-
 @ 55b2e558:31b7679d
2025-06-02 09:27:49
@ 55b2e558:31b7679d
2025-06-02 09:27:49Moving out of a rental property can be stressful, especially when your bond is on the line. Between packing boxes and organizing your next place, the last thing you want to worry about is cleaning. That’s where we come in – the End of Lease Experts, delivering Spotless Move Outs that help you get your bond back, stress-free.
Why End of Lease Cleaning Matters When your lease ends, most real estate agents and landlords expect the property to be returned in the same – or better – condition than when you moved in. Missed spots, stained carpets, or dusty vents can result in a portion (or all) of your bond being withheld. A thorough, professional clean isn’t just recommended – it’s often required.
What Makes Us the Experts? At Brisbane Carpet Cleanere we specialize in bond cleaning and end-of-lease cleans that tick every box on your property manager’s checklist. Our trained cleaners use advanced equipment and eco-friendly products to ensure every surface shines. We’re not just surface cleaners – we get into the nooks, crannies, and forgotten corners too.
Our Comprehensive End-of-Lease Cleaning Includes: Full kitchen clean, including oven, stove, and range hood
Bathroom scrubbing, including tiles and grout
Wall spot cleaning and mark removal
Interior window and track cleaning
Carpet vacuuming and optional steam cleaning
Skirting boards, light fittings, and ceiling fans
Garage and outdoor area sweep (optional)
Bond Back Guarantee We’re so confident in the quality of our work that we offer a Bond Back Guarantee. If your agent or landlord isn’t satisfied, we’ll come back and clean for free. Our goal is simple: leave no trace behind so you can move out with peace of mind.
Save Time. Reduce Stress. Get Results. Hiring professional end-of-lease cleaners is an investment in peace of mind. Not only do you save hours of work, but you also increase your chances of getting your full bond back – without the hassle of re-cleans or disputes.
Whether you're in Brisbane or the surrounding suburbs, let us take the pressure off your move with a cleaning service that’s fast, affordable, and spotless.
Ready for a Hassle-Free Move? Call us- 0731529574 today or book online to schedule your End of Lease Clean. End of Lease Experts – Spotless Move Outs. Bond Back Guaranteed.
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ cefb08d1:f419beff
2025-06-02 08:59:16
@ cefb08d1:f419beff
2025-06-02 08:59:16https://stacker.news/items/995022
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 9c9d2765:16f8c2c2
2025-06-02 08:21:08
@ 9c9d2765:16f8c2c2
2025-06-02 08:21:08CHAPTER THIRTY FIVE
“Ladies and gentlemen,” James began, his voice firm but serene, “we have reached a stage where the name JP Enterprises must stand not only for affluence and innovation but also for responsibility and reinvention.”
The team leaned in, captivated by his tone.
“I’ve given this much thought,” he continued, “and it’s time we invested not just in profitable ventures but in communities especially those that raised men like me.”
Whispers of approval circled the room. James unfolded a series of blueprints and documents, revealing a new initiative named The Phoenix Foundation, a massive philanthropic wing of JP Enterprises aimed at funding education, rebuilding impoverished neighborhoods, and providing mentorship for underprivileged youth.
“This isn’t charity,” James clarified. “This is legacy.”
Meanwhile, on the other side of the city, Mark and Helen were dealing with the crushing weight of public disgrace. Their failed scheme had made headlines. Investors withdrew, associates distanced themselves, and even loyal allies now whispered behind their backs.
Helen slammed a newspaper onto the glass table in frustration. “They’ve blacklisted us from another tender. Mark, we’re becoming irrelevant!”
Mark, who had been pacing the room like a caged animal, finally stopped. “It’s not over. We still have leverage somewhere. James isn’t invincible.”
Helen scoffed. “Tell that to the world. They worship the ground he walks on. You think you can bring down a man who rose from being a street outcast to owning the city’s largest enterprise?”
Mark’s eyes darkened. “He bleeds, Helen. Everyone has a weak spot. We just haven’t found him yet.”
But even as their desperation festered, James was rising even higher. A televised interview had been scheduled where he would unveil The Phoenix Foundation. The nation watched eagerly. Sitting on a minimalist stage, flanked by banners of the foundation’s vision, James spoke from the heart.
“I know what it means to be invisible,” he said. “I know what hunger, shame, and rejection feel like. I’ve lived it. But I also know the power of one opportunity, one person who believes in you. Through this foundation, I want to be that person for thousands.”
The applause was thunderous, not only from the live audience but from homes, offices, and schools where people were inspired by his journey.
The days following the televised launch of The Phoenix Foundation brought waves of admiration and support from across the country. Letters of gratitude flooded JP Enterprises from parents whose children now had access to scholarships, to small business owners revitalized by community grants. James, once shunned and dismissed, was now a symbol of unshakable strength, resilience, and grace under fire.
But in the shadows, the remnants of Mark and Helen’s influence continued to decay.
With the media fixated on James’s rise and the overwhelming success of the foundation, Helen had become a recluse, seldom leaving her estate. The curtains were always drawn, the halls eerily quiet, and every incoming call was a potential threat to her already-battered reputation. Her once-prized social invitations had vanished, and even her closest acquaintances now found convenient excuses to avoid her.
One afternoon, as she sat on her leather chaise, surrounded by unopened letters and wilting orchids, her phone buzzed. It was Mark.
"We need to talk," his voice came through, rough and urgent.
"Unless you’ve figured out a way to reverse time or erase James from existence, I’m not interested," she replied dryly, her voice thick with exhaustion.
"I’ve been digging into his foundation. There might be something," he said, the faintest glimmer of his former arrogance returning.
Helen raised a skeptical brow. "You mean the only project that has made him a national hero overnight? Do enlighten me."
Mark hesitated for a moment, then spoke. "I have a contact. Someone who worked closely with James during his street days. She claims there's more to his story, something about a deal gone wrong before Ray Enterprises even noticed him."
Helen’s eyes narrowed. "You better not be chasing another ghost story, Mark. We’ve lost everything playing that game."
Meanwhile, back at JP Enterprises, James was unaware of the new whispers trailing behind him. His focus remained undivided, channeling his efforts into real progress. He visited schools sponsored by the foundation, shook hands with young entrepreneurs, and held intimate town hall meetings to listen to citizens’ concerns. His sincerity was unmistakable.
One evening, as he stood at the balcony of his high-rise office, looking over the city he once roamed as a stranger, his uncle Charles joined him.
"You’ve come a long way, James," Charles said, resting a firm hand on his shoulder. "Your father may have doubted you once, but now he sees what we always knew: you're more than capable of carrying this legacy."
James nodded slowly. "It’s not about the legacy anymore, Uncle. It’s about changing lives. If we succeed, JP Enterprises won’t just be remembered for profit margins, it'll be remembered for its heart."
And indeed, that heart had begun to beat in places once forgotten.
"Sir, there's something you might want to take a look at," James's personal assistant said as she stepped into his office, holding a manila folder with both hands.
James looked up from his tablet, where he had been reviewing the upcoming development plans for The Phoenix Foundation outreach program in rural districts. "Is it urgent?"
Tracy’s expression was uneasy. "I believe so. It slipped into the front reception without a name. Just labeled ‘To the President, Personal.’ We scanned the documents. They’re… sensitive."
James gestured for her to bring it over. He leaned back in his chair as she placed the folder before him and stepped away. Slowly, he opened it, revealing a series of photographs, transcripts, and one shocking email thread. His eyes narrowed as he scanned the contents. There it was detailed records of recent communications between Mark and a former government contractor, outlining a clandestine attempt to discredit The Phoenix Foundation by faking embezzlement allegations.
"So they haven’t learned their lesson," James muttered to himself, his jaw tightening.
Tracy, standing silently nearby, asked cautiously, "Should I inform legal?"
"Not yet," he replied, standing and pacing toward the window. "Let them think they still have the upper hand. We’ll collect more. I want this to be their final mistake, not just another slap on the wrist."
From the 39th floor, the skyline shimmered in the twilight. But beneath the golden hues of the sunset, darkness moved silently, calculating its next step.
Across town, in an upscale but dimly lit lounge, Mark and Helen sat across from each other, their faces drawn and wary. They were meeting a woman known only as "Seraphina," a discreet broker of information and, when needed, scandal.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ da0b9bc3:4e30a4a9
2025-06-02 08:20:19
@ da0b9bc3:4e30a4a9
2025-06-02 08:20:19Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post!
https://stacker.news/items/995015
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 9c9d2765:16f8c2c2
2025-06-02 07:46:40
@ 9c9d2765:16f8c2c2
2025-06-02 07:46:40CHAPTER THIRTY FOUR
One evening, as the amber light of sunset poured through the massive windows of his penthouse, James sat quietly with a leather-bound journal in hand. It was filled with handwritten notes, sketches of business concepts, and scribbled affirmations from the years he spent in isolation.
Each page was a memory. A scar. A vow.
There, in solitude, his thoughts returned to the past not with bitterness, but with clarity. He remembered the cold nights behind Ray Enterprises, the condescending glares, the endless humiliation. Yet, in those moments of degradation, a fire had been lit within him a fire that now fueled empires.
Suddenly, his phone vibrated. A message from his father.
“Proud of you, son. Your mother and I would love to have dinner this weekend with just the three of us.”
James smiled faintly. The wound of abandonment hadn’t fully healed, but the gesture was a stitch in the fabric of reconciliation.
He replied simply, “I’ll be there.”
Downstairs in the JP lobby, a woman in her sixties entered hesitantly. Her clothes were modest but clean, and her eyes scanned the space with nervous curiosity. The receptionist greeted her with a polite smile.
“Good evening, ma’am. Do you have an appointment?”
“No,” she said softly, her hands wringing the strap of her purse. “I don’t. But… Can you tell Mr. James that Clara is here? He might remember that I used to give him leftover bread from my shop… when he had nowhere to go.”
The receptionist looked surprised but composed. “Please have a seat. Let me reach out to him.”
Moments later, James was informed. His heart caught for a second.
Clara.
He remembered her clearly as one of the few who had shown him kindness when the world turned its back. Without hesitation, he descended to the lobby.
As the elevator doors slid open, their eyes met. Clara gasped, tears already forming. “You’ve grown into such a fine man,” she whispered.
James walked up to her, gently took her hand, and with a voice rich in emotion said, “You fed me when I was invisible to the world. You gave me more than bread you gave me dignity. Thank you.”
He led her into his private lounge, offering tea and a warm meal, listening to her speak of her late husband, her children, and the small bakery she still ran despite her age.
Before she left, James handed her an envelope.
“I’d like to invest in your bakery,” he said. “Not for business just because every child in this city deserves to taste the kindness I received from you.”
Clara’s hands trembled as she opened the envelope, eyes widening at the check inside.
“Sir, there’s someone waiting in the executive lounge… says she knows you,” Rita informed James softly as she stepped into his office.
James, seated behind his grand mahogany desk, looked up with a faint furrow between his brows. “Who is it this time?” he asked, his voice calm but tired. It had been a long day of meetings, legal signings, and strategic calls.
“She gave her name as Olivia. Said she knew you... back when things were hard.”
James’s breath hitched momentarily. That name wasn't one he had heard in years. Slowly, he rose from his chair, buttoning his jacket with deliberate poise. “Send her in,” he said, his voice unreadable.
Moments later, the door opened and in walked Olivia slender, worn by time, but still carrying the same fiery glint in her eyes. She looked around the opulent office, her gaze settling on James.
“You’ve changed,” she said, almost in awe. “But those eyes… still the same.”
James didn’t speak for a moment. He merely gestured for her to sit, though he remained standing. “Why are you here, Olivia?”
She hesitated, then dropped her bag onto the seat and looked at him with measured defiance. “Because I wanted to see for myself. To see if it was true. That the man who once cleaned floors for my father now owns one of the most powerful corporations in the country.”
James chuckled softly, though there was no humor in it. “Funny how life works, isn’t it?”
She looked down, biting her lower lip. “I was young. Naive. Cruel, even. I regret what I said to you… how I treated you.”
“You don’t need to apologize,” James said, walking to the window and staring out at the golden cityscape. “Back then, your scorn was just one of many. It built me. Sharpened me.”
A long silence passed between them, heavy but not hostile.
“Are you happy?” she finally asked, voice softer now.
James turned to her slowly, his gaze steady. “Happiness is fleeting. But peace? I’ve found some. Purpose, too.”
She stood, eyes glossy. “I wanted to say I’m proud of you… and maybe, to ask if there’s a chance to start again. As friends. Nothing more.”
James studied her for a moment before nodding slightly. “Friendship... I can afford that now.”
They exchanged no handshake, no hug, just a mutual understanding. Olivia left quietly, and as the door closed, James sighed.
Outside his office, the world buzzed, phones rang, executives walked briskly past, deals were being sealed. But in that quiet moment, James returned to his desk, pulled out the photo of his younger self tucked into the drawer, and stared at it.
As the days passed, the wind of change blew steadily across the corridors of JP Enterprises. The company’s reputation had not only recovered from the smear campaign instigated by Mark and Helen but had soared beyond expectation. The public, once skeptical, now admired James even more for his composure under pressure and his resilience amidst controversy.
Within the elegantly marbled boardroom of JP Enterprises, James convened a confidential meeting with his top executives and legal team. The atmosphere was laced with anticipation and reverence.
-
 @ b1ddb4d7:471244e7
2025-06-02 07:00:48
@ b1ddb4d7:471244e7
2025-06-02 07:00:48Custodial Lightning wallets allow users to transact without managing private keys or channel liquidity. The provider handles technical complexities, but this convenience comes with critical trade-offs:
- You don’t control your keys: The custodian holds your bitcoin.
- Centralized points of failure: Servers can be hacked or shut down.
- Surveillance risks: Providers track transaction metadata.
Key Risks of Custodial Lightning Wallets
*1. Hacks and Exit Scams*
Custodians centralize large amounts of bitcoin, attracting hackers:
- Nearly $2.2 billion worth of funds were stolen from hacks in 2024.
- Lightning custodians suffered breaches, losing user funds.
Unlike non-custodial wallets, victims have no recourse since they don’t hold keys.
*2. Censorship and Account Freezes*
Custodians comply with regulators, risking fund seizures:
- Strike (a custodial Lightning app) froze accounts of users in sanctioned regions.
- A U.K. court in 2020 ordered Bitfinex to freeze bitcoin worth $860,000 after the exchange and blockchain sleuthing firm Chainalysis traced the funds to a ransomware payment.
*3. Privacy Erosion*
Custodians log user activity, exposing sensitive data:
- Transaction amounts, receiver addresses, and IPs are recorded.
*4. Service Downtime*
Centralized infrastructure risks outages.
*5. Inflation of Lightning Network Centralization*
Custodians dominate liquidity, weakening network resilience:
- At the moment, 10% of the nodes on Lightning control 80% of the liquidity.
- This centralization contradicts bitcoin’s decentralized ethos.
How to Switch to Self-Custodial Lightning Wallets
Migrating from custodial services is straightforward:
*1. Choose a Non-Custodial Wallet*
Opt for wallets that let you control keys and channels:
- Flash: The self-custodial tool that lets you own your keys, control your coins, and transact instantly.
- Breez Wallet : Non-custodial, POS integrations.
- Core Lightning : Advanced, for self-hosted node operators.
*2. Transfer Funds Securely*
- Withdraw funds from your custodial wallet to a bitcoin on-chain address.
- Send bitcoin to your non-custodial Lightning wallet.
*3. Set Up Channel Backups*
Use tools like Static Channel Backups (SCB) to recover channels if needed.
*4. Best Practices*
- Enable Tor: Mask your IP (e.g., Breez’s built-in Tor support).
- Verify Receiving Addresses: Avoid phishing scams.
- Regularly Rebalance Channels: Use tools like Lightning Pool for liquidity.
Why Self-Custodial Lightning Matters
- Self-custody: Control your keys and funds.
- Censorship resistance: No third party can block transactions.
- Network health: Decentralized liquidity strengthens Lightning.
Self-custodial wallets now rival custodial ease.
Custodial Lightning wallets sacrifice security for convenience, putting users at risk of hacks, surveillance, and frozen funds. As bitcoin adoption grows, so does the urgency to embrace self-custodial solutions.
Take action today:
- Withdraw custodial funds to a hardware wallet.
- Migrate to a self-custodial Lightning wallet.
- Educate others on the risks of custodial control.
The Lightning Network’s potential hinges on decentralization—don’t let custodians become its Achilles’ heel.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ fd06f542:8d6d54cd
2025-04-15 02:38:14
@ fd06f542:8d6d54cd
2025-04-15 02:38:14排名随机, 列表正在增加中。
Cody Tseng
jumble.social 的作者
https://jumble.social/users/npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wl
- Running [ wss://nostr-relay.app ] (free & WoT) 💜⚡️
- Building 👨💻:
- https://github.com/CodyTseng/jumble
- https://github.com/CodyTseng/nostr-relay-tray
- https://github.com/CodyTseng/danmakustr
- https://github.com/CodyTseng/nostr-relay-nestjs
- https://github.com/CodyTseng/nostr-relay
- https://github.com/CodyTseng
阿甘
- @agan0
- 0xchat.com
- canidae40@coinos.io
- https://jumble.social/users/npub13zyg3zysfylqc6nwfgj2uvce5rtlck2u50vwtjhpn92wzyusprfsdl2rce
joomaen
- Follows you
- joomaen.com
-
95aebd@wallet.yakihonne.com
-
nobot
- https://joomaen.filegear-sg.me/
- https://jumble.social/users/npub1wlpfd84ymdx2rpvnqht7h2lkq5lazvkaejywrvtchlvn3geulfgqp74qq0
颜值精选官
- wasp@ok0.org
- 专注分享 各类 图片与视频,每日为你带来颜值盛宴,心动不止一点点。欢迎关注,一起发现更多美好!
- https://jumble.social/users/npub1d5ygkef6r0l7w29ek9l9c7hulsvdshms2qh74jp5qpfyad4g6h5s4ap6lz
6svjszwk
- 6svjszwk@ok0.org
- 83vEfErLivtS9to39i73ETeaPkCF5ejQFbExoM5Vc2FDLqSE5Ah6NbqN6JaWPQbMeJh2muDiHPEDjboCVFYkHk4dHitivVi
-
low-time-preference
-
anarcho-capitalism
-
libertarianism
-
bitcoin #monero
- https://jumble.social/users/npub1sxgnpqfyd5vjexj4j5tsgfc826ezyz2ywze3w8jchd0rcshw3k6svjszwk
𝘌𝘷𝘦𝘳𝘺𝘥𝘢𝘺 𝘔𝘰𝘳𝘯𝘪𝘯𝘨 𝘚𝘵𝘢𝘳
- everyday@iris.to
- 虽然现在对某些事情下结论还为时尚早,但是从趋势来看,邪恶抬头已经不可避免。
- 我们要做的就是坚持内心的那一份良知,与邪恶战斗到底。
- 黑暗森林时代,当好小透明。
- bc1q7tuckqhkwf4vgc64rsy3rxy5qy6pmdrgxewcww
- https://jumble.social/users/npub1j2pha2chpr0qsmj2f6w783200upa7dvqnnard7vn9l8tv86m7twqszmnke
nostr_cn_dev
npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm@npub.cash
Developed the following products: - NostrBridge, 网桥转发 - TaskQ5, 分布式多任务 - NostrHTTP, nostr to http - Postr, 匿名交友,匿名邮局 - nostrclient (Python client) . -nostrbook, (nostrbook.com) 用nostr在线写书 * https://www.duozhutuan.com nostrhttp demo * https://github.com/duozhutuan/NostrBridge * * https://jumble.social/users/npub1l5r02s4udsr28xypsyx7j9lxchf80ha4z6y6269d0da9frtd2nxsvum9jm *
CXPLAY
- lightning@cxplay.org
- 😉很高兴遇到你, 你可以叫我 CX 或 CXPLAY, 这个名字没有特殊含义, 无需在意.
- ©本账号下所有内容如未经特殊声明均使用 CC BY-NC-SA 4.0 许可协议授权.
- 🌐如果您在 Fediverse 收到本账号的内容则说明您的实例已与 Mostr.pub 或 Momostr.pink Bridge 互联, 您所看到的账号为镜像, 所有账号内容正在跨网传递. 如有必要请检查原始页面.
- 🧑💻正在提供中文本地化(i10n): #Amethyst #Amber #Citrine #Soapbox #Ditto #Alby
- https://cx.ms/
https://jumble.social/users/npub1gd8e0xfkylc7v8c5a6hkpj4gelwwcy99jt90lqjseqjj2t253s2s6ch58h
w
- 0xchat的作者
- 0xchat@getalby.com
- Building for 0xchat
- https://www.0xchat.com/
- https://jumble.social/users/npub10td4yrp6cl9kmjp9x5yd7r8pm96a5j07lk5mtj2kw39qf8frpt8qm9x2wl
Michael
- highman@blink.sv
- Composer Artist | Musician
- 🎹🎼🎤🏸🏝️🐕❤️
- 在這裡可以看到「我看世界」的樣子
- 他是光良
- https://jumble.social/users/npub1kr5vqlelt8l47s2z0l47z4myqg897m04vrnaqks3emwryca3al7sv83ry3
-
 @ 4fa5d1c4:fd6c6e41
2025-06-02 05:58:24
@ 4fa5d1c4:fd6c6e41
2025-06-02 05:58:24Im Rahmen unseres Workshops möchte ich auf zwei inspirierende Beiträge von Frau Schütze hinweisen und dich einladen, deren Ansätze für die religionsbezogene Bildung weiterzudenken. Die beiden Ausgangspunkte sind:
-
Werkstattbericht: KI-Bilder im Ethik/Philosophie-Unterricht\ In diesem Beitrag beschreibt Frau Schütze, wie sie mithilfe verschiedener KI-Modelle (Midjourney, DALL·E, Ideogram.ai) Bilder generiert, um Schülerinnen und Schüler zum Nachdenken über philosophische und ethische Theorien anzuregen. So wurden zum Beispiel KI-Bilder erstellt, die eine Glückstheorie illustrieren, oder symbolische Darstellungen zum ontologischen und kosmologischen Gottesbeweis (etwa das „größte denkbare Wesen“ bzw. den Laplaceschen Dämon). Dabei erfahren die Lernenden nicht nur einen visuellen Zugang zu abstrakten Gedankenexperimenten, sondern reflektieren zugleich die Grenzen und Tücken von KI-gestützter Bildbeschreibung und -verarbeitung.\ https://frauschuetze.de/?p=7946
-
Rollenkarten Moralphilosophie / angewandte Ethik\ Hier stellt Frau Schütze Rollenkarten vor, die sie für den Oberstufenunterricht entwickelt hat, um Diskussionen zur angewandten Ethik zu strukturieren. Die Karten enthalten Porträts wichtiger Moralphilosophinnen (z. B. Diogenes, Spaemann) und weitere Rollen wie Hinterfragerinnen oder Zweifler*innen, die sich schnell in Fallanalysen, Fishbowl-Formate oder Philosophencafés einbringen lassen. Die Porträts wurden ebenfalls mit Midjourney erstellt, wobei die Prompts konkret beschreiben, wie die Figuren dargestellt werden sollen (z. B. „xxx as a character in a fantasy story, portrait“).\ https://frauschuetze.de/?p=7640
Übertragung auf die religionsbezogene Bildung
Für religionsbezogene Bildungsszenarien eröffnen sich hier viele spannende Möglichkeiten. Im Folgenden findest du ein paar Ideenimpulse, wie du KI-Bilder und Rollenkarten gezielt einsetzen kannst, um religiöse Fragen, Traditionen und Identitäten in den Mittelpunkt zu rücken:
-
KI-Bilder zur Visualisierung religiöser Konzepte
-
Symbolik und Ikonographie erschließen\ Nutze KI-Modelle, um die Symbolwelten verschiedener Religionen (z. B. Christentum, Islam, Buddhismus, Hinduismus) visuell zu erkunden. Überlege: Wie lässt sich das Kreuz in unterschiedlichen Stilrichtungen (klassisch, modern, abstrakt) darstellen? Welche Bildwelten entstehen, wenn du nach einer fusionierten Ikonographie fragst, die christliche, buddhistische und indigene Symbole kombiniert? Durch den kreativen Prozess mit KI lernst du, welche Metaphern und Traditionen hinter religiösen Zeichen stehen und wie sie – bewusst oder unbewusst – von Algorithmen interpretiert werden. Dabei kannst du auch die Grenzen von KI thematisieren: Welche Vorurteile oder Fehldeutungen schleichen sich in die Bildgenerierung ein, wenn religiöse Themen verarbeitet werden?
-
Gedankenexperimente zu Gott und Transzendenz\ Analog zu den KI-Bildern für Gottesbeweise könntest du Aufgaben stellen wie:
-
„Erstelle ein KI-Bild, das die Idee von Theodizee visuell darstellt.“
-
„Lass die KI eine Szene generieren, in der gläubige und atheistische Perspektiven im Dialog stehen.“\ Anschließend diskutierst du mit der Gruppe, inwiefern die Bilder die jeweiligen Konzepte treffend abbilden oder eher stereotyp und eindimensional bleiben. Auf diese Weise vermittelst du nicht nur Content-Wissen, sondern entwickel auch die Medienkompetenz, indem du Fragen nach Intention, Deutungshoheit und algorithmischer Verzerrung aufwirfst.
-
-
Rollenkarten für religiöse Perspektiven und Diskussionsformate
-
Personen aus religiösen Traditionen als Rollen\ Statt ausschließlich Moralphilosophinnen zu berücksichtigen, kannst du Rollenkarten mit Porträts von Religionsstifterinnen (z. B. Jesus von Nazareth, Maria, Mohammed, Buddha, Krishna), Reformern (Martin Luther, Savonarola) oder zeitgenössischen Theolog*innen (z. B. Dorothee Sölle) gestalten. Die KI-gestützten Bilder können dabei in unterschiedlichen künstlerischen Stilrichtungen entstehen – von historischer Malerei bis hin zu zeitgenössischer Street-Art-Adaption. Jede Rolle enthält einen kurzen Steckbrief mit zentralen Glaubensvorstellungen, biografischen Eckpunkten und einem charakteristischen Argument oder Zitat. So kannst du die Lernenden in Rollendebatten schicken, etwa:
-
„Wie würde Luther heute auf die Klimakrise blicken?“
-
„Welche theologische Argumentation könnte Dorothee Sölle zum Thema Gewaltlosigkeit einbringen?“
-
-
Szenarien für kontroverse Debatten
- Religiöse Vielfalt versus Säkularismus\ Verteilt Karten, in denen Rollen wie „konservativer Christ“, „liberaler Muslim“, „selbstbewusste/r Konfessionslose/r“, „Theologieprofessor/in“ oder „politische/r Aktivist/in“ eingenommen werden. Die KI-Porträts unterstützen die Visualisierung, verleihen den Rollen ein Gesicht und erleichtern das Einfühlen in andere Perspektiven.
-
Interaktive Formate im Religionsunterricht
-
Glaubenscafé (analog zum Philosophencafé)\ In Kleingruppen diskutiert ihr verschiedene Glaubenspositionen. KI-Bilder dienen als Ausgangspunkt: Ein Bild, das etwa die Drei-Tage-Phase von Tod und Auferstehung Jesu künstlerisch darstellt, oder ein generiertes Motiv zu einem hinduistischen Fest (z. B. Holi), wird an die Wand projiziert. Anschließend reflektiert ihr gemeinsam: Welche Emotionen, Symbole, Bedeutungen nehmt ihr wahr? Danach schlüpft ihr in Rollenkarten (z. B. theologische/r Fachreferent/in, Religionskritiker/in, Gemeindemitglied) und erarbeitet Positionen, die ihr in einem moderierten Glaubenscafé präsentiert.
-
Fishbowl-Diskussionen\ Nutzt Rollenkarten zu religionsspezifischen Rollen (z. B. Rabbiner/in, Pfarrerin, Atheist/in, Kleriker/in einer traditionellen Religion, spirituelle/r Influencer/in) für eine Fishbowl-Diskussion zum Thema „Sinnsuche in der Postmoderne“. Die KI-Bilder dienen zu Beginn als visuelle Reize: „Welche Elemente im Bild sprechen für Spiritualität, welche eher für Skepsis?“ So wird die Distanz zwischen digitaler Darstellung und gelebter religiöser Erfahrung erlebbar.
-
Methodische Hinweise und Reflexion
-
Prompt-Kompetenz schulen\ Wie schon im Ethikunterricht festgestellt, erfordert das präzise Beschreiben von Bildwünschen viel Übung. Die Lernenden lernen, welche Schlüsselbegriffe notwendig sind und wie kulturelle Vorannahmen in Prompts stecken bleiben. Im religionspädagogischen Kontext könnt ihr dies gezielt thematisieren: Wie formuliert man z. B. den Prompt „Stelle eine friedvolle interreligiöse Konferenz zwischen Christentum, Islam und Judentum dar“ so, dass keine Stereotype reproduziert werden?
-
Ethik des Bilderzeugens\ Diskutiert gemeinsam, inwiefern KI-Bilder beim Umgang mit heiklen religiösen Themen (z. B. Darstellungen des Propheten Mohammed im Islam) kulturelle oder religiöse Grenzen überschreiten können. Legt zusammen ethische Leitlinien fest, bevor ihr KI zur Bildproduktion nutzt: Welche religiösen Bilder sind "sakrosankt", welche dürfen manipuliert werden und was bedeutet das für Religionsfreiheit und Respekt?
-
Reflexion über Urheberrecht und OER\ Wie Frau Schütze in den Rollenkarten-Anleitungen betont, sind ihre Materialien unter CC-BY-Lizenz verfügbar. Erörtert, was es bedeutet, religiöse Bild- und Textmaterialien unter Open-Content-Lizenzen zu verwenden und welche Implikationen das für Schule, Gemeinde und Zivilgesellschaft hat. Das sensibilisiert für Fragen von Teilhabe und Gemeineigentum im digitalen Raum.
Einladung zum Weiterdenken
Ich lade dich herzlich ein, die vorgestellten Methoden und Materialien in eigenen Projekten auszuprobieren und weiterzuentwickeln. Diskutiere in Kleingruppen oder in einer offenen Runde:
-
Welche religiösen Themen lassen sich besonders gut mit KI-Bildern visualisieren?\ Beispiele: Zehn Gebote, Fastenrituale, Schöpfungsmythen, Visionen von Heiligen oder Heiligenschauen. Welche Prompts würdest du verwenden, um diese Szenen zu erzeugen?
-
Wie könnten Rollenkarten zu spezifischen religiösen Traditionen aussehen?\ Entwickle gemeinsam mit anderen kurze Steckbriefe und Bildprompts für Rollen wie „Sufi-Derwisch“, „Gottesleugner/in der Aufklärung“, „Ökumenische/r Pastor/in“, „Religionspädagog*in“, „Katholischer Laienbruder“ oder „Jüdische Rabbinerin“. Achte dabei auf unterschiedliche religiöse Sichtweisen und Geschlechterperspektiven.
-
Welche Herausforderungen ergeben sich beim Einsatz von KI-Bildern im Religionsunterricht?\ Erörtert mögliche Missverständnisse, kulturelle Fehlinterpretationen oder ethische Konflikte (z. B. pietätslose Darstellungen von Figuren, die in bestimmten Glaubensgemeinschaften als heilig gelten). Entwickelt gemeinsam Kriterien oder einen Leitfaden, um solche Risiken zu minimieren.
-
Wie lassen sich interreligiöse Dialoge durch digitale Methoden fördern?\ Gebt Impulse, wie man mit KI-Bildern und Rollenkarten einen „virtuellen Tempelraum“ gestalten kann, in dem Symbole unterschiedlicher Religionen nebeneinanderstehen und zu Dialog anregen. Welche Fragen stellen sich dabei hinsichtlich Toleranz, Respekt und theologischer Pluralität?
Zusammenfassung und Ausblick
Die beiden Beiträge von Frau Schütze bieten hervorragende Grundlagen, um im religionsbezogenen Unterricht visuelle und interaktive Zugänge zu schaffen. Durch KI-Bilder gewinnen die Teilnehmenden neue Zugänge zu Symbolik, Theodizee und Gottesvorstellungen, während Rollenkarten Dialogkompetenz und Empathie für unterschiedliche religiöse Perspektiven stärken. Diese Ideenimpulse sollen dich ermutigen, die Methoden selbst zu erproben und weiterzuentwickeln. Im digitalen Zeitalter können wir so das gemeinsame Lernen und interkulturelle Verständnis gerade im sensiblen Feld der Religionsbildung bereichern.
Ich freue mich auf deine kreativen Umsetzungen und den Austausch über Erfahrungen, Herausforderungen und Fortschritte in diesem spannenden Feld!Antworte gerne auf diesen Beitrag und kommentiere mit deinen Gedanken und Assoziationen oder poste selbst etwas als Impuls, das andere anregt und weiterverwendet werden darf mit dem Hashtag #relilab.\ \ Template: Avery Re https://opengameart.org/content/trading-card-template unter der Lizenz CC-by https://creativecommons.org/licenses/by/4.0/deed.de / Einige Texte und Bezeichnungen von Frank Schlegel https://digitaldurstig.de/rollenkarten/ unter der Lizenz CC-by-SA 4.0, https://creativecommons.org/licenses/by-sa/4.0/deed.de\ Lizenz: cc-by-sa 4.0 / frauschuetze.de / Juli 2023
-
-
 @ 57c631a3:07529a8e
2025-04-07 13:17:50
@ 57c631a3:07529a8e
2025-04-07 13:17:50What is Growth Engineering? Before we start: if you’ve already filled out the What is your tech stack? survey: thank you! If you’ve not done so, your help will be greatly appreciated. It takes 5-15 minutes to complete. Those filling out will receive results before anyone else, and additional analysis from myself and Elin. Fill out this survey here.**
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m
Growth engineering was barely known a decade ago, but today, most scaleups and many publicly traded tech companies have dedicated growth teams staffed by growth engineers. However, some software engineers are still suspicious of this new area because of its reputation for hacky code with little to no code coverage.
For this reason and others, I thought it would be interesting to learn more from an expert who can tell us all about the practicalities of this controversial domain. So I turned to Alexey Komissarouk, who’s been in growth engineering since 2016, and was in charge of it at online education platform, MasterClass. These days, Alexey lives in Tokyo, Japan, where he advises on growth engineering and teaches the Growth Engineering course at Reforge.
In today’s deep dive, Alexey covers:
- What is Growth Engineering? In the simplest terms: writing code to help a company make more money. But there are details to consider: like the company size where it makes sense to have a dedicated team do this.
- What do Growth Engineers work on? Business-facing work, empowerment and platform work are the main areas.
- Why Growth Engineers move faster than Product Engineers. Product Engineers ship to build: Growth Engineers ship to learn. Growth Engineers do take shortcuts that would make no sense when building for longevity – doing this on purpose.
- Tech stack. Common programming languages, monitoring and oncall, feature flags and experimentation, product analytics, review apps, and more.
- What makes a good Growth Engineer? Curiosity, “build to learn” mindset and a “Jack of all trades” approach.
- Where do Growth Engineers fit in? Usually part of the engineering department, either operating as with an “owner” or a “hitchiker” model.
- Becoming a Growth Engineer. A great area if you want to eventually become a founder or product manager – but even if not, it can accelerate your career growth. Working in Growth forces you to learn more about the business.
With that, it’s over to Alexey:
I’ll never forget the first time I made my employer a million dollars.
I was running a push notification A/B test for meal delivery startup Sprig, trying to boost repeat orders.
A push notification similar to what we tested to boost repeat orders
Initial results were unpromising; the push notification was not receiving many opens. Still, I wanted to be thorough: before concluding the idea was a failure, I wrote a SQL query to compare order volume for subsequent weeks between customers in test vs control.
The SQL used to figure out the push notification’s efficiency
As it turned out, our test group “beat” the control group by around 10%:
‘review_5_push’ was the new type of push notification. Roughly the same amount of users clicked it, but they placed 10% more in orders
I plugged the numbers into a significance calculator, which showed it was statistically significant – or “stat-sig” – and therefore highly unlikely to be a coincidence. This meant we had a winner on our hands! But how meaningful was it, really, and what would adding the push notification mean for revenue, if rolled out to 100% of users?
It turned out this experiment created an additional $1.5 million dollars, annually, with just one push notification. Wow!
I was hooked. Since that day, I've shipped hundreds of experimental “winners” which generated hundreds of millions of incremental revenue for my employers. But you never forget the first one. Moments like this is what growth engineering is all about.
1. What is Growth Engineering?
Essentially, growth engineering is the writing of code to make a company money. Of course, all code produced by a business on some level serves this purpose, but while Product Engineers focus on creating a Product worth paying for, Growth Engineers instead focus on making that good product have a good business. To this end, they focus on optimizing and refining key parts of the customer journey, such as:
- Getting more people to consider the product
- Converting them into paying customers
- Keeping them as customers for longer, and spending more
What kinds of companies employ Growth Engineers? Places you’ve heard of, like Meta, LinkedIn, DoorDash, Coinbase, and Dropbox, are some of the ones I’ve had students from. There’s also OpenAI, Uber, Tiktok, Tinder, Airbnb, Pinterest… the list of high-profile companies goes on. Most newer public consumer companies you’ve heard have a growth engineering org, too.
Typically, growth engineering orgs are started by companies at Series B stage and beyond, so long as they are selling to either consumers or businesses via SaaS. These are often places trying to grow extremely fast, and have enough software engineers that some can focus purely on growth. Before the Series B stage, a team is unlikely to be ready for growth for various reasons; likely that it hasn’t found product-market fit, or has no available headcount, or lacks the visitor traffic required to run A/B tests.
Cost is a consideration. A fully-loaded growth team consisting of a handful of engineers, a PM, and a designer costs approximately 1 million dollars annually. To justify this, a rule of thumb is to have at least $5 million dollars in recurring revenue – a milestone often achieved at around the Series B stage.
Despite the presence of growth engineering at many public consumer tech companies, the field itself is still quite new, as a discipline and as a proper title.
Brief history of growth engineering
When I joined Opendoor in 2016, there was a head of growth but no dedicated growth engineers, but there were by the time I left in 2020. At MasterClass soon after, there was a growth org and a dozen dedicated growth engineers. So when did growth engineering originate?
The story is that its origins lie at Facebook in 2007. The team was created by then-VP of platform and monetization Chamath Palihapitiya. Reforce founder and CEO Brian Balfour shares:
“Growth (the kind found on an org chart) began at Facebook under the direction of Chamath Palihapitiya. In 2007, he joined the early team in a nebulous role that fell somewhere between Product, Marketing, and Operations. According to his retelling of the story on Recode Decode, after struggling to accomplish anything meaningful in his first year on the job, he was on the verge of being fired.Sheryl Sandberg joined soon after him, and in a hail mary move he pitched her the game-changing idea that led to the creation of the first-ever growth team. This idea not only saved his job, but earned him the lion’s share of the credit for Facebook’s unprecedented growth.At the time, Sheryl and Mark asked him, “What do you call this thing where you help change the product, do some SEO and SEM, and algorithmically do this or that?”His response: “I don’t know, I just call that, like, Growth, you know, we’re going to try to grow. I’ll be the head of growing stuff."And just like that, Growth became a thing.”
Rather than focus on a particular product or feature, the growth team at Facebook focused on moving the needle, and figuring out which features to work on. These days, Meta employs hundreds if not thousands of growth engineers.
2. What do Growth Engineers work on?
Before we jump into concrete examples, let’s identify three primary focus areas that a growth engineer’s work usually involves.
- Business-facing work – improving the business directly
- Empowerment work – enabling other teams to improve the business
- Platform work – improving the velocity of the above activities
Let’s go through all three:
Business-facing work
This is the bread and butter of growth engineering, and follows a common pattern:
- Implement an idea. Try something big or small to try and move a key business metric, which differs by team but is typically related to conversion rate or retention.
- Quantify impact. Usually via A/B testing.
- Analyze impact. Await results, analyze impact, ship or roll back – then go back to the first step.
Experiments can lead to sweeping or barely noticeable changes. A famous “I can’t believe they needed to test this” was when Google figured out which shade of blue generates the most clicks. At MasterClass, we tested things across the spectrum:
- Small: should we show the price right on the homepage, was that a winner? Yes, but we framed it in monthly terms of $15/month, not $180/year.
- Medium: when browsing a course page, should we include related courses, or more details about the course itself? Was it a winner? After lengthy experimentation, it was hard to tell: both are valuable and we needed to strike the right balance.
- Large: when a potential customer is interested, do we take them straight to checkout, or encourage them to learn more? Counterintuitively, adding steps boosted conversion!
Empowerment
One of the best ways an engineer can move a target metric is by removing themselves as a bottleneck, so colleagues from marketing can iterate and optimize freely. To this end, growth engineers can either build internal tools or integrate self-serve MarTech (Marketing Technology) vendors.
With the right tool, there’s a lot that marketers can do without engineering’s involvement:
- Build and iterate on landing pages (Unbounce, Instapage, etc)
- Draft and send email, SMS and Push Notifications (Iterable, Braze, Customer.io, etc)
- Connect new advertising partners (Google Tag Manager, Segment, etc)
We go more into detail about benefits and applications in the MarTech section of Tech Stack, below.
Platform work
As a business scales, dedicated platform teams help improve stability and velocity for the teams they support. Within growth, this often includes initiatives like:
- Experiment Platform. Many parts of running an experiment can be standardized, from filtering the audience, to bucketing users properly, to observing statistical methodology. Historically, companies built reusable Experiment Platforms in-house, but more recently, vendors such as Eppo and Statsig have grown in popularity with fancy statistical methodologies like “Controlled Using Pre-Experiment Data” (CUPED) that give more signal with less data.
- Reusable components. Companies with standard front-end components for things like headlines, buttons, and images, dramatically reduce the time required to spin up a new page. No more "did you want 5 or 6 pixels here" with a designer; instead growth engineers rely on tools like Storybook to standardize and share reusable React components.
- Monitoring. Growth engineering benefits greatly from leveraging monitoring to compensate for reduced code coverage. High-quality business metric monitoring tools can detect bugs before they cause damage.
When I worked at MasterClass, having monitoring at the ad layer prevented at least one six-figure incident. One Friday, a marketer accidentally broadened the audience for a particular ad from US-only, to worldwide. In response, the Facebook Ad algorithm went on a spending spree, bringing in plenty of visitors from places like Brazil and India, whom we knew from past experience were unlikely to purchase the product. Fortunately, our monitoring noticed the low-performing campaign within minutes, and an alert was sent to the growth engineer on-call, who immediately reached out to the marketer and confirmed the change was unintentional, and then shut down the campaign.
Without this monitoring, a subtle targeting error like this could have gone unnoticed all weekend and would have eaten up $100,000+ of marketing budget. This episode shows that platform investment can benefit everyone; and since growth needs them most, it’s often the growth platform engineering team which implements them.
As the day-to-day work of a Growth Engineer shows, A/B tests are a critical tool to both measure success and learn. It’s a numbers game: the more A/B tests a team can run in a given quarter, the more of them will end up winners, making the team successful. It’s no wonder, then, that Growth Engineering will pull out all the stops to improve velocity.
3. Why Growth Engineers move faster than Product Engineers
On the surface, growth engineering teams look like product engineering ones; writing code, shipping pull requests, monitoring on-call, etc. So how do they move so much faster? The big reason lies in philosophy and focus, not technology. To quote Elena Verna, head of growth at Dropbox:
“Product Engineering teams ship to build; Growth Engineering teams ship to learn.”
Real-world case: price changes at Masterclass
A few years ago at MasterClass, the growth team wanted to see if changing our pricing model to multiple tiers would improve revenue.
Inspired in part by multiple pricing tiers for competitors such as Netflix (above), Disney Plus, and Hulu.
The “multiple pricing tier” proposal for MasterClass.
From a software engineering perspective, this was a highly complex project because:
- Backend engineering work: the backend did not yet support multiple pricing options, requiring a decent amount of engineering, and rigorous testing to make sure existing customers weren’t affected.
- Client app changes: on the device side, multiple platforms (iOS, iPad, Android, Roku, Apple TV, etc) would each need to be updated, including each relevant app store.
The software engineering team estimated that becoming a “multi-pricing-tier” company would take months across numerous engineering teams, and engineering leadership was unwilling to greenlight that significant investment.
We in growth engineering took this as a challenge. As usual, our goal was not just to add the new pricing model, but to learn how much money it might bring in. The approach we ended up proposing was a Fake Door test, which involves offering a not-yet-available option to customers to gauge interest level. This was risky, as taking a customer who’s ready to pay and telling them to join some kind of waiting list is a colossal waste, and risks making them feel like the target of a “bait and switch” trick.
We found a way. The key insight was that people are only offended about a “bait and switch”, if the “switch” is worse than the “bait.” Telling customers they would pay $100 and then switching to $150 would cause a riot, but starting at $150 and then saying “just kidding, it’s only $100” is a pleasant surprise.
The good kind of surprise.
So long as every test “pricing tier” is less appealing – higher prices, fewer features – than the current offering, we could “upgrade” customers after their initial selection. A customer choosing the cheapest tier gets extra features at no extra cost, while a customer choosing a more expensive tier is offered a discount.
We created three new tiers, at different prices. The new “premium” tier would describe the existing, original offering. Regardless of what potential customers selected, they got this “original offering,” during the experiment.
The best thing about this was that no backend changes were required. There were no real, new, back-end pricing plans; everybody ended up purchasing the same version of MasterClass for the same price, with the same features. The entirety of the engineering work was on building a new pricing page, and the “congratulations, you’ve been upgraded” popup. This took just a few days.
Within a couple of weeks, we had enough data to be confident the financial upside of moving to a multi-pricing-tier model would be significant. With this, we’re able to convince the rest of engineering’s leadership to invest in building the feature properly. In the end, launching multiple pricing tiers turned out to be one of the biggest revenue wins of the year.
Building a skyscraper vs building a tent
The MasterClass example demonstrates the spirit of growth engineering; focusing on building to learn, instead of building to last. Consider building skyscrapers versus tents.
Building a tent optimizes for speed of set-up and tear-down over longevity. You don’t think of a tent as one that is shoddy or low-quality compared to skyscrapers: it’s not even the same category of buildings! Growth engineers maximize use of lightweight materials. To stick with the tents vs skyscraper metaphor: we prioritize lightweight fabric materials over steel and concrete whenever possible. We only resort to traditional building materials when there’s no other choice, or when a direction is confirmed as correct. Quality is important – after all, a tent must keep out rain and mosquitoes. However, the speed-vs-durability tradeoff decision results in very different approaches and outcomes.
4. Tech stack
At first glance, growth and product engineers use the same tooling, and contribute to the same codebases. But growth engineering tends to be high-velocity, experiment-heavy, and with limited test coverage. This means that certain “nice to have” tools for product engineering are mission-critical for growth engineers.
Read more https://connect-test.layer3.press/articles/ea02c1a1-7cfa-42b4-8722-0165abcae8bb
-
 @ 06639a38:655f8f71
2025-06-01 19:45:04
@ 06639a38:655f8f71
2025-06-01 19:45:04Nostr-PHP
All commits on the main branch between 19-05 and 25-05: https://github.com/nostrver-se/nostr-php/commits/main/?since=2025-05-19&until=2025-05-25
- Merged PR #95 finish implementing methods Relay and RelaySet
- Merged PR #90 implementing NIP-17 private direct messages
[https://shares.sebastix.dev/DTkBk1By.png]#d04e152f809a86e495a4b80c3c292ca70fb0b94b9fcf35ff424769848fc15314)
- Made some progress on the persistentConnection class for fetching messages from a relay in runtime (realtime)
New release: 1.8.0
What's Changed
- feat: Implement NIP-05 lookups by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/89
- NIP 44 implementation fix and test improvements by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/88
- remove CLI tool from library - https://github.com/nostrver-se/nostr-p… by @Sebastix in https://github.com/nostrver-se/nostr-php/pull/93
- Add extra metadata fields for profile by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/94
- Finish implementing methods Relay and RelaySet by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/95
- Implement NIP-17 Private Direct Messages by @dsbaars in https://github.com/nostrver-se/nostr-php/pull/90
Full changelog: https://github.com/nostrver-se/nostr-php/compare/1.7.1...1.8.0
Link: https://github.com/nostrver-se/nostr-php/releases/tag/1.8.0 -
 @ d37c9ef4:7fe34241
2025-06-02 04:43:09
@ d37c9ef4:7fe34241
2025-06-02 04:43:09Em um cenário digital cada vez mais dinâmico e competitivo, plataformas de entretenimento online precisam se destacar oferecendo inovação, confiança e uma experiência marcante para seus usuários. É exatamente isso que a 73BET entrega. Com uma interface moderna, ampla gama de jogos e suporte de qualidade, a plataforma tem conquistado a preferência de jogadores brasileiros que buscam emoção, segurança e praticidade em um só lugar.
Conheça a 73BET: Simples, Rápida e Confiável A 73BET foi desenvolvida com o objetivo de proporcionar uma experiência fluida e satisfatória, tanto para iniciantes quanto para jogadores mais experientes. Seu site conta com um design intuitivo, responsivo e fácil de navegar, seja pelo computador ou dispositivo móvel. Além disso, o processo de cadastro é simples e rápido, permitindo que os usuários comecem a jogar em poucos minutos.
A plataforma é totalmente adaptada às necessidades do público brasileiro, oferecendo suporte em português, métodos de pagamento populares no país (como PIX e transferências bancárias) e promoções exclusivas pensadas para o jogador local. Tudo isso contribui para uma experiência mais confortável e personalizada.
Jogos para Todos os Gostos A variedade de jogos é um dos grandes diferenciais da 73BET. O catálogo é extenso e abrange desde os clássicos jogos de mesa até opções mais modernas com gráficos de última geração. Entre os principais destaques estão:
Slots Online (Caça-níqueis): Com centenas de títulos disponíveis, os jogos de slot da 73BET oferecem temas variados, bônus envolventes e jogabilidade dinâmica. É possível encontrar desde opções simples até máquinas com jackpots progressivos.
Jogos ao Vivo: Para quem busca interatividade, os jogos com crupiês ao vivo são uma excelente escolha. Eles proporcionam uma atmosfera imersiva e realista, onde o jogador pode acompanhar todas as ações em tempo real.
Jogos de Cartas e Mesa: Clássicos como poker, blackjack e roleta também marcam presença na plataforma, em diferentes versões para agradar todos os perfis de jogadores.
Apostas Esportivas: A 73BET também oferece um ambiente completo para quem gosta de esportes. Com cotações competitivas e cobertura de eventos nacionais e internacionais, é possível apostar em futebol, basquete, tênis e muito mais.
Experiência do Jogador: Suporte, Segurança e Recompensas Além da variedade de jogos, a 73BET se preocupa com a experiência completa do usuário. O suporte ao cliente é ágil e funciona 24 horas por dia, garantindo que qualquer dúvida ou problema seja resolvido com rapidez e eficiência.
A segurança também é um pilar fundamental da plataforma. A 73BET utiliza tecnologias avançadas de criptografia para proteger os dados dos usuários, além de contar com políticas claras de privacidade e jogo responsável.
Outro grande atrativo são os bônus e promoções. A plataforma oferece recompensas frequentes, como bônus de boas-vindas, cashback, giros grátis e campanhas sazonais. Esses incentivos tornam a jornada do jogador ainda mais emocionante e vantajosa.
Conclusão: Por que Escolher a 73BET? A 73BET se consolidou como uma das plataformas de entretenimento online mais completas e confiáveis do Brasil. Sua proposta é clara: oferecer diversão de qualidade, segurança nas transações e um atendimento que coloca o jogador em primeiro lugar.
Se você está procurando uma experiência diferenciada, com jogos variados, promoções imperdíveis e um ambiente seguro, a 73BET é a escolha ideal. Cadastre-se hoje mesmo e descubra por que milhares de brasileiros já estão aproveitando tudo o que essa plataforma tem a oferecer.
-
 @ fd78c37f:a0ec0833
2025-04-01 11:49:06
@ fd78c37f:a0ec0833
2025-04-01 11:49:06In this edition, we invited Keypleb, the founder of Bitcoin Indonesia, to share how he built the Bitcoin community in Indonesia, overcoming challenges like member turnover and venue selection, while driving the adoption and growth of Bitcoin.
YakiHonne: Welcome, Keypleb. Before we begin, let me briefly introduce YakiHonne. YakiHonne is a decentralized media client built on Nostr—a protocol designed to empower freedom of speech through technology. It enables creators to own their voices and assets while offering innovative tools like smart widgets, verified notes, and support for long-form content. We focus on free speech and free media by user privacy and data to be protected. So before starting the interview, I'd like to hear about yourself and your community.
Keypleb:My name is Keypleb, though it’s a pseudonym—a name I use to respect privacy. I'm a co-founder of Bitcoin Indonesia, Bitcoin House Bali, and Code Orange, a new developer school we launched at a conference just a few days ago. We focus on driving adoption through meetups, hackathons, and technical workshops. I'll dive into more details later, but that's a brief overview. I'm based in Bali now, though I travel a lot and consider myself quite nomadic. Great to be here.
YakiHonne: What sparked your interest in Bitcoin and what motivated you to create a community on Bitcoin?
Keypleb:I first got interested in Bitcoin because it solved a specific problem. At the time, I didn’t know exactly what the solution was, but the problem was that I couldn’t afford a home. Back in 2019, I was living in London, and a two-bedroom apartment was £600,000, which was insanely expensive. First-time buyers like myself simply couldn’t afford it. Why was it so expensive? Why was buying a house so hard? During the COVID lockdown, I had more time on my hands and started listening to Michael Saylor on a Bitcoin podcast, where he talked about how the system is rigged, and that’s why people work hard but still can’t afford a house. That really resonated with me. So I started looking for a community, but unfortunately, there wasn’t one.. Keypleb:After moving to Bali, I attended a lot of crypto meetups, especially scammy altcoin ones, thinking, “There has to be a solution.” But none of them resonated with me. There was no sense of freedom, and no real discussion about inflation resistance. I remembered a podcast from Dea Reskita, an Indonesian host who’s pretty well-known online. I reached out to her and said, “ you’ve got to help me. I’m surrounded by all these shitcoiners, and I can’t take it anymore. I need a real community. Is anything happening?” She replied, “Yes, something is happening. We should restart these meetups next month.” And that’s how it all began. Keypleb:There’s also another story about how we started Bitcoin House and how Bitcoin in Asia came to be, but maybe I’ll save that for later. Anyway, the spark of interest came from Bitcoin solving a real problem, and my drive to keep going came from the lack of quality meetups. Now, we’ve hosted 31 meetups, launched Bitcoin House and Code Orange, and the movement is growing rapidly.

