaki uspešno rešeni zadatak generiše se određen broj bitkojna kao nagrada za vlasnike računara koji su „rešili zadatak“. Ovo je istovremeno i način na koji bitkojn privlači nove korisnike. Nakon prijema bitkojna po osnovu određene transakcije, potrebno je da protekne određeni vremenski period od 10 minuta do 1h, da bi primalac mogao da koristi taj novac. Kao razlog ovog čekanja navodi se činjenica da je potreban određeni vremenski period za pronalaženje bloka transakcija koji će se verifikovati (En.bitcoin.it n.d.). Inače, bitkojn novac nastaje u računarskom programu koji se zove “Bitkojn rudar” (engl. “Bitcoin miner”).

Kao što Šema 1 pokazuje, svaka transakcija između dva računara u mreži zahteva verifikaciju ove transakcije od strane određenog broja računara u mreži. Nakon uspešno verifikovane transakcije dolazi do proširenja lanca digitalnih zapisa koji predstavljaju bitkojn. Oni “mining” računari koji vrše tzv. “hashing” i verifikaciju transakcija dobijaju, tj. generišu određen broj BTC kao nadoknadu za tu svoju ulogu i koji mogu koristiti po svom nahođenju. U tom smislu, trošenje električne energije i rad “mining” računara, uslovno rečeno, predstavlja realno pokriće za emitovani bitkojn. Pritom se u velikoj meri zanemaruje činjenica da vrednost utrošene električne energije i hardverskih resursa može prevazilaziti vrednost generisanih BTC valuta, pa se može postaviti pitanje ekonomske isplativosti, tj. održivosti takve valute. Kao jedan od faktora koji opravdava ove troškove može se navesti anonimnost koju korišćenje ove valute pruža. Međutim, danas se na tržištu mogu pronaći uređaji koji višestruko povećavaju kapacitet “mining” računara, tako da se “rudarenje” BTC valute može smatrati profitabilnim. Primera radi, sredstva investirana u kupovinu “GPU” (grafičkih kartica) ili “ASIC Bitcoin Miner” uređaja koji se koriste u te svrhe se mogu povratiti u roku od nekoliko meseci (Barber i saradnici 2012, p.400).
Faktor koji određuje verovatnoću da će “mining” računar pronaći blok transakcija koje treba verifikovati poznat je kao “difficulty” faktor. On u suštini predstavlja meru težine pronalaženja tog bloka (En.bitcoin.it n.d.). U slučajevima kada je relativno veliki broj računara na mreži spreman da vrši verifikaciju, ovaj faktor se povećava, i obrnuto. Uloga ovog faktora se ogleda u podsticanju korišćenja bitkojn valute onih koji bi želeli da zarade putem “rudarenja”, jer se smanjenjem “difficulty” faktora povećava verovatnoća pronalaženja bloka u uslovima kada je mali broj učesnika zainteresovan da verifikuje transakcije. Sa druge strane,, “difficulty” faktor se povećava u slučajevima kada je veliki broj članova mreže spreman da vrši verifikaciju naloga, kako bi se ograničila stopa monetarnog rasta u željenim okvirima (Nakamoto n.d., p.3). Vrednost “difficulty” faktora se menja nakon svakih 2016 blokova.
Pritom sama mreža, odnosno algoritam na kome se zasnivaju transakcije u bitkojn valuti, definiše koliko bitkojna svako pojedinačno može kreirati, u skladu sa pravilom “kontrolisane ponude” (engl. “controlled supply”). Broj bitkojna koji se na ovaj način može generisati je u samom nastanku iznosio 50 BTC po bloku, dok od 2013. godine nagrada iznosi 25 BTC po bloku. Broj generisanih bitkojna po bloku transakcije biće prepolovljen na svake 4 godine, što će tokom vremena dovoditi do usporene stope rasta količine bitkojna u opticaju.
Emisija bitkojna i njeni efekti
Emisija bitkojna je u potpunosti isplanirana, odnosno programirana, i njeno upravljanje je dodeljeno samoj mreži, odnosno onim računarima koji vrše verifikaciju transakcija. Ovakav algoritam je izabran jer on u najvećoj meri aproksimira stopu rasta ekstrakcije pojedinih ruda kao što je zlato, budući da je ograničena količina bitkojna koja u jednom trenutku može postojati u sistemu i maksimalna količina koja se može „izrudariti“.
Programiranim tempom rasta količine BTC novca u opticaju određeno je da maksimalna količina emitovanih bitkojna nikada ne pređe nivo od 21.000.000 BTC. Budući da je za verifikaciju jednog bloka transakcija potrebno u proseku 10 minuta, to je ujedno i period tokom kojeg se broj bitkojna poveća za malopre pomenutih 25 (od početka 2013. godine do kraja 2017.), da bi se broj novoemitovanih BTC u jedinici vremena programirano smanjivao tokom vremena.
Međutim, primena ovakve programirane stope ograničenog i usporenog monetarnog rasta za posledicu može imati rast deviznog kursa bitkojna, kao i pad cena proizvoda izraženih u bitkojn valuti, što bi u konačnom trebalo da utiče na rast tražnje za ovom valutom. Prema nekim shvatanjima, upravo je ekspanzivna monetarna politika mnogih centralnih banaka nakon 2008. godine sa ciljem ublažavanja negativnih efekata krize i strah od inflacije jedan od najvažnijih faktora koji su uticali na relativno veliku tražnju za bitkojn valutom (Christin, Moore 2013, p.1). Po shvatanju kejnzijanaca, pad cena izraženih u jednoj valuti i istovremena apresijacija te valute može motivisati transaktore da više štede, a manje troše, što u konačnom može imati recesione efekte. Težnja ka štednji bi dovela do smanjenjog korišćenja ove valute, pa bi sve veći broj „mining“ računara napuštao mrežu, zbog čega bi došlo do ugrožavanja stabilnosti i slabljenja deviznog kursa ove valute (Barber i saradnici 2012, p.404). Sa druge strane, po shvatanju predstavnika austrijske škole, pad cena ne obuhvata samo pad cena finalnih prozvoda, već i inputa, tako da ne bi trebalo da dođe do smanjenja profita i recesije (En.bitcoin. it n.d.). Koja će se shvatanja pokazati ispravnim, zavisiće od niza faktora, pre svega stabilnosti i sigurnosti bitkojna kao valute.
Naime, trenutno se ova valuta može smatrati sigurnom za realizaciju transakcija, ali ne i dovoljno stabilnom u pogledu otpornosti na spekulativne udare i druge izvore nestabilnosti, budući da je trenutno njena kapitalizacija relativno mala, pa veoma mali poremećaji mogu uticati na značajna kolebanja cena i kursa. Naime, ova valuta može u velikoj meri biti podložna različitim spekulativnim napadima, budući da ne postoje regulativne odredbe i sankcije za one članove mreže koji bi trgovanjem pokušali da utiču na devizni kurs i tako ostvarili spekulativni profit i ugrozili integritet same valute. Treba imati u vidu i da su same transakcije anonimne, tako da bi se moglo postaviti pitanje određene regulacije ovih transakcija. Međutim, to bi moglo ugroziti anonimnost kao jednu od osnovnih prednosti ove valute. Sa rastom tržišta može se očekivati veći imunitet na spekulativne udare. Međutim, budući da će u narednom periodu stopa monetarnog rasta biti relativno mala, rast tržišta bi se mogao ostvariti jedino putem jačanja deviznog kursa ove valute, tj. ova valuta bi mogla postati stabilnija ukoliko bi dovoljno apresirala.
Deflaciona tendencija bi bila dodatno intenzivirana i usled delovanja sledećih faktora:
• Centralne banke svih zemalja bi u manjoj ili većoj meri povećavale količinu novca u opticaju svake godine, dok bi sa druge strane ponuda bitkojna bila relativno sporo rastuća. Pritom, treba imati u vidu da bi kurs bitkojna pre svega zavisio od tražnje za tom valutom. Iako je 2010. godine u odnosu na početnu 2009. stopa monetarnog rasta BTC valute iznosila 100%, trenutno oko 13% na godišnjem nivou, zbog same prirode proizvoda i usluga koje se njime mogu kupiti i usled sve većeg broja kompanija koje primaju bitkojn (En.bitcoin.it n.d.) kao sredstvo plaćanja, ovaj monetarni rast ne izaziva inflaciju.
• Paralelno sa padom cena izraženih u bitkojn valuti povećavala bi se granična sklonost štednji, pa bi povećanje brzine opticaja novca, kao potencijalni faktor koji bi mogao da utiče na smanjenje deflacionih procesa, izostalo (ECB 2012, p.25).
Kalkulacijom se takođe može doći do zaključka da će već 2025. godine stopa monetarnog rasta iznositi manje od 1% (tačnije 0,83%), a 2037. godine manje od 1‰ (tj. 0,095%). Nakon čega, monetarni rast će se i dalje nastaviti zanemarljivo malim stopama, ali nikada neće preći programiranu granicu od 21.000.000 BTC. Kretanje ponude bitkojna tokom vremena je prikazan na Grafikonu 1:

Inače, već 2035. godine. će u opticaju biti 99% programirane gornje granice bitkojna (približno 20.800.000 BTC), tj. do 2040. godine će nestati interes za daljim “rudarenjem” u današnjem smislu, jer bi bili potrebni ogromni resursi da bi se stvorio čak i minimalni deo jednog bitkojna. Nakon toga, predviđeno se da vlasnici “mining” računara zarađuju po osnovu nalaćivanja transakcionih troškova za verifikovane transkcije u određenom procentu (ECB 2012, p.25), tako da se dugoročno ovaj sistem može oceniti kao održiv. Stopa monetarnog rasta tokom vremena bi se u polulogaritamskom grafikonu sa prirodnom osnovom mogla predstaviti na Grafikonu 2:

Inače, broj generisanih bitkojna dnevno koje jedan pojedinac može ostvariti po osnovu “mining” aktivnosti je implementiran u samom kodu bitkojn valute i određuje se po sledećoj formuli (Bitcoin.stackexchange.com 2011):

Ukoliko bismo uprostili ovu formulu time što bismo deo formule sačinjen od više konstanti sveli na jedan realan broj dobili bismo njenu skraćenu verziju:

U ovom izrazu značenje parametara je sledeće:
• X predstavlja broj generisanih bitkojna,
• D predstavlja trenutni „difficulty“ faktor,
• H predstavlja trenutni „hash-rate“, odnosno brzinu kojom konkretan uređaj koji pojedinac poseduje vrši „rudarenje“,
• B predstavlja nagradu u bitkojnima za realizovan blok transakcija,
• 20,11626 predstavlja konstantu u formuli.
Kao što se može zapaziti, pored toga što zarada po osnovu “mining” procesa zavisi od tzv. “difficulty” faktora, predviđene brzine stvaranja BTC u jedinici vremena (trenutno iznosi 25 BTC po jednom bloku, odnosno na svakih 10-ak minuta), ovaj proces zavisi od brzine kojom računari vrše “rudarenje”. Brzina se izražava u h/s (engl. “hash per second”), odnosno u Mh/s ili Gh/s. Na osnovu kalkulacija se može zaključiti da zarada i brzina otplate po osnovu “mining” procesa zavisi od kvaliteta uređaja koji se koristi za taj proces. Inače, zarada po osnovu korišćenja klasičnih grafičkih kartica koje su se do nedavno koristile za ovaj proces je trenutno neuporedivo manja (nekoliko desetina do nekoliko hiljada puta) u odnosu na najsavremenije uređaje za “rudarenje” (En.bitcoin.it n.d.)). Budući da se tokom narednih godina može očekivati povećanje “difficulty” faktora (u skladu sa dosadašnjom tendencijom (Bitcoinx.com n.d.)) i smanjenje broja generisanih bitkojna po bloku transakcija, profitabilnost će se, pod pretpostavkom nepromenljivog kursa i nepromenjenih cena uređaja za “rudarenje” i električne energije višestruko smanjivati.
U Tabeli 1 su prikazani osnovni statistički podaci o bitkojn valuti na dan 22.03.2013. i na dan 30.08.2013. godine:

Kao što se može zapaziti, u odnosu na period pre 5 meseci, došlo je do povećanja bitkojn novčanih jedinica u opticaju, što je i očekivano, budući da je u pitanju programiran proces. Takođe, došlo je do povećanja tržišne kapitalizacije BTC valute, što je pre svega posledica njene apresijacije. Uvećanje kapitalizacije tokom vremena od samog nastanka 2009. godine, a naročito tokom 2013. godine, kako usred povećanja broja bitkojna, tako i usled apresijacije njegovog deviznog kursa može se uočiti sa Grafikona 3:

Može se reći da BTC valutni sistem ima određene sličnosti sa zlatnim standardom, jer postoji gornja granica rasta količine valute u opticaju, tako da, slično sistemu zlatnog važenja, može postati kočnica daljem razvoju, budući da onemogućuje povećanje tražnje putem povećanja količine novca u opticaju. Povezano sa pravilom “kontrolisane ponude”, poželjno je naglasiti da je čak i sam Milton Fridman smatrao da je monetarnu politiku programirane ili konstantne stope monetarnog rasta moguće uspešno implementiratu pomoću računara (Econlib.org 2006). Inače, pristalice bitkojna kritikuju sistem frakcionih rezervi. Takođe, smatraju da je nastanak ove valute početni korak u ukidanju monopola centralne banke kao ekskluzivnog emitenta novca (ECB 2012, p.22). Postoje i shvatanja da je kreator ove valute kao inspiraciju imao zlatni standard. Međutim, ono po čemu se ovaj sistem razlikuje od zlatnog standarda jeste nedostatak unutrašnje, tj. materijalne vrednosti koja je svojstvena robnom novcu kao što su to plemeniti metali, dok bitkojn poseduje samo funkcionalnu vrednost koja zavisi od njegove kupovne snage.
Postoje, međutim, i shvatanja da bitkojn valuta u suštini funkcioniše kao Ponzijeva šema, budući da onima koji ranije počnu sa njenim korišćenjem pruža mogućnost ostvarenja značajnog profita ukoliko prodaju svoje bitkojne u uslovima rasta cena. Međutim, kao razlike ovog sistema u odnosu na Ponzijevu šemu možemo izdvojiti (ECB 2012, p.27):
• Ne postoji očekivani finansijski prinos koji se može ostvariti niti se prilikom prvog korišćenja bitkojn valute potpisuje ugovor koji garantuje visok prinos, čak ni za početne ulagače. U praksi, profit se može ostvariti kako po osnovu rudarenja, čime nastaju novi bitkojni, tako i po osnovu jačanja deviznog kursa ove valute. Međutim, taj profit je neizvestan, pre svega komponenta koja se odnosi na apresijaciju deviznog kursa.
• Ne postoji centralna institucija ili kompanija koja bi mogla da pokupi novac od korisnika sistema i „nestane“. Iako u praksi oni koji su prvi počeli da „rudare“ uspevaju da najviše i zarade, svaki profit ostvaren po osnovu „rudarenja“ i kasnijeg izlaska iz sistema bi se pre mogao okarakterisati kao spekulacija („kupiti jeftino, prodati skupo“) nego Ponzijeva šema. Međutim, u praksi je ipak postojao primer koji demantuje ovaj argument, a u pitanju je slučaj kompanije „Bitcoin Savings and Trust“ (“BTCST”) koja je tokom 2011. i 2012, godine koristeći klasičnu Ponzijevu šemu proneverila novac svojih korisnika. Ipak, ovaj primer se može oceniti samo kao izuzetak, odnosno kao zloupotreba sistema, ali ne i kao dokaz da bitkojn valuta funkcioniše kao Ponzijeva šema.
Devizni kurs bitkojna
Devizni kurs bitkojna se, kao i u slučaju bilo koje druge valute formira na berzi, na bazi sučeljavanja ponude i tražnje za tom valutom. U odnosu na početak godine kada je BTC/USD kurs iznosio približno 13, krajem avgusta je vrednost bitkojna prema američkom dolaru približno 10 puta veća i BTC/USD kurs iznosi oko 130. Očigledno je da 1 BTC ima višestruko veću vrednost od bilo koji zvanične svetske valute, pri čemu se njegova vrednost uglavnom izražava u USD, budući da se na bitkojn berzama najveći deo bitkojna razmeni za američki dolar.
Krajem avgusta se u opticaju nalazi ukupno skoro 12 miliona BTC, pri čemu njihova ukupna vrednost izražena u USD približno iznosi preko 1,4 milijarde USD. Konkretno, to znači da je ukupna vrednost svih emitovanih bitkojna nominalno veća od bruto društvenog proizvoda pojedinih zemalja. Budući da je cena zlata približno 50 USD/g, možemo zaključiti da 1 bitkojn vredi nešto više od 2,5 grama zlata. Prevedeno u RSD po kursu od približno 85 RSD/USD, za kupovinu jednog bitkojna je na dan 29.08.2013. godine potrebno više od 11.000 RSD. Pritom, 1 bitkojn je jednak 100.000.000 „satoshis“-a (naziv „satoshis“ potiče od pseudonima Satoshi Nakamoto, tj. pseudonima kreatora ili grupe ljudi koji su stvorili bitkojn).
Inače, kurs bitkojna zavisi od ponude i tražnje za ovom valutom. Kretanje srednjeg ponderisanog dnevnog kursa BTC valute u odnosu na USD može se uočiti na osnovu Grafikona 4:

Na osnovu dostupnih podataka od početka 2013. godine statističkom analizom može se doći do zaključka da linearna funkcija trenda najbolje opisuje kretanje vrednosti BTC valute. Ocenjena linearna funkcija trenda glasi:
BTC/USD = 27.95 + 0.45t
pri čemu je bazni period 1. januar 2013. godine, a to je ceo broj koji predstavlja broj dana nakon 1.januara. Međutim, budući da je koeficijent determinacije svega r²= 0.52, ocenjena funkcija trenda se ne može primeniti za ekstrapolaciju, odnosno ne bismo mogli sa velikim stepenom sigurnosti da procenimo kretanje vrednosti bitkojna u budućnosti. Ovako nizak koeficijent determinacije ukazuje na činjenicu da je devizni kurs bitkojna veoma nestabilan. Nestabilnosti deviznog kursa bitkojna u velikoj meri doprinosi i podložnost različitim šokovima, o čemu će više reči biti kasnije.
Prednosti i nedostaci bitkojn valute
Kao osnovne prednosti bitkojna u odnosu na ostale, kako nacionalne, tako i alternativne valute, obično se navode:
• Za razliku od transakcija klasičnim elektronskim novcem koji se nalazi na računima banaka, u slučaju bitkojna ne postoje transakcioni troškovi ili su oni svedeni na minimum, dok sa druge strane ne postoji ograničenje u pogledu minimalnog iznosa transakcije koju je moguće realizovati (Nakamoto n.d., p.1).
• Kontrolu transakcija i emisiju BTC valute vrše kompjuterski algoritmi, čime se onemogućava pojava veštački izazvane inflacije. Takođe, ovom verifikacijom se izbegava “duplo plaćanje” (engl. “double-spending”), čime bi se mogao zloupotrebiti sistem (Bitcoin.org/en/ about n.d.) i nekontrolisano povećavala količina novca u opticaju. Sigurnost plaćanja je pritom zasnovana na korišćenju kriptografije.
• Praktično je gotovo nemoguće falsifikovati bitkojn. Teoretski, to bi bilo moguće ukoliko bi se isti BTC iskoristio za istovremeno obavljanje dva plaćanja. Međutim, lanac digitalnih potpisa onemogućava takve transakcije (Stanford Bitcoin Group n.d.).
• Omogućena je potpuna anonimnost transaktora. Međutim, iako ovo predstavlja pogodnost za određene grupe ekonomskih subjekata, sa aspekta poreskih i regulatornih organa ova osobina bitkojna bi se definitivno mogla oceniti kao njen nedostatak. Za razliku od elektronskog novca u platnom prometu kod kojeg su informacije o učesnicima u transakciji javnog, a informacije o transakcijama privatnog karaktera, u slučaju bitkojn valute su informacije o transaktorima privatnog karaktera, tj. veoma često ni samim transaktorima nije poznato kome vrše plaćanja, dok su same karakteristike realizovane transakcije javnog karaktera.
Sa druge strane, kao neke od osnovnih nedostataka bitkojn valute možemo izdvojiti sledeće:
• Bitkojn nije široko prihvaćen kao sredstvo plaćanja. Naime, veoma je mali broj privrednih subjekata koji primaju bitkojn za prodaju prodaju robe, odnosno pružanje usluga. Iako je broj ovih subjekata sve veći, uloga bitkojna kao sredstva plaćanja je još uvek veoma ograničena. Razlog ovoj pojavi leži kako u činjenici da postoji niz proizvoda koji se ne mogu kupiti za bitkojn, tako i u činjenici da ova valuta ne postoji u svojoj fizičkoj verziji, tako da se može koristiti jedino za elektronska plaćanja.
• Devizni kurs bitkojna je veoma nestabilan. Tome u velikoj meri doprinosi i nepostojanje centralnog entiteta poput centralne banke koja bi putem intervencija na deviznom tržištu ili nekom drugom merom monetarne politike mogla pozitivno da utiče na njegovu stabilizaciju.
• Transakcije bitkojn valutama nisu reverzibilne, što znači da nije moguće poništiti već realizovanu transakciju. Iako se ova osobina bitkojn valute može smatrati njenim nedostatkom, značajno je zapaziti da bitkojn u suštini više liči na keš nego na elektronski novac, pa samim tim nema nikakvu mogućnost poništavanja transakcija, jer po definiciji ne postoji sistem za praćenje toka novca. Drugim rečima, transakcije realizovane elektronskim novcem koji se nalazi na računima banaka se mogu poništiti u određenom roku. Sa druge strane, u najvećem broju slučajeva gotovinu potrošenu u prodavnici uglavnom nećemo moći da povratimo, osim ukoliko nije u pitanju roba sa garancijom i sl. Upravo u ovome i leži jedan od najvećih problema vezan za korišćenje bitkojn valute, a koji se odnosi na teškoće prilikom povraćaja novca u slučaju kupovine neispravnih proizvoda bez adekvatno regulisane garancije. Sa druge strane, ovo je odličan mehanizam zaštite prodavaca od zloupotreba, jer im ovaj mehanizam omogućuje sigurnu i momentalnu naplatu svojih potraživanja po osnovu prodate robe (Nakamoto n.d., p.1). Vezano za reverzibilnost transakcija, značajno je naglasiti da je osnovni uzrok ove osobine bitkojna činjenica da, u opštem slučaju, ne postoji posrednik u plaćanju, odnosno, sve plaćanja se vrše direktno između tržišnih subjekata. Iako se nererzibilnost može oceniti kao nedostatak bitkojna, treba imati u vidu da nepostojanje posrednika za posledicu ima nepostojanje provizija koje bi u suprotnom naplaćivale banke ili drugi posrednici u platnom prometu. Međutim, ne treba zanemariti činjenicu da postoje opcione provizije koje plaćaju oni koji žele da transakcija u bitkojn valuti bude brže realizovana (Stanford Bitcoin Group n.d.).
• Iako je reč o vidu elektronskog novca, postoji mogućnost njegovog gubitka. Naime, jedna od specifičnosti ove valute jeste da ona postoji samo u svojoj elektronskoj verziji. Pritom se nalog koji se koristi za plaćanja razlikuje od klasičnog transakcionog računa u banci po tome što ne postoji institucija poput banke koja bi transaktorima zatvorila ili blokirala nalog. Takođe, ne postoje nikakva ograničenja u pogledu korišćenja bitkojna. Nalog mogu deaktivirati sami korisnici sistema time što bi prestali da ga koriste i time što bi se oslobodila svih BTC valuta na svom nalogu. Nalog se inače gubi i ukoliko se prilikom oporavka operativnog sistema na računaru ne obezbedi skladištenje (engl. “backup”) bitkojna. Time se faktički taj novac trajno gubi iz sistema. U tome se faktički i ogleda sličnost između bitkojn valute i običnog novca, budući da on praktično može biti izgubljen ili uništen (Kaplanov 2012, p.116). Međutim, za razliku od običnog novca koji može biti dodatno otštampan od strane centralne banke, u slučaju bitkojna ne postoji entitet koji bi emitovao novu količinu novčanih jedinica koje bi zamenile nestale ili uništene bitkojne.
• Kao poslednji nedostatak bitkojna bismo mogli navesti sve one probleme koji se odnose na zloupotrebe kojima je on podložan, a koji se odnose na mogućnost obavljanja nelegalnih aktivnosti, pranje novca, stvaranja “crnih tržišta”, ali i poreskih rajeva, mogućnost poreske evazije, ali i neotpornost na različite napade kompjuterskih virusa itd.
Korišćenje BTC valute se preporučuje manjim kompanijama i preduzetnicima, budući da im omogućuje prodaju proizvoda i njihovu naplatu uz niže transakcione troškove, tj. bez provizija različitih finansijskih institucija, kao i zahvaljujući činjenici da je veoma lako implementirati ovaj oblik prodaje i naplate prodaje putem Interneta. Međutim, time se može dovesti u pitanje legalnost obavljanja takvih aktivnosti, naročito kada je reč o prodaji digitalnih proizvoda (softvera, muzike,…) koji se mogu neograničen broj puta umnožavati i prodavati bez ikakve evidencije, čime se može izbeći izvršenje poreske obaveze.
Finansijske institucije koje posluju sa bitkojnima
Trenutno postoji oko 50 aktivnih berzi na kojima se zvanične valute mogu razmeniti za bitkojn, od kojih je najznačajnija “MtGox” na kojoj se dnevno razmeni oko 64% ukupnog prometa bitkojn valutom za ostale zvanične valute i obrnuto. Inače, bitkojn se najviše razmenjuje za USD (74%) i EUR (14%), dok je značaj svih ostalih valuta zanemarljiv (Bitcoincharts.com n.d.). Inače, statistička analiza aktivnih i ugašenih bitkojn berzi je pokazala nekoliko zakonitosti (Christin, Moore 2013, p.7):
• Sa povećanjem prometa na nekoj berzi smanjuje se verovatnoća da će doći do njenog zatvaranja
• S druge strane, što je promet na nekoj berzi veći, postojaće i veća šansa da dođe do različitih oblika zloupotreba i prekršaja.
Pritom treba imati u vidu da je u ovoj analizi apstrahovan niz faktora koji bi potencijalno mogli da utiču na dobijanje drugačijih rezultata. Primera radi, nije uzeta u obzir reputacija samih berzi, odnosno činjenica da će atraktivnost same berze zavisiti od sigurnosti koju ona pruža svojim korisnicima.
Takođe, iako je kao jedna od osnovnih karakteristika kriptovaluta, a samim tim i bitkojna, navedena činjenica da ovakve valute u opštem slučaju funkcionišu bez posredovanja finansijskijh institucija, ne treba zanemariti činjenicu da se marta 2013. godine pojavio prvi hedž fond „Exante“ koji investira u bitkojn. Treba međutim naznačiti da ovaj fond ima širok portfolio aktivnosti, pri čemu su operacije sa bitkojnom samo jedna od njih. Fond kao naknadu za svoje usluge ne naplaćuje procentualni deo ostvarenog profita, već fiksnu proviziju od 0,5% neto vrednosti Bitcoin Fund-a. Pritom, ovaj fond ogroman akcenat stavlja na zaštitu podataka i sigurnost fonda. Marta 2013. godine vrednost fonda je iznosila približno 3,2 miliona USD. Inače, za pristup fondu su neophodna inicijalna ulaganja od minimum 100.000 USD (Forbes.com 2013). Ovaj fond ostvaruje zaradu po osnovu kapitalnih dobitaka na kupljene bitkojne, pri čemu jedna akcija ovog fonda vredi tačno jedan BTC. S obzirom na vrtoglavi rast vrednosti bitkojn valute, očekuju se visoki prinosi po osnovu plasmana ovog fonda. Kao osnovne prednosti investiranja u fond umesto direktne kupovine BTC valute navode se (Exante.eu/press/news2013[a]):
• Lakše je kupiti akcije/investicione jedinice fonda nego bitkojn.
• Sredstva investirana u fondove umesto u direktnu kupovinu bitkojn valute se smatraju sigurnijim, budući da takvi fondovi, između ostalog i Exante, značajan akcenat stavljaju na kriptografsku sigurnost sredstava svojih korisnika.
Inače, od juna 2013. godine ovaj fond svojim klijentima nudi „Automatic Trading Platform“ (ATP), odnosno elektronsku platformu za trgovinu koja im omogućuje niz usluga koje se, između ostalog, odnose na različite statističke alate i portfolio menadžment (Exante.eu/press/news 2013[b]).
Međutim, ovaj fond nije prva finansijska institucija koja je radila sa bitkojn valutom. Naime, ne treba zaboraviti ni na „Bitcoin Savings and Trust“ (“BTCST”) kompaniju koja je, koristeći klasičnu Ponzijevu šemu, od 2011. do septembra 2012. godine prikupila oko 700.000 BTC (vrednih više od 4,5 miliona USD) od svojih klijenata obećavši im nedeljne stope prinosa od čak 7%, a zatim taj novac proneverila. Tim povodom je jula 2013. godine američka “Komisija za hartije od vrednosti i berzu” (engl. “Securities and Exchange Commission” - SEC) optužila ovu kompaniju i Trendon Shaversa, njenog osnivača (Wang 2013).
Takođe, postoje i najave da će vlasnici BTC valute moći da na realnim bankomatima da povlače zvaničan novac čiji je emitent centralna banka u ekvivalentnom iznosu (eventualno umanjenom za određenu proviziju), kao i da će se moći koristiti prilikom kupovine u prodavnicama na POS terminalima (Newscientist.com 2012).
Kao što se može zaključiti, iako je bitkojn po svojoj prirodi decentralizovana valuta koja čak i eliminiše potrebu za finansijskim posrednicima, same potrebe njegovih korisnika očigledno nameću potrebu za odgovarajućim finansijskim institucijama koje bi imale različite funkcije u bitkojn transakcijama. Kao neke od finansijskih institucija koje za sada posluju sa bitkojn valutom za sada su se izdvojile berze koje omogućuju razmenu najpoznatijih svetskih valuta za bitkojn i obratno. Takođe, sve češće se javljaju i druge finansijske institucije kao posrednici u plaćanju bitkojnima, a koje svojim klijentima nude veći stepen zaštite podataka i sigurnosti pri obavljanju transakcija u odnosu na direktna plaćanja bez korišćenja usluga finansijskih posrednika. U tom smislu, ukoliko izvršimo komparaciju razvoja decentralizovane bitkojn valute sa razvojem klasičnog novca, pojava nekog oblika centralnog entiteta u ovom sistemu (po osnovu ekonomske moći ili po osnovu nekih zakonskih odredbi) koji bi preuzeo neke od funkcija klasične centralne banke više ne deluje kao naučna fantastika. Naime, prvi oblici novca su, kao što je poznato, bili stoka, koža, so, med, krzno, kasnije metali kao što su gvožđe, bakar i plemeniti metali (srebro i zlato), a zatim i novčanice. Paralelno sa razvojem sredstava plaćanja javljali su se novi učesnici u privrednom životu kao što su zlatari koji su izdavali certifikate po osnovu deponovanog novca i međusobno vršili kliring potraživanja svojih klijenata. Nakon toga nastaju i privilegovane banke koje su bile jedine ovlašćene od strane države da emituju banknote, da bi prve centralne banke nastale tek u 17. veku (Đurović-Todorović 2010, str.18- 23). U tom smislu, iako prve oblike novca nije emitovala nijedna centralna institucija, već sami ljudi, nije isključena mogućnost da nekada u budućnosti kriptovalute kao što je bitkojn, koje su po svojoj prirodi decentralizovane, dobiju centralnu instituciju. Međutim, budući da, prema mnogim shvatanjima, upravo decentralizovanost ovakve valute predstavlja faktor koji u najvećoj meri pozitivno utiče na tražnju za takvom valutom, postoji verovatnoća da bi u slučaju pojave centralnog entiteta u takvim sistemima opala tražnja za tim valutama, a povećala se tražnja za drugim valutama koje još uvek nisu centralizovane. U konačnom, ceteris paribus, pokušaj regulacije i centralizacije neke kriptovalute bi u konačnom samo mogao dovesti do napuštanja tih valuta, erozije njihovog značaja i migracije korisnika i tranfera njihovih sredstava u druge valute.
Problemi funkcionisanja i regulacija bitkojna
Bitkojn valuta je gotovo u potpunosti van regulacionog spektra centralne banke i poreskih organa. Stoga je pojedini autori pogodnim instrumentom za stvaranje “crnog tržišta” različitih roba i usluga, a najznačajnija opasnost postoji ukoliko bi se koristila za obavljanje nelegalnih aktivnosti. Primera radi, zabeleženi su slučajevi kada se bitkojn valuta koristila za kupovinu droge putem Interneta (Manchin. senate.gov 2011).
Takođe, ništa beznačajniji nisu problemi po osnovu krađe (koje su se već dešavale) ili potencijalnog nekontrolisanog umnožavanja ove valute od strane cyber-kriminalaca (što je za sada praktično neizvodljivo). Usled toga, može doći i do značajnih fluktuacija kursa bitkojn valute. Između ostalog, postoje i procene stručnjaka za kriptografiju i sigurnost podataka na Internetu da se sigurnost ove valute može oceniti kao veoma niska (Economist.com 2012). Primera radi, 2011. godine se pojavio kompjuterski virus, tj. „Trojanac“ koji “krade bitkojn novčanike” (engl. „Bitcoin wallet“), tj. koji, ukoliko se nađe na računaru onog ko koristi bitkojn valutu, preuzima i šalje putem Interneta na odgovarajuću adresu kompjuterske fajlove pomoću kojih je moguće sa nekog drugog računara koristiti tuđ bitkojn novac (Symantec.com 2011). Usled tog sigurnosnog kolapsa, vrednost bitkojna je pala sa 30,99 USD 08.06.2011. na svega 0,10 USD 20.06.2011. Do decembra 2011. godine vrednost valute se vratila na nešto više od 3 USD (ECB 2012, p.38). Sledeći značajan udarac na bitkojn valutu dogodio se 10. aprila 2013. godine. Tog dana je trgovina BTC valutom otpočela po ceni od 200 USD, da bi tokom dana dostigla svoj istorijski maksimum od čak 266 USD, da bi u roku od par sati njena vrednost pala ispod 100 USD. Iako su se prve sumnje odnosile na dv. DDoS napad, zvaničnici MtGox berze su izjavili da je uzrok ovog problema preveliki obim trgovine.
Inače, DDoS napad (engl. „distributed denial- of-service attack“) predstavlja napad na tržišni centar putem masovnog ispostavljanja naloga za trgovinu kako bi se izazvala blokada u trgovini i izvršio uticaj na cenu. Međutim, pravi DDoS napad je ubrzo zaista usledio, pa je berza prekinula proces trgovanja u periodu od 2 sata, mada je i narednih 8 sati postojao problem u pristupu mreži. Prekid trgovanja se desio na još nekim bitkojn berzama. Ovaj kolaps je ukazao na neke od osnovnih slabosti bitkojn valute, a koje se odnose kako na dominantan položaj MtGox berze, tako i na činjenicu da je veliki broj elektronskih berzi za trgovanje bitkojn valutom razvijan od strane web developer-a koji jesu iskusni profesionalci, ali nisu poznavali u dovoljnoj meri način funkcionisanja finansijskih berzi (Bitcoinmagazine.com 2013).
Jedno od osnovnih pitanja koje se postavlja od same pojave bitkojn valute odnosi se na legalnost njegove primene. Inače, kao razlozi zbog kojih bi bitkojn trebalo smatrati potpuno legalnom valutom navode se: pravo na slobodnu razmenu, činjenica da bitkojn ne predstavlja alternativu američkom dolaru kao zvaničnoj valuti, odnosno ni na koji način ne predstavljaju njegov falsifikat, niti se nalaze u širokoj upotrebi. Sa druge strane, kao razlozi zbog kojih bi trebalo zakonski preciznije regulisati korišćenje bitkojna navode se povećana mogućnost poreske evazije i činjenica da bitkojn otvara mogućnost za kreiranje poreskih rajeva i crnog tržišta različite robe (pre svega droge), kao i za pranje novca.
Naime, transakcije u bitkojnima prema nekim ocenama imaju klasične elemente bartera, odnosno trampe, a takve transakcije su oporezive. Međutim, bitkojn po svojoj prirodi nudi anonimnost i mogućnost prikrivanja brojnih transakcija od poreskih organa čime se izbegava izvršenje poreske obaveze. Takođe, značajno pitanje se odnosi i na nadležno zakonodavstvo u slučaju transakcija u bitkojn valuti na međunarodnom nivou, kada bi bilo veoma teško utvrditi nadležnu poresku vlast. Sa jedne strane, kriptovalute (među kojima je trenutno najaktuelniji bitkojn) su sve popularnije. Sa druge strane, finansijske institucije su pod sve većim pritiskom da dostavljaju potrebne informacije o svojim klijentima poreskim organima i sarađuju sa njima kako bi se sprečila poreska evazija. Iako je reč o potpuno nezavisnim procesima, činjenica je da oni u sve većoj meri konvergiraju (Marian 2013, p.38). U tom smislu, korišćenje kriptovaluta je po svojim efektima dosta slično poslovanju u ofšor zonama, budući da profit ostvaren u, primera radi, bitkojn valuti nije predmet oporezivanja, a takođe korisnici ovih valuta imaju obezbeđenu anonimnost. Praktično, sa nastankom kriptovaluta poreski obveznici su dobili novo oružje za poresku evaziju. Štaviše, ne postoji ni institucija od koje bi poreski organi mogli da zahtevaju dostavljanje informacija o vlasnicima računa u toj valuti. U sistemima plaćanja zasnovanim na kriptovalutama ne postoje ni centralne banke kao emitenti, ni klasične finansijske institucije koje bi mogle biti predmet različitih pritisaka poreskih organa. Drugim rečima, korišćenje kriptovaluta za sada, uslovno rečeno, poreske vlasti ne mogu uspešno da kontrolišu, odnosno da detektuju korišćenje ovih valuta na sistematičan način, osim eventualno u pojedinačnim slučajevima. Prema nekim shvatanjima, postoji opasnost da će se u budućnosti poreska evazija sve više odvijati putem korišćenja kriptovaluta, a na štetu sadašnjih ofšor zona, odnosno mogu im predstavljati direktnu konkurenciju. Međutim, sa druge strane treba imati u vidu relativno malu vrednost virtuelne ekonomije u okviru koje se koriste te vrituelne valute, tako da je za sada prisutno i relativno malo interesovanje nadležnih poreskih organa za većom kontrolom ovih tokova. Takođe, trenutni ekonomski potencijal kriptovaluta im ne omogućuje da postanu značajnija konkurencija ofšor zonama.
Pored poreske evazije, anonimnost koja je imanentna bitkojn valuti pruža i niz mogućnosti za prikrivanje različitih kriminalnih aktivnosti. Pod tim pre svega imamo u vidu trgovinu drogom, pranje novca, i niz drugih kriminalnih aktivnosti.
Stoga, kao potencijalna rešenja za rizike koje primena ove valute sa sobom nosi mogu se izdvojiti sledeći predlozi (www-cs-faculty. stanford.edu n.d.[2]):
• Forsirano licenciranje - Budući da u slučaju bitkojna ne postoji centralni entitet niti klasične finansijske institucije koje bi mogle biti primorane da izvrše registraciju kao posrednici u plaćanju (engl. „money transmitters“), postoje predlozi da bi se registracija trebala odnositi samo na vlasnike „mining“ računara. Međutim, to bi predstavljalo isuviše komplikovanu proceduru, a takođe bi postojao problem vezan za regulaciju ukoliko bi se „rudarenje“ vršilo iz drugih zemalja u kojima ne postoji ovakav oblik regulacije.
• Zahtevi za poreskim izveštajima - Postoji ideja da bi svi korisnici bitkojna trebalo da automatski budu u obavezi da poreskim organima dostavljaju sve izveštaje o transakcijama u ovoj valuti. Međutim, primenom ovakve mere poreski organi bi se suočili sa preprekama kao što su: mogućnost obavljanja transakcija iz inostranstva, teška izvodljivost s obzirom na neophodnost saglasnosti korisnika, nestabilna vrednost bitkojn valute i niz drugih.
• Prinudno gašenje - Kao jedan od načina za gašenje ove i sličnih valuta može se navesti i formalna zabrana korišćenja ovakvih valuta kao sredstava plaćanja i donošenje niza restriktivnih zakonskih odredbi kojima bi se suzbijalo ili kontrolisalo korišćenje ovih valuta. Takođe, postoje ideje da bi virtuelne valute, s obzirom na relativno mali ekonomski značaj, mogle da budu u potpunosti otkupljene od strane centralne banke ili da centralna banka angažuje resurse koje bi koristila za „rudarenje“ tih valuta, čime bi one bile eliminisane iz dalje upotrebe (Marian 2013, p.47). Međutim, to bi uvek iziskivalo manje ili veće troškove. Takođe, tu bi se možda pojavila i mogućnost različitih zloupotreba.
Međutim, i pored izdvojenih teorijskih shvatanja o nužnosti i načinu regulacije transakcija u bitkojn valuti, zanemarljivo mali broj zemalja je učinio nešto konkretno po tom pitanju. Primera radi, u slučaju SAD-a ne postoji nijedna zakonska odredba kojom se izričito zaključuje zabrana korišćenja ove valute i definiše njeno korišćenje ilegalnom aktivnošću (www-cs-faculty.stanford.edu n.d.[1]). Sa druge strane, postoje i određeni pokušaji da se različitim preporukama, direktivama i podzakonskim aktima daju smernice za regulaciju alternativnih valuta, uključujući i decentralizovane virtuelne valute kao što je bitkojn. Jedan od njih je i „Primena FinCEN- ove regulacije na osobe koje administriraju, razmenjuju i koriste virtuelne valute” (engl. „Application of FinCEN’s Regulations to Persons Administering, Exchanging, or Using Virtual Currencies”). U pitanju je preporuka kojom je “Financial Crimes Enforcement Network” kao departman Trezora SAD-a pokušao da da sugeriše način implementacije „Bank Secrecy Act“ regulative na virtuelne valute. Prema ovoj preporuci, ekonomski subjekt koji kreira virtuelnu valutu i koristi je za kupovinu realnih dobara i usluga se smatra korisnikom te valute i njegove aktivnosti nisu predmet regulacije. Sa druge strane, subjekt koji kreira virtuelnu valutu i prodaje je za zvanično sredstvo plaćanja se smatra posrednikom u plaćanju i njihove aktivnosti su predmet regulacije (Fincen.gov 2013, p.5). Međutim, osim ovog pojmovnog razgraničenja ovom preporukom nije dat odgovor na niz dodatnih pitanja vezanih za regulaciju ovih transakcija.
U Nemačkoj je ove godine bitkojn dobio status „privatnog novca“ (engl. „private money“), čime je načinjen značajan korak napred ka širem zakonskom obuhvatu i masovnijem korišćenju ove valute. Korišćenje bitkojna i njegova emisija nisu zabranjeni, međutim, profit po osnovu korišćenja bitkojna podleže poreskim zakonima. Naime, prihodi ostvareni po osnovu prodaje proizvoda i pružanja usluga ostvareni u bitkojn valuti se oporezuju porezom na dodatu vrednost, dok se sav ostali profit po osnovu emisije ili korišćenja bitkojna oporezuje porezom na dohodak, odnosno dobit (Dw.de 2013). Međutim, nije naglašeno na koji bi način bilo rešeno pitanje poreske evazije.
Iako po pitanju regulacije bitkojna nije mnogo učinjeno ni u Francuskoj, značajno je zapaziti činjenicu da su regulatorni organi Bitcoin-Central-i, jednoj od bitkojn berzi, dali dozvolu za obavljanje određenih bankarskih poslova, pre svega onih vezanih za usluge platnog prometa. Time će njenim klijentima biti omogućeno da deponuju sredstva u evrima ili bitkojnima i da ih jednostavno konvertuju (Tagteam.harvard.edu n.d.). Takođe, ova sredstva su deponovana na računu druge finansijske institucije, i u skladu sa tim su osigurana do iznosa od 100.000 EUR od strane francuskog “Fonda za garanciju depozita” (franc. „Fonds de garantie des dépôts “) (En. bitcoin.it n.d.).
Međutim, i pored ovih pojedinačnih izuzetaka, u opštem slučaju područje alternativnih valuta, a pre svega decentralizovanih kriptovaluta kao što je bitkojn do sada nije adekvatno, nedvosmisleno i u potpunosti regulisano ni u jednoj od relevantnih jurisdikcija.
Zaključak
Bitkojn predstavlja specifičnu valutu koja se po svojim karakteristikama razlikuje od svih svojih prethodnika. Otkad se pojavila pokrenula je niz kontroverzi vezanih za pozitivne i negativne efekte njene primene. Emisija ove valute je kompjuterski programirana i ograničena, zasnovana na „peer-to-peer“ tehnologiji i tehnologiji enkripcije podataka čime se faktički eliminiše mogućnost dvostrukog plaćanja, falsifikovanja i sličnih zloupotreba. To je ujedno i jedan od glavnih razloga zbog čega se ova valuta smatra sigurnom iako ne postoji centralna emisiona institucija. Transakcioni troškovi su veoma niski, gotovo su zanemarljivi, ali same transakcije nisu reverzibilne, što se može oceniti značajnim nedostatkom ove valute.
Međutim, s obzirom na činjenicu da je makroekonomski značaj bitkojna zanemarljivo mali, čak i manji šokovi mogu negativno uticati na njegovu stabilnost i izazvati drastične fluktuacije deviznog kursa. Pritom ne postoji centralna institucija koja bi mogla svojim merama pozitivno da utiče na njegovu stabilizaciju, a što može predstavljati značajnu prepreku za masovnije korišćenje ove valute. Budući da ova valuta svojim korisnicima praktično pruža potpunu anonimnost i netransparentnost njihovih aktivnosti, postoje kritike da se na taj način kreira pogodan ambijent za pranje novca, kreiranje crnih tržišta nelegalne robe, poresku evaziju i niz drugih kriminalnih radnji. Takođe, postojali su slučajevi različitih zloupotreba poput Ponzijevih šema i kompjuterskih Trojanaca koji su korišćeni za krađu elektronskih novčanika korisnika bitkojn valuta.
Stoga se vodi sve češća diskusija o potrebi regulisanja ovakvih kriptovaluta. Iako je određen broj zemalja počeo da reguliše bitkojn transakcije, i dalje je relativno malo učinjeno po tom pitanju budući da ovakvo pitanje zahteva veliku opreznost. Naime, bilo koji oblik kontrole i regulacije ovakvih valuta bi za posledicu mogao imati preusmeravanje korisnika tih valuta na korišćenje drugih kriptovaluta koje još uvek nisu predmet regulative ili transfer bitkojn transakcija u one jurisdikcije u kojima one nisu regulisane. U tom smislu, jedan od najvećih izazova za centralne banke i nacionalne regulatorne organe u budućem periodu će se vrlo verovatno odnositi na praćenje efekata korišćenja ovakvih valuta i njihovu regulaciju, odnosno preduzimanje adekvatnih mera u slučaju različitih zloupotreba ili izazivanja nestabilnosti. Kakva će biti budućnost bitkojna i sličnih kriptovaluta zavisiće kako od regulacije ovakvih valuta, tako i od njihove sigurnosti i stabilnosti.
-
Barber Simon, Boyen Xavier, Shi Elaine, Uzun Ersin, “Bitter to Better - How to Make Bitcoin a Better Currency”, Financial Cryptography, Volume 7397 of Lecture Notes in Computer Science, page 399-414. Springer (2012), crypto.stanford.edu/~xb/fc12/bitcoin.pdf, Vreme pristupa: 02.08.2013.
-
Bitcoin.org/en/about, “About Bitcoin”, n.d., bitcoin.org/en/about, Vreme pristupa: 01.08.2013.
-
Bitcoin.stackexchange.com, “How Much Bitcoin Will I Mine Right Now With Hardware X?”, 2011, bitcoin.stackexchange.com/questions/118/how-much-bitcoin-will-i-mine-right-now-with-hardware-x, Vreme pristupa: 08.08.2013.
-
Bitcoinbalkan.com, “Uvod u Bitcoin”, 2012, bitcoinbalkan.com/uvod-u-bitcoin, Vreme pristupa: 24.08.2013.
-
Bitcoincharts.com, n.d., bitcoincharts.com, Vreme pristupa: 28.08.2013.
-
Bitcoinmagazine.com, “The Bitcoin Crash:An Examination”, 2013, bitcoinmagazine.com/markets/the-bitcoin-crash-an-examination-1365911041, Vreme pristupa: 22.08.2013.
-
Bitcoinx.com, n.d., bitcoinx.com/charts/, Vreme pristupa: 29.08.2013.
-
Christin Nicolas, Moore Tyler, “Beware the Middleman: Empirical Analysis of Bitcoin Exchange Risk”, Financial Cryptography, Volume 7859 of Lecture Notes in Computer Science, pages 25-33. Springer (2013), andrew.cmu.edu/user/nicolasc/publications/MC-FC13.pdf, Vreme pristupa: 07.08.2013.
- Dw.de, “Germany lends real value to bitcoin virtual money”, 2013, dw.com/en/germany-lends-real-value-to-bitcoin-virtual-money/a-17038675, Vreme pristupa: 25.08.2013.
- Đurović-Todorović Jadranka, „Monetarna ekonomija“, Ekonomski fakultet u Nišu, Niš, 2010.
- ECB, “Virtual Currency Schemes”, 2012, ecb.europa.eu/pub/pdf/other/virtualcurrencyschemes201210en.pdf, Vreme pristupa: 01.08.2013.
- Econlib.org, “An Interview with Milton Friedman”, 2006, econlib.org/library/Columns/y2006/Friedmantranscript.html Vreme pristupa: 21.08.2013.
- Economist.com, “Monetarists Anonymous”, 2012, economist.com/node/21563752, Vreme pristupa: 24.08.2013.
- En.bitcoin.it, “Bitcoin Central”, n.d., en.bitcoin.it/wiki/Bitcoin-Central, Vreme pristupa: 22.08.2013.
- Exante.eu/press/news , “Bitcoin Fund aims to make Bitcoin Investing easy”, 2013[a], exante.eu/press/news/297/, Vreme pristupa: 27.08.2013.
- Exante.eu/press/news, “EXANTE Opens Up an Automatic Trading Platform for Bitcoin Funds”, 2013[b], exante.eu/press/news/314/, Vreme pristupa: 27.08.2013.
- Fincen.gov Fincen.gov, “Application of FinCEN’s Regulations to Persons Administering, Exchanging, or Using Virtual Currencies”, 2013, fincen.gov/statutes_regs/guidance/pdf/FIN-2013-G001.pdf, Vreme pristupa: 15.8.2013.
- Forbes.com, “First Bitcoin Hedge Fund Launches From Malta”, 2013, Vreme pristupa: 27.08.2013. forbes.com/sites/jonmatonis/2013/03/08/first-bitcoinhedge-fund-launches-from-malta/, Vreme pristupa: 28.08.2013.
- Kaplanov Nikolei M., “Nerdy Money: Bitcoin, The Private Digital Currency, And The Case Against Its Regulation”, Temple University Legal Studies Research Paper, 2012, luc.edu/media/lucedu/law/ students/publications/clr/pdfs/kaplanov. pdf, Vreme pristupa: 05.08.2013.
- Manchin.senate.gov, “Manchin Urges Federal Law Enforcement to Shut Down Online Black Market for Illegal Drugs”, 2011, manchin.senate.gov/public/ index.cfm/press-releases?ID=284ae54a-acf1- 4258-be1c-7acee1f7e8b3, Vreme pristupa: 25.08.2013.
- Nakamoto Satoshi, “Bitcoin: A Peer-to-Peer Electronic Cash System”, n.d., bitcoin.org/bitcoin.pdf, Vreme pristupa: 04.08.2013.
- Newscientist.com, “Bitcoin credit card to let users withdraw cash”, 2012, newscientist.com/blogs/onepercent/2012/08/bitcoincredit-card-to-let-use.html, Vreme pristupa: 27.08.2013.
- Marian Omri Y., “Are Cryptocurrencies 'Super' Tax Havens?”, 112 Michigan Law Review First Impressions (2013), ssrn.com/abstract=2305863, Vreme pristupa: 23.08.2013.
- Sh.wikipedia.org/wiki/Kriptografija, “Kriptografija”, n.d., sh.wikipedia.org/wiki/Kriptografija, Vreme pristupa: 12.08.2013.
- Stanford Bitcoin Group, “The Basics of Bitcoin”, n.d., bitcoin.stanford.edu/basics, Vreme pristupa: 15.08.2013.
- Symantec.com, “Infostealer. Coinbit”, 2011, symantec.com/security_response/writeup.jsp?docid=2011-061615-3651-99, Vreme pristupa: 23.08.2013.
- Tagteam.harvard.edu, “Feed Item: Bitcoin going mainstream? Exchange approved to operate as a bank”, n.d., tagteam.harvard.edu/hub_feeds/1785/feed_items/69431, Vreme pristupa: 26.08.2013.
- Wang Mengyi, “SEC Charges Texas Man with Running a Bitcoin Ponzi Scheme”, 2013, jolt.law.harvard.edu/digest/patent/flash-digest-news-in-brief-144, Vreme pristupa: 23.08.2013.
- Www-cs-faculty.stanford.edu, “Current Legal Status”, n.d.[1], cs- faculty.stanford.edu/~eroberts/cs181/ projects/2010-11/Bitcoins/current-legal- status.html, Vreme pristupa: 21.08.2013.
- Www-cs-faculty.stanford.edu, “Regulating Bitcoin”, n.d.[2], cs.stanford.edu/people/eroberts/cs201/projects/2010-11/Bitcoins/regulating-bitcoin.html, Vreme pristupa: 21.08.2013.
-
-
 @ 2cde0e02:180a96b9
2025-06-07 16:16:39
@ 2cde0e02:180a96b9
2025-06-07 16:16:39桜の姫
https://stacker.news/items/999877
-
 @ 318ebaba:9a262eae
2025-06-08 10:15:56
@ 318ebaba:9a262eae
2025-06-08 10:15:56✒️ My articles
-
 @ dfa02707:41ca50e3
2025-06-07 16:01:40
@ dfa02707:41ca50e3
2025-06-07 16:01:40Contribute to keep No Bullshit Bitcoin news going.
- Wasabi Wallet v2.6.0 "Prometheus" is a major update for the project, focused on resilience and independence from centralized systems.
- Key features include support for BIP 158 block filters for direct node synchronization, a revamped full node integration for easier setup without third-party reliance, SLIP 39 share backups for flexible wallet recovery (sponsored by Trezor), and a Nostr-based update manager for censorship-resistant updates.
- Additional improvements include UI bug fixes, a new fallback for transaction broadcasting, updated code signing, stricter JSON serialization, and options to avoid third-party rate providers, alongside various under-the-hood enhancements.
This new version brings us closer to our ultimate goal: ensuring Wasabi is future-proof," said the developers, while also highlighting the following key areas of focus for the project:
- Ensuring users can always fully and securely use their client.
- Making contribution and forks easy through a codebase of the highest quality possible: understandable, maintainable, and improvable.
"As we achieve our survival goals, expect more cutting-edge improvements in Bitcoin privacy and self-custody. Thank you for the trust you place in us by using Wasabi," was stated in the release notes.
What's new
- Support for Standard BIP 158 Block Filters. Wasabi now syncs using BIP 158 filters without a backend/indexer, connecting directly to a user's node. This boosts sync speed, resilience, and allows full sovereignty without specific server dependency.
- Full Node Integration Rework. The old integration has been replaced with a simpler, more adaptable system. It’s not tied to a specific Bitcoin node fork, doesn’t need the node on the same machine as Wasabi, and requires no changes to the node’s setup.
- "Simply enable the RPC server on your node and point Wasabi to it," said the developers. This ensures all Bitcoin network activities—like retrieving blocks, fee estimations, block filters, and transaction broadcasting—go through your own node, avoiding reliance on third parties.
- Create & Recover SLIP 39 Shares. Users now create and recover wallets with multiple share backups using SLIP 39 standard.
"Special thanks to Trezor (SatoshiLabs) for sponsoring this amazing feature."
- Nostr Update Manager. This version implements a pioneering system with the Nostr protocol for update information and downloads, replacing reliance on GitHub. This enhances the project's resilience, ensuring updates even if GitHub is unavailable, while still verifying updates with the project's secure certificate.
- Updated Avalonia to v11.2.7, fixes for UI bugs (including restoring Minimize on macOS Sequoia).
- Added a configurable third-party fallback for broadcasting transactions if other methods fail.
- Replaced Windows Code Signing Certificate with Azure Trusted Signing.
- Many bug fixes, improved codebase, and enhanced CI pipeline.
- Added the option to avoid using any third-party Exchange Rate and Fee Rate providers (Wasabi can work without them).
- Rebuilt all JSON Serialization mechanisms avoiding default .NET converters. Serialization is now stricter.

