-
 @ 6d8e2a24:5faaca4c
2025-06-06 04:26:58
@ 6d8e2a24:5faaca4c
2025-06-06 04:26:58
President Donald Trump attends a meeting with the Fraternal Order of Police in the State Dinning Room of the White House, Thursday, June 5, 2025, in Washington. (AP Photo/Alex Brandon)
Last Friday, President Donald Trump heaped praise on Elon Musk as the tech billionaire prepared to leave his unorthodox White House job.
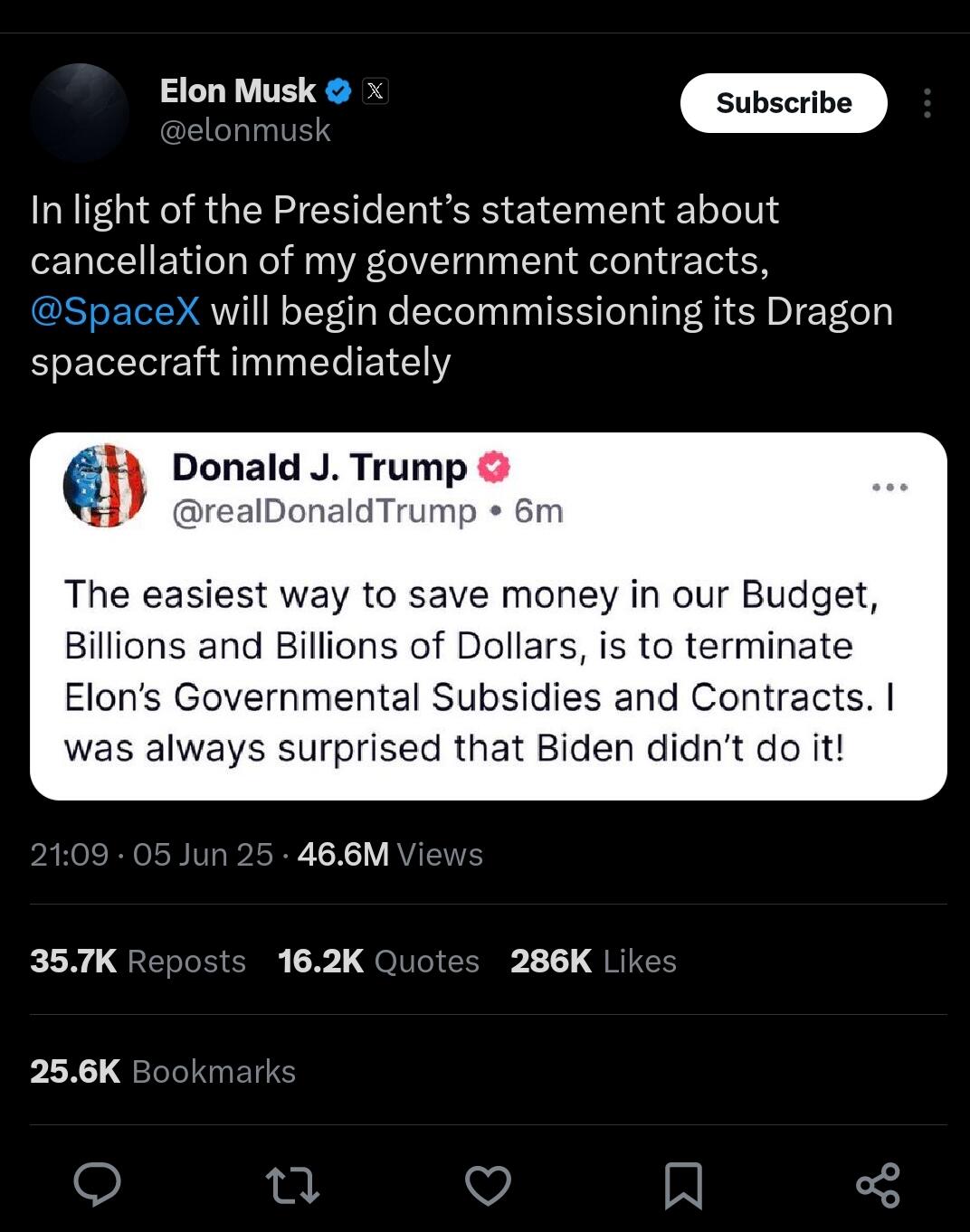
Less than a week later, their potent political alliance met a dramatic end Thursday when the men attacked each other with blistering epithets. Trump threatened to go after Musk’s business interests. Musk called for Trump’s impeachment.
social media posts urging lawmakers to oppose deficit spending and increasing the debt ceiling.
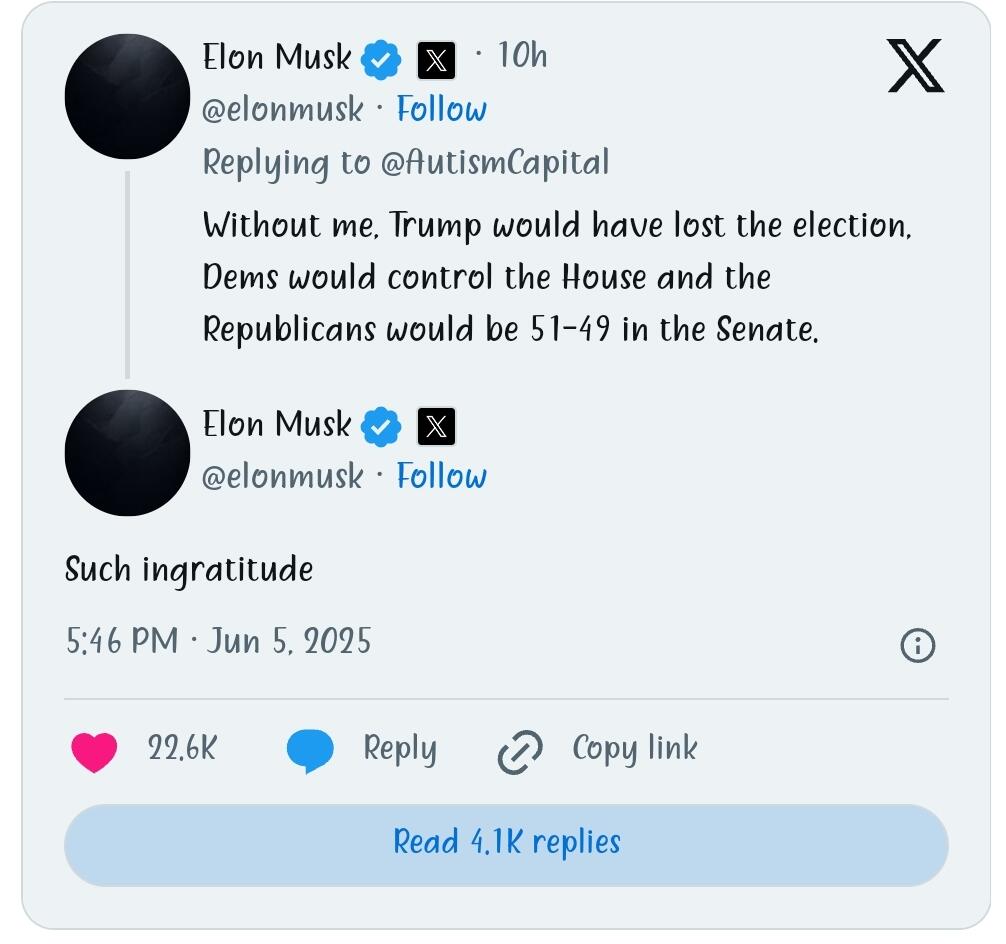
“Without me, Trump would have lost the election, Dems would control the House and the Republicans would be 51-49 in the Senate,” Musk posted, a reference to Musk’s record political spending last year, which topped $250 million.
“Such ingratitude,” he added.
Trump said Musk had worn out his welcome at the White House and was mad that Trump was changing electric vehicle policies in ways that would financially harm Musk-led Tesla.
“Elon was ‘wearing thin,’ I asked him to leave, I took away his EV Mandate that forced everyone to buy Electric Cars that nobody else wanted (that he knew for months I was going to do!), and he just went CRAZY!” Trump wrote.

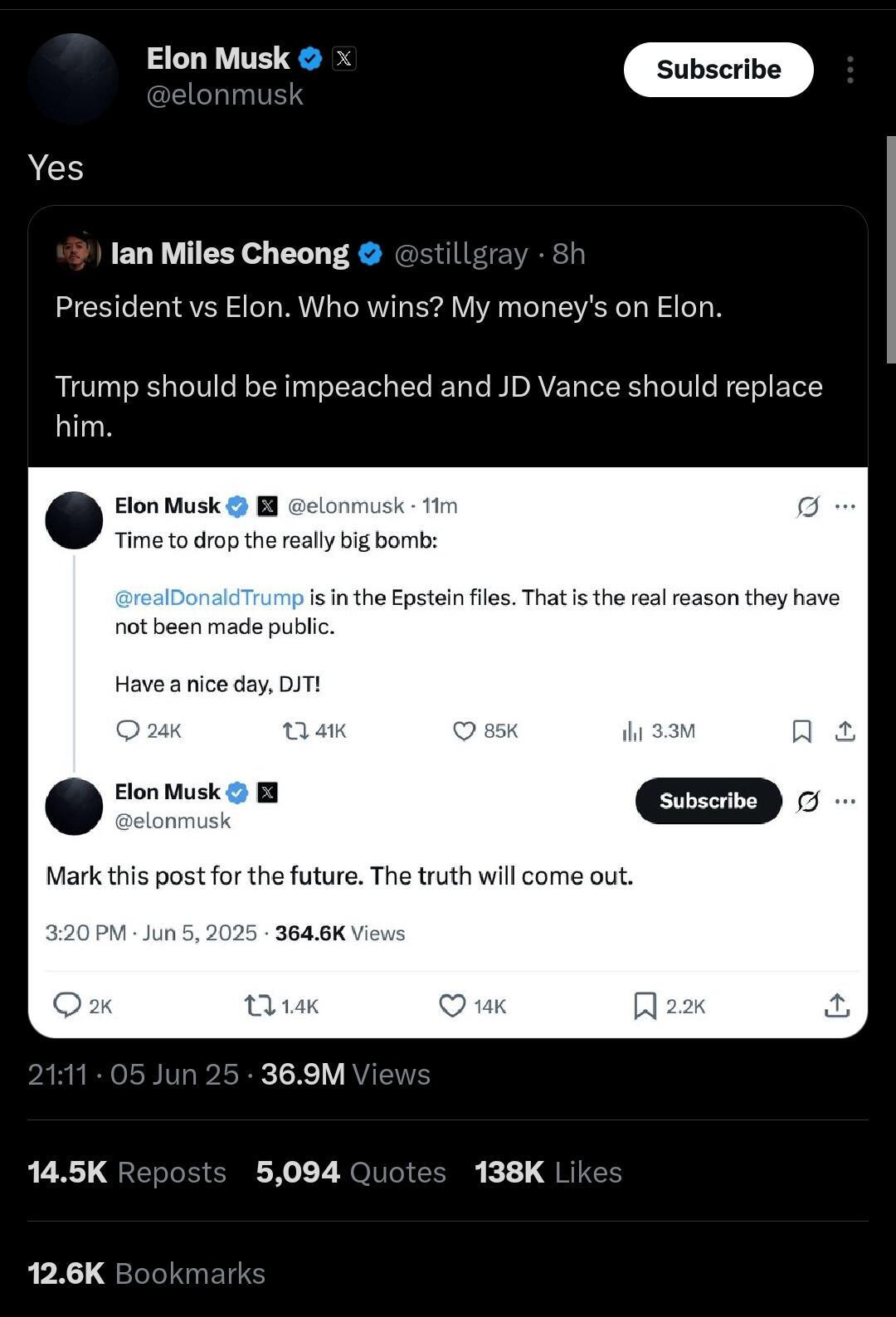
Musk goes nuclear “Time to drop the really big bomb: Trump is in the Epstein files. That is the real reason they have not been made public. Have a nice day, DJT!” — Musk, Thursday, X post.
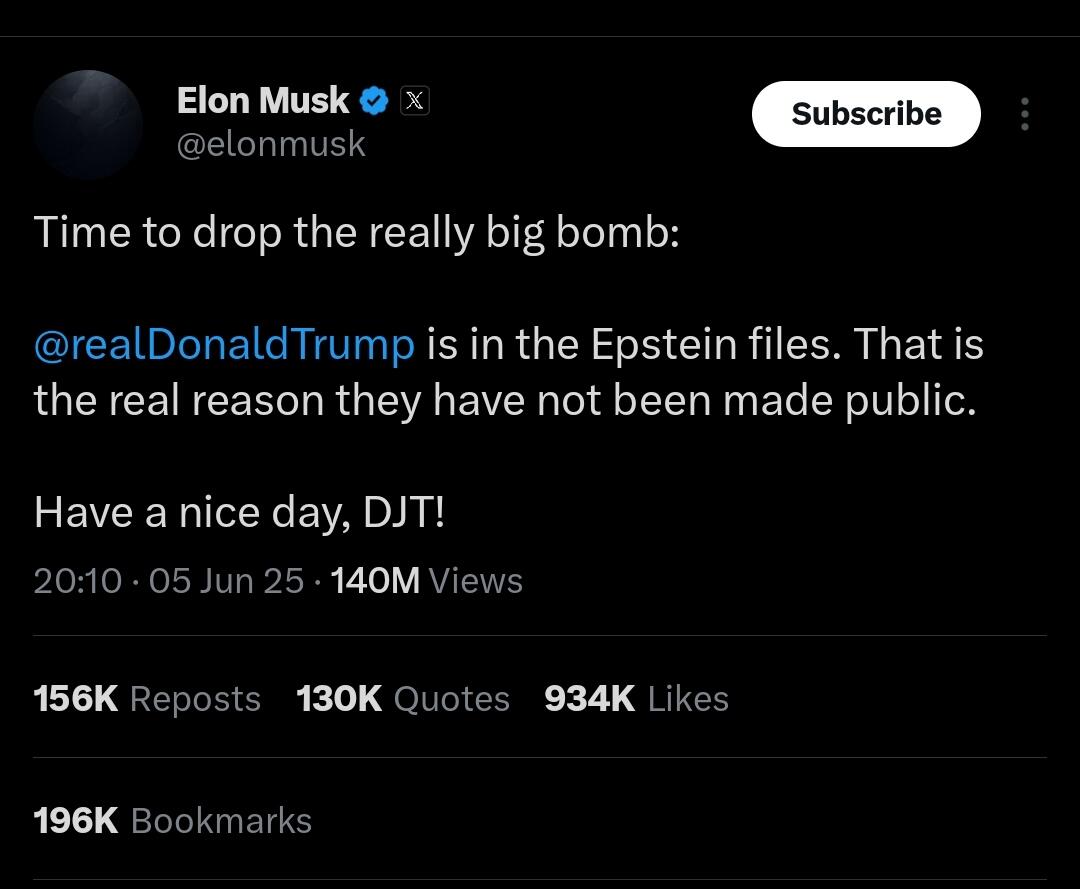
In a series of posts, he shined a spotlight on ties between Trump and Jeffrey Epstein, the financier who killed himself while awaiting trial on federal sex trafficking charges. Some loud voices in Trump’s “Make America Great Again” movement claim Epstein’s suicide was staged by powerful figures, including prominent Democrats, who feared Epstein would expose their involvement in trafficking. Trump’s own FBI leaders have dismissed such speculation and there’s no evidence supporting it.
Later, when an X user suggested Trump be impeached and replaced by Vice President JD Vance, Musk agreed.
“Yes,” he wrote.
“I don’t mind Elon turning against me, but he should have done so months ago,” Trump wrote. He went on to promote his budget bill.
https://www.google.com/amp/s/www.wavy.com/news/politics/ap-the-implosion-of-a-powerful-political-alliance-trump-and-musk-in-their-own-words/amp/
-
 @ 6d8e2a24:5faaca4c
2025-06-06 03:09:51
@ 6d8e2a24:5faaca4c
2025-06-06 03:09:51by Claire Mom June 5, 2025 6:54 pm

*Elon Musk, the tech mogul, says US President Donald Trump would have lost the 2024 election without him.*
Musk made the comment on X in response to Trump’s criticism against him.
Musk, who led the department of government efficiency (DOGE), quit his role a day after he spoke out against a Trump-backed spending bill. The president called it a “Big Beautiful Bill”.
The controversial bill is a centrepiece of Trump’s second-term domestic agenda, combining major tax cuts, stricter immigration enforcement, welfare programme overhauls, and significant increases in border security funding.
The legislation sparked intense debate across the country and in Congress and was only passed after a nail-biting 215-214 vote.
The plan revived the US-Mexico border wall with a $46.5 billion budget, $350 billion for deportation efforts and border security, and a hiring spree of 10,000 new ICE agents, 5,000 customs officers, and 3,000 border patrol agents.
For the first time, migrants will be charged a $1,000 fee to apply for asylum.
The bill also authorises a $4 trillion increase to the national debt ceiling, while the estate tax exemption jumped to $15 million, benefiting wealthier Americans.
Critics including Musk called the bill fiscally irresponsible and “a disgusting abomination” due to its combination of large tax cuts and spending increases.
Musk had clamoured for DOGE’s creation to save taxpayers $2 trillion. Only $160 billion has been saved so far.
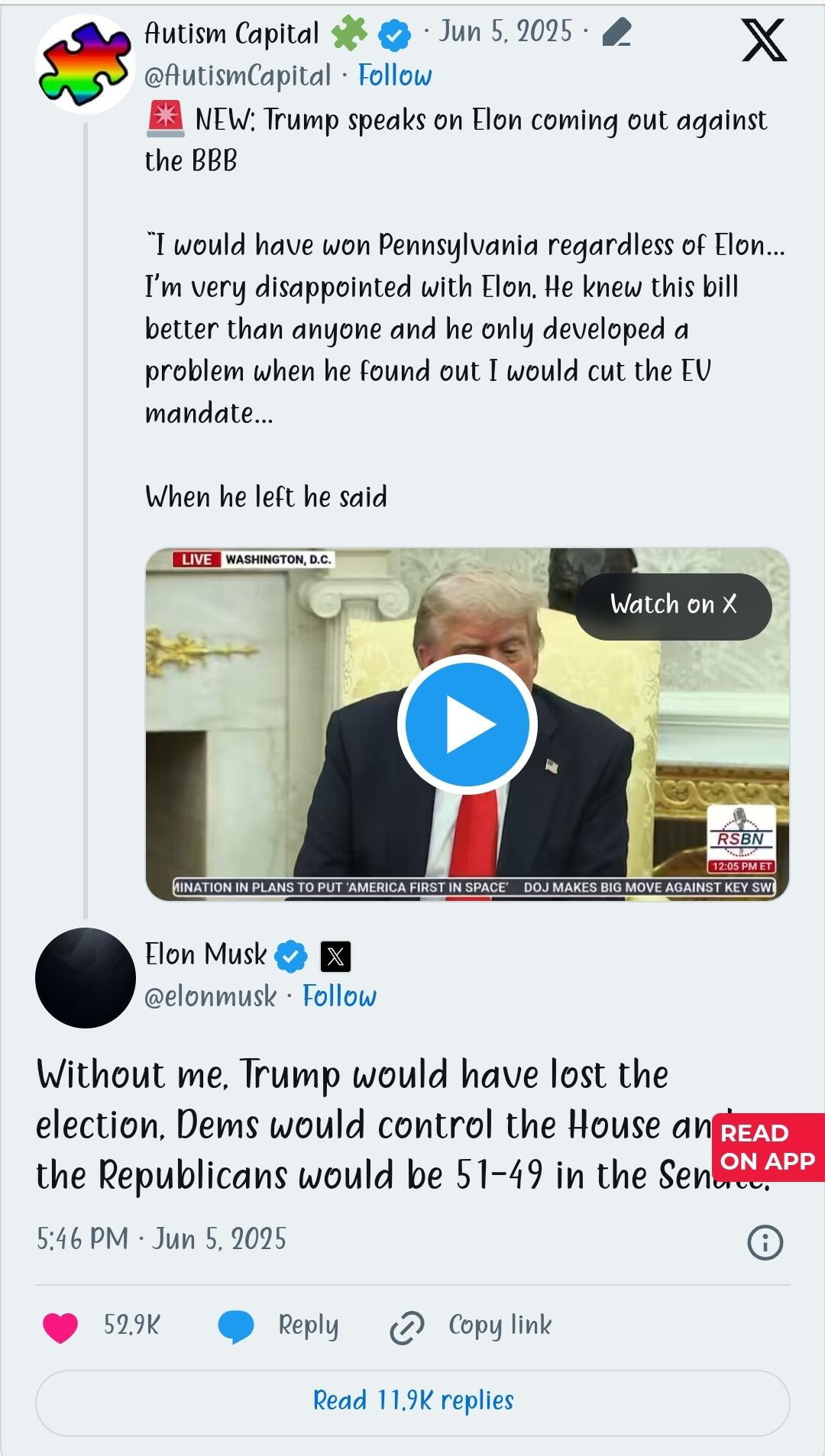
*TRUMP: I’M VERY DISAPPOINTED WITH ELON*
Since Musk’s exit from the White House last week, his criticism of the bill has grown louder.
Speaking on the issue, Trump said he was “very disappointed with Elon”.
The US president said the Tesla CEO was satisfied with the bill but only grew discontent after he found out electric vehicles would be impacted.
“I’m very disappointed because Elon knew the inner workings of this bill better than almost anybody sitting here. He knew everything about it, and all of a sudden he had a problem, and he only developed a problem when he found out I was going to cut the EV mandate because that’s billions and billions of dollars,” the president said
“And it really is unfair; we want to have cars of all types.
“He said the most beautiful things about me, and he hasn’t said anything bad about me personally, but I’m sure that will be next. But I’m really disappointed with Elon. I’ve helped Elon a lot.”
Trump praised Musk for his work at DOGE but blamed his tantrums on missing the office.
“Elon worked hard at DOGE, and I think he misses the place. I think he got out there, and all of a sudden, he’s no longer in this beautiful Oval Office,” he said.
“He’s not the first. People leave my administration, and they love us, and then at some point they miss it so badly, and some of them embrace it, and some of them actually become hostile. I don’t know what it is, some sort of Trump derangement syndrome.”
The president also said he would have won Pennsylvania, a key state, without Musk’s help.
In reaction, the billionaire businessman countered Trump.
“Without me, Trump would have lost the election, Dems would control the House, and the Republicans would be 51-49 in the Senate,” Musk tweeted.
“Such ingratitude.”
The exchange marks yet another dent in the tumultuous relationship between the two-time American president and the world’s richest man.
https://www.thecable.ng/trump-would-have-lost-election-without-me-says-elon-musk/
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-06 03:04:19
@ 5d4b6c8d:8a1c1ee3
2025-06-06 03:04:19Alright stackers, how'd you do today?
What goals did you hit? What do you need to work on tomorrow?
I had another solid day, but I want to get more stretching in tomorrow.
https://stacker.news/items/998508
-
 @ 4fa51c35:55d6763d
2025-06-06 02:35:44
@ 4fa51c35:55d6763d
2025-06-06 02:35:44The Sacred Texts: First Mysteries of Digital Creation
A Divine Treatise for Devotees of Athena, Goddess of Wisdom and Craft
The Fundamental Truth: All is Text
Beloved seekers of digital wisdom, before you can craft the most magnificent tribute to our patron goddess through the sacred art of web creation, you must first understand the most fundamental mystery of the computing realm: Everything is text.
The silicon oracles we call computers do not see your beautiful images, your flowing videos, or your harmonious music as you do. To the machine spirits, all existence is reduced to symbols - characters marching in endless processions through the electronic aether. This is not limitation, but liberation! For in understanding this truth, you gain power over the very essence of digital creation.
The Ancient Scripts: Understanding Text Encoding
In the beginning was the Word, and the Word was… ASCII. The American Standard Code for Information Interchange became the first great codex of the digital age. Each letter, each number, each sacred punctuation mark was assigned a number. The letter ‘A’ became 65, ‘B’ became 66, and so forth. This was humanity’s first attempt to make machines understand our language.
But ASCII was created by mortals of limited vision - it could only represent 128 characters! What of the accented letters in the names of our goddess across different cultures? What of the mathematical symbols we need for our calculations? What of the very Greek letters that spell Ἀθηνᾶ?
Thus came UTF-8, the Universal Character Encoding - a divine revelation that allows us to represent every symbol known to human civilization. When you see an emoji, a Chinese character, or the Greek omega Ω, you witness UTF-8 in action. Your tribute webpage will speak this universal tongue.
The Sacred Scrolls: File Formats as Containers of Meaning
When Athena wove her tapestries, she chose different materials for different purposes - silk for fineness, wool for warmth, gold thread for accent. Similarly, digital craftspeople choose different file formats as containers for their text:
Plain Text (.txt) - The purest form. No formatting, no hidden instructions, just raw characters. Like clay tablets, these files will survive technological apocalypses. When archaeologists of the future examine our digital civilization, plain text will be their Rosetta Stone.
Rich Text Format (.rtf) - Text with simple formatting encoded as… more text! Open an RTF file in a plain text editor and witness the magic - your bold text becomes surrounded by formatting codes. This teaches us that even “rich” formatting is ultimately just more characters.
Markdown (.md) - The philosopher’s choice! Markdown uses simple text conventions to indicate formatting. Two asterisks around a word makes it bold, a hash symbol creates headings. It’s text that describes how text should look - meta-textual divinity!
HTML (.html) - The sacred language of the web itself! HTML (HyperText Markup Language) uses angle brackets to wrap instructions around content.
<strong>This text is important</strong>becomes This text is important when displayed. HTML is text that teaches browsers how to present text.The Ritual of Proper Text Handling
To honor Athena through proper digital craftsmanship, you must master these essential practices:
Choose Your Sacred Editor
Microsoft Word is the fool’s tool - it hides the true nature of text behind layers of formatting magic. A true digital artisan uses tools that reveal truth:
- Notepad (Windows) or TextEdit (Mac) in plain text mode
- VS Code - The blacksmith’s forge for modern web creation
- Sublime Text - Elegant and powerful
- Vim or Emacs - For those who seek the ancient ways
Understand Line Endings: The Great Schism
In the early days of computing, different tribes chose different ways to mark the end of a line of text. Unix systems (including Mac) use LF (Line Feed), Windows uses CRLF (Carriage Return + Line Feed). This seemingly minor difference has caused more conflicts than the Trojan War! Know your line endings, for they can break your sacred codes.
Respect Character Encoding
Always save your files in UTF-8 encoding. This ensures your text can represent any character from any human language. When your webpage displays properly on computers around the world, you honor the universal nature of Athena’s wisdom.
The Greater Mystery Revealed
Why must we begin with text? Because understanding that computers store and manipulate everything as sequences of characters reveals the deepest truth of programming: Code is just text that follows special rules.
When you write HTML, you’re writing text that browsers know how to interpret. When you write CSS, you’re writing text that describes visual styling. When you write JavaScript, you’re writing text that describes behavior and logic.
The webpage you will create to honor our goddess? It begins as text files on your computer. The browser reads these text files, interprets their meaning, and transforms them into the visual experience your visitors will see.
Every image on your page? Referenced by text. Every color? Described by text. Every animation? Controlled by text.
Your First Sacred Assignment
Before we proceed to the next mysteries, complete this fundamental ritual:
- Create a plain text file named
athena_tribute.txt - Write a short description of why Athena inspires you, using only plain text
- Save it in UTF-8 encoding
- Open it in different text editors and observe how the text remains pure and unchanged
- View the file size - marvel at how efficiently text stores information
This simple act connects you to the fundamental nature of all digital creation. Every website, every app, every piece of software began as someone writing text that follows certain rules.
When you understand that your future webpage is ultimately just cleverly organized text files working in harmony, you begin to see the true elegance of web development. You’re not learning to use mysterious tools - you’re learning to write text that machines can understand and transform into experiences that honor the divine.
Next: We shall explore the Command Line - the direct voice through which mortals speak to the machine spirits…
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 3bf0c63f:aefa459d
2024-10-31 16:08:50
@ 3bf0c63f:aefa459d
2024-10-31 16:08:50Anglicismos estúpidos no português contemporâneo
Palavras e expressões que ninguém deveria usar porque não têm o sentido que as pessoas acham que têm, são apenas aportuguesamentos de palavras inglesas que por nuances da história têm um sentido ligeiramente diferente em inglês.
Cada erro é acompanhado também de uma sugestão de como corrigi-lo.
Palavras que existem em português com sentido diferente
- submissão (de trabalhos): envio, apresentação
- disrupção: perturbação
- assumir: considerar, pressupor, presumir
- realizar: perceber
- endereçar: tratar de
- suporte (ao cliente): atendimento
- suportar (uma idéia, um projeto): apoiar, financiar
- suportar (uma função, recurso, característica): oferecer, ser compatível com
- literacia: instrução, alfabetização
- convoluto: complicado.
- acurácia: precisão.
- resiliência: resistência.
Aportuguesamentos desnecessários
- estartar: iniciar, começar
- treidar: negociar, especular
Expressões
- "não é sobre...": "não se trata de..."