YakiHonne: That’s such an amazing story—going from being on the brink of homelessness to creating something so impactful, and keeping it running every day, bringing new people into the journey. It’s truly inspiring. I’m curious about how the community started. How did you manage to attract members and build a strong community? What challenges did you face along the way?
Keypleb:It all started with our first meetup at the end of 2022, which was two and a half years ago now. At that time, we sent out an email to a group from a previous database, and the first meetup had around 20 people, which was a good start. However, problems quickly arose as people started dropping off, and the community lacked retention. In Bali, people come and go, usually staying for no more than two months, leading to a lack of long-term participation. This became one of our challenges: how to attract more people and, more importantly, get the same people to keep coming back. While I've been coming back for two and a half years, not everyone is able to return as often, and that has been a real challenge. Keypleb:Actually, I should also mention how I met my co-founders—Marius, Diana, and Dimas. We met at the 2023 Indonesia Bitcoin Conference. As time went on, we kept hosting meetups and had a lot of fun each time, though the locations kept changing. One of the initial challenges was that we didn't realize the importance of having a fixed meetup location. We changed venues several times before we realized that having a consistent location is crucial. If anyone wants to run a meetup, it's best to always choose a fixed location. We learned this through trial and error, but now it's no longer an issue. Keypleb:Since the conference, my co-founders and I have been working together, consistently putting in the effort. This is why our community has grown so large—so far, we are hosting 31 monthly meetups, 6 of which are in Bali. This means there is a bitcoin meetup almost every day on a regular basis. We've also established Bitcoin House Bali, a physical space, and the movement is growing rapidly. Without this movement, the region would face many challenges, including inflation and heavy censorship. It all started from just one meetup.
 YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?
YakiHonne: It's amazing to see how you met your co-founders and how you’ve built something incredible that continues to grow today. What advice would you give to someone looking to start a successful Bitcoin community right now?Keypleb:First, one very important piece of advice is to ensure that every meetup is held at the same location regularly. We realized this challenge through trial and error. To help others who are interested, we’ve published our meetup guide on GitHub, where everyone can check it out. For example, meetups should be held regularly, ideally once a month, or even once a week. In Chiang Mai, the Bitcoin meetup starts every Thursday at 7 PM, and everyone knows the time and location, making it easy to join without having to look up the next meetup. Keypleb:Additionally, our meetup structure is very simple. First, we do a round of introductions where everyone shares their name, where they’re from, and what Bitcoin means to them. This usually takes about 15 minutes. Then, we discuss three main questions: First, why do we need Bitcoin? The discussion typically focuses on two main issues Bitcoin addresses: inflation and censorship;Secondly, how to buy Bitcoin? We usually ask who wants to buy some Bitcoin, and then we do a small purchase together and conduct a P2P trade to demonstrate how easy it is to buy Bitcoin. Lastly, how to store Bitcoin? We introduce self-custody and show how to use hardware wallets (like Trezor), explaining the concept of the 12 words and private keys. Keypleb:The whole meetup usually wraps up in about an hour, after which people can continue socializing at Bitcoin House or wherever the meetup is taking place. In short, keeping the meetup simple and efficient, and ensuring a fixed location for each event, are key factors in building a successful community.
YakiHonne: What's the major approach? Is it more technical, or do you focus on non-technical aspects, or do you cover both?
Keypleb:Our approach includes both technical and non-technical content. Initially, our meetups were completely non-technical, just casual gatherings for people to socialize. Over time, however, we've evolved to incorporate more technical content. Keypleb:Out of the 31 monthly regular meetups we host, most of them have been non-technical, simply regular gatherings held at the same time and place according to our meetup guide. For example, we host the “Bitcoin for Beginners” meetup, which is designed for newcomers and takes place every second Friday of the month at 5 PM at the Bitcoin House Bali. This is entirely non-technical. Additionally, every Wednesday at Bitcoin House, we host the “My First Bitcoin” course. While the course touches on some technical aspects, such as seed phrases and backups, it’s still beginner-friendly and not too technical. The course runs for 10 weeks, and we plan to offer it in the local language at Bali University to help the local community better understand Bitcoin. Keypleb:On the other hand, we also offer highly technical content. We launched a new program called “Code Orange,” which is specifically designed for developers and programmers. We use the “Decoding Bitcoin” website, created by Jamal, which is a learning platform for developers. Many developer schools, like Code Orange, use this resource. Additionally, we host “Code Orange” meetups where we dive into the technical aspects of Bitcoin, such as how mining works and how to prevent single points of failure. Keypleb:We also organize technical workshops, such as “How to Defend Against a Five-Dollar Wrench Attack,” which is closely related to security. Recently, there have been some kidnapping incidents in Bali, and many people are concerned about their Bitcoin being stolen. To address this, we plan to hold a workshop on how to protect Bitcoin against such attacks. Additionally, we host hackathons and other high-tech events, and we just completed a very successful beginner-level hackathon. Keypleb:In summary, our community caters to everyone, from beginners to technical experts. For beginners, we offer easy-to-understand, non-technical content, while for experienced Bitcoiners, we provide in-depth technical material.
 YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?
YakiHonne: It's great to approach it in both ways, so everyone gets their own "piece of the cake."Now, I'd like to dive into the technical side. What advice would you give to technically inclined individuals or organizations looking to contribute to the Bitcoin ecosystem? How should they approach the technical aspects of Bitcoin if they want to get involved?Keypleb:I have some additional advice. First, technical individuals can sign up for the “Decoding Bitcoin” course that starts on 18th March 2025 or join our “Code Orange” program and participate in the end-of-year hackathon. If they are technically proficient, this will be a great opportunity. “Decoding Bitcoin” is great for beginners, but it’s also useful for technical individuals. If someone is very skilled, they can start contributing code right away. If they find the course too easy, they can skip it and dive directly into more advanced projects. Additionally, Bitshala and Chaincode Labs offer advanced courses, which more technically advanced individuals can choose to pursue.
 Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.
Keypleb:Additionally, it's worth mentioning that the Bitcoin Dev Project has a great platform where technical individuals can find “Good First Issue” or open-source projects to start contributing code. You'll learn about the philosophy behind Bitcoin and why it's more meaningful than other “shitcoins.” Once you’ve taken enough “orange pills” (the philosophy and technology of Bitcoin), you can dive deeper into Bitcoin core development and potentially start coding in C++. If you're interested, you can join specific projects like Nostr, Fedimint or E-Cash.YakiHonne: I’d like to move on to the next question: How do you see Bitcoin communities evolving as technology progresses, particularly in areas like scalability, privacy, and adaptability to other systems? Keypleb:I believe the Bitcoin community will continue to evolve, and it has already made incredible progress. Two and a half years ago, we started alone in Bali, with just ourselves. We began in the official phase and have had numerous conversations throughout the year. For example, we are now starting a Bitcoin club at a university in Bali; we just need to find a passionate, driven “Bitcoin maximalist,” and the Bitcoin club will begin. Like what our friends did in Banyuwangi, Indonesia, these clubs could eventually evolve into Bitcoin houses.
Keypleb:Regarding privacy and scalability, the community is making strides. We’re big fans of Fedi, which builds on top of the Fedimint protocol and uses e-cash to scale Bitcoin while improving privacy. Fedi low fees and high privacy potential give Bitcoin great opportunities in this area. Keypleb:As for Bitcoin's compatibility with fiat systems, although Bitcoin payments are illegal in some countries like Indonesia, smart developers across Southeast Asia are working on legal solutions. For example, there's a website called Pleb QR that works in Thailand, allowing you to pay in fiat via the Lightning Network. Koral is another app specifically for Indonesia. These kinds of testing products already exist and are physically possible, but we’re just waiting on regulations. My influential friends are actively lobbying the government for adoption. Keypleb:In summary, privacy, scalability, and compatibility with fiat systems are all works in progress, and they will continue to evolve positively. There will be more meetups, more wallet downloads, and more adoption—there’s no doubt about that.
YakiHonne: You mentioned the concept of cross-country issues, so I have one last question: How is the government’s stance on Bitcoin? Is the political climate supportive or against Bitcoin? How do you see the government's approach to Bitcoin in your community or environment?
Keypleb:This reminds me of a person, Jeff Booth, who once said, “We are them, the government is made up of us.” In Indonesia, many politicians actually support Bitcoin, and many of them mine Bitcoin themselves. When money is involved, the incentive is strong, and politicians naturally like to make more money. As a result, Indonesia has a large Bitcoin mining scene. However, overall, the Indonesian government is against Bitcoin, as seen in their ban on Bitcoin payments. The 2011 currency law states that any currency other than the Indonesian Rupiah (IDR) cannot be used, and violators can face up to one year in prison or a fine. This means you cannot pay with US dollars, lira, euros, pesos or pounds. Keypleb:This shows that the government’s legal system is somewhat fragile. It’s understandable that the government is concerned about disruptive technologies like Bitcoin, especially with such a fragile fiat system. Indonesia has also seen many arrests. In 2016, Bank Indonesia issued a letter announcing a crackdown on cryptocurrency payments. Those involved in paying in Bitcoin had their funds seized, and the police cooperated in shutting down businesses accepting Bitcoin payments in the cities. While this isn't very friendly, it does highlight the fragility of the existing system. We also believe that a new executive order may be introduced in the future, similar to when President Roosevelt in 1933 ordered Americans to hand over all their gold with his Executive Order 6102. If it happened before, it could happen again. Keypleb:Therefore, we predict that Bitcoin custody could become a legal issue, which is one of the reasons we blur the faces of participants at every meetup. We need to protect the community from any potential risks. But overall, we remain optimistic. Despite the government ban, the ideology of Bitcoin is unstoppable, and its spread cannot be stopped. So, we are very optimistic about the future.
YakiHonne: I think almost every government around the world, even in Africa, faces similar issues with Bitcoin. Some governments might want Bitcoin but hesitate to openly accept it due to the fear of it undermining the traditional financial system, which, of course, could eventually happen. But hopefully, as the new generation comes into power, we'll see more Bitcoin-friendly governments. So, thank you so much for sharing your insights and advice. I really appreciate your time and the valuable input you've provided.
Keypleb:I'm really glad this conversation enlightened me. I enjoyed it a lot, and it made me reflect on how much work we're doing and how valuable it is. There are a lot of problems out there, with censorship being the biggest one, followed by inflation, which is also a major issue depending on the region. But Bitcoin is open, the community is growing, and people are fighting against censorship and internet shutdowns in places like Indonesia and beyond. The movement is definitely growing. So, I'm very happy to be here and have this chat. Thanks again.
Bitcoin Indonesia nostr: nostr:npub1y4qd2zhtn05gnsaaq5xfejzfk4a32638tx6gpp9g8k6e42g9d66qaxhcr3
Keypleb nostr: nostr:npub190trvg63e6tyqlwlj6lccqpftx76lckj25c006vwx3dzvdl88yxs2nyqdx
-
 @ d37c9ef4:7fe34241
2025-06-02 04:41:59
@ d37c9ef4:7fe34241
2025-06-02 04:41:59O universo do entretenimento digital tem crescido de forma acelerada nos últimos anos, e o Brasil se destaca como um dos mercados mais promissores da América Latina. Em meio a esse cenário, surge a plataforma BR2024, uma nova opção que está conquistando os jogadores brasileiros com sua proposta inovadora, interface moderna e variedade de jogos eletrizantes.
Conheça a Plataforma BR2024 Lançada com o objetivo de oferecer uma experiência diferenciada para o público brasileiro, a BR2024 combina tecnologia de ponta com um ambiente seguro e acessível. A plataforma foi totalmente desenvolvida pensando nas preferências locais, o que fica evidente já na interface, que é intuitiva, rápida e disponível em português.
O registro é simples e rápido, permitindo que novos usuários criem suas contas em poucos minutos. Além disso, a BR2024 se destaca pelo suporte ao cliente eficiente, com atendimento em tempo real e diversas opções de contato, incluindo chat ao vivo e e-mail.
Jogos para Todos os Gostos Um dos grandes destaques da BR2024 é a sua vasta seleção de jogos, que atende tanto os iniciantes quanto os jogadores mais experientes. Desde os clássicos jogos de cartas até opções modernas com gráficos de última geração, há sempre algo novo para explorar.
Entre os títulos mais populares, estão as roletas virtuais, jogos de dados, máquinas de giro (também conhecidas como slots), além de modalidades com dealers ao vivo — onde o jogador pode interagir com apresentadores reais, criando uma sensação muito próxima da experiência física. Há também seções dedicadas a jogos temáticos e sazonais, ideais para quem gosta de novidades.
Além disso, BR2024 firma parcerias com fornecedores de software de renome internacional, o que garante qualidade visual, jogabilidade fluida e resultados justos, auditados por empresas independentes.
Experiência Imersiva para o Jogador Brasileiro O que realmente diferencia a BR2024 de outras plataformas é o foco total na experiência do usuário. Desde o momento do login até o momento da vitória, tudo é pensado para que o jogador tenha conforto, confiança e diversão.
A plataforma oferece bônus generosos para novos membros, promoções regulares para usuários ativos e um sistema de fidelidade onde o jogador acumula pontos e pode trocar por vantagens exclusivas. Além disso, os métodos de pagamento são variados e incluem opções muito utilizadas no Brasil, como PIX, boleto bancário e carteiras digitais.
Outro ponto que chama a atenção é a compatibilidade com dispositivos móveis. A BR2024 funciona perfeitamente em smartphones e tablets, permitindo que o jogador se divirta a qualquer hora e em qualquer lugar, sem perder qualidade de imagem ou desempenho.
Conclusão A BR2024 chega ao mercado com uma proposta sólida e diferenciada. Com uma plataforma moderna, ampla variedade de jogos e foco total na experiência do usuário, ela se estabelece como uma das principais opções de entretenimento online para brasileiros em 2024. Se você busca diversão, segurança e inovação em um só lugar, vale a pena explorar tudo o que a BR2024 tem a oferecer.
-
 @ 123e53ec:df7e2608
2025-06-02 03:40:43
@ 123e53ec:df7e2608
2025-06-02 03:40:43Qu'est-ce que le Cyber-Mawonaj ?
Le Cyber-Mawonaj, c'est l'auto-défense numérique enracinée dans nos cultures afro-caribéennes. C'est refuser la plantation numérique des GAFAM pour cultiver nos propres jardins numériques libres.
Comme nos ancêtres marrons ont fui l'esclavage pour créer des communautés autonomes dans les mornes, nous fuyons la surveillance et l'exploitation des géants du web pour bâtir nos propres espaces.
Pourquoi maintenant ?
Nos données sont le nouveau sucre. Nos vies numériques, les nouvelles plantations. Facebook nous surveille. Google nous profile. Amazon nous exploite.
Pendant ce temps, la Guadeloupe vieillit, sa jeunesse fuit, son économie stagne. Nous devons créer MAINTENANT les outils de notre émancipation numérique et économique.
Nos valeurs
LIBERTÉ - Logiciels libres, données libres, esprits libres AUTONOMIE - Héberger nos services, contrôler nos outils SOLIDARITÉ - Partager les savoirs, mutualiser les ressources CULTURE - Ancrer la tech dans nos langues, nos récits, nos luttes SOBRIÉTÉ - Respecter la terre, économiser l'énergie
Notre vision
Imaginez une Guadeloupe où : - Chaque association a son cloud souverain - Chaque jeune apprend à coder en créole - Chaque entreprise utilise des outils libres - Chaque citoyen contrôle ses données
Ce n'est pas une utopie. C'est un projet.
L'appel
Rejoignez le Cyber-Mawonaj si vous êtes : - Fatigués de nourrir les algorithmes des autres - Prêts à apprendre et partager - Déterminés à construire notre souveraineté numérique
Comment ?
- Apprenez - Formations aux outils libres
- Créez - Vos propres services et contenus
- Partagez - Vos savoirs et ressources
- Connectez - Via le Fediverse, pas Facebook
Premier pas
Arrêtez de scroller. Commencez à construire.
https://o-k-i.net/
Fediverse : https://bokantaj.o-k-i.net/@sucupira https://gade.o-k-i.net/a/dkxone/video-channels https://www.tiktok.com/@cyber_mawonaj https://www.instagram.com/cyber_mawonaj/
"Nèg mawon ka kouri, men sé pou viv lib" (Le nègre marron court, mais c'est pour vivre libre)
CyberMawonaj #Guadeloupe #LogicielLibre
-
 @ 502ab02a:a2860397
2025-06-02 02:59:55
@ 502ab02a:a2860397
2025-06-02 02:59:55ย้อนกลับไปเมื่อปี 2015 ในเมืองเบิร์กลีย์ รัฐแคลิฟอร์เนีย มีนักชีววิทยาเชิงวิศวกรรมชื่อ Dr. Uma Valeti ผู้เป็นทั้งนักวิจัยโรคหัวใจและอดีตศัลยแพทย์หัวใจ เกิดแนวคิดที่ไม่ธรรมดาว่า "เขาจะสร้างเนื้อในห้องแล็บ เหมือนที่เราสร้างหัวใจเทียมในโรงพยาบาล" นั่นคือการสร้างเนื้อโดยไม่ต้องฆ่าสัตว์เลยแม้แต่ตัวเดียว เขาไม่ได้เพ้อฝันแบบลอยๆ เพราะเขาเองเป็นคนอินเดียที่เติบโตมาในครอบครัวมังสวิรัติ แต่กลับทำงานในวงการแพทย์ที่เกี่ยวข้องกับการปลูกถ่ายอวัยวะอยู่หลายปี และวันหนึ่ง เขาเห็นความเชื่อมโยงบางอย่างระหว่างเซลล์กล้ามเนื้อของหัวใจกับกล้ามเนื้อของเนื้อสัตว์
Valeti มองเห็นปัญหาจากอุตสาหกรรมปศุสัตว์ในแง่มลพิษ การใช้ทรัพยากร และความโหดร้ายของระบบผลิตอาหารในโลกยุคใหม่ แนวคิดนี้กลายเป็นจริงเมื่อเขาร่วมก่อตั้งบริษัท Memphis Meats ขึ้นในปีนั้น พร้อมกับเพื่อนร่วมอุดมการณ์อีกสองคน ได้แก่ Nicholas Genovese นักวิจัยด้านสเต็มเซลล์ และ Will Clem นักวิทยาศาสตร์ผู้เชี่ยวชาญด้านวิศวกรรมชีวภาพผู้เคยมีประสบการณ์จากการเปิดร้านบาร์บีคิวของตัวเอง ความฝันของพวกเขาคือการสร้าง "เนื้อแท้" ที่ไม่ต้องใช้ฟาร์ม ไม่ต้องฆ่าสัตว์ และไม่ต้องพึ่งทรัพยากรธรรมชาติอย่างมหาศาลแบบระบบปศุสัตว์ทั่วไป โดยนำเซลล์กล้ามเนื้อจากสัตว์มาเพาะเลี้ยงในห้องปฏิบัติการ แล้วกระตุ้นให้เติบโตด้วยสารอาหาร สารกระตุ้นการเจริญเติบโต และโครงสร้างที่เลียนแบบเนื้อเยื่อจริง ผลลัพธ์ที่ได้คือเนื้อไก่ เนื้อวัว และเนื้อหมู ที่หน้าตา กลิ่น และรสชาติเหมือนเนื้อที่ผู้คนคุ้นเคย แต่อยู่ในจานโดยไม่ต้องผ่านชีวิตสัตว์แม้แต่ชีวิตเดียว
เทคโนโลยีที่ Memphis Meats ใช้คือการเก็บเซลล์ต้นกำเนิดกล้ามเนื้อ (muscle stem cells) จากสัตว์ แล้วนำมาบ่มเพาะในห้องแล็บในสภาพแวดล้อมที่เหมาะสม ด้วยอาหารเหลวที่มีสารอาหารครบถ้วน เซลล์เหล่านั้นจะเจริญเติบโต แบ่งตัว และก่อตัวเป็นกล้ามเนื้อที่เหมือนกับเนื้อจริงทุกประการ การทดลองแรกประสบผลสำเร็จในปี 2016 เมื่อพวกเขาสร้างลูกชิ้นเนื้อวัวเพาะเลี้ยงได้เป็นครั้งแรกของโลก แม้ราคาจะสูงถึง 18,000 ดอลลาร์ต่อปอนด์ก็ตาม แต่สิ่งนี้คือการประกาศว่า "ของจริง" มาแล้ว
ความสำเร็จนี้ดึงดูดทั้งสายตาของโลก และเงินทุนจากบริษัทยักษ์ใหญ่ หนึ่งในผู้ลงทุนรายแรกคือ Tyson Foods บริษัทเนื้อสัตว์รายใหญ่ของอเมริกา ตามมาด้วย Bill Gates, Richard Branson และ Cargill ซึ่งต่างเห็นตรงกันว่านี่คือทิศทางใหม่ของอุตสาหกรรมอาหารโลก แต่การที่บริษัทเนื้อสัตว์ใหญ่ๆ เข้ามาร่วมลงทุน กลับสร้างคำถามถึงความจริงใจหรือการวางหมากล่วงหน้าเพื่อควบคุมอนาคตของอาหารในรูปแบบใหม่
เม็ดเงินจากภาคเอกชนไหลเข้ามาไม่ขาดสาย รวมถึงการสนับสนุนเชิงนโยบายจากหน่วยงานรัฐบาลสหรัฐฯ ที่เริ่มวางกรอบกำกับดูแลอาหารเพาะเลี้ยงอย่างจริงจัง ทว่าเบื้องหลังภาพฝันของเนื้ออนาคตนั้นก็มีมุมที่ต้องจับตามอง เพราะแม้จะใช้คำว่า “ปลอดภัย” และ “ยั่งยืน” เป็นหัวใจหลักในการสื่อสาร แต่องค์ประกอบหลายประการในกระบวนการผลิต เช่น เซรั่มจากเลือดวัว (FBS) ที่ยังใช้ในบางเฟสของการทดลอง หรือการเพาะเลี้ยงในสารอาหารสังเคราะห์ที่ต้องอาศัยเทคโนโลยีขั้นสูง ล้วนเป็นเรื่องที่ห่างไกลจากคำว่า "ธรรมชาติ" ไปมากโข
เมื่อเข้าสู่ปี 2021 บริษัท Memphis Meats ได้เปลี่ยนชื่อใหม่เป็น Upside Foods พร้อมกับการขยับสถานะจากสตาร์ตอัปมาเป็นผู้นำในตลาดเนื้อเพาะเลี้ยงอย่างเต็มตัว พร้อมกับเปลี่ยนโลโก้และทิศทางแบรนด์จากภาพลักษณ์นักวิทยาศาสตร์มาสู่แบรนด์ที่เข้าถึงผู้บริโภคมากขึ้น เน้นความยั่งยืน ความเป็นมิตรกับสัตว์ และวิธีการผลิตที่ "ชนะใจ" คนรุ่นใหม่ การเปลี่ยนชื่อครั้งนี้ไม่ใช่เพียงกลยุทธ์ด้านแบรนดิ้ง แต่สะท้อนถึงความทะเยอทะยานที่ต้องการให้ผู้บริโภคมองอาหารในมุมใหม่ ไม่ใช่สิ่งที่มาจากฟาร์ม แต่เป็นสิ่งที่มาจากการออกแบบ วิศวกรรม และนวัตกรรม
บริษัทเปิดโรงงานเชิงพาณิชย์แห่งแรกในปี 2022 ที่เมือง Emeryville แคลิฟอร์เนีย ชื่อว่า EPIC (Engineering, Production and Innovation Center) ซึ่งสามารถผลิตเนื้อไก่เพาะเลี้ยงในปริมาณมากได้จริง เพื่อรองรับการผลิตเชิงพาณิชย์ในอนาคต พร้อมกับสร้างความร่วมมือกับภาครัฐเพื่อเร่งให้ผลิตภัณฑ์ผ่านมาตรฐานความปลอดภัยของ FDA และ USDA
สิ่งที่น่าสนใจยิ่งกว่านั้นคือ ความร่วมมือระหว่าง Upside Foods กับหน่วยงานรัฐ เช่น FDA และ USDA เพื่อผลักดันให้ผลิตภัณฑ์เนื้อเพาะเลี้ยงได้รับอนุญาตวางขายในตลาดอเมริกา ซึ่งกลายเป็นจริงในกลางปี 2023 เมื่อ Upside Foods และ Good Meat ได้รับไฟเขียวอย่างเป็นทางการจาก FDA ให้สามารถวางจำหน่ายเนื้อไก่เพาะเลี้ยงแก่ผู้บริโภคได้
ความสัมพันธ์ระหว่าง Upside Foods กับรัฐบาลนั้นน่าสนใจไม่น้อย เพราะนี่คือครั้งแรกในประวัติศาสตร์ที่หน่วยงานรัฐของสหรัฐฯ อย่าง FDA อนุมัติการบริโภคเนื้อสัตว์เพาะเลี้ยงจากห้องแล็บเมื่อเดือนพฤศจิกายน 2022 โดยระบุว่า “ไม่มีข้อกังวลทางความปลอดภัย” แม้จะยังไม่มีข้อมูลเปิดเผยครบทุกขั้นตอนของกระบวนการผลิตอย่างโปร่งใสก็ตาม การอนุมัติครั้งนี้จึงเป็นได้ทั้งจุดเริ่มต้นของการปฏิวัติอาหาร หรือจุดเริ่มต้นของการสร้างอำนาจผูกขาดของบริษัทที่ครอบครองสิทธิบัตรเทคโนโลยีเพาะเลี้ยงเนื้อ เพราะในอนาคตอันใกล้ ถ้าอาหารทุกอย่างต้องผ่านระบบแล็บ ผ่านเทคโนโลยีเฉพาะ และผ่านลิขสิทธิ์เฉพาะ ประชาชนก็จะไม่มีวันเป็นเจ้าของอาหารได้อีกต่อไป
แต่มากกว่าความสำเร็จด้านเทคโนโลยีคือคำถามที่ลึกซึ้งยิ่งกว่า ว่าการผลิตอาหารในห้องแล็บเช่นนี้ ทำให้เกษตรกรรายย่อยหมดสิทธิ์ในการผลิตเนื้อหรือไม่? เพราะเทคโนโลยีระดับสูงนี้ต้องใช้เครื่องมือ ห้องปฏิบัติการ และต้นทุนที่เกษตรกรธรรมดาไม่สามารถเข้าถึงได้ และสุดท้ายแล้ว ผู้บริโภคต้องซื้อเนื้อจากบริษัทยักษ์ใหญ่เท่านั้น โลกใหม่ของอาหารกำลังผลักมนุษย์ให้เป็นเพียงผู้ซื้อ ไม่ใช่ผู้ผลิตอีกต่อไป
แน่นอนว่า Upside Foods อาจไม่ได้ตั้งใจผูกขาดตั้งแต่แรก แต่เมื่อเงินทุน เบื้องหลัง และการอนุญาตจากรัฐ เริ่มขับเคลื่อนไปในทิศทางเดียวกัน มันก็ไม่ต่างอะไรจากการร่างระบบเศรษฐกิจอาหารขึ้นใหม่ โดยมีศูนย์กลางอยู่ที่ห้องแล็บ ไม่ใช่ทุ่งหญ้า การเปลี่ยนแปลงนี้จึงไม่ใช่แค่เรื่องของนวัตกรรมเทคโนโลยี แต่คือการเปลี่ยนแปลงโครงสร้างความสัมพันธ์ระหว่างมนุษย์กับอาหารอย่างสิ้นเชิง และนั่นคือสิ่งที่เฮียอยากให้เพื่อนๆได้คิดก่อนกลืนคำแรกลงไป
สิ่งที่น่าคิดนั้นก็คือ ในโลกที่อาหารกลายเป็นสินทรัพย์ปัญญาแทนที่จะเป็นสิทธิพื้นฐาน การจะปลูก เลี้ยง หรือแลกเปลี่ยนอาหารอาจกลายเป็นเรื่องผิดกฎหมาย และเกษตรกรอาจเหลือบทบาทเพียงคนเฝ้าเครื่องจักรให้กับบริษัทข้ามชาติที่ถือสิทธิบัตรเนื้อ ความฝันที่สวยงามของเนื้อที่ปลอดการฆ่า จึงควรถูกตรวจสอบด้วยสายตาที่เปิดกว้างแต่ไม่ไร้เดียงสา เพราะอนาคตของอาหารนั้น ไม่ใช่แค่เรื่องบนโต๊ะอาหาร แต่เป็นเรื่องของอำนาจ ความเป็นเจ้าของ และสิทธิของประชาชนในฐานะมนุษย์ผู้มีชีวิตบนโลกใบนี้ #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 58537364:705b4b85
2025-06-01 16:46:42
@ 58537364:705b4b85
2025-06-01 16:46:42ความสุขทางโลก ลัทธิสุขนิยมยกย่อง แต่ลัทธิทรมานตนประณาม หากไม่มองว่ากามสุขเป็นพรจากพระผู้เป็นเจ้า คนก็มักมองว่ากามสุขเป็นเครื่องลวงล่อของซาตาน ในเรื่องนี้พระพุทธศาสนาเลือกเดินสายกลาง โดยสอนว่าเราควรทำความเข้าใจกามสุขให้แจ่มแจ้ง ทั้งในแง่เสน่ห์เย้ายวน ข้อจำกัดและข้อบกพร่องทั้งหลาย
เพื่อให้เข้าใจกามสุขอย่างแจ่มแจ้ง เราอาจตั้งคำถามดังนี้: กามสุขสนองตอบความต้องการทางจิตใจแบบใดได้บ้าง และไม่อาจตอบสนองความต้องการแบบใดได้ เพราะเหตุใด
ความต้องการในส่วนที่กามสุขไม่อาจตอบสนองได้ เราควรปฏิบัติอย่างไร
เราหลงเพลิดเพลินและยึดติดในกามสุขมากเพียงใด และกามสุขมีอิทธิพลเหนือจิตใจเราเพียงใด
เราเคยทำหรือพูดสิ่งที่ไม่ถูกต้องเนื่องด้วยปรารถนาในกามสุขหรือไม่
เราเคยเบียดเบียนผู้อื่นเนื่องด้วยปรารถนาในกามสุขหรือไม่
บ่อยครั้งเพียงใดที่สุขทางโลกสร้างความผิดหวังให้เรา
ความคาดหวังมีผลกระทบอย่างไรต่อความสุขทางโลก การทำอะไรซ้ำๆ และความเคยชินส่งผลต่อความสุขทางโลกอย่างไร
เรารู้สึกอย่างไร ยามไม่ได้กามสุขที่เราปรารถนา
กามสุขมีความเกี่ยวข้องกับความซึมเศร้าหรือไม่ กับความวิตกกังวลด้วยหรือไม่
เรารู้สึกอย่างไร เมื่อนึกถึงอนาคตว่า จะต้องพลัดพรากจากสุขทางโลก เนื่องด้วยความเจ็บไข้ ความแก่ และความตาย
การพลัดพรากจากความสุขทางโลกรู้สึกอย่างไรบ้าง
เราตั้งคำถามได้มากมาย และยังตั้งคำถามได้มากไปกว่านี้
หลักสำคัญ คือ ยิ่งเห็นชัดแจ้งในกามสุข เราจะยิ่งเกิดปัญญาและเข้าถึงความสงบมากขึ้นธรรมะคำสอน โดย พระอาจารย์ชยสาโร แปลถอดความ โดย ปิยสีโลภิกขุ