Full Changelog: v2.5.1...v2.6.0
-
 @ eac63075:b4988b48
2025-06-07 15:14:03
@ eac63075:b4988b48
2025-06-07 15:14:03Ever imagined sending a Bitcoin transaction without an internet connection? Or talking to your friends during a total blackout when the cell network just vanishes? It sounds like science fiction, but this technology is an accessible reality, built with low-cost hardware and open-source software. Welcome to the world of mesh networks, Meshtastic, and the BTC Mesh project.
This guide explores the universe of decentralized communication networks, showing how they work, why they are vital for our digital sovereignty, and how you can use them to strengthen your privacy and resilience—not just in communication, but in your Bitcoin transactions as well.
https://fountain.fm/episode/nr8qWgi7XNoBbDkc8GZj
https://open.spotify.com/episode/6vKW7Lhi3uOUhlRogAtgej
What Are Mesh Networks and Why Should You Care?
Our connected world runs on a fragile, centralized infrastructure. Cell towers, internet providers, data centers—if one of these points fails, communication stops. A mesh network turns this logic on its head.
Here, each participant (or "node") connects directly to other nodes within its reach, forming a web of P2P (peer-to-peer) connections. Instead of data passing through a central server, it hops from node to node until it reaches its destination. The true strength of this approach is decentralization and resilience. If a node goes down, the others simply find a new path for the information. The network reconfigures and heals itself.
 Source: meshtastic.org
Source: meshtastic.orgLoRa and Meshtastic: The Dynamic Duo
To create these networks in the real world, the enthusiast community has rallied around a powerful duo:
- LoRa (Long Range): Think of LoRa as the physical layer—the "radio waves" of our network. It's a technology that allows for long-range wireless communication with incredibly low power consumption. We're talking about cheap little radios that can send small data packets for miles, running for days on a single battery.
- Meshtastic: If LoRa is the physical medium, Meshtastic is the brain. It's open-source software that equips these radios to form a smart, easy-to-use mesh network. Meshtastic handles everything: discovering other nodes, managing routes, encrypting messages, and providing an interface on your phone, connected via Bluetooth.
Meshtastic was originally created as an off-grid communicator, but its usefulness goes far beyond that. Here, privacy is a fundamental pillar. To join a group channel, you need the encryption key. Direct messages are end-to-end encrypted. It's like having a "hardware wallet" for your communication: your private key is secure on your radio, ensuring that only you and the recipient can read the messages.
While Meshtastic is the most popular, alternatives like MeshCore exist, which aim to optimize packet routing. However, the network effect is powerful, and the vast majority of users today are on the Meshtastic platform.
Introducing BTC Mesh: Bitcoin Transactions Via Radio
This is where Bitcoin enters the picture. The inspiration for the BTC Mesh project came from a mix of necessity and chance. After buying a LoRa radio on AliExpress that, to my frustration, couldn't transmit over long distances—and the seller simply stopped responding—I discovered it worked perfectly within my apartment. With two radios in hand, one for the base and another "defective" one, I had the perfect test environment for a new use case: sending Bitcoin transactions over the mesh network.
GitHub - eddieoz/btcmesh: BTC Mesh Relay is designed to send Bitcoin payments via LoRa Meshtastic.
BTC Mesh is a simple application that allows anyone on a Meshtastic network to send a Bitcoin transaction (on-chain, layer 1) over the radio network, without needing a direct internet connection.
How the Magic Works
The system has two parts: a client and a server.
- The Server: Someone on the network with internet access runs the "server node." This is a computer (a Raspberry Pi can handle it) connected to a LoRa radio and a full Bitcoin node (Bitcoin Core). It acts as the bridge between the off-grid mesh world and the global Bitcoin network.
- The Client: Anyone else on the network, even miles away and without internet, can use the "client" on their laptop or phone.
The process is a choreographed dance designed for the low-speed LoRa network:
- Preparing the Transaction: In a wallet like Sparrow, you create and sign your transaction. Instead of clicking "Broadcast," you copy the "Raw Transaction"—a long hexadecimal text.
- Sending Over the Mesh: In the terminal, you run a simple command, pointing to the server's radio and pasting your raw transaction.
- The Communication: Since the transaction is too large for a single LoRa packet, the client splits it into chunks and starts a conversation with the server:
- Client: "Hey server! I have a transaction in 15 parts. Can we start?"
- Server: "Roger that! Awaiting 15 parts. Send the first one."
- Client: (sends part 1)
- Server: "Part 1 received. Send part 2."
- This "handshake" continues until all parts are confirmed, ensuring the transaction arrives complete.
- Validation and Broadcast: Upon receiving everything, the server reconstructs the transaction, validates it, and hands it off to its local Bitcoin node, which finally broadcasts it to the worldwide network.
And that's it! Your transaction is sent to the blockchain, broadcast from a radio, without your IP address ever being exposed.
Maximum Privacy and Sovereignty
BTC Mesh's power lies in its layers of privacy:
- No IP Trail: Since the transaction is sent via radio, there is no record of your IP address. To the Bitcoin network, the transaction simply originated from the server node.
- End-to-End Encryption: The communication between the radios is encrypted by Meshtastic. No one in between can see the content of your transaction.
- Extra Layer with Tor: For maximum privacy, the server node can connect to the internet through the Tor network. This way, not even the server's IP is exposed in the final broadcast.
This combination creates a powerful system for censorship-resistant Bitcoin transactions with high privacy.
Building Your Kit: The Hardware
Excited to build your own station? The hardware is cheap and accessible.
- Frequency is Key: First, know the legal LoRa frequency in your country. In Brazil, use 915 MHz. In Europe, 868 MHz. Buying the wrong frequency will render your radio useless.
- Popular Brands:
- Heltec: Very popular, with boards like the T114, V3, and the Wireless Bridge, which comes with a practical design and an e-ink screen.
- RAK Wireless: Considered more "professional." The RAK4631 model (which I use for my base) is excellent, and the WisBlock line is modular, requiring no soldering.
- LilyGo: Famous in the "maker" community. Offers boards like the T-Beam (with GPS), T-Echo (small and practical), and the T-Deck (a full communicator with a keyboard).
- Seeed Studio (SenseCAP): Offers robust devices like the T1000-e (waterproof) and the XIAO ESP32S3 (tiny, perfect for compact projects).
- Antennas: Don't underestimate the antenna! And a crucial warning: never, ever, turn on your radio without an antenna connected, or you could burn out the transmitter.
- 3 dBi: A more "rounded" signal (a sphere), great for short distances with vertical obstacles.
- 10 dBi: A "flatter," more directional signal (a frisbee), for long distances with a clear line of sight.
- Power: Many boards have connectors for batteries and small solar panels, allowing you to create autonomous nodes.
Limitations and Considerations
Despite its power, LoRa technology has its limits:
- Low Bandwidth: The network is slow. Think 140-character Twitter. It's perfect for messages, but forget about web browsing.
- Regulation: Many regions limit the amount of data a radio can transmit per hour ("duty cycle"). Meshtastic respects these limits, which reinforces the need for optimized applications.
- Need for a Bridge: For a transaction to reach the global network, one node on the mesh needs internet. The network can be fully off-grid for internal communication, but the bridge to the outside world is necessary for certain applications. MQTT servers can play this role, connecting distant mesh networks over the internet.
Use Cases: Beyond Bitcoin
- Disaster Communication: Projects like Disaster.Radio focus on using LoRa to coordinate rescue teams during catastrophes.
- Outdoor Activities: Essential for hiking and camping in remote locations.
- Internet of Things (IoT): In agriculture, sensors can cover vast areas. On farms, they can monitor livestock.
- Private Communication: In a world of surveillance, having a communication channel that you control is an act of sovereignty.
The Future is Decentralized
Projects like BTC Mesh offer a glimpse into a more resilient, private, and decentralized future. They give us the tools to build our own communication and financial networks, free from centralized control.
The technology is cheap, the software is free, and the community is vibrant. Building your first node might seem intimidating, but it's a rewarding project and a practical step toward personal sovereignty.
So, are you ready to get off the grid?
-
 @ 9ca447d2:fbf5a36d
2025-06-07 15:02:22
@ 9ca447d2:fbf5a36d
2025-06-07 15:02:22Trump Media & Technology Group (TMTG), the company behind Truth Social and other Trump-branded digital platforms, is planning to raise $2.5 billion to build one of the largest bitcoin treasuries among public companies.
The deal involves the sale of approximately $1.5 billion in common stock and $1.0 billion in convertible senior secured notes.
According to the company, the offering is expected to close by the end of May, pending standard closing conditions.
Devin Nunes, CEO of Trump Media, said the investment in bitcoin is a big part of the company’s long-term plan.
“We view Bitcoin as an apex instrument of financial freedom,” Nunes said.
“This investment will help defend our Company against harassment and discrimination by financial institutions, which plague many Americans and U.S. firms.”
He added that the bitcoin treasury will be used to create new synergies across the company’s platforms including Truth Social, Truth+, and the upcoming financial tech brand Truth.Fi.
“It’s a big step forward in the company’s plans to evolve into a holding company by acquiring additional profit-generating, crown jewel assets consistent with America First principles,” Nunes said.
The $2.5 billion raise will come from about 50 institutional investors. The $1 billion in convertible notes will have 0% interest and be convertible into shares at a 35% premium.
TMTG’s current liquid assets, including cash and short-term investments, are $759 million as of the end of the first quarter of 2025. With this new funding, the company’s liquid assets will be over $3 billion.
Custody of the bitcoin treasury will be handled by Crypto.com and Anchorage Digital. They will manage and store the digital assets.
Earlier this week The Financial Times reported Trump Media was planning to raise $3 billion for digital assets acquisitions.
The article said the funds would be used to buy bitcoin and other digital assets, and an announcement could come before a major related event in Las Vegas.
Related: Bitcoin 2025 Conference Kicks off in Las Vegas Today
Trump Media denied the FT report. In a statement, the company said, “Apparently the Financial Times has dumb writers listening to even dumber sources.”
There was no further comment. However, the official $2.5 billion figure, which was announced shortly after by Trump Media through a press release, aligns with its actual filing and investor communication.
Trump Media’s official announcement
This comes at a time when the Trump family and political allies are showing renewed interest in Bitcoin.
President Donald Trump who is now back in office since the 2025 election, has said he wants to make the U.S. the “crypto capital of the world.”
Trump Media is also working on retail bitcoin investment products including ETFs aligned with America First policies.
These products will make bitcoin more accessible to retail investors and support pro-Trump financial initiatives.
But not everyone is happy.
Democratic Senator Elizabeth Warren recently expressed concerns about Trump Media’s Bitcoin plans. She asked U.S. regulators to clarify their oversight of digital-asset ETFs, warning of investor risk.
Industry insiders are comparing Trump Media’s plans to Strategy (MSTR) which has built a multi-billion dollar bitcoin treasury over the last year. They used stock and bond sales to fund their bitcoin purchases.
-
 @ 553b8217:e6e84118
2025-06-07 14:41:21
@ 553b8217:e6e84118
2025-06-07 14:41:21The Lightning Network is a revolutionary layer-2 solution built on top of the Bitcoin blockchain, designed to enhance transaction speed, reduce costs, and improve scalability. By integrating with Bitcoin wallets, the Lightning Network significantly improves user experience, making Bitcoin more practical for everyday payments. Here’s how it benefits both wallets and users.
A.Faster Transactions - Traditional Bitcoin transactions can take 10 minutes or more to confirm, especially during network congestion.
- The Lightning Network enables near-instant transactions (often under a second), making Bitcoin wallets ideal for real-time payments like buying coffee or tipping content creators .B.Lower Fees - On-chain Bitcoin transactions can have high fees during peak times, sometimes exceeding $50.
- Lightning Network transactions cost a fraction of a cent, making micropayments (even as small as a few satoshis) economically viable .C.Enhanced Scalability - Bitcoin’s base layer processes only 7 transactions per second (TPS),limiting its use for mass adoption.
- The Lightning Network can theoretically handle millions of TPS,allowing wallets to support high-volume transactions without clogging the blockchain .D. Improved Privacy - On-chain Bitcoin transactions are publicly recorded, exposing user activity.
- Lightning transactions occur off-chain, reducing visibility and enhancing privacy for wallet users .E. Better User Experience - Lightning-integrated wallets (e.g., Phoenix, Wallet of Satoshi, BlueWallet) automate complex processes like channel management, making it easy for beginners to send/receive Bitcoin instantly .
- Features like Lightning Addresses(e.g.,user@wallet.com) simplify payments, replacing long blockchain addresses .F. New Use Cases - Enables micropayments for streaming services, pay-per-minute content, and gaming.
- Supports cross-border remittances with minimal fees, benefiting unbanked populations .Therefore By integrating the Lightning Network, Bitcoin wallets become faster, cheaper, and more scalable, unlocking Bitcoin’s potential as a global payment system. Whether for daily spending or innovative financial applications, the Lightning Network is transforming how users interact with Bitcoin wallets.
bitcoin #lightingnetwork #bitcoinwallet #blochchain
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-07 14:19:37
@ 5d4b6c8d:8a1c1ee3
2025-06-07 14:19:37I'll do more specific deep dives into the interesting teams, but let's start with the big picture. Which teams are buyers and sellers this offseason and who will be the biggest moving pieces?
Sellers
These are the teams that I expect to be bailing on their valuable assets: - Celtics: Even before Tatum's horrible injury, there was Last Dance talk around this old expensive roster. I think they'll use this year to get the roster more aligned with Tatum's timeline. That likely means moving on from Horford, Holliday, and Porzingis for salary savings and promising young players. - Bucks: With Dame injured and the roster being both old and not very good, they'll be putting Giannis on the auction block, as well as anyone else with trade value. They aren't tanking, though, unless they can get their picks back. - Phoenix: They desperately need to turn KD into assets that will be valuable in the future. The situation may even be bleak enough that they look to move on from Booker. - Memphis: A badly injured superstar and a roster that probably isn't good enough anyway, means it's time to sell the parts that don't quite fit and look to get back on track after next season.
Buyers
These are the teams looking to add high-end talent: - Houston: They had a great season, but lack a true number one player. Fortunately for them, they have a ton of draft picks and promising young players. - San Antonio: They also have a ton of assets and are ready to build a competitor around Wemby and Fox.
Both
These teams are pretty good, but they probably need to make pretty big roster tweaks: - Cavs: The two-big lineup looked too big against the Pacers. They probably need to move either Garland or Allen for another good player that fits the roster needs better. - Minnesota: Randle looked good for most of the playoffs, but Randle and Gobert aren't the right frontcourt for Ant. - Lakers: I'm not sure who they should part with, but they need a center.
Run it back
These teams don't need to do more than small tweaks around the edges, either because they're close already, they're developing a young promising roster, or there's just not much they can do: - Detroit - New York - Indiana - OKC - Golden State
???
I don't know what they need to do, but they need to do something: - Clippers: Kawhi and Harden went as far as they're gonna go, but I doubt anyone wants to give up assets for either of them. - Philly: Hahahahaha! - Orlando: Great defense, miserable offense. Something's gotta give - Dallas: Are they trying to win now or build around Flagg? - New Orleans: They have way too much talent to be as bad as they've been. - Denver: They looked great against OKC, but it seems like they need more around Jokic. Is MPJ worth anything as a trade asset, though?
Who cares? They suck
Everyone else
Let me know what you're looking at this offseason.
https://stacker.news/items/999795
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:22
@ dfa02707:41ca50e3
2025-06-07 14:01:22Contribute to keep No Bullshit Bitcoin news going.
- The latest firmware updates for COLDCARD devices introduce two major features: COLDCARD Co-sign (CCC) and Key Teleport between two COLDCARD Q devices using QR codes and/or NFC with a website.

What's new
- COLDCARD Co-Sign: When CCC is enabled, a second seed called the Spending Policy Key (Key C) is added to the device. This seed works with the device's Main Seed and one or more additional XPUBs (Backup Keys) to form 2-of-N multisig wallets.
- The spending policy functions like a hardware security module (HSM), enforcing rules such as magnitude and velocity limits, address whitelisting, and 2FA authentication to protect funds while maintaining flexibility and control, and is enforced each time the Spending Policy Key is used for signing.
- When spending conditions are met, the COLDCARD signs the partially signed bitcoin transaction (PSBT) with the Main Seed and Spending Policy Key for fund access. Once configured, the Spending Policy Key is required to view or change the policy, and violations are denied without explanation.
"You can override the spending policy at any time by signing with either a Backup Key and the Main Seed or two Backup Keys, depending on the number of keys (N) in the multisig."
-
A step-by-step guide for setting up CCC is available here.
-
Key Teleport for Q devices allows users to securely transfer sensitive data such as seed phrases (words, xprv), secure notes and passwords, and PSBTs for multisig. It uses QR codes or NFC, along with a helper website, to ensure reliable transmission, keeping your sensitive data protected throughout the process.
- For more technical details, see the protocol spec.
"After you sign a multisig PSBT, you have option to “Key Teleport” the PSBT file to any one of the other signers in the wallet. We already have a shared pubkey with them, so the process is simple and does not require any action on their part in advance. Plus, starting in this firmware release, COLDCARD can finalize multisig transactions, so the last signer can publish the signed transaction via PushTX (NFC tap) to get it on the blockchain directly."
- Multisig transactions are finalized when sufficiently signed. It streamlines the use of PushTX with multisig wallets.
- Signing artifacts re-export to various media. Users are now provided with the capability to export signing products, like transactions or PSBTs, to alternative media rather than the original source. For example, if a PSBT is received through a QR code, it can be signed and saved onto an SD card if needed.
- Multisig export files are signed now. Public keys are encoded as P2PKH address for all multisg signature exports. Learn more about it here.
- NFC export usability upgrade: NFC keeps exporting until CANCEL/X is pressed.
- Added Bitcoin Safe option to Export Wallet.
- 10% performance improvement in USB upload speed for large files.
- Q: Always choose the biggest possible display size for QR.
Fixes
- Do not allow change Main PIN to same value already used as Trick PIN, even if Trick PIN is hidden.
- Fix stuck progress bar under
Receiving...after a USB communications failure. - Showing derivation path in Address Explorer for root key (m) showed double slash (//).
- Can restore developer backup with custom password other than 12 words format.
- Virtual Disk auto mode ignores already signed PSBTs (with “-signed” in file name).
- Virtual Disk auto mode stuck on “Reading…” screen sometimes.
- Finalization of foreign inputs from partial signatures. Thanks Christian Uebber!
- Temporary seed from COLDCARD backup failed to load stored multisig wallets.
Destroy Seedalso removes all Trick PINs from SE2.Lock Down Seedrequires pressing confirm key (4) to execute.- Q only: Only BBQr is allowed to export Coldcard, Core, and pretty descriptor.

-
 @ dfa02707:41ca50e3
2025-06-07 14:01:19
@ dfa02707:41ca50e3
2025-06-07 14:01:19Contribute to keep No Bullshit Bitcoin news going.
-
Version 1.3 of Bitcoin Safe introduces a redesigned interactive chart, quick receive feature, updated icons, a mempool preview window, support for Child Pays For Parent (CPFP) and testnet4, preconfigured testnet demo wallets, as well as various bug fixes and improvements.
-
Upcoming updates for Bitcoin Safe include Compact Block Filters.
"Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions. They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK," writes the project's developer Andreas Griffin.
- Learn more about the current and upcoming features of Bitcoin Safe wallet here.
What's new in v1.3
- Redesign of Chart, Quick Receive, Icons, and Mempool Preview (by @design-rrr).
- Interactive chart. Clicking on it now jumps to transaction, and selected transactions are now highlighted.

- Speed up transactions with Child Pays For Parent (CPFP).
- BDK 1.2 (upgraded from 0.32).
- Testnet4 support.
- Preconfigured Testnet demo wallets.
- Cluster unconfirmed transactions so that parents/children are next to each other.
- Customizable columns for all tables (optional view: Txid, Address index, and more)
- Bug fixes and other improvements.

