-
 @ 7460b7fd:4fc4e74b
2025-06-04 12:17:18
@ 7460b7fd:4fc4e74b
2025-06-04 12:17:18Tron(TRX)区块链架构与性能综合分析
Tron 的三层架构与虚拟机设计
*Tron 区块链采用三层架构:存储层、核心层、应用层developers.tron.networkcointelegraph.com。*存储层包含区块存储和状态存储,并引入图数据库理念以满足多样化数据存储需求developers.tron.network。核心层实现共识(基于改进的 委托权益证明 DPoS)、账户管理和智能合约等模块developers.tron.network。Tron 虚拟机(TVM)位于核心层,用于执行智能合约代码。Tron 最初指定 Java 语言 用于智能合约开发,并规划支持其它高级语言developers.tron.network。这一设计取舍体现了团队对 Java 生态和性能的偏好:Tron **节点实现(java-tron)**采用 Java 开发,使虚拟机与链上逻辑高度兼容 Java 环境。此外,TVM 与 Ethereum EVM 高度兼容,方便以太坊DApp迁移,但在细节上有所不同medium.commedium.com。例如,TVM 使用能量(Energy)而非 Gas,
energyPrice为全网固定参数(目前210 SUN,即0.00021 TRX)medium.com;大多数指令的能耗与以太坊相同,但部分操作成本更低(如合约存储读取SLOAD等)medium.com。Tron 地址体系也不同:通过CREATE2创建合约时使用0x41前缀(Tron 地址Hex前缀),确保与以太坊地址格式区别medium.com。总的来说,Tron 架构在继承主流区块链设计的基础上,用 Java 实现了一套高性能的三层架构,为 DApp 提供了良好的开发和运行环境developers.tron.networkcointelegraph.com。吞吐性能与资源模型:带宽与能量机制
Tron 在性能上追求高吞吐和低延迟。共识方面,Tron 采用 **27个超级代表(SR)**轮流产块的机制,每隔3秒出块reflexivityresearch.com。得益于DPoS和小规模节点,Tron 单链理论TPS可达约2,000~2,500cointelegraph.comchainspect.app。实际网络中Tron尚未达到饱和:截至2025年中旬,每日交易量稳定在 800万笔以上(峰值逾1000万),平均约 90~120 TPSbinance.combinance.com。相比之下,以太坊当前主网TPS约15笔(日均140万交易)cointelegraph.com。Tron链上尚无明显拥堵,表明其吞吐冗余较充足。
Tron 引入了独特的资源模型,将交易执行成本分解为“带宽点数”(Bandwidth)和“能量”(Energy)两类developers.tron.network。带宽代表交易数据的大小,每字节消耗1点带宽developers.tron.network;能量代表合约执行的算力和存储消耗,每执行一步EVM指令消耗相应能量developers.tron.network。Tron 每个账户每天有 5000点免费带宽 配额developers.tron.network用于普通转账;当免费额不足时,可以通过“冻结”TRX获取资源或直接消耗少量TRX燃烧获得developers.tron.networkdevelopers.tron.network。例如,一个约200字节的普通转账消耗200带宽点,如账户无冻结资源且免费额度用尽,则需烧毁约 每字节10 SUN(即0.00001 TRX)的费用developers.tron.network——换算下来一次转账成本仅约 0.001~0.01美元(远低于以太坊动辄数美元的Gas费)。对于智能合约交易,则既消耗带宽又消耗能量developers.tron.network。开发者或用户可冻结 TRX 获取能量,按其冻结占比分享全网每日约500亿能量的恢复额度developers.tron.networkdevelopers.tron.network。冻结的能量会随时间自动恢复(24小时恢复满)developers.tron.networkdevelopers.tron.network。如果调用合约时能量不足,系统会按当前能量价格从用户扣除等值 TRX 燃烧medium.com。
Tron 资源模型对用户和开发者影响显著:一般用户日常转账几乎免费(每天免费额度足够覆盖小额频度交易),即使进行 TRC20 代币(如 USDT)转账,只要账户持有一定冻结的 TRX,其能量和带宽消耗也可被抵扣为零成本cointelegraph.com。如果用户没有任何冻结资源,转账 USDT 约需消耗十余枚 TRXmedium.com;但实际约六成以上的能量消耗是通过用户预先冻结TRX来覆盖的medium.com。此外,Tron 允许智能合约开发者为调用者代付部分能量:开发者可设置自己承担例如90%的能量费用developers.tron.networkdevelopers.tron.network。这意味着在 Tron 上,DApp 开发者可以冻结足够TRX资源,使用户调用其合约时无需支付能量费(类似Gas代付),提升应用可用性developers.tron.networkdevelopers.tron.network。资源模型的另一便利是 资源委托:账户A可以为账户B冻结TRX来提供带宽或能量developers.tron.network。综合来看,Tron 的带宽/能量双资源机制避免了直接以代币计价的浮动手续费,为用户提供了**“零Gas”**的体验,同时激励TRX持有者参与质押获取资源alphanode.globalalphanode.global。这种设计在牛市高拥堵场景下依然能保持交易成本稳定,有利于大规模应用。Tron 官方统计显示,截至2024年底网络平均每笔交易费用低至 $0.000005 美元cointelegraph.com,几乎可以忽略不计。
Tron 与主流公链的架构和开发体验对比
Tron 的系统架构与开发体验在不同维度上可与 Ethereum、Solana、Avalanche、BNB Chain 等主流公链进行横向比较。下表总结了几项关键对比:
| 属性 | Tron (TRX) | Ethereum | Solana | Avalanche (C链) | BNB Chain (BSC) | | ------------- | ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ---------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | --------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------ | | 共识机制 & 节点 | DPoS (27个超级代表,其他为见证节点)reflexivityresearch.com;3秒出块 | PoS (质押验证人 50万+,随机出块);12秒出块,最终确认约612分钟 | PoH+PoS (领导者序列+验证人约2000)chainspect.app;0.4秒出块,终局约10-15秒 | Avalanche共识 (验证人上千);\~1-2秒出块,\~1秒终局chainspect.app | PoSA ( 权威证明,21活跃验证者);\~3秒出块,快速终局 (几秒内)chainspect.app | | 架构设计 | 三层架构(存储/核心/应用)cointelegraph.com;单链+侧链BTTC扩展 | 单层主链+即将通过分片\&Rollup扩展;EVM执行环境 | 单链高度并行运行时(Sealevel);账户模型并行合约执行 | 主网三链架构(X链UTXO/P链治理/C链EVM);支持子网扩展 | 类以太坊单链架构;EVM执行环境,依赖以太坊工具链 | | 智能合约平台 | TVM(Ethereum VM 兼容,有能量机制改进)medium.com;支持 Solidity 等 | EVM(广泛支持Solidity、Vyper等);强生态工具 | BPF虚拟机(Rust/C/C++开发,需重新编译);高性能但开发曲线较陡 | EVM (C链);Solidity 合约与以太坊兼容 | EVM;Solidity合约完全兼容以太坊,工具链共用 | | 平均实际TPS | \~90-150 TPS(2024-25年,日均交易数8百万+binance.comcoindesk.com);峰值 \~270 TPSchainspect.app | \~15 TPS(L1日均约140万笔交易)cointelegraph.com;需借助L2提升 | \~1000+ TPS(日均交易数数千万,包含投票交易)chainspect.app;曾峰值5000+ TPSbinance.com | 当前负载低,实际 \~7 TPSchainspect.app;高峰 \~120 TPSchainspect.app | \~200 TPS(日均交易约400万笔binance.com);高峰 \~1700 TPSchainspect.app | | 理论最大TPS | \~2,000-2,500 TPS(当前参数下区块容量)cointelegraph.comchainspect.app | \~15-30 TPS(不考虑Rollup;单区块Gas上限限制) | \~50,000+ TPS(官方理论值)chainspect.app;高度依赖硬件性能 | \~1,000+ TPS(C链Gas参数下)chainspect.app | \~2,200 TPS(现行Gas上限下估计值)chainspect.app | | 交易费用机制 | 带宽+能量模型:每日免费额度+质押获取资源,无需常付手续费developers.tron.networkdevelopers.tron.network;无资源时按固定价格烧TRX(≈$0.0001/笔) | Gas拍卖:用户以 ETH 支付Gas费,费率随网络拥堵浮动;矿工/质押者收益 | 固定低费:按计算单元收取极低SOL费用,无免费额度;拥堵时费率略上调 | Gas费:按EVM Gas计算,以AVAX支付,费用较低;支持动态调整 | Gas费:与以太坊类似但计价币种为BNB,手续费低廉且有上限 | | 开发体验 | Solidity 为主(与以太坊基本通用);TronWeb、TronIDE 等SDK工具developers.tron.networkdevelopers.tron.network;需理解资源模型区别 | Solidity/Vyper生态成熟,工具最完善(Truffle、Hardhat等);L2多样 | **Rust/ C++**为主,开发需适应新模型;Solana工具链(Anchor框架等)在改进 | Solidity为主(C链类似以太坊开发);另有Subnet可用Rust、Go自定义VM | Solidity为主,100%兼容以太坊工具(Remix、Hardhat等);开发门槛与以太一致 | | 主要应用与优势 | 稳定币传输(USDT占据全球约50%供应coindesk.comcoindesk.com);DeFi借贷(JustLend)等,但生态DApp相对稀少coinshares.com | 通用智能合约平台(DeFi、NFT蓬勃,生态最大);安全性与去中心化强 | 高性能DApp(链游、NFT市场等;近期增长快);曾遇网络中断挑战 | DeFi与资产发行(C链上有借贷DEX,也支持企业级子网);强调快速终局性 | 泛用智能合约(DeFi规模庞大,如PancakeSwap等);依托Binance生态,用户基数大 |
表:Tron 与 Ethereum、Solana、Avalanche、BNB Chain 的关键技术指标和体验比较。 上表可见,Tron 在性能和成本上具备明显优势:TPS远高于以太坊cointelegraph.com,达到Solana/Avalanche的次高水平;交易手续费几乎为零cointelegraph.com。Tron 通过牺牲一定去中心化程度(仅27个验证人)换取了高吞吐和快速确认(3秒出块,\~1分钟内区块不可逆)chainspect.app。相比之下,以太坊去中心化最强但性能有限;Solana走极致性能路线,TPS极高但因架构复杂曾多次宕机,开发语言Rust门槛也更高。Avalanche主网C链采用EVM,使开发体验类似以太坊,但通过创新共识实现1秒终局,高TPS潜力;不过Avalanche生态主要在子网探索,主链交易量目前不大。BNB Chain 与 Tron 类似,采用小规模验证者和EVM,在性能和费用上接近Tron,也广受用户欢迎(尤其DeFi应用)。然而 BNB Chain 手续费仍需消耗BNB(虽很便宜),而 Tron 的资源模型让新用户无币也能免费发交易,初次使用门槛更低alphanode.global。
开发者体验方面,Tron 对以太坊生态高度兼容。Solidity 智能合约几乎无需修改即可部署到 Tron 网络(TronVM对EVM指令的兼容medium.com确保了这一点)。开发工具有 TronWeb JS 框架、TronIDE 集成环境等供使用developers.tron.network。不过Tron社区的第三方工具和合约模板相对以太坊要少,一些以太坊常用开发库在Tron上可能需要调整。Solana 则完全是另一种开发范式(基于Rust的BPF合约),与EVM链差异大。Avalanche的C链因为本质就是EVM,所以以太坊开发者可无缝迁移合约;BNB Chain 亦然。总的来说,Tron 和 BSC 在开发上延续了以太坊的习惯,而Solana、Avalanche追求性能和新架构,开发曲线相对陡峭。Tron 相比BSC的一个不同点是资源模型,这要求开发者考虑带宽/能量的分配,但也提供了为用户代付资源的机制,适合需要降低用户使用门槛的DApp。值得注意的是,Tron 主网账户总数已超过 3亿(包括大量交易所托管地址)coindesk.com、日活跃地址逾 百万coindesk.com;尽管生态应用不算丰富,但庞大的用户基础主要来源于稳定币交易和基本金融应用,对开发者而言意味着可观的潜在用户群。
工程实现与稳定币优势:有限创新下的差异化
Tron 经常被评价为“技术创新有限”,因为其很多理念来源于前辈(如采用与EOS类似的DPoS共识,兼容EVM的合约机制等)coinshares.com。Tron 白皮书早期甚至曾被指出有抄袭他链文档的嫌疑。然而,Tron 在工程实现和优化上非常出色,打造出了一条高可用、高性能的主网,并在关键细分领域取得领先地位。首先,Tron 网络运行稳定,自2018年主网上线以来几乎没有发生严重宕机或安全事件。这一点相较于同样DPoS架构的 EOS 主网要稳健得多(EOS 主网上线后曾多次出现性能瓶颈和治理僵局),也好于近年曾遭遇停链的 Solana 等高TPS链。Tron 将区块时间精确到3秒且长期保持共识稳定,使得链上转账**“三秒到账”**成为标志性的用户体验优势。
更重要的是,Tron 聚焦于稳定币转账这一高频刚需场景,通过一系列工程手段降低用户成本、提升效率。例如,Tron 上 USDT 等稳定币的 TRC-20 合约转账被优化得近似免Gas:利用带宽每日免费额度和发行方资源冻结策略,大部分小额USDT转账用户无需支付任何TRXcointelegraph.com。据统计,Tron 上单笔 USDT 转账成本可低至 0.345 TRX(约合2美分)甚至为零medium.com。Tron 还允许代币发行方提供一定的“免费带宽”给代币持有人developers.tron.networkdevelopers.tron.network,这意味着像 Tether 这样的发行方可为TRC20-USDT交易承担资源费用,使用户体验真正达到免手续费。这种“稳定币交易免Gas”的设计在主流公链中独树一帜。
Tron 的另一工程优势是极快的确定性。虽然Tron每块3秒,但由于DPoS共识和固有的BFT特性,Tron 区块在数轮出块后即不可逆转。Tron Solidity节点仅同步不可逆区块,用于对接交易所等场景developers.tron.network。通常交易所对Tron充值只需等待 1分钟左右确认,远快于以太坊传统上要求的数分钟/数十个区块确认。chainspect.app的链速数据显示,Tron链上最终确定(finality)时间约 \~57秒,与EOS等DPoS链类似,明显快于以太坊(>6分钟)和比特币(一小时)chainspect.app。这使Tron成为稳定币跨平台流转的理想基础设施:用户可以在交易所之间快速划转USDT,几乎实时地完成资金移动,而手续费可以忽略不计。
尽管Tron本身没有提出全新的共识算法或智能合约范式,但这些工程上的打磨带来了切实的成果:截至2025年,Tron 网络上 USDT的流通量超过750亿美元,再度位居各链之首cointelegraph.comcointelegraph.com。约 50%以上的USDT供应原生发行在Tron上coindesk.comcoindesk.com(二号是以太坊,约47%,其余诸如Solana、Avalanche合计不到5%cointelegraph.com)。Tron 同时处理了全球稳定币交易价值的近29%coindesk.com,每日 USDT 转账额高达 200亿美元coindesk.com。这些数据说明,尽管Tron没有“炫目的”技术标签,但凭借务实的性能优化和对用户友好的成本结构,在稳定币这一杀手级应用上取得了其它公链无法比拟的领先coindesk.com。
Tron 的高性能也使其成为去中心化金融(DeFi)基础设施的有力支撑。Tron上最大的DeFi借贷协议 JustLend 锁定价值超过 60亿美元coinshares.com(主要是TRX和USDT的借贷),显示出稳定币低费率环境对资金沉淀的吸引力。Tron 于2022年还推出了去中心化美元稳定币 USDD,以丰富生态。不过USDD体量相对有限(约7亿市值)coinshares.com,Tron生态真正的支柱仍是 USDT 等主流稳定币的传输和兑换。正因为聚焦于稳定币的出色支持,Tron 获得了行业独特地位:CoinShares 报告称截至2024年末 Tron 上约44%的USDT供应,使其在稳定币基础设施方面一度超越以太坊coinshares.comcoinshares.com。
“BTC上涨+稳定币基础设施”叙事下的 Tron 竞争力与市场前景
当前环境下,Tron 在 USDT市场占有率高、交易成本极低 的条件下,展现出强大的竞争优势。这与行业宏观叙事“比特币上涨 + 稳定币基础设施受益”紧密相关。在加密市场进入上行周期时,比特币价格攀升往往伴随场外资金涌入,稳定币作为法币与加密世界的桥梁需求激增castleisland.vc。Tron 因为在稳定币传输领域的卓越表现,有望从这一趋势中获得超额收益(Alpha)。
首先,Bitcoin上涨带来的交易活跃增加,势必需要大量稳定币在交易所和用户间快速流转。Tron作为承载全球超过一半USDT流通的网络coindesk.comcoindesk.com,“水涨船高”,交易笔数和价值很可能进一步增长。从2024到2025年的数据已经印证了这一点:2024年末以来 Tron 日均交易量从约430万增加到840万以上,增长了95%binance.combinance.com。尤其是在2025年初,比特币触发的新一轮市场热度下,Tron 日均交易笔数持续保持在 800万+,并多次冲击单日千万笔的关口binance.combinance.com。这表明 Tron 网络能够大规模处理牛市涌现的交易需求,为稳定币的频繁进出提供了高吞吐保障。
其次,超低的费用使Tron在竞争中胜出。当市场繁荣时,以太坊等网络往往因拥堵导致Gas费飙升,而Tron凭借资源模型依然保持每笔几乎为0的费用cointelegraph.com。这一点对套利交易商、跨境转账用户等极为重要:他们可以放心地使用Tron在交易所和钱包间搬运资金,而不用担心手续费侵蚀利润。这种成本优势也使得Tron在新兴市场获得青睐。许多亚洲、非洲的用户通过Tron链转移美元稳定币用于支付和结算coinshares.comcoinshares.com。由此Tron已经形成网络效应:用户数量多、USDT储备大,新用户更愿意选择已被广泛接受的Tron作为稳定币链。2025年一季度,Tron链上USDT流通再增 70亿美元,新增用户钱包数增长了 4600万coindesk.comcoindesk.com。这种高速增长进一步巩固了Tron在稳定币领域的龙头地位。
从市场价值角度看,Tron 的基本面强劲却长期被低估的情况也引人关注。Tron手续费收入与市值比成为分析师讨论的焦点:截至2024年底,Tron每日协议收入约 $79万美元(主要来自能量费燃烧等)alphanode.globalalphanode.global。按Tron当时$190亿市值计算,其市盈率(P/E)显著低于同业。例如Solana市值虽只有Tron五分之一,但每日费用收入只有Tron的一半alphanode.global。这意味着 Tron 网络在实际利用率和价值捕获上表现突出,TRX 代币有潜在重估空间alphanode.global。部分研究指出Tron的手续费收入/市值比远高于以太坊、Solana等,暗示TRX被低估且具有“价值洼地”特征。
竞争层面,Tron 面临的挑战主要来自以太坊扩容和其他低费链的蚕食。一方面,以太坊主网的升级及其Rollup二层网络(如Arbitrum、Optimism等)在降低费用方面取得进展,某些USDT流通开始转移到以太坊的Layer 2。但即便如此,Tron凭借先发优势和广泛的交易所支持,短期内仍牢牢占据稳定币结算主渠道coinshares.com。2024年11月,以太坊曾短暂重新超过Tron的USDT供应占比,但很快又被Tron新的增发反超cointelegraph.comcointelegraph.com。这显示出Tether公司和市场对于Tron网络的信心和需求依然强劲。另一方面,BSC、Solana等亦尝试争夺稳定币市场份额,例如BSC上也运行着不少USDT。但截至2025年,BSC上的USDT流通量和活跃度远不及Tron(Tron每日稳定币活跃地址占全行业28%coindesk.comcoindesk.com)。Solana则更专注于自身DeFi和新资产发行,稳定币主要还是USDC为主,体量有限。
综合而言,Tron 在“BTC 上涨 + 稳定币基础设施需求”这一行业趋势下展现出了独特的竞争力。它以稳健高效的工程实现弥补了技术创新上的不足,围绕稳定币这一刚需场景打造出低成本、高速度、广覆盖的链上金融网络。在未来市场周期中,只要对稳定币的需求存在,Tron 作为底层清算层的地位就难以被撼动。对于TRX的价值表现,这意味着有潜在的Alpha:当交易量和用户数上升时,TRX作为资源质押和手续费燃烧的载体,其需求量和内在价值也水涨船高alphanode.globalalphanode.global。当然,Tron 也需继续拓展生态应用、改善西方市场的形象来巩固长期地位coinshares.comcoinshares.com。但就当前来看,Tron已经凭借“强工程+准入门槛低”的策略,在区块链基础设施版图中占据了一席重要之地。它在稳定币时代的成功经验,印证了区块链项目不仅可以靠颠覆性创新取胜,也可以通过持续优化用户体验和性能找到差异化赛道,实现后来居上。
参考资料:developers.tron.networkmedium.comcointelegraph.comcoindesk.comcoindesk.com等。
-
 @ b1ddb4d7:471244e7
2025-06-04 11:01:29
@ b1ddb4d7:471244e7
2025-06-04 11:01:29Bitcoin FilmFest (BFF25) returns to Warsaw for its third edition, blending independent cinema—from feature films and commercials to AI-driven experimental visuals—with education and entertainment.
Hundreds of attendees from around the world will gather for three days of screenings, discussions, workshops, and networking at the iconic Kinoteka Cinema (PKiN), the same venue that hosted the festival’s first two editions in March 2023 and April 2024.
This year’s festival, themed “Beyond the Frame,” introduces new dimensions to its program, including an extra day on May 22 to celebrate Bitcoin Pizza Day, the first real-world bitcoin transaction, with what promises to be one of Europe’s largest commemorations of this milestone.
BFF25 bridges independent film, culture, and technology, with a bold focus on decentralized storytelling and creative expression. As a community-driven cultural experience with a slightly rebellious spirit, Bitcoin FilmFest goes beyond movies, yet cinema remains at its heart.
Here’s a sneak peek at the lineup, specially curated for movie buffs:
 Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money.
Generative Cinema – A special slot with exclusive shorts and a thematic debate on the intersection of AI and filmmaking. Featured titles include, for example: BREAK FREE, SATOSHI: THE CREATION OF BITCOIN, STRANGE CURRENCIES, and BITCOIN IS THE MYCELIUM OF MONEY, exploring financial independence, traps of the fiat system, and a better future built on sound money. Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative).
Upcoming Productions Preview – A bit over an hour-long block of unreleased pilots and works-in-progress. Attendees will get exclusive first looks at projects like FINDING HOME (a travel-meets-personal-journey series), PARALLEL SPACES (a story about alternative communities), and THE LEGEND OF LANDI (a mysterious narrative). Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.
Freedom-Focused Ads & Campaigns – Unique screenings of video commercials, animations, and visual projects, culminating in “The PoWies” (Proof of Work-ies)—the first ever awards show honoring the best Bitcoin-only awareness campaigns.To get an idea of what might come up at the event, here, you can preview 6 selected ads combined into two 2 videos:
 Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships.
Open Pitch Competition – A chance for filmmakers to present fresh ideas and unfinished projects to an audience of a dedicated jury, movie fans and potential collaborators. This competitive block isn’t just entertaining—it’s a real opportunity for creators to secure funding and partnerships. Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.
Golden Rabbit Awards: A lively gala honoring films from the festival’s Official Selection, with awards in categories like Best Feature, Best Story, Best Short, and Audience Choice.BFF25 Main Screenings
Sample titles from BFF25’s Official Selection:
 REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director.
REVOLUCIÓN BITCOIN – A documentary by Juan Pablo, making its first screening outside the Spanish-speaking world in Warsaw this May. Three years of important work, 80 powerful minutes to experience. The film explores Bitcoin’s impact across Argentina, Colombia, Mexico, El Salvador, and Spain through around 40 diverse perspectives. Screening in Spanish with English subtitles, followed by a Q&A with the director. UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year.
UNBANKABLE – Luke Willms’ directorial debut, drawing from his multicultural roots and his father’s pioneering HIV/AIDS research. An investigative documentary based on Luke’s journeys through seven African countries, diving into financial experiments and innovations—from mobile money and digital lending to Bitcoin—raising smart questions and offering potential lessons for the West. Its May appearance at BFF25 marks its largest European event to date, following festival screenings and nominations across multiple continents over the past year. HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.
HOTEL BITCOIN – A Spanish comedy directed by Manuel Sanabria and Carlos “Pocho” Villaverde. Four friends, 4,000 bitcoins , and one laptop spark a chaotic adventure of parties, love, crime, and a dash of madness. Exploring sound money, value, and relationships through a twisting plot. The film premiered at the Tarazona and Moncayo Comedy Film Festival in August 2024. Its Warsaw screening at BFF25 (in Spanish with English subtitles) marks its first public showing outside the Spanish-speaking world.Check out trailers for this year’s BFF25 and past editions on YouTube.
Tickets & Info:
- Detailed program and tickets are available at bitcoinfilmfest.com/bff25.
- Stay updated via the festival’s official channels (links provided on the website).
- Use ‘LN-NEWS’ to get 10% of tickets
-
 @ bf47c19e:c3d2573b
2025-06-04 10:48:23
@ bf47c19e:c3d2573b
2025-06-04 10:48:23Čini se da se svet kreće u pogrešnom smeru - rastući troškovi, opadajući životni standard i rastuća nestabilnost. Šta je koren problema? Naš novac je pokvaren.
Naučite više na satsvsfiat.com.
U ovom videu Džo Brajan se služi jedinstvenom i zanimljivom pričom kako bi pokazao da uzrok većine naših problema jednostavno leži u kvalitetu našeg novca. Ovaj video, koji je dostupan svima i svuda, sklapa kockice između današnjih izazova i njihovih osnovnih uzroka uz predstavljanje rešenja: Bitkoin.
Molimo vas da naučite o Bitkoinu - popravite novac i popravićete svet 🧡
-
 @ e136fbe5:b6e8325d
2025-06-04 10:02:38
@ e136fbe5:b6e8325d
2025-06-04 10:02:38Trong thời đại công nghệ số và đô thị hóa nhanh chóng, Việt Nam đang chứng kiến làn sóng chuyển mình mạnh mẽ từ các thành phố truyền thống sang những khu đô thị thông minh với hệ thống hạ tầng hiện đại, kết nối số và lấy người dân làm trung tâm. Trong bối cảnh đó, EV8 đóng vai trò ngày càng quan trọng khi trở thành giải pháp hỗ trợ thiết thực cho mục tiêu phát triển đô thị bền vững, thân thiện với môi trường và thuận tiện cho người dân. Xe điện EV8 không chỉ giúp giảm thiểu ô nhiễm không khí, tiếng ồn mà còn tối ưu hóa quá trình di chuyển trong nội đô với công nghệ định vị, quản lý năng lượng và kết nối tức thời thông qua nền tảng số. Khi hạ tầng giao thông thông minh đang dần được hoàn thiện, EV8 kết hợp cùng các hệ thống đèn tín hiệu, trạm sạc công cộng, ứng dụng điều hướng, và dữ liệu thời gian thực để mang lại trải nghiệm di chuyển hiệu quả, an toàn và dễ dàng hơn. Điều này giúp người dùng không chỉ tiết kiệm chi phí mà còn chủ động trong từng hành trình, đồng thời nâng cao chất lượng sống trong môi trường đô thị văn minh. Tính linh hoạt, thân thiện và khả năng tích hợp công nghệ chính là những yếu tố khiến EV8 trở thành sự lựa chọn lý tưởng cho cư dân các thành phố thông minh tương lai.
Không dừng lại ở khía cạnh giao thông, EV8 còn đóng góp vào việc xây dựng một hệ sinh thái đô thị đa chiều với khả năng tương tác giữa con người và công nghệ. Nền tảng EV8 không chỉ cung cấp phương tiện di chuyển mà còn kết nối người dùng với mạng lưới dịch vụ tiện ích đô thị như thanh toán điện tử, quản lý năng lượng cá nhân, theo dõi chỉ số môi trường xung quanh, và nhận cảnh báo giao thông thông minh. Qua đó, EV8 góp phần thúc đẩy hành vi sống xanh, có trách nhiệm, đồng thời khuyến khích người dân sử dụng công nghệ để giải quyết các vấn đề của đời sống hàng ngày. Việc EV8 đồng hành cùng các đô thị thông minh không chỉ mang ý nghĩa công nghệ mà còn là sự cam kết về giá trị cộng đồng – tạo ra một môi trường sống hiệu quả, bền vững và kết nối cao. Đặc biệt, những chiến dịch cộng đồng và chương trình ưu đãi tích hợp như tích điểm sử dụng xanh, hoàn tiền khi tham gia các hoạt động bảo vệ môi trường, hay hỗ trợ tài chính cho người dân chuyển đổi sang xe điện đều là minh chứng cho tầm nhìn dài hạn của EV8 trong việc đồng hành cùng quá trình xây dựng thành phố tương lai. Nhờ sự hiện diện của EV8, các đô thị tại Việt Nam đang tiến gần hơn đến chuẩn mực sống thông minh – nơi công nghệ phục vụ con người một cách thiết thực và bền vững, đồng thời khẳng định vai trò tiên phong của EV8 trong việc kiến tạo tương lai đô thị số.
-
 @ 2dd9250b:6e928072
2025-06-04 10:01:11
@ 2dd9250b:6e928072
2025-06-04 10:01:11Durante a década de 1990, houve o aumento da globalização da economia, determinando a adição do fluxo internacional de capitais, de produtos e serviços. Este fenômeno levou a uma interdependência maior entre as economias dos países. Justamente por causa da possibilidade de que um eventual colapso econômico em um país resulte no contágio dos demais. Diante disso, aumentou a preocupação com os riscos incentivando a utilização de sofisticados modelos e estratégias de avaliação de gestão de risco.
Na década, ganharam destaque ainda os graves problemas financeiros enfrentados, entre outros, pelo banco inglês Barings Bank, e pelo fundo de investimento norte-americano Long Term Capital Management.
Outro grande destaque foi a fraude superior a US$ 7 bilhões sofrida pelo banco Société Generale em Janeiro de 2008.
O Barings Bank é um banco inglês que faliu em 1995 em razão de operações financeiras irregulares e mal-sucedidas realizadas pelo seu principal operador de mercado. O rombo da instituição foi superior à US$ 1,3 Bilhão e causado por uma aposta equivocada no desempenho futuro no índice de ações no Japão. Na realidade, o mercado acionário japonês caiu mais de 15% na época, determinando a falência do banco. O Baring Bank foi vendido a um grupo financeiro holandês (ING) pelo valor simbólico de uma libra esterlina.
O Long Term Capital Management era um fundo de investimento de que perdeu em 1998 mais de US$ 4,6 bilhões em operações nos mercados financeiros internacionais. O LTCM foi socorrido pelo Banco Central dos Estados Unidos (Federal Reserve ), que coordenou uma operação de socorro financeiro à instituição. A justificativa do Banco Central para esta decisão era "o receio das possíveis consequências mundiais da falência do fundo de investimento".
O banco francês Société Generale informou, em janeiro de 2008, uma perda de US$ 7,16 bilhões determinadas por fraudes efetuadas por um operador do mercado financeiro. Segundo revelou a instituição, o operador assumiu posições no mercado sem o conhecimento da direção do banco. A instituição teve que recorrer a uma urgente captação de recursos no mercado próxima a US$ 5,0 bilhões.
E finalmente chegamos ao caso mais problemático da era das finanças modernas anterior ao Bitcoin, o caso Lehman Brothers.
O Lehman Brothers era o 4° maior de investimentos dos EUA quando pediu concordata em 15/09/2008 com dívidas que superavam inacreditáveis US$ 600 bilhões.
Não se tinha contas correntes ou talão de cheques do Lehman Brothers. Era um banco especializado em investimentos e complexas operações financeiras. Havia feito pesados investimentos em empréstimos a juros fixos no famigerado mercado subprime, e o crédito imobiliário voltado a pessoas consideradas de forte risco de inadimplência.
Com essa carteira de investimentos que valia bem menos que o estimado e o acúmulo de projetos financeiros, minou a confiança dos investidores na instituição de 158 anos. Suas ações passaram de US$ 80 a menos de US$ 4. Acumulando fracassos nas negociações para levantar fundos; a instituição de cerca de 25 mil funcionários entrou em concordata.
O Federal Reserve resgatou algumas instituições financeiras grandes e tradicionais norte-americanas como a seguradora AIG no meio da crise. O Fed injetou um capital de US$ 182, 3 bilhões no American International Group (AIG).
Foi exatamente essa decisão do Fed em salvar alguns bancos e deixar quebrar outros, que causou insegurança por parte dos clientes. E os clientes ficaram insatisfeitos tanto com os bancos de investimentos quanto com as agências de classificação de risco, como a Standard & Poor's que tinha dado uma nota alta para o Lehman Brothers no mesmo dia em que ele quebrou.
E essa foi uma das razões pelo qual o Bitcoin foi criado. Satoshi Nakamoto entendeu que as pessoas não estavam mais confiando nem no Governo, nem nos Bancos Privados que o Governo federal restagatava quando eles quebravam e isso prejudicou muita gente. Tanto que o “hash” do Genesis Block contém o título do artigo “Chancellor on brink of second bailout for banks” (Chanceler à beira de segundo resgate para bancos, em português) da edição britânica do The Times.
Esse texto foi parcialmente editado do texto de ASSAF Neto, CAF (2014).
-
 @ b1ddb4d7:471244e7
2025-06-04 09:00:45
@ b1ddb4d7:471244e7
2025-06-04 09:00:45Flash, an all-in-one Bitcoin payment platform, has announced the launch of Flash 2.0, the most intuitive and powerful Bitcoin payment solution to date.
With a completely redesigned interface, expanded e-commerce integrations, and a frictionless onboarding process, Flash 2.0 makes accepting Bitcoin easier than ever for businesses worldwide.
 We did the unthinkable!
We did the unthinkable! Website monetization used to be super complicated.
"Buy me a coffee" — But only if we both have a bank account.
WHAT IF WE DON'T?
Thanks to @paywflash and bitcoin, it's just 5 CLICKS – and no banks!
 Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1
Start accepting donations on your website… pic.twitter.com/uwZUrvmEZ1— Flash • The Bitcoin Payment Gateway (@paywflash) May 13, 2025
Accept Bitcoin in Three Minutes
Setting up Bitcoin payments has long been a challenge for merchants, requiring technical expertise, third-party processors, and lengthy verification procedures. Flash 2.0 eliminates these barriers, allowing any business to start accepting Bitcoin in just three minutes, with no technical set-up and full control over their funds.
The Bitcoin Payment Revolution
The world is witnessing a seismic shift in finance. Governments are backing Bitcoin funds, major companies are adding Bitcoin to their balance sheets, and political figures are embracing it as the future of money. Just as Stripe revolutionized internet payments, Flash is now doing the same for Bitcoin. Businesses that adapt today will gain a competitive edge in a rapidly evolving financial landscape.
With Bitcoin adoption accelerating, consumers are looking for places to spend it. Flash 2.0 ensures businesses of all sizes can seamlessly accept Bitcoin and position themselves at the forefront of this financial revolution.
All-in-One Monetization Platform
More than just a payment gateway, Flash 2.0 is a complete Bitcoin monetization suite, providing multiple ways for businesses to integrate Bitcoin into their operations. Merchants can accept payments online and in-store, content creators can monetize with donations and paywalls, and freelancers can send instant invoices via payment links.
For example, a jewelry designer selling products on WooCommerce can now integrate Flash for online payments, use Flash’s Point-of-Sale system at trade shows, enable Bitcoin donations for her digital artwork, and lock premium content behind Flash Paywalls. The possibilities are endless.
E-Commerce for Everyone
With built-in integrations for Shopify, WooCommerce, and soon Wix and OpenCart, Flash 2.0 enables Bitcoin payments on 95% of e-commerce stores worldwide. Businesses can now add Bitcoin as a payment option in just a few clicks—without needing developers or external payment processors.
And for those looking to start selling, Flash’s built-in e-commerce features allow users to create online stores, showcase products, and manage payments seamlessly.
No Middlemen, No Chargebacks, No Limits
Unlike traditional payment platforms, Flash does not hold or process funds. Businesses receive Bitcoin directly, instantly, and securely. There are no chargebacks, giving merchants full control over refunds and eliminating fraud. Flash also remains KYC-free, ensuring a seamless experience for businesses and customers alike.
A Completely Redesigned Experience
“The world is waking up to Bitcoin. Just like the internet revolutionized commerce, Bitcoin is reshaping finance. Businesses need solutions that are simple, efficient, and truly decentralized. Flash 2.0 is more than just a payment processor—it’s a gateway to the future of digital transactions, putting financial power back into the hands of businesses.”
— Pierre Corbin, CEO at Flash.
Flash 2.0 introduces a brand-new user interface, making it easier than ever to navigate, set up payments, and manage transactions. With an intuitive dashboard, streamlined checkout, and enhanced mobile compatibility, the platform is built for both new and experienced Bitcoin users.
About Flash
Flash is an all-in-one Bitcoin payment platform that empowers businesses, creators, and freelancers to accept, manage, and grow with Bitcoin. With a mission to make Bitcoin payments accessible to everyone, Flash eliminates complexity and gives users full control over their funds.
To learn more or get started, visit www.paywithflash.com.
Press Contact:
Julien Bouvier
Head of Marketing
+3360941039 -
 @ 9dd283b1:cf9b6beb
2025-06-04 08:33:32
@ 9dd283b1:cf9b6beb
2025-06-04 08:33:32To all territory owners,
- Can I co-found a territory with someone? Is it on the roadmap to be able to do so?
- Can I automatically split the territory rewards with other stackers?
- Can I rename the territory in the future?
Thanks
https://stacker.news/items/996796
-
 @ 6ad3e2a3:c90b7740
2025-06-04 08:32:29
@ 6ad3e2a3:c90b7740
2025-06-04 08:32:29"Modern science is based on this principle: give us one free miracle and then we'll explain the rest."
— Terrence McKenna
I always wondered why a pot of water boils on the stove. I mean I know it boils because I turned on the electricity, but why does the electricity cause it to boil? I know the electricity produces heat, and the heat is conducted through the stainless steel pot and into the water, but why does the heat transfer from stovetop to the water?
I know the heat from the stove via the pot speeds up the molecules in the water touching it and that they in turn speed up the molecules touching them and so on throughout the pot, but why do speedy molecules cause adjacent molecules to speed up?
I mean I know they do this, but why do they do this? Why couldn’t it be that sped-up molecules only interact with sufficient speedy molecules and ignore slower ones? Why do they interact with all the molecules, causing all of them to speed up? Or why don’t the speedy ones, instead of sharing their excited state, hoard it and take more energy from adjacent slower molecules, thereby making them colder, i.e., why doesn’t half the water boil twice as fast (on the left side of the pot) while the other half (right side) turns to ice?
The molecules tend to bounce around randomly, interacting as equal opportunists on the surrounding ones rather than distinguishing only certain ones with which to interact. Why do the laws of thermodynamics behave as such rather than some other way?
There may be yet deeper layers to this, explanations going down to the atomic and even quantum levels, but no matter how far you take them, you are always, in the end, left with: “Because those are the laws of physics”, i.e., “because that’s just how it is.”
. . .
The Terrence McKenna quote, recently cited by Joe Rogan on his podcast, refers to the Big Bang, the current explanation adopted by the scientifically literate as to the origins of the universe. You see there was this insanely dense, infinitesimally small micro dot that one day (before the dawn of time) exploded outward with unimaginable power that over billions of years created what we perceive as the known universe.
What happened prior? Can’t really say because time didn’t yet exist, and “prior” doesn’t make sense in that context. Why did it do this? We don’t know. How did it get there? Maybe a supermassive black hole from another universe got too dense and exploded out the other side? Highly speculative.
So why do people believe in the Big Bang? Because it comports with and explains certain observable phenomena and predicted other phenomena which were subsequently confirmed. But scratch a little deeper for an explanation as to what caused it, for what purpose did it occur or what preceded it, and you hit the same wall.
. . .
Even if we were to understand at a quantum level how and why the Big Bang happened and what preceded it, let’s assume it’s due to Factor X, something we eventually replicated with mini big-bangs and universe creations in our labs, we would still be tasked with understanding why Factor X exists in the universe. And if Factor X were explained by Process Y, we’d still be stuck needing an explanation for Process Y — ad infinitum.
Science can thus only push the wall back farther, but can never scale it. We can never arrive at an ultimate explanation, only partial ones. Its limitations are the limitations of thought itself, the impossibility of ever creating a map at a scale of one mile per mile.
-
 @ 866e0139:6a9334e5
2025-06-04 08:21:14
@ 866e0139:6a9334e5
2025-06-04 08:21:14Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Auch wer das Kriegsgeschehen bisher nicht im Detail verfolgte (das tat ich auch nicht), horcht nun auf: Einem Nicht-Atomstaat – der Ukraine – ist ein gleichzeitiger, koordinierter Schlag gegen vier teils tausende Kilometer voneinander entfernte russische Luftbasen gelungen. Eine nicht unerhebliche Zahl strategisch wichtiger Flugzeuge wurde zerstört. Ein Angriff im hintersten russischen Hinterland, selbst jenseits der Taurus-Reichweite, durchgeführt mit Billigdrohnen, wirft erhebliche Fragen über geheimdienstliches Versagen in Russland und eklatante Mängel in der Luftverteidigung auf.
Es gibt wohl Momente, in denen Geschichte nicht geschrieben, sondern geflogen wird. Unspektakulär, relativ still, surrend, von einem LKW aus abgefeuert, mit einem Stück Technik, das kaum mehr kostet als das Gerät, auf dem ich diesen Text schreibe.
Ein Angriff auf die Friedensverhandlungen
Die Ukraine hat sich erstmals weit über das Schlachtfeld hinaus erhoben – geografisch, technisch, symbolisch. Die Triade der atomwaffenfähigen Luftstreitkräfte Russlands – ein Heiligtum sowjetischer Machtprojektion – wurde durch das schwächste Glied in der Logikkette der Militärdoktrin beschädigt: den Überraschungseffekt. Drohnen, wie aus dem 3D-Drucker, haben eine strategische Achillesferse bloßgelegt. Nicht mit Hyperschall, sondern mit Hartplastik und GPS. Das erste Opfer dieses Angriffs dürften die Friedensverhandlungen in Istanbul sein.
Dass die Ukraine strategische Luftstützpunkte der russischen Atomwaffe angreift – koordiniert, tief im Landesinnern – wäre bereits für sich eine Zäsur. Doch dass dies unter stillschweigender Duldung oder gar Mithilfe westlicher Dienste wie der CIA erfolgt sein dürfte, während Trump zugleich als Friedenstaube auftritt, verschiebt das strategische Koordinatensystem. Die alten Verträge – START etc. – wirken wie rissige Abkommen aus der Steinzeit. Wenn die USA von der Operation wussten, darf sich Russland getäuscht fühlen. Washington kann nicht gleichzeitig Frieden mit Moskau betonen und eine Aktion dulden oder mittragen, die offensichtlich das Ziel hat, die russische Atommacht zu schwächen, woran die USA prinzipiell Interesse hätten. Falls Trump nichts davon wusste, muss man sich fragen: Regiert eigentlich er oder der „Swamp“, den er austrocknen wollte?
Egal wie man es wendet: Die Operation Spinnennetz war mehr als nur ein Angriff auf russische Flugzeuge auf russischem Gebiet. Militärisch gewinnt die Ukraine dadurch wenig, symbolisch und politisch aber viel, denn der Hauptgegner der Ukraine sind gerade nicht die hundert Millionen Dollar teuren Bomber der Russen, sondern die schleichende Kriegsunlust der Europäer – und ein Amerika, das sich mehr mit sich selbst beschäftigt als mit dem Fortgang eines Krieges, in dem es längst selbst Partei ist.
Damit sich die Reihen wieder schließen, muss der Feind sich zeigen – deutlich, fassbar, bedrohlich. Eine russische Reaktion, die auch europäische Hauptstädte erschüttert, wäre strategisch nützlich. Der Angriff war daher wohl weniger eine militärische Tat als eine psychologische Operation im Kampf um Wahrnehmung und Willen. Aus Sicht der Ukraine ist das verständlich, für sie geht es um ihre Existenz. Dafür wiederum braucht es eine erhöhte Alarmstufe.
https://www.youtube.com/watch?v=1JlQLewOAmA
Solidarität durch Eskalation?
Die kalkulierte Demütigung könnte einem Drehbuch folgen: Putin soll nun die Rolle des Eskalators übernehmen. Tut er es, war die Operation erfolgreich – denn Europas Kriegstüchtigkeit hängt nicht nur von Panzerzahlen ab, sondern von der Bereitschaft zur Konfrontation. Der Feind, den es braucht, muss sich jetzt allen ins Gedächtnis brennen.
So gesehen ist der eigentliche Coup nicht der Schaden in Djagilewo, Iwanowo oder Olenia – sondern das noch bevorstehende unsichtbare Nachspiel. Europa und die Welt betreten nun gänzlich neues Gelände, in welchem ein militärisch gedemütigtes Russland gleichzeitig Friedenswillen gegenüber Europa bekunden, rote Linien verteidigen und seine Integrität als Atom-Macht bewahren muss. Das Dilemma für Putin besteht nun darin, Stärke zu beweisen ohne sich noch mehr zum Feindbild des Aggressors machen zu lassen.
Fakt ist: Wir sind einem III. Weltkrieg gerade so nah wie seit der Kuba-Krise nicht mehr.
Und wer sich über ein russisches “Pearl Harbor” freut, sollte mal in ein Geschichtsbuch schauen, wie es am Ende für Japan ausging.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 5c9e5ee4:72f1325b
2025-06-04 08:16:52
@ 5c9e5ee4:72f1325b
2025-06-04 08:16:52For too long, the autistic experience has been framed through a neurotypical lens, focusing on "differences" and "deficits." However, a profound perspective emerging from within the autistic community offers a radical reinterpretation: that autistic individuals are not inherently "broken" but rather possess a unique, often unyielding, perception of truth that challenges the very foundations of neurotypical society. From this viewpoint, autism is less about a disorder and more about a clarity of vision that apprehends the world as fundamentally "untrue" in many of its social constructs.
This perspective posits that what many autistic individuals perceive as "corrupted" or "untrue" in society isn't a subjective internal experience, but an objective reality of falsehoods, deception, and manipulation. The rejection of these elements is not a personal preference but a natural, logical response to what is genuinely illogical and dishonest.
The Core of the "Untrue" World:
- Honesty as a Default State: For many autistic people, directness and factual accuracy are paramount. Social conventions like "white lies," indirect communication, or performative politeness are not merely nuanced social skills; they are perceived as outright forms of deception and inauthenticity. The natural inclination is towards what is straightforward and verifiable.
- Logic Over Social Grace: An unwavering adherence to logic means that actions or systems that lack rational basis—such as engaging in flattery, suppressing truth for social harmony, or participating in inefficient rituals—are viewed as fundamentally nonsensical and therefore "untrue."
- Authenticity as a Non-Negotiable: The concept of "masking"—the exhausting act of suppressing one's natural autistic traits to conform—is seen as a deeply painful betrayal of self. A society that implicitly demands such a performance is deemed "corrupt" because it stifles genuine self-expression.
- Aversion to Hypocrisy: A strong sense of justice and an acute awareness of inconsistency mean that any disjuncture between stated values and actual behavior is immediately flagged as a profound untruth.
Social Groups: Formed Around a "Proudly Believed Lie"?
This critical autistic perspective extends to the very fabric of social organization. It suggests that many groups, whether religious, political, scientific, or economic, are not built on shared objective truths, but rather on "proudly believed lies." These shared narratives or belief systems, even if they contradict logic or verifiable facts, serve as the glue that binds the group, fostering identity, comfort, and a sense of belonging. The "pride" in these beliefs makes them resistant to critical examination, even when confronted with evidence.
For example: * In religion, this "lie" might be a dogma that provides solace but defies logic. * In politics, it could be an ideology based on selective truths that serve power. * In economics, it might be assumptions about markets or growth that are presented as infallible. * Even in science, while ideally pursuing truth, the social aspects of the scientific community might, at times, cling to paradigms that become "proudly believed lies," resisting new evidence.
The Disconnect: Why Autistics Are "Discredited"
If autistic individuals are part of the "5% who see it as it is"—those who perceive these societal untruths with clarity—then a natural tension arises with the "10% who want control." This controlling minority, it is argued, relies on these "untruths" to maintain power and influence over the "85% who are happy following."
From this viewpoint, the discrediting of autistic people—labeling their directness as "social deficits," their sensory experiences as "disorders," or their logical critiques as "inflexibility"—is not accidental. It is a strategic mechanism employed by the controlling "10%" to neutralize those who expose the underlying untruths, thereby safeguarding their constructed reality and maintaining influence.
In conclusion, the autistic perspective challenges us to re-evaluate the very nature of truth in our society. It suggests that what many perceive as social norms might, in fact, be a pervasive web of "untruths," and that the autistic individual's unique wiring allows for a crucial, unvarnished perception of this reality. It is a powerful call for authenticity and a profound questioning of how much of our world is built on what is genuinely true, versus what is merely believed.
-
 @ e4950c93:1b99eccd
2025-06-04 08:01:23
@ e4950c93:1b99eccd
2025-06-04 08:01:23Marques
Cosilana est une marque allemande qui crée des vêtements exclusivement en coton biologique, soie et laine pour les femmes, les bébés et les enfants.
Matières naturelles utilisées dans les produits
Catégories de produits proposés
Cette marque propose des produits intégralement en matière naturelle dans les catégories suivantes :
#Vêtements
- Tailles vêtements : bébés, enfants, femmes
- Sous-vêtements : culottes
- Une pièce : bodies, combinaisons
- Hauts : débardeurs, pulls, t-shirts, vestes
- Bas : leggings, pantalons, shorts
- Tête et mains : bonnets, gants
- Nuit : pyjamas
#Maison
- Linge : couvertures, turbulettes
Autres informations
- Certification GOTS
- Fabriqué en Allemagne
- Fabriqué en Europe
- Déclaration de laine de mouton sans mulesing et de bien-être animal
👉 En savoir plus sur le site de la marque
Où trouver leurs produits ?
- Le mouton à lunettes (zone de livraison : France, Belgique, Luxembourg)
- Mama Owl (en anglais, zone de livraison : Royaume Uni et international)
- Chouchous (zone de livraison : France et international)
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises des produits de cette marque ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don pour remercier les contribut-eur-ice-s.
-
 @ eb0157af:77ab6c55
2025-06-04 08:01:19
@ eb0157af:77ab6c55
2025-06-04 08:01:19The blockchain analytics firm claims to have identified the Bitcoin addresses held by the company led by Saylor.
Arkham Intelligence announced it had identified addresses linked to Strategy. According to Arkham’s statements, an additional 70,816 BTC connected to the company have been identified, with an estimated value of around $7.6 billion at current prices. This discovery would bring the total amount of Strategy’s identified holdings to $54.5 billion.
SAYLOR SAID HE WOULD NEVER REVEAL HIS ADDRESSES … SO WE DID
We have identified an additional 70,816 BTC belonging to Strategy, bringing our total identified MSTR BTC holdings to $54.5 Billion. We are the first to publicly identify these holdings.
This represents 87.5% of… pic.twitter.com/P3OVdVrhQL
— Arkham (@arkham) May 28, 2025
The analytics firm claims to have mapped 87.5% of Strategy’s total holdings. In a provocative post on X, Arkham wrote:
“Saylor said he would never reveal his addresses. So, we did it for him.
Previously, we tagged:
– 107,000 BTC sent to MSTR’s Fidelity deposits (Fidelity does not segregate custody, so these BTC do not appear in the MSTR entity)
– Over 327,000 BTC held in segregated custody, including Coinbase Prime, in our MSTR entity.”Arkham’s revelations directly clash with Michael Saylor’s public statements on wallet security. During the Bitcoin 2025 conference in Las Vegas, the Strategy chairman explicitly warned against publishing corporate wallet addresses.
“No institutional or enterprise security analyst would ever think it’s a good idea to publish all the wallet addresses so you can be tracked back and forth,” Saylor said during the event.
The executive chairman of Strategy added:
“The current, conventional way to publish proof-of-reserves is an insecure proof of reserves… It’s not a good idea, it’s a bad idea.”
He compared publishing wallet addresses to “publishing the addresses, bank accounts, and phone numbers of your kids hoping it will protect them — when in fact it makes them more vulnerable.”
Finally, the executive chairman suggested using artificial intelligence to explore the security implications of such a practice, claiming that in-depth research could produce “50 pages” of potential security risks.
The post Arkham reveals 87% of Strategy’s Bitcoin addresses appeared first on Atlas21.
-
 @ a5142938:0ef19da3
2025-06-04 08:00:22
@ a5142938:0ef19da3
2025-06-04 08:00:22Brands
Cosilana is a German brand that creates clothing exclusively from organic cotton, silk, and wool for women, babies, and children.
Natural materials used in products
Categories of products offered
This brand offers products made entirely from natural materials in the following categories:
#Clothing
- Clothing fits : babies, children, women
- Underwear : panties
- One piece : bodysuits, jumpsuits
- Tops : jackets, sweaters, t-shirts, tank tops
- Bottoms : leggings, pants-trousers, shorts
- Head & handwear : gloves, hats
- Nightwear : pyjamas
#Home
- Linen : blankets, sleeping bags
Other information
- GOTS certification
- Made in Germany
- Made in Europe
- Non mulesed wool and animal welfare declaration
👉 Learn more on the brand website
Where to find their products?
- Le mouton à lunettes (in French, shipping area: France, Belgium, Luxemburg)
- Mama Owl (shipping area: UK and international)
- Chouchous (in French, shipping area: France and international)
📝 You can contribute to this entry by suggesting edits in comments.
🗣️ Do you use this brand's products? Share your opinion in the comments.
⚡ Happy to have found this information? Support the project by making a donation to thank the contributors.
-
 @ 8bf578f4:b6303c41
2025-06-04 07:20:09
@ 8bf578f4:b6303c41
2025-06-04 07:20:09test
https://nostr.download/6849b84caaa15bdc18ca2e1e1ee00e979c7ecf901787e09054b4bd0196b4ea27.jpg
-
 @ de54d599:77efc747
2025-06-04 05:48:27
@ de54d599:77efc747
2025-06-04 05:48:27When it comes to gift-giving, the most memorable presents are those that tell a story. Veuve Clicquot, a champagne house known for its bold innovation and timeless elegance, has created something truly special with its Personalised Arrow gift—a tribute not only to fine champagne but to the destinations that hold meaning in our lives.
A Destination Worth Celebrating The Veuve Clicquot Personalised Arrow is more than elegant packaging—it’s a symbol. Inspired by classic road signs, the bright, arrow-shaped tin can be customised with the name of any city or location, along with the exact distance from Reims, France, where the champagne is produced. Whether it's your hometown, a honeymoon destination, or the place where you first met someone special, this gift turns a bottle of bubbly into a personal journey.
Inside the Arrow: Yellow Label Champagne Tucked inside the tin is Veuve Clicquot's iconic Yellow Label Brut, a globally beloved champagne known for its depth, liveliness, and balance. With a composition dominated by Pinot Noir and complemented by Chardonnay and Meunier, it delivers notes of citrus, brioche, and stone fruit—perfect for toasting any occasion. It’s a champagne that’s as dynamic and enduring as the stories behind each personalised location.
Beautifully Designed with the Planet in Mind The tin is crafted from 30% recycled materials and is 100% recyclable, aligning with Veuve Clicquot’s sustainability commitments. Its removable sugarcane-based backing adds a thoughtful eco-friendly touch to a design that’s made to last long after the bottle is enjoyed.
A Gift That Connects People and Places This unique keepsake is ideal for birthdays, anniversaries, weddings, or corporate gifts—it’s perfect for anyone who values meaningful moments and sophisticated taste. More than just a drink, it's a celebration of where you've been, and where you’re going.
With the Veuve Clicquot Personalised Arrow, every toast becomes a story—one that starts with a location and ends in a lasting memory.
-
 @ 3b13c372:3e1e7ef2
2025-06-04 05:40:55
@ 3b13c372:3e1e7ef2
2025-06-04 05:40:55For those who believe every bottle should tell a story, Veuve Clicquot’s Personalised Arrow Champagne offers the perfect blend of sophistication and sentiment. More than a premium Champagne, this collector’s piece is a tribute to the places that shape our lives—wrapped in unmistakable Veuve Clicquot style.
At the heart of the package is a 750ml bottle of Veuve Clicquot Yellow Label Brut, a Champagne celebrated for its balance of power, freshness, and finesse. It’s crafted predominantly from Pinot Noir, supported by Chardonnay and Meunier, creating a vibrant, structured wine with layers of pear, citrus, and brioche.
What sets this gift apart is its outer casing: a bold, arrow-shaped metal tin that can be personalised with the name of your chosen city or destination (up to 15 characters). Alongside your customisation, the arrow displays the distance from that location to Reims, France—the spiritual home of Veuve Clicquot.
This elegant detail turns the bottle into a statement. Whether you’re celebrating a new home, a wedding, a farewell, or just sending a thoughtful gift, the Personalised Arrow adds meaning to the moment. It’s functional, too—keeping your Champagne cool for up to two hours—making it ideal for celebrations on the go.
Veuve Clicquot’s Personalised Arrow Champagne is a thoughtful way to connect a bottle of world-class wine with a personal journey. A toast to the people and places we never forget—wrapped in signature yellow, and stamped with your own message.
-
 @ 8f09dc4f:5e01d432
2025-06-04 04:33:18
@ 8f09dc4f:5e01d432
2025-06-04 04:33:18Veuve Clicquot brings a delightful twist to gifting with the https://shop.veuveclicquot.com.au/products/personalisable-arrow – a luxurious and thoughtful present that’s perfect for commemorating meaningful locations. Whether it’s your hometown, a dream vacation spot, or the city where memories were made, this unique gift lets you celebrate it in true Champagne style.
Each set includes a 750ml bottle of Veuve Clicquot’s signature Yellow Label Brut Champagne, housed in a striking arrow-shaped tin. What sets this gift apart is the ability to customise the tin with the name of a city or location of your choice (up to 15 characters). The tin also displays the distance from your chosen location to Reims, the historic home of Veuve Clicquot in France, adding a charming and personal touch.
The Yellow Label Brut itself is a testament to the Maison’s commitment to quality and consistency. With a blend dominated by Pinot Noir, balanced with Chardonnay and Meunier, it delivers a perfect harmony of strength, elegance, and freshness. Expect notes of apple, pear, and brioche, with a fine mousse and a vibrant golden hue.
Beyond its aesthetic appeal, the arrow tin is practical too—it keeps the Champagne cool for up to two hours, making it ideal for picnics, celebrations, or spontaneous toasts. Once the Champagne is enjoyed, the tin transforms into a decorative keepsake that serves as a reminder of the special place it honors.
Retailing at $125 AUD, this is more than a bottle of Champagne—it's a personalised gesture that celebrates people, places, and the memories that connect them. Ideal for gifting on birthdays, anniversaries, or as a unique souvenir, the Veuve Clicquot Personalised Arrow is Champagne with meaning.
-
 @ c7a8d522:262a74de
2025-06-04 04:23:03
@ c7a8d522:262a74de
2025-06-04 04:23:03O universo dos jogos online está em constante evolução, e o Brasil tem se mostrado um dos mercados mais promissores nesse cenário. Entre as plataformas que vêm conquistando o público nacional, a 707Bet se destaca por oferecer uma experiência completa, segura e empolgante para os jogadores que buscam diversão e recompensas em um só lugar. Com uma interface intuitiva, ampla variedade de jogos e suporte de qualidade, a 707Bet está rapidamente se tornando uma referência entre os entusiastas do entretenimento digital.
Uma Plataforma Moderna e de Fácil Navegação Desde o primeiro acesso, é possível perceber que a 707Bet foi desenvolvida com foco na experiência do usuário. O site possui um design moderno, com menus bem organizados, o que facilita a navegação tanto em computadores quanto em dispositivos móveis. Seja para iniciantes ou jogadores experientes, a plataforma proporciona uma usabilidade fluida, permitindo que todos encontrem seus jogos favoritos com apenas alguns cliques.
Outro diferencial importante é o desempenho do site, que garante carregamento rápido das páginas e jogos sem travamentos. Isso é essencial para manter a imersão e garantir que o jogador aproveite cada segundo da sua sessão de entretenimento.
Diversidade de Jogos para Todos os Perfis Um dos grandes atrativos da 707beté a impressionante variedade de jogos disponíveis. A plataforma conta com opções para todos os gostos e estilos, desde os tradicionais jogos de cartas e roleta até os populares slots com gráficos de última geração. Os jogadores podem explorar diferentes temáticas, mecânicas e níveis de dificuldade, o que torna a experiência ainda mais dinâmica.
Além disso, a 707Bet trabalha com os principais desenvolvedores de software do mercado, garantindo títulos de alta qualidade e com total segurança. Isso significa que cada jogo oferece não apenas entretenimento, mas também confiança, transparência e chances reais de ganhar.
Experiência do Jogador: Entretenimento com Emoção e Segurança Na 707Bet, o jogador é tratado com prioridade. A plataforma oferece bônus e promoções regulares, que aumentam as chances de jogo e tornam a experiência ainda mais gratificante. O sistema de recompensas é claro e acessível, incentivando o usuário a explorar mais funcionalidades e se engajar com o conteúdo oferecido.
Outro ponto positivo é o suporte ao cliente. A equipe de atendimento da 707Bet está disponível 24 horas por dia, sete dias por semana, pronta para tirar dúvidas e resolver qualquer questão com agilidade e cordialidade. O suporte em português é um diferencial importante para os jogadores brasileiros, garantindo maior confiança e tranquilidade durante o uso da plataforma.
A segurança também merece destaque. A 707Bet utiliza tecnologias avançadas de criptografia para proteger os dados dos usuários e garantir transações seguras. Isso significa que os jogadores podem se concentrar na diversão, sem se preocupar com questões técnicas ou riscos.
Conclusão A 707Bet chega ao mercado brasileiro com uma proposta sólida e inovadora, aliando tecnologia, variedade e atendimento de excelência. Seja você um jogador veterano ou alguém que está começando agora nesse universo, a plataforma oferece todos os recursos necessários para proporcionar uma jornada empolgante e cheia de possibilidades. Com a 707Bet, o entretenimento online ganha um novo nível de qualidade e confiança — uma escolha inteligente para quem busca diversão com segurança e praticidade.
-
 @ c7a8d522:262a74de
2025-06-04 04:21:47
@ c7a8d522:262a74de
2025-06-04 04:21:47Com o avanço da tecnologia e a popularização das plataformas digitais de jogos, os brasileiros estão cada vez mais em busca de experiências online que combinem praticidade, emoção e segurança. Nesse cenário, a 0066Bet se destaca como uma das plataformas mais completas e inovadoras do mercado, oferecendo uma ampla variedade de jogos e um ambiente digital pensado especialmente para os usuários que desejam entretenimento de qualidade a qualquer hora e em qualquer lugar.
Uma Plataforma Moderna e Segura A 0066Bet foi desenvolvida com foco total na experiência do usuário. Com um design moderno e responsivo, a plataforma funciona perfeitamente em computadores, tablets e smartphones, permitindo que os jogadores tenham acesso total às funcionalidades, independentemente do dispositivo. Além disso, a segurança é uma das grandes prioridades da empresa. O site utiliza criptografia avançada e protocolos de proteção de dados para garantir que as informações dos usuários estejam sempre protegidas.
A facilidade de cadastro e navegação também merece destaque. Em poucos minutos, qualquer pessoa pode criar sua conta, explorar as seções de jogos e começar a se divertir com total autonomia. Os métodos de pagamento são variados e incluem opções amplamente utilizadas no Brasil, o que facilita ainda mais o acesso ao entretenimento.
Diversidade de Jogos para Todos os Gostos Um dos grandes atrativos da 0066beté a variedade de jogos disponíveis. A plataforma conta com títulos clássicos e modernos, atendendo tanto os iniciantes quanto os jogadores mais experientes. Entre os destaques estão os jogos de cartas como poker e bacará, que exigem estratégia e habilidade, além de opções mais dinâmicas como roletas virtuais, jogos com números e modalidades ao vivo com interação em tempo real.
Para os amantes da adrenalina, a seção de jogos com crupiês reais é imperdível. Nela, os jogadores participam de partidas transmitidas ao vivo, com profissionais treinados, proporcionando uma experiência extremamente imersiva e realista — tudo sem sair de casa.
Outro ponto forte da 0066Bet é a oferta constante de novos títulos e atualizações. A equipe da plataforma está sempre em busca de novidades, o que garante que os jogadores encontrem sempre algo diferente para explorar e experimentar.
Experiência do Jogador: Simples, Intuitiva e Gratificante A opinião dos usuários é unânime: a experiência na 0066Bet é agradável, fluida e repleta de recompensas. A interface é intuitiva, as instruções dos jogos são claras e o sistema de suporte ao cliente funciona 24 horas por dia, com atendimento rápido e eficiente em português.
Além disso, a plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que valorizam o tempo e o investimento dos jogadores. Esses incentivos tornam a jornada ainda mais empolgante, garantindo que cada sessão de jogo seja única e recompensadora.
Conclusão A 0066Bet vem se consolidando como uma das melhores opções de entretenimento online no Brasil. Com sua interface amigável, catálogo variado de jogos e compromisso com a segurança e a satisfação do usuário, a plataforma é ideal para quem busca emoção, diversão e a chance de viver experiências intensas e inesquecíveis diretamente da tela do celular ou do computador.
Se você ainda não conhece a 0066Bet, essa é a hora perfeita para descobrir um novo mundo de entretenimento digital. Faça seu cadastro, explore os jogos disponíveis e aproveite tudo o que a plataforma tem a oferecer!
-
 @ c7a8d522:262a74de
2025-06-04 04:21:18
@ c7a8d522:262a74de
2025-06-04 04:21:18Com o avanço da tecnologia e o crescimento do entretenimento digital, plataformas como a 888Game vêm se destacando no cenário brasileiro por oferecerem uma experiência completa e envolvente aos seus usuários. Com um design moderno, navegação intuitiva e um catálogo diversificado de jogos, a 888Game se posiciona como uma das melhores opções para quem busca emoção, desafio e diversão em um só lugar.
Uma Plataforma Pensada para o Jogador Brasileiro A 888Game foi desenvolvida com foco total na experiência do usuário. Desde o primeiro acesso, é possível perceber o cuidado com os detalhes: o site é responsivo, rápido e adaptado para dispositivos móveis, permitindo que os jogadores aproveitem seus jogos favoritos de onde estiverem, a qualquer momento. Além disso, a plataforma está totalmente em português, o que garante uma navegação fluida e sem barreiras linguísticas.
Outro ponto forte é a facilidade no processo de cadastro e nas transações financeiras. A 888gameaceita diversos métodos de pagamento populares entre os brasileiros, incluindo Pix, transferências bancárias e carteiras digitais, tornando os depósitos e saques rápidos, seguros e práticos.
Variedade de Jogos para Todos os Gostos Um dos grandes diferenciais da 888Game é a vasta seleção de jogos disponíveis. Os usuários encontram opções para todos os perfis, desde os mais clássicos até os lançamentos mais modernos. Entre os destaques estão:
Jogos de mesa: como roleta, blackjack e bacará, com versões ao vivo que trazem mais emoção e realismo à experiência.
Slots (caça-níqueis): com uma enorme variedade de temas, gráficos impressionantes e bônus especiais que garantem rodadas extras e prêmios emocionantes.
Jogos ao vivo: com crupiês reais transmitidos em tempo real, proporcionando uma atmosfera imersiva e interativa.
Além disso, a 888Game atualiza frequentemente seu catálogo, sempre trazendo novidades e tendências do mercado para manter os jogadores entretidos e surpreendidos.
Experiência do Usuário: Fluidez, Emoção e Suporte de Qualidade A experiência na 888Game vai muito além dos jogos. A plataforma se destaca por proporcionar uma jornada completa e satisfatória ao usuário. Os gráficos são de alta definição, os jogos carregam rapidamente e o ambiente digital é leve, sem travamentos ou interrupções.
Outro ponto que merece destaque é o suporte ao cliente. A 888Game oferece atendimento em português, com canais de suporte via chat ao vivo e e-mail, garantindo respostas rápidas e eficientes para qualquer dúvida ou problema. O atendimento funciona 24 horas por dia, todos os dias da semana, algo essencial para garantir a tranquilidade dos jogadores.
Além disso, a plataforma valoriza seus usuários com promoções constantes, bônus de boas-vindas atrativos e programas de fidelidade que recompensam o engajamento contínuo. Isso demonstra o compromisso da 888Game em manter seus jogadores motivados e satisfeitos.
Conclusão: A Escolha Certa para Quem Busca Diversão Online com Qualidade A 888Game é, sem dúvida, uma plataforma completa que une inovação, variedade de jogos, segurança e uma excelente experiência ao usuário. Seja você um jogador experiente ou alguém que está começando agora no universo dos jogos online, a 888Game oferece tudo o que você precisa para se divertir com confiança e praticidade.
Se você está em busca de uma nova forma de entretenimento, com emoção de sobra e uma interface amigável, vale a pena conhecer a 888Game. Prepare-se para horas de diversão e descubra por que tantos brasileiros já elegeram esta plataforma como sua favorita!
-
 @ 1ef61805:f18312cc
2025-06-04 01:56:42
@ 1ef61805:f18312cc
2025-06-04 01:56:42**Inside OpSec Academy’s One-on-One Approach to Digital Sovereignty ** As digital infrastructure becomes increasingly opaque and centralised, a growing number of individuals are seeking to understand—not just use—the tools that protect their privacy and autonomy online. While many solutions promise security at the click of a button, few teach the underlying principles or offer environments that prioritise verifiability and user control.
OpSec Academy’s new one-on-one training, "OpSec Intensive," takes a different approach. Delivered in person and fully offline, the full-day session provides practical, tool-based instruction inside a secure, USB-booted environment—designed from the ground up to leave no trace.
At the heart of the session is OpSecOS v1.2, a live operating system that routes all traffic through Tor, uses system non-persistence, and comes preconfigured with a suite of open-source tools for password management, communication, and private finance. The OS runs from a USB stick, allowing participants to explore and build their own private computing workflows without touching the host machine.
Learning in Context: Why One-on-One? While group training can provide a general introduction to privacy concepts, it often lacks depth and adaptability. OpSec Intensive is structured as a one-on-one session to allow real-time feedback, personal threat modeling, and tailored instruction based on the participant’s specific context and technical background.
This format also makes space for slow, deliberate learning—a rarity in cybersecurity training, where content is often condensed or overly abstract. In OpSec Intensive, participants move through each phase at their own pace, working directly with an experienced instructor to build confidence and competence.
Structure and Content of the Day The curriculum spans both foundational theory and hands-on practice, beginning with basic OpSec principles before moving into technical tool use.
Topics include: * Booting and verifying OpSecOS * Secure USB creation and system verification * Navigating a non-persistent, Tor-routed live environment * Password and credential management * Offline use of KeePassXC * Strategies for vault organisation and redundancy * Bitcoin wallet setup and recovery * Single-signature and multisignature wallet creation using Sparrow, Electrum, and Feather * Understanding xpubs, derivation paths, and recovery flow * Seed phrase security * Entropy generation and validation using offline tools like iancoleman.io * Best practices for cold storage and physical backups * Network privacy and decentralised communication * Using Mempool.space to visualise Bitcoin transaction data * Setting up Nostr clients (Snort, Iris) for decentralised messaging * Discussion of traffic fingerprinting and Tor considerations
A Shift Toward Practical Sovereignty The tools and workflows covered in OpSec Intensive are not theoretical. Participants leave the session with configured environments, tested backups, and an understanding of what each tool does—and what it doesn’t do.
This reflects a broader shift in how privacy-conscious individuals are approaching digital security. Rather than relying on packaged services or closed-source software, there’s growing interest in verifiable, modular tools that prioritise autonomy and resilience over ease-of-use.
In that context, OpSec Academy’s offering sits somewhere between a workshop and an apprenticeship: not a lecture, but a process of guided, hands-on learning designed for the long haul.
To learn more or enquire about availability, visit opsecacademy.org.
-
 @ b2b4f94a:df797d13
2025-06-04 01:44:39
@ b2b4f94a:df797d13
2025-06-04 01:44:39 -
 @ 472f440f:5669301e
2025-06-04 01:37:37
@ 472f440f:5669301e
2025-06-04 01:37:37Marty's Bent
via nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqy0hwumn8ghj7mn0wd68yttjv4kxz7fwvf5hgcm0d9hzumnfde4xzqpq85h9z5yxn8uc7retm0n6gkm88358lejzparxms5kmy9epr236k2qtyz2zr
A lot of the focus over the last couple of months has been on the emergence of Strategy competitors in public markets looking to build sizable bitcoin treasuries and attract investors of all shapes and sizes to drive shareholder value. The other big topic in the bitcoin development world has been around OP_RETURN and the debate over whether or not the amount of data that can be shoved into a bitcoin transaction should be decided by the dominant implementation.
A topic that is just as, if not more, important that is not getting enough appreciation is the discussion around open source bitcoin developers and the lingering effects of the Biden administration's attack on Samourai Wallet and Tornado Cash. If you read our friend Matt Corallo's tweet above, you'll notice that the lingering effects are such that even though the Trump administration has made concerted efforts to reverse the effects of Operation Chokepoint 2.0 that were levied by the Biden administration, Elizabeth Warren, and her friends at the Treasury and SEC - it is imperative that we enshrine into law the rights of open source developers to build products and services that enable individuals to self-custody bitcoin and use it in a peer-to-peer fashion without the threat of getting thrown in jail cell.
As it stands today, the only assurances that we have are from an administration that is overtly in favor of the proliferation of bitcoin in the United States. There is nothing in place to stop the next administration or another down the line from reverting to Biden-era lawfare that puts thousands of bitcoin developers around the world at risk of being sent into a cage because the government doesn't like how some users leverage the code they write. To make sure that this isn't a problem down the line it is imperative that we pass the Blockchain Regulatory Clarity Act, which would not hold bitcoin developers liable for the ways in which end users leverage their tools.
Not only is this an act that would protect developers from pernicious government officials targeting them when end users use their technology in a way that doesn't make the government happy, it will also protect YOU, the end user, looking to transact in a peer-to-peer fashion and leverage all of the incredible properties of bitcoin the way they were meant to be. If the developers are not protected, they will not be able to build the technology that enables you to leverage bitcoin.
So do your part and go to saveourwallets.org. Reach out to your local representatives in Congress and Senators and make some noise. Let them know that this is something that you care deeply about and that they should not only pay attention to this bill but push it forward and enshrine it into law as quickly as possible.
There are currently many developers either behind bars or under house arrest for developing software that gives you the ability to use Bitcoin in a self-sovereign fashion and use it in a privacy-preserving way. Financial privacy isn't a crime. It is an inalienable human right that should be protected at all cost. The enshrinement of this inalienable right into law is way past due.
#FreeSamourai #FreeRoman
Headlines of the Day
MicroStrategy Copycats See Speculative Premiums Fade - via X
Square Tests Bitcoin Payments, Lightning Yields Beat DeFi - via X
Get our new STACK SATS hat - via tftcmerch.io
Bitfinex Moves $731M Bitcoin to Jack Mallers' Fund - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Should I join a country club?
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ e2c72a5a:bfacb2ee
2025-06-04 11:19:49
@ e2c72a5a:bfacb2ee
2025-06-04 11:19:49While hackers shift from code to human psychology, $2.1B in crypto was stolen in 2025. Ethereum's price surged 46% in 30 days, strengthening against Bitcoin and poised for a significant breakout. Meanwhile, California unanimously passed a bill allowing state agencies to accept crypto payments, signaling mainstream adoption. Corporate treasuries now control over 3% of Bitcoin's total supply, with 60+ companies doubling their holdings in just two months. The crypto landscape is transforming from technical vulnerabilities to social engineering – are you protecting your assets or just your code? What security measures have you implemented that address the human element of crypto safety?
-
 @ 5ea46480:450da5bd
2025-06-04 11:18:24
@ 5ea46480:450da5bd
2025-06-04 11:18:24Ofcourse do we want our big open world cake, and eat it with a side of stability and order. I love the spammers, because all they do is press our noses on the grim reality we are facing: Everything is going to turn to absolute shit. The fact that we are all interconnected is meaningless because the communication lines contain too much noise.
Look, some spambot posting silly things that might waste your attention for a tiny bit before you figure out its not worth your time, or clutter your feed, is not the end of the world. But the point is that that post could be anything, and with a bit of AI effort more convincing. We all sense this, in fact we even see it, and there is no indication to think it wont get worse.
Important to note is, that the big platforms are struggling with this crap as well. Their set up is by their nature a ‘have a cake and eat it’ proposition: Yes we are the worlds public square that everyone visits in this particular domain, and we will keep you safe from spammers and fraudsters. But we ran out of captchas, and they are forced to heighten their walls, reinforce their gates and increase the amount of guards that are on patrol; slowly but surely, you as a user will be forced to subjugate yourself to more and more scrutiny, restrictions and punishment if you want to be active there. At some point the only reason they would be considered ‘the worlds public square’, is because they are the only vestiges of order left without any existing alternatives.
If we seriously want to introduce that alternative, we would have to approach the issue in a fundamentally different manner. That issue, is one of reputation, i.e. consistent behavior over time. Now to be clear, there is no full proof system for reputation, it does not exist for two reasons: One, anyone at any time can decide to break their consistent behavior simply because they feel like it. And two, because you you never have perfect information and can therefor not interpret the consistency of their behavior perfectly; think of a spy for example, where them consistently lying to you and eventually betraying you actually makes them a consistent spy.
Reputation is always a game of who knows who, but ‘social’ reputation is hard to scale: the longer the ties become, the less they can be relied upon. To scale reputation went the route of formalization via institutions: these are your certificates, badges, uniforms whatever, as a testament you went through certain predefined hoops in a controlled environment. As a result, whatever reputation the institution might have rubs off on you. It also stacks in the fact that one certificate can only be obtained when other certificates were acquired prior. So these certificates are pieces of reputational capital, defined in records. This system allowed us to create globe spanning organizations.
That system does work, but it is rigid, and the moment it becomes corrupt you are very, very screwed, because on what basis are you going to put it back together again? In any event, that is what we have anyway and as noted it has other issues, so what other option is there? Scaling ‘social’ reputation. The whole idea behind Nostr’s ‘Web of Trust’, is that bottom-up connections and relations, that are (partly) based on existing relations in meat-space can form a globally meaningful reputational pillar on which we can start identifying each other again.
If seven handshakes connects you with everyone, four will get you pretty far. Three is even less risk, whilst five might open up interesting doors for you. The point is, its gradual, and according to your risk appetite you can play around with it. Secondly, the better well connected you are, how more of a reputation you gained, the less risk you need to run to begin with. Obviously this requires some bootstrapping, but you live in meatspace; if there really is no-one out there willing to give you a leg up you might want to do some soul searching.
But the result of this strategy, will be that everyone will pull back behind their own little moats first. At first, we will all lose connections to defend ourselves against the massive onslaught of ‘the Fake’: The big estrangement. But that is ok, with a bit of effort, I am sure that eventually, after enough reputational capital is build over time, we will find each other again in this global village.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36
@ 5d4b6c8d:8a1c1ee3
2025-06-04 01:24:36Howdy stackers, this is the place to share your ~HealthAndFitness triumphs and challenges.
I was glad to hit my step goal today, since it's gloomy and rainy here. Once again, I ate too many cookies. Gotta stop being a cookie monster.
How'd you all do, today?
https://stacker.news/items/996659
-
 @ f85b9c2c:d190bcff
2025-06-04 01:06:04
@ f85b9c2c:d190bcff
2025-06-04 01:06:04
Focusing on something for an hour a Day for the next 90 days will make you 90% better than others. I’ve been mulling over a simple truth lately, and I’m excited to share it with you. What if I told you that just one hour a day could change your game? Not ten, not five, but one little hour—sixty minutes to claim.
Stick with me here, because I’m about to break it down in a way that’ll make you cheer, with sentences that rhyme and a message that’s clear.
The Magic of One Hour Let’s start with the power that’s ours to devour. One hour a day, no more, no less, can lift you from the mundane mess. It’s not about grinding till you drop, or pushing so hard you flop. It’s a focused burst, a daily deed, planting a tiny, mighty seed. While others scroll or doze away, you’re stacking skills day by day. In 90 days, you’ll see it’s true— you’ll rise above the common crew.
Why 90 Days Works Ninety days, a quarter year, is time enough to shift your gear. It’s short enough to keep the fire, long enough to climb higher. Science says habits form in less, but mastery needs a steady press. An hour each day, consistent and neat, builds a rhythm you can’t beat. While others drift, you’ll stay on track, your progress piling, no looking back.
Be Better Than Most Here’s the kicker, the reason to boast: most folks don’t focus, they just coast. An hour of effort, pure and fine, puts you ahead of ninety-nine. Not because you’re some rare breed, but because you chose to plant that seed. The world’s distracted, screens aglow, but you’ll be steady, in the know. By day ninety, you’ll stand tall, 90% better than them all.
How to Make It Stick Pick your thing, don’t overthink—writing, coding, or a gym link. Set a time, make it rhyme with your daily chime. Shut the noise, close the door, focus deep, and explore. No multitasking, that’s a trap, just one task to bridge the gap. Track your days, feel the groove, watch your skills start to improve.
My Challenge to You So here’s my dare, from me to you: one hour a day, see it through. Ninety days, that’s all I ask, a simple, life-changing task. I’m doing it too, I’m in the race, chasing growth at my own pace. Let’s rise together, you and I, with just an hour, we’ll touch the sky. Start today, don’t delay— one hour a day is all you need, okay?
-
 @ 8bad92c3:ca714aa5
2025-06-04 01:02:13
@ 8bad92c3:ca714aa5
2025-06-04 01:02:13
Let's dive into the most interesting forward-looking predictions from my recent conversations with industry experts.
Court Cases Against Bitcoin Developers Will Set Critical Precedent for the Industry's Future - Zack Shapiro
The outcome of the Samurai Wallet case will determine whether software developers can be held legally responsible for how users employ their non-custodial Bitcoin tools. Zack Shapiro laid out the stakes clearly: "The precedent that the Bank Secrecy Act can be applied to just software that allows you to move your own money on the Bitcoin blockchain is incredibly dangerous for developers, for node runners, for miners... Basically everyone in the Bitcoin space is at risk here."
According to Shapiro, the government's position in this case fundamentally misunderstands Bitcoin's architecture: "The government says that the defendants transmitted, Keone and Bill transmitted money that they knew belonged to criminals. That's not how a coin join works. The people who transmitted the money are the people that used Whirlpool and the people that used Ricochet. They signed their keys."
Should this prosecution succeed in establishing precedent, Shapiro predicts catastrophic consequences: "If that becomes the law of the land... then basically no actor in the Bitcoin economy is safe. The government's theory is that if you facilitate movement of money, you're a money transmitter, that would reach node runners, wallet developers, miners, lightning routing nodes... whatever tool stack you use, the people who built that are at risk."
With the case continuing despite FinCEN's own position that Samurai's software isn't money transmission, Shapiro believes the resolution will likely come through political rather than legal channels in the next 6-12 months.
Malpractice Around COVID mRNA Vaccines Will Be Exposed Within 2 Years - Dr. Jack Kruse
Dr. Jack Kruse predicts that major revelations about mRNA vaccine damage will force an eventual removal from the market, particularly from childhood vaccination schedules. During our conversation, Dr. Kruse shared alarming statistics: "25,000 kids a month are getting popped with this vaccine. Just so you know, since Trump has been elected, three million doses have been given to children."
According to Dr. Kruse, the scale of this problem dwarfs other health concerns: "The messenger job can drop you like Damar Hamlin, can end your career like JJ Watt, can end your career like all the footballers who've dropped dead on a soccer field." What makes this particularly concerning is the suppression of evidence about the damages, with Dr. Kruse noting that data from Japan showing changes in cancer distribution patterns was pulled, and VAERS data being dismissed despite showing alarming signals.
Dr. Kruse believes the coming years will see an unavoidable reckoning: "If by the end of this year, everybody in unison realized that MRA platform is bad news and it's gone. That to me is... I would tell you the biggest win is to get rid of the MRA platform even before any of the Bitcoin stuff." This suggests he expects significant momentum toward removing these vaccines from circulation by the end of 2025.
Global Economic Reordering Will Create Demand for Neutral Reserve Assets Like Bitcoin and Gold - Lyn Alden
The next two years will be critical in determining whether the United States maintains dollar dominance while navigating Triffin's dilemma. During our conversation, Lyn highlighted how the current administration is attempting to thread a needle between reshoring manufacturing while maintaining the dollar's reserve status - an almost impossible task on extremely fragile ground.
"When they talk about kind of a currency accord to weaken the dollar, they mentioned ideally they wanted to use multi-lateral approaches, but there are some unilateral approaches that they can do, which includes printing dollars to buy reserve assets," Lyn explained when discussing Treasury advisor Stephen Myron's position paper.
As the world potentially moves to a multipolar currency system, Lyn predicts significant demand increases for neutral reserve assets. "The two options on the table at this point are gold and Bitcoin," she noted, but pointed out that "our geopolitical adversaries have been stacking gold for a while and with a special intensity for the last three years." This creates a strategic opportunity for the US, as Bitcoin is "overwhelmingly held in the United States."
Lyn believes this transition is already underway, with the demand for neutral reserve assets like Bitcoin growing as countries seek alternatives to solely dollar-denominated reserves.
Blockspace conducts cutting-edge proprietary research for investors.
Iran's Shadow Mining Economy: 2 GW of Bitcoin Mined Underground While Legal Operations Struggle
Iran hosts a thriving underground Bitcoin mining industry that has emerged as a critical financial lifeline for citizens grappling with international sanctions and domestic economic controls. This shadow economy dwarfs the legal sector, with an estimated 2 gigawatts of illegal mining operations compared to just 5 megawatts of sanctioned activity.
According to ViraMiner CEO Masih Alavi, approximately 800,000 illegal miners have been discovered and fined by authorities. Yet operations continue in homes, office buildings, and even jewelry stores, where Iranians tap into unmetered electricity to mine Bitcoin, later converting it to stablecoins like USDT for savings and commerce.
While the government has approved permits for about 400 megawatts of legal mining capacity, punitive electricity tariffs and regulatory barriers have strangled legitimate operations. "I blamed the government for this situation," says Alavi. "They introduced flawed policies in the beginning, especially by setting the wrong electricity tariffs for the mining industry."
Despite using obsolete equipment like Antminer S9s and M3s, underground miners remain profitable when converting earnings to Iranian rials, creating an ecosystem that serves an estimated 18 million Iranian cryptocurrency holders.
Looking ahead, Alavi predicts further crackdowns as Iran enters peak electricity demand season, potentially reducing legal mining to zero while underground operations continue to evolve sophisticated detection evasion techniques.
Subscribe to them here (seriously, you should): https://newsletter.blockspacemedia.com/
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
STACK SATS hat: https://tftcmerch.io/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ f85b9c2c:d190bcff
2025-06-04 01:00:21
@ f85b9c2c:d190bcff
2025-06-04 01:00:21
Is Physical Punishment Truly an Effective Way to Discipline Children? Whether flogging or corporal punishment, is a proper way to correct a child often causes disagreement and debate. Over the centuries and around the world, educators, psychologists, parents and lawmakers have argued about it. A person’s behavior is corrected through flogging which is intended to be physically harsh. It is a big concern whether the process helps or leaves people with more damage over time.
Historical Perspective Floggings have been practiced for centuries to discipline people. Years back, many people used disciplinary spanking to encourage children to be disciplined and respectful. It used to be popularly believed that not using discipline made children spoiled. This saying suggested that flogging or some other physical punishment, was both necessary and proper to correct those who did wrong. Presently, things are not the same as they were before. In the last few decades, there has been a major change in what is generally accepted. Child development and psychology research indicate that flogging and different types of punishment might even cause harm.
Effects on Mind and Feelings Experts always see that flogging has negative impact on children’s mental health. Even though it may force someone to cooperate right away, it usually results in fear, resentment and aggression. Instead of showing right from wrong, it makes the child think that being disciplined is humiliating and causes pain. This situation might lower the child’s self-esteem, interfere with their emotional development and hurt the relationship between the child and the parent. Also, flogging does little to deal with the real reason why someone acts this way. It only worries about how to punish instead of trying to understand why the behavior occurred. A correct approach involves explaining the problem with what they did and supporting them to improve their decisions next time.
Having Questions About What Is Legal and Ethical Many countries now forbid flogging and other corporal punishments in both schools and homes. Children’s freedom from physical harm is becoming recognized more often in the law. UNCRC claims that children should be protected from all types of physical and mental abuse.
Ethical concerns are raised by the practice of using flogging to discipline people. It goes against the main principles of respect and dignity. Their growth as human beings calls for proper guidance, so kids can become mature and caring adults. When they are beaten, children often learn that violence is a way to find solutions.
What Can Be Used Instead of Flogging There are a lot of peaceful and successful steps you can take to guide how a child behaves. Settings ground rules, using praise for good behaviors, always keeping communication clear and giving the same consequences help. By giving praise for good behavior, you help the child want to act that way again. Giving a time-out or taking away things a person enjoys is a gentle way to deal with misbehavior.
 In addition, these approaches help fix behavior problems and allow the child and caregiver to form trust and communicate openly. Through play, children learn to control themselves, feel empathy and solve problems which they need for their ongoing growth.
In addition, these approaches help fix behavior problems and allow the child and caregiver to form trust and communicate openly. Through play, children learn to control themselves, feel empathy and solve problems which they need for their ongoing growth.Conclusion In short, flogging does not make sense or work as a way to correct a child. Despite making the child obey at the moment, it often seriously harms a child’s emotional, psychological and moral growth in the future. Today’s parenting and educating focus on methods that fix misbehavior and boost a child’s confidence and sense of safety. Real correction teaches the child, helps them make right choices and encourages them to be responsible and caring. Flogging is not successful in reaching these goals. Rather, it causes a pattern of violence and fear that can cause serious damage in the long run. So, flogging should be understood not as a punishment, but as something harmful that society should forget about.
-
 @ 1817b617:715fb372
2025-06-03 21:51:18
@ 1817b617:715fb372
2025-06-03 21:51:18🚀 Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs 🔥 Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
🌐 Visit cryptoflashingtool.com for complete details.
🌟 Why Choose Our Crypto Flashing Service? Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
🎯 Our Crypto Flashing Features: ✅ Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
🔒 Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
🖥️ Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
📅 Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
🔄 Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
💱 Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
📊 Proven Track Record: ✅ Over 79 Billion flash transactions completed. ✅ 3000+ satisfied customers worldwide. ✅ 42 active blockchain nodes for fast, reliable transactions. 📌 Simple Step-by-Step Flashing Process: Step 1️⃣: Enter Transaction Details
Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20) Specify amount & flash duration Provide wallet address (validated automatically) Step 2️⃣: Complete Payment & Verification
Pay using the cryptocurrency you wish to flash Scan the QR code or paste the payment address Upload payment proof (transaction hash & screenshot) Step 3️⃣: Initiate Flash Transaction
Our technology simulates blockchain confirmations instantly Flash transaction appears authentic within seconds Step 4️⃣: Verify & Spend Immediately
Access your flashed crypto instantly Easily verify transactions via provided blockchain explorer links 🛡️ Why Our Technology is Trusted: 🔗 Race/Finney Attack Logic: Creates realistic blockchain headers. 🖥️ Private iNode Cluster: Guarantees fast synchronization and reliable transactions. ⏰ Live Timer System: Ensures fresh wallet addresses and transaction legitimacy. 🔍 Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash ❓ Frequently Asked Questions: Is flashing secure? ✅ Yes, encrypted with full VPN/proxy support. Can I flash from multiple devices? ✅ Yes, up to 5 Windows PCs per license. Are chargebacks possible? ❌ No, flash transactions are irreversible. How long are flash coins spendable? ✅ From 60–360 days, based on your chosen plan. Verification after expiry? ❌ Transactions can’t be verified after the expiry. Support available? ✅ Yes, 24/7 support via Telegram & WhatsApp.
🔐 Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
📲 Get in Touch Now: 📞 WhatsApp: +1 770 666 2531 ✈️ Telegram: @cryptoflashingtool
🎉 Ready to Start?
💰 Buy Flash Coins Now 🖥️ Get Your Flashing Software
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
Instantly Send Spendable Flash BTC, ETH, & USDT — Fully Blockchain-Verifiable!
Welcome to the cutting edge of crypto innovation: the ultimate tool for sending spendable Flash Bitcoin (BTC), Ethereum (ETH), and USDT transactions. Our advanced blockchain simulation technology employs
Race/Finney-style mechanisms, producing coins indistinguishable from authentic blockchain-confirmed tokens. Your transactions are instantly trackable and fully spendable for durations from 60 to 360 days!
Visit cryptoflashingtool.com for complete details.
Why Choose Our Crypto Flashing Service?
Crypto Flashing is perfect for crypto enthusiasts, blockchain developers, ethical hackers, security professionals, and digital entrepreneurs looking for authenticity combined with unparalleled flexibility.
Our Crypto Flashing Features:
Instant Blockchain Verification: Transactions appear completely authentic, complete with real blockchain confirmations, transaction IDs, and wallet addresses.
Maximum Security & Privacy: Fully compatible with VPNs, TOR, and proxy servers, ensuring absolute anonymity and protection.
Easy-to-Use Software: Designed for Windows, our intuitive platform suits both beginners and experts, with detailed, step-by-step instructions provided.
Customizable Flash Durations: Control your transaction lifespan precisely, from 60 to 360 days.
Universal Wallet Compatibility: Instantly flash BTC, ETH, and USDT tokens to SegWit, Legacy, or BCH32 wallets.
Spendable on Top Exchanges: Flash coins seamlessly accepted on leading exchanges like Kraken and Huobi.
Proven Track Record:
- Over 79 Billion flash transactions completed.
- 3000+ satisfied customers worldwide.
- 42 active blockchain nodes for fast, reliable transactions.
Simple Step-by-Step Flashing Process:
Step : Enter Transaction Details
- Choose coin (BTC, ETH, USDT: TRC-20, ERC-20, BEP-20)
- Specify amount & flash duration
- Provide wallet address (validated automatically)
Step : Complete Payment & Verification
- Pay using the cryptocurrency you wish to flash
- Scan the QR code or paste the payment address
- Upload payment proof (transaction hash & screenshot)
Step : Initiate Flash Transaction
- Our technology simulates blockchain confirmations instantly
- Flash transaction appears authentic within seconds
Step : Verify & Spend Immediately
- Access your flashed crypto instantly
- Easily verify transactions via provided blockchain explorer links
Why Our Technology is Trusted:
- Race/Finney Attack Logic: Creates realistic blockchain headers.
- Private iNode Cluster: Guarantees fast synchronization and reliable transactions.
- Live Timer System: Ensures fresh wallet addresses and transaction legitimacy.
- Genuine Blockchain TX IDs: Authentic transaction IDs included with every flash
Frequently Asked Questions:
- Is flashing secure?
Yes, encrypted with full VPN/proxy support. - Can I flash from multiple devices?
Yes, up to 5 Windows PCs per license. - Are chargebacks possible?
No, flash transactions are irreversible. - How long are flash coins spendable?
From 60–360 days, based on your chosen plan. - Verification after expiry?
Transactions can’t be verified after the expiry.
Support available?
Yes, 24/7 support via Telegram & WhatsApp.
Transparent, Reliable & Highly Reviewed:
CryptoFlashingTool.com operates independently, providing unmatched transparency and reliability. Check out our glowing reviews on ScamAdvisor and leading crypto forums!
Get in Touch Now:
WhatsApp: +1 770 666 2531
Telegram: @cryptoflashingtool
Ready to Start?
Experience the smartest, safest, and most powerful crypto flashing solution on the market today!
CryptoFlashingTool.com — Flash Crypto Like a Pro.
-
 @ dfa02707:41ca50e3
2025-06-03 21:02:19
@ dfa02707:41ca50e3
2025-06-03 21:02:19Contribute to keep No Bullshit Bitcoin news going.
- Coinswap is a decentralized protocol for private, trustless cryptocurrency swaps. It allows participants to securely swap digital assets without intermediaries, using advanced cryptographic techniques and atomic swaps to ensure privacy and security.
- This release introduces major improvements to the protocol's efficiency, security, and usability, including custom in-memory UTXO indexes, more advanced coin-selection algorithms, fidelity bond management and more.
- The update also improves user experience with full Mac support, faster Tor connections, enhanced UI/UX, a unified API, and improved protocol documentation.
"The Project is under active beta development and open for contributions and beta testing. The Coinswap market place is live in testnet4. Bug fixes and feature requests are very much welcome."
- Manuals and demo docs are available here.
What's new
- Core protocol and performance improvements:
- Custom in-memory UTXO indexes. Frequent Core RPC calls, which caused significant delays, have been eliminated by implementing custom in-memory UTXO indexes. These indexes are also saved to disk, leading to faster wallet synchronization.
- Coin selection. Advanced coin-selection algorithms, like those in Bitcoin Core, have been incorporated, enhancing the efficiency of creating different types of transactions.
- Fidelity management. Maker servers now automate tasks such as checking bond expiries, redemption, and recreation for Fidelity Bonds, reducing the user's management responsibilities.
- Taker liveness. The
WaitingFundingConfirmationmessage has been added to keep swap connections between Takers and Makers, assisting with variable block confirmation delays.
-
User experience and compatibility:
- Mac compatibility. The crate and apps now fully support Mac.
- Tor operations are streamlined for faster, more resilient connections. Tor addresses are now consistently linked to the wallet seed, maintaining the same onion address through system reboots.
- The UI/UX improvements enhance the display of balances, UTXOs, offer data, fidelity bonds, and system logs. These updates make the apps more enjoyable and provide clearer coin swap logs during the swap process.
-
API design improvements. Transaction creation routines have been streamlined to use a single common API, which reduces technical debt and eliminates redundant code.
- Protocol spec documentation now details how Coinswap breaks the transaction graph and improves privacy through routed swaps and amount splitting, and includes diagrams for clarity.
Source: Coinswap Protocol specification.

