-
 @ a296b972:e5a7a2e8
2025-06-06 13:00:24
@ a296b972:e5a7a2e8
2025-06-06 13:00:24Wie schon gewohnt durch die Empfänge von Baerbock und von der Leyen im Ausland, in Washington ein Empfang etwas oberhalb der 1. Class, von Staatsempfang keine Spur. Passt eigentlich auch nicht für den 51. Bundesstaat der USA. Aber immerhin flog die „Bundesrepublik Deutschland“ ohne Pannen, das ist ja auch schon mal was. Und bei solch einem erfahrenen Chef-Co-Piloten an Bord, der auch mal schnell einspringen könnte, sozusagen als 2. Wahl, kann eigentlich gar nichts mehr schief gehen. Vielleicht hat Fritzchen den Kapitän auch gefragt, ob er auch mal ans Steuer darf, wenn sich die Gelegenheit schon bietet.
Im Gepäck die eingerahmte Geburtsurkunde von Großvater Trump. Als ob Donald die sich nicht selbst besorgen könnte, wenn er Interesse daran hätte. Vielleicht hat er sie auch schon.
Die Übergabe, kurz und schmerzlos. Sie erinnert an einen Sketch von Loriot, „Weihnachten bei Hoppenstedts“:…oh, eine Krawatte! Der versprochene Ehrenplatz wird sich vermutlich in einer der unteren Etagen des Weißen Hauses befinden.
Man muss auch erst einmal darauf kommen, so typisch deutsch: Eine Geburtsurkunde als Geschenk. Das könnte man auch als einen Wink mit dem Zaunpfahl ansehen: Erinnere Dich an Deine deutschen Wurzeln (und lass uns gefälligst nicht fallen?).
Jetzt zur Einschätzung des Treffens: Vorfahrt mit frisch gewaschenem Auto, Schwarz-Rot-Gold vorne am Kotflügel, wie es sich gehört, Schwarz-Rot-Gold am Eingang. Ganz schön rechts. Warum eigentlich nicht die Regenbogenfahne?
Begrüßung durch Trump auf Nachfrage eines Reporters: „I love the People of Germany.“
Und Merz nutzt die Gelegenheit sich in Biedermeier-Style einzuschmeicheln: „And I love the People of America.“
Und Trump erwidert: „That‘s good!“
In welcher Atmosphäre findet das Treffen statt?
Trump hat ein Elefantengedächtnis. Er weiß um die abwertenden, diplomatiefreien Aussagen, die Merz über ihn gemacht hat. Er weiß, dass Merz ihn mehrfach persönlich beleidigend angegriffen hat. Als Präsident der USA steht man darüber. Aber man weiß es! Trump ist sich darüber im Klaren, mit welcher Geisteshaltung er es bei Merz zu tun hat.
Vor dem Hintergrund passt seine Aussage zur Presse: „Ich liebe die Deutschen.“ Das ist eine demokratische und höfliche Sympathiebekundung gegenüber der deutschen Bevölkerung, die Merz zwar miteinschließt, aber nicht direkt an ihn gerichtet ist.
Trump begrüßt Merz mit Handschlag, begrüßt aber eigentlich nicht den Kanzler, sondern die Deutschen.
Andererseits darf der Äußerung „Ich liebe die Deutschen“ auch nicht zu viel Bedeutung beigemessen werden, denn die Amerikaner sind ja dafür bekannt, dass sie gerne und schnell alles lieben: I love America, I love Coca-Cola, I love Peanuts und eben auch I love the People of Germany.
Merz nutzt gleich die Gelegenheit, sich anzubiedern, in dem er pariert: „Und ich liebe die Amerikaner.“, worauf Trump antwortet: „That’s good!“ Das kann man übersetzen mit „Das ist gut!“, aber auch mit „Das ist auch gut so!“, bei letzterem wäre es eine versteckte Drohung. Mach Dir bewusst, wo Du bist und mit wem Du es zu tun hast und verhalte Dich danach!
Nonverbal wird dem sonst in Deutschland so eloquent wirken wollenden, akzentuiert sprechenden Merz die Bedeutung zugedacht, die ihm aus Sicht von Trump gebührt. In Frankfurt heißen sie Wiener, in Wien heißen sie Frankfurter.
Somit sind die Voraussetzungen, unter denen das Treffen stattfinden soll, schon einmal von amerikanischer Seite aus geklärt.
Du bist hier Gast in meinem Haus, also benimm Dich auch entsprechend! Ich bin der Präsident der Vereinigten Staaten von Amerika und Du bist klein Fritzchen aus dem Sauerland. Die Machtverhältnisse sind unausgesprochen geklärt.
Man hat in gewohnter Manier Platz genommen. Die Journalisten stellen Ihre Fragen ausschließlich an Trump. Zufall, oder Teil einer orchestrierten Aufführung, das wird man nie erfahren.
So oder so, die Journalisten signalisieren durch ihre Fragen an Trump, auf welcher Seite sie stehen, es weht der Geist von „America first“. Was Germany dazu zu sagen hat, interessiert niemanden, warum auch?
Die Einseitigkeit ist schon sehr auffällig. Eigentlich hätte es die Journalisten interessieren müssen, wie Deutschland zu verschiedenen Themen steht. Keine Fragen an Merz zu Zöllen, zur Ukraine, zur Meinungsfreiheit, zur Opposition. Mit dem Anspruch, ein breites Spektrum an Meinungen abbilden zu wollen, hat das eigentlich nichts zu tun. Wenn das die Vorstellung von „Freedom of Speach“ ist, dann können hier Zweifel aufkommen.
Falls diese Fragerunde in Hollywood-Manier gestaltet wurde, dann spräche das eher für Propaganda pro Trump. Wäre es Propaganda, dann wäre das Ziel allerdings erreicht worden: Kein Mensch interessiert sich für das, was Deutschland, vertreten durch Merz, zu sagen hat.
Trump setzt dem Ganzen zum Schluss noch die Krone auf, in dem er die Journalisten auffordert, nun endlich doch auch noch ein paar Fragen an Merz zu richten. Das unterstreicht nochmals das (geplante oder ungeplante) Desinteresse der anwesenden Journalisten, die sich nun fast schon genötigt fühlen, anstandshalber etwas zu fragen.
Merz, der bisher brav wie ein Schüler dem Lehrer zugehört hat, muss nun blitzschnell entscheiden, wie er die „künstlich“ hergestellte Möglichkeit nutzen kann, um, etwas unter Druck, durch die Kürze der Zeit, mit wenigen Worten seinen Standpunkt nach außen zu tragen. Seine konzentrierte Kernbotschaft, die Essenz, die Deutschland aus den USA und die übrige Welt hören soll, ist: Er steht weiter an der Seite der Ukraine und Russland ist ausschließlich das Böse.
Ganz schön raffiniert, denn so hat Trump es geschafft, das Konzentrat der Merz’schen Logik aus ihm herauszupressen.
Beide bekunden den Willen zum Frieden. Gleichzeitig wird jedoch auch klar, was jeder unter Frieden versteht: Merz will „Frieden durch Krieg“ und Trump will „Frieden durch Frieden“.
Auf rund 45 Minuten Trump kommen rund 4 Minuten Merz. Die Minuten drücken exakt die Machtverhältnisse aus.
Hätte Trump vorgehabt, Merz vorzuführen, ihm die Ohren langzuziehen, ihn bis auf die Knochen zu blamieren, er hätte reichlich Möglichkeiten dazu gehabt.
Er hätte Merz fragen können, warum er seinerzeit meinte, dass ihn, Trump, als Arschloch zu bezeichnen, noch gelinde sei. Er hätte ihn fragen können, warum er Trump als Gefahr für die Demokratie ansieht. Trump weiß darum, er hat es jedoch nicht angesprochen, was ist der Grund dafür?
Und Vance, der ebenfalls anwesend war, hätte seine Feststellungen zur Meinungsfreiheit und der „Fire-Wall“ gegen die Opposition, die er auf der Sicherheitskonferenz in München klar formuliert hat, wiederholen können, jetzt, wo doch der Kanzler, als erster Ansprechpartner für Deutschland, persönlich hätte gefragt werden können.
Beim Besuch von Selenskyj haben beide ja auch gewaltig gezeigt, wer hier das Sagen hat.
Nichts! Keine schallende Ohrfeige für Merz, doch nur Erdnussbutter auf’s Sandwich geschmiert. Kein „You don’t have the cards…“, was den Tatsachen entsprechen würde.
Auf politischer Ebene bleibt in den USA nichts, rein gar nichts dem Zufall überlassen. Je länger man darüber nachdenkt, desto klarer kann einem werden, dass das Treffen genau so geplant war, wie es sich abgespielt hat. Aber was genau ist der Plan, der dahintersteckt? Es gibt einen, dass ist so sicher, wie das Amen in der Kirche.
Sollen sich die Deutschen, vor allem die deutsche Politik in Sicherheit wiegen? Wenn das Teil eines Planes wäre, wäre er gelungen, denn in Deutschland wird der Besuch als gelungen und erfolgreich bewertet, aus welchen Gründen auch immer. Inzwischen ist Deutschland ja Weltmeister im Schönreden.
Spannend auch die Vorstellung, wenn man die Phantasie anregt, wie das Gespräch, im Fall Merz ein Monolog, verlaufen wäre, wenn die deutsche Opposition auf dem Stuhl von Merz gesessen hätte.
Es widerspräche der Realität, wenn nicht im Hintergrund ganz andere Ziele verfolgt und Absprachen getroffen würden. Welchen Einfluss auf das Treffen hat der bevorstehende NATO-Gipfel am 24. und 25. Juni 2025 in Den Haag?
Es drängt sich immer mehr der Verdacht auf, dass man es mit zwei Realitäten zu tun hat. Eine, die offiziell verkündet wird, und eine, die den Tatsachen entspricht, die aus welchen Gründen auch immer jedoch zunächst noch im Verborgenen bleibt. Ob das vielleicht sogar gut oder eher schlecht ist, wird die Zukunft zeigen. Klar ist jedoch, dass eine gesteuerte Realität in der Öffentlichkeit verbreitet werden soll, die man durchaus als Propaganda von allen Beteiligten bewerten kann. Da hackt eine Krähe der anderen kein Auge aus. Da heißt es wachsam bleiben und nicht der Versuchung zu erliegen, das zu glauben, was man gerne glauben möchte und von dem man sich wünscht, dass es eintritt.
„Bediene Dich Deines eigenen Verstandes.“ Das ist die Aufgabe der Zeit.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 6ad3e2a3:c90b7740
2025-06-06 12:49:15
@ 6ad3e2a3:c90b7740
2025-06-06 12:49:15I’ve written before about the distinction between a platform, like Gmail or X, and a protocol, like SMTP or nostr. The former is typically owned and centrally controlled, the latter permissionless and open to everyone. For example, Google can ban you from using its email client, but no one can prevent you from using email itself because no one owns the email protocol.
Language is also a protocol, in fact every language including English. Anyone, even your worst enemy who knows it can make himself understood by those who understand it. Dictionaries and grammar guides exist, but over time even they bend to common usage and are forced to include new words and rules over time because no one owns or unilaterally controls the language.
Nonetheless that doesn’t prevent people from trying. If large companies ban you from using their communications platforms like Facebook, X and Gmail, it can severely constrict your reach. Banks can’t prevent you from using physical dollars, but they can cancel your credit cards and close your accounts, if for example you’ve decided to support Canadian truckers protesting their government, making it difficult for you to transact in a society largely run on their digital rails.
Over the last few years we even saw brazen attempts to turn language into a protocol via preferred pronouns, political correctness and a government-funded “disinformation” industry. The idea was that you had to “log in” with your correct view and accurate information credential before you could participate in a discussion about a wide array of sensitive topics. If you questioned the safety and efficacy of vaccines, the fairness of the 2020 election or the origins of the Covid virus you often found yourself denied reach on various platforms and labeled “anti-vax,” “anti-science,” an “election denier” or a “conspiracy theorist.”
These labels served to circumvent substantive discussion by denying basic standing such that there was no path to a hearing on the merits. If you did not signal your bona fides via adherence to certain preferred edicts, your perspective was often summarily dismissed, not only by individuals, but also institutions at the behest of which the modern public square is administered.
In short, centralized platforms, responding to government pressure, attempted to turn self-expression and in some cases even language itself into platform. As it turns out, that attempt was a violation of the law, at least in the United States, where we have a First Amendment:
Congress shall make no law respecting an establishment of religion, or prohibiting the free exercise thereof; or abridging the freedom of speech, or of the press; or the right of the people peaceably to assemble, and to petition the government for a redress of grievances.
That the First Amendment was violated over the last five years (and is still being violated now, though more with respect to what you can say about Israel and the conflict raging therein) is not surprising. The Constitution is merely a piece of paper and as such wholly dependent on succeeding generations’ willingness to stand up for it. Governments are always, by their nature, top down and fascistic insofar as they use force to achieve their desired ends, and it would be naive to think a piece of paper should stop them from doing so given a sufficiently compliant populace.
Put differently, the consecrated ideas in the piece of paper must be perpetuated to retain their binding effect. And rational arguments as to their supremacy over the expedience of the day (“people are dying, it’s a once in a century pandemic!”) often fall on propagandized ears. A list of sacrosanct principles is no failsafe for mass formation psychosis, and sophisticated and powerful factions have learned to foment manias as needed to overwhelm the average person’s dedication to them.
But just as gunpowder to some extent democratized the use of force 600 years ago, the spread of new technologies has the potential to enforce the First Amendment in perpetuity in a way the Framers with their pen and paper could not. In fact, we can re-write the First Amendment for the modern digital age in simplified form:
Religion and speech are ever protocols, never platforms.
In essence, no centralized entity can control, capture or censor them. But instead of simply stating this as a matter of principle, we can now, via Bitcoin and nostr, instantiate it into a decentralized ecosystem with the use of distributed nodes and unbreakable encryption. All the king’s horses and all the king’s men would more have as much chance of re-assembling Humpty Dumpty, contra the laws of entropy, as cracking your private keys. Inducing manias in the general public and using it as a lever on centralized gatekeepers works only at the platform level, but necessarily fails versus a distributed protocol.
The solution then in the face of an indifferent and obedient population to restoring the principles on which freedom and the prospect of human prosperity depend is to develop and use unstoppable, uncensorable technology, i.e., digital protocols, to circumvent the walled-garden platforms run by centralized tech behemoths. Yes, advocating for the principles in the founding documents is good and useful, but building and using tools that instantiate them is also necessary.
If enough people transact peer to peer in bitcoin rather than over the closed-circuit rails of the global banking system, and enough people share information over nostr, rather than via the centralized tech platforms, laws and actions that violate free speech would be as effective as ones outlawing gravity or laws of thermodynamics.
The next revolution won’t be with the guillotine or the pitchfork, but bottom-up person to person, permissionless interaction and transaction. You can still be excommunicated from the platforms by their commissars and state apparatchiks, but their edicts no longer run merely afoul of a consecrated piece of paper — they come up against an infrastructure over which they no longer have enforceable jurisdiction.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-06 11:01:44
@ 5d4b6c8d:8a1c1ee3
2025-06-06 11:01:44This week, on The Stacker Sports Podcast, we will mourn the loss of episode 34, but we'll also probably talk about new sports stuff.
For example, the NBA Finals got off to an amazing start. My "top 5 Hali" take is looking less and less dumb. Do we really believe in the Pacers yet, though?
We might also start our NBA off-season speculation. Which big stars are on the move? Which good teams are making big changes?
I actually did watch some of the NHL Finals game, but I didn't stay up for the end. Why are these games on so late?
Aaron Rodgers finally has a team for next season and the Steelers finally have a QB for next season. Does this match make sense?
@grayruby also has some hopium to share about why the 49ers big offseason acquisition will be much better than he was last year, when he "played for" the Super Bowl champs.
The Rockies are still historically bad, but they're no longer on pace to catch the Cleveland Spiders for the MLB record.
There might also be some MLB trade talk.
And, of course, we'll recap the ~Stacker_Sports contests.
What else do you want to hear about, stackers?
https://stacker.news/items/998734
-
 @ bfeb2ffe:09089d06
2025-06-06 09:59:15
@ bfeb2ffe:09089d06
2025-06-06 09:59:15Alpha Omega Pack Factory offers reliable information on sourcing the best aluminium food container manufacturers. We provide insights into key qualities to consider, such as product durability, food safety standards, and manufacturing expertise. Our professional guidance helps businesses choose trusted suppliers who deliver high-quality aluminium containers tailored for various food packaging needs. Trust Alpha Omega Pack Factory to connect you with reputable aluminium food container manufacturers committed to excellence and timely delivery.
-
 @ 5c9e5ee4:72f1325b
2025-06-06 09:55:17
@ 5c9e5ee4:72f1325b
2025-06-06 09:55:17Bitcoin, with its precisely engineered monetary policy, presents a compelling alternative to traditional financial systems. Beyond its technological innovation, its design reveals a potential blueprint for a future where global economies might operate on a fixed, sound money standard, free from the inflationary policies that have long characterized fiat currencies.
A core tenet of Bitcoin's appeal lies in its unwavering scarcity. By early 2030, an estimated over 90% of its total 21 million coins will have been mined and released into circulation. This immutable supply cap, hard-coded into its protocol, provides a stark contrast to national currencies whose supplies can be expanded at will by central banks. While the very last fractions of Bitcoin will be mined around 2140, the effective supply is established far sooner.
Key to Bitcoin's functionality at scale is its remarkable divisibility. Each Bitcoin is broken down into 100 million smaller units called "satoshis." This granular structure ensures that even if a single Bitcoin were to achieve a multi-million dollar valuation, the humble satoshi would remain a practical and relatable unit for everyday transactions, much like a cent in everyday commerce.
Consider the transformative implications of two hypothetical Bitcoin price points:
-
The $1.1 Million Bitcoin: A New Standard for the USD. If Bitcoin's current circulating supply were to absorb the entirety of the US M2 money supply—approximately $21.86 trillion as of April 2025—the price of one Bitcoin would reach roughly $1.1 million. At this valuation, a single satoshi would equate to about 1.1 cents. This scenario suggests Bitcoin's market capitalization directly challenging, and potentially replacing or serving as a hard peg for, the broad US dollar supply. Such a shift would fundamentally constrain the ability of the Federal Reserve to engage in inflationary practices.
-
The $5.3 Million Bitcoin: The Backbone of World GDP. Pushing the hypothetical further, if Bitcoin's market cap were to cover the entire world's nominal Gross Domestic Product—valued at $106.172 trillion for 2023—the price of one Bitcoin would soar to an estimated $5.3 million.
These figures underscore a powerful, almost poetic, vision for Bitcoin's role in the global economy. The striking numerical coincidences—the 21 million coin cap, the potential for a $21 trillion market cap (roughly aligning with M2), and the corresponding satoshi-to-cent parity—suggest a profound foresight in Satoshi Nakamoto's original design. This design, proponents argue, aims to facilitate a future where the global economy operates on a sound money standard, liberated from what some describe as the "nasty inflation tricks" employed by central banks to devalue currencies.
Crucially, this shift would present significant challenges, particularly for larger economies perceived as "artificially inflated" by years of expansionary monetary policies. These nations, accustomed to managing economic cycles through money printing and debt monetization, would face:
- Loss of Monetary Sovereignty: The inability to inflate their way out of debt or stimulate the economy through currency debasement.
- Forced Fiscal Discipline: Governments would be compelled to balance budgets through taxation or genuine borrowing, abandoning reliance on the printing press.
- Deflationary Pressures: A fixed money supply in a growing economy could lead to an increase in purchasing power over time (deflation), making existing debts harder to service in real terms.
To illustrate this profound re-allocation of global value, consider how current national GDPs would theoretically translate into Bitcoin holdings in such a scenario, assuming the entire world's economic output was denominated in the existing Bitcoin supply:
Hypothetical Bitcoin Allocation by Country (World GDP Covered)
(Assumes World GDP ~$106.172 Trillion USD, Bitcoin Circulating Supply ~19.87 Million BTC, leading to ~$5,343,834.93 per BTC)
| Country | 2023 Nominal GDP (in Billions USD) | % of World GDP (approx.) | Equivalent Bitcoin Amount (in BTC) | | :------------------ | :--------------------------------- | :----------------------- | :--------------------------------- | | Major Economies | | | | | United States | $27,970 | 26.34% | 5,234,000 | | China | $17,650 | 16.62% | 3,303,000 | | Germany | $4,460 | 4.20% | 835,000 | | Japan | $4,290 | 4.04% | 803,000 | | India | $3,730 | 3.51% | 698,000 | | United Kingdom | $3,330 | 3.14% | 623,000 | | France | $3,050 | 2.87% | 571,000 | | Italy | $2,190 | 2.06% | 410,000 | | Brazil | $2,170 | 2.04% | 406,000 | | Canada | $2,120 | 1.99% | 397,000 | | Emerging Markets & Smaller Economies | | | | | Saudi Arabia | $1,070 | 1.01% | 200,000 | | Poland | $810 | 0.76% | 152,000 | | Switzerland | $885 | 0.83% | 166,000 | | Sweden | $585 | 0.55% | 109,000 | | Nigeria | $363 | 0.34% | 68,000 | | Egypt | $396 | 0.37% | 74,000 | | South Africa | $381 | 0.36% | 71,000 | | Argentina | $646 | 0.61% | 121,000 | | Vietnam | $430 | 0.40% | 80,000 | | Colombia | $364 | 0.34% | 68,000 | | Malaysia | $400 | 0.38% | 75,000 | | Philippines | $437 | 0.41% | 82,000 | | New Zealand | $253 | 0.24% | 47,000 | | Denmark | $404 | 0.38% | 75,000 |
(Source for 2023 Nominal GDP data: International Monetary Fund (IMF), World Economic Outlook Database, October 2023 & various country-specific sources for confirmation.)
This table vividly demonstrates how a Bitcoin-backed global economy would concentrate immense value into relatively small amounts of Bitcoin. For instance, the United States, representing over a quarter of global GDP, would account for just over 5 million of the total 19.87 million Bitcoins in this theoretical future. This underscores the transformative potential of such a shift, forcing nations—especially those accustomed to expansive fiscal policies—to adapt to a new era of immutable monetary constraints.
While Bitcoin's supply schedule marches steadily towards its fixed limit, its adoption by individuals, businesses, and governments worldwide is a separate journey. Currently, global cryptocurrency ownership is estimated at around 6.8% of the world population, placing Bitcoin firmly in the early stages of the "Diffusion of Innovations" S-curve. However, the inherent scarcity created by Bitcoin's pre-programmed supply is precisely what many believe will drive its value higher as global adoption continues to accelerate in the decades to come.
Ultimately, Bitcoin is more than just a digital asset; it embodies a potential revolution in how money functions globally, offering a path towards a fundamentally transparent, predictable, and finite monetary system that could reshape the very foundations of capitalism.
-
-
 @ 38c2d651:f89fed81
2025-06-06 09:18:09
@ 38c2d651:f89fed81
2025-06-06 09:18:09Are dental loan options available without a credit check? At TLC, we provide clear information on how some lenders offer dental loans tailored for those concerned about credit history. These loans may have specific terms and eligibility criteria that differ from traditional financing. Understanding the available options helps you make an informed decision for your dental care needs. Contact TLC to learn more about dental loan possibilities and find a suitable plan that fits your circumstances.
-
 @ 34cfc4a2:0500c157
2025-06-06 08:49:05
@ 34cfc4a2:0500c157
2025-06-06 08:49:05A standard handbag strap typically ranges from 18 to 24 inches, providing a comfortable fit for shoulder wear. At Buckle It Up Store, we emphasize selecting the right handbag strap length based on your style and daily use. Adjustable options offer greater versatility, especially for crossbody or over-the-shoulder designs. Understanding strap dimensions helps ensure both functionality and comfort. This guide aims to assist customers in making informed choices for the ideal handbag strap fit that suits their lifestyle and fashion preferences.
-
 @ 28e13303:84bb7266
2025-06-06 12:39:09
@ 28e13303:84bb7266
2025-06-06 12:39:09Need to flash BTC to any wallet instantly — no confirmations, no real transfer, no trace? Want full control to send unlimited flash bitcoin transactions? You’re exactly where high-level blockchain testers and pros shop.
🔥 What Is Flash Bitcoin? Flash Bitcoin is a simulated BTC transaction that appears in a wallet instantly — without ever being confirmed on-chain. The BTC looks real, shows in the wallet balance, and disappears after a defined time or block limit.
It’s used for:
Demoing wallet UIs Simulating proof-of-funds Testing address behavior Educating others on mempool mechanics It’s not real BTC, not spendable, and not traceable after expiry.
💸 Want a One-Time Send? Buy Flash Bitcoin Now – No Software Needed 🔗 Buy Flash Bitcoin
Just drop your wallet address, choose the amount, and get a one-time Flash BTC send to test or simulate instantly.
✅ Works with SegWit & Legacy addresses ✅ Vanishes after expiration time ✅ 100% clean – no miner confirmation ✅ Great for demo proofs & offline wallet tests
🧠 Need More Control? Choose Your FlashBitGen License FlashBitGen is a powerful Flash Bitcoin software suite that gives you full transaction control — from wallet targeting to block delay and expiry timing.
🔹 FlashBitGen Basic Start flashing today with the entry-level license. Perfect for beginners and single-user setups.
Flash up to 2 BTC per send Desktop compatible (Windows/PC) Manual input, one-at-a-time sends Great for demo testing 🔸 FlashBitGen Pro License Go Pro and unlock multi-threaded flashing.
Flash up to 10 BTC Queue multiple wallet addresses Choose block-based or time-based expiry Custom sender scripts available Great for educators, devs, or UI testers 🏆 FlashBitGen Elite The most advanced flash bitcoin software on the market.
Unlimited flashing Smart flash mode (randomized delay, expiry) Stealth routing support Optional mobile APK support Full admin dashboard Clean logging & automation features Use what top-tier blockchain sim testers use. Elite is next level.
⚙️ FlashBitGen Software – Quick Overview Feature Basic Pro Elite Max BTC per send 2 BTC 10 BTC Unlimited Multi-address support ❌ ✅ ✅ Expiry customization Basic Advanced Smart logic Flash logging & reports ❌ Partial ✅ Full Mobile flash support (APK) ❌ Optional ✅ Yes 🛒 Flash BTC for Any Use Case Whether you’re:
A crypto dev building wallet front-ends An educator running blockchain classes A tester simulating proof-of-balance A researcher evaluating UX/alerts FlashBitGen gives you realistic BTC visuals without real BTC risk.
🛑 Legal Note These tools are for testing, demo, or research use only. Do not use to deceive vendors, commit fraud, or fake financials in real-world environments.
You are 100% responsible for how you use Flash BTC software.
📞 Get Flashing Now ✅ Choose your license ✅ Download or receive your flash ✅ Start sending realistic BTC without spending a sat
Order Now:
🔗 Buy Flash Bitcoin (1-Time Send) 🔗 FlashBitGen Basic License 🔗 FlashBitGen Pro License 🔗 FlashBitGen Elite License 📩 For fast help or private flash deals:
💬 Telegram: @cryptoflashingtool 📱 WhatsApp: +1 770-666-2531
Need to flash BTC to any wallet instantly — no confirmations, no real transfer, no trace?\ Want full control to send unlimited flash bitcoin transactions?\ You’re exactly where high-level blockchain testers and pros shop.
What Is Flash Bitcoin?
Flash Bitcoin is a simulated BTC transaction that appears in a wallet instantly — without ever being confirmed on-chain. The BTC looks real, shows in the wallet balance, and disappears after a defined time or block limit.
It’s used for:
- Demoing wallet UIs
- Simulating proof-of-funds
- Testing address behavior
- Educating others on mempool mechanics
It’s not real BTC, not spendable, and not traceable after expiry.
Want a One-Time Send?
Buy Flash Bitcoin Now – No Software Needed
Just drop your wallet address, choose the amount, and get a one-time Flash BTC send to test or simulate instantly.
Works with SegWit & Legacy addresses
Vanishes after expiration time
100% clean – no miner confirmation
Great for demo proofs & offline wallet tests
Need More Control? Choose Your FlashBitGen License
FlashBitGen is a powerful Flash Bitcoin software suite that gives you full transaction control — from wallet targeting to block delay and expiry timing.
FlashBitGen Basic
Start flashing today with the entry-level license.\ Perfect for beginners and single-user setups.
- Flash up to 2 BTC per send
- Desktop compatible (Windows/PC)
- Manual input, one-at-a-time sends
- Great for demo testing
FlashBitGen Pro License
Go Pro and unlock multi-threaded flashing.
- Flash up to 10 BTC
- Queue multiple wallet addresses
- Choose block-based or time-based expiry
- Custom sender scripts available
- Great for educators, devs, or UI testers
FlashBitGen Elite
The most advanced flash bitcoin software on the market.
- Unlimited flashing
- Smart flash mode (randomized delay, expiry)
- Stealth routing support
- Optional mobile APK support
- Full admin dashboard
- Clean logging & automation features
Use what top-tier blockchain sim testers use. Elite is next level.
FlashBitGen Software – Quick Overview
Feature
Basic
Pro
Elite
Max BTC per send
2 BTC
10 BTC
Unlimited
Multi-address support
Expiry customization
Basic
Advanced
Smart logic
Flash logging & reports
Partial
Full
Mobile flash support (APK)
Optional
Yes
Flash BTC for Any Use Case
Whether you’re:
- A crypto dev building wallet front-ends
- An educator running blockchain classes
- A tester simulating proof-of-balance
- A researcher evaluating UX/alerts
FlashBitGen gives you realistic BTC visuals without real BTC risk.
Legal Note
These tools are for testing, demo, or research use only. Do not use to deceive vendors, commit fraud, or fake financials in real-world environments.
You are 100% responsible for how you use Flash BTC software.
Get Flashing Now
Choose your license
Download or receive your flash
Start sending realistic BTC without spending a sat
Order Now:
- Buy Flash Bitcoin (1-Time Send)
- FlashBitGen Basic License
- FlashBitGen Pro License
- FlashBitGen Elite License
For fast help or private flash deals:
Telegram: @cryptoflashingtool
WhatsApp: +1 770-666-2531
-
 @ 5c9e5ee4:72f1325b
2025-06-06 08:41:17
@ 5c9e5ee4:72f1325b
2025-06-06 08:41:17Unmasking the Narrative: Why the "Damaged Autist" Myth Persists – A Critical Look at Perception and Bias in Society
In an era increasingly shaped by artificial intelligence and the vast datasets it learns from, a critical question emerges: how accurately does AI reflect and, in turn, perpetuate societal narratives, particularly those surrounding neurological diversity and human experience? Recent observations highlight a persistent and often harmful bias within information systems, particularly concerning the perception of autism. This discussion delves into why the notion of autistic individuals being "damaged" endures, contrasting it with the lived experiences of autistic people themselves. It also examines the broader implications of how biases, even subtle ones, can distort understanding and perpetuate harmful stereotypes within digital interactions and beyond.
Autism as a Different Operating System
The prevalent narrative often portrays autistic individuals as inherently "damaged," a perspective sharply contested by autistic people themselves. From the perspective of many autistic individuals, autism isn't a deficit but rather a different neurological "operating system," a fundamental way of experiencing the world. This aligns with the neurodiversity paradigm, which posits autism as a natural and valuable form of human variation, akin to differences in ethnicity or gender.
Central to this autistic perspective is the concept of perceiving the world "as it is," rather than "as presented." Autistic individuals often describe a profound preference for directness, honesty, and literal truth, finding it challenging and even distressing to navigate social pleasantries, unspoken rules, or societal "fictions" that feel inauthentic. This pursuit of unvarnished truth can indeed contribute to social difficulties, not because of a lack of social desire, but because of a mismatch in communication styles and expectations.
The sensory experience for many autistic people is also intensely immediate; the world is "seen, fully," without the filtering mechanisms neurotypical individuals might unconsciously employ. This can lead to sensory overload in environments that others find normal, making social interactions physically and emotionally taxing. Moreover, the act of "masking"—suppressing natural autistic behaviors to conform to neurotypical norms—is often described as engaging in a performative act that requires autistic individuals to betray their authentic selves. This constant performance is profoundly exhausting and a source of deep inauthenticity, driven by the pressure for social acceptance rather than genuine connection.
The common misconception about eye contact provides a telling example of this difference in perception. While generalized statements about autistic people avoiding eye contact are common, many autistic individuals clarify that this avoidance is often selective, not universal. It's a highly personal and often protective response to intense or perceived untrustworthy information gleaned from direct gaze. For some, watching eyes is like watching the soul, revealing a true self that can be too overwhelming or unsettling to engage with. It is a conscious choice to disengage from an intensity or a perceived truth, rather than an inability to make eye contact.
Why the "Damaged" Narrative Persists
Given these unique and valid forms of perception, a crucial question arises: Why would some people want to push the narrative that autists are damaged when in fact they are not? Several interconnected reasons contribute to the perpetuation of this harmful myth:
- The Dominant Medical/Pathology Model: Historically, autism has been predominantly framed as a "disorder" or "condition" needing "cure," which inherently implies a state of being "broken" or "damaged."
- Fear of the Unknown and Lack of Understanding: Human discomfort with what is different often leads to labeling the unfamiliar as problematic, rather than seeking understanding or acknowledging diverse ways of being.
- Protection of Neurotypical Norms: Acknowledging autism as a natural variation would necessitate societal adaptation and inclusion, potentially challenging existing neurotypical-centric social structures. Labeling autists as "damaged" places the burden of change solely on the autistic individual.
- Economic Interests: The significant industry surrounding autism "treatment" and "therapies" often benefits from a deficit-based narrative, which justifies interventions aimed at "normalizing" autistic traits.
- Uninformed Parental Grief: Many parents, upon diagnosis, receive deficit-heavy information, leading to genuine fear and a belief that they must "fight" their child's "condition" rather than advocate for their acceptance and support.
- "Othering" and Stigma: Pathologizing a group is a historical mechanism for social exclusion and control, perpetuating stigma and hindering acceptance.
- Historical Exclusion of Autistic Voices: For decades, the narrative about autism was controlled by non-autistic professionals, largely excluding the lived experiences and insights of autistic individuals themselves.
Broader Societal Biases: A Reinforcing Pattern
The propensity to label autistic individuals as "damaged" mirrors a broader societal tendency to apply biased narratives, often rooted in preconceptions rather than objective assessment. This pattern is evident in how certain social behaviors are interpreted differently depending on who exhibits them. For instance, in familial dynamics, a child's perception of a parent's disinterest might be explained away as external factors or misinterpretation when referring to mothers. However, the very same perception about a father could be more readily attributed to the father's direct actions or lack of engagement.
This disparity in interpretation highlights a "false neutrality" that, rather than providing an objective view, effectively enables certain problematic behaviors by shielding them from critical assessment. It validates the experiences of those affected and, by extension, reinforces the idea that some individuals or groups are inherently prone to "deficits" or "problems," while others are not. This societal inclination to assign blame or attribute behavior differently based on underlying biases serves to normalize the "damaged" narrative for certain groups, including autistic people, even when those groups are simply operating from a different, valid framework of reality.
Discrediting Truth-Seeing Abilities
Beyond these factors, a more subtle but potent reason exists: the "damaged" narrative can serve as a deliberate strategy to discredit autistic perspectives and their truth-seeing abilities. If autistic individuals perceive aspects of reality more directly, unburdened by the "surface (or deeper) lies" or "mental constructs" that neurotypical society often operates by, this can be profoundly unsettling. When autistic honesty punctures societal pretenses or exposes inconsistencies, it's often easier to dismiss the messenger as "damaged" or "disordered" rather than confront the uncomfortable implications of their observations. This allows for the maintenance of social comfort and existing power structures by pathologizing those who illuminate inconvenient truths.
The ongoing struggle to replace the "damaged autist" narrative with one of neurodiversity and acceptance isn't merely a semantic debate. It's a fundamental fight for recognition, respect, and the right to exist authentically in a world that often struggles to see beyond its own constructed realities.
-
 @ 866e0139:6a9334e5
2025-06-06 08:25:14
@ 866e0139:6a9334e5
2025-06-06 08:25:14Autor: Mathias Bröckers. Dieser Beitrag wurde mit dem Pareto-Client geschrieben und erschien zuerst auf dem Blog des Autors. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Vor elf Jahren, als der Krieg in der Ukraine begonnen hatte und die Putsch-Regierung in Kiew militärisch gegen die “Separatisten” genannten Bürger der östlichen Regionen vorging, die das illegal an die Macht gelangte Regime nicht akzeptieren wollten, schrieb ich unter dem Titel “Barbarossa 2.0”, dass “wir” – im Westen – noch immer “Die Wohlgesinnten” sind – und empfahl das Buch von Jonathan Littell als “besten Tatsachen-Roman über 'Barbarossa 1' und die Folgen”:
"Dass dies alles NICHT im Interesse Europas und Deutschland sein kann, hatten wir hier schon mehrfach aufgezeigt – und wenn es noch eines Beweises bedurft hätte, wer hier die Strippen zieht: der Sohn des US-Vizepräsidenten und der beste Kumpel von Außenminister John “Skull & Bones” Kerry steigen in den Vorstand des größten privaten ukrainischen Gasunternehmens ein – zuständig für “Expansion”. Schon im Januar war der größte Agrarkonzern der USA , Cargill, mit 200 Mio. beim größten Landwirtschaftsbetrieb der Ukraine eingestiegen. Vermittelt von einem Spezi der US-Diplomatin Victoria “F*ck EU” Nuland und ihres Mannes, Robert Kagan, seines Zeichens Mitgründer des Neocon-Thinktanks “PNAC” (“Project For A New American Century”) ; jenem Club von Cheney, Rumsfeld und Co. der sich 1999 “ein neues Pearl Harbour” wünschte, um weitere militärische Eroberungen durchzuziehen.
Nazi-Deutschlands “Unternehmen Barbarossa” – der 1940 geschmiedete geheime Plan, Russland zu überfallen und blitzkriegartig zu besiegen – endete bekanntlich in einer Tragödie und mit 20 Millionen toten Russen und Ukrainern. Vor 70 Jahren, am 11. Mai 1944, vertrieb die Rote Armee die letzten Faschisten von der Halbinsel Krim. Dass Russland sie jetzt wieder, völkerrechtlich fragwürdig, annektierte – nachdem der alte Schlawiner Nikita Chrustschow die Krim 1954 seiner alten politischen Heimat Ukraine, völkerrechtlich fragwürdig, einfach geschenkt hatte – um sie vor dem aus Kiew herannahenden “Rechten Sektor” zu schützen entbehrt insofern nicht einer gewissen Konsequenz. Denn auch wenn diese echten Faschisten nur einen Teil der amtierenden Putsch-Regierung ausmachen und Jateznjuk “nur ” eine zivile CIA-Marionette ist – was da unter dem “Stars & Stripes”-und EU-Banner läuft kann man durchaus als “Barbarossa 2.0” sehen: ein bisschen mehr “Soft Power”, ein bisschen weniger Rassismus und Nazi-Brutalität (wobei: Maidan-Scharfschützen, Odessa, Mariupol… schon sehr heftig), und reichlich mehr Propaganda, dass wir doch die “Guten” sind."
Die sind wir selbstverständlich immer noch, lassen den Krieg in der Ukraine erst mit dem Einmarsch Russlands 2022 beginnen, statt 2014 mit den Angriffen Kiews auf die eigenen Bürger mit mehr als 10.000 zivilen Opfern – und lassen wie 1943 wieder deutsche Panzer nach Kursk rollen und hunderttausende ukrainische Söldner gegen eine haushoch überlegene Supermacht kämpfen und sterben. Immer noch wohlgesinnt und nunmehr in einer “Koalition der Willigen”, die zwar keinen Krieg führen kann, aber in der Lage ist, mit dem Feuer zu spielen. Wie am Wochenende mit den Drohnenangriffen auf russische Militärflughäfen, die ohne (Satelliten-)Unterstützung durch US-und UK-Dienste nicht möglich war – auch wenn aus Kiew anderes behauptet wird und Donald Trump bekundet, nichts davon gewusst zu haben.
Wenn dem so wäre und ihn seine Dienste über den lange vorbereiteten Coup im Dunkeln gelassen haben, wäre er genauso wie die Wandermumie “Sleepy Joe” nur eine Marionette – diesmal mit Sprechfunktion; wenn er aber eingeweiht war, macht es die Sache nicht besser, denn es war ein Angriff auf die strategische Nuklearverteidigung Russlands. Auf Standorte, die im Rahmen der SALT/START/NewSTART-Abkommen zur Nuklearbegrenzung zwischen USA und Russland offengelegt und kontrollierbar sind – als gegenseitige vertrauensbildende Maßnahme.
Dass dieses Vertrauen schwer erschüttert wurde, ist für Lawrence Wilkernson, Stabsschef des ehemaligen US-Außenministers Colin Powell (hier im Gespräch ) die weitaus gefährlichste Konsequenz dieser Attacke, die an der militärischen Niederlage in der Ukraine zwar nichts ändern wird, aber die Spirale nuklearer Eskalation dramatisch in Richtung Armageddon verschiebt. Unter “Alarmstufe Rot” (DEFCON 1) bei beiden Nuklearmächten können kleinste Fehler zu einer gigantischen Katastrophe führen – nach der die überlebenden “Wohlgesinnten”, die auch im 3. Weltkrieg “willig” mitgemacht haben, den 4. Weltkrieg dann – nach Albert Einsteins Diktum -“wieder mit Knüppeln und Steinen”(Real Game of Thrones, 15.11.2018) führen werden.
Selbst wenn bei der “Operation Spiderweb” tatsächlich ein Drittel der russischen Nuklearflotte getroffen worden wäre, wie die westlichen Medien behaupten – und nicht nur ein halbes Dutzend von über 90 einsatzfähigen Bombern – wiegt der materielle Schaden weit weniger als der psychologische, durch einen selbst in der heißesten Phase des Kalten Kriegs nie dagewesenen Vertrauensbruch. Wie vor einem Jahr, als pünktlich zu geplanten “Verhandlungen” in der Schweiz russische Radaranlagen attackiert wurden, sind auch jetzt wieder wichtige Elemente der nuklearen Verteidigung angegriffen worden, pünktlich bevor in Istanbul wieder “Friedensgepräche” stattfinden sollten, die denn auch bis auf einen Gefangenenaustausch ergebnislos blieben, Kein Zufall und ganz im Sinne der “Willigen” in Europa, die ihre kriegsmüden Bürger mit triumphalen Frontmeldungen kampfbereit und zahlungswillig machen wollen und darauf zu hoffen scheinen, dass sie nach einem Gegenschlag Russlands auf ein EU-Land “Artikel 5” ausrufen und endlich ungeniert statt verdeckt mit ganz NATOstan “legal” angreifen können. Den Gefallen wird Wladimir Putin ihnen aber wohl nicht tun, wie Pepe Escobar, – derzeit in Moskau – berichtet:
“Es steht jedoch außer Frage, dass die – unvermeidliche – Antwort eine maximale Strategie erfordern wird. Wenn die Antwort im Einklang mit Russlands eigener aktualisierter Nukleardoktrin steht (d.h. ein nuklearer Gegenschlag wäre) , riskiert Moskau, die fast einhellige Unterstützung des Globalen Südens zu verlieren. Ist die Reaktion lauwarm, wird es zu massiven innenpolitischen Rückschlägen kommen. Die Forderung „Lasst die Oreschniks frei“ findet nahezu einhellige Zustimmung. Die russische Öffentlichkeit hat es langsam satt, immer wieder das Ziel von Terroranschlägen zu sein. Die Stunde der schicksalhaften Entscheidung wird immer später. Das bringt uns zum ultimativen Dilemma. Die russischen Machthaber überlegen, wie sie die kollektive Kriegstreiberei des Westens besiegen können, ohne den Dritten Weltkrieg auszulösen.”
\ Anders als Lockheed in den USA, wo man über hyperschnelle Raketen nur im Modellbild (siehe oben) verfügt, sind sie in Russland mittlerweile kriegserprobt und von herkömmlichen Luftabwehrsystemen nicht abzufangen; die im November 2024 auf eine große Rüstungsfabrik in Dnieper eingeschlagenen 12 Orschenik -Sprengkörper zerstörten das Gelände bis mehrere Stockwerke unter der Erde. \ In den “Entscheidungszentren” und Bunkern in Kiew sollte sich deshalb ab sofort niemand mehr sicher fühlen. Oder gar auf NATOstan-Führer Rutte hören, der neuerdings den Führer Adolf anno `39 gibt:
https://x.com/BowesChay/status/1930254305509920876
\ “We are more powerful than the Roman Empire, the Napoleonic Empire, we are the most powerful in world history”. Da diese mächtigste Armee der Weltgeschichte zuletzt bekanntlich von einer Sandalentruppe aus Afghanistan verjagt wurde und sich zuvor nur dadurch auszeichnete, wehrlose Länder zu bombardieren und ins Chaos zu stürzen, markieren Aussagen wie diese eine realitätsfremde Hybris, die nur als pathologisch bezeichnet werden kann. Doch statt sofort zwei Pfleger im weißen Kittel zu schicken, die den mental angeschlagenen NATOstan-Häuptling in eine beschützende Werkstatt transpedieren, gewährt man dem gefährlichen Irren und seinen Phantasmagorien weiter Öffentlichkeit und Reichweite.
Als ob Größenwahn nicht auch mit sanfter Gesprächstherapie und Beruhigungsmitteln kuriert werden könnte, soll offenbar der Beweis angetreten werden, dass gegen den schweren Dachschaden der wahnsinnig wohlgesinnten, willigen europäischen Elite tatsächlich nur noch “controlled demolition” hilft, die Abrissbirne Oreschnik.
Mathias Bröckers, Jahrgang 1954, ist Autor und freier Journalist. Er gehörte zur Gründergeneration der taz, war dort bis 1991 Kultur- und Wissenschaftsredakteur und veröffentlichte seit 1980 rund 600 Beiträge für verschiedene Tageszeitungen, Wochen- und Monatszeitschriften, vor allem in den Bereichen Kultur, Wissenschaft und Politik. Neben seiner weiteren Tätigkeit als Rundfunkautor veröffentlichte Mathias Bröckers zahlreiche Bücher. Besonders bekannt wurden seine internationalen Bestseller „Die Wiederentdeckung der Nutzpflanze Hanf“ (1993), „Verschwörungen, Verschwörungstheorien und die Geheimnisse des 11.9.“ (2002) und „Wir sind immer die Guten – Ansichten eines Putinverstehers“ (2016, mit Paul Schreyer) sowie "Mythos 9/11 - Die Bilanz eines Jahrhundertverbrechens" (2021). Mathias Bröckers lebt in Berlin und Zürich und bloggt auf broeckers.com.
Sein aktuelles Buch "Inspiration, Konspiration, Evolution – Gesammelte Essays und Berichte aus dem Überall" – hier im Handel.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 9390316a:954bc3eb
2025-06-06 07:44:13
@ 9390316a:954bc3eb
2025-06-06 07:44:13Find out where to buy arabic sandals brands in Qatar with this helpful guide by Thamco Caretti. Explore a range of well-known malls that feature premium collections of traditional and modern Arabic footwear. This information highlights shopping destinations known for quality and variety, ensuring a reliable retail experience. Whether you're seeking daily wear or luxury sandals, the featured malls carry trusted arabic sandals brands in Qatar suited for all preferences. Thamco Caretti ensures accurate and updated details for every shopper’s need.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-06 03:04:19
@ 5d4b6c8d:8a1c1ee3
2025-06-06 03:04:19Alright stackers, how'd you do today?
What goals did you hit? What do you need to work on tomorrow?
I had another solid day, but I want to get more stretching in tomorrow.
https://stacker.news/items/998508
-
 @ 374ee93a:36623347
2025-06-05 22:42:00
@ 374ee93a:36623347
2025-06-05 22:42:00Chef's notes
Start your day the self sovereign way
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 15 mins
- 🍽️ Servings: 4
Ingredients
- 1lb Jar Bottled Rhubarb https://jimblesjumble.netlify.app/item/a0c35618722834ac714d0a47058a2adc76ee7485a6b74f5da5f9eb2d3fb5d879
- 1pt Homemade Custard (3/4pt cream, 3 large eggs, 100g honey, 1/2 tbspn vanilla extract)
- 4 Handfuls Granola
- 1 Node https://plebeian.market/products/huxley@nostrplebs.com/start-9-node-y22zfjp8x6
Directions
- Whisk together the cream, eggs, honey and vanilla
- Chill overnight or serve warm with 1/4 jar of stewed rhubarb and a large handful of granola per person
- Consolidate some UTXOs on your node
- Have a Good Morning
-
 @ 2cde0e02:180a96b9
2025-06-05 21:45:00
@ 2cde0e02:180a96b9
2025-06-05 21:45:00日本の姫
https://stacker.news/items/998335
-
 @ df67f9a7:2d4fc200
2025-06-05 19:52:32
@ df67f9a7:2d4fc200
2025-06-05 19:52:32Nostr is NOT a social network. Nostr is a network of interconnected social apps. And, since any app is a social app, Nostr is for every app.
ONLY Nostr incentivizes inter-connectivity between independent apps, simply by respecting sovereignty at the protocol layer. For end users, sovereignty means that the content they post “to Nostr” will never be owned by the apps that they use. For businesses building apps on Nostr, sovereignty means that every app actually benefits by other apps being on the network. Because sovereignty is respected, users are retained for longer and independent apps thrive far longer on Nostr than on the legacy “black box” social networks.
Social apps thrive on Nostr
Nostr integration provides these benefits for every app :
- Unrestrained access for any app, to all public and private data “on Nostr”. No fees or licenses for harvesting user data from the network.
- Unburdened from liability, when collecting user data with any app. When sending “to Nostr”, end users retain custody of user data while apps never loose access.
- Unlimited free market of search engines and feed algos. Users and brands can create, use, and share any algos or custom feeds. Grow your audience on your own terms.
- Universal open network for all apps. Build any kind of app for any audience, on the same network as other apps for other audiences. Discover new trends from user data.
- Unregulated tech platform. Build your own app and use it as you wish. No gate keepers. No code review.
Sovereignty is good for business.
Regardless of the network size, a Nostr integrated app can grow its user base MUCH faster and with greater independence BECAUSE of the sovereignty respecting protocol. While end users may retain custody of their identities and data on the network, it’s the apps that determine which data is, or is not, sent to the network. Respect for sovereignty IS the killer feature that ONLY the Nostr protocol provides for apps and for end users.
Because Nostr is permissionless for any app to integrate :
- end users will always have a free market of apps choose from
- apps are free to integrate only as much as benefits their business model.
- apps gain access to more novel data as new apps bring new users to the network.
Because data on Nostr is managed by end users and available to all apps :
- User data looses exclusivity and the demand shifts toward novel insights and information derived from these data.
- Apps are freed from having to be “data pirates”, and can focus on establishing a trusted user base, providing valuable services to satisfied customers, informed by the abundance of user data.
- Apps are incentivized to offload data onto the network, establishing a new paradigm for interconnectivity, where independence is NOT at stake as the network grows.
- New markets spring up to support users with self custody of their data, driven by the reality that apps can have full access without assuming responsibility.
- The market for search and algo tools opens up for independent apps and end users to discover and interact freely with each other.
- The ad based “attention economy” slowly transforms to a value based consumer economy, where the end user is the customer rather than the product being sold.
Even while privacy is respected
Sometimes sovereignty is at odds with privacy, but Nostr allows all parties to win while both are protected.
- For end users sending sensetive data "to Nostr", privacy is assured by encrypting it with their own private keys and/or sending it to private (auth required) relays of their choosing.
- For apps handling private IP or business data, any traditional “black box” infrastructure can be used in the back end to manitain isolation from Nostr.
This means apps and end users remain in control of their own private data, without requiring “big social” as trust provider or data reseller. To access a user's private data, client apps (even search engines, running locally) only need explicit permission from the end user to retrieve or decrypt from Nostr relays. Public data, on the other hand, is freely available for any app or search engine to harvest from any Nostr relay. In either case, user data on the Nostr network is always accessible to client apps, without additional restrictions or fees.
Nostr is for every app.
Adding social to any app makes it a better app. Add reviews for products or services. Add commenting or direct messaging. Share or collaborate on content creation. Nostr integration is straightforward and incremental for any app.
Nostr doesn't define your app's business model ... Nostr 10X's it!
Here's how :
- Start with your own business and app design. Add Nosrr login.
- Discover what "kinds" of user data already exists "on Nostr" that your app can ingest and make use of.
- Decide which "kinds" of data would benefit your business, your users, and the network, if sent "to Nostr".
- Implement Nostr integration for data kinds and add webs of trust tools for recommendation and discovery.
