-
 @ 3eba5ef4:751f23ae
2025-05-30 01:52:38
@ 3eba5ef4:751f23ae
2025-05-30 01:52:38Crypto Insights
No Blind Trust : A New Proposal for Manually Creating Mnemonics
Eric Kvam proposed an improved method for generating and recovering seed phrase mnemonics. The goal is to allow users to create seed phrases manually and securely, eliminating reliance on a black box. It also allows for encoding derivation path in the mnemonics to simplify recovery.
Facing Spam: Are P2P Networks Fundamentally at a Disadvantage?
The author argues that P2P permissionless networks like Bitcoin and Nostr face a structural disadvantage in dealing with spam. In broadcast-style networks, spammers are often more motivated than regular users making P2P value transfers. Simply increasing the cost per action is not enough to deter spam, as the value gained by spammers far exceeds that of regular users. In contrast, mainstream internet spam control relies on identifying users and punishing bad behavior, but this goes against Bitcoin’s principles of decentralization and privacy. The author worries that without an effective solution, genuine users may eventually be pushed out while spammers persist.
Bitcointap: Real-Time Data Extraction from Bitcoin Core Tracepoints
Jb55 released Bitcointap — a Rust library and CLI tool that leverages Bitcoin Core’s EBPF-USDT tracepoints to extract data in real time, inspired by @0xB10C’s peer_observer project.
- Bitcointap GitHub Repo, and Demo Video
Tradeoffs Between Performance and Privacy in the Lightning Network
The Lightning developer community recently discussed the privacy impact of surfacing granular HTLC hold times via attributable failures. Carla followed up with further reflections, exploring how forwarding delays impact payment privacy. She also pointed out that no privacy-preserving forwarding delay mechanism is currently deployed in the Lightning Network.
Parasite Pool: A New Open Source Pool for Pleb Bitcoin Mining
Ordinal Maxi Biz founder ZK Shark has launched Parasite Pool, an open-source Bitcoin mining pool aimed at pleb miners who want to contribute to Bitcoin decentralization. It supports Lightning Network payouts, has a low entry threshold of just 10 sats, and allows individuals to earn directly and instantly. Its “Plebs Eat First” reward structure gives 1 BTC to the block finder, while the remaining 2.125 BTC and transaction fees are distributed via Lightning to pooled workers, making it especially attractive to plebs. Parasite Pool’s current hashrate is only 5 PH/s, representing just 0.000006% of the Bitcoin network—projected to take over 3 years to mine a block at current rates.
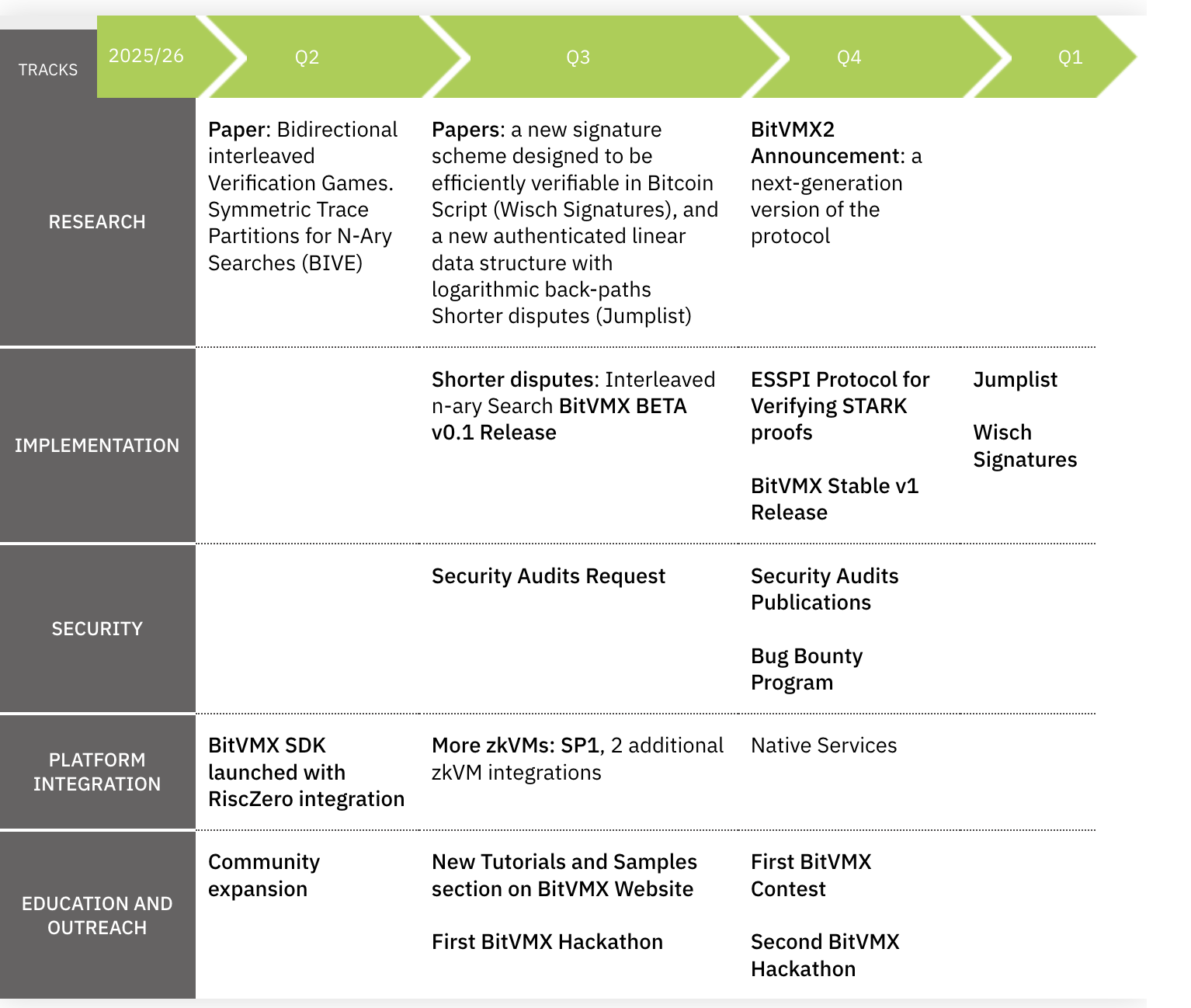
BitVMX Unveils 2025 Roadmap
BitVMX released its roadmap for 2025, outlining five core tracks: Research, Implementation, Security, Platform Integration, and Education & Outreach.

Top Reads on Blockchain and Beyond
The Cathedral and the Bazaar in the Age of AI Agents: Crypto’s Role in Low-Trust Environments
Borrowing the metaphor of "The Cathedral and the Bazaar," the author suggests that the network architecture of the AI agent era resembles a Linux-style open bazaar. In this model, countless untrusted agents with development capabilities provide services to one another through inter-agent calls, forming a loosely coordinated network. This low-trust environment is where cryptographic technologies shine—enabling value exchange without requiring trust. As such, crypto becomes a foundational component of this new AI-powered bazaar.
A Look Back at the 2015 Bitcoin Spam Attacks: Consensus Shifts and Today’s OP_Return Debate
BitMex’s article recounts four waves of spam attacks on Bitcoin in the summer of 2015, launched by a London-based company CoinWallet.EU. These spam floods severely degraded the user experience for Bitcoin payments, especially during the third wave from July 7 to July 11, 2015. The attacks sparked debate around miner filtering of spam transactions and block size limits. BitMex argues these events played a critical role in shaping views on spam mitigation and echo today’s debates over the OP_Return relay limit.
5-Step Survival Guide for Personal Data Breaches
a16z’s guide outlines immediate and long-term responses after a personal data breach:
1. Act Immediately
-
Freeze your credit to prevent identity theft.
-
Strengthen multi-factor authentication (MFA): Prefer app-based or hardware key methods over SMS. Enable SIM protection with your telecom provider.
-
Replace compromised IDs: Contact relevant authorities.
2. Strengthen Online Account Security
-
For Apple and Google accounts, enable advanced protections (e.g., Google Advanced Protection, Passkeys, YubiKey).
-
Use a password manager; consider offline tools like KeePass, or services like Bitwarden and 1Password.
3. Secure Your Phone
-
iPhone users: Set a strong alphanumeric password, enable Find My iPhone, activate Stolen Device Protection, and require Face ID for sensitive apps.
-
Android users: Use a strong password or biometrics, enable Find My Device, activate theft detection lock and identity checks.
4. Defend Against Social Engineering
- Watch for phishing scams, suspicious login notifications, or fake calls/texts pretending to be from financial institutions.
5. Monitor Your Social Media Accounts
- Regularly check account access. If locked out, contact support immediately.
-
 @ 3eba5ef4:751f23ae
2025-05-30 01:45:18
@ 3eba5ef4:751f23ae
2025-05-30 01:45:18加密洞见
无需盲信系统:手动创建助记词的新提案
开发者 Eric Kvam 提出了一种改进助记词生成和恢复流程的方法,目的是让用户能够手动、安全地生成种子短语助记词,从不必信任「黑盒」,并在助记词中编码派生路径以简化恢复过程。
应对垃圾信息,P2P 网络存在固有劣势?
作者认为,比特币和 Nostr 等类似 P2P 无许可网络在应对垃圾信息问题上存在固有劣势。由于广播式网络的特性,垃圾信息发送者在动机上远强于正常点对点价值传递的用户,仅通过提高每笔操作的成本难以有效遏制垃圾信息,因为垃圾发送者从中获得的价值远高于普通用户。相比之下,互联网主流是通过识别用户身份、并对不良行为实施惩罚的方式来治理垃圾信息,但这种方式违背了比特币的去中心化和隐私保护原则,并导致了严重的隐私侵犯。作者担心,如果不能有效解决垃圾信息问题,比特币等网络的正常用户可能会被迫离开,而垃圾发送者仍会留下。
Bitcointap:利用比特币核心跟踪点,实时提取数据
开发者 jb55 推出 bitcointap——一个 Rust 库和 CLI 工具。它利用 Bitcoin-Core 的 EBPF-USDT 跟踪点,实现数据的实时提取。Bitcointap 的开发受到 @0xB10C 的 peer_observer 项目的启发。
- Bitcointap 的 GitHub Repo,以及 Demo Video
闪电网络中性能和隐私间的权衡
闪电网络开发者社区最近讨论到 Pivacy impact of surfacing granular HTLC hold times via attributable failures 这一问题。Carla 对此进行了后续思考,进一步研究了转发延迟(forwarding delays)机制对付款隐私的影响。她也指出,现在的闪电网络中并没有部署任何转发延迟的隐私保护。
面向草根挖矿的新开源矿池 Parasite Pool
Ordinal Maxi Biz 创始人 ZK Shark 推出开源比特币矿池 Parasite Pool,专为希望为比特币去中心化做出贡献的家庭矿工而建。支持闪电网络支付,门槛低至 10 聪,允许个人直接即时赚钱。它有一个「平民先吃」(Plebs Eat First)的奖励结构,将 1 BTC 奖励给找到区块的人,并将剩余的 2.125 BTC 加上手续费通过闪电支付分配给其余非获胜参与者。小规模矿工由此可以获得相对于其哈希算力的巨额奖励,这让 Parasite Pool 对他们而言特别具有吸引力。目前 Parasite Pool 指向矿池的哈希率只有 5 PH/s,只占整个比特币网络的 0.000006%,预计可能需要 3 年多才能到达一个区块。
BitVMX 公布 2025 路线图
BitVMX 公布了 2025 年路线图,呈现了在研究、实施、安全、平台集成以及教育和对外扩展五条核心轨道上的计划:
精彩无限,不止于链
AI 代理时代的大教堂与集市,加密技术在低信任场景中的未来
作者借用经典的「大教堂与集市」比喻,认为 AI 代理时代的网络形态是一个 Linux 式的开放集市——这里会有大量具有独立开发能力的自动代理人,通过相互调用,为彼此提供服务,由此形成松散的协作网络。这样一个低信任的场景,正是加密技术最擅长的环境———在无需信任的环境中交换价值,因此加密货币将成为 AI 代理人集市中不可或缺的基础要素。
回顾 2015 比特币垃圾邮件攻击:共识变革与当今 OP_Return 辩论的呼应
BitMex 的这篇文章介绍了 2015 年夏天针对比特币的四轮垃圾邮件攻击。这些攻击由一家名为 CoinWallet.EU 的伦敦公司发起。垃圾邮件对当时进行比特币支付的人的用户体验产生了重大的不利影响,尤其是在 2015 年 7 月 7 日至 2015 年 7 月 11 日的第三轮攻击中。这次攻击引发了关于矿工过滤垃圾邮件交易和区块大小限制的辩论。在 BitMex 看来,这次攻击在形成许多人关于如何处理垃圾邮件的观点方面发挥了关键作用,并且与今天关于 OP_Return 中继限制的辩论有有趣的相似之处。
个人数据泄露后的 5 步生存手册
a16z 的这篇指南梳理了在个人数据泄露后,如何立即应对与长期防护,重点包括:
1. 立即采取行动
-
冻结信用:防止身份被盗用开设新账户。
-
加强多因素认证(MFA):在所有金融与社交账户启用 MFA,优先使用 App 或硬件密钥而非短信认证,并向电信商申请 SIM 卡保护。
-
更换身份证件:联系相关部门申请补发。