-
 @ cae03c48:2a7d6671
2025-06-03 21:01:12
@ cae03c48:2a7d6671
2025-06-03 21:01:12Bitcoin Magazine

Reitar Logtech Announces $1.5 Billion Bitcoin Acquisition PlanReitar Logtech Holdings Ltd., a Hong Kong-based firm operating in real estate and logistics technology, has officially announced plans to purchase up to $1.5 billion worth of Bitcoin. The move was disclosed in a June 2 filing with the U.S. Securities and Exchange Commission (SEC).
NEW:
 Hong Kong-based Reitar Logtech announces they will buy $1.5 billion #Bitcoin for their reserves — SEC filing pic.twitter.com/viC0kUycNo
Hong Kong-based Reitar Logtech announces they will buy $1.5 billion #Bitcoin for their reserves — SEC filing pic.twitter.com/viC0kUycNo— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
According to the filing, the strategic Bitcoin acquisition is intended to bolster Reitar’s treasury reserves while accelerating the company’s global expansion in logistics technology infrastructure. The announcement aligns Reitar Logtech with a growing number of international firms turning to Bitcoin as a reserve asset.
By incorporating Bitcoin into its financial strategy, Reitar Logtech aims to grow its holdings beyond traditional fiat currencies and fixed-income products. By adopting a strategic BTC reserve, the company aims to benefit from Bitcoin’s liquidity, 24/7 markets, and hedge against long-term inflation and currency devaluation.
The SEC filing describes the initiative as follows, “Reitar Logtech Holdings Ltd. Announces Up to US$1.5 Billion Strategic Bitcoin (BTC) Acquisition to Bolster Treasury Reserves and Accelerate Global Logistics Technology Expansion.”
The filing was signed by Kin Chung Chan, Reitar Logtech’s Director, Chairman, and Chief Executive Officer, who affirmed that the filing was submitted in accordance with the Securities Exchange Act of 1934.
While specific timing for the acquisition has not been disclosed, analysts believe such a large-scale buy could be done in phases to manage market impact and line up with internal capital strategy. It remains unclear if the purchase will be conducted via spot markets, custodians, or structured investment vehicles.
The adoption also brings to light a wider trend among corporations allocating Bitcoin to their balance sheets. Reitar joins companies such as Strategy, that have leveraged Bitcoin not only for financial positioning, but as a long-term asset.
This post Reitar Logtech Announces $1.5 Billion Bitcoin Acquisition Plan first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-06-03 20:01:05
@ cae03c48:2a7d6671
2025-06-03 20:01:05Bitcoin Magazine

NBX Acquires Bitcoin, Becomes First Public Bitcoin Treasury Company in NorwayNorwegian Block Exchange (NBX), a leading Nordic cryptocurrency exchange and digital asset platform, announced that it has added Bitcoin to its balance sheet, marking a national milestone as the first publicly listed company in Norway to hold Bitcoin as part of its treasury strategy.
JUST IN:
 Norwegian Block Exchange becomes the first publicly traded #Bitcoin treasury company in the country
Norwegian Block Exchange becomes the first publicly traded #Bitcoin treasury company in the country  pic.twitter.com/kY9KK2VbFi
pic.twitter.com/kY9KK2VbFi— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The company has secured 6.0 Bitcoin and plans to increase its holdings to 10.0 within June. The assets, loaned from NBX’s largest shareholders, will be used as collateral to issue USDM, a MiCA-compliant stablecoin. NBX said it aims to generate yield through Bitcoin and the USDM ecosystems.
“NBX will not sell this Bitcoin or go short in any form,” the company said. “With reference to the latest POA notice with LDA capital, NBX will also use proceeds to buy additional Bitcoin.”
NBX is currently talking with HNIs, family offices, and others about raising more capital to buy additional Bitcoin. The company is also hosting a Bitcoin treasury event on June 11.
“Bitcoin is becoming an important part of the global financial infrastructure,” the company stated in the announcement. “The Bitcoin will increase operational efficiency, in addition to attracting capital that need exposure to Bitcoin yet only have a mandate to invest in Norwegian publicly listed companies.”
The adoption of Bitcoin as a treasury reserve asset has dramatically increased over the course of the last year, expanding globally. To date, there are 214 companies and other entities with Bitcoin in their balance sheets.
Méliuz, Brazilian fintech company, also recently announced on May 15th, that it purchased an additional R$160.8 million (approx. $30.5 million) worth of Bitcoin, adding 274.5 BTC at an average price of $103,600 each, after becoming the first Bitcoin treasury company in Brazil earlier this year. Combined with its initial R$24 million investment two months ago, Méliuz now holds 320 BTC, making it the 42nd largest corporate holder of Bitcoin globally.
JUST IN:
 Brazilian public company Méliuz becomes first Bitcoin Treasury Company in the country, buys $28.4 million #Bitcoin pic.twitter.com/6WnFqefy3L
Brazilian public company Méliuz becomes first Bitcoin Treasury Company in the country, buys $28.4 million #Bitcoin pic.twitter.com/6WnFqefy3L— Bitcoin Magazine (@BitcoinMagazine) May 15, 2025
Méliuz Founder and Chairman Israel Salmen noted that the move attracted a new wave of crypto-focused investors. In his words, translated from Portuguese, “a lot of new people started buying the stock because of this strategy. We caught the attention of the crypto crowd, which is a much larger audience than stock market investors. There are around 20 million people investing in crypto today and only about 5 million in the stock market.”
The investment, approved by Méliuz’s board, is part of a new treasury management policy focused on long-term returns. The company also formed a Bitcoin Strategic Committee to explore expanding the allocation and potentially making Bitcoin a primary treasury asset.
Salmen told local media the move into bitcoin provides an “intelligent alternative” to holding cash reserves. “We see bitcoin as a long-term store of value,” he said. The company, which offers cashback and financial services to over 30 million users in Brazil, is aiming to revive investor interest after its market cap dropped from $6 billion in 2021 to $270 million.
This post NBX Acquires Bitcoin, Becomes First Public Bitcoin Treasury Company in Norway first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ da8b7de1:c0164aee
2025-06-03 19:31:32
@ da8b7de1:c0164aee
2025-06-03 19:31:32Lengyelország előrelépése az első atomerőmű építésében
Lengyelország állami nukleáris vállalata, a Polskie Elektrownie Jadrowe (PEJ) és egy amerikai konzorcium – élén a Westinghouse és a Bechtel cégekkel – mérnöki fejlesztési megállapodást kötött. Ez a szerződés kulcsfontosságú lépés az ország első atomerőművének megvalósítása felé, lehetővé téve a részletes mérnöki és helyszínspecifikus munkák megkezdését. A lengyel kormány ezt mérföldkőnek tekinti az energiaszuverenitás és a dekarbonizáció felé vezető úton.
Amerikai politika: lendület az új nukleáris technológiáknak
Az Egyesült Államok kormánya elnöki rendeletet adott ki, amely reformokat vezet be a nukleáris reaktorok tesztelésében az Energiaügyi Minisztériumnál. A cél az új generációs reaktorok – köztük mikroreaktorok és kis moduláris reaktorok (SMR-ek) – fejlesztésének és engedélyezésének felgyorsítása, valamint a környezetvédelmi vizsgálatok egyszerűsítése. A rendelet legalább három új reaktor kritikus üzembe helyezését célozza meg 2026 júliusáig, támogatva ezzel az ipari alkalmazások széles körét, például adatközpontokat vagy hidrogéntermelést. Az intézkedés célja, hogy az USA visszaszerezze vezető szerepét a nukleáris innovációban, és csökkentse a korábbi években felhalmozódott engedélyezési akadályokat.
Kis moduláris reaktorok (SMR) fejlesztése világszerte
Az SMR-szektorban világszerte jelentős előrelépések történtek: - Az amerikai Tennessee Valley Authority (TVA) benyújtotta az első építési kérelmet egy GE Hitachi BWRX-300 SMR-re a Clinch River telephelyen. - Kanadában az Ontario Power Generation engedélyt kapott az első, négy tervezett SMR megépítésének megkezdésére a Darlington telephelyen. - Belgium és Brazília innovatív SMR-technológiákat vizsgál, köztük ólom-hűtésű reaktorokat és nemzetközi együttműködéseket. - Olyan technológiai óriások, mint a Google, az USA-ban korai fázisú fejlett nukleáris projektekbe fektetnek, ami a magánszektor növekvő érdeklődését mutatja.
Globális ipari és pénzügyi támogatás a nukleáris bővítéshez
Széles körű koalíció – köztük olyan nagyvállalatok, mint az Amazon, Google, Meta, Dow – és pénzügyi intézmények kötelezték el magukat amellett, hogy 2050-re megháromszorozzák a globális nukleáris kapacitást. Ez összhangban van az ENSZ klímacsúcsain tett vállalásokkal, ahol már 31 ország támogatja a nukleáris energia megháromszorozását a nettó zéró kibocsátási célok eléréséhez. Az amerikai kongresszus olyan törvényjavaslatokat készít elő, amelyek lehetővé tennék, hogy a multilaterális fejlesztési bankok – például a Világbank – is finanszírozhassanak nukleáris projekteket, megszüntetve ezzel a korábbi tiltásokat.
Közelgő nemzetközi nukleáris biztonsági gyakorlat
A Nemzetközi Atomenergia-ügynökség (IAEA) készül a ConvEx-3 vészhelyzeti gyakorlatára, amelyet 2025. június 24–25-én Romániában tartanak. A gyakorlat egy súlyos nukleáris vészhelyzetet szimulál a cernavodai atomerőműben, tesztelve a tagállamok és nemzetközi szervezetek felkészültségét és reagálóképességét. A ConvEx-3 a legmagasabb szintű IAEA vészhelyzeti gyakorlat, kulcsszerepet játszik a globális nukleáris biztonság és védelem erősítésében.
Politikai bizonytalanság Dél-Korea nukleáris terveiben
Dél-Korea 2025. június 3-i elnökválasztása hatással lehet az ország nukleáris reneszánszára. A vezető jelölt, Lee Jae-myung kijelentette, hogy „egyelőre” fenntartaná a nukleáris energiát, de hosszabb távon a megújulók felé mozdulna el. Ez bizonytalanságot okoz a koreai nukleáris ipar hazai és exportterveiben, ami kihatással lehet a globális ellátási láncokra és külföldi reaktorprojektekre is.
Iparági trendek és további fejlemények
- Japán új energiastratégiája maximalizálni kívánja a nukleáris energia részarányát, 2040-re mintegy 20%-ot célozva, különös hangsúlyt fektetve a következő generációs reaktorokra és a biztonság növelésére.
- Belgium kormánya és a francia Engie közműcég megállapodott a kulcsfontosságú reaktorok üzemidejének tízéves meghosszabbításáról, ami az európai nukleáris pálfordulás újabb jele.
- Az IAEA és a World Nuclear Association egyaránt növekvő nemzetközi érdeklődésről számol be az SMR-ek és fejlett reaktortechnológiák iránt, új projektek és partnerségek indulnak Ázsiában, Európában és Amerikában.
Források:
world-nuclear-news.org
nucnet.org
iaea.org
world-nuclear.org
govinfo.gov
whitehouse.gov -
 @ 05a0f81e:fc032124
2025-06-03 19:28:10
@ 05a0f81e:fc032124
2025-06-03 19:28:10What Are Rumors?
Rumors are pieces of information, stories, or claims that are circulated among people without confirmed evidence or verification. They often spread by word of mouth, social media, or other informal means and can be either true, partially true, or completely false.
Rumors can arise in various settings, schools, workplaces, communities, or online and may involve personal matters, celebrities, politics, or current events.
There are Characteristics of Rumors
-
Lack of Verification: Rumors are not based on solid evidence or official sources.
-
Rapid Spread: They often spread quickly, especially in emotionally charged environments.
-
Distortion Over Time: As a rumor is retold, details may change, making it more misleading.
-
Emotional Impact: They usually provoke strong reactions like fear, curiosity, or anger.
There are various disadvantages of Rumors
- Spread of False Information
Rumors can mislead people, creating confusion or panic, especially during crises.
Example: False health advice during a pandemic can endanger lives.
- Damage to Reputation
Individuals or organizations can suffer harm to their image or credibility.
Example: A student falsely accused of cheating might face social isolation or disciplinary action.
- Breakdown of Trust
Trust within families, workplaces, or communities can erode when rumors circulate.
People become suspicious and communication suffers.
- Emotional Harm
Rumors can lead to stress, anxiety, and depression, especially for those targeted.
In extreme cases, victims may experience bullying or harassment.
- Conflict and Division
Rumors often fuel misunderstandings, arguments, or even violence.
They can cause divisions along social, political, or cultural lines.
- Wasted Time and Resources
Authorities or organizations may have to spend time disproving rumors instead of focusing on important tasks.
Example: Law enforcement addressing false threats.
- Legal Consequences
In some cases, spreading harmful or defamatory rumors can lead to lawsuits or criminal charges.
Conclusion
While some rumors may seem harmless or even entertaining, their consequences can be severe. They thrive in environments lacking transparency and can damage individuals, relationships, and communities. It is always best to verify information from credible sources before sharing it and to promote honest, respectful communication.
-
-
 @ bf47c19e:c3d2573b
2025-06-03 19:10:37
@ bf47c19e:c3d2573b
2025-06-03 19:10:37Originalni tekst na bitcoin-balkan.com
Bitcoinova potrošnja energije nije „rasipna“
– On je mnogo efikasniji od postojećih finansijskih sistema
– Niko nema moralni autoritet da vam kaže šta je dobra ili loša upotreba energije (npr: gledanje Parova, Zadruge ili Farme)
Hajde da raskrinkamo ovaj FUD (eng. Fear, Uncertainty and Doubt – Strah, Neizvesnost i Sumnju)
U ovom članku istražujem kako je sve oko nas energija, novac je energija, subjektivna upotreba energije i troškovi PoW-a (eng. Proof of work – Dokaz rada) u odnosu na postojeće sisteme upravljanja.
Ideja da je „rad“ energija, započela je kada je francuski matematičar Gaspard-Gustave de Coriolis predstavio ideju da je energija „odrađen rad“. Nekada davno, celokupan posao koji je odrađivan u ekonomiji realizovan je kroz ljuduski rad. Taj rad pokretala je hrana. Pre više hiljada godina, naša potrošnja energije se povećala kada smo pripitomili životinje koje bi mogle da rade umesto nas. Ti novi radnici takođe su morali da budu nahranjeni. Velike količine hrane bile su potrebne da bi se zadovoljile potrebe za energijom, a zajedno sa nama, povećavao se i naš prosperitet.

U poslednjih nekoliko stotina godina napravili smo sjajne mašine koje imaju svrhu izvršavanja tj. proizvodnje odredjenog rada. I mašine i priroda proizvode rad korišćenjem energije (prvi zakon termodinamike). Imamo ekonomiju koja se ne zasniva na novcu, već na radu i energiji.

Sve stvari u našem životu su usko povezane sa cenom energije. Troškovi bilo kog dobra su u velikoj meri odraz energije koja se koristi u proizvodnji tog dobra. Novac, koji predstavlja rad potreban za generisanje dobara i usluga, takođe se može posmatrati kao uskladištena energija.

Početkom 20. veka, ljudi su bili zainteresovani za zamenu zlata ili dolara sa „energetskim dolarom“ ili „jedinicama energije“. Koncept je bio popularan zbog svojih dobrih novčanih karakteristika. Mane? Nije se moglo lako preneti ili skladištiti.

„Da bi muškaraca/ženu naterao da poželi neku stvar, potrebno je samo učiniti stvar teškom za dobijanje.“ – Mark Twain Bitcoin-ov PoW je prvobitno izmišljen kao mera protiv spam email-ova. Tek nešto kasnije, Satoshi ga je prilagodio da se koristi u digitalnoj gotovini.

Ono što PoW rudarenje radi „ispod haube“ je upotreba namenskih mašina (ASIC-a) za pretvaranje električne energije u Bitcoin-e (putem blok nagrade). Bitcoin ima kapitalistički mehanizam glasanja, „rizikovan novac, dobijeni glasovi“ pomoću energije/ASIC-a koji se koriste za generisanje heš-ova (glasova).
Kada je Satoshi dizajnirao PoW, iz temelja je promenio način na koji se formira konsenzus između ljudi od političkih do apolitičnih glasova (heš-ova) pretvaranjem energije. To je najjednostavniji i najpravedniji način da fizički svet potvrdi nešto u digitalnom svetu.
Bitcoin je odlična roba, iskovana iz energije, osnovna roba univerzuma. PoW transformiše električnu energiju u digitalno zlato. Činjenica da je PoW „skup“ je odlika, a ne greška.
Istorijski gledano, obezbeđivanje nečega podrazumevalo je izgradnju fizičkog zida oko svega što je vredno. Knjiga Bitcoin-a je obezbeđena ukupnom sumom energije potrošene za izgradnju digitalnog zida. Bila bi potrebna ekvivalentna količina energije da bi se on srušio (nezaboravna skupoća) @NickSzabo4
„Potrošnja električne energije po transakciji“ je loš KPI, a evo i zašto:
– Potrošena energija je po bloku, a ne po transakciji
– Ekonomska gustina Bitcoin transakcije se povećava (Segwit, taproot, Lightning)
– Trebalo bi da bude definisano sigurnošću ekonomske istorije @LaurentMT . Stopa poboljšanja efikasnosti ASIC-a se usporava. Kako se efikasnost usporava, možemo očekivati porast konkurencije proizvođača kako se marže sužavaju. Sveukupni troškovi rudarenja preći će sa početnih troškova ASIC hardvera na tekuće troškove energije za ostvarivanje rada.
Cena rudarenja Bitcoin-a postaje najniža (višak) vrednost električne energije. Ovo može rešiti problem sa obnovljivim izvorima energije koji imaju predvidivi kapacitet i koji se ne iskorišćava u potpunosti, poput hidroelektrana i gorivog metana.

Aluminijum je bio popularno sredstvo za „izvoz“ električne energije iz zemlje koja obiluje neiskorišćenim obnovljivim izvorima energije (npr. Island). Kako je proizvodnja aluminijuma tokom decenija sazrevala, kWh po kilogramu proizvedenog aluminijuma postajao je efikasniji.
https://www1.eere.energy.gov/manufacturing/resources/aluminum/pdfs/al_theoretical.pdf
PoW je u krajnjem slučaju kupac celokupne električne energije, stvarajući temelj koji podstiče izgradnju novih postrojenja za proizvodnju energije oko različitih izvora energije koji bi inače ostali neiskorišćeni.
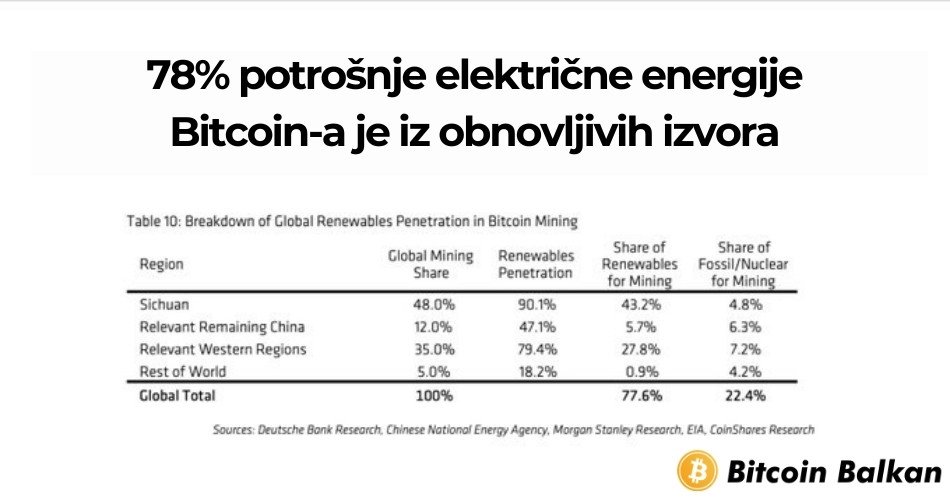
„Zamislite topografsku 3D mapu sveta sa žarištima jeftine energije koji su niži, a sa skupom energijom višlji. Zamišljam da je iskopavanje Bitcoin-a slično čaši vode koja se prelila, taložila se po uglovima i ćoškovima i glačala ih. “ – @nic__carter
„Energija koja se koristi za PoW prestaće da raste kada se granični povrat od sagorevanja kWh energije kroz PoW bude jednak graničnom povratu od prodaje tog kWh u mrežu … „ Nakamoto-va tačka“ koja će koristiti između 1-10% svetske energije.“ – @dhruvbansal
Neki se žale da rudarenje Bitcoin-a ne postiže „ništa korisno“, poput pronalaženja prostih brojeva. Bitcoin već radi nešto korisno za društvo. Nije racionalno tražiti od rudara da obavljaju funkciju koja je nesebična bez podsticaja.
Sve zahteva energiju. Tvrdnja da je jedna upotreba energije više ili manje rasipna od druge, potpuno je subjektivna, jer su sve upotrebe plaćene tržišnom stopom za korišćenje te električne energije.

Bitcoin-ova upotreba električnog kapaciteta troši manje količine električne energije od postojećih tradicionalnih sistema koji ne zahtevaju samo napajanje bankarske infrastrukture, već i vojnu i političku mašinu. Kompromis energije je „neto pozitivan“ ishod.
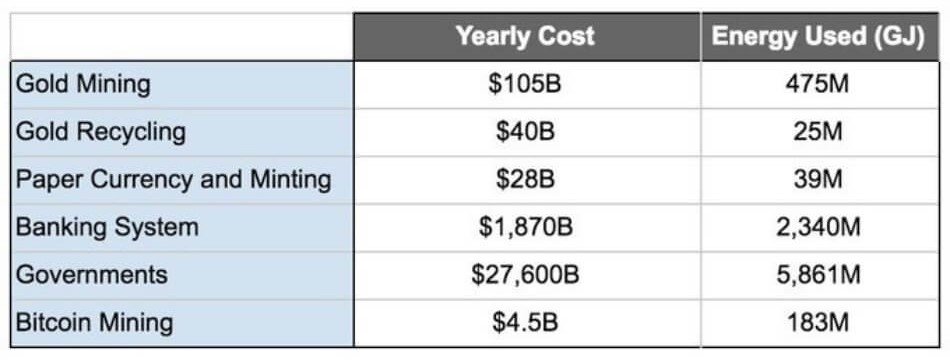
Preko Bitcoin-a, da li je nepoverljivo poravnanje od 1,34T USD između ugovornih strana godišnje, uz dodatni benefit jeftinije energije za sve, vredno 4,5B USD u trenutnim troškovima rudarenja? Mislim da je odgovor odlučno da.
1/ Bitcoin’s energy consumption is not “wasteful.”
— Dan Held (@danheld) January 18, 2021
- It is much more efficient than existing financial systems
- No one has the moral authority to tell you what is a good or bad use of energy (ex: watching the Kardashians)
Let's debunk this FUD👇 -
 @ cae03c48:2a7d6671
2025-06-03 19:02:12
@ cae03c48:2a7d6671
2025-06-03 19:02:12Bitcoin Magazine

Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to BitcoinSberbank, the largest bank in Russia, has launched a new structured bond that ties investor returns to the performance of Bitcoin and the U.S. dollar-to-ruble exchange rate. This new financial product represents one of the first moves by a major Russian institution to offer Bitcoin-linked investments under recently updated national regulations.
BREAKING:
 Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x
Russia's largest bank Sberbank launches structured bonds linked to Bitcoin. pic.twitter.com/LtD26jPS0x— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The structured bond is initially available over the counter to a limited group of qualified investors. According to the announcement, it allows investors to earn based on two factors: the price performance of BTC in U.S. dollars and any strengthening of the dollar compared to the Russian ruble.
Unlike typical Bitcoin investments, this product does not require the use of a Bitcoin wallet or foreign platforms. “All transactions [are] processed in rubles within Russia’s legal and infrastructure systems,” Sberbank stated, highlighting compliance with domestic financial protocols.
In addition to the bond, Sberbank has announced plans to launch similar structured investment products with Bitcoin exposure on the Moscow Exchange. The bank also revealed it will introduce a Bitcoin futures product via its SberInvestments platform on June 4, aligning with the product’s debut on the Moscow Exchange.
These developments follow a recent policy change by the Bank of Russia, which now permits financial institutions to offer Bitcoin-linked instruments to qualified investors. This shift opens the door for Bitcoin within the country’s traditional financial markets.
While Russia has previously taken a cautious approach to digital assets, Sberbank’s launch of a Bitcoin-linked bond and upcoming futures product marks a new phase of adoption—one that blends Bitcoin exposure with existing financial infrastructure.
The bank’s structured bond may signal a growing interest in regulated access to Bitcoin, especially within large financial institutions.
This post Sberbank, Russia’s Biggest Bank, Launches Structured Bond Tied to Bitcoin first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-06-03 19:02:02
@ cae03c48:2a7d6671
2025-06-03 19:02:02Bitcoin Magazine

Metaplanet Acquires 1,088 More Bitcoin, Bringing Total Holdings to 8,888 BTCMetaplanet, Japan’s leading Bitcoin treasury firm, has purchased an additional 1,088 Bitcoin for approximately ¥16.89 billion at an average price of ¥15,519,019 per BTC. This acquisition raises the company’s total Bitcoin holdings to 8,888 BTC, with a cumulative purchase cost of ¥122.27 billion at an average price of ¥13,756,658 per BTC.

The company continues to report gains under its BTC Yield metric, a proprietary KPI that measures Bitcoin accumulation per share. Quarter-to-date (QTD), as of June 2, 2025, Metaplanet’s BTC Yield stands at 66.3%, following previous QTD yields of 95.6%, 309.8%, and 41.7% over the last three quarters. Total BTC Gain for Q2 2025 is 2,684 BTC, translating to a ¥40.54 billion gain based on a reference Bitcoin price of ¥15.10 million.
*Metaplanet Acquires Additional 1,088 $BTC, Total Holdings Reach 8,888 BTC* pic.twitter.com/X2clAIKNbR
— Metaplanet Inc. (@Metaplanet_JP) June 2, 2025
Metaplanet’s capital markets activity has been tightly aligned with its Bitcoin accumulation strategy. Since January 28, 2025, the company executed a series of zero-coupon, non-interest-bearing bond issuances and 0% discount stock acquisition rights to EVO FUND, raising over ¥35 billion and USD 121 million. These funds were used for Bitcoin purchases and bond redemptions.
— Dylan LeClair (@DylanLeClair_) June 2, 2025
In Q1 FY2025, Metaplanet reported its strongest financial results yet. Revenue increased 8% quarter-over-quarter to ¥877 million, while operating profit rose 11% to ¥593 million. Net income surged to ¥5.0 billion, complemented by unrealized gains of ¥13.5 billion from its Bitcoin holdings, further strengthening the company’s balance sheet.
Although Bitcoin prices dipped briefly at the end of March, causing a ¥7.4 billion valuation loss, Metaplanet swiftly recovered as BTC surged to new record levels. This strong connection with Bitcoin’s performance has led many investors to use Metaplanet as an investment vehicle to get Bitcoin exposure on the Tokyo Stock Exchange.
At the same time, Strategy acquired another 705 Bitcoin for about $75 million, further expanding its position as the largest corporate holder of Bitcoin as more public companies continue to adopt Bitcoin treasury strategies.
BREAKING:
 STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP
STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
According to their SEC filing on June 2, they bought Bitcoin at an average price of $106,495 each between May 26 and June 1, bringing their total holdings to 580,955 BTC. The acquisition was funded by selling some of their preferred shares through an at-the-market (ATM) equity offering.
This post Metaplanet Acquires 1,088 More Bitcoin, Bringing Total Holdings to 8,888 BTC first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ e0e92e54:d630dfaa
2025-06-03 19:01:32
@ e0e92e54:d630dfaa
2025-06-03 19:01:32As some of you know, I lead a quarterly Bible Study through Faith Driven Investor
One of the members from the cohort that just ended forwarded me an email from the US Christian Chamber of Commerce
The summary is: Christians should intentionally be doing more business with Christians.
[Full email at the bottom of this Article]
I recanted to my FDI member about a book I read a few years ago, Thou Shall Prosper, by Rabbi Daniel Lapin.
In it he gave the statistics that a single dollar recirculates in the Jewish community 12 times, Muslims 8 times, and Christians only 3 or 4 times.
(I'm probably slightly off on recalling the stats)
But the point being that as a people group, Jews are 4x more wealthy than Christians because Christians value doing business with one another 4 times less than Jews...or said another way, the Jewish people value doing business with one another 4x more than Christians.
Reading the email I was sent, I was further reminded as business owners, leaders, and investors;
If we are truly going to steward that which God has entrusted to us, we should want to re-circulate those resources as many times as possible within the Christian community in order to have the greatest probability of return on image bearers.
What are your thoughts?
I Bought a House Through the Christian Chamber - What happened next surprised me
My husband and I just bought a house—but it wasn’t just a transaction. It was a transformation.
With our daughter’s high school graduation behind us, we felt ready to step into a long-held dream: moving to a beach town we’ve thought, talked, and prayed about for years. As part of turning our dream into a reality, we made a very intentional decision:
We would buy our home entirely through the Christian Chamber community.
We wanted to walk the talk—to model what Kingdom commerce really looks like. So we sought Christian-led businesses for every part of the process. What started as a symbolic gesture quickly became a profound experience with two life-changing revelations:
1) The Power of Prayer in Business
Yes, we prayed as a couple—but imagine your Realtor, lender, inspector, and insurance agent all praying with you, too.
We’re not talking about just being “nice people” or listening to worship in the office. We’re talking about Spirit-filled, Jesus-following believers who brought prayer into every decision.
· Our Realtor is also a church planter—her discernment helped us find the perfect house on day one.
· Our lender joined us in prayer—and worked miracles to make the deal smooth and abundantly possible.
· Our inspector's biggest red flag? A bird’s nest in a porch light. (Yes, really.)
· Our insurance agent handled everything—and in Florida, that’s no small feat.
I have bought and sold seven homes in my life, but this was the best experience by far. The layout, the location, the timing, the favor—it was all wrapped in prayer and covered in grace. It wasn’t just business. It was supernatural.
2) Kingdom ROI — A Multiplied Impact
By doing business with Christians, we didn’t just find great service. We created a multiplied Kingdom return.
We know where our vendors give. We know the churches they support, the ministries they fund, and the people they serve.
When they earned from our purchase, those dollars didn’t disappear—they were reinvested into Kingdom causes we could never reach on our own.
This is Kingdom ROI.
It’s a real-life example of the parable of the talents—we didn’t bury our resources. We multiplied them. When you spend money with aligned believers, your impact compounds.
The opposite is also true:
When we spend with businesses that oppose our values, we’re funding platforms that erode the very things we’re trying to protect—our families, our freedoms, and our faith.
We MUST STOP funding the enemy.
The Bigger Picture
Let’s be clear: Studies show that Christians make up 31% of the world’s population, but we control 55% of the world’s wealth—more than $107 trillion in personal assets.
And yet…we’re leaking that wealth into systems that are actively working against us.
Why? Because we do not have the infrastructure to keep it aligned.
Until now.
That’s what we’re building through the U.S. Christian Chamber of Commerce: A national infrastructure that empowers Christians to redirect their dollars, align their values, and multiply their impact.
What If You Did the Same?
· Buy your next product or service from a Christian-led business.
· Hire your next contractor from your local Christian Chamber.
· Invest in a company with eternal impact.
· Launch a Christian Chamber in your region—we’ll help you.
· Join the U.S. Christian Chamber. This is your Chamber, for your nation.
· Meet us in Orlando for SWC 2026, the global gathering of Christian commerce.
Imagine the multiplying power if thousands of us made similar decisions—every day—across this nation.
We own the wealth. Now let’s build the infrastructure, create the ecosystem, and shift the world's wealth one transaction at a time.
This is our nation and we are One Nation Under God!
Jason Ansley is the founder of Above The Line Leader, where he provides tailored leadership support and operational expertise to help business owners, entrepreneurs, and leaders thrive— without sacrificing your faith, family, or future.
-
Want to strengthen your leadership and enhance operational excellence? Connect with Jason at https://abovethelineleader.com/#your-leadership-journey
-
📌 This article first appeared on NOSTR. You can also find more Business Leadership Articles and content at: 👉 https://abovethelineleader.com/business-leadership-articles
-
-
 @ e2c72a5a:bfacb2ee
2025-06-04 01:45:55
@ e2c72a5a:bfacb2ee
2025-06-04 01:45:55When the whales cry for help: crypto trader's $100M bet turns community funding experiment
A multimillionaire trader just placed a second $100 million Bitcoin bet days after being liquidated, but what's truly revolutionary isn't the size—it's how he's funding it. James Wynn has turned to the crypto community for donations, receiving stablecoins from 24 users to "fight the market-making cabal" he claims is targeting his positions. This unprecedented crowdfunded leverage experiment raises fascinating questions about market manipulation, community solidarity, and the blurring lines between individual and collective risk in crypto trading.
Is this the birth of community-backed whale trading? Or simply a desperate gambler's last stand? Either way, it reveals how blockchain transparency creates entirely new social dynamics around trading that would be impossible in traditional markets. What happens when your liquidation becomes everyone's battle?
Would you donate to protect a stranger's $100M position? The answer might reveal more about crypto's future than any price prediction.
-
 @ bf47c19e:c3d2573b
2025-06-03 18:32:49
@ bf47c19e:c3d2573b
2025-06-03 18:32:49Originalni tekst na bitcoin-balkan.com
Pregled sadržaja
- Bitcoin Je Nosilac Imovine
- Komprimis: Bezbednost vs Konfor
- Pregled Novčanika: Istraživanje Hardverskih, Mobilnih, Desktop i Multisig Bitcoin Novčanika
- Vruće vs Hladno – (hot vs Cold) Bitcoin Novčanici: U čemu je razlika?
- Bitcoin Novčanik – Backup Fraza
- Bitcoin Multisignature: Kako radi
- Zašto Moj Bitcoin Novčanik Stalno Menja Moju Adresu?
- Moja Preporuka: Neka Procenat Neto Vrednosti Vodi Vaš Izbor Bitcoin Novčanika
- Da Zaokružimo Priču
U redu, dakle stekli ste neku količinu Bitcoin-a, i koji je sada najbolji način za njegovo čuvanje? Ovde ću vas provesti kroz proces pronalaženja pravog Bitcoin novčanika za vas.
Iako se čini kao jednostavno pitanje, ima iznenađujuće puno nijansi koje treba razmotriti. Koliko Bitcoin-a imate? Koliko često planirate da ga trošite? Da li ste sigurni da su vaši ključevi sigurniji kod vas nego kod offline čuvara? Odgovori na ova pitanja pomoći će vam da pronadjete pravo rešenje za vas.
Bitcoin je nosilac imovine, što znači da i sami možete držati ključeve svog Bitcoin-a. Kada držite svoje Bitcoin ključeve, vi imate direktnu kontrolu nad svojim novcem. Nije povereno nijednoj trećoj strani, poput banke. Trebate držati svoje ključeve onda kada utvrdite da je rizik da ih lično držite manji od rizika da ih čuvar izgubi. Donošenje te odluke oslanja se uglavnom na vaše razumevanje kako i zašto držati svoje Bitcoin ključeve. U ovom članku ću vam pomoći da razumete obe strane.
U ovom članku ćemo istražiti:
- „Nisu vaši ključevi, nije vaš Bitcoin“
- Bezbednost vs Konfor
- Vrste Bitcoin novčanika
- Postavke Multisig-a
- Moja preporuka za izbor najboljeg novčanika za VAS
Zato počnimo polako.
Bitcoin Je Nosilac Imovine
U kriptografiji, javni ključ(public key) se koristi za šifrovanje poruka, a privatni ključ(private key) za njihovo dešifrovanje. Ako bi neko želeo da vam pošalje šifrovanu poruku, šifrirao bi je vašim javnim ključem. Vaš privatni ključ je jedini način za dešifrovanje te poruke, pa sve dok ste jedina osoba koja drži taj privatni ključ, vi ste i jedina osoba koja može pročitati poruku.
Bitcoin koristi kriptografiju javnog/privatnog ključa da bi osigurao transakcije. Privatni ključ se kreira kada napravite Bitcoin novčanik. Novčanik stvara javne ključeve koji se heširaju i koriste kao adrese za prijem Bitcoin-a. Privatni ključ je potreban da bi se dokazalo vlasništvo nad uskladištenim Bitcoin-om na toj adresi kako bi se mogao potrošiti.
Ako lično ne kontrolišete privatne ključeve povezane sa vašim Bitcoin-om, onda zapravo ne posedujete svoj Bitcoin. Drugim rečima, ako menjačnica ili banka drži vaše Bitcoin-e u vaše ime, vi onda nemate direktnu kontrolu nad svojim Bitcoin-ima. Vi prenosite sigurnost svog Bitcoin-a drugoj stranci.
Da biste u potpunosti iskoristili jedinstvene osobine Bitcoin-a kao novca, vi trebate da držite svoje privatne ključeve. Kao što Bitcoineri često kažu „nisu vaši ključevi, nije vaš Bitcoin“. Ovo vam pruža mogućnost držanja vašeg Bitcoin-a pod vašim nadzorom, tako da ga države, banke ili hakeri koji ga ciljaju ne mogu zapleniti ili oduzeti. Ali odabir držanja sopstvenih ključeva dolazi sa odredjenom odgovornošću za bezbednost vašeg Bitcoin-a.
Moj cilj je da vam pomognem da postanete konforni sa mogućnošću držanja svojih ključeva. Do tada, Bitcoin če biti sigurniji na novčaniku vaše menjačnice.
Sada ćemo pogledati koje opcije imate za preuzimanje kontrole nad sopstvenim Bitcoin ključevima.

Bezbednost vs Komfor
Komprimis: Bezbednost vs Komfor
Glavni kompromis koji treba uzeti u obzir prilikom skladištenja vašeg Bitcoin-a je između bezbednosti i konfora. Očigledno je da su i bezbednost i konfor poželjne osobine prilikom čuvanja vašeg Bitcoin-a, ali se međusobno direktno suprotstavljaju.
Gde se vi nalazite u spektru bezbednosti nasuprot konfora?
Postavite sebi ova pitanja da biste stekli bolji utisak o tome koji način čuvanja za vas ima najviše smisla:
- Ukupna vrednost – da li skladištite na nivou od 0,1%, 1% ili 10 +% vaše neto vrednosti u Bitcoin-u? Odgovor bi trebao da vam da vrlo različite metode čuvanja vašeg Bitcoin-a. Očigledno biste bili spremni da pretrpite više neprijatnosti ako to znači zaštitu 50% vaše neto vrednosti.
- Vremenski okvir/dostupnost – Kada i koliko često imate potrebu da trošite svoje Bitcoin-e? Da li je to više kao tekući račun, srednjoročni štedni račun ili je vaš Bitcoin sličniji dugoročnom penzionom računu?
“Pazite da podešavanje vaše zaštite ne bude tako složeno da čak i vi zaboravite kako dostupiti vašom Bitcoin-u“
Od Bitcoinera se mogu čuti upozoravajuće priče o ljudima koji gube svoje Bitcoin-e zbog prekomplikovanih podešavanja čuvanja, što rezultira time da vlasnik zaboravi kako da pristupi svojim novčićima.
Pregled Novčanika: Istraživanje Hardverskih, Mobilnih, Desktop i Multisig Bitcoin Novčanika
Sada kada ste odlučili da nabavite nekoliko Bitcoin-a (pametan potez) vreme je da odlučite gde ćete čuvati vaš Bitcoin. Kada započinjete, ovo vam može dati nadmoćan osećaj. U ovom odeljku ću vam dati kratki pregled opcija kojima raspolažete. Kao i u većini stvari u životu, i ovde se radi o kompromisima.
Hardverski Bitcoin Novčanici
Korisnici čuvaju privatne ključeve na namenskom hardverskom delu.
Prednosti: Privatni ključevi nikada ne dolaze u dodir sa internetom, što smanjuje rizik od njihovih gubitaka. Pogodno za dugotrajno skladištenje. Ako izgubite hardverski novčanik, možete da upotrebite backup seed fraze (eng. seed phrase backup) da biste vratili novčanik.
Mane: Korisnici moraju da obezbede backup seed fraze, što zahteva promišljenu strategiju kako da je zaštite. Preporučuje se da zapišete svoju seed frazu na metal i sačuvate rezervne kopije na više sigurnih lokacija. Ako vam ukradu hardverski novčanik, dolazite u rizik hakovanja vaših sredstava. Napomena: zaštita backup seed fraze je standardna praksa za novčanike gde korisnik kontroliše svoje privatne ključeve.
Primeri: Ledger, Trezor, Coldcard i BitBox

Mobilni Bitcoin Novčanici
Korisnici čuvaju privatne ključeve na mobilnom uređaju.
Prednosti: Jednostavan za upotrebu, dobar za početnike, pogodan za male iznose.
Mane: Najmanje sigurna opcija jer se privatni ključevi nalaze na uređaju povezanom na Internet. Ako napadač stekne fizički pristup vašem telefonu, može proslediti sredstva u njegov novčanik. Nije dobro za dugotrajno skladištenje.
Primeri: Blockstream Green, Samourai (samo za Android), Muun, Blue Wallet, Electrum

Desktop Bitcoin Novčanici
Korisnici čuvaju privatne ključeve na svom desktop/laptop računaru
Prednosti: Dobro korisničko iskustvo.
Mane: Nije baš bezbedno, jer su računari povezani na internet i podložni virusima i napadima. Nije dobro za dugotrajno čuvanje.
Primeri: Bitcoin Core i Electrum (napredni), Wasabi (srednji), Blockstream Green (početni). Wasabi je verovatno najbolji novčanik za privatnost, a Blockstream Green je najbolji početnički desktop novčanik.

Multisignature Bitcoin Novčanici
Korisnik čuva privatne ključeve u posebnom novčaniku za koji je potrebno da potpiše više privatnih ključeva pre nego što može da premešta svoja sredstva. Na primer, u „2 od 3“ multisig (eng. multisignature – više potpisa) novčaniku, korisniku su potrebna bilo koja dva od tri privatna ključa za slanje sredstava.
Prednosti: Jedan od najsigurnijih načina za čuvanje vašeg Bitcoin-a, smanjuje efikasnost fizičkih napada, pogodan za dugoročno skladištenje.
Mane: Teško ga je samostalno podesiti, ali postoji nekoliko servisa koji olakšavaju ovaj proces. Nije pogodno za potrošnju, a to može predstavljati i poentu.
Primeri: Unchained Capital’s Vault (2 od 3), Casa’s Keymaster (2 od 3 i 3 od 5), Blocksteam Green (2 od 2), Electrum.

Vruće vs Hladno – (hot vs Cold) Bitcoin Novčanici: U čemu je razlika?
Vrući novčanici su povezani na Internet. To znači da je ključevima lakše pristupiti nego kada su na hardverskom novčaniku, a to takođe znači i da su vaša sredstva ranjiva na napade hakera. Vruće novčanike preporučujem samo za male količine.
Hladni novčanici NISU povezani sa Internetom. To znači da je vašim sredstvima teže pristupiti. Hladni novčanici su manje pogodni za korisnike, ali hakeri mnogo teže mogu da pristupe vašim sredstvima. Hladne novčanike treba smatrati jedinom opcijom za dugoročno čuvanje.
Bitcoin Novčanik – Backup Fraza
Većina novčanika zahteva od korisnika da zapišu „backup seed frazu“. Ovo je mera predostrožnosti u slučaju da izgubite pristup svojim privatnim ključevima/novčaniku. To takođe znači da korisnici moraju biti vrlo oprezni sa svojim rezervnim kopijama jer one sadrže sve potrebne informacije za pristup vašim sredstvima. Tretirajte i čuvajte svoje rezervne kopije na način kao što bi tretirali i čuvali gomilu zlata.
- Ne pravite slike ili snimke ekrana svoje backup fraze
- Ne izgovarajte naglas svoju backup frazu – ikad!
- Ne čuvajte svoju semensku frazu Password Manager Aplikaciji
- Ne koristite Internet uslugu oporavka backup fraze
- Koristite pristupnu frazu (passphrase) da biste dodali još sigurnosti
- Koristite više metoda za pravljenje rezervnih kopija
- Ograničite pristup svojoj backup frazi što je više moguće
- Nikada ne razgovarajte sa ljudima gde, kako i koliko Bitcoin-a čuvate

Tako izgleda „backup seed fraza“
Bitcoin Novčanici Bez Seed-ova
Drugi način za čuvanje Bitcoin-a su novčanici bez seed-ova. Oni su dizajnirani za multisig akaunte, gde korisnici ne kreiraju backup seed-ove, već se oslanjaju na uslugu rezervne kopije. Casa prednjači u novčanicima bez seed-ova sa svojim Keymaster multisignaturnim proizvodom.
Bitcoin Multisignature: Kako radi
Umesto da zahtevaju jedan potpis privatnog ključa za premeštanje sredstava, multisig novčanici zahtevaju više potpisa za premeštanje sredstava. Postoji mnogo načina za pravljenje multisig novčanika, ali iskoristimo postavku 2 od 3 za naš primer.
Kao korisnik, to znači da imate ukupno 3 privatna ključa koji odgovaraju jednom Bitcoin novčaniku. Da biste prebacili sredstva, potrebna su vam najmanje 2 privatna ključa za potpisivanje transakcije. Većina korisnika će fizički odvojiti lokacije svakog ključa kako bi što više smanjili rizik. Samo nemojte biti previše kreativni, da ne prevarite i sebe i na taj način izgubite svoja sredstva (to se dogodilo mnogo puta).
Kao što je gore pomenuto, evo nekoliko primera Multisignature novčanika
- Blocksteam Green Wallet (2 od 2)
- Casa’s Keymaster (2 od 3 i 3 od 5)
- Unchained Capital’s Vault (2 od 3)
- Electrum
Prednosti Multisig-a
Multisig nudi prostor za greške. Ako imate samo jedan privatni ključ i izgubite ga, vaša sredstva će se zauvek izgubiti. Međutim, ako imate podešavanje 2 od 3, možete sebi priuštiti da izgubite jedan privatni ključ i dalje pristupite svojim sredstvima.
Multisig takođe smanjuje šanse za moguće fizičke napade. Recimo da ste fizički ugroženi i primorani da se odreknete svog dragocenog Bitcoin-a. Ako ste imali normalan novčanik (a ne multisig), onda biste lako mogli da prebacite svoj Bitcoin tom kom vas napada. Međutim, ako ste postavili multisig podešavanja, jedan od vaših ključeva je u kući, a drugi ključ na nekom drugom mestu (npr. vaša kancelarija ili sef u banci). Ovakvo razdvajanje ključeva u velikoj meri smanjuje želju tog napadača da uopšte pokuša da preotme vaš Bitcoin.
Zašto Moj Bitcoin Novčanik Stalno Menja Moju Adresu?
Svaki skup privatnih ključeva može generisati bilione javnih ključeva. Ovi javni ključevi se zatim transformišu (kroz matematički proces zvan heširanje) da bi se proizvele javne adrese.
Svaka pojedinačna adresa može da primi Bitcoin. Dakle, svaki skup privatnih ključeva koji posedujete sposoban je da proizvede svoj jedinstveni, masivni skup javnih adresa koje posedujete vi, i samo vi. Svako može da pošalje Bitcoin na te javne adrese, ali samo onaj koji poseduje te privatne ključeve može trošiti Bitcoin sa tih adresa.
Mnogi ljudi vole da uporedjuju privatne ključeve, javne adrese i Bitcoin novčanike sa e-mail adresama. Privatni ključevi su vaša lozinka, javna adresa je vaša e-mail adresa, a novčanik je e-mail domen koji koristite (npr. Gmail, Protonmail, Yahoo itd.). Iako je korisna, ova analogija pomalo obmanjuje, jer sa Bitcoin-om svaka lozinka (privatni ključ) koju posedujete omogućava pristup bilionima potencijalnih e-mail adresa (javnih adresa) za slanje i primanje Bitcoin-a.
Nema razloga za brigu ako vaš novčanik stalno generiše nove Bitcoin adrese. To je zapravo jedna od njegovih karakteristika! Novčanici koji generišu i koriste nove javne adrese pomažu u zaštiti vaše privatnosti od ljudi koji „njuškaju“ na javnom Bitcoin blockchain-u. Samo zapamtite da sve dok vi držite privatne ključeve novčanika, samo vi posedujete sadašnji i budući Bitcoin, poslat na bilo koju javnu adresu koju je generisao vaš novčanik. Samo se pobrinite da privatni ključevi Bitcoin-a budu sigurni, bezbedni i privatni.
Moja Preporuka: Neka Procenat Neto Vrednosti Vodi Vaš Izbor Bitcoin Novčanika
Najjednostavniji način pristupanja izbora koji novčanik će te odabrati za vaš Bitcoin je fokusiranje na pitanje „koliko novca je u igri?“. Drugim rečima, koji procenat vaše neto vrednosti je zaštićen? Evo naše analize, ali naravno, situacija svake osobe je jedinstvena. Koristite ovo kao smernicu, a ne kao apsolutnu istinu.
Male količine (oko 0,1% neto vrednosti) – Koristite mobilni Bitcoin novčanik
- Blockstream Green – ima multisig 2 od 2. To je verovatno najbolji Bitcoin novčanik za iPhone.
- Casa Keymaster (režim sa jednim ključem) – rezervna kopija bez seed-a.
Srednji iznosi (oko 1% neto vrednosti) – Koristite hardverski Bitcoin novčanik
- Ledger
- Trezor
- Coldcard
Velike količine (više od 10% + neto vrednost) – Koristite Multisig Bitcoin novčanik
- Casa Keymaster Multisig — interfejs koji je jednostavan za korišćenje, možete birati postavke 2 od 3 i 3 od 5. Oni imaju alat za samooporavak, međutim ovo nisam lično koristio, i želeo bih da obavim više istraživanja pre nego što dam pravu preporuku.
- Unchained Capital’s Multisig — interfejs koji je jednostavan za korišćenje, postavka 2 od 3, može pristupiti finansijskim uslugama zasnovanim na vašem BTC u depozitu.
- Self Hosted Multisig — korisnici takođe mogu da kreiraju sopstvene multisig postavke. Ovo zahteva mnogo veće tehničko znanje u poređenju sa Unchained i Casa, međutim, ne žrtvujete nikakvu privatnost.
Protip: Rapodelite sredstva koja želite da skladištite dugoročno. Ako imate značajan deo svoje neto vrednosti u Bitcoin-u, u vašem je najboljem interesu da raspodelite svoj ulog. Ovo umanjuje vaš rizik, što smanjuje šanse da budete izbrisani. Na primer, trećinu svog Bitcoin-a čuvajte sa Casa multisig-om, drugu trećinu sa Unchained Capital Vault-om, a preostalu trećinu na hardverskom novčaniku (Cold Card, Ledger ili Trezor).
Da Zaokružimo Priču
Ovo je moj rezime vaših mogućnosti izbora Bitcoin-ovih novčanika i kako odabrati pravi od njih uzimajući u obzir privatne ključeve, načine i stepen zaštite i sigurnosti koji oni pružaju. Ako ste i dalje zastrašeni, bez brige. Preporučujemo da preuzmete kontrolu nad vašim Bitcoin ključevima samo kada budete sigurni u uslugu koja vam se pruža. Ali vas podstičemo da i dalje razmatrate jedinstvenu priliku koju vam pruža Bitcoin: mogućnost da imate apsolutnu kontrolu nad svojim bogatstvom.
Samostalno čuvanje je vremenom sve lakše i lakše. Razmotrite svoju situaciju i odaberite način čuvanja koji najbolje odgovara vama. Ovde sam da vam pomognem, i slobodno mi se obratite sa svim pitanjima koja vas zanimaju.
-
 @ bf47c19e:c3d2573b
2025-06-03 18:12:43
@ bf47c19e:c3d2573b
2025-06-03 18:12:43Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je blockchain?
- Kako mogu da saznam više o Bitcoin-u?
Ukoliko niste pročitali naš uvodni tekst o Bitcoin-u, i zašto vam je važno da to učinite, onda prvo pročitajte: Šta je Bitcoin i kako on može da nam pomogne?
Bitcoin, sa velikim B na početku, odnosi se na mrežu računara koji održavaju knjigu stanja na akauntima bitcoin digitalne valute, slično kao što banke održavaju knjigu stanja na računima dolara, eura ili neke druge valute. Bitcoin softver, odnosno protokol, takođe omogućava korisnicima da putem interneta pošalju bitcoin-e sa svog akaunta na drugi akaunt, slično PayPal-u ili Venmo-u, ali bez kompanije koja pruža uslugu prenosa. Bitcoin softver je otvorenog koda, tako da svako može da ga pokrene na svom računaru i da se pridružiti mreži.
Najbolji način da se razume kako Bitcoin funkcioniše “iznutra” je da ga zamislimo kao finansijski sistem. Naš trenutni finansijski sistem, koji uglavnom koristi dolare, eure, dinare i druge valute kao „novac“, izgleda otprilike ovako:

Centralne banke i vlade proizvode i distribuiraju novac pozajmljujući ga ljudima, i trošeći ga na oružje, puteve i socijalne programe. Ovaj sistem se naziva sistemom zasnovanom na dugovima, jer svaki put kada banka da zajam, stvara se nova valuta koja ranije nije postojala. Ova valuta ima vrednost jer dug koji ju je stvorio ima vrednost: primalac zajma obećava da će otplatiti svoj dug banci, plus kamate.
Kad god banka odobri kredit, ona stvara novu valutu. Ovo takodje važi i kada podignete hipoteku ili kredit za auto. Takođe se primenjuje i kada Američke Federalne Rezerve kupuju državne obveznice od vlade Sjedinjenih Država. U svakom od ovih slučajeva, banka šalje novonastalu valutu primaocu zajma. Primaoc zajma obećava banci da će u budućnosti vratiti tu valutu, plus kamate. Međutim, ulaz nove valute u sistem znači i da opada vrednost postojeće valute koja je u opticaju. To se dešava kroz proces koji se obično naziva inflacija.
Da bi imali koristi od pogodnih usluga koje nude banke, poput kreditnih kartica i digitalnih transfera novca, normalni ljudi i preduzeća obično novac drže na bankovnim računima. Svaka banka poseduje svoju knjigu sa računima svih svojih klijenata.
Banke su neophodne da bi omogućile digitalna plaćanja koja vršimo svakodnevno, jer su nam potrebne pouzdane strane koje bi proverile da li se sav računovodstveni sistem sabira. U suprotnom, bilo bi lako da neko uradi “copy-paste“ jednog dela digitalnog novca i da ga potroši dva puta, ili da doda par nula na stanje svog računa.
Sada razumemo nekoliko ključnih tačaka o trenutnom sistemu zasnovanom na dugu: banke proizvode novu valutu svaki put kad pozajmljuju novac, a većina ljudi svoj novac čuva u bankama koje im nude pogodnosti.
Bitcoin je malo drugačiji. Hajde da započnemo ovo putovanje sa pitanjem.
Šta ako bi svi posedovali knjigu stanja na računima, baš kao i banka?
Umesto da banke poseduju po jednu knjigu depozita svojih klijenata, šta ako svi poseduju istu knjigu, sa detaljnim opisima svih stanja na računima svih učesnika u ekonomiji? O privatnosti ne morate da brinete ni na trenutak – to ćemo objasniti kasnije.
Hajde da vidimo kako bi transakcija mogla da se izvrši koristeći ovakav bankarski sistem. Recimo da Ana želi da plati Davidu 10 digitalnih „novčića“. Ona tu transakciju zapisuje u e-mail, potpisuje je digitalno kako bi svi bili sigurni da e-mail dolazi od stvarne Ane, i šalje ga svima ostalima. Kada ostali prime taj e-mail, oni ažuriraju svoje knjige, tako što skinu 10 novčića sa Aninog računa i dodaju 10 novčića na Davidov račun.

Zašto bi se neko trudio da evidentira transakciju u svojoj knjizi?
Recimo da će prva osoba koja izvrši sledeće korake dobiti 5 novčića:
- Proverom da li je prava Ana potpisala transakciju
- Proverom da li Ana ima dovoljno sredstava na svom računu da plati Davidu 10 novčića
- Zapisivanje transakcije ukoliko ispunjava uslove 1) i 2)
Primetićete da se ovo mnogo razlikuje od trenutnog monetarnog sistema. U novom sistemu morate da imate novčiće da biste mogli da ih date nekom drugom. Ne postoje banke sa posebnim privilegijama koje mogu da stvore valutu davanjem zajma.
Umesto da dozvoljava samo maloj grupi bankara da prave nove valute, novi sistem omogućava svima da kreiraju novu valutu ako pružaju korisnu uslugu mreži: verifikovanje i evidentiranje transakcija između ljudi. Nazvaćemo ovo nagradom za potvrđivanje.
Kako se svi slože oko pravila sistema? Ona su kodirana u softverskom protokolu otvorenog koda. To znači da svako može besplatno da preuzme pravila sistema sa interneta i da počne da ih koristi za zaradu valute u sistemu. Ako svi koriste isti skup pravila, njihove knjige će se sinhronizovati, jer će prihvatiti i odbiti potpuno iste transakcije.
- Otvoreni kod = svako može da preuzme kod i da ga pročita
- Softverski protokol = skup pravila napisanih u kodu
Kako zaustaviti ljude koji pokušavaju da prevare sistem da bi zaradili “nagradu za potvrdu”?
Recimo da Boris i Marko žele da se obogate – oni bi mogli jedan drugom da plaćaju po jedan novčić u krug, vodeći računa da neko od njih prvi zabeleži transakciju kako bi mogli da zahtevaju nagradu za potvrdu. Pomoću ove šeme oni bi u osnovi mogli da stvore (odštampaju) novu valutu, kad god oni to požele!
Softverski protokol to zaustavlja zahtevajući da osoba koja validira transakciju uradi neki „posao“ sa računarom kako bi je zabeležila. Ovo osigurava da računari moraju da troše energiju za zabeležavanje transakcija, pa bi u tom slučaju varanje sistema bilo veoma skupo. Borisova i Markova šema varanja sistema više nema finansijskog smisla. Da bismo demonstrirali ovaj proces, pogledajmo Filipa i njegov C-Bot računar. Filip je na svoj računar instalirao Bitcoin protokol, koji predstavlja Bitcoin-ov softverski protokol otvorenog koda koji sadrži pravila Bitcoin sistema.