Announcement / Archive
Blog Post / Archive
GitHub Repo
Website -
-
 @ 8bad92c3:ca714aa5
2025-06-07 14:01:15
@ 8bad92c3:ca714aa5
2025-06-07 14:01:15
Another week of conversations with sharp minds thinking about Bitcoin's future and the broader economic landscape. Here are the three most compelling predictions from recent episodes.
Bitcoin Core Will Face a Major Governance Crisis Over Covenant Proposals in 2025 - James O'Beirne
James made a prediction that sent chills through the Bitcoin development community - he believes Bitcoin Core's current governance structure will reach a breaking point this year over covenant proposals like CTV. After working as a Core developer for nearly a decade, he's convinced that the organization's inability to make progress on scaling solutions will force alternative implementations.
His timeline is specific and urgent. James believes that if Core doesn't show "substantive review discussion about how we get this stuff in" within six months, credible developers will start building alternate activation clients. The technical argument is compelling: covenants like CheckTemplateVerify have been thoroughly reviewed for seven years, with a 5 BTC bounty (worth over $500,000) still unclaimed for finding material bugs.
The stakes couldn't be higher for Bitcoin's future. James noted that currently "just over two and a half percent of Americans would be able to, on a monthly basis, buy Bitcoin on an exchange, withdraw it to self-custody, and then maybe make a spend." Without scaling solutions, this number won't improve meaningfully. His prediction reflects growing frustration with Core's de facto monopoly over protocol development. "You simply can't ignore that there is a social reality to being in that world," he said, referring to the concentrated funding and decision-making power that has created what he sees as an unsustainable bottleneck for Bitcoin's evolution.
The U.S. Will See Widespread Energy Blackouts as AI Data Centers Strain the Grid - Anas Alhajji
Dr. Anas delivered a sobering prediction about America's energy infrastructure failing to keep pace with exploding AI demand. He expects we'll see significant blackouts in major cities within the next few years, with a particularly concerning scenario where AI facilities maintain power while residential areas go dark. "I will not be surprised if we end up with a situation like this in some states and some cities," he warned.
The mathematics behind his prediction are stark. Energy consumption is skyrocketing due to multiple factors: urbanization, AI data centers, and simple population growth. When migrants move from rural areas to U.S. cities, their energy consumption increases by 30-70 times. Meanwhile, AI facilities require massive baseload power that renewable sources simply cannot provide reliably.
The infrastructure problems run deeper than just generation capacity. Anas explained that America's electrical grid is aging and wasn't designed for this level of demand. Even worse, we lack the manufacturing capacity to produce enough natural gas turbines - the only realistic solution for reliable baseload power at scale. He predicts this will create a dangerous political dynamic where tech companies with guaranteed power contracts maintain operations during blackouts while regular citizens lose electricity. "We might see a backlash from the population, and we will see politicians basically being forced to fight them because of that."
AI Will Force Millennials Into Career Reinvention Within the Next Decade - Bram Kanstein
Bram made a stark prediction about the collision between artificial intelligence and millennial career paths. He believes that traditional knowledge-based jobs will become obsolete much faster than people expect, forcing an entire generation to completely rethink their working lives. "If you think you're going to work for the next 30 years of your life, think again," he warned during our conversation.
His argument centers on the rapid advancement of AI capabilities that he's witnessed firsthand. After spending just 12 hours working with AI tools, Bram claims he developed what could be "a top 10 cybersecurity invention" - despite having no cybersecurity background. This experience convinced him that jobs requiring strict knowledge and logic are already dead. The implications are massive for millennials who built their careers around expertise that AI can now replicate instantly.
The timing couldn't be worse, as Bram notes that this technological disruption is happening precisely when millennials need stable income to support families and prepare for retirement. His solution? Use Bitcoin to create the time and space needed to figure out how to function in an AI-dominated world. "You need to be aware of that. This is where it's going. So how do you protect yourself in an age of AI? Bitcoin is the perfect way to do that."
Blockspace conducts cutting-edge proprietary research for investors.
New Bitcoin Mining Pool Flips Industry Model: "Plebs Eat First" Could Threaten Corporate Dominance
Parasite Pool's radical zero-fee structure challenges mining giants by guaranteeing payouts to small miners while rewarding block finders with instant Bitcoin. It disrupts traditional mining with a hybrid payout model that gives block discoverers 1 BTC immediately, while distributing remaining rewards (~2.125 BTC plus fees) among all pool participants. This "plebs eat first" approach targets the 22% discount miners typically accept in exchange for guaranteed income.
Key innovations that matter:
- Lightning Network integration bypasses Bitcoin's 100-block maturity rule, delivering instant payouts to Lightning wallets
- 10-sat minimum withdrawal eliminates traditional barriers for small miners
- Block withholding protection through substantial honest-miner rewards reduces pool attacks
The pool currently commands just 5 PH/s (0.000006% of Bitcoin's network), meaning an expected 3+ years before hitting a block. But this represents a growing counterculture against Full Pay Per Share (FPPS) pools that dominate corporate mining.
Industry impact: If successful, Parasite Pool could attract commercial miners seeking downside protection while maintaining the lottery appeal that drives pleb participation. The model challenges the structural advantages of corporate mining pools.
What's next: ZK Shark plans to open-source components over time, with the current beta suggesting this is just "V1" of a broader disruption strategy.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
STACK SATS hat: https://tftcmerch.io/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 8bad92c3:ca714aa5
2025-06-07 14:01:14
@ 8bad92c3:ca714aa5
2025-06-07 14:01:14Marty's Bent
via me

I think we'll look back at last weekend as one of the most pivotal points in human history. Ukraine's Operation Spider Web is one of the more shocking things I've seen in terms of military operations in my life. It validates something that many bitcoiners, many cypherpunks, and many prescient individuals have been talking about for decades now at this point, which is asymmetric drone warfare.
The Sovereign Individual is a book that many bitcoiners have talked about throughout the years due to how prescient it was in terms of the inevitable emergence of a digital currency outside the control of central banks and governments. The book was written in the mid-90s, so the fact that the two authors were able to predict that something like bitcoin would emerge less than 20 years after writing the book is pretty incredible. However, digital currencies leveraging cryptography were not the sole focus of the book. Another portion of the book was dedicated to the idea of asymmetric drone warfare and its effects on society overall.
It seems pretty clear today that this is another call from The Sovereign Individual that is coming true. Obviously, unless you've been living under a rock, you've noticed that Ukraine has been using drones in the battlefield to target strategic Russian assets and individual soldiers over the last year. The amount of battlefield videos I've seen of Russian soldiers running from autonomous drones that are hunting them down has been increasing significantly over the last six months. The footage is truly harrowing. It is a death that I wouldn't wish on anybody. With Operation Spider Web Ukraine has increased the stakes of this type of drone warfare by going deep into Russian territory and targeting strategic long-range bombers, some of which had the ability to deploy nuclear warheads. This is sure to incite a reaction from Russia. No one will be surprised if, by the end of the week, Russia has started a shock and awe campaign that goes deep into Ukrainian territory in retaliation for the kamikaze drone strikes on their long-range aircraft. I pray for peace and a quick resolution to this war, and every other war for that matter.
I didn't come here to pontificate and give my thoughts on this particular war, but I would like to focus on this new tactic of war and what it means for military budgets moving forward. The Sovereign Individual laid it out clearly when they wrote in the 1990s that at some point in the future autonomous drones would be leveraged in the battlefield and prove to be asymmetric because of the fact that they are extremely cheap to produce. When you compare the price it cost to produce one of these drones to the price of the equipment they are destroying, things get pretty crazy. With tens of thousands of dollars of drone equipment the Ukrainian army destroyed tens if not hundreds of millions of dollars worth of long-range missile aircraft. And it did so without putting any Ukrainian military personnel in harm's way. Directly, at least.
When you consider the return on investment of deploying these drones compared to sending in soldiers, tanks, and your own aircraft, it becomes pretty obvious that this is going to quickly become the most logical way to fight a war moving forward. The question that remains is how quickly do other governments recognize this and implement it into their own defense strategies? As an American looking at our military budget, which is quickly approaching $1 trillion in annual spend, I'm forced to question whether or not most of that money is simply being wasted, considering the fact that we live in a time where these asymmetric battlefield strategies now exist. Why build new fighter jets when a Somali pirate, or nefarious individual for that matter, could use a $200 drone to destroy it in a matter of seconds with no threat of direct physical harm?
I'm no military expert, but if I were at the helm of the Defense Department, I would seriously be forcing those below me to focus a ton of effort on this problem and create plans to make sure that we are sufficiently protected from these risks. The only way to protect from these risks is to build the capabilities yourself. When it comes to the risk reward from a defense tech investment perspective I think a majority of the effort should be focused on defensive drone technologies and capabilities.
With that being said, it does seem like the US military is privy to this asymmetric reality that we currently live in. Defense contracts with Andruil make this pretty clear. Andruil is certainly ahead of the curve when it comes to autonomous drone warfare and defense against it. As an American, even though I don't like war, or the military industrial complex, knowing that the military is working with companies like Andruil does give me some comfort. However, the other side of that coin is that it is very unnerving when you consider that the government creating these public-private partnerships could lead to some Orwellian outcomes here at home. It may make some of you feel uncomfortable, but I believe the ideal scenario is that any individual has access to these types of defensive drone technologies in the future. The end goal being to create a nuclear game theoretical outcome where violence is reduced because one always has to assume that anyone they intend to attack has access to sufficient and formidable defensive technologies.
It's truly scary times we're living in as we transition further into the Digital Age. Part of the reason that I've dedicated my whole life to bitcoin is because I truly do believe that if you fix the money, you can fix the world. That is not to say that kinetic wars or physical violence will not exist in the future. It certainly will. But I believe sound money and open access to these systems and tools creates conditions which are much more suitable for cooperation and less so for conflict.
Multi-Signature Bitcoin Custody Is Replacing Single-Point Solutions
Jesse Gilger made a compelling case for why multi-signature Bitcoin custody represents the future of secure storage. He explained how Gannett Trust's approach ensures "not all of the keys are going to be at any one entity," fundamentally reducing the honeypot risk that plagues centralized custodians. This distributed model means no single point of failure can compromise your Bitcoin, whether through hacking, internal fraud, or regulatory seizure.
"I was on the list. I got the email. 'You were affected.'" - Jesse Gilger
Jesse's firsthand experience with the Coinbase data breach drives home why centralized custody is fundamentally flawed. While Coinbase holds keys for 10 of 12 Bitcoin ETFs, smart money is moving toward multi-institutional setups where Gannett holds a key, Unchained holds a key, and a third party holds a key. This alignment with Bitcoin's decentralized ethos isn't just philosophically pure—it's pragmatically superior for protecting generational wealth.
Check out the full podcast here for more on MSTY risks, Bitcoin retirement strategies and nation-state adoption dynamics.
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Trying to imagine the future my children are going to live in gets harder by the day.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients
-
 @ f85b9c2c:d190bcff
2025-06-07 13:16:28
@ f85b9c2c:d190bcff
2025-06-07 13:16:28
To understand the value of a cryptocurrency, it’s vital to know how many coins are currently in circulation and at what price they’re being sold. Market capitalization of coins are calculated by multiplying the number of coins in circulation with their current market selling rate per coin.
What is Market Capitalization? Market capitalization is the total dollar value of all shares in a company. For Bitcoin or another cryptocurrency it’s calculated by multiplying a total number of coins mined by their current price at that particular time. The market cap is a great way to measure an asset’s stability. The larger it gets, the less likely you’ll have any fluctuations in pricing because more people are using this currency. This means that its price will remain consistent over time no matter what happens with the markets.
Why is a Market Cap Necessary? Cryptocurrencies are collected and catalogued by market cap which helps investors better understand their value. This statistic can indicate if a cryptocurrency is safe to buy or sell compared with others in the industry — it may also provide an idea of what kind of growth potential they have ahead.
What Can You Do With the Market Cap? It’s essential for crypto enthusiasts like yourself to keep track of what kind of project might be worth investing in.
Cryptocurrencies are divided into three categories based on their market cap: 1.Large-cap Cryptocurrencies Large-cap cryptocurrencies are considered lower-risk investments because they’ve demonstrated growth and high liquidity. This means that even if many people sell their investment, its value won’t decrease too much.
2.Mid-cap Cryptocurrencies Mid-cap cryptocurrencies have a lot of potential but are also riskier than large-cap coins.
3.Small-cap Cryptocurrencies Small-cap cryptocurrencies could be your best bet for those looking to invest in a more volatile market with the potential for greater returns.
Last thoughts Even though cryptocurrency market caps allow for an easy way to compare the values of different coins you should consider all factors when investing in any project. You can’t just go into cryptocurrency investing without doing your research. It would help if you looked at each coin’s market trends and stability and whether it’s right for you financially.
-
 @ 1817b617:715fb372
2025-06-07 13:15:04
@ 1817b617:715fb372
2025-06-07 13:15:04Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
🔗 Buy Flash USDT Now This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
✅ Perfect for: Simulating token inflows Wallet stress testing “Proof of funds” display Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
🧠 What Is Flash USDT? Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
Visible on wallet interfaces Time-limited (auto-disappears cleanly) Undetectable on block explorers after expiry It’s the smartest, safest way to simulate high-value transactions without real crypto.
🛠️ Flash USDT Software – Your Own USDT Flasher at Your Fingertips Want to control the flash? Run your own operations? Flash unlimited wallets?
🔗 Buy Flash USDT Software
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
Send custom USDT amounts Set custom expiry time (e.g., 30–360 days) Flash multiple wallets Choose between networks (Tron, ETH, BSC) You can simulate any amount, to any supported wallet, from your own system.
No third-party access. No blockchain fee. No trace left behind.
💥 Why Our Flash USDT & Software Stands Out Feature Flash USDT Flash USDT Software One-time flash send ✅ Yes Optional Full sender control ❌ No ✅ Yes TRC20 / ERC20 / BEP20 ✅ Yes ✅ Yes Custom duration/expiry Limited ✅ Yes Unlimited usage ❌ One-off ✅ Yes Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
🛒 Ready to Buy Flash USDT or the Software? Skip the wait. Skip the scammers. You’re one click away from real control.
👉 Buy Flash USDT 👉 Buy Flash USDT Software
📞 Support or live walkthrough?
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
🚫 Legal Notice These tools are intended for:
Educational purposes Demo environments Wallet and UI testing They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call: Need to flash USDT? Want full control? Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
🔗 Buy Now → Flash USDT 🔗 Buy Now → Flash USDT Software 💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531Looking to simulate a USDT deposit that appears instantly in a wallet — with no blockchain confirmation, no real spend, and no trace?
You’re in the right place.
Buy Flash USDT Now\ This product sends Flash USDT directly to your TRC20, ERC20, or BEP20 wallet address — appears like a real deposit, but disappears after a set time or block depth.
Perfect for:
- Simulating token inflows
- Wallet stress testing
- “Proof of funds” display
Flash USDT is ideal for developers, trainers, UI testers, and blockchain researchers — and it’s fully customizable.
What Is Flash USDT?
Flash USDT is a synthetic transaction that mimics a real Tether transfer. It shows up instantly in a wallet balance, and it’s confirmed on-chain — and expires after a set duration.
This makes it:
- Visible on wallet interfaces
- Time-limited (auto-disappears cleanly)
- Undetectable on block explorers after expiry
It’s the smartest, safest way to simulate high-value transactions without real crypto.
Flash USDT Software – Your Own USDT Flasher at Your Fingertips
Want to control the flash?\ Run your own operations?\ Flash unlimited wallets?
This is your all-in-one USDT flasher tool, built for TRC20, ERC20, and BEP20 chains. It gives you full control to:
- Send custom USDT amounts
- Set custom expiry time (e.g., 30–360 days)
- Flash multiple wallets
- Choose between networks (Tron, ETH, BSC)
You can simulate any amount, to any supported wallet, from your own system.
No third-party access.\ No blockchain fee.\ No trace left behind.
Why Our Flash USDT & Software Stands Out
Feature
Flash USDT
Flash USDT Software
One-time flash send
Yes
Optional
Full sender control
No
Yes
TRC20 / ERC20 / BEP20
Yes
Yes
Custom duration/expiry
Limited
Yes
Unlimited usage
One-off
Yes
Whether you’re flashing for wallet testing, demoing investor dashboards, or simulating balance flows, our tools deliver realism without risk.
Ready to Buy Flash USDT or the Software?
Skip the wait. Skip the scammers.\ You’re one click away from real control.
Support or live walkthrough?
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
Legal Notice
These tools are intended for:
- Educational purposes
- Demo environments
- Wallet and UI testing
They are not for illegal use or financial deception. Any misuse is your full responsibility.
Final Call:
Need to flash USDT? Want full control?\ Don’t wait for another “maybe” tool.
Get your Flash USDT or Flashing Software today and simulate like a pro.
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ bf47c19e:c3d2573b
2025-06-07 12:49:02
@ bf47c19e:c3d2573b
2025-06-07 12:49:02Originalni tekst na armantheparman.com / Autor: @parman_the
Puno sam razmišljao o ovom pitanju i konačno se osećam spremnim da ponudim sveobuhvatan odgovor.
UKRATKO – ako imamo novac rođen na slobodnom tržištu, u slobodnom društvu, koji treba da zameni fiat novac, onda on ne može biti ravnomerno raspoređen od samog početka dok istovremeno svi ljudi cene njegovu vrednost – nužno mora proći kroz period kada ga samo nekolicina ljudi vrednuje.
Jednakost i pravičnost
Želim da počnem sa značenjem reči „pravično“. Mnogi ljudi, posebno oni koji pripadaju političkoj levici, smatraju da nešto mora biti jednako da bi bilo pravično. Na prvi pogled i bez dubljeg razmišljanja, to deluje ispravno ali zapravo je veoma netačno. Možda verujete da je jednakost instinktivno očekivanje od strane jednakih ljudi. Greška nastaje kada se taj prirodni instinkt nesvesno prenosi na druge stvari.
Zamislimo prirodan osećaj nepravde koji dete može doživeti kada njegov brat ili sestra (vršnjak) dobiju više slatkiša od njega – „Zašto on/ona zaslužuje više od mene?“ Ovo uvodi dodatnu promenljivu – „zaslužiti“, o čemu ću govoriti u kasnijem odeljku. Za sada ću se fokusirati na jednakost i pravičnost.
Nerazumno je i nelogično očekivati da sve u prirodi bude jednako. S obzirom na to da u prirodi postoje razlike u sposobnostima i drugim karakteristikama, rezultati tih razlika će, naravno, biti nejednako raspoređeni. Poricanje toga znači poricanje stvarnosti i poricanje uzročno-posledične veze. Mešati se u to znači „igrati se Boga“.
Na primer, neka stabla dobijaju više sunčeve svetlosti i kiše od drugih i bujnije napreduju; neke životinje jedu druge životinje; neki ljudi su mudriji, jači, brži, privlačniji ili produktivniji od drugih. Takva je priroda i to je srž prirodne selekcije i evolucije i na taj način prirodni ekosistemi postižu ravnotežu.
Iako biste možda želeli da se mešate u ravnotežu prirode u svojoj bašti s povrćem, primenjivanje svojih želja na živote drugih ljudi protiv njihove volje može biti nemoralno. Na primer, oduzimanje bogatstva/imetka (silom) koje je zaradio neko ko je sposobniji ili više doprinosi društvu i ustupanje tog bogatstva nekome siromašnom i manje produktivnom (suština socijalizma) je autoritativno, dugoročno kontraproduktivno za sve i vodi ka konačnom kolapsu civilizacije (Ajn Rend je ovo istraživala u svom remek-delu od 1244 strane, romanu Pobunjeni Atlas (engl. Atlas Shrugged), koji toplo preporučujem). Ovo „forsiranje“ jednakih nagrada za rezultate različitih sposobnosti koristi „pravičnost“ kao opravdanje ali je suštinski NEPRAVIČNO, jer ide protiv prirode.
Uzimanje (silom) od onih koji su zaradili više i preraspodela onima koji su zaradili manje predstavlja ideal JEDNAKOSTI u ishodima ali, da bi se to postiglo, ljude tretirate nejednako.
Nagrade raspoređene na osnovu prirodnih razlika (npr. sposobnosti, predviđanja, iskustva) ili razlika u uloženom trudu, bez mešanja spoljnih sila koje nameću svoju volju (autoritarizam) – to je PRAVIČNOST. Ovo je u skladu s jednakim tretiranjem ljudi shodno prirodnim zakonima, pa čak i zakonima vlasti.
Alternativni pogled na pravičnost je da nagrade treba da se zasnivaju na moralu – iako to zvuči lepo, to je čista fantazija.
Ljudska prava
Ništa od ovoga ne znači da neke stvari ne bi trebalo da budu jednake. Na primer, ljudska prirodna prava su zapravo jednaka. Ona NE zavise od sposobnosti, potreba, morala, kriminalne prošlosti, političkih uverenja, sreće, truda, statusa, važnosti, slave – nimalo.
Ona se zasnivaju na tome što smo ljudi.
Zašto je ovo relevantno postaće jasno veoma brzo. Svi imaju jednaka prirodna prava. Neki primeri su pravo na život, slobodu, govor i privatnost. Ova prava postoje bez potrebe za dozvolom da postoje – mogu biti prekršena ili poštovana/zaštićena – ali nisu nam dodeljena ili data, niti nam mogu biti oduzeta. Ona su nezavisna od zakona.
Da pojasnim, sva ova prava ne zahtevaju da neko drugi nešto uradi za vas. „Pravo na život“ izgleda kao da krši ovo pravilo ali zapravo bi trebalo da se zove „pravo da ne budete ubijeni“; niko nema ljudsko pravo da primorava nekoga da ga održava u životu. Slično je i sa slobodom govora, niko nema pravo da mu se obezbedi platforma za govor ali ima pravo da ne bude ućutkan. Prava značenja se mogu izgubiti u jednostavnom jeziku/rečima koje smo navikli da koristimo.
Sledeće je veoma važno razumeti: prirodno ljudsko pravo je nešto što imamo na osnovu našeg inteligentnog RAZMIŠLJANJA o tome šta je ispravno i pogrešno i ne podleže diskreciji autoritativne vlasti. Međutim, autoritativna vlast ima sposobnost da to pravo prekrši ili zaštiti.
To što imam ljudska prava ne znači da će trenutni autoritet današnjice (vlada) zaštititi ta prava. Umesto toga, odgovornost dobronamerne autoritativne vlasti je da ih zaštiti.
Da sumiram:
Prirodno ljudsko pravo je nešto što svi ljudi imaju (ali zakon ne štiti uvek).
Ovo se razlikuje od zakonskog prava:
Zakonsko pravo je nešto što daje autoritativna vlast.
Sada kada su ljudska prava površno objašnjena, želim da ponovo naglasim nešto veoma važno:
Dok je jednakost ljudskih prava prirodna stvar koju treba očekivati između svih ljudi, veoma je različito očekivati jednakost nagrada za naše sposobnosti ili trud. Da bismo postigli jednake nagrade, moramo ljude tretirati različito, što je suštinski nepravično.
Ne mislim da je potreban dalji logički argument. Ako se još uvek ne slažete, predlažem da ponovo pročitate ono što sam rekao i razmislite o tome.
Povezujući se sa temom ovog teksta, distribucijom bitkoina – bogatstvo nije ljudsko pravo, ono je NAGRADA. Jednakost bogatstva između ljudi takođe nije ljudsko pravo. Međutim, ljudsko je pravo biti slobodan da posedujete imovinu i da vaša imovina ne bude narušena. Odgovornost svake postojeće vlade je da zaštiti ta ljudska prava. Za dalje čitanje, pogledajte libertarijanizam.
Zasluživanje
Vraćajući se na „zasluživanje“ – ovo je ljudski konstrukt, zasnovan na dobru i zlu: „Dobri ljudi zaslužuju dobre stvari, a loši ljudi zaslužuju kaznu.“
U stvarnosti, međutim, loše stvari se dešavaju dobrim ljudima, a dobre stvari se dešavaju lošim ljudima. Mnogima je teško da to prihvate.
Koristeći logiku, i dalje može imati savršenog smisla zašto ljudi ne dobijaju uvek ono što zaslužuju – jer priroda ne dodeljuje nagrade savršeno na osnovu ljudskih konstrukata dobra i zla.
Čovek je taj koji pokušava da nadgleda ravnotežu između posledica i morala. Ljudi zamišljaju kako stvari treba izgledaju ali što više budu obraćali pažnju na prirodu, to će više biti razočarani stvarnošću.
Umesto toga, u prirodi postoje uzrok i posledica. Postoji određena predvidljivost ali takođe postoji i izvesna slučajnost, sviđalo se to nama ili ne. Mnogima se to ne sviđa.
Ne shvatite ovo kao poziv na ukidanje nagrađivanja i kažnjavanja u društvu. Ono što razmatram je da nije moguće da čovečanstvo uspešno nadgleda celokupnu prirodu na osnovu onoga što je zasluženo (koristeći moralnu definiciju „zasluživanja“). Pretpostavljam da bi visoko napredna autoritarna država mogla pokušati.
Pravična raspodela novog novca
Da bismo odlučili kako bi distribucija Bitkoina trebalo da izgleda u idealnom svetu, najpre razmotrimo šta je poželjno I moguće za novi novac, a zatim možemo videti koliko je Bitkoinov dizajn to veličanstveno postigao:
Kreiraćemo hipotetički novi novac. Dajmo mu neke neupitne karakteristike relevantne za ovu diskusiju (ovo nije potpuna lista):
- Novac će biti digitalan.
- Jer fizički novac, zlato, nije uspeo.
-
U globalnom društvu, sa bilo kojim fizičkim novcem (nedigitalnim), potrebne su treće strane (za digitalizaciju fizičkog novca i omogućavanje plaćanja na daljinu), što dovodi do razvoja fiat novca.
-
Novac će biti rođen na slobodnom tržištu.
-
Odnosno, vrednost nije nametnuta zakonom. Setimo se da je Bitkoin izmišljen da odvoji novac od države.
-
Niko ne kontroliše njegovo izdavanje niti može promeniti ponudu novca.
-
Pristup ovom novcu dostupan je svima.
-
U razumnim granicama – ne treba novoj monetarnoj jedinici nametati teret rešavanja svakog zamislivog problema u svetu
-
Zavisnost od država ili banaka za čuvanje novca u ime pojedinaca neće postojati, iako je to dozvoljeno i opcionalno.
- Ako je to obavezno, ponovo ćemo završiti sa fiat novcem.
Sada moramo distribuirati ovaj novac koji smo upravo stvorili. Kako to učiniti što je „pravičnije“ moguće? Hajde da pokušamo da damo svakom čoveku na Zemlji jednak deo, kao jedan razuman pokušaj „pravičnosti“.
Da bi to bilo izvodljivo, svaki čovek mora biti u nekoj bazi podataka – pretpostavimo da to imamo. Možda moramo prihvatiti da će neki ljudi naći način da budu višestruko upisani u toj bazi i tako prevare sistem ali zamislimo da pronađemo način da to uglavnom sprečimo.
Sada moramo dodeliti sredstva tako da svaka osoba ima privatni ključ za svoja sredstva i niko drugi – to je suština digitalnog vlasništva. Ko god ima privatni ključ ima moć da troši sredstva i time poseduje novac. Dakle, svaki čovek mora biti jedina osoba koja ima pristup svojim privatnim ključevima (uz neke izuzetke kada je u pitanju pomoć od strane pouzdanih članova porodice). Pretpostavimo da postoji neko novo tehnološko otkriće koje to nekako čini izvodljivim i lakim za sve, bez potrebe za centralnom institucijom poput banke koja bi obezbedila sigurnost.
Veoma važno i gotovo neostvarivo – svi koji imaju privatni ključ treba da ga zaštite – odnosno, ne smeju ga izgubiti, trebalo bi da znaju njegovu važnost i da im ne bude ukraden (katastrofe sa privatnim ključevima dogodile su se mnogim ranim korisnicima Bitkoina) ili da ne budu prevareni da ga poklone ili prodaju jeftino.
Za sada nam dobro ide ali uz neke optimistične pretpostavke.
Zamislimo da nekim čudom možemo efikasno preneti informacije o novim novčićima i privatnim ključevima svim ljudima na Zemlji bez obzira na njihove okolnosti (u razumnim granicama). Naravno, oni bi na početku imali NULTU vrednost (jer su besplatno stvoreni i nemaju drugu upotrebu osim kao novac).
Setimo se, kao što je navedeno u početnim uslovima, ovde nema autoritativne vlasti i ne možemo prisiliti ljude da vrednuju ovaj novac i koriste ga, kao što države koriste silu za fiat novac. Ovde je svrha oslobađanje od fiat novca.
Čestitamo, sada imamo hipotetičku alternativu Bitkoinu koja je RAVNOMERNO raspoređena svakom čoveku na Zemlji i svaki čovek ima kontrolu nad svojim novcem. Da li je ovo bolje od lansiranja/distribucije Bitkoina u januaru 2009. godine? Da li je ovo rešilo problem jednake raspodele?
Još uvek ne, a razlog je što smo distribuirali nešto što je bezvredno.
Potrebna nam je još jedna stvar – svi moraju ISTOVREMENO vrednovati novostečeni novac KAO NOVAC i prihvatati/trošiti ga na otprilike istoj vrednosti. Očigledno, ovo nije moguće u slobodnom društvu.
Ovo je veoma važno - „slobodno društvo“. Moramo dozvoliti ljudima da rade šta žele sa ovim novoraspoređenim novcem. Šta će se desiti? Neki ljudi će ga visoko vrednovati, a neki neće – ljudi koji ga visoko vrednuju kupiće ga od onih koji ga ne vrednuju. I šta nam onda ostaje? Mali deo sveta koji veruje u ovaj novac i sada poseduje većinu ponude.
Čekajte, zar nije upravo to slučaj sa Bitkoinom? Zar se ljudi nisu baš zbog toga žalili?
Kada je Bitkoin u pitanju, većina nas je imala otprilike jednak pristup početnim novčićima. Svi su mogli da rudare, a novčići su u početku bili gotovo bezvredni. Rani korisnici su trgovali troškovima električne struje, svojim vremenom i trudom u zamenu za novoizrudarene bitkoine.
Ne, Satoši nije „unapred“ rudario (eng. pre-mine), on JESTE RUDARIO zajedno sa svima ostalima (počevši od 3. januara 2009.) dva meseca nakon najave novog sistema (31. oktobra 2008.).
Nije postojalo znanje da će Bitkoin sigurno imati neku vrednost. Rani rudari su zaradili svoj deo bitkoina jer su posedovali predviđanje o njegovoj budućoj vrednost i preuzeli su RIZIK sa svojim resursima, vremenom i trudom. Vi i ja, mi smo to ignorisali. Smejali smo se tome. Nadali smo se da će propasti. „Zaslužili“ smo da propustimo priliku.
Postoji izreka među Bitkoinerima: „Svi će kupiti bitkoin po ceni koju zaslužuju.“
Zašto smo pogrešili i šta se desilo da vremenom dobije na vrednosti? Činjenica da su mu neki ljudi, rani korisnici, DAVALI vrednost (vrednost je subjektivna ljudska odluka), a zatim su se vremenom pridružili i drugi. Rani korisnici su bili u pravu što su verovali da će ga drugi kasnije vrednovati nakon što su oni preuzeli rizike, a Bitkoin nije propao. Što kasnije ulazite u Bitkoin, to je rizik manji, a cena koju plaćate za njegovo sticanje je viša – ovo je prikladno.
Zbog neizvesnosti, mnogi ljudi nisu rudarili, niti su odvojili vreme da ozbiljno razmotre ili kupe bitkoin kada su imali priliku. To bi bio slučaj sa BILO KOJIM novostvorenim novcem, čak i ako je ravnomerno raspoređen.
Drugim rečima, ponuditi ravnomernu raspodelu od samog početka je suštinski isto kao i ponuditi podjednake šanse za sticanje bitkoina.
Kao što sam rekao na početku:
Ako imamo novac rođen na slobodnom tržištu, u slobodnom društvu, koji treba da zameni fiat novac – onda on ne može biti ravnomerno raspodeljen od početka, a da ga svi ljudi istovremeno vrednuju. Neminovno mora proći kroz period kada ga samo nekolicina ljudi vrednuje.
Satoši je odlično obavio posao dizajnirajući protokol tako da se izdavanje odvija tokom vremena. Može se raspravljati o tome da li je mogao učiniti izdavanje malo drugačijim ali on/ona/oni je samo čovek (verovatno), tako da imamo ono što imamo i to se sada ne može promeniti.
U početku su rudari bili nagrađivani sa 50 novčića svakih 10 minuta (svaki blok), a ovaj iznos se prepolovljava svakih 210.000 blokova (otprilike svake 4 godine). Trenutno je nagrada za svaki blok 6.25 bitkoina, a izdato je 19.5 miliona od 21 milion novčića. U 2024. godini nagrada će biti prepolovljena na 3.125 bitkoina svakih 10 minuta.
Pored pružanja jednakih prilika tokom raspodele novčića, Satošijev dizajn postepene distribucije takođe jača kvalitet novca i njegov potencijal za uspeh. U sledećem odeljku ću diskutovati o tome kako distribucija utiče na kvalitet novca.
Idealna distribucija novca na slobodnom tržištu
Ostavljajući po strani pravičnost i moral, želeo bih ovde da iznesem argument da raspodela ne-fiat novca kroz populaciju predstavlja promenljivu koja utiče na kvalitet novca.
Da su svi bitkoini bili dostupni od samog početka, onda bi veoma mali broj ljudi posedovao celokupnu ponudu. To bi zapravo dovelo do rizika od neuspeha Bitkoina jer, da bi novac bio koristan, mora biti široko distribuiran. Jedna od funkcija rudarenja bila je distribucija novčića – Satošijev dizajn je osigurao da distribucija bude dovoljna kako bi novac vremenom stekao vrednost, što bi zatim omogućilo trošenje i dalju distribuciju.
Razmišljanje o ekstremima pomaže. Zamislite da jedna osoba poseduje celokupnu ponudu svetskog novca. U tom slučaju, da li bi ta jedinica imala ikakvu vrednost kao novac? Tvrdim bi da bi imala nultu monetarnu vrednost ali, u zavisnosti od toga šta je, mogla bi imati neku robnu vrednost (neki ljudi kažu „intrinzična vrednost“ kada zapravo misle na robnu vrednost ili nemonetarnu vrednost. Dublja diskusija o ovome može se pronaći ovde).
Možda već znate kako novac evoluira iz stanja trampe, što je detaljno objašnjeno ovde, a ukratko je sledeće: U društvu zasnovanom na trampi, potencijalno monetarno dobro inicijalno ima vrednost zbog svoje nemonetarne upotrebe (nemonetarna vrednost), pa počinje sa monetarnom premijom koja je jednaka nuli. Ako ga poseduje dovoljan broj ljudi, postaje praktično koristiti ga kao sredstvo razmene kako bi se prevazišla ograničenja trampe, čime se povećava trgovina, smanjuje rizik specijalizacije i povećava prosperitet tog društva. Kako ovaj tip razmene postaje sve rasprostranjeniji, jedinica postaje poželjnija, što povećava vrednost iznad robne vrednosti. Ova dodatna vrednost je monetarna premija. Monetarna premija zatim uzrokuje da više ljudi poseduje jedinicu i putem pozitivne povratne sprege, ona na kraju postaje univerzalno prihvaćena, što dovodi do toga da monetarna premija dostigne pun potencijal – tj. potpuno usvojena kao novac.
Vraćajući se na hipotetičku situaciju u kojoj jedna osoba drži sav raspoloživi novac na svetu – to predstavlja suprotnost celokupnom procesu gde se monetarna premija razvila iz trampe. Ako se proces potpuno obrne, završavamo na početnom stanju gde jedinica ima nultu monetarnu premiju.
Uporedite to sa suprotnim ekstremom – šta ako svi na svetu poseduju ovaj novac u podjednakoj meri? U tom slučaju, imali biste maksimalno poverenje da će jedinica biti prihvaćena u trgovini.
Sada razmotrimo sredinu između dva ekstrema – ako postoji populacija ljudi koja uopšte ne poseduje ovaj novac, vaša sigurnost u to gde i kod koga možete potrošiti svoj novac u budućnosti bila bi niža – pa je stoga i kvalitet novca niži. Vidim da bi mogao da postoji kontinuum ali u nekom trenutku raspodela će biti dovoljna da novac funkcioniše dobro, a svaka dalja promena ka ravnomernijoj distribuciji imaće zanemarljiv efekat.
Nakon što sam ovo shvatio, postavio sam pitanje: da li je zaista distribucija novca ono što je ovde važno, ili je to prihvatanje tog novca kao sredstva plaćanja, tj. potražnja? Zaključio sam da su one blisko povezane.
Čini se intuitivnim da ako jedna osoba ima sav novac na svetu, više ljudi bi odbilo tu jedinicu kao novac, bilo zato što bi se bunili protiv nejednakosti bogatstva, bilo zato što ne bi bili sigurni da li će je drugi prihvatiti. A ako svi poseduju deo novca, intuitivno je verovati da bi ga više ljudi prihvatilo.
Što se tiče Bitkoina, distribucija je počela sa jednom osobom koja je držala celokupnu raspoloživu ponudu. To se dogodilo u prvom bloku, 3. januara 2009. kada je Satoši izrudario prvi blok i bio nagrađen sa 50 bitkoina. U to vreme nije mogao dobiti više bitkoina zbog pravila protokola – morao je nastaviti da rudari i akumulira novčiće tokom vremena.
U prvim danima, samo su Satoši i Hal Fini rudarili. Zatim su se pridružili drugi i sada je to svetski fenomen. Postepeno izdavanje novih novčića značajno je pomoglo distribuciji. Kako su novi novčići izdavani tokom vremena, oni koji su kasnije ušli još uvek su mogli da se takmiče sa ranijim korisnicima.
Trinaest godina kasnije, većina digitalnih kovanica (oko 19,5 miliona od 21 milion) distribuirana je rudarenjem.
"Zar najbogatiji Bitkoineri neće samo gomilati novčiće i kontrolisati mrežu da bi uvećali svoje bogatstvo što bi dovelo do smanjene distribucije?
Shvatio sam da ono što je važno nije široka distribucija, već široka potražnja. To će povećati cenu i podstaći rane korisnike da oslobode (potroše) deo svojih novčića kako bi poboljšali kvalitet svog života i to je prirodno; na ovaj način, vlasništvo nad bitkoinima postaje ravnomernije raspoređeno tokom vremena, a sa ovom raspodelom njegova vrednost kao novca raste, što dodatno pomaže potražnji, što dalje pomaže ranim usvojiteljima da potroše novčiće.
Veoma važna razlika u poređenju sa fiat novcem je da oni sa najviše novca nemaju nepošten uticaj u cilju povećanja svog bogatstva. Šanse su jednake. U fiat sistemu, oni koji su najbogatiji prvi imaju pristup štampariji novca (npr. bailout-ovi, državne subvencije velikim kompanijama koje formiraju monopole ili pristup jeftinom kreditu koji je zapravo oblik štampanja novca) i oni troše taj novac u ekonomiji pre nego što cene porastu kako bi se prilagodile povećanju ponude novca (Kantiljonov efekat).
Kod Bitkoina nema štampanja novca. Oni sa najvećim bitkoin bogatstvom uživaju u tom bogatstvu trošeći ga onima koji rade za njega (kada bitkoin postane univerzalno prihvaćen kao novac), omogućavajući veću distribuciju.
Naravno, najbogatiji Bitkoineri mogu povećati svoje bogatstvo ali to će biti učinjeno razmenom nečega vrednog sa onima koji im plaćaju bitkoinom (tj. dobrovoljna razmena), nasuprot suštinskoj „krađi“ kao što je slučaj kod Kantiljonovog efekta.
U slobodnom svetu, ako bogati Bitkoiner pruža uslugu, a siromašni Bitkoiner mu plati, OBOJICA poboljšavaju svoju situaciju. Bogati Bitkoiner je zaradio više bitkoina, a siromašni Bitkoiner je, razmotrivši prednosti i nedostatke, odlučio da će njegov/njen život biti bolji trošenjem nešto bitkoina. Ne izmišljam ovde ništa, ovo je osnovno učenje austrijske ekonomske škole i prilično intuitivno.
Ali pogledaj, gotovo niko ne troši. Kako Bitkoin može biti novac? Novac mora da se troši
O ovome sam već pisao ali vredi ponoviti ovde jer sam siguran da će ovo pitanje iskrsnuti kada se razmatra distribucija novčića.
Pomalo je zbunjujuće jer da bi žeton/jedinica bila novac, mora se koristiti kao novac. To je drugačije od jezika – jezik je i dalje jezik čak i ako ga niko ne govori.
Da bi jedinica postala novac, ne samo da mora imati TEHNIČKE osobine novca (retkost, deljivost, prepoznatljivost, prenosivost, zamenjivost, itd.), već mora imati i DRUŠTVENE osobine – tj. mrežu ljudi koji ga vrednuju kao novac - na veoma sličan način kao što je jeziku potrebno da poseduje određene tehničke osobine (zvuci, simboli i pravila) da bi bio koristan ali i mrežu ljudi koji komuniciraju njime.
Sada kada je ovo razjašnjeno, razmotrimo Bitkoin. On ima odlične tehničke monetarne osobine ali ga nedovoljno ljudi koristi kao novac. To bi trebalo da vas navede da zaključite da on nije dobar novac u celini – ALI, to ne znači da neće postati dobar novac. Bitkoineri veruju da hoće i zato ga i prihvataju čekajući da ostatak sveta uhvati priključak.
Samo zato što možete čuti neke Bitkoinere koji promovišu Bitkoin kao novac, to ne znači da greše i da će Bitkoin zato propasti. Oni se pozivaju na superiorne tehničke osobine Bitkoina kao novca. Njihovi protivnici se raspravljaju koristeći drugačiju definiciju, žaleći se da se Bitkoin ne koristi kao novac.
Zaključak
Objasnio sam da se distribucija Bitkoina razvija otprilike onako kako bi se razvijala distribucija bilo kog novca na slobodnom tržištu i da je očekivanje ravnomerne raspodele nerealno. Priroda novca je takva kakva je, nekima se to možda ne sviđa ali to ne daje valjanost argumentu da bi od Bitkoina trebalo odustati i vratiti se novcu koji se nalazi pod neposrednom kontrolom određenih ljudi (altkoini ili fiat).
Dalje čitanje
https://www.danheld.com/blog/2019/1/6/bitcoins-distribution-was-fair
Bakšiš
Statička Lightning adresa: dandysack84@walletofsatoshi.com
-
 @ b1ddb4d7:471244e7
2025-06-07 12:01:52
@ b1ddb4d7:471244e7
2025-06-07 12:01:52Breez, a leader in Lightning Network infrastructure, and Spark, a bitcoin-native Layer 2 (L2) platform, today announced a groundbreaking collaboration to empower developers with tools to seamlessly integrate self-custodial bitcoin payments into everyday applications.
The partnership introduces a new implementation of the Breez SDK built on Spark’s bitcoin-native infrastructure, accelerating the evolution of bitcoin from “digital gold” to a global, permissionless currency.
The Breez SDK is expanding