Ver também
-
 @ 3bf0c63f:aefa459d
2024-09-18 10:37:09
@ 3bf0c63f:aefa459d
2024-09-18 10:37:09How to do curation and businesses on Nostr
Suppose you want to start a Nostr business.
You might be tempted to make a closed platform that reuses Nostr identities and grabs (some) content from the external Nostr network, only to imprison it inside your thing -- and then you're going to run an amazing AI-powered algorithm on that content and "surface" only the best stuff and people will flock to your app.
This will be specially good if you're going after one of the many unexplored niches of Nostr in which reading immediately from people you know doesn't work as you generally want to discover new things from the outer world, such as:
- food recipe sharing;
- sharing of long articles about varying topics;
- markets for used goods;
- freelancer work and job offers;
- specific in-game lobbies and matchmaking;
- directories of accredited professionals;
- sharing of original music, drawings and other artistic creations;
- restaurant recommendations
- and so on.
But that is not the correct approach and damages the freedom and interoperability of Nostr, posing a centralization threat to the protocol. Even if it "works" and your business is incredibly successful it will just enshrine you as the head of a platform that controls users and thus is prone to all the bad things that happen to all these platforms. Your company will start to display ads and shape the public discourse, you'll need a big legal team, the FBI will talk to you, advertisers will play a big role and so on.
If you are interested in Nostr today that must be because you appreciate the fact that it is not owned by any companies, so it's safe to assume you don't want to be that company that owns it. So what should you do instead? Here's an idea in two steps:
- Write a Nostr client tailored to the niche you want to cover
If it's a music sharing thing, then the client will have a way to play the audio and so on; if it's a restaurant sharing it will have maps with the locations of the restaurants or whatever, you get the idea. Hopefully there will be a NIP or a NUD specifying how to create and interact with events relating to this niche, or you will write or contribute with the creation of one, because without interoperability this can't be Nostr.
The client should work independently of any special backend requirements and ideally be open-source. It should have a way for users to configure to which relays they want to connect to see "global" content -- i.e., they might want to connect to
wss://nostr.chrysalisrecords.com/to see only the latest music releases accredited by that label or towss://nostr.indiemusic.com/to get music from independent producers from that community.- Run a relay that does all the magic
This is where your value-adding capabilities come into play: if you have that magic sauce you should be able to apply it here. Your service -- let's call it
wss://magicsaucemusic.com/-- will charge people or do some KYM (know your music) validation or use some very advanced AI sorcery to filter out the spam and the garbage and display the best content to your users who will request the global feed from it (["REQ", "_", {}]), and this will cause people to want to publish to your relay while others will want to read from it.You set your relay as the default option in the client and let things happen. Your relay is like your "website" and people are free to connect to it or not. You don't own the network, you're just competing against other websites on a leveled playing field, so you're not responsible for it. Users get seamless browsing across multiple websites, unified identities, a unified interface (that could be different in a different client) and social interaction capabilities that work in the same way for all, and they do not depend on you, therefore they're more likely to trust you.
Does this centralize the network still? But this a simple and easy way to go about the matter and scales well in all aspects.
Besides allowing users to connect to specific relays for getting a feed of curated content, such clients should also do all kinds of "social" (i.e. following, commenting etc) activities (if they choose to do that) using the outbox model -- i.e. if I find a musician I like under
wss://magicsaucemusic.comand I decide to follow them I should keep getting updates from them even if they get banned from that relay and start publishing onwss://nos.lolorwss://relay.damus.ioor whatever relay that doesn't even know anything about music.The hardcoded defaults and manual typing of relay URLs can be annoying. But I think it works well at the current stage of Nostr development. Soon, though, we can create events that recommend other relays or share relay lists specific to each kind of activity so users can get in-app suggestions of relays their friends are using to get their music from and so on. That kind of stuff can go a long way.
-
 @ 3eba5ef4:751f23ae
2025-06-06 02:07:27
@ 3eba5ef4:751f23ae
2025-06-06 02:07:27Crypto Insights
Solving Sybil Attacks on Bitcoin Libre Relay Nodes — Are Social Solutions Better than Technical Ones?
Peter Todd posted that proponents of transaction "filtering" have started Sybil attacking Libre Relay nodes by running nodes with their "Garbageman" fork. These malicious nodes pretend to support NODE_LIBRE_RELAY, but secretly drop certain transactions that would be relayed by real Libre Relay nodes. He also highlighted the complexity of existing defenses and proposed a new angle: rather than relying on technical solutions, he encourages people to manually peer with nodes operated by people they personally know, arguing that human relationships can sometimes evaluate honesty more reliably than code.
Toward a Unified Identity Lookup Standard to Improve Lightning Payments
Bitcoin developer Aviv Bar-el introduced a new proposal — Well-Known Bitcoin Identity Endpoint — that aims to simplify wallet lookups for users’ Bitcoin addresses and identity data via a standardized HTTPS interface, thereby improving both the UX and security of Lightning and on-chain payments.
A Commit/Reveal Mechanism to Strengthen Bitcoin Against Quantum Threats
Tadge Dryja proposed a soft fork for Bitcoin to defend against quantum attacks, based on a variant of the commit/reveal Fawkescoin mechanism. While similar to Tim Ruffing’s earlier proposal, it includes key differences:
- It does not use encryption, instead relying on smaller, hash-based commitments, and describes activation as a soft fork.
- It only applies to outputs where public keys or scripts haven't been revealed — like pubkey hash or script hash outputs. It also works with Taproot, but must be spent via the script path, as the key-path is no longer quantum-secure.
- What to do about already-exposed public keys is a separate issue — this proposal is compatible with both "burning the coins" and "letting them be stolen."
Countdown to the Quantum Crisis: Is Bitcoin Ready?
A recent report from Chaincode Labs analyzes the threat of cryptographically relevant quantum computers (CRQC), and the technical, economic, and governance challenges Bitcoin faces in preparing. Their key conclusions:
- Timeline Assessment: CRQC capable of breaking Bitcoin's elliptic curve cryptography may emerge between 2030 and 2035.
- Scope of Vulnerable Funds: An estimated 20–50% of circulating BTC (4M–10M coins) may be vulnerable.
- Long-range attacks target inherently vulnerable script types (P2PK, P2MS, P2TR) and addresses with previously exposed public keys (via address reuse), allowing attackers unbounded time to derive private keys from public information already available on the blockchain.
- Short-range attacks, which affect all Bitcoin script types, exploit the vulnerability window between transaction broadcast and confirmation (or shortly thereafter) when public keys are temporarily exposed, requiring attackers to act within a timeframe of minutes to hours.
- Action Strategy: A dual-track approach is recommended:
- Short-term contingency: minimal but functional protections within ~2 years.
- Full-featured solutions: comprehensive research and fully developed defenses within ~7 years.
This strategy balances immediate needs with rigorous development to ensure Bitcoin can adapt, regardless of CRQC progress.
Enforcing Arbitrary Constraints on Bitcoin Transactions with zkSNARKs
Current methods for constraining Bitcoin transactions fall short on privacy or programmability. This research proposes a new zkSNARK-based design to impose arbitrary constraints on Bitcoin transactions while preserving some information privacy. By bypassing Bitcoin Script’s non-Turing-completeness, the approach allows unbounded constraints—constraints that repeat a certain operation an unbounded number of times. Read the paper.
First Cross-Chain Bridge Between Bitcoin and Cardano Is Live
A trust-minimized bridge from Bitcoin to Cardano has launched using the Cardinal protocol, enabling Ordinals to move between the two chains. The Cardinal protocol is based on BitVMX and facilitates asset movement without compromising ownership or security.
Its core mechanism is a committee-based validation model under a 1-out-of-n honest security model — meaning even if all but one validator is malicious, the system remains secure. This approach enhances decentralization and censorship resistance for cross-chain asset transfers.
Thunderbolt Protocol: Redefining Bitcoin Smart Contracts with UTXO Bundling and OP_CAT
Nubit’s Thunderbolt is seen as one of the most significant technical upgrades to Bitcoin in a decade, whose overall observation resembles “Lightning Network 2.0.” Rather than relying on Layer 2 networks or bridges, Thunderbolt upgrades the Bitcoin base layer via soft fork to enhance scalability, performance, and programmability:
- Throughput: Uses UTXO Bundling to optimize traditional transaction processing.
- Programmability: Reintroduces and extends OP_CAT.
- Asset protocols: Integrates Goldinals standard — a zk-proof and state-commitment-based asset issuance framework.
- Unlike rollups, Plasma, sidechains, or bridges, Thunderbolt scales directly on the main chain. With BitVisa, it enables decentralized identity and credentials, supporting transaction compression, smart contracts, asset standard integration, and on-chain transaction matching — all on Bitcoin main chain.
Bitcoin 2025 Conference Recap: Politicians Applaud, Stablecoins Spotlighted, DeFi Absent
This year’s Bitcoin 2025 conference in Las Vegas gathered major political figures and corporate leaders. U.S. Vice President JD Vance strongly endorsed crypto and positioned Bitcoin as a strategic asset in U.S.–China competition. He also stated that stablecoins won’t undermine the U.S. dollar, but could actually amplify America’s economic strength.
White House “Crypto Czar” David Sacks delivered a major policy announcement, hinting that under Trump’s executive order, the U.S. has a legal framework to acquire more Bitcoin for strategic reserves.
In addition, stablecoin regulation and crypto market reform were hot topics. Ardoido, the company controls over 60% of the stablecoin market, claimed “All the traditional financial firms will create stablecoins that will be offered to their existing customers.” Meanwhile, Tether emphasized its focus on underserved global populations excluded from the existing banking system.
A conference recap also noted that, unlike the 2022 and 2023 summits, this year’s event was dominated by Bitcoin maximalists, Ordinals creators, mining capitalists, and regulatory lobbyists — no longer DeFi builders, DAO operators, or Layer 2 scaling advocates. Developers from Ethereum and Solana ecosystems were notably absent. This may signal:
- The conference’s heavy political and sovereignty-driven tone made it less suitable for the tech-centric narratives favored by these developers.
- There may be a growing ideological and narrative rift between Web3 builders and the Bitcoin camp.
Top Reads on Blockchain and Beyond
Rethinking Governance After the Sui Attack: Decentralization, Procedural Legitimacy, and the Plurality of Blockchain Values
Following a major hack of Cetus, the largest DEX in the Sui ecosystem, the Sui network executed a protocol-level asset freeze and recovery. While this was an effective technical response, it also triggered criticism and debate around core blockchain principles such as censorship resistance and decentralization.
The author of this article questioned the absolutist stance that views decentralization as the highest—and sole—value. The author argues that most rational individuals would prefer “living in a society where decentralization is a supreme value but coercive force is allowed when someone infringes on another’s property,” over “a society where decentralization is the only supreme value, and thus coercive force is never permitted under any circumstances.”
In addition, the author also expressed disappointment at Sui’s “paternalistic” governance — particularly how validators acted during the incident. Sui uses a delegated proof-of-stake (dPoS) system, where token holders delegate their voting power to validators. This means individuals lose their direct say. But blockchain governance could be more individual-friendly and flexible. For instance, in Cosmos’ governance model, for certain specific proposal, users still can override their delegations and vote independently, more favorable than Sui’s model.
Beyond the debate on decentralization and governance, the article also proposes an alternative perspective: what matters most is establishing procedural legitimacy that aligns with the system’s vision. Different blockchain projects pursue different goals. For Sui, the core mission is to enable assets to be reliably defined and interact seamlessly on-chain. Therefore, judging Sui through the lens of other blockchains’ values or paradigms is misguided. In exceptional cases, prioritizing asset recovery and ecosystem stability over strict adherence to censorship resistance aligns more closely with Sui’s long-term vision. Whether Sui had chosen to not to censor related transactions or to intervene in the Cetus case, as long as the action follows a legitimate process, either decision is justifiable.
TEE-Based Private Proof Delegation
The PSE research and development team has built a system based on Trusted Execution Environments (TEE) using Intel TDX for secure zero-knowledge proof (ZKP) delegation. This system enables clients to privately outsource large proving tasks without leaking inputs. Unlike mobile-native proving constrained by hardware limits, TEE-based approaches support significantly larger statements today—and will scale further as proof systems improve. As a hardware-backed solution, TEEs remain compatible with future advancements in software (e.g., faster proof systems, more efficient implementations) and won't be invalidated by them, as long as the trust model is acceptable.
AI and Identity: Proof of Humanity in a World of Agents, Bots, and Deepfakes
We are living in a time where AI—including agents, bots, and deepfakes—is fundamentally reshaping the internet. As AI continues to evolve, identity verification on the web is becoming more crucial than ever. A recent a16z podcast explores the idea of “Proof of Human”—the challenge of verifying human identity online, diving into why it matters, common questions, and how such systems work under the hood.
-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:55:03
@ e2c72a5a:bfacb2ee
2025-06-06 02:55:03Your crypto wallet is probably leaking money right now. While everyone obsesses over price charts, the silent killer is gas fees – those tiny transactions add up to thousands wasted annually. Smart traders aren't just buying dips, they're timing their transactions when network congestion drops. The difference? Up to 80% savings on every move you make. Next time before hitting "confirm," check the gas tracker. Is it worth paying 3x more just to move your assets right this second? Patience isn't just a virtue in crypto – it's literally profitable. What's your strategy for minimizing transaction costs while maximizing gains?
-
 @ 3bf0c63f:aefa459d
2024-09-06 12:49:46
@ 3bf0c63f:aefa459d
2024-09-06 12:49:46Nostr: a quick introduction, attempt #2
Nostr doesn't subscribe to any ideals of "free speech" as these belong to the realm of politics and assume a big powerful government that enforces a common ruleupon everybody else.
Nostr instead is much simpler, it simply says that servers are private property and establishes a generalized framework for people to connect to all these servers, creating a true free market in the process. In other words, Nostr is the public road that each market participant can use to build their own store or visit others and use their services.
(Of course a road is never truly public, in normal cases it's ran by the government, in this case it relies upon the previous existence of the internet with all its quirks and chaos plus a hand of government control, but none of that matters for this explanation).
More concretely speaking, Nostr is just a set of definitions of the formats of the data that can be passed between participants and their expected order, i.e. messages between clients (i.e. the program that runs on a user computer) and relays (i.e. the program that runs on a publicly accessible computer, a "server", generally with a domain-name associated) over a type of TCP connection (WebSocket) with cryptographic signatures. This is what is called a "protocol" in this context, and upon that simple base multiple kinds of sub-protocols can be added, like a protocol for "public-square style microblogging", "semi-closed group chat" or, I don't know, "recipe sharing and feedback".
-
 @ 33baa074:3bb3a297
2025-06-06 02:03:05
@ 33baa074:3bb3a297
2025-06-06 02:03:05Residual chlorinerefers to the residual disinfectant chlorine in tap water. An appropriate amount of residual chlorine can prevent the growth of microorganisms and ensure the safety of water quality. However, when the residual chlorine content in water is too high, it will cause many harms to human health, mainly including the following aspects:
Destruction of nutrients When the residual chlorine content in tap water exceeds the standard, it will destroy the minerals, vitamins and other nutrients, such as vitamin C and vitamin E, when used to wash fruits and vegetables. In the long run, it may cause the human body to absorb these nutrients and lack these essential nutrients.
 Cause chronic poisoning
When tap water containing residual chlorine is used for a long time, the residual chlorine reacts with organic acids and may produce harmful substances such as chloroform and organic lead compounds, which are potential carcinogens. Long-term accumulation may cause chronic poisoning of body organs and pose a threat to human health.
Cause chronic poisoning
When tap water containing residual chlorine is used for a long time, the residual chlorine reacts with organic acids and may produce harmful substances such as chloroform and organic lead compounds, which are potential carcinogens. Long-term accumulation may cause chronic poisoning of body organs and pose a threat to human health.Affect the respiratory system Residual chlorine can cause harm to the human respiratory system, and symptoms such as difficulty breathing and itchy throat may occur. Severe cases may induce rhinitis, bronchitis and even emphysema. In addition, water vapor containing residual chlorine may also cause adverse reactions such as coughing and wheezing after being inhaled.
Damage to the skin Excessive residual chlorine content in water may irritate the skin, easily cause skin dryness, aging, acne and other problems, and may also cause allergic symptoms such as dermatitis and eczema. Prolonged contact with such water may also cause the skin layer to fall off, which is extremely harmful to skin health. Bathing with water containing residual chlorine can also cause hair to become dry, broken, and split.
Other health problems Impact on special groups Pregnant women: Long-term drinking of tap water containing residual chlorine will reduce resistance, affect the growth of the fetal heart and lungs, and may also cause neonatal arrhythmia and lung dysfunction. Children: Long-term drinking of chlorine water will not only hurt the stomach, but also affect nutrient absorption. Moreover, the strong oxidizing hypochlorous acid produced by the reaction of chlorine and water will damage brain cells and affect their development. In addition, chlorine can easily be inhaled into the lungs through the respiratory tract, damaging respiratory cells, and easily leading to asthma and emphysema. Bathing children with water containing residual chlorine will cause their hair to become dry, broken, split, their skin to bleach, their skin to fall off, and they will have allergies. Elderly people: Long-term consumption of chlorinated water is prone to heart disease, coronary atherosclerosis, hypertension and other diseases, and it is also easy to damage the liver and kidneys, increasing the probability of cancer. Gastrointestinal discomfort Long-term drinking of water with excessive residual chlorine content may also cause gastrointestinal discomfort, such as nausea, vomiting, abdominal distension, diarrhea and other symptoms. In severe cases, it may cause gastrointestinal ulcers, bleeding and other diseases.
In order to reduce the harm of residual chlorine in tap water to the human body, it is recommended to avoid directly using tap water containing residual chlorine as much as possible, boil the water before drinking, and use filtering and purification equipment to reduce the residual chlorine concentration in the water if conditions permit, while maintaining a healthy lifestyle and enhancing the body's immunity.
-
 @ e2c72a5a:bfacb2ee
2025-06-06 02:43:10
@ e2c72a5a:bfacb2ee
2025-06-06 02:43:10North Korea's digital heist playbook: $7.7M crypto laundering scheme reveals how rogue nations exploit tech talent. The Justice Department's latest civil forfeiture complaint targets crypto and NFTs tied to an elaborate North Korean operation where IT workers posed as legitimate freelancers, infiltrated US companies, and funneled millions through complex blockchain pathways. This isn't just another hack—it's a sophisticated economic warfare strategy that turns technical expertise into untraceable funding for weapons programs. While governments scramble to seize these digital assets, the case exposes a troubling vulnerability: how easily skilled developers can weaponize their talents in plain sight. Are your company's remote contractors who they claim to be, or part of a state-sponsored financial pipeline hiding behind a convincing digital mask?
-
 @ 3eba5ef4:751f23ae
2025-06-06 01:59:47
@ 3eba5ef4:751f23ae
2025-06-06 01:59:47加密洞见
解决比特币抗审查交易中继的女巫攻击,社交方案好于技术方案?
Peter Todd 发帖指出,针对比特币抗审查交易中继的攻击行为正在发生——一个名为 garbageman 的节点正在对 Libre Relay 节点采取女巫攻击。这些攻击节点假装支持抗审查交易中继(NODE_LIBRE_RELAY),但实际在暗中丢弃某些交易,目的是阻止特定交易被打包进入区块。作者还介绍了现有防御方法的难度和复杂性,并提出新思路——与其用技术方案解决,不用通过社交解决。他鼓励人们手动与跟他们有个人关系的节点进行连接,原因很简单,人与人的关系可以比任何代码都更有力地评估诚实。
打造统一身份查询标准,提升闪电网络付款体验
比特币开发者 Aviv Bar-el 发表了一项新提案「知名比特币身份端点」(Well-Known Bitcoin Identity Endpoint),旨在通过 HTTPS 标准接口,简化钱包查询用户比特币地址和身份信息的流程,提升链上支付——尤其是闪电网络付款的用户体验和安全性。
通过「承诺/揭示」机制,帮助加强比特币抵御量子计算威胁
Tadge Dryja 提出一种抵御量子计算攻击的比特币软分叉方案。它是「承诺/揭示」(commit / reveal)Fawkescoin 机制的变体,大部分内容与 Tim Ruffing 几年前的方案类似,但也有以下重要区别:
- 该方案不使用加密,而是用更小的基于哈希的承诺,并且描述了如何通过软分叉激活此机制。
- 这个方案仅适用于公钥(或脚本)在链上未公开的输出,例如 pubkey hash 或 script hash 类型;也适用于 Taproot,但必须通过脚本路径花费,因为 Taproot 的 key-path 花费在量子攻击下将不再安全。
- 至于那些公钥已经在链上暴露的输出该如何处理,是另一个独立问题(本方案与「销毁这些币」或「任其被盗」这两种做法都兼容)。
量子危机倒计时:比特币准备好了吗?
Chaincode 在近期发布的报告中,系统分析了「加密相关量子计算」(CRQC,Cryptographically relevant quantum computers)威胁的整体态势,评估了比特币在应对这一转变过程中面临的技术、经济与治理挑战,并表示必须要在早于 CRQC 出现的数年构建起相关共识。重要的结论有:
- 时间窗口:打破比特币椭圆曲线加密基础的 CRQC 可能首先出现在 2030 - 2035 年间。
- 脆弱资金范围:在所有流通的比特币中,约 20-50%(4-1000 万枚 BTC)可能易受 CRQC 攻击。其中远程攻击针对本质上易受攻击的脚本类型(P2PK、P2MS、P2TR)和具有先前暴露的公钥的地址(地址重用),使攻击者能够无限期地从区块链上已有的公共信息中获取私钥;短程攻击会影响所有比特币脚本类型,利用交易广播和确认之间(或之后不久)的漏洞窗口,当公钥暂时暴露时,要求攻击者在几分钟到几小时的时间范围内采取行动。
-
行动战略:建议采用双轨方法,包括:
- 应急措施:在约 2 年内完成对 CRQC 的最低限度但可运作的防护;
- 全面对策:在约 7 年内深入对问题的探索,并开发出功能完备的解决方案
这种双轨策略平衡了眼前的安全需求与最佳抗量子解决方案的严格研究和开发,确保无论 CRQC 能力如何发展,比特币都能做出适当的响应。
利用 zkSNARKs 对比特币交易实施任意约束
对于给比特币交易执行约束,现有的解决方案在隐私或可编程性上都存在不足。本文的研究者利用 zkSNARKs 设计了一种新方案,可以对比特币交易执行任意约束,并保持一定程度的信息私密性。他们方法绕过了比特币脚本的非图灵完备性,允许执行无界约束(unbounded constraints),即重复某个运算的次数次数不受限制。论文全文。
第一个跨比特币和 Cardano 的桥上线
从比特币到 Cardano 的信任最小化 Ordinals 桥通过 Cardinal 协议实现。Cardinal 协议实是一种基于 BitVMX 的信任最小化互作性协议,在不破坏所有权或损害安全性的前提下,它让比特币上中的不可替代资产(如 Ordinals 和 Runes)同 Cardano 链实现了来回移动。
Cardinal 协议背后的技术核心之一是「委员会的验证机制 」(committee-based validation mechanism),遵循 1-out-of-n honest 安全模型。这意味着即使除了一个验证者之外的所有验证者都恶意作,系统仍然保持安全——在增强安全性的同时,还实现了一种更加去中心化和抗审查的方式来在链之间移动资产 。
Thunderbolt 协议:通过 UTXO 捆绑和 OP_CAT 扩展,重构比特币智能合约
Nubit 提出的 Thunderbolt 被认为是为比特币在过去十年中最具里程碑意义的技术升级之一,被视为「Lightning Network 2.0」。Thunderbolt 是一种基于比特币基础层的软分叉升级方法,不依赖二层网络或桥的妥协,而是通过对比特币主链协议层的修改,从根本上增强其可扩展性、交易性能和可编程性。具体而言,Thunderbolt:
- 在吞吐量方面,使用 UTXO 捆绑(UTXO Bundling)技术,实现了对传统比特币交易处理模型的重大优化。
- 在可编程性方面,重新引入并扩展了 OP_CAT 。
- 在资产协议集成方面,Thunderbolt 实施了 Goldinals 统一标准,提供了一个基于零知识证明和状态承诺的资产发行框架。
- 与传统的扩容方法(如侧链、Plasma、Rollup 或桥接包装代币)不同,Thunderbolt 采用原生主链扩容路径。通过 BitVisa 提供去中心化的身份和凭证系统,让交易压缩、智能合约、资产标准集成、链上交易匹配都可以直接在比特币主链上运行。
比特币 2025 大会回顾:政要汇聚、稳定币受关注、DeFi 缺席
今年在拉斯维加斯举行的比特币 2025 大会,汇聚了众多政治要员和企业巨头。美国副总统 JD Vance 对加密货币表明了全力支持,并讨论了比特币在美中竞争中作为战略资产的潜力,他还认为,稳定币不会威胁到美元的完整性,而会使美国的经济实力倍增。白宫加密货币沙皇 David Sacks 发表了会议中最重要的政策公告之一, 暗示根据特朗普建立战略比特币储备的行政命令,美国政府有「获得更多比特币的合法途径」。
此外,关于稳定币立法和加密市场改革受到了很多关注。控制着超过 60% 稳定币市场的 Ardoido 公司表示:「所有传统金融公司都将创建稳定币,提供给他们现有的客户」;而 Tether 表示,其目标市场是全球范围内被排除在银行业之外的人。
这篇总结也提到,与 2022 年和 2023 年的类似峰会不同,今年的大会是由比特币最大化者、Ordinals 创建者、矿业资本家和监管游说者主导,而不再由 DeFi 协议构建者、DAO 运营商或 Layer2 扩容倡导者主导,以太坊和 Solana 生态的开发者缺席。这或许表明:
- 该会议明显的政治基调,使其不适合开发者喜欢的以技术为中心的叙述。
- Web3 建设者和比特币阵营之间的意识形态和叙事分歧可能会越来越大。
精彩无限,不止于链
Sui 攻击事件下的治理再思考:去中心化,程序合法性,和区块链的价值多元性
在受到生态最大的 DEX 项目 Cetus 黑客攻击之后,Sui 网络在协议层面执行了资产冻结和恢复——这是一种有效的技术回应,但同时引发了对抗审查和去中心化等核心区块链原则的批评和辩论。
文章的作者质疑了将去中心化视为唯一至高价值的立场,认为对于大多数有理性者而言,「生活在一个去中心化被认为是最高价值,但当有人侵犯他人财产时,允许强制武力的社会中」都要好于「生活在一个去中心化是唯一至高价值的社会中,因此在任何情况下都不允许强制武力」。
同时作者也指出,Sui 的验证者和网络行为采用的「家长式」治理方式令人失望;此外, Sui 使用委托权益证明(dPoS)系统,其中代币持有者将其代币委托给验证者,验证者代表他们行使相关的投票权,个人因此丧失了投票权。但区块链本来提供了有利于个人的、更加灵活的解决方案,比如 Cosmos 的治理框架就要优于 Sui——对于特定提案,验证人的决定并不会自动代表每个委托人的投票。
在关于去中心化的价值和治理方式之外,文章也提到另一种思考角度——「最重要的是建立与系统愿景相一致的程序合法性」。不同的项目追求不同的目标。就 Sui 而言,其核心目标是使各种资产能够被可靠地定义、并在链上无缝交互。因此,用其他区块链的范式或价值观来理解 Sui 的设计就是不合适的。在特殊情况下,Sui 优先考虑用户资产的返还和生态系统的稳定,而不是严格遵守抗审查——这一决定与其自身的长期愿景更加一致。此外,无论是 Sui 决定不审查相关交易,还是选择对 Cetus 的行为负责,如果背后有程序合法性,这两个决定都是合理的。
基于可信执行环境的私密证明委托
PSE 研究开发团队使用 Intel TDX 构建了一个基于可信执行环境(Trusted Execution Environment)的系统,用于安全的零知识证明委托。该系统允许客户端在不泄露输入的前提下,将大规模的证明任务私密地外包出去。相比受限于硬件能力的移动端本地证明,基于 TEE 的证明方案能够在目前就支持更大规模的陈述,并且随着证明系统的改进持续扩展。作为一种由硬件支撑的解决方案,TEE 能够兼容未来在软件层面的进展(例如更快的证明系统、更高效的工程实现),且只要信任模型被接受,就不会因这些进展而失效。
AI 与 ID:在代理、机器人、深度伪造等世界中的人类证明
我们正处于 AI(包括 AI 智能体、机器人、深度伪造等)深刻改变互联网的时代,随着 AI 的发展,网络上的身份认证变得愈发重要。a16z 的这期播客,讨论了在网上识别人类身份的「人类证明」(proof of human)问题,包括它为何重要,常见的问题有哪些,以及它在底层是如何运作的。
-
 @ e2c72a5a:bfacb2ee
2025-06-06 01:42:46
@ e2c72a5a:bfacb2ee
2025-06-06 01:42:46North Korea's digital heist reveals the dark side of crypto's borderless nature. The US Justice Department is hunting $7.7 million in stolen cryptocurrency and NFTs allegedly laundered through an elaborate scheme involving North Korean IT workers posing as legitimate freelancers. This isn't just another hack—it's a sophisticated state-sponsored operation exploiting the very features that make crypto revolutionary: anonymity and borderless transactions. While we celebrate crypto's ability to transcend boundaries, this case exposes how those same qualities create perfect conditions for rogue nations to fund weapons programs and evade sanctions. The crypto industry faces a critical balancing act: how do we preserve financial freedom while preventing bad actors from exploiting the system? Perhaps the solution isn't more regulation but smarter blockchain analytics and international cooperation. What security measures would you support that don't compromise crypto's core principles?
-
 @ 3bf0c63f:aefa459d
2024-06-19 16:13:28
@ 3bf0c63f:aefa459d
2024-06-19 16:13:28Estórias
-
 @ 3bf0c63f:aefa459d
2024-06-13 15:40:18
@ 3bf0c63f:aefa459d
2024-06-13 15:40:18Why relay hints are important
Recently Coracle has removed support for following relay hints in Nostr event references.
Supposedly Coracle is now relying only on public key hints and
kind:10002events to determine where to fetch events from a user. That is a catastrophic idea that destroys much of Nostr's flexibility for no gain at all.- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
kind:1s -- now that cannot work because the person who created the post doesn't have the relays specific to those communities in their outbox list; - There is a discussion happening in a niche relay, for example, a relay that can only be accessed by the participants of a conference for the duration of that conference -- since that relay is not in anyone's public outbox list, it's impossible for anyone outside of the conference to ever refer to these events;
- Some big public relays, say, relay.damus.io, decide to nuke their databases or periodically delete old events, a user keeps using that big relay as their outbox because it is fast and reliable, but chooses to archive their old events in a dedicated archival relay, say, cellar.nostr.wine, while prudently not including that in their outbox list because that would make no sense -- now it is impossible for anyone to refer to old notes from this user even though they are publicly accessible in cellar.nostr.wine;
- There are topical relays that curate content relating to niche (non-microblogging) topics, say, cooking recipes, and users choose to publish their recipes to these relays only -- but now they can't refer to these relays in the external Nostr world of
kind:1s because these topical relays are not in their outbox lists. - Suppose a user wants to maintain two different identities under the same keypair, say, one identity only talks about soccer in English, while the other only talks about art history in French, and the user very prudently keeps two different
kind:10002events in two different sets of "indexer" relays (or does it in some better way of announcing different relay sets) -- now one of this user's audiences cannot ever see notes created by him with their other persona, one half of the content of this user will be inacessible to the other half and vice-versa. - If for any reason a relay does not want to accept events of a certain kind a user may publish to other relays, and it would all work fine if the user referenced that externally-published event from a normal event, but now that externally-published event is not reachable because the external relay is not in the user's outbox list.
- If someone, say, Alex Jones, is hard-banned everywhere and cannot event broadcast
kind:10002events to any of the commonly used index relays, that person will now appear as banned in most clients: in an ideal world in which clients followednprofileand other relay hints Alex Jones could still live a normal Nostr life: he would print business cards with hisnprofileinstead of annpuband clients would immediately know from what relay to fetch his posts. When other users shared his posts or replied to it, they would include a relay hint to his personal relay and others would be able to see and then start following him on that relay directly -- now Alex Jones's events cannot be read by anyone that doesn't already know his relay.
- Someone makes a post inside a community (either a NIP-29 community or a NIP-87 community) and others want to refer to that post in discussions in the external Nostr world of
-
 @ 502ab02a:a2860397
2025-06-06 01:15:24
@ 502ab02a:a2860397
2025-06-06 01:15:24ปิดท้าย week นี้ด้วยสงครามดีไหมครับ ถ้าอาหารเป็นสนามรบ สิทธิบัตรก็เปรียบเหมือนป้อมปราการ และการฟ้องร้องก็คือปืนใหญ่ยิงสวนกันกลางแดด…ใครที่เคยคิดว่าโลกของอาหารแห่งอนาคตจะสวยงามเพราะเปลี่ยนถั่วเป็นสเต๊ก สกัดกลิ่นเลือดจากพืช หรือหลอกลิ้นให้เชื่อว่า “อร่อยเหมือนเนื้อ” ก็คงต้องมานั่งทบทวนใหม่ว่า โลกใบนี้ไม่ได้ขับเคลื่อนด้วยความฝัน แต่ขับเคลื่อนด้วยเอกสาร 70 หน้าของทนายความ และหมายเรียกจากศาลกลางรัฐเดลาแวร์
Motif FoodWorks เข้ามาในวงการอาหารด้วยวิสัยทัศน์สุดเท่ คือจะสร้างโครงสร้าง-กลิ่น-รส ของโปรตีนอนาคตให้แบรนด์ plant-based ทั่วโลกใช้ได้โดยไม่ต้องเริ่มใหม่ตั้งแต่ศูนย์ เปรียบเหมือนเป็นเบื้องหลังของวงการ มีซอสลับคือ HEMAMI™ ที่สกัดกลิ่นเนื้อจากยีสต์ ผ่านวิธีการทางวิทยาศาสตร์สุดซับซ้อน ฟังแล้วดูดี แต่ปัญหาคือซอสลับของเขาดัน “คล้ายเกินไป” กับของ Impossible Foods ที่ใช้ heme protein เหมือนกัน
แล้วอะไรคือจุดเปราะบางที่ทำให้ Motif ต้องร่วง?
เฮียอยากให้ลองคิดแบบนี้ครับ สมมุติว่ามีร้านกาแฟใหม่ที่ตั้งใจจะขายกาแฟแนวใหม่ ใช้เมล็ดกาแฟหมักยีสต์กลิ่นกล้วยหอม รสชาตินุ่มลึก เป็นของตัวเอง เขาไม่ได้ก็อปสูตรใคร แต่ดันไปใช้กระบวนการคล้ายกับแบรนด์เจ้าตลาดที่เขียนจดสิทธิบัตรเอาไว้ก่อนแล้ว แค่คล้ายก็พอจะโดนลากขึ้นศาลได้ เพราะในโลกของสิทธิบัตร “ความใหม่” และ “ความไม่เหมือน” คือสิ่งศักดิ์สิทธิ์ แม้จะไม่ได้ก็อปตรง ๆ
Impossible Foods เห็นช่องนี้ชัด พวกเขายื่นฟ้องทันที โดยระบุว่า HEMAMI™ ของ Motif ละเมิดสิทธิบัตรเทคนิคการใช้ heme เพื่อสร้างรสชาติเหมือนเนื้อในผลิตภัณฑ์ plant-based ซึ่งเป็นหัวใจหลักที่ Impossible ใช้มัดใจตลาดมาหลายปี
ในเดือนมีนาคม 2022, Impossible Foods ก็ลุกขึ้นมาฟ้อง Motif FoodWorks ต่อศาลรัฐบาลกลางของสหรัฐฯ โดยอ้างว่า HEMAMI™ ละเมิดสิทธิบัตรของตนที่เกี่ยวข้องกับการใช้โปรตีน heme ในการสร้างรสชาติและกลิ่นที่คล้ายเนื้อจริงในผลิตภัณฑ์จากพืช จุดนี้ดูผิวเผินเหมือนแค่ “บริษัท A เหมือนของบริษัท B เลยโดนฟ้อง” แต่ความจริงซับซ้อนและลึกกว่านั้นมาก เพราะทั้งสองบริษัทต่างก็ใช้วิธีผลิตโปรตีน heme ที่คล้ายกันมาก นั่นคือการดัดแปลงพันธุกรรมจุลินทรีย์ให้ผลิตโปรตีนเฉพาะ แล้วหมักออกมาในถังขนาดใหญ่ แต่ต่างกันที่วัตถุดิบและดีไซน์โปรตีน
Impossible Foods ใช้ “soy leghemoglobin” ซึ่งเป็นโปรตีน heme จากรากถั่วเหลือง ส่วน Motif ใช้ “bovine myoglobin” ซึ่งเลียนแบบของวัวจริง ๆ โดยตรง ความคล้ายคือโปรตีนทั้งสองต่างก็ให้กลิ่นคาวแบบเนื้อเมื่อโดนความร้อน และสร้างสีแดงแบบ rare steak ได้เหมือนกัน ทั้งยังถูกหมักด้วยจุลินทรีย์ GMO แบบใกล้เคียงกันอีกด้วย แม้จะต่างสายพันธุ์ของโปรตีน แต่การฟ้องครั้งนี้ตั้งอยู่บนแนวคิดว่า “วิธีการใช้” โปรตีน heme ในอาหารจากพืชอาจเข้าข่ายละเมิดสิทธิบัตร
จากนั้นไม่กี่เดือน Motif ก็สวนกลับโดยการยื่นคำร้อง “Inter Partes Review” (IPR) กับสำนักงานสิทธิบัตรของสหรัฐฯ (USPTO) ผ่าน PTAB ซึ่งเป็นขั้นตอนที่ใช้เพื่อขอให้ตรวจสอบความถูกต้องของสิทธิบัตรที่กำลังมีปัญหา แนวคิดคือถ้าพิสูจน์ได้ว่าสิทธิบัตรของ Impossible นั้นไม่ใหม่จริง หรือมี prior art อยู่ก่อนแล้ว (เช่น งานวิจัยเก่า ๆ ที่ตีพิมพ์ก่อน) ก็จะทำให้สิทธิบัตรนั้นกลายเป็นโมฆะ
Motif ยื่นคำร้องโจมตีสิทธิบัตรถึง 7 ฉบับของ Impossible แบบกระหน่ำชุดใหญ่ ยิงทีเดียวหวังให้สั่นคลอนทั้งระบบ แต่ PTAB รับพิจารณาเพียงฉบับเดียว (หมายเลขสิทธิบัตร 10,933,018) และท้ายที่สุดในเดือนเมษายน 2023 ศาลตัดสินยกเลิกฉบับนั้นจริง โดยให้เหตุผลว่า “ไม่เป็นสิ่งประดิษฐ์ใหม่อย่างเพียงพอ” ซึ่งถือเป็นชัยชนะเล็ก ๆ ของ Motif และสร้างแรงกระเพื่อมในแวดวงวิทยาศาสตร์อาหารอยู่พอสมควร
แต่แม้จะมีชัยบางส่วน อีก 6 ฉบับที่เหลือ PTAB กลับไม่รับพิจารณา โดยบอกว่า “หลักฐานไม่ชัดเจนพอจะเข้าขั้นพิจารณาใหม่” นั่นทำให้ฝั่ง Impossible ยังถือสิทธิบัตรส่วนใหญ่ไว้อยู่เหมือนเดิม แล้วก็เริ่มกลับมาเร่งกระบวนการฟ้องร้องในศาลต่อ ซึ่งหมายความว่า Motif ยิ่งต้องใช้เงินมากขึ้นเรื่อย ๆ ในการสู้รบทั้งสองด้าน ทั้งในศาลและในระบบสิทธิบัตร
ชัยชนะเล็ก ๆ นี้กลายเป็นดาบสองคม เพราะในขณะที่ Motif ดีใจว่าล้มได้ 1 ฉบับ ตลาดกลับมองว่าพวกเขาสู้แบบดิ้นสุดตัว ซึ่งในมุมของนักลงทุน นั่นแปลว่า "ขาดเงินทุนหมุนเวียน" หรือ “มีแนวโน้มขาดทุนต่อเนื่อง” มากกว่าจะมองว่าเป็นฮีโร่สู้เพื่อความถูกต้อง
ระหว่างนี้ Motif ยังพยายาม “spin” ภาพลักษณ์ตัวเองในเชิงบวกอย่างหนัก พวกเขาเปิดตัวผลิตภัณฑ์ใหม่ชื่อ “Motif MoBeef™” และ “Motif MoChicken™” โดยใช้ HEMAMI™ ผสมอยู่ พร้อมโชว์ผลงานให้เชฟชื่อดังระดับ Michelin มาชิมและออกสื่อ โดยหวังว่าจะสร้างความเชื่อมั่นให้ตลาดว่า “ผลิตภัณฑ์เรายังไปต่อได้” และอาจดึงดีลใหม่หรือการลงทุนเพิ่มเข้ามาเพื่อบรรเทาภาระจากการฟ้องร้อง
และในขณะที่ Motif เดินหน้าเปิดตัวผลิตภัณฑ์ใหม่เพื่อแสดงพลังให้ตลาดเห็นว่า “เรายังไปต่อได้” ฝั่ง Impossible กลับเดินเกม PR อย่างเงียบ ๆ ด้วยการแจ้งเตือนสื่อและผู้ถือหุ้นว่า “Motif ยังใช้เทคโนโลยีละเมิดอยู่ต่อเนื่อง” พร้อมแนบเอกสารคำฟ้องเพิ่มในปี 2023 ซึ่งแปลความได้ว่า “ศึกยังไม่จบ อย่าเพิ่งส่งเงินให้คู่แข่งเรา” เพราะในเอกสารคำฟ้องของปี 2023 พวกเขาเสริมข้อกล่าวหาใหม่ว่าการที่ Motif ออกสื่อและใช้ HEMAMI™ ต่อไป “เป็นการจงใจละเมิด” และอาจเข้าข่ายการทำลายคุณค่าของแบรนด์ Impossible โดยตรง จุดนี้ยิ่งทำให้ Motif อยู่ในมุมที่เสี่ยงและลำบากมากขึ้น
การต่อสู้ของทั้งสองบริษัทจึงไม่ใช่แค่เรื่องใครเลียนแบบใคร แต่มันคือเกมยืดเวลา เผาเงิน ปั่นมูลค่า และวัดใจนักลงทุนว่าใครจะถอยก่อนกัน และสุดท้ายคนที่หมดลมหายใจก่อนก็คือ Motif แม้จะมีนักวิทยาศาสตร์เก่ง ๆ เทคโนโลยีล้ำ ๆ หรือวัตถุดิบดีแค่ไหน แต่เมื่อต้องมาสู้กับยักษ์ที่มีสิทธิบัตรในมือ บารมีในตลาด และชื่อเสียงติดหูผู้บริโภค…ก็ยากที่จะเอาชนะด้วยวิทยาศาสตร์เพียงอย่างเดียว
ศึกนี้จึงไม่ได้จบแค่ในศาล แต่มันลากไปถึงห้องประชุมนักลงทุน พาดหัวข่าวใน Business Insider และบอร์ด Reddit ที่คุยกันว่า “Motif จะไปไม่รอดหรือเปล่า” ซึ่งในยุคที่เงินทุนคือออกซิเจน การที่ภาพลักษณ์ของบริษัทเริ่มสั่นคลอน ก็เหมือนถังอากาศรั่วในห้องแล็บใต้ทะเล…ไม่นานนัก Motif ก็เริ่มลดจำนวนพนักงาน ลดเป้าการผลิต และสุดท้าย “ลดบทบาทตัวเองในตลาด”
หากดูเผิน ๆ หลายคนอาจคิดว่านี่คือเรื่องของสองบริษัทใหญ่ในโลก plant-based ที่ทะเลาะกันเอง แต่จริง ๆ แล้วนี่คือบทเรียนใหญ่ของ “วงการอาหารแห่งอนาคต” ที่กำลังเติบโตบนหลังคำว่า IP Intellectual Property ใครถือสิทธิบัตรก่อน คนนั้นตั้งกฎได้ ใครมาใหม่ ถ้าไม่จดให้ไว ก็อาจต้องจ่ายค่าต๋งตลอดชีวิต
และที่เจ็บปวดที่สุดคือบางทีของที่คุณคิดขึ้นมาเอง อาจไม่ใช่ของคุณอีกต่อไปแล้ว ถ้าคุณไม่มีเอกสารในมือ
นี่แหละครับ วงการที่ดูเหมือนจะขาย “นวัตกรรมอาหาร” แต่จริง ๆ แล้วขาย “สิทธิบัตรในกล่องข้าว” ใครจะอยู่ใครจะไป บางทีก็ไม่เกี่ยวกับว่า “ของอร่อยแค่ไหน” แต่เกี่ยวกับว่า “ใครมีทนายเก่งกว่า”
และในขณะที่สองยักษ์ใหญ่ยิงกันด้วยเอกสารละเมิดสิทธิ์ เหยื่อเงียบ ๆ อย่างเกษตรกรรายย่อยที่ยังอยากปลูกผักจริง เลี้ยงวัวจริง หรือแม้แต่ผู้บริโภคที่แค่อยากรู้ว่า “กินอะไรแล้วร่างกายจะดีขึ้น” กลับวนเวียนในทางอยู่ในโลกที่อาหารทุกคำถูกควบคุมโดยทุน จดหมายเรียกจากศาล และวัตถุดิบสังเคราะห์ที่มีรหัสมากกว่าชื่อจริง
สงครามสิทธิบัตรเหล่านี้ไม่เคยมีพื้นที่ให้ชาวไร่ หรือผู้บริโภคธรรมดาเข้าไปมีเสียงเลยสักนิด เพราะมันคือการต่อสู้ระหว่างนักล่าที่ฟาดฟันกันบนยอดห่วงโซ่อาหาร แต่เบื้องล่างของพีระมิด กลับมีแต่เหยื่อที่ถูกเลี้ยงให้งุนงง อยู่กับของปลอม และเชื่อว่า “นี่แหละคืออนาคตของอาหาร”
แล้วใครจะบอกเราว่า...ทางรอดคืออะไร?
คำตอบอาจอยู่ไม่ไกล แค่เราต้องกลับมาถามคำถามง่าย ๆ ที่ใครก็ลืมไปว่า “จริง ๆ แล้ว เราต้องการอาหารแบบไหนกันแน่” อาหารที่กินแล้วแข็งแรง หรืออาหารที่บริษัทแข็งแรง?
เพราะตราบใดที่เรายังปล่อยให้กล่องข้าวอยู่ในมือคนจดสิทธิบัตร เราอาจไม่มีวันได้กลับไปจับจอบเอง ปลูกเอง กินเอง แบบที่มนุษย์เคยเป็นมาก่อนโลกจะกลายเป็นห้องทดลองขนาดยักษ์
ศึกระหว่างผู้ล่ายังรุนแรงขนาดนี้ แล้วศึกระหว่างผู้ล่ากับเหยื่อ จะเหลืออะไรครับ
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 3bf0c63f:aefa459d
2024-05-24 12:31:40
@ 3bf0c63f:aefa459d
2024-05-24 12:31:40About Nostr, email and subscriptions
I check my emails like once or twice a week, always when I am looking for something specific in there.
Then I go there and I see a bunch of other stuff I had no idea I was missing. Even many things I wish I had seen before actually. And sometimes people just expect and assume I would have checked emails instantly as they arrived.
It's so weird because I'm not making a point, I just don't remember to open the damn "gmail.com" URL.
I remember some people were making some a Nostr service a while ago that sent a DM to people with Nostr articles inside -- or some other forms of "subscription services on Nostr". It makes no sense at all.
Pulling in DMs from relays is exactly the same process (actually slightly more convoluted) than pulling normal public events, so why would a service assume that "sending a DM" was more likely to reach the target subscriber when the target had explicitly subscribed to that topic or writer?
Maybe due to how some specific clients work that is true, but fundamentally it is a very broken assumption that comes from some fantastic past era in which emails were 100% always seen and there was no way for anyone to subscribe to someone else's posts.
Building around such broken assumptions is the wrong approach. Instead we should be building new flows for subscribing to specific content from specific Nostr-native sources (creators directly or manual or automated curation providers, communities, relays etc), which is essentially what most clients are already doing anyway, but specifically Coracle's new custom feeds come to mind now.
This also reminds me of the interviewer asking the Farcaster creator if Farcaster made "email addresses available to content creators" completely ignoring all the cryptography and nature of the protocol (Farcaster is shit, but at least they tried, and in this example you could imagine the interviewer asking the same thing about Nostr).
I imagine that if the interviewer had asked these people who were working (or suggesting) the Nostr DM subscription flow they would have answered: "no, you don't get their email addresses, but you can send them uncensorable DMs!" -- and that, again, is getting everything backwards.
-
 @ df478568:2a951e67
2025-06-05 23:34:01
@ df478568:2a951e67
2025-06-05 23:34:01About 156,000 blocks ago, I went to a Taco Shop for a bitcoin meetup. I asked my favorite question, “Do you accept bitcoin?”
“Yes," he said as he handed me a Toast Terminal with a BTCpayServer QR code.
 ]
]Awesome!
12,960 blocks later, I took my dad to the taco shop. We ordered food. I asked my favorite question once again.
“Uh…Yeah, but I don't know how to work the machine.”
"Dough!🤦"
It's been a problem in the past, but now lightning payments are about to be ubiquitous. Steak N Shake is taking bitcoin using Speed Wallet and Block is implementing bitcoin payments by 2026 in all legal jurisdictions. I have tested both of these so you don't have to. Just kidding. I geek out on this stuff, but both work great. You can pay with your sats by scanning a screen on a QR code. The employees don't need to be bitcoin lightning network experts. You can just pay as easy as a credit card.
There were 35,000 people at the bitcoin conference, and 4,187 transactions were made. It was a world record. Wait, I thought they said there could only be 7 transactions per second! No, not anymore. Now we can use bitcoin for shopping. I can pay for tacos at taco trucks.

How You Can Accept Bitcoin At Your Business
Coinos is a simple bitcoin point of sale information that acts like a cash register. Bitcoin is peer-to-peer electronic cash. Coinos is a cash register and you should treat it as such. If you make a few hundred thousand sats at the end of the night, you should sweep the bitcoin into your own wallet.. You can use Aqua, AlbyHub, Bull Bitcoin wallet, or whatever your favorite lightning enabled wallet is to withdraw. You'll need a password. Do not lose this. I have tried the automatic withdraws, but it did not work for me. I'm no concerned because this is not a wallet I intend to keep a lot of sats in for a long time.
Here is my coinos payment terminal.
https://coinos.io/ZapthisBlog/receive
I made the QR code with libreqr.com/

Now I have an online bitcoin cash register. The Bitcoiners know how to pay for stuff with sats. They will be proud to show you too. If you're nerdy, you can use all the cool kid tools now, but we will just focus on the lightning address. Anyone can send you sats with a lightning address with just a QR code.
At the end of the night, you cash out to your own wallet. Again, this assumes you have an Aqua Wallet or any other lightning enabled wallet, but all it takes to accept bitcoin at your brick and mortar store is to create an account with Coinos and print out a QR code. It's a quick and easy way to start accepting bitcoin even if you don't expect many clients to shop with sats.
Tips
This is not just a cash register. Employees can also make their own Coinos wallet and receive tips from bitcoiners. Anyone can accept payments using this system. Your kids could use it to sell lemonade for sats. You are only limited by your imagination. When will you begin accepting bitcoin payments? It is easier than ever. You do not need to train employees. You do not need to be in the store. Bitcoin is peer-to-peer electronic cash so you can give it away like cash. I don't know what the tax rules on cash are. You need to verify that with your own jurisdiction. This is not financial or tax advice. This is for informational purposes only.
Remember, this is a custodial wallet. Not your keys not your bitcoin. Don't keep more sats than you are willing to lose on custodial wallets. Sweep your wallet early and often. Loss of funds is possible. There is a small fee for liquidity management too. Do your own research.
-
 @ f85b9c2c:d190bcff
2025-06-06 01:02:16
@ f85b9c2c:d190bcff
2025-06-06 01:02:16
Cristiano Ronaldo stands out as a recognized and accomplished football player on a scale. His inspiring journey, from beginnings in Portugal to attaining superstar status serves as an inspiration, to individuals.
Ronaldo’s prodigious talent was evident from a young age. His coach at Sporting CP famously said “He was skinny when he arrived here but with tremendous skill”. Through hard work and dedication, Ronaldo honed his skills
Some Work Ethic and Ambition that Fuelled his success .A key factor in Ronaldo’s success story is his incredible work ethic and winning mentality. He is renowned for his strict training regimen, nutrition plan, and diligent recovery routines. Ronaldo’s dedication to self-improvement paved the way for his success. .Throughout his career, Ronaldo has shown insatiable hunger and ambition to be the best. His drive to succeed and break records is unmatched. Even in the twilight of his career, Ronaldo’s success story continues as he plies his trade in Italy with Juventus.
Lessons from Ronaldo’s Success Story 1. Dedication and hard work are essential Ronaldo showed how training relentlessly can make dreams come true. 2. Believe in your talent Ronaldo had the confidence and work ethic to fulfill his potential. 3. Handle pressure with grace Ronaldo embraced the spotlight and thrived under pressure. 4. Be ambitious and hungry Ronaldo set new benchmarks by constantly raising the bar. 5. Lead by example Ronaldo inspires teammates with his exemplary attitude. 6. Learn and improve Even at the top Ronaldo keeps evolving and adding new skills. 7. Give back Ronaldo uses his global fame and fortune for charity work.
Sum Up Cristiano Ronaldo's remarkable journey showcases the heights that can be reached through a combination of talent and relentless effort. His success serves as an inspiration for anyone with dreams and the determination to make them a reality.
-
 @ f57bac88:6045161e
2025-06-06 04:19:25
@ f57bac88:6045161e
2025-06-06 04:19:25تاریخچه پیدایش پروتکل اردینالز
پروتکل اردینالز در ژانویه 2023 توسط کیسی رودرمور معرفی شد. این پروتکل حاصل دو بهروزرسانی مهم در بیتکوین است:
-
سگویت (2017): جدا کردن دادههای امضا از بدنه تراکنشها برای افزایش فضای بلاک.
-
تپروت (2021): افزایش حریم خصوصی و انعطافپذیری در تراکنشها.
رودرمور با استفاده از این دو ویژگی، سیستمی را طراحی کرد که به هر ساتوشی یک شناسه اختصاص میدهد و امکان الصاق داده به آن را فراهم میکند. اولین اینسکریپشن رسمی در دسامبر 2022 یک تصویر پیکسلی از یک جمجمه بود.
اینسکریپشن چیست؟
اینسکریپشن به معنای «حکاکی» دیجیتال است و در اینجا به ثبت دادههایی مانند تصویر، ویدئو یا متن بر روی بلاکچین بیتکوین اشاره دارد. برخلاف انافتی های سنتی که اغلب فقط لینک یا متادیتا ثبت میکنند، اینسکریپشنها کل داده را در بخش ویتنس تراکنش ذخیره میکنند و به یک ساتوشی خاص متصل میشوند.
پروتکل اردینالز چگونه کار میکند؟
پروتکل اردینالز به هر ساتوشی یک شماره منحصربهفرد میدهد و آن را غیرقابلتعویض میکند. مراحل اصلی آن:
-
شمارهگذاری: به هر ساتوشی یک شناسه اختصاص مییابد.
-
اینسکریپشن: با ابزارهایی مثل ابزار داده به ساتوشی الصاق میشود.
-
ذخیرهسازی: در بخش ویتنس با حجم حداکثر ۴ مگابایت.
-
مالکیت: از طریق کلید خصوصی قابلانتقال است.
سایتهایی مانند ordinals.com و ord.io برای مشاهده این دادهها توسعه یافتهاند.
انواع اینسکریپشنها
کاربران دادههای متنوعی را روی بیتکوین ثبت کردهاند:
-
تصاویر: از هنر پیکسلی تا عکسهای شخصی.
-
متن: پیام، شعر یا اسناد.
-
ویدئو/صوت: نسخههای فشرده و کوتاه.
-
بازیها: نسخههای ساده مانند دووم.
مزایای اینسکریپشن و اردینالز
-
تغییرناپذیری: دادهها دائمی و مقاوم در برابر سانسور هستند.
-
ارزش ذاتی: هر اینسکریپشن به یک ساتوشی متصل است.
-
درآمدزایی برای ماینرها: افزایش تراکنشها = کارمزد بیشتر.
-
کاربرد بیشتر بیتکوین: فراتر از پول دیجیتال.
-
امنیت بالا: بدون نیاز به سرور خارجی.
معایب و چالشها
-
افزایش حجم بلاکچین: رشد حجم تا بالای ۵۰۰ گیگابایت تا مارس 2025.
-
کارمزد بالا: گاهی تا ۴۰ دلار در سال 2023.
-
پیچیدگی فنی: راهاندازی نود و ساخت اینسکریپشن ساده نیست.
-
اختلافنظر: برخی معتقدند این کاربرد با فلسفه بیتکوین در تضاد است.
-
مقیاسپذیری: ممکن است شبکه را کند کند.
تأثیرات بر اکوسیستم بیتکوین
1. تأثیر اقتصادی
در سال 2023، بیش از ۲۰ میلیون اینسکریپشن ثبت شد. این روند در 2024 نیز ادامه داشت و منجر به شکلگیری بازار انافتی های بیتکوینی شد.
2. تأثیر فنی
ابزارهای جدید مانند کیف پول اسپرو و پلتفرمهای معاملاتی مانند پلتفرم معاملاتی مجیک ادن توسعه یافتند.
3. تأثیر اجتماعی
جامعه به دو دسته تقسیم شد: موافقان نوآوری و مخالفان تغییر مسیر بیتکوین.
مقایسه اینسکریپشن و انافتی های اتریوم
| ویژگی | اینسکریپشن بیتکوین | انافتی اتریوم | | -------------- | ------------------- | --------------- | | محل ذخیره داده | روی بلاکچین | خارج از بلاکچین | | تغییرناپذیری | بسیار بالا | وابسته به سرور | | هزینه ساخت | متغیر (کارمزد) | متغیر (گس) | | امنیت | بسیار بالا | متوسط تا بالا | | انعطافپذیری | محدود | بالا | | دسترسی | پیچیده | ساده |
تحولات اخیر (2024 و اوایل 2025)
-
پس از هاوینگ: وابستگی بیشتر ماینرها به کارمزد و رشد اینسکریپشن.
-
پشتیبانی صرافیها: اضافه شدن قابلیت معامله در بایننس و کراکن.
-
کاربردهای نو: ثبت اسناد قانونی، بازیهای تعاملی و هنر دیجیتال.
آینده اینسکریپشن و اردینالز
چشمانداز آینده بستگی به:
-
پذیرش کاربران.
-
راهکارهای مقیاسپذیری.
-
رقابت با دیگر بلاکچینها.
-
تحولات قانونی.
در بهترین حالت، بیتکوین به پلتفرمی چندمنظوره تبدیل خواهد شد.
نتیجهگیری
اینسکریپشن و پروتکل اردینالز فرصتی برای نوآوری در بیتکوین ایجاد کردهاند. اگرچه چالشهایی وجود دارد، اما پتانسیل این فناوری برای ایجاد داراییهای دیجیتال دائمی، غیرقابلتغییر و امن بسیار بالاست. آینده این ابزار به مسیر فنی، پذیرش اجتماعی و سیاستگذاریهای جهانی بستگی خواهد داشت.
منابع
-
مقالات CoinDesk (2023–2024)
-
تحلیلهای Bitcoin Magazine (2023–2025)
-
آمارهای Blockchain.com
-
کانال ترجمهی مقالههای بیتکوین در تلگرام
کلمات و اصطلاحات ترجمه شده و موجود در متن:
-
پروتکل (Protocol) → قرارداد فنی / پروتکل
-
اردینالز (Ordinals) → ترتیبیها / اردینالز
-
ژانویه (January) → دیماه / ژانویه
-
کیسی رودرمور (Casey Rodarmor) → نام فرد
-
SegWit (Segregated Witness) → تفکیک شاهد / سگویت
-
Taproot → تپروت
-
ساتوشی (Satoshi) → کوچکترین واحد بیتکوین
-
اینسکریپشن (Inscription) → حکاکی / ثبت
-
تصویر پیکسلی (Pixel image) → تصویر نقطهای
-
جمجمه (Skull) → Skull
-
انافتی (NFT - Non-Fungible Token) → توکن غیرقابل تعویض
-
متادیتا (Metadata) → فراداده
-
بلاکچین (Blockchain) → زنجیره بلوکی
-
ویتنس (Witness) → بخش شاهد در تراکنش
-
Ord (ابزار) → ابزار Ord
-
کلید خصوصی (Private Key) → رمز اختصاصی
-
ordinals.com** / **ord.io → نام وبسایت
-
Doom (بازی) → دوم (نام بازی معروف)
-
ماینر (Miner) → استخراجکننده
-
تراکنش (Transaction) → مبادله
-
هاوینگ (Halving) → نصف شدن پاداش استخراج
-
Binance / Kraken → نام صرافیها
-
Sparrow Wallet → کیف پول اسپرو
-
Magic Eden → پلتفرم معاملاتی مجیک ادن
-
**Ethereum NFTs **→ توکنهای غیرقابل تعویض در شبکه اتریوم
-
گس (Gas) → هزینه پردازش در اتریوم
-
سرور (Server) → خدمتدهنده
-
اسناد قانونی (Legal documents) → مدارک حقوقی
-
بازیهای تعاملی (Interactive games) → گیمهای تعاملی
-
هنر دیجیتال (Digital art) → آثار هنری دیجیتال
-
مقیاسپذیری (Scalability) → توان گسترش
-
پلتفرم (Platform) → بستر نرمافزاری
-
چشمانداز (Outlook/Future vision) → آیندهنگری
-
سیاستگذاری (Policy-making) → برنامهریزی راهبردی
-
-
 @ 3bf0c63f:aefa459d
2024-05-21 12:38:08
@ 3bf0c63f:aefa459d
2024-05-21 12:38:08Bitcoin transactions explained
A transaction is a piece of data that takes inputs and produces outputs. Forget about the blockchain thing, Bitcoin is actually just a big tree of transactions. The blockchain is just a way to keep transactions ordered.
Imagine you have 10 satoshis. That means you have them in an unspent transaction output (UTXO). You want to spend them, so you create a transaction. The transaction should reference unspent outputs as its inputs. Every transaction has an immutable id, so you use that id plus the index of the output (because transactions can have multiple outputs). Then you specify a script that unlocks that transaction and related signatures, then you specify outputs along with a script that locks these outputs.

As you can see, there's this lock/unlocking thing and there are inputs and outputs. Inputs must be unlocked by fulfilling the conditions specified by the person who created the transaction they're in. And outputs must be locked so anyone wanting to spend those outputs will need to unlock them.
For most of the cases locking and unlocking means specifying a public key whose controller (the person who has the corresponding private key) will be able to spend. Other fancy things are possible too, but we can ignore them for now.
Back to the 10 satoshis you want to spend. Since you've successfully referenced 10 satoshis and unlocked them, now you can specify the outputs (this is all done in a single step). You can specify one output of 10 satoshis, two of 5, one of 3 and one of 7, three of 3 and so on. The sum of outputs can't be more than 10. And if the sum of outputs is less than 10 the difference goes to fees. In the first days of Bitcoin you didn't need any fees, but now you do, otherwise your transaction won't be included in any block.