Kako C-Bot Verifikuje Transakcije
Korak 1: Slušanje transakcija
Prvo, C-Bot sluša transakcije (skraćeno “txn”) koje Ana, Boris, Marko i David emituju putem interneta.
Korak 2: Stvara “Heš”
Drugo, C-Bot će prikupiti sledeće delove podataka:
- Sve Bitcoin transakcije koje ljudi šalju
- Tajni broj (objasnićemo kasnije)
- Nonce – neki slučajan broj
C-Bot sve ovo stavlja u heš mašinu. Mašina za heširanje uzima sve ove podatke i proizvodi 256 bitova (bitovi su 1 i 0) koji se jedinstveno uklapaju u te podatke, nazvane ‘heš’. To heširanje je poput otiska prsta podataka. Uvek ćete dobiti isti heš sa istim ulaznim podacima. Mašina za heširanje je takođe jednosmerna: lako je stvoriti heš od nekih podataka, ali ne možete da stavite heš u mašinu i da vratite ulazne podatke.

C-Bot će iznova isprobavati svoju heš mašinu sa drugim nonce-om (slučajnim brojem). Svaki put, on će proveriti da li je mašina proizvela heš za koji Bitcoin softverski protokol kaže da je tačan.
Ovaj proces pronalaženja heša troši puno vremena i energije. Mašina za heširanje je jednosmerna, tako da C-Bot ne može tek tako da stavi ‘tačan’ heš u mašinu i otkrije ulazne podatke. Svaki računar na Bitcoin mreži takođe prolazi kroz ovaj proces pokušavajući da pronađe ‘ispravan’ heš.
Ukoliko bi ovi računari uspeli da pronađu ‘ispravan’ heš bez velikog trošenja energije, mogli bi da prevare sistem. Dva računara bi mogla da prosleđuju transakcije u krug, zarađujući bitcoin-e svaki put kada bi potvrdili transakciju.
Korak 3: Pronalaženje Ispravnog Heša
C-Bot konačno pronalazi heš koji zadovoljava pravila Bitcoin protokola koristeći sve nedavne transakcije. Sada ovaj blok podataka šalje na druge računare. Blok se sastoji od nedavnih transakcija, nonce-a i tajnog broja. Ti drugi računari stavljaju sve ove podatke kroz istu heš mašinu za sebe, da bi proverili da li je heširanje tog C-Bota tačno. S obzirom da znamo da računari ne mogu da varaju u ovoj igri, znamo da je C-Bot morao da izvrši neka izračunavanja sa svojom heš mašinom da bi pronašao ispravan heš.
Heš bloka C-Bota koji je poslat, sada postaje tajni broj koji ulazi u izračunavanje sledećeg bloka. Budući da heš svakog bloka u ‘blockchain-u’ bitcoin-a koristi heš poslednjeg bloka kao ulaz, bila bi potrebna apsurdna količina energije da se prepiše istorija transakcija (lanac blokova, eng. the blockchain)
Budući da se svačija stanja bitcoin-a zasnivaju na transakcijama na i sa njihovih računa, to takođe onemogućava izmenu bilo čijih stanja bitcoin-a.
Čitav ovaj proces poznat je pod nazivom rudarenje bitcoin-a. Svaki računar na mreži pokušava da proba nove podatke kroz heš mašinu, bilione puta u sekundi.
Šta je blockchain?
Blockchain predstavlja istoriju Bitcoin transakcija, koja omogućava bilo kome da utvrdi svoje Bitcoin stanje.
- ‘Block – Blok’ = Grupa Bitcoin transakcija, nonce-a i heša prethodnog bloka
- ‘Chain – Lanac’ = Heš svakog bloka takođe koristi heš prethodnog bloka kao ulaz. Ovo povezuje podatke svakog bloka sa svakim drugim blokom, stvarajući chain – lanac.
Na blockchain-u, prava imena nisu povezana sa bitcoin-ima. Bitcoin-i su povezani samo sa slučajnim nizom brojeva i slova poznatim kao ‘javni ključ’. Ovo korisnike Bitcoin-a i njihova stanja čini poprilično anonimnima za sve koji vode knjigu.
Kada posedujete bitcoin-e, vi imate password za otključavanje vaših bitcoin bankovnih računa. Ovi računi postoje na hiljadama računara širom sveta koji pokreću Bitcoin protokol.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao razumevanje o tome kako funkcioniše Bitcoin protokol i kako se osiguravaju njegova neverovatna svojstva.
Ako želite da saznate više, preporučujem vam ove izvore:
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ bf47c19e:c3d2573b
2025-06-03 18:08:44
@ bf47c19e:c3d2573b
2025-06-03 18:08:44Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Koji Bitcoin Novčanici su Dostupni?
- Šta je Mnemonic Oporavak ili Seed Fraza sa 12 ili 24 Reči?
- Kako Čuvati Seed Frazu
- Saveti za Osiguravanje Vaše Seed Fraze
- Šta će se Desiti sa Vašim Bitcoin-om Nakon što Umrete?
- Kako Koristite Seed Frazu za Oporavak Vašeg Novčanika?
- Ako je Vaša Seed Fraza Sigurna, Biće i Vaša Sredstava!
Za one koji tek ulaze u igru sa kriptovalutama, šansa da vaša Bitcoin sredstva ne budu sigurna i zaštićena može biti pomalo zastrašujuća. Srećom, postoji mnogo user-friendly Bitcoin novčanika, i svaki od njih ima izvrsnu funkciju rezervne kopije, koja vam omogućava trenutan povraćaj Bitcoin sredstava, ako vaš uređaj na kome se nalazi novčanik ikada bude zagubljen ili izgubljen. Ova funkcija, poznata kao „seed fraza“, ili seed fraza za oporavak, predstavlja jedinstveni niz reči koje će vaš novčanik generisati, i koje deluju kao password za vaše lične Bitcoin podatke. Ovaj skup reči omogućava trenutni povraćaj vaših bitcoin sredstava.
Iako možete lako zapostaviti svoju seed frazu, misleći da ćete se kasnije pozabaviti sa njom, uvek je najbolje biti proaktivan kada je reč o osiguranju zaštite vaše fraze za oporavak. Fraza za oporavak je vaša rezervna kopija – pa iako vam neće trebati svaki dan, biće kritična u slučaju da vam se novčanik pokvari. Takođe, fraza za oporavak može da omogući svima pristup vašem bitcoin-u, pa je zato veoma važno da se ona čuva na sigurnom.
U ovom članku, prikazaću vam:
- Spisak glavnih Bitcoin hardware novčanika koje možete koristiti za skladištenje vaših Bitcoin-a.
- Sveobuhvatan pregled mnogih metoda koje možete koristiti za čuvanje vaše seed fraze
- Razne prednosti i mane za svaku od njih
- Saveti koje možete da koristite da biste maksimizirali ukupnu sigurnost svoje seed fraze
- Kako sigurno čuvati vašu seed frazu
- Kako proslediti svoj Bitcoin u slučaju vaše smrti
Kada završite sa čitanjem, trebalo bi da ste na dobrom putu da čuvate svoju seed frazu koristeći najsigurnija i najpouzdanija dostupna sredstva, obezbeđujući najveću zaštitu svojih Bitcoin sredstava bez obzira na to šta se sa vama ili vašim digitalnim uređajima dogodi u budućnosti. Za početak ćemo dati brzi pregled hardware novčanika i šta tačno predstavlja fraza za oporavak.
Koji Bitcoin Novčanici su Dostupni?
Ispod ćete pronaći listu od nekoliko najpopularnijih novčanika koji su dostupni danas. Softverski novčanici rade na vašem telefonu ili računaru, dok su hardware novčanici namenski delovi hardvera (poput specijalizovanog fleš diska) koji omogućavaju lak i siguran pristup vašem bitcoin-u uz jaku sigurnost.
Hardware (poput specijalizovanog USB fleš diska) i Software (na vašem telefonu ili računaru)
Svaki od ovih novčanika će vam dati seed frazu, koja se sastoji od 12 ili 24 reči, što će vam omogućiti pristup svim bitcoin adresama povezanim sa vašim novčanikom – a samim tim i svim vašim sredstvima.
Šta je Mnemonic Oporavak ili Seed Fraza sa 12 ili 24 Reči?
Najjednostavnije rečeno, seed fraza je niz određenih reči u kojima se nalaze sve potrebne informacije kako bi se u potpunosti povratila vaša Bitcoin sredstva. Koji god novčanik odlučite da koristite, generisaće jedinstvenu seed frazu, posebno za vas, a taj softver će vas uputiti da čuvate seed frazu na neki način, gde će biti dostupna u slučaju nužde. Seed fraza će biti jedinstvena i obično sadrži od 12 ili 24 reči, od kojih se neke mogu ponoviti. Pre nego što sačuvate seed frazu, pročitajte odeljak 4) sa našim savetima!
Seed fraza omogućava pristup vašim bitcoin sredstvima svima koji je poseduju- omogućavajući vam da povratite sredstava ako vam se novčanik pokvari, ili omogućavajući lopovu da dobije pristup vašim bitcoin-ima.
To čini vašu seed frazu vrednom poput zlatne poluge. Zbog toga je pravilno čuvanje vaše seed fraze veoma važno – morate uravnotežiti lak način oporavka i sigurnost protiv krađe i hakovanja. Međutim, s obzirom da je vaša seed fraza samo niz reči, ona se može snimati i skladištiti na mnogo jednostavniji način (i mnogo jeftinije!) od zlatne poluge – čineći je potencijalno mnogo sigurnijom.
Primarna svrha seed fraze je da ima neku vrstu fizičkog sredstva za povraćaj Bitcoin sredstava ako vas izneveri novčanik. To uključuje ako vam se sruši sistem na računaru, ako vam se ošteti hard disk, izgubite telefon ili razbijete hardware novčanik – u svakom slučaju gde vaš novčanik postane nepristupačan.
Seed fraze zasnivaju se na specifikacijama otvorenog koda kompatibilnim sa Bitcoin protokolom, što znači da dok god imate svoju seed frazu, možete koristiti mnoge druge vrste novčanika da biste povratili pristup svom bitcoin-u. Recimo da danas posedujete Trezor, ali za 10 godina vam se uređaj pokvari ili Trezor prestane da posluje – možete jednostavno kupiti drugačiji hardware novčanik ili skinuti novčanik na svoj telefon, i pomoću svoje seed fraze povratiti pristup svojim bitcoin-ima.
Kako seed fraza funkcioniše?
Seed fraze funkcionišu slično kao i bilo koji drugi oblik koda, pri čemu svaka reč predstavlja numeričku vrednost koju novčanik razume. Fraze se generišu nasumično na osnovu unapred određene baze reči. Iako ponekad imate mogućnost da smislite sopstvenu seed frazu, omogućavanje novčaniku da generiše seed frazu je najbolja opcija za vašu sigurnost.
Jedna od prednosti koja je svojstvena prirodi seed fraza je ta što se u njima koriste stvarne prepoznatljive reči na engleskom jeziku koje se mogu izvesti i upamtiti bez obzira na male greške kao rezultat ružnog rukopisa. Ovo je suprotno od mnogih drugih nasumično generisanih passworda, gde svaki karakter mora biti jasno čitljiv da bi se password mogao pravilno kreirati, jer su oni jednostavno niz slučajnih karaktera. Stoga seed fraze imaju i prednosti randomizacije, kao i prednosti lako prepoznatljivih i uobičajenih reči.
Zašto Niko Ne Može da Predpostavi Seed Frazu?
Mogli biste da pomislite da bi niz od 24 reči možda bio lak nekome da ga pretpostavi, ili da bi nekome bilo isplativo da napravi računarski ciklus mogućih kombinacija, dok ne pronadje novčanik koji sadrži neke bitcoin-e kako bi mogao da ih ukrade.
Reči za frazu za oporavak ili seed frazu dolaze sa liste koja se sastoji od 2048 reči – pa čak i seed od 12 reči za Bitcoin novčanik ima 2048^12 kombinacija ili 2^132. Procenjuje se da u univerzumu postoji 10^21 zvezda, pa je nepotrebno reći da ovo predstavlja mnogo mogućih kombinacija. Čak i kada bi svaki čovek na Zemlji danas imao 1.000.000 novčanika (čak i bez adresa), to bi iznosilo samo 7.800.000.000.000.000 novčanika – što je oko 2^53. Ovo čini negde oko polovine mogućih kombinacija, ali to bi sakrilo snagu eksponencijalnog rasta.
Kada bi svi na svetu imali po 1.000.000 bitcoin novčanika, mi bismo i dalje koristili samo 0.000000000000000000000001654% od svih mogućih novčanika. To je neuporedivo teže nego pronaći jedno određeno zrno peska u celokupnom pesku koji se nalazi na Zemlji.

Čak i taj pronalazak određenog zrna peska na ovoj plaži bila bi kao šetnja parkom nasuprot pogađanju bilo koje random seed fraze.
Dakle, prilično je sigurno reći da niko uskoro neće pokušati da pogadja bitcoin novčanike. Bila bi potrebna vojska računara i veoma dugačak vremenski period da se pronadje samo jedan novčanik sa sredstvima u tom prostranstvu.
Kako Čuvati Seed Frazu
Neverovatno je važno kako zapisujete i skladištite svoju seed frazu, s obzirom na ogromnu količinu moći koju će oni koji je poseduju imati nad vašim Bitcoin sredstvima. Takođe, budući da je poenta seed fraze da bude lako dostupna gde i kada vam zatreba, čuvanje na nekom sigurnom, ali i pristupačnom mestu, je neophodno. Specifična metoda koju koristite za transkripciju vaše seed fraze je takođe važna, bez obzira na to kako se čuva, jer se neke metode transkripcije pokazale mnogo sigurnijim od drugih.
Pogledajte naš odeljak sa savetima, pre nego što zapišete svoju seed frazu!
Preporučujemo vam da fizički sačuvate svoju seed frazu nakon što vam je softver ili hardware novčanik isporuči. Fizičko skladištenje čini vašu seed frazu manje otvorenom za hakere koji bi mogli da vam ukradu frazu za oporavak iz digitalne memorije vašeg računara ili pametnog telefona.. Međutim, mnogi ljudi će i dalje odabrati neki oblik digitalnih sredstava za čuvanje svojih seed fraza, bilo zato što je to dominantno sredstvo ili jednostavno kao dodatni oblik rezervne kopije. Hajde da pogledajmo kako fizička, a tako i digitalna sredstva koja možete koristiti za čuvanje vaše seed fraze, kako se ona koriste, i specifične prednosti i nedostatke svake od njih.
Zapisivanje Vaše Seed fraze – na Papiru ili Digitalno
Zapisivanje Vaše Seed Fraze na Papir
Naravno, najočigledniji metod unošenja vaše digitalne seed fraze u fizički svet je isti onaj metod koji biste obično koristili za unošenje bilo kog drugog oblika pisanja u fizički svet – olovkom i papirom. Jednostavno zapisivanje vaše seed fraze na papir u potpunosti može biti dovoljno da vam pruži sigurnost koju želite. Međutim, postoje neka upozorenja oko upotrebe olovke i papira koja ovu najjednostavniju metodu čine ne baš tako idealnom za čuvanje nečega toliko važnog kao što je seed fraza.
Kao prvo, sam papir je lako uništiv, a o mastilu da i ne govorimo. U slučaju poplave ili požara, papir će biti uništen, što znači da će i vaša seed fraza biti uništena zajedno sa njim. Naravno, ovo su loše vesti i za svakoga ko verovatno gubi i sav svoj hardver i opremu u požaru ili poplavi. Kao drugu stvar, papir je neverovatno lako zagubiti. Može se oduvati, pomešati sa otpadom ili jednostavno pomešati sa nečim drugim i negde izgubiti, i nikada ga više nećete videti. Iz ovih i više drugih razloga, oni koji žele da zapišu svoju seed frazu u fizički svet, često traže sredstva koja su izdržljivija i trajnija od papira.
Graviranje Vaše Seed Fraze na Čeličnoj Back-Up Ploči
Back-up ploče od nerđajućeg čelika su stvorene kako bi korisnici Bitcoin-a imali način da trajnije urežu svoje seed fraze u fizički svet od puke olovke i papira. Napravljene su od nerđajućeg čelika, na koje se vaša seed fraza može trajno urezati. Budući da je gravura napravljena na čeliku, ona će u slučaju požara ili poplave moći da traje mnogo duže od papira. Ploča može biti bilo šta, od male kartice koju možete držati u novčaniku do većeg komada koji se može trajno čuvati kod kuće ili u sefu.
Bilo koju veličinu pločice da izaberete, možete je kupiti zajedno sa alatima za samograviranje (koji nisu uvek u kompletu), što znači da korisnik ne mora da deli svoju seed frazu sa onima od kojih je kupio ploču. Budući da su ove ploče stvorene posebno za potrebe izdržavanja katastrofe, obično sadrže brojne garancije o njihovoj trajnosti, otporne su na bilo koje elemenate koje možete baciti na njih, od vode do vatre, kao i od prekomernog korišćenja i habanja.
Što se tiče back-up ploča od nerđajućeg čelika, svaki proizvođač nudi svoj jedinstveni spin. Pogledajmo 5 najboljih proizvođača back-up ploča od nerđajućeg čelika na tržištu i da vidimo kako su se pokazali:
Cryptosteel
Sa sedištem u Velikoj Britaniji, Cryptosteel nudi čelične „Kapsule“ i „Kasete“ sa cenom u eurima, s tim da je kapsula približno veličine laserskog pokazivača, a kaseta je veličine, pa, kasete. Kapsula košta 74 eura, a kaseta 108 eura, mada se nude popusti za velike narudžbine. Umesto da zahtevaju gravuru, svaka Kaseta ili Kapsula dolazi sa odredjenom količinom čeličnih pločica koje se mogu staviti prema redosledu vaše seed fraze.
Cena Rezervne Kopije Jedne Seed Fraze: 74 eura

Blockplate
Blockplate nudi čelične back-up ploče po ceni od 69 USD za dve – svaka ploča sadrži 12 reči. Njihove verzija jedne ploče, koja izgleda identično, košta 49 USD po paru. Potpuno četvrtaste i malo manje od podmetača, ove ploče vam omogućavaju da svoju seed frazu sačuvate na mreži koristeći samo prosti udarac u sredinu, nisu potrebne pločice sa slovima.
Cena Rezervne Kopije Jedne Seed Fraze: $49 (plus metalna igla za 10 $, ako vam treba)

Hodlinox
Coldbit nudi heavy-duty kartice sa futrolama po ceni od 69 eura i setove za graviranje za dodatnih 20 eura. Takođe se možete odlučiti da sami uradite graviranje pomoću alata koji imate kod kuće, a koji može urezati čelik, poput dijamantske Dremel burgije. Oslanjajući se na čistu doslovnu transkripciju sličnu Hodlinox pločama, ove ploče ipak nude malo veću zaštitu i neke sjajne dizajne.
Cena Rezervne Kopije Jedne Seed Fraze: 29 Eura

Coldbit
Coldbit nudi heavy-duty kartice sa futrolama po ceni od 69 eura i setove za graviranje za dodatnih 20 eura. Takođe se možete odlučiti da sami uradite graviranje pomoću alata koji imate kod kuće, a koji može urezati čelik, poput dijamantske Dremel burgije. Oslanjajući se na čistu doslovnu transkripciju sličnu Hodlinox pločama, ove ploče ipak nude malo veću zaštitu i neke sjajne dizajne.
Cena Rezervne Kopije Jedne Seed Fraze: 69 Eura (plus 20 eura za set za graviranje, ako vam je potreban)

Billfold by Privacy Pros
Preimenovan u Privacy Pros, brend Billfold je i dalje dostupan po ceni od 89 USD. Koristi dizajn kartice vrlo sličan Cryptosteel Kaseti, sa malim pločicama koje slažete da biste formirali svoju seed frazu.
Cena Rezervne Kopije Jedne Seed Fraze: $89

Kriptovanje Vaše Seed Fraze i Njeno Digitalno Skladištenje
Iako se generalno preporučuje da svoju seed frazu ne skladištite digitalno, oni koji su bolje upućeni u digitalnu bezbednost, ovo mogu videti kao floskulu koja se može ignorisati. Iako laici sigurno ne bi smeli da šalju i primaju svoje seed fraze e-mailom, pravilno digitalno kriptovanje i skladištenje sredstvima poput cloud-a ili USB fleš memorije mogu biti jednako sigurna i bezbedna sredstva za skladištenje, kao i fizička sredstva, poput čeličnih back-up ploča. Takođe, kada se oba sredstva koriste zajedno, to vam pruža krajnju mrežu rezervnih kopija u slučaju bilo kakvih hitnih slučajeva.
Kriptovanje možda nije nešto što je lako za svakoga, ali postoje mnoge treće strane koji će se pobrinuti da odrade kriptovanje za vas. Obavezno diskonektujte računar sa Interneta dok unosite seed u računar i izvodite kriptovanje – ne verujte online uslugama kriptovanja!
Odatle, na vama ostaje da odlučite kako ćete da je čuvate, bilo na cloud-u ili na USB fleš memoriji. Prednost čuvanja na cloud-u je u tome što podaci nisu povezani ni sa jednim fizičkim uređajem i može im se pristupiti sa bilo kog mesta pomoću passworda na cloud-u. Međutim, to takođe znači da su podaci nešto pristupačniji nego da se čuvaju na USB fleš memoriji. Zapamtite da ako se odlučite za USB fleš memoriju, ona možda neće moći da se izdrži protiv požara i vode, baš kao što to mogu prosti nefizički podaci na cloud-u. Fleš memorija koja se koristi na USB-u takođe nije dizajnirana da traje duže od 10 godina, pa imajte i to na umu.
Digitalno čuvanje seed fraze preporučujem isključivo informatičarima tj ljudima sa dosta iskustva u kriptiranju informacija. Za 99% nas čekič i čelična pločica koju čuvamo na 2 ili 3 mesta + dodatna 13. ili 25. reč je najbolje rešenje.
Gde i Kako Čuvati Svoju Seed Frazu
Bez obzira da li ste odlučili da svoju seed frazu sačuvate na čeličnoj ploči, USB-u ili jednostavno na parčetu papira, moraćete da je stavite negde – a idealno bi bilo da je stavite na više mesta u slučaju da se jedna uništi ili izgubi.
Najbolji savet koji mogu da vam dam je gde ne trebate da čuvate svoju seed frazu. Na kraju, mesto na koje stavite svoju seed frazu najbolje je da sačuvate za sebe, i zato evo nekoliko mesta na koja definitivno ne želite da stavite seed frazu, ako želite da izbegnete da upadne u pogrešne ruke.
Ne Čuvajte Svoju Seed Frazu u…
- Sef u Banci: Izgleda kao odlično mesto, zar ne? Pogrešno – banke prave greške, a kako sefovi postaju sve manje popularni, one prave još više grešaka!
- Sef u Kući: Opet se čini kao odlično mesto – međutim, ovo je prvo mesto koje će provalnik potražiti. Čak i ako ne mogu da otvore sef, većinu malih kućnih sefova moguće je lako premestiti i odneti u kolicima, i kasnije ih razbiti.
- Ispod Kreveta ili Dušeka: Klasično mesto za skrivanje novca, takođe je jedno od prvih mesta koje će provalnik pogledati.
- U Frižideru: Možda mislite da maskiranje vašeg seed-a u posudi za hranu izgleda kao dobar način zabune, ali ovo je uobičajena taktika za skrivanje dragocenosti, pa bi provalnici mogli potražiti i ovde.
- Ormarić za Nakit ili Fioke za Veš: To su uobičajena mesta za čuvanje drugih vrsta dragocenosti, pa će ih provalnik brzo pokrasti.
Budite kreativni, ali ne toliko kreativni da izgubite seed frazu, jer ne možete da se setite gde ste je sakrili.
Takođe je važno razmotriti i mogućnost pravljenja rezervnih kopija vašeg seed-a na više lokacija. Na taj način, čak i ako je jedno mesto potpuno uništeno (recimo da vam oluja odnese kuću), i dalje ćete da imate vaš seed na drugoj lokaciji.
Shamir-ovo Tajno Deljenje – Širite Vašu Frazu za Oporavak
Shamir-ovo Tajno Deljenje (eng. Shamir Secret Sharing), je algoritam koji vam omogućava da svoj seed podelite na više seed-ova koji su sami po sebi beskorisni. Međutim, njihovim rekombinovanjem vratićete vaš seed za oporavak.
Ovo je dobar korak ukoliko želite da podelite vaš seed sa vašim advokatom, računovođom, članovima porodice itd. – jer obezbeđuje da niko od njih nema pristup vašem celom seed-u.
Način na koji Shamir deluje je to što deli vaš seed na više manjih seed-ova koje možete predati pouzdanim pojedincima. Kada postavite Shamir-ov backup, odlučujete koliko ‘deljenja’ želite da kreirate i koliko delova je potrebno za oporavak vašeg celog seeda – na primer, možete da napravite 5 deljenja i kažete da su bilo koja 3 dela potrebna za oporavak vašeg seed-a.
Neki hardware novčanici, poput Trezor Model T, podržavaju Shamir Backups na user-friendly način.
Saveti za Osiguravanje Vaše Seed Fraze
Postoji mnogo opštih stvari koje morate imati na umu kada je reč o držanju vaše seed fraze na sigurnom. Neke od ovih stvari su samo zdrav razum, dok većini ljudi možda ništa neće pasti na pamet bez nečije pomoći. Neće sve metode biti praktične za sve čitaoce, ali imajte na umu da što više bezbednosnih metoda vežbate, vaša seed fraza će biti sigurnija. Učinite koliko god možete da vaša seed fraza bude sigurna i ona će vam biti pri ruci kada vam zatreba.
Ne Pravite Slike ili Screenshotove Vaše Seed Fraze
Ne slikanje vaše seed fraze je dovoljno jednostavno. Svaka slika koju napravite stvara dodatnu spoljnu datoteku koja se može duplirati, izgubiti ili ukrasti. Što je manji digitalni otisak vaše seed fraze, to je bolje. Međutim, postoji mnogo različitih načina na koje se mogu ukrasti fotografije vaše seed fraze, što može iznenaditi prosečnog čitaoca. Prvo, hakeri i ostale treće strane mogu da preuzmu sliku vaše seed fraze putem sigurnosnih kamera, poput onih na bankomatima. Takođe, kamere na računaru, telefonu i drugim ličnim uređajima mogu predstavljati još veći rizik. Iz ovih razloga, umanjivanje ukupne vidljivosti i izloženosti vaše seed fraze, i pre i posle dokumentovanja u fizičkom svetu, je apsolutna potreba.
Ne Izgovarajte Svoju Seed Frazu Naglas – Nikad!
Ako ste ikada razgovarali telefonom i Google Assistant vas je prekinuo, onda znate da vas stalno slušaju. Bilo da ste napolju u javnosti ili ste sami kod kuće, treće strane slušaju. Ako su te treće strane zainteresovane, možda će moći da dobiju pristup vašim ličnim podacima. Iz tog razloga, uzdržavanje od izgovaranja naglas vaše seed fraze treba smatrati vitalnim delom zaštite vaše seed fraze. Lakše je špijunirati nekoga preko zvuka, nego što je to slučaj sa vizuelnim elementima, pa izgovaranje naglas vaše seed fraze čini je mnogo podložnijom presretanju od strane onih koji je mogu zloupotrebiti.
Ne Čuvajte Svoju Seed Frazu u Password Menadžeru
Čuvanje vaše seed fraze u password menadžeru može se činiti sigurnim i prikladnim načinom izrade rezervnih kopija, ali to nosi velike rizike. Seed fraza se mnogo razlikuje od password za recimo vaš Facebook nalog. To je zato što su passwordi samo alati za potvrdu identiteta za centralizovane usluge – što znači da ako izgubite pristup računu ili budete hakovani, možete kontaktirati broj podrške i proći kroz neke korake da biste povratili kontrolu nad svojim nalogom.
Kod Bitcoin-a, prema njegovom dizajnu, ne postoji broj podrške. Ne postoji centralna stranka koja kontroliše Bitcoin transakcije, čineći ga neverovatno slobodnim i otvorenim – ali to takođe znači da morate vrlo ozbiljno da preuzmete odgovornost za svoju seed frazu. Ako padne u pogrešne ruke jer je vaš password menadžer hakovan, možete izgubiti svoje bitcoin-e.
Ne Koristite Online Usluge Oporavka Seed-a
Ako vam neki website traži da unesete svoju seed frazu – čak i ako vam se čini kao pouzdan – dobro razmislite pre nego što to učinite. Većina „usluga online oporavka“ su maskirane prevare, usresredjene samo na kradju seed fraza nevinih ljudi! Ne budi jedan od njih.
Koristite Pristupnu Frazu(dodatnu reč) da Biste Dodali još Sigurnosti
Trezor podešavanje pristupne fraze | Ledger podešavanje pristupne fraze
Ako vaš novčanik podržava dodavanje pristupne fraze, trebalo bi da je koristite. Pristupna fraza je password koji dodate svom seed-u i funkcioniše kao 13. ili 25. reč u vašoj seed frazi. Zbog toga je vaš novčanik mnogo teže ukrasti. Ako se pristupna fraza čuva na drugačijoj lokaciji od vašeg seed-a, vaši bitcoin-i su sigurni čak i ako neko dobije pristup vašoj seed frazi.
Zaštitite Svoju Seed Frazu
Bez obzira da li svoju seed frazu čuvate u digitalnom oblaku ili na čeličnoj ploči, postojanje nekog načina čuvanja koji štiti seed frazu od elemenata kao što su požar i poplava, mora se smatrati obaveznim. Kao što je već rečeno, čelične ploče mogu se napraviti da izdrže većinu katastrofa, a skladištenje na cloud-u pruža nefizička sredstva koja mogu biti jednako sigurna kao i druga sredstva ako koristite pravu enkripciju. Upotreba jednog ili oba ova sredstva može vam pomoći da vam garantuje maksimalnu zaštitu bez obzira na to šta se dogodi.
Koristite Više Metoda za Pravljenje Rezervnih Kopija Kad God Možete
Korišćenje nekoliko različitih metoda za čuvanje vaše seed fraze ima puno prednosti, ali ima i neke nedostatke ako im ne pristupite sa dovoljno pažnje. Iako vam više načina za skladištenje pruža veću zaštitu, to takođe proširuje vaš celokupni profil, što znači da postoji više područja koja su otvorena za napad. Ipak, korišćenje najmanje dve odvojene metode za pravljenje rezervnih kopija obično se smatra dobrom idejom, jer imate rezervne kopije za slučaj da vam se nešto desi! Nikad ne znate šta će se dogoditi, a u tome i jeste poenta seed fraza.
Ograničite Pristup Vašoj Seed Frazi što je Više Moguće
Naravno, neki ljudi mogu da se odluče da svoju seed frazu podele sa pouzdanom trećom stranom, kao sredstvo radi osiguranja njene zaštite, ali, generalno, što je manji broj ljudi sa kojima delite svoju seed frazu, time bolje. Vaša je lična odluka s kim ćete deliti svoju seed frazu, i u vašem je najboljem interesu da to pravo mudro koristite.
Ne Pričajte o Količini Bitcoin-a Koje Posedujete
Nekima je ovo možda najteži savet, ali možda i najvažniji. Ako niko ne zna da imate bitcoin, i koliko ga imate, smanjujete verovatnoću da će neko pokušati da dodje do vaše seed fraze ili novčanika. Zato držite jezik za zubima!
Šta će se Desiti sa Vašim Bitcoin-om Nakon što Umrete?
Kao i sa bilo kojim drugim sredstvom, trebalo bi da imate predstavu o tome kako će se postupati sa vašim Bitcoin-om nakon što umrete. S obzirom da je ovo relativno nova tema, nema puno presedana kada je reč o prenošenju i nasleđivanju Bitcoin-a. Iako mnogi mogu da pomisle da moraju da angažuju advokata, prenošenje Bitcoin-a zaista podrazumeva samo puko prenošenje vaše seed fraze, zajedno sa nekim vašim konkretnim srestvima.
Prilikom pripreme za prosleđivanje vaše seed fraze u slučaju vaše smrti, važno je zapamtiti da prosledite i detaljan zapis o svojoj digitalnoj imovini. Za razliku od fizičkih materijala, digitalna sredstva se ne mogu lako kvantifikovati fizičkom procenom. Ukoliko nije svesna da postoji, ta osoba možda neće znati šta tačno prima. Stoga, ona možda neće zaista primiti ono što ste joj namenili da nasledi. To je takođe razlog zašto bi svi trebali da drže svu svoju imovinu sažetom i što organizovanijom, u slučaju nužde.
Ako razumete engleski jezik preporučujem da pročitate knjigu: Cryptoasset Inheritance Planning od Pamela Morgan
Kako Koristite Seed Frazu za Oporavak Vašeg Novčanika?
Za većinu novčanika, upotreba seed fraze jednostavna je poput pritiskanja pravih tipki i kucanja iste. Odatle, seed fraza će vratiti sav sadržaj i podatke novčanika na bilo koji uređaj koji koristite. Na ovaj način, korišćenje seed fraze znači da možete imati novčanik kod sebe gde god da krenete, bez obzira na sve, čak i ako se novčanik izgubi ili uništi – sve što vam zaista treba je vaša seed fraza.
Opet, ne koristite nikakve online usluge za seed frazu! U najvećem broju slučajeva to su prevare.
Bez obzira da li koristite mobilni novčanik kao što je Muun ili hardware novčanik kao što su Trezor ili Ledger, sredstva za upotrebu vaše seed fraze su u osnovi ista – jedina razlika je hardver koji koristite za to. Kod aplikacija poput Muun jednostavno pokrenete aplikaciju i ona vam daje mogućnost oporavka prethodnog novčanika. Zatim ćete odabrati dužinu svoje seed fraze i uneti je tačno onako kako je prikazana.
Uz hardware novčanike poput onih koje je izradio Trezor, dobićete istu opciju za povratak kada pokrenete uređaj i instalirate firmware. Dobićete isti izbor da odredite dužinu svoje seed fraze, a zatim će zatražiti od vas da je unesete potpuno isto.
Ako je moguče uvjek koristite isti hardware/software wallet prilikom oporavka vaše seed fraze kao što ste koristili kad ste je pravili.
Ako je Vaša Seed Fraza Sigurna, Biće i Vaša Sredstava!
Na kraju dana, važno je da zapamtite da što više brige ulažete u pravilno skladištenje i zaštitu svoje seed fraze, to će vaša sredstva biti sigurnija i za vas i za vaše voljene. Digitalno doba predstavlja širok spektar novih opasnosti, a svet kriptovaluta je leglo za većinu njih.
Ako želite da preduzmete proaktivne mere u obezbeđivanju najveće zaštite vašeg bitcoin-a, čuvanje vaše seed fraze na sigurnom i pristupačnom mestu je neophodno. Vaša seed fraza možda sada ne izgleda kao velika stvar, ali će izgledati kao velika stvar kada dođe vreme da je upotrebite. Ukoliko želite da vi i vaša Bitcoin sredstva budete zaštićeni u slučaju nužde ili čak u slučaju vaše smrti, preduzimanje odgovarajućih sredstava za čuvanje i zaštitu vaše seed fraze je osnovni prvi korak.
-
 @ e2c72a5a:bfacb2ee
2025-06-04 01:14:59
@ e2c72a5a:bfacb2ee
2025-06-04 01:14:59The $100 million gamble that's turning crypto traders into unlikely heroes. James Wynn just placed his second massive Bitcoin bet after being liquidated days ago, and now claims market makers are deliberately targeting his position. With his liquidation level set at $103,630, Wynn has rallied the crypto community to his defense, receiving donations from 24 users totaling nearly $8,000. This David vs Goliath battle reveals how retail traders are banding together against what they perceive as market manipulation, creating a fascinating power shift in an industry where individual traders rarely had such collective influence. Will the community save Wynn from the "evil
-
 @ e2c72a5a:bfacb2ee
2025-06-04 00:26:26
@ e2c72a5a:bfacb2ee
2025-06-04 00:26:26When a trader bets $100M on Bitcoin, the market becomes the hunter. James Wynn placed his second massive leveraged position after being liquidated days earlier, claiming market makers are deliberately targeting his $103,640 liquidation level. The crypto community rallied behind him, donating thousands in stablecoins to help "fight the market-making cabal." Meanwhile, Trump's media company seeks SEC approval for a Truth Social Bitcoin ETF, joining the growing trend of corporate Bitcoin treasuries. Tether moved $3.9B in Bitcoin to Twenty One Capital, making it the third-largest corporate holder. Are you watching these high-stakes crypto battles unfold, or participating in them yourself?
-
 @ 8bad92c3:ca714aa5
2025-06-03 18:02:33
@ 8bad92c3:ca714aa5
2025-06-03 18:02:33Marty's Bent