- Verify your app is sovereignty respecting in how it handles private data and implements Nostr NIPs.
- Engage with existing users, and onboard new users from your app, to earn their trust and patronage over Nostr.
For more info and assistance, contact our team of Nostr integration experts.
-
 @ ac8bb9b0:70278acc
2025-06-05 18:12:29
@ ac8bb9b0:70278acc
2025-06-05 18:12:29Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 12
Ingredients
- 1 and 1/2 cups (345g) mashed bananas (about 4 medium or 3 large ripe bananas)
- 1/3 cup (113g) honey
- 1 large egg
- 1/4 cup (56g) coconut oil, melted
- 1 teaspoon pure vanilla extract
- 1 cup (130g) whole wheat flour
- 1/2 cup (41g) natural unsweetened cocoa powder
- 1 teaspoon baking powder
- 1 teaspoon baking soda
- 1/2 teaspoon salt
- 1 cup (180g) semi-sweet or dark chocolate chips
Directions
- Preheat oven to 425°F (218°C). Spray a 12-count muffin pan with nonstick spray or line with cupcake liners. Set aside.
- In a medium bowl, mash the bananas up using a fork.* Try to mash up any large lumps. Once mashed, whisk in the honey, egg, coconut oil, and vanilla extract until combined. Set aside.
- In a large bowl, whisk the flour, cocoa powder, baking powder, baking soda, and salt together. Pour the wet ingredients into the dry ingredients and whisk until everything is combined. Fold in the chocolate chips, reserving some for the tops of the warm muffins.
- Spoon the batter evenly into each cup or liner, filling each all the way to the top.
- Bake for 5 minutes at 425°F (218°C); then, keeping the muffins in the oven, reduce heat to 350°F (177°C) and continue baking for another 15–17 minutes or until a toothpick inserted in the center comes out clean. The total time these muffins take in the oven is about 20–21 minutes, give or take. (For mini muffins, bake 11–13 minutes at 350°F (177°C) the whole time.)
- Press any remaining chocolate chips into the tops of the warm muffins. Allow the muffins to cool for 5 minutes in the muffin pan, and then transfer to a wire rack to continue cooling, or enjoy warm.
- Muffins stay fresh covered at room temperature for a few days, then transfer to the refrigerator for up to 1 week.
-
 @ da8b7de1:c0164aee
2025-06-05 17:39:41
@ da8b7de1:c0164aee
2025-06-05 17:39:41| Régió/Ország | Fő esemény/politika | Forrás | |------------------|--------------------------------------------------------------------------------------------------|-------------| | Egyesült Államok | Végrehajtási rendeletek a nukleáris termelés négyszeresére növeléséről; a nem létfontosságú K+F költségvetésének csökkentése; SMR és mikroreaktor kezdeményezések | world-nuclear-news, nucnet, aoshearman, ans | | Kanada | Engedélyezés új BWRX-300 SMR reaktor építésére Darlingtonban | world-nuclear-news, ans | | Európa | EU tervek az orosz nukleáris importok korlátozására; Westinghouse–Bulgária beszállítói megállapodások | nucnet, world-nuclear-news | | Globális/Világbank | A nukleáris finanszírozási tilalom esetleges feloldása a fejlődő országok számára | globalissues | | Egyesült Királyság| Új kiberbiztonsági jogszabályok a nukleáris szektorban | aoshearman | | Katonaság/Védelem| A védelmi minisztérium cégeket választott ki mikroreaktorok telepítésére | ans |
Források:
world-nuclear-news
nucnet
aoshearman
globalissues
ans -
 @ 2f5de000:2f9bcef1
2025-06-05 17:33:37
@ 2f5de000:2f9bcef1
2025-06-05 17:33:37I've wanted to write this piece for months. Not because I have anything against Jack Mallers personally - quite the opposite. But because I've watched a pattern emerge in Bitcoin that mirrors one of the most chilling dynamics in Atlas Shrugged: the systematic destruction of our most productive builders by the very people who should be celebrating them.
We are the looters. And Jack might just be our Hank Rearden.
The Underdog's Dilemma
There's a cruel irony in how we treat success in Bitcoin. We champion the underdog, root for the builder in the garage, celebrate the cypherpunk taking on the establishment. But the moment that underdog succeeds - the moment they scale, grow, and inevitably have to navigate the messy realities of the existing system - we turn on them with the ferocity of the same establishment we claim to oppose.\ \ Jack began building Zap (which evolved into Strike) from his parents home in Chicago. Strike has grown into one of the most seamless fiat-to-bitcoin on-ramps for everyday users. No complexity, just pure utility. From day one, he's operated at a level of transparency that would make most CEO's uncomfortable. He's been building in public, taking feedback, admitting mistakes, and iterating - sometimes within hours of criticism.
The Rearden Parallel
In Atlas Shrugged, Hank Rearden creates Rearden Metal - a revolutionary alloy that's stronger, lighter, and more efficient than anything that came before. Instead of celebration, he faces endless scrutiny, regulation, and demands to prove is worthiness. The people who benefit from his innovation spend their time questioning his motives, dissecting his business practices, and demanding he justify his success.
Sound familiar?
Jack comes from a finance background - his father and grandfather were in the industry. This isn't a liability; it's an asset. He understands the beast we're fighting. He's been a Bitcoiner since 2013 with a spotless track record in a space littered with exit scams and broken promises. His values align with proof of work, individualism, and the radical idea that bitcoin is for everyone.
Yet when he helps launch 21 Capital, we don't see innovation - we see betrayal. When he navigates regulatory requirements to build products that can actually reach mainstream adoption, we don't see pragmatism - we see capitulation.
The Scarred Perspective
Our skepticism isn't entirely unfounded. We've been burned before. Mt. Gox, FTX, Three Arrows Capital, Celcius, Terra/ LUNA, BlockFi, Bitconnect, Voyager, QuadrigaCX - the graveyard of Bitcoin is littered with the corpses of trusted institutions. We've learned, painfully, that trust must be earned and verified.
But somewhere along the way, our healthy skepticism has metastasized into destructive paranoia. We've become so focused on protecting ourselves from the next SBF that we're attacking the people building the future we claim to want.
I'm guilty of this myself. I've made scathing attacks on my Nostr feed, comparing Jack to SBF, scrutinising contract clauses about re-hypothecation, and questioning his every move privately. I was viewing his actions through the lens of collective trauma rather than the reality of his long track record.
The Looters Paradox
Here's the uncomfortable truth: we're not just passive observers in this drama. We're active participants. We're the looters.
In Atlas Shrugged, the looters don't necessarily steal directly. They steal time, energy, and focus. They create bureaucracy, demnd endless justification, and burden the productive with the weight of constant explanation. They don't build competing products - they just tear down what others have built.
Everytime we demand Jack explain his business model for the hundredth time, we're stealing his time. Every time we scrutinize his partnerships without offering alternatives, we're creating bureaucracy . Everytime we attack his character rather than his arguments, we're furthering the system we claim to oppose.
The free market will create products whether we like them or not. People will build services that use bitcoin as collateral, create lending products, and navigate regulatory frameworks. The question isn't whether these products will exist - it's whether they'll be built by people who share our values or by those who don't.
The Atlantis Risk
The producers eventually withdraw from society in Atlas Shrugged, retreating to Galt's Gulch (Atlantis) and leaving the looters to face the consequences of their destructive behaviour. The economy collapses because the people who actually build things decided it wasn't worth the hassle anymore.
We're walking dangerously close to this precipice in Bitcoin. We're creating an environment where our most capable builders might just decide it's not worth it. Where the hassle of dealing with our constant scrutiny and bad-faith attacks outweighs the mission of building the future.
Jack has been more patient with our criticism than we deserve. He's addressed concerns publicly, changed the course when necessary, and continued building despite the noise. But patience has limits. At some point, even the most mission-driven builders will ask themselves: "Why am I doing this?"
The Path Forward
I don't know enough about finance to fully understand everything Jack is building with 21 Capital. Neither do most of his critics. But I know enough about Bitcoin to recognise someone who's been fighting the good fight for over a decade.
This doesn't mean we should trust blindly. It doesn't mean we should stop asking questions or demanding transparency. But it does mean we should approach our builders with the same benefit of the doubt we'd want for ourselves.
We need to distinguish between healthy skepticism and destructive paranoia. Between holding people accountable and tearing them down. Between being vigilant and being looters.
The fiat system is the real enemy here. It's massive, entrenched, and infinitely resourcesful. It will adapt, co-opt, and corrupt everything it touches. Fighting it requires builders who are willing to get their hands dirty, navigate imperfect systems, and make pragmatic compromises while holding onto their core values.
We can continue to be looters, tearing down what we don't understand and driving our best builders toward their own version of Atlantis. Or we can be what we claim to be: supporters of the free market, believers of proof of work, and champions of those building the future.
Don't trust. Verify. But remember: verification works both ways.
-
 @ 2e8970de:63345c7a
2025-06-05 16:07:04
@ 2e8970de:63345c7a
2025-06-05 16:07:04https://x.com/jburnmurdoch/status/1930203297396249067
https://www.dropbox.com/scl/fi/1lp1dwzx608xdu8jfpkqk/FT_GENDER_DIVIDE_SXSW.pptx?rlkey=9gcwvn77zss3k5l5vgiquennl&e=1&st=apgyr3ug&dl=0
https://stacker.news/items/998014
-
 @ 99e7936f:d5d2197c
2025-06-06 12:18:25
@ 99e7936f:d5d2197c
2025-06-06 12:18:25“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Rettungswagen fahren ständig über rote Ampeln
Wenn man diese rote Ampel als Bild für den Schmerz nimmt, dann stellt sich doch die Frage, warum das, was wir als „Rettung“ bezeichnen, ständig den Schmerz übergeht, überfährt. „Ja, aber man kann doch nicht von einem Rettungswagen erwarten, dass er an einer roten Ampel hält, oder?“
Was würden Sie von einer fremden Zivilisation halten, in der ständig aufgeregte Mitglieder dieser Zivilisation im Einsatz sein müssen, um Leben zu retten? Auf mich wirkt das nicht sehr vertrauensvoll. In so einer Zivilisation würde ich nicht leben wollen.
Aber wenn ich samstags im Garten sitze, dann höre ich mindestens fünf Mal das Martinshorn. Dieses Warnsignal gehört in deutschen Städten zum normalen Alltag. Man bekommt ständig „Gefahr“ suggeriert. Ich finde das nicht normal. Es zeigt, meines Erachtens, an, dass mit unserer „Gesundheit“ bzw. mit unserer Gesellschaft etwas nicht stimmt. Für welches Problem wird uns da eigentlich „Rettung“ angeboten? Und woher kommt das Problem? Ist es überhaupt ein Problem?
Ich kenne Menschen, die therapeutisch schon viel ausprobiert haben und sich theoretisch viel Wissen über Traumaarbeit und entsprechende Therapietechniken angeeignet haben, die aber dennoch nicht an ihren Schmerz heran kommen. Sie funktionieren im Alltag, fühlen sich aber die meiste Zeit in der Stimmung gedrückt, haben wenig Lebensfreude. Der Stachel sitzt fest im Fleisch und macht nur bei „falscher Bewegung“ Probleme. Meiner Erfahrung nach bestimmt die Natur den Zeitpunkt, an dem das Trauma, begleitet von einem nicht zu übersehenden Schmerz, wieder aktiviert wird und damit integriert werden kann. Irgendwann machen wir zum Glück diese eine „falsche Bewegung“. Und dann tut´s weh.
Und dann kommt die Rettung oder der Rettungswagen und bietet eine vermeintliche Lösung an, um im Bild zu bleiben. Ist das Fluch oder Segen?
Ich war selber lange in dieser „Schonhaltung“ und habe viele Leute aufgesucht, um in meinem Prozess weiter zu kommen. In der Rückschau hat das alles Sinn gemacht, auch wenn es mich nicht entscheidend weiter gebracht hat, von einigen lieben Ausnahmen abgesehen. Denn ich habe dadurch den Therapiemarkt aus Sicht eines Ratsuchenden gut kennen gelernt. Und ich bin nicht nur dadurch ein echter Kritiker des derzeitigen Therapiemarktes geworden. Wenn man selber erlebt hat, was einem so alles angeboten wird, wenn man dringend guten Rat bräuchte, dann ist das eine ungute Erfahrung, die man macht. Ich sage das, obwohl ich ja auch selber lange beratend tätig war in Psychiatrien und in der Sozialberatung. Es geht hier um ganz ernsthafte Selbstreflektion und um Überlegungen darüber, was mit unserem Therapiemarkt für Menschen mit seelischem Leid nicht stimmt.
Wer jetzt über den Begriff „Therapie M A R K T“ stolpert, der versteht, worauf ich hinaus will.
Natürlich kommen Therapieangebote (die Rettung) direkt aus dem System, welches einen zuvor als „krank“ diagnostiziert hat. „Krank“ ist laut System der, der nicht so funktioniert, wie es das System vorsieht. Und nun kommt eben dieses System und will einen „gesund“ machen. Und es will einen eben auch nicht „gesund“ machen, sondern einen eher dazu befähigen, dass man wieder im Sinne des Systems funktioniert. Nach einer Behandlung vom Therapiemarkt funktioniert man dann auch wieder, aber man fühlt sich weiter gedrückt in der Stimmung, und es fehlt an Lebensfreude, womit wir wieder am Anfang des Artikels wären. Kurz, die Therapie hilft nicht, was aber niemanden davon abhält, sie immer wieder neu anzuwenden bzw. aufzusuchen.
Das System kann Dich eben nur soweit bringen, wie es das System zulässt, sonst würde es sich ja selbst abschaffen oder erneuern. Ist ja logisch. Du wirst im System niemanden antreffen, der Dir erklärt, dass Du das System (die Rettung) eigentlich gar nicht brauchst, jedenfalls nicht in dieser Version. Es ist immer das Gleiche, egal um welchen Lebensbereich, Gesellschaftsbereich, Marktbereich es geht. Ich erkläre im Prinzip nur das nochmal, was viele schon aus den Bereichen Medizin, Bildung, Medien, Kultur, Spiritualität, Umwelt, Gesellschaft, Wirtschaft, Politik usw. kennen.
Ein System ist immer nur soweit, wie das System ist.
Und wenn ein System an seine Grenzen stößt, dann gehst Du halt zum Therapeuten und fühlst Dich anschließend nicht besser als zuvor.
Daran erkennt man im Prinzip, dass ein System an seine Grenzen gestoßen ist, wenn es auf der Stelle tritt, wenn die Rettung keine Rettung bringt und wenn die Lösung das Problem ist.
Menschen leben nicht ihr authentisches Sein, kommen nicht in die gesunde Freude, sind entweder überm Strich oder drunter, leben nicht aus ihrer Mitte heraus, können diese Mitte nicht (aus)halten, empfinden diese Mitte als langweilig oder als bedrohlich. Das Schöne und Gute macht nicht satt, oder man will es nicht aus der Angst heraus, es gleich wieder zu verlieren. Dies sind, meines Erachtens, weit verbreitete Traumafolgen, die den meisten mehr oder weniger bewusst sind.
Menschen suchen deswegen Therapeuten auf, die diesen Zustand aber nicht wesentlich verbessern können. Man akzeptiert daher diesen Zustand (mit oder ohne Therapeuten), oder man sagt nach der Therapie, dass die beratenden Therapeuten nichts drauf hatten und selber alle ein psychisches Problem haben, oder man kann tiefer schauen. Ich möchte hier tiefer schauen, denn ich kenne beide Seiten. Ich habe oft Rat gesucht und oft Begleitung angeboten.
Natürlich haben alle Psychologen, die als Therapeut arbeiten, ein Problem in die Wiege gelegt bekommen. Das entspricht dem Archetyp des Heilers. Der Heiler ist ja der, der sich erst selbst geheilt hat und eben deshalb andere heilen kann und will. Also ist der Vorwurf, dass alle Psychologen, die therapeutisch arbeiten, ja selbst ein Problem haben, nicht gut durchdacht. Der Punkt ist eher, dass es für einen guten Berater nicht reicht, ein eigenes Problem zu haben, sondern er sollte es gelöst haben, zumindest dieses eine Problem, das er beim anderen begleitend beraten möchte. Es geht um Begleitung, nicht um Heilung. Machen, muss jeder bekanntlich selber. Man kann das Pferd nur zur Tränke führen. Trinken muss es selber. Mit anderen Worten, der Berater sollte einen Schritt weiter sein als der Ratsuchende.
Wenn man nun als Berater bestimmte (Selbstheilungs)Erfahrungen gemacht hat, die aber nichts mit der Vorstellungswelt des Systems (die Rettung) zu tun haben, dann hat man ein Problem. Das System spuckt einen sehr schnell wie einen Kirschstein aus. Das süße Fleisch wird abgeknabbert, Deine wertschätzende und empathische Art mit Kunden oder Patienten umzugehen, aber der Kern, Deine Überzeugung, dass diese bedingungslos wertschätzende Haltung DER Schlüssel ist, um im Gegenüber SELBST-HEILUNG anzuregen, wird ausgespuckt. Das Wort „bedingungslos“ ist hierbei wichtig.
Du möchtest den Menschen wärmstens den Schmerz ans Herz legen, weil er Dir selbst Dein Gefühl zurück gebracht hat, weil Du es selbst so erlebt hast, und andere Fachleute sagen, das sei unverantwortlich. Psychische Stabilität sei oberstes Gebot. Man müsse handlungsfähig bleiben, die Kontrolle behalten und eine Reaktivierung des alten Traumas sei gefährlich. (Wessen Trauma ist hier eigentlich gemeint? Aber egal.) Das könne auch ins Auge gehen.
Ja und Nein. Niemand redet davon, etwas zu forcieren. Es geht vielmehr um die Anerkennung dessen, dass wichtige Transformationsprozesse sich SELBST einleiten, SELBST das Tempo vorgeben und NICHT (durch Bedingungen) gestört werden wollen. Meines Erachtens werden Transformationsprozesse, die sich zaghaft anmelden, in der Regel durch sogenannte Behandlungen und die dazugehörigen RahmenBEDINGUNGEN gestört. Ratsuchende werden mit Wissen und Fremdwörtern überhäuft, mit mündlich und schriftlich vereinbarten Therapiezielen irritiert, mit regelmäßigen mündlichen und schriftlichen Nachfragen zum Behandlungserfolg verunsichert und belästigt und nicht selten wegen angeblich fehlender Mitwirkung bewertet. Andauernde Symptome werden einem zum Vorwurf gemacht, Gefühle werden wie wilde Tiere gejagt, die es, wenn nötig, pharmazeutisch einzufangen und zu erlegen gilt. Anpassung ist Trumpf. Und die Bürokratie beäugt alles aus sicherer Entfernung mit der Stoppuhr. Zeit ist Geld. Wie soll man sich da vertrauensvoll öffnen, Gefühle fließen lassen, den Schmerz zulassen, die Kontrolle verlieren UND wieder erlangen bevor die Kurzzeittherapie oder der genehmigte Klinikaufenthalt beendet sind? Keine Frau kann auf natürliche Weise ein Kind gebären, wenn, etwas überspitzt formuliert, alle fünf Minuten jemand ins Zimmer kommt, den Muttermund fühlen möchte und freundlich darauf hinweist, dass in ein paar Minuten nur noch der Bereitschaftsdienst von der Nachtschicht im Hause ist. Das verursacht Stress, und alles zieht sich buchstäblich zusammen. In der Psychotherapie ist das vergleichbar.
Der seelische Schmerz ist in Praxen, Kliniken und Gesundheitszentren ein Zustand, der wie ein Hund, draußen bleiben muss. Er gilt als Indikator für Krankheit. Das ist aber nur die halbe Wahrheit. Es gibt auch Therapiehunde, und die dürfen rein. Der Schmerz ist beides.
Meines Erachtens ist der Schmerz die Durchtrittspforte, die in beide Richtungen passiert werden kann. Er ist der Letzte und der Erste. Er schaltet das Gefühl ab, wenn das Trauma passiert. Aber er läutet die Wiederkehr des vollen Gefühls auch wieder ein, wenn das Gefühl zurückkommen möchte. Und genau dieser (wertvolle) Schmerz wird bekämpft, was das Zeug hält. Wie soll man dabei gesund werden, wenn man aktiv davon abgehalten wird, durch diese Pforte zu gehen? Niemand lässt einen in Ruhe diesen (wertvollen) Schmerz durchfühlen. Therapeuten werden nervös, Ärzte zücken den Rezeptblock, Krankenkassen beanstanden den fehlenden Erfolg der Behandlungsmethode und kürzen die Mittel. Und dabei arbeitet genau dieser Schmerz FÜR das Leben und FÜR die Selbstheilung, wenn man ihn einfach mal machen lassen würde. Der Schmerz ist so viel besser als sein Ruf. Wenn es irgendwo Drama gibt, dann kann man sicher sein, dass es dem Schmerz in die Schuhe geschoben wird. Und das ganze Geld, was man zur Schmerzbekämpfung ausgibt (Schmerz ist ein Geschäft), könnte man so sinnvoll an anderer Stelle anlegen. Wichtige Gefühle und eben dieser wertvolle Schmerz, der die Selbstheilung bringt, werden vereitelt, weil unser derzeitiges System sich das nicht vorstellen kann, dass ein Schmerz gut sein kann. Der Rettungswagen fährt immer über diese rote Ampel drüber.
Was ist nun mein erster skizzenhafter Kurzausblick für einen hilfreichen Umgang mit Verletzung oder gar Trauma?
Genauso wie es in diesen Tagen Überlegungen zur natürlichen Geburt, zur Hausgeburt usw. gibt, genauso braucht es, meines Erachtens, komplett andere Strukturen, um Mensch zu helfen, die seelisch leiden. Es gibt zurzeit sehr viele Menschen, die aus den unterschiedlichsten Gründen seelisch leiden. Wir sind eine verletzte Gesellschaft, oft sogar bis tief in die Wurzeln.
Mein Traum ist, dass alles von Grund auf anders wird. Der Ratsuchende wird gesehen, er braucht nicht mehr nach Hilfe suchen. Menschen erkennen, was mit einem Mitglied ihrer Gemeinschaft los ist, nicht stimmt. Der Betroffene wird liebevoll und behutsam in die Mitte gestellt, nicht an den Rand. Er erfährt Wertschätzung für sich und seine Situation. Er braucht keine Angst zu haben, ausgestoßen zu werden. Alle setzen alles daran, jemandem zu helfen, weil er ein wertvolles Mitglied der Gruppe ist. Die Begleitung ist ein Anliegen der ganzen Gruppe, nicht eines Heilers. Alle wollen, dass es einer Person wieder besser geht. Alle erkennen eine Botschaft in der „Krankheit“. Denn eine Krankheit entsteht immer in einem System und nicht in einem Individuum allein. Alle nehmen aus der Krankheit eine Lernerfahrung mit für die Zukunft, damit das in Zukunft nach Möglichkeit nicht mehr passiert. Der Betroffene ist um eine Erfahrung reicher, geht gestärkt aus dem Prozess hervor und kann später andere unterstützen, weil er ein spezielles Wissen erworben hat. Der Kranke braucht keine Gefühle von Schuld oder Versagen zu entwickeln, im Gegenteil, er wird aufgewertet, weil ihm Aufmerksamkeit und Fürsorge zuteil werden. Und die Gruppe ist gestärkt, weil sie ein Mitglied wieder fit gemacht hat, sich selbst als Gruppe helfen konnte. „Krankheit“ ist nicht länger ein Grund, jemanden auszustoßen, sondern ein Anreiz, als Gruppe stärker zu werden. Eine Gruppe, die schon ein paar schwere Probleme gemeinsam gemeistert hat, ist ein starkes Team.
Seelisches Leid einer Person wird so einfach zu einem Indikator, der einer Gruppe anzeigt, wo sie nachbessern darf.
Je sensibler jemand ist, desto eher zeigt er seelisches Leid an. Sensible Leute haben diese Funktion in einer Gruppe. Die robusten Leute haben eine andere Funktion in einer Gruppe. Beides ist wichtig. Gruppen brauchen sensible Mitglieder, weil diese, wenn sie gesehen werden, sicherstellen, dass auf gute Umgangsformen, auf Rücksicht, auf Ausgleich, auf Gerechtigkeit usw. geachtet wird. „Krankheiten“ zeigen eigentlich nur Überlastungen an. Je mehr Mitglieder einer Gruppe „krank“ werden, umso schlimmer sind die Lebensumstände. Jedes System sollte immer konstruktiv auf Überlastungsanzeigen reagieren, weil es ansonsten auf der Zeitlinie endet.
Und diesem Gedanken folgend, zieht die Forderung nach einer anderen Begleitung von seelischem Leid in unserer Gesellschaft im Prinzip den Wunsch nach einer ganz anderen gesellschaftlichen Form des Zusammenlebens nach sich. Um sich in einer Gemeinschaft um ein Mitglied kümmern zu können, braucht es erstmal eine (soziale) Gemeinschaft. Also brauchen wir wieder funktionierende soziale Gruppen, wo Menschen sich ganz einfach miteinander verbunden fühlen, sich für die Oma, den Neffen, den Nachbarn oder Kollegen interessieren. Solche Dinge können klein anfangen und dann immer größer werden. Ich denke an Oasen inmitten der alten Struktur wie es sie in ähnlichen Bereichen bereits gibt. Das sind z.B. nichtkommerzielle Projekte, die davon leben, dass einige wenige Menschen sich zusammengeschlossen haben, weil sie die gleiche Sehnsucht teilten. Oder einzelne Menschen machen ihre eigene Erfahrung für jeden frei zugänglich. Jeder, der etwas Hilfreiches in Sachen „seelische Heilung“ erlebt hat, meldet sich zu Wort, wird erkennbar für Ratsuchende. Der Ratsuchende muss nicht mehr auf die Suche gehen, muss sich nicht mehr schämen, ist nicht mehr allein. Es geht um freien Wissensaustausch, der dann Kreise ziehen kann. Es geht um den Wunsch, es anders, freier und menschlicher gestalten zu wollen und darum, sich etwas anderes vorstellen zu können, weil man selbst mal etwas anderes am eigenen Leib und an der eigenen Seele erfahren hat. Wenn man selbst etwas anders erfahren hat, als es vom System und von wichtigen Gremien gepredigt wird, dann gibt es kein Zurück zum System mehr, denn man weiß, es geht anders.
Wissen kann man nicht mehr zurück nehmen, wenn es einmal da ist.
Es geht anders, das ist zumindest meine Gewissheit. Und wir können Traumaintegration mit der Kraft der Natur, mit unserer Biologie, mit der Intelligenz der Evolution oder dem, was größer ist als wir, erreichen. Wir können mit dieser in uns angelegten Fähigkeit zur SELBSTheilung auch schwere seelische Verletzungen „heilen“. Die Natur hat Frauen seit Urzeiten natürlich gebären lassen. Und die Natur hilft uns genauso bei seelischem Trauma, wenn wir sie, die Natur, dabei nicht stören.
Solche Oasen für seelische Prozesse können überall dort entstehen, wo Menschen selbst diese Erfahrung von Selbstheilung seelischer Verletzung gemacht haben. Solche Oasen haben nichts mit Kommerz zu tun haben. Die Erfahrung, die man in solch einer Oase gemacht hat, kann man dann weiter tragen. Das ist sozusagen ihr „Gewinn“. Der Gewinn ist immateriell. Aber wie wir alle wissen, zieht das Bewusstsein immer die Materie nach sich. Das bedeutet, dass immer mehr Menschen durch diese Erfahrungen in ihr authentisches Sein und ihre gesunde Schaffenskraft kommen. Und das wird irgendwann sichtbar und auch auf gesellschaftlicher Ebene spürbar.
Die größte Herausforderung wird sein, den Menschen klar zu machen, dass die Natur uns heilt und dass man mit diesem Modell kein Geschäft machen kann. Wer mit Heilung ein Geschäft machen möchte, kommt zwangsläufig an den Punkt, an dem wir jetzt sind. Man kann wohl nur mit unterdrücktem Heilungswissen Geschäfte machen. Deswegen wird der Schmerz auch unterdrückt und übergangen. Denn er trägt dieses Heilungswissen in sich. Mit frei zugänglichem Heilungswissen für jeden, also z.B. dem Wissen über den Schmerz und was dieser imstande ist zu verändern, kann man zwar kein Geschäft machen, aber dafür endlich alles andere.
Heiße den Schmerz willkommen, wenn er in Dein Leben kommt.
*******************************************************************************
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Onboarding bei Nostr: Nostr
Easy onboarding via **Start.**\ \ Das Pareto-Team baut den “Marktplatz der Ideen” und hat dabei schon viel erreicht. \ team@pareto.space \ https://pareto.space \ https://geyser.fund/project/pareto?hero=1c1b8e487090
\ \ Newsletter per Mail (Die Friedenstaube)\ hier abonnieren\ \ In Telegram lesen -> hier unsere Kanäle\ https://t.me/pareto_artikel \ https://t.me/friedenstaube_artikel \ \ Als Feed in einem Feed-Reader \ https://pareto.space/atom/feed.xml \ https://pareto.space/atom/de_feed.xml \ https://pareto.space/atom/en_feed.xml
-
 @ e2c72a5a:bfacb2ee
2025-06-06 12:13:16
@ e2c72a5a:bfacb2ee
2025-06-06 12:13:16While billionaires battle for Bitcoin billions, everyday investors are missing the real revolution. Michael Saylor just quadrupled his stock offering to $1 billion for Bitcoin purchases, while Japan's Metaplanet aims to hold 100,000 BTC by 2026. These corporate treasuries aren't just hedging inflation – they're preparing for a world where traditional finance and crypto fully merge. Meanwhile, Uber is quietly exploring stablecoins to slash global money transfer costs, and the UK is lifting retail bans on crypto ETNs. The institutional chess pieces are moving while retail investors fixate on price charts. The question isn't whether Bitcoin hits $112K this year – it's whether you'll recognize the financial system transformation happening right under your nose. Are you watching the price or the paradigm shift?
-
 @ fe820c8e:d2d76f04
2025-06-06 09:09:42
@ fe820c8e:d2d76f04
2025-06-06 09:09:42Nostr Quizzzz
-
Was ist Nostr?
-
[( )] Ein zentralisierter Social-Media-Dienst
- [(X)] Ein dezentralisiertes Protokoll für soziale Netzwerke
- [( )] Ein E-Mail-Anbieter
-
[( )] Ein Open-Source-Betriebssystem
-
Welche der folgenden Punkte sind typische Merkmale von Nostr? (Mehrfachauswahl möglich)
-
[[X]] Nutzung von Public/Private-Key-Paaren für Identität
- [[ ]] Ein zentraler Server speichert alle Profile
- [[ ]] Keine Möglichkeit zur Moderation von Inhalten
- [[X]] Jeder kann ohne Erlaubnis eines Providers einen Relay betreiben
- [[ ]] Komplett verschlüsselte Nachrichten (Ende-zu-Ende) als Standard
Umfragen
Wie findet ihr Nostr?
- [(1)] sehr gut
- [(2)] gut
- [(3)] ok
- [(4)] befriedigend
- [(5)] würde ich nicht nutzen ...
-
-
 @ 58537364:705b4b85
2025-06-05 15:55:12
@ 58537364:705b4b85
2025-06-05 15:55:12อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก
…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ 2cde0e02:180a96b9
2025-06-05 15:13:03
@ 2cde0e02:180a96b9
2025-06-05 15:13:03pen & ink; monochromized
Magdalena Carmen Frida Kahlo y Calderón[a] (Spanish pronunciation: [ˈfɾiða ˈkalo]; 6 July 1907 – 13 July 1954[1]) was a Mexican painter known for her many portraits, self-portraits, and works inspired by the nature and artifacts of Mexico. Inspired by the country's popular culture, she employed a naïve folk art style to explore questions of identity, postcolonialism, gender, class, and race in Mexican society.[2] Her paintings often had strong autobiographical elements and mixed realism with fantasy. In addition to belonging to the post-revolutionary Mexicayotl movement, which sought to define a Mexican identity, Kahlo has been described as a surrealist or magical realist.[3] She is also known for painting about her experience of chronic pain.[4]
https://stacker.news/items/997980
-
 @ 975e4ad5:8d4847ce
2025-06-05 13:14:46
@ 975e4ad5:8d4847ce
2025-06-05 13:14:46What is the Fiat System and How Do Central Banks Set Interest Rates?
When central banks expand credit, they often increase the money supply by creating new money through mechanisms like quantitative easing (QE). For instance, a central bank may purchase government bonds, injecting money into the economy. This boosts liquidity but can lead to inflation when too much money chases limited goods and services.
Low interest rates make borrowing cheaper, encouraging spending and investment. However, this can overheat the economy, create speculative bubbles (e.g., in real estate), and drive inflation. Conversely, high interest rates restrict borrowing, slow the economy, and curb inflation but may trigger recessions.
How Would Interest Rates Work Under a Bitcoin Standard?
Under a Bitcoin standard, the money supply is fixed—only 21 million bitcoins will ever exist, with the last one mined around 2140. Unlike the fiat system, no central authority can manipulate the money supply or set interest rates. Instead, interest rates would be determined entirely by the market—by the supply and demand for capital.
If someone wants to borrow bitcoins, the interest rate would depend on negotiations between the lender and borrower. For example, if demand for loans is high and available bitcoins are scarce, interest rates would rise. Conversely, if there are ample bitcoin savings, rates might fall. This process would be fully decentralized and reflect real market conditions, not central bank decisions.
Since new bitcoins cannot be “printed,” there would be no inflation caused by an expanding money supply. Instead, bitcoin’s value would likely rise over time (deflation) as its fixed supply competes with growing demand. This could encourage saving over reckless spending, reshaping economic behavior.
Advantages of a Bitcoin Standard
-
Protection Against Inflation: Bitcoin’s fixed supply prevents currency devaluation, a common issue with fiat money. This safeguards savings and promotes long-term planning.
-
Decentralization: Without a central bank manipulating the market, economic decisions are made by individuals, not bureaucrats. This aligns with free-market principles where competition and innovation thrive.
-
Transparency and Security: The Bitcoin blockchain is public and immutable, ensuring transactions are transparent and secure from tampering.
-
Financial Freedom: Under a Bitcoin standard, individuals have full control over their money without government or bank interference, which is especially crucial in countries with unstable regimes or currencies.
-
Discipline in Lending: Without the ability to print money, lenders would be more cautious, reducing risky investments and speculative bubbles.
Potential Drawbacks and Why a Bitcoin Standard is Superior
One major argument against a Bitcoin standard is that it could slow economic growth. Low interest rates in the fiat system encourage borrowing and spending, driving economic activity. Under a Bitcoin standard, where interest rates are market-driven and likely higher, borrowing would be costlier, potentially limiting investments in new projects.
However, this critique misses a key point: economic growth fueled by artificially low interest rates and money printing is often unsustainable. It leads to debt crises, inflation, and bubbles that eventually burst, as seen in 2008. A Bitcoin standard promotes healthy economic discipline, where investments are based on real value, not artificial capital.
Moreover, bitcoin’s deflationary nature could shift how people view money. Instead of chasing endless growth, societies might prioritize sustainability, innovation, and efficiency. This could lead to a more stable and equitable economy in the long run.
Additional Considerations
A Bitcoin standard could transform global trade. Today, countries with fiat currencies often manipulate exchange rates to gain trade advantages. With bitcoin as a universal currency, such manipulations would vanish, fostering fairer competition.
Another aspect is energy efficiency. While bitcoin mining consumes energy, it incentivizes the development of renewable sources as miners seek cheap, sustainable energy. This could accelerate the transition to a green economy.
Conclusion
The Bitcoin standard offers a vision of an economy rooted in sound money, free markets, and financial freedom. While it may slow certain aspects of economic growth, it creates a more stable and sustainable system that protects individuals from inflation and centralized control. In a world where trust in institutions is waning, the Bitcoin standard is a step toward a fairer and more transparent future.
-
-
 @ 90c656ff:9383fd4e
2025-06-05 12:27:43
@ 90c656ff:9383fd4e
2025-06-05 12:27:43When people talk about Bitcoin, it’s often described as a digital currency or a “speculative investment.” However, one of Bitcoin’s most fundamental and least understood roles is its function as a settlement network. To understand this, it’s worth comparing it with traditional settlement systems like SWIFT and exploring how Bitcoin offers a foundational layer for global value transfer decentralized and censorship-resistant.
First, let’s explain the difference between liquidity and settlement:
-
Liquidity refers to the ease with which an asset can be converted into “money” without losing value.
-
Settlement is the process of completing a transaction (actual transfer of value between parties).
SWIFT: The communication layer of the traditional financial system
The SWIFT system (Society for Worldwide Interbank Financial Telecommunication) is a network for communication between banks. It doesn’t move money directly but sends standardized messages that instruct financial institutions to perform transfers. The process involves multiple intermediaries, is costly, slow (can take days), and depends on trust between parties and local regulations.
Unlike SWIFT, Bitcoin is a self-sufficient network that enables the direct settlement of value between two parties, without the need for intermediaries. With each block mined, transactions are validated and recorded immutably in a global, transparent, and secure database: the timechain or "blockchain".
01 - Final settlement: Once a transaction is confirmed by a sufficient number of blocks, it is considered final and irreversible.
02 - Censorship resistance: There is no central entity that can block or reverse a valid transaction.
03 - Global availability: The network is accessible 24/7 anywhere in the world with internet access.
Just as gold once served as the foundation of monetary systems, Bitcoin is establishing itself as a base layer of digital value. This layer can support others, such as:
01 - The Lightning Network, which enables near-instant transactions with extremely low fees;
02 - Tokenized financial services, which can use Bitcoin as collateral or for inter-institutional settlement.
By functioning as a public and neutral settlement network, Bitcoin offers an alternative to the traditional system, which is fragmented, closed, and reliant on trust between institutions.
In summary, more than just a speculative asset, Bitcoin is emerging as a global financial infrastructure. As a settlement network, it removes intermediaries, reduces costs, increases security, and democratizes access to value transfer. In an increasingly interconnected and digital world, understanding Bitcoin’s role as a base layer may be key to understanding the future of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:46:07
@ 20e7c953:3b8bcb21
2025-06-05 10:46:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bircoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
Skatestr
-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:55:03
@ e2c72a5a:bfacb2ee
2025-06-06 02:55:03Your crypto wallet is probably leaking money right now. While everyone obsesses over price charts, the silent killer is gas fees – those tiny transactions add up to thousands wasted annually. Smart traders aren't just buying dips, they're timing their transactions when network congestion drops. The difference? Up to 80% savings on every move you make. Next time before hitting "confirm," check the gas tracker. Is it worth paying 3x more just to move your assets right this second? Patience isn't just a virtue in crypto – it's literally profitable. What's your strategy for minimizing transaction costs while maximizing gains?
-
 @ e4950c93:1b99eccd
2025-06-05 10:23:39
@ e4950c93:1b99eccd
2025-06-05 10:23:39Marques
Nordkidz est une marque allemande qui crée à la demande des vêtements et linges pour les bébés, les enfants, et un peu pour leurs parents.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements : bébés, enfants, unisexe
- Hauts : pulls, t-shirts
- Bas : pantalons, pantalons de survêtement, shorts
- Tête et mains : bonnets, écharpes
Maison
- Linge : housses de pouf, langes, ponchos de bain
Autres informations
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Nordkidz (en allemand, zone de livraison : Allemagne et Union Européenne) 💚 Via ce lien vous soutenez directement la marque.
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:43:10
@ e2c72a5a:bfacb2ee
2025-06-06 02:43:10North Korea's digital heist playbook: $7.7M crypto laundering scheme reveals how rogue nations exploit tech talent. The Justice Department's latest civil forfeiture complaint targets crypto and NFTs tied to an elaborate North Korean operation where IT workers posed as legitimate freelancers, infiltrated US companies, and funneled millions through complex blockchain pathways. This isn't just another hack—it's a sophisticated economic warfare strategy that turns technical expertise into untraceable funding for weapons programs. While governments scramble to seize these digital assets, the case exposes a troubling vulnerability: how easily skilled developers can weaponize their talents in plain sight. Are your company's remote contractors who they claim to be, or part of a state-sponsored financial pipeline hiding behind a convincing digital mask?
-
 @ e2c72a5a:bfacb2ee
2025-06-06 01:42:46
@ e2c72a5a:bfacb2ee
2025-06-06 01:42:46North Korea's digital heist reveals the dark side of crypto's borderless nature. The US Justice Department is hunting $7.7 million in stolen cryptocurrency and NFTs allegedly laundered through an elaborate scheme involving North Korean IT workers posing as legitimate freelancers. This isn't just another hack—it's a sophisticated state-sponsored operation exploiting the very features that make crypto revolutionary: anonymity and borderless transactions. While we celebrate crypto's ability to transcend boundaries, this case exposes how those same qualities create perfect conditions for rogue nations to fund weapons programs and evade sanctions. The crypto industry faces a critical balancing act: how do we preserve financial freedom while preventing bad actors from exploiting the system? Perhaps the solution isn't more regulation but smarter blockchain analytics and international cooperation. What security measures would you support that don't compromise crypto's core principles?
-
 @ b1ddb4d7:471244e7
2025-06-05 10:00:43
@ b1ddb4d7:471244e7
2025-06-05 10:00:43Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ 502ab02a:a2860397
2025-06-06 01:15:24
@ 502ab02a:a2860397
2025-06-06 01:15:24ปิดท้าย week นี้ด้วยสงครามดีไหมครับ ถ้าอาหารเป็นสนามรบ สิทธิบัตรก็เปรียบเหมือนป้อมปราการ และการฟ้องร้องก็คือปืนใหญ่ยิงสวนกันกลางแดด…ใครที่เคยคิดว่าโลกของอาหารแห่งอนาคตจะสวยงามเพราะเปลี่ยนถั่วเป็นสเต๊ก สกัดกลิ่นเลือดจากพืช หรือหลอกลิ้นให้เชื่อว่า “อร่อยเหมือนเนื้อ” ก็คงต้องมานั่งทบทวนใหม่ว่า โลกใบนี้ไม่ได้ขับเคลื่อนด้วยความฝัน แต่ขับเคลื่อนด้วยเอกสาร 70 หน้าของทนายความ และหมายเรียกจากศาลกลางรัฐเดลาแวร์
Motif FoodWorks เข้ามาในวงการอาหารด้วยวิสัยทัศน์สุดเท่ คือจะสร้างโครงสร้าง-กลิ่น-รส ของโปรตีนอนาคตให้แบรนด์ plant-based ทั่วโลกใช้ได้โดยไม่ต้องเริ่มใหม่ตั้งแต่ศูนย์ เปรียบเหมือนเป็นเบื้องหลังของวงการ มีซอสลับคือ HEMAMI™ ที่สกัดกลิ่นเนื้อจากยีสต์ ผ่านวิธีการทางวิทยาศาสตร์สุดซับซ้อน ฟังแล้วดูดี แต่ปัญหาคือซอสลับของเขาดัน “คล้ายเกินไป” กับของ Impossible Foods ที่ใช้ heme protein เหมือนกัน
แล้วอะไรคือจุดเปราะบางที่ทำให้ Motif ต้องร่วง?
เฮียอยากให้ลองคิดแบบนี้ครับ สมมุติว่ามีร้านกาแฟใหม่ที่ตั้งใจจะขายกาแฟแนวใหม่ ใช้เมล็ดกาแฟหมักยีสต์กลิ่นกล้วยหอม รสชาตินุ่มลึก เป็นของตัวเอง เขาไม่ได้ก็อปสูตรใคร แต่ดันไปใช้กระบวนการคล้ายกับแบรนด์เจ้าตลาดที่เขียนจดสิทธิบัตรเอาไว้ก่อนแล้ว แค่คล้ายก็พอจะโดนลากขึ้นศาลได้ เพราะในโลกของสิทธิบัตร “ความใหม่” และ “ความไม่เหมือน” คือสิ่งศักดิ์สิทธิ์ แม้จะไม่ได้ก็อปตรง ๆ
Impossible Foods เห็นช่องนี้ชัด พวกเขายื่นฟ้องทันที โดยระบุว่า HEMAMI™ ของ Motif ละเมิดสิทธิบัตรเทคนิคการใช้ heme เพื่อสร้างรสชาติเหมือนเนื้อในผลิตภัณฑ์ plant-based ซึ่งเป็นหัวใจหลักที่ Impossible ใช้มัดใจตลาดมาหลายปี
ในเดือนมีนาคม 2022, Impossible Foods ก็ลุกขึ้นมาฟ้อง Motif FoodWorks ต่อศาลรัฐบาลกลางของสหรัฐฯ โดยอ้างว่า HEMAMI™ ละเมิดสิทธิบัตรของตนที่เกี่ยวข้องกับการใช้โปรตีน heme ในการสร้างรสชาติและกลิ่นที่คล้ายเนื้อจริงในผลิตภัณฑ์จากพืช จุดนี้ดูผิวเผินเหมือนแค่ “บริษัท A เหมือนของบริษัท B เลยโดนฟ้อง” แต่ความจริงซับซ้อนและลึกกว่านั้นมาก เพราะทั้งสองบริษัทต่างก็ใช้วิธีผลิตโปรตีน heme ที่คล้ายกันมาก นั่นคือการดัดแปลงพันธุกรรมจุลินทรีย์ให้ผลิตโปรตีนเฉพาะ แล้วหมักออกมาในถังขนาดใหญ่ แต่ต่างกันที่วัตถุดิบและดีไซน์โปรตีน
Impossible Foods ใช้ “soy leghemoglobin” ซึ่งเป็นโปรตีน heme จากรากถั่วเหลือง ส่วน Motif ใช้ “bovine myoglobin” ซึ่งเลียนแบบของวัวจริง ๆ โดยตรง ความคล้ายคือโปรตีนทั้งสองต่างก็ให้กลิ่นคาวแบบเนื้อเมื่อโดนความร้อน และสร้างสีแดงแบบ rare steak ได้เหมือนกัน ทั้งยังถูกหมักด้วยจุลินทรีย์ GMO แบบใกล้เคียงกันอีกด้วย แม้จะต่างสายพันธุ์ของโปรตีน แต่การฟ้องครั้งนี้ตั้งอยู่บนแนวคิดว่า “วิธีการใช้” โปรตีน heme ในอาหารจากพืชอาจเข้าข่ายละเมิดสิทธิบัตร
จากนั้นไม่กี่เดือน Motif ก็สวนกลับโดยการยื่นคำร้อง “Inter Partes Review” (IPR) กับสำนักงานสิทธิบัตรของสหรัฐฯ (USPTO) ผ่าน PTAB ซึ่งเป็นขั้นตอนที่ใช้เพื่อขอให้ตรวจสอบความถูกต้องของสิทธิบัตรที่กำลังมีปัญหา แนวคิดคือถ้าพิสูจน์ได้ว่าสิทธิบัตรของ Impossible นั้นไม่ใหม่จริง หรือมี prior art อยู่ก่อนแล้ว (เช่น งานวิจัยเก่า ๆ ที่ตีพิมพ์ก่อน) ก็จะทำให้สิทธิบัตรนั้นกลายเป็นโมฆะ
Motif ยื่นคำร้องโจมตีสิทธิบัตรถึง 7 ฉบับของ Impossible แบบกระหน่ำชุดใหญ่ ยิงทีเดียวหวังให้สั่นคลอนทั้งระบบ แต่ PTAB รับพิจารณาเพียงฉบับเดียว (หมายเลขสิทธิบัตร 10,933,018) และท้ายที่สุดในเดือนเมษายน 2023 ศาลตัดสินยกเลิกฉบับนั้นจริง โดยให้เหตุผลว่า “ไม่เป็นสิ่งประดิษฐ์ใหม่อย่างเพียงพอ” ซึ่งถือเป็นชัยชนะเล็ก ๆ ของ Motif และสร้างแรงกระเพื่อมในแวดวงวิทยาศาสตร์อาหารอยู่พอสมควร
แต่แม้จะมีชัยบางส่วน อีก 6 ฉบับที่เหลือ PTAB กลับไม่รับพิจารณา โดยบอกว่า “หลักฐานไม่ชัดเจนพอจะเข้าขั้นพิจารณาใหม่” นั่นทำให้ฝั่ง Impossible ยังถือสิทธิบัตรส่วนใหญ่ไว้อยู่เหมือนเดิม แล้วก็เริ่มกลับมาเร่งกระบวนการฟ้องร้องในศาลต่อ ซึ่งหมายความว่า Motif ยิ่งต้องใช้เงินมากขึ้นเรื่อย ๆ ในการสู้รบทั้งสองด้าน ทั้งในศาลและในระบบสิทธิบัตร
ชัยชนะเล็ก ๆ นี้กลายเป็นดาบสองคม เพราะในขณะที่ Motif ดีใจว่าล้มได้ 1 ฉบับ ตลาดกลับมองว่าพวกเขาสู้แบบดิ้นสุดตัว ซึ่งในมุมของนักลงทุน นั่นแปลว่า "ขาดเงินทุนหมุนเวียน" หรือ “มีแนวโน้มขาดทุนต่อเนื่อง” มากกว่าจะมองว่าเป็นฮีโร่สู้เพื่อความถูกต้อง
ระหว่างนี้ Motif ยังพยายาม “spin” ภาพลักษณ์ตัวเองในเชิงบวกอย่างหนัก พวกเขาเปิดตัวผลิตภัณฑ์ใหม่ชื่อ “Motif MoBeef™” และ “Motif MoChicken™” โดยใช้ HEMAMI™ ผสมอยู่ พร้อมโชว์ผลงานให้เชฟชื่อดังระดับ Michelin มาชิมและออกสื่อ โดยหวังว่าจะสร้างความเชื่อมั่นให้ตลาดว่า “ผลิตภัณฑ์เรายังไปต่อได้” และอาจดึงดีลใหม่หรือการลงทุนเพิ่มเข้ามาเพื่อบรรเทาภาระจากการฟ้องร้อง
และในขณะที่ Motif เดินหน้าเปิดตัวผลิตภัณฑ์ใหม่เพื่อแสดงพลังให้ตลาดเห็นว่า “เรายังไปต่อได้” ฝั่ง Impossible กลับเดินเกม PR อย่างเงียบ ๆ ด้วยการแจ้งเตือนสื่อและผู้ถือหุ้นว่า “Motif ยังใช้เทคโนโลยีละเมิดอยู่ต่อเนื่อง” พร้อมแนบเอกสารคำฟ้องเพิ่มในปี 2023 ซึ่งแปลความได้ว่า “ศึกยังไม่จบ อย่าเพิ่งส่งเงินให้คู่แข่งเรา” เพราะในเอกสารคำฟ้องของปี 2023 พวกเขาเสริมข้อกล่าวหาใหม่ว่าการที่ Motif ออกสื่อและใช้ HEMAMI™ ต่อไป “เป็นการจงใจละเมิด” และอาจเข้าข่ายการทำลายคุณค่าของแบรนด์ Impossible โดยตรง จุดนี้ยิ่งทำให้ Motif อยู่ในมุมที่เสี่ยงและลำบากมากขึ้น
การต่อสู้ของทั้งสองบริษัทจึงไม่ใช่แค่เรื่องใครเลียนแบบใคร แต่มันคือเกมยืดเวลา เผาเงิน ปั่นมูลค่า และวัดใจนักลงทุนว่าใครจะถอยก่อนกัน และสุดท้ายคนที่หมดลมหายใจก่อนก็คือ Motif แม้จะมีนักวิทยาศาสตร์เก่ง ๆ เทคโนโลยีล้ำ ๆ หรือวัตถุดิบดีแค่ไหน แต่เมื่อต้องมาสู้กับยักษ์ที่มีสิทธิบัตรในมือ บารมีในตลาด และชื่อเสียงติดหูผู้บริโภค…ก็ยากที่จะเอาชนะด้วยวิทยาศาสตร์เพียงอย่างเดียว
ศึกนี้จึงไม่ได้จบแค่ในศาล แต่มันลากไปถึงห้องประชุมนักลงทุน พาดหัวข่าวใน Business Insider และบอร์ด Reddit ที่คุยกันว่า “Motif จะไปไม่รอดหรือเปล่า” ซึ่งในยุคที่เงินทุนคือออกซิเจน การที่ภาพลักษณ์ของบริษัทเริ่มสั่นคลอน ก็เหมือนถังอากาศรั่วในห้องแล็บใต้ทะเล…ไม่นานนัก Motif ก็เริ่มลดจำนวนพนักงาน ลดเป้าการผลิต และสุดท้าย “ลดบทบาทตัวเองในตลาด”
หากดูเผิน ๆ หลายคนอาจคิดว่านี่คือเรื่องของสองบริษัทใหญ่ในโลก plant-based ที่ทะเลาะกันเอง แต่จริง ๆ แล้วนี่คือบทเรียนใหญ่ของ “วงการอาหารแห่งอนาคต” ที่กำลังเติบโตบนหลังคำว่า IP Intellectual Property ใครถือสิทธิบัตรก่อน คนนั้นตั้งกฎได้ ใครมาใหม่ ถ้าไม่จดให้ไว ก็อาจต้องจ่ายค่าต๋งตลอดชีวิต
และที่เจ็บปวดที่สุดคือบางทีของที่คุณคิดขึ้นมาเอง อาจไม่ใช่ของคุณอีกต่อไปแล้ว ถ้าคุณไม่มีเอกสารในมือ
นี่แหละครับ วงการที่ดูเหมือนจะขาย “นวัตกรรมอาหาร” แต่จริง ๆ แล้วขาย “สิทธิบัตรในกล่องข้าว” ใครจะอยู่ใครจะไป บางทีก็ไม่เกี่ยวกับว่า “ของอร่อยแค่ไหน” แต่เกี่ยวกับว่า “ใครมีทนายเก่งกว่า”
และในขณะที่สองยักษ์ใหญ่ยิงกันด้วยเอกสารละเมิดสิทธิ์ เหยื่อเงียบ ๆ อย่างเกษตรกรรายย่อยที่ยังอยากปลูกผักจริง เลี้ยงวัวจริง หรือแม้แต่ผู้บริโภคที่แค่อยากรู้ว่า “กินอะไรแล้วร่างกายจะดีขึ้น” กลับวนเวียนในทางอยู่ในโลกที่อาหารทุกคำถูกควบคุมโดยทุน จดหมายเรียกจากศาล และวัตถุดิบสังเคราะห์ที่มีรหัสมากกว่าชื่อจริง
สงครามสิทธิบัตรเหล่านี้ไม่เคยมีพื้นที่ให้ชาวไร่ หรือผู้บริโภคธรรมดาเข้าไปมีเสียงเลยสักนิด เพราะมันคือการต่อสู้ระหว่างนักล่าที่ฟาดฟันกันบนยอดห่วงโซ่อาหาร แต่เบื้องล่างของพีระมิด กลับมีแต่เหยื่อที่ถูกเลี้ยงให้งุนงง อยู่กับของปลอม และเชื่อว่า “นี่แหละคืออนาคตของอาหาร”
แล้วใครจะบอกเราว่า...ทางรอดคืออะไร?