If you're still interested in transactions maybe you could take a look at this small chapter of that Andreas Antonopoulos book.
If you hate Andreas Antonopoulos because he is a communist shitcoiner or don't want to read more than half a page, go here: https://en.bitcoin.it/wiki/Coin_analogy
-
 @ f85b9c2c:d190bcff
2025-06-06 00:24:22
@ f85b9c2c:d190bcff
2025-06-06 00:24:22
Inflation is one of the most significant factors affecting personal wealth and the economy yet it goes unnoticed until its effects become unavoidable. As the cost of goods and services rises, your purchasing power decreases, and this makes long-term financial planning more challenging.
What is inflation? Inflation is the general increase in prices of goods and the reduction of the purchasing power of money. It is commonly measured by : 1.Consumer Price Index (CPI)
2.Core Inflation
3.Producer Price Index (PPI)
Inflation occurs due to various factors, including increased demand and supply chain disruptions
Why is Inflation Important? Inflation is crucial because it affects the cost of living, purchasing power, and the economy as a whole. As prices rise money loses value making it harder for consumers to afford essentials if wages don’t keep up. It also influences interest rates as central banks ,adjust policies to control inflation, borrowing, savings, and investments.
How Inflation Affects Personal Wealth 1. Erosion of Purchasing Power As prices rise, the same amount of money used to buy more before now buys fewer goods and services. 2. Impact on Savings Your money sitting in savings accounts with little or no interest rates loses value over time. If the inflation rate exceeds the interest or profit earned on your savings, then it becomes affected 3. Effects on Investments Their impact is the most because inflation reduces the real value of future payments. 4.Wages & Employment Some businesses may cut costs by reducing roles in a department or reducing pay to keep the team members.
Everyone is affected by inflation.
How Do You Protect Your Wealth from Inflation? 1.Invest in Inflation-Protected Assets Stocks and real estate investments offer long-term growth potential.They give you ownership of a product, which you can use, resell or repackage as you please. 2.Alternative Investments If you have the stomach, commodities, cryptocurrency, and other non-traditional assets may provide inflation releaved. 3. Increase Income Streams Side hustles, passive income, and career advancements can help offset inflation’s impact. 4.Reduce Debt Nigerians are aware of Credit Houses pretending as Loan Sharks chasing debtors around with ridiculous messages of loved ones. In a period of inflation, those loans feel like a double punishment because of ridiculous interest rates and overwhelmed inflation. Whatever you can do to reduce your debt during this period will be life-changing. Also, non-interest debts should always be considered before going down a slippery slope.
Summary Nigeria — A Few Word One thing is clear — inflation persists in almost every corridor of the economy. Inflation is an inevitable part of economic cycles, but understanding its impact allows you to take proactive steps in protecting your wealth. But I believe you can maintain financial stability by following some of the steps above.
Be proactive!
-
 @ 374ee93a:36623347
2025-06-05 22:42:00
@ 374ee93a:36623347
2025-06-05 22:42:00Chef's notes
Start your day the self sovereign way
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 15 mins
- 🍽️ Servings: 4
Ingredients
- 1lb Jar Bottled Rhubarb https://jimblesjumble.netlify.app/item/a0c35618722834ac714d0a47058a2adc76ee7485a6b74f5da5f9eb2d3fb5d879
- 1pt Homemade Custard (3/4pt cream, 3 large eggs, 100g honey, 1/2 tbspn vanilla extract)
- 4 Handfuls Granola
- 1 Node https://plebeian.market/products/huxley@nostrplebs.com/start-9-node-y22zfjp8x6
Directions
- Whisk together the cream, eggs, honey and vanilla
- Chill overnight or serve warm with 1/4 jar of stewed rhubarb and a large handful of granola per person
- Consolidate some UTXOs on your node
- Have a Good Morning
-
 @ 3bf0c63f:aefa459d
2024-03-23 08:57:08
@ 3bf0c63f:aefa459d
2024-03-23 08:57:08Nostr is not decentralized nor censorship-resistant
Peter Todd has been saying this for a long time and all the time I've been thinking he is misunderstanding everything, but I guess a more charitable interpretation is that he is right.
Nostr today is indeed centralized.
Yesterday I published two harmless notes with the exact same content at the same time. In two minutes the notes had a noticeable difference in responses:
The top one was published to
wss://nostr.wine,wss://nos.lol,wss://pyramid.fiatjaf.com. The second was published to the relay where I generally publish all my notes to,wss://pyramid.fiatjaf.com, and that is announced on my NIP-05 file and on my NIP-65 relay list.A few minutes later I published that screenshot again in two identical notes to the same sets of relays, asking if people understood the implications. The difference in quantity of responses can still be seen today:
These results are skewed now by the fact that the two notes got rebroadcasted to multiple relays after some time, but the fundamental point remains.
What happened was that a huge lot more of people saw the first note compared to the second, and if Nostr was really censorship-resistant that shouldn't have happened at all.
Some people implied in the comments, with an air of obviousness, that publishing the note to "more relays" should have predictably resulted in more replies, which, again, shouldn't be the case if Nostr is really censorship-resistant.
What happens is that most people who engaged with the note are following me, in the sense that they have instructed their clients to fetch my notes on their behalf and present them in the UI, and clients are failing to do that despite me making it clear in multiple ways that my notes are to be found on
wss://pyramid.fiatjaf.com.If we were talking not about me, but about some public figure that was being censored by the State and got banned (or shadowbanned) by the 3 biggest public relays, the sad reality would be that the person would immediately get his reach reduced to ~10% of what they had before. This is not at all unlike what happened to dozens of personalities that were banned from the corporate social media platforms and then moved to other platforms -- how many of their original followers switched to these other platforms? Probably some small percentage close to 10%. In that sense Nostr today is similar to what we had before.
Peter Todd is right that if the way Nostr works is that you just subscribe to a small set of relays and expect to get everything from them then it tends to get very centralized very fast, and this is the reality today.
Peter Todd is wrong that Nostr is inherently centralized or that it needs a protocol change to become what it has always purported to be. He is in fact wrong today, because what is written above is not valid for all clients of today, and if we drive in the right direction we can successfully make Peter Todd be more and more wrong as time passes, instead of the contrary.
See also:
-
 @ 2cde0e02:180a96b9
2025-06-05 21:45:00
@ 2cde0e02:180a96b9
2025-06-05 21:45:00日本の姫
https://stacker.news/items/998335
-
 @ df67f9a7:2d4fc200
2025-06-05 19:52:32
@ df67f9a7:2d4fc200
2025-06-05 19:52:32Nostr is NOT a social network. Nostr is a network of interconnected social apps. And, since any app is a social app, Nostr is for every app.
ONLY Nostr incentivizes inter-connectivity between independent apps, simply by respecting sovereignty at the protocol layer. For end users, sovereignty means that the content they post “to Nostr” will never be owned by the apps that they use. For businesses building apps on Nostr, sovereignty means that every app actually benefits by other apps being on the network. Because sovereignty is respected, users are retained for longer and independent apps thrive far longer on Nostr than on the legacy “black box” social networks.
Social apps thrive on Nostr
Nostr integration provides these benefits for every app :
- Unrestrained access for any app, to all public and private data “on Nostr”. No fees or licenses for harvesting user data from the network.
- Unburdened from liability, when collecting user data with any app. When sending “to Nostr”, end users retain custody of user data while apps never loose access.
- Unlimited free market of search engines and feed algos. Users and brands can create, use, and share any algos or custom feeds. Grow your audience on your own terms.
- Universal open network for all apps. Build any kind of app for any audience, on the same network as other apps for other audiences. Discover new trends from user data.
- Unregulated tech platform. Build your own app and use it as you wish. No gate keepers. No code review.
Sovereignty is good for business.
Regardless of the network size, a Nostr integrated app can grow its user base MUCH faster and with greater independence BECAUSE of the sovereignty respecting protocol. While end users may retain custody of their identities and data on the network, it’s the apps that determine which data is, or is not, sent to the network. Respect for sovereignty IS the killer feature that ONLY the Nostr protocol provides for apps and for end users.
Because Nostr is permissionless for any app to integrate :
- end users will always have a free market of apps choose from
- apps are free to integrate only as much as benefits their business model.
- apps gain access to more novel data as new apps bring new users to the network.
Because data on Nostr is managed by end users and available to all apps :
- User data looses exclusivity and the demand shifts toward novel insights and information derived from these data.
- Apps are freed from having to be “data pirates”, and can focus on establishing a trusted user base, providing valuable services to satisfied customers, informed by the abundance of user data.
- Apps are incentivized to offload data onto the network, establishing a new paradigm for interconnectivity, where independence is NOT at stake as the network grows.
- New markets spring up to support users with self custody of their data, driven by the reality that apps can have full access without assuming responsibility.
- The market for search and algo tools opens up for independent apps and end users to discover and interact freely with each other.
- The ad based “attention economy” slowly transforms to a value based consumer economy, where the end user is the customer rather than the product being sold.
Even while privacy is respected
Sometimes sovereignty is at odds with privacy, but Nostr allows all parties to win while both are protected.
- For end users sending sensetive data "to Nostr", privacy is assured by encrypting it with their own private keys and/or sending it to private (auth required) relays of their choosing.
- For apps handling private IP or business data, any traditional “black box” infrastructure can be used in the back end to manitain isolation from Nostr.
This means apps and end users remain in control of their own private data, without requiring “big social” as trust provider or data reseller. To access a user's private data, client apps (even search engines, running locally) only need explicit permission from the end user to retrieve or decrypt from Nostr relays. Public data, on the other hand, is freely available for any app or search engine to harvest from any Nostr relay. In either case, user data on the Nostr network is always accessible to client apps, without additional restrictions or fees.
Nostr is for every app.
Adding social to any app makes it a better app. Add reviews for products or services. Add commenting or direct messaging. Share or collaborate on content creation. Nostr integration is straightforward and incremental for any app.
Nostr doesn't define your app's business model ... Nostr 10X's it!
Here's how :
- Start with your own business and app design. Add Nosrr login.
- Discover what "kinds" of user data already exists "on Nostr" that your app can ingest and make use of.
- Decide which "kinds" of data would benefit your business, your users, and the network, if sent "to Nostr".
- Implement Nostr integration for data kinds and add webs of trust tools for recommendation and discovery.
- Verify your app is sovereignty respecting in how it handles private data and implements Nostr NIPs.
- Engage with existing users, and onboard new users from your app, to earn their trust and patronage over Nostr.
For more info and assistance, contact our team of Nostr integration experts.
-
 @ dfa02707:41ca50e3
2025-06-05 22:01:48
@ dfa02707:41ca50e3
2025-06-05 22:01:48
Good morning (good night?)! The No Bullshit Bitcoin news feed is now available on Moody's Dashboard! A huge shoutout to sir Clark Moody for integrating our feed.
Headlines
- Spiral welcomes Ben Carman. The developer will work on the LDK server and a new SDK designed to simplify the onboarding process for new self-custodial Bitcoin users.
- The Bitcoin Dev Kit Foundation announced new corporate members for 2025, including AnchorWatch, CleanSpark, and Proton Foundation. The annual dues from these corporate members fund the small team of open-source developers responsible for maintaining the core BDK libraries and related free and open-source software (FOSS) projects.
- Strategy increases Bitcoin holdings to 538,200 BTC. In the latest purchase, the company has spent more than $555M to buy 6,556 coins through proceeds of two at-the-market stock offering programs.
- Spar supermarket experiments with Bitcoin payments in Zug, Switzerland. The store has introduced a new payment method powered by the Lightning Network. The implementation was facilitated by DFX Swiss, a service that supports seamless conversions between bitcoin and legacy currencies.
- The Bank for International Settlements (BIS) wants to contain 'crypto' risks. A report titled "Cryptocurrencies and Decentralised Finance: Functions and Financial Stability Implications" calls for expanding research into "how new forms of central bank money, capital controls, and taxation policies can counter the risks of widespread crypto adoption while still fostering technological innovation."
- "Global Implications of Scam Centres, Underground Banking, and Illicit Online Marketplaces in Southeast Asia." According to the United Nations Office on Drugs and Crime (UNODC) report, criminal organizations from East and Southeast Asia are swiftly extending their global reach. These groups are moving beyond traditional scams and trafficking, creating sophisticated online networks that include unlicensed cryptocurrency exchanges, encrypted communication platforms, and stablecoins, fueling a massive fraud economy on an industrial scale.
- Slovenia is considering a 25% capital gains tax on Bitcoin profits for individuals. The Ministry of Finance has proposed legislation to impose this tax on gains from cryptocurrency transactions, though exchanging one cryptocurrency for another would remain exempt. At present, individual 'crypto' traders in Slovenia are not taxed.
- Circle, BitGo, Coinbase, and Paxos plan to apply for U.S. bank charters or licenses. According to a report in The Wall Street Journal, major crypto companies are planning to apply for U.S. bank charters or licenses. These firms are pursuing limited licenses that would permit them to issue stablecoins, as the U.S. Congress deliberates on legislation mandating licensing for stablecoin issuers.
"Established banks, like Bank of America, are hoping to amend the current drafts of [stablecoin] legislation in such a way that nonbanks are more heavily restricted from issuing stablecoins," people familiar with the matter told The Block.
- Charles Schwab to launch spot Bitcoin trading by 2026. The financial investment firm, managing over $10 trillion in assets, has revealed plans to introduce spot Bitcoin trading for its clients within the next year.
Use the tools
- Bitcoin Safe v1.2.3 expands QR SignMessage compatibility for all QR-UR-compatible hardware signers (SpecterDIY, KeyStone, Passport, Jade; already supported COLDCARD Q). It also adds the ability to import wallets via QR, ensuring compatibility with Keystone's latest firmware (2.0.6), alongside other improvements.
- Minibits v0.2.2-beta, an ecash wallet for Android devices, packages many changes to align the project with the planned iOS app release. New features and improvements include the ability to lock ecash to a receiver's pubkey, faster confirmations of ecash minting and payments thanks to WebSockets, UI-related fixes, and more.
- Zeus v0.11.0-alpha1 introduces Cashu wallets tied to embedded LND wallets. Navigate to Settings > Ecash to enable it. Other wallet types can still sweep funds from Cashu tokens. Zeus Pay now supports Cashu address types in Zaplocker, Cashu, and NWC modes.
- LNDg v1.10.0, an advanced web interface designed for analyzing Lightning Network Daemon (LND) data and automating node management tasks, introduces performance improvements, adds a new metrics page for unprofitable and stuck channels, and displays warnings for batch openings. The Profit and Loss Chart has been updated to include on-chain costs. Advanced settings have been added for users who would like their channel database size to be read remotely (the default remains local). Additionally, the AutoFees tool now uses aggregated pubkey metrics for multiple channels with the same peer.
- Nunchuk Desktop v1.9.45 release brings the latest bug fixes and improvements.
- Blockstream Green iOS v4.1.8 has renamed L-BTC to LBTC, and improves translations of notifications, login time, and background payments.
- Blockstream Green Android v4.1.8 has added language preference in App Settings and enables an Android data backup option for disaster recovery. Additionally, it fixes issues with Jade entry point PIN timeout and Trezor passphrase input.
- Torq v2.2.2, an advanced Lightning node management software designed to handle large nodes with over 1000 channels, fixes bugs that caused channel balance to not be updated in some cases and channel "peer total local balance" not getting updated.
- Stack Wallet v2.1.12, a multicoin wallet by Cypher Stack, fixes an issue with Xelis introduced in the latest release for Windows.
- ESP-Miner-NerdQAxePlus v1.0.29.1, a forked version from the NerdAxe miner that was modified for use on the NerdQAxe+, is now available.
- Zark enables sending sats to an npub using Bark.
- Erk is a novel variation of the Ark protocol that completely removes the need for user interactivity in rounds, addressing one of Ark's key limitations: the requirement for users to come online before their VTXOs expire.
- Aegis v0.1.1 is now available. It is a Nostr event signer app for iOS devices.
- Nostash is a NIP-07 Nostr signing extension for Safari. It is a fork of Nostore and is maintained by Terry Yiu. Available on iOS TestFlight.
- Amber v3.2.8, a Nostr event signer for Android, delivers the latest fixes and improvements.
- Nostur v1.20.0, a Nostr client for iOS, adds
-
 @ ac8bb9b0:70278acc
2025-06-05 18:12:29
@ ac8bb9b0:70278acc
2025-06-05 18:12:29Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 20 min
- 🍽️ Servings: 12
Ingredients
- 1 and 1/2 cups (345g) mashed bananas (about 4 medium or 3 large ripe bananas)
- 1/3 cup (113g) honey
- 1 large egg
- 1/4 cup (56g) coconut oil, melted
- 1 teaspoon pure vanilla extract
- 1 cup (130g) whole wheat flour
- 1/2 cup (41g) natural unsweetened cocoa powder
- 1 teaspoon baking powder
- 1 teaspoon baking soda
- 1/2 teaspoon salt
- 1 cup (180g) semi-sweet or dark chocolate chips
Directions
- Preheat oven to 425°F (218°C). Spray a 12-count muffin pan with nonstick spray or line with cupcake liners. Set aside.
- In a medium bowl, mash the bananas up using a fork.* Try to mash up any large lumps. Once mashed, whisk in the honey, egg, coconut oil, and vanilla extract until combined. Set aside.
- In a large bowl, whisk the flour, cocoa powder, baking powder, baking soda, and salt together. Pour the wet ingredients into the dry ingredients and whisk until everything is combined. Fold in the chocolate chips, reserving some for the tops of the warm muffins.
- Spoon the batter evenly into each cup or liner, filling each all the way to the top.
- Bake for 5 minutes at 425°F (218°C); then, keeping the muffins in the oven, reduce heat to 350°F (177°C) and continue baking for another 15–17 minutes or until a toothpick inserted in the center comes out clean. The total time these muffins take in the oven is about 20–21 minutes, give or take. (For mini muffins, bake 11–13 minutes at 350°F (177°C) the whole time.)
- Press any remaining chocolate chips into the tops of the warm muffins. Allow the muffins to cool for 5 minutes in the muffin pan, and then transfer to a wire rack to continue cooling, or enjoy warm.
- Muffins stay fresh covered at room temperature for a few days, then transfer to the refrigerator for up to 1 week.
-
 @ 374ee93a:36623347
2025-06-05 21:49:45
@ 374ee93a:36623347
2025-06-05 21:49:45Chef's notes
Start your day the self sovereign way
Details
- ⏲️ Prep time: 10 mins
- 🍳 Cook time: 15 mins
- 🍽️ Servings: 4
Ingredients
- 1lb Jar Bottled Rhubarb https://jimblesjumble.netlify.app/item/a0c35618722834ac714d0a47058a2adc76ee7485a6b74f5da5f9eb2d3fb5d879
- 1pt Homemade Custard (3/4pt cream, 3 large eggs, 100g honey, 1/2 tbspn vanilla extract)
- 4 Handfuls Granola
- 1 Node https://plebeian.market/products/huxley@nostrplebs.com/start-9-node-y22zfjp8x6
Directions
- Whisk together the cream, eggs, honey and vanilla
- Chill overnight or serve warm with 1/4 jar of stewed rhubarb and a large handful of granola per person
- Consolidate some UTXOs on your node
- Have a Good Morning
-
 @ da8b7de1:c0164aee
2025-06-05 17:39:41
@ da8b7de1:c0164aee
2025-06-05 17:39:41| Régió/Ország | Fő esemény/politika | Forrás | |------------------|--------------------------------------------------------------------------------------------------|-------------| | Egyesült Államok | Végrehajtási rendeletek a nukleáris termelés négyszeresére növeléséről; a nem létfontosságú K+F költségvetésének csökkentése; SMR és mikroreaktor kezdeményezések | world-nuclear-news, nucnet, aoshearman, ans | | Kanada | Engedélyezés új BWRX-300 SMR reaktor építésére Darlingtonban | world-nuclear-news, ans | | Európa | EU tervek az orosz nukleáris importok korlátozására; Westinghouse–Bulgária beszállítói megállapodások | nucnet, world-nuclear-news | | Globális/Világbank | A nukleáris finanszírozási tilalom esetleges feloldása a fejlődő országok számára | globalissues | | Egyesült Királyság| Új kiberbiztonsági jogszabályok a nukleáris szektorban | aoshearman | | Katonaság/Védelem| A védelmi minisztérium cégeket választott ki mikroreaktorok telepítésére | ans |
Források:
world-nuclear-news
nucnet
aoshearman
globalissues
ans -
 @ f57bac88:6045161e
2025-06-06 03:52:51
@ f57bac88:6045161e
2025-06-06 03:52:51شروع ماجرا:
همه چیز از 1401 شروع شد، زمانی که به خاطر وارد کردن ضربات متعدد به بیضه توسط بسیجیان و لباس شخصی های جمهوری اسلامی و شروع درد مبهم و تیر کشیدن توی بیضههام حس میکردم که با گذشت زمان شدیدتر میشد. اول فکر کردم یه چیز سادهایه و خود به خود خوب میشه، اما با گذشت زمان متوجه شدم که این درد داره بدتر میشه که همون شب توی یازداشتگاه چندبار دکتر اومد بالای سرم و آمپول هایی برای کاهش دردم تزریق کرد و قرار شد بعد از آزادی به دکتر مراجعه کنم، اما چون فرصت مراجعه به دکتر رو نداشتم و کمی هم بیخیال بودم، این چک کردن دو سال طول کشید و در 1403 به دکتر مراجعه کردم
بعد از دو سال به دلیل اینکه میزان اسپرمم به شدت کاهش یافته بود و بیضه م داشت به شکل عجیب غریبی در میومد به پزشک مراجعه کردم، و بعد از انجام آزمایش سونوگرافی و اسپرم، دکتر سونوگرافی گفت بیضه چپم تخلیه شده، و علاوه بر اون رگ های خونی بیضه م هم آسیب دیده بوده که این یعنی واریکوسل گرید سه به همراه التهاب و ... که این یعنی سریعا عمل میشدم که حداقل بشه برای رگ ها و ورید های بیضه کاری کرد.
واریکوسل به وضعیتی گفته میشود که در آن وریدهای بیضه بزرگ و متورم میشوند، چیزی شبیه به واریس پا. این مشکل میتواند تأثیری بر کیفیت اسپرم و در نتیجه باروری داشته باشد و در گرید های بالا میتواند به عقیم شدن و عدم باروری منجر شود.
تصمیم برای عمل:
بعد از شنیدن تشخیص دکتر، خیلی ناراحت و نگران شدم. اما دکترم بهم اطمینان داد که با عمل جراحی میتونم این مشکل رو حل کنم. اولش خیلی ترسیدم، اما بعد از کلی تحقیق و مشورت با دوستان و خانواده، تصمیم گرفتم که عمل کنم.
زیر میزی قبل از عمل:
متاسفانه در ایران دکتر های جراح قبل از عمل درخواست واریز وجه به حساب خودشون یا دیگران(برای رد گم کردن و عدم شکایت بیمار) میکنند
روز عمل: استرس و آرامش
روز عمل فرا رسید. قبل از جراحی استرس داشتم، اما کادر درمان و خود دکتر بسیار حرفهای و دلسوز و مهربان بودند و حس اطمینان خوبی به من دادند. عمل تحت بیحسی از ستون فقرات و بیهوشی عمومی انجام شد و حدود یک ساعت طول کشید. وقتی به هوش آمدم، احساس درد نداشتم ولی تا چند ساعت از کمر به پایین بی حس بودم و حس خوابآلودگی داشتم.
نکته: بعد از عمل حتما آب، آبمیوه و اگر میتونید میوه و غذا بخورید!
دوران بهبودی: صبر و مراقبت
دوره نقاهت بعد از عمل، یه کم سخت بود. درد داشتم و فعالیتهای روزمرهام محدود شده بود. اما با گذشت زمان، کم کم بهتر شدم و دردهام کمتر شد.
دوره بهبودی برای من حدود یک هفته طول کشید. پزشک توصیههایی از جمله استراحت کافی، اجتناب از فعالیتهای سنگین و مصرف داروهای مسکن برای کاهش درد داده بود. در روزهای اول کمی ورم و ناراحتی داشتم، اما به مرور زمان بهتر شدم. نکتهای که برای من بسیار مهم بود، که بعد از 6 روز سرکار برگشتم و شروع به فعالیت کردم، و بعد از یک هفته بخیه ها کشیده شد.
حدود یک ماه پس از عمل، دوباره به پزشک مراجعه کردم تا روند بهبودی بررسی شود. خوشبختانه همه چیز خوب پیش رفته بود و احساس سبکی و راحتی بیشتری داشتم. درد و حس سنگینی که قبل از عمل داشتم، کاملاً از بین رفته بود.
نتیجهگیری: چرا این تصمیم ارزشش را داشت
وقتی به گذشته نگاه میکنم، از اینکه تصمیم به انجام عمل واریکوسل گرفتم، کاملاً راضیام. گرچه گرفتن تصمیم برای جراحی همیشه با ترس و تردید همراه است، اما تأثیری که این عمل بر کیفیت زندگیام گذاشت، بدون تردید ارزشش را داشت. بعد از عمل، نه تنها از درد و ناراحتی رهایی یافتم، بلکه آرامش ذهنی بیشتری هم پیدا کردم. احساس سبکی و راحتی در فعالیتهای روزمره، و از بین رفتن نگرانیهایی مثل احتمال ناباروری، باعث شد دوباره حس کنم به زندگی عادی برگشتم.
به همه کسانی که با واریکوسل درگیر هستند، پیشنهاد میکنم به بدنشان گوش دهند و حتماً از نظر پزشکان متخصص بهره بگیرند. هر کسی شرایط خاص خودش را دارد و تصمیم نهایی باید بر اساس بررسی دقیق و مشورت با پزشک گرفته شود. اما مهمترین نکته این است که سلامتیتان را در اولویت بگذارید و اجازه ندهید ترس یا تردید، مانع رسیدن به بهبودی شود.
برای من، عمل واریکوسل مثل یک تولد دوباره بود. حالا با خیال راحت و بدون درد، زندگی میکنم و از این تصمیم مهم کاملاً خوشحالم. اگر شما هم با این مشکل مواجه هستید، نگران نباشید؛ با آگاهی و مشورت درست، میتوانید آن را پشت سر بگذارید و به زندگی عادی خودتان بازگردید.
نکات مهم:
-
اگر درد یا ناراحتی در ناحیه بیضهها دارید، حتما به پزشک اورولوژی مراجعه کنید.
-
از خود درمانی خودداری کنید.
-
عمل واریکوسل یک عمل ساده و بی خطر است.
-
بعد از عمل به توصیههای پزشک عمل کنید.
-
-
 @ cae03c48:2a7d6671
2025-06-05 21:01:38
@ cae03c48:2a7d6671
2025-06-05 21:01:38Bitcoin Magazine

Moscow Exchange Launches Bitcoin Futures For Qualified InvestorsThe Moscow Exchange, Russia’s largest exchange group, announced the launch of Bitcoin futures contracts on June 4th, 2025. The new derivatives will allow qualified investors in Russia to gain exposure to bitcoin prices without directly owning it.
The bitcoin futures contracts are cash-settled in Russian rubles and will be tied to the iShares Bitcoin Trust ETF (IBIT) that trades on U.S. exchanges. The IBIT ETF tracks the price of bitcoin, with each share representing 0.00068 bitcoin.
BREAKING:
 Russia’s largest exchange, Moscow Exchange launches #Bitcoin futures trading for qualified investors. pic.twitter.com/J9htJUWpLw
Russia’s largest exchange, Moscow Exchange launches #Bitcoin futures trading for qualified investors. pic.twitter.com/J9htJUWpLw— Bitcoin Magazine (@BitcoinMagazine) June 4, 2025
Trading for the new bitcoin futures kicked off on Wednesday, with the first contracts expiring in September 2025. Each futures contract will be denominated in U.S. dollars per bitcoin but settled in rubles.
The launch of bitcoin futures on the Moscow Exchange comes after increased interest in Bitcoin exposure from Russian financial institutions. In May, Russia’s central bank formally permitted the offering of crypto-linked securities and derivatives to qualified investors. Prior to this, direct investment in Bitcoin was discouraged.
Sberbank, Russia’s largest bank, also announced plans to unveil its own bitcoin futures product in addition to the Moscow Exchange’s offering. The bank is launching exchange-traded notes that track Bitcoin’s price without direct ownership.
Bitcoin futures and other crypto-derivatives have seen surging interest recently as the Bitcoin and crypto industry matures. The move comes as an increasing number of countries have started adding Bitcoin to their reserves.
As Bitcoin adoption increases, investors and financial institutions are seeking more routes to gain exposure to Bitcoin. The launch of futures on the Moscow Exchange provides regulated bitcoin exposure to qualified Russian investors. But direct ownership of “physical” bitcoin remains off limits for most in Russia’s traditional finance sector.
This post Moscow Exchange Launches Bitcoin Futures For Qualified Investors first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:45:07
@ 20e7c953:3b8bcb21
2025-06-05 10:45:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bitcoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
-
 @ 3bf0c63f:aefa459d
2024-03-19 14:32:01
@ 3bf0c63f:aefa459d
2024-03-19 14:32:01Censorship-resistant relay discovery in Nostr
In Nostr is not decentralized nor censorship-resistant I said Nostr is centralized. Peter Todd thinks it is centralized by design, but I disagree.
Nostr wasn't designed to be centralized. The idea was always that clients would follow people in the relays they decided to publish to, even if it was a single-user relay hosted in an island in the middle of the Pacific ocean.
But the Nostr explanations never had any guidance about how to do this, and the protocol itself never had any enforcement mechanisms for any of this (because it would be impossible).
My original idea was that clients would use some undefined combination of relay hints in reply tags and the (now defunct)
kind:2relay-recommendation events plus some form of manual action ("it looks like Bob is publishing on relay X, do you want to follow him there?") to accomplish this. With the expectation that we would have a better idea of how to properly implement all this with more experience, Branle, my first working client didn't have any of that implemented, instead it used a stupid static list of relays with read/write toggle -- although it did publish relay hints and kept track of those internally and supportedkind:2events, these things were not really useful.Gossip was the first client to implement a truly censorship-resistant relay discovery mechanism that used NIP-05 hints (originally proposed by Mike Dilger) relay hints and
kind:3relay lists, and then with the simple insight of NIP-65 that got much better. After seeing it in more concrete terms, it became simpler to reason about it and the approach got popularized as the "gossip model", then implemented in clients like Coracle and Snort.Today when people mention the "gossip model" (or "outbox model") they simply think about NIP-65 though. Which I think is ok, but too restrictive. I still think there is a place for the NIP-05 hints,
nprofileandneventrelay hints and specially relay hints in event tags. All these mechanisms are used together in ZBD Social, for example, but I believe also in the clients listed above.I don't think we should stop here, though. I think there are other ways, perhaps drastically different ways, to approach content propagation and relay discovery. I think manual action by users is underrated and could go a long way if presented in a nice UX (not conceived by people that think users are dumb animals), and who knows what. Reliance on third-parties, hardcoded values, social graph, and specially a mix of multiple approaches, is what Nostr needs to be censorship-resistant and what I hope to see in the future.
-
 @ 2f5de000:2f9bcef1
2025-06-05 17:33:37
@ 2f5de000:2f9bcef1
2025-06-05 17:33:37I've wanted to write this piece for months. Not because I have anything against Jack Mallers personally - quite the opposite. But because I've watched a pattern emerge in Bitcoin that mirrors one of the most chilling dynamics in Atlas Shrugged: the systematic destruction of our most productive builders by the very people who should be celebrating them.
We are the looters. And Jack might just be our Hank Rearden.
The Underdog's Dilemma
There's a cruel irony in how we treat success in Bitcoin. We champion the underdog, root for the builder in the garage, celebrate the cypherpunk taking on the establishment. But the moment that underdog succeeds - the moment they scale, grow, and inevitably have to navigate the messy realities of the existing system - we turn on them with the ferocity of the same establishment we claim to oppose.\ \ Jack began building Zap (which evolved into Strike) from his parents home in Chicago. Strike has grown into one of the most seamless fiat-to-bitcoin on-ramps for everyday users. No complexity, just pure utility. From day one, he's operated at a level of transparency that would make most CEO's uncomfortable. He's been building in public, taking feedback, admitting mistakes, and iterating - sometimes within hours of criticism.
The Rearden Parallel
In Atlas Shrugged, Hank Rearden creates Rearden Metal - a revolutionary alloy that's stronger, lighter, and more efficient than anything that came before. Instead of celebration, he faces endless scrutiny, regulation, and demands to prove is worthiness. The people who benefit from his innovation spend their time questioning his motives, dissecting his business practices, and demanding he justify his success.
Sound familiar?
Jack comes from a finance background - his father and grandfather were in the industry. This isn't a liability; it's an asset. He understands the beast we're fighting. He's been a Bitcoiner since 2013 with a spotless track record in a space littered with exit scams and broken promises. His values align with proof of work, individualism, and the radical idea that bitcoin is for everyone.
Yet when he helps launch 21 Capital, we don't see innovation - we see betrayal. When he navigates regulatory requirements to build products that can actually reach mainstream adoption, we don't see pragmatism - we see capitulation.
The Scarred Perspective
Our skepticism isn't entirely unfounded. We've been burned before. Mt. Gox, FTX, Three Arrows Capital, Celcius, Terra/ LUNA, BlockFi, Bitconnect, Voyager, QuadrigaCX - the graveyard of Bitcoin is littered with the corpses of trusted institutions. We've learned, painfully, that trust must be earned and verified.
But somewhere along the way, our healthy skepticism has metastasized into destructive paranoia. We've become so focused on protecting ourselves from the next SBF that we're attacking the people building the future we claim to want.
I'm guilty of this myself. I've made scathing attacks on my Nostr feed, comparing Jack to SBF, scrutinising contract clauses about re-hypothecation, and questioning his every move privately. I was viewing his actions through the lens of collective trauma rather than the reality of his long track record.
The Looters Paradox
Here's the uncomfortable truth: we're not just passive observers in this drama. We're active participants. We're the looters.
In Atlas Shrugged, the looters don't necessarily steal directly. They steal time, energy, and focus. They create bureaucracy, demnd endless justification, and burden the productive with the weight of constant explanation. They don't build competing products - they just tear down what others have built.
Everytime we demand Jack explain his business model for the hundredth time, we're stealing his time. Every time we scrutinize his partnerships without offering alternatives, we're creating bureaucracy . Everytime we attack his character rather than his arguments, we're furthering the system we claim to oppose.
The free market will create products whether we like them or not. People will build services that use bitcoin as collateral, create lending products, and navigate regulatory frameworks. The question isn't whether these products will exist - it's whether they'll be built by people who share our values or by those who don't.
The Atlantis Risk
The producers eventually withdraw from society in Atlas Shrugged, retreating to Galt's Gulch (Atlantis) and leaving the looters to face the consequences of their destructive behaviour. The economy collapses because the people who actually build things decided it wasn't worth the hassle anymore.
We're walking dangerously close to this precipice in Bitcoin. We're creating an environment where our most capable builders might just decide it's not worth it. Where the hassle of dealing with our constant scrutiny and bad-faith attacks outweighs the mission of building the future.
Jack has been more patient with our criticism than we deserve. He's addressed concerns publicly, changed the course when necessary, and continued building despite the noise. But patience has limits. At some point, even the most mission-driven builders will ask themselves: "Why am I doing this?"
The Path Forward
I don't know enough about finance to fully understand everything Jack is building with 21 Capital. Neither do most of his critics. But I know enough about Bitcoin to recognise someone who's been fighting the good fight for over a decade.
This doesn't mean we should trust blindly. It doesn't mean we should stop asking questions or demanding transparency. But it does mean we should approach our builders with the same benefit of the doubt we'd want for ourselves.
We need to distinguish between healthy skepticism and destructive paranoia. Between holding people accountable and tearing them down. Between being vigilant and being looters.
The fiat system is the real enemy here. It's massive, entrenched, and infinitely resourcesful. It will adapt, co-opt, and corrupt everything it touches. Fighting it requires builders who are willing to get their hands dirty, navigate imperfect systems, and make pragmatic compromises while holding onto their core values.
We can continue to be looters, tearing down what we don't understand and driving our best builders toward their own version of Atlantis. Or we can be what we claim to be: supporters of the free market, believers of proof of work, and champions of those building the future.
Don't trust. Verify. But remember: verification works both ways.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:14:50
@ e2c72a5a:bfacb2ee
2025-06-05 17:14:50The silent revolution: Ethereum's pivot to 'digital oil' could redefine crypto's future. While Bitcoin grabs headlines as digital gold, Ethereum is quietly transforming into something potentially more valuable—the essential infrastructure powering our digital economy. Ryan Berckmans reveals Ethereum's strategic shift from being just another cryptocurrency to becoming the foundation for stablecoins, tokenized assets, and global financial systems. With $480 billion in stablecoin volume and institutional players entering the space, Ethereum isn't just competing with Bitcoin—it's creating an entirely different value proposition. The question isn't whether ETH will hit $3K, but whether we're underestimating its long-term potential as the backbone of digital finance. Are you positioning yourself for the real crypto revolution happening right under our noses?
-
 @ 3eab247c:1d80aeed
2025-06-05 08:51:39
@ 3eab247c:1d80aeed
2025-06-05 08:51:39Global Metrics
Here are the top stats from the last period:
- Total Bitcoin-accepting merchants: 15,306 → 16,284
- Recently verified (1y): 7,540 → 7,803 (the rest of our dataset is slowly rotting; help us before it's too late!)
- Avg. days since last verification: 398 → 405 (more mappers, please)
- Merchants boosted: 22 (for a total of 4,325 days, someone is feeling generous)
- Comments posted: 34
Find current stats over at the 👉 BTC Map Dashboard.
Merchant Adoption
Steak n’ Shake
The US 🇺🇸 is a massive country, yet its BTC Map footprint has been lagging relative to other countries ... that is until now!

In what came as a nice surprise to our Shadowy Supertaggers 🫠, the Steak ’n Shake chain began accepting Bitcoin payments across hundreds of its locations nationwide (with some international locations too).
According to CoinDesk, the rollout has been smooth, with users reporting seamless transactions powered by Speed.
This marks a significant step towards broader Bitcoin adoption in the US. Now to drop the capital gains tax on cheesburgers!
SPAR Switzerland
In other chain/franchise adoption news, the first SPAR supermarket in Switzerland 🇨🇭 to begin accepting Bitcoin was this one in Zug. It was quickly followed by this one in Rossrüti and this one in Kreuzlingen, in what is believed to be part of a wider roll-out plan within the country powered by DFX's Open CryptoPay.
That said, we believe the OG SPAR crown goes to SPAR City in Arnhem Bitcoin City!
New Features
Merchant Comments in the Web App
Web App users are now on par with Android users in that they can both see and make comments on merchants.
This is powered by our tweaked API that enables anyone to make a comment as long as they pass the satswall fee of 500 sats. This helps keep spam manageable and ensure quality comments.
And just in case you were wondering what the number count was on the merchant pins - yep, they're comments!
Here is an 👉 Example merchant page with comments.
Merchant Page Design Tweaks
To support the now trio of actions (Verify, Boost & Comment) on the merchant page, we've re-jigged the design a little to make things a little clearer.
What do you think?
Technical
Codebase Refactoring
Thanks to Hannes’s contributions, we’ve made progress in cleaning-up the Web App's codebase and completing long overdue maintenance. Whilst often thankless tasks, these caretaking activities help immensely with long-term maintainability enabling us to confidently build new features.
Auth System Upgrades
The old auth system was held together with duct tape and prayers, and we’re working on a more robust authentication system to support future public API access. Updates include:
- Password hashing
- Bearer token support
- Improved security practices
More enhancements are in progress and we'll update you in the next blog post.
Better API Documentation
Instead of relying on tribal knowledge, we're finally getting around to writing actual docs (with the help/hindrance of LLMs). The "move fast, break everything" era is over; now we move slightly slower and break slightly less. Progress!
Database Improvements
We use SQLite, which works well but it requires careful handling in async Rust environments. So now we're untangling this mess to avoid accidental blocking queries (and the ensuing dumpster fires).
Backup System Enhancements
BTC Map data comes in three layers of fragility:
- Merchants (backed up by OS - the big boys handle this)
- Non-OSM stuff (areas, users, etc. - currently stored on a napkin)
- External systems (Lightning node, submission tickets - pray to Satoshi)
We're now forcing two core members to backup everything, because redundancy is good.
Credits
Thanks to everyone who directly contributed to the project this period:
- Comino
- descubrebitcoin
- Hannes
- Igor Bubelov
- Nathan Day
- Rockedf
- Saunter
- SiriusBig
- vv01f
Support Us
There are many ways in which you can support us:
-
Become a Shadowy Supertagger and help maintain your local area or pitch-in with the never-ending global effort.
-
Consider a zapping this note or make a donation to the to the project here.
-
 @ 3bf0c63f:aefa459d
2024-01-29 02:19:25
@ 3bf0c63f:aefa459d
2024-01-29 02:19:25Nostr: a quick introduction, attempt #1
Nostr doesn't have a material existence, it is not a website or an app. Nostr is just a description what kind of messages each computer can send to the others and vice-versa. It's a very simple thing, but the fact that such description exists allows different apps to connect to different servers automatically, without people having to talk behind the scenes or sign contracts or anything like that.
When you use a Nostr client that is what happens, your client will connect to a bunch of servers, called relays, and all these relays will speak the same "language" so your client will be able to publish notes to them all and also download notes from other people.
That's basically what Nostr is: this communication layer between the client you run on your phone or desktop computer and the relay that someone else is running on some server somewhere. There is no central authority dictating who can connect to whom or even anyone who knows for sure where each note is stored.
If you think about it, Nostr is very much like the internet itself: there are millions of websites out there, and basically anyone can run a new one, and there are websites that allow you to store and publish your stuff on them.
The added benefit of Nostr is that this unified "language" that all Nostr clients speak allow them to switch very easily and cleanly between relays. So if one relay decides to ban someone that person can switch to publishing to others relays and their audience will quickly follow them there. Likewise, it becomes much easier for relays to impose any restrictions they want on their users: no relay has to uphold a moral ground of "absolute free speech": each relay can decide to delete notes or ban users for no reason, or even only store notes from a preselected set of people and no one will be entitled to complain about that.
There are some bad things about this design: on Nostr there are no guarantees that relays will have the notes you want to read or that they will store the notes you're sending to them. We can't just assume all relays will have everything — much to the contrary, as Nostr grows more relays will exist and people will tend to publishing to a small set of all the relays, so depending on the decisions each client takes when publishing and when fetching notes, users may see a different set of replies to a note, for example, and be confused.
Another problem with the idea of publishing to multiple servers is that they may be run by all sorts of malicious people that may edit your notes. Since no one wants to see garbage published under their name, Nostr fixes that by requiring notes to have a cryptographic signature. This signature is attached to the note and verified by everybody at all times, which ensures the notes weren't tampered (if any part of the note is changed even by a single character that would cause the signature to become invalid and then the note would be dropped). The fix is perfect, except for the fact that it introduces the requirement that each user must now hold this 63-character code that starts with "nsec1", which they must not reveal to anyone. Although annoying, this requirement brings another benefit: that users can automatically have the same identity in many different contexts and even use their Nostr identity to login to non-Nostr websites easily without having to rely on any third-party.
To conclude: Nostr is like the internet (or the internet of some decades ago): a little chaotic, but very open. It is better than the internet because it is structured and actions can be automated, but, like in the internet itself, nothing is guaranteed to work at all times and users many have to do some manual work from time to time to fix things. Plus, there is the cryptographic key stuff, which is painful, but cool.
-
 @ 42a071ab:3391e086
2025-06-05 20:06:56
@ 42a071ab:3391e086
2025-06-05 20:06:5688VIN đã từng bước khẳng định vị thế của mình trên thị trường bằng cách không ngừng đầu tư vào chất lượng dịch vụ và sự hài lòng của người dùng. Khác với những nền tảng thông thường, 88VIN chú trọng vào việc xây dựng một hệ sinh thái vận hành bài bản, nơi mọi quy trình đều được chuẩn hóa và tối ưu để đem lại hiệu suất cao nhất. Từ bước đăng ký tài khoản, xác thực thông tin, cho đến nạp – rút tiền và hỗ trợ khách hàng, tất cả đều được thiết kế một cách khoa học, rõ ràng và minh bạch. Sự tiện lợi trong thao tác và tính linh hoạt trong hệ thống đã giúp 88VIN tạo được sự tin tưởng vững chắc từ phía người dùng. Hệ thống hoạt động ổn định, tốc độ xử lý nhanh chóng, cùng đội ngũ chăm sóc khách hàng chuyên nghiệp, nhiệt tình 24/7 chính là những yếu tố làm nên thành công bền vững của 88VIN. Không chỉ vậy, nền tảng còn tích hợp công nghệ bảo mật hiện đại, bảo vệ an toàn tuyệt đối cho mọi thông tin và giao dịch cá nhân, giúp người dùng yên tâm tuyệt đối khi sử dụng.
Bên cạnh sự hoàn hảo về hệ thống, 88VIN còn gây ấn tượng bởi chính sách hỗ trợ người dùng rõ ràng, minh bạch và đầy tính nhân văn. Thay vì chỉ chú trọng vào mặt kỹ thuật, 88VIN hiểu rằng yếu tố con người mới là cốt lõi cho sự phát triển lâu dài. Chính vì vậy, đội ngũ chăm sóc khách hàng tại đây không chỉ được đào tạo bài bản mà còn luôn sẵn sàng lắng nghe, thấu hiểu và đồng hành cùng người dùng trong mọi tình huống. Mỗi phản hồi, dù là nhỏ nhất, đều được ghi nhận nghiêm túc để làm cơ sở nâng cấp chất lượng dịch vụ. Điều này giúp tạo nên một cộng đồng sử dụng 88VIN văn minh, gắn bó và ngày càng phát triển. Đồng thời, việc tối ưu hóa trải nghiệm người dùng được thể hiện qua từng chi tiết nhỏ, từ giao diện hiển thị, bố cục chức năng đến tốc độ phản hồi trên mọi thiết bị. Chính nhờ sự chăm chút tỉ mỉ đó, 88VIN không chỉ đáp ứng nhu cầu trước mắt mà còn luôn sẵn sàng cải tiến để bắt kịp xu hướng trong tương lai.
88VIN không đơn thuần là một nền tảng cung cấp dịch vụ chất lượng cao mà còn là biểu tượng của sự cam kết lâu dài đối với người dùng. Mỗi thành viên khi đến với 88VIN đều được đảm bảo quyền lợi rõ ràng, được đồng hành trong môi trường minh bạch và công bằng. Sự khác biệt của 88VIN chính là khả năng duy trì sự ổn định trong khi vẫn không ngừng đổi mới và hoàn thiện. Những giá trị mà 88VIN theo đuổi không chỉ nằm ở hiệu quả vận hành mà còn là sự tận tâm trong từng trải nghiệm của người dùng. Đây là yếu tố quyết định giúp nền tảng ngày càng chiếm được lòng tin và sự lựa chọn của cộng đồng. Trong thời đại mà sự cạnh tranh ngày càng khốc liệt, việc giữ vững đạo đức kinh doanh, coi trọng người dùng và luôn đặt chất lượng lên hàng đầu chính là con đường bền vững mà 88VIN đang theo đuổi. Nhờ vậy, 88VIN ngày càng khẳng định vị trí vững chắc, trở thành điểm đến tin cậy cho những ai tìm kiếm một nền tảng chuyên nghiệp, ổn định và thực sự vì lợi ích của người dùng.
-
 @ 2e8970de:63345c7a
2025-06-05 16:07:04
@ 2e8970de:63345c7a
2025-06-05 16:07:04https://x.com/jburnmurdoch/status/1930203297396249067
https://www.dropbox.com/scl/fi/1lp1dwzx608xdu8jfpkqk/FT_GENDER_DIVIDE_SXSW.pptx?rlkey=9gcwvn77zss3k5l5vgiquennl&e=1&st=apgyr3ug&dl=0
https://stacker.news/items/998014
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45
@ 1c5ff3ca:efe9c0f6
2025-06-05 06:29:45Just calling it Open is not enough - Herausforderungen öffentlicher Bildungsinfrastrukturen und wie Nostr helfen könnte
Ich möchte gerne mit euch teilen, an welchen Konzepten ich arbeite, um die öffentliche Bildungsinfrastruktur mit Hilfe von Nostr zugänglicher und offener zu gestalten. Ich arbeite im Bereich öffentlicher Bildungsinfrastrukturen, besonders im Feld von Open Educational Resources (#OER). OER sind offen lizenzierte Bildungsmaterialien, die mit einer offenen Lizenz, meist einer Creative Commons Lizenz, versehen sind (CC-0, CC-BY, CC-BY-SA). Durch die klare und offene Lizenzierung ist es leicht möglich, die Lernmaterialien auf die individuellen Bedarfe anzupassen, sie zu verbessern und sie erneut zu veröffentlichen.
Seit vielen Jahren wird einerseits die Entwicklung freier Bildungsmaterialien gefördert, andererseits werden Plattformen, insbesondere Repositorien gefördert, die diese Materialien verfügbar machen sollen. Denn irgendwo müssen diese Materialien zur Verfügung gestellt werden, damit sie auch gefunden werden können.
Das klappt allerdings nur so mittelgut.
Herausforderungen
Nach vielen Jahren Förderung kann die einfache Frage: "Wo kann ich denn mein OER-Material bereitstellen" nicht einfach beantwortet werden. Es gibt Services, bei denen ich mein OER hochladen kann, jedoch bleibt es dann eingeschlossen in dieser Plattform und wird nicht auf anderen Plattformen auffindbar. Außerdem sind diese Services häufig an bestimmte Bildungskontexte gebunden oder geben Content erst nach einer Qualitätsprüfung frei. Dies führt dazu, dass ein einfaches und gleichzeitig öffentliches Teilen nicht möglich ist.
Diese und weitere Herausforderungen haben ihren Ursprung darin, dass Service und Infrastruktur in der Architektur öffentlichen Bildungsarchitektur ungünstig vermischt werden. Als Infrastruktur verstehe ich hier die Bereitstellung einer öffentlichen und offen zugänglichen Bildungsinfrastruktur, auf der Daten ausgetauscht, also bereitgestellt und konsumiert werden können. Jedoch existiert eine solche Infrstruktur momentan nicht unabhängig von den Services, die auf ihr betrieben werden. Infrastrukturbetreiber sind momentan gleichzeitig immer Servicebetreiber. Da sie aber die Hand darüber haben wollen, was genau in ihrem Service passiert (verständlich), schränken sie den Zugang zu ihrer Infrastruktur mit ein, was dazu führt, dass sie Lock-In Mechanismen großer Medienplattformen in der kleinen öffentlichen Bildungsinfrastruktur replizieren.
Es ist in etwas so, als würde jeder Autobauer auch gleichzeitig die Straßen für seine Fahrzeuge bauen. Aber halt nur für seine Autos.
Anhand einiger beispielhafter Services, die bestehende Plattformen auf ihren Infrastrukturen anbieten, möchte ich die Herausforderungen aufzeigen, die ich im aktuellen Architekturkonzept sehe:
- Upload von Bildungsmaterial
- Kuration: Zusammenstellung von Listen, Annotation mit Metadaten
- Crawling, Indexierung und Suche
- Plattfformübergreifende Kollaboration in Communities -> Beispiel: Qualitätssicherung (was auch immer das genau bedeutet)
- KI- Services -> Beispiel: KI generierte Metadaten für BiIdungsmaterial
Material Upload
Der Service "Material-Upload" oder das Mitteilen eines Links zu einem Bildungsmaterial wird von verschiedenen OER-Pattformen bereitgestellt (wirlernenonline.de, oersi.org, mundo.schule).
Dies bedeutet konkret: Wenn ich bei einer der Plattformen Content hochlade, verbleibt der Content in der Regel auch dort und wird nicht mit den anderen Plattformen geteilt. Das Resultat für die User: Entweder muss ich mich überall anmelden und dort mein Material hochladen (führt zu Duplikaten) oder damit leben, dass eben nur die Nutzer:innen der jeweiligen Plattform meinen Content finden können.
Der "Open Educational Resource Search Index" (OERSI) geht diese Herausforderung an, indem die Metadaten zu den Bildungsmaterialien verschiedener Plattformen in einem Index bereitgestellt werden. Dieser Index ist wiederum öffentlich zugänglich, sodass Plattformen darüber auch Metadaten anderer Plattformen konsumieren können. Das ist schon sehr gut. Jedoch funktioniert das nur für Plattformen, die der OERSI indexiert und für alle anderen nicht. Der OERSI ist auf den Hochschulbereich fokussiert, d.h. andere Bildungskontexte werden hier ausgeschlossen. Der Ansatz für jeden Bildungsbereich einen passenden "OERSI" daneben zustellen skaliert und schlecht und es bleibt die Herausforderung bestehen, dass für jede Quelle, die indexiert werden soll, ein entsprechender Importer/Crawler geschrieben werden muss.
Dieser Ansatz (Pull-Ansatz) rennt den Materialien hinterher.
Es gibt jedoch noch mehr Einschränkungen: Die Plattformen haben sich jeweils auf spezifische Bildungskontexte spezialisiert. D.h. auf die Fragen: Wo kann ich denn mein OER bereitstellen, muss immer erst die Gegenfrage: "Für welchen Bildungsbereich denn?" beantwortet werden. Wenn dieser außerhalb des allgemeinbildendenden Bereichs oder außerhalb der Hochschule liegt, geschweige denn außerhalb des institutionellen Bildungsrahmens, wird es schon sehr, sehr dünn. Kurzum:
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Kuration
Unter Kuration verstehe ich hier die Zusammenstellung von Content in Listen oder Sammlungs ähnlicher Form sowie die Annotation dieser Sammlungen oder des Contents mit Metadaten.
Einige Plattformen bieten die Möglichkeit an, Content in Listen einzuordnen. Diese Listen sind jedoch nicht portabel. Die Liste, die ich auf Plattform A erstelle, lässt sich nicht auf Plattform B importieren. Das wäre aber schön, denn so könnten die Listen leichter auf anderen Plattformen erweitert oder sogar kollaborativ gestaltet werden, andererseits werden Lock-In-Effekte zu vermieden.
Bei der Annotation mit Metadaten treten verschiedene zentralisierende Faktoren auf. In der momentanen Praxis werden die Metadaten meist zum Zeitpunkt der Contentbereitstellung festgelegt. Meist durch eine Person oder Redaktion, bisweilen mit Unterstützung von KI-Services, die bei der Metadateneingabe unterstützen. Wie aber zusätzliche eigene Metadaten ergänzen? Wie mitteilen, dass dieses Material nicht nur für Biologie, sondern auch für Sport in Thema XY super einsetzbar wäre? Die momentanen Ansätze können diese Anforderung nicht erfüllen. Sie nutzen die Kompetenz und das Potential ihrer User nicht.
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Crawling, Indexierung und Suche

Da die Nutzer:innen nicht viele verschiedene Plattformen und Webseiten besuchen wollen, um dort nach passendem Content zu suchen, crawlen die "großen" OER-Aggregatoren diese, um die Metadaten des Contents zu indexieren. Über verschiedene Schnittstellen oder gerne auch mal über das rohe HTML. Letztere Crawler sind sehr aufwändig zu schreiben, fehleranfällig und gehen bei Design-Anpassungen der Webseite schnell kaputt, erstere sind etwas stabiler, solange sich die Schnittstelle nicht ändert. Durch den Einsatz des Allgemeinen Metadatenprofils für Bildungsressourcen (AMB) hat sich die Situation etwas verbessert. Einige Plattformen bieten jetzt eine Sitemap an, die Links zu Bildungsmaterial enthalten, die wiederum eingebettet
script-tags vom Typapplication/ld+jsonenthalten, sodass die Metadaten von dort importiert werden können.Beispiel: e-teaching.org bietet hier eine Sitemap für ihre OER an: https://e-teaching.org/oer-sitemap.xml und auf den jeweiligen Seiten findet sich ein entsprechendes script-Tag.
Das ist schon viel besser, aber da geht noch mehr:
Zunächst ist dieser Ansatz nur für Plattformen und Akteure praktikabel, die über IT-Ressourcen verfügen, um entsprechende Funktionalitäten bei sich einbauen zu können. Lehrende können dies nicht einfach auf ihrem privaten Blog oder ähnliches umsetzen. Zum anderen besteht immer noch ein Discovery Problem. Ich muss nach wie vor wissen, wo ich suchen muss. Ich muss die Sitemaps kennen, sonst finde ich nichts. Statt eines Ansatzes, bei dem Akteure eigenständig mitteilen können, dass sie neuen Content haben (Push-Ansatz), verfolgen wir derzeit einen Ansatz, bei dem jede Plattform für sich Content im Pull-Verfahren akquiriert. Dies führt an vielen Stellen zu Doppelarbeiten, ist ineffizient (mehrere Personen bauen genau die gleichen Crawler, aber halt immer für ihre Plattform) und schliesst vor allem kleine Akteure aus (lohnt es sich einen Crawler zu programmieren, wenn die Webseite "nur" 50 Materialien bereitstellt?).
Anstatt erschlossene Daten zu teilen, arbeiten die Plattformen für sich oder stellen es höchstens wieder hinter eigenen (offenen oder geschlossenen) Schnittstellen bereit. Das ist wohl nicht das, was wir uns unter einer offenen und kollaborativen Gemeinschaft vorstellen, oder?
Bei der Suche stehen wir vor ähnlichen Herausforderungen, wie bereits oben geschildert. Obwohl verschiedene OER-Aggregatoren in Form von Repositorien oder Referatorien bereits viele der "kleineren" Plattformen indexieren und somit eine übergreifende Suche anbieten, ist es nicht möglich, diese Aggregatoren gemeinsam zu durchsuchen. Dies führt im Endeffekt dazu, dass die User wieder verschiedene Plattformen ansteuern müssen, wenn sie den gesamten OER-Fundus durchsuchen wollen.
- An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform
- Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können
- Es gibt keine plattformübergreifenden Suchmöglichkeiten
Plattformübergreifende Kollaboration
Das wäre schön, oder? Mir ist schleierhaft, wie #OEP (Open Educational Practices, genaue Definition durch die Community steht noch aus) ohne funktionieren soll. Aber es gibt meines Wissens nach nicht mal Ansätze, wie das technisch umgesetzt werden soll (oder doch? let me hear).
Ein Szenario für solche plattformübergreifende Kollaboration könnte Qualitätssicherung sein. Gesetzt, dass sich zwei Plattformen / Communities auf etwas verständigt haben, dass sie als "Qualität" bezeichnen, wie aber dieses Gütesiegel nun an den Content bringen?
Plattform A: Na, dann kommt doch alle zu uns. Hier können wir das machen und dann hängt auch ein schönes Badge an den Materialien.
Plattform B: Ja, aber dann hängt es ja nicht an unseren Materialien. Außerdem wollen/müssen wir bei uns arbeiten, weil welche Existenzberechtigung hat denn meine Plattform noch, wenn wir alles bei dir machen?
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
KI-Services
Was ist heute schon komplett ohne das Thema KI zu erwähnen? Mindestens für den nächsten Förderantrag muss auch irgendetwas mit KI gemacht werden...
Verschiedene Projekte erarbeiten hilfreiche und beeindruckende KI-Services. Beispielsweise, um die Annotation von Content mit Metadaten zu erleichtern, Metadaten automatisch hinzuzufügen, Content zu bestimmten Themen zu finden oder (halb-)automatisch zu Sammlungen hinzuzufügen. Aber (vielleicht habt ihr es schon erraten): Funktioniert halt nur auf der eigenen Plattform. Vermutlich, weil die Services nah am plattformeigenen Datenmodell entwickelt werden. Und da die Daten dieses Silo nicht verlassen, passt das schon. Das führt dazu, dass an mehreren Stellen die gleichen Services doppelt entwickelt werden.
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Zusammenfassung der Probleme
Wir machen übrigens vieles schon sehr gut (Einsatz des AMB, Offene Bidungsmaterialien, wir haben eine großartige Community) und jetzt müssen wir halt weiter gehen.
(Die OER-Metadatengruppe, die das Allgemeine Metadatenprofil für Bildungsressourcen (AMB) entwickelt hat, bekommt für ihre Arbeit keine direkte Förderung. Gleichzeitig ist sie eine zentrale Anlaufstelle für alle, die mit Metadaten in offenen Bildungsinfrastukturen hantieren und das Metadatenprofil ist eines der wenigen Applikationsprofile, das öffentlich einsehbar, gut dokumentiert ist und Validierungsmöglichkeiten bietet.)
Betrachten wir die gesamten Plattformen und die beschriebenen Herausforderungen aus der Vogelperspektive, so lassen sich drei ineinander verschränkte Kernbestandteile unterscheiden, die helfen, die beschriebenen Probleme besser zu verstehen:
- User
- Service
- Daten
User: Auf (fast) allen Plattformen agieren User. Sie laden Material hoch, annotieren mit Metadaten, sind in einer Community, suchen Content usw. Egal, ob sie sich einloggen können/müssen, irgendetwas bieten wir unseren Usern an, damit sie daraus hoffentlich Mehrwerte ziehen
Service: Das ist dieses irgendetwas. Die "Webseite", die Oberfläche, das, wo der User klicken und etwas tun kann. Es ist das, was den Daten oft eine "visuelle" Form gibt. Der Service ist der Mittler, das Interface zwischen User und Daten. Mithilfe des Services lassen sich Daten erzeugen, verändern oder entfernen (Es gibt natürlich auch viele nicht-visuelle Services, die Interaktion mit Daten ermöglichen, aber für die meisten normalen Menschen, gibt es irgendwo was zu klicken).
Daten: Die Informationen in strukturierter maschinenlesbarer Form, die dem User in gerenderter Form durch einen Service Mehrwerte bieten können. Ungerenderte Daten können wir schwieirg erfassen (wir sind ja nicht Neo). Das können entweder die Metadaten zu Bildungmaterialien sein, die Materialien selbst, Profilinformationen, Materialsammlungen o.ä.