We’re joining forces with @buildonspark to release a new nodeless implementation of the Breez SDK — giving developers the tools they need to bring Bitcoin payments to everyday apps.
Bitcoin-Native
Powered by Spark’s…— Breez
 (@Breez_Tech) May 22, 2025
(@Breez_Tech) May 22, 2025A Bitcoin-Native Leap for Developers
The updated Breez SDK leverages Spark’s L2 architecture to deliver a frictionless, bitcoin-native experience for developers.
Key features include:
- Universal Compatibility: Bindings for all major programming languages and frameworks.
- LNURL & Lightning Address Support: Streamlined integration for peer-to-peer transactions.
- Real-Time Interaction: Instant mobile notifications for payment confirmations.
- No External Reliance: Built directly on bitcoin via Spark, eliminating bridges or third-party consensus.
This implementation unlocks use cases such as streaming content payments, social app monetization, in-game currencies, cross-border remittances, and AI micro-settlements—all powered by Bitcoin’s decentralized network.
Quotes from Leadership
Roy Sheinfeld, CEO of Breez:
“Developers are critical to bringing bitcoin into daily life. By building the Breez SDK on Spark’s revolutionary architecture, we’re giving builders a bitcoin-native toolkit to strengthen Lightning as the universal language of bitcoin payments.”Kevin Hurley, Creator of Spark:
“This collaboration sets the standard for global peer-to-peer transactions. Fast, open, and embedded in everyday apps—this is bitcoin’s future. Together, we’re equipping developers to create next-generation payment experiences.”David Marcus, Co-Founder and CEO of Lightspark:
“We’re thrilled to see developers harness Spark’s potential. This partnership marks an exciting milestone for the ecosystem.”Collaboration Details
As part of the agreement, Breez will operate as a Spark Service Provider (SSP), joining Lightspark in facilitating payments and expanding Spark’s ecosystem. Technical specifications for the SDK will be released later this year, with the full implementation slated for launch in 2025.About Breez
Breez pioneers Lightning Network solutions, enabling developers to embed self-custodial bitcoin payments into apps. Its SDK powers seamless, secure, and decentralized financial interactions.About Spark
Spark is a bitcoin-native Layer 2 infrastructure designed for payments and settlement, allowing developers to build directly on Bitcoin’s base layer without compromises. -
 @ 8bad92c3:ca714aa5
2025-06-07 11:01:49
@ 8bad92c3:ca714aa5
2025-06-07 11:01:49Marty's Bent

If you do one thing today, take the time to spend an hour to watch this YouTube video. As someone creating content who has become very cognizant of the effects of the algorithm and the pressures to cater to it, this video was unexpectedly and incredibly satisfying. We're coming up on the eight year anniversary of this newsletter and the podcast that accompanies it and over that eight year period, the pressures to compete in the world of ever increasing digital soy slop grow at an accelerating rate.
If you've seen our YouTube channel recently, you'll probably notice that we've bent the knee to the thumbnail and title clickbait game in an attempt to get our content out to a wider audience. This is something I've held out on for many years now at this point, but recently became convinced that it's something we simply have to do if we want to get our message out to a wider audience. As I write this, I'm thinking that maybe the fact that we have to do that in the first place says something about the content we're putting out there and whether or not it is actually valuable. But I do think the high velocity trash economy becoming completely saturated with digital soy slop has made it so people who truly want to get their message out have to play that game.
I want to make one thing clear. I certainly do not think I'm an artist, but I do like to think that over the last eight years we've been putting out information via content mediums that is valuable to you, dear reader. However, the informational content we put out there, particularly the audio and video content, is put on platforms where it is forced to compete with others who cater to the lowest common denominators of dopamine hijacking and in-group signaling that draws the masses like moths to a flame.
If you haven't watched the YouTube video yet, which I'm assuming 99.9% of you haven't, this may seem like a nonsensical ramble. So, I'll keep this one short and urge you to go watch the social commentary from comedian Jarrett Moore about the state of art, "content" and its effect on culture as it stands today. I'm assuming this isn't too much of a spoiler alert, but the situation is pretty dire. The world needs better art and people who are willing to support artists who are truly creative and take risks. This has nothing to do with bitcoin. But I think it highlights an interesting part of our society that is deteriorating at a rapid clip. And it's something that all of us should feel compelled to attend to lest we speed run into Idiocracy.
It made me feel uneasy about parts of my approach to this business, and that's a good thing.
Don't forget to buy a Bitkey!
Iran's Nuclear Ambitions Create a "Never-Ending Crisis"
In our latest discussion, energy expert Dr. Anas Alhajji described what he called Iran's "never-ending crisis" – a thesis he first published over 20 years ago that has proven remarkably accurate. As Alhajji explained, this crisis persists because of a fundamental contradiction: the U.S. sees any Iranian nuclear program (even peaceful) as strengthening a hostile regime, while Iran views nuclear energy as essential for domestic stability and economic survival.
"Iran is not going to negotiate over the bomb. They want to drag everything for the longest period until they get the bomb." - Dr. Anas Alhajji
What's particularly concerning is Iran's resilience against sanctions. Alhajji detailed how Iran has masterfully circumvented oil export restrictions through China, using a dedicated Chinese bank to process payments outside the international system. Iran's leadership appears willing to endure temporary geopolitical losses in Syria, Lebanon, and potentially Yemen, calculating that obtaining nuclear weapons will fundamentally transform regional politics and their treatment by the United States.
Check out the full podcast here for more on Trump's Middle East strategy, the future of BRICS, and critical challenges facing global energy infrastructure.
Headlines of the Day
Standard Chartered Predicts Bitcoin Will Reach $500K by 2028 - via X
Lummis: Genius Act Makes US Leader in Digital Asset Policy - via X
Get our new STACK SATS hat - via tftcmerch.io
Jake Tapper's Admission on Biden's Decline Sparks Media Ethics Debate - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
My oldest is already at the "faking sick to get out of school" stage and I'm extremely proud.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 9ca447d2:fbf5a36d
2025-06-07 11:01:31
@ 9ca447d2:fbf5a36d
2025-06-07 11:01:31LAS VEGAS, May 28 2025 — Blockstream, the global leader in Bitcoin-powered financial infrastructure, has today revealed its strategic vision to support Bitcoin’s next pivotal phase of growth, building on over a decade of pioneering work at the forefront of Bitcoin innovation.
Unveiled in a keynote by Blockstream Co-Founder and CEO Dr. Adam Back at Bitcoin 2025 in Las Vegas and anchored by a bold new tagline, The Future of Finance Runs on Bitcoin, the vision introduces a clear framework based on three core business units—Consumer, Enterprise and Blockstream Asset Management (BAM).
This framework represents a unified approach to onboarding users across the rapidly growing Bitcoin economy, from individuals to institutions.
“The past year has shown clearly that Bitcoin no longer sits on the margins of the global financial system—it is rapidly becoming the foundation,” said Dr. Back.
“Our vision is simple: The Future of Finance Runs on Bitcoin. Guided by this idea, Blockstream is working hard to build the vertically integrated platform to support that transition, from individual self-custody to enterprise-scale asset issuance and regulated investment products.”
A New Era for Bitcoin-Native Finance
According to crypto ETF analytics platform SoSoValue, Bitcoin has attracted over $41 billion in net ETF inflows alone since the launch of U.S. spot ETFs in early 2024, led by major institutions such as BlackRock, Fidelity, and Franklin Templeton.
At the same time, New Hampshire and Arizona have become the first U.S. states to pursue Strategic Bitcoin Reserves and the number of corporate treasuries holding bitcoin continues to climb.
With a market cap of just over $2 trillion and trillions settled annually on-chain, Bitcoin’s role as a legitimate financial layer is becoming increasingly clear, hastening the need for scalable infrastructure.
Blockstream has been building that infrastructure for over a decade.
Founded in 2014 by Dr. Adam Back—inventor of Bitcoin’s proof-of-work (PoW) mechanism—the company has focused from the outset on expanding Bitcoin’s functionality without compromising its foundational principles.
Blockstream Research, led by renowned cryptographer Andrew Poelstra, is a key contributor to Bitcoin Core and drives advances in applied cryptography and protocol development.
On the product side, Blockstream maintains Core Lightning (CLN) for scalable payments, the Liquid Network and Blocksteam Asset Management Platform (AMP) for tokenized asset issuance and settlement, as well as self-custody tools including the open-source Jade hardware wallet.
The All-New Blockstream App—Self Custody on Your Terms
Headlining today’s keynote was the launch of the all-new Blockstream app—a streamlined, self-custodial experience that lets users buy bitcoin and secure it immediately in their own wallet.
Built on the foundation of the trusted Blockstream Green wallet, the updated app offers seamless support for managing bitcoin and Liquid assets within a redesigned interface tailored to both new and experienced users.
The Blockstream app is designed to make onboarding intuitive from day one, minimizing friction while staying true to the principles of self-custody.
Users can begin simply and gradually adopt more advanced features at their own pace—including hardware signing and air-gapped transactions with the Blockstream Jade.
Current Blockstream Green users will find all existing functionality preserved within the redesigned interface.
With support for 31 languages, the app makes Bitcoin accessible to anyone with a smartphone, opening the door to secure, sovereign finance worldwide
“The new Blockstream app isn’t just a wallet,” said Peter Bain, VP of Consumer Products at Blockstream.
“It’s a gateway to the full power of Bitcoin—enabling secure savings, fast payments, and seamless management of tokenized assets, all within an intuitive interface designed for both newcomers and hardcore bitcoiners.”
Blockstream Enterprise: Bitcoin-Native Financial Infrastructure
Dr. Back also used his keynote to highlight the growing importance of Blockstream Enterprise, the company’s evolving platform for corporations, governments and participants across the broader financial sector.
Underpinned by the Liquid Network and Blockstream AMP, the platform enables secure asset issuance, as well as treasury and balance sheet management.
It also facilitates integration with custodians, exchanges and core financial systems via industry-standard FIX and REST APIs.
With the first iteration of AMP already available and additional features rolling out over time, the platform builds on Liquid’s momentum, which recently surpassed $3.27 billion in total value locked (TVL).
In doing so, it provides a Bitcoin-native foundation for tokenization and institutional settlement focused on regulated custody, compliant off-exchange settlement, and programmable financial instruments.
“As capital markets evolve, businesses, institutions, and governments will need infrastructure that is secure, programmable and built directly on Bitcoin’s rapidly growing network,” said Dr. Back.
“Blockstream Enterprise brings that infrastructure together—enabling asset issuance, management, and settlement on Liquid, Bitcoin’s first and most battle-tested sidechain.”
Unifying Consumer, Enterprise, and Institutional Products
Today’s keynote marks a strategic inflection point, aligning Blockstream’s efforts across the three market segments it serves.
In 2024, the company raised $210 million to accelerate development and launched Blockstream Asset Management (BAM), a dedicated division focused on institutional-grade Bitcoin investment products.
The company has also deepened collaborations with regulated custodians, corporate treasuries and financial service providers to support the integration of Liquid and AMP into existing financial infrastructure.
The Future of Finance Runs on Bitcoin
The vision laid out by Dr. Back reflects Blockstream’s conviction that Bitcoin is no longer just a $2 trillion asset class but a settlement layer, a development platform, and the most credible foundation for building the next financial system.
“The financial world is waking up to what we’ve known for years,” said Dr. Back. “Bitcoin is here to stay —and it’s never been easier to build on it.”
“From first-time users to trillion-dollar institutions, our aim is to give everyone the tools to participate in this new economy, with the transparency, security and resilience that only Bitcoin can provide.”
To learn more visit Booth 2121 at Bitcoin 2025 or visit www.blockstream.com.
Download the new Blockstream app today and take control of your bitcoin—on your terms.
Institutions, enterprises, and governments interested in building on Bitcoin with Liquid and AMP can connect with the Blockstream team directly at business@blockstream.com.
Media contact:
Edward Moore – Head of PR, Blockstream
emoore@blockstream.comAbout Blockstream
Founded in 2014, Blockstream is a global leader in Bitcoin and blockchain infrastructure, with offices and team members distributed around the world.
Serving as the technology provider for the Liquid Network, Blockstream offers a sidechain solution that enables secure, trustless Bitcoin swap settlements and robust smart contracts, empowering financial institutions to tokenize assets efficiently.
The company’s Core Lightning is a leading implementation of the open Lightning Network protocol, widely adopted for enterprise Bitcoin Lightning Network deployments.
Blockstream Jade, an open-source hardware wallet, delivers advanced security for Bitcoin and Liquid assets in an easy-to-use form factor.
For consumers, Blockstream app is a highly secure and user-friendly Bitcoin wallet.
Disclaimer
This press release contains forward-looking statements, including but not limited to statements regarding the expected launch timeline of the Blockstream Enterprise platform and time to market of Blockstream Asset Management products.
Other “forward looking statements” may, without limitation, include statements that are preceded by, followed by, or include the words “believes,” “expects,” “anticipates,” “intends,” “plans,” “estimates,” “foresees,” or similar expressions, and other statements concerning anticipated future events and expectations that are not historical facts.
_Actual results may differ materially due to regulatory developments, competition from other hardware and technology services providers (in the case of Jade and the app) and both traditional finance and crypto native managers (in the case of BAM), market conditions and other risks. Actual results may differ materially. Blockstream undertakes no oblig
-
 @ 6a6be47b:3e74e3e1
2025-06-07 09:28:14
@ 6a6be47b:3e74e3e1
2025-06-07 09:28:14Hi frens! 📕
How are you today? How’s your weekend going? I hope you’ve found a moment to rest and recharge—even just for a few minutes. If you’re on the hunt for your next great read, I’ve got something exciting to share!
I just found out that the new book from Robert Galbraith (aka J.K. Rowling) "The Hallmarked Man" has finally been announced! It’s coming out this September, and I’ll admit—I screamed and did a little happy dance. The last book ended on such a major cliffhanger!
🕵️♂️ If you’re not familiar, Robert Galbraith is Rowling’s pen name for her detective series featuring the duo Cormoran Strike and Robin Ellacott. Strike is the founder of their private investigation agency, and Robin, who started as a temp secretary, quickly proved she’s a natural-born detective (and it’s been her dream job for years).
If you’re wondering whether you need to read the earlier books first, I get it. The story of Robin and Strike definitely makes more sense if you start from the beginning, but Rowling is clever—she avoids major spoilers, so you can jump in out of order if you want (like I did!). Just be warned: you’ll get hooked and want to know what happens next.
Each book centers on a new crime for Strike and Robin to solve, so you’re pulled into the mystery first—and then deeper into their lives. That’s part of what makes the series so addictive.
📖 Why am I so hyped for the new release? The last book, The Running Grave, was a wild ride: tense, heart-wrenching, and impossible to put down. I was on the edge of my seat the whole time! For me, it’s the best in the series so far. By the end, I was fully invested in all the characters—even the secondary ones. I just had to know what would happen to them.
Of course, not everyone is a fan of Rowling’s style, and some say her books could use a bit of editing. But I think she weaves tension, character development, and mystery together brilliantly. To each their own, though!
❤️ I have really high hopes for the next book this fall. If you love mysteries with complex characters and dark twists, I hope you’ll give this series a shot. Sometimes the truth is even darker than you expect!
Let me know what you think if you’ve read them—or if you’re planning to start.
🌟 Enjoy your weekend and godspeed!
https://stacker.news/items/999611
-
 @ 57d1a264:69f1fee1
2025-06-07 06:08:19
@ 57d1a264:69f1fee1
2025-06-07 06:08:19In the rural areas of Vietnam, people tend to give the land plot next to their house to their grown up children to build a new home – thus a new family. This poses many interesting problems about the two generation’s living spaces. In the case of Ai Nghia House, we pay close attention to the connection and privacy between the two families.
The skylit courtyard
Learning from the structure of traditional houses in Hoi An, we create a courtyard in the middle of the house, connecting the parents’ house and the children’s new house. The courtyard plays its role as a funnel collecting sunlight and natural wind, also, it’s a place for sharing daily stories, common or private. It’s a place where parents watch over the house and the kids, where families pass over a little spice in cooking time, or simply a place where the sky is only one perk away. The courtyard is thus shared naturally between the families as a continuation between generations.
The framed garden
The front garden is framed into a red brick facade, making the greenery stand out. Voids are boldly cut to allow sunlight to reach the plants, making the garden comes to life. Altogether that frame becomes a lively picture of nature and many daily moments of each member in the family.
Read more about Naqi & Partners at https://naqipartners.com/project/ai-nghia-house-quang-nam/
https://stacker.news/items/999526
-
 @ 57d1a264:69f1fee1
2025-06-07 05:48:57
@ 57d1a264:69f1fee1
2025-06-07 05:48:57There is only one item on my CSS wishlist for 2025: a slower pace!
After years of rapid innovation, now feels like the right time for browser vendors to take a beat to consolidate, fix browser inconsistencies, and let the rest of us catch up.
After all, we might've heard about
subgrid, :has(), scroll-drivenanimations, and all the other recent CSS improvements – but how many of us can say that we've actually used all these features, let alone mastered them?This is why this year's survey will be so interesting. It'll be a chance to see which of the past few year's new CSS additions have already been adopted by the community, and which ones are still on our to-do list.
So once again, please join me for this year's State of CSS!
Take the survey at https://survey.devographics.com/en-US/survey/state-of-css/2025
https://stacker.news/items/999510
-
 @ 044da344:073a8a0e
2025-06-07 07:49:53
@ 044da344:073a8a0e
2025-06-07 07:49:53Es ist merkwürdig, wie sich die Dinge manchmal fügen. Himmelfahrt bin ich mit den beiden größeren Enkeln, 2 und 4, in einen Zirkus gegangen. Wir mussten ein wenig suchen, okay, haben das Zelt aber irgendwann entdeckt am Ufer des Regen. Ich könnte schreiben: klein, aber fein, so richtig trifft es das jedoch nicht. Klein schon. Ich will hier auch nicht schimpfen, weil sich die Zirkusfamilie alle Mühe gegeben hat, einen preisgekrönten Artisten dabeihatte (Silberner Clown in Monte Carlo) und sogar reichlich Tiere in die Manege brachte. Vier Araberpferde, zwei Dromedare, einen Esel und Ziegen.
Dann aber kamen die Katzen. Richtig gelesen. Katzen dort, wo es Tiger, Löwen, Bären gegeben hat, als ich selbst noch ein Kind war. Ich meine gar nicht die großen Zelte in der DDR, Berolina, Busch oder Aeros. Diese Riesen verirrten sich nicht in einen Badeort auf Rügen. Die Wiese gleich hinter unserem Haus gehörte ab Anfang der 1980er Rüdiger Probst, alle paar Jahre wieder. Ein junger Mann, der gar nicht so viel älter war als ich, keine Angst vor großen Tieren hatte und mit einem Salto von Pferd zu Pferd sprang. In einem kleinen Zirkus wie gesagt, für ein paar Groschen und meist vor vollem Haus. Mit den Enkeln hatte ich jetzt allen Platz der Welt und hinterher ein leeres Portemonnaie. Sieben Euro allein für Popcorn (es gab nur eine Tütengröße) und fünf (freiwillig) für ein paar Möhrenstücke, damit die Kinder in der Pause was zum Füttern in der Hand hatten.
Am Abend dann das neue Buch von Matthias Krauß. „Die falschen Fragen gestellt“. Ich habe mich ein wenig gewundert, als das Paket im Kasten lag, weil der Autor vor gar nicht allzu langer Zeit einen „einseitigen Waffenstillstand“ ausgerufen hatte und Schluss machen wollte mit seinem Kampf gegen die „Aufarbeitungsindustrie“ und mit der Verteidigung der DDR. Ich zitiere einfach aus meiner Rezension von 2019:
Matthias Krauß, 1960 in Hennigsdorf geboren, weiß natürlich, was da alles im Argen lag. Er hat selbst an der Sektion Journalistik studiert und in den späten 1980ern noch ein wenig für die Parteipresse gearbeitet. „Apologetisch“, sagt er. Vor allem Innen- und Wirtschaftspolitik. Sein Aber: erstens die Kultur. Begegnungen vor allem mit dem, was in Osteuropa so an Filmen, Serien, Kunst produziert wurde. Punkt zwei: „der einfache Mensch“. „Ungleich häufiger“ im Bild als heute. Und drittens „gab es eine prinzipielle und grundsätzliche Kritik“ am Westen und am Kapitalismus.
Der Zirkus am Ufer des Regen. Ein totes Pferd soll man nicht reiten. Deshalb tauche ich ein in ein Buch, das etwas schafft, was selbst ich nicht für möglich gehalten habe. Matthias Krauß singt ein Loblied auf den DDR-Journalismus, ohne dass es peinlich wird. Er bleibt dabei ganz bei sich – bei der Mappe mit Zeitungsausschnitten, die er als Schüler angelegt hat, bei den Aktbildern im Magazin, das sein Vater abonniert hatte und das dem Sohn auch jenseits der Erotik ganze Welten öffnete, bei einem Porträt, das ihm die Lokalzeitung 1977 widmete.
Das Schöne ist: Matthias Krauß hat das alles aufgehoben und darf jetzt als reifer Mann zurückschauen – als Journalist, der später auch die andere Seite erlebt hat, folglich vergleichen kann und vor allem niemandem mehr nach dem Mund reden muss. Die „Qualität der Bilder“, okay. Eher „Kartoffeldruck“ als Zeitung. Die immer gleichen alten Männer, klar. Die Grenzen, die jedes Parteiorgan hat und die auch ein junger Mann wie Krauß schon zu spüren bekam. Aber eben auch Texte, die nah dran waren am Leben (vor allem an der Arbeit) und ihre Leser ernst nahmen. Matthias Krauß ist nach dem Studium 1986 Redakteur der Jugendseite des Potsdamer SED-Blatts geworden und ruft den Journalismusforschern heute zu: Vergleicht doch einfach die Bravo mit dem Neuen Leben, einer Zeitschrift, die damals sein Leitstern war und immer ausverkauft. These von Matthias Krauß: Das Neue Leben
war vielseitiger, anspruchsvoller und in jeder Hinsicht höherwertiger als die Bravo-Post, mit dem endlos einfältigen Star-Rummel, den auf Kauf und Konsum orientierten Modetipps, dem Klatsch und Abklatsch und den klischeehaften Rollenbildern – Ausdruck des insgesamt unpolitischen Grundanspruchs. Nun gut, aus exakt diesem Grund wird dieser Vergleich wohl niemals stattfinden. (S. 103)
Matthias Krauß hat ein kaum zu schlagendes Argument auf seiner Seite: Er, der SED-Propagandist, hatte nach 1990 schnell wieder das Vertrauen des Publikums, das er „bei Lichte besehen“ vielleicht gar nicht verdiente, aber allein wegen seiner Herkunft bekam (S. 116). Und: Er kann sogar jemanden zitieren, der die Ernte-Berichterstattung vermisst, Hassobjekt von Lesern wie von Journalisten – einen Landwirt aus dem Westen, der dort sehen konnte, wie weit die Kollegen waren, was sie wie machten und wie sie auf das Wetter reagierten (S. 166).
Ich gebe zu: Ich habe eine Schwäche für autobiografische Texte. Solche Bücher erlauben mir, all das mit Leben zu füllen, was in den Akten bald zu Staub zerfällt. Ich habe ein Fußballregal (gleich zweimal Lothar Matthäus!), eine DDR-Abteilung, Erinnerungen von Wissenschaftlern und natürlich Journalisten. Da längst nicht jeder schreibt, der etwas zu sagen hat, helfe ich immer wieder nach und sammle als Interviewer Lebensgeschichten ein. Matthias Krauß dürfte einer der ersten ostdeutschen Medienmenschen aus der Geburtskohorte um 1960 sein, der sich öffentlich äußert und dabei nicht einfach das nachbetet, was ohnehin schon überall steht.
Das gilt auch jenseits des Themas Journalismus. Der Wehrdienst, für mich bis heute ein Albtraum, wird von Matthias Krauß als „Entscheidung für eine Art persönlicher Freiheit“ interpretiert (S. 43). Mit 18 unabhängig sein von den Eltern und dann auch ohne Geldsorgen studieren können. Leipzig war für ihn in den 1980ern nicht nur Uni-Standort, sondern auch „Messestadt“ und damit „Weltstadt“ (S. 50). Und der Aufregung um jede DDR-Exmatrikulation, die er keineswegs schönredet, werden „die Millionen Opfer der Demokratisierung“ gegenübergestellt und das laute gesamtdeutsche Schweigen nicht nur in diesem Punkt (S. 58).
Was das alles mit dem Zirkus zu tun hat? Matthias Krauß hat in der DDR das Motto für sein Leben als Journalist gefunden – bei der Arbeit mit einem Parteisoldaten, der einfach nicht rauswollte aus dem Korsett, das die Genossen über sein Leben geworfen hatten.
Ja, sagte ich mir, stelle immer die falschen Fragen. (S. 153)
In Sachen Zirkus liegen alle Antworten auf dem Tisch. Meine Trauer habe ich schon vor mehr als zehn Jahren verarbeitet. Mal schauen, was die Enkel eines Tages dazu sagen.

Matthias Krauß: Die falschen Fragen gestellt. Journalist in zwei deutschen Staaten. Berlin: Das Neue Berlin 2025, 189 Seiten, 18 Euro.
-
 @ 57d1a264:69f1fee1
2025-06-07 05:38:49
@ 57d1a264:69f1fee1
2025-06-07 05:38:49Every purchase we make ties us to a vast, hidden network of people, machines, and resources — whether we see it or not.
Supply chains are large industrial systems. They are composed of heterogeneous elements, such as ships, aircraft, trains, and trucks, but also systems of labor, information, and finance that build them and connect them together. Usually the goods flow in one direction and money flows in the opposite direction. Their physical substrates are themselves industrial products, relying on ships, trucks, cranes, fossil fuels, and electric power, tied together by skilled human operators, supervisors, managers, and other industrial roles.
Few of us would likely condone every moment of every supply chain for every product we consume.
Consider any product in your home. Where was it made? (That should be written on the label somewhere.) Where were the parts made? Who put them all together? How did it get to your doorstep?
Continue reading at https://thereader.mitpress.mit.edu/supply-chains-are-us/
https://stacker.news/items/999509
-
 @ 57d1a264:69f1fee1
2025-06-07 05:28:26
@ 57d1a264:69f1fee1
2025-06-07 05:28:26In the early days of computer vision, when memory was scarce and every byte counted, innovation thrived under constraint. “An Efficient Chain-Linking Algorithm,” developed at Inria in the late 1980s, is a brilliant example of this spirit. Now preserved and shared by Software Heritage, this compact yet powerful piece of C code showcases how elegance and efficiency went hand in hand in outlining the future of image processing—one pixel chain at a time.
The code resulted from research work carried out between 1985 and 1991 at Inria, by Gérard Giraudon (research and principal investigator), Philippe Garnesson (a PhD student), and Patrick Cipière (software engineer). Down in sunny Sophia Antipolis, a tech park 20 minutes inland from Antibes, the team tackled computer vision with a distinctly local flavor. They called themselves PASTIS, a playful nod to the anise drink. Still, the acronym – Scene Analysis and Symbolic Image Processing Project (Projet d’Analyse de Scène et de Traitement d’Image Symbolique) – hinted at their serious mission.
Continue reading at https://www.softwareheritage.org/2025/06/04/history_computer_vision/
https://stacker.news/items/999507
-
 @ dfa02707:41ca50e3
2025-06-07 14:01:22
@ dfa02707:41ca50e3
2025-06-07 14:01:22
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ da8b7de1:c0164aee
2025-06-07 04:42:05
@ da8b7de1:c0164aee
2025-06-07 04:42:05Nukleáris technológiai és projektfejlesztési hírek
Több jelentős nemzetközi fejlemény történt a nukleáris energia területén. A Westinghouse Electric Company megkapta az amerikai Energiaügyi Minisztériumtól a kulcsfontosságú biztonsági jóváhagyást az eVinci mikroreaktorához, ami fontos lépés ennek az innovatív nukleáris technológiának a bevezetése felé. A vállalat Idaho államban tervezi egy tesztreaktor létesítését, ami jól mutatja, hogy a mikroreaktorok piaca egyre nagyobb lendületet kap.
Eközben a nukleáris kapacitás gyors bővítéséhez szükséges ellátási lánc felkészültsége volt a fő témája a World Nuclear Association első konferenciájának. Jelentős projektfrissítések között szerepel a kritikus turbinakomponensek beszerelése a kínai Haiyang atomerőműben, az indiai Mahi Banswara Rajasthan Atomerőmű négy blokkjára vonatkozó szabályozói engedély, valamint egy új olaszországi partnerség, a Nuclitalia, amely fejlett nukleáris technológiákra fókuszál. Belgiumban a Nukleáris Kutatóközpont hivatalos konzultációkat indított egy ólom-hűtésű kis moduláris reaktor (SMR) ügyében, Brazília pedig bejelentette, hogy Oroszországgal közösen fejleszt SMR-projektet.
Szabályozási és biztonsági aktualitások
A Nemzetközi Atomenergia-ügynökség (IAEA) meghosszabbította a tanulmányok benyújtási határidejét a közelgő, nukleáris létesítmények ellenállóképességéről szóló konferenciájára, hangsúlyozva a nukleáris létesítmények alkalmazkodásának fontosságát a klímaváltozás jelentette növekvő kockázatokhoz. A konferenciát 2025 októberében rendezik Bécsben, és fő témája a nukleáris létesítmények biztonságának és ellenállóképességének növelése lesz, különös tekintettel a külső eseményekre, mint az árvizek és földrengések.
Kanadában a Nukleáris Biztonsági Bizottság engedélyezte az Ontario Power Generation számára, hogy megkezdje egy BWRX-300 típusú reaktor építését a Darlington New Nuclear Project helyszínén, ami a nukleáris építkezések folyamatos szabályozói támogatását mutatja. Az Egyesült Államokban a Nukleáris Szabályozási Bizottság további 20 évvel meghosszabbította a Duke Energy Oconee atomerőművi blokkjainak üzemeltetési engedélyét, valamint támogatást nyújtott a michigani Palisades atomerőmű újraindításához.
Iparági és gazdasági trendek
Az iparági vezetők optimistán nyilatkoztak a nukleáris energia jelenlegi helyzetéről, kiemelve az Egyesült Államokban zajló aktív projekteket (például a TerraPower Wyomingban és az X-energy együttműködése a Dow vállalattal), valamint a fejlett nukleáris üzemanyaggyártásba irányuló magánbefektetések növekedését. Felmerült az is, hogy a Világbank nukleáris projekteket is finanszírozhatna, ami tovább ösztönözhetné a globális beruházásokat, és megerősítené a nukleáris energia szerepét az energetikai átmenetben.
Belgiumban a kormány és az Engie közüzemi vállalat végleges megállapodást kötött a Tihange 3 és Doel 4 reaktorok üzemidejének tíz évvel történő meghosszabbításáról, amely az energiabiztonságot és a radioaktív hulladék kezelését is szolgálja. Németországban a nukleáris technológiai szövetség hangsúlyozta, hogy akár hat, nemrégiben leállított reaktor újraindítása technikailag megvalósítható, és a nukleáris energia biztonságos, gazdaságos, valamint klímabarát alternatívát jelent.
Nemzetközi együttműködés és kutatás
Kanadában a Prodigy Clean Energy és a Serco közel jár a szállítható atomerőművek tesztprogramjának befejezéséhez, amelynek középpontjában a biztonság és az extrém helyzetekben való ellenállóképesség áll. Az EnergySolutions és a WEC Energy Group új nukleáris kapacitás létesítését vizsgálja a wisconsini Kewaunee helyszínen, és előzetes engedélyeket kívánnak szerezni a jövőbeni telepítéshez.
Az IAEA ismételten hangsúlyozta, hogy kész támogatni a Zaporizzsjai Atomerőműre vonatkozó megállapodásokat, amely továbbra is orosz katonai ellenőrzés alatt áll, kiemelve a térségben fennálló geopolitikai és biztonsági kihívásokat.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
ans.org -
 @ dfa02707:41ca50e3
2025-06-07 14:01:20
@ dfa02707:41ca50e3
2025-06-07 14:01:20Contribute to keep No Bullshit Bitcoin news going.
- RoboSats v0.7.7-alpha is now available!
NOTE: "This version of clients is not compatible with older versions of coordinators. Coordinators must upgrade first, make sure you don't upgrade your client while this is marked as pre-release."
- This version brings a new and improved coordinators view with reviews signed both by the robot and the coordinator, adds market price sources in coordinator profiles, shows a correct warning for canceling non-taken orders after a payment attempt, adds Uzbek sum currency, and includes package library updates for coordinators.

Source: RoboSats.
- siggy47 is writing daily RoboSats activity reviews on stacker.news. Check them out here.
- Stay up-to-date with RoboSats on Nostr.
What's new
- New coordinators view (see the picture above).
- Available coordinator reviews signed by both the robot and the coordinator.
- Coordinators now display market price sources in their profiles.