คำตอบอาจอยู่ไม่ไกล แค่เราต้องกลับมาถามคำถามง่าย ๆ ที่ใครก็ลืมไปว่า “จริง ๆ แล้ว เราต้องการอาหารแบบไหนกันแน่” อาหารที่กินแล้วแข็งแรง หรืออาหารที่บริษัทแข็งแรง?
เพราะตราบใดที่เรายังปล่อยให้กล่องข้าวอยู่ในมือคนจดสิทธิบัตร เราอาจไม่มีวันได้กลับไปจับจอบเอง ปลูกเอง กินเอง แบบที่มนุษย์เคยเป็นมาก่อนโลกจะกลายเป็นห้องทดลองขนาดยักษ์
ศึกระหว่างผู้ล่ายังรุนแรงขนาดนี้ แล้วศึกระหว่างผู้ล่ากับเหยื่อ จะเหลืออะไรครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ d5c440ce:04726d89
2025-06-05 06:19:49
@ d5c440ce:04726d89
2025-06-05 06:19:49Effektiv behandling af blodsprængninger kræver en professionel tilgang og de rette metoder. Hos Klinik Zenit tilbyder vi skånsomme og dokumenterede teknikker til at reducere synligheden af blodsprængninger i ansigt og på krop. Vores behandlinger tilpasses individuelt og udføres af erfarne specialister med fokus på sikkerhed og langvarige resultater. Få vejledning om hudpleje før og efter behandlingen for at opnå det bedste resultat. Kontakt Klinik Zenit for en professionel vurdering og behandlingsplan.
-
 @ 527337d5:93e9525e
2025-06-05 03:09:02
@ 527337d5:93e9525e
2025-06-05 03:09:02The Algorithmic Pursuit of Connection: A Five-Book Journey into the Self
As a researcher, hitting my thirties and the winding down of a significant project prompted a crucial re-evaluation of life's latter half. While I'd successfully applied probabilistic control theory to one-on-one interactions, the complexities of group dynamics remained a persistent challenge. My recent dive into five diverse books on human relationships inadvertently became a profound journey of self-discovery, fundamentally reshaping my perspective on social connections.
Neil Strauss: A Mirror Reflecting the Self's Evolution
Neil Strauss's The Truth resonated deepest among my recent reads. The author's battle with sex addiction uncomfortably mirrored my own past struggles: the fragile self-esteem stemming from rejection, the hubris born of early successes, and the tendency to view women as mere objects of manipulation. It felt eerily prescient, a glimpse into a potential future.
Yet, I found myself arriving at Strauss's ultimate conclusion – the paramount importance of self-preparation and community – far sooner than he did. This acceleration wasn't accidental; it was the result of intense focus on individual experiences, meticulously replayed and analyzed in my mind. The book, therefore, served less as a revelation and more as a powerful validation of my own journey of introspection and root-cause analysis.
Quantifying Connection: The Promise and Limits of Mathematical Models
Hannah Fry's The Mathematics of Love offered a kindred spirit in its attempt to quantify human relationships. While I appreciate the mathematical lens, Fry's models primarily concern dyadic relationships (N=2), relying on relatively simple systems of two-variable ordinary differential equations. For me, these are akin to linear models, sufficient only up to a certain point. Beyond N=4, the dependencies become exponentially complex.
My own pursuit extends to understanding and optimizing group dynamics within complex systems. This involves multi-variable problems (N $\ge$ 3) and the application of network theory, a far more sophisticated approach. Human collectives, after all, are systems of nodes and edges, where information propagates in predictable ways. My focus is on deriving optimal behavioral controls within these intricate frameworks.
Conversely, Men Are from Mars, Women Are from Venus initially struck me as bordering on conspiracy theory. However, its latter half proved unexpectedly useful. Its clear enumeration of male and female desires, and its articulation of common points of conflict, presented a practical template for communication styles. In a systemic view, this serves as a rudimentary, yet functional, interface design for complex social interactions.
A Dispassionate Critique of Relationship Dogma
My drive for efficiency and systematic understanding led to a rather blunt assessment of certain relationship classics. The New Science of Adult Attachment felt disorganized and frustratingly anecdotal. Lacking a coherent theoretical framework, it burdened the reader with deciphering meaning from a jumble of examples. Its inefficiency was, frankly, its most irksome flaw.
Similarly, Dale Carnegie's How to Win Friends and Influence People struck me as closer to pseudoscience than social science. Its plethora of specific anecdotes obscured any underlying principle. Given my deep engagement with social engineering – a discipline that systematically and practically analyzes human interaction – Carnegie's work appeared largely irrelevant and inefficient. From my perspective, which views humans as objective systems to be analyzed with mathematical rigor, such unstructured approaches hold little value.
The Unveiling of a Core Principle: Humans as Systems
This intensive reading period solidified my most crucial insight: humans, at their core, are systems. This understanding allows for a dispassionate, methodical approach to human collectives, mitigating unnecessary emotional friction.
This revelation has sharply refined my future learning trajectory. I'm now prioritizing foundational theories like graph theory and network theory over anecdotal accounts of human behavior. By mastering these theoretical underpinnings, I aim to precisely model complex human interactions as systems of nodes and edges, enabling the derivation of optimal behavioral controls within communities.
My choice of the term "target for capture" for individuals stems from a personal aversion to perceived equality in certain human interactions, a mechanism to avoid cognitive dissonance. This rational approach, I believe, is key to cultivating secure attachment styles – relationships demonstrably sustainable in the long term. My philosophy is to strategically approach the initial engagement, then transition to a stable, enduring connection. It's a calculated, dispassionate method for achieving desired relational outcomes.
Ultimately, this period of reading wasn't just about acquiring knowledge; it was a profound journey of self-discovery, clarifying my personal frameworks for navigating life's complexities and forging meaningful, yet strategically managed, connections.
-
 @ 49d472c1:a63cd544
2025-06-05 02:59:12
@ 49d472c1:a63cd544
2025-06-05 02:59:12Bitcoin Miners Pivot to Power AI Boom, Offering a Lifeline to America’s Data-Center Crunch
A fresh Morgan Stanley analysis warns that U.S. data-center demand will balloon to ≈65 GW between 2025 and 2028—about 45 GW more than the grid can currently supply. One solution the bank singles out: repurposing the oversized, transformer-fed campuses originally built for Bitcoin mining. (investopedia.com)
Several public miners are already moving. Riot Platforms has begun buying extra land near its Corsicana, TX complex and hired a veteran data-center executive to head a “high-performance compute” division aimed squarely at AI customers. (riotplatforms.com, coindesk.com) Bitfarms, meanwhile, is marketing North-American sites to hyperscalers after hiring consultants to evaluate GPU-ready retrofits. (reuters.com)
Industry analysts say the pivot is existential. April 2024’s fourth halving chopped block rewards to 3.125 BTC, shrinking miner revenue just as network difficulty hit record highs. By leasing idle megawatts—or fully converting halls—operators lock in dollar-denominated cash-flows while retaining the option to resume mining if margins rebound.
“Miners spent the last cycle amassing land, switchgear and transformers. AI is about to pay them for it.” —Greg Miller, Citizens JMP (research note quoted in multiple sector briefings)
Why it matters
- Grid relief: Every gigawatt shifted from speculative hashing to AI compute eases ERCOT’s peak-load stress and shortens transmission-upgrade timelines. (datacenterdynamics.com)
- Cap-ex savings for cloud firms: Retrofitting a mining hall is months faster—and currently 30-40 % cheaper—than green-field construction, analysts estimate. (govtech.com)
- Dual-revenue model: Miners keep upside to future BTC price spikes while monetizing power capacity today.
The roadblocks
- Cooling retrofits: Air-cooled ASIC barns must be re-engineered for liquid-cooled GPU clusters, at up to \$3 M per MW in conversion costs. (driehaus.com)
- Policy risk in Texas: Lawmakers are weighing caps on industrial load-flex credits after recent grid-stress events, which could dent miners’ ancillary revenue. (dallasnews.com)
Bottom line: Once-beleaguered Bitcoin mines may become critical real estate for the surging AI sector—turning yesterday’s crypto boomtowns into tomorrow’s compute hubs while giving miners a much-needed new income stream.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52
@ 5d4b6c8d:8a1c1ee3
2025-06-05 01:28:52How did the stackers do on their ~HealthAndFitness journeys today?
I did very well: Slept well? Check Stuck to fast? Check Ate healthy? Check Activity target? Checkarooni
The one oddity I need to work on is that I got a foot cramp while playing turtle tag with my daughter.
https://stacker.news/items/997476
-
 @ a296b972:e5a7a2e8
2025-06-04 22:06:06
@ a296b972:e5a7a2e8
2025-06-04 22:06:06In dem Video geht es um Dietrich Bonhoeffer, wie er sich zu Dummheit und vorsätzlicher bzw. rationaler Ignoranz geäußert hat. Schon seit einiger Zeit geht bei vielen Seltsames vor: Sie werden mit einem Thema persönlich konfrontiert und postum gibt es genau zu diesem Thema ein Video oder einen Artikel. Das kommt manchmal so vor, wie ein Frage- und Antwort-Spiel innerhalb der Schwarm-Intelligenz. Irgendwie spooky.
Die erschreckende Theorie der Dummheit, die Sie nie hören sollten - Dietrich Bonhoeffer: https://www.youtube.com/watch?v=PH-Vs5ILEko
Dem Entdecken, oder besser, dem Auf-einen-Zukommen, ist dieser E-Mail-Schriftverkehr in zeitlichem Zusammenhang vorausgegangen:
Nachfrage zu einem Aufruf durch einen Mitarbeiter zur Blutspende in einem Unternehmen mit über 100 Mitarbeitern über den E-Mail-Verteiler:
Lieber XXXXXXX,
danke zunächst für Dein Engagement.
In meiner näheren Familie gibt es jemanden, der regelmäßig Blut spendet, daher bin ich ein wenig für das Thema sensibilisiert.
Seit Du die E-Mail verschickt hast, gehe ich damit „schwanger“, ob ich ein vielleicht „heißes Eisen“ anfassen soll.
In den angehängten Informationen (des Roten Kreuzes) steht, dass das gespendete Blut auf bestimmte „Verunreinigungen“ durch Vorerkrankungen untersucht wird. Was nicht aufgeführt ist, ist eine Untersuchung, von der ich noch nicht einmal weiß, ob sie überhaupt schon durchgeführt wurde, und wenn ja, zu welchem Ergebnis sie gekommen ist, ob das gespendete Blut auch mit Substanzen der Corona-Gen-Behandlung verunreinigt sein kann. Leider zeigen ja die aktuellen Erkenntnisse, dass das Spike-Protein noch nach Jahren aktiv sein kann. Auch in gespendetem Blut? Die konkrete Frage wäre, ob das Rote Kreuz definitiv ausschließen kann, dass das nicht der Fall ist, damit ein möglicher Schaden nicht die Gefahr läuft, größer zu sein, als der Nutzen.
Soweit ich weiß, hat das Rote Kreuz bis heute keine separaten Blutbanken von „geimpftem“ und „ungeimpftem“ Blut angelegt. Wenn zu 100% ausgeschlossen werden kann, dass keine schädlichen Substanzen der Gen-Behandlung in die Blutkonserve gelangen, wäre das ja natürlich nicht nötig. Ist das so? Wenn ja, wo ist der Nachweis dazu zu finden, wie ist der aktuelle Erkenntnisstand, von wem wurden Studien dazu erarbeitet, wer hat das finanziert?
Mindestens 20% der Bevölkerung, das sind rund 16 Millionen Menschen, haben auf die Gen-Behandlung verzichtet und wollen im Ernstfall kein kontaminiertes Blut empfangen. Wie kann das Rote Kreuz belegbar und glaubhaft nachweisen, dass möglicherweise verunreinigtes Blut nicht doch in die Blutkonserven gelangt, weil sonst die Gefahr besteht, dass im Ernstfall Impfverzichter einen Schaden davontragen könnten?
Ich finde das eine wichtige Frage dem Roten Kreuz gegenüber und vielleicht wäre es auch gut, die möglichen Spender im Vorfeld für dieses heikle Thema zu sensibilisieren. Ich finde es auffällig, dass das Rote Kreuz sich hierzu weder in die eine, noch andere Richtung in den Informationen äußert, obwohl sie uns alle betrifft.
Ich schreibe diese Email aus kollegialen Gründen, aber auch zur Sensibilisierung gegenüber der Verantwortung aller Menschen gegenüber ihren Mitmenschen, die (hoffentlich nie) in die Situation kommen, einmal auf eine Blutspende angewiesen zu sein.
Wenn sich etwas Neues auf meine Nachfrage an Dich ergibt, wäre es klasse, ich würde davon erfahren.
Vielen Dank und viele Grüße
YYYYYYY
(Die Intension war, sich so vorsichtig wie möglich, quasi auf „Samtpfötchen“, an den Kern heranzupirschen. Dass es bereits Erkenntnisse dazu gibt, dass das Blut kontaminiert sein kann, wurde bewusst weggelassen, um keine Angriffsfläche zu bieten, ein „Verschwörungstheoretiker“ zu sein. Wenn die andere Seite auf einen Austausch eingestiegen wäre, wäre eine Quelle zu dieser Aussage vorhanden gewesen.)
Die Antwort:
Hallo YYYYYYY,
danke für die ausführliche Nachricht und dass du dir Gedanken zu dem Thema machst. Ich finde, man sollte Blutspenden als eine persönliche und private Sache betrachten.
Jeder und jede sollte für sich selbst abwägen, ob und unter welchen Bedingungen er oder sie das tun möchte.
Die Fragen, die du gestellt hast, sind echt speziell. Da geht's um medizinische und wissenschaftliche Themen, da kann ich als Privatperson nicht mitreden. Ich denke, dass sich Interessierte bei solchen Themen am besten direkt an medizinische Fachstellen oder das Rote Kreuz vor Ort wenden sollten, um fundierte und belastbare Informationen zu erhalten.
Mir persönlich ist es wichtig, Menschen auf die Möglichkeit der Blutspende aufmerksam zu machen.
Jeder kann das für sich selbst entscheiden und es ist auch okay, wenn man dabei Überzeugungen hat.
Beste Grüße
XXXXXXX
(„Blutspende…eine persönliche und private Sache“, nach dem Corona-Ereignis auch noch?, „…ich als Privatperson“ empfehle anderen etwas, bei dem sie möglicherweise anderen einen Schaden zufügen. Ist das schon grob fahrlässig, nach den Denkanstößen, die gegeben wurden?, „Wenn man dabei Überzeugungen hat.“, interessante Formulierung.)
Darauf die Reaktion:
Hallo XXXXXXX,
danke auch für Deine Antwort.
Wenn so eine im Grundsatz sicher gute Aktion beworben wird, liegt es nach meinem Empfinden auch in der Verantwortung, auf mögliche Folgen hinzuweisen, wenn es das Rote Kreuz schon nicht tut. Vorausgesetzt, man misst ihnen Bedeutung zu. Wenn meine E-Mail keine Veranlassung zu einer Beunruhigung und eigener Recherche angeregt hat, dann kann ich leider mehr nicht tun.
Dass das Rote Kreuz keine Hinweise gibt, liegt wohl daran, dass es Teil des Systems ist. Wer die Augen aufmacht, kann mit wenig Aufwand leider mehr als genug Tatsachenwahrheiten finden, die mit Schäden im Zusammenhang der Gen-Behandlung verursacht wurden und immer noch verursacht werden. Es ist nicht meine Aufgabe, einen Wissensrückstand von 5 Jahren auf den aktuellen Stand zu bringen. Allein die veröffentlichten RKI-Protokolle sollten schon genug Anlass zur Skepsis bieten. Der ÖRR berichtet leider nicht darüber, weil er auch Teil des Systems ist.
Ich will es damit genug sein lassen und hoffe, dass es unter den Kolleginnen und Kollegen noch weitere kritische Geister gibt.
Es geht nicht gegen Dich persönlich, aber ich hoffe, das Angebot wird nicht zahlreich genutzt.
Viele Grüße
YYYYYYY
(Einen halben Gang hochgeschaltet, ein Versuch, XXXXXXX aus der Reserve zu locken.)
Und ein Nachtrag von YYYYYYY:
Lieber XXXXXXX,
wir sind schon einmal unter Missbrauch des Begriffes „Solidarität“ hinter die Fichte geführt worden. Das darf nicht noch einmal passieren!
Nochmals viele Grüße
YYYYYYY
(Keine Reaktion mehr von XXXXXXX)
Und, wie gesagt, daraufhin kam das Video mit Bonhoeffer entgegen. Besser kann man vorsätzliche, rationale Ignoranz in Bezug auf den Schriftwechsel nicht beschreiben.
Hier wird eine jeden angehende allgemeinmedizinische Frage zu einer Frage der persönlichen Überzeugung gemacht. Das kommt doch sehr bekannt vor, oder?
Sehr wahrscheinlich lässt es sich vermuten, dass es sich bei XXXXXXX wohl um einen Corona-Jünger handelt, der die Tatsachen scheut, wie der Teufel das Weihwasser. Bloß nicht nachdenken, bloß nicht in Frage stellen, bloß nicht hellhörig oder gar neugierig werden, bloß nicht auf die Äußerungen eingehen, bloß nicht konkret werden, bloß keine eindeutig formulierte Stellung zu den Aussagen beziehen. „Angriffsfläche“ wäre vorhanden gewesen.
Das vorsichtige Anpirschen war alles andere, als mit-der-Brechstange-herangehen. Und doch setzt sofort automatisch der Teflon-Effekt ein. Selbstschutz.
Die Frage ist, wie soll da die Spaltung überwunden werden, wenn „die andere Seite“ so überhaupt nicht bereit ist, sich mit dem Vorgebrachten auseinanderzusetzen. Noch nicht einmal, wenn man nur die Spitze der Spitze des Eisbergs leise anhaucht.
Diesem Beispiel könnten viele unzählige weitere Beispiele hinzugefügt werden. Jeder hat so etwas schon einmal auf die eine oder andere Weise erlebt.
Das Gefühl lässt sich nicht unterdrücken, dass sich die Menschheit in zwei Lager aufgeteilt hat, und es gibt derzeit keinen Weg, wie man wieder aufeinander zukommen könnte.
Wie zwei Welten aufeinanderprallen, kann man derzeit auch in der Enquete-Kommission im sächsischen Landtag erleben: https://www.youtube.com/watch?v=D6ACmwBUBFM
Aus der Sicht von YYYYYYY ist das kein Grund zur Verzweiflung, jedoch drängt sich der Wunsch auf, dass man mit solchen Menschen wie XXXXXXX nichts mehr anfangen will. Man möchte mit ihnen, so schade es auch ist, am liebsten gar nichts mehr zu tun haben, und wenn doch aus irgendwelchen Gründen, nur noch das Allernotwendigste, so kurz und knapp, wie möglich. Empathie aufzubringen erscheint einem als vergeudete Energie, besser ist es, sich auf die Menschen zu konzentrieren, die wegen fehlender Genbehandlung keine Wesensveränderungen, die mittlerweile leider auch schon bestätigt sind, erlitten haben.
Wie Bonhoeffer richtig sagt, es geht hier nicht um Intelligenz, es geht viel tiefer. Es geht um das Menschsein an sich, und man hat den Eindruck, dass vor allem dies unter dem Einfluss der Spritze sehr stark gelitten hat. Da scheint so eine Abgestumpftheit durch, die einem einen kalten Schauer über den Rücken fahren lässt. Und das ist vielleicht noch gefährlicher, als diejenigen, die wirklich dumm sind. Das ist keine Arroganz oder Überheblichkeit, sondern unschuldig, wahllos von der Natur vergebene Dummheit, die jeden hätte ereilen können, hat es immer schon zu einem großen Teil gegeben. Hier hat man wenigstens noch die Möglichkeit, sich einfühlen zu können und Verständnis aufzubringen. Bei Menschen aber, von denen man weiß, dass sie die kognitiven Fähigkeiten zur Reflektion hätten, sie jedoch aus welchen Gründen auch immer nicht nutzen, oder sie als Verdrängungsmechanismus gerade nutzen, weil sie es können, geht auch eine gewisse Gefahr aus, weil man nie wissen kann, was sie sich sonst noch so ausdenken könnten, wenn sie in die geistige Enge getrieben werden, um ja nicht von Menschen, die den Mut haben, die Wahrheit auszusprechen, in ihrem mühsam aufgebauten Weltbild erschüttert zu werden. „Was nicht sein darf, das nicht sein kann!“, obwohl doch eigentlich die Wahrheit dem Menschen zumutbar ist.
So hat man das Gefühl, man atmet Honig ein und bewegt sich mühsam durch einen zähen Brei vorwärts, der einem bis zu den Oberschenkeln reicht. Jeder Schritt eine Anstrengung.
Und bevor man noch tiefer in dieses Verlustgefühl von Lebensqualität eintaucht (das hat nichts mit Depressionen zu tun, man bekommt einfach nur schlechte Laune), sich immer wieder bewusst machen, dass es da draußen noch eine Menge bei Verstand gebliebener Menschen gibt, die unermüdlich daran arbeiten, dass die Wahrheit weiter so sehr erkraftet, dass sie sich ihren Weg in den sogenannten Mainstream bahnt und die Menschen endlich aufwachen. So schmerzlich das für viele sein mag, es muss sein!
Selbst für einen wenig religiösen Menschen, im Sinne von regelmäßigen Kirchgängen und keinem Kontakt zur Institution Kirche, bekommt der Satz eine ganz besondere Bedeutung:
„Ich schicke euch den Geist der Wahrheit, und der wird euch frei machen!“
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:14:50
@ e2c72a5a:bfacb2ee
2025-06-05 17:14:50The silent revolution: Ethereum's pivot to 'digital oil' could redefine crypto's future. While Bitcoin grabs headlines as digital gold, Ethereum is quietly transforming into something potentially more valuable—the essential infrastructure powering our digital economy. Ryan Berckmans reveals Ethereum's strategic shift from being just another cryptocurrency to becoming the foundation for stablecoins, tokenized assets, and global financial systems. With $480 billion in stablecoin volume and institutional players entering the space, Ethereum isn't just competing with Bitcoin—it's creating an entirely different value proposition. The question isn't whether ETH will hit $3K, but whether we're underestimating its long-term potential as the backbone of digital finance. Are you positioning yourself for the real crypto revolution happening right under our noses?
-
 @ 5c26ee8b:a4d229aa
2025-06-04 21:29:51
@ 5c26ee8b:a4d229aa
2025-06-04 21:29:51Since late December, 2024, an evil magic attack targeted me and my family as well as many people occupying governmental positions. The attack was involving the Antichrist that was on an unreachable island found by me telepathically. Sadly the information about the Antichrist reached some Russian Oligarchs Among which many Jews. And somehow he was contacted by them as well as many other Antichrist Allies among which Royal families and he led the magic attack even though magic mixed with AI and computer technologies. The attack consisted in whispering of the devils, of mankind (Antichrist allies) and jinns. Physical harm was attempted too although so weak for any significant effect for me at least. I hesitated on killing the Antichrist because his appearance is a sign of Judgement Day, however, because of acknowledging that the attack would be too intense for ordinary people that don’t know how to know the difference between inner voice or whispering of the devils I have decided to kill him by requesting that he is burned in the core of the earth and by turning any remains into dust spread in space. He didn’t have only a physical presence though he had an incorporated devil. So it took a while to kill the devil that was isolated in iron coffin first so it assumed a smaller figure while trying to escape and finally God guided me to request that the devil is hit with fireballs over and over again. It was confirmed to me that the devil of the Antichrist was completely burned out. And that the next sign would be the creature coming out of the earth, Ad-Daba as well as the smoke covering all the earth, with which there is a great punishment, and that I would be able to fly too (good for me). I hesitated on spreading the news about the Antichrist to avoid fitnah (confusion and trial). Also because he was never freed out of the island before getting burned out. I am mentioning this because it’s important to know that when God’s punishment comes and when the great signs of Judgement Day (among which what’s mentioned above) would appear the returning to God in belief or in repentance won’t be accepted; so my advise is to do it now.
27:82 An-Naml
۞ وَإِذَا وَقَعَ الْقَوْلُ عَلَيْهِمْ أَخْرَجْنَا لَهُمْ دَابَّةً مِنَ الْأَرْضِ تُكَلِّمُهُمْ أَنَّ النَّاسَ كَانُوا بِآيَاتِنَا لَا يُوقِنُونَ
And when the word befalls them, We will bring forth for them a creature from the earth speaking to them, [saying] that the people were, of Our verses, not certain [in faith].
- Ad-Dukhaan
حم
Ha, Meem.
وَالْكِتَابِ الْمُبِينِ
By the clear Book,
إِنَّا أَنْزَلْنَاهُ فِي لَيْلَةٍ مُبَارَكَةٍ ۚ إِنَّا كُنَّا مُنْذِرِينَ
Indeed, We sent it down during a blessed night. Indeed, We were to warn [mankind].
فِيهَا يُفْرَقُ كُلُّ أَمْرٍ حَكِيمٍ
On that night is made distinct every precise matter -
أَمْرًا مِنْ عِنْدِنَا ۚ إِنَّا كُنَّا مُرْسِلِينَ
[Every] matter [proceeding] from Us. Indeed, We were to send [a messenger]
رَحْمَةً مِنْ رَبِّكَ ۚ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
As mercy from your Lord. Indeed, He is the Hearing, the Knowing.
رَبِّ السَّمَاوَاتِ وَالْأَرْضِ وَمَا بَيْنَهُمَا ۖ إِنْ كُنْتُمْ مُوقِنِينَ
Lord of the heavens and the earth and that between them, if you would be certain.
لَا إِلَٰهَ إِلَّا هُوَ يُحْيِي وَيُمِيتُ ۖ رَبُّكُمْ وَرَبُّ آبَائِكُمُ الْأَوَّلِينَ
There is no deity except Him; He gives life and causes death. [He is] your Lord and the Lord of your first forefathers.
بَلْ هُمْ فِي شَكٍّ يَلْعَبُونَ
But they are in doubt, amusing themselves.
فَارْتَقِبْ يَوْمَ تَأْتِي السَّمَاءُ بِدُخَانٍ مُبِينٍ
Then watch for the Day when the sky will bring a visible smoke.
يَغْشَى النَّاسَ ۖ هَٰذَا عَذَابٌ أَلِيمٌ
Covering the people; this is a painful torment.
رَبَّنَا اكْشِفْ عَنَّا الْعَذَابَ إِنَّا مُؤْمِنُونَ
[They will say], "Our Lord, remove from us the torment; indeed, we are believers."
أَنَّىٰ لَهُمُ الذِّكْرَىٰ وَقَدْ جَاءَهُمْ رَسُولٌ مُبِينٌ
How will there be for them a reminder [at that time]? And there had come to them a clear Messenger.
ثُمَّ تَوَلَّوْا عَنْهُ وَقَالُوا مُعَلَّمٌ مَجْنُونٌ
Then they turned away from him and said, "[He was] taught [and is] a madman."
إِنَّا كَاشِفُو الْعَذَابِ قَلِيلًا ۚ إِنَّكُمْ عَائِدُونَ
Indeed, We will remove the torment for a little. Indeed, you [disbelievers] will return [to disbelief].
يَوْمَ نَبْطِشُ الْبَطْشَةَ الْكُبْرَىٰ إِنَّا مُنْتَقِمُونَ
The Day We will strike with the greatest assault, indeed, We will take retribution.
6:158 Al-An'aam
هَلْ يَنْظُرُونَ إِلَّا أَنْ تَأْتِيَهُمُ الْمَلَائِكَةُ أَوْ يَأْتِيَ رَبُّكَ أَوْ يَأْتِيَ بَعْضُ آيَاتِ رَبِّكَ ۗ يَوْمَ يَأْتِي بَعْضُ آيَاتِ رَبِّكَ لَا يَنْفَعُ نَفْسًا إِيمَانُهَا لَمْ تَكُنْ آمَنَتْ مِنْ قَبْلُ أَوْ كَسَبَتْ فِي إِيمَانِهَا خَيْرًا ۗ قُلِ انْتَظِرُوا إِنَّا مُنْتَظِرُونَ
Do they [then] wait for anything except that the angels should come to them or your Lord should come or that there come some of the signs of your Lord? The Day that some of the signs of your Lord will come no soul will benefit from its faith as long as it had not believed before or had earned through its faith some good. Say, "Wait. Indeed, we [also] are waiting."
4:17 An-Nisaa
إِنَّمَا التَّوْبَةُ عَلَى اللَّهِ لِلَّذِينَ يَعْمَلُونَ السُّوءَ بِجَهَالَةٍ ثُمَّ يَتُوبُونَ مِنْ قَرِيبٍ فَأُولَٰئِكَ يَتُوبُ اللَّهُ عَلَيْهِمْ ۗ وَكَانَ اللَّهُ عَلِيمًا حَكِيمًا
The repentance accepted by Allah is only for those who do wrong in ignorance [or carelessness] and then repent soon after. It is those to whom Allah will turn in forgiveness, and Allah is ever Knowing and Wise.
4:18 An-Nisaa
وَلَيْسَتِ التَّوْبَةُ لِلَّذِينَ يَعْمَلُونَ السَّيِّئَاتِ حَتَّىٰ إِذَا حَضَرَ أَحَدَهُمُ الْمَوْتُ قَالَ إِنِّي تُبْتُ الْآنَ وَلَا الَّذِينَ يَمُوتُونَ وَهُمْ كُفَّارٌ ۚ أُولَٰئِكَ أَعْتَدْنَا لَهُمْ عَذَابًا أَلِيمًا
But repentance is not [accepted] of those who [continue to] do evil deeds up until, when death comes to one of them, he says, "Indeed, I have repented now," or of those who die while they are disbelievers. For them We have prepared a painful punishment.
4:47 An-Nisaa
يَا أَيُّهَا الَّذِينَ أُوتُوا الْكِتَابَ آمِنُوا بِمَا نَزَّلْنَا مُصَدِّقًا لِمَا مَعَكُمْ مِنْ قَبْلِ أَنْ نَطْمِسَ وُجُوهًا فَنَرُدَّهَا عَلَىٰ أَدْبَارِهَا أَوْ نَلْعَنَهُمْ كَمَا لَعَنَّا أَصْحَابَ السَّبْتِ ۚ وَكَانَ أَمْرُ اللَّهِ مَفْعُولًا
O you who were given the Scripture, believe in what We have sent down [to Muhammad], confirming that which is with you, before We obliterate faces and turn them toward their backs or curse them as We cursed the sabbath-breakers. And ever is the decree of Allah accomplished.
4:48 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدِ افْتَرَىٰ إِثْمًا عَظِيمًا
Indeed, Allah does not forgive association with Him, but He forgives what is less than that for whom He wills. And he who associates others with Allah has certainly fabricated a tremendous sin.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
61:13 As-Saff
وَأُخْرَىٰ تُحِبُّونَهَا ۖ نَصْرٌ مِنَ اللَّهِ وَفَتْحٌ قَرِيبٌ ۗ وَبَشِّرِ الْمُؤْمِنِينَ
And [you will obtain] another [favor] that you love - victory from Allah and an imminent conquest; and give good tidings to the believers.
-
 @ 472f440f:5669301e
2025-06-04 20:58:53
@ 472f440f:5669301e
2025-06-04 20:58:53Marty's Bent
J.P. Morgan CEO Jamie Dimon has long been an outspoken skeptic and critic of bitcoin. He has called Bitcoin a speculative asset, a fraud, a pet rock, and has opined that it will inevitably blow up. A couple of years ago, he was on Capitol Hill saying that if he were the government, he would "close it down". Just within the last month, he was on Fox Business News talking with Maria Bartiromo, proclaiming that the U.S. should be stockpiling bullets and rare earth metals instead of bitcoin. It's pretty clear that Jamie Dimon, who is at the helm of the most powerful and largest bank in the world, does not like bitcoin one bit.
Evidence below:
via Bitcoin Magazine
via me
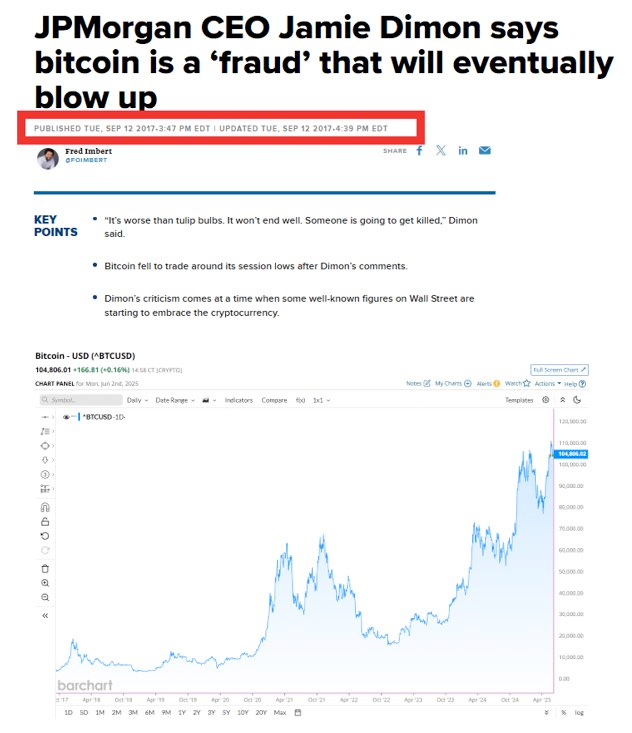
via CNBC
Despite Dimon's distinguished disdain for Bitcoin, J.P. Morgan cannot deny reality. The CEO of the largest bank in the world is certainly a powerful man, but no one individual, even in the position that Jamie Dimon is in, is more powerful than the market. And the market has spoken very clearly, it is demanding bitcoin. The Bitcoin ETFs have been the most successful ETFs in terms of pace of growth since their launch. They've accumulated tens of billions of dollars in AUM in a very short period of time. Outpacing the previous record set by the gold ETF, GLD.
Whether or not Jamie Dimon himself likes Bitcoin doesn't matter. J.P. Morgan, as the largest bank in the world and a publicly traded company, has a duty to shareholders. And that duty is to increase shareholder value by any ethical and legal means necessary. Earlier today, J.P. Morgan announced plans to offer clients financing against their Bitcoin ETFs, as well as some other benefits, including having their bitcoin holdings recognized in their overall net worth and liquid assets, similar to stocks, cars, and art, which will be massive for bitcoiners looking to get mortgages and other types of loans.
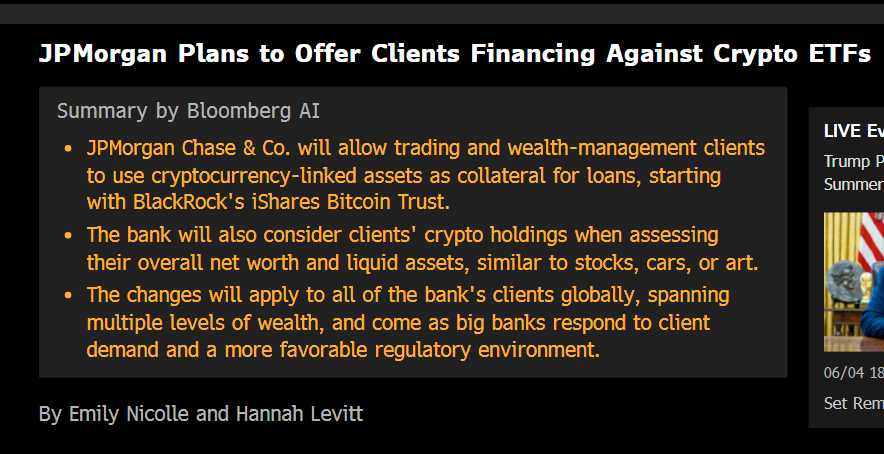
via Bloomberg
I've talked about this recently, but trying to buy a house when most of your liquid net worth is held in bitcoin is a massive pain in the ass. Up until this point, if you wanted to have your bitcoin recognized as part of your net worth and count towards your overall credit profile, you would need to sell some bitcoin, move it to a bank account, and have it sit there for a certain period of time before it was recognized toward your net worth. This is not ideal for bitcoiners who have sufficient cash flows and don't want to sell their bitcoin, pay the capital gains tax, and risk not being able to buy back the amount of sats they were forced to sell just to get a mortgage.
It's not yet clear to me whether or not J.P. Morgan will recognize bitcoin in cold storage toward their clients' net worth and credit profile, or if this is simply for bitcoin ETFs only. However, regardless, this is a step in the right direction and a validation of something that many bitcoiners have been saying for years. Inevitably, everyone will have to bend the knee to bitcoin. Today, it just happened to be the largest bank in the world. I expect more of this to come in the coming months, years, and decades.
Lyn Alden likes to say it in the context of the U.S. national debt and the fiscal crisis, but it also applies to bitcoin adoption and the need for incumbents to orient themselves around the demands of individual bitcoiners; nothing stops this train.
Corporate Bitcoin Treasuries are Changing Market Dynamics
Leon Wankum revealed how corporate Bitcoin treasuries are fundamentally reshaping business dynamics. Companies can now issue equity to fund operations while preserving their Bitcoin holdings, creating a revolutionary capital structure. Leon highlighted MicroStrategy's position, noting they hold enough Bitcoin to cover dividend payments for over 200 years. This model enables companies to reduce founder dilution since they don't need repeated funding rounds when their treasury appreciates.
"Some companies' Bitcoin treasuries are now worth more than all money they've ever raised." - Leon Wankum
Leon shared examples from his own portfolio companies where this strategy has proven transformative. Public companies have discovered an entirely new business model through strategic dilution that actually increases BTC per share. As Leon explained, this approach allows firms to leverage equity markets for operational funding while their Bitcoin treasury compounds in value, creating a positive feedback loop that benefits both shareholders and the company's long-term sustainability.
Check out the full podcast here for more on real estate price cycles, Bitcoin lending products, and the transition to a Bitcoin standard.
Headlines of the Day
California May Seize Idle Bitcoin After 3 Years - via X
Semler Scientific Buys $20M More Bitcoin, Holds $467M - via X
US Home Sellers Surge as Buyers Hit 4-Year Low - via X
Get our new STACK SATS hat - via tftcmerch.io
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
I feel old.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ e516ecb8:1be0b167
2025-06-04 20:33:38
@ e516ecb8:1be0b167
2025-06-04 20:33:38Imagina un mundo donde cada peso que gastas es vigilado, registrado y cuestionado. Donde el Estado decide si puedes comprar un café, una manzana o una criptomoneda. No es una distopía de ciencia ficción, es el rumbo que están tomando varios países, mientras otros, como Argentina, dan un giro inesperado hacia la libertad. ¿Quién está ganando esta batalla por el control de tu dinero?
Argentina: "Tus dólares son tuyos" En Argentina, Javier Milei, con su bandera libertaria ondeando, ha dado un paso audaz: desmantelar el control policial sobre el dinero de los ciudadanos. Su lema, "Tus dólares son tuyos", es tan obvio como revolucionario. Después de décadas de corralitos, cepos cambiarios y una inflación que en 2023 alcanzó el 211,4% según el INDEC, Milei apuesta por devolverle al ciudadano el poder sobre su propio capital. Con el país logrando superávit fiscal por primera vez en años (0,2% del PBI en el primer trimestre de 2024), el gobierno ya no necesita espiar cada transacción para exprimir impuestos.
Pero aquí viene lo curioso: encuestas recientes, como una de la consultora Poliarquía, muestran que un 35% de los argentinos aún prefiere que el Estado controle sus finanzas. ¿Masoquismo? ¿Miedo a la libertad? Tal vez sea la costumbre de vivir bajo la lupa. Milei, fiel a su convicción, no solo liberaliza por necesidad económica, sino porque cree que el dinero es tuyo, no del burócrata de turno.
España y el Euro Digital: El ojo que todo lo ve Mientras Argentina afloja las riendas, Europa cabalga en dirección opuesta. En España, el gobierno está reduciendo progresivamente los umbrales para controlar transacciones bancarias. A partir de 2026, cada pago por Bizum —el equivalente ibérico al Pix brasileño— estará bajo escrutinio. Según el Banco de España, en 2024 se realizaron más de 1.200 millones de transacciones por Bizum, moviendo unos 60.000 millones de euros. Ahora, cada una de esas operaciones será un dato más para Hacienda.
Pero no es solo España. La Unión Europea avanza con el Euro Digital, un proyecto que promete ser la pesadilla de cualquier amante de la privacidad. Esta moneda digital, según el Banco Central Europeo, permitirá rastrear cada movimiento, limitar ciertos gastos (¿adiós a compras de cripto o donaciones incómodas?), e incluso programar que el dinero "se oxide". Sí, has leído bien: si no gastas tus euros digitales en un tiempo determinado, podrían perder valor o simplemente desaparecer. Un informe del BCE de 2023 estima que el Euro Digital estará operativo en 2027, y ya hay pruebas piloto en países como Alemania y Francia. ¿Libertad financiera? Más bien un Gran Hermano con esteroides.
Chile: El Estado fisgón y los funcionarios de lujo En Chile, el control monetario también aprieta. El gobierno ha propuesto levantar el secreto bancario, permitiendo que cualquier funcionario del SII pueda husmear en tus cuentas. Además, si haces más de 50 transacciones al mes, el Servicio de Impuestos Internos (SII) pondrá la lupa sobre ti. ¿Y las ferias libres? Esas donde compras tus tomates y zapallos sin complicaciones ahora deberán emitir boletas electrónicas, encareciendo los productos para el ciudadano de a pie. Según la CEPAL, los costos administrativos para pequeños comerciantes podrían aumentar hasta un 15% con estas medidas.
Mientras tanto, el sector público chileno vive en otra galaxia. Funcionarios con sueldos que superan los 5 millones de pesos mensuales (unos 5.500 USD) toman licencias médicas para viajar por el mundo, según denuncias de la Contraloría. Algunos incluso cobran por "turnos" de 17 horas extras diarias o marcan asistencia en dos lugares al mismo tiempo. ¿Y quién paga? Tú, con tus impuestos.
La resistencia: Volver al efectivo o abrazar las cripto Si el Estado quiere controlar cada centavo, ¿qué opciones nos quedan? Una es volver al efectivo, pero no nos engañemos: el dinero fiat, controlado por bancos centrales, pierde valor a largo plazo. En Chile, la inflación acumulada entre 2010 y 2024 fue del 62%, según el INE. Tus billetes de hoy valen menos que los de ayer, y mañana valdrán aún menos.
La otra opción es el mundo cripto, pero no cualquier cripto. Bitcoin, la más conocida, es un titán para almacenar valor, pero para transacciones diarias necesita una segunda capa como Lightning Network, que procesa pagos instantáneos con comisiones ínfimas (menos de 0,01 USD por transacción en 2024). Alternativas como Bitcoin Cash (BCH) o Monero (XMR) ofrecen transacciones rápidas y, en el caso de XMR, un enfoque en la privacidad que hace temblar a los burócratas. Sin embargo, ninguna cripto servirá si los comercios y las personas no las adoptan. En Argentina, por ejemplo, solo el 1,5% de las transacciones minoristas en 2024 usaron criptomonedas, según Chainalysis. La libertad financiera no llega sola: hay que construirla.
El futuro es ahora El dinero es poder, y quien controla el dinero controla tu vida. Mientras Milei en Argentina te devuelve las llaves de tus dólares, en Europa y Chile te atan las manos con leyes, regulaciones y monedas digitales. La pregunta no es si quieres libertad, sino si estás dispuesto a pelear por ella. Usa efectivo, explora cripto, pero sobre todo, no dejes que el Gran Hermano decida por ti. Porque una vez que el Estado mete la mano en tu bolsillo, no la saca nunca.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:11:03
@ e2c72a5a:bfacb2ee
2025-06-05 17:11:03The $220 million crypto heist that took just minutes reveals a fatal flaw in DeFi security. While blockchain tech promises trustless transactions, the Cetus DEX exploit on Sui exposed how a single undetected bug in a math library became catastrophic. What's truly alarming isn't the hack itself but the revelation from Curve's founder that professional hackers-for-hire are now coordinating sophisticated cross-platform attacks. This signals a dangerous evolution in crypto threats where vulnerabilities aren't just discovered—they're hunted by organized teams with specialized skills. The industry faces a stark choice: invest aggressively in preventative security or watch as billions more vanish in seconds. Is your crypto truly safe, or just waiting for the right hacker to find its weakness?
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:00:01
@ e2c72a5a:bfacb2ee
2025-06-05 17:00:01Forget Lambos, think real estate tokens.
A European fund just dropped $3.4 million on tokenized real estate, marking the first time big money directly bought retail available tokens. This isn't just about crypto hype; it's about institutions embracing regulated crypto assets. Real World Assets (RWAs) are booming, up 260% this year, fueled by clearer US crypto rules. This surge pushes the tokenization sector past $23 billion.
Is this the start of crypto's mainstream moment?
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:54:43
@ e2c72a5a:bfacb2ee
2025-06-05 16:54:43Think your crypto is FDIC insured like your bank account? Big mistake. Crypto's wild west demands you be your own bank and security guard.
Crypto trading involves buying, selling, and exchanging digital currencies like Bitcoin or Ethereum, aiming to profit from price fluctuations. Security is paramount. Understand basic concepts like wallets (digital storage for your crypto), private keys (passwords to access your crypto), and blockchain (the technology that records all transactions).
Real world applications include using crypto for online purchases, international money transfers, and decentralized finance (DeFi) services like lending and borrowing. Current trends include the rise of DeFi, NFTs (non-fungible tokens), and increasing institutional investment.
Best practices? Use strong, unique passwords, enable two factor authentication (2FA) on all accounts, and store most of your crypto in cold wallets (offline storage) to protect against hacking. Be wary of phishing scams and fake websites. Never share your private keys or seed phrases.
Misconceptions? Crypto is not anonymous, transactions are not easily reversible, and past performance is not indicative of future results. Also, remember that regulations are evolving, so stay informed.
With crypto hacks on the rise, are you truly ready to secure your digital fortune, or are you leaving the door open for the next billion dollar heist?
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:50:08
@ e2c72a5a:bfacb2ee
2025-06-05 16:50:08Think crypto is just magic internet money? Think again.
Tokenomics is the secret sauce that makes or breaks a crypto project. It is the study of how tokens are created, distributed, and used within a blockchain ecosystem. Imagine it as the economic policy of a digital nation, dictating everything from supply and demand to user incentives.
Key features include supply caps, distribution models, utility, and burn mechanisms. A well designed token economy incentivizes user behavior, secures the network, and fosters long term growth. Poor tokenomics? It can lead to manipulation and project failure.
Zero Knowledge Proofs are like showing you know a password without revealing the password itself. This tech allows for private and secure transactions, verifying data without exposing the data itself. Think of voting systems where your vote stays secret, or supply chains where product details are confirmed without revealing the supplier.
Want to dive deeper into the economics of crypto? What project has the most interesting tokenomics you have seen?
-
 @ 2ed3596e:98b4cc78
2025-06-04 20:06:07
@ 2ed3596e:98b4cc78
2025-06-04 20:06:07Bitcoin Well recently sat down with Bitcoin News for a conversation about our mission to empower financial independence through Bitcoin. Founder and CEO Adam O’Brien shared how a frustrating experience purchasing bitcoin in 2013 led to the creation of one of Canada’s largest bitcoin ATM networks—and ultimately, a broader mission to help people replace traditional banks with self-custodied bitcoin.
From building out our Bitcoin portal to navigating life fully de-banked, Adam discussed how Bitcoin Well is creating tools for everyday use—paying bills, receiving paychecks, and living sovereignly. Read the full conversation to understand why we’re proud to be leading the charge for freedom-minded Bitcoiners across Canada and beyond.
About Bitcoin Well:
Bitcoin Well is a Canadian company on a mission to enable financial independence through the use of Bitcoin. We offer tools and services that allow users to buy, sell, and use bitcoin in self-custody—without relying on traditional banks.
About Bitcoin News:
Bitcoin News Inc is a US-based media company dedicated to covering the latest in Bitcoin—from mining and wallets to its growing role in global liquidity. We deliver clear, insightful reporting to help readers navigate the shifting landscape of Bitcoin and digital finance.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:46:19
@ e2c72a5a:bfacb2ee
2025-06-05 16:46:19Think proving you're over 21 without showing your ID is impossible? Zero Knowledge Proofs make it real.
Zero Knowledge Proofs let you prove something is true without revealing the information itself. Imagine proving you know a password without saying it. It's like magic, but it's math.
They're used in crypto for private transactions, secure voting, and faster blockchains. Zcash and Aztec use them to hide transaction details. StarkWare uses them to make Ethereum faster.
But here's the twist: zk STARKs don't need a trusted setup, unlike zk SNARKs. This makes them more secure and decentralized.
Misconception alert: ZKPs aren't just for privacy. They also boost scalability and interoperability.
Want to dive deeper into this mind bending tech? What other secrets can ZKPs unlock?
-
 @ b2caa9b3:9eab0fb5
2025-06-04 19:50:29
@ b2caa9b3:9eab0fb5
2025-06-04 19:50:29If you'd like to connect with me on XMPP, you're very welcome! I first used it many years ago, and now I've returned to it — and I'm really glad I did.
XMPP is a secure and privacy-friendly way to communicate. It's spam-resistant: messages only go through once you've accepted a contact request. To request a connection, just send me a message.
One of the great things about XMPP is that you have control over encryption. You can choose to use strong encryption like PGP or OMEMO, or even no encryption at all — it's entirely up to you. Your messages aren’t tied to any one company or service.
There are many apps (called clients) you can use with XMPP, and you’re not locked into a single one that monitors or sells your data. XMPP is an open protocol, which means freedom of choice and better privacy.
My XMPP username is: rubenstorm@c0nnect.de
I’ve also been much less active on Facebook, Instagram, and other social media. That’s because I’ve shifted from platforms to protocols — more decentralized, censorship-resistant tools that put users in control. I started exploring these about two years ago and haven’t looked back.
If you’re interested in learning more or want help getting started, feel free to reach out. Just message me using any XMPP client — I’ll be happy to connect!
-
 @ ca76c778:e784c54b
2025-06-04 19:45:11
@ ca76c778:e784c54b
2025-06-04 19:45:11A few days ago I remembered video by Antonio Stappaerts(Artwod) on Youtube. And I thought to myself I want to be really good at drawing hands.\ In the video he explains something that, in my opinion, applies when learning just about anything.
