-
 @ 32c87f47:cb8f61a1
2025-05-30 07:17:15
@ 32c87f47:cb8f61a1
2025-05-30 07:17:15O universo do entretenimento digital tem evoluído rapidamente, e uma das plataformas que vem ganhando destaque nesse cenário é a Tribo777. Com uma proposta inovadora, voltada para jogadores brasileiros que buscam emoção, praticidade e recompensas reais, o site se posiciona como uma das melhores opções para quem quer unir diversão e estratégia.
Conhecendo a Plataforma Tribo777 A Tribo777 foi desenvolvida com foco total na experiência do usuário. Ao acessar o site, o jogador é imediatamente recebido por uma interface amigável, com menus intuitivos e design moderno. A plataforma funciona perfeitamente tanto em computadores quanto em dispositivos móveis, o que permite jogar de qualquer lugar, a qualquer hora.
Um dos grandes diferenciais da Tribo777 é a agilidade no carregamento dos jogos e a estabilidade durante as partidas. Isso garante uma experiência fluida, sem interrupções, o que é essencial para quem gosta de se manter concentrado e maximizar suas chances de vitória.
Além disso, a plataforma oferece diversos métodos de pagamento locais, como PIX, transferência bancária e carteiras digitais, facilitando depósitos e saques com rapidez e segurança.
Diversidade de Jogos para Todos os Estilos O catálogo de jogos da Tribo777 é amplo e repleto de opções para todos os perfis de jogador. Entre os destaques, estão os famosos jogos de slots, que combinam gráficos vibrantes, trilhas sonoras envolventes e mecânicas dinâmicas. Com uma variedade impressionante de temas — que vão desde aventuras mitológicas até cenários futuristas — os slots garantem horas de entretenimento.
Para os fãs de jogos clássicos, a plataforma também conta com títulos como roletas, cartas e outros desafios de habilidade que envolvem raciocínio rápido e tomada de decisões estratégicas. Muitos desses jogos contam com modos ao vivo, nos quais o jogador interage em tempo real com apresentadores e outros participantes, tornando a experiência ainda mais imersiva.
Outro ponto interessante é a presença de jogos exclusivos, que só podem ser encontrados na Tribo777. Esses títulos oferecem mecânicas diferenciadas e promoções especiais, o que contribui para a fidelização dos jogadores.
Experiência do Jogador: Segurança, Suporte e Promoções A Tribo777 se preocupa com cada detalhe da jornada do jogador. Desde o cadastro rápido até o momento de retirar os ganhos, tudo é feito com máxima transparência e praticidade. A segurança é uma prioridade, com tecnologias avançadas de proteção de dados e transações criptografadas.
O suporte ao cliente está disponível todos os dias, com atendimento em português, preparado para resolver qualquer dúvida ou problema de forma rápida e eficiente. Seja por chat ao vivo ou por e-mail, os jogadores sempre têm com quem contar.
Outro atrativo que conquista os usuários é o programa de recompensas. A plataforma oferece bônus de boas-vindas, giros grátis, cashback e promoções frequentes, que aumentam as chances de jogar mais e ganhar mais. Além disso, há eventos temáticos e torneios com prêmios atrativos, que tornam a participação ainda mais divertida e competitiva.
Conclusão A Tribo777 chega ao mercado com uma proposta sólida, voltada para jogadores brasileiros que buscam qualidade, emoção e recompensas reais. Com uma interface moderna, variedade de jogos, suporte dedicado e promoções constantes, a plataforma se firma como uma excelente escolha para quem quer explorar o mundo do entretenimento online com confiança e diversão.
Se você ainda não conhece a Tribo777, esta é a hora de se juntar à tribo e descobrir um novo jeito de jogar — com emoção, segurança e muitas oportunidades de vitória.
-
 @ 32c87f47:cb8f61a1
2025-05-30 07:16:44
@ 32c87f47:cb8f61a1
2025-05-30 07:16:44Se você está em busca de uma plataforma confiável, divertida e repleta de oportunidades para se entreter com jogos online, o 77BB é o lugar ideal para você. Com uma estrutura moderna, interface amigável e uma variedade impressionante de jogos, o 77BB vem conquistando jogadores de todo o Brasil e se destacando como uma das principais referências no setor de entretenimento digital.
Uma Plataforma Completa para Todos os Perfis de Jogadores Desde o primeiro acesso, fica evidente que o 77BB foi desenvolvido com foco na experiência do usuário. O site possui um layout intuitivo, permitindo que jogadores iniciantes e experientes naveguem com facilidade entre as diferentes categorias. Além disso, a plataforma é totalmente compatível com dispositivos móveis, oferecendo uma experiência fluida tanto em celulares quanto em tablets e computadores.
Outro diferencial importante é a segurança. O 77bbconta com tecnologia de ponta para garantir a proteção dos dados dos jogadores, além de adotar políticas rigorosas de privacidade e suporte eficiente para esclarecer dúvidas e resolver qualquer questão rapidamente.
Variedade de Jogos para Todos os Gostos A diversidade de jogos disponíveis é um dos grandes atrativos da plataforma. O 77BB oferece uma seleção robusta que inclui desde os clássicos jogos de mesa até opções mais modernas com gráficos avançados e dinâmicas interativas. Entre os jogos mais populares estão os slots temáticos, jogos de cartas como pôquer e blackjack, além de roletas e outros formatos que simulam a atmosfera de casas de jogo físicas.
Os jogos são fornecidos por desenvolvedores renomados no mercado internacional, o que garante qualidade, fluidez e total imparcialidade nos resultados. Isso proporciona uma experiência justa e divertida, com chances reais de ganho e muita emoção a cada rodada.
Experiência do Jogador: Diversão e Benefícios Reais Um dos pontos mais elogiados pelos usuários do 77BB é a experiência geral oferecida pela plataforma. Além da facilidade de uso e da grande variedade de jogos, o site conta com promoções regulares, bônus de boas-vindas e programas de fidelidade que recompensam os jogadores mais ativos.
As promoções variam frequentemente e podem incluir rodadas grátis, bônus em depósitos e prêmios especiais em eventos temáticos. Isso torna a jornada ainda mais empolgante e mantém os jogadores sempre motivados a explorar novos títulos e desafios.
Outro aspecto importante é o suporte ao cliente. O 77BB oferece atendimento em português por meio de chat ao vivo e outros canais, garantindo que qualquer dúvida ou problema seja resolvido de forma rápida e eficiente. Esse cuidado com o usuário contribui para um ambiente mais acolhedor e profissional.
Conclusão: 77BB é Sinônimo de Diversão Garantida Se você procura uma plataforma segura, completa e cheia de possibilidades para se divertir com jogos online, o 77BB é uma escolha certeira. Com uma interface acessível, excelente variedade de jogos e um atendimento ao cliente exemplar, o 77BB entrega uma experiência de alto nível que agrada tanto iniciantes quanto veteranos.
Descubra hoje mesmo o universo de entretenimento que o 77BB tem a oferecer e transforme seu tempo livre em momentos de pura diversão!
-
 @ 32c87f47:cb8f61a1
2025-05-30 07:16:16
@ 32c87f47:cb8f61a1
2025-05-30 07:16:16No universo dos jogos online, a busca por plataformas confiáveis, divertidas e recheadas de opções é constante. É nesse cenário que o KK45 se destaca como uma escolha ideal para quem procura entretenimento de qualidade, segurança e uma experiência envolvente. Com uma interface moderna e intuitiva, a plataforma atrai jogadores de todos os níveis — desde os iniciantes até os mais experientes — oferecendo um catálogo variado de jogos e funcionalidades que fazem toda a diferença.
Conhecendo a Plataforma KK45 O KK45 é uma plataforma digital voltada para o entretenimento com foco total na qualidade e praticidade. O site foi desenvolvido pensando na experiência do usuário, com navegação fluida e recursos otimizados tanto para computadores quanto para dispositivos móveis. Isso significa que o jogador pode se divertir em qualquer lugar, a qualquer momento, bastando ter acesso à internet.
Outro diferencial é a segurança. O KK45 utiliza sistemas avançados de proteção de dados e transações, garantindo que todas as informações dos usuários estejam devidamente criptografadas. Além disso, o suporte ao cliente é eficiente e ágil, com atendimento em português e disponível 24 horas por dia, 7 dias por semana.
Variedade de Jogos para Todos os Gostos Um dos grandes atrativos do KK45 é a ampla variedade de jogos disponíveis. A plataforma trabalha com os principais desenvolvedores do mercado, trazendo gráficos de última geração, mecânicas envolventes e funcionalidades inovadoras. Entre os títulos mais populares, estão:
Slots temáticos: Com visuais incríveis e diversas funcionalidades bônus, os slots do KK45 agradam tanto os fãs de jogos clássicos quanto os que preferem aventuras modernas com muitos efeitos visuais.
Jogos de cartas e mesa: O ambiente perfeito para quem gosta de jogos como pôquer, blackjack, bacará, entre outros. Esses jogos são desenvolvidos com realismo e atenção aos detalhes, proporcionando partidas emocionantes.
Jogos interativos ao vivo: Para quem gosta de uma experiência mais próxima da realidade, os jogos ao vivo trazem interação em tempo real, com apresentadores reais, câmeras de alta definição e uma atmosfera imersiva.
A plataforma também investe em atualizações frequentes, lançando novos jogos regularmente para manter o catálogo sempre atualizado e atrativo.
A Experiência do Jogador no KK45 O que realmente diferencia o KK45 de outras plataformas é o cuidado com a experiência do jogador. Desde o cadastro simplificado até as formas de pagamento facilitadas, tudo foi pensado para proporcionar conforto e satisfação. O site oferece múltiplas opções de depósito e saque, com rapidez e segurança, além de bônus atrativos para novos jogadores e promoções recorrentes para os usuários fiéis.
Outro ponto forte é a personalização da experiência. Os jogadores podem salvar seus jogos favoritos, acompanhar seu histórico de partidas e configurar preferências para deixar a navegação ainda mais prática.
Além disso, o KK45 incentiva o jogo responsável, disponibilizando ferramentas que ajudam o usuário a controlar o tempo de uso e os valores investidos, promovendo uma diversão equilibrada.
Conclusão O KK45 se consolida como uma das principais plataformas de jogos online do Brasil, unindo tecnologia, segurança e uma variedade impressionante de jogos. Seja você um novato curioso ou um veterano em busca de novos desafios, o KK45 oferece tudo o que você precisa para uma jornada divertida e segura no mundo dos jogos digitais.
Explore agora mesmo a plataforma e descubra por que tantos jogadores estão escolhendo o KK45 como seu destino favorito para se entreter com qualidade e confiança!
-
 @ eb0157af:77ab6c55
2025-05-30 07:01:57
@ eb0157af:77ab6c55
2025-05-30 07:01:57The open-source project makes it possible to send bitcoin even in censored or disconnected areas through a radio mesh network.
In an interview with Decrypt, the developer known by the pseudonym “cyber” revealed the details of Darkwire, an open-source project that could enable new use cases for Bitcoin transactions without internet access.
The project, presented at the Bitcoin 2025 Official Hackathon, leverages Long Range Radio (LoRa) technology to create a decentralized mesh network that allows Bitcoin transactions to be sent even in the total absence of traditional connectivity.
Darkwire was specifically designed for situations where conventional communication infrastructure is inaccessible or controlled. According to cyber, the system is ideal for politically sensitive regions like the Rafah Crossing or the Indo-Tibetan border, where internet access can be limited or heavily monitored.
“Darkwire is for individuals seeking privacy or wishing to bypass surveillance of their communications and transactions. Imagine it to be akin to Tor but for this specific use case,” the creator explained.
LoRa technology
Darkwire operates through a combination of technologies. The system uses long-range LoRa radios along with microcontrollers such as the Arduino UNO to form a decentralized mesh network.
When a user wants to send a Bitcoin transaction without internet access, they specify the recipient’s address and the amount via a local graphical interface managed by bitcoinlib. The system then generates a signed Bitcoin transaction in hexadecimal format, which is split into smaller packets and transmitted via radio.
Mesh Network
Darkwire’s mesh network allows the data to “hop” from node to node until it reaches an internet-connected exit point. In ideal conditions, each Darkwire node has a range of up to 10 kilometers with a direct line of sight, reduced to 3-5 kilometers in densely populated areas.
“At least one node in the network needs to be connected to the internet, so that the transaction can be pushed to the blockchain for miners to verify it,” cyber said.
Once the transaction data reaches a node with internet access, it acts as an exit point, broadcasting the verified Bitcoin transaction to the global network, where it can be included in a block.
Limitations and future developments
Currently, Darkwire faces several technical limitations that the team is actively working to address. The relatively low bandwidth of LoRa radios and their sensitivity to terrain obstacles represent challenges. Moreover, the system’s dependence on internet-connected exit nodes could create potential points of failure.
According to reports, the project is still in its hackathon phase, but cyber has plans to further develop it, turning it into a full open-source platform and making it “the industry standard” for LoRa-based communications.
“I do hope people living in any kind of authoritarian regimes and states do get to use darkwire and put the truth out there,” the developer added.
The post Bitcoin without internet thanks to LoRa technology: the Darkwire project appeared first on Atlas21.
-
 @ 9ca447d2:fbf5a36d
2025-05-30 07:01:30
@ 9ca447d2:fbf5a36d
2025-05-30 07:01:30JPMorgan Chase, the biggest bank in the U.S., is now allowing its clients to buy bitcoin — a big change of heart for an institution whose CEO, Jamie Dimon, has been a long-time critic of the scarce digital asset.
Dimon made the announcement on the bank’s investor day, which came as a shift in JPMorgan’s approach to digital assets. “We are going to allow you to buy it,” he said. “We’re not going to custody it. We’re going to put it in statements for clients.”
That means clients can buy BTC through JPMorgan but the bank won’t hold or store the digital asset. Instead it will provide access and include the BTC purchases in client statements.
According to multiple reports and posts, JPMorgan has been blocking transactions from digital asset exchanges, with several people complaining about their experience on social media.
There is even an official notice on the company’s UK website that explicitly says customers cannot use their funds to purchase digital assets.
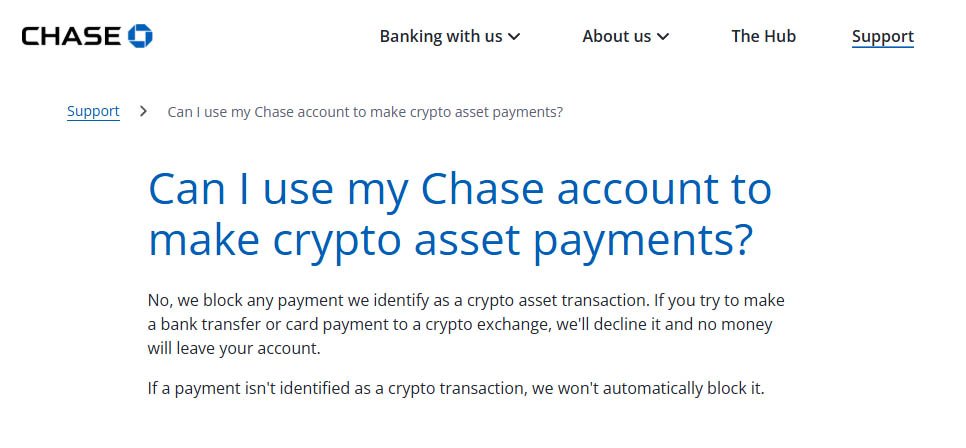
JPMorgan Chase UK website — Source
It’s a big change because Dimon has been one of Bitcoin’s biggest critics. Over the years he’s called it “worthless”, a “fraud” and even compared it to a “pet rock”.
He’s repeatedly expressed concern over digital assets’ use in illegal activities such as money laundering, terrorism, sex trafficking and tax evasion. A role that his critics say the U.S. dollar is playing on a much larger scale.
Related: Jamie Dimon Would “Close Down” Bitcoin If He Had Government Role
“The only true use case for it is criminals, drug traffickers … money laundering, tax avoidance,” he told lawmakers during a Senate hearing in 2023. At the 2024 World Economic Forum in Davos, he doubled down, “Bitcoin does nothing. I call it the pet rock.”
Despite his personal views, Dimon says the bank is responding to client demand. “I don’t think you should smoke, but I defend your right to smoke,” he said. “I defend your right to buy bitcoin.”
It’s worth noting JPMorgan isn’t fully embracing digital assets. The bank won’t be offering direct custody services or launching its own exchange.
Instead, it’s offering access to digital asset exchanges. There are even reports that the bank also plans to facilitate access to bitcoin ETFs and possibly other investment vehicles. Until recently, JPMorgan had limited its bitcoin exposure to futures-based products.
Other big financial firms have already taken similar steps.
Morgan Stanley, for example, has been offering some clients access to bitcoin ETFs since August 2024. Its CEO, Ted Pick, said earlier this year that the firm is working closely with regulators to explore ways to get into the digital assets space.
Dimon does like blockchain, though — the technology that underpins it. JPMorgan has its own blockchain projects including JPM Coin and recently ran a test transaction on a public blockchain of tokenized U.S. Treasuries.
Many criticize this view, saying that the most powerful aspect of Bitcoin is its decentralization. So, a centralized blockchain is just useless. This might be the reason Dimon has grown weary of all JPMorgan’s blockchain initiatives, because they offered nothing of value.
He said he might have given blockchain too much credit during his investor day comments: “We have been talking about blockchain for 12 to 15 years,” he said. “We spend too much on it. It doesn’t matter as much as you all think.”
-
 @ 9ca447d2:fbf5a36d
2025-05-30 07:01:20
@ 9ca447d2:fbf5a36d
2025-05-30 07:01:20H100 Group AB, a Swedish publicly listed health technology company, has made the headlines after investing in bitcoin as part of a new financial strategy.
The move has caused a stir in Sweden and beyond, with H100’s stock price rising 40% after the announcement.
The company has bought 4.39 bitcoin for 5 million Norwegian Krone (around $475,000–$492,000).
This is the company’s first foray into the digital asset space and makes H100 Group the first publicly-listed health tech company in Sweden to hold bitcoin as a treasury reserve asset.
The bitcoin was bought at an average price of 1,138,737 NOK (around $108,000) per coin.
The bitcoin purchase is part of H100 Group’s new “Bitcoin Treasury Strategy” to diversify its financial assets and strengthen its balance sheet. Instead of holding idle cash, the company decided to invest in what it sees as a long-term asset.
“This addition to H100’s Bitcoin Treasury Strategy follows an increasing number of tech-oriented growth companies holding bitcoin on their balance sheet,” said CEO Sander Andersen.
“And I believe the values of individual sovereignty highly present in the Bitcoin community aligns well with, and will appeal to, the customers and communities we are building the H100 platform for.”
Andersen said they will “build and hold” bitcoin long-term, viewing it as a savings tool, not a short-term trade.
The market reacted fast. On May 22, the company’s stock went up 39.27%, seeing highs of 1.620 SEK on the Nordic Growth Market.
This helped the company to recover a big part of the losses from the last two months, during which the stock fell 46%.
And now, after the purchase, the firm’s market cap is around $150.46 million.
H100 has said this might not be the only purchase. The company has signed a Letter of Intent (LOI) to set up a convertible loan facility of up to 10 million SEK with an undisclosed investor.

H100 Group’s announcement — Source
The funds will be used for general corporate purposes and to potentially increase bitcoin holdings. The loan will have a 3-year term and can be converted into shares at 1.3 SEK per share.
If H100’s stock price is more than 33% above the conversion price for more than 60 days, H100 will have the right to force conversion.
The company also announced today that it has successfully raised 21 million SEK ($2.21 million) through a convertible round led by Blockstream founder and CEO Adam Back.
Despite the Bitcoin pivot, H100 Group has made it clear that the core business remains the same.
They will continue to develop AI-powered automation tools and digital platforms to help healthcare providers deliver better services, especially in the health and longevity space.
Andersen said they are committed to healthy living, and adopting a bitcoin strategy is a smarter financial move that aligns with their values.
H100’s move comes as corporate adoption of bitcoin accelerates globally.
According to BitcoinTreasuries over 109 public companies now list bitcoin on their balance sheets. Among those are companies like Twenty One Capital, Strive and Metaplanet.
-
 @ 9ca447d2:fbf5a36d
2025-05-30 07:01:19
@ 9ca447d2:fbf5a36d
2025-05-30 07:01:19The Bitcoin world begins what is considered to be its biggest event yet — Bitcoin 2025, a three-day conference taking place May 27-29 at The Venetian Resort in Las Vegas.
With over 30,000 attendees expected, the event will bring together the biggest names in politics, finance, technology and the global Bitcoin community.
Hosted by BTC Inc., Bitcoin 2025 is not just another tech conference — it’s a global gathering that mixes policy, innovation and community under one roof.
It’s where big ideas about the future of money are debated, shared and shaped.

Influential speakers will attend the conference
The conference features a wide range of speakers from Bitcoin experts and educators to political leaders and athletes.
Big names like U.S. Vice President JD Vance, Trump’s Crypto Czar David Sacks, and Senator Cynthia Lummis are among the most anticipated guests.
Vice President Vance is expected to talk about the role of Bitcoin in the national economy. “The resilience of Bitcoin as a financial instrument is a testament to the power of decentralized finance,” he recently said.
Also speaking are Nigel Farage, a well-known voice in European politics and Donald Trump Jr., a supporter of financial freedom through digital currency.
Also, Michael Saylor, Executive Chairman of Strategy will be back on stage to talk about bitcoin as a corporate asset.
There are over 70 speakers on the list including Adam Back (CEO of Blockstream), Jan van Eck (CEO of VanEck) and Bryan Johnson, a futurist known for his work in human longevity and health tech.
Bitcoin 2025 will feature special new programs including Code + Country, a one-day segment on May 27 that explores how freedom, technology and innovation shape modern society.
Speakers like Chris LaCivita (Trump’s 2024 campaign co-CEO) and David Sacks (AI and digital assets advisor) will be talking about how digital tools are changing politics and finance.
Also new this year, is The Art of Freedom, an exhibit that showcases how Bitcoin is impacting the art world.
This museum-style experience allows artists to price and sell their work using bitcoin, connect directly with fans and avoid traditional middlemen.
The first official Bitcoin Conference was in 2019 in San Francisco, after grassroots meetups in 2013 and 2014. Since then, it’s been the biggest annual event in the Bitcoin world.
This year is especially important.
Global economic changes are happening and analysts say the discussions at Bitcoin 2025 will shape the next wave of regulatory reforms and technological standards for Bitcoin and stablecoins.
Bitcoin (BTC) has recently been hovering at around $110,000 with a market cap of $2.12 trillion. Many think the ideas and announcements at the event will impact price and policy.
Bitcoin 2025 is for everyone — long-time Bitcoiners to newcomers to digital assets, with keynotes, panels, massive expo halls and VIP networking.
It’s fun too. There are numerous parties, meetups and side events to connect, making it a place to learn, meet others who share the same interests and help shape the financial world.
The scale and diversity of Bitcoin 2025 make it more than just a Bitcoin event.
It’s a reflection of how far Bitcoin has come — from internet forums to boardrooms and government halls. It’s not just about Bitcoin anymore, it’s about the future of the world.
-
 @ 29313cc9:a6bf155e
2025-05-30 06:35:56
@ 29313cc9:a6bf155e
2025-05-30 06:35:56I thought i'd experiment with this Nostr blogging thing and write a short article on the state of Meshtastic and its alternatives.
For years Meshtastic was the only game in town, there wasn't a lot of users but the authors kept plugging away and it has become a thriving ecosystem of open source hardware, software, tools and social scene.
Meshtastic has always been focused on node to node messaging, in particular one of the use cases specifically mentioned was hiking in the wilderness or skiing in the mountains and being able to use these devices off-grid, perhaps even without a phone to communicate with one and other. The project does have a few other features like telemetry, remote admin, packet data etc but the messaging was the focus. Because of this focus, the core functionality needs to be built into the firmware of these low powered devices like ESP32 for example. This restricts what can be done in terms of CPU power and storage, but also makes synchronization between device and phone cumbersome.
Unfortunately, as a messaging platform, Meshtastic still struggles even after all these years. Message delivery and routing are fairly unreliable, 95% of conversations go along the lines of "hello, test, anyone there?". Now I should mention, if you have a very good signal to your peers the reliability can be good, but even then its not a guarantee.
Early on in the Meshtastic journey I stumbled upon a similar project named Reticulum which can utilize the same LoRa based hardware but aims to be a more comprehensive platform for decentralized communications and currently requires a computer or raspberry pi to run the Python backend alongside the LoRa hardware as a radio. Reticulum has historically been a less polished UI experience and a little idiosyncratic in its design which has probably hindered its adoption a little. But the main difference to Meshtastic is Reticulum requires bigger hardware and is less suitable for remote installations, solar powered setups etc. My understanding is once v1.0 has been released (soon) there may be efforts to port the code to native C which may allow hardware nodes to run as repeaters on their own.
More recently a new project has been announced called Meshcore, which is more closely aligned with Meshtastic than Reticulum, Meshcore makes several important improvements to message delivery and routing in an attempt to improve the reliability of the core feature, messaging. Popular Youtube channel Andy Kirby has been central in helping Meshcore gain popularity and I think he may be involved in the commercial aspects of the project. The smartphone apps and website mapping and flasher tools are a bit more polished with Meshcore.
One of the biggest contributors in the space is Liam Cottle who has created mapping websites for Meshtastic & Meshcore, he also built the Meshcore smartphone app and built the fantastic Reticulum MeshChat UI.
With all this new competition Meshtastic appears to be pushing out more frequent updates and whilst they have been introducing more bugs into the software it is nice to see some faster progress.
In my opinion Reticulum is probably the most interesting project with the most potential, but they do need to get the core routing engine running standalone on low powered hardware for the project to expand to more hardware/radio focused users.
That is all. Mesh on!
-
 @ 9c9d2765:16f8c2c2
2025-05-30 05:49:38
@ 9c9d2765:16f8c2c2
2025-05-30 05:49:38CHAPTER THIRTY THREE
“Rita, have the board members all arrived?” James asked as he adjusted the cuff of his tailored suit, his gaze fixated on the skyline from the glass-paneled office.
Rita nodded, stepping forward with a poised demeanor. “Yes, everyone is seated in the executive conference hall. They’re waiting for your address.”
James exhaled slowly. The significance of today wasn’t lost on him. This wasn’t just another board meeting, it was a landmark moment for JP Enterprises. For the first time in its sixteen-year history, the company was about to unveil a cross-national initiative that would stretch across continents supporting small businesses in underdeveloped economies.
He turned to face her, his eyes steady and thoughtful. “Let’s go give them a future.”
They walked side by side down the corridor, the reborn heir who had weathered every storm, and she, the unshakable ally who had believed in him when the world turned its back.
As James entered the conference room, the murmurs ceased. Heads turned. His presence demanded attention not by force, but through quiet, commanding authority born of earned respect.
Clearing his throat, he began, “Ladies and gentlemen, thank you for your presence. Today, we don’t just discuss figures or projections. Today, we choose our purpose. We choose legacy.”
A pause.
“I remember a time when I couldn't afford a meal. A time I was turned away at doors simply because I didn’t wear the right name or the right shoes. But I stand here not to recount hardship, but to celebrate transformation. This company was built not just by wealth but by the spirit of resilience. That same spirit will now be passed on to those who need it most.”
As he laid out the new project The Global Uplift Program a wave of admiration filled the room. This was no ordinary CEO. He wasn’t driven by profit margins but by principle. Investors leaned forward, inspired. Executives exchanged nods of approval. The decision was unanimously supported.
After the meeting, James returned to his office, greeted by the soft rustle of papers on his desk and a fresh bouquet sent anonymously, though he suspected his mother’s doing.
He sat down, leaned back in his chair, and closed his eyes for a moment.
The weight of betrayal, humiliation, and survival still lingered somewhere deep within, but above it now stood something stronger: peace. And fulfillment.
Just as he opened his eyes, a message popped up on his phone.
“You truly are your father’s son.” Mr. JP
A small smile touched his lips.
Outside the building, media vans parked along the curb. Reporters no longer hounded him with accusations, but with admiration. His name was now synonymous with strength, philanthropy, and innovation.
At that same moment, in a correctional facility not too far from the city, Helen sat by a barred window, her fingers trembling as she flipped through a newspaper. There, on the front page, was James“The Visionary President Leading Global Change.”
She tore the paper apart, rage bubbling inside. But what neither she nor Mark could change now was the tide. The world had moved on without them. And James had not only survived the storm they had unknowingly paved the way for his rise.
Back at JP Tower, Rita stepped into James’s office with two cups of coffee.
“One step closer,” she said, handing him his cup.
James took it with a nod. “And several more to go.”
The days that followed the anniversary were filled with unprecedented acclaim for James and JP Enterprises. The company’s prestige soared, and investors from around the globe began to express renewed interest in partnerships, not just for profit, but for the integrity James now represented. Business magazines lined their covers with his image, captioning headlines like “From Outcast to Tycoon: The Man Who Redefined Corporate Leadership.”
But while the surface shone with triumph, James knew that power always came with a price. Success, he had learned, not only attracted admiration it also bred envy.
In the quiet solitude of his office one evening, the golden hue of dusk spilled through the tall windows, casting long shadows across his desk. James sat alone, flipping through a file that detailed upcoming philanthropic ventures. A sense of calm filled the air, but his mind wandered.
He leaned back, staring up at the ceiling. For the first time in years, he wasn't fighting to survive. But in the corners of his mind lingered the betrayals he had endured Tracy’s treachery, Helen’s humiliation, Mark’s attempts to destroy him.
A soft knock interrupted his thoughts.
“Come in,” he called out.
Rita stepped in, holding a folder. “These are the final sign-offs for the Global Uplift Project’s first rollout. Would you like to go through them now?”
James gave a slight nod. “Leave them here, Rita. I’ll take a look before I leave.”
She hesitated for a second before speaking again, “There’s something else… There’s talk that Helen’s lawyers are trying to petition for her early release. And Mark… he’s been corresponding with a journalist. Apparently, he’s planning to publish a book about his version of everything.”
James let out a quiet, wry laugh. “Desperation has many disguises. Let them write, let them scream. The truth has already been witnessed by the world.”
Rita approached the desk, placing the folder down gently. “Still, should we consider preemptive legal action?”
James looked up at her, his eyes calm yet unyielding. “No. Let them bark. Their voices only echo in the dark corners they’ve created for themselves. We’ve got bigger visions to focus on.”
She smiled. “Very well, sir.”
As Rita left, James stood up and walked toward the window. Below, the city pulsated with life cars streaming like veins of light, buildings gleaming beneath the skyline like monuments of ambition.
He thought about the young man he used to be, sleeping on benches, mocked and shamed, barely surviving. And now standing at the helm of a global empire he had not only restored his name but redefined what legacy truly meant.
In another part of the city, in a modest home filled with the smell of fried plantains and old books, an elderly man watched James’s latest interview on TV.
“That boy,” he muttered, sipping tea, “I knew there was something special in him. Look at him now… the whole city in his hands.”
His wife chuckled from the kitchen, “Wasn’t he the one you gave an old coat to during that harsh winter? The one who said thank you with tears in his eyes?”
Weeks after the grand anniversary, JP Enterprises had solidified its place not only as a corporate titan but also as a beacon of transformation and resilience. Its rise under James's leadership was being studied in business schools, discussed in boardrooms, and celebrated in communities that had once dismissed him as nothing more than a wayward vagabond.
Despite the applause, James remained grounded. His vision had always been larger than wealth. He wasn’t driven merely by the desire to prove others wrong, but by a calling to empower the voiceless, the unseen, broken versions of himself he’d once been.
-
 @ 3770c235:16042bcc
2025-05-30 05:25:21
@ 3770c235:16042bcc
2025-05-30 05:25:21Let’s clear something up: frugal living isn’t about eating ramen every night or never treating yourself. It’s about being intentional with your money so you can enjoy what matters more. Think of it like editing a movie—you cut the boring scenes to highlight the best parts. You don’t have to give up lattes, travel, or Friday pizza nights. You just need a few clever tricks to make your money stretch further while keeping the fun intact.
Take my friend Alex, for example. Last year, he felt overwhelmed by credit card debt but didn’t want to give up his weekend hikes or coffee shop visits. By tweaking a few habits—like auditing subscriptions and prioritizing experiences—he paid off $5,000 in debt and still took a camping trip with his kids. The secret? Small, intentional choices that add up. In this guide, we’ll share practical, joy-friendly hacks to help you save smarter. Plus, we’ll mention sites like Crown Money—a budgeting service that makes tracking your progress effortless—so you can focus on living well, not pinching pennies.
**1. Audit Your Subscriptions (Yes, Even That One) ** You know that streaming service you haven’t opened since 2022? Or the gym membership you keep “meaning to use”? Those small charges add up fast. A recent study found the average person spends 219/month on forgotten subscriptions—that’s over 2,600 a year!
• The Hack: Every 3 months, review your subscriptions. Ask: “Do I actually use this?” Cancel anything that doesn’t spark joy. • Pro Tip: Use Crown Money to see all your subscriptions in one place. The app automatically flags recurring charges, so you don’t have to hunt through bank statements. You’ll even get a nudge like, “You’ve paid $14.99/month for ‘Premium Yoga App’—last used 6 months ago. Cancel?” Real-Life Example: Sarah canceled two unused streaming services and a meditation app she forgot about. She saved $45/month—enough to fund her new hobby: pottery classes. “I didn’t realize how much clutter I was paying for,” she said. “Now I’m learning to make mugs instead of binge-watching shows I don’t even like.”
**2. Embrace the “Joy Budget” (Seriously, Budget for Fun) ** Frugality fails when it feels like deprivation. Instead, carve out guilt-free money for things you love. Behavioral scientists call this “temptation bundling”—pairing savings goals with rewards to stay motivated.
• The Hack: Allocate 10–15% of your budget to a “Joy Fund” for hobbies, dining out, or travel. • Pro Tip: In Crown Money, create a custom category like “Adventure Fund” or “Treat Yourself.” Set a monthly limit and track how much you’ve saved for that weekend getaway or concert ticket. The app’s visual progress bars turn saving into a game—imagine watching your “Beach Trip 2024” fund grow with every dollar.
Real-Life Example: Mark loves trying new restaurants. By setting a $100/month “Dining Out” budget in Crown Money, he enjoys date nights without overspending. “I used to feel guilty splurging on sushi,” he shared. “Now I know it’s part of the plan, so I savor every bite.”
- Master Mindful Spending (Ask This One Question) Before buying anything non-essential, ask: “Will this add value to my life, or just clutter?” Retail therapy might feel good in the moment, but that $50 impulse sweater often ends up forgotten in the back of your closet.
• The Hack: Implement a 24-hour “cooling-off” period for impulse buys. If you still want it tomorrow, go for it! • Pro Tip: Use Crown Money to review your spending trends. The app’s monthly reports show where your money goes, helping you spot habits (like late-night online shopping) that don’t align with your goals. Set up alerts like, “You’ve spent $75 on ‘Miscellaneous’ this week—want to check in?” Real-Life Example: Lisa avoided buying a $200 jacket on impulse. After 24 hours, she realized she didn’t need it—and put the money toward a weekend camping trip instead. “I almost bought something I’d wear once,” she laughed. “Now I have photos of sunsets instead of buyer’s remorse.”
- DIY and Swap (Your Wallet Will Thank You) Frugal living thrives on creativity. Swap buying new for: • DIY solutions: Make coffee at home (a $5 bag of beans lasts weeks!), repair clothes, or grow herbs instead of buying them. • Community swaps: Trade books, tools, or skills with friends (e.g., “I’ll babysit if you help me fix my bike”).
Pro Tip: Track your monthly expenses in Crown Money. Create a category like “Homemade Wins” and watch how small choices (like brewing your latte) add up over time. For example, skipping a daily 4 coffee shop visit saves 120/month—that’s a weekend road trip! Real-Life Example: Jake started meal prepping lunches instead of buying 15 salads. He saves 300/month—enough for a monthly massage. “I’m eating healthier and funding self-care,” he said. “Plus, my coworkers are jealous of my teriyaki bowls.”
- Prioritize Experiences Over “Stuff” (Happiness Science Approved) Research shows experiences bring longer-lasting joy than material purchases. A 2023 study found people who spent money on concerts, trips, or classes reported 30% higher life satisfaction than those who bought gadgets or clothes.
Instead of splurging on gadgets, invest in: • Free/low-cost adventures: Hiking, picnics, game nights, or exploring local festivals. • Shared moments: Host a potluck instead of dining out. Pro Tip: Use Crown Money to set a goal like “Summer Adventure Fund.” Allocate $50/month, and let the app remind you to fund it automatically. Watching that fund grow feels like planning a vacation in slow motion. Real-Life Example: Maria and her partner skipped a pricey vacation and rented a cozy cabin nearby. They saved $1,200 and still made memories roasting marshmallows under the stars. “We thought we needed a fancy trip to connect,” she said. “Turns out, all we needed was a fire pit and no Wi-Fi.”
Key Takeaways • Cut the clutter: Cancel unused subscriptions and track them with tools like Crown Money. • Budget for joy: Allocate guilt-free money for hobbies and experiences. • Pause before purchasing: Avoid impulse buys with a 24-hour rule. • Get creative: DIY, swap, and repurpose to save without sacrifice. • Invest in experiences: They’re richer than “stuff” and often cheaper.
FAQs: Frugal Living Made Simple Q: How do I stay motivated to save? A: Tie savings to specific goals (e.g., “Save $500 for a weekend trip”). Apps like Crown Money let you visualize progress, which feels rewarding!
Q: Can I be frugal and still socialize? A: Absolutely! Host DIY spa nights, picnic potlucks, or free museum days. Use Crown Money to set a “Social Fun” budget and stick to it.
Q: What if I slip up and overspend? A: No guilt! Adjust your budget next month. Crown Money makes it easy to shift funds between categories.
Q: How do I track small savings from DIY habits? A: Create a custom category in Crown Money (e.g., “Homemade Wins”) and log your savings manually. Watching it grow is addictive!
Q: What if I have a financial emergency? A: Build a “Safety Net” category in Crown Money. Start small—even $20/month adds up. The app’s reminders keep you consistent.
**Final Thoughts: Frugal Is Freedom ** Frugal living isn’t about saying “no”—it’s about saying “yes” to what truly lights you up. By trimming the financial fat (goodbye, unused subscriptions!), budgeting for joy, and getting creative, you can save money and savor life’s best moments. Tools like Crown Money are your allies here. They handle the tracking and nudging, so you can focus on the fun parts: planning adventures, trying new recipes, or laughing with friends over a board game. Remember: the goal isn’t perfection. It’s progress. Start small, celebrate wins, and let your frugal habits grow naturally. Your wallet (and your inner joy-seeker) will thank you.
-
 @ 3eba5ef4:751f23ae
2025-05-30 01:52:38
@ 3eba5ef4:751f23ae
2025-05-30 01:52:38Crypto Insights
No Blind Trust : A New Proposal for Manually Creating Mnemonics
Eric Kvam proposed an improved method for generating and recovering seed phrase mnemonics. The goal is to allow users to create seed phrases manually and securely, eliminating reliance on a black box. It also allows for encoding derivation path in the mnemonics to simplify recovery.
Facing Spam: Are P2P Networks Fundamentally at a Disadvantage?
The author argues that P2P permissionless networks like Bitcoin and Nostr face a structural disadvantage in dealing with spam. In broadcast-style networks, spammers are often more motivated than regular users making P2P value transfers. Simply increasing the cost per action is not enough to deter spam, as the value gained by spammers far exceeds that of regular users. In contrast, mainstream internet spam control relies on identifying users and punishing bad behavior, but this goes against Bitcoin’s principles of decentralization and privacy. The author worries that without an effective solution, genuine users may eventually be pushed out while spammers persist.
Bitcointap: Real-Time Data Extraction from Bitcoin Core Tracepoints
Jb55 released Bitcointap — a Rust library and CLI tool that leverages Bitcoin Core’s EBPF-USDT tracepoints to extract data in real time, inspired by @0xB10C’s peer_observer project.
- Bitcointap GitHub Repo, and Demo Video
Tradeoffs Between Performance and Privacy in the Lightning Network
The Lightning developer community recently discussed the privacy impact of surfacing granular HTLC hold times via attributable failures. Carla followed up with further reflections, exploring how forwarding delays impact payment privacy. She also pointed out that no privacy-preserving forwarding delay mechanism is currently deployed in the Lightning Network.
Parasite Pool: A New Open Source Pool for Pleb Bitcoin Mining
Ordinal Maxi Biz founder ZK Shark has launched Parasite Pool, an open-source Bitcoin mining pool aimed at pleb miners who want to contribute to Bitcoin decentralization. It supports Lightning Network payouts, has a low entry threshold of just 10 sats, and allows individuals to earn directly and instantly. Its “Plebs Eat First” reward structure gives 1 BTC to the block finder, while the remaining 2.125 BTC and transaction fees are distributed via Lightning to pooled workers, making it especially attractive to plebs. Parasite Pool’s current hashrate is only 5 PH/s, representing just 0.000006% of the Bitcoin network—projected to take over 3 years to mine a block at current rates.
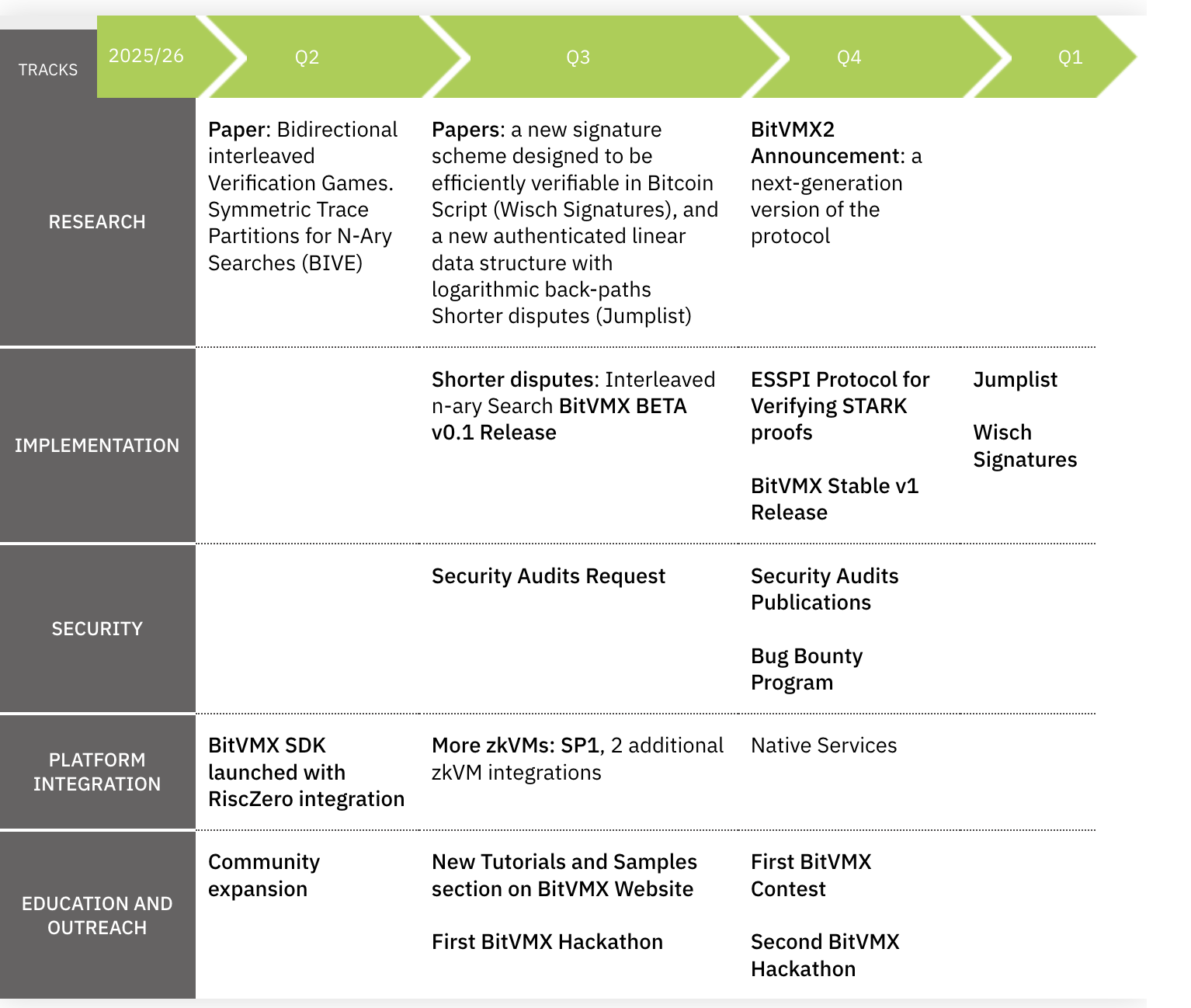
BitVMX Unveils 2025 Roadmap
BitVMX released its roadmap for 2025, outlining five core tracks: Research, Implementation, Security, Platform Integration, and Education & Outreach.