Source: RoboSats.
- Fix for wrong message on cancel button when taking an order. Users are now warned if they try to cancel a non taken order after a payment attempt.
- Uzbek sum currency now available.
- For coordinators: library updates.
- Add docker frontend (#1861).
- Add order review token (#1869).
- Add UZS migration (#1875).
- Fixed tests review (#1878).
- Nostr pubkey for Robot (#1887).
New contributors

Full Changelog: v0.7.6-alpha...v0.7.7-alpha
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-07 02:18:51
@ 5d4b6c8d:8a1c1ee3
2025-06-07 02:18:51This is the place to reflect on how well you met your ~HealthAndFitness goals today.
Where did you succeed? What do you need to keep working on?
I probably didn't get enough sleep and overcompensated with caffeine. Otherwise, today was pretty solid. Other than a big cookie, I ate well and kept it within a decent window. Activity level was good, not great.
I meant to stretch more today, which I didn't really do, but I suppose I can do now.
https://stacker.news/items/999453
-
 @ 523a8281:fc94329a
2025-06-07 05:11:07
@ 523a8281:fc94329a
2025-06-07 05:11:07The Darkest Hour of the GameFi Market and the Glimmer of Hope Amid the prolonged downturn of the cryptocurrency market, the GameFi sector is undergoing an unprecedented trial. According to CoinGecko data, the total market capitalization of the GameFi sector shrank by 35% from its peak in the first half of 2024. DappRadar statistics further confirm the industry's decline—numerous projects have struggled to maintain sustainable economic models, leading to severe user attrition. Although the number of daily active users has grown by 18%, this "volume up, price down" phenomenon reflects the market's painful transition from speculation-driven to value-driven development.
Even more alarming is that 93% of projects in the industry have either stagnated or perished, with the average project lifespan lasting a mere four months. Token prices have fallen more than 95% from their historical highs, extinguishing the enthusiasm of countless investors and players. The once-glorious "Play-to-Earn" and "X to Earn" models collapsed after the profit bubbles burst, exposing the fatal flaws of over-reliance on financial speculation while neglecting the essence of gaming.
However, crises often breed opportunities. The GameFi sector has not been crushed by the bear market but has instead started to clarify its future direction amid the turbulence. This deep market adjustment acts as a brutal filter, leaving only those projects that abandon token speculation, focus on player experience, and build sustainable economic systems to stand out during this industry-wide reshuffle.
- Neo Fantasy: A Game-Changer Breaking the Deadlock Neo Fantasy is not just a blockchain game; it is a gateway to the ACGN metaverse. In the mysterious land of Loren, players become brave adventurers tasked with reclaiming wealth from the forces of darkness. The game seamlessly integrates compelling storylines with cutting-edge blockchain technology, allowing players to immerse themselves in epic adventures while earning significant rewards through diverse gameplay. From the moment players step into the game, they are captivated by its unique charm—whether it's the vividly designed characters or the grand battle scenes, everything reflects Neo Fantasy's relentless pursuit of quality.
Looking back at the development trajectory of the GameFi industry, its collapse was no accident. Many past projects focused entirely on speculative financial incentives, neglecting the refinement of game content and the construction of community ecosystems. Complex and obscure tokenomics and flashy but impractical DeFi concepts attracted attention in the short term but failed to mask the lack of gameplay. Once token rewards diminished, users quickly scattered, leading to the project's rapid decline. This blind pursuit of short-term gains ultimately triggered a full-blown industry crisis, serving as a wake-up call for future projects.
Neo Fantasy has keenly identified these industry pitfalls and introduced a series of innovative measures to break the deadlock:
Enhancing User Experience: The team accurately addressed traditional gamers' aversion to complex blockchain interfaces by developing an independent application that combines the seamless operation of traditional games with the "play-to-earn" features of Web3. New players can easily get started without deep knowledge of blockchain technology. This low-barrier design significantly broadens the user base, attracting many players who were previously deterred by blockchain games.
Community and Market Expansion: Neo Fantasy has demonstrated strong strategic foresight by establishing deep collaborations with renowned platforms like Nextype, quickly amassing a large user base. Moreover, its plan to launch on mainstream app stores such as Google Play and the App Store aims to tap into the billion-user Web2 gaming market. This move will undoubtedly break the barriers of blockchain gaming, allowing more ordinary players to experience Neo Fantasy's unique charm and paving the way for broader growth.
Innovative Gameplay: Sustained innovation in gameplay is key to Neo Fantasy's vitality. The team has abandoned the outdated model of solely relying on token-driven user engagement and continuously introduces new features. PvE dungeons are filled with challenges and surprises, requiring strategic cooperation to overcome; the PvP arena is packed with skilled players, offering intense real-time battles; auto chess combines strategy and luck, making each match unpredictable; and guild tournaments emphasize teamwork, fostering strong bonds among players. Future plans for open-world and virtual-world experiences will further expand the game's boundaries, delivering unprecedented immersive experiences.
Sustainable Tokenomics: The construction of the token economy showcases the team's wisdom and vision. Centered around the ERT token, the system serves as both a governance tool and a utility token. Through a carefully designed economic cycle model, every in-game action—whether upgrading heroes, enhancing equipment, or participating in events—is closely tied to ERT. This design ensures the token's utility while avoiding unsustainable high-yield promises, achieving self-sufficient and healthy economic circulation. Additionally, offering free hero characters to new players lowers the participation barrier, attracting a diverse and loyal community of traditional gamers.
-
Breaking Through the Bear Market: Neo Fantasy's Keys to Success and Industry Insights Under the severe challenges of the bear market, Neo Fantasy's development strategy has pointed the way forward for GameFi projects. Gameplay is the foundation of survival; only with outstanding fun and playability can players truly immerse themselves. A strong community is the cornerstone of development; an active player community not only enhances user retention but also injects continuous vitality into the project. Leveraging mainstream platforms to expand the market is the necessary path to breaking through barriers and achieving large-scale growth. Meanwhile, a sustainable and transparent tokenomics model is the core element to ensure the long-term stability of the project. Continuous innovation is the key to standing out in a fiercely competitive market; only by consistently introducing new features can a project retain players' attention and maintain its competitiveness.
-
Looking Ahead: Concrete Actions to Lead the Next GameFi Revolution While the GameFi sector has suffered significant losses during the bear market, Neo Fantasy's rise offers hope for the industry's recovery. In the future, Neo Fantasy will take a series of practical actions to solidify its strengths and drive industry transformation:
Expanding Community Collaboration and Listening to Players: Neo Fantasy will broaden its community partnerships, working with global gaming forums, blockchain communities, and player groups. By hosting regular online and offline events and conducting surveys, the project will gather feedback on gameplay, economic systems, and social features. These insights will guide targeted improvements to ensure the game aligns with player needs, enhancing satisfaction and loyalty.
Optimizing Game Content for Premium Experiences: Resources will continue to be invested in developing and refining game content. This includes enriching storylines for immersive narratives, fine-tuning PvE dungeon difficulty curves and reward mechanisms, and improving PvP balance and fairness. The development of open-world and virtual-world features will also be accelerated, introducing innovative gameplay and interaction elements to provide players with more opportunities for exploration and creativity.
Strengthening Guild Systems to Promote Ecosystem Prosperity: Neo Fantasy will actively support in-game guild development by offering exclusive benefits and activities such as guild quests and rewards. A guild ranking system will incentivize growth, while cross-game and cross-platform collaborations will encourage interaction among players from different communities, expanding the game's influence and ecosystem.
Expanding the Ecosystem and Exploring New Possibilities: Beyond core gameplay, Neo Fantasy will actively expand its ecosystem. On the technical side, it will accelerate cross-chain compatibility to enable seamless flow of $ERT tokens and game assets across networks, attracting more external resources and users. In content creation, the project will support an ACGN creator program, encouraging community members to produce comics, novels, animations, and other content related to Neo Fantasy, enriching the game's cultural value and building a diverse ecosystem.
By focusing on player experience, community building, and sustainable development, Neo Fantasy has proven that GameFi can thrive even in a bear market. The future belongs to projects that prioritize high-quality gaming content and earn players' trust. Neo Fantasy not only survives but actively positions itself as a leader, driving the next GameFi revolution. For the GameFi industry, abandoning hype and focusing on quality is the key to standing out in a fiercely competitive market. Neo Fantasy is steadfastly walking this path, writing its own legend.
Follow Neo Fantasy on: Twitter: https://x.com/NeoFantasy_Game
Telegram: https://t.me/NeoFantasy2024
Youtube: https://www.youtube.com/@NeoFantasy2024
Medium: https://medium.com/@neofantasy419
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-07 00:40:06
@ 5d4b6c8d:8a1c1ee3
2025-06-07 00:40:06https://youtu.be/YA1Lkl3h9AQ
"...and then, like so many Pacers games, things just happened."
I think that's about as well as any of us understand what's going on.
https://stacker.news/items/999389
-
 @ cae03c48:2a7d6671
2025-06-06 22:00:31
@ cae03c48:2a7d6671
2025-06-06 22:00:31Bitcoin Magazine

President Trump’s Truth Social Files S-1 Form For Bitcoin ETFToday, Trump Media and Technology Group Corp. (Nasdaq, NYSE Texas: DJT) filed with the US Securities and Exchange Commission (SEC) a Form S-1 for their upcoming Truth Social Bitcoin ETF.

The ETF, which will hold bitcoin directly, is designed to track the bitcoin’s price performance.
“Truth Social Bitcoin ETF, B.T. is a Nevada business trust that issues beneficial interests in its net assets,” stated the Form S-1. “The assets of the Trust consist primarily of bitcoin held by a custodian on behalf of the Trust. The Trust seeks to reflect generally the performance of the price of bitcoin.”
The ETF is sponsored by Yorkville America Digital, LLC and will trade under NYSE Arca. The Trust’s assets primarily consist of bitcoin held by Foris DAX Trust Company, LLC, the designated bitcoin custodian. Crypto.com will act as the ETF’s prime execution agent and liquidity provider.
“Shares will be offered to the public from time to time at varying prices that will reflect the price of bitcoin and the trading price of the Shares on New York Stock Exchange Arca, Inc. at the time of the offer,” mentioned the Form S-1.
While the ETF offers investors a regulated avenue for bitcoin exposure, the Trust warned of several risks related to digital assets:
- Loss, theft, or compromise of private keys could result in permanent loss of bitcoin.
- Bitcoin’s reliance on blockchain and Internet technologies makes it vulnerable to disruptions and cyber threats.
- Environmental and regulatory pressures tied to high electricity use in bitcoin mining could impact market stability.
- Potential forks or protocol failures in the Bitcoin Network may lead to volatility and uncertainty in asset value.
Last week, during an interview at the 2025 Bitcoin Conference, Donald Trump Jr. announced that TMTG and Truth Social were forming a Bitcoin treasury with $2.5 billion. “We’re seriously on crypto—we’re seriously on Bitcoin,” said Trump Jr. “We’re in three major deals. I believe we’re at the beginning of what will be the future of finance. And the opportunity is massive.”
The day after that interview, Eric Trump and Donald Trump Jr., joined by American Bitcoin Executive Chairman and Board Member Mike Ho, CEO Matt Prusak, and Altcoin Daily founder Aaron Arnold, discussed the future of Bitcoin.
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric Trump. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric added.
This post President Trump’s Truth Social Files S-1 Form For Bitcoin ETF first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 9ca447d2:fbf5a36d
2025-06-07 14:00:47
@ 9ca447d2:fbf5a36d
2025-06-07 14:00:47CANNES, FRANCE – May 2025 — Bitcoin mining made its mark at the world’s most prestigious film gathering this year as Puerto Rican director and producer Alana Mediavilla introduced her feature documentary Dirty Coin: The Bitcoin Mining Documentary at the Marché du Film during the Cannes Film Festival.
The film puts bitcoin mining at the center of a rising global conversation about energy, technology, and economic freedom.
Dirty Coin is the first feature-length documentary to explore bitcoin mining through immersive, on-the-ground case studies.
From rural towns in the United States to hydro-powered sites in Latin America and the Congo, the film follows miners and communities navigating what may be one of the most misunderstood technologies of our time.
The result is a human-centered look at how bitcoin mining is transforming local economies and energy infrastructure in real ways.
To mark its Cannes debut, Mediavilla and her team hosted a packed industry event that brought together leaders from both film and finance.

Dirty Coin debut ceremony at the Marché du Film
Sponsors Celestial Management, Sangha Renewables, Nordblock, and Paystand.org supported the program, which featured panels on mining, energy use, and decentralized infrastructure.
Attendees had the rare opportunity to engage directly with pioneers in the space. A special session in French led by Seb Gouspillou spotlighted mining efforts in the Congo’s Virunga region.
Dirty Coin builds on Mediavilla’s award-winning short film Stranded, which won over 20 international prizes, including Best Short Documentary at Cannes in 2024.
That success helped lay the foundation for the feature and positioned Mediavilla as one of the boldest new voices in global documentary filmmaking.

Alana Mediavilla speaks at the Marché du Film — Cannes Film Festival
“If we’ve found an industry that can unlock stranded energy and turn it into real power for people—especially in regions with energy poverty—why wouldn’t we look into it?” says Mediavilla. “Our privilege blinds us.
“The same thing we criticize could be the very thing that lifts the developing world to our standard of living. Ignoring that potential is a failure of imagination.”
Much like the decentralized network it explores, Dirty Coin is spreading globally through grassroots momentum.
Local leaders are hosting independent screenings around the world, from Roatán and Berlin to São Paulo and Madrid. Upcoming events include Toronto and Zurich, with more cities joining each month.
Mediavilla, who previously worked in creative leadership roles in the U.S. — including as a producer at Google — returned to Puerto Rico to found Campo Libre, a studio focused on high-caliber, globally relevant storytelling from the Caribbean.
She was also accepted into the Cannes Producers Network, a selective program open only to producers with box office releases in the past four years.
Mediavilla qualified after independently releasing Dirty Coin in theaters across Puerto Rico. Her participation in the network gave her direct access to meetings, insights, and connections with the most active distributors and producers working today.
The film’s next public screening will take place at the Anthem Film Festival in Palm Springs on Saturday, June 14 at 2 PM. Additional screenings and market appearances are planned throughout the year at Bitcoin events and international film platforms.

Dirty Coin at the Cannes Film Festival
Watch the Trailer + Access Press Materials
📂 EPK
🎬 Screener
🌍 Host a Screening
Follow the Movement
Instagram: https://www.instagram.com/dirty_coin_official/
Twitter: https://x.com/DirtyCoinDoc
Website: www.dirtycointhemovie.com -
 @ 3c7dc2c5:805642a8
2025-06-06 21:32:46
@ 3c7dc2c5:805642a8
2025-06-06 21:32:46🧠Quote(s) of the week:
"The real Bitcoin Strategic Reserve is the Bitcoin held in the wallets of individual citizens. A strong nation of citizens who have strong Bitcoin reserves is going to be okay." - Marty Bent https://i.ibb.co/rRNJWsJX/Gr4-W7-ZEXc-AAZ4i-U.jpg
🧡Bitcoin news🧡
"The premise required for the universe to function is the conservation of energy. A person without energy is a ghost. An object without energy is an image. Money without energy is credit." —Michael Saylor https://i.ibb.co/N61ZL8sv/Gr4-Xcwg-XQAI5m-Hz.png
On the 26th of May:
➡️'Bitcoin capital flows could exceed $120B by the end of 2025 and reach $300B in 2026, per Bitwise. U.S. spot Bitcoin ETFs attracted over $36.2B in net inflows during 2024, outperforming expectations and exceeding early SPDR Gold Shares (GLD) performance by 20x.' -Bitcoin News
https://i.ibb.co/TMx3mbV6/Gr3kg-LZW8-AAj-TN3.jpg
➡️Michael Saylor's STRATEGY becomes the first company to hold over 500,000 Bitcoin on its balance sheet. Over the last 64 days, Saylor has purchased approximately 80,000 Bitcoin.
➡️River: '2-3% inflation per year sounds harmless... until you zoom out. Every line on this chart is a reason Bitcoin exists.'
https://i.ibb.co/fYPW6RRh/Gr6-LXts-Ww-AEj4no.jpg
➡️State Street Corporation has bought 1.13 million Strategy₿ $MSTR stocks for 344.78 million dollars at an average price of $304.41 per share in Q1 2025. Their total holdings are 4.98 million shares worth over 1.84 billion dollars.
On the 27th of May:
➡️Cantor Fitzgerald officially launches $2 BILLION Bitcoin-backed lending with first loans, partnering with Anchorage Digital and Copper. - Bloomberg
➡️Trump Media Announces Approximately $2.5 Billion Bitcoin Treasury Deal. Trump Media is following the MSTR playbook. With that amount, you can now buy over 22,500 BTC. TMTG would then enter the list of largest corporate Bitcoin holders in fourth place.
Pledditor: "Trump just sabotaged Cynthia Lummis's BITCOIN ACT by doing this I see no future where Trump buys billions of dollars of bitcoin and then Congress codifies SBR into law. The corruption is just too brazen." Spot on! Considering the brazen corruption so far this actually makes it more likely.
➡️'Jack Dorsey’s Block to launch Bitcoin Lightning Payments on all Square terminals!' -Bitcoin Archive
Jack Dorsey’s Block is launching Bitcoin payments on Square at the Bitcoin Conference. Merchants can choose to hold the BTC or automatically convert it to fiat. The feature will expand to more sellers later this year.
➡️Sminston With: "But yes, I'm sure this cycle has peaked."
'Bitcoin cycles @ power law fit, a la 365-day SMA At ~$110,000/coin today, the 365-dSMA is only touching the trendline; History shows each cycle moving 2-3x higher than this. Have a nice day!'
https://i.ibb.co/gMHhq3FP/Gr9rka-ZXg-AAI5-Ck.jpg
➡️Whales have shifted to net distribution with a score around 0.3, reversing their earlier accumulation pattern during this year's price rallies, according to data from Glassnode.
➡️Fast food giant Steak 'n Shake announced they're saving 50% in processing fees accepting Bitcoin payments '#Bitcoin is faster than credit cards'
➡️BlackRock increases Bitcoin exposure for their own funds. The Strategic Income Opportunities Portfolio now holds 2,123,592 shares of IBIT as of March 31 (worth $99.4M) up from 1,691,143 shares on December 31.
➡️Interesting, so Michael Saylor is refusing to publish on-chain proof of Bitcoin reserves...
If Metaplanet and El Salvador can do proof of reserves, why not Strategy? At the end of the day, it's investors' money that is being used to buy Bitcoin. What am I missing?
Arkham: 'SAYLOR SAID HE WOULD NEVER REVEAL HIS ADDRESSES ... SO WE DID We have identified an additional 70,816 BTC belonging to Strategy, bringing our total identified MSTR BTC holdings to $54.5 Billion. We are the first to identify these holdings publicly. This represents 87.5% of total MSTR holdings (including assets in Fidelity Digital’s omnibus custody).'
https://intel.arkm.com/explorer/entity/microstrategy
Don't Trust, Verify!
On the 28th of May:
➡️GameStop CEO says the company bought 4,700 #Bitcoin because it's better than gold. "It has asymmetric upside."
Parker Lewis: Gamestop bought 4,710 Bitcoin (or 471 billion bitcoins) and the CEO says things like "if the thesis is correct." That is a scary place to be, relying on some thesis. "But, we'll see what happens."
Zero vision, great. This pretty much sums up the Bitcoin conference from last week: a repetitive parroting of Bitcoin fundamentals with zero substance beyond “buy Bitcoin, it’s the future.”
Most of the time these people will do the following thing. Sell low after buying high. Anyway, Gamestop is up 4.20% in pre-market after announcing a purchase of 4,710 Bitcoin. They're now the 13th largest public company holder of BTC in the world.
➡️IMF says "efforts will continue" to prevent El Salvador from acquiring more Bitcoin.
➡️The U.S. Department of Labor has officially reversed its 2022 guidance on Bitcoin and crypto in retirement plans.
➡️ UK MP @EmmaforWycombe writes that the “UK government currently has no plans to adopt a strategic bitcoin reserve.” She believes Bitcoin’s “properties as an asset nonetheless remain inconsistent with the objectives and investment principles that govern the Government's foreign exchange reserves.” The UK government appears dead set on fumbling a bag of 61,000 BTC. HFSP! https://i.ibb.co/1tMHmqKw/Gs-C3-D54-Wc-AAdg0d.jpg
➡️Ryan Gentry: 'The biggest news at @TheBitcoinConf just dropped. @milessuter shared that the c= routing node is earning 9.7% APR on its bitcoin liquidity (which I’d estimate at ~$10M, 50% of its 184 BTC of public capacity). True non-custodial yield based on the utility of bitcoin payments.'
Great response on the matter by Sam Callahan: "Imagine a treasury company with 1,000 BTC earning ~10% annual yield. Sovereign, Bitcoin-native yield without counterparty risk that’s tied to the economic activity of Lightning instead of interest rate policy. At $1M per BTC, that’s $100M in annual recurring revenue."
9.7% REAL yield on a payment network while holding the keys to their BTC the entire time!! Madness! The constant claims that no one uses lightning are ridiculous.
On the 29th of May:
➡️ Investors are selling gold for Bitcoin - Bloomberg Gold ETF outflows: -$2.8 billion Bitcoin ETF inflows: +$9 billion.
➡️'Spanish banking giant Banco Santander looking to make Bitcoin and stablecoins available to retail clients. Santander has 175 million customers worldwide and is the BIGGEST lender in the Eurozone.' - Bitcoin Archive
➡️The U.S. Department of Labor rescinded 2022 guidance discouraging 401(k) plans from including Bitcoin and cryptocurrency, allowing retirement plans to potentially include Bitcoin and other digital assets. If just 1% of the $8 trillion in 401k funds flows into Bitcoin, that’s $80 billion of new demand, and 2x more than what’s flowed into Bitcoin ETFs.
➡️ Blockstream launches the Blockstream App, enabling users to buy Bitcoin directly and store it in a self-custodial wallet, eliminating the need for third-party custodians.
➡️$550 billion DBS bank says Bitcoin mining could help stabilize the grid and reduce emissions.
➡️Tether reveals that it owns over 100,000 Bitcoin & +50 tons of gold.
➡️Paris Saint Germain adopts Bitcoin as a Treasury Reserve asset.
➡️'The supply of BTC held by long-term holders has now increased by OVER 1.4 MILLION in under 3 months! The market's most experienced participants are refusing to sell Bitcoin at these prices, and soon there won't be enough $BTC left for those late to the party...' - Bitcoin Magazine Pro
On the 30th of May:
➡️Joe Consorti:
It was foretold. Should Bitcoin follow global M2 all the way down on this correction, we may see $97,500. May not happen, may see lower, nobody knows. The only certainty is that the global aggregate of fiat denominated in USD will rise, and so too will BTC follow it in time.
https://i.ibb.co/5gpq4c53/Gs-Pp-SWua-MAUwzj-T.jpg
➡️Buy Real Bitcoin, and NOT:
⇒ BTC Companies,
⇒ Wrapped BTC
⇒ BTC IOU's
⇒ ...
Bitcoin in self-custody is the only way you get all the benefits of BTC.
https://i.ibb.co/0pZgdQjP/Gs-ND795-Xs-AA23-Yx.jpg
And please, as Wicked described it perfectly: 'Don’t run a node for Bitcoin, run and use it for yourself. Your humble little node isn’t saving the network, but it can protect your privacy and verify that the coins you receive are legit…if you’re actually using it.'
On the 31st of May:
➡️The Texas legislature has passed the Strategic Bitcoin Reserve bill. It now goes to Governor Abbott who is expected to sign it into law. This is a historic moment for Bitcoin and Texas, one of the largest (8th largest) economies in the world.
➡️Bitcoin News: 'Norwegian digital asset firm K33 has raised 60 million SEK (about $5.6 million) to expand its Bitcoin treasury. The funds were secured from insiders and strategic investors, including Klein Group and Modiola AS. CEO Torbjørn Bull Jenssen said the move reflects K33’s belief in Bitcoin’s long-term role in global finance and strengthens the company’s balance sheet as it grows its presence as a leading crypto broker in Europe.'
➡️ IMF raises concern over Pakistan‘s Bitcoin mining power plans. They want everyone under their control. They can't do it with Bitcoin. They might be losing another 'customer'. The IMF sees all the debt slaves becoming financially sovereign and independent by embracing Bitcoin.
https://i.ibb.co/BV0V1c6S/Gs-Sj-NP5-WIAAZv-Fo.jpg
I have rewritten Daniel Batten's quote/post on this matter:
**
'Why Pakistan’s Bitcoin Plans May Not Survive the IMF"
**
While I’m an optimist by nature—and I truly hope I’m wrong—I believe Pakistan will struggle to follow through on its Bitcoin and Bitcoin mining ambitions.
Short Answer: The IMF
Mid-Length Explanation:
- Bitcoin poses a significant threat to the IMF’s influence—on at least five fronts.
- Pakistan is heavily indebted to the IMF, and history shows a clear pattern: the IMF has already derailed or scaled back Bitcoin initiatives in all of the three countries that attempted adoption—El Salvador, Argentina, and the Central African Republic.
- Pakistan will likely face similar pushback.
- And given Pakistan’s economic vulnerabilities, it’s equally likely that the IMF will succeed.
What the IMF’s Next Steps Might Look Like
-
Manufacturing Doubt and Delay The IMF will likely begin by generating fear, uncertainty, and doubt (FUD) around the viability of Pakistan’s Bitcoin program. Expect references to:
-
“Energy shortages”
- “High electricity costs”
- “Unclear regulatory frameworks”
- “Anti-money laundering (AML) concerns”
These will be framed as responsible concerns by a seasoned financial guardian. The IMF may also imply that Pakistan acted prematurely, noting the country did not consult the IMF before announcing its Bitcoin initiative—suggesting a lack of due diligence. However, these objections are highly debatable. Multiple peer-reviewed studies show that Bitcoin mining can improve grid stability and lower electricity costs. Moreover, examples like Bhutan and El Salvador demonstrate how Bitcoin can enhance economic sovereignty. But that’s precisely the issue: economic sovereignty reduces the IMF’s lending relevance, and that’s not in the IMF’s institutional interest.
- Weaponizing Debt and Conditionality
Under its $7 billion Extended Fund Facility program, the IMF is likely to:
- Demand FATF-compliant crypto regulation
- Prohibit state-level Bitcoin accumulation
- Tie loan disbursements to rollbacks on Bitcoin and mining-related policies
This approach exploits Pakistan’s financial dependence on IMF loans to meet external debt obligations and maintain its foreign exchange reserves.
- Enforcing Compliance Through Vulnerability
Pakistan’s financial position leaves little room for defiance:
- It faces $12.7 billion in debt repayments in FY 2025.
- Without IMF support, reserves could fall below $4 billion, covering less than one month of imports—far below the threshold needed for macroeconomic stability.
- A repeat of early 2023, when reserves fell to $2.92 billion, would likely trigger another balance-of-payments crisis.
This would pressure the Pakistani rupee, already having depreciated from PKR 100 to over 330 per USD since 2017, and could push the country closer to default. Given its past FATF grey-listing, Pakistan cannot afford another multilateral funding freeze.
So What Does This All Mean?
It means the gloves are off.
The IMF is no longer merely advising—it’s actively resisting. Bitcoin threatens its long-standing monopoly over financially vulnerable nations, and Pakistan is shaping up to be the fourth test case of this resistance. If the IMF pressures Pakistan into reversing course, it will mark a 4-for-4 track record in blocking Bitcoin adoption efforts by countries under its financial umbrella.
The Bigger Picture
This is how entrenched institutions behave when facing disruption. They won’t stand aside—they’ll use every tool available to defend the system they control.
If a nation wants to adopt Bitcoin, it must either:
- Be financially independent, like Bhutan or even the United States, or
- Secure alternative funding, so IMF leverage becomes ineffective.
Bitcoin isn’t just a financial network. It’s a threat to the debt-based global order—and that means those invested in the status quo will fight back.'
➡️'Recent analysis by market research firm Alphractal suggests that, based on its current Sharpe Ratio, a key measure of risk-adjusted returns, Bitcoin still has room to run. The metric, which compares excess returns to volatility, is trending upward but remains well below the historical levels that have marked past market tops in 2013, 2017, and 2021.' - Bitcoin News
https://i.ibb.co/r245Smsm/Gs-PZ3f-XXMAATui8.jpg
➡️Publicly-listed Brazilian fintech Méliuz to raise $78m to buy more Bitcoin, after buying $26.5m Bitcoin yesterday.
On the 1st of June:
➡️Bitcoin made its Highest Monthly Close ever last night!
➡️ Someone just donated 300 Bitcoin worth +$30m to Ross Ulbricht, founder of SilkRoad.
https://intel.arkm.com/explorer/entity/ross-ulbricht
ZakeXBT: 'Interestingly the 300 BTC appears to come from Jambler outputs (sketchy centralized mixing service) Whereas normal privacy enthusiasts use decentralized mixers (Wasabi, Samourai, etc).'
Even if he is washing his own Bitcoin, (I don't think he is that stupid) not everyone is a sheep what he does is his own business no need to attract attention to it. I really don't give a damn if he still had those funds, or if it's donations. Good for him in any case.
➡️ New Record Bitcoin Hashrate 920,000,000,000,000,000,000x per second.
https://i.ibb.co/YFSWWYfD/Gs-W829f-XAAAr-KI5.jpg
Bitcoin's global hashrate has reached a new all-time high, with data from Hashrate Index showing a 7-day simple moving average peak of 943 EH/s.
➡️Top Bitcoin holders: 1. Satoshi Nakamoto: 1.1M BTC ($114B) 2. Coinbase: 983K BTC ($103B) 3. Binance: 619K BTC ($65B) 4. BlackRock: 600K BTC ($63B) 5. Strategy: 580K BTC ($47B) 6. Fidelity: 346K BTC ($36B) 7. Grayscale: 218K BTC ($23B) 8. U.S. Government: 196K BTC ($20B)
On the 2nd of June:
➡️IG Group becomes the first UK-listed firm to offer Bitcoin trading to retail investors - Financial Times “Customer demand [for bitcoin] is reaching a tipping point,” says MD Michael Healy
➡️Tether moved 14,000 Bitcoin worth +$1.4 BILLION to Twenty-One Capital (XXI) as part of its investment.
➡️Hong Kong-based Reitar Logtech announces they will buy $1.5 billion Bitcoin for their reserves — SEC filing The logistics and real estate company says the move strengthens its financial foundation as it scales its global tech platform.
➡️Russia's largest bank Sberbank launches structured bonds tied to Bitcoin. Source
"No power on earth can stop an idea whose time has come"
https://i.ibb.co/pvk8dMrM/Gsc-Vld-Ww-AACSLI.png
➡️Australian Bitcoin ETFs took in 60x more funds thant Gold ETFs in May - AFR Bitcoin = $87.3m Gold = $1.5m
💸Traditional Finance / Macro:
👉🏽No news
🏦Banks:
On the 21st of May: 👉🏽No news
🌎Macro/Geopolitics:
So last week we received the latest Google Veo 3 AI videos. Prompt Theory (Made with Veo 3). What if AI-generated characters refused to believe they were AI-generated?
People were going nuts online with statements like: "Inevitably, this is going to end up destroying life as we know it. AI growth from just two years ago to now is insane. We are dooming ourselves. I promise you, this all ends badly for humanity."
I don't think so. Yes, in some cases it will be a bad thing. But as Guy Swann said: "They said even worse about photography No it won’t end the world. You just won’t trust anything online because you see it. We know what the solution to that is already, build local communities and use cryptographic signatures online. It just makes trust a much more valuable commodity. Which is a good thing, imo."
In the end, it will be a good thing to use Bitcoin. Build again trust, and build local communities.
On the 26th of May:
👉🏽'Japan's bond market is EXPLODING: Japan's 40-year government bond yield has SKYROCKETED over the last 3 years and is trading at record highs. In 45 days, Japan's 30Y Government Bond Yield rose a MASSIVE +100 basis points, to a record 3.20%. Over $500 BILLION worth of "safe" 40Y Japanese Government Bonds have lost 20%+ in 6 weeks.
Will this trigger bank failures? Is carry trade at risk? Is the Bank of Japan going to step in? The financial system is fragile.' - Global Markets Investor
https://i.ibb.co/CKbmNDQx/Gr6-Ud-WOW8-AA3-Vj0.png
On the 27th of May:
👉🏽Michael A. Arouet: 'Many people will lose their well-paid jobs. Investment bankers, lawyers, consultants, accountants, doctors, designers, architects, and others. It will be brutal folks, buckle up.'
https://i.ibb.co/Zz0rMyM5/Gr8p6u-Xg-AA-Mp5.jpg
👉🏽38% of the U.S. debt maturity needs to be rolled over into long-term Treasuries by 2026.
https://i.ibb.co/8np5KF04/Gr6-Iupi-XYAArmx6.jpg
👉🏽'Unrealized losses on domestic bond holdings for 4 of Japan’s largest life insurers rose to a record $60 billion in Q1 2025. This is 4 TIMES more than the unrealized losses seen in Q1 2024. Nippon Life, the largest Japanese insurer and the world’s sixth-largest life insurance company posted $25 billion in paper losses, marking a +260% jump YoY. This comes as Japan’s 30-year and 40-year bonds have seen one of their most violent price declines in history. Japan’s financial system is on the edge.' -TKL
https://i.ibb.co/nqHCKFGn/Gr0-KYx-MX0-AA0-BCo.png
👉🏽 'Gold's funds posted $2.9 billion net OUTFLOW last week, the biggest since April 2013 and the 3rd-largest on record. This comes after a massive rally year-to-date. Much needed correction has finally come.' -Global Markets Investor
👉🏽Japan's bond market liquidity has currently dropped to 2008 Lehman crisis levels. Remember when troubles started in Iceland in 2007? Today we have Japan, the UK, and Switzerland in a similar spot…
On the 28th of May:
👉🏽France Running Out Of Money? Auditors Warn State Has "Lost Control" Of Welfare Spending, IMF Demands Cuts
https://www.zerohedge.com/economics/france-running-out-money-auditors-warn-state-has-lost-control-welfare-spending-imf
👉🏽The US M2 money supply hits a new all-time high in April for the first in three years. Got Bitcoin?
https://i.ibb.co/GQLzsjgt/Gr-2ihc-Xg-AAy-D4-U.jpg
👉🏽McKinsey terminates 10% of staff (largest in 100 years) due to a sharp slowdown in revenue growth across the consulting market. It’s actually over for MBA consultants. McKinsey said: “Generative AI enables new levels of productivity for our teams.” Source: https://archive.ph/Q2zm8
👉🏽What a graph. The median age of first-time home buyers is spiking, now approaching 40.
https://i.ibb.co/QFdnCf9V/Gs-Cm-YUv-XAAAI0ck.jpg
Russ Greene: "When boomers are done, the median first-time home buyer will be 48, the national debt will be 60 trillion, the code of federal regulations will be a quarter million pages long, and they will not at any point have been vaguely aware of what they did to this nation."
Unfortunately, this is also happening in the Netherlands.
👉🏽'Saving becomes impossible in the Netherlands with the new draconian Box 3 regulation.
Monthly contribution: €150
Investment horizon: 40 years
Annual return: 10%
Model 1: 1.2% wealth tax per year on total assets (the old tax system) Model 2: 36% tax per year on unrealized gains
The difference between having enough saved for retirement or not…
Due to the compound interest effect, you miss out on it. Even if you never sell over those 40 years and only invest in S&P 500 ETFs, you still miss out on hundreds of thousands of euros…
No rights can be derived from these calculations. Obviously, I'm too lazy to do the math myself, so all calculations were done by AI.' - Tsartoshi
https://i.ibb.co/nsnTZV08/Gs-Cbc-CW0-AA0-Qe-I.jpg https://i.ibb.co/DD72kNsS/Gs-Cc-Fet-Wg-AA7g-W5.png
👉🏽The White House says there will be no increase in the US deficit under President Trump’s tax bill. Recent estimates have suggested the bill would increase the US deficit by $3.8 trillion.
On the 29th of May:
👉🏽Alex Recouso: 'The recent capital gains tax increase in the UK was expected to bring additional tax revenue. Instead, high-net-worth individuals and families are leaving the country, leading to a 10% fall in net capital gains tax revenue. Welcome to the Laffer curve, suckers.'
https://i.ibb.co/KjbtDNwT/Gs-Ij-Ay-Ua-UAEz-Cbm.jpg
Amazing how so many people in governments around the world don’t understand human nature. Same story in every country that tries this. Socialists are a strange species, they always repeat the same mistakes and are surprised that the results are always the same. Why are they so detached from reality? I suspect future attempts will include banning people from leaving entirely.
Another example...
👉🏽North Sea electricity grid leads to a sharp increase in energy bills. Source NOS 'The construction of infrastructure for offshore wind farms in the North Sea could lead to significantly higher energy bills for Dutch households. Over the next 15 years, a staggering €88 billion will be spent on laying cables and building platforms, according to government calculations made earlier this year. While energy companies currently receive no subsidies for building wind farms, that doesn’t mean it won’t cost us money.'
That makes sense, right?
Sun and wind are free. So the more we invest in that free energy, the more expensive energy becomes.
The climate…
The following I have asked chat GPT:
What Could €88 Billion Buy in Nuclear Energy?
Let’s take a closer look at what €88 billion could achieve if invested in nuclear power, using realistic and conservative estimates.
Average Cost of a Nuclear Power Plant
The construction of a modern nuclear power plant—such as an EPR or AP1000—typically ranges between €8 and €12 billion, depending on factors like location, scale, regulatory environment, and potential delays.
For this estimate, we'll use a conservative average of:
👉 €10 billion per plant How Many Plants for €88 Billion? Dividing the total investment by the average cost: €88 billion ÷ €10 billion = 8.8 nuclear plants
👉 This means approximately 8 to 9 large-scale nuclear power plants could be built. Electricity Output Comparison
A single 1.6 GW nuclear plant generates around 12 to 13 TWh annually. Therefore, 8 plants would produce approximately 100 TWh per year. This output would cover roughly 50% of the Netherlands’ current annual electricity consumption—and do so with a stable, low-carbon baseload supply.
Now as you might already know I am apolitical. But sjeezzzz
'How is this possible, Frans Timmerman? “You hardly need any public money to invest in renewables,” he said! Was this ignorance or deliberate misinformation? Socialist “solutions” should always come with a clear warning label:
🚨 Warning: Past socialist outcomes guarantee deep misery for the future.
Plenty of examples. Everyone is equally poor! “Climate justice.” Who comes up with this stuff?'
Sources: https://www.euronews.com/2021/11/26/you-hardly-need-any-public-money-to-invest-in-renewables-frans-timmermans
Again, I am not picking a political side, just stating the obvious... Check out the next example...
On the 30th of May:
👉🏽'It’s really time for the West to rethink its economic model, moving to a service-based economy creates security and geopolitical risks. We need to rebuild our manufacturing base.' - Michael A. Arouet Chart @econovisuals
https://i.ibb.co/QvFTQrtx/Gs-Lf-Wl5-XMAALw6t.jpg
Funny isn't it how regulatory burden distorts incentives away from manufacturing and atoms to services and bytes? We traded short-term corporate profits for long-term civilizational power. Is this the point of no return, or can the West still rebuild what it systematically dismantled?
👉🏽The European dream. Work 40 hours per week and get taxed close to 50%, if not more, to fund a bloated government and mass immigration. And because it's so much fun, you get to do it until you're 70. https://i.ibb.co/YF0HZzMs/Gs-Mm-Ti-HWUAAf-IRb.png
👉🏽Argentina's economy expands 8% year-over-year in april according to EMAE
👉🏽TKL: 'The US government's default risk is rising: 1-year US credit default swaps (CDS) have risen to 52 basis points, near the highest since 2023.
Excluding the 2023 debt ceiling crisis, the cost of insurance against the US government's default is at its highest in 12 years. Furthermore, the outstanding volume of credit default swaps has risen by ~$1 billion this year, to $3.9 billion, the second-highest since 2014. This comes as investors are increasingly concerned about the US government's rising deficit.
The US reached its statutory borrowing limit in January and employed “extraordinary measures” to avoid a default. The debt ceiling crisis has never truly been resolved.'
On the 31st of May:
👉🏽'Global debt just hit $324 TRILLION. That’s 3x the size of the world’s entire economy. This isn’t just a number, it’s a ticking time bomb.' - Stockmarket News
Why Bitcoin, well this:
https://i.ibb.co/MkT77MDD/Gs-TWuir-WQAAr3-Q6.jpg
👉🏽Japanese Stocks just saw a weekly outflow of almost $12 Billion, the largest in history.
On the 2nd of June:
👉🏽JEROME POWELL: "The end of the Breton-Woods era fundamentally changed monetary policy" He just told you "WTF Happened in 1971?".
The end of the Bretton Woods system in 1971, as Jerome Powell noted, shifted global monetary policy from fixed exchange rates, where currencies were pegged to the U.S. dollar (tied to gold at $35/ounce), to floating rates driven by market forces. This gave central banks like the Federal Reserve more flexibility to manage domestic issues like inflation and jobs but made global economic ties more complex. The collapse happened due to U.S. dollar surpluses from spending on the Vietnam War and trade deficits, leading to gold reserve losses as countries like France swapped dollars for gold. Nixon ended dollar-gold convertibility to protect reserves. This shift caused trends like higher inflation and inequality, often linked to "WTF Happened in 1971?" debates.
Here is the video: https://x.com/RadarHits/status/1929611410100937125
Meanwhile...
👉🏽The US will never default on its debt, says Treasury Secretary Scott Bessent. "We are on the warning track and we will never hit the wall."
👉🏽Gold prices surge above $3400/oz as markets react to rising geopolitical tensions between Russia and Ukraine.
👉🏽Sminston With: "Nothing stops this (already completely derailed) train. - - - If you haven't seen this, you should: the correlation between M2 money supply and US total debt (USD). In the early COVID-19 days, the money supply was way ahead of debt, and now the debt is way ahead of the money supply. Can you say "mean reversion?".
https://i.ibb.co/zHN91wsR/Gsaw-Hy-Zag-AAo-HHV.jpg
🎁If you have made it this far, I would like to give you a little gift:
Lysander: "Lyn Alden gave one of the clearest breakdowns of why the U.S. is on an unstoppable fiscal path—and why Bitcoin matters more than ever because of it.
Lyn Alden walks through the numbers behind the federal deficit, interest expenses, Social Security, and the structural changes that happened post-2008. The short version? We’re in a new era. One where the government can’t slow down even if it wants to.
The debt is compounding. The interest expense is rising. The trust funds are running dry. And the political will to do anything about it doesn’t exist.
Her phrase: “Nothing stops this train.” Not because of ideology, but because of math—and human nature.
This isn’t hyperinflation doom-talk. It’s a sober look at what happens when a system built on ever-growing debt reaches its limits—and why Bitcoin, with its fixed supply and transparent rules, is the opposite of that system.
Highly recommend watching this one all the way through."
https://x.com/UnderCoercion/status/1928280669764931860
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ b1ddb4d7:471244e7
2025-06-07 14:00:42
@ b1ddb4d7:471244e7
2025-06-07 14:00:42When Sergei talks about bitcoin, he doesn’t sound like someone chasing profits or followers. He sounds like someone about to build a monastery in the ruins.
While the mainstream world chases headlines and hype, Sergei shows up in local meetups from Sacramento to Cleveland, mentors curious minds, and shares what he knows is true – hoping that, with the right spark, someone will light their own way forward.
We interviewed Sergei to trace his steps: where he started, what keeps him going, and why teaching bitcoin is far more than explaining how to set up a node – it’s about reaching the right minds before the noise consumes them. So we began where most journeys start: at the beginning.