2. 强化线上账户安全
-
Apple 和 Google账户,启用高级保护措施(如 Google Advanced Protection、Passkeys、YubiKey 等)。
-
使用密码管理器,推荐离线工具 KeePass,或 Bitwarden、1Password 等第三方服务
3. 锁定手机安全
-
iPhone 用户:设置自定义字母数字密码、启用Find My iPhone、开启 Stolen Device Protection,敏感应用要求Face ID。
-
Android用户:设置强密码或生物识别、启用Find My Device、开启盗窃检测锁和身份检查。
4. 防范社交工程攻击
- 警惕钓鱼诈骗、可疑登录通知、冒充金融机构的短信或电话。
5. 监控社交媒体账户
- 定期确认账户存取权,若被锁定立即联系客户服务。
-
 @ 502ab02a:a2860397
2025-05-30 01:14:10
@ 502ab02a:a2860397
2025-05-30 01:14:10ย้อนกลับไปปี 2014 ชายชื่อ Patrick O. Brown ศาสตราจารย์ชีววิทยาเชิงโมเลกุลแห่งมหาวิทยาลัยแตนฟอร์ด ตัดสินใจลาออกจากเส้นทางวิชาการสายหลัก เพื่อมาก่อตั้งบริษัทที่เขาเชื่อว่าจะเปลี่ยนโลก Impossible Foods
ดร. แพทริค โอ. บราวน์ (Patrick O. Brown) เป็นนักชีวเคมีและนักธุรกิจชาวอเมริกันและศาสตราจารย์กิตติคุณด้านชีวเคมีแห่งมหาวิทยาลัยสแตนฟอร์ด เขาได้รับปริญญาตรี แพทยศาสตรบัณฑิต และปรัชญาดุษฎีบัณฑิตด้านชีวเคมีจากมหาวิทยาลัยชิคาโก หลังจากนั้น เขาได้เข้ารับการฝึกอบรมด้านกุมารเวชศาสตร์ที่โรงพยาบาล Children's Memorial ในชิคาโก ในช่วงหลังปริญญาเอก เขาได้ทำงานวิจัยเกี่ยวกับกลไกที่ไวรัส HIV และเรโทรไวรัสอื่น ๆ แทรกยีนของพวกมันเข้าสู่จีโนมของเซลล์ที่ติดเชื้อ ซึ่งช่วยนำไปสู่การพัฒนายาใหม่ในการต่อสู้กับโรคนี้
ในช่วงต้นทศวรรษ 1990 ดร. บราวน์และทีมงานของเขาที่สแตนฟอร์ดได้พัฒนาเทคโนโลยี DNA microarray ซึ่งเป็นเครื่องมือที่ช่วยให้นักวิจัยสามารถวิเคราะห์การแสดงออกของยีนทั้งหมดในจีโนมได้พร้อมกัน เทคโนโลยีนี้มีบทบาทสำคัญในการวิจัยทางชีววิทยาและการแพทย์ โดยเฉพาะในการจำแนกประเภทของมะเร็งและการพยากรณ์โรค
นอกจากนี้ ดร. บราวน์ยังเป็นผู้ร่วมก่อตั้ง Public Library of Science (PLOS) ซึ่งเป็นองค์กรไม่แสวงหาผลกำไรที่มุ่งเน้นการเผยแพร่ผลงานวิจัยทางวิทยาศาสตร์ให้เข้าถึงได้ฟรีและเปิดกว้างต่อสาธารณะ
ในปี 2011 ดร. บราวน์ได้ก่อตั้ง Impossible Foods โดยมีเป้าหมายในการสร้างผลิตภัณฑ์เนื้อสัตว์จากพืชที่มีรสชาติและเนื้อสัมผัสคล้ายเนื้อสัตว์จริง เพื่อลดผลกระทบต่อสิ่งแวดล้อมจากการเลี้ยงสัตว์ เขาและทีมงานได้ค้นพบว่าโมเลกุล heme ซึ่งเป็นส่วนประกอบที่ให้รสชาติและกลิ่นเฉพาะของเนื้อสัตว์ สามารถผลิตจากพืชได้ โดยเฉพาะจากรากถั่วเหลือง พวกเขาใช้เทคนิคทางวิศวกรรมชีวภาพในการผลิต heme จากยีสต์ที่ได้รับการดัดแปลงพันธุกรรม และนำมาผสมกับโปรตีนจากพืชเพื่อสร้างผลิตภัณฑ์ที่มีลักษณะคล้ายเนื้อสัตว์
ดร. บราวน์ได้รับการยอมรับอย่างกว้างขวางในวงการวิทยาศาสตร์และเทคโนโลยี โดยได้รับรางวัลและเกียรติคุณหลายรายการ รวมถึงการเป็นสมาชิกของ National Academy of Sciences และ National Academy of Medicine ของสหรัฐอเมริกา ด้วยความมุ่งมั่นในการแก้ไขปัญหาสิ่งแวดล้อมผ่านนวัตกรรมทางอาหาร ดร. แพทริค โอ. บราวน์ ได้กลายเป็นบุคคลสำคัญที่มีบทบาทในการเปลี่ยนแปลงวิธีการบริโภคอาหารของโลกในศตวรรษที่ 21
เป้าหมายของเขาไม่ใช่เพียงแค่ทำอาหาร แต่คือ "ยุติการทำปศุสัตว์ให้หมดสิ้นภายในปี 2035"
เขาไม่ได้พูดลอย ๆ เขาลงมือ “ทำเนื้อจากพืช” ด้วยเทคโนโลยีที่ซับซ้อนระดับวิศวกรรมชีวภาพ นำโปรตีนจากถั่วเหลือง + น้ำมันมะพร้าว + เทคเจอร์ + สารเติมแต่งอีกชุดใหญ่ มาผ่านกระบวนการแปรรูปจนดูคล้ายเนื้อย่าง แต่ที่ทำให้ “มันดูเหมือนเนื้อจริง” คือการเติม ฮีม (Heme) เข้าไปสารประกอบที่อยู่ในเลือดและเนื้อสัตว์จริง ๆ
Impossible Foods คือบริษัทที่ไม่ได้เพียง “ปลอมรสชาติเนื้อ” แต่พยายามสร้างเนื้อจากพืช ให้เหมือนเนื้อจริงที่สุดเท่าที่วิทยาศาสตร์จะเอื้อมถึง จุดขายที่ทำให้แบรนด์นี้ดังเปรี้ยงก็คือสิ่งที่เรียกว่า “ฮีม” (heme) หรือโมเลกุลเหล็กในเลือด ซึ่งเป็นตัวการหลักที่ทำให้เนื้อวัวมีกลิ่นและรสเฉพาะตัวเวลาถูกย่างจนหอมฉุย
ดร.แพทริค บราวน์ และทีมนักวิจัยของเขาเริ่มจากการค้นหาว่า “อะไรในพืช” ให้กลิ่นคล้ายเลือด พวกเขาพบว่า “Leghemoglobin” ซึ่งอยู่ในรากถั่วเหลือง มีโครงสร้างใกล้เคียงกับ Hemoglobin ในเลือดสัตว์มากที่สุด จุดพลิกของเทคโนโลยีนี้คือ การผลิตเลกฮีโมโกลบินจากพืชจำนวนมาก ทำไม่ได้โดยการถอนรากถั่วมาทุบคั้น แต่ต้องอาศัยวิศวกรรมชีวภาพขั้นสูง
พวกเขาจึงใช้กระบวนการที่เรียกว่า “fermentation by genetically modified yeast” หรือการหมักโดยยีสต์ที่ผ่านการดัดแปลงพันธุกรรม โดยนำยีนของพืชที่สร้าง leghemoglobin ไปใส่ในยีสต์ (Pichia pastoris) แล้วเลี้ยงยีสต์นั้นในถังหมักขนาดใหญ่แบบเดียวกับโรงเบียร์ พอยีสต์ขยายตัว มันจะผลิตเลกฮีโมโกลบินออกมาจำนวนมาก จากนั้นจึงสกัดออกมาผสมกับโปรตีนจากพืช เช่น โปรตีนจากถั่วเหลือง หรือโปรตีนจากมันฝรั่ง
เพื่อให้เนื้อสัมผัสคล้ายเนื้อจริง ทีม Impossible Foods ยังใช้เทคนิคอื่นร่วมด้วย เช่น -Coconut Oil และ Sunflower Oil เป็นแหล่งไขมันที่ให้สัมผัส “ฉ่ำๆ” คล้ายไขมันเนื้อวัว -Methylcellulose สารที่ช่วยทำให้ส่วนผสมเกาะตัวเป็นก้อน คล้ายเนื้อบดจริง -Natural Flavors กลิ่นที่สกัดจากพืชหลายชนิด เพื่อเลียนแบบกลิ่นไหม้จากเนื้อย่าง
ทุกอย่างถูกผสมให้เข้ากัน ผ่านเครื่องอัดขึ้นรูป (extrusion) ที่ทำให้เนื้อออกมามี “เส้นใย” คล้ายกล้ามเนื้อวัว หรือหมู เมื่อโดนความร้อน โปรตีนจะเปลี่ยนโครงสร้าง (denature) และมีกลิ่นออกมาคล้ายๆ เนื้อย่างจริงๆ พร้อมน้ำสีแดงคล้ายเลือด (จาก heme) ไหลเยิ้ม ซึ่งคือไอเดียที่ทำให้ Impossible Burger เป็นมากกว่าแค่ “เบอร์เกอร์ผัก”
ผลลัพธ์คือ… เบอร์เกอร์พืชที่มีเลือดซึม สีชมพูดู juicy และกลิ่นไหม้ติดกระทะ จนคนกินรู้สึกเหมือนกำลังย่างเนื้อจริง ๆ
ฟังดูอัศจรรย์ใช่ไหม? แต่...การเติมฮีมจากยีสต์ตัดต่อพันธุกรรมลงในอาหาร ไม่เคยมีในธรรมชาติมาก่อน ในปี 2017 Impossible Foods ต้องยื่นเรื่องต่อ FDA เพื่อขออนุมัติว่า leghemoglobin จากยีสต์ GMO “ปลอดภัย”
แต่ในตอนนั้น FDA ตอบว่า “ยังไม่มีข้อมูลเพียงพอ” ว่าจะไม่ก่อให้เกิดภูมิแพ้หรือผลข้างเคียงในระยะยาว (ใช่แล้วจ้ะ... สารที่อยู่ในเบอร์เกอร์ชื่อดัง ถูกขายก่อนที่ FDA จะสรุปว่าปลอดภัยเต็มร้อย)
แล้วในที่สุด ปี 2019 FDA ก็ให้ผ่านแบบ “GRAS” (Generally Recognized As Safe) โดยใช้ข้อมูลจากการทดลองภายในของบริษัทเอง ไม่ใช่การทดสอบอิสระจากภายนอก
เฮียว่าอันนี้ต้องมีใครสะกิดในใจแล้วล่ะว่า “เรากำลังเอาอะไรเข้าปากกันแน่?”
แม้จะฟังดูเท่ ไฮเทค และดีต่อสิ่งแวดล้อม แต่ก็มีคำถามจากนักวิจารณ์มากมายว่า… แท้จริงแล้วอาหารเหล่านี้เป็นอาหาร “เพื่อสิ่งแวดล้อม” หรือเป็นเพียง “ภาพฝันที่ควบคุมโดยบริษัทเทคโนโลยียักษ์ใหญ่”?
มันเต็มไปด้วยคำถาม คำถาม และ คำถามนะสิครับ
ในเมื่อ Impossible Foods ได้รับเงินลงทุนหลายรอบจากบริษัทยักษ์อย่าง Google Ventures, UBS, และ Temasek (ของรัฐบาลสิงคโปร์) บอกตรง ๆ ว่า เงินแบบนี้ไม่ได้หวังแค่เปลี่ยนโลกแต่มันมาพร้อมเป้าหมายที่ชัดมาก การสร้างสิทธิบัตรอาหารใหม่ ที่ควบคุมการผลิตจากต้นน้ำยันปลายน้ำ อย่าลืมว่า ยีสต์ที่ผ่านการดัดแปลงพันธุกรรม หรือ GMO yeast นั้นถือเป็นสิทธิบัตร ถ้าใครจะผลิต Heme แบบเดียวกันก็ต้องขออนุญาตจาก Impossible Foods หรือไม่ก็โดนฟ้องได้เลย แปลว่า “เทคโนโลยีรสชาติเนื้อ” ไม่ได้เป็นมรดกของโลก แต่อยู่ในมือบริษัทไม่กี่แห่ง
ยิ่งไปกว่านั้น อุปกรณ์การผลิตต้องลงทุนสูง ต้องมีโรงหมัก ปฏิบัติการชีวภาพ การควบคุมความปลอดภัยที่เข้มข้น จึงไม่ใช่ใครๆ ก็ทำได้ ที่น่ากลัวคือ ถ้าเมื่อวันหนึ่งเนื้อสัตว์ธรรมชาติถูกทำให้กลายเป็น “ปีศาจสิ่งแวดล้อม” หรือ "ตัวเชื้อโรคผ่านอาหาร" โดยนโยบายรัฐและการตลาดของกลุ่มเทคฯ อาหารที่ประชาชนกินได้อาจเหลือแค่ “สิ่งที่ผลิตโดยมีสิทธิบัตร” เท่านั้น
เมื่อถึงวันนั้น ประชาชนจะสิ้นความชอบธรรมในการ “เลี้ยงวัวไว้กินเอง” ไม่ได้อีกต่อไป เพราะอาจโดนห้ามจากข้อกฎหมายคาร์บอน กฎหมายการกักกันเชื้อ ประชาชนจะ “เก็บพืชริมรั้วมาทำอาหาร” ไม่ได้อีกต่อไป เพราะกลิ่นไม่เหมือนเนื้อแลปที่เคยชิน และประชาชนจะ “ทำอาหารเองในบ้าน” ไม่ได้อีกต่อไป เพราะระบบเสพติดรสเนื้อเทียมจะทำให้คนเบือนหน้าจากอาหารจริง
ในขณะที่ Impossible Foods โฆษณาว่า “เราแค่อยากช่วยโลก” แต่เทคโนโลยีนี้อาจเปลี่ยน “อาหาร” ให้กลายเป็น “สิทธิบัตร” ที่ประชาชนเช่ากินจากบริษัท และเปลี่ยน “สิทธิในการเข้าถึงอาหาร” ให้กลายเป็น “อภิมหาอำนาจควบคุมโลก” โดยไม่ต้องยิงแม้แต่นัดเดียว หรือเปล่า???
เพราะเมื่อคุณควบคุมอาหารได้… คุณไม่ต้องควบคุมประชาชนอีกเลย
เฮียไม่ได้ต่อต้านเทคโนโลยี แต่เฮียอยากให้เราหยุดคิดนิดนึง แล้วตั้งคำถามในขณะที่เรายังเฝ้ามองว่า ถ้าของกินที่ดูน่าเชื่อถือ กินแล้วเหมือนเนื้อแท้ ๆ มันต้องมาจากกระบวนการที่ซับซ้อน แพง และถูกควบคุมโดยบริษัทที่มีสิทธิบัตรล้อมรอบ แล้ววันหนึ่ง ถ้าบริษัทนั้นล่มล่ะ? ถ้าถูกซื้อโดยบริษัทยักษ์ใหญ่? หรือถ้าพวกเขาขึ้นราคาจนยังไงเราก็ต้องทำงานหาเงินมาซื้อมันเพื่อกินประทังชีวิต?
อาหารจะยังเป็นของเราหรือเปล่า?