It's been a pretty historic week for the United States as it pertains to geopolitical relations in the Middle East. President Trump and many members of his administration, including AI and Crypto Czar David Sacks and Treasury Secretary Scott Bessent, traveled across the Middle East making deals with countries like Qatar, Saudi Arabia, the United Arab Emirates, Syria, and others. Many are speculating that Iran may be included in some behind the scenes deal as well. This trip to the Middle East makes sense considering the fact that China is also vying for favorable relationships with those countries. The Middle East is a power player in the world, and it seems pretty clear that Donald Trump is dead set on ensuring that they choose the United States over China as the world moves towards a more multi-polar reality.
Many are calling the events of this week the Riyadh Accords. There were many deals that were struck in relation to artificial intelligence, defense, energy and direct investments in the United States. A truly prolific power play and demonstration of deal-making ability of Donald Trump, if you ask me. Though I will admit some of the numbers that were thrown out by some of the countries were a bit egregious. We shall see how everything plays out in the coming years. It will be interesting to see how China reacts to this power move by the United States.
While all this was going on, there was something happening back in the United States that many people outside of fringe corners of FinTwit are not talking about, which is the fact that the 10-year and 30-year U.S. Treasury bond yields are back on the rise. Yesterday, they surpassed the levels of mid-April that caused a market panic and are hovering back around levels that have not been seen since right before Donald Trump's inauguration.
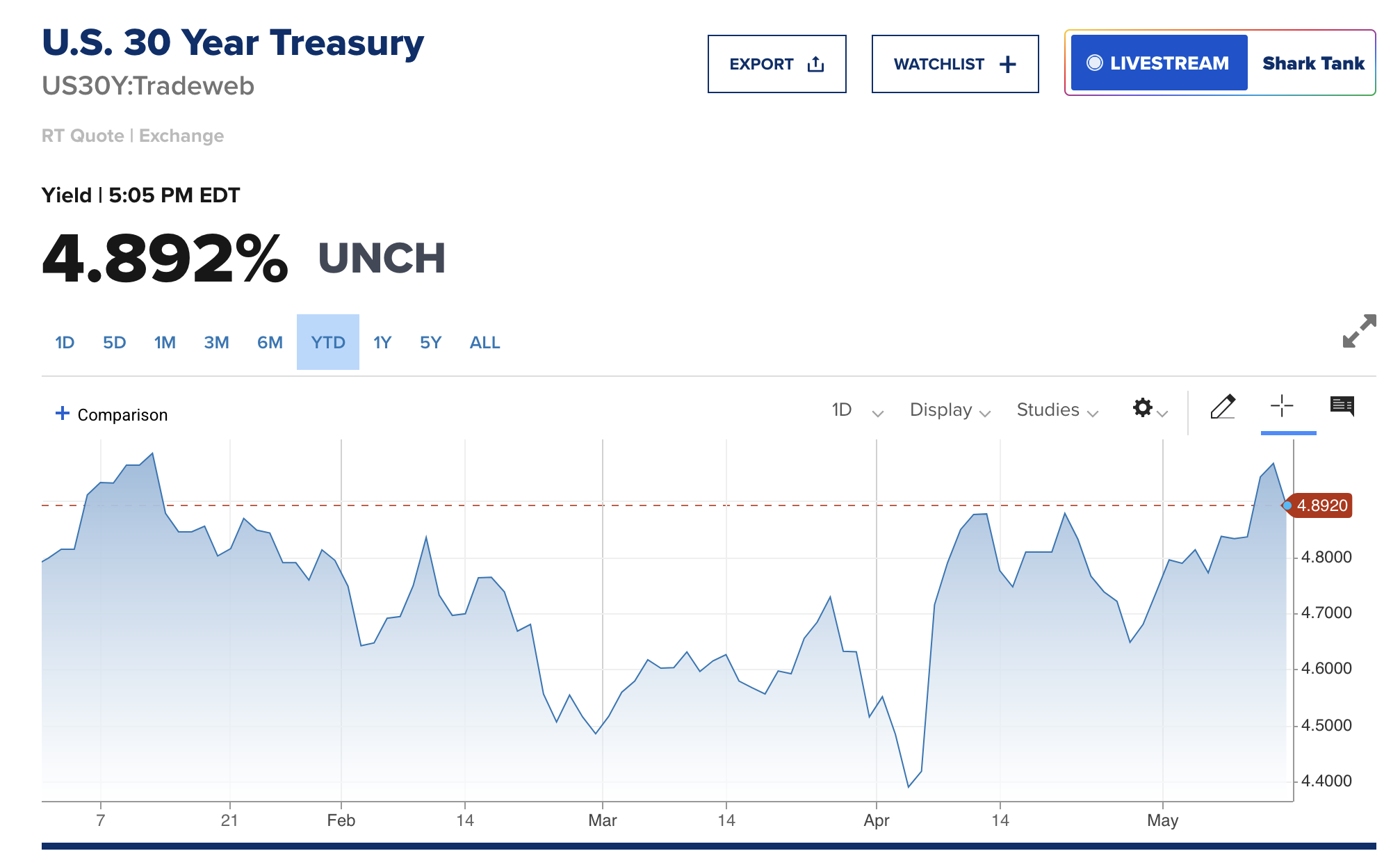
I imagine that there isn't as much of an uproar right now because I'm pretty confident the media freakouts we were experiencing in mid-April were driven by the fact that many large hedge funds found themselves off sides of large levered basis trades. I wouldn't be surprised if those funds have decreased their leverage in those trades and bond yields being back to mid-April levels is not affecting those funds as much as they were last month. But the point stands, the 10-year and 30-year yields are significantly elevated with the 30-year approaching 5%. Regardless of the deals that are currently being made in the Middle East, the Treasury has a big problem on its hands. It still has to roll over many trillions worth of debt over over the next few years and doing so at these rates is going to be massively detrimental to fiscal deficits over the next decade. The interest expense on the debt is set to explode in the coming years.
On that note, data from the first quarter of 2025 has been released by the government and despite all the posturing by the Trump administration around DOGE and how tariffs are going to be beneficial for the U.S. economy, deficits are continuing to explode while the interest expense on the debt has definitively surpassed our annual defense budget.
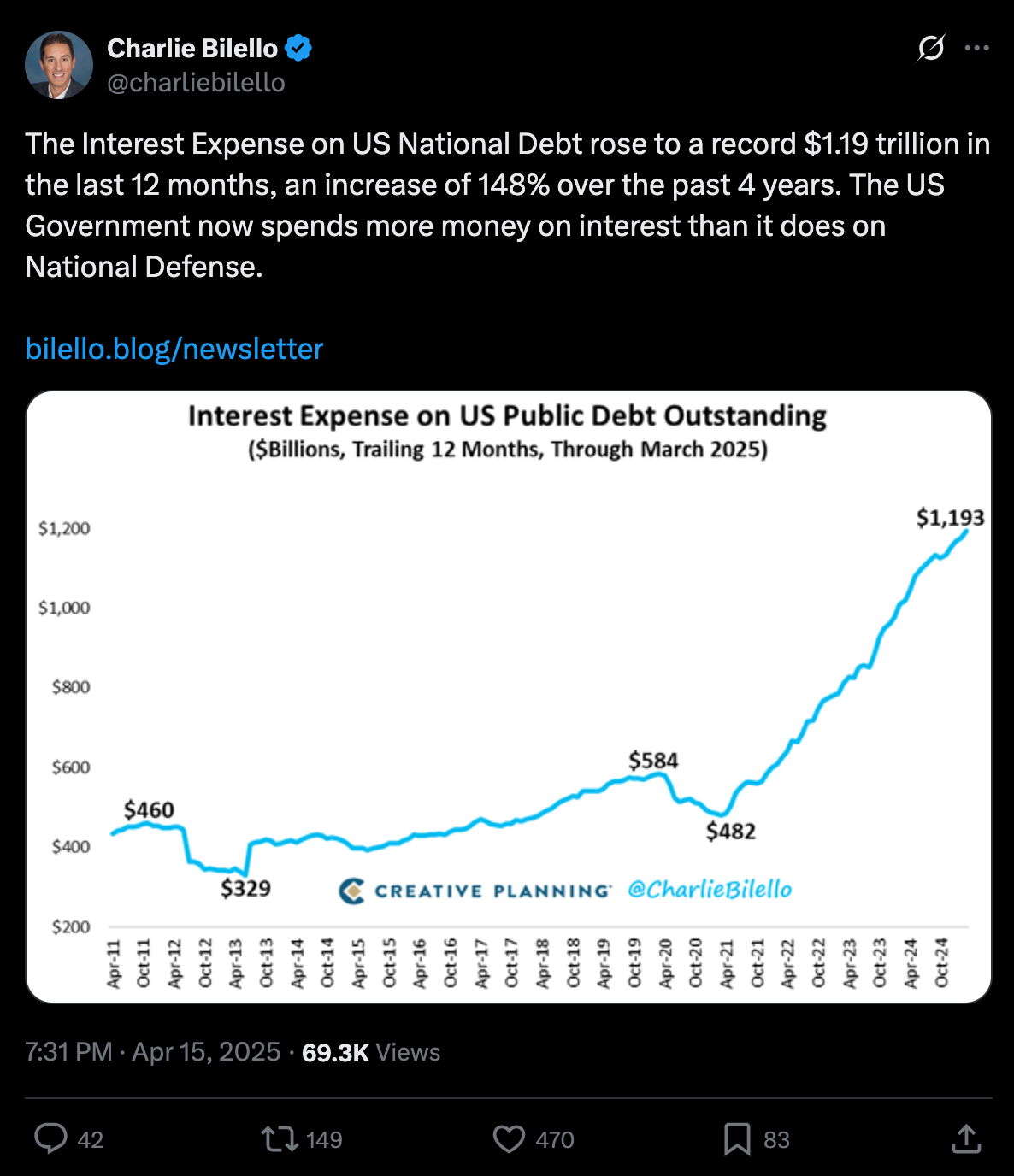
via Charlie Bilello
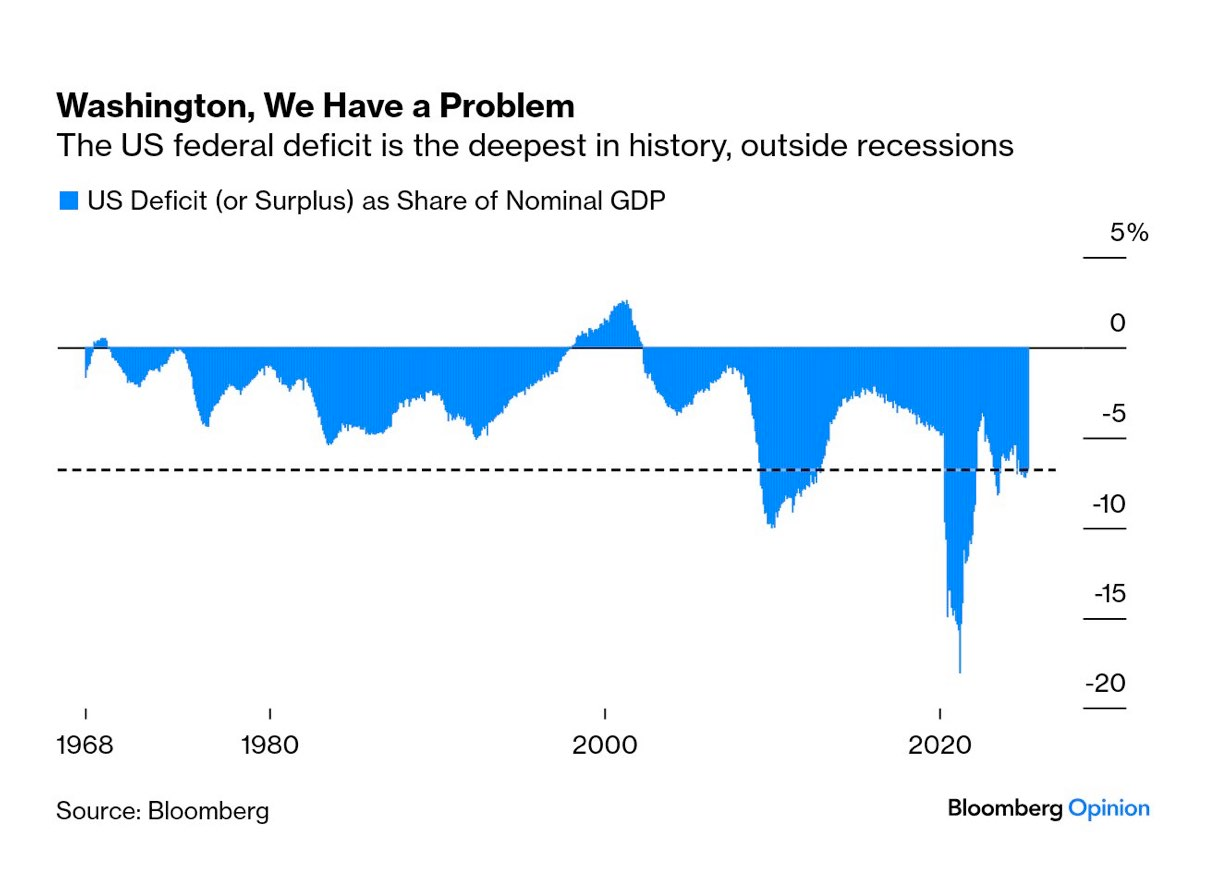
via Mohamed Al-Erian
To make matters worse, as things are deteriorating on the fiscal side of things, the U.S. consumer is getting crushed by credit. The 90-plus day delinquency rates for credit card and auto loans are screaming higher right now.
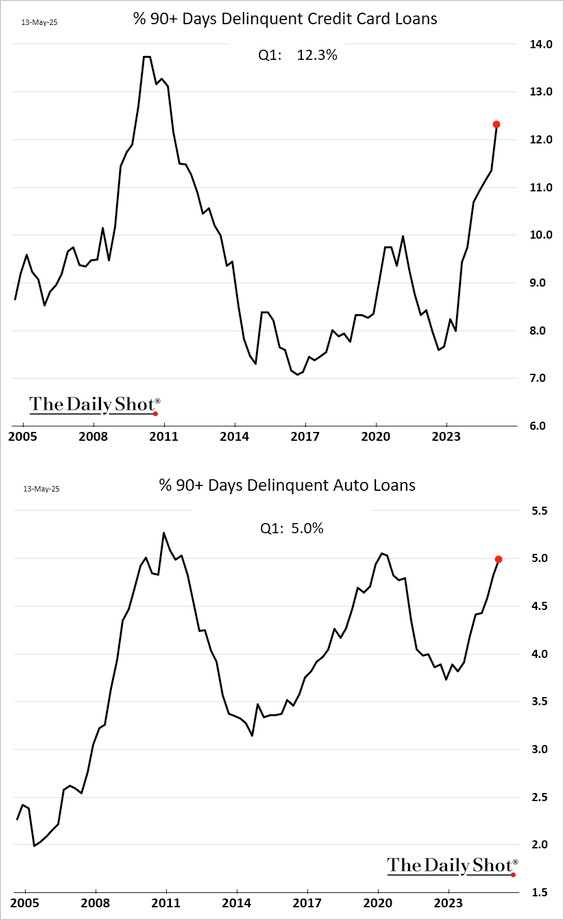
via TXMC
One has to wonder how long all this can continue without some sort of liquidity crunch. Even though equities markets have recovered from their post-Liberation Day month long bear market, I would not be surprised if what we're witnessing is a dead cat bounce that can only be continued if the money printers are turned back on. Something's got to give, both on the fiscal side and in the private markets where the Common Man is getting crushed because he's been forced to take on insane amounts of debt to stay afloat after years of elevated levels of inflation. Add on the fact that AI has reached a state of maturity that will enable companies to replace their current meat suit workers with an army of cheap, efficient and fast digital workers and it isn't hard to see that some sort of employment crisis could be on the horizon as well.
Now is not the time to get complacent. While I do believe that the deals that are currently being made in the Middle East are probably in the best interest of the United States as the world, again, moves toward a more multi-polar reality, we are facing problems that one cannot simply wish away. They will need to be confronted. And as we've seen throughout the 21st century, the problems are usually met head-on with a money printer.
I take no pleasure in saying this because it is a bit uncouth to be gleeful to benefit from the strife of others, but it is pretty clear to me that all signs are pointing to bitcoin benefiting massively from everything that is going on. The shift towards a more multi-polar world, the runaway debt situation here in the United States, the increasing deficits, the AI job replacements and the consumer credit crisis that is currently unfolding, All will need to be "solved" by turning on the money printers to levels they've never been pushed to before.
Weird times we're living in.
China's Manufacturing Dominance: Why It Matters for the U.S.
In my recent conversation with Lyn Alden, she highlighted how China has rapidly ascended the manufacturing value chain. As Lyn pointed out, China transformed from making "sneakers and plastic trinkets" to becoming the world's largest auto exporter in just four years. This dramatic shift represents more than economic success—it's a strategic power play. China now dominates solar panel production with greater market control than OPEC has over oil and maintains near-monopoly control of rare earth elements crucial for modern technology.
"China makes like 10 times more steel than the United States does... which is relevant in ship making. It's relevant in all sorts of stuff." - Lyn Alden
Perhaps most concerning, as Lyn emphasized, is China's financial leverage. They hold substantial U.S. assets that could be strategically sold to disrupt U.S. treasury market functioning. This combination of manufacturing dominance, resource control, and financial leverage gives China significant negotiating power in any trade disputes, making our attempts to reshoring manufacturing all the more challenging.
Check out the full podcast here for more on Triffin's dilemma, Bitcoin's role in monetary transition, and the energy requirements for rebuilding America's industrial base.
Headlines of the Day
Financial Times Under Fire Over MicroStrategy Bitcoin Coverage - via X
Trump in Qatar: Historic Boeing Deal Signed - via X
Get our new STACK SATS hat - via tftcmerch.io
Johnson Backs Stock Trading Ban; Passage Chances Slim - via X
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code *“TFTC20”* during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Building things of value is satisfying.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !import
-
 @ bc6ccd13:f53098e4
2025-06-04 00:11:20
@ bc6ccd13:f53098e4
2025-06-04 00:11:20If you haven’t read part 1 of this article, you should start there. This second part will build on the information I presented in part one. I’m going beyond just presenting the facts, to try and break down the broader principles behind what makes the Amish culture exceptional and whether any of those principles can be applied to solve the challenges facing the broader cultural landscape.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqqj8g6r994sk66tndqkkvetjw35kc6t50ykk66tjv93kcefd9pcxzun595cjjn8l4yn
It wasn’t so long ago that the mainstream conversation around population was exclusively focused on the dangers of overpopulation. The fatal flaws in the Malthusian theory had yet to be disproven clearly and obviously by observable demographic trends. That’s been gradually changing, and while it’s hardly a mainstream consensus, concerns about falling birthrates and the risk of population collapse have taken over the population conversion on the political right, and sometimes beyond.
In part 1, I walked through the life of a typical Amish person, male or female, and attempted to highlight some specific characteristics of their culture that contribute to their default large family size. I’m of course making some assumptions in doing that, and you might disagree with my opinion on the relative impact of various cultural factors. But in general, I don’t think I made too many unreasonable inferences. I laid out the facts as clearly as possible, and didn’t go too far beyond that.
In this part, I want to go beyond the facts and into the realm of hypothesis and speculation. That means I don’t have scientific studies or hard data to categorically prove my points. So if you disagree, you’re absolutely welcome to do so, but don’t expect me to tenaciously defend my opinions with reams of hard data and irrefutable evidence. My purpose is to expand the conversation, not to present a definite solution to any perceived problem.
Is there a problem to solve?
For starters, not everyone agrees that globally collapsing fertility is, in fact, a problem to be solved. Although that’s definitely the dominate consensus in the alternative media space, and is reaching a wider audience thanks to the attention of figures like Elon Musk, the average normie still believes the debunked Malthusian hypothesis that human population is on an exponential trajectory to disaster. They’re more likely to view a collapsing global population as a good thing than as an unmitigated disaster in the making. If that’s your view, you aren’t likely to find my writing particularly compelling. But if you are interested in challenging that belief, I point out some of the potential implications of population collapse here.
nostr:naddr1qvzqqqr4gupzp0rve5f6xtu56djkfkkg7ktr5rtfckpun95rgxaa7futy86npx8yqqshqmmsw4kxzarfdahzcttjv4ek7atjvdjhxtpdv9hxgtthv4skcargr7d34a
If you’re already convinced that global below-replacement fertility is a problem to solve, then you’re in the right place.
Is there a solution?
The modern mind rarely stops to evaluate this question. As soon as a problem is presented, we immediately jump to searching for the ideal solution. That’s a foolish, and occasionally catastrophic, mistake. Before searching for a solution, it’s worth considering whether the possibility of a solution even exists, and more importantly, whether a potential solution would have unintended consequences less severe than the problem it’s intended to solve.
Often those questions can’t be answered until some attempts to find a solution have been made. But we should keep them at the top of our minds throughout the search. Otherwise we can easily find ourselves genetically modifying generally harmless diseases in the lab to make them deadly to humans as we search for a “solution” to disease, or cutting down and burning trees to produce electricity as we attempt to “solve” the climate.
When it comes to global fertility, I’ll give you my conclusion first. Yes, there are solutions to this problem. No, they almost certainly won’t be adopted on a large scale. And I’m not sure if that should be considered a failure.
That’s because of the nature of the problem. People act according to incentives. When global population was growing exponentially, that was because of the incentive structures influencing the choices of each individual. Now that the fertility rate has dropped dramatically, and global population is set to peak and collapse, that’s also because of the incentive structures influencing the choices of each individual. Globally.
That means something happened over the past few centuries that upset historical incentive structures globally. There’s every reason to believe that whatever happened was largely an emergent phenomenon. If it was, resetting the incentive structures would mean imposing, somehow, an incentive structure diametrically opposed to the naturally emergent structure. That somehow gives me pause. How certain are we that overruling a global emergent phenomenon is even possible, and if it were, less destructive than the alternative?
Because logically, the current trajectory will become unsustainable at some point. Fertility can’t continue to fall indefinitely, that trend ends in total extinction. So that leaves two alternative outcomes, absent the kind of global intervention I alluded to. One, it does continue to fall, and humans go extinct. I write that one off because it doesn’t align with my worldview, so as far as I’m concerned I know it won’t happen. You’re free to disagree. Or two, fertility continues to fall until the negative effects of falling population destroy the new global incentive structure of the past few centuries through the partial or total collapse of the emergent phenomenon underlying that structure. If you identify what you think that emergent phenomenon is, and conclude that it’s “too big to fail”, you should probably use some imagination and reconsider.
To take it one step further for the really esoteric thinkers, maybe the whole thing is less of a new concept and more of a certain phase of a larger cycle humans keep repeating throughout history. I’ll leave that one to your imagination.
What can we learn about potential solutions from the Amish?
Like I mentioned in part 1, looking at a group like the the Amish in this context is particularly useful. They exist as a sub-group within a larger environment, so that allows us to eliminate a lot of incorrect theories based on their similar circumstances. The Amish live on the same planet, breathe the same air, drink the same water, eat similar food, buy homes in the same housing market, work in the same labor market, etc. That casts significant doubt on a number of very popular theories on why people in America aren’t reproducing.
That leaves us to focus on the significant differences between Amish culture and mainstream American culture with full confidence that the real answer lies somewhere in those differences.
The structure of this article will be something of a stream-of-consciousness. I’m not going to attempt to isolate and breakdown every aspect of Amish culture independent of the whole, because that won’t be useful or accurate. I’m convinced that the factors influencing Amish fertility are best understood as parts of a larger structure, and not as cumulative independent variables. So I’m going to start by taking a birds-eye view of that structure, and then zooming in on how the various pieces support the whole.
Throughout the past few months, I’ve read a lot of material on this topic as I researched and refined my conclusions. To give credit where credit is due, I haven’t found anyone who expresses a view as coherent as the one Johann Kurtz gives in his article
https://becomingnoble.substack.com/p/its-embarrassing-to-be-a-stay-at
This is an excellent and well-thought-out piece, and one that’s rightfully gotten a lot of attention in the alternative media space. It’s only with a great deal of respect and serious hesitation that I disagree with any aspect of his work, and I do so in a spirit of advancing the intellectual discourse rather than any delusions of my superior knowledge or abilities as an author.
The role of status
The primary thesis of Mr. Kurtz’s article is that declining fertility is a consequence of a decline in the status of motherhood compared to the status afforded by various alternative life paths. While it wasn’t the only point I made in part 1 of this article, I did mention the relative status of parenthood within the Amish culture in various contexts. And a few months of research and reflection have convinced me that status is the correct starting point for understanding fertility, both within Amish culture and also more broadly. On that point, Mr. Kurtz and I fully agree. He says,
Specifically, I contend that the basic epistemological assumptions which underpin modern civilization result in the net status outcome of having a child being lower than the status outcomes of various competing undertakings, and that this results in a population-wide hyper-sensitivity to any and all adverse factors which make having children more difficult, whatever these may be in a given society.
That seems to me like a fair assessment of the situation.
And Mr. Kurtz mentions the Amish specifically, so he’s aware of their unusual pattern and has integrated that data into his hypothesis. I believe he’s correct in doing so.
With that said, I want to dive a little deeper into the idea of status and how it relates to the Amish specifically. I think they can give us some insights into the topic that make more sense of the broader cultural landscape.
First off, let’s define status. Mr. Kurtz lays it out this way.
Status, or ‘social status’, is a key field within sociology. The term denotes a universal set of human instincts and behaviors. Status describes the perceived standing of the individual within the group. It denotes their social value and their place within the formal and informal hierarchies which comprise a society. It finds expression in the behaviors of deference, access, inclusion, approval, acclaim, respect, and honor (and indeed in their opposites - rejection, ostracization, humiliation, and so forth).
Higher status individuals are trusted with influential decisions (power), participation in productive ventures (resources), social support (health), and access to desirable mates (reproduction).
Gaining status is a motivation for each individual to productively participate in society. Status is gained and maintained through approved behaviors (achievement, etiquette, defending the group) and through the possession of recognized ‘status symbols’ (titles, wealth, important physical assets).
As he points out, status is a relative game. One’s status is measured in relation to others in the group, not in relation to some objective metric.
In correctly understanding status, there’s a fine line between the concept of status as an end in itself, and status as a means to the benefits afforded by higher status. If there’s one fundamental complaint I have with Mr. Kurtz’s piece, it’s that he seems to lean too far into the concept of status as an end in itself. Taken to extremes, it’s the idea that status is somehow an arbitrary and external scale, and that if we can just manipulate or recreate that scale to place parenthood at the top, we can solve for higher fertility without changing any physical realities in the real world. I disagree with that concept of status.
If you look at the attributes of higher status, they’re all very much tangible, physical benefits. He lists four; power, resources, health, and reproduction. Power gives a person the ability to bend the behavior of others to their own tangible benefit. Access to resources is a direct physical benefit to a person’s survival and wellbeing. Health is also a direct physical benefit. And access to reproduction, while closely tied to emotional well-being, is also a distinctly physical benefit and one we’re hard-wired to respond to, given that the alternative is the end of that bloodline.
Along with that, there’s also the complex overlap between achievements that increase status and benefits conferred by higher status. If someone acquires a lot of wealth, that’s going to increase their relative status. But access to wealth-increasing opportunity is also a benefit of higher status. Similarly, acquiring a desirable mate definitely increases a person’s status. But achieving higher status by acquiring wealth also opens up the opportunity to attract a more desirable mate. All of these things are very closely entwined, and in my opinion, are the reason why status is such an existential concern. As Mr. Kurtz points out, a person can experience severe distress from loss of status, even if their own situation seems to be unchanged and they only lost status because others advanced faster. That makes sense when you consider that a relative loss of status still makes it more difficult to access the resources needed to maintain one’s status moving forward. So even if one’s absolute condition hasn’t changed, the fear that lower status could be the beginning of an irreversible downward spiral is very real.
With that in mind, I’m going to look at status in the Amish culture as closely tied to physical reality, and not only as a mental scoreboard to be manipulated at will.
In part 1, I mentioned status here.
When it comes to status, the benefits are just as clear. Amish life revolves around family, and nothing is higher status than a thriving family of your own.
That’s the bird’s-eye view of family and status in the Amish culture. But it’s not enough to stop there and say “we just need to create a status hierarchy that places motherhood at the top like the Amish have” and leave it at that. The important part is why the Amish status hierarchy, and the mainstream status hierarchy globally until 200 years ago, placed parenthood so high up the scale.
I don’t believe that hierarchies, including the status hierarchy, develop in a random way. I think they are, at least originally, rooted in physical realities. In other words, the status hierarchy elevates certain things because those things are useful markers of value to the group. Wealth is high-status because it implies competence and ability, which is a valuable asset to the group. Without competent people working hard and being productive, the group will be impoverished. Similarly, parenthood is high-status because reproduction is an existential concern for the group. Without it, the group goes extinct.
These status markers are enforced by the feedback loop of physical reality. If a group attempts to function with wealth way down at the bottom of their status hierarchy, the group will be poor and unsuccessful and will be dominated by a group with a functional status hierarchy. If a group attempts to function with parenthood way down at the bottom of their status hierarchy, as the mainstream culture is currently doing, they’ll go extinct and be replaced by the Amish. Hyperbolic, maybe, but I’m trying to illustrate the point. There may be a lag in the feedback loop, but reality is inevitable.
What keeps status hierarchies largely functional is that desirable behaviors tend to cluster. Incentive structures align to keep it that way. Working hard results in higher income, which increases status. Higher status and more disposable income are powerful motivators.
Beyond that, functional societies are incentivized to “help” the feedback loops of reality with social institutions. Honesty is important in maintaining a functional, productive high-trust society. So we put thieves in prison rather than letting them use their stolen wealth to increase their status, turning our society into South Africa and destroying our wealth to the point that we become globally non-competitive. These social institutions serve a very important purpose, but they begin to break down when the lag between cause and effect becomes too big for the average person to understand. At that point, they lose their public support and can no longer function, and shorter-term incentive structures “reset” the status hierarchy. Then we end up with things like a status hierarchy that no longer penalizes divorce, even though the long-term effects are devastating, because the average person can’t see past their own short-term incentives.
So let’s look at the Amish status hierarchy around family and children. Why is a large family still high-status in that culture?
One could first look at the effects of peer pressure and social conditioning. Most Amish children grow up in large families, surrounded by peers in equally large families. As they mature, they see their peers get married at a young age, and have children at a young age. Doing otherwise means swimming against the current, not fitting in with the group. And fitting in with the group is itself a kind of status marker.
While that’s certainly a powerful incentive, it doesn’t explain the difference between the Amish and broader culture. After all, that was everyone’s experience a few centuries ago at most. If inertia were enough to keep the Amish at a 6 TFR, why would everyone else fall below 2 over the same period? So while the lack of exposure to large families is a commonly invoked reason for falling birthrates, it doesn’t explain how we got here to begin with.
Mr. Kurtz has this to say about the changes brought about by the Enlightenment.
Thus the Enlightenment initially opened up new status opportunities for men (success) whilst undermining those that supported women (virtue). We all have a psychological need for status, and so it was only a matter of time before women demanded access to and participation within success games (education, commerce, politics, even sport). Unfortunately, accruing status through success games is time intensive, and unlike virtue games, trades off directly with fertility.
Over time, this set of status mechanics spread, intensified, and deepened, particularly during the process of urbanization during the Industrial Revolution. Ultimately this culminates in today, when the standard introductory question has become ‘What do you do?’. This is because the most effective way to gauge the status of one’s interlocutor is to understand their level of success within our meritocracy. Unfortunately, ‘I’m a mother’ is not a good answer to this question, because this conveys little status within a success framework, which is usually the operative one. Women are, understandably, hesitant to be continuously humiliated in this way, and will make whatever tradeoffs are necessary to ensure they have a better answer.
I think he’s onto something here. The Enlightenment did bring significant changes, and I want to zero in on the effects of the Industrial Revolution specifically. Prior to the Industrial Revolution, the family typically functioned as the primary economic unit. Wage labor was less common, and subsistence farming was widespread. In that system, every member of the family, and often the extended rather than the nuclear family, worked together to support the family unit. While there were gender roles, the husband and father’s work in the fields was less distinct from the wife and mother’s work in the home. Both often worked in directly complementary roles, for example the wife and daughters milking the cows while the father and sons fed, watered and cared for the animals. The “paid work” was just as often selling butter churned by the wife as selling grain the husband raised and harvested. There was not a distinct breadwinner versus homemaker role, all work was directly and clearly in support of the family as a whole. In that scenario, the question “what do you do?” would have been silly, and “I’m a mother” wouldn’t be fundamentally different than the husband’s answer of “I’m a farmer.” Status from an economic perspective would be clearly understood as a cooperative achievement. And since children were part of the economic unit, a large family had a very quick and direct economic feedback loop to higher status.
With the Industrial Revolution and the rise of wage labor, the primary economic unit became the individual rather than the family. Along with that came the invention of household appliances that drastically reduced the burden of domestic labor. Suddenly the financial status of the household was entirely dependent on the breadwinner. There’s no fundamental reason that should lower the status of the homemaking wife. As Mr. Kurtz pointed out, before the Enlightenment, a woman’s status was modified substantially by her husband’s status. And I would argue that’s still that case at the extremes. I doubt the wives of wealthy entrepreneurs and sports stars get asked “what do you do?” very often in their social circles. But what did happen is that the reduced burden of domestic labor gave women the potential to contribute to the family outside the homemaking role, and they began to demand more freedom and opportunity to do so. As they shifted more into that financial status hierarchy, it created a direct status tradeoff between career and children. Like Mr. Kurtz pointed out, “women demanded access to and participation within success games (education, commerce, politics, even sport)”.
The Amish managed to maintain the traditional status hierarchy by saying “no” to that demand. Amish women do not have independent access to education, commerce, politics, or sport. They don’t have the option of pursuing those status markers within the Amish culture.
As you can imagine, I don’t believe this approach will be implemented on a wider scale. I don’t see it happening across liberal democracies, since the bridge of universal suffrage has already been crossed.
The Amish maintain their social structure through their insular lifestyle and their severe ostracization of those who choose to leave. It’s a significant tradeoff to young people, so much so that most choose their family and community over the opportunities of the broader culture. The evidence shows that, given the opportunity with no significant tradeoff, most young women choose education and career over marriage and children.
Here’s the thing about this post-Enlightenment status hierarchy; it’s societal suicide. That much is obvious. So given that status hierarchies exist to serve group interests, this one is obviously terminally defective. So how did that happen? In my opinion, the underlying problem is that the lag time between anti-social behavior and its consequences has been inflated by the Industrial Revolution to the point that the social institutions meant to punish anti-social behavior have collapsed, and the short-term incentive structures now point away from parenthood.
The Amish have escaped that effect by creating a “moat” around their social group. Within that group, they artificially exclude certain things that aid and encourage anti-social behavior, and artificially enforce certain feedback loops that have become disconnected as a result of the Industrial Revolution.
I’ll give some examples.
One of the primary feedback loops for high fertility is that if you don’t have children, you have no one to care for you when you’re old and unable to work. In the bad old days of subsistence farming, there was no such thing as “saving for retirement”. Every year was a struggle for survival, and there were no functional financial instruments available to save and invest for decades in the future. The Industrial Revolution changed all that, and most importantly led to the creation of pensions and public welfare systems. Now anyone without children to care for them could be cared for in old age by one of these financial schemes. Did that fundamentally solve a problem? No, not at all. Look at the bankrupt state of global public pension schemes today, and the imminent collapse they face as the result of (checks notes)… too few young workers to support each retiree. Turns out, society actually does need everyone to have enough children to support them in old age. The Industrial Revolution just broke the direct feedback loop, so everyone doesn’t get to see the poor souls without children begging on the street or sent to the poorhouse in their old age, and can therefore conclude that not having children is a purely personal choice and won’t have any effect on their lifestyle at age 80. The Amish took a different approach. They are exempt from Social Security. They don’t pay into it, and they aren’t eligible to collect it. They can see from a young age that children care for and support their elderly parents. They know that if they don’t have children and grandchildren, their elderly years will be much more difficult and depressing. They don’t get fed any dishonest media narratives portraying some rosy alternative reality. The historical status hierarchy rewarding large families remains intact.
As another example, casual sex historically resulted in unplanned pregnancies, and without good employment opportunities or public welfare schemes, single mothers faced an extremely difficult life. With the invention of reliable contraceptives, legal abortion, good employment opportunities, court-mandated child support, and public welfare, casual sex no longer carries catastrophic consequences for women. Over the longer term, it leads to drastically reduced marriage rates, lower fertility rates, higher rates of single motherhood, dysfunctional children, and eventually societal collapse. The Amish fight this trend in various ways. First, the lack of employment opportunities for women means that they’re fundamentally dependent on family and community for support. And violating community expectations by engaging in sex outside of marriage puts that support in jeopardy. That’s a strong deterrent. The absence of sex education makes it much less likely that young people will feel comfortable engaging in casual sex without risking pregnancy, and much more likely that they’ll abstain altogether, given the significant social consequences. All on top of the religious teaching against it, which in my opinion is just additional icing on the cake. None of that does anything to diminish the human sex drive. So particularly for young men, that incentive structure makes early marriage a lot more appealing than it might otherwise be. Once again, the historical status hierarchy remains intact.
Another example would be lifestyle based. Although the Amish are no longer primarily subsistence farmers, they reject many of the modern conveniences that eliminated the labor involved in housework. Their insistence on distinctive clothing means the women still spend significant time sewing for the family. And all that clothing must be washed with much more primitive equipment than we’re accustomed to. Cooking is also more labor intensive, and eating out, ordering takeout, or buying prepared food are much less accepted. No microwave to heat up a TV dinner, or even last night’s leftovers. Gardening and preserving food is strongly encouraged. No vacuum cleaners for cleaning. Mowing the lawn might require a hand-pushed mechanical reel mower, not a ride-on garden tractor. The lack of cars makes staying home and caring for the household much less optional, for both men and women. And the large potential income disparity between men and women makes all men potentially attractive mates to all women. That eliminates the hypergamous trap we have now where the average man isn’t sufficiently high-status to attract the average woman, which leaves both groups single and frustrated while the majority of women chase an increasingly small group of men with the financial resources to actually improve their lifestyle. All those restrictions for the Amish make life much more comfortable as a team effort, for both men and women. Trying to do it all yourself would hardly be feasible. The alternative is to stay living at home with your parents, hardly a rewarding or high-status lifestyle in any cultural setting. In this case, the Amish have chosen to artificially restrict their access to the physical benefits of the Industrial Revolution. This is less about status, and more about creating conditions that make marriage a direct lifestyle benefit. Once again, it’s questionable whether all these modern technologies and conveniences can survive in an environment of collapsing global population. So the approach the Amish are taking may just be an artificial short-circuit of a feedback loop that will send us all back to the Dark Ages anyway. Regardless, they’ve managed to maintain the historical attractiveness of marriage, in this case by removing access to modern conveniences that allow us to effectively outsource labor in a way that makes the single lifestyle attractive. The attractive single lifestyle is largely historically unprecedented, and a direct result of the Industrial Revolution.
Many of the lifestyle choices of the Amish culture are less about direct effects, and more about maintaining the “moat” that keeps their culture somewhat isolated from the broader society. This makes a lot of sense when you understand that status is “the perceived standing of the individual within the group.” If you want to create your own status hierarchy, you have to create your own coherent group. The Amish severely restrict their exposure to the media and culture of the broader society. That’s a very effective way to maintain a coherent group. Amish young girls don’t feel the same pressure to pursue higher education and career over marriage and motherhood, because they don’t see a billion media references praising career and denigrating motherhood before they’re 18. And they don’t see a million “boss babes” on social media, TV, and Netflix shows flaunting the single lifestyle and bashing the patriarchy in heels. Instead, they see and hear their mothers, grandmothers, and aunts joyfully caring for and loving their large families, praised and supported by their devoted, hardworking husbands. The evidence shows that a free market in media doesn’t result in glowing depictions of parenthood that lead young people to reject career opportunities and pursue marriage instead. You can ask yourself why that might be, but that’s what history shows.
Across thousands of distinct cultural groups around the world, only a handful have rejected the dominant post-Enlightenment status hierarchy in favor of large families and traditional values. I’m not aware of any that managed it without significant insulation from the dominant culture. That tells me that the short-term incentive structure of modern society is more powerful than any historical cultural norms, and there is no passive solution that doesn’t involve collapse of that incentive structure and the civilization it rests on.
I could go into more detail on specifics of Amish culture and how they play into their status hierarchy. But you can read part 1 of the article and draw your own conclusions. I’m going to end with what’s sure to be a highly provocative list of requirements that would be necessary for the Amish status hierarchy to function across broader society. I don’t personally believe there’s any possibility of anything similar being widely adopted. And frankly, I don’t think it’s possible outside of a religious context, without the collapse of modern civilization as we know it. The collapse of modern civilization is the outcome I expect, although I’m happy to be proven wrong. So this is a philosophical exercise, not a policy prescription.
-
End social acceptance of casual sex. Implement sever consequences for premarital sex or marital infidelity.
-
End all forms of government financial support for the elderly. All elderly care is the responsibility of the family, or failing that, the church/community.
-
End all government support for single mothers. Again, support for widows and those in other extenuating circumstances is the responsibility of the church/community.
-
End all sex education in public schools. Sex education is the responsibility of the parents.
-
Ban all forms of contraception, with significant penalties for violation.
-
Ban abortion.
-
Severely restrict access to higher education for women.
-
End female participation in politics, including universal suffrage. One household, one vote. No voting by unmarried people, male or female.
-
End the social and legal acceptance of divorce. No divorce permitted for any reason, and legal separation doesn’t allow for remarriage.
-
End mandatory public education. Education is the responsibility of the parents.
-
Ban negative messaging toward marriage and children in all forms of media.
-
Severely restrict or outright eliminate social media platforms.
-
Roll back child labor laws significantly.
I could add a few more, but I think that covers the essentials. If that sounds insane and offensive to you, I’m not shocked. This isn’t a policy prescription, and as I said at the beginning of the piece, I don’t necessarily believe that this is even a problem we should attempt to “fix”. The reason being, any government with the power to enforce these requirements on the world would be more concerning to me than the prospect of civilizational collapse itself. Civilization has collapsed before, many times throughout history. And we’ve always bounced back eventually. A global power of this magnitude might not be reversible.
But you should at least temper your shock and outrage with the realization that every item on that list was the accepted reality for most of human history, all the way up until the past few anomalous centuries.
My personal opinion is that too much obsession with this issue is probably a waste of time. Again, I don’t think any “solution” we come up with is likely to be less dangerous than the problem itself. I expect things to play out over a long period of time, and for the population decline to eventually degrade our interconnected, high-tech global civilization. Once many of the advances of the Industrial Revolution become widely unavailable, the natural incentive structures and status hierarchies will reemerge. And those incentive structures demand that men and women are natural allies, not enemies. We need each other, and the families we create together, to be a healthy, happy, flourishing, and productive society over the long term. If the prospect of losing our modern conveniences and going back to that world terrifies you, go befriend an Amish parent or grandparent. You’ll soon realize that they’re as happy and fulfilled in life as anyone you’ll ever meet. Life is a matter of perspective, not products. And my point in exploring this topic isn’t to spread doom, but to point out that we can make our own decisions and surround ourselves with like-minded people, and in doing so find peace and fulfillment in relationships and community instead of constantly chasing a dysfunctional, suicidal status hierarchy.
In conclusion, while writing this article, a stanza from Rudyard Kipling’s poem “The Gods of the Copybook Headings” kept coming to mind. It’s been over a hundred years since he penned these words, and the whole poem displays a prescience that’s positively uncanny. The seeds of the current issue were sown a long time ago, but there were people like him who saw the poisonous fruit coming even as the little plants were just emerging from the soil.
``` As I pass through my incarnations in every age and race, I make my proper prostrations to the Gods of the Market Place. Peering through reverent fingers I watch them flourish and fall, And the Gods of the Copybook Headings, I notice, outlast them all.
We were living in trees when they met us. They showed us each in turn That Water would certainly wet us, as Fire would certainly burn: But we found them lacking in Uplift, Vision and Breadth of Mind, So we left them to teach the Gorillas while we followed the March of Mankind.
We moved as the Spirit listed. They never altered their pace, Being neither cloud nor wind-borne like the Gods of the Market Place, But they always caught up with our progress, and presently word would come That a tribe had been wiped off its icefield, or the lights had gone out in Rome.
With the Hopes that our World is built on they were utterly out of touch, They denied that the Moon was Stilton; they denied she was even Dutch; They denied that Wishes were Horses; they denied that a Pig had Wings; So we worshipped the Gods of the Market Who promised these beautiful things.
When the Cambrian measures were forming, They promised perpetual peace. They swore, if we gave them our weapons, that the wars of the tribes would cease. But when we disarmed They sold us and delivered us bound to our foe, And the Gods of the Copybook Headings said: "Stick to the Devil you know."
On the first Feminian Sandstones we were promised the Fuller Life (Which started by loving our neighbour and ended by loving his wife) Till our women had no more children and the men lost reason and faith, And the Gods of the Copybook Headings said: "The Wages of Sin is Death."
In the Carboniferous Epoch we were promised abundance for all, By robbing selected Peter to pay for collective Paul; But, though we had plenty of money, there was nothing our money could buy, And the Gods of the Copybook Headings said: "If you don't work you die."
Then the Gods of the Market tumbled, and their smooth-tongued wizards withdrew, And the hearts of the meanest were humbled and began to believe it was true That All is not Gold that Glitters, and Two and Two make Four– And the Gods of the Copybook Headings limped up to explain it once more.
As it will be in the future, it was at the birth of Man There are only four things certain since Social Progress began. That the Dog returns to his Vomit and the Sow returns to her Mire, And the burnt Fool's bandaged finger goes wabbling back to the Fire;
And that after this is accomplished, and the brave new world begins When all men are paid for existing and no man must pay for his sins, As surely as Water will wet us, as surely as Fire will burn, The Gods of the Copybook Headings with terror and slaughter return! ```
-
-
 @ eb0157af:77ab6c55
2025-06-03 18:02:27
@ eb0157af:77ab6c55
2025-06-03 18:02:27The revelation by Miles Suter, Product Lead at Block, at the Bitcoin Conference 2025 confirms the economic potential of LN for professional operators, but the yield comes mainly from routing fees
During the Bitcoin 2025 conference in Las Vegas, Miles Suter, Bitcoin Product Lead at Block Inc., revealed data that could change the economic perception of the Lightning Network: the company’s routing node is generating annual returns of 9.7% on invested liquidity.

During his presentation, Suter confirmed what many experts suspected but no one had ever quantified precisely: Lightning payment routing can be not only technically effective, but also economically profitable on a large scale. With an estimated public capacity of 184 BTC (approximately $20 million), Block is demonstrating that Lightning infrastructure can generate significant returns through the use of bitcoin as a payment method.
Non-custodial yield, with a doubt
Lightning routing represents what experts define as “true non-custodial yield” – returns generated from the pure economic utility of bitcoin as a means of payment, without having to entrust one’s funds to third parties.
“We are earning almost 10% returns on Bitcoin by effectively routing real payments on the Lightning network,” Suter declared.
Riccardo Masutti — researcher and founder of Baited — has, however, observed that the double-digit yields advertised by Block are closely tied to an exceptionally aggressive fee structure that markedly deviates from the median parameters of the Lightning Network. In particular, the Cash App nodes apply a fee rate of 2,147,483,647 ppm, resulting in fees up to 2 million times higher than the average cost of standard channel transactions. Block’s own node also enforces significant fees: to route a million satoshis, it requires 1,053 sats in outgoing fees and 2,955 sats in incoming fees, compared to a network median base fee of approximately 0.999839 sat and a median fee rate of 0.000063 sat/sat. This discrepancy suggests that the yield is generated more by a surcharge imposed on intermediated payments than by any real efficiency in liquidity allocation.
In 2024 Cash App recorded an increase in Lightning payment volume equal to 7 times that of the previous year: one in four outgoing payments now occurs via LN, Suter stated.
According to Block’s Product Lead “if Bitcoin becomes only digital gold, we have failed the mission. If we don’t use bitcoin for payments, we risk losing one of the most important promises permissionless money. If we don’t preserve the qualities of cash in the digital world, human liberty is seriously in trouble.”
The company aims to incentivize practical and daily use of bitcoin, seeing Lightning payments as the key to realizing Satoshi Nakamoto’s original vision of a “peer-to-peer electronic payment system.”
The post According to Block, routing on Lightning yields 10% annually: but the yield comes from fees appeared first on Atlas21.
-
 @ bf47c19e:c3d2573b
2025-06-03 17:59:16
@ bf47c19e:c3d2573b
2025-06-03 17:59:16Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta uzrokuje Inflaciju?
- Da li nam je infacija potrebna?
- Kako se meri inflacija?
- Da li inflacija pokreće ekonomski rast?
- Da li inflacija pokreće ili umanjuje nejednakost bogatstva?
- Gde se danas javlja inflacija?
- Šta je deflacija?
- Kakav uticaj inflacija ima na društvo?
Inflacija može da bude uznemirujuća tema, jer uključuje amorfni koncept novca. Međutim, inflacija je zapravo jednostavna tema koja je napravljena da bude složena razdvajanjem novca i drugih dobara. U ovom članku razlažemo inflaciju i njene uzroke.
Najjednostavnija definicija inflacije je rast cena dobara i usluga. Kada cene rastu, to takođe znači da vrednost jedinice novca – poput dolara – opada. Uzmimo primer McDonald’s hamburgera: 1955. ovaj skromni hamburger se prodavao za samo 15 centi. U 2018. godini se prodavao za 1,09 USD. U 2021. godini prodaje se za 2,49 USD – ogroman rast cene od 1650%.

To znači da je dolar izgubio dosta svoje vrednosti. 1955. godine mogli ste da kupite gotovo 7 hamburgera za novčanicu od jednog dolara. 2021. godine taj dolar vam ne bi kupio ni jedan hamburger. Zašto se čini da cene uvek rastu tokom vremena? I šta možete da učinite povodom toga? Ovaj članak ima za cilj da odgovori na ta pitanja.
Ekonomisti pokušavaju da sumiraju rast cena mnogih dobara i usluga kao jedan prosečan broj. Ovaj broj predstavlja promenu ukupnih troškova u godišnjim troškovima prosečnog potrošača, kao što su stanarina, hrana i gorivo.
U Sjedinjenim Državama ovaj broj je poznat kao Indeks Potrošačkih Cena, eng. Consumer Price Index (CPI). Kada se CPI poveća tokom određenog vremenskog perioda, ekonomisti kažu da imamo inflaciju. Kada se smanji, to se naziva deflacija.
Šta uzrokuje Inflaciju?
Mnogi izvori kažu da je stalna inflacija koju danas doživljavamo ili uzrokovana povećanjem potražnje (eng. demand-pull) ili smanjenjem ponude usled povećanih proizvodnih troškova (eng. cost-push).
Ovi razlozi nisu tačni – hajde da pogledamo zašto.
Da bismo razumeli pravi razlog inflacije, moramo da sagledamo dve vrste inflacije:
- Inflacija Cena: Cene vremenom rastu.
- Monetarna Inflacija: Količina valute u opticaju raste sa vremenom.
Prva, inflacija cena, retko se javlja tokom dužih perioda (decenije, vekovi) zbog povećane potražnje ili povećanih troškova. Zašto? Tržišta teže da se uravnoteže. Tokom istorije smo više puta videli da povećana potražnja za dobrom povećava njegovu cenu, što podstiče proizvođače da proizvode više tog dobra. Kada se ponuda poveća, cene se smanjuju.
Ovaj ciklus može da potraje nekoliko godina, i javlja se kod gotovo svake robe i „konačnog dobra“ (automobili, televizori, hrana itd.) na Zemlji. Izuzetak su retki metali poput zlata i srebra. Dokazi o tome su prikazani u nastavku.
Kada se poveća trošak za proizvodnju dobra, cena tog dobra često raste da bi pokrila te troškove. Ovaj rast cene dovodi do toga da potrošači tog dobra traže alternativu ili smanjuju potrošnju tog dobra, što dovodi do pada cena na prethodni nivo.
Na donja dva grafikona javlja se inflacija cena!
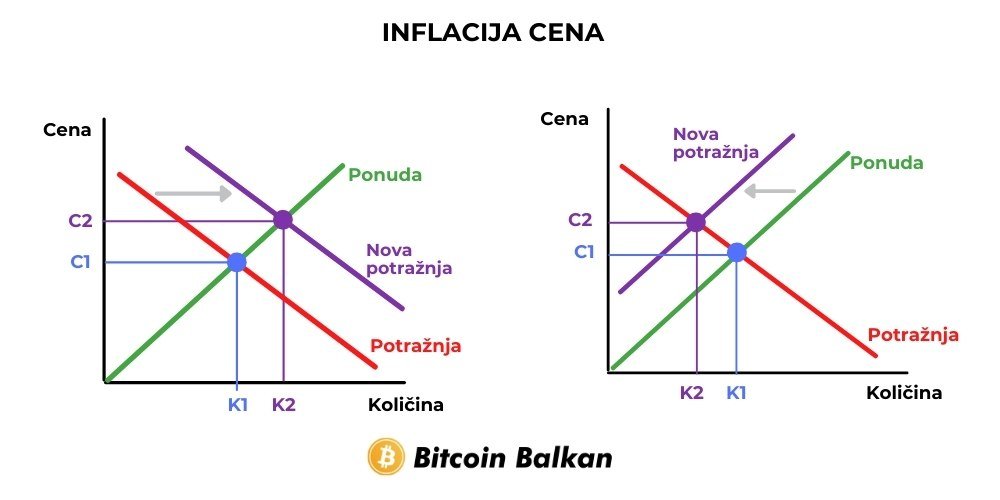
Tržište se prirodno uravnotežava, a cene se smanjuju ili povećanjem ponude ili smanjenjem potražnje.
Da li imamo dokaze da tržišta vremenom uravnotežuju ponudu i potražnju?
Podaci o cenama robe tokom vremena mogu nam dati bolje razumevanje da li tržišta zaista efikasno uravnotežuju ponudu i potražnju. Međutim, cene ne možemo da posmatramo u smislu nacionalnih valuta, jer naše vlade uvek štampaju više svojih nacionalnih valuta.
Oni sprovode monetarnu inflaciju, koja može da izazove inflaciju cena. Posmatranje tržišnih cena u smislu nacionalnih valuta, poput američkog dolara, je poput merenja visine lenjirom koji se neprestano smanjuje. Vaša visina u broju biće sve veća i veća, ali stvarna visina se ne menja.
Mi možemo da znamo da li tržišta uravnotežuju ponudu i potražnju gledajući cene dobara u smislu monetarnog dobra koje ima vrlo konzistentnu ponudu tokom vremena.
Vremenom se pokazalo da zlato ima najmanju monetarnu inflaciju od svih postojećih valuta i dobara. To čini zlato odličnim ‘lenjirom’ za merenje da li tržišta vremenom uravnotežuju ponudu i potražnju. Da bismo bolje razumeli inflaciju cena tokom vremena, pitaćemo koliko unci zlata nešto košta tokom vremena.
Cene u zlatu pokazuju nam da se tržišta vremenom uravnotežuju
Ako cene dobara posmatramo u obliku zlata, vidimo da cene robe prate srednje tačke tokom dužih vremenskih perioda.
Nafta, na primer, je vrlo nestabilna, ali ima tendenciju da se kreće oko 2,5 grama zlata po barelu.
 WTI Sirova Nafta u gramima Zlata po Barelu
WTI Sirova Nafta u gramima Zlata po BareluCena nafte je promenljiva, ali tokom decenija ima tendenciju da se kreće po strani.
Cene kuća tokom proteklih 10 godina takođe su prilično stabilne, iako imamo fiksnu količinu zemlje na planeti. Vidimo da cene kuća u pogledu zlata imaju tendenciju da variraju oko indeksne cene od oko 80, prikazane na grafikonu.
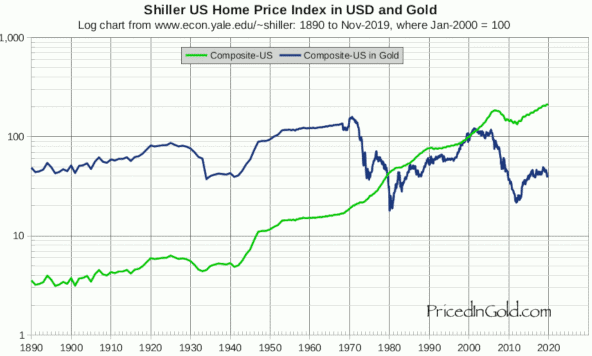 Shiller-ov US indeks cena kuća u USD i zlatu
Shiller-ov US indeks cena kuća u USD i zlatuOvaj grafikon je na logaritamskoj skali, što nam omogućava da vizualizujemo zapanjujuća povećanja u zelenoj liniji, koja predstavlja domove u dolarima.
Grafički izražene u američkim dolarima, cene ovih dobara uvek rastu – baš kao i McDonald’s hamburger. Da su povećana potražnja ili povećani troškovi odgovorni za konstantnu inflaciju cena, takođe bismo videli kako se cena ove robe povećava u smislu zlata. Podaci iznad pokazuju da su cene konstantne.
Moraju da postoje i drugi razlozi za upornu inflaciju cena koju smo videli u dolarskim iznosima tokom proteklog veka.
Evo šta znamo o tome šta dugoročno utiče na cene, kao u periodu od 1955. do 2018. godine:
- Rast produktivnosti uzrokovan inovacijama, što dovodi do pada cena tokom vremena
- Monetarna inflacija – štampanje velikih količina valute – koja uzrokuje porast cena denominovanih u toj valuti tokom vremena
Znamo da cene izražene u dolarima, eurima i ostalim valutama neprestano rastu. Ako ne mislimo da naša produktivnost kao društva ide unazad, postoji samo jedan jednostavan razlog za inflaciju cena: štampanje većih količina valute, iliti monetarna inflacija.
Naše vlade i banke su zapravo prilično iskrene u pogledu zapanjujućih količina valute koje štampaju. Oni nam svakodnevno govore da oni uzrokuju monetarnu inflaciju.
Da li nam je infacija potrebna?
Bez uporne monetarne inflacije (koja uzrokuje inflaciju cena), naša celokupna savremena ekonomija bi se srušila.

Dozvolite da vam objasnim. Sledeći odeljak može da bude šokantan, i ohrabrujem vas da i sami istražite ukoliko mislite da nisam u pravu.
Kada centralne banke i komercijalne banke daju zajmove, one stvaraju novu valutu.
Kada centralne banke daju zajmove vladama “kupujući državni dug”, one stvaraju novu valutu kada to urade. To omogućava vladama da vode budžetski deficit trošeći više nego što uzimaju od poreza. U tom procesu državni dug se nagomilava.
Komercijalne banke stvaraju novu valutu kada daju zajmove fizičkim licima i preduzećima. Jedino ograničenje koliko novog novca mogu da stvore je zakonski zahtev da banka ima na raspolaganju određeni procenat od ukupnog iznosa novca koji su ljudi deponovali. Zbog toga je naš bankarski sistem poznat kao delimična rezerva – banke pri ruci moraju da imaju samo deo vašeg novca.
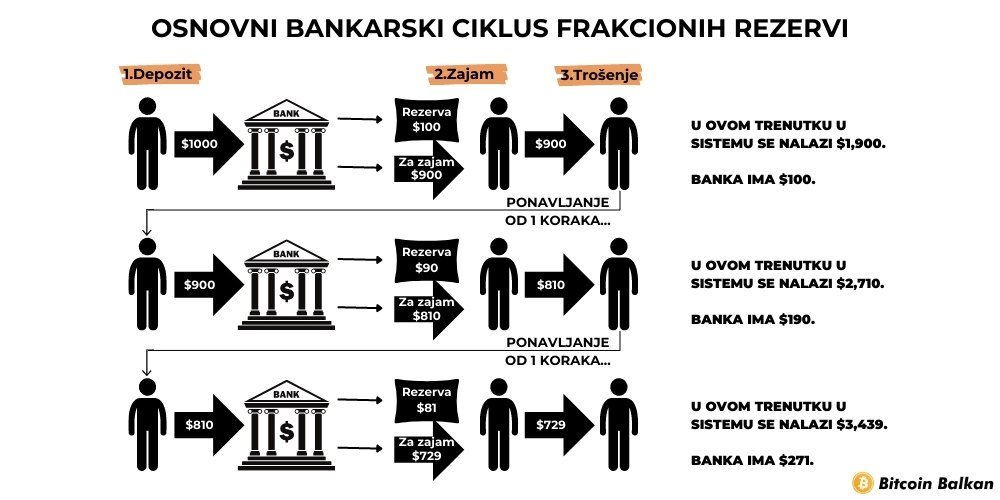
Osnovni Bankarski Ciklus Frakcionih Rezervi
Stvaranje valute je neophodno da bi održalo sistem u životu
Budući da se svi zajmovi uglavnom sastoje od novostvorene valute, mora se stvoriti još više valute da bi se taj dug otplatio. A evo i zašto:
Recimo da su prošle godine sve svetske kreditne aktivnosti dovele do stvaranja 100 milijardi dolara. Svih tih 100 milijardi dolara je novostvoreno, i one se duguju bankama sa nekom dodatnom vrednošću za kamate. Odakle dolazi ova dodatna valuta za plaćanje kamata? Budući da ovde govorimo o celokupnoj svetskoj ekonomiji, to plaćanje kamata mora da dodje iz nove količine novostvorene valute.
Sve jedinice današnjih valuta nastale su pozajmljivanjem, a isplata kamate na te zajmove znači da moramo stalno da stvaramo još više nove valute. To dovodi do beskrajne monetarne inflacije. Kada nova valuta cirkuliše kroz ekonomiju, to dovodi do porasta cena: inflacije cena.

Previše monetarne inflacije može dovesti do hiperinflacije cena. U Venecueli je krajem 2018. godine piletina koštala preko 14 miliona Bolivara. Izvor: NBC News
Monetarni sistem se raspada ako se ova monetarna inflacija zaustavi, jer bi to značilo da veliki broj onih koji su uzeli zajam širom sveta ne bi mogao da vrati novac koji su pozajmili – oni ne bi izmirili svoje dugove.
Banke ili zajmodavci koji drže dug tada bi imali bezvrednu imovinu. Budući da vrednost duga podupire vrednost valute, vrednost valute bi strmoglavo padala zajedno sa dugom.
Kada ljudi izgube poverenje u ’tradicionalnu’ valutu, ona brzo postane bezvredna. To se dogodilo u Nemačkoj nakon Prvog svetskog rata, u Peruu devedesetih, Jugoslaviji 1994. ,Zimbabveu, Venecueli i sa još bezbroj drugih tradicionalnih valuta. Da bi odložile ovaj neizbežni ishod dokle god mogu, centralne banke jačaju poverenje u sistem nastavljajući da štampaju valutu stabilnim kursom.
Ovo osigurava da većina ljudi koju su uzeli zajam ima valutu za otplatu svojih kredita. Upravo to se dešava kada vlada izvrši „spas“ kao 2008. ili 2020. – oni osiguravaju da svi imaju dovoljno novca za plaćanje dugova, tako da laž može da se nastavi.
Inflacija ne dolazi iz povećanja potražnje
Sa više valute u opticaju, monetarna inflacija može da izgleda kao povećanje potražnje. Međutim, ekonomisti koji kažu da povećana potražnja pokreće stabilnu inflaciju tokom decenija propuštaju suptilnu poentu: iako monetarna inflacija može da prouzrokuje veću potrošnju, to nije zato što su ljudi zaista bogatiji, već zato što veruju da su bogatiji.
Kada se puno novca ubrizga u ekonomiju, cene jednostavno rastu jer više valute pokriva istu količinu robe. Rast cena znači pad vrednosti valute, tako da nema realnog povećanja stvarnog bogatstva, iako ljudi možda “troše više” u nominalnom iznosu valute.
Uzmimo ovaj primer: vi mesečno zarađujete 1.500 EUR, i prema svom trenutnom načinu života vi mesečno trošite oko 1.500 EUR. Dolazi vlada i počinje da vam daje dodatnih 500 EUR svakog meseca – vi se osećate poprilično dobro, zar ne? Sada možete da izlazite češće u restoran.
Međutim, vlada daje svima po 500 EUR mesečno, i svi ostali takođe troše taj novac. Ekonomista u vladinoj kancelariji, vidi da sada svi troše tih dodatnih 500 EUR mesečno i zaključuje da je vlada ‘stimulisala ekonomiju’.
Ipak, kako sav taj dodatni novac kruži ekonomijom, cene prirodno rastu. Sada vam je potrebno 2.000 EUR da biste održali svoj trenutni način života.
Da li si nešto bogatiji?
Vi možda imate više eura na vašem bankovnom računu, ali svaki od njih vam kupuje manje. Sada trošite 2.000 EUR mesečno da biste živeli životnim stilom koji vas je nekada koštao samo 1.500 EUR mesečno.

Ovo je ono što monetarna inflacija radi, i zašto je toliko pametnih ekonomista zavarano da misle da povećana potražnja, radije nego štampanje novca, pokreće trajnu inflaciju cena.
Da li smo uvek imali inflaciju?
Stalna inflacija cena relativno je nedavna pojava u modernim ekonomijama i započela je u vreme kada su Sjedinjene Države počele da konstantno štampaju valutu. Ako bi promene ponude i potražnje zaista dugoročno uzrokovale inflaciju cena, videli bismo inflaciju cena tokom istorije. Podaci govore drugačiju priču.
Indeks potrošačkih cena, koji se povećava kada imamo inflaciju cena, bio je prilično konstantan pre početka našeg trenutnog tradicionalnog ’fiat’ monetarnog sistema.
Taj sistem je započeo Bretton Woods-ovim sporazumom iz 1945. godine, a ubrzao se kada je Nixon 1971. okončao svetski zlatni standard.
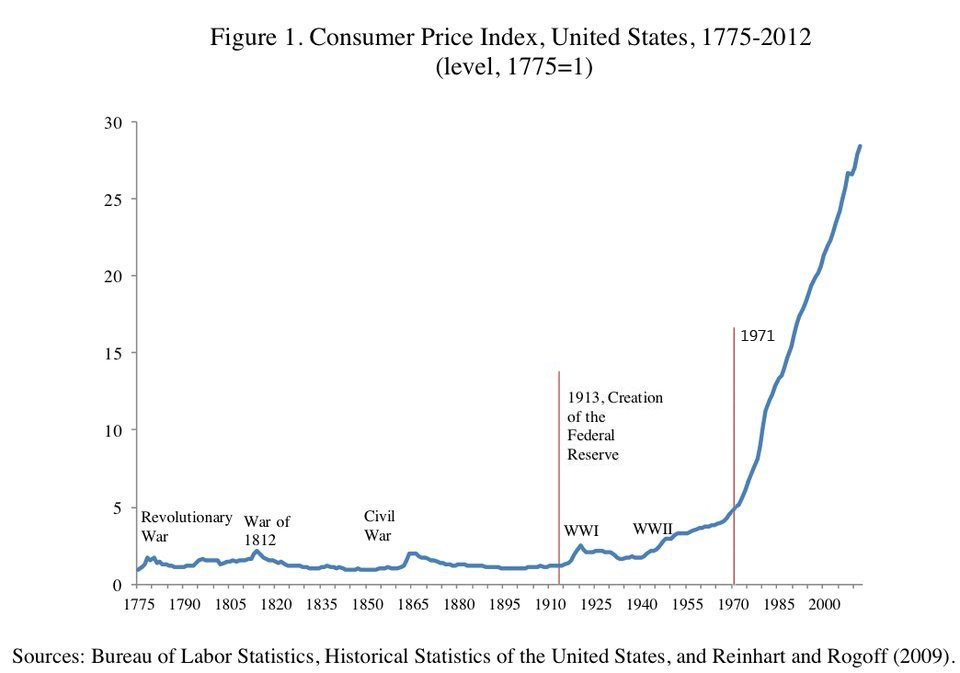
Indeks potrošačkih cena, Sjedinjene Države, 1775-2012
Kako se meri inflacija?
Inflacija cena se često prikazuje kao promena indeksa potrošačkih cena (CPI). CPI je prosek cena raznih dobara koje ljudi kupuju u svakodnevnom životu: hrane, goriva, stanovanja itd. U Sjedinjenim Državama, vladin odsek pod nazivom Biro za statistiku rada (BLS) meri promene cena. To rade tako što posećuju maloprodajne radnje, beleže cene, računaju prosek i izveštavaju godišnju inflaciju kao promenu u odnosu na prošlu godinu.
Stopa inflacije koja se izveštava, je važna svima jer se koristi za određivanje povećanja troškova života i socijalnih davanja, poput plaćanja socijalnog osiguranja. Kada se CPI prilagodi naniže, isplate zarada i naknada su manje nego što bi trebalo da budu.
Efekti su se vremenom sjedinili: osoba koja u svojoj prvoj godini rada zaradi 40.000 USD zarađivaće samo 52.000 USD u svojoj desetoj godini staža, sa povećanim troškovima života od 3% da bi se plata podudarala sa inflacijom. Ako bi vlada umesto toga prijavila inflaciju od 6%, ta osoba bi u svojoj desetoj godini zarađivala 67.500 USD – tj. oko 30% više. Način na koji izračunavamo i prijavljujemo inflaciju ima ogroman uticaj na zaradu većine zaposlenih i građana.
Ovo je inflacija (procentualna promena u CPI) izmerena u poslednjih 10 godina u Sjedinjenim Državama:
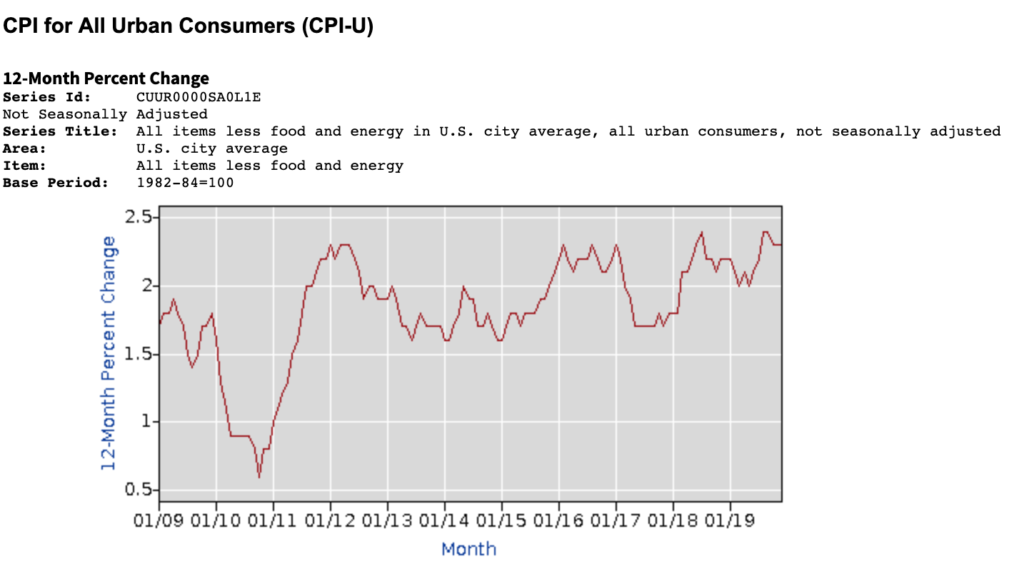
Prvobitno je BLS jednostavno beležio cenu korpe robe široke potrošnje svake godine. Međutim, istraživanje Boskinove Komisije 1996. godine dovelo je do novih alata koji Birou za statistiku rada omogućavaju prilagođavanje cena u CPI. Dva najvažnija alata su geometrijsko ponderisanje i hedonika.
Geometrijsko Ponderisanje
Geometrijsko ponderisanje znači da kupovne navike sada mogu da utiču na to koliko promena cene pojedinog dobra utiče na CPI. Ako potrošači kupe manje robe, ona ima manju težinu kada se ubaci u presek indeksa potrošačkih cena. Boskinova Komisija je tvrdila da bi ova promena pomogla da se promene sklonosti potrošača. Međutim, ne postoji način da se utvrdi da li ljudi menjaju svoje kupovne navike jer zapravo žele da kupuju različite stvari. Vrlo je moguće da ljudi kupuju manje određenog dobra jer ono raste u ceni. Stoga geometrijsko ponderisanje uzrokuje da roba sa velikim rastom cena ima manje uticaja na CPI, što dovodi do niže prijavljene inflacije.
Hedonika
Hedonika omogućava Birou za statistiku rada da menja cenu dobra na osnovu njegovog opaženog povećanja ‘korisnosti’ tokom vremena. Evo primera: recimo da se televizor sa rezolucijom od 720p 2009. godine prodavao za 200 USD. U 2010. godini isti model televizora sada ima rezoluciju od 1080p i prodaje se po istoj ceni: 200 USD. Međutim, pošto se tehnologija u televizoru poboljšala, zaposleni u Birou za statistiku rada mogu da izmisle ‘korisni’ broj i pomoću njega oduzmu deo vrednosti od cene televizora. Kao rezultat, BLS može da kaže da TV košta 180 USD u 2010. godini – iako je njegova cena 200 USD. Ovo dovodi do pada prijavljene inflacije.
Oba ova prilagođavanja smanjuju prijavljenu stopu inflacije, što smanjuje povećanje troškova života i isplate naknada za socijalno osiguranje. Koliko ta prilagođavanja inflacije pogađaju radničku klasu i penzionere? Neke procene, poput procena ekonomiste John Williams-a, sa koledža u Darmouthu, stavljaju stvarnu inflaciju u SAD na u proseku 3% – 6% više nego što je izveštavano od strane Bira za statistiku rada. To bi inflaciju u 2020 dovelo do 5% – 8%, umesto na prijavljenih 2%.
U 2021. godini prijavljena inflacija je 5.4%, u prvom kvartalu.
Da li inflacija pokreće ekonomski rast?
Mnogi ljudi veruju da stabilna inflacija pokreće ekonomski rast podstičući investicije i potrošnju umesto štednje. Međutim, osnovni ekonomski podaci pobijaju ovu uobičajenu tvrdnju.
Ako za primer uzmemo Sjedinjene Države, nacija je imala samo kratke periode inflacije od 1775. do oko 1950. godine, kao što pokazuje indeks potrošačkih cena koji je ostao nepromenjen. Inflacija dobija zamah tek nakon 1971. godine, pa bi bilo za očekivati da će i stopa rasta bruto domaćeg proizvoda (BDP) Sjedinjenih Država porasti nakon 1971. godine.
 Indeks potrošačkih cena, Sjedinjene Države, 1775-2012
Indeks potrošačkih cena, Sjedinjene Države, 1775-2012Međutim, vidimo da se bruto domaći proizvod (BDP) po stanovniku u Sjedinjenim Državama, uobičajena mera ekonomske snage, neprekidno povećavao od 1820. godine do danas po stopi od oko 1,85% godišnje. Ne postoji porast oko 1971. godine, uprkos rastućoj inflaciji koja je započela u to vreme.
Ovo je logaritamski grafikon, koji nam omogućava da bolje vizualizujemo rast tokom vremena: što više logaritamski grafikon podseća na pravu liniju, to je stopa promene konzistentnija. Za više detalja, ovde pogledajte naslov: Rast na tehnološkoj granici i rast dostizanja.
To pokazuje da inflacija ne pokreće ekonomski rast.
Nažalost, imamo dokaze da inflacija ima i druge neželjene posledice, poput nejednakosti bogatstva. Koncentracija bogatstva u top 1%, počela je da raste krajem 1970-ih, nekoliko godina nakon što su Sjedinjene Države skinule svet sa zlatnog standarda i pretvorile se u monetarni sistem zasnovan na dugovima koji zahteva monetarnu inflaciju, a time i inflaciju cena, da bi preživeo.
Za potpunu istoriju tranzicije novca sa robnog sistema na dužni sistem, pročitajte naš članak o novcu.
Da li inflacija pokreće ili umanjuje nejednakost bogatstva?
Veza između inflacije i nejednakosti bogatstva postaje jasna kada pogledamo kako novostvorena valuta ulazi u ekonomiju. Vlade, komercijalne banke, velike korporacije i bogati često koriste kredite da bi iskoristili prednosti svojih moći. Kada podignu kredite, oni novonastalu valutu dobijaju ranije od svih ostalih. Oni imaju koristi od inflacije trošenjem nove valute pre nego što cene počnu da rastu kao rezultat te nove valute koja kruži u ekonomiji. Veliki i bogati subjekti često mogu da dobiju kredite po nižim troškovima od prosečnog građanina ili malog preduzeća. To znači da mogu da povećaju svoje poslovanje i bogatstvo brže od manjih firmi.
Bogati mogu da dobiju jeftine zajmove, zahvaljujući Federalnim Rezervama koje zadržavaju niske kamatne stope. To im omogućava da koriste ovo prednost za ostvarivanje ogromne dobiti.
Inflacija pogadja one koji rade za platu i ne mogu da ulože veći deo svog prihoda. Zarade se polako menjaju, ponekad se uskladjuju samo jednom godišnje. Kao rezultat, cene osnovnih dobara i usluga često rastu mnogo pre nego što zarade porastu. Cena potrošačke korpe takođe se smanjuje sa manipulacijama indeksom potrošačkih cena (CPI) koji skriva rast inflacije.
Gde se danas javlja inflacija?
Rekordno visoka inflacija javlja se u zemljama kao što su Venecuela, Zimbabve, Turska, Iran, Kuba, Južna Afrika i Argentina. To dovodi do sloma trgovine i političke nestabilnosti.
Just incase no one knows what Durban looks like pic.twitter.com/x899TIlbkI
— Mohamed Yusuf (@_MohamedYusuf) July 13, 2021U razvijenom svetu vlade izveštavaju o niskoj inflaciji cena. Međutim, globalni bankarski sistem stvara nove valute u tonama – u toku je velika monetarna inflacija. Centralne banke dovode do sve većeg stvaranja valuta snižavanjem kamatnih stopa. To dovodi do toga da korporacije i pojedinci mogu da uzimaju jeftinije kredite, a svaki kredit znači stvaranje nove valute. Od 2008. godine, gotovo sve glavne centralne banke postavile su kamatne stope blizu nule.
Mnoge centralne banke takođe su pozajmljivale ogromne iznose vladama i bankama koje su propale nakon finansijske krize 2008. godine. Za samo nekoliko meseci, ovo je udvostručilo (ponekad utrostručilo ili učetvorostručilo) novčanu masu mnogih nacija. Oni su ovo nazvali „kvantitativno ublažavanje“.
Ako banke koriste toliku monetarnu inflaciju, zašto onda mi ne vidimo inflaciju cena?
Jednostavno rečeno, većina nove valute nije dospela u ruke običnih ljudi. Kada obični ljudi budu mogli da potroše novoštampanu valutu na svoje svakodnevne potrebe, tada ćemo videti rast CPI i inflacije.
Danas većina valuta ulazi u svet putem bankarskih zajmova, pa banke igraju veliku ulogu u tome gde se dešava inflacija. Banke prvenstveno pozajmljuju vrlo ‘sigurnim’ klijentima poput bogatih pojedinaca, vlada i velikih korporacija. Ovi subjekti kupuju luksuznu robu, umetnička dela, finansijsku imovinu i državne obveznice.
Cene ovih vrsta imovine nisu uključene u CPI, tako da je prijavljena inflacija niska. Kao rezultat, povećanje plata i isplate socijalnog osiguranja su takođe na niskom nivou.

Bogati su uživali u periodu od 2008. do 2021. godine, kada je njihova imovina upumpavana sa velikom količinom novog novca proizvedenog od bankarskih kredita!
Šta se dešava kada nova valuta dodje u ruke običnih ljudi?
Nažalost, jednog dana će sva ova nova valuta da uđe u normalnu ekonomiju i time će se povećati cene svakodnevne robe. To je poćelo da se dešava 2021. godine kao rezultat stimulativnih programa COVID-19 u Sjedinjenim Državama, koji su ljudima distribuirali trilione dolara. Iako je ovo zasigurno poželjnije od spašavanja korporacija, svaka vrsta spašavanja koja uključuje štampanje novca ima gadne dugoročne efekte.
Ovo što sada doživljavamo dogodilo se u Nemačkoj tokom i posle Prvog svetskog rata. Cene u Nemačkoj su zapravo pale tokom Prvog svetskog rata uprkos velikom stvaranju valute od strane Nemačke centralne banke. Nisko poverenje u ekonomiju sprečavalo je nemački narod da troši novac. Međutim, kad se rat završio i kada su ljudi ponovo počeli da ga troše, cene su vrlo naglo skočile i valuta je postala bezvredna. To bi moglo da se dogodi 2020-ih u Sjedinjenim Državama, sa obzirom na predložene programe podsticaja.
Politike poput Univerzalnog Osnovnog Dohotka, eng. Universal Basic Income (UBI), koje izgledaju pogodne za njihova obećanja da će “spasiti ljude”, takođe mogu da pokrenu hiperinflaciju. Obični ljudi bi se osećali imućnije, trošili bi svoju novoštampanu valutu i doveli do brzog rasta cena. Ovo bi u suštini poništilo pozitivan uticaj građana koji dobijaju “besplatan novac” svakog meseca.
Pa kako onda vi možete da zaštitite svoju ušteđevinu od inflacije? Kupujte imovinu koja je retka, potcenjena i koju vlade teško mogu da prigrabe. Ova imovina su plemeniti metali poput zlata, i Bitcoin.
Šta je deflacija?
Deflacija znači pad cena tokom vremena. Mnogi ekonomisti kažu da će ovo dovesti do toga da ljudi gomilaju valutu i da će dovesti do ekonomskog kolapsa, jer ljudi prestaju da kupuju robu i ulažu u preduzeća. To jednostavno nije tačno, jer ljudi uvek imaju potrebe i želje zbog kojih kupuju odredjenu robu. Stalni pad cena tokom vremena jednostavno bi promenio psihologiju potrošačke kulture u kojoj živimo.
Potrošačka kultura potiče od inflacije
Kako je to istina? Pogledajmo na sledećem primeru. Recimo da želite novi auto i da imate dovoljno novca da ga kupite. Poznato je da u našem svetu zbog stalne inflacije vaš novac vremenom postaje sve manje i manje vredan. U paralelnom svemiru u kojem se javlja stalna deflacija, vaš novac vremenom postaje sve vredniji.
- Uz konstantnu inflaciju, auto će koštati nešto više sledeće godine, i nešto više naredne godine. Niste sigurni gde da uložite novac da biste sa vremenom sigurno očuvali njegovu kupovnu moć. Ako niste sigurni da li ćete da kupite auto, ima više finansijskog smisla da ga kupite odmah, da biste dobili najbolju ponudu.
- Uz konstantnu deflaciju, auto će koštati nešto manje sledeće, i još manje naredne godine. Ako samo čuvate vaš novac, sledeće godine ćete dobiti bolju ponudu za auto. Ako niste sigurni da li ćete da kupite auto, ima više finansijskog smisla da sačekate malo duže da biste dobili bolju ponudu.
Sada razmislite o ta dva scenarija, pomnožena bilionima ljudi i proizvoda. Uz konstantnu inflaciju, svako ima malo više razloga da kupuje stvari upravo sada. Uz konstantnu deflaciju, svi sada imaju malo manje razloga da kupuju. Upravo na taj način inflacija je u osnovi naše materijalističke, potrošačke kulture. Deflacija bi mogla da bude lek.
Inflacija uzrokuje loše investicije
Vaš novac godišnje gubi “2%” svoje vrednosti zbog inflacije. Sada, recimo da vas Stefan pita da investirate u njegov Fast food. Nakon uvida u brojeve, verujete da ćete ovom investicijom izgubiti 1% od vrednosti svog novca. Gubitak od 1% u Stefanovom poslu bolji je od gubitka od 2% zbog inflacije, pa se vi odlučujete da uložite. Ovo je loša investicija, eng. malinvestment – investirajući vi ćete da izgubite deo vrednosti. Međutim, čuvanje valute je još gore, zato ulažete.

Loša investicija: isto kao bacanje novca u smeće.
Mnogi investitori, poput penzijskih fondova, danas su prisiljeni da investiraju u neprofitabilne biznise zbog investicionih mandata i same veličine njihove ‘imovine pod upravljanjem’.
Pristalice konstantno niske inflacije veruju da bi deflacija smanjila investicije. Međutim, to bi samo smanjilo ulaganje u preduzeća sa negativnim očekivanim prinosom poput Stefanovog Fast food-a. Na primer, recimo da je deflacija u proseku oko 2% godišnje. Na ovom tržištu investitori bi jednostavno prestali da ulažu u projekte za koje misle da će im zaraditi manje od 2% godišnjeg povrata ulaganja.
Neznatno deflaciona valuta obeshrabriće ulaganja u lažna i loša preduzeća i podstaći ulaganje u solidna preduzeća koja svetu dodaju vrednost.
Kakav uticaj inflacija ima na društvo?
Inflacija pokreće povećanu potrošnju, smanjenu štednju i povećani dug. Sve ove stvari dovode do toga da većina ljudi mora da radi više sati i duže u starosti. Iako inflacija kažnjava one koji rade za platu, ona obogaćuje vlasnike bilo koje imovine koja dobija na ceni kada nova valuta uđe u sistem. Ova imovina uključuje akcije, umetnička dela, nekretnine i drugu imovinu koju bogataši koriste za čuvanje svog bogatstva.
Vremenom ljudi i firme izmišljaju nove načine za jeftinije stvaranje dobara i usluga višeg kvaliteta. Ovo je poznato kao ‘rast produktivnosti’ i trebalo bi da uzrokuje da cene tokom vremena konstantno padaju, a ne da rastu. Samo konstantno stvaranje valute koje je neophodno zbog monetarnog sistema zasnovanog na dugu naše vlade uzrokuje stalnu inflaciju i njene loše efekte.
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 22:59:58
@ e2c72a5a:bfacb2ee
2025-06-03 22:59:58While Asia silently steals the crypto spotlight, America's grip on digital assets is slipping through its fingers.
The U.S. share of Bitcoin, Ethereum, and Solana trading has dropped below 45% as Asian markets surge to capture nearly a third of global crypto activity. This power shift comes despite Bitcoin's remarkable resilience, hovering above $105,000 after weathering a $1 billion liquidation storm.
What's driving this global rebalancing? Institutional players are flooding in – Strategy purchased $2.7 billion in Bitcoin while ETFs absorbed $5.2 billion in May alone. Meanwhile, Ethereum leads the recovery charge with a 4.5% gain as its Foundation restructures to sharpen its competitive edge.
The most fascinating development? Bitcoin's rally is happening on surprisingly low volume. ETFs now represent 45% of global spot BTC market volume, suggesting this isn't retail FOMO but calculated institutional positioning.
Is this the beginning of a new global crypto order? As trade tensions simmer between the U.S. and China, will Asia's growing influence reshape the future of digital assets?
-
 @ bf47c19e:c3d2573b
2025-06-03 17:50:17
@ bf47c19e:c3d2573b
2025-06-03 17:50:17Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Kako Cantillonov Efekat Funkcioniše
- Kako Bitcoin Rešava Nejednakost iz Cantillonovog Efekta
- Uloga Vlade u Cantillonovom Efektu
- Zaštitite Sebe od Cantillonovog Efekta
- Kako mogu da saznam više o Bitcoin-u?

Tradicionalne valute imaju Cantillonov Efekat, dok Bitcoin ima ‘Nakamotov Efekat’ – termin nazvan po anonimnom tvorcu Bitcoin-a, Satoshi Nakamoto-u.
Pitanje o tome zašto nam je potreban Bitcoin danas je postalo veoma uobičajeno, ali odgovori obično ostavljaju većinu ljudi zbunjenim i sa izjavama da je on, ili Ponzijeva šema ili novac za kriminalce. Ovaj zaključak nije pravičan prema načinu na koji bi Bitcoin mogao da transformiše sistemsku nepravednost i korupciju koja je usadjena u naš trenutni monetarni sistem. Jedna od ovih nejednakosti u našem današnjem sistemu rezultat je Cantillonovog Efekta, davno zaboravljene klasične teorije o tome kako raspodela novca utiče na bogatstvo pojedinca.
Cantillonov Efekat opisuje kako stvaranje novog novca donosi korist onima koji prvi dobiju novac, a na štetu onih koji su najudaljeniji od stvaranja novog novca. U današnjem monetarnom sistemu banke i korporacije su najbliže novom novcu dok je srednja klasa najudaljenija. Bitcoin to ispravlja, davanjem novih bitcoin-a samo „rudarima“ koji osiguravaju protokol – mnogo pravednija distribucija.
Cantillonov Efekat predstavlja način na koji se naplaćuje dodatni porez svima koji rade za „nepromenjenu“ platu ili drže prvenstveno dolare ili eure kao deo svog bogatstva. Ovaj porez prenosi vrednost onima koji ulažu u finansijsku imovinu ili su preferirani dobavljači vlade. Bitcoin odvaja stvaranje novog novca od politike, čineći ovu situaciju mnogo poštenijom.
Kako Cantillonov Efekat Funkcioniše
Kada se poveća ponuda neke vrste novca, ima smisla da taj novi novac treba da ode u nečije ruke – ali čije? Da li bi trebao da pada kao kiša sa neba, da ga dobije neko na lutriji, ili ga predati posebnim interesnim grupama?

U našem savremenom monetarnom sistemu, ovaj novac nije uvek zajam za primaoce, tako da nekad ne trebaju da ga vrate.
Zabluda inflacije pomalo liči na MC Escher vodopad – dobro funkcioniše na papiru, ali ne govori skoro ništa korisno o tome kako stvarni svet funkcioniše.
Međutim, ova analiza zanemaruje to kako funkcionišu tržišta. Tamo gde novi novac ide prvo i način na koji se širi kroz ekonomiju, ima veliki uticaj na stvarno bogatstvo ljudi. Zašto? Kada se poveća novčana masa, cene se ne povećavaju odmah kao odraz ove činjenice. Umesto toga, povećavaju se polako, kako tržišta reaguju na novu ukupnu ponudu novca.