First Steps
- So, where did it all begin for you and what made you stay curious?
I first heard about bitcoin from a friend’s book recommendation, American Kingpin, the book about Silk Road (online drug marketplace). He is still not a true bitcoiner, although I helped him secure private keys with some bitcoin.
I was really busy at the time – focused on my school curriculum, running a 7-bedroom Airbnb, and working for a standardized test prep company. Bitcoin seemed too technical for me to explore, and the pace of my work left no time for it.
After graduating, while pursuing more training, I started playing around with stocks and maximizing my savings. Passive income seemed like the path to early retirement, as per the promise of the FIRE movement (Financial Independence, Retire Early). I mostly followed the mainstream news and my mentor’s advice – he liked preferred stocks at the time.
I had some Coinbase IOUs and remember sending bitcoin within the Coinbase ledger to a couple friends. I also recall the 2018 crash; I actually saw the legendary price spike live but couldn’t benefit because my funds were stuck amidst the frenzy. I withdrew from that investment completely for some time. Thankfully, my mentor advised to keep en eye on bitcoin.
Around late 2019, I started DCA-ing cautiously. Additionally, my friend and I were discussing famous billionaires, and how there was no curriculum for becoming a billionaire. So, I typed “billionaires” into my podcast app, and landed on We Study Billionaires podcast.
That’s where I kept hearing Preston Pysh mention bitcoin, before splitting into his own podcast series, Bitcoin Fundamentals. I didn’t understand most of the terminology of stocks, bonds, etc, yet I kept listening and trying to absorb it thru repetition. Today, I realize all that financial talk was mostly noise.
When people ask me for a technical explanation of fiat, I say: it’s all made up, just like the fiat price of bitcoin! Starting in 2020, during the so-called pandemic, I dove deeper. I religiously read Bitcoin Magazine, scrolled thru Bitcoin Twitter, and joined Simply Bitcoin Telegram group back when DarthCoin was an admin.
DarthCoin was my favorite bitcoiner – experienced, knowledgeable, and unapologetic. Watching him shift from rage to kindness, from passion to despair, gave me a glimpse at what a true educator’s journey would look like.
The struggle isn’t about adoption at scale anymore. It’s about reaching the few who are willing to study, take risks, and stay out of fiat traps. The vast majority won’t follow that example – not yet at least… if I start telling others the requirements for true freedom and prosperity, they would certainly say “Hell no!”
- At what point did you start teaching others, and why?
After college, I helped teach at a standardized test preparation company, and mentored some students one-on-one. I even tried working at a kindergarten briefly, but left quickly; Babysitting is not teaching.
What I discovered is that those who will succeed don’t really need my help – they would succeed with or without me, because they already have the inner drive.
Once you realize your people are perishing for lack of knowledge, the only rational thing to do is help raise their level of knowledge and understanding. That’s the Great Work.
I sometimes imagine myself as a political prisoner. If that were to happen, I’d probably start teaching fellow prisoners, doctors, janitors, even guards. In a way we already live in an open-air prison, So what else is there to do but teach, organize, and conspire to dismantle the Matrix?