Meines Erachtens nach haben viele der oben beschriebenen Herausforderungen ihren Ursprung darin, dass die drei Kernbestandteile User, Service, Daten ungünstig miteinander verbunden wurden. Was kein Vorwurf sein soll, denn das ist genau die Art und Weise, wie die letzten Jahre (Jahrzehnte?) Plattformen immer gebaut wurden:
- User, Service und Daten werden in einer Plattform gebündelt
Das heisst durch meinen Service agieren die User mit den Daten und ich kann sicherstellen, dass in meiner kleinen Welt alles gut miteinander funktioniert. Sinnvoll, wenn ich Microsoft, Facebook, X oder ähnliches bin, weil mein Geschäftsmodell genau darin liegt: User einschließen (lock-in), ihnen die Hohheit über ihren Content nehmen (oder kannst du deine Facebook Posts zu X migrieren?) und nach Möglichkeit nicht wieder rauslassen.
Aber unsere Projekte sind öffentlich. Das sind nicht die Mechanismen, die wir replizieren sollten. Also was nun?
Bildungsinfrasstrukturen auf Basis des Nostr-Protokolls
Nostr
Eine pseudonyme Person mit dem Namen "fiatjaf" hat 2019 ein Konzept für ein Social Media Protokoll "Nostr - Notes and Other Stuff Transmitted By Relays" wie folgt beschrieben:
It does not rely on any trusted central server, hence it is resilient, it is based on cryptographic keys and signatures, so it is tamperproof, it does not rely on P2P techniques, therefore it works.
Fiatjaf, 2019
Die Kernbestandsteile des Protokolls bestehen aus:
- JSON -> Datenformat
- SHA256 & Schnorr -> Kryptographie
- Websocket -> Datenaustausch
Und funktionieren tut es so:
User besitzen ein "Schlüsselpaar": einen privaten Schlüssel (den behälst du für dich, nur für dich) und einen öffentlichen Schlüssel, den kannst du herumzeigen, das ist deine öffentliche Identität. Damit sagst du anderen Usern: Hier schau mal, das bin ich. Die beiden Schlüssel hängen dabei auf eine "magische" (kryptografische) Weise zusammen: Der öffentliche Schlüssel lässt sich aus dem privaten Schlüssel generieren, jedoch nicht andersherum. D.h. falls du deinen öffentlichen Schlüssel verlierst: Kein Problem, der lässt sich immer wieder herstellen. Wenn du deinen privaten Schlüssel verlierst: Pech gehabt, es ist faktisch unmöglich, diesen wieder herzustellen.
Die Schlüsselmagie geht jedoch noch weiter: Du kannst mit deinem privaten Schlüssel "Nachrichten" signieren, also wie unterschreiben. Diese Unterschrift, die du mit Hilfe des privaten Schlüssels erstellst, hat eine magische Eigenschaft: Jeder kann mithilfe der Signatur und deinem öffentlichen* Schlüssel nachprüfen, dass nur die Person, die auch den privaten Schlüssel zu diesem öffentlichen Schlüssel besitzt, diese Nachricht unterschrieben haben kann. Magisch, richtig? Verstehst du nicht komplett? Nicht schlimm, du benutzt es bereits vermutlich, ohne dass du es merkst. Das ist keine fancy neue Technologie, sondern gut abgehangen und breit im Einsatz.
Merke: User besitzen ein Schlüsselpaar und können damit Nachrichten signieren.
Dann gibt es noch die Services. Services funktionieren im Grunde wie bereits oben beschrieben. Durch sie interagieren die User mit Daten. Aber bei Nostr ist es ein kleines bisschen anders als sonst, denn: Die Daten "leben" nicht in den Services. Aber wo dann?
Wenn ein User einen Datensatz erstellt, verändert oder entfernen möchte, wird dieses "Event" (so nennen wir das bei Nostr) mit deinem privaten Schlüssel signiert (damit ist für alle klar, nur du kannst das gemacht haben) und dann mehrere "Relays" gesendet. Das sind die Orte, wo die Daten gehalten werden. Wenn ein User sich in einen Service einloggt, dann holt sich der Service die Daten, die er braucht von diesen Relays. User, Service und Daten sind also entkoppelt. Der User könnte zu einem anderen Service wechseln und sich dieseleben Daten von den Relays holen. Keine Lock-In Möglichkeiten.
Merke: User, Service und Daten sind entkoppelt.
Zuletzt gibt es noch die Relays. Relays sind Orte. Es sind die Orte, zu denen die Events, also die Daten der User, ihre Interaktionen, gesendet und von denen sie angefragt werden. Sie sind sowas wie das Backend von Nostr, allerdings tun sie nicht viel mehr als das: Events annehmen, Events verteilen. Je nach Konfiguration dürfen nur bestimmte User auf ein Relay schreiben oder davon lesen.
Das Protokoll ist von seinem Grunddesign auf Offenheit und Interoperabilität ausgelegt. Keine Registrierung ist nötig, sondern nur Schlüsselpaare. Durch kryptografische Verfahren kann dennoch die Authentizitität eines Events sichergestellt werden, da nur die Inhaberin des jeweiligen Schlüsselpaares dieses Event so erstellen konnte. Die Relays sorgen dafür die Daten an die gewünschten Stellen zu bringen und da wir mehr als nur eines benutzen, haben wir eine gewisse Ausfallsicherheit. Da die Daten nur aus signierten JSON-Schnipseln bestehen, können wir sie leicht an einen anderen Ort kopieren, im Falle eines Ausfalls. Durch die Signaturen ist wiederum sichergestellt, dass zwischendurch keine Veränderungen an den Daten vorgenommen wurden.
Beispiel: Ein Nostr Event
Hier ein kleiner technischer Exkurs, der beschreibt, wie Nostr Events strukturiert sind. Falls dich die technischen Details nicht so interessieren, überspringe diesen Abschnitt ruhig.
Jedes Nostr Event besitzt die gleiche Grundstruktur mit den Attributen:
id: Der Hash des Eventspubkey: Der Pubkey des Urhebers des Eventscreated_at: Der Zeitstempel des Eventskind: Der Typ des Eventstags: Zusätzliche Metadaten für das Event können in diesem Array hinterlegt werdencontent: Der textuelle Inhalt eines Eventssig: Die Signatur des Events, um die Integrität der Daten zu überprüfen
json { "id": <32-bytes lowercase hex-encoded sha256 of the serialized event data>, "pubkey": <32-bytes lowercase hex-encoded public key of the event creator>, "created_at": <unix timestamp in seconds>, "kind": <integer between 0 and 65535>, "tags": [ [<arbitrary string>...], // ... ], "content": <arbitrary string>, "sig": <64-bytes lowercase hex of the signature of the sha256 hash of the serialized event data, which is the same as the "id" field> }Die verwendeten Eventtypen sowie die existierenden Spezifikationen lassen sich unter https://github.com/nostr-protocol/nips/ einsehen.
Wichtig ist auch: Du kannst einfach anfangen, Anwendungen zu entwickeln. Die Relays werden alle Events akzeptieren, die dem o.g. Schema folgen. Du musst also niemanden um Erlaubnis fragen oder warten, bis deine Spezifikation akzeptiert und hinzugefügt wurde.
You can just build things.
Exkurs: Nostr für Binärdaten - Blossom
Ja, aber... das ist doch nur für textbasierte Daten geeignet? Was ist denn mit den Binärdaten (Bilder, Videos, PDFs, etc)
Diese Daten sind oft recht groß und es wurde sich auf das Best-Practice geeignet, diese Daten nicht auf Relays abzulegen, sondern einen besser geeigneten Publikationsmechanismus für diese Datentypen zu finden. Der Ansatz wird als "Blossom - Blobs stored simply on mediaservers" bezeichnet und ist recht unkompliziert.
Blossom Server (nichts anderes als simple Medienserver) nutzen Nostr Schlüsselpaare zur Verwaltung Identitäten und zum Signieren von Events. Die Blobs werden über ihren sha256 Hash identifiziert. Blossom definiert einige standardisierte Endpunkte, die beschreiben wie Medien hochgeladen werden können, wie sie konsumiert werden können usw.
Die Details, wie Authorisierung und die jeweiligen Endpunkte funktionieren, werden in der genannten Spezifikation beschrieben.
Nostr 🤝 Öffentliche Bildungsinfrastrukturen
Wie könnten Herausforderungen gelöst werden, wenn wir Nostr als Basis für die öffentliche Bildungsinfrastruktur einsetzen?
Material-Upload
- Es ist nicht einfach möglich OER bereitzustellen, sodass es auch auf verschiedenen Plattformen gefunden werden kann.
Mit Nostr als Basis-Infrastruktur würden die Metadaten und die Binärdaten nicht an den Service gekoppelt sein, von dem aus sie bereitgestellt wurden. Binärdaten können auf sogenannten Blossom-Servern gehostet werden. Metadaten, Kommentare und weitere textbasierte Daten werden über die Relay-Infrastruktur verteilt. Da Daten und Service entkoppelt sind, können die OER Materialien von verschiedenen Anwendungen aus konsumiert werden.
Kuration
- Es gibt keine interoperablen Sammlungen
- Metadaten-Annotation ist zentralisiert
- User können keine eigenen Metadaten hinzufügen
Sammlungen sind per se interoperabel. Auf Protokollebene ist definiert, wie Listen funktionieren. Die Annotation mit Metadaten ist an keiner Stelle zentralisiert. Das Versprechen der RDF-Community "Anyone can say anything about any topic" wird hier verwirklicht. Ich muss mir ja nicht alles anhören. Vielleicht konsumiere ich nur Metadaten-Events bestimmter Redaktionen oder User. Vielleicht nur diejenigen mit einer Nähe zu meinem sozialen Graphen. Jedenfalls gibt es die Möglichkeit für alle User entsprechende Metadaten bereit zu stellen.
Crawling, Indexierung und Suche * An vielen Stellen wird Content doppelt erschlossen, aber immer für die eigene Plattform * Es gibt keinen geteilten Datenraum, in den Akteure Content "pushen" können * Es gibt keine plattformübergreifenden Suchmöglichkeiten
Keine Doppelerschließungen mehr. Wenn ein User im Netzwerk ein Metadatenevent veröffentlicht hat, ist es für alle konsumierbar. Der Datenraum ist per se geteilt. Plattformübergreifende Suche wird durch die Kombination aus Relays und NIPs ermöglicht. In den NIPs können spezielle Query-Formate für die jeweiligen NIPs definiert werden. Relays können anzeigen, welche NIPs sie untersützten. Eine plattformübergreifende Suche ist im Nostr eine relay-übergreifende Suche.
Plattformübergreifende Kollaboration
- Obwohl nun #OEP in aller Munde sind, gibt es keine technischen Ansätze, wie (plattformübergreifende) Kollaboration technisch abgebildet werden kann
Nostr ist der technische Ansatz.
KI-Services
- KI-Services funktionieren oft nur auf der Plattform für die sie entwickelt werden
Es gibt im Nostr das Konzept der Data Vending Machines (s. auch data-vending-machines.org). Statt also einfach nur eine API zu bauen (was auch schon sehr schön ist, wenn sie offen zugänglich ist), könnten diese Services auch als Akteure im Nostr Netzwerk fungieren und Jobs annehmen und ausführen. Die Art der Jobs kann in einer Spezifikation beschrieben werden, sodass die Funktionsweise für alle interessierten Teilnehmer im Netzwerk einfach nachzuvollziehen ist.
Die Services könnten sogar monetarisiert werden, sodass sich hier auch Möglichkeiten böten, Geschäftsmodelle zu entwickeln.
Fazit
Die Open Education Community ist großartig. Es sind einzigartige und unglaublich engagierte Menschen, die sich dem hehren Ziel "Zugängliche Bildung für Alle" -> "Offene Bildung" verschrieben haben. Wir verwenden Creative Commons Lizenzen -> Commons -> Gemeingüter. Es ist okay, dass viele Projekte von Sponsoren und Förderungen abhängig sind. Was wir machen, ist im Sinne eines Gemeingutes: Öffentliche Bildung für alle. Also zahlen wir als Gemeinschaft alle dafür.
Was nicht okay ist: Dass das, wofür wir alle gezahlt haben, nach kurzer Zeit nicht mehr auffindbar ist. Dass es eingeschlossen wird. In öffentlich finanzierten Datensilos. Es muss für alle auch langfristig verfügbar sein. Sonst ist es nicht zugänglich, nicht offen. Dann ist das O in OER nur ein Label und Marketing, um für eine ABM-Maßnahme 3 Jahre Geld zu bekommen. Denn nichts anderes ist Content-Entwicklung, wenn der Content nach drei Jahren weggeschmissen wird.
Und dasselbe gilt für OEP. Offene Lernpraktiken, sind auch nur eine Phrase, wenn wir die passende technische Infrastruktur nicht mitdenken, die wirkliche Offenheit und Kollaboration und damit die Umsetzung offener Lernpraktiken ermöglicht.
Und wenn wir uns jetzt nicht Gedanken darüber machen, die Infrastruktur für offenes Lernen anzupassen, dann werden wir vermutlich in einigen Jahren sehen können, was bei politischen Umorientierungen noch davon übrig bleiben wird. Wenn die Fördertöpfe komplett gestrichen werden, was bleibt dann übrig von dem investierten Geld?
Wir brauchen Lösungen, die engagierte Communities weiter betreiben können und denen kein Kopf abgeschlagen werden kann, ohne dass wir zwei neue daneben setzen könnten.
Wir müssen uns jetzt Gedanken darüber machen.
Wie offen will öffentliche Bildungsinfrastruktur sein?
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:11:03
@ e2c72a5a:bfacb2ee
2025-06-05 17:11:03The $220 million crypto heist that took just minutes reveals a fatal flaw in DeFi security. While blockchain tech promises trustless transactions, the Cetus DEX exploit on Sui exposed how a single undetected bug in a math library became catastrophic. What's truly alarming isn't the hack itself but the revelation from Curve's founder that professional hackers-for-hire are now coordinating sophisticated cross-platform attacks. This signals a dangerous evolution in crypto threats where vulnerabilities aren't just discovered—they're hunted by organized teams with specialized skills. The industry faces a stark choice: invest aggressively in preventative security or watch as billions more vanish in seconds. Is your crypto truly safe, or just waiting for the right hacker to find its weakness?
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16bitcoinddecentralizationIt is better to have multiple curator teams, with different vetting processes and release schedules for
bitcoindthan a single one."More eyes on code", "Contribute to Core", "Everybody should audit the code".
All these points repeated again and again fell to Earth on the day it was discovered that Bitcoin Core developers merged a variable name change from "blacklist" to "blocklist" without even discussing or acknowledging the fact that that innocent pull request opened by a sybil account was a social attack.
After a big lot of people manifested their dissatisfaction with that event on Twitter and on GitHub, most Core developers simply ignored everybody's concerns or even personally attacked people who were complaining.
The event has shown that:
1) Bitcoin Core ultimately rests on the hands of a couple maintainers and they decide what goes on the GitHub repository[^pr-merged-very-quickly] and the binary releases that will be downloaded by thousands; 2) Bitcoin Core is susceptible to social attacks; 2) "More eyes on code" don't matter, as these extra eyes can be ignored and dismissed.
Solution:
bitcoinddecentralizationIf usage was spread across 10 different
bitcoindflavors, the network would be much more resistant to social attacks to a single team.This has nothing to do with the question on if it is better to have multiple different Bitcoin node implementations or not, because here we're basically talking about the same software.
Multiple teams, each with their own release process, their own logo, some subtle changes, or perhaps no changes at all, just a different name for their
bitcoindflavor, and that's it.Every day or week or month or year, each flavor merges all changes from Bitcoin Core on their own fork. If there's anything suspicious or too leftist (or perhaps too rightist, in case there's a leftist
bitcoindflavor), maybe they will spot it and not merge.This way we keep the best of both worlds: all software development, bugfixes, improvements goes on Bitcoin Core, other flavors just copy. If there's some non-consensus change whose efficacy is debatable, one of the flavors will merge on their fork and test, and later others -- including Core -- can copy that too. Plus, we get resistant to attacks: in case there is an attack on Bitcoin Core, only 10% of the network would be compromised. the other flavors would be safe.
Run Bitcoin Knots
The first example of a
bitcoindsoftware that follows Bitcoin Core closely, adds some small changes, but has an independent vetting and release process is Bitcoin Knots, maintained by the incorruptible Luke DashJr.Next time you decide to run
bitcoind, run Bitcoin Knots instead and contribute tobitcoinddecentralization!
See also:
[^pr-merged-very-quickly]: See PR 20624, for example, a very complicated change that could be introducing bugs or be a deliberate attack, merged in 3 days without time for discussion.
-
 @ 05a0f81e:fc032124
2025-06-05 18:36:08
@ 05a0f81e:fc032124
2025-06-05 18:36:08Akhenaten (originally named Amenhotep IV) was a pharaoh of ancient Egypt known for radically transforming Egyptian religion, art, and culture. He is most famous for promoting the worship of one god—Aten, the sun disk—marking one of the earliest recorded movements toward monotheism.
Early Life and Rise to Power of pharaoh Akhenaten.
The Birth Name was Amenhotep IV, and he was born Around 1380 BCE. By Pharaoh Amenhotep III, and the mother Likely Queen Tiye. He grew up and married a Wife, Nefertiti, one of Egypt's most iconic queens. He have children, Including daughters and likely the father of Tutankhamun (King Tut).
Amenhotep IV ascended the throne around 1353 BCE, succeeding his father, a powerful and prosperous pharaoh, and there was a Religious Revolution.
A Shift Toward Monotheism
Around his 5th regnal year, Amenhotep IV changed his name to Akhenaten, meaning "Effective for Aten".
He abandoned the traditional Egyptian pantheon, especially the powerful god Amun, and elevated Aten as the sole god.
This was a dramatic break from Egypt's deeply rooted polytheistic religion.
The capital city Akhetaten (Modern-day Amarna). Akhenaten moved the capital from Thebes to a new city he built from scratch: Akhetaten (Horizon of Aten).
The city was dedicated entirely to the Aten religion and became a center of art, culture, and politics.
Nefertiti was not just a queen but a powerful co-ruler. Some theories suggest she may have ruled independently for a time after Akhenaten’s death (possibly as Neferneferuaten).
They had at least six daughters. The identity of Akhenaten's sons is debated, but Tutankhamun is widely believed to be his son, possibly by a secondary wife.
Decline and Death
Akhenaten died around 1336 BCE after a 17-year reign.
After his death, his successors (including Tutankhamun) restored traditional religion, abandoned Atenism, and moved the capital back to Thebes.
His monuments were defaced, and his name was erased from king lists, a process known as damnatio memoriae (damnation of memory).
Legacy
Akhenaten is remembered as:
A visionary who introduced monotheism before it appeared in other cultures.
A heretic who defied over a thousand years of religious tradition.
A reformer whose bold changes caused cultural upheaval.
His religious revolution was short-lived, but modern historians and archaeologists regard him as one of the most fascinating and controversial figures in ancient history.
The reasons why Pharaoh Akhenaten introduced monotheism, the worship of Aten, the sun disk, as the one true god are still debated by historians, but several key political, religious, personal, and philosophical factors likely contributed.
✅ Main Reasons Why Akhenaten Introduced Monotheism
- Religious Reform: Belief in a Universal Power
Akhenaten may have genuinely believed in Aten as the supreme creator and life-giver.
The sun was already important in Egyptian religion (Ra, Amun-Ra), but Akhenaten stripped away all personification, choosing the sun's disk (Aten) as a pure, abstract symbol of divine power.
He saw Aten as omnipresent, providing light and life to everything and everyone equally.
- Political Motivation: Weaken the Power of the Priests
The priesthood of Amun at Thebes had become extremely wealthy and powerful, almost a state within a state. By elevating Aten and banning Amun's worship, Akhenaten dismantled the influence of the Amun priests and centralized religious power in his own hands. He made himself the sole mediator between Aten and the people, increasing royal control.
- Personal Vision and Identity
Akhenaten may have had a personal religious experience or conviction that shaped his devotion to Aten.
His new name, “Akhenaten,” meaning “Effective for the Aten,” reflects a deep, personal connection to this god.
He often depicted himself and his family in direct contact with Aten, showing a highly intimate and unique belief system.
- Philosophical and Artistic Shift
Akhenaten's reign saw a revolution in art, emphasizing naturalism, emotion, and individuality.
This change in thinking may reflect a broader philosophical shift toward a more abstract and spiritual understanding of the divine unified in Aten.
Atenism removed the idea of gods with human forms, replacing them with a universal force (the sun's light).
- Reaction Against Religious Corruption or Complexity
Traditional Egyptian religion had hundreds of gods, rituals, and temple hierarchies.
Akhenaten may have seen the system as corrupt, ritualistic, and too complex for ordinary people.
Atenism was simple, focused, and accessible, with the sun’s light reaching everyone equally.
- Political Instability or Health Issues (Speculative)
Some theories suggest Akhenaten’s appearance (depicted with elongated head, wide hips, etc.) may reflect a genetic disorder (e.g., Marfan syndrome or Froehlich's syndrome).
If he was sickly, he may have been drawn to religious introspection or spiritual reform.
Others suggest that political instability or unrest during his early reign may have motivated a bold unifying reform.
Summary
Akhenaten’s monotheism was unprecedented in Egypt’s long religious history. Whether he was a spiritual visionary, a political tactician, or both, his religious revolution stands out as one of the most dramatic and controversial in ancient history.
-
 @ b2caa9b3:9eab0fb5
2025-06-04 19:50:29
@ b2caa9b3:9eab0fb5
2025-06-04 19:50:29If you'd like to connect with me on XMPP, you're very welcome! I first used it many years ago, and now I've returned to it — and I'm really glad I did.
XMPP is a secure and privacy-friendly way to communicate. It's spam-resistant: messages only go through once you've accepted a contact request. To request a connection, just send me a message.
One of the great things about XMPP is that you have control over encryption. You can choose to use strong encryption like PGP or OMEMO, or even no encryption at all — it's entirely up to you. Your messages aren’t tied to any one company or service.
There are many apps (called clients) you can use with XMPP, and you’re not locked into a single one that monitors or sells your data. XMPP is an open protocol, which means freedom of choice and better privacy.
My XMPP username is: rubenstorm@c0nnect.de
I’ve also been much less active on Facebook, Instagram, and other social media. That’s because I’ve shifted from platforms to protocols — more decentralized, censorship-resistant tools that put users in control. I started exploring these about two years ago and haven’t looked back.
If you’re interested in learning more or want help getting started, feel free to reach out. Just message me using any XMPP client — I’ll be happy to connect!
-
 @ e2c72a5a:bfacb2ee
2025-06-05 17:00:01
@ e2c72a5a:bfacb2ee
2025-06-05 17:00:01Forget Lambos, think real estate tokens.
A European fund just dropped $3.4 million on tokenized real estate, marking the first time big money directly bought retail available tokens. This isn't just about crypto hype; it's about institutions embracing regulated crypto assets. Real World Assets (RWAs) are booming, up 260% this year, fueled by clearer US crypto rules. This surge pushes the tokenization sector past $23 billion.
Is this the start of crypto's mainstream moment?
-
 @ 58537364:705b4b85
2025-06-05 15:55:12
@ 58537364:705b4b85
2025-06-05 15:55:12อารมณ์ คือ โลก - โลก คือ อารมณ์ อารมณ์ ในโลกปัจจุบันรวมอยู่ที่ วัตถุนิยม อารมณ์ จึงเป็นปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก
…. “ เดี๋ยวนี้คําว่า “อารมณ์” ในภาษาไทยนั้น หมายถึงความรู้สึกในใจมากกว่า; เช่น พื้นเพของจิตใจในขณะนั้นเป็นอย่างไร, เรียกว่าอารมณ์ของเขาเป็นอย่างไร, อารมณ์กําลังดี อารมณ์กําลังไม่ดี, นี่ คําว่าอารมณ์ในภาษาไทยใช้กันไปเสียอย่างนี้ ; มันคนละเรื่องกับในภาษาบาลี ซึ่งคําว่า “อารมณ์” หมายถึง สิ่งที่จะเข้ามากระทบ ตา หู จมูก ลิ้น กาย ใจ.
…. ถ้ากระทบแล้วเกิดความรู้สึกอย่างไร งุ่นง่านอยู่ในใจ อันนั้นไม่ได้เรียกว่าอารมณ์; อันนั้นก็เรียกว่ากิเลสอย่างอื่น เช่น เรียกว่าตัณหาบ้าง อุปาทานบ้าง; ถ้าจัดเป็นพวกขันธ์ ก็เรียกว่า เวทนาขันธ์บ้าง สัญญาขันธ์บ้าง สังขารขันธ์บ้าง; ถ้าเป็นความคิดที่งุ่นง่านก็เรียกว่า “สังขารขันธ์” ทั้งนั้น ดังนั้น เราจะต้องถือเอาคําว่าอารมณ์ในบาลีมาเป็นหลัก …. คําว่า อารมณ์ ที่จะเข้าใจกันง่ายๆ ก็หมายความว่า รูป เสียง กลิ่น รส โผฏฐัพพะ ที่จะมากระทบ ตา หู จมูก ลิ้น กาย นี้ ๕ อย่าง แล้วก็ความรู้สึกเก่าแก่ที่จะมาผุดขึ้นในใจอีก เรียกว่า ธัมมารมณ์ ที่จะมากระทบใจในปัจจุบันนี้ นี้ก็เป็นอันหนึ่ง เลยได้เป็นอารมณ์ ๖. อารมณ์กระทบ ตา หู จมูก ลิ้น กาย ๕ อย่างข้างนอกนี้ก็สําคัญไปพวกหนึ่ง ที่ปรุงขึ้นภายในสําหรับกระทบใจโดยไม่ต้องอาศัย ตา หู จมูก ลิ้น กาย ใจ เลย ในเวลานั้นก็ยังมีอยู่นี้เรียกว่าธัมมารมณ์ นี้ก็ยิ่งสําคัญ: แต่ว่ารวมกันแล้วก็เรียกว่า อารมณ์ ได้ด้วยกันทั้งนั้น แปลว่า สิ่งที่จะมากระทบกับ ตา หู จมูก ลิ้น กาย ใจ นั่นเอง
…. นี้ ดูให้ละเอียดตามตัวหนังสือ คําว่า “อารมณ์” แปลว่า ที่หน่วงบ้าง แปลว่า ที่ยินดีบ้าง, มันมีความหมายละเอียดมาก. ถ้าถือเอาความหมายอย่างคนที่มีตัวตนเป็นหลัก ธรรมะในฝ่ายฮินดูหรือฝ่ายพรหมณ์เขาก็จะพูดว่า สําหรับจิตหรืออาตมันเข้าไปจับฉวยเอา. แต่ถ้าพูดอย่างภาษาชาวพุทธพูดอย่างนั้นไม่ได้ เพราะไม่มีจิตไม่มีอาตมันชนิดนั้น แล้วจิตนี้ก็เพิ่งเกิดขึ้นหลังอารมณ์กระทบแล้ว; เลยต้องพูดตามพระบาลีที่ว่า อาศัยตาด้วย อาศัยรูปด้วย ย่อมเกิดจักษุวิญญาณ; ตาอาศัยกับรูปคืออารมณ์นั้นได้แล้วจึงจะเกิดจักษุวิญญาณ วิญญาณหรือจิตนี้เกิดทีหลัง
…. ฉะนั้น จึงไม่พูดว่า อารมณ์นี้เป็นสิ่งสําหรับจิตหรือตัวตนเข้าไปจับฉวยยึดเอา; ถ้าพูดอย่างนั้นมันก็จะเป็นฮินดูหรือพราหมณ์ไป คือมีตัวตนไป. พูดอย่างพุทธไม่มีตัวตน ทุกอย่างไม่ใช่ตัวตน เป็นสักว่าธาตุ, ได้การปรุงแต่งที่เหมาะแล้วมันก็ปรุงแต่งเป็นสิ่งใหม่ขึ้นมา ในนั้นอาจจะมีความรู้สึกโง่ไปว่าเป็นตัวเราก็ได้
…. ฉะนั้น คําว่าอารมณ์ ถ้าถือตามหลักในทางพุทธศาสนา ก็แปลว่า สิ่งที่อาศัยกันกับจิต จะเรียกว่าเป็นที่หน่วงของจิตมันก็ยังได้: ถ้าเข้าใจผิดมันก็ผิดได้: เรียกว่าสิ่งที่อาศัยกับอายตนะ แล้วก็เกิดเป็นความรู้สึกเป็นจิตขึ้นมา จิตกําลังหน่วงสิ่งนั้นเป็นอารมณ์ก็ได้ แต่จะให้เป็นตัวตนนั้นไม่ได้
…. โดยพยัญชนะก็มีอยู่อย่างนี้ ตัวพยัญชนะก็ยังกํากวม อารมฺมณํ หรือที่มาจาก อาลมฺพนํ ก็แปลว่า ที่หน่วงของจิต. ถ้าจะถือว่ามาจาก รม ที่แปลว่า ยินดี ก็แปลว่า มันเป็นสิ่งที่หลงใหลยินดีของจิต อย่างนี้ก็ยังได้อีก
…. แต่ขอให้รู้จักจากภายในดีกว่าที่จะมารู้จักจากตัวหนังสือ เมื่อตากระทบรูป เมื่อหูกระทบเสียง เป็นต้น มันเกิดขึ้นในใจ, แล้วสังเกตเอาที่นั่นก็แล้วกัน ว่ารูปที่มากระทบตานั้นมันคืออะไร? เสียงที่มากระทบหูนั้นมันคืออะไร? จะค่อยเข้าใจแจ่มแจ้งขึ้นทีละน้อยๆ ว่าอารมณ์นั้นคืออะไร? แต่ให้เข้าใจไว้ทีหนึ่งก่อนว่าสิ่งที่เรียกว่าอารมณ์ๆที่มากระทบนี้ มันยังไม่ดีไม่ชั่ว ยังไม่จัดเป็นสิ่งดีสิ่งชั่ว มันต้องผสมปรุงแต่งเป็นความคิดอย่างนั้นอย่างนี้เสียก่อน จึงจะจัดเป็นดีเป็นชั่ว อารมณ์ล้วนๆยังไม่ดีไม่ชั่ว จะได้รู้จักป้องกัน อย่าให้เป็นไปในทางชั่ว, ให้เป็นไปแต่ในทางดีได้ตามปรารถนา
…. นี้เรียกว่าโดยพยัญชนะ โดยตัวหนังสือ คําว่า “อารมณ์” แปลว่า เป็นที่ยินดีแห่งจิต, เป็นที่ยึดหน่วงแห่งจิต; โดยเฉพาะภาษาอภิธรรมแล้วก็ใช้คําว่า “เป็นที่หน่วงเอาของจิต”, คือจิตย่อมหน่วงสิ่งใดสิ่งหนึ่งเป็นอารมณ์ แปลคําว่าอารมณ์บ้าง, อาลัมพนะ แปลว่า เป็นที่หน่วงเอา.
…. เดี๋ยวนี้เราเรียนพุทธศาสนาไม่ใช่เรามาเรียนหนังสือบาลี, เราจะเรียนพระธรรมคําสอนของพระพุทธเจ้า เราก็ต้องดูสิ่งที่เรียกว่าอารมณ์ โดยหลักของธรรมชาติที่ปรุงแต่งกันอยู่ในใจดีกว่า; ก็อย่างพระบาลีที่ได้ว่ามาแล้วข้างต้นว่า จกฺขุญฺจ ปฏิจฺจ รูเป จ อุปฺปชฺชติ จกฺขุวิญฺญาณํ = เพราะอาศัยตาด้วย รูปด้วย ย่อมบังเกิดจักษุวิญญาณ ติณฺณํ ธมฺมานํ สงฺคติ ผสฺโส - การประจวบกันของ ๓ สิ่งนี้เรียกว่า “ผัสสะ”, ผสฺสปจฺจยา เวทนา = เพราะผัสสะเป็นปัจจัยจึงเกิดเวทนา, อย่างนี้เรื่อยไปจนเกิดทุกข์ จนเกิดความทุกข์, นี้เรียกว่าโดยธรรมชาติ
…. สิ่งที่เรียกว่าอารมณ์มีอยู่โดยธรรมชาติที่จะเข้ามาอาศัยกันกับตาข้างใน ที่มีอยู่ในตัวคน. แล้วจะเกิดจักษุวิญญาณ เป็นต้น ขึ้นในตัวคน; จะเกิด ผัสสะ เวทนา ตัณหา อุปาทาน ภพ ชาติ ขึ้นในตัวคน; นี้โดยธรรมชาติ พระพุทธเจ้าท่านบันดาลอะไรไม่ได้ : ธรรมชาติเป็นอยู่อย่างนี้ แต่ท่านรู้เรื่องนี้ท่านจึงนํามาสอนว่า ธรรมชาติมันมีอยู่อย่างนี้ เราจะต้องเข้าใจให้ถูกต้อง โดยที่จะป้องกันความทุกข์ไม่ให้เกิดขึ้นมาได้, หรือถ้าเกิดขึ้นมาได้ก็จะดับเสียได้
…. เราควรจะรู้จักอารมณ์ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ แล้วที่จะเข้ามาทําเรื่องทําราวขึ้นในจิตใจของคนเราให้เกิดปัญหายุ่งยากนี้ให้ดีๆ นี้เรียกว่ารู้จักอารมณ์จากธรรมชาติโดยตรงอย่างนี้ ดีกว่าที่จะรู้จักตามตัวหนังสือ, ดีกว่าที่จะรู้จักตามคําบอกเล่าบางอย่างบางประการที่มันไม่มีประโยชน์อะไร. รู้จักตามคําบอกเล่าก็รู้จักตามที่พระพุทธเจ้าท่านตรัสดีกว่า แต่แล้วยังไม่รู้จักตัวจริง จนกว่าจะมารู้จักจากที่เมื่ออารมณ์มากระทบตา หู จมูก ลิ้น กาย ใจ เข้าจริงๆ : นั่นจึงจะรู้จักอารมณ์ รู้จักผลที่เกิดขึ้นจากการกระทบของอารมณ์, รู้จักต่อไปตามลําดับ จนแก้ปัญหาต่างๆ ได้
…. นี่ ขอร้องให้รู้จักสิ่งที่เรียกว่า อารมณ์ ในฐานะที่เป็นธรรมชาติอันหนึ่ง ที่มีอยู่ตามธรรมชาติ ที่จะเข้ามากระทบอายตนะภายใน คือ กระทบ ตา หู จมูก ลิ้น กาย ใจ แล้วมีเรื่องมีราวมีปัญหา
อารมณ์ คือ โลก - โลก คือ อารมณ์ …. “ ที่นี้จะให้ดูต่อไปอีก ว่าโดยข้อเท็จจริงที่เป็นอยู่แล้ว อารมณ์นั้นคืออะไร? ถ้าจะพูดโดยข้อเท็จจริงหรือตามสถานการณ์ที่เป็นอยู่จริงในชีวิตของคนเรา อารมณ์มันก็คือ “โลก” นั่นเอง. เดี๋ยวนี้เราไม่รู้จักโลกในฐานะอย่างนี้, เราไปเข้าใจความหมายของคําว่าโลกแคบไปบ้าง หรือว่าเขวไปบ้าง.
…. ถ้าจะรู้ตามหลักพระพุทธศาสนาแล้ว โลกทั้งหมดก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ของเรา, เรามีเพียง ๖ อย่าง, แล้วมันก็ ปรากฏได้เพียง ๖ ทาง, มากกว่านั้นมันปรากฏไม่ได้ ดังนั้น โลกก็คือสิ่งที่จะมาปรากฏแก่ ตา หู จมูก ลิ้น กาย ใจ ๖ อย่างของเรา. “โลก” ก็คือ รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ ๖ ประการเท่านั้น, ไม่มีอะไรมากไปกว่านั้น
…. ฉะนั้น รูป เสียง กลิ่น รส โผฏฐัพพะ ธัมมารมณ์ แต่ละอย่าง ๆ ก็คือ โลกในแต่ละแง่ละมุม นั่นเอง, ที่เป็น รูป เสียง กลิ่น รส โผฏฐัพพะ ก็อยู่ข้างนอก จะเรียกว่าอยู่ข้างนอกก็ได้, ที่เป็นอารมณ์เกิดขึ้นในใจ ปรุงขึ้นในใจก็เรียกว่าโลกข้างในก็ได้ แต่มันก็เป็นโลกอยู่นั่นแหละ เพราะมันเป็นสิ่งที่จิตจะต้องรู้สึก จิตรู้สึกก็เรียกว่าโลกสําหรับจิต ตา หู จมูก ลิ้น กาย รู้สึก ก็เรียกว่าโลกสำหรับ ตา หู จมูก ลิ้น กาย. นี้ขอให้มองให้เห็นชัดตามพระพุทธประสงค์ว่า โลก ก็คือ อารมณ์, อารมณ์ ก็คือ โลก.
…. แต่ทีนี้ พระพุทธเจ้าท่านมองลึกกว่านั้น ท่านตรัสถึงข้อที่ว่า ถ้ามันมาเกิดเป็นปัญหาแก่เราเมื่อไรจึงจะเรียกว่า “มันมี” พอมันมาเป็นปัญหาแก่เราเมื่อไรก็เรียกว่า “เป็นทุกข์”; เพราะว่าเราได้ไปจับฉวยยึดถือเอาตามประสาตามวิสัยของคนที่ไม่รู้จักโลก ถ้าพูดว่าไม่รู้จักโลกแล้วคนก็มักจะไม่ยอมรับ เพราะว่าเขาจะพูดว่าเขารู้จักโลกดี. ยิ่งพวกฝรั่งสมัยนี้ นักวิทยาศาสตร์ปราดเปรื่องนั้น เขาจะไม่ยอมรับว่าเขาไม่รู้จักโลก. แต่ถ้าพูดตามหลักพุทธศาสนาแล้วก็จะพูดได้ว่ายังไม่รู้จักโลกเลย เป็นคนตาบอดยิ่งกว่าตาบอด; เพราะว่าฝรั่งเหล่านั้นรู้จักโลกแต่ในแง่สําหรับจะยึดมั่นถือมั่นเป็น “ตัวกู ของกู” จะครองโลกจะอะไร เอาประโยชน์ทุกอย่าง; เขารู้จักโลกในแง่นี้ อย่างนี้พุทธบริษัทไม่เรียกว่า “รู้จักโลก”; แต่ถือว่าเป็นคนตาบอดต่อโลก, หลงยึดมั่นถือมั่นในโลก. เพราะว่าคนเหล่านั้นไม่รู้จักโลกโดยความเป็นอารมณ์ ๖ ประการ คือ รูป เสียง กลิ่นรส โผฏฐัพพะ ธัมมารมณ์, แล้วเป็น “มายา” คือ เอาจริงไม่ได้ เป็นของชั่วคราวๆ หลอกให้เกิดความรู้สึกยึดมั่นถือมั่น
…. นี้เรารู้จัก เราไม่ไปหลงยึดมั่นถือมั่นกับมัน นี้จึงเรียกว่า “คนที่รู้จักโลก” ไปตามหลักของพุทธศาสนา, ฉะนั้น จึงไม่ยึดมั่นถือมั่นสิ่งใดโดยความเป็นตัวตน หรือโดยความเป็นของตน, เรียกว่าเป็นผู้รู้จักอารมณ์ ๖ ประการนั้นก็คือรู้จักโลกทั้งปวง, แล้วก็ไม่หลงไปในโลกในแง่ใดแง่หนึ่ง นี้เรียกว่า อารมณ์ ก็คือ โลก นั่นเอง ในความหมายที่ลึกที่สุดของพระพุทธสาสนา ไม่ใช่โลกก้อนดิน, ไม่ใช่โลกก้อนกลมๆ นี้. แต่มันหมายถึงคุณค่าอะไรที่มันมีอยู่ในโลกกลมๆ นี้ ที่จะเข้ามามาทําให้เกิดปัญหา ที่ตา ที่หู ที่จมูก ที่ลิ้น ที่กาย ที่ใจ ของคน. นั่นแหละคือตัวร้ายกาจของสิ่งที่เรียกว่า โลก เราจะต้องรู้จักในส่วนนี้ให้เพียงพอ
อารมณ์ในโลกปัจจุบันมารวมที่วัตถุนิยม …. ทีนี้ ดูอีกแง่หนึ่งก็โดยปัญหาที่กําลังมีอยู่ อารมณ์ในโลกนี้ในฐานะที่มันเป็นตัวปัญหาที่กําลังมีอยู่ มันมารวมอยู่ที่คําว่า “วัตถุนิยม”: หมายความว่า ตา หู จมูก ลิ้น กาย ใจ นี้ มันเป็นฝ่ายชนะ ไปหลงใหลในอารมณ์ รูป เสียง กลิ่น รส โผฏฐัพพะ ฯลฯ, แล้วก็เกิดนิยมหลงใหลในวัตถุเหล่านั้น จนเกิดความคิดใหม่ๆ, ปรุงแต่งไปในทางที่จะให้หลงใหลในโลกยิ่งขึ้นๆ, ความเจริญก้าวหน้า ในโลกสมัยนี้เป็นไปแต่ในทางอย่างนี้ ฉะนั้น จึงไกลความสงบ, ไกลสันติภาพ ไกลอะไรออกไปทุกที. การที่มนุษย์ที่มีปัญญาในโลกสมัยนี้ โดยเฉพาะฝรั่งที่ก้าวหน้านั้นเขาก็จัดโลกไปแต่ในแง่ของวัตถุมากขึ้นๆ: มันก็ไกลจากสันติภาพ ไกลจากความสงบสุขยิ่งขึ้นทุกที
…. ความสะดวกสบายที่ทําให้เกิดขึ้นมาได้นั้น ไม่ได้ช่วยส่งเสริมเกิดสันติภาพ; แต่มันช่วยให้เกิดความหลงในโลกนั้นเองมากขึ้น แล้วก็ช่วยให้หลงใหลใน “ตัวกู ของกู”, ยึดมั่นถือมั่นเห็นแก่ตัวมากขึ้น รวมกันแล้วมันไม่มีทางที่จะเกิดสันติภาพหรือสันติสุขในโลกได้เลย, จึงกลายเป็นความหลอกลวงเหลือประมาณ โลกจึงกลายเป็นความหลอกลวง, หรือสิ่งที่หลอกลวงเหลือประมาณใน เวลานี้ เราเรียกกันว่า ติดบ่วง หรือว่า ติดเหยื่อของวัตถุนิยม. คําพูดทั้งหมดนี้ ล้วนแต่เป็นการแสดงให้เห็นว่า อารมณ์นี้คืออะไร สิ่งที่เรียกว่าอารมณ์นั้น คือตัวโลกที่กําลังหลอกลวงเราอยู่ทุกวันอย่างยิ่ง โดยเฉพาะในปัจจุบันนี้เป็นวัตถุนิยม นี้คืออารมณ์”
พุทธทาสภิกขุ ที่มา : ธรรมบรรยายภาคมาฆบูชา ครั้งที่ ๗ หัวข้อเรื่อง “อารมณ์ คือ ปัจจัยแห่งเหตุการณ์ทุกอย่างในโลก” เมื่อวันที่ ๑๖ กุมภาพันธ์ ๒๕๑๗ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ก ข ก กา ของการศึกษาพุทธศาสนา”
หมายเหตุ
“อารมณ์ ” ในทางพุทธศาสนา มี ๖ คือ... * ๑. รูปะ = รูป, สิ่งที่เห็น หรือ วัณณะ คือ สี * ๒. สัททะ = เสียง * ๓. คันธะ = กลิ่น * ๔. รสะ = รส * ๕. โผฏฐัพพะ = สัมผัสทางกาย * ๖. ธรรมารมณ์ = สิ่งที่ใจนึกคิด, อารมณ์ที่เกิดกับใจ
…. ทั้ง ๖ อย่างนี้ เป็นสิ่งสำหรับให้จิตยึดหน่วง เรียกอีกอย่างว่า "อายตนะภานนอก" ก็ได้
“อายตนะภายใน ๖” คือ ที่เชื่อมต่อให้เกิดความรู้, แดนต่อความรู้ฝ่ายภายใน มี * ๖ อย่าง คือ... * ๑. จักษุ - ตา * ๒. โสตะ - หู * ๓. ฆานะ - จมูก * ๔. ชิวหา - ลิ้น * ๕. กาย - กาย * ๖. มโน - ใจ
… หรือจะเรียกอีกอย่างว่า “อินทรีย์ ๖” ก็ได้ เพราะเป็นใหญ่ในหน้าที่ของตนแต่ละอย่าง เช่น จักษุ เป็นเจ้าการ(เป็นใหญ่)ในการเห็น เป็นต้น
ท. ส. ปัญญาวุฑโฒ – รวบรวม.
-
 @ 2cde0e02:180a96b9
2025-06-05 15:13:03
@ 2cde0e02:180a96b9
2025-06-05 15:13:03pen & ink; monochromized
Magdalena Carmen Frida Kahlo y Calderón[a] (Spanish pronunciation: [ˈfɾiða ˈkalo]; 6 July 1907 – 13 July 1954[1]) was a Mexican painter known for her many portraits, self-portraits, and works inspired by the nature and artifacts of Mexico. Inspired by the country's popular culture, she employed a naïve folk art style to explore questions of identity, postcolonialism, gender, class, and race in Mexican society.[2] Her paintings often had strong autobiographical elements and mixed realism with fantasy. In addition to belonging to the post-revolutionary Mexicayotl movement, which sought to define a Mexican identity, Kahlo has been described as a surrealist or magical realist.[3] She is also known for painting about her experience of chronic pain.[4]
https://stacker.news/items/997980
-
 @ 3bf0c63f:aefa459d
2024-01-14 14:52:16
@ 3bf0c63f:aefa459d
2024-01-14 14:52:16Drivechain
Understanding Drivechain requires a shift from the paradigm most bitcoiners are used to. It is not about "trustlessness" or "mathematical certainty", but game theory and incentives. (Well, Bitcoin in general is also that, but people prefer to ignore it and focus on some illusion of trustlessness provided by mathematics.)
Here we will describe the basic mechanism (simple) and incentives (complex) of "hashrate escrow" and how it enables a 2-way peg between the mainchain (Bitcoin) and various sidechains.
The full concept of "Drivechain" also involves blind merged mining (i.e., the sidechains mine themselves by publishing their block hashes to the mainchain without the miners having to run the sidechain software), but this is much easier to understand and can be accomplished either by the BIP-301 mechanism or by the Spacechains mechanism.
How does hashrate escrow work from the point of view of Bitcoin?
A new address type is created. Anything that goes in that is locked and can only be spent if all miners agree on the Withdrawal Transaction (
WT^) that will spend it for 6 months. There is one of these special addresses for each sidechain.To gather miners' agreement
bitcoindkeeps track of the "score" of all transactions that could possibly spend from that address. On every block mined, for each sidechain, the miner can use a portion of their coinbase to either increase the score of oneWT^by 1 while decreasing the score of all others by 1; or they can decrease the score of allWT^s by 1; or they can do nothing.Once a transaction has gotten a score high enough, it is published and funds are effectively transferred from the sidechain to the withdrawing users.
If a timeout of 6 months passes and the score doesn't meet the threshold, that
WT^is discarded.What does the above procedure mean?
It means that people can transfer coins from the mainchain to a sidechain by depositing to the special address. Then they can withdraw from the sidechain by making a special withdraw transaction in the sidechain.
The special transaction somehow freezes funds in the sidechain while a transaction that aggregates all withdrawals into a single mainchain
WT^, which is then submitted to the mainchain miners so they can start voting on it and finally after some months it is published.Now the crucial part: the validity of the
WT^is not verified by the Bitcoin mainchain rules, i.e., if Bob has requested a withdraw from the sidechain to his mainchain address, but someone publishes a wrongWT^that instead takes Bob's funds and sends them to Alice's main address there is no way the mainchain will know that. What determines the "validity" of theWT^is the miner vote score and only that. It is the job of miners to vote correctly -- and for that they may want to run the sidechain node in SPV mode so they can attest for the existence of a reference to theWT^transaction in the sidechain blockchain (which then ensures it is ok) or do these checks by some other means.What? 6 months to get my money back?
Yes. But no, in practice anyone who wants their money back will be able to use an atomic swap, submarine swap or other similar service to transfer funds from the sidechain to the mainchain and vice-versa. The long delayed withdraw costs would be incurred by few liquidity providers that would gain some small profit from it.
Why bother with this at all?
Drivechains solve many different problems:
It enables experimentation and new use cases for Bitcoin
Issued assets, fully private transactions, stateful blockchain contracts, turing-completeness, decentralized games, some "DeFi" aspects, prediction markets, futarchy, decentralized and yet meaningful human-readable names, big blocks with a ton of normal transactions on them, a chain optimized only for Lighting-style networks to be built on top of it.
These are some ideas that may have merit to them, but were never actually tried because they couldn't be tried with real Bitcoin or inferfacing with real bitcoins. They were either relegated to the shitcoin territory or to custodial solutions like Liquid or RSK that may have failed to gain network effect because of that.
It solves conflicts and infighting
Some people want fully private transactions in a UTXO model, others want "accounts" they can tie to their name and build reputation on top; some people want simple multisig solutions, others want complex code that reads a ton of variables; some people want to put all the transactions on a global chain in batches every 10 minutes, others want off-chain instant transactions backed by funds previously locked in channels; some want to spend, others want to just hold; some want to use blockchain technology to solve all the problems in the world, others just want to solve money.
With Drivechain-based sidechains all these groups can be happy simultaneously and don't fight. Meanwhile they will all be using the same money and contributing to each other's ecosystem even unwillingly, it's also easy and free for them to change their group affiliation later, which reduces cognitive dissonance.
It solves "scaling"
Multiple chains like the ones described above would certainly do a lot to accomodate many more transactions that the current Bitcoin chain can. One could have special Lightning Network chains, but even just big block chains or big-block-mimblewimble chains or whatnot could probably do a good job. Or even something less cool like 200 independent chains just like Bitcoin is today, no extra features (and you can call it "sharding"), just that would already multiply the current total capacity by 200.
Use your imagination.
It solves the blockchain security budget issue
The calculation is simple: you imagine what security budget is reasonable for each block in a world without block subsidy and divide that for the amount of bytes you can fit in a single block: that is the price to be paid in satoshis per byte. In reasonable estimative, the price necessary for every Bitcoin transaction goes to very large amounts, such that not only any day-to-day transaction has insanely prohibitive costs, but also Lightning channel opens and closes are impracticable.
So without a solution like Drivechain you'll be left with only one alternative: pushing Bitcoin usage to trusted services like Liquid and RSK or custodial Lightning wallets. With Drivechain, though, there could be thousands of transactions happening in sidechains and being all aggregated into a sidechain block that would then pay a very large fee to be published (via blind merged mining) to the mainchain. Bitcoin security guaranteed.
It keeps Bitcoin decentralized
Once we have sidechains to accomodate the normal transactions, the mainchain functionality can be reduced to be only a "hub" for the sidechains' comings and goings, and then the maximum block size for the mainchain can be reduced to, say, 100kb, which would make running a full node very very easy.
Can miners steal?
Yes. If a group of coordinated miners are able to secure the majority of the hashpower and keep their coordination for 6 months, they can publish a
WT^that takes the money from the sidechains and pays to themselves.Will miners steal?
No, because the incentives are such that they won't.
Although it may look at first that stealing is an obvious strategy for miners as it is free money, there are many costs involved:
- The cost of ceasing blind-merged mining returns -- as stealing will kill a sidechain, all the fees from it that miners would be expected to earn for the next years are gone;
- The cost of Bitcoin price going down: If a steal is successful that will mean Drivechains are not safe, therefore Bitcoin is less useful, and miner credibility will also be hurt, which are likely to cause the Bitcoin price to go down, which in turn may kill the miners' businesses and savings;
- The cost of coordination -- assuming miners are just normal businesses, they just want to do their work and get paid, but stealing from a Drivechain will require coordination with other miners to conduct an immoral act in a way that has many pitfalls and is likely to be broken over the months;
- The cost of miners leaving your mining pool: when we talked about "miners" above we were actually talking about mining pools operators, so they must also consider the risk of miners migrating from their mining pool to others as they begin the process of stealing;
- The cost of community goodwill -- when participating in a steal operation, a miner will suffer a ton of backlash from the community. Even if the attempt fails at the end, the fact that it was attempted will contribute to growing concerns over exaggerated miners power over the Bitcoin ecosystem, which may end up causing the community to agree on a hard-fork to change the mining algorithm in the future, or to do something to increase participation of more entities in the mining process (such as development or cheapment of new ASICs), which have a chance of decreasing the profits of current miners.
Another point to take in consideration is that one may be inclined to think a newly-created sidechain or a sidechain with relatively low usage may be more easily stolen from, since the blind merged mining returns from it (point 1 above) are going to be small -- but the fact is also that a sidechain with small usage will also have less money to be stolen from, and since the other costs besides 1 are less elastic at the end it will not be worth stealing from these too.
All of the above consideration are valid only if miners are stealing from good sidechains. If there is a sidechain that is doing things wrong, scamming people, not being used at all, or is full of bugs, for example, that will be perceived as a bad sidechain, and then miners can and will safely steal from it and kill it, which will be perceived as a good thing by everybody.
What do we do if miners steal?
Paul Sztorc has suggested in the past that a user-activated soft-fork could prevent miners from stealing, i.e., most Bitcoin users and nodes issue a rule similar to this one to invalidate the inclusion of a faulty
WT^and thus cause any miner that includes it in a block to be relegated to their own Bitcoin fork that other nodes won't accept.This suggestion has made people think Drivechain is a sidechain solution backed by user-actived soft-forks for safety, which is very far from the truth. Drivechains must not and will not rely on this kind of soft-fork, although they are possible, as the coordination costs are too high and no one should ever expect these things to happen.
If even with all the incentives against them (see above) miners do still steal from a good sidechain that will mean the failure of the Drivechain experiment. It will very likely also mean the failure of the Bitcoin experiment too, as it will be proven that miners can coordinate to act maliciously over a prolonged period of time regardless of economic and social incentives, meaning they are probably in it just for attacking Bitcoin, backed by nation-states or something else, and therefore no Bitcoin transaction in the mainchain is to be expected to be safe ever again.
Why use this and not a full-blown trustless and open sidechain technology?
Because it is impossible.
If you ever heard someone saying "just use a sidechain", "do this in a sidechain" or anything like that, be aware that these people are either talking about "federated" sidechains (i.e., funds are kept in custody by a group of entities) or they are talking about Drivechain, or they are disillusioned and think it is possible to do sidechains in any other manner.
No, I mean a trustless 2-way peg with correctness of the withdrawals verified by the Bitcoin protocol!
That is not possible unless Bitcoin verifies all transactions that happen in all the sidechains, which would be akin to drastically increasing the blocksize and expanding the Bitcoin rules in tons of ways, i.e., a terrible idea that no one wants.
What about the Blockstream sidechains whitepaper?
Yes, that was a way to do it. The Drivechain hashrate escrow is a conceptually simpler way to achieve the same thing with improved incentives, less junk in the chain, more safety.
Isn't the hashrate escrow a very complex soft-fork?
Yes, but it is much simpler than SegWit. And, unlike SegWit, it doesn't force anything on users, i.e., it isn't a mandatory blocksize increase.
Why should we expect miners to care enough to participate in the voting mechanism?
Because it's in their own self-interest to do it, and it costs very little. Today over half of the miners mine RSK. It's not blind merged mining, it's a very convoluted process that requires them to run a RSK full node. For the Drivechain sidechains, an SPV node would be enough, or maybe just getting data from a block explorer API, so much much simpler.
What if I still don't like Drivechain even after reading this?
That is the entire point! You don't have to like it or use it as long as you're fine with other people using it. The hashrate escrow special addresses will not impact you at all, validation cost is minimal, and you get the benefit of people who want to use Drivechain migrating to their own sidechains and freeing up space for you in the mainchain. See also the point above about infighting.
See also
-
 @ b1ddb4d7:471244e7
2025-06-04 15:01:25
@ b1ddb4d7:471244e7
2025-06-04 15:01:25Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A violência é uma forma de comunicação
A violência é uma forma de comunicação: um serial killer, um pai que bate no filho, uma briga de torcidas, uma sessão de tortura, uma guerra, um assassinato passional, uma briga de bar. Em todos esses se pode enxergar uma mensagem que está tentando ser transmitida, que não foi compreendida pelo outro lado, que não pôde ser expressa, e, quando o transmissor da mensagem sentiu que não podia ser totalmente compreendido em palavras, usou essa outra forma de comunicação.
Quando uma ofensa em um bar descamba para uma briga, por exemplo, o que há é claramente uma tentativa de uma ofensa maior ainda pelo lado do que iniciou a primeira, a briga não teria acontecido se ele a tivesse conseguido expressar em palavras tão claras que toda a audiência de bêbados compreendesse, o que estaria além dos limites da linguagem, naquele caso, o soco com o mão direita foi mais eficiente. Poderia ser também a defesa argumentativa: "eu não sou um covarde como você está dizendo" -- mas o bar não acreditaria nessa frase solta, a comunicação não teria obtido o sucesso desejado.
A explicação para o fato da redução da violência à medida em que houve progresso da civilização está na melhora da eficiência da comunicação humana: a escrita, o refinamento da expressão lingüística, o aumento do alcance da palavra falada com rádio, a televisão e a internet.
Se essa eficiência diminuir, porque não há mais acordo quanto ao significado das palavras, porque as pessoas não estão nem aí para se o que escrevem é bom ou não, ou porque são incapazes de compreender qualquer coisa, deve aumentar proporcionalmente a violência.
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:54:43
@ e2c72a5a:bfacb2ee
2025-06-05 16:54:43Think your crypto is FDIC insured like your bank account? Big mistake. Crypto's wild west demands you be your own bank and security guard.
Crypto trading involves buying, selling, and exchanging digital currencies like Bitcoin or Ethereum, aiming to profit from price fluctuations. Security is paramount. Understand basic concepts like wallets (digital storage for your crypto), private keys (passwords to access your crypto), and blockchain (the technology that records all transactions).
Real world applications include using crypto for online purchases, international money transfers, and decentralized finance (DeFi) services like lending and borrowing. Current trends include the rise of DeFi, NFTs (non-fungible tokens), and increasing institutional investment.
Best practices? Use strong, unique passwords, enable two factor authentication (2FA) on all accounts, and store most of your crypto in cold wallets (offline storage) to protect against hacking. Be wary of phishing scams and fake websites. Never share your private keys or seed phrases.
Misconceptions? Crypto is not anonymous, transactions are not easily reversible, and past performance is not indicative of future results. Also, remember that regulations are evolving, so stay informed.
With crypto hacks on the rise, are you truly ready to secure your digital fortune, or are you leaving the door open for the next billion dollar heist?
-
 @ 975e4ad5:8d4847ce
2025-06-05 13:14:46
@ 975e4ad5:8d4847ce
2025-06-05 13:14:46What is the Fiat System and How Do Central Banks Set Interest Rates?
When central banks expand credit, they often increase the money supply by creating new money through mechanisms like quantitative easing (QE). For instance, a central bank may purchase government bonds, injecting money into the economy. This boosts liquidity but can lead to inflation when too much money chases limited goods and services.
Low interest rates make borrowing cheaper, encouraging spending and investment. However, this can overheat the economy, create speculative bubbles (e.g., in real estate), and drive inflation. Conversely, high interest rates restrict borrowing, slow the economy, and curb inflation but may trigger recessions.
How Would Interest Rates Work Under a Bitcoin Standard?
Under a Bitcoin standard, the money supply is fixed—only 21 million bitcoins will ever exist, with the last one mined around 2140. Unlike the fiat system, no central authority can manipulate the money supply or set interest rates. Instead, interest rates would be determined entirely by the market—by the supply and demand for capital.
If someone wants to borrow bitcoins, the interest rate would depend on negotiations between the lender and borrower. For example, if demand for loans is high and available bitcoins are scarce, interest rates would rise. Conversely, if there are ample bitcoin savings, rates might fall. This process would be fully decentralized and reflect real market conditions, not central bank decisions.
Since new bitcoins cannot be “printed,” there would be no inflation caused by an expanding money supply. Instead, bitcoin’s value would likely rise over time (deflation) as its fixed supply competes with growing demand. This could encourage saving over reckless spending, reshaping economic behavior.
Advantages of a Bitcoin Standard
-
Protection Against Inflation: Bitcoin’s fixed supply prevents currency devaluation, a common issue with fiat money. This safeguards savings and promotes long-term planning.
-
Decentralization: Without a central bank manipulating the market, economic decisions are made by individuals, not bureaucrats. This aligns with free-market principles where competition and innovation thrive.
-
Transparency and Security: The Bitcoin blockchain is public and immutable, ensuring transactions are transparent and secure from tampering.
-
Financial Freedom: Under a Bitcoin standard, individuals have full control over their money without government or bank interference, which is especially crucial in countries with unstable regimes or currencies.
-
Discipline in Lending: Without the ability to print money, lenders would be more cautious, reducing risky investments and speculative bubbles.
Potential Drawbacks and Why a Bitcoin Standard is Superior
One major argument against a Bitcoin standard is that it could slow economic growth. Low interest rates in the fiat system encourage borrowing and spending, driving economic activity. Under a Bitcoin standard, where interest rates are market-driven and likely higher, borrowing would be costlier, potentially limiting investments in new projects.
However, this critique misses a key point: economic growth fueled by artificially low interest rates and money printing is often unsustainable. It leads to debt crises, inflation, and bubbles that eventually burst, as seen in 2008. A Bitcoin standard promotes healthy economic discipline, where investments are based on real value, not artificial capital.
Moreover, bitcoin’s deflationary nature could shift how people view money. Instead of chasing endless growth, societies might prioritize sustainability, innovation, and efficiency. This could lead to a more stable and equitable economy in the long run.
Additional Considerations
A Bitcoin standard could transform global trade. Today, countries with fiat currencies often manipulate exchange rates to gain trade advantages. With bitcoin as a universal currency, such manipulations would vanish, fostering fairer competition.
Another aspect is energy efficiency. While bitcoin mining consumes energy, it incentivizes the development of renewable sources as miners seek cheap, sustainable energy. This could accelerate the transition to a green economy.
Conclusion
The Bitcoin standard offers a vision of an economy rooted in sound money, free markets, and financial freedom. While it may slow certain aspects of economic growth, it creates a more stable and sustainable system that protects individuals from inflation and centralized control. In a world where trust in institutions is waning, the Bitcoin standard is a step toward a fairer and more transparent future.
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Problemas com Russell Kirk
A idéia central da “política da prudência[^1]” de Russell Kirk me parece muito correta, embora tenha sido melhor formulada pior no seu enorme livro do que em uma pequena frase do joanadarquista Lucas Souza: “o conservadorismo é importante, porque tem muita gente com idéia errada por aí, e nós podemos não saber distingüi-las”.
Porém, há alguns problemas que precisam ser esclarecidos, ou melhor explicados, e que me impedem de enxergar os seus argumentos como refutação final do meu já tão humilde (embora feroz) anarquismo. São eles:
I Percebo alguma coisa errada, não sei bem onde, entre a afirmação de que toda ideologia é ruim, ou “todas as ideologias causam confusão[^2]”, e a proposta conservadora de “conservar o mundo da ordem que herdamos, ainda que em estado imperfeito, de nossos ancestrais[^3]”. Ora, sem precisar cair em exemplos como o do partido conservador inglês -- que conservava a política inglesa sempre onde estava, e se alternava no governo com o partido trabalhista, que a levava cada vez mais um pouco à esquerda --, está embutida nessa frase, talvez, a idéia, que ao mesmo tempo é clara e ferrenhamente combatida pelos próprios conservadores, de que a história é da humanidade é uma história de progresso linear rumo a uma situação melhor.
Querer conservar o mundo da ordem que herdamos significa conservar também os vários erros que podem ter sido cometidos pelos nossos ancestrais mais recentes, e conservá-los mesmo assim, acusando toda e qualquer tentativa de propôr soluções a esses erros de ideologia? Ou será que conservar o mundo da ordem é escolher um período determinado que seja tido como o auge da história humana e tentar restaurá-lo em nosso próprio tempo? Não seria isto ideologia?
Ou, ainda, será que conservar o mundo da ordem é selecionar, entre vários períodos do passado, alguns pedaços que o conservador considerar ótimos em cada sociedade, fazer dali uma mistura de sociedade ideal baseada no passado e então tentar implementá-la? Quem saberia dizer quais são as partes certas?
II Sobre a questão do que mantém a sociedade civil coesa, Russell Kirk, opondo-a à posição libertária de que o nexo da sociedade é o autointeresse, declara que a posição conservadora é a de que “a sociedade é uma comunidade de almas, que une os mortos, os vivos e os ainda não nascidos, e que se harmoniza por aquilo que Aristóteles chamou de amizade e os cristãos chamam de caridade ou amor ao próximo”.
Esta é uma posição muito correta, mas me parece estar em contradição com a defesa do Estado que ele faz na mesma página e na seguinte. O que me parece errado é que a sociedade não pode ser, ao mesmo tempo, uma “comunidade baseada no amor ao próximo” e uma comunidade que “requer não somente que as paixões dos indivíduos sejam subjugadas, mas que, mesmo no povo e no corpo social, bem como nos indivíduos, as inclinações dos homens, amiúde, devam ser frustradas, a vontade controlada e as paixões subjugadas” e, pior, que “isso somente pode ser feito por um poder exterior”.
Disto aí podemos tirar que, da mesma forma que Kirk define a posição libertária como sendo a de que o autointeresse é que mantém a sociedade civil coesa, a posição conservadora seria então a de que essa coesão vem apenas do Estado, e não de qualquer ligação entre vivos e mortos, ou do amor ao próximo. Já que, sem o Estado, diz, ele, citando Thomas Hobbes, a condição do homem é “solitária, pobre, sórdida, embrutecida e curta”?
[^1]: este é o nome do livro e também um outro nome que ele dá para o próprio conservadorismo (p.99). [^2]: p. 101 [^3]: p. 102
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:50:08
@ e2c72a5a:bfacb2ee
2025-06-05 16:50:08Think crypto is just magic internet money? Think again.
Tokenomics is the secret sauce that makes or breaks a crypto project. It is the study of how tokens are created, distributed, and used within a blockchain ecosystem. Imagine it as the economic policy of a digital nation, dictating everything from supply and demand to user incentives.
Key features include supply caps, distribution models, utility, and burn mechanisms. A well designed token economy incentivizes user behavior, secures the network, and fosters long term growth. Poor tokenomics? It can lead to manipulation and project failure.
Zero Knowledge Proofs are like showing you know a password without revealing the password itself. This tech allows for private and secure transactions, verifying data without exposing the data itself. Think of voting systems where your vote stays secret, or supply chains where product details are confirmed without revealing the supplier.
Want to dive deeper into the economics of crypto? What project has the most interesting tokenomics you have seen?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28
A command line utility to create and manage personal graphs, then write them to dot and make images with graphviz.
It manages a bunch of YAML files, one for each entity in the graph. Each file lists the incoming and outgoing links it has (could have listen only the outgoing, now that I'm tihnking about it).
Each run of the tool lets you select from existing nodes or add new ones to generate a single link type from one to one, one to many, many to one or many to many -- then updates the YAML files accordingly.
It also includes a command that generates graphs with graphviz, and it can accept a template file that lets you customize the
dotthat is generated and thus the graphviz graph.rel
-
 @ 8d34bd24:414be32b
2025-06-04 13:21:20
@ 8d34bd24:414be32b
2025-06-04 13:21:20It is hard going through difficult situations. Health problems, family problems, financial problems, feeling alone, feeling stuck in the wrong place, and persecution are all situations that Christians regularly find themselves. The question is “How will we respond to pain?”
Advice for the Suffering
Some Christians pull away from God when it feels like everything is going wrong. They think God doesn’t care or can’t fix things. They resent every minute of pain and accuse God of wrongdoing. Even Job, who fell on his face in worship after losing everything had a moment of weakness.
“Oh that my grief were actually weighed\ And laid in the balances together with my calamity!\ For then it would be heavier than the sand of the seas;\ Therefore my words have been rash.” (Job 6:2-3) {emphasis mine}
After a moment of doubt, he did, however, repent of his rash words, as should we all.
Job should be an example to us all in dealing with pain and difficult situations. This is the verse that inspired this post.
But it is still my consolation,\ And I rejoice in unsparing pain,\ That I have not denied the words of the Holy One. \ (Job 6:10) {emphasis mine}
What an example! “I rejoice in unsparing pain.” When we trust God so much that we can rejoice in unsparing pain, we are trusting God as we should. We are accepting that God is working good in our life and we can trust Him even when nothing makes sense to us.
I also love how he says that his consolation is that “I have not denied the words of the Holy One.” Job is hurting terribly. His heart is broken. He is destitute. He lost 8 children in one day. His friends, that came to console him, have instead accused him of wrongdoing. He doesn’t understand what God is doing and why, but he has “NOT denied the words of the Holy One.” He is still putting his faith in God and his word. He is still submitting to God when he feels mistreated. He is still trusting \ God, even when he doesn’t understand what God is doing and why so many bad things are raining down on him in a torrent. Despite it all, he refuses to deny God. I hope if I am ever put through similar situations, that I can trust God and not deny His goodness.
Advice for friends
The book of Job, in addition to advice to those who are suffering, also gives advice to friends of those who are suffering. (or maybe more accurately, what not to do)
Job’s friends came with the intention to encourage and console Job. Every time Job would confess his thoughts, concerns, and questions, the response by his friends would get harsher and harsher. In the beginning they were gentle corrections, but they quickly escalated to accusing Job of great sins, that they had to know were not true, and blaming Job for every hard thing that had happened to him.
I’ve talked to other Christians who have confessed to being dragged down by other Christians who would tell them that every difficult thing that happened to them was due to their sin or lack of faith. In the case of Job, his difficulties were due to his faithfulness, in order to prove to Satan and all of history that a faithful man would stay faithful to God in good times and in bad.
Can Christians suffer as a consequence of sins and poor decisions? Of course, but there are many times that the faithful suffer. In Scripture, the people who suffered most were frequently the most faithful.
Job’s correction of his friends was accurate.
“For the despairing man there should be kindness from his friend;\ So that he does not forsake the fear of the Almighty.\ My brothers have acted deceitfully like a wadi,\ Like the torrents of wadis which vanish, (Job 6:14-15)
For those who don’t know, a wadi is a streambed that has water running in the wet season, but is bone dry during the dry season. Job accused his friends of being encouraging and helpful when he was prospering, then showing up and providing no encouragement or help when he needed it most. He thought refreshment was coming to visit, and instead what hope he had left was drained from him by his “friends.”
We need to make sure we aren’t one of those who decreases hope and decreases faith in one who is hurting. We need to have mercy when a hurting person works through their confusion and doubts and help lead them back to God instead of driving a wedge between them and God.
May the God of heaven protect us and lead us through the trials of life and may our trials lead us into the arms of our Savior. May God help us to merciful and to help guide the hurting into the Savior’s care.
Trust Jesus
-
 @ 90c656ff:9383fd4e
2025-06-05 12:27:43
@ 90c656ff:9383fd4e
2025-06-05 12:27:43When people talk about Bitcoin, it’s often described as a digital currency or a “speculative investment.” However, one of Bitcoin’s most fundamental and least understood roles is its function as a settlement network. To understand this, it’s worth comparing it with traditional settlement systems like SWIFT and exploring how Bitcoin offers a foundational layer for global value transfer decentralized and censorship-resistant.
First, let’s explain the difference between liquidity and settlement:
-
Liquidity refers to the ease with which an asset can be converted into “money” without losing value.
-
Settlement is the process of completing a transaction (actual transfer of value between parties).
SWIFT: The communication layer of the traditional financial system
The SWIFT system (Society for Worldwide Interbank Financial Telecommunication) is a network for communication between banks. It doesn’t move money directly but sends standardized messages that instruct financial institutions to perform transfers. The process involves multiple intermediaries, is costly, slow (can take days), and depends on trust between parties and local regulations.
Unlike SWIFT, Bitcoin is a self-sufficient network that enables the direct settlement of value between two parties, without the need for intermediaries. With each block mined, transactions are validated and recorded immutably in a global, transparent, and secure database: the timechain or "blockchain".
01 - Final settlement: Once a transaction is confirmed by a sufficient number of blocks, it is considered final and irreversible.
02 - Censorship resistance: There is no central entity that can block or reverse a valid transaction.
03 - Global availability: The network is accessible 24/7 anywhere in the world with internet access.
Just as gold once served as the foundation of monetary systems, Bitcoin is establishing itself as a base layer of digital value. This layer can support others, such as:
01 - The Lightning Network, which enables near-instant transactions with extremely low fees;
02 - Tokenized financial services, which can use Bitcoin as collateral or for inter-institutional settlement.
By functioning as a public and neutral settlement network, Bitcoin offers an alternative to the traditional system, which is fragmented, closed, and reliant on trust between institutions.
In summary, more than just a speculative asset, Bitcoin is emerging as a global financial infrastructure. As a settlement network, it removes intermediaries, reduces costs, increases security, and democratizes access to value transfer. In an increasingly interconnected and digital world, understanding Bitcoin’s role as a base layer may be key to understanding the future of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
-
 @ e2c72a5a:bfacb2ee
2025-06-05 16:46:19
@ e2c72a5a:bfacb2ee
2025-06-05 16:46:19Think proving you're over 21 without showing your ID is impossible? Zero Knowledge Proofs make it real.
Zero Knowledge Proofs let you prove something is true without revealing the information itself. Imagine proving you know a password without saying it. It's like magic, but it's math.
They're used in crypto for private transactions, secure voting, and faster blockchains. Zcash and Aztec use them to hide transaction details. StarkWare uses them to make Ethereum faster.
But here's the twist: zk STARKs don't need a trusted setup, unlike zk SNARKs. This makes them more secure and decentralized.
Misconception alert: ZKPs aren't just for privacy. They also boost scalability and interoperability.
Want to dive deeper into this mind bending tech? What other secrets can ZKPs unlock?
-
 @ 20e7c953:3b8bcb21
2025-06-05 10:46:07
@ 20e7c953:3b8bcb21
2025-06-05 10:46:0721… That number means something. A reminder that limits create value - both in Bitcoin and in life.
Every June 21st, skaters around the world remind us that freedom is something you make yourself - one push at a time only constrained by your own limitations.
This year in Vientiane, we’re proud to support one of the few real skate spots in Laos. A place built and held together by skaters for skaters.
Expect around 50 locals - from young kids to older heads - showing up not just to skate, but to hold space for each other. No ego, no filters, just boards, fun and respect.
Bircoiners have lots to learn from these communities on this regard. Go skate and you'll find out.