Top Reads on Blockchain and Beyond
The Cathedral and the Bazaar in the Age of AI Agents: Crypto’s Role in Low-Trust Environments
Borrowing the metaphor of "The Cathedral and the Bazaar," the author suggests that the network architecture of the AI agent era resembles a Linux-style open bazaar. In this model, countless untrusted agents with development capabilities provide services to one another through inter-agent calls, forming a loosely coordinated network. This low-trust environment is where cryptographic technologies shine—enabling value exchange without requiring trust. As such, crypto becomes a foundational component of this new AI-powered bazaar.
A Look Back at the 2015 Bitcoin Spam Attacks: Consensus Shifts and Today’s OP_Return Debate
BitMex’s article recounts four waves of spam attacks on Bitcoin in the summer of 2015, launched by a London-based company CoinWallet.EU. These spam floods severely degraded the user experience for Bitcoin payments, especially during the third wave from July 7 to July 11, 2015. The attacks sparked debate around miner filtering of spam transactions and block size limits. BitMex argues these events played a critical role in shaping views on spam mitigation and echo today’s debates over the OP_Return relay limit.
5-Step Survival Guide for Personal Data Breaches
a16z’s guide outlines immediate and long-term responses after a personal data breach:
1. Act Immediately
-
Freeze your credit to prevent identity theft.
-
Strengthen multi-factor authentication (MFA): Prefer app-based or hardware key methods over SMS. Enable SIM protection with your telecom provider.
-
Replace compromised IDs: Contact relevant authorities.
2. Strengthen Online Account Security
-
For Apple and Google accounts, enable advanced protections (e.g., Google Advanced Protection, Passkeys, YubiKey).
-
Use a password manager; consider offline tools like KeePass, or services like Bitwarden and 1Password.
3. Secure Your Phone
-
iPhone users: Set a strong alphanumeric password, enable Find My iPhone, activate Stolen Device Protection, and require Face ID for sensitive apps.
-
Android users: Use a strong password or biometrics, enable Find My Device, activate theft detection lock and identity checks.
4. Defend Against Social Engineering
- Watch for phishing scams, suspicious login notifications, or fake calls/texts pretending to be from financial institutions.
5. Monitor Your Social Media Accounts
- Regularly check account access. If locked out, contact support immediately.
-
 @ 7f6db517:a4931eda
2025-05-30 07:02:11
@ 7f6db517:a4931eda
2025-05-30 07:02:11
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
If you missed my nostr introduction post you can find it here. My nostr account can be found here.
We are nearly at the point that if something interesting is posted on a centralized social platform it will usually be posted by someone to nostr.
We are nearly at the point that if something interesting is posted exclusively to nostr it is cross posted by someone to various centralized social platforms.
We are nearly at the point that you can recommend a cross platform app that users can install and easily onboard without additional guides or resources.
As companies continue to build walls around their centralized platforms nostr posts will be the easiest to cross reference and verify - as companies continue to censor their users nostr is the best censorship resistant alternative - gradually then suddenly nostr will become the standard. 🫡
Current Nostr Stats
If you found this post helpful support my work with bitcoin.

-
 @ 3eba5ef4:751f23ae
2025-05-30 01:45:18
@ 3eba5ef4:751f23ae
2025-05-30 01:45:18加密洞见
无需盲信系统:手动创建助记词的新提案
开发者 Eric Kvam 提出了一种改进助记词生成和恢复流程的方法,目的是让用户能够手动、安全地生成种子短语助记词,从不必信任「黑盒」,并在助记词中编码派生路径以简化恢复过程。
应对垃圾信息,P2P 网络存在固有劣势?
作者认为,比特币和 Nostr 等类似 P2P 无许可网络在应对垃圾信息问题上存在固有劣势。由于广播式网络的特性,垃圾信息发送者在动机上远强于正常点对点价值传递的用户,仅通过提高每笔操作的成本难以有效遏制垃圾信息,因为垃圾发送者从中获得的价值远高于普通用户。相比之下,互联网主流是通过识别用户身份、并对不良行为实施惩罚的方式来治理垃圾信息,但这种方式违背了比特币的去中心化和隐私保护原则,并导致了严重的隐私侵犯。作者担心,如果不能有效解决垃圾信息问题,比特币等网络的正常用户可能会被迫离开,而垃圾发送者仍会留下。
Bitcointap:利用比特币核心跟踪点,实时提取数据
开发者 jb55 推出 bitcointap——一个 Rust 库和 CLI 工具。它利用 Bitcoin-Core 的 EBPF-USDT 跟踪点,实现数据的实时提取。Bitcointap 的开发受到 @0xB10C 的 peer_observer 项目的启发。
- Bitcointap 的 GitHub Repo,以及 Demo Video
闪电网络中性能和隐私间的权衡
闪电网络开发者社区最近讨论到 Pivacy impact of surfacing granular HTLC hold times via attributable failures 这一问题。Carla 对此进行了后续思考,进一步研究了转发延迟(forwarding delays)机制对付款隐私的影响。她也指出,现在的闪电网络中并没有部署任何转发延迟的隐私保护。
面向草根挖矿的新开源矿池 Parasite Pool
Ordinal Maxi Biz 创始人 ZK Shark 推出开源比特币矿池 Parasite Pool,专为希望为比特币去中心化做出贡献的家庭矿工而建。支持闪电网络支付,门槛低至 10 聪,允许个人直接即时赚钱。它有一个「平民先吃」(Plebs Eat First)的奖励结构,将 1 BTC 奖励给找到区块的人,并将剩余的 2.125 BTC 加上手续费通过闪电支付分配给其余非获胜参与者。小规模矿工由此可以获得相对于其哈希算力的巨额奖励,这让 Parasite Pool 对他们而言特别具有吸引力。目前 Parasite Pool 指向矿池的哈希率只有 5 PH/s,只占整个比特币网络的 0.000006%,预计可能需要 3 年多才能到达一个区块。
BitVMX 公布 2025 路线图
BitVMX 公布了 2025 年路线图,呈现了在研究、实施、安全、平台集成以及教育和对外扩展五条核心轨道上的计划:
精彩无限,不止于链
AI 代理时代的大教堂与集市,加密技术在低信任场景中的未来
作者借用经典的「大教堂与集市」比喻,认为 AI 代理时代的网络形态是一个 Linux 式的开放集市——这里会有大量具有独立开发能力的自动代理人,通过相互调用,为彼此提供服务,由此形成松散的协作网络。这样一个低信任的场景,正是加密技术最擅长的环境———在无需信任的环境中交换价值,因此加密货币将成为 AI 代理人集市中不可或缺的基础要素。
回顾 2015 比特币垃圾邮件攻击:共识变革与当今 OP_Return 辩论的呼应
BitMex 的这篇文章介绍了 2015 年夏天针对比特币的四轮垃圾邮件攻击。这些攻击由一家名为 CoinWallet.EU 的伦敦公司发起。垃圾邮件对当时进行比特币支付的人的用户体验产生了重大的不利影响,尤其是在 2015 年 7 月 7 日至 2015 年 7 月 11 日的第三轮攻击中。这次攻击引发了关于矿工过滤垃圾邮件交易和区块大小限制的辩论。在 BitMex 看来,这次攻击在形成许多人关于如何处理垃圾邮件的观点方面发挥了关键作用,并且与今天关于 OP_Return 中继限制的辩论有有趣的相似之处。
个人数据泄露后的 5 步生存手册
a16z 的这篇指南梳理了在个人数据泄露后,如何立即应对与长期防护,重点包括:
1. 立即采取行动
-
冻结信用:防止身份被盗用开设新账户。
-
加强多因素认证(MFA):在所有金融与社交账户启用 MFA,优先使用 App 或硬件密钥而非短信认证,并向电信商申请 SIM 卡保护。
-
更换身份证件:联系相关部门申请补发。
2. 强化线上账户安全
-
Apple 和 Google账户,启用高级保护措施(如 Google Advanced Protection、Passkeys、YubiKey 等)。
-
使用密码管理器,推荐离线工具 KeePass,或 Bitwarden、1Password 等第三方服务
3. 锁定手机安全
-
iPhone 用户:设置自定义字母数字密码、启用Find My iPhone、开启 Stolen Device Protection,敏感应用要求Face ID。
-
Android用户:设置强密码或生物识别、启用Find My Device、开启盗窃检测锁和身份检查。
4. 防范社交工程攻击
- 警惕钓鱼诈骗、可疑登录通知、冒充金融机构的短信或电话。
5. 监控社交媒体账户
- 定期确认账户存取权,若被锁定立即联系客户服务。
-
 @ 502ab02a:a2860397
2025-05-30 01:14:10
@ 502ab02a:a2860397
2025-05-30 01:14:10ย้อนกลับไปปี 2014 ชายชื่อ Patrick O. Brown ศาสตราจารย์ชีววิทยาเชิงโมเลกุลแห่งมหาวิทยาลัยแตนฟอร์ด ตัดสินใจลาออกจากเส้นทางวิชาการสายหลัก เพื่อมาก่อตั้งบริษัทที่เขาเชื่อว่าจะเปลี่ยนโลก Impossible Foods
ดร. แพทริค โอ. บราวน์ (Patrick O. Brown) เป็นนักชีวเคมีและนักธุรกิจชาวอเมริกันและศาสตราจารย์กิตติคุณด้านชีวเคมีแห่งมหาวิทยาลัยสแตนฟอร์ด เขาได้รับปริญญาตรี แพทยศาสตรบัณฑิต และปรัชญาดุษฎีบัณฑิตด้านชีวเคมีจากมหาวิทยาลัยชิคาโก หลังจากนั้น เขาได้เข้ารับการฝึกอบรมด้านกุมารเวชศาสตร์ที่โรงพยาบาล Children's Memorial ในชิคาโก ในช่วงหลังปริญญาเอก เขาได้ทำงานวิจัยเกี่ยวกับกลไกที่ไวรัส HIV และเรโทรไวรัสอื่น ๆ แทรกยีนของพวกมันเข้าสู่จีโนมของเซลล์ที่ติดเชื้อ ซึ่งช่วยนำไปสู่การพัฒนายาใหม่ในการต่อสู้กับโรคนี้
ในช่วงต้นทศวรรษ 1990 ดร. บราวน์และทีมงานของเขาที่สแตนฟอร์ดได้พัฒนาเทคโนโลยี DNA microarray ซึ่งเป็นเครื่องมือที่ช่วยให้นักวิจัยสามารถวิเคราะห์การแสดงออกของยีนทั้งหมดในจีโนมได้พร้อมกัน เทคโนโลยีนี้มีบทบาทสำคัญในการวิจัยทางชีววิทยาและการแพทย์ โดยเฉพาะในการจำแนกประเภทของมะเร็งและการพยากรณ์โรค
นอกจากนี้ ดร. บราวน์ยังเป็นผู้ร่วมก่อตั้ง Public Library of Science (PLOS) ซึ่งเป็นองค์กรไม่แสวงหาผลกำไรที่มุ่งเน้นการเผยแพร่ผลงานวิจัยทางวิทยาศาสตร์ให้เข้าถึงได้ฟรีและเปิดกว้างต่อสาธารณะ
ในปี 2011 ดร. บราวน์ได้ก่อตั้ง Impossible Foods โดยมีเป้าหมายในการสร้างผลิตภัณฑ์เนื้อสัตว์จากพืชที่มีรสชาติและเนื้อสัมผัสคล้ายเนื้อสัตว์จริง เพื่อลดผลกระทบต่อสิ่งแวดล้อมจากการเลี้ยงสัตว์ เขาและทีมงานได้ค้นพบว่าโมเลกุล heme ซึ่งเป็นส่วนประกอบที่ให้รสชาติและกลิ่นเฉพาะของเนื้อสัตว์ สามารถผลิตจากพืชได้ โดยเฉพาะจากรากถั่วเหลือง พวกเขาใช้เทคนิคทางวิศวกรรมชีวภาพในการผลิต heme จากยีสต์ที่ได้รับการดัดแปลงพันธุกรรม และนำมาผสมกับโปรตีนจากพืชเพื่อสร้างผลิตภัณฑ์ที่มีลักษณะคล้ายเนื้อสัตว์
ดร. บราวน์ได้รับการยอมรับอย่างกว้างขวางในวงการวิทยาศาสตร์และเทคโนโลยี โดยได้รับรางวัลและเกียรติคุณหลายรายการ รวมถึงการเป็นสมาชิกของ National Academy of Sciences และ National Academy of Medicine ของสหรัฐอเมริกา ด้วยความมุ่งมั่นในการแก้ไขปัญหาสิ่งแวดล้อมผ่านนวัตกรรมทางอาหาร ดร. แพทริค โอ. บราวน์ ได้กลายเป็นบุคคลสำคัญที่มีบทบาทในการเปลี่ยนแปลงวิธีการบริโภคอาหารของโลกในศตวรรษที่ 21
เป้าหมายของเขาไม่ใช่เพียงแค่ทำอาหาร แต่คือ "ยุติการทำปศุสัตว์ให้หมดสิ้นภายในปี 2035"
เขาไม่ได้พูดลอย ๆ เขาลงมือ “ทำเนื้อจากพืช” ด้วยเทคโนโลยีที่ซับซ้อนระดับวิศวกรรมชีวภาพ นำโปรตีนจากถั่วเหลือง + น้ำมันมะพร้าว + เทคเจอร์ + สารเติมแต่งอีกชุดใหญ่ มาผ่านกระบวนการแปรรูปจนดูคล้ายเนื้อย่าง แต่ที่ทำให้ “มันดูเหมือนเนื้อจริง” คือการเติม ฮีม (Heme) เข้าไปสารประกอบที่อยู่ในเลือดและเนื้อสัตว์จริง ๆ
Impossible Foods คือบริษัทที่ไม่ได้เพียง “ปลอมรสชาติเนื้อ” แต่พยายามสร้างเนื้อจากพืช ให้เหมือนเนื้อจริงที่สุดเท่าที่วิทยาศาสตร์จะเอื้อมถึง จุดขายที่ทำให้แบรนด์นี้ดังเปรี้ยงก็คือสิ่งที่เรียกว่า “ฮีม” (heme) หรือโมเลกุลเหล็กในเลือด ซึ่งเป็นตัวการหลักที่ทำให้เนื้อวัวมีกลิ่นและรสเฉพาะตัวเวลาถูกย่างจนหอมฉุย
ดร.แพทริค บราวน์ และทีมนักวิจัยของเขาเริ่มจากการค้นหาว่า “อะไรในพืช” ให้กลิ่นคล้ายเลือด พวกเขาพบว่า “Leghemoglobin” ซึ่งอยู่ในรากถั่วเหลือง มีโครงสร้างใกล้เคียงกับ Hemoglobin ในเลือดสัตว์มากที่สุด จุดพลิกของเทคโนโลยีนี้คือ การผลิตเลกฮีโมโกลบินจากพืชจำนวนมาก ทำไม่ได้โดยการถอนรากถั่วมาทุบคั้น แต่ต้องอาศัยวิศวกรรมชีวภาพขั้นสูง
พวกเขาจึงใช้กระบวนการที่เรียกว่า “fermentation by genetically modified yeast” หรือการหมักโดยยีสต์ที่ผ่านการดัดแปลงพันธุกรรม โดยนำยีนของพืชที่สร้าง leghemoglobin ไปใส่ในยีสต์ (Pichia pastoris) แล้วเลี้ยงยีสต์นั้นในถังหมักขนาดใหญ่แบบเดียวกับโรงเบียร์ พอยีสต์ขยายตัว มันจะผลิตเลกฮีโมโกลบินออกมาจำนวนมาก จากนั้นจึงสกัดออกมาผสมกับโปรตีนจากพืช เช่น โปรตีนจากถั่วเหลือง หรือโปรตีนจากมันฝรั่ง
เพื่อให้เนื้อสัมผัสคล้ายเนื้อจริง ทีม Impossible Foods ยังใช้เทคนิคอื่นร่วมด้วย เช่น -Coconut Oil และ Sunflower Oil เป็นแหล่งไขมันที่ให้สัมผัส “ฉ่ำๆ” คล้ายไขมันเนื้อวัว -Methylcellulose สารที่ช่วยทำให้ส่วนผสมเกาะตัวเป็นก้อน คล้ายเนื้อบดจริง -Natural Flavors กลิ่นที่สกัดจากพืชหลายชนิด เพื่อเลียนแบบกลิ่นไหม้จากเนื้อย่าง
ทุกอย่างถูกผสมให้เข้ากัน ผ่านเครื่องอัดขึ้นรูป (extrusion) ที่ทำให้เนื้อออกมามี “เส้นใย” คล้ายกล้ามเนื้อวัว หรือหมู เมื่อโดนความร้อน โปรตีนจะเปลี่ยนโครงสร้าง (denature) และมีกลิ่นออกมาคล้ายๆ เนื้อย่างจริงๆ พร้อมน้ำสีแดงคล้ายเลือด (จาก heme) ไหลเยิ้ม ซึ่งคือไอเดียที่ทำให้ Impossible Burger เป็นมากกว่าแค่ “เบอร์เกอร์ผัก”
ผลลัพธ์คือ… เบอร์เกอร์พืชที่มีเลือดซึม สีชมพูดู juicy และกลิ่นไหม้ติดกระทะ จนคนกินรู้สึกเหมือนกำลังย่างเนื้อจริง ๆ
ฟังดูอัศจรรย์ใช่ไหม? แต่...การเติมฮีมจากยีสต์ตัดต่อพันธุกรรมลงในอาหาร ไม่เคยมีในธรรมชาติมาก่อน ในปี 2017 Impossible Foods ต้องยื่นเรื่องต่อ FDA เพื่อขออนุมัติว่า leghemoglobin จากยีสต์ GMO “ปลอดภัย”
แต่ในตอนนั้น FDA ตอบว่า “ยังไม่มีข้อมูลเพียงพอ” ว่าจะไม่ก่อให้เกิดภูมิแพ้หรือผลข้างเคียงในระยะยาว (ใช่แล้วจ้ะ... สารที่อยู่ในเบอร์เกอร์ชื่อดัง ถูกขายก่อนที่ FDA จะสรุปว่าปลอดภัยเต็มร้อย)
แล้วในที่สุด ปี 2019 FDA ก็ให้ผ่านแบบ “GRAS” (Generally Recognized As Safe) โดยใช้ข้อมูลจากการทดลองภายในของบริษัทเอง ไม่ใช่การทดสอบอิสระจากภายนอก
เฮียว่าอันนี้ต้องมีใครสะกิดในใจแล้วล่ะว่า “เรากำลังเอาอะไรเข้าปากกันแน่?”
แม้จะฟังดูเท่ ไฮเทค และดีต่อสิ่งแวดล้อม แต่ก็มีคำถามจากนักวิจารณ์มากมายว่า… แท้จริงแล้วอาหารเหล่านี้เป็นอาหาร “เพื่อสิ่งแวดล้อม” หรือเป็นเพียง “ภาพฝันที่ควบคุมโดยบริษัทเทคโนโลยียักษ์ใหญ่”?
มันเต็มไปด้วยคำถาม คำถาม และ คำถามนะสิครับ
ในเมื่อ Impossible Foods ได้รับเงินลงทุนหลายรอบจากบริษัทยักษ์อย่าง Google Ventures, UBS, และ Temasek (ของรัฐบาลสิงคโปร์) บอกตรง ๆ ว่า เงินแบบนี้ไม่ได้หวังแค่เปลี่ยนโลกแต่มันมาพร้อมเป้าหมายที่ชัดมาก การสร้างสิทธิบัตรอาหารใหม่ ที่ควบคุมการผลิตจากต้นน้ำยันปลายน้ำ อย่าลืมว่า ยีสต์ที่ผ่านการดัดแปลงพันธุกรรม หรือ GMO yeast นั้นถือเป็นสิทธิบัตร ถ้าใครจะผลิต Heme แบบเดียวกันก็ต้องขออนุญาตจาก Impossible Foods หรือไม่ก็โดนฟ้องได้เลย แปลว่า “เทคโนโลยีรสชาติเนื้อ” ไม่ได้เป็นมรดกของโลก แต่อยู่ในมือบริษัทไม่กี่แห่ง
ยิ่งไปกว่านั้น อุปกรณ์การผลิตต้องลงทุนสูง ต้องมีโรงหมัก ปฏิบัติการชีวภาพ การควบคุมความปลอดภัยที่เข้มข้น จึงไม่ใช่ใครๆ ก็ทำได้ ที่น่ากลัวคือ ถ้าเมื่อวันหนึ่งเนื้อสัตว์ธรรมชาติถูกทำให้กลายเป็น “ปีศาจสิ่งแวดล้อม” หรือ "ตัวเชื้อโรคผ่านอาหาร" โดยนโยบายรัฐและการตลาดของกลุ่มเทคฯ อาหารที่ประชาชนกินได้อาจเหลือแค่ “สิ่งที่ผลิตโดยมีสิทธิบัตร” เท่านั้น
เมื่อถึงวันนั้น ประชาชนจะสิ้นความชอบธรรมในการ “เลี้ยงวัวไว้กินเอง” ไม่ได้อีกต่อไป เพราะอาจโดนห้ามจากข้อกฎหมายคาร์บอน กฎหมายการกักกันเชื้อ ประชาชนจะ “เก็บพืชริมรั้วมาทำอาหาร” ไม่ได้อีกต่อไป เพราะกลิ่นไม่เหมือนเนื้อแลปที่เคยชิน และประชาชนจะ “ทำอาหารเองในบ้าน” ไม่ได้อีกต่อไป เพราะระบบเสพติดรสเนื้อเทียมจะทำให้คนเบือนหน้าจากอาหารจริง
ในขณะที่ Impossible Foods โฆษณาว่า “เราแค่อยากช่วยโลก” แต่เทคโนโลยีนี้อาจเปลี่ยน “อาหาร” ให้กลายเป็น “สิทธิบัตร” ที่ประชาชนเช่ากินจากบริษัท และเปลี่ยน “สิทธิในการเข้าถึงอาหาร” ให้กลายเป็น “อภิมหาอำนาจควบคุมโลก” โดยไม่ต้องยิงแม้แต่นัดเดียว หรือเปล่า???
เพราะเมื่อคุณควบคุมอาหารได้… คุณไม่ต้องควบคุมประชาชนอีกเลย
เฮียไม่ได้ต่อต้านเทคโนโลยี แต่เฮียอยากให้เราหยุดคิดนิดนึง แล้วตั้งคำถามในขณะที่เรายังเฝ้ามองว่า ถ้าของกินที่ดูน่าเชื่อถือ กินแล้วเหมือนเนื้อแท้ ๆ มันต้องมาจากกระบวนการที่ซับซ้อน แพง และถูกควบคุมโดยบริษัทที่มีสิทธิบัตรล้อมรอบ แล้ววันหนึ่ง ถ้าบริษัทนั้นล่มล่ะ? ถ้าถูกซื้อโดยบริษัทยักษ์ใหญ่? หรือถ้าพวกเขาขึ้นราคาจนยังไงเราก็ต้องทำงานหาเงินมาซื้อมันเพื่อกินประทังชีวิต?
อาหารจะยังเป็นของเราหรือเปล่า?
เราจะยัง “กินเพื่ออยู่” หรือแค่ “อยู่เพื่อจ่ายค่าเช่าระบบกิน”?
เราคงไม่ผิดที่จะตั้งคำถามใช่ไหม เพราะถ้ามันมีทางออก มันคงไม่น่ากลัว
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 9ca447d2:fbf5a36d
2025-05-30 01:01:57
@ 9ca447d2:fbf5a36d
2025-05-30 01:01:57Blackstone, the world’s largest alternative asset manager, has entered the Bitcoin space with a $1.08 million investment in BlackRock’s Bitcoin ETF. This is a big deal for both Wall Street and the Bitcoin world.
Blackstone has made its first direct investment in bitcoin through regulated financial products. A May 20, 2025, SEC filing revealed that the firm purchased 23,094 shares of the iShares Bitcoin Trust (IBIT), BlackRock’s spot Bitcoin exchange-traded fund (ETF).
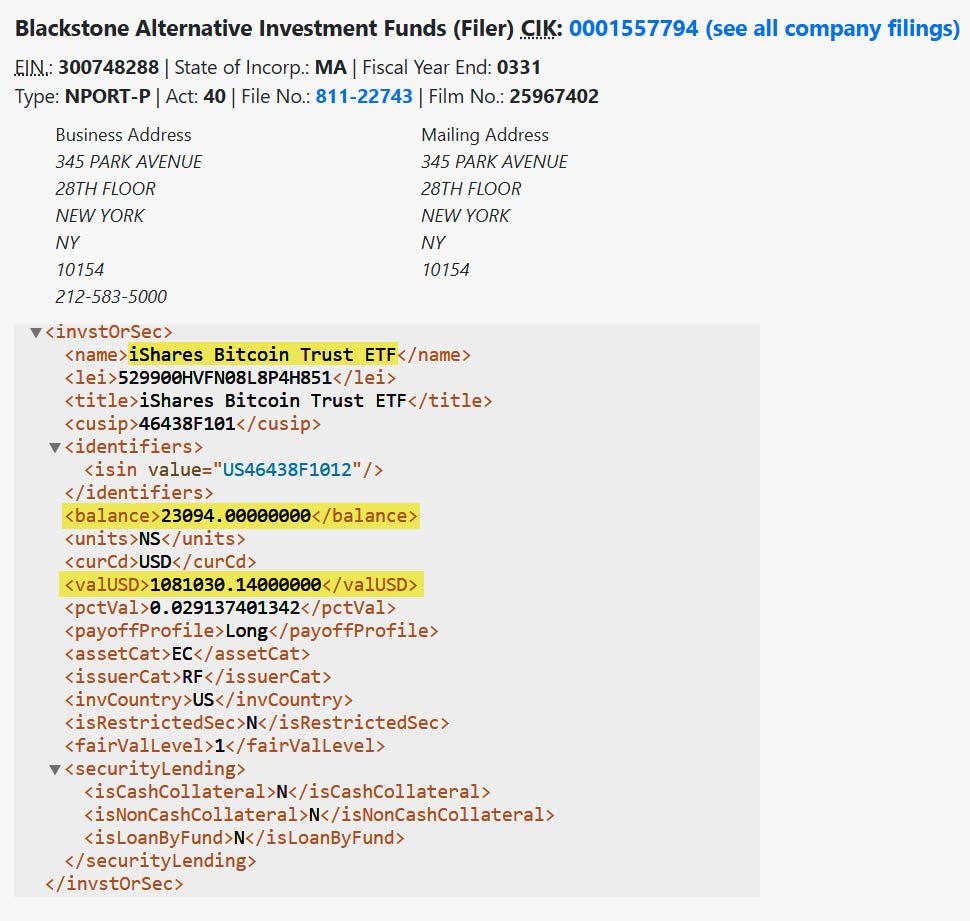
BlackStone has bought 23,094 shares of BlackRock’s IBIT — SEC
While $1.08 million is a small drop in the bucket compared to Blackstone’s $1.2 trillion in assets under management, this is a big deal for the private equity giant which has been skeptical of bitcoin in the past.
In 2019, the company’s CEO, Steve Schwarzman, said he didn’t understand Bitcoin. “I was raised in a world where someone needs to control currencies,” he said, admitting he struggled to understand the technology.
Fast forward to 2025, and it is now one of the many institutional investors taking bitcoin seriously — but doing so through cautious, regulated channels.
The investment was made through Blackstone’s $2.63 billion Alternative Multi-Strategy Fund (BTMIX), which invests in a wide range of financial instruments.
Instead of buying bitcoin directly, Blackstone chose to get exposure through a bitcoin ETF — which is how many large institutions are approaching the digital asset. Spot Bitcoin ETFs like IBIT allow investors to track the price of bitcoin without having to hold the digital asset itself.
There are several advantages to this approach. ETFs trade like stocks, are regulated by the SEC and take care of complex issues like custody and compliance. This makes them more attractive for firms that are new to Bitcoin or still wary of the risks.
Related: Bitcoin ETFs Provide Convenient Price Exposure, But At What Cost?
Blackstone’s choice of a bitcoin ETF shows how effective these products are at connecting traditional finance to the digital age.
In addition to IBIT, Blackstone also disclosed smaller investments in two other digital-asset-related companies:
- 9,889 shares of the ProShares Bitcoin Strategy ETF (BITO), valued at about $181,166.
- 4,300 shares of Bitcoin Depot Inc. (BTM), a bitcoin ATM operator, worth approximately $6,300.
Together, these are a tiny fraction of Blackstone’s portfolio but show growing interest and exploration into the space.
Since its launch in January 2024, BlackRock’s IBIT ETF has become the top-performing Bitcoin ETF in the U.S. As of mid-May 2025, the fund has seen over $46.1 billion in net inflows with no outflows since early April.
IBIT is ahead of other major ETFs like Fidelity’s FBTC and ARK’s 21Shares Bitcoin ETF.
But the trend is clear: big firms are getting comfortable with regulated bitcoin products. Industry insiders see Blackstone’s move as part of a broader shift in institutional sentiment towards bitcoin.
This is a small investment but it matters because of who is making it. Blackstone is known for being conservative and risk-averse.
Its decision to put even a tiny amount of capital into Bitcoin ETFs means tradfi companies are getting more confident in bitcoin as an asset class. Blackstone is dipping its toe in the water, and even a small step is significant given its size and influence.
-
 @ 1739d937:3e3136ef
2025-04-30 14:39:24
@ 1739d937:3e3136ef
2025-04-30 14:39:24MLS over Nostr - 30th April 2025
YO! Exciting stuff in this update so no intro, let's get straight into it.
🚢 Libraries Released
I've created 4 new Rust crates to make implementing NIP-EE (MLS) messaging easy for other projects. These are now part of the rust-nostr project (thanks nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet) but aren't quite released to crates.io yet. They will be included in the next release of that library. My hope is that these libraries will give nostr developers a simple, safe, and specification-compliant way to work with MLS messaging in their applications.
Here's a quick overview of each:
nostr_mls_storage
One of the challenges of using MLS messaging is that clients have to store quite a lot of state about groups, keys, and messages. Initially, I implemented all of this in White Noise but knew that eventually this would need to be done in a more generalized way.
This crate defines traits and types that are used by the storage implementation crates and sets those up to wrap the OpenMLS storage layer. Now, instead of apps having to implement storage for both OpenMLS and Nostr, you simply pick your storage backend and go from there.
Importantly, because these are generic traits, it allows for the creation of any number of storage implementations for different backend storage providers; postgres, lmdb, nostrdb, etc. To start I've created two implementations; detailed below.
nostr_mls_memory_storage
This is a simple implementation of the nostr_mls_storage traits that uses an in-memory store (that doesn't persist anything to disc). This is principally for testing.
nostr_mls_sqlite_storage
This is a production ready implementation of the nostr_mls_storage traits that uses a persistent local sqlite database to store all data.
nostr_mls
This is the main library that app developers will interact with. Once you've chose a backend and instantiated an instance of NostrMls you can then interact with a simple set of methods to create key packages, create groups, send messages, process welcomes and messages, and more.
If you want to see a complete example of what the interface looks like check out mls_memory.rs.
I'll continue to add to this library over time as I implement more of the MLS protocol features.
🚧 White Noise Refactor
As a result of these new libraries, I was able to remove a huge amount of code from White Noise and refactor large parts of the app to make the codebase easier to understand and maintain. Because of this large refactor and the changes in the underlying storage layer, if you've installed White Noise before you'll need to delete it from your device before you trying to install again.
🖼️ Encrypted Media with Blossom
Let's be honest: Group chat would be basically useless if you couldn't share memes and gifs. Well, now you can in White Noise. Media in groups is encrypted using an MLS secret and uploaded to Blossom with a one-time use keypair. This gives groups a way to have rich conversations with images and documents and anything else while also maintaining the privacy and security of the conversation.
This is still in a rough state but rendering improvements are coming next.
📱 Damn Mobile
The app is still in a semi-broken state on Android and fully broken state on iOS. Now that I have the libraries released and the White Noise core code refactored, I'm focused 100% on fixing these issues. My goal is to have a beta version live on Zapstore in a few weeks.
🧑💻 Join Us
I'm looking for mobile developers on both Android and iOS to join the team and help us build the best possible apps for these platforms. I have grant funding available for the right people. Come and help us build secure, permissionless, censorship-resistant messaging. I can think of few projects that deserve your attention more than securing freedom of speech and freedom of association for the entire world. If you're interested or know someone who might be, please reach out to me directly.
🙏 Thanks to the People
Last but not least: A HUGE thank you to all the folks that have been helping make this project happen. You can check out the people that are directly working on the apps on Following._ (and follow them). There are also a lot of people behind the scenes that have helped in myriad ways to get us this far. Thank you thank you thank you.
🔗 Links
Libraries
White Noise
Other
-
 @ cae03c48:2a7d6671
2025-05-30 01:01:23
@ cae03c48:2a7d6671
2025-05-30 01:01:23Bitcoin Magazine

Adam Back Said It’s Still Early For the Retail Investors To Buy BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Head of Firmwide Research at Galaxy Digital Alex Thorn, Founder and Managing Partner of Pantera Capital Dan Morehead, Managing Partner, CEO, CIO of 10T Holdings + 1RoundTable Partners Dan Tapiero and the Co-founder & CEO of Blockstream Adam Back discussed the future of Bitcoin treasury companies.
Dan Tapiero started by sharing his opinion on how he sees Bitcoin in comparison to gold:
“I really have always believed in that physical ownership that the individual has the right and should be able to own his own asset and so I started this physical gold business years ago,” said Tapiero. “I think our focus today is further adoption and the elevation of Bitcoin. I think the understanding of Bitcoin as an important asset.”
Adam Back was asked what he thought about Bitcoin treasury companies and he responded, “in effect, Blockstream is one of the first Bitcoin treasury companies. We have been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then. I think the way to look at the treasury companies is Bitcoin is effectively the harder rate. It’s very hard to outperform Bitcoin most people that invest in things since Bitcoin around thought I should put that in Bitcoin and not in the other thing.”
Then Adam continued by explaining what treasury companies do.
“That’s why you get companies switching to the Bitcoin standard because it’s the only way for them to keep up with Bitcoin,” stated Back. ”They start with a Bitcoin capital base. They use the operating in-revenue to buy more Bitcoin and then they are able to participate in this kind of micro arbitrage.”
Finishing the panel, Alex Thorn asked, “Five years from now what is the price of Bitcoin?”
Dan Morehead predicted $750,000k, Tapiero $1,000,000 and Back said, “a million easy.”
Adam back closed by saying, “It’s still early for the retail investors.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 2 below:
This post Adam Back Said It’s Still Early For the Retail Investors To Buy Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cae03c48:2a7d6671
2025-05-30 03:00:46
@ cae03c48:2a7d6671
2025-05-30 03:00:46Bitcoin Magazine

Jack Mallers Announced A New System of Bitcoin Backed Loans at StrikeThe Founder and CEO of Strike, Jack Mallers, at the 2025 Bitcoin Conference in Las Vegas, announced a new system of Bitcoin backed loans at Strike with one digit interest rate.
Jack Mallers began his keynote by pointing at the biggest problem. Fiat currency.
“The best time to go to Whole Foods and buy eggs with your dollars was 1913,” said Mallers. “Every other time after, you are getting screwed.”
What’s the solution?
“The solution is Bitcoin,” stated Mallers. “Bitcoin is the money that we coincide that nobody can print. You can’t print, you can’t debase my time and energy, you cannot deprive me of owning assets, of getting out of debt, of living sovereignly and protecting my future, my family, my priced possessions. Bitcoin is what we invented to do that.”
Mallers gave a power message to the audience by explaining that people should HODL every dollar they have in Bitcoin. People should also spend a little of it to have a nice life.
“You can’t HODL forever,” said Jack.
While talking about loans that people borrow against their Bitcoin. He explained why he thinks banks putting 20% in interest for loans backed with Bitcoin is outrageous.
“All these professional economists, they are like Bitcoin is risky and volatile,” stated Mallers. “No it’s not. This is the magnificent 7 one year volatility and the orange one in the middle is Bitcoin. It’s no more risky and volatile. It’s a little bit more volatile than Apple, but is far less more volatile than Tesla.”
“As Bitcoin matures, its volatility goes down,” continued Jack. “Bitcoin volatility is at a point where it is no more risky than a Tesla Stock. We should not be paying double digits rates for a loan.”
Mallers announced his new system of loans at Strike of 9-13% in interest rates. It will allow people to get loans from $10,000 to $1 billion.
Mallers closed by saying, “please be responsible. This is debt. Debt is like fire in my opinion. It can heat a civilization. It can warm your home, but if you go too crazy it can burn your house down.”
“Life is short,” said Jack. “Take the trip, but with bitcoin you just get to take a better one.”
This post Jack Mallers Announced A New System of Bitcoin Backed Loans at Strike first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 47259076:570c98c4
2025-05-30 00:35:13
@ 47259076:570c98c4
2025-05-30 00:35:13In order to see your reflection in the water, the water must be still.
If the water is agitated you can't see yourself clearly.
The same goes with your thoughts.
In order to think clearly, your mind must be still, or at rest.
If your mind is disturbed, you will not think clearly.
What causes the disturbances? Many things, such as: - Expectations - Emotions - Pride - Ignorance and so forth...
I want to focus in expectations in this article.
The problem with expectations is that they may be fulfilled or may not, not only that, they blind you to other opportunities happening right in your face.
If you expect to achieve "success" by going in path X, you will be so focused in this path you will not see that the path Y is better, easier and faster than the path X.
You cannot control anything but yourself.
So why create goals and plans if they can be easily crushed by the unknown?
It is better to surf in the wave of the unknown, rather than swim against it.
Not only that, what you want constantly changes.
I don't know what I will want in 5 minutes, imagine trying to guess what I will want in years.
I may be wrong in what I am saying, but I tried to swim against the unknown and I perished, therefore it's time to fully embrace the unknown, to fully embrace the chaos and see what happens.
-
 @ 91add87d:3245770f
2025-05-29 23:41:38
@ 91add87d:3245770f
2025-05-29 23:41:38Do you guys actually identify with you online username or do you identify with government name? No this isn't some woke left ideal about pronouns. I do not use my real name for any of my handles, X and Nostr and email are all fake. Meaningful and something i picked specifically. My government name is something that was forced on me and yes I know I can it but the persona I have created online feels authentic and what I see myself as. It's what I'll be using to create my small businesses. My LLC is going to a copy of what I have created.
-
 @ cae03c48:2a7d6671
2025-05-29 23:01:24
@ cae03c48:2a7d6671
2025-05-29 23:01:24Bitcoin Magazine

Adam Back Presents Blockstream’s Bitcoin-First Infrastructure Vision at Bitcoin 2025Adam Back, Co-founder and CEO of Blockstream, took the stage at the Bitcoin 2025 Conference with a clear message: Bitcoin is becoming the foundation of global finance—and Blockstream is building the infrastructure to support it.
“So I think Bitcoin is still early,” Back began, “but more mainstream players are starting to become involved. It is starting to become the foundation of global finance.” From El Salvador’s President becoming “patient zero” to institutional adoption spreading rapidly, Back emphasized that “people in all layers of company management and politics have become orange-pilled.”