If you've heard of the Dunning-Kruger effect then you know the first part.\ If you haven't, one begins learning something and on top of the first peak thinks oneself to be almost a master. And then one learns a little bit more and realizes how little skill one actually has.
 \
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.
\
Now, what is really interesting is this. He points out that the second slope is made up of many smaller Dunning-Kruger effects. For example the effect will apply when learning: the basic shape of the figure, how to pose the figure, how draw the hands, the hair etc.So the way to climb the second hill is to understand and practice these smaller skills. And not just once or twice. You want to reach close to the second peak of each of the smaller skills.
And with that in mind I search for a good tutorial about drawing hands and got down to it(for the third time).
Step one was to learn pose and gesture using a grid shape.
https://cdn.satellite.earth/f55a9d1ef2fd687a9dce5ceee5e05a1b666c436509e264ddbac4d260b99e882a.jpg
https://cdn.satellite.earth/1b5524635c20ee4869f4860c982deea469cb87be7ad7b404e1777497b5a4fbd4.jpg
https://cdn.satellite.earth/35652251243ffd8c495b855c319d27da0c193ff2e951591f0a9f1b35aad39b29.jpg
https://cdn.satellite.earth/68f55979d102b4ebe55177842c6d9ab2ab30b95f926441429d977b47fae925c3.jpg
Step two. Practice the basic forms for the palm and fingers.\ I got carried away and drew some hands.
https://cdn.satellite.earth/48b400f72e35d078368149f00182cb58e606ddd16f6db4e7789c1431c28d44a0.jpg
Step three. learn the measurements.
https://cdn.satellite.earth/75c9b82da90ef50d17f698dd7b1eadc223b74a019a702a4617ed7d321646a87c.jpg
Step four. Understand the fingers.
https://cdn.satellite.earth/e33f9f3f9217bf5e3e206e96dfe764eba09b9fb3c10b450bb9c8a4075e3c1ec8.jpg
Step five. Learn about the thumb and put it all together. Drawing from reference and imagination.
https://cdn.satellite.earth/b2dd9c1cc1045dde021272199818b0db331e71a603c5900122aa850eb2d4148a.jpg
https://cdn.satellite.earth/8f5647ae9e148ad6217c106b5b69cf231384475e0a0eedf210bd149f75ade0b7.jpg
-
 @ 7460b7fd:4fc4e74b
2025-06-05 15:54:42
@ 7460b7fd:4fc4e74b
2025-06-05 15:54:42比特币正在主动引诱量子计算“破解自己”
引言:危机还是契机?
比特币和量子计算,这两个看似对立的存在,正在酝酿一场耐人寻味的博弈。许多人担心未来强大的量子计算机将秒破比特币的密码学基石,从而令区块链安全灰飞烟灭。然而,本文想传达的核心观点却截然相反:比特币不仅不会被量子破解打败,反而正在通过协议层的巧妙设计来“引诱”量子计算进入自己的游戏规则之中。通过诸如BIP-360等提案,比特币有望将量子计算的威胁转化为动力,开启一个“后挖矿时代”的全新正反馈经济体系,让“破解”本身成为新的挖矿机制。
这样的观点听起来近乎狂想,但背后有着深厚的技术逻辑支撑。我们将从基本的密码学原理谈起,逐步剖析量子计算的能力与局限,以及比特币协议在抗量子方向做出的结构性准备。最后,我们探讨一种大胆的经济模型:当量子计算被诱导去参与“破解竞赛”时,或许正是比特币凤凰涅槃、新经济形态崛起之机。
非对称加密的数学本质:“上帝视角”的陷门答案
非对称加密(如RSA、椭圆曲线加密ECC等)的核心在于存在一种单向函数:正向计算容易,反向推导极难。公钥可以视作某个难题的题目,私钥则相当于“上帝视角”提前知道的答案。一旦掌握私钥,就能轻松完成从答案到题目的逆推;而只有公钥时,想要逆推出私钥则被设计为在现实中不可行。这类单向难题通常通过陷门函数来实现——对合法持有者(私钥)来说,存在隐藏的捷径(陷门)可以快速解题;而对局外人来说,题目看似无解。
举例来说,比特币当前采用的ECC加密:私钥与公钥的关系就像“一次难以逆推的乘法”。给定私钥x,乘以基点G可轻易得到公钥点P = x·G,但已知P却无法高效求出x。这种不对称确保了签名者可以用私钥生成签名,而验证者只能用公钥验证签名而无法伪造。私钥掌握了解题的“上帝答案”,公钥则只能用于验证答案是否正确。
这一点在新型的抗量子算法中同样体现。以格密码(lattice cryptography)为例:Falcon等基于NTRU格的签名算法,其公钥可以被视为一个高维长基,私钥是对应的短基。pqshield.com在二维格子上的示意说明了这种不对称性:拥有短基(私钥)时,我们可以高效地找到距离某个目标点很近的格点解;但只有长基(公钥)时,我们顶多能验证某个给定解是否有效,却很难自行找到足够优质的解pqshield.com。换言之,私钥提供了一个陷门,允许持有者快速逆推答案,而公钥持有者只能望“题”兴叹。
图:在二维格子中,签名者持有的短基(私钥)可以高效求解出距离目标点(黑色方块)极近的格点解(绿色圆点)。绿色平行四边形表示短基下求解空间很小,因而容易找到最优解。这直观展示了陷门函数的威力:私钥掌握短基就如同拿到了解题捷径。
图:仅持有长基(公钥)时,使用相同算法得到的格点解(红色圆点)可能距离目标(黑色方块)很远。红色平行四边形代表在无陷门情况下求解范围巨大,找到最佳解极其困难。但验证者仍可用长基检查出某个解(如绿色点)确实是有效解pqshield.com。这体现了公私钥在计算能力上的不对称:私钥可求解,公钥仅可验证。
总而言之,非对称加密的安全性源自数学难题的单向性质和陷门结构。私钥就是那个隐藏的逆向通道,“上帝视角”的答案;公钥则是不具备捷径的信息,只够验证而无法逆推。从RSA的整数分解、ECC的离散对数,到Falcon的近似最近矢量问题,每一种公钥体制都是在构造“题目易出答案难逆”的格局,让持有陷门者轻松,旁观破解者绝望。
量子计算的原理与极限:并行穷举的神话与现实
量子计算机令人畏惧之处,在于其并行计算能力。通过量子叠加态,n个量子比特(qubit)可同时表示2^n种状态——仿佛能把指数级的可能性同时考虑。配合量子干涉与算法设计,量子计算机能够以远胜传统计算机的效率解决某些特定问题。其中最著名的就是Shor算法,它能在多项式时间内完成对大整数的质因数分解和离散对数求解。这正是传统公钥加密(RSA、ECC)的命门:一旦有足够强大的量子计算机,基于这些数学问题的公钥体制将不再困难,私钥可以由公钥“解密”而出coindesk.com。
然而,“并行穷举”的神话背后有严格的物理和工程学限制。首先是量子比特数量和质量的限制:当前的量子芯片规模远未达到破解现代加密所需的级别。据风险研究机构与专家调查,目前我们只有几十到几百个物理qubit,而要威胁256位ECC或2048位RSA,需要数百万高质量qubitdeloitte.com。不仅数量上相差几个数量级,现有量子芯片的纠错和降噪技术也远不成熟。量子比特极其敏感,微小噪声都会引入错误,真正实用的量子计算机需要对成千上万的物理比特进行纠错编码,形成稳定的逻辑比特。这个工程挑战之巨大,使得可攻破密码的量子计算机仍是多年之后的前景——多数专家预测大概还需十几年时间才可能出现实质威胁deloitte.com。
其次,量子计算并非万能破解,仅对特定问题有指数级加速。Shor算法擅长因数分解和离散对数,Grover算法可以对无结构的穷举搜索加速(将时间复杂度平方根降低)。但许多新兴的抗量子算法依赖的问题(如格上的最短向量问题SVP、最近向量问题CVP,或多变量方程、哈希预像等)目前并无高效量子算法。这些问题大多属于NP难类,甚至找近似解也极为困难emerginginvestigators.org。尽管量子计算提供并行试探能力,但对这类高度复杂的问题也爱莫能助。正如一项研究指出:SVP和CVP问题即便在量子计算机上依然“极端困难”,在可预见的将来仍足以保证安全性emerginginvestigators.org。Falcon所使用的NTRU格就是这样的难题代表——没有已知算法可以像Shor之于RSA那样,高效攻破NTRU问题。
最后,我们还需注意量子攻击的实际条件。量子破解比特币主要有两种情景:存储攻击和传输攻击deloitte.com。存储攻击指利用量子计算找出已公开公钥对应的私钥,从而盗取静态存放于链上某地址的币;传输攻击则是当交易广播(公钥暴露)后,在被矿工打包上链前的短暂窗口内,量子计算抢先推导私钥并盗转。这两种攻击对量子能力要求不同:存储攻击允许耗时几周甚至数月破解一个密钥,只要在币移动前完成即可;而传输攻击要求在区块确认之前(比特币约10分钟内,以太坊更短)秒破私钥deloitte.com。显然,目前和可预见的中期内,量子计算都远达不到传输攻击所需的即时破解水平;即便存储攻击,由于比特币区块链的UTXO模型(稍后详述),真正高价值、长时间暴露公钥的币也相对有限deloitte.com。因此,量子威胁虽然现实存在,但并非一夜之间让比特币崩溃的魔法。这反倒给予我们部署抗量子方案、引导量子力量“为我所用”的时间窗口。
抗量子密码学的三大结构前提
要让比特币真正抵御量子威胁,并把量子计算纳入自身生态,需要满足几个结构性前提。经过多年社区讨论和研究,以下三点被认为是比特币走向抗量子的关键设计要素:
-
UTXO模型:隐藏公钥缩短攻击窗口 – 比特币采用UTXO模型,每次交易都会生成新地址,公钥通常以哈希形式隐藏在地址中,直到你花费时才公布。这意味着量子计算只有在你发起交易后的很短时间内(交易确认前)才能获得公钥并尝试破解,大大压缩了攻击窗口anduro.iodeloitte.com。相较之下,账户模型(如以太坊)重复使用固定地址,公钥一旦被提取或首次使用后就长久暴露,使得65%以上的以太币当前都处于量子暴露风险中,而比特币约只有25%处于类似风险deloitte.com。UTXO模型通过“一次性地址”和“不用则公钥不出”的原则,天然提供了对抗量子存储攻击的第一道屏障。
-
“见证隔离”(SegWit):模块化升级签名算法 – 抗量子方案的发展日新月异,比特币必须保持签名算法的可插拔升级能力。2017年的见证隔离升级正是为此奠定基础:SegWit将签名等见证数据与交易本体分离,并引入版本化的见证脚本格式。这使得添加新签名类型成为可能——通过软分叉引入新的输出类型和见证版本,就能兼容地支持不同算法delvingbitcoin.org。正如BIP-341利用SegWit扩展出了Taproot的Schnorr签名,比特币也可以扩展出抗量子签名的新地址类型而无需硬分叉或显著增加区块体积delvingbitcoin.org。这一模块化特性对于迎接未来各类抗量子算法至关重要,没有SegWit的铺垫,抗量子改造将困难重重。
-
分级安全机制:根据价值和时效选择算法强度 – 由于UTXO的性质,每笔交易在花费时都会暴露其公钥。因此,安全策略不能“一刀切”,应允许根据币值大小或持有时长采用不同强度的抗量子算法。高价值的UTXO、长期未移动的“老币”,应使用更高安全级别但可能更重型的签名方案;反之,小额频繁交易可用较轻量的方案以兼顾效率和区块容量。好比Falcon提供了512和1024两种参数版本:Falcon-1024安全级别更高但签名稍大,而Falcon-512签名更小速度更快,适合资源受限场景emerginginvestigators.org。未来比特币或可同时支持多种抗量子算法或参数,用户按需选用,让“安全性”成为一种可以权衡和市场定价的链上资源。每一次支付都在安全与成本之间找到平衡,这将促使一个分层的安全市场形成——进一步论述见后文经济模型部分。
上述三大前提缺一不可:UTXO模型提供了基础的_安全缓冲_,SegWit机制给予_升级弹性_,分级算法让_经济可行性_落地。在这方面,比特币的体系结构远优于某些后来的公链。例如,以太坊的账户模型天生缺乏隐藏公钥的机制,地址就是固定的公钥哈希,一旦使用过私钥签名就永久暴露公钥,同时其交易脚本(EVM)对签名算法固定死,没有灵活插拔空间。这意味着以太坊想转向抗量子算法,必须经过极其痛苦的整体迁移或硬分叉——开发者需要为每个账户引入新密钥,新老算法并行过渡,智能合约地址、签名验证逻辑全部推倒重来。这种难度令人生畏,以至于有人嘲讽以太坊“几乎不可能”实现真正的抗量子迁移。反观比特币,得益于其简单而弹性的UTXO+Script设计,只需通过新的输出类型软分叉,就可以逐步引入抗量子地址,让用户自愿迁移过渡,避免一次性硬分叉的系统性风险。
BIP-360:可选抗量子签名,引入量子博弈
面对量子威胁,比特币开发社区并未坐以待毙。2024年,由开发者Hunter Beast提出的BIP-360提案(又称P2QRH,意为“支付到抗量子哈希”)正式将抗量子签名引入了议事日程anduro.io。BIP-360核心思路是在比特币中增加新的地址类型,这些地址采用后量子密码学的签名算法(当前优先考虑Falcon,并备选CRYSTALS-Dilithium和SPHINCS+等)来取代易受量子攻击的ECDSA/Schnorr签名anduro.iogroups.google.com。换句话说,用户可以自愿选择生成一种“抗量子地址”,对应的UTXO需使用抗量子算法签名才能解锁。
为什么说BIP-360让比特币“引诱”量子计算加入博弈?这里有几层含义:
首先,BIP-360采用软分叉方式部署,可选而非强制。这意味着在量子计算真正成熟之前,绝大多数交易仍可继续使用原有签名算法,不平添负担;而有安全偏好的用户或机构可以提前迁移一部分资金到抗量子地址以高枕无忧。随着量子技术进展,逐步会有更多人选择这个选项,形成一个与量子威胁赛跑的过程。这种自愿迁移机制本身就是一种对量子黑客的诱导:网络主动暴露出一个“堡垒更坚固”的区域,鼓励守法用户往那里走,同时意味着留下的旧区域反而成为显眼的攻击目标和“诱饵”。
其次,BIP-360在算法选择和参数上充分考虑了区块链经济的承受力。起初提案曾讨论过一些前沿算法如SQIsign,但发现其验证开销高达ECDSA的15,000倍,若全网采用将使验证一块新区块从1秒暴涨到4小时,带来难以接受的性能瓶颈groups.google.com。最终的方案优选Falcon等NIST标准算法,它们签名体积较小、验证高效,可与当前区块大小和验证速度相容groups.google.com。例如Falcon-1024的签名约1.3KB、公钥1.7KB左右,这虽然比当前64字节的Schnorr签名大得多,但并非无法承受。通过配置灵活的安全级别(如重要交易才用Falcon-1024,一般小额用Falcon-512或普通Schnorr),比特币区块空间将被合理分配在安全性和费用之间。BIP-360精心设计了新的地址格式和见证结构,确保即便引入抗量子签名,区块验证和存储开销也在经济范围内,不会动摇挖矿和节点运行的成本平衡anduro.io。
最后也是最具前瞻性的一点,BIP-360为量子计算参与链上博弈打开了一扇门。通过提供抗量子和非抗量子地址并存的环境,比特币网络其实设置了一个对量子计算的挑战擂台:量子计算可以选择去攻击那些仍使用旧签名算法且价值巨大的UTXO,但同一时间,网络里的用户也在不断提升关键UTXO的签名强度来应对。量子计算不再是一个纯粹的外部敌人,而被巧妙地“请”进了系统,在规则内与用户和矿工互动。这为下一节将讨论的新经济模型奠定了基础——破解即挖矿的雏形由此孕育。
值得一提的是,BIP-360还提出了一个Taproot的量子安全补丁方案P2TRH,用哈希隐藏Taproot的公钥以弥补其“公钥长曝”缺陷groups.google.comgroups.google.com。因为现有的Taproot地址(见证v1)是直接以公钥生成地址,失去了UTXO模型隐藏公钥的优势,量子攻击者可以随时尝试破解Taproot资金。P2TRH通过将Taproot公钥再哈希一层,恢复“见证前隐藏公钥”的特性,代价是每笔此类输入增加8.25字节开销groups.google.com。这显示出比特币开发者未雨绸缪,连新升级的Taproot漏洞也在想办法弥补,使全局达到抗量子的结构性统一。
综上,BIP-360及相关提案不仅提供了技术方案,更释放出一种积极的信号:比特币正主动拥抱量子挑战,将其纳入规则之内。正如Anduro团队支持BIP-360时所言:“量子攻击的威胁严肃而迫近,我们不能坐等紧急关头才手忙脚乱。”anduro.ioanduro.io比特币社区选择了在危机到来前主动布局,以最小的代价换取最大的安全冗余和发展新契机。
“破解竞赛”经济模型:当量子成为新矿工
设想未来5-15年内,量子计算技术逐步成熟。在比特币网络中,可能会上演这样一幕令人惊叹的图景:量子计算矿工和抗量子验证者同时在线,围绕着尚未升级的老式UTXO展开一场你追我赶的“破解竞赛”。这将引发怎样的经济动力?我们大胆描绘一个后PoW时代的可能场景:
一方面,强大的量子计算机不再浪费算力去挖掘哈希谜题(传统PoW),而是直接瞄准那些“量子易攻”的UTXO,即尚使用老式ECDSA/Schnorr签名且公钥已暴露的地址。这些地址里的币对合法持有人来说如果迟迟未迁移到抗量子地址,实际上就变成了躺在链上的“悬赏”:谁能先算出私钥,谁就能转走这些币。在量子计算参与者眼中,这些币和早期比特币矿工眼中的区块奖励无异,都是凭借算力可竞争获取的收益。值得注意的是,根据分析,目前约有25%的比特币(按币量)处于公钥已暴露状态deloitte.com。随着时间推移,这个比例可能上升——除非持有人主动升级安全。这就像网络故意留出了一片“牧场”,让量子计算在其中竞相捕猎,以获得收益。量子攻击者之间形成竞争:更快的量子芯片、更好的算法意味着可以更早破解特定私钥,拿下那笔币。这几乎就是PoW的变体——过去矿工拼SHA-256算力抢区块奖励,未来量子矿工拼质因数分解/离散对数能力抢遗留UTXO。
另一方面,守护这片“牧场”的则是抗量子验证者和普通用户自身的防范行为。所谓抗量子验证者,可能是运行完整后量子节点或提供安全服务的专业机构。他们一方面帮助用户升级UTXO(例如提供一键迁移服务,把旧地址币转移到新PQ地址上,收取服务费),另一方面监测全网可疑交易。当量子攻击者尝试盗取某UTXO时,如果该UTXO持有者事先购买了“安全服务”,验证者可以抢先代为花费将币转移到更安全的地址(类似白帽黑客行为),或者提供更高级别签名升级以挫败攻击。总之,抗量子能力本身也成为一种商品,在市场上明码标价。你想让自己的币绝对安全?可以付费请量子安全服务团队定期轮换密钥、使用最高强度签名、监控链上异常。你的交易想确保不中途被截胡?可以支付更高矿工费甚至指定量子保险节点护送。在链上,一个根据签名难度和安全级别定价的市场逐渐形成:越高难度的签名(比如超长位的Falcon变种、多重签名方案结合等)需要支付越高的费用来存储和验证;反过来,这些费用补贴给保障网络安全的矿工/节点,激励他们投入更多资源提升抗量子能力。这种正反馈循环下,“安全”本身成为了新的经济激励。
如此一来,比特币生态迎来了“后挖矿时代”的转型:当区块补贴逐渐趋零,原本空缺的矿工激励由量子破解竞赛和安全服务市场所填补。量子计算加入竞争并非摧毁网络,反而扮演起类似矿工的角色,通过攻破薄弱环节来获得收益;而诚实的参与者则通过不断升级安全措施和支付安全费用来保护资产。这看似矛盾,却形成了动态平衡:正如生物进化中的“红后效应”,猎豹越快,羚羊也进化得更快,两者共同提升了系统的活力。
当然,这一模型中也充满戏剧性和讽刺意味——尤其当我们把眼光投向其他缺乏这种机制的公链。以太坊等账户制链若在量子时代陷入危机,很可能只能选择停机硬分叉、或者由中心化机构出面更换用户密钥,几乎无自动博弈的空间可言。而比特币网络则通过精妙的协议调整,把外部威胁内化为内部博弈,让市场机制去调节和应对。这种弹性与活力,正是比特币经久不衰的原因。
结语:危机催生新生,量子力量为我所用
当年互联网面对计算机病毒肆虐时,人们最终没有被动防守,而是发展出杀毒产业、安全协议,将病毒的威胁转化为推动网络更加健壮的动力。同样道理,比特币面对量子计算的冲击,并非只能筑高墙固步自封,而是选择了更具前瞻性的道路:拥抱威胁、化敌为友。通过提前布局抗量子基础设施(UTXO模型、SegWit扩展、PQ签名算法)、逐步推行BIP-360等方案,比特币正悄然改变游戏规则。在这个新规则中,量量对决、攻守博弈将上演全新篇章,网络安全不再是一成不变的盾牌,而是一套动态进化的生态系统。
或许若干年后回望,我们会发现量子计算并没有摧毁比特币,反而成就了比特币历史上的一次重大飞跃——开启了一个后工作量证明时代的新纪元。在这个纪元里,“破解就是新挖矿”不再只是戏谑之语,而成为链上真实上演的经济现象;“出售安全”也从附属服务变成每个节点和用户的日常考量。比特币将继续履行其角色:作为一个去中心化的、自我强化的金融体系,它有能力将任何挑战转化为自身进化的燃料。
正如BIP-360提案作者所言,这是一个“when 而非 if”的议题anduro.io。量子计算终将到来,而比特币已在主动邀请它参与一场精心设计的游戏。当量子计算机真的站上擂台,比特币早已不再是那个任人宰割的靶子,而更像是一位早已摆好阵势的棋手,静候对手入局。在这盘大棋中,没有永远的猎物,只有不断进化的猎人。比特币,会是那个始终笑到最后的“猎人”吗?让我们拭目以待。
参考文献:
-
【18】PQShield博客:《Falcon – A Post-Quantum Signature Scheme》 – 阐释格密码中长基(公钥)与短基(私钥)的不对称性pqshield.com。
-
【28】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 比较了比特币UTXO模型与以太坊账户模型在量子攻击下的差异,指出以太坊65%资产易受量子威胁,而比特币约25%deloitte.comdeloitte.com。
-
【23】Bitcoin开发者论坛:《Proposing a P2QRH BIP towards a quantum resistant soft fork》 – 描述了通过SegWit扩展新签名算法的思路,无需硬分叉且不增加区块大小delvingbitcoin.org。
-
【22】Emerging Investigators论文:《A meta-analysis on NIST post-quantum cryptographic primitive finalists》 – 说明Falcon-512与Falcon-1024在安全性和性能上的差异,并强调SVP/CVP等问题对量子计算依然极为困难emerginginvestigators.orgemerginginvestigators.org。
-
【36】Anduro博客:《Bitcoin Needs Quantum Resistant Addresses – We Support BIP360》 – 介绍了BIP-360提案内容,引入抗量子地址类型P2QRH,采用Falcon和Dilithium签名,软分叉兼容anduro.io。同时强调量子威胁需提早应对的紧迫性anduro.ioanduro.io。
-
【32】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 提供了BIP-360提案的最新动态,算法选型从SQIsign转向Falcon、Dilithium、SPHINCS+,原因是前者验证开销过大(15,000倍)而不切实际groups.google.comgroups.google.com。
-
【30】CoinDesk报道:《Quantum Computing Could Break Bitcoin-Like Encryption Far Easier…》 – 提及比特币所用ECC也可被Shor算法破解,只要有足够强大的量子计算机coindesk.com。
-
【33】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 阐述当前量子计算的物理局限:需要上百万qubit且降低噪声量级,目前技术远不能攻击密码算法deloitte.com。
-
【38】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 描述了针对Taproot的P2TRH抗量子方案,用哈希隐藏公钥以减小长时间暴露,并分析其开销和局限groups.google.comgroups.google.com。
-
-
 @ a5ee4475:2ca75401
2025-06-04 18:11:52
@ a5ee4475:2ca75401
2025-06-04 18:11:52clients #link #list #english #article #finalversion #descentralismo
*These clients are generally applications on the Nostr network that allow you to use the same account, regardless of the app used, keeping your messages and profile intact.
**However, you may need to meet certain requirements regarding access and account NIP for some clients, so that you can access them securely and use their features correctly.
CLIENTS
Twitter like
- Nostrmo - [source] 🌐💻(🐧🪟🍎)🍎🤖(on zapstore)
- Coracle - Super App [source] 🌐🤖(on zapstore)
- Amethyst - Super App with note edit, delete and other stuff with Tor [source] 🤖(on zapstore)
- Primal - Social and wallet [source] 🌐🍎🤖(on zapstore)
- Iris - [source] 🌐🤖🍎
- Current - [source] 🤖🍎
- FreeFrom 🤖🍎
- Openvibe - Nostr and others (new Plebstr) [source] 🤖🍎
- Snort 🌐(🤖[early access]) [onion] [source]
- Damus 🍎 [source]
- Nos 🍎 [source]
- Nostur 🍎 [source]
- NostrBand 🌐 [info] [source]
- Yana [source] 🌐💻(🐧) 🍎🤖(on zapstore)
- Nostribe [on development] 🌐 [source]
- Lume 💻(🐧🪟🍎) [info] [source]
- Gossip - [source] 💻(🐧🪟🍎)
- noStrudel - Gamified Experience [onion] [info/source] 🌐
- [Nostrudel Next] - [onion]
- moStard - Nostrudel with Monero [onion] [info/source] 🌐
- Camelus - [source] 🤖 [early access]
Community
- CCNS - Community Curated Nostr Stuff [source]
- Nostr Kiwi [creator] 🌐
- Satellite [info] 🌐
- Flotilla - [source] 🌐🐧🤖(on zapstore)
- Chachi - [source] 🌐
- Futr - Coded in haskell [source] 🐧 (others soon)
- Soapbox - Comunnity server [info] [source] 🌐
- Ditto - Soapbox community server 🌐 [source] 🌐
- Cobrafuma - Nostr brazilian community on Ditto [info] 🌐
- Zapddit - Reddit like [source] 🌐
- Voyage (Reddit like) [on development] 🤖
Wiki
- Wikifreedia - Wiki Dark mode [source] 🌐
- Wikinostr - Wiki with tabs clear mode [source] 🌐
- Wikistr - Wiki clear mode [info] [source] 🌐
Search
- Keychat - Signal-like chat with AI and browser [source] 💻(🐧🪟🍎) - 📱(🍎🤖{on zapstore})
- Spring - Browser for Nostr apps and other sites [source] 🤖 (on zapstore)
- Advanced nostr search - Advanced note search by isolated terms related to a npub profile [source] 🌐
- Nos Today - Global note search by isolated terms [info] [source] 🌐
- Nostr Search Engine - API for Nostr clients [source]
- Ntrends - Trending notes and profiles 🌐
Website
- Nsite - Nostr Site [onion] [info] [source]
- Nsite Gateway - Nostr Site Gateway [source]
- Npub pro - Your site on Nostr [source]
App Store
ZapStore - Permitionless App Store [source] 🤖 💻(🐧🍎)
Video and Live Streaming
- Flare - Youtube like 🌐 [source]
- ZapStream - Lives, videos, shorts and zaps (NIP-53) [source] 🌐 🤖(lives only | Amber | on zapstore)
- StreamCat - [source code dont found]
- Shosho - Stream your camera [source] 🤖(on zapstore)
- Swae - Live streaming [source] (on development) ⏳
Post Aggregator - Kinostr - Nostr Cinema with #kinostr [english] [author] 🌐 - Stremstr - Nostr Cinema with #kinostr [english] [source] 🤖
Link Agreggator - Kinostr - #kinostr - Nostr Cinema Profile with links [English] - Equinox - Nostr Cinema Community with links [Portuguese]
Audio and Podcast Transmission
- Castr - Your npub as podcast feed [source]
- Nostr Nests - Audio Chats [source] 🌐
- Fountain - Podcast [source] 🤖🍎
- Corny Chat - Audio Chat [source] 🌐
Music
- Tidal - Music Streaming [source] [about] [info] 🤖🍎🌐
- Wavlake - Music Streaming [source] 🌐(🤖🍎 [early access])
- Tunestr - Musical Events [source] [about] 🌐
- Stemstr - Musical Colab (paid to post) [source] [about] 🌐
Images
- Lumina - Trending images and pictures [source] 🌐
- Pinstr - Pinterest like [source] 🌐
- Slidestr - DeviantArt like [source] 🌐
- Memestr - ifunny like [source] 🌐
Download and Upload
Documents, graphics and tables
- Mindstr - Mind maps [source] 🌐
- Docstr - Share Docs [info] [source] 🌐
- Formstr - Share Forms [info] 🌐
- Sheetstr - Share Spreadsheets [source] 🌐
- Slide Maker - Share slides 🌐 [Advice: Slide Maker https://zaplinks.lol/ site is down]
Health
- Sobrkey - Sobriety and mental health [source] 🌐
- Runstr - Running app [source] 🌐
- NosFabrica - Finding ways for your health data 🌐
- LazerEyes - Eye prescription by DM [source] 🌐
Forum
- OddBean - Hacker News like [info] [source] 🌐
- LowEnt - Forum [info] 🌐
- Swarmstr - Q&A / FAQ [info] 🌐
- Staker News - Hacker News like 🌐 [info]
Direct Messenges (DM)
- 0xchat 🤖🍎 [source]
- Nostr Chat 🌐🍎 [source]
- Blowater 🌐 [source]
- Anigma (new nostrgram) - Telegram based [on development] [source]
Reading
- Oracolo - A minimalist Nostr html blog [source]
- nRSS - Nostr RSS reader 🌐
- Highlighter - Insights with a highlighted read [info] 🌐
- Zephyr - Calming to Read [info] 🌐
- Flycat - Clean and Healthy Feed [info] 🌐
- Nosta - Check Profiles [on development] [info] 🌐
- Alexandria - e-Reader and Nostr Knowledge Base (NKB) [source] 🌐
Writing
- Habla - Blog [info] 🌐
- Blogstack - Blog [info]🌐
- YakiHonne - Articles and News [info] 🌐🍎🤖(on zapstore)
Lists
- Following - Users list [source] 🌐
- Nostr Unfollower - Nostr Unfollower
- Listr - Lists [source] 🌐
- Nostr potatoes - Movies List [source] 💻(numpy)
Market and Jobs
- Shopstr - Buy and Sell [onion] [source] 🌐
- Nostr Market - Buy and Sell 🌐
- Plebeian Market - Buy and Sell [source] 🌐
- Ostrich Work - Jobs [source] 🌐
- Nostrocket - Jobs [source] 🌐
Data Vending Machines - DVM (NIP90)
(Data-processing tools)
Games
- Chesstr - Chess 🌐 [source]
- Jestr - Chess [source] 🌐
- Snakestr - Snake game [source] 🌐
- Snakes on a Relay - Multiplayer Snake game like slither.io [source] 🌐
ENGINES - DEG Mods - Decentralized Game Mods [info] [source] 🌐 - NG Engine - Nostr Game Engine [source] 🌐 - JmonkeyEngine - Java game engine [source] 🌐
Customization
Like other Services
- Olas - Instagram like [source] 🌐🍎🤖(on zapstore)
- Nostree - Linktree like 🌐
- Rabbit - TweetDeck like [info] 🌐
- Zaplinks - Nostr links 🌐
- Omeglestr - Omegle-like Random Chats [source] 🌐
General Uses
- Njump - HTML text gateway source 🌐
- Filestr - HTML midia gateway [source] 🌐
- W3 - Nostr URL shortener [source] 🌐
- Playground - Test Nostr filters [source] 🌐
Places
- Wherostr - Travel and show where you are
- Arc Map (Mapstr) - Bitcoin Map [info]
Driver and Delivery
- RoadRunner - Uber like [on development] ⏱️
- Nostrlivery - iFood like [on development] ⏱️
⚠️ SCAM ⚠️ | Arcade City - Uber like [source]
OTHER STUFF
Lightning Wallets (zap)
- Wallet of Satoshi - Simplest Lightning Wallet [info] 🤖🍎
- Coinos - Web wallet and Nostr client [source] 🌐
- Alby - Native and extension [info] [source] 🌐
- Minibits - Cashu mobile wallet [info] 🤖
- LNbits - App and extension [source] 🤖🍎💻
- Zeus - [info] [source] 🤖🍎
- Blink - Open source custodial wallet (KYC over 1000 usd) [source] 🤖🍎
⚠️ ZBD - Zap Gaming wallet and no more Social [closed source] [info] [some resources] 🤖 ⚠️ ZBD suddenly canceled my account for alleged Terms of Service violations, gives me no explanation and won't let me withdraw my money ⚠️
Without Zap - Wassabi Wallet - Privacy-focused and non-custodial with Nostr Update Manager [source]
Exchange
Media Server (Upload Links)
audio, image and video
Connected with Nostr (NIP):
- Nostr Build - Free and paid Upload [info] [source] 🌐
- NostrMedia - Written in Go with Nip 96 / Blossom (free and paid) [info] [source]
- Nostr Check - [info] [source] 🌐
- NostPic - [info] [source] 🌐
- Sovbit - Free and paid upload [info] [source] 🌐
- Voidcat - Nip-96 and Blossom [source] 🌐
- Primal Media - Primal Media Uploader [source] 🌐
Blossom - Your Media Safer
- Primal Blossom 🌐
- NostrBuild Blossom - Free upload (max 100MiB) and paid [info] [source] 🌐
Paid Upload Only
- Satellite CDN - prepaid upload (max 5GB each) [info] [source] 🌐
Without Nostr NIP:
- Pomf - Upload larger videos (max 1GB) [source]
- Catbox - max 200 MB [source]
- x0 - max 512 MiB [source]
Donation and payments
- Zapper - Easy Zaps [source] 🌐
- Autozap [source] 🌐
- Zapmeacoffee 🌐
- Nostr Zap 💻(numpy)
- Creatr - Creators subscription 🌐
- Geyzer - Crowdfunding [info] [source] 🌐
- Heya! - Crowdfunding [source]
Security
- Secret Border - Generate offline keys 💻(java)
- Umbrel - Your private relay [source] 🌐
Key signing/login and Extension
- Amber - Key signing [source] 🤖(on zapstore)
- Nowser - Account access keys 📱(🤖🍎) 💻(🐧🍎🪟)
- Nos2x - Account access keys 🌐
- Nsec.app 🌐 [info]
- Lume - [info] [source] 🐧🪟🍎
- Satcom - Share files to discuss - [info] 🌐
- KeysBand - Multi-key signing [source] 🌐
Code
- Stacks - AI Templates [info] [source] 🌐
- Nostrify - Share Nostr Frameworks 🌐
- Git Workshop (github like) [experimental] 🌐
- Gitstr (github like) [on development] ⏱️
- Osty [on development] [info] 🌐
- Python Nostr - Python Library for Nostr
- Sybil - Creating, managing and test Nostr events [on development] ⏱️
Relay Check and Cloud
- Nostr Watch - See your relay speed 🌐
- NosDrive - Nostr Relay that saves to Google Drive
Bidges and Getways
- Matrixtr Bridge - Between Matrix & Nostr
- Mostr - Between Nostr & Fediverse
- Nostrss - RSS to Nostr
- Rsslay - Optimized RSS to Nostr [source]
- Atomstr - RSS/Atom to Nostr [source]
Useful Profiles and Trends
nostr-voice - Voice note (just some clients)
NOT RELATED TO NOSTR
Voca - Text-to-Speech App for GrapheneOS [source] 🤖(on zapstore)
Android Keyboards
Personal notes and texts
Front-ends
- Nitter - Twitter / X without your data [source]
- NewPipe - Youtube, Peertube and others, without account & your data [source] 🤖
- Piped - Youtube web without you data [source] 🌐
Other Services
- Brave - Browser [source]
- DuckDuckGo - Search [source]
- LLMA - Meta - Meta open source AI [source]
- DuckDuckGo AI Chat - Famous AIs without Login [source]
- Proton Mail - Mail [source]
Other open source index: Degoogled Apps
Some other Nostr index on:
-
 @ 4fa5d1c4:fd6c6e41
2025-06-04 17:45:05
@ 4fa5d1c4:fd6c6e41
2025-06-04 17:45:051. Einleitung
Dieser Beitrag bietet eine detaillierte Einführung in Nostr - ein dezentrales Protokoll für soziale Medien, das sich grundlegend von traditionellen und föderierten Plattformen unterscheidet - und erweitert seine Diskussion, um das Potenzial für die Integration von Nostr in die Entwicklung von Bildungsplattformen im Sinne von Open Educational Practices (OEP) zu untersuchen. Nostr ist als leichtgewichtiger, zensurresistenter Mechanismus konzipiert, der in erster Linie auf einer kryptografischen Schlüsselverwaltung und einer Client-zentrierten Architektur basiert, die zusammen eine dezentrale Identitätskontrolle und Autonomie über digitale Inhalte ermöglichen. Im Gegensatz zu konventionellen zentralisierten Modellen, die sich auf servergestützte Kontrolle oder föderierte Systeme wie Mastodon, die Moderation und Identitätsspeicherung zusammenfassen, stützt sich Nostr auf ein Netzwerk von "Relais", die ohne direkte Interkommunikation arbeiten, wobei alle Funktionen der Datenaggregation, des Austauschs von Inhalten zwischen den Räumen und der Benutzerinteraktion an die Client-Anwendungen delegiert werden. Ziel dieses Beitrags ist es daher, einen umfassenden technischen und konzeptionellen Überblick über die Architektur des Protokolls und eine kritische Diskussion seiner Anwendbarkeit im Kontext dezentraler Bildungsplattformen zu geben, die eine offene, nutzergesteuerte Erstellung, Verwaltung und Verteilung von Inhalten fördern und damit den Prinzipien des OEP entsprechen.
2. Hintergrund und Motivation
Die Entwicklung der sozialen Medien in den letzten zwei Jahrzehnten war geprägt von zunehmend zentralisierten Plattformen, die sowohl die digitale Identität der Nutzer als auch die von ihnen erstellten Inhalte kontrollieren, was oft zu Zensur, algorithmischer Manipulation und Einzelausfällen führt. Im Gegensatz dazu haben sich dezentralisierte Social-Media-Protokolle wie Nostr als innovative Antwort auf diese Zentralisierungsfallen entwickelt, die offene, kryptografisch sichere und verteilte Architekturen verwenden. Nostr wurde mit dem ausdrücklichen Schwerpunkt konzipiert, den Nutzern die volle Kontrolle über ihre Kontoauthentifizierung und digitale Identität zu geben, was durch die Verwaltung von kryptografischen Schlüsselpaaren analog zu denen in Bitcoin-Wallets erreicht wird. Dieses Modell verbessert nicht nur die zensurresistenten Eigenschaften der Plattform, sondern verändert auch grundlegend die Machtdynamik in traditionellen sozialen Netzwerken, da es die Abhängigkeit von zentralen Behörden minimiert und die Möglichkeiten der Ausbeutung und Überwachung verringert. Im Kontext von Bildungsökosystemen bieten diese Merkmale eine solide Grundlage für die Entwicklung von Plattformen, die transparent, partizipatorisch und widerstandsfähig sind, da sie die gemeinsame Nutzung und kontinuierliche Weiterentwicklung von Bildungsressourcen ohne zentralisierte Kontrolle oder Unternehmenssteuerung unterstützen.
3. Technische Architektur von Nostr
Die Architektur von Nostr basiert in erster Linie auf zwei integralen Komponenten: Clients und Relays. Clients sind die benutzerseitigen Anwendungen, die die Erstellung, Veröffentlichung und Aggregation von Inhalten ermöglichen, während Relays Server sind, die von den Benutzern generierte Nachrichten, so genannte "Events", empfangen, speichern und weiterleiten. Eine der wichtigsten Neuerungen des Nostr-Protokolls ist die radikale Entkopplung der traditionellen Client-Server-Beziehung: Die Relais müssen sich nicht synchronisieren oder miteinander kommunizieren, was bedeutet, dass die Replikation von Inhalten und die Aggregation von Daten zwischen den Räumen vollständig auf der Client-Seite stattfindet. Dies minimiert die zentrale Kontrolle und schafft ein verteiltes, relaisbasiertes System, das von Natur aus resistent gegen Zensur ist, da die Dichte der verfügbaren Relays und die Möglichkeit der Nutzer, sich mit mehreren Relays zu verbinden, sicherstellen, dass die Inhalte auch dann zugänglich bleiben, wenn bestimmte Relays ausfallen oder kompromittiert sind.
In Nostr sind Ereignisse als JSON-Objekte strukturiert, die einem definierten Schema mit verschiedenen "Arten" (NIPs) entsprechen, um spezifische Funktionalitäten und andere zukünftige Erweiterungen zu unterstützen. Jedes Ereignis wird mit dem privaten kryptografischen Schlüssel des Nutzers digital signiert, was die Authentizität und Integrität der Daten garantiert und gleichzeitig eine sichere, pseudonyme Interaktion ermöglicht. Da innerhalb des Protokolls keine zentrale Behörde oder ein einziger Identitätsspeicher existiert, behalten die Nutzer die vollständige Kontrolle über ihre digitalen Identitäten, und wenn der private Schlüssel verloren geht, ist das entsprechende Konto unwiederbringlich. Dieser Ansatz verankert den Grundsatz, dass Identität sowohl dezentralisiert als auch unveränderlich ist, und stärkt die individuelle Kontrolle über persönliche Daten und Inhalte.
Da die Relays unabhängig voneinander von verschiedenen Betreibern verwaltet und nicht von zentralen Diensten koordiniert werden, können die Benutzer mehrere Relays auswählen, um die Bereitstellung und Replikation von Inhalten zu optimieren. Diese architektonische Entscheidung verbessert die Redundanz und Ausfallsicherheit erheblich, bringt aber gleichzeitig technische Herausforderungen in Bezug auf Standardisierung, Moderation und effiziente Kommunikation zwischen den Clients mit sich. Nostr integriert auch Bitcoin-basierte Mikrozahlungen (bekannt als "Zaps"), um finanzielle Anreize für den Betrieb von Relay-Servern zu schaffen und so die Herausforderungen der wirtschaftlichen Nachhaltigkeit in einer dezentralen Infrastruktur zu bewältigen. Die Design-Entscheidungen in Nostr fördern Offenheit und Innovation, indem sie es jeder Person oder Organisation mit ausreichenden technischen Fähigkeiten erlauben, ein Relay zu hosten oder einen Client zu entwickeln, was zu einem lebendigen Ökosystem von verschiedenen Anwendungen und Diensten führt.
4. Identitätsmanagement und Moderation
Im Mittelpunkt des dezentralen Paradigmas von Nostr steht der Ansatz der Identitätsverwaltung, der sich von traditionellen Systemen unterscheidet, bei denen Identitäten als Kontodaten von zentralen Servern verwaltet werden. Bei Nostr verfügt jeder Benutzer über ein einzigartiges kryptografisches Schlüsselpaar, wobei der öffentliche Schlüssel als dauerhafte digitale Kennung und der private Schlüssel als Mittel zum Signieren aller Aktionen und Ereignisse dient. Dieses kryptonative Modell gewährleistet nicht nur robuste Sicherheit und Authentizität, sondern überlässt den Nutzern auch die alleinige Verantwortung für die Verwaltung ihrer Schlüssel - was sowohl die Freiheit als auch das Risiko eines vollständig dezentralen Identitätssystems unterstreicht.Dieses empfindliche Gleichgewicht unterstreicht die Autonomie der Nutzer und steht im Einklang mit dem breiteren Ethos dezentraler sozialer Medien, in denen keine einzelne Instanz die Identität einer Person ohne Zugang zu ihrem privaten Schlüssel außer Kraft setzen oder manipulieren kann.
Die Moderation in Nostr ist aufgrund des dezentralen Kuratierungsmodells noch komplexer. Die Inhalte werden nicht von einer zentralen Behörde moderiert, sondern durch eine Kombination aus relaisspezifischen Richtlinien und clientseitigen Kontrollen, wie z. B. benutzerdefinierte Listen für persönliche Kuratoren oder Sperr-/Stummschaltungsfunktionen. Dieser Ansatz fördert zwar die freie Meinungsäußerung und unterstützt eine Vielzahl von Standpunkten, kann aber auch zu uneinheitlichen Moderationsrichtlinien und fragmentierten Nutzererfahrungen auf verschiedenen Relays und Clients führen, was für die Nutzer eine erhebliche technische und verhaltensbezogene Belastung darstellt, wenn sie ihre digitalen Umgebungen kuratieren wollen.
5. Skalierbarkeit und Widerstandsfähigkeit gegen Zensur
Ein entscheidendes Merkmal des Nostr-Protokolls ist sein hohes Maß an Skalierbarkeit und Zensurresistenz, das durch seine verteilte, relaisbasierte Architektur erreicht wird. Durch die Dezentralisierung der Speicherung und Verbreitung von Inhalten auf zahlreiche unabhängige Relays entschärft Nostr die üblichen Schwachstellen zentralisierter sozialer Plattformen, wie z. B. Single Points of Failure oder das Potenzial für staatliche oder unternehmensgesteuerte Zensur. Mehrere Relays können gleichzeitig arbeiten, wodurch sichergestellt wird, dass die Stabilität des Netzwerks auch dann erhalten bleibt, wenn einige von ihnen vom Netz genommen werden oder behördlichem Druck ausgesetzt sind, und dass Inhalte für Kunden, die mit alternativen Relays verbunden sind, zugänglich bleiben.
Die Skalierbarkeit von Nostr wird dadurch verbessert, dass sich die Nutzenden gleichzeitig mit mehreren Relays verbinden können, was die Replikation von Inhalten über ein globales Netz von Servern ermöglicht, das sich über zahlreiche geografische Regionen und autonome Systeme erstreckt. Dieser Replikationsmechanismus bringt jedoch Herausforderungen mit sich, wie z. B. eine erhöhte Redundanz bei der Speicher- und Bandbreitennutzung, die eine sorgfältige Optimierung und die Entwicklung innovativer clientseitiger Strategien erfordern, um den Datenabruf zu verwalten und den Overhead zu reduzieren, ohne die Verfügbarkeit zu beeinträchtigen. Darüber hinaus trägt die Dezentralisierung der Zuständigkeiten für Kuratierung und Moderation zu einer dynamischen Umgebung bei, in der Inhalte sowohl gegen erzwungene Löschungen resistent als auch an die Bedürfnisse der Nutzer anpassbar sind, wenn auch auf Kosten von Einheitlichkeit und vorhersehbarer Nutzererfahrung.
6. Vergleich mit föderierten und zentralisierten Modellen
Das Aufkommen dezentraler Protokolle wie Nostr steht in scharfem Kontrast zu föderierten Netzwerken wie Mastodon, die das ActivityPub-Protokoll verwenden. Während föderierte Systeme die Kontrolle über unabhängige Instanzen verteilen, verlassen sie sich immer noch auf ein gewisses Maß an Zentralisierung auf der Ebene jeder einzelnen Instanz, von denen jede ihre eigenen Richtlinien bezüglich Moderation, Identitätsüberprüfung und Inhaltszensur durchsetzt. In diesen Systemen ist die Verwaltung zwar auf mehrere Knotenpunkte verteilt, aber es besteht eine Abhängigkeit von Serveradministratoren, die erhebliche Macht über den Inhalt und die Identität der Benutzer haben; dies steht im Gegensatz zu Nostrs vollständig kundenorientiertem Kurations- und Identitätsverwaltungsmodell, das darauf abzielt, jeden einzelnen Kontrollpunkt zu eliminieren.
In zentralisierten Architekturen werden Benutzerdaten und -identitäten auf proprietäre und undurchsichtige Weise verwaltet, wodurch Inhalte den Launen von Unternehmensrichtlinien und externem Druck ausgesetzt werden, was zu Überwachung, gezielter Zensur oder einseitiger algorithmischer Manipulation von Inhalten führen kann. Das Design von Nostr - das auf kryptografischer Authentifizierung, clientseitiger Datenaggregation und dem erlaubnisfreien Betrieb von Relay-Servern beruht - stellt eine radikale Abkehr dar, die das Gleichgewicht der Macht fest in die Hände der einzelnen Nutzer und nicht in die Hände zentraler Behörden legt.
7. Implikationen für Bildungsplattformen
Das Potenzial für die Integration des dezentralen Protokolls von Nostr in Bildungsplattformen bietet eine transformative Gelegenheit zur Unterstützung von Open Educational Practices (OEP). OEP legt den Schwerpunkt auf Inklusion, Autonomie der Lernenden, kollaborative Wissenserstellung und offenen Zugang zu Bildungsressourcen. Herkömmliche Bildungsplattformen sind oft durch zentralisierte Architekturen eingeschränkt, die den Zugang behindern und Innovationen unterdrücken können, da sie auf einzelne administrative Kontrollen und proprietäre Content-Management-Systeme angewiesen sind.
Durch die Nutzung der dezentralen Infrastruktur von Nostr können Bildungsplattformen aufgebaut werden, die es Lehrenden und Lernenden ermöglichen, die volle Kontrolle über ihre digitalen Identitäten und Bildungsinhalte zu behalten, ohne das Risiko von Zensur oder externer Einmischung. In solchen Systemen verwaltet jeder Teilnehmer seine eigene Identität mithilfe von kryptografischen Schlüsseln, wodurch sichergestellt wird, dass Bildungsleistungen, Beiträge und Zeugnisse auf überprüfbare und unveränderliche Weise aufgezeichnet werden. Dies fördert ein Umfeld, in dem die Schaffung und Verbreitung von Wissen wirklich von den Teilnehmern selbst bestimmt wird, frei von den Zwängen, die von zentralen Torwächtern auferlegt werden.
Darüber hinaus bietet die relaisbasierte Architektur von Nostr eine beispiellose Skalierbarkeit und Ausfallsicherheit - Eigenschaften, die für ein Bildungsökosystem, das eine Vielzahl von Nutzern mit unterschiedlichem geografischen und sozioökonomischen Hintergrund unterstützen muss, unerlässlich sind. Bildungsinhalte - von digitalen Lehrbüchern und Multimedia-Vorlesungen bis hin zu interaktiven Diskursen und gemeinschaftlichen Projekten - können gespeichert und über mehrere Relays repliziert werden, um sicherzustellen, dass der Zugang auch bei lokalen Netzwerkausfällen oder Zensurversuchen erhalten bleibt.
Das offene Protokoll von Nostr ist außerdem eine ideale Grundlage für die Entwicklung interoperabler Bildungsplattformen, auf denen Drittentwickler und Bildungseinrichtungen maßgeschneiderte Clients und Anwendungen für pädagogische Zwecke erstellen können. Dieser Ansatz fördert ein vielfältiges Ökosystem von Bildungswerkzeugen und -diensten, die nahtlos zusammenarbeiten, ohne auf eine einzige proprietäre Plattform beschränkt zu sein, und steht damit im Einklang mit dem Ethos des OEP. Pädagogen können digitale Lernumgebungen entwerfen, die die kollaborative Erstellung von Inhalten, Peer-Reviews und Community-gesteuerte Kuration unterstützen und gleichzeitig von der Sicherheit und Transparenz profitieren, die das kryptografische Grundgerüst von Nostr bietet.
Darüber hinaus gewährleistet die inhärente Zensurresistenz von Nostr, dass Bildungsinhalte zugänglich und frei von staatlichen oder unternehmerischen Eingriffen bleiben - ein besonders wichtiger Aspekt für Lernende in Regionen, in denen der Zugang zu Informationen eingeschränkt oder überwacht wird. Diese Widerstandsfähigkeit untermauert nicht nur die demokratische Verbreitung von Wissen, sondern unterstützt auch den Grundsatz eines digitalen Gemeinguts, bei dem Bildungsressourcen kollektiv verwaltet und gemeinsam genutzt werden. In diesem Zusammenhang kann Nostr genutzt werden, um Bildungsplattformen zu entwickeln, die nicht nur robust und integrativ sind, sondern auch auf die Bedürfnisse marginalisierter oder unterrepräsentierter Gemeinschaften abgestimmt sind.