SnF
Laostr
Skateboardingisfun
Skate4Fun
Skatestr
-
 @ b1ddb4d7:471244e7
2025-06-04 09:00:44
@ b1ddb4d7:471244e7
2025-06-04 09:00:44Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28GraphQL vs REST
Today I saw this: https://github.com/stickfigure/blog/wiki/How-to-(and-how-not-to)-design-REST-APIs
And it reminded me why GraphQL is so much better.
It has also reminded me why HTTP is so confusing and awful as a protocol, especially as a protocol for structured data APIs, with all its status codes and headers and bodies and querystrings and content-types -- but let's not talk about that for now.
People complain about GraphQL being great for frontend developers and bad for backend developers, but I don't know who are these people that apparently love reading guides like the one above of how to properly construct ad-hoc path routers, decide how to properly build the JSON, what to include and in which circumstance, what status codes and headers to use, all without having any idea of what the frontend or the API consumer will want to do with their data.
It is a much less stressful environment that one in which we can just actually perform the task and fit the data in a preexistent schema with types and a structure that we don't have to decide again and again while anticipating with very incomplete knowledge the usage of an extraneous person -- i.e., an environment with GraphQL, or something like GraphQL.
By the way, I know there are some people that say that these HTTP JSON APIs are not the real REST, but that is irrelevant for now.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36
@ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36Howdy stackers, this is the place to share your ~HealthAndFitness triumphs and challenges.
I was glad to hit my step goal today, since it's gloomy and rainy here. Once again, I ate too many cookies. Gotta stop being a cookie monster.
How'd you all do, today?
https://stacker.news/items/996659
-
 @ e4950c93:1b99eccd
2025-06-05 10:23:39
@ e4950c93:1b99eccd
2025-06-05 10:23:39Marques
Nordkidz est une marque allemande qui crée à la demande des vêtements et linges pour les bébés, les enfants, et un peu pour leurs parents.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque contiennent des matières non naturelles, dont :
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
Vêtements
- Tailles vêtements : bébés, enfants, unisexe
- Hauts : pulls, t-shirts
- Bas : pantalons, pantalons de survêtement, shorts
- Tête et mains : bonnets, écharpes
Maison
- Linge : housses de pouf, langes, ponchos de bain
Autres informations
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Nordkidz (en allemand, zone de livraison : Allemagne et Union Européenne) 💚 Via ce lien vous soutenez directement la marque.
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ cae03c48:2a7d6671
2025-06-05 16:01:20
@ cae03c48:2a7d6671
2025-06-05 16:01:20Bitcoin Magazine

Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury StrategyToday, H100 Group AB announced it has entered a SEK 21 million convertible loan from an investment agreement with Adam Back, with the option to expand his investment to SEK 277 million through a five-tranche convertible loan deal. The proceeds will be used to buy Bitcoin in alignment with H100 Group’s long-term Bitcoin treasury strategy.
H100 Group AB (Ticker: H100) secures a SEK 21M ($2.1M) commitment from @adam3us , with rights to invest an additional SEK 128M ($12.8M) in tranches—bringing the total contemplated raise to SEK 277M (~$27.7M). pic.twitter.com/c0HgMSRxut
— H100 (@H100Group) June 3, 2025
Under the agreement, Back may invest up to SEK 128 million across four additional tranches, with guaranteed participation of at least 50%. Each tranche is twice his committed amount, demonstrating his support for H100’s long-term growth.
The press release said, “Adam Back may request the Second Tranche within 90 days from signing of the Initial Tranche, the Third Tranche within 90 days from signing of the Second Tranche, the Fourth Tranche within 90 days from signing of the Third Tranche and the Fifth Tranche within ninety 90 days from signing of the Fourth Tranche. In the event Adam Back does not request a Future Tranche within the deadline, the right to request subsequent Future Tranches lapses.”
The convertible loans have no interest and have a five year maturity. At any time, Back may convert the loans into shares of the Company. Conversion prices are fixed per tranche: SEK 1.75 per share for the initial tranche, rising to SEK 5.00 by the fifth tranche. H100 retains the right to force conversion if the stock price exceeds the conversion rate by 33% over a 20 day period. Full conversion of the initial tranche would result in 12 million new shares and a 9.3% dilution.
“Upon request of a tranche Adam Back is obliged to invest in the relevant Tranche with SEK 15,750,000 in the second tranche, SEK 23,625,000 in the third tranche, SEK 35,437,500 in the fourth tranche, and SEK 53,156,250 in the fifth tranche,” stated the press release. “The contemplated size for each tranche is twice the entitled amount of Adam Back.”
Blockstream has “been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then,” said Adam Back at the 2025 Bitcoin Conference. “I think the way to look at the treasury companies is that Bitcoin is effectively the hurdle rate; it’s very hard to outperform bitcoin. Most people that have invested in things since bitcoin has been around have thought, ‘oh, I should have put that in bitcoin and not in the other thing.”
This post Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury Strategy first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ a74cf7d3:37b9b82e
2025-06-05 17:03:04
@ a74cf7d3:37b9b82e
2025-06-05 17:03:04Lava is the most secure way to borrow against your bitcoin. Lava Loans allow you to borrow dollars using your bitcoin as collateral, all without giving up self-custody. No need to wait days, sign paperwork, bridge your bitcoin, or trust third-party custodians to take out a loan. All you have to do is set the terms of your loan within your Lava Vault, and you can get your loan capital within seconds.
Unlike other bitcoin-backed lending options, Lava is entirely self-custodial. You control your own keys and never have to transfer your bitcoin to a third party. Historically, most bitcoin-backed lending solutions required users to trust custodians with their bitcoin, exposing them to hacks, rehypothecation risk, insolvency, and seizures. This resulted in more than $24B in user funds lost in 2022 alone. Lending protocols on other chains like Ethereum or Solana require users to bridge their bitcoin, introducing additional custodial, bridge, smart contract, and platform risks. Both options are clunky, risky, and slow.
Lava Loans introduces a better model. We’ve built a borrowing protocol that works entirely on native bitcoin. Taking out a loan on Lava takes seconds, doesn't require paperwork, and allows you to maintain self-custody. Lava is the best option for simple, low-cost, and safe bitcoin-backed loans.
In this article we’ll dive into the key features of Lava Loans, how it is different from other borrowing options on the market, and explain how it works at a technical level.
Key Features of Lava
-
Instant loans: No paperwork. Just answer 2 questions and get your loan within seconds.
-
Low cost: We minimize costs by reducing loan risk, allowing us to offer the lowest rates on the market. All fees are made transparent at the start.
-
Flexible amounts: Borrow exactly what you need.
-
No Custodial Risk: Your BTC never leaves your control. There’s no risk of hacks, seizure, or rehypothecation. You can verify this yourself on-chain. Lava is the only loan product where you can independently verify—on-chain and in real time—that your bitcoin is not being rehypothecated.
-
No Loan Initiation Risk: Using atomic swaps, your collateral only moves if your loan capital is already secured.
-
No Repayment Risk: Repay your loan and your BTC is automatically returned, guaranteed by cryptography.
-
Reduced Liquidation Risk: You choose your own blinded, off-chain price source, minimizing the chance of unfair liquidation.
-
Bug-Minimized: Lava uses formally verified smart contracts on bitcoin (Discreet Log Contracts), meaning all contract outcomes are known and signed ahead of time. Execution is private and secure.
How It Works
The Lava Loans Protocol is built on top of bitcoin-native smart contracts, called Discreet Log Contracts (DLCs). DLCs enable conditional (oracle-based) contracts on bitcoin, meaning they can execute transactions based on pre-specified and approved conditions. Lava Loans are executed via custom DLCs that allow the borrower and lender to agree to the terms of a loan, enter into a contract based on those terms, and have the contract enforce the terms on-chain— all without requiring a third-party custodian.
DLCs allow for a trust-minimized borrowing experience, and they avoid many of the risks inherent with smart contracts on other platforms like Ethereum. DLCs operate on Bitcoin itself— you don’t need to move your coins to another chain or layer. They also mitigate bug risk because they are formally verified, meaning the output conditions of the contract are known from the beginning. This helps to avoid the exploits commonly seen in Ethereum. Because the contracts use off-chain oracles, they aren't susceptible to oracle manipulation by miners. Not only that, but these contracts are private, customizable (choose your own oracle), and scalable (minimal on-chain cost because execution happens off-chain).
Lava Loans are on-chain contracts between borrowers and lenders. The borrower and the lender agree on a loan amount (in USD), a collateral amount (in BTC), the loan duration, the interest rate, the loan-to-value (LTV) ratio at which liquidation happens, and a data feed (oracle) that will provide the Bitcoin price. When the contract is initialized, the collateral is locked and the loan capital is transferred to the borrower. The oracle feeds the price of Bitcoin into the contract on a continuous basis, and the contract executes according to its pre-defined parameters. As long as the borrower maintains a healthy LTV and repays their loan, their collateral is automatically returned to them upon completion.
Each Lava Loan goes through three phases:
Phase 1: Loan Initiation
- The loan is initialized via an atomic swap; the bitcoin collateral is locked in the smart contract and the loan capital is transferred from the lender to the borrower. Because this is done via an atomic swap, the borrower and lender do not have to trust one another or use an escrow. The collateral moves into the smart contract, and the loan capital is automatically sent to the borrower.
Phase 2: Active Loan
-
Once the atomic swap is complete, the loan is active. The bitcoin collateral remains locked in the smart contract, and the borrower has access to their loan capital.
-
While the loan is active, the oracle feeds the bitcoin price into the contract on an ongoing basis. This allows the contract to monitor the LTV.
Phase 3: Loan Termination
Once the loan is active, it can terminated in one of the following ways:
-
Repaid: If the borrower repays the loan, the collateral is released to the borrower atomically.
-
Liquidated: If the loan value reaches a pre-determined LTV or the borrower misses a payment, the collateral is immediately released to the lender for liquidation.
-
Expired: If the borrower does not repay the loan before the loan term ends, some of the collateral, equivalent to principal plus interest, is released to the lender, and the rest is sent to the borrower.
-
Fail-Safe: In rare scenarios where the loan process cannot be completed as expected due to unresponsive oracles, the protocol has built-in fail-safe mechanisms. These mechanisms ensure that the collateral is not lost.
As you can see, all of the loan terms and conditions are built into the smart contract. The borrower and lender agree on the terms, enter into the loan, and then the contract executes the pre-specified and approved transactions based on either the actions taken by the borrow/lender, or the price changes in BTC. As a user, you can verify at any point that your collateral sits on-chain, is locked in the contract, and isn’t being used or rehypothecated in any way.
Security
Lava Loans are designed to be the most secure option for Bitcoiners who want to borrow against their holdings. Lava’s approach is trust-minimized, bug-minimized, and verifiable for users.
Trust-Minimized
-
Traditional platforms expose you to bridge, custodian, or bank risk. Lava lets you borrow against native-BTC directly in your vault. This means there can’t be rehypothecation, funds lost in custodial hacks, or asset confiscation.
-
While other platforms require blind trust during loan initiation, Lava uses atomic swaps to ensure your BTC collateral only moves to the escrowed smart contract once the loan is in your hands.
-
The uncertainty of receiving collateral post-repayment is a concern with many platforms. Lava uses cryptographic guarantees to ensure that once you fulfill your repayment, your BTC is promptly returned.
-
You don’t have to trust a lender who can liquidate your BTC unjustly. With Lava, you choose your off-chain, blinded oracles per loan to provide price data, drastically reducing risks from malicious entities.
Bug-Minimized
-
Lava’s bitcoin smart contract is formally-verified, meaning the output conditions to the contract are known ahead of time, minimizing technical risk. DLCs, the underlying technology Lava uses, use pre-signed, encrypted transactions to specify the output conditions to a contract ahead of time. Since all the output conditions to the contract are specified ahead of time, and then encrypted using adaptor signatures, the output conditions are known (money can only move to borrower/lender).
-
Lava’s contracts have been audited by the best auditors in the industry, Antoine Riard from thelab31 and Conduition, as well as the core contributors to the cryptography behind DLCs.
Verifiable
-
Lava is the only loan product where you can independently verify—on-chain and in real time—that your bitcoin is not being rehypothecated. When you borrow using Lava, you have cryptographic proof, not just legal or reputational assurances, that your collateral is secure.
-
Lava’s oracle implementation is open-source.
-
Lava’s oracles make daily attestations and calculate a median price across various price feeds to avoid flash crash and unreliable margin call risk.
How Lava Compares