เราจะยัง “กินเพื่ออยู่” หรือแค่ “อยู่เพื่อจ่ายค่าเช่าระบบกิน”?
เราคงไม่ผิดที่จะตั้งคำถามใช่ไหม เพราะถ้ามันมีทางออก มันคงไม่น่ากลัว
#pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก #siamstr
-
 @ 9ca447d2:fbf5a36d
2025-05-30 01:01:57
@ 9ca447d2:fbf5a36d
2025-05-30 01:01:57Blackstone, the world’s largest alternative asset manager, has entered the Bitcoin space with a $1.08 million investment in BlackRock’s Bitcoin ETF. This is a big deal for both Wall Street and the Bitcoin world.
Blackstone has made its first direct investment in bitcoin through regulated financial products. A May 20, 2025, SEC filing revealed that the firm purchased 23,094 shares of the iShares Bitcoin Trust (IBIT), BlackRock’s spot Bitcoin exchange-traded fund (ETF).
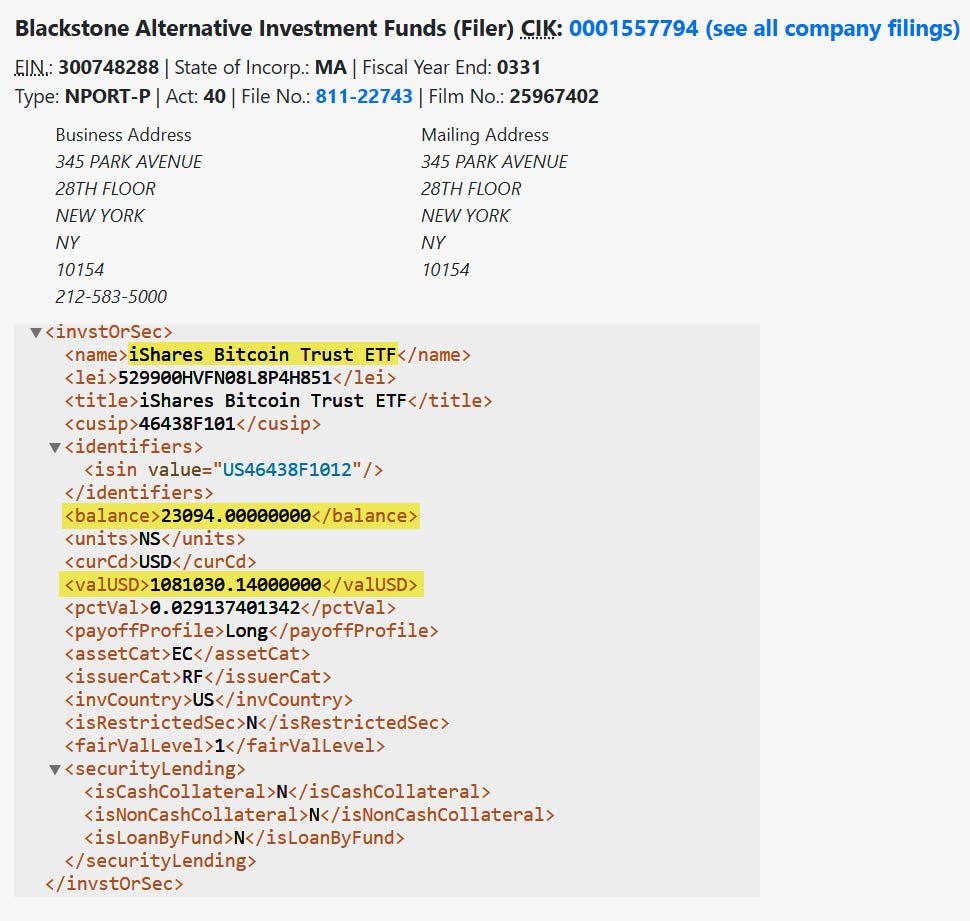
BlackStone has bought 23,094 shares of BlackRock’s IBIT — SEC
While $1.08 million is a small drop in the bucket compared to Blackstone’s $1.2 trillion in assets under management, this is a big deal for the private equity giant which has been skeptical of bitcoin in the past.
In 2019, the company’s CEO, Steve Schwarzman, said he didn’t understand Bitcoin. “I was raised in a world where someone needs to control currencies,” he said, admitting he struggled to understand the technology.
Fast forward to 2025, and it is now one of the many institutional investors taking bitcoin seriously — but doing so through cautious, regulated channels.
The investment was made through Blackstone’s $2.63 billion Alternative Multi-Strategy Fund (BTMIX), which invests in a wide range of financial instruments.
Instead of buying bitcoin directly, Blackstone chose to get exposure through a bitcoin ETF — which is how many large institutions are approaching the digital asset. Spot Bitcoin ETFs like IBIT allow investors to track the price of bitcoin without having to hold the digital asset itself.
There are several advantages to this approach. ETFs trade like stocks, are regulated by the SEC and take care of complex issues like custody and compliance. This makes them more attractive for firms that are new to Bitcoin or still wary of the risks.
Related: Bitcoin ETFs Provide Convenient Price Exposure, But At What Cost?
Blackstone’s choice of a bitcoin ETF shows how effective these products are at connecting traditional finance to the digital age.
In addition to IBIT, Blackstone also disclosed smaller investments in two other digital-asset-related companies:
- 9,889 shares of the ProShares Bitcoin Strategy ETF (BITO), valued at about $181,166.
- 4,300 shares of Bitcoin Depot Inc. (BTM), a bitcoin ATM operator, worth approximately $6,300.
Together, these are a tiny fraction of Blackstone’s portfolio but show growing interest and exploration into the space.
Since its launch in January 2024, BlackRock’s IBIT ETF has become the top-performing Bitcoin ETF in the U.S. As of mid-May 2025, the fund has seen over $46.1 billion in net inflows with no outflows since early April.
IBIT is ahead of other major ETFs like Fidelity’s FBTC and ARK’s 21Shares Bitcoin ETF.
But the trend is clear: big firms are getting comfortable with regulated bitcoin products. Industry insiders see Blackstone’s move as part of a broader shift in institutional sentiment towards bitcoin.
This is a small investment but it matters because of who is making it. Blackstone is known for being conservative and risk-averse.
Its decision to put even a tiny amount of capital into Bitcoin ETFs means tradfi companies are getting more confident in bitcoin as an asset class. Blackstone is dipping its toe in the water, and even a small step is significant given its size and influence.
-
 @ cae03c48:2a7d6671
2025-05-30 01:01:23
@ cae03c48:2a7d6671
2025-05-30 01:01:23Bitcoin Magazine

Adam Back Said It’s Still Early For the Retail Investors To Buy BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Head of Firmwide Research at Galaxy Digital Alex Thorn, Founder and Managing Partner of Pantera Capital Dan Morehead, Managing Partner, CEO, CIO of 10T Holdings + 1RoundTable Partners Dan Tapiero and the Co-founder & CEO of Blockstream Adam Back discussed the future of Bitcoin treasury companies.
Dan Tapiero started by sharing his opinion on how he sees Bitcoin in comparison to gold:
“I really have always believed in that physical ownership that the individual has the right and should be able to own his own asset and so I started this physical gold business years ago,” said Tapiero. “I think our focus today is further adoption and the elevation of Bitcoin. I think the understanding of Bitcoin as an important asset.”
Adam Back was asked what he thought about Bitcoin treasury companies and he responded, “in effect, Blockstream is one of the first Bitcoin treasury companies. We have been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then. I think the way to look at the treasury companies is Bitcoin is effectively the harder rate. It’s very hard to outperform Bitcoin most people that invest in things since Bitcoin around thought I should put that in Bitcoin and not in the other thing.”
Then Adam continued by explaining what treasury companies do.
“That’s why you get companies switching to the Bitcoin standard because it’s the only way for them to keep up with Bitcoin,” stated Back. ”They start with a Bitcoin capital base. They use the operating in-revenue to buy more Bitcoin and then they are able to participate in this kind of micro arbitrage.”
Finishing the panel, Alex Thorn asked, “Five years from now what is the price of Bitcoin?”
Dan Morehead predicted $750,000k, Tapiero $1,000,000 and Back said, “a million easy.”
Adam back closed by saying, “It’s still early for the retail investors.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 2 below:
This post Adam Back Said It’s Still Early For the Retail Investors To Buy Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 000002de:c05780a7
2025-05-29 21:17:37
@ 000002de:c05780a7
2025-05-29 21:17:37Resist the black pill. If the evolution of the "bitcoin community" bothers you, I'm with you. It's very likely that you need to shift your expectations but not your principles.
Lately, I've been hearing many bitcoiners and non-bitcoiners point out how the bitcoin world is embracing the suits—the politicians and traditional finance. This is on full display at Bitcoin 2025. I haven't watched the conference, but I have seen a few clips that seem to trigger people, and I get it. Believe me, I do. Please read this as kind advice for your own good.
We have many memes in the bitcoin space.
- Bitcoin Fixes This
- Not Your Keys Not Your Coins
- Never Sell Your Bitcoin
- HODL
There are many more. Memes are meant to compress a large amount of info into a small package. They work very well. But just because people repeat memes doesn't mean they understand the meaning and dense knowledge that caused them to develop. I think many bitcoiners, disappointed in the status quo, have miscalculated their fellow bitcoiners. After all, it is easy to repeat memes and seem like you are in the club. Many are not. Many do not share our values.
The Inevitability of Where We Are
I've been aware of bitcoin for a long time now. I didn't get it for many years. I didn't realize where it was coming from. As I started to understand how it was a technical application for many economic and technological things I already believed in, it started to come together. By this point in my life, though, I had already realized that most people are just going with the flow. They don't think deeply about the issues I care about. They are too practical. It took some time for me to realize that this doesn't make me superior to them, just different. I began to realize that these people matter, but it is a waste of time to try to convince them intellectually. Practical solutions are the only way. You see, most people do not even understand or care about how the current system works. They just want what they want for their families. Many are very good at it. They play the game. They don't wonder why the game was made or who made it. There are also many people that understand the issues with the system but simply want to use them to enrich themselves. They see what we see but don't care to change it as long as they can profit from it.
As bitcoin becomes more commonly used/bought/traded, it will move into these camps. The number of people that are hard-core bitcoiners is small. Very small. It's not going to become a significant portion of the population. Just as those that get economics aren't, nor are those that understand technology on a deep level. Don't get me wrong. It will grow, but it's never going to be the majority.
So with all this in mind, it is inevitable that a scarce money/asset would attract people that simply want to use it to make themselves wealthy. It's inevitable that bitcoin will become integrated into the financial system. The state will not be able to kill it, so it tries to use it. Is this good? Well, I don't think it is, but that doesn't really matter now, does it? Bitcoin doesn't care about what I think. Just as gold doesn't care how murderous and evil the man is that holds it.
Bitcoin Doesn't Fix This... Not Yet At Least
I'm beginning to think that many that are decrying the current state of bitcoin actually believed that "bitcoin fixes this." I mean, they believed it might do it overnight. I am having a hard time not thinking that many people actually think that when someone buys bitcoin, they have some sort of "born-again" experience. That's nonsense, and I doubt anyone would say this, but I think many might have believed it. Bitcoin, once it replaces the fiat system and revolutionizes banking, will fix many problems we see. The thing is, before fiat money printing, we still had many problems. The incentives that fiat money printing creates are not all the problems that exist. It just amplifies them. Bitcoin doesn't magically make people hate taxes and the state. We've had many years to win over those people to bitcoin, and frankly, we have a long way to go to even get those people. Maybe we should adjust our time preference.
The Vanguard
So what's my point? If you are triggered by all this bitcoin conference nonsense, all this statist boot-licking, I'm with you. It's pathetic. Bitcoin was started by cypherpunks. By people that opposed the state. But they aren't here now. You are. Also, while I'm on this point, I think we overstate the early bitcoiners. I think plenty of them thought bitcoin, if it succeeded, would become very valuable. It's baked into the design. Don't kid yourself. Fiat has no bottom, and bitcoin has no top. But it was more than that. So bitcoin needs to be sovereign and censorship-resistant. If you care about these things, live it. Run a node. Run a lightning node. Use open-source software stacks. Dump your MacBook Pro and use Linux. Support devs. Be an uncle Jim to your friends and family. Do the work. We are the vanguard, and we should be principled. That doesn't mean a vow of poverty, but it does mean spending bitcoin. You can spend and replace. There always needs to be people that push back on the normies. It's better to do this with actions over words.
Keep holding onto your values. Live them out. Values are literally what you value. And if you aren't doing things that align with your values, they really aren't your values. You are larping. Just don't lie to yourself most of all. Lies are like poison. Sometimes you have to be honest with where you are in the moment. Take stock and adjust your frame. What do you really value, and are you living it? If not, why not. Maybe you are lying to yourself. Maybe you just aren't aware. Take stock and adjust.
https://stacker.news/items/992238
-
 @ 2cde0e02:180a96b9
2025-05-29 11:19:56
@ 2cde0e02:180a96b9
2025-05-29 11:19:56pen; monochromized
https://stacker.news/items/991836
-
 @ 47259076:570c98c4
2025-05-30 00:35:13
@ 47259076:570c98c4
2025-05-30 00:35:13In order to see your reflection in the water, the water must be still.
If the water is agitated you can't see yourself clearly.
The same goes with your thoughts.
In order to think clearly, your mind must be still, or at rest.
If your mind is disturbed, you will not think clearly.
What causes the disturbances? Many things, such as: - Expectations - Emotions - Pride - Ignorance and so forth...
I want to focus in expectations in this article.
The problem with expectations is that they may be fulfilled or may not, not only that, they blind you to other opportunities happening right in your face.
If you expect to achieve "success" by going in path X, you will be so focused in this path you will not see that the path Y is better, easier and faster than the path X.
You cannot control anything but yourself.
So why create goals and plans if they can be easily crushed by the unknown?
It is better to surf in the wave of the unknown, rather than swim against it.
Not only that, what you want constantly changes.
I don't know what I will want in 5 minutes, imagine trying to guess what I will want in years.
I may be wrong in what I am saying, but I tried to swim against the unknown and I perished, therefore it's time to fully embrace the unknown, to fully embrace the chaos and see what happens.
-
 @ 7d33ba57:1b82db35
2025-05-29 08:40:35
@ 7d33ba57:1b82db35
2025-05-29 08:40:35Lingen (Ems) is a peaceful town in Lower Saxony, near the Dutch border, known for its historic old town, green surroundings, and relaxed pace of life. It may not be on the typical tourist radar, but it offers a taste of small-town Germany with plenty of charm and local culture.