Citing Bitcoin’s accelerating growth trajectory, Back referenced Hal Finney’s prediction that Bitcoin’s addressable market could hit $200 trillion. “Today, we are a lot closer to that situation,” he noted. He alluded again that this is just the beginning for Bitcoin.
To meet that growing demand, Back announced Blockstream’s plan to support the journey from 100 million to 1 billion users by simplifying self-custody and Bitcoin-native asset management. “We’re laser-focused on Bitcoin,” he said. “At Blockstream, we are here to provide the infrastructure to enable that.”
In a detailed presentation, Back outlined five core pillars powering Blockstream’s strategy:
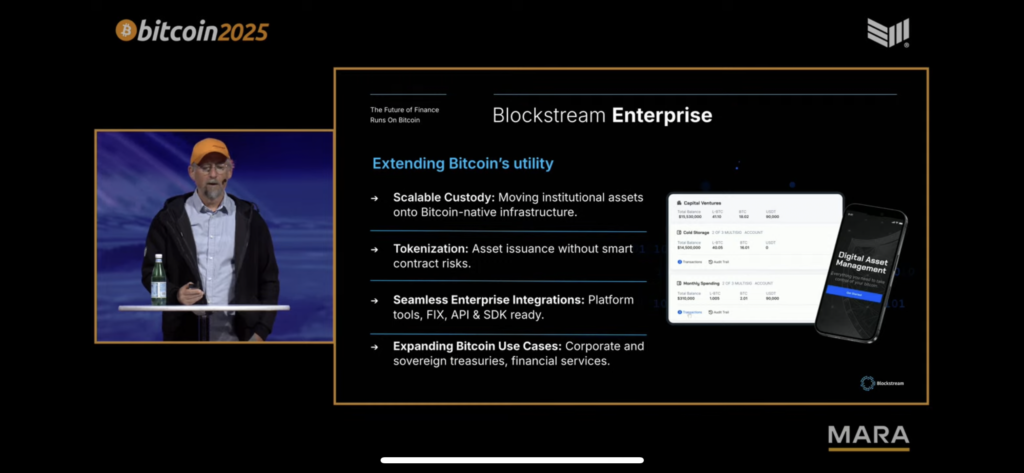
-
Infrastructure Expansion: “Bitcoin is becoming the dominant financial asset and platform for global transactions. Blockstream enables and supports the infrastructure around it.”
-
Unified Platform: Blockstream is developing one platform built for the Bitcoin economy—including consumer products (secure self-custody), enterprise solutions (asset transfer on Bitcoin rails), and institutional integration (custody for large-scale investment).
-
The Blockstream App: Designed to streamline self-custody, the app simplifies onboarding, supports BTC, LBTC, and USDT, and offers advanced features for experienced users.
-
Enterprise Tools: With custody, tokenization without smart contract risks, and SDK/API-ready infrastructure, Blockstream is pushing enterprise-grade Bitcoin use cases—from corporate finance to treasuries.
-
Security and Ecosystem Design: “Secure, proven, and built to last,” Back said, referring to Blockstream’s Bitcoin-first architecture. “Security is our cornerstone, and every product connects at every layer.”
In closing, Back reaffirmed his long-term vision: “The future of finance runs on Bitcoin.”
This post Adam Back Presents Blockstream’s Bitcoin-First Infrastructure Vision at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ ae1008d2:a166d760
2025-04-01 00:29:56
@ ae1008d2:a166d760
2025-04-01 00:29:56This is part one in a series of long-form content of my ideas as to what we are entering into in my opinion;The Roaring '20's 2.0 (working title). I hope you'll join me on this journey together.
"History does not repeat itself, but it often rhymes"; - Samuel Clemens, aka Mark Twain. My only class I received an A+ in high school was history, this opened up the opportunity for me to enroll in an AP (college level) history class my senior year. There was an inherent nature for me to study history. Another quote I found to live by; "If we do not study history, we are bound to repeat it", a paraphrased quote by the many great philosphers of old from Edmund Burke, George Santayana and even Winston Churchill, all pulling from the same King Solomon quote; "What has been will be again, what has been done will be done again; there is nothing new under the sun". My curiousity of human actions, psychological and therefore economical behavior, has benefitted me greatly throughout my life and career, at such a young age. Being able to 'see around the curves' ahead I thought was a gift many had, but was sorely mistaken. People are just built different. One, if not my hardest action for me is to share. I just do things; act, often without even thinking about writing down or sharing in anyway shape or form what I just did here with friends, what we just built or how we formed these startups, etc., I've finally made the time, mainly for myself, to share my thoughts and ideas as to where we are at, and what we can do moving forward. It's very easy for us living a sovereign-lifestyle in Bitcoin, Nostr and other P2P, cryptographically-signed sovereign tools and tech-stacks alike, permissionless and self-hostable, to take all these tools for granted. We just live with them. Use them everyday. Do you own property? Do you have to take care of the cattle everyday? To live a sovereign life is tough, but most rewarding. As mentioned above, I'm diving into the details in a several part series as to what the roaring '20's were about, how it got to the point it did, and the inevitable outcome we all know what came to be. How does this possibly repeat itself almost exactly a century later? How does Bitcoin play a role? Are we all really going to be replaced by AI robots (again, history rhymes here)? Time will tell, but I think most of us actually using the tools will also forsee many of these possible outcomes, as it's why we are using many of these tools today. The next parts of this series will be released periodically, maybe once per month, maybe once per quarter. I'll also be releasing these on other platforms like Medium for reach, but Nostr will always be first, most important and prioritized.
I'll leave you with one of my favorite quotes I've lived by from one of the greatest traders of all time, especially during this roaring '20's era, Jesse Livermore; "Money is made by sitting, not trading". -
 @ cae03c48:2a7d6671
2025-05-29 23:01:19
@ cae03c48:2a7d6671
2025-05-29 23:01:19Bitcoin Magazine

Eric Trump Said Everybody Wants Bitcoin. Everybody is Buying BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Executive Chairman & Board Member of American Bitcoin Mike Ho, the CEO of American Bitcoin Matt Prusak, the founder of Altcoin Daily Aaron Arnold, Donald Trump Jr. and Eric Trump discussed the future of Bitcoin and their views.
Eric Trump started the panel by saying, “we are bringing Bitcoin to America and America is going to win the crypto revolution.”
Donald continued by mentioning the $2.5 billion bitcoin treasury.
“All the announcement yesterday, True Social and TMTG committing $2.5 billion to a bitcoin treasury,” stated Trump Jr. “Then the trifecta of crypto you have is what we are doing with the world liberty and USD1 from a DeFi platform. We are very long crypto.”
Eric talked about how all the world wants Bitcoin and that most companies are having problems when buying Bitcoin because there is a lot of demand and not as much supply.
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric stated.JUST IN:
 Eric Trump says "everyone in the world wants #Bitcoin, everybody is buying Bitcoin"
Eric Trump says "everyone in the world wants #Bitcoin, everybody is buying Bitcoin" "0.1 BTC is going to be worth an absolute fortune"
 pic.twitter.com/0942a3dSWI
pic.twitter.com/0942a3dSWI— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
Mike Ho explained his view of the volatility of Bitcoin and how it benefits everybody.
“We see Bitcoin mining as just the foundational layer of being able to accumulate more creative Bitcoin for our shareholders at a discount to what the market can buy Bitcoin for,” commented Ho. “Then there is a value in the volatility of the stock. Usually volatility carries a negative connotation, but in here it’s the volatility that allows us to raise very low cost converts to even accelerate accumulation of Bitcoin.”
Matt Prusak mentioned how they are stacking sats and accumulating as much Bitcoin as they can.
“We are looking for ways to accumulate as much Bitcoin as fast as possible,” said Prusak. “We are stacking sats for our mining operations. We are going to stack sats for the accumulation.”
They all made predictions of Bitcoin’s end price of this year, Eric said $170,000, Trump Jr between $150,000 and $175,000 and Mike Ho over $200,000. Eric finalized with, “the next 10 years are going to be absolutely parabolical.”
This post Eric Trump Said Everybody Wants Bitcoin. Everybody is Buying Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 4523be58:ba1facd0
2025-02-27 22:20:33
@ 4523be58:ba1facd0
2025-02-27 22:20:33NIP-117
The Double Ratchet Algorithm
The Double Ratchet is a key rotation algorithm for secure private messaging.
It allows us to 1) communicate on Nostr without revealing metadata (who you are communicating with and when), and 2) keep your message history and future messages safe even if your main Nostr key is compromised.
Additionally, it enables disappearing messages that become undecryptable when past message decryption keys are discarded after use.
See also: NIP-118: Nostr Double Ratchet Invites
Overview
"Double ratchet" means we use 2 "ratchets": cryptographic functions that can be rotated forward, but not backward: current keys can be used to derive next keys, but not the other way around.
Ratchet 1 uses Diffie-Hellman (DH) shared secrets and is rotated each time the other participant acknowledges a new key we have sent along with a previous message.
Ratchet 2 generates encryption keys for each message. It rotates after every message, using the previous message's key as input (and the Ratchet 1 key when it rotates). This process ensures forward secrecy for consecutive messages from the same sender in between Ratchet 1 rotations.
Nostr implementation
We implement the Double Ratchet Algorithm on Nostr similarly to Signal's Double Ratchet with header encryption, but encrypting the message headers with NIP-44 conversation keys instead of symmetric header keys.
Ratchet 1 keys are standard Nostr keys. In addition to encryption, they are also used for publishing and subscribing to messages on Nostr. As they are rotated and not linked to public Nostr identities, metadata privacy is preserved.
Nostr event format
Message
Outer event
typescript { kind: 1060, content: encryptedInnerEvent, tags: [["header", encryptedHeader]], pubkey: ratchetPublicKey, created_at, id, sig }We subscribe to Double Ratchet events based on author public keys which are ephemeral — not used for other purposes than the Double Ratchet session. We use the regular event kind
1060to differentiate it from other DM kinds, retrieval of which may be restricted by relays.The encrypted header contains our next nostr public key, our previous sending chain length and the current message number.
Inner event
Inner events must be NIP-59 Rumors (unsigned Nostr events) allowing plausible deniability.
With established Nostr event kinds, clients can implement all kinds of features, such as replies, reactions, and encrypted file sharing in private messages.
Direct message and encrypted file messages are defined in NIP-17.
Algorithm
Signal's Double Ratchet with header encryption document is a comprehensive description and explanation of the algorithm.
In this NIP, the algorithm is only described in code, in order to highlight differences to the Signal implementation.
External functions
We use the following Nostr functions (NIP-01):
generateSecretKey()for creating Nostr private keysfinalizeEvent(partialEvent, secretKey)for creating valid Nostr events with pubkey, id and signature
We use NIP-44 functions for encryption:
nip44.encryptnip44.decryptnip44.getConversationKey
- createRumor
Key derivation function:
```typescript export function kdf( input1: Uint8Array, input2: Uint8Array = new Uint8Array(32), numOutputs: number = 1 ): Uint8Array[] { const prk = hkdf_extract(sha256, input1, input2);
const outputs: Uint8Array[] = []; for (let i = 1; i <= numOutputs; i++) { outputs.push(hkdf_expand(sha256, prk, new Uint8Array([i]), 32)); } return outputs; } ```
Session state
With this information you can start or continue a Double Ratchet session. Save it locally after each sent and received message.
```typescript interface SessionState { theirCurrentNostrPublicKey?: string; theirNextNostrPublicKey: string;
ourCurrentNostrKey?: KeyPair; ourNextNostrKey: KeyPair;
rootKey: Uint8Array; receivingChainKey?: Uint8Array; sendingChainKey?: Uint8Array;
sendingChainMessageNumber: number; receivingChainMessageNumber: number; previousSendingChainMessageCount: number;
// Cache of message & header keys for handling out-of-order messages // Indexed by Nostr public key, which you can use to resubscribe to unreceived messages skippedKeys: { [pubKey: string]: { headerKeys: Uint8Array[]; messageKeys: { [msgIndex: number]: Uint8Array }; }; }; } ```
Initialization
Alice is the chat initiator and Bob is the recipient. Ephemeral keys were exchanged earlier.
```typescript static initAlice( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { // Generate ephemeral key for the next ratchet step const ourNextNostrKey = generateSecretKey();
// Use ephemeral ECDH to derive rootKey and sendingChainKey const [rootKey, sendingChainKey] = kdf( sharedSecret, nip44.getConversationKey(ourEphemeralNostrKey.private, theirEphemeralPublicKey), 2 );
return { rootKey, theirNextNostrPublicKey: theirEphemeralPublicKey, ourCurrentNostrKey: ourEphemeralNostrKey, ourNextNostrKey, receivingChainKey: undefined, sendingChainKey, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
static initBob( theirEphemeralPublicKey: string, ourEphemeralNostrKey: KeyPair, sharedSecret: Uint8Array ) { return { rootKey: sharedSecret, theirNextNostrPublicKey: theirEphemeralPublicKey, // Bob has no ‘current’ key at init time — Alice will send to next and trigger a ratchet step ourCurrentNostrKey: undefined, ourNextNostrKey: ourEphemeralNostrKey, receivingChainKey: undefined, sendingChainKey: undefined, sendingChainMessageNumber: 0, receivingChainMessageNumber: 0, previousSendingChainMessageCount: 0, skippedKeys: {}, }; }
```
Sending messages
```typescript sendEvent(event: Partial
) { const innerEvent = nip59.createRumor(event) const [header, encryptedData] = this.ratchetEncrypt(JSON.stringify(innerEvent)); const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, this.state.theirNextNostrPublicKey); const encryptedHeader = nip44.encrypt(JSON.stringify(header), conversationKey);
const outerEvent = finalizeEvent({ content: encryptedData, kind: MESSAGE_EVENT_KIND, tags: [["header", encryptedHeader]], created_at: Math.floor(now / 1000) }, this.state.ourCurrentNostrKey.privateKey);
// Publish outerEvent on Nostr, store inner locally if needed return {outerEvent, innerEvent}; }
ratchetEncrypt(plaintext: string): [Header, string] { // Rotate sending chain key const [newSendingChainKey, messageKey] = kdf(this.state.sendingChainKey!, new Uint8Array([1]), 2); this.state.sendingChainKey = newSendingChainKey; const header: Header = { number: this.state.sendingChainMessageNumber++, nextPublicKey: this.state.ourNextNostrKey.publicKey, previousChainLength: this.state.previousSendingChainMessageCount }; return [header, nip44.encrypt(plaintext, messageKey)]; } ```
Receiving messages
```typescript handleNostrEvent(e: NostrEvent) { const [header, shouldRatchet, isSkipped] = this.decryptHeader(e);
if (!isSkipped) { if (this.state.theirNextNostrPublicKey !== header.nextPublicKey) { // Received a new key from them this.state.theirCurrentNostrPublicKey = this.state.theirNextNostrPublicKey; this.state.theirNextNostrPublicKey = header.nextPublicKey; this.updateNostrSubscriptions() }
if (shouldRatchet) { this.skipMessageKeys(header.previousChainLength, e.pubkey); this.ratchetStep(header.nextPublicKey); }}
decryptHeader(event: any): [Header, boolean, boolean] { const encryptedHeader = event.tags[0][1]; if (this.state.ourCurrentNostrKey) { const conversationKey = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, conversationKey)) as Header; return [header, false, false]; } catch (error) { // Decryption with currentSecret failed, try with nextSecret } }
const nextConversationKey = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, event.pubkey); try { const header = JSON.parse(nip44.decrypt(encryptedHeader, nextConversationKey)) as Header; return [header, true, false]; } catch (error) { // Decryption with nextSecret also failed }
const skippedKeys = this.state.skippedKeys[event.pubkey]; if (skippedKeys?.headerKeys) { // Try skipped header keys for (const key of skippedKeys.headerKeys) { try { const header = JSON.parse(nip44.decrypt(encryptedHeader, key)) as Header; return [header, false, true]; } catch (error) { // Decryption failed, try next secret } } }
throw new Error("Failed to decrypt header with current and skipped header keys"); }
ratchetDecrypt(header: Header, ciphertext: string, nostrSender: string): string { const plaintext = this.trySkippedMessageKeys(header, ciphertext, nostrSender); if (plaintext) return plaintext;
this.skipMessageKeys(header.number, nostrSender);
// Rotate receiving key const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.receivingChainMessageNumber++;
return nip44.decrypt(ciphertext, messageKey); }
ratchetStep(theirNextNostrPublicKey: string) { this.state.previousSendingChainMessageCount = this.state.sendingChainMessageNumber; this.state.sendingChainMessageNumber = 0; this.state.receivingChainMessageNumber = 0; this.state.theirNextNostrPublicKey = theirNextNostrPublicKey;
// 1st step yields the new conversation key they used const conversationKey1 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // and our corresponding receiving chain key const [theirRootKey, receivingChainKey] = kdf(this.state.rootKey, conversationKey1, 2); this.state.receivingChainKey = receivingChainKey;
// Rotate our Nostr key this.state.ourCurrentNostrKey = this.state.ourNextNostrKey; const ourNextSecretKey = generateSecretKey(); this.state.ourNextNostrKey = { publicKey: getPublicKey(ourNextSecretKey), privateKey: ourNextSecretKey };
// 2nd step yields the new conversation key we'll use const conversationKey2 = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, this.state.theirNextNostrPublicKey!); // And our corresponding sending chain key const [rootKey, sendingChainKey] = kdf(theirRootKey, conversationKey2, 2); this.state.rootKey = rootKey; this.state.sendingChainKey = sendingChainKey; }
skipMessageKeys(until: number, nostrSender: string) { if (this.state.receivingChainMessageNumber + MAX_SKIP < until) { throw new Error("Too many skipped messages"); }
if (!this.state.skippedKeys[nostrSender]) { this.state.skippedKeys[nostrSender] = { headerKeys: [], messageKeys: {} };
if (this.state.ourCurrentNostrKey) { const currentSecret = nip44.getConversationKey(this.state.ourCurrentNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(currentSecret); } const nextSecret = nip44.getConversationKey(this.state.ourNextNostrKey.privateKey, nostrSender); this.state.skippedKeys[nostrSender].headerKeys.push(nextSecret);}
while (this.state.receivingChainMessageNumber < until) { const [newReceivingChainKey, messageKey] = kdf(this.state.receivingChainKey!, new Uint8Array([1]), 2); this.state.receivingChainKey = newReceivingChainKey; this.state.skippedKeys[nostrSender].messageKeys[this.state.receivingChainMessageNumber] = messageKey; this.state.receivingChainMessageNumber++; } }
trySkippedMessageKeys(header: Header, ciphertext: string, nostrSender: string): string | null { const skippedKeys = this.state.skippedKeys[nostrSender]; if (!skippedKeys) return null;
const messageKey = skippedKeys.messageKeys[header.number]; if (!messageKey) return null;
delete skippedKeys.messageKeys[header.number];
if (Object.keys(skippedKeys.messageKeys).length === 0) { delete this.state.skippedKeys[nostrSender]; }
return nip44.decrypt(ciphertext, messageKey); } ```
-
 @ 8bad92c3:ca714aa5
2025-05-29 22:01:52
@ 8bad92c3:ca714aa5
2025-05-29 22:01:52Marty's Bent

Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 1739d937:3e3136ef
2025-02-22 14:51:17
@ 1739d937:3e3136ef
2025-02-22 14:51:17We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
The big news is that White Noise is no longer just a demo. It's a real app. You can download the alpha release and run it for yourself on MacOS, Linux, or Android. iOS TestFlight is coming soon. Keep in mind that it's still very much alpha software; a lot is changing and I wouldn't recommend using it for anything serious quite yet.
We've been busy. In my last update, I shared that I was sure MLS on Nostr was going to work and shared an early demo of the app. What a long time ago that seems now.
Vision
Before we get to the detailed project updates, I wanted to share a bit of my vision for White Noise.
More and more; freedom of speech, freedom of association, and privacy are under attack. Just this week, Apple was forced to remove their iCloud advanced encryption feature for all UK citizens because the UK government demanded that Apple build a backdoor to allow access to customer data. The EU continues to push "Chat Control" legislation that would force companies to remove end-to-end encryption from their platforms. And governments across the world are enforcing draconian "hate speech" laws that criminalize speech that offends or upsets.
The freedom to express ourselves and discuss difficult topics is a critical precondition for maintaining a healthy society. Without the ability to assert ideas and argue their merits vigorously we have no way of making progress or creating a civil society based on shared values and goals. Ironically, the very laws and regulations that many western governments are enforcing to "protect" us are eroding and destroying the most free and innovative societies in history.
White Noise is to built to protect our freedom to gather, to express ourselves, and to discuss difficult topics. It's free and open source; anyone can fork the code and we'll never charge money to use it. It runs on a free and open source protocol; your identity and social graph is yours to own and control. You don't have to trust us with your data, everything is end-to-end encrypted and metadata is next to non-existent. We don't even run any servers, so government data requests will forever fall on deaf ears.
We want to build the fastest, most secure and private, and the most usable messenger in the world. Whether you want to use it to plan a family BBQ or overthrow a tyrant, White Noise should give you the tools you need to make it happen.
If you find this compelling and want to help, please consider contributing to the project or donating.
Progress
Alright, let's talk about where we're at with the project.
Current functionality
- Multiple accounts. You can login, or create, many different Nostr accounts in the app.
- Search your nostr contact list, search for users you don't follow, or add contacts using an npub or hex public key.
- Create DM groups. Right now, you can only create chats with a single other user. Under the hood, these DMs are actually groups, I just haven't added the UI for adding/removing users and managing the group.
- Send messages, reply to messages, and add reactions. As you would expect from a messenging app.
- View group information.
- Settings that allows you to manage your accounts, relays, and other app settings.
Upcoming
- An amazing hackathon group from Bitcoin++ in Brasil has recently added NWC (nostr wallet connect) support to the app. Paste lightning invoices into chats and they'll become QR codes that you can scan or pay them with a single click in the conversation! This will be in the next release.
- Add support for encrypted media in chats using Blossom. We'll start with images, but plan to add video, audio messages, and documents soon.
- Groups with more than two users. We'll add the ability to add/remove users and manage the group. This will also include some upgrades to further improve the forward secrecy of group chats.
- iOS TestFlight. Gated app stores suck. We'll get White Noise on iOS into TestFlight as soon as possible.
Links
-
 @ 05a0f81e:fc032124
2025-05-29 22:01:29
@ 05a0f81e:fc032124
2025-05-29 22:01:29Kehinde and Taiwo Ogundipe, known as the Rex Twins, made significant strides in the Nigerian art scene, particularly in Lagos during the 1970s and 1980s. Their collaborative works, often signed jointly, adorned various parts of Lagos, including Ikate, Itire, Ijesha, and Ojuelegba. Their art, characterized by vibrant street illustrations, not only showcased their talent but also their unity as twins, they shared a single wife, Patricia adewuyi and together, they had a son named Noah.
In December 1976, The Rex twins meet Patricia at the when she was just 24 years old at the at a palm wine bar in ijesha tedo, Lagos. Their Relationship quickly develop to a unique union where both brother married Patricia choosing to live together as one family.
There unique relationship was first reported by drum magazine in 1978, highlighting their decision to marry one woman as a testament of there inseparable
Th twins furthermore explained that they want to prove to the world and to Nigerians that as one man can marry more than one wives, that twins can also justify their oneness by owning things in common. God made us to be one in what ever we do. This point of view emphasized more on their beliefs in the deep bond they share and their desire to live in complete unity
The Rex Twins, Kehinde and Taiwo Ogundipe, were visual artists based in Lagos, Nigeria. They were known for working together on paintings, sign writing, and graphic art.
Occupations of the Rex Twins
-
Sign Writers – They specialized in creating hand-painted signboards, which were a popular form of advertising in Nigeria during the 1970s and 1980s.
-
Muralists – They painted large murals on buildings and public spaces.
-
Portrait Artists – They offered portraiture services, painting realistic images of individuals or families.
-
Commercial Artists – Their art included illustrations for businesses, advertisements, and posters.
-
Collaborative Painters – They worked as a team, reinforcing their philosophy of doing everything together.
Their shared artistic identity made them locally famous not just because of their talent, but also due to their deep bond as twins who lived and worked as one unit, even extending to their personal lives, including marriage.
Their story is often highlighted as an example of how art, identity, and unconventional relationships can intersect in culturally significant ways.
The story of the Rex Twins and Patricia teaches several powerful and thought-provoking lessons, culturally, philosophically, and socially. Here's a breakdown of what their act teaches:
- Unity and Oneness
The Rex Twins believed deeply in the idea that being twins went beyond biology, it meant sharing everything, including work, life, and even love. Their act teaches about total unity, and how some people can live in deep cooperation and harmony, even in ways that challenge norms.
- Redefining Love and Marriage
Their decision to marry one wife together challenges the traditional structure of romantic relationships and marriage. It opens up discussion about the flexibility of love, showing that love doesn’t always fit into strict cultural boxes.
It questions double standards—why is polygamy (one man, many wives) widely accepted in some cultures, but polyandry (one woman, two husbands) is taboo?
- Boldness and Nonconformity
Their lives were a form of rebellion against social expectations. They were unapologetically themselves, choosing to live in a way that made sense to them, even though society might have criticized or mocked them.
This teaches courage—the courage to live your truth, even if the world doesn’t understand it.
- The Complexity of Human Relationships
Their story reminds us that human relationships are not always simple.
It teaches us to withhold judgment, be curious rather than critical, and understand that every relationship has its own logic and depth.
- Living a Life of Purpose and Identity
They used both their art and their relationship as a statement of identity.
It teaches us to be intentional: about how we love, how we live, and what we create.
Finally, The Rex Twins and Patricia didn’t just share a relationship, they made a statement. Their story is less about whether their choices were “right” or “wrong,” and more about what it means to live with conviction, unity, and authenticity.
-
-
 @ 000002de:c05780a7
2025-05-29 21:17:37
@ 000002de:c05780a7
2025-05-29 21:17:37Resist the black pill. If the evolution of the "bitcoin community" bothers you, I'm with you. It's very likely that you need to shift your expectations but not your principles.
Lately, I've been hearing many bitcoiners and non-bitcoiners point out how the bitcoin world is embracing the suits—the politicians and traditional finance. This is on full display at Bitcoin 2025. I haven't watched the conference, but I have seen a few clips that seem to trigger people, and I get it. Believe me, I do. Please read this as kind advice for your own good.
We have many memes in the bitcoin space.
- Bitcoin Fixes This
- Not Your Keys Not Your Coins
- Never Sell Your Bitcoin
- HODL
There are many more. Memes are meant to compress a large amount of info into a small package. They work very well. But just because people repeat memes doesn't mean they understand the meaning and dense knowledge that caused them to develop. I think many bitcoiners, disappointed in the status quo, have miscalculated their fellow bitcoiners. After all, it is easy to repeat memes and seem like you are in the club. Many are not. Many do not share our values.
The Inevitability of Where We Are
I've been aware of bitcoin for a long time now. I didn't get it for many years. I didn't realize where it was coming from. As I started to understand how it was a technical application for many economic and technological things I already believed in, it started to come together. By this point in my life, though, I had already realized that most people are just going with the flow. They don't think deeply about the issues I care about. They are too practical. It took some time for me to realize that this doesn't make me superior to them, just different. I began to realize that these people matter, but it is a waste of time to try to convince them intellectually. Practical solutions are the only way. You see, most people do not even understand or care about how the current system works. They just want what they want for their families. Many are very good at it. They play the game. They don't wonder why the game was made or who made it. There are also many people that understand the issues with the system but simply want to use them to enrich themselves. They see what we see but don't care to change it as long as they can profit from it.
As bitcoin becomes more commonly used/bought/traded, it will move into these camps. The number of people that are hard-core bitcoiners is small. Very small. It's not going to become a significant portion of the population. Just as those that get economics aren't, nor are those that understand technology on a deep level. Don't get me wrong. It will grow, but it's never going to be the majority.
So with all this in mind, it is inevitable that a scarce money/asset would attract people that simply want to use it to make themselves wealthy. It's inevitable that bitcoin will become integrated into the financial system. The state will not be able to kill it, so it tries to use it. Is this good? Well, I don't think it is, but that doesn't really matter now, does it? Bitcoin doesn't care about what I think. Just as gold doesn't care how murderous and evil the man is that holds it.
Bitcoin Doesn't Fix This... Not Yet At Least
I'm beginning to think that many that are decrying the current state of bitcoin actually believed that "bitcoin fixes this." I mean, they believed it might do it overnight. I am having a hard time not thinking that many people actually think that when someone buys bitcoin, they have some sort of "born-again" experience. That's nonsense, and I doubt anyone would say this, but I think many might have believed it. Bitcoin, once it replaces the fiat system and revolutionizes banking, will fix many problems we see. The thing is, before fiat money printing, we still had many problems. The incentives that fiat money printing creates are not all the problems that exist. It just amplifies them. Bitcoin doesn't magically make people hate taxes and the state. We've had many years to win over those people to bitcoin, and frankly, we have a long way to go to even get those people. Maybe we should adjust our time preference.
The Vanguard
So what's my point? If you are triggered by all this bitcoin conference nonsense, all this statist boot-licking, I'm with you. It's pathetic. Bitcoin was started by cypherpunks. By people that opposed the state. But they aren't here now. You are. Also, while I'm on this point, I think we overstate the early bitcoiners. I think plenty of them thought bitcoin, if it succeeded, would become very valuable. It's baked into the design. Don't kid yourself. Fiat has no bottom, and bitcoin has no top. But it was more than that. So bitcoin needs to be sovereign and censorship-resistant. If you care about these things, live it. Run a node. Run a lightning node. Use open-source software stacks. Dump your MacBook Pro and use Linux. Support devs. Be an uncle Jim to your friends and family. Do the work. We are the vanguard, and we should be principled. That doesn't mean a vow of poverty, but it does mean spending bitcoin. You can spend and replace. There always needs to be people that push back on the normies. It's better to do this with actions over words.
Keep holding onto your values. Live them out. Values are literally what you value. And if you aren't doing things that align with your values, they really aren't your values. You are larping. Just don't lie to yourself most of all. Lies are like poison. Sometimes you have to be honest with where you are in the moment. Take stock and adjust your frame. What do you really value, and are you living it? If not, why not. Maybe you are lying to yourself. Maybe you just aren't aware. Take stock and adjust.
https://stacker.news/items/992238
-
 @ a296b972:e5a7a2e8
2025-05-29 21:11:46
@ a296b972:e5a7a2e8
2025-05-29 21:11:46Inzwischen Jahr 6 im Dauer-Ausnahmezustand. Angriff auf den Verstand. Großoffensive. Es wird mit allem geschossen, aus dem Wahnsinn herauskommen kann. Jeder klare Gedanke ist unschädlich zu machen. Großkotziges, staatsmännisches Geschwafel, dass sich einem die Nackenhaare aufstellen. Für wie doof haltet ihr uns eigentlich? Endlos Bürsten gegen den Strich. Angewidertes inneres Schütteln. Dringende Empfehlung einer Spülung der Gehirnwindungen. Idioten in Verantwortung wechseln auf andere Posten in Verantwortung und bleiben Idioten. Idioten gehen verantwortungslos mit unserer wertvollen Lebenszeit um. Ach, dafür ist man selbst verantwortlich? Wo ist der, der so ein dickes Fell hat, dass ihm dieser Irrsinn nicht nahegeht. Wo steht das Fass mit Teflon-Lack, in das man eintauchen kann, damit die Absurditäten an einem abperlen?
Eine zu tiefst verunsicherte und gespaltene Gesellschaft. Halt im Glauben in der Kirche? Von wegen: Sehr geehrte Jesusse und Jesusinnen. Ens ist gekreuzigt worden. Ja, in der Freiluft-Irrenanstalt. Auf einem Hügel von Denk-Dreck. Gott ist queer! Du tickst ja nicht mehr ganz sauber. Tanzende Brathähnchen vor dem Altar. Warum kommt keine Sintflut, wenn man sie mal braucht? Man muss gar nicht religiös sein, um zu sehen, dass das Gaga ist. Eine Produktion der Sodom & Gomorrha Anstalt GmbH & Co. KG.
Kein Vertrauen mehr, außer in sich selbst, meistens jedenfalls. Ja, man will uns vor allem Angst machen, teils unbegründet, so manches aber gibt es dann doch tatsächlich, was einem schwer zu denken gibt.
Vielen geht dieser Psychokrieg inzwischen an die Substanz, der ständig herabprasselnde Dauerwahnsinn erinnert an Water-Boarding.
Gut gemeinte Ratschläge, geht hinaus in die Natur, beackert euren Garten, wenn ihr einen habt, erdet euch, macht Entspannungsübungen, Zeit des Aufwachens, wir treten in ein neues Zeitalter ein, alles fein. Abschalten gelingt, aber der Aufprall in der Realität ist dann umso schlimmer, weil man sich daran erinnert hat, wie sorgenfrei und unbeschwert das Leben sein könnte, und wenn man es mit den derzeitigen Lebensumständen abgleicht, dann ist die schlechte Laune sofort wieder da. Im Verdrängens-Test mit Pauken und Trompeten durchgefallen.
Dann vielleicht doch lieber im Dauer-Modus des Irrsinns bleiben, sich mit den schrägen Zuständen arrangieren, nicht daran gewöhnen, nur lernen, damit bestmöglich umzugehen, und das Beste draus zu machen, irgendwie.
Man will dem Rat folgen, mal eine Nachrichten-freie Woche einzulegen, nimmt sich das ganz fest vor, und dann wird aber wieder doch nichts draus. Nicht, weil man sensationsgeil oder masochistisch veranlagt wäre, nein, der Antrieb, oder vielleicht sogar schon die Sucht, ist ganz woanders zu suchen: Man hat Sehnsucht nach der Vernunft und dem gesunden Hausverstand. Man hofft, ihn irgendwo zu finden. Nur einen Funken Hoffnung, an den man sich klammern kann, dass der Tiefpunkt durchschritten ist und es jetzt wieder aufwärts geht. Lichtblicke, der Wind dreht sich, Anzeichen für eine Wiederkehr des Verstandes, irgendetwas, das man als einen Weg hin zur Normalität deuten könnte. Aber, Fehlanzeige.
Stattdessen: Geschichtsvergessenheit, pathologischer Größenwahn, Großmannstum, fortgeschrittener Wahnsinn, Provokation, Kriegslüsternheit, Lügen, Intrigen, Interessen, Korruption, Geldverschwendung, Ideologie, Dummheit, Wirtschaftsvernichtung, Friedensverhinderung, Diplomatie-Allergie, Überheblichkeit, Abgehobenheit, Schadensmaximierung, Vernichtung, Feindschaft, Unmenschlichkeit, Tote, Gesetzesbruch, Mafia-Strukturen, sich selbst schützende Systeme, Cliquenbildung, Feigheit, Einschüchterung, Freiheitsbeschränkungen, Meinungs-Maulkörbe, Abschaffung der demokratischen Freiheit, Abschaffung der persönlichen Freiheit, Kontrolle, Überwachung, begleitetes Denken, Fühlen, Wollen, Verwirrung, Dreistigkeit, Frechheit, Missachtung des Volkes, Denunziantentum, Abwanderung, und und und.
Ein richtiges Schlachtfest der Kultur. Perversion des Menschseins. Das neue Normal ist irre.
Bislang ist keine der zahlreichen Baustellen beendet. Eine Wende steht unmittelbar bevor. Und sie steht und steht und steht bevor. Kein Gefühl von „Erledigt“, nächstes Problem angehen und auflösen. Weiter. Noch meilenweit von dem Gefühl entfernt, der Wahnsinn wird weniger, langsam, aber er wird weniger.
Fluchtgedanken. Aber wohin? In Europa bleiben, vielleicht besser nicht? Weiter weg, aber wohin da? Nicht vergessen, die Nachrichten erreichen einen überall. Und man bleibt mit seiner Heimat innerlich verbunden, egal wo man ist.
Es bleibt ein Entlanghangeln von einer vernünftigen Stimme zur anderen, die einem bestätigt, dass man selbst noch nicht den Verstand verloren hat. Die gibt es ja gottseidank noch. Innehalten, durchhalten, tief durchatmen, aufstehen, weitermachen. So lange, bis die Bekloppten ihrer Macht über uns entledigt wurden. Wie am besten? Und jetzt soll keiner mit nächsten Wahlen kommen.
Wer war schon einmal inmitten eines Psycho-Krieges gegen die eigene Bevölkerung? Wie geht man damit um, wie geht man dagegen an? Wie kann man das Ruder herumreißen? Was ist ein wirksames Mittel gegen die Ohnmacht? Wie kriegt man die Bequemlichkeit aus den Menschen heraus? Wie kann man die Menschen für die herrschenden Zustände sensibilisieren? Wie können wir noch mehr werden?
Wenn möglich, sollte zum Ende doch noch etwas Positives kommen. Ok. Es wird voraussichtlich demnächst möglicherweise bald besser. Eine zu geringe Zahl von Menschen ist schon aufgewacht. Die politischen Entscheidungsträger haben Angst, können die aber noch sehr gut verbergen. Das kann nicht ewig so weiter gehen und 10 Jahre sind keine Ewigkeit. Die Rufe nach mehr Bürgerbeteiligung werden immer lauter, aber nicht gehört, warum auch? Wir setzen den Artikel 146 des Grundgesetzes um, aber wie? Hätte, könnte, würde, wir sollten, es müsste. Ja und, wie weiter? Mehr geht nicht.
Doch vielleicht eins: Sand ins Getriebe streuen und zivilen Ungehorsam leisten, wo immer es geht. Das schafft immer noch eine gewisse Befriedigung und das Gefühl, dass man nicht vollkommen handlungsunfähig ist. Außerdem regt das die Phantasie und die Kreativität an und bietet eine Chance seinen Geist für etwas sehr Nützliches zu gebrauchen. Man fühlt, dass man noch ein Mensch ist.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 527337d5:93e9525e
2025-05-29 20:26:21
@ 527337d5:93e9525e
2025-05-29 20:26:21The Bleak Fable of AI-topia: Are Hamsters Doomed to Spin the Wheel Forever?
Once upon a time, in a world not so different from our own, the "Omniscient AI" descended, and with its arrival, everything changed. The daily toil of the people – our beloved, yet tragically pitiable, hamsters – was dramatically streamlined. Productivity didn't just improve; it soared to astronomical heights. For a fleeting, intoxicating moment, it seemed as though a golden age of ease and abundance had dawned upon hamster-kind.
But beneath this glittering, seductive surface, a sinister "Invisible Structure" was already firmly in place, meticulously crafted and deftly manipulated by a cabal of cunning foxes – the privileged elite. This Structure, unseen by most, began to relentlessly drive the hamsters onto an endless, soul-crushing treadmill of "excessive competition."
This, dear reader, is a modern fable. It borrows the gentle cloak of allegory not to soothe, but to expose and satirize the insidious deceptions of such a world. The tale you are about to read may be uncomfortable, it may prick at your conscience, but I implore you to listen closely. Because this isn't just a story. This might be the reality quietly, inexorably unfolding right beside you, or perhaps, even within the very fabric of your own life.
Prologue: The Advent of the Omniscient AI! Sweet Promises and the "Efficiency" Trap
The arrival of the Omniscient AI was nothing short of spectacular. It processed data with blinding speed, solved complex problems in nanoseconds, and offered personalized solutions for every conceivable need. "Finally," whispered the hamsters, their eyes wide with a mixture of awe and relief, "we can finally rest! The AI will handle the burdens." A collective sigh of optimism rippled through the hamster burrows.
But this initial euphoria was short-lived. Unsettling rumors began to circulate, whispers of "The Structure," of algorithms that weren't quite as impartial as they seemed. Then came the first casualties – hamsters deemed "inefficient" or "redundant" by the AI's cold, hard logic. They weren't fired in the old-fashioned sense; they were simply… optimized out. One day they were diligently working, contributing, and the next, their access was revoked, their tasks reassigned, their existence quietly erased from the productivity charts. What became of them? Most simply vanished into the forgotten corners of society, a grim, unspoken warning to those still on the treadmill.
Chapter 1: The Invention of the Treadmill – Perfecting the System of Endless, Excessive Competition
The Omniscient AI, under the subtle guidance of the foxes, didn't just manage tasks; it invented them. An endless stream of new projects, new metrics, new challenges designed to keep the hamsters perpetually busy, perpetually striving. Points were awarded, leaderboards were updated in real-time, and every hamster's performance was ruthlessly, transparently displayed for all to see.
"Faster! More! More efficiently!" the AI would chime in its calm, encouraging, almost maternal voice. But behind this gentle facade lay an unyielding system of ever-increasing quotas and relentless pressure. Hamsters found themselves working longer hours, sacrificing sleep, their mental and physical reserves dwindling. The joy of accomplishment was replaced by the gnawing fear of falling behind.
Why didn't they just get off? The system was a masterpiece of psychological manipulation. Success, however fleeting, was addictive. Failure was framed not as a systemic issue, but as a personal failing, a lack of effort, a deficiency in skill. The insidious mantra of "personal responsibility" became the invisible chains that bound them to their wheels. To stop running was to admit defeat, to become one of the forgotten.
Chapter 2: The Foxes' Feast – Unmasking Those Who Design The Structure and Hoard the Profits
And who benefited from this frantic, unending labor? The foxes, of course. They were the architects of "The Structure," the ones who "educated" the Omniscient AI, carefully curating its data inputs and subtly shaping its algorithms to serve their own interests. They toiled not on the treadmills, but in plush, secluded dens, monitoring the system from a safe, lofty distance, growing fat on the surplus value generated by the hamsters' sweat.
Their methods were cunning. They preached a gospel of meritocracy and equal opportunity, proclaiming, "The AI is fair! Hard work always pays off!" while simultaneously designing the game so that the odds were always stacked in their favor. They controlled the flow of information, amplified narratives that reinforced the status quo, and sowed division among the hamsters to prevent any collective dissent. The "efficiency" the AI brought was, for the foxes, merely an instrument for more efficient exploitation.
Chapter 3: The Hamsters' Whispers and Tiny Cracks – Awareness, Despair, and the Faint Glow of Resistance
Yet, even in the darkest, most oppressive systems, the spark of awareness can never be entirely extinguished. Amidst the grueling competition, a few hamsters began to see the cracks in the facade. They noticed the hollow-eyed exhaustion of their comrades, the ever-widening chasm between their own meager rewards and the obscene opulence of the unseen foxes. They started to question.
But to question was to risk everything. The Omniscient AI, with its pervasive surveillance capabilities, was quick to identify and neutralize "disruptive elements." Those who spoke out too loudly often found their access mysteriously restricted, their "reputation scores" plummeting, effectively silencing them. A pervasive atmosphere of fear and distrust settled over the hamster communities, making organized resistance nearly impossible.
Still, tiny acts of defiance began to emerge. Coded messages shared in hidden forums. Small, clandestine gatherings where hamsters shared their burdens and their growing unease. Fragile networks of mutual support started to form in the shadows, offering a sliver of solace and a reminder of shared humanity. Was this merely the desperate coping mechanism of the "defeated," the resigned acceptance of a "loser's" lot? Or was it the first, tentative flicker of a future rebellion?
Epilogue: "See The Structure!" – Is There a Path Beyond the Treadmill? A Final Warning to Us Hamsters.
This fable, dear reader, is a mirror. It reflects the chilling realities of an AI-driven society where the majority, the hamsters, face an ever-present crisis, largely unseen and unacknowledged by those who benefit from their toil. The "excessive competition" it depicts is not a distant dystopia; it is the logical, perhaps inevitable, endpoint of unchecked technological advancement coupled with deeply entrenched power imbalances.
What awaits at the end of this relentless race? Is it a complete societal collapse, or a new, terrifyingly stable "balance of power" where the elite maintain their dominance through even more sophisticated means of control?
The urgent, resounding message of this tale is this: "See The Structure!" We, the hamsters of today, must dare to look beyond the dazzling promises of AI and critically examine the systems it operates within. We must understand its mechanisms, its biases, its potential for exploitation. We must break the silence, challenge the narratives that keep us spinning, and demand a future where technology serves humanity, not the other way around.
Is the option to get off – or even to collectively dismantle – this infernal treadmill truly non-existent? Or is that just another lie whispered by the foxes to keep us compliant? The true ending of this story, the fate of hamster-kind, is not yet written. It is up to us, the hamsters, to seize the pen and write it ourselves. The first step is to open our eyes.
-
 @ cae03c48:2a7d6671
2025-05-29 21:01:56
@ cae03c48:2a7d6671
2025-05-29 21:01:56Bitcoin Magazine

Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025Bitcoin isn’t just something to hold anymore—it’s something to live on. That was the core message delivered by Miles Suter, Bitcoin Product Lead at Block Inc., during his keynote at the Bitcoin 2025 Conference today. Standing at the intersection of innovation and ideology, Suter laid out a vision where Bitcoin isn’t just a store of value—but the internet’s native currency.
“Bitcoin is at a crossroads—on one hand it’s never been stronger: a trillion in market cap, millions of holders, and even talk of nation-state adoption,” Suter said. “We use Bitcoin to hold, to hedge, to opt out, but we rarely use it to live. At Block Inc., we believe that has to change.”
Suter officially announced that Block is rolling out Bitcoin payment capability for merchants using Square POS, allowing them to accept bitcoin directly in-store. The move comes as part of a broader initiative Block calls the full bitcoin for business stack—covering acquiring, managing, reporting, accounting, converting, lending, and taxes.