Loan Payments + Fees
Users who take out a Lava Loan pay a one-time origination fee (currently 2%) to open a loan, and each loan has a determined, fixed interest rate for the duration of the loan. Interest rates depend on the length of the loan, but they currently start at 5% annually. Users can also extend their loan by paying an extension fee (currently 2%) at the time that the loan is extended.
Loans that are longer than one month in duration require users to make monthly payments on their loans. Because the terms of Lava Loans are set programmatically in the smart contract, users must make their monthly payments on time in order to avoid being liquidated. You can make your monthly payments using digital dollars (either those held in your Lava Vault, or by depositing USDC into the vault) or via bank transfer. Bank transfers may take several days to clear, so it’s important to plan ahead in order to make the payments on time. Lava offers notifications in advance of payment deadlines in order to allow you sufficient time to plan and make payments.
FAQ
What are oracles?
Oracles are independent data feeds that attest to the price of Bitcoin and feed that price into the contract. At Lava, we’ve built Sibyls, an open-source oracle implementation for bitcoin. Users can choose their own oracles, and oracles have zero knowledge about the contracts they influence. In the case of the Lava Loans Protocol, oracles also make off-chain attestations, and in doing so, this helps us avoid the increased fees and miner manipulation that comes from on-chain oracles. You can learn more about our oracles here.
Why does Lava use digital dollars?
To ensure a fast, trust-minimized loan, Lava uses smart contracts that require HTLC compatibility. Fiat doesn’t support this, so we use digital dollars (like USDC on Solana) — which you can instantly withdraw to your bank account.
What are bitcoin smart contracts?
Bitcoin smart contracts (also known as discreet log contracts) enable conditional (oracle-based) contracts on bitcoin. The way it works is that each party to a contract creates and shares encrypted signatures for each output condition to the contract. Each counterparty has confidence they can decrypt the encrypted signatures and use them correctly at the right time because they can verify the encryption: verify when they can decrypt the signatures and that the signatures are valid.
Bitcoin smart contracts are a better way to do smart contracts because they are secure, private, customizable, and scalable. They mitigate bug risk because they are formally verified, meaning the output conditions of the contract are known from the beginning. This helps avoid exploits you constantly see in Ethereum. Since these contracts use off-chain oracles, they aren't susceptible to oracle manipulation by miners. Not only that, but these contracts are private, customizable (choose your own oracle), and scalable (minimal on-chain cost because execution happens off-chain).
These contracts are zero knowledge in that the blockchain has zero knowledge about the contract, the oracles have zero knowledge about the contract, and the counterparty can verify the encryption without needing the decrypted material.
Where can I learn more?
If you want to learn more about the Lava Loans Protocol, check out the loans paper here: https://github.com/lava-xyz/loans-paper/tree/main
Ready to borrow? Download the Lava Vault on iOS or Android and take out your first bitcoin-secured loan in seconds.
-
-
 @ 8bad92c3:ca714aa5
2025-06-03 17:01:39
@ 8bad92c3:ca714aa5
2025-06-03 17:01:39Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
via Charlie Bilello
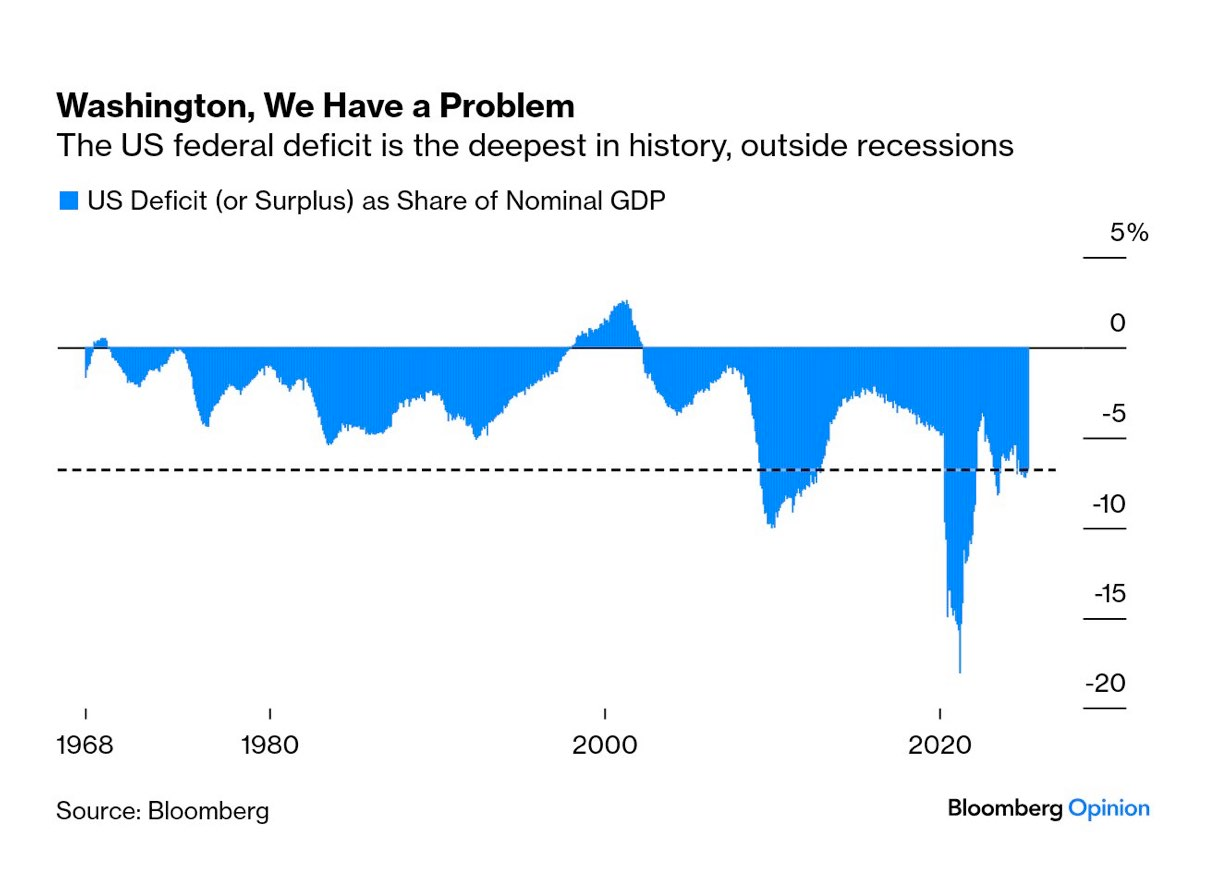
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
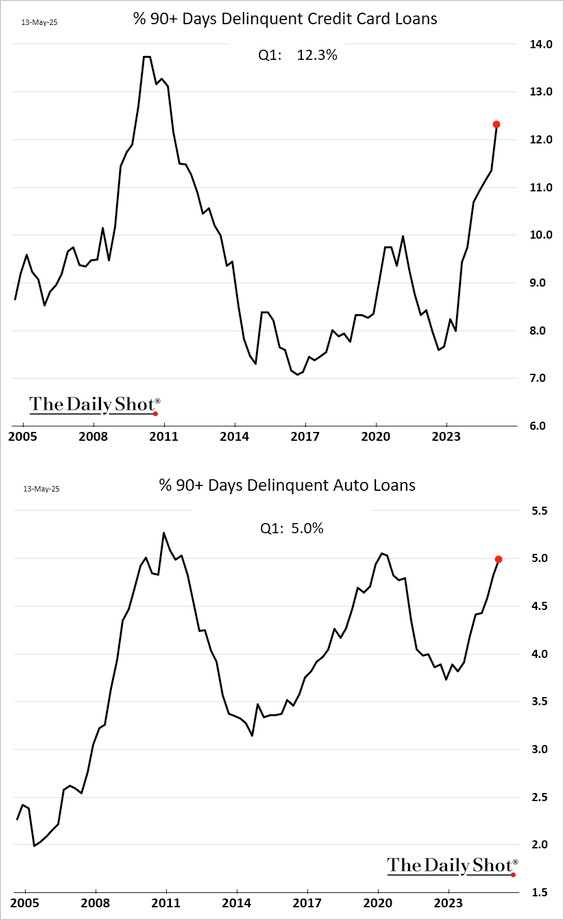
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ cae03c48:2a7d6671
2025-06-03 16:01:01
@ cae03c48:2a7d6671
2025-06-03 16:01:01Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28nostr - Notes and Other Stuff Transmitted by Relays
The simplest open protocol that is able to create a censorship-resistant global "social" network once and for all.
It doesn't rely on any trusted central server, hence it is resilient; it is based on cryptographic keys and signatures, so it is tamperproof; it does not rely on P2P techniques, therefore it works.
Very short summary of how it works, if you don't plan to read anything else:
Everybody runs a client. It can be a native client, a web client, etc. To publish something, you write a post, sign it with your key and send it to multiple relays (servers hosted by someone else, or yourself). To get updates from other people, you ask multiple relays if they know anything about these other people. Anyone can run a relay. A relay is very simple and dumb. It does nothing besides accepting posts from some people and forwarding to others. Relays don't have to be trusted. Signatures are verified on the client side.
This is needed because other solutions are broken:
The problem with Twitter
- Twitter has ads;
- Twitter uses bizarre techniques to keep you addicted;
- Twitter doesn't show an actual historical feed from people you follow;
- Twitter bans people;
- Twitter shadowbans people.
- Twitter has a lot of spam.
The problem with Mastodon and similar programs
- User identities are attached to domain names controlled by third-parties;
- Server owners can ban you, just like Twitter; Server owners can also block other servers;
- Migration between servers is an afterthought and can only be accomplished if servers cooperate. It doesn't work in an adversarial environment (all followers are lost);
- There are no clear incentives to run servers, therefore they tend to be run by enthusiasts and people who want to have their name attached to a cool domain. Then, users are subject to the despotism of a single person, which is often worse than that of a big company like Twitter, and they can't migrate out;
- Since servers tend to be run amateurishly, they are often abandoned after a while — which is effectively the same as banning everybody;
- It doesn't make sense to have a ton of servers if updates from every server will have to be painfully pushed (and saved!) to a ton of other servers. This point is exacerbated by the fact that servers tend to exist in huge numbers, therefore more data has to be passed to more places more often;
- For the specific example of video sharing, ActivityPub enthusiasts realized it would be completely impossible to transmit video from server to server the way text notes are, so they decided to keep the video hosted only from the single instance where it was posted to, which is similar to the Nostr approach.
The problem with SSB (Secure Scuttlebutt)
- It doesn't have many problems. I think it's great. In fact, I was going to use it as a basis for this, but
- its protocol is too complicated because it wasn't thought about being an open protocol at all. It was just written in JavaScript in probably a quick way to solve a specific problem and grew from that, therefore it has weird and unnecessary quirks like signing a JSON string which must strictly follow the rules of ECMA-262 6th Edition;
- It insists on having a chain of updates from a single user, which feels unnecessary to me and something that adds bloat and rigidity to the thing — each server/user needs to store all the chain of posts to be sure the new one is valid. Why? (Maybe they have a good reason);
- It is not as simple as Nostr, as it was primarily made for P2P syncing, with "pubs" being an afterthought;
- Still, it may be worth considering using SSB instead of this custom protocol and just adapting it to the client-relay server model, because reusing a standard is always better than trying to get people in a new one.
The problem with other solutions that require everybody to run their own server
- They require everybody to run their own server;
- Sometimes people can still be censored in these because domain names can be censored.
How does Nostr work?
- There are two components: clients and relays. Each user runs a client. Anyone can run a relay.
- Every user is identified by a public key. Every post is signed. Every client validates these signatures.
- Clients fetch data from relays of their choice and publish data to other relays of their choice. A relay doesn't talk to another relay, only directly to users.
- For example, to "follow" someone a user just instructs their client to query the relays it knows for posts from that public key.
- On startup, a client queries data from all relays it knows for all users it follows (for example, all updates from the last day), then displays that data to the user chronologically.
- A "post" can contain any kind of structured data, but the most used ones are going to find their way into the standard so all clients and relays can handle them seamlessly.
How does it solve the problems the networks above can't?
- Users getting banned and servers being closed
- A relay can block a user from publishing anything there, but that has no effect on them as they can still publish to other relays. Since users are identified by a public key, they don't lose their identities and their follower base when they get banned.
- Instead of requiring users to manually type new relay addresses (although this should also be supported), whenever someone you're following posts a server recommendation, the client should automatically add that to the list of relays it will query.
- If someone is using a relay to publish their data but wants to migrate to another one, they can publish a server recommendation to that previous relay and go;
- If someone gets banned from many relays such that they can't get their server recommendations broadcasted, they may still let some close friends know through other means with which relay they are publishing now. Then, these close friends can publish server recommendations to that new server, and slowly, the old follower base of the banned user will begin finding their posts again from the new relay.
-
All of the above is valid too for when a relay ceases its operations.
-
Censorship-resistance
- Each user can publish their updates to any number of relays.
-
A relay can charge a fee (the negotiation of that fee is outside of the protocol for now) from users to publish there, which ensures censorship-resistance (there will always be some Russian server willing to take your money in exchange for serving your posts).
-
Spam
-
If spam is a concern for a relay, it can require payment for publication or some other form of authentication, such as an email address or phone, and associate these internally with a pubkey that then gets to publish to that relay — or other anti-spam techniques, like hashcash or captchas. If a relay is being used as a spam vector, it can easily be unlisted by clients, which can continue to fetch updates from other relays.
-
Data storage
- For the network to stay healthy, there is no need for hundreds of active relays. In fact, it can work just fine with just a handful, given the fact that new relays can be created and spread through the network easily in case the existing relays start misbehaving. Therefore, the amount of data storage required, in general, is relatively less than Mastodon or similar software.
-
Or considering a different outcome: one in which there exist hundreds of niche relays run by amateurs, each relaying updates from a small group of users. The architecture scales just as well: data is sent from users to a single server, and from that server directly to the users who will consume that. It doesn't have to be stored by anyone else. In this situation, it is not a big burden for any single server to process updates from others, and having amateur servers is not a problem.
-
Video and other heavy content
-
It's easy for a relay to reject large content, or to charge for accepting and hosting large content. When information and incentives are clear, it's easy for the market forces to solve the problem.
-
Techniques to trick the user
- Each client can decide how to best show posts to users, so there is always the option of just consuming what you want in the manner you want — from using an AI to decide the order of the updates you'll see to just reading them in chronological order.
FAQ
- This is very simple. Why hasn't anyone done it before?
I don't know, but I imagine it has to do with the fact that people making social networks are either companies wanting to make money or P2P activists who want to make a thing completely without servers. They both fail to see the specific mix of both worlds that Nostr uses.
- How do I find people to follow?
First, you must know them and get their public key somehow, either by asking or by seeing it referenced somewhere. Once you're inside a Nostr social network you'll be able to see them interacting with other people and then you can also start following and interacting with these others.
- How do I find relays? What happens if I'm not connected to the same relays someone else is?
You won't be able to communicate with that person. But there are hints on events that can be used so that your client software (or you, manually) knows how to connect to the other person's relay and interact with them. There are other ideas on how to solve this too in the future but we can't ever promise perfect reachability, no protocol can.
- Can I know how many people are following me?
No, but you can get some estimates if relays cooperate in an extra-protocol way.
- What incentive is there for people to run relays?
The question is misleading. It assumes that relays are free dumb pipes that exist such that people can move data around through them. In this case yes, the incentives would not exist. This in fact could be said of DHT nodes in all other p2p network stacks: what incentive is there for people to run DHT nodes?
- Nostr enables you to move between server relays or use multiple relays but if these relays are just on AWS or Azure what’s the difference?
There are literally thousands of VPS providers scattered all around the globe today, there is not only AWS or Azure. AWS or Azure are exactly the providers used by single centralized service providers that need a lot of scale, and even then not just these two. For smaller relay servers any VPS will do the job very well.
-
 @ 7460b7fd:4fc4e74b
2025-06-05 15:54:42
@ 7460b7fd:4fc4e74b
2025-06-05 15:54:42比特币正在主动引诱量子计算“破解自己”
引言:危机还是契机?
比特币和量子计算,这两个看似对立的存在,正在酝酿一场耐人寻味的博弈。许多人担心未来强大的量子计算机将秒破比特币的密码学基石,从而令区块链安全灰飞烟灭。然而,本文想传达的核心观点却截然相反:比特币不仅不会被量子破解打败,反而正在通过协议层的巧妙设计来“引诱”量子计算进入自己的游戏规则之中。通过诸如BIP-360等提案,比特币有望将量子计算的威胁转化为动力,开启一个“后挖矿时代”的全新正反馈经济体系,让“破解”本身成为新的挖矿机制。
这样的观点听起来近乎狂想,但背后有着深厚的技术逻辑支撑。我们将从基本的密码学原理谈起,逐步剖析量子计算的能力与局限,以及比特币协议在抗量子方向做出的结构性准备。最后,我们探讨一种大胆的经济模型:当量子计算被诱导去参与“破解竞赛”时,或许正是比特币凤凰涅槃、新经济形态崛起之机。
非对称加密的数学本质:“上帝视角”的陷门答案
非对称加密(如RSA、椭圆曲线加密ECC等)的核心在于存在一种单向函数:正向计算容易,反向推导极难。公钥可以视作某个难题的题目,私钥则相当于“上帝视角”提前知道的答案。一旦掌握私钥,就能轻松完成从答案到题目的逆推;而只有公钥时,想要逆推出私钥则被设计为在现实中不可行。这类单向难题通常通过陷门函数来实现——对合法持有者(私钥)来说,存在隐藏的捷径(陷门)可以快速解题;而对局外人来说,题目看似无解。
举例来说,比特币当前采用的ECC加密:私钥与公钥的关系就像“一次难以逆推的乘法”。给定私钥x,乘以基点G可轻易得到公钥点P = x·G,但已知P却无法高效求出x。这种不对称确保了签名者可以用私钥生成签名,而验证者只能用公钥验证签名而无法伪造。私钥掌握了解题的“上帝答案”,公钥则只能用于验证答案是否正确。
这一点在新型的抗量子算法中同样体现。以格密码(lattice cryptography)为例:Falcon等基于NTRU格的签名算法,其公钥可以被视为一个高维长基,私钥是对应的短基。pqshield.com在二维格子上的示意说明了这种不对称性:拥有短基(私钥)时,我们可以高效地找到距离某个目标点很近的格点解;但只有长基(公钥)时,我们顶多能验证某个给定解是否有效,却很难自行找到足够优质的解pqshield.com。换言之,私钥提供了一个陷门,允许持有者快速逆推答案,而公钥持有者只能望“题”兴叹。
图:在二维格子中,签名者持有的短基(私钥)可以高效求解出距离目标点(黑色方块)极近的格点解(绿色圆点)。绿色平行四边形表示短基下求解空间很小,因而容易找到最优解。这直观展示了陷门函数的威力:私钥掌握短基就如同拿到了解题捷径。
图:仅持有长基(公钥)时,使用相同算法得到的格点解(红色圆点)可能距离目标(黑色方块)很远。红色平行四边形代表在无陷门情况下求解范围巨大,找到最佳解极其困难。但验证者仍可用长基检查出某个解(如绿色点)确实是有效解pqshield.com。这体现了公私钥在计算能力上的不对称:私钥可求解,公钥仅可验证。
总而言之,非对称加密的安全性源自数学难题的单向性质和陷门结构。私钥就是那个隐藏的逆向通道,“上帝视角”的答案;公钥则是不具备捷径的信息,只够验证而无法逆推。从RSA的整数分解、ECC的离散对数,到Falcon的近似最近矢量问题,每一种公钥体制都是在构造“题目易出答案难逆”的格局,让持有陷门者轻松,旁观破解者绝望。
量子计算的原理与极限:并行穷举的神话与现实
量子计算机令人畏惧之处,在于其并行计算能力。通过量子叠加态,n个量子比特(qubit)可同时表示2^n种状态——仿佛能把指数级的可能性同时考虑。配合量子干涉与算法设计,量子计算机能够以远胜传统计算机的效率解决某些特定问题。其中最著名的就是Shor算法,它能在多项式时间内完成对大整数的质因数分解和离散对数求解。这正是传统公钥加密(RSA、ECC)的命门:一旦有足够强大的量子计算机,基于这些数学问题的公钥体制将不再困难,私钥可以由公钥“解密”而出coindesk.com。
然而,“并行穷举”的神话背后有严格的物理和工程学限制。首先是量子比特数量和质量的限制:当前的量子芯片规模远未达到破解现代加密所需的级别。据风险研究机构与专家调查,目前我们只有几十到几百个物理qubit,而要威胁256位ECC或2048位RSA,需要数百万高质量qubitdeloitte.com。不仅数量上相差几个数量级,现有量子芯片的纠错和降噪技术也远不成熟。量子比特极其敏感,微小噪声都会引入错误,真正实用的量子计算机需要对成千上万的物理比特进行纠错编码,形成稳定的逻辑比特。这个工程挑战之巨大,使得可攻破密码的量子计算机仍是多年之后的前景——多数专家预测大概还需十几年时间才可能出现实质威胁deloitte.com。
其次,量子计算并非万能破解,仅对特定问题有指数级加速。Shor算法擅长因数分解和离散对数,Grover算法可以对无结构的穷举搜索加速(将时间复杂度平方根降低)。但许多新兴的抗量子算法依赖的问题(如格上的最短向量问题SVP、最近向量问题CVP,或多变量方程、哈希预像等)目前并无高效量子算法。这些问题大多属于NP难类,甚至找近似解也极为困难emerginginvestigators.org。尽管量子计算提供并行试探能力,但对这类高度复杂的问题也爱莫能助。正如一项研究指出:SVP和CVP问题即便在量子计算机上依然“极端困难”,在可预见的将来仍足以保证安全性emerginginvestigators.org。Falcon所使用的NTRU格就是这样的难题代表——没有已知算法可以像Shor之于RSA那样,高效攻破NTRU问题。
最后,我们还需注意量子攻击的实际条件。量子破解比特币主要有两种情景:存储攻击和传输攻击deloitte.com。存储攻击指利用量子计算找出已公开公钥对应的私钥,从而盗取静态存放于链上某地址的币;传输攻击则是当交易广播(公钥暴露)后,在被矿工打包上链前的短暂窗口内,量子计算抢先推导私钥并盗转。这两种攻击对量子能力要求不同:存储攻击允许耗时几周甚至数月破解一个密钥,只要在币移动前完成即可;而传输攻击要求在区块确认之前(比特币约10分钟内,以太坊更短)秒破私钥deloitte.com。显然,目前和可预见的中期内,量子计算都远达不到传输攻击所需的即时破解水平;即便存储攻击,由于比特币区块链的UTXO模型(稍后详述),真正高价值、长时间暴露公钥的币也相对有限deloitte.com。因此,量子威胁虽然现实存在,但并非一夜之间让比特币崩溃的魔法。这反倒给予我们部署抗量子方案、引导量子力量“为我所用”的时间窗口。
抗量子密码学的三大结构前提
要让比特币真正抵御量子威胁,并把量子计算纳入自身生态,需要满足几个结构性前提。经过多年社区讨论和研究,以下三点被认为是比特币走向抗量子的关键设计要素:
-
UTXO模型:隐藏公钥缩短攻击窗口 – 比特币采用UTXO模型,每次交易都会生成新地址,公钥通常以哈希形式隐藏在地址中,直到你花费时才公布。这意味着量子计算只有在你发起交易后的很短时间内(交易确认前)才能获得公钥并尝试破解,大大压缩了攻击窗口anduro.iodeloitte.com。相较之下,账户模型(如以太坊)重复使用固定地址,公钥一旦被提取或首次使用后就长久暴露,使得65%以上的以太币当前都处于量子暴露风险中,而比特币约只有25%处于类似风险deloitte.com。UTXO模型通过“一次性地址”和“不用则公钥不出”的原则,天然提供了对抗量子存储攻击的第一道屏障。
-
“见证隔离”(SegWit):模块化升级签名算法 – 抗量子方案的发展日新月异,比特币必须保持签名算法的可插拔升级能力。2017年的见证隔离升级正是为此奠定基础:SegWit将签名等见证数据与交易本体分离,并引入版本化的见证脚本格式。这使得添加新签名类型成为可能——通过软分叉引入新的输出类型和见证版本,就能兼容地支持不同算法delvingbitcoin.org。正如BIP-341利用SegWit扩展出了Taproot的Schnorr签名,比特币也可以扩展出抗量子签名的新地址类型而无需硬分叉或显著增加区块体积delvingbitcoin.org。这一模块化特性对于迎接未来各类抗量子算法至关重要,没有SegWit的铺垫,抗量子改造将困难重重。
-
分级安全机制:根据价值和时效选择算法强度 – 由于UTXO的性质,每笔交易在花费时都会暴露其公钥。因此,安全策略不能“一刀切”,应允许根据币值大小或持有时长采用不同强度的抗量子算法。高价值的UTXO、长期未移动的“老币”,应使用更高安全级别但可能更重型的签名方案;反之,小额频繁交易可用较轻量的方案以兼顾效率和区块容量。好比Falcon提供了512和1024两种参数版本:Falcon-1024安全级别更高但签名稍大,而Falcon-512签名更小速度更快,适合资源受限场景emerginginvestigators.org。未来比特币或可同时支持多种抗量子算法或参数,用户按需选用,让“安全性”成为一种可以权衡和市场定价的链上资源。每一次支付都在安全与成本之间找到平衡,这将促使一个分层的安全市场形成——进一步论述见后文经济模型部分。
上述三大前提缺一不可:UTXO模型提供了基础的_安全缓冲_,SegWit机制给予_升级弹性_,分级算法让_经济可行性_落地。在这方面,比特币的体系结构远优于某些后来的公链。例如,以太坊的账户模型天生缺乏隐藏公钥的机制,地址就是固定的公钥哈希,一旦使用过私钥签名就永久暴露公钥,同时其交易脚本(EVM)对签名算法固定死,没有灵活插拔空间。这意味着以太坊想转向抗量子算法,必须经过极其痛苦的整体迁移或硬分叉——开发者需要为每个账户引入新密钥,新老算法并行过渡,智能合约地址、签名验证逻辑全部推倒重来。这种难度令人生畏,以至于有人嘲讽以太坊“几乎不可能”实现真正的抗量子迁移。反观比特币,得益于其简单而弹性的UTXO+Script设计,只需通过新的输出类型软分叉,就可以逐步引入抗量子地址,让用户自愿迁移过渡,避免一次性硬分叉的系统性风险。
BIP-360:可选抗量子签名,引入量子博弈
面对量子威胁,比特币开发社区并未坐以待毙。2024年,由开发者Hunter Beast提出的BIP-360提案(又称P2QRH,意为“支付到抗量子哈希”)正式将抗量子签名引入了议事日程anduro.io。BIP-360核心思路是在比特币中增加新的地址类型,这些地址采用后量子密码学的签名算法(当前优先考虑Falcon,并备选CRYSTALS-Dilithium和SPHINCS+等)来取代易受量子攻击的ECDSA/Schnorr签名anduro.iogroups.google.com。换句话说,用户可以自愿选择生成一种“抗量子地址”,对应的UTXO需使用抗量子算法签名才能解锁。
为什么说BIP-360让比特币“引诱”量子计算加入博弈?这里有几层含义:
首先,BIP-360采用软分叉方式部署,可选而非强制。这意味着在量子计算真正成熟之前,绝大多数交易仍可继续使用原有签名算法,不平添负担;而有安全偏好的用户或机构可以提前迁移一部分资金到抗量子地址以高枕无忧。随着量子技术进展,逐步会有更多人选择这个选项,形成一个与量子威胁赛跑的过程。这种自愿迁移机制本身就是一种对量子黑客的诱导:网络主动暴露出一个“堡垒更坚固”的区域,鼓励守法用户往那里走,同时意味着留下的旧区域反而成为显眼的攻击目标和“诱饵”。
其次,BIP-360在算法选择和参数上充分考虑了区块链经济的承受力。起初提案曾讨论过一些前沿算法如SQIsign,但发现其验证开销高达ECDSA的15,000倍,若全网采用将使验证一块新区块从1秒暴涨到4小时,带来难以接受的性能瓶颈groups.google.com。最终的方案优选Falcon等NIST标准算法,它们签名体积较小、验证高效,可与当前区块大小和验证速度相容groups.google.com。例如Falcon-1024的签名约1.3KB、公钥1.7KB左右,这虽然比当前64字节的Schnorr签名大得多,但并非无法承受。通过配置灵活的安全级别(如重要交易才用Falcon-1024,一般小额用Falcon-512或普通Schnorr),比特币区块空间将被合理分配在安全性和费用之间。BIP-360精心设计了新的地址格式和见证结构,确保即便引入抗量子签名,区块验证和存储开销也在经济范围内,不会动摇挖矿和节点运行的成本平衡anduro.io。
最后也是最具前瞻性的一点,BIP-360为量子计算参与链上博弈打开了一扇门。通过提供抗量子和非抗量子地址并存的环境,比特币网络其实设置了一个对量子计算的挑战擂台:量子计算可以选择去攻击那些仍使用旧签名算法且价值巨大的UTXO,但同一时间,网络里的用户也在不断提升关键UTXO的签名强度来应对。量子计算不再是一个纯粹的外部敌人,而被巧妙地“请”进了系统,在规则内与用户和矿工互动。这为下一节将讨论的新经济模型奠定了基础——破解即挖矿的雏形由此孕育。
值得一提的是,BIP-360还提出了一个Taproot的量子安全补丁方案P2TRH,用哈希隐藏Taproot的公钥以弥补其“公钥长曝”缺陷groups.google.comgroups.google.com。因为现有的Taproot地址(见证v1)是直接以公钥生成地址,失去了UTXO模型隐藏公钥的优势,量子攻击者可以随时尝试破解Taproot资金。P2TRH通过将Taproot公钥再哈希一层,恢复“见证前隐藏公钥”的特性,代价是每笔此类输入增加8.25字节开销groups.google.com。这显示出比特币开发者未雨绸缪,连新升级的Taproot漏洞也在想办法弥补,使全局达到抗量子的结构性统一。
综上,BIP-360及相关提案不仅提供了技术方案,更释放出一种积极的信号:比特币正主动拥抱量子挑战,将其纳入规则之内。正如Anduro团队支持BIP-360时所言:“量子攻击的威胁严肃而迫近,我们不能坐等紧急关头才手忙脚乱。”anduro.ioanduro.io比特币社区选择了在危机到来前主动布局,以最小的代价换取最大的安全冗余和发展新契机。
“破解竞赛”经济模型:当量子成为新矿工
设想未来5-15年内,量子计算技术逐步成熟。在比特币网络中,可能会上演这样一幕令人惊叹的图景:量子计算矿工和抗量子验证者同时在线,围绕着尚未升级的老式UTXO展开一场你追我赶的“破解竞赛”。这将引发怎样的经济动力?我们大胆描绘一个后PoW时代的可能场景:
一方面,强大的量子计算机不再浪费算力去挖掘哈希谜题(传统PoW),而是直接瞄准那些“量子易攻”的UTXO,即尚使用老式ECDSA/Schnorr签名且公钥已暴露的地址。这些地址里的币对合法持有人来说如果迟迟未迁移到抗量子地址,实际上就变成了躺在链上的“悬赏”:谁能先算出私钥,谁就能转走这些币。在量子计算参与者眼中,这些币和早期比特币矿工眼中的区块奖励无异,都是凭借算力可竞争获取的收益。值得注意的是,根据分析,目前约有25%的比特币(按币量)处于公钥已暴露状态deloitte.com。随着时间推移,这个比例可能上升——除非持有人主动升级安全。这就像网络故意留出了一片“牧场”,让量子计算在其中竞相捕猎,以获得收益。量子攻击者之间形成竞争:更快的量子芯片、更好的算法意味着可以更早破解特定私钥,拿下那笔币。这几乎就是PoW的变体——过去矿工拼SHA-256算力抢区块奖励,未来量子矿工拼质因数分解/离散对数能力抢遗留UTXO。
另一方面,守护这片“牧场”的则是抗量子验证者和普通用户自身的防范行为。所谓抗量子验证者,可能是运行完整后量子节点或提供安全服务的专业机构。他们一方面帮助用户升级UTXO(例如提供一键迁移服务,把旧地址币转移到新PQ地址上,收取服务费),另一方面监测全网可疑交易。当量子攻击者尝试盗取某UTXO时,如果该UTXO持有者事先购买了“安全服务”,验证者可以抢先代为花费将币转移到更安全的地址(类似白帽黑客行为),或者提供更高级别签名升级以挫败攻击。总之,抗量子能力本身也成为一种商品,在市场上明码标价。你想让自己的币绝对安全?可以付费请量子安全服务团队定期轮换密钥、使用最高强度签名、监控链上异常。你的交易想确保不中途被截胡?可以支付更高矿工费甚至指定量子保险节点护送。在链上,一个根据签名难度和安全级别定价的市场逐渐形成:越高难度的签名(比如超长位的Falcon变种、多重签名方案结合等)需要支付越高的费用来存储和验证;反过来,这些费用补贴给保障网络安全的矿工/节点,激励他们投入更多资源提升抗量子能力。这种正反馈循环下,“安全”本身成为了新的经济激励。
如此一来,比特币生态迎来了“后挖矿时代”的转型:当区块补贴逐渐趋零,原本空缺的矿工激励由量子破解竞赛和安全服务市场所填补。量子计算加入竞争并非摧毁网络,反而扮演起类似矿工的角色,通过攻破薄弱环节来获得收益;而诚实的参与者则通过不断升级安全措施和支付安全费用来保护资产。这看似矛盾,却形成了动态平衡:正如生物进化中的“红后效应”,猎豹越快,羚羊也进化得更快,两者共同提升了系统的活力。
当然,这一模型中也充满戏剧性和讽刺意味——尤其当我们把眼光投向其他缺乏这种机制的公链。以太坊等账户制链若在量子时代陷入危机,很可能只能选择停机硬分叉、或者由中心化机构出面更换用户密钥,几乎无自动博弈的空间可言。而比特币网络则通过精妙的协议调整,把外部威胁内化为内部博弈,让市场机制去调节和应对。这种弹性与活力,正是比特币经久不衰的原因。
结语:危机催生新生,量子力量为我所用
当年互联网面对计算机病毒肆虐时,人们最终没有被动防守,而是发展出杀毒产业、安全协议,将病毒的威胁转化为推动网络更加健壮的动力。同样道理,比特币面对量子计算的冲击,并非只能筑高墙固步自封,而是选择了更具前瞻性的道路:拥抱威胁、化敌为友。通过提前布局抗量子基础设施(UTXO模型、SegWit扩展、PQ签名算法)、逐步推行BIP-360等方案,比特币正悄然改变游戏规则。在这个新规则中,量量对决、攻守博弈将上演全新篇章,网络安全不再是一成不变的盾牌,而是一套动态进化的生态系统。
或许若干年后回望,我们会发现量子计算并没有摧毁比特币,反而成就了比特币历史上的一次重大飞跃——开启了一个后工作量证明时代的新纪元。在这个纪元里,“破解就是新挖矿”不再只是戏谑之语,而成为链上真实上演的经济现象;“出售安全”也从附属服务变成每个节点和用户的日常考量。比特币将继续履行其角色:作为一个去中心化的、自我强化的金融体系,它有能力将任何挑战转化为自身进化的燃料。
正如BIP-360提案作者所言,这是一个“when 而非 if”的议题anduro.io。量子计算终将到来,而比特币已在主动邀请它参与一场精心设计的游戏。当量子计算机真的站上擂台,比特币早已不再是那个任人宰割的靶子,而更像是一位早已摆好阵势的棋手,静候对手入局。在这盘大棋中,没有永远的猎物,只有不断进化的猎人。比特币,会是那个始终笑到最后的“猎人”吗?让我们拭目以待。
参考文献:
-
【18】PQShield博客:《Falcon – A Post-Quantum Signature Scheme》 – 阐释格密码中长基(公钥)与短基(私钥)的不对称性pqshield.com。
-
【28】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 比较了比特币UTXO模型与以太坊账户模型在量子攻击下的差异,指出以太坊65%资产易受量子威胁,而比特币约25%deloitte.comdeloitte.com。
-
【23】Bitcoin开发者论坛:《Proposing a P2QRH BIP towards a quantum resistant soft fork》 – 描述了通过SegWit扩展新签名算法的思路,无需硬分叉且不增加区块大小delvingbitcoin.org。
-
【22】Emerging Investigators论文:《A meta-analysis on NIST post-quantum cryptographic primitive finalists》 – 说明Falcon-512与Falcon-1024在安全性和性能上的差异,并强调SVP/CVP等问题对量子计算依然极为困难emerginginvestigators.orgemerginginvestigators.org。
-
【36】Anduro博客:《Bitcoin Needs Quantum Resistant Addresses – We Support BIP360》 – 介绍了BIP-360提案内容,引入抗量子地址类型P2QRH,采用Falcon和Dilithium签名,软分叉兼容anduro.io。同时强调量子威胁需提早应对的紧迫性anduro.ioanduro.io。
-
【32】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 提供了BIP-360提案的最新动态,算法选型从SQIsign转向Falcon、Dilithium、SPHINCS+,原因是前者验证开销过大(15,000倍)而不切实际groups.google.comgroups.google.com。
-
【30】CoinDesk报道:《Quantum Computing Could Break Bitcoin-Like Encryption Far Easier…》 – 提及比特币所用ECC也可被Shor算法破解,只要有足够强大的量子计算机coindesk.com。
-
【33】Deloitte报告:《Quantum risk to the Ethereum blockchain》 – 阐述当前量子计算的物理局限:需要上百万qubit且降低噪声量级,目前技术远不能攻击密码算法deloitte.com。
-
【38】Bitcoin开发邮件列表:《P2QRH/BIP-360 Update》 – 描述了针对Taproot的P2TRH抗量子方案,用哈希隐藏公钥以减小长时间暴露,并分析其开销和局限groups.google.comgroups.google.com。
-
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Parallel Chains
We want merged-mined blockchains. We want them because it is possible to do things in them that aren't doable in the normal Bitcoin blockchain because it is rightfully too expensive, but there are other things beside the world money that could benefit from a "distributed ledger" -- just like people believed in 2013 --, like issued assets and domain names (just the most obvious examples).
On the other hand we can't have -- like people believed in 2013 -- a copy of Bitcoin for every little idea with its own native token that is mined by proof-of-work and must get off the ground from being completely valueless into having some value by way of a miracle that operated only once with Bitcoin.
It's also not a good idea to have blockchains with custom merged-mining protocol (like Namecoin and Rootstock) that require Bitcoin miners to run their software and be an active participant and miner for that other network besides Bitcoin, because it's too cumbersome for everybody.
Luckily Ruben Somsen invented this protocol for blind merged-mining that solves the issue above. Although it doesn't solve the fact that each parallel chain still needs some form of "native" token to pay miners -- or it must use another method that doesn't use a native token, such as trusted payments outside the chain.
How does it work
With the
SIGHASH_NOINPUT/SIGHASH_ANYPREVOUTsoft-fork[^eltoo] it becomes possible to create presigned transactions that aren't related to any previous UTXO.Then you create a long sequence of transactions (sufficient to last for many many years), each with an
nLockTimeof 1 and each spending the next (you create them from the last to the first). Since theirscriptSig(the unlocking script) will useSIGHASH_ANYPREVOUTyou can obtain a transaction id/hash that doesn't include the previous TXO, you can, for example, in a sequence of transactionsA0-->B(B spends output 0 from A), include the signature for "spending A0 on B" inside thescriptPubKey(the locking script) of "A0".With the contraption described above it is possible to make that long string of transactions everybody will know (and know how to generate) but each transaction can only be spent by the next previously decided transaction, no matter what anyone does, and there always must be at least one block of difference between them.
Then you combine it with
RBF,SIGHASH_SINGLEandSIGHASH_ANYONECANPAYso parallel chain miners can add inputs and outputs to be able to compete on fees by including their own outputs and getting change back while at the same time writing a hash of the parallel block in the change output and you get everything working perfectly: everybody trying to spend the same output from the long string, each with a different parallel block hash, only the highest bidder will get the transaction included on the Bitcoin chain and thus only one parallel block will be mined.See also
[^eltoo]: The same thing used in Eltoo.
-
 @ b1ddb4d7:471244e7
2025-06-05 10:00:43
@ b1ddb4d7:471244e7
2025-06-05 10:00:43Starting January 1, 2026, the United Kingdom will impose some of the world’s most stringent reporting requirements on cryptocurrency firms.
All platforms operating in or serving UK customers-domestic and foreign alike-must collect and disclose extensive personal and transactional data for every user, including individuals, companies, trusts, and charities.
This regulatory drive marks the UK’s formal adoption of the OECD’s Crypto-Asset Reporting Framework (CARF), a global initiative designed to bring crypto oversight in line with traditional banking and to curb tax evasion in the rapidly expanding digital asset sector.
What Will Be Reported?
Crypto firms must gather and submit the following for each transaction:
- User’s full legal name, home address, and taxpayer identification number
- Detailed data on every trade or transfer: type of cryptocurrency, amount, and nature of the transaction
- Identifying information for corporate, trust, and charitable clients
The obligation extends to all digital asset activities, including crypto-to-crypto and crypto-to-fiat trades, and applies to both UK residents and non-residents using UK-based platforms. The first annual reports covering 2026 activity are due by May 31, 2027.
Enforcement and Penalties
Non-compliance will carry stiff financial penalties, with fines of up to £300 per user account for inaccurate or missing data-a potentially enormous liability for large exchanges. The UK government has urged crypto firms to begin collecting this information immediately to ensure operational readiness.
Regulatory Context and Market Impact
This move is part of a broader UK strategy to position itself as a global fintech hub while clamping down on fraud and illicit finance. UK Chancellor Rachel Reeves has championed these measures, stating, “Britain is open for business – but closed to fraud, abuse, and instability”. The regulatory expansion comes amid a surge in crypto adoption: the UK’s Financial Conduct Authority reported that 12% of UK adults owned crypto in 2024, up from just 4% in 2021.
Enormous Risks for Consumers: Lessons from the Coinbase Data Breach
While the new framework aims to enhance transparency and protect consumers, it also dramatically increases the volume of sensitive personal data held by crypto firms-raising the stakes for cybersecurity.
The risks are underscored by the recent high-profile breach at Coinbase, one of the world’s largest exchanges.
In May 2025, Coinbase disclosed that cybercriminals, aided by bribed offshore contractors, accessed and exfiltrated customer data including names, addresses, government IDs, and partial bank details.
The attackers then used this information for sophisticated phishing campaigns, successfully deceiving some customers into surrendering account credentials and funds.
“While private encryption keys remained secure, sufficient customer information was exposed to enable sophisticated phishing attacks by criminals posing as Coinbase personnel.”
Coinbase now faces up to $400 million in compensation costs and has pledged to reimburse affected users, but the incident highlights the systemic vulnerability created when large troves of personal data are centralized-even if passwords and private keys are not directly compromised. The breach also triggered a notable drop in Coinbase’s share price and prompted a $20 million bounty for information leading to the attackers’ capture.
The Bottom Line
The UK’s forthcoming crypto reporting regime represents a landmark in financial regulation, promising greater transparency and tax compliance. However, as the Coinbase episode demonstrates, the aggregation of sensitive user data at scale poses a significant cybersecurity risk.
As regulators push for more oversight, the challenge will be ensuring that consumer protection does not become a double-edged sword-exposing users to new threats even as it seeks to shield them from old ones.
-
 @ a296b972:e5a7a2e8
2025-06-03 15:08:50
@ a296b972:e5a7a2e8
2025-06-03 15:08:50***Achtung Spreng-Arbeiten!***
Der verbliebene intakte Strang der Nordstream Pipeline soll jetzt von Deutschland mit einem hochexplosiven 18. Sanktionspaket gesprengt werden, damit Putin nicht, wie schon in Kursk, Truppen durch das Rohr schickt, und so doch noch in Schwedt anlandend auf deutschem Boden eine russische Invasion stattfinden kann.
***Kriegserklärung***
Deutschland hat Deutschland den Krieg erklärt. Zunächst freiwillig, doch wenn es nicht von allein noch schlimmer wird, wird es eine Kriegspflicht geben müssen. Kriegstreibende Propaganda und der intensive Ausbau des Feindbilds sollen die Bevölkerung dahingehend umstimmen, weil Frieden doch auf die Dauer sehr langweilig ist.
***Verwechslung***
Bei der Einstellung der Außenbeauftragten der Europäischen Union ist es zu einer Verwechslung gekommen. Ursprünglich wollte man Maria Callas einstellen, doch dann stellte man fest, dass diese begnadete Stimme leider nicht mehr unter uns weilt.
***Bedingungslose Kapitulation***
Anlässlich der Bereicherung der UN durch die Präsidentschaft der ehemaligen deutschen Außen-Dings, haben die Vereinten Nationen direkt nach der unerklärlichen Wahl vorsorglich ihre Bedingungslose Kapitulation gegenüber allen Nationen bekannt gegeben. Alle von der Präsidentin getroffenen Aussagen haben vorläufigen Charakter und werden aufgrund der Fremdsprachlichkeit der Präsidentin auf ihren korrekten Inhalt hin nachträglich überprüft.
***Mehrfach gesichert ***
Ein gesichert staatsfinanziertes Rechercheportal hat durch investigative Recherche herausgefunden, dass der neue Papst gesichert katholisch ist. Es konnte nicht nur eine Nähe festgestellt werden, sondern es wurde sogar gesichert nachgewiesen, dass es sich um dieselbe katholische Kirche handelt, die schon seinerzeit in der Inquisition Hexen und Ketzer verbrannt hat.
***Gleichbehandlung***
Nachdem es in Spanien und Portugal und zuletzt auch in Südfrankreich zu einem Stromausfall gekommen ist, hat die deutsche Regierung beim Europäischen Gerichtshof Klage eingereicht. Im Zuge der Gleichbehandlung aller Nationen will Deutschland nun das Recht auf einen eigenen Black-Out für mindestens zwei Tage einklagen.
***Problem fehlender Wohnungen gelöst***
Aufgrund der Wohnungsknappheit hat die deutsche Regierung nun einen Fond aufgelegt, aus dem jede Familie 35.000 Euro Starthilfe erhält, wenn sie für mindestens 10 Jahre das Land verlässt. Es kam bereits zu ersten Ausreisen, bevor noch die Starthilfe ausgezahlt werden konnte.
***Bürokratieabbau***
Zum schnellen und effizienten Bürokratieabbau wird ein neues Ministerium für Komplikationen mit mindestens 5.000 Mitarbeitern eingerichtet, um den überbordenden Verordnungs- und Bürokratiesumpf auszutrocknen. Derzeit warten nur noch wenige 100 Beamte darauf, dass ihnen Arbeit zugewiesen wird.
***‘Aufruf an die deutsche Bevölkerung***
Die deutschen Haushalte werden gebeten, vorhandene Küchensiebe der Bundesregierung zur Verfügung zu stellen. Die vorhandenen Sieblöcher sollen zugelötet und die Siebe so als Alu- oder Edelstahlhelme für die Bundeswehr zur bevorstehenden gemeinsamen Invasion der USA und Russlands in Deutschland verwendet werden. Weiter sollen ausgediente Heizöltanks auf die Ladeflächen offener Pritschenwagen installiert werden, um die in Deutschland verbliebenen Panzer betanken zu können.
***Long-Pipeline oder Post-Gas?***
Deutschland will nicht, dass Nordstream wieder in Betrieb genommen wird, weil das russische Gas Verunreinigungen, unter anderem auch Nano-Partikel enthält, dass den deutschen Gasthermen Schaden zufügen könnte. Das erklärt auch, warum die deutsche Aufklärung zur Sprengung der Nordstream-Pipelines im Sande verlaufen ist: Zu explosiv!
***Mielke: Ich liebe doch alle Menschen…***
Gerüchten zufolge soll der berühmt gewordene Satz von Erich Mielke in seiner ersten und einzigen Rede vor der DDR-Volkskammer am 13.11.1989 den amtierenden deutschen Außenminister sehr inspiriert haben: Ich hasse…ich hasse doch alle, alle Russen… ich hasse doch, ich setze mich dafür ein… dass Russland immer unser Feind sein wird!
***Durchbruch in der Quantenphysik***
Deutschen Quantenphysikern ist es gelungen, dass Taurus zur gleichen Zeit sowohl noch in Deutschland, als auch schon in der Ukraine sein kann. Lediglich die Eingabe der Zielkoordinaten bereitet den Programmierern noch Schwierigkeiten. Je nachdem, wo sich der Taurus gerade befindet, kann das Hauptstadt-Ziel sowohl Berlin, als auch Moskau sein.
***Selbstjustiz***
Die verantwortlichen Politiker während des Corona-Ereignisses haben ein Gerichtsverfahren ins Leben gerufen, in dem sie sich gegenseitig beschuldigt und verurteilt haben. Anschließend begab man sich unter Polizeischutz in ein bekanntes Promi-Lokal in Berlin und fuhr danach weiter zur Selbsteinweisung nach Bauzen.
***Kaiser’s Sektsteuer***
Um die seinerzeit eingeführte Sektsteuer zum Aufbau der deutschen Kriegsmarine wieder ihrem ursprünglichen Zweck zuzuführen, hat die Meyer-Werft sich bereit erklärt, Fregatten zu bauen, mit der die Deutsche Marine dann Panzerkreuzerfahrten in der Ostsee vor Königsberg veranstalten will. Schon wenige Tage nach Bekanntgabe waren die ersten Vergnügungsdampferfahrten mit „Meine Fregatte“ komplett ausgebucht.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
* *
(Bild von pixabay)
-
 @ fbf0e434:e1be6a39
2025-06-05 14:08:24
@ fbf0e434:e1be6a39
2025-06-05 14:08:24Hackathon 概要
ETHBratislava Hackathon Vol.2 汇聚 54 名开发者并审核通过 11 个项目,成为以太坊社区的重要盛事。此次黑客马拉松在斯洛伐克技术大学举办,参与者可免费参与 ETHBratislava 大会,这一安排助力开发者探索区块链技术的前沿进展。
项目在解决以太坊可扩展性与互操作性问题上成果显著,尤其在 “World Computer” 赛道表现突出。“Zircuit Restaking Track” 赛道也带来重要创新,聚焦通过 AI 驱动的 zk rollups 技术提升安全性与扩展性。“European Stablecoin EURØP Challenge” 则致力于开发欧元背书的稳定币,推动欧洲监管数字货币概念落地。
参与者不仅获得资深导师指导、与行业领袖建立连接的机会,现场更有招聘方挖掘技术人才。活动在兼具庆祝与社交属性的派对中落幕。总计 4,000 欧元奖金的设置,营造了开发者之间竞争与合作并存的创新氛围。ETHBratislava Vol.2 成功孵化出影响以太坊未来的创新构想,同时强化了社区联结。
Hackathon 获奖者
World Computer 奖项获奖者
此类别着重于利用以太坊能力的面向消费者的应用程序。开发者创建了解决方案,旨在增强包容性、金融工具和教育平台。获奖者包括:
- Zhar: 该去中心化平台使用AI和以太坊区块链来管理、执行和激励使用智能合约和代币的链上挑战。
- Ledger Lens: 一个Web应用程序,促进对以太坊多层生态系统的可视化和分析,强调代币流动和跨链桥使用等指标。
现实世界代币化奖项获奖者
此类别集中于在欧洲利用EUR锚定的稳定币EURØP构建效用。项目目标是在此数字货币之上部署初步技术增强。
- dEST: 一个去中心化平台,利用NFTs和智能合约来促进无中介的代币化房地产交易。
- EnergyHub: 一个提供去中心化平台以货币化多余绿色能源并通过智能合约和用户友好的仪表板实现能源捐赠的应用程序。
Restaking 奖项获奖者
此类别鼓励团队在Zircuit生态系统内的AI驱动zkEVM上进行构建,着重于支持AI增强安全性和创新zk rollup技术的项目。
- RestakerX: 一个仪表板应用程序,设计用于跟踪Zircuit网络上的数字资产,提供算法建议以最大化收益。
有关所有项目的更多详细信息和此次黑客马拉松中展示的创新理念的进一步见解,请访问 ETHBratislava Hackathon页面。
关于组织者
Ethereum Bratislava
Ethereum Bratislava 是中欧和东欧地区区块链和技术领域的一个重要社区,致力于推进以太坊的开发和整合。由一支专家团队支持,该组织在增强以太坊在中欧和东欧地区的可扩展性和安全性的项目中作出了重大贡献。积极参与社区活动和教育活动强调了他们在区块链领域促进技术创新和知识共享的承诺。Ethereum Bratislava 继续支持技术改进和生态系统增长,旨在增强以太坊的能力和跨各行业的采用。
-
 @ 00ea1f73:71c6e344
2025-06-03 09:59:07
@ 00ea1f73:71c6e344
2025-06-03 09:59:07Je suis en train de construire un outil de référencement collectif de marques et fabricants proposant des produits 100 % en matière naturelle (ce qui veut essentiellement dire "sans plastique").
Voici les étapes de ma progression ces dernières semaines en tant que non développeur pour créer cela tout en privilégiant des outils open source.
Etape 1 : faisons simple, du texte organisé
J'ai commencé par réunir mes idées dans Anytype. Leur approche "tout est un objet" laisse une flexibilité incroyable pour organiser ses données. On peut s'en servir comme simple outil de prise de note ou comme outil de gestion de projet. Le fonctionnement "local first" de l'application me donne la main sur mes données : elles sont stockées en local sur mon ordinateur et mon téléphone, qui se synchronisent entre eux.
Anytype permet depuis peu de publier sur Internet les "objets" de son choix (pages, notes, albums…) mais cela reste limité pour proposer à des visiteur une navigation fluide entre des objets liés (dans mon cas des marques et des matières par exemple). De plus, il n'est pas encore possible d'y automatiser la mise en forme de contenus à partir de données.
Ainsi, après avoir réuni les informations et préparé les contenus "à la main" pour trois marques seulement dans Anytype, j'ai eu besoin d'automatisation, et donc d'une vraie base de données. Je conserve quand même Anytype pour organiser mes idées et la suite du projet. Je l'utilise aussi pour la vie quotidienne (liste de course partagée, journal…).
Etape 2 : structurons une base de données
Baserow est une alternative à Airtable qui permet de gérer une base de données comme un tableur. Les formules utilisables dans les tableaux m'ont aidé à générer automatiquement les contenus de marque à partir des données que je réunissais. J'ai obtenu des données bien ordonnés dans de beaux tableaux sans avoir plus besoin de réécrire tout le contenu pour chaque marque.
J'ai passé un peu de temps à apprendre la syntaxe des formules de Baserow, j'ai mis à jour le contenu des trois premières marques, généré automatiquement celui d'une quatrième et… je me suis rendu compte que ça n'allait pas le faire.
Un point crucial de mon projet est la gestion et l'affichage des catégories de produits proposés par chaque marque, histoire que cela soit pratique de trouver les alternatives naturelles pour ce que l'on cherche sur le site. Or, dans Baserow il n'y avait pas moyen de générer mes contenus catégorisés de manière dynamique. J'étais contraint de modifier sans cesse des formules de plus en plus complexes, et donc avec un risque d'erreur de plus en plus grand. Cela reste un tableur, plus net pour gérer des données, mais moins fourni en termes de formules.
Avec une seule marque traitée en plus, mon "backend" v2 n'aura pas duré longtemps !
Etape 3 : courage, passons aux choses sérieuses
A ce moment là, j'ai sérieusement douté de ma capacité a créer ce site avec des outils open source et j'ai été tenté de retourner vers Bubble. À mon avis, Bubble est l'outil "no code" (ou de "programmation visuelle") le plus abouti. Je l'avais déjà utilisé efficacement avec We Do Good pour réaliser des prototypes de fonctionnalités, même utilisés provisoirement en production.
C'est génial, avec Bubble, des semaines de travail classique entre développeurs et designers pour arriver à une version utilisable se transforment en heures, voire en jours pour tester et valider des prototypes.
Mais… avec Bubble on n'a pas accès à ce qui se passe derrière l'interface de programmation. On devient en fait prisonnier de leur langage de programmation propriétaire. Si on a besoin de faire différemment, s'ils augmentent leurs prix de manière inadaptée, ou si un blocage se présente pour une autre raison, il faut tout refaire à zéro ou faire développer des nouvelles fonctionnalités (plugins) qui enrichissent Bubble.
J'ai alors décidé de passé au niveau supérieur en terme de technicité, avec des outils tout de même accessible aux non initiés motivés : une base de données dans Supabase connectée à une interface créée avec Plasmic. Avec Supabase j'ai accès aux paramétrages les plus fins sur les données et avec Plamic je construis visuellement ce dont j'ai besoin, comme avec Bubble.
Malgré l'interface visuelle très complètes de Plasmic, certaines fonctions dont j'ai besoin demandent des formules personnalisées utilisant un peu de code. L'avantage, c'est que là ou j'avais appris le language Bubble utilisable seulement avec Bubble, j'apprends maintenant les languages ouverts et universels du web sql et javascript, avec un peu d'aide de l'"IA" pour comprendre les fonctions et erreurs de syntaxe.
J'apprendre en faisant directement ce que j'ai envie, et c'est beaucoup plus efficace et motivant !
Plasmic me laisse aussi récupérer et réutiliser l'ensemble du code source ailleurs si j'en ai besoin un jour.
Je devais en passer par là
Chaque version de mon "backend" a été utile et même nécessaire à la suivante.
Avec mon expérience d'entrepreneur du web, je sentais depuis le départ que j'aurais besoin d'une solution robuste de base de données ainsi que de pouvoir intervenir sur le code facilement. Cependant, au démarrage, je n'avais pas envie de me plonger là-dedans. Finalement, bien m'en a pris ! La structuration de données que j'avais initialement imaginée est très différente de celle à laquelle j'arrive maintenant.
Je n'aurais pas eu une base de données claire et bien organisée dans Supabase si je n'avais pas fait précédemment une itération dans Baserow. Je n'aurais pas créé les tables et liaisons utiles dans Baserow si je n'avais pas créé les premiers contenus sous forme de texte avec liaisons dans Anytype.
De plus, je n'aurais pas trouvé l'énergie de me lancer sur ce nouveau projet si je n'avais pas commencé par une version très simple et non "scalable". C'est un vrai progrès personnel : j'ai toujours travaillé en essayant de concevoir le maximum de choses d'avances, pour me rassurer et limiter les risques, et parce que c'est ce qu'on apprend à l'école. Les problèmes, c'est que je dépensais pour cela une énergie folle et que bien sûr, la réalité ne correspond jamais vraiment aux prévisions.
En me lançant avec une première version pas du tout aboutie mais fonctionnelle, je me suis autorisé à faire plus d'erreur, à m'exposer et à me concentrer sur du concret.
Références
Pour moi, favoriser l'open source est essentiel car cela fait partie des outils fondamentaux pour défendre ma liberté et celle des autres.
Tous les outils que j'utilise ou ai utilisé pour ce projet sont open source, sauf Anytype qui est juste "open core" (c'est à dire qu'ils publient leur code mais n'autorisent pas tous les usages avec). Ils présentent aussi tous des plans gratuits bien pratiques pour se lancer sans contrainte financière.
- Anytype : https://anytype.io/
- Baserow : https://baserow.io/
- Supabase : https://supabase.com/
- Plasmic : https://www.plasmic.app/
J'ai aussi testé ou envisagé sans les retenir quelques autres solutions comme WordPress ou Silex. Provisoirement, en attendant d'avoir créé toutes les interfaces dont j'ai besoin avec Plasmic, j'utilise NocoDB, connecté à Supabase, pour disposer d'une interface visuelle équivalente à Baserow (avec des formules moins avancées mais la possibilité de me connecter plusieurs bases de données si besoin).
J'utilise beaucoup Alternative.to pour trouver les outils dont j'ai besoin, on y peut filtrer les applications selon de nombreux critère, je le recommande.
Ensuite, il faut tester et se lancer, voire tester en se lançant !
opensource #nocode #lowcode #vibecoding #ia #produitsnaturels #zeroplastique #nostrfr
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28A estrutura lógica do livro didático
Todos os livros didáticos e cursos expõem seus conteúdos a partir de uma organização lógica prévia, um esquema de todo o conteúdo que julgam relevante, tudo muito organizadinho em tópicos e subtópicos segundo a ordem lógica que mais se aproxima da ordem natural das coisas. Imagine um sumário de um manual ou livro didático.
A minha experiência é a de que esse método serve muito bem para ninguém entender nada. A organização lógica perfeita de um campo de conhecimento é o resultado final de um estudo, não o seu início. As pessoas que escrevem esses manuais e dão esses cursos, mesmo quando sabem do que estão falando (um acontecimento aparentemente raro), o fazem a partir do seu próprio ponto de vista, atingido após uma vida de dedicação ao assunto (ou então copiando outros manuais e livros didáticos, o que eu chutaria que é o método mais comum).
Para o neófito, a melhor maneira de entender algo é através de imersões em micro-tópicos, sem muita noção da posição daquele tópico na hierarquia geral da ciência.
- Revista Educativa, um exemplo de como não ensinar nada às crianças.
- Zettelkasten, a ordem surgindo do caos, ao invés de temas se encaixando numa ordem preexistentes.
-
 @ a296b972:e5a7a2e8
2025-06-03 07:04:39
@ a296b972:e5a7a2e8
2025-06-03 07:04:39So sehr man sich auch Mühe gibt, es will vielen einfach nicht gelingen, Russland als den Feind anzusehen.
Wenn ein fremder Mann eine Frau unfreiwillig zum Tanz auf’s Parkett zerrt und der Ehemann dem fremden Mann wie auch immer zu verstehen gibt, dass das so nicht geht, dann kann man nicht sagen, der Ehemann habe einen Streit vom Zaun gebrochen.
Eine Reaktion setzt immer eine Aktion voraus.
Nicht Russland ist der NATO auf die Pelle gerückt, sondern die NATO mit der Osterweiterung Russland.
Russland wollte mit Auflösung des Warschauer Pakts eine gemeinsame europäische Militärlösung, die die Neuordnung der NATO oder gar ebenfalls ihre Auflösung zur Folge gehabt hätte.
Der sogenannte Wertewesten ist maßgeblich für den Krieg in der Ukraine verantwortlich. Völkerrechtswidrigkeit kann man weglassen, da es auch im Westen, von den USA, mehrfach Beispiele für völkerrechtswidrige Angriffe auf andere Staaten gibt. Und Deutschland hat im Kosovo auch nicht nur Kaffee für die Truppen gekocht.
Wer im Glashaus sitzt, sollte nicht mit Steinen werfen.
Wenn Deutschland, vertreten durch einen Kanzler 2. Wahl über die nicht mehr vorhandene Reichweitenbeschränkung spricht, das Wahlvieh, den ehemaligen Souverän, im Ungewissen über die Lieferung des Stiers lässt, und dann, wie aus heiterem Himmel, Taurus, mit deutschem Kompass und deutschen Kompassbedienern, auf einmal Richtung Krim-Brücke oder gar Moskau unterwegs sein sollte, wen würde es dann wundern, wenn Moskau seine „Liebesgrüße“, schon allein aus reiner Höflichkeit und Anstand, nach Schrobenhausen sendet?
Würde das passieren, würde man in Deutschland sagen: Seht ihr, wir haben es euch ja immer gesagt, ihr wolltet es nur nicht glauben. Russland, mit seinem imperialen Anspruch und seinem aggressiven Verhalten, der Friedensverhinderer, der böse Putin, der böse Russ‘, wird uns angreifen! Die geforderte Kriegstüchtigkeit war also absolut berechtigt!
Wer das dann immer noch glaubt, dem möchte man eine Rakete in den Kamin seiner Doppelhaushälfte mit Gänsemuster-Gardinen am Küchenfenster stecken.
Wenn man jemanden bis auf’s Blut reizt, ist es ihm dann zu verdenken, wenn ihm irgendwann der Geduldsfaden reißt, nachdem schon mehrere Rote Linien überschritten wurden?
Und warum reizt man Russland bis auf’s Blut? Man kann zu keinem anderen Grund kommen, als dass die Geistesgrößen in Deutschland unbedingt einen Krieg wollen. Wozu? Ist das die von wem auch immer geplante Vollendung der Zerstörung Deutschlands? Der zukünftige Ex-Kanzler redet einen Haufen vermeintlich kluges Zeug daher, aber Russland handelt klug. Kleiner Unterschied.
Rheingold ist in gewöhnliches Rheinmetall, wohl durch Geheim-Alchimie, verwandelt worden. Geheim wird ja jetzt wieder modern. Man kann nur hoffen, dass es in der Taurussland-Rakete tatsächlich US-amerikanische Komponenten gibt, die (vielleicht sogar in Wiesbaden?) abgeschaltet werden können, damit der Stier nicht fliegen kann. Und man kann auch nur hoffen, dass die USA sie dann auch wirklich abschalten.
Die Meyer-Werft in Papenburg soll demnächst auch „Meine Fregatte“ und „Kreuzer grau I bis IX“ bauen. Panzerkreuzerfahrten in der Ostsee mit Blick auf Königsberg, na bravo, tolle Idee. (Da war doch mal was?). Gute Erholung schon jetzt. Da wird die vom Kaiser für den Aufbau der Marine eingeführte Sektsteuer endlich wieder ihrem eigentlichen Zweck zugeführt.
Und wie der ehemalige Masken-Chef-Einkäufer erst jüngst in einer der unsäglichen Staatsfunk-Aufführungen lichtblitzartig erkannt haben muss, spricht Putin Deutsch. Nein, doch, oh! Man stelle sich das einmal vor. Ganz was Neues! Die jetzt für die deutsche Bevölkerung geheim gehaltenen militärischen Absprachen werden nun in einer Sprache in Berlin besprochen, von denen man vorher sorgfältig, wie immer, recherchiert hat, dass Putin sie sicher nicht spricht, damit er nichts mitbekommt. Pssst, Feind hört mit! Den Beruf des Dolmetschers oder Übersetzers hat das Arbeitsamt in der Berufsberatung in der Schulzeit des Bankkaufmanns wahrscheinlich nicht vorgestellt, daher existieren sie für ihn nicht.
Und welche militärischen Entscheidungen von den deutschen "Chef-Diplomaten" getroffen wurden, das erfährt die Bevölkerung ja spätestens, wenn es knallt. Das reicht ja auch.
Was kommt als nächstes? Nach selbst genähten Maulwindeln jetzt eine Nähanleitung für schwere Gardinen zur Fenster-Verdunkelung? Oder gibt es die bald schon fertig in allen Größen zu kaufen, bei einem Discounter, wie in Berlin jetzt Macheten, damit man sich im Garten wieder den Weg zum Geräteschuppen bahnen kann.
Ils sont fous ces Allemands!
„Das große Karthago führte drei Kriege. Nach dem ersten war es noch mächtig. Nach dem zweiten war es noch bewohnbar. Nach dem dritten war es nicht mehr aufzufinden“, Berthold Brecht.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 74fb3ef2:58adabc7
2025-06-02 22:59:39
@ 74fb3ef2:58adabc7
2025-06-02 22:59:39I'm actually glad that COVID happened. If it weren't for COVID, I would not have woken up.
Before COVID, I hated the government like any tax-paying slave does, but I never questioned the narrative. I believed the full statist propaganda—that the government had my best interest in mind and that we couldn't live without them.
I always believed they were thieves. I always knew they were idiots. I think it takes barely a few minutes of actual thinking to realize that. But I was very anti-"conspiracy theory." I used to ridicule non-statists and bitcoiners too.
COVID was the switch for me. I started doing research, but I was skeptical at first. Then, in a random Discord server about political debate, a certain user's messages stood out.
Most users were statists, left and right NPCs screaming about which geriatric and demented person should be the new monarch of a country I don't even live in and will likely never visit anymore.
But this one person was different. I don't think it's up to me to share his name since he's a very private person (you know who you are, and thank you). But I talked with this person almost every week. I presented argument after argument for my "side," essentially advocating for my own slavery to people who value me less than a pawn in a game of chess.
There was no argument I would bring up that he wouldn't destroy me on with logic and data.
Slowly, over a few months, he convinced me and turned me into the free person I am today.
I owe so much to this person: - The fact that I quit my main job a while back and only do freelance now - The fact that I don't use any big tech products anymore - The fact that I'm a bitcoiner - The fact that I self-host a lot of servers, despite living in a small apartment - The fact that I'm becoming less reliant on the slavery system - The fact that I'm now living free - The fact that I'm writing this very article on nostr
Once you start questioning one widely-accepted narrative, it becomes natural to ask "what else might I have wrong?" or "what other assumptions haven't I examined?"
Thank you, government, for COVID. And thank you, mystery person, for calling me a retard and showing me how I was being retarded.
-
 @ cae03c48:2a7d6671
2025-06-05 15:01:26
@ cae03c48:2a7d6671
2025-06-05 15:01:26Bitcoin Magazine
How Strategy (MSTR) Built Their Capital Stack to Accelerate Bitcoin AccumulationMicroStrategy—now operating as Strategy
 —has built the most aggressive Bitcoin treasury in the world. But its true innovation isn’t just holding Bitcoin. It’s in how it finances the accumulation of Bitcoin at scale without giving up control or diluting shareholder value.
—has built the most aggressive Bitcoin treasury in the world. But its true innovation isn’t just holding Bitcoin. It’s in how it finances the accumulation of Bitcoin at scale without giving up control or diluting shareholder value.The engine behind this? A meticulously designed capital stack—a multi-tiered structure of debt, preferred stock, and equity that appeals to different types of investors, each with unique risk, yield, and volatility preferences.
This is more than corporate finance—it’s a blueprint for Bitcoin-native capital formation.
What Is a Capital Stack?
A capital stack refers to the layers of capital a company uses to finance its operations and strategic goals. Each layer has its own return profile, risk level, and repayment priority in the event of liquidation.
Strategy’s capital stack is designed to do one thing exceptionally well: convert fiat capital into Bitcoin exposure—efficiently, at scale, and without compromise.
The Stack: Ordered by Priority
Strategy’s capital stack comprises five core instruments:
1. Convertible Notes
2. Strife Preferred Stock ($STRF)
3. Strike Preferred Stock ($STRK)
4. Stride Preferred Stock ($STRD)
5. Common Equity ($MSTR)These layers are ranked from highest to lowest in repayment priority. What makes this structure unique is how each layer balances downside protection, yield, and Bitcoin exposure—offering institutional investors fixed-income alternatives with varying degrees of correlation to Bitcoin.
Strategy’s Capital Stack illustrated by Chris Millas
Convertible Notes: Senior Debt with Optional Upside
Strategy’s capital stack begins with convertible notes—senior unsecured debt that can convert into equity.
- Downside: Low risk, high priority in liquidation
- Upside: Modest unless converted
- Appeal: Institutional debt investors seeking protection with optional Bitcoin-adjacent upside
These notes were Strategy’s earliest fundraising tools, enabling the company to raise billions in low-interest environments to accumulate Bitcoin without issuing equity.
Strife ($STRF): Investment-Grade Yield
Strife is a perpetual preferred stock designed to mimic high-grade fixed income.
- 10% cumulative dividend, paid in cash
- $100 liquidation preference
- No conversion rights or Bitcoin upside
- Compounding penalties on unpaid dividends
- Low volatility, medium risk profile
Strife targets conservative capital—allocators who want predictable income without equity or crypto exposure. It’s senior to other preferreds and common stock, making it a high-quality fixed-income proxy built atop a Bitcoin treasury.
Strike ($STRK): Yield + Bitcoin Optionality
Strike is convertible preferred stock—bridging fixed income and equity upside.
- 8% cumulative dividend
- Convertible into $MSTR at $1,000 strike
- Paid in cash or Class A shares
- Bitcoin exposure via conversion option
- Medium volatility, low risk
Strike appeals to investors who want income with optional participation in Bitcoin upside. In bullish Bitcoin cycles, the conversion option becomes valuable—offering a hybrid between bond-like stability and equity-like potential.
Stride ($STRD): High Yield, High Risk
Stride is the most junior preferred—non-cumulative, perpetual stock issued with high yield and few protections.
- >10% dividend, only if declared
- No compounding, no conversion, no voting rights
- Highest relative risk among preferreds
- Liquidation priority above common equity, but below all others
Stride plays a crucial role. Its issuance improves the credit quality of Strife, adding a subordinate capital buffer beneath it—similar to how mezzanine debt protects senior tranches in structured finance.
Stride attracts yield-hungry investors, enabling Strategy to raise capital without compromising more senior layers.
Common Equity ($MSTR): Pure Bitcoin Beta
At the base is Strategy’s common equity—the most volatile, least protected, but highest potential instrument in the stack.
- Unlimited upside
- No dividend, no priority
- Full exposure to Bitcoin volatility
- Voting rights, long-term ownership
Common equity is for conviction-driven investors. Over the past four years, this layer has attracted capital from funds and individuals aligned with Strategy’s Bitcoin thesis—investors who want maximal upside from a corporate Bitcoin strategy.
The Big Picture: Saylor Is Targeting the Fixed Income Market
This isn’t just a financing mechanism—it’s a direct challenge to the $130 trillion global bond market.
By issuing instruments like $STRF, $STRK, and $STRD, Strategy is offering Bitcoin-adjacent yield vehicles that absorb demand from across the capital spectrum:
- Institutional investors seeking investment-grade yield
- Hedge funds chasing structured upside
- Yield hunters willing to go down the stack for returns
Each instrument behaves like a synthetic bond, yet all are backed by a Bitcoin accumulation engine.
As Director of Bitcoin Strategy at Metaplanet, Dylan LeClair put it: “Saylor is coming for the entire fixed income market.”
Rather than issue traditional bonds, Saylor is constructing a Bitcoin-native capital stack—one that unlocks liquidity without ever selling the underlying asset.
Why It Matters: A Model for Bitcoin Treasury Strategy
Strategy’s capital structure is more than innovation—it’s a financial operating system for any public company that wants to monetize Bitcoin’s rise while maintaining capital discipline.
Key takeaways:
- Every layer matches a specific investor need: From low-risk debt to speculative yield
- Capital flows in, Bitcoin stays put: Preserving treasury position while scaling
- No single instrument dominates: The stack is diversified by design
- Control is retained: Most securities are non-voting, non-convertible
For corporations serious about building a Bitcoin-native balance sheet, this is the playbook to study.
Saylor isn’t just stacking Bitcoin—he’s engineering the financial infrastructure for a monetary paradigm shift.
Disclaimer: This content was written on behalf of Bitcoin For Corporations. This article is intended solely for informational purposes and should not be interpreted as an invitation or solicitation to acquire, purchase, or subscribe for securities.
This post How Strategy (MSTR) Built Their Capital Stack to Accelerate Bitcoin Accumulation first appeared on Bitcoin Magazine and is written by Nick Ward.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Boardthreads
This was a very badly done service for turning a Trello list into a helpdesk UI.
Surprisingly, it had more paying users than Websites For Trello, which I was working on simultaneously and dedicating much more time to it.
The Neo4j database I used for this was a very poor choice, it was probably the cause of all the bugs.