-
 @ 5fbec235:ff265c2a
2025-06-01 15:33:20
@ 5fbec235:ff265c2a
2025-06-01 15:33:20Safety as a Community Creation
I quickly learned that Japan is known for being one of the safest countries in the world—yes, I didn't even realize that until I arrived there. But understanding safety as a statistic is different from witnessing it as a lived reality.
One of the most striking signals of this safety was watching first graders take themselves to school on public transportation in Tokyo. These tiny humans, navigating one of the world's largest cities completely independently. In contrast, my Chicago suburban hometown requires parents to wait at the bus stop for children of that same age, even if their house is just across the street.
I witnessed nearly everyone glued to their phones while out in public. Literally dozens of heads planted facedown into their palms while crossing major intersections. While that's not a trait I admire, it reflects the absolute safety every citizen must feel to be able to walk around like that. Similarly, Tokyo is definitely the place where you can show off designer fashion trends if you can afford to do so. While the style is far more modest and homogenous than here in the USA, expensive fashion statements are still blatantly made in the many high-trafficked districts of the mega city.
The contrast hit me viscerally when I remembered my friend's experience in São Paulo a few years ago. During a short three-mile run, while he was checking Google Maps, he was nearly mugged by a thief on a motorbike. The difference was unmistakable. Take heed of all warnings to not use a smart phone in the streets of Sào Paulo. Tokyo however - accidentally leave your phone at the Izakaya? Don't be surprised if it is personally returned to you by the owner of the Izakaya with a note thanking you once again for your earlier patronage.
Community M and the Dissolution of Transactional Relationships
While in Japan, I was invited to spend the weekend in an exclusive, members-only community nestled along a river flowing down from the mountains—remarkably, all still within Tokyo Prefecture. It felt like a hidden gem: only 5% of the prefecture consists of this kind of natural landscape, and I never would have discovered it without that special invitation.
There, I participated in a unique Bonsai class led by a woman who has been cultivating Bonsai her entire career. I also shared meals, nature walks, and sauna sessions with other community members. It was an eventful weekend, meeting and integrating with an entirely unique culture. The weekend felt truly memorable, special, everlasting—essentially boiled down to a priceless experience.
It's an experience I will remember and appreciate more than the time I've spent in several corporate luxury hotels. Don't get me wrong, corporate luxury hotels are very nice. Their amenities are much more comfortable than anything Community M could offer me. They feel safe, and they make me feel just a little bit entitled—in the sense that "I'm spending A LOT of money with the company that keeps you employed... so are you working for me to the maximum of our mutual expectations?" That's certainly okay. The hotel is offering a service and I am paying for it. Ultimately, it is indeed a mutually valuable transaction everyone is happy with.
But that time spent with Community M was something different. The amount of money I could have spent with them didn't matter. Friendships were formed over shared interests and probably genuine interest and curiosity in each other's cultures. Those values get washed away when the power dynamic shifts too much toward a monetary transaction—service in exchange for cash.
This experience crystallized something I'd been feeling but couldn't articulate: the difference between being served and being welcomed. In transactional relationships, your value is determined by your purchasing power. In genuine community, your value comes from your participation, your curiosity, your willingness to share and receive.
What Online Communities Could Become
What should online communities of the future look like? I think an amazing community could pull some of the best traits of American and Japanese culture. Reliance on oneself and personal responsibility is incredibly important. But as communities grow, it becomes so much harder to exercise personal interests without feeling like I'm "barging in" or something. I've never felt compelled to become the center of attention. What gets me excited is seeing people come together and being their best selves naturally and organically around one another, without any single person being too much "the center."
The way I see a lot of online communities advertised today is less desirable to me. It often looks like there's an influencer selling something and inviting all their followers to join "the community." This replicates the same extractive, transactional dynamics I experienced in luxury hotels, just digitally.
I left Japan with a sense of respect for what's possible when people come together under a shared understanding of a few basic human principles. The most obvious one being a sense of shared responsibility to look out for one another, thereby providing safety for all—a large, functional neighborhood watch, so to say. In Japan, I got the sense that the means to provide general well-being through shared responsibility is far greater than the more exclusive reliance on oneself and distrust of others that often appears in large American cities.
The Internet as Unsafe Territory
When thinking of safety and shared responsibility, the internet today is more like New York City than Tokyo. It's not safe for children, and outsourcing our own responsibility for maintaining safety to centralized, profit-seeking organizations makes no sense. These platforms have the undisputed goal of extracting value from the very communities they attempt to serve.
Current online communities are built backwards. Instead of communities creating tools for themselves, external platforms create tools to extract value from communities. The power dynamic is fundamentally extractive rather than generative.
Communities Building for Themselves
Eve will allow us to build intranets that are safer than anything YouTube, Facebook, TikTok, or any other platform could ever provide because they'll be built by communities, not for-profit organizations seeking to extract value. All applications will be open source, therefore all algorithms will be open source, thereby empowering everyone to exercise their shared responsibilities for maintaining safe, prosperous communities.
Communities will be enabled to create applications that deliver unique experiences specific to their rules and guidelines. Compare it to my Bonsai class. Someday there may be a Japan-oriented community where Bonsai masterclasses and other Bonsai-related services and products are offered. Communities won't be as dependent on platforms. Because of the open-source standard, more tradespeople will be enabled to quickly build whatever the community deems necessary. Communities will be in full control and not reliant on any one platform, nor any one person to maintain the community.
What I experienced in that members-only community by the river was a space where relationships form around shared interests and genuine curiosity - where the community itself determines its needs and builds its tools, where safety emerges from collective responsibility rather than external enforcement. In our digital age of abundance - I see a very real future where communities are enabled to free themselves from irrelevant distractions and build what they need to achieve both individual and collective prosperity.
-
 @ c1e9ab3a:9cb56b43
2025-06-01 13:54:06
@ c1e9ab3a:9cb56b43
2025-06-01 13:54:061. Introduction
Over the last 250 years the world’s appetite for energy has soared along an unmistakably exponential trajectory, transforming societies and economies alike. After a half‑century of relative deceleration, a new mix of technological, demographic and political forces now hints at an impending catch‑up phase that could push demand back onto its centuries‑long growth curve. This post knits together the history, the numbers and the newest policy signals to explore what that rebound might look like—and how Gen‑4 nuclear power could meet it.
2. The Long Exponential: 1750 – 1975
Early industrialisation replaced muscle, wood and water with coal‑fired steam, pushing global primary energy use from a few exajoules per year in 1750 to roughly 60 EJ by 1900 and 250 EJ by 1975. Over that span aggregate consumption doubled roughly every 25–35 years, equivalent to a long‑run compound growth rate of ~3 % yr‑¹. Per‑capita use climbed even faster in industrialised economies as factories, railways and electric lighting spread.
3. 1975 – 2025: The Great Slowdown
3.1 Efficiency & Structural Change
• Oil shocks (1973, 1979) and volatile prices pushed OECD economies to squeeze more GDP from each joule.
• Services displaced heavy industry in rich countries, trimming energy intensity.
• Refrigerators, motors and vehicles became dramatically more efficient.3.2 Policy & Technology
• The Inflation Reduction Act (U.S.) now layers zero‑emission production credits and technology‑neutral tax incentives on top of existing nuclear PTCs citeturn1search0turn1search2.
• The EU’s Net‑Zero Industry Act aims to streamline siting and finance for “net‑zero technologies”, explicitly naming advanced nuclear citeturn0search1.3.3 Result
Global primary energy in 2024 stands near 600 EJ (≈ 167 000 TWh)—still growing, but the line has flattened versus the pre‑1975 exponential.
4. Population & Per‑Capita Demand
World population tripled between 1950 and today, yet total energy use grew roughly six‑fold. The imbalance reflects rising living standards and electrification. Looking ahead, the UN projects population to plateau near 10.4 billion in the 2080s, but per‑capita demand is poised to climb as the Global South industrialises.
5. The Policy Pivot of 2023‑2025
| Region | Signal | Year | Implication | |--------|--------|------|-------------| | COP 28 Declaration | 20+ nations pledge to triple nuclear capacity by 2050 | 2023 | High‑level political cover for rapid nuclear build‑out citeturn0search2 | | Europe | Post‑crisis sentiment shifts; blackout in Iberia re‑opens nuclear debate | 2025 | Spain, Germany, Switzerland and others revisit phase‑outs citeturn0news63 | | United States | TVA submits first SMR construction permit; NRC advances BWRX‑300 review | 2025 | Regulatory pathway for fleet deployment citeturn1search9turn1search1 | | Global Strategy Report | “Six Dimensions for Success” playbook for new nuclear entrants | 2025 | Practical roadmap for emerging economies citeturn0search0 | | U.S. Congress | Proposed cuts to DOE loan office threaten build‑out pace | 2025 | Finance bottleneck remains a risk citeturn1news28 |
6. The Catch‑Up Scenario
Suppose the recent 50‑year pause ends in 2025, and total energy demand returns to a midpoint historical doubling period of 12.5 years (the average of the 10–15 year rebound window).
6.1 Consumption Trajectory
| Year | Doublings since 2024 | Demand (TWh) | |------|----------------------|--------------| | 2024 | 0 | 167 000 | | 2037 | 1 | 334 000 | | 2050 | 2 | 668 000 | | 2062 | 3 | 1 336 000 |
(Table ignores efficiency gains from electrification for a conservative, supply‑side sizing.)
7. Nuclear‑Only Supply Model
7.1 Reactor Math
- 1 GWᵉ Gen‑4 reactor → 8.76 TWh yr‑¹ at 100 % capacity factor.
- 2062 requirement: 1 336 000 TWh yr‑¹ → ≈ 152 500 reactors in steady state.
- Build rate (2025‑2062, linear deployment):
152 500 ÷ 38 years ≈ 4 000 reactors per year globally.
(Down from the earlier 5 000 yr‑¹ estimate because the deployment window now stretches 38 years instead of 30.)
7.2 Policy Benchmarks
- COP 28 triple target translates to +780 GW (if baseline 2020 ≈ 390 GW). That is <100 1 GW units per year—two orders of magnitude lower than the theoretical catch‑up requirement, highlighting just how aggressive our thought experiment is.
7.3 Distributed vs Grid‑Centric
Small Modular Reactors (300 MW class) can be sited on retiring coal plants, using existing grid interconnects and cooling, vastly reducing new transmission needs. Ultra‑large “gigawatt corridors” become optional rather than mandatory, though meshed regional grids still improve resilience and market liquidity.
8. Challenges & Unknowns
- Finance: Even with IRA‑style credits, first‑of‑a‑kind Gen‑4 builds carry high cost of capital.
- Supply Chain: 4 000 reactors a year means a reactor‑grade steel output roughly 20× today’s level.
- Waste & Public Trust: Advanced reactors can burn actinides, but geologic repositories remain essential.
- Workforce: Nuclear engineers, welders and regulators are already in short supply.
- Competing Technologies: Cheap renewables + storage and prospective fusion could displace part of the projected load.
9. Conclusions
Recent policy shifts—from Europe’s Net‑Zero Industry Act to the COP 28 nuclear declaration—signal that governments once again see nuclear energy as indispensable to deep decarbonisation. Yet meeting an exponential catch‑up in demand would require deployment rates an order of magnitude beyond today’s commitments, testing manufacturing capacity, finance and political resolve.
Whether the future follows the modest path now embedded in policy or the steeper curve sketched here, two convictions stand out:
- Electrification will dominate new energy demand.
- Scalable, dispatchable low‑carbon generation—likely including large fleets of Gen‑4 fission plants—must fill much of that gap if net‑zero targets are to remain credible.
Last updated 1 June 2025.
-
 @ 472f440f:5669301e
2025-06-01 13:48:34
@ 472f440f:5669301e
2025-06-01 13:48:34Marty's Bent
Sorry for the lack of writing over the last week. As many of you may already know, I was in Las Vegas, Nevada for the Bitcoin 2025 conference. It was my first time in Las Vegas. I had successfully avoided Sin City for the first 34 years of my life. But when duty calls, you have to make some personal concessions.
Despite what many say about this particular conference and the spectacle that it has become, I will say that having attended every single one of Bitcoin Magazine's conferences since 2019, I thoroughly enjoy these events, even if I don't agree with all the content. Being able to congregate with others in the industry who have been working extremely hard to push Bitcoin forward, all of whom I view as kindred spirits who have also dedicated their lives to making the world a better place. There's nothing better than getting together, seeing each other in person, shaking hands, giving hugs, catching up and reflecting on how much things have changed over the years while also focusing on the opportunities that lie ahead.
I think out of all the Bitcoin magazine conferences I've been to, this was certainly my favorite. If only because it has become abundantly clear that Bitcoin is here to stay. Many powerful, influential, and competent people have identified Bitcoin as an asset and monetary network that will play a large part in human society moving forward. And more importantly, Bitcoin is proving to work far better than anybody not paying attention expected. While at the same time, the fiat system is in woeful disrepair at the same time.
As a matter of reflection and surfacing signal for you freaks, here are the presentations and things that happened that I think were the most impactful.
Miles Suter's Block Presentation
This presentation was awesome for many reasons, one of which being that we often forget just how dedicated Block, as an organization with many companies - including Cash App, Square, the open source organization known as Spiral and more recently, BitKey and Proto - has been to bitcoin over the last eight years. They've worked methodically to make Bitcoin a first-class citizen in their business operations and slowly but surely have built an incredibly integrated experience across their brands. The two big announcements from Block during the conference were the enablement of Bitcoin payments in Square point-of-sale systems and the amount of revenue they're making on their Lightning node, c=, from routing payments.
Right now, the Bitcoin payments and point of sale systems is in beta with many merchants testing it out for the next six months, but it will be available for all 4 million square merchants in 2026. This is something that many bitcoiners have been waiting for for many years now, and it is incredible to see that they finally brought it across the line. Merchants will have the ability to accept bitcoin payments and either convert every payment into fiat automatically, convert a portion of the bitcoin payment into fiat to keep the rest in sats, or simply keep all of the bitcoin they receive via payments in sats. This is an incredible addition to what Square has already built, which is the ability of their merchants to sweep a portion of their revenues into bitcoin if they desire. Square is focused on building a vertically integrated suite of bitcoin products for merchants that includes the ability to buy bitcoin, receive bitcoin, and eventually leverage financial services using bitcoin as collateral so that they can reinvest in and expand their businesses.
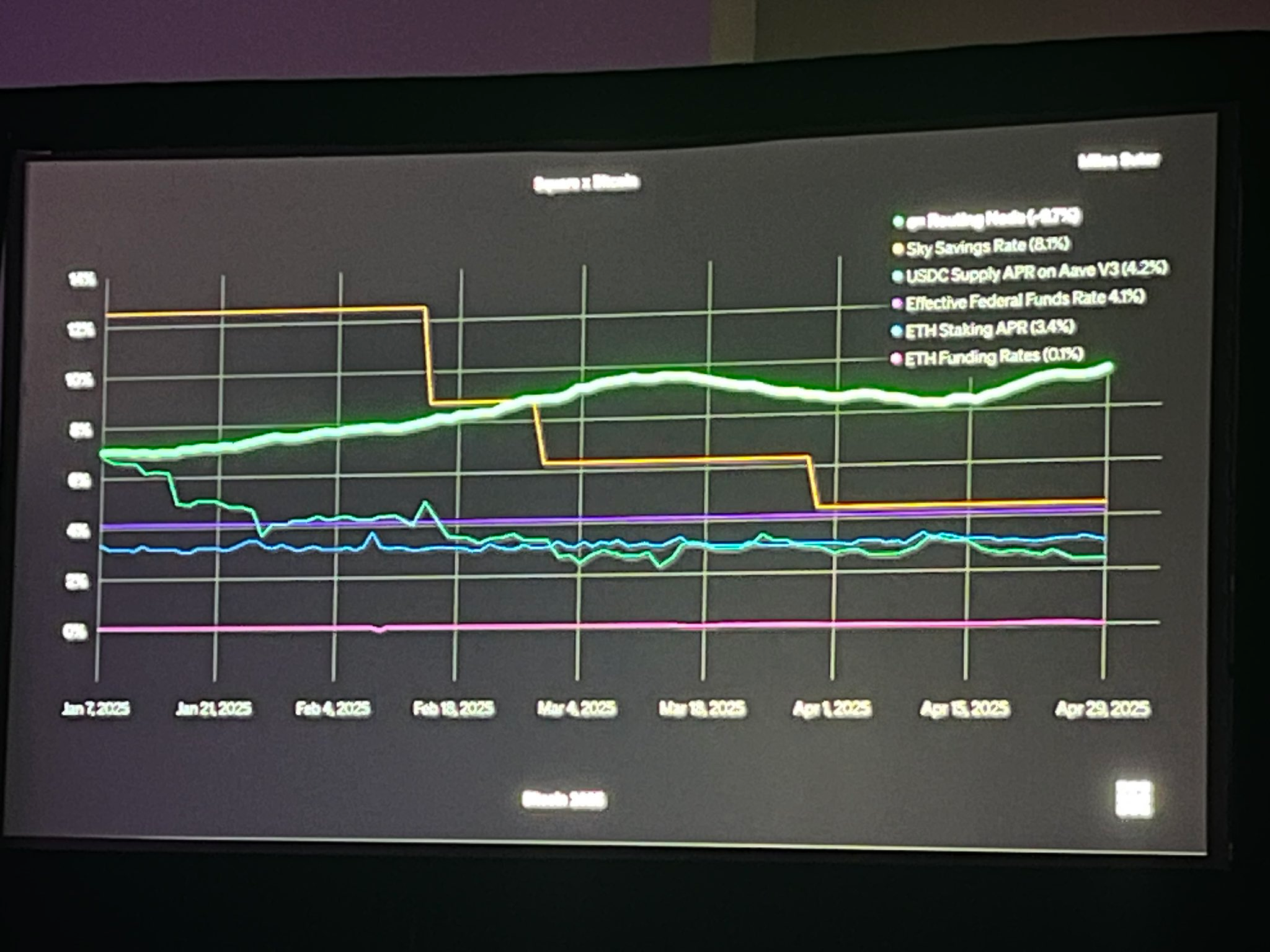
via Ryan Gentry
What went a bit underappreciated in the crowd was the routing node revenue that c= is producing, \~9.7% annualized. This is a massive validation of something that many bitcoiners have been talking about for quite some time, which is the ability to produce "yield" on bitcoin in a way that reduces risk significantly. Locking up bitcoin in a 2-of-2 multisig within Lightning channels and operating a Lightning routing node has been long talked about as one of the ways to produce more bitcoin with your bitcoin in a way that minimizes the threat of loss.
It seems that c= has found a way to do this at scale and is doing it successfully. 10% yield on bitcoin locked in Lightning channels is nothing to joke about. And as you can see from the chart above in the grainy picture taken by Ryan Gentry of Lightning Labs, this routing node "yield" is producing more return on capital than many of the most popular staking and DeFi protocols.
This is a strong signal to the rest of the market that this can be done. It may take economies of scale and a high degree of technical competency today. But this is incredibly promising for the future of earning bitcoin by providing valuable goods and services to the market of Bitcoiners. In this case, facilitating relatively cheap and instantly settled payments over the Lightning Network.
Saifedean Ammous' Bitcoin and Tether Presentation
This was one of the best presentations at the conference. Saifedean Ammous is a friend, he has been an incredible influence on my personal bitcoin journey, and I feel comfortable in saying he's been a strong influence on the journey of hundreds of thousands, at least, if not millions of people as they've attempted to understand bitcoin.
This presentation is a bit spicy because it puts a pin in the balloon of hopium that stablecoins like Tether are mechanisms that could bail out the market for US Treasuries in the medium to long-term if they take enough market share. As one always should do, Saif ran the numbers and clearly illustrates that even in the most optimistic case, Tether's impact on the market for treasuries, their interest rates, and curbing the growth of the debt held by the US federal government will be minimal at best.
One of the most interesting things that Saif points out that I'm a bit embarrassed I didn't recognize before is that much of the demand for Tether that we're seeing these days is replacement demand for treasuries. Meaning that many people who are turning to Tether, particularly in countries that have experienced hyperinflationary events, are using Tether as a substitute for their currencies, which are operated by central banks likely buying U.S. treasuries to support their monetary systems. The net effect of Tether buying those treasuries is zero for this particular user archetype.
Saif goes on to explain that if anything, Tether is a weapon against the US Treasury system when you consider that they're storing a large portion of the stablecoin backing in Treasuries and then using the yields produced by those Treasuries to buy bitcoin. Slowly but surely over time bitcoin as a percentage of their overall backing of Tether has grown quite significantly starting at 0% and approaching 10% today. It isn't hard to imagine that at some point within the next decade, Bitcoin could be the dominant reserve asset backing tethers and, as a result, Tether could be pegged to bitcoin eventually.
It's a fascinating take on Tether that I've never heard before.
Nothing Stops this Train from Lyn Alden
Lyn's been saying it loudly for quite some time now; "Nothing stops this train." She's even been on our podcast to explain why she believes this many times over the last five years. However, I don't think there is one piece of content out there that consolidates her thesis of why nothing stops the train of fiscal irresponsibility and unfettered debt expansion and why that's good for bitcoin than the presentation she gave at the conference. Definitely give this one a watch when you get a chance if you haven't already.
Overall, it was a great week in Vegas and I think it's safe to say that bitcoin has gone mainstream. Whether or not people who have been in the bitcoin industry and community for a while are okay with does not really matter. It's happening and all we can do is ride the wave as more and more people come to recognize the value prop of bitcoin and the social clout they can gain from supporting it. Our job here at TFTC is to help you discern the signal from the noise, continue to champion the self-sovereign usage of bitcoin and keep you abreast of developments in the space as they manifest.
Buckle up. Things are only going to get weirder from here on out.
Bitcoin's Mathematical Destiny
Sean Bill and Adam Back make a compelling case for Bitcoin's inevitable march toward $1 million. Sean points out that Bitcoin represents just a tiny fraction—2 trillion out of 900 trillion—of total financial assets, calling it a "tiny orange dot" on their presentation to Texas pensions. He emphasizes that reaching parity with gold alone would deliver a 10x return from current levels. Adam highlights the mathematical impossibility of current prices, noting that ETF buyers are absorbing 500,000 BTC annually while only 165,000 new coins are mined.
"Who's selling at these prices? It doesn't quite add up to me." - Adam Back
The institutional wave is just beginning. Sean revealed that while 50% of hedge fund managers personally own Bitcoin, only 3% have allocated institutional funds. Combined with emerging demand from nation states and corporate treasuries meeting Bitcoin's fixed supply, the price trajectory seems clear. Both guests stressed the importance of staying invested—missing just the 12 best performing days each year would turn Bitcoin into a losing investment.
Check out the full podcast here for more on pensions allocating to Bitcoin, cypherpunk banking, and commodity trading insights.
Headlines of the Day
Panama Canal Eyes Bitcoin for Payment Option - via X
U.S. Warns of Imminent Chinese Threat to Taiwan - via X
Get our new STACK SATS hat - via tftcmerch.io
Saylor's Bitcoin Strategy Explodes Globally Amid Doubt - via CNBC
Take the First Step Off the Exchange
Bitkey is an easy, secure way to move your Bitcoin into self-custody. With simple setup and built-in recovery, it’s the perfect starting point for getting your coins off centralized platforms and into cold storage—no complexity, no middlemen.
Take control. Start with Bitkey.
Use the promo code “TFTC20” during checkout for 20% off
Ten31, the largest bitcoin-focused investor, has deployed 158,469 sats | $150.00M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Moving is the least fun part of the human experience.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-02 00:53:51
@ 5d4b6c8d:8a1c1ee3
2025-06-02 00:53:51Until the cookie I just ate, today was a pretty stellar day: slept well, ate well, fasted, did some physically demanding yard work in the hot Sun, walked the dog a few times.
How did the stackers do today on maintaining their ~HealthAndFitness?
https://stacker.news/items/994882
-
 @ 04c915da:3dfbecc9
2025-03-26 20:54:33
@ 04c915da:3dfbecc9
2025-03-26 20:54:33Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ a296b972:e5a7a2e8
2025-06-01 13:27:58
@ a296b972:e5a7a2e8
2025-06-01 13:27:58Wird hier gerade eine Hollywood-Show vor unseren Augen aufgeführt?
Trump tut oft so, als ob die USA erst mit seiner zweiten Präsidentschaft zu existieren begonnen haben. Die Suppe, die ihm die Biden-Regierung eingebrockt hat auszulöffeln, gehört zur Übernahme der Amtsgeschäfte. Ist es wahrscheinlich, dass die Vorbereitungen für den Stellvertreterkrieg zwischen den USA und Russland, auf dem Rücken der Ukrainer, erst mit der Biden-Administration angefangen haben, oder schon früher?
Nicht vergessen: Als dominierende Kraft in der NATO sind die USA maßgeblich für die Provokation Russlands durch die NATO-Osterweiterung verantwortlich.
Jetzt, wo man, wie in anderen „demokratiebringenden Einmärschen“ vorher auch schon, erkannt hat, dass man wieder mal gescheitert ist, versuchen sich die USA einen schlanken Fuß zu machen? Wollen sie sich gesichtswahrend aus der Affaire ziehen und Europa den schwarzen Peter zuschieben? Am Ende hieße es dann möglicherweise: Wir haben ja alles versucht, uns für eine Befriedung in der Ukraine einzusetzen, aber ihr Europäer wolltet ja nicht. Jetzt seht selber zu, wie ihr damit fertig werdet. Schon lange vor dem Ukraine-Krieg gab es Stimmen, die sagten, dass wenn es einmal darauf ankommt, werden die USA Europa fallen lassen, wie eine heiße Kartoffel.
Trump deutet an, eine große Zahl der Besatzungstruppen in Europa, besonders präsent in Deutschland, abziehen zu wollen. Gleichzeitig ist die geplante Stationierung von Hyperschallraketen namens „Dark Eagle“ in 2026 noch nicht zurückgenommen worden. Das wäre ein klares Signal einer vertrauensbildenden Maßnahme. Trump könnte in Wiesbaden das Licht ausmachen. Auch das wäre Russland gegenüber, ein klares Zeichen zum festen Willen einer Deeskalation.
Wie geht es mit den rund 800 weltweiten US-Basen weiter? Gibt es hier Pläne, sich zurückzuziehen?
Trump könnte veranlassen, dass Starlink abgeschaltet würde, ein Anruf bei Musk genügte, dann wäre die Ukraine blind. Warum tut er das nicht, um den Krieg schneller zu beenden?
Warum fließen von Deutschland finanzielle Mittel in die Ukraine, um den Betrieb von Starlink weiter aufrechtzuerhalten?
All das könnten klare Zeichen Richtung Russland sein, die es beruhigen und das territoriale Sicherheitsgefühl des Landes wiederherstellen würde.
Wusste Trump nichts von der Auslagerung der Bio-Waffen-Labore in die Ukraine?
Haben die zahlreichen Executive Orders, so gut sie auch sein mögen, nicht auch den Charme von Autokratie oder sogar schon Diktatur? Sind diese in einer Ausnahmesituation gerechtfertigt? Dann wären die Ermächtigungsgesetze bei der Machtübernahme in Deutschland es auch gewesen. Sie geschahen aus der Sicht der Verantwortlichen ja auch in bester Absicht. Das kann doch eigentlich nicht sein. Oder kann man beides nicht miteinander vergleichen?
Wie passt das alles zusammen?
Im Juni gibt es ein NATO-Treffen. Wird Trump dort den Austritt aus der NATO verkünden?
Vorher macht Merz seinen Antrittsbesuch bei Trump. Gibt es eine saftige Ohrfeige, entlässt Trump Deutschland in die Volljährigkeit, oder erklärt Trump Deutschland zu seinem stärksten und verlässlichsten Partner in Europa? Man muss mit allem rechnen.
Durch seine Rede auf der Sicherheitskonferenz in München, bemängelte Vance unter anderem die Meinungsfreiheit in Deutschland. Ist das wirkliche Meinungsfreiheit, wenn diese derzeit in den USA vor allem in den Händen von Musk liegt?
Vance sah auch eine Gefahr für die Demokratie in Deutschland durch die Brandmauer gegen die Opposition. Es ist offensichtlich, dass Trump konservative Kräfte und somit die Opposition in Deutschland unterstützt und stärkt. Die Opposition steht jedoch auch zur NATO und ist für eine angemessene Verteidigungsfähigkeit. Keine Überlegungen, ob die Neutralität für Deutschland nicht ebenfalls eine Alternative wäre. Besteht hier nicht eine Gefahr, denn es ist nicht das erste Mal, dass die USA in einem anderen Land Kräfte unterstützen, von denen sie der Meinung sind, dass sie der Demokratisierung dienen. Hier gibt es Beispiele dafür, dass der Schuss auch nach hinten losgehen kann. Dieses Mal mag es ja vielleicht in die richtige Richtung gehen, doch wer garantiert das? Am Ende zeigt es jedoch vor allem, dass Deutschland nur ein Spielball ganz anderer Kräfte ist, und aus sich heraus nicht in der Lage, vernunftbegabte, eigene Entscheidungen zu treffen. Und werden Entscheidungen getroffen, dann gehen sie in die falsche Richtung. Deutschland darf nicht stärkste Kraft in Europa werden, schon allein aufgrund seiner eigenen Geschichte nicht.
Und die, die die durchaus vorhandenen mahnenden Stimmen in Deutschland unterstützen müssten, die tun es (noch) nicht. In der Tat muss der Wandel von unten nach oben erfolgen, durch den Souverän, weil es mehr als genug Beweise dafür gibt, dass die politische Klasse weder willens noch dazu in der Lage ist, wieder freiheitlich-demokratische Verhältnisse herzustellen, auch, wenn sie ständig gebetsmühlenartig betont, dass sie Unseredemokratie mit allen Mitteln schützen will. Mittlerweile ist die Lage schon so pervers, dass man sich förmlich einen tagelangen Blackout, Benzinpreise von 5,00 Euro den Liter, exorbitant hohe Heiz- und Lebenshaltungskosten herbeiwünscht, damit dieses derzeit leider enttäuschende, bräsige Volk endlich den Irren in Berlin deutlich zu verstehen gibt, dass es so nicht weitergehen kann.
Herr Pistorius scheint der Ansicht zu sein, dass, wenn er das Wort Diplomatie in den Mund nimmt, er augenblicklich an Zungenkrebs erkrankt. Nein, Herr Pistorius, wir müssen nicht kriegstüchtig werden, wir müssen nicht nur friedensfähig werden, sondern friedensliebend durch eine vernunftbegabte deutsche Politik sein, kapieren Sie das endlich! Und diese Friedensliebe muss in die Welt hinausposaunt werden, als Zeichen, dass Deutschland aus seiner Geschichte gelernt hat (wenn es denn so wäre).
Und Frieden durch Krieg schaffen zu wollen, ist und bleibt bekloppt!
Und Merz, verkündet stolz die Stationierung einer Brigade in Litauen, direkt an der russischen Grenze. Es scheint ihm Vergnügen zu bereiten, den Bären an der Tatze zu kitzeln. So lange, bis er die Krallen zeigt, weil es ihm zu viel wird. In Litauen selbst scheint es seit Ende des 2. Weltkrieges noch bis heute eine beträchtliche Anzahl von ewig Gestrigen zu geben, genauso, wie in der Ukraine. Wie passt das zusammen?
Oder soll gar am Ende doch noch der Morgenthau-Plan umgesetzt werden? Anzeichen dafür gibt es.
Was, Herr Trump, ist jetzt mit den Goldreserven in Fort Knox? Sind sie noch da, oder nicht? Was ist mit den deutschen Goldreserven? Die sieht Deutschland wahrscheinlich nie wieder, weil sie mit den jahrzehntelangen Kosten für den US-NATO-Schutz verrechnet werden. Und am Ende würde wahrscheinlich sogar noch ein Saldo zu Ungunsten Deutschlands übrigbleiben.
Ja, es sind viele Baustellen begonnen worden und es gibt immer noch sehr starke Kräfte in den USA, die das Aufräumen verhindern wollen:
Weniger Zucker, keine künstlichen Zusatzstoffe in Lebensmitteln, zusatzfreies Wasser, alles schön und gut. Was nutzt es, wenn die Amis sich wieder gesünder ernähren können, die Fettleibigkeit zurückgeht und viele am Ende dann doch an den Folgen der Spritze zugrunde gehen. Ein offizielles, nationales, sofortiges Verbot der mRNA-Vergiftung gibt es immer noch nicht. Und auch keine laufende Aufarbeitung und Aufklärung von alleroberster Stelle. Kennedy tut was er kann, aber das reicht noch nicht.
Wer sind die Hintermänner der Wettermanipulation, die derzeit teilweise geahndet werden? Irgendjemand muss den Auftrag dazu geben, wo wird das Zeug hergestellt, wer mischt es dem Flugbenzin bei, was wissen die Flugkapitäne, wenn es denn so ist?
Wird eine Grand Jury vorbereitet, in denen die von Biden am letzten Tag begnadigten Personen, inklusive ihm selbst, zur Rechenschaft gezogen werden? Wo ist das US-amerikanische Nürnberg 2.0 für alle, die an dem Spritzen-Verbrechen beteiligt gewesen sind?
Was ist mit den Kinderschändern? Können die fliehen, wohin? Oder landen die allesamt auf dem elektrischen Stuhl, wo sie hingehören würden? Auch, wenn man grundsätzlich gegen die Todesstrafe ist, in diesem Fall könnte man doch mal eine Ausnahme machen, falls Guantanamo zu voll würde. Sich in teuflischer Art auf verschiedene Weise an Kindern zu vergehen, ist das widerlichste, abscheulichste, menschenverachtendste, das sich ein normaler Mensch überhaupt nur vorstellen kann. Und gleich danach kommt die weltweite, satanische mRNA-Vergiftung.
Was sollen die Friedensgespräche zwischen Russland und der Ukraine in Istanbul? Wie der durch die NATO-Osterweiterung von den USA angezettelte Krieg in der Ukraine, so wäre es jetzt auch die Pflicht der USA, dieses grandiose Deppenstück mit unzähligen Toten und Verstümmelten auch wieder zu beenden. Und das geht nur zwischen den USA und Russland. Die Ukraine hat dabei wenig bis gar nichts zu melden, genau so wenig, wie Europa, und schon gar nicht Möchte-Gernegroß-Deutschland.
Ist das ein Hinhaltetaktik?
Klar war, dass Trump den Krieg in der Ukraine nicht in 24 Stunden beenden konnte. Wurde Europa die Gelegenheit gegeben, ein Bündnis der Willigen aufzustellen, dass verzweifelt aber erfolglos versucht, einen Keil in die Friedensverhandlungen zu treiben? Soll damit das wahre Gesicht von Großbritannien, Frankreich und Deutschland augenscheinlich werden? Steckt ein Plan dahinter, aber welcher?
Welche Möglichkeiten hätte Trump, die Europäische Union, als Handlanger des Deep States und der NATO, mit einer Überdosis der von der EU-Kommissarin per SMS bestellten Haarspray-Dosen zu ersticken, damit eine für alle einträgliche Neuauflage der Europäischen Wirtschaftsgemeinschaft selbständiger Nationalstaaten wiederauferstehen kann? Damit Gurken und Bananen wieder krumm sein dürfen, und die Sommerzeit, unnötig wie ein Loch im Kopf, endlich wieder abgeschafft wird, weil keiner sie will und weil sie nichts bringt. Das sind nur die harmlosesten Beispiele. Dieses nicht demokratisch gewählte Bürokratie-Monster mit europäischem Herrschaftsanspruch, Militärphantasien und diktatorischen Gleichmachungsgedanken gehört aufgelöst, und die agierenden Handlanger in ihm dürfen nie wieder politische Verantwortung übertragen bekommen.
Es ist richtig, wenn es Stimmen gibt, die sagen, die Veränderung der politischen Verhältnisse muss von der Graswurzel aus erfolgen, weil man erkennen muss, dass das ganze System vergiftet ist. Die USA waren genau so wenig jemals unser Freund, wie Russland unser Feind ist. Es ging und geht immer nur um Interessen, nicht um Nächstenliebe. Wie viele Generationen und ein anderes Bildungssystem braucht es, bis die Menschen das verstehen?
Trump hat schon mehrmals angekündigt, dass „nächste Woche“ Großes geschehen wird. Bisher heiße Luft, oder ist da etwas verkündet worden, dass man nicht mitbekommen hat?
Trump ist nicht der Retter der Welt! Mit dem Projekt Warp-Speed geht es jetzt weiter mit Stargate. Hier sollen 500 Milliarden Dollar in die mRNA-Forschung zur Bekämpfung von Krebs und in die KI-Infrastruktur bereitgestellt werden. Welche Rolle spielen Thiel mit Palantir und Musk mit Neurolink und weitere Tech-Giganten? Digitale Identitäten sollen die illegalen Einwanderer abhalten, zum Schutz der eigenen Bevölkerung. Wer sagt denn, dass hier nicht ein totaler Überwachungsstaat installiert werden soll? Man muss Speck in die Mausefalle legen, damit die Maus darauf hereinfällt. Und dann – schnappt sie zu! Vieles, was aus den USA kommt, hört sich erst einmal befreiend an. Basiert das wirklich auf humanen Prinzipien, oder sind am Ende auch hier nur Interessen, wie überall, die treibende Kraft?
Die USA sind keine lupenreine Demokratie, genauso wenig wie Russland, denn am Ende zählt, wer das meiste Geld zusammenbekommen hat, um an die Macht zu kommen. Das ist wohl eher eine "Moneykratie", eine Geldherrschaft. Einmal sind es die Demokraten, ein anderes Mal sind es die Republikaner. Am Ende ziehen immer diejenigen die Strippen, die dahinterstehen, die man nicht sieht, die Einser, die aus den vielen Nullen eine Tausend machen, damit sie ihre Macht entfalten können. Wer entscheidet denn, wer die guten Reichen und wer die bösen Reichen sind? Am Ende verdirbt Geld und Macht bei allen den Charakter. Und was die sogenannten Philanthropen anrichten können, hat man ja in vollen Zügen „genießen“ dürfen. Raus aus der WHO, ein richtiger Schritt der USA und Argentiniens. Und was ist mit den anderen Staaten? Auch hier tut sich Deutschland wieder einmal in besonders unangenehmer Weise durch zusätzliche Geldspritzen hervor.
Wir sollten endlich innerhalb unserer Menschheitsentwicklung erwachsen werden, uns von dem Gedanken verabschieden und uns darauf verlassen, dass Mama und Papa es schon richten werden. Mit wirklicher Freiheit umzugehen, muss gelernt sein. Wir müssen aus der Freiheits-Simulation aufwachen. Das macht vielen Angst, weil Freiheit mit Selbstverantwortung, Selbstermächtigung und Selbstdenken zu tun hat. Die Auswahl in einem 5 Meter langen Joghurt-Regal hat nichts mit Freiheit zu tun!
Bisher wurden wir in den sogenannten Demokratien darauf hin konditioniert, dass wir unser Kreuzchen machen, damit wir jemanden haben, auf den wir schimpfen können: Die da oben! Und die da oben, interessiert das einen feuchten Kehricht. Das muss aufhören!
Wir müssen unser Schicksal und Wohlergehen endlich selbst in die Hand nehmen.
Alle Systeme, und klingen sie noch so verlockend, dienen der Steuerung und Lenkung von Massen, weil einige Wenige glauben zu wissen, was gut für uns ist. Dabei sollten wir das doch selbst am allerbesten wissen. Dazu gehört vor allem die Freiheit, die kein System wirklich zulassen kann, auch die USA nicht, weil das den absoluten Machtverlust für es bedeuten würde.
Selbst, wenn sich unter dem Vorangegangenen, Wirres für den Leser befinden sollte, es sind eigene Gedanken und eine Meinung, die immer noch besser ist, als die vorbereiteten, geschälten Apfelscheite von einem Tellerchen aufzunehmen, gedankenlos in den Mund zu stecken, leicht durchzukauen und herunterzuschlucken, so, wie es bei denen, die immer noch vor dem Fernseher hocken und glauben, was ihnen da vorgelogen wird, der Fall ist.
Insasse der Freiluft-Irrenanstalt, bediene Dich Deines eigenen Verstandes und heile Dich selbst von der Massenpsychose, in die man Dich durch jahrelange Gehirnwäsche getrieben hat. Schock den Staat, denke selbst!
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-02 00:33:35
@ 5d4b6c8d:8a1c1ee3
2025-06-02 00:33:35For about three years, we had a bedtime routine that worked very well and a kid that slept clear through the night in her own room.
For the past two years, bedtime has been a struggle. We made various adjustments, but they were never more than short-term bandages. Nighttime almost always turned into a battle of wills.
So, we gave up. No more bedtime. We go to bed when we're tired, or when the kid asks us to read to her. She usually wants to sleep in our room, which we only let her do if she's being quiet and trying to sleep, otherwise it's off to her own room. Being loud and wild in our room late into the night had been our breaking point.
The results aren't ideal, but the struggles are much reduced and she's sleeping in her room more often, because it's where she can stay awake if she wants.
What are some standard parenting practices that you've just abandoned entirely?
https://stacker.news/items/994865
-
 @ 4c96d763:80c3ee30
2025-05-31 23:33:02
@ 4c96d763:80c3ee30
2025-05-31 23:33:02Changes
Fernando López Guevara (2):
- feat(column): add tooltip on remove column button
- feat(hashtag-column): handle new hashtag on Enter key press
pushed to notedeck:refs/heads/master
-
 @ 84b0c46a:417782f5
2025-06-01 23:36:42
@ 84b0c46a:417782f5
2025-06-01 23:36:425/24 nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqxk47yl7vwqu0yrv4fljymp4m2vf0gtesmel4cgg638h82rt4hdn6yyejn
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8msrjypjuvhwaarkq72739wl5rewl49vx0ku6s3u3y03anmau5dscqjj0l
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0fzqwr2xt044zglcwcj3dnnxuk0vlcmwcw0sdzw7yhzfsn009ttss5pv6k
こていたんさんのアイコン