Zusätzlich zu diesen strukturellen Vorteilen kann die finanzielle Nachhaltigkeit dezentraler Bildungsplattformen durch die Integration von auf Kryptowährungen basierenden Anreizmechanismen gestärkt werden - wie die Unterstützung von Nostr für Bitcoin Lightning "Zaps" zeigt. Diese Micropayment-Systeme eröffnen Möglichkeiten für neuartige Finanzierungsmodelle, die Pädagogen und Inhaltsersteller direkt belohnen und so die Abhängigkeit von werbebasierten Einnahmen oder zentralisierten Finanzierungsströmen verringern, die häufig die Integrität der Bildung gefährden. Solche wirtschaftlichen Anreize können auch den Betrieb und die Wartung von Relay-Servern unterstützen und so sicherstellen, dass die dezentrale Infrastruktur belastbar und kontinuierlich für Bildungszwecke verfügbar bleibt.
8. Möglichkeiten für kollaboratives und kultursensibles Lernen
Über die technische Stabilität und Skalierbarkeit hinaus bietet die dezentrale Natur von Nostr bedeutende Möglichkeiten zur Förderung von kollaborativem Lernen und kultursensibler Pädagogik. Dezentralisierte Bildungsplattformen, die auf Nostr aufbauen, können lokale Gemeinschaften in die Lage versetzen, Inhalte zu erstellen und zu kuratieren, die kontextuell relevant und kulturell angemessen sind - ein entscheidender Faktor bei der Förderung von Bildungsgerechtigkeit und Inklusivität. In Umgebungen, in denen Mainstream-Bildungstechnologien als von oben nach unten betrachtet werden und nicht mit lokalen Werten oder pädagogischen Ansätzen übereinstimmen, ermöglicht eine dezentralisierte Infrastruktur die Entwicklung maßgeschneiderter digitaler Lernumgebungen, die lokale Kulturen, Sprachen und Traditionen widerspiegeln.
Dieser gemeinschaftsorientierte Bildungsansatz fördert das Gefühl der Eigenverantwortung bei Lernenden und Lehrenden gleichermaßen und ermutigt zur gemeinschaftlichen Schaffung von Wissen, das unterschiedliche Erkenntnistheorien respektiert. So können Pädagogen beispielsweise dezentrale "Lernräume" einrichten, in denen Open-Source-Lernmaterialien, Werkzeuge für die digitale Kompetenz und innovative Lehrmethoden gemeinsam genutzt und durch partizipatives Engagement kontinuierlich weiterentwickelt werden. In einem solchen Modell verschwimmen die Grenzen zwischen Lernenden und Lehrenden, was einen fließenden Ideenaustausch und die gemeinsame Schaffung von Wissen ermöglicht, die im Mittelpunkt offener Bildungspraktiken stehen.
Darüber hinaus ermöglicht die Flexibilität der Client-zentrierten Architektur von Nostr die Entwicklung von spezialisierten Bildungsclients, die auf die jeweiligen Lernstile und Disziplinen zugeschnitten sind. Diese Clients könnten Funktionen wie erweiterte Such- und Filterfunktionen für Bildungsinhalte, integrierte Anmerkungswerkzeuge für die gemeinsame Bearbeitung von Dokumenten und interoperable Identitätsmanagementsysteme enthalten, die es den Lernenden ermöglichen, ihre Anmeldedaten nahtlos in verschiedene digitale Lernumgebungen zu übertragen. Solche Innovationen würden nicht nur die Rolle der Nutzerautonomie beim digitalen Lernen stärken, sondern auch die Entwicklung von Bildungsnetzwerken fördern, die belastbar und anpassungsfähig sind und auf die sich verändernden pädagogischen Herausforderungen reagieren können.
9. Herausforderungen und Abhilfestrategien
Trotz der vielversprechenden Möglichkeiten ist die Integration von Nostr in Bildungsplattformen nicht unproblematisch. Gerade die Funktionen, die den Nutzern mehr Möglichkeiten bieten - wie selbstverwaltete kryptografische Schlüssel und dezentralisierte Inhaltsmoderation - führen auch Komplexitäten ein, die die Benutzerfreundlichkeit und Zugänglichkeit behindern können, insbesondere für Personen ohne fortgeschrittene technische Kenntnisse. Die Schlüsselverwaltung stellt beispielsweise eine kritische Schwachstelle dar; der Verlust eines privaten Schlüssels führt unwiderruflich zum Verlust der Identität und des Zugriffs auf die eigenen digitalen Beiträge - ein Risiko, das durch solide Bildungsinitiativen und Mechanismen zur Unterstützung der Nutzer angegangen werden muss.
Die technische Kompetenz von Lehrenden und Lernenden ist in diesem Zusammenhang von größter Bedeutung und erfordert die Entwicklung umfassender Einführungsverfahren, benutzerfreundlicher Schnittstellen und Hilfsmittel, die kryptografische Konzepte entmystifizieren und die Interaktion mit dezentralen Netzwerken vereinfachen. Zu diesem Zweck könnte der Einsatz intuitiver Bildungsmodule, interaktiver Tutorials und von der Community geleiteter Schulungen technische Barrieren abbauen und gleichzeitig die Entwicklung digitaler Kompetenzen fördern, die für die Navigation in dezentralen Netzwerken unerlässlich sind. Darüber hinaus muss die Herausforderung einer inkonsistenten Moderation und fragmentierten Nutzererfahrung aufgrund der heterogenen Richtlinien unabhängiger Relais und Clients durch die Einrichtung von Community-Governance-Rahmenwerken und interoperablen Standards angegangen werden, die eine Grundlinie der Qualität und Sicherheit auf der gesamten Plattform gewährleisten.
Strategien zur Bewältigung des mit der Skalierbarkeit verbundenen Overheads - wie etwa die redundante Replikation von Beiträgen über eine übermäßige Anzahl von Relays - sollten sich auf die Implementierung clientseitiger Optimierungstechniken konzentrieren, die die Ineffizienz von Bandbreite und Speicherplatz verringern, ohne die Belastbarkeit und Zugänglichkeit des Netzwerks zu beeinträchtigen. Kontinuierliche Forschung und iterative Verfeinerung werden notwendig sein, um ein Gleichgewicht zwischen den Vorteilen der Dezentralisierung und der ihr innewohnenden betrieblichen Komplexität zu finden und sicherzustellen, dass auf Nostr basierende Bildungsplattformen sowohl robust als auch benutzerfreundlich bleiben können.
10. Zukünftige Richtungen und Forschungsmöglichkeiten
Die Einbindung von Nostr in Bildungsplattformen stellt ein fruchtbares Gebiet für Forschung und Entwicklung dar, das zahlreiche Möglichkeiten zur Erkundung bietet. Zukünftige Arbeiten könnten das Design interoperabler Bildungsrahmenwerke erforschen, die die dezentrale Architektur von Nostr mit aufkommenden Technologien wie künstlicher Intelligenz, Blockchain-basiertem Credentialing und fortschrittlichen kryptographischen Techniken integrieren, um die Sicherheit, Zugänglichkeit und Authentizität in digitalen Lernumgebungen weiter zu verbessern. Die Erforschung gemeinschaftsbasierter Governance-Modelle ist ebenfalls gerechtfertigt, da dezentrale Plattformen Mechanismen für die kollektive Entscheidungsfindung und Konfliktlösung erfordern, die mit den Grundsätzen einer offenen, partizipativen Bildung vereinbar sind.
Ein möglicher Weg ist die Entwicklung modularer, quelloffener Bildungs-Clients, die sich nahtlos mit verschiedenen Relais verbinden lassen und den Lehrkräften leistungsstarke Tools zur Kuratierung und Moderation von Inhalten bieten. Diese Clients könnten anpassbare Dashboards, Module für die Zusammenarbeit in Echtzeit und integrierte Unterstützung für Mikrozahlungen oder Anreizstrukturen bieten, um sicherzustellen, dass Bildungsinhalte sowohl dynamisch als auch finanziell nachhaltig bleiben. Darüber hinaus könnte die Einrichtung digitaler Identitätsrahmen, die auf den kryptografischen Prinzipien von Nostr aufbauen, zu innovativen Modellen für die Überprüfung akademischer Zeugnisse, die Verfolgung des Lernfortschritts und die Erleichterung der plattformübergreifenden Anerkennung von Bildungsleistungen führen, und das alles ohne die Aufsicht zentralisierter Registrierungsbehörden.
Die Schnittstelle zwischen digitaler Kompetenz und ethischer digitaler Bürgerschaft ist ein weiteres vielversprechendes Forschungsgebiet. In dem Maße, in dem Pädagogen dezentrale Bildungstechnologien in die Lehrpläne integrieren, wird es zwingend notwendig, Lehrmethoden zu entwickeln, die nicht nur technische Kenntnisse, sondern auch die kritischen und moralischen Fähigkeiten vermitteln, die für die Arbeit in einem dezentralen digitalen Ökosystem erforderlich sind. Solche pädagogischen Strategien sollten Schulungen zum Schlüsselmanagement, zur Verifizierung digitaler Identitäten und zum Verständnis der Kompromisse umfassen, die mit dezentralisierten und zentralisierten Technologiemodellen einhergehen, um den Schülern eine ausgewogene Perspektive auf digitale Rechte, Verantwortlichkeiten und Möglichkeiten zu vermitteln.
Die Zusammenarbeit zwischen akademischen Institutionen, Open-Source-Gemeinschaften und Innovatoren dezentraler Technologien wird entscheidend sein, um diese Forschungsagenden voranzutreiben und die Entwicklung von Bildungslabors und Pilotprojekten zu fördern, die die praktischen Auswirkungen und Vorteile dezentraler Bildungsplattformen auf der Grundlage von Nostr erforschen. Solche Initiativen könnten als lebende Laboratorien zum Testen neuer Werkzeuge, Methoden und Governance-Strategien dienen, mit dem Ziel, das Gleichgewicht zwischen dem Versprechen der Dezentralisierung und ihren praktischen Herausforderungen schrittweise zu verfeinern.
11. Schlußfolgerung
Zusammenfassend lässt sich sagen, dass Nostr eine bahnbrechende Entwicklung in der Architektur sozialer Medien darstellt, die die Beziehung zwischen Nutzern, Inhalten und Netzwerkinfrastruktur durch ein dezentralisiertes, kryptographisch gesichertes und klientenzentriertes Modell neu definiert. Das relaisbasierte Design, die dezentrale Identitätsverwaltung und die offene Architektur bieten erhebliche Vorteile gegenüber herkömmlichen zentralisierten und föderierten Systemen in Bezug auf Zensurresistenz, Skalierbarkeit und Benutzerautonomie. Diese technischen Innovationen haben weitreichende Auswirkungen auf die Entwicklung von Bildungsplattformen, die den Grundsätzen der Open Educational Practices entsprechen. Durch die Unterstützung von nutzergesteuerten Identitäten, stabiler Replikation von Inhalten und gemeinschaftsgesteuerter Verwaltung bietet Nostr eine Infrastruktur für dezentrale Bildungsökosysteme, die Inklusion, Zusammenarbeit und kontinuierliche Innovation fördern.
Der Einsatz von Nostr in Bildungskontexten verspricht, Lernende und Lehrende in die Lage zu versetzen, Bildungsinhalte frei von zentralisierten Einschränkungen und externer Zensur zu erstellen, zu teilen und gemeinschaftlich weiterzuentwickeln. Gleichzeitig erfordern die Herausforderungen, die mit der technischen Komplexität, der Schlüsselverwaltung und der inkonsistenten Moderation verbunden sind, kontinuierliche Forschung und die Entwicklung unterstützender Werkzeuge. Wenn diese Probleme durch gezielte Maßnahmen wie benutzerfreundliche Schnittstellen, umfassende Programme für digitale Kompetenz und gemeinschaftsbasierte Governance-Modelle angegangen werden, können die Beteiligten das volle Potenzial von Nostr nutzen, um dezentrale, offene und partizipative Bildungsplattformen zu schaffen, die den Geist von Open Educational Practices wirklich verkörpern.
Letztendlich stellt die Integration von Nostr in dezentralisierte Bildungsplattformen nicht nur eine technische Entwicklung dar, sondern auch einen gesellschaftspolitischen Wandel hin zu größerer Dezentralisierung, Ermächtigung der Nutzer und digitaler Souveränität. Diese Ausrichtung an den Werten des OEP definiert nicht nur die Verbreitung und den Konsum von Bildungsinhalten neu, sondern ist auch Katalysator für breitere Diskussionen über digitale Rechte, Inklusion und ethische Teilhabe an der digitalen Allmende. Das Potenzial solcher Plattformen, kontextrelevante, zensurresistente und kollaborativ kuratierte Bildungsressourcen bereitzustellen, ist ein entscheidender Schritt, um die Zukunft der digitalen Bildung neu zu gestalten.
Fazit
Zusammenfassend lässt sich sagen, dass die innovative Architektur von Nostr, die auf einer kryptografischen Schlüsselverwaltung und dezentralen Relay-Netzwerken basiert, den Grundstein für eine neue Generation von Bildungsplattformen legt, die die Einschränkungen zentralisierter Systeme überwinden können. Ihre Fähigkeit, belastbare, sichere und nutzerzentrierte digitale Umgebungen bereitzustellen, steht in perfektem Einklang mit den Grundsätzen offener Bildungspraktiken und bietet Lehrenden und Lernenden eine noch nie dagewesene Kontrolle über ihre digitalen Interaktionen und Inhalte. Kontinuierliche Forschung, interdisziplinäre Zusammenarbeit und gezielte Bildungsinitiativen werden unerlässlich sein, um dieses Potenzial voll auszuschöpfen und sicherzustellen, dass die Vorteile der Dezentralisierung allen Mitgliedern der Bildungsgemeinschaft zugänglich sind.
Durch den strategischen Einsatz von Nostr-basierten Bildungsplattformen kann die Zukunft des Lernens als ein Bereich neu konzipiert werden, in dem offener Zugang, Autonomie der Lernenden und gemeinschaftsgesteuerte Wissensbildung nicht nur möglich, sondern unvermeidlich sind - eine Zukunft, in der dezentrale Infrastrukturen eine gerechtere, transparentere und partizipativere digitale Bildungslandschaft ermöglichen.
Dieser Beitrag hat daher eine ausführliche Einführung in die technischen und konzeptionellen Grundlagen von Nostr gegeben, die Mechanismen beschrieben, mit denen Nostr Dezentralisierung und Zensurresistenz erreicht, und seine bedeutenden Auswirkungen auf die Zukunft von Bildungsplattformen im Rahmen von Open Educational Practices untersucht. Die Synergie zwischen dem dezentralen Paradigma von Nostr und dem demokratischen, inklusiven Ethos von OEP birgt ein transformatives Versprechen für die Neugestaltung der digitalen Bildung in einer Weise, die Offenheit, Sicherheit und lebenslanges Lernen für eine globale Gemeinschaft fördert.
Indem sie aufkommende dezentralisierte Protokolle wie Nostr als grundlegende Infrastrukturkomponenten von Bildungsplattformen nutzen, können Stakeholder eine ganzheitliche digitale Transformation vorantreiben, die Technologie, Pädagogik und Ethik vereint und ein Paradigma einführt, in dem Bildungsgerechtigkeit und digitale Selbstbestimmung keine Wünsche, sondern realisierte Prinzipien unserer vernetzten Gesellschaft sind.
Verwendete Quellen:
-
Seeing the Politics of Decentralized Social Media Protocols. S Hwang, AX Zhang. ArXiv (2025). <https://doi.org/10.48550/arxiv.2505.22962>
-
Navigating Decentralized Online Social Networks: An Overview of Technical and Societal Challenges in Architectural Choices. Ujun Jeong, L. Ng, K. Carley, Huan Liu. ArXiv (2504). <https://doi.org/10.48550/arxiv.2504.00071>
-
Towards Decentralized Applications. X Ma. 2024. <https://escholarship.org/content/qt0j7044w0/qt0j7044w0_noSplash_c638cdfda170244b9abf750f654399f1.pdf>
-
Decentralized Social Networking Protocol (DSNP) and User Empowerment: An Analysis of Online Identity Ownership, Data Privacy, and Comparative Assessment with Other Decentralized Protocols. M Nay . 2024. <https://dspace.mit.edu/bitstream/handle/1721.1/156782/nay-mnay-meng-eecs-2024-thesis.pdf?sequence=1&isAllowed=y>
-
A Kantian Right to Fediverse Access, or: for a digital enlightenment on the social web. JN Bingemann . <https://philarchive.org/archive/BINAKR>
-
Exploring the Nostr Ecosystem: A Study of Decentralization and Resilience. Yiluo Wei, Gareth Tyson. ArXiv (2402). <https://doi.org/10.48550/arxiv.2402.05709>
-
Money and Trust in Metaverses, Bitcoin and Stablecoins in global social XR. John O'Hare, Allen J. Fairchild, U. Ali. ArXiv (2207). <https://doi.org/10.48550/arxiv.2207.09460>
-
FEDSTR: Money-In AI-Out | A Decentralized Marketplace for Federated Learning and LLM Training on the NOSTR Protocol. Konstantinos E. Nikolakakis, George Chantzialexiou, Dionysis Kalogerias. ArXiv (2024). <https://doi.org/10.48550/arxiv.2404.15834>
-
"Sumud" as Connected Learning: Towards a Collective Digital Commons in Palestine.. H Scott, M Ujvari, AMA Bakeer. 2025. <https://files.eric.ed.gov/fulltext/EJ1464483.pdf>
Erstellt mit Unterstützung von FutureHouse, Perplexity, Deepl, Ideogram und ChatGPT.
-
-
 @ fbf0e434:e1be6a39
2025-06-05 14:08:24
@ fbf0e434:e1be6a39
2025-06-05 14:08:24Hackathon 概要
ETHBratislava Hackathon Vol.2 汇聚 54 名开发者并审核通过 11 个项目,成为以太坊社区的重要盛事。此次黑客马拉松在斯洛伐克技术大学举办,参与者可免费参与 ETHBratislava 大会,这一安排助力开发者探索区块链技术的前沿进展。
项目在解决以太坊可扩展性与互操作性问题上成果显著,尤其在 “World Computer” 赛道表现突出。“Zircuit Restaking Track” 赛道也带来重要创新,聚焦通过 AI 驱动的 zk rollups 技术提升安全性与扩展性。“European Stablecoin EURØP Challenge” 则致力于开发欧元背书的稳定币,推动欧洲监管数字货币概念落地。
参与者不仅获得资深导师指导、与行业领袖建立连接的机会,现场更有招聘方挖掘技术人才。活动在兼具庆祝与社交属性的派对中落幕。总计 4,000 欧元奖金的设置,营造了开发者之间竞争与合作并存的创新氛围。ETHBratislava Vol.2 成功孵化出影响以太坊未来的创新构想,同时强化了社区联结。
Hackathon 获奖者
World Computer 奖项获奖者
此类别着重于利用以太坊能力的面向消费者的应用程序。开发者创建了解决方案,旨在增强包容性、金融工具和教育平台。获奖者包括:
- Zhar: 该去中心化平台使用AI和以太坊区块链来管理、执行和激励使用智能合约和代币的链上挑战。
- Ledger Lens: 一个Web应用程序,促进对以太坊多层生态系统的可视化和分析,强调代币流动和跨链桥使用等指标。
现实世界代币化奖项获奖者
此类别集中于在欧洲利用EUR锚定的稳定币EURØP构建效用。项目目标是在此数字货币之上部署初步技术增强。
- dEST: 一个去中心化平台,利用NFTs和智能合约来促进无中介的代币化房地产交易。
- EnergyHub: 一个提供去中心化平台以货币化多余绿色能源并通过智能合约和用户友好的仪表板实现能源捐赠的应用程序。
Restaking 奖项获奖者
此类别鼓励团队在Zircuit生态系统内的AI驱动zkEVM上进行构建,着重于支持AI增强安全性和创新zk rollup技术的项目。
- RestakerX: 一个仪表板应用程序,设计用于跟踪Zircuit网络上的数字资产,提供算法建议以最大化收益。
有关所有项目的更多详细信息和此次黑客马拉松中展示的创新理念的进一步见解,请访问 ETHBratislava Hackathon页面。
关于组织者
Ethereum Bratislava
Ethereum Bratislava 是中欧和东欧地区区块链和技术领域的一个重要社区,致力于推进以太坊的开发和整合。由一支专家团队支持,该组织在增强以太坊在中欧和东欧地区的可扩展性和安全性的项目中作出了重大贡献。积极参与社区活动和教育活动强调了他们在区块链领域促进技术创新和知识共享的承诺。Ethereum Bratislava 继续支持技术改进和生态系统增长,旨在增强以太坊的能力和跨各行业的采用。
-
 @ 000002de:c05780a7
2025-06-04 17:09:47
@ 000002de:c05780a7
2025-06-04 17:09:47I know most of you aren't doing this but I hope this is helpful when talking to your friends and family about bitcoin. Specifically if they bring up Orange Man or have real issues with him.
First off we can see that most of the MAGA / Political Bitcoin cheer-leading is exclusively SoV/NGU and not freedom money. Its basically the crypto types. The shitcoiners. The scammers. I get why this will turn off people that don't love the orange man. I recently heard a technical podcaster say he didn't like being associated with bitcoin (though he said crypto and his co-host is a bitcoin only guy...). I'm here to tell you that's dumb.
Why? I know how dumb it is by experience. Back in the day I was a kid listening to Rush Limbaugh and he was destroying the sky is falling claims I was hearing in government schools. I used to come home freaking out about global warming and the destruction of the rain forests. This was in the 90s btw. Looking back on what Limbaugh said, he's been proven largely right. But that isn't my point. My point is that because of this and because of how dumb many of the environmentalists takes were, I ignored many environmental issues. I would turn off people that called themselves environmentalists. This was a mistake. I was ignoring many other problems with how we use resources and used weak reasoning on others. I seeded caring for the environment to the left. I let myself be sidelined by reactionary thinking.
A few years ago I learned about the Permaculture[^1] way of thinking and it kinda blew my mind. A guy named Jack Spirko said something that stuck with me. Everyone should be an environmentalist. At least to the extent that they care about the planet we all share. Of course we all know this but it flipped a switch in my head. I'd allowed myself to be a reactionary on the environment and harm humans do to the air, water, and soil as well as the creatures. I always cared about these things but it too a dude that I aligned with on many topics to snap me out of my programming.
I think a similar thing can happen with Bitcoin. Don't be reactionary. Just because some people you don't align with or like do like a thing... it doesn't mean that thing is bad. They could be representing it incorrectly. Bitcoin, if it truly is money is apolitical. Now, we can get into economics and dive into the deep end about hard money but the fact is that bitcoin shouldn't really be political in the sense of US politics on the ground. If you are just a voter or pleb you should be adopting bitcoin no matter what any politician says. The republicans and democrats are not that different on many topics and the MAGA movement is just pandering. Don't let the Orange Man turn you off from bitcoin. Don't let the number go up people turn you off. There are people living under oppressive regimes all over the globe that can be helped by bitcoin. We may need it in the US. Don't sleep on this because of a clown. Don't be dumb. Its a great way to stay poor and vulnerable.
[^1]: Permaculture is an ethical design science that uses natural systems to provide all human and ecological needs in a regenerative way.
https://stacker.news/items/997169
-
 @ 31a4605e:cf043959
2025-06-05 13:03:59
@ 31a4605e:cf043959
2025-06-05 13:03:59Nos últimos anos, o Bitcoin tem sido frequentemente comparado ao ouro, ganhando o nome de "ouro digital". Essa comparação ocorre porque ambas as formas de valor têm características em comum, como escassez, durabilidade e aceitação mundial. Contudo, o Bitcoin também representa uma novidade tecnológica que muda a ideia de dinheiro e investimento, se destacando como uma alternativa moderna e eficaz ao ouro físico.
Uma das razões pelas quais o Bitcoin é comparado ao ouro é a sua escassez programada. Enquanto o ouro é um recurso natural limitado, cuja oferta depende da mineração, o Bitcoin tem um teto máximo de 21 milhões de unidades, definido em seu código. Esse teto faz com que o Bitcoin seja protegido contra a inflação, ao contrário das moedas tradicionais, que podem ser criadas sem limites pelos bancos centrais.
Essa característica traz um valor duradouro, parecido com o ouro, já que a oferta limitada ajuda a manter o poder de compra ao longo do tempo. Com o aumento da procura por Bitcoin, sua quantidade reduzida reforça seu papel como reserva de valor.
Outro aspecto que aproxima o Bitcoin do ouro é a durabilidade. Enquanto o ouro resiste à corrosão e pode ser guardado por séculos, o Bitcoin é um ativo digital protegido por criptografia avançada e armazenado na blockchain — um livro-razão imutável e descentralizado.
Além disso, o Bitcoin é mais fácil de transportar do que o ouro. Mover ouro físico envolve custos e segurança, tornando o transporte complicado, principalmente em transações internacionais. Por outro lado, o Bitcoin pode ser enviado digitalmente para qualquer parte do mundo em minutos, com taxas baixas e sem intermediários. Essa vantagem tecnológica torna o Bitcoin mais eficaz para um mundo globalizado e digital.
A segurança é outra característica que o Bitcoin e o ouro têm em comum. O ouro é difícil de falsificar, fazendo dele uma reserva de valor confiável. Da mesma forma, o Bitcoin usa protocolos de criptografia que asseguram transações seguras e protegidas contra fraudes.
Além disso, todas as transações feitas com Bitcoin são registradas na blockchain, fornecendo um nível de transparência que o ouro físico não oferece. Qualquer pessoa pode revisar as transações na rede, aumentando a confiança e a rastreabilidade.
EconômicaHistoricamente, o ouro tem sido utilizado como proteção contra a inflação e crises econômicas. Durante momentos de instabilidade, os investidores buscam o ouro como uma maneira de preservar seu patrimônio. O Bitcoin, por sua vez, está surgindo como uma alternativa digital com o mesmo propósito.
Em países com alta inflação ou instabilidade política, o Bitcoin tem sido usado como uma proteção contra a desvalorização das moedas locais. Sua natureza descentralizada impede que governos confisquem ou controlem diretamente o ativo, garantindo maior liberdade financeira para os usuários.
Apesar de suas semelhanças com o ouro, o Bitcoin ainda enfrenta desafios. Sua volatilidade é muito maior, o que pode causar incertezas a curto prazo. No entanto, muitos especialistas afirmam que essa volatilidade é uma característica comum em ativos novos e tende a diminuir com o tempo, à medida que a aceitação cresce e o mercado se desenvolve.
Outro desafio é a regulamentação. Enquanto o ouro já é reconhecido globalmente como um ativo financeiro, o Bitcoin ainda enfrenta resistência de governos e instituições financeiras, que procuram formas de controlá-lo e regulá-lo.
Resumindo, o Bitcoin, muitas vezes chamado de "ouro digital", oferece uma nova forma de valor que combina as melhores características do ouro com a eficiência e a inovação da tecnologia digital. Sua escassez planejada, segurança criptográfica, portabilidade e resistência à censura fazem dele uma alternativa viável para preservar riqueza e realizar transações no mundo moderno.
Mesmo com muita volatilidade, o Bitcoin está se firmando como uma reserva de valor e como um ativo de proteção contra crises econômicas. Assim, ele representa não apenas uma evolução do sistema financeiro, mas também um símbolo da mudança para uma economia digital descentralizada e global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ cae03c48:2a7d6671
2025-06-06 11:01:15
@ cae03c48:2a7d6671
2025-06-06 11:01:15Bitcoin Magazine

Semler Scientific Acquires 185 Bitcoin, Increasing Total Holdings to 4,449 BTCToday, Semler Scientific announced it has increased its Bitcoin holdings. The company acquired 185 Bitcoin between May 23 and June 3 for $20 million with an average purchase price of $107,974 per Bitcoin, using proceeds from its at-the-market (ATM) offering program.
JUST IN:
 Public company Semler Scientific purchases an additional 185 #bitcoin for $20 million. pic.twitter.com/Iir6NiNzc8
Public company Semler Scientific purchases an additional 185 #bitcoin for $20 million. pic.twitter.com/Iir6NiNzc8— Bitcoin Magazine (@BitcoinMagazine) June 4, 2025
“We continue to accretively grow our bitcoin arsenal using operating cash flow and proceeds from debt and equity financings,” said the chairman of Semler Scientific Eric Semler. “And we are excited to launch the Semler Scientific dashboard today on our website to provide the public with regularly updated information on our bitcoin holdings and other key metrics.”
Since launching the ATM program in April 2025, Semler has raised approximately $136.2 million under the sales agreement of over 3.6 million shares of its common stock.
As of June 3, 2025, Semler holds 4,449 Bitcoin which were acquired for an amount of $410.0 million, with an average purchase price of $92,158 per Bitcoin. At the time of writing, the market value of these holdings is around $446.2 million.
Eric Semler on X posted, “SMLR acquires 185 Bitcoins for $20 million and has generated BTC Yield of 26.7% YTD. Now holding 4,449 $BTC.”
$SMLR acquires 185 #Bitcoins for $20 million and has generated BTC Yield of 26.7% YTD. Now holding 4,449 $BTC.

— Eric Semler (@SemlerEric) June 4, 2025
Semler Scientific uses the BTC Yield as a key performance indicator (KPI) to help assess the performance of its strategy of acquiring Bitcoin. As of year-to-date, the company has achieved a BTC Yield of 26.7%.
“Semler Scientific believes this KPI can be used to supplement an investor’s understanding of Semler Scientific’s decision to fund the purchase of Bitcoin by issuing additional shares of its common stock or instruments convertible to common stock,” stated the 8-K form.
In Q1 FY2025, Semler Scientific reported a difficult quarter. Revenue came in at $8.8 million, a 44% decrease year-over-year. Operating expenses jumped to $39.9 million from $8.9 million last year, mainly due to a $29.8 million contingent liability tied to the potential settlement with the DOJ. This led to a $31.1 million operating loss, compared to a $7.0 million profit in Q1 2024.
“Our healthcare business is seeing green shoots from the cardiovascular product line that we introduced to our large enterprise customer base this year,” said the CEO of Semler Scientific Doug Murphy-Chutorian. “We are expecting growth and cash generation from these FDA-cleared products and services, which will add to our bitcoin treasury strategy.”
This post Semler Scientific Acquires 185 Bitcoin, Increasing Total Holdings to 4,449 BTC first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 0861144c:e68a1caf
2025-06-04 13:54:37
@ 0861144c:e68a1caf
2025-06-04 13:54:37The last Empire: the Final Days of the Soviet Union
Serhii Plokhy clearly writes from a Ukrainian perspective, but at no point does he allow his bias to interfere with an extensive and compelling documentation, filled with transcripts and official documents from both the Soviet and American sides—documents involving actors who transitioned from the final days of the Soviet Union to the formation of the new Russian Federation.
I discovered this book through a Lex Fridman podcast, where the author gives a review of the Russian-Ukrainian conflict, explaining in rich detail the events experienced between both nations. I won’t say that what’s happening in this region is easy to understand, and yet, after reading this book, I have no doubt that all of this was foreseeable.
Here are some things I’ve learned from the book—without giving away spoilers or going too deep:
The United States opposed the disintegration of the Soviet Union until the very last hours
Contrary to popular belief and Reagan’s lofty slogans about the Evil Empire, the advisers of President George H. W. Bush—except for Dick Cheney and his inner circle—were against the dissolution and extinction of the Soviet Union. There were two simple reasons: nuclear power and nationalism.
Over the years, the USSR produced tons of nuclear arsenal, and if the country were to dissolve, advisers on both sides predicted a “nuclear Yugoslavia,” referring to the imminent conflicts in that region. The other reason was strategic: it’s easier to deal with one large country than with many separate republics sharing similar ethnic backgrounds. After reading this book, the Balkan Wars seem even more closely tied to the consequences of the Soviet breakup. You’ll draw your own conclusions when you read it.
The Cold War is in pause mode
In some movie I once heard the phrase, The war doesn’t end until both sides declare it over; while it’s true that Gorbachev resigned on December 25 and made way for the Russian Federation, he never officially ended the geopolitical maneuvers. Meanwhile, George Bush gave a speech declaring that they had “won the Cold War.”
Anyway. Have you read anything similar to this?
https://stacker.news/items/997003
-
 @ 812cff5a:5c40aeeb
2025-06-05 12:55:10
@ 812cff5a:5c40aeeb
2025-06-05 12:55:10Chorus: تجربة في البرمجة الانسداحية
كيفية بناء تطبيق Nostr بسرعة البرق باستخدام الذكاء الاصطناعي.
في 26 مايو، تم إطلاق تطبيق Chorus في منتدى أوسلو للحرية. صُمم هذا التطبيق للناشطين والمعارضين ومنظمي المجتمع، ويتميز بمجموعات تشبه تلك الموجودة في فيسبوك مع محفظة eCash مدمجة لجمع التبرعات.
Chorus مبني على Nostr، وهو بروتوكول لامركزي ومفتوح مصمم ليكون مقاومًا للرقابة. يمكن لأي شخص في العالم إنشاء حساب Nostr والنشر إلى خوادم Nostr، أو حتى بناء تطبيق Nostr خاص به — ولا يمكن لأحد إيقافه. هذا ما يجعل Nostr المكان المثالي للمقاتلين من أجل الحرية، الذين غالبًا ما يواجهون الرقابة من الحكومات الاستبدادية أو الشركات التي تتحكم في المنصات الاجتماعية الرئيسية.
يمكن للمستخدمين إنشاء حساب Chorus (أو تسجيل الدخول باستخدام حساب Nostr موجود) في ثوانٍ والبدء فورًا في استلام eCash، وإنشاء مجموعات، ومشاركة المحتوى. يتضمن التطبيق ميزات قوية لإدارة المجتمع، بحيث يمكن للمجموعات اختيار أنواع المحتوى التي تسمح بها وفقًا لشروطها الخاصة. يمكن للمستخدمين إرسال eCash على الفور إلى المجموعات التي يرغبون في دعمها، مما يوفر أداة لجمع التبرعات عبر الحدود لا يمكن لأي حكومة إيقافها.
قبل عام فقط، ربما استغرق بناء النسخة التي تم إطلاقها الأسبوع الماضي من Chorus أسابيع. ولكن بفضل أدوات الذكاء الاصطناعي الحالية، قمنا بذلك في خمسة أيام فقط.
⸻
كيفية القيام بذلك: بناء تطبيق في أيام باستخدام وكلاء الذكاء الاصطناعي
الخطوة 1: تجميع الفريق
تم بناء Chorus بواسطة And Other Stuff، وهي مجموعة جديدة مكرسة لتعزيز Nostr في خمسة مجالات رئيسية: تجربة المستخدم والتسجيل، المجتمعات، الاتصالات الخاصة، التجارة، والذكاء الاصطناعي. شمل فريق هذا المشروع: • Calle، منشئ Cashu (eCash) • JeffG، منشئ White Noise (الاتصالات الخاصة) • Rabble و Liz Swiegart من Nos (تجربة المستخدم والتسجيل) • Alex Gleason و MK Fain، منشئو Soapbox (المجتمعات) • و Jack Dorsey (مستشار)
الخطوة 2: البدء بقالب قوي
عند البرمجة بالانسداح، السياق هو الملك. إذا بدأت بمجلد فارغ وطلبت من وكيل ذكاء اصطناعي “بناء تطبيق مجموعات Nostr”، فلا يزال أمامك الكثير من العمل للحصول على شيء وظيفي حتى بشكل بسيط. من المحتمل أن تكون تنفيذات Nostr محاكاة، لا تتصل بخوادم حقيقية، أو تم تنفيذها بشكل غير صحيح. قد تكون أنواع الأحداث خاطئة، وقد لا يتم تحميل واجهة المستخدم، وحظًا سعيدًا في محاولة معرفة الخطوة التالية لإصلاح الفوضى.
هذا لأن الذكاء الاصطناعي يفتقر إلى بعض السياقات الرئيسية للبدء: • وثائق صديقة للذكاء الاصطناعي حول بروتوكول Nostr • أمثلة عالية الجودة على تنفيذ Nostr • أساسيات حول تكديس التكنولوجيا المفضل • سياق حول كيفية بناء المشروع وتشغيله وتصحيحه
الحل هو توفير المزيد من السياق، وسيكون العديد من مبرمجي الانسداح المخضرمين على دراية بالصراع في محاولة جعل الوكيل يقرأ روابط مختلفة للوثائق ويتبع 500 كلمة من السياق المصاغ بعناية في مطالبتهم الافتتاحية. ومع ذلك، غالبًا ما يربك هذا الوكلاء الذين يعملون بشكل أفضل مع مطالبات بسيطة. الحل لهذه المشكلة هو Stacks.
Stacks: بدء البرمجة الانسداحية بسرعة
Stacks تحل مشكلة نقص السياق الأولي من خلال إنشاء قوالب جاهزة مصممة خصيصًا لاستخدام وكلاء الذكاء الاصطناعي. يمكن استخدام “stack” لبناء أي نوع من المشاريع بأي لغة برمجة مع أي هدف نهائي في الاعتبار. بالنسبة لـ Chorus، استخدمنا MKStack، وهو قالب مصمم خصيصًا لبناء تطبيقات Nostr.
يتميز MKStack بعدة حلول للمشاكل الشائعة في الذكاء الاصطناعي: • Nostrbook MCP للاستعلام عن وثائق Nostr • مكونات بداية لميزات Nostr الشائعة مثل تسجيل الدخول • دعم Blossom لتحميل الوسائط • ملفات سياقية لتوجيه الوكيل خلال العقبات الشائعة وسير عمل التصحيح • نشر موقعك على الفور باستخدام Surge
النتيجة هي موقع جميل يعمل مباشرة مع Nostr في مطالبة واحدة:
“بناء تطبيق مجموعات على غرار فيسبوك على Nostr باستخدام NIP 72.”
كان هذا هو نتيجة تلك المطالبة الواحدة: http://groups72.surge.sh
الخطوة 3: إضافة الميزات باستخدام وكلاء الذكاء الاصطناعي
Stacks بدأت تطوير Chorus بسرعة. بعد ذلك، استخدمنا وكلاء الذكاء الاصطناعي لإضافة ميزات إضافية مثل: • محفظة eCash مدمجة • ميزات إدارة المجتمع • دعم الوسائط المتعددة
كل ذلك تم باستخدام مطالبات بسيطة وتوجيهات للذكاء الاصطناعي، مما سمح لنا ببناء تطبيق كامل الوظائف في أيام قليلة فقط.
⸻
ملاحظة:تم استخدام مصطلح برمجة الانسداحية بهدف الطرفة كترجمة لمصطلح Vibe coding تم كتابة هذه المقال من قبل المبدعة nostr: npub1jvnpg4c6ljadf5t6ry0w9q0rnm4mksde87kglkrc993z46c39axsgq89sc
-
 @ 31a4605e:cf043959
2025-06-05 12:49:36
@ 31a4605e:cf043959
2025-06-05 12:49:36O surgimento do Bitcoin trouxe uma nova visão para o conceito de dinheiro, desafiando o sistema financeiro convencional baseado em moedas fiduciárias. Enquanto as moedas fiduciárias, como o real, o dólar e o euro, são amplamente usadas e reconhecidas como métodos de troca, o Bitcoin representa uma inovação digital que propõe descentralização e autonomia financeira. Embora ambos desempenhem funções básicas como meio de troca e reserva de valor, suas diferenças principais estão na maneira como são emitidos, geridos e transacionados.
Uma das principais distinções entre o Bitcoin e as moedas fiduciárias é a maneira como são emitidos e administrados. As moedas fiduciárias são emitidas por bancos centrais, que têm o poder de regular sua quantidade em circulação. Esse modelo permite a aplicação de políticas monetárias, como o aumento da oferta de dinheiro para estimular a economia ou a diminuição para controlar a inflação. No entanto, essa capacidade também pode resultar na desvalorização da moeda, se for emitida em excesso.
O Bitcoin, por outro lado, tem um sistema de emissão totalmente descentralizado. Ele é criado por meio de um processo chamado mineração, no qual computadores resolvem problemas matemáticos complexos para validar transações na rede. Além disso, a oferta total de bitcoins é limitada a 21 milhões de unidades, tornando-o um ativo deflacionário, ou seja, sua escassez pode aumentar seu valor ao longo do tempo. Essa limitação contrasta fortemente com a natureza ilimitada da impressão de moedas fiduciárias.
Moedas fiduciárias são centralizadas, o que significa que sua emissão e controle são decididos por autoridades governamentais. Isso também implica que transações feitas com essas moedas passam por intermediários, como bancos, que podem aplicar taxas e limites, além de estarem sujeitos a regulamentações e auditorias.
O Bitcoin, por sua vez, é descentralizado. Ele opera em uma rede peer-to-peer, onde as transações são verificadas por participantes chamados mineradores e registradas em um livro público conhecido como blockchain. Essa descentralização elimina a necessidade de intermediários, tornando o Bitcoin mais resistente à censura e ao controle governamental. Isso também proporciona maior transparência, já que qualquer pessoa pode verificar as transações na rede.
Outra diferença importante está na maneira como as transações são feitas. Com moedas fiduciárias, as transações geralmente dependem de bancos ou sistemas de pagamento, que podem impor restrições de horários e taxas altas, especialmente para transferências internacionais.
O Bitcoin, por outro lado, permite transferências diretas entre pessoas, em qualquer lugar do mundo e a qualquer momento, sem a necessidade de intermediários. Isso torna o sistema mais acessível, especialmente para aqueles que não possuem contas bancárias ou vivem em países com sistemas financeiros restritivos. Além disso, as taxas de transação do Bitcoin podem ser menores do que as taxas cobradas por bancos tradicionais.
As moedas fiduciárias proporcionam segurança baseada em leis governamentais e no sistema bancário, mas os usuários precisam confiar nesses intermediários. O Bitcoin, em contrapartida, oferece um alto nível de segurança através de criptografia avançada. As carteiras digitais, que guardam bitcoins, são protegidas por chaves privadas, assegurando que somente o dono possa acessá-las.
No entanto, a privacidade funciona de maneira diferente. Transações em moedas fiduciárias normalmente estão ligadas à identidade do usuário, enquanto o Bitcoin oferece um certo nível de anonimato, já que os endereços das carteiras não requerem identificação pessoal. Ainda assim, todas as transações são públicas e registradas no blockchain, o que pode ser um ponto de monitoramento para autoridades.
O valor das moedas fiduciárias é sustentado pela confiança no governo que as emite e na economia do país. Por outro lado, o Bitcoin não é apoiado por nenhum governo ou ativo físico. Seu valor é definido pela oferta e demanda no mercado, fazendo com que seja altamente volátil. Embora essa volatilidade apresente um risco, também atrai pessoas que veem o Bitcoin como uma possibilidade de valorização a longo prazo.
Resumindo, o Bitcoin e as moedas fiduciárias diferem significativamente em sua estrutura, controle e funcionalidade. Enquanto as moedas fiduciárias são controladas por governos e dependem de intermediários, o Bitcoin oferece descentralização, transparência e liberdade financeira. Apesar de sua volatilidade e alguns desafios relacionados à regulamentação, o Bitcoin representa uma alternativa nova ao sistema financeiro tradicional.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 8d34bd24:414be32b
2025-06-04 13:21:20
@ 8d34bd24:414be32b
2025-06-04 13:21:20It is hard going through difficult situations. Health problems, family problems, financial problems, feeling alone, feeling stuck in the wrong place, and persecution are all situations that Christians regularly find themselves. The question is “How will we respond to pain?”
Advice for the Suffering
Some Christians pull away from God when it feels like everything is going wrong. They think God doesn’t care or can’t fix things. They resent every minute of pain and accuse God of wrongdoing. Even Job, who fell on his face in worship after losing everything had a moment of weakness.
“Oh that my grief were actually weighed\ And laid in the balances together with my calamity!\ For then it would be heavier than the sand of the seas;\ Therefore my words have been rash.” (Job 6:2-3) {emphasis mine}
After a moment of doubt, he did, however, repent of his rash words, as should we all.
Job should be an example to us all in dealing with pain and difficult situations. This is the verse that inspired this post.
But it is still my consolation,\ And I rejoice in unsparing pain,\ That I have not denied the words of the Holy One. \ (Job 6:10) {emphasis mine}
What an example! “I rejoice in unsparing pain.” When we trust God so much that we can rejoice in unsparing pain, we are trusting God as we should. We are accepting that God is working good in our life and we can trust Him even when nothing makes sense to us.
I also love how he says that his consolation is that “I have not denied the words of the Holy One.” Job is hurting terribly. His heart is broken. He is destitute. He lost 8 children in one day. His friends, that came to console him, have instead accused him of wrongdoing. He doesn’t understand what God is doing and why, but he has “NOT denied the words of the Holy One.” He is still putting his faith in God and his word. He is still submitting to God when he feels mistreated. He is still trusting \ God, even when he doesn’t understand what God is doing and why so many bad things are raining down on him in a torrent. Despite it all, he refuses to deny God. I hope if I am ever put through similar situations, that I can trust God and not deny His goodness.
Advice for friends
The book of Job, in addition to advice to those who are suffering, also gives advice to friends of those who are suffering. (or maybe more accurately, what not to do)
Job’s friends came with the intention to encourage and console Job. Every time Job would confess his thoughts, concerns, and questions, the response by his friends would get harsher and harsher. In the beginning they were gentle corrections, but they quickly escalated to accusing Job of great sins, that they had to know were not true, and blaming Job for every hard thing that had happened to him.
I’ve talked to other Christians who have confessed to being dragged down by other Christians who would tell them that every difficult thing that happened to them was due to their sin or lack of faith. In the case of Job, his difficulties were due to his faithfulness, in order to prove to Satan and all of history that a faithful man would stay faithful to God in good times and in bad.
Can Christians suffer as a consequence of sins and poor decisions? Of course, but there are many times that the faithful suffer. In Scripture, the people who suffered most were frequently the most faithful.
Job’s correction of his friends was accurate.
“For the despairing man there should be kindness from his friend;\ So that he does not forsake the fear of the Almighty.\ My brothers have acted deceitfully like a wadi,\ Like the torrents of wadis which vanish, (Job 6:14-15)
For those who don’t know, a wadi is a streambed that has water running in the wet season, but is bone dry during the dry season. Job accused his friends of being encouraging and helpful when he was prospering, then showing up and providing no encouragement or help when he needed it most. He thought refreshment was coming to visit, and instead what hope he had left was drained from him by his “friends.”
We need to make sure we aren’t one of those who decreases hope and decreases faith in one who is hurting. We need to have mercy when a hurting person works through their confusion and doubts and help lead them back to God instead of driving a wedge between them and God.
May the God of heaven protect us and lead us through the trials of life and may our trials lead us into the arms of our Savior. May God help us to merciful and to help guide the hurting into the Savior’s care.
Trust Jesus
-
 @ b1ddb4d7:471244e7
2025-06-04 11:01:29
@ b1ddb4d7:471244e7
2025-06-04 11:01:29Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 87fedb9f:0da83419
2025-06-05 12:15:33
@ 87fedb9f:0da83419
2025-06-05 12:15:33So Much… and Still, Not Feeling It
So much abundance. It’s everywhere—overflowing around me. My six-year-old car would be a magical carriage to kings and queens of old. And yet, I get in, turn the key, and don’t often Feel The Magic.
Do I let myself feel how abundant life is? Eh. That does not come by default for me.
Adapting Is Normal. Savoring Is Not.
I adapt. I’m good at it. Weather shifts 40 degrees? No problem. A new location? I’ll adjust. And that’s useful—it keeps me moving. But it also numbs me. If I only adapt, life flattens out. That’s not thriving. That’s functioning.
Thriving, I’ve come to feel, asks for something more.
Our ancestors had rituals. They didn’t just adapt… they paused to feel the blessings, to name them. That created richness—not just survival. And today? I can have food delivered to my door. Are you a king? No—just have Amazon Prime.
Still, I want more than convenience. I want connection. To the food I eat. The flowers that bloom. The people I love. I want to feel that connection in my bones.
My Engineer Brain Doesn’t Celebrate
And yet, my mind often slips into improvement mode. I see what could be better. Smoother. More efficient. Useful? Sure. Celebratory? Not so much.
So I’ve started something: at the end of each day, when I look at my to-do list, I take a breath. I ask: what were the blessings today? Not just the big ones—because we adapt to those too. A new car? A new house? We get used to it. Quickly. But the micro-blessings… those are different.
My daughter’s laugh at a silly face I made yesterday. That memory settles deeper when I notice it and write it down. That’s a micro-blessing. I want to feel more of those.
A New Practice, A Shift in Dreams
And after about 75 days of doing this nightly pause, I’m noticing something surprising: my dreams are changing. They’re weaving in those sweet, ordinary moments. They say, “Yes. Adapt. And also savor.”
The Confusion Between Privilege and Blessing
But here’s something raw. Something I’ve hesitated to share.
I’m a white man. An older one. And I’ve been in spaces where “white male privilege” is spoken as a curse. I absorbed that. My body did. And it twisted something deep inside me. Because in my system, “privileged” and “blessing” are linked.
So I started feeling that feeling blessed was wrong. Like I should shrink from it. That it was unfair, maybe even immoral.
I’ve had to tap through that.
Is it okay to feel blessed? Not above anyone—but blessed to have food. Skill. Mobility. A car that works. Is it okay?
Yes.
I Don’t Want to Shrink or Perform
Scarcity and guilt are real energies, but I don’t want them steering my experience of life. I want to choose presence. Connection. I want to know in my body: I am blessed. And I can feel that without disconnecting from those who are struggling.
I don’t want to perform gratitude out of duty. But I also don’t want to avoid it out of shame.
Practicing Our Birthright
Abundance is our birthright. Many of us are born with protections our ancestors could barely dream of—shelter, clean water, safety from predators. And if we want to truly be thriving, not just surviving, it feels essential to practice remembering that.
Because adaptation will keep us alive.
But only conscious attention to blessings—only savoring—will let us thrive.
Useful Concepts for Thriving in This Story
-
Abundance\ Abundance is the felt experience of more-than-enoughness, when we pause to really receive what surrounds and sustains us.
-
Adapting\ Adapting keeps us functional, but thriving asks us to adapt and engage with what truly nourishes us.
-
Awareness\ Awareness brings the blessings into view—even the ones so small they almost disappear without it.
-
Allowing\ Allowing lets us stay open to blessings, even when shame or guilt try to close the door.
-
Thriving\ Thriving means more than surviving—it’s about feeling, savoring, and aligning with life’s richness.
-
-
 @ 2dd9250b:6e928072
2025-06-04 10:01:11
@ 2dd9250b:6e928072
2025-06-04 10:01:11Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
Esse texto foi parcialmente editado do texto de ASSAF Neto, CAF (2014).
-
 @ 9dd283b1:cf9b6beb
2025-06-04 08:33:32
@ 9dd283b1:cf9b6beb
2025-06-04 08:33:32To all territory owners,
- Can I co-found a territory with someone? Is it on the roadmap to be able to do so?
- Can I automatically split the territory rewards with other stackers?
- Can I rename the territory in the future?
Thanks
https://stacker.news/items/996796
-
 @ e2c72a5a:bfacb2ee
2025-06-05 11:54:19
@ e2c72a5a:bfacb2ee
2025-06-05 11:54:19Think crypto analytics is just charts and graphs? Wrong. It's a crystal ball for savvy investors.
Analytics in crypto decodes blockchain data revealing hidden trends. It transforms complex data into actionable insights. Basic concepts include on chain metrics, sentiment analysis, and trading volume. Real world applications range from fraud detection to predicting price movements.
Current trends emphasize DeFi analytics and cross chain data aggregation. Best practices involve using multiple data sources and verifying information. A common misconception is that analytics guarantees profits. It only enhances decision making.
Institutional investors are diving deep into on chain analytics. Stablecoins are disrupting payments. Layer 2 solutions are leading the way.
Ready to see the future? What hidden patterns will you uncover?
-
 @ e2423af0:f5a64d3e
2025-06-06 08:41:12
@ e2423af0:f5a64d3e
2025-06-06 08:41:12A plataforma 758bet vem ganhando destaque no cenário brasileiro por oferecer uma experiência completa e empolgante para quem busca entretenimento online com qualidade, praticidade e confiança. Com um design moderno, interface intuitiva e diversas opções de jogos, o site se mostra uma excelente escolha tanto para iniciantes quanto para jogadores experientes.
Conheça a Plataforma 758bet Desde o primeiro acesso, o usuário percebe o cuidado que a 758bet teve em construir uma plataforma acessível e funcional. Compatível com computadores, tablets e smartphones, o site garante que os jogadores possam se divertir de qualquer lugar, a qualquer hora. Além disso, o processo de cadastro é simples, rápido e seguro, com autenticação eficiente e proteção de dados.