-
 @ b1ddb4d7:471244e7
2025-06-05 14:01:57
@ b1ddb4d7:471244e7
2025-06-05 14:01:57This article was originally published on aier.org
Even after eleven years experience, and a per Bitcoin price of nearly $20,000, the incredulous are still with us. I understand why. Bitcoin is not like other traditional financial assets.
Even describing it as an asset is misleading. It is not the same as a stock, as a payment system, or a money. It has features of all these but it is not identical to them.
What Bitcoin is depends on its use as a means of storing and porting value, which in turn rests of secure titles to ownership of a scarce good. Those without experience in the sector look at all of this and get frustrated that understanding why it is valuable is not so easy to grasp.
In this article, I’m updating an analysis I wrote six years ago. It still holds up. For those who don’t want to slog through the entire article, my thesis is that Bitcoin’s value obtains from its underlying technology, which is an open-source ledger that keeps track of ownership rights and permits the transfer of these rights. Bitcoin managed to bundle its unit of account with a payment system that lives on the ledger. That’s its innovation and why it obtained a value and that value continues to rise.
Consider the criticism offered by traditional gold advocates, who have, for decades, pushed the idea that sound money must be backed by something real, hard, and independently valuable. Bitcoin doesn’t qualify, right? Maybe it does.
Bitcoin first emerged as a possible competitor to national, government-managed money in 2009. Satoshi Nakamoto’s white paper was released October 31, 2008. The structure and language of this paper sent the message: This currency is for computer technicians, not economists nor political pundits. The paper’s circulation was limited; novices who read it were mystified.
But the lack of interest didn’t stop history from moving forward. Two months later, those who were paying attention saw the emergence of the “Genesis Block,” the first group of bitcoins generated through Nakamoto’s concept of a distributed ledger that lived on any computer node in the world that wanted to host it.
Here we are all these years later and a single bitcoin trades at $18,500. The currency is held and accepted by many thousands of institutions, both online and offline. Its payment system is very popular in poor countries without vast banking infrastructures but also in developed countries. And major institutions—including the Federal Reserve, the OECD, the World Bank, and major investment houses—are paying respectful attention and weaving blockchain technology into their operations.
Enthusiasts, who are found in every country, say that its exchange value will soar even more in the future because its supply is strictly limited and it provides a system vastly superior to government money. Bitcoin is transferred between individuals without a third party. It is relatively low-cost to exchange. It has a predictable supply. It is durable, fungible, and divisible: all crucial features of money. It creates a monetary system that doesn’t depend on trust and identity, much less on central banks and government. It is a new system for the digital age.
Hard lessons for hard money
To those educated in the “hard money” tradition, the whole idea has been a serious challenge. Speaking for myself, I had been reading about bitcoin for two years before I came anywhere close to understanding it. There was just something about the whole idea that bugged me. You can’t make money out of nothing, much less out of computer code. Why does it have value then? There must be something amiss. This is not how we expected money to be reformed.
There’s the problem: our expectations. We should have been paying closer attention to Ludwig von Mises’ theory of money’s origins—not to what we think he wrote, but to what he actually did write.
In 1912, Mises released The Theory of Money and Credit. It was a huge hit in Europe when it came out in German, and it was translated into English. While covering every aspect of money, his core contribution was in tracing the value and price of money—and not just money itself—to its origins. That is, he explained how money gets its price in terms of the goods and services it obtains. He later called this process the “regression theorem,” and as it turns out, bitcoin satisfies the conditions of the theorem.
Mises’ teacher, Carl Menger, demonstrated that money itself originates from the market—not from the State and not from social contract. It emerges gradually as monetary entrepreneurs seek out an ideal form of commodity for indirect exchange. Instead of merely bartering with each other, people acquire a good not to consume, but to trade. That good becomes money, the most marketable commodity.
But Mises added that the value of money traces backward in time to its value as a bartered commodity. Mises said that this is the only way money can have value.
The theory of the value of money as such can trace back the objective exchange value of money only to that point where it ceases to be the value of money and becomes merely the value of a commodity…. If in this way we continually go farther and farther back we must eventually arrive at a point where we no longer find any component in the objective exchange value of money that arises from valuations based on the function of money as a common medium of exchange; where the value of money is nothing other than the value of an object that is useful in some other way than as money…. Before it was usual to acquire goods in the market, not for personal consumption, but simply in order to exchange them again for the goods that were really wanted, each individual commodity was only accredited with that value given by the subjective valuations based on its direct utility.
Mises’ explanation solved a major problem that had long mystified economists. It is a narrative of conjectural history, and yet it makes perfect sense. Would salt have become money had it otherwise been completely useless? Would beaver pelts have obtained monetary value had they not been useful for clothing? Would silver or gold have had money value if they had no value as commodities first? The answer in all cases of monetary history is clearly no. The initial value of money, before it becomes widely traded as money, originates in its direct utility. It’s an explanation that is demonstrated through historical reconstruction. That’s Mises’ regression theorem.
Bitcoin’s Use Value
At first glance, bitcoin would seem to be an exception. You can’t use a bitcoin for anything other than money. It can’t be worn as jewelry. You can’t make a machine out of it. You can’t eat it or even decorate with it. Its value is only realized as a unit that facilitates indirect exchange. And yet, bitcoin already is money. It’s used every day. You can see the exchanges in real time. It’s not a myth. It’s the real deal.
It might seem like we have to choose. Is Mises wrong? Maybe we have to toss out his whole theory. Or maybe his point was purely historical and doesn’t apply in the future of a digital age. Or maybe his regression theorem is proof that bitcoin is just an empty mania with no staying power, because it can’t be reduced to its value as a useful commodity.
And yet, you don’t have to resort to complicated monetary theory in order to understand the sense of alarm surrounding bitcoin. Many people, as I did, just have a feeling of uneasiness about a money that has no basis in anything physical. Sure, you can print out a bitcoin on a piece of paper, but having a paper with a QR code or a public key is not enough to relieve that sense of unease.
How can we resolve this problem? In my own mind, I toyed with the issue for more than a year. It puzzled me. I wondered if Mises’ insight applied only in a pre-digital age. I followed the speculations online that the value of bitcoin would be zero but for the national currencies into which it is converted. Perhaps the demand for bitcoin overcame the demands of Mises’ scenario because of a desperate need for something other than the dollar.
As time passed—and I read the work of Konrad Graf, Peter Surda, and Daniel Krawisz—finally the resolution came. Bitcoin is both a payment system and a money. The payment system is the source of value, while the accounting unit merely expresses that value in terms of price. The unity of money and payment is its most unusual feature, and the one that most commentators have had trouble wrapping their heads around.
We are all used to thinking of currency as separate from payment systems. This thinking is a reflection of the technological limitations of history. There is the dollar and there are credit cards. There is the euro and there is PayPal. There is the yen and there are wire services. In each case, money transfer relies on third-party service providers. In order to use them, you need to establish what is called a “trust relationship” with them, which is to say that the institution arranging the deal has to believe that you are going to pay.
This wedge between money and payment has always been with us, except for the case of physical proximity.
If I give you a dollar for your pizza slice, there is no third party. But payment systems, third parties, and trust relationships become necessary once you leave geographic proximity. That’s when companies like Visa and institutions like banks become indispensable. They are the application that makes the monetary software do what you want it to do.
The hitch is that
-
 @ 0b884d0d:9abbd54a
2025-06-02 21:42:29
@ 0b884d0d:9abbd54a
2025-06-02 21:42:29Conceitos chaves
Neste artigo você vai entender um pouco dos conceitos chave desse novo conjunto de ferramentas para aplicar justiça de forma descentralizada e anárquica.
Antes de continuar a leitura, quero elucidar alguns termos que serão constantemente usados neste artigo.
- Private Law Society (PLS)
- Uma organização sem fins lucrativos com o objetivo de criar novas soluções para tornar cada vez mais viável a aplicabilidade de uma justiça privada e descentralizada
- Ao mesmo tempo, um conjunto de protocolos e softwares de código aberto com o mesmo propósito
- Links úteis
- Perfil Nostr: nostr:npub1p79dx59d5gctllar73cqnucqft89gpkfmydxj4mmk2jj69s7hn3sfjatxx
- GitHub: https://github.com/PrivateLawSociety
- Sobre: https://privatelawsociety.net
- Bitcoin Justice Protocol (BJP)
- Um protocolo estabelecido pela Private Law Society
- Também um software de código aberto disponível no GitHub da Private Law Society
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-bjp
- Sobre: https://privatelawsociety.net/bjp
- Implementação oficial da PLS: https://pls-bjp.vercel.app/
- Web Of Trust (WoT)
- Uma base de dados com avaliações entre usuários Nostr relatando confiança/desconfiança e se um usuário teve relações comerciais ou não com outro
- O objetivo é ser um repositório de reputação para chaves Nostr
- Links úteis
- GitHub: https://github.com/PrivateLawSociety/pls-wot
- Sobre: https://privatelawsociety.net/wot
- Implementação oficial da PLS: https://pls-wot.vercel.app/
- Meu fork com o grafo: https://pls-wot-kiuusai.vercel.app/
Prefácio
Recentemente saiu um episódio no BetterMoney podcast sobre o projeto de justiça privada Private Law Society.
Muitos bons pontos foram levantados neste excelente episódio pelos participantes nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju e nostr:npub1wsl3695cnz7skvmcfqx980fmrv5ms3tcfyfg52sttvujgxk3r4lqajteft. Mas neste entorno permanecem ainda muitas dúvidas sobre o projeto em si, seu funcionamento, princípios, objetivos e funcionalidades.
Venho através deste artigo, apresentar resumidamente o projeto, a filosofia por trás do mesmo e dar a minha visão de como este conjunto de protocolos chamado Private Law Society tem a capacidade de não só transformar o mundo como o conhecemos, mas de tornar boa parte do "poder judiciário" obsoleto e irrelevante em vários aspectos, se assim os indivíduos o quiserem.
Mas afinal, o que é essa tal de PLS?
PLS é um acrônimo para Private Law Society (Sociedade de Leis Privadas em uma tradução livre). Além de uma organização sem fins lucrativos e totalmente Open Source, trata-se de um conjunto de softwares disponíveis no GitHub de forma a estruturar um protocolo de justiça privada descentralizado com colateral em Bitcoin. Falei grego para você? Vamos com calma dissecar estes conceitos...
Sociedade de leis privadas, a "utopia" libertária se tornando realidade
Quem é adepto do movimento libertário e/ou estuda o tema, provavelmente já ouviu falar nesse termo. Originalmente cunhado por David Hume, o filósofo e idealista escocẽs. O projeto toma este nome com o intúito, talvez de forma ambiciosa, mas com certeza visionária e audaz, de trazer uma solução prática e simples de estabelecer contratos voluntários entre duas ou mais partes, as quais livremente escolhem os seus "árbitros" ou "juízes" para fazer valer a lei. Como realmente uma justiça paralela a qual o contrato faz lei entre as partes.
Para uma introdução sobre o conceito, indico este vídeo do canal AnCapSu que trata sobre o tema de forma resumida.
Essa ideia, simples a priori esbarra no problema da aplicabilidade da força, ou ao menos era o que se pensava, antes da criação de ferramentas como o Bitcoin e soluções como Taproot e Bitcoin Scripts. Agora, com uma propriedade realmente soberana, programável e incensurável, essa ideia começa a ganhar forma.
Basicamente, uma dúvida plausível para uma pessoa leiga no assunto seria: "Tá, entendi. Esse tal de bitcoin é realmente bom, seguro e o Estado não tem poder de controle sobre ele. Mas como isso pode gerar essa tal de sociedade de leis privadas? É só uma forma de dinheiro."
A resposta para isso é: Dinheiro programável, chaves privadas e reputação!
BJP: contratos colateralizados em Bitcoin
Bitcoin, Nostr e Taproot: a chave para a aplicação da justiça privada
Se você já está minimamente envolvido com o ambiente Bitcoin, Nostr e afins, deve saber o que é um par de chaves públicas e privadas e como isso funciona. Existe uma chave pública e privada, a pública é a forma de identificação no sistema e a privada é a que gera as assinaturas. Daí é possível determinar que quem publicou a mensagem, seja na blockchain do Bitcoin, seja na rede Nostr, é o dono daquela chave pública em específico. Assim, se institui uma forma de identidade digital.
O que muita gente não sabe, ou não dá o devido valor, é que depois do soft fork Taproot da rede Bitcoin (ocorrido em 2021), os antigos Bitcoin Scripts tomaram outra forma e maior capacidade, se tornando mais práticos, leves e funcionais. Isso é o que dá base hoje para "contratos inteligentes" no Bitcoin e toda a parafernalha de Ordinals, Runes e coisas do gênero. O que pra muitos foi uma maldição que encheu a mempool, na verdade também se provou uma bênção, a qual é a base do BJP (Bitcoin Justice Protocol) da Private Law Society. A atualização permitiu com que scripts mais complexos pudessem ser desenvolvidos de forma mais simples, fossem mais leves e tivessem uma melhor privacidade. O BJP se empodera disso, fornecendo uma solução ao mesmo tempo que simples, inovadora para casos de uso de contratos. Primariamente na camada nobre do Bitcoin e posteriormente na Liquid Network, para aqueles que querem poupar em taxas e terem mais privacidade.
Por sua vez, o Nostr funciona também com criptografia de curvas elípticas, assim como nosso querido Bitcoin. Para ser mais preciso, o mesmo algoritmo é usado tanto no Nostr quanto no Bitcoin. O Secp256k1. Na prática isso significa que toda chave Nostr também é uma chave Bitcoin em potencial. O BJP se apropria dessa interconexão para possibilitar a criação de contratos jurídicos.
BJP: uma multisig sofisticada?
Ok, até agora vimos o que torna esse tal de BJP possível, mas como ele funciona e como eu posso usá-lo na prática?
Bem grosseiramente falando, o BJP é um software que facilita a criação de carteiras multisig específicas para contratos jurídicos. Com ele, você constrói uma multisig não convencional com Taproot que assegura o cumprimento do contrato mediante concordância de todas as partes "clientes" do contrato ou do número mínimo de árbitros configurados previamente + um dos clientes.
Na prática, um script Taproot é montado com a seguinte lógica:
``` Clientes = {Lista de chaves públicas dos clientes}
Árbitros = {Lista de chaves públicas dos árbitros}
Quorum = Número mínimo de árbitros para aprovar a transação
Se todos os Clientes concordarem: Libera gasto Senão se 1 dentre todos os Clientes concorda e ao menos o Quorum de Árbitros concorda: Libera gasto Senão Bloqueia gasto ```
Esse algoritmo garante que o contrato seja efetuado e esteja de acordo com a vontade de todas as partes envolvidas, ou, se entrar em "disputa judicial", o número mínimo de árbitros designados para "fazer valer a lei", concorde junto com a parte lesada para onde os fundos devem ir.
Um exemplo prático:
Aqui temos um exemplo prático de aplicabilidade de um contrato feito através do BJP. Nesse caso, tendo a concordar com o nostr:npub1narc0ect9jf0ffnvcwg8kdqlte69yxfcxgxwaq35eygw42t3jqvq4hxv0r e discordar do nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju quando o primeiro comenta no recente episódio do BetterMoney Podcast:
19:30 Eu discordo do Júlio. Acho que a PLS seria perfeita pro contrato de aluguel. O locatário coloca o colateral e o proprietário vai ter certeza de que não vai tomar calote.
E se uma das partes tentar levar pra justiça estatal, não vai ter nenhum nome no contrato, apenas chaves públicas.
E está certo. O exemplo prático que acabei de citar reforça isso. Não há nada que impeça também, de no contrato, ter uma cláusula a qual envolver a justiça estatal cause algum prejuízo ou perda de causa imediata para a parte expositora. Não estou fazendo recomendação alguma, fazendo apologia a qualquer prática ou aconselhando usar deste tipo de artifício, se o que falo possa ser interpretado como crime pela lei positivada (não sou advogado). Mas, no campo das ideias e das possibilidades no mundo real, é uma possível solução/alternativa.
Vamos ao exemplo...
Adriano Calango quer alugar um apartamento de Beto Lagartixa. Só que ambos não se conhecem e não confiam suficientemente um no outro para fazer um contrato. Ambos decidem então escrever um documento. Word, Pdf ou um texto puro. Não importa. Lá estão todas as cláusulas, o caução do aluguel, multas estabelecidas para uso indevido, penalidades, dia de pagamento, decisão sobre multa de atraso, enfim, qualquer detalhe desse contrato.
Adriano Calango, escolhe Célsio Jacaré, seu amigo como seu árbitro pessoal. Beto Lagartixa escolhe Danilo Crocodilo, seu amigo, como seu árbitro pessoal. Ambos escolhem Eduardo Cobra, um réptil íntegro, com reputação ilibada e que já fez vários julgamentos, como um árbitro em comum para seu contrato. Daqui temos: dois contratantes, duas testemunhas e um juíz.
Adriano Calango então, acessa o site da PLS BJP para criar o contrato. Configura os clientes (ele e Beto Lagartixa), configura todos os árbitros, anexa o arquivo e cria o contrato na rede Bitcoin.
Um evento Nostr criptografado é criado e um link de compartilhamento do contrato é disponibilizado. Adriano Calango compartilha esse link com todos os usuários disponíveis.
Todos os usuários verificam os detalhes do contrato e se o documento do contrato bate com o contrato assinado. Todas as partes ativamente concordando, a nossa multisig é criada.
Um arquivo do contrato é disponibilizado para acessar a multisig do contrato posteriormente. Todos os usuários salvam esse arquivo e o mantém guardado em um local seguro. O objetivo disso é ter redundância. Se um dos participantes perder este arquivo, outro pode compartilhar o mesmo para possibilitar o acesso à multisig do contrato.
Adriano Calango e Beto Lagartixa depositam os devidos colaterais no contrato. Seja o caução de aluguel ou um montante separado para ser empenhorado. Isso é definido pelo acordo feito previamente.
Se tudo ocorrer bem, assim que Adriano Calango resolver se mudar e Beto Lagartixa não tiver nenhuma objeção quanto a isso, ambos voltam para o contrato previamente feito e concordam quanto aos montantes que cada um receberá de volta. Dividem o preço da taxa entre si e cada um tem sua propriedade de volta.
Digamos que Adriano Calango não cumpriu com parte do contrato, atrasando o pagamento de alguns meses. Por outro lado, Beto Lagartixa também não cumpriu parte de seu acordo, deixando de fornecer serviços prescritos no contrato como segurança de condomínio e um elevador funcional. O caso então é levado aos árbitros. Célsio Jacaré argumenta a favor de Adriano Calango, questionando Beto Lagartixa sobre os serviços não prestados pelo mesmo e que claramente no contrato estavam previstos como parte inclusa no custo do aluguel. Danilo Crocodio retruca sobre a inadimplência de Adriano Calango, defendendo seu amigo/cliente, Beto Lagartixa. Eduardo Cobra, ao ouvir calmamente todos os argumentos de ambos os lados, então decide: - Adriano Calango foi inadimplente por três meses. Portanto terá uma multa de 35% sobre seu patrimônio - Beto Lagartixa terá uma multa de 25% sobre o seu patrimônio, pois não prestou o serviço com a devida qualidade - O restante do patrimônio será devolvido para seus respectivos donos - Dos valores da multa: - 90% será dividido entre cada árbitro. 30% para cada - Os 10% restantes serão queimados em taxas para os mineradores
Note que não foi usado nenhum meio coercitivo para solucionar o caso e penalizar os réus em seus devidos processos. Tudo foi aceito voluntariamente previamente, inclusive da parte dos árbitros. As multas aplicadas são meramente ilustrativas. Em um cenário real, tais penalidades seriam acordadas previamente e na falta das mesmas, todas as partes discutiriam até entrar em um acordo quanto a decisão. É totalmente plausível que, por exemplo, a penalidade fosse queimar todo o valor das multas em taxas para os mineradores, se assim todos aceitassem. O mecanismo de mineração nesse cenário também se torna um possivel meio de aplicação de força em um julgamento.
Só esta parte do ecosistema já faz boa parte dos casos de uso da justiça estatal obsoleta, dando maior descentralização, privacidade e soberania para os indivíduos.
Nesse cenário temos novamente a "utopia" libertária sendo definitivamente aplicada. Não há dedo do Estado no meio, todos os contratos foram previamente acordados entre as partes e não houve violação ao PNA (Princípio da Não Agressão). Todo o processo foi estritamente voluntário desde o começo.
WoT: A digitalização da reputação
Quem vê o projeto a primeira vista, pode pensar:
Ah Calango. Legal essa solução com bitcoin e tal. Mas eu vou sempre precisar gastar meus bitcoins toda vida que fizer um contrato? Tem contratos que isso não vale a pena!
Sim. Isso é verdade. Tanto que foi genialmente um caso citado pelo nostr:npub12mllp29adf2fw0eeahmseczcu3y4625qyn3v4uwfvkpzlshnmj3qs903ju. Há casos que os valores são tão pequenos que não compensa criar todo um documento de contrato para, por exemplo, comprar um livro ou algo do tipo. Ou, algumas vezes, o próprio indivíduo não quer gastar dinheiro ou travar valores para manter esse contrato. Mas não é o único caso de uso. Lembre-se que mesmo com colaterais aplicados, normalmente as pessoas não gostam de entrar em decisões judiciais ou confusões em geral. Idealmente todos querem traçar o caminho feliz da história. Então, mesmo para firmar contratos com colateral em Bitcoin usando o BJP, é plausível que um usuário queira pesquisar o "histórico" de outro usuário na rede para averiguar se é uma boa ideia ou não se envolver com aquele indivíduo em específico.
Naturalmente o ser humano já pratica esse cálculo de reputação e analisa o ambiente a sua volta para entender a hierarquia e reputação dele e de outros indivíduos em um grupo. Somos seres sociais e naturalmente na nossa cabeça já montamos uma espécie de rede de confiança na nossa cabeça com a imagem que formamos de um indivíduo X ou Y com base na nossa comunidade. Hierarquia, lideranças, influência, são características naturais do ser humano.
A partir desse cenário, surgiu a ideia de gerar uma solução para uma melhor visualização da reputação entre usuários do protocolo. O objetivo é ser primariamente um repositório com avaliações de usuários sobre outros usuários, os classificando positivamente ou negativamente e informando se houve ou não negócios/fechamento de contratos com o mesmo. A ideia é realmente simples e o objetivo é deixar o protocolo aberto para as mais diversas formas de interpretação desses dados. Seja com modelos matemáticos, visualização e interpretação pessoal ou até mesmo o uso de inteligência artificial para o auxiliar o usuário a tomar suas decisões.
WoT: o nome é conhecido, mas a proposta é diferente
Veja que há uma diferença prática na WoT da PLS e outros projetos de WoT espalhados pela internet afora e pelo Nostr. A maioria dos projetos de WoT são para determinar se uma pessoa/chave privada é ou não relevante a partir da visão de outra chave privada. É o caso de serviços de WoT como o da Coracle.Social, Vertexlab.io e mais recentemente da nova implementação de WoT Relays. Serviços como estes tem o objetivo de reduzir ou eliminar spam e falsidade ideológica (fakes), assim como oferecer uma espécie de algoritmo de recomendação, similar ao que é feito em redes sociais como YouTube e Instagram.
Note que em nenhum momento o objetivo da WoT da PLS é definir por A + B quem é ou deixa de ser confiável ou inconfiável, afinal, confiança é algo estritamente relativo. Nenhum projeto pode ter a audácia de tentar classificar pessoas como confiáveis ou inconfiáveis a nível de estabelecimento de contratos. A PLS entende isso e respeita esse caráter subjetivo da confiança. De igual maneira, nunca foi o objetivo de qualquer projeto de WoT sério fazer algo similar ao que é feito em países como a China, onde pessoas têm alguma espécie de "crédito social". Fique tranquilo. Nosso objetivo não é tornar os episódios distópicos de Black Mirror em realidade 🤣
Visualização em grafo: uma proposta elegante
Desde que entrei de cabeça no projeto da PLS, uma coisa que veio sendo falada nas reuniões era sobre a criação de novas ferramentas para visualizar a rede de formas mais intuitivas, que ajudassem os usuários ao julgar pessoas como confiáveis ou não para estabelecer contratos, e ao mesmo tempo, resolvessem o problema de UX que é uma simples tabela com avaliações entre usuários da rede. A tendência é, a partir do momento que o projeto comece a ter adesão, que o número de notas cresça exponencialmente, e com isso, a visualização da reputação dos indivíduos seja pouco intuitiva. Uma solução apresentada para este problema foi a criação de um frontend com grafos, ou melhor, a criação de uma forma de visualização da sua rede de confiança em particular. A partir disso, foi gerada uma bounty no projeto para a implementação desta solução, a qual eu orgulhosamente estou construindo (na verdade está pronta para uso. Mas ainda quero melhorar algumas coisas). O objetivo é simples: dar ao usuário mais uma forma de contemplar os dados da WoT, de forma mais particular e intuitiva. Facilitando a tomada de decisões.
A natureza da confiança humana em sintonia com a tecnologia
Bolhas virtuais, vilarejos e mineiros
Uma possível crítica que o projeto possa receber é a possibilidade de ataques de spam ou cancelamento em massa corroer ou inviabilizar a utilidade do protocolo. Ataque Sybil também. Entretanto, são espantalhos até bem inocentes quanto ao projeto em questão.
Como havia mencionado anteriormente, a base do projeto em si é propositalmente simples e não se propõe a dar uma solução definitiva para a visualização dos dados postos no protocolo. A tabela de avaliações hoje existente no site da WoT da PLS é apenas uma das inúmeras formas de interpretar estes dados. E uma forma efetiva para problemas como esse, é justamente a implementação de uma visualização por grafo, onde os usuários podem ver redes de confiança sendo tracejadas a partir do ponto de vista específico de uma npub em particular.
Aqui a lógica de um antigo ditado é aplicada:
"O amigo do meu amigo é meu amigo"
Da mesma maneira também podemos formular outras afirmações como:
"O inimigo do meu inimigo é meu amigo"
"O inimigo do meu amigo é meu inimigo"
"O amigo do meu inimigo é meu inimigo"
Se tais derivações fazem sentido para você ou não, não cabe a mim dizer. Novamente, confiança é intrinsecamente algo de caráter subjetivo. Vai de cada um decidir quem é ou não confiável. É justamente por isso que estou implementando diversos filtros de avaliações no meu fork da PLS.
Na prática é o velho jogo de política de sempre. Como bem citado uma vez pelo filósofo e youtuber Platinho, ao citar Carl Schmitt:
Isso também se reflete na cultura mineira (e rural do Brasil em geral), por exemplo. O clássico "cê é fi de quem?". Perceba que essa é uma forma de procurar por um caminho de confiança já estabelecido. Quem tem parente em interior sabe, que uma das coisas mais comuns é os mais velhos, seja ou tio, mãe ou avô perguntar sobre um amigo que você leve para o ambiente familiar (meu filho, esse seu amigo é filho de quem?) É algo até instintivo do ser humano procurar por rotas de confiança e trabalhar de certa forma com o QI (Quem Indica). Goste você ou não, é assim que a natureza humana se expressa e é assim que a dinâmica social é montada.
Vendo que é natural a formação de bolhas, não é uma boa ideia em si interpretar os dados da WoT da PLS simplesmente de uma forma numérica bruta. A melhor forma é fazer uma abordagem individual, com base na sua rede de confiança ao invés de puramente o número de avaliações positivas e negativas.
O grafo da PLS busca justamente tornar mais intuitivo, prático e sistemático essa pesquisa natural. Essa implementação é além de uma ferramenta, uma forma de expressão social muito forte, tanto em âmbito social quanto jurídico, à medida em que a dinâmica social e jurídica se entrelaçam no tecido social.
Adriano Calango ataca novamente
Para um exemplo prático, voltemos a falar dele, Adriano Calango.
Adriano Calango conhece a WoT da PLS já faz um tempo e já avaliou todos os seus parceiros comerciais e amigos aos quais tem laços de confiança já firmes e maduros. Ele procura alguém para alugar uma casa Rolante, RS. ´Ele vê alguns perfis de síndicos no Nostr que moram na mesma cidade que ele com casas disponíveis para alugar. Mas quer ter uma noção que não está se metendo em encrenca ou lidando com algum síndico chato que inferniza a vida dos inquilinos.
Dito isso, ele acessa a WoT da PLS e vai na página do grafo. Percebe que seu amigo Bruno Jabuti, ao qual já havia avaliado positivamente anteriormente, avaliou positivamente um professor de Jiu-jitsu, conhecido como Carlos Camaleão. Que além de ser avaliado positivamente por Bruno Jabuti, recebeu várias avaliações positivas de outros usuários conhecidos de Adriano Calango. Carlos Camaleão, por sua vez, avaliou positivamente um síndico da região chamado Diego Iguana. Na descrição Carlos Camaleão descreve como em todo o tempo que ele foi inquilino de Diego Iguana sempre foi bem tratado e como seu condomínio estava sempre bem organizado e era cuidadosamente zelado, e como sempre que havia alguma falha de infraestrutura, o problema era rapidamente resolvido. Adriano Calango considera firmar um contrato de aluguel com Diego Iguana.
Assim, temos o seguinte caminho de confiança estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👍 -> Diego Iguana
Passando-se alguns dias, Adriano Calango é abordado por Denis Jacaré em uma DM no Nostr oferecendo aluguel baratíssimo e com poucas exigências. Denis Jacaré foi informado que Adriano Calango estava a procura de um imóvel novo para residir. Adriano Calango, então, pega a chave Nostr de Denis Jacaré e joga na parte de "target" na página do grafo na PLS WoT. Ele percebe que Denis Jacaré tem várias avaliações negativas de inúmeros usuários, mas não consegue ainda bater o martelo quanto a confiabilidade de Denis Jacaré. Ele então insere sua própria chave Nostr no campo de "main rater" e vê que tem um caminho tracejado entre a sua npub e a de Denis Jacaré. Pra sua surpresa, ele vê que Carlos Camaleão deu a Denis Jacaré uma avaliação negativa, por conta que no período em que sua filha era inquilina do mesmo, prestou um péssimo serviço. O condomínio vivia com o elevador quebrado, a portaria muitas vezes não funcionava e tinha falta de luz constante. Denis Jacaré não tomava providẽncia nenhuma quanto a isso e ainda fazia questão de causa intriga entre os inquilinos e tentar jogar uns contra os outros. Adriano Calango, então percebe que Denis Jacaré não é confiável com base na rede de confiança definida por Adriano Calango.
Nesse caso temos o seguinte circuito estabelecido:
Adriano Calango 👍 -> Bruno Jabuti 👍 -> Carlos Camaleão 👎 -> Denis Jacaré
Adriano Calango aborda Diego Iguana para estabelecer um contrato. Agora é a vez de Diego Iguana pesquisar o histórico de Adriano Calango. Pois ele quer manter a comunidade de seu condomínio saudável e não deseja aceitar inquilinos baderneiros ou barraqueiros.
Diego Iguana faz então o caminho inverso de Adriano Calango, pondo a npub de Adriano Calango como "target" e a própria npub como "main rater". Daí Diego Iguana consegue ver que Carlos camaleão deu uma nota positiva para Bruno Jabuti e Bruno Jabuti deu uma nota positiva para Adriano Calango. Os dois então fecham negócio.
Neste exemplo, o grafo da WoT da PLS serviu como uma "bússola de confiança" para Adriano Calango e Diego Iguana firmarem um contrato no BJP com seus árbitros e advogados.
Considerações finais
Neste artigo você pôde aprender os conceitos básicos da Private Law Society, motivos de certas escolhas de design, viu exemplos práticos de casos de uso e um pouco das bases filosóficas que norteiam o ecosistema da PLS. Também pôde compreender um pouco mais sobre o conceito de WoT na PLS e como isso pode ser útil com o passar do tempo e a adesão de novos usuários no sistema.
Se este conteúdo te agregou de forma positiva em algo, considere mandar um ZAP ou fazer uma doação anônima por um dos meios disponibilizados na descrição do meu perfil Nostr. Este artigo foi feito com muito carinho e dedicação. Sua doação me encoraja a continuar produzindo e lhe mantendo informado. Se não pode ou não quer contribuir financeiramente, considere engajar no conteúdo reagindo, compartilhando e comentando. Toda a ajuda é bem vinda. Agradeço de coração sua paciência e atenção para ler até aqui.
Em breve trarei novidades sobre o desenvolvimento do grafo da WoT e logo mais, vídeo novo no meu canal do YouTube. Até mais!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Channels without HTLCs
HTLCs below the dust limit are not possible, because they're uneconomical.
So currently whenever a payment below the dust limit is to be made Lightning peers adjust their commitment transactions to pay that amount as fees in case the channel is closed. That's a form of reserving that amount and incentivizing peers to resolve the payment, either successfully (in case it goes to the receiving node's balance) or not (it then goes back to the sender's balance).
SOLUTION
I didn't think too much about if it is possible to do what I think can be done in the current implementation on Lightning channels, but in the context of Eltoo it seems possible.
Eltoo channels have UPDATE transactions that can be published to the blockchain and SETTLEMENT transactions that spend them (after a relative time) to each peer. The barebones script for UPDATE transactions is something like (copied from the paper, because I don't understand these things):
OP_IF # to spend from a settlement transaction (presigned) 10 OP_CSV 2 As,i Bs,i 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIFDuring a payment of 1 satoshi it could be updated to something like (I'll probably get this thing completely wrong):
OP_HASH256 <payment_hash> OP_EQUAL OP_IF # for B to spend from settlement transaction 1 in case the payment went through # and they have a preimage 10 OP_CSV 2 As,i1 Bs,i1 2 OP_CHECKMULTISIGVERIFY OP_ELSE OP_IF # for A to spend from settlement transaction 2 in case the payment didn't went through # and the other peer is uncooperative <now + 1day> OP_CHECKLOCKTIMEVERIFY 2 As,i2 Bs,i2 2 OP_CHECKMULTISIGVERIFY OP_ELSE # to spend from a future update transaction <Si+1> OP_CHECKLOCKTIMEVERIFY 2 Au Bu 2 OP_CHECKMULTISIGVERIFY OP_ENDIF OP_ENDIFThen peers would have two presigned SETTLEMENT transactions, 1 and 2 (with different signature pairs, as badly shown in the script). On SETTLEMENT 1, funds are, say, 999sat for A and 1001sat for B, while on SETTLEMENT 2 funds are 1000sat for A and 1000sat for B.
As soon as B gets the preimage from the next peer in the route it can give it to A and them can sign a new UPDATE transaction that replaces the above gimmick with something simpler without hashes involved.
If the preimage doesn't come in viable time, peers can agree to make a new UPDATE transaction anyway. Otherwise A will have to close the channel, which may be bad, but B wasn't a good peer anyway.
-
 @ cae03c48:2a7d6671
2025-06-05 15:01:20
@ cae03c48:2a7d6671
2025-06-05 15:01:20Bitcoin Magazine

MARA Announces Over $100 Million in Bitcoin Mined in May 2025Today, MARA Holdings, Inc. (NASDAQ: MARA) reported a record high month of bitcoin production in May 2025, mining 950 BTC worth over $100 million at the time of writing. A 35% increase from April and the highest monthly output since the April 2024 halving event. MARA did not sell any bitcoin in May.
JUST IN: MARA mined 950 #Bitcoin worth over $100 MILLION in May

They HODLed all of it
 pic.twitter.com/Z4v1zoEfga
pic.twitter.com/Z4v1zoEfga— Bitcoin Magazine (@BitcoinMagazine) June 3, 2025
“May was a record-breaking month for MARA with 282 blocks won, a 38% increase over April and a new monthly high,” said the Chairman and CEO of MARA Fred Thiel. “Our total bitcoin holdings surpassed 49,000 BTC during May and the 950 bitcoin produced were the most since the halving event in April 2024.”
The company mined 282 blocks during the month, a 38% rise over the previous month, and now holds 49,179 BTC, worth roughly $5.23 billion at the time of writing.
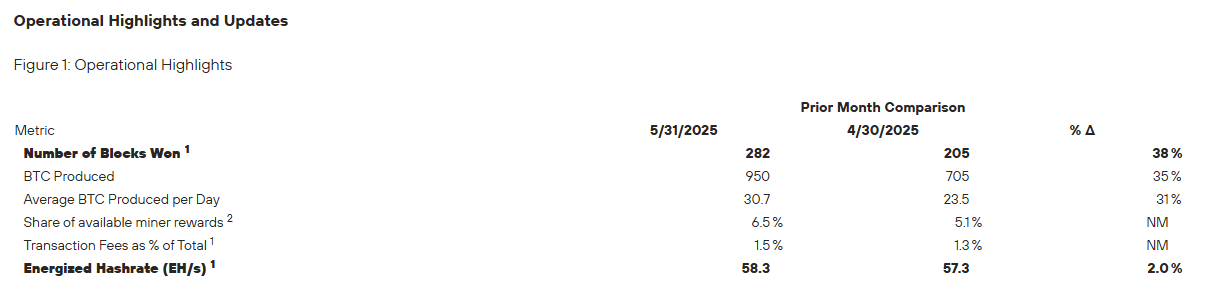
“Our fully integrated tech stack is a key differentiator, and MARA Pool is the only self-owned and operated mining pool among public miners, offering greater control and efficiency,” stated Thiel. “Operating our pool means no fees to external operators and retention of the full value of block rewards. Production in May also benefitted from block reward luck. Since launch, MARA Pool’s block reward luck has outperformed the network average by over 10%, contributing to our industry-leading block production.”
Operational efficiency also improved, with energized hashrate rising 2% from 57.3 EH/s to 58.3 EH/s. MARA’s average daily bitcoin production hit 30.7 BTC, which is 31% more than the last month from April.
“We remain laser-focused on transforming MARA into a vertically integrated digital energy and infrastructure company,” commented Thiel. “We believe this model gives us tighter operational control, improves cost-efficiency, and makes us more resilient to shifts in the broader economy.”
Earlier this month, on May 8, MARA released its first quarter 2025 earnings, posting 213.9 million dollars in revenue. A 30 percent increase over the same period last year. The company’s bitcoin holdings surged 174 percent year over year, rising from 17,320 BTC to 47,531 BTC as of March 31, with an estimated value of 3.9 billion dollars at the time. In Q1, MARA mined 2,286 BTC and acquired an additional 340 BTC. Operational performance also strengthened, with energized hashrate nearly doubling from 27.8 EH/s to 54.3 EH/s, and cost per petahash per day improving by 25 percent.
This post MARA Announces Over $100 Million in Bitcoin Mined in May 2025 first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Criteria for activating Drivechain on Bitcoin
Drivechain is, in essence, just a way to give Bitcoin users the option to deposit their coins in a hashrate escrow. If Bitcoin is about coin ownership, in theory there should be no objection from anyone on users having the option to do that: my keys, my coins etc. In other words: even if you think hashrate escrows are a terrible idea and miners will steal all coins from that, you shouldn't care about what other people do with their own money.
There are only two reasonable objections that could be raised by normal Bitcoin users against Drivechain:
- Drivechain adds code complexity to
bitcoind - Drivechain perverts miner incentives of the Bitcoin chain
If these two objections can be reasonably answered there remains no reason for not activating the Drivechain soft-fork.
1
To address 1 we can just take a look at the code once it's done (which I haven't) but from my understanding the extra validation steps needed for ensuring hashrate escrows work are very minimal and self-contained, they shouldn't affect anything else and the risks of introducing some catastrophic bug are roughly zero (or the same as the risks of any of the dozens of refactors that happen every week on Bitcoin Core).
For the BMM/BIP-301 part, again the surface is very small, but we arguably do not need that at all, since anyprevout (once that is merged) enables blind merge-mining in way that is probably better than BIP-301, and that soft-fork is also very simple, plus already loved and accepted by most of the Bitcoin community, implemented and reviewed on Bitcoin Inquisition and is live on the official Bitcoin Core signet.
2
To address 2 we must only point that BMM ensures that Bitcoin miners don't have to do any extra work to earn basically all the fees that would come from the sidechain, as competition for mining sidechain blocks would bid the fee paid to Bitcoin miners up to the maximum economical amount. It is irrelevant if there is MEV on the sidechain or not, everything that reaches the Bitcoin chain does that in form of fees paid in a single high-fee transaction paid to any Bitcoin miner, regardless of them knowing about the sidechain or not. Therefore, there are no centralization pressure or pervert mining incentives that can affect Bitcoin land.