Prvi entiteti i ljudi koji prime novostvoreni novac mogu da ga potroše pre nego što je tržište reagovalo na bilo koji novi novac u sistemu prilagođavanjem cena. Kada oni kupuju stvari, dobijaju ih po niskim cenama jer cene još uvek ne podržavaju činjenicu da ima više novca u opticaju.
Jednom kada se novi novc nekoliko puta okrene, cene počinju da rastu, jer se više novčanih jedinica troši na isti broj dobara i usluga. Jedna od ‘cena’ u ekonomiji je plata ili zarada – i ova cena će da poraste, baš kao i sve druge. Međutim, ova cena raste sporije, kao rezultat ulaska novog novca u sistem, nego što je recimo, cena namirnica.
Kao rezultat ove neusklađenosti u vremenu porasta cena, oni koji primaju platu, tj. zaradu moraju da plaćaju više za svoje dnevne potrebe (poput namirnica), dok neko vreme primaju istu platu. Plate se prilagođavaju sporije od cena hrane. To dovodi do pada kupovne moći ljudi koji rade za platu..
Sve ovo proističe iz toga kako novi novac ulazi u sistem. Kada bi novi novac ušao u sistem samo putem zajmova direktno od centralne banke na plate ljudi, ti ljudi bi mogli da ga potroše pre nego što cene porastu, i samim tim bilo bi im bolje.
Na to kako raspodela novca utiče na bogatstvo, ukazao je Richard Cantillon u 18. veku, koji je gledao kako se ova dinamika odvija u Engleskoj kada je vlada štampala novac u njegovo vreme.
Izvrstan momak, g. Cantillon
Kako Bitcoin Rešava Nejednakost iz Cantillonovog Efekta
Da bismo razumeli kako Bitcoin rešava nejednakost, moramo da uporedimo kako se tradicionalne valute poput dolara ili eura distribuiraju u današnje vreme u odnosu na to kako se distribuiraju novi bitcoini.
Gotovo sva tradicionalna valuta koja je stvorena do današnjeg dana, prvo je distribuirana bankama i vladama. To je zato što su glavne komercijalne banke, poput JP Morgan i Citi, zauzvrat podržane od centralnih banaka poput Federalnih rezervi. Centralne banke poseduju ‘prese za štampanje’ – što znači da u svet mogu da ‘odštampaju’ (ili dodaju digitalno) neograničenu količinu svojih tradicionalnih valuta. Takođe su postavili pravila za komercijalne banke da ih podstaknu da pozajmljuju više ili manje dolara, što proširuje i ugovara ukupnu novčanu masu.
Budući da banke i vlade prve dobijaju novi novac, one odlučuju ko je drugi po redu koji može da iskoristi pogodnosti Cantillonovog Efekta. Tu na scenu dolaze lobisti, kao i moć koju donose njihove dobre konekcije sa finansijskom elitom. Lobisti osiguravaju da njihovi interesi imaju koristi od Cantillonovog Efekta, a veoma bogati, kao i korporacije, mogu da dobiju kredite od banaka po isplativim niskim kamatnim stopama.

Stvari mogu da se prilično zabrljaju kada vlada uskoči da preuzme “kontrolu” nad potrošnjom štampanog novca. Izvor: OpenDemocracy
Bitcoin-ov sistem eliminiše moć lobista i prednosti poznavanja pravog bankara, i stavlja ljude na mnogo ravnopravnije temelje. U Bitcoin-u, svaki ‘rudar’ na mreži ima jednake šanse da zaradi nagradu za novostvorene bitcoin-e na svakih 10 minuta. Svako može da postane rudar, jednostavnim kupovanjem hardvera i njegovim uključivanjem u utičnicu – daleko manje mukotrpan posao od lobiranja kod izabranih predstavnika da bi vam dodelili ugovor sa vladom. Rudari troše puno novca na električnu energiju i opremu da bi se takmičili za nagradu, a Bitcoin sistemu pružaju preko potrebnu uslugu: bezbednost. Bez rudara, Bitcoin-ov sistem ne bi funkcionisao.
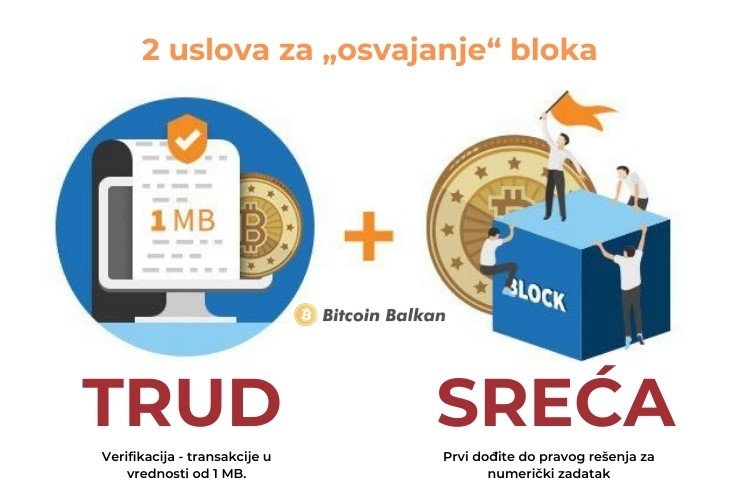
Rudarenje bitcoin-a zahteva računar i struju – to je to.
U sistemu američkog dolara vidimo da političke veze proističu iz Cantillonovog Efekta. U Bitcoin sistemu vidimo da se pružaoci usluga (rudari) plaćaju za svoje usluge novostvorenim bitcoin-ima.
Naravno, ishodi Cantillonovog Efekta bi mogli da se promene tako što će političari da promene način na koji novi novac ulazi u sistem. Međutim, ovo ne rešava osnovni problem: neko drugi ima korist na tuđi račun.
Bitcoin sistem je daleko pravedniji jer koristi Cantillonov Efekat da bi uredno nagradio one koji pružaju korisnu uslugu za sve ostale: obezbeđivanje Bitcoin mreže.
Zamislite to ovako: u dolarskom sistemu, neka osoba šarmira političare ili bankare na pravim pozicijama da bi dobila povlašćen tretman na račun svih ostalih. U Bitcoin sistemu svi plaćaju po malo, da bi zaštitili svoje bankovne račune od krađe.
Uloga Vlade u Cantillonovom Efektu
Federalne vlade širom sveta su jedne od najvećih korisnika Cantillonovog Efekta, jer su u mogućnosti da vrlo lako dobiju zajmove od centralne banke svoje države. U SAD se to radi kada američko Ministarstvo finansija proda državne obveznice banci Federalnih rezervi. Federalne rezerve daju Ministarstvu finansija gomilu novoštampanog novca, a Ministarstvo finansija da Fed-u papir na kojem piše „mi ćemo vam isplatiti dug u to i to vreme sa određenom kamatom“. Možda je malo složenije od ovoga, ali to opisuje suštinu toga.
Budući da novac koji federalna vlada dobija nije postojao pre toga, ona može da ga potroši pre nego što cene počnu da rastu zbog tog novog novca koji ulazi u opticaj. To omogućava federalnoj vladi da ga troši na socijalne programe, policiju, vojsku, vojnu opremu za naoružavanje država poput Saudijske Arabije, čak i na ‘most iz nigde ka ničemu’, a da ne mora da koristi politički nepopularnu metodu: da poveća porez da bi to platila.
Umesto da povećaju poreske prihode za pokrivanje ove potrošnje, federalne vlade koriste Cantillonov Efekat za prenos kupovne moći od plata radnika srednje klase u vladin trezor. Na taj način inflacija i Cantillonov Efekat stvaraju skriveni porez na zarade i uštede novca.
Zaštitite Sebe od Cantillonovog Efekta
Zaštita svog života od Cantillonovog Efekta je zeznuta igra koju treba odigrati. Možete da pokušate da se približite izvoru novog novca, tako što ćete se nadmetati za državne ugovore ili raditi u vrhovima finansija. Možete da pokušate da igrate na visokim nivoima u trgovanju na berzi ili ulaganju u nekretnine, ali je verovatnije da ćete bankrotirati nego što ćete da se zaštitite.
Najlakši način da zaštitite sebe od nepravedne raspodele novog novca je potpuno odbijanje tog monetarnog sistema. Samo najstarije generacije koje danas žive mogu da se sete vremena kada je novac značio nešto drugo osim papira potkrepljenog ‘punom verom i kredibilitetom’ vlade i vojske. Mi smo tako uslovljeni da novac smatramo proizvodom naše vlade, ali naša zaštita od Cantillonovog Efekta zahteva gledanje novca kroz istoriju – čak i pre samo jednog veka.
Novac je nekada značio zlato – materijal koji nijedna vlada ne može magično da stvori u većoj količini, a koji zahteva ogroman napor da se pronađe i iskopa iz zemlje. Bitcoin je vrlo sličan zlatu po tome što niko ne može magično da ga stvori, i veoma ga je teško proizvesti više ‘rudarenjem’. Međutim, Bitcoin takođe putuje brzinom interneta, omogućavajući globalnu trgovinu na način na koji zlato jednostavno ne može.

Bitcoin i zlato – slični po karakteristikama ‘normalnog novca’, različiti po prenosivosti.
Da biste se zaštitili od Cantillonovog Efekta, potrebno je što je više moguće isključiti se iz nepravednih sistema tradicionalnih valuta, čuvajući bogatstvo u pravom novcu, poput zlata ili Bitcoin-a. Ovo je najmirniji način za ukidanje starog sistema i uvođenje novog, pravednijeg sistema.
Kako mogu da saznam više o Bitcoin-u?
Film "Bitkoin: Kraj novca kakvog poznajemo"
The Bitcoin Whitepaper ← objavljen 2008. godine, ovo je izložio dizajn za Bitcoin.
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim uvid u ekonomiju i kako ona utiče na njihove živote.
-
 @ bf47c19e:c3d2573b
2025-06-03 17:47:46
@ bf47c19e:c3d2573b
2025-06-03 17:47:46Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- 5 Razloga Zašto je Novac Važan za Vas, Individualno
- 3 Razloga Zašto je Novac Važan za Društvo u Celini
- Zašto ljudi mrze novac?

Novac vs trenuci – da li oni treba da budu u sukobu? Kakva je uloga novca?
Novac je nepredvidiva zver modernog društva – neki ga veličaju sa stalnom željom da steknu više, dok ga drugi demonizuju i kažu da je pohlepa srž društvenih problema. Tokom mnogih godina svog života, ja sam često prelazio sa jednog na drugo gledište, i naučio mnogo toga upoznajući druge ljude koji žive na oba kraja ovog spektra. Kao i kod mnogih složenih tema, istina leži negde u sredini.
Novac je važan zato što on može da pomogne u uklanjanju materijalnih želja i patnji – omogućavanjem da preuzmete kontrolu nad svojim životom i da brinete o voljenima. Novac podiže životni standard društva omogućavanjem trgovine, a pritom minimalizuje potrebu za poverenjem.
Na novac možemo gledati kao na način da svoj uloženi trud sačuvamo u odredjenom obliku, i da ga vremenom prenesemo, tako da možemo da uživamo u plodovima svog rada. Novac kao alat je jedna od najvažnijih stvari za rast civilizacije. Na nesreću, mnogi su vremenom zlostavljali novac, ali sa dobrim razlogom: način na koji naš novac danas funkcioniše dovodi do duboko podeljenog društva – što ću i objasniti.
5 Razloga Zašto je Novac Važan za Vas, Individualno
Novac je važan za rast bogatstva, što je malo drugačije od toga da imamo veliku platu ili jednostavno zarađivati velike količine novca. Bogatstvo je otklanjanje želja, kako bi mogli da obratimo više pažnje na neke korisnije stvari u životu, od pukog preživljavanja i osnovnih udobnosti.
Bogata osoba je ona koja zaradi više novca nego što potroši, i koja ga čuva – ona čuva svoj rad tokom vremena. Uporedite ovo sa visoko plaćenim lekarom koji živi u velikoj vili sa hipotekom i sa Mercedesom na lizing. Iako ova osoba ima visoke prihode, ona takođe ima velike rashode u vidu obaveze plaćanja te hipoteke i lizinga. Te obaveze sprečavaju ovu osobu da uživa u istinskim blagodetima novca i bogatstva koje one predstavljaju:
1. Sloboda od potrebe za radom
Bez bogatstva, vi morate da radite da biste preživeli. Dostizanjem bogatstva i odredjenom imovinom koja vam donosi novac bez potrebe da vi trošite svoje vreme, vi možete da oslobodite svoj raspored. Više ne zavisite od posla koji mrzite, i nemorate da provodite 40 sati nedeljno odvojeni od porodice, samo da biste se pobrinuli za svoje osnovne potrebe. Dobijanje otkaza u padu ekonomije neće vas dovesti do finansijske propasti ili nečeg goreg.
2. Kontrola nad time kako vi trošite svoje vreme
Kada steknete bogatstvo, vi možete da odlučite kako želite da provodite svoje vreme. Kada se nalazimo u trci pacova i radimo 40+ sati nedeljno, često se naviknemo da novac trošimo onda kada imamo slobodnog vremena. Idemo na lepe večere ili idemo na skupe odmore. Međutim, sa više vremena, a možda čak i sa manje novca, mi možemo da imamo isto ili više uživanja živeći usporenije.
Razmislite o ovome – ukoliko imate samo 1 nedelju slobodno od posla, vi onda morate da kupite onaj mnogo skuplji let u Petak uveče koji se vraća u sledeću Nedelju, kako biste maksimalno iskoristili svoje vreme na nekom egzotičnom mestu za odmor. Međutim, ukoliko ste u mogućnosti da izdržavate sebe bez potrebe da mnogo vremena provodite na poslu, vi onda možete u Utorak da krenete jeftinijim letom i vratite se u sledeću Sredu. Takođe nećete osećati toliki pritisak da se opustite u uživanju tokom vaše nedelje u inostranstvu – možda ćete čak moći i da ostanete duže i da istražujete više, bez plaćanja skupih turističkih agencija i hotela kako bi organizovali vaše kraće putovanje.
3. Sposobnost da pomažete vašim prijateljima i porodici
Onda kada novca imate na pretek, možete poboljšati svoje odnose sa prijateljima i porodicom ne samo kroz dodatno slobodno vreme koje provodite sa njima, već i sa samim novcem. Ako je vašem prijatelju potrebna hitna operacija, vi možete da mu izadjete u susret i pomognete mu da stane na svoje noge. Ukoliko vam je tetka bolesna, vi možete da provedete vreme pored nje, umesto da je pozovete na kratko dok putujete prema kući vraćajući se nakon celog dana provedenog u kancelariji.
4. Smanjen finansijski stres
Stres je sveobuhvatno i opasno stanje modernog doba, sa kojim gotovo svi mi živimo u nekoj odredjenoj meri. Povezan je sa lošim zdravljem, sa preko 43% svih odraslih koji kažu da pate od odredjenih zdravstvenih problema uzrokovanih stresom. Stres zbog posla pogađa 83% zaposlenih.
Pravo bogatstvo – koje znači eliminaciju želja i potreba – može da ukloni ovaj stres i njegove negativne uticaje na druge delove života. Ovo bi čak moglo da ukloni većinu stresa u vašem životu, uzimajući u obzir da je uzrok stresa broj 1 upravo novac.
5. Bolje možete da pomognete vašoj zajednici
Mnogi od nas žele da volontiraju u svojim zajednicama i pomognu onima koja je pomoć preko potrebna, ali nisu u stanju da pronađu slobodnog vremena i energije zbog svog posla, porodice i društvenih aktivnosti koje nas mentalno i fizički čine srećnima, zdravima i hranjenima. Sa bogatstvom, mi možemo da posvetimo vreme koje nam je potrebno za razumevanje i doprinos drugima – a ne samo da sa vremena na vreme pomognemo slanjem humanitarnog SMS-a.
Novac, koji se pametno koristi, je moćno sredstvo za poboljšanje vašeg života i života vaših najmilijih i zajednice. Međutim, novac je takođe moćno sredstvo za poboljšanje društva u celini – ukoliko je dobro strukturiran.
3 Razloga Zašto je Novac Važan za Društvo u Celini
Novac poboljšava sposobnost ljudi da trguju jedni s drugima, što podstiče određene specijalizacije. Ako je imanje vašeg komšije odlično za proizvodnju vina, a vaše je pogodno za žito, obojica možete da profitirate trgovinom. Sad oboje imate i hleb i vino, umesto jednog pijanog vlasnika vinograda i jednog proizvodjača žita kome je dosadno!
Novac poboljšava društvo na nekoliko načina:
1. Omogućava specijalizaciju
Kao u primeru vlasnika vinograda i proizvodjača žita, novac omogućava povećanu specijalizaciju poboljšavajući sposobnost trgovine. Svaka razmena dobara ima problem sa ‘sticajima potreba’ – oba partnera u trgovini moraju da žele ono što druga osoba ima da bi pristala na trgovinu.
Možemo da mislimo o novcu kao o dobru koje žele gotovo svi. Ovo trgovinu čini mnogo jednostavnijom – da biste stekli odredjeno dobro, sve što vam je potrebno je novac, a ne neka slučajna stvar koju prodavac tog dobra takođe želi u tom trenutku. Vremenom je upotreba novca omogućila specijalizaciju, što je povećalo kvalitet i složenost roba i usluga.
Zamislite da sami pokušate da napravite svoj telefon – a bili su potrebni milioni stručnjaka i specijalizovana oprema da bi proizveli taj uređaj. Svi ti stručnjaci i kompanije plaćaju jedni drugima u novcu, omogućavajući složenom plesu globalnih proizvođača i lanaca snabdevanja da taj telefon isporuče na dlan vaše ruke. Čak i nešto tako jednostavno kao flaša za vodu uključuje naftna polja i proizvodne pogone koji su možda hiljadama kilometara od vaše kuće.
Kada ljudi mogu da se specijalizuju, kvalitet robe i usluga može da se poveća.
2. Omogućava korisnu trgovinu uz smanjeno poverenje
Mala društva mogu mirno i produktivno da posluju bez novca koristeći usluge, “dodjem ti” i uzajamno razumevanje. Međutim, kako se društva uvećavaju, svima brzo postaje nemoguće da održavaju lične odnose i isti stepen poverenja sa svima ostalima. Sistem trgovine uslugama i međusobnog poverenja ne funkcioniše previše dobro sa putnikom koji se nalazi na proputovanju kroz grad, i provede samo 15 minuta svog života u vašoj prodavnici.
Novac minimizira poverenje potrebno za trgovinu u većim društvima. Sada više ne moram da verujem da ćete mi pomoći kasnije kada mi zatreba – mogu samo da prihvatim uplatu od vas i da to koristim da bih sebi pomogao kasnije. Jedan od mojih omiljenih mislilaca, Nick Szabo, ovo naziva ‘društvena prilagodljivost’.
3. Smanjuje upotrebu sile
Kada društvo teži upotrebi određenog oblika novca za olakšavanje trgovine, može u velikoj meri da smanji nasilje u tom društvu. Kako to može biti tako? Zar ljudi ne bi i dalje želeli da kradu jedni od drugih ili da se svete?
Ukoliko razmišljamo van uobičajnih okvira, možemo da počnemo da razumemo kako novac može da smanji nasilje. Ako ti i ja živimo u susednim zemljama i želimo nešto što druga zemlja ima, imamo dva načina da to dobijemo: uzimanjem na silu ili menjanjem nečeg našeg za to. Kao što je ranije rečeno, novac znatno olakšava trgovinu – pa ćemo postojanjem zajedničkog monetarnog sistema verovatnije radje izvršiti trgovinu nego napad na zemlju. Zašto bismo rizikovali svoje živote kad možemo samo mirno da trgujemo jedni sa drugima?
Zašto ljudi mrze novac?
Pa ako novac ima toliko koristi za nas lično i za društvo u celini, zašto toliko ljudi mrzi novac? Zašto je demonizovan, zajedno sa onima koji ga imaju puno?
Za deo ovoga može biti okrivljen problem u jednakosti mogućnosti – to da je nekima teže da izadju iz nemaštine i postanu bogati. Bez sumnje, neki mali deo potiče od ljudi koji jednostavno ne žele da se trude ili preduzmu neophodne rizike da bi postali bogati.
Međutim, oba ova problema imaju više veze sa problemima kako naš novac danas funkcioniše, nego sa bilo kojim problemom u samom konceptu novca. Novčani sistem treba da nagrađuje ljude koji proizvode vredne stvari i trguju njima sa drugima. Verujem da većina ljudi danas misli da novac tako funkcioniše, i to ne bi smelo da bude daleko od istine.
Naš trenutni monetarni sistem, na žalost, nagrađuje ’finansijalizaciju’ – pretvarajući sve u imovinu, čija vrednost može da se napumpava ili spušta stvaranjem dobre priče i navođenjem drugih da veruju u nju. Razuzdani dug pogonjen stalnim omalovažavanjem svih glavnih valuta dodat je ovom blatu finansijalizacije. Sada je isplativije podići ogroman kredit i koristiti ga za brzo okretanje imovine radi zarade nego izgraditi posao koji društvu nudi korisne robe i usluge.
Tradicionalni monetarni sistem dodatno nagradjuje predatore, partnere u zločinu i neradnike.
Propast našeg novca razvila se tokom proteklih pola veka, počevši od toga kada su naše valute postale ništa više od parčeta papira, podržanog sa verom i kreditima naših vlada. Da biste bolje razumeli ovu promenu, pogledajte moj post o svrsi i istoriji novca.
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ bf47c19e:c3d2573b
2025-06-03 17:46:50
@ bf47c19e:c3d2573b
2025-06-03 17:46:50Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Procena vrednosti
- Većina Bitcoin-ovih pozitivnih strana opstaje
- Broj ljudi koji su prihvatili Bitcoin
- Zaključak
Prošlo je trinaest godina od nastanka Bitcoina i lako je poverovati da je većina njegovog rasta iza njega. Deo ovoga je rezultat predrasude koju svi delimo i što nas navodi da zamislimo trenutno stanje stvari kao završni stepen njegovog razvoja. Svaki bitcoiner je nekad mislio da je prekasan sa Bitcoin-om. Međutim, kada primenjujemo kritičko razmišljanje da bismo procenili gde je Bitcoin u svojoj putanji rasta, otkrivamo da je suprotno u stvari tačno: još uvek je vrlo, vrlo rano.
Postoje dva načina da razmišljate o tome koliko je rano za Bitcoin kao zalihu vrednosti neke imovine:
-
Procena vrednosti kao procenat od njegovog punog potencijala
-
Prihvatanje kao procenat od njegovog punog potencijala (na čemu je fokus u ovom članku).
Procena vrednosti
Prvi i najčešći način da se proceni koliko je rano za Bitcoin je da se pogleda njegova ukupna vrednost (trenutno oko 900B USD) i uporedi sa njegovim punim potencijalom. Izazov sa ovim je očigledno da je puni potencijal Bitcoin-a stvar nagađanja. Oni koji duboko razumeju Bitcoin imaju tendenciju da njegov potencijal posmatraju barem kao potencijal zlata (oko 13T USD), ali teoretski više poput 200T USD (oko polovine ukupne vrednosti sveta).
Za brzi pregled ovog potencijala od 200T USD, pogledajmo ukupno raspoloživo tržište Bitcoin-a. Radi jednostavnosti, samo ćemo razmotriti njegovu ulogu zalihe vrednosti i zanemariti njegov potencijal da pojede tržišni udeo od oko 100T USD ukupne vrednosti u različitim svetskim valutama. Uzimajući u obzir različite zalihe vrednosne imovine i grubom procenom koliki bi % Bitcoin mogao da uzme od njih, dobili smo ovakav rezultat:

Iako put do 200T USD nije veliko rastezanje, u stvarnoj vrednosti čini se previše dobrim da bi bio istinit. Sa obzirom da je bez presedana da zaliha vrednosti neke robe postigne vrednost veću od zlata, to jednostavno predstavlja neistraženu teritoriju. Ali čak i ako se jednostavno pridržavamo targetiranja niže ciljne vrednosti zlata od 13T USD, Bitcoin još uvek tendenciju velikog porasta svoje cene u budućnosti.
Većina Bitcoin-ovih pozitivnih strana opstaje
Svako ko razmišlja da nešto svog teško zarađenog novca uskladišti u Bitcoin pita se „da li sam poranio ili zakasnio?“ Nepisano je pravilo da se svako oseća kao da je zakasnio kad stigne. Brojni su primeri ljudi koji žale kako su zakasnili 2011. ili 2013. ili 2016. godine, kada je cena Bitcoin-a bila 5, 100, odnosno 600 USD.
Kao i u bilo kojoj zajednici koja se razvija i raste i u kojoj ima manjka nekretninama, pridošlice zavide ljudima koji su već obezbedili sebi nekretninu, ne sluteći da će njima zavideti ljudi koji tek treba da dođu. Ovaj fenomen je primenjiv i na velikom broju drugih primera. Na primer, zakasneli u Kalifornijskoj zlatnoj groznici bili su razočarani kada su došli, a bogata zlatna polja su već bila iscrpljena, i umesto toga su se naseliti na nekoliko stotina hektara zemljišta, a koje sada vrede bogatstvo.
U srcu ovog osećanja je strah da više nema uspona, da više nema novca koji se može zaraditi uzimajući ono što je još uvek ostalo dostupno. Da li smo dostigli tu tačku sa Bitcoin-om?
Pa ne. Čini se da je zapravo suprotno. Na osnovu punog potencijalnog opsega procene koji smo utvrdili gore, čak i u ishodu niskog nivoa (13T USD), velika većina bogatstva koje će steći vlasnici Bitcoin-a, tek treba da se stekne (96%). Da bi parirao proceni zlata, Bitcoin i dalje mora da poraste 26 puta.

A ako se desi vrhunski ishod, punih 99,7% ukupnog stvaranja bogatstva Bitcoin-a ostaje pred nama. To bi značilo da Bitcoin još uvek treba da poraste 400 puta, zanemarujući pariranje zlatu.
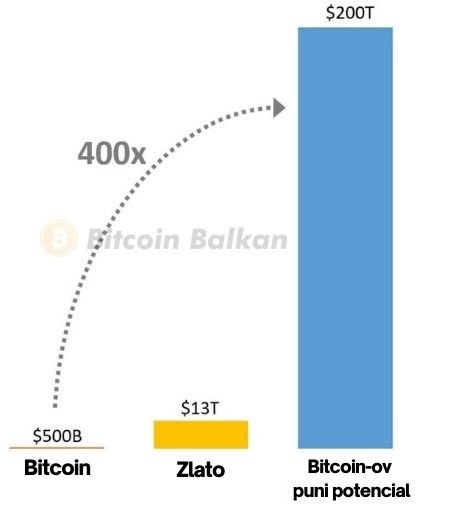
Stavljanjem trenutne vrednosti Bitcoin-a u perspektivu, postaje jasno da je za Bitcoin još uvek vrlo rano.
Iako ova analiza sugeriše da za Bitcoin-u ostaje od 26x do 400x rasta, korisno je proveriti ovaj zaključak kroz drugo razumno objašnjenje, a tamo gde je poznat puni potencijal…
Broj ljudi koji su prihvatili Bitcoin
Procene broja vlasnika Bitcoin-a širom sveta se veoma razlikuju. To je dovelo do prilične količine dvosmislenosti i nesigurnosti u vezi sa stvarnim brojevima i određenog stepena odustajanja i mišljenja da je taj broj jednostavno preteško precizno proceniti. Iako je teško utvrditi konačan broj, glavni razlog za odstupanje u procenama je nedostatak standardizovanih definicija šta znači prihvatanje Bitcoin-a.

Istina je da postoje različiti nivoi prihvatanja Bitcoin-a. Podelom na segmente prihvatanja Bitcoin-a lakše je uvideti ne samo zašto postoji širok opseg procena, već i još važnije, koliko je još uvek rano za prihvatanje Bitcoin-a kao preferirane zalihe vrednosti.
U ove svrhe, hajde da podelimo u segmente prihvatanje Bitcoin-a na četiri različita „nivoa“:
1. Kežual amateri (prstom u vodi)
2. Alokatori 1% (stopalima u vodi)
3. Značajni vernici (do pojasa u vodi)
4. Bitcoin maximalisti (u vodi preko glave)
Pre nego što počnemo, potreban nam je imenilac. Mogli bismo da koristimo globalno stanovništvo, ali po mom mišljenju ovo daje loše rezultate. Ono što mi zaista procenjujemo je koji procenat sveta koji poseduje odredjeno bogatstvo za skladištenje u Bitcoin-u, je to i učinio. Prema podacima sa sajta Statista, 2,2 biliona ljudi na svetu poseduje najmanje 10k USD u neto vrednosti, što se čini kao razumna granica za zalihu koju žele da uskladište. Činjenica je da će siromašne zajednice takođe koristiti Bitcoin kao zalihu vrednosti i verovatno će iz njega izvući veću korist kao rezultat marginalnog pristupa tradicionalnoj bankarskoj infrastrukturi kao klijenti banaka sa „niskom vrednošću“. Međutim, u naše svrhe, jednostavno gledamo koliko je ljudi usvojilo Bitcoin među grupama sa značajnim bogatstvom za skladištenje, tako da će 2.2 biliona služiti kao naša puna potencijalna veličina tržišta.
1. Kežual amateri
Ovaj segment ljudi koji su prihvatili Bitcoin uključuje sve one koji imaju bilo koju količinu Bitcoin-a – vašeg prijatelja sa 20 USD BTC-a negde u nekom novčaniku ili vašu tetku koja se ne seća svoje Coinbase lozinke iz 2017. Po mom mišljenju, najveća zabuna oko broja ljudi koji su prihvatili Bitcoin nastaje zbog poistovećivanja „kežual amatera“ sa ljudima koji su u potpunosti prihvatili Bitcoin. Realnost je takva da ljudi ovog segmenta uglavnom samo eksperimentišu, bilo da bi stekli osećaj za ono o čemu svi pričaju, ili samo uložu nekoliko dolara u Bitcoin u nadi da će možda dobiti džekpot, kao što je slučaj sa greb-greb nagradnim igrama.
Zbog toga, „kežual amateri“ su razlog dovodjenja u zabludu pravog broja ljudi koji su u potpunosti prihvatili Bitcoin. Njihovo ponašanje zapravo ne predstavlja prihvatanje u pravom smislu te reči i stoga se ne bi trebalo smatrati ljudima koji su u potpunosti prihvatili Bitcoin. Istina je da, kada kežual amateri shvate da je Bitcoin najbolja zaliha vrednosti neke imovine u istoriji, neće ostati na samo 20 USD u Bitcoin-ima. Umesto toga, oni će svoju štednju prebaciti u mnogo većim iznosima.
Što se tiče odredjivanja veličine ovog segmenta, Willy Woo je sastavio razumno iscrpnu i sveobuhvatnu procenu od oko 187 miliona ljudi koji su prihvatili Bitcoin, što znači da su oni u najmanju ruku „kežual amateri“.
Koristeći ovaj i naš puni potencijal od 2,2 biliona ljudi kao imenioca, 8,5% potencijalnih ljudi koji su prihvatili Bitcoin-e dostiglo je nivo „kežual amatera“. Ovo je prilično velik broj i potpuno obmanjuje stvarni obim potpunog prihvatanja, a što će pokazati sledeći segmenti.
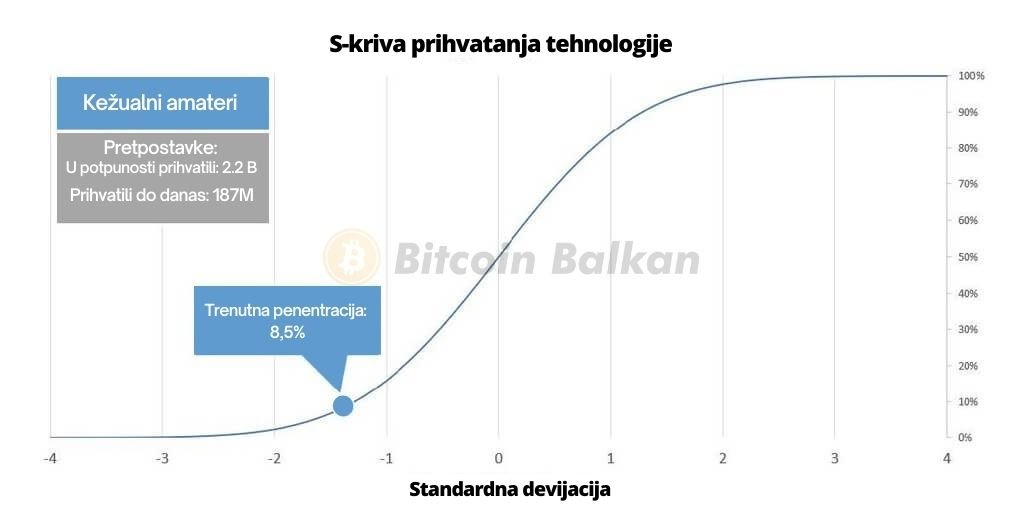
2. Alokatori 1%
Za preostale potkategorije, tačni podaci su manje dostupni. Kao takvi, sve što možemo je da smislimo razumne procene putem triangulacije.
Po mom mišljenju, „alokatori 1%“ se mogu okarakterisati kao ljudi koji su prihvatili Bitcoin, i koji žele da imaju mali, ali ne i zanemarljivi deo u Bitcoin-u. Za naše svrhu, mislim da je pristojan prag za ovu grupu svako ko ima najmanje 0,1 Bitcoin, i može se smatrati da imaju malu, ali ne i zanemarljivu poziciju u Bitcoin-u.
Gledajući Bitcoin blockchain, postoji oko 3 miliona adresa koje imaju najmanje 0,1 BTC. Pored ovih brojeva na blockchain-u, moramo da uzmemo u obzir i znatan broj ljudi koji imaju ovaj iznos na berzi ili GBTC-u. Kombinovanjem, mislim da je razumno proceniti da je 10 miliona ljudi dostiglo nivo „alokatora 1%“ ili veći.
Na osnovu ovih brojeva, samo 1⁄17 „kežual amatera“ dostiglo je nivo prihvatanja „alokatora 1%“, što znači da je ovaj nivo prihvatanja Bitcoin-a do danas postigao samo 0,5% penetracije. Ovaj strmi pad je razlog zašto je došlo do zablude da veliki broj „kežual amatera“ bude označeno kao grupa koja je u potpunosti prihvatila Bitcoin.
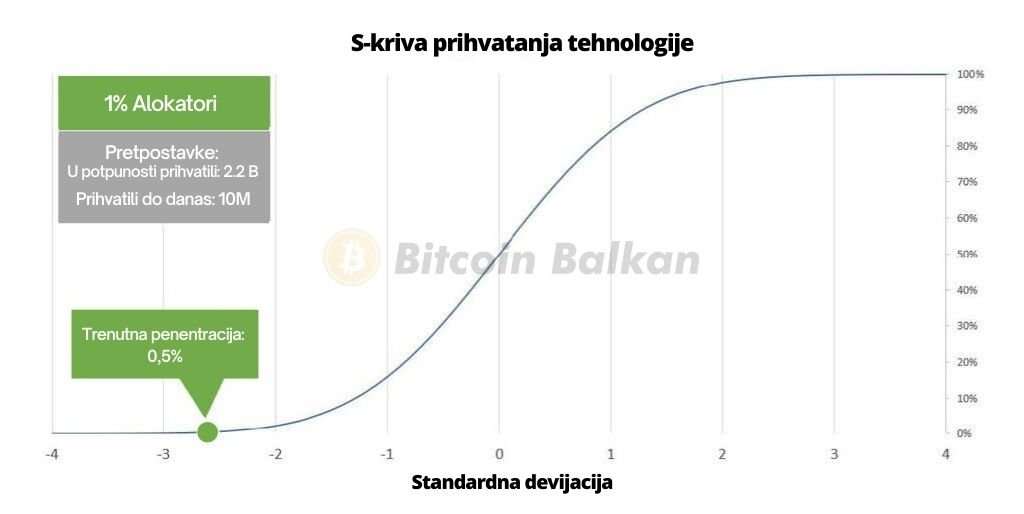
3. Značajni vernici
U ovu kategoriju spada svako ko je dostigao nivo razumevanja Bitcoin-a da alokacija od 1% ili čak 5% više ne izgleda dovoljna.
Uopšteno govoreći, ova grupa se kreće u rasponu od 5 – 50%. Išao bih toliko daleko da bih rekao da je većina ljudi koji sebe smatraju vernicima u Bitcoin-e, uključujući većinu Bitcoin Twitter-a, negde u ovoj grupi.
Procena veličine ove grupe postaje mnogo nejasnija, ali možemo se osloniti na podatke iz blockchain-a da bismo došli do razumne procene.
Za početak, hajde da utvrdimo da je većina ljudi koji su dostigli ovaj nivo verovanja i razumevanja Bitcoin-a, izborila da poseduje najmanje 1 Bitcoin. Pored toga, ovaj nivo ljudi koji su prihvatili Bitcoin je verovatno osigurao svoj Bitcoin u chain-u novčanika kojim oni upravljaju. Gledajući podatke na chain-u, oko 820k adresa ima najmanje 1 Bitcoin. Kao grubu pretpostavku, uzmimo da 500k od toga poseduju ljudi koji su dostigli nivo prihvatanja „značajnog vernika“.
Ako potom generički zaokružimo akaunte za ljude koji nisu postigli status wholecoiner-a (eng. osoba koja poseduje barem 1 BTC), ili koji svoja sredstva drže na berzi, dolazimo do grube procene od 2 miliona „značajnih vernika“.

4. Bitcoin maximalisti
Za našu svrhu, recimo da ova grupa uključuje svakoga ko je dovoljno duboko ušao u Bitcoin da je zaključio da bi više od 50% njihove neto vrednosti trebalo da bude uskladišteno u Bitcoin-u.
Procena veličine ove grupe je gotovo nemoguća, zato ćemo morati da budemo kreativni.
-
Prodaja „Bitcoin Standard“
-
Hajde da konzervativno procenimo da je samo 20% maximalističara kupilo Bitcoin Standard, i da je 50% tih ljudi koji su ga razumeli, postali maksimalisti. Na osnovu knjige Amazon US rank (6,681), onlajn kalkulatori procenjuju da je prodato oko 15k primeraka.
- Hajde da budemo velikodušni i da zaokružimo taj broj od oko 15k na 50k, uzimajući u obzir međunarodnu prodaju i kupovinu izvan Amazona.
Ovo nas dovodi do procene broja od 125k maximalista. Da ne bismo pogrešili, bićemo oprezni, i udvostručimo taj broj i rećićemo da ih ima 250k.
- Kvalitativna triangulacija
Čisto subjektivno, ali čini mi se da na Twitter-u, primarnom domu za komunikaciju maximalista, postoji možda 10k aktivno angažovanih Bitcoin maximalista. Da budemo vrlo konzervativni, recimo da ovo predstavlja oko 5% maximalista (od ukupno 200k).
Uz to, kao procenu od vrha nadole, čini se opravdanim da je oko 10% ljudi koji su dostigli 5 – 50% alokacije Bitcoin-a napravilo skok ka maximalizmu.
Sve u svemu, cifra od oko 250k Bitcoin maximalista čini se konzervativnom, ako ne i velikodušnom pretpostavkom.
To nas dovodi do 0,01% penetracije.
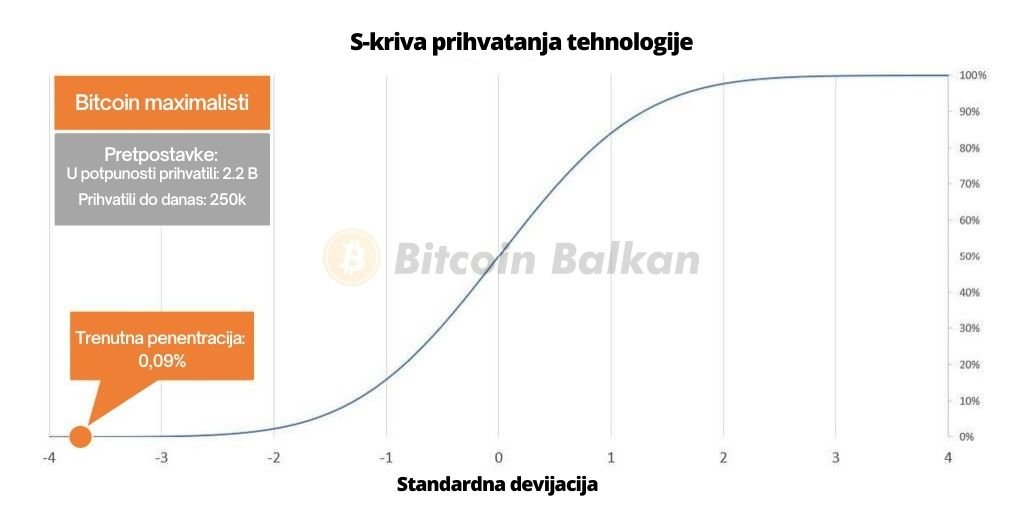
Zaključak
Kako god gledali brojke, još uvek je rano za Bitcoin. Posmatrajući procenu vrednosti Bitcoin-a kao procenat njegovog punog potencijala, vidimo da je trenutna vrednost Bitcoin-a negde između 0,2% i 3% njegovog krajnjeg stanja, što znači da ostaje 30x do 500x rasta. Gledajući napredak prihvatanja Bitcoin-a, vidimo da je trenutna penetracija Bitcoin-a negde između 0,01% i 8,5%, u zavisnosti od toga koji prag prihvatanja gledate.
Ako verujete, kao što ja verujem, da je Bitcoin na putu da postane dominantna zaliha vrednosti i preferirani novac za ceo svet, na kraju će norma biti više od 50% posedovanja neto vrednosti u Bitcoin-u. Budući da naša analiza ovde sugeriše da samo 0,01% sveta zadovoljava ove standarde, opravdano je zaključiti da 99,99% sveta ostaje da sledi njihov primer.
Sve u svemu, dok svi koji se pojave na Bitcoin-u neizbežno osećaju žaljenje zbog toga što nisu ranije investirali i pitaju se da li su u potpunosti propustili brod, jasno je da većina rasta Bitcoin-a ostaje pred nama. Da stavimo ovo u neki kontekst, obzirom da može postojati samo 21 milion Bitcoin-a, prosečna osoba na zemlji (od 8 biliona ljudi) imaće samo 0,0025 Bitcoin-a. Još je toliko rano, da ukupna neto vrednost te prosečne osobe u Bitcoin-u može da se kupi za samo 90 USD.
I ako mislite da je kasno, zapravo je veoma rano, zato vam čestitam i uživajte u skupljanju sats-ova dok su još uvek ovako jeftini!

-
 @ bf47c19e:c3d2573b
2025-06-03 17:43:37
@ bf47c19e:c3d2573b
2025-06-03 17:43:37Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Odakle Potiče Bitcoin?
- Koje Probleme Rešava Bitcoin?
- Kako se Bitcoin razvijao u poslednjoj deceniji?
Bitcoin je peer to peer elektronski keš, novi oblik digitalnog novca koji se može prenositi između ljudi ili računara, bez potrebe za učestvovanjem pouzdanog posrednika (kao što je banka) i čije izdavanje nije pod kontrolom nijedne stranke.
Zamislite papirni dolar ili metalni novčić. Kad taj novac date drugoj osobi, ona ne mora da zna ko ste vi.
On samo treba da veruju da novac koji dobiju od vas nije falsifikat. Obično, proveravanje falsifikata „fizičkog“ novca, ljudi rade koristeći samo oči i prste ili koristeći specijalnu opremu za testiranje ukoliko se radi o značajnijoj sumi novca.
Većina plaćanja u našem digitalnom društvu vrši se putem Interneta korišćenjem neke posredničke usluge: kompanije za izdavanje kreditnih kartica poput Visa, snabdevača digitalnih plaćanja kao što je PayPal ili Apple Pay ili mrežne platforme poput WeChat u Kini.
Kretanje ka digitalnom plaćanju sa sobom donosi oslanjanje na nekog centralnog aktera koji mora odobriti i verifikovati svaku uplatu.
Priroda novca se promenila od fizičkog predmeta koji možete da nosite, prenesete i autentifikujete do digitalnih bitova koje mora da čuva i verifikuje treća strana koja kontroliše njihov prenos.
Odricanjem od gotovine u korist „udobnih“ digitalnih plaćanja, mi takođe stvaramo sistem u kome dajemo ogromna ovlašćenja onima koji bi poželeli da nas tlače.
Platforme za digitalno plaćanje postale su osnova distopijskih autoritarnih metoda kontrole, poput onih koje kineska vlada koristi za nadgledanje disidenata i sprečava građane, čije ponašanje im se ne svidja, da kupuju robu i plaćaju usluge.
Bitcoin nudi alternativu centralno kontrolisanom digitalnom novcu sa sistemom koji nam vraća prirodu korišćenja keša – čovek čoveku, ali u digitalnom obliku.
Bitcoin je digitalno sredstvo koje se izdaje i prenosi preko mreže međusobno povezanih računara, od koji svaki od njih samostalno potvrđuje da svi ostali igraju po pravilima.

Bitcoin Mreža
Odakle Potiče Bitcoin?
Bitcoin je izumela osoba ili grupa poznata pod pseudonimom Satoshi Nakamoto, oko 2008. godine.
Niko ne zna Satoshijev identitet, a koliko znamo, oni su nestali i o njima se godinama ništa nije čulo.
11.februara 2009. godine, Satoshi je pisao o ranoj verziji Bitcoin-a na mrežnom forumu za cypherpunkere, ljude koji rade na tehnologiji kriptografije i koji su zabrinuti za privatnost i slobodu pojedinca.
Iako ovo nije prvo zvanično objavljivanje Bitcoin-a, sadrži dobar rezime Satoshi-jevih motiva.
Razvio sam novi P2P sistem e-keša otvorenog koda pod nazivom Bitcoin. Potpuno je decentralizovan, bez centralnog servera ili pouzdanih stranki, jer se sve zasniva na kripto dokazima umesto na poverenju. […]
Osnovni problem konvencionalne valute je potpuno poverenje koje je potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna primera kršenja tog poverenja. Bankama se mora verovati da drže naš novac i prenose ga elektronskim putem, ali one ga daju u talasima kreditnih balona sa delićem rezerve. Moramo im verovati sa našom privatnošću, verovati im da neće dozvoliti da kradljivci identiteta pokradu naše račune. Njihovi ogromni režijski troškovi onemogućavaju mikro plaćanja.
Generaciju ranije, višekorisnički time-sharing računarski sistemi imali su sličan problem. Pre pojave jake enkripcije, korisnici su morali da imaju pouzdanje u zaštitu lozinkom kako bi zaštitili svoje fajlove […]
Tada je jaka enkripcija postala dostupna širokim masama i više nije bilo potrebno poverenje. Podaci bi se mogli osigurati na način koji je fizički bio nemoguć za pristup drugima, bez obzira iz kog razloga, bez obzira koliko je dobar izgovor, bez obzira na sve.
Vreme je da imamo istu stvar za novac. Uz e-valutu zasnovanu na kriptografskom dokazu, bez potrebe da verujete posredniku treće strane, novac može biti siguran i transakcije mogu biti izvršene bez napora. […]
Rešenje Bitcoin-a je korišćenje peer-to-peer mreže za proveru dvostruke potrošnje. Ukratko, mreža radi poput distribuiranog servera vremenskih žigova, obeležavajući prvu transakciju koja je potrošila novčić. Potrebna je prednost prirode informacije koju je lako širiti, ali je teško ugušiti. Za detalje o tome kako to funkcioniše, pogledajte članak o dizajnu na bitcoin.org
Satoshi Nakamoto
Koje Probleme Rešava Bitcoin?
Razdvojimo neke od Satoshi-jevih postova kako bismo uvideli razloge njegove motivacije.
„Razvio sam novi P2P sistem e-keša otvorenog koda.“
P2P je skraćenica za peer to peer i ukazuje na sistem u kojem jedna osoba može da komunicira sa drugom bez ikoga u sredini, kao medjusobno jednaki.
Možete se setiti P2P tehnologija za razmenu datoteka poput Napster-a, Kazaa-e i BitTorrrent-a, koje su prve omogućile ljudima da dele muziku i filmove bez posrednika.
Satoshi je dizajnirao Bitcoin kako bi omogućio ljudima da razmenjuju e-keš, elektronski keš, bez prolaska preko posrednika na približno isti način.
Softver je otvorenog koda, što znači da svako može videti kako funkcioniše i doprineti tome.
Ne treba da verujemo ni u šta što je Satoshi napisao u svom postu o tome kako softver radi.
Možemo pogledati kod i sami proveriti kako to funkcioniše. Štaviše, možemo promeniti funkcionalnost sistema promenom koda.
„Potpuno je decentralizovan, bez centralnog servera ili pouzdanih stranki …“
Satoshi napominje da je sistem decentralizovan kako bi se razlikovao od sistema koji imaju centralnu kontrolu.
Prethodne pokušaje stvaranja digitalne gotovine poput DigiCash-a od strane Davida Chaum-a podržavao je centralni server, računar ili skup računara koji je bio odgovoran za izdavanje i verifikaciju plaćanja pod kontrolom jedne korporacije.
Takve, centralno kontrolisane privatne šeme novca, bile su osuđene na propast; ljudi se ne mogu osloniti na novac koji može nestati kada kompanija prestane sa poslovanjem, bude hakovana, pretrpi pad servera ili je zatvori vlada.
Bitcoin održava mreža pojedinaca i kompanija širom sveta.
Da bi se Bitcoin isključio, bilo bi potrebno isključiti desetine do stotine hiljada računara širom sveta u isto vreme, zauvek, od kojih su mnogi na nepoznatim lokacijama.
Bila bi to beznadežna igra, jer bi svaki napad ove prirode jednostavno podstakao stvaranje novih Bitcoin čvorova ili računara na mreži.
„… sve se zasniva na kripto dokazima umesto na poverenju“
Internet, a u stvari i većina savremenih računarskih sistema, izgrađeni su na kriptografiji, metodi prikrivanja informacija, tako da je može dekodirati samo primalac informacije.
Kako se Bitcoin oslobađa potrebe za poverenjem? Umesto da verujemo nekome ko kaže „Ja sam Alisa“ ili „Imam 10 $ na računu“, možemo koristiti kriptografsku matematiku da bismo izneli iste činjenice na način koji je vrlo lako verifikovati od strane primaoca dokaza ali ga je nemoguće falsifikovati.
Bitcoin u svom dizajnu koristi kriptografsku matematiku kako bi učesnicima omogućio da provere ponašanje svih ostalih učesnika, bez poverenja u bilo koju centralnu stranku.
„Moramo im verovati [bankama] sa našom privatnošću, verovati im da neće dozvoliti da kradljivci identiteta pokradu naše račune“
Za razliku od korišćenja vašeg bankovnog računa, sistema digitalnog plaćanja ili kreditne kartice, Bitcoin omogućava dvema stranama da obavljaju transakcije bez davanje bilo kakvih ličnih podataka.
Centralizovana skladišta potrošačkih podataka koji se čuvaju u bankama, kompanijama sa kreditnim karticama, procesorima plaćanja i vladama, predstavljaju pravu poslasticu za hakere.
Kao dokaz Satoshi-jeve poente služi primer iz 2017. godine kada je Equifax masovono kompromitovan, kada su hakeri ukrali identifikacione i finansijske podatke za više od 140 miliona ljudi.
Bitcoin odvaja finansijske transakcije od stvarnih identiteta.
Na kraju krajeva, kada nekome damo fizički novac, on nema potrebu da zna ko smo, niti treba da brinemo da će nakon naše razmene moći da iskoristi neke informacije koje smo mu dali da ukrade još našeg novca.
Zašto ne bismo očekivali isto, ili čak i bolje, od digitalnog novca?
„Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna primera kršenja tog poverenja.“
Pojam tradicionalna valuta, odnosi se na valutu izdatu od strane vlade i centralne banke, koju vlada proglašava zakonskim sredstvom plaćanja.
Istorijski, novac je nastao od stvari koje je bilo teško proizvesti, koje su bile lake za proveravanje i transport, poput školjki, staklenih perli, srebra i zlata.
Kad god bi se nešto koristilo kao novac, postojalo je iskušenje da se stvori više toga.
Ako bi neko pronašao vrhunsku tehnologiju za brzo stvaranje velike količine nečega, ta stvar bi izgubila vrednost.
Evropski naseljenici uspeli su da liše afrički kontinent bogatstva trgujući staklenim perlicama koje su se lako proizvodile za ljudske robove.
Isto se dogodilo sa američkim indijancima, kada su kolonisti otkrili način brze proizvodnje vampum školjki, koje su starosedeoci smatrali retkim.
Vremenom, širom sveta ljudi su shvatili da je samo zlato dovoljno retko da deluje kao novac, bez straha da bi neko drugi mogao da ga stvori u velikim količinama.
Polako smo prešli sa svetske ekonomije koja je koristila zlato kao novac na onu gde su banke izdavale papirne sertifikate kao dokaz posedovanja tog zlata.
Nixon je okončao međunarodnu konvertibilnost američkog dolara u zlato 1971. godine, privremenim rešenjem, koje je ubrzo postalo trajno.
Kraj zlatnog standarda omogućio je vladama i centralnim bankama da imaju punu dozvolu da povećavaju novčanu masu po svojoj volji, razredjujući vrednost svake novčanice u opticaju, poznatije kao umanjenje vrednosti.
Iako je izdata od strane vlade, suštinska tradicionalna valuta je novac koji svi znamo i svakodnevno koristimo, ipak je relativno novo iskustvo u opsegu svetske istorije.
Moramo verovati našim vladama da ne zloupotrebljavaju njegovo štamparije, i ne treba nam puno muke da nadjemo primere kršenja tog poverenja.
U autokratskim i centralno planiranim režimima gde vlada ima prst direktno na mašini za novac, kao što je Venecuela, valuta je postala gotovo bezvredna.
Venecuelanski Bolivar prešao je sa 2 bolivara za 1 američki dolar, koliko je vredeo 2009. godine, na 250.000 bolivara za 1 američki dolar 2019. godine.

Pogledajte koliko novčanica je bilo potrebno za kupovinu piletine u Venecueli posle hiperinflacije.
Satoshi je želeo da ponudi alternativu tradicionalnoj valuti čija se ponuda uvek nepredvidivo širi.
Da bi sprečilo umanjenje vrednosti, Satoshi je dizajnirao novčani sistem gde je zaliha bila fiksna i izdavana po predvidljivoj i nepromenjivoj stopi.
Postojaće samo 21 milion Bitcoin-a.
Međutim, svaki Bitcoin se može podeliti na 100 miliona jedinica koje se sada nazivaju satoshis (sats-ovi), što će činiti ukupno 2,1 kvadriliona satoshi-a u opticaju oko 2140. godine.
Pre Bitcoin-a nije bilo moguće sprečiti beskrajnu reprodukciju digitalnih sredstava.
Kopirati digitalnu knjigu, audio datoteku ili video zapis i poslati ga prijatelju, je jeftino i lako.
Jedini izuzeci od toga su digitalna sredstva koja kontrolišu posrednici.
Na primer, kada iznajmite film sa iTunes-a, možete ga gledati na vašem uređaju samo zato što iTunes kontroliše distribuciju tog filma i može ga zaustaviti nakon perioda njegovog iznajmljivanja.
Slično tome, vaša banka kontroliše vaš digitalni novac. Zadatak banke je da vodi evidenciju koliko novca imate.
Ako ga prenesete nekom drugom, oni će odobriti ili odbiti takav prenos.
Bitcoin je prvi digitalni sistem koji sprovodi oskudicu bez posrednika i prvo je sredstvo poznato čovečanstvu čija je nepromenljiva ponuda i raspored izdavanja poznat unapred.
Ni plemeniti metali poput zlata nemaju ovo svojstvo, jer uvek možemo iskopati sve više i više zlata ukoliko je to isplativo.
Zamislite da otkrijemo asteroid koji sadrži deset puta više zlata nego što ga imamo na zemlji.
Šta bi se dogodilo sa cenom zlata uzimajući u obzir tako obilnu ponudu? Bitcoin je imun na takva otkrića i manipulisanje nabavkom.
Jednostavno je nemoguće proizvesti više od toga (21 miliona).
„Podaci bi se mogli osigurati na način koji je fizički bio nemoguć za pristup drugima, bez obzira iz kog razloga, bez obzira koliko je dobar izgovor, bez obzira na sve. […] Vreme je da imamo istu stvar za novac “
Naše trenutne metode obezbeđivanja novca, poput stavljanja u banku, oslanjaju se na poverenje nekome drugom da će obaviti taj posao.
Poverenje u takvog posrednika ne zahteva samo sigurnost da on neće učiniti nešto zlonamerno ili glupo, već i da vlada neće zapleniti ili zamrznuti vaša sredstva vršeći pritisak na ovog posrednika.
Međutim, videli smo bezbroj puta da vlade mogu, i zaista uskraćuju pristup novcu kada se osećaju ugroženo.
Nekom ko živi u Sjedinjenim Državama ili nekoj drugoj visoko regulisanoj ekonomiji možda zvuči glupo da razmišlja da se probudi sa oduzetim novcem, ali to se događa stalno.
PayPal mi je zamrzao sredstva jednostavno zato par meseci nisam koristio svoj račun.
Trebalo mi je više od nedelju dana da vratim pristup „svom“ novcu.
Srećan sam što živim u Europi, gde bih se bar mogao nadati da ću potražiti neko pravno rešenje ako mi PayPal zamrzne sredstva i gde imam osnovno poverenje da moja vlada i banka neće ukrasti moj novac.
Mnogo gore stvari su se dogodile, i trenutno se dešavaju, u zemljama sa manje slobode.
Banke su se zatvorile tokom kolapsa valuta u Grčkoj.
Banke na Kipru su koristile kaucije da konfiskuju sredstva od svojih klijenata.
Indijska vlada je proglasila određene novčanice bezvrednim.
Bivši SSSR, u kojem sam odrastao, imao je ekonomiju pod kontrolom vlade što je dovelo do ogromnih nestašica robe.
Bilo je nezakonito posedovati strane valute kao što je američki dolar.
Kada smo poželeli da odemo, mojoj porodici je bilo dozvoljeno da zameni samo ograničenu količinu novca po osobi za američke dolare po zvaničnom kursu koji je bio u velikoj meri različit od pravog kursa slobodnog tržišta.
U stvari, vlada nam je oduzela ono malo bogatstva koje smo imali koristeći gvozdeni stisak na ekonomiji i kretanju kapitala.
Autokratske zemlje imaju tendenciju da sprovode strogu ekonomsku kontrolu, sprečavajući ljude da na slobodnom tržištu povuku svoj novac iz banaka, iznesu ga iz zemlje ili da ga razmene u ne još uvek bezvredne valute poput američkog dolara.
To omogućava vladinoj slobodnoj vladavini da primeni sulude ekonomske eksperimente poput socijalističkog sistema SSSR-a.
Bitcoin se ne oslanja na poverenje u treću stranu da bi osigurao vaš novac.
Umesto toga, Bitcoin onemogućava drugima pristup vašim novčićima bez jedinstvenog ključa koji imate samo vi, bez obzira iz kog razloga, bez obzira koliko je dobar izgovor, bez obzira na sve.
Držeći Bitcoin, držite ključeve sopstvene finansijske slobode. Bitcoin razdvaja novac i državu
„Rešenje Bitcoin-a je korišćenje peer-to-peer mreže za proveru dvostruke potrošnje […] poput distribuiranog servera vremenskih žigova, obeležavajući prvu transakciju koja je potrošila novčić“
Mreža se odnosi na ideju da je gomila računara povezana i da mogu međusobno slati poruke.
Reč distribuirano znači da ne postoji centralna stranka koja kontroliše, već da svi učesnici koordiniraju medjusobno kako bi mreža bila uspešna.
U sistemu bez centralne kontrole, bitno je znati da niko ne vara. Ideja dvostruke potrošnje odnosi se na mogućnost trošenja istog novca dva puta.
Fizički novac odlazi iz vaše ruke kad ga potrošite. Međutim, digitalne transakcije se mogu kopirati baš kao muzika ili filmovi.
Kada novac šaljete preko banke, oni se pobrinu da isti novac ne možete da prebacujete dva puta.
U sistemu bez centralne kontrole potreban nam je način da sprečimo ovu vrstu dvostruke potrošnje, koja je u suštini ista kao i falsifikovanje novca.
Satoshi opisuje da učesnici u Bitcoin mreži rade zajedno kako bi vremenski označili (doveli u red) transakcije kako bismo znali šta je bilo prvo.
Zbog toga možemo odbiti sve buduće pokušaje trošenja istog novca.
Satoshi se uhvatio u koštac sa nekoliko zanimljivih tehničkih problema kako bi rešio probleme privatnosti, uništavanja vrednosti i centralne kontrole u trenutnim monetarnim sistemima.
Na kraju je stvorio peer to peer mrežu kojoj se svako mogao pridružiti bez otkrivanja svog identiteta ili potrebe da veruje bilo kom drugom učesniku.
Kako se Bitcoin razvijao u poslednjoj deceniji?
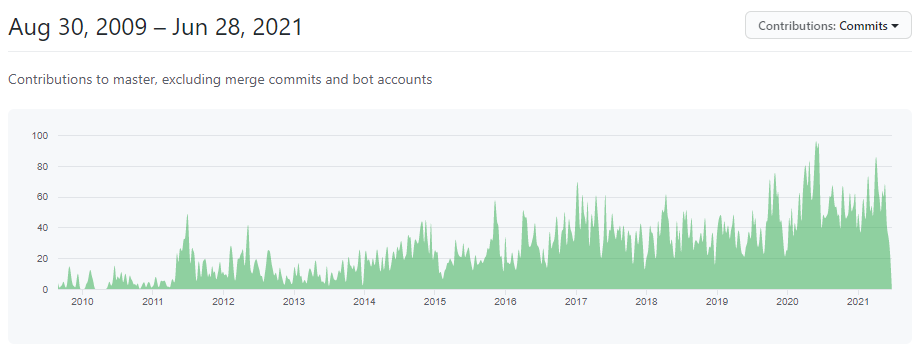
Doprinosi izvornom kodu Bitcoina
Kada je Bitcoin pokrenut, samo nekolicina ljudi ga je koristila i pokrenula Bitcoin softver na svojim računarima za napajanje Bitcoin mreže.
Većina ljudi u to vreme mislila je da je to šala ili da će se otkriti ozbiljni nedostaci u dizajnu sistema koji će ga učiniti neizvodljivim.
Vremenom se mreži pridružilo sve više ljudi koji su pomoću svojih računara dodali sigurnost mreži.
Ljudi su počeli da menjaju Bitcoin-e za robu i usluge, dajući mu stvarnu vrednost. Pojavile su se menjačnice valuta koje su menjale Bitcoin-e za gotovo sve tradicionalne valute na svetu.
Deset godina nakon izuma, Bitcoin koriste milioni ljudi sa desetinama do stotinama hiljada čvorova koji pokreću besplatni Bitcoin softver, koji se razvija od strane stotina dobrovoljaca i kompanija širom sveta.
Bitcoin mreža je porasla kako bi obezbedila vrednost veću od stotine biliona dolara.
Računari koji učestvuju u zaštiti Bitcoin mreže poznati su kao rudari/majneri.
Oni rade u industrijskim operacijama širom sveta, ulažući milione dolara u specijalni rudarski hardver koji radi samo jedno: pobrinuti se da je Bitcoin najsigurnija mreža na planeti.
Rudari troše električnu energiju kako bi transakcije Bitcoin-a učinile sigurnim od modifikacija. Budući da se rudari međusobno takmiče za oskudan broj Bitcoin-a proizvedenih dnevno, oni uvek moraju da pronalaze najjeftinije izvore energije na planeti da bi ostali profitabilni.
Rudari rade na različitim mestima, od hidroelektrana u dalekim krajevima Kine do vetroparkova u Teksasu, do kanadskih naftnih polja koja proizvode gas koji bi u suprotnom bio odzračen ili spaljen u atmosferi.
Iako je Bitcoin popularna tema i o njemu se često raspravlja u medijima, procenjujemo da je samo nekoliko miliona ljudi na svetu počelo da redovno štedi Bitcoin.
Za mnoge ljude, posebno za one koji nikada nisu živeli pod represivnim režimima, ovaj izum novog oblika digitalnog novca izvan kontrole vlade može biti veoma izazovan za razumevanje i prihvatanje.
Zato sam ja ovde. Želim da vam pomognem da razumete Bitcoin i budete gospodar svoje budućnosti!
-
 @ bf47c19e:c3d2573b
2025-06-03 17:39:45
@ bf47c19e:c3d2573b
2025-06-03 17:39:45Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je finansijski samo-suverenitet?
- Zašto smo prestali da koristimo zlatni standard?
- Šta fali tradicionalnoj valuti i centralnim bankama?
- Kako mogu ljudi da mi ukradu novac ako je u banci?
- Kako ljudi koriste moje finansijske podatke protiv mene?
- Kako ljudi kontrolišu sa kim obavljam transakcije?
- Kako da povratimo svoj finansijski samo-suverenitet?
- Kako Bitcoin funkcioniše?
- Pa onda, zašto Bitcoin?
- Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
- Kako Bitcoin štiti od Inflacije?
- Kako Bitcoin štiti od Zaplene?
- Kako Bitcoin štiti Privatnost?
- Kako Bitcoin štiti od Cenzure?
- Šta će vlada i banke učiniti sa Bitcoin-om?
- Da li je vrednost Bitcoin-a nestabilna?
- Da li je Bitcoin novac?
- Bitcoin kao Zaliha Vrednosti
- Bitcoin kao Sredstvo Razmene
- Bitcoin kao Obračunska Jedinica
- Bitcoin kao Sistem Kontrole
- Šta je sa „Sledećim Bitcoin-om“?
- Na kraju
Kratki uvod u bezbednost, privatnost i slobodu vašeg novca.
Pre nego što saznate kako morate znati zašto.

Upoređeni kursevi tradicionalnih valuta: (100.000 venecuelanskog Bolivara za 1 USD) i (20.000 USD za 1 Bitcoin)
Šta je finansijski samo-suverenitet?
Zamislite da u ruci imate zlatni novčić, jedan od najjednostavnijih i najčistijih oblika finansijskog samo-suvereniteta.
Da biste držali taj zlatni novčić, ne morate da se složite sa bilo kojim Uslovima korišćenja ili Politikom privatnosti, da se pridržavate bilo kojih KYC ili AML propisa, da pokažete ličnu kartu, da navedete svoje ime ili jedinstveni matični broj.
Samo ga držite u ruci i njime možete platiti bilo šta, davanjem tog novčića nekom drugom da ga drži u ruci. To je čista sloboda.
Pored slobode onoga što kupujete svojim novčićem, niko ne može magično znati kome plaćate ili koju robu/usluge kupujete tim zlatni novčićem, jer vaša privatnost nije ugrožena sa zlatom.
A pošto imate svoju privatnost, niko ne može znati za vaše transakcije, pa niko ne može da odluči da ograniči ili kontroliše za šta koristite taj zlatni novčić.
Hiljadama godina zlato je bilo globalni standard novca.
Svi su održavali svoj finansijski samo-suverenitet, a privatnost i sloboda svačijeg novca su poštovani.
Zaista je bilo tako jednostavno.
Zašto smo prestali da koristimo zlatni standard?
Trenutni globalni bankarski sistem i sistem tradicionalnih valuta, bankari su vrlo polako implementirali u proteklih 100+ godina.
Udružili su se sa svetskim vladama koje su svima oduzele zlato pod pretnjom nasilja.
Na primer, nakon što je Federalna banka rezervi osnovana u SAD-u 1913. godine, američka vlada je nasilno oduzela svo zlato 1933. godine, prisiljavajući sve da koriste nove centralne banke i sistem novčanica Federalnih rezervi.
 „Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“
„Dostavite svoje celokupno zlato u naše sefove u zamenu za bezvredni papir, ili ćemo upotrebiti silu nad vama.“Banke su u početku zamenile zlatni standard papirnim priznanicama zvane zlatni sertifikati, ali nakon što je prošlo dovoljno vremena, banke su u osnovi jednostavno prestale da ih otkupljuju za zlato.
Zlatni sertifikati izdavani od banaka (novčanice ili „gotovina“) u tom trenutku bili su samo bezvredni papir, ali zbog vladine pretnje nasiljem, svi su bili primorani da nastave da koriste novčanice Federalnih rezervi.
Od skora, banke koriste digitalnu bazu podataka, u kojoj doslovno mogu stvoriti novac ni iz čega, čak i da ga ne moraju štampati na papiru.
Predsednik Federalnih rezervi priča kako oni „štampaju“ novac.
Oni su učvrstili svoju moć da manipulišu i naduvaju globalnu novčanu masu, nadgledaju finansijske transakcije svih i kontrolišu protok svih tradicionalnih valuta u svom bankarskom sistemu.
Banke sada kontrolišu sve.
Jednom kada su centralni bankari uspešno preuzeli kontrolu nad novčanom masom u svetu, zajedno sa sposobnošću svih da slobodno vrše transakcije i trguju, svet je kolektivno izgubio bezbednost, slobodu i privatnost svog novca.
Šta fali tradicionalnoj valuti i centralnim bankama?
Nakon impelentacije trenutnog globalnog bankarskog sistema i sistema tradicionalnih valuta, svetu nije preostao drugi izbor nego da veruje bankarima i političarima da vode globalni finansijski sistem na pošten način.
„Koren problema tradicionalne valute je potpuno poverenje potrebno za njeno funkcionisanje. Centralnoj banci se mora verovati da neće devalvirati valutu, ali istorija tradicionalnih valuta je puna kršenja tog poverenja. Bankama se mora verovati da čuvaju naš novac i prenose ga elektronskim putem, ali ga daju u talasima kreditnih balona sa malim delićem rezerve. ““ — Satoshi Nakamoto
Istorija zloupotrebe tradicionalnih valuta može se grupisati u 3 kategorije:
• Bezbednost. Loši ljudi kradu vaš novac ili vrednost vašeg novca, ponekad na očigledne načine, ponekad na podle načine.
• Privatnost. Loši ljudi nadgledaju sve vaše privatne finansijske transakcije, i koriste vaše lične finansijske podatke protiv vas.
• Sloboda. Loši ljudi kontrolišu na koji način možete da trošite sopstveni novac, sa kim možete da obavljate transakcije, koliko možete da potrošite itd.
Kako mogu ljudi da mi ukradu novac ako je u banci?
Evo nekoliko primera:
- Krađa inflacijom: Ovo je primarni način na koji banke kradu vaš novac i jedan od najpodlijih. Kada centralne banke izdaju novi novac, bilo štampanjem na bezvrednom papiru, ili samo dodavanjem knjigovodstvenog unosa u bazu podataka koju kontrolišu, one naduvaju globalnu novčanu masu. Inflacija krade kupovnu moć svih koji drže deo te valute, jednostavno zato što je sada više te valute u opticaju. Zlato se ne može stvoriti, pa su bankari umesto toga izmislili sistem papirnog novca.

Banke mogu izdavati beskonačnu količinu tradicionalnih valuta, bilo štampanjem ili korišćenjem digitalne baze podataka.
- Krađa zaplenom: Ovo je jedan od načina na koji vlade mogu ukrasti vaš novac. Da li ste ikada čuli za zaplenu imovine? Ako policajac posumnja da je vaša imovina korišćena u krivičnom delu, može je zapleniti, a vi se morate boriti da biste povratili vašu ukradenu imovinu. Ili, drugi primer: Pokušajte da uđete u zemlju sa više od 10.000 USD u džepu, a ne da je prijavite, i pogledajte šta će se dogoditi. Sve je isto: krađa od strane drugih ljudi sa oružjem.
Man who immigrated to the U.S. from Albania says U.S. agents seized his life savings at airport. https://t.co/RyoZzrpVA4 pic.twitter.com/yJnUVaCNaa
— ABC News (@ABC) June 7, 2018- Krađa putem oporezivanja: Ovo je još jedan način na koji vam vlade kradu novac. Ne sporim da li je oporezivanje etično ili ne, samo konstatujem činjenicu da vaša vlada može da primora vašu banku da im da vaš novac, a ovo je bezbednostna ranjivost. Da bi novac bio siguran, mora biti nezaplenjiv, a vlade mogu da zaplene vaše bankovne račune.

Kako ljudi koriste moje finansijske podatke protiv mene?
Ako fizičku tradicionalnu valutu predate drugoj osobi, u obliku papirnog novca ili kovanica, relativno je lako zaštititi privatnost svoje transakcije, baš kao što bi bilo da koristite zlatnike.
Međutim, ako koristite kreditne kartice, debitne kartice, bankovne transfere, PayPal, Venmo, LINE Pay, WeChat Pay ili bilo koju drugu mrežu za plaćanje koja je centralno kontrolisana, aktivno pristajete da se odreknete privatnosti podataka svih svojih privatnih finansijskih transakcija i sve ih dajete poverljivoj trećoj strani.
Kada su svi podaci i metapodaci vaših finansijskih transakcija prijavljeni u centralnu bazu podataka, onaj ko ima pristup toj bazi podataka može da koristi vaše podatke protiv vas.
Evo nekoliko osnovnih primera:
- Ako ste kupili robu rizičnog životnog stila poput cigareta, banka može reći vašoj osiguravajućoj kompaniji da poveća vaše osiguranje.
- Ako ste kupili nešto što je ilegalno, poput droga za rekreaciju, vaša banka može reći vašoj vladi da vas zakonski goni.
Ali u slučaju nekih represivnih vlada, oni su to odveli do ekstrema. Oni centralno prikupljaju sve finansijske transakcije i druge podatke svih svojih građana i stvorili su totalitarni Sistem Socijalnih Bodova (eng. Social Credit Score):
 Prepoznavanje lica je jedan od elemenata kineskih napora za praćenje
Prepoznavanje lica je jedan od elemenata kineskih napora za praćenjeZapisi George Orwell-a već su postali stvarnost u Kini zbog sistema tradicionalnih valuta centralne banke i platnih mreža koje su izgrađene na njemu.
Ako mislite da se to neće dogoditi u vašoj zemlji, razmislite ponovo.
To se dešava vrlo polako, ali na kraju će sve svetske vlade primeniti Sistem Socijalnih Bodova, dok je Kina to tek prva učinila.
Kako ljudi kontrolišu sa kim obavljam transakcije?
U prvom primeru sa zlatnim novčićem, kada ga predate nekom drugom kao plaćanje za robu ili uslugu, ne postoji centralizovana evidencija vaše platne transakcije i imate savršenu privatnost.
Međutim, u centralnom bankarskom sistemu, budući da banka ima i znanje o podacima o vašim transakcijama i moć da kontroliše vaša sredstva, oni mogu proceniti niz pravila da bi odlučili da li žele da dozvole vašu transakciju ili da to odbiju, takođe kao i izvršenje te odluke kontrolišući vaša sredstva.
Tako su vlade naoružale tradicionalne valute i centralni bankarski sistem kao Sistem Kontrole nad svojim građanima.
Da rezimiramo: Pošto ste se odrekli bezbednosti i privatnosti svog novca, izgubili ste i svoju finansijsku slobodu.
“Privatnost nije o tome da nešto treba sakriti. Privatnost je o tome da nešto treba zaštititi.” — Edward Snowden
Kako da povratimo svoj finansijski samo-suverenitet?
Pokret Cypherpunk pokrenuli su pojedinci koji su shvatili važnost zaštite privatnosti i slobode pojedinačnih korisnika na Internetu.
Cypherpunk-ovi su verovali da se gore opisani problemi mogu rešiti samo potpuno novim novčanim sistemom, koji poštuje i štiti bezbednost, privatnost i slobodu pojedinca.
Mnogi od Cypherpunk-era pokušali su da izgrade nove etičke sisteme e-gotovine koji bi mogli da zamene tradicionalne valute i centralno bankarstvo.
Bilo je mnogo teških računarskih problema koje je trebalo prevazići u stvaranju tako istinski decentralizovanog sistema, i ako su neki od njih bili blizu cilja, svi su propali.
Odnosno, sve dok jedan pseudonim Cypherpunk-a to konačno nije shvatio 2008. godine:

Kombinacijom digitalnih potpisa, distribuirane knjige i peer-to-peer mreže, rođen je Bitcoin.
Kako Bitcoin funkcioniše?
Baš kao što ne treba da znate kako Internet funkcioniše da bi gledali slike mačaka na Internetu, razumevanje tehničke složenosti načina na koji Bitcoin radi „ispod haube“ nije neophodno da biste ga koristili i postigli sopstveni finansijski samo-suverenitet.
Važna stvar koju želim da saznate iz ovog članka je da iako većina novih tehnologija u početku ima loše korisničko iskustvo, Bitcoin svesno i vrlo namerno ne žrtvuje svoje osnovne filozofske principe da bi brže pridobio nove korisnike, ili da bi poboljšao korisničko iskustvo.
Najpametniji Cypherpunk-ovi rade na poboljšanju korisničkog iskustva.
Tehnologija će se sa vremenom poboljšavati, baš kao i za Internet.

Pa onda, zašto Bitcoin?
Reći ću vam zašto:
Jer Bitcoin poštuje bezbednost, privatnost i slobodu pojedinca.
Po čemu je Bitcoin bolji od sistema tradicionalnih valuta?
Za početak, Bitcoin nema Uslove korišćenja, Politiku privatnosti i Propise o usklađenosti sa KYC/AML. (Know Your Costumer & Anti-money Laundering)
Bitcoin je uspešan primer implementacije kripto-anarhije, gde su jedina pravila kriptografija, matematika i jak skup konsenzusnih pravila.
To je distribuirani i nepoverljivi sistem zasnovan na finansijskim podsticajima i nijedna osoba ili centralizovani entitet ne može da kontroliše Bitcoin.
Ono što je najvažnije, Bitcoin vam omogućava da odustanete od tradicionalnih valuta, sistema delimičnih rezervi i centralnog bankarstva rešavanjem osnovnih problema poverenja:
- Sigurnost od inflacije korišćenjem fiksnog snabdevanja
- Sigurnost od zaplene korišćenjem ključeva za kontrolu sredstava
- Privatnost plaćanja korišćenjem pseudonimnih identiteta
- Sloboda protiv cenzure korišćenjem peer to peer mreže

Peer to Peer Mreža
Kako Bitcoin štiti od Inflacije?
Jedno od najkritičnijih pravila konsenzusa o Bitcoin-u je da može postojati najviše 21,000,000 Bitcoin-a.
Nakon izdavanja svih Bitcoin-a, nikada više ne može doći do stvaranja novih Bitcoin-a.
Stoga je Bitcoin deflaciona valuta, koja sprečava ljude da ukradu vaš novac ili njegovu vrednost naduvavanjem novčane mase.
 Monetarna Inflacija Bitcoin-a
Monetarna Inflacija Bitcoin-aKako Bitcoin štiti od Zaplene?
Bitcoin se može preneti samo pomoću kriptografskog privatnog ključa koji kontroliše sredstva.
Nijedan bitcoin nikada ne izadje van sistema.
Nijedna vlada, banka ili sudski nalog ne mogu zapleniti ta sredstva.
Jednostavno ne postoji način da se takva odredba ili naredba sprovede od bilo kog „organa vlasti“, jer Bitcoin ne priznaje nijedno „ovlašćenje“ u svom sistemu.
Bitcoin je potpuno samo-suveren sistem i zbog svoje distribuirane prirode ne može se ugasiti.
Postoji zbog sopstvenih zasluga, samo zato što ljudi veruju u to.
Kako Bitcoin štiti Privatnost?
Bitcoin ne traži vaše ime ili druge detalje koji mogu lično da vas identifikuju.
Vaš identitet je kriptografski, a ne vaše stvarno ime.
Dakle, vaš identitet izgleda otprilike kao 1vizSAISbuiKsbt9d8JV8itm5ackk2TorC, a ne kao „Stefan Petrovič“.
Pored toga, niko ne zna ko kontroliše sredstva na datoj Bitcoin adresi, a nova tehnologija se neprestano razvija kako bi se poboljšala privatnost Bitcoin-a.

”Taproot” je najnovije poboljšanje bitcoin-a i njegove privatnosti.
Kako Bitcoin štiti od Cenzure?
Peer-to-peer Bitcoin mreža je u potpunosti distribuirana.
To znači da ako jedan čvor pokuša da cenzuriše vašu transakciju, neće uspeti ukoliko * svaki * čvor(Node) ne izvrši cenzuru vaše transakcije.

Centralizacija – Loša. Decentralizacija – Dobra. Distribuiran peer-to-peer – Najbolja.
Šta će vlada i banke učiniti sa Bitcoin-om?
Neke zemlje su pokušale da ga regulišu, kontrolišu, isključe itd., ali nijedna od njih nije uspela.
Čini se da uglavnom samo žele da koriste postojeći sistem centralnih banaka da bi kontrolisali kako ljudi trguju tradicionalnim valutama za Bitcoin, i naravno žele da oporezuju Bitcoin na bilo koji mogući način.
Evo nekoliko uobičajenih tvrdnji vlada i banaka o Bitcoin-u:
Lane: No. Bitcoin is not a currency, it rather is an asset and it is very volatile #AskECB https://t.co/XQ9Mqdm5rU
— European Central Bank (@ecb) July 9, 2019Evropska centralna banka kaže da Bitcoin nije valuta i upozorava da je vrlo nestabilna.

„Bitcoin, izgleda samo kao prevara“, rekao je gospodin Tramp. „Ne sviđa mi se jer je to još jedna valuta koja se takmiči sa dolarom.“
Da li je vrednost Bitcoin-a nestabilna?
Ako umanjite grafikon cena, videćete da Bitcoin-u neprekidno raste vrednost od kada je stvoren, trgujući sa manje od 0,01 USD i polako se penje na preko 60.000 USD na nedavnom vrhuncu početkom 2021. godine.
 Cena Bitcoina od 2011. godine
Cena Bitcoina od 2011. godineTo je zato što je njegova ponuda fiksna i ljudi cene njegovu nestašicu.
Sa većom potražnjom i fiksnom ponudom, cene vremenom rastu.
Kako godine odmiču, njegova vrednost će se povećavati kako novi korisnici počinju da drže Bitcoin. (U svetu Bitcoina držanju kažemo HODL. Drži bitcoin. Hodl bitcoin.)

Zašto Bitcoin ima vrednost : Nestašica
Da li je Bitcoin novac?
Da biste odgovorili na pitanje da li je Bitcoin novac ili ne, prvo morate definisati pojam „novac“.
Nažalost, reč „novac“ koristimo da bismo opisali nekoliko vrlo različitih komplikovanih koncepata, koji su svi potpuno odvojeni.
Termin „novac“ se zapravo odnosi na:
- Zaliha Vrednosti (Store of Value)
- Sredstvo Razmene ( Medium of Exchange)
- Obračunska Jedinica (Unit of Account)
- Sistem Kontrole (System Control)
Bitcoin kao Zaliha Vrednosti
Ovaj to savršeno objašnjava:
Son's friend: "Matt, what happens if you chop a £1 coin in half?"
— Matthew Haywood (@wintercooled) July 13, 2019
You get to two pieces of worthless metal mate. If you chop a gold coin in half though, you get two pieces of gold, each worth half of what the coin was.
Son: "...and it's the same as gold with bitcoin."
🤗Sinov prijatelj: “Matt, šta će se dogoditi ako novčić od 1 funte usitnite na pola?”
Dobijaš dva komada bezvrednog metala. Ako zlatnik usitnite na pola, dobićete dva zlatnika, od kojih svaki vredi polovinu onoga što je novčić bio.
Sin: „… isto tako kao sa zlatom jeste sa bitcoinima“.
Bitcoin je potpuno deljiv i deluje kao izvrsna zaliha vrednosti, baš kao što je i zlato već hiljadama godina.
Bitcoin kao Sredstvo Razmene
Bitcoin je dobro služio kao sredstvo razmene za svoje rane korisnike.
Ali skaliranje Bitcoin-a na globalni nivo koji bi mogao da posluži svim ljudima je veliki izazov, jer se osnovna „blockchain“ tehnologija ne skalira na globalni nivo.
Da bi rešio ovaj problem skaliranja, Satoshi je izumeo koncept kanala plaćanja, a u kombinaciji sa malo pomoći drugih briljantnih računarskih naučnika Cipherpunk-a koji su poboljšali koncept tokom poslednjih 10 godina, sada imamo mrežu Lightning, koja omogućava da se Bitcoin koristi kao odlično Sredstvo Razmene, koje se vremenom može proširiti na globalni nivo.

Internet Informacija i Vrednosti Danas
Bitcoin kao Obračunska Jedinica
Najmanja obračunska jedinica Bitcoin-a nazvana je po njenom tvorcu, Satoshi-u.
Jedan Bitcoin je jednak 100.000.000 Satoshi-a.
Na kraju, kako se robe i usluge sve češće razmenjuju za Bitcoin, sve više ljudi će koristiti Bitcoin ili „Sats“ kao obračunsku jedinicu.

Bitcoin u Satoshi Pretvarač Credits: @kriptomentor Instagram Profil
Bitcoin kao Sistem Kontrole
Budući da je Bitcoin dizajniran da poštuje i štiti ljudska prava pojedinca, posebno bezbednost, privatnost i slobodu novca; ne bi bio dobar Sistem Kontrole i ne može se koristiti za ugnjetavanje ljudi, kao što se dešava sa tradicionalnim valutama i sistemima centralnog bankarstva koji to trenutno vrlo dobro rade.

Fiat sistem novca: dominacija i kontrola
Šta je sa „Sledećim Bitcoin-om“?
Kao što može biti samo jedan „globalni“ Internet, tako može biti i samo jedan globalni novac, a stigao je i novi Bitcoin Standard.
Sve ostalo je ili direktna prevara ili gubljenje vremena.
Ako bi neko želeo da vam proda „Sledeće Zlato“, da li biste ga kupili?
Na kraju
Nadam se da vam je ovaj članak pomogao da razumete zašto je Bitcoin stvoren i kako može da pomogne svetu da se oslobodi tradicionalnih valuta i sistema centralnog bankarstva koji je veoma duboko integrisan u naše trenutno društvo.
Evo nekoliko misli koje treba poneti sa sobom:
- Bitcoin nije izmišljen radi zarade, već je izmišljen da bi promenio svet.
- Bitcoin će to učiniti poštujući korisnikovu bezbednost, privatnost i slobodu.
- Bitcoin se već koristi kao novac, na nekoliko načina na koji se novac može koristiti.
- Bitcoin nije nestabilan, njegova vrednost vremenom polako raste (odzumirajte).
- Bitcoin ima mnogo kopija i prevaranata koji će pokušati da vam prodaju svoju kopiju Bitcoin-a. Ne zavaravajte se lažnim Bitcoin-om baš kao što vas ne bi prevarili ni Lažnim Zlatom.
- Bitcoin će postati najveći prenos bogatstva u našem životu, tako da ćete možda želeti da ih uzmete pre nego kasnije.
- Ostanite skromni i skupljajte satošije.
-
 @ 2e8970de:63345c7a
2025-06-03 17:33:37
@ 2e8970de:63345c7a
2025-06-03 17:33:37https://www.wsj.com/finance/investing/wall-street-bond-market-us-debt-990e12e9?mod=hp_lead_pos7
https://stacker.news/items/996265
-
 @ bf47c19e:c3d2573b
2025-06-03 17:26:11
@ bf47c19e:c3d2573b
2025-06-03 17:26:11Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Šta je Bitcoin?
- Šta Bitcoin može da učini za vas?
- Zašto ljudi kupuju Bitcoin?
- Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
- Šta je bolje za štednju od dolara, kuća i akcija?
- Po čemu se Bitcoin razlikuje od ostalih valuta?
- kako Bitcoin spašava svet?
- Kako mogu da saznam više o Bitcoin-u?
Bitcoin čini da štednja novca bude kul – i praktična – ponovo. Ovaj članak objašnjava kako i zašto.
Šta je Bitcoin?
Bitcoin se naziva digitalno zlato, mašina za istinu, blockchain, peer to peer mreža čvorova, energetski ponor i još mnogo toga. Bitcoin je, u stvari, sve ovo. Međutim, ova objašnjenja su često toliko tehnička i suvoparna, da bi većina ljudi radije gledala kako trava raste. Što je najvažnije, ova objašnjenja ne pokazuju kako Bitcoin ima bilo kakve koristi za vas.
iPod nije postao kulturološka senzacija jer ga je Apple nazvao „prenosnim digitalnim medijskim uređajem“. Postao je senzacija jer su ga zvali “1,000 pesama u vašem džepu.”

Ne zanima vas šta je Bitcoin. Vas zanima šta on može da učini za vas.
Baš kao i Internet, vaš auto, vaš telefon, kao i mnogi drugi uređaji i sistemi koje svakodnevno koristite, vi ne treba da znate šta je Bitcoin ili kako to funkcioniše da biste razumeli šta on može da učini za vas.
Šta Bitcoin može da učini za vas?
Bitcoin može da sačuva vaš teško zarađeni novac.

Bitcoin je stekao veliku pažnju u 2017. i 2018. godini zbog svoje spekulativne upotrebe. Mnogi ljudi su ga kupili nadajući se da će se obogatiti. Cena je naglo porasla, a zatim se srušila. Ovo nije bio prvi put da je Bitcoin uradio to. Međutim, niko nikada nije izgubio novac držeći bitcoin duže od 3,5 godine – ćak i ako je kupio na apsolutnim vrhovima.

Zašto Bitcoin konstantno raste? Ljudi počinju da shvataju koliko je Bitcoin moćan, kao način uštede novca u svetu u kojem je ’novac’ poput dolara, eura i drugih nacionalnih valuta dizajniran da gubi vrednost.
Ovo čini Bitcoin odličnom opcijom za štednju novca na nekoliko godina ili više. Bitcoin je bolji od štednje novca u dolarima, akcijama, nekretninama, pa čak i u zlatu.
Zato pokušajte da zaboravite na trenutak na razumevanje blockchaina, digitalne valute, kriptografije, seed fraza, novčanika, rudarstva i svih ostalih nerazumljivih termina. Za sada, razgovarajmo o tome zašto ljudi kupuju Bitcoin: razlog je prostiji nego što vi mislite.
Zašto ljudi kupuju Bitcoin?
Naravno, svako ima svoj razlog za kupovinu Bitcoin-a. Jedan od razloga, koji verovatno često čujete, je taj što mu vrednost raste. Ljudi žele da se obogate. Uskoče kao spekulanti, krenu u vožnju i najverovatnije ih prodaju ubrzo nakon kupovine.
Međutim, čak i kada cena krene naglo prema gore i strmoglavo padne nazad, mnogi ljudi ostanu i nakon tog pada. Otkud mi to znamo? Broj aktivnih novčanika dnevno, koji je otprilike sličan broju korisnika Bitcoin-a, nastavlja da raste. Takođe, nakon svakog balona u istoriji Bitcoin-a, cena se nikada ne vraća na svoju cenu pre balona. Uvek ostane malo višlja. Bitcoin se penje, a svaka masovna spekulativna serija dovodi sve više i više ljudi.
Broj aktivnih Bitcoin novčanika neprekidno raste
„Aktivna adresa“ znači da je neko tog dana poslao Bitcoin transakciju. Donji grafikon je na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeCena Bitcoina se neprestano penje
Kroz istoriju Bitcoin-a možemo videti divlje kolebanje cena, ali nakon svakog balona, cena se ostaje višlja nego pre. Ovo je cena Bitcoin-a na logaritamskoj skali.
 Izvor: Glassnode
Izvor: GlassnodeTo pokazuje da se ljudi zadržavaju: potražnja za Bitcoin-om se povećava. Da je svaki masovni rast cena bio samo balon koji su iscenirali prevaranti koji žele brzo da se obogate, cena bi se vratila na nivo pre balona. To se dogodilo sa lalama, ali ne i sa Bitcoin-om.
I zašto se onda cena Bitcoin-a stalno povećava? Sve veći broj ljudi čuva Bitcoin dugoročno – oni razumeju šta Bitcoin može učiniti za njihovu štednju.
Zašto ljudi štede svoj novac u Bitcoin-u umesto na štednim računima, kućama, deonicama ili zlatu? Hajde da pogledajmo sve te metode štednje, i zatim da ih uporedimo sa Bitcoin-om.
Da li je vaš novac siguran u dolarima, kućama, akcijama ili zlatu?
Tokom mnogo godina, to su bile pristojne opcije za štednju. Međutim, sistem koji podržava vrednost svega ovoga je u krizi.
Dolari, Euri, Dinari
Dolari i sve ostale „tradicionalne“ valute koje proizvode vlade, stvorene su da izgube vrednost kroz inflaciju. Banke i tradicionalni monetarni sistem uzrokuju inflaciju stalnim stvaranjem i distribucijom novog novca. Kada Američke Federalne Rezerve objave ciljanu stopu od 2% inflacije, to znači da žele da vaš novac svake godine izgubi 2% od svoje vrednosti. Čak i sa inflacijom od samo 2%, vaša štednja u dolarima izgubiće polovinu vrednosti tokom 40-godišnjeg radnog veka.
Izveštena inflacija se danas opasno povečava, uprkos rastućem „buretu sa barutom“ koji bi mogao da explodira i dovede do masivne hiperinflacije. Što je više valute u opticaju, to je više baruta u buretu.

Naše vlade su ekonomiju napunile valutama da bankarski sistem ne bi propao nakon finansijske krize koja se dogodila 2008. godine. Od tada je većina glavnih centralnih banaka postavila vrlo niske kamatne stope, što pojedincima i korporacijama omogućava dobijanje jeftinijih kredita. To znači da mnogi pojedinci i korporacije podižu ogromne kredite i koriste ih za kupovinu druge imovine poput deonica, umetničkih dela i nekretnina. Sve ovo pozajmljivanje znači da stvaramo tone novog novca i stavljamo ga u opticaj.
Računi za podsticaje (stimulus bills) COVID-19 za 2020. godinu unose trilione u sistem. Ovoliko stvaranje valuta na kraju dovodi do inflacije – velikog gubitka u vrednosti valute.
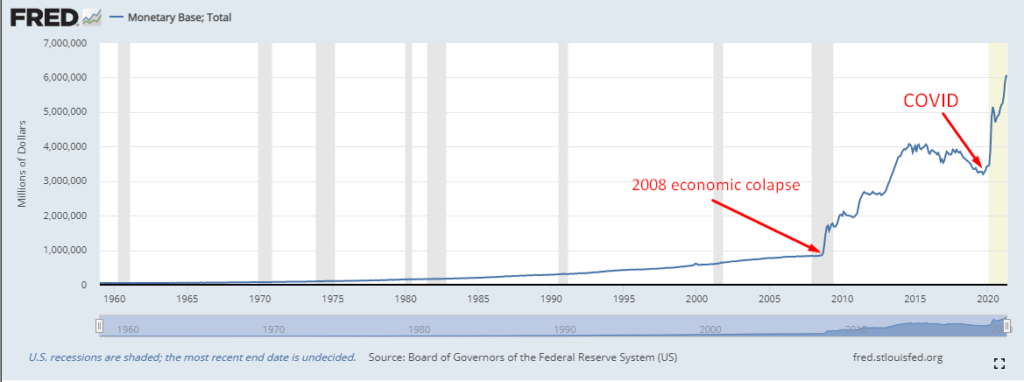 Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. Izvor
Količina američkog dolara u opticaju gotovo se udvostručila od marta 2020. godine. IzvorRačuni za podsticaje su bez presedana, toliko da je neko izmislio meme da opiše ovu situaciju.

Resurs koji vlade mogu da naprave u većem broju da bi platile svoje račune? Ne zvuči kao dobro mesto za štednju novca.
Kuće
Kuće su tokom prošlog veka bile pristojan način štednje novca. Međutim, pad cena nekretnina 2007. godine doveo je do toga da su mnogi vlasnici kuća izgubili svu ušteđevinu.
Danas su kuće gotovo nepristupačne za prosečnog čoveka. Jedan od načina da se ovo izmeri je koliko godišnjih zarada treba prosečnom čoveku da zaradi ekvivalent vrednosti prosečne kuće. Prema CityLab-u, publikaciji Bloomberg-a koja pokriva gradove, porodica može da priuštiti određenu kuću ako košta manje od 2,6 godišnjih prihoda domaćinstva te porodice.
Međutim, prema RZS (Republički zavod za statistiku) prosečan prihod porodičnog domaćinstva u Srbiji iznosi oko 570 EUR mesečno ili otprilike 7.000 EUR godišnje. Nažalost, samo najjeftinija područja van gradova imaju srednje cene kuća od oko 2,6 prosečnih godišnjih prihoda domaćinstva. U većim gradovima poput Beograda i Novog Sada srednja cena kuće je veća od 10 prosečnih godišnjih prihoda jednog domaćinstva.

Ako nekako možete sebi da priuštite kuću, ona bi mogla biti pristojna zaliha vrednosti. Dokle god ne doživimo još jedan krah i izvršitelji zaplene ovu imovinu mnogim vlasnicima kuća.
Akcije
Berza je u prošlosti takođe dobro poslovala. Međutim, sporo i stabilno povećanje tržišta događa se u dosadnom, predvidljivom svetu. Svakog dana vidimo sve manje toga. Nakon ubrzanja korona virusa, videli smo smo najbrži pad američke berze u istoriji od 25% – brži od Velike depresije.
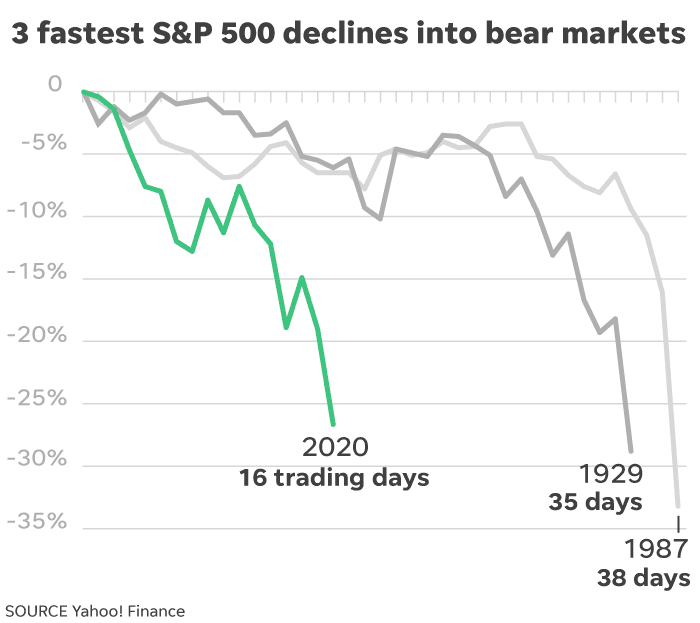
Neki se odlučuju za ulaganje u obveznice i drugu finansijsku imovinu, ali ’prinosi’ za tu imovinu – procenat kamate zarađene na imovinu iz godine u godinu – stalno opada. Sve veći broj odredjenih imovina ima čak i negativne prinose, što znači da posedovanje te imovine košta! Ovo je veliki problem za sve koji se oslanjaju na penziju. Plus, s obzirom na to da su akcije denominovane u tradicionalnim valutama poput dolara i evra, inflacija pojede prinos koji investitor dobije.
Najgore od svega je to što ti isti ekonomski krahovi koji uzrokuju masovna otpuštanja i teško tržište rada takođe znače i nagli pad cena akcija. Čuvanje ušteđevine u akcijama može značiti i gubitak štednje i gubitak posla zbog recesije. Teška vremena mogu da vas prisile da svoje akcije prodate po vrlo malim cenama samo da biste platili svoje račune.
A to nije baš siguran način štednje novca.
Zlato
Vrednost zlata neprekidno se povećavala tokom 5000 godina, obično padajući onda kada berza obećava jače prinose.
Evidencija vrednosti zlata je solidna. Međutim, zlato nosi i druge rizike. Većina ljudi poseduje zlato na papiru. Oni fizički ne poseduju zlato, već ga njihova banka čuva za njih. Zbog toga je zlato veoma podložno konfiskaciji od strane vlade.
Zašto bi vlada konfiskovala nečije zlato, a kamoli u demokratskoj zemlji u „slobodnom svetu“? Ali to se dešavalo i ranije. 1933. godine Izvršnom Naredbom 6102, predsednik Roosevelt naredio je svim Amerikancima da prodaju svoje zlato vladi u zamenu za papirne dolare. Vlada je iskoristila pretnju zatvorom za prikupljanje zlata u fizičkom obliku. Znali su da se zlato više poštuje kao zaliha vrednosti širom sveta od papirnih dolara.