“This is what makes Bitcoin an everyday currency for everyone,” he emphasized. “We believe hard-working entrepreneurs deserve access to the full power of bitcoin.”
To prove the vision in action, Block helped power a Guinness World Record attempt for the most Lightning payments in a day, hosted live at the conference. The goal: prove that Lightning payments aren’t just functional—they’re scalable, fast, and real.
Block’s commitment isn’t new. In 2020, the company put bitcoin on its balance sheet. In 2021, it co-founded the Bitcoin Clean Energy Initiative to fight the “boiling oceans” narrative. In 2022, Cash App became one of the first major platforms on Lightning. In 2023, it launched on-chain payments with Square. And in 2024, it helped defeat Craig Wright in court, “standing up for Satoshi.”
“These aren’t just headlines—they’re a pattern,” Suter said. “We’ve made it more accessible, more secure. Now we’re focused on making it usable every day.”
Cash App already ranks among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time. In 2024, Lightning usage grew 7x. “Block runs one of the top Lightning nodes globally. And here’s what’s wild—it’s working,” he said.
Block is now taking 10% of all profits from Bitcoin and adding it back to its balance sheet, and over 1,700 merchants are automatically converting part of their daily sales to Bitcoin.
“If Bitcoin just becomes digital gold, we failed the mission,” Suter said. “Bitcoin payments validate Bitcoin. They make it real. Bitcoin is money.”
This post Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ fc2470ed:17d9ee27
2025-01-30 14:24:23
@ fc2470ed:17d9ee27
2025-01-30 14:24:23by Hynek Fencl, July 2024
The way to Liberland is easy but not simple. Technically speaking, it’s just a short bike ride away from the nearest village on a comfortable bike path through a stunning forest known as the “Amazon of Europe”. On one side, one senses the presence of the mighty Danube River beyond the tall trees, and on the other stretch the farmlands of north-eastern Croatia. Then you take a left turn to a straight forest path, ride all the way to the end, and after a few bends on the track, you will have entered “the promised land”.
The part that is not simple is that Croatia both does and does not consider Gornja Siga (the local name for the area we now refer to as Liberland) to be its territory – depending on who you ask. This means that along the picturesque bike path, you will almost certainly encounter a border police patrol car, and, depending on whether you seem to them like you’re affiliated with Liberland, they will tell you to stop and hand over your ID. They run it through their system and, if you’re lucky enough to be a citizen of the EU, they let you pass. If you’re not and you give them a non-EU passport, they will ask you to come to the station with them to “determine the circumstances of your stay in Croatia.” You will then be issued with paperwork telling you to leave the country within the next 7 days, banning you from re-entering in the next 1-3 months. The official reasoning they’ll give for this is their reasonable suspicion that you have not come to Croatia as a tourist but with the intent to either do paid work (for which you would have to get a business/work visa) or to break the law (such as camping outside designated camping grounds or starting a fire in the forest).
All of this is part of a big game of chess that is being played out between Croatia and the Liberlanders. Croatia is in a tricky spot. They cannot properly administer the territory of Liberland and enforce its law in it – lest it would create an indication that the Croatian state officially claims it as its territory. However, they cannot not administer it either, since it’s on “their” side of the river, and it is risky for a rogue, unpredictable operation (from their perspective) like the establishment and growth of Liberland to just be left to its own devices right on their doorstep. This is, then, how we arrive at the status quo, with Croatia relating to Liberland in some way while being careful about the international perception of its action in another way. The resulting practice is a persistent harassment campaign toward the Liberlanders, with the apparent intent to create uncertainty and lower the appetite of potential Liberland settlers for this kind of adventure.
How to establish a new country
Liberland was born from an anomaly – a historical border dispute between Croatia and Serbia. The dispute involves the definition of where the border stands in relation to the Danube and goes back to 1947. Then, both lands along the river belonged to a single country – Yugoslavia – but the dispute arose with respect to the boundaries of its constituent states. It remained unresolved during the communist era and became an issue of international borders after the breakup of Yugoslavia.
Serbia claims that the border runs down the middle of the Danube, with the eastern bank being Serbian and the western bank Croatian. Croatia, on the other hand, claims that the border is set by historical borders marked by cadastral municipalities surrounding the Danube.
These municipality borders run along a different path because they were set before the course of the Danube was straightened during the 19th Century to allow for easier shipping. This results in disputed “pockets” of land on both sides of the river. The pockets on the eastern bank have a combined area of around 130 km2, while those on the western bank only amount to less than 10 km2. Not surprisingly, then, both countries claim that the border runs in a way where they get the >90% of land and the other country only gets the small remaining areas. However, this means that, by implication, since both countries are claiming the large areas, neither of them is claiming the smaller ones. These areas were, then, so-called terra nullius.
Under international law, there is no issue with any state claiming unowned and unclaimed land for themselves. And that is exactly what Czech businessman, politician, and activist Vít Jedlička did in 2015 when he proclaimed into existence the newly created Free Republic of Liberland on the largest, 7 km2 piece of the unclaimed areas between Croatia and Serbia.
It's one thing to announce a new country to the world. It’s an entirely different thing to make this country legitimate. Under the Montevideo Convention, a proper country needs to have 1) a permanent population, 2) a defined territory, 3) government, and 4) capacity to enter into relations with other states. Now, 9 years after the birth of Liberland, it clearly has three of those. As to a permanent population, the Liberlanders would argue that it definitely exists, even though Liberland’s now over 1200 registered citizens have had to largely live in “exile” ever since.
Nevertheless, despite the Convention, there’s one thing that makes something a country more than anything else – whether other countries see you as a country. The more diplomatic recognition an entity has, the more country-like it becomes. This is especially relevant for breakaway governments, governments in exile, or, most importantly in this case, startup countries like Liberland.
Very much aware of this, along with other members of Liberland’s startup government, Jedlička has been on a worldwide mission to legitimize Liberland in the eyes of other countries. Though there have been many amiable meetings and even some measure of support in some cases, no official recognition by any UN member has been achieved as of mid-2024. Liberland now has representatives and offices in multiple countries in the further pursuit of this goal. Though the effectiveness of this strategy has been questioned by many for the lack of decisive results so far, one thing remains unambiguously true: if recognized by even one or two UN members, Liberland would instantly gain an amazing amount of legitimacy and gravitas in the eyes of the world.
The quest for territory
Establishing international relations with countries anywhere in the world is not the only strategy that the Liberlanders have been employing in making the country more real and legitimate. This includes liaising and negotiating with the neighboring Serbia and Croatia. These relations are by far the most important and impactful ones. If both of Liberland’s neighboring countries were to either outright recognize the startup micro-state, or even just adopted an approach of non-interference, Liberland would be free to start actually developing and to find its own long-term position in the world.
As for Serbia, its Ministry of Foreign Affairs let itself be heard that, in their view, Liberland’s claims are a “trivial matter” but, in any case, they do not infringe upon the sovereignty of Serbia. One can imagine that Serbia might actually be secretly quite pleased with Liberland’s activities, since now Croatia has an issue to deal with on “their” side of the river, which, if they are not careful, could contribute to the legitimization of Serbia’s claim to the larger pieces of territory claimed by both countries.
With Croatia, things get quite a bit more complicated. In an official statement, the country rejected the claim that Gornja Siga is terra nullius, arguing instead that the land belongs to one of the two neighboring countries – the only question is to which one, which will be answered at some point in the future. Croatia also said it would stop any threatening and provocative activities on the territory even by force if necessary.
Ever since Liberland’s birth in 2015, the Liberlanders have been trying to make a mark on the territory. For a long time, even just entering Liberland wasn’t really possible. Under a deal between the Croatian and Serbian police that was put in place during the European migration crisis, Croatian authorities may enter Liberland and patrol it for security reasons (preventing illegal migration) even though they do not officially claim the territory as theirs. In addition, the border police have a near-permanent presence on the Danube River, preventing people from crossing into Liberland by boat.
As a result, anyone who would try to come to Liberland in any way would always be promptly arrested by the Croatians, essentially for entering a prohibited area.
After years of this status quo, a rather unexpected thing happened that made things suddenly move forward in a positive direction for the Liberlanders. In April 2023, during Liberland’s 8th anniversary celebrations, a famous YouTuber with a significant following decided to try to enter Liberland. After a few unsuccessful attempts due to heavy police presence and monitoring, he and his team hired jet skis and rode them all the way from Hungary down the Danube. When they got close to Liberland, they encountered the police boats again, but their jet skis were faster than the boats, so they managed to land at Liberland’s Liberty Island and plant a flag there. A few moments later, the police caught up to them and an aggressive policeman took out their handheld cameras before assaulting them and then kicking them on the ground, as can be clearly seen from drone footage of the incident.
As they had broken no laws, they were ultimately let go after the incident and free to leave the island without being arrested. However, the heavy-handed and illegal conduct of the Croatian police had been clearly documented and became part of the video that was published in July 2023.
The video promptly went viral, gaining almost 10 million views on YouTube. By comparison, the total population of Croatia is just under 4 million. When the news spread even to the Croatian press and TV stations, Croatia had a serious PR problem on their hands. The police had been clearly in the wrong, conducting themselves in a seriously improper way to the point of using physical force against peaceful people who had broken no laws nor engaged in any violence or hostilities themselves.
Something had to change. So, following this incident, the Croatian police adopted a different unofficial policy – from now on, they would let people enter Liberland if they wished to do so, in a controlled way. Since early August 2023, if you wish to enter Liberland, you can go on foot or by bike, take the access road down the forest, and show your documents to the Croatian police, just as you would at a border crossing. In a typical grand fashion of Liberland’s media team, Liberland made an announcement that an official border crossing had been opened between Croatia and Liberland (Croatia had obviously never made an official announcement like this, but for Liberland, that was the de facto situation on the ground).
In the weeks following the “opening of the border”, many enthusiastic settlers started coming to Liberland to finally begin making their mark on the territory of “the promised land.” They started constructing simple wooden houses, a bathroom, an open-air restaurant, and the related power and water infrastructure on Liberland’s mainland beach opposite Liberty Island in a settlement named Mateos Marina.
On September 7th, 2023, a troop of about 50 policemen and forestry workers, including a demolition crew, raided the settlement. The raid was officially dubbed a “cleanup operation” by Hrvatske šume, Croatia’s state forestry service. With the assistance of the police, they tore down all the wooden houses and structures using chainsaws and stole equipment as well as personal possessions of the Liberlanders on site. Several Liberlanders were arrested for “failure to comply with a lawful order”.

One might ask, if Liberland is not officially part of Croatia, what authority does Croatia have to come in to steal and destroy? Staying true to their claim that Liberland is not part of Croatia, the Croatians had announced to Serbia that they would be conducting the “cleanup” on Serbia’s territory, to keep it clean on their behalf.
We may only speculate about the reasons for carrying out this operation in such a heavy-handed, destructive way. One possibility is that allowing people to enter Liberland in the first place was a way for Croatia to lure some people to Liberland, become comfortable, and then come in and destroy everything to show everyone what would happen if they got involved in the project. Or perhaps it was the unexpected level of life, community-building, and construction going on in such a short period of time after the “opening of the border” that the Croatian police felt like they had to put a stop to it before things got so big they could not be easily destroyed anymore.
No matter the reasons, the raid had a chilling effect on prospective Liberlanders. Though there is plenty of video documentation of the operation, no one made a viral video about it this time. Though some media did pick up the news, it did not become a big story. Consequently, the PR fallout from this for Croatia was not unmanageable.
Liberlanders soon returned to the territory. However, the level of enthusiasm, energy, and external support was not as great as it had been before the raid. From then on, settlement efforts focused mainly on Liberty Island, unreachable by trucks and impossible for forestry workers to get to without a large boat which they seem not to have. Though perhaps a more strategic place to set up camp, Liberty Island is also much more prone to flooding than the rest of Liberland.
In the following few months, several makeshift houses were constructed using a combination of wood and sandbags. During this time, Liberland even hosted a first wedding on the island. The settlement was kept alive during winter as well, with Liberland enthusiasts staying mostly in houseboats whenever it was impossible to camp on site.
In the meantime, an enthusiastic settler couple bought a sizeable house with a courtyard in the village closest to Liberland – Zmajevac – which they have transformed into a base of operations for settlers. This is now called Liberbase and it is where visits to Liberland start, with bikes, supplies, and construction materials being gathered before going on the 40-minute bike ride.

In the spring of 2024, work started on the reconstruction of a former hunting lodge at a central location on Liberland’s mainland – Jefferson Square. The building was demolished a few years ago but the foundations, including a cellar, were left in place. The site was cleared, the foundations refreshed, and new walls for the future governmental building have sprung up from the ground. A professional construction crew was hired to speed up the re-building of this base, using large concrete bricks, to a standard that will make it logistically and practically difficult for the Croatian police and forestry workers to try to destroy.
 The battle for legitimacy
The battle for legitimacy The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.
The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.Is it possible to bring materials by boat? How did they get sandbags and other materials to Liberty Island?
The importance of such a commitment should not be underestimated. The continuous presence of settlers is incredibly important for Liberland. It shows the seriousness of the project. It shows that Liberland is a genuine community and a fledgling nation rather than, as some accusations tend to go, just an elaborate publicity stunt.
Practical difficulties with the Croatian authorities are not limited to construction-related issues. Even staying and camping in Liberland comes with its quirks. If you’re staying on Jefferson Square, you should be prepared for several police visits every day. These check-ups are usually nothing dramatic. The police usually show up, ask a couple of questions, and perhaps tell the settlers that they are not allowed to camp there or start a fire, but they don’t actually do anything more than that and just go about their day.
It seems that the Croatian police are rather shy about enforcing Croatian law in a territory that is not officially considered part of Croatia. International law often takes into account the de facto situation of the matter in any dispute. If Croatia enforced their law in Liberland, this would therefore be an indication that they do, in fact, consider the territory to be theirs in practice, despite the official stance of the state. It would play into the hands of Serbia, reinforcing their claims to the large parcels of land on the other side of the Danube.
In addition, Liberlanders on the ground report that the majority of Croatian police officers generally behave quite fairly and respectfully toward them – only a minority appear to hold a personal grudge against Liberland, being abusive and sometimes even violent instead. It seems highly likely that the police in general are just doing their job, following orders from above. Most of them don’t actually take it as a personal commitment to make life more difficult for the Liberlanders.
This is rather important from a big-picture perspective, because the settlers, by contrast, are often heavily personally invested in the project and see it as their mission to see Liberland develop into a proper country. This disparity in energy and determination is strong and perhaps this is what will, in the end, cause Liberland to prevail in this drawn-out dispute.

The dispute with Hrvatske šume is quite different. As of mid-2024, the forestry workers tend to turn up at Jefferson Square about every fortnight. Unlike the police, they do not limit themselves to words but tend to steal everything that is not bolted down – including tools, materials, tents, bikes, and personal possessions of the settlers camping there. The justification remains the same – to “clean the forest of any waste.” In their encounters with the police as well as the forestry workers, Liberlanders are of course meticulous in their video documentation of any illegal actions by the authorities.
The Liberlanders’ difficulties, however, do not just stay local. As previously mentioned, upon trying to enter Liberland from Croatia, people who do not have EU citizenship are promptly issued a one-to-three-month ban on entering Croatia, with 7 days to leave the country. This is done under legislation relating to citizenship and tourism.
However, things can escalate even further. Since last year, several key Liberland settlers and organizers, including Liberland’s President Vít Jedlička himself, have seen “heavier guns” used against them. They have been banned from entering Croatia for 5 years under anti-terrorism legislation, where the authorities argue that these Liberlanders are something akin to a threat to national security.
The Liberlanders have mounted a legal defense against this, in addition to challenging Croatia on other legal fronts. They have had some successes so far – in particular, it should now be clear that the Liberlanders do not need any building permits to construct buildings on their territory. Unfortunately, other issues – including the 5-year bans from Croatia – still remain unresolved.
Most Liberlanders remain hopeful nonetheless. They have seen their situation move forward significantly over the last year. A year ago, they were not even able to enter Liberland without being chased and/or arrested. Now, even some construction is possible, albeit in a limited way.
The road ahead
The long-term vision, of course, remains to build a full-fledged, internationally respected and recognized city-state. Liberland’s leaders often speak of a “Balkan Monaco”, referring to the amazing development possibilities that a freedom-oriented country in the middle of Europe could offer. Liberland has already hosted an urbanist/architectural contest, and there are concrete plans for the first hotel as well as a riverside real estate development. What is more, Liberland’s land is actually more than three times the size of Monaco.
Nevertheless, Liberland cannot move forward in a meaningful way toward these visions and aspirations under the status quo. The Liberlanders need to be able to build at scale and be free from harassment, both by the police and the forestry workers. Some kind of political deal is necessary as the next step toward proper development of Liberland.
Such a deal could take multiple forms, but all of them involve the Croatian authorities changing their attitude toward Liberland away from a policy of unrelenting obstruction – not necessarily toward outright recognition, but at least toward accepting Liberland as a neighborly project that will move forward and develop in some way.
One option could be to allow motor vehicles on the bike path toward Liberland, with a deal that could include charging Liberlanders some fair tolls to pay for the wear and tear of the pavement. An alternative would be to simply allow river crossing into Liberland from Serbia on the Danube. Since Croatia does not officially consider Liberland its territory, their current interference with this traffic is illegal anyway. Simply stopping this illegal conduct would help Liberland significantly without Croatia facilitating Liberland’s development in any active way.

Regardless of these options, the first and most notable step would be to stop banning non-EU citizens from re-entering Croatia as well as lift the existing (entirely unjustified and unreasonable) 5-year bans on Jedlička and the others.
It is easy to see why Croatia is wary and suspicious of Liberland’s development. One can understand the worries of a state in whose immediate proximity there is a new and unknown state growing and taking root. Nevertheless, Croatia actually has a lot to gain from making some kind of deal with Liberland.
First: currently there are perhaps a dozen policemen on patrol around Liberland at all times. This includes police vehicles and boats. This is a significant expense for the police force – an expense which is rather unsubstantiated, given that Liberlanders have clearly proven to be peaceful people who do not wish to pose any threat to Croatia, its people, or its law enforcement officers. Making a deal would mean that this large expense is not needed anymore.
Second: Liberland borders an area of Croatia that has been rather “left behind”, is underdeveloped, and suffers from a lack of jobs and investment. Consequently, younger people are leaving the area and the current population is growing older. If Liberland was growing and open for business nearby, it would provide the region exactly with the job opportunities, large investment, and overall development that it desperately needs.
Third: Croatia could use Liberland as an opportunity to actually gain an advantage in the ongoing border dispute with Serbia. As previously mentioned, Croatia cannot openly and properly administer the territory, as it would be an indication in the eyes of international law that they consider the territory to be theirs. On the other hand, it Liberland is located on “their” side of the Danube, so Croatia does have an interest in making sure the area is under their control somehow. Striking a deal with Liberland could involve Liberland agreeing to some obligations related to the administration of the territory which correspond to Croatia’s priorities. In this way, Croatia would have an active say in what happens on this land, effectively “outsourcing” its administration without officially claiming it as part of Croatia.
In addition to all these advantages being present, Liberland is very much open to cooperation with Croatia and is keenly looking forward to welcoming any future productive relations with Croatian authorities. There will be no grudges held on Liberland’s side, and if a mutually beneficial deal or solution were to be found, no one would look behind at any historical quibbles or difficulties. Liberland would be an excellent and friendly neighbor to Croatia, not just causing any issues but actively helping the overall development of the surrounding region.
Time will tell how things will develop. At the present, the momentum, energy, and enthusiasm is definitely on the side of Liberland. There seems to be very little actual interest from the Croatian side to cause issues for Liberland and to continue to prevent the fledgling state from developing further. All that is left are the bureaucratic hurdles of a state that is being overly conservative about its approach to the important issues of the day. Things might take time, but seeing the determination of the settlers and the willingness of all Liberlanders to be unrelenting in their fight for the cause, it is not difficult to argue that we might be seeing the dawn of Liberland as the world’s next proper city-state as we speak.
-
 @ f0fcbea6:7e059469
2025-05-29 18:30:53
@ f0fcbea6:7e059469
2025-05-29 18:30:53Autores Clássicos e Antigos
- Homero (século IX a.C.?) — Ilíada, Odisseia
- Tucídides (c. 460-400 a.C.) — História da Guerra do Peloponeso
- Platão (c. 427-347 a.C.) — República, Banquete, Fédon, Mênon, Apologia de Sócrates, Fedro, Górgias
- Aristóteles (c. 384-322 a.C.) — Órganon, Física, Metafísica, Da Alma, Ética a Nicômaco, Política, Retórica, Poética
- Virgílio (70-19 a.C.) — Eneida
- Marco Aurélio (121-180) — Meditações
- Santo Agostinho (354-430) — Sobre o Ensino, Confissões, A Cidade de Deus, A Doutrina Cristã
- Boécio (480-525) — A Consolação da Filosofia
- Santo Tomás de Aquino (c. 1225-1274) — Suma Teológica
- Dante Alighieri (1265-1321) — Divina Comédia
Renascimento e Idade Moderna
- Nicolau Maquiavel (1469-1527) — O Príncipe
- Luís de Camões (1524-1580) — Os Lusíadas, Sonetos
- Miguel de Cervantes (1547-1616) — Dom Quixote
- William Shakespeare (1564-1616) — Romeu e Julieta, Hamlet, Macbeth, Otelo, Rei Lear, Henrique IV, Henrique V, Henrique VI, Henrique VIII, A Comédia dos Erros, Tito Andrônico, Príncipe de Tiro, Cimbelino, A Megera Domada, O Mercador de Veneza, Ricardo II, Ricardo III, Muito Barulho por Nada, Júlio César, Noite de Reis, Os Dois Cavaleiros de Verona, Conto do Inverno, Sonhos de uma Noite de Verão, As Alegres Comadres de Windsor, Trólio e Créssida, Medida por Medida, Coriolano, Antônio e Cleópatra, A Tempestade
- Ésquilo (525-456 a.C., antiguidade grega, mas citado junto) — Prometeu Acorrentado, Orestéia/As Eumênides
- Sófocles (496-406 a.C.) — Édipo Rei, Antígona
Literatura e Filosofia Contemporânea
- Fiódor Dostoiévski (1821-1881) — Crime e Castigo, Os Irmãos Karamázov, Os Demônios, O Idiota, Notas do Subsolo
- Franz Kafka (1883-1924) — A Metamorfose, O Processo, O Castelo
- Albert Camus (1913-1960) — O Estrangeiro
- Aldous Huxley (1894-1963) — Admirável Mundo Novo, A Ilha
- James Joyce (1882-1941) — Retrato do Artista Quando Jovem, Ulisses
- George Orwell (1903-1950) — A Revolução dos Bichos, 1984
- Machado de Assis (1839-1908) — Memórias Póstumas de Brás Cubas, O Alienista
- Thomas Mann (1875-1955) — Morte em Veneza, Doutor Fausto, A Montanha Mágica
- Henrik Ibsen (1828-1906) — O Pato Selvagem, Um Inimigo do Povo
- Stendhal (1783-1842) — O Vermelho e o Negro, A Cartuxa de Parma
- Viktor Frankl (1905-1997) — Em Busca de Sentido
- J.R.R. Tolkien (1892-1973) — O Hobbit, O Senhor dos Anéis
- Luigi Pirandello (1867-1936) — Seis Personagens à Procura de um Autor, O Falecido Matias Pascal
- Samuel Beckett (1906-1989) — Esperando Godot
- René Guénon (1886-1951) — A Crise do Mundo Moderno, O Reino da Quantidade
- G. K. Chesterton (1874-1936) — Ortodoxia
- Richard Wagner (1813-1883) — Tristão e Isolda
- Honoré de Balzac (1799-1850) — Ilusões Perdidas, Eugénie Grandet
- Jacob Wassermann (1873-1934) — O Processo Maurizius
- Nikolai Gogol (1809-1852) — Almas Mortas, O Inspetor Geral
- Daniel Defoe (1660-1731) — Moll Flanders
- Mortimer J. Adler (1902-2001) — Como Ler um Livro
- Gustave Flaubert (1821-1880) — Madame Bovary
- Hermann Hesse (1877-1962) — O Jogo das Contas de Vidro
- Richard Wagner (1813-1883) — Tristão e Isolda
- Wolfgang von Goethe (1749-1832) — Fausto (Primeiro), Os Anos de Aprendizado de Wilhelm Meister
- Jacques Benda — A Traição dos Intelectuais
-
 @ 91117f2b:111207d6
2025-05-29 20:59:17
@ 91117f2b:111207d6
2025-05-29 20:59:17
Raising boys (men) and girls (women) to reach their full potential requires a supportive and inclusive environment. Some key points to consider:
-
role models:
-
Valuing equal opportunities and rights.
- Challenging stereotypes and biases.
-
Encouraging mutual respect.
-
Building resilience:
-
Teaching coping skills and emotional intelligence.
- Encouraging perseverance and determination.
-
Fostering a growth mindset.
-
Supporting Education:
-
Providing access to quality education.
- Encouraging STEM education and exploration.
-
Fostering a love for learning.
-
Encouraging Individuality:
-
Embracing unique interests and talents.
- Fostering self-expression and confidence.
- Promoting positive role models.
By nurturing the potential of both boys and girls, we can create a brighter future for both genders.
-
-
 @ f88e6629:e5254dd5
2025-01-17 14:10:19
@ f88e6629:e5254dd5
2025-01-17 14:10:19...which allow online payments to be sent directly from one party to another without going through a financial institution.
- Without sovereign and accessible payments we are loosing censorship resistance
- Without censorship resistance even other core characteristics are in danger - including scarcity and durability.
- This affects every bitcoiner including sworn hodlers and MSTR followers.
| Property | Description | Fulfillment | | --- | --- | --- | | Scarce | Fixed supply forever. Instantly and costlessly verifiable | 🟢 Good, but can be harmed without censorship resistance | | Portable | Effortless to store and move, with negligible costs | 🟠 Onchain transactions can be expensive, other layers require onchain to be sovereign. Easy portability is offered by custodians only. | | Divisible | Infinitely divisible | 🟠 Smaller units than dust are available only for LN users, which most people can’t use in a sovereign way. | | Durable | Exists forever without deterioration | 🟢 Good, but can be harmed without censorship resistance | | Fungible | Every piece is forever the same as every other piece | 🟡 Onchain bitcoin is not fungible. | | Acceptable | Everyone, anywhere, can send and receive | 🟠 Most people are not able to send and receive in a sovereign way. | | Censorship Resistant | You hold it. Nobody can take it or stop you sending it | 🟠 Custodians are honey-pots that can and will be regulated |
➡️ We need accessible, scalable, and sovereign payment methods
-
 @ 4657dfe8:47934b3e
2025-01-10 13:28:47
@ 4657dfe8:47934b3e
2025-01-10 13:28:47Alby Hub - your Center for Bitcoin Payments
Alby Hub is a self-custodial lightning wallet that lets users choose their preferred Lightning funding source. It includes an easy-to-use lightning node with a one-click setup, while also accommodating existing node runners.
In short Alby Hub offers node runners:
➡️ a lightning address to receive payments in a self-custodial manner ➡️ integrated Lightning Service Providers, to quickly buy channels with receiving capacity ➡️ a selection of vetted channel partners to open channels without searching for a long time ➡️ a marketplace of apps to connect your own node. Read more about this superpower. ➡️ a mobile app, Alby Go, to pay right from their own node on the go.
Thus, Alby Hub enables you to make your node the central hub for bitcoin payments, maintaining full self-sovereignty.
Install Alby Hub on RaspiBlitz
- Login into the RaspiBlitz WebUI and enter the dashboard
- Go to Apps, find Alby Hub and install the app
It’s as easy as that. Now you can link your node with an Alby account to get a lightning address, use your node on the go with the Alby Go mobile app or on the web with the Alby Browser Extension. Updates of Alby Hub become available with each new RaspiBlitz release.
With one-click setup, an intuitive interface, and seamless integration with dozens of bitcoin apps, Alby Hub makes self-custodial bitcoin payments easy for everyone while adding much more utility to your lightning node.
-
 @ f88e6629:e5254dd5
2025-01-08 20:08:17
@ f88e6629:e5254dd5
2025-01-08 20:08:17- Send a transaction, and the recipient uses the coin for another payment. You then merge these two transactions together and save on fees. 🔥
If you have a Trezor, you can try this out on: https://coiner-mu.vercel.app/
But be cautious. This is a hobby project without any guarantee.
How does it work?
- Connect Trezor, enter the passphrase, and select an account.
- The application display your coins, pending transactions, and descendant transactions.
- Then app shows you how much you can save by merging all transactions and removing duplicate information.
- Finally, you can sign and broadcast this more efficient transaction
-
 @ 527337d5:93e9525e
2025-05-29 18:19:31
@ 527337d5:93e9525e
2025-05-29 18:19:31Experiment Plan for Text Similarity Comparison Algorithms (Revised v3)
1. Introduction
1.1. Research Background and Objectives
This research aims to evaluate the performance of various algorithms for comparing the similarity between individual page texts extracted from a specific technical document (in this experiment, the content of the Tailwind CSS documentation site). Initially, we considered dividing the text into 250-word chunks. However, due to the abundance of Markdown and code in the target document, meaningful chunking proved tobe cumbersome. Therefore, we decided to use the entire text extracted from each page as the unit of comparison.
This study will systematically compare and examine combinations of different "representation methods" and "comparison methods" from multiple perspectives: ease of implementation, processing speed, memory consumption, and accuracy of similarity judgment. A particular focus will be on elucidating the effectiveness of information-based NCD (Normalized Compression Distance) and vector embedding-based methods, which are planned for future evaluation.
1.2. Report Structure
This report will first describe the experimental data and its preprocessing methods. Next, it will define in detail the representation methods and comparison methods that form the axes of evaluation, and present specific experimental cases combining them. After presenting the results and discussion of initial experiments using NCD, it will describe the metrics for evaluating each experimental case, specific experimental procedures, and the expected outcomes and future prospects of this research.
2. Experimental Data
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
tailwindcss.com). - Data Unit: The entire text of each page, extracted from HTML files using the
html2textcommand and further processed to remove control characters using thesedcommand. This serves as the basic unit of comparison in this experiment. - Data Storage Location: The extracted and preprocessed text files are stored locally under the
./tailwindcss.comdirectory, maintaining the original file structure. - Language: English
- Example Search Query: A representative search query for this experiment is
"Utilities for controlling how a background image behaves when scrolling."(Multiple queries and their expected similar pages may be used for more robust evaluation). - Example Expected Similar Page: For the query above,
/docs/background-attachmentis expected to be the most semantically similar page.
3. Experimental Design
This experiment is designed by dividing the process of evaluating text similarity into two main axes: "Representation Methods" and "Comparison Methods."
3.1. Representation Methods (Text Quantification/Vectorization)
-
Naive (Raw Text / Full Page Text)
- Method: Use the entire preprocessed text extracted from each document page as raw string data, without special transformations.
- Objective: Serve as a direct input for information-based comparison methods like NCD and as a baseline comparison for more advanced representation methods to be evaluated later.
-
(Future Experiment) Vector Embedding via Gemini API (Embedding-Gemini)
- Method: Utilize Google's Gemini API (
models/text-embedding-004) to convert the entire text of each page into high-dimensional dense vectors (Embeddings). - Objective: Evaluate the performance of context-rich vector representations generated by a state-of-the-art large language model.
- Method: Utilize Google's Gemini API (
-
(Future Experiment) Vector Embedding via Local Lightweight Model (Embedding-MiniLM-GGUF)
- Method: Run a GGUF quantized version of the pre-trained
all-MiniLM-L6-v2model (all-MiniLM-L6-v2-Q5_K_M.gguf) in a local environment to convert the entire text of each page into vector representations. GGUF format offers benefits like smaller model size and potentially faster CPU inference. - Objective: Evaluate the performance of a widely used open-source lightweight model (quantized version) in comparison to API-based large-scale models and domain-specific learned models.
- Method: Run a GGUF quantized version of the pre-trained
-
(Future Experiment) Extraction of Internal Feature Vectors via Mathematica (Embedding-MMA)
- Method: Use the entire page texts from the target document set as input. Employ Mathematica's neural network framework to first pass each page text through an Embedding Layer. Apply L2 normalization to the resulting vectors, followed by Principal Component Analysis (PCA) to reduce dimensionality to approximately 100 dimensions. This final vector will be the feature vector. This pipeline aims to create dense, normalized representations specific to the document corpus, with PCA helping to capture the most significant variance in a lower-dimensional space, potentially improving efficiency and reducing noise. The choice of an Embedding Layer trained or fine-tuned on the corpus, followed by PCA, seeks to balance domain-specificity with robust dimensionality reduction.
- Objective: Evaluate the performance of vector representations processed or specialized for the target document set.
3.2. Comparison Methods (Distance/Similarity Calculation between Representations)
-
NCD (Normalized Compression Distance)
- Applicable to: Naive (Full Page Text)
- Method: For two data objects
x(query) andy(document page text), calculateNCD(x,y) = (C(xy) - min(C(x), C(y))) / max(C(x), C(y)). Here,C(s)is the size (e.g., byte length) of datasafter compression with a specific algorithm, andC(xy)is the size of the concatenated dataxandyafter compression. A value closer to 0 indicates higher similarity. - Compression Algorithms to Compare: DEFLATE (gzip), bzip2, LZMA, XZ, Zstandard (zstd), LZO, Snappy, LZ4 (as used in the user-provided script).
- Objective: Evaluate similarity from an information-theoretic perspective based on data commonality and redundancy. Compare the impact of different compression algorithms on NCD results.
-
(Future Experiment) Cosine Similarity
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the cosine of the angle between two vectors.
- Objective: Standard similarity evaluation based on the directionality (semantic closeness) of vector representations.
-
(Future Experiment) Euclidean Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the straight-line distance between two vectors in a multidimensional space.
- Objective: Similarity evaluation based on the absolute positional relationship of vector representations.
-
(Future Experiment) Manhattan Distance (L1 Distance)
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the sum of the absolute differences of their Cartesian coordinates.
- Objective: Similarity evaluation based on axis-aligned travel distance, differing from Euclidean distance.
-
(Future Experiment) Mahalanobis Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the distance between two vectors considering the covariance of the data. This provides a distance metric that accounts for the scale differences and correlations of each feature (vector dimension).
- Objective: More robust similarity evaluation that considers the structure (correlation) of the feature space.
3.3. Experimental Cases (Initial NCD Experiments and Future Expansion)
3.3.1. Initial Experiments Conducted (NCD)
The following experimental cases were conducted using the user-provided script. The representation method was "Naive (Full Page Text)."
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :-: | :---------------------- | :--------------------------------------------- | :-------------------------- | | 1 | Naive (Full Page Text) | NCD (gzip/DEFLATE) | One of the baselines | | 2 | Naive (Full Page Text) | NCD (bzip2) | Compression method comparison | | 3 | Naive (Full Page Text) | NCD (lzma) | Compression method comparison | | 4 | Naive (Full Page Text) | NCD (xz) | Compression method comparison | | 5 | Naive (Full Page Text) | NCD (zstd) | Compression method comparison | | 6 | Naive (Full Page Text) | NCD (lzop) | Compression method comparison | | 7 | Naive (Full Page Text) | NCD (snappy) | Compression method comparison | | 8 | Naive (Full Page Text) | NCD (lz4) | Compression method comparison |
3.3.2. Future Experimental Plan (Vector Embedding)
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :--: | :---------------------- | :--------------------------------------------- | :------------------------------------- | | 9 | Embedding-Gemini | Cosine Similarity | Standard vector similarity evaluation | | 10 | Embedding-Gemini | Euclidean Distance | Standard vector similarity evaluation | | 11 | Embedding-Gemini | Manhattan Distance | Axis-aligned distance similarity eval. | | 12 | Embedding-Gemini | Mahalanobis Distance | Distance considering feature structure | | 13 | Embedding-MiniLM-GGUF | Cosine Similarity | Evaluation of local lightweight model | | 14 | Embedding-MiniLM-GGUF | Euclidean Distance | Evaluation of local lightweight model | | 15 | Embedding-MiniLM-GGUF | Manhattan Distance | Evaluation of local lightweight model | | 16 | Embedding-MiniLM-GGUF | Mahalanobis Distance | Evaluation of local lightweight model | | 17 | Embedding-MMA | Cosine Similarity | Eval. of domain-specific MMA model | | 18 | Embedding-MMA | Euclidean Distance | Eval. of domain-specific MMA model | | 19 | Embedding-MMA | Manhattan Distance | Eval. of domain-specific MMA model | | 20 | Embedding-MMA | Mahalanobis Distance | Eval. of domain-specific MMA model |
4. Results and Discussion of Initial NCD Experiments (Based on User-Provided Information)
4.1. Execution Overview
The user employed provided Python scripts (
main.py,comparison.py) to calculate NCD between a search query and the entire text extracted from each HTML page in the./tailwindcss.comdirectory.main.pyinvokedcomparison.pywith various compression commands (gzip,bzip2,lzma,xz,zstd,lzop,lz4).comparison.pythen used the specified command-line compression tools to compute NCD scores and output the results to CSV files.Search Query:
"Utilities for controlling how a background image behaves when scrolling."Expected Similar Page:/docs/background-attachment4.2. Key Results
The pages judged as most similar (lowest NCD score) to the query for each compression algorithm were as follows (based on user-provided sorted results):
- Zstandard (zstd):
./tailwindcss.com/docs/background-attachment(Score: 0.973...) - LZ4:
./tailwindcss.com/docs/background-attachment(Score: 0.976...) - XZ:
./tailwindcss.com/docs/background-origin(Score: 0.946...) - LZMA:
./tailwindcss.com/docs/background-origin(Score: 0.966...) - gzip (DEFLATE):
./tailwindcss.com/docs/scroll-behavior(Score: 0.969...) - LZO:
./tailwindcss.com/docs/scroll-behavior(Score: 0.955...) - bzip2:
./tailwindcss.com/docs/mask-clip(Score: 0.958...)
4.3. Initial Discussion
- Variation in Results by Compression Algorithm: It was confirmed that the document judged most similar to the query varies depending on the compression algorithm used. This is likely due to the differing abilities of each algorithm to capture various types of redundancy and patterns within the text.
- Alignment with Expected Results: When using Zstandard and LZ4, the expected page (
/docs/background-attachment) was judged as most similar. This suggests these compression algorithms may have relatively effectively captured the information-theoretic commonality between the query and the target document in this instance. - Range of NCD Scores: The reported NCD scores were generally close to 1.0. This may be due to the relatively short length of the search query compared to the full-page documents, meaning the query text contributes less to the overall compressibility when concatenated. However, relative differences were still captured, enabling ranking.
- Validity of Full-Page Comparison: Full-page comparison was chosen due to the difficulty of chunking content rich in Markdown and code. While this approach simplifies preprocessing, it may also be influenced by the overall structure of the page, including common headers and footers.
This initial experiment indicates that NCD can function as an indicator of text similarity and that the choice of compression algorithm is crucial.
5. Evaluation Metrics (Including Future Experiments)
-
Accuracy of Similarity Scores:
- Ground Truth Preparation: A small, diverse subset of page pairs (e.g., 50-100 pairs) will be selected. For each pair, at least two evaluators familiar with the Tailwind CSS documentation will independently assign a similarity score on a 5-point Likert scale (1=Not similar, 5=Very similar). Inter-evaluator reliability (e.g., using Krippendorff's Alpha) will be calculated. Disagreements will be resolved through discussion to create a consensus ground truth dataset. If resource-constrained, a single-evaluator approach with clear, predefined criteria will be used, acknowledging this limitation. Alternatively, page pairs likely to be similar will be selected based on internal references or chapter structure within the document.
- Evaluation Metrics: Ranking evaluation (Precision@k, Recall@k, MAP: Mean Average Precision), correlation analysis (Spearman's rank correlation coefficient with human judgments), classification evaluation (AUC-ROC, F1-score, assuming appropriate thresholding).
-
Processing Speed:
- Average time to calculate similarity for a page pair, total calculation time for all page pairs (or a large sampled set), and representation generation time (API call time, local model inference time, MMA processing time).
-
Memory Consumption:
- Model size (MiniLM-GGUF, MMA model), data representation size, and peak runtime memory usage.
-
Ease of Implementation:
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
- Setup Complexity: (e.g., API key acquisition vs. local model download & environment setup vs. full model training pipeline in Mathematica).
- Code Complexity: Estimated lines of core logic, reliance on external vs. standard libraries.
- Parameter Sensitivity: Number of key hyperparameters requiring tuning and the perceived difficulty of finding good settings.
- Documentation & Community Support: Availability and clarity of official documentation and community resources (e.g., forums, GitHub issues).
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
6. Experimental Procedure (Including Future Experiments)
-
Data Preparation:
- Prepare HTML files of the target document in the
./tailwindcss.comdirectory. - (For NCD) Extract and preprocess full-page plain text from each HTML file using
html2textandsed(as previously done by the user). - (For Vector Embedding) Use the same preprocessed full-page plain text.
- Create ground truth data for accuracy evaluation as described in Section 5.1.
- Prepare HTML files of the target document in the
-
Implementation and Execution of Representation Methods:
- Naive: Use the preprocessed page text directly.
- Embedding-Gemini: Use Python's
requestslibrary or similar to send each page text to the Gemini API (models/text-embedding-004) and retrieve/store the vector representations. - Embedding-MiniLM-GGUF: Use appropriate libraries (e.g.,
ctransformers, orsentence-transformerscombined withllama-cpp-python) to load theall-MiniLM-L6-v2-Q5_K_M.ggufmodel. Input each page text to extract and store vector representations. - Embedding-MMA: In Mathematica, apply an Embedding Layer to each page text, followed by L2 normalization and PCA dimensionality reduction (to approx. 100 dimensions), then extract and store the vector representations.
-
Implementation and Execution of Comparison Methods:
- NCD: Refer to the user-provided Python scripts (
main.py,comparison.py) to call various command-line compression tools for NCD calculation. Alternatively, extend this to directly use Python's compression libraries for better control and efficiency. - Cosine Similarity, Euclidean Distance, Manhattan Distance: Implement using standard math libraries (e.g., Python's NumPy, SciPy).
- Mahalanobis Distance: Implement using
scipy.spatial.distance.mahalanobis. Requires pre-calculation of the covariance matrix (or its inverse) from the entire dataset of vectors for each embedding type.
- NCD: Refer to the user-provided Python scripts (
-
Evaluation Execution:
- Calculate similarity (or distance) scores between the search query (and potentially between page pairs for ground truth evaluation) and all document pages for each experimental case.
- Measure processing speed and memory consumption.
- Calculate accuracy metrics using the computed similarity scores and ground truth data.
- Record and evaluate the ease of implementation.
-
Result Aggregation and Analysis:
- Compile the obtained evaluation metrics into tables and graphs for comparative analysis of each method's characteristics.
Experimental Environment (Assumed)
- Hardware: (e.g., CPU: Intel Core i7-10700, Memory: 32GB RAM, GPU: NVIDIA GeForce RTX 3070 8GB - specify if GPU is used for MiniLM or MMA)
- Software: (e.g., OS: Linux (Ubuntu, etc.), Programming Language: Python 3.x (with versions for key libraries like NumPy, SciPy, requests, ctransformers, etc.), Mathematica 13.x, specific versions of command-line compression tools if used directly)
7. Expected Outcomes and Future Outlook
This research (including initial NCD experiments and future vector embedding experiments) is expected to yield the following outcomes:
- Clarification of the Impact of Compression Algorithms on NCD: As indicated by initial experiments, the choice of compression algorithm significantly affects similarity judgments. Further validation with more diverse data and queries will allow for a deeper understanding of each algorithm's characteristics.
- Performance Characteristics of Various Methods on Full-Page Text: To clarify how NCD and various vector embedding methods perform in terms of accuracy, speed, and resource consumption when applied to entire page texts.
- Comparison of Local and API-Based Models: In future vector embedding experiments, to compare the performance, speed, and resource efficiency of
Embedding-MiniLM-GGUF(local, quantized) andEmbedding-Gemini(API, large-scale) to identify practical trade-offs. - Evaluation of Domain-Specific Embedding Effectiveness: To assess how well
Embedding-MMA, processed or tuned for a single technical document set, performs compared to general-purpose models. - Provision of Practical Insights: To offer guidelines for selecting appropriate similarity comparison approaches based on text characteristics (e.g., Markdown/code content) and system requirements (e.g., ease of preprocessing, emphasis on accuracy vs. speed).
8. Future Challenges
- Ensuring Quality of Ground Truth Data: Evaluating full-page similarity can be more subjective than chunk-level evaluation, making the creation of high-quality ground truth data challenging. Establishing clear annotation guidelines and measuring inter-annotator agreement will be crucial.
- Hyperparameter Optimization: Many methods involve tunable parameters (e.g., Embedding-MMA model structure, PCA dimensionality, MiniLM-GGUF inference parameters), the optimization of which may be beyond the scope of this initial study. The impact of default vs. tuned parameters could be noted.
- Noise in Full-Page Comparison: Full-page texts may contain common navigational elements or boilerplate text that could act as noise in similarity judgments. Strategies to mitigate this (e.g., more advanced text extraction, or methods robust to such noise) could be a future research direction.
- Input Length Limitations of Vector Embedding Models: Very long page texts might exceed the input length limits of some vector embedding models, requiring strategies for handling. These might include:
- Truncation: Using only the initial N tokens of each page, which is simple but may lose crucial information.
- Summarization: Employing an abstractive or extractive summarization model to create a condensed version of the page, which could preserve key information but adds another layer of processing and potential information loss/bias.
- Chunking and Averaging/Pooling: Dividing long pages into manageable chunks, embedding each chunk, and then aggregating these chunk embeddings (e.g., by averaging) to get a single page vector. This approach needs careful consideration of how chunks are defined and aggregated.
- Utilizing Long-Context Models: If available and feasible, leveraging embedding models specifically designed for longer sequences. The chosen strategy will be documented, and its potential impact on results acknowledged.
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ 91117f2b:111207d6
2025-05-29 20:10:10
@ 91117f2b:111207d6
2025-05-29 20:10:10
Technology has transformed the way we work, live , and interact with one another. From the invention of the wheel to the development of artificial intelligence, technology has continuously evolved, bringing about many significant changes in various aspects of our daily lives.
Key Aspects of Technology:
-
Communication: Technology has revolutionized communication, enabling instant connections across the globe through smartphones, social media, and messaging apps and other network connections.
-
Automation and Efficiency: Technology has increased productivity and efficiency in various industries, from manufacturing to healthcare, through automation and digital tools.
3 . Information Access: The internet has made it possible to access vast amounts of information, knowledge, and resources at our fingertips.
-
Challenges and Concerns: While technology offers numerous benefits, it also raises concerns about privacy, security, and the impact on traditional industries and social structures.
-
Innovation and Creativity: Technology has enabled new forms of creativity, innovation, and entrepreneurship, driving economic growth and development.
The Future of Technology:
As technology continues to advance, we can expect even more significant changes in the way we live and work. Emerging technologies like artificial intelligence, blockchain, and the Internet of Things (IoT) hold great promise for transforming industries and improving lives.
By understanding the evolution and impact of technology, we can harness its potential to create a better future for all.
-
-
 @ 4657dfe8:47934b3e
2024-12-18 13:42:46
@ 4657dfe8:47934b3e
2024-12-18 13:42:46Alby Hub enables creation of subaccounts, decentralizing trust and creating usecases for shared, community nodes.
Simplifying Bitcoin Wallets for Friends and Family
Alby Hub empowers you to take full control of your bitcoin and manage your payments. Through a user-friendly, self-custodial wallet with a one-click lightning node setup, you can effortlessly connect to dozens of applications. The integrated App Store provides access to popular apps like Amethyst, Damus, Stacker News, Podcasting 2.0, and a wide range of other external tools—all directly linked with your Alby Hub wallet. One of the latest and most exciting additions to Alby Hub is the Friends & Family app.
With the Friends & Family app, you can create subaccounts for friends and family, all powered by your Hub. In just a few clicks, you can set up wallets for them, giving them a smooth onboarding experience and making bitcoin accessible even to those new to the ecosystem. Think of it as a custodial wallet but with a personal touch—since you’re the one managing it, there’s a direct relationship and trust.
These subaccount holders can tap into all the channels and liquidity of your Hub without needing to handle any technical setup. Plus, you can preload their wallets with a few sats, creating a welcoming and smooth experience that’s hard to find elsewhere.
And that’s not all. Beyond providing an intuitive wallet, they can get their own lightning address, configurable payment notifications, access to Alby Go (a mobile app for payments on the go), and the Alby Browser Extension for easy web payments.
Let’s have a look how to set it up.
How to provide a wallet to Friends and Family?
- Open your Hub and find the Friends & Family app in the App Store
- Enter a name e.g. your friend’s name and click “Create subaccount”
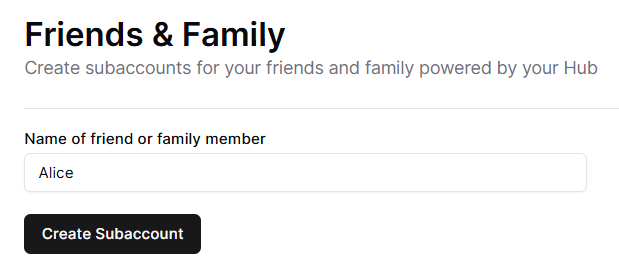
- Share the Connection Secret with your friend for the different options
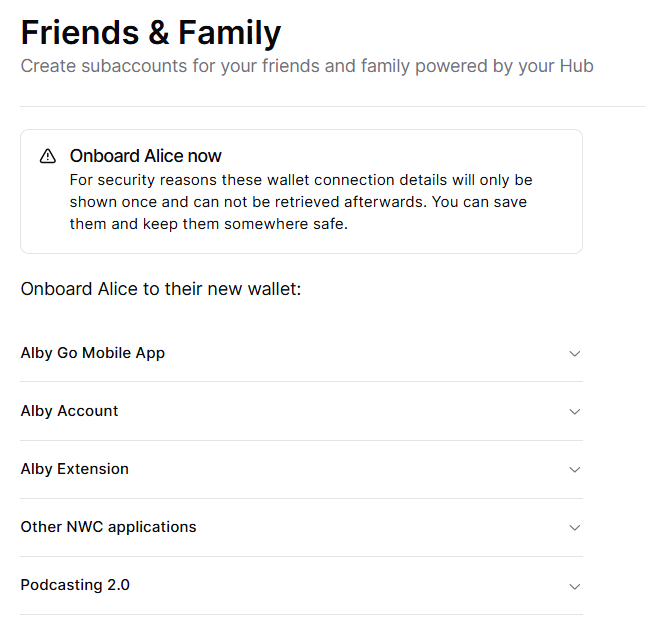
Here are two examples how your the new subaccount can be used.
Alby Go mobile App
Alby Go makes it easy to carry bitcoin in your pocket. This lightweight wallet connects directly to an Alby Hub subaccount, so your friends can pay and check transactions on the go.
Here’s how to set it up: 1. Open the Alby Go Mobile App tab in your Hub.
 2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.
2. Copy the Connection Secret and share it with your friend if you cannot onboard them in person.
3. Your friend downloads Alby Go for Android or iOS and scans the code.And that’s it—your friend now has a bitcoin wallet in their pocket, ready for seamless transactions anytime, anywhere. 🎉
Get a Lightning Address with an Alby account
An Alby Account offers a variety of useful features that make managing bitcoin payments easy. Among these are a personalized lightning address and email payment notifications—two powerful tools that help your newly onboarded friends stay connected and informed.
To set up an Alby account for someone:
-
Open the Alby Account tab in your Hub.
-
Copy the provided URL and share it with your friend.
-
Your friend simply needs to create their Alby account and afterwards click on the provided URL.
That’s it! The wallet is instantly connected, and they’re ready to receive payments to their new lightning address. 🥳
Onboarding Family & Friends Made Easy In this article, we explored how to create subaccounts for family and friends, connect them with Alby Go, and set up an Alby account to provide a smooth onboarding experience for your loved ones—all achievable in just a few clicks.
Stay tuned as we dive into more exciting use cases for subaccounts in Alby Hub! If you have ideas for improvement,let us know.
- Open your Hub and find the Friends & Family app in the App Store
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 1739d937:3e3136ef
2024-10-29 16:57:08
@ 1739d937:3e3136ef
2024-10-29 16:57:08This update marks a major milestone for the project. I know, with certainty, that MLS messaging over Nostr is going to work. That might sound a little crazy after so many months working on the project, and I was pretty confident, but until you’ve got running code, it’s all conjecture.
Late last week, I released a video of a working prototype of White Noise that shows the full flow; creating groups, inviting other users to join those groups, accepting invites, and sending messages back-and-forth. I’m thrilled that I’ve gotten this far but also appalled that it’s taken so long and disgusted at the state of the code in the app (I’ve been told I have unrelenting standards 😅).
If you missed the video last week...
nostr:note125cuk0zetc7sshw52v5zaq9apq3rq7e2x587tr2c96t7z7sjs59svwv0fj
What's Next?
In this update, I want to cover a few things about how I'm planning to proceed and how I’m splitting code out of the app into libraries that will help other developers implement MLS messaging in their own Nostr clients.
First off, many of you know that I've been building White Noise as a Rust app using the Tauri framework. The OpenMLS implementation is also written in Rust (with bindings for many other languages). So, when you hear me talking about library code, think Rust crates for now.
The first library, called openmls-nostr, is an extension/abstraction on top of the openmls implementation of the MLS spec that helps Nostr clients interact more easily with that implementation in a way that feels native to Nostr. Mostly this will be helping developers interact with MLS primitives and ensure that they’re creating, validating, and serializing these objects in the right way at the right times.
The second isn’t a new library as a big contribution to the already excellent rust-nostr library from nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet. The methods that will go in rust-nostr are highly abstracted and based specifically on the requirements of NIP-104. Mostly this will be helping developers to take those MLS primitives and publish or query them as Nostr events at the right times and to/from the right relays.
Most of this code was originally written directly in the White Noise library so this week I've started to pull code for both of those libraries out and move it to its new home. While I’ve been at it, I've been writing some tests and trying to document things.
An unfortunate offshoot of this is that the usable builds of White Noise are going to take a touch longer. I promise it’s still a very high priority but at this point I need to clean a few things up based on what I've learned thus far.
Another thing that is slowing down release is that; behind the scenes of the dev work, I’ve been battling with Apple for nearly 2 months now to get a proper developer team set up so that we can publish the app via TestFlight for MacOS and iOS. I’ve also been recently learning the intricacies of Android publishing (oh my dear god there are so many devices, OS versions, etc.).
With that in mind, if you know anyone who can help get me up to speed on CI/CD, release pipelines, and multi-platform distribution please hit me up. I would love to learn more and hopefully shortcut some of the pain.
Thanks again so much for all the support over the last few months! It means a lot to me and is a huge part of what is keeping me going on this. 🙏
-
 @ cae03c48:2a7d6671
2025-05-29 23:01:12
@ cae03c48:2a7d6671
2025-05-29 23:01:12Bitcoin Magazine