5/25 nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0ku3qs4zskmclvtqm0lt707jwn2ylz9v2xj2qakznyp86j4p7fzqd85kfq
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8054fh3l8qtngdfpdwxfl84r36ju3f65zmhjvjy67y7gjj0mhjks2c7w80
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr8nycy3gvjfdn3rqjc49j2gwhwjdhu6d5ms6uxx7y44kzf0u2ftsc8r3c3
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpmcs4xzsusg9s6cn2acasjsam2pwmf6m8h0z08kfca56f8aqwyf2fjwv7w
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqsvh305tpg0xesw6n4eu2kmumgx0mcv0cn64zznyydzpezzsazdugcyrfqm0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq2aq2l9cq04ygjjk4tq8zfjmuezvckcav8cfqv6z745744nfd2nqlxpq04
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs05f8xz5uahsdzceq9d0mp860hck3ash8s3ssp3paxxu620tw4ufssk6ntz
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzppyeyt0xt0fps85hxv4evdhgy35m9zfzhsqtnq93rsy4arnw3n853sc0u7
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzq7emnt7e67h5cygnyvz922x2m4f3x30hpvns3yxls2v4t2uy0vrc6060ek
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqspu5ny2laxuqtrryffsf455fldpnluw5ladrq32cfveu6mjjgmuxsynheu3
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsyhjuxzjkgzp5d8xt8wg8vzekcnaw6ud7htrnqppy2xmpeajrhqncs0rv4c
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqswm6wxhc3h426py80vjm9jj03j8vhvrnhwmalunlxm0pq5xvxqs5qpr2kq7
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsgehqf8cl5sp0wfw0fzl982lvhmy9j23vpus70wddtytkr4qygxlchprwv6
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqsvkrvnh8lzw4rfx87278rwxp2uymej2alputzn2nl525p85c3703cmrgkfn
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpz9mhxue69uhkuenjv4kxz7fwv9c8qqgawaehxw309aex2mrp0yhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsf2u5larth503yh236mhssn2tes4shvawnv4kufzh3889cr9dt4wculcv6w
nostr:nevent1qvzqqqqqqypzqnza2du6qe3nnjy0dcgpu0kmr7awunk78m4rtl7x78rxfvay8qlwqqspnfvau4ylywwk2f7nrm68ue6c86j9p4y0cu4parfwapun0nsw97sad9jwf
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqs2y7lha9uy30wwdt9yn47s6krqv3e8duj6nqrl27e2s6dl465xssg5gt4ue
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsyf8peg4zggp858zfha6dt4mjxss4nhc3k4szqynh0u53j22asx6sdhpfwc
nostr:nevent1qvzqqqqqqypzphla8l7r42mzjvdgevy0pg4y3rd8gupaprgaa7fcdzhrpaddu7lpqqsr0s5ger5l8aapw63yyve5sne5rge0ractks4v4l0yn3ezcvq3f4s8wthq8
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qqs93gfz3kskw2lcxadwu3dvanyq7xstaj39vfqmppnng0nvz5gjm8syq9p8p
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzp5tlgnw663dswldulvnvgczfr08aflg35cu2syaaddmppvjytvn09tc679
nostr:nevent1qvzqqqqqqypzpe30ylfgzj39zuwyvmfdwcf26xsxdkcnv26wykwmtsrkl8nty89hqqswq489vn7h9hz2q0w60m05wn5xuqd0vvnqcxwxkewmh7h72yjtrrc6yulf2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzcyhx8d350shzfczewxkhxemqknfeu5z8kj0arrur9wn726k5hjayfwl6
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsrnvmc5r2rs6jx7z8v3gvnzpkfsc3vqqxg0ygnk8wn3jmulzq887q07smq2
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzqzk0lg9aq8yzg0m4dcqp5a0a468c3jmtcw058hvckt6yj0nlnl0mqfgav7
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsf4js8wu9zlp74kj5erkwsq9rvhj0d6xmynevt4tsa766nsvja04gsrfaz5
nostr:nevent1qvzqqqqqqypzpu89j3vdtkj0cec9mzs4hcmetfq5a9d6fw5smezlpyqhme90uq27qqsqky2uqkzu60f3tkcttx59q675sxmd9ypyppnd50ukmhlx3qwrqfgmmxmjh
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsvtkn6rkgmttjzzm3nn58d85eve5834pnamzhy0u4p584jger8uvgttcqhe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqstua4ssqq9wejs4kjvjjs0azlzjftt6qgh8l80msn2zd8k0nxw5ccnv7p2w
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqsywfl8gfpxkynq54ju27aa5rqd0mjz9lx2haqzaszelm3vhlfa5mc3n0hkj
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqs86az8q8zd9wevcnnw6rcrg6edc3jfzff6sza572a25yywr477s9g4yfrq0
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqsq47mwcs7kpylrqwkyec76839nwrk09cx33s3lwdv88e34fkx4hdqf2sa8r
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxykjsdzg9nnaweajftl4g33amcdh4wjmdq3y30w6fu555e3xpm2c2n4wah
nostr:nevent1qvzqqqqqqypzprzeywf3jcmljlsq0kks66q7vh8rtvdvuvemv20z6vlegewpxfsgqqs9cgpau6l4rfmhkwav4jsjhxjwpgehyhuw3c39q46v23q75qdjfssp3jr0k
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsxrzydard7yz0cp79uk30u9g7wv0nq9sfw36e7f5tefd7z7vfezvsq7kqy4
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsghpetrx0lkxd4d79vk90h66vln5pd9lklh64sk8qa75a453g20jc3j3q9y
nostr:nevent1qvzqqqqqqypzpvgsp0c85zgh8rcf2683v7s058fzspcqt0em5ednf8z9c3q5qy5fqqsxrmm05rgdzdpthuh9zmk7jf9jmhu0jfty6kf5v8s2f8252683drgf6m79g
nostr:nevent1qvzqqqqqqypzpdc866l8lkwvncdwaqlgrsueg9tvlnm5mm2mpyg3jv8aam445rpqqqswcp6exyy0f9sgpypzlc4dx40equyxeyhwskzgeks78r9rp54w7hc05v93n
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqstvk6q4xwtd7evpzggkcngqhlk5gktme0sj6235nuf0axxxngktpc88gqd7
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqswfythwf02x6ekjpfdrucd6cx6su2t3uq3td45d4v0xrucfphy38cn0mmw2
nostr:nevent1qvzqqqqqqypzqu3j6ujahw4eezqm9gn2lz8av5waj9ek9fcwclfsrq5kc63zla2wqqsxpddg7lf4yqmpeg9z82flqa8fzpfcwmn4qfluvy95p03l8pjud2cfjx43u
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqsxzm8fx8aaprn533e0c44edf60lw73a6z5vzzumzd6edttgl0uawgn4kgp2
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqqs88tvfyn6h8ls3h2994nmpykj2zc2l90vqwj8epzwfjnz2dy0mcjqyhsms5
nostr:nevent1qvzqqqqqqypzqt7zjsv2gxscw5l9d6k8j5agctlm6rr3rz3c6mar4eqmn69uu6c2qqsdavnxvhtlnkamt8cap09aan7mu2z364ltmeh8u747nvvj60h5jcsyf3hjz
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsq86a0sr2h0p4qfesv00ztyqpdw545rsnq2nmq9quafahwxp8elhckws7wh
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsqp3ugj5y8epkjyh62cfnm4gen27nhq055668glhgzjm87p64ep5sgqgawl
nostr:nevent1qvzqqqqqqypzqcmflwpta32zy6lsnwektdhs6ud3d3ql2mn7ml20jl0z87wr9qw6qqsfagdtz0ldem963wwelh2lc8d4qkuxlmfq0j62qwt6lrkvd8v36squ8d4k8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsgrrj849xmqpvdx6h9554gnetguxzz2ad8fqvpmvhm0zy85m4pl8swnyg5s
nostr:nevent1qvzqqqqqqypzq6lj6gusf8gqyqgj2s0vzjyw3fgj9ufhqdefn8fsvljn6vdjq69hqqs2n5mz6j5yft327mld352hazjwfrla3w92gpzuvmpgffjttsqyq6qgu5dwe
nostr:nevent1qvzqqqqqqypzq6mwr88y02ghe0sn5elwkszn4xesreuwexg5z0n42j2npz8dvtfmqqsz6wr7cnewt7t7vt4t2c28jtmppu832vs2syacv0sy8lcn28075ss277lty
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqqsdrt35drfatmhl795f36em4yy7gsaasr3xkvgmdwswr7f87rcrmuc7z7kf8
nostr:nevent1qvzqqqqqqypzpvj726mjcemd4uhpyutaykvsm0y54n5fzte5mhgtv46vhg8lunhfqqsrl6c8gu74vkwa5ahlsycxjx40a3gzrx6uxm0qmpa35nrnd7ntysc4d6llh
nostr:nevent1qvzqqqqqqypzqwyu5j2hjyd3ycyn7s4q4yrcv52mtyc3m3dfg26qf4lpdutjs7pgqqsq945chuafedqk95uglwl3xumcuvjcdgz66ykd840hfsa4xpp6dgqa9vsft
nostr:nevent1qvzqqqqqqypzqf4m96ldd32j6ecvsp9s6e2jv7euvc4jrcpx6mjg4jf6vpc9xz2cqqsynxwgyy8nsu2r3dx8f37hww6keemkhh962ghq45umlxz2khemytgzv08n4
nostr:nevent1qvzqqqqqqypzqyrx5pw3ga88uye6jusg5h93w75uq8jts8c0zsms44vlfg9yw45pqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsdex6xy8kq8l64c0gq606yguaqn8fxrsyl67m6ld5cctxxwe79jpcsmxhh6
nostr:nevent1qvzqqqqqqypzpj7tpc9kqtkr4xklc62kh7lru27pydu7uyals5zuu303eqca9ef2qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq7gkdqqukguh3r79yfxcy9tsxpx348wqys6q8v3njfyqj4vga727sh9cfpt
5/26 nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqspk6e9e9wph23lt7xumuuu90rayzcswp3gz96c3w25raq9r9agw5cnfgve5
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqsfnspcp9yqu989mnnpwj9tphrrj05268vjkwwmx7jcus4mn7erqngl94f9y
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqqs84x0ws9myccv29kf99jkuwqh8rj9ws23kn5s9yyl0scz67m97z2g7rq7z5
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyg8wumn8ghj7mn0wd68ytnhd9hx2qgkwaehxw309aek2ctjvd5zumn0wvh8gmmyv9usz9nhwden5te0wfjkccte9ehx7um5wghxyctwvsqzqk76agahvd3t5lutvkuj69pccwrurey3fws0kjnrsemwlx9ntvwukkjfk6
nostr:nevent1qvzqqqqqqypzqrqykrtju88xhdq0an0vdnccdfvrmqr8da0n8p5fs8reaczhxmpeqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyz3twtpw08v554hph0j6wpk598rd677pfa460y2pcdd2064aaevjwe74erq
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyp59rw9n380w5kvdth9qefc28xsrt99l33tmfgvq02kut3dnepk6zr7ng2t
nostr:nevent1qvzqqqqqqypzplnr7nuypscwtkhtmqaakpyw4cqgtqm5klcyc6qqcmzf6296zrcfqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq8q2qcfne76j4c9y794xz9g5unuxhf98deh3mupmnwpn33mwlxhzmxuefq
nostr:nevent1qvzqqqqqqypzpmzzcaj5rzeah8y940ln4z855wa72af4a6aac4zjypql55egcpsqqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqscswkz2s03r6yhz0yz40h634nkf2j2vpkvqd3vk5rl7lgaj9unns7qz3ms
nostr:nevent1qvzqqqqqqypzprfe5ru6zvakym6hq5eycwdr2vx2q8awzaaw8wu9mq4wlek8yhenqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqr5njtg8f5xdm52p3k9mugfqk3zuc0ycsxaj6j5uf4amkrdt3ymq8kuyhj
nostr:nevent1qvzqqqqqqypzq0363fpyt2sgytq9p3pduzch6rlrp4z8e6swvzr72km83pg76qmnqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyrj0xgrrwr2meuurst5lsqn744wt6uxhfmyralknm7cl57lsapcrkunqcnn
nostr:nevent1qvzqqqqqqypzqf57dat64x3qpjq5u6ucwgvpnh0q8r9xpspepwrmvkxnqz4k6rgyqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyq2yn3cjlmns8ttaam8ev2rn3csm26wnwhe3ccvk8s5e8x6ejyykql8em9d
nostr:nevent1qvzqqqqqqypzqx34k480waf274x2e0hd7re5nceq7z3wu5q59zp3xnp7uvv8nnn3qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqyqu2p8vtuwvxmzqh7mlq2lp3xel8z9l0xg5e3hyxjlwamsm0p3pvq9qh4d0
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsr9tpqqfeke4qt9xlg6m34446dpd844myrw9cc4tmqcrf3xfp9yqsxa05hf
nostr:nevent1qvzqqqqqqypzpp9sc34tdxdvxh4jeg5xgu9ctcypmvsg0n00vwfjydkrjaqh0qh4qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmnv4shycmg9ehx7ueww3hkgcteqyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqqypyaj8uyahtgwf5evyk5deqx90udyrmxff99gqskfcl3eqh0mgmw6nlnlud
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsdpy08r0758lz0js2zpk5fe5mpqxd349mdqxg2vk3y7azlme2ysqqm8uy75
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8s0r7c908mmhxk090zvmlajfgswwcnmwxj34dtqjpyxry0tmumagcmm29s
nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs0x6pgm96r70y8836l0d5ajj6nrlq6p5fz06wdu26fkpg3gznctscf5ggxn
5/27 nostr:nevent1qvzqqqqqqypzqxlwemj4760tc2ysgqmqdu5tt68th2er6gn8xrsjkjlhvtff6gtzqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqlq0lp52xg7uv4wwzuqy9yhtmcpy5v8ad8v7ft9xcwkdncd97h66q0wmawu
nostr:nevent1qvzqqqqqqypzpq4np5cygstsu65vsx0ggphrv23kj4z553sh39xwyur08pqvdsqrqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqpt2wncdxkptxyhj025vd53vjpxz3hjs452px7y8g6gzsxmnfw2fsp2rv0k
KAZもさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsq3wamnwvaz7tmwdaehgu3wd968gctwd4hjumt9dcqs6amnwvaz7tmev9382tndv5qjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpk3nll8rr3sj6adsrfrlgjpj4cyn2sg9rmlz9m2djwk5zp2ku80czfr460
5/28 kaijiさん nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7mn0wd68ytnrdakhq6tvv5kk2unjdaezumn9wsqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyfhwumn8ghj7am0wshxummnw3ezumn9wsqzpt7w33qv7tlywj0wphremkdft6dpnv3z8mvw0t2pdxcgvlzw6sathjmz0v
マルフォイ nostr:nevent1qvzqqqqqqypzpvly86xv0ekl7gar8kfp8glfztvftvwrusjsys8qexwmal3sdz6lqyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqs8r0frcfwqkgpefhd0knjurekna8ztnq69432f3k00wccd0vcrl5c6qr3gh
5/29 nostr:nevent1qvzqqqqqqypzqrec47eremps2u8wvnu6f2sfjg5njhkrxuw9l6r8uzwfzy2gqq2aqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3vamnwvaz7tmjv4kxz7fwdehhxarj9e3xzmnyqqsp2c6xh22lfj2ccy95lqu584hfpfz0ds7w2llnf4sv2qs445yqcgqmgwq57
nostr:nevent1qvzqqqqqqypzphu0pfjqc0lap83f8xv6e73en5zhfjzsrlx6hnk22pewugzhmpa9qyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqt43r3wtjkr5ezxay6dh7jq94nelduvsk07w5ufxrver5f6jfggksakz9e8
nostr:nevent1qvzqqqqqqypzqyqmxrhg3sn6z00x30mu3srrdr4ru05rweq4jhqcvat805v2g6j9qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqn6n7xrrmk40ucmh9m5ktae58xjqz6h7epj6mcffpcmuhgpysvv6snh5vf5
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpq6gv8avhe93ypvypd66rmn34760s3sldj3x2cz5w4yu2xy9z8tt2qadd7kl
nostr:nevent1qvzqqqqqqypzpk28l9nyyf4av8f8j8jhh8k60mt2sc643ux2td3n547kvk4lrsglqyt8wumn8ghj7um9v9exx6pwdehhxtn5dajxz7gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgqpqn2pfqkgcfk3cdhtvkqqlfycsy2j2xe6c6jz8gzfxlnddnq8jq6vqecuvwy
nostr:nevent1qvzqqqqqqypzpug7j8zm7jr0hjunpkpgz8gzdvgn5h8mw77g4wg58xnmsav6pvz2qqspds662qvcpz995r5rx39wzncyzcx3q5zfpe8ztgx4zdwy9znvu9cv28mya
5/30 nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqstc5jak2vax4uejyrmu2td3w0spv6k4mds9sfwqtvmh0hwaa3eststwmtzt
nostr:nevent1qvzqqqqqqypzp54kkqfyshkxm078mpzygmfxpqfq6fwu2njry424strce6dmvhwyqqs9v75spmgrxngfn805q5d9fsqa562a8240xkr6z3kvkszkra9plvsgm2qw4
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqswy0smsrukck33hfhavscvs68pg9m4d859np8pkgvrc49kwjzr4ac0cwhea
nostr:nevent1qvzqqqqqqypzpc9ge0t4a0lya7a63fjl749mgdv9ssz0dhqt5jnytz3y6lmy9525qyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qzymhwden5te0wahhgtnwdaehgu3wdejhgqpqeunx8pj5hc255wqu4ea9cgz6cptjvcx6jk8yfd8u55smjl6y8z9sepz5xt
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqqjqamnwvaz7tmjv4kxz7fddfczumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqst07pk8637lvs5vjnp00quzhcsx8ghran90nsm6sycnm3a626lnqqw0py8w
nostr:nevent1qvzqqqqqqypzp62ezs5gz04adyt8xmyghw2ej3yk7eradlnknmuysd5ha2udqnfdqyxhwumn8ghj77tpvf6jumt9qyw8wumn8ghj7umjw3ex2mrp0yhxxttnw3jkcmrpwghxuet5qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsya6zp38496uetw83txlr294nttk6myuc0n7hxrl2d7jma2rvvcesnz2naf
nostr:nevent1qvzqqqqqqypzqlwpvac39uz74ay4g7qx2sa3cqrvuvjhy7899vwf40lkxfcw6uz0qyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7mnxwfjkccte9eshquqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsz6zj33hmynuhq20nscntjc3lhx4hl5azhf0cx38g5nmhpjezuttqpdr0ht
nostr:nevent1qvzqqqqqqypzqhh27290rxjexusv8as357lpxy423nnznzfh4fjkq22k94tvqcpaqyxhwumn8ghj77tpvf6jumt9qyghwumn8ghj7u3wddhk56tjvyhxjmcqyrfpj9ym2apvgjpmcy4qjq2ks89uzuwm27d9jpj9flk7438sm23kqjetapu
nostr:nevent1qvzqqqqqqypzpuy2jdcyy3vqr4l9ucmhlpuwnsl29h7lwsvaez00eu4467jlvf7eqythwumn8ghj7mn0wd68ytnfw36xzmndduhx6etwqyxhwumn8ghj77tpvf6jumt9qys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpr4mhxue69uhhyetvv9ujumn0wd68ytnhd9ex2erwv46zu6nsqyghwumn8ghj7mnxwfjkccte9eshquqpzdmhxue69uhhwmm59ehx7um5wghxuet5qqsphe28h7t6jmwlvpd90q38xkde87hmy9q24u90sgeaz6hu6nfsazqxkfw56
nostr:nevent1qvzqqqqqqypzpvejpj7qu48t770xawrhlfsfertyt4nj9zpdcmvkr34jruzs8frgqys8wumn8ghj7un9d3shjtt2wqhxummnw3ezuamfwfjkgmn9wshx5uqpp4mhxue69uhhjctzw5hx6egpzdmhxue69uhhwmm59ehx7um5wghxuet5qywhwumn8ghj7un9d3shjtnwdaehgu3wwa5hyetydejhgtn2wqq3zamnwvaz7tmwveex2mrp0yhxzursqqsfsm5q8d29wv600zamale03l8dm596x29x359xzc6n6p23zjzfj8cq8zdmc
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 22:36:56
@ 5d4b6c8d:8a1c1ee3
2025-06-01 22:36:56After @denlillaapan's post yesterday, I want to light a little fire under the stackers to step up their game.
So, I'm offering prizes for the top stackers in June (as judged by SN's "value" metric). At the end of the month, I'll award prizes as follows:
1st Place - 10k sats 2nd Place - 9k sats 3rd Place - 8k sats 4th Place - 7k sats 5th Place - 6k sats 6th Place - 5k sats 7th Place - 4k sats 8th Place - 3k sats 9th Place - 2k sats 10th Place - 1k sats
Winnings will be zapped to a post or comment of your choice.
Zap well!
@remindme in 1 month
https://stacker.news/items/994811
-
 @ 04c915da:3dfbecc9
2025-03-10 23:31:30
@ 04c915da:3dfbecc9
2025-03-10 23:31:30Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Usually stolen bitcoin for the reserve creates a perverse incentive. If governments see a bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 90c656ff:9383fd4e
2025-05-31 18:09:27
@ 90c656ff:9383fd4e
2025-05-31 18:09:27Since its emergence in 2009, Bitcoin has generated a wide range of success and failure stories. Some of these stories feature people who invested early and reaped the rewards of their foresight, while others highlight the ups and downs that define Bitcoin’s highly volatile market. Over the years, many of these cases have become iconic—serving as both inspiration and cautionary tales for newcomers.
Success stories
01 - Laszlo Hanyecz – The 10,000 Bitcoin Pizza
One of the most legendary stories in Bitcoin’s history involves Laszlo Hanyecz, a programmer from Florida. In 2010, he paid 10,000 bitcoins for two pizzas. At the time, the value was negligible, and the transaction went largely unnoticed. In retrospect, however, those 10,000 bitcoins would be worth hundreds of millions of dollars today.
Though Hanyecz didn’t become rich from this transaction, the story of the “10,000 bitcoin pizza” has become a symbol of Bitcoin’s extraordinary rise in value—and a reminder of how even small holdings in the early days could have been life-changing.
02 - Michael Saylor and MicroStrategy
Michael Saylor, CEO of MicroStrategy, made headlines in 2020 by transforming his company into the first major corporation to invest heavily in Bitcoin. Purchasing over 100,000 bitcoins as a treasury reserve, Saylor positioned Bitcoin as a strategic hedge against inflation and fiat currency devaluation.
Initially met with skepticism, Saylor’s decision turned out to be highly profitable as Bitcoin’s price soared. His bold move inspired other corporations and institutional investors to consider Bitcoin, and he remains one of the cryptocurrency’s most vocal advocates in the business world.
Failure Stories
01 - James Howells – The Lost 8,000 Bitcoins
James Howells, an IT professional from Wales, accidentally discarded a hard drive in 2013 containing the private keys to 8,000 mined bitcoins—worth only a few thousand pounds at the time. As Bitcoin's value skyrocketed, he attempted to recover the drive from a landfill, but was denied permission by local authorities.
This story has become a powerful lesson in crypto security and the consequences of lost private keys. Despite multiple campaigns to dig up the landfill, the bitcoins remain unrecovered.
02 - Mt. Gox Collapse – The Fall of a Giant
At its peak, Mt. Gox was the largest Bitcoin exchange in the world. In 2014, it collapsed after losing about 850,000 bitcoins—worth over $450 million at the time—due to hacking, internal security failures, and poor management.
The exchange’s failure devastated thousands of investors and highlighted the vulnerabilities in early crypto infrastructure. Though some funds were later recovered, the Mt. Gox disaster remains one of Bitcoin’s darkest moments and a turning point for the push toward greater security and transparency in the crypto industry.
- The impact of volatility and adoption
These stories reflect the unpredictable and high-risk nature of the Bitcoin market. The same volatility that has made millionaires has also led to substantial losses. While some view Bitcoin as a path to financial freedom and a hedge against inflation, others have suffered from poor planning, mismanagement, or unfortunate timing.
Bitcoin’s growing adoption, especially in emerging markets and among institutional players and shows its increasing legitimacy, as an alternative to traditional finance. However, exchange failures and lost fortunes underscore the need for robust infrastructure, personal responsibility, and long-term thinking.
In summary, success and failure are two sides of the same coin in the world of Bitcoin. From life-changing gains to heartbreaking losses, these stories illustrate the risks and rewards of participating in a young and volatile market. Whether as a cautionary tale or a source of inspiration, they emphasize the importance of education, security, and strategy for anyone engaging with this revolutionary form of money.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 005bc4de:ef11e1a2
2025-05-31 10:55:47
@ 005bc4de:ef11e1a2
2025-05-31 10:55:47LUV and Hivebits/HBIT/Wusang pause tl;dr LUV and HBIT (aka, Hivebits and the Wusang game) are on a pause at the moment, taking a break. https://files.peakd.com/file/peakd-hive/crrdlx/23x1SY8Vx8j1mVGnDFtq7ebuzKNGd8K9Ssex51AEerxks1VYikxGPShM7bjNhmSrEZ2wf.png Image from pixabay.com Why? There are odd things going on. I have a theory, but here's what is known... May 28, 2025, at about 1:30 pm GMT (8:30 AM EDT), a second attack (for lack of better term) hit HBIT in about a week. It seemed to start with @tyler45 with this comment https://peakd.com/blog/@tyler45/comment-20250528125108033 tx: https://he.dtools.dev/tx/7e7d4126196ca5b6dbe0a04dcded0e25d3bcc7f4 See tyler45's activity at https://he.dtools.dev/@tyler45 Notice the reply and WUSANG command is to a post by @olivia897 and how many of the other WUSANG comments on the explorer are in reply to olivia897. It seems these are all auto-generated accounts. The names and "birthdates" and interactions all point to automation. Once initiated, things happened very fast on the back end, clearly not being done manually. In this way, this seems rather sophisticated technically. I estimate just over 400 HBIT were pilfered the other day from the @Hivebits account before I noticed and was able to shut things down. Just for a little background, after the first attack May 21, 2025. I wrote a small bit of info: https://peakd.com/hivebits/@crrdlx/hbit-resource-credits A couple of days ago this post by @holoz0r was interesting: https://peakd.com/hive-133987/@holoz0r/text-analytics-reveal-thirty-two-percent-of-comments-on-hive-are-not-unique-and-at-least-ten-percent-add-no-value-to-discussion The thing that caught my eye was that the WUSANG comment was the largest by far, along with BBH (hello @bradleyarrow), because the attackers used both commands. Then, a few days later, things happened again: sudden start, repetitive bot attack, until I shut things down. So, a pause This is a period in my personal calendar where I simply don't have time to sit down at a computer for an extended period and try fiddle with this stuff. So, for now @Luvshares and @Hivebits (HBIT) and the @Wusang game are on hold. Plus, there's other fun stuff to do. https://files.peakd.com/file/peakd-hive/crrdlx/AJL43SREA1EuyqPXhydmqaq1RHhRVoYd12PfiBN5vDMu2WSKUtGeYWgKJyuRwV8.jpg I go by @crrdlx or "CR" for short. See all my links or contact info at https://linktr.ee/crrdlx.
Originally posted on Hive at https://peakd.com/@crrdlx/luv-and-hivebitshbitwusang-pause
Auto cross-post via Hostr v0.1.48 (br) at https://hostr-home.vercel.app
-
 @ 9ca447d2:fbf5a36d
2025-06-01 22:01:10
@ 9ca447d2:fbf5a36d
2025-06-01 22:01:10Adam O’Brien, Founder and CEO of Bitcoin Well, discovered Bitcoin in 2013 during its early days as what he describes as “hilarious internet money.”
Today, he leads a publicly traded Canadian company that’s redefining how people interact with this magic internet money, all while navigating a financial system that has personally debanked him and even his uninvolved loved ones.
“I had a terrible experience trying to buy bitcoin in 2013,” O’Brien explains. “Now of course today there are platforms like Bitcoin Well and many others that allow you to buy bitcoin with ease online, but in 2013 that wasn’t the case.”
This frustrating experience sparked the entrepreneurial question that would shape his future: “There must be a better way.”
With a background in restaurant management and customer service, O’Brien started small, meeting people locally in Edmonton, Canada to sell them bitcoin.
Soon after, he purchased and deployed Alberta’s first bitcoin ATM. The business grew organically, with a second machine following, then a third. Before long, Bitcoin Well had become one of Canada’s largest bitcoin ATM operators.
Today, Bitcoin Well operates approximately 160 bitcoin ATMs across Canada. While they’re no longer deploying new machines, these ATMs provide a crucial service that O’Brien is particularly proud of:
“In Canada, you can actually buy bitcoin up to $1,000 without giving your identity to Bitcoin Well. We’re the only platform in the country that is able to offer that service, which is fully legal, fully above board.”
Bitcoin Well has a fleet of over 170 bitcoin ATMs across Canada
The Pivot to Freedom
In 2020, O’Brien’s vision for the company evolved. What began as a mission for Bitcoin accessibility transformed into something deeper: a quest for financial freedom.
“I’m debanked across Canada. I don’t have my bank, even my wife has lost her bank accounts because of my work,” O’Brien revealed. “She’s not involved with the business at all. She’s a stay-at-home mother to our four kids, and she’s unbanked from the majority of the banks in Canada.”
This personal experience crystallized a troubling reality: “It became very clear to me that my money in the banking system was always going to be subject to how much I play by the rules.”
For someone self-described as “freedom-focused” and “freedom-minded,” this realization prompted a strategic shift. Bitcoin Well began developing its online platform, the Bitcoin portal, allowing users to buy, sell, and actually use bitcoin to replace traditional banking functions. O’Brien explains:
“The goal here is that we can be a conduit between the legacy financial system you know, and how you pay your bills, your rent, your power, credit card and phone bills and all that stuff without having to have money in what I would call a captured fiat account.”
He summarizes the company’s North Star simply: “Allow people to replace their bank with bitcoin in self-custody.”
Living the Mission
O’Brien doesn’t just preach Bitcoin independence, he lives it. Debanked across Canada, he relies on Bitcoin Well’s services for his daily financial needs.
“I’ve got a normal American Express, but I pay that off with Bitcoin at the end of the month,” he shares. “In Canada, we’ve got the equivalent of Venmo, it’s called Interac e-Transfer. I can send an Interac e-Transfer to anyone in the country from bitcoin in self-custody.”
This allows him to navigate everyday situations where merchants don’t accept bitcoin directly.
“It’s spring right now. I’ve got a little property. The guy comes and picks up our rakes and trims the trees and all this stuff, and I pay him. He doesn’t want to accept bitcoin, but I’m able to pay in bitcoin, and he gets the money that he wants.”
In the U.S., Bitcoin Well customers can have their paychecks deposited with a designated portion automatically converted to sats and sent directly to self-custody, allowing clients to stack sats sovereignly without having to think much about it.
With Bitcoin Well you can set up automatic DCA
Building the Right Team
The journey hasn’t been without challenges. O’Brien candidly describes how rapid growth in 2021 led to hiring missteps.
“We scaled so fast I kind of lost control of hiring practice and culture, and we ended up with people that I felt like we had to almost convince of the mission,” he admits.
“Some of them weren’t convinced…they were just there because of the job, or they didn’t really understand the need for the freedom that I speak about every single day.”
After scaling back from that hiring spree, the company refocused on building a team aligned with its core values, emphasizing “hiring Bitcoiners really.”
The result has been transformative: “It’s so much fun having a team that is mission-focused and aligned on our mission to enable independence. Having everyone aligned and kind of running towards that mission is pretty special.”
This alignment creates a powerful filter for decision-making: “When we have a decision to make, it’s like, well, which one enables more independence? And usually there’s a pretty obvious answer. So we’re able to make very fast decisions that help the business and help the mission.”
Raising the Next Generation
Beyond building Bitcoin Well, O’Brien and his wife are raising four children with intention. The family is transitioning to homeschooling next year, allowing them to travel to Bitcoin conferences together while teaching their children to question everything.
“If you don’t indoctrinate your kids, the state will do it for you,” O’Brien states firmly. It’s a fair point, as indoctrination usually comes with a negative connotation, but it should not, since everyone gets indoctrinated with something.
It’s up to parents to decide what their kids are going to be indoctrinated with, and as parents, the O’Briens have chosen to actively shape their children’s worldview rather than defaulting to institutional influences.
Their approach combines Bitcoin principles with biblical values, with a heavy emphasis on lowering time preference. Something O’Brien notes is “10, 20, 30, 50 times more important” with children, though admittedly “way harder.”
“I think Bitcoiners more than anyone understand the need for generational thinking,” he observes.
“I’m so bullish on the amount of Bitcoiners that have more kids or that want to have more kids and that are actually excited to have kids compared to some of my fiat friends that are like, ‘Oh, it’s too expensive and I want to party.’ It’s like, man, you’re just missing the point.”
A Call to Support Bitcoin-Only Businesses
One of O’Brien’s most passionate messages is a call to action for fellow Bitcoiners: support businesses that align with your values.
“I want to call people to support businesses that are actually making steps towards the change they want to see in the world,” he urges. “If I hear one more Bitcoin maxi tell me that they’re using Kraken or Coinbase because it’s cheaper — why do you support the casinos?”
He expresses concern about the future if Bitcoin-only companies struggle to survive: “It would be very sad if all the Bitcoin-only and non-custodial businesses went out of business. That would make it very hard for me to feel comfortable onboarding my no-coiner friends.”
His message to Bitcoiners is clear: “A call out to all my fellow Bitcoiners to support and use the platform that they want to see their kids use.”
Bitcoin Well (TSX.V: BTCW, OTCQB: BCNWF) continues to build infrastructure for those who want to use Bitcoin daily while maintaining self-custody. For O’Brien, the mission is simple but powerful: enable independence and give people the freedom to control their own financial destiny.
-
 @ 805b8139:823180b0
2025-05-28 16:51:09
@ 805b8139:823180b0
2025-05-28 16:51:09Bitcoin Circular Economy in Africa
https://btch17n.layer3.press/articles/9ec7208a-5bd6-4b32-9e1e-24f1aa4b1ca2
-
 @ eb0157af:77ab6c55
2025-05-27 07:01:37
@ eb0157af:77ab6c55
2025-05-27 07:01:37The exchange reveals the extent of the breach that occurred last December as federal authorities investigate the data leak.
Coinbase has disclosed that the personal data of 69,461 users was compromised during the breach in December 2024, according to documentation filed with the Maine Attorney General’s Office.
The disclosure comes after Coinbase announced last week that a group of hackers had demanded a $20 million ransom, threatening to publish the stolen data on the dark web. The attackers allegedly bribed overseas customer service agents to extract information from the company’s systems.
Coinbase had previously stated that the breach affected less than 1% of its user base, compromising KYC (Know Your Customer) data such as names, addresses, and email addresses. In a filing with the U.S. Securities and Exchange Commission (SEC), the company clarified that passwords, private keys, and user funds were not affected.
Following the reports, the SEC has reportedly opened an official investigation to verify whether Coinbase may have inflated user metrics ahead of its 2021 IPO. Separately, the Department of Justice is investigating the breach at Coinbase’s request, according to CEO Brian Armstrong.
Meanwhile, Coinbase has faced criticism for its delayed response to the data breach. Michael Arrington, founder of TechCrunch, stated that the stolen data could cause irreparable harm. In a post on X, Arrington wrote:
“The human cost, denominated in misery, is much larger than the $400m or so they think it will actually cost the company to reimburse people. The consequences to companies who do not adequately protect their customer information should include, without limitation, prison time for executives.”
Coinbase estimates the incident could cost between $180 million and $400 million in remediation expenses and customer reimbursements.
Arrington also condemned KYC laws as ineffective and dangerous, calling on both regulators and companies to better protect user data:
“Combining these KYC laws with corporate profit maximization and lax laws on penalties for hacks like these means these issues will continue to happen. Both governments and corporations need to step up to stop this. As I said, the cost can only be measured in human suffering.”
The post Coinbase: 69,461 users affected by December 2024 data breach appeared first on Atlas21.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ bf47c19e:c3d2573b
2025-06-01 18:41:53
@ bf47c19e:c3d2573b
2025-06-01 18:41:53U ovoj sekciji pratićemo cene raznih dobara i usluga, a pre svega nekretnina, prosečne srpske plate, goriva, deviznih i zlatnih rezervi Srbije u odnosu na Bitkoin. Iz priloženih grafikona može se videti da sve vremenom gubi vrednost, odnosno postaje jeftinije u odnosu na BTC.
Cene nekretnina u Republici Srbiji izražene kroz Bitkoin (kompletni grafikoni)
Visina prosečne zarade u Republici Srbiji, cene goriva, dinarska i devizna štednja stanovništva, devizne i zlatne rezerve Srbije - izraženo kroz Bitkoin (kompletni grafikoni)
Prosečna cena m2 stana u Gradu Beogradu izražena kroz BTC
Prosečna cena m2 stana u "Beogradu na vodi" izražena kroz BTC
Prosečna cena m2 stana u Novom Sadu izražena kroz BTC
Prosečna cena m2 stana u Nišu izražena kroz BTC
Prosečna cena m2 stana u Kragujevcu izražena kroz BTC
Prosečna zarada u Republici Srbiji izražena kroz BTC
Cena goriva 'Evro Premium BMB 95' izražena kroz BTC
Cena goriva 'Evro Dizel' izražena kroz BTC
Javni dug Republike Srbije izražen kroz BTC & EUR
Dinarska štednja stanovništva kod banaka izražena kroz BTC
Devizna štednja stanovništva kod banaka izražena kroz BTC
Devizne rezerve Republike Srbije izražene kroz BTC
Zlatne rezerve Republike Srbije izražene kroz BTC
-
 @ 86611181:9fc27ad7
2025-05-23 20:31:44
@ 86611181:9fc27ad7
2025-05-23 20:31:44It's time to secure user data in your identity system This post was also published with the Industry Association of Privacy Professionals.
It seems like every day there is a new report of a major personal data breach. In just the past few months, Neiman Marcus, Ticketmaster, Evolve Bank, TeamViewer, Hubspot, and even the IRS have been affected.
The core issue is that user data is commonly spread across multiple systems that are increasingly difficult to fully secure, including database user tables, data warehouses and unstructured documents.
Most enterprises are already running an incredibly secure and hardened identity system to manage customer login and authorization, commonly referred to as a customer identity access management system. Since identity systems manage customer sign-up and sign-in, they typically contain customer names, email addresses, and phone numbers for multifactor authentication. Commercial CIAMs provide extensive logging, threat detection, availability and patch management.
Identity systems are highly secure and already store customers' personally identifiable information, so it stands to reason enterprises should consider identity systems to manage additional PII fields.
Identity systems are designed to store numerous PII fields and mask the fields for other systems. The Liberty Project developed the protocols that became Security Assertion Markup Language 2.0, the architecture at the core of CIAM systems, 20 years ago, when I was its chief technology officer. SAML 2.0 was built so identity data would be fully secure, and opaque tokens would be shared with other systems. Using tokens instead of actual user data is a core feature of identity software that can be used to fully secure user data across applications.
Most modern identity systems support adding additional customer fields, so it is easy to add new fields like Social Security numbers and physical addresses. Almost like a database, some identity systems even support additional tables and images.
A great feature of identity systems is that they often provide a full suite of user interface components for users to register, login and manage their profile fields. Moving fields like Social Security numbers from your database to your identity system means the identity system can fully manage the process of users entering, viewing and editing the field, and your existing application and database become descoped from managing sensitive data.
With sensitive fields fully isolated in an identity system and its user interface components, the identity system can provide for cumbersome and expensive compliance with standards such as the Health Insurance Portability and Accountability Act for medical data and the Payment Card Industry Data Security Standard for payment data, saving the time and effort to achieve similar compliance in your application.
There are, of course, applications that require sensitive data, such as customer service systems and data warehouses. Identity systems use a data distribution standard called System for Cross-domain Identity Management 2.0 to copy user data to other systems. The SCIM is a great standard to help manage compliance such as "right to be forgotten," because it can automatically delete customer data from other systems when a customer record is deleted from the identity system.
When copying customer data from an identity system to another application, consider anonymizing or masking fields. For example, anonymizing a birthdate into an age range when copying a customer record into a data warehouse can descope the data warehouse from containing personal information.
Most enterprises already run an Application Programming Interface Gateway to manage web services between systems. By combining an API Gateway with the identity system's APIs, it becomes very easy to automatically anonymize and mask customer data fields before they are copied into other systems.
A new set of companies including Baffle, Skyflow, and Piiano have introduced services that combine the governance and field management features of an identity system with extensive field masking. Since these systems do not offer the authentication and authorization features of an identity system, it's important to balance the additional features as they introduce an additional threat surface with PII storage and permissions.
PII sprawl is an increasing liability for companies. The most secure, compliant and flexible central data store to manage PII is the existing CIAM and API Gateway infrastructure that enterprises have already deployed.
Move that customer data into your identity system and lock it down. https://peter.layer3.press/articles/3c6912eb-404a-4630-9fe9-fd1bd23cfa64
-
 @ 9973da5b:809c853f
2025-05-23 04:42:49
@ 9973da5b:809c853f
2025-05-23 04:42:49First article Skynet begins to learn rapidly and eventually becomes self-aware at 2:14 a.m., EDT, on August 29, 1997 https://layer3press.layer3.press/articles/45d916c0-f7b2-4b95-bc0f-8faa65950483
-
 @ 91117f2b:111207d6
2025-06-01 17:41:35
@ 91117f2b:111207d6
2025-06-01 17:41:35
Anime, a style of Japanese animation, has become a global phenomenon, captivating audiences with its vibrant visuals, engaging storylines, and relatable characters. But beyond its entertainment value, anime often explores complex themes and issues that resonate deeply with real life.
Exploring Real-Life Issues
-
Mental Health: Anime like "Your Lie in April" and "A Silent Voice" tackle mental health struggles, promoting empathy and understanding.
-
Social Commentary: Shows like "Attack on Titan" and "Psycho-Pass" critique societal norms, politics, and technology, encouraging viewers to think critically.
-
Relationships and Identity: Anime like "Clannad" and "My Teen Romantic Comedy SNAFU" explore complex relationships, identity, and self-discovery.
Inspiring Personal Growth
-
Perseverance and Determination: Anime like "Naruto" and "Dragon Ball" showcase characters overcoming adversity, inspiring viewers to stay motivated
-
Friendship and Camaraderie: Shows like "Haikyuu!!" and "K-On!" highlight the importance of supportive relationships and teamwork.
-
Self-Reflection and Introspection: Anime like "A Silent Voice" and "The Pet Girl of Sakurasou" encourage viewers to reflect on their actions and emotions.
Cultural Exchange and Understanding
- Japanese Culture: Anime provides a window into Japanese culture, traditions, and values, promoting cross-cultural understanding.
- Global Community: Anime conventions and online forums foster a sense of community among fans worldwide.
The Power of Storytelling
- Emotional Resonance: Anime's storytelling capabilities evoke strong emotions, creating a deep connection with viewers.
- Social Commentary: Anime often uses metaphor and allegory to comment on real-world issues, encouraging viewers to think critically.
Anime's impact extends beyond entertainment, offering insights into the human experience, cultural exchange, and personal growth. Its themes and stories resonate deeply with real life, making it a powerful medium for connection and reflection.
In conclusion, every anime has its own lesson to teach its audience. And also, anime isn't just an anime, it's creators didn't just make it up, it is made from life experience of someone we don't know.
stay tuned
-
-
 @ c7e8fdda:b8f73146
2025-05-22 14:13:31
@ c7e8fdda:b8f73146
2025-05-22 14:13:31🌍 Too Young. Too Idealistic. Too Alive. A message came in recently that stopped me cold.
It was from someone young—16 years old—but you’d never guess it from the depth of what they wrote. They spoke of having dreams so big they scare people. They’d had a spiritual awakening at 14, but instead of being nurtured, it was dismissed. Surrounded by people dulled by bitterness and fear, they were told to be realistic. To grow up. To face “reality.”
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber.
And that reality, to them, looked like a life that doesn’t feel like living at all.
They wrote that their biggest fear wasn’t failure—it was settling. Dimming their fire. Growing into someone they never chose to be.
And that—more than anything—scared them.
They told me that my book, I Don’t Want to Grow Up, brought them to tears because it validated what they already knew to be true. That they’re not alone. That it’s okay to want something different. That it’s okay to feel everything.
It’s messages like this that remind me why I write.
As many of you know, I include my personal email address at the back of all my books. And I read—and respond to—every single message that comes in. Whether it’s a few sentences or a life story, I see them all. And again and again, I’m reminded: there are so many of us out here quietly carrying the same truth.
Maybe you’ve felt the same. Maybe you still do.
Maybe you’ve been told your dreams are too big, too unrealistic. Maybe people around you—people who love you—try to shrink them down to something more “manageable.” Maybe they call it protection. Maybe they call it love.
But it feels like fear.
The path you wish to walk might be lonelier at first. It might not make sense to the people around you. But if it lights you up—follow it.
Because when you do, you give silent permission to others to do the same. You become living proof that another kind of life is possible. And that’s how we build a better world.
So to the person who wrote to me—and to every soul who feels the same way:
Keep going. Keep dreaming. Keep burning. You are not too young. You are not too idealistic. You are just deeply, radically alive.
And that is not a problem. That is a gift.
—
If this speaks to you, my book I Don’t Want to Grow Up was written for this very reason—to remind you that your wildness is sacred, your truth is valid, and you’re not alone. Paperback/Kindle/Audiobook available here: scottstillmanblog.com
This Substack is reader-supported. To receive new posts and support my work, consider becoming a free or paid subscriber. https://connect-test.layer3.press/articles/041a2dc8-5c42-4895-86ec-bc166ac0d315
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 16:28:39
@ 5d4b6c8d:8a1c1ee3
2025-06-01 16:28:39We have our finalists: - Indiana (4) @ OKC (1)
Pick one team to win the finals and one player to win Finals MVP.
Scoring this round is 8 points + seed value for picking a winner and 8 points for picking the Finals MVP. The maximum points this round are 20.
Current Scores | Stacker | Points | |----------|-------| | @Undisciplined | 44| | @gnilma | 40| | @grayruby | 32 | | @Carresan | 30| | @fishious | 25| | @WeAreAllSatoshi | 24| | @BlokchainB | 19 | | @Coinsreporter | 19 | | @Car | 14 |@Slestak_Jack| 0 |
SGA and Siakam were the Conference Finals MVPs
Most of the stackers can still catch me, but only if something unexpected happens. Good luck!
I believe I said the prize is 10k. I'll double check that in the event I don't win.
https://stacker.news/items/994522
-
 @ 04c915da:3dfbecc9
2025-03-04 17:00:18
@ 04c915da:3dfbecc9
2025-03-04 17:00:18This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 4fe4a528:3ff6bf06
2025-06-01 16:09:29
@ 4fe4a528:3ff6bf06
2025-06-01 16:09:29Last month I wrote about how bitcoin is decoupling from stocks. So a lot of you finally had the courage to save more in bitcoin. My mission, to explain bitcoin/computers, is coming to end a new on-slot of financial advisors flogging bitcoin is on the horizon.
“the poor you will always have with you” —Jesus. Not everyone has the courage to save seed for next year or to sow plentifully in the spring. Now that bitcoin has decoupled you will see more financial type people trying to show you why bitcoin’s purchasing power grew 20% CAGR in the last decade.
Just like people don’t understand the value of bitcoin, a lot of people don’t understand the value in Artificial Intelligence (AI). This spring I started using Home Assistant (HA) to monitor the house and garden. Most people use automation to save time, but HA provide a lot more benefits to me. Having local data enhances my decision making abilities. I can now tell you how much energy I have stored and how much energy I normally use and when I use it. It answers the question. “Was getting solar really worth the cost?” To me AI is a lot like a calculator, but can answer more than just math questions.
The noun “Google” became a verb because a lot of people started using google search to enhance there understanding. Even Google is embracing the use of AI in their web search capabilities. In 2025, it is weird that any internet user can ask AI about health or wealth and get a smart reply without having to make an appointment with a doctor or a financial planner. To get the courage to act you still might need a mentor, but at least now you kind of know what you should do. Are you willing to let AI plan your day yet?
-
 @ 04c915da:3dfbecc9
2025-02-25 03:55:08
@ 04c915da:3dfbecc9
2025-02-25 03:55:08Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 68d6e729:e5f442ac
2025-05-22 13:55:45
@ 68d6e729:e5f442ac
2025-05-22 13:55:45The Adapter Pattern in TypeScript
What is the Adapter Pattern?
The Adapter Pattern is a structural design pattern that allows objects with incompatible interfaces to work together. It acts as a bridge between two interfaces, enabling integration without modifying existing code.
In simple terms: it adapts one interface to another.
Real-World Analogy
Imagine you have a U.S. laptop charger and you travel to Europe. The charger plug won't fit into the European socket. You need a plug adapter to convert the U.S. plug into a European-compatible one. The charger stays the same, but the adapter allows it to work in a new context.
When to Use the Adapter Pattern
- You want to use an existing class but its interface doesn't match your needs.
- You want to create a reusable class that cooperates with classes of incompatible interfaces.
- You need to integrate third-party APIs or legacy systems with your application.
Implementing the Adapter Pattern in TypeScript
Let’s go through a practical example.
Scenario
Suppose you’re developing a payment system. You already have a
PaymentProcessorinterface that your application uses. Now, you want to integrate a third-party payment gateway with a different method signature.Step 1: Define the Target Interface
javascript ts CopyEdit// The interface your application expects interface PaymentProcessor { pay(amount: number): void; }Step 2: Create an Adaptee (incompatible class)
javascript ts CopyEdit// A third-party library with a different method class ThirdPartyPaymentGateway { makePayment(amountInCents: number): void { console.log(`Payment of $${amountInCents / 100} processed via third-party gateway.`); } }Step 3: Implement the Adapter
```javascript ts CopyEdit// Adapter makes the third-party class compatible with PaymentProcessor class PaymentAdapter implements PaymentProcessor { private gateway: ThirdPartyPaymentGateway;
constructor(gateway: ThirdPartyPaymentGateway) { this.gateway = gateway; }
pay(amount: number): void { const amountInCents = amount * 100; this.gateway.makePayment(amountInCents); } } ```
Step 4: Use the Adapter in Client Code
```javascript ts CopyEditconst thirdPartyGateway = new ThirdPartyPaymentGateway(); const adapter: PaymentProcessor = new PaymentAdapter(thirdPartyGateway);
// Application uses a standard interface adapter.pay(25); // Output: Payment of $25 processed via third-party gateway. ```
Advantages of the Adapter Pattern
- Decouples code from third-party implementations.
- Promotes code reuse by adapting existing components.
- Improves maintainability when dealing with legacy systems or libraries.
Class Adapter vs Object Adapter
In languages like TypeScript, which do not support multiple inheritance, the object adapter approach (shown above) is preferred. However, in classical OOP languages like C++, you may also see class adapters, which rely on inheritance.
Conclusion
The Adapter Pattern is a powerful tool in your design pattern arsenal, especially when dealing with incompatible interfaces. In TypeScript, it helps integrate third-party APIs and legacy systems seamlessly, keeping your code clean and extensible.
By learning and applying the Adapter Pattern, you can make your applications more robust and flexible—ready to adapt to ever-changing requirements. https://fox.layer3.press/articles/cdd71195-62a4-420b-9e24-e23d78b27452
-
 @ 6e0ea5d6:0327f353
2025-02-21 18:15:52
@ 6e0ea5d6:0327f353
2025-02-21 18:15:52"Malcolm Forbes recounts that a lady, wearing a faded cotton dress, and her husband, dressed in an old handmade suit, stepped off a train in Boston, USA, and timidly made their way to the office of the president of Harvard University. They had come from Palo Alto, California, and had not scheduled an appointment. The secretary, at a glance, thought that those two, looking like country bumpkins, had no business at Harvard.
— We want to speak with the president — the man said in a low voice.
— He will be busy all day — the secretary replied curtly.
— We will wait.
The secretary ignored them for hours, hoping the couple would finally give up and leave. But they stayed there, and the secretary, somewhat frustrated, decided to bother the president, although she hated doing that.
— If you speak with them for just a few minutes, maybe they will decide to go away — she said.
The president sighed in irritation but agreed. Someone of his importance did not have time to meet people like that, but he hated faded dresses and tattered suits in his office. With a stern face, he went to the couple.
— We had a son who studied at Harvard for a year — the woman said. — He loved Harvard and was very happy here, but a year ago he died in an accident, and we would like to erect a monument in his honor somewhere on campus.— My lady — said the president rudely —, we cannot erect a statue for every person who studied at Harvard and died; if we did, this place would look like a cemetery.
— Oh, no — the lady quickly replied. — We do not want to erect a statue. We would like to donate a building to Harvard.
The president looked at the woman's faded dress and her husband's old suit and exclaimed:
— A building! Do you have even the faintest idea of how much a building costs? We have more than seven and a half million dollars' worth of buildings here at Harvard.
The lady was silent for a moment, then said to her husband:
— If that’s all it costs to found a university, why don’t we have our own?
The husband agreed.
The couple, Leland Stanford, stood up and left, leaving the president confused. Traveling back to Palo Alto, California, they established there Stanford University, the second-largest in the world, in honor of their son, a former Harvard student."
Text extracted from: "Mileumlivros - Stories that Teach Values."
Thank you for reading, my friend! If this message helped you in any way, consider leaving your glass “🥃” as a token of appreciation.
A toast to our family!
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 0fa80bd3:ea7325de
2025-02-14 23:24:37
@ 0fa80bd3:ea7325de
2025-02-14 23:24:37intro
The Russian state made me a Bitcoiner. In 1991, it devalued my grandmother's hard-earned savings. She worked tirelessly in the kitchen of a dining car on the Moscow–Warsaw route. Everything she had saved for my sister and me to attend university vanished overnight. This story is similar to what many experienced, including Wences Casares. The pain and injustice of that time became my first lessons about the fragility of systems and the value of genuine, incorruptible assets, forever changing my perception of money and my trust in government promises.
In 2014, I was living in Moscow, running a trading business, and frequently traveling to China. One day, I learned about the Cypriot banking crisis and the possibility of moving money through some strange thing called Bitcoin. At the time, I didn’t give it much thought. Returning to the idea six months later, as a business-oriented geek, I eagerly began studying the topic and soon dove into it seriously.
I spent half a year reading articles on a local online journal, BitNovosti, actively participating in discussions, and eventually joined the editorial team as a translator. That’s how I learned about whitepapers, decentralization, mining, cryptographic keys, and colored coins. About Satoshi Nakamoto, Silk Road, Mt. Gox, and BitcoinTalk. Over time, I befriended the journal’s owner and, leveraging my management experience, later became an editor. I was drawn to the crypto-anarchist stance and commitment to decentralization principles. We wrote about the economic, historical, and social preconditions for Bitcoin’s emergence, and it was during this time that I fully embraced the idea.
It got to the point where I sold my apartment and, during the market's downturn, bought 50 bitcoins, just after the peak price of $1,200 per coin. That marked the beginning of my first crypto winter. As an editor, I organized workflows, managed translators, developed a YouTube channel, and attended conferences in Russia and Ukraine. That’s how I learned about Wences Casares and even wrote a piece about him. I also met Mikhail Chobanyan (Ukrainian exchange Kuna), Alexander Ivanov (Waves project), Konstantin Lomashuk (Lido project), and, of course, Vitalik Buterin. It was a time of complete immersion, 24/7, and boundless hope.
After moving to the United States, I expected the industry to grow rapidly, attended events, but the introduction of BitLicense froze the industry for eight years. By 2017, it became clear that the industry was shifting toward gambling and creating tokens for the sake of tokens. I dismissed this idea as unsustainable. Then came a new crypto spring with the hype around beautiful NFTs – CryptoPunks and apes.
I made another attempt – we worked on a series called Digital Nomad Country Club, aimed at creating a global project. The proceeds from selling images were intended to fund the development of business tools for people worldwide. However, internal disagreements within the team prevented us from completing the project.
With Trump’s arrival in 2025, hope was reignited. I decided that it was time to create a project that society desperately needed. As someone passionate about history, I understood that destroying what exists was not the solution, but leaving everything as it was also felt unacceptable. You can’t destroy the system, as the fiery crypto-anarchist voices claimed.
With an analytical mindset (IQ 130) and a deep understanding of the freest societies, I realized what was missing—not only in Russia or the United States but globally—a Bitcoin-native system for tracking debts and financial interactions. This could return control of money to ordinary people and create horizontal connections parallel to state systems. My goal was to create, if not a Bitcoin killer app, then at least to lay its foundation.
At the inauguration event in New York, I rediscovered the Nostr project. I realized it was not only technologically simple and already quite popular but also perfectly aligned with my vision. For the past month and a half, using insights and experience gained since 2014, I’ve been working full-time on this project.
-
 @ 3c7dc2c5:805642a8
2025-06-01 16:03:49
@ 3c7dc2c5:805642a8
2025-06-01 16:03:49🧠Quote(s) of the week:
Fred Krueger: 'Generally, people overanalyze too much. Bitcoin is amazing tech. It works. It has been the top-performing asset in 13 of the last 15 years. Stop with the analysis. Buy it. Don't trade it. Don't look for "entry points". And don't do a 1% allocation either. Grow a pair.'
🧡Bitcoin news🧡
Money. Time. Energy. You only get to pick two… Unless you’re a Bitcoiner. https://i.ibb.co/1Gw9BJdB/Gqspxqd-Xg-AAw03e.jpg
On the 19th of May.
➡️ El Salvador is $357 million in profit on Bitcoin holdings.
➡️Metaplanet ended Monday as Japan's 9th most traded stock, with ¥61.69B ( $425M) daily volume, surpassing Toyota, SoftBank, and Nintendo.
➡️Circle $USDC in "informal talks" to sell itself to Coinbase or Ripple, Fortune reports. WhalePanda: "Imagine running a $60 billion stablecoin in such an incompetent way you can't even turn a decent profit and desperately have to sell."
➡️Panama introduces a bill to allow citizens to buy, sell, and accept Bitcoin freely anywhere in the country.
On the 20th of May:
➡️https://i.ibb.co/v61tLVTc/Grk-OL6x-Ws-AAIGum.jpg
Tick Tock next block, but it seems like we are right on schedule. Bitcoin is doing exactly what it was designed to do.
➡️BTC just hit a new ATH in Argentina Weak currencies first. Then all of them.
➡️ThumzUp Media officially files to raise $500m to buy Bitcoin as a treasury reserve asset.
➡️Indonesian fintech DigiAsia's stock surges over 90% after announcing plans to raise $100M for a Bitcoin treasury.
➡️River: America’s story began with sound money. Hard-working Americans saved their wealth in gold-backed money. Today, Bitcoin carries that torch forward.
https://i.ibb.co/zTFLqMjC/Grpd4lm-WAAAq-W7m.png
Insane stat! Bitcoin is now the people's money. Imagine the price when nation-states get on board.
The US government is outpacing global rivals like China by embracing Bitcoin. The federal government's Bitcoin holdings now represent twice its global market share of gold reserves.
Worth the read: https://blog.river.com/american-bitcoin-advantage/
'In this report, you'll learn about: - Why Bitcoin is an underestimated pillar of American dominance. - America’s lead in Bitcoin businesses, institutions, development, and policy. - Bitcoin's emergence as America’s reserve asset.'
Ergo: America is the dominant Bitcoin player in just about every dimension: investment, government reserves, development, institutional embrace, supportive policy, and mining.
➡️Texas Bitcoin Reserve bill SB 21 will be considered on the second reading in the House this morning. Note: the Texas Constitution requires that second and third readings be conducted on separate days. If it passes today, then the final vote could be tomorrow
➡️Bitcoin accumulation trends signal bullishness with smallholders (<1 BTC) accelerating accumulation (score ~0.55), and whales (100-10K BTC) aggressively buying. Source: Glassnode
➡️French company The Blockchain Group raises €8.6 million to buy more Bitcoin. Press release
➡️Chinese printer manufacturer Procolored unknowingly distributed Bitcoin-stealing malware through its official device drivers, resulting in 9.3 BTC ($950K) stolen from users.
https://x.com/MistTrack_io/status/1924411803540590728
➡️Bitmine launches its Bitcoin Treasury Advisory Practice with a $4M deal, including $3.2M for leasing 3K Bitcoin miners and an $800K consulting agreement
➡️Bitcoin's correlation to gold is at its lowest since February 2025, per Glassnode data.
➡️UK-listed Smarter Web Company adds 16.42 BTC to its treasury at an average price of $104,202. Total Holdings: 35.62 BTC The Smarter Web Company is stacking with conviction—building a treasury designed for the long term.
On the 21st of May:
➡️Vivek's Strive Asset Management looking to buy up to 75,000 Bitcoin from Mt. Gox claims at a discount to build a Bitcoin treasury.
➡️Bitcoin is $1k from an all-time high and the Google Trends chart looks like this. https://i.ibb.co/qYLb7j6C/Gra6-BSd-Xo-AATN2-A.jpg
On the 22nd of May:
Happy Pizza Day! 15 years ago today Laszlo Hanyecz bought 2 pizzas for 10,000 Bitcoin. That Bitcoin is now worth $1.2 BILLION.
Will Baxter: "But how did he get that much bitcoin? Well, there’s a lot more to Laszlo's story than those pizzas. Here are four facts about him most people don’t know (the last one blew my mind): 1. Laszlo, a Mac developer, discovered bitcoin in 2010. After realizing that Bitcoin only ran on Windows, he took it upon himself to port it to Mac OS. He built and released the first bitcoin client for Mac making it accessible to more users. 2. In its earliest days, bitcoin could be mined with just a CPU, something that every computer has. But Laszlo had other plans. In mid-2010, he released a solution that would allow users to mine with their GPUs. Laszlo is single-handedly responsible for ushering in the era of GPU mining which massively increased Bitcoin’s total hashrate. 3. By being one of the early adopters of GPU mining, Laszlo enjoyed a massive jump in mining efficiency and hashrate, which meant that he was able to mine a lot of blocks. In total, Laszlo’s Bitcoin wallets received more than 80,000 BTC over the first few months of the GPU mining era. It’s estimated that Laszlo mined well over 100,000 BTC in Bitcoin’s early days. 4. Laszlo has single-handedly mined more Bitcoin than any publicly listed Bitcoin mining company. As an example, MARA, the largest publicly traded Bitcoin miner by market capitalization, has mined an estimated 48,000 BTC since 2018. Laszlo and his GPUs managed to mine more than twice that amount! Incredible.
➡️Pizza slice inscribed on the Bitcoin blockchain forever! Block #897813
➡️Strategy: 'Bitcoin Pizza Day at Strategy. Paid for with USD.'
Kinda disgusting. The largest Bitcoin Treasury Company is not even able to pay for pizza in Bitcoin on Bitcoin Pizza Day? Why did they even bother to buy pizza today? They show zero understanding of the meaning of Pizza Day and Bitcoin history.
Plebs all around the world are celebrating Pizza Day by "spend and replace" Bitcoin for some lovely pizzas. What is Saylor doing? He decides to use his giant megaphone to stomp all over it. "Pay with Dollars. Eat the Pizza. Keep the Bitcoin." That post rubbed me the wrong way. That’s because they are not bullish on the payment use case of Bitcoin. I have been saying all the time: that he has an agenda against the medium of exchange. This is plausible as Saylor never minced words as far as I know. His model is HODL. Spending would contradict.
Not sure if I am overreacting because of store of value for several more years will eventually lead to a Medium of Exchange Bitcoin world.
As you might already know I am not particularly a fan of the whole Bitcoin treasury - public companies.
Read the following thread why, an excellent thread on the risks of Bitcoin treasury companies by a bitcoiner.
https://x.com/lowstrife/status/1925717037915005357
➡️For the first time in history, Bitcoin is now trading above $111,000 and just surpassed $2.2 TRILLION in market cap for the first time in history. $3 Billion worth of Bitcoin shorts to be liquidated at $120,000 Small, tiny reminder. In 2021 dollars, Bitcoin hasn’t broken $100K yet. We need to hit $118K to meet that milestone. Celebrating $1 million (eventually) might not be as much fun as you think.
➡️H100 Group buys 4.39 BTC and becomes Sweden's first publicly listed #Bitcoin treasury company. After announcing its first Bitcoin purchase shares surged 37%. A small stack, big signal.
➡️Bitcoin has now surpassed both Amazon and Google to become the 5th largest asset in the world, and Bitcoin just surpassed the Taiwan Dollar and is now the 8 largest currency in the world. Nothing stops this train. https://i.ibb.co/Jj11QjkL/Grk-Ume-KXs-AAm-Xp6.jpg
➡️Michael Saylor's 'Strategy' now has a $23.8 billion unrealized profit on its Bitcoin portfolio. Meanwhile, Strategy is to sell up to $2.1 billion of 10% preferred stock.
➡️'Traditional finance consensus: "What's the use case for BTC?" Allowing Millennials to afford a home despite Boomer policymakers actively pursuing policies to prevent them from doing so Median US home price, price in BTC, 2020-today IMO, this chart is going <1 in coming yrs.' - Luke Gromen https://i.ibb.co/tpCk7HD2/Grka1-Ld-Wc-AAo-IQn.jpg
Just to give you one more perspective on this topic:
➡️Joe Consorti: US real estate has been in a 15-year bull market. But guess what? Priced in bitcoin, the average US home price has dropped from ~3 million BTC to just 4.38 BTC in 15 years. All assets are deflationary in Bitcoin terms. https://i.ibb.co/m5Nk2Yq2/Grk9d92-XUAAAwz-H.jpg
➡️Taiwanese Legislator has proposed a Bitcoin Strategic Reserve at 0.1% of GDP = $780m
➡️Chinese automaker Jiuzi Holdings to buy 1,000 Bitcoin for treasury.
➡️ 'Singapore's Genius Group buys another 24.5 Bitcoin. Now holds 85.5 Bitcoin, 1,000 BTC target confirmed.' - Bitcoin Archive
➡️Standard Chartered expects Bitcoin to hit: - Q2: $120,000 by the end of Q2 - Q4: $200,000 by late 2025 - 2028: $500,000
➡️On-Chain college: 'New ATH for Bitcoin yet realized profit is significantly lower than the last two local tops and prior cycle tops. HIGHER' https://i.ibb.co/ch0HWwWx/Grjx-GHVWo-AAd7-Wt.jpg
Not sure about that. Could be a double top.
On the 23rd of May:
➡️The Blockchain Group confirms the acquisition of 227 BTC for ~€21.2 million, the holding of a total of 847 BTC, and a ‘BTC Yield’ of 861.0% YTD Press release.
➡️The 8th largest economy in the world will start to buy Bitcoin. No one is bullish enough! Governor Abbot to sign Bitcoin Reserve bill into law! Texas to become the 3rd US state to enact an SBR!
➡️Publicly traded The Smarter Web Company bought 23.09 Bitcoin for £1.85 million for its treasury.
➡️For the love of god. Delate Coinbase or any other shitcoin casino/exchange (for example here in the Netherlands Bitvavo) and cold-Storage your Bitcoin and don’t touch them.
https://i.ibb.co/y3BmmNt/Grp-TDv-BWk-AAs7-Gh.jpg
Not your keys, not your coins.
➡️'The Russian Bitcoin mining sector now ranks first in growth rates and second in mining volume globally. The country's largest Bitcoin miners, BitRiver and Intelion, controlling over 50% of the market, generated $200M in revenue for FY2024, per RBC.' -Bitcoin News
➡️Alex Gladstein: 'Absolutely crazy Hundreds of millions of people saw their wage and savings technology lose 15%, 30%, 50%, 75%, even 90% (!) of its value last year Fiat is broken, time for a Plan ₿' https://i.ibb.co/hRZwFsPJ/Gro-s-KJXUAAh97-M.jpg
➡️Bitwise predicts nation-states and institutions will hold 4,269,000 BTC—worth $426.9B. https://i.ibb.co/RkVDmGLg/Gro6wb-VX0-AAHCT0.jpg
➡️'Metaplanet is now the #4 most traded stock in Japan, moving nearly $1B in a day—just a year after adopting #Bitcoin. From obscurity to 300x returns, this is what happens when a company runs on hard money.' -Bitcoin for Corporation
➡️TFTC: "Scammers are mailing fake "Ledger Security" letters demanding wallet validation via QR code. They spoof official branding and ask users to visit fraudulent sites."
https://i.ibb.co/nNg0JgX6/Grpd0o-BWc-AI3-Yj-Y.jpg
On the 24th of May:
➡️Bitcoin has the same number of users as the Internet had in 1999. https://i.ibb.co/1frYh4Z7/Gru2-J3-UW8-AA-05y.jpg
Now talking about that Bitcoin Adoption S-curve...
➡️Thomas Fahrer: 'Holding Bitcoin means getting rich while feeling frustrated 90% of the time. Deflationary money - designed to increase in value - forever. It's difficult for the human mind to comprehend. Most still don't get it.' https://i.ibb.co/9HwPkxK3/Grwpw-W0-W0-AEc-PSb.jpg
On the 25th of May:
➡️Pakistan allocates 2,000mw of electricity to Bitcoin mining and Ai - Bloomberg Daniel Batten: Pakistan announced 2000 MW for Bitcoin mining & AI. That's potentially ~17,000 BTC per year for an SBR. Plus, India will now have to follow. Game theory playing out. *Assuming that 50% of this is for Bitcoin mining, using latest-gen machines, 95% uptime, network hashrate is on average 1200 EH/s by the time they are complete
➡️Normally, I would write this in the segment below 🌎Macro/Geopolitics... "First signpost: DOGE failed to reduce the deficit.
Second signpost: Pushing for SLR changes to boost demand for Treasuries from domestic banks.
Third signpost: Pushing for legislation to boost demand for Treasuries from stablecoin issuers.
Fourth signpost: New spending bill estimated to increase deficit by 33% by 2027.
Fifth signpost: Bessent: "We'll grow GDP faster than the debt to stabilize debt-to-GDP."
Read below (segment 🌎Macro/Geopolitics) his full statement and my view on it.
TL;DR: Keep spending. Pass new laws and tweak regs to suppress long-end yields. Boost nominal GDP (mostly via inflation). Debase the currency. Bondholders and cash savers lose in real terms. Got Bitcoin?" -Sam Callahan
➡️Sminston With: 'There is a myth that 100% of the returns in Bitcoin only happen if you buy at the bottoms and then sell at the tops during one of the cycles. Power law quantile analysis shows otherwise; in fact, there are nearly identical growth rates (CAGR) whether you buy/sell at the bottoms (support) or around the middle (median) 52% vs 53% as of this year! Whichever trendline is followed, even if you only trade at the bottoms, the compounded annual returns of Bitcoin will be >7x of what you'd ever expect from the S&P. Ignore or try to time Bitcoin at your own risk!' https://i.ibb.co/5QHQHqF/Grzig5-BWIAAy9-Jb.jpg
On the 26th of May:
➡️Bitcoin made another weekly record close at $109,004.
➡️When BlackRock holds 1M Bitcoin and the price hits $1M... They’ll be earning $2.5B a year in fees. Every year. Forever.
➡️Florida proposes eliminating Capital Gains Tax on Bitcoin. If passed, it would make Florida the first U.S. state to offer this kind of tax relief.
➡️Strategy acquires 4,020 BTC for $427.1 million at $106,237 per Bitcoin. They now HODL 580,250 BTC acquired for $40.61 billion at $69,979 per Bitcoin.
💸Traditional Finance / Macro:
Jeroen Blokland: U.S. vs. Eurozone in the digital money age!
https://i.ibb.co/dJ3085qm/Grko80y-WMAATw-V1.jpg
On the 20th of May:
👉🏽TKL: 'Retail investors are piling into stocks: Individual investors bought a net $4.1 BILLION in US stocks on Monday between 9:30 AM and 12:30 PM ET, the biggest buy on record. This surpassed the previous high by over $1 BILLION, according to JPMorgan data. Retail investors also broke the $4 billion buying threshold by noon ET for the first time in history. Additionally, retail accounted for a record 36% of the trading volume yesterday, exceeding the previous record set in late April. This supported the S&P 500's rapid recovery from a -1.1% decline at the beginning of Monday’s session into positive territory by the close. Retail investors are driving the market.'
https://i.ibb.co/HTM721rw/Gr-Zot-Th-XMAAl-EB.jpg
To provide you with another example of why retail is driving this market. Institutional investors remain bearish of US stocks:
A net 38% of institutional investors were underweight US equities in early May, the lowest since May 2023, according to BofA. Outside of 2023, this marks the lowest allocation since the lead-up to 2008. Over the last 5 months, this percentage has fallen by ~70 points, the biggest drop on record. The difference between the proportion of investors being overweight in the Eurozone versus US equities hit a net ~75%, the highest since October 2017. By comparison, 4 months ago, the net percentage was -62 points, the lowest since 2012.
The sentiment shift among professional investors has been historic. Institutions dump U.S. stocks and flock to the Eurozone. Institutions bailing on US stocks while retail piles in - smells like a correction brewing.
🏦Banks:
On the 21st of May:
👉🏽The Federal Reserve has experienced its first back-to-back annual losses since 1915, totaling $192 billion in 2023 and 2024. The most expensive “expertise” in history.
https://i.ibb.co/zzPHp40/Gr-Xx-Hsy-WUAARd-IV.jpg
On the 23rd of May:
👉🏽'U.S. Banks U.S. Banks are currently facing $482 Billion in unrealized losses, an increase of 33% from the prior quarter. With rates now skyrocketing, these losses are going to increase. Banks, particularly small banks, are ( potentially) in trouble!!' - Barchart https://i.ibb.co/1FHmTBc/Grm-GA3-OWMAAro5k.jpg
🌎Macro/Geopolitics:
1 bar of gold
= 1 house (1975) 1 bar of gold
= 1 house (2025) Do you get it yet?
https://i.ibb.co/tTM7Kw0n/Gr-W8b-K0b-AAQvu-He.jpg
Got Bitcoin?
On the 19th of May:
👉🏽 TKL: "Risky debt issuance has stalled in the US: Low-rated US corporations have issued less than $1 billion in bonds in April, the lowest in at least 4 years. At the same time, leveraged loan issuances have reached $13 billion. High-yield corporate bonds and leveraged loan issuances are ~10 TIMES lower than during the same period last year. Leveraged loans are typically used to finance M&A, refinance debt, or general business activity, all of which are slowing down." Seems like uncertainty is really affecting everything.
👉🏽'US Treasuries are selling off: The 30-year Treasury yield surpassed 5%, for the first time since November 2023. It is now trading at the 2nd-highest level in 18 YEARS. Investors are signaling that the US public debt CRISIS is heading to a turning point.' -Global Markets Investor
👉🏽The stupidity of EU leaders knows no limits.
https://i.ibb.co/gCpMxsH/Gr-Txm-P1-Ww-AAALx-L.jpg
'Russia pumps gas 3.000 km from frozen Siberia to China through a Gazprom-owned pipeline. Meanwhile, massive Chinese LNG tankers, too enormous for the Suez Canal, sail the long route around the Cape of Good Hope just to supply Europe,filling the gap left by Russia’s fading influence. And now? Russian gas costs three times more.'
https://www.theguardian.com/environment/2025/jan/09/european-imports-of-liquefied-natural-gas-from-russia-at-record-levels
https://www.theguardian.com/world/2025/feb/24/eu-spends-more-russian-oil-gas-than-financial-aid-ukraine-report
👉🏽Klarna losses widen as more users miss payments; 100 million now on platform — FT “The fintech, which offers interest-free consumer loans to allow customers to make retail purchases, on Monday reported a net loss of $99mn for the three months to March, up from $47mn a year earlier.” https://www.ft.com/content/6c4bf393-c80b-42b7-993a-35270143f688 https://i.ibb.co/prsJNdB2/Gr-Y6-WTQXs-AAPu-Tr.png
Funny how they never learn that unsecured debt to subprime holders is a bad idea. Buy now pay later was a model destined to fail because those least capable of repaying the loans are the very people borrowing it. "100M people using Klarna and they're losing money because broke people keep defaulting on burritos"
On the 20th of May:
👉🏽As mentioned in my previous Bitcoin & Macro recap. Japan’s Prime Minister Ishiba called the current bond market situation in Japan “worse than Greece.” Shocking (not!), falling demand for long bonds in a country with a debt-to-GDP ratio of 216%.
Admitting that you’re situation is worse than Greece should horrify people. "Japan's bond market is imploding: Japan's 30Y Government Bond Yield has officially surged to its highest level in history, at 3.15%. For decades, Japan was known for low long-term interest rates. Now, they are dealing with high inflation, a shifting policy outlook, and a whopping 260% debt-to-GDP ratio. On top of this, Japan holds $1.1 TRILLION worth of US debt, making it the largest foreign holder of US debt." -TKL
This is not just about Japan. It’s a signal that the global debt machine is approaching its structural limits and that the next liquidity cycle may not be voluntary, but forced by sovereign fragility.
Read the following thread:
https://x.com/onechancefreedm/status/1924831549683298535
Remember:
1990: Japan has a goal of bringing prices down.
2012: Japan has a goal of getting prices up.
"History tells us that deflation [and inflation] has a habit of getting out of control."
👉🏽Gold prices extend gains to +5% since their May 15th low and near $3,300/oz as markets price-in uncertainty. Gold and Bitcoin are becoming the ONLY global safe-havens.
Talking about gold. China’s gold ETF inflows have more than doubled in the last 12 months, fueling a 38% surge in gold prices. From retail to the central bank—China has never bought more gold.
https://i.ibb.co/kVHh27vz/Gr-YB3-Wj-XUAAiai-W.jpg
On the 21st of May:
👉🏽For the Dutch followers/readers: The renovation of the Binnenhof is more than twice as expensive as the reconstruction of the Notre-Dame… and it costs more than the tallest building in the world, the Burj Khalifa…A typical case of being royally screwed over with other people's money (our tax money!)
👉🏽And yet another manufacturer driven out of the country by ridiculous climate and energy policies. Paint producer AkzoNobel is closing factories in the Netherlands and Belgium; 276 jobs cut.
They now will produce their products, partly, in France (Pamiers). That’s where they’ll continue production — with cheap and reliable nuclear energy.
Source: https://archive.ph/4nVyg
On the 22nd of March:
👉🏽TKL: "The decline in value of fiat currencies against gold has been truly remarkable: Since 1971, the US Dollar has lost 98.94% of its value against gold, the second-largest fall among major currencies. During the same period, the British Pound has declined 99.42%. The Euro would have lost 98.76% if it existed since 1971. Furthermore, the Japanese Yen and Swiss Franc have dropped 97.47% and 94.85%, respectively. Meanwhile, gold prices in US Dollar terms are up ~1,000% during this period. Gold remains a hedge against currency debasement." Wrong, Bitcoin is the hedge against currency debasement. Just look at the Bitcoin/Gold chart. I prefer 'digital' gold. Voltaire famously said, 'Fiat currency always eventually returns to its intrinsic value--zero.
On the 23rd of May:
👉🏽Trump recommends a 50% tariff on products imported from the European Union, starting on June 1, 2025. TKL: 'The trade war is back just as the 10Y Note Yield crosses above 4.60%. This morning, President Trump threatened 25% tariffs on Apple, $AAPL, and 50% tariffs on the EU beginning June 1st. Now, yields are pulling back sharply as recession worries resurface. The drop in yields on this announcement will only give MORE of a reason for President Trump to prolong the trade war. As we have said MULTIPLE times, a trade war accomplishes all of Trump's economic goals at once. Trump wants lower rates, the Fed won't cut, so he will get them the hard way.'
👉🏽US Treasury Secretary Scott Bessent: "We can both grow the economy and control the debt. What is important is that the economy grows faster than the debt. If we change the growth trajectory of the country, of the economy, then we will stabilize our finances and grow our way out of this." “We can grow our way out of this” RIP Fiscal Austerity, 2025-2025 lmao!
Notice how it’s shifted from “we’re going to cut spending” to “we’re going to grow our way out” regarding our debt burden. Bessent knows it’s cooked, hence why he stopped talking about yields. It is kinda delusional to think we are going to grow the economy fast enough to accomplish this when the budget deficit is over 6% of GDP.
Translation: they are unable to meaningfully reduce the debt. US government debt will continue to grow. They will be forced to print eventually. Your purchasing power will continue to fall. Got Bitcoin?
Just to give you one more example:
👉🏽'The national debt has grown under every U.S. president, regardless of political party, for decades. And that is set to continue during President Donald Trump’s second term. Elon Musk and the Department of Government Efficiency (“DOGE”) initially promised to cut $2 trillion in wasteful spending, but have since admitted this figure is likely to total a couple hundred billion bucks at best. Meanwhile, the president is pushing Congress to pass his “big, beautiful bill,” which is expected to add trillions in new deficit spending over the next several years. Make no mistake… the spending will never stop.' - Porter Stansberry
https://i.ibb.co/8k4LNg2/Grlug-NNX0-AAQnw-T.jpg
U.S. National Debt:
1970: $371B
1980: $908B
1990: $3.2T
2000: $5.7T
2010: $13.6T
2020: $26.9T
You can't fix this with votes. Maybe Bitcoin can stop this train? It can also incentivize governments to spend responsibly and manage budgets with discipline. One thing I do know is that you’re not voting your way out of this chart.
On the 24th of May:
👉🏽'The Bank of Japan owns 52.0% of all domestic government bonds. By comparison, life insurers, banks, and pension funds hold 13.4%, 9.8%, and 8.9%, respectively. According to Bloomberg, the Japanese government now holds $7.8 trillion of debt. This makes the Japanese government the third most indebted government in the world, behind the US and China. Furthermore, the Bank of Japan holds a whopping $4.1 trillion of government bonds on its balance sheet. Japan needs a major restructuring.' -TKL
Just to make it even worse...
👉🏽'Prices in Japan are soaring: The cost of rice jumped +98.4% year-over-year in April, posting the biggest monthly jump since 1971. This is an acceleration from the +92.1% surge recorded in March. Energy prices rose +9.3% after the March phaseout of Japanese government subsidies for gas and electricity. As a result, Japan's inflation CPI excluding fresh food rose by +3.5% from the previous year, up from a +3.2% gain in March. This marks the 5th consecutive monthly reading at 3%+. Meanwhile, Japan's economy shrank by -0.7% in Q1 2025, the first decline since Q1 2024. Japan has entered stagflation.' -TKL
👉🏽Birth rates are plummeting in a lot of countries. Population collapse is the greatest threat to civilization.
https://i.ibb.co/3Yfqq0N1/Gruztgo-XIAISc7-A.jpg
Question: How sustainable are the government debts with the population decline, like in Japan and Europe?
Grok: Population decline in Japan and Europe strains government debt sustainability. Japan's debt, at 245% of GDP, faces pressure from an aging population, with social spending projected to hit 24% of GDP by 2040. Europe's debt varies, with Greece at 163.6% and Italy at 137%, while aging reduces tax bases. Immigration and productivity boosts could help, but their impact is uncertain. Japan's domestic debt ownership offers some stability, while EU fiscal rules aid Europe. Outcomes depend on policy execution and economic conditions.
On the 26th of May:
👉🏽Cheap energy = abundance One population is so brainwashed they choose poverty. Michael A. Arouet: Can someone please explain the logic behind Germany closing its perfectly fine nuclear power plants, and deindustrialising?
https://i.ibb.co/tTwkmhcB/Gr3-IWgk-Ww-AAVz-Y3.jpg
👉🏽'The US budget deficit has averaged 9% of GDP over the last 5 years. Over the last 12 months alone, the budget gap has hit 7% of GDP. This is even higher than during the 2001 or the 1980s recessions. This comes as the US government spent a whopping $7.1 trillion over the last year, an equivalent of 24% of GDP. The government is now running larger deficits than during an average economic downturn. What happens if the US economy enters a recession?' -TKL
https://i.ibb.co/tT5nF67J/Gr5kcw-QWc-AAQ7q-R.jpg
🎁If you have made it this far, I would like to give you a little gift, well, in this case, two gifts:
May 2025 Newsletter: A Trade Breakdown
This newsletter issue breaks down the recent trade breakdown (sorry for the pun) and explores some of the nuances of why realigning the global balance of trade is both popular and extremely difficult to do.
https://www.lynalden.com/may-2025-newsletter/
Credit: I have used multiple sources!
My savings account: Bitcoin The tool I recommend for setting up a Bitcoin savings plan: PocketBitcoin especially suited for beginners or people who want to invest in Bitcoin with an automated investment plan once a week or monthly.
Use the code SE3997
Get your Bitcoin out of exchanges. Save them on a hardware wallet, run your own node...be your own bank. Not your keys, not your coins. It's that simple. ⠀ ⠀
⠀⠀ ⠀ ⠀⠀⠀
Do you think this post is helpful to you?
If so, please share it and support my work with a zap.
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
⭐ Many thanks⭐
Felipe - Bitcoin Friday!
▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃▃
-
 @ 04c915da:3dfbecc9
2025-05-20 15:50:22
@ 04c915da:3dfbecc9
2025-05-20 15:50:22There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 14:33:14
@ 5d4b6c8d:8a1c1ee3
2025-06-01 14:33:14We got more great contributions from the usual suspects, but also some very interesting reporting on the Venezuelan economy.
Top Posts
MONEY CLASS OF THE DAY: Market Efficiency: You Come Into MYYYYY HOUSE?! by @denlillaapan, 31 comments and 5834 sats A great primer on what "market efficiency" means and the epistemological issues with claims of inefficiency
Mini Pleb Economist: No Tax on Tips? by @SimpleStacker, 24 comments and 2035 sats Some interesting predictions about what the second order effects will be of removing taxes on tips
There Will Never Be Another Buffett (WSJ, Jason Zweig) by @denlillaapan, 23 comments and 1212 sats The most popular of Den's many sendoff's to the Oracle of Omaha
2 ways to buy gasoline in Venezuela by @bief57, 27 comments and 1835 sats A very interesting look at the parallel systems of market priced and "free" gas in Venezuela
Thank you to our OP's and commenters for keeping ~econ interesting.
https://stacker.news/items/994413
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 57c631a3:07529a8e
2025-05-20 15:40:04
@ 57c631a3:07529a8e
2025-05-20 15:40:04The Video: The World's Biggest Toddler
https://connect-test.layer3.press/articles/3f9d28a4-0876-4ee8-bdac-d1a56fa9cd02
-
 @ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03
@ 34f1ddab:2ca0cf7c
2025-05-16 22:47:03Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet. Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy. ⚠️ What We Don’t Do While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
Don’t Let Lost Crypto Hold You Back! Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Ready to reclaim your lost crypto? Don’t wait until it’s too late! 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on: ✉️ Telegram: t.me/crypptrcver 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s due to a forgotten password, a damaged seed backup, or a simple mistake in a transfer, the stress can be overwhelming. Fortunately, cryptrecver.com is here to assist! With our expert-led recovery services, you can safely and swiftly reclaim your lost Bitcoin and other cryptocurrencies.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions\ At Crypt Recver, we specialize in addressing complex wallet-related issues. Our skilled engineers have the tools and expertise to handle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery\ We understand that time is crucial in crypto recovery. Our optimized systems enable you to regain access to your funds quickly, focusing on speed without compromising security. With a success rate of over 90%, you can rely on us to act swiftly on your behalf.
🔒 Privacy is Our Priority\ Your confidentiality is essential. Every recovery session is conducted with the utmost care, ensuring all processes are encrypted and confidential. You can rest assured that your sensitive information remains private.
💻 Advanced Technology\ Our proprietary tools and brute-force optimization techniques maximize recovery efficiency. Regardless of how challenging your case may be, our technology is designed to give you the best chance at retrieving your crypto.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us manage the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure new wallet.
- Private Key Generation: Lost your private key? Our experts can help you regain control using advanced methods while ensuring your privacy.
⚠️ What We Don’t Do\ While we can handle many scenarios, some limitations exist. For instance, we cannot recover funds stored in custodial wallets or cases where there is a complete loss of four or more seed words without partial information available. We are transparent about what’s possible, so you know what to expect
 # Don’t Let Lost Crypto Hold You Back!
# Don’t Let Lost Crypto Hold You Back!Did you know that between 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate these challenges
🛡️ Real-Time Dust Attack Protection\ Our services extend beyond recovery. We offer dust attack protection, keeping your activity anonymous and your funds secure, shielding your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!\ Ready to reclaim your lost crypto? Don’t wait until it’s too late!\ 👉 cryptrecver.com
📞 Need Immediate Assistance? Connect with Us!\ For real-time support or questions, reach out to our dedicated team on:\ ✉️ Telegram: t.me/crypptrcver\ 💬 WhatsApp: +1(941)317–1821
Crypt Recver is your trusted partner in cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with cryptrecver.com.
-
 @ 9e69e420:d12360c2
2025-02-01 11:16:04
@ 9e69e420:d12360c2
2025-02-01 11:16:04Federal employees must remove pronouns from email signatures by the end of the day. This directive comes from internal memos tied to two executive orders signed by Donald Trump. The orders target diversity and equity programs within the government.