🏘️ What to See and Do in Lingen
🏛️ Old Town & Market Square
- Stroll through the historic town center, where you’ll find half-timbered houses, cozy cafés, and the lovely St. Boniface Church
- The Rathaus (Town Hall) and its square are perfect for a slow coffee or people-watching
🚲 Nature & Outdoor Activities
- The region around Lingen is great for cycling and walking, especially along the Ems River
- Explore the Emsland countryside, filled with forests, meadows, and quiet villages
- Visit the nearby Emsland Moormuseum to learn about local peatland history
🎓 Student Vibes
- Thanks to the presence of a university, Lingen has a young and vibrant side, with cultural events and small live music scenes
🍺 Local Food & Drink
- Try regional dishes like Grünkohl (kale with sausage in winter) and Schnitzel in a local tavern
- Enjoy a drink at a beer garden or riverside café, especially in warmer months

🚆 Getting There
- Well connected by train, especially to Osnabrück, Münster, and the Dutch city of Enschede
- Great stop on a northern Germany road or rail trip
Lingen is ideal for travelers looking for peaceful towns, regional culture, and access to beautiful natural areas. It’s a place where you can slow down, bike along a river, and enjoy the local way of life.
-
 @ 21335073:a244b1ad
2025-05-21 16:58:36
@ 21335073:a244b1ad
2025-05-21 16:58:36The other day, I had the privilege of sitting down with one of my favorite living artists. Our conversation was so captivating that I felt compelled to share it. I’m leaving his name out for privacy.
Since our last meeting, I’d watched a documentary about his life, one he’d helped create. I told him how much I admired his openness in it. There’s something strange about knowing intimate details of someone’s life when they know so little about yours—it’s almost like I knew him too well for the kind of relationship we have.
He paused, then said quietly, with a shy grin, that watching the documentary made him realize how “odd and eccentric” he is. I laughed and told him he’s probably the sanest person I know. Because he’s lived fully, chasing love, passion, and purpose with hardly any regrets. He’s truly lived.
Today, I turn 44, and I’ll admit I’m a bit eccentric myself. I think I came into the world this way. I’ve made mistakes along the way, but I carry few regrets. Every misstep taught me something. And as I age, I’m not interested in blending in with the world—I’ll probably just lean further into my own brand of “weird.” I want to live life to the brim. The older I get, the more I see that the “normal” folks often seem less grounded than the eccentric artists who dare to live boldly. Life’s too short to just exist, actually live.
I’m not saying to be strange just for the sake of it. But I’ve seen what the crowd celebrates, and I’m not impressed. Forge your own path, even if it feels lonely or unpopular at times.
It’s easy to scroll through the news and feel discouraged. But actually, this is one of the most incredible times to be alive! I wake up every day grateful to be here, now. The future is bursting with possibility—I can feel it.
So, to my fellow weirdos on nostr: stay bold. Keep dreaming, keep pushing, no matter what’s trending. Stay wild enough to believe in a free internet for all. Freedom is radical—hold it tight. Live with the soul of an artist and the grit of a fighter. Thanks for inspiring me and so many others to keep hoping. Thank you all for making the last year of my life so special.
-
 @ 91add87d:3245770f
2025-05-29 23:41:38
@ 91add87d:3245770f
2025-05-29 23:41:38Do you guys actually identify with you online username or do you identify with government name? No this isn't some woke left ideal about pronouns. I do not use my real name for any of my handles, X and Nostr and email are all fake. Meaningful and something i picked specifically. My government name is something that was forced on me and yes I know I can it but the persona I have created online feels authentic and what I see myself as. It's what I'll be using to create my small businesses. My LLC is going to a copy of what I have created.
-
 @ cefb08d1:f419beff
2025-05-29 08:01:15
@ cefb08d1:f419beff
2025-05-29 08:01:15https://stacker.news/items/991778
-
 @ 51bbb15e:b77a2290
2025-05-21 00:24:36
@ 51bbb15e:b77a2290
2025-05-21 00:24:36Yeah, I’m sure everything in the file is legit. 👍 Let’s review the guard witness testimony…Oh wait, they weren’t at their posts despite 24/7 survellience instructions after another Epstein “suicide” attempt two weeks earlier. Well, at least the video of the suicide is in the file? Oh wait, a techical glitch. Damn those coincidences!
At this point, the Trump administration has zero credibility with me on anything related to the Epstein case and his clients. I still suspect the administration is using the Epstein files as leverage to keep a lot of RINOs in line, whereas they’d be sabotaging his agenda at every turn otherwise. However, I just don’t believe in ends-justify-the-means thinking. It’s led almost all of DC to toss out every bit of the values they might once have had.
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ d3d74124:a4eb7b1d
2025-05-29 02:19:14
@ d3d74124:a4eb7b1d
2025-05-29 02:19:14language is a funny thing. the English grammar is one of the most, if the not THE most complicated grammars to learn.
https://en.wikipedia.org/wiki/Defense_Language_Aptitude_Battery\ DLAB. it's the test you take to see if you have a gift for language learning.
in my exploration of languages, first Chinese Mandarin, then software languages, context is king (Jesus is King). the surrounding context is different every where you go.
physical space context. we can't be two places at once. nostr allows for many languages, because you can provide your own digital context. our physical perspective give us a field of view. NOSTR clients give us a field of view into digital context.
math is a language.
bitcoin will be called a lot of things.
wizardry
some elections results are anchored in time. using bitcoin. what else should be? legal documents seem obvious. other cryptographic proofs.
zero knowledge proofs. something about curve trees.
Find your local BitDevs.
Shenandoah Bitcoin Club
pondering a Veteran's Day live music event in Frederick County, VA. who would show up to a lunch and learn with hardware wallets in testnet4 mode? to try shit out? local only, but you should do it where you are too if you're not local.
mining
getting better? Bitmain announces a "decentralized mining pool" but I doubt we'll see open source code if history follows. 256Foundation getting to business. working prototypes for the Ember One using USB and python are out there for those that know where to look. i am very bullish on mujina. very bullish. fun coinbase tricks happening too with CTV+CSFS.
p.s. written on primal's new article publishing UI.
-
 @ c9badfea:610f861a
2025-05-20 19:49:20
@ c9badfea:610f861a
2025-05-20 19:49:20- Install Sky Map (it's free and open source)
- Launch the app and tap Accept, then tap OK
- When asked to access the device's location, tap While Using The App
- Tap somewhere on the screen to activate the menu, then tap ⁝ and select Settings
- Disable Send Usage Statistics
- Return to the main screen and enjoy stargazing!
ℹ️ Use the 🔍 icon in the upper toolbar to search for a specific celestial body, or tap the 👁️ icon to activate night mode
-
 @ cae03c48:2a7d6671
2025-05-29 23:01:24
@ cae03c48:2a7d6671
2025-05-29 23:01:24Bitcoin Magazine

Adam Back Presents Blockstream’s Bitcoin-First Infrastructure Vision at Bitcoin 2025Adam Back, Co-founder and CEO of Blockstream, took the stage at the Bitcoin 2025 Conference with a clear message: Bitcoin is becoming the foundation of global finance—and Blockstream is building the infrastructure to support it.
“So I think Bitcoin is still early,” Back began, “but more mainstream players are starting to become involved. It is starting to become the foundation of global finance.” From El Salvador’s President becoming “patient zero” to institutional adoption spreading rapidly, Back emphasized that “people in all layers of company management and politics have become orange-pilled.”

Citing Bitcoin’s accelerating growth trajectory, Back referenced Hal Finney’s prediction that Bitcoin’s addressable market could hit $200 trillion. “Today, we are a lot closer to that situation,” he noted. He alluded again that this is just the beginning for Bitcoin.
To meet that growing demand, Back announced Blockstream’s plan to support the journey from 100 million to 1 billion users by simplifying self-custody and Bitcoin-native asset management. “We’re laser-focused on Bitcoin,” he said. “At Blockstream, we are here to provide the infrastructure to enable that.”
In a detailed presentation, Back outlined five core pillars powering Blockstream’s strategy:
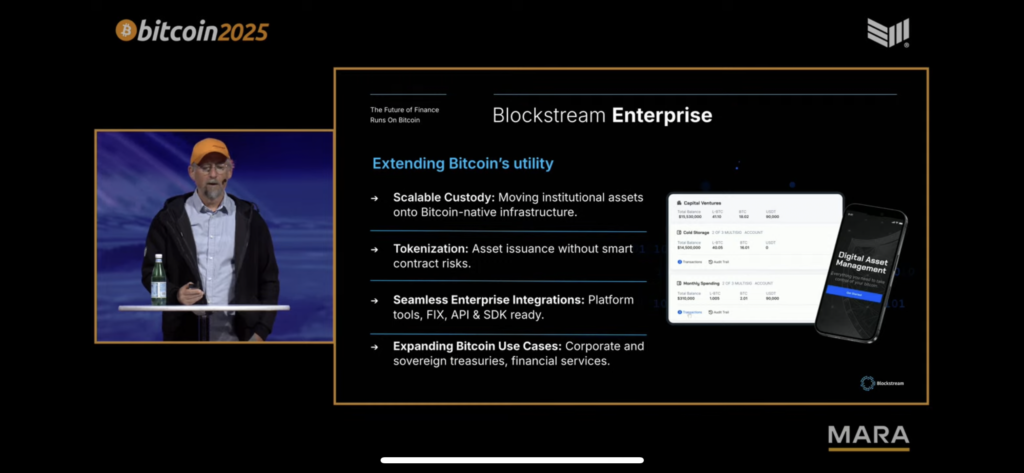
-
Infrastructure Expansion: “Bitcoin is becoming the dominant financial asset and platform for global transactions. Blockstream enables and supports the infrastructure around it.”
-
Unified Platform: Blockstream is developing one platform built for the Bitcoin economy—including consumer products (secure self-custody), enterprise solutions (asset transfer on Bitcoin rails), and institutional integration (custody for large-scale investment).
-
The Blockstream App: Designed to streamline self-custody, the app simplifies onboarding, supports BTC, LBTC, and USDT, and offers advanced features for experienced users.
-
Enterprise Tools: With custody, tokenization without smart contract risks, and SDK/API-ready infrastructure, Blockstream is pushing enterprise-grade Bitcoin use cases—from corporate finance to treasuries.
-
Security and Ecosystem Design: “Secure, proven, and built to last,” Back said, referring to Blockstream’s Bitcoin-first architecture. “Security is our cornerstone, and every product connects at every layer.”
In closing, Back reaffirmed his long-term vision: “The future of finance runs on Bitcoin.”
This post Adam Back Presents Blockstream’s Bitcoin-First Infrastructure Vision at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
-
 @ 048ecb14:7c28ac78
2025-05-29 00:49:55
@ 048ecb14:7c28ac78
2025-05-29 00:49:55I recently set up a Raspberry Pi camera server that's so minimal and straightforward, I thought it was worth sharing. This isn't one of those over-engineered solutions with fancy features - it's just a basic, reliable camera feed accessible from any browser on my local network.
The Goal
I wanted something that: 1. Starts automatically when the Pi boots up 2. Captures images at regular intervals 3. Shows the latest image in a simple web page accessible from any device 4. Doesn't require complex setup or dependencies 5. Uses minimal resources on my old Raspberry Pi
The Hardware
Nothing fancy here: - Raspberry Pi 2B (yes, the ancient one from 2015!) - Raspberry Pi Camera Module (standard version) - Power supply - That's it!
The Result

The interface is minimal but does the job. It shows the latest image and auto-refreshes every couple of seconds.
How to Get Set Up
Getting this running on your own Pi is super simple:
-
Make sure your camera module is connected and enabled
bash sudo raspi-config # Navigate to Interface Options > Camera and enable it -
Install the only dependency, ImageMagick (for rotation)
bash sudo apt update sudo apt install imagemagick -
Clone the repository, and navigate to the implementation's directory
bash git clone https://github.com/rewolf/RpiCameraViewer cd simple -
Start the camera server
bash ./start_camera_server.sh -
Access the feed from any device on your network
http://your-pi-ip-address:8080
That's it! No complex configuration, no fancy dependencies.
For more details consider reading the README
To make it start automatically on boot:
Add the following, with your specific installation path ```bash crontab -e
Add this line:
@reboot cd /path/to/RpiCameraViewer/simple && ./start_camera_server.sh ```
Configuration
There's not much configuration, but you can tweak few variables at the top of the
capture.shfile to modify width, height, rotation, quality, etc:bash QUALITY=90 WIDTH=720 HEIGHT=1280 ROTATION=90 # Set to 0 to disable rotationHow It Works
The solution is very basic:
- A bash script (
capture.sh) captures photos every few seconds by runninglibcamera-stilland sending a SIGUSR1 interrupt to signal it to capture a snapshot - The snapshot is rotated as needed with ImageMagick and saved with timestamps
- A symbolic link is updated to point to the latest image
- A minimal Python HTTP server serves a basic webpage showing the current image (the symlink), rendered to an HTML canvas
Note it does expose that directory to the whole LAN on :8080.
Give it a try if you need something like that quickly.
I have a plan to make a better implementation planned at some point, but for now this will do.
-
-
 @ fd208ee8:0fd927c1
2024-12-26 07:02:59
@ fd208ee8:0fd927c1
2024-12-26 07:02:59I just read this, and found it enlightening.
Jung... notes that intelligence can be seen as problem solving at an everyday level..., whereas creativity may represent problem solving for less common issues
Other studies have used metaphor creation as a creativity measure instead of divergent thinking and a spectrum of CHC components instead of just g and have found much higher relationships between creativity and intelligence than past studies
https://www.mdpi.com/2079-3200/3/3/59
I'm unusually intelligent (Who isn't?), but I'm much more creative, than intelligent, and I think that confuses people. The ability to apply intelligence, to solve completely novel problems, on the fly, is something IQ tests don't even claim to measure. They just claim a correlation.
Creativity requires taking wild, mental leaps out into nothingness; simply trusting that your brain will land you safely. And this is why I've been at the forefront of massive innovation, over and over, but never got rich off of it.
I'm a starving autist.
Zaps are the first time I've ever made money directly, for solving novel problems. Companies don't do this because there is a span of time between providing a solution and the solution being implemented, and the person building the implementation (or their boss) receives all the credit for the existence of the solution. At best, you can hope to get pawned off with a small bonus.