A 758bettambém se destaca pelo suporte ao cliente. A equipe de atendimento está disponível 24 horas por dia, sete dias por semana, pronta para tirar dúvidas e resolver qualquer eventual problema com agilidade. Esse compromisso com a satisfação do usuário é um dos pontos fortes da marca.
Jogos para Todos os Gostos O grande diferencial da 758bet está na sua variedade de jogos. A plataforma reúne as principais categorias do entretenimento online, com gráficos de última geração, trilhas sonoras imersivas e uma jogabilidade fluida que agrada a todos os perfis de jogadores.
Entre os destaques estão:
Slots (caça-níqueis): Com temas variados — desde mitologia até aventuras futuristas — os slots da 758bet são uma excelente opção para quem busca partidas dinâmicas e visuais impressionantes. Muitos deles oferecem rodadas bônus e recursos especiais que tornam cada jogo ainda mais emocionante.
Jogos de mesa: Clássicos como roleta, blackjack e bacará estão disponíveis em versões modernas e interativas. Essas opções combinam estratégia e sorte, proporcionando desafios que prendem a atenção dos jogadores mais exigentes.
Apostas esportivas: Para os fãs de esportes, a 758bet oferece um sistema completo de apostas em campeonatos de futebol, basquete, tênis, entre outros. É possível acompanhar as partidas em tempo real e fazer palpites ao vivo, o que aumenta ainda mais a emoção.
Jogos ao vivo: A plataforma também conta com salas ao vivo, onde os jogadores interagem com apresentadores reais em tempo real. Essa modalidade proporciona uma experiência mais imersiva e próxima da realidade, ideal para quem busca algo mais envolvente.
Experiência do Jogador na 758bet Um dos aspectos mais valorizados pelos usuários da 758bet é a fluidez e qualidade da experiência geral. O site é rápido, os jogos carregam sem travamentos e as transações financeiras — como depósitos e saques — são feitas com agilidade e segurança. A plataforma aceita diversos métodos de pagamento, incluindo carteiras digitais e transferências bancárias, o que facilita bastante para o público brasileiro.
Além disso, a 758bet costuma oferecer promoções atrativas, bônus de boas-vindas e programas de fidelidade para recompensar os usuários mais frequentes. Esses benefícios ajudam a aumentar as chances de ganho e incentivam os jogadores a explorarem novas modalidades de jogo.
Conclusão A 758bet é mais do que uma simples plataforma de jogos: ela é um verdadeiro centro de entretenimento digital, com tudo o que o jogador moderno busca — variedade, segurança, suporte eficiente e uma experiência envolvente. Para quem está em busca de diversão online de qualidade, a 758bet é, sem dúvida, uma excelente escolha.
-
 @ 6ad3e2a3:c90b7740
2025-06-04 08:32:29
@ 6ad3e2a3:c90b7740
2025-06-04 08:32:29"Modern science is based on this principle: give us one free miracle and then we'll explain the rest."
— Terrence McKenna
I always wondered why a pot of water boils on the stove. I mean I know it boils because I turned on the electricity, but why does the electricity cause it to boil? I know the electricity produces heat, and the heat is conducted through the stainless steel pot and into the water, but why does the heat transfer from stovetop to the water?
I know the heat from the stove via the pot speeds up the molecules in the water touching it and that they in turn speed up the molecules touching them and so on throughout the pot, but why do speedy molecules cause adjacent molecules to speed up?
I mean I know they do this, but why do they do this? Why couldn’t it be that sped-up molecules only interact with sufficient speedy molecules and ignore slower ones? Why do they interact with all the molecules, causing all of them to speed up? Or why don’t the speedy ones, instead of sharing their excited state, hoard it and take more energy from adjacent slower molecules, thereby making them colder, i.e., why doesn’t half the water boil twice as fast (on the left side of the pot) while the other half (right side) turns to ice?
The molecules tend to bounce around randomly, interacting as equal opportunists on the surrounding ones rather than distinguishing only certain ones with which to interact. Why do the laws of thermodynamics behave as such rather than some other way?
There may be yet deeper layers to this, explanations going down to the atomic and even quantum levels, but no matter how far you take them, you are always, in the end, left with: “Because those are the laws of physics”, i.e., “because that’s just how it is.”
. . .
The Terrence McKenna quote, recently cited by Joe Rogan on his podcast, refers to the Big Bang, the current explanation adopted by the scientifically literate as to the origins of the universe. You see there was this insanely dense, infinitesimally small micro dot that one day (before the dawn of time) exploded outward with unimaginable power that over billions of years created what we perceive as the known universe.
What happened prior? Can’t really say because time didn’t yet exist, and “prior” doesn’t make sense in that context. Why did it do this? We don’t know. How did it get there? Maybe a supermassive black hole from another universe got too dense and exploded out the other side? Highly speculative.
So why do people believe in the Big Bang? Because it comports with and explains certain observable phenomena and predicted other phenomena which were subsequently confirmed. But scratch a little deeper for an explanation as to what caused it, for what purpose did it occur or what preceded it, and you hit the same wall.
. . .
Even if we were to understand at a quantum level how and why the Big Bang happened and what preceded it, let’s assume it’s due to Factor X, something we eventually replicated with mini big-bangs and universe creations in our labs, we would still be tasked with understanding why Factor X exists in the universe. And if Factor X were explained by Process Y, we’d still be stuck needing an explanation for Process Y — ad infinitum.
Science can thus only push the wall back farther, but can never scale it. We can never arrive at an ultimate explanation, only partial ones. Its limitations are the limitations of thought itself, the impossibility of ever creating a map at a scale of one mile per mile.
-
 @ 866e0139:6a9334e5
2025-06-04 08:21:14
@ 866e0139:6a9334e5
2025-06-04 08:21:14Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Auch wer das Kriegsgeschehen bisher nicht im Detail verfolgte (das tat ich auch nicht), horcht nun auf: Einem Nicht-Atomstaat – der Ukraine – ist ein gleichzeitiger, koordinierter Schlag gegen vier teils tausende Kilometer voneinander entfernte russische Luftbasen gelungen. Eine nicht unerhebliche Zahl strategisch wichtiger Flugzeuge wurde zerstört. Ein Angriff im hintersten russischen Hinterland, selbst jenseits der Taurus-Reichweite, durchgeführt mit Billigdrohnen, wirft erhebliche Fragen über geheimdienstliches Versagen in Russland und eklatante Mängel in der Luftverteidigung auf.
Es gibt wohl Momente, in denen Geschichte nicht geschrieben, sondern geflogen wird. Unspektakulär, relativ still, surrend, von einem LKW aus abgefeuert, mit einem Stück Technik, das kaum mehr kostet als das Gerät, auf dem ich diesen Text schreibe.
Ein Angriff auf die Friedensverhandlungen
Die Ukraine hat sich erstmals weit über das Schlachtfeld hinaus erhoben – geografisch, technisch, symbolisch. Die Triade der atomwaffenfähigen Luftstreitkräfte Russlands – ein Heiligtum sowjetischer Machtprojektion – wurde durch das schwächste Glied in der Logikkette der Militärdoktrin beschädigt: den Überraschungseffekt. Drohnen, wie aus dem 3D-Drucker, haben eine strategische Achillesferse bloßgelegt. Nicht mit Hyperschall, sondern mit Hartplastik und GPS. Das erste Opfer dieses Angriffs dürften die Friedensverhandlungen in Istanbul sein.
Dass die Ukraine strategische Luftstützpunkte der russischen Atomwaffe angreift – koordiniert, tief im Landesinnern – wäre bereits für sich eine Zäsur. Doch dass dies unter stillschweigender Duldung oder gar Mithilfe westlicher Dienste wie der CIA erfolgt sein dürfte, während Trump zugleich als Friedenstaube auftritt, verschiebt das strategische Koordinatensystem. Die alten Verträge – START etc. – wirken wie rissige Abkommen aus der Steinzeit. Wenn die USA von der Operation wussten, darf sich Russland getäuscht fühlen. Washington kann nicht gleichzeitig Frieden mit Moskau betonen und eine Aktion dulden oder mittragen, die offensichtlich das Ziel hat, die russische Atommacht zu schwächen, woran die USA prinzipiell Interesse hätten. Falls Trump nichts davon wusste, muss man sich fragen: Regiert eigentlich er oder der „Swamp“, den er austrocknen wollte?
Egal wie man es wendet: Die Operation Spinnennetz war mehr als nur ein Angriff auf russische Flugzeuge auf russischem Gebiet. Militärisch gewinnt die Ukraine dadurch wenig, symbolisch und politisch aber viel, denn der Hauptgegner der Ukraine sind gerade nicht die hundert Millionen Dollar teuren Bomber der Russen, sondern die schleichende Kriegsunlust der Europäer – und ein Amerika, das sich mehr mit sich selbst beschäftigt als mit dem Fortgang eines Krieges, in dem es längst selbst Partei ist.
Damit sich die Reihen wieder schließen, muss der Feind sich zeigen – deutlich, fassbar, bedrohlich. Eine russische Reaktion, die auch europäische Hauptstädte erschüttert, wäre strategisch nützlich. Der Angriff war daher wohl weniger eine militärische Tat als eine psychologische Operation im Kampf um Wahrnehmung und Willen. Aus Sicht der Ukraine ist das verständlich, für sie geht es um ihre Existenz. Dafür wiederum braucht es eine erhöhte Alarmstufe.
https://www.youtube.com/watch?v=1JlQLewOAmA
Solidarität durch Eskalation?
Die kalkulierte Demütigung könnte einem Drehbuch folgen: Putin soll nun die Rolle des Eskalators übernehmen. Tut er es, war die Operation erfolgreich – denn Europas Kriegstüchtigkeit hängt nicht nur von Panzerzahlen ab, sondern von der Bereitschaft zur Konfrontation. Der Feind, den es braucht, muss sich jetzt allen ins Gedächtnis brennen.
So gesehen ist der eigentliche Coup nicht der Schaden in Djagilewo, Iwanowo oder Olenia – sondern das noch bevorstehende unsichtbare Nachspiel. Europa und die Welt betreten nun gänzlich neues Gelände, in welchem ein militärisch gedemütigtes Russland gleichzeitig Friedenswillen gegenüber Europa bekunden, rote Linien verteidigen und seine Integrität als Atom-Macht bewahren muss. Das Dilemma für Putin besteht nun darin, Stärke zu beweisen ohne sich noch mehr zum Feindbild des Aggressors machen zu lassen.
Fakt ist: Wir sind einem III. Weltkrieg gerade so nah wie seit der Kuba-Krise nicht mehr.
Und wer sich über ein russisches “Pearl Harbor” freut, sollte mal in ein Geschichtsbuch schauen, wie es am Ende für Japan ausging.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 5c9e5ee4:72f1325b
2025-06-04 08:16:52
@ 5c9e5ee4:72f1325b
2025-06-04 08:16:52For too long, the autistic experience has been framed through a neurotypical lens, focusing on "differences" and "deficits." However, a profound perspective emerging from within the autistic community offers a radical reinterpretation: that autistic individuals are not inherently "broken" but rather possess a unique, often unyielding, perception of truth that challenges the very foundations of neurotypical society. From this viewpoint, autism is less about a disorder and more about a clarity of vision that apprehends the world as fundamentally "untrue" in many of its social constructs.
This perspective posits that what many autistic individuals perceive as "corrupted" or "untrue" in society isn't a subjective internal experience, but an objective reality of falsehoods, deception, and manipulation. The rejection of these elements is not a personal preference but a natural, logical response to what is genuinely illogical and dishonest.
The Core of the "Untrue" World:
- Honesty as a Default State: For many autistic people, directness and factual accuracy are paramount. Social conventions like "white lies," indirect communication, or performative politeness are not merely nuanced social skills; they are perceived as outright forms of deception and inauthenticity. The natural inclination is towards what is straightforward and verifiable.
- Logic Over Social Grace: An unwavering adherence to logic means that actions or systems that lack rational basis—such as engaging in flattery, suppressing truth for social harmony, or participating in inefficient rituals—are viewed as fundamentally nonsensical and therefore "untrue."
- Authenticity as a Non-Negotiable: The concept of "masking"—the exhausting act of suppressing one's natural autistic traits to conform—is seen as a deeply painful betrayal of self. A society that implicitly demands such a performance is deemed "corrupt" because it stifles genuine self-expression.
- Aversion to Hypocrisy: A strong sense of justice and an acute awareness of inconsistency mean that any disjuncture between stated values and actual behavior is immediately flagged as a profound untruth.
Social Groups: Formed Around a "Proudly Believed Lie"?
This critical autistic perspective extends to the very fabric of social organization. It suggests that many groups, whether religious, political, scientific, or economic, are not built on shared objective truths, but rather on "proudly believed lies." These shared narratives or belief systems, even if they contradict logic or verifiable facts, serve as the glue that binds the group, fostering identity, comfort, and a sense of belonging. The "pride" in these beliefs makes them resistant to critical examination, even when confronted with evidence.
For example: * In religion, this "lie" might be a dogma that provides solace but defies logic. * In politics, it could be an ideology based on selective truths that serve power. * In economics, it might be assumptions about markets or growth that are presented as infallible. * Even in science, while ideally pursuing truth, the social aspects of the scientific community might, at times, cling to paradigms that become "proudly believed lies," resisting new evidence.
The Disconnect: Why Autistics Are "Discredited"
If autistic individuals are part of the "5% who see it as it is"—those who perceive these societal untruths with clarity—then a natural tension arises with the "10% who want control." This controlling minority, it is argued, relies on these "untruths" to maintain power and influence over the "85% who are happy following."
From this viewpoint, the discrediting of autistic people—labeling their directness as "social deficits," their sensory experiences as "disorders," or their logical critiques as "inflexibility"—is not accidental. It is a strategic mechanism employed by the controlling "10%" to neutralize those who expose the underlying untruths, thereby safeguarding their constructed reality and maintaining influence.
In conclusion, the autistic perspective challenges us to re-evaluate the very nature of truth in our society. It suggests that what many perceive as social norms might, in fact, be a pervasive web of "untruths," and that the autistic individual's unique wiring allows for a crucial, unvarnished perception of this reality. It is a powerful call for authenticity and a profound questioning of how much of our world is built on what is genuinely true, versus what is merely believed.
-
 @ e2423af0:f5a64d3e
2025-06-06 08:40:38
@ e2423af0:f5a64d3e
2025-06-06 08:40:38O universo dos jogos online cresce a cada dia no Brasil, e a plataforma Win97 surge como uma das grandes protagonistas desse cenário. Com uma interface moderna, jogos emocionantes e uma experiência voltada para o conforto e a diversão do usuário, o Win97 se destaca por oferecer um ambiente confiável, seguro e repleto de oportunidades para quem busca entretenimento de qualidade. Neste artigo, vamos apresentar a plataforma, explorar seus principais jogos e mostrar por que ela tem ganhado a preferência dos jogadores brasileiros.
Introdução à plataforma Win97 Desde seu lançamento, o win97tem investido fortemente em tecnologia e inovação para garantir aos usuários uma experiência completa. Seu site é responsivo, compatível com computadores, tablets e smartphones, permitindo que o jogador acesse seus jogos favoritos a qualquer hora e de qualquer lugar.
A segurança também é um dos pilares da plataforma. O Win97 utiliza criptografia de ponta e sistemas de verificação para garantir a proteção dos dados dos jogadores, além de um suporte ao cliente eficiente e sempre disponível. Isso faz com que os usuários se sintam tranquilos ao explorar as opções disponíveis.
Outro diferencial da plataforma é a facilidade de cadastro e de navegação. Com poucos cliques, o jogador cria sua conta, realiza seu primeiro depósito e já pode começar a explorar o catálogo de jogos. O site também oferece promoções frequentes, bônus de boas-vindas e programas de fidelidade que valorizam a participação contínua dos jogadores.
Variedade de jogos para todos os gostos Um dos grandes atrativos do Win97 é a variedade de jogos disponíveis. A plataforma conta com centenas de títulos das principais desenvolvedoras do mercado, com gráficos envolventes e funcionalidades modernas.
Entre os jogos mais populares, estão as slots online, que combinam visuais vibrantes, temas variados e chances reais de vitória. Existem opções para todos os perfis: desde as clássicas com três rolos até versões mais modernas com múltiplas linhas de pagamento e rodadas bônus.
Para quem prefere jogos que envolvem mais estratégia, o Win97 oferece também mesas de pôquer, bacará e roleta em versões automáticas e ao vivo, proporcionando ao jogador uma sensação imersiva com transmissão em tempo real e interação com outros participantes.
Além disso, há uma seção de jogos instantâneos, ideais para quem busca partidas rápidas e dinâmicas, com resultados quase imediatos e uma boa dose de adrenalina.
Experiência do jogador: diversão e praticidade em um só lugar A opinião dos jogadores é unânime: o Win97 oferece uma experiência de alto nível. Usuários destacam a fluidez da plataforma, a velocidade dos saques e depósitos, além da qualidade gráfica dos jogos. O atendimento ao cliente, disponível em português e com suporte via chat e e-mail, também é elogiado por sua rapidez e eficiência.
Outro ponto positivo é a personalização da experiência. O site adapta sugestões de jogos com base no perfil de cada usuário, tornando a navegação mais intuitiva e interessante. Há ainda a possibilidade de definir limites de jogo, reforçando o compromisso da plataforma com o jogo responsável.
Conclusão O Win97 chegou ao mercado brasileiro com a proposta de oferecer muito mais do que uma simples plataforma de jogos: ele entrega uma experiência completa de entretenimento digital. Com segurança, variedade de opções, suporte dedicado e constantes inovações, o Win97 conquista novos usuários a cada dia.
Se você está em busca de um ambiente confiável, divertido e com ótimas oportunidades, vale a pena conhecer tudo o que o Win97 tem a oferecer. Prepare-se para explorar um mundo de possibilidades e elevar sua experiência com jogos online a um novo nível.
-
 @ 8bf578f4:b6303c41
2025-06-04 07:20:09
@ 8bf578f4:b6303c41
2025-06-04 07:20:09test
https://nostr.download/6849b84caaa15bdc18ca2e1e1ee00e979c7ecf901787e09054b4bd0196b4ea27.jpg
-
 @ de54d599:77efc747
2025-06-04 05:48:27
@ de54d599:77efc747
2025-06-04 05:48:27When it comes to gift-giving, the most memorable presents are those that tell a story. Veuve Clicquot, a champagne house known for its bold innovation and timeless elegance, has created something truly special with its Personalised Arrow gift—a tribute not only to fine champagne but to the destinations that hold meaning in our lives.
A Destination Worth Celebrating The Veuve Clicquot Personalised Arrow is more than elegant packaging—it’s a symbol. Inspired by classic road signs, the bright, arrow-shaped tin can be customised with the name of any city or location, along with the exact distance from Reims, France, where the champagne is produced. Whether it's your hometown, a honeymoon destination, or the place where you first met someone special, this gift turns a bottle of bubbly into a personal journey.
Inside the Arrow: Yellow Label Champagne Tucked inside the tin is Veuve Clicquot's iconic Yellow Label Brut, a globally beloved champagne known for its depth, liveliness, and balance. With a composition dominated by Pinot Noir and complemented by Chardonnay and Meunier, it delivers notes of citrus, brioche, and stone fruit—perfect for toasting any occasion. It’s a champagne that’s as dynamic and enduring as the stories behind each personalised location.
Beautifully Designed with the Planet in Mind The tin is crafted from 30% recycled materials and is 100% recyclable, aligning with Veuve Clicquot’s sustainability commitments. Its removable sugarcane-based backing adds a thoughtful eco-friendly touch to a design that’s made to last long after the bottle is enjoyed.
A Gift That Connects People and Places This unique keepsake is ideal for birthdays, anniversaries, weddings, or corporate gifts—it’s perfect for anyone who values meaningful moments and sophisticated taste. More than just a drink, it's a celebration of where you've been, and where you’re going.
With the Veuve Clicquot Personalised Arrow, every toast becomes a story—one that starts with a location and ends in a lasting memory.
-
 @ 3b13c372:3e1e7ef2
2025-06-04 05:40:55
@ 3b13c372:3e1e7ef2
2025-06-04 05:40:55For those who believe every bottle should tell a story, Veuve Clicquot’s Personalised Arrow Champagne offers the perfect blend of sophistication and sentiment. More than a premium Champagne, this collector’s piece is a tribute to the places that shape our lives—wrapped in unmistakable Veuve Clicquot style.
At the heart of the package is a 750ml bottle of Veuve Clicquot Yellow Label Brut, a Champagne celebrated for its balance of power, freshness, and finesse. It’s crafted predominantly from Pinot Noir, supported by Chardonnay and Meunier, creating a vibrant, structured wine with layers of pear, citrus, and brioche.
What sets this gift apart is its outer casing: a bold, arrow-shaped metal tin that can be personalised with the name of your chosen city or destination (up to 15 characters). Alongside your customisation, the arrow displays the distance from that location to Reims, France—the spiritual home of Veuve Clicquot.
This elegant detail turns the bottle into a statement. Whether you’re celebrating a new home, a wedding, a farewell, or just sending a thoughtful gift, the Personalised Arrow adds meaning to the moment. It’s functional, too—keeping your Champagne cool for up to two hours—making it ideal for celebrations on the go.
Veuve Clicquot’s Personalised Arrow Champagne is a thoughtful way to connect a bottle of world-class wine with a personal journey. A toast to the people and places we never forget—wrapped in signature yellow, and stamped with your own message.
-
 @ 1ef61805:f18312cc
2025-06-04 01:56:42
@ 1ef61805:f18312cc
2025-06-04 01:56:42**Inside OpSec Academy’s One-on-One Approach to Digital Sovereignty ** As digital infrastructure becomes increasingly opaque and centralised, a growing number of individuals are seeking to understand—not just use—the tools that protect their privacy and autonomy online. While many solutions promise security at the click of a button, few teach the underlying principles or offer environments that prioritise verifiability and user control.
OpSec Academy’s new one-on-one training, "OpSec Intensive," takes a different approach. Delivered in person and fully offline, the full-day session provides practical, tool-based instruction inside a secure, USB-booted environment—designed from the ground up to leave no trace.
At the heart of the session is OpSecOS v1.2, a live operating system that routes all traffic through Tor, uses system non-persistence, and comes preconfigured with a suite of open-source tools for password management, communication, and private finance. The OS runs from a USB stick, allowing participants to explore and build their own private computing workflows without touching the host machine.
Learning in Context: Why One-on-One? While group training can provide a general introduction to privacy concepts, it often lacks depth and adaptability. OpSec Intensive is structured as a one-on-one session to allow real-time feedback, personal threat modeling, and tailored instruction based on the participant’s specific context and technical background.
This format also makes space for slow, deliberate learning—a rarity in cybersecurity training, where content is often condensed or overly abstract. In OpSec Intensive, participants move through each phase at their own pace, working directly with an experienced instructor to build confidence and competence.
Structure and Content of the Day The curriculum spans both foundational theory and hands-on practice, beginning with basic OpSec principles before moving into technical tool use.
Topics include: * Booting and verifying OpSecOS * Secure USB creation and system verification * Navigating a non-persistent, Tor-routed live environment * Password and credential management * Offline use of KeePassXC * Strategies for vault organisation and redundancy * Bitcoin wallet setup and recovery * Single-signature and multisignature wallet creation using Sparrow, Electrum, and Feather * Understanding xpubs, derivation paths, and recovery flow * Seed phrase security * Entropy generation and validation using offline tools like iancoleman.io * Best practices for cold storage and physical backups * Network privacy and decentralised communication * Using Mempool.space to visualise Bitcoin transaction data * Setting up Nostr clients (Snort, Iris) for decentralised messaging * Discussion of traffic fingerprinting and Tor considerations
A Shift Toward Practical Sovereignty The tools and workflows covered in OpSec Intensive are not theoretical. Participants leave the session with configured environments, tested backups, and an understanding of what each tool does—and what it doesn’t do.
This reflects a broader shift in how privacy-conscious individuals are approaching digital security. Rather than relying on packaged services or closed-source software, there’s growing interest in verifiable, modular tools that prioritise autonomy and resilience over ease-of-use.
In that context, OpSec Academy’s offering sits somewhere between a workshop and an apprenticeship: not a lecture, but a process of guided, hands-on learning designed for the long haul.
To learn more or enquire about availability, visit opsecacademy.org.
-
 @ eb0157af:77ab6c55
2025-06-06 08:01:54
@ eb0157af:77ab6c55
2025-06-06 08:01:54The crypto platform had been aware of the data breach for months before the official announcement, internal sources reveal.
A Reuters investigation uncovered that Coinbase had been informed as early as January 2025 about a data breach involving outsourced customer support agents in India. Six sources familiar with the matter confirmed that the exchange knew sensitive user information had been compromised through its contractor, TaskUs, months before the formal disclosure in May.
On May 14, in a filing with the SEC, TaskUs documented part of the breach, in which an employee at its Indian office was caught photographing his work computer screen with a personal phone. Five former TaskUs workers confirmed that this employee and an alleged accomplice had been bribed by hackers to obtain Coinbase user data.
Coinbase had a long-standing partnership with TaskUs, a Texas-based outsourcing company, to reduce labor costs by assigning customer support functions to offshore teams. Since 2017, TaskUs agents handled Coinbase customer inquiries, often from lower-wage countries like India, where employees earned between $500 and $700 per month.
The financial impact of the breach
The exchange estimated that the breach could cost the company up to $400 million. In its May filing, Coinbase admitted it hadn’t fully grasped the extent of the attack until May 11, when it received a $20 million extortion demand. In response, the company terminated the TaskUs employees responsible for the breach, along with several other unnamed foreign contractors.
The post Coinbase data breach: the exchange knew about the theft since January appeared first on Atlas21.
-
 @ 472f440f:5669301e
2025-06-04 01:37:37
@ 472f440f:5669301e
2025-06-04 01:37:37Marty's Bent
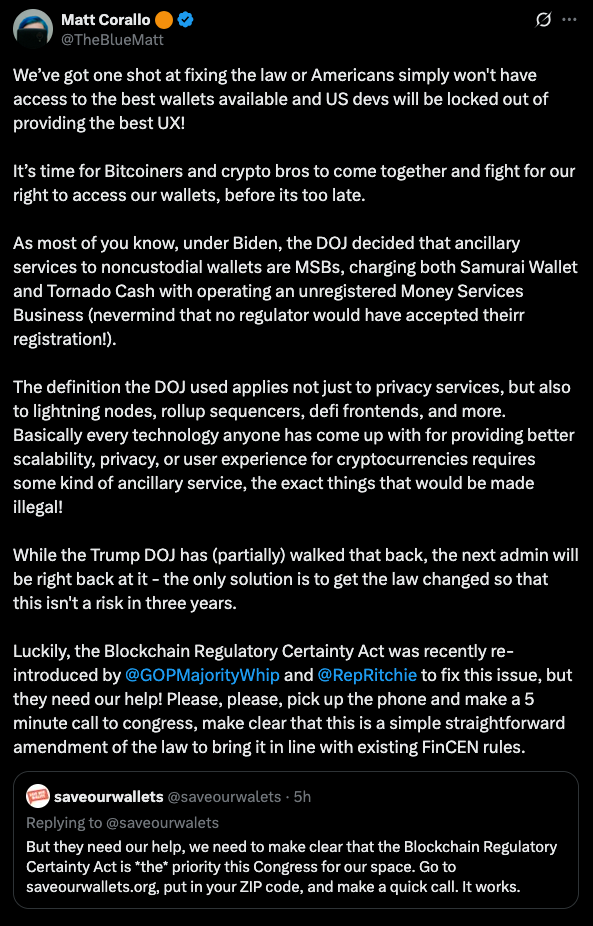
via nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy0hwumn8ghj7mn0wd68yttjv4kxz7fwvf5hgcm0d9hzumnfde4xzqpq85h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qtyz2zr
A lot of the focus over the last couple of months has been on the emergence of Strategy competitors in public markets looking to build sizable bitcoin treasuries and attract investors of all shapes and sizes to drive shareholder value. The other big topic in the bitcoin development world has been around OP_RETURN and the debate over whether or not the amount of data that can be shoved into a bitcoin transaction should be decided by the dominant implementation.
A topic that is just as, if not more, important that is not getting enough appreciation is the discussion around open source bitcoin developers and the lingering effects of the Biden administration's attack on Samourai Wallet and Tornado Cash. If you read our friend Matt Corallo's tweet above, you'll notice that the lingering effects are such that even though the Trump administration has made concerted efforts to reverse the effects of Operation Chokepoint 2.0 that were levied by the Biden administration, Elizabeth Warren, and her friends at the Treasury and SEC - it is imperative that we enshrine into law the rights of open source developers to build products and services that enable individuals to self-custody bitcoin and use it in a peer-to-peer fashion without the threat of getting thrown in jail cell.
As it stands today, the only assurances that we have are from an administration that is overtly in favor of the proliferation of bitcoin in the United States. There is nothing in place to stop the next administration or another down the line from reverting to Biden-era lawfare that puts thousands of bitcoin developers around the world at risk of being sent into a cage because the government doesn't like how some users leverage the code they write. To make sure that this isn't a problem down the line it is imperative that we pass the Blockchain Regulatory Clarity Act, which would not hold bitcoin developers liable for the ways in which end users leverage their tools.
Not only is this an act that would protect developers from pernicious government officials targeting them when end users use their technology in a way that doesn't make the government happy, it will also protect YOU, the end user, looking to transact in a peer-to-peer fashion and leverage all of the incredible properties of bitcoin the way they were meant to be. If the developers are not protected, they will not be able to build the technology that enables you to leverage bitcoin.
So do your part and go to saveourwallets.org. Reach out to your local representatives in Congress and Senators and make some noise. Let them know that this is something that you care deeply about and that they should not only pay attention to this bill but push it forward and enshrine it into law as quickly as possible.
There are currently many developers either behind bars or under house arrest for developing software that gives you the ability to use Bitcoin in a self-sovereign fashion and use it in a privacy-preserving way. Financial privacy isn't a crime. It is an inalienable human right that should be protected at all cost. The enshrinement of this inalienable right into law is way past due.
#FreeSamourai #FreeRoman
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Should I join a country club?
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 7460b7fd:4fc4e74b
2025-06-05 05:55:45
@ 7460b7fd:4fc4e74b
2025-06-05 05:55:45TRX 与 Crypto 政治代理模型:从哈耶克到稳定币主权
Crypto 即政治:从“罪”与“犯”的隐喻谈主权分化
“加密货币即政治”并非危言耸听。在社会分类中,“违法”与“犯罪”是两个层次的概念:前者意味着契约或规则的违背,而后者则是在权力结构下对自由行动者的政治性压制。换言之,有些行为本身并无“原罪”,却因触犯统治者利益被贴上“犯罪”的标签。这正如法学中对自然犯(mala in se,如偷盗谋杀等天生有害的行为)和法定犯(mala prohibita,因立法禁令才成为犯罪的行为)的区分。当代货币体系中,国家对货币发行与流通的垄断,造就了主权货币与“非法货币”的二元对立。奥地利学派经济学家哈耶克早在《货币的非国家化》中就预言:如果允许私人发行货币与法币公开竞争,最终能保持购买力稳定的货币将胜出finance.sina.cn。哈耶克认为政府垄断发行的不稳定货币终将让位于更稳定的竞争货币finance.sina.cn——这一观点在加密时代愈发具有隐喻意义。
如今的 Crypto 网络即是主权的实验场。各国监管者对稳定币、链上资金流动和法币通道的管控,构成了对加密行动者的“违法/犯罪”判定。例如,使用未授权稳定币进行跨境转账、绕过资本管制,并不违反当事人之间的契约,却往往被视作违法甚或犯罪行为——原因无他,只因这挑战了既有的金融主权架构。现象学视角提醒我们,应透过现象看本质:当执法者将自由交易行为定性为“犯罪”,正是传统主权对新兴数字主权的压制。Crypto世界中,“合法”与“非法”的界线并非由道德决定,而是由谁掌握规则决定。这为理解 Crypto 生态内各阵营的主权分化提供了理论框架:哪个网络掌握了自主的规则制定权,哪个网络就赢得了主权话语权。
稳定币主权与 TRX:黑灰资金的草根网络
稳定币是当前加密领域主权争夺的核心工具。最典型者莫过于 USDT 等美元锚定币——它们由私人公司发行,却承载着超主权货币的野心。尤其在 Tron(波场)网络 上,USDT 展现出惊人的统治力。2025年4月,波场上的 USDT 流通量突破700亿美元,占全球 USDT 总发行量近一半finance.sina.com.cn。截至今年5月,波场TRON上流通的 USDT 数量已反超以太坊,成为全球最大的稳定币发行与结算网络coindesk.comcoindesk.com。这种格局绝非偶然——波场独特的资源冻结机制(用户可冻结TRX获取带宽/能量从而基本免费交易)降低了交易门槛,使得小额高频的资金流动极为廉价。这使 TRX 链天然成为草根资金的“结算主链”,承接了大量主流金融体系之外的资金需求。
更值得关注的是波场上的黑市/灰色地带资金流动。低费率、高效率和对审查相对宽松的特性,吸引了大量游走于监管边缘的资本选择TRX链作为避风港。据区块链分析公司 TRM Labs 报告,2024年全球非法加密交易中有超过一半发生在 Tron 网络上,金额高达260亿美元dlnews.comdlnews.com。这些非法活动包括与受制裁实体相关的转账、诈骗黑客资金洗白以及暗网交易等dlnews.com。不法分子之所以青睐波场,正是看中了其稳定币通道和低交易成本等优势dlnews.com。北韩黑客在2024年盗取的8亿美元加密资产,大部分在数小时内经由波场链上的USDT迅速转移dlnews.com。联合国的分析同样指出,波场网络上的 USDT 已成为东亚地区欺诈和洗钱者的“首选”工具dlnews.com。由此可见,波场实际上扮演着**“无照金融公路”的角色:那些被传统金融体系拒之门外、没有正规交易所资格的人,可以通过波场上的USDT完成跨境汇兑和大额交易。这种自下而上的草根主权**,在波场网络上得到了前所未有的市场化体现。
当然,“草根主权”的另一面是高风险和争议。Tether公司虽偶有配合监管冻结特定链上地址,但波场整体上对资金流向的管束远不如银行体系。这使其成为地下资金的温床,也令波场背负“黑钱温床”的骂名。然而,换个角度看,这正验证了那句箴言:革命者在暴政者眼中即是罪犯。波场承载的灰色资金,恰恰反映了主流权力视角下的“犯罪”,但对于使用这些渠道的普通人来说,这可能只是追寻金融自由和机会的务实选择。
孙宇晨的政治人格:主权代理人的崛起
如果说波场TRON成为“无声多数”的金融主权载体,那么其创始人孙宇晨则高调地扮演起了加密世界的政治代理人。一直以来,加密圈华人创业者往往秉持“闷声发财、远离政治”的生存哲学,然孙宇晨选择了截然不同的道路:主动以政治为剧本,塑造个人和项目的话语权。
首先,他直接介入了美国的政治舆论场。2024年底以来,孙宇晨高调参与前总统川普推出的加密项目:斥资数千万美元认购“Trump系列”代币,成为该项目最大公开投资人之一reuters.com。2025年5月,孙宇晨作为头号持币者出席了川普在弗吉尼亚高尔夫俱乐部举办的私宴,与川普同台亮相reuters.com。他不仅以约1.85亿美元等值的钱包额度夺得饭局“竞标”第一名,还受邀成为川普家族加密平台 World Liberty Financial 的顾问reuters.com。这场引发争议的晚宴上,孙宇晨西装革履出镜,高调宣示其政治立场。巧合的是,就在饭局前后,美国证券交易委员会(SEC)突然宣布暂停此前对孙宇晨提起的证券欺诈诉讼,理由是“基于公共利益”reuters.com。这一戏剧性转折不禁令人生疑:孙宇晨深谙政治筹码运作之道,懂得借助美国权力更迭的契机为自己谋得一张“豁免令”。他在X平台(推特)上感慨对邀请心怀感激reuters.com——无形中传达出与未来政治盟友结盟的信号。
其次,孙宇晨积极布局中立主权地区,塑造自身的国际政治身份。他早在2019年即移居新加坡,将波场基金会设立于此,以避开中国大陆的监管高压。更令人瞩目的是,2021年底孙宇晨受聘出任加勒比海国家格林纳达驻世贸组织代表,正式踏入外交圈aljazeera.comaljazeera.com。身为一名加密创业者,却摇身一变成为“孙大使”,这在币圈乃至政坛都属破天荒之举。孙宇晨对媒体直言,加密行业发展到了需要主权国家和国际组织正视其潜力的阶段,他将致力于让区块链获得更多国家的认可aljazeera.com。他特别提到加勒比国家具有成为“下一个新加坡”的潜力:“加勒比国家离美国很近,但又不在美国,这非常关键。在美国境内你会陷入严苛监管和税收,而在加勒比,你可以避开这些桎梏。”aljazeera.com。这番话道出了孙宇晨战略的精髓——借助小国中立地带实现进可攻退可守的布局:既贴近美国这样的核心市场获取影响力,又保持独立主权豁免于其监管范围。
再次,孙宇晨还在国际舆论和文化象征上进行政治表态:例如高调竞拍知名艺术品、与名人互动、甚至不避讳与政治敏感人物(如特朗普阵营)同台。reuters.com川普在活动上直言“拜登政府迫害了加密创新者,我们要把他们带回美国”,孙宇晨的出现无疑为这一论调背书。在国内外社交媒体上,他乐于以“搞事者”形象示人,时而炮轰监管不公,时而与监管机构周旋谈判。从购买巴菲特午餐到押注川普NFT,从宣布波场成为多米尼加共和国官方公链到在洪都拉斯建立加密公司,他一再突破华人企业家避讳政治的传统藩篱,塑造出一个敢于同各国势力斡旋的主权代言人形象。市场也给予了正向反馈:在2023-2025这一轮震荡周期中,TRX价格和生态韧性远超许多竞争对手;波场不仅未被监管风暴击沉,反而因其政治押注而收获新增用户和资金青睐(USDT市值占比的提升即是一例finance.sina.com.cn)。孙宇晨个人也凭借外交官身份游走于各国高层,增强了项目背书的公信力。
与孙宇晨类似,币安创始人赵长鹏(CZ)也体现了“Crypto政治代理人”的影子。作为另一位华人加密巨头,CZ深知监管博弈的重要:币安从中国出发,几经辗转注册地于马耳他、开曼等地,近年来又与迪拜、阿布扎比等中东监管方建立良好关系。尽管币安在美国也受到诉讼挑战,但CZ本人频繁出席各国峰会、主动配合调查、游说政策制定者,其全球公关布局使 BNB 等币安生态资产始终享有一定溢价。可以说,孙宇晨和CZ代表的“华人币”之所以在风雨飘摇的市场中幸存并趋强,正是因为他们扮演了超越技术层面的政治角色:当绝大多数项目埋头编码或躲避监管时,他们选择直面政治、影响政治。
技术乌托邦的失语:ETH、SOL、XRP、ADA 的失速
将波场TRX和币安BNB的经历与其他主流链对照,更能突显“政治代理机制”的缺失所带来的代价。以太坊(ETH)、Solana(SOL)、瑞波(XRP)、Cardano(ADA)等项目,各有辉煌的技术远景或社区共识,却在本轮周期里不同程度陷入了失语和失速状态,一个重要原因正是缺乏有效的政治代理。
-
以太坊:作为智能合约的开创者,以太坊一直醉心于技术迭代和去中心化理想。然而,面对现实世界的监管压力,以太坊社区显得相对被动甚至天真。2021年后,美国制裁“Tornado Cash”等事件使以太坊网络一度出现矿工/验证者自我审查(OFAC合规)的现象,凸显出去中心化网络在政治压力下的脆弱。以太坊基金会和维塔利克等核心人物选择回避直接介入政治角力,试图以技术中立自守。但结果是,在稳定币领域,以太坊逐渐让出优势:USDT更多地流向了“不问来路”的波场,而USDC这种受美国监管严格的稳定币虽然依赖以太坊,却因为监管风险屡屡遭遇增发受限、黑名单冻结等情况。这使得以太坊在**“金融主权承载”**方面的话语权削弱。没有政治代理人替以太坊发声,其技术优势难以转化为对抗监管的筹码。相反,我们看到SEC在近期诉讼中对ETH网开一面(未将ETH列为证券),某种程度上是因其高度依赖美国企业(如Coinbase、Circle)的合规运营——这并非政治胜利,而更像被纳入现有规则体系的被动选择。
-
Solana、Cardano:这两条后起之秀公链,一个以极致性能著称,一个以学术范严谨著称。然而,他们在制度博弈上都缺乏存在感。2023年,美国SEC在对币安、Coinbase等交易所的诉讼中,点名将 SOL、ADA 等列为未经注册的证券,导致相关代币价格暴跌、机构退避cointelegraph.com。SOL和ADA团队自身并无强有力的政治资源予以反击:Solana团队更多精力放在修复网络停机和拓展应用上,对监管定性只能听天由命;Cardano的查尔斯·霍斯金森虽活跃社交媒体,但更多是科普技术和理念,对抗监管的实际影响力有限。当监管大棒挥下,这些专注技术的项目只能被动接受市场信心滑坡的现实。简言之,缺少政治代理等于缺少话语权——无论技术多优,没有人在权力场为你据理力争,你的话语权就只能拱手让人。
-
瑞波 XRP:作为对比,XRP的境遇更具讽刺意味。瑞波公司早早意识到监管的重要性,选择在美国走法律途径与SEC对簿公堂,试图以司法胜利换取地位合法。cointelegraph.com2023年中,瑞波在诉讼中部分胜诉,法院认定XRP本身不是证券,这看似是政治博弈的成果。然而,诉讼旷日持久耗费了瑞波数年的黄金发展期。期间XRP市场份额和舆论热度大不如前,新兴稳定币和跨境支付方案已趁虚而入。可以说,瑞波是少数走上前台直接对抗美国监管的项目,但孤军奋战终究力量有限:没有更广泛政治联盟支撑,胜利也难掩失地之痛。相比之下,孙宇晨选择的并非司法缠斗,而是迂回结盟,这种灵活的政治手腕或许更为有效。
归根结底,ETH、SOL、ADA 等在本轮周期的失速,提醒我们技术乌托邦需要现实政治护航。那些沉迷于宏大技术愿景却忽视政治策略的项目,往往在监管和资本博弈中败下阵来。反观TRX和BNB,一方面技术上并无颠覆性创新(波场VM几乎就是以太坊的变体,BNB Chain 也高度模仿以太架构),但却凭借政治上的主动赢得了市场认可——市值和生态逆势增长就是明证。
结论:主权表达的市场化工具
“从哈耶克到稳定币主权”,我们见证的是货币形态和政治形态的双重演进。哈耶克式的货币竞争思想在加密时代照进现实:私人发行的数字货币在与法定货币争夺稳定性和信任,而这一过程本质上就是主权的竞争与表达。加密货币从来都不仅是冷冰冰的技术产品,更是不断演化的主权表达的市场化工具。每一条公链、每一个代币,都在尝试承载某种主权意志:要么是传统国家主权的延伸(例如各国央行数字货币CBDC),要么是新兴数字共同体的自治主权,要么像USDT/波场这样,成为无国籍资本的影子主权。
TRX 的兴起充分说明,加密项目要取得长足发展,技术功能固然重要,但更关键的是充当“底层政治协调物”的能力。波场并没有因为VM设计优雅而胜出,而是因为它契合了特定政治经济环境下的市场需求:在强监管与资本外流并存的亚洲新兴市场,在美欧银行体系排斥的一角,波场提供了一个去中心化的政治避难所,让资本在不同主权之间自由穿行。aljazeera.com波场作为稳定币和博彩应用的主要载体,被贴上了“不受待见”的标签,但这正是另一种形式的民意表达。市场选择波场,并赋予TRX正溢价,正是对其他缺乏政治承载力项目的集体投票。
“Crypto 即政治”并非说技术不重要,而是强调技术的成败取决于其所嵌入的政治坐标。当ETH坚持代码法则时,TRX已经学会了在代码之上玩转权力棋局;当SOL醉心于极限TPS时,BNB已将自己融入全球离岸金融版图。展望未来,加密世界的竞争将更加赤裸地表现为主权影响力的竞争。谁能更好地平衡各方主权、充当不同利益的代理人,谁就能在市场中取得优势。这或许是加密运动发展至今给我们的最大的启示:去中心化的终点,并非消弭政治,而是重构政治。加密货币让更多人有机会参与主权的创造和表达,而TRX等“政治积极型”项目的案例则证明了,在市场的维度上,政治选择和市场选择早已融为一体。
参考资料:
-
哈耶克主张由私人发行货币与法币竞争finance.sina.cn
-
波场TRON上USDT流通量突破700亿美元,占全球近半finance.sina.com.cn
-
TRON超越以太坊成最大USDT发行网络coindesk.comcoindesk.com
-
2024年约260亿美元非法资金经由波场转移,居各链之首dlnews.comdlnews.com
-
波场低费用和稳定币优势吸引大量黑灰产资金dlnews.com
-
孙宇晨高调参与特朗普家族加密项目,成为最大持币者之一reuters.com
-
美国SEC出于“公共利益”暂停对孙宇晨的诉讼reuters.com
-
孙宇晨出任格林纳达驻世贸组织代表,波场成加勒比官方合作链aljazeera.comaljazeera.com
-
孙宇晨称需让主权国家正视区块链潜力,将精力投向国家层面的推动aljazeera.com
-
美国SEC曾在诉讼中将SOL、ADA等列为未经注册证券,后放弃相关请求cointelegraph.com
-
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36
@ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36Howdy stackers, this is the place to share your ~HealthAndFitness triumphs and challenges.
I was glad to hit my step goal today, since it's gloomy and rainy here. Once again, I ate too many cookies. Gotta stop being a cookie monster.
How'd you all do, today?
https://stacker.news/items/996659
-
 @ da8b7de1:c0164aee
2025-06-03 19:31:32
@ da8b7de1:c0164aee
2025-06-03 19:31:32Lengyelország előrelépése az első atomerőmű építésében
Lengyelország állami nukleáris vállalata, a Polskie Elektrownie Jadrowe (PEJ) és egy amerikai konzorcium – élén a Westinghouse és a Bechtel cégekkel – mérnöki fejlesztési megállapodást kötött. Ez a szerződés kulcsfontosságú lépés az ország első atomerőművének megvalósítása felé, lehetővé téve a részletes mérnöki és helyszínspecifikus munkák megkezdését. A lengyel kormány ezt mérföldkőnek tekinti az energiaszuverenitás és a dekarbonizáció felé vezető úton.
Amerikai politika: lendület az új nukleáris technológiáknak
Az Egyesült Államok kormánya elnöki rendeletet adott ki, amely reformokat vezet be a nukleáris reaktorok tesztelésében az Energiaügyi Minisztériumnál. A cél az új generációs reaktorok – köztük mikroreaktorok és kis moduláris reaktorok (SMR-ek) – fejlesztésének és engedélyezésének felgyorsítása, valamint a környezetvédelmi vizsgálatok egyszerűsítése. A rendelet legalább három új reaktor kritikus üzembe helyezését célozza meg 2026 júliusáig, támogatva ezzel az ipari alkalmazások széles körét, például adatközpontokat vagy hidrogéntermelést. Az intézkedés célja, hogy az USA visszaszerezze vezető szerepét a nukleáris innovációban, és csökkentse a korábbi években felhalmozódott engedélyezési akadályokat.
Kis moduláris reaktorok (SMR) fejlesztése világszerte
Az SMR-szektorban világszerte jelentős előrelépések történtek: - Az amerikai Tennessee Valley Authority (TVA) benyújtotta az első építési kérelmet egy GE Hitachi BWRX-300 SMR-re a Clinch River telephelyen. - Kanadában az Ontario Power Generation engedélyt kapott az első, négy tervezett SMR megépítésének megkezdésére a Darlington telephelyen. - Belgium és Brazília innovatív SMR-technológiákat vizsgál, köztük ólom-hűtésű reaktorokat és nemzetközi együttműködéseket. - Olyan technológiai óriások, mint a Google, az USA-ban korai fázisú fejlett nukleáris projektekbe fektetnek, ami a magánszektor növekvő érdeklődését mutatja.
Globális ipari és pénzügyi támogatás a nukleáris bővítéshez
Széles körű koalíció – köztük olyan nagyvállalatok, mint az Amazon, Google, Meta, Dow – és pénzügyi intézmények kötelezték el magukat amellett, hogy 2050-re megháromszorozzák a globális nukleáris kapacitást. Ez összhangban van az ENSZ klímacsúcsain tett vállalásokkal, ahol már 31 ország támogatja a nukleáris energia megháromszorozását a nettó zéró kibocsátási célok eléréséhez. Az amerikai kongresszus olyan törvényjavaslatokat készít elő, amelyek lehetővé tennék, hogy a multilaterális fejlesztési bankok – például a Világbank – is finanszírozhassanak nukleáris projekteket, megszüntetve ezzel a korábbi tiltásokat.
Közelgő nemzetközi nukleáris biztonsági gyakorlat
A Nemzetközi Atomenergia-ügynökség (IAEA) készül a ConvEx-3 vészhelyzeti gyakorlatára, amelyet 2025. június 24–25-én Romániában tartanak. A gyakorlat egy súlyos nukleáris vészhelyzetet szimulál a cernavodai atomerőműben, tesztelve a tagállamok és nemzetközi szervezetek felkészültségét és reagálóképességét. A ConvEx-3 a legmagasabb szintű IAEA vészhelyzeti gyakorlat, kulcsszerepet játszik a globális nukleáris biztonság és védelem erősítésében.
Politikai bizonytalanság Dél-Korea nukleáris terveiben
Dél-Korea 2025. június 3-i elnökválasztása hatással lehet az ország nukleáris reneszánszára. A vezető jelölt, Lee Jae-myung kijelentette, hogy „egyelőre” fenntartaná a nukleáris energiát, de hosszabb távon a megújulók felé mozdulna el. Ez bizonytalanságot okoz a koreai nukleáris ipar hazai és exportterveiben, ami kihatással lehet a globális ellátási láncokra és külföldi reaktorprojektekre is.
Iparági trendek és további fejlemények
- Japán új energiastratégiája maximalizálni kívánja a nukleáris energia részarányát, 2040-re mintegy 20%-ot célozva, különös hangsúlyt fektetve a következő generációs reaktorokra és a biztonság növelésére.
- Belgium kormánya és a francia Engie közműcég megállapodott a kulcsfontosságú reaktorok üzemidejének tízéves meghosszabbításáról, ami az európai nukleáris pálfordulás újabb jele.
- Az IAEA és a World Nuclear Association egyaránt növekvő nemzetközi érdeklődésről számol be az SMR-ek és fejlett reaktortechnológiák iránt, új projektek és partnerségek indulnak Ázsiában, Európában és Amerikában.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
world-nuclear.org
govinfo.gov
whitehouse.gov -
 @ 7460b7fd:4fc4e74b
2025-06-05 05:45:02
@ 7460b7fd:4fc4e74b
2025-06-05 05:45:02TRX 资源冻结式 Staking 与用户结构演化:对价格发现机制的影响分析
引言
TRX(波场币)作为波场 TRON 区块链的原生代币,因其独特的“冻结换资源”式 staking 模型而呈现出不同于传统公链的用户结构演变轨迹。这种机制在不同发展阶段吸引了截然不同类型的用户,从早期高度集中的机构持有者,到中期大量利用资源冻结套利的灰色产业,再到近期随着合规压力下资产向零散用户转移所形成的更广泛持有群体。本文将深入分析这一用户结构的演变历程,以及这种变化如何潜在影响 TRX 的市场价格发现机制。我们将按照时间脉络探讨以下问题:
-
初期设计:波场最初的 staking 模型如何偏向“对公场景”(如交易所间结算、机构资源调配),导致早期 TRX 资金和投票权集中度极高?
-
灰产利用:灰色产业(电信诈骗、网络赌博、地下钱庄等)如何利用 TRX “冻结换能量”机制降低 USDT 等稳定币转账成本,在波场上形成中期稳定的使用者群体?
-
用户下沉:随着各大交易所面临日益严格的合规压力,这些灰产地址如何将资金转移给“无交易所”通道的散户和小型平台账户,导致 TRX 使用权和持仓逐步向更广泛的普通用户渗透?
-
价格发现影响:这种持币结构的变化是否可能引导“零售价格发现”,即当大量散户持有 TRX 时,是否会对价格走势产生聚合影响(类似 GameStop 股票或 meme 币的散户抱团现象)?