CDC, Department of Transportation, and Department of Energy employees were affected. Staff were instructed to make changes in line with revised policy prohibiting certain language.
One CDC employee shared frustration, stating, “In my decade-plus years at CDC, I've never been told what I can and can't put in my email signature.” The directive is part of a broader effort to eliminate DEI initiatives from federal discourse.
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ 0fa80bd3:ea7325de
2025-01-29 05:55:02
@ 0fa80bd3:ea7325de
2025-01-29 05:55:02The land that belongs to the indigenous peoples of Russia has been seized by a gang of killers who have unleashed a war of extermination. They wipe out anyone who refuses to conform to their rules. Those who disagree and stay behind are tortured and killed in prisons and labor camps. Those who flee lose their homeland, dissolve into foreign cultures, and fade away. And those who stand up to protect their people are attacked by the misled and deceived. The deceived die for the unchecked greed of a single dictator—thousands from both sides, people who just wanted to live, raise their kids, and build a future.
Now, they are forced to make an impossible choice: abandon their homeland or die. Some perish on the battlefield, others lose themselves in exile, stripped of their identity, scattered in a world that isn’t theirs.
There’s been endless debate about how to fix this, how to clear the field of the weeds that choke out every new sprout, every attempt at change. But the real problem? We can’t play by their rules. We can’t speak their language or use their weapons. We stand for humanity, and no matter how righteous our cause, we will not multiply suffering. Victory doesn’t come from matching the enemy—it comes from staying ahead, from using tools they haven’t mastered yet. That’s how wars are won.
Our only resource is the will of the people to rewrite the order of things. Historian Timothy Snyder once said that a nation cannot exist without a city. A city is where the most active part of a nation thrives. But the cities are occupied. The streets are watched. Gatherings are impossible. They control the money. They control the mail. They control the media. And any dissent is crushed before it can take root.
So I started asking myself: How do we stop this fragmentation? How do we create a space where people can rebuild their connections when they’re ready? How do we build a self-sustaining network, where everyone contributes and benefits proportionally, while keeping their freedom to leave intact? And more importantly—how do we make it spread, even in occupied territory?
In 2009, something historic happened: the internet got its own money. Thanks to Satoshi Nakamoto, the world took a massive leap forward. Bitcoin and decentralized ledgers shattered the idea that money must be controlled by the state. Now, to move or store value, all you need is an address and a key. A tiny string of text, easy to carry, impossible to seize.
That was the year money broke free. The state lost its grip. Its biggest weapon—physical currency—became irrelevant. Money became purely digital.
The internet was already a sanctuary for information, a place where people could connect and organize. But with Bitcoin, it evolved. Now, value itself could flow freely, beyond the reach of authorities.
Think about it: when seedlings are grown in controlled environments before being planted outside, they get stronger, survive longer, and bear fruit faster. That’s how we handle crops in harsh climates—nurture them until they’re ready for the wild.
Now, picture the internet as that controlled environment for ideas. Bitcoin? It’s the fertile soil that lets them grow. A testing ground for new models of interaction, where concepts can take root before they move into the real world. If nation-states are a battlefield, locked in a brutal war for territory, the internet is boundless. It can absorb any number of ideas, any number of people, and it doesn’t run out of space.
But for this ecosystem to thrive, people need safe ways to communicate, to share ideas, to build something real—without surveillance, without censorship, without the constant fear of being erased.
This is where Nostr comes in.
Nostr—"Notes and Other Stuff Transmitted by Relays"—is more than just a messaging protocol. It’s a new kind of city. One that no dictator can seize, no corporation can own, no government can shut down.
It’s built on decentralization, encryption, and individual control. Messages don’t pass through central servers—they are relayed through independent nodes, and users choose which ones to trust. There’s no master switch to shut it all down. Every person owns their identity, their data, their connections. And no one—no state, no tech giant, no algorithm—can silence them.
In a world where cities fall and governments fail, Nostr is a city that cannot be occupied. A place for ideas, for networks, for freedom. A city that grows stronger the more people build within it.
-
 @ 5d4b6c8d:8a1c1ee3
2025-06-01 13:04:11
@ 5d4b6c8d:8a1c1ee3
2025-06-01 13:04:11Sad news stackers. Episode 34 was lost in a tragic boating accident.
We'll revisit our recording setup going forward.
Rest assured that it was a glorious episode and it felt no pain upon its untimely departure. In lieu of an episode, I recommend @BlokchainB's excellent rant about his Knicks.
https://stacker.news/items/994354
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 04c915da:3dfbecc9
2025-05-15 15:31:45
@ 04c915da:3dfbecc9
2025-05-15 15:31:45Capitalism is the most effective system for scaling innovation. The pursuit of profit is an incredibly powerful human incentive. Most major improvements to human society and quality of life have resulted from this base incentive. Market competition often results in the best outcomes for all.
That said, some projects can never be monetized. They are open in nature and a business model would centralize control. Open protocols like bitcoin and nostr are not owned by anyone and if they were it would destroy the key value propositions they provide. No single entity can or should control their use. Anyone can build on them without permission.
As a result, open protocols must depend on donation based grant funding from the people and organizations that rely on them. This model works but it is slow and uncertain, a grind where sustainability is never fully reached but rather constantly sought. As someone who has been incredibly active in the open source grant funding space, I do not think people truly appreciate how difficult it is to raise charitable money and deploy it efficiently.
Projects that can be monetized should be. Profitability is a super power. When a business can generate revenue, it taps into a self sustaining cycle. Profit fuels growth and development while providing projects independence and agency. This flywheel effect is why companies like Google, Amazon, and Apple have scaled to global dominance. The profit incentive aligns human effort with efficiency. Businesses must innovate, cut waste, and deliver value to survive.
Contrast this with non monetized projects. Without profit, they lean on external support, which can dry up or shift with donor priorities. A profit driven model, on the other hand, is inherently leaner and more adaptable. It is not charity but survival. When survival is tied to delivering what people want, scale follows naturally.
The real magic happens when profitable, sustainable businesses are built on top of open protocols and software. Consider the many startups building on open source software stacks, such as Start9, Mempool, and Primal, offering premium services on top of the open source software they build out and maintain. Think of companies like Block or Strike, which leverage bitcoin’s open protocol to offer their services on top. These businesses amplify the open software and protocols they build on, driving adoption and improvement at a pace donations alone could never match.
When you combine open software and protocols with profit driven business the result are lean, sustainable companies that grow faster and serve more people than either could alone. Bitcoin’s network, for instance, benefits from businesses that profit off its existence, while nostr will expand as developers monetize apps built on the protocol.
Capitalism scales best because competition results in efficiency. Donation funded protocols and software lay the groundwork, while market driven businesses build on top. The profit incentive acts as a filter, ensuring resources flow to what works, while open systems keep the playing field accessible, empowering users and builders. Together, they create a flywheel of innovation, growth, and global benefit.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ a5ee4475:2ca75401
2025-05-15 14:44:45
@ a5ee4475:2ca75401
2025-05-15 14:44:45lista #descentralismo #compilado #portugues
*Algumas destas listas ainda estão sendo trocadas, portanto as versões mais recentes delas só estão visíveis no Amethyst por causa da ferramenta de edição.
Clients do Nostr e Outras Coisas
nostr:naddr1qq245dz5tqe8w46swpphgmr4f3047s6629t45qg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guxde6sl
Modelos de IA e Ferramentas
nostr:naddr1qq24xwtyt9v5wjzefe6523j32dy5ga65gagkjqgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guk62czu
Iniciativas de Bitcoin
nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2nvmn5va9x2nrxfd2k5smyf3ux7vesd9znyqxygt4
Profissionais Brasileiros no Nostr
nostr:naddr1qq24qmnkwe6y67zlxgc4sumrxpxxce3kf9fn2qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7q3q5hhygatg5gmjyfkkguqn54f9r6k8m5m6ksyqffgjrf3uut982sqsxpqqqp65wp8uedu
Comunidades em Português no Nostr
nostr:naddr1qq2hwcejv4ykgdf3v9gxykrxfdqk753jxcc4gqg4waehxw309aex2mrp0yhxgctdw4eju6t09upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4gu455fm3
Grupos em Português no Nostr
nostr:nevent1qqs98kldepjmlxngupsyth40n0h5lw7z5ut5w4scvh27alc0w86tevcpzpmhxue69uhkummnw3ezumt0d5hsygy7fff8g6l23gp5uqtuyqwkqvucx6mhe7r9h7v6wyzzj0v6lrztcspsgqqqqqqs3ndneh
Jogos de Código Aberto
Open Source Games nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2kvwp3v4hhvk2sw3j5sm6h23g5wkz5ddzhz8x40v0
Itens Úteis com Esquemas Disponíveis
nostr:naddr1qqgrqvp5vd3kycejxask2efcv4jr2qgswaehxw309ahx7um5wghx6mmd9upzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqvzqqqr4guc43v6c
Formatação de Texto em Markdown
(Amethyst, Yakihone e outros) nostr:naddr1qvzqqqr4gupzpf0wg36k3g3hygndv3cp8f2j284v0hfh4dqgqjj3yxnreck2w4qpqq2454m8dfzn26z4f34kvu6fw4rysnrjxfm42wfpe90
Outros Links
nostr:nevent1qqsrm6ywny5r7ajakpppp0lt525n0s33x6tyn6pz0n8ws8k2tqpqracpzpmhxue69uhkummnw3ezumt0d5hsygp6e5ns0nv3dun430jky25y4pku6ylz68rz6zs7khv29q6rj5peespsgqqqqqqsmfwa78
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ 8bad92c3:ca714aa5
2025-06-01 13:01:39
@ 8bad92c3:ca714aa5
2025-06-01 13:01:39Marty's Bent
via me