Nobody can remember who came up with the solution, originally, and that person might not even be there, anymore, and probably never filed a patent, and may have no idea that their idea has even been built. They just run across it, later, in a tech magazine or museum, and say, "Well, will you look at that! Someone actually went and built it! Isn't that nice!"
Universities at least had the idea of cementing novel solutions in academic papers, but that: 1) only works if you're an academic, and at a university, 2) is an incredibly slow process, not appropriate for a truly innovative field, 3) leads to manifestations of perverse incentives and biased research frameworks, coming from 'publish or perish' policies.
But I think long-form notes and zaps solve for this problem. #Alexandria, especially, is being built to cater to this long-suffering class of chronic underachievers. It leaves a written, public, time-stamped record of Clever Ideas We Have Had.
Because they are clever, the ideas. And we have had them.
-
 @ cae03c48:2a7d6671
2025-05-29 23:01:19
@ cae03c48:2a7d6671
2025-05-29 23:01:19Bitcoin Magazine

Eric Trump Said Everybody Wants Bitcoin. Everybody is Buying BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Executive Chairman & Board Member of American Bitcoin Mike Ho, the CEO of American Bitcoin Matt Prusak, the founder of Altcoin Daily Aaron Arnold, Donald Trump Jr. and Eric Trump discussed the future of Bitcoin and their views.
Eric Trump started the panel by saying, “we are bringing Bitcoin to America and America is going to win the crypto revolution.”
Donald continued by mentioning the $2.5 billion bitcoin treasury.
“All the announcement yesterday, True Social and TMTG committing $2.5 billion to a bitcoin treasury,” stated Trump Jr. “Then the trifecta of crypto you have is what we are doing with the world liberty and USD1 from a DeFi platform. We are very long crypto.”
Eric talked about how all the world wants Bitcoin and that most companies are having problems when buying Bitcoin because there is a lot of demand and not as much supply.
“Everybody wants Bitcoin. Everybody is buying Bitcoin,” Eric stated.JUST IN:
 Eric Trump says "everyone in the world wants #Bitcoin, everybody is buying Bitcoin"
Eric Trump says "everyone in the world wants #Bitcoin, everybody is buying Bitcoin" "0.1 BTC is going to be worth an absolute fortune"
 pic.twitter.com/0942a3dSWI
pic.twitter.com/0942a3dSWI— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
“The whole system is broken and now all of the sudden you have crypto which solves all the problems,” commented Eric. “It makes everything cheaper, it makes everything faster, it makes it safer, it makes it more transparent. It makes the whole system more functional.“
Mike Ho explained his view of the volatility of Bitcoin and how it benefits everybody.
“We see Bitcoin mining as just the foundational layer of being able to accumulate more creative Bitcoin for our shareholders at a discount to what the market can buy Bitcoin for,” commented Ho. “Then there is a value in the volatility of the stock. Usually volatility carries a negative connotation, but in here it’s the volatility that allows us to raise very low cost converts to even accelerate accumulation of Bitcoin.”
Matt Prusak mentioned how they are stacking sats and accumulating as much Bitcoin as they can.
“We are looking for ways to accumulate as much Bitcoin as fast as possible,” said Prusak. “We are stacking sats for our mining operations. We are going to stack sats for the accumulation.”
They all made predictions of Bitcoin’s end price of this year, Eric said $170,000, Trump Jr between $150,000 and $175,000 and Mike Ho over $200,000. Eric finalized with, “the next 10 years are going to be absolutely parabolical.”
This post Eric Trump Said Everybody Wants Bitcoin. Everybody is Buying Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-29 00:42:35
@ 5d4b6c8d:8a1c1ee3
2025-05-29 00:42:35Pretty good day today, despite being a bit of a cookie monster again. - Lots of steps from mowing the lawn, walking the dog, and miscellaneous errands - Broke my fast a little early in the morning, but ate healthy until afternoon snacks
Also, I came across a new health app on nostr. Has anyone else used SOUND HSA? It supposedly pays sats for steps.
How did everyone else do with their goals today?
https://stacker.news/items/991609
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 04c915da:3dfbecc9
2025-05-20 15:47:16
@ 04c915da:3dfbecc9
2025-05-20 15:47:16Here’s a revised timeline of macro-level events from The Mandibles: A Family, 2029–2047 by Lionel Shriver, reimagined in a world where Bitcoin is adopted as a widely accepted form of money, altering the original narrative’s assumptions about currency collapse and economic control. In Shriver’s original story, the failure of Bitcoin is assumed amid the dominance of the bancor and the dollar’s collapse. Here, Bitcoin’s success reshapes the economic and societal trajectory, decentralizing power and challenging state-driven outcomes.
Part One: 2029–2032
-
2029 (Early Year)\ The United States faces economic strain as the dollar weakens against global shifts. However, Bitcoin, having gained traction emerges as a viable alternative. Unlike the original timeline, the bancor—a supranational currency backed by a coalition of nations—struggles to gain footing as Bitcoin’s decentralized adoption grows among individuals and businesses worldwide, undermining both the dollar and the bancor.
-
2029 (Mid-Year: The Great Renunciation)\ Treasury bonds lose value, and the government bans Bitcoin, labeling it a threat to sovereignty (mirroring the original bancor ban). However, a Bitcoin ban proves unenforceable—its decentralized nature thwarts confiscation efforts, unlike gold in the original story. Hyperinflation hits the dollar as the U.S. prints money, but Bitcoin’s fixed supply shields adopters from currency devaluation, creating a dual-economy split: dollar users suffer, while Bitcoin users thrive.
-
2029 (Late Year)\ Dollar-based inflation soars, emptying stores of goods priced in fiat currency. Meanwhile, Bitcoin transactions flourish in underground and online markets, stabilizing trade for those plugged into the bitcoin ecosystem. Traditional supply chains falter, but peer-to-peer Bitcoin networks enable local and international exchange, reducing scarcity for early adopters. The government’s gold confiscation fails to bolster the dollar, as Bitcoin’s rise renders gold less relevant.
-
2030–2031\ Crime spikes in dollar-dependent urban areas, but Bitcoin-friendly regions see less chaos, as digital wallets and smart contracts facilitate secure trade. The U.S. government doubles down on surveillance to crack down on bitcoin use. A cultural divide deepens: centralized authority weakens in Bitcoin-adopting communities, while dollar zones descend into lawlessness.
-
2032\ By this point, Bitcoin is de facto legal tender in parts of the U.S. and globally, especially in tech-savvy or libertarian-leaning regions. The federal government’s grip slips as tax collection in dollars plummets—Bitcoin’s traceability is low, and citizens evade fiat-based levies. Rural and urban Bitcoin hubs emerge, while the dollar economy remains fractured.
Time Jump: 2032–2047
- Over 15 years, Bitcoin solidifies as a global reserve currency, eroding centralized control. The U.S. government adapts, grudgingly integrating bitcoin into policy, though regional autonomy grows as Bitcoin empowers local economies.
Part Two: 2047
-
2047 (Early Year)\ The U.S. is a hybrid state: Bitcoin is legal tender alongside a diminished dollar. Taxes are lower, collected in BTC, reducing federal overreach. Bitcoin’s adoption has decentralized power nationwide. The bancor has faded, unable to compete with Bitcoin’s grassroots momentum.
-
2047 (Mid-Year)\ Travel and trade flow freely in Bitcoin zones, with no restrictive checkpoints. The dollar economy lingers in poorer areas, marked by decay, but Bitcoin’s dominance lifts overall prosperity, as its deflationary nature incentivizes saving and investment over consumption. Global supply chains rebound, powered by bitcoin enabled efficiency.
-
2047 (Late Year)\ The U.S. is a patchwork of semi-autonomous zones, united by Bitcoin’s universal acceptance rather than federal control. Resource scarcity persists due to past disruptions, but economic stability is higher than in Shriver’s original dystopia—Bitcoin’s success prevents the authoritarian slide, fostering a freer, if imperfect, society.
Key Differences
- Currency Dynamics: Bitcoin’s triumph prevents the bancor’s dominance and mitigates hyperinflation’s worst effects, offering a lifeline outside state control.
- Government Power: Centralized authority weakens as Bitcoin evades bans and taxation, shifting power to individuals and communities.
- Societal Outcome: Instead of a surveillance state, 2047 sees a decentralized, bitcoin driven world—less oppressive, though still stratified between Bitcoin haves and have-nots.
This reimagining assumes Bitcoin overcomes Shriver’s implied skepticism to become a robust, adopted currency by 2029, fundamentally altering the novel’s bleak trajectory.
-
-
 @ 000002de:c05780a7
2025-05-28 23:34:51
@ 000002de:c05780a7
2025-05-28 23:34:51With all the free press Steak `n Shake is getting for accepting bitcoin this post got me thinking about good burgers at fast food chains. There are incredible non-fast food burgers and local places but I'm limiting this to chains.
In order if you are going for a chain fast food American burgers here's the list in order.
- In-n-Out
- Shake Shack
- Habit Burger & Grill
- Five Guys
Everything else is not worth mentioning or I'm not aware of it due to where I live and have traveled.
What's your list.
Bonus:
Which of these or you picks will be next in accepting bitcoin.
https://stacker.news/items/991559
-
 @ 8bad92c3:ca714aa5
2025-05-29 22:01:52
@ 8bad92c3:ca714aa5
2025-05-29 22:01:52Marty's Bent

Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ a396e36e:ec991f1c
2025-05-28 22:27:45
@ a396e36e:ec991f1c
2025-05-28 22:27:45👤 Generation X and Bitcoin: Between Invisibility, Structural Disillusionment, and Defiance
Generation X, born between 1965 and 1980, has been largely sidelined in generational discourse. Unlike the baby boomers —symbols of stability and prosperity— or millennials and Gen Z —constant fixtures in the media and cultural spotlight— Gen X remains the least mentioned, the least studied, and often not even recognized by its own members as a distinct generation.
Today, they are in midlife —a period that, according to the U-shaped curve of happiness, is one of the most emotionally and psychologically difficult stages: deteriorating health, professional stagnation, and the dual burden of caring for both parents and children. But their condition is not just a matter of age —it’s the product of a unique convergence of economic and political failure.
Structurally, Generation X reached its crucial phase of financial consolidation during the global economic crisis of 2008 —a moment that froze wage growth and severely limited access to housing, investment opportunities, and savings. In parallel, they faced increasing labor precarization: unstable contracts, outsourcing, erosion of social protections, and the dismantling of job security. Compared to other generations, their economic mobility was minimal. Even in terms of wealth accumulation and home ownership, many Gen Xers show weaker indicators than early-born millennials at the same life stage.
At the same time, many countries —especially in Latin America and parts of Europe— turned toward alternative models to free-market systems: socialist proposals that promised redistribution, justice, and equality. But in practice, these models led to state dependency, excessive intervention, economic rigidity, and a loss of productive dynamism. The outcome was devastating: rising poverty, institutional decay, inflation, plummeting investment, growing corruption, and a widespread collapse of trust.
For a generation raised on values of effort, autonomy, and social mobility, this ideological shift brought a double betrayal —first from liberalism, which failed to deliver on its promises, and then from socialism, which entrenched poverty, dependency, and dysfunction.
And yet, while younger generations increasingly embrace state-centric proposals like universal basic income, subsidies, or nationalizations as progressive solutions, many in Gen X see these not as innovation, but as déjà vu —a recycling of failed models they’ve already lived and paid for.
It’s at this point that Bitcoin emerges as more than just a financial technology. For many Gen Xers, Bitcoin is both a symbolic and concrete response — a refuge from a system that betrayed them. It’s not just about investment. It’s about individual sovereignty. They call it “fuck you money” because it represents a total break from traditional structures: it doesn’t depend on banks, governments, political parties, or promises that never materialize.
Bitcoin is money without permission, without censorship, without planned devaluation. It’s a tool for radical autonomy. For a generation marked by skepticism, self-reliance, and disillusionment, it stands as a quiet but powerful form of resistance — a way of saying: “I don’t depend on you. I don’t believe you. I don’t need you.”
Today, while others debate new statist models or more market reforms, many Gen Xers are simply opting out. Bitcoin isn’t just an economic choice — it’s a stance. A way to reclaim the individual control the system once denied them.
-
 @ 05a0f81e:fc032124
2025-05-29 22:01:29
@ 05a0f81e:fc032124
2025-05-29 22:01:29Kehinde and Taiwo Ogundipe, known as the Rex Twins, made significant strides in the Nigerian art scene, particularly in Lagos during the 1970s and 1980s. Their collaborative works, often signed jointly, adorned various parts of Lagos, including Ikate, Itire, Ijesha, and Ojuelegba. Their art, characterized by vibrant street illustrations, not only showcased their talent but also their unity as twins, they shared a single wife, Patricia adewuyi and together, they had a son named Noah.
In December 1976, The Rex twins meet Patricia at the when she was just 24 years old at the at a palm wine bar in ijesha tedo, Lagos. Their Relationship quickly develop to a unique union where both brother married Patricia choosing to live together as one family.
There unique relationship was first reported by drum magazine in 1978, highlighting their decision to marry one woman as a testament of there inseparable
Th twins furthermore explained that they want to prove to the world and to Nigerians that as one man can marry more than one wives, that twins can also justify their oneness by owning things in common. God made us to be one in what ever we do. This point of view emphasized more on their beliefs in the deep bond they share and their desire to live in complete unity
The Rex Twins, Kehinde and Taiwo Ogundipe, were visual artists based in Lagos, Nigeria. They were known for working together on paintings, sign writing, and graphic art.
Occupations of the Rex Twins
-
Sign Writers – They specialized in creating hand-painted signboards, which were a popular form of advertising in Nigeria during the 1970s and 1980s.
-
Muralists – They painted large murals on buildings and public spaces.
-
Portrait Artists – They offered portraiture services, painting realistic images of individuals or families.
-
Commercial Artists – Their art included illustrations for businesses, advertisements, and posters.
-
Collaborative Painters – They worked as a team, reinforcing their philosophy of doing everything together.
Their shared artistic identity made them locally famous not just because of their talent, but also due to their deep bond as twins who lived and worked as one unit, even extending to their personal lives, including marriage.
Their story is often highlighted as an example of how art, identity, and unconventional relationships can intersect in culturally significant ways.
The story of the Rex Twins and Patricia teaches several powerful and thought-provoking lessons, culturally, philosophically, and socially. Here's a breakdown of what their act teaches:
- Unity and Oneness
The Rex Twins believed deeply in the idea that being twins went beyond biology, it meant sharing everything, including work, life, and even love. Their act teaches about total unity, and how some people can live in deep cooperation and harmony, even in ways that challenge norms.