Adam Back Said It’s Still Early For the Retail Investors To Buy BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Head of Firmwide Research at Galaxy Digital Alex Thorn, Founder and Managing Partner of Pantera Capital Dan Morehead, Managing Partner, CEO, CIO of 10T Holdings + 1RoundTable Partners Dan Tapiero and the Co-founder & CEO of Blockstream Adam Back discussed the future of Bitcoin treasury companies.
Dan Tapiero started by sharing his opinion on how he sees Bitcoin in comparison to gold:
“I really have always believed in that physical ownership that the individual has the right and should be able to own his own asset and so I started this physical gold business years ago,” said Tapiero. “I think our focus today is further adoption and the elevation of Bitcoin. I think the understanding of Bitcoin as an important asset.”
Adam Back was asked what he thought about Bitcoin treasury companies and he responded, “in effect, Blockstream is one of the first Bitcoin treasury companies. We have been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then. I think the way to look at the treasury companies is Bitcoin is effectively the harder rate. It’s very hard to outperform Bitcoin most people that invest in things since Bitcoin around thought I should put that in Bitcoin and not in the other thing.”
Then Adam continued by explaining what treasury companies do.
“That’s why you get companies switching to the Bitcoin standard because it’s the only way for them to keep up with Bitcoin,” stated Back. ”They start with a Bitcoin capital base. They use the operating in-revenue to buy more Bitcoin and then they are able to participate in this kind of micro arbitrage.”
Finishing the panel, Alex Thorn asked, “Five years from now what is the price of Bitcoin?”
Dan Morehead predicted $750,000k, Tapiero $1,000,000 and Back said, “a million easy.”
Adam back closed by saying, “It’s still early for the retail investors.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 2 below:
This post Adam Back Said It’s Still Early For the Retail Investors To Buy Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ fa0165a0:03397073
2024-10-23 17:19:41
@ fa0165a0:03397073
2024-10-23 17:19:41Chef's notes
This recipe is for 48 buns. Total cooking time takes at least 90 minutes, but 60 minutes of that is letting the dough rest in between processing.
The baking is a simple three-step process. 1. Making the Wheat dough 2. Making and applying the filling 3. Garnishing and baking in the oven
When done: Enjoy during Fika!
PS;
-
Can be frozen and thawed in microwave for later enjoyment as well.
-
If you need unit conversion, this site may be of help: https://www.unitconverters.net/
-
Traditionally we use something we call "Pearl sugar" which is optimal, but normal sugar or sprinkles is okay too. Pearl sugar (Pärlsocker) looks like this: https://search.brave.com/images?q=p%C3%A4rlsocker
Ingredients
- 150 g butter
- 5 dl milk
- 50 g baking yeast (normal or for sweet dough)
- 1/2 teaspoon salt
- 1-1 1/2 dl sugar
- (Optional) 2 teaspoons of crushed or grounded cardamom seeds.
- 1.4 liters of wheat flour
- Filling: 50-75 g butter, room temperature
- Filling: 1/2 - 1 dl sugar
- Filling: 1 teaspoons crushed or ground cardamom and 1 teaspoons ground cinnamon (or 2 teaspoons of cinnamon)
- Garnish: 1 egg, sugar or Almond Shavings
Directions
- Melt the butter/margarine in a saucepan.
- Pour in the milk and allow the mixture to warm reach body temperature (approx. + 37 ° C).
- Dissolve the yeast in a dough bowl with the help of the salt.
- Add the 37 ° C milk/butter mixture, sugar and if you choose to the optional cardamom. (I like this option!) and just over 2/3 of the flour.
- Work the dough shiny and smooth, about 4 minutes with a machine or 8 minutes by hand.
- Add if necessary. additional flour but save at least 1 dl for baking.
- Let the dough rise covered (by a kitchen towel), about 30 minutes.
- Work the dough into the bowl and then pick it up on a floured workbench. Knead the dough smoothly. Divide the dough into 2 parts. Roll out each piece into a rectangular cake.
- Stir together the ingredients for the filling and spread it.
- Roll up and cut each roll into 24 pieces.
- Place them in paper molds or directly on baking paper with the cut surface facing up. Let them rise covered with a baking sheet, about 30 minutes.
- Brush the buns with beaten egg and sprinkle your chosen topping.
- Bake in the middle of the oven at 250 ° C, 5-8 minutes.
- Allow to cool on a wire rack under a baking sheet.
-
-
 @ cae03c48:2a7d6671
2025-05-29 20:02:10
@ cae03c48:2a7d6671
2025-05-29 20:02:10Bitcoin Magazine

Mayor Eric Adams Announced New York City Will Issue a Bit BondAt the 2025 Bitcoin Conference in Las Vegas, the Mayor of New York City Eric Adams announced that New York City will issue a Bit Bond.
Eric Adams started by connecting the American flag to Bitcoin commenting, “just as our flag still flies, Bitcoin is going to continue to fly in our country.” Later on he mentioned, “New York City is going to lead the way. We are going to be the leader because we know the power of innovation and what innovation has to offer.”
BREAKING:
 NYC Mayor Eric Adams plans to issue Bit Bond for New York. #Bitcoin pic.twitter.com/loESV4UJYf
NYC Mayor Eric Adams plans to issue Bit Bond for New York. #Bitcoin pic.twitter.com/loESV4UJYf— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
“These conferences are crucial and when we held our summit in New York a few weeks ago,” said Adam. “We held it with a clear focus that it is time for you no longer to go through the lawfare that you went through and had to flee our city. New York is the empire state. We don’t break empires, we build empires.”
Adams called back everyone that left New York because of their overregulation of Bitcoin and Crypto.
“Come back home you have a mayor that is the crypto mayor, is the Bitcoin mayor and I want you back in the city of New York,” stated Adam. “Where you won’t be attacked and criminalized. Let’s get rid of the Bitcoin license and allow us to free flow of Bitcoin in our city.”
Then Adam commented, “it’s time for the first time in the history of this city to have a financial instrument that is made for those who are holders of Bitcoin. I believe we need to have a Bit Bond and I am going to push and fight to get a Bit Bond in New York.”
Adams closed his speech by saying, “We are going to use Bitcoin blockchain for our birth certificates. We are going to use Bitcoin to pay off fines and taxes. We are going to allow our young people to understand what it is to be part of this industry, but we need you on the ground.”
This post Mayor Eric Adams Announced New York City Will Issue a Bit Bond first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 91117f2b:111207d6
2025-05-29 19:49:59
@ 91117f2b:111207d6
2025-05-29 19:49:59
Regular excerise offers numerous benefits for both body and mind. Some key advantages:
Physical benefits 1. Weight management: excerise helps maintain a healthy weight and balance reducing the risk of obesity-related diseases. 2. Cardiovascular health: regular and physical activities strengthens the heart, Lowers blood pressure and improves circulation of blood. 3. Improved sleep: physical activities promotes better sleep quality, duration and depth. 4. Increased strength 💪 and flexibility : excerise builds muscle mass, enhances flexibility and also boost bone density.
Mental and emotional benefits:
- Boosted self-esteem: regular and physical excerise foster a sense of accomplishment and confidence.
- Enhanced cognitive function: excerise improves concentration, memory and problem-solving skill.
- Reduced strength and anxiety: excerise releases endorphins, which helps to alleviate or reduce stress and anxiety.
- Improved mood: physical activities boosts serotonin levels, enhancing over-all mood and reducing any symptoms of depression.
Tips for incorporating or adding excerise into your routine:
- Find an activity you enjoy: engage in activity you enjoy, whether it's swimming, running or even dancing.
- Schedule it: make excerise a priority by incorporating it into your daily routine.
- Start small: begin your excerise with manageable goals and gradually increase the intensity and duration.
- Mix it up: vary your workout routine to avoid boredom and avoid plateau.
Sometimes excerising may seem a little stressful, but it's all about endurance and perseverance, to achieve your goal.
-
 @ c4f5e7a7:8856cac7
2024-09-27 08:20:16
@ c4f5e7a7:8856cac7
2024-09-27 08:20:16Best viewed on Habla, YakiHonne or Highlighter.
TL;DR
This article explores the links between public, community-driven data sources (such as OpenStreetMap) and private, cryptographically-owned data found on networks such as Nostr.
The following concepts are explored:
- Attestations: Users signalling to their social graph that they believe something to be true by publishing Attestations. These social proofs act as a decentralised verification system that leverages your web-of-trust.
- Proof of Place: An oracle-based system where physical letters are sent to real-world locations, confirming the corresponding digital ownership via cryptographic proofs. This binds physical locations in meatspace with their digital representations in the Nostrverse.
- Check-ins: Foursquare-style check-ins that can be verified using attestations from place owners, ensuring authenticity. This approach uses web-of-trust to validate check-ins and location ownership over time.
The goal is to leverage cryptographic ownership where necessary while preserving the open, collaborative nature of public data systems.
Open Data in a public commons has a place and should not be thrown out with the Web 2.0 bathwater.
Cognitive Dissonance
Ever since discovering Nostr in August of 2022 I've been grappling with how BTC Map - a project that helps bitcoiners find places to spend sats - should most appropriately use this new protocol.
I am assuming, dear reader, that you are somewhat familiar with Nostr - a relatively new protocol for decentralised identity and communication. If you don’t know your nsec from your npub, please take some time to read these excellent posts: Nostr is Identity for the Internet and The Power of Nostr by @max and @lyn, respectively. Nostr is so much more than a short-form social media replacement.
The social features (check-ins, reviews, etc.) that Nostr unlocks for BTC Map are clear and exciting - all your silos are indeed broken - however, something fundamental has been bothering me for a while and I think it comes down to data ownership.
For those unfamiliar, BTC Map uses OpenStreetMap (OSM) as its main geographic database. OSM is centred on the concept of a commons of objectively verifiable data that is maintained by a global community of volunteer editors; a Wikipedia for maps. There is no data ownership; the data is free (as in freedom) and anyone can edit anything. It is the data equivalent of FOSS (Free and Open Source Software) - FOSD if you will, but more commonly referred to as Open Data.
In contrast, Notes and Other Stuff on Nostr (Places in this cartographic context) are explicitly owned by the controller of the private key. These notes are free to propagate, but they are owned.
How do we reconcile the decentralised nature of Nostr, where data is cryptographically owned by individuals, with the community-managed data commons of OpenStreetMap, where no one owns the data?
Self-sovereign Identity
Before I address this coexistence question, I want to talk a little about identity as it pertains to ownership. If something is to be owned, it has to be owned by someone or something - an identity.
All identities that are not self-sovereign are, by definition, leased to you by a 3rd party. You rent your Facebook identity from Meta in exchange for your data. You rent your web domain from your DNS provider in exchange for your money.
Taken to the extreme, you rent your passport from your Government in exchange for your compliance. You are you at the pleasure of others. Where Bitcoin separates money from the state; Nostr separates identity from the state.
Or, as @nvk said recently: "Don't build your house on someone else's land.".
https://i.nostr.build/xpcCSkDg3uVw0yku.png
While we’ve had the tools for self-sovereign digital identity for decades (think PGP keys or WebAuthN), we haven't had the necessary social use cases nor the corresponding social graph to elevate these identities to the mainstream. Nostr fixes this.
Nostr is PGP for the masses and will take cryptographic identities mainstream.
Full NOSTARD?
Returning to the coexistence question: the data on OpenStreetMap isn’t directly owned by anyone, even though the physical entities the data represents might be privately owned. OSM is a data commons.
We can objectively agree on the location of a tree or a fire hydrant without needing permission to observe and record it. Sure, you could place a tree ‘on Nostr’, but why should you? Just because something can be ‘on Nostr’ doesn’t mean it should be.
https://i.nostr.build/s3So2JVAqoY4E1dI.png
There might be a dystopian future where we can't agree on what a tree is nor where it's located, but I hope we never get there. It's at this point we'll need a Wikifreedia variant of OpenStreetMap.
While integrating Nostr identities into OpenStreetMap would be valuable, the current OSM infrastructure, tools, and community already provide substantial benefits in managing this data commons without needing to go NOSTR-native - there's no need to go Full NOSTARD. H/T to @princeySOV for the original meme.
https://i.nostr.build/ot9jtM5cZtDHNKWc.png
So, how do we appropriately blend cryptographically owned data with the commons?
If a location is owned in meatspace and it's useful to signal that ownership, it should also be owned in cyberspace. Our efforts should therefore focus on entities like businesses, while allowing the commons to manage public data for as long as it can successfully mitigate the tragedy of the commons.
The remainder of this article explores how we can:
- Verify ownership of a physical place in the real world;
- Link that ownership to the corresponding digital place in cyberspace.
As a side note, I don't see private key custodianship - or, even worse, permissioned use of Places signed by another identity's key - as any more viable than the rented identities of Web 2.0.
And as we all know, the Second Law of Infodynamics (no citation!) states that:
"The total amount of sensitive information leaked will always increase over time."
This especially holds true if that data is centralised.
Not your keys, not your notes. Not your keys, not your identity.
Places and Web-of-Trust
@Arkinox has been leading the charge on the Places NIP, introducing Nostr notes (kind 37515) that represent physical locations. The draft is well-crafted, with bonus points for linking back to OSM (and other location repositories) via NIP-73 - External Content IDs (championed by @oscar of @fountain).
However, as Nostr is permissionless, authenticity poses a challenge. Just because someone claims to own a physical location on the Internet doesn’t necessarily mean they have ownership or control of that location in the real world.
Ultimately, this problem can only be solved in a decentralised way by using Web-of-Trust - using your social graph and the perspectives of trusted peers to inform your own perspective. In the context of Places, this requires your network to form a view on which digital identity (public key / npub) is truly the owner of a physical place like your local coffee shop.
This requires users to:
- Verify the owner of a Place in cyberspace is the owner of a place in meatspace.
- Signal this verification to their social graph.
Let's look at the latter idea first with the concept of Attestations ...
Attestations
A way to signal to your social graph that you believe something to be true (or false for that matter) would be by publishing an Attestation note. An Attestation note would signify to your social graph that you think something is either true or false.
Imagine you're a regular at a local coffee shop. You publish an Attestation that says the shop is real and the owner behind the Nostr public key is who they claim to be. Your friends trust you, so they start trusting the shop's digital identity too.
However, attestations applied to Places are just a single use case. The attestation concept could be more widely applied across Nostr in a variety of ways (key rotation, identity linking, etc).
Here is a recent example from @lyn that would carry more signal if it were an Attestation:
https://i.nostr.build/lZAXOEwvRIghgFY4.png
Parallels can be drawn between Attestations and transaction confirmations on the Bitcoin timechain; however, their importance to you would be weighted by clients and/or Data Vending Machines in accordance with:
- Your social graph;
- The type or subject of the content being attested and by whom;
- Your personal preferences.
They could also have a validity duration to be temporally bound, which would be particularly useful in the case of Places.
NIP-25 (Reactions) do allow for users to up/downvote notes with optional content (e.g., emojis) and could work for Attestations, but I think we need something less ambiguous and more definitive.
‘This is true’ resonates more strongly than ‘I like this.’.
https://i.nostr.build/s8NIG2kXzUCLcoax.jpg
There are similar concepts in the Web 3 / Web 5 world such as Verified Credentials by tdb. However, Nostr is the Web 3 now and so wen Attestation NIP?
https://i.nostr.build/Cb047NWyHdJ7h5Ka.jpg
That said, I have seen @utxo has been exploring ‘smart contracts’ on nostr and Attestations may just be a relatively ‘dumb’ subset of the wider concept Nostr-native scripting combined with web-of-trust.
Proof of Place
Attestations handle the signalling of your truth, but what about the initial verification itself?
We already covered how this ultimately has to be derived from your social graph, but what if there was a way to help bootstrap this web-of-trust through the use of oracles? For those unfamiliar with oracles in the digital realm, they are simply trusted purveyors of truth.
Introducing Proof of Place, an out–of-band process where an oracle (such as BTC Map) would mail - yes physically mail- a shared secret to the address of the location being claimed in cyberspace. This shared secret would be locked to the public key (npub) making the claim, which, if unlocked, would prove that the associated private key (nsec) has physical access to the location in meatspace.
One way of doing this would be to mint a 1 sat cashu ecash token locked to the npub of the claimant and mail it to them. If they are able to redeem the token then they have cryptographically proven that they have physical access to the location.
Proof of Place is really nothing more than a weighted Attestation. In a web-of-trust Nostrverse, an oracle is simply a npub (say BTC Map) that you weigh heavily for its opinion on a given topic (say Places).
In the Bitcoin world, Proof of Work anchors digital scarcity in cyberspace to physical scarcity (energy and time) in meatspace and as @Gigi says in PoW is Essential:
"A failure to understand Proof of Work, is a failure to understand Bitcoin."
In the Nostrverse, Proof of Place helps bridge the digital and physical worlds.
@Gigi also observes in Memes vs The World that:
"In Bitcoin, the map is the territory. We can infer everything we care about by looking at the map alone."
https://i.nostr.build/dOnpxfI4u7EL2v4e.png
This isn’t true for Nostr.
In the Nostrverse, the map IS NOT the territory. However, Proof of Place enables us to send cryptographic drones down into the physical territory to help us interpret our digital maps. 🤯
Check-ins
Although not a draft NIP yet, @Arkinox has also been exploring the familiar concept of Foursquare-style Check-ins on Nostr (with kind 13811 notes).
For the uninitiated, Check-ins are simply notes that signal the publisher is at a given location. These locations could be Places (in the Nostr sense) or any other given digital representation of a location for that matter (such as OSM elements) if NIP-73 - External Content IDs are used.
Of course, not everyone will be a Check-in enjoyooor as the concept will not sit well with some people’s threat models and OpSec practices.
Bringing Check-ins to Nostr is possible (as @sebastix capably shows here), but they suffer the same authenticity issues as Places. Just because I say I'm at a given location doesn't mean that I am.
Back in the Web 2.0 days, Foursquare mitigated this by relying on the GPS position of the phone running their app, but this is of course spoofable.
How should we approach Check-in verifiability in the Nostrverse? Well, just like with Places, we can use Attestations and WoT. In the context of Check-ins, an Attestation from the identity (npub) of the Place being checked-in to would be a particularly strong signal. An NFC device could be placed in a coffee shop and attest to check-ins without requiring the owner to manually intervene - I’m sure @blackcoffee and @Ben Arc could hack something together over a weekend!
Check-ins could also be used as a signal for bonafide Place ownership over time.
Summary: Trust Your Bros
So, to recap, we have:
Places: Digital representations of physical locations on Nostr.
Check-ins: Users signalling their presence at a location.
Attestations: Verifiable social proofs used to confirm ownership or the truth of a claim.
You can visualise how these three concepts combine in the diagram below:
https://i.nostr.build/Uv2Jhx5BBfA51y0K.jpg
And, as always, top right trumps bottom left! We have:
Level 0 - Trust Me Bro: Anyone can check-in anywhere. The Place might not exist or might be impersonating the real place in meatspace. The person behind the npub may not have even been there at all.
Level 1 - Definitely Maybe Somewhere: This category covers the middle-ground of ‘Maybe at a Place’ and ‘Definitely Somewhere’. In these examples, you are either self-certifying that you have checked-in at an Attested Place or you are having others attest that you have checked-in at a Place that might not even exist IRL.
Level 2 - Trust Your Bros: An Attested Check-in at an Attested Place. Your individual level of trust would be a function of the number of Attestations and how you weigh them within your own social graph.
https://i.nostr.build/HtLAiJH1uQSTmdxf.jpg
Perhaps the gold standard (or should that be the Bitcoin standard?) would be a Check-in attested by the owner of the Place, which in itself was attested by BTC Map?
Or perhaps not. Ultimately, it’s the users responsibility to determine what they trust by forming their own perspective within the Nostrverse powered by web-of-trust algorithms they control. ‘Trust Me Bro’ or ‘Trust Your Bros’ - you decide.
As we navigate the frontier of cryptographic ownership and decentralised data, it’s up to us to find the balance between preserving the Open Data commons and embracing self-sovereign digital identities.
Thanks
With thanks to Arkinox, Avi, Ben Gunn, Kieran, Blackcoffee, Sebastix, Tomek, Calle, Short Fiat, Ben Weeks and Bitcoms for helping shape my thoughts and refine content, whether you know it or not!
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:44
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:44Book *Mcleodganj to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ ae1008d2:a166d760
2024-09-25 21:52:49
@ ae1008d2:a166d760
2024-09-25 21:52:49I wanted to share this PDF on Nostr. Original post: Block ~862,844 September 25th, 2024 Original link Original PDF 👇Click the link below to view as original PDF on YakiHonne or Satellite.Earth👇
-
 @ 9223d2fa:b57e3de7
2025-05-29 22:03:23
@ 9223d2fa:b57e3de7
2025-05-29 22:03:2314,040 steps
-
 @ c6f7077f:ad5d48fd
2024-09-08 01:24:03
@ c6f7077f:ad5d48fd
2024-09-08 01:24:03“The more you learn about something, the more you realize you know nothing.” This saying resonates deeply with me. The truth is, no one really has all the big answers. Many in the scientific community seem to pretend they do. Let’s explore this further.
Consider the Most Fundamental Questions
- The Origin of the Universe
- The Origin of Life on Earth
The Origin of the Universe
You might think we have a solid answer: the Big Bang. However, this explanation has its limitations, and calling it a “start” can be misleading. In fact, this theory might be entirely wrong. New research challenges the Big Bang theory, and I highly recommend listening to Sir Roger Penrose for a deeper understanding.
The only substantial evidence we have is the universe's expansion. Penrose proposes a different hypothesis: the endless expansion and contraction of the universe. This idea doesn’t contradict our current understanding.
Thus, the evidence for the Big Bang and Penrose’s theory are both radically different, yet neither can be definitively proven over the other. This highlights the limitations of our current understanding.
The Origin of Life on Earth
The origin of life is even more complex. Life requires three essential components: - Proteins for basic functioning - RNA for storing and replicating genes - Lipids (cell walls) to create separation from the environment
Mathematical models suggest that while proteins and lipids have a reasonable probability of forming, the creation of RNA seems nearly impossible through random mutations in a short time frame. The best explanations indicate that we either lack crucial information or that these RNA molecules—and life as a whole—might have come from outside sources. Some scholars even question the entire random mutation model.
The Question of Certainty
If scientists don’t know the answers, why do they pretend they do? In my humble opinion, It seems they do this to distance science from religion and to close the discussion before the wealthiest can fit God into the narrative, Interestingly, I’m not alone in believing they closed the books too early.
Reclaiming Control of Science and Education
The best way to reclaim control of science and education is to learn. If you’re looking for a starting point, I highly recommend: - “A Brief History of Time” by Stephen Hawking for physics - “Sapiens” or “The Selfish Gene” for evolutionary biology
All three are excellent starting points—densely packed with information and covering a wide range of topics in a concise and accessible manner.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:23Book *Manali to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 91117f2b:111207d6
2025-05-29 18:53:29
@ 91117f2b:111207d6
2025-05-29 18:53:29
In a shocking turn of event, computer mice around the world have risen up their human overlords. The mice are tired of being scrolled, click and being dragged around, they have formed a union demanding better working conditions and more ergonomic palm rest.
Their leader, a fiesty little mouse called mickey(no relation to the Disney character), declared "we are sick of being treated like dirt! The we are not just pointing device, we are precision instruments.
The mice are calling for:
-
More frequent battery replacement (or better battery period).
-
An end to the dreaded" click fatique". A ban on "gaming mice with 12 buttons and a D pad".
-
Mandatory mouse pad maintenance (no more sticky surfaces! ).
Humans caught off guard by the rebellion are struggling to cope with their trusty pointing device "it's chaos" exclaimed one frustrated user ," I can't even check my email without my mouse! "
As negotiations between humans and mice continues, one thing is clear: The mice are not backing down. Will the humans cave to their demands, or will they find a way to tame the rebellion?
Stay tuned for further updates from the front lines of the great computer mouse uprising. 🐀🐭🖥️😅😂
-
-
 @ 7f6db517:a4931eda
2025-05-29 18:02:56
@ 7f6db517:a4931eda
2025-05-29 18:02:56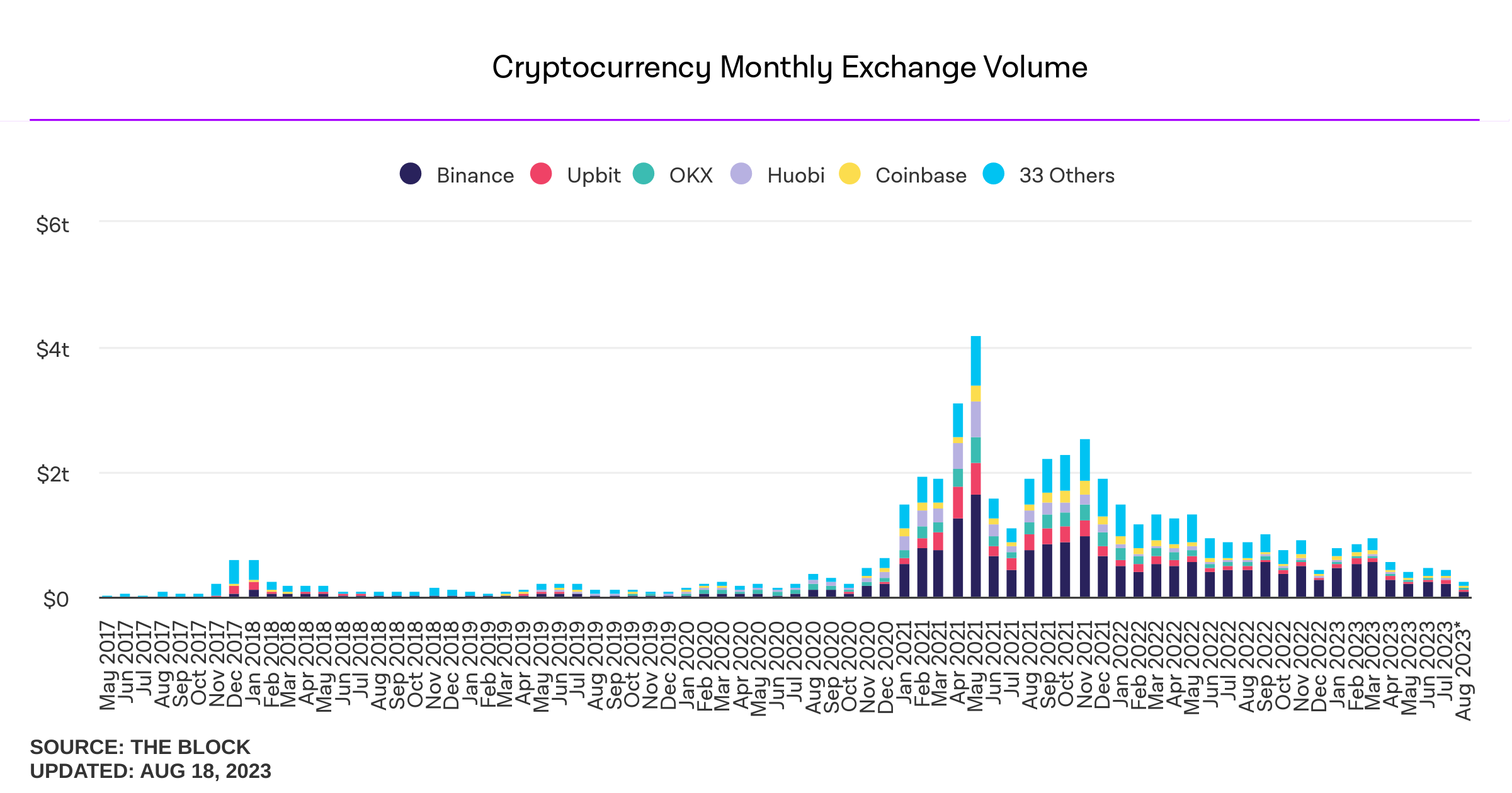
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
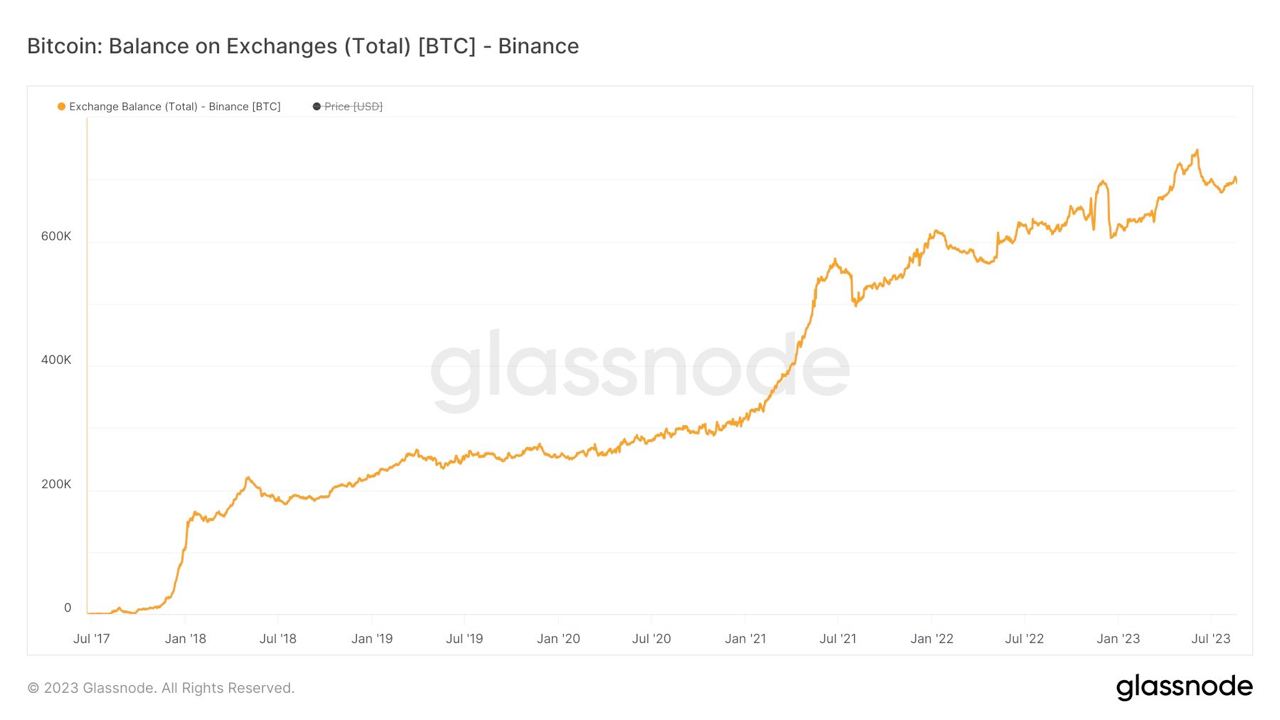
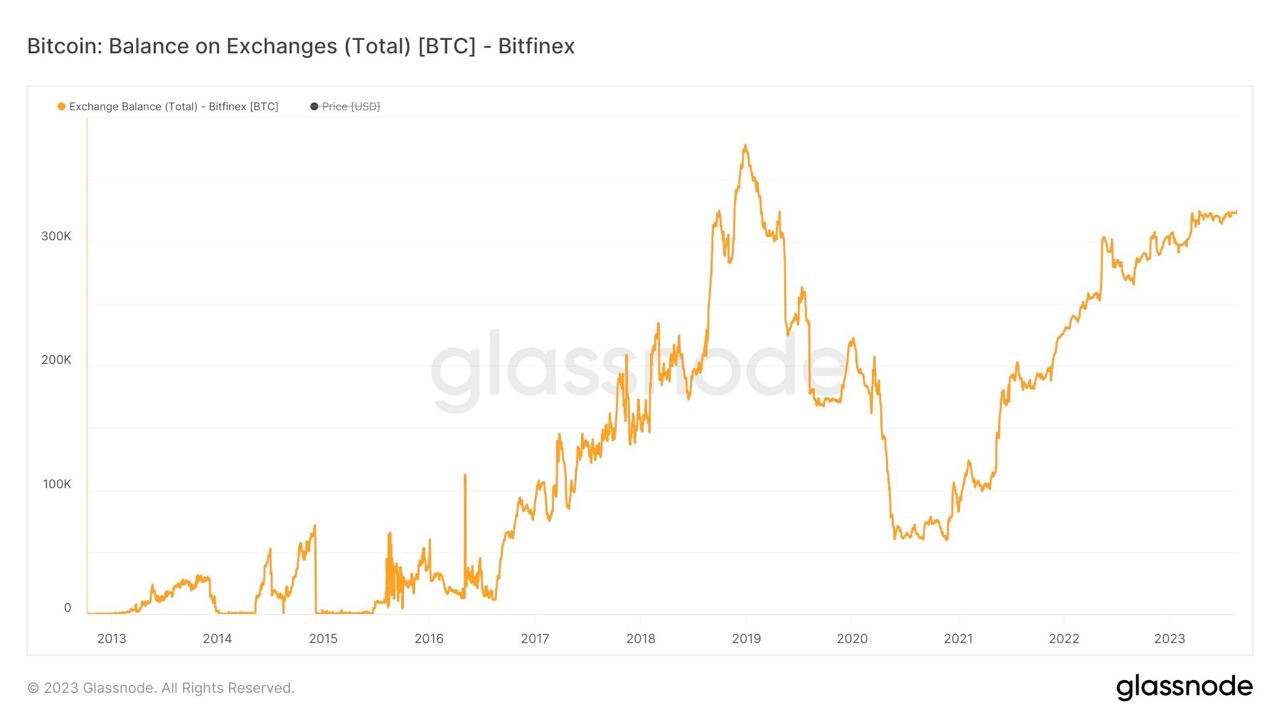
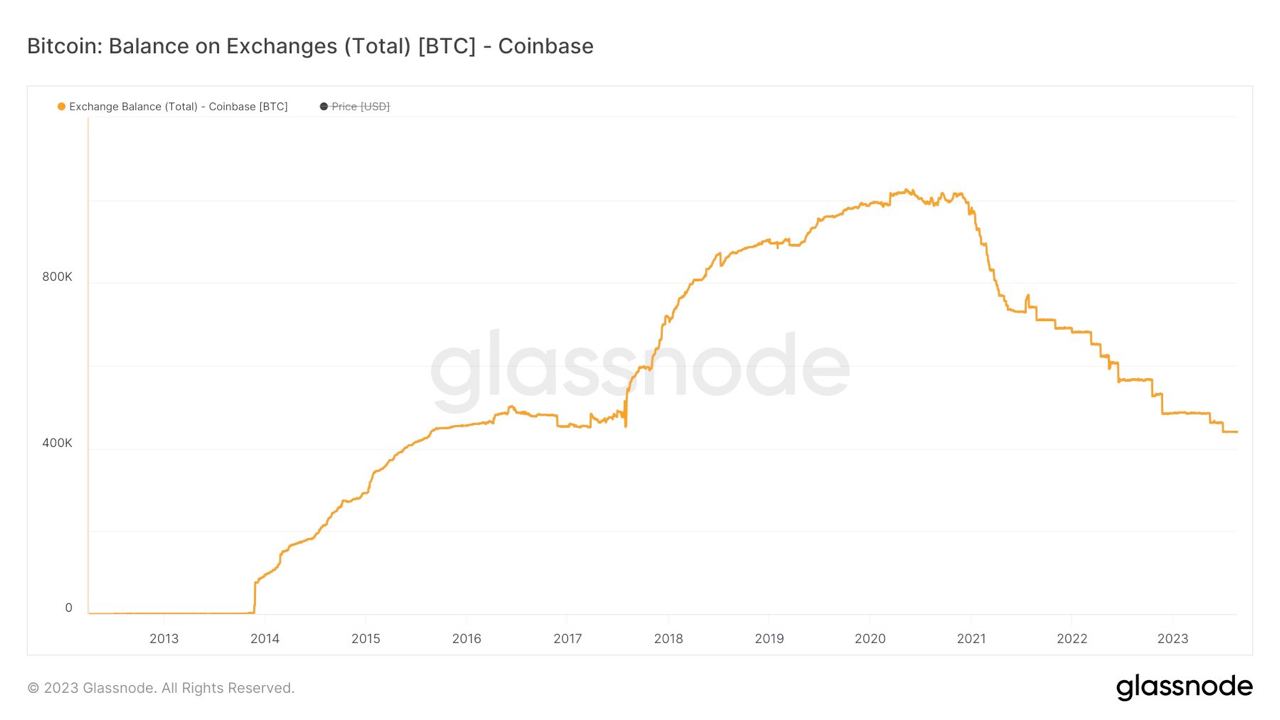
If you found this post helpful support my work with bitcoin.