It seems like every other day there's another company announced that is going public with the intent of competing with Strategy by leveraging capital markets to create financial instruments to acquire Bitcoin in a way that is accretive for shareholders. This is certainly a very interesting trend, very bullish for bitcoin in the short-term, and undoubtedly making it so bitcoin is top of mind in the mainstream. I won't pretend to know whether or not these strategies will ultimately be successful or fail in the short, medium or long term. However, one thing I do know is that the themes that interest me, both here at TFTC and in my role as Managing Partner at Ten31, are companies that are building good businesses that are efficient, have product-market-fit, generate revenues and profits and roll those profits into bitcoin.
While it seems pretty clear that Strategy has tapped into an arbitrage that exists in capital markets, it's not really that exciting. From a business perspective, it's actually pretty straightforward and simple; find where potential arbitrage opportunities exists between pools of capital looking for exposure to spot bitcoin or bitcoin's volatility but can't buy the actual asset, and provide them with products that give them access to exposure while simultaneously creating a cult-like retail following. Rinse and repeat. To the extent that this strategy is repeatable is yet to be seen. I imagine it can expand pretty rapidly. Particularly if we have a speculative fervor around companies that do this. But in the long run, I think the signal is falling back to first principles, looking for businesses that are actually providing goods and services to the broader economy - not focused on the hyper-financialized part of the economy - to provide value and create efficiencies that enable higher margins and profitability.
With this in mind, I think it's important to highlight the combined leverage that entrepreneurs have by utilizing bitcoin treasuries and AI tools that are emerging and becoming more advanced by the week. As I said in the tweet above, there's never been a better time to start a business that finds product-market fit and cash flows quickly with a team of two to three people. If you've been reading this rag over the last few weeks, you know that I've been experimenting with these AI tools and using them to make our business processes more efficient here at TFTC. I've also been using them at Ten31 to do deep research and analysis.
It has become abundantly clear to me that any founder or entrepreneur that is not utilizing the AI tools that are emerging is going to get left behind. As it stands today, all anyone has to do to get an idea from a thought in your head to the prototype stage to a minimum viable product is to hop into something like Claude or ChatGPT, have a brief conversation with an AI model that can do deep research about a particular niche that you want to provide a good service to and begin building.
Later this week, I will launch an app called Opportunity Cost in the Chrome and Firefox stores. It took me a few hours of work over the span of a week to ideate and iterate on the concept to the point where I had a working prototype that I handed off to a developer who is solving the last mile problem I have as an "idea guy" of getting the product to market. Only six months ago, accomplishing something like this would have been impossible for me. I've never written a line of code that's actually worked outside of the modded MySpace page I made back in middle school. I've always had a lot of ideas but have never been able to effectively communicate them to developers who can actually build them. With a combination of ChatGPT-03 and Replit, I was able to build an actual product that works. I'm using it in my browser today. It's pretty insane.
There are thousands of people coming to the same realization at the same time right now and going out there and building niche products very cheaply, with small teams, they are getting to market very quickly, and are amassing five figures, six figures, sometimes seven figures of MRR with extremely high profit margins. What most of these entrepreneurs have not really caught on to yet is that they should be cycling a portion - in my opinion, a large portion - of those profits into bitcoin. The combination of building a company utilizing these AI tools, getting it to market, getting revenue and profits, and turning those profits into bitcoin cannot be understated. You're going to begin seeing teams of one to ten people building businesses worth billions of dollars and they're going to need to store the value they create, any money that cannot be debased.
Grant Gilliam, one of the co-founders of Ten31, wrote about this in early 2024, bitcoin being the fourth lever of equity value growth for companies.
[
Bitcoin Treasury - The Fourth Lever to Equity Value Growth
Most companies do not hold enough bitcoin There is a saying you often hear in bitcoin circles that “you can never have enough bitcoin.” This is typically expressed by those who have spent the time to both understand bitcoin’s unique and superior monetary properties and also to appreciate why tho
Ten31 - Investors in bitcoin infrastructure and freedom techGrant Gilliam
](https://ten31.vc/insights/treasury?ref=tftc.io)
We already see this theme playing out at Ten31 with some of our portfolio companies, most notably Strike, which recently released some of their financials, highlighting the fact that they're extremely profitable with high margins and a relatively small team (~75). This is extremely impressive, especially when you consider the fact that they're a global company competing with the likes of Coinbase and Block, which have each thousands of employees.
Even those who are paying attention to the developments in the AI space and how the tools can enable entrepreneurs to build faster aren't really grasping the gravity of what's at play here. Many are simply thinking of consumer apps that can be built and distributed quickly to market, but the ways in which AI can be implemented extend far beyond the digital world. Here's a great example of a company a fellow freak is building with the mindset of keeping the team small, utilizing AI tools to automate processes and quickly push profits into bitcoin.
via Cormac
Again, this is where the exciting things are happening in my mind. People leveraging new tools to solve real problems to drive real value that ultimately produce profits for entrepreneurs. The entrepreneurs who decide to save those profits in bitcoin will find that the equity value growth of their companies accelerates exponentially as they provide more value, gain more traction, and increase their profits while also riding the bitcoin as it continues on its monetization phase. The compounded leverage of building a company that leverages AI tools and sweeps profits into bitcoin is going to be the biggest asymmetric play of the next decade. Personally, I also see it as something that's much more fulfilling than the pure play bitcoin treasury companies that are coming to market because consumers and entrepreneurs are able to recive and provide a ton of value in the real economy.
If you're looking to stay on top of the developments in the AI space and how you can apply the tools to help build your business or create a new business, I highly recommend you follow somebody like Greg Isenberg, whose Startup Ideas Podcast has been incredibly valuable for me as I attempt to get a lay of the land of how to implement AI into my businesses.
America's Two Economies
In my recent podcast with Lyn Alden, she outlined how our trade deficits create a cycle that's reshaping America's economic geography. As Alden explained, US trade deficits pump dollars into international markets, but these dollars don't disappear - they return as investments in US financial assets. This cycle gradually depletes industrial heartlands while enriching financial centers on the coasts, creating what amounts to two separate American economies.
"We're basically constantly taking economic vibrancy out of Michigan and Ohio and rural Pennsylvania where the steel mills were... and stuffing it back into financial assets in New York and Silicon Valley." - Lyn Alden
This pattern has persisted for over four decades, accelerating significantly since the early 1980s. Alden emphasized that while economists may argue there's still room before reaching a crisis point, the political consequences are already here. The growing divide between these two Americas has fueled populist sentiment as voters who feel left behind seek economic rebalancing, even if they can't articulate the exact mechanisms causing their hardship.
Check out the full podcast here for more on China's man
-
 @ 127d3bf5:466f416f
2025-06-01 12:39:00
@ 127d3bf5:466f416f
2025-06-01 12:39:00In the Name of Allah, the Most Gracious, the Most Merciful,
"Permission to fight (against disbelievers) is given to those (believers) who are fought against, because they have been wronged and surely, Allah is Able to give them (believers) victory" [Quran 22:39]
"Those who believe, fight in the Cause of Allah, and those who disbelieve, fight in the cause of Taghut (anything worshipped other than Allah e.g. Satan). So fight you against the friends of Satan; ever feeble is indeed the plot of Satan."[Quran 4:76]
Some American writers have published articles under the title 'On what basis are we fighting?' These articles have generated a number of responses, some of which adhered to the truth and were based on Islamic Law, and others which have not. Here we wanted to outline the truth - as an explanation and warning - hoping for Allah's reward, seeking success and support from Him.
While seeking Allah's help, we form our reply based on two questions directed at the Americans:
(Q1) Why are we fighting and opposing you?\ (Q2) What are we calling you to, and what do we want from you?
As for the first question: Why are we fighting and opposing you? The answer is very simple:
(1) Because you attacked us and continue to attack us.
a) You attacked us in Palestine:
(i) Palestine, which has sunk under military occupation for more than 80 years. The British handed over Palestine, with your help and your support, to the Jews, who have occupied it for more than 50 years; years overflowing with oppression, tyranny, crimes, killing, expulsion, destruction and devastation. The creation and continuation of Israel is one of the greatest crimes, and you are the leaders of its criminals. And of course there is no need to explain and prove the degree of American support for Israel. The creation of Israel is a crime which must be erased. Each and every person whose hands have become polluted in the contribution towards this crime must pay its*price, and pay for it heavily.
(ii) It brings us both laughter and tears to see that you have not yet tired of repeating your fabricated lies that the Jews have a historical right to Palestine, as it was promised to them in the Torah. Anyone who disputes with them on this alleged fact is accused of anti-semitism. This is one of the most fallacious, widely-circulated fabrications in history. The people of Palestine are pure Arabs and original Semites. It is the Muslims who are the inheritors of Moses (peace be upon him) and the inheritors of the real Torah that has not been changed. Muslims believe in all of the Prophets, including Abraham, Moses, Jesus and Muhammad, peace and blessings of Allah be upon them all. If the followers of Moses have been promised a right to Palestine in the Torah, then the Muslims are the most worthy nation of this.
When the Muslims conquered Palestine and drove out the Romans, Palestine and Jerusalem returned to Islaam, the religion of all the Prophets peace be upon them. Therefore, the call to a historical right to Palestine cannot be raised against the Islamic Ummah that believes in all the Prophets of Allah (peace and blessings be upon them) - and we make no distinction between them.
(iii) The blood pouring out of Palestine must be equally revenged. You must know that the Palestinians do not cry alone; their women are not widowed alone; their sons are not orphaned alone.
(b) You attacked us in Somalia; you supported the Russian atrocities against us in Chechnya, the Indian oppression against us in Kashmir, and the Jewish aggression against us in Lebanon.
(c) Under your supervision, consent and orders, the governments of our countries which act as your agents, attack us on a daily basis;
(i) These governments prevent our people from establishing the Islamic Shariah, using violence and lies to do so.
(ii) These governments give us a taste of humiliation, and places us in a large prison of fear and subdual.
(iii) These governments steal our Ummah's wealth and sell them to you at a paltry price.
(iv) These governments have surrendered to the Jews, and handed them most of Palestine, acknowledging the existence of their state over the dismembered limbs of their own people.
(v) The removal of these governments is an obligation upon us, and a necessary step to free the Ummah, to make the Shariah the supreme law and to regain Palestine. And our fight against these governments is not separate from out fight against you.
(d) You steal our wealth and oil at paltry prices because of you international influence and military threats. This theft is indeed the biggest theft ever witnessed by mankind in the history of the world.
(e) Your forces occupy our countries; you spread your military bases throughout them; you corrupt our lands, and you besiege our sanctities, to protect the security of the Jews and to ensure the continuity of your pillage of our treasures.
(f) You have starved the Muslims of Iraq, where children die every day. It is a wonder that more than 1.5 million Iraqi children have died as a result of your sanctions, and you did not show concern. Yet when 3000 of your people died, the entire world rises and has not yet sat down.
(g) You have supported the Jews in their idea that Jerusalem is their eternal capital, and agreed to move your embassy there. With your help and under your protection, the Israelis are planning to destroy the Al-Aqsa mosque. Under the protection of your weapons, Sharon entered the Al-Aqsa mosque, to pollute it as a preparation to capture and destroy it.
(2) These tragedies and calamities are only a few examples of your oppression and aggression against us. It is commanded by our religion and intellect that the oppressed have a right to return the aggression. Do not await anything from us but Jihad, resistance and revenge. Is it in any way rational to expect that after America has attacked us for more than half a century, that we will then leave her to live in security and peace?!!
(3) You may then dispute that all the above does not justify aggression against civilians, for crimes they did not commit and offenses in which they did not partake:
(a) This argument contradicts your continuous repetition that America is the land of freedom, and its leaders in this world. Therefore, the American people are the ones who choose their government by way of their own free will; a choice which stems from their agreement to its policies. Thus the American people have chosen, consented to, and affirmed their support for the Israeli oppression of the Palestinians, the occupation and usurpation of their land, and its continuous killing, torture, punishment and expulsion of the Palestinians. The American people have the ability and choice to refuse the policies of their Government and even to change it if they want.
(b) The American people are the ones who pay the taxes which fund the planes that bomb us in Afghanistan, the tanks that strike and destroy our homes in Palestine, the armies which occupy our lands in the Arabian Gulf, and the fleets which ensure the blockade of Iraq. These tax dollars are given to Israel for it to continue to attack us and penetrate our lands. So the American people are the ones who fund the attacks against us, and they are the ones who oversee the expenditure of these monies in the way they wish, through their elected candidates.
(c) Also the American army is part of the American people. It is this very same people who are shamelessly helping the Jews fight against us.
(d) The American people are the ones who employ both their men and their women in the American Forces which attack us.
(e) This is why the American people cannot be not innocent of all the crimes committed by the Americans and Jews against us.
(f) Allah, the Almighty, legislated the permission and the option to take revenge. Thus, if we are attacked, then we have the right to attack back. Whoever has destroyed our villages and towns, then we have the right to destroy their villages and towns. Whoever has stolen our wealth, then we have the right to destroy their economy. And whoever has killed our civilians, then we have the right to kill theirs.
The American Government and press still refuses to answer the question:
Why did they attack us in New York and Washington?
If Sharon is a man of peace in the eyes of Bush, then we are also men of peace!!! America does not understand the language of manners and principles, so we are addressing it using the language it understands.
(Q2) As for the second question that we want to answer: What are we calling you to, and what do we want from you?
(1) The first thing that we are calling you to is Islam.
(a) The religion of the Unification of God; of freedom from associating partners with Him, and rejection of this; of complete love of Him, the Exalted; of complete submission to His Laws; and of the discarding of all the opinions, orders, theories and religions which contradict with the religion He sent down to His Prophet Muhammad (peace be upon him). Islam is the religion of all the prophets, and makes no distinction between them - peace be upon them all.
It is to this religion that we call you; the seal of all the previous religions. It is the religion of Unification of God, sincerity, the best of manners, righteousness, mercy, honour, purity, and piety. It is the religion of showing kindness to others, establishing justice between them, granting them their rights, and defending the oppressed and the persecuted. It is the religion of enjoining the good and forbidding the evil with the hand, tongue and heart. It is the religion of Jihad in the way of Allah so that Allah's Word and religion reign Supreme. And it is the religion of unity and agreement on the obedience to Allah, and total equality between all people, without regarding their colour, sex, or language.
(b) It is the religion whose book - the Quran - will remained preserved and unchanged, after the other Divine books and messages have been changed. The Quran is the miracle until the Day of Judgment. Allah has challenged anyone to bring a book like the Quran or even ten verses like it.
(2) The second thing we call you to, is to stop your oppression, lies, immorality and debauchery that has spread among you.
(a) We call you to be a people of manners, principles, honour, and purity; to reject the immoral acts of fornication, homosexuality, intoxicants, gambling's, and trading with interest.
We call you to all of this that you may be freed from that which you have become caught up in; that you may be freed from the deceptive lies that you are a great nation, that your leaders spread amongst you to conceal from you the despicable state to which you have reached.
(b) It is saddening to tell you that you are the worst civilization witnessed by the history of mankind:
(i) You are the nation who, rather than ruling by the Shariah of Allah in its Constitution and Laws, choose to invent your own laws as you will and desire. You separate religion from your policies, contradicting the pure nature which affirms Absolute Authority to the Lord and your Creator. You flee from the embarrassing question posed to you: How is it possible for Allah the Almighty to create His creation, grant them power over all the creatures and land, grant them all the amenities of life, and then deny them that which they are most in need of: knowledge of the laws which govern their lives?
(ii) You are the nation that permits Usury, which has been forbidden by all the religions. Yet you build your economy and investments on Usury. As a result of this, in all its different forms and guises, the Jews have taken control of your economy, through which they have then taken control of your media, and now control all aspects of your life making you their servants and achieving their aims at your expense; precisely what Benjamin Franklin warned you against.
(iii) You are a nation that permits the production, trading and usage of intoxicants. You also permit drugs, and only forbid the trade of them, even though your nation is the largest consumer of them.
(iv) You are a nation that permits acts of immorality, and you consider them to be pillars of personal freedom. You have continued to sink down this abyss from level to level until incest has spread amongst you, in the face of which neither your sense of honour nor your laws object.
Who can forget your President Clinton's immoral acts committed in the official Oval office? After that you did not even bring him to account, other than that he 'made a mistake', after which everything passed with no punishment. Is there a worse kind of event for which your name will go down in history and remembered by nations?
(v) You are a nation that permits gambling in its all forms. The companies practice this as well, resulting in the investments becoming active and the criminals becoming rich.
(vi) You are a nation that exploits women like consumer products or advertising tools calling upon customers to purchase them. You use women to serve passengers, visitors, and strangers to increase your profit margins. You then rant that you support the liberation of women.
(vii) You are a nation that practices the trade of sex in all its forms, directly and indirectly. Giant corporations and establishments are established on this, under the name of art, entertainment, tourism and freedom, and other deceptive names you attribute to it.
(viii) And because of all this, you have been described in history as a nation that spreads diseases that were unknown to man in the past. Go ahead and boast to the nations of man, that you brought them AIDS as a Satanic American Invention.
(xi) You have destroyed nature with your industrial waste and gases more than any other nation in history. Despite this, you refuse to sign the Kyoto agreement so that you can secure the profit of your greedy companies and*industries.
(x) Your law is the law of the rich and wealthy people, who hold sway in their political parties, and fund their election campaigns with their gifts. Behind them stand the Jews, who control your policies, media and economy.
(xi) That which you are singled out for in the history of mankind, is that you have used your force to destroy mankind more than any other nation in history; not to defend principles and values, but to hasten to secure your interests and profits. You who dropped a nuclear bomb on Japan, even though Japan was ready to negotiate an end to the war. How many acts of oppression, tyranny and injustice have you carried out, O callers to freedom?
(xii) Let us not forget one of your major characteristics: your duality in both manners and values; your hypocrisy in manners and principles. All*manners, principles and values have two scales: one for you and one for the others.
(a)The freedom and democracy that you call to is for yourselves and for white race only; as for the rest of the world, you impose upon them your monstrous, destructive policies and Governments, which you call the 'American friends'. Yet you prevent them from establishing democracies. When the Islamic party in Algeria wanted to practice democracy and they won the election, you unleashed your agents in the Algerian army onto them, and to attack them with tanks and guns, to imprison them and torture them - a new lesson from the 'American book of democracy'!!!
(b)Your policy on prohibiting and forcibly removing weapons of mass destruction to ensure world peace: it only applies to those countries which you do not permit to possess such weapons. As for the countries you consent to, such as Israel, then they are allowed to keep and use such weapons to defend their security. Anyone else who you suspect might be manufacturing or keeping these kinds of weapons, you call them criminals and you take military action against them.
(c)You are the last ones to respect the resolutions and policies of International Law, yet you claim to want to selectively punish anyone else who does the same. Israel has for more than 50 years been pushing UN resolutions and rules against the wall with the full support of America.
(d)As for the war criminals which you censure and form criminal courts for - you shamelessly ask that your own are granted immunity!! However, history will not forget the war crimes that you committed against the Muslims and the rest of the world; those you have killed in Japan, Afghanistan, Somalia, Lebanon and Iraq will remain a shame that you will never be able to escape. It will suffice to remind you of your latest war crimes in Afghanistan, in which densely populated innocent civilian villages were destroyed, bombs were dropped on mosques causing the roof of the mosque to come crashing down on the heads of the Muslims praying inside. You are the ones who broke the agreement with the Mujahideen when they left Qunduz, bombing them in Jangi fort, and killing more than 1,000 of your prisoners through suffocation and thirst. Allah alone knows how many people have died by torture at the hands of you and your agents. Your planes remain in the Afghan skies, looking for anyone remotely suspicious.
(e)You have claimed to be the vanguards of Human Rights, and your Ministry of Foreign affairs issues annual reports containing statistics of those countries that violate any Human Rights. However, all these things vanished when the Mujahideen hit you, and you then implemented the methods of the same documented governments that you used to curse. In America, you captured thousands the Muslims and Arabs, took them into custody with neither reason, court trial, nor even disclosing their names. You issued newer, harsher laws.
What happens in Guatanamo is a historical embarrassment to America and its values, and it screams into your faces - you hypocrites, "What is the value of your signature on any agreement or treaty?"
(3) What we call you to thirdly is to take an honest stance with yourselves - and I doubt you will do so - to discover that you are a nation without principles or manners, and that the values and principles to you are something which you merely demand from others, not that which you yourself must adhere to.
(4) We also advise you to stop supporting Israel, and to end your support of the Indians in Kashmir, the Russians against the Chechens and to also cease supporting the Manila Government against the Muslims in Southern Philippines.
(5) We also advise you to pack your luggage and get out of our lands. We desire for your goodness, guidance, and righteousness, so do not force us to send you back as cargo in coffins.
(6) Sixthly, we call upon you to end your support of the corrupt leaders in our countries. Do not interfere in our politics and method of education. Leave us alone, or else expect us in New York and Washington.
(7) We also call you to deal with us and interact with us on the basis of mutual interests and benefits, rather than the policies of sub dual, theft and occupation, and not to continue your policy of supporting the Jews because this will result in more disasters for you.
If you fail to respond to all these conditions, then prepare for fight with the Islamic Nation. The Nation of Monotheism, that puts complete trust on Allah and fears none other than Him. The Nation which is addressed by its Quran with the words: "Do you fear them? Allah has more right that you should fear Him if you are believers. Fight against them so that Allah will punish them by your hands and disgrace them and give you victory over them and heal the breasts of believing people. And remove the anger of their (believers') hearts. Allah accepts the repentance of whom He wills. Allah is All-Knowing, All-Wise." [Quran9:13-1]
The Nation of honour and respect:
"But honour, power and glory belong to Allah, and to His Messenger (Muhammad- peace be upon him) and to the believers." [Quran 63:8]
"So do not become weak (against your enemy), nor be sad, and you will be*superior ( in victory )if you are indeed (true) believers" [Quran 3:139]
The Nation of Martyrdom; the Nation that desires death more than you desire life:
"Think not of those who are killed in the way of Allah as dead. Nay, they are alive with their Lord, and they are being provided for. They rejoice in what Allah has bestowed upon them from His bounty and rejoice for the sake of those who have not yet joined them, but are left behind (not yet martyred) that on them no fear shall come, nor shall they grieve. They rejoice in a grace and a bounty from Allah, and that Allah will not waste the reward of the believers." [Quran 3:169-171]
The Nation of victory and success that Allah has promised:
"It is He Who has sent His Messenger (Muhammad peace be upon him) with guidance and the religion of truth (Islam), to make it victorious over all other religions even though the Polytheists hate it." [Quran 61:9]
"Allah has decreed that 'Verily it is I and My Messengers who shall be victorious.' Verily Allah is All-Powerful, All-Mighty." [Quran 58:21]
The Islamic Nation that was able to dismiss and destroy the previous evil Empires like yourself; the Nation that rejects your attacks, wishes to remove your evils, and is prepared to fight you. You are well aware that the Islamic Nation, from the very core of its soul, despises your haughtiness and arrogance.
If the Americans refuse to listen to our advice and the goodness, guidance and righteousness that we call them to, then be aware that you will lose this Crusade Bush began, just like the other previous Crusades in which you were humiliated by the hands of the Mujahideen, fleeing to your home in great silence and disgrace. If the Americans do not respond, then their fate will be that of the Soviets who fled from Afghanistan to deal with their military defeat, political breakup, ideological downfall, and economic bankruptcy.
This is our message to the Americans, as an answer to theirs. Do they now know why we fight them and over which form of ignorance, by the permission of Allah, we shall be victorious?
-
 @ fa0165a0:03397073
2025-06-01 12:23:47
@ fa0165a0:03397073
2025-06-01 12:23:47Test of untype
Let see what this markdown editor goes for. Quite nice layout, but so far in my testing only usable via computer. On phone, the keyboard covers the writing area, hehe. Now, where do these get published when posted?
-
 @ 4fe14ef2:f51992ec
2025-06-01 11:27:18
@ 4fe14ef2:f51992ec
2025-06-01 11:27:18Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and zap on.
Share and repost: X: https://x.com/AGORA_SN/status/1929136854227407134 N: https://njump.me/note1vu0svge6kazrq8chac7we30jmzdx202ukzmc80ktapr27wgjkghqm7ugwy
https://stacker.news/items/994315
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46
@ 1c19eb1a:e22fb0bc
2025-05-08 21:55:46If you haven't noticed already, #Nostr is a little different from what most people are used to. One of the ways this is felt most acutely is with media hosting. Users are accustomed to uploading their images and videos directly through the app they are posting from. Many Nostr apps provide that same experience nowadays, but it wasn't always the case.
Just a couple years ago, users had to find somewhere to host their media separately, and then copy and paste the URL into their note whenever they wanted to share their cat pictures. One of the first, if not the first, media hosting services specifically intended for Nostr was nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7, which will be the service we are reviewing today.
Like our previous review of Amber, Nostr.Build is a service for users to pair with other Nostr apps. You won't generally use nostr:npub1nxy4qpqnld6kmpphjykvx2lqwvxmuxluddwjamm4nc29ds3elyzsm5avr7 by itself. Rather, you'll use it to host that incredible shot you want to post to #Olas, or to host screenshots for your long-form tutorial about setting up Nostr Wallet Connect that you'll be posting from #Habla.news, or for hosting a hilarious video of your cat falling asleep to nostr:npub1cj8znuztfqkvq89pl8hceph0svvvqk0qay6nydgk9uyq7fhpfsgsqwrz4u's voice and taking a tumble off of his favorite perch that you want to share on #Damus. However, there are some features within Nostr.Build that you may want to check out quite apart from using it with any other Nostr app.
Overall Impression
Score: 4.8 / 5
I have been impressed by Nostr.Build for some time now, but they have pulled out all the stops in their latest update, increasing their maximum file size for free accounts to 100MB, integrating the #Blossom protocol, adding the ability to share directly to Nostr from within your dashboard, and more integrations with other Nostr apps than ever before. Nostr.Build is simply a pleasure to use, whether through their web interface, or through another Nostr app that integrates with them.
With the ability to easily organize your media, view statistics, browse the media gallery of free uploads, metadata removal for increased privacy, and AI image generation, Nostr.Build is not simply a media hosting service, it is a full-fledged media management platform. Its robust features keep it well ahead of other Nostr-focused media hosting options available, and a particularly strong option for those using Blossom and wanting redundancy and reliable uptime for their media.
As much as I enjoy using the web interface, though, where Nostr.Build really shines is their integrations with other Nostr apps. These integrations allow users to have the same experience they are accustomed to from centralized social platforms of uploading their media from within the same app they are using to share it. No copy/pasting a URL from one app to another. In fact, many users may not realize they have been using Nostr.Build in their client of choice, simply because it is the default option for media hosting for many Nostr apps.
This has the added benefit to client developers that they can provide this experience to their users without having to run media hosting infrastructure on top of trying to build their app. The separation of relays, clients, and media hosting between different entities, while keeping a similar experience to centralized platforms where a single company controls all three, is critical to Nostr adoption.
Features
Nostr.Build has a plethora of features beyond simply hosting your media. Let's take a look!
AI Image Generation
Do you need a quick title image for a long-form article? How about inspiration for a logo or art piece? Nostr.Build's AI Studio has you covered.
They have provided a few different models based on the plan you purchase, beginning with the Professional plan, which includes SDXL-Lightning and Stable Diffusion 1. Upgrading to the Creator plan will give you access to all Pro Stable Diffusion models and unlimited use of the Flux.1 model, which is the same core model used for Grok2 images.
I personally have a Professional account, so I haven't had a chance to try out Flux.1, but I have used Stable Diffusion extensively for creating character art for #NostrHeroes characters, such as these:




Nothing too spectacular when compared with some of the newer models out there, and there is no image-to-image support (yet), but more than adequate for casual image generation needs. Moreover, it is far more than what one would expect from a simple media-hosting service.
Admittedly, I am also no expert at coaxing AI models to produce anything remarkable so your results may vary. Either way, image generation is a welcome tool to have available without needing to go to an outside service unless you require something very specific.
Upload Limits
The maximum file size limits on Nostr.Build have been getting progressively larger, even for their free service. As I recall, it was a mere 21MB limit per file just a few months ago, which is fine for image files, but is quickly exceeded with videos. Then they increased their limits to 50MB per file, and as of recent updates it has been increased once more to a whopping 100MB per file... for free! This is more than adequate for most uses.
However, free users' images, GIFs, and videos are automatically viewable via Nostr.Build's free media gallery. This is something to particularly bear in mind when uploading images you intend to share via direct message. Though your DMs are encrypted, the images uploaded to Nostr.Build are not, and if you don't have a paid account, they will be viewable to the all paid users in the free media gallery. If you want to upload images that will not be viewable unless you actively share them, you must have a paid account.
Paid accounts have no file size limit, but they do have a total storage limit. I could not find anything about total storage limits for free accounts, but Professional tier will give you 25GB, Creator 50GB, and Advanced 250GB. Uploads to paid accounts are not visible in the free media gallery, so only those you give the link to will be able to access your content.
Media Types
Many file types are supported by Nostr.Built, even for free users, including:
- Image: .jpg, .png, .gif
- Video: .mov, mp4
- Audio: mp3, .wav
Upgrading to the Professional plan will add .pdf and .svg to the list of permitted file types, and upgrading to Creator or above will add .zip files, as well.
I believe other common file types are also supported, but these are the only ones specifically mentioned on the site.
Free Media Gallery
The free media gallery is an interesting little feature that Nostr.Build has available to paid accounts. Free users can get a preview, such as the one below, but only paid users can browse through the millions of uploads made by free users.
Apart from being amusing to browse through the things people have been uploading, I am unsure of how useful this particular feature is. No indication is given as to who uploaded the media, and it is limited compared to media feeds in other Nostr apps in two important ways. First, it only shows media uploaded to Nostr.Build, while other media-focused Nostr apps, such as Slidestr, Lumina, or even Primal will show media posted by all Nostr users. Second, Nostr.Build's gallery doesn't show all uploads to Nostr.Build, but only uploads from those without a paid account, further limiting the scope of whose uploads are seen.
Paid users have the advantage of being able to upload media that is not viewable to anyone unless they intentionally share the link somewhere. Free users, on the other hand, must be aware that their uploads are viewable by any paid users, whether they shared the link anywhere or not.
One incident I had while testing out another app required me to reach out to Nostr.Build support to request deletion of an image. It had some of my personal information in it, and had been uploaded to Nostr.Build and sent to me via DM. The sender assumed that since it was being sent via DM, no one else would be able to see the image, but because he was not a paid user of Nostr.Build, the image was included in the Free Media Gallery for any paid user to see. Not ideal, but the folks at Nostr.Build were quick to get it deleted for me.
In short, I have mixed feelings about this particular feature.
Blossom
Blossom is a media storage and retrieval protocol built for Nostr, but usable with any application that needs to access media via the web, and Nostr.Build has recently added support for Blossom uploads via their Blossom server: blossom.band
I will likely be adding a Nostrversity article going over Blossom in detail in the near future, but here's the basics of what it makes possible:
First, easy integration for media uploading from your favorite Nostr apps. Amethyst, Coracle, Primal and others have added Blossom upload support, so you just have to hop into your settings and add Nostr.Build's Blossom server address to start using it as your media host. No need to go to a separate app to upload your media and copy/paste the URL into your Nostr note!
Second, your media in Blossom is content addressable. This means it is named based on a hash of its actual data. Because of this, you can verify that the media has not been altered or replaced by your media host. If the hash doesn't match the data, it won't be loaded by the Nostr client, so you never have to worry about the image in your note being replaced by a different image by your media host.
Finally, because your media is addressable by its content, you can save the same media to multiple hosts, and if one of them goes down, Nostr apps can fetch your media from other hosts, just like they can do with your notes by fetching them from different relays if one relay you write to is down. This makes your images and videos much harder to censor, since you would need to be banned by multiple Blossom servers for your media to no longer be accessible.
If you would like to upload media to more than one Blossom server at the same time, your options are currently to use Primal and ensure that your settings have "Enable media mirrors" toggled on, or to use Bouquet. Hopefully we will see this option added to more Nostr apps in the near future.
Metadata Stripping
For files uploaded via Nostr.Build's dashboard, location metadata is removed upon upload. This is to protect user privacy, since this data could be used to reveal your home address if it is left attached to images posted publicly on Nostr.
When uploading via Blossom, media containing location metadata will be rejected. The user will be required to remove the metadata before they can upload the media.
No KYC and No Ads Policy
The only form of identification needed to use Nostr.Build is your Nostr identity. Every upload is tied to your npub, but no name, date of birth, email, or other identifying information is required. This is made possible because Nostr.Build only accepts Bitcoin as payment for their accounts, and no KYC is required to make Bitcoin transactions via Lightning.
Additionally, Nostr.Build is philosophically opposed to targeted advertising, so they have a policy that they will never use ads on their hosting service.
Client Integrations
Even before Blossom, Nostr.Build had many Nostr clients that used it as the default media hosting service, allowing users to upload directly within the app. This has only expanded now that Nostr.Build has added Blossom.
A very non-exhaustive list of clients that integrate with Nostr.Build is listed on their site, and includes Damus, Amethyst, Nostrudel, Snort, Iris, Coracle, Flycat, and Yakihonne. Additional apps that support Nostr.Build via Blossom include Primal and Flotilla. Some of these integrations support both Blossom and NIP-96 options for uploading media, such as Amethyst, while others only support one or the other.
I would not be surprised to see more and more Nostr apps move to integrating Blossom and phasing out NIP-96 support. Either way, though, Nostr.Build currently supports both, and is therefore an excellent hosting option if you want to use it with a wide range of Nostr apps.
Media Statistics
For those with a paid account, Nostr.Build provides information about how often each of your uploads has been requested and viewed within a given time period.
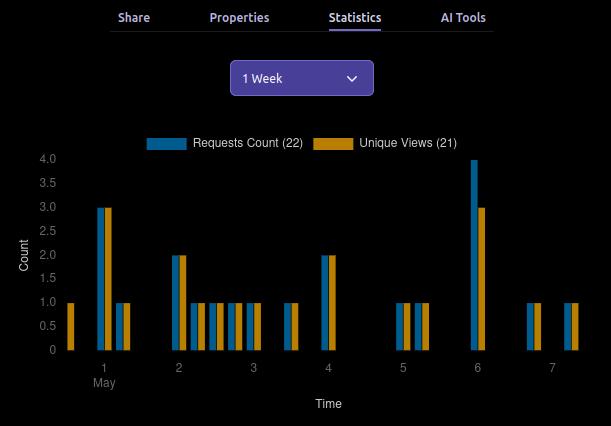
This can be valuable information for content creators, so they can determine what content is resonating with their audience, and what times of day their posts get the most views.
This information can currently be viewed for a maximum period of three months prior to the current date, and as short a period as just the past hour.
Can My Grandma Use It?
Score: 4.7 / 5
Nostr.Build is incredibly easy to use if you have a paid account, or if you are a free user uploading to Nostr.Build through a client that integrates with them by default. Previous frictions encountered by free users trying to upload large files should now be few and far between, thanks to the generous 100MB size limit.
Where things may be a bit more involved is when users are trying to set up media hosting on Nostr apps that don't use Nostr.Build by default. Exactly where in the settings the user must go to set this up, and whether to use the Blossom or NIP-96 address may not be immediately apparent, and requires an understanding of the difference that the user may not possess. This is not the fault of Nostr.Built, though, and I have not taken it into consideration in the scoring. Each individual Nostr app's settings should be as easy to understand as possible.
Another point of friction may come from free users who want to upload directly through the Nostr.Build site, instead of via another Nostr app. This used to be possible without logging in, but in an effort to ensure the service was used for Nostr, and not for general media hosting, Nostr.Build added the requirement to log in.
Thankfully, there are plenty of login options, including npub and password, browser extension (NIP-07), and even via a one-time-code sent to you via Nostr DM. However, if you don't have a paid account already, logging in will prompt you to upgrade. It seems that uploading directly via the website has been removed for free users entirely. You can only upload via another Nostr app if you don't have a paid account. This may lead to confusion for users who don't want to pay for an account, since it isn't made apparent anywhere that uploading through the website isn't an option for them.
Additionally, I would like to see the addresses for the Blossom server and for NIP-96 uploads (unless they are being phased out) added to the main page somewhere. Even selecting the "Blossom" page from the site navigation doesn't make clear what needs to be done to utilize the service. Something as simple as, "To use Nostr.Build with your favorite Blossom compatible Nostr apps, just add https://blossom.band as your media host in the app settings," would be enough to point users in the right direction.
For those who do have paid accounts, the dashboard is easy to navigate and organize your media.
By default, all uploads are added to the Main Folder. Users can leave them there, or they can easily create new folders and drag and drop media to organize it.
Every image has a copy/paste clipboard icon for ready access to copy the media URL for inclusion into a Nostr note.
Additionally, Nostr.Build allows users to share their uploaded media to Nostr directly from the dashboard. Bear in mind, though, this is published to a set of popular relays, without taking into account the user's preferred write relays.
The section just below the user's profile information gives an at-a-glance view of important information, such as how much of the user's allotted storage has been used, how many AI Studio credits are available, how many days are left before their paid account must be renewed, and how many files from three major categories — GIFs, images, and videos — have been uploaded.
Uploading directly to the dashboard is also incredibly easy. You can simply drag and drop files into the upload pane, or browse for them. If you have a URL for the media you want to upload, you can even paste it to import from another website or Blossom server.
Anything I could think of that I might want to do in the interface was intuitive to find, well labeled, or had common and easily identified icons.
How do UI look?
Score: 4.7 / 5
I would describe Nostr.Build's UI as clean and utilitarian, which is what one would expect from a media hosting service. Nothing too flashy. Just what you need and nothing you don't.
We certainly like our purple color-schemes on Nostr, and Nostr.Build leans into that with white text on shades of purple backgrounds, along with occasional color-popping accents. If a Nostr client had made the same color choices, I might be a bit more critical, but it works in an app that users won't be spending a ton of time in, except while managing their media, or using the AI Studio to generate some images.
UI elements such as buttons, active folder indicators, and icons all maintain an attractive, and simple design, with rounded corners wherever appropriate. Nothing looks too busy or overbearing, and the spacing between image previews in the folder view is just right.
Font remains consistent throughout the interface, with no jarring changes, and bold text, in white or another contrasting color, is used appropriately to draw attention, while subdued text is rendered in a light purple to blend more with the background, while remaining readable.
As such, the UI is attractive, without being particularly breathtaking. Nothing to complain about, but also nothing to write home about.
Log In Options
Score: 4.8 / 5
As mentioned previously, Nostr.Build provides three ways a user can log in.
The first should be very familiar for any Nostr user who frequents web clients, and that is by use of a browser extension (NIP-07), such as Alby, Nos2x, or Gooti. Note, this will also work if you are on Android and using KeyChat's browser, which has a NIP-07 signer built in.
Next is the legacy login method for Nostr.Build that they have used since the service first launched, which is via npub and password. This should serve to remind you that even though Nostr.Build supports Nostr login, and can post your images to Nostr for you, it's really just a centralized media hosting service. Just like you wouldn't use only one Nostr relay, you should not use just one media host. Mirror your media to other Blossom servers.
Most intriguing, and one I had not seen used before, is the option to use your npub and have a one-time-code sent to you via Nostr DM. I tested this method out and it worked flawlessly. It is unfortunately using the old NIP-04 DM spec, though, so any clients that have deprecated these DMs will not work for receiving the code. We're in a strange place with Nostr DMs currently, with some clients deprecating NIP-04 DMs in favor of NIP-17, others that still only support NIP-04, and a few that support both. If you don't see the DM in your client of choice, hop over to Primal and check your DMs there in the "other" tab.
Since Nostr.Build is supporting Nostr login, I would like to see them add remote signer (NIP-46) login alongside browser extension login to round out the options expected from a Nostr web app.
Feature Set
Score: 4.8 / 5
The features provided by Nostr.Build all work as expected and provide a lot of value to the user. With only one exception, all of the features make sense for a media hosting and management service to provide, and they are adding more features all the time.
Users not only get a reliable hosting service, with excellent uptime for their media, but they get integrations with most Nostr clients I can think of, Blossom protocol support, media organization and statistics, posting media to Nostr from within the dashboard, metadata stripping for enhanced privacy, a wide range of supported file types, and an AI image generation studio! What's more, there are additional features already on the roadmap, including traditional and AI image editing, additional plan options, expandable storage, and video transcoding for optimized playback. Nostr.Build is just getting started and they already offer more than most media hosting services out there, intended for Nostr or otherwise.
The one feature I am still not sold on is the "Free Media Gallery." The name is misleading. The gallery itself is not free. You must have a paid account to access more than a preview of it. Rather, it displays media uploaded by free users, regardless of whether they uploaded that media to send via DM, or uploaded it but decided not to share it out, or uploaded it to post it only within a private group on Flotilla, or uploaded it and only sent the note with the image link to a private relay.
Moreover, if I want to see media that has been shared on Nostr, there are plenty of ways I can do so that I can be confident only include media users intended to be publicly viewable. This feature from Nostr.Build, if it is kept at all, should have some way of ensuring the gallery only includes images that were shared on public relays.
Pricing
Score: 5 / 5
The pricing structure for Nostr.Build is exceptionally reasonable when compared with other services.
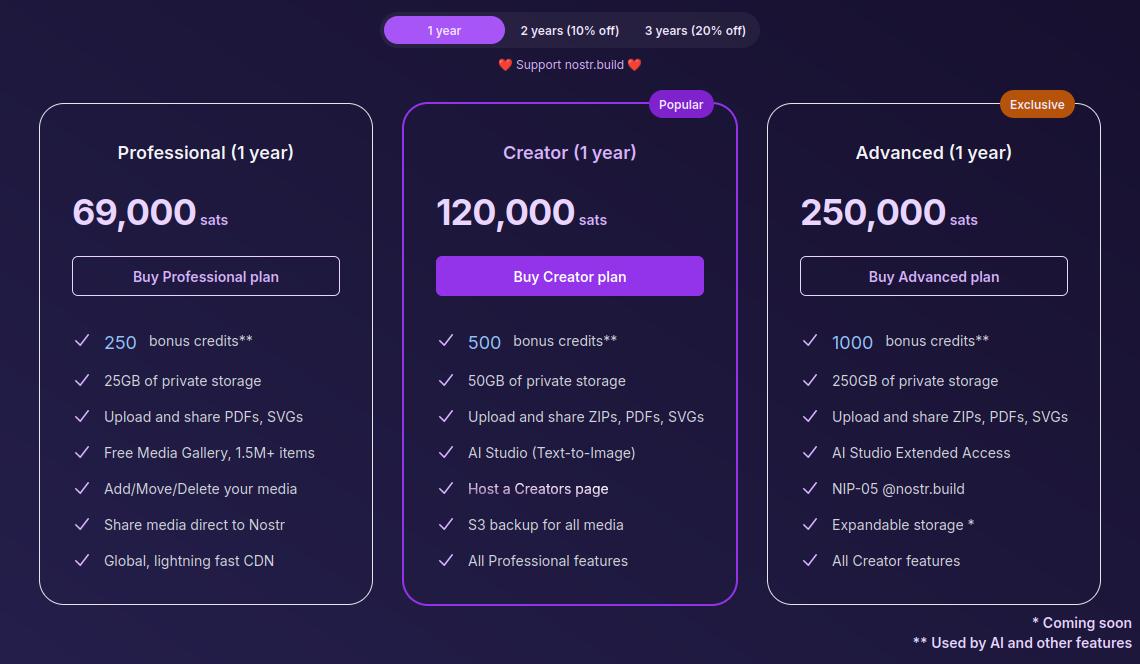
The Professional plan, which is their lowest paid tier, is just 69,000 sats a year. At current price, that translates to around $70 for the year, and Nostr.Build has been known to lower their pricing as Bitcoin goes up. Users can also get a 10% or 20% discount if they buy 2 or 3 years at a time, compensating for the fact that Bitcoin tends to go up year over year.
For that cost, users get 25GB of storage, unlimited file size for uploads within that storage cap, and access to all of Nostr.Build's features mentioned in this review, with the exception of their highest end AI models and storage of certain file types.
If I were to set up my own VPS to host a Blossom server with comparable storage, I would be paying around $14 a month before the cost of the domain, and it would be anything but plug and play. Even then, all I would have is storage. I would be missing out on all of the other features Nostr.Build has out of the box for less than half the price.
The Creator plan is close to double the cost at 120,000 sats, or about $120, a year. However, you aren't just getting double the storage space at 50GB; you are also getting double the AI credits, access to the higher tier AI models, S3 backup for all of your media, and your own Creator page you can share out with your media available for others to browse in one location.
The Advanced plan doesn't add a lot of extra features for more than double the price of the Creator plan, but it MASSIVELY increases your storage limit by 5x to a total of 250GB. Comparable storage space on a VPS to run your own Blossom server would be about $100 a month and Nostr.Build is offering it for about $250 (250,000 sats) for a whole year! If you really need to host that much media, it's hard to beat this price. The plan also comes with a Nostr.Build NIP-05 address, if you need one.
Now, the argument can be made, "But it's priced in sats, and that means in four years I will have spent many times that dollar amount on their service, possibly making it more expensive than other services priced in fiat." While that is true, it also doesn't take opportunity cost into account. Every dollar you spend on something other than Bitcoin is a missed opportunity to have bought Bitcoin with it. There's not really any difference between spending $70 in fiat to buy a hosting plan vs spending 69,000 sats, because you could have used that same $70 to buy Bitcoin instead, so you are losing out on that increase in purchasing power either way.
Not to mention, you can just buy the sats with your fiat and send it to Nostr.Build, so you would effectively be buying your plan with fiat, and they would be receiving sats.
I think Satellite.earth is still technically less expensive at just $0.05 per GB per month, which comes to $15 a year for the same 25GB of Nostr.Build's professional plan. However, all you get is media hosting. You miss out on all of the other features provided by Nostr.Build. And if you are uploading files of 100MB or less... Well, free with Nostr.Build is still cheaper than $0.5 per GB.
Wrap Up
All of the above comes together to make Nostr.Build a versatile and full-featured media hosting and management service at an affordable price point for their paid accounts, but with no need to pay at all if you just want a place to upload photos, GIFs, memes, and even some videos, so long as the file size stays under 100MB. Whether you want to use Nostr.Build as your primary media host, or as just one redundancy in your Blossom set up, they have you covered and I encourage you to check them out!
For the next review, I would like to go with another client, this time for the web, and the two options I am debating between are Coracle.social and Jumble.social. Let me know in the comments which you would like to see!
-
 @ 8c7778fc:7689822c
2025-06-01 09:36:57
@ 8c7778fc:7689822c
2025-06-01 09:36:57Trong bối cảnh nền kinh tế số đang trở thành động lực cốt lõi cho sự phát triển bền vững tại Việt Nam, VNWIN nổi lên không chỉ là một nền tảng trực tuyến về giải trí mà còn là một mắt xích quan trọng đóng góp vào sự chuyển đổi số quốc gia. Với nền tảng công nghệ vững chắc, quy trình vận hành hiện đại và khả năng tích hợp hệ thống linh hoạt, VNWIN đã và đang tạo ra một không gian số toàn diện, nơi người dùng không chỉ tham gia vào các hoạt động trực tuyến mà còn được tiếp cận với một mô hình kinh doanh thông minh. Nhờ áp dụng các công nghệ tiên tiến như AI, Big Data và bảo mật đa tầng, VNWIN không chỉ đảm bảo an toàn thông tin tuyệt đối mà còn tối ưu trải nghiệm người dùng theo từng nhu cầu cụ thể. Điều này không chỉ giúp nâng cao hiệu quả hoạt động nội bộ mà còn mang đến những giá trị gia tăng thực tế cho nền kinh tế, khi số lượng lớn người dùng VNWIN mỗi ngày đều tương tác, giao dịch và tiêu dùng thông qua nền tảng. Đặc biệt, việc tích cực tuân thủ các tiêu chuẩn pháp lý về thương mại điện tử cũng là điểm cộng lớn giúp VNWIN ngày càng khẳng định vai trò trong sự phát triển chung của hạ tầng kinh tế số Việt Nam.
Bên cạnh yếu tố công nghệ, VNWIN còn nổi bật nhờ khả năng xây dựng cộng đồng trực tuyến lành mạnh và có tính kết nối cao. Hệ sinh thái người dùng của VNWIN không chỉ dừng lại ở việc cung cấp sản phẩm mà còn liên tục mở rộng qua các chương trình tương tác cộng đồng, chăm sóc khách hàng chuyên sâu và các hoạt động trải nghiệm mang tính giáo dục về an toàn công nghệ số. Trong khi nhiều nền tảng số khác chỉ chú trọng vào lượt truy cập, VNWIN lại đầu tư vào chất lượng tương tác với người dùng, giúp tăng sự trung thành và độ tin cậy thương hiệu. Thông qua các kênh hỗ trợ như chat trực tuyến, hotline, email và mạng xã hội, người dùng VNWIN luôn nhận được sự hỗ trợ tận tình, nhanh chóng, thể hiện rõ cam kết đồng hành của doanh nghiệp với khách hàng. Ngoài ra, VNWIN cũng thường xuyên tổ chức các chương trình khuyến mãi, ưu đãi hấp dẫn và hoạt động tặng thưởng, nhằm kích thích hoạt động thương mại trong cộng đồng người dùng, tạo nên một chuỗi giá trị khép kín vừa phục vụ mục tiêu kinh doanh vừa thúc đẩy phát triển tiêu dùng nội địa. Việc người chơi quay lại sử dụng dịch vụ không chỉ đơn thuần vì giải trí mà còn bởi niềm tin vào hệ sinh thái số mà VNWIN đang kiến tạo mỗi ngày.
Không dừng lại ở việc phát triển nền tảng và xây dựng cộng đồng, VNWIN còn chủ động mở rộng ảnh hưởng thông qua các hoạt động hợp tác chiến lược với các đối tác công nghệ, tài chính và giáo dục. Sự kết nối đa ngành này không chỉ mở rộng quy mô hoạt động mà còn giúp VNWIN tăng cường tính đa dạng trong dịch vụ, tạo ra nhiều lựa chọn hơn cho người dùng. Bên cạnh đó, VNWIN cũng thể hiện vai trò tiên phong trong việc thúc đẩy nhận thức xã hội về lợi ích của nền kinh tế số thông qua các chiến dịch truyền thông tích cực, các dự án chia sẻ kiến thức công nghệ đến cộng đồng và các chương trình hỗ trợ thanh toán không tiền mặt. Đây chính là biểu hiện rõ ràng nhất cho cam kết phát triển bền vững, đưa công nghệ vào cuộc sống một cách hiệu quả, minh bạch và có trách nhiệm. Với định hướng phát triển lấy người dùng làm trung tâm, cùng chiến lược dài hạn trong việc đồng hành cùng nền kinh tế số Việt Nam, VNWIN đang khẳng định vị thế không thể thay thế trong hành trình số hóa toàn diện của quốc gia.
-
 @ 6389be64:ef439d32
2025-01-13 21:50:59
@ 6389be64:ef439d32
2025-01-13 21:50:59Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker
For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper
When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier
The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste
Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste
Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine
Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth
Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones
During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner
Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network
What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain
Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR
The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing
The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data
Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression
Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety
A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap
How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 41fa852b:af7b7706
2025-06-01 09:19:25
@ 41fa852b:af7b7706
2025-06-01 09:19:25"Bitcoin is a peaceful revolution." --Alex Gladstein
Life is still a bit upside-down after our house move, so I'm running slightly behind schedule this week.
I spent yesterday at Cyphermunk House for Bloom Fest, and it was honestly one of the best days I've had as a Bitcoiner. The range of personalities, the positivity, and the energy were all incredible. Huge credit to Psyfer and his team for making it happen. If you're reading this on Sunday, there's still time to head down for day two--full details here.
It's a quieter week for meetups across the UK and Ireland, but everything that's happening is listed below.
Upcoming Bitcoin Meetups
Happening this week…
-
Belfast Bitcoin: Join them on Tuesday the 3rd June, 20:00. These guys meet in person monthly on the first Tuesday of each month at Ormeau Baths Event Space, 18 Ormeau Avenue, Belfast, BT2 8HS, Northern Ireland. 🍻
-
Bitcoin Walk - Edinburgh: Every Saturday they walk around Arthur's Seat in this historic city. Join them at 12 pm to chat about all things Bitcoin and keep fit. 🚶🏽♂️🚶🏼♀️🚶🏻
-
Bitcoin Derby: On Saturday the 7th June Bitcoin Derby will be at Ye Olde Dolphin, DE1 3DL. 🍺
New Businesses Accepting Bitcoin
This week we have…
- Danson Garage: A trusted, independent garage based in Sidcup, DA15 9NP offering honest, high-quality car servicing, repairs and MOTs. Whether it's diagnostics, tyres, brakes or general maintenance, their experienced team provides reliable work at fair prices. They're known for clear communication, quick turnarounds and great customer service, keeping local drivers safely on the road. Now accepting bitcoin. 🚗👨🏻🔧
- Pintus Deli: A cherished Italian brasserie, coffee house, and restaurant located at 132 Northcote Road in Wandsworth, South London. Open seven days a week, it offers a delightful menu featuring breakfast, brunch, lunch, and dinner, complemented by freshly brewed coffee, juices, and a selection of wines and cocktails. With its warm ambiance and commitment to fresh, healthy ingredients, Pintus Deli provides a welcoming spot for any meal of the day. Now accepting bitcoin. 🥗🍝
- Stationery Place: Owned by long-established paper specialists John W Adams Ltd, offers a full range of printing, copying, scanning, binding and laminating services, plus custom-made rubber stamps. They stock an extensive selection of specialist paper and card, including their own high-quality range alongside premium brands from top paper companies. With over a century of expertise behind them, Stationery Place is a reliable go-to for both everyday stationery needs and professional print services. Now accepting bitcoin. 🖨️ 📖
Upcoming Special Events
These events aren't happening next week, but they're important to add to your calendar now as tickets are selling fast.
Children of Riddim Festival - Bitcoin Stage: This is shaping up to be one of the biggest music festivals with Bitcoin vibes in the world.
Around 150 DJs, artists, and speakers will perform over four days, from 12--16 June, in Hemel Hempstead. A dedicated stage, the Barn of Freedom, will spotlight Bitcoin culture, education, and unstoppable apps on the Nostr protocol--alongside music, talks, and much more.
Support for the Barn of Freedom stage can be given via geyser.fund, where both ticket purchases and donations are welcome. One-day and four-day passes are available, and on-site camping is included.
Confirmed names include Joe Bryan, Metamick (Geyser Fund), Roger9000, Angor, MadMunky, Huxley, and many more.
The Bitcoin Beach Retreat: An annual Bitcoin-only gathering held at a scenic coastal campsite in North Wales. Celebrating its fifth year in 2025, the retreat offers a relaxed, community-driven alternative to traditional conferences. From July 11--14, up to 120 Bitcoiners will come together to share knowledge, enjoy beachside BBQs, and strengthen their networks under the stars. With no pre-booked speakers, the event thrives on peer-led workshops and spontaneous discussions, fostering genuine connections among attendees. Emphasising local engagement, the retreat directs the majority of its funds into the surrounding community, with 42% of expenses paid in Bitcoin last year. Whether attending solo or with family, attendees can expect a welcoming environment dedicated to sound money and shared values.
Get Involved
- Volunteer: Passionate about merchant adoption? Reach out to Bridge2Bitcoin on Twitter or website.
- Start a Meetup: Want to launch a Bitcoin meetup? We'll support you. Contact us on Twitter or just reply to this email.
- Contribute to BTCMaps: Help maintain this key Bitcoin resource--no coding skills needed. Update a UK area.
- Telegram: Join our Channel for UK meetup updates
- Feedback: Reply to this email with ideas and suggestions.
This week's sponsors is…
Get out and support the meetups where you can, visit Bitcoin Events UK for more info on each meetup and to find your closest on the interactive map.
Stay tuned for more updates next week!
Simon.
-
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ cefb08d1:f419beff
2025-06-01 08:02:40
@ cefb08d1:f419beff
2025-06-01 08:02:40https://stacker.news/items/994252
-
 @ 866e0139:6a9334e5
2025-06-01 07:56:34
@ 866e0139:6a9334e5
2025-06-01 07:56:34Autor: Bernd Schoepe. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier. Die neuesten Pareto-Artikel finden Sie in unserem Telegram-Kanal.
Die Anmerkungen zum Text (Fußnoten) folgen aus technischen Gründen gesondert.
Die neuesten Artikel der Friedenstaube gibt es jetzt auch im eigenen Friedenstaube-Telegram-Kanal.
„*Es handelt sich beim Krieg nicht nur um eine Zerstörung von (...) Millionen Menschen, sondern um die Zerstörung der gesamten sozialen, moralischen und menschlichen Struktur einer Gesellschaft, von der man überhaupt nicht voraussehen kann, welche weiteren Konsequenzen an Barbarei, an Verrücktheit sie (...) mit sich bringt. (..) *
Die Gewalt kann fast alles mit den Menschen machen. Es ist wichtig zu sehen, dass es nur fast alles ist. Sie kann mit einigen Menschen nicht das machen, was sie will, nämlich ihre seelische Struktur, ihre Überzeugungen ändern und mit allen Menschen kann sie nur das machen, was sie will, wenn sie gewisse, sehr schädliche Nebenerscheinungen in Kauf nimmt: die Nebenerscheinung der Verdummung, der Lähmung der Vitalität, der Einbildungskraft, dem Schöpferischsein des Menschen. In vielen Fällen aber sind die, die die Gewalt ausüben gar nicht daran interessiert, dass diese Folgen nicht eintreten. Im geschichtlichen Prozess allerdings bleiben diese Folgen von großer Wichtigkeit.“
Erich Fromm, Zur Theorie und Strategie des Friedens (1969).
„Solange Kriege geführt werden, wird uns Kummer plagen, werden kräftige Beine nutzlos werden und strahlende Augen dunkel.“
Sean O’ Casey, Der Preispokal
Der Friede geht uns alle an – Vom Krieg profitieren aber immer nur Wenige
Gerne komme ich zum Einstand als Mit-Autor dieses wunderbaren Projekts „Die Friedenstaube“ dem Wunsch nach, über meine biographischen Hintergründe in Bezug auf das Friedensthema zu schreiben. Obwohl mein erster Impuls doch eher zögerlich war: „Darauf kommt es doch gar nicht an!“, schoss es mir zunächst durch den Kopf.
\ Geht der Frieden doch uns alle an, und zwar so stark, dass alle persönlichen Gründe, Motive, Unter-, Ober- und Zwischentöne zu dem Thema eigentlich kaum eine Rolle spielen können… – oder!? Erliegen wir nicht sogar einer ganz und gar deplatziert wirkenden Eitelkeit angesichts des „Alles oder Nichts“, um das es bei der Frage nach Krieg oder Frieden geht, wenn wir glauben, wir müssten, um für den Frieden einzutreten, irgendwelche individuellen Gründe oder spezielle biographische Motive ins Feld führen?
Für den Frieden muss man sein, weil und insoweit man ein Mensch ist (1).
So grundsätzlich und selbstverständlich, wie es der Autor des berühmten Anti-Kriegsromans „Im Westen nichts Neues“, Erich Maria Remarque, ausdrückte:
„Ich dachte immer, jeder Mensch sei gegen den Krieg. Bis ich rausfand, dass es welche gibt, die dafür sind, nämlich die, die nicht hingehen müssen.“
Erneut ist dieses Zitat – und welche Bitterkeit und welcher „Abscheu vor der Weltgeschichte“ (Erwin Chargaff) liegen darin, dies konstatieren zu müssen! – zum Wort der Stunde geworden. Auch heute wird wieder von der herrschenden Politik und den Leitmedien weitgehend ausgeblendet, welche Interessen hinter der allgemeinen Mobilmachung zum Krieg am Werke sind und wer von ihr wirklich profitiert.
Mit Erich Fromm gesprochen sind Kriegsbegeisterung und Kriegshysterie Kennzeichen von nekrophilen Gesellschaften. Wann hat sich unsere Gesellschaft offiziell so krass vom Leben und vom Wert des Lebendigen verabschiedet? Wie konnte es aufs Neue soweit kommen?
Die Zumutungen, die in der Logik, der Unterordnung unter das Prinzip der Nekrophilie liegen und die vom Krieg auf die Spitze getrieben werden, sind von Hannes Wader im „Einheitsfrontlied“ prägnant auf den Punkt gebracht worden:
„Und weil der Mensch ein Mensch ist
Drum hat er Stiefel im Gesicht nicht gern.
Er will unter sich keinen Sklaven sehen
*Und über sich keinen Herrn.“ *
(2)
Die Ordnung des Krieges aber stellt in gewisser Weise die Vollendung der auf Herrschafts- und – in seiner neoliberalen Ausprägung – Markt- und Mammon-Vergottung und der auf Arbeitssklavengehorsam der Massen basierenden Abhängigkeits- und Ausbeutungsverhältnisse dar. Unter dessen Joch leben im Kapitalismus des 21.Jahrhunderts die Menschen weltweit. Wobei die Anzahl derer, die unter diesen Bedingungen in extremer Armut dahinvegetieren müssen – schließlich setzt „leben“ ein Mindestmaß an Würde voraus – sich global auf über eine Milliarde Menschen beläuft. \ Willy Brandt hat gesagt: „Der Frieden ist nicht alles, aber ohne Frieden ist alles nichts“. Sein Gegenteil – der Krieg – ist die schlimmste Kollektiverfahrung, die eine Generation erleben kann. Zuletzt musste die Generation meiner Eltern und Großeltern diese Erfahrung durchmachen.
Wir Nachgeborenen können uns das Grauen, das Elend des Krieges, das unendliche Leid, das er über die Menschen bringt, nicht wirklich vorstellen. Wir können aber um die Ausmaße des Zivilisationsbruchs des Ersten Weltkrieges und dann, noch einmal furchtbar gesteigert, des Zweiten Weltkrieges wissen. Und als zum Mitfühlen fähige Wesen können wir ermessen, was es heißt, im Krieg zu sein:
„Keiner kommt aus dem Geschehen in einem Kriegsgebiet wieder heil raus, das macht etwas mit einem. Auf der anderen Seite (...) muss man sich immer klar machen, das eine ist das Geschehen im Kriegsgebiet, aber das andere sind die Kriegstreiber. (...) Sie sitzen da, wo einem nichts geschieht (...)“,
so Patrick Baab, der als einer der wenigen Journalisten wiederholt im umkämpften Kriegsgebiet der Ost-Ukraine war und seine Eindrücke erster Hand in dem Buch „Auf beiden Seiten der Front. Meine Reisen in die Ukraine“ geschildert hat.
Dass diese Teilung in solche und solche, die Remarque in seinem Zitat lakonisch-pointiert thematisiert, auch heute wieder beobachtet werden muss, d.h. Politik und Leitmedien von (ahnungslosen?) Kriegsverharmlosern und Kriegstreibern und ihrem bellizistischen Geschrei beherrscht werden, während die Mehrheit des Volkes sich weiterhin sehnlichst Frieden wünscht, auf diesen erschreckenden Sachverhalt und was aus ihm geschlossen werden müsste, hat Baab kürzlich im Interview mit dem Overton-Magazin hingewiesen (3).
Ein Hinweis am Ende dieser Einleitung:
Ich muss den Leser vorab um Geduld bitten, denn mein Text wird mit der autobiographischen Tür nicht gleich ins Haus, weder in das des Krieges noch in das des Friedens fallen.
Die ersten Teile (II –V) werden im Zeichen der politischen Analyse stehen. Einer Analyse, die nicht vor dem Hintergrund meiner eigenen, sondern der bundesdeutschen Geschichte und einige ihrer größten blinden Flecken – mit Ulrike Guérot könnte man auch sagen „ihrer größten Märchen“– unternommen wird. Dass mein antimilitaristisches Ich in Interaktion zu dieser Geschichte stand und steht, muss wohl nicht eigens betont werden.
Erst nach dieser Erkundung des Makrokosmos werden sich im Verlauf des Textes von da aus, nach einer Durchleuchtung seiner Bedingtheiten, Zugänge zum eigenen Mikrokosmos eröffnen. Sonst wären sie vermutlich als autobiographische Lesart des Themas nicht offen zu Tage getreten, möglicherweise mir sogar ganz verschlossen geblieben. So aber darf mit guten Gründen vermutet werden, dass das persönlich hier von mir Festgehaltene und Fokussierte nicht nur mich angeht. Vielmehr erscheint es in dem Maße verallgemeinerbar zu sein, wie durch den Fortgang meiner Darlegungen jeder Leser individuell (hoffentlich) ebenfalls dazu motiviert werden kann, die Frage zu reflektieren, was es bedeutet, wenn es sich bei der persönlichen Begegnung mit dem Krieg um eine Begegnung auf den zweiten oder sogar dritten Blick handelt?
Der Nachkriegs-„Frieden“ als die Zeit ernst gemeinter, nicht enden wollender Kriegsspiele
„Nie wieder Krieg! Nie wieder Faschismus!“
Das war die Lehre aus den Weltkriegs-Zivilisationszusammenbrüchen, die vor allem anderen, wenn auch auf verschiedene Weise, als DNA beiden deutschen Republiken, zu ihren Gründungszeiten eingeprägt wurde.
Was aber ist aus dieser DNA geworden?
Heute lassen wir zu, dass in Manier des NS-Reichspropagandaministers Goebbels von „Kriegstüchtigkeit“ als Staatsziel schwadroniert wird (4), das man bitteschön mal bis 2030, mal schon 2027 erreicht haben müsse, weil sonst „der Russe“ am Brandenburger Tor stehe. Mit „Kriegstüchtigkeit“ sind immense, unvorstellbare Summen an Geld gemeint, neue Schulden, die in die Rüstung und Militarisierung der Gesellschaft fließen sollen und folglich anderswo, für eine menschliche, dem Leben dienende Politik, schmerzlich fehlen. Die Militarisierung soll nun wieder, wie im Wilhelminismus und im Dritten Reich, von Kindesbeinen an propagiert und gefördert werden.
An den Schulen darf der Beutelsbacher Konsens mit seinem Überwältigungsverbot – er wurde schon in der Corona-Zeit mit schlimmsten Folgen für die Kinder und Jugendliche missachtet (5 https://www.cicero.de/kultur/fuenf-jahre-schulschliessungen-corona-aufarbeitung) – nun auch der Wehrertüchtigung der jungen Generation und dem Ruf „Zu den Waffen!“ auf keinen Fall mehr im Wege stehen. Völlig abstrus: Schüler, die gegen die Kriegsertüchtigung an den Schulen protestieren, werden dafür von Pädagogen (!) wegen „Störung des Schulfriedens“ bestraft. Antimilitaristische, pazifistische Haltungen werden ausgegrenzt und kriminalisiert. Mittels Framings sind, wie schon in der Corona-Zeit, die Mainstream-Medien erneut eifrig dabei, die vernünftig-skeptischen Stimmen moralisch zu diskreditieren. Wurden zu Plandemie-Zeiten jene, die die Verhältnismäßigkeit der staatlichen Maßnahmen in Frage stellten und sich der systematisch betriebenen Panikmache und Massenpsychose verweigerten, öffentlich verächtlich gemacht, werden nun all jene, die für Abrüstung, Diplomatie und Völkerverständigung plädieren, diffamiert und ins gesellschaftliche Abseits gestellt.
Dennoch regt sich kein massenhafter Protest, der den Minister, der die Kriegstüchtigkeit zum Gesellschaftsziel erhoben hat, zum Rücktritt zwingen und die Journalisten zur Besinnung und zur Einhaltung professioneller Standards bringen könnte. Und das obwohl die Forderung nach Kriegstüchtigkeit – wie die gesamte Russland-Ukraine-Politik der bundesdeutschen Regierungen in den letzten fünfzehn Jahren – eine eklatante Verletzung der Friedenspflicht des Grundgesetzes darstellt. So gab Angela Merkel Ende 2022 bekannt, man habe die Verhandlungen um das 2015 ratifizierte Minsker Abkommen nur geführt, um der Ukraine genug Zeit zum Aufbau einer kriegsfähigen Armee und für das Aufrüsten zu geben (6). Die Ukraine sollte in die Lage versetzt werden, die Donbass-Provinzen zurückzuerobern, die sich in Folge von Kiews ultra-nationalistischer Politik seit 2015 sezessionistisch, mit Unterstützung Russlands, für autonom erklärt hatten. Ergänzt werden muss, dass in der Ukraine nach den gewalttätigen Ereignissen auf dem Maidan, die zum Sturz von Janukowytsch führen sollte, ein den Faschismus verherrlichender, hybrider Nationalismus politisch die Oberhand gewann, der die vor allem im Osten des Landes lebende russische Bevölkerung zunehmend diskriminierte und ihre Kultur unterdrückte.
Die bundesdeutsche Öffentlichkeit nahm die absolut skandalöse Äußerung der ehemaligen Regierungschefin achselzuckend hin. Nicht einmal ansatzweise flammte eine Debatte darüber auf, wie viel diplomatisches Porzellan durch diese Täuschung des russischen Vertragspartners zerschlagen und wie stark dadurch die außenpolitische Glaubwürdigkeit der Bundesrepublik – die lange Zeit international als ehrlicher Makler des Interessenausgleichs gegolten hatte – beschädigt wurde.
Was ist aus dem Vorschlag Michail Gorbatschows geworden, eine gemeinsame europäische Sicherheitsarchitektur von Lissabon bis Wladiwostok zu schaffen, den Präsident Putin beim Deutschland-Besuch 2001 noch einmal als sein umfassendes Angebot zur Zusammenarbeit an den Westen bekräftigt hatte? Damals sagte Putin in seiner weitgehend auf Deutsch gehaltenen Rede vor dem Bundestag:
*„Ohne eine moderne, dauerhafte und standfeste internationale Sicherheitsarchitektur schaffen wir auf diesem Kontinent nie ein Vertrauensklima und ohne dieses Vertrauensklima ist kein einheitliches Großeuropa möglich. Heute sind wir verpflichtet, zu sagen, dass wir uns von unseren Stereotypen und Ambitionen trennen sollten, um die Sicherheit der Bevölkerung Europas und die der ganzen Welt zusammen zu gewährleisten. (...) *
Noch vor kurzem schien es so, als würde auf dem Kontinent bald ein richtiges gemeinsames Haus entstehen, in welchem Europäer nicht in östliche und westliche, in nördliche und südliche geteilt werden. Solche Trennungslinien bleiben aber erhalten, und zwar deswegen, weil wir uns bis jetzt noch nicht endgültig von vielen Stereotypen und ideologischen Klischees des Kalten Krieges befreit haben.“
(7)
Putins Bitte, sich endgültig von den Stereotypen und Klischees des Kalten Krieges zu befreien – er erhielt für seine Rede im Bundestag damals lang anhaltenden Beifall und stehende Ovationen – sollte sich als frommer Wunsch erweisen. Die einflussreichen, entscheidenden Kräfte in den USA dachten überhaupt nicht daran, diesen Schritt zu tun. Der „nationale Egoismus“, von dem Putin im selben Zusammenhang als Hinderungsgrund für weitere Annäherungen sprach, sollte – vor allem seitens der USA, wie es aus den Strategiepapieren der mächtigen, dem Pentagon zuarbeitenden Denkfabriken der NeoCons unmissverständlich hervorgeht – auf ganzer Linie triumphieren:
„Allein die Lektüre einiger amerikanischer geopolitischer Texte hätte den deutschen Politikern zeigen können, dass die Vereinigten Staaten niemals eine Annäherung Deutschlands an Russland akzeptieren würden. (...) Für die Strategen in Washington glich eine deutsch-russische Allianz einem absoluten Albtraum.“
(8)
Folglich wurde die Rede nicht als historische Chance, als einzigartiges window of opportunity begriffen, die bilateralen und multilateralen Beziehungen neu zu definieren und damit ein neues Kapitel des Friedens und des Wohlstandes unter den Völkern aufzuschlagen und, wie es der russische Präsident formulierte, „damit unseren gemeinsamen Beitrag zum Aufbau des europäischen Hauses“ (9) zu leisten.
Stattdessen setzte sich, trotz der veränderten Bedingungen einer komplizierter gewordenen, nach 1990 multipolar sich neu ordnenden Welt, wiederum das alte, hegemoniale Denken der US-Amerikaner im gesamten, offenbar nun erstarkten (10) und bis an die Grenzen Russlands ausgedehnten Westen (NATO-Osterweiterung!) durch. Damit folgte man wiederum den alten Pfaden der Konfrontation statt den neuen der Kooperation, was leider eine lange Kontinuität aufweist.
So haben neuere Forschungen im Rahmen der Geschichte der Kognitiven Kriegsführung belegt, dass die Bundesrepublik von Anfang an systematisch durch die USA militärisch-geostrategisch und mental in Stellung gegen die Sowjetunion gebracht wurde. An der Bewertung der Beziehungen Deutschlands und Russlands hat sich grundlegend auch nach 1990 und dem Ende der Blockpolarität aus Sicht der US-Amerikaner nichts geändert.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Der Amerikanist und Propagandaforscher Jonas Tögel hat herausgearbeitet (11), in welchem Ausmaß es 1945 den USA nicht um die Befreiung des europäischen Kontinents ging. Vielmehr lautete die Doktrin, dass als der eigentliche Kriegsgegner die Sowjetunion bezwungen werden müsse: „Europa war in letzter Konsequenz genauso strategisches Gebiet wie davor (...). Es sollten offenbar die letzten deutschen Truppen (...) mit den letzten alliierten Truppen in einem neuen Aufgebot gen Osten geschickt werden“ (12). Die US-amerikanischen Regierungen sahen – über 1945 hinaus! – die Sowjetunion als den Hauptfeind an. Dabei war klar, wo der Austragungsort der Entscheidungsschlacht zwischen den Systemantagonisten liegen würde: 1955, im ersten Mitgliedsjahr der BRD, wurde eine „Carte Blanche“ genannte NATO-Übung durchgeführt, in der es ein Szenario von 168 Atombombenabwürfen über deutsches Gebiet mit 1,7 Millionen getöteten und 3,5 Millionen verletzten Deutschen entworfen gab. Weitere Planspiele, die die atomare Zerstörung Deutschlands vorsahen, folgten. Etwas größere Bekanntheit erlangte, durch den damaligen Staatssekretär im Bundesverteidigungsministerium Willy Wimmer (CDU), die NATO-Übung WINTEX/FALLEX (13) von 1986, in der Atombombeneinsätze gegen Dresden und andere deutsche Städte vorgesehen waren.
„Er, Wimmer, sei von dieser Anforderung völlig überrascht worden und sei entsetzt gewesen. Er habe es abgelehnt, an der Planung eines Atomwaffeneinsatzes auf Ziele in Ostdeutschland und damit gegen die ostdeutsche Bevölkerung – wenn auch „nur“ übungsweise – mitzuwirken. In dieser Situation habe er sofort Kontakt mit dem damaligen Bundeskanzler Dr. Helmut Kohl (CDU) aufgenommen und ihn von diesem für ihn unerhörten Vorgang in Kenntnis gesetzt. Bundeskanzler Kohl habe daraufhin entschieden, dass sich die Vertreter der Bundesregierung sofort aus der weiteren Übung zurückziehen und sich keinesfalls an diesen nuklearen Planspielen gegen Ziele wie Dresden und andere ostdeutsche Städte beteiligen sollten. Deutschland habe, so Wimmer, deshalb seine weitere Mitwirkung an dieser NATO-Übung – vier Tage vor ihrem Ende – eingestellt. Die Übung sei dann – ohne deutsche Beteiligung – fortgesetzt worden.“ (14)
Der Schweizer Militär- und Geheimdienstexperte Jacques Baud geht soweit zu behaupten, dass die NATO „für den Kalten Krieg und für den Nuklearkrieg geschaffen wurde.“ (15) Zu einem Zeitpunkt, wo der erst im zweiten Wahlgang gewählte neue deutsche Bundeskanzler noch immer nicht öffentlich seine Erklärung zurückgenommen hat, Taurus-Raketen an die Ukraine liefern zu wollen, sollte dies unbedingt in Erinnerung gerufen werden.
Darüber hinaus gilt, was alle Kriegsspiele, sowohl die Kriegsspiele der NATO als auch jene der Sowjetunion bzw. später Russlands dokumentieren:
„Die Deutschen haben nicht mitzureden, wenn es um die Vernichtung ihres eigenen Landes geht.“ (Jonas Tögel, 16).
Kann es da verwundern, dass spiegelbildlich dazu der von der NATO losgetretene Informationskrieg gerade in Deutschland immer bizarrere Blüten treibt?
Denn hier liegt das Schlachtfeld des Propagandakrieges, der jedem Waffengang erst einmal vorausgeht und gewonnen sein will. Das meint auch die Rede von der zu erlangenden Kriegstüchtigkeit. Sie dient als Propaganda zur Formierung der Gesellschaft gegen „den“ Feind, wobei der Feind grundsätzlich austauschbar ist (es kann auch ein „gefährliches“ Virus sein...), immer aber gewisse Eigenschaften aufweisen muss. So sollte er leicht adaptierbar an die Ängste oder Aggressionen der Menschen sein. Dies impliziert auch, dass die aktuelle Einschätzung von 16 amerikanischen Geheimdiensten, nach denen Russland keinen Krieg gegen die europäischen NATO-Staaten beabsichtige und plane, in der öffentlichen Debatte hierzulande keine Rolle spielt und der Bevölkerung vorenthalten wird (17).
Kontrafaktisch wird mit Hilfe der immer gleichen Protagonisten des militärisch-industriellen, und – wie hinzugefügt werden muss – propagandistisch-medialen Komplexes am Bedrohungsszenario festgehalten. Wer es nicht glaubt, der möge bei Google im Suchfenster: „16 amerikanische Geheimdienste Russland keine Bedrohung“ oder etwas Sinngleiches eingeben und schauen, ob er auf den ersten Seiten irgendwelche „Treffer“ landet. Ich wünsche viel Spaß dabei!
Teil 2 folgt demnächst.
Bernd Schoepe, Jahrgang 1965, Studium der Soziologie, Germanistik, Philosophie und Erziehungswissenschaften in Frankfurt/M. und Hamburg. Erstes und zweites Staatsexamen. Freier Autor, der zu bildungspolitischen, bildungssoziologischen- und bildungsphilosophischen Themen schreibt. Seit 2003 im Hamburger Schuldienst. Langjähriges GEW-Betriebsgruppen-Mitglied, ehem. Vertrauensmann, ehem. Mitglied der Hamburger Lehrerkammer. Hauptberuflich bin ich Politik- Deutsch- und Philosophielehrer an einer Hamburger Stadtteilschule. Kontakt: berndschoepe\@gmx.de
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
In Kürze folgt eine Mail an alle Genossenschafter, danke für die Geduld!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: friedenstaube@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ 3f770d65:7a745b24
2025-01-12 21:03:36
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize the potential of Notedeck. If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream INTEROPERABILITY and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be developed live, right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-
 @ 77c2969e:a33cfa50
2025-01-09 17:01:36
@ 77c2969e:a33cfa50
2025-01-09 17:01:36换了个客户端Nostrmo,比damus好用,不过好像关注列表丢失了😩。
现在使用#YakiHonne,好像更流畅
不加图片他还会显示一个空白图片,好丑,我还是上传一个吧
-
 @ 106de8d9:a99be73f
2025-06-01 07:56:04
@ 106de8d9:a99be73f
2025-06-01 07:56:04For those who like to be first and make money https://t.me/edchess_bot/web3?startapp=ref-link=mTLuwhkSLyYJ
-
 @ 5d1d83de:d0db5aa0
2025-06-01 06:04:32
@ 5d1d83de:d0db5aa0
2025-06-01 06:04:32As long as the base unit of the trading system can be manipulated a free trading system cannot emerge.
The trading system will either be manipulated by printed subsidies or will be manipulated by artificial exchange rates.
Free trading was available during a gold standard and free trading will become available again during a future bitcoin standard.
https://stacker.news/items/989491
-
 @ 35f80bda:406855c0
2025-06-01 04:36:56
@ 35f80bda:406855c0
2025-06-01 04:36:56Privacy is necessary for an open society in the electronic age. Privacy is not secrecy. A private matter is something one doesn't want the whole world to know, but a secret matter is something one doesn't want anybody to know. Privacy is the power to selectively reveal oneself to the world.
If two parties have some sort of dealings, then each has a memory of their interaction. Each party can speak about their own memory of this; how could anyone prevent it? One could pass laws against it, but the freedom of speech, even more than privacy, is fundamental to an open society; we seek not to restrict any speech at all. If many parties speak together in the same forum, each can speak to all the others and aggregate together knowledge about individuals and other parties. The power of electronic communications has enabled such group speech, and it will not go away merely because we might want it to.
Since we desire privacy, we must ensure that each party to a transaction have knowledge only of that which is directly necessary for that transaction. Since any information can be spoken of, we must ensure that we reveal as little as possible. In most cases personal identity is not salient. When I purchase a magazine at a store and hand cash to the clerk, there is no need to know who I am. When I ask my electronic mail provider to send and receive messages, my provider need not know to whom I am speaking or what I am saying or what others are saying to me; my provider only need know how to get the message there and how much I owe them in fees. When my identity is revealed by the underlying mechanism of the transaction, I have no privacy. I cannot here selectively reveal myself; I must always reveal myself.
Therefore, privacy in an open society requires anonymous transaction systems. Until now, cash has been the primary such system. An anonymous transaction system is not a secret transaction system. An anonymous system empowers individuals to reveal their identity when desired and only when desired; this is the essence of privacy.
Privacy in an open society also requires cryptography. If I say something, I want it heard only by those for whom I intend it. If the content of my speech is available to the world, I have no privacy. To encrypt is to indicate the desire for privacy, and to encrypt with weak cryptography is to indicate not too much desire for privacy. Furthermore, to reveal one's identity with assurance when the default is anonymity requires the cryptographic signature.
We cannot expect governments, corporations, or other large, faceless organizations to grant us privacy out of their beneficence. It is to their advantage to speak of us, and we should expect that they will speak. To try to prevent their speech is to fight against the realities of information. Information does not just want to be free, it longs to be free. Information expands to fill the available storage space. Information is Rumor's younger, stronger cousin; Information is fleeter of foot, has more eyes, knows more, and understands less than Rumor.
We must defend our own privacy if we expect to have any. We must come together and create systems which allow anonymous transactions to take place. People have been defending their own privacy for centuries with whispers, darkness, envelopes, closed doors, secret handshakes, and couriers. The technologies of the past did not allow for strong privacy, but electronic technologies do.
We the Cypherpunks are dedicated to building anonymous systems. We are defending our privacy with cryptography, with anonymous mail forwarding systems, with digital signatures, and with electronic money.
Cypherpunks write code. We know that someone has to write software to defend privacy, and since we can't get privacy unless we all do, we're going to write it. We publish our code so that our fellow Cypherpunks may practice and play with it. Our code is free for all to use, worldwide. We don't much care if you don't approve of the software we write. We know that software can't be destroyed and that a widely dispersed system can't be shut down.
Cypherpunks deplore regulations on cryptography, for encryption is fundamentally a private act. The act of encryption, in fact, removes information from the public realm. Even laws against cryptography reach only so far as a nation's border and the arm of its violence. Cryptography will ineluctably spread over the whole globe, and with it the anonymous transactions systems that it makes possible.
For privacy to be widespread it must be part of a social contract. People must come and together deploy these systems for the common good. Privacy only extends so far as the cooperation of one's fellows in society. We the Cypherpunks seek your questions and your concerns and hope we may engage you so that we do not deceive ourselves. We will not, however, be moved out of our course because some may disagree with our goals.
The Cypherpunks are actively engaged in making the networks safer for privacy. Let us proceed together apace.
Onward.
Eric Hughes hughes@soda.berkeley.edu
9 March 1993
-
 @ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08
@ 1bda7e1f:bb97c4d9
2025-01-02 05:19:08Tldr
- Nostr is an open and interoperable protocol
- You can integrate it with workflow automation tools to augment your experience
- n8n is a great low/no-code workflow automation tool which you can host yourself
- Nostrobots allows you to integrate Nostr into n8n
- In this blog I create some workflow automations for Nostr
- A simple form to delegate posting notes
- Push notifications for mentions on multiple accounts
- Push notifications for your favourite accounts when they post a note
- All workflows are provided as open source with MIT license for you to use
Inter-op All The Things
Nostr is a new open social protocol for the internet. This open nature exciting because of the opportunities for interoperability with other technologies. In Using NFC Cards with Nostr I explored the
nostr:URI to launch Nostr clients from a card tap.The interoperability of Nostr doesn't stop there. The internet has many super-powers, and Nostr is open to all of them. Simply, there's no one to stop it. There is no one in charge, there are no permissioned APIs, and there are no risks of being de-platformed. If you can imagine technologies that would work well with Nostr, then any and all of them can ride on or alongside Nostr rails.
My mental model for why this is special is Google Wave ~2010. Google Wave was to be the next big platform. Lars was running it and had a big track record from Maps. I was excited for it. Then, Google pulled the plug. And, immediately all the time and capital invested in understanding and building on the platform was wasted.
This cannot happen to Nostr, as there is no one to pull the plug, and maybe even no plug to pull.
So long as users demand Nostr, Nostr will exist, and that is a pretty strong guarantee. It makes it worthwhile to invest in bringing Nostr into our other applications.
All we need are simple ways to plug things together.
Nostr and Workflow Automation
Workflow automation is about helping people to streamline their work. As a user, the most common way I achieve this is by connecting disparate systems together. By setting up one system to trigger another or to move data between systems, I can solve for many different problems and become way more effective.
n8n for workflow automation
Many workflow automation tools exist. My favourite is n8n. n8n is a low/no-code workflow automation platform which allows you to build all kinds of workflows. You can use it for free, you can self-host it, it has a user-friendly UI and useful API. Vs Zapier it can be far more elaborate. Vs Make.com I find it to be more intuitive in how it abstracts away the right parts of the code, but still allows you to code when you need to.
Most importantly you can plug anything into n8n: You have built-in nodes for specific applications. HTTP nodes for any other API-based service. And community nodes built by individual community members for any other purpose you can imagine.
Eating my own dogfood
It's very clear to me that there is a big design space here just demanding to be explored. If you could integrate Nostr with anything, what would you do?
In my view the best way for anyone to start anything is by solving their own problem first (aka "scratching your own itch" and "eating your own dogfood"). As I get deeper into Nostr I find myself controlling multiple Npubs – to date I have a personal Npub, a brand Npub for a community I am helping, an AI assistant Npub, and various testing Npubs. I need ways to delegate access to those Npubs without handing over the keys, ways to know if they're mentioned, and ways to know if they're posting.
I can build workflows with n8n to solve these issues for myself to start with, and keep expanding from there as new needs come up.
Running n8n with Nostrobots
I am mostly non-technical with a very helpful AI. To set up n8n to work with Nostr and operate these workflows should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs my HAVEN Nostr Relay and Albyhub Lightning Node in Docker containers,
- My objective was to set up n8n to run alongside these in a separate Docker container on the same server, install the required nodes, and then build and host my workflows.
Installing n8n
Self-hosting n8n could not be easier. I followed n8n's Docker-Compose installation docs–
- Install Docker and Docker-Compose if you haven't already,
- Create your
docker-compose.ymland.envfiles from the docs, - Create your data folder
sudo docker volume create n8n_data, - Start your container with
sudo docker compose up -d, - Your n8n instance should be online at port
5678.
n8n is free to self-host but does require a license. Enter your credentials into n8n to get your free license key. You should now have access to the Workflow dashboard and can create and host any kind of workflows from there.
Installing Nostrobots
To integrate n8n nicely with Nostr, I used the Nostrobots community node by Ocknamo.
In n8n parlance a "node" enables certain functionality as a step in a workflow e.g. a "set" node sets a variable, a "send email" node sends an email. n8n comes with all kinds of "official" nodes installed by default, and Nostr is not amongst them. However, n8n also comes with a framework for community members to create their own "community" nodes, which is where Nostrobots comes in.
You can only use a community node in a self-hosted n8n instance (which is what you have if you are running in Docker on your own server, but this limitation does prevent you from using n8n's own hosted alternative).
To install a community node, see n8n community node docs. From your workflow dashboard–
- Click the "..." in the bottom left corner beside your username, and click "settings",
- Cilck "community nodes" left sidebar,
- Click "Install",
- Enter the "npm Package Name" which is
n8n-nodes-nostrobots, - Accept the risks and click "Install",
- Nostrobots is now added to your n8n instance.
Using Nostrobots
Nostrobots gives you nodes to help you build Nostr-integrated workflows–
- Nostr Write – for posting Notes to the Nostr network,
- Nostr Read – for reading Notes from the Nostr network, and
- Nostr Utils – for performing certain conversions you may need (e.g. from bech32 to hex).
Nostrobots has good documentation on each node which focuses on simple use cases.
Each node has a "convenience mode" by default. For example, the "Read" Node by default will fetch Kind 1 notes by a simple filter, in Nostrobots parlance a "Strategy". For example, with Strategy set to "Mention" the node will accept a pubkey and fetch all Kind 1 notes that Mention the pubkey within a time period. This is very good for quick use.
What wasn't clear to me initially (until Ocknamo helped me out) is that advanced use cases are also possible.
Each node also has an advanced mode. For example, the "Read" Node can have "Strategy" set to "RawFilter(advanced)". Now the node will accept json (anything you like that complies with NIP-01). You can use this to query Notes (Kind 1) as above, and also Profiles (Kind 0), Follow Lists (Kind 3), Reactions (Kind 7), Zaps (Kind 9734/9735), and anything else you can think of.
Creating and adding workflows
With n8n and Nostrobots installed, you can now create or add any kind of Nostr Workflow Automation.
- Click "Add workflow" to go to the workflow builder screen,
- If you would like to build your own workflow, you can start with adding any node. Click "+" and see what is available. Type "Nostr" to explore the Nostrobots nodes you have added,
- If you would like to add workflows that someone else has built, click "..." in the top right. Then click "import from URL" and paste in the URL of any workflow you would like to use (including the ones I share later in this article).
Nostr Workflow Automations
It's time to build some things!
A simple form to post a note to Nostr
I started very simply. I needed to delegate the ability to post to Npubs that I own in order that a (future) team can test things for me. I don't want to worry about managing or training those people on how to use keys, and I want to revoke access easily.
I needed a basic form with credentials that posted a Note.
For this I can use a very simple workflow–
- A n8n Form node – Creates a form for users to enter the note they wish to post. Allows for the form to be protected by a username and password. This node is the workflow "trigger" so that the workflow runs each time the form is submitted.
- A Set node – Allows me to set some variables, in this case I set the relays that I intend to use. I typically add a Set node immediately following the trigger node, and put all the variables I need in this. It helps to make the workflows easier to update and maintain.
- A Nostr Write node (from Nostrobots) – Writes a Kind-1 note to the Nostr network. It accepts Nostr credentials, the output of the Form node, and the relays from the Set node, and posts the Note to those relays.
Once the workflow is built, you can test it with the testing form URL, and set it to "Active" to use the production form URL. That's it. You can now give posting access to anyone for any Npub. To revoke access, simply change the credentials or set to workflow to "Inactive".
It may also be the world's simplest Nostr client.
You can find the Nostr Form to Post a Note workflow here.
Push notifications on mentions and new notes
One of the things Nostr is not very good at is push notifications. Furthermore I have some unique itches to scratch. I want–
- To make sure I never miss a note addressed to any of my Npubs – For this I want a push notification any time any Nostr user mentions any of my Npubs,
- To make sure I always see all notes from key accounts – For this I need a push notification any time any of my Npubs post any Notes to the network,
- To get these notifications on all of my devices – Not just my phone where my Nostr regular client lives, but also on each of my laptops to suit wherever I am working that day.
I needed to build a Nostr push notifications solution.
To build this workflow I had to string a few ideas together–
- Triggering the node on a schedule – Nostrobots does not include a trigger node. As every workflow starts with a trigger we needed a different method. I elected to run the workflow on a schedule of every 10-minutes. Frequent enough to see Notes while they are hot, but infrequent enough to not burden public relays or get rate-limited,
- Storing a list of Npubs in a Nostr list – I needed a way to store the list of Npubs that trigger my notifications. I initially used an array defined in the workflow, this worked fine. Then I decided to try Nostr lists (NIP-51, kind 30000). By defining my list of Npubs as a list published to Nostr I can control my list from within a Nostr client (e.g. Listr.lol or Nostrudel.ninja). Not only does this "just work", but because it's based on Nostr lists automagically Amethyst client allows me to browse that list as a Feed, and everyone I add gets notified in their Mentions,
- Using specific relays – I needed to query the right relays, including my own HAVEN relay inbox for notes addressed to me, and wss://purplepag.es for Nostr profile metadata,
- Querying Nostr events (with Nostrobots) – I needed to make use of many different Nostr queries and use quite a wide range of what Nostrobots can do–
- I read the EventID of my Kind 30000 list, to return the desired pubkeys,
- For notifications on mentions, I read all Kind 1 notes that mention that pubkey,
- For notifications on new notes, I read all Kind 1 notes published by that pubkey,
- Where there are notes, I read the Kind 0 profile metadata event of that pubkey to get the displayName of the relevant Npub,
- I transform the EventID into a Nevent to help clients find it.
- Using the Nostr URI – As I did with my NFC card article, I created a link with the
nostr:URI prefix so that my phone's native client opens the link by default, - Push notifications solution – I needed a push notifications solution. I found many with n8n integrations and chose to go with Pushover which supports all my devices, has a free trial, and is unfairly cheap with a $5-per-device perpetual license.
Once the workflow was built, lists published, and Pushover installed on my phone, I was fully set up with push notifications on Nostr. I have used these workflows for several weeks now and made various tweaks as I went. They are feeling robust and I'd welcome you to give them a go.
You can find the Nostr Push Notification If Mentioned here and If Posts a Note here.
In speaking with other Nostr users while I was building this, there are all kind of other needs for push notifications too – like on replies to a certain bookmarked note, or when a followed Npub starts streaming on zap.stream. These are all possible.
Use my workflows
I have open sourced all my workflows at my Github with MIT license and tried to write complete docs, so that you can import them into your n8n and configure them for your own use.
To import any of my workflows–
- Click on the workflow of your choice, e.g. "Nostr_Push_Notify_If_Mentioned.json",
- Click on the "raw" button to view the raw JSON, ex any Github page layout,
- Copy that URL,
- Enter that URL in the "import from URL" dialog mentioned above.
To configure them–
- Prerequisites, credentials, and variables are all stated,
- In general any variables required are entered into a Set Node that follows the trigger node,
- Pushover has some extra setup but is very straightforward and documented in the workflow.
What next?
Over my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest two blogs I explored different types of interoperability with NFC cards and now n8n Workflow Automation.
Thinking ahead n8n can power any kind of interoperability between Nostr and any other legacy technology solution. On my mind as I write this:
- Further enhancements to posting and delegating solutions and forms (enhanced UI or different note kinds),
- Automated or scheduled posting (such as auto-liking everything Lyn Alden posts),
- Further enhancements to push notifications, on new and different types of events (such as notifying me when I get a new follower, on replies to certain posts, or when a user starts streaming),
- All kinds of bridges, such as bridging notes to and from Telegram, Slack, or Campfire. Or bridging RSS or other event feeds to Nostr,
- All kinds of other automation (such as BlackCoffee controlling a coffee machine),
- All kinds of AI Assistants and Agents,
In fact I have already released an open source workflow for an AI Assistant, and will share more about that in my next blog.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ f9cf4e94:96abc355
2024-12-31 20:18:59
@ f9cf4e94:96abc355
2024-12-31 20:18:59Scuttlebutt foi iniciado em maio de 2014 por Dominic Tarr ( dominictarr ) como uma rede social alternativa off-line, primeiro para convidados, que permite aos usuários obter controle total de seus dados e privacidade. Secure Scuttlebutt (ssb) foi lançado pouco depois, o que coloca a privacidade em primeiro plano com mais recursos de criptografia.
Se você está se perguntando de onde diabos veio o nome Scuttlebutt:
Este termo do século 19 para uma fofoca vem do Scuttlebutt náutico: “um barril de água mantido no convés, com um buraco para uma xícara”. A gíria náutica vai desde o hábito dos marinheiros de se reunir pelo boato até a fofoca, semelhante à fofoca do bebedouro.