- Redefining Love and Marriage
Their decision to marry one wife together challenges the traditional structure of romantic relationships and marriage. It opens up discussion about the flexibility of love, showing that love doesn’t always fit into strict cultural boxes.
It questions double standards—why is polygamy (one man, many wives) widely accepted in some cultures, but polyandry (one woman, two husbands) is taboo?
- Boldness and Nonconformity
Their lives were a form of rebellion against social expectations. They were unapologetically themselves, choosing to live in a way that made sense to them, even though society might have criticized or mocked them.
This teaches courage—the courage to live your truth, even if the world doesn’t understand it.
- The Complexity of Human Relationships
Their story reminds us that human relationships are not always simple.
It teaches us to withhold judgment, be curious rather than critical, and understand that every relationship has its own logic and depth.
- Living a Life of Purpose and Identity
They used both their art and their relationship as a statement of identity.
It teaches us to be intentional: about how we love, how we live, and what we create.
Finally, The Rex Twins and Patricia didn’t just share a relationship, they made a statement. Their story is less about whether their choices were “right” or “wrong,” and more about what it means to live with conviction, unity, and authenticity.
-
-
 @ 6a6be47b:3e74e3e1
2025-05-28 17:37:11
@ 6a6be47b:3e74e3e1
2025-05-28 17:37:11Hi frens! 🌞
How was your day? Mine was pretty great! Not to brag—I just try to see things in a positive light. Even when a day is “meh” or downright awful, I look for at least one good thing in it. Sometimes, let’s be real, there isn’t even one. Some days, weeks, or even months can just be tough. But even that shall pass.
✨ So, let’s try to focus on at least one good thing around us, or within us. Who knows—maybe a little magic can happen…
🎨 Today, I made time for some drawing on Procreate—yaaay! If you caught yesterday’s discussion, you know I drew a butterfly 🦋. Maybe with today’s drawing, you’ll be able to guess my next blog entry 👀
Today’s subject: Cytisus scoparius, better known as “Scotch broom” (or Scots broom).
🔍 I used to mix it up with gorse, but there are some telltale differences:
“Broom is similar to common gorse in size, shape and flower colour, but it lacks the spines and has short, flattened leaves and larger flowers.” — The Wildlife Trusts
⭐️Fun fact: I actually painted a gorse not too long ago for my Beltane post.
🚨 A word of caution though—don’t get too close! Scotch broom is harmful if eaten, so keep an eye out for your pets when you’re out and about, according to rhs.org.uk
🌼 I love spotting these bright yellow blooms by the highway or just outside town. That color is chef’s kiss—it really brightens up any drive!
💐That’s all for today. I’m super excited to hear what you think!
Take care and godspeed, my frens! 🚀✨
https://stacker.news/items/991324
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 18:06:46
@ 04c915da:3dfbecc9
2025-05-16 18:06:46Bitcoin has always been rooted in freedom and resistance to authority. I get that many of you are conflicted about the US Government stacking but by design we cannot stop anyone from using bitcoin. Many have asked me for my thoughts on the matter, so let’s rip it.
Concern
One of the most glaring issues with the strategic bitcoin reserve is its foundation, built on stolen bitcoin. For those of us who value private property this is an obvious betrayal of our core principles. Rather than proof of work, the bitcoin that seeds this reserve has been taken by force. The US Government should return the bitcoin stolen from Bitfinex and the Silk Road.
Using stolen bitcoin for the reserve creates a perverse incentive. If governments see bitcoin as a valuable asset, they will ramp up efforts to confiscate more bitcoin. The precedent is a major concern, and I stand strongly against it, but it should be also noted that governments were already seizing coin before the reserve so this is not really a change in policy.
Ideally all seized bitcoin should be burned, by law. This would align incentives properly and make it less likely for the government to actively increase coin seizures. Due to the truly scarce properties of bitcoin, all burned bitcoin helps existing holders through increased purchasing power regardless. This change would be unlikely but those of us in policy circles should push for it regardless. It would be best case scenario for American bitcoiners and would create a strong foundation for the next century of American leadership.
Optimism
The entire point of bitcoin is that we can spend or save it without permission. That said, it is a massive benefit to not have one of the strongest governments in human history actively trying to ruin our lives.
Since the beginning, bitcoiners have faced horrible regulatory trends. KYC, surveillance, and legal cases have made using bitcoin and building bitcoin businesses incredibly difficult. It is incredibly important to note that over the past year that trend has reversed for the first time in a decade. A strategic bitcoin reserve is a key driver of this shift. By holding bitcoin, the strongest government in the world has signaled that it is not just a fringe technology but rather truly valuable, legitimate, and worth stacking.
This alignment of incentives changes everything. The US Government stacking proves bitcoin’s worth. The resulting purchasing power appreciation helps all of us who are holding coin and as bitcoin succeeds our government receives direct benefit. A beautiful positive feedback loop.
Realism
We are trending in the right direction. A strategic bitcoin reserve is a sign that the state sees bitcoin as an asset worth embracing rather than destroying. That said, there is a lot of work left to be done. We cannot be lulled into complacency, the time to push forward is now, and we cannot take our foot off the gas. We have a seat at the table for the first time ever. Let's make it worth it.
We must protect the right to free usage of bitcoin and other digital technologies. Freedom in the digital age must be taken and defended, through both technical and political avenues. Multiple privacy focused developers are facing long jail sentences for building tools that protect our freedom. These cases are not just legal battles. They are attacks on the soul of bitcoin. We need to rally behind them, fight for their freedom, and ensure the ethos of bitcoin survives this new era of government interest. The strategic reserve is a step in the right direction, but it is up to us to hold the line and shape the future.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30
@ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30https://rumble.com/embed/v6rp3fh/?pub=4e023h
I know some of our stackers are follicly challenged, so I thought I'd pass along this video.
Have any of you tried topical onion juice for hair regrowth?
I'll eat more onion and rosemary and get more Sun, just to be safe.
https://stacker.news/items/991118
-
 @ 005bc4de:ef11e1a2
2025-05-28 09:05:10
@ 005bc4de:ef11e1a2
2025-05-28 09:05:10
BIP-2,100,000,000,000,000,000
So, you're telling me...
- 21 million bitcoins is out, and...
- 2.1 quadrillion sats is in, except that...
- sats are out, so...
- 2.1 quadrillion bitcoins is in, except that...
- there are actually millisats, but...
- millisats are out, so...
- millibitcoins are in, so now...
- there are 2.1 quintillion millibitcoins, except that...
- millibitcoins are the basic base unit of bitcoin, so...
- millibitcoins are out, and now...
- 2.1 quintillion bitcoins are in

-
 @ 04c915da:3dfbecc9
2025-05-16 17:59:23
@ 04c915da:3dfbecc9
2025-05-16 17:59:23Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ a296b972:e5a7a2e8
2025-05-29 21:11:46
@ a296b972:e5a7a2e8
2025-05-29 21:11:46Inzwischen Jahr 6 im Dauer-Ausnahmezustand. Angriff auf den Verstand. Großoffensive. Es wird mit allem geschossen, aus dem Wahnsinn herauskommen kann. Jeder klare Gedanke ist unschädlich zu machen. Großkotziges, staatsmännisches Geschwafel, dass sich einem die Nackenhaare aufstellen. Für wie doof haltet ihr uns eigentlich? Endlos Bürsten gegen den Strich. Angewidertes inneres Schütteln. Dringende Empfehlung einer Spülung der Gehirnwindungen. Idioten in Verantwortung wechseln auf andere Posten in Verantwortung und bleiben Idioten. Idioten gehen verantwortungslos mit unserer wertvollen Lebenszeit um. Ach, dafür ist man selbst verantwortlich? Wo ist der, der so ein dickes Fell hat, dass ihm dieser Irrsinn nicht nahegeht. Wo steht das Fass mit Teflon-Lack, in das man eintauchen kann, damit die Absurditäten an einem abperlen?
Eine zu tiefst verunsicherte und gespaltene Gesellschaft. Halt im Glauben in der Kirche? Von wegen: Sehr geehrte Jesusse und Jesusinnen. Ens ist gekreuzigt worden. Ja, in der Freiluft-Irrenanstalt. Auf einem Hügel von Denk-Dreck. Gott ist queer! Du tickst ja nicht mehr ganz sauber. Tanzende Brathähnchen vor dem Altar. Warum kommt keine Sintflut, wenn man sie mal braucht? Man muss gar nicht religiös sein, um zu sehen, dass das Gaga ist. Eine Produktion der Sodom & Gomorrha Anstalt GmbH & Co. KG.
Kein Vertrauen mehr, außer in sich selbst, meistens jedenfalls. Ja, man will uns vor allem Angst machen, teils unbegründet, so manches aber gibt es dann doch tatsächlich, was einem schwer zu denken gibt.
Vielen geht dieser Psychokrieg inzwischen an die Substanz, der ständig herabprasselnde Dauerwahnsinn erinnert an Water-Boarding.
Gut gemeinte Ratschläge, geht hinaus in die Natur, beackert euren Garten, wenn ihr einen habt, erdet euch, macht Entspannungsübungen, Zeit des Aufwachens, wir treten in ein neues Zeitalter ein, alles fein. Abschalten gelingt, aber der Aufprall in der Realität ist dann umso schlimmer, weil man sich daran erinnert hat, wie sorgenfrei und unbeschwert das Leben sein könnte, und wenn man es mit den derzeitigen Lebensumständen abgleicht, dann ist die schlechte Laune sofort wieder da. Im Verdrängens-Test mit Pauken und Trompeten durchgefallen.
Dann vielleicht doch lieber im Dauer-Modus des Irrsinns bleiben, sich mit den schrägen Zuständen arrangieren, nicht daran gewöhnen, nur lernen, damit bestmöglich umzugehen, und das Beste draus zu machen, irgendwie.
Man will dem Rat folgen, mal eine Nachrichten-freie Woche einzulegen, nimmt sich das ganz fest vor, und dann wird aber wieder doch nichts draus. Nicht, weil man sensationsgeil oder masochistisch veranlagt wäre, nein, der Antrieb, oder vielleicht sogar schon die Sucht, ist ganz woanders zu suchen: Man hat Sehnsucht nach der Vernunft und dem gesunden Hausverstand. Man hofft, ihn irgendwo zu finden. Nur einen Funken Hoffnung, an den man sich klammern kann, dass der Tiefpunkt durchschritten ist und es jetzt wieder aufwärts geht. Lichtblicke, der Wind dreht sich, Anzeichen für eine Wiederkehr des Verstandes, irgendetwas, das man als einen Weg hin zur Normalität deuten könnte. Aber, Fehlanzeige.
Stattdessen: Geschichtsvergessenheit, pathologischer Größenwahn, Großmannstum, fortgeschrittener Wahnsinn, Provokation, Kriegslüsternheit, Lügen, Intrigen, Interessen, Korruption, Geldverschwendung, Ideologie, Dummheit, Wirtschaftsvernichtung, Friedensverhinderung, Diplomatie-Allergie, Überheblichkeit, Abgehobenheit, Schadensmaximierung, Vernichtung, Feindschaft, Unmenschlichkeit, Tote, Gesetzesbruch, Mafia-Strukturen, sich selbst schützende Systeme, Cliquenbildung, Feigheit, Einschüchterung, Freiheitsbeschränkungen, Meinungs-Maulkörbe, Abschaffung der demokratischen Freiheit, Abschaffung der persönlichen Freiheit, Kontrolle, Überwachung, begleitetes Denken, Fühlen, Wollen, Verwirrung, Dreistigkeit, Frechheit, Missachtung des Volkes, Denunziantentum, Abwanderung, und und und.
Ein richtiges Schlachtfest der Kultur. Perversion des Menschseins. Das neue Normal ist irre.
Bislang ist keine der zahlreichen Baustellen beendet. Eine Wende steht unmittelbar bevor. Und sie steht und steht und steht bevor. Kein Gefühl von „Erledigt“, nächstes Problem angehen und auflösen. Weiter. Noch meilenweit von dem Gefühl entfernt, der Wahnsinn wird weniger, langsam, aber er wird weniger.
Fluchtgedanken. Aber wohin? In Europa bleiben, vielleicht besser nicht? Weiter weg, aber wohin da? Nicht vergessen, die Nachrichten erreichen einen überall. Und man bleibt mit seiner Heimat innerlich verbunden, egal wo man ist.
Es bleibt ein Entlanghangeln von einer vernünftigen Stimme zur anderen, die einem bestätigt, dass man selbst noch nicht den Verstand verloren hat. Die gibt es ja gottseidank noch. Innehalten, durchhalten, tief durchatmen, aufstehen, weitermachen. So lange, bis die Bekloppten ihrer Macht über uns entledigt wurden. Wie am besten? Und jetzt soll keiner mit nächsten Wahlen kommen.
Wer war schon einmal inmitten eines Psycho-Krieges gegen die eigene Bevölkerung? Wie geht man damit um, wie geht man dagegen an? Wie kann man das Ruder herumreißen? Was ist ein wirksames Mittel gegen die Ohnmacht? Wie kriegt man die Bequemlichkeit aus den Menschen heraus? Wie kann man die Menschen für die herrschenden Zustände sensibilisieren? Wie können wir noch mehr werden?
Wenn möglich, sollte zum Ende doch noch etwas Positives kommen. Ok. Es wird voraussichtlich demnächst möglicherweise bald besser. Eine zu geringe Zahl von Menschen ist schon aufgewacht. Die politischen Entscheidungsträger haben Angst, können die aber noch sehr gut verbergen. Das kann nicht ewig so weiter gehen und 10 Jahre sind keine Ewigkeit. Die Rufe nach mehr Bürgerbeteiligung werden immer lauter, aber nicht gehört, warum auch? Wir setzen den Artikel 146 des Grundgesetzes um, aber wie? Hätte, könnte, würde, wir sollten, es müsste. Ja und, wie weiter? Mehr geht nicht.