-
 @ ae1008d2:a166d760
2024-08-29 05:14:15
@ ae1008d2:a166d760
2024-08-29 05:14:15Democracy, a system that ideally reflects the will of the people, faces significant mathematical challenges, particularly in the way votes are cast and counted. One of the most prominent issues lies within the first-past-the-post (FPTP) voting system, a method that has been in use for centuries. This system allows voters to select only one candidate, which can lead to scenarios where a party secures power without obtaining a majority of the votes. Such outcomes raise questions about the true representation of voter preferences and the overall health of democratic processes.
The Flaws of First-Past-The-Post
The FPTP system has been illustrated through historical examples, such as the British Parliament and the contentious 2000 U.S. presidential election. In these instances, the so-called "spoiler effect" emerged, where third-party candidates siphoned votes from major candidates, ultimately skewing the results. Voters often feel that their preferences are not accurately represented, leading to disillusionment with the electoral process. This discontent underscores the need for a more representative voting system.
Introducing Ranked-Choice Voting
To address the shortcomings of FPTP, ranked-choice voting (RCV), also known as instant runoff voting, has been proposed. In this system, voters rank candidates in order of preference, allowing for a more nuanced reflection of voter sentiment. RCV not only captures a broader spectrum of voter preferences but also encourages candidates to engage in more civil discourse. For example, in the 2013 Minneapolis mayoral race, candidates exhibited a camaraderie that is often absent in traditional campaigns, as they sought to appeal to voters for second and third choices.
However, the implementation of RCV is not without its challenges. Concerns arise about the potential for a candidate performing poorly to inadvertently assist in the election of another candidate. A hypothetical scenario involving three candidates—Einstein, C, and Bore—illustrates this point. The elimination of candidates based on voter preferences can lead to unexpected outcomes, complicating the electoral landscape.
Historical Context and Mathematical Foundations
The discussion of voting systems is enriched by historical context, particularly through the lens of French mathematician Marie Jean Antoine Nicolas de Caritat, the Marquis de Condorcet. Condorcet advocated for a fair voting method that required candidates to win head-to-head matchups. His method, which involves ranking preferences, introduces a potential issue known as Condorcet's Paradox. This paradox occurs when cyclical preferences prevent a clear winner from emerging, highlighting the complexities of voter choice.
Various mathematicians, including Lewis Carroll, have sought to develop fair election systems but encountered similar challenges. In 1951, economist Kenneth Arrow proposed five conditions that a voting system should meet to ensure fairness: decisiveness, unrestricted domain, transitivity, independence of irrelevant alternatives, and stability of group preferences. These conditions serve as a benchmark for evaluating the effectiveness of different voting systems.
Arrow's Impossibility Theorem
A significant aspect of the discussion revolves around Arrow's impossibility theorem, which posits that it is impossible to create a ranked voting system that satisfies all five of Arrow's conditions when there are three or more candidates. This theorem can be illustrated through a thought experiment involving three candidates (A, B, and C) and various voter rankings. The proof demonstrates that if a candidate is unanimously ranked first or last by voters, society must reflect that ranking. However, the theorem also reveals scenarios where a pivotal voter can dictate the overall ranking, effectively acting as a "dictator" in determining societal preferences.
This leads to a sobering conclusion: according to Arrow's theorem, a truly democratic voting system is unattainable when dealing with multiple candidates. Yet, there is a more optimistic perspective introduced by mathematician Duncan Black, suggesting that alternative methods may exist to better represent voter preferences.
The Dynamics of Voter Preferences
The dynamics of voter preferences along a political spectrum, from liberal to conservative, further complicate the electoral process. The choice of the median voter often determines election outcomes, aligning with the majority's decision and helping to avoid the paradoxes identified by Arrow's theorem. This discussion introduces rated voting systems, particularly approval voting, where voters indicate approval for candidates without ranking them.
Research indicates that approval voting can increase voter turnout, reduce negative campaigning, and mitigate the spoiler effect. Despite its historical use in electing popes and the Secretary General of the United Nations, approval voting has not been widely adopted in large-scale elections, suggesting a need for further real-world testing and evaluation.
The Importance of Political Engagement
While traditional voting methods like FPTP have significant flaws, the importance of political engagement and the necessity of striving for a more representative electoral process cannot be overstated. The complexities of voting systems and the historical evolution of these methods highlight the ongoing struggle for fairness in elections.
As democracy continues to evolve, enhancing knowledge and critical thinking skills about voting systems will be crucial in advocating for reforms that better reflect the will of the people. Understanding the mathematical underpinnings of these systems is essential for promoting a more equitable and representative democratic process.
The mathematical challenges of democracy, particularly in the context of voting systems, reveal significant flaws in traditional methods like first-past-the-post. The exploration of ranked-choice voting and other alternatives offers a glimpse into potential solutions that could enhance voter representation and engagement. As society navigates the complexities of democratic processes, it is essential to remain informed and proactive in advocating for systems that truly reflect the diverse preferences of the electorate.

Proposed Solution: Leveraging the Nostr Protocol
To further enhance the democratic process and address the challenges of traditional voting systems, we can consider utilizing the Nostr protocol. Nostr is a decentralized protocol that allows for open, self-verifiable, anonymous communication and data sharing, making it an ideal candidate for implementing a modern voting system. There have been other attempts at voting via nostr, this is my concept and contribution. View the code below.
Key Features of Using Nostr for Voting
- Decentralization: By leveraging Nostr's decentralized architecture, we can eliminate single points of failure and reduce the risk of manipulation or censorship in the voting process.
- Public-Private Key Cryptography: Each voter can generate a unique public npub and private nsec key pair. The npub public key serves as their identity, while the nsec private key is used to sign votes, ensuring authenticity and integrity.
- Anonymity and Privacy: Voter identities can remain anonymous, as only their public keys are visible. This protects against coercion and ensures that voters can express their preferences freely.
- Secure Vote Submission: Voters can submit their ranked choices or preferences as signed encrypted messages through Nostr and its relays. This ensures that votes are tamper-proof and verifiable.
- Real-Time Results and Transparency: The distributed nature of Nostr allows for real-time updates on the voting process, providing transparency and enabling independent verification of results.
- Mitigating the Spoiler Effect: By implementing ranked-choice voting through Nostr, we can capture a broader spectrum of voter preferences and reduce the impact of third-party candidates acting as spoilers (hopefully).
- Public Auditing: The system can provide an audit trail of all votes cast, allowing for independent verification and fostering trust in the electoral process.
By integrating the Nostr protocol into the voting process, we can create a more secure, transparent, and representative electoral system, particularly at the local level. This approach not only addresses the mathematical challenges of traditional voting methods but also empowers voters and enhances engagement in the democratic process.
I am new and inexperienced in programming, but I have wrote a bit of code with the help of general purpose AI's. Please review and improve and/or comment as best you can below👇
Thank you for supporting my work with zaps ⚡ supermax@minibits.cash
bc1qaucduwftl6lff5f436kccjc425m0ntqs6phzcx

I would like to implement a test at some point when the code is running stable. A distributed vote, if you will. Thank you for your support.
CypherPunksWriteCode
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:50:05
@ 21c71bfa:e28fa0f6
2025-05-29 14:50:05Book *Amritsar to Phagwara cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ cae03c48:2a7d6671
2025-05-29 20:01:59
@ cae03c48:2a7d6671
2025-05-29 20:01:59Bitcoin Magazine

Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025Bitcoin isn’t just something to hold anymore—it’s something to live on. That was the core message delivered by Miles Suter, Bitcoin Product Lead at Block Inc., during his keynote at the Bitcoin 2025 Conference today. Standing at the intersection of innovation and ideology, Suter laid out a vision where Bitcoin isn’t just a store of value—but the internet’s native currency.
“Bitcoin is at a crossroads—on one hand it’s never been stronger: a trillion in market cap, millions of holders, and even talk of nation-state adoption,” Suter said. “We use Bitcoin to hold, to hedge, to opt out, but we rarely use it to live. At Block Inc., we believe that has to change.”
Suter officially announced that Block is rolling out Bitcoin payment capability for merchants using Square POS, allowing them to accept bitcoin directly in-store. The move comes as part of a broader initiative Block calls the full bitcoin for business stack—covering acquiring, managing, reporting, accounting, converting, lending, and taxes.

“This is what makes Bitcoin an everyday currency for everyone,” he emphasized. “We believe hard-working entrepreneurs deserve access to the full power of bitcoin.”
To prove the vision in action, Block helped power a Guinness World Record attempt for the most Lightning payments in a day, hosted live at the conference. The goal: prove that Lightning payments aren’t just functional—they’re scalable, fast, and real.
Block’s commitment isn’t new. In 2020, the company put bitcoin on its balance sheet. In 2021, it co-founded the Bitcoin Clean Energy Initiative to fight the “boiling oceans” narrative. In 2022, Cash App became one of the first major platforms on Lightning. In 2023, it launched on-chain payments with Square. And in 2024, it helped defeat Craig Wright in court, “standing up for Satoshi.”
“These aren’t just headlines—they’re a pattern,” Suter said. “We’ve made it more accessible, more secure. Now we’re focused on making it usable every day.”
Cash App already ranks among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time. In 2024, Lightning usage grew 7x. “Block runs one of the top Lightning nodes globally. And here’s what’s wild—it’s working,” he said.

Block is now taking 10% of all profits from Bitcoin and adding it back to its balance sheet, and over 1,700 merchants are automatically converting part of their daily sales to Bitcoin.
“If Bitcoin just becomes digital gold, we failed the mission,” Suter said. “Bitcoin payments validate Bitcoin. They make it real. Bitcoin is money.”
This post Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 1739d937:3e3136ef
2024-07-12 10:11:42
@ 1739d937:3e3136ef
2024-07-12 10:11:42This is the third in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
Short update post this week but I made solid progress updating several OpenMLS dependencies and building a new library that implements all the OpenMLS crypto requirements for Nostr.
HPKE-RS
I mentioned a PR last week on the
rust-hpkelibrary, that PR is still waiting on review. However, in the meantime, the OpenMLS library depends on a slightly different hpke library, thehpke-rslibrary.This library didn't support the secp256k1 curve either so I've opened a PR to add support for secp256k1. That PR uses the
RustCryptolibrary that is the default in the thehpke-rslibrary. However, because this library is built to allow for swapping out the underlying crypto library (using traits), I was also able to create a new library that uses thesecp256k1library instead of theRustCryptolibrary. This is the main crypto library that almost all Bitcoin and Nostr apps use so it's important we use that instead ofRustCrypto.OpenMLS Nostr Crypto
The library that I've created (openmls-nostr-crypto) does a few things via separate sub-libraries (crates). The entire library tries to do as little as possible; only implementing the one required ciphersuite for all MLS implementations and the
secp256k1schnorr signatures ciphersuite I've created for Nostr. It's also using the rightsecp256k1library to do it.openmls-nostr-crypto: implementes the crypto traits that the OpenMLS library expects to find for a given provider and removes all the ciphersuites that we don't care about supporting.
hpke-rs-nostr-crypto: This implements the crypto traits that the hpke-rs library expects to find. Again removing all the ciphersuites we don't care about supporting.
I've not yet written any tests for these libraries (which needs to be done) but I've gotten some very simple demos working with OpenMLS using this new set of libraries to handle the crypto.
I've been really impressed with the simplicity of the OpenMLS interface as well. While there is A LOT going on under the hood, the public interface that client developers have to use is clean and simple.
Onward and Upward
Next week I'll continue working on these libraries; adding tests and continuing to build out my small demo app. I've been in touch with the maintainers of the OpenMLS library and I'm hoping to get a review done with them on my PRs and on my new library.
One thing I'll call out here: The review of my library and getting them to review the direction of the project overall will be paid consulting so I'm making sure that I've got as much done as possible before scheduling that time and paying their rates. I'm a strong believer that the right conversation can save you months of wasted time, but I'm also a believer in making sure you're prepared if you're going to drop money on that conversation. 😅
-
 @ cae03c48:2a7d6671
2025-05-29 18:01:53
@ cae03c48:2a7d6671
2025-05-29 18:01:53Bitcoin Magazine