Building on Bitcoin
- You hosted some in-person meetups in Sacramento. What did you learn from those?
My first presentation was on MultiSig storage with SeedSigner, and submarine swaps through Boltz.exchange.
I realized quickly that I had overestimated the group’s technical background. Even the meetup organizer, a financial advisor, asked, “How is anyone supposed to follow these steps?” I responded that reading was required… He decided that Unchained is an easier way.
At a crypto meetup, I gave a much simpler talk, outlining how bitcoin will save the world, based on a DarthCoin’s guide. Only one person stuck around to ask questions – a man who seemed a little out there, and did not really seem to get the message beyond the strength of cryptographic security of bitcoin.
Again, I overestimated the audience’s readiness. That forced me to rethink my strategy. People are extremely early and reluctant to study.
- Now in Ohio, you hold sessions via the Orange Pill App. What’s changed?
My new motto is: educate the educators. The corollary is: don’t orange-pill stupid normies (as DarthCoin puts it).
I’ve shifted to small, technical sessions in order to raise a few solid guardians of this esoteric knowledge who really get it and can carry it forward.
The youngest attendee at one of my sessions is a newborn baby – he mostly sleeps, but maybe he still absorbs some of the educational vibes.
- How do local groups like Sactown and Cleveland Bitcoiners influence your work?
Every meetup reflects its local culture. Sacramento and Bay Area Bitcoiners, for example, do camping trips – once we camped through a desert storm, shielding our burgers from sand while others went to shoot guns.
Cleveland Bitcoiners are different. They amass large gatherings. They recently threw a 100k party. They do a bit more community outreach. Some are curious about the esoteric topics such as jurisdiction, spirituality, and healthful living.
I have no permanent allegiance to any state, race, or group. I go where I can teach and learn. I anticipate that in my next phase, I’ll meet Bitcoiners so advanced that I’ll have to give up my fiat job and focus full-time on serious projects where real health and wealth are on the line.
Hopefully, I’ll be ready. I believe the universe always challenges you exactly to your limit – no less, no more.
- What do people struggle with the most when it comes to technical education?
The biggest struggle isn’t technical – it’s a lack of deep curiosity. People ask “how” and “what” – how do I set up a node, what should one do with the lightning channels? But very few ask “why?”
Why does on-chain bitcoin not contribute to the circular economy? Why is it essential to run Lightning? Why did humanity fall into mental enslavement in the first place?
I’d rather teach two-year-olds who constantly ask “why” than adults who ask how to flip a profit. What worries me most is that most two-year-olds will grow up asking state-funded AI bots for answers and live according to its recommendations.
- One Cleveland Bitcoiner shows up at gold bug meetups. How valuable is face-to-face education?
I don’t think the older generation is going to reverse the current human condition. Most of them have been under mind control for too long, and they just don’t have the attention span to study and change their ways.
They’re better off stacking gold and helping fund their grandkids’ education. If I were to focus on a demographic, I’d go for teenagers – high school age – because by college, the indoctrination is usually too strong, and they’re chasing fiat mastery.
As for the gold bug meetup? Perhaps one day I will show up with a ukulele to sing some bitcoin-themed songs. Seniors love such entertainment.
- How do you choose what to focus on in your sessions, especially for different types of learners?
I don’t come in with a rigid agenda. I’ve collected a massive library of resources over the years and never stopped reading. My browser tab and folder count are exploding.
At the meetup, people share questions or topics they’re curious about, then I take that home, do my homework, and bring back a session based on those themes. I give them the key takeaways, plus where to dive deeper.
Most people won’t – or can’t – study the way I do, and I expect attendees to put in the work. I suspect that it’s more important to reach those who want to learn but don’t know how, the so-called nescient (not knowing), rather than the ignorant.
There are way too many ignorant bitcoiners, so my mission is to find those who are curious what’s beyond the facade of fake reality and superficial promises.
That naturally means that fewer people show up, and that’s fine. I’m not here for the crowds; I’m here to educate the educators. One bitcoiner who came decided to branch off into self-custody sessions and that’s awesome. Personally, I’m much more focused on Lightning.
I want to see broader adoption of tools like auth, sign-message, NWC, and LSPs. Next month, I’m going deep into eCash solutions, because let’s face it – most newcomers won’t be able to afford their own UTXO or open a lightning channel; additionally, it has to be fun and easy for them to transact sats, otherwise they won’t do it. Additionally, they’ll need to rely on
-
 @ 523a8281:fc94329a
2025-06-07 04:53:12
@ 523a8281:fc94329a
2025-06-07 04:53:12As the global financial landscape continues to evolve, the interaction between the cryptocurrency market and traditional financial systems is becoming increasingly intertwined. Crypto payment cards, serving as a critical bridge between the two, are emerging as a new force in the payments sector. According to a report by The Brainy Insights, the global crypto credit card market was valued at $25 billion in 2023 and is projected to surpass $400 billion by 2033, showcasing astonishing growth potential. Behind this rapid development is the relentless effort of payment providers to bridge the gap between crypto and traditional payment methods, striving to meet users' diverse payment needs. Currently, crypto payment card products are springing up like mushrooms after a rain and have already integrated with mainstream payment methods like Google Pay, Apple Pay, and Alipay, greatly enhancing their usability. Products like the Crypto. com Visa Card, Binance Card, Bybit Card, and Bitget Card, mostly launched by major cryptocurrency exchanges, hold significant influence in the market. In terms of technological innovation, some card issuers have even integrated DeFi protocols such as Ethena, Morpho, and USUAL, offering asset appreciation services to users and successfully building a comprehensive financial service ecosystem that extends from payments to wealth management. This further expands the application scope and value of crypto payment cards. Despite the unique advantages of cryptocurrency payments in terms of speed (46% of users choose it), cross-border cost efficiency (37% value low fees), and financial autonomy (32% pursue decentralization), a survey by Bitget Wallet reveals that their actual application scale still lags significantly behind traditional payment systems. The traditional payment market, worth trillions of dollars, covers the vast majority of daily transactions globally, while crypto payments occupy only a small share, mainly concentrated in niche scenarios like cross-border remittances and digital asset transactions. Users' preference for traditional payment methods primarily stems from concerns about trust and security. The security risks of crypto payments (e.g., hacking and fraud) leave users apprehensive, while traditional payments, backed by mature banking systems, legal protections, and dispute resolution mechanisms, significantly reduce transaction risks. Additionally, the price volatility of cryptocurrencies makes them unsuitable as stable transaction mediums, whereas the stability of traditional fiat currencies better aligns with daily consumer needs. Traditional payments also achieve seamless coverage through extensive POS terminals and online integrations, whereas the limited merchant acceptance of crypto payments restricts their practicality. Furthermore, the low operational barriers of traditional payment tools and the habitual usage formed over time, combined with the complexity and technical barriers of crypto wallets, pose challenges to the widespread adoption of crypto payments. Against this market backdrop, the VooPay digital asset card stands out, showcasing core advantages such as multi-chain technology integration, global compliance frameworks, and real-time payment innovations, redefining the crypto payment experience: 1. Breaking Efficiency Barriers with Multi-Chain Interoperability and Real-Time Payment Technology The VooPay digital asset card supports major cryptocurrencies like Bitcoin, Ethereum, USDT, and BNB (compatible with multi-chain protocols such as BEP-20 and TRC-20). Through an integrated cross-chain bridge, users can freely transfer assets across major blockchains like Ethereum, BNB Chain, and TRON without manual conversion. For instance, a freelancer in the UK receiving USDT payments from a U.S. client can directly convert it to GBP for consumption via the card, with the entire process settling in minutes and fees as low as 1.8%-2%. This represents a more than 90% improvement in efficiency and a 60%-80% reduction in costs compared to traditional bank cross-border transfers (5%-10% fees + 3-5 days settlement). The platform employs Layer 2 scaling technologies (e.g., zk-Rollups) to further optimize transaction throughput, supporting high-frequency, low-value payment scenarios. Additionally, its dynamic exchange rate locking feature helps users mitigate cryptocurrency price volatility risks, ensuring payment amount stability—for example, even if Bitcoin drops from $101,867 in January 2025 to $94,500 in February, users can still settle payments at the real-time exchange rate during consumption without needing to pre-convert to fiat currency. 2. Building Trust with a Global Payment Network and Compliance System Leveraging deep collaborations with Visa and MasterCard, the VooPay digital asset card covers 210 countries/regions and 150 million merchants (including offline retail, online e-commerce, and ATM networks). It supports integration with third-party platforms like Alipay, WeChat Pay, and Apple Pay, enabling seamless transitions between "crypto-to-fiat" payment scenarios. For instance, in the $20.5 billion spent by Canadians in the U.S. in 2024, using the VooPay card could bypass traditional bank exchange rate losses (averaging about 3%) and high fees, requiring only a fixed rate of 1.8%-2%. In terms of compliance, VooPay holds financial licenses in Europe and North America, strictly adhering to KYC (Know Your Customer) and AML (Anti-Money Laundering) standards. Users must complete identity verification to activate their cards. The digital asset cards are issued by banks in Hong Kong and the U.S., with funds segregated from platform operating assets and regularly audited by third-party institutions to ensure security. This ensures that every transaction complies with global regulatory requirements, especially under the backdrop of tightened financial regulations driven by Trump-era policies, providing users with reliable safeguards. 3. Revolutionizing User Experience and Extending the Ecosystem to Make Crypto Payments Mainstream The VooPay card is designed to balance high spending limits and operational convenience: the Gold Card has a daily spending limit of $7,500 and a monthly limit of $50,000, while the virtual card can be activated with as little as 10 USDT. It supports instant card issuance and multilingual interfaces (including Chinese). Users can view multi-chain asset distributions, transaction records, and real-time exchange rates via the app, significantly lowering the operational barriers compared to traditional crypto wallets. Moreover, the card integrates Zero-Knowledge Proof (ZKP) technology, protecting transaction privacy while meeting compliance requirements, allowing users to complete payment verification without disclosing sensitive information. On the ecosystem front, VooPay's native token, VOO, has diverse use cases, including payment fee discounts (20%), participation in liquidity mining, and community governance voting. Future plans include deep integration with DeFi protocols, enabling users to directly participate in staking, lending, and other financial activities via the card, building an integrated ecosystem of "payments-wealth management-governance." As a core project incubated by M3 DAO, VooPay is deeply embedded in its community ecosystem, which spans over 100 countries and includes more than 200,000 members. It serves as the designated payment hub for incubated projects like Rocket and MetaMars. Rocket, an IDO platform in the DeFi space, collaborates with VooPay to achieve seamless integration of crypto asset subscriptions and payments. Users can invest in Rocket projects using the VooPay card and enjoy VOO token fee discounts and priority benefits. MetaMars, on the other hand, extends VooPay's practical applications in metaverse scenarios, enabling users to purchase NFTs or virtual services with cryptocurrencies stored in their cards, with the system automatically converting to platform tokens at low fees. Together, the three entities drive VooPay's construction of an integrated ecosystem of "payments + investments + applications," promoting the adoption of cryptocurrencies in diverse scenarios. 4. Differentiated Competitiveness to Address Market Challenges Compared to traditional payments and competitors, VooPay's core advantages lie in: ●Dual-Driven by Technology and Compliance: Enhancing efficiency through cross-chain interoperability and Layer 2 technologies while building trust with financial licenses in Europe and North America and segregated fund custody. ●Deep Integration of Scenarios and Ecosystems: Covering diverse scenarios such as personal consumption, enterprise cross-border acquiring, and DeFi finance, rather than being limited to single-use transaction functions. ●Accurate Matching of User Needs: Addressing pain points in cross-border payments (low cost, real-time), privacy and security demands (ZKP technology), and operational barriers (one-click integration with mainstream payments) with systematic solutions. Looking ahead, as blockchain technology matures and global regulatory environments gradually open up, VooPay is poised to carve out a larger space in the crypto payment card market with its triple advantages of "technological innovation + compliance framework + ecosystem expansion." It aims to drive cryptocurrencies from "marginal payments" to "daily necessities," becoming a mainstream gateway connecting Web3 and the real economy.
-
 @ bf47c19e:c3d2573b
2025-06-06 21:07:19
@ bf47c19e:c3d2573b
2025-06-06 21:07:19Originalni tekst na bitcoin-balkan.com
Dobrodošli u Bitcoin Q+A
Naša misija je jednostavna, da vam pružimo kratke i lako svarljive odgovore na najčešće postavljana pitanja o Bitcoin-u. Ako ne možete da pronađete odgovor, obavezno nas kontaktirajte. Postoji jako puno informacija o Bitcoin-u i lako je zaglaviti se u gužvi i postati zbunjen. Da bismo se borili protiv toga, naše odgovore u ovom vodiču održavamo kratkim i preciznim. Predlažemo da započnete sa vrha stranice i prođete jedan po jedan kroz odeljke.
Kao i kod svih stvari vezanih za tehnologiju, stvari se brzo kreću, ali nastojaćemo da informacije ovde uvek budu ažurne. S tim u vezi, i mi smo ljudi, pa ako primetite nešto netačno, obratite nam se.
- Uobičajena pitanja - Odgovori na najčešća pitanja o Bitcoin-u
- Uobičajene greške - Naveli smo uobičajene zamke da bismo vam pomogli da ih izbegnete
- Novčanici - Šta su novčanici? Čemu služe? Koji su različiti tipovi?
- Nodes (Čvorovi) - Šta je to čvor? Zašto pokrenuti jedan? Koji su različiti tipovi?
- Lightning - Odgovori na vaša uobičajena pitanja o Lightning Network-u
- Coinjoin - Odgovori na vaša uobičajena pitanja o Coinjoin-u
- Mitovi - Uobičajeni mitovi o Bitcoin-u, razotkriveni
- Rečnik - Bitcoin žargoni, pojednostavljeno
Uobičajena pitanja
Jednostavni odgovori na vaša Bitcoin pitanja
Šta je Bitcoin?
Bitcoin je peer to peer mreža u kojoj svako može da učestvuje. Omogućava vam da bezbedno čuvate vrednost tokom vremena i da je prenesete bilo kome drugom u bilo kom trenutku bez potrebe za trećom stranom. Ima fiksni i transparentni raspored inflacije koji se ne može menjati po volji poput „običnog“ novca. To je novac, za internet.
Zašto je Bitcoin važan?
Omogućava kriptografski sigurna prekogranična plaćanja koja su otporna na cenzuru. To je prvi i jedini oblik apsolutne digitalne nestašice i njime ne upravlja nijedna osoba ili grupa. Kao rezultat toga, nijedna svetska vlada se ne može mešati u njega.
Kako Bitcoin funkcioniše?
Ana šalje transakciju iz svog novčanika koju prima 1000 učesnika mreže, koji jedni drugima govore da Ana želi da pošalje Marku. Transakciju vidi rudar (majner) koji posvećuje računarsku snagu grupišući Aninu transakciju u blok, zajedno sa puno drugih transakcija. Jednom kada se Anina transakcija iskopa u blok, Marko će u novčaniku imati odgovarajuću količinu Bitcoin-a.
Ko je izumeo Bitcoin?
Svet je saznao za Bitcoin 2008. godine kada je anonimni mrežni entitet pod nazivom „Satoshi Nakamoto“ podelio Bitcoin White Paper na online mailing listu. Satoshi je nestao 2011. godine i od tada nikada nije viđen online. Tokom godina, stotine programera širom sveta nastavili su da doprinose i poboljšavaju Bitcoin protokol.
Šta daje vrednost Bitcoinu?
Oskudan je (biće ih samo 21 milion) i to može da proveri svako ko ima običan računar od 30 dolara. Ima ogromnu količinu računarske snage posvećene osiguranju svoje distribuirane knjige. Mreža doslovno plaća ljudima da zaštite njen integritet i deluju u dobroj nameri. „Cena“ Bitcoin-a u $ ili € određuje se jednostavnom tržišnom ponudom i potražnjom.
Ko kontroliše mrežu?
Pojednostavljeno, svi i niko. Svako kontroliše sopstveno učešće u mreži i mreža je strukturirana tako da loši akteri ne mogu uspeti. Nijedan programer ne može da podstakne bilo kakve promene koda. Nijedan rudar ne može cenzurisati određene transakcije. Nijedan korisnik ne može prevariti sistem i trošiti Bitcoin koji nema ili koji mu ne pripada.
Da li je Bitcoin anoniman?
Na mrežnom nivou, Bitcoin-i nisu ’označeni’ ni za jedan javni identitet. Protokol zna samo za nizove slova i brojeva poznate kao adresa. Međutim, preduzeća izgrađena na vrhu Bitcoin-a, poput KYC menjačnica, na kojima je moguće kupiti Bitcoin, mogu povezati vaš stvarni identitet sa Bitcoin-om kupljenim preko njih. Knjiga transakcija Bitcoin-a je potpuno javna, tako da je moguće pratiti poznate javne entitete preko mreže.
Šta je to blockchain?
Blockchain (lanac blokova) je javna knjiga koja sadrži kopiju svake pojedinačne bitcoin transakcije koja je ikada završena. Rudari se takmiče ko će proizvoditi blokove za naknade za transakcije i blok subvencije. Svaki uspešni blok je kriptografski povezan ili „vezan lancem” za svog prethodnika.
Mogu li vlade to zaustaviti?
Vlade bi apsolutno mogle učiniti Bitcoin nezakonitim u njihovoj nadležnosti. U stvari, Kina i Nigeria su to već učinile, više puta, ali ekosistem i dalje cveta. Distribuirana priroda Bitcoin-a znači da bi u stvarnosti bio potreban monumentalni koordinirani napad mnogih svetskih sila da zaustavi njegov rast.
Zar ga ne koriste kriminalci?
Bitcoin je novac, i bilo koji novac može biti korišćen od strane kriminalaca. U 2017. godini procenjeno je da celokupno tržište trgovine drogom vredi $500,000,000,000 (500 biliona) dolara. Po trenutnim cenama to bi moglo kupiti celokupnu Bitcoin mrežu! Verovatno je pošteno reći da se ogromna većina nelegalnih aktivnosti finansira iz tradicionalnih valuta.
Zar ne troši energiju?
Tačno je da Bitcoin mreža troši mnogo energije, ali trošenje energije za obezbeđivanje i upravljanje globalnom mrežom za plaćanja koja pružaju ogromne vrednosti milionima ljudi ne bi trebalo smatrati „rasipnim“. Rudarstvo Bitcoin-a je već počelo da podstiče inovacije u korišćenju alternativnih (često rasipanih) izvora energije kao što je gorivi gas ili obnovljivi izvori energije. Bitcoin mreža u 2021 godini troši 0.1% energije koja se proizvede.
Koliko ima bitcoin-a?
U vreme pisanja ovog dokumenta, iskopano je nešto manje od 19 miliona bitcoin-a. Može postojati samo 21 milion, a poslednji će se iskopati oko 2140. godine. Svaki bitcoin može se podeliti na 100 miliona Satošija ili "sats-ova", tako da ima mnogo toga u ponudi.
Kako nastaju bitcoin-i?
Novi bitcoin-i nastaju kao rezultat globalno distribuiranog i visoko konkurentnog rudarskog procesa. Svaki novo izrudareni blok nagrađuje uspešnog rudara subvencijom. U vreme pisanja ovog teksta, ova subvencija je 6,25 bitcoin-a. Ponovo će se prepoloviti 2024. godine na 3,125 bitcoin-a nakon još 210 000 blokova (otprilike svake 4 godine).
Šta je to rudarenje?
Proces učesnika koji doprinose velikim količinama računarske snage za obradu transakcija u blokove. Jednom kada grupišu ove transakcije, rudar izvršava ponavljajući računski zadatak na njima, pokušavajući da pronadje odgovor koji je ispod određenog cilja. Ako su uspešni, blok je iskopan - majnovan, i rudar prima naknade za transakcije i subvenciju bloka. Proces zatim započinje ponovo, kao i sledeća grupa transakcija.
Gde ga mogu kupiti?
Postoji mnoštvo online menjačnica na kojima možete kupiti bitcoin-e, mada biste trebali da obratite pažnju kada tražite mesto za kupovinu. Najbolji način da dobijete vaš prvi deo bitcoin-a je da ga kupite od pouzdanog prijatelja ili člana porodice. Zapamtite - Možete kupiti delić bitcoin-a (u svakom je 100 miliona sats-ova)! Pogledajte ovde neke od preporuka.
Uobičajene greške
Saveti kako ne biste napravili iste greške kao i mi
Bitcoin alternative
„Kripto“ prostor je preplavljen alternativnim valutama, takozvanim aplikacijama „decentralizovanog finansiranja“, i nekim čistim prevarama. Može izgledati vrlo primamljivo da se uključite u ove projekte jer oni imaju puno zvučnih reči i izgledaju „jeftino“ u poređenju sa Bitcoin-om. Gotovo svi ovi projekti nisu ništa drugo do marketinške i modne priče i treba ih istraživati sa oprezom.
Kupovina KYC bitcoin-a
Kupovina KYC bitcoin-a od nekih kao što je ECD menjačnica je dosta brz i jednostavan način kupovine bitcoin-a. Ne kažemo da to apsolutno ne bi trebalo da radite, ali želimo da znate koji su kompromisi. Kada se registrujete kod ovih kompanija, moraćete da dostavite neki oblik foto-ID-a koji označava bitcoin koji kupujete za vaš javni identitet. Zbog javne prirode Bitcoin bloka, nadzorne kompanije mogu da vas ‘prate’ i gledaju vaše buduće transakcije.
Neistraživanje drugih mogućnosti kupovine
Dakle, ne sviđa vam se zvuk KYC bitcoin-a, i koje su druge opcije? To su Peer to Peer menjačnice kao što su Bisq i HodlHodl koje koriste uslugu pratnje kako bi vam omogućile da kupujete bitcoin-e od nekoga bilo gde u svetu, ali one uglavnom nisu tako jednostavne za upotrebu kao alternative KYC. Ubedljivo najlakša opcija za počinjanje je da kupite neku količinu od prijatelja ili člana porodice. Raspitajte se, napolju je mnogo više Bitcoin-era nego što mislite!
Ne pokrećete svoj Node
Jednostavno, ako ne koristite svoj čvor (eng. node), onda koristite tuđi, bilo da ga poznajete ili ne. Tako Bitcoin funkcioniše. Povezivanje novčanika sa sopstvenim čvorom znači da se ne oslanjate na bilo koga drugog da izvršava transakcije, što daje ogromne prednosti privatnosti. Korišćenjem sopstvenog čvora takođe možete biti uvereni da su podaci prikazani u novčaniku tačni i da se pridržavaju pravila vašeg Bitcoin čvora.
Ostavljanje Bitcoin-a na menjačnicama
Da, kupio sam KYC Bitcoin i pošto nisam znao kako da upravljam novčanikom, ostavio sam ga na menjačnici. Ako imate bitcoin na menjačnici, nemate bitcoin. Imate IOU (zadužnica) i trebali biste naučiti dovoljno (uz našu pomoć, nadamo se) da taj bitcoin izvadite sa menjačnice i prebacite u novčanik nad kojim vi kontrolišete privatne ključeve. U prošlosti je bilo više slučajeva hakovanja na menjačnici, i ljudi su izgubili velike količine bitcoin-a, zato ne dozvolite da to budete vi.
Slanje vaših privatnih ključeva nekome
Srećom ja nikada nisam pao na ovo, ali mnogi ljudi jesu. Sasvim je uobičajeno u javnim čet grupama poput telegrama, da se prevaranti predstavljaju kao neko iz zajednice Bitcoin-a koji nude podršku nekome ko možda traži pomoć. NIKADA.....ALI NIKADA ne dajte svoje privatne ključeve ili seed reči nikome, posebno ne na Internetu.
Nesigurno čuvanje seed reči
Vaše seed reči su ključevi vašeg bitcoin-a, i svako ko ima kontrolu nad njima može pristupiti vašim sredstvima. Trebalo bi da ih čuvate na siguran način, ali imajte na umu da ih ne čuvate tako sigurno, da i vi zaboravite gde su. Verovali ili ne, to se jako često dešava. Nije dobra ideja da ih čuvate na računaru.
Slanje na pogrešnu adresu
Zahvaljujući QR kodovima koji se mogu skenirati i funkcijama za otkrivanje grešaka koje su implementirane u novčanike, ovo danas postaje prilično teško učiniti. Bitcoin adrese su dugi nizovi brojeva i slova, tako da je uvek dobra praksa koristiti QR kodove ili u najmanju ruku copy/paste kada šaljete nekome. Takođe je dobar savet da bar jednom vizuelno proverite adresu pre slanja.
Postajete uzbudjeni
Što više naučite, to ćete biti više uzbuđeni zbog Bitcoin-a. Meni se još uvek to dešava! Ovo se može desiti ako provedete dosta vremena na Bitcoin Twitter-u, tamo je vrlo lako postati previše uzbudjen, i kupiti više nego što možete priuštiti sebi. Bitcoin je mlada i izuzetno nestabilna imovina, trebalo bi sami da je istražite i nikada ne kupujete više nego što možete priuštiti da izgubite. Postoji izreka u zajednici koja je vrlo dobro pravilo za život ... ‘Ostanite skromni, skupljajte sats-ove’.
Pokušavaš da trguješ
Bitcoin je izuzetno nestabilan, nije neobično kada se cena od 20% kreće u bilo kom smeru u jednom danu. Ako niste iskusni i pokušate da igrate na ovim tržištima, GUBIĆETE novac. Hodajte pažljivo.
Ne tražite pomoć
Bitcoin zajednica je živahna i korisna. Postoje stotine različitih telegram grupa, GitHub ili reddit stranica i ljudi na Twitteru koji su spremni da pomognu. Slobodno nas pitajte ako vas nešto zanima. Zapamtite, ako niste sigurni, pitajte.
Nekorišćenje 2FA
Sve što danas radimo online dolazi sa nalogom povezanim sa našim e-mailom. Ako vaš nalog e-maila postane ugrožen, to mogu biti otvorena vrata u vaš život za prevarante. Dvofaktorska autentifikacija pruža i dodatni sigurnosni sloj koji vas štiti od hakovanja. Izbegavajte upotrebu SMS autentikacije, puno bolja opcija je aplikacija ili ključ. Uobičajeni primeri uključuju Authy ili Google Authenticator.
Govoriti ljudima koliko imate Bitcoina
Bitcoin živi na Internetu, koji je, slično kao što je stvarni svet, prepun ljudi voljnih da vam uzmu vaše stvari. Govoreći o posedovanju Bitcoin-a online ili u stvarnom svetu možete sasvim bukvalno da postavite metu na svoja leđa za lopove ili prevarante. Uobičajeni pristup za ljude koji komuniciraju sa mrežom Bitcoin zajednice je stvaranje online ličnosti potpuno odvojene od njihovog stvarnog identiteta.
Novčanici Q+A
Jednostavni odgovori na vaša uobičajena pitanja o Bitcoin novčaniku
Šta je to novčanik?
Bitcoin novčanik je baš kao i vaš pravi novčanik, to je način čuvanja vrednosti. Glavna razlika sa bitcoin novčanikom je u tome što on zapravo ne skladišti bitcoin u sebi, jer Bitcoin-i postoje samo na distribuiranoj knjizi (blockchain). Bitcoin novčanik čuva ključeve potrebne za slanje i primanje vašeg Bitcoin-a preko blockchain-a.
Šta su to seed reči?
Seed reči (ili backup reči) su nizovi od 12 ili 24 engleskih nasumično generisanih reči stvorenih kada se napravi novi novčanik. Ove reči su vaša glavna rezervna kopija za čitav novčanik i ne smeju se deliti ni sa kim, niti čuvati bilo gde, gde bi mogle biti ugrožene. Svako ko ima pristup ovim rečima može vam ukrasti vaš bitcoin.
Šta je to pristupna fraza?
Pristupna fraza (eng. passphrase), često se naziva i 13./25. reč, je korisnički definisana dodatna reč ili fraza dizajnirana da doda dodatni nivo zaštite vašoj rezervnoj kopiji. Ako vaše početne reči postanu ugrožene, a vi ste definisali dodatnu pristupnu frazu, napadaču će biti potrebna vaša pristupna fraza da bi dobio pristup vašem bitcoin-u. Nikada ne čuvajte svoje seed reči i pristupnu frazu zajedno.
Šta je to privatni ključ? (private key)
Generisan iz vaših seed reči, privatni ključ je dokaz da subjekt koji ga kontroliše ima pristup trošenju sa odgovarajuće adrese. Novčanik će generisati privatni ključ za svaku adresu koju kreira. Većina korisnika Bitcoin-a danas nikada neće direktno stupiti u interakciju sa privatnim ključem, njime se automatski upravlja softverom novčanika.
Šta je to javni ključ? (public key)
Javni ključevi se koriste u transakciji da bi se verifikovalo da je vlasnik odgovarajućeg privatnog ključa kreirao važeći potpis kao dokaz o vlasništvu nad sredstvima. Opet, iz opšte perspektive korisnika, javni ključevi se nikada neće direktno koristiti ili videti.
Šta je to prošireni javni ključ? (Xpub)
Prošireni javni ključ (ili Xpub) može se gledati kao glavni pogled u vaš bitcoin novčanik. Xpub je sposoban da generiše i pregleda svaku adresu koja se nalazi u novčaniku, tako da treba da imate na umu sa kime i sa kojima delite proširene javne ključeve. Ako niste povezani sa sopstvenim node-om, velika je verovatnoća da neko drugi zna vaš Xpub. Varijacije Xpub-a uključuju Ipub i Zpub, svi rade isti posao.
Šta je to mobilni novčanik?
Mobilni novčanik je onaj koji radi na vašem mobilnom telefonu. Omogućuju brz pristup vašem bitcoin-u, ali nose rizik da ćete izgubiti svoj bitcoin ako izgubite ili slomite vaš telefon. Ovo ne bi trebalo da predstavlja problem pod uslovom da imate bezbedno spremljene seed reči kako biste mogli da vratite novčanik na drugi uređaj. Nikad ne koristite novčanik koji vam ne pruža opciju da sačuvate svoj private key (backup reči).
Šta je to desktop novčanik?
Desktop novčanik je onaj novčanik koji se pokreće na računaru. Desktop novčanici uglavnom imaju više funkcionalnosti od mobilnih, ali mogu biti i složeniji. Budući da su računari uređaji povezani na Internet i koji su podložni zlonamernim softverima, budite oprezni sa softverima koje instalirate, ne čuvajte velike količine Bitcoina na novčanicima koji su povezani sa internetom.
Šta je to hardware novčanik?
Hardverski, eng. hardware, novčanik (HWW) je uređaj posvećen stvaranju i čuvanju vaših privatnih ključeva. Većina HWW-a se smatra sigurnijim od hardvera opšte namene, poput računara ili mobilnih telefona. To je zato što je površina napada mnogo manja za uređaj napravljen za jedan određeni zadatak. HWW je još sigurniji kada je air-gapped, što znači da uređaj nikada nije priključen na računar. Kada je air-gapped, kod slanja transakcija koriste se QR kodovi ili prenosna datoteka na SD kartici.
Šta je to multi-sig novčanik?
Multi-signature novčanik je novčanik kojem je potrebno više od jednog privatnog ključa za potpisivanje transakcije. Ovo može biti bilo šta, 2 od moguća 3 ključa zbog potpisa ili 15 od 20, a to je na korisniku kada kreira novčanik. Multi-sig je sigurniji od single-siga, ali je mnogo komplikovaniji kada je reč o kreiranju, pravljenju rezervnih kopija i transakcijama. Novi korisnici bi trebali biti pažljivi sa ovim.
Šta je to watch only novčanik?
Watch only novčanik je kreiran pomoću vašeg proširenog javnog ključa (Xpub) koji vam omogućava da pratite stanje novčanika. Watch only novčanici ne sadrže privatne ključeve i sa njih se ne mogu trošiti Bitcoin-i. Budite pažljivi sa kime delite svoje Xpub, svako ko ima pristup ovome može pratiti vaše bitcoin stanje.
Šta je to custodial novčanik?
Custodial novčanik je novčanik u kome vi ne kontrolišete privatne ključeve. Custodial novčanici su često u stanju da prikriju neku složenost bitcoin novčanika, ali to dolazi sa rizikom da ne kontrolišete svoj bitcoin. Custodial novčanicima uglavnom upravljaju menjačnice i korisnici ne bi trebalo da drže velike količine bitcoin-a u njima.
Šta je to non custodial novčanik?
Non custodial novčanik je novčanik u kome imate kontrolu nad svojim privatnim ključevima. To je način na koji je bitcoin dizajniran za upotrebu i uvek treba da se pobrinite da novčanik koji koristite bude non custodial. Brzi način da saznate - da li ste morali da zapišete svoje seed reči kada ste otvorili novčanik? Ako je odgovor da, onda imate novčanik koji je non custodial.
Kako da znam koje naknade da koristim?
Ovo u potpunosti zavisi od toga koliko brzo treba da vaša transakcija bude obrađena i koliko je mreža zauzeta u trenutku kada želite da pošaljete bitcoin. Većina novčanika će vam dati procenu na osnovu ovih parametara i omogućiti vam da se prilagodite prema vašoj potrebi.
Šta je to QR kod?
QR kod je vizuelni prikaz podataka. Najčešće se koriste u Bitcoin-u za pretvaranje dugačkih i teško čitljivih adresa u oblik bar-koda koji može da se skenira pomoću novčanika pošiljalaca. Ovo uklanja potrebu za unošenjem adrese koja bi mogla dovesti do grešaka i slanja bitcoin-a na pogrešnu adresu.
Šta je to block explorer?
Istraživač blokova, eng. block explorer, je website ili aplikacija koja vam omogućava da pronađete detalje bilo kog bloka na blockchain-u. Možete pronaći podatke kao što su broj transakcija u bloku, adresa pošiljaoca, adresa primaoca, plaćene naknade, poslati iznos, visina bloka i vreme bloka.
Čvorovi - Nodes Q+A
Jednostavni odgovori na uobičajena pitanja o Bitcoin čvorovima
Ovde možete saznati više o različitim vrstama čvorova
Šta je to čvor?
Čvor, eng. node, je računar koji pokreće Bitcoin softver. Vaš čvor je vaša verzija Bitcoin blockchain-a i skupa pravila. Zamislite to kao sopstveni ulaz u ekosistem Bitcoin-a. Emituje transakcije, potvrđuje da su bitcoin-i koje primate legitimni i održava vašu privatnost, omogućavajući vam da učestvujete bez oslanjanja na bilo koga drugog.
Kako pokrenuti čvor?
Vaš čvor = vaša pravila. Kada povežete vaš novčanik sa vašim čvorom, ne verujete nikome drugom da će verifikovati vaše transakcije. Čvor vas štiti od loših aktera i takođe održava mrežu decentralizovanom. Ako nemate svoj, vi verujete u tuđi čvor, koji vam govori koliko imate bitcoin-a, i da biste slali/primali svoje transakcije.
Šta treba razmotriti pre pokretanja čvora?
Čvorovi su dizajnirani da rade 24/7, tako da će u zavisnosti od korištenog hardvera biti i neki troškovi napajanja. Većina čvorova radi na računarima sa jednom pločom male snage kao što je Raspberry Pi, tako da su troškovi rada zanemarljivi. Takođe bi trebalo da imate konstantnu internet vezu, jer će čvor koristiti oko 20 GB mesečno. Obavezno kupite ili napravite čvor koji dovršava početni blok ispočetka, inače verujete nečijim tudjim blockchain podacima.
Koje vrste čvorova postoje?
Moguće je pokrenuti čvor na računaru koji trenutno posedujete, jednostavnim preuzimanjem Bitcoin Core softvera. Najčešći čvorovi ‘plug + play’ su MyNode ili Nodl. Oni dolaze sa svime što je potrebno za početak. Mnogi korisnici se odluče da kupe sopstveni hardver i sami instaliraju Bitcoin softver. Uobičajeni izbor softvera su Umbrel, MyNode, Ronin Dojo ili Raspiblitz. Kliknite ovde da biste videli čvorove koje ja preporučujem.
Šta još čvor može da uradi?
Ovo veoma zavisi od konfiguracije koju imate. Neke uobičajene „dodatne funkcije“ uključuju lightning node, electrum server, block explorer, mempool viewer, whirlpool implementation i infrastrukturu plaćanja, poput BTC Pay Server-a.
Šta je to inicijalno preuzimanje blokova?
Inicijalno preuzimanje blokova, eng. initial block download (IBD), odvija se kada prvi put pokrenete čvor. Vaš softver preuzima čitav Bitcoin blockchain i proverava celokupnu istoriju transakcija(410gb). Kada se sinhronizuje, ovo omogućava vašem čvoru da potvrdi da su bitcoin-i koje primate legitimni i odbijaju svakoga ko pokušava da prevari sistem. Vreme sinhronizacije će se razlikovati u zavisnosti od brzine hardvera i interneta, ali u proseku postupak traje oko 4-7 dana.
Šta je to pruned čvor?
Pruning čvor je opcija za vaš čvor da odbaci sve stare podatke koji mu nisu potrebni, nakon što u potpunosti potvrdi čitav blockchain. To može biti korisno ako imate ograničenja za skladištenje, ali to znači da kada je omogućen, vaš čvor ne podržava mrežu, i ne dopušta novim čvorovima koji dolaze na mrežu da preuzimaju informacije iz vašeg blockchain-a.
Šta je to lightning node?
Lightning node je vaš ulaz u lightning network, što je eksperimentalno rešenje za skaliranje izgrađeno na vrhu Bitcoin-a. Obično se pokreće na istom uređaju kao i vaš Bitcoin čvor, i slično kao i vaš Bitcoin čvor koristi se za interakciju sa drugim ljudima na toj mreži slanjem i primanjem uplata.
Mogu li ja da koristim tuđi čvor?
Da, možete se povezati sa tuđim čvorom. Ovo je podrazumevano za veliki broj novčanika, ali treba da budete oprezni iz gore navedenih razloga. Ako imate prijatelja kome verujete, a koji ima pokrenut čvor, ovo bi bila bolja alternativa od davanja vašeg poverenja nekoj nezavisnoj kompaniji. Krajnji način da učestvujete u Bitcoin mreži je pokretanje sopstvenog čvora.
Lightning Q+A
Jednostavni odgovori na uobičajena pitanja o Lightning Network-u
Za detaljniji pregled Lightning Network-a, pogledajte ovde
Šta je to Lightning Network?
Lightning Network je rešenje za skaliranje izgrađeno na vrhu Bitcoin protokola. Omogućava manja, skoro trenutna plaćanja između korisnika po vrlo niskim troškovima. Sprečava potrebu da se svaka izvršena transakcija odvija na „osnovnom sloju“ Bitcoin-a, istovremeno osiguravajući da vrednost koja se šalje poštuje osnovna pravila i vrednosti Bitcoin mreže. Ne možete obavljati transakcije na Lightning-u bez posedovanja bitcoin-a.
Zašto nam je potreban Lightning?
Trenutno nam zaista NE treba Lightning network, jer su normalne bitcoin transakcije (obično se nazivaju „on chain transakcijama“) relativno jeftine, čak i ako želite brzo vreme potvrde. Lightning zaista počinje da blista kada se naknade za ‘on chain’ povećavaju kako se baza korisnika Bitcoin povećava, a subvencija blokova smanjuje. Lightning takođe odlično obećava u manjim, češćim slučajevima plaćanja za stvari poput otključavanja online sadržaja.
Kako Lightning Network radi?
Ana otvara kanal za plaćanje sa Markom pravljenjem on chain „finansijske transakcije“. Veličina ove finansijske transakcije diktira koliku vrednost Ana može da prenese koristeći Lightning. Jednom kada se finansijska transakcija potvrdi na osnovnom sloju, Ana može slobodno da trguje s Markom preko Lightning-a onoliko puta koliko želi, dok jedan ili oboje ne odluče da žele da zatvore kanal. Svaka Lightning transakcija ažurira trenutno stanje kanala tako da jedna strana ne može da prevari drugu za bilo kakva sredstava. Kada se kanal zatvori, najnovije „stanje kanala“ emituje se na Bitcoin mrežu i obe strane će dobiti odgovarajuće stanje natrag u svoj novčanik.
Ali šta ako Ana želi da plati nekome drugom?
Ovde Lightning zaista blista. Kanali za plaćanje mogu biti povezani zajedno da bi se pronašao put do primaoca. Ana ne treba da ima otvoren kanal sa Davidom da bi mu poslala nekoliko sats-ova, mreža će pronaći optimalan put za usmeravanje plaćanja preko drugih kanala. Moglo bi izgledati otprilike ovako Ana> Marko> Petar> David. Tokom čitave rute uplata je kriptografski osigurana tako da bilo koji posrednik ne može ukrasti bilo koje sredstvo koje im ne pripada.
Ko poseduje i kontroliše Lightning Network?
Kao i Bitcoin, Lightning Network je u potpunosti otvorenog koda i nije u vlasništvu nijednog entiteta. Svako može pokrenuti čvor i učestvovati u mreži sa potpunom dozvolom. Postoji više popularnih primena Lightning -a koje uključuju LND, C Lightning i Eclair. Sve ove implementacije su gotovo 100% interoperabilne.
Ima li rudara na Lightning Network-u?
Ne, Lightning Network je izgrađen na vrhu osnovnog sloja Bitcoin-a i zadržava sve iste sigurnosne funkcije. Minimalne naknade koje plaćate na Lightning-u idu učesnicima mreže koji čine deo rute kojom ide vaša uplata, tako da to može biti bukvalno svako ko pokreće Lightning čvor.
Da li Lightning ima svoj blockchain?
Ne, Lightning je mreža kanala za plaćanja u kojoj su svi međusobno povezani. Sve transakcije otvaranja i zatvaranja Lightning kanala odvijaju se na osnovnom Bitcoin protokolu. Lightning nasleđuje sigurnost Bitcoin blockchain-a.
Koje su loše strane Lightning-a?
Za nekoga ko često koristi Lightning Network sa više kanala, upravljanje likvidnošću može postati zamorno. Mreža je relativno mlada i neka plaćanja ponekad mogu propasti, ali kako se razvoj nastavlja ovi slučajevi postaju daleko ređi. Zbog strukture mreže, nije toliko pogodna za veća plaćanja zbog ograničenja likvidnosti svakog kanala. To bi se moglo promeniti kako mreža raste, a ljudi dobijaju poverenje u njenu pouzdanost.
Da li mi treba čvor da bih koristio Lightning?
Slično kao i Bitcoin, nije vam potreban čvor za interakciju sa Lightning mrežom, ali je preporučljivo. Zapamtite, ako ne pokrećete svoj čvor, oslanjate se na tuđi. Dobra vest je da većina Bitcoin čvorova danas dolazi sa ugrađenim Lightning čvorom, tako da ne biste trebali imati previše dodatnog posla da biste se postavili na Lightning.
Šta je to dolazna likvidnost?
Dolazna likvidnost, eng. inbound liquidity, je mera koliko bitcoin-a možete dobiti preko Lightning Network-a. Ako jednostavno otvorite kanal prema nekom drugom, u početku možete samo da šaljete bitcoin-e. To je zato što su sva sredstva na vašoj strani kanala. Ako otvorite kanal za 100k sats-ova, a zatim potrošite 25k, vaša dolazna likvidnost bi bila 25k sats-ova. Bolji način za postizanje dolazne likvidnosti je ako vam neko otvori kanal ka vama, tako da bi sav bilans bio na njihovoj strani kanala.
Šta je to odlazna likvidnost?
Odlazna likvidnost, eng. outbound liquidity, je mera koliko bitcoin-a možete poslati preko Lightning Network-a. Ako otvorite kanal za 100k sats-ova i potrošite 75k, tada vaša odlazna likvidnost iznosi 25k sats-ova. Dobijanje odlazne likvidnosti je jednostavno poput primanja sats-ova na postojećim kanalima ili otvaranja novog kanala sa još sats-ova. Zapamtite, nikada ne možete potrošiti više od ukupne veličine vašeg najvećeg kanala. Mada, ovo će se promeniti kada se uvedu Multi Path Payments.
Gde da počnem?
Pogledajte našu preporučenu stranicu za čvorove koje treba pokrenuti, a zatim odlučite da li želite mobilni ili desktop Lightning novčanik. Naš lični favorit je Zap koji nudi i mobilne i desktop, u kombinaciji sa vrlo dobrim korisničkim interfejsom. Pogledajte Lightning Network guide za detaljniji pogled na Lightning.
Coinjoin Q+A
Jednostavni odgovori na uobičajena Coinjoin pitanja
Šta je to Coinjoin?
Coinjoin (ponekad se naziva i mešanje) je on chain rešenje za privatnost za Bitcoin, koje je prvi put 2013. predložio Gregory Maxwell. Dizajniran je da razbije „heuristiku zajedničkog vlasništva“, koja pretpostavlja da svi unosi u transakciju pripadaju istom entitetu. Bitcoin adrese nisu direktno povezane sa stvarnim identitetima, ali svako ko ima dovoljno vremena i resursa (poput firmi za analizu lanca), mogu početi da prave ove veze gledajući javnu knjigu Bitcoin-a. Coinjoin pomaže da se ovo spreči.
Zašto nam je potreban Coinjoin?
Bitcoin blockchain je potpuno javan, pa ako imate bitcoin koji je vezan za vaš lični identitet (recimo sa KYC menjačnice), može vas na lancu pratiti bilo ko raspolaže sa pravim resursima, a koji nadgleda blockchain. Ovaj problem se pogoršava ako nehotice kombinujete bitcoin-e iz različitih izvora prilikom obavljanja transakcija. Može vam izgledati kao da ovo nije problem i da nemate šta da krijete, ali ako ne biste dozvolili da nepoznati čovek pogleda vaš izvod iz banke, pa zašto onda to dozvoliti sa Bitcoin-om?
Kako CoinJoin funkcioniše?
Postoje različite vrste implementacija Coinjoin-a, svaka sa svojim vlastitim mišljenjem oko iste osnovne ideje. Dva ili više korisnika udružuju svoje UTXO-ove u zajedničku transakciju koja se formira na jedinstven način. Način na koji je transakcija konstruisana otežava nadzornim firmama da tačno znaju čija izlazna transakcija pripada kom ulaznom vlasniku. U najboljem slučaju, svako ko posmatra transakciju može da smisli niz mogućih scenarija ko poseduje koji deo bitcoin-a, ali nikada ne može biti 100% siguran.
Postoje li različiti tipovi Coinjoin-a?
Postoje tri popularne primene Coinjoin-a, 1) Joinmarket koji deluje na strukturi tvorca/primaoca, gde tvorac nudi svoje bitcoin-e (uz naknadu) da bi postao deo transakcije primaoca. 2) Wasabi novčanik koji koristi aplikaciju za desktop računare i nudi velike coinjoin-ove. 3) Samourai Whirlpool nudi male, ali efikasne Coinjoin-ove zajedno sa mobilnim interfejsom koji je lak za upotrebu. To je jedini protokol koji koristim.
Da li je mixer isto što i Coinjoin?
Ne, mixer se obično smatra centralizovanom uslugom kojoj vi šaljete bitcoin-e, a on ih zatim meša i vraća vam tuđi bitcoin. Ove usluge treba izbegavati jer svoje potpuno poverenje stavite u entitet za mešanje da vam u stvari pošalje neki bitcoin nazad nakon što ga vi pošaljete. Uvek biste trebali da imate kontrolu nad svojim privatnim ključevima!
Da li moram da platim za Coinjoin?
Da, sve gore navedene usluge Coinjoin naplaćuju naknade. Svaka od njih ima malo drugačiju strukturu naknada, pa biste uvek trebali sami da istražite pre nego što počnete da koristite bilo koju od njih.
Mogu li izgubiti svoj bitcoin učestvujući u Coinjoin-u?
Kada koristite uslugu Coinjoin poput onih gore navedenih, oni su strukturirani na takav način da uvek imate kontrolu nad svojim privatnim ključevima. Trenutno nismo upoznati sa slučajem da su korisnici izgubili bitcoin kao rezultat greške u protokolu ili zbog bilo kog lošeg aktera koji stoji iza jednog od njih.
Sa kojim problemima mogu da se suočim kada koristim Coinjoin?
Bilo je nekoliko slučajeva kada je menjačnica označila korisnike koji su praćeni do, ili iz usluge Coinjoin. To je rezultiralo time da su neki morali da pruže KYC informacije, a drugima je njihov nalog stavljen na crnu listu, što znači da nisu mogli da koriste menjačnicu. Radi transparentnosti moramo navesti da su svi ovi korisnici povezani sa implementacijom Wasabi novčanika. Nisu zabeleženi problemi sa označenim korisnicima Joinmarket ili Samourai Whirlpool-a. Često zanemareni aspekt Coinjoin-a je ono šta radite nakon što se coinjoin dogodi. Vaše navike trošenja nakon udruživanja, ako se ne urade pravilno mogu u potpunosti poništiti svu stečenu privatnost. Potrošnja nakon mešanja može biti složena tema, ali alati kao što su Stonewall i Stowaway, koje primenjuje Samourai novčanik, čine ovaj postupak mnogo lakšim.
Šta je to Payjoin?
Ponekad nazvan Pay-to-end-point (P2EP), Payjoin je posebna vrsta Coinjoin-a između dve strane kod kojih jedna zapravo plaća drugoj. Zbog strukture transakcije nemoguće je tačno odrediti iznos kojim se transakcija obavlja. Još jedna sjajna stvar u vezi sa Payjoin-om je da Payjoin za firme za nadzor blockchain-a izgleda baš kao redovna Bitcoin transakcija. Ako se široko usvoji, Payjoin će zauvek uništiti zajedničku heuristiku vlasništva nad ulazima.
Šta je to analiza chain-a?
Analiza chain-a je praksa entiteta koji nadgleda blockchain kako bi tražio klastere i obrasce u transakcijama, kako bi pokušao da prati ljude ili da razume njihove navike trošenja. Firme za analizu chain-a to rade pod maskom da pokušavaju da zaustave kriminalce ili terorizam. Iako se slažemo sa sentimentom borbe protiv ilegalnih aktivnosti koje bi mogle naneti štetu drugima, ne slažemo se sa drag net alatima za nadzor koje koriste i koji narušavaju privatnost uobičajenog korisnika bitcoin-a.
Gde mogu da saznam više o Coinjoin-u?
Coinjoin je vrlo složena tema sa puno nijansi, tako da je marljivo istraživanje apsolutno neophodno. Slušajte ovaj podcast Stephan Livera o „zašto“ Coinjoin-a. Ovaj repository od @6102Bitcoin je sjajan niz od tri glavne Coinjoin implementacije.
Bitcoin Mitovi
Otklanjanje najčešćih zabluda o Bitcoin-u.
Bitcoin nema suštinsku vrednost
Parker Lewis najbolje sumira ovaj odgovor u svom članku. „Kao i sav novac, i Bitcoin je podržan kredibilitetom svojih monetarnih svojstava“. Bitcoin je vredan jer je pouzdano oskudan, svako može tačno da proveri koliko je bitcoin-a u opticaju u bilo kom trenutku. Vredan je jer je osiguran sredstvima vrednim milionima dolara širom sveta putem svojih distribuiranih rudarskih i konsenzusnih mehanizama. Vredan je jer je prvi i jedini oblik novca u kojem može učestvovati svako ko ima internet vezu. Ne diskriminiše i ne cenzuriše.
Bitcoin je anoniman
To nije tačno, Bitcoin je ‘pseudonim’. To znači da na mrežnom nivou novčanik ili adresa nisu direktno povezani sa stvarnim identitetom. To znači da firme za nadzor chain-a mogu da prate i povezuju ‘Bitcoin identitete’, a da ne znaju ko su pojedinci koji stoje iza njih. Ali, ako bitcoin kupujete preko entiteta koji zahteva lične podatke, te kompanije mogu povezati stvarnu osobu i bitcoin adresu. Uvek imajte na umu kome dajete ove informacije.
Bitcoin kod se može lako promeniti
Ovo je jednostavno netačno. Bitcoin je postao poznat (i ponekad kritikovan) zbog vremena koje je potrebno da se primene promene u njegovoj bazi kodova. To je zato što sve veće promene Bitcoin-ovog koda moraju da prođu kroz rigorozni postupak stručne provere pre primene. Ako bi ova promena koda rezultirala nedostatkom povratne kompatibilnosti (što znači da stariji softver možda nije kompatibilan), tada proces postaje još sporiji i rigorozniji.
Bitcoin se može kopirati
Na mrežnom nivou vi možete, a mnogo ljudi i jeste. Postoji bukvalno stotine kopija Bitcoin-a, od kojih svaka obično ima malo podešavanja svog koda da bi ga ‘poboljšala’. Gotovo uvek ova ‘poboljšanja‘ dolaze sa ogromnim kompromisima koji im sprečavaju da steknu bilo kakvu privlačnost na ogromnim mrežnim efektima Bitcoin-a. Ove kopije obično imaju nepravedno lansiranje koje se generalno obavljaja radi obogaćivanja njihovih osnivača. Njihov dizajn obično otežava prosečnom korisniku pokretanje čvora. To znači da projekat postaje veoma centralizovan i da nekoliko strana ima veliki uticaj nad bilo kakvim promenama.
Nema dovoljno Bitcoin-a za sve na zemlji
Postojaće samo 21 milion bitcoin-a. Svaki bitcoin sadrži 100 miliona satoshis-a. Što znači da će biti dostupno ukupno 2,1 kvadriliona satoshis-a (to je 2,100,000,000,000,000) na raspolaganju za cirkulaciju oko Bitcoin mreže. Na populaciju sveta od 8 biliona (zaokruženo) to iznosi 262,500 sats-ova za svaku osobu na planeti. Prilično dosta u opticaju, zar ne?
Bitcoin je novac za kriminalce
Bitcoin je novac, i kao i svaki drugi novac mogu ga koristiti i kriminalci. U 2017. godini procenjeno je da celokupno tržište trgovine drogom vredno 500,000,000,000 (500 biliona) dolara. Po trenutnim cenama, to bi umalo moglo kupiti celokupnu Bitcoin mrežu! Verovatno je pošteno reći da se ogromna većina nelegalnih aktivnosti finansira iz normalnih „tradicionalnih“ valuta. Takođe bi se moglo tvrditi da ga javna priroda Bitcoin-ovog blockchain-a može zapravo učiniti manje poželjnim za kriminalce.
Naknade će učiniti Bitcoin neupotrebljivim u budućnosti
Bitcoin mreža ima vrlo efikasno tržište naknada. Bilo je nekih kratkotrajnih skokova kada je obim transakcija eksponencijalno rastao što je rezultiralo višim naknadama. Prosečna naknada za Bitcoin transakciju za poslednjih 12 meseci iznosi $4.77. Kako cena bitcoin-a i broj koristinka raste, tako bitcoin transakcije na mreži (on-chain) postaju vrednije i skuplje u dollar vrednosti, kada one neizbežno porastu, imamo Lightning koji je rešenje za skaliranje. Više o Lightning-u možete pročitati ovde.
Rudari kontrolišu Bitcoin
Iako je istina da rudari igraju ključnu ulogu u radu Bitcoin-a, reći da oni kontrolišu mrežu, nije. Rudari su finansijski podstaknuti da deluju u dobroj nameri, a mreža zahteva samo nešto više od 50% rudara koji su iskreni da bi mreža i dalje funkcionisala. U krajnje malo verovatnom slučaju da većina "podlih" rudara dobije kontrolu nad mrežom, koštaće ih preko 3.6M dolara na sat da bi je održavali. Ako bi uspeli, ne samo da bi to bilo izuzetno skupo, već bi i cena bitcoin-a verovatno naglo pala, čineći njihove napore još manje plodonosnim.
Rudari će prestati sa kopanjem kada padne subvencija za blokove
Očigledno niko ne može biti siguran u ovo, jer je to buduća pojava. Ali zajedničko očekivanje je da će, kako opada subvencija za blokove, naknade će rasti, a rudari će i dalje dobijati kompenzaciju za svoje transakcije obrade posla i obezbeđivanje mreže. Do tog trenutka, verovatnoća postojanja opšteprihvaćenog rešenja za skaliranje, kao što je Lightning, biće daleko veća. Čak i ako bi neki rudari prestali da kopaju, zahvaljujući mrežnom pravilu ‘difficulty adjustment‘, i dalje bi funkcionisalo sasvim u redu i blokovi bi se i dalje proizvodili u proseku svakih 10 minuta. Da difficulty adjustment sjajno funkcionise i kad su veliki procenti u pitanju (27 %) smo videli u Junu 2021 godine kad su Kineski majneri morali ugasiti masine zbog bana bitcoin mininga u kini.
Rudarenje je loše za životnu sredinu
Tačno je da Bitcoin-ov dokaz o radu, eng. proof of work, rudarskog procesa troši ogromne količine energije, ali većina toga sada dolazi iz obnovljivih izvora. Bitcoin takođe podstiče razvoj korišćenja energije iz izvora koji bi inače bili bačeni, poput gorivog prirodnog gasa. Bitcoin troši energiju samo za apetit tržišta. Ako se više ljudi odluči da vrednuje i koristi Bitcoin-e, tada će se više energije posvetiti njegovom obezbeđivanju. Suprotno je takodje tačno. Više o tome dali je bitcoin rudarenje štetno možete pročitati ovdje.
Bitcoin je previše nestabilan
Svakako nije tajna da Bitcoin ima volatilno kretanje cene. To je relativno novo finansijsko sredstvo koje tržište još uvek pokušava da razume. Zbog toga je uvek dobar savet da ne pokušavate da trgujete marketom radi zarade. Usvajanjem strategije obavljanja manjih ali češćih kupovina, vi efektivno ignorišete volatilnost cena Bitcoin-a i dobijate cenu ‘prosečnog tržišta‘. Nefinansijski savet.
Bitcoin je previše spor
Ako bi Starbucks sutra prihvatio bitcoin-e, onda da, čekanje od 10 minuta na potvrdu za plaćanje vašeg lattea možda nije idealna situacija. Za skoro trenutne uplate poput te imamo Lightning. Iako korisničko iskustvo nije toliko uglađeno kao CashApp ili Venmo, ono sigurno stiže. Recimo da želite da prebacite 50,000 USD na drugi kraj sveta, u poređenju sa trenutno dostupnim opcijama, 10 minuta ne deluje tako sporo?
Bitcoin je previše težak za upotrebu
Ovo je krajnje subjektivno gledište i zavisi od svakog pojedinca. Ali da, trenutno se slažem da je lakše dodirnuti bankovnu karticu na terminalu nego izvaditi telefon, skenirati QR kod i sačekati potvrdu. Mislimo da je dodatnih nekoliko koraka za izvršavanje Bitcoin transakcije mala cena koju treba platiti za beneficije koje mreža nudi. Postoje hiljade developera širom sveta koji rade danonoćno kako bi olakšali korisničko iskustvo. Kao i u svim tehnologijama, potrebno je vreme za razvoj i usavršavanje.
Bitcoin Rečnik
Jednostavna objašnjenja uobičajenih Bitcoin termina.
-
Adresa - Bitcoin adresa je niz slova i brojeva. Vaš novčanik može da ih generiše beskonačno mnogo,i svaka je jedinstvena
-
Bip - Predlog za poboljšanje bitkoina, eng. 'Bitcoin Improvement Proposal‘ predstavlja način na koji se promene protokola podnose, odobravaju i označavaju
-
bitcoin (malo ‘b’) - Kada se izrazi sa malim „b“, reč bitcoin odnosi se na jedinicu valute
-
Blok - Skup transakcija koje je rudar grupisao i uspešno iskopao
-
Blockchain - Lanac uspešnih blokova koji se grade jedan na drugom. Svaka je vezana za svog prethodnika
-
Hladno Skladištenje (cold storage) - Metoda čuvanja privatnih ključeva bitcoin-a u okruženju koje nije povezano sa Internetom
-
Potvrda (Confirmation) - Kada se transakcija rudari, deo bloka je jedna potvrda. Svaki sledeći blok je dodatna potvrda
-
Pravila konsenzusa (Consensus rules) - Skup pravila koje mora da poštuje svako ko želi da učestvuje u mreži
-
Težina (Difficulty) - Podesiva vrednost koja diktira kolika je računarska snaga potrebna rudarima za kopanje novih blokova.
-
Naknade (Fees) - Vrednost koja se plaća rudaru za uključivanje transakcije u blok
-
Hardware novčanik - Namenski sigurni uređaj za čuvanje bitcoin privatnih ključeva u oflajn okruženju
-
Hash - Termin dat radnji pretvaranja podataka. Hashing koriste rudari za obradu transakcija
-
Brzina Hasha (Hash Rate) - Ukupan broj hashova koje je izvršio rudar ili grupa rudara, eng. mining pool, izražen u hashovima u sekundi
-
KYC - ‘Znajte svog kupca, eng. Know Your Customer‘ je propis koji zahteva od preduzeća koja prodaju bitcoin-e da prikupljaju identifikacione informacije o kupcu
-
Lightning Network - Dodatni sloj izgrađen na vrhu Bitcoin-a koji omogućava korisnicima da šalju/primaju male uplate sa vrlo niskim naknadama
-
Mempool - Grupa transakcija koja čeka da ih rudar uključi u blok
-
Rudar - Učesnik mreže koji doprinosi računarskoj snazi za obradu transakcija u želji da zaradi naknade i blok nagradu
-
Multisig - Multi-Signature je postavka novčanika koja može zahtevati više privatnih ključeva za autorizaciju transakcije
-
Čvor (Node) - Računar povezan na Bitcoin mrežu koji koristi softver potreban za emitovanje, prenošenje i verifikaciju transakcija
-
Papirni novčanik - Komad papira koji sadrži neophodne podatke za skladištenje Bitkoina zaštićenog od pristupa internetu
-
Privatni ključ - Jedinstveni niz slova i brojeva potreban za čuvanje i transakciju bitcoin-a. Ovo ne biste trebali da delite ni sa kim
-
Proof of Work - Metod kojim rudari nastoje da osiguraju mrežu i uključuju transakcije u blokove
-
Javni ključ - Izveden iz privatnog ključa, javni ključ se koristi prilikom provere potpisa u transakciji
-
Block Reward - Blok nagrada se dodeljuje prvom rudaru koji postigne dovoljan dokaz o radu, eng. Proof of Work. Nagrada = Blok subvencija + sve naknade za transakcije za taj blok. Trenutna blok subvencija je 6,25 BTC.
-
Satoshi or ‘sat’ - Nazvan po anonimnom tvorcu Bitcoin-a i ponekad skraćenici „sat“, Satoshi je najmanja jedinica bitcoin-a. 1 bitcoin = 100 miliona satoshis
-
Satoshi Nakamoto - Pseudonim koji je koristio Bitcoin-ov tvorac (ili tvorci) pre nego što je nestao sa interneta
-
SegWit - Odvojeni svedok, eng. Segregated Witness, je poboljšanje napravljeno 2017. godine kako bi se povećala skalabilnost mreže. Segwit transakcije su jeftinije.
-
Subvencija (Subsidy) - Subvencija se isplaćuje rudaru koji postigne dovoljan dokaz o radu za svaki blok. Trenutna subvencija je 6,25 BTC. Ona se prepolovljava na svakih 210.000 blokova (otprilike 4 godine)
-
Testnet - Odvojena mreža sa gotovo identičnim dizajnom kao Bitcoin, koja služi programerima za testiranje poboljšanja
-
Tor - The Onion Router je alternativna mreža koju koriste korisnici koji žele da sačuvaju svoju privatnost na mreži
-
Txid - Identifikator transakcije, eng. Transaction Identifier, je jedinstveni niz brojeva i slova koji se koristi za označavanje transakcije
-
UTXO - Nepotrošeni izlaz transakcije, eng. Unspent Transaction Output, je deo bitcoin-a potrošen na novu adresu koji se može koristiti kao ulaz u budućim transakcijama
-
 @ 97c70a44:ad98e322
2025-06-06 20:48:33
@ 97c70a44:ad98e322
2025-06-06 20:48:33Vibe coding is taking the nostr developer community by storm. While it's all very exciting and interesting, I think it's important to pump the brakes a little - not in order to stop the vehicle, but to try to keep us from flying off the road as we approach this curve.
In this note Pablo is subtweeting something I said to him recently (although I'm sure he's heard it from other quarters as well):
nostr:nevent1qvzqqqqqqypzp75cf0tahv5z7plpdeaws7ex52nmnwgtwfr2g3m37r844evqrr6jqy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qghwaehxw309aex2mrp0yh8qunfd4skctnwv46z7qg6waehxw309ac8junpd45kgtnxd9shg6npvchxxmmd9uqzq0z48d4ttzzkupswnkyt5a2xfkhxl3hyavnxjujwn5k2k529aearwtecp4
There is a naive, curmudgeonly case for simply "not doing AI". I think the intuition is a good one, but the subject is obviously more complicated - not doing it, either on an individual or a collective level, is just not an option. I recently read Tools for Conviviality by Ivan Illich, which I think can help us here. For Illich, the best kind of tool is one which serves "politically interrelated individuals rather than managers".
This is obviously a core value for bitcoiners. And I think the talks given at the Oslo Freedom Forum this year present a compelling case for adoption of LLMs for the purposes of 1. using them for good, and 2. developing them further so that they don't get captured by corporations and governments. Illich calls both the telephone and print "almost ideally convivial". I would add the internet, cryptography, and LLMs to this list, because each one allows individuals to work cooperatively within communities to embody their values in their work.
But this is only half the story. Illich also points out how "the manipulative nature of institutions... have put these ideally convivial tools at the service of more [managerial dominance]."
Preventing the subversion and capture of our tools is not just a matter of who uses what, and for which ends. It also requires an awareness of the environment that the use of the tool (whether for virtuous or vicious ends) creates, which in turn forms the abilities, values, and desires of those who inhabit the environment.
The natural tendency of LLMs is to foster ignorance, dependence, and detachment from reality. This is not the fault of the tool itself, but that of humans' tendency to trade liberty for convenience. Nevertheless, the inherent values of a given tool naturally gives rise to an environment through use: the tool changes the world that the tool user lives in. This in turn indoctrinates the user into the internal logic of the tool, shaping their thinking, blinding them to the tool's influence, and neutering their ability to work in ways not endorsed by the structure of the tool-defined environment.
The result of this is that people are formed by their tools, becoming their slaves. We often talk about LLM misalignment, but the same is true of humans. Unreflective use of a tool creates people who are misaligned with their own interests. This is what I mean when I say that AI use is anti-human. I mean it in the same way that all unreflective tool use is anti-human. See Wendell Berry for an evaluation of industrial agriculture along the same lines.
What I'm not claiming is that a minority of high agency individuals can't use the technology for virtuous ends. In fact, I think that is an essential part of the solution. Tool use can be good. But tools that bring their users into dependence on complex industry and catechize their users into a particular system should be approached with extra caution. The plow was a convivial tool, and so were early tractors. Self-driving John Deere monstrosities are a straightforward extension of the earlier form of the technology, but are self-evidently an instrument of debt slavery, chemical dependency, industrial centralization, and degradation of the land. This over-extension of a given tool can occur regardless of the intentions of the user. As Illich says:
There is a form of malfunction in which growth does not yet tend toward the destruction of life, yet renders a tool antagonistic to its specific aims. Tools, in other words, have an optimal, a tolerable, and a negative range.
The initial form of a tool is almost always beneficial, because tools are made by humans for human ends. But as the scale of the tool grows, its logic gets more widely and forcibly applied. The solution to the anti-human tendencies of any technology is an understanding of scale. To prevent the overrun of the internal logic of a given tool and its creation of an environment hostile to human flourishing, we need to impose limits on scale.
Tools that require time periods or spaces or energies much beyond the order of corresponding natural scales are dysfunctional.
My problem with LLMs is:
- Not their imitation of human idioms, but their subversion of them and the resulting adoption of robotic idioms by humans
- Not the access they grant to information, but their ability to obscure accurate or relevant information
- Not their elimination of menial work, but its increase (Bullshit Jobs)
- Not their ability to take away jobs, but their ability to take away the meaning found in good work
- Not their ability to confer power to the user, but their ability to confer power to their owner which can be used to exploit the user
- Not their ability to solve problems mechanistically, but the extension of their mechanistic value system to human life
- Not their explicit promise of productivity, but the environment they implicitly create in which productivity depends on their use
- Not the conversations they are able to participate in, but the relationships they displace
All of these dysfunctions come from the over-application of the technology in evaluating and executing the fundamentally human task of living. AI work is the same kind of thing as an AI girlfriend, because work is not only for the creation of value (although that's an essential part of it), but also for the exercise of human agency in the world. In other words, tools must be tools, not masters. This is a problem of scale - when tool use is extended beyond its appropriate domain, it becomes what Illich calls a "radical monopoly" (the domination of a single paradigm over all of human life).
So the important question when dealing with any emergent technology becomes: how can we set limits such that the use of the technology is naturally confined to its appropriate scale?
Here are some considerations:
- Teach people how to use the technology well (e.g. cite sources when doing research, use context files instead of fighting the prompt, know when to ask questions rather than generate code)
- Create and use open source and self-hosted models and tools (MCP, stacks, tenex). Refuse to pay for closed or third-party hosted models and tools.
- Recognize the dependencies of the tool itself, for example GPU availability, and diversify the industrial sources to reduce fragility and dependence.
- Create models with built-in limits. The big companies have attempted this (resulting in Japanese Vikings), but the best-case effect is a top-down imposition of corporate values onto individuals. But the idea isn't inherently bad - a coding model that refuses to generate code in response to vague prompts, or which asks clarifying questions is an example. Or a home assistant that recognized childrens' voices and refuses to interact.
- Divert the productivity gains to human enrichment. Without mundane work to do, novice lawyers, coders, and accountants don't have an opportunity to hone their skills. But their learning could be subsidized by the bots in order to bring them up to a level that continues to be useful.
- Don't become a slave to the bots. Know when not to use it. Talk to real people. Write real code, poetry, novels, scripts. Do your own research. Learn by experience. Make your own stuff. Take a break from reviewing code to write some. Be independent, impossible to control. Don't underestimate the value to your soul of good work.
- Resist both monopoly and "radical monopoly". Both naturally collapse over time, but by cultivating an appreciation of the goodness of hand-crafted goods, non-synthetic entertainment, embodied relationship, and a balance between mobility and place, we can relegate new, threatening technologies to their correct role in society.
I think in all of this is implicit the idea of technological determinism, that productivity is power, and if you don't adapt you die. I reject this as an artifact of darwinism and materialism. The world is far more complex and full of grace than we think.
The idea that productivity creates wealth is, as we all know, bunk. GDP continues to go up, but ungrounded metrics don't reflect anything about the reality of human flourishing. We have to return to a qualitative understanding of life as whole, and contextualize quantitative tools and metrics within that framework.
Finally, don't believe the hype. Even if AI delivers everything it promises, conservatism in changing our ways of life will decelerate the rate of change society is subjected to and allow time for reflection and proper use of the tool. Curmudgeons are as valuable as technologists. There will be no jobspocalypse if there is sufficient political will to value human good over mere productivity. It's ok to pump the breaks.
-
 @ c9badfea:610f861a
2025-06-06 20:05:26
@ c9badfea:610f861a
2025-06-06 20:05:26- Install Food You (it's free and open source)
- Launch the app and tap the ⚙️ icon
- Tap Meals and set up your meal schedule (these items will appear on the main screen)
- Go back and then tap Calorie Goal to configure your daily intake goal
- Return to the main screen
- Now you can tap + on a card (e.g. Breakfast) to add a meal
- Tap + and select Product
- You can now fill in the details manually
- Or tap Download Product, paste the URL of the product from OpenFoodFacts (e.g. https://world.openfoodfacts.org/product/6111242101180/lait-entier-uht-jaouda), and then tap Download
- Tap Create
- You can now adjust intake details like servings
- Tap Save
- Add more products and recipes and start tracking your nutrition!
ℹ️ Once you have created enough products, you can tap + on a meal card on the main screen, then tap + and select Recipe to create recipes from products
ℹ️ Internet connection is only used to optionally fetch product details via URLs; otherwise, the app works completely offline
-
 @ cae03c48:2a7d6671
2025-06-06 20:01:23
@ cae03c48:2a7d6671
2025-06-06 20:01:23Bitcoin Magazine