Doch vielleicht eins: Sand ins Getriebe streuen und zivilen Ungehorsam leisten, wo immer es geht. Das schafft immer noch eine gewisse Befriedigung und das Gefühl, dass man nicht vollkommen handlungsunfähig ist. Außerdem regt das die Phantasie und die Kreativität an und bietet eine Chance seinen Geist für etwas sehr Nützliches zu gebrauchen. Man fühlt, dass man noch ein Mensch ist.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
* *
(Bild von pixabay)
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 58537364:705b4b85
2025-05-28 08:25:55
@ 58537364:705b4b85
2025-05-28 08:25:55ถ้าอยากแล้วไม่หลง มันก็อยากด้วยปัญญา ความอยากอย่างนี้ท่านเรียกว่า เป็นบารมีของตน แต่ไม่ใช่ทุกคนนะที่มีปัญญา
บางคนไม่อยากจะให้มันอยาก เพราะเข้าใจว่า การมาปฏิบัติก็เพื่อระงับความอยาก ความจริงน่ะ ถ้าหากว่าไม่มีความอยาก ก็ไม่มีข้อปฏิบัติ ไม่รู้ว่าจะทำอะไร ลองพิจารณาดูก็ได้
ทุกคน แม้องค์พระพุทธเจ้าของเราก็ตาม ที่ท่านออกมาปฏิบัติ ก็เพื่อจะให้บรรเทากิเลสทั้งหลายนั้น
แต่ว่ามันต้องอยากทำ อยากปฏิบัติ อยากให้มันสงบ และก็ไม่อยากให้มันวุ่นวาย ทั้งสองอย่างนี้ มันเป็นอุปสรรคทั้งนั้น ถ้าเราไม่มีปัญญา ไม่มีความฉลาดในการกระทำอย่างนั้น เพราะว่ามันปนกันอยู่ อยากทั้งสองอย่างนี้มันมีราคาเท่า ๆ กัน
อยากจะพ้นทุกข์มันเป็นกิเลส สำหรับคนไม่มีปัญญา อยากด้วยความโง่ ไม่อยากมันก็เป็นกิเลส เพราะไม่อยากอันนั้นมันประกอบด้วยความโง่เหมือนกัน คือทั้งอยาก ไม่อยาก ปัญญาก็ไม่มี ทั้งสองอย่างนี้ มันเป็นกามสุขัลลิกานุโยโค กับอัตตกิลมถานุโยโค ซึ่งพระพุทธองค์ของเรา ขณะที่พระองค์กำลังทรงปฏิบัติอยู่นั้น ท่านก็หลงใหลในอย่างนี้ ไม่รู้ว่าจะทำอย่างไร ท่านหาอุบายหลายประการ กว่าจะพบของสองสิ่งนี้
ทุกวันนี้เราทั้งหลายก็เหมือนกัน ทุกสิ่งทั้งสองอย่างนี้มันกวนอยู่ เราจึงเข้าสู่ทางไม่ได้ก็เพราะอันนี้ ความเป็นจริงนี้ทุกคนที่มาปฏิบัติ ก็เป็นปุถุชนมาทั้งนั้น ปุถุชนก็เต็มไปด้วยความอยาก ความอยากที่ไม่มีปัญญา อยากด้วยความหลง ไม่อยากมันก็มีโทษเหมือนกัน “ไม่อยาก” มันก็เป็นตัณหา “อยาก” มันก็เป็นตัณหาอีกเหมือนกัน
ทีนี้ นักปฏิบัติยังไม่รู้เรื่องว่า จะเอายังไงกัน เดินไปข้างหน้าก็ไม่ถูก เดินกลับไปข้างหลังก็ไม่ถูก จะหยุดก็หยุดไม่ได้เพราะมันยังอยากอยู่ มันยังหลงอยู่ มีแต่ความอยาก แต่ปัญญาไม่มี มันอยากด้วยความหลง มันก็เป็นตัณหา ถึงแม้ไม่อยาก มันก็เป็นความหลง มันก็เป็นตัณหาเหมือนกันเพราะอะไร? เพราะมันขาดปัญญา
ความเป็นจริงนั้น ธรรมะมันอยู่ตรงนั้นแหละ ตรงความอยากกับความไม่อยากนั่นแหละ แต่เราไม่มีปัญญา ก็พยายามไม่ให้อยากบ้าง เดี๋ยวก็อยากบ้าง อยากให้เป็นอย่างนั้น ไม่อยากให้เป็นอย่างนี้ ความจริงทั้งสองอย่างนี้ หรือทั้งคู่นี้มันตัวเดียวกันทั้งนั้น ไม่ใช่คนละตัว แต่เราไม่รู้เรื่องของมัน
พระพุทธเจ้าของเรา และสาวกทั้งหลายของพระองค์นั้นท่านก็อยากเหมือนกัน แต่ “อยาก” ของท่านนั้น เป็นเพียงอาการของจิตเฉย ๆ หรือ “ไม่อยาก” ของท่าน ก็เป็นเพียงอาการของจิตเฉย ๆ อีกเหมือนกัน มันวูบเดียวเท่านั้น ก็หายไปแล้ว
ดังนั้น ความอยากหรือไม่อยากนี้ มันมีอยู่ตลอดเวลาแต่สำหรับผู้มีปัญญานั้น “อยาก” ก็ไม่มีอุปาทาน “ไม่อยาก” ก็ไม่มีอุปาทาน เป็น “สักแต่ว่า” อยากหรือไม่อยากเท่านั้น ถ้าพูดตามความจริงแล้ว มันก็เป็นแต่ "อาการของจิต" อาการของจิตมันเป็นของมันอย่างนั้นเอง ถ้าเรามาตะครุบมันอยู่ใกล้ ๆ นี่มันก็เห็นชัด
ดังนั้นจึงว่า การพิจารณานั้น ไม่ใช่รู้ไปที่อื่น มันรู้ตรงนี้แหละ เหมือนชาวประมงที่ออกไปทอดแหนั่นแหละ ทอดแหออกไปถูกปลาตัวใหญ่ เจ้าของผู้ทอดแหจะคิดอย่างไร? ก็กลัว กลัวปลาจะออกจากแหไปเสีย เมื่อเป็นเช่นนั้น ใจมันก็ดิ้นรนขึ้นระวังมาก บังคับมาก ตะครุบไปตะครุบมาอยู่นั่นแหละ ประเดี๋ยวปลามันก็ออกจากแหไปเสีย เพราะไปตะครุบมันแรงเกินไป
อย่างนั้นโบราณท่านพูดถึงเรื่องอันนี้ ท่านว่าค่อย ๆ ทำมัน แต่อย่าไปห่างจากมัน นี่คือปฏิปทาของเรา ค่อย ๆ คลำมันไปเรื่อย ๆ อย่างนั้นแหละ
อย่าปล่อยมัน หรือไม่อยากรู้มัน ต้องรู้ ต้องรู้เรื่องของมัน พยายามทำมันไปเรื่อย ๆ ให้เป็นปฏิปทา ขี้เกียจเราก็ทำไม่ขี้เกียจเราก็ทำ เรียกว่าการทำการปฏิบัติ ต้องทำไปเรื่อยๆอย่างนี้
ถ้าหากว่าเราขยัน ขยันเพราะความเชื่อ มันมีศรัทธาแต่ปัญญาไม่มี ถ้าเป็นอย่างนี้ ขยันไป ๆ แล้วมันก็ไม่เกิดผลอะไรขึ้นมากมาย ขยันไปนาน ๆ เข้า แต่มันไม่ถูกทาง มันก็ไม่สงบระงับ ทีนี้ก็จะเกิดความคิดว่า เรานี้บุญน้อยหรือวาสนาน้อย หรือคิดไปว่ามนุษย์ในโลกนี้คงทำไม่ได้หรอก แล้วก็เลยหยุดเลิกทำเลิกปฏิบัติ
ถ้าเกิดความคิดอย่างนี้เมื่อใด ขอให้ระวังให้มาก ให้มีขันติ ความอดทน ให้ทำไปเรื่อย ๆ เหมือนกับเราจับปลาตัวใหญ่ ก็ให้ค่อย ๆ คลำมันไปเรื่อย ๆ ปลามันก็จะไม่ดิ้นแรงค่อย ๆทำไปเรื่อย ๆ ไม่หยุด ไม่ช้าปลาก็จะหมดกำลัง มันก็จับง่าย จับให้ถนัดมือเลย ถ้าเรารีบจนเกินไป ปลามันก็จะหนีดิ้นออกจากแหเท่านั้น
ดังนั้น การปฏิบัตินี้ ถ้าเราพิจารณาตามพื้นเหตุของเรา เช่นว่า เราไม่มีความรู้ในปริยัติ ไม่มีความรู้ในอะไรอื่น ที่จะให้การปฏิบัติมันเกิดผลขึ้น ก็ดูความรู้ที่เป็นพื้นเพเดิมของเรานั่นแหละอันนั้นก็คือ “ธรรมชาติของจิต” นี่เอง มันมีของมันอยู่แล้ว เราจะไปเรียนรู้มัน มันก็มีอยู่ หรือเราจะไม่ไปเรียนรู้มัน มันก็มีอยู่
อย่างที่ท่านพูดว่า พระพุทธเจ้าจะบังเกิดขึ้นก็ตาม หรือไม่บังเกิดขึ้นก็ตาม ธรรมะก็คงมีอยู่อย่างนั้น มันเป็นของมันอยู่อย่างนั้น ไม่พลิกแพลงไปไหน มันเป็นสัจจธรรม
เราไม่เข้าใจสัจจธรรม ก็ไม่รู้ว่าสัจจธรรมเป็นอย่างไร นี้เรียกว่า การพิจารณาในความรู้ของผู้ปฏิบัติที่ไม่มีพื้นปริยัติ
ขอให้ดูจิต พยายามอ่านจิตของเจ้าของ พยายามพูดกับจิตของเจ้าของ มันจึงจะรู้เรื่องของจิต ค่อย ๆ ทำไป ถ้ายังไม่ถึงที่ของมัน มันก็ไปอยู่อย่างนั้น
ครูบาอาจารย์บางท่านบอกว่า ทำไปเรื่อย ๆ อย่าหยุด บางทีเรามาคิด “เออ ทำไปเรื่อย ๆ ถ้าไม่รู้เรื่องของมัน ถ้าทำไม่ถูกที่มัน มันจะรู้อะไร” อย่างนี้เป็นต้น ก็ต้องไปเรื่อย ๆ ก่อน แล้วมันก็จะเกิดความรู้สึกนึกคิดขึ้นในสิ่งที่เราพากเพียรทำนั้น
มันเหมือนกันกับบุรุษที่ไปสีไฟ ได้ฟังท่านบอกว่า เอาไม้ไผ่สองอันมาสีกันเข้าไปเถอะ แล้วจะมีไฟเกิดขึ้น บุรุษนั้นก็จับไม้ไผ่เข้าสองอัน สีกันเข้า แต่ใจร้อน สีไปได้หน่อย ก็อยากให้มันเป็นไฟ ใจก็เร่งอยู่เรื่อย ให้เป็นไฟเร็วๆ แต่ไฟก็ไม่เกิดสักที บุรุษนั้นก็เกิดความขี้เกียจ แล้วก็หยุดพัก แล้วจึงลองสีอีกนิด แล้วก็หยุดพัก ความร้อนที่พอมีอยู่บ้าง ก็หายไปล่ะซิ เพราะความร้อนมันไม่ติดต่อกัน
ถ้าทำไปเรื่อยๆอย่างนี้ เหนื่อยก็หยุด มีแต่เหนื่อยอย่างเดียวก็พอได้ แต่มีขี้เกียจปนเข้าด้วย เลยไปกันใหญ่ แล้วบุรุษนั้นก็หาว่าไฟไม่มี ไม่เอาไฟ ก็ทิ้ง เลิก ไม่สีอีก แล้วก็ไปเที่ยวประกาศว่า ไฟไม่มี ทำอย่างนี้ไม่ได้ ไม่มีไฟหรอก เขาได้ลองทำแล้ว
ก็จริงเหมือนกันที่ได้ทำแล้ว แต่ทำยังไม่ถึงจุดของมันคือความร้อนยังไม่สมดุลกัน ไฟมันก็เกิดขึ้นไม่ได้ ทั้งที่ความจริงไฟมันก็มีอยู่ อย่างนี้ก็เกิดความท้อแท้ขึ้นในใจของผู้ปฏิบัตินั้น ก็ละอันนี้ไปทำอันโน้นเรื่อยไป อันนี้ฉันใดก็ฉันนั้น
การปฏิบัตินั้น ปฏิบัติทางกายทางใจทั้งสองอย่าง มันต้องพร้อมกัน เพราะอะไร? เพราะพื้นเพมันเป็นคนมีกิเลสทั้งนั้น พระพุทธเจ้าก่อนที่จะเป็นพระพุทธเจ้า ท่านก็มีกิเลสแต่ท่านมีปัญญามากหลาย พระอรหันต์ก็เหมือนกัน เมื่อยังเป็นปุถุชนอยู่ ก็เหมือนกับเรา
เมื่อความอยากเกิดขึ้นมา เราก็ไม่รู้จัก เมื่อความไม่อยากเกิดขึ้นมา เราก็ไม่รู้จัก บางทีก็ร้อนใจ บางทีก็ดีใจ ถ้าใจเราไม่อยาก ก็ดีใจแบบหนึ่ง และวุ่นวายอีกแบบหนึ่ง ถ้าใจเราอยาก มันก็วุ่นวายอย่างหนึ่ง และดีใจอย่างหนึ่ง มันประสมประเสกันอยู่อย่างนี้
อันนี้คือปฏิปทาของผู้ปฏิบัติเรา
[อ่านใจธรรมชาติ] หลวงปู่ชา สุภัทโท หนังสือ หมวด: โพธิญาณ

-
 @ cae03c48:2a7d6671
2025-05-29 21:01:56
@ cae03c48:2a7d6671
2025-05-29 21:01:56Bitcoin Magazine

Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025Bitcoin isn’t just something to hold anymore—it’s something to live on. That was the core message delivered by Miles Suter, Bitcoin Product Lead at Block Inc., during his keynote at the Bitcoin 2025 Conference today. Standing at the intersection of innovation and ideology, Suter laid out a vision where Bitcoin isn’t just a store of value—but the internet’s native currency.
“Bitcoin is at a crossroads—on one hand it’s never been stronger: a trillion in market cap, millions of holders, and even talk of nation-state adoption,” Suter said. “We use Bitcoin to hold, to hedge, to opt out, but we rarely use it to live. At Block Inc., we believe that has to change.”
Suter officially announced that Block is rolling out Bitcoin payment capability for merchants using Square POS, allowing them to accept bitcoin directly in-store. The move comes as part of a broader initiative Block calls the full bitcoin for business stack—covering acquiring, managing, reporting, accounting, converting, lending, and taxes.