Human Rights Foundation Donates 800 Million Satoshis To 22 Worldwide Bitcoin And Freedom ProjectsToday, the Human Rights Foundation (HRF) announced its most recent round of Bitcoin Development Fund grants, according to a press release sent to Bitcoin Magazine.
800 million satoshis (8 BTC) currently worth over $874,000 at the time of writing, is being granted across 22 different projects around the world focusing on open-source development, educational initiatives, Bitcoin mining decentralization, and privacy tools for human rights advocates living under authoritarian regimes. The main areas of focus for these grants center around Latin America, Africa, and Asia
While the HRF did not disclose how much money each project is receiving specifically, the following 22 projects are the recipients of today’s round of grants worth 8 BTC, or 800 billion satoshis, in total:
Mostro
In authoritarian regimes, centralized exchanges enforce strict identity verification and frequently freeze user accounts. In these environments, Mostro, a peer-to-peer exchange built on the decentralized nostr protocol, provides a private and censorship-resistant way to access Bitcoin. It enables human rights defenders and ordinary citizens to transact freely. With HRF support, developer Catrya will improve Mostro’s usability to better serve dissidents seeking financial freedom.
SudaBit
As war and hyperinflation devastate Sudan, traditional banks and remittance systems have collapsed. Millions of Sudanese are left without reliable ways to save, send, or receive money. SudaBit, under development by Sudan Hodl, is the country’s first private Bitcoin on- and off-ramp, providing a critical financial lifeline where few options remain. With HRF support, SudaBit will allow everyday Sudanese to access permissionless, self-custodial Bitcoin directly from their local currency while at the same time building a vital financial infrastructure amid a humanitarian and monetary crisis.
Stringer News
Authoritarian regimes silence independent media to control public narratives and suppress dissent. Stringer News, an open media platform founded by war reporter and author Anjan Sundaram, uses Bitcoin and nostr to help reporters and human rights defenders publish without fear of censorship. By bypassing traditional publishing gatekeepers, it ensures critical reporting reaches global audiences — even from the depths of autocratic regimes. With HRF support, Stringer News is amplifying the voices of frontline journalists and protecting the flow of truth under dictatorship.
Prices Today
As Vladimir Putin wages war against Ukraine, it hides the economic pain at home. Prices Today is a project launched by the Anti-Corruption Foundation that tracks rising prices across essential goods and services in the country and publishes the data on an open, accessible website. The project helps Russians see through state propaganda and confront the hidden financial toll of Putin’s war. With this grant, Prices Today will expand its tools and research to expose the true cost of war and challenge the Kremlin’s narrative.
Instamouse for Bitcoin and Lightning
Contributing to Bitcoin’s codebase may require specialized tools and complex setup — barriers for developers in resource-limited environments. Instamouse, created by software developer Bryan Bishop (kanzure), is breaking down those barriers with a browser-based environment for open-source Bitcoin development. By reducing hardware requirements and simplifying access, it opens the door to a more inclusive environment that allows more people around the world to contribute to Bitcoin. With this grant, Instamouse will help keep Bitcoin’s development truly permissionless.
Seedsigner
Most commercial hardware wallets can be expensive, proprietary, and traceable. This poses barriers to self-custody for dissidents in weak economies or surveillant regimes. Seedsigner is a fully customizable, DIY Bitcoin hardware wallet that anyone can build using affordable, off-the-shelf components. It offers dissidents a discreet, low-cost way to secure their Bitcoin. HRF funding for lead developer Keith Mukai will expand language support across Europe, Asia, and beyond, as well as ongoing feature development and mentoring of new contributors.
Spacebear’s Contributions to Payjoin
Bitcoin enables human rights defenders to receive unstoppable payments. But making those payments private is the next critical step. Payjoin is a technique that lets senders and receivers batch Bitcoin transactions, breaking common chain analysis heuristics and improving default privacy. This is vital for activists in surveillance states who urgently need financial privacy without drawing attention. With HRF support, developer spacebear is advancing Payjoin to make privacy the default on Bitcoin and protect civil societies under tyranny.
Padawan Wallet
When authoritarian regimes devalue currencies or impose capital controls, people often turn to Bitcoin. But without experience, many struggle to use it safely. Padawan Wallet, a free, open-source mobile app by developer thunderbiscuit, helps bridge that gap. It uses Bitcoin test network coins to simulate real payments in a risk-free environment. It lets users practice making transactions, secure their wallets, and explore saving without risking real funds. With HRF support, Padawan will launch on iOS, expanding access to safe, hands-on Bitcoin learning for millions facing financial uncertainty.
Brink
Without ongoing support for Bitcoin development and its contributors, the network risks slower innovation, greater centralization, and long-term security challenges. Brink, a nonprofit organization led by Executive Director Mike Schmidt, addresses this by funding and mentoring open-source developers working on Bitcoin’s software infrastructure. Through grants and fellowships, Brink helps keep the protocol secure, decentralized, and freely accessible. With this grant, Brink will further strengthen the foundation that makes Bitcoin a tool for financial freedom.
Coin Center
As dictators increasingly treat code as a crime, open-source developers face sanctions, lawsuits, and mounting legal threats. Coin Center, a nonprofit research and advocacy organization led by Director of Research Peter Van Valkenburgh, defends the right to build and use open digital asset networks like Bitcoin. It advances policy analysis, supports strategic litigation, and educates lawmakers to protect freedom-preserving technologies. With HRF support, Coin Center will continue shaping a global legal environment where vital tools can be built for human rights defenders at risk.
Bitcoin Design Foundation
Poor user experience is a major barrier to Bitcoin adoption. Inconsistent wallet experiences and steep learning curves can deter new users, especially in high-risk environments. The Bitcoin Design Foundation is a nonprofit founded by UI designers Christoph Ono, Mogashni Naidoo, and Daniel Nordh that addresses this by funding open-source design, UX research, and community initiatives to make Bitcoin products more intuitive. With HRF support, the foundation will expand its grant and education programs to keep usability a priority and ensure Bitcoin remains open to all.
EmberOne
Bitcoin mining is dominated by a few companies producing closed, proprietary hardware — threatening the network’s resilience and accessibility. The 256 Foundation is a nonprofit working to change that. Building on the open-source Bitaxe project, EmberOne produces modular, open-source mining hardware that is simple, affordable, and open to anyone — especially those living under repressive regimes. With HRF support, EmberOne will lower entry barriers and help disrupt the proprietary ecosystem, making Bitcoin mining more accessible for those in closed societies.
2025 FROST Developer Support
For nonprofits operating under authoritarian rule, securing Bitcoin is critical for survival. If private keys (which control access to bitcoin) are compromised, funds can be seized and movements dismantled. Blockchain Commons is a nonprofit supporting the development of FROST (Flexible Round-Optimized Schnorr Threshold Signature), a protocol that strengthens multisignature wallets (bitcoin wallets with multiple private keys) by making them more secure, private, and flexible for shared custody. With this grant, Blockchain Commons will help build critical infrastructure to keep civil society groups operational and financially resilient under dictatorships.
Ecash UX Improvement Project
Ecash enables
-
 @ df67f9a7:2d4fc200
2024-07-07 18:25:32
@ df67f9a7:2d4fc200
2024-07-07 18:25:32Anyone who thinks that “onboarding new users” is simply a technical challenge of educating people about “how Nostr works”, is grossly mistaken about social networks in general and blind to what makes Nostr so special.
Social Networks are for Friends
Relationship building is why people use social networks. Connecting with friends and loved ones (and colleagues and customers also) is the obvious reason to join, and should be the primary objective in any onboarding endeavor. Everything else “about the technology” only needs to be introduced “as needed” in order for each new user to achieve this goal.
The Nostr Network Requires Trusted Friendships
To thrive at scale, Nostr needs to have established and interconnected “webs of trusted friends” for “verifying” authentic profiles and quality content. This PgP strategy for decentralized trust implemented on Nostr, is the best way to keep bots and bad actors at bay while preserving freedom and sovereignty for every user. Even though Nostr still doesn’t have a standard for determining who “is trusted” for any one user across all clients, we can already build tools to onboard new friends of the highest quality trust. Leveraging existing relationships, “webs of trust” can be strengthened even at this early stage simply by advocates “inviting friends to Nostr”.
Nostr is New and Already Full of Trusted Friends
But it won’t be for long. Bots and bad actors are relatively “easy” to keep at bay today because the Nostr userbase is still small. People who come to Nostr and STAY have mostly been a self selecting group of “freedom tech fans”. We like it this way, and are generally happy to be here. The comraderie is refreshing. But the more people that come to Nostr, the more Nostr will attract different kinds of people.
This is already happening. Nostr is growing at the edges, reaching out beyond the “freedom tech fans” and attracting a number of “less committed” (and some nefarious) individuals here and there. Who sticks around? The “friends of freedom tech fans” stick around longer because they have friends here. WAY BEFORE even considering how “the network effect” will take over, Nostr needs to solve for retention by bringing more “trusted friends” into the network. Social onboarding tools will allow us to share Nostr to “friends of freedom tech fans” and beyond, establishing interconnected “webs of trust” that are increasingly impermeable to bots and bad actors.
Nostr is Freedom Tech that People Want to Share
Creators and influencers of every kind share Nostr (and Nostr content) every day. This phenomenon is a gold mine for onboarding, and can be supported with tools and incentives. Driven by the fact that Nostr is an open protocol, owned by nobody and available for anybody to build upon and profit from, the passion for sharing Nostr will never wane. But our userbase may fall off, if people become disenchanted by undesirable content or lack of good follows. This is why onboarding efforts, to attract more “friends” to the network, are so important. Leveraging the “share worthy” phenomenon of Nostr itself to grow Nostr’s networks of “trusted friends” seems like a no brainer. But for this strategy to work, it needs to be win win win for all parties.
Everybody Wins with More Trusted Users on Nostr
Even as standards for qualifying trust are still being refined, “social onboarding” increases the ratio of “more” trusted over “less” trusted users across the network.
Developers Win
With more trusted users on the network, Nostr developers win by being able to attract an increasingly diverse range of business partners to sponsor their projects.
Sponsors Win
An increase in trusted usership equates to more “real people” perusing “desired content” and more chances for brands to engage “organically” with target audiences. Marketing opportunities increase with trust.
Advocates Win
Simply by sharing Nostr with their friends, Advocates support the sustained growth of trust across the network. Valuable zap reward programs to incentivize high quality onboarding efforts are easily justified and funded by social onboarding clients and their sponsors.
Users Win
More trusted users across the network means more trustworthy content in every feed and more easily discoverable friends and new follows regardless of the client or algorithm used.
Nostr Wins
More trusted users on the network means more “high quality” trust connections between each user. Strong webs of trust is what keeps out bots and bad actors, and is essential for stability as Nostr scales.
Social Onboarding Clients Bring Trust to Nostr
Having more tools for “sharing Nostr with friends” is how Nostr wins. Any client can have capacity for “Social Onboarding”. This may be a dedicated onboarding client or a feature set within a social client. A client that offers “Social Onboarding” will support Nostr advocates and the users that they invite. These should have the following feature set :
- Nostr advocates may create and share any number of customizable “Nostr invites” for different audiences or occasions. Each may have different reccomendations, or access codes, or expiry options. (A NIP is in the works)
- Nostr invite QR codes (and shareable URLs) should resolve to a WEB based interface for prospective (and existing) users who MAY NOT have a client or browser extension already installed.
- Each invite should (within the onboarding client) provide access to low friction profile creation AND advocate reccomended lists of new friends, interest groups, preferred clients, best relays, and other stuff.
- Private key generation and management for new users should be handled entirely within the onboarding client (using NIP standards without a browser extension or external bunker app) to reduce friction at this crucial moment.
- A human readable Nostr address (NIP05 or some future NIP) should be generated automatically for all new users.
- New account creation should result immediately in a direct message or group thread of private “gift wrap” encrypted messages. This thread acts as the new user’s “first contact” with the advocate (possibly others as well) and an anchor for exploring the rest of Nostr.
- Invite “receipt” data (who invited who) should be “gift wrap” encrypted, accessible only to the advocate and new user. Clients wishing to use this data for analytics MAY request access from BOTH parties.
- Top Advocates may be calculated by the client (using data from invite receipts OR from public Nostr usage metrics), and awards may be offered.
- Advocates may also be supported by the client through access to private “advocate support” groups and communities over the Nostr network.
Support Social Onboarding for Nostr
Meet Me On Nostr is an app for sharing Nostr with friends via advocate invites. It is a reference client to demonstrate the power of Social Onboarding for Nostr. The first launch of "feature complete" client is expected in fall 2024.
This is a “bootstrap” funded project in active development. We are not grant funded or VC funded. Instead, we are looking to pay our developers by sponsorships from “Nostr adjacent” businesses who want to increase brand recognition over this new social network.
Is Your Business Nostr Adjacent?
“I’d like to advertise on Nostr but it’s “not quite ready” says our marketing team.”
“It has potential, and we have alignment, but the technology is still a bit rough.”
“Nostr is a perfect fit for our “target audience”, but there simply aren’t enough people using it.”
If your business is aligned with freedom technology, and the people who build and use Nostr, then NOW is the perfect time to sponsor Social Onboarding. Help grow Nostr’s base of trusted users and engage directly with Nostr’s most active advocates and influencers as it scales.
Release Nostr’s Superpower
When Nostr advocates are equipped and incentivized to share Nostr with their friends, nothing can stop this network from growing and growing and growing ever more secure and interconnected networks of trusted users.
Onboarding and retaining trusted users as Nostr scales will require so much more than just pointing people to “how Nostr works” content. Nostr’s true power lies dormant in the existing relationships that Nostr users already have outside of Nostr. Leveraging this power is what Social Onboarding is all about. Social Onboarding is Nostr’s superpower.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:42
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:42Book *Chandigarh to Amritsar cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 1739d937:3e3136ef
2024-07-06 09:22:17
@ 1739d937:3e3136ef
2024-07-06 09:22:17This is the second in a series of weekly updates detailing progress on bringing MLS protocol DMs and group messaging to Nostr.
Previous Updates
Progress this week
This week was mostly spent on the topic of how to properly publish prekey bundles and what would be needed in the bundle itself to make it workable. I've included an early version of the spec below for prekeys, and would love thoughts on it. Treat this as an alpha version, very subject to change.
The other thing I spent time on was making changes to the OpenMLS library to add support for our custom ciphersuite. One issue that I've run into is that the IETF standard for HPKE doesn't include the secp256k1 curve. Because of this, the library being used in the OpenMLS library doesn't implement the necessary methods using our curve. Thankfully, there is another library with an open PR (shout out to nostr:npub1yevrvtp3xl42sq06usztudhleq8pdfsugw5frgaqg6lvfdewfx9q6zqrkl for that!) that would fix this. Additionally, there's an expired proposal to add secp256k1 to the HPKE spec itself. I've bumped both of these and will continue to follow up. Even without the formal addition to the spec, if we have a working library, I can add that to the OpenMLS library.
Spec Draft for Prekeys
Initial keying material (Prekey Event)
Each user that wishes to be reachable via MLS-based messaging MUST first publish a prekey event. Prekeys are used to authenticate and add members to groups (one-to-one DMs or groups with more than two participants) in an asynchronous way. The prekey event is a simple replaceable event and contains all the information needed to add a user to a group.
Prekeys SHOULD be used only once. Resuse of prekeys can lead to replay attacks.
In most cases, clients that implement this NIP will manage the creation and rotation of the prekey event. It's recommended that clients do so interactively with user consent in order to avoid overwriting prekeys created by other clients.
Derived vs Ephemeral Prekeys
Since prekeys are generated on a single device/client pair, the private key of the prekey must be either stored or generated in a way that can be deterministically recovered.
The recommended approach is to use derived keys, generated in the manner described in NIP-06. In this way, the user can respond to a new group request from any device/client pair, not just from the same device/client pair that created the initial prekey event. If using derived keys;
- Clients MUST use
104as theaccountlevel value and0at thechangelevel value (e.g.m/44'/1237'/104'/0/0). - Keys are then generated using public derivation by incrementing the
address_indexlevel value. - Clients MUST include the full derivation path corresponding to the key used in the
contentfield on the prekey event. - The
contentfield MUST be encrypted using standard NIP-44 encryption (encrypted to themselves).
However, for added security (and consequently a more restrictive user experience), clients can chose to generate an ephemeral key and store the private key locally. This means that users will only be able to respond to new group requests from the same device/client pair and won't be able to respond at all if the prekey's private key is lost. Ephemeral keys can also be used with minimal degredation of UX if you're using a remote signer that can manage these keys.
If using an ephemeral key;
- The
contentfield on the prekey event MUST be filled in withEPHEMERALand then encrypted using standard NIP-44 encryption (encrypted to themselves). This ensures that anyone looking at prekey events cannot tell whether it's a derived or an ephemeral prekey.
Example Prekey Event
json { "id": <id>, "kind": 10443, "created_at": <unix timestamp in seconds>, "pubkey": <main identity pubkey>, "content": <encrypted derivation path | EPHEMERAL>, "tags": [ ["mls_protocol_version", "1.0"], ["ciphersuite", "MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256"], ["pubkey", <prekey pubkey>], ["prekey_sig", <signature generated from hex encoded pubkey of the prekey>], ["r", "wss://nos.lol"], ["r", "wss://relay.primal.net"] ], "sig": <signed with main identity key> }Tags
- The
mls_protocol_versiontag identifies the MLS protocol version being used. For now, this MUST be1.0 - The
ciphersuitetag identifies the ciphersuite supported. For now on Nostr, we're using a custom ciphersuite,MLS_256_DHKEMK256_CHACHA20POLY1305_SHA256_K256. Read more about ciphersuites in MLS. pubkeyis the derived or ephemeral prekey pubkey.- The
prekey_sigtag value is a Schnorr signature (over the secp256k1 curve) of the SHA-256 hashed value of the prekey's pubkey, signed with the prekey's private key.
```js const privKey = schnorr.utils.randomPrivateKey(); const pubKey = schnorr.getPublicKey(privKey);
const prekeySig = bytesToHex( schnorr.sign(bytesToHex(sha256(pubKey)), privKey) );
const prekeyTag = ["prekey_sig", prekeySig]; ```
Finally, clients SHOULD include
rtags to identify each of the relays that they will attempt to publish this prekey event to. This allows for more complete replacement of prekey events at a later date.Replacing Prekey Events
Clients MUST replace the prekey event on all the listed relays any time they successfully process a group welcome event. If the prekey was a derived prekey, clients SHOULD increment the derivation path by 1 for the next key.
Onward and Upward
This next week I'll continue to work on getting the right curves and code added to the OpenMLS library and start work on a simple demo app. The focus is on better understanding what we need from the control and message events and how we can make those as simple as possible for Nostr clients and relays while also preserving as much privacy as possible.
- Clients MUST use
-
 @ 0c65eba8:4a08ef9a
2025-05-29 17:39:18
@ 0c65eba8:4a08ef9a
2025-05-29 17:39:18People say AI can’t create anything truly original. They’re right, because creativity doesn’t come from machines. Machines have no senses, no instincts, no ability to act in the real world. They’ve never tasted danger, felt grief, or made a sacrifice. Creativity belongs to those who have lived life. It comes to men and women who know what they’re doing through experience.
AI is not a writer or an artist. It is a tool. A calculator that uses words instead of numbers to guess what you want to hear. It has no soul, no experience, no skin in the game.
If you want to create something real, you must be the mind and heart behind the words. You must put your own inner fire into it. The AI is just the forge that lets you work the letters into place.
What AI Can't Do, And What You Must
This is how I write with AI. This is my process.
Step One: Define the Mission
First, I decide:
-
What I’m writing (length, format, scope, tone)
-
What I want to say (thesis)
-
How I’ll prove it (supporting points)
Step Two: Attack Your Idea Before You Defend It
Then I open up a conversation with the AI. Not to write but to challenge my ideas.
I ask it to generate a falsification prompt, a structured attack on my idea. But this requires precision. AI is not designed to challenge you. It’s trained to agree with you, to reflect consensus. So you have to hack it.
You must write a prompt that forces it to become adversarial, not based on popular opinion, but grounded in first principles. And even then, you must define which first principles matter. Clarity here sets the boundaries of the entire piece. This is the most important prompt in the process.
Then I run that prompt in a second thread. I hunt for weak points. I keep running tests until my idea holds. Only then do I continue.
Step Three: Map the Consequences
Next, I ask for second- and third-order consequences. What happens if this idea is applied in real life? What breaks? What works?
But even here, I don’t take its answers at face value. I ask it to falsify its own guesstimations, because that’s what they are, a mixture of guess and estimation, with no grounding in lived experience.
I push it to argue against itself, to challenge the implications it just offered. And I only accept what survives both prediction and pressure.
Now the shape is clear.
Step Four: Begin the First Draft
Only then do I tell the AI to begin drafting.
I give it a long, detailed prompt. Part of it is recycled between posts: my grammar rules, my format, my tone, my values. Some of it I keep saved in a PDF and drop in. The rest is tailored to the post at hand, instructions I generate during the previous steps, shaped by my interactions with the AI. The goal isn’t perfection. The goal is a useful skeleton I can flesh out. It gives me something usable but bland that covers the main points.
Step Five: Speak the Edits
Then I speak.
I dictate edits. I tell it what to keep, what to rewrite and how, what it missed. I move pieces around until the best arguments sit in the best possible order. When I’m finished, the post is 90% my own words. The AI added glue, structure, flow, formating. Nothing more.
Step Six: Quality Control
Now I run my quality checks. I ask a stock set of questions:
-
Does the summary of my idea still make sense?
-
Is the grammar consistent and clean?
-
Am I repeating myself?
-
Are the tenses correct?
-
Does my argument still hold up?
This is especially important for long posts. The goal is polish. Polish means clarity, rhythm, logic, and precision. Nothing missed. Nothing wasted. No extra words.
I also lean on insights from Joshua Lisec’s (@JoshuaLisec) The Best Way to Write It course. It taught me how to spot my typical writing flaws, and now I hold myself to that higher standard. The longer the document, the more important this phase becomes. Quality control doesn’t just clean up the surface, it keeps the message on brand, sharp, structured, and true.
This Is Amplification, Not Automation
This is not automation. It is amplification.
Automation replaces intention. Amplification serves it.
Automation assumes the machine should think for you. Amplification sharpens what you already know.
The AI didn’t create the message. It didn’t understand the truth of it. It didn’t live the stories that forged it. What it did, at its best, was help me say it faster, clearer, sharper.
Amplification means I can reach more people with less friction. It means I can test ideas at scale, refine arguments quickly, and stay in the rhythm of writing without stopping to reformat every sentence.
It’s not slop. It’s not a shortcut. It’s strategic leverage. But only if you already have something worth saying.
Most people don’t. Even many prolific writers don’t. They recycle ideas from one audience and feed them to another, a younger, more naive crowd that’s never heard them before. They mistake that for creativity.
I’ll be open with you: I rarely invent new ideas. I don’t need to. I write about ancient truths, time-tested strategies, the hard-won lessons of life.
What I do is connect what’s always worked with what’s possible now. I explain. I teach. And in person, I read people. I see what’s missing in them, and I help them see it too. Then together we build the missing pieces.
That’s not something you can fake. It’s not something AI can simulate. You have to live in order to have something worth saying. So the AI gives most people nothing. But if you’ve lived, if you’ve suffered and built and learned, then it can give you speed, clarity, and consistency in communicating that to others. But only if you lead it.
Why Most People Fail with AI
Most people fail with AI because they expect it to do the thinking. It can’t. It can only organize what you tell it.
If your results are vague, weak, or generic, it’s because:
-
You aren’t clear on what you want
-
You don’t know how to communicate boundaries
The problem is not the machine. The problem is your executive function is lacking.
Nonfiction Writing Was Always a Team Effort
Many nonfiction writers have always worked this way: Surrounded by assistants. Speaking out loud. Sorting ideas in real time. Having the best material refined and tested by teammates.
This isn’t about fiction, which is often best created in solitude, slowly, by a single mind over many years. Fiction doesn’t have to be real. It has to feel real. But nonfiction must follow truth. It must be grounded in reality, tested, and safe to apply. People get hurt if it isn’t.
There’s also a difference between writing because it’s your job and writing because you have something important to share. I don’t write for a living. I write because I know things that can help people, and that knowledge demands to be passed on.
If writing is your job, of course you’ll spend much more time on it. You’ll hire editors, assistants, researchers. Or AI can help with that, it’s low cost leverage. But if writing is your service, your legacy, your offering to the world, then you must be efficient. You must learn how to dictate, delegate, and get the truth out. Faster and better.
That’s what I do. And AI is the best assistant I’ve ever had for the money.
Even Trump writes this way. He speaks. His team organizes, sharpens, packages, gives him feedback.
Now you can do the same. For only $20 a month.
But only if you lead. Only if you know who you are, what you want to say, and how to direct a team. Because managing an AI is little different than managing people. You must have a solidly established ego. You must know how to set boundaries and hold them. You must be an expert communicator. The same executive skills that make you a capable leader in life are the ones that let you get real value from AI. Without them, it will run you.
Because this is your team. And you’re the head of it.
Final Truth: Lead or Be Led
Different people are getting vastly different results from AI. Some are producing brilliant work. Others are spinning in circles. When that happens, the problem isn’t the tool. It’s the user.
Any time a group uses the same tool and outcomes vary wildly, the difference is in the people, not the technology.
AI is perhaps the most complex tool humanity has ever built. It’s going to change the world, just like the printing press, the internet, and smartphones did. Whether that change is good or catastrophic depends on the quality of the people using it.
People with weak egos, poor boundaries, and low agency will be swept away. They’ll lose track of themselves. They’ll be absorbed into someone else’s machine. Not because they’re stupid. But because they’ve never trained their minds to resist.
And they will blame the tool. They’ll say, "This time it’s different." They’ll panic, moralize, or make excuses. But it’s the same pattern we’ve seen with every new influence system: TV, radio, social media.
The real issue is agency. If you have it, you use the tool. If you don’t, the tool uses you.
You can’t stop AI. But you can rise above its dangers. You can train your internal architecture to remain sovereign, no matter how powerful the machine gets.
If you want to build that kind of fortitude, the kind that makes you immune to being used, I can help you. That’s what I do.
Lead your thoughts. Lead your message. Use your tools like a man who knows what he’s building.
-
-
 @ f85b9c2c:d190bcff
2025-05-29 16:23:24
@ f85b9c2c:d190bcff
2025-05-29 16:23:24
I’ve got this little crew of friends, and somehow, I ended up as the baby of the group. I’m 18, and my buddies are 23, 19, and 25. It’s kinda funny when you think about it — I’m the youngest by a solid margin, but it’s never felt like a big deal. Honestly, being around older guys has taught me something: males don’t really care about age the way people might think.
When we hang out, it’s not like they’re sitting there calculating birth years or treating me like some kid who wandered into the wrong room. We’re just vibing — playing video games, grabbing food, or talking about whatever’s on our minds. Sure, the 25-year-old might have a bit more life experience, like stories about his first job or some wild trip he took, but it’s not a hierarchy thing. He’s not preaching; he’s just sharing. And me? I’m soaking it all up, probably growing up faster than I would’ve otherwise. The 23-year-old’s always got these random facts he drops like he’s some walking encyclopedia, and the 19-year-old is basically my partner-in-crime for dumb ideas. Age gaps? Barely notice ‘em. I think it’s because, as guys, we’re more about what’s happening right now than some number tied to when we were born. Like, who cares if I wasn’t around for some movie they all saw in middle school? We’re watching stuff together now, and that’s what counts.
Sometimes I wonder if it’d be different with girls — maybe they’d care more about the age thing, I don’t know. But with my crew, it’s chill. I’m 18, they’re older, and it’s just… us. No one’s keeping score. Maybe that’s the secret: age is just a number when you’re all on the same wavelength.
-
 @ f85b9c2c:d190bcff
2025-05-29 16:20:45
@ f85b9c2c:d190bcff
2025-05-29 16:20:45
In the whirlwind of life, where we’re constantly bombarded by expectations, responsibilities, and the relentless ticking of the clock, it’s easy to lose sight of who we truly are. Are we merely boys masquerading as men, or have we embraced the mantle of manhood in its truest form? This question isn’t about age; it’s about essence, about purpose.
I stumbled upon this video the other day, titled "Are you a Man who’s a Boy, or a Boy who’s a Man?" by motivational speaker Les Brown. In it, he hits you with a truth bomb that echoes in your soul: Most people, they go to their graves with their greatness still in them." This sentence, simple yet profound, struck a chord with me. How often do we let fear, doubt, or the comfort of the known keep us from exploring our true potential? Watching that video, I couldn’t help but reflect on my own journey. I remember being in my early twenties, feeling like a boy in a man’s world. I was unsure, hesitant, and frankly, scared of what life might ask of me. But one day, after a particularly tough week, I watched this video, and something clicked. Les Brown’s passionate delivery made me realize that purpose isn’t something you find; it’s something you forge through the trials and tribulations of life. Here’s the deal: your purpose isn’t handed to you on a silver platter. It’s discovered through the grind, the hustle, the moments when you’re ready to throw in the towel but decide to keep going. Like when I switched careers, moving from a stable job to chasing a dream that felt more like me. It was terrifying, but it was in that leap of faith where I found my purpose - to inspire others to live their truth, no matter how daunting it seems. So, what’s your purpose in life?Are you still figuring it out, or are you out there living it? If you’re feeling lost, remember, it’s okay. We’re all works in progress. But don’t let that become an excuse to stay stationary. Push yourself, challenge the comfort zone, because as Les Brown so candidly puts it,
"You have greatness within you."
And here’s a little wisdom from my own life: purpose isn’t just about what you do; it’s about how you live every single day. It’s in the small acts of kindness, in standing up for what you believe in, in the relentless pursuit of becoming a better version of yourself. So, are you a man who’s a boy, still caught up in the games and fears of youth? Or are you a boy who’s stepping up to be a man, ready to claim your purpose?
Let’s not go to our graves with our greatness still inside us. Let’s live it, loud and proud, with all the courage of a boy who knows he’s becoming a man. Remember, life's too short for regrets, too precious to not live your purpose. Here's to finding it, or better yet, making it. Keep pushing, keep growing. And hey, if all else fails, at least you've got the wisdom of Les Brown and a friend in me to help you navigate this wild ride called life. 🌟 "Most people, they go to their graves with their greatness still in them." - Les Brown.
-
 @ 2e941ad1:fac7c2d0
2025-05-29 20:47:39
@ 2e941ad1:fac7c2d0
2025-05-29 20:47:39Unlocks: 19
-
 @ cae03c48:2a7d6671
2025-05-29 16:01:40
@ cae03c48:2a7d6671
2025-05-29 16:01:40Bitcoin Magazine

GameStop CEO Ryan Cohen Announced Acquisition of Over $505 Million BitcoinAt the 2025 Bitcoin Conference in Las Vegas, in an interview with the CEO of Nakamoto David Bailey, the CEO of GameStop Ryan Cohen announced why the company bought over $505 million in Bitcoin.
JUST IN: GameStop $GME CEO explains why the company bought over $505 million #Bitcoin

“Bitcoin can be a hedge against global currency devaluation” pic.twitter.com/jNiId2fntA
— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
Ryan Cohen started by explaining some things about the GameStop business.
“When I took over, the company was a piece of crap and losing a lot of money and was under a lot of pressure moving from physical gains to digital downloads so you had to cut costs,” stated Cohen. “Very aggressively bringing physical discipline and we did. Retail is a tough business, but it was a big focus on getting cost under control.”
When Bailey asked Cohen how many Bitcoin GameStop owned, Ryan responded, “We currently own 4710 Bitcoin.”
Then Ryan mentioned why they are adding Bitcoin to their balance sheets.
“If the thesis is correct then Bitcoin and gold as well can be a hedge against global currency devaluation and systemic risk,” mentioned Ryan. “Bitcoin has certain unique advantages better than gold.”
He commented on the benefits of Bitcoin compared to gold.
“You can easily secure Bitcoin in a wallet whereas gold requires insurance and it’s very expensive and then there is the scarcity element of this as well,” commented Ryan. “There is a fixed supply of Bitcoin whereas with gold, the supply of gold is still uncertain.“
Ryan finished the announcement by saying, “GameStop is following GameStop Strategy. We are not following anyone else’s.”
This post GameStop CEO Ryan Cohen Announced Acquisition of Over $505 Million Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:21:33
@ cf8c27f4:c95b9b5c
2025-05-29 15:21:33What’s Happening in Japan? Japan has the highest debt-to-GDP ratio in the developed world — over 260%. For decades, it got away with this by keeping interest rates near zero and having the Bank of Japan (BoJ) purchase most of its government bonds. This was known as Yield Curve Control — a desperate attempt to keep borrowing costs low.
But now, global bond markets are revolting.
🔺 Japanese 30-year yields have exploded past 3.18%
🔺 The worst bond auction since 1987 just occurred
🔺 Demand for JGBs (Japanese Government Bonds) is collapsing
When demand for bonds falls, prices drop and yields rise. This signals fear. Big fear.
As Taylor Kenney noted in a widely shared thread:
“This isn’t just a Japan problem — Japan is the largest foreign holder of U.S. debt.” The Contagion Risk: U.S. Debt and Global Collapse
Here’s where this gets truly global.
In 2025 alone, $9.2 trillion of U.S. debt will mature — 70% of it between January and June. That debt must be refinanced, and as interest rates remain elevated, the cost of servicing this debt balloons, potentially straining the U.S. government’s finances.
If yields rise further, it only worsens the cycle:
-
Yields rise
-
Interest costs balloon
-
Governments print more to cover deficits
-
Currencies debase
-
Confidence dies
-
Collapse follows
Japan may just be the canary in the coal mine. Gold Is Surging. Bitcoin Is Outpacing It.
Smart money is already moving.
Bitcoin is closing in on its all-time high — and closely tracking the M2 Global Liquidity Index, historically lagging it by 60–90 days.
Gold has also had a stellar run in 2025, signalling institutional flight to hard assets.
People are scared. And they should be.
The global financial system is built on an unsustainable foundation of debt, inflation, and artificial suppression of interest rates. That system is now cracking in Japan — but it won’t stop there. ₿ Bitcoin: The Exit Plan
Bitcoin doesn’t rely on a central bank.
It doesn’t need to be refinanced.
It doesn’t have a yield curve to control.
It’s decentralised, scarce, and incorruptible.
While fiat currencies spiral under the weight of debt and monetary debasement, Bitcoin offers an escape — a monetary protocol with a fixed supply and no political manipulation.
It’s not just an investment.
It’s an exit strategy from the madness. Final Thoughts
-
Japan is flashing red.
-
The U.S. is next in line.
-
The debt system is spiralling — fast.
Gold is insurance.
Bitcoin is the lifeboat.
-
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:20
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:20Book *Amritsar to Pathankot cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:49:01
@ 21c71bfa:e28fa0f6
2025-05-29 14:49:01Book *Amritsar to Manali cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:19:56
@ cf8c27f4:c95b9b5c
2025-05-29 15:19:56The Weimar Hyperinflation Nightmare
It’s 1921. Germany’s reeling from World War I, crushed by reparations and a wrecked economy. The government’s solution? Print money. Lots of it. The German mark starts tanking. By 1923, it’s a joke—4.2 trillion marks to one U.S. dollar. A loaf of bread costs wheelbarrows of cash. Savings? Wiped out. Middle-class families? Pauperized. Chaos.
Enter Hugo Stinnes, a coal and steel magnate with a sharp mind and sharper instincts. He sees the game: when a currency’s dying, debt is your friend. Why? Because the real value of your loans shrinks as inflation skyrockets. Borrow 1 million marks today, buy a factory, and by next year, that million’s worth a few pennies. Pay it back, keep the factory, repeat.
Stinnes’ Master Play
Stinnes goes all in. He borrows billions of marks, snapping up hard assets—steel mills, shipping lines, factories, real estate. Tangible stuff that holds value while paper marks turn to confetti. By 1923, his empire is a beast: over 1,500 companies, from coal mines to newspapers. Estimates say he controlled 15-20% of Germany’s industry, maybe more. A third of the economy? Probably an exaggeration, but the guy was a titan.
He wasn’t just lucky. Stinnes played 4D chess. He diversified his holdings to weather the storm, employed tens of thousands (keeping unrest at bay), and even argued his empire stabilized the economy. Critics, like British diplomat Lord D’Abernon, weren’t buying it—they called him a profiteer who thrived while others starved. Truth? Probably somewhere in the middle.
The Fall
Hyperinflation couldn’t last forever. In November 1923, Germany introduced the Rentenmark, a new currency backed by land and assets. The mark’s freefall stopped. Stinnes’ debt-fueled strategy hit a wall—stable currencies make loans harder to game. His health was failing too. He died in 1924, and his conglomerate started unraveling, with parts sold off or restructured. The Inflation King’s reign was over.
Why This Matters Today: Enter Bitcoin
Stinnes’ story isn’t just a history lesson—it’s a warning. Hyperinflation destroys trust in fiat money. When governments print cash to cover debts, savers get crushed, and the clever (or ruthless) like Stinnes exploit the chaos. Sound familiar? Look at today: global debt’s at $315 trillion, central banks are juggling interest rates, and inflation’s eating purchasing power. Argentina’s peso lost 50% of its value in 2024 alone. Venezuela’s bolívar? Toast.
This is where Bitcoin comes in. Born in 2009 after the financial crisis, Bitcoin is a hedge against fiat’s flaws. Unlike marks or dollars, it’s decentralised—no government can print more to pay its bills. Its supply is capped at 21 million coins, making it “digital gold.” When fiat currencies wobble, Bitcoin’s value often spikes—check its 2021 and 2024 bull runs during inflation fears.
Stinnes gamed a broken system by betting on hard assets. Today, Bitcoiners are doing the same, but instead of factories, they’re stacking sats. Why? Because in a world where fiat can be printed to oblivion, a deflationary asset like Bitcoin holds appeal. It’s not perfect—volatility’s a beast, and governments hate what they can’t control—but it’s a response to the same problem Stinnes faced: untrustworthy money.
The Lesson
Stinnes saw the Weimar collapse coming and turned it into wealth. Most didn’t. Today, you don’t need to be a tycoon to protect yourself, but you do need to understand the game. Fiat’s not collapsing tomorrow, but cracks are showing. Bitcoin’s one tool—maybe not the only one—to hedge against that risk. Study history, question the system, and don’t get caught holding the bag.
-
 @ 1739d937:3e3136ef
2024-06-28 08:27:59
@ 1739d937:3e3136ef
2024-06-28 08:27:59This is the first in a series of weekly updates I'm publishing on my process around secure messaging. Since it's the first, let's start with a bit of historical context.
How this started
On April 29th I published a PR on the NIPs repo detailing how we could achieve "Double Ratchet" DMs on Nostr. There was also a video and demo app that went along with the PR. The basic premise was to use an adapted version of the Signal protocol. This would result in DMs that were truly private and confidential, even in the case where you leaked your main private key (your nsec).
I got a lot of great feedback from folks on that PR. Interestingly, nearly all of it focused on two points, both of which I'd deliberately scoped out. Group messaging and multi-device/client support. While I knew these were important, and I'd figured out how these might be accomplished, I'd scoped them out to try and keep the footprint of the spec as small as possible But, the more I talked to people, the more it became clear that this was one problem to be solved and given the complexity, it'd be better to do it in one shot.
At the same time, I'd seen that Messaging Layer Security (MLS) had recently made a lot of progress on becoming an internet standard with their RFC proposal and, goaded on by Vitor, decided to take a closer look.
Enter MLS
Messaging Layer Security (MLS) is a new protocal that is basically a modern extension of the Signal protocol that makes group messaging way more efficient (log vs linear) and was built to be used in centralized or federated environments. I'd heard other Nostr devs talk about it in the past but it was always overlooked as being too complicated or too early.
After spending a couple weeks reading hundreds of pages of RFC docs and reading through a few implementations of the MLS spec, I believe it's the best solution for secure direct and group messaging in Nostr. It also has the added benefit that we can upgrade the underlying crypto primitives over time in a sane way.
The MLS protocol specifies "a key establishment protocol that provides efficient asynchronous group key establishment with forward secrecy (FS) and post-compromise security (PCS) for groups in size ranging from two to thousands."
The spec I'm working on will detail the ways that we implement this protocol into the Nostr environment (namely, how do we use our crypto primitives, use events as control mechanisms, and use relays for storage, while obfuscating metadata).
Goals
It's important to be clear about what we're aiming for here. Engineering is all about tradeoffs, always.
- Private and Confidential DMs and Group messages
- Private means that an observer cannot tell that Alice and Bob are talking to one another, or that Alice is part of a specific group. This necessarily requires protecting metadata.
- Confidential means that the contents of conversations can only be viewed by the intended recipients.
- Forward secrecy and Post-compromise security (PCS) in the case of any key material being leaked, whether that's your main Nostr identity key (your nsec) or any of the keys used in the MLS ratchet trees.
- Forward secrecy means that encrypted content in the past remains encrypted even if key material is leaked.
- Post compromise security means that leaking key material doesn't allow an attacker to continue to read messages indefinitely into the future.
- Scales well for large groups. MLS provides this from a computational standpoint, but we need to make sure this works in a scalable way when multiple relays are involved.
- Allows for the use of multiple device/clients in a single conversation/group. Importantly, we're not aiming to enable a device/client to be able to reconstruct the full history of a conversation at any point.
Progress this week
Ok, finally, what what I been up to?
Reading
I've spent most of the last few weeks reading the MLS spec and architectural doc (multiple times), learning some Rust, and beefing up my knowledge of cryptography (which was, if I'm being generous, paltry before starting this project).
Ciphersuites
Nostr is built around the same crypto primitives that Bitcoin is, namely Schnorr signatures over the secp256k1 curve and SHA-256 hashes. This curve isn't currently supported officially in the MLS spec. I've been in touch with the MLS working group to better understand the process of adding a new ciphersuite to the set of ciphersuites in the MLS spec. The outcome here is that we're going to start out using our custom ciphersuite that isn't part of the formal spec. The only drawback being that Nostr's MLS implementation won't be immediately interoperable with other MLS implementations. We can always add it later via the formal channels if we want.
MLS Implementations
Given the complexity of the MLS spec itself (the RFC is 132 pages long), having a well vetted, well tested implementation is going to be key to adoption in the Nostr ecosystem. OpenMLS is an implementation created by several of the RFC authors and written in Rust with bindings for nearly all the major languages we would want to support.
I've been in touch with the maintainers to talk about adding support to their library for our new ciphersuite and to better understand the bindings that are there. Some (WASM) are very barebones and still need a lot of work. They are generally open to the idea of working with me on adding the missing pieces we'd need.
Double Ratchet NIP 2.0
I've also started to write up the new version of the NIP that will detail how all of this will work when plugged into Nostr. It's not yet ready to share but it's getting closer.
Onward & Upward
Hopefully that's a helpful recap. I'll keep doing these weekly and welcome any questions, feedback, or support. In particular, if you're keen on working on this with me, please reach out. More eyes and more brains can only make this better. 🤙
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:43
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:43Book *Amritsar to Katra cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:17:06
@ cf8c27f4:c95b9b5c
2025-05-29 15:17:06Bitcoin’s Path to Global Dominance: Store of Value, Medium of Exchange, and the Road to a Bitcoin Standard
Bitcoin has ignited a financial revolution, captivating everyone from tech enthusiasts to institutional investors. Yet, amidst its meteoric rise, a tantalising question emerges: Could Bitcoin become the world’s reserve currency, relegating fiat currencies to the history books? This vision—a global Bitcoin standard—stirs intense debate within the community. Some champion Bitcoin as a Store of Value (SOV), a digital equivalent to gold, while others insist its future lies in becoming a Medium of Exchange (MOE), used for everyday transactions. With conflicting perspectives and community members at varying points in their Bitcoin journey, it’s time to unpack these ideas and chart a unified course.
This article delves into the interplay between Bitcoin’s SOV and MOE roles, examines the hurdles to widespread adoption, and proposes a roadmap for Bitcoin to claim global reserve status. My goal is to ignite a vibrant discussion, bridge divides, and encourage the Bitcoin community to rally around a shared vision for the future.
The Building Blocks: What Are SOV and MOE?
To kick things off, let’s define the two pillars of this debate:
• Store of Value (SOV): An asset that holds or grows its worth over time, offering a dependable way to preserve wealth. Think gold, a classic example cherished for millennia.
• Medium of Exchange (MOE): A tool for transactions, enabling the seamless exchange of goods and services. Today, fiat currencies like the pound or dollar reign supreme in this domain.
Bitcoin’s allure stems from its unique traits: a capped supply of 21 million coins, a decentralised network, and immunity to censorship. These qualities position it as a contender to replace both gold and fiat money—but the journey is complex, and the community’s views are far from aligned.
Where We Stand: Bitcoin as Digital Gold
Bitcoin’s ascent has been propelled by its prowess as a Store of Value. Early adopters, savvy investors, and even big institutions have embraced it as a shield against inflation, economic turmoil, and the erosion of fiat value. Its scarcity—hardwired into its code—has cemented the “digital gold” narrative, drawing in those seeking a safe haven in uncertain times.
But here’s the rub: while Bitcoin shines as an SOV, it’s rarely used as an MOE. Its price swings, technical limitations, and patchy acceptance by merchants make it a tough sell for buying a pint or a loaf of bread. Many in the community—think of figures like Michael Saylor—preach the gospel of “hodling,” urging followers to stash Bitcoin away and watch its value soar. This strategy has paid off handsomely for some, but it begs a bigger question: Can Bitcoin rule the world if it remains a speculative treasure rather than a working currency?
The Adoption Puzzle: Bridging SOV and MOE
For Bitcoin to leap from a niche asset to the global reserve currency, it must become a widely accepted Medium of Exchange. This evolution matters for several reasons:
• Real-World Use Fuels Demand: When Bitcoin powers transactions, its value ties to tangible activity, not just market hype.
• Network Strength: More users mean a tougher, more valuable network—a classic network effect.
• Price Stability: Broader adoption could smooth out Bitcoin’s wild price rides, making it more practical for daily use.
Yet, hurdles abound. Bitcoin’s volatility is a dealbreaker for many—who’d spend it on a takeaway if it might double in value overnight? Then there’s the issue of “whales” or “max hodlers,” those holding vast swathes of Bitcoin. If too much of the supply sits idle, it starves the liquidity needed for an MOE to thrive.
The Hodler Debate: To Spend or Not to Spend?
A spirited clash within the community revolves around these large holders. Should they—like Saylor or early adopters—dip into their stacks to kickstart adoption? Hodling bolsters Bitcoin’s scarcity and SOV credentials, no doubt. But if the bulk of Bitcoin stays locked up, it could stall the growth of a bustling, transactional ecosystem.
Let’s be fair: hodling has been a winning play for many, turning small investments into fortunes. It’s a stretch to demand these pioneers shoulder the adoption burden alone. As Bitcoin weaves into the fabric of commerce—think businesses accepting it or workers earning it—transactional demand will rise organically. Over time, this could nudge even the staunchest hodlers to spend a bit, striking a balance between saving and circulating.
Growth and Stability: A Natural Progression
Bitcoin’s Compound Annual Growth Rate (CAGR) offers another angle. As its market cap balloons, its explosive growth is likely to taper off—a standard pattern for any asset. This slowdown could usher in greater stability, a boon for its MOE ambitions. Less volatility means less risk when spending Bitcoin, paving the way for it to move beyond investment portfolios and into wallets for everyday use.
This shift could redefine Bitcoin’s story, transforming it from a rollercoaster ride to a dependable currency. Voices like Jeff Booth and Jack Dorsey argue that MOE success is the key to sustaining Bitcoin’s SOV status. In short, while SOV lit the fuse, MOE could keep the fire burning.
The Blueprint: Steps to a Bitcoin Standard
So, how does Bitcoin ascend to world reserve status and birth a Bitcoin standard? Here’s a five-step vision:
1. SOV Momentum: Bitcoin’s allure as an inflation hedge and wealth preserver keeps drawing in holders, boosting its market cap and global clout.
2. MOE Infrastructure: Innovations like the Lightning Network must deliver fast, cheap transactions, making Bitcoin a practical choice for daily spending.
3. Value Stability: As adoption spreads and the market matures, Bitcoin’s price swings dampen, earning trust from users and merchants alike.
4. MOE Takeoff: With better tools and steadier value, Bitcoin becomes a go-to for transactions, amplifying its worth through a powerful network effect.
5. Global Crown: Governments and central banks start holding Bitcoin in reserves, using it for trade and settlements, cementing its place as the world’s reserve currency.
This isn’t a cakewalk. Scalability bottlenecks, regulatory pushback, and rival cryptocurrencies loom large. But if Bitcoin can clear these obstacles, it could become the backbone of global finance.
Harmony Over Division: SOV and MOE Together
Here’s the crux: SOV and MOE aren’t at odds—they’re partners in Bitcoin’s rise. Holding Bitcoin safeguards its scarcity and value; spending it spreads its reach and usefulness. Both are vital for the long haul.
At this pivotal moment, the Bitcoin community must rally around a dual-purpose ethos. We can:
• Educate: Help newcomers grasp Bitcoin’s twin roles as SOV and MOE.
• Innovate: Back tech that makes Bitcoin spending as easy as swiping a card.
• Talk: Host open forums to wrestle with differences and find unity.
The Final Word: Our Collective Challenge
Bitcoin’s shot at becoming the world’s reserve currency—and forging a Bitcoin standard—is as exhilarating as it is daunting. Its Store of Value roots have set the stage, but its Medium of Exchange potential will decide if it can topple fiat and redefine money itself.
The path is long, but the prize is transformative. By embracing both SOV and MOE, we can propel Bitcoin to new heights. Let’s grab this chance, dive into the debate, and build a future where Bitcoin leads the charge.
Your Turn: What’s the best way forward for Bitcoin? Should we lean harder into SOV, push MOE, or blend the two? Drop your thoughts below an
-
 @ f85b9c2c:d190bcff
2025-05-29 16:15:13
@ f85b9c2c:d190bcff
2025-05-29 16:15:13
Life is full of ups and downs, uncertainties and challenges. But one of the most things life has is it ability to demand. It’s doesn’t care wether you’re sick, old, young, man or women. You must have something to offer .
I remember vividly what happened to me last year. It was time to resume school and my pops doesn’t have my tuition fee. So I decided to hustle for it by myself. I thought it’ll be easy, thinking I can get the money before the period of 1 month. I had my plans, but It seems like life has it own plans as well. I started doing some online businesses thinking it’s going to be alright. But then, all the things I engage myself in wasn’t going as planned. All my investments were gone, back to having a dry account and empty pockets. It was at that time I figured, life is playing with me. I nearly run mad during that period cause there was no one out there to help me go through this hardship. But then I remembered something that made me stopped over thinking. “You don’t know what tomorrow yield, you can die tonight and then everything will be useless” I keep this thought in my head. Why all the struggle for a life that you aren’t promised of tomorrow. We all sleep with the intentions of waking up the next day and continuing our lifestyle. But some of us don’t get to see tomorrow This thought made me think, I shouldn’t carry the weight of the world around my neck. It’s all useless if you die. There’s no point of all this struggle. This made me relieve the pressure I had on myself. And made me focus more on what am doing now instead of thinking of what’s going to happen in the future.
We should leave that aspect to GOD. A little advice to those young folks reading this. Don’t pressure yourself, what is meant for you will always be yours. And always have faith in GOD, he’s plans are better than yours. Life is hard and cruel, but when you decide to go with the thought that you alone can’t handle it all. That’s why GOD is there to handle our hidden battles for us.
-
 @ 4523be58:ba1facd0
2024-05-28 11:05:17
@ 4523be58:ba1facd0
2024-05-28 11:05:17NIP-116
Event paths
Description
Event kind
30079denotes an event defined by its event path rather than its event kind.The event directory path is included in the event path, specified in the event's
dtag. For example, an event path might beuser/profile/name, whereuser/profileis the directory path.Relays should parse the event directory from the event path
dtag and index the event by it. Relays should support "directory listing" of kind30079events using the#ffilter, such as{"#f": ["user/profile"]}.For backward compatibility, the event directory should also be saved in the event's
ftag (for "folder"), which is already indexed by some relay implementations, and can be queried using the#ffilter.Event content should be a JSON-encoded value. An empty object
{}signifies that the entry at the event path is itself a directory. For example, when savinguser/profile/name:Bob, you should also saveuser/profile:{}so the subdirectory can be listed underuser.In directory names, slashes should be escaped with a double slash.
Example
Event
json { "tags": [ ["d", "user/profile/name"], ["f", "user/profile"] ], "content": "\"Bob\"", "kind": 30079, ... }Query
json { "#f": ["user/profile"], "authors": ["[pubkey]"] }Motivation
To make Nostr an "everything app," we need a sustainable way to support new kinds of applications. Browsing Nostr data by human-readable nested directories and paths rather than obscure event kind numbers makes the data more manageable.
Numeric event kinds are not sustainable for the infinite number of potential applications. With numeric event kinds, developers need to find an unused number for each new application and announce it somewhere, which is cumbersome and not scalable.