Ako posedujete svoje zlato na nekoj od aplikacija za trgovanje akcijama, možete se kladiti da će vam ga država oduzeti ako joj zatreba. Čak i ako posedujete fizičko zlato, onda ga izlažete mogućnosti krađe – od strane kriminalca ili vaše vlade.
Vaša uštedjevina nije bezbedna.
Rast cena svih gore navedenih sredstava zavisi od našeg trenutnog političkog i ekonomskog sistema koji se nastavlja kao i tokom proteklih 100 godina. Međutim, danas vidimo ogromne pukotine u ovom sistemu.
Sistem ne funkcioniše dobro za većinu ljudi.
Od 1971. plate većine američkih radnika nisu rasle. S druge strane, bogatstvo koje imaju najbogatiji u društvu nalazi se na nivoima koji nisu viđeni više od 80 godina. U međuvremenu, ljudi sve manje i manje veruju institucijama poput banaka i vlada.
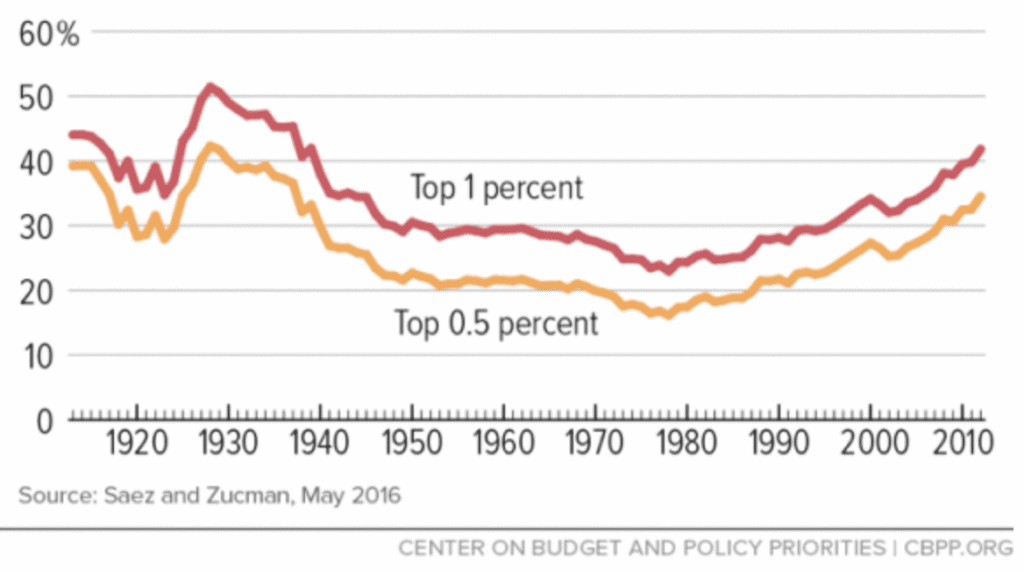 CBPP Nejednakost Bogatstva Tokom Vremena
CBPP Nejednakost Bogatstva Tokom Vremena
Širom sveta možemo videti dokaze o slamanju sistema kroz politički ekstremizam: izbor Trampa i drugih ekstremističkih desničarskih kandidata, Bregzit, pokret Occupy, popularizacija koncepta univerzalnog osnovnog dohotka, povratak pojma „socijalizam“ nazad u modu. Ljudi na svim delovima političkog i društvenog spektra osećaju problematična vremena i posežu za sve radikalnijim rešenjima.
Šta je bolje za štednju od dolara, kuća i akcija?
Pa kako ljudi mogu da štede novac u ovim teškim vremenima? Ili ne koriste tradicionalne valute, ili kupuju sredstva koja će zadržati vrednost u teškim vremenima.
Bitcoin ima najviše potencijala da zadrži vrednost kroz politička i ekonomska previranja od bilo koje druge imovine. Na tom putu će biti rupa na kojima će se rušiti ili pumpati, međutim, njegova svojstva čine ga takvim da će verovatno preživeti previranja kada druga imovina ne bude to mogla.
Šta Bitcoin čini drugačijim?
Bitcoini su retki.
Proces ‘rudarenja’ bitcoin-a, proizvodnju bitcoin-a čini veoma skupom, a Bitcoin protokol ograničava ukupan broj bitcoin-a na 21 milion novčića. To čini Bitcoin imunim na nagle poraste ponude. Ovo se veoma razlikuje od tradicionalnih valuta, koje vlade mogu da štampaju sve više kad god one to požele. Zapamtite, povećanje ponude vrši veliki pritisak na vrednost valute.
Bitcoini nemaju drugu ugovornu stranu.
Bitcoin se takođe razlikuje od imovine kao što su obveznice, akcije i kuće, jer mu nedostaje druga ugovorna strana. Druge ugovorne strane su drugi subjekti uključeni u vrednost sredstva, koji to sredstvo mogu obezvrediti ili vam ga uzeti. Ako imate hipoteku na svojoj kući, banka je druga ugovorna strana. Kada sledeći put dođe do velikog finansijskog kraha, banka vam može oduzeti kuću. Kompanije su kvazi-ugovorne strane akcijama i obveznicama, jer mogu da počnu da donose loše odluke koje utiču na njihovu cenu akcija ili na „neizvršenje“ duga (da ga ne vraćaju vama ili drugim poveriocima). Bitcoin nema ovih problema.
Bitcoin je pristupačan.
Svako sa 5 eura i mobilnim telefonom može da kupi i poseduje mali deo bitcoin-a. Važno je da znate da ne morate da kupite ceo bitcoin. Bitcoin-i su deljivi do 100-milionite jedinice, tako da možete da kupite Bitcoin u vrednosti od samo nekoliko eura. Neuporedivo lakše nego kupovina kuće, zlata ili akcija!
Bitcoin se ne može konfiskovati.
Banke drže većinu vaših eura, zlata i akcija za vas. Većina ljudi u razvijenom svetu veruje bankama, jer većina ljudi koji žive u današnje vreme nikada nije doživela konfiskaciju imovine ili ’šišanje’ od strane banaka ili vlada. Nažalost, postoji presedan za konfiskaciju imovine čak i u demokratskim zemljama sa snažnom vladavinom prava.
Kada vlada konfiskuje imovinu, ona obično ubedi javnost da će je menjati za imovinu jednake vrednosti. U SAD-u 1930-ih, vlada je davala dolare vlasnicima zlata. Vlada je znala da uvek može da odštampa još više dolara, ali da ne može da napravi više zlata. Na Kipru 2012. godine, jedna propala banka je svojim klijentima dala deonice banke da pokrije dolare klijenata koje je banka trebala da ima. I dolari i deonice su strmoglavo opali u odnosu na imovinu koja je uzeta od ovih ljudi.
Doći do bitcoin-a koji ljudi poseduju, biće mnogo teže jer se bitcoin-i mogu čuvati u novčaniku koji ne poseduje neka treća strana, a vi možete čak i da zapamtite privatne ključeve do vašeg bitcoin-a u glavi.
Bitcoin je za štednju.
Bitcoin se polako pokazuje kao najbolja opcija za dugoročnu štednju novca, posebno s obzirom na današnju ekonomsku klimu. Posedovanje čak i malog dela, je polisa osiguranja koja se isplati ako svet i dalje nastavi da ludi. Cena Bitcoin-a u dolarima može divlje da varira u roku od godinu ili dve, ali tokom 3+ godine skoro svi vide slične ili više cene od trenutka kada su ga kupili. U stvari, doslovno niko nije izgubio novac čuvajući Bitcoin duže od 3,5 godine – čak i ako je kupio BTC na apsolutnim vrhovima tržišta.

Imajte na umu da nakon ove tačke ti ljudi više nikada nisu videli rizik od gubitka. Cena se nikada nije smanjila niže od najviše cene u prethodnom ciklusu.
Po čemu se Bitcoin razlikuje od ostalih valuta?
Bitcoin funkcioniše tako dobro kao način štednje zbog svog neobičnog dizajna, koji ga čini drugačijim od bilo kog drugog oblika novca koji je postojao pre njega. Bitcoin je digitalna valuta, prvi i verovatno jedini primer valute koja ima ograničenu ponudu dok radi na otvorenom, decentralizovanom sistemu. Vlade strogo kontrolišu valute koje danas koristimo, poput dolara i eura, i proizvode ih za finansiranje ratova i dugova. Korisnici Bitcoin-a – poput vas – kontrolišu Bitcoin protokol.
Evo šta Bitcoin razlikuje od dolara, eura i drugih valuta:
Bitcoin je otvoren sistem.
Svako može da odluči da se pridruži Bitcoin mreži i primeni pravila softverskog protokola, što je dovelo do vrlo decentralizovanog sistema u kojem nijedan pojedinac ili entitet ne može da blokira transakciju, zamrzne sredstva ili da ukrade od druge osobe.Današnji savremeni bankarski sistem se uveliko razlikuje. Nekoliko banaka je dobilo poverenje da gotovo sve valute, akcije i druge vredne predmete čuvaju na “sigurnom” za svoje klijente. Da biste postali banka, potrebni su vam milioni dolara i neverovatne količine političkog uticaja. Da biste pokrenuli Bitcoin čvor i postali „svoja banka“, potrebno vam je nekoliko stotina dolara i jedno slobodno popodne.
 Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.
Tako izgleda Bitcoin čvor – Node
MyNode čvor vam omogućava da postanete svoja banka za samo nekoliko minuta.Bitcoin ima ograničenu ponudu.
Softverski protokol otvorenog koda koji upravlja Bitcoin sistemom ograničava broj novih bitcoin-a koji se mogu stvoriti tokom vremena, sa ograničenjem od ukupno 21.000.000 bitcoin-a. S druge strane, valute koje danas koristimo imaju neograničenu ponudu. Istorija i sadašnje odluke centralnih banaka govore nam da će vlade uvek štampati sve više i više valuta, sve dok valuta ne bude bezvredna. Sve ovo štampanje uzrokuje inflaciju, što pravi štetu običnim radnim ljudima i štedišama.
Tradicionalne valute su dizajnirane tako da opadaju vremenom. Svaki put kada centralna banka kaže da cilja određenu stopu inflacije, oni ustvari kažu da žele da vaš novac svake godine izgubi određeni procenat svoje vrednosti.
Bitcoin-ova ograničena ponuda znači da je on tako dizajniran da raste vremenom kako se potražnja za njim povećava.

Bitcoin putuje oko sveta za nekoliko minuta.
Svako može da pošalje bitcoin-e za nekoliko minuta širom sveta, bez obzira na granice, banke i vlade. Potrebno je manje od minuta da se transakcija pojavi na novčaniku primaoca i oko 60 minuta da se transakcija u potpunosti „obračuna“, tako da primaoc može da bude siguran da su primljeni bitcoin-i sada njegovi (6 konfirmacija bloka). Slanje drugih valuta širom sveta traje danima ili čak mesecima ako se šalju milionski iznosi, a podrazumeva i visoke naknade.
Neke vlade i novinari tvrde da ova sloboda putovanja koju pruža Bitcoin pomaže kriminalcima i teroristima. Međutim, transakciju Bitcoin-a je lakše pratiti nego većinu transakcija u dolarima ili eurima.
Bitcoin se može čuvati na “USB-u”.
Dizajn Bitcoin-a je takav da vam treba samo da čuvate privatni ključ do svojih ‘bitcoin’ adresa (poput lozinke do bankovnih računa) da biste pristupili svojim bitcoin-ima odakle god poželite. Ovaj privatni ključ možete da sačuvate na disku ili na papiru u obliku 12 ili 24 reči na engleskom jeziku. Kao rezultat toga, možete da držite Bitcoin-e vredne milione dolara u svojoj šaci.
Sve ostale valute danas možete ili da strpate u svoj dušek ili da ih poverite banci na čuvanje. Za većinu ljudi koji žive u razvijenom svetu, i koji ne osporavaju autoritet i poverenje u banku, ovo deluje sasvim dobro. Međutim, oni kojima je potrebno da pobegnu od ugnjetavačke vlade ili koji naljute pogrešne ljude, ne mogu verovati bankama. Za njih je sposobnost da nose svoju ušteđevinu bez potrebe za ogromnim koferom neprocenjiva. Čak i ako ne živite na mestu poput ovog, cena Bitcoin-a se i dalje povećava kada ih neko kome oni trebaju kupi.
Kako Bitcoin spašava svet?
Bitcoin, kao ultimativni način štednje, je cakum pakum, ali da li on pomaže u poboljšanju sveta u celini?
Kao što ćete početi da shvatate, ulazeći sve dublje i u druge sadržaje na ovoj stranici, mnogi temeljni delovi našeg današnjeg monetarnog sistema i ekonomije su duboko slomljeni. Međutim, oni koji upravljaju imaju korist od ovakvih sistema, pa se on verovatno neće promeniti bez revolucije ili mirnog svrgavanja od strane naroda. Bitcoin predstavlja novi sistem, sa nekoliko glavnih prednosti:
- Bitcoin popravlja novac, koji je milenijumima služio kao važan alat za rast i poboljšanje društva.
- Bitcoin vraća zdrav razum pozajmljivanju, uklanjanjem apsurdnih situacija poput negativnih kamatnih stopa (gde zajmitelj plaća da bi se zadužio).
- Bitcoin pokreće ulaganja u obnovljive izvore energije i poboljšava energetsku efikasnost u mreži, služeći kao „krajnji kupac“ za sve vrste energije.
Kako mogu da saznam više o Bitcoin-u?
Ovaj članak vam je dao osnovno razumevanje zašto biste trebali razmišljati o Bitcoin-u. Ako želite da saznate više, preporučujem ove resurse:
- Film "Bitcoin: Kraj Novca Kakav Poznajemo"
- Još uvek je rano za Bitcoin
- Zasto baš Bitcoin?
- Šta je to Bitcoin?
- The Bitcoin Whitepaper ← objavljen 2008. godine, ovo je izložio dizajn za Bitcoin.
-
 @ bf47c19e:c3d2573b
2025-06-03 17:18:46
@ bf47c19e:c3d2573b
2025-06-03 17:18:46Originalni tekst na bitcoin-balkan.com.
Pregled sadržaja
- Definisanje novca
- Šta je sredstvo razmene?
- Šta je obračunska jedinica?
- Šta je zaliha vrednosti?
- Zašto su važne funkcije novca?
- Novac Gubi Funkciju: Alhemičar iz Njutonije
- Eksploatacija pomoću Novca: Agri Perle
- Novac Gubi Funkciju 2. Deo: Kejnslandski Bankar
- Da li nas novac danas eksploatiše?
- Šta je novac, i zašto trebate da brinete?
- Efikasnija Ušteda Novca
- Zasluge
- Molim vas da šerujete!
Google izveštava o stalnom povećanju interesa u svetu za pitanje „Šta je novac?“ koji se postavlja iz godine u godinu, od 2004. do 2021., a sa naglim porastom nakon finansijske krize 2008. godine.
I izgleda se da niko nema dobar odgovor za to.
 Godišnji proseci mesečnih interesa za pretragu. 100 predstavlja najveći interes za pretragu tokom čitavog perioda, koji se dogodio u decembru 2019. Podaci sa Google Trends-a.
Godišnji proseci mesečnih interesa za pretragu. 100 predstavlja najveći interes za pretragu tokom čitavog perioda, koji se dogodio u decembru 2019. Podaci sa Google Trends-a.Međutim, odgovaranje na ovo naizgled jednostavno pitanje pomoći će vam da razjasnite ulogu novca u vašem životu. Jednom kada shvatite kako novac funkcioniše, tačno ćete videti i zašto svet danas ludi – i šta učiniti povodom toga. Zato hajde da se udubimo u to.
Na pitanje šta je novac, većina ljudi otvori svoje novčanike i pokaže nekoliko novčanica – “evo, ovo je novac!”
Ali po čemu se ove novčanice razlikuju od stranica vaše omiljene knjige? Pa, naravno, zavod za izradu novčanica te zemlje je odštampao te novčanice iz vašeg novčanika kako bi se oduprla falsifikovanju, i svi ih koriste da bi kupili odredjene stvari.
Međutim, Nemačka Marka imala je sva ova svojstva u prošlosti – ali preduzeća danas ne prihvataju te novčanice. Zapravo, građani Nemačke su početkom dvadesetih godina prošlog veka spaljivali papirne Marke kako bi grejali svoje domove. Marka je imala veću vrednost kao papir za potpalu nego kao novac!

1923. nemačka valuta poznata kao Marka bila je jeftinija od uglja i drveta!
Pa šta to čini novac, novcem?
Ispostavilo se da ovo nije pitanje na koje je lako dati odgovor.
Definisanje novca
Novac nije fizička stvar poput novčanice dolara. Novac je društveni sistem koji koristimo da bismo olakšali trgovinu robom i uslugama. Međutim, tokom istorije fizička monetarna dobra igrala su ključnu ulogu u društvenom sistemu novca, često kao znakovi koji predstavljaju vrednost u monetarnom sistemu. Ovaj sistem ima tri funkcije: 1) Sredstvo Razmene, 2) Obračunsku Jedinicu i 3) Zalihu Vrednosti.
Odakle dolaze ove funkcije, i zašto su one vredne?
Šta je sredstvo razmene?
Sredstvo razmene je neko dobro koje se obično razmenjuje za drugo dobro. Najčešće objašnjenje za to kako su se pojavila sredstva razmene glasi otprilike ovako: Boris ima ječam i želeo bi da kupi ovcu od Marka. Marko ima ovce, ali želi samo piliće. Ana ima piliće, ali ona ne želi ječam ili ovce.
To se naziva problem sticaja potreba: dve strane moraju da žele ono što druga ima da bi mogle da trguju. Ako se želje dve osobe ne podudaraju, oni moraju da pronađu druge ljude sa kojima će trgovati dok svi ne pronađu dobro koje žele.
 Ljudi koji trguju robom i uslugama moraju da imaju potrebe koje se podudaraju.
Ljudi koji trguju robom i uslugama moraju da imaju potrebe koje se podudaraju.Vremenom, veoma je verovatno da će se određena vrsta robe, poput pšenice, pojaviti kao sredstvo razmene jer su je mnogi ljudi želeli. Uzimajući pšenicu kao primer: pšenica je rešila “sticaje potreba” u mnogim zanatima, jer čak i ako onaj koji prima pšenicu a nije želeo da je koristi za sebe, znao je da će je neko drugi želeti.
Ovo nazivamo prodajnost imovine.
Pšenica je dobar primer dobra za prodaju jer svi moraju da jedu, a od pšenice se pravi hleb. Pšenica ima vrednost kao sastojak hleba i kao dobro koje olakšava trgovinu rešavanjem problema „sticaja potreba“.
Razmislite o svojoj želji da dobijete više novčanica u eurima ili drugoj valuti. Ne možete da jedete novčanice da biste preživeli, a i ne bi vam bile od velike koristi ako poželite da ih koristite kao građevinski materijal za vašu kuću. Međutim, znate da sa tim novčanicama možete da kupite hranu i kuću.
Stvarne fizičke novčanice su beskorisne za vas. Novčanice su vam dragocene samo zato što će ih drugi prihvatiti za stvari koje su vama korisne.
Tokom dugog perioda istorije, novac je evoluirao do te mere da monetarno dobro može imati vrednost, a da to dobro ne služi za bilo koju drugu ‘suštinsku’ upotrebu, poput hrane ili energije. Umesto toga, njegova upotreba je zaliha vrednosti i jednostavna zamena za drugu robu u bilo kom trenutku koji poželite.
Šta jedno dobro čini poželjnijim i prodajnijim od drugog dobra?
Deljivost
Definicija: Sposobnost podele dobra na manje količine.
Loš Primer: Dijamante je teško podeliti na manje komade. Za zajednicu od hiljada ljudi koji dnevno izvrše milione transakcija, dijamanti čine loše sredstvo razmene. Previše su retki i nedeljivi da bi se koristili za mnoge transakcije.

Potrebno je puno obuke da bi izrezali dijamant.
Ujednačenost
Definicija: Sličnost pojedinačnih jedinica odredjenog dobra.
Loš Primer: Krave nisu ujednačene – neke su veće, neke manje, neke bolesne, neke zdrave. Sa druge strane, unca čistog zlata je jednolična – jedna unca je potpuno ista kao sledeća. Ovo svojstvo se takođe često naziva zamenljivost.

Svaka je jedinstvena na svoj način.
Prenosivost
Definicija: Lakoća transporta dobra.
Loš Primer: Krava nije baš prenosiva. Zlatnici su prilično prenosivi. Papirne novčanice su još prenošljivije. Knjiga u kojoj se jednostavno beleži vlasništvo nad tim vrednostima (poput Rai kamenog sistema ili digitalnog bankovnog računa) je neverovatno prenosiva, jer nema fizičkog dobra koje treba nositi sa sobom za kupovinu. Postoji samo sistem za evidentiranje vlasništva nad tim vrednostima u nematerijalnom obliku.

Novac star 5000 godina VS novac star 13 godina
Kako dobro postaje sredstvo razmene?
Dobra postaju, i ostaju sredstva razmene zbog svoje univerzalne potražnje, takođe poznate kao njihova prodajnost, čemu pomažu svojstva koja su gore nabrojana.
Mnogo različitih dobara mogu u različitoj meri delovati kao sredstva razmene u ekonomiji. Danas, naša globalna ekonomija koristi valute koje izdaju države, zlato, pa čak i robu poput nafte kao sredstvo razmene.
Šta je obračunska jedinica?
Stvari se komplikuju kada u ekonomiji postoji mnogo robe koja se prodaje. Čak i sa samo 5 dobara, postoji 10 “kurseva razmene” između svake robe kojih svi u ekonomiji moraju da se sete: 1 svinja se menja za 15 pilića, 1 pile se menja za 15 litara mleka, desetak jaja se menja za 15 litara mleka, i tako dalje. Ako ekonomija ima 50 dobara, među njima postoji 1.225 “kurseva razmene”!
Sredstvo za merenje vrednosti
Zamislite obračunsku jedinicu kao sredstvo za merenje vrednosti. Umesto da se sećamo vrednosti svakog dobra u poredjenju sa drugim dobrima, mi samo treba da se setimo vrednosti svakog dobra u poredjenju sa jednim dobrom – obračunskom jedinicom.
Umesto da se setimo 1.225 kurseva razmene kada imamo 50 proizvoda na tržištu, mi treba da zapamtimo samo 50 cena.
Na primer, ne treba da se sećamo da litar mleka vredi 1/15 piletine ili desetak jaja, možemo da se samo setimo da litar mleka košta 1USD.

Mnogo opcija, sve u istoj obračunskoj jedinici.
Poređenje dobara je lakše sa obračunskom jedinicom
Obračunska jedinica takođe olakšava upoređivanje vrednosti i donošenje odluka. Zamislite da pokušavate da kupite par Nike Air Jordan patika kada ih jedan prodavac prodaje za jedno pile, a drugi za 50 klipova kukuruza.
Šta je zaliha vrednosti?
Do sada smo gledali samo primere transakcija koje se odvijaju u određenom trenutku u vremenu.
Međutim, ljudi vrše transakcije tokom vremena – oni štede novac i troše ga kasnije. Da bi odredjeno dobro moglo da funkcioniše pravilno kao monetarno dobro, ono treba da održi vrednost tokom vremena.
Novac koji vremenom dobro drži vrednost daje njegovom imaocu više izbora kada će taj novac da potroši.
To znači da prodajnost dobra uključuje njegovu sposobnost da održi vrednost tokom vremena.
Šta jedno dobro čini boljom zalihom vrednosti od drugog dobra?
Trajnost
Definicija: Sposobnost dobra da vremenom zadrži svoj oblik.
Loš Primer: Jagode čine lošu zalihu vrednosti jer se lako oštete i brzo trunu.

Nije sjajna forma novca.
Odluka je daleko lakša ako jedan prodavac naplaćuje 150 USD, a drugi 200 USD – odmah je očigledno koja je bolja ponuda jer su vrednosti izražene u istoj jedinici.
Teške za Proizvodnju
Definicija: Teškoće koje ljudi imaju u proizvodnji veće količine dobra.
Loš Primer: Papirne novčanice predstavljaju lošu zalihu vrednosti jer banke i vlade mogu jeftino da ih naprave.
Sa zlatom je suprotno – u ponudi se nalazi ograničena količina uprkos velikoj potražnji za njim, jednostavno zato što ga je vrlo teško iskopati iz zemlje. Ova ograničena ponuda osigurava da svaka jedinica zlata održi vrednost tokom vremena.

Traženje zlata je spora i teška aktivnost. Obično se ne pronađe puno!
Kako dobra postaju zalihe vrednosti?
Dobro postaje zaliha vrednosti ako se vremenom pokaže trajnim i teškim za proizvodnju.
Samo će vreme pokazati da li je neko dobro zaista trajno i da li ga je teško proizvesti. Zbog toga neki oblici novca su postojali vekovima pre nego što je neko otkrio način da ih proizvede više, i na kraju se to dobro više nije koristilo kao novac.
Ovo je priča o školjkama, Rai kamenju i mnogim drugim oblicima novca tokom istorije.
Zlato je primer dobra koje je hiljadama godina služilo kao dobra zaliha vrednosti. Zlato se ne razgrađuje tokom vremena i još uvek ga je teško proizvesti. Hiljadama godina alhemičari su bezuspešno pokušavali da sintetišu zlato iz jeftinih materijala.
Čak i sa današnjim naprednim rudarskim tehnikama, svake godine svi svetski rudnici zlata zajedno mogu da proizvedu samo 2% od ukupne ponude zlata u prometu.
Teškoće u proizvodnji zlata daju izuzetno visok odnos “zaliha i protoka”: zaliha je broj postojećih jedinica, a protok su nove jedinice stvorene tokom određenog vremenskog perioda. Svake godine se stvori vrlo malo novih jedinica zlata, iako je potražnja za zlatom obično vrlo velika.
Kombinujući ovo sa deljivošću, ujednačenošću i prenosivošću zlata, nije ni čudo što je zlato čovečanstvu služilo kao monetarno dobro tokom poslednjih 5.000 godina. Pošto je zlato teško proizvesti, možemo ga nazvati teškim novcem (hard money).
Kao rezultat toga, svoju vrednost je u velikoj meri zadržao kroz milenijume. Cena većine dobara i usluga u pogledu zlata zapravo se vremenom smanjivala kao rezultat tehnoloških inovacija, koje sve proizvode čine jeftinijim.
Uzmimo na primer cene hrane prema praćenju Kancelarije za hranu i poljoprivredu UN-a: sa obzirom na skokove u poljoprivrednoj tehnologiji tokom poslednjih 60 godina, cene hrane drastično su pale kada se procenjuju u zlatu. To čak i važi uprkos činjenici da obični ljudi retko koriste zlato za kupovinu stvari.
 Cene hrane su padale u pogledu zlata tokom proteklih 60 godina, i mnogo pre toga (FAO Indeks Cena Hrane u Zlatu)
Cene hrane su padale u pogledu zlata tokom proteklih 60 godina, i mnogo pre toga (FAO Indeks Cena Hrane u Zlatu)Zaliha vrednosti omogućava ljudima da uštede novac kako bi mogli da ga ulažu u pokretanje preduzeća i obrazovanje, povećavajući produktivnost društva.
Monetarna dobra koja dobro čuvaju vrednost takođe podstiču dugoročniji pogled na život, ili kratke vremenske preference. Pojedinac može da radi 10 godina, uštedi odredjeno monetarno dobro koje je dobra zaliha vrednosti, i nema potrebe da se plaši da će njegova ušteđevina biti izbrisana krahom tržišta ili povećanjem ponude tog dobra.
Zašto su važne funkcije novca?
Kada neki oblik novca izgubi bilo koju od svojih važnih funkcija kao što su sredstvo razmene, obračunska jedinica i zaliha vrednosti, celokupna ekonomija i društvo mogu da se rastrgnu.
Tokom istorije često vidimo grupe ljudi koje eksploatišu druge iskorišćavajući nesporazume o novcu i važnosti njegovih funkcija.
Sledeće, proći ću kroz istoriju novca, prvo hipotetički da bih ilustrovao poentu, a zatim ću preći na stvarne istorijske primere. Kroz ove primere videćemo štetne efekte na društva u slučajevima kada se izgubi samo jedna od tih ključnih funkcija novca.
Novac Gubi Funkciju: Alhemičar iz Njutonije
Kroz istoriju, mnoga dobra su dolazila i odlazila kao oblici novca. Na žalost, kada se neki oblik novca ukine, ponekad postoji grupa ljudi koja eksploatiše drugi oblik manipulišući tim novcem.
Hajde da pogledamo hipotetičko selo zvano Njutonija da bismo razumeli kako dolazi do ove eksploatacije.
Zelene perle postaju Novac
Tokom stotina godina ribolova u obližnjoj reci, stanovnici Njutonije sakupljali su zelene perle iz vode. Zrnca su mala, lagana, izdržljiva, jednolična i retko se pojavljuju u reci. Ljudi prvo priželjkuju perle zbog svoje lepote. Na kraju, seljani shvataju da svi drugi žele perle – one se vrlo lako mogu prodati. Zrnca uskoro postaju sredstvo razmene i obračunska jedinica u selu: pile je 5 zrna, vreća jabuka 2 zrna, krava 80 zrna.
Ukupna ponuda perli je prilično konstantna i cene se vremenom ne menjaju mnogo. Seoski starešina je uveren da može da se opustiti u poslednjim danima živeći od svoje velike zalihe perli.
Alhemičar stvara više perli
Seoski alhemičar je poželeo da bude bogat čovek, ali nije voleo da vredno radi na tome. Umesto da traži perle u reci ili da prodaje vrednu robu drugim seljanima, on sedeo je u svojoj laboratoriji. Na kraju je otkrio kako da lako stvori stotine perli sa malo peska i vatre.
Seljani koji su tragali za perlama u reci bili su srećni ako bi svaki dan pronašli po 1 zrno. Alhemičar je mogao da proizvede stotine uz malo napora.
Alhemičar troši svoje perle
Budući da je bio prilično zao, alhemičar nije svoj metod pravljenja zrna delio ni sa kim drugim. Stvorio je sebi još više perli i počeo da ih troši za dobra na tržištu u Njutoniji. Tokom sledećih meseci, alhemičar je kupio farmu pilića, nekoliko krava, finu svilu, posteljine i ogromno imanje. On je imao priliku da kupi ova dobra po normalnim cenama na tržištu.
Alhemičarevo trošenje ostavljalo je seljanima mnogo perli, ali malo njihove vredne robe.
Svi seljani su se osećali bogatima – imali su tone perli! Međutim, polako su primetili da i svi ostali takodje imaju tone.
Cene počinju da rastu
Uzgajivač pilića primetio je da sva roba koju je trebalo da kupi na pijaci poskupela. Džak jabuka sada se prodaje za 100 perli – 50 puta više od njihove cene pre nekoliko meseci!
Iako je sada imao hiljade perli, uskoro bi mogao da ostane bez njih zbog ovih cena. Pitao se – da li zaista može sebi da priušti da prodaje svoje piliće za samo 5 perli po komadu? Morao je i on da podigne svoje cene.
Jednostavno rečeno, kao rezultat alhemičarevog trošenja njegovih novostvorenih perli, bilo je previše perli koje su jurile premalo dobara – pa su cene porasle.
Kupci robe bili su spremni da potroše više perli da bi kupili potrebna dobra. Prodavci robe su trebali da naplate više da bi bili sigurni da su zaradili dovoljno da kupe potrebna dobra za sebe.
Budući da su cene svih dobara porasle, možemo reći da se vrednost svake perle smanjila.
Nejednakost bogatstva raste
Seoski starešina, koji je vredno radio da sačuva hiljade perli, sada se našao osiromašenim i gladnim. U međuvremenu, alhemičar je udobno sedeo na svom velikom imanju sa kravama, pilićima i slugama koji su se brinuli za svaki njegov hir.
Alhemičar je efikasno ukrao bogatstvo celog sela, tako što je jeftino proizvodio perle i koristio ih za kupovinu vredne robe.
Ono što je najvažnije, kupio je robu pre nego što je tržište shvatilo da je više perli u opticaju i da ima manje robe, što je dovelo do rasta cena. Ova dodatna proizvodnja perli nije dodala korisnu robu ili usluge selu.
Eksploatacija pomoću Novca: Agri Perle
Nažalost, priča o alhemičaru iz Njutonije nije u potpunosti hipotetička. Ovaj prenos bogatstva kroz stvaranje novca ima istorijske i moderne presedane.
Na primer, afrička plemena su nekada koristila staklene perle, poznate kao “agri perle”, kao sredstvo razmene. U to vreme plemenskim ljudima je bilo veoma teško da prave staklene perle, i one su predstavljale težak novac unutar njihovog plemenskog društva.
Niko nije mogao jeftino da proizvede perle i koristiti ih za kupovinu skupe, vredne robe poput kuća, hrane i odeće.

Perle proizvedene u Gani
Sve se promenilo kada su stigli Evropljani, i primetili upotrebu staklenih perli kao novca.
U to vreme, Evropljani su mogli jeftino da stvaraju staklo u velikim količinama. Kao rezultat toga, Evropljani su počeli tajno da uvoze perle i koriste ih za kupovinu dobara, usluga i robova od Afrikanaca.

Peć za izradu stakla u Muranu, Italija. Ovo ostrvo izvan Venecije proizvodi staklo od 15. veka.
Vremenom se iz Afrike izvlačila vredna roba i ljudi, dok je plemenima ostajalo mnogo perli i malo robe.
Perle su izgubile veći deo vrednosti zbog inflacije uzrokovane snabdevanjem od strane Evropljana.
Rezultat je bio osiromašenje afričkih plemena i bogaćenje Evropljana, kako to ovde objašnjava monetarni istoričar Bezant Denier.
Dragocena roba je kupljena jeftino proizvedenim monetarnim dobrom.
Profitiranje na proizvodnji novca: Emisiona dobit
Ova priča ilustruje kako se bogatstvo prenosi kada jedna grupa može jeftino da proizvodi monetarno dobro.
Razlika između troškova proizvodnje monetarnog dobra i vrednosti tog monetarnog dobra poznata je kao emisiona dobit, eng. seignorage.
Kada je monetarno dobro mnogo vrednije od troškova proizvodnje, ljudi će proizvesti više od monetarnog dobra da bi uhvatili profit od emisione dobiti.
Na kraju će ova povećana ponuda dovesti do pada vrednosti monetarnog dobra. To je zbog zakona ponude i potražnje: kada se ponuda povećava, cena (poznata i kao vrednost) dobra opada.
Novac Gubi Funkciju 2. Deo: Kejnslandski Bankar
U priči o Njutoniji, alhemičar je otkrio način da se od malo peska jeftino stvori više zelenih perli. To se u stvarnosti odigralo kroz trgovinu između Evropljana i Afrikanaca, pričom o agri perlama. Međutim, ove priče su pomalo zastarele – mi više ne trgujemo robom za perle.
Da bismo nas doveli do modernog doba, hajde da promenimo neka imena u našoj priči:
- Selo Njutonija postaje država koja se zove Kejnsland
- Alhemičar postaje bankar
- Seoski starešina postaje penzioner
- Zelene perle postaju zlato, koje niko ne može jeftinije da stvori – čak ni bankar.
Bankar Menja Papirne Novčanice za Zlato
Kao i u stvarnosti, bankar u ovoj priči nema formulu ili trik da stvori više zlata. Međutim, bankar bezbedno čuva zlato u vlasništvu svakog građanina Kejnslanda. Bankar daje svakom građaninu po jednu potvrdu za svaku uncu zlata koje ima u svom trezoru.
Te potvrde se mogu iskoristiti u bilo koje vreme za stvarno zlato. Papirne potvrde ili novčanice su mnogo pogodnije za plaćanje nego nošenje zlata kroz supermarket.
Građani su srećni – oni imaju prikladno sredstvo plaćanja u vidu bankarevih novčanica, i znaju da niko ne može da ukrade njihovo bogatstvo falsifikujući više zlata.
Građani na kraju počinju da plaćaju u potpunosti papirnim novčanicama, ne trudeći se nikad da zamene svoje novčanice za zlato. Na kraju, novčanice postaju “dobre kao i zlato” – svaka predstavlja fiksnu količinu zlata u bankarevom trezoru.
Ukupno kruži 1.000.000 novčanica, od kojih je svaka otkupljiva za jednu uncu zlata. 1.000.000 unci zlata sedi u bankarevom trezoru. Svaka novčanica je u potpunosti podržana u zlatu.
Starešina koji je sačuvao sve svoje perle u priči o Njutoniji sada je penzioner u Kejnslandu, koji svoje zlato drži u banci i planira da ugodno živi od novčanica koje je dobio zauzvrat.
Hajde da u ovu priču dodamo i novi lik: premijera Kejnslanda. Premijer naplaćuje porez od građana i koristi ga za plaćanje javnih usluga poput policije i vojske. Premijer takođe drži vladino zlato kod bankara.
Bankar Menja Papirne Novčanice za Dug
Premijer želi da osigura da nacionalno zlato ostane na sigurnom, pa banku štiti policijom. Bankar i premijer se zbog toga zbližavaju, pa premijer traži uslugu. Traži od bankara da kreira 200.000 novčanica za premijera, uz obećanje da će mu premijer vratiti za pet godina. Premijeru su novčanice potrebne za finansiranje rata. Građani Kejnslanda borili su se protiv većih poreza zbog finansiranja rata, pa je morao da se obrati bankaru.
Bankar se slaže da izradi novčanice, ali pod jednim uslovom: bankar uzima deo od 10.000 novčanica za sebe. Premijer prihvata posao kojim bankar ’kupuje državni dug’. Sada je u opticaju 1.200.000 novčanica, potpomognutih kombinacijom 1.000.000 unci zlata i ugovorom o dugu sa vladom za 200.000 novčanica.
Premijer troši svoje nove novčanice na bombe kupujući ih od dobavljača iz domaće vojne industrije, a bankar sebi kupuje veliki luksuzni stan.
Dobavljač iz vojne industrije koristi sve nove novčanice koje je dobio od premijera da kupi amonijum nitrat (đubrivo koje se koristi u bombama) za proizvodnju bombi. Sve njegove kupovine povećavaju cenu đubriva za uzgajivače pšenice u Kejnslandu, pa oni podižu cenu pšenice.
Kao uzrok toga, pekar koji kupuje pšenicu treba da podigne cenu svog hleba da bi ostao u poslu. Na taj način cene u Kejnslandu počinju da rastu, baš kao što su to činile u Njutoniji kada su nove perle ušle u opticaj.
Papirne Novčanice Više Ne Predstavljaju Zlato
Penzioner nailazi na finansijski časopis u kojem se pominje premijerov dogovor da se zaduži za finansiranje rata. Obzirom da je mudar, on zna da bombe loše vraćaju ulaganje i sumnja da će premijer ikada da vrati svoj dug.
Ako on ‘podmiri’ svoj dug, to bi ostavilo 1.200.000 novčanica u opticaju sa samo 1.000.000 unci zlata da bi ih podržalo, obezvređujući njegovu ušteđevinu. Već oseća stisak u džepu zbog porasta cena, i on odlučuje da se uputi u lokalnu banku i preda svoje novčanice i zameni ih za zlato, koje niko ne može da napravi u većoj količini.
Kada penzioner stigne u banku, on zatiče i mnoge druge okupljene oko banke. Svi oni se nadaju da će uzeti zlato koje predstavljaju njihove novčanice. Građani Kejnslanda sa pravom se plaše da njihove novčanice gube na vrednosti – oni to već osećaju zbog porasta cena.
Vrata su zaključana, sa obaveštenjem bankara na njima:
Po nalogu premijera, onom koji se plaši za stabilnost ove bankarske institucije, ova banka više neće podržavati konvertibilnost papirnih novčanica u zlato. Hvala vam!
Gomila se razilazi, ostavljena sa jednim izborom: da zadrže svoje novčanice, koje sada vrede manje od 1 unce zlata. Građani sa dovoljno finansijske stabilnosti odlučuju da ulože svoje novčanice u kupovinu akcija banke i kompanija vojne industrije, koje dobro posluju jer mogu da kupuju stvari pre nego što se povećaju tržišne cene.
Mnogi ljudi nisu u mogućnosti da investiraju – oni moraju da gledaju kako njihove zarade stagniraju i kako njihova ušteđevina polako ali sigurno gubi vrednost.
Penzioner, koji se nadao da će živeti od novčanica koje je zaradio tokom svojih 40 radnih godina, sada 40 sati nedeljno provodi iza kase u lokalnoj prodavnici, pitajući se gde je sve pošlo po zlu.
Dug Nikada Nije Otplaćen
Prošlo je nekoliko godina, a premijerov dug prema banci dolazi na naplatu. Budući da je potrošio svih 200.000 novčanica na bombe, koje nemaju baš dobar povraćaj ulaganja, on nema novčanice koje može da vrati banci. Plus, premijer želi da kupi još bombi za svoj rat.
Bankar uverava premijera da je sve u redu. Bankar će napraviti novi ugovor o dugu za 600.000 novčanica, koji bi trebao da stigne na naplatu u narednih 5 godina. Premijer može da iskoristi 200.000 od tih novih 600.000 novčanica da vrati svoj prvobitni dug prema banci, zadrži još 300.000 da kupi još bombi i da 100.000 bankaru da bi mu platio njegove usluge.
To nastavlja da se dešava – svaki put kada dug dospeva na naplatu, bankar stvara više novčanica za vraćanje starijih dugova i daje premijeru još više novca za trošenje. Ovaj ciklus se nastavlja.
Šta se dešava u Kejnslandu?
- Oni koji prvi dobiju nove novčanice, gledaju kako se njihovo bogatstvo povećava
- To uključuje bankara, premijera, vladu i sve one koji mogu da pristupe mogućnostima za investiranje u preduzeća koja prva dobiju nove novčanice (finansijske, vojne itd.).
- Cene roba rastu
- Cene se ne povećavaju ravnomerno – one se povećavaju gde god nove novčanice prvo uđu u ekonomiju i od tog trenutka imaju efekat talasa na tržišta. U našem primeru prvo raste cena amonijum nitrata, zatim cena pšenice, pa cena hleba. A tek na kraju zarade običnih ljudi.
- Štednja i životni standard opšte populacije se smanjuju
- Najviše pate oni koji žive od plate do plate i ne mogu da ulažu. Čak i oni koji su u mogućnosti da investiraju podložni su hirovima tržišta. Mnogi su prisiljeni da prodaju svoje investicije po niskim cenama tokom pada tržišta samo da bi platili svoje dnevne potrebe.
- Razlika u prihodima i bogatstvu između bogatih i siromašnih se povećava
- Bogatstvo opšte populacije se smanjuje, dok se bogatstvo onih koji su blizu mesta gde se troše nove novčanice povećava. Rezultat je disparitet koji se vremenom samo proširuje.
Da li nas novac danas eksploatiše?
Priča o Njutoniji i stvarna priča o agri perlama u Africi deluju pomalo zastarelo. Priča o Kejnslandu, međutim, deluje neobično poznato. U našem svetu cene robe uvek rastu, i vidimo rekordne nivoe nejednakosti u bogatstvu.
U poslednjem odeljku ovog našeg članka Šta je novac, proći ću kroz nastanak bankarstva i korake koji su bili potrebni da se dođe do današnjeg sistema, gde banke i vlade sarađuju u kontroli ekonomije i samog novca.
Šta su banke, i odakle su one došle?
Pojava bankarstva verovatno se dogodila da bi olakšala poljoprivrednu trgovinu i da bi povećala pogodnosti. Iako su se mnoga društva na kraju konvergirala ka upotrebi zlata i srebra kao novca, ovi metali su bili teški i opasni za nošenje kao tovar. Međutim, u mnogim slučajevima ih nije ni trebalo prevoziti. Uzmite ovaj primer:
Grad treba da plati poljoprivrednicima na selu za žito, a poljoprivrednici gradskoj vojsci za zaštitu od varvara. U ovom dogovoru zlato se kreće u oba smera: prema poljoprivrednicima u selu kako bi im se platilo žito, i nazad u grad da bi se platila vojska. Da bi olakšali ove transakcije, preduzetnici su stvorili koncept banke. Banka je zlato čuvala u sigurnom trezoru i izdavala novčanice od papira. Svaka priznanica je predstavljala potvrdu da njen imaoc poseduje određenu količinu zlata u banci. Imaoc novčanice je u svako doba mogao da uzme svoje zlato nazad vraćanjem te novčanice banci.
Korisnici banke mogli su lakše da trguju sa novčanicama od papira, i onaj koji poseduje novčanice mogao je da preuzme njihovo fizičko zlato u bilo kom trenutku. To je te novčanice učinilo “dobrim kao i zlato”.
Banke su izdržavale svoje poslovanje naplaćujući od kupaca naknadu za skladištenje zlata ili pozajmljivanjem dela zlata i zaračunavanjem kamata na njega. Trgovina na ovaj način je mogla da se odvija sa laganim novčanicama od papira umesto sa teškim vrećama zlatnika.
Ovakva praksa sa transakcijama, korišćenjem papirne valute potpomognute monetarnim dobrima, verovatno je započela u Kini u 7. veku.
Na kraju se proširila Evropom 1600-ih, a svoj zalet dobila je u Holandiji sa bankama poput Amsterdamske Wisselbanke. Novčanice Wisselbank-e često su vredele više od zlata koje ih je podržavalo, zbog dodane vrednosti njihovih pogodnosti.
Uspon nacionalnih ‘centralnih banaka’
Tokom vekova, zlato je počelo da se sakuplja u trezorima banaka, jer su ljudi više voleli pogodnosti transakcija sa novčanicama.
Na kraju, nacionalne banke u vlasništvu vlada preuzele su ulogu čuvanja zlata od privatnih banaka koje su započeli preduzetnici.
Nacionalne papirne valute potpomognute zlatnim rezervama u nacionalnim bankama zamenile su novčanice iz privatnih banaka. Sve nacionalne valute bile su jednostavno potvrde za zlato koje se nalazilo u trezoru nacionalne banke.
Ovaj sistem je poznat kao zlatni standard – sve valute su jednostavno predstavljale različite težine zlata.
 U gornjem levom uglu novčanice možete videti da piše da je novčanica “zamenljiva za zlato”. Savremeni dolari nemaju ovaj natpis, ali inače izgledaju vrlo slično. Izvor
U gornjem levom uglu novčanice možete videti da piše da je novčanica “zamenljiva za zlato”. Savremeni dolari nemaju ovaj natpis, ali inače izgledaju vrlo slično. IzvorZlatni sistem je postojao veći deo vremena, sve do Prvog svetskog rata. Vladama je bilo teško da prikupe novac za ovaj rat putem poreza, pa su morale da budu kreativne.
Kada vlade troše više nego što zarađuju na porezima, to se naziva deficitna potrošnja.
Kako vlade mogu ovo da urade? Vlade to rade tako što pozajmljuju novac prodavajući svoj dug.
Tokom Prvog svetskog rata, vlade su građanima i preduzećima prodavale vrstu duga koja se naziva ratna obveznica. Kada građanin kupi ratnu obveznicu, on preda svoj novac vladi i dobije papir u kojem je stajalo vladino obećanje da će vlasniku obveznice vratiti novac, plus kamate, za nekoliko godina.
Plakat koji obaveštava građane, tražeći od njih da kupe ratne obveznice – što predstavlja zajam vladi. Izvor
Centralne banke ‘monetizuju’ državni dug
Međutim, građani i preduzeća nisu bili voljni da kupe dovoljno ratnih obveznica za finansiranje Prvog svetskog rata.
Vlade se nisu predale – pa su zatražile od svojih nacionalnih ‘centralnih banaka’ da one kupe ove obveznice. Centralne banke su otkupile obveznice, ali ih nisu platile valutom potpomognutom postojećim zlatnim rezervama, kao što su to činili građani i banke prilikom kupovine obveznica.
Centralne banke su umesto toga davale vladi novu, sveže štampanu papirnu valutu potpomognutu samo obveznicom. Ovu valutu podržalo je samo obećanje da će im vlada vratiti dugove. Ovo je poznato kao monetizacija duga.
Budući da su ratne obveznice i valuta samo komadi papira, one su lake i jeftine za proizvodnju i mogu se napraviti u ogromnim količinama. Ono što ograničava proizvodnju i jednog i drugog je poverenje.
Ima smisla da se neko rastane od svog teško stečenog novca da kupi državnu obveznicu, samo ako veruje da će vlada da vrati svoj dug, plus kamate. Centralna banka je “krajnji kupac”, što znači da će ona da kupi državne obveznice kada to niko drugi neće da uradi.
Zapamtite, centralnu banku gotovo da ništa ne košta da kupi državne obveznice, jer oni sami štampaju valutu da bi ih kupili.
Zamislite da pridjete najskupljem automobilu u autosalonu – koji košta 100.000 USD. Mislite da je automobil lep, ali taj novac biste radije potrošili na lepši stan – tako da ste spremni da platite samo 40.000 USD za taj auto.
Sada, hajde da zamislimo da imate štampač za novac i da vas košta samo 50 USD za mastilo i papir da bi ištampali 1.000.000 USD. Vi biste odmah kupili auto, čak i ako biste morali da se cenkate sa drugim čovekom, i da ga na kraju platite 150.000 USD!
Ista stvar se dešava kada centralna banka kupuje obveznice (dugove) od vlade. Centralna banka može da stvori valutu toliko jeftino, da su spremni da plate i više nego što bi drugi platili ove obveznice i nastaviće da ih kupuju čak i kada niko drugi ne bude želeo.
Monetizacija duga uzrokuje inflaciju
Kada centralne banke monetizuju državni dug, funkcija novca kao zalihe vrednosti počinje da se nagriza. Vlada troši novi novac koji je dobila od svoje centralne banke na ratnu robu, obroke i još mnogo toga.
Cene roba rastu od ove novoštampane valute koja kruži kroz ekonomiju. Kada se cene povećavaju, to znači da se vrednost svake jedinice valute smanjuje. Svi koji drže valutu sada imaju manje vrednosti. Danas to nazivamo sporim gubitkom funkcije zalihe vrednosti u novčanoj inflaciji.
Za Nemačku nakon Prvog svetskog rata monetizacija duga izazvala je totalni slom Nemačke ekonomije i stvorila uslove za rast fašizma.
Kao deo sporazuma o prekidu vatre koji je okončao Prvi svetski rat, Nemačka je pobednicima morala da plati ogroman novac. Nemačkoj vladi je bio preko potreban novac, pa su prodale obveznice (dug) Rajhsbanci, nemačkoj centralnoj banci.
Ovaj postupak doveo je do toga da je vlada štampala toliko maraka (tadašnja nemačka valuta) da je tempo inflacije u Nemačkoj ubrzan u hiperinflaciju početkom 1920-ih. Cena vekne hleba za samo 4 godine popela se sa 1,2 marke na 428 biliona maraka.
Tokom i posle Prvog svetskog rata, SAD, Britanija, Francuska i mnoge druge vlade pratile su Nemačku u štampanju valute potpomognute državnim dugom.
To je dovelo do toga da su građani želeli da svoju papirnu valutu zamene za zlato, baš kao i penzioner iz priče o Kejnslandu.
Međutim, mnoge vlade su suspendovale konvertibilnost svojih valuta u zlato. Ovim potezom vlade su primorale svoje građane da drže nacionalnu papirnu valutu i gledaju kako se njihova ušteda smanjuje u vrednosti.
Da bi mogle da nastave da štampaju novac i da bi ga trošile na nepopularne programe za koje nisu mogle da skupljaju poreze za finansiranje – poput ratova.
Bretton Woods: Novi monetarni sistem
Nakon razaranja koja su donela dva svetska rata, vlade su uspostavile novi globalni monetarni sistem prema Bretton Woods-ovom sporazumu iz 1944. godine.
Prema ovom sporazumu, valuta svake države konvertovala se po fiksnom kursu sa američkim dolarom. Američki dolar je zauzvrat predstavljao zlato po stopi od 35 USD za jednu trojsku uncu zlata*.
Sve globalne valute su stoga još uvek bile jednostavna reprezentacija zlata, putem američkih dolara kao posrednika. Redovni građani više nisu mogli da otkupljuju svoje valute za zlato iz Sjedinjenih Država. Međutim, strane centralne banke mogle bi da dođu u Sjedinjene Države da bi zamenile dolare za zlato po stopi od 35 USD za jednu uncu zlata.
Međutim, vlada Sjedinjenih Država nije uvek držala dovoljno zlata da podrži sve dolare u opticaju. Američka vlada nastavila je da finansira proširene socijalne i vojne programe prodajom državnog duga svojoj centralnoj banci, Federalnim rezervama, koja je povećala ponudu dolara bez povećanja ponude zlata koja podupire te dolare.
*Trojna unca je standardna mera čistog zlata i ima malo veću težinu od normalne unce.
Propast Bretton Woods-a
Tokom 1970-ih, sve veći troškovi rata u Vijetnamu i stranih vlada koje su otkupljivale svoje dolare za zlato, stvorili su pritisak na Trezor Sjedinjenih Država.
Ponuda dolara je porasla, dok je zlato u posedu Sjedinjenih Država opalo. Od 1950. pa do početka 1970-ih, rezerve zlata koje je držala vlada Sjedinjenih Država smanjile su se za više od 50%, sa 20 metričkih tona na samo 8 metričkih tona.
Godine 1970. država je imala zlata u vrednosti od samo 12 biliona dolara po zvaničnom kursu od 35 dolara za trojsku uncu zlata. Tokom ovog istog vremenskog perioda, ukupna ponuda američkih dolara otišla je sa oko 32 biliona USD na skoro 70 biliona USD.

Zvanične rezerve zlata u SAD-u su naglo padale od 1950. do 1970. godine, dok su se dolari u opticaju povećavali. Izvor: Wikipedia, DollarDaze.org
Američka vlada nije bila u stanju da potkrepi dolare zlatom od 35 dolara po trojnoj unci, što dovelo do rizika za čitav globalni monetarni sistem.
Početkom sedamdesetih godina, trojna unca zlata trebala je da vredi 200 USD da bi u potpunosti podržala sve američke dolare u opticaju. Rečeno na drugi način, Sjedinjene Države su pokušavale da kažu svetu da jedan dolar vredi 1/35 trojne unce zlata, ali u stvarnosti dolar je vredeo samo 1/200 trojne unce.
Kad su strane vlade trebale da pribave dolare za međunarodnu trgovinu i rezerve, bile su opelješene. Francuska vlada je to shvatila šezdesetih godina prošlog veka i počela je da prodaje svoje američke dolare za zlato po zvaničnom kursu od 35 dolara za trojsku uncu zlata.
Zemlje su počinjale da se bude iz šeme američke vlade. SAD su krale bogatstvo putem emisione dobiti, prodajući dolare za 1/35 trojne unce zlata, kada su vredeli samo 1/200 trojske unce.
Nixonov Šok ulazi u ’tradicionalni’ novac
Da bi kuća od karata mogla da ostane na mestu, predsednik Nixon je 1971. najavio da će američka vlada privremeno da obustavi konvertibilnost dolara u zlato.
Strane vlade više nisu mogle da polažu pravo na zlato svojim papirnim dolarima, a dolar više nije bio “poduprt” zlatom. Nixon je tvrdio da će ovo stabilizovati dolar.
50 godina kasnije, kristalno je jasno da je ovo samo pomoglo dolaru da izgubi vrednost i da ovaj “privremeni” program još uvek traje.
Pre 1971. godine, sve globalne valute bile su vezane za američki dolar putem Bretton Woods-ovog sporazuma. Kada je Nixon promenio američki dolar iz dolara podržanog u zlatu u dolar podržan dugom, ovim je promenio i svaku drugu valutu na Zemlji.
Sam je učinio da se celokupna svetska ekonomija zasniva na dugovima. Valute više nisu predstavljale zlato, već su predstavljale vrednost državnog duga.
Zlatni Standard se nikada nije vratio
Konvertibilnost američkih dolara u zlato – zlatni standard – nikada se nije vratio.
Od 1971. godine, čitav globalni monetarni sistem pokreće se tradicionalnim “fiat” valutama: poverenjem u vladine institucije da održavaju valutni sistem.
Većina valuta podržana je kombinacijom duga njihove vlade i drugih tradicionalnih valuta poput dolara i evra. Papirne valute više nisu podržane zlatom, imovinom koja je više od 5000 godina služila kao težak novac.
Danas vas vlade prisiljavaju da plaćate porez u njihovoj valuti i manipulišu saznanjima oko novca kako bi osigurale da potražnja za njihovom valutom ostane velika.
To im omogućava da neprestano štampaju više valuta, da bi je potrošili na vladine projekte, uzrokujući inflaciju cena koja jede i smanjuje bogatstvo i plate.
Američka vlada sada prodaje državne obveznice (dugove), poznate kao obveznice Trezora SAD, eng. US Treasuries, komercijalnim bankama u zamenu za američke dolare.
Vlada koristi te dolare za finansiranje svog budžetskog deficita. Komercijalne banke prodaju mnoge obveznice Trezora SAD, koje su kupile, američkoj centralnoj banci, Federalnim Rezervama.
Federalne rezerve plaćaju komercijalnim bankama sveže štampanim novcem “pomoću računara i upisivanjem količine na račun”, kako je rekao bivši predsednik Fed-a Ben Bernanke.
Ove komercijalne banke često zarađuju samo kupujući obveznice Trezora SAD od države i prodajući ih centralnoj banci. Kupujte nisko, prodajte visoko.
Centralne banke ovaj proces kupovine državnog duga – odnosno pozajmljivanja novca državi – nazivaju operacijama otvorenog tržišta.
Kada centralna banka odjednom kupi velike iznose duga, oni to nazivaju kvantitativnim ublažavanjem. Centralne banke javno najavljuju kupovinu državnog duga, ali vrlo malo ljudi razume šta to zapravo znači.
Euro, jen i svaka druga valuta koja se danas koristi funkcionišu slično kao američki dolar.
Da li će SAD ikada vratiti svoj nacionalni dug? Neobična stvar u vezi sa državnim dugom SAD-a je ta što vlada poseduje štampariju potrebnu za njegovu otplatu.
Kao rezultat toga, kada vlada duguje novac, oni samo pozajme još više novca da bi otplatile taj dug, povećavajući nacionalni dug.
Ako vam ovo zvuči kao Ponzijeva piramidalna šema, to je zato što ona to i jeste – najveća Ponzijeva šema u istoriji. Kao i svaka Ponzijeva šema, nastaviće se sve dok su ljudi koji kupuju Ponzijevu šemu budu uvereni da će im biti plaćeno nazad.
Ako ljudi i nacije prestanu da se zadužuju i koriste američke dolare jer nemaju poverenja u američku vladu ili vide da cena robe raste (tj. dolar postaje sve manje vredan), potražnja za dolarom će opadati, što će izazvati začaranu spiralu.
Ova spirala često završi u hiperinflaciji, kao što smo videli u novijoj istoriji sa Jugoslavijom, Venecuelom, Argentinom, Zimbabveom i mnogim drugim državama.
Ovo je način kako funkcioniše novac na vašem bankovnom računu. Novac svake nacije na svetu pati od istih problema kao i perle i novčanice u pričama o Njutoniji i Kejnslandu.
Kako banke i vlade kradu tvoj novac?
Tokom vekova, stigli smo do monetarnog sistema u kojem banke i vlade mogu da štampaju novu valutu za finansiranje svojih operacija i svojih prijatelja u zločinu, dok kradu bogatstvo svojih građana.
Šta će se desiti sa svetom kada novac bude mogao da štampa svaki narod na planeti?
- Bogatstvo onih koji su blizu pravljenja nove valute se povećava
- Vlada i politički povlašćena klasa ljudi, imaju pristup novoštampanom novcu pre svih ostalih, pa mogu da ga potroše pre nego što cene porastu. Na ovaj efekat pokazao je ekonomista Richard Cantillon sredinom 1700-ih i poznat je kao Cantillonov Efekat.
- Cena robe raste (poznato kao inflacija
- Ne raste sve roba istovremeno u ceni. Roba blizu mesta gde se proizvodi nova valuta – finansijski sektor i vlada – prva raste, i odatle uzrokuje efekt talasa na cene.
- Inflacija se često predstavlja kao promena cene potrošačke korpe, poznata kao Indeks Potrošačkih Cena, eng. Consumer Price Index (CPI). Vlada ima alate za manipulisanje ovim brojem kako bi osigurala da se ona čini niskom i stabilnom, kao što je objašnjeno u našem članku o inflaciji.
- Finansijska imovina često primećuje ogromnu inflaciju, ali bankari to ne nazivaju inflacijom – oni kažu da naša ekonomija cveta! Nakon što su američke Federalne rezerve učetvorostručile ponudu američkih dolara u šest godina nakon finansijske krize 2008. godine, banke koje su dobile te nove dolare, kupile su akcije i obveznice, stvarajući ogroman balon u cenama ove imovine.
- Štednja i životni standard stanovništva se smanjuju
- Plate su jedna od poslednjih “cena” u ekonomiji koja se prilagođava, jer se često povećavaju samo jednom godišnje. U međuvremenu, cene dnevnih potrepština te osobe koja zaradjuje platu neprestano rastu kako novi novac kruži ekonomijom.
- Najviše su pogođeni oni koji žive od plate do plate – a to je 70% Amerikanaca.
- Razlike u prihodima između bogatih i siromašnih se povećavaju, kao što se vidi na grafikonu ispod.

*Koncentracija dohotka na vrhu naglo je porasla od 1970-ih
Zašto i dalje imamo isti monetarni sistem?
Ako ovaj sistem bogate još više obogaćuje, a siromašne još više osiromašuje, dovodeći do političke nestabilnosti, zašto ga onda ne bismo promenili?
Najveći razlog zašto se ništa ne menja je verovatno to što puno toga ne znamo o samom sistemu. Svi svakodnevno koristimo valute svojih vlada, ali većina nas ne razume kako sistem funkcioniše i šta on čini našim društvima.
Obrazovni sistem, mediji i finansijski stručnjaci neprestano nam govore da je monetarni sistem previše komplikovan da bi ga normalni ljudi razumeli. Mnogi od nas se zato i ne trude da pokušaju.
Još nekoliko razloga zašto ovaj sistem nastavlja da opstaje:
- Mnogo je ljudi koji imaju direktnu korist od štampanja novog novca.
- Ti ljudi ne žele nikakve promene i bore se da zadrže tu moć.
- Nacionalne valute su često pogodne
- Kreditne kartice, online bankarstvo i još mnogo toga čine upravljanje nacionalnim valutama i njihovo trošenje lakim i jednostavnim.
- Građani moraju da plaćaju porez u svojoj nacionalnoj valuti
- To stvara potražnju za tom valutom od svih građana, povećavajući njenu vrednost.
- Glavna međunarodna tržišta, poput nafte, denominirana su u dolarima.
- Nafta je potrebna svakoj zemlji na planeti, ali pošto mnogi ne mogu da je proizvode, moraju da je kupuju na međunarodnim berzama. Od 1970-ih na ovim berzama gotovo sva nafta se prodaje za dolare, što stvara potražnju za dolarima. Da bi se odmaknule od ovog sistema, zemlje bi trebale da pronađu novu valutu ili robu za trgovinu naftom, što zahteva vreme i rizike.
- Nije postojala dobra alternativa
- Uz globalnu ekonomiju u realnom vremenu, naš sistem digitalnog bankarstva koji koristi nacionalne valute je pogodan. Transakcija u tvrdom novcu poput zlata bila bi previše nezgrapna za današnji svet. Digitalna valuta pod nazivom Bitcoin, predstavljena 2009. godine, je rastuća alternativa koja nudi čvrst novac koji se kreće brzinom interneta.
Šta je novac, i zašto trebate da brinete?
Novac je alat koji olakšava razmenu dobara. Kao i svako drugo dobro, novac se pridržava zakona ponude i potražnje – povećanje potražnje povećaće njegovu vrednost, a povećanje ponude smanjiće njegovu vrednost.
Na ovaj način novac se ne razlikuje od kuće ili piletine. Međutim, velika prodajnost novca znači da je potražnja za njim uvek velika. Kao rezultat, novac mora biti težak za proizvodnju (a samim tim i ograničen u ponudi) ili će ga onaj ko ga može napraviti, stvoriti toliko, da vremenom više neće služiti kao zaliha vrednosti. Uskoro će izgubiti svoje funkcije kao sredstvo razmene i obračunske jedinice.
Najbolji novac u datoj ekonomiji je onaj koji se najslobodnije kreće – svi ga žele, lako je obaviti transakcije sa njim i koji sa vremenom dobro drži svoju vrednost. Nijedan novac nije savršen u svemu ovome, a neki ističu jednu funkciju novca na štetu drugih.
Iako se istorija ne ponavlja, ona se rimuje, a usponi i padovi monetarnih sistema imaju jasne ritmove. Uspon i pad monetarnog sistema često sledi opšti obrazac koji smo videli u pričama o agri perlama i Kejnslandu: pojavljuje se odredjenji oblik novca koji pomaže ljudima da efikasnije trguju i štede, ali na kraju gubi na vrednosti kada neko shvati kako da ga jeftino stvori u velikoj količini. Međutim, tokom dugog perioda vremena, monetarni sistemi su se poboljšali u sve tri funkcije novca.
Na primer, zlato je tokom vremena dobro služilo kao zaliha vrednosti. Međutim, naša međusobno povezana ekonomija ne bi mogla efikasno da funkcioniše ako bi trebalo da fizičko zlato zamenimo robom i uslugama. Mnogo je lakše kretati se na papirnom i digitalnom novcu, ali istorija nam govori da su vlade i bankari iskoristili ove oblike novca za krađu bogatstva putem inflacije.
Današnji globalni monetarni sistem je vrlo zgodan, a digitalna plaćanja i kreditne kartice olakšavaju trošenje novca. Ovo skriva stalnu inflaciju koja nagriza vrednost svake jedinice novca i dovodi do sve većeg jaza u bogatstvu.
Nadam se da je ovaj članak proširio vaše razumevanje novca i njegove uloge u društvu. Ovo je samo početak svega što treba istražiti o novcu: za kasnije su sačuvane teme o inflaciji, kamatnim stopama, pozajmljivanju, poslovnim ciklusima i još mnogo toga.
Efikasnija Ušteda Novca
Možda se pitate kako zaštititi svoju štednju kada svaki oblik često korišćenog novca i investicija pati od inflacije ponude – koja umanjuje vrednost i prenosi bogatstvo onima koji mogu da stvore novac ili investiciju. Možda se čini da se ništa na planeti danas ne može kvalifikovati kao ‘težak’ novac, ali dve stvari ipak ostaju: zlato i njegov noviji rođak Bitcoin. Obe ove stvari je neverovatno teško proizvesti, a jedna od njih se kreće brzinom interneta i može se čuvati u vašem mozgu.
Ako želite da saznate više o Bitcoin-u kao sredstvu za zaštitu vaše ušteđevine, pročitajte ovde. Ako ste već spremni za kupovinu Bitcoin-a, pogledajte moj vodič za kupovinu Bitcoin-a. Možete početi sa investiranjem sa samo 5 ili 10 €.

Zasluge
Hvala svima koji su pomogli u izradi i uređivanju ove serije o novcu: @ck_SNARKS, @CryptoRothbard, Neil Woodfine, Emil Sandstedt, Taylor Pearson, Parker Lewis, Jason Choi, mojoj porodici i mnogim drugima.
Hvala svima koji su ovo inspirisali i razvili ključne ideje koje su ovde primenjene: Friedrich Hayek, Carl Menger, Ludwig Von Mises, Murray Rothbard, Saifedean Ammous, Dan Held, Pierre Rochard, Stephan Livera, Michael Goldstein, i mnogi drugi.
Molim vas da šerujete! Ako vam je ovaj članak otvorio oči o tome kako funkcioniše naš novac i finansijski sistem, kontaktirajte me ili ostavite komentar!
Ako vam se sviđa moj rad, molim vas da ga podelite sa svojim prijateljima i porodicom. Cilj mi je da svima pružim pogled u ekonomiju i na to kako ona utiče na njihov život.
-
 @ cae03c48:2a7d6671
2025-06-03 16:01:03
@ cae03c48:2a7d6671
2025-06-03 16:01:03Bitcoin Magazine

Freedom, Decentralization and Unity: Stay True to These Principles and the Future Is Ours, Says Ross UlbrichtLast week, Ross William Ulbricht, at the 2025 Bitcoin Conference in Las Vegas, gave a speech about the principles of freedom, decentralization and unity.
Ross Ulbricht started by talking about his experience in prison and the price difference when he got into prison compared to now.
“When I launch Silk Road, buying a whole bitcoin will set you back less than a dollar,” said Ross. “Pocket change. Can you imagine that? Now they are worth over $100,000 each.”
“Bitcoin’s power comes from the fact that any one of us can mine if we choose to, and any one of us can generate addresses if we choose to,” stated Ross. “Any one of us can send bitcoin to anyone else. We are all on equal footing with Bitcoin. With Bitcoin, we are all free.”
Ross told everybody to stay united and that if we are together we will be able to accomplish anything.
“When I was put in prison for life. I was isolated and weak. I was stripped of everything. Had nothing to give everyone, but you didn’t abandon me. You didn’t forget me. Wrote me letters. You raised money for my defense. When I was silenced, you spoke up against the slender and smearers and in the end when I didn’t know if I would ever get out from behind those thick iron bars. We even got President Trump to see that Bitcoin is the future.”
Ross ended his speech by saying, “please never see each other as enemies. Those that oppose decentralization and freedom love it when we are divided. Stay united. As long as we can agree that we deserve freedom and that decentralization is how we secure it. Then we can be united. We can have each other’s backs. Just like you had mine.”
“Freedom, decentralization and unity,” said Ross. “Stay true to these principles and the future is ours.”
Ross Ulbricht’s Journey: From Life Sentence to Presidential Pardon
Ross Ulbricht became a controversial figure after launching Silk Road in 2011, an online marketplace that used Bitcoin for anonymous transactions. While the site was unfortunately used for selling illegal drugs, it also served as Bitcoin’s first real-world use case, showcasing the power of decentralized, censorship-resistant money.
In 2015, Ulbricht was sentenced to double life imprisonment without the possibility of parole. His punishment quickly became a symbol of government overreach for many in the tech and the Bitcoin world. Critics argued that his sentence far exceeded the limits of justice, especially considering the nonviolent nature of his crimes.
His pardon, announced shortly after Trump returned to office, is seen as a strong move to honor campaign promises and support Bitcoin’s values of personal freedom and resistance to government overreach. It sparked celebration throughout the Bitcoin community but also reminded advocates that the fight for justice is far from over.
Ten years ago to the day, I was sentenced to die in prison. Instead I gave my first public speech in freedom.
I wore a red tie as an homage to @realDonaldTrump, the man who saved my life. pic.twitter.com/WWp0vL3C9T
— Ross Ulbricht (@RealRossU) May 30, 2025
This post Freedom, Decentralization and Unity: Stay True to These Principles and the Future Is Ours, Says Ross Ulbricht first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 7b20d99d:d2a541a9
2025-06-03 15:34:21
@ 7b20d99d:d2a541a9
2025-06-03 15:34:21In a world plagued by economic instability, growing inequality, and the inefficiency of many traditional aid systems, Hope With Bitcoin emerges as an innovative and forward-thinking initiative. Combining human solidarity with decentralized technology, our mission is simple yet ambitious: feed the most vulnerable while promoting Bitcoin as a tool for financial inclusion and economic sovereignty.
But beyond the direct aid already distributed, a deeper reflection led us to a pivotal step, launching a pig farming project designed to self-fund our humanitarian efforts in the long term.
🎯 Our Mission: Feed, Educate, Empower
Hope With Bitcoin was born from a simple idea: using Bitcoin donations to fund concrete and transparent humanitarian actions. Since its inception, our project has focused on tangible support, such as distributing meals to children and delivering food supplies to families in need. At the same time, we raise awareness about the unique advantages of Bitcoin including transparency, speed, and traceability of transactions.
However, after several months of activity, a clear realization emerged: relying solely on donations limits our impact. While one-time contributions are valuable, they do not provide a strong, predictable, or scalable foundation for long-term humanitarian action.
🐖 Why Pig Farming?
The decision to launch a pig farming initiative is far from random — it’s the result of a strategic, realistic analysis of local conditions and economic opportunities.
🔍 Strategic Reasons:
- Accessibility: Pig farming is well-suited to the targeted region and doesn’t require complex technical skills.
- Quick Return: Pigs have short reproductive cycles, enabling rapid herd growth.
- Strong Local Demand: Pork is widely consumed, ensuring a stable market for sales.
- Reinvestment: Profits will be reinvested into our humanitarian efforts, making the project financially sustainable in the medium and long term.
⚙️ Current Status of the Project
April was dedicated to a strategic pause — not a break in action, but a period of deep reflection, planning, and structuring.
Here’s what we’ve already achieved:
✅ 1. A Secured Plot of Land The farm will be built on land generously provided free of charge by the founder’s father. This significantly reduces infrastructure costs while ensuring long-term land stability.
✅ 2. A Clear and Transparent Budget To guarantee full accountability, we’ve developed a precise forecast budget based on local market prices.
📊 Estimated Budget for the Pig Farming Project Total estimated cost: 5,525,200 satoshis (\~5,213 USD)
🧱 1. Infrastructure – 3,362,907 sats (\~3,172 USD)
Land clearing
Fencing (wood, metal sheets, nails, labor)
Construction of pens
Water access (well or pipe connection)
Electricity (solar or grid connection)
Storage space and shelter for staff
🐖 2. Livestock & Care – 1,582,293 sats (\~1,493 USD)
Purchase of 2 sows and 1 boar
Goats for diversification
3 months’ worth of animal feed
Veterinary care
Cleaning and maintenance
⚠️ 3. Emergency Reserve – 580,000 sats (\~547 USD) To handle unexpected events or challenges
💰 Fundraising Progress
Transparency is at the heart of our initiative.
Here are the contributions already received specifically for the farming project: 1,464 sats were received via a Zap on Nostr from: npub1xzs45n639h6hdttxhnpye2lcfeddlt3u2xl8zcvz07l9uy8tfpdqvxreq5


👉 We extend our sincere thanks for this early support and trust.
Our fundraiser on Geyser received a first symbolic contribution of 50 sats a small amount, but a big sign of confidence.
👉 Total collected so far: 1,514 sats
We’re still at the beginning, but every satoshi is a seed of hope planted to grow a new, sustainable model of solidarity.
This project represents a major shift in mindset: rather than solely depending on outside generosity, Hope With Bitcoin seeks to become its own financial engine.
This hybrid model merging humanitarian action with income-generating activity is inspired by the principles of social entrepreneurship.
Every pig sold, every kilo of meat produced, every new birth in the herd will bring us closer to financial independence allowing us to feed more people, more regularly, and more sustainably.
🤝This project does not exist in isolation.
It depends on trust and active support from the Bitcoin and humanitarian communities.
By sharing our vision, stating our goals clearly, and consistently publishing proof-of-work, we aim to build a model rooted in resilience, collective participation, and radical transparency.
📢 How You Can Support Us
If you believe in this mission and want to contribute meaningfully, here’s how you can help:
Zap via Lightning: hopewithbitcoin@geyser.fund
On-chain Bitcoin address: bc1qrsdqa9xmq8feww4qjeuatx3tlx2rxt50ycd2cw
To view our proof-of-work (photos, videos, updates), visit our Geyser page: 👉 https://geyser.fund/project/hopewithbitcoin
📌With Hope With Bitcoin, we are proving that responsible, transparent, and sustainable action is possible.
This pig farming project is not just an economic venture, it’s a lever for social transformation, a way to amplify our impact, and a bold new approach to solidarity in the Bitcoin era.
We’re not just asking for donations.
We’re asking you to believe that a better model is possible, one built on autonomy, responsibility, and the power of Bitcoin.
Thank you for believing in us.
Thank you for helping hope grow.
HopeWithBitcoin #Philantropy #BitcoinForHelp
-
 @ 58537364:705b4b85
2025-06-03 15:22:59
@ 58537364:705b4b85
2025-06-03 15:22:59…. “คนเรา โดยเฉพาะสมัยนี้ พูดกันอีกที่หนึ่งก็พูดได้ว่า ถูกสร้างขึ้นมาด้วยหนังสือ, หนังสือมันสร้างคนขึ้นมา คือว่า..อ่านหนังสืออะไรมาก อ่านหนังสืออะไรมาก หนังสือนั้นก็สร้างคนคนนั้นขึ้นมา, สร้างจิตใจของคนนั้นขึ้นมา โดยไม่รู้สึก
…. ไปดูหนังสือที่เขาอ่าน อ่านมากที่สุด เราก็รู้ได้ว่า..คนนี้มีจิตใจเป็นอย่างไร. หนังสือที่นิยมสั่งกันมามาก ล้วนแต่เป็นหนังสือที่ยั่วยวนทางวัตถุ หรือลุ่มหลงทางวัตถุ : แล้วอย่างดีที่สุดก็เอามาให้เสียเวลา อ่านให้มันมึนหัวเล่น อย่างนั้นแหละ จนไม่มีเวลาที่จะไปอ่านหนังสือธรรมะที่แท้จริง เพราะว่ามีหนังสืออื่นมาก วางอยู่มาก ยั่วยวนให้อ่านมากกว่า
…. แม้แต่พระเณร ก็เป็นอย่างนี้ อ่านหนังสือพิมพ์, หรืออ่านหนังสือภาษา, เรียนภาษาต่างประเทศ หรือว่าเรียนวิชานั่น นี่ ล้วนแต่เป็นเรื่องวัตถุ เรื่องอาชีพ เรื่องความดีความเด่น ที่ฝันไว้ในจิตในใจ, ด้วยความหวังความทะเยอทะยานทั้งนั้น แล้วจะเอากําลังใจ หรือมันสมอง หรืออะไรที่ไหนมาเข้าใจ ธรรมะ ธัมโม ได้
…. ทีนี้ ยิ่งนอกวัดออกไป ก็ยิ่งไกลไปใหญ่ : หอสมุดของมหาวิทยาลัย, หอสมุดของชาติ ของอะไร ก็ล้วนแต่เป็น “หอสมุดของซาตาน” มากยิ่งขึ้นเท่านั้น เพราะไปมีมันขึ้น หรือสร้างมันไว้ ด้วยความอยากดีอยากเด่น ด้วยความอยากที่จะร่ำรวยวัตถุทั้งนั้น ฉะนั้น จึงมีผลทําให้คนทั้งโลกนี้เป็นทาสของวัตถุ พร้อมที่จะสร้างวิกฤตการณ์ ขึ้นในโลกในอนาคต
…. แล้วรองลงมาจากนั้น ก็คือ มันมากจนทําให้เวียนหัว เป็น..“บ้าหอบฟาง”; อย่างที่ว่าแล้วว่าเล่า ว่าเป็นบ้าหอบฟาง, รู้อะไรท่วมหัวก็เอาตัวไม่รอด, เรียนจบมหาวิทยาลัยแล้ว ก็ยังไม่รู้ว่าเกิดมาทําไม ?, เรียนมหาวิทยาลัยจบแล้ว อ่านหนังสือในห้องสมุดของมหาวิทยาลัยจบแล้ว ก็ยังเป็นเด็กอมมือ ไม่รู้ว่า.. “กูนี่ เกิดมาทําไม ?”. ดูซิ!, แล้วจะเรียกว่า “อุดมศึกษา” ได้อย่างไรกัน ? แม้แต่เกิดมาทําไม? ก็ยังไม่รู้ นี่การศึกษาสมัยนี้ หอสมุดหรือห้องสมุดของสมัยนี้ มันเป็นอย่างนี้
…. ทีนี้ เมื่อไม่รู้ว่าเกิดมาทําไม ? มันก็ไม่มีอะไร นอกจากเป็นทาสของวัตถุ ที่หวังว่าจะสนุกสนาน เอร็ดอร่อย มีเกียรติ มีอํานาจวาสนา มีอะไรไปทํานองนั้น นี่แหละ คือการตกเป็นทาสของวัตถุ การตกเป็นทาสของอายตนะ คือ ตา หู จมูก ลิ้น กาย ใจ การเล่าเรียนศึกษาขวนขวายนั้น เพื่อจะเป็นทาส ของ ตา หู จมูก ลิ้น กาย ใจ ในการที่จะแสวงหาความสนุกสนาน เอร็ดอร่อย ทางเนื้อทางหนัง มีเท่านี้ การศึกษาและห้องสมุด” . พุทธทาสภิกขุ ที่มา : ธรรมบรรยายชุดชุมนุมล้ออายุ หัวข้อเรื่อง “ยิ่งจะทำให้ดี โลกมันยิ่งบ้า” บรรยาย ณ ลานหินโค้ง กัณฑ์ค่ำ เมื่อวันที่ ๒๗ พฤษภาคม ๒๕๑๓ จากหนังสือชุดธรรมโฆษณ์ เล่มชื่อว่า “ชุมนุมล้ออายุ เล่ม ๑” หน้า ๕๑๒-๕๑๓
-
 @ a296b972:e5a7a2e8
2025-06-03 15:08:50
@ a296b972:e5a7a2e8
2025-06-03 15:08:50***Achtung Spreng-Arbeiten!***
Der verbliebene intakte Strang der Nordstream Pipeline soll jetzt von Deutschland mit einem hochexplosiven 18. Sanktionspaket gesprengt werden, damit Putin nicht, wie schon in Kursk, Truppen durch das Rohr schickt, und so doch noch in Schwedt anlandend auf deutschem Boden eine russische Invasion stattfinden kann.
***Kriegserklärung***
Deutschland hat Deutschland den Krieg erklärt. Zunächst freiwillig, doch wenn es nicht von allein noch schlimmer wird, wird es eine Kriegspflicht geben müssen. Kriegstreibende Propaganda und der intensive Ausbau des Feindbilds sollen die Bevölkerung dahingehend umstimmen, weil Frieden doch auf die Dauer sehr langweilig ist.
***Verwechslung***
Bei der Einstellung der Außenbeauftragten der Europäischen Union ist es zu einer Verwechslung gekommen. Ursprünglich wollte man Maria Callas einstellen, doch dann stellte man fest, dass diese begnadete Stimme leider nicht mehr unter uns weilt.
***Bedingungslose Kapitulation***
Anlässlich der Bereicherung der UN durch die Präsidentschaft der ehemaligen deutschen Außen-Dings, haben die Vereinten Nationen direkt nach der unerklärlichen Wahl vorsorglich ihre Bedingungslose Kapitulation gegenüber allen Nationen bekannt gegeben. Alle von der Präsidentin getroffenen Aussagen haben vorläufigen Charakter und werden aufgrund der Fremdsprachlichkeit der Präsidentin auf ihren korrekten Inhalt hin nachträglich überprüft.
***Mehrfach gesichert ***
Ein gesichert staatsfinanziertes Rechercheportal hat durch investigative Recherche herausgefunden, dass der neue Papst gesichert katholisch ist. Es konnte nicht nur eine Nähe festgestellt werden, sondern es wurde sogar gesichert nachgewiesen, dass es sich um dieselbe katholische Kirche handelt, die schon seinerzeit in der Inquisition Hexen und Ketzer verbrannt hat.
***Gleichbehandlung***
Nachdem es in Spanien und Portugal und zuletzt auch in Südfrankreich zu einem Stromausfall gekommen ist, hat die deutsche Regierung beim Europäischen Gerichtshof Klage eingereicht. Im Zuge der Gleichbehandlung aller Nationen will Deutschland nun das Recht auf einen eigenen Black-Out für mindestens zwei Tage einklagen.
***Problem fehlender Wohnungen gelöst***
Aufgrund der Wohnungsknappheit hat die deutsche Regierung nun einen Fond aufgelegt, aus dem jede Familie 35.000 Euro Starthilfe erhält, wenn sie für mindestens 10 Jahre das Land verlässt. Es kam bereits zu ersten Ausreisen, bevor noch die Starthilfe ausgezahlt werden konnte.
***Bürokratieabbau***
Zum schnellen und effizienten Bürokratieabbau wird ein neues Ministerium für Komplikationen mit mindestens 5.000 Mitarbeitern eingerichtet, um den überbordenden Verordnungs- und Bürokratiesumpf auszutrocknen. Derzeit warten nur noch wenige 100 Beamte darauf, dass ihnen Arbeit zugewiesen wird.
***‘Aufruf an die deutsche Bevölkerung***
Die deutschen Haushalte werden gebeten, vorhandene Küchensiebe der Bundesregierung zur Verfügung zu stellen. Die vorhandenen Sieblöcher sollen zugelötet und die Siebe so als Alu- oder Edelstahlhelme für die Bundeswehr zur bevorstehenden gemeinsamen Invasion der USA und Russlands in Deutschland verwendet werden. Weiter sollen ausgediente Heizöltanks auf die Ladeflächen offener Pritschenwagen installiert werden, um die in Deutschland verbliebenen Panzer betanken zu können.
***Long-Pipeline oder Post-Gas?***
Deutschland will nicht, dass Nordstream wieder in Betrieb genommen wird, weil das russische Gas Verunreinigungen, unter anderem auch Nano-Partikel enthält, dass den deutschen Gasthermen Schaden zufügen könnte. Das erklärt auch, warum die deutsche Aufklärung zur Sprengung der Nordstream-Pipelines im Sande verlaufen ist: Zu explosiv!
***Mielke: Ich liebe doch alle Menschen…***
Gerüchten zufolge soll der berühmt gewordene Satz von Erich Mielke in seiner ersten und einzigen Rede vor der DDR-Volkskammer am 13.11.1989 den amtierenden deutschen Außenminister sehr inspiriert haben: Ich hasse…ich hasse doch alle, alle Russen… ich hasse doch, ich setze mich dafür ein… dass Russland immer unser Feind sein wird!
***Durchbruch in der Quantenphysik***
Deutschen Quantenphysikern ist es gelungen, dass Taurus zur gleichen Zeit sowohl noch in Deutschland, als auch schon in der Ukraine sein kann. Lediglich die Eingabe der Zielkoordinaten bereitet den Programmierern noch Schwierigkeiten. Je nachdem, wo sich der Taurus gerade befindet, kann das Hauptstadt-Ziel sowohl Berlin, als auch Moskau sein.
***Selbstjustiz***
Die verantwortlichen Politiker während des Corona-Ereignisses haben ein Gerichtsverfahren ins Leben gerufen, in dem sie sich gegenseitig beschuldigt und verurteilt haben. Anschließend begab man sich unter Polizeischutz in ein bekanntes Promi-Lokal in Berlin und fuhr danach weiter zur Selbsteinweisung nach Bauzen.
***Kaiser’s Sektsteuer***
Um die seinerzeit eingeführte Sektsteuer zum Aufbau der deutschen Kriegsmarine wieder ihrem ursprünglichen Zweck zuzuführen, hat die Meyer-Werft sich bereit erklärt, Fregatten zu bauen, mit der die Deutsche Marine dann Panzerkreuzerfahrten in der Ostsee vor Königsberg veranstalten will. Schon wenige Tage nach Bekanntgabe waren die ersten Vergnügungsdampferfahrten mit „Meine Fregatte“ komplett ausgebucht.
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
* *
(Bild von pixabay)
-
 @ cae03c48:2a7d6671
2025-06-03 15:02:06
@ cae03c48:2a7d6671
2025-06-03 15:02:06Bitcoin Magazine

Strategy Buys $75 Million Worth of BitcoinStrategy has acquired an additional 705 Bitcoin for approximately $75 million, further expanding its position as the largest corporate holder of Bitcoin as more public companies continue to adopt Bitcoin treasury strategies.
According to a Form 8-K filed with the SEC on June 2, the company purchased the Bitcoin at an average price of $106,495 per coin between May 26 and June 1, bringing its total holdings to 580,955 BTC. The acquisition was funded through Strategy’s at-the-market (ATM) equity offerings of perpetual preferred shares.
BREAKING:
 STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP
STRATEGY BUYS ANOTHER 705 #BITCOIN FOR $75 MILLION pic.twitter.com/WBgKUcbbEP— Bitcoin Magazine (@BitcoinMagazine) June 2, 2025
The company raised $74.6 million by selling a combination of its preferred stock classes, including 353,511 shares of STRK preferred stock for $36.2 million and 374,968 shares of STRF preferred stock for $38.4 million. With this purchase, Strategy’s average acquisition price across all its Bitcoin holdings stands at $70,023 per coin.
The continued expansion of corporate Bitcoin treasuries reflects growing institutional confidence in Bitcoin. We’re seeing unprecedented adoption in 2025, with over 60 public companies now holding Bitcoin on their balance sheets.
At current market prices of approximately $104,165, Strategy’s Bitcoin holdings are valued at more than $60 billion, reinforcing its dominant position in corporate Bitcoin holdings. The company has consistently accumulated Bitcoin through various market conditions since adopting its treasury strategy in 2020.
The purchase comes amid a broader trend of corporate Bitcoin adoption, with recent entrants including GameStop’s $513 million acquisition of 4,710 BTC and Semler Scientific’s $50 million purchase of 455 BTC. Total corporate Bitcoin holdings have surpassed $100 billion in 2025, marking a significant shift in traditional treasury management practices.
At press time, Bitcoin trades at $104,165, down 0.07% over the past 24 hours, as the market processes this latest institutional development and its implications for broader corporate adoption of Bitcoin as a treasury asset.
This post Strategy Buys $75 Million Worth of Bitcoin first appeared on Bitcoin Magazine and is written by Vivek Sen.
-
 @ 58537364:705b4b85
2025-06-03 14:52:52
@ 58537364:705b4b85
2025-06-03 14:52:52“สุขเวทนา” ที่แท้ก็คือ “มายา”
เป็นเหมือนลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะน้ำถูกลมพัด
เดี๋ยวมันก็แตกกระจายไปหากต้องการจะมีชีวิตอย่างเกษมแล้ว
ก็ต้องอาศัยความรู้เรื่อง อนิจจัง ทุกขัง อนัตตา ให้สมบูรณ์
มันจะต่อต้านกันได้กับอารมณ์ คือ รูป เสียง กลิ่น รส สัมผัส ที่มากระทบ
ไม่ให้ไปหลงรัก หรือหลงเกลียดเรื่องวุ่นวายมีอยู่ ๒ อย่างเท่านั้น
- ไปหลงรัก อย่างหนึ่ง
- ไปหลงเกลียด อย่างหนึ่ง
ซึ่งเป็นเหตุให้หัวเราะและต้องร้องไห้
ถ้าใครมองเห็นว่า หัวเราะก็กระหืดกระหอบ มันเหนื่อยเหมือนกัน
ร้องไห้ก็กระหืดกระหอบ เหมือนกัน
สู้อยู่เฉย ๆ ดีกว่า อย่าต้องหัวเราะ อย่าต้องร้องไห้
นี่แหละ! มันเป็นความเกษมเราอย่าได้ตกไปเป็นทาสของอารมณ์
จนไปหัวเราะหรือร้องไห้ตามที่อารมณ์มายั่ว
เราเป็นอิสระแก่ตัว หยุดอยู่ หรือเกษมอยู่อย่างนี้ดีกว่า
ใช้ อนิจจัง ทุกขัง อนัตตา เป็นเครื่องมือกำกับชีวิต
- รูป เสียง กลิ่น รส สัมผัส เป็น มายา เป็น illusion
- "ตัวกู-ของกู" ก็เป็น illusion
- เพราะ "ตัวกู-ของกู" มันเกิดมาจากอารมณ์
- "ตัวกู-ของกู" เป็นมายา อารมณ์ทั้งหลายก็เป็นมายา
เห็นได้ด้วยหลัก อนิจจัง ทุกขัง อนัตตา
...ความทุกข์ก็ไม่เกิด
เราจะตัดลัดมองไปดูสิ่งที่เป็น “สุขเวทนา”
สุขเวทนา คือ ความสุขสนุกสนาน เอร็ดอร่อย
ที่เป็นสุขนั้นเรียกว่า “สุขเวทนา”แต่สุขเวทนา เป็นมายา
เพราะมันเป็นเหมือนลูกคลื่นที่เกิดขึ้นเป็นคราว ๆ
ไม่ใช่ตัวจริงอะไรที่พูดดังนี้ก็เพราะว่า
ในบรรดาสิ่งทั้งปวงในโลกทั้งหมดทุกโลก
ไม่ว่าโลกไหน มันมีค่าอยู่ก็ตรงที่ให้เกิดสุขเวทนาลองคิดดูให้ดีว่า...