Matador Technologies Raises C$1.64M To Invest in Their Bitcoin ReserveMatador Technologies Inc. (TSXV: MATA, OTCQB: MATAF), a Bitcoin-focused tech company, announced that it has closed the second tranche of its non-brokered private placement, raising C$1,644,300 through the issuance of 2,652,097 units at a price of $0.62 per unit, with the proceeds going towards investing in their Bitcoin reserve.
 Matador (TSXV: MATA | OTCQB: MATAF | FSE: IU3) closes $1.64M second tranche at $0.62/unit
Matador (TSXV: MATA | OTCQB: MATAF | FSE: IU3) closes $1.64M second tranche at $0.62/unit
 Each unit: 1 share + ½ warrant @ $0.77
Each unit: 1 share + ½ warrant @ $0.77
Proceeds:
 Buy more Bitcoin
Buy more Bitcoin
 Expand gold & Grammies
Expand gold & Grammies
 General corporate growth
General corporate growth  https://t.co/nUm0bFWtO0#Bitcoin #TreasuryStrategy…
https://t.co/nUm0bFWtO0#Bitcoin #TreasuryStrategy…— Matador Technologies (@buymatador) June 4, 2025
“Each Unit consists of one common share and one-half of one common share purchase warrant,” stated in the press release. “Each Warrant entitles the holder to acquire one additional common share of the Company at a price of $0.77 for a period of twelve months from the date of issuance.”
The warrants are subject to acceleration if Matador’s shares trade at or above $1.15 for five consecutive trading days at any time following the date which is four months and one day after the closing date.
The securities from the second tranche are under a hold period that lasts until October 5, 2025. As part of the deal, the company also paid finder’s fees totaling $95,582 and issued 152,165 broker warrants on the same terms.
This follows the first tranche of the offering, announced on May 30, 2025, which included a CAD$1.5 million investment from Arrington Capital, a digital asset management firm co-founded by Michael Arrington.
“We’re thrilled to welcome Arrington Capital as a strategic investor,” said the CEO of Matador Technologies Inc. Deven Soni. “Their deep conviction in the Bitcoin ecosystem and global perspective on digital assets align perfectly with Matador’s vision. This investment enhances our ability to accelerate development of Bitcoin-native financial products and scale our platform globally.”
In that tranche, Matador issued 2,419,354 units under the same terms. Each including one common share and one-half warrant, with full warrants exercisable at $0.77 for one year. Like the second tranche, those warrants are also subject to acceleration if the share price hits $1.15 for five consecutive trading days following the initial four-month period.
“This is more than just a capital raise—it’s a signal that the world’s top digital asset investors see the same future we do,” said the Chief Visionary Officer of Matador Mark Moss.
“At Matador, we believe the next wave of global financial infrastructure will be built on digital assets,” commented Moss. “By aligning with HODL, we’re not just expanding geographically—we’re expanding the reach of the digital assets’ ecosystem into a key innovation hub.”
This post Matador Technologies Raises C$1.64M To Invest in Their Bitcoin Reserve first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-06-06 20:01:16
@ cae03c48:2a7d6671
2025-06-06 20:01:16Bitcoin Magazine

Botanix Launches Federated Sidechain with 16 Members On TestnetBotanix Labs has launched Botanix on testnet as a federated sidechain built on Bitcoin with a 16-node founding federation that includes XBTO, Fireblocks, Antpool, UTXO Management, and other entities (full list below).
The federation ensures that no single entity — including Botanix Labs — controls the network. Botanix Labs has relinquished operational responsibilities, transferring governance and consensus to the node operators. The network plans to evolve into a dynamic federation that supports hundreds of nodes, with the long-term goal of enabling anyone to run a Botanix node. The network’s mainnet is scheduled to launch later this quarter.
Willem Schroé, CEO and co-founder of Botanix Labs, stated in a press release that, “The Bitcoin economy cannot be built on centralized rails. With this 16-node founding federation, we’ve stripped out centralized control and laid the groundwork for a fully permissionless future.”
Botanix’s design emphasizes resilience, with geographically distributed nodes and different kinds of security hardware to minimize single points of failure. The goal is to support consistent availability and uncensorable transaction processing, aligning with Bitcoin’s principles of security and open access. Their use of what they call the “Spiderchain” protocol enables Ethereum Virtual Machine compatibility, allowing applications like lending and staking directly on the network without wrapped assets or bridges.
Philippe Bekhazi, co-founder and CEO of XBTO, commented, “Institutional interest in Bitcoin continues to grow, but that growth depends on secure, decentralized infrastructure that can meet the standards of professional markets.”
Bekhazi also noted XBTO’s commitment to supporting Botanix.
Founded in 2023, Botanix Labs developed the Spiderchain protocol and initiated Botanix. With the network now independently operated, the lab focuses on research, developer tools, and ecosystem support. Botanix enables developers to build financial applications while maintaining Bitcoin’s base layer integrity.
The network’s decentralized structure supports scalability and security for Bitcoin-related applications. As Botanix prepares for its mainnet launch, it aims to expand its federation and move toward further decentralization.
The full founding Botanix federation includes Botanix, Galaxy, Fireblocks, Alchemy, XBTO, Antpool, UTXO Management, Kiln, Chorus One, UndefinedXBlockPI, DAIC, Pier Two, Stakin, Vertex, Stake.fish, and Hashkey Cloud.
Bitcoin Magazine is wholly owned by BTC Inc., which operates UTXO Management, a regulated capital allocator focused on the digital assets industry. UTXO invests in a variety of Bitcoin businesses, and maintains significant holdings in digital assets.
This post Botanix Launches Federated Sidechain with 16 Members On Testnet first appeared on Bitcoin Magazine and is written by Juan Galt.
-
 @ 91117f2b:111207d6
2025-06-06 19:36:06
@ 91117f2b:111207d6
2025-06-06 19:36:06
When news broke out that a superhero was living in Nigeria, Nigerians had mixed reactions.
The Skeptics
- "Oga, which superpower be this? Can you use am make I get scholarship?"
- "I no believe am. Na juju or what?"
- "If you be superhero, why you no use your powers help yourself get good job?"
The Supporters
- "Ahah! We need more superheroes like you in Nigeria! You go make us proud!"
- "Oga superhero, use your powers help us fight corruption and poverty!"
- "We welcome you with open arms! Come, chop jollof rice with us!"
The Entrepreneurs
- "Superhero brother, I get small business wey sell superhero merchandise. You fit be our brand ambassador?"
- "Oga, I get idea! We fit create superhero-themed restaurant, and you fit be the face!"
- "You fit use your powers help me transport goods to other parts of the country?"
The Pragmatists
- "Oga superhero, make sure say you no use your powers cause trouble or break things. We no get money pay for damages."
- "Just make sure you're not one of those superheroes who forgets about the real issues in Nigeria."
- "Use your powers wisely, and don't make us look foolish in front of the world."
What's the most humorous reaction you'd expect from a Nigerian about a superhero in their midst?
stay tuned for more
Part 2
-
 @ 91117f2b:111207d6
2025-06-06 19:13:30
@ 91117f2b:111207d6
2025-06-06 19:13:30
Growth often happens outside our comfort zones, but what if we told you that comfort and growth aren't mutually exclusive? In fact, they can complement each other beautifully.
The Comfort Zone
- Safety and security: A sense of familiarity and control.
- Reduced stress: No unexpected challenges or surprises.
- Predictability: Knowing what to expect.
The Growth Mindset
- Embracing challenges: Stepping out of your comfort zone to learn and grow.
- Learning from failures: Using setbacks as opportunities for growth.
- Resilience: Developing coping mechanisms and bouncing back.
Finding Comfort in Growth
- Embracing the unknown: Finding comfort in the uncertainty of growth.
- Building resilience: Developing coping mechanisms to navigate challenges.
- Celebrating small wins: Acknowledging progress and celebrating milestones.
The Benefits
- Increased confidence: Growing and overcoming challenges builds self-assurance.
- New perspectives: Expanding your horizons and gaining new insights.
- Personal growth: Developing as a person and reaching your full potential.
The Takeaway
Comfort and growth aren't opposing forces; they can work together. By embracing challenges and finding comfort in the process, you can:
- Grow as a person: Develop new skills and perspectives.
- Build resilience: Learn to navigate uncertainty and overcome obstacles.
- Find comfort in the journey: Embracing the process of growth and self-improvement.
What's the most significant growth experience you've had recently?
-
 @ 91117f2b:111207d6
2025-06-06 18:54:04
@ 91117f2b:111207d6
2025-06-06 18:54:04
Emotional pain: the ultimate party crasher. It shows up uninvited, overstays its welcome, and makes you wonder if you'll ever dance again. It is the worst pain you can feel, worse than injuries because it can be treated easily but the one you feel inside can't.
The Symptoms
- Random mood swings (like a hormonal teenager)
- Overthinking (hello, brain hamster wheel)
- Emotional exhaustion (like running a marathon... blindfolded)
The Coping Mechanisms
- Netflix binge-watching (because who needs human connection?)
- Ice cream therapy (the answer to all life's problems)
- Creative expression (art, music, or writing – take your pick)
The Silver Lining
Emotional pain can be a catalyst for:
- Growth: Learning to navigate your emotions and develop resilience.
- Empathy: Understanding others' struggles and forming deeper connections.
- Creativity: Channeling your emotions into art, music, or writing.
The Takeaway
Emotional pain might be awkward, but it's also a chance to:
- Learn to dance again: Find your rhythm and move forward.
- Connect with others: Share your story and find solidarity.
- Create something beautiful: Turn your pain into art.
-
 @ c631e267:c2b78d3e
2025-06-06 18:54:04
@ c631e267:c2b78d3e
2025-06-06 18:54:04Willst du den Charakter eines Menschen kennenlernen, \ so gib ihm Macht. \ Abraham Lincoln
Vermutlich war Friedrich Merz erleichtert nach seinem Besuch beim US-Präsidenten im Oval Office. Dem Bundeskanzler kam zwar neben der Wortgewalt Donald Trumps eher eine Statistenrolle in der Medienrunde zu, aber es hätte natürlich viel schlimmer kommen können. Deswegen hatte er sich wohl vorher Ratschläge geholt, wie man hört unter anderem vom ukrainischen Präsidenten Wolodymyr Selenskyj. Offiziell gab der deutsche Regierungschef sogar an, «außerordentlich zufrieden» mit seinem Antrittsbesuch zu sein.
Dabei gibt es aktuell doch mehr Differenzen als Gemeinsamkeiten. Zu den Themen, mit denen es eine sehr unterschiedliche Umgehensweise hier und dort gibt, gehört die Gesundheit. Trumps Gesundheitsminister, Robert F. Kennedy Jr., kritisiert zum Beispiel, die meisten US-Universitäten würden den Studenten zu wenig über die Bedeutung gesunder Ernährung beibringen. Im Vordergrund der medizinischen Ausbildung stünde zu sehr die Behandlung der Menschen mit Medikamenten. Daher plant er, den Fakultäten die Bundesmittel zu streichen, wenn sie ihren Studenten keine Ernährungskurse anbieten.
Der oft als Verschwörungstheoretiker diffamierte RFK Jr. ist auch Teil des wachsenden Widerstands gegen Geoengineering-Aktivitäten. Die Manipulation von Wetter und Klima beispielsweise durch das Freisetzen von Chemikalien in die Atmosphäre kann kaum gesund sein und soll daher mit Louisiana jetzt in einem weiteren US-Bundesstaat verboten werden. Kennedy hatte derartige Maßnahmen auch schon als ein Verbrechen bezeichnet, das es zu stoppen gelte.
Indes ist der deutsche Beitrag in diesem Kontext, dass Ex-Gesundheitsminister und Covid-Impfpflicht-Befürworter Karl Lauterbach jetzt zum Klimaexperten mutiert. Laut Spiegel soll er Mitglied einer Kommission für Klima und Gesundheit bei der Weltgesundheitsorganisation werden, angeblich unentgeltlich. Vermutlich möchte die WHO im Sinne ihrer One-Health-Initiative mit solcher Lobbyarbeit für «Klimaschutz als Teil des Gesundheitsschutzes» ihren globalen Führungsanspruch untermauern.
Das Thema «Corona» ist im Übrigen noch lange nicht erledigt und das Narrativ bekommt weitere Risse. Nachdem Kennedy in den USA den Covid-«Impfstoff» für gesunde Kinder und schwangere Frauen aus dem empfohlenen Impfplan gestrichen hat, ist eine CDC-Beraterin zurückgetreten, die die Gen-Injektionen für Schwangere gefördert hatte. Auch die australische Regierung hat ihre Impfempfehlungen aktualisiert. Sie räumt jetzt ein, dass der Nutzen des «Impfstoffs» die Schäden für gesunde Jugendliche nicht überwiegt.
Gleichzeitig berichten Medien von einer neuen, anhaltenden «Covid-19-Welle» in China. Es gebe Befürchtungen, dass es zu erneuten Lockdowns und anderen drastischen Maßnahmen kommen könnte, obwohl sich die «Infektionen» laut den Gesundheitsbehörden auf einem Abwärtstrend befinden. In einigen Schulen seien Schüler isoliert und unter Quarantäne gestellt worden.
Isolierung, Überwachung und Kontrolle sind ebenfalls ein höchst ungesundes Erbe der «Coronazeit». Die weltweit vielfach eingeführten digitalen «Impfpässe» wurden als Instrument benutzt, um Kampagnen für digitale Identitäten zu fördern und die entsprechenden Systeme aufzubauen. Gerade hat auch Griechenland mit der Einführung seiner «Personal Citizen Number» den Grundstein für ein einheitliches digitales ID-System gelegt.
Derweil schlagen Datenschützer Alarm wegen des Tracking-Potenzials der sogenannten «Phone Home»-Funktion vieler digitaler Ausweise. Dieses «Feature», bei dem im Hintergrund jedesmal der Aussteller kontaktiert wird, um eine Angabe zu überprüfen, werde ganz leise in der Gesellschaft eingeführt, warnen sie. Das gebe den Regierungen den Vorgeschmack auf eine Macht, die sie kaum jemals wieder loslassen würden. Dagegen hilft nur eins: wachsam sein, hinterfragen und im Zweifel «Nein» sagen, anstatt auf eine vermeintliche Bequemlichkeit hereinzufallen.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ e2c72a5a:bfacb2ee
2025-06-06 18:01:32
@ e2c72a5a:bfacb2ee
2025-06-06 18:01:32The 8-Month Prison Sentence That Changed Crypto's Security Landscape
Freedom comes at a price. Just ask Tigran Gambaryan, who finally resigned from Binance after spending 8 months in a Nigerian prison for doing his job.
While headlines focus on Bitcoin's price swings and Trump-Musk feuds, the real story is how vulnerable crypto executives have become on the global stage. Gambaryan's detention wasn't random – it was a warning shot to compliance officers worldwide.
The former IRS investigator joined Binance to strengthen their compliance, only to be detained while traveling for work. His crime? Being too good at his job in an industry where borders mean nothing but local governments still control everything.
This pattern repeats across jurisdictions: executives detained, exchanges pressured, and compliance officers caught in geopolitical crosshairs. Meanwhile, companies like Uber quietly explore stablecoins to move money globally while avoiding similar risks.
What security measures are you implementing to protect your crypto assets and identity when traveling internationally? The next detention story could impact your investments more than any market dip.
-
 @ 91117f2b:111207d6
2025-06-06 18:32:33
@ 91117f2b:111207d6
2025-06-06 18:32:33
The weight of unspoken words can be a heavy burden, but it's a burden that can be lifted. By expressing ourselves authentically, we can:
- Release pent-up emotions: Sharing our feelings can help us process and understand them better.
- Form deeper connections: Vulnerability can lead to more meaningful relationships and a sense of community.
- Find our voice: Expressing ourselves can help us discover our unique perspective and style.
Creative Outlets for Expression
- Writing: Journaling, poetry, or short stories can be powerful ways to express emotions.
- Art: Painting, drawing, or photography can provide a visual outlet for feelings.
- Conversation: Talking to a trusted friend, family member, or therapist can help you process your emotions.
The Courage to Be Vulnerable
Being vulnerable takes courage, but it's a courage that can lead to:
- Deeper self-awareness: Understanding your emotions and needs.
- More authentic relationships: Building connections based on trust and empathy.
- Personal growth: Developing resilience and confidence.
Your Story Matters
Your experiences, thoughts, and feelings are unique and valuable. By sharing your story, you can:
- Inspire others: Your words can motivate, comfort, or empower others.
- Process your emotions: Sharing your story can help you heal and grow.
- Leave a legacy: Your words can outlast you, leaving a lasting impact.
Everyone has a way to express themselves, what's yours?
-
 @ 502ab02a:a2860397
2025-06-06 17:27:33
@ 502ab02a:a2860397
2025-06-06 17:27:33เฮียไปเจอบทความต่างประเทศของเมื่อราวๆปี 2022 ที่เล่าเรื่องการจับมือกันระหว่าง CP Foods หรือที่คนไทยเรารู้จักกันดีในชื่อ “ซีพี” กับบริษัทจากอิสราเอลที่ชื่อ Future Meat Technologies ชื่อดูเหมือนจะหลุดมาจากหนังไซไฟ แต่สิ่งที่เขาทำไม่ใช่ยานอวกาศ ไม่ใช่หุ่นยนต์ แต่เป็น “เนื้อ” ใช่แล้ว เนื้อจริง ๆ แต่ไม่ต้องฆ่าสัตว์ เป็นเนื้อเพาะเลี้ยงจากเซลล์ในห้องแล็บ ที่เขาเรียกกันว่า cultivated meat หรือเนื้อเพาะเลี้ยง เฮียเห็นชื่อครั้งแรกก็แอบคิดว่ามันจะเป็นของเล่นของคนไฮเทคหรือเปล่า แต่พออ่านลึกเข้าไป มันกลายเป็นเรื่องจริงจังมาก เพราะมันเกี่ยวกับอนาคตของอาหารที่คนทั้งโลกอาจจะต้องพึ่งพาโดยไม่รู้ตัว
บริษัท Future Meat ทำเรื่องนี้ได้ล้ำมาก เขาสามารถเพาะเลี้ยงเซลล์ของสัตว์ให้เติบโตเป็นเนื้อได้โดยไม่ต้องฆ่าใครเลย ฟังดูเป็นมิตรกับโลกกับสัตว์มาก แต่มันมีโจทย์ที่ยากกว่านั้น คือจะทำอย่างไรให้เนื้อเพาะเลี้ยงนี้ “น่ากิน” สำหรับคนเอเชีย เพราะถ้าจะขายแค่ฝรั่งที่ชอบอกไก่จืด ๆ ก็ง่ายหน่อย แต่คนเอเชียเรานี่สิ ชอบเนื้อที่เรียกว่าเนื้อดำ ซึ่งจะเข้มข้น แน่นๆ มัน ๆ หอม ๆ สีเข้ม รสชัดแบบสะโพกไก่ น่องไก่ หรือเนื้อวัวที่เอาไปทำกะเพรา ทำแกง ทำผัดเผ็ดได้ CP เขาเข้าใจรสนิยมนี้ดี และนั่นแหละคือเหตุผลที่เขาไปจับมือกับบริษัทนี้ เฮียว่ามันไม่ใช่แค่เรื่องเทคโนโลยี แต่มันคือการจับมือกันระหว่างห้องแล็บกับตลาดรสนิยมบนจานข้าวของคนจริง ๆ
สิ่งที่เฮียว่าน่าสนใจคือ CP เข้ามาเติมเต็มสิ่งที่บริษัทเทคโนโลยีขาด นั่นคือความเข้าใจตลาดเอเชียแบบลึกซึ้ง ซีพีมีเครือข่ายทั่วภูมิภาค รู้ว่าคนไทย คนจีน คนอินโดฯ กินอะไร ชอบรสไหน จะเข้าไปวางขายในตลาดไหนต้องระวังวัฒนธรรมการกินอะไรบ้าง มันไม่ใช่แค่จะเอาเนื้อเพาะเลี้ยงมาย่างแล้ววางใส่เบอร์เกอร์แล้วขายได้เหมือนกันหมด CP เลยเป็นเหมือนสะพานเชื่อมจากโลกห้องแล็บเข้าสู่โลกจริงที่มีคนกินจริง ๆ นั่งรออยู่
แต่ในขณะที่หลายคนมองว่าเนื้อเพาะเลี้ยงคือความหวังใหม่ของโลก ที่ไม่ต้องฆ่าสัตว์ ไม่ปล่อยคาร์บอน ไม่ใช้พื้นที่มหาศาล เฮียก็อดคิดไม่ได้ว่า ถ้าระบบอาหารในอนาคตถูกควบคุมโดยไม่กี่บริษัท ใครเป็นคนควบคุมสูตร ใครถือสิทธิ์ในเซลล์ต้นแบบ ใครควบคุมแหล่งวัตถุดิบที่ใช้เพาะเลี้ยง แล้วคนกินอย่างเราจะเหลืออิสระแค่ไหนในการเลือกอาหารของตัวเอง มันอาจจะดูดีในระยะสั้น แต่ในระยะยาว ถ้าเราต้องพึ่งของพวกนี้เป็นหลัก แล้วของจริงที่โตจากดิน มีชีวิต กำลังถูกแทนที่ด้วยของเพาะในถัง เฮียว่าความเป็นมนุษย์ของเราก็อาจจะค่อย ๆ หายไปเหมือนกันโดยไม่รู้ตัว ถ้าในอนาคต “เนื้อ” ไม่ได้มาจากสัตว์ แต่กลายเป็นของเพาะเลี้ยงที่ออกแบบโดยใครบางคนในห้องแล็บ เราจะยังมีสิทธิ์เลือกรสชาติชีวิตของตัวเองอยู่มั้ย หรือเรากำลังค่อย ๆ โดนโปรแกรมผ่านของที่เรียกว่าอาหาร โดยไม่รู้เลยว่าใครคือคนเขียนโค้ดนั้น
siamstr #pirateketo
-
 @ e2c72a5a:bfacb2ee
2025-06-06 17:23:32
@ e2c72a5a:bfacb2ee
2025-06-06 17:23:32The Freedom Paradox: Why Bitcoin's Biggest Threat Isn't Regulation
Bitcoin was designed to escape government control. Now it's becoming the darling of presidents, corporations, and nation-states.
Japan's Metaplanet just announced plans to acquire 91,000 Bitcoin in the next 18 months. Michael Saylor's Strategy quadrupled its stock offering to $1 billion for more Bitcoin purchases. Even Pakistan's crypto minister is meeting with Wall Street and NYC's mayor.
The very institutions Bitcoin was created to circumvent are now its biggest champions.
This isn't just ironic – it's potentially dangerous. As Bitcoin becomes institutionalized, the revolutionary spirit that made it valuable risks being diluted. When presidents tweet about it and corporations hoard it, does Bitcoin still represent financial freedom?
The true test isn't Bitcoin's price but whether it remains censorship-resistant when those same powerful entities decide they want control.
Is Bitcoin being captured by the establishment, or has it simply arrived? Your answer determines whether you're investing in revolution or just another asset class.
What do you think happens when the rebels become the rulers?
-
 @ 91117f2b:111207d6
2025-06-06 18:17:24
@ 91117f2b:111207d6
2025-06-06 18:17:24
Nigeria, land of vibrant culture, delicious jollof rice, and... creepy crawlies! Yes, our beloved country is home to some insects that might just make you shudder. But don't worry, we've got you covered!
The Top 5 Most Feared (and Fascinating) Insects in Nigeria
-
Mosquitoes: The Unwelcome Guests- These tiny terrors are notorious for their itchy bites and malaria-spreading abilities. But let's be real, who needs personal space when you're trying to enjoy a peaceful evening outdoors?
-
Cockroaches: The Ultimate Survivors- These resilient critters can thrive in even the most inhospitable environments. They're like the Nigerian version of The Terminator – unstoppable and unkillable!
-
Scorpions: The Stinging Sensations- With their menacing stingers and armored shells, scorpions are the ultimate party crashers. Just don't invite them to your next outdoor gathering!
-
Tsetse Flies: The Biting Buzz- These pesky flies are known for their painful bites and ability to transmit diseases. But hey, at least they're consistent – they'll always bring their A-game to the biting party!
-
Ants: The Marching Army- Some ant species in Nigeria are infamous for their painful stings and organized invasions. It's like they're trying to take over the world, one crumb at a time!
The Silver Lining
While these insects might seem daunting, they play a vital role in Nigeria's ecosystem. They pollinate, decompose, and even serve as a food source for other animals. So, let's appreciate these creepy crawlies from a safe distance!
Survival Tips
To coexist with Nigeria's insects, remember:
- Wear protective clothing when outdoors
- Keep your home clean and tidy
- Use insect repellent (preferably the strong stuff)
- Don't mess with ants – they'll retaliate!
The Nigerian Insect Brigade
While we might joke about these insects, it's essential to respect their place in our ecosystem. Who knows, maybe one day we'll learn to appreciate their quirky charm?
In Nigeria, we don't have aliens, to pose as a threat "(alien invasion)" , we already have insect invasion.
-
-
 @ 4898fe02:4ae46cb0
2025-06-06 16:56:23
@ 4898fe02:4ae46cb0
2025-06-06 16:56:23I had a bit of extra time this week to attend a call organized by npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc regarding a privacy focused project he's been working on for the last year-or-so. Shout-out to npub1e0z776cpe0gllgktjk54fuzv8pdfxmq6smsmh8xd7t8s7n474n9smk0txy for encouraging me to do so, pushing my somewhat out of my comfort zone in reporting on technical updates.
Also, if you know of or are involved in similar dev calls and would like a report done, please reach out and feel free to share calendar updates.
--npub1f4www6qjx43mckpkjld4apyyr76j3aahprvkduh9gc5xec78ypmsmakqh9 would be awesome to see this talked about on SNL later today, as it seems to be a very important/overlooked project for the future of privacy, nostr and bitcoin broadly.
Anyway, here's the unschooled report--my technical explanations may sometimes be scant, but I've done my best to provide more qualified sources where necessary.
Bringing Secure, Confidential Group Chats to Nostr - A Monthly MLS on Nostr Dev Call
Posted originally to Stacker News \~nostr territory
Developers met Tuesday, 3 Jun at 1600UTC at what would be the first of a monthly series of community calls to discuss updates and respond to questions about the implementation of the MLS (Messaging Layer Security) standard over nostr.
npub1klkk3vrzme455yh9rl2jshq7rc8dpegj3ndf82c3ks2sk40dxt7qulx3vt, npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn, npub1klkk3vrzme455yh9rl2jshq7rc8dpegj3ndf82c3ks2sk40dxt7qulx3vt and npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc among others attended and contributed to a discussion about the latter's research and development on implementing a new messaging standard on nostr using MLS.
The call highlighted some of the features of MLS, a relatively new (as of 2023) secure and confidential messaging and group-chat protocol standard. It is modeled to achieve a similar level of security as Signal, prioritizing forward-secrecy and post-compromise security, multi-device compatibility, as well as the ability to scale for large groups.
For those not familiar,
Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.\ Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future. ^1
Developers working on the project indicated that it will be an improvement on current instant-messaging standards commonly used by nostr clients, such as nip17, for a relatively simple implementation.
Those in attendance overall showed enthusiasm to push this project forward and developers interested are being encouraged to fork the the Nostr-MLS Rust Library to begin working it into their stack. Notably, jeffg and Hillebrand are keen to see new contributors work on the project.
Participants had the opportunity to ask technical questions about how the library handles some features as well as how to begin contributing.
Discussion also centered around issues with MLS (such as potential key-package rotation DOS attack vectors and de-syncing) as well as some key concepts for the new messaging standard such as how key-packages are signed by a users nsec and published to key-package inbox relays before being rotated.
Proofs of Concept
White Noise and 0xchat both have implemented MLS on nostr. These are the first to prove that the concept of secure-confidential group messaging is possible over the distributed nostr-relay protocol.
Learn More
jeffg has kept detailed project updates on his nostr account. Notably, the post MLS Over Nostr explains the vision he has for the project and his presentation The Past and Future of Messaging on Nostr (youtube) gives a high-level overview of messaging on nostr and the problems he is working to solve.
Follow npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc on your favourite nostr client for call updates.
Link to join.
Related:
-
 @ e2c72a5a:bfacb2ee
2025-06-06 16:35:04
@ e2c72a5a:bfacb2ee
2025-06-06 16:35:04The secret map whales use to liquidate you isn't actually secret anymore.
Bitcoin liquidation maps reveal exactly how market makers target overleveraged positions. When too many traders pile into the same price level with borrowed money, it creates a juicy target.
These maps show concentrated liquidation points where thousands of traders have set their stop losses. Whales don't randomly move markets - they strategically push prices to trigger these cascading liquidations, creating artificial price movements that benefit their positions.
The most dangerous part? Most retail traders have no idea they're swimming in predatory waters. While they're busy following technical patterns and news cycles, institutional players are simply following the money - your money.
Learning to read these liquidation heat maps isn't just a trading edge - it's survival. The difference between profitable traders and liquidated ones often comes down to position sizing and avoiding the obvious liquidation zones where everyone else has clustered.
Are you monitoring the liquidation map before your next leveraged trade, or are you just another dot on someone else's profit target?
-
 @ 4d41a7cb:7d3633cc
2025-06-06 18:16:08
@ 4d41a7cb:7d3633cc
2025-06-06 18:16:08Have you ever stopped to think how retarded our monetary system is? If the U.S. is the most powerful nation on earth, has the biggest gold reserves, and has the monopoly over the global reserve currency... Why the fuck are they still 34 trillion in debt? One reporter finally asked this important question to the Chair of the Council of Economic Advisors (whatever that means): Jared Bernstein.
> JB: They, they, um, they, yeah, they, they, um, they sell bonds. Yeah, they sell bonds, right? Since they sell bonds and people buy the bonds and lend them the money. Yeah, so, yeah, I guess I'm just, I don't, I can't really talk. I don't, I don't get it. I don't know what they're talking about.
BANKSTERS DON'T WANT US TO KNOW HOW THIS MECHANISM WORKS BECAUSE THEY KNOW THAT IF WE KNOW, WE ARE GOING TO GET MAD. NOT EVEN POLITICIANS AND HIGH-RANKED OFFICIALS UNDERSTAND WHAT I AM ABOUT TO EXPLAIN.
THE CORRECT QUESTION TO ASK IS: IF THE U.S. PRINTS DOLLARS, WHY DOES IT HAVE SUCH A BIG DEBT? IF YOU HAD THIS QUESTION BEFORE: GOOD FOR YOU!
THE ANSWER IS: The U.S. has debt because every Federal Reserve Note, a.k.a. FRN ("DOLLAR"), that the Federal Reserve prints is a NOTE that the government owes plus interest. The FRNs are debt instruments! How is this possible? You may ask... Who do they owe this debt to? "The government does not print "dollars" out of thin air."
The government prints bonds (debt) out of thin air, and the Federal Reserve buys these bonds, printing FRNs out of thin air. And that is how "dollars" come into existence. This doesn't make sense, right? Thomas Edison thought the same when he said:
> “If the government can issue bonds, it can issue currency. Both are promises to pay, but one promise fattens the usurer and the other helps the people.”
New York Times, 6 de diciembre de 1921The U.S. could print its own debt-free, non-interest-bearing Treasury notes. Like Lincoln printed the Greenbacks to finance the Civil War, Kennedy issued treasury notes with E.O. 11110. What's the difference between a United States note and a Federal Reserve note?
ONE PROMISE FATTENS THE USURER, AND THE OTHER HELPS THE PEOPLE.
The truth is the Federal Reserve took over the U.S. government in 1933 when it declared bankruptcy and the power was passed to its creditors: the Federal Reserve. This institution artificially inflated and contracted the currency supply to create the Great Depression (1929) and finally bankrupted the U.S. government in 1933. They forced the Gold Standard Act in the 1900s, and then they officially took the U.S. out of it in 1934. This bank stole the gold of the American people, and then they stole the gold of other nations in 1971!!!
I want to clarify that I am not making this up, but I am standing on the shoulders of giants like Alfred Owen Crozier (1863-1939). This legend was lobbying against the Federal Reserve Act in 1912, and he wrote the book U.S. Money vs. Corporate Currency, where he documented the intent of this private group of banksters to create a private central bank that would counterfeit currency and take over the republic, bankrupting it. He literally predicted the Great Depression. His worst nightmares turned into a reality. Here you have my top 3 books from him:

Most recently, another legendary character that did a monumental work in dismantling this giant fraud was Thomas Schauf (1949). He lived years out of his savings to prove this giant fraud to the American people. He is a certified CPA who became a full-time lecturer on “money and debt” after the 1987 crash. He dismantled the Federal Reserve cartel, and he also explains the fraud of the commercial bank's credit creation process using the Federal Reserve's own publications.

Both Alfred and Thomas prove that the Federal Reserve is an unconstitutional private central bank that took the power to coin currency from the government, unlawfully transferring that sovereignty to private corporations. Crozier provided the original historical record, and Thomas provided the insider accounting documentation.
CROZIER CONTRIBUTIONS
-
Introduced the term “corporate currency” to flag that the new notes would be liabilities of a private cartel, not of the U.S. Treasury.
-
Warned about the non gold redeem-ability of this private paper: any emergency suspension of specie payments would convert the notes into a floating, unbacked claim—“irredeemable except in more paper.”
-
National bankruptcy forecast: once Treasury debt became the key collateral behind private notes, taxpayers would shoulder every panic, culminating in “the insolvency of the Republic.”
THOMAS SCHAUF UNIQUE CONTRIBUTIONS
-
FOIA stock-subscription ledgers (1991): first public list of the individual banks and share counts that capitalized each of the 12 Reserve Banks.
-
Annotated FRB H-4-1 balance sheets (weekly releases): line-by-line notes showing how “Federal Reserve Notes outstanding” are booked as a liability to member banks, not to the public.
-
Discount-window flow charts: traced how reserves created in New York are pyramided 30-to-1 in downstream banks, then recycled into Treasuries.
-
Internal circulars on surplus rebates: revealed the dividend formula (6 % to stock-holding banks) and the legally mandated tax exemption on that income.
Thomas Schauf is the researcher who turned the Federal Reserve’s own accounting records into hard evidence of private ownership and systemic leverage.
The Federal Reserve is the biggest fraud in human history and the most profitable business on earth: it prints currency out of thin air, and it lends it to the government at interest, buying treasury bills. For every FRN they print at no cost they earn $1 plus interest.
NEW YORK FEDERAL RESERVE OWNERS
• Chase Manhattan Bank N.A. • Citibank N.A. • Morgan Guaranty Trust • Chemical Bank • Bankers Trust Co. • Manufacturers Hanover
HOW CAN AMERICA END THIS FRAUD?
Alfred Owen Crozier, Thomas Schauf, and I will agree on the same solution: Convert existing Federal Reserve notes into U.S. notes on a one-for-one basis. This will automatically end the interest on the U.S. debt: THE BIGGEST U.S GOVERNMENT LIABILITY.
You cannot fix the deficit if you don't nationalize the Federal Reserve Inc and replace every interest-bearing Federal Reserve Note with a non-interest-bearing U.S. Note.
YOU CAN LITERALLY ELIMINATE THE U.S. PUBLIC DEBT BY ISSUING AN EXECUTIVE ORDER REPLACING FRNs FOR U.S notes. Then force private banks to lend only their own capital or time deposits, ending the credit-creation privilege and the boom and bust cycle.
Ron Paul will also agree with this. Every person that understands the monetary system will agree with this.
All freedom-loving Americans who believe in the Revolutionary War, the Constitution, and the Bill of Rights need to join their efforts to fight this corrupt system, abolish the federal system, the national debt, and most of the taxes, and re-establish an honest monetary system.
The American population needs to understand the truth and why they fought the Revolutionary War: FOR THIS SAME REASON! WAKE UP, AMERICA!
This cannot be fixed with Bitcoin TODAY, but probably in the coming decades. But in the meantime it can be done with Treasury notes. This needs to be done if you want to avoid hyperinflation and a state of emergency, martial law, and total disaster.
Time is running out and you need to take action fast. Interest rates are eating up all the revenue of the government and your tax money is going into an unpayable black hole for this very reason.
Americans have two choices: stay and fight or escape before disaster strikes. And no, I am not being extremist, it is a sad reality. Read this books, study this and talk about this with all you fellow Americans.
This is the most important issue you should be discussing about.
-