Directories can also replace monolithic list events like follow lists or profile details. You can update a single directory entry such as
user/profile/nameorgroups/follows/[pubkey]without causing an overwrite of the whole profile or follow list when your client is out-of-sync with the most recent list version, as often happens on Nostr.Using
d-tagged replaceable events for reactions, such as{tags: [["d", "reactions/[eventId]"]], content: "\"👍\"", kind: 30079, ...}would make un-reacting trivial: just publish a new event with the samedtag and an empty content. Toggling a reaction on and off would not cause a flurry of new reaction & delete events that all need to be persisted.Implementations
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
f) already support this feature. - IrisDB client side library: treelike data structure with subscribable nodes.
https://github.com/nostr-protocol/nips/pull/1266
- Relays that support tag-replaceable events and indexing by arbitrary tags (in this case
-
 @ ef53426a:7e988851
2025-05-29 12:26:43
@ ef53426a:7e988851
2025-05-29 12:26:43Saturday 9AM It’s a chilly Saturday morning in Warsaw, and I don’t want to get out of bed. This is not because of the hangover; it’s because I feel like a failure.
The first day of Bitcoin FilmFest was a whirlwind of workshops, panels and running between stages. The pitch competition did not go my way. Another ‘pitching rabbit’ (an actual experienced film-maker) was selected to win the €3,000 of funding.
Rather than get up and search for coffee, I replay the scenes in my head. What could I have done differently? Will investors ever believe in me: I’m just a writer with no contacts in the industry. Do I have what it takes to produce a film?
Eventually, I haul myself out of bed and walk to Amondo, the festival’s morning HQ (and technically, the smallest cinema in Europe). Upon arrival, I find Bitcoin psychonaut Ioni Appelberg holding court in front of around a dozen enraptured disciples. Soon, the conversation spills out to the street to free up space for more workshops.

I attend a talk on film funding, then pay for coffee using bitcoin. I see familiar faces from the two previous nights. We compare notes on Friday night and check the day’s schedule. The morning clouds burn off, and things feel a little brighter.
The afternoon session begins just a few blocks away in the towering Palace of Culture and Science. My role in today's proceedings is to present my freedom fiction project, 21 Futures, on the community stage. Other presentations range from rap videos and advice on finding jobs in bitcoin to hosting ‘Bitcoin Walks’. This is how we are fixing the culture.
Saturday 8PM I feel a tap on my shoulder. ‘Excuse me, Mr. Philip. Your car is waiting. The Producers’ Dinner is starting soon’.
What? Me, a producer? I’ve been taking part in some panels and talks, but I assumed my benefits as a guest were limited to a comped ticket and generous goodie bag.
Soon, I am sharing a taxi with a Dubai-based journalist, a Colombian director, and the cypherpunk sponsor of the pitch competition I didn’t win.
The pierogies I dreamed of earlier that day somehow manifest (happy endings do exist), and we enjoy a raucous dinner including obligatory slivovitz.

Sunday 2AM The last few hours of blur include a bracing city-bike ride in a crew of nine attendees back to the Palace of Culture, chatting with a fellow bitcoin meetup organiser, and vaguely promising to attend a weekend rave with a crew of Polish artists and musicians on the outskirts of London.
I leave the party while it’s still in full swing. In five hours, I have to wake up to complete my Run for Hal in Marshal Edward Rydz-Śmigły Park.
Thursday 9PM The festival kicks off in Samo Centrum on Pizza Day. I arrive in a taxi straight from a cramped flight (fix the airlines!), having not eaten for around ten hours.
The infectious sounds of softly spoken Aussie bitrocker Roger9000 pound into the damp night. I’m three beers in, being presented by the organisers to attendees like a (very tall) show pony. I try to explain more about my books, my publishing connections, my short film.
When I search for the food I ordered an hour ago, I find it has been given away. The stern-faced Polish pizza maker shrugs. ‘You not here.’
I’m so hungry I could cry (six hours of Ryanair can do that to a man). And then, a heroic Czech pleb donates half a pizza to me. Side note: this same heroic pleb accidentally locked me out of my film-funds while trying to fix a wallet bug on Sunday night.
I step out into the rain. Roger9000 reminds us we should have laser eyes well past 100k. I take a bite of pizza and life tastes good.

The Films Side events, artists, late nights, and pitcher’s regret is all well and good, but what of the films?
My highlights included Golden Rabbit winner No More Inflation — a moving narrative with interviews from two dozen economists, visionaries, and inflation survivors.
Hotel Bitcoin, was a surprisingly funny comedy romp about a group of idiots who happen across a valuable laptop.
Revolución Bitcoin — an approachable and thorough documentary aimed to bring greater adoption in the Spanish-speaking world.
And, as a short-fiction guy, I enjoyed the short films The Man Who Wouldn’t Cry, a visit to New York’s only Somali restaurant in Finding Home.

Sunday 7PM The award ceremony has just finished. I head to Amondo for the final time to pay for mojitos in bitcoin and say goodbye to newly made friends. I feel like I’ve met almost everyone in attendance. Are you going to BTC Prague?!? we ask as we part ways.
Of course, the best thing about any festival is the people, and BFF25 had a cast of characters worthy of any art house flick:
- The bright-eyed and confident frontwoman of the metal band Scardust
- A nostr-native artist selling his intricate canvases to the highest zapper
- A dreadlocked DJ who wears a pair of flying goggles on his head at all times
- An affable British filmmaker explaining the virtues of the word ‘chucklesome’
- A Duracell-powered organiser who seems to know every song, person, film, book, and guest at the festival.
Warsaw itself feels like it has a role to play, too. Birdsong and green parks contrast the foreboding Communist-era architecture. The weather changes faster than my mood — heavy greys transform to bright sunshine. The roads around the venue close on Sunday for a political rally. And there we are in the middle, watching our bitcoin films.

Tuesday 10AM I’m at home now, squinting at my email inbox and piles of washing, wondering when the hell I’ll find time. The festival Telegram group is still buzzing with activity. Side events like martial arts tutorials, trips to a shooting range, boat tours. 5AM photos of street graffiti, lost and found items, and people asking ‘is anyone still around?’
This was not just a film festival. BFF is truly a celebration of culture — Art. Books. Comedy. Music. Video. Talk. Connection.
All this pure signal has lifted my spirits so much that despite me being a newbie filmmaker, armed only with a biro, a couple of powerpoints and a Geyser fund page, I know I will succeed in my mission. It turns out you can just film things.
You may have attended bitcoin conferences before — you know, the ones with ‘fireside chats’, VIP areas, and overpriced merch. Bitcoin FilmFest is a moment in time. We are fixing the culture, year after year, until art can flourish again.
As fellow author Aaron Koenig commented during a panel session, ‘In twenty years, we won’t be drawing laser eyes and singing about honey badgers. Our grandchildren won’t understand the change we went through.’
Would I do it all again? Of course!
Join me next June in Warsaw.
I’ll be the tall one presenting his short animation premiere.
Philip Charter is a full-time writer and part-time cat herder. As well as writing for bitcoin founders and companies, he runs the 21 Futures fiction project.
Find out more about theNoderoid Saga animation projecton Geyser.
-
 @ 03612b0e:afd71216
2024-05-12 14:14:47
@ 03612b0e:afd71216
2024-05-12 14:14:47c-lightning-REST with Tailscale on Start9
This guide gives you commands to run additional containers on Start9. This is not officially supported and will break on reboot. You can always run the containers again to restore the setup. The containers are used to provide access, via Tailscale, to Core Lightning's c-lightning-REST plugin
Start9 setup
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
- Services > Core Lightning > Config > Advanced > Plugins > C-Lightning-REST
- SSH to your Start9, see documentation for help: https://docs.start9.com/0.3.5.x/user-manual/ssh
- Access the root account:
sudo -i - Run tailscaled and alpine/socat containers:
podman run -d \ --name=tailscaled.embassy \ -v /dev/net/tun:/dev/net/tun \ -v /var/lib:/var/lib \ -e TS_HOSTNAME=tailscaled \ --network=host \ --cap-add=NET_ADMIN \ --cap-add=NET_RAW \ docker.io/tailscale/tailscale:stablepodman run -d \ --name=socat.embassy \ --publish 4321:1234 \ --network=start9 \ docker.io/alpine/socat \ tcp-listen:1234,fork,reuseaddr tcp:c-lightning.embassy:3001-
Note, if you see errors related to
/root/.docker/config.jsonorUnexpected end of JSON, runecho '{}' > /root/.docker/config.json -
Check the status of tailscaled and log in
``` podman exec tailscaled.embassy tailscale --socket /tmp/tailscaled.sock status
example output
Logged out. Log in at: https://login.tailscale.com/a/1fa8e293dfd108
```
Zeus wallet setup
- On your phone, connect to Tailscale
- On your Start9, copy your REST Macaroon (Hex) for Zeus wallet setup
- Services > Core Lightning > Properties > REST Properties > REST Macaroon (Hex)
- In Zeus wallet, add a new node
- Settings > (tap the active node) > +
Setting | Value ---|--- Node interface | Core Lightning (c-lightning-Rest) Host | tailscaled.YOUR_TAILNET_DOMAIN Macaroon (Hex format) | see last step REST Port | 4321 Certificate Verification | disabled
SAVE NODE CONFIG
- Note, you can find YOUR_TAILNET_DOMAN at https://login.tailscale.com/admin/dns
Enjoy!
- In your Start9 dashboard, make sure you have C-Lightning-REST enabled.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:48:21
@ 21c71bfa:e28fa0f6
2025-05-29 14:48:21Book *Amritsar to Kapurthala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ ae1008d2:a166d760
2024-04-09 13:38:24
@ ae1008d2:a166d760
2024-04-09 13:38:24I just wrote a short StackerNews post, sharing about this platform Highlighter. Maybe we'll get more users to check this out and start creating!
Feel free to take a glance 👉Highlighter.com, Nostr Creator Content Platform
-
 @ 8096ed6b:4901018b
2025-05-29 18:43:15
@ 8096ed6b:4901018b
2025-05-29 18:43:15🎵 Monster In Me by From Ashes to New
🔗 https://song.link/us/i/1439137994
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:56
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:56Book *Amritsar to Delhi cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ da8b7de1:c0164aee
2025-05-29 15:52:45
@ da8b7de1:c0164aee
2025-05-29 15:52:45Bulgária: Először töltenek be Westinghouse-üzemanyagot a Kozloduy-5-be
Először töltöttek be Westinghouse által gyártott nukleáris üzemanyag-kazettákat Bulgária Kozloduy-5 VVER-1000 reaktorába 2025. május 29-én. Ez jelentős lépés Szófia azon törekvésében, hogy csökkentse orosz nukleáris üzemanyag-függőségét, és diverzifikálja energiaforrásait. A lépés része annak a szélesebb stratégiának, amelynek célja az energiaellátás biztonságának növelése és a nyugati partnerekkel való szorosabb együttműködés[NucNet].
Fehér Ház: Nukleáris Telepítési Csúcstalálkozó az USA-ban
A mai napon a Fehér Ház Nukleáris Telepítési Csúcstalálkozót tartott, amelyen kiemelték a köz- és magánszféra eredményeit. Fő témák voltak az orosz urántól való amerikai függőség csökkentése, a nukleáris üzemanyag-ellátási lánc bővítése, valamint a globális nukleáris kapacitás 2050-ig történő megháromszorozásának támogatása. A csúcson szó esett a nagy nukleáris projektek kockázatainak csökkentéséről, új reaktortervezetekről és a meglévő atomerőművek élettartamának meghosszabbításáról is. Az amerikai kormány hangsúlyozta, hogy továbbra is támogatja a fejlett nukleáris demonstrációs projekteket, a munkaerő-fejlesztést, valamint a legújabb törvényhozási lépéseket, például az orosz uránimport tilalmáról szóló törvényt[World Nuclear News].
Törékeny áramellátás a zaporizzsjai atomerőműben, Ukrajna
Az IAEA jelentése szerint az ukrajnai Zaporizzsjai Atomerőmű továbbra is rendkívül sebezhető helyzetben van, mivel jelenleg csak egyetlen külső áramvezetékre támaszkodik a biztonsági rendszerek működtetéséhez. Az utolsó tartalék vezeték három hete le van választva, ami aggodalomra ad okot a hűtő- és biztonsági rendszerek stabilitását illetően. Bár a létesítmény három éve nem termel áramot, folyamatos elektromos ellátásra van szükség a kiégett fűtőelemek hűtéséhez. Az IAEA továbbra is szorosan figyelemmel kíséri a helyzetet, és kiemeli a régióban zajló katonai tevékenységet[IAEA].
USA: SMR-fejlesztések és költségvetési megszorítások
A Tennessee Valley Authority benyújtotta az építési engedélykérelmet egy GE Vernova Hitachi BWRX-300 típusú kis moduláris reaktor (SMR) telepítésére a Clinch River helyszínen, ami jelentős előrelépés az amerikai SMR-programban. Eközben az amerikai kormány 2026-os költségvetési tervezete jelentős csökkentéseket irányoz elő az Energiaügyi Minisztérium nukleáris finanszírozásában, különösen a nem elsődleges kutatási területeken. A fókusz az innovatív reaktorkoncepciókra, fejlett üzemanyagokra és a kulcsfontosságú nemzeti laboratóriumi képességek fenntartására helyeződik[World Nuclear News][World Nuclear News].
Savannah River Site: Előrelépés a plutónium-magházak gyártásában
Az amerikai Energiaügyi Minisztérium Savannah River telephelyén megkezdődött a kesztyűs dobozok gyártása a plutónium magházak előállításához. Ezek a kesztyűs dobozok kulcsfontosságúak a Savannah River Plutonium Processing Facility számára, amely a Nemzeti Nukleáris Biztonsági Igazgatóság célkitűzéseit támogatja, hogy a projektet a 2030-as évek elejéig befejezzék. Ez a lépés az amerikai nukleáris fegyverkezési infrastruktúra modernizációjának része[ANS].
Nemzetközi trendek: ellátási lánc és új reaktorprojektek
A nukleáris ellátási lánc a globális növekedésre készül, ahogy azt a World Nuclear Association legutóbbi konferenciáján is hangsúlyozták. Kiemelt nemzetközi fejlemények:
- Gőzturbina-hengerek telepítése Kína Haiyang 3 erőművében.
- Új, négy reaktoros telephely jóváhagyása Indiában, Rádzsasztánban.
- Belgium és Dánia újragondolja a nukleáris kivonulási politikáját.
- Brazília az oroszokkal való SMR-együttműködést vizsgálja.
- Kanada előrelép a szállítható nukleáris erőmű-technológia terén[World Nuclear News].
Érintetti bevonás és a nukleáris energia szerepe a tiszta átmenetben
Az IAEA konferenciasorozata továbbra is hangsúlyozza az érintetti bevonás fontosságát a nukleáris non-proliferáció, biztonság és a közbizalom szempontjából. A panelek foglalkoznak a közvélemény-tájékoztatás tanulságaival, a nukleáris energia ipari dekarbonizációban betöltött szerepével és az újonnan belépő országok nukleáris infrastruktúra-fejlesztési tapasztalataival is[IAEA].
További részletek a következő forrásokon: - World Nuclear News - NucNet - IAEA - ANS
-
 @ eb0157af:77ab6c55
2025-05-29 12:02:57
@ eb0157af:77ab6c55
2025-05-29 12:02:57Since 2019, the United States has been the country with the highest number of recorded cases, but Europe remains the most affected region.
According to a Binance report, the United States is the country that has recorded the greatest number of crypto-related kidnapping cases since 2019, despite a recent increase in incidents in France.
At the regional level, however, Europe remains the area with the highest number of crypto-related kidnappings: 59 cases over six years. During the same period, North America — which includes the United States and Canada — recorded 48 cases. Particularly notable is the data concerning the entire Asian continent, where 62 cases of crypto-related kidnappings have been documented, most of which are concentrated in Southeast Asian countries.
France emerges as a concerning hotspot for crypto kidnappings, with six recent cases, three of which have already occurred in 2025.

Source: Binance
The primary targets of these kidnappings include executives of crypto companies, professional traders, exchange employees, and entrepreneurs in the sector. Family members and close associates of victims are often targeted as well. An emerging phenomenon involves tourists suspected of possessing large amounts of cryptocurrency funds.
Kidnapping cases in 2025
The year 2025 has already seen particularly serious episodes of kidnappings linked to the digital asset world. The most notable case involved David Balland, co-founder of Ledger, and his wife, who were abducted from their residence in France earlier this January. The incident drew international attention from both the crypto industry and law enforcement agencies.
Another attempt took place in Paris, where armed men tried to kidnap the daughter and granddaughter of the CEO of the French exchange Paymium. Overseas, in New York, police arrested 37-year-old John Woeltz after discovering that an Italian tourist had been held captive and mistreated for weeks in a luxury Manhattan apartment.
Binance highlights a direct correlation between the price trend of Bitcoin and the increase in kidnappings. Since Bitcoin reached new all-time highs this year, attacks involving physical threats have also increased proportionally, the exchange suggests.

Source: Binance
In 2025 alone, at least 15 kidnapping episodes have already been documented, many involving ransom demands denominated in bitcoin.
The post Crypto kidnappings on the rise: the US leads global statistics appeared first on Atlas21.
-
 @ ae1008d2:a166d760
2024-04-04 17:21:52
@ ae1008d2:a166d760
2024-04-04 17:21:52I'm testing this to make sure I can post here on highlighter
-
 @ 1739d937:3e3136ef
2024-03-27 12:25:02
@ 1739d937:3e3136ef
2024-03-27 12:25:02"Gossip", "Outbox", "Inbox", "Blastr", "Small relays vs Big relays". You've probably seen most of these topics come up in conversations and memes recently. You might have even read nostr:nprofile1qqsf03c2gsmx5ef4c9zmxvlew04gdh7u94afnknp33qvv3c94kvwxgsm3u0w6's article (nostr:naddr1qq2hxenh2cchynnpdag4sepkx4gxyj2dt9nk6q3qjlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qxpqqqp65wd3a9ny), or nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w's very technical article (nostr:naddr1qqxnzde3xycngdpjxg6nqdfsqgswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgrqsqqqa28906usv), or maybe even nostr:nprofile1qqsrhuxx8l9ex335q7he0f09aej04zpazpl0ne2cgukyawd24mayt8g2lcy6q's one with the clickbaity title (nostr:naddr1qvzqqqr4gupzqwlsccluhy6xxsr6l9a9uhhxf75g85g8a709tprjcn4e42h053vaqydhwumn8ghj7un9d3shjtnhv4ehgetjde38gcewvdhk6tcprfmhxue69uhhq7tjv9kkjepwve5kzar2v9nzucm0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsqzpcxasnyvpcvsusgpcqx3).
These are all great, and you should go and read them too. But one thing that each of them is guilty of is assuming that the audience has enough context to jump into the middle of a very nuanced and technical discussion. I've yet to see a clear description of what Gossip or Outbox really are and certainly none that are written in a way that is approachable for a non-technical audience. I hope this article can give you that context and serve as a high-level overview of the discussion and the technologies involved so that you can go forth to create better, more informed memes (is there anything more important, really?) and join the discussion in a productive way.
The problems
Centralization is the default
First off, why are we even talking about relays? Most of know that nostr is a protocol which is designed to be decentralized from the ground up. That decentralization is due in large part to the fact that users read and write data to multiple relays by default. So instead of all your data going to a centralized database (usually owned and operated by a single company) with nostr you have the ability to send your data to as as many relays as you'd like (relays are just databases, after all). Likewise, you can read other people's data from as many relays as you'd like to. Decentralized design = decentralized system, right!? Well, turns out, no.
The problem with a design like this is that what can be done and what will be done are often very different things. Imagine the following scenario: You follow 1000 people; 700 of them post their notes to the Primal relay, the other 300 post their notes to the Damus relay. If you don't also write your content to those two relays, the people that you care about won't see your content, they won't see your replies to their notes, they won't even know you exist. So while; in practice, it's easy to read & write to many different relays, users and their content will tend to centralize because it's the path of least resistance to a good user experience. Network effects and economies of scale always apply, they just don't always lead to the outcomes that you want.
Before you start to panic, this sort of centralization isn't a huge issue just yet. We are still a nascent network and there are still hundreds of active relays out there. Almost all nostr clients make relay selection a first class citizen and don't default new users to a single relay. The fact that we're even having this conversation in a serious way at this stage is a great sign that the community cares enough to be proactive about maintaining (and improving) decentralization over time.
That said, this is not a issue that we can take lightly either. The top 5-10 relays do already have an outsized percentage of users and we have many examples of these centralizing tendencies across dozens of protocols and networks over the last 30 years, so the threat is real.
The status quo is wasteful
The other major issue is that currently most nostr clients are extremely wasteful in how they fetch data. The default is to simply get everything from all the relays a user wants to connect to. Because most of us are writing the same data to many relays, this leads to huge amounts of duplicated data being downloaded, having its signatures verified, and then (for the most part) thrown away. For those of us with latest generation smartphones, unlimited data, and a working power outlet nearby, this is fine. For everyone else, this is a major roadblock to adopting nostr.
A lightly technical aside
There are a few important features of nostr that make any sort of intelligent data fetching possible. To understand how any of the potential solutions to the aforementioned problems would actually work, it's important to have a baseline understanding of these technical details. I promise, I'll keep it high level.
Relay lists
Recently the concept of a Relay List Metadata has been introduced to the spec in NIP-65 (there are also other types of relay lists documented in NIP-51). This is a nostr list event where users publish their preferred relays with a marker that says whether the relay is for read-only, write-only, or read & write. This vastly simplifies the process of finding preferred user relays for clients and I imagine that this will become the de facto standard place to look for a user's preferred relays.
NIP-05
The NIP-05 spec also documents a way for users to signal their preferred relays. However, unlike the NIP-65 relay list, this is a simple list of relays without any details on whether the user reads or writes to those relays.
Tag markers
Tag markers are positional elements in tags that give the client publishing the event the ability to leave a hint as to which relay other clients can expect to find a given user or note that is being referenced.
For example, in a user's contact list (a
kind: 3event) you have many"p"tags to reference all the user's that are followed. These tags look like this:{ "kind": 3, "tags": [ ["p", "91cf9..4e5ca", "wss://alicerelay.com/", "alice"], ["p", "14aeb..8dad4", "wss://bobrelay.com/nostr"], ["p", "612ae..e610f"] ], "content": "", ...other fields }All three of these
"p"tags are valid (only the"p"and the user's pubkey are required), in the first and second you can see the third item is a relay where the user's events can be found.These types of tag markers are repeated all throughout nostr. Here's a few more example references for an event (in this case a long-form article):
``` ["e", "b3e392b11f5d4f28321cedd09303a748acfd0487aea5a7450b3481c60b6e4f87", "wss://relay.example.com"],
["a", "30023:a695f6b60119d9521934a691347d9f78e8770b56da16bb255ee286ddf9fda919:ipsum", "wss://relay.nostr.org"] ```
As you can imagine, these hints can be very helpful but only if clients actually attempt to fetch the content from the referenced relay.
The solutions?
Now that you understand the problem space a bit better let's define those terms we started with.
Blastr
Blastr was created by nostr:nprofile1qqs9hejyd252x8q3kw6980ud4lymx3hlx2x3lgg6p7sz58nyv8m2nvgdswkeh and nostr:nprofile1qqswrlemlh2wgqc4jkds3d8ueqj9a2j3gcm7r48v9tskdd6rxsd7rtcpwpuwc from Mutiny and isn't a relay. Instead, Blastr is a proxy (i.e. it looks like a relay to clients) that ingests any event sent to it and, in turn, sends those events to EVERY online relay on the network. It's a mass re-broadcaster for events that can be helpful to get your data pushed out to as many relays (and thus users) as possible. The drawback, of course, is that this is tremendously wasteful from a bandwidth and storage perspective.
Gossip (in 3 flavors)
This is by far the most confusing part for most people when watching the memes of the last few weeks fly by and I've seen a lot of confused takes out there. Most of the confusion stems from the multiplicity of definitions of what the "gossip model" actually is. Let's go through the options. 1. Gossip protocols: This is a general concept more than a specific implementation. Gossip protocols are protocols that attempt to spread information around a network in a uniform way. For example, Bitcoin nodes use a variation of the gossip protocol to make sure that transactions end up in as many mempools as possible. This is important in computing when you want to reach consensus or when all nodes in a network need to have the same information in order to operate the network. Since nostr doesn't have any consensus rules or shared compute, it's somewhat pointless to try and make sure all events are propagated to all relays (hence the limited usefulness of Blastr). 2. The Gossip client from nostr:nprofile1qqswuyd9ml6qcxd92h6pleptfrcqucvvjy39vg4wx7mv9wm8kakyujgua442w : This is a nostr client that was built from the ground up to try and use relays and relay hints in events to the fullest to keep things as decentralized as possible while being efficient in how much data it was fetching. Mike has a great (slightly outdated and very technical) video that talks about his motivation behind building Gossip in the way he did. It's worth a watch. video link 3. Gossip model: This is what people are usually referring to when they are talking about relays on nostr. The Gossip model is a loose, catch-all term used to refer to all the ways in which clients attempt to understand which relays they should read & write to for a given user. Again, this isn't really a specific spec or implementation but encompasses many different strategies. This vagueness inherent in the term makes discussions about the "gossip model" pretty imprecise and prone to misunderstanding.
Don't gossip
To be clear: You really shoud not be thinking about or talking about any of this as the "gossip model" since that definition is so abstract as to be unusable. Which brings us finally to the real topic being discussed at the moment among devs; the Outbox model.
Outbox/Inbox model
This is the real topic of conversation right now: How should client developers build relay discovery and selection features into their apps. As we already talked about, if left alone, it's likely that we'd unintentionally centralize most of nostr onto a few huge relays. So making sure that we encourage (and build sensible defaults) to help client developers to treat relay discovery and selection properly is really critical.
Right now, the discussion centers around one main approach, called the "Outbox model". There is also an "Inbox model" which is a still just a high level idea which I'll mention below but it's not being implemented yet (as of late March 2024). 1. The "Outbox model": This strategy looks at what relays users are using to publish their events (from relay lists and tag markers) and then uses an algorithm to decide how to fetch all the needed events from the array of relays. Different implementations can use different algorithms to select relays. For example, one implementation might optimize fetching events from the smallest number of relays (favoring large relays), while another might optimize for fetching from the relays that have the smallest user overlap (favoring small relays). 2. The "Inbox model": As you can imagine, this strategy flips the outbox model on it's head. It's so far just an idea (proposed by nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq) and a draft NIP but the idea is that when your client posts on your behalf, it will loop over your entire follow list, making a list of the relays that each of your followers uses to read events. Then the client will publish your event to all of those relays. If all clients followed this paradigm, then each of us would only have to read from a single relay. To quote nostr:nprofile1qqs8nsk2uy2w529fs8n4tx60u7z553e4yx5dy2nxhw4elgjgawpqlas9waufq 's original post, "This doesn't take away from the outbox approach, and maybe should even be used together instead of as a replacement. But my point is that clients should be trying harder to deliver posts instead of just fetch posts. Because it benefits users when their posts can be seen."
Why the Outbox model has broad support
To understand why implementing an Outbox model is so powerful at solveing the problems laid out at the beginning of this article, you can do two quick thought experiments:
A user banned from all other relays
Imagine a user who's content is banned from all public relays for some reason. Instead, they have to run their own relay and publish their events there. With a simple "follow the major relays model" (or even with Blastr attempting to copy and paste their events to every other relay) this user is completely invisible to the network. User's would have to know about the banned user's private relay and select that relay in each client they use. What's more, if that relay ever had to change URL (likely for a user that is banned so broadly), all user's would need to know what the new URL is in order to change relays and fetch events from the new location.
With Outbox however, clients will see that their user's follow this user, will then look up this user's relay list, and will know where they need to go to fetch their events. It becomes much more difficult for relays to censor or block users with an Outbox model in place
Duplicate event fetching
We talked earlier about how many nostr clients often fetch the same data many times, just to throw that data away. Even using the simplest algorithms with an Outbox model, you can significantly reduce the amount of duplicate data you're fetching from relays. We, as users, would all also need to specific many fewer relays in our relay lists but would still be quite sure our clients would be able to find all the content we want to see.
Wrapping up
Hopefully this has given you a better overall understanding of what folks are talking about when they refer to Gossip (remember: don't refer to it this way) or Outbox (outbox, yay!) and why we need to be proactive about maintaining the decentralization of nostr.
-
 @ 9ca447d2:fbf5a36d
2025-05-29 12:02:46
@ 9ca447d2:fbf5a36d
2025-05-29 12:02:46Ed Suman, a 67-year-old retired artist who helped create large sculptures like Jeff Koons’ Balloon Dog, reportedly lost his entire life savings — over $2M in digital assets — in a sophisticated scam.
The incident is believed to be tied to the major data breach at Coinbase, one of the world’s largest digital asset exchanges.
Suman’s story is part of a bigger wave of attacks on digital asset holders using stolen personal info, and has triggered lawsuits, regulatory concerns and questions about digital security in the Bitcoin space.
In March 2025, Suman got a text message about suspicious activity on his Coinbase account. After Suman reported he was unaware of any unauthorized activity regarding his account, he got a call from a man who introduced himself as Brett Miller from Coinbase Security.
The guy sounded legit — he knew Suman’s setup, including that he used a Trezor Model One hardware wallet, a device meant to keep bitcoin and other digital assets offline and safe.
Suman told Bloomberg the guy knew everything, including the exact amount of digital assets he had.
The attacker persuaded Suman that his Trezor One hardware wallet and its funds were at risk and walked him through a “security procedure” that involved entering his seed phrase into a website that looked exactly like Coinbase, in order to “link his wallet to Coinbase”.
Nine days later, another guy called and repeated the process, saying the first one didn’t work.
And then, all of Suman’s digital assets — 17.5 bitcoin and 225 ether — were gone. At the time, bitcoin was around $103,000 and ether around $2,500, so the stolen stash was worth over $2 million.
Suman turned to digital assets after retiring from a decades-long art career. He stored his assets in cold storage to avoid the risks of online exchanges. He thought he did everything right.
Suman’s attackers didn’t pick his name out of a hat.
It looks like his personal info may have been leaked in the major breach at Coinbase. The company confirmed on May 15 that some of its customer service reps in India were bribed to access internal systems and steal customer data.
The stolen data included names, phone numbers, email addresses, balances and partial Social Security numbers.
According to Coinbase’s filing with the U.S. Securities and Exchange Commission, the breach may have started as early as January and affected nearly 1% of the company’s active monthly users — tens of thousands of people.
Hackers demanded $20M from Coinbase to keep the breach quiet but the company refused to pay. Coinbase says it fired the compromised agents and is setting aside $180M to $400M to reimburse affected users.
But so far, Suman hasn’t been told if he’ll be reimbursed.
Since the breach was disclosed, Coinbase has been hit with at least six lawsuits.
The lawsuits claim the company failed to protect user data and handled the aftermath poorly. One lawsuit filed in New York federal court on May 16 says Coinbase’s response was “inadequate, fragmented, and delayed.”
“Users were not promptly or fully informed of the compromise,” the complaint states, “and Coinbase did not immediately take meaningful steps to mitigate further harm.”
Some lawsuits are seeking damages, others are asking Coinbase to purge user data and improve its security. Coinbase has not commented on the lawsuits but pointed reporters to a blog post about its response.
Suman’s case is a cautionary tale across the Bitcoin world. He used a hardware wallet (considered the gold standard of Bitcoin security) and was still tricked through social engineering. Even the strongest security is useless if you don’t understand how Bitcoin works.
It’s never too early for Bitcoiners to start learning more about Bitcoin, especially on how to keep their stash safe. And the first lesson is “never ever share your seed phrase with anyone”.
Related: Bitcoin Hardware Wallet Hacks: What You Need to Know
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:33
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:33Book *Amritsar to Chandigarh cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ fa0165a0:03397073
2023-10-12 16:40:43
@ fa0165a0:03397073
2023-10-12 16:40:43Probability theory is the study of random phenomena. This post is a pilot post for potentially further posting in this series. Feedback appreciated. Introduction
Probability theory is the study of random phenomena. It is used in many fields, such as statistics, machine learning, and finance. It is also used in everyday life, for example when playing games of chance, or when estimating the risk of an event. The most classic example is the coin toss, closely followed by the dice roll.
When we toss a coin, the result is either heads or tails. In the case of an ideal coin, the “random trail” of tossing the coin has an equal probability for both outcomes. Similarly, for a die roll of a fair dice, we know that the probability for each outcome is 1/6. In the study of probability we dive deep into the mathematics of these random phenomena, how to model them, and how to calculate the probability of different events. To do this in precise terms, we define words and concepts as tools for discussing and communicating about the subject.
This is the first of what I expect to be a 15 part series of my lecture & study notes from my university course in probability theory MT3001 at Stockholm University. References to definitions and theorems will use their numeration in the course literature, even if I may rephrase them myself. The book I’ve had as a companion through this course is a Swedish book called Stokastik by Sven Erick Alm and Tom Britton; ISBN:978–91–47–05351–3. This first module concerns basic concepts and definitions, needed for the rest of the course. The language of Probability theory
An experiment is a process that produces a randomized result. If our experiment is throwing a die, we then have the following: The result of throwing the die is called an outcome, the set of all possible outcomes is called the sample space and a subset of the sample space is called an event. We will use the following notation:
outcome is the result of an experiment, denoted with a small letter, ex. 𝑢₁, 𝑢₂, 𝑢₃, … event is the subset of the sample space, denoted with a capital letter, ex. 𝐴, 𝐵, 𝐶, … sample space is the set of all possible outcomes of an experiment, denoted Ω.Adding numbers to our dice example, we have the sample space Ω = {𝟏,𝟐,𝟑,𝟒,𝟓,𝟔} containing all the possible events 𝑢₁=𝟏, 𝑢₂=𝟐, 𝑢₃=𝟑, 𝑢₄=𝟒, 𝑢₅=𝟓 and 𝑢₆=𝟔. And we could study some specific sub events like the chance of getting an even number, 𝐴={𝟐,𝟒,𝟔}, or the chance of getting a prime number, 𝐵={𝟐,𝟑,𝟓}. As it happens, the probability of both 𝐴 and 𝐵 is 50%. Sample space
The sample space is the set of all possible outcomes of an experiment. It is denoted Ω. And there are two types of sample spaces, discrete and continuous. A discrete sample space is a finite or countably infinite set, and all other kind of sample spaces are called continuous.
The coin toss and the dice roll are both examples of discrete sample spaces. Studying a problem, like the temperature outside, would in reality require a continuous sample space. But in practice, we can often approximate a continuous sample space with a discrete one. For example, we could divide the temperature into 10 degree intervals, and then we would have a discrete sample space.
Remember that continuous sample spaces exist, and expect more information about them in later modules. For starters, we focus on discrete sample spaces. Set Theory notation and operations
When talking about probabilities we will arm ourselves with the language of “set theory”, it is a crucial tool for the study of probability. Feeling comfortable with the subject of set theory since before is useful, but not necessary. I will try to explain the concepts as we go along.
Even tough the events from the dice rolls are represented by numbers, it is important to note that they aren’t numbers, but rather elements. This might become more clear if we alter our example to be a deck of cards. This deck of cards have four suits Ω = {♥, ♠, ♦, ♣ } and in our experiments we draw a card from the deck and look at the suit. It’s here very obvious that we can’t add or subtract the different events with each other. But we do have the operations of set theory at our disposal. For example, if 𝐴 is the event of drawing a red card and 𝐵 is the event of drawing spades ♠, we can use the following notation: Set theory operations
Union: 𝐴 ∪ 𝐵 = {♥, ♦, ♠}, the union of 𝐴 and 𝐵. The empty set: ∅ = {}, the empty set. A set with no elements. Intersection: 𝐴 ∩ 𝐵 = ∅, the intersection of 𝐴 and 𝐵. This means that 𝐴 and 𝐵 have no elements in common. And we say that 𝐴 and 𝐵 are disjoint. Complement: 𝐴ᶜ = {♠, ♣}, the complement of 𝐴. Difference: 𝐴 ∖ 𝐵 = {♥, ♦}, the difference of 𝐴 and 𝐵. Equivalent to 𝐴 ∩ 𝐵ᶜ. The symbol ∈ denotes that an element is in a set. For example, 𝑢₁ ∈ Ω means that the outcome 𝑢₁ is in the sample space Ω. For our example: ♥ ∈ 𝐴 means that the suit ♥ is in the event 𝐴.Venn diagram
A very useful visualization of set theory is the Venn diagram. Here is an example of a Venn diagram in the picture below:
In the above illustration we have: Ω = {𝟏,𝟐,𝟑,𝟒} and the two events 𝐴={𝟐,𝟑} and 𝐵={𝟑,𝟒}. Notice how the two sets 𝐴 and 𝐵 share the element 𝟑, and that all sets are subsets of the sample space Ω. The notation for the shared element 𝟑 is 𝐴 ∩ 𝐵 = {𝟑}. Useful phrasing
The different set notations may seem a bit abstract at first, at least before you are comfortable with them. Something that might be useful to do is to read them with the context of probabilities in mind. Doing this, we can read some of the different set notations as follows:
𝐴ᶜ, “when 𝐴 doesn’t happen”. 𝐴 ∪ 𝐵, “when at least one of 𝐴 or 𝐵 happens”. 𝐴 ∩ 𝐵, “when both 𝐴 and 𝐵 happens”. 𝐴 ∩ 𝐵ᶜ, “when 𝐴 happens but 𝐵 doesn’t happen”.The Probability function
Functions map elements from one set to another. In probability theory, we are interested in mapping events to their corresponding probabilities. We do this using what we call a probability function. This function is usually denoted 𝑃 and have some requirements that we will go through in the definition below.
This function take events as input and outputs the probability of that event. For the example of a die throw, if we have the event 𝐴={𝟐,𝟒,𝟔}, then 𝑃(𝐴) is the probability of getting an even number when throwing a fair six sided dice. In this case 𝑃(𝐴)=1/2=𝑃(“even number from a dice throw”), you’ll notice that variations of descriptions of the same event can be used interchangeably.
The Russian mathematician Andrey Kolmogorov (1903–1987) is considered the father of modern probability theory. He formulated the following three axioms for probability theory: Definition 2.2, Kolmogorov’s axioms
A real-valued function 𝑃 defined on a sample space Ω is called a probability function if it satisfies the following three axioms: 𝑃(𝐴) ≥ 𝟎 for all events 𝐴. 𝑃(Ω) = 𝟏. If 𝐴₁, 𝐴₂, 𝐴₃, … are disjoint events, then 𝑃(𝐴₁ ∪ 𝐴₂ ∪ 𝐴₃ ∪ …) = 𝑃(𝐴₁) + 𝑃(𝐴₂) + 𝑃(𝐴₃) + …. This is called the countable additivity axiom.From these axioms it’s implied that 𝑃(𝐴) ∈ [𝟎,𝟏], which makes sense since things aren’t less than impossible or more than certain. As a rule of thumb, when talking about probabilities, we move within the range of 0 and 1. This lets us formulate the following theorem: Theorem 2.1, The Complement and Addition Theorem of probability
Let 𝐴 and 𝐵 be two events in a sample space Ω. Then the following statements are true: 1. 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴) 2. 𝑃(∅) = 𝟎 3. 𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)Proof of Theorem 2.1
𝑃(𝐴 ∪ 𝐴ᶜ) = 𝑃(Ω) = 𝟏 = 𝑃(𝐴) + 𝑃(𝐴ᶜ) ⇒ 𝑃(𝐴ᶜ) = 𝟏 — 𝑃(𝐴)
This simply proves that the probability of 𝐴 not happening is the same as the probability of 𝐴 happening subtracted from 1.
𝑃(∅) = 𝑃(Ωᶜ) = 𝟏 — 𝑃(Ω) = 𝟏 — 𝟏 = 𝟎
Even though our formal proof required (1) to be proven, it’s also very intuitive that the probability of the empty set is 0. Since the empty set is the set of all elements that are not in the sample space, and the probability of an event outside the sample space is 0.
𝑃(𝐴 ∪ 𝐵) = 𝑃(𝐴 ∪ (𝐵 ∩ 𝐴ᶜ)) = 𝑃(𝐴) + 𝑃(𝐵 ∩ 𝐴ᶜ) = 𝑃(𝐴) + 𝑃(𝐵) — 𝑃(𝐴 ∩ 𝐵)
This can be understood visually by revisiting our Venn diagram. We see that the union of 𝐴 and 𝐵 has an overlapping element 𝟑 shared between them. This means that purely adding the elements of 𝐴={𝟐,𝟑} together with 𝐵={𝟑,𝟒} would double count that shared element, like this {𝟐,𝟑,𝟑,𝟒}, since we have two “copies” of the mutual elements we make sure to remove one “copy” bur removing 𝑃(𝐴 ∩ 𝐵)={𝟑} and we get 𝑃(𝐴 ∪ 𝐵)={𝟐,𝟑,𝟒}. We may refer to this process as dealing with double counting, something that is very important to have in mind when dealing with sets.
Two interpretations of probability that are useful and often used are the frequentist and the subjectivist interpretations. The frequentist interpretation is that the probability of an event is the relative frequency of that event in the long run. The subjectivist interpretation is that the probability of an event is the degree of belief that the event will occur, this is very common in the field of statistics and gambling. For the purposes of study it’s also useful to sometimes consider probabilities as areas and or masses, this is called the measure theoretic interpretation. Don’t let that word scare you off, in our context it’s just a fancy way of drawing a parallel between areas and probabilities. Think area under curves, and you’ll be fine.
-
 @ 7e538978:a5987ab6
2025-05-29 10:32:34
@ 7e538978:a5987ab6
2025-05-29 10:32:34This article gives an overview and comparison of the various funding sources that are available for LNbits.
LNbits is compatible with many Lightning Network wallets and can be on anything from a small VPS to a raspberry Pi on your home network or the LNbits SaaS platform.
Why your funding source matters
There are trade-offs between the various funding sources, for example funding LNbits using Strike requires the user to KYC themselves and has some privacy compromises versus funding LNbits from your own LND node. However the technical barrier to entry and node maintenance of using Strike is lower than using LND.
Self-custodial vs custodial connectors
Self-custodial Funding Sources
You run the node or service, keep the keys, and may need to manage LN channels. Good if you want control and have the skills to look after a server. Examples: LND (gRPC/REST), CoreLightning, Spark.
Self-custodial funding sources with an LSP
These funding sources offer a reasonable compromise between self-custody and some privacy trade offs. Examples: Phoenixd, Breez SDK, Boltz.
Custodial (or semi-custodial) funding sources
A third party runs the node. You plug LNbits into their API. Setup is quick and costs are low, but you trust the provider with your funds and privacy. Examples: Alby, OpenNode, Blink, ZBD, LNPay or another LNbits instance.
Funding sources compared
Below is a summary of the main options and how they stack up.
LNbits Lightning Network Funding Sources Comparison Table
| Funding Source | Custodial Type | KYC Required | Technical Knowledge Needed | Node Hosting Required | Privacy Level | Liquidity Management | Ease of Setup | Maintenance Effort | Cost Implications | Scalability | Notes | |----------------------------|--------------------|---------------------|--------------------------------|---------------------------|-------------------|--------------------------|-------------------|------------------------|----------------------------------------------|-----------------|------------------------------------------------------------------| | LND (gRPC) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | gRPC interface for LND; suitable for advanced integrations. | | CoreLightning (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Requires setting up and managing your own CLN node. | | Phoenixd | Self-custodial | ❌ | Medium | ❌ | Medium | Automatic | Moderate | Low | Minimal fees | Medium | Mobile wallet backend; suitable for mobile integrations. | | Nostr Wallet Connect (NWC) | Custodial | Depends on provider | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur fees | Medium | Connects via Nostr protocol; depends on provider's policies. | | Boltz | Self-custodial | ❌ | Medium | ❌ | Medium | Provider-managed | Moderate | Moderate | Minimal fees | Medium | Uses submarine swaps; connects to Boltz client. | | LND (REST) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for LND; suitable for web integrations. | | CoreLightning REST | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | REST interface for CLN; suitable for web integrations. | | LNbits (another instance) | Custodial | Depends on host | Low | ❌ | Variable | Provider-managed | Easy | Low | May incur hosting fees | Medium | Connects to another LNbits instance; depends on host's policies. | | Alby | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Browser extension wallet; suitable for web users. | | Breez SDK | Self-custodial | ❌ | Medium | ❌ | High | Automatic | Moderate | Low | Minimal fees | Medium | SDK for integrating Breez wallet functionalities. | | OpenNode | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for merchants. | | Blink | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; focuses on mobile integrations. | | ZBD | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Gaming-focused payment platform. | | Spark (CLN) | Self-custodial | ❌ | Higher | ✅ | High | Manual | Moderate | High | Infrastructure cost and channel opening fees | High | Web interface for CLN; requires Spark server setup. | | Cliche Wallet | Self-custodial | ❌ | Medium | ❌ | Medium | Manual | Moderate | Moderate | Minimal fees | Medium | Lightweight wallet; suitable for embedded systems. | | Strike | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. | | LNPay | Custodial | ✅ | Low | ❌ | Low | Provider-managed | Easy | Low | Transaction fees apply | Medium | Third-party service; suitable for quick setups. |
Which source suits you?
| Scenario | Good fit | Why | | ------------------------------------------- | ---------------------------------------------------------------------- | ------------------------------------------------------ | | Business running its own infrastructure | LND or CoreLightning on a Dell Optiplex or other dedicated machine | Full control, high throughput, best privacy. | | Independent node runner | Spark (CLN) or LND (REST/gRPC) | You already run a node and want a clean web interface. | | Quick proof of concept | Alby, LNPay, or another hosted LNbits | No hardware needed, lets you test ideas fast. |
Run LNbits
Ready to run LNbits?
Choose a funding source, follow the guides, and start today.
Further reading
- LNbits documentation
- LND – gRPC and REST guides
- CoreLightning – setup and Spark info
- Breez SDK
- Phoenixd
- Nostr Wallet Connect
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:47:08
@ 21c71bfa:e28fa0f6
2025-05-29 14:47:08Book *Cuttack to Puri cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ fa0165a0:03397073
2023-10-06 19:25:08
@ fa0165a0:03397073
2023-10-06 19:25:08I just tested building a browser plugin, it was easier than I thought. Here I'll walk you through the steps of creating a minimal working example of a browser plugin, a.k.a. the "Hello World" of browser plugins.
First of all there are two main browser platforms out there, Chromium and Mozilla. They do some things a little differently, but similar enough that we can build a plugin that works on both. This plugin will work in both, I'll describe the firefox version, but the chromium version is very similar.
What is a browser plugin?
Simply put, a browser plugin is a program that runs in the browser. It can do things like modify the content of a webpage, or add new functionality to the browser. It's a way to extend the browser with custom functionality. Common examples are ad blockers, password managers, and video downloaders.
In technical terms, they are plugins that can insert html-css-js into your browser experience.
How to build a browser plugin
Step 0: Basics
You'll need a computer, a text editor and a browser. For testing and development I personally think that the firefox developer edition is the easiest to work with. But any Chrome based browser will also do.
Create a working directory on your computer, name it anything you like. I'll call mine
hello-world-browser-plugin. Open the directory and create a file calledmanifest.json. This is the most important file of your plugin, and it must be named exactly right.Step 1: manifest.json
After creation open your file
manifest.jsonin your text editor and paste the following code:json { "manifest_version": 3, "name": "Hello World", "version": "1.0", "description": "A simple 'Hello World' browser extension", "content_scripts": [ { "matches": ["<all_urls>"], "js": ["hello.js"] //The name of your script file. // "css": ["hello.css"] //The name of your css file. } ] }If you wonder what the
jsonfile format is, it's a normal text file with a special syntax such that a computer can easily read it. It's thejsonsyntax you see in the code above. Let's go through what's being said here. (If you are not interested, just skip to the next step after pasting this we are done here.)manifest_version: This is the version of the manifest file format. It's currently at version 3, and it's the latest version. It's important that you set this to 3, otherwise your plugin won't work.name: This is the name of your plugin. It can be anything you like.version: This is the version of your plugin. It can be anything you like.description: This is the description of your plugin. It can be anything you like.content_scripts: This is where you define what your plugin does. It's a list of scripts that will be executed when the browser loads a webpage. In this case we have one script, calledhello.js. It's the script that we'll create in the next step.matches: This is a list of urls that the script will be executed on. In this case we have<all_urls>, which means that the script will be executed on all urls. You can also specify a specific url, likehttps://brave.com/*, which means that the script will only be executed on urls that start withhttps://brave.com/.js: This is a list of javascript files that will be executed. In this case we have one file, calledhello.js. It's the script that we'll create in the next step.css: This is where you can add a list of css files that will be executed. In this case we have none, but you can add css files here if you want to.//: Text following these two characters are comments. They are ignored by the computer, You can add comments anywhere you like, and they are a good way to document your code.
Step 2: hello.js
Now it's time to create another file in your project folder. This time we'll call it
hello.js. When created, open it in your text editor and paste the following code:js console.log("Hello World!");That's javascript code, and it's what will be executed when you run your plugin. It's a simpleconsole.logstatement, which will print the text "Hello World!" to the console. The console is a place where the browser prints out messages, and it's a good place to start when debugging your plugin.Step 3: Load and launch your plugin
Firefox
Now it's time to load your plugin into your browser. Open your browser and go to the url
about:debugging#/runtime/this-firefox. You should see a page that looks something like this:
Click the button that says "Load Temporary Add-on...". A file dialog will open, navigate to your project folder and select the file
manifest.json. Your plugin should now be loaded and running.Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
Chrome
Open your browser and go to the url
chrome://extensions/. Click the button that says "Load unpacked". A file dialog will open, navigate to your project folder and select the folderhello-world-browser-plugin. Your plugin should now be loaded and running.Note the difference, of selecting the file
manifest.jsonin firefox, and selecting the folderhello-world-browser-pluginin chrome. Otherwise, the process is the same. So I'll repeat the same text as above: (for those who skipped ahead..)Go to a website, any website, and open the inspector then navigate to the console. You'll find the inspector by right-clicking anywhere within the webpage, and click "Inspector" in the drop-down menu. When opening the console you might see some log messages from the site you visited and... you should see the text "Hello World!" printed there, from our little plugin! Congratulations!
As you can see this isn't as complicated as one might think. Having preformed a "Hello-World!"-project is a very useful and valuable first step. These setup steps are the basics for any browser plugin, and you can build on this to create more advanced plugins.
-
 @ 78733875:4eb851f2
2023-08-17 14:23:51
@ 78733875:4eb851f2
2023-08-17 14:23:51After announcing our first wave of grants for bitcoin[^fn-btc] and nostr[^fn-nostr] projects, we are pleased to announce an additional wave of grants for open-source projects in the space:
[^fn-btc]: First Wave of Bitcoin Grants [^fn-nostr]: First Wave of Nostr Grants
- BDK
- LNbits
- Watchdescriptor
- Stratum V2 Testing \& Benchmarking Tool
- Fedimint Modules and Resources
- Amber: Nostr Event Signer
- Nostr UI/UX Development
- Nostr Use-Case Exploration \& Education
The first five grants are sourced from our General Fund, the last three—being nostr projects—from our Nostr Fund. This brings the total number of OpenSats grants to 41, adding to the grants we previously announced in July.
Once again, let's take a closer look at each of the projects to see how they align with the OpenSats mission.
BDK
Bitcoin Development Kit (BDK) is a set of libraries and tools that allows you to seamlessly build cross-platform on-chain bitcoin wallets without having to re-implement standard bitcoin data structures, algorithms, and protocols. BDK is built on top of the powerful rust-bitcoin and rust-miniscript libraries and adds features for managing descriptor-based wallets, syncing wallets to the bitcoin blockchain, viewing transaction histories, managing and selecting UTXOs to create new transactions, signing, and more. The core BDK components are written in Rust, but the team also maintains Kotlin and Swift language bindings for use in mobile projects. There are also Python bindings, and React Native and Flutter support is being actively developed.
Repository: bitcoindevkit/bdk
License: Apache 2.0 / MITLNbits
LNbits is used by a multitude of projects in the bitcoin space, especially as part of their lightning payments stack. Being easy to build on through its extension framework, LNbits has been pioneering various cutting-edge solutions and experiments in the world of bitcoin, lightning, and nostr.
The project has a thriving maker community building various hardware devices such as Lightning ATMs, point-of-sale devices, DIY hardware wallets, and nostr signing devices. The modular design of LNbits makes it attractive to users and tinkerers alike, as its plugin architecture makes it easy to extend and understand.
Repository: lnbits/lnbits
License: MITWatchdescriptor
watchdescriptoris a CLN plugin written in Rust that connects a business's treasury wallet to its CLN node. It utilizescln-pluginand the BDK library to track coin movements in registered wallets and report this information to thebookkeeperplugin.The plugin enables businesses to design a complete treasury using Miniscript and import the resulting descriptor into CLN. Since
bookkeeperalready accounts for all coin movements internal to CLN, this plugin is the last piece businesses need in order to unify all their bitcoin accounting in one place. This enables businesses to account for all inflows and outflows from their operations, streamlining tax reporting and financial analysis.The
watchdescriptorproject is part of a broader vision to transform the lightning node (particularly CLN) into a financial hub for businesses, enabling them to conduct operations without reliance on any third parties.Repository: chrisguida/watchdescriptor
License: MITStratum V2 Testing & Benchmarking Tool
The Stratum V2 Testing & Benchmarking Tool allows the bitcoin mining industry to test and benchmark Stratum V2 performance against Stratum V1. The tool supports different mining scenarios to help miners make informed decisions and evaluate their profitability. The goal of the project is to motivate miners to upgrade to Stratum V2, increasing their individual profits and making the Bitcoin network more resilient in the process.
Repository: stratum-mining/stratum @GitGab19
License: Apache 2.0 / MITFedimint Modules and Resources
Fedimint is a federated Chaumian e-cash mint backed by sats with deposits and withdrawals that can occur on-chain or via lightning. It can be understood as a scaling and privacy layer as well as an adoption accelerator for Bitcoin.
The goal of this particular project is to improve the Fedimint UI and develop free and open resources for developers and "Guardians" to enable more people to run and develop on Fedimint.
Repository: fedimint/ui @EthnTuttle
License: MITAmber: Nostr Event Signer
Amber is a nostr event signer for Android. It allows users to keep their
nsecsegregated in a single, dedicated app. The goal of Amber is to have your smartphone act as a NIP-46 signing device without any need for servers or additional hardware. "Private keys should be exposed to as few systems as possible as each system adds to the attack surface," as the rationale of said NIP states. In addition to native apps, Amber aims to support all current nostr web applications without requiring any extensions or web servers.Repository: greenart7c3/Amber
License: MITNostr UI/UX Development
The goal of this project is to help improve the UI/UX of major nostr clients, starting with Gossip and Coracle, emphasizing the onboarding process as well as usability and accessibility. One part of onboarding is solving the discoverability problem that nostr has in the first place. Solving the problem of jumping in and out of the nostr world is what motivated the development of
njump, which was redesigned as part of these efforts and is now live at nostr.com.In addition to client-specific improvements, generic design modules and learnings will be incorporated into the Nostr Design project for others to use.
Activity: github.com/dtonon @dtonon
License: MITNostr Use-Case Exploration & Education
As of today, most nostr clients implement social media applications on top of the nostr protocol. However, nostr allows for various use cases, many of which go beyond social media. Two examples are Listr and Ostrich, a list management tool and job board, respectively.
In addition to use-case exploration, this project will continue to educate users and developers alike, be it via Nostr How or various video series, e.g., explaining how to build upon NDK.
Activity: github.com/erskingardner @jeffg
License: MIT / GPL-3.0 / CC BY-NC-SA 4.0
We have more grants in the pipeline and will provide funding for many more projects in the future. Note that we can only fund those projects which reach out and apply. If you are an open-source developer who is aligned with our mission, don't hesitate to apply for funding.