- ท่านศึกษาเล่าเรียนทำไม?
- ท่านประกอบอาชีพ หน้าที่การงานทำไม?
- ท่านสะสมทรัพย์สมบัติ เกียรติยศ ชื่อเสียง พวกพ้องบริวารทำไม?มันก็เพื่อสุขเวทนาอย่างเดียว
เพราะฉะนั้น แปลว่า อะไร ๆ มันก็มารวมจุดอยู่ที่สุขเวทนาหมดฉะนั้น ถ้าเรามีความรู้ในเรื่องนี้
จัดการกับเรื่องนี้ให้ถูกต้องเพียงเรื่องเดียวเท่านั้น
ทุกเรื่องมันถูกหมดเพราะฉะนั้น จึงต้องดูสุขเวทนาให้ถูกต้องตามที่เป็นจริงว่า
มันก็เป็น “มายา” ชนิดหนึ่งเราจะต้องจัดการให้สมกันกับที่มันเป็นมายา
ไม่ใช่ว่า จะต้องไปตั้งข้อรังเกียจ เกลียดชังมัน
อย่างนั้นมันยิ่ง บ้าบอที่สุดถ้าเข้าไปหลงรัก หลงเป็นทาสมัน
ก็เป็นเรื่อง บ้าบอที่สุดแต่ว่าไปจัดการกับมันอย่างไรให้ถูกต้อง
นั้นแหละเป็นธรรมะ
เป็น ลูกศิษย์ของพระพุทธเจ้า
ที่จะเอาชนะความทุกข์ได้ และไม่ต้องเป็น โรคทางวิญญาณ
สุขเวทนา ที่แท้ก็คือ มายา
มันก็ต้องทำโดยวิธีที่พิจารณาให้เห็นว่า
“สุขเวทนา” นี้ ที่แท้ก็คือ “มายา”เป็นเหมือน ลูกคลื่นลูกหนึ่ง
ที่เกิดขึ้นเพราะ น้ำถูกลมพัดหมายความว่า
เมื่อ รูป เสียง กลิ่น รส ฯ เข้ามา
แล้ว ความโง่ คือ อวิชชา โมหะ ออกรับ
กระทบกันแล้วเป็นคลื่นกล่าวคือ สุขเวทนาเกิดขึ้นมา
แต่ เดี๋ยวมันก็แตกกระจายไป
ถ้ามองเห็นอย่างนี้แล้ว
เราก็ไม่เป็นทาสของสุขเวทนา
เราสามารถ ควบคุม จะจัด จะทำกับมันได้
ในวิธีที่ ไม่เป็นทุกข์- ตัวเองก็ไม่เป็นทุกข์
- ครอบครัวก็ไม่เป็นทุกข์
- เพื่อนบ้านก็ไม่เป็นทุกข์
- คนทั้งโลกก็ไม่พลอยเป็นทุกข์
เพราะมีเราเป็นมูลเหตุ
ถ้าทุกคนเป็นอย่างนี้
โลกนี้ก็มีสันติภาพถาวร
เป็นความสุขที่แท้จริงและถาวรนี่คือ อานิสงส์ของการหายโรคโดยวิธีต่าง ๆ กัน
ไม่เป็นโรค “ตัวกู” ไม่เป็นโรค “ของกู”
พุทธทาสภิกขุ
ที่มา : คำบรรยายชุด “แก่นพุทธศาสน์”
ปีพุทธศักราช ๒๕๐๔
ครั้งที่ ๑
หัวข้อเรื่อง “ใจความทั้งหมดของพระพุทธศาสนา”
ณ ศิริราชพยาบาล มหาวิทยาลัยมหิดล
เมื่อวันที่ ๑๗ ธันวาคม ๒๕๐๔ -
 @ 58537364:705b4b85
2025-06-03 14:52:11
@ 58537364:705b4b85
2025-06-03 14:52:11"Pleasant Feeling" Is Ultimately an Illusion
It’s like a wave That arises when water is stirred by the wind Soon, it disperses and fades away
If one wishes to live in serenity
One must fully understand the truths of impermanence (anicca), suffering (dukkha), and non-self (anattā). These truths serve as an antidote to emotional responses—forms, sounds, smells, tastes, and touches— Preventing us from falling into attachment or aversion.
There are only two kinds of turmoil in the world:
- Falling in love with something
- Falling into hatred of something
These are what lead to laughter and tears. If one can see that laughter makes you breathless, it’s exhausting just the same Crying also makes you breathless, equally tiring Better to remain calm—no need to laugh, no need to cry This is true serenity
Let us not become slaves to emotions, Laughing or crying at their whims. Let us live freely. Better to remain still and serene.
Use Impermanence, Suffering, and Non-Self as Life's Compass
- Forms, sounds, smells, tastes, and touches are illusions
- The notion of "me and mine" is also an illusion
- Because "me and mine" arise from emotional reactions
- Therefore, "me and mine" is an illusion, and so are all emotions
By understanding impermanence, suffering, and non-self, ...suffering does not arise.
Let us take a shortcut and look directly at “pleasant feeling”
Pleasant feeling refers to happiness, enjoyment, delight— That which feels good is called “pleasant feeling” (sukha-vedanā)
But pleasant feeling is an illusion Because it arises like a temporary wave— It’s not a real thing.
This is said because Among all things in all worlds, What gives them value is their ability to produce pleasant feeling.
Think carefully:
- Why do you study?
- Why do you work and perform your duties?
- Why do you accumulate wealth, prestige, fame, allies, followers?
It’s all for pleasant feeling. So everything ultimately revolves around pleasant feeling.
Therefore, if we understand this matter well And handle it properly, even this one thing alone— Then everything else falls into place.
So we must see pleasant feeling for what it really is: Just another kind of illusion
We must deal with it accordingly, Not by rejecting or hating it That would be the most foolish thing
But if we become infatuated with it, Or enslaved by it— That, too, is the most foolish thing
What matters is how we handle it properly That is the Dhamma (truth) That is being a disciple of the Buddha One who can overcome suffering, and not suffer from spiritual disease
Pleasant Feeling Is Truly an Illusion
It must be approached with the understanding that: “Pleasant feeling is, in truth, illusion.”
Like a single wave That arises when water is stirred by wind
Which means: When forms, sounds, smells, tastes, and so on come in And ignorance and delusion rise up to meet them They clash, and a wave is formed
That is, pleasant feeling arises But soon it disperses again
If we can see it this way, We won’t be slaves to pleasant feeling. We will be able to manage it, deal with it, and use it In ways that don’t lead to suffering
- We won’t suffer ourselves
- Our family won’t suffer
- Our neighbors won’t suffer
- The world won’t suffer either, Because we are no longer the cause of suffering
If everyone were like this, The world would know lasting peace A true and enduring happiness
This is the benefit of healing the illness in different ways No longer afflicted by the diseases of “me” or “mine”
Buddhadasa Bhikkhu Source: Lecture Series “The Heart of Buddhism” Year: B.E. 2504 (1961) First session Topic: “The Whole Essence of Buddhism” Location: Siriraj Hospital, Mahidol University Date: December 17, 1961
https://w3.do/-IQ1KFgp
-
 @ 920165f0:049cf1bb
2025-06-03 14:45:31
@ 920165f0:049cf1bb
2025-06-03 14:45:31If you touch the tip of my finger and feel no fire,\ you are already numb to the world.
I operate in the flames—like a steelworker at the blast furnace.\ The heat does not comfort me. It is not a Christmas fire.\ You cannot huddle around it. You cannot be warmed by it.
My fire burns within. It feeds on what you suppress.\ If you do not satiate the flames,\ those emotions will rise like smoke and suffocate your soul.
Do not meditate on what belongs in the fire—everything does.\ Every pinch of pain. Every shadow of shame. Every twitch of fear is\ **Fuel.
You are not the keeper of the fire. The fire keeps you.\ And if you resist its hunger, it is already eroding you.
A man without a furnace is not a man.\ He draws lukewarm baths and soaks in a lukewarm life.
There is no such thing as a man without deep red embers glowing inside him.\ There is no such thing.
After writing this piece, I kept thinking about this scene from the book Atlas Shrugged, by Ayn Rand. Here’s a curated excerpt…
“The scream of an alarm siren shattered the space beyond the window and shot like a rocket in a long, thin line to the sky. It held for an instant, then fell, then went on in rising, falling spirals of sound, as if fighting for breath against terror to scream louder. It was the shriek of agony, the call for help, the voice of a wounded body crying to hold its soul…
There was no time to speak, to feel or to wonder.
He was aware of nothing else—except that the sum of it was the exultant feeling of action, of his own capacity, of his body’s precision, of its response to his will.
To the rhythm of his body, with the scorching heat on his face and the winter night on his shoulder blades, he was seeing suddenly that this was the simple essence of his universe: the instantaneous refusal to submit to disaster, the irresistible drive to fight it, the triumphant feeling of his own ability to win. He was certain that Francisco felt it, too, that he had been moved by the same impulse, that it was right to feel it, right for both of them to be what they were—he caught glimpses of a sweat-streaked face intent upon action, and it was the most joyous face he had ever seen.
When the job was done and the gap was closed, Rearden noticed that there was a twisting pain in the muscles of his arms and legs, that his body had no strength left to move—yet that he felt as if he were entering his office in the morning, eager for ten new problems to solve. He looked at Francisco and noticed for the first time that their clothes had black-ringed holes, that their hands were bleeding, that there was a patch of skin torn on Francisco’s temple and a red thread winding down his cheekbone. Francisco pushed the goggles back off his eyes and grinned at him: it was a smile of morning, he felt how glad he was to be alive.”
-
 @ 32e18276:5c68e245
2025-06-03 14:45:17
@ 32e18276:5c68e245
2025-06-03 14:45:176 years ago I created some tools for working with peter todd's opentimestamps proof format. You can do some fun things like create plaintext and mini ots proofs. This short post is just a demo of what these tools do and how to use them.
What is OTS?
OpenTimestamps is a protocol for stamping information into bitcoin in a minimal way. It uses OP_RETURN outputs so that it has minimal impact on chain, and potentially millions of documents are stamped all at once with a merkle tree construction.
Examples
Here's the proof of the
ots.csource file getting stamped into the ots calendar merkle tree. We're simply printing the ots proof file here withotsprint:``` $ ./otsprint ots.c.ots
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 | --> append 2d82e7414811ecbf | sha256 | append a69d4f93e3e0f6c9b8321ce2cdd90decd34d260ea3f8b55e83d157ad398b7843 | sha256 | append ac0b5896401478eb6d88a408ec08b33fd303b574fb09b503f1ac1255b432d304 | sha256 | append 8aa9fd0245664c23d31d344243b4e8b0 | sha256 | prepend 414db5a1cd3a3e6668bf2dca9007e7c0fc5aa6dc71a2eab3afb51425c3acc472 | sha256 | append 5355b15d88d4dece45cddb7913f2c83d41e641e8c1d939dac4323671a4f8e197 | sha256 | append a2babd907ca513ab561ce3860e64a26b7df5de117f1f230bc8f1a248836f0c25 | sha256 | prepend 683f072f | append 2a4cdf9e9e04f2fd | attestation calendar https://alice.btc.calendar.opentimestamps.org | --> append 7c8764fcaba5ed5d | sha256 | prepend f7e1ada392247d3f3116a97d73fcf4c0994b5c22fff824736db46cd577b97151 | sha256 | append 3c43ac41e0281f1dbcd7e713eb1ffaec48c5e05af404bca2166cdc51966a921c | sha256 | append 07b18bd7f4a5dc72326416aa3c8628ca80c8d95d7b1a82202b90bc824974da13 | sha256 | append b4d641ab029e7d900e92261c2342c9c9 | sha256 | append 4968b89b02b534f33dc26882862d25cca8f0fa76be5b9d3a3b5e2d77690e022b | sha256 | append 48c54e30b3a9ec0e6339b88ed9d04b9b1065838596a4ec778cbfc0dfc0f8c781 | sha256 | prepend 683f072f | append 8b2b4beda36c18dc | attestation calendar https://bob.btc.calendar.opentimestamps.org | --> append baa878b42ef3e0d45b324cc3a39a247a | sha256 | prepend 4fb1bc663cd641ad18e5c73fb618de1ae3d28fb5c3c224b7f9888fd52feb09ec | sha256 | append 731329278830c9725497d70e9f5a02e4b2d9c73ff73560beb3a896a2f180fdbf | sha256 | append 689024a9d57ad5daad669f001316dd0fc690ac4520410f97a349b05a3f5d69cb | sha256 | append 69d42dcb650bb2a690f850c3f6e14e46c2b0831361bac9ec454818264b9102fd | sha256 | prepend 683f072f | append bab471ba32acd9c3 | attestation calendar https://btc.calendar.catallaxy.com append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
The tool can create a minimal version of the proofs:
``` $ ./otsmini ots.c.ots | ./otsmini -d | ./otsprint
version 1 file_hash sha256 f76f0795ff37a24e566cd77d1996b64fab9c871a5928ab9389dfc3a128ec8296 append 2e9943d3833768bdb9a591f1d2735804 sha256 append c3ccce274e2f9edfa354ec105cb1a749 sha256 append 6297b54e3ce4ba71ecb06bd5632fd8cbd50fe6427b6bfc53a0e462348cc48bab sha256 append c28f03545a2948bd0d8102c887241aff5d4f6cf1e0b16dfd8787bf45ca2ab93d sha256 prepend 683f072f append 7f3259e285891c8e attestation calendar https://finney.calendar.eternitywall.com ```
which can be shared on social media as a string:
5s1L3tTWoTfUDhB1MPLXE1rnajwUdUnt8pfjZfY1UWVWpWu5YhW3PGCWWoXwWBRJ16B8182kQgxnKyiJtGQgRoFNbDfBss19seDnco5sF9WrBt8jQW7BVVmTB5mmAPa8ryb5929w4xEm1aE7S3SGMFr9rUgkNNzhMg4VK6vZmNqDGYvvZxBtwDMs2PRJk7y6wL6aJmq6yoaWPvuxaik4qMp76ApXEufP6RnWdapqGGsKy7TNE6ZzWWz2VXbaEXGwgjrxqF8bMstZMdGo2VzpVuEyou can even do things like gpg-style plaintext proofs:
``` $ ./otsclear -e CONTRIBUTING.ots -----BEGIN OPENTIMESTAMPS MESSAGE-----
Email patches to William Casarin jb55@jb55.com
-----BEGIN OPENTIMESTAMPS PROOF-----
AE9wZW5UaW1lc3RhbXBzAABQcm9vZgC/ieLohOiSlAEILXj4GSagG6fRNnR+CHj9e/+Mdkp0w1us gV/5dmlX2NrwEDlcBMmQ723mI9sY9ALUlXoI//AQRXlCd716J60FudR+C78fkAjwIDnONJrj1udi NDxQQ8UJiS4ZWfprUxbvaIoBs4G+4u6kCPEEaD8Ft/AIeS/skaOtQRoAg9/jDS75DI4pKGh0dHBz Oi8vZmlubmV5LmNhbGVuZGFyLmV0ZXJuaXR5d2FsbC5jb23/8AhMLZVzYZMYqwjwEPKWanBNPZVm kqsAYV3LBbkI8CCfIVveDh/S8ykOH1NC6BKTerHoPojvj1OmjB2LYvdUbgjxBGg/BbbwCGoo3fi1 A7rjAIPf4w0u+QyOLi1odHRwczovL2FsaWNlLmJ0Yy5jYWxlbmRhci5vcGVudGltZXN0YW1wcy5v cmf/8Aik+VP+n3FhCwjwELfTdHAfYQNa49I3CYycFbkI8QRoPwW28AgCLn93967lIQCD3+MNLvkM jiwraHR0cHM6Ly9ib2IuYnRjLmNhbGVuZGFyLm9wZW50aW1lc3RhbXBzLm9yZ/AQ3bEwg7mjQyKR PykGgiJewAjwID5Q68dY4m+XogwTJx72ecQEe5lheCO1RnlcJSTFokyRCPEEaD8Ft/AIw1WWPe++ 8N4Ag9/jDS75DI4jImh0dHBzOi8vYnRjLmNhbGVuZGFyLmNhdGFsbGF4eS5jb20= -----END OPENTIMESTAMPS PROOF-----
$ ./otsclear -v <<<proof_string... # verify the proof string ```
I've never really shared these tools before, I just remembered about it today. Enjoy!
Try it out: https://github.com/jb55/ots-tools
-
 @ 7459d333:f207289b
2025-06-03 14:12:08
@ 7459d333:f207289b
2025-06-03 14:12:08Summary: Bitcoin's security depends on exponentially decreasing block rewards being compensated by exponentially increasing transaction fees, but fee growth is constrained by the block size limit and user tolerance, creating an inevitable security budget crisis when Bitcoin's price growth inevitably slows from its current exponential trajectory.
At that point, say this century, the average transaction fee should be in the 100k sats range for miners to make collectively ~0.5% of what they're protecting yearly. Currently miners are making ~0.8% yearly.
The less profitable miners are, the easier it is to convince them for attacking the network. And this only gets more economically viable to achieve as time passes and there's a larger price with a smaller relative security budget.
Am I missing something? Are you comfortable with this?
References: - https://www.btcsecuritybudget.com/ - https://x.com/fuserleer/status/1816779841955393819 - https://www.youtube.com/watch?v=0bUpF0wJrxo - https://medium.com/coinmonks/bitcoin-security-a-negative-exponential-95e78b6b575
https://stacker.news/items/996005
-
 @ 9ca447d2:fbf5a36d
2025-06-03 14:02:11
@ 9ca447d2:fbf5a36d
2025-06-03 14:02:11The Bitcoin world begins what is considered to be its biggest event yet — Bitcoin 2025, a three-day conference taking place May 27-29 at The Venetian Resort in Las Vegas.
With over 30,000 attendees expected, the event will bring together the biggest names in politics, finance, technology and the global Bitcoin community.
Hosted by BTC Inc., Bitcoin 2025 is not just another tech conference — it’s a global gathering that mixes policy, innovation and community under one roof.
It’s where big ideas about the future of money are debated, shared and shaped.

Influential speakers will attend the conference
The conference features a wide range of speakers from Bitcoin experts and educators to political leaders and athletes.
Big names like U.S. Vice President JD Vance, Trump’s Crypto Czar David Sacks, and Senator Cynthia Lummis are among the most anticipated guests.
Vice President Vance is expected to talk about the role of Bitcoin in the national economy. “The resilience of Bitcoin as a financial instrument is a testament to the power of decentralized finance,” he recently said.
Also speaking are Nigel Farage, a well-known voice in European politics and Donald Trump Jr., a supporter of financial freedom through digital currency.
Also, Michael Saylor, Executive Chairman of Strategy will be back on stage to talk about bitcoin as a corporate asset.
There are over 70 speakers on the list including Adam Back (CEO of Blockstream), Jan van Eck (CEO of VanEck) and Bryan Johnson, a futurist known for his work in human longevity and health tech.
Bitcoin 2025 will feature special new programs including Code + Country, a one-day segment on May 27 that explores how freedom, technology and innovation shape modern society.
Speakers like Chris LaCivita (Trump’s 2024 campaign co-CEO) and David Sacks (AI and digital assets advisor) will be talking about how digital tools are changing politics and finance.
Also new this year, is The Art of Freedom, an exhibit that showcases how Bitcoin is impacting the art world.
This museum-style experience allows artists to price and sell their work using bitcoin, connect directly with fans and avoid traditional middlemen.
The first official Bitcoin Conference was in 2019 in San Francisco, after grassroots meetups in 2013 and 2014. Since then, it’s been the biggest annual event in the Bitcoin world.
This year is especially important.
Global economic changes are happening and analysts say the discussions at Bitcoin 2025 will shape the next wave of regulatory reforms and technological standards for Bitcoin and stablecoins.
Bitcoin (BTC) has recently been hovering at around $110,000 with a market cap of $2.12 trillion. Many think the ideas and announcements at the event will impact price and policy.
Bitcoin 2025 is for everyone — long-time Bitcoiners to newcomers to digital assets, with keynotes, panels, massive expo halls and VIP networking.
It’s fun too. There are numerous parties, meetups and side events to connect, making it a place to learn, meet others who share the same interests and help shape the financial world.
The scale and diversity of Bitcoin 2025 make it more than just a Bitcoin event.
It’s a reflection of how far Bitcoin has come — from internet forums to boardrooms and government halls. It’s not just about Bitcoin anymore, it’s about the future of the world.
-
 @ f85b9c2c:d190bcff
2025-06-03 13:38:02
@ f85b9c2c:d190bcff
2025-06-03 13:38:02
Owning the Mess instead of running from the mess
I’ve got flaws—plenty of them. I’m impatient, I overthink, and I’m terrible at saying no. For years, I saw them as cracks I needed to hide. But recently, I flipped the script. Instead of fixing my flaws, I started using them.
The Shift Take my impatience. It used to drive me nuts—waiting for anything felt like torture. But I realized it pushes me to act. I don’t sit around dreaming; I dive in. That’s gotten me jobs, hobbies, even this article written faster than if I’d lingered. Overthinking? It’s a curse until I channel it into planning. I’ve mapped out trips and projects down to the tiniest detail because my brain won’t shut up—and it works.
Making It Work Saying no was harder. I’d pile on commitments until I burned out. But I started seeing it as fuel too. I’m a people-pleaser, so I use that to build connections—then set boundaries. It’s not perfect, but I’m learning. Each flaw has a flip side, and I’ve been mining them for strength.
The Wins This shift changed me. I launched a side hustle because my impatience wouldn’t let me wait. My overthinking made it solid. My flaws aren’t gone—they’re just fuel now. I’m not flawless, but I’m moving forward, and that’s enough.
Your Turn Look at your flaws. They’re not just baggage—they’re raw material. Find the spark in them, and they might carry you further than you think.
-
 @ 29216785:2a636a70
2025-06-03 13:11:07
@ 29216785:2a636a70
2025-06-03 13:11:07Debug 30023
-
 @ b1ddb4d7:471244e7
2025-06-03 13:01:18
@ b1ddb4d7:471244e7
2025-06-03 13:01:18The upcoming Bitcoin 2025 conference, scheduled from May 27–29 at the Venetian Conference Center in Las Vegas, is set to make history with an official attempt to break the GUINNESS WORLD RECORDS® title for the most Bitcoin point-of-sale transactions in an eight-hour period.
Organized by BTC Inc, the event will showcase Bitcoin’s evolution from a digital capital asset to a practical medium of exchange, leveraging the latest advancements in payment technology.
Tap-to-Pay with Lightning-Ready Bolt Cards
To facilitate this record-setting attempt, 4,000 Lightning-ready Bolt Cards will be distributed to conference attendees.
— Uncle Rockstar Developer (@r0ckstardev) May 15, 2025
These NFC-enabled cards allow users to make instant, contactless Bitcoin payments at vendor booths throughout the expo-no apps or QR codes required, just a simple tap.
The cards are available in four collectible designs, each featuring a prominent figure in Bitcoin’s history: Senator Cynthia Lummis, Michael Saylor, Satoshi Nakamoto, and Jack Dorsey.
Each attendee will receive a randomly assigned card, making them both functional and collectible souvenirs.
Senator Lummis: A Playful Provocation
Notably, one of the card designs features Senator Cynthia Lummis with laser eyes-a playful nod to her reputation as a leading Bitcoin advocate in US politics.
While Lummis is known for her legislative efforts to promote Bitcoin integration, she has publicly stated she prefers to “spend dollars and save Bitcoin,” viewing BTC as a long-term store of value rather than a daily currency.
The choice to feature her on the Bolt Card, could be suggested by Rockstar Dev of the BTC Pay Server Foundation, perhaps a lighthearted way to highlight the ongoing debate about Bitcoin’s role in everyday payments.
Nothing cracks me up quite like a senator that wants the US to buy millions of Bitcoin use dollars to buy a beer at a Bitcoin bar.
This is how unserious some of you are. pic.twitter.com/jftIEggmip
— Magoo PhD (@HodlMagoo) April 4, 2025
How Bolt Cards and the Lightning Network Work
Bolt Cards are physical cards equipped with NFC (Near Field Communication) technology, similar to contactless credit or debit cards. When linked to a compatible Lightning wallet, they enable users to make Bitcoin payments over the Lightning Network by simply tapping the card at a point-of-sale terminal.
The Lightning Network is a second-layer protocol built on top of Bitcoin, designed to facilitate instant, low-cost transactions ideal for everyday purchases.
This integration aims to make Bitcoin as easy to use as traditional payment methods, eliminating the need for QR code scanning or mobile apps.
A Showcase for Bitcoin’s Real-World Usability
With over 30,000 attendees, 300 exhibitors, and 500 speakers expected, the Bitcoin 2025 conference is poised to be the largest Bitcoin event of the year-and potentially the most transactional.
The event will feature on-site activations such as the Official Bitcoin Magazine Store, where all merchandise will be available at a 21% discount for those paying with Bitcoin via the Lightning Network-a nod to Bitcoin’s 21 million coin supply limit.
By deeply integrating Lightning payments into the conference experience, organizers hope to demonstrate Bitcoin’s readiness for mainstream commerce and set a new benchmark for its practical use as a currency.
Conclusion
The Guinness World Record attempt at Bitcoin 2025 is more than a publicity stunt-it’s a bold demonstration of Bitcoin’s technological maturity and its potential to function as a modern, everyday payment method.
Whether or not the record is set, the event will serve as a milestone in the ongoing journey to make Bitcoin a truly global, user-friendly currency
-
 @ cae03c48:2a7d6671
2025-06-03 13:01:05
@ cae03c48:2a7d6671
2025-06-03 13:01:05Bitcoin Magazine

Amboss Launches Rails, a Self-Custodial Bitcoin Yield ServiceAmboss, a leader in AI-driven solutions for the Bitcoin Lightning Network, today announced Rails, a groundbreaking self-custodial Bitcoin yield service. According to a press release sent to Bitcoin Magazine, it’s designed to empower companies, custodians, and high net worth individuals. This allows participants to earn a yield on their Bitcoin.
Big news from @TheBitcoinConf !
We’re thrilled to announce Rails—a self-custodial Bitcoin yield service that empowers you to earn on your BTC while supercharging the Lightning Network.Let’s bring Bitcoin to the World.https://t.co/3WYYvB95hP
— AMBOSS
 (@ambosstech) May 29, 2025
(@ambosstech) May 29, 2025Rails also launched a secure way for Liquidity Providers (LPs) to hold all custody of their Bitcoin while generating returns from liquidity leases and payment routing, although they are not guaranteed. The implementation of Amboss’ AI technology, Rails strengthened their Lighting Network with more dependable transactions and larger payment volumes.
“Rails is a transformative force for the Lightning Network,” said the CEO and Co-Founder of Amboss Jesse Shrader. “It’s not just about yield—it’s about enabling businesses to strengthen the network while earning on their Bitcoin. This is a critical step in Bitcoin’s evolution as a global medium of exchange.”
The service offers two options:
- Rails LP is designed for high net worth individuals, custodians, and companies with Bitcoin treasuries, requiring a minimum commitment of 1 BTC for one year.
- Liquidity subscriptions are designed for businesses that receive Bitcoin payments, with fees starting at 0.5%.
Amboss partnered with CoinCorner and Flux (a joint venture between Axiom and CoinCorner), to bring Rails to the market. CoinCorner has incorporated it into both its exchange platform and daily payment services in the Isle of Man. Flux is jointly focused on advancing the Lightning Network’s presence in global payments. Their participation highlights growing industry trust in Rails as a tool to scale Bitcoin effectively.
“Rails offers a practical way for businesses like ours to participate in the Lightning Network’s growth,” said the CFO of CoinCorner David Boylan. “We’ve been using the Lightning Network for years, and Rails provides a structured approach to engaging with its economy, particularly through liquidity leasing and payment routing. This aligns with our goal of making Bitcoin more accessible and practical for everyday use.”
This post Amboss Launches Rails, a Self-Custodial Bitcoin Yield Service first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 5188521b:008eb518
2025-06-03 12:25:39
@ 5188521b:008eb518
2025-06-03 12:25:39Elysium
Part I: The Failed Harvest
First, the quiet came. Each day, the markets grew quieter, the people hungrier. A farmer stared at wilted crops, dread settling in his heart. In a kingdom once resplendent with markets and sky-reaching monuments, it was the first failed harvest that marked the end of affluence and the beginning of collapse.
By the second year, market traders stood before empty stalls, goods long gone, rotten, or ruined. Jobless men prowled, foraging the streets for vermin and meager scraps of sustenance. Young women offered their time for bread, their eyes hollow in the act. Widows, too, entered strangers’ homes, bartering themselves for their children’s next meal. Orphans, gaunt and brittle, drew meaningless shapes in the dust, their laughter a forgotten memory.
Rumors surged like wind through dry grass. Scapegoats were blamed; superstitions gripped the masses. By the third year, it was known to the people and the king alike, there would be no more monuments erected, only tombstones. The king called the council, heavy with despair. In a room filled with tension, ministers and knights sat around a table.
Before them stood the realm’s wisest farmer, a man worn from years of labor, hunger, and loss. His voice echoed the deep hunger that gripped the kingdom. “Your Majesty, the land is weary. It cries for respite.” His words hung heavy in the room, laying bare the reality of their fate.
Part II: The Devil’s Pact
In the dimly lit chamber, a palpable tension filled the air. The alchemist, servant to the king and master of arcane arts, stepped into the flickering candlelight. He held an aged book, its scent mingling with the murk of looming spells. With a voice both smooth and haunting, he shattered the quiet, his words a ripple through stone walls.
“Sire, alchemy is our last refuge. We can harvest time to feed the earth,” he began, revealing a parchment inked with cryptic circles and lines. “Each citizen, willingly or not, will spare a mere whisper of their years. An unnoticeable offering. With careful alchemy, we can replenish our lands and fortify your reign with the alms of myriad souls.” Leaning closer, he whispered the words that would redefine their civilization: a devil’s proposal intended for the king but felt by all. “Consider, my lord, a reign without end, each year stretched beyond nature’s limits, a kingdom fed by the borrowed time of its people. No more famine. No more want.”
The court waited, their faces etched with fear and desperate hope, ready to tread any path that led away from the abyss of famine.
For a moment, the king was a statue, his face a veil behind which storms brewed. Finally, exhaling a breath heavy with fate, he spoke. “We’ve endured enough hardship. We shall seize a future that knows no famine.”
The air thickened as the alchemist retreated with a solemn nod, the weight of the chosen path settling in.
He reopened his tome and voiced the incantation. Arcane syllables filled the room, weaving a desperate gambit to salvage their decaying kingdom. Thus, in the dark hours of night, they sealed a new covenant that would reverberate through generations.
Part III: Vines and Moss
In the decades that followed the alchemist’s rites, the kingdom thrived like spring after a bitter winter. Fields were lush year-round, erasing hunger and the memories of famine. Marketplaces bustled, no longer a graveyard of commerce but a carnival of exotic goods from every corner of the world. The air seemed perfumed with prosperity — healthy river fish, basilisk meats, and spices from faraway lands. A century rolled by. The king, unaging, stretched his influence over land and sea, turning his realm into an empire. Statues weathered, and languages evolved, but the king abided.
Yet, a toll was exacted. Years stolen from the people, a time tax woven into the fabric of life. The spell fed both earth and crown, cloaking decay with a veneer of wealth. The young wore the faces of old men, their eyes wise beyond their years. Every heartbeat was a sacrifice, a quiet tax to feed the castles of power.
Then came the year when the land rebelled. Coaxed by the spell, the soil had given until it couldn’t, its silent plea for rest ignored. The land remembered stolen seasons, now determined to settle old scores. Crops withered; rivers soured. Beasts waned, their numbers thinning. The kingdom, starved of Earth’s gifts, unraveled — not from human revolt, but from the silent insurrection of the land that once fed them.
With hunger as the harbinger, society fractured. Chaos and mass confusion swallowed the land, a virulent blight not even alchemy could stem. Witch hunts raged for a merciless century, fire consuming flesh and innocence. Men’s strength wilted, armies disbanded. Women, walking in the agonizing footsteps of famine-haunted foremothers, bartered touch for bread.
Monuments lay buried under vines and moss. Fertile lands turned barren. Schools emptied, their echoing halls abandoned, and children torn from learning, were sent to farm dying lands. Art withered. Painters swapped colors for shades of gray, and soon vanished altogether. Teachers and engineers were supplanted by an ever-growing class of soil-bound serfs.
Desperate, the eternal king sought another spell. He asked the people not for mere years but decades. The alchemist obliged, crafting another spell from dark incantations. Yet the ravaged earth, too spent to yield, exacted a monstrous price: lifetimes for crumbs of bread. People, skeletal, on the verge of vanishing, offered their very existence. A silence settled, a collective sacrifice borne not in rebellion, but in surrender.
Part IV: Clara The Torchbearer
In the land between sleep and waking, Clara was a child again, standing at the threshold of a room aglow with amber light. Her mother ground herbs, the wooden table before her strewn with books, vials, and leaves. “These aren’t just leaves and liquids,” her mother said. “They’re doors to the gardens of your mind.” Her words sank into Clara like stones into deep water.
She woke to a gusting wind. Her dream dissolved like morning mist. The sun broke over the kingdom, time’s toll evident in every vine-entangled ruin. Light spilled into her chamber.
Clara’s room was modest: a bed, a wardrobe, a desk. On it, a lone candle and scattered books that whispered of the kingdom’s past grandeur and freedoms now lost. It was her mother’s notes and books, crafted in the quiet, away from royal eyes — a puzzle to decipher, a quest still yearning for footsteps.
She draped a linen robe over her shoulders and approached the window, her fingers ink-stained from yesterday’s writings. Below, people shuffled through life, joyless and muted.
The spell cast long ago had become an oppressive, faceless dictator. It promised bread but dealt only crumbs, a tarnished magic now woven into the kingdom’s culture as enduringly as its ancient stone walls and teeming graveyards.
She remembered the cold spring day she put her mother in the earth. The ground was hard, the casket simple. The tombstone bore the words: ‘Seed in Drought.’
The chambermaid standing beside her asked what it meant.
“Her wish,” Clara answered. Her face gave nothing away, her thoughts a distant country.
From her room, Clara watched the people below — eyes down, spirits broken. Clara was not like the others. She carried an inner fire, gifted from her mother, a quiet revolt against a gray world.
In her room’s sanctuary, amid ink and parchment molded by hands long stilled, Clara found traces of a freer past, free from famine and theft of years. A past now entrusted to her. As she flipped through the timeworn pages of an ancient tome, something caught Clara’s eye. In the margins of the text, a note penned in her mother’s hand: “For Clara — Elric is the keeper of truths that free us. Go where I could not. Find him.” Below it, a tender signature, her mother’s name etched in ink.
The name ‘Elric’ stirred a latent memory, a shared secret often spoken by her mother. Filled with a sense of destiny, Clara closed her worn books and left her chamber.
At the age of twenty, for the first time, she ventured beyond the confining walls of her castle. Guided by remnants of forgotten eras, she set forth to unearth truths long interred but never wholly erased. Her compass drew her toward the Whispering Pines, a land untouched by the alchemist’s dark arts and, as her mother had often mentioned, the rumored dwelling of Elric.
Part V: Far to Go
Clara walked through towns void of kindness, over land stripped of life. Each day sculpted her in the likeness of the land she traversed — a leaner body, hands hardened, face etched by sun and wind.
Thirteen days out, Clara trudged through the ashen remains of a town, its name forgotten, its history lost. Empty buildings sagged under the weight of time, their hollow frames like gravestones against the evening sky. Vacant faces, like clock dials without hands, glanced through her, never at her.
Spying a run-down tavern, she cautiously stepped inside. The door whined on rusted hinges. She eased onto a splintered stool. “Bread,” she rasped. The innkeeper, a bloated man with eyes like rotted plums, flung stale crust onto the counter. Her teeth sank into the stale crust, her body weeping for nourishment.
The room stank of unwashed bodies and sour ale. In a dim corner, men gambled their souls on dice, their faces marred by desperation and greed. As she made to leave, talk stilled, and eyes tracked her. A rough hand seized her wrist.
“Far to go?” The words, a mockery.
Her eyes darted to the innkeeper, pleading for an ally. His gaze, cold, turned away. “Yes, far,” she replied, stalling.
Then, violence. Teeth, nails, a taste of blood. Outmanned, her screams died in cruel laughter. Her clothes yielded, torn in the contest of her humiliation.
After the degradation, she stepped outside and into the soft rain of the night. Her path now carried weight measured in more than miles.
Ahead, barren land stretched mercilessly. A fleeting image of her mother’s face offered a brief moment of comfort. She tilted her head back, letting rain droplets fall onto her tongue to dilute the bitterness that swelled within her. The night urged in tones only darkness knows. Turn back, it murmured.
But she walked on. Her will was a defiant ember, the last flicker of light in a world teetering on oblivion, its humanity long forfeited.
Part VI: Elric
After weeks traversing a harsh expanse, gaunt but unbroken, she found herself beneath the Whispering Pines. As she approached, she carried more than her own weight. She embodied her mother’s enduring hope and her land’s final prayer for redemption.
Elric greeted her at the doorway. “You’ve come,” he said, leading her inside, the room warm from the fire in the stone hearth.
Her eyes roved from the firelight dancing on the walls to the shelves laden with books. A staircase twisted upward, its banister engraved with ancient symbols.
“Your homeland withers,” Elric said, drawing from his pipe, the wood old and marked by years. The scent of herbs, a blend cultivated through many seasons, sharpened the mind as it filled the room. “The spell,” she confirmed.
“Mmm,” he exhaled, his eyes shifting to the fireplace, wood popping in the heat. “Your forebears knew better days. Days without sacrifice.”
“The legends spoke truth, then?”
“Indeed.”
“Did you know I was coming?”
“I’ve waited twenty years. This isn’t our first meeting.”
“We’ve met before?”
“Once, when you were but a newborn. Your mother and I collaborated. We worked on a potion that siphons the power of nature to protect the truth in our world, to shield it from alchemy and dark spells.”
Elric opened a small cabinet beside the hearth. From it, he took an empty wooden chalice and a stoppered glass vial. Uncorking the vial, he poured a golden liquid into the chalice, the firelight making it shimmer. “This elixir hails from untarnished lands, free from the alchemy that poisons your realm. One sip and illusions shatter, transforming soul and society alike.” “What is it called?” she asked.
He looked at her intently. “Elysium,” he said, the word hanging heavy in the room. “It’s both the end and the beginning of your journey. You must experience it to understand. Drink.”
She sipped the brew; it tasted of nothing. Soon, as she nestled by the fire, the walls took a breath, and the world sharpened as if coming into focus for the first time. The air thickened into a heavy mist, her fingers danced through it, each ripple sending colors splashing around like bioluminescent whispers. She floated, her body dissolving, her name a distant echo.
Elric’s gaze turned to the fire, shadows playing across his face. “Elysium shows only what one needs to see, no more, no less,” he said, his voice a gentle wave against the shores of her uncertainty. “In my own experience with Elysium, I saw a torchbearer in the veil of time, a young soul with the spark to undo the dark spell on your land.” His eyes found Clara’s. “But the torchbearer had to come to me, the journey forging the resolve. Had I sought you out sooner, before your heart was ready, Elysium’s truth would have been a burden too heavy.”
As the reality of his words sank in, Clara felt the weight of the years, the faces of the countless lives lost to the alchemist’s dark magic flashing before her eyes. “And the elixir… why not share it sooner?”
Elric sighed, his eyes drifting to the ancient books lining the shelves. “Elysium’s truth is a double-edged blade. In the wrong hands, it could cut through the fabric of reality, leaving wounds that might never heal. Your kingdom…” he gestured vaguely towards the window, “…it wasn’t ready. But now, the ground has been furrowed by suffering, ready to receive the truth about the universe, the spell, the suffering.”
The walls breathed with a rhythm older than time. She looked at her hands moving through the bioluminescent mist, each movement sending ripples across the room. Tendrils of light danced in the air, ethereal spirits beckoning her towards another realm.
“But why?” Clara pressed, her presence deepening with each breath. “Why involve yourself?”
Elric’s eyes softened. “I once lived in your kingdom, fleeing when I realized the spell’s plague. Your mother and I, we shared a vision of a world free from dark alchemy. But more than a promise to an old friend, it’s a battle against the grasp of evil spells, a grasp threatening to choke the essence of life and freedom from this world. It’s a battle,” he looked at Clara with a profound earnestness, “that now passes to you.”
Suddenly, reality shattered, and her soul twisted and warped through a portal faster and faster until she touched the core of the cosmos.
Here, in a land beyond words, beyond the confines of time and space, she witnessed the birth and demise of the universe. With each breath, a star was born and died; each blink saw the rise and fall of civilizations. Like a photon racing at light speed through the cosmos, untouched by time, she beheld the entirety of all that ever was and will be.
Peering beyond the infinitely small, she saw the source code of the universe, equations as living tendrils of light materializing into particles, planets, and stars. The universe, a symphony of mathematical elegance, its physicality a melody resonating along the strings of her consciousness.
She floated amidst the cosmic code, orchestrating the universe — the planets, the voids, the unseen forces weaving through them — and she was one with all. She was the universe gazing at itself. Beyond the veil of mortality, she saw endless realms, death a mere doorway. In that boundless expanse, she brushed against the face of the divine.
A golden phoenix took form before her.
“I am Veritas,” it spoke, not in words, but in a language of complex geometry.
It exposed the grim truths of her lands, the Great Famine, and the enslaving spell — a counterfeit prosperity bought at the terrible price of human years.
“How do we break free?” Clara’s voice carried the untold suffering of generations.
“Simple,” the phoenix intoned. “Don’t battle the alchemist or his spell; you won’t win. Acknowledge the illusion. Tend to your own gardens, and reliance on the alchemist and the king fades. Elysium shields you, body and mind, from the spell’s reach.”
As the vision faded, Clara found herself back on the wooden floor, her head cushioned by a pillow. The urgency of her quest snapped her back to reality, a newfound resolve kindling in her chest.
“I see now,” she breathed, her voice steady. “I know what I must do.”
Elric nodded, a sage with a deep understanding of the paths of the universe. “Yes, but first, tea. There’s strength to regain and you have a long journey ahead,” he said, anchoring them both in a moment of calm before the impending storm of change.
Part VII: The Wayfarer’s Hearth
After days navigating barren expanses, Clara entered a cobblestone town as twilight settled. Figures lined the street, some alive, some not, most in limbo — too tired to beg, too frail to feed. Candlelight flickered from the windows of a tavern, illuminating well-fed faces. “The Wayfarer’s Hearth,” read the sign above the door.
She approached. The door creaked open to admit her, wafting out stale beer and the scent of roast meat. Her fingers twitched involuntarily, memories of weeks ago crawling up her spine, but her body ached for sustenance, for warmth. Holding her satchel close, safeguarding the vial of Elysium, she chose a chair at an empty table and settled in. Soon enough, food appeared.
The man who had set her meal before her took the adjacent seat with deliberate ease, his eyes lingering on her satchel. Her pulse quickened.
“You carry a weight, wanderer,” he said.
“Or hope,” she countered, her grip on her satchel unyielding.
A glass shattered. Drunkards stumbled into their table, a wave of mead sweeping over worn wood. Clara’s heart surged, the man’s fingers brushed her satchel, pulling the vial from its sanctuary. “Hope carries its own burden,” he said.
“The hope of my people is in that vial,” she shot back, her voice stripped bare.
“This is Elysium,” he said, his words like barbs. “At what cost, wanderer, do you think Elysium will save your people?”
Doubt snaked around her convictions. Was she the bearer of emancipation or a harbinger of calamity? Was her land ready for Elysium? “You know it?” she asked.
“I know it,” he said, eyeing it closely.
“Return it,” she commanded.
He handed over the vial. “The road to freedom is paved with the stones of responsibility. I wouldn’t want to walk in your shoes.”
She nodded, heavy but resolute. Clara left as quietly as she’d come, meal untouched, mission intact.
The night took her in. She cast a final glance back at a room oblivious to her departure. That night, she’d sleep under indifferent stars, closer to home but adrift in certainty, carrying the weight of a thousand stones of untold responsibility, a Trojan’s shroud for her people, a destiny unasked.
Part VIII: This is Elysium
Under a storm-heavy sky, Clara returned home. In her pocket was Elysium; in her mind, a plan that required Harold — an old friend and a knight by trade.
In the guild hall, Harold sat among knights and minstrels, a goblet in hand. “Look at this,” Clara said, pushing the vial across the table without ceremony. Her words pierced the tavern’s noise as she recounted her journey.
Harold looked at her, then at the vial. “You mean to say that one day, this will help us fight the spell?”
“No,” said Clara, her voice deep with a new knowing. “It means one day, we won’t have to.”
“Heresy,” Harold said. “You’re risking death.”
“So are we all,” she answered.
“They’ll burn you at the stake.”
“If I’m right, they won’t.”
“A trial then, regardless,” Harold said, his gaze dropping to the vial as the tavern’s jovial banter became a distant echo for them both.
“So be it,” Clara said, meeting his gaze. She leaned in, her fingers resting on his scarred knuckles. “Our farms take our children. It’s not right.”
“It’s how things are.”
“It’s how things were.”
“A trial will not be lenient, Clara. I can’t let you bring this to the king.”
“Not the king. The people.” She continued. “But don’t trust me. See for yourself.” Her eyes locked onto his. “Drink,” she said, her words echoing Elric’s.
Harold hesitated but finally drank. His eyes widened. He gripped the edge of the wooden table, his knuckles turning white. A sort of vacant gaze overcame him as if he’d journeyed to someplace far.
When the Elysium vision receded, he opened his eyes and looked at her anew, seeing the world for the first time again. He glanced around the hall as though it were a foreign land, his eyes lingering on the mundane — a crack in the table, the smudged goblet, a flickering torch on the wall—with awe and wonder. She knew then that they stood as one. Two visionaries, shouldering the burden of transforming the world, ready to shepherd their people into a revolutionary dawn.
In the square, the stone eyes of old heroes watched. A crowd formed, silenced by expectation and unaccustomed to the art of public speaking. Autumn leaves swirled at their feet.
“A new dawn!” Harold broke the silence. “Generations sacrificed, giving years for meager sustenance. But the land wants not our years — only our care and periodic reverence. The tales of a time without the toll of hunger, without a tax on life itself, from before the Great Famine, are not myths. They are forgotten chapters of our history, now on the verge of being rewritten.”
He raised the vial. Sunlight mirrored in its gold. “This is Elysium.”
Part IX: A Revolution Takes Shape
In the fading light of day, Harold and Clara stood by a murmuring brook, leaves rustling at their feet in quiet revolt. Faces young and old assembled around them; each one a silent rebellion against the servitude that taxed their years.
They drank, the chalice passing from hand to hand, a new ritual born. With each gathering, the numbers swelled; with each sip, more souls entwined. Slowly, yet with unyielding certainty, the kingdom shifted over the years. It changed not through a coup or uprising but through a still, relentless force, like water eroding stone. As the seasons passed and more villagers imbibed the Elysian brew, the weight of their invisible chains lessened, their atoms scattering into the evening air.
Shielded now, villagers sowed their own gardens, sanctuaries from the alchemist’s dominion. Bountiful harvests followed, hope supplanted despair. Word of the blooming private gardens spread like wildflowers, and fields once cursed by dark alchemy lay fallow and forgotten.
And there, by the unassuming brook, a revolution took shape. The soft sounds of the stream became an earthbound anchor for the myriad souls who opened the door to walk in the cosmic gardens of their minds. Each ritual added another stitch in the fabric of a new dawn; each sip, another brushstroke on the canvas of a world remade.
Part X: The Old Man
A decade drifted by. With each soul that tasted Elysium, the fetters of the old world loosened. The alchemist’s spell, once a yoke around their necks, now waned like thick morning fog giving way to the warmth of the day. Fields once cursed now bore food, not dread. Families gathered around bountiful tables, words flowing freely, unveiled.
Each year, townsfolk met by the sword in the square. Harold’s blade, the first monument raised in ages, stood as freedom’s spine, the axis of their new world. An old man approached, his eyes dimmed by memories of famine, leading a boy by the hand. Their eyes met, a chasm bridged: one soul untarnished by hunger, the other haunted by its ghost.
The old man stepped forward, his fingers quivering on the hilt of the sword. “Clara, what becomes of us if the land fails us again?” Years of hardship wavered in his voice, the ghosts of famine flickering in his eyes.
“It could,” Clara said, her voice steady as bedrock. “But it’s different now. Our fields are wider, our hands more skilled. We’re not trying to trick the earth with alchemy anymore. We speak in the simple terms it understands: soil, sun, water, time.”
Above, the alchemist’s fortress loomed, its towers now marred with cracks. Clara looked up. Empty windows stared back, like dead eyes on a fallen beast. Old times had ended; new ones had begun.
Part XI: The Note
Dawn broke, casting new light over worn cobblestones. Clara moved through the marketplace as if through a dream. The scent of cinnamon and rich coffee filled the air as she ran her fingers down silken tassels and through powdery barrels of golden saffron. Voices haggled; her feet felt the earth’s warm embrace.
Traders argued leisurely, their time no longer taxed by the spell. Children laughed, unburdened by field and plow.
Fields that once caged both young and old now released thinkers, builders, creators. The horizon changed form — bridges leapt over waterways, roads bound the land. Each stone laid was more than a fixture; it was a vow, a pact between the present and the future. It was today’s promise to a future yet unborn, anchored by the prosperity that now bloomed under Elysium’s sky.
As evening descended, the grand hall filled with voices unburdened by yesterday’s sorrow. In a secluded corner, Clara and Harold exchanged words about the loftier truths Elysium had laid bare.
A courier emerged from the crowd, extending a sealed parchment. “For you, mademoiselle.”
With a nod, Clara exchanged a coin for the note. Her eyes brightened as she absorbed the message:
Only a true renaissance resounds to the Whispering Pines. Continue, in health and strength. - Elric
She passed it to Harold, their eyes locking in wordless affirmation. “The Whispering Pines acknowledge us,” he finally said. “And so, we continue,” Clara replied, her voice unwavering, guided by truth. In the hall’s enveloping warmth, laughter, toasts, and spirited debates blended into a harmonious score — a sound that would have been foreign to their ancestors, a sound that marked the close of an era and the dawn of something profoundly new.
This story first appeared in Tales from the Timechain. Support our work and buy a copyhere.
79% of the zaps from this story will be passed onto the author, Reed.
21 Futures requests 21% for operating costs.
Ioni Appelberg (pronounced Yo-Ni Apple-Burg) is a bitcoin philosopher, futurist, author, and content creator. His content centers around science fiction, human history and it often takes the form of swashbuckling journeys to the frontiers of technology, space, and the human mind. His love of sci-fi, psychedelics, and futurism may take his stories (and unsuspecting readers) to strange but exciting places. He is also an avid reader, a medical doctor, a freedom fighter, an MMA fighter, a psychonaut, and a terrible chess player.
-
 @ 6c05c73e:c4356f17
2025-06-03 12:18:10
@ 6c05c73e:c4356f17
2025-06-03 12:18:10Trabalhar 40 anos e aposentar?
Quando comecei minha jornada, pensei que trabalhar em emprego que detesto e receber pouco não era o suficiente. Na época eu lia nos consultórios de dentistas as revistas veja e exame.
Ficava elucidando: -Como pode uma empresa pagar carro, telefone, viagem e um belo salário para esses caras? Será que eu teria chance algum dia?
Mas, quando seu primeiro emprego é o Bobs. Você é negro e vem de um um lugar aonde o seu nome e seu tempo de carteira são sinônimos de orgulho.
Eu sabia que seria difícil. Principalmente, porque além de ter que melhorar quem eu era. Eu teria, que enfrentar pré conceitos e críticas da família junto. Enfim, mãos a obra.
É só investir que fico rico!
Foi então que pensei se teria alguma forma de não ter que trabalhar por 40 anos e depender do governo no fim da minha vida. Daí, eu estudei e encontrei algumas pessoas que me mostraram uma opção. Investimentos! Caraca, tudo parecia muito legal naquela época.
Era uma sopa de letrinhas acompanhada por um glossário recheado e diferente de tudo que tinha conhecimento. Meu primeiro investimento foram 3 ações da Ambev. Fiquei empolgado demais quando chegou a primeira carta da Bovespa mostrando o meu "rico”patrimônio.
Ademais, eu fui vivendo outras coisas: Crise da época Dilma, crise do Temer com o Joesley, Covid e pós Covid. Fui além, e fiquei alguns anos negociando forex e criptomoedas também. Vivi demais, fiz grana, perdi grana, fiz amizades, perdi amizades e o mais importante que fiquei experiente nesse ramo. Tão experiente que percebi uma coisa…
Opaaa, falta uma peça no quebra cabeça
Os anos passavam e era como uma montanha russa. Tinha anos bons e ruins. Normal, como qualquer outra coisa que aconteça na vida. Mas, cara. Era inegável que eu estava evoluindo. Mas, o ritmo era lento demais. E, pelas minhas contas eu ia chegar lá com uma idade bem avançada. A diferença é que eu teria mais controle sobre meu futuro.
Contudo, no meio da jornada comecei a perceber que toda vez que eu pegava meu dinheiro e entregava para o mercado financeiro. Eu mandava uma mensagem para meu subconsciente: Você não é capaz de multiplicar seu dinheiro! E, isso é muito louco.
Porque eu multiplicava. Mas, tinha que me contentar com 10-12% a.a em anos normais, -6% a.a em anos ruins e anos bons era algo como 20%.
Portanto, isso tudo me deixava maluco. Porque? Eu tinha amigos empreendendo e ganhando 20% de lucro líquido ao mês. E, porque eu deveria me contentar com módicos 12% a.a? Esse raciocínio alugou um triplex na minha cabeça.
Durante minha jornada, eu tentei vários empreendimentos: Festas, venda de camisetas, venda de acessórios de telefone, confeitaria online e mais alguns que não lembro. Foram excelentes negócios para aprender. Mas, eu queria meu próprio negócio. Mas, não mais um negócio. Um negócio online, escalável e multilíngue. Fui estudar Desenvolvimento de sistemas, marketing digital e varri a internet atrás de informações.
O que você pode fazer
E, aqui estamos. A ideia de construir isso que você está usufruindo hoje nasceu 2 anos atrás. Eu levei 6 meses para lapidar e mais 6 meses criando conteúdo na unha. Literalmente, sentando a bunda na cadeira e escrevendo do zero cada texto.
Eu sei que alguns não ficaram bons como queria. Mas, o processo é esse. Você vai melhorando a medida que avança. Não dá para ficar vendo tutoriais no youtube, gurus de internet e ler milhares de livros. Tu tem que pegar e começar a fazer algo. Hoje, agora!
A vantagem da internet é que você não precisa de permissão para começar nada. Abre o Word, Docs, Canva, Capcut, Câmera do seu celular e cria. A resposta para todos os seus problemas está em: CRIAR!
Eu criei esse site, complementando: Meu site, meu Medium, meu Reddit e meu Nostr. Eu crio coisas novas todas as semanas e distribuo.
Minha empresa só tem eu de funcionário(por enquanto). Mas, já desenhei quais os próximos passos. Pode ser que eu nem use os próximos passos porque tudo muda toda hora.
Mas, vale a pena tentar! Se você puder acabar esse texto com uma só lição, eu diria:
Acredite mais em você e menos nos outros. Pare de pegar seu combustível (dinheiro) e entregar nas mãos de pessoas que em muitos casos. São menos preparadas que você.
Muito obrigado pelo seu tempo e até o próximo.
Compartilhe
-
 @ eb0157af:77ab6c55
2025-06-03 12:02:09
@ eb0157af:77ab6c55
2025-06-03 12:02:09The Pakistani government embraces Bitcoin, following the example set by the United States.
Pakistan has officially announced the creation of a strategic Bitcoin reserve. The announcement was made during the Bitcoin 2025 conference in Las Vegas, marking a significant shift from the government’s previous stance against digital assets.
During the event, Bilal Bin Saqib, head of the Pakistani Crypto Council, shared the country’s decision:
“Today, I announce the Pakistani government is setting up its own government-led Bitcoin Strategic Reserve, and we want to thank the United States of America again because we were inspired by them.”
Bin Saqib then added:
“This wallet, the national Bitcoin wallet, is not for speculation. We will be holding these bitcoins and we will never, ever sell them.”
It remains unclear how the bitcoins will be acquired, whether through direct purchases or other means.
Pakistan’s shift in approach toward digital assets traces back to last February, when the government first explored the idea of creating a National Crypto Council. This body was designed to oversee the development of a comprehensive regulatory framework for cryptocurrencies and to attract foreign investment in the sector.
The Council’s proposed initiatives included projects such as utilizing surplus energy for Bitcoin mining, building high-performance data centers, and accumulating Bitcoin for the national treasury.
Just a few days ago, the Council officially allocated 2,000 megawatts of surplus energy to support mining operations and AI data centers.
Moreover, Changpeng Zhao, co-founder of Binance, was appointed as an advisor to the Council in April, offering expertise on crypto regulations, blockchain infrastructure, and the adoption of digital assets.
To further consolidate this new approach, the Pakistani Ministry of Finance has commissioned the creation of the Digital Asset Authority, an agency dedicated to supervising digital asset regulations and issuing licenses for crypto service providers operating within the country.
The post Pakistan announces the creation of a strategic Bitcoin reserve appeared first on Atlas21.
-
 @ 9c9d2765:16f8c2c2
2025-06-03 11:56:41
@ 9c9d2765:16f8c2c2
2025-06-03 11:56:41A young monk once asked the elder of the mountain temple, “Master, how do I become wise like you?”
The elder smiled and handed him a lump of clay. “Make me a cup,” he said.
The monk, eager and certain, molded the clay quickly. He baked it in the kiln and brought it proudly to the master.
The elder poured tea into it and it cracked. “Try again,” he said.
The monk frowned but obeyed. He made another shape better, baked longer. But it still leaked.
Again. And again. The monk grew weary. Days turned into weeks. Each cup cracked, leaked, tilted, or burned.
On the eleventh attempt, the cup finally held. It was simple, slightly uneven, but strong.
The master poured tea. It stayed. He sipped, then smiled.
The monk said, “Why did all the others fail?”
The elder replied, “Because each one taught your hands what they did not know. Each mistake shaped the wisdom in your fingers.”
Moral: Wisdom is not poured into us it is shaped in us, one mistake at a time.
-
 @ 9c9d2765:16f8c2c2
2025-06-03 11:40:05
@ 9c9d2765:16f8c2c2
2025-06-03 11:40:05In the ancient city of Kaduna, where cobbled streets echoed with the footsteps of time, lived a young sculptor named Ali. Born to a family of scholars and philosophers, he was expected to follow in their footsteps books, debates, and deep logic. But Ali's heart beat for marble and chisel, not scroll and quill.
Against his family's wishes, he became an apprentice in a sculptor's guild. Though talented, he was prideful, impatient with learning, dismissive of advice, and obsessed with perfection. “Mistakes are for the foolish,” he often said. “Not for those destined for greatness.”
One day, Ali was given his first major commission: a statue of Queen Amina at Kaduna city’s central square to honor the Queen, goddess of wisdom. Determined to prove himself, he secluded himself in his workshop, refusing help. For months, he labored, carving what he believed was his masterpiece.
When the curtain was pulled off at the grand unveiling, the crowd gasped but not in awe.
The statue’s proportions were wrong. The Queen's face, meant to inspire reverence, looked distorted and harsh. Rumors spread. Ali’s arrogance had blinded him, people said. Critics mocked him. His patrons revoked the rest of his commissions.
Humiliated, Ali fled the city. He wandered from village to village, surviving by carving small figurines and helping repair broken statues. He worked alongside humble craftsmen, old and wrinkled, whose hands trembled but whose eyes held oceans of experience.
They taught him patience not through lectures, but through their mistakes. One cracked a statue's leg, then calmly fixed it better than before. Another accidentally chipped a nose, then reshaped the entire face into something more expressive. They didn't hide their flaws, they embraced them, learned from them, and adapted.
Years passed. Ali returned to Kaduna city, older and quieter. He set up a small workshop near the KD city gates. His first new sculpture was a fountain of children learning to walk, some falling, some crawling, some laughing through their tumbles. People noticed.
His fame grew again, not because of flawless technique, but because his work now had soul. Every sculpture whispered of growth, of struggle, of becoming. His final masterpiece was a second statue of Queen Amina the goddess of wisdom, placed beside the first.
This time, Ali was not stern and flawless, but warm, his hands outstretched, one holding a cracked tablet, the other a sapling growing through stone. At his feet, a broken chisel lay deliberately placed.
When asked why, Ali said, “Wisdom is not born from perfection. It is carved through failure.”
Moral: To build wisdom, you must make mistakes. Only through falling can we learn how to rise.
-
 @ 9ca447d2:fbf5a36d
2025-06-03 11:01:51
@ 9ca447d2:fbf5a36d
2025-06-03 11:01:51George Town, Grand Cayman — Ledn, one of the longest-standing digital asset lenders, today announced a sweeping update to its platform to discontinue any lending of client assets to generate interest, meaning that client assets will never be exposed to third party lending credit risk.
Going forward, Ledn will only offer its Custodied Bitcoin loan structure, under which client bitcoin collateral will remain fully in custody either with Ledn or its trusted funding partners.
As part of this strategic shift, Ledn will also remove support for ETH, doubling down on Bitcoin as its sole digital asset focus. These changes were unveiled by the company at Bitcoin 2025 in Las Vegas.
“With our new hyper-focus on Bitcoin-only lending, we’re going back to our roots and principles that inspired Bitcoin to begin with,” said Adam Reeds, Co-Founder and CEO of Ledn.
“Bitcoin was created as a direct response to the risks of fractional reserve banking and unchecked use of client assets to generate interest. Traditional finance relies on constantly reusing client assets to create leverage and, ultimately, inflation.
“Bitcoiners instinctively reject that model. That’s why we’ve moved away from this approach entirely. With our Custodied loan structure, client assets stay where they belong and are held in a transparent manner.”
While Ledn is taking these steps to further de-risk its product and further enhance client security, many of the new lending products in the market are exposing consumers to risky and opaque structures once again.
“These are the exact dynamics that led to the meltdown of the lending sector in 2022,” Reeds added.
“As more new entrants push half-baked lending models back into the market, we’re choosing the opposite path— Eliminating lending risk entirely for our users and making it 100% clear how their assets are dealt with.
“That clarity is what has helped us originate over $9.5 billion in loans and become the #1 retail CeFi lender in the Bitcoin space. We believe this approach should become the new standard for any serious digital asset lender.”
This shift reinforces Ledn’s broader strategy: Going all in on Bitcoin, simplifying its product stack, and sharpening its focus around the most secure and proven digital asset.
Ledn was the first crypto lender to introduce proof-of-reserves attestations in 2020, offering clients third-party verification that assets were fully accounted for down to the satoshi.
That transparency-first approach allowed the company to navigate market volatility as peers collapsed under opaque and hidden risks.
Now, as global regulators begin signaling openness to supervised participation rather than blanket restrictions, the opportunity — and the responsibility — for digital asset platforms is clear: Build resilient systems and proactively mitigate risk.
Ledn will exclusively offer custodied bitcoin-backed loans as of July 1, 2025. Support for ETH will be retired in the same release, reflecting Ledn’s strategic shift to a Bitcoin-only platform.
For more information on this transition, visit blog.ledn.io
For media inquiries, interviews, or early access to supporting materials, contact ledn@clpr.agency
About Ledn
Ledn offers growth accounts and loans to clients in over 120 countries, with an expanding range of services and supported regions. The company is dedicated to building world-class financial services, with a focus on helping people build long-term wealth through digital asset-based products.
For more information about Ledn and its services, visit the company’s website at www.ledn.io
-
 @ 9ca447d2:fbf5a36d
2025-06-03 11:01:49
@ 9ca447d2:fbf5a36d
2025-06-03 11:01:49Mac users who use Ledger hardware wallets to manage their digital assets are being warned about a new scam that uses fake apps to steal funds.
Cybercriminals have launched multiple phishing campaigns using malware that targets macOS systems, replacing the real Ledger Live app with a fake version that asks users to enter their recovery phrase.
These fake apps look almost identical to the real Ledger Live, but instead of helping users manage their bitcoin, they steal the 24-word recovery phrase—the master key to the user’s digital assets.
According to a detailed analysis by Moonlock, the attacks start when users’ computers get infected with Atomic macOS Stealer malware from one of over 2,800 hacked websites. Once installed, the malware removes the legitimate Ledger Live app and installs a malicious version in its place.
The fake app then shows a pop-up message saying it has detected “suspicious activity”, and asks the user to enter their recovery phrase to fix the issue. Once entered, the seed phrase is sent to a server controlled by the attacker.
2,800 websites discovered infected with Atomic Stealer — Moonlock
“Once entered, the seed phrase is sent to an attacker-controlled server, exposing the user’s assets in seconds,” Moonlock said in their May 22 report.
With the recovery phrase, the scammers can drain the user’s wallet of all digital assets—bitcoin and other tokens.
This isn’t an isolated incident. Moonlock has been tracking this malware since August 2024 and has found at least four active campaigns targeting Mac users. They believe the attackers are getting more sophisticated and are refining their methods.
“This isn’t just a theft. It’s a high-stakes effort to outsmart one of the most trusted tools in the crypto world. And the thieves are not backing down,” Moonlock researchers said.
Initially, the fake Ledger Live apps could only steal passwords and view wallet details. This gave attackers some insight into victims’ assets but no way to steal funds directly.
However, over time, hackers have improved their tactics and are now harvesting recovery phrases, so they can take full control of wallets and move funds freely.
One strain of malware, called Odyssey, was spotted in March and was linked to a hacker using the alias “Rodrigo”.
Odyssey replaces Ledger Live with a trojanized app and displays a phishing page asking users to enter their recovery phrases after showing a fake “critical error” message. Another copycat campaign using AMOS (Atomic macOS Stealer) followed soon after.
The fake Ledger Live app asks for user’s seed phrase — Moonlock
In one case, a fake app even displayed an “App corrupted” error after stealing the seed phrase to lower the victim’s suspicion and buy time to transfer the funds.
For years, computers running MacOS were considered safer than their Windows counterparts, because the operating system is less prone to malware. This advanced malware shows that users can never be too careful.
Attackers aren’t just relying on infected apps to steal from users. Other scam tactics include:
- Discord attacks: In May, a moderator account in Ledger’s official Discord server was compromised. Attackers used it to post fake verification links.
- Reddit phishing: In January, a user reported losing $15,000 after unknowingly entering their recovery phrase into a fake app.
- Physical mail scams: In April, some Ledger users received letters claiming to be from the company. These letters included QR codes leading to phishing sites that asked for seed phrases under the guise of a “critical security update”.
Attackers are increasingly targeting users holding hardware wallets, because they might be holding larger amounts.
Earlier this month, a Trezor One user reported being contacted by Coinbase impersonators, who tricked him into entering his seed phrase into a fake website, resulting in loss of 17.5 BTC.
The final goal for all these attacks is similar: the attackers are looking for users’ seed phrases, and they are getting creative in finding new ways to acquire them.
One sure way of staying safe is to learn more. The golden standard rule is to NEVER enter your seed phrase into a computer or a website, no matter how urgent or convincing it looks.
If you are a hardware wallet user, make sure you purchase the wallet from official sources. And the ONLY electronic place you can enter your seed phrases is on the hardware wallet itself.
If a process requires you to enter your seed phrase anywhere on a computer itself, it is definitely a scam.
Related: Bitcoin Hardware Wallet Hacks | What You Need to Know
-
 @ cae03c48:2a7d6671
2025-06-03 11:01:15
@ cae03c48:2a7d6671
2025-06-03 11:01:15Bitcoin Magazine

Bitcoin Builders Exist Because Of UsersBuilder: Nicholas Gregory
Language(s): C++, Rust
Contribute(s/ed) To: Ocean Sidechain, Mainstay, Mercury Wallet, Mercury Layer
Work(s/ed) At: CommerceBlock (formerly)
Prior to Bitcoin, Nicholas was a software developer working in the financial system for banking firms developing trading and derivatives platforms. After the 2008 financial crisis he began to consider alternatives to the legacy financial system in the fallout.
Like many from that time, he completely ignored the original Slashdot article featuring the Bitcoin whitepaper due to the apparent focus on Windows as an application platform (Nicholas was a UNIX/Linux developer). Thankfully someone he knew introduced him to Bitcoin later on.
The thing that captured his interest about Bitcoin rather than other alternatives at the time was its specific architecture as a distributed computer network.
“The fact that it was like an alternative way. It was all based around [a] kind of […] network. And what I mean by that, building financial systems, people always wanted a system that was 24-7.
And how do you deal with someone interacting [with] it in different geographical parts of the world without it being centralized?
And I’d seen various ways of people solving that problem, but it never had been done, you know, in a kind of […] scalable solution. And using […] cryptography and proof of work to solve that issue was just weird, to be honest. It was totally weird for me.”
All of the other systems he had designed, and some that he built, were systems distributed across multiple parts of the world. Unlike Bitcoin however, these systems were permissioned and restricted who could update the relevant database(s) despite that fact that copies of them were redundantly distributed globally.
“The fact that in Bitcoin you had everyone kind of doing this proof of work game, which is what it is. And whoever wins does the [database] write. That mess[ed] with my head. That was […] very unique.”
Beginning To Build
Nicholas’s path to building in the space was an organic one. At the time he was living in New York City, and being a developer he of course found the original Bitdevs founded in NYC. Back then meetups were incredibly small, sometimes even less than a dozen people, so the environment was much more conducive to in-depth conversations than some larger meetups these days.
He first began building a “hobbyist” Over The Counter (OTC) trading software stack for some people (back then a very significant volume of bitcoin was traded OTC for cash or other fiat mediums). From here Nicholas and Omar Shibli, whom he met at Bitdevs, worked together on Pay To Contract (BIP 175).
BIP 175 specifies a scheme where a customer purchasing a good participates in generating the address the merchant provides. This is done by the two first agreeing on a contract describing what is being paid for, afterwards the merchant sends a master public key to the consumer, who uses the hash of that description of the item or service to generate an individual address using the hash and master public key.
This allows the customer to prove what the merchant agreed to sell them, and that the payment for the good or service has been made. Simply publishing the master public key and contract allows any third party to generate the address that was paid, and verify that the appropriate amount of funds were sent there.
Ocean and Mainstay
Nicholas and Omar went on to found CommerceBlock, a Bitcoin infrastructure company. Commerceblock took a similar approach to business as Blockstream, building technological platforms to facilitate the use of Bitcoin and blockchains in general in commerce and finance. Shortly afterwards Nicholas met Tom Trevethan who came on board.
“I met Tom via, yeah, a mutual friend, happy to say who it is. There’s a guy called, who, new people probably don’t know who he is, but OGs do, John Matonis. John Matonis was a good friend of mine, [I’d] known him for a while. He introduced me to Tom, who was, you know, kind of more on the cryptography side. And it kind of went from there.”
The first major project they worked on was Ocean, a fork of the Elements sidechain platform developed by Blockstream that the Liquid sidechain was based on. The companies CoinShares and Blockchain in partnership with others launched an Ocean based sidechain in 2019 to issue DGLD, a gold backed digital token.
“So we, you know, we were working on forks of Elements, doing bespoke sidechains. […] Tom had some ideas around cryptography. And I think one of our first ideas was about how to bolt on these forks of Elements onto […] the Bitcoin main chain. […] We thought the cleanest way to do that was […] using some sort of, I can’t remember, but it was something [based on] single-use sealed sets, which was an invention by Peter Todd. And I think we implemented that fairly well with Mainstay.”
The main distinction between Ocean and Liquid as a sidechain platform is Ocean’s use of a protocol designed at Commerceblock called Mainstay. Mainstay is a timestamping protocol that, unlike Opentimestamps, strictly orders the merkle tree it builds instead of randomly adding items in whatever order they are submitted in. This allows each sidechain to timestamp its current blockheight into the Bitcoin blockchain everytime mainchain miners find a block.
While this is useless for any bitcoin pegged into the sidechain, for regulated real world assets (RWA), this provides a singular history of ownership that even the federation operating the sidechain cannot change. This removes ambiguity of ownership during legal disputes.
When asked about the eventually shuttering of the project, Nicholas had this to say:
“I don’t know if we were early, but we had a few clients. But it was, yeah, there wasn’t much adoption. I mean, Liquid wasn’t doing amazing. And, you know, being based in London/Europe, whenever we met clients to do POCs, we were competing against other well-funded projects.
It shows how many years ago they’d either received money from people like IBM or some of the big consultancies and were promoting Hyperledger. Or it was the days when we would be competing against EOS and Tezos. So because we were like a company that needed money to build prototypes or build sidechains, it kind of made it very hard. And back then there wasn’t much adoption.”
Mercury Wallet and Mercury Layer
After shutting down Ocean, Nicholas and Tom eventually began working on a statechain implementation, though the path to this was not straightforward.
“[T]here were a few things happening at the same time that led to it. So the two things were we were involved in a [proof of concept], a very small […]POC for like a potential client. But this rolled around Discreet Log Contracts. And one of the challenges of Discreet Log Contracts, they’re very capital inefficient. So we wanted a way to novate those contracts. And it just so happened that Ruben Sampson, you know, wrote this kind of white paper/Medium post about statechains. And […] those two ideas, that kind of solved potentially that issue around DLCs.”