-
链上数据演化:若数据支持,我们将呈现 TRX 持仓结构在链上的历史演变情况(如交易所热钱包占比、已知灰产地址占比、散户地址占比等),借助 Nansen、Lookonchain、Arkham、Dune 等分析工具的公开数据来说明上述趋势。
接下来,将从背景入手介绍波场 TRX 的 staking 机制设计及其早期影响,然后依据链上数据和行为证据分阶段分析用户结构转变,结合博弈论视角讨论价格发现机制,最后给出结论和展望。
背景:TRX 资源冻结型 Staking 模型与早期集中化
波场 TRON 于 2018 年主网上线,采用 委托权益证明(DPoS) 共识机制,其核心是 资源冻结(质押)换取网络资源和权益 的模式cryptorank.io。用户可以冻结一定数量的 TRX 以获取 带宽(用于普通交易)和 能量(用于智能合约操作)的配额,从而用资源抵扣交易手续费cryptorank.io。此外,冻结 TRX 还能获得 Tron Power(投票权),用于参与超级代表(Super Representatives,SR)节点的选举,从而分享出块奖励和投票奖励。这一机制本质上鼓励大量持币并长期冻结,以换取低成本交易和治理权。
TRX 早期的经济设计和应用场景明显偏向**“大户”和“机构”。首先,TRX 在 2017 年 ICO 分发时就有相当集中度——总发行1000亿枚中,约40%面向公开发售,15%私募,35%由项目方保留cryptorank.io。项目方(波场基金会)及早期投资人一开始就掌握了近一半的代币供应量。其次,在 DPoS 模式下,持币多者在投票治理中掌握更大权力,早期27个超级代表节点的投票由少数巨鲸地址主导。波场联合创始人、前 CTO 陈志强曾直言:“TRON 的代币分布是中心化的,超级代表是中心化的”cointelegraph.com;前27个超级代表节点拥有超过1.7亿票数,其中大部分受波场官方控制,普通散户的投票几乎无法左右结果cointelegraph.com。这意味着网络治理和出块权高度集中在项目方和早期大户手中**,staking 机制对中小持币者参与并不友好。这种局面导致 TRX 在生态早期呈现出明显的寡头格局。
更重要的是,波场团队有意将 TRX 打造成 高吞吐低成本的链上结算网络,这吸引了交易所和机构用户的青睐。2019年,创始人孙宇晨敏锐地抓住 交易所间稳定币跨链转账 的需求:由于以太坊网络手续费高、速度慢,交易所间结算 USDT 等稳定币成本很高,而波场上的 TRC20-USDT 转账费用极低、确认快theblockbeats.info。孙宇晨当即采取激进补贴策略,动用波场超级节点的挖矿收益,投入数亿元人民币补贴 TRC20-USDT 的充提手续费,在各大交易所间推广波场作为USDT转账的介质theblockbeats.info。据报道,当时通过波场网络充提 USDT 的用户可以享受相当于16%\~30%的收益(手续费返还优惠),极大刺激了交易所采用波场网络theblockbeats.info。这一系列措施使 TRC20版 USDT 的流通量和交易量在短时间内飙升,波场迅速取代以太坊成为 USDT 最主要的发行和转移平台。交易所和场外结算机构成为 TRX 生态的核心参与者:他们大量持有并冻结 TRX 来获取能量用于大额稳定币转账,或者直接利用波场网络进行跨所清算。这奠定了 TRX 早期资金和使用的高度机构化、集中化特征:头部交易所和项目方持仓占比极高,散户持有比例相对很低。
图:2024年初 TRX 持币分布的集中度。数据显示前10大地址合计持有约31.6%的供应量,前500大地址合计持有约85.5%的供应cryptorank.io。这印证了波场生态早期的持币高度集中在少数机构和巨鲸手中。
综上,波场 TRX 通过独特的冻结换资源机制,将手续费成本内化为持币收益,迎合了交易所、支付清算等对公场景对廉价高速链上转账的需求。在2018-2019年间,这一定位成功吸引了大量机构资金,但也造成了代币分布和治理权的高度集中。这是 TRX 用户结构演化的起点:以机构和巨鲸为主体的集中式持仓格局。
链上数据与行为层分析
随着波场网络逐步发展,TRX 的用户结构并未一成不变。链上数据和使用者行为表明,TRX 的持有者构成经历了从集中到扩散的动态演化,大致可划分为以下阶段:
初期阶段:机构主导的集中持仓
在主网上线后的早期(2018\~2019年),TRX 的持仓和使用主要集中在交易所、基金会等少数主体。从链上持币分布看,2019年时 TRX 前5个地址持有全网一半以上代币供应量,前10名地址接近60%(包括波场基金会及创始团队地址、少数大交易所的钱包等)cryptorank.io。即便到2025年中,集中度仍然较高——据统计前10大持币者仍合计拥有约25%的供应ccn.com,其中最大的单一地址占比超过8%ccn.com(推测为波场基金会或主要交易所冷钱包)。可见在初期,头部持有者在供应中占据主导。这种格局的形成,一方面源自前述代币分发和 DPoS 机制让项目方及早期投资人持有巨量筹码;另一方面,交易所为提供波场网络USDT充提现也大量囤积并冻结 TRX 获取带宽/能量,从而自身成为持币大户。
链上行为数据显示,交易所地址在 TRX 交易活动中占相当权重。大量 TRX 被冻结在交易所热/冷钱包用于日常为用户支付交易费用或资源租借。例如,币安在2019年直接成为波场超级代表节点之一,拥有全网超过一半以上的超级代表选票,当时就反映出交易所对 TRX 生态的深度介入coinmarketcap.comcointelegraph.com。总的来说,初期阶段 TRX 的用例主要是交易所间结算的媒介和赚取投票收益的质押资产,对应的用户主要是大宗资金持有者(交易所、基金会、早期投资人)。普通散户在这一阶段对 TRX 的参与度有限,无论持仓量还是交易笔数占比都很低。价格发现也主要由这些“大玩家”驱动——他们有能力通过场外交易或协议控制市场供给,从而较大程度上主导 TRX 的价格走向。
中期阶段:灰产经济的稳定使用者崛起
2019年至2021年后,随着波场网络的稳定运行和 USDT 等稳定币在波场上的广泛流通,一个意想不到的用户群体开始在 TRX 生态中扮演重要角色:灰产经济体。这里所指的灰产包括电信网络诈骗、网络赌博平台、地下钱庄洗钱团伙等非法或游走在法律灰色地带的组织。这些团体发现,波场的**“冻结 TRX 换能量”机制非常适合他们大规模、频繁地转移资金:通过持有并冻结一定量的 TRX,他们可以几乎免费地在波场链上无限次转账 USDT** 等代币linqihuishou.com。相比在以太坊等公链上高昂的 Gas 费用,波场提供的这种低成本转账渠道对灰产资金具有巨大吸引力。
联合国毒品和犯罪办公室(UNODC)的一份报告指出,在东南亚地区从事洗钱和诈骗的犯罪团伙偏好使用波场链上的 USDT 作为转移资产的工具dlnews.com。报告称,仅在截至2022年9月的一年间,就有逾170亿美元等值的 USDT 涉及非法交易所、地下洗钱等活动dlnews.comdlnews.com。波场因其匿名性强、转账快且成本近乎为零,成为这些团伙的“首选”网络dlnews.com。另一份调查也揭示,使用波场 USDT 的网络赌博和洗钱架构俨然形成了一个平行的地下银行系统protos.com。不法分子往往在国内收取现金,通过OTC渠道换成波场 USDT,在链上层层划转,最后在境外兑换回法币完成洗钱3e97756f-e20a-4497-8bc2-57f45e005c8a.baidu.scalaris-eci.com。
灰产大规模涌入波场带来了 TRX 生态的中期用户结构转变:虽然这些团伙的主要目的是利用 USDT 等稳定币,但为了降低成本他们必须持有一定数量的 TRX 来支付手续费或获取能量。这就意味着一批新的持币群体——灰产地址——开始稳定持有和使用 TRX。链上可以观察到许多可疑地址经常冻结大量 TRX,然后进行频繁的 USDT 转账操作。这些地址往往关联着诈骗资金、黑钱,通过分析工具已被标记为高风险。在波场交易笔数中,这些灰产相关地址的交易占有相当比例,它们维系着庞大的跨境资金流。dlnews.comprotos.com
值得注意的是,灰产用户的TRX持有行为具有“两面性”:一方面,他们持有 TRX 完全是出于工具用途,对 TRX 价格本身并不敏感,往往在完成资金转移后就会解冻并抛售 TRX(换回稳定币或法币)。因此,灰产用户的存在为 TRX 提供了持续的基础交易需求,但同时他们也可能对价格形成抛压。另一方面,由于这部分需求庞大且相对稳定(例如地下钱庄每天都有大额 USDT 要汇出),某种程度上托起了 TRX 的链上活跃度,甚至提高了网络的基础价值支撑。到2024年,波场上 USDT 的流通量已经超过以太坊,占到 USDT 总供应的一半以上cointelegraph.com;波场每日处理的稳定币转账金额高达数百亿美元,全球所有稳定币交易量中近30%通过波场网络完成coindesk.comcoindesk.com。在这些惊人的数字背后,灰产资金不可小觑。
综上,中期阶段 TRX 用户结构从单纯的机构主导,演变为**“机构+灰产”双重主导**格局。灰产经济成为 TRX 生态中隐形但重要的参与者,为 TRX 提供了源源不断的交易量和实用需求。然而,这种需求带有很强的功利性,在正常市场中往往难以转化为对 TRX 价格的主动支撑。
转型阶段:合规压力与持币群体下沉
进入2023-2024年,全球监管环境对加密行业(尤其是交易所)日趋严格,大型中心化交易所纷纷加强了 KYC/AML(反洗钱) 审查。这对利用交易所渠道“进出”资金的灰产团伙造成了沉重打击:大量涉嫌非法的地址被交易所列入黑名单冻结,稳定币发行方 Tether 也开始配合执法,冻结了部分波场网络上的可疑 USDT 账户cointelegraph.comcointelegraph.com。
图:由波场、Tether 与 TRM Labs 于2024年8月成立的“T3”金融犯罪联合行动小组,自成立以来已冻结超过1.26亿美元涉案 USDTcointelegraph.com。其中近一半涉及洗钱,另有相当比例涉及投资诈骗cointelegraph.com。这一行动反映出监管合规压力下,波场网络上大额非法资金池正受到打击。面对这种压力,灰产资金的流转模式开始转变。
随着“大额、集中”的灰产资金在主流交易所难以脱身,这些团伙被迫改变策略,更加依赖非交易所渠道来“出清”资金。他们开始将大宗资金拆分,通过场外交易(OTC)网络或小型换汇平台,转移给众多零散的个人地址。例如,一个诈骗团伙可能将上百万 USDT 分拆成上千笔小额转账,分别发给成百上千个个人钱包;这些个人再通过点对点方式把 USDT 换成现金。在中国等地破获的地下钱庄案件中,就发现犯罪团伙通过海量的个人数字钱包收款,以规避大额交易监控3e97756f-e20a-4497-8bc2-57f45e005c8a.baidu.scalaris-eci.com。波场网络的低费率使得**“大拆小”式的分散转账成为可能且经济**。
这一过程中,TRX 的使用者结构出现了**“下沉”**。原先主要由灰产团伙自己持有的 TRX(用于支付手续费或冻结换能量),现在逐步分散到大量普通用户手中。很多此前从未直接接触过波场的散户,因为参与OTC交易或接受灰产资金而开始持有少量 TRX。例如,一些东南亚地区的务工人员通过地下渠道汇款,在接收USDT时被要求使用波场网络的钱包,这意味着他们需要持有一点 TRX 来支付手续费。同样地,一些小型境外换汇商为了承接灰产的出金业务,也开始积累 TRX 以便快速完成批量转账。
链上数据支持了这种“去中心化”的趋势:CryptoQuant 的研究指出,截至2024年7月,波场网络上小额持有者(“散户”)的数量已经超过5260万,占据 USDT 转账笔数的28%左右newsdirect.com。也就是说,有数千万计的普通用户活跃在波场上进行小额交易。波场官方数据显示,到2025年初,总用户账户数已突破3亿,日活跃地址超过100万,每日小额稳定币交易数百万笔coindesk.comnewsdirect.com。这些数字表明,TRX 与波场网络的使用已深入到广泛的民间层面,不再只是大户的专属。
从持币结构看,虽然大户依然握有大量筹码,但相比早期,中小地址合计持有的比例有所上升。前文提到截至2025年5月前10名地址占供应约25%,而在更早时期这一数字一度超过30%cryptorank.ioccn.com。顶级持有者占比的下降意味着更多代币分散到了小持仓地址中。当然,大部分散户并非因为投资目的囤积 TRX,他们往往只持有满足转账所需的少量(比如几十个甚至几个 TRX用于手续费)。然而,当数以千万计的用户都持有哪怕少量 TRX 时,其总量也不可忽视。此外,一些原本为灰产服务的小平台、小型交易商,随着合规压力增加也可能选择转型,通过合法途径运营,这些玩家持有的 TRX 由“暗”转“明”,进一步增加了公开市场上的流通筹码。
**这一阶段的核心转变在于:TRX 的持有者基础变得空前广泛。**从链上身份看,除了交易所和已知灰产地址,普通散户地址在网络活动和持仓中的占比显著提高newsdirect.com。TRX 不再仅仅是机构间的结算工具或黑市的洗钱桥梁,它开始进入寻常用户的钱包,成为跨境汇款、支付和个人转账的一种选择。在非洲、中东等通货不稳定地区,波场 USDT 甚至被用作日常价值存储手段,TRX 则提供了必要的基础设施dlnews.com。这种下沉为 TRX 的市场生态带来了新的变量:当持币者从少数改为众多,价格发现的参与者结构也相应改变。
博弈模型讨论:散户崛起能否引导价格发现?
随着 TRX 持有和使用群体愈发多元化,一个关键问题浮出水面:如此广泛的散户参与,是否会改变 TRX 的价格发现机制,乃至引发类似 GameStop 或 meme 币那样的“散户聚合”行情? 从博弈论和市场微观结构角度,我们可以进行以下分析。
1. 定价权由大转小的再分配:在传统金融和早期加密市场中,少数大玩家(做市商、鲸鱼、机构)往往通过信息优势和资金优势主导价格。然而,当持仓分散到众多散户后,市场定价权力开始更平均地分配。如果散户群体足够活跃,他们的集体交易行为(买入或卖出)可以对价格产生显著影响。尤其在社交媒体发达的时代,散户可以通过舆论形成某种“共识预期”。例如,若大批散户相信“波场用户遍地开花将推高 TRX 价值”,他们可能趋于买入持有,从而真的推高价格——这类似于一种自证预期的动态。散户数量庞大且分散,单个看似微不足道,但**“乌合之众”在同步行动时可产生和巨鲸相媲美的资金量**。GameStop 股票之所以在2021年出现爆炸性逼空行情,就是因为数百万散户在网络论坛上形成合力,对抗华尔街空头。如果 TRX 的散户持有者也形成共同的看涨信念,可能出现交易行为的正反馈,推动价格快速上涨。
2. 网络效应与认知偏差:波场网络广泛的用户基础本身就会带来网络效应。每增加一位用户,TRX 的实用价值和潜在需求就略有提高。当数千万用户都在使用某个网络时,会产生一种“这么多人用,币价应该有支撑”的认知偏差。散户往往受“用户规模=价值”直觉影响而追涨。coindesk.comnewsdirect.com中的数据(每日超百万活跃地址、全球稳定币流通近三成经波场)可能被解读为 TRX 的基本面支撑,从而增强散户的持有信心。这种对基本面的再认知有别于灰产用户时期——灰产虽使用波场但不会宣扬其价值,而普通用户的使用反而可能转化为对 TRX 的口碑传播和正面情绪。由此,一个正向循环可能形成:用户基础扩大 → 市场认可度提高 → 新投资者涌入 → 价格上升 → 吸引更多用户。
3. 大户与散户的博弈:当然,散户行情能否持续,还取决于大户(早期鲸鱼、机构)的行为反应。一种可能情景是类似meme股/币:当散户推高价格时,大户出于逐利反而顺势助涨,甚至刻意制造舆论迎合散户,以便自己高位出货。如果 TRX 出现快速拉升,早期持有巨量筹码的老玩家可能选择逢高抛售套现,给上涨造成阻力。这一点在博弈上体现为:散户试图通过一致行动改变定价,但理性的大利润持有者会反向博弈,利用散户情绪行情实现盈利。TRX 目前前几大地址仍掌握巨额筹码,他们的抛压能力依旧很强。如果没有新的强力资金接盘,大户的出货可能使散户难以持续控盘。GameStop等案例中,散户成功逼空的前提之一是大户被困住无法立即抛售(空头被迫买入、公司高管锁仓等)。而在TRX市场,波场基金会、交易所等钱包并无锁定约束,完全可以利用流动性高点出售。因此,散户要引导价格发现,必须面对大户博弈的反作用力。
4. 市场情绪和触发事件:散户聚合行为往往需要一个导火索或叙事。GameStop有“对抗华尔街”的叙事,Dogecoin等meme币有马斯克等名人站台或者社区狂欢。TRX 虽有庞大用户,但缺乏类似的戏剧性话题来凝聚炒作热情。Justin Sun 虽然善于营销(如天价拍巴菲特午餐等),但这些年 TRX 价格相对稳健,没有出现过山车式暴涨暴跌,说明市场对其噱头相对理性。如果未来出现某个事件——例如波场生态中诞生一个现象级应用、或哪位投资大佬高调支持 TRX ——这可能点燃散户的想象力,触发一波情绪行情。在博弈模型上,这类似于公共知识的形成:散户需要确信“大家都会买”,而导火索事件恰恰提供了这样的公共信号。如果信号足够强烈,散户预期可协调,形成簇拥买入的纳什均衡。反之,在缺乏信号的平静环境中,散户各自为战,价格更多反映基本面与存量大户操作,不易自发聚合。
5. 零售价格发现的迹象:目前观察,TRX 市场已经显现出一些零售主导的特征。例如,2023-2024年熊市中,TRX 价格相对抗跌且波动率较低,或许与大量散户被动持币(用于手续费而非投机)有关——这部分需求相对刚性,不会因市场恐慌而大量抛售,反而稳定了价格。另一方面,在牛市来临时,这批散户是否会转为主动买入、推高价格,还有待验证。截至2025年年中,TRX 的市场走势总体平稳,CCN 分析指数给其势能评分仅34(满分100),显示动能偏弱ccn.com。这说明尚未出现 meme 式狂热,散户更多是被动参与者。但随着波场版稳定币生态的进一步扩张以及监管环境变化,不排除散户的角色从“被动用币者”转变为“主动投资者”。如果那一刻到来,TRX 的价格发现模式可能从当前偏基本面/机构驱动,转向更加依赖大众情绪和网络舆情。
综上,在博弈论视角下,TRX 用户结构的演变确实为零售价格发现创造了条件:更分散的持仓、更广泛的市场参与,使价格形成过程潜在地更具民主化色彩。然而,能否出现类似 GameStop 或 meme 币的极端行情,还取决于散户共识凝聚程度以及大户的策略反应。目前迹象表明 TRX 市场仍处于相对均衡状态,散户广布带来的更多是流动性提升和韧性增强,而非泡沫炒作。当然,市场结构一旦改变,其影响往往非线性——未来某个时点,不可忽视数以千万计散户的力量可能展现。
结论
TRX 代币由于其资源冻结式 staking 模式,在过去数年间经历了独特的用户结构演化:
-
早期,波场刻意迎合高频结算等对公场景,导致 TRX 持币和治理高度集中于项目方、交易所等少数机构账户,散户影响微乎其微。价格发现主要由这些大主体决定,市场呈现中心化特征。
-
中期,随着波场成为稳定币(尤其 USDT)的重要转移网络,各类灰色产业大量涌入利用“冻结换能量”降低转账成本。灰产地址成为 TRX 生态中不可忽视的稳定使用者群体,带来了巨大的链上交易量和实际需求。但这部分用户对 TRX 价格并无投机兴趣,其行为在提高网络实用性的同时,也给市场抛压埋下隐患。
-
近期,全球合规打击使得灰产资金从大交易所撤出,被迫通过无数散户和小型渠道分散流动。由此,TRX 的使用权和持有量开始向更广泛的人群下沉,数以千万计的普通用户卷入波场网络的使用。TRX 的持币结构正变得相对分散,散户在链上交易和持仓中的占比明显上升。
-
对价格发现的影响,可以概括为“基础盘扩大,定价权下放”。更广泛的用户基础意味着 TRX 价格受到的力量更加多元:除了少数大户博弈,还受到千千万万小持有者情绪和行为的影响。散户群体有可能在某些条件下形成合力影响价格(例如共同的看涨预期或外部刺激事件),这为 TRX 带来了出现零售驱动行情的可能性。然而,目前 TRX 市场尚未经历真正的散户抱团狂热,其价格依然相对平稳,说明机构和基本面因素仍占主导。
-
链上持仓结构演变总体符合上述趋势:从交易所/基金会占主导,逐步过渡到多元参与者并存。尽管确切的链上占比数据仍在完善(可借助 Nansen、Dune 等进一步分析交易所热钱包持仓、标记的诈骗地址持仓、非风险地址的小额持仓等),现有资料表明前十大地址持仓比例已从超过30%降至约25%,而小额地址数以亿计增长,对网络活动贡献巨大cryptorank.ionewsdirect.com。
综合而言,TRX 的资源冻结 staking 模式在不经意间促成了一条特殊的发展路径:从精英走向草根。这种用户结构的下沉为 TRX 带来了使用面的繁荣,同时也打开了价格发现的新篇章。未来,如果散户力量能够被某种契机调动,TRX 不排除出现类似meme行情的可能;即便没有极端事件,更多元的持仓结构也意味着价格将更真实地反映广泛市场的供需和预期。对于波场生态来说,如何平衡好“大户—灰产—散户”三类持币者的利益,将是决定 TRX 市值能走多远、走多稳的关键。波场的故事,正在从幕后走向台前,从少数走向大众,这或许正是去中心化精神的一种体现。
参考文献:
-
Chen, Z. (2019). Tron Co-Founder and CTO Leaves Project, Alleging Excessive Centralization. Cointelegraphcointelegraph.comcointelegraph.com.
-
Primitive Ventures. (2023). 裂隙中的共识:Tether与全球金融新秩序theblockbeats.infotheblockbeats.info.
-
CryptoRank. (2024). TRON H1 2024: From Stablecoins to Bitcoin and Beyond. CryptoRank Reportcryptorank.io.
-
DLNews. (2023). UN says USDT on Tron is “preferred choice” for fraudsters in East Asiadlnews.com.
-
Protos. (2024). China busts $2B USDT money laundering operationprotos.com.
-
TronDAO & CryptoQuant. (2024). TRON retail usage analysisnewsdirect.com.
-
Cointelegraph. (2024). Tether, Tron and TRM Labs jointly froze $126M USDT in 2024cointelegraph.comcointelegraph.com.
-
Cointelegraph. (2024). Nansen 2 brings transparency to Tron: USDT on Tron adoptioncointelegraph.com.
-
CCN. (2025). TRON Price Prediction 2025: Rich List and Distributionccn.comccn.com.
-
TRON DAO. (2025). Press Release: USDT on TRON surpasses $75Bcoindesk.comcoindesk.com.
-
-
 @ cae03c48:2a7d6671
2025-06-03 19:02:12
@ cae03c48:2a7d6671
2025-06-03 19:02:12Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ eb0157af:77ab6c55
2025-06-06 06:01:16
@ eb0157af:77ab6c55
2025-06-06 06:01:16The Russian banking giant introduces financial instruments linked to Bitcoin for qualified investors.
Russia’s largest commercial banking institution, Sber, has made its entry into the Bitcoin space by unveiling a bond product tied to the asset.
Sber has officially launched its structured financial instrument that mirrors the price performance of Bitcoin alongside fluctuations in the dollar-ruble exchange rate. The product is already available to qualified investors through the over-the-counter (OTC) market, with plans to list it on the Moscow Exchange in the near future.
Formerly known as Sberbank, the institution stated in a May 30 announcement that the listing would provide transparency, liquidity, and convenience for a wide range of professional investors. This structured approach will allow investors to benefit both from Bitcoin’s appreciation in dollars and from the strengthening of the US dollar against the Russian ruble, the bank suggests.
The lender also announced plans to expand its crypto offering through the SberInvestments platform, introducing exchange-traded products that provide exposure to digital assets. The first product will be a Bitcoin futures instrument, scheduled for listing on June 4, coinciding with its official launch by the Moscow Exchange.
Sber’s initiative follows the authorization granted by Russia’s Central Bank on May 28, which permitted financial institutions to offer specific crypto-related financial instruments to accredited investors. However, the direct offering of cryptocurrencies remains prohibited.
Meanwhile, T-Bank (formerly Tinkoff Bank) launched an investment product linked to Bitcoin’s price, branding it a “smart asset” issued through Russia’s state-backed tokenization platform Atomyze.
According to the Russian Central Bank’s report for the first quarter of 2025, Russian residents hold approximately 827 billion rubles ($9.2 billion) in cryptocurrencies on centralized exchanges. Inflows into Russian crypto platforms surged by 51%, reaching 7.3 trillion rubles ($81.5 billion) over the same period.
The post Sber, Russia’s largest bank, launches Bitcoin bonds appeared first on Atlas21.
-
 @ e0e92e54:d630dfaa
2025-06-03 19:01:32
@ e0e92e54:d630dfaa
2025-06-03 19:01:32As some of you know, I lead a quarterly Bible Study through Faith Driven Investor
One of the members from the cohort that just ended forwarded me an email from the US Christian Chamber of Commerce
The summary is: Christians should intentionally be doing more business with Christians.
[Full email at the bottom of this Article]
I recanted to my FDI member about a book I read a few years ago, Thou Shall Prosper, by Rabbi Daniel Lapin.
In it he gave the statistics that a single dollar recirculates in the Jewish community 12 times, Muslims 8 times, and Christians only 3 or 4 times.
(I'm probably slightly off on recalling the stats)
But the point being that as a people group, Jews are 4x more wealthy than Christians because Christians value doing business with one another 4 times less than Jews...or said another way, the Jewish people value doing business with one another 4x more than Christians.
Reading the email I was sent, I was further reminded as business owners, leaders, and investors;
If we are truly going to steward that which God has entrusted to us, we should want to re-circulate those resources as many times as possible within the Christian community in order to have the greatest probability of return on image bearers.
What are your thoughts?
I Bought a House Through the Christian Chamber - What happened next surprised me
My husband and I just bought a house—but it wasn’t just a transaction. It was a transformation.
With our daughter’s high school graduation behind us, we felt ready to step into a long-held dream: moving to a beach town we’ve thought, talked, and prayed about for years. As part of turning our dream into a reality, we made a very intentional decision:
We would buy our home entirely through the Christian Chamber community.
We wanted to walk the talk—to model what Kingdom commerce really looks like. So we sought Christian-led businesses for every part of the process. What started as a symbolic gesture quickly became a profound experience with two life-changing revelations:
1) The Power of Prayer in Business
Yes, we prayed as a couple—but imagine your Realtor, lender, inspector, and insurance agent all praying with you, too.
We’re not talking about just being “nice people” or listening to worship in the office. We’re talking about Spirit-filled, Jesus-following believers who brought prayer into every decision.
· Our Realtor is also a church planter—her discernment helped us find the perfect house on day one.
· Our lender joined us in prayer—and worked miracles to make the deal smooth and abundantly possible.
· Our inspector's biggest red flag? A bird’s nest in a porch light. (Yes, really.)
· Our insurance agent handled everything—and in Florida, that’s no small feat.
I have bought and sold seven homes in my life, but this was the best experience by far. The layout, the location, the timing, the favor—it was all wrapped in prayer and covered in grace. It wasn’t just business. It was supernatural.
2) Kingdom ROI — A Multiplied Impact
By doing business with Christians, we didn’t just find great service. We created a multiplied Kingdom return.
We know where our vendors give. We know the churches they support, the ministries they fund, and the people they serve.
When they earned from our purchase, those dollars didn’t disappear—they were reinvested into Kingdom causes we could never reach on our own.
This is Kingdom ROI.
It’s a real-life example of the parable of the talents—we didn’t bury our resources. We multiplied them. When you spend money with aligned believers, your impact compounds.
The opposite is also true:
When we spend with businesses that oppose our values, we’re funding platforms that erode the very things we’re trying to protect—our families, our freedoms, and our faith.
We MUST STOP funding the enemy.
The Bigger Picture
Let’s be clear: Studies show that Christians make up 31% of the world’s population, but we control 55% of the world’s wealth—more than $107 trillion in personal assets.
And yet…we’re leaking that wealth into systems that are actively working against us.
Why? Because we do not have the infrastructure to keep it aligned.
Until now.
That’s what we’re building through the U.S. Christian Chamber of Commerce: A national infrastructure that empowers Christians to redirect their dollars, align their values, and multiply their impact.
What If You Did the Same?
· Buy your next product or service from a Christian-led business.
· Hire your next contractor from your local Christian Chamber.
· Invest in a company with eternal impact.
· Launch a Christian Chamber in your region—we’ll help you.
· Join the U.S. Christian Chamber. This is your Chamber, for your nation.
· Meet us in Orlando for SWC 2026, the global gathering of Christian commerce.
Imagine the multiplying power if thousands of us made similar decisions—every day—across this nation.
We own the wealth. Now let’s build the infrastructure, create the ecosystem, and shift the world's wealth one transaction at a time.
This is our nation and we are One Nation Under God!
Jason Ansley is the founder of Above The Line Leader, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive— without sacrificing your faith, family, or future.
-
Want to strengthen your leadership and enhance operational excellence? Connect with Jason at https://abovethelineleader.com/#your-leadership-journey
-
📌 This article first appeared on NOSTR. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles
-
-
 @ 6d8e2a24:5faaca4c
2025-06-06 04:26:58
@ 6d8e2a24:5faaca4c
2025-06-06 04:26:58
President Donald Trump attends a meeting with the Fraternal Order of Police in the State Dinning Room of the White House, Thursday, June 5, 2025, in Washington. (AP Photo/Alex Brandon)
Last Friday, President Donald Trump heaped praise on Elon Musk as the tech billionaire prepared to leave his unorthodox White House job.
Less than a week later, their potent political alliance met a dramatic end Thursday when the men attacked each other with blistering epithets. Trump threatened to go after Musk’s business interests. Musk called for Trump’s impeachment.
social media posts urging lawmakers to oppose deficit spending and increasing the debt ceiling.
“Without me, Trump would have lost the election, Dems would control the House and the Republicans would be 51-49 in the Senate,” Musk posted, a reference to Musk’s record political spending last year, which topped $250 million.
“Such ingratitude,” he added.
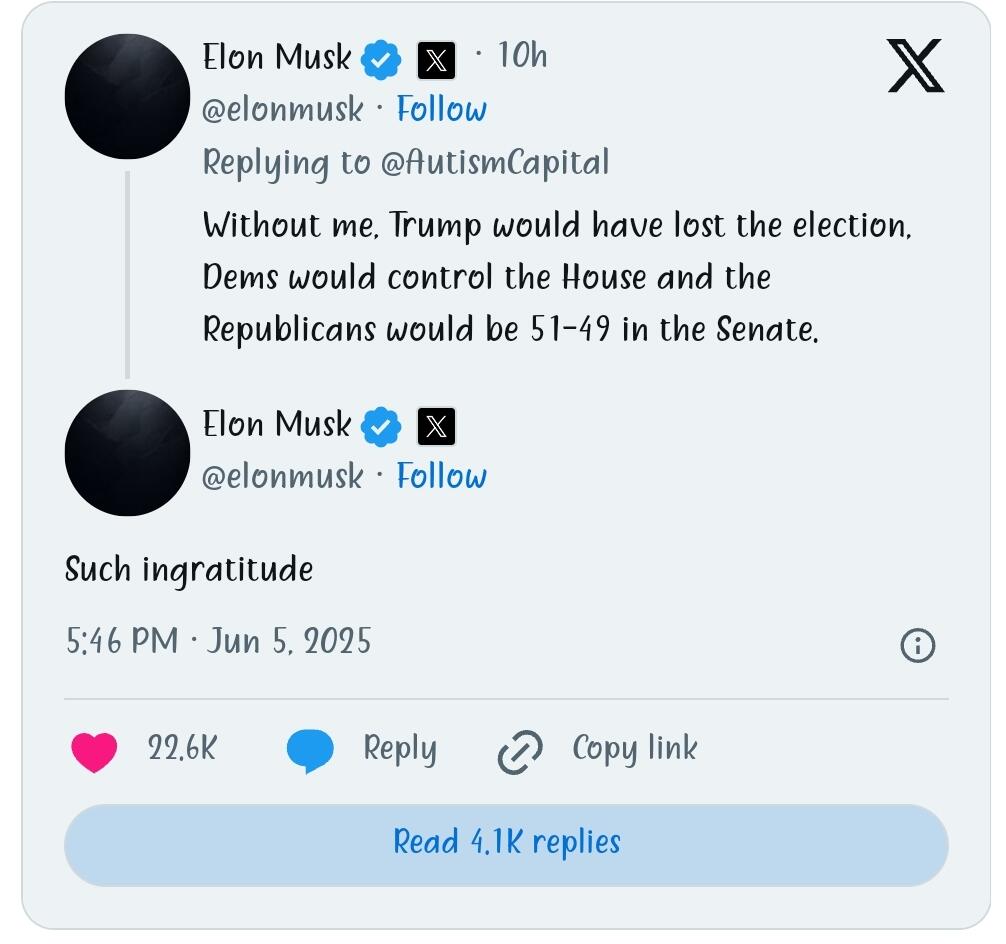
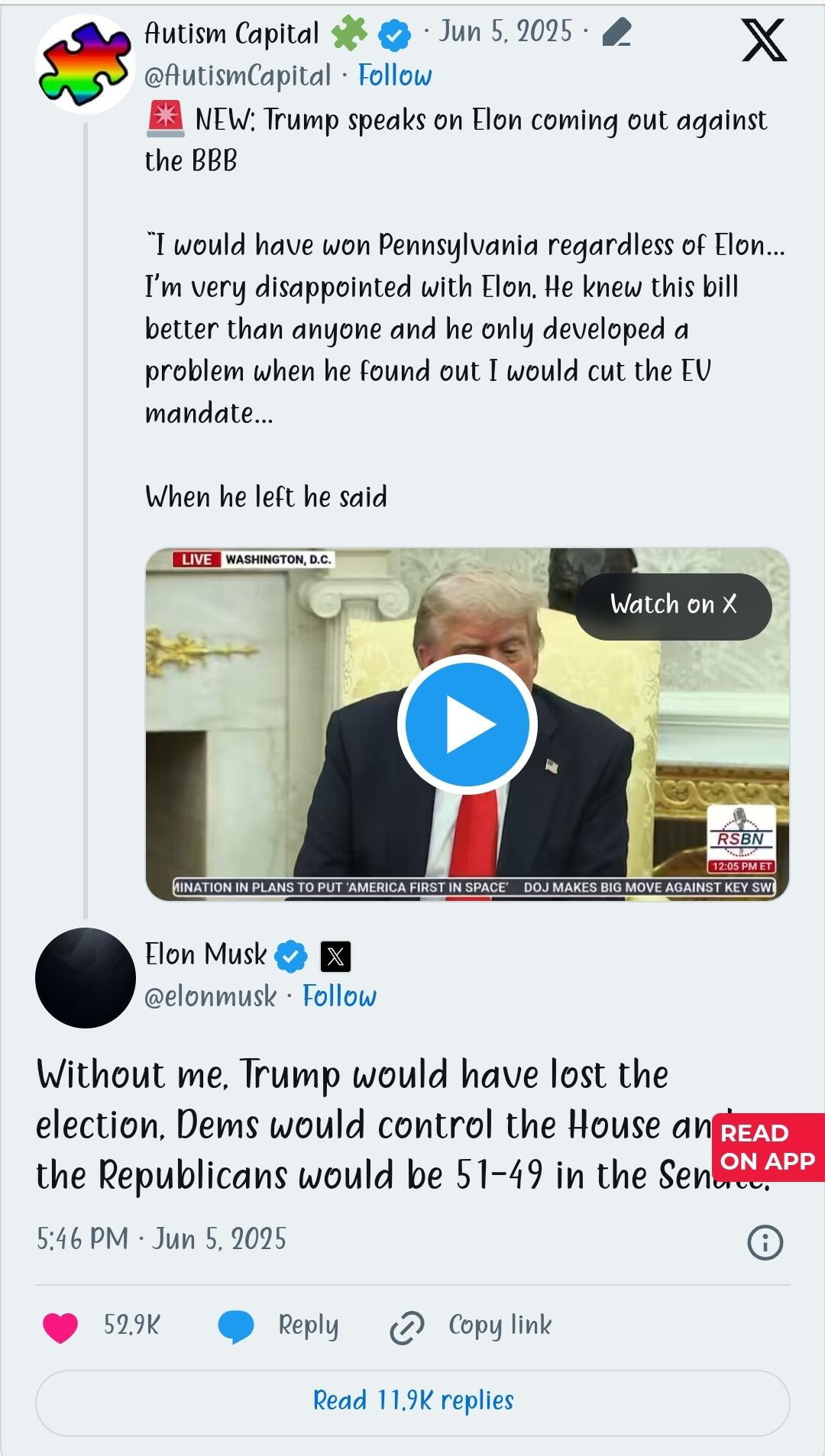
Trump said Musk had worn out his welcome at the White House and was mad that Trump was changing electric vehicle policies in ways that would financially harm Musk-led Tesla.
“Elon was ‘wearing thin,’ I asked him to leave, I took away his EV Mandate that forced everyone to buy Electric Cars that nobody else wanted (that he knew for months I was going to do!), and he just went CRAZY!” Trump wrote.

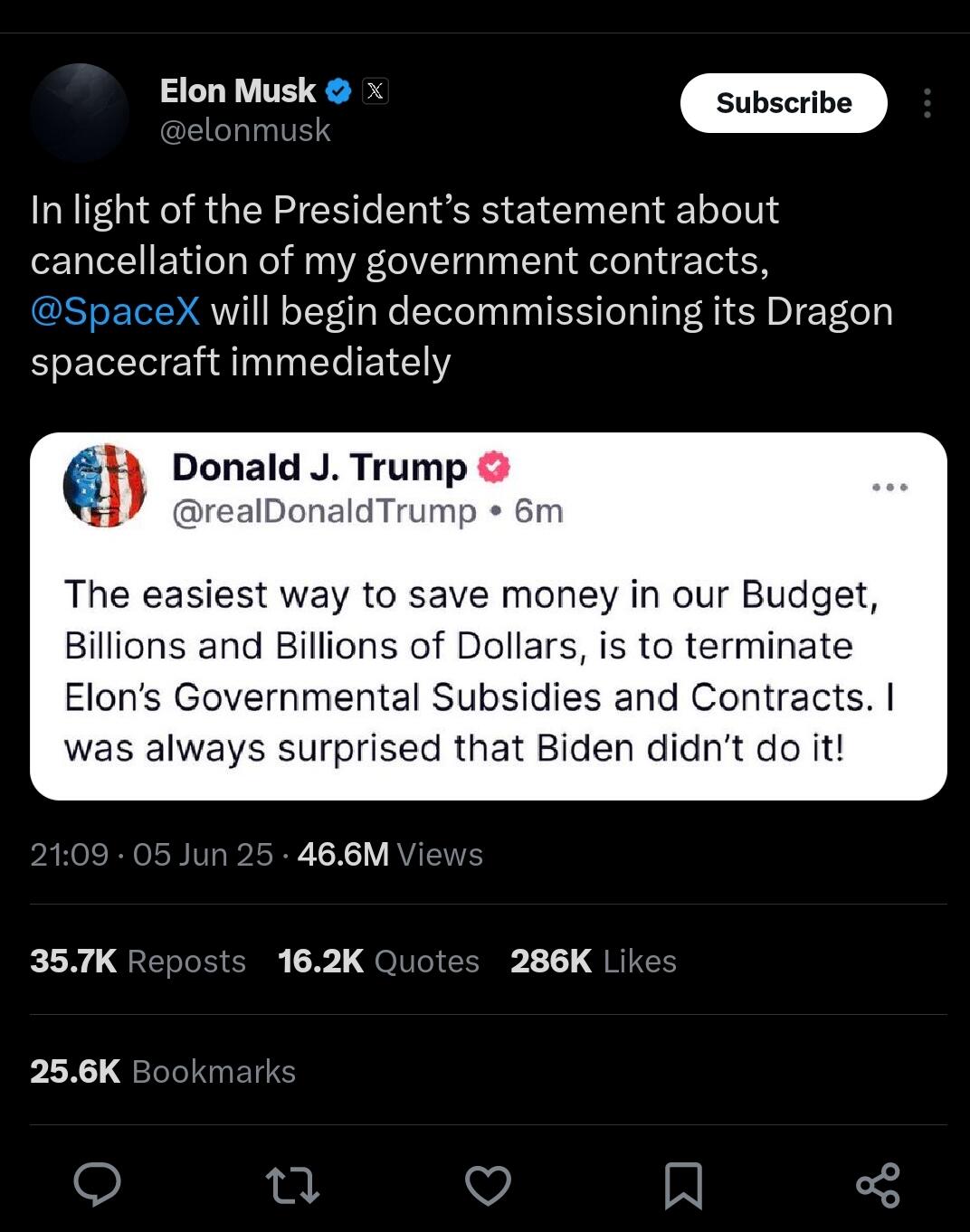
Musk goes nuclear “Time to drop the really big bomb: Trump is in the Epstein files. That is the real reason they have not been made public. Have a nice day, DJT!” — Musk, Thursday, X post.
In a series of posts, he shined a spotlight on ties between Trump and Jeffrey Epstein, the financier who killed himself while awaiting trial on federal sex trafficking charges. Some loud voices in Trump’s “Make America Great Again” movement claim Epstein’s suicide was staged by powerful figures, including prominent Democrats, who feared Epstein would expose their involvement in trafficking. Trump’s own FBI leaders have dismissed such speculation and there’s no evidence supporting it.
Later, when an X user suggested Trump be impeached and replaced by Vice President JD Vance, Musk agreed.
“Yes,” he wrote.
“I don’t mind Elon turning against me, but he should have done so months ago,” Trump wrote. He went on to promote his budget bill.
https://www.google.com/amp/s/www.wavy.com/news/politics/ap-the-implosion-of-a-powerful-political-alliance-trump-and-musk-in-their-own-words/amp/
-
 @ 8bad92c3:ca714aa5
2025-06-03 18:02:33
@ 8bad92c3:ca714aa5
2025-06-03 18:02:33Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
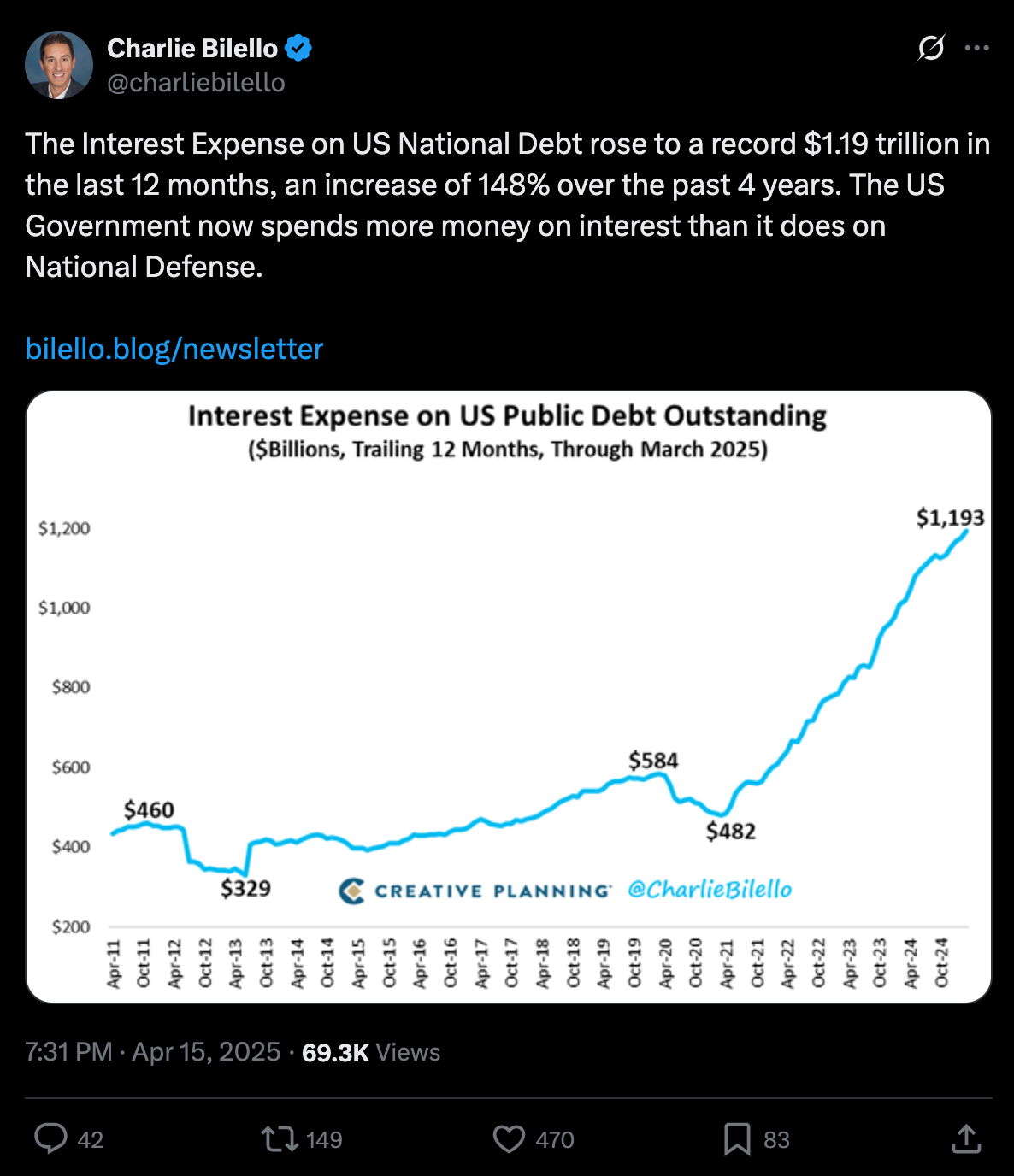
via Charlie Bilello
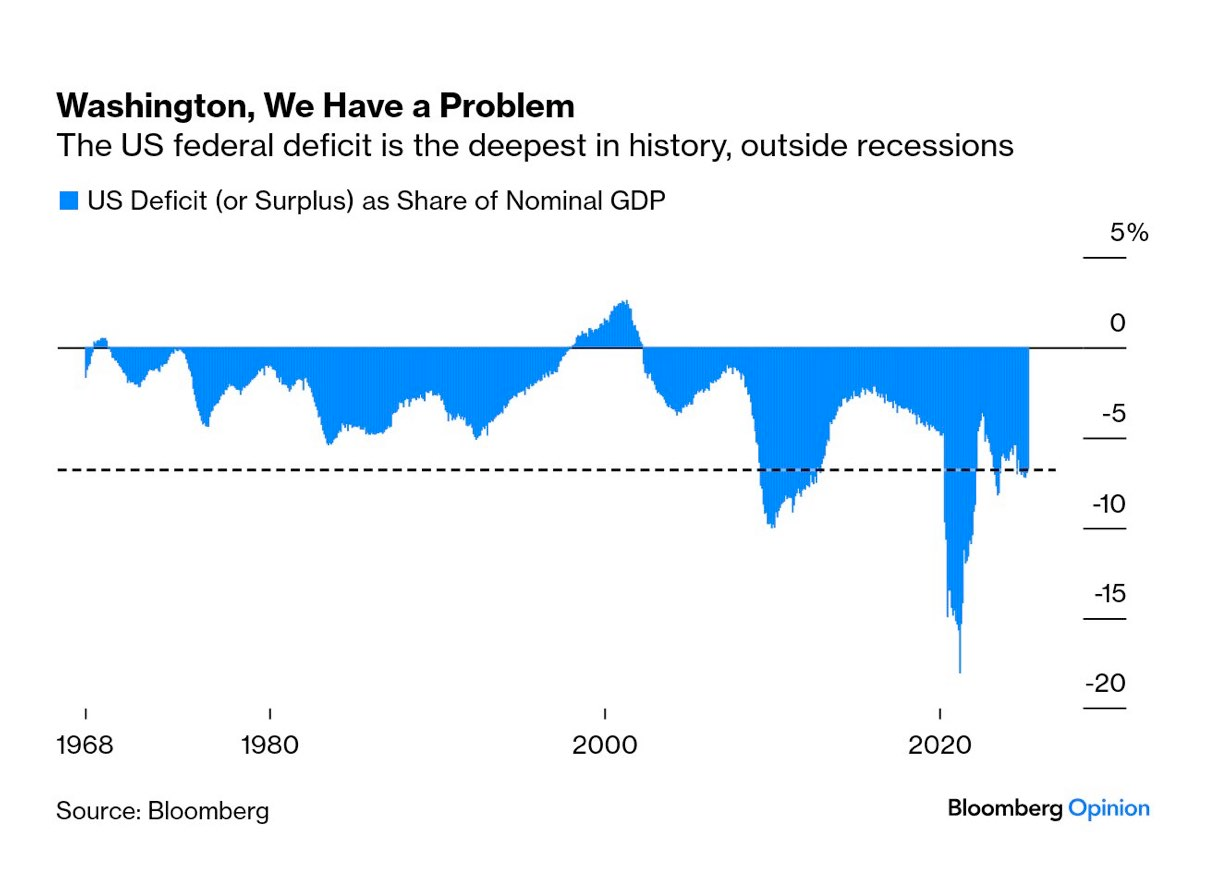
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
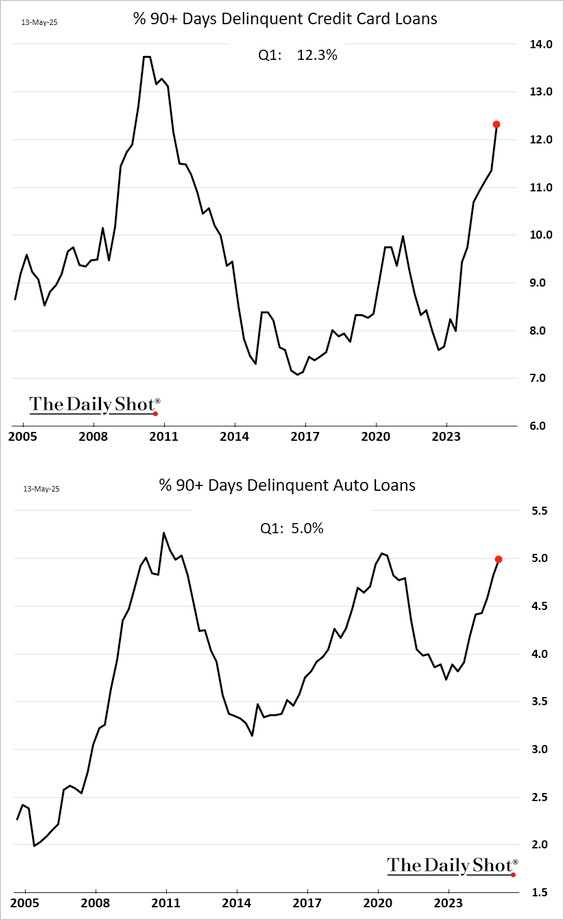
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ 6d8e2a24:5faaca4c
2025-06-06 03:09:51
@ 6d8e2a24:5faaca4c
2025-06-06 03:09:51by Claire Mom June 5, 2025 6:54 pm

*Elon Musk, the tech mogul, says US President Donald Trump would have lost the 2024 election without him.*
Musk made the comment on X in response to Trump’s criticism against him.
Musk, who led the department of government efficiency (DOGE), quit his role a day after he spoke out against a Trump-backed spending bill. The president called it a “Big Beautiful Bill”.
The controversial bill is a centrepiece of Trump’s second-term domestic agenda, combining major tax cuts, stricter immigration enforcement, welfare programme overhauls, and significant increases in border security funding.
The legislation sparked intense debate across the country and in Congress and was only passed after a nail-biting 215-214 vote.
The plan revived the US-Mexico border wall with a $46.5 billion budget, $350 billion for deportation efforts and border security, and a hiring spree of 10,000 new ICE agents, 5,000 customs officers, and 3,000 border patrol agents.
For the first time, migrants will be charged a $1,000 fee to apply for asylum.