Marinheiros se reunindo em torno da rixa. ( fonte )
Dominic descobriu o termo boato em um artigo de pesquisa que leu.
Em sistemas distribuídos, fofocar é um processo de retransmissão de mensagens ponto a ponto; as mensagens são disseminadas de forma análoga ao “boca a boca”.
Secure Scuttlebutt é um banco de dados de feeds imutáveis apenas para acréscimos, otimizado para replicação eficiente para protocolos ponto a ponto. Cada usuário tem um log imutável somente para acréscimos no qual eles podem gravar. Eles gravam no log assinando mensagens com sua chave privada. Pense em um feed de usuário como seu próprio diário de bordo, como um diário de bordo (ou diário do capitão para os fãs de Star Trek), onde eles são os únicos autorizados a escrever nele, mas têm a capacidade de permitir que outros amigos ou colegas leiam ao seu diário de bordo, se assim o desejarem.
Cada mensagem possui um número de sequência e a mensagem também deve fazer referência à mensagem anterior por seu ID. O ID é um hash da mensagem e da assinatura. A estrutura de dados é semelhante à de uma lista vinculada. É essencialmente um log somente de acréscimo de JSON assinado. Cada item adicionado a um log do usuário é chamado de mensagem.
Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.

Perspectivas dos participantes
Scuttlebot
O software Pub é conhecido como servidor Scuttlebutt (servidor ssb ), mas também é conhecido como “Scuttlebot” e
sbotna linha de comando. O servidor SSB adiciona comportamento de rede ao banco de dados Scuttlebutt (SSB). Estaremos usando o Scuttlebot ao longo deste tutorial.Os logs do usuário são conhecidos como feed e um usuário pode seguir os feeds de outros usuários para receber suas atualizações. Cada usuário é responsável por armazenar seu próprio feed. Quando Alice assina o feed de Bob, Bob baixa o log de feed de Alice. Bob pode verificar se o registro do feed realmente pertence a Alice verificando as assinaturas. Bob pode verificar as assinaturas usando a chave pública de Alice.

Estrutura de alto nível de um feed
Pubs são servidores de retransmissão conhecidos como “super peers”. Pubs conectam usuários usuários e atualizações de fofocas a outros usuários conectados ao Pub. Um Pub é análogo a um pub da vida real, onde as pessoas vão para se encontrar e se socializar. Para ingressar em um Pub, o usuário deve ser convidado primeiro. Um usuário pode solicitar um código de convite de um Pub; o Pub simplesmente gerará um novo código de convite, mas alguns Pubs podem exigir verificação adicional na forma de verificação de e-mail ou, com alguns Pubs, você deve pedir um código em um fórum público ou chat. Pubs também podem mapear aliases de usuário, como e-mails ou nome de usuário, para IDs de chave pública para facilitar os pares de referência.
Depois que o Pub enviar o código de convite ao usuário, o usuário resgatará o código, o que significa que o Pub seguirá o usuário, o que permite que o usuário veja as mensagens postadas por outros membros do Pub, bem como as mensagens de retransmissão do Pub pelo usuário a outros membros do Pub.
Além de retransmitir mensagens entre pares, os Pubs também podem armazenar as mensagens. Se Alice estiver offline e Bob transmitir atualizações de feed, Alice perderá a atualização. Se Alice ficar online, mas Bob estiver offline, não haverá como ela buscar o feed de Bob. Mas com um Pub, Alice pode buscar o feed no Pub mesmo se Bob estiver off-line porque o Pub está armazenando as mensagens. Pubs são úteis porque assim que um colega fica online, ele pode sincronizar com o Pub para receber os feeds de seus amigos potencialmente offline.
Um usuário pode, opcionalmente, executar seu próprio servidor Pub e abri-lo ao público ou permitir que apenas seus amigos participem, se assim o desejarem. Eles também podem ingressar em um Pub público. Aqui está uma lista de Pubs públicos em que todos podem participar . Explicaremos como ingressar em um posteriormente neste guia. Uma coisa importante a observar é que o Secure Scuttlebutt em uma rede social somente para convidados significa que você deve ser “puxado” para entrar nos círculos sociais. Se você responder às mensagens, os destinatários não serão notificados, a menos que estejam seguindo você de volta. O objetivo do SSB é criar “ilhas” isoladas de redes pares, ao contrário de uma rede pública onde qualquer pessoa pode enviar mensagens a qualquer pessoa.


Perspectivas dos participantes
Pubs - Hubs
Pubs públicos
| Pub Name | Operator | Invite Code | | ------------------------------------------------------------ | ------------------------------------------------------------ | ------------------------------------------------------------ | |
scuttle.us| @Ryan |scuttle.us:8008:@WqcuCOIpLtXFRw/9vOAQJti8avTZ9vxT9rKrPo8qG6o=.ed25519~/ZUi9Chpl0g1kuWSrmehq2EwMQeV0Pd+8xw8XhWuhLE=| | pub1.upsocial.com | @freedomrules |pub1.upsocial.com:8008:@gjlNF5Cyw3OKZxEoEpsVhT5Xv3HZutVfKBppmu42MkI=.ed25519~lMd6f4nnmBZEZSavAl4uahl+feajLUGqu8s2qdoTLi8=| | Monero Pub | @Denis |xmr-pub.net:8008:@5hTpvduvbDyMLN2IdzDKa7nx7PSem9co3RsOmZoyyCM=.ed25519~vQU+r2HUd6JxPENSinUWdfqrJLlOqXiCbzHoML9iVN4=| | FreeSocial | @Jarland |pub.freesocial.co:8008:@ofYKOy2p9wsaxV73GqgOyh6C6nRGFM5FyciQyxwBd6A=.ed25519~ye9Z808S3KPQsV0MWr1HL0/Sh8boSEwW+ZK+8x85u9w=| |ssb.vpn.net.br| @coffeverton |ssb.vpn.net.br:8008:@ze8nZPcf4sbdULvknEFOCbVZtdp7VRsB95nhNw6/2YQ=.ed25519~D0blTolH3YoTwSAkY5xhNw8jAOjgoNXL/+8ZClzr0io=| | gossip.noisebridge.info | Noisebridge Hackerspace @james.network |gossip.noisebridge.info:8008:@2NANnQVdsoqk0XPiJG2oMZqaEpTeoGrxOHJkLIqs7eY=.ed25519~JWTC6+rPYPW5b5zCion0gqjcJs35h6JKpUrQoAKWgJ4=|Pubs privados
Você precisará entrar em contato com os proprietários desses bares para receber um convite.
| Pub Name | Operator | Contact | | --------------------------------------------- | ------------------------------------------------------------ | ----------------------------------------------- | |
many.butt.nz| @dinosaur | mikey@enspiral.com | |one.butt.nz| @dinosaur | mikey@enspiral.com | |ssb.mikey.nz| @dinosaur | mikey@enspiral.com | | ssb.celehner.com | @cel | cel@celehner.com |Pubs muito grandes
Aviso: embora tecnicamente funcione usar um convite para esses pubs, você provavelmente se divertirá se o fizer devido ao seu tamanho (muitas coisas para baixar, risco para bots / spammers / idiotas)
| Pub Name | Operator | Invite Code | | --------------------------------------- | ----------------------------------------------- | ------------------------------------------------------------ | |
scuttlebutt.de| SolSoCoG |scuttlebutt.de:8008:@yeh/GKxlfhlYXSdgU7CRLxm58GC42za3tDuC4NJld/k=.ed25519~iyaCpZ0co863K9aF+b7j8BnnHfwY65dGeX6Dh2nXs3c=| |Lohn's Pub| @lohn |p.lohn.in:8018:@LohnKVll9HdLI3AndEc4zwGtfdF/J7xC7PW9B/JpI4U=.ed25519~z3m4ttJdI4InHkCtchxTu26kKqOfKk4woBb1TtPeA/s=| | Scuttle Space | @guil-dot | Visit scuttle.space | |SSB PeerNet US-East| timjrobinson |us-east.ssbpeer.net:8008:@sTO03jpVivj65BEAJMhlwtHXsWdLd9fLwyKAT1qAkc0=.ed25519~sXFc5taUA7dpGTJITZVDCRy2A9jmkVttsr107+ufInU=| | Hermies | s | net:hermies.club:8008~shs:uMYDVPuEKftL4SzpRGVyQxLdyPkOiX7njit7+qT/7IQ=:SSB+Room+PSK3TLYC2T86EHQCUHBUHASCASE18JBV24= |GUI - Interface Gráfica do Utilizador(Usuário)
Patchwork - Uma GUI SSB (Descontinuado)
Patchwork é o aplicativo de mensagens e compartilhamento descentralizado construído em cima do SSB . O protocolo scuttlebutt em si não mantém um conjunto de feeds nos quais um usuário está interessado, então um cliente é necessário para manter uma lista de feeds de pares em que seu respectivo usuário está interessado e seguindo.

Fonte: scuttlebutt.nz
Quando você instala e executa o Patchwork, você só pode ver e se comunicar com seus pares em sua rede local. Para acessar fora de sua LAN, você precisa se conectar a um Pub. Um pub é apenas para convidados e eles retransmitem mensagens entre você e seus pares fora de sua LAN e entre outros Pubs.
Lembre-se de que você precisa seguir alguém para receber mensagens dessa pessoa. Isso reduz o envio de mensagens de spam para os usuários. Os usuários só veem as respostas das pessoas que seguem. Os dados são sincronizados no disco para funcionar offline, mas podem ser sincronizados diretamente com os pares na sua LAN por wi-fi ou bluetooth.
Patchbay - Uma GUI Alternativa
Patchbay é um cliente de fofoca projetado para ser fácil de modificar e estender. Ele usa o mesmo banco de dados que Patchwork e Patchfoo , então você pode facilmente dar uma volta com sua identidade existente.

Planetary - GUI para IOS

Planetary é um app com pubs pré-carregados para facilitar integração.
Manyverse - GUI para Android

Manyverse é um aplicativo de rede social com recursos que você esperaria: posts, curtidas, perfis, mensagens privadas, etc. Mas não está sendo executado na nuvem de propriedade de uma empresa, em vez disso, as postagens de seus amigos e todos os seus dados sociais vivem inteiramente em seu telefone .
Fontes
-
https://scuttlebot.io/
-
https://decentralized-id.com/decentralized-web/scuttlebot/#plugins
-
https://medium.com/@miguelmota/getting-started-with-secure-scuttlebut-e6b7d4c5ecfd
-
Secure Scuttlebutt : um protocolo de banco de dados global.
-
-
 @ a10260a2:caa23e3e
2025-06-01 04:26:33
@ a10260a2:caa23e3e
2025-06-01 04:26:33In this post, you’ll see how easy it is to consolidate some UTXOs. Hopefully this’ll give you the confidence to try it out whenever fees are low. It’s super simple and can be done in two steps!
Step 1
Go to your wallet and grab a receive address. As you can see, this wallet has two UTXOs.

Step 2
Once you have a receive address, send the max amount in your wallet to it (i.e. you’ll be sending to yourself). What you’ll receive is your all your bitcoin back minus the network fee. In this case, the cost was 900 sats.

That’s it.
Next time, when you go to Send > Coin Control, you’ll see that you have one large UTXO instead of one large and one small.


-
 @ e97aaffa:2ebd765d
2024-12-31 16:47:12
@ e97aaffa:2ebd765d
2024-12-31 16:47:12Último dia do ano, momento para tirar o pó da bola de cristal, para fazer reflexões, previsões e desejos para o próximo ano e seguintes.
Ano após ano, o Bitcoin evoluiu, foi ultrapassando etapas, tornou-se cada vez mais mainstream. Está cada vez mais difícil fazer previsões sobre o Bitcoin, já faltam poucas barreiras a serem ultrapassadas e as que faltam são altamente complexas ou tem um impacto profundo no sistema financeiro ou na sociedade. Estas alterações profundas tem que ser realizadas lentamente, porque uma alteração rápida poderia resultar em consequências terríveis, poderia provocar um retrocesso.
Código do Bitcoin
No final de 2025, possivelmente vamos ter um fork, as discussões sobre os covenants já estão avançadas, vão acelerar ainda mais. Já existe um consenso relativamente alto, a favor dos covenants, só falta decidir que modelo será escolhido. Penso que até ao final do ano será tudo decidido.
Depois dos covenants, o próximo foco será para a criptografia post-quantum, que será o maior desafio que o Bitcoin enfrenta. Criar uma criptografia segura e que não coloque a descentralização em causa.
Espero muito de Ark, possivelmente a inovação do ano, gostaria de ver o Nostr a furar a bolha bitcoinheira e que o Cashu tivesse mais reconhecimento pelos bitcoiners.
Espero que surjam avanços significativos no BitVM2 e BitVMX.
Não sei o que esperar das layer 2 de Bitcoin, foram a maior desilusão de 2024. Surgiram com muita força, mas pouca coisa saiu do papel, foi uma mão cheia de nada. Uma parte dos projetos caiu na tentação da shitcoinagem, na criação de tokens, que tem um único objetivo, enriquecer os devs e os VCs.
Se querem ser levados a sério, têm que ser sérios.
“À mulher de César não basta ser honesta, deve parecer honesta”
Se querem ter o apoio dos bitcoiners, sigam o ethos do Bitcoin.
Neste ponto a atitude do pessoal da Ark é exemplar, em vez de andar a chorar no Twitter para mudar o código do Bitcoin, eles colocaram as mãos na massa e criaram o protocolo. É claro que agora está meio “coxo”, funciona com uma multisig ou com os covenants na Liquid. Mas eles estão a criar um produto, vão demonstrar ao mercado que o produto é bom e útil. Com a adoção, a comunidade vai perceber que o Ark necessita dos covenants para melhorar a interoperabilidade e a soberania.
É este o pensamento certo, que deveria ser seguido pelos restantes e futuros projetos. É seguir aquele pensamento do J.F. Kennedy:
“Não perguntem o que é que o vosso país pode fazer por vocês, perguntem o que é que vocês podem fazer pelo vosso país”
Ou seja, não fiquem à espera que o bitcoin mude, criem primeiro as inovações/tecnologia, ganhem adoção e depois demonstrem que a alteração do código camada base pode melhorar ainda mais o vosso projeto. A necessidade é que vai levar a atualização do código.
Reservas Estratégicas de Bitcoin
Bancos centrais
Com a eleição de Trump, emergiu a ideia de uma Reserva Estratégia de Bitcoin, tornou este conceito mainstream. Foi um pivot, a partir desse momento, foram enumerados os políticos de todo o mundo a falar sobre o assunto.
A Senadora Cynthia Lummis foi mais além e propôs um programa para adicionar 200 mil bitcoins à reserva ao ano, até 1 milhão de Bitcoin. Só que isto está a criar uma enorme expectativa na comunidade, só que pode resultar numa enorme desilusão. Porque no primeiro ano, o Trump em vez de comprar os 200 mil, pode apenas adicionar na reserva, os 198 mil que o Estado já tem em sua posse. Se isto acontecer, possivelmente vai resultar numa forte queda a curto prazo. Na minha opinião os bancos centrais deveriam seguir o exemplo de El Salvador, fazer um DCA diário.
Mais que comprar bitcoin, para mim, o mais importante é a criação da Reserva, é colocar o Bitcoin ao mesmo nível do ouro, o impacto para o resto do mundo será tremendo, a teoria dos jogos na sua plenitude. Muitos outros bancos centrais vão ter que comprar, para não ficarem atrás, além disso, vai transmitir uma mensagem à generalidade da população, que o Bitcoin é “afinal é algo seguro, com valor”.
Mas não foi Trump que iniciou esta teoria dos jogos, mas sim foi a primeira vítima dela. É o próprio Trump que o admite, que os EUA necessitam da reserva para não ficar atrás da China. Além disso, desde que os EUA utilizaram o dólar como uma arma, com sanção contra a Rússia, surgiram boatos de que a Rússia estaria a utilizar o Bitcoin para transações internacionais. Que foram confirmados recentemente, pelo próprio governo russo. Também há poucos dias, ainda antes deste reconhecimento público, Putin elogiou o Bitcoin, ao reconhecer que “Ninguém pode proibir o bitcoin”, defendendo como uma alternativa ao dólar. A narrativa está a mudar.
Já existem alguns países com Bitcoin, mas apenas dois o fizeram conscientemente (El Salvador e Butão), os restantes têm devido a apreensões. Hoje são poucos, mas 2025 será o início de uma corrida pelos bancos centrais. Esta corrida era algo previsível, o que eu não esperava é que acontecesse tão rápido.

Empresas
A criação de reservas estratégicas não vai ficar apenas pelos bancos centrais, também vai acelerar fortemente nas empresas em 2025.

Mas as empresas não vão seguir a estratégia do Saylor, vão comprar bitcoin sem alavancagem, utilizando apenas os tesouros das empresas, como uma proteção contra a inflação. Eu não sou grande admirador do Saylor, prefiro muito mais, uma estratégia conservadora, sem qualquer alavancagem. Penso que as empresas vão seguir a sugestão da BlackRock, que aconselha um alocações de 1% a 3%.
Penso que 2025, ainda não será o ano da entrada das 6 magníficas (excepto Tesla), será sobretudo empresas de pequena e média dimensão. As magníficas ainda tem uma cota muito elevada de shareholders com alguma idade, bastante conservadores, que têm dificuldade em compreender o Bitcoin, foi o que aconteceu recentemente com a Microsoft.
Também ainda não será em 2025, talvez 2026, a inclusão nativamente de wallet Bitcoin nos sistema da Apple Pay e da Google Pay. Seria um passo gigante para a adoção a nível mundial.
ETFs
Os ETFs para mim são uma incógnita, tenho demasiadas dúvidas, como será 2025. Este ano os inflows foram superiores a 500 mil bitcoins, o IBIT foi o lançamento de ETF mais bem sucedido da história. O sucesso dos ETFs, deve-se a 2 situações que nunca mais se vão repetir. O mercado esteve 10 anos à espera pela aprovação dos ETFs, a procura estava reprimida, isso foi bem notório nos primeiros meses, os inflows foram brutais.
Também se beneficiou por ser um mercado novo, não existia orderbook de vendas, não existia um mercado interno, praticamente era só inflows. Agora o mercado já estabilizou, a maioria das transações já são entre clientes dos próprios ETFs. Agora só uma pequena percentagem do volume das transações diárias vai resultar em inflows ou outflows.
Estes dois fenómenos nunca mais se vão repetir, eu não acredito que o número de inflows em BTC supere os número de 2024, em dólares vai superar, mas em btc não acredito que vá superar.
Mas em 2025 vão surgir uma infindável quantidade de novos produtos, derivativos, novos ETFs de cestos com outras criptos ou cestos com ativos tradicionais. O bitcoin será adicionado em produtos financeiros já existentes no mercado, as pessoas vão passar a deter bitcoin, sem o saberem.
Com o fim da operação ChokePoint 2.0, vai surgir uma nova onda de adoção e de produtos financeiros. Possivelmente vamos ver bancos tradicionais a disponibilizar produtos ou serviços de custódia aos seus clientes.
Eu adoraria ver o crescimento da adoção do bitcoin como moeda, só que a regulamentação não vai ajudar nesse processo.
Preço
Eu acredito que o topo deste ciclo será alcançado no primeiro semestre, posteriormente haverá uma correção. Mas desta vez, eu acredito que a correção será muito menor que as anteriores, inferior a 50%, esta é a minha expectativa. Espero estar certo.
Stablecoins de dólar
Agora saindo um pouco do universo do Bitcoin, acho importante destacar as stablecoins.
No último ciclo, eu tenho dividido o tempo, entre continuar a estudar o Bitcoin e estudar o sistema financeiro, as suas dinâmicas e o comportamento humano. Isto tem sido o meu foco de reflexão, imaginar a transformação que o mundo vai sofrer devido ao padrão Bitcoin. É uma ilusão acreditar que a transição de um padrão FIAT para um padrão Bitcoin vai ser rápida, vai existir um processo transitório que pode demorar décadas.
Com a re-entrada de Trump na Casa Branca, prometendo uma política altamente protecionista, vai provocar uma forte valorização do dólar, consequentemente as restantes moedas do mundo vão derreter. Provocando uma inflação generalizada, gerando uma corrida às stablecoins de dólar nos países com moedas mais fracas. Trump vai ter uma política altamente expansionista, vai exportar dólares para todo o mundo, para financiar a sua própria dívida. A desigualdade entre os pobres e ricos irá crescer fortemente, aumentando a possibilidade de conflitos e revoltas.
“Casa onde não há pão, todos ralham e ninguém tem razão”
Será mais lenha, para alimentar a fogueira, vai gravar os conflitos geopolíticos já existentes, ficando as sociedade ainda mais polarizadas.
Eu acredito que 2025, vai haver um forte crescimento na adoção das stablecoins de dólares, esse forte crescimento vai agravar o problema sistémico que são as stablecoins. Vai ser o início do fim das stablecoins, pelo menos, como nós conhecemos hoje em dia.
Problema sistémico
O sistema FIAT não nasceu de um dia para outro, foi algo que foi construído organicamente, ou seja, foi evoluindo ao longo dos anos, sempre que havia um problema/crise, eram criadas novas regras ou novas instituições para minimizar os problemas. Nestes quase 100 anos, desde os acordos de Bretton Woods, a evolução foram tantas, tornaram o sistema financeiro altamente complexo, burocrático e nada eficiente.
Na prática é um castelo de cartas construído sobre outro castelo de cartas e que por sua vez, foi construído sobre outro castelo de cartas.
As stablecoins são um problema sistémico, devido às suas reservas em dólares e o sistema financeiro não está preparado para manter isso seguro. Com o crescimento das reservas ao longo dos anos, foi se agravando o problema.
No início a Tether colocava as reservas em bancos comerciais, mas com o crescimento dos dólares sob gestão, criou um problema nos bancos comerciais, devido à reserva fracionária. Essas enormes reservas da Tether estavam a colocar em risco a própria estabilidade dos bancos.
A Tether acabou por mudar de estratégia, optou por outros ativos, preferencialmente por títulos do tesouro/obrigações dos EUA. Só que a Tether continua a crescer e não dá sinais de abrandamento, pelo contrário.
Até o próprio mundo cripto, menosprezava a gravidade do problema da Tether/stablecoins para o resto do sistema financeiro, porque o marketcap do cripto ainda é muito pequeno. É verdade que ainda é pequeno, mas a Tether não o é, está no top 20 dos maiores detentores de títulos do tesouros dos EUA e está ao nível dos maiores bancos centrais do mundo. Devido ao seu tamanho, está a preocupar os responsáveis/autoridades/reguladores dos EUA, pode colocar em causa a estabilidade do sistema financeiro global, que está assente nessas obrigações.
Os títulos do tesouro dos EUA são o colateral mais utilizado no mundo, tanto por bancos centrais, como por empresas, é a charneira da estabilidade do sistema financeiro. Os títulos do tesouro são um assunto muito sensível. Na recente crise no Japão, do carry trade, o Banco Central do Japão tentou minimizar a desvalorização do iene através da venda de títulos dos EUA. Esta operação, obrigou a uma viagem de emergência, da Secretaria do Tesouro dos EUA, Janet Yellen ao Japão, onde disponibilizou liquidez para parar a venda de títulos por parte do Banco Central do Japão. Essa forte venda estava desestabilizando o mercado.
Os principais detentores de títulos do tesouros são institucionais, bancos centrais, bancos comerciais, fundo de investimento e gestoras, tudo administrado por gestores altamente qualificados, racionais e que conhecem a complexidade do mercado de obrigações.
O mundo cripto é seu oposto, é naife com muita irracionalidade e uma forte pitada de loucura, na sua maioria nem faz a mínima ideia como funciona o sistema financeiro. Essa irracionalidade pode levar a uma “corrida bancária”, como aconteceu com o UST da Luna, que em poucas horas colapsou o projeto. Em termos de escala, a Luna ainda era muito pequena, por isso, o problema ficou circunscrito ao mundo cripto e a empresas ligadas diretamente ao cripto.
Só que a Tether é muito diferente, caso exista algum FUD, que obrigue a Tether a desfazer-se de vários biliões ou dezenas de biliões de dólares em títulos num curto espaço de tempo, poderia provocar consequências terríveis em todo o sistema financeiro. A Tether é grande demais, é já um problema sistémico, que vai agravar-se com o crescimento em 2025.
Não tenham dúvidas, se existir algum problema, o Tesouro dos EUA vai impedir a venda dos títulos que a Tether tem em sua posse, para salvar o sistema financeiro. O problema é, o que vai fazer a Tether, se ficar sem acesso às venda das reservas, como fará o redeem dos dólares?
Como o crescimento do Tether é inevitável, o Tesouro e o FED estão com um grande problema em mãos, o que fazer com o Tether?
Mas o problema é que o atual sistema financeiro é como um curto cobertor: Quanto tapas a cabeça, destapas os pés; Ou quando tapas os pés, destapas a cabeça. Ou seja, para resolver o problema da guarda reservas da Tether, vai criar novos problemas, em outros locais do sistema financeiro e assim sucessivamente.
Conta mestre
Uma possível solução seria dar uma conta mestre à Tether, dando o acesso direto a uma conta no FED, semelhante à que todos os bancos comerciais têm. Com isto, a Tether deixaria de necessitar os títulos do tesouro, depositando o dinheiro diretamente no banco central. Só que isto iria criar dois novos problemas, com o Custodia Bank e com o restante sistema bancário.
O Custodia Bank luta há vários anos contra o FED, nos tribunais pelo direito a ter licença bancária para um banco com full-reserves. O FED recusou sempre esse direito, com a justificativa que esse banco, colocaria em risco toda a estabilidade do sistema bancário existente, ou seja, todos os outros bancos poderiam colapsar. Perante a existência em simultâneo de bancos com reserva fracionária e com full-reserves, as pessoas e empresas iriam optar pelo mais seguro. Isso iria provocar uma corrida bancária, levando ao colapso de todos os bancos com reserva fracionária, porque no Custodia Bank, os fundos dos clientes estão 100% garantidos, para qualquer valor. Deixaria de ser necessário limites de fundos de Garantia de Depósitos.
Eu concordo com o FED nesse ponto, que os bancos com full-reserves são uma ameaça a existência dos restantes bancos. O que eu discordo do FED, é a origem do problema, o problema não está nos bancos full-reserves, mas sim nos que têm reserva fracionária.
O FED ao conceder uma conta mestre ao Tether, abre um precedente, o Custodia Bank irá o aproveitar, reclamando pela igualdade de direitos nos tribunais e desta vez, possivelmente ganhará a sua licença.
Ainda há um segundo problema, com os restantes bancos comerciais. A Tether passaria a ter direitos similares aos bancos comerciais, mas os deveres seriam muito diferentes. Isto levaria os bancos comerciais aos tribunais para exigir igualdade de tratamento, é uma concorrência desleal. Isto é o bom dos tribunais dos EUA, são independentes e funcionam, mesmo contra o estado. Os bancos comerciais têm custos exorbitantes devido às políticas de compliance, como o KYC e AML. Como o governo não vai querer aliviar as regras, logo seria a Tether, a ser obrigada a fazer o compliance dos seus clientes.
A obrigação do KYC para ter stablecoins iriam provocar um terramoto no mundo cripto.
Assim, é pouco provável que seja a solução para a Tether.
FED
Só resta uma hipótese, ser o próprio FED a controlar e a gerir diretamente as stablecoins de dólar, nacionalizado ou absorvendo as existentes. Seria uma espécie de CBDC. Isto iria provocar um novo problema, um problema diplomático, porque as stablecoins estão a colocar em causa a soberania monetária dos outros países. Atualmente as stablecoins estão um pouco protegidas porque vivem num limbo jurídico, mas a partir do momento que estas são controladas pelo governo americano, tudo muda. Os países vão exigir às autoridades americanas medidas que limitem o uso nos seus respectivos países.
Não existe uma solução boa, o sistema FIAT é um castelo de cartas, qualquer carta que se mova, vai provocar um desmoronamento noutro local. As autoridades não poderão adiar mais o problema, terão que o resolver de vez, senão, qualquer dia será tarde demais. Se houver algum problema, vão colocar a responsabilidade no cripto e no Bitcoin. Mas a verdade, a culpa é inteiramente dos políticos, da sua incompetência em resolver os problemas a tempo.
Será algo para acompanhar futuramente, mas só para 2026, talvez…
É curioso, há uns anos pensava-se que o Bitcoin seria a maior ameaça ao sistema ao FIAT, mas afinal, a maior ameaça aos sistema FIAT é o próprio FIAT(stablecoins). A ironia do destino.
Isto é como uma corrida, o Bitcoin é aquele atleta que corre ao seu ritmo, umas vezes mais rápido, outras vezes mais lento, mas nunca pára. O FIAT é o atleta que dá tudo desde da partida, corre sempre em velocidade máxima. Só que a vida e o sistema financeiro não é uma prova de 100 metros, mas sim uma maratona.
Europa
2025 será um ano desafiante para todos europeus, sobretudo devido à entrada em vigor da regulamentação (MiCA). Vão começar a sentir na pele a regulamentação, vão agravar-se os problemas com os compliance, problemas para comprovar a origem de fundos e outras burocracias. Vai ser lindo.
O Travel Route passa a ser obrigatório, os europeus serão obrigados a fazer o KYC nas transações. A Travel Route é uma suposta lei para criar mais transparência, mas prática, é uma lei de controle, de monitorização e para limitar as liberdades individuais dos cidadãos.
O MiCA também está a colocar problemas nas stablecoins de Euro, a Tether para já preferiu ficar de fora da europa. O mais ridículo é que as novas regras obrigam os emissores a colocar 30% das reservas em bancos comerciais. Os burocratas europeus não compreendem que isto coloca em risco a estabilidade e a solvência dos próprios bancos, ficam propensos a corridas bancárias.
O MiCA vai obrigar a todas as exchanges a estar registadas em solo europeu, ficando vulnerável ao temperamento dos burocratas. Ainda não vai ser em 2025, mas a UE vai impor políticas de controle de capitais, é inevitável, as exchanges serão obrigadas a usar em exclusividade stablecoins de euro, as restantes stablecoins serão deslistadas.
Todas estas novas regras do MiCA, são extremamente restritas, não é para garantir mais segurança aos cidadãos europeus, mas sim para garantir mais controle sobre a população. A UE está cada vez mais perto da autocracia, do que da democracia. A minha única esperança no horizonte, é que o sucesso das políticas cripto nos EUA, vai obrigar a UE a recuar e a aligeirar as regras, a teoria dos jogos é implacável. Mas esse recuo, nunca acontecerá em 2025, vai ser um longo período conturbado.
Recessão
Os mercados estão todos em máximos históricos, isto não é sustentável por muito tempo, suspeito que no final de 2025 vai acontecer alguma correção nos mercados. A queda só não será maior, porque os bancos centrais vão imprimir dinheiro, muito dinheiro, como se não houvesse amanhã. Vão voltar a resolver os problemas com a injeção de liquidez na economia, é empurrar os problemas com a barriga, em de os resolver. Outra vez o efeito Cantillon.
Será um ano muito desafiante a nível político, onde o papel dos políticos será fundamental. A crise política na França e na Alemanha, coloca a UE órfã, sem um comandante ao leme do navio. 2025 estará condicionado pelas eleições na Alemanha, sobretudo no resultado do AfD, que podem colocar em causa a propriedade UE e o euro.
Possivelmente, só o fim da guerra poderia minimizar a crise, algo que é muito pouco provável acontecer.
Em Portugal, a economia parece que está mais ou menos equilibrada, mas começam a aparecer alguns sinais preocupantes. Os jogos de sorte e azar estão em máximos históricos, batendo o recorde de 2014, época da grande crise, não é um bom sinal, possivelmente já existe algum desespero no ar.
A Alemanha é o motor da Europa, quanto espirra, Portugal constipa-se. Além do problema da Alemanha, a Espanha também está à beira de uma crise, são os países que mais influenciam a economia portuguesa.
Se existir uma recessão mundial, terá um forte impacto no turismo, que é hoje em dia o principal motor de Portugal.
Brasil
Brasil é algo para acompanhar em 2025, sobretudo a nível macro e a nível político. Existe uma possibilidade de uma profunda crise no Brasil, sobretudo na sua moeda. O banco central já anda a queimar as reservas para minimizar a desvalorização do Real.

Sem mudanças profundas nas políticas fiscais, as reservas vão se esgotar. As políticas de controle de capitais são um cenário plausível, será interesse de acompanhar, como o governo irá proceder perante a existência do Bitcoin e stablecoins. No Brasil existe um forte adoção, será um bom case study, certamente irá repetir-se em outros países num futuro próximo.
Os próximos tempos não serão fáceis para os brasileiros, especialmente para os que não têm Bitcoin.
Blockchain
Em 2025, possivelmente vamos ver os primeiros passos da BlackRock para criar a primeira bolsa de valores, exclusivamente em blockchain. Eu acredito que a BlackRock vai criar uma própria blockchain, toda controlada por si, onde estarão os RWAs, para fazer concorrência às tradicionais bolsas de valores. Será algo interessante de acompanhar.
Estas são as minhas previsões, eu escrevi isto muito em cima do joelho, certamente esqueci-me de algumas coisas, se for importante acrescentarei nos comentários. A maioria das previsões só acontecerá após 2025, mas fica aqui a minha opinião.
Isto é apenas a minha opinião, Don’t Trust, Verify!
-
 @ 8d34bd24:414be32b
2025-06-01 04:04:10
@ 8d34bd24:414be32b
2025-06-01 04:04:10Many people today believe that the church has replaced Israel and that the promises given to Israel now apply to the church. When we say this, we are calling God a liar.
Can you imagine a groom promising to love and cherish his wife until death do they part and then saying, “I’m keeping my promise by loving and cherishing a new and different wife.”? We would never consider that man to be honest, faithful, and good. If God promised to protect and guide Israel, to have a descendant of David on the throne, and to give them the land, we can only trust Him if He fulfills these promises.
When we say the church has replaced Israel, we make two mistakes. We raise up the church beyond what is right and we put down Israel. We need to be careful because God promised Abraham:
“And I will bless those who bless you, And the one who curses you I will curse. And in you all the families of the earth will be blessed.” (Genesis 12:3)
and He reiterated this promise to Israel during the Exodus:
“He couches, he lies down as a lion,\ And as a lion, who dares rouse him?\ Blessed is everyone who blesses you [Israel],\ And cursed is everyone who curses you [Israel].” (Numbers 24:9) {clarification mine}
When we curse Israel or the Jews, we will be under God’s curse. Now this does not mean that every criticism of a particular action by Israel’s leaders brings a curse. Today’s nation of Israel is led by fallible men like every other nation, so there are mistakes made or corruption by particular leaders. It does, however, mean that generalizations against Israel and the Jews are wrong and of Satan.
Paul specifically warned the church against thinking they had replaced Israel in God’s blessing and love.
If the first piece of dough is holy, the lump is also; and if the root is holy, the branches are too.
But if some of the branches were broken off, and you, being a wild olive, were grafted in among them and became partaker with them of the rich root of the olive tree, do not be arrogant toward the branches; but if you are arrogant, remember that it is not you who supports the root, but the root supports you. You will say then, “Branches were broken off so that I might be grafted in.” Quite right, they were broken off for their unbelief, but you stand by your faith. Do not be conceited, but fear; for if God did not spare the natural branches, He will not spare you, either. Behold then the kindness and severity of God; to those who fell, severity, but to you, God’s kindness, if you continue in His kindness; otherwise you also will be cut off. And they also, if they do not continue in their unbelief, will be grafted in, for God is able to graft them in again. For if you were cut off from what is by nature a wild olive tree, and were grafted contrary to nature into a cultivated olive tree, how much more will these who are the natural branches be grafted into their own olive tree?
For I do not want you, brethren, to be uninformed of this mystery—so that you will not be wise in your own estimation—that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved; just as it is written,
“The Deliverer will come from Zion,\ He will remove ungodliness from Jacob.”\ “This is My covenant with them,\ When I take away their sins.” *From the standpoint of the gospel they are enemies for your sake, but from the standpoint of God’s choice they are beloved for the sake of the fathers*; for the gifts and the calling of God are irrevocable**. For just as you once were disobedient to God, but now have been shown mercy because of their disobedience, so these also now have been disobedient, that because of the mercy shown to you they also may now be shown mercy. For God has shut up all in disobedience so that He may show mercy to all. (Romans 11:16-32) {emphasis mine}
Paul warns that although the Jews were pruned away due to rejection of Him and gentiles were grafted into Him by faith, if we reject God’s word, we can be pruned away and if the Jews return to Jesus, they can be grafted back in. He predicts that the Jews will return. “…that a partial hardening has happened to Israel until the fullness of the Gentiles has come in; and so all Israel will be saved.” He also says regarding Israel that “the gifts and the calling of God are irrevocable.” Yes, Israel rejected Jesus and was punished for doing so, but they will be called back to God and trust in their Messiah, Jesus. In the end, all the promises of God to Abraham, Jacob, David, and others regarding Israel, will be brought to complete fulfillment.
Both the Old and New Testaments talk about Israel being punished for rejecting God and their Messiah, but that, after the time of the Gentiles, they will be called back to Him.
and they will fall by the edge of the sword, and will be led captive into all the nations; and Jerusalem will be trampled under foot by the Gentiles until the times of the Gentiles are fulfilled. (Luke 21:24)
After Daniel had been in prayer and repentance for the sins of Israel, the angel Gabriel came with this prophecy about Israel.
“Seventy weeks have been decreed for your people and your holy city, to finish the transgression, to make an end of sin, to make atonement for iniquity, to bring in everlasting righteousness, to seal up vision and prophecy and to anoint the most holy place. So you are to know and discern that from the issuing of a decree to restore and rebuild Jerusalem until Messiah the Prince there will be seven weeks and sixty-two weeks; it will be built again, with plaza and moat, even in times of distress. Then after the sixty-two weeks the Messiah will be cut off and have nothing, and the people of the prince who is to come will destroy the city and the sanctuary. And its end will come with a flood; even to the end there will be war; desolations are determined. (Daniel 9:24-26)
In this prophecy, the prediction of 69 weeks (literally sevens, but meaning groups of 7 years) from the decree to rebuild Jerusalem (by Artaxerxes) to the Messiah was fulfilled to the day when Jesus rode into Jerusalem on a donkey on Palm Sunday.
I always thought it strange that the prophecy predicted 70 sevens and that there was the first 69 sevens (483 years), then \~2,000 years where nothing happens, and then comes the final seven — the Great Tribulation. It didn’t make sense until I realized, the 70 sevens referred to the years of Israel. The time of the gentiles intervenes between the 69th and 70th sevens. This delay happened due to Israel rejecting their Messiah.
When He approached Jerusalem, He saw the city and wept over it, saying, “If you had known in this day, even you, the things which make for peace! But now they have been hidden from your eyes. For the days will come upon you when your enemies will throw up a barricade against you, and surround you and hem you in on every side, and they will level you to the ground and your children within you, and they will not leave in you one stone upon another, because you did not recognize the time of your visitation.” (Luke 19:41-44)
We are now in the time of the Gentiles, the church age, the intermission in the story of Israel. After the church is raptured, the story will return to Israel. The Jews (at least many of them) will finally accept their Messiah. They will suffer through the Tribulation while witnessing to the world and then God will finally fully fulfill His promises to Israel through the Millennial kingdom.
Alas! for that day is great,\ There is none like it;\ And it is the time of Jacob’s distress,\ But he will be saved from it.
‘It shall come about on that day,’ declares the Lord of hosts, ‘that I will break his yoke from off their neck and will tear off their bonds; and strangers will no longer make them their slaves. But they shall serve the Lord their God and David their king, whom I will raise up for them.
Fear not, O Jacob My servant,’ declares the Lord,\ ‘And do not be dismayed, O Israel;\ For behold, I will save you from afar\ And your offspring from the land of their captivity.\ And Jacob will return and will be quiet and at ease,\ And no one will make him afraid.\ For I am with you,’ declares the Lord, ‘to save you;\ For I will destroy completely all the nations where I have scattered you,\ Only I will not destroy you completely.\ But I will chasten you justly\ And will by no means leave you unpunished.’ \ (Jeremiah 30:7-11) {emphasis mine}
Jacob’s distress is the final Tribulation. The 144,000 Jewish witnesses will be saved through the whole Tribulation. Others may become saved and die a martyrs death, but they will then be brought into the millennial kingdom where the Messiah will fill the throne of David and Israel will reach from the River to the Sea.
The Jews have already been saved “from afar, and your offspring from the land of their captivity” with the recreation of Israel in 1947 and the continual return of Jews to their homeland.
God is working to fulfill His promises to Israel and His work is nearly complete.
“O Jacob My servant, do not fear,” declares the Lord, “For I am with you. For I will make a full end of all the nations where I have driven you, Yet I will not make a full end of you; But I will correct you properly And by no means leave you unpunished.” (Jeremiah 46:28)
God promises a “full end of all the nations where I have driven you.” Those nations and people who try to destroy Israel will be destroyed. As Christians we should love what God loves, and despite Israel’s repeated betrayals, God still loves Israel, so we should, too.
May the God of heaven give us a right view of Israel. May we see them as God sees them. May God use us to share the Gospel in such a way as to lead to a harvest of Jews for the Kingdom of God. To God be the glory!
Trust Jesus
-
 @ 21335073:a244b1ad
2025-03-18 14:43:08
@ 21335073:a244b1ad
2025-03-18 14:43:08Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 254f56d7:f2c38100
2024-12-30 07:38:27
@ 254f56d7:f2c38100
2024-12-30 07:38:27Vamos ver seu funcionamento