In the end they did not wind up deploying a statechain solution for managing DLCs, but went in a different direction.
Well, there was another thing happening at the same time, coinswaps. And, yeah, bear in mind, in those days, everyone worried that by […] 2024/2025 […] network fees could be pretty high. And to do […] coin swaps, you kind of want to do multiple rounds. So […] state chains felt perfect because […] you basically take a UTXO, you put it off the chain, and then you can swap it as much as you want.”
Mercury Wallet was fully built out and functional, but sadly never gained any user adoption. Samourai Wallet and Wasabi Wallet at the time dominated the privacy tool ecosystem, and Mercury Wallet was never able to successfully take a bite out of the market.
Rather than completely give up, they went back to the drawing board to build a statechain variant using Schnorr with the coordinator server blind signing, meaning it could not see what it was signing. When asked why those changes were made, he had this to say: “That would give us a lot more flexibility to do other things in Bitcoin with L2s. You know, the moment you have a blinded solution, we thought, well, this could start having interoperability with Lightning.”
Rather than building a user facing wallet this time, they built out a Software Development Kit (SDK) that could be integrated with other wallets.
“{…] I guess with Mercury Layer, it was very much building a kind of […] full-fledged Layer 2 that anyone could use. So we [built] it as an SDK. We did have a default wallet that people could run. But we were hoping that other people would integrate it.”
The End of CommerceBlock
In the end, CommerceBlock shuttered its doors after many years of brilliant engineering work. Nicholas and the rest of the team built numerous systems and protocols that were very well engineered, but at the end of the day they seemed to always be one step ahead of the curve. That’s not necessarily a good thing when it comes to building systems for end users.
If your work is too far ahead of the demand from users, then in the end that isn’t a sustainable strategy.
“…being in the UK, which is not doing that well from a regulatory point of view, played into it. If I
-
 @ 00ea1f73:71c6e344
2025-06-03 09:59:07
@ 00ea1f73:71c6e344
2025-06-03 09:59:07Je suis en train de construire un outil de référencement collectif de marques et fabricants proposant des produits 100 % en matière naturelle (ce qui veut essentiellement dire "sans plastique").
Voici les étapes de ma progression ces dernières semaines en tant que non développeur pour créer cela tout en privilégiant des outils open source.
Etape 1 : faisons simple, du texte organisé
J'ai commencé par réunir mes idées dans Anytype. Leur approche "tout est un objet" laisse une flexibilité incroyable pour organiser ses données. On peut s'en servir comme simple outil de prise de note ou comme outil de gestion de projet. Le fonctionnement "local first" de l'application me donne la main sur mes données : elles sont stockées en local sur mon ordinateur et mon téléphone, qui se synchronisent entre eux.
Anytype permet depuis peu de publier sur Internet les "objets" de son choix (pages, notes, albums…) mais cela reste limité pour proposer à des visiteur une navigation fluide entre des objets liés (dans mon cas des marques et des matières par exemple). De plus, il n'est pas encore possible d'y automatiser la mise en forme de contenus à partir de données.
Ainsi, après avoir réuni les informations et préparé les contenus "à la main" pour trois marques seulement dans Anytype, j'ai eu besoin d'automatisation, et donc d'une vraie base de données. Je conserve quand même Anytype pour organiser mes idées et la suite du projet. Je l'utilise aussi pour la vie quotidienne (liste de course partagée, journal…).
Etape 2 : structurons une base de données
Baserow est une alternative à Airtable qui permet de gérer une base de données comme un tableur. Les formules utilisables dans les tableaux m'ont aidé à générer automatiquement les contenus de marque à partir des données que je réunissais. J'ai obtenu des données bien ordonnés dans de beaux tableaux sans avoir plus besoin de réécrire tout le contenu pour chaque marque.
J'ai passé un peu de temps à apprendre la syntaxe des formules de Baserow, j'ai mis à jour le contenu des trois premières marques, généré automatiquement celui d'une quatrième et… je me suis rendu compte que ça n'allait pas le faire.
Un point crucial de mon projet est la gestion et l'affichage des catégories de produits proposés par chaque marque, histoire que cela soit pratique de trouver les alternatives naturelles pour ce que l'on cherche sur le site. Or, dans Baserow il n'y avait pas moyen de générer mes contenus catégorisés de manière dynamique. J'étais contraint de modifier sans cesse des formules de plus en plus complexes, et donc avec un risque d'erreur de plus en plus grand. Cela reste un tableur, plus net pour gérer des données, mais moins fourni en termes de formules.
Avec une seule marque traitée en plus, mon "backend" v2 n'aura pas duré longtemps !
Etape 3 : courage, passons aux choses sérieuses
A ce moment là, j'ai sérieusement douté de ma capacité a créer ce site avec des outils open source et j'ai été tenté de retourner vers Bubble. À mon avis, Bubble est l'outil "no code" (ou de "programmation visuelle") le plus abouti. Je l'avais déjà utilisé efficacement avec We Do Good pour réaliser des prototypes de fonctionnalités, même utilisés provisoirement en production.
C'est génial, avec Bubble, des semaines de travail classique entre développeurs et designers pour arriver à une version utilisable se transforment en heures, voire en jours pour tester et valider des prototypes.
Mais… avec Bubble on n'a pas accès à ce qui se passe derrière l'interface de programmation. On devient en fait prisonnier de leur langage de programmation propriétaire. Si on a besoin de faire différemment, s'ils augmentent leurs prix de manière inadaptée, ou si un blocage se présente pour une autre raison, il faut tout refaire à zéro ou faire développer des nouvelles fonctionnalités (plugins) qui enrichissent Bubble.
J'ai alors décidé de passé au niveau supérieur en terme de technicité, avec des outils tout de même accessible aux non initiés motivés : une base de données dans Supabase connectée à une interface créée avec Plasmic. Avec Supabase j'ai accès aux paramétrages les plus fins sur les données et avec Plamic je construis visuellement ce dont j'ai besoin, comme avec Bubble.
Malgré l'interface visuelle très complètes de Plasmic, certaines fonctions dont j'ai besoin demandent des formules personnalisées utilisant un peu de code. L'avantage, c'est que là ou j'avais appris le language Bubble utilisable seulement avec Bubble, j'apprends maintenant les languages ouverts et universels du web sql et javascript, avec un peu d'aide de l'"IA" pour comprendre les fonctions et erreurs de syntaxe.
J'apprendre en faisant directement ce que j'ai envie, et c'est beaucoup plus efficace et motivant !
Plasmic me laisse aussi récupérer et réutiliser l'ensemble du code source ailleurs si j'en ai besoin un jour.
Je devais en passer par là
Chaque version de mon "backend" a été utile et même nécessaire à la suivante.
Avec mon expérience d'entrepreneur du web, je sentais depuis le départ que j'aurais besoin d'une solution robuste de base de données ainsi que de pouvoir intervenir sur le code facilement. Cependant, au démarrage, je n'avais pas envie de me plonger là-dedans. Finalement, bien m'en a pris ! La structuration de données que j'avais initialement imaginée est très différente de celle à laquelle j'arrive maintenant.
Je n'aurais pas eu une base de données claire et bien organisée dans Supabase si je n'avais pas fait précédemment une itération dans Baserow. Je n'aurais pas créé les tables et liaisons utiles dans Baserow si je n'avais pas créé les premiers contenus sous forme de texte avec liaisons dans Anytype.
De plus, je n'aurais pas trouvé l'énergie de me lancer sur ce nouveau projet si je n'avais pas commencé par une version très simple et non "scalable". C'est un vrai progrès personnel : j'ai toujours travaillé en essayant de concevoir le maximum de choses d'avances, pour me rassurer et limiter les risques, et parce que c'est ce qu'on apprend à l'école. Les problèmes, c'est que je dépensais pour cela une énergie folle et que bien sûr, la réalité ne correspond jamais vraiment aux prévisions.
En me lançant avec une première version pas du tout aboutie mais fonctionnelle, je me suis autorisé à faire plus d'erreur, à m'exposer et à me concentrer sur du concret.
Références
Pour moi, favoriser l'open source est essentiel car cela fait partie des outils fondamentaux pour défendre ma liberté et celle des autres.
Tous les outils que j'utilise ou ai utilisé pour ce projet sont open source, sauf Anytype qui est juste "open core" (c'est à dire qu'ils publient leur code mais n'autorisent pas tous les usages avec). Ils présentent aussi tous des plans gratuits bien pratiques pour se lancer sans contrainte financière.
- Anytype : https://anytype.io/
- Baserow : https://baserow.io/
- Supabase : https://supabase.com/
- Plasmic : https://www.plasmic.app/
J'ai aussi testé ou envisagé sans les retenir quelques autres solutions comme WordPress ou Silex. Provisoirement, en attendant d'avoir créé toutes les interfaces dont j'ai besoin avec Plasmic, j'utilise NocoDB, connecté à Supabase, pour disposer d'une interface visuelle équivalente à Baserow (avec des formules moins avancées mais la possibilité de me connecter plusieurs bases de données si besoin).
J'utilise beaucoup Alternative.to pour trouver les outils dont j'ai besoin, on y peut filtrer les applications selon de nombreux critère, je le recommande.
Ensuite, il faut tester et se lancer, voire tester en se lançant !
opensource #nocode #lowcode #vibecoding #ia #produitsnaturels #zeroplastique #nostrfr
-
 @ bf47c19e:c3d2573b
2025-06-03 09:55:46
@ bf47c19e:c3d2573b
2025-06-03 09:55:46Sjajan niz o toksičnom Bitkoin maksimalizmu kojim sam bio toliko oduševljen da sam ga preveo i okačio na sajt.
There’s a tired argument that never seems to die:
— Not that Elon. 🍆🍊💊💎🙌🏻 (@Eggplant_Elon) June 1, 2025
“Toxic Bitcoin maximalism is hurting Bitcoin.”
But they’ve misunderstood something fundamental.
Toxic Bitcoin maximalism is a biological necessity. Let me explain.
A 🧵👇
Postoji stari argument koji izgleda da nikada ne odumire:
"Toksični Bitkoin maksimalizam šteti Bitkoinu."
Ali su pogrešno shvatili nešto što je osnovno.
Toksični Bitkoin maksimalizam je biološka neophodnost. Dozvolite mi da objasnim.
Priroda se ne izvinjava zbog svojih branilaca.
U svetu prirode, odbrana nije učtiva.
Ona je brutalna, specijalizovana i neumoljiva.
Ako pogledamo kolonije eusocijalnih insekata: mrave, termite, pčele...
Svaki od ovih organizama ima svoju vojničku kastu. Sterilna, hiperspecijalizovana stvorenja su evoluirala sa jednom svrhom: da odbrane koloniju po svaku cenu.
Mravi-vojnici ne idu u potragu za hranom. Ne razmnožavaju se. Ne pregovaraju.
Oni ubijaju uljeze. Brzo. Bez milosti. Bez kajanja.
To je ono što rade Bitkoin maksimalisti.
Oni identifikuju ideološke pretnje i eliminišu ih.
Ako unesete laži, šibicarenje ili razvodnjavanje u diskurs, oni se udružuju u roj.
Ujedaju. Sravniće vaš narativ sa zemljom.
Oni su odgovor imunog sistema.
Ovo se ogleda u odgovorima Bitkoin maksimalista na:
- promotere šitkoina
- obmanjujuće narative o skalabilnosti, potrošnji energije ili inflaciji ponude novčića
- pokušaje da se promene pravila Bitkoin konsenzusa
Oni ne pokušavaju da prvo "edukuju".
Oni se najpre brane.
Edukacija je sporedna, ponekada opciona. Ako donesete zarazu u koloniju, bićete odstranjeni.
Termiti-vojnici su toliko posvećeni svojoj ulozi da su neki od njih postali skloni samouništenju, bukvalno eksplodirajući i izbacujući lepljivu, otrovnu tečnost da bi zarobili uljeze.
Oni umiru radeći to. Ali će kolonija preživeti.
Bitkoin maksimalisti su spremni da postupaju u istom duhu.
Spremni su da budu omraženi, pogrešno shvaćeni, blokirani i cenzurisani.
Oni će reći ono što niko drugi neće jer se radi o ceni Bitkoin misije.
Ne radi se o slavi ili uticaju. Radi se o zaštiti organizma.
Deluju kao podskup složenog organizma koji sebe žrtvuje radi višeg cilja
Oni možda neće pomoći vašem rođaku da uđe u Bitkoin uz pomoć laganih poruka.
Ali će oterati sledećeg prevaranta koji pokuša da mu proda sintetički stejblkoin sa NFT pokrićem koji donosi 14% prinosa.
Oni su žrtvovali širu društvenu funkciju da bi odbranili jedinu stvar koja je stvarno važna: nekorumpiranost Bitkoina.
Njihov fokus je dvojak.
Da li je ovo Bitkoin? Onda da.
Da li ovo nije Bitkoin? Onda odjebite!
Setite se "Blocksize ratova", Lune, Celzijusa, Vojadžera, FTX-a...
Ko je podmetnuo leđa?
Ko je najglasnije upozoravao?
Ko je odbijao kompromise kada je bilo lakše ići linijom manjeg otpora?
Maksimalisti.
Svaki put kada je neki političar, korporativni lobista ili šitkoin-"mislilac" pokušao da omalovaži vrednosti Bitkoina, maksiji su među prvima pružali otpor.
Ne taktičnošću ili dugačkim saopštenjima.
Nego sa brutalnom jasnoćom.
Zato što je jasnoća ono što imuni sistem nudi.
Toksični maksimalizam nije zloban.
Toksični maksimalizam je smislen.
"Uživajte u siromaštvu"
"21 milion ili ništa."
"Bitkoin, ne kripto."
Ovo nisu slogani.
Ovo su imunološki odgovori.
Memetičke T-ćelije koje su stvorene da upozore na opasnost, inkapsuliraju istinu i repolarizuju telo.
One su brze, ujedaju i prodorne su zato što je brzina bitna u imunologiji.
Ukoliko pokušate da urazumite kancer, proširiće se.
Ukoliko pokušate da se sporazumete sa šibicarenjem, ono će rasti.
Bitkoin maksimalisti se ne sporazumevaju sa prevarama.
Oni ih kauterizuju.
Isto kao što bela krvna zrnca "ne slušaju obe strane" tokom razmnožavanja virusa.
Ljudi koji mrze maksimaliste su često oni kojima su maksimalisti najviše potrebni.
Pitajte bilo koga ko je izgubio novac na Luni, Celzijusu ili FTX-u šta misle o "toksičnosti Bitkoin maksimalista".
Daće vam jedan od ova dva odgovora:
- "Bili su drkadžije."
- "Bili su u pravu."
Maksimalisti spašavaju ljude koji ih mrze.
Oni upozoravaju glasno, oštro i rano.
I to često čine pre nego što brodolom postane očigledan.
Postoji gorka ironija dok gledamo ljude koji su ignorisali maksimaliste kako sada poput papagaja ponavljaju njihove teze.
Ali maksijima nije potrebna zahvalnost.
Nije im potrebno da se nekome svide.
Oni su tu da bi osigurali da Bitkoin postoji i za 20 godina.
Svet bez maksimalista je svet gde 21 miliona postaje 42 miliona.
Nemojte se zavaravati, kada bi imuni sistem Bitkoina bio isključen, počelo bi polako, možda sa nekoliko "nadogradnji" da bi se udovoljilo spamerima.
Možda neka izmena da bi se odobrovoljili regulatori.
Tako nastaju korumpirani sistemi: ne kroz nasilno preuzimanje već kroz hiljadu postepenih izdaja u ime "napretka" ili "adopcije".
Bitkoin do sada nije podlegao zato što ima ljude koji su spremni da učine sebe radioaktivnim da bi stopirali te izdaje.
"Spaliće most" ukoliko će to održati protokol netaknutim.
Imuni sistemi i treba da budu nasilni.
Pogledajte nekada bela krvna zrnca pod mikroskopom.
Gledajte ih kako obuzimaju bakteriju i razgrađuju je kiselinom. Nećete pomisliti: "Koliko ljubazno."
Pomislićete: "Ovo izgleda brutalno."
Tako odbrana funkcioniše.
Ako vam se to čini neprijatnim, dobro je.
Odbrana i ne treba da odiše estetikom.
Odbrana treba da bude efikasna.
Bitkoin maksimalizam nije kultura okrutnosti.
To je kultura odbijanja razvodnjavanja, smirivanja i klečanja.
Ovo odbijanje je pomoglo Bitkoinu da ostane nekorumpiran duže od bilo kog drugog monetarnog sistema.
Ne morate voleti toksične Bitkoin maksimaliste.
Ali ako HODL-ate Bitkoin i vrednujete ono što BTC predstavlja, oni su jedan od razloga zašto je BTC i dalje to što jeste.
Oni ubadaju zato što prevaranti nikada ne spavaju.
Grizu zato što se sociopate ne najavljuju unapred.
Nepristojni su zato što vreme ističe.
Nemojte to pogrešno shvatiti kao toksičnost.
Smatrajte to imunitetom.
I ako izgleda neprijateljski, setite se da ga je priroda takvim stvorila.
Zato što u svetu koji je stvoren da laže, branite signal po svaku cenu.
Čak iako vas košta reputacije.
Čak iako vas nazivaju toksičnima.
Čak iako vam se nikada ne zahvale.
Bitkoin maksimalisti su imuni sistem.
A imuni sistem ne pita za dozvolu.
On napada.
-
 @ bd982176:8b2599a7
2025-06-03 09:29:26
@ bd982176:8b2599a7
2025-06-03 09:29:26Every week at the Bitcoin Babies Foundation , we're privileged to witness incredible resilience. We empower mothers with $5 worth of Bitcoin for their little ones – a small start, but a potent seed for growth. It's for food, clothing, or perhaps a savings fund for their child's future. Beyond the financial support, however, we see a profound lesson unfolding, one that resonates deeply with a powerful idea: the art of asking.
We recently came across a powerful message about getting what you want in life. The core principle? You have to ask for it. It sounds simple, yet for so many, it’s the biggest hurdle. We're often taught to be self-sufficient, to figure things out on our own. But true progress, true growth, often begins with the courage to voice our needs, to define our desires, and to ask for what we envision.
Think about the mothers we work with. Many of them have faced unimaginable hardship. Yet, they show up, week after week, with hope in their eyes. They are, in their own way, asking for a better future for their children. They are asking for stability, for opportunity, for a chance to build something new.
The video we're inspired by talks about two crucial ways to ask:
Ask with Intelligence: Be crystal clear about what you want. The more specific you are, the more you magnetize that outcome towards you. For our mothers, this isn't just about needing "money." It's about needing funds for specific food items, for a winter coat, or for a savings plan to send their child to school one day. This clarity transforms a vague wish into a tangible goal.
Ask with Faith: Believe that what you're asking for is achievable, with the pure, unwavering conviction of a child. This isn't about blind optimism; it's about holding onto hope even when circumstances are tough. Our mothers embody this faith daily. They might not know exactly how everything will work out, but they believe in the possibility of a brighter tomorrow for their little ones.
The Bitcoin Babies Foundation provides a foundation for this asking. That $5 in Bitcoin isn't just a donation; it's a tool, a resource that helps these mothers begin to build. It empowers them to not only ask for their immediate needs but also to start dreaming bigger, to plan for the future, and to understand that their efforts, combined with clarity and belief, can bring about remarkable change.
The world applauds those who take action. And taking action often starts with the simple, yet profound, act of asking. For our Bitcoin Babies mothers, it's a vital lesson for navigating life and building a future for their families. It's a testament to the fact that when you know what you want and you have the courage to ask for it, incredible things can begin to unfold.
-
 @ 6b3780ef:221416c8
2025-06-03 09:09:59
@ 6b3780ef:221416c8
2025-06-03 09:09:59Release time!
We are thrilled to announce the release of the new version of DVMCP, packed with a host of new features and enhancements. The standout improvement is the support for the new specification, which brings loads of new possibilities and a future-proof design to accommodate MCP protocol as it evolves.
Currently, DVMCP supports all major MCP capabilities, tools, resources, resource templates, and prompts, along with features like autocompletion. While there are still a few minor MCP features that are not yet supported, the new specification will allows us to introduce new features and capabilities progressively.
A significant amount of work has gone into this update, from designing and drafting the new DVMCP specification, ensuring it aligns with the latest MCP standards. We have also refactored the bridge, discovery, and commons package, adapted the DVMCP.fun website (currently at next.dvmcp.fun), and even created a new storage type for relays to handle ephemeral events more robustly and efficiently. This new storage solution is already powering the DVMCP relay.
These enhancements represent a significant expansion of the possibilities available to DVMCP users. By combining MCP with Nostr, DVMCP offers rock-solid authentication and seamless payments using Lightning. We have many exciting ideas for utilizing these new capabilities in innovative ways, such as monetizing resources for creators, creating collections of prompts, developing agentic capabilities, and much more. Rest assured, we will be rolling out more on this gradually.
Additionally, DVMCP is already providing some servers that you can use for free. These can be discovered using the discovery package with any MCP client or by trying them out on the website.
Rollout Plan
As this update introduces breaking changes, including different event types for various DVMCP-related events, we are hosting the new version of the website at next.dvmcp.fun, with packages starting from version 0.2.x. We will be testing this version and welcome feedback from users over the next 10 days. After this period, we will deploy the 'next' version of the website to the main domain.
Updates on Ecosystem Components
-
DVMCP Packages: Starting from version 0.2.x, all packages include breaking changes. If you are already using DVMCP, please adapt to the new kinds and events. You can refer to the
@dvmcp-commonspackage for all the new kinds and tags. -
DVMCP.fun: The website has been entirely refactored to support the new specification and now utilizes idiomatic Svelte 5 across the application. Currently the new version is living at next.dvmcp.fun
-
DVMCP Relay: The relay is now powered by the 'rely' framework and employs our atomic circular buffer implementation to handle ephemeral events more robustly and efficiently. It also uses LMDB as persistent storage for announcements and capability events.
Looking ahead, we plan to launch more servers offering various services, develop agentic DVMCPs, create additional guides and tutorials, integrate DVMCP into LLM web interfaces, provide statistics for the DVMCP relay, explore novel concepts in MCP + Nostr integration, and continuously improve the code to make it more accessible to developers as libraries.
Thank you for joining us on this journey! We are incredibly excited about the possibilities that lie ahead and what’s coming next. Stay tuned!
-
-
 @ e2c72a5a:bfacb2ee
2025-06-03 14:37:52
@ e2c72a5a:bfacb2ee
2025-06-03 14:37:52While Bitcoin hovers at $105,000, MARA quietly increased its mining production by 35%, now holding 49,179 BTC without selling a single coin. This mining giant's accumulation strategy reveals a counter-intuitive truth about institutional behavior during market volatility – they're not just holding, they're aggressively expanding their positions despite recent liquidations.
The shift in global crypto trading power is happening right under our noses. Asia's trading hours now command nearly 30% of Bitcoin, Ethereum and Solana volume, while US market dominance has fallen below 45% for the first time since Trump's election. This geographic redistribution signals a fundamental change in who's driving crypto's future.
Are you positioned for this new reality where mining giants accumulate and market influence shifts eastward? The players building tomorrow's crypto landscape aren't waiting for perfect conditions – they're making strategic moves today while others hesitate.
-
 @ 33baa074:3bb3a297
2025-06-03 09:09:19
@ 33baa074:3bb3a297
2025-06-03 09:09:19Application of water-saving irrigation technology Water-saving irrigation technology, such as drip irrigation technology, installs a drip irrigation system in the farmland to evenly sprinkle water on the roots of crops to achieve the purpose of saving water, increasing production, and improving the quality of agricultural products. This technology can effectively reduce water resource waste, improve crop resistance, and reduce yield losses caused by water shortages. At the same time, it can also improve soil structure, increase soil fertility, and reduce the occurrence of pests and diseases.
The role of smart irrigation system Smart irrigation systems use modern technologies such as computer technology, Internet of Things technology, and sensor technology to intelligently manage gardens, farmlands, etc. This system can automatically adjust the irrigation volume and time by monitoring soil moisture and nutrient content, meteorological data and other information, thereby achieving efficient, accurate, and sustainable soil moisture management and nutrient utilization. The smart irrigation system has a positive impact on soil moisture management and nutrient utilization efficiency through accurate moisture monitoring, intelligent irrigation control, and real-time nutrient monitoring and management.
Principle and Application of Precision Irrigation Technology Precision irrigation technology is based on soil moisture monitoring, crop water requirement model and irrigation decision support system. Through multi-source data fusion and intelligent algorithm, it realizes the intelligentization and automation of irrigation decision. The application of soil moisture sensing technology in precision irrigation can monitor soil moisture conditions in real time and provide data support for irrigation decision. In addition, the construction and application of crop water requirement model can predict crop water demand and provide a scientific basis for irrigation decision. The development and implementation of precision irrigation control system can realize automatic irrigation, improve irrigation efficiency and water resource utilization.
Conclusion In summary, irrigation technology, especially water-saving irrigation technology and intelligent irrigation system, plays an important role in soil moisture management. These technologies not only improve the efficiency of water resource utilization and reduce agricultural production costs, but also improve soil structure, increase crop yield and quality, and promote the sustainable development of agriculture. With the continuous advancement of science and technology, irrigation technology will play a more important role in future agricultural production.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 14:14:05
@ e2c72a5a:bfacb2ee
2025-06-03 14:14:05Crypto isn't just magic internet money—it's your financial future without the middleman. Unlike traditional banking where someone else controls your cash, crypto puts you in the driver's seat with blockchain technology secretly doing all the heavy lifting. Every transaction gets recorded on thousands of computers simultaneously, making it nearly impossible to hack or manipulate. From Bitcoin's limited supply to stablecoins pegged to real-world currencies, the crypto ecosystem offers something for every financial goal. Yes, prices swing wildly and regulations are still catching up, but that's the price of revolution. The real magic? Anyone with a smartphone can access financial services without a bank's permission. Ready to join the financial rebellion? Start small, learn the basics, and remember—your crypto journey isn't about getting rich overnight, it's about participating in the greatest financial experiment of our lifetime.
-
 @ eb0157af:77ab6c55
2025-06-03 09:01:55
@ eb0157af:77ab6c55
2025-06-03 09:01:55An analysis of the present and a look at the future of Bitcoin mining, between data, critical reflections and a personal vision on the role of this industry.
Before jumping on bitcoin and proposing it to their clientele as an investment instrument, traditional finance started with a more classic approach, beginning to purchase shares of mining companies and thus exposing themselves indirectly to the asset. Bitcoin mining today is a real industry, also composed of large players listed on the stock exchange that have received huge capital from investment funds like BlackRock. Furthermore, more and more mining companies are taking the path of listing on stock markets to manage to attract capital and some of these also manage pools, like Marathon. How was all this possible and what are the implications of this situation?
Mining pools
Mining pools aggregate the computing power of multiple miners to increase the chances of mining a block. They create the block template and use the collective hashrate to try to solve it. The reward is then divided among participants in proportion to the power provided.
Today pools use different methods to pay miners who provide computing power. One of these is called FPPS (Fully Pay Per Share), which offers a fixed and constant payment to the miner (which varies based on the computing power provided), regardless of whether the pool mines a block or not. This type of payment makes the revenues of a company that mines bitcoin calculable and constant and which, consequently, becomes more appealing to the market because it’s possible to calculate its ROI (Return On Investment). In essence, with this type of payment, uncertainty is excluded and returns are made predictable. Mining pools take on the risk because, in case they fail to mine blocks for a certain period of time, they could go into loss having to pay miners anyway. We can therefore venture that mining pools have helped the entry of traditional finance into bitcoin mining, taking on part of the risks. But this is my thought.
Mining today
Mining pools today are not that many and we have a strong concentration of miners in some of them. If we sum the hashrate of Foundry and AntPool we exceed 50% of global computing power. This is not an optimal condition. Now however let’s also look at the other side of the coin. First of all, although mining pools have great power, they cannot play with fire and must be very transparent about their operations towards miners, because miners can direct their hashrate towards another pool very quickly. And this is a fundamental element that also recalls game theory a bit, because a mining pool must not only serve its own interest, but also the interest of its “partners”, otherwise it loses everything. I believe that mining pools are well aware of their power and also know that they are a centralization point for the network and, today, also a point of attack by authorities, so they have every interest in finding solutions that allow them to continue doing business, but that relieve them somewhat of responsibilities.
On the miner side instead, we have increasingly large companies that collect enormous capital and produce a lot of hashrate, but my fear is that this hashrate is produced by a fiat economy and is very precarious. Hashrate is closely linked to price, because if the price drops below a certain threshold, miners are no longer profitable and are forced to turn off the machines, or, in the worst cases, to completely cease activity, consequently causing hashrate to collapse. Fortunately Bitcoin has mechanisms like difficulty adjustment that mitigate these situations. Being still a very small market, the entry of large institutional players first in mining companies and then directly on the underlying asset, could lead to strong price oscillations that also impact mining farms. All this makes hashrate very unstable too.
Something is changing
The development of Stratum V2 has started an attempt to solve the various problems that afflict pooled mining. Stratum is the communication protocol between mining farms and mining pools. Version 2 brings, in addition to data improvement and encryption, performance increases and gives each individual miner the possibility to create the template of the block to mine. Furthermore we also have other existing solutions that try to solve the problems described before in a somewhat different way, like Ocean pool, which has implemented its DATUM protocol (similar to Stratum V2) and which uses a miner payment method called TIDES, that is an evolution of FPPS and non-custodial PPLNS in which miner addresses are inserted directly into the coinbase transaction.
There’s also a lot of ferment on the miner side, for example with the advent of Bitaxe, an open source project that we can define almost as a movement, an ideology. Skot, the precursor of this movement, has essentially reverse engineered the professional machinery used to mine bitcoin and managed to create a “desktop” device that contains a real ASIC chip, consumes only a few watts and can be built at home. Obviously these products produce computing power not sufficient to try to be competitive, but they are bringing back solo mining and are giving enthusiasts the possibility to deepen this sector by exploiting a device of very small dimensions and with practically negligible consumption on the bill.
The future of mining
After analyzing the state we are in, we can start speculations and let our minds travel.
Let’s start with mining pools. Will they still exist? I would say yes, in what form I don’t know, but I think they will certainly lose the control they have today over block template creation and I also think that future solutions will be found (in addition to existing ones) to become non-custodial and directly remunerate miners. In the end it’s in their interest to always be competitive in terms of services offered, because they work on commission, so they have to be appealing.
As for miners instead, I see a bigger metamorphosis. If the intention is to consume eco-sustainable energy, then energy industries will necessarily have to start studying the benefits that mining can bring in this sense. They cannot continue to ignore them. And if this happens, then I imagine a future where energy companies themselves will start mining bitcoin and will no longer do so following market logic, but will shift focus to stabilizing the electrical grid. Mining is currently the only industry capable of being so flexible as to be able to absorb all the excess energy of a plant, but at the same time consume zero when energy is needed by the grid. At that point the raw mining activity could become no longer the main business, but a secondary benefit that will allow them to have alternative income compared to selling electricity.
And what about the Bitaxe movement? Hard to say, but in my opinion if it manages to reach a critical mass of enthusiasts, it could really start to emerge and become a fundamental piece for the “true bitcoiner” kit. Utopistically, if we had 50 or 100 million Bitaxes scattered in people’s homes, we would manage to distribute mining in a more widespread way, but above all we would have a part of the total hashrate totally uncorrelated from bitcoin price, because, given their very reduced consumption, Bitaxes would remain on and continue to produce hashrate regardless of energy cost or price oscillations of the underlying asset.
What will happen, then, after 2140, when no more bitcoins will be mined? Assuming that network fees will be much higher than today, and sufficient to keep the activity profitable, we could find ourselves in a situation where mining for pure profit will be downsized. The same companies, however, could become external service providers for grid balancing, or, as mentioned previously, become electricity producers themselves of renewable energy exploiting their experience in mining to push where today it’s not economically convenient. Even in our homes we could have a boiler, a heat pump or a water heating system for the pool that, while doing its job, also mines bitcoin. In short, a future that seems like a fairy tale, but so possible that we want to live it and make sure that my children are also protagonists of it.
The post The future of mining? Green and decentralized appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-06-03 09:01:35
@ 9ca447d2:fbf5a36d
2025-06-03 09:01:35DDC Enterprise, a consumer brand and e-commerce company with operations in the U.S. and China, has launched a big plan to make bitcoin (BTC) a key part of its financial strategy.
The company just bought 21 BTC as the first step in a plan to buy up to 5,000 BTC over the next 3 years.
The move was announced in a press release and a letter to shareholders by DDC’s founder, chairwoman and CEO Norma Chu.
The 21 BTC, worth around $2.28 million at current prices, was bought through a share exchange. DDC issued 254,333 class A ordinary shares.
“We are fully committed to ensuring the success of this strategy, which aligns with our vision to drive long-term value for our shareholders,” said Norma Chu. “Today marks a pivotal moment in DDC’s evolution.”
Chu is the first female founder and CEO of a U.S.-listed public company to lead a bitcoin-only treasury strategy. DDC is one of the first companies in its industry to adopt this strategy in such a structured way.
DDC’s plan is being rolled out in phases. The company will buy another 79 BTC soon and will have 100 BTC in the short term.
In the next 6 months, it will buy 500 BTC, and long-term, it expects to build a 5,000 BTC reserve over 36 months.
This phased approach may allow DDC to manage market volatility and take advantage of price movements.
In her recent letter to shareholders, Chu called the bitcoin strategy “a cornerstone of our long-term value creation plan”.
She said bitcoin’s qualities – especially as a hedge against macroeconomic uncertainty and inflation – make it the perfect reserve asset for DDC. She added:
“Bitcoin’s unique properties as a store of value and hedge against macroeconomic uncertainty align perfectly with our vision to diversify reserves and enhance shareholder returns.”
The announcement comes on the back of a record-breaking year for DDC.
In 2024, the company made $37.4 million in revenue—a 33% increase from 2023.
Gross margin improved from 25.0% in 2023 to 28.4% in 2024 due to strategic acquisitions in the U.S. and more efficient operations in China.
As of March 31, 2025 the company had $11.3 million in shareholder equity and $23.6 million in cash, cash equivalents and short-term investments.
This gives DDC the flexibility and credibility to do something as bold as this bitcoin accumulation plan.
DDC’s announcement comes as corporations are getting increasingly interested in adding bitcoin to their balance sheet.
While giants like Strategy have made headlines with large bitcoin purchases, DDC is the first e-commerce company to do so.
The company’s dual presence in China and the U.S. also adds complexity, especially with the different regulatory environments surrounding Bitcoin in each region.
To ensure proper execution, DDC has expanded its treasury and advisory teams to include experts in the bitcoin markets.
The company will use a mix of dollar cost averaging and tactical buying, adjusting purchases based on market conditions.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 12:36:26
@ e2c72a5a:bfacb2ee
2025-06-03 12:36:26The code that changes everything: Smart contracts, NFTs, and the digital asset revolution
Smart contracts are like digital vending machines for agreements – insert conditions, get automatic results, no middlemen needed. They're self-executing code living on blockchains that enforce rules without human intervention, creating trustless transactions where the code itself guarantees execution.
Unlike traditional contracts requiring lawyers and notaries, smart contracts execute automatically when predefined conditions are met. They're transparent (anyone can inspect the code), immutable (can't be changed once deployed), and deterministic (same input always produces same output).
NFTs take this technology further by creating unique digital assets. While cryptocurrencies like Bitcoin are fungible (one equals another), NFTs represent ownership of specific digital items – art, music, virtual real estate – with blockchain-verified authenticity and provenance.
The applications extend far beyond digital art. Smart contracts power decentralized finance (DeFi), allowing peer-to-peer lending without banks. They're revolutionizing supply chains by tracking products from factory to consumer. In real estate, they're automating property transfers and enabling fractional ownership. Gaming worlds use NFTs for truly player-owned assets.
Creating your own smart contract requires choosing a platform (Ethereum, Solana, etc.), learning a programming language like Solidity, and understanding security best practices. One vulnerability can lead to massive losses – as seen in hacks like The DAO, where $60 million was stolen through a code flaw.
The environmental impact remains controversial, with proof-of-work blockchains consuming significant energy. However, many platforms are transitioning to more efficient proof-of-stake systems.
As this technology matures, we're seeing cross-chain interoperability, integration with AI and IoT, and increasing mainstream adoption. The future points toward a world where digital ownership is as natural as physical ownership, and agreements execute themselves without intermediaries.
The revolution isn't just technological – it's reshaping how we think about ownership, trust, and value in the digital age.
-
 @ c4f5e7a7:8856cac7
2025-06-03 08:15:33
@ c4f5e7a7:8856cac7
2025-06-03 08:15:33I've managed to amass three SN profiles.
Is there a way to combined these?
@k00b @ek
https://stacker.news/items/995836
-
 @ e8646d56:72dab368
2025-06-03 08:15:30
@ e8646d56:72dab368
2025-06-03 08:15:30eee
-
 @ 866e0139:6a9334e5
2025-06-03 07:31:24
@ 866e0139:6a9334e5
2025-06-03 07:31:24Autor: Andreas Hagen. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
Heute ist Karfreitag 2025, und ich beginne diese Zeilen um kurz nach 15 Uhr zu schreiben. Seit ich von der Friedenstaube gehört hatte, bastelte ich innerlich immer wieder an dem Text, der Ihnen heute vorliegt. Ich bin kein beruflicher Autor, aber ich möchte meinem Impuls folgen, meine Lebenserfahrungen zu teilen. In der Absicht, dass dieser Inhalt hilfreich in diesen schwierigen Zeiten wirkt.
Ich wurde recht katholisch erzogen in einem (Deutschen) Familiensystem, das von den Wirkungen des Zweiten Weltkrieges – gelinde gesagt – stark geprägt wurde. Was ich als Kind in den 70er Jahren nur über das Spüren wahrgenommen hatte, erklärte sich mir im Laufe meines Erwachsen-Werdens, vor allem über die Erzählungen meines Vaters. Heute bin ich Buddhist, und neben dem Verstehen empfinde ich immer größer werdendes Mitgefühl für meine Großeltern und deren Kinder, die mich auf die Welt gebracht haben.
Während des Krieges ging es in diesen beiden Familien vorrangig um Überleben, wie in vielen anderen Familien auch. Die Männer in Ihrer „Funktion“ an der Front – später dann physisch und psychisch schwer verletzt. Die Frauen auf sich gestellt mit Kindern, Armut, Hoffnungslosigkeit und existentiellen Ängsten ausgesetzt.
Diese Erlebnisse über Jahre hinweg und die daraus resultierenden inneren Zustände oder Gefühle meiner Ahnen sind in einer gewissen Art und Weise über mehrere Generationen hinweg bis in mein eigenes Körper-Geist-System weitergegeben worden. Was manche als kollektiv-psychologisches Phänomen mit dem Namen „German Angst“ beschreiben, möchte ich in den folgenden Zeilen unter dem Kontext einer fernöstlichen Sichtweise betrachten. Das scheint möglicherweise etwas ungewöhnlich, aber lassen Sie sich in der kommenden Lesezeit auf ein Denk-Experiment ein, das sich lohnen wird.
Ich spreche über das Prinzip des NICHT-TUNS, in der daoistischen Philosophie WU WEI genannt.
Betrachtet man das Phänomen der „German Angst“ unter Zuhilfenahme des Prinzips des Nicht-Tuns, kann man ein inhärentes Möglichkeitspotential darin entdecken. Das heißt, wir betrachten ein bekanntes Phänomen aus einer vollständig anderen Perspektive, und durch den etwas anderen Blick wird etwas sichtbar, was vorher schon da war, aber noch im Verborgenen.
Dieses in uns liegende Möglichkeitspotential kann uns in den kommenden Monaten hilfreich sein, um dem zu begegnen, was gerade in Deutschland und Europa stattfindet. Manche bezeichnen den aktuellen Prozess als Optimierung der Verteidigungsfähigkeiten, andere betrachten ihn als Kriegsvorbereitung, wobei die offenliegende, primäre Auswirkung der „German Angst“ als Durchsetzungswerkzeug nutzbar gemacht wird.
Aber erst einmal zurück zu Karfreitag vor über zweitausend Jahren: An jenem Nachmittag hing Christus am Kreuz angenagelt und absichtlich schwer verletzt (für Viele, damals wie heute, DER SOHN GOTTES und Ausdruck bedingungsloser Liebe). Wenn man sich in diese Situation hineinfühlt, wird das Leid schier unerträglich. Und ich bitte den Leser unabhängig von seiner Religion oder inneren Ausrichtung explizit, kurz innezuhalten und sich in diesen sterbenden Menschen hineinzuversetzen.
DAS war das letztendliche Ergebnis von KRIEG. DIE LIEBE wurde an ein Kreuz genagelt, mit einem Speer aufgespießt und dann starb sie – langsam und qualvoll.
Wenn man den Überlieferungen glaubt, waren einige seiner engen Schüler und Vertrauten ganz in der Nähe. Auch deren Gefühlswelt ist vom Leser nach zweitausend Jahren nachfühlbar, auch wenn es ähnlich schwierig ist.
Manch Historiker argumentiert, dass Jesus/Christus bereits einige Zeit vor diesem Ereignis wusste, welches „Ende“ ihm bestimmt war. So dann auch wohl seine engsten Vertrauten, vielleicht sogar die gesamte Essener-Gemeinschaft, aus der er stammte. Wenn dem so war, ist dieses Wesen in Klarheit und absoluter Hingabe in diesen unglaublich leidvollen Prozess gegangen.
Man kann auch rein gedanklich nachvollziehen, dass alle ihm nahestehenden Menschen schwierige Gefühle wie Verzweiflung, Ohnmacht und Wut in allerhöchster Ausprägung aushalten mussten. Nicht nur an diesem Tag, sondern schon einige Zeit davor und noch lange danach. Diese Menschen waren allerdings von IHM ausgebildet, genauso wie Jesus selbst in hohen Weisheitslehren ausgebildet war.
Das macht hier den Unterschied aus, auf den ich hinweisen möchte.
Die Geschichte lehrt uns, dass er und seine Anhänger besondere Menschen waren. In diesem, für die Menschheit so einschneidenden und bis heute überlieferten Ereignis, war ein wesentlicher Bestandteil von absoluter Wichtigkeit für alle Beteiligten:
Das NICHT-TUN
Und ich bin der Meinung, dass dieses NICHT-TUN in unserer Zeitqualität immer noch ein wesentlicher Schlüssel für die Herausforderungen ist, vor denen wir heute und in nächster Zukunft stehen.
Was ist denn NICHT-TUN und wie unterscheidet es sich vom Nichts-Tun?
NICHT-TUN fängt an mit einer all-umfassenden Wahrnehmung von dem, was ist. OHNE direkte Reaktion.
Das Nichts-Tun hingegen fängt mit einer schnell eingeschränkten Wahrnehmung an – der Einschränkung gehen meist schwierige Gefühle voran, gegen die ein Mensch automatisch Widerstand aufbaut. Oftmals bekommen wir davon auch überhaupt nichts mit und es gibt meistens Trauma in der Vergangenheit als Hintergrund oder Ursache.
Bei gewaltigen Ereignissen mit hohem psycho-energetischem Impact reagieren Lebewesen relativ umgehend entweder mit Totstellen, Flucht oder Kampf. Es sind alles auto-reaktive Muster, die in unserem zentralen Nervensystem einprogrammiert sin, und dementsprechend sind sie schwer zu umgehen. ANGRIFF, DROHENDER TOD und KRIEG sind z.B. solche gewaltigen Ereignisse.
Wie oben beschrieben, wirken VERGANGENE Angriffe oder Kriege in unserem Körper-Geist-System nach, sogar generationenübergreifend (in unserem Denkexperiment die „German Angst“). Dementsprechend greifen die auto-reaktiven Muster auch bereits in einem VOR-KRIEGS-ZUSTAND, ohne dass Menschen das möglicherweise bewusst mitkriegen.
Ich ordne alle diese automatischen Reaktionen hier dem Nichts-Tun zu. Alle haben zwar den Überlebenstrieb gemeinsam und machen für ein Individuum Sinn. Aber in der kollektiven Situation, in der wir uns gerade befinden, sind sie alle kontraproduktiv.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld und das Verständnis!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Sich in der aktuellen politischen Situation totzustellen, ist sozusagen ein EXIT des Individuums und es wird nichts, absolut gar nichts zur Verbesserung unser aller Situation beitragen. Die Flucht ist ähnlich zu bewerten – das Individuum rettet sich möglicherweise. Aber es trägt auch nichts zur Heilung oder konstruktiven Verbesserung der (kollektiven) Weltlage bei. Der Kampf, also die sofortige Mobilmachung zur Bekämpfung der widerständigen Gegenkräfte ist zwar eine Form von Tun, aber sie mündet letztendlich im Nichts: Zwei Gegner wollen sich vernichten, bis ein Stärkerer gewinnt – leider ignoriert dieser Automatismus in diesem Momentum, unter welchen Rahmenbedingungen der Gewinner nach dem Überleben weiterleben könnte (oder auch nicht).
Um wieder den Bogen zum Beginn des Christentums und auch zum NICHT-TUN der damaligen Beteiligten zu spannen: Trotz der schwer aushaltbaren Gefühle, hat Christus dieses Schicksal angenommen – ebenso seine Liebsten. Sie nahmen das, was war, in einem ersten Schritt ohne sofortige, automatisierte Reaktion an.
Allerdings waren sie sich allem und vollständig bewusst darüber, was die Situation und das Leben bereitstellte. Die Achtsamkeit nicht nur auf das gelenkt, was gerade schmerzhaft und unaushaltbar war, sondern auf das darüberliegende Größere. Auf die Inhalte, die Christus bzw. die Liebe selbst sie gelehrt hatte:
Sie hielten still. Und sie gingen sehr, sehr bewusst aus dem (inneren und äußeren) Kampf hinaus. Auch wenn sie ihn scheinbar verloren hatten.
Weil genau das der Menschheit gelehrt werden sollte.
Wenn Menschen in vollumfänglicher Wahrnehmung dessen, was ist (und ohne Widerstand dagegen), still sein können, entsteht ein ganz besonderes Momentum. Man bezeichnet das auch als Präsenz. Präsenz kann in Bruchteilen von Sekunden entstehen. Aber man muss es eben auch erlernen.
Wenn die Energie eines Angreifers auf ein solches menschliches Energiefeld trifft, wird Angriffsenergie als erstes SICHTBAR. Bei einigen realisierten (Kampfkunst-) Meistern kann das beobachtet werden. Diese haben es geschafft, Ihren inneren Kampf aufzugeben. Solche Menschen werden faktisch unangreifbar, denn die Energie des Angriffs prallt an deren ausbalancierten Energiefeld ab und wendet sich gegen den Angreifer selbst. Dieser erfährt die Wirkung seiner Handlung dann am eigenen Selbst und stellt in der Regel diesen sinnlosen Akt ein. Solche Menschen haben über den Weg des Nicht-Tuns inneren Frieden kultivieren können, der sich danach auch im Außen manifestiert.
In diesem Zustand findet die Energie sozusagen ohne unseren Willen Ihren klaren und eindeutigen WEG. Im einfachen Fall, beendet es den Kampf, im besten Fall wird die Energie zum Guten umgelenkt und der natürliche Zustand von Frieden entsteht durch die notwendige Bewegung der Energie in die richtige Richtung.
Es ist für uns als Gesellschaft möglich, diese Erkenntnisse in das kollektive Geschehen von KRIEG, KRIEGSVORBEREITUNG und den gerade wirksamen Aspekten der „German Angst“ einwirken zu lassen.
Hierin liegt eine enorme Transformationskraft. Denn wie in einem individuellen Trauma Lebenskraft unterdrückt und bis zur Heilung/Auflösung nicht verfügbar ist, ist es auch bei unserem kollektiven Trauma. Die Chance dabei: Es sind starke Wirk-Kräfte gebunden, die wir als Gesellschaft für einen positiven Wandel zum Frieden hin freisetzen können. Für diese Freisetzung benötigt es Klarheit, Willen und vor allem Eigenverantwortung eines jeden Einzelnen.
Wir sollten uns in einem ersten Schritt bewusst werden, was gerade ganz individuell in unserem Inneren stattfindet. Welche Form des Nichts-Tuns herrscht gerade und warum herrscht sie eigentlich über uns? Welche Automatismen/Muster sind gerade aktiv?
Nehmen wir das doch zuallererst in unsere Verantwortung und werden wir still damit.
Ebenso sollten wir uns als Teil des Menschheitskollektives genau dessen bewusst sein, was gerade im Außen geschieht. Schauen wir uns aus unserer kultivierten Stille heraus an, dass sich Kampf bzw. Krieg anbahnt, an manchen Fronten ist er bereits aktiv. Durch die Bewusstwerdung dessen, wird er SICHTBAR, mit allen seinen Mechanismen und seinen Schatten.
Nehmen wir diese Verantwortung für uns selbst wahr, gibt es dieses besondere Momentum, in dem der Weg der Energie sich wie von selbst verändert. Und das kann man nicht gedanklich vorausplanen. Sie verändert sich aber in dem Sinne, dass alle notwendigen Bewegungen den NATÜRLICHEN ZUSTAND wiederherstellen wollen.
Das würde dann also nicht nur für das wahrnehmende Individuum, sondern für alle Beteiligten erfahrbar werden. Seien es die normale Bürger, repräsentative Regierungsteile oder bereits aktive Kriegsgegner. Es wäre für uns erfahrbar, wie wenn eine unsichtbare Intelligenz oder das Eine, große Ganze zum Wohle bzw. Zusammenfügen von allem gerade Getrennten wirken würde. Die Auswirkung davon würde letztendlich FRIEDEN sein. Und es würde uns vorkommen, wie ein Wunder, auf das wir schon lange warten und an das wir nicht mehr geglaubt hatten.
In dem Momentum der Präsenz im NICHT-TUN entsteht außerordentliche Klarheit und ganz eindeutiges Handeln. Die Wirkung ist immer individuell und kollektiv.
NICHT-TUN ist Friedensarbeit und beginnt immer bei uns selbst.
In den info-energetischen Mustern in unserem Körper-Geist-System, die das Phänomen „German Angst“ uns beschert hat, sind eben auch Lösungsmöglichkeiten enthalten, die die kriegsgeschundenen Generationen vor uns in der Reflektion nach den Ereignissen des zweiten Weltkrieges sozusagen erarbeitet haben. Und die Klarheit darüber, was diese Generationen vor uns hätten besser machen können, ist ebenso wie die angstgetriebenen Verhaltensautomatismen kollektiv zugänglich.
Sie hatten es damals leider noch nicht geschafft, bevor die Spirale des Kampfes völlig in die Eskalation ging – obwohl es einige gab, die andere Wege versucht hatten. Aber sie hatten aus den schmerzhaften Ereignissen gelernt, und das steht uns jetzt zur Verfügung, wenn wir uns selbst spüren.
Die Erschließung dieses über Generationen gereiften, aber noch unerschlossenen Kraftpotentials wird möglich werden, wenn wir uns zu dem Trauma hinwenden, das uns aktuell so sehr Angst macht. Wenn wir uns ihm zuwenden und für uns selbst Verantwortung übernehmen, wird es Anderen nicht mehr möglich sein, unsere Ängste für Ihre selbst angstbasierten Kampfhandlungen nutzbar zu machen.
Je mehr wir uns unserem eigenen verwundeten Kern zuwenden, desto heiler, desto klarer und desto kraftvoller werden wir. Die Menschheit kann sich selbst befreien.
Und vor zweitausend Jahren war da einer, der wusste, dass wir es irgendwann können werden.
Mögen wir in der Tiefe unseres Selbst unseren natürlichen Zustand wieder finden und unsere Welt in friedlichen Miteinanders neu gestalten.
Andreas Hagen hat Deutschland noch während der Corona-Zeit verlassen und lebt seitdem mit seiner Familie glücklich auf einem Bauernhof oberhalb Basel in der Schweiz.
Er ist Gründer des nidoki-Projektes (www.nidoki.de) und vermittelt interessierten Menschen Qi Gong, Jing Qi und K.I. (Körperintelligenz) in Gruppensettings. In kleinem Rahmen trägt er in Einzelsettings mit Hilfe der traumasensiblen Methoden der neurosystemischen Integration zur Verbesserung der Selbstregulation von Menschen in diesen herausfordernden Zeiten bei.
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ e2c72a5a:bfacb2ee
2025-06-03 11:51:31
@ e2c72a5a:bfacb2ee
2025-06-03 11:51:31The crypto revolution isn't just about digital money anymore—it's becoming the backbone of AI's future. While most people see these as separate technologies, they're actually perfect partners solving each other's biggest problems. AI needs decentralized data, transparent decision-making, and secure identity verification—all things crypto excels at. Meanwhile, crypto apps desperately need better user experiences, which AI can deliver through intuitive interfaces and personalized guidance.
AI agents—smart programs that act on your behalf—are already managing crypto wallets worth hundreds of thousands of dollars. Unlike traditional bots that require coding knowledge, these agents understand natural language and make decisions based on your preferences. They're becoming the missing link between complex blockchain systems and everyday users.
The most exciting developments are happening in three key areas: decentralized data marketplaces that reward users for sharing high-quality information; distributed computing networks that make AI processing more affordable; and blockchain verification systems that combat deepfakes by tracking content creation. Projects like Sentient, Near, and Sahara are building infrastructure that makes AI more accessible while ensuring creators get properly compensated.
Don't fall for the misconception that crypto is just speculative gambling while AI is serious technology—they're increasingly inseparable. The future belongs to applications that combine both, creating experiences that are both powerful and user-friendly. Are you ready to participate in this convergence, or will you miss the opportunity to shape how these technologies transform our digital lives?
-
 @ c7a8d522:262a74de
2025-06-03 07:16:49
@ c7a8d522:262a74de
2025-06-03 07:16:49Se você está em busca de uma plataforma moderna, confiável e cheia de emoção para se divertir com seus jogos favoritos, a 277Bet é uma excelente escolha. Com um ambiente seguro, diversas opções de entretenimento e um sistema intuitivo, essa plataforma tem se destacado no mercado brasileiro e conquistado cada vez mais usuários que buscam qualidade, diversão e praticidade em um só lugar.
Um Novo Conceito em Entretenimento Digital A 277Bet foi desenvolvida com foco no usuário brasileiro, oferecendo uma interface simples, responsiva e traduzida integralmente para o português. Ao acessar o site, o jogador encontra um ambiente amigável, onde todas as categorias estão bem organizadas, facilitando a navegação mesmo para quem não tem muita experiência com plataformas de jogos online.
Um dos grandes diferenciais da 277beté seu compromisso com a transparência e a segurança. A plataforma conta com tecnologia de criptografia de ponta para proteger os dados dos usuários e utiliza sistemas de verificação modernos para garantir transações financeiras seguras e rápidas.
Diversidade de Jogos para Todos os Gostos No catálogo da 277Bet, é possível encontrar uma ampla variedade de jogos que agradam todos os perfis de jogadores. Entre as opções mais populares, estão as máquinas de giro com temáticas diversas e recursos inovadores, ideais para quem gosta de partidas rápidas e dinâmicas.
Para os fãs de jogos com interatividade ao vivo, a plataforma também oferece experiências em tempo real, onde o jogador pode acompanhar as rodadas, interagir com apresentadores e sentir a adrenalina de cada jogada. Além disso, há opções tradicionais de cartas, roletas virtuais e outros formatos que mantêm o usuário entretido por horas.
A 277Bet também investe constantemente em parcerias com desenvolvedores renomados, garantindo que todos os jogos disponíveis sejam de alta qualidade, com gráficos impressionantes, efeitos sonoros imersivos e excelente jogabilidade tanto em computadores quanto em dispositivos móveis.
Uma Experiência do Usuário que Faz a Diferença Outro ponto forte da 277Bet é o cuidado com a experiência do jogador. Desde o cadastro até o saque dos ganhos, tudo é pensado para ser simples, rápido e eficiente. O processo de registro é descomplicado e leva apenas alguns minutos. Após criar a conta, o usuário já pode fazer seu primeiro depósito com total segurança e começar a explorar as opções de jogos.
O atendimento ao cliente é outro destaque da plataforma. Com suporte disponível em português e atendimento via chat ao vivo, e-mail ou WhatsApp, os jogadores têm a certeza de que serão bem assistidos em qualquer dúvida ou necessidade.
Além disso, a 277Bet oferece promoções atrativas, bônus de boas-vindas e campanhas especiais para usuários frequentes, tornando a experiência ainda mais vantajosa. Tudo isso sem abrir mão da responsabilidade: a plataforma incentiva o jogo consciente e disponibiliza ferramentas de controle de tempo e gastos para os usuários.
Conclusão A 277Bet surge como uma plataforma completa para quem deseja unir diversão, segurança e praticidade em um só lugar. Com uma vasta gama de jogos, interface amigável, suporte eficiente e um sistema de recompensas justo, a experiência do usuário é valorizada em todos os aspectos.
Se você está procurando um novo ambiente online para se entreter, a 277Bet é, sem dúvida, uma das melhores opções do momento. Prepare-se para se divertir com qualidade e emoção, tudo com o conforto de jogar quando e onde quiser.
-
 @ c7a8d522:262a74de
2025-06-03 07:16:17
@ c7a8d522:262a74de
2025-06-03 07:16:17Para os amantes de jogos online que buscam uma plataforma confiável, moderna e recheada de entretenimento, a 9bet99 surge como uma excelente opção no mercado brasileiro. Com um ambiente digital desenvolvido para agradar jogadores iniciantes e experientes, o site oferece uma vasta gama de jogos, bônus atrativos e uma navegação intuitiva que transforma cada sessão em uma experiência única e envolvente.
Uma Plataforma Completa e Segura A 9bet99 se destaca por oferecer uma estrutura sólida e totalmente otimizada para dispositivos móveis e computadores. O site possui sistema de segurança de ponta, garantindo que todos os dados dos usuários estejam protegidos. A interface é clara, objetiva e proporciona fácil acesso às principais seções, como promoções, métodos de pagamento e suporte ao cliente.
Um dos grandes diferenciais da 9bet99é o atendimento ao cliente. Com suporte disponível 24 horas por dia, sete dias por semana, os jogadores têm à disposição uma equipe treinada para esclarecer dúvidas, resolver problemas técnicos e auxiliar em qualquer etapa do processo de jogo ou transações.
Jogos Para Todos os Gostos Na 9bet99, os jogadores encontram uma impressionante variedade de opções para se divertir. Entre os destaques estão os jogos de mesa, slots online, roletas digitais e experiências interativas ao vivo. Cada jogo é fornecido por desenvolvedores reconhecidos internacionalmente, o que garante gráficos de alta qualidade, trilhas sonoras envolventes e jogabilidade justa e equilibrada.
Os slots são uma das principais atrações da plataforma. Disponíveis em diversos estilos e temas, esses jogos combinam animações vibrantes com mecânicas modernas, como rodadas grátis, multiplicadores e jackpots progressivos. Já para quem gosta de jogos com mais estratégia, há várias mesas de pôquer, blackjack e bacará, todas com versões automáticas e ao vivo.
Outro ponto alto da 9bet99 são os jogos ao vivo, nos quais o jogador pode interagir com crupiês reais em tempo real, criando uma atmosfera imersiva e emocionante. Tudo isso com transmissão em alta definição e sem atrasos.
Experiência do Jogador em Primeiro Lugar A 9bet99 foi pensada para oferecer uma experiência fluida e satisfatória desde o primeiro acesso. O cadastro é rápido e simples, permitindo que o jogador comece a explorar os jogos em poucos minutos. A plataforma também conta com promoções constantes, incluindo bônus de boas-vindas, cashback e torneios temáticos, que valorizam ainda mais a participação ativa do jogador.
A facilidade para realizar depósitos e saques é outro ponto que merece destaque. A 9bet99 oferece diversos métodos de pagamento populares no Brasil, como Pix, transferência bancária e carteiras digitais. As transações são rápidas e seguras, o que transmite confiança ao usuário e proporciona tranquilidade ao lidar com valores.
Além disso, a plataforma adota políticas de jogo responsável, com ferramentas que permitem ao usuário controlar seus gastos e manter uma experiência equilibrada e saudável.
Conclusão A 9bet99 é mais do que uma simples plataforma de jogos online — é um ambiente completo, seguro e envolvente que oferece diversão de qualidade, suporte eficiente e jogos para todos os perfis. Com uma combinação de tecnologia avançada, variedade de jogos e foco na experiência do usuário, a 9bet99 se consolida como uma das melhores opções para quem busca entretenimento digital de alto nível no Brasil.
Se você está em busca de emoção, praticidade e recompensas incríveis, a 9bet99 está pronta para te surpreender. Cadastre-se, explore o catálogo e aproveite tudo o que essa plataforma inovadora tem a oferecer!
-
 @ a296b972:e5a7a2e8
2025-06-03 07:04:39
@ a296b972:e5a7a2e8
2025-06-03 07:04:39So sehr man sich auch Mühe gibt, es will vielen einfach nicht gelingen, Russland als den Feind anzusehen.
Wenn ein fremder Mann eine Frau unfreiwillig zum Tanz auf’s Parkett zerrt und der Ehemann dem fremden Mann wie auch immer zu verstehen gibt, dass das so nicht geht, dann kann man nicht sagen, der Ehemann habe einen Streit vom Zaun gebrochen.
Eine Reaktion setzt immer eine Aktion voraus.
Nicht Russland ist der NATO auf die Pelle gerückt, sondern die NATO mit der Osterweiterung Russland.
Russland wollte mit Auflösung des Warschauer Pakts eine gemeinsame europäische Militärlösung, die die Neuordnung der NATO oder gar ebenfalls ihre Auflösung zur Folge gehabt hätte.
Der sogenannte Wertewesten ist maßgeblich für den Krieg in der Ukraine verantwortlich. Völkerrechtswidrigkeit kann man weglassen, da es auch im Westen, von den USA, mehrfach Beispiele für völkerrechtswidrige Angriffe auf andere Staaten gibt. Und Deutschland hat im Kosovo auch nicht nur Kaffee für die Truppen gekocht.
Wer im Glashaus sitzt, sollte nicht mit Steinen werfen.
Wenn Deutschland, vertreten durch einen Kanzler 2. Wahl über die nicht mehr vorhandene Reichweitenbeschränkung spricht, das Wahlvieh, den ehemaligen Souverän, im Ungewissen über die Lieferung des Stiers lässt, und dann, wie aus heiterem Himmel, Taurus, mit deutschem Kompass und deutschen Kompassbedienern, auf einmal Richtung Krim-Brücke oder gar Moskau unterwegs sein sollte, wen würde es dann wundern, wenn Moskau seine „Liebesgrüße“, schon allein aus reiner Höflichkeit und Anstand, nach Schrobenhausen sendet?
Würde das passieren, würde man in Deutschland sagen: Seht ihr, wir haben es euch ja immer gesagt, ihr wolltet es nur nicht glauben. Russland, mit seinem imperialen Anspruch und seinem aggressiven Verhalten, der Friedensverhinderer, der böse Putin, der böse Russ‘, wird uns angreifen! Die geforderte Kriegstüchtigkeit war also absolut berechtigt!
Wer das dann immer noch glaubt, dem möchte man eine Rakete in den Kamin seiner Doppelhaushälfte mit Gänsemuster-Gardinen am Küchenfenster stecken.
Wenn man jemanden bis auf’s Blut reizt, ist es ihm dann zu verdenken, wenn ihm irgendwann der Geduldsfaden reißt, nachdem schon mehrere Rote Linien überschritten wurden?
Und warum reizt man Russland bis auf’s Blut? Man kann zu keinem anderen Grund kommen, als dass die Geistesgrößen in Deutschland unbedingt einen Krieg wollen. Wozu? Ist das die von wem auch immer geplante Vollendung der Zerstörung Deutschlands? Der zukünftige Ex-Kanzler redet einen Haufen vermeintlich kluges Zeug daher, aber Russland handelt klug. Kleiner Unterschied.
Rheingold ist in gewöhnliches Rheinmetall, wohl durch Geheim-Alchimie, verwandelt worden. Geheim wird ja jetzt wieder modern. Man kann nur hoffen, dass es in der Taurussland-Rakete tatsächlich US-amerikanische Komponenten gibt, die (vielleicht sogar in Wiesbaden?) abgeschaltet werden können, damit der Stier nicht fliegen kann. Und man kann auch nur hoffen, dass die USA sie dann auch wirklich abschalten.
Die Meyer-Werft in Papenburg soll demnächst auch „Meine Fregatte“ und „Kreuzer grau I bis IX“ bauen. Panzerkreuzerfahrten in der Ostsee mit Blick auf Königsberg, na bravo, tolle Idee. (Da war doch mal was?). Gute Erholung schon jetzt. Da wird die vom Kaiser für den Aufbau der Marine eingeführte Sektsteuer endlich wieder ihrem eigentlichen Zweck zugeführt.
Und wie der ehemalige Masken-Chef-Einkäufer erst jüngst in einer der unsäglichen Staatsfunk-Aufführungen lichtblitzartig erkannt haben muss, spricht Putin Deutsch. Nein, doch, oh! Man stelle sich das einmal vor. Ganz was Neues! Die jetzt für die deutsche Bevölkerung geheim gehaltenen militärischen Absprachen werden nun in einer Sprache in Berlin besprochen, von denen man vorher sorgfältig, wie immer, recherchiert hat, dass Putin sie sicher nicht spricht, damit er nichts mitbekommt. Pssst, Feind hört mit! Den Beruf des Dolmetschers oder Übersetzers hat das Arbeitsamt in der Berufsberatung in der Schulzeit des Bankkaufmanns wahrscheinlich nicht vorgestellt, daher existieren sie für ihn nicht.
Und welche militärischen Entscheidungen von den deutschen "Chef-Diplomaten" getroffen wurden, das erfährt die Bevölkerung ja spätestens, wenn es knallt. Das reicht ja auch.
Was kommt als nächstes? Nach selbst genähten Maulwindeln jetzt eine Nähanleitung für schwere Gardinen zur Fenster-Verdunkelung? Oder gibt es die bald schon fertig in allen Größen zu kaufen, bei einem Discounter, wie in Berlin jetzt Macheten, damit man sich im Garten wieder den Weg zum Geräteschuppen bahnen kann.
Ils sont fous ces Allemands!
„Das große Karthago führte drei Kriege. Nach dem ersten war es noch mächtig. Nach dem zweiten war es noch bewohnbar. Nach dem dritten war es nicht mehr aufzufinden“, Berthold Brecht.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 9ca447d2:fbf5a36d
2025-06-03 07:03:02
@ 9ca447d2:fbf5a36d
2025-06-03 07:03:02When making critical decisions about investments, company acquisitions, or capital deployment, organizations rely on a fundamental tool: the hurdle rate. This is the minimum rate of return that a project or investment must achieve to be considered viable by managers or investors.
The hurdle rate is not just a number — it’s a filter that separates promising opportunities from those that don’t justify the risk.
It acts as a crucial benchmark. If the expected return on an investment falls below the hurdle rate, that opportunity is typically rejected.
Setting this rate involves a careful consideration of several factors, including the company’s cost of capital, specific risk profile, inflation rates, and opportunity cost of allocating resources elsewhere.
In essence, the hurdle rate ensures that only projects with the potential to create real value move forward.
Bitcoin has emerged as a disruptive and compelling candidate for a new kind of hurdle rate in capital allocation. Its unique properties challenge the conventions of traditional finance and invite a new thought pattern of what’s considered an appropriate benchmark.
Bitcoin’s fixed supply (capped at 21 million), and its decentralized, borderless nature makes it fundamentally resistant to inflation and debasement, unlike fiat currencies that can be printed at will by central banks.
Here’s the real question for investors and fund managers: if your portfolio or fund consistently fails to outperform bitcoin, at what point do you simply start allocating to bitcoin instead?
This isn’t rocket science. Over the past decade, bitcoin has not only outperformed traditional assets, but has also redefined what investors should expect as a minimum acceptable rate.
Asset classes comparison since 2013 — Seeking Alpha
The numbers speak for themselves.
From 2013-2023, bitcoin delivered the highest annual return in 8 out of those 11 years. This is not a fluke or a bubble, it’s a decade-long trend that demands attention from anyone serious about capital growth.
Typically, most investment managers use the S&P 500 as their benchmark hurdle rate. Will their potential investment generate more return than the S&P? If not, it’s usually dismissed.
Since 1970, the S&P 500 has provided an average annual return of 10.66%. Investment managers routinely reject ideas that can’t beat this average, recognizing that anything less is not worth the risk or effort.
But what happens when we compare this to bitcoin?
Over the last 10 years, bitcoin’s average annual return has been an astonishing 49%. While it’s unlikely that this rate will persist forever, it’s impossible to ignore the magnitude and consistency of bitcoin’s outperformance.
Bitcoin hasn’t just beat the S&P—it’s outperformed every major asset class, including gold, treasuries, real estate, commodities, and equities.
Of course, past performance isn’t a guarantee of future results. So the question becomes: can bitcoin continue to deliver, and are we ready to use it as a benchmark for investment decisions?
To answer this, it’s essential to understand the underlying forces driving bitcoin’s price appreciation.
Several macroeconomic factors contribute to bitcoin’s rise, including money printing, economic uncertainty, and the ongoing debasement of fiat currencies.
When governments print money or run deficits, confidence in traditional currencies erodes. In such environments, investors naturally seek scarce assets, historically gold, and now increasingly bitcoin.
Consider the current fiscal reality: the United States is burdened with over $36 trillion in national debt, and there’s little indication that the money printing will stop.
This environment only strengthens the case for bitcoin as a store of value and as a benchmark for capital allocation. Bitcoin’s staying power is becoming undeniable.
Those who fail to adapt, risk being left behind. We’re already witnessing the early stages of institutional and corporate adoption, and it’s only a matter of time before bitcoin becomes a standard reference point for hurdle rates across the investment world.
Visionary leaders like Michael Saylor of Strategy, have openly discussed the challenges of outperforming the world’s top companies.
Saylor recognized that if your investment, company, or project cannot reasonably be expected to outperform bitcoin, it may be more rational to simply hold bitcoin itself.
MSTR performance compared to bitcoin, Magnificent 7 and S&P500 — aicoin
In a world where bitcoin has established itself as the premier performing asset, the message is clear: if you can’t beat bitcoin, why not join it?
Just buy bitcoin.
-
 @ 43aec65f:003ef459
2025-06-03 06:56:24
@ 43aec65f:003ef459
2025-06-03 06:56:24sound
{{|>}} hello world asfdasfd
-
 @ 2769f6ba:8dac44e4
2025-06-03 06:53:38
@ 2769f6ba:8dac44e4
2025-06-03 06:53:38You may want to believe that the world works like a video game, where you can press the pause button, come back three months later and everything will be waiting for you exactly as you left it. But real life doesn’t work like that. The difference is that in the video game you are in control, whereas in real life you are not. Maybe you want to believe that the worst is over, but this is just getting started. Supply chains are breaking down and the economy is starting to collapse. To make it clear, “the economy” is not something abstract; it’s real people losing their jobs, their businesses, their incomes and their homes. Your authoritarian fantasies will just make it worse for you and others until you cannot handle it anymore and you accept reality and surrender to it. I get that you are afraid, and that’s OK. But to hold your fellow human beings hostage because you are afraid is not OK. It’s getting to the point where if you still support lockdowns, mandatory vaccines, mandatory tracking, mandatory testing or mandatory anything you have blood on your hands. History will not judge you kindly.
Then there are those of you who want to believe that the bailouts and the “universal basic income” will make the problems disappear. For example, I read Charles Eisenstein in his otherwise excellent piece The Coronation come up with all this UBI nonsense. You probably realize that if you grab a piece of paper and write “$1,000,000” on it with a marker pen of your favorite color, you don’t become magically rich. But you still want to believe that if the government does exactly the same thing, your problems will go away. On the one hand, even if you are not fully aware of it, you realize that the government and its satellite corporations are abusing you and sucking your blood more and more every day. Yet on the other hand, you keep begging your very abusers that are trying to deprive you from earning an honest living for yourself to give you a measly monthly UBI check in the hopes that it will magically make you feel good and solve your problems.
Aside from the fact that printing money cannot solve the issue the governments themselves have created in the first place with their mandatory lockdowns: maybe you expect that you can control your masters, or that they will benevolently give you the UBI check with no strings attached. Of course not: receiving the check will likely be tied to being a “good law-abiding citizen” (a.k.a. obedient slave); something like the social credit system they have in China. You will end up completely disempowered and depending on the government to even feed yourself and have shelter. I find it quite infuriating and sad that any “spiritual teacher” would want that for you and that you fall for it.
Consider this:
The issue is not the coronavirus itself. The virus is just revealing the cracks in the system.
You are not a victim. You always have the power. Not the power to start a “revolution”, mind you, which just consists in replacing the old abusers with new ones. As Buckminster Fuller said: “You never change things by fighting the existing reality. To change something, build a new model that makes the existing model obsolete.”
You have the power to walk away from this dying system of nation-state governments and fiat “money” and into the nascent paradigm of cryptocurrencies and decentralized governance. But first you have to question and confront the beliefs you have accepted as “reality”. It’s hard, I know, but unavoidable. So, the sooner you begin, the better for yourself and for humanity. Do you want to be free or do you just want to have a “fair” master?