The bill also authorises a $4 trillion increase to the national debt ceiling, while the estate tax exemption jumped to $15 million, benefiting wealthier Americans.
Critics including Musk called the bill fiscally irresponsible and “a disgusting abomination” due to its combination of large tax cuts and spending increases.
Musk had clamoured for DOGE’s creation to save taxpayers $2 trillion. Only $160 billion has been saved so far.
*TRUMP: I’M VERY DISAPPOINTED WITH ELON*
Since Musk’s exit from the White House last week, his criticism of the bill has grown louder.
Speaking on the issue, Trump said he was “very disappointed with Elon”.
The US president said the Tesla CEO was satisfied with the bill but only grew discontent after he found out electric vehicles would be impacted.
“I’m very disappointed because Elon knew the inner workings of this bill better than almost anybody sitting here. He knew everything about it, and all of a sudden he had a problem, and he only developed a problem when he found out I was going to cut the EV mandate because that’s billions and billions of dollars,” the president said
“And it really is unfair; we want to have cars of all types.
“He said the most beautiful things about me, and he hasn’t said anything bad about me personally, but I’m sure that will be next. But I’m really disappointed with Elon. I’ve helped Elon a lot.”
Trump praised Musk for his work at DOGE but blamed his tantrums on missing the office.
“Elon worked hard at DOGE, and I think he misses the place. I think he got out there, and all of a sudden, he’s no longer in this beautiful Oval Office,” he said.
“He’s not the first. People leave my administration, and they love us, and then at some point they miss it so badly, and some of them embrace it, and some of them actually become hostile. I don’t know what it is, some sort of Trump derangement syndrome.”
The president also said he would have won Pennsylvania, a key state, without Musk’s help.
In reaction, the billionaire businessman countered Trump.
“Without me, Trump would have lost the election, Dems would control the House, and the Republicans would be 51-49 in the Senate,” Musk tweeted.
“Such ingratitude.”
The exchange marks yet another dent in the tumultuous relationship between the two-time American president and the world’s richest man.
https://www.thecable.ng/trump-would-have-lost-election-without-me-says-elon-musk/
-
 @ 4fa51c35:55d6763d
2025-06-06 02:35:44
@ 4fa51c35:55d6763d
2025-06-06 02:35:44The Sacred Texts: First Mysteries of Digital Creation
A Divine Treatise for Devotees of Athena, Goddess of Wisdom and Craft
The Fundamental Truth: All is Text
Beloved seekers of digital wisdom, before you can craft the most magnificent tribute to our patron goddess through the sacred art of web creation, you must first understand the most fundamental mystery of the computing realm: Everything is text.
The silicon oracles we call computers do not see your beautiful images, your flowing videos, or your harmonious music as you do. To the machine spirits, all existence is reduced to symbols - characters marching in endless processions through the electronic aether. This is not limitation, but liberation! For in understanding this truth, you gain power over the very essence of digital creation.
The Ancient Scripts: Understanding Text Encoding
In the beginning was the Word, and the Word was… ASCII. The American Standard Code for Information Interchange became the first great codex of the digital age. Each letter, each number, each sacred punctuation mark was assigned a number. The letter ‘A’ became 65, ‘B’ became 66, and so forth. This was humanity’s first attempt to make machines understand our language.
But ASCII was created by mortals of limited vision - it could only represent 128 characters! What of the accented letters in the names of our goddess across different cultures? What of the mathematical symbols we need for our calculations? What of the very Greek letters that spell Ἀθηνᾶ?
Thus came UTF-8, the Universal Character Encoding - a divine revelation that allows us to represent every symbol known to human civilization. When you see an emoji, a Chinese character, or the Greek omega Ω, you witness UTF-8 in action. Your tribute webpage will speak this universal tongue.
The Sacred Scrolls: File Formats as Containers of Meaning
When Athena wove her tapestries, she chose different materials for different purposes - silk for fineness, wool for warmth, gold thread for accent. Similarly, digital craftspeople choose different file formats as containers for their text:
Plain Text (.txt) - The purest form. No formatting, no hidden instructions, just raw characters. Like clay tablets, these files will survive technological apocalypses. When archaeologists of the future examine our digital civilization, plain text will be their Rosetta Stone.
Rich Text Format (.rtf) - Text with simple formatting encoded as… more text! Open an RTF file in a plain text editor and witness the magic - your bold text becomes surrounded by formatting codes. This teaches us that even “rich” formatting is ultimately just more characters.
Markdown (.md) - The philosopher’s choice! Markdown uses simple text conventions to indicate formatting. Two asterisks around a word makes it bold, a hash symbol creates headings. It’s text that describes how text should look - meta-textual divinity!
HTML (.html) - The sacred language of the web itself! HTML (HyperText Markup Language) uses angle brackets to wrap instructions around content.
<strong>This text is important</strong>becomes This text is important when displayed. HTML is text that teaches browsers how to present text.The Ritual of Proper Text Handling
To honor Athena through proper digital craftsmanship, you must master these essential practices:
Choose Your Sacred Editor
Microsoft Word is the fool’s tool - it hides the true nature of text behind layers of formatting magic. A true digital artisan uses tools that reveal truth:
- Notepad (Windows) or TextEdit (Mac) in plain text mode
- VS Code - The blacksmith’s forge for modern web creation
- Sublime Text - Elegant and powerful
- Vim or Emacs - For those who seek the ancient ways
Understand Line Endings: The Great Schism
In the early days of computing, different tribes chose different ways to mark the end of a line of text. Unix systems (including Mac) use LF (Line Feed), Windows uses CRLF (Carriage Return + Line Feed). This seemingly minor difference has caused more conflicts than the Trojan War! Know your line endings, for they can break your sacred codes.
Respect Character Encoding
Always save your files in UTF-8 encoding. This ensures your text can represent any character from any human language. When your webpage displays properly on computers around the world, you honor the universal nature of Athena’s wisdom.
The Greater Mystery Revealed
Why must we begin with text? Because understanding that computers store and manipulate everything as sequences of characters reveals the deepest truth of programming: Code is just text that follows special rules.
When you write HTML, you’re writing text that browsers know how to interpret. When you write CSS, you’re writing text that describes visual styling. When you write JavaScript, you’re writing text that describes behavior and logic.
The webpage you will create to honor our goddess? It begins as text files on your computer. The browser reads these text files, interprets their meaning, and transforms them into the visual experience your visitors will see.
Every image on your page? Referenced by text. Every color? Described by text. Every animation? Controlled by text.
Your First Sacred Assignment
Before we proceed to the next mysteries, complete this fundamental ritual:
- Create a plain text file named
athena_tribute.txt - Write a short description of why Athena inspires you, using only plain text
- Save it in UTF-8 encoding
- Open it in different text editors and observe how the text remains pure and unchanged
- View the file size - marvel at how efficiently text stores information
This simple act connects you to the fundamental nature of all digital creation. Every website, every app, every piece of software began as someone writing text that follows certain rules.
When you understand that your future webpage is ultimately just cleverly organized text files working in harmony, you begin to see the true elegance of web development. You’re not learning to use mysterious tools - you’re learning to write text that machines can understand and transform into experiences that honor the divine.
Next: We shall explore the Command Line - the direct voice through which mortals speak to the machine spirits…
-
 @ 3eba5ef4:751f23ae
2025-06-06 02:07:27
@ 3eba5ef4:751f23ae
2025-06-06 02:07:27Crypto Insights
Solving Sybil Attacks on Bitcoin Libre Relay Nodes — Are Social Solutions Better than Technical Ones?
Peter Todd posted that proponents of transaction "filtering" have started Sybil attacking Libre Relay nodes by running nodes with their "Garbageman" fork. These malicious nodes pretend to support NODE_LIBRE_RELAY, but secretly drop certain transactions that would be relayed by real Libre Relay nodes. He also highlighted the complexity of existing defenses and proposed a new angle: rather than relying on technical solutions, he encourages people to manually peer with nodes operated by people they personally know, arguing that human relationships can sometimes evaluate honesty more reliably than code.
Toward a Unified Identity Lookup Standard to Improve Lightning Payments
Bitcoin developer Aviv Bar-el introduced a new proposal — Well-Known Bitcoin Identity Endpoint — that aims to simplify wallet lookups for users’ Bitcoin addresses and identity data via a standardized HTTPS interface, thereby improving both the UX and security of Lightning and on-chain payments.
A Commit/Reveal Mechanism to Strengthen Bitcoin Against Quantum Threats
Tadge Dryja proposed a soft fork for Bitcoin to defend against quantum attacks, based on a variant of the commit/reveal Fawkescoin mechanism. While similar to Tim Ruffing’s earlier proposal, it includes key differences:
- It does not use encryption, instead relying on smaller, hash-based commitments, and describes activation as a soft fork.
- It only applies to outputs where public keys or scripts haven't been revealed — like pubkey hash or script hash outputs. It also works with Taproot, but must be spent via the script path, as the key-path is no longer quantum-secure.
- What to do about already-exposed public keys is a separate issue — this proposal is compatible with both "burning the coins" and "letting them be stolen."
Countdown to the Quantum Crisis: Is Bitcoin Ready?
A recent report from Chaincode Labs analyzes the threat of cryptographically relevant quantum computers (CRQC), and the technical, economic, and governance challenges Bitcoin faces in preparing. Their key conclusions:
- Timeline Assessment: CRQC capable of breaking Bitcoin's elliptic curve cryptography may emerge between 2030 and 2035.
- Scope of Vulnerable Funds: An estimated 20–50% of circulating BTC (4M–10M coins) may be vulnerable.
- Long-range attacks target inherently vulnerable script types (P2PK, P2MS, P2TR) and addresses with previously exposed public keys (via address reuse), allowing attackers unbounded time to derive private keys from public information already available on the blockchain.
- Short-range attacks, which affect all Bitcoin script types, exploit the vulnerability window between transaction broadcast and confirmation (or shortly thereafter) when public keys are temporarily exposed, requiring attackers to act within a timeframe of minutes to hours.
- Action Strategy: A dual-track approach is recommended:
- Short-term contingency: minimal but functional protections within ~2 years.
- Full-featured solutions: comprehensive research and fully developed defenses within ~7 years.
This strategy balances immediate needs with rigorous development to ensure Bitcoin can adapt, regardless of CRQC progress.
Enforcing Arbitrary Constraints on Bitcoin Transactions with zkSNARKs
Current methods for constraining Bitcoin transactions fall short on privacy or programmability. This research proposes a new zkSNARK-based design to impose arbitrary constraints on Bitcoin transactions while preserving some information privacy. By bypassing Bitcoin Script’s non-Turing-completeness, the approach allows unbounded constraints—constraints that repeat a certain operation an unbounded number of times. Read the paper.
First Cross-Chain Bridge Between Bitcoin and Cardano Is Live
A trust-minimized bridge from Bitcoin to Cardano has launched using the Cardinal protocol, enabling Ordinals to move between the two chains. The Cardinal protocol is based on BitVMX and facilitates asset movement without compromising ownership or security.
Its core mechanism is a committee-based validation model under a 1-out-of-n honest security model — meaning even if all but one validator is malicious, the system remains secure. This approach enhances decentralization and censorship resistance for cross-chain asset transfers.
Thunderbolt Protocol: Redefining Bitcoin Smart Contracts with UTXO Bundling and OP_CAT
Nubit’s Thunderbolt is seen as one of the most significant technical upgrades to Bitcoin in a decade, whose overall observation resembles “Lightning Network 2.0.” Rather than relying on Layer 2 networks or bridges, Thunderbolt upgrades the Bitcoin base layer via soft fork to enhance scalability, performance, and programmability:
- Throughput: Uses UTXO Bundling to optimize traditional transaction processing.
- Programmability: Reintroduces and extends OP_CAT.
- Asset protocols: Integrates Goldinals standard — a zk-proof and state-commitment-based asset issuance framework.
- Unlike rollups, Plasma, sidechains, or bridges, Thunderbolt scales directly on the main chain. With BitVisa, it enables decentralized identity and credentials, supporting transaction compression, smart contracts, asset standard integration, and on-chain transaction matching — all on Bitcoin main chain.
Bitcoin 2025 Conference Recap: Politicians Applaud, Stablecoins Spotlighted, DeFi Absent
This year’s Bitcoin 2025 conference in Las Vegas gathered major political figures and corporate leaders. U.S. Vice President JD Vance strongly endorsed crypto and positioned Bitcoin as a strategic asset in U.S.–China competition. He also stated that stablecoins won’t undermine the U.S. dollar, but could actually amplify America’s economic strength.
White House “Crypto Czar” David Sacks delivered a major policy announcement, hinting that under Trump’s executive order, the U.S. has a legal framework to acquire more Bitcoin for strategic reserves.
In addition, stablecoin regulation and crypto market reform were hot topics. Ardoido, the company controls over 60% of the stablecoin market, claimed “All the traditional financial firms will create stablecoins that will be offered to their existing customers.” Meanwhile, Tether emphasized its focus on underserved global populations excluded from the existing banking system.
A conference recap also noted that, unlike the 2022 and 2023 summits, this year’s event was dominated by Bitcoin maximalists, Ordinals creators, mining capitalists, and regulatory lobbyists — no longer DeFi builders, DAO operators, or Layer 2 scaling advocates. Developers from Ethereum and Solana ecosystems were notably absent. This may signal:
- The conference’s heavy political and sovereignty-driven tone made it less suitable for the tech-centric narratives favored by these developers.
- There may be a growing ideological and narrative rift between Web3 builders and the Bitcoin camp.
Top Reads on Blockchain and Beyond
Rethinking Governance After the Sui Attack: Decentralization, Procedural Legitimacy, and the Plurality of Blockchain Values
Following a major hack of Cetus, the largest DEX in the Sui ecosystem, the Sui network executed a protocol-level asset freeze and recovery. While this was an effective technical response, it also triggered criticism and debate around core blockchain principles such as censorship resistance and decentralization.
The author of this article questioned the absolutist stance that views decentralization as the highest—and sole—value. The author argues that most rational individuals would prefer “living in a society where decentralization is a supreme value but coercive force is allowed when someone infringes on another’s property,” over “a society where decentralization is the only supreme value, and thus coercive force is never permitted under any circumstances.”
In addition, the author also expressed disappointment at Sui’s “paternalistic” governance — particularly how validators acted during the incident. Sui uses a delegated proof-of-stake (dPoS) system, where token holders delegate their voting power to validators. This means individuals lose their direct say. But blockchain governance could be more individual-friendly and flexible. For instance, in Cosmos’ governance model, for certain specific proposal, users still can override their delegations and vote independently, more favorable than Sui’s model.
Beyond the debate on decentralization and governance, the article also proposes an alternative perspective: what matters most is establishing procedural legitimacy that aligns with the system’s vision. Different blockchain projects pursue different goals. For Sui, the core mission is to enable assets to be reliably defined and interact seamlessly on-chain. Therefore, judging Sui through the lens of other blockchains’ values or paradigms is misguided. In exceptional cases, prioritizing asset recovery and ecosystem stability over strict adherence to censorship resistance aligns more closely with Sui’s long-term vision. Whether Sui had chosen to not to censor related transactions or to intervene in the Cetus case, as long as the action follows a legitimate process, either decision is justifiable.
TEE-Based Private Proof Delegation
The PSE research and development team has built a system based on Trusted Execution Environments (TEE) using Intel TDX for secure zero-knowledge proof (ZKP) delegation. This system enables clients to privately outsource large proving tasks without leaking inputs. Unlike mobile-native proving constrained by hardware limits, TEE-based approaches support significantly larger statements today—and will scale further as proof systems improve. As a hardware-backed solution, TEEs remain compatible with future advancements in software (e.g., faster proof systems, more efficient implementations) and won't be invalidated by them, as long as the trust model is acceptable.
AI and Identity: Proof of Humanity in a World of Agents, Bots, and Deepfakes
We are living in a time where AI—including agents, bots, and deepfakes—is fundamentally reshaping the internet. As AI continues to evolve, identity verification on the web is becoming more crucial than ever. A recent a16z podcast explores the idea of “Proof of Human”—the challenge of verifying human identity online, diving into why it matters, common questions, and how such systems work under the hood.
-
 @ 2e8970de:63345c7a
2025-06-03 17:33:37
@ 2e8970de:63345c7a
2025-06-03 17:33:37https://www.wsj.com/finance/investing/wall-street-bond-market-us-debt-990e12e9?mod=hp_lead_pos7
https://stacker.news/items/996265
-
 @ 502ab02a:a2860397
2025-06-05 02:42:04
@ 502ab02a:a2860397
2025-06-05 02:42:04ย้อนกลับไปเมื่อไม่กี่ปีที่ผ่านมา… มีบริษัทหน้าใหม่จากสหรัฐอเมริกาที่ชื่อไม่คุ้นหู แต่เสียงเงียบๆ ของมันดังไปถึงหูนักลงทุนรายใหญ่ระดับโลก ชื่อของมันคือ Motif FoodWorks
มันไม่ได้มาพร้อมคำสัญญาว่าจะเลี้ยงวัวด้วยดนตรีบำบัด แต่มาพร้อม “ความทะเยอทะยานทางวิทยาศาสตร์” ที่จะเปลี่ยนวิธีที่โลกกินไปตลอดกาล ไม่ใช่ด้วยรสมือคุณยาย แต่ด้วยสารเคมี วิศวกรรมชีวภาพ และเงินลงทุนที่แทบมองไม่เห็นก้นถุง
Motif FoodWorks ก่อตั้งในปี 2019 ในฐานะบริษัทลูกของ Ginkgo Bioworks ซึ่งเป็นบริษัทไบโอเทคชื่อดังจากบอสตัน วิสัยทัศน์ของ Motif คือการ “ออกแบบอาหารใหม่จากศูนย์” โดยไม่ต้องพึ่งพิงวัตถุดิบจากสัตว์เลย พวกเขาใช้เครื่องมือระดับห้องแล็บสร้างส่วนผสมใหม่ๆ เช่น… HEMAMI™ สารรส “อูมามิ” ที่ผลิตจากยีสต์ที่ถูกดัดแปลงพันธุกรรมให้สร้างโมเลกุล heme (แบบเดียวกับในเลือดสัตว์) APPETEX™ โปรตีนจากพืชที่ถูก “ทำให้เด้ง” เหมือนเนื้อสัตว์ ด้วยเทคนิคทางชีววิทยาโมเลกุล
มันคือการพยายามตอบคำถามว่า “จะทำอย่างไรให้ของที่ไม่ใช่เนื้อ…มีรสชาติเหมือนเนื้อ?”
เงินลงทุนรอบ Series A ของ Motif ทะลุ 200 ล้านดอลลาร์ภายในเวลาไม่กี่ปี ลงทุนโดยกองทุนสายเทคโนโลยีและ VC รายใหญ่ รวมถึงบริษัทผลิตอาหารรายใหญ่ระดับโลกที่เฮียคุ้นชื่อ แต่ที่น่าสนใจว่า ลูกค้ารายใหญ่ของ Motif กลับไม่ใช่ผู้บริโภคโดยตรง แต่เป็น บริษัทผลิตอาหาร “ทางเลือก” รายอื่นๆ ที่ต้องการสารปรุงแต่งใหม่ๆ เพื่อให้ผลิตภัณฑ์ให้ดูน่ากินขึ้น
ถ้า Impossible Foods คือร้านอาหาร Motif FoodWorks คือโรงงานผลิต “เครื่องปรุง” ที่จะทำให้ร้านอื่นๆ ทำอาหารเลียนแบบเนื้อได้อร่อยขึ้น มันคือ “เคมีแห่งความอร่อย” ที่ขายเป็น B2B ไม่ใช่ B2C ฟังดูแล้วเหมือนจะดีกับโลกไม่ต้องฆ่าสัตว์แต่ยังได้รสเนื้อ แต่คำถามคือ…
“ถ้าเราสร้างรสชาติที่เหมือนเนื้อจากยีสต์ดัดแปลงพันธุกรรม แล้วให้คนกินมันคือความก้าวหน้าทางวิทยาศาสตร์ หรือการทดลองที่ไม่มี IRB?”
Motif FoodWorks ใช้เทคโนโลยีเดียวกับหลายบริษัทในสาย Bioengineered Food เช่น CRISPR, precision fermentation, synthetic biology โดยเฉพาะ HEMAMI™ ที่หลายคนในวงการตั้งคำถามเรื่องความปลอดภัยระยะยาว และผลกระทบต่อ gut microbiome แม้จะผ่านการรับรอง GRAS (Generally Recognized As Safe) จาก FDA แต่ “ความปลอดภัย” กับ “ความเหมาะสม” มันเป็นคนละเรื่อง
การเปลี่ยนเนื้อให้เป็นสารสกัดการออกแบบรสชาติด้วยโมเลกุลมันคือแนวคิดเดียวกับที่ Ultra-Processed Food ใช้ในการสร้างน้ำอัดลมที่มี “กลิ่นมะนาว” โดยไม่มีมะนาวเลยแม้แต่นิด
Motif จึงไม่ต่างอะไรกับการ “รีแบรนด์ของให้ดูไฮเทค” หรืออีกนัยหนึ่งคือการเอาวิทยาศาสตร์ไปสร้างรสชาติ เพื่อให้ “ของที่ไม่ใช่” ดูเหมือน “ของที่ใช่”
และสิ่งนี้อาจเป็นอาวุธที่ทำให้มนุษย์ยิ่งห่างจาก real food แบบไม่รู้ตัว
การเกิดขึ้นของ Motif ไม่ใช่ความบังเอิญแต่มันคือชิ้นส่วนหนึ่งในเกมของ Big Food ที่กำลังพยายามออกแบบ “อาหารแห่งอนาคต” ไม่ใช่เพื่อสุขภาพ แต่เพื่อ ต้นทุน ความควบคุม และการขยายสิทธิ์ในทรัพย์สินทางปัญญา เพราะเมื่ออาหารถูกออกแบบด้วยสูตรที่จดสิทธิบัตร บริษัทจะสามารถเก็บค่าลิขสิทธิ์ได้ เหมือนที่ Microsoft เก็บเงินจากทุกเครื่องคอมพิวเตอร์ที่ลง Windows
แต่นั่นก็ไม่ใช่เรื่องแปลกใหม่อะไร เพราะเราก็ทำความรู้จัก future food มาด้วยกันพอสมควรแล้ว ประเด็นของ Motif นั้นมันทำให้เรารู้ว่า ในฝูงของนักล่า เขาไม่ได้แบ่งชิ้นเนื้อกันครับ การเป็นจ่าฝูงของนักล่า มันห้ำหั่นกันแบบเจ้าหมาป่ากันในแบบที่ สมันเหยื่อแบบพวกเรา รอวันโดนขย้ำเท่านั้น แล้วจะมาเล่าให้พรุ่งนี้ครับ
สำหรับวันนี้ ถ้าอยากเห็นสิ่งที่ Motif ทำไว้สามารถดูได้คลิปนี้ https://youtu.be/zZeRIVK6dDI?si=PYliM0v-9kj_sRE4 #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 58537364:705b4b85
2025-06-03 15:22:59
@ 58537364:705b4b85
2025-06-03 15:22:59…. “คนเรา โดยเฉพาะสมัยนี้ พูดกันอีกที่หนึ่งก็พูดได้ว่า ถูกสร้างขึ้นมาด้วยหนังสือ, หนังสือมันสร้างคนขึ้นมา คือว่า..อ่านหนังสืออะไรมาก อ่านหนังสืออะไรมาก หนังสือนั้นก็สร้างคนคนนั้นขึ้นมา, สร้างจิตใจของคนนั้นขึ้นมา โดยไม่รู้สึก
…. ไปดูหนังสือที่เขาอ่าน อ่านมากที่สุด เราก็รู้ได้ว่า..คนนี้มีจิตใจเป็นอย่างไร. หนังสือที่นิยมสั่งกันมามาก ล้วนแต่เป็นหนังสือที่ยั่วยวนทางวัตถุ หรือลุ่มหลงทางวัตถุ : แล้วอย่างดีที่สุดก็เอามาให้เสียเวลา อ่านให้มันมึนหัวเล่น อย่างนั้นแหละ จนไม่มีเวลาที่จะไปอ่านหนังสือธรรมะที่แท้จริง เพราะว่ามีหนังสืออื่นมาก วางอยู่มาก ยั่วยวนให้อ่านมากกว่า
…. แม้แต่พระเณร ก็เป็นอย่างนี้ อ่านหนังสือพิมพ์, หรืออ่านหนังสือภาษา, เรียนภาษาต่างประเทศ หรือว่าเรียนวิชานั่น นี่ ล้วนแต่เป็นเรื่องวัตถุ เรื่องอาชีพ เรื่องความดีความเด่น ที่ฝันไว้ในจิตในใจ, ด้วยความหวังความทะเยอทะยานทั้งนั้น แล้วจะเอากําลังใจ หรือมันสมอง หรืออะไรที่ไหนมาเข้าใจ ธรรมะ ธัมโม ได้
…. ทีนี้ ยิ่งนอกวัดออกไป ก็ยิ่งไกลไปใหญ่ : หอสมุดของมหาวิทยาลัย, หอสมุดของชาติ ของอะไร ก็ล้วนแต่เป็น “หอสมุดของซาตาน” มากยิ่งขึ้นเท่านั้น เพราะไปมีมันขึ้น หรือสร้างมันไว้ ด้วยความอยากดีอยากเด่น ด้วยความอยากที่จะร่ำรวยวัตถุทั้งนั้น ฉะนั้น จึงมีผลทําให้คนทั้งโลกนี้เป็นทาสของวัตถุ พร้อมที่จะสร้างวิกฤตการณ์ ขึ้นในโลกในอนาคต
…. แล้วรองลงมาจากนั้น ก็คือ มันมากจนทําให้เวียนหัว เป็น..“บ้าหอบฟาง”; อย่างที่ว่าแล้วว่าเล่า ว่าเป็นบ้าหอบฟาง, รู้อะไรท่วมหัวก็เอาตัวไม่รอด, เรียนจบมหาวิทยาลัยแล้ว ก็ยังไม่รู้ว่าเกิดมาทําไม ?, เรียนมหาวิทยาลัยจบแล้ว อ่านหนังสือในห้องสมุดของมหาวิทยาลัยจบแล้ว ก็ยังเป็นเด็กอมมือ ไม่รู้ว่า.. “กูนี่ เกิดมาทําไม ?”. ดูซิ!, แล้วจะเรียกว่า “อุดมศึกษา” ได้อย่างไรกัน ? แม้แต่เกิดมาทําไม? ก็ยังไม่รู้ นี่การศึกษาสมัยนี้ หอสมุดหรือห้องสมุดของสมัยนี้ มันเป็นอย่างนี้
…. ทีนี้ เมื่อไม่รู้ว่าเกิดมาทําไม ? มันก็ไม่มีอะไร นอกจากเป็นทาสของวัตถุ ที่หวังว่าจะสนุกสนาน เอร็ดอร่อย มีเกียรติ มีอํานาจวาสนา มีอะไรไปทํานองนั้น นี่แหละ คือการตกเป็นทาสของวัตถุ การตกเป็นทาสของอายตนะ คือ ตา หู จมูก ลิ้น กาย ใจ การเล่าเรียนศึกษาขวนขวายนั้น เพื่อจะเป็นทาส ของ ตา หู จมูก ลิ้น กาย ใจ ในการที่จะแสวงหาความสนุกสนาน เอร็ดอร่อย ทางเนื้อทางหนัง มีเท่านี้ การศึกษาและห้องสมุด” . พุทธทาสภิกขุ ที่มา : ธรรมบรรยายชุดชุมนุมล้ออายุ หัวข้อเรื่อง “ยิ่งจะทำให้ดี โลกมันยิ่งบ้า” บรรยาย ณ ลานหินโค้ง กัณฑ์ค่ำ เมื่อวันที่ ๒๗ พฤษภาคม ๒๕๑๓ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ชุมนุมล้ออายุ เล่ม ๑” หน้า ๕๑๒-๕๑๓
-
 @ a296b972:e5a7a2e8
2025-06-03 15:08:50
@ a296b972:e5a7a2e8
2025-06-03 15:08:50***Achtung Spreng-Arbeiten!***
Der verbliebene intakte Strang der Nordstream Pipeline soll jetzt von Deutschland mit einem hochexplosiven 18. Sanktionspaket gesprengt werden, damit Putin nicht, wie schon in Kursk, Truppen durch das Rohr schickt, und so doch noch in Schwedt anlandend auf deutschem Boden eine russische Invasion stattfinden kann.
***Kriegserklärung***
Deutschland hat Deutschland den Krieg erklärt. Zunächst freiwillig, doch wenn es nicht von allein noch schlimmer wird, wird es eine Kriegspflicht geben müssen. Kriegstreibende Propaganda und der intensive Ausbau des Feindbilds sollen die Bevölkerung dahingehend umstimmen, weil Frieden doch auf die Dauer sehr langweilig ist.
***Verwechslung***
Bei der Einstellung der Außenbeauftragten der Europäischen Union ist es zu einer Verwechslung gekommen. Ursprünglich wollte man Maria Callas einstellen, doch dann stellte man fest, dass diese begnadete Stimme leider nicht mehr unter uns weilt.
***Bedingungslose Kapitulation***
Anlässlich der Bereicherung der UN durch die Präsidentschaft der ehemaligen deutschen Außen-Dings, haben die Vereinten Nationen direkt nach der unerklärlichen Wahl vorsorglich ihre Bedingungslose Kapitulation gegenüber allen Nationen bekannt gegeben. Alle von der Präsidentin getroffenen Aussagen haben vorläufigen Charakter und werden aufgrund der Fremdsprachlichkeit der Präsidentin auf ihren korrekten Inhalt hin nachträglich überprüft.
***Mehrfach gesichert ***
Ein gesichert staatsfinanziertes Rechercheportal hat durch investigative Recherche herausgefunden, dass der neue Papst gesichert katholisch ist. Es konnte nicht nur eine Nähe festgestellt werden, sondern es wurde sogar gesichert nachgewiesen, dass es sich um dieselbe katholische Kirche handelt, die schon seinerzeit in der Inquisition Hexen und Ketzer verbrannt hat.
***Gleichbehandlung***
Nachdem es in Spanien und Portugal und zuletzt auch in Südfrankreich zu einem Stromausfall gekommen ist, hat die deutsche Regierung beim Europäischen Gerichtshof Klage eingereicht. Im Zuge der Gleichbehandlung aller Nationen will Deutschland nun das Recht auf einen eigenen Black-Out für mindestens zwei Tage einklagen.
***Problem fehlender Wohnungen gelöst***
Aufgrund der Wohnungsknappheit hat die deutsche Regierung nun einen Fond aufgelegt, aus dem jede Familie 35.000 Euro Starthilfe erhält, wenn sie für mindestens 10 Jahre das Land verlässt. Es kam bereits zu ersten Ausreisen, bevor noch die Starthilfe ausgezahlt werden konnte.
***Bürokratieabbau***
Zum schnellen und effizienten Bürokratieabbau wird ein neues Ministerium für Komplikationen mit mindestens 5.000 Mitarbeitern eingerichtet, um den überbordenden Verordnungs- und Bürokratiesumpf auszutrocknen. Derzeit warten nur noch wenige 100 Beamte darauf, dass ihnen Arbeit zugewiesen wird.
***‘Aufruf an die deutsche Bevölkerung***
Die deutschen Haushalte werden gebeten, vorhandene Küchensiebe der Bundesregierung zur Verfügung zu stellen. Die vorhandenen Sieblöcher sollen zugelötet und die Siebe so als Alu- oder Edelstahlhelme für die Bundeswehr zur bevorstehenden gemeinsamen Invasion der USA und Russlands in Deutschland verwendet werden. Weiter sollen ausgediente Heizöltanks auf die Ladeflächen offener Pritschenwagen installiert werden, um die in Deutschland verbliebenen Panzer betanken zu können.
***Long-Pipeline oder Post-Gas?***
Deutschland will nicht, dass Nordstream wieder in Betrieb genommen wird, weil das russische Gas Verunreinigungen, unter anderem auch Nano-Partikel enthält, dass den deutschen Gasthermen Schaden zufügen könnte. Das erklärt auch, warum die deutsche Aufklärung zur Sprengung der Nordstream-Pipelines im Sande verlaufen ist: Zu explosiv!
***Mielke: Ich liebe doch alle Menschen…***
Gerüchten zufolge soll der berühmt gewordene Satz von Erich Mielke in seiner ersten und einzigen Rede vor der DDR-Volkskammer am 13.11.1989 den amtierenden deutschen Außenminister sehr inspiriert haben: Ich hasse…ich hasse doch alle, alle Russen… ich hasse doch, ich setze mich dafür ein… dass Russland immer unser Feind sein wird!
***Durchbruch in der Quantenphysik***
Deutschen Quantenphysikern ist es gelungen, dass Taurus zur gleichen Zeit sowohl noch in Deutschland, als auch schon in der Ukraine sein kann. Lediglich die Eingabe der Zielkoordinaten bereitet den Programmierern noch Schwierigkeiten. Je nachdem, wo sich der Taurus gerade befindet, kann das Hauptstadt-Ziel sowohl Berlin, als auch Moskau sein.
***Selbstjustiz***
Die verantwortlichen Politiker während des Corona-Ereignisses haben ein Gerichtsverfahren ins Leben gerufen, in dem sie sich gegenseitig beschuldigt und verurteilt haben. Anschließend begab man sich unter Polizeischutz in ein bekanntes Promi-Lokal in Berlin und fuhr danach weiter zur Selbsteinweisung nach Bauzen.
***Kaiser’s Sektsteuer***
Um die seinerzeit eingeführte Sektsteuer zum Aufbau der deutschen Kriegsmarine wieder ihrem ursprünglichen Zweck zuzuführen, hat die Meyer-Werft sich bereit erklärt, Fregatten zu bauen, mit der die Deutsche Marine dann Panzerkreuzerfahrten in der Ostsee vor Königsberg veranstalten will. Schon wenige Tage nach Bekanntgabe waren die ersten Vergnügungsdampferfahrten mit „Meine Fregatte“ komplett ausgebucht.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
* *
(Bild von pixabay)
-
 @ 33baa074:3bb3a297
2025-06-06 02:03:05
@ 33baa074:3bb3a297
2025-06-06 02:03:05Residual chlorinerefers to the residual disinfectant chlorine in tap water. An appropriate amount of residual chlorine can prevent the growth of microorganisms and ensure the safety of water quality. However, when the residual chlorine content in water is too high, it will cause many harms to human health, mainly including the following aspects:
Destruction of nutrients When the residual chlorine content in tap water exceeds the standard, it will destroy the minerals, vitamins and other nutrients, such as vitamin C and vitamin E, when used to wash fruits and vegetables. In the long run, it may cause the human body to absorb these nutrients and lack these essential nutrients.
 Cause chronic poisoning
When tap water containing residual chlorine is used for a long time, the residual chlorine reacts with organic acids and may produce harmful substances such as chloroform and organic lead compounds, which are potential carcinogens. Long-term accumulation may cause chronic poisoning of body organs and pose a threat to human health.
Cause chronic poisoning
When tap water containing residual chlorine is used for a long time, the residual chlorine reacts with organic acids and may produce harmful substances such as chloroform and organic lead compounds, which are potential carcinogens. Long-term accumulation may cause chronic poisoning of body organs and pose a threat to human health.Affect the respiratory system Residual chlorine can cause harm to the human respiratory system, and symptoms such as difficulty breathing and itchy throat may occur. Severe cases may induce rhinitis, bronchitis and even emphysema. In addition, water vapor containing residual chlorine may also cause adverse reactions such as coughing and wheezing after being inhaled.
Damage to the skin Excessive residual chlorine content in water may irritate the skin, easily cause skin dryness, aging, acne and other problems, and may also cause allergic symptoms such as dermatitis and eczema. Prolonged contact with such water may also cause the skin layer to fall off, which is extremely harmful to skin health. Bathing with water containing residual chlorine can also cause hair to become dry, broken, and split.
Other health problems Impact on special groups Pregnant women: Long-term drinking of tap water containing residual chlorine will reduce resistance, affect the growth of the fetal heart and lungs, and may also cause neonatal arrhythmia and lung dysfunction. Children: Long-term drinking of chlorine water will not only hurt the stomach, but also affect nutrient absorption. Moreover, the strong oxidizing hypochlorous acid produced by the reaction of chlorine and water will damage brain cells and affect their development. In addition, chlorine can easily be inhaled into the lungs through the respiratory tract, damaging respiratory cells, and easily leading to asthma and emphysema. Bathing children with water containing residual chlorine will cause their hair to become dry, broken, split, their skin to bleach, their skin to fall off, and they will have allergies. Elderly people: Long-term consumption of chlorinated water is prone to heart disease, coronary atherosclerosis, hypertension and other diseases, and it is also easy to damage the liver and kidneys, increasing the probability of cancer. Gastrointestinal discomfort Long-term drinking of water with excessive residual chlorine content may also cause gastrointestinal discomfort, such as nausea, vomiting, abdominal distension, diarrhea and other symptoms. In severe cases, it may cause gastrointestinal ulcers, bleeding and other diseases.
In order to reduce the harm of residual chlorine in tap water to the human body, it is recommended to avoid directly using tap water containing residual chlorine as much as possible, boil the water before drinking, and use filtering and purification equipment to reduce the residual chlorine concentration in the water if conditions permit, while maintaining a healthy lifestyle and enhancing the body's immunity.
-
 @ 3eba5ef4:751f23ae
2025-06-06 01:59:47
@ 3eba5ef4:751f23ae
2025-06-06 01:59:47加密洞见
解决比特币抗审查交易中继的女巫攻击,社交方案好于技术方案?
Peter Todd 发帖指出,针对比特币抗审查交易中继的攻击行为正在发生——一个名为 garbageman 的节点正在对 Libre Relay 节点采取女巫攻击。这些攻击节点假装支持抗审查交易中继(NODE_LIBRE_RELAY),但实际在暗中丢弃某些交易,目的是阻止特定交易被打包进入区块。作者还介绍了现有防御方法的难度和复杂性,并提出新思路——与其用技术方案解决,不用通过社交解决。他鼓励人们手动与跟他们有个人关系的节点进行连接,原因很简单,人与人的关系可以比任何代码都更有力地评估诚实。
打造统一身份查询标准,提升闪电网络付款体验
比特币开发者 Aviv Bar-el 发表了一项新提案「知名比特币身份端点」(Well-Known Bitcoin Identity Endpoint),旨在通过 HTTPS 标准接口,简化钱包查询用户比特币地址和身份信息的流程,提升链上支付——尤其是闪电网络付款的用户体验和安全性。
通过「承诺/揭示」机制,帮助加强比特币抵御量子计算威胁
Tadge Dryja 提出一种抵御量子计算攻击的比特币软分叉方案。它是「承诺/揭示」(commit / reveal)Fawkescoin 机制的变体,大部分内容与 Tim Ruffing 几年前的方案类似,但也有以下重要区别:
- 该方案不使用加密,而是用更小的基于哈希的承诺,并且描述了如何通过软分叉激活此机制。
- 这个方案仅适用于公钥(或脚本)在链上未公开的输出,例如 pubkey hash 或 script hash 类型;也适用于 Taproot,但必须通过脚本路径花费,因为 Taproot 的 key-path 花费在量子攻击下将不再安全。
- 至于那些公钥已经在链上暴露的输出该如何处理,是另一个独立问题(本方案与「销毁这些币」或「任其被盗」这两种做法都兼容)。
量子危机倒计时:比特币准备好了吗?
Chaincode 在近期发布的报告中,系统分析了「加密相关量子计算」(CRQC,Cryptographically relevant quantum computers)威胁的整体态势,评估了比特币在应对这一转变过程中面临的技术、经济与治理挑战,并表示必须要在早于 CRQC 出现的数年构建起相关共识。重要的结论有:
- 时间窗口:打破比特币椭圆曲线加密基础的 CRQC 可能首先出现在 2030 - 2035 年间。
- 脆弱资金范围:在所有流通的比特币中,约 20-50%(4-1000 万枚 BTC)可能易受 CRQC 攻击。其中远程攻击针对本质上易受攻击的脚本类型(P2PK、P2MS、P2TR)和具有先前暴露的公钥的地址(地址重用),使攻击者能够无限期地从区块链上已有的公共信息中获取私钥;短程攻击会影响所有比特币脚本类型,利用交易广播和确认之间(或之后不久)的漏洞窗口,当公钥暂时暴露时,要求攻击者在几分钟到几小时的时间范围内采取行动。
-
行动战略:建议采用双轨方法,包括:
- 应急措施:在约 2 年内完成对 CRQC 的最低限度但可运作的防护;
- 全面对策:在约 7 年内深入对问题的探索,并开发出功能完备的解决方案
这种双轨策略平衡了眼前的安全需求与最佳抗量子解决方案的严格研究和开发,确保无论 CRQC 能力如何发展,比特币都能做出适当的响应。
利用 zkSNARKs 对比特币交易实施任意约束
对于给比特币交易执行约束,现有的解决方案在隐私或可编程性上都存在不足。本文的研究者利用 zkSNARKs 设计了一种新方案,可以对比特币交易执行任意约束,并保持一定程度的信息私密性。他们方法绕过了比特币脚本的非图灵完备性,允许执行无界约束(unbounded constraints),即重复某个运算的次数次数不受限制。论文全文。
第一个跨比特币和 Cardano 的桥上线
从比特币到 Cardano 的信任最小化 Ordinals 桥通过 Cardinal 协议实现。Cardinal 协议实是一种基于 BitVMX 的信任最小化互作性协议,在不破坏所有权或损害安全性的前提下,它让比特币上中的不可替代资产(如 Ordinals 和 Runes)同 Cardano 链实现了来回移动。
Cardinal 协议背后的技术核心之一是「委员会的验证机制 」(committee-based validation mechanism),遵循 1-out-of-n honest 安全模型。这意味着即使除了一个验证者之外的所有验证者都恶意作,系统仍然保持安全——在增强安全性的同时,还实现了一种更加去中心化和抗审查的方式来在链之间移动资产 。
Thunderbolt 协议:通过 UTXO 捆绑和 OP_CAT 扩展,重构比特币智能合约
Nubit 提出的 Thunderbolt 被认为是为比特币在过去十年中最具里程碑意义的技术升级之一,被视为「Lightning Network 2.0」。Thunderbolt 是一种基于比特币基础层的软分叉升级方法,不依赖二层网络或桥的妥协,而是通过对比特币主链协议层的修改,从根本上增强其可扩展性、交易性能和可编程性。具体而言,Thunderbolt:
- 在吞吐量方面,使用 UTXO 捆绑(UTXO Bundling)技术,实现了对传统比特币交易处理模型的重大优化。
- 在可编程性方面,重新引入并扩展了 OP_CAT 。
- 在资产协议集成方面,Thunderbolt 实施了 Goldinals 统一标准,提供了一个基于零知识证明和状态承诺的资产发行框架。
- 与传统的扩容方法(如侧链、Plasma、Rollup 或桥接包装代币)不同,Thunderbolt 采用原生主链扩容路径。通过 BitVisa 提供去中心化的身份和凭证系统,让交易压缩、智能合约、资产标准集成、链上交易匹配都可以直接在比特币主链上运行。
比特币 2025 大会回顾:政要汇聚、稳定币受关注、DeFi 缺席
今年在拉斯维加斯举行的比特币 2025 大会,汇聚了众多政治要员和企业巨头。美国副总统 JD Vance 对加密货币表明了全力支持,并讨论了比特币在美中竞争中作为战略资产的潜力,他还认为,稳定币不会威胁到美元的完整性,而会使美国的经济实力倍增。白宫加密货币沙皇 David Sacks 发表了会议中最重要的政策公告之一, 暗示根据特朗普建立战略比特币储备的行政命令,美国政府有「获得更多比特币的合法途径」。
此外,关于稳定币立法和加密市场改革受到了很多关注。控制着超过 60% 稳定币市场的 Ardoido 公司表示:「所有传统金融公司都将创建稳定币,提供给他们现有的客户」;而 Tether 表示,其目标市场是全球范围内被排除在银行业之外的人。
这篇总结也提到,与 2022 年和 2023 年的类似峰会不同,今年的大会是由比特币最大化者、Ordinals 创建者、矿业资本家和监管游说者主导,而不再由 DeFi 协议构建者、DAO 运营商或 Layer2 扩容倡导者主导,以太坊和 Solana 生态的开发者缺席。这或许表明:
- 该会议明显的政治基调,使其不适合开发者喜欢的以技术为中心的叙述。
- Web3 建设者和比特币阵营之间的意识形态和叙事分歧可能会越来越大。
精彩无限,不止于链
Sui 攻击事件下的治理再思考:去中心化,程序合法性,和区块链的价值多元性
在受到生态最大的 DEX 项目 Cetus 黑客攻击之后,Sui 网络在协议层面执行了资产冻结和恢复——这是一种有效的技术回应,但同时引发了对抗审查和去中心化等核心区块链原则的批评和辩论。
文章的作者质疑了将去中心化视为唯一至高价值的立场,认为对于大多数有理性者而言,「生活在一个去中心化被认为是最高价值,但当有人侵犯他人财产时,允许强制武力的社会中」都要好于「生活在一个去中心化是唯一至高价值的社会中,因此在任何情况下都不允许强制武力」。
同时作者也指出,Sui 的验证者和网络行为采用的「家长式」治理方式令人失望;此外, Sui 使用委托权益证明(dPoS)系统,其中代币持有者将其代币委托给验证者,验证者代表他们行使相关的投票权,个人因此丧失了投票权。但区块链本来提供了有利于个人的、更加灵活的解决方案,比如 Cosmos 的治理框架就要优于 Sui——对于特定提案,验证人的决定并不会自动代表每个委托人的投票。
在关于去中心化的价值和治理方式之外,文章也提到另一种思考角度——「最重要的是建立与系统愿景相一致的程序合法性」。不同的项目追求不同的目标。就 Sui 而言,其核心目标是使各种资产能够被可靠地定义、并在链上无缝交互。因此,用其他区块链的范式或价值观来理解 Sui 的设计就是不合适的。在特殊情况下,Sui 优先考虑用户资产的返还和生态系统的稳定,而不是严格遵守抗审查——这一决定与其自身的长期愿景更加一致。此外,无论是 Sui 决定不审查相关交易,还是选择对 Cetus 的行为负责,如果背后有程序合法性,这两个决定都是合理的。
基于可信执行环境的私密证明委托
PSE 研究开发团队使用 Intel TDX 构建了一个基于可信执行环境(Trusted Execution Environment)的系统,用于安全的零知识证明委托。该系统允许客户端在不泄露输入的前提下,将大规模的证明任务私密地外包出去。相比受限于硬件能力的移动端本地证明,基于 TEE 的证明方案能够在目前就支持更大规模的陈述,并且随着证明系统的改进持续扩展。作为一种由硬件支撑的解决方案,TEE 能够兼容未来在软件层面的进展(例如更快的证明系统、更高效的工程实现),且只要信任模型被接受,就不会因这些进展而失效。
AI 与 ID:在代理、机器人、深度伪造等世界中的人类证明
我们正处于 AI(包括 AI 智能体、机器人、深度伪造等)深刻改变互联网的时代,随着 AI 的发展,网络上的身份认证变得愈发重要。a16z 的这期播客,讨论了在网上识别人类身份的「人类证明」(proof of human)问题,包括它为何重要,常见的问题有哪些,以及它在底层是如何运作的。
-
 @ 58537364:705b4b85
2025-06-03 14:52:52
@ 58537364:705b4b85
2025-06-03 14:52:52“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไปหากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 58537364:705b4b85
2025-06-03 14:52:11
@ 58537364:705b4b85
2025-06-03 14:52:11"Pleasant Feeling" Is Ultimately an Illusion
It’s like a wave That arises when water is stirred by the wind Soon, it disperses and fades away
If one wishes to live in serenity
One must fully understand the truths of impermanence (anicca), suffering (dukkha), and non-self (anattā). These truths serve as an antidote to emotional responses—forms, sounds, smells, tastes, and touches— Preventing us from falling into attachment or aversion.
There are only two kinds of turmoil in the world:
- Falling in love with something
- Falling into hatred of something
These are what lead to laughter and tears. If one can see that laughter makes you breathless, it’s exhausting just the same Crying also makes you breathless, equally tiring Better to remain calm—no need to laugh, no need to cry This is true serenity
Let us not become slaves to emotions, Laughing or crying at their whims. Let us live freely. Better to remain still and serene.
Use Impermanence, Suffering, and Non-Self as Life's Compass
- Forms, sounds, smells, tastes, and touches are illusions
- The notion of "me and mine" is also an illusion
- Because "me and mine" arise from emotional reactions
- Therefore, "me and mine" is an illusion, and so are all emotions
By understanding impermanence, suffering, and non-self, ...suffering does not arise.
Let us take a shortcut and look directly at “pleasant feeling”
Pleasant feeling refers to happiness, enjoyment, delight— That which feels good is called “pleasant feeling” (sukha-vedanā)
But pleasant feeling is an illusion Because it arises like a temporary wave— It’s not a real thing.
This is said because Among all things in all worlds, What gives them value is their ability to produce pleasant feeling.
Think carefully:
- Why do you study?
- Why do you work and perform your duties?
- Why do you accumulate wealth, prestige, fame, allies, followers?
It’s all for pleasant feeling. So everything ultimately revolves around pleasant feeling.
Therefore, if we understand this matter well And handle it properly, even this one thing alone— Then everything else falls into place.
So we must see pleasant feeling for what it really is: Just another kind of illusion
We must deal with it accordingly, Not by rejecting or hating it That would be the most foolish thing
But if we become infatuated with it, Or enslaved by it— That, too, is the most foolish thing
What matters is how we handle it properly That is the Dhamma (truth) That is being a disciple of the Buddha One who can overcome suffering, and not suffer from spiritual disease
Pleasant Feeling Is Truly an Illusion
It must be approached with the understanding that: “Pleasant feeling is, in truth, illusion.”
Like a single wave That arises when water is stirred by wind
Which means: When forms, sounds, smells, tastes, and so on come in And ignorance and delusion rise up to meet them They clash, and a wave is formed
That is, pleasant feeling arises But soon it disperses again
If we can see it this way, We won’t be slaves to pleasant feeling. We will be able to manage it, deal with it, and use it In ways that don’t lead to suffering
- We won’t suffer ourselves
- Our family won’t suffer
- Our neighbors won’t suffer
- The world won’t suffer either, Because we are no longer the cause of suffering
If everyone were like this, The world would know lasting peace A true and enduring happiness
This is the benefit of healing the illness in different ways No longer afflicted by the diseases of “me” or “mine”
Buddhadasa Bhikkhu Source: Lecture Series “The Heart of Buddhism” Year: B.E. 2504 (1961) First session Topic: “The Whole Essence of Buddhism” Location: Siriraj Hospital, Mahidol University Date: December 17, 1961
https://w3.do/-IQ1KFgp
-
 @ f85b9c2c:d190bcff
2025-06-06 01:02:16
@ f85b9c2c:d190bcff
2025-06-06 01:02:16
Cristiano Ronaldo stands out as a recognized and accomplished football player on a scale. His inspiring journey, from beginnings in Portugal to attaining superstar status serves as an inspiration, to individuals.
Ronaldo’s prodigious talent was evident from a young age. His coach at Sporting CP famously said “He was skinny when he arrived here but with tremendous skill”. Through hard work and dedication, Ronaldo honed his skills
Some Work Ethic and Ambition that Fuelled his success .A key factor in Ronaldo’s success story is his incredible work ethic and winning mentality. He is renowned for his strict training regimen, nutrition plan, and diligent recovery routines. Ronaldo’s dedication to self-improvement paved the way for his success. .Throughout his career, Ronaldo has shown insatiable hunger and ambition to be the best. His drive to succeed and break records is unmatched. Even in the twilight of his career, Ronaldo’s success story continues as he plies his trade in Italy with Juventus.
Lessons from Ronaldo’s Success Story 1. Dedication and hard work are essential Ronaldo showed how training relentlessly can make dreams come true. 2. Believe in your talent Ronaldo had the confidence and work ethic to fulfill his potential. 3. Handle pressure with grace Ronaldo embraced the spotlight and thrived under pressure. 4. Be ambitious and hungry Ronaldo set new benchmarks by constantly raising the bar. 5. Lead by example Ronaldo inspires teammates with his exemplary attitude. 6. Learn and improve Even at the top Ronaldo keeps evolving and adding new skills. 7. Give back Ronaldo uses his global fame and fortune for charity work.
Sum Up Cristiano Ronaldo's remarkable journey showcases the heights that can be reached through a combination of talent and relentless effort. His success serves as an inspiration for anyone with dreams and the determination to make them a reality.