“This is what makes Bitcoin an everyday currency for everyone,” he emphasized. “We believe hard-working entrepreneurs deserve access to the full power of bitcoin.”
To prove the vision in action, Block helped power a Guinness World Record attempt for the most Lightning payments in a day, hosted live at the conference. The goal: prove that Lightning payments aren’t just functional—they’re scalable, fast, and real.
Block’s commitment isn’t new. In 2020, the company put bitcoin on its balance sheet. In 2021, it co-founded the Bitcoin Clean Energy Initiative to fight the “boiling oceans” narrative. In 2022, Cash App became one of the first major platforms on Lightning. In 2023, it launched on-chain payments with Square. And in 2024, it helped defeat Craig Wright in court, “standing up for Satoshi.”
“These aren’t just headlines—they’re a pattern,” Suter said. “We’ve made it more accessible, more secure. Now we’re focused on making it usable every day.”
Cash App already ranks among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time. In 2024, Lightning usage grew 7x. “Block runs one of the top Lightning nodes globally. And here’s what’s wild—it’s working,” he said.
Block is now taking 10% of all profits from Bitcoin and adding it back to its balance sheet, and over 1,700 merchants are automatically converting part of their daily sales to Bitcoin.
“If Bitcoin just becomes digital gold, we failed the mission,” Suter said. “Bitcoin payments validate Bitcoin. They make it real. Bitcoin is money.”
This post Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 01:29:24
@ 5d4b6c8d:8a1c1ee3
2025-05-28 01:29:24I finished my Workit step challenge today, but still ate too many snacks and kept eating too late into the evening. I also was just more active in general: chores, errands, playing with the kid and dog, etc.
How did you all do today?
https://stacker.news/items/990849
-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ b7274d28:c99628cb
2025-05-28 01:11:43
@ b7274d28:c99628cb
2025-05-28 01:11:43In this second installment of The Android Elite Setup tutorial series, we will cover installing the nostr:npub10r8xl2njyepcw2zwv3a6dyufj4e4ajx86hz6v4ehu4gnpupxxp7stjt2p8 on your #Android device and browsing for apps you may be interested in trying out.
Since the #Zapstore is a direct competitor to the Google Play Store, you're not going to be able to find and install it from there like you may be used to with other apps. Instead, you will need to install it directly from the developer's GitHub page. This is not a complicated process, but it is outside the normal flow of searching on the Play Store, tapping install, and you're done.
Installation
From any web browser on your Android phone, navigate to the Zapstore GitHub Releases page and the most recent version will be listed at the top of the page. The .apk file for you to download and install will be listed in the "Assets."
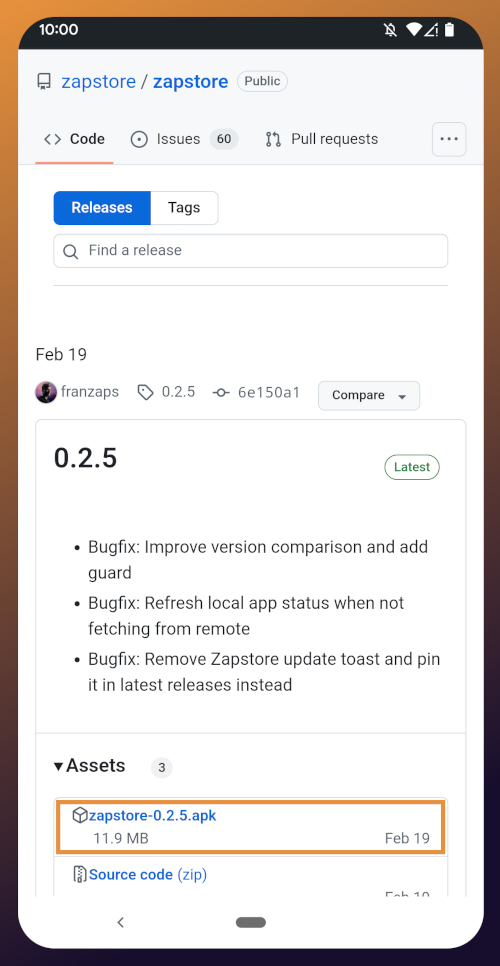
Tap the .apk to download it, and you should get a notification when the download has completed, with a prompt to open the file.
You will likely be presented with a prompt warning you that your phone currently isn't allowed to install applications from "unknown sources." Anywhere other than the Play Store is considered an "unknown source" by default. However, you can manually allow installation from unknown sources in the settings, which the prompt gives you the option to do.
In the settings page that opens, toggle it to allow installation from this source, and you should be prompted to install the application. If you aren't, simply go to your web browser's downloads and tap on the .apk file again, or go into your file browser app and you should find the .apk in your Downloads folder.
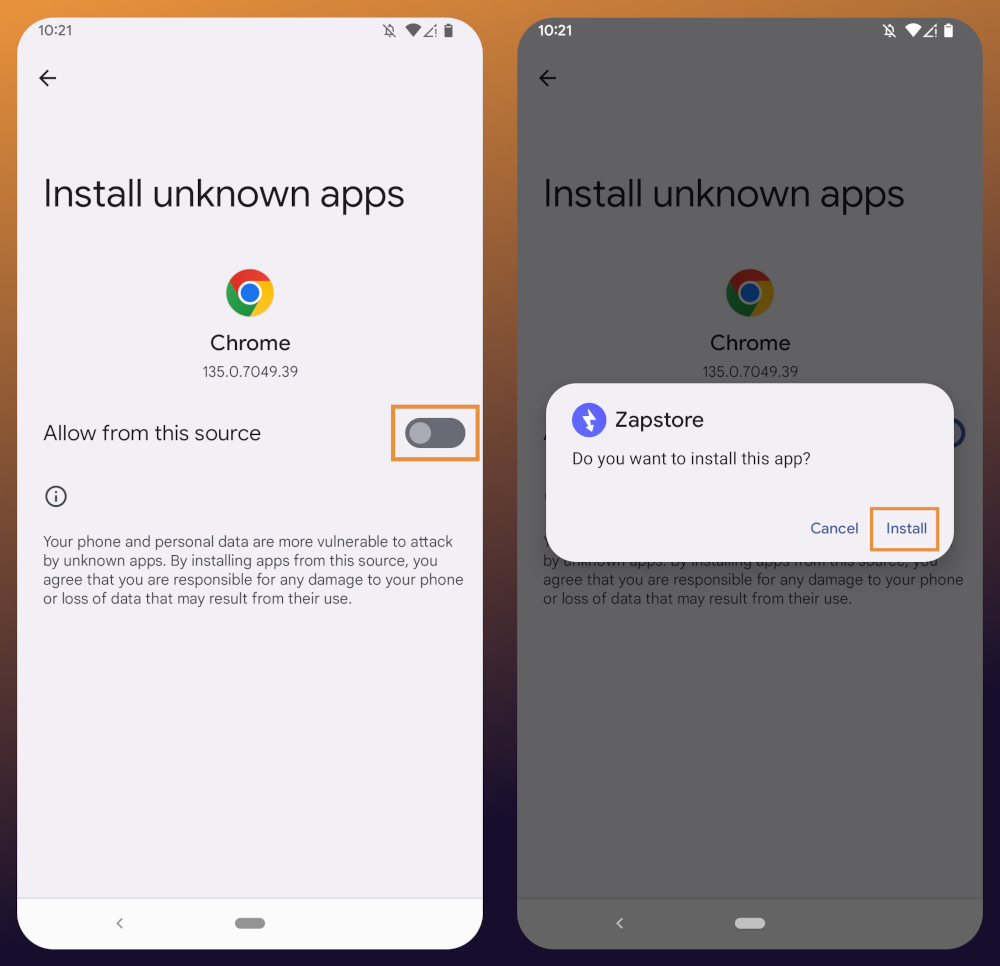
If the application doesn't open automatically after install, you will find it in your app drawer.

Home Page
Right at the top of the home page in the Zapstore is the search bar. You can use it to find a specific app you know is available in the Zapstore.
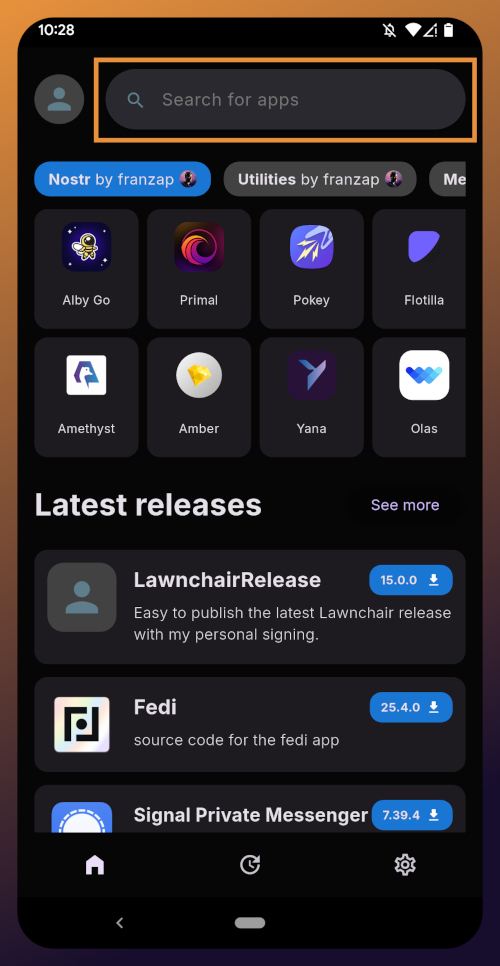
There are quite a lot of open source apps available, and more being added all the time. Most are added by the Zapstore developer, nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but some are added by the app developers themselves, especially Nostr apps. All of the applications we will be installing through the Zapstore have been added by their developers and are cryptographically signed, so you know that what you download is what the developer actually released.
The next section is for app discovery. There are curated app collections to peruse for ideas about what you may want to install. As you can see, all of the other apps we will be installing are listed in nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9's "Nostr" collection.
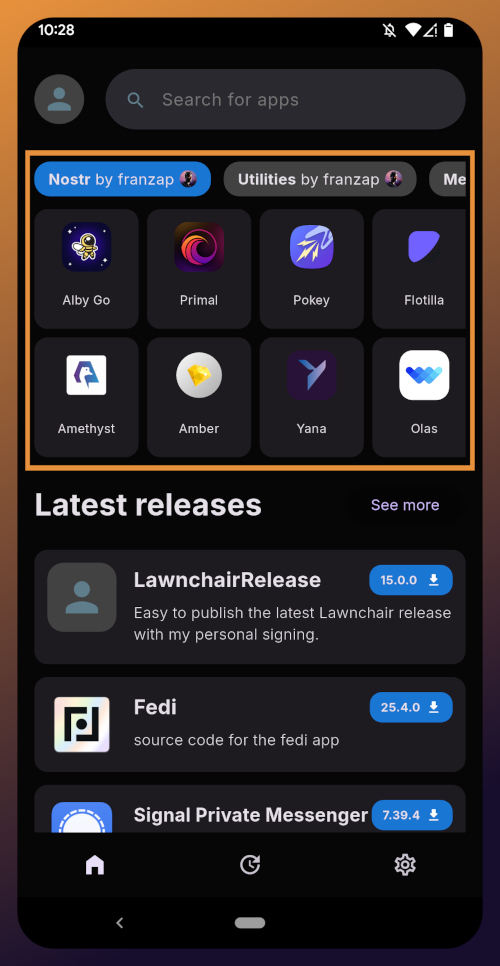
In future releases of the Zapstore, users will be able to create their own app collections.
The last section of the home page is a chronological list of the latest releases. This includes both new apps added to the Zapstore and recently updated apps. The list of recent releases on its own can be a great resource for discovering apps you may not have heard of before.
Installed Apps
The next page of the app, accessed by the icon in the bottom-center of the screen that looks like a clock with an arrow circling it, shows all apps you have installed that are available in the Zapstore. It's also where you will find apps you have previously installed that are ready to be updated. This page is pretty sparse on my test profile, since I only have the Zapstore itself installed, so here is a look at it on my main profile:

The "Disabled Apps" at the top are usually applications that were installed via the Play Store or some other means, but are also available in the Zapstore. You may be surprised to see that some of the apps you already have installed on your device are also available on the Zapstore. However, to manage their updates though the Zapstore, you would need to uninstall the app and reinstall it from the Zapstore instead. I only recommend doing this for applications that are added to the Zapstore by their developers, or you may encounter a significant delay between a new update being released for the app and when that update is available on the Zapstore.
Tap on one of your apps in the list to see whether the app is added by the developer, or by the Zapstore. This takes you to the application's page, and you may see a warning at the top if the app was not installed through the Zapstore.
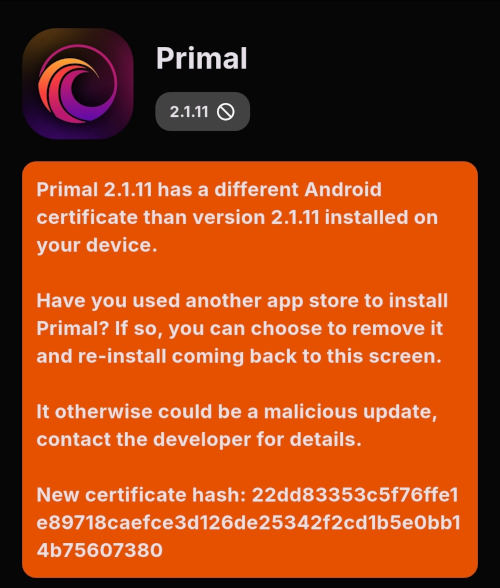
Scroll down the page a bit and you will see who signed the release that is available on the Zapstore.
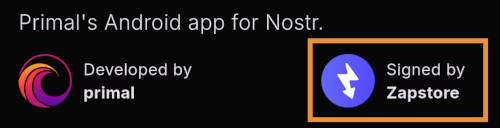
In the case of Primal, even though the developer is on Nostr, they are not signing their own releases to the Zapstore yet. This means there will likely be a delay between Primal releasing an update and that update being available on the Zapstore.
Settings
The last page of the app is the settings page, found by tapping the cog at the bottom right.
Here you can send the Zapstore developer feedback directly (if you are logged in), connect a Lightning wallet using Nostr Wallet Connect, delete your local cache, and view some system information.
We will be adding a connection to our nostr:npub1h2qfjpnxau9k7ja9qkf50043xfpfy8j5v60xsqryef64y44puwnq28w8ch wallet