Sometimes it's argued that Drivechain may facilitate the ocurrence of a transaction paying a fee so high it would create incentives for reorging the Bitcoin chain. There is no reason to believe Drivechain would make this more likely than an actual attack than anyone can already do today or, as has happened, some rich person typing numbers wrong on his wallet. In fact, if a drivechain is consistently paying high fees on its BMM transactions that is an incentive for Bitcoin miners to keep mining those transactions one after the other and not harm the users of sidechain by reorging Bitcoin.
Moreover, there are many factors that exist today that can be seen as centralization vectors for Bitcoin mining: arguably one of them is non-blind merge mining, of which we have a (very convoluted) example on the Stacks shitcoin, and introducing the possibility of blind merge-mining on Bitcoin would basically remove any reasonable argument for having such schemes, therefore reducing the centralizing factor of them.
- Drivechain adds code complexity to
-
 @ 31a4605e:cf043959
2025-06-05 13:03:59
@ 31a4605e:cf043959
2025-06-05 13:03:59Nos últimos anos, o Bitcoin tem sido frequentemente comparado ao ouro, ganhando o nome de "ouro digital". Essa comparação ocorre porque ambas as formas de valor têm características em comum, como escassez, durabilidade e aceitação mundial. Contudo, o Bitcoin também representa uma novidade tecnológica que muda a ideia de dinheiro e investimento, se destacando como uma alternativa moderna e eficaz ao ouro físico.
Uma das razões pelas quais o Bitcoin é comparado ao ouro é a sua escassez programada. Enquanto o ouro é um recurso natural limitado, cuja oferta depende da mineração, o Bitcoin tem um teto máximo de 21 milhões de unidades, definido em seu código. Esse teto faz com que o Bitcoin seja protegido contra a inflação, ao contrário das moedas tradicionais, que podem ser criadas sem limites pelos bancos centrais.
Essa característica traz um valor duradouro, parecido com o ouro, já que a oferta limitada ajuda a manter o poder de compra ao longo do tempo. Com o aumento da procura por Bitcoin, sua quantidade reduzida reforça seu papel como reserva de valor.
Outro aspecto que aproxima o Bitcoin do ouro é a durabilidade. Enquanto o ouro resiste à corrosão e pode ser guardado por séculos, o Bitcoin é um ativo digital protegido por criptografia avançada e armazenado na blockchain — um livro-razão imutável e descentralizado.
Além disso, o Bitcoin é mais fácil de transportar do que o ouro. Mover ouro físico envolve custos e segurança, tornando o transporte complicado, principalmente em transações internacionais. Por outro lado, o Bitcoin pode ser enviado digitalmente para qualquer parte do mundo em minutos, com taxas baixas e sem intermediários. Essa vantagem tecnológica torna o Bitcoin mais eficaz para um mundo globalizado e digital.
A segurança é outra característica que o Bitcoin e o ouro têm em comum. O ouro é difícil de falsificar, fazendo dele uma reserva de valor confiável. Da mesma forma, o Bitcoin usa protocolos de criptografia que asseguram transações seguras e protegidas contra fraudes.
Além disso, todas as transações feitas com Bitcoin são registradas na blockchain, fornecendo um nível de transparência que o ouro físico não oferece. Qualquer pessoa pode revisar as transações na rede, aumentando a confiança e a rastreabilidade.
EconômicaHistoricamente, o ouro tem sido utilizado como proteção contra a inflação e crises econômicas. Durante momentos de instabilidade, os investidores buscam o ouro como uma maneira de preservar seu patrimônio. O Bitcoin, por sua vez, está surgindo como uma alternativa digital com o mesmo propósito.
Em países com alta inflação ou instabilidade política, o Bitcoin tem sido usado como uma proteção contra a desvalorização das moedas locais. Sua natureza descentralizada impede que governos confisquem ou controlem diretamente o ativo, garantindo maior liberdade financeira para os usuários.
Apesar de suas semelhanças com o ouro, o Bitcoin ainda enfrenta desafios. Sua volatilidade é muito maior, o que pode causar incertezas a curto prazo. No entanto, muitos especialistas afirmam que essa volatilidade é uma característica comum em ativos novos e tende a diminuir com o tempo, à medida que a aceitação cresce e o mercado se desenvolve.
Outro desafio é a regulamentação. Enquanto o ouro já é reconhecido globalmente como um ativo financeiro, o Bitcoin ainda enfrenta resistência de governos e instituições financeiras, que procuram formas de controlá-lo e regulá-lo.
Resumindo, o Bitcoin, muitas vezes chamado de "ouro digital", oferece uma nova forma de valor que combina as melhores características do ouro com a eficiência e a inovação da tecnologia digital. Sua escassez planejada, segurança criptográfica, portabilidade e resistência à censura fazem dele uma alternativa viável para preservar riqueza e realizar transações no mundo moderno.
Mesmo com muita volatilidade, o Bitcoin está se firmando como uma reserva de valor e como um ativo de proteção contra crises econômicas. Assim, ele representa não apenas uma evolução do sistema financeiro, mas também um símbolo da mudança para uma economia digital descentralizada e global.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Um algoritmo imbecil da evolução
Suponha que você queira escrever a palavra BANANA partindo de OOOOOO e usando só alterações aleatórias das letras. As alterações se dão por meio da multiplicação da palavra original em várias outras, cada uma com uma mudança diferente.
No primeiro período, surgem BOOOOO e OOOOZO. E então o ambiente decide que todas as palavras que não começam com um B estão eliminadas. Sobra apenas BOOOOO e o algoritmo continua.
É fácil explicar conceber a evolução das espécies acontecendo dessa maneira, se você controlar sempre a parte em que o ambiente decide quem vai sobrar.
Porém, há apenas duas opções:
- Se o ambiente decidir as coisas de maneira aleatória, a chance de você chegar na palavra correta usando esse método é tão pequena que pode ser considerada nula.
- Se o ambiente decidir as coisas de maneira pensada, caímos no //design inteligente//.
Acredito que isso seja uma enunciação decente do argumento "no free lunch" aplicado à crítica do darwinismo por William Dembski.
A resposta darwinista consiste em dizer que não existe essa BANANA como objetivo final. Que as palavras podem ir se alterando aleatoriamente, e o que sobrar sobrou, não podemos dizer que um objetivo foi atingido ou deixou de sê-lo. E aí os defensores do design inteligente dirão que o resultado ao qual chegamos não pode ter sido fruto de um processo aleatório. BANANA é qualitativamente diferente de AYZOSO, e aí há várias maneiras de "provar" que sim usando modelos matemáticos e tal.
Fico com a impressão, porém, de que essa coisa só pode ser resolvida como sim ou não mediante uma discussão das premissas, e chega um ponto em que não há mais provas matemáticas possíveis, apenas subjetividade.
Daí eu me lembro da minha humilde solução ao problema do cão que aperta as teclas aleatoriamente de um teclado e escreve as obras completas de Shakespeare: mesmo que ele o faça, nada daquilo terá sentido sem uma inteligência de tipo humano ali para lê-las e perceber que não se trata de uma bagunça, mas sim de um texto com sentido para ele. O milagre se dá não no momento em que o cão tropeça no teclado, mas no momento em que o homem olha para a tela.
Se o algoritmo da evolução chegou à palavra BANANA ou UXJHTR não faz diferença pra ela, mas faz diferença para nós, que temos uma inteligência humana, e estamos observando aquilo. O homem também pensaria que há //algo// por trás daquele evento do cão que digita as obras de Shakespeare, e como seria possível alguém em sã consciência pensar que não?
-
 @ fbf0e434:e1be6a39
2025-06-05 14:06:35
@ fbf0e434:e1be6a39
2025-06-05 14:06:35Hackathon 概要
Verifiable AI Hackathon 由 cheqd 主办,聚焦通过安全、可验证的道德系统构建可信 AI 生态。活动吸引 278 名开发者参与,共提交 21 个项目,致力于推动可信 AI 环境的建立。开发者针对 AI 技术滥用问题(如 deepfake 欺诈)及透明化、道德化 AI 系统构建挑战提出解决方案。
参与者围绕自主经济、AI 验证、安全数据应用等主题,借助 cheqd 的去中心化标识符(DID)与可验证凭证(VC)技术展开探索。核心成果包括内容认证创新方案,以及通过验证数据集防范虚假信息的应用实践。
本次黑客松凸显了 AI 解决方案需以透明度和用户权益为核心的发展方向,旨在通过区块链工具为开发者赋能,夯实安全可靠的 AI 应用基础。这一举措致力于将数字身份与 AI 的交互模式,升级为兼顾可持续性与隐私保护的新型范式。
Hackathon 获奖者
AI Agents 奖项获奖者
- Kith: 这个去中心化系统利用加密的可验证凭证,通过去中心化标识符(DIDs)确保 AI 代理的隐私、认证和可信度。
- Identone: 该项目通过在电话交谈中验证身份来保障人与AI语音代理之间的互动可信度。
- SNAILS.: 利用去中心化数字身份来验证内容的机器人,从而增强 AI 环境中的信任。
其他奖项获奖者
- CheqDeep: 利用区块链技术认证媒体内容,通过 DID 链接资源验证人类来源和真实性。
- Trusty Bytes: 为 AI 代理提供一个获取经过验证数据的市场,使用基于区块链的验证来确保可信交易。
- crdbl: 一个平台,通过可验证凭证、去中心化身份、加密签名和AI验证来提升在线可信度。
构建一个整合私人用户数据的Agent奖项获奖者
- Viskify: 一个AI辅助手的平台,用于人才验证,利用可验证凭证和确定性去中心化标识符,并与 Stripe 和 Verida 集成以进行账单和私人数据管理。
有关所有项目的更多信息,请访问 The Verifiable AI Hackathon。
关于主办方
cheqd
cheqd 是区块链行业的重要参与者,专注于数字身份解决方案。该组织以其在建立支持安全和注重隐私数据管理的去中心化身份基础设施中所扮演的角色而闻名。通过利用最前沿的区块链技术,cheqd 在身份生态系统的标准开发中发挥了关键作用。其努力包括建立战略合作伙伴关系,以创建可互操作的身份服务。秉承加强数字信任框架的承诺,cheqd 继续通过先进且有效的身份管理解决方案来赋能个人和组织。
-
 @ 06639a38:655f8f71
2025-06-02 18:23:34
@ 06639a38:655f8f71
2025-06-02 18:23:34You might notice the styling of this site has changed. That's because I've made a custom Drupal theme using TailwindCSS and daisyUI. For these CSS frameworks / components I've also seperate Drupal theme everyone could use:
https://www.drupal.org/project/tailwind_css
https://www.drupal.org/project/daisy_uiWhat else?
- Wrote my third OpenSats progress report, read it here
- Added Nostr-PHP RelayListMetadata class (NIP-65) and tests, see PR
- Added Nostr-PHP PersistentConnection class and tests, see PR
-
 @ da8b7de1:c0164aee
2025-06-02 16:24:06
@ da8b7de1:c0164aee
2025-06-02 16:24:06Amerikai nukleáris végrehajtási rendeletek és szakpolitikai fejlemények
2025.05.23-án az amerikai kormány négy jelentős végrehajtási rendeletet adott ki, amelyek célja egy „nukleáris reneszánsz” felgyorsítása a következő 25 évben. Ezek a rendeletek egy, az egész kormányzatra kiterjedő tervet határoznak meg a 400 GW nukleáris kapacitás elérésére 2050-ig, lefedve az ipar minden területét: engedélyezés, üzemanyagciklus, reaktortechnológia, ellátási lánc, munkaerő, hulladékkezelés, finanszírozás és nemzetközi megállapodások. Azonnali intézkedések között szerepel a biztonságos hazai üzemanyag-ellátás megteremtése, szabályozási reformok, a reaktor-telepítések felgyorsítása, valamint pénzügyi és diplomáciai eszközök alkalmazása az amerikai nukleáris technológia belföldi és nemzetközi előmozdítására. A rendeletek gyorsított szabályozási eljárásokat írnak elő – például az NRC-nek (Nuclear Regulatory Commission) 18 hónapon belül kell elbírálnia az új reaktorokra vonatkozó kérelmeket –, valamint kibővített szerepet adnak az Energiaügyi és Védelmi Minisztériumoknak az engedélyezésben és telepítésben, beleértve a szövetségi földeken való elhelyezést is.
Az NRC jóváhagyta a NuScale kis moduláris reaktor (SMR) tervét
Az amerikai NRC jóváhagyta a NuScale Power 462 MW kapacitású kis moduláris reaktor (SMR) erőművének tervét, ami jelentős mérföldkő az új típusú nukleáris technológiák bevezetésében. Ez az engedélyezés a tervezettnél korábban történt, így a NuScale az egyetlen SMR, amely NRC-tervjóváhagyással rendelkezik, és technológiája hivatkozási alap lehet a jövőbeli építési és üzemeltetési engedélykérelmekben. A tervet kifejezetten nagy adatközpontok és ipari ügyfelek számára fejlesztették, a gyártási kapacitás már elérhető a dél-koreai Doosan vállalatnál. A NuScale várhatóan 2025 végéig szerzi meg első amerikai ügyfelét, és az első erőmű akár 2030-ra üzembe léphet, ha sikerül gyorsan szerződést kötni. Az NRC jóváhagyása szélesebb körű lendületet ad az amerikai fejlett nukleáris iparnak, beleértve a közelmúltbeli végrehajtási rendeleteket is, amelyek célja a reaktor-telepítések bővítése és a hazai ellátási láncok megerősítése.
Amerikai uránellátás és piaci helyzet
Az amerikai uránszektor kritikus ponthoz érkezett, kétpárti politikai támogatással és az adatközpontok, valamint az alapvető villamosenergia-igények növekvő keresletével. Az iparági vezetők egy közelgő kínálati hiányra figyelmeztetnek, mivel a magas minőségű készletek kimerülnek, és az új termelés beindítása nehézségekbe ütközik. Az új termelés ösztönző ára jelenleg 100 dollár felett van fontonként, ami meghaladja a jelenlegi spot árakat, így a már működő termelők előnyben vannak. A legutóbbi végrehajtási rendeletek és a Section 232 vizsgálatok megerősítik a kormány elkötelezettségét a hazai urántermelés és az ellátási lánc biztonsága mellett. Az orosz urán tilalom, amely 2028-ban lép teljesen életbe, tovább szűkíti a nyugati ellátást, a mentességek várhatóan a geopolitikai feszültségek miatt hamarabb megszűnnek. Kína gyors nukleáris fejlesztése tovább növeli a keresletet, ami kettéosztott globális uránpiacot eredményez.
Az amerikai urándúsítási kapacitás bővítése
Az Urenco USA megkezdte a termelést legújabb gázcentrifuga-egységében a New Mexico-i National Enrichment Facility-ben, ezzel mintegy 15%-kal bővítve a hazai dúsítási kapacitást. Ez a bővítés célja, hogy csökkentse az orosz ellátástól való függőséget, és támogassa az amerikai nukleáris üzemanyag-ellátási láncot. Az Urenco USA, az ország egyetlen kereskedelmi dúsított urán előállítója, jelenleg az amerikai atomerőművek szükségletének mintegy egyharmadát fedezi, és további bővítést fontolgat a piaci kereslet függvényében.
Nemzetközi nukleáris energetikai fejlemények
Globális nukleáris reaktor-építési hullám van kibontakozóban, élen az Egyesült Királysággal, Törökországgal, Lengyelországgal, valamint ázsiai és afrikai országokkal. Több mint 30 ország vállalta, hogy 2050-ig megháromszorozza a globális nukleáris kapacitást a nettó zéró kibocsátás és az energiabiztonság érdekében. Az atomtechnológia exportja továbbra is jelentős bevételi forrás Oroszország számára, miközben az Egyesült Államok jogalkotási és szakpolitikai lépéseket tesz a nukleáris export és együttműködés vezető szerepének biztosítására; a Szenátus Külügyi Bizottsága hamarosan tárgyalja azt a törvényjavaslatot, amely az amerikai nukleáris exportot hivatott erősíteni, hogy Kínát és Oroszországot megelőzze a globális piacon.
Ipari partnerségek és katonai alkalmazások
Az amerikai Védelmi Minisztérium nyolc céget választott ki mikroreaktor-technológiák fejlesztésére katonai létesítmények számára, azzal a céllal, hogy decentralizált, skálázható mikroreaktor-rendszereket hozzanak létre kritikus energiaigények kielégítésére. Ez a kezdeményezés a kereskedelmi mikroreaktor-fejlesztést és a kapcsolódó ellátási láncok megerősítését is ösztönzi, az NRC szabályozási útvonalainak kihasználásával.
Érintetti bevonás és konferenciák
A Nemzetközi Atomenergia Ügynökség (IAEA) nemrégiben zárta első, a nukleáris programok érintetti bevonásáról szóló nemzetközi konferenciáját Bécsben, amely hangsúlyozta a nyilvánosság és az érintettek bevonásának fontosságát a nukleáris energiafejlesztés minden szakaszában, hogy bizalmat építsenek és megalapozott döntéshozatalt támogassanak.
Források:
- world-nuclear-news.org
- nucnet.org
- iaea.org
- utilitydive.com
- observer.co.uk
- ans.org
-
 @ cae03c48:2a7d6671
2025-06-05 15:01:14
@ cae03c48:2a7d6671
2025-06-05 15:01:14Bitcoin Magazine

Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury StrategyToday, H100 Group AB announced it has entered a SEK 21 million convertible loan from an investment agreement with Adam Back, with the option to expand his investment to SEK 277 million through a five-tranche convertible loan deal. The proceeds will be used to buy Bitcoin in alignment with H100 Group’s long-term Bitcoin treasury strategy.
H100 Group AB (Ticker: H100) secures a SEK 21M ($2.1M) commitment from @adam3us , with rights to invest an additional SEK 128M ($12.8M) in tranches—bringing the total contemplated raise to SEK 277M (~$27.7M). pic.twitter.com/c0HgMSRxut
— H100 (@H100Group) June 3, 2025
Under the agreement, Back may invest up to SEK 128 million across four additional tranches, with guaranteed participation of at least 50%. Each tranche is twice his committed amount, demonstrating his support for H100’s long-term growth.
The press release said, “Adam Back may request the Second Tranche within 90 days from signing of the Initial Tranche, the Third Tranche within 90 days from signing of the Second Tranche, the Fourth Tranche within 90 days from signing of the Third Tranche and the Fifth Tranche within ninety 90 days from signing of the Fourth Tranche. In the event Adam Back does not request a Future Tranche within the deadline, the right to request subsequent Future Tranches lapses.”
The convertible loans have no interest and have a five year maturity. At any time, Back may convert the loans into shares of the Company. Conversion prices are fixed per tranche: SEK 1.75 per share for the initial tranche, rising to SEK 5.00 by the fifth tranche. H100 retains the right to force conversion if the stock price exceeds the conversion rate by 33% over a 20 day period. Full conversion of the initial tranche would result in 12 million new shares and a 9.3% dilution.
“Upon request of a tranche Adam Back is obliged to invest in the relevant Tranche with SEK 15,750,000 in the second tranche, SEK 23,625,000 in the third tranche, SEK 35,437,500 in the fourth tranche, and SEK 53,156,250 in the fifth tranche,” stated the press release. “The contemplated size for each tranche is twice the entitled amount of Adam Back.”
Blockstream has “been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then,” said Adam Back at the 2025 Bitcoin Conference. “I think the way to look at the treasury companies is that Bitcoin is effectively the hurdle rate; it’s very hard to outperform bitcoin. Most people that have invested in things since bitcoin has been around have thought, ‘oh, I should have put that in bitcoin and not in the other thing.”
This post Adam Back Invests SEK 21 Million to H100 Group Bitcoin Treasury Strategy first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 812cff5a:5c40aeeb
2025-06-05 12:55:10
@ 812cff5a:5c40aeeb
2025-06-05 12:55:10Chorus: تجربة في البرمجة الانسداحية
كيفية بناء تطبيق Nostr بسرعة البرق باستخدام الذكاء الاصطناعي.
في 26 مايو، تم إطلاق تطبيق Chorus في منتدى أوسلو للحرية. صُمم هذا التطبيق للناشطين والمعارضين ومنظمي المجتمع، ويتميز بمجموعات تشبه تلك الموجودة في فيسبوك مع محفظة eCash مدمجة لجمع التبرعات.
Chorus مبني على Nostr، وهو بروتوكول لامركزي ومفتوح مصمم ليكون مقاومًا للرقابة. يمكن لأي شخص في العالم إنشاء حساب Nostr والنشر إلى خوادم Nostr، أو حتى بناء تطبيق Nostr خاص به — ولا يمكن لأحد إيقافه. هذا ما يجعل Nostr المكان المثالي للمقاتلين من أجل الحرية، الذين غالبًا ما يواجهون الرقابة من الحكومات الاستبدادية أو الشركات التي تتحكم في المنصات الاجتماعية الرئيسية.
يمكن للمستخدمين إنشاء حساب Chorus (أو تسجيل الدخول باستخدام حساب Nostr موجود) في ثوانٍ والبدء فورًا في استلام eCash، وإنشاء مجموعات، ومشاركة المحتوى. يتضمن التطبيق ميزات قوية لإدارة المجتمع، بحيث يمكن للمجموعات اختيار أنواع المحتوى التي تسمح بها وفقًا لشروطها الخاصة. يمكن للمستخدمين إرسال eCash على الفور إلى المجموعات التي يرغبون في دعمها، مما يوفر أداة لجمع التبرعات عبر الحدود لا يمكن لأي حكومة إيقافها.
قبل عام فقط، ربما استغرق بناء النسخة التي تم إطلاقها الأسبوع الماضي من Chorus أسابيع. ولكن بفضل أدوات الذكاء الاصطناعي الحالية، قمنا بذلك في خمسة أيام فقط.
⸻
كيفية القيام بذلك: بناء تطبيق في أيام باستخدام وكلاء الذكاء الاصطناعي
الخطوة 1: تجميع الفريق
تم بناء Chorus بواسطة And Other Stuff، وهي مجموعة جديدة مكرسة لتعزيز Nostr في خمسة مجالات رئيسية: تجربة المستخدم والتسجيل، المجتمعات، الاتصالات الخاصة، التجارة، والذكاء الاصطناعي. شمل فريق هذا المشروع: • Calle، منشئ Cashu (eCash) • JeffG، منشئ White Noise (الاتصالات الخاصة) • Rabble و Liz Swiegart من Nos (تجربة المستخدم والتسجيل) • Alex Gleason و MK Fain، منشئو Soapbox (المجتمعات) • و Jack Dorsey (مستشار)
الخطوة 2: البدء بقالب قوي
عند البرمجة بالانسداح، السياق هو الملك. إذا بدأت بمجلد فارغ وطلبت من وكيل ذكاء اصطناعي “بناء تطبيق مجموعات Nostr”، فلا يزال أمامك الكثير من العمل للحصول على شيء وظيفي حتى بشكل بسيط. من المحتمل أن تكون تنفيذات Nostr محاكاة، لا تتصل بخوادم حقيقية، أو تم تنفيذها بشكل غير صحيح. قد تكون أنواع الأحداث خاطئة، وقد لا يتم تحميل واجهة المستخدم، وحظًا سعيدًا في محاولة معرفة الخطوة التالية لإصلاح الفوضى.
هذا لأن الذكاء الاصطناعي يفتقر إلى بعض السياقات الرئيسية للبدء: • وثائق صديقة للذكاء الاصطناعي حول بروتوكول Nostr • أمثلة عالية الجودة على تنفيذ Nostr • أساسيات حول تكديس التكنولوجيا المفضل • سياق حول كيفية بناء المشروع وتشغيله وتصحيحه
الحل هو توفير المزيد من السياق، وسيكون العديد من مبرمجي الانسداح المخضرمين على دراية بالصراع في محاولة جعل الوكيل يقرأ روابط مختلفة للوثائق ويتبع 500 كلمة من السياق المصاغ بعناية في مطالبتهم الافتتاحية. ومع ذلك، غالبًا ما يربك هذا الوكلاء الذين يعملون بشكل أفضل مع مطالبات بسيطة. الحل لهذه المشكلة هو Stacks.
Stacks: بدء البرمجة الانسداحية بسرعة
Stacks تحل مشكلة نقص السياق الأولي من خلال إنشاء قوالب جاهزة مصممة خصيصًا لاستخدام وكلاء الذكاء الاصطناعي. يمكن استخدام “stack” لبناء أي نوع من المشاريع بأي لغة برمجة مع أي هدف نهائي في الاعتبار. بالنسبة لـ Chorus، استخدمنا MKStack، وهو قالب مصمم خصيصًا لبناء تطبيقات Nostr.
يتميز MKStack بعدة حلول للمشاكل الشائعة في الذكاء الاصطناعي: • Nostrbook MCP للاستعلام عن وثائق Nostr • مكونات بداية لميزات Nostr الشائعة مثل تسجيل الدخول • دعم Blossom لتحميل الوسائط • ملفات سياقية لتوجيه الوكيل خلال العقبات الشائعة وسير عمل التصحيح • نشر موقعك على الفور باستخدام Surge
النتيجة هي موقع جميل يعمل مباشرة مع Nostr في مطالبة واحدة:
“بناء تطبيق مجموعات على غرار فيسبوك على Nostr باستخدام NIP 72.”
كان هذا هو نتيجة تلك المطالبة الواحدة: http://groups72.surge.sh
الخطوة 3: إضافة الميزات باستخدام وكلاء الذكاء الاصطناعي
Stacks بدأت تطوير Chorus بسرعة. بعد ذلك، استخدمنا وكلاء الذكاء الاصطناعي لإضافة ميزات إضافية مثل: • محفظة eCash مدمجة • ميزات إدارة المجتمع • دعم الوسائط المتعددة
كل ذلك تم باستخدام مطالبات بسيطة وتوجيهات للذكاء الاصطناعي، مما سمح لنا ببناء تطبيق كامل الوظائف في أيام قليلة فقط.
⸻
ملاحظة:تم استخدام مصطلح برمجة الانسداحية بهدف الطرفة كترجمة لمصطلح Vibe coding تم كتابة هذه المقال من قبل المبدعة nostr: npub1jvnpg4c6ljadf5t6ry0w9q0rnm4mksde87kglkrc993z46c39axsgq89sc
-
 @ d5c440ce:04726d89
2025-06-05 06:19:49
@ d5c440ce:04726d89
2025-06-05 06:19:49Effektiv behandling af blodsprængninger kræver en professionel tilgang og de rette metoder. Hos Klinik Zenit tilbyder vi skånsomme og dokumenterede teknikker til at reducere synligheden af blodsprængninger i ansigt og på krop. Vores behandlinger tilpasses individuelt og udføres af erfarne specialister med fokus på sikkerhed og langvarige resultater. Få vejledning om hudpleje før og efter behandlingen for at opnå det bedste resultat. Kontakt Klinik Zenit for en professionel vurdering og behandlingsplan.
-
 @ e516ecb8:1be0b167
2025-06-02 15:22:40
@ e516ecb8:1be0b167
2025-06-02 15:22:40Bitcoin was born as a middle finger to the financial establishment. Its 2008 whitepaper, penned by the enigmatic Satoshi Nakamoto, promised a peer-to-peer (P2P) electronic cash system—a decentralized rebellion against state-controlled money, sparked in the ashes of the global financial crisis. It was a cypherpunk dream: a currency free from banks, governments, and middlemen. But somewhere along the way, Bitcoin lost its soul. What was meant to be a fluid, practical currency has morphed into a clunky, expensive digital vault—a gilded cage for your wealth. Let’s unpack why Bitcoin is broken, why its fixes are flimsy, and why its rebellious spirit is fading into a state-backed shadow of its former self.
The P2P Promise: Shattered by Sky-High Fees Bitcoin’s core idea was simple: send money directly to anyone, anywhere, without a bank skimming off the top. Fast forward to today, and that vision is in tatters. Imagine you’ve got $34 in Bitcoin to send to a friend. By the time it arrives, after transaction fees, they might get a measly $2. According to data from BitInfoCharts, the average Bitcoin transaction fee in early 2025 hovers around $20–$30, with spikes as high as $60 during network congestion. For context, that’s more than the cost of a Venmo transfer or even some international wire fees.
This isn’t a one-off issue. Wallets like Guarda, Exodus, or even hardware wallets like Ledger face the same problem: Bitcoin’s base layer (Layer 1) is so congested that fees make small transactions absurdly impractical. Want to buy a $5 coffee with Bitcoin? You’d lose more in fees than the coffee’s worth. This isn’t P2P money—it’s confiscatory, inefficient, and anything but user-friendly.
Lightning Network: A Band-Aid on a Broken System Cue the Bitcoin maximalists: “But we have the Lightning Network!” Sure, Lightning was introduced as a second-layer solution to scale Bitcoin for smaller, faster transactions. It’s a network of off-chain payment channels designed to handle microtransactions with lower fees. Sounds great, right? Except it’s a patchwork fix that betrays Bitcoin’s original vision.
First, Lightning wasn’t part of Satoshi’s plan—it’s an afterthought, a kludge to address the base layer’s limitations. Second, it’s not universally adopted. According to 1ML, as of early 2025, only about 15% of Bitcoin wallets natively support Lightning. Major wallets like Coinbase Wallet and Trust Wallet still require workarounds or third-party integrations. Why? Because implementing Lightning is complex, and for most users, it involves trusting third-party nodes or custodians to route payments. So much for “be your own bank.”
Worse, running your own Lightning node requires technical know-how—think Linux commands, channel management, and constant monitoring. A 2024 survey by Bitcoin Magazine found that only 8% of Bitcoin users run their own nodes, Lightning or otherwise. For the average person, Lightning isn’t a solution; it’s a hurdle. And if you’re relying on a third party, you’re back to square one: trusting someone else with your money.
Take Adrián Bernabeu, author of Bitcoinismo, who preaches the gospel of self-custody while simultaneously hyping Lightning for micropayments. It’s a contradiction. You can’t champion “not your keys, not your crypto” while pushing a system that often requires third-party intermediaries for practical use. It’s like telling someone to live off-grid but handing them a generator that only works with a utility company’s permission.
A Gilded Cage: Bitcoin as a Store of Value So, if Bitcoin isn’t practical for payments, what’s it good for? The narrative has shifted: Bitcoin is now a “store of value,” a digital gold. Its price has soared—hitting $80,000 in late 2024, per CoinGecko—and its fixed supply of 21 million coins makes it a hedge against inflation. But this shift isn’t just about market dynamics; it’s a consequence of Bitcoin’s own flaws.
Moving Bitcoin is so expensive that it’s often smarter to hodl than to spend. Your wallet becomes an orange-tinted cage, trapping your wealth in a system where transferring value eats away at your holdings. Sure, you could wait for fees to drop, but that’s another nail in the P2P coffin. Real money doesn’t make you wait for a discount to use it. Imagine telling someone, “Hold off on buying groceries until the dollar’s transaction fees go down.” It’s absurd.
OP_RETURN and the Spam Problem: A Network Clogged with Junk Bitcoin’s blockchain isn’t just struggling with fees; it’s also drowning in digital clutter. The OP_RETURN function, meant for embedding small amounts of data (like metadata for smart contracts), has become a dumping ground for everything from NFT inscriptions to random spam. In 2023, Glassnode reported that OP_RETURN transactions accounted for nearly 20% of Bitcoin’s block space during peak periods, crowding out legitimate transactions and driving up fees.
Proposed fixes from Bitcoin Core and Knots—like limiting OP_RETURN data size or tweaking mempool rules—are more Band-Aids. They don’t address the root issue: Bitcoin’s block size limit. Capped at 1MB (or roughly 4MB with SegWit), Bitcoin can only process about 3–7 transactions per second, compared to Visa’s 24,000. Increasing the block size could ease congestion and lower fees, but Bitcoin Core developers have resisted this for years, citing concerns about centralization.
Here’s the kicker: Bitcoin Cash (BCH), a 2017 fork of Bitcoin, raised its block size to 32MB and processes transactions at a fraction of the cost. BCH’s average fee in 2025 is under $0.01, per BitInfoCharts. Bitcoin maximalists dismiss BCH as a failed experiment, but it’s hard to argue with the numbers. A larger block size reduces spam’s impact because legitimate transactions dominate. Admitting this, though, would mean conceding defeat in a years-long ideological battle. And Bitcoiners hate losing.
From Rebellion to Regulatory Lapdog Bitcoin’s cypherpunk roots are fading fast. What started as a revolt against state control is cozying up to governments. El Salvador made Bitcoin legal tender in 2021, but its state-backed Chivo wallet (built on Lightning) is riddled with bugs and usability issues, according to a 2024 Reuters report. Meanwhile, Bitcoin Core developers have lobbied for institutional adoption, with figures like Michael Saylor advocating for Bitcoin as a strategic reserve asset for governments and corporations.
This is a far cry from Satoshi’s vision. A 2023 post on X revealed that Core developers met with U.S. regulators to discuss Bitcoin’s role in national reserves—a move that reeks of compromise. The same system Bitcoin was meant to disrupt is now being courted. If governments start subsidizing Bitcoin mining to protect their reserves, as some speculate, the irony will be complete: a decentralized dream bankrolled by fiat.
The Looming Threats: Quantum and Mining Woes Bitcoin’s problems don’t end with fees and politics. Quantum computing looms on the horizon. A 2024 MIT Technology Review article estimated that quantum computers capable of breaking Bitcoin’s ECDSA cryptography could emerge by 2030. This threatens “Satoshi-era” wallets—those holding early, unspent coins—potentially undermining trust in the entire blockchain.
Then there’s mining. Bitcoin’s proof-of-work system is energy-intensive, with global mining consuming 150 TWh annually, per the Cambridge Bitcoin Electricity Consumption Index. As block rewards halve (the next halving is in 2028), miners will rely more on transaction fees. Higher fees mean even less practicality for P2P payments, locking Bitcoin further into its “digital gold” trap. If states step in to subsidize mining, as some X posts have speculated, Bitcoin’s anti-establishment ethos will be dead in the water.
The Final Irony: Paying for Freedom with Fiat Bitcoin promised to replace fiat currency, but its flaws are pushing it toward a bizarre dependency on the very system it sought to destroy. If governments subsidize mining or adopt Bitcoin as a reserve asset, we’ll be left with a bitter irony: a supposedly revolutionary asset propped up by fiat. The cypherpunk dream will have come full circle, not as a triumph, but as a compromise.
So, is Bitcoin broken? Yes. It’s a victim of its own success—too valuable to spend, too clunky to use, and too compromised to stay true to its roots. The question isn’t whether Bitcoin can be fixed; it’s whether its community has the courage to admit what’s wrong. Until then, your Bitcoin wallet remains a shiny, orange prison—a relic of a rebellion that forgot how to fight.
-
 @ 527337d5:93e9525e
2025-06-05 03:09:02
@ 527337d5:93e9525e
2025-06-05 03:09:02The Algorithmic Pursuit of Connection: A Five-Book Journey into the Self
As a researcher, hitting my thirties and the winding down of a significant project prompted a crucial re-evaluation of life's latter half. While I'd successfully applied probabilistic control theory to one-on-one interactions, the complexities of group dynamics remained a persistent challenge. My recent dive into five diverse books on human relationships inadvertently became a profound journey of self-discovery, fundamentally reshaping my perspective on social connections.
Neil Strauss: A Mirror Reflecting the Self's Evolution
Neil Strauss's The Truth resonated deepest among my recent reads. The author's battle with sex addiction uncomfortably mirrored my own past struggles: the fragile self-esteem stemming from rejection, the hubris born of early successes, and the tendency to view women as mere objects of manipulation. It felt eerily prescient, a glimpse into a potential future.
Yet, I found myself arriving at Strauss's ultimate conclusion – the paramount importance of self-preparation and community – far sooner than he did. This acceleration wasn't accidental; it was the result of intense focus on individual experiences, meticulously replayed and analyzed in my mind. The book, therefore, served less as a revelation and more as a powerful validation of my own journey of introspection and root-cause analysis.
Quantifying Connection: The Promise and Limits of Mathematical Models
Hannah Fry's The Mathematics of Love offered a kindred spirit in its attempt to quantify human relationships. While I appreciate the mathematical lens, Fry's models primarily concern dyadic relationships (N=2), relying on relatively simple systems of two-variable ordinary differential equations. For me, these are akin to linear models, sufficient only up to a certain point. Beyond N=4, the dependencies become exponentially complex.
My own pursuit extends to understanding and optimizing group dynamics within complex systems. This involves multi-variable problems (N $\ge$ 3) and the application of network theory, a far more sophisticated approach. Human collectives, after all, are systems of nodes and edges, where information propagates in predictable ways. My focus is on deriving optimal behavioral controls within these intricate frameworks.
Conversely, Men Are from Mars, Women Are from Venus initially struck me as bordering on conspiracy theory. However, its latter half proved unexpectedly useful. Its clear enumeration of male and female desires, and its articulation of common points of conflict, presented a practical template for communication styles. In a systemic view, this serves as a rudimentary, yet functional, interface design for complex social interactions.
A Dispassionate Critique of Relationship Dogma
My drive for efficiency and systematic understanding led to a rather blunt assessment of certain relationship classics. The New Science of Adult Attachment felt disorganized and frustratingly anecdotal. Lacking a coherent theoretical framework, it burdened the reader with deciphering meaning from a jumble of examples. Its inefficiency was, frankly, its most irksome flaw.
Similarly, Dale Carnegie's How to Win Friends and Influence People struck me as closer to pseudoscience than social science. Its plethora of specific anecdotes obscured any underlying principle. Given my deep engagement with social engineering – a discipline that systematically and practically analyzes human interaction – Carnegie's work appeared largely irrelevant and inefficient. From my perspective, which views humans as objective systems to be analyzed with mathematical rigor, such unstructured approaches hold little value.
The Unveiling of a Core Principle: Humans as Systems
This intensive reading period solidified my most crucial insight: humans, at their core, are systems. This understanding allows for a dispassionate, methodical approach to human collectives, mitigating unnecessary emotional friction.
This revelation has sharply refined my future learning trajectory. I'm now prioritizing foundational theories like graph theory and network theory over anecdotal accounts of human behavior. By mastering these theoretical underpinnings, I aim to precisely model complex human interactions as systems of nodes and edges, enabling the derivation of optimal behavioral controls within communities.
My choice of the term "target for capture" for individuals stems from a personal aversion to perceived equality in certain human interactions, a mechanism to avoid cognitive dissonance. This rational approach, I believe, is key to cultivating secure attachment styles – relationships demonstrably sustainable in the long term. My philosophy is to strategically approach the initial engagement, then transition to a stable, enduring connection. It's a calculated, dispassionate method for achieving desired relational outcomes.
Ultimately, this period of reading wasn't just about acquiring knowledge; it was a profound journey of self-discovery, clarifying my personal frameworks for navigating life's complexities and forging meaningful, yet strategically managed, connections.
-
 @ 31a4605e:cf043959
2025-06-05 12:49:36
@ 31a4605e:cf043959
2025-06-05 12:49:36O surgimento do Bitcoin trouxe uma nova visão para o conceito de dinheiro, desafiando o sistema financeiro convencional baseado em moedas fiduciárias. Enquanto as moedas fiduciárias, como o real, o dólar e o euro, são amplamente usadas e reconhecidas como métodos de troca, o Bitcoin representa uma inovação digital que propõe descentralização e autonomia financeira. Embora ambos desempenhem funções básicas como meio de troca e reserva de valor, suas diferenças principais estão na maneira como são emitidos, geridos e transacionados.
Uma das principais distinções entre o Bitcoin e as moedas fiduciárias é a maneira como são emitidos e administrados. As moedas fiduciárias são emitidas por bancos centrais, que têm o poder de regular sua quantidade em circulação. Esse modelo permite a aplicação de políticas monetárias, como o aumento da oferta de dinheiro para estimular a economia ou a diminuição para controlar a inflação. No entanto, essa capacidade também pode resultar na desvalorização da moeda, se for emitida em excesso.
O Bitcoin, por outro lado, tem um sistema de emissão totalmente descentralizado. Ele é criado por meio de um processo chamado mineração, no qual computadores resolvem problemas matemáticos complexos para validar transações na rede. Além disso, a oferta total de bitcoins é limitada a 21 milhões de unidades, tornando-o um ativo deflacionário, ou seja, sua escassez pode aumentar seu valor ao longo do tempo. Essa limitação contrasta fortemente com a natureza ilimitada da impressão de moedas fiduciárias.
Moedas fiduciárias são centralizadas, o que significa que sua emissão e controle são decididos por autoridades governamentais. Isso também implica que transações feitas com essas moedas passam por intermediários, como bancos, que podem aplicar taxas e limites, além de estarem sujeitos a regulamentações e auditorias.
O Bitcoin, por sua vez, é descentralizado. Ele opera em uma rede peer-to-peer, onde as transações são verificadas por participantes chamados mineradores e registradas em um livro público conhecido como blockchain. Essa descentralização elimina a necessidade de intermediários, tornando o Bitcoin mais resistente à censura e ao controle governamental. Isso também proporciona maior transparência, já que qualquer pessoa pode verificar as transações na rede.
Outra diferença importante está na maneira como as transações são feitas. Com moedas fiduciárias, as transações geralmente dependem de bancos ou sistemas de pagamento, que podem impor restrições de horários e taxas altas, especialmente para transferências internacionais.
O Bitcoin, por outro lado, permite transferências diretas entre pessoas, em qualquer lugar do mundo e a qualquer momento, sem a necessidade de intermediários. Isso torna o sistema mais acessível, especialmente para aqueles que não possuem contas bancárias ou vivem em países com sistemas financeiros restritivos. Além disso, as taxas de transação do Bitcoin podem ser menores do que as taxas cobradas por bancos tradicionais.
As moedas fiduciárias proporcionam segurança baseada em leis governamentais e no sistema bancário, mas os usuários precisam confiar nesses intermediários. O Bitcoin, em contrapartida, oferece um alto nível de segurança através de criptografia avançada. As carteiras digitais, que guardam bitcoins, são protegidas por chaves privadas, assegurando que somente o dono possa acessá-las.
No entanto, a privacidade funciona de maneira diferente. Transações em moedas fiduciárias normalmente estão ligadas à identidade do usuário, enquanto o Bitcoin oferece um certo nível de anonimato, já que os endereços das carteiras não requerem identificação pessoal. Ainda assim, todas as transações são públicas e registradas no blockchain, o que pode ser um ponto de monitoramento para autoridades.
O valor das moedas fiduciárias é sustentado pela confiança no governo que as emite e na economia do país. Por outro lado, o Bitcoin não é apoiado por nenhum governo ou ativo físico. Seu valor é definido pela oferta e demanda no mercado, fazendo com que seja altamente volátil. Embora essa volatilidade apresente um risco, também atrai pessoas que veem o Bitcoin como uma possibilidade de valorização a longo prazo.
Resumindo, o Bitcoin e as moedas fiduciárias diferem significativamente em sua estrutura, controle e funcionalidade. Enquanto as moedas fiduciárias são controladas por governos e dependem de intermediários, o Bitcoin oferece descentralização, transparência e liberdade financeira. Apesar de sua volatilidade e alguns desafios relacionados à regulamentação, o Bitcoin representa uma alternativa nova ao sistema financeiro tradicional.
Muito obrigado por teres lido o texto até aqui, espero que esteja tudo bem contigo e um abraço enorme do teu madeirense bitcoiner maximalista favorito. Viva a liberdade!
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Gerador de tabelas de todos contra todos
I don't remember exactly when I did this, but I think a friend wanted to do software that would give him money over the internet without having to work. He didn't know how to program. He mentioned this idea he had which was some kind of football championship manager solution, but I heard it like this: a website that generated a round-robin championship table for people to print.
It is actually not obvious to anyone how to do it, it requires an algorithm that people will not reach casually while thinking, and there was no website doing it in Portuguese at the time, so I made this and it worked and it had a couple hundred daily visitors, and it even generated money from Google Ads (not much)!
First it was a Python web app running on Heroku, then Heroku started charging or limiting the amount of free time I could have on their platform, so I migrated it to a static site that ran everything on the client. Since I didn't want to waste my Python code that actually generated the tables I used Brython to run Python on JavaScript, which was an interesting experience.
In hindsight I could have just taken one of the many
round-robinJavaScript libraries that exist on NPM, so eventually after a couple of more years I did that.I also removed Google Ads when Google decided it had so many requirements to send me the money it was impossible, and then the money started to vanished.
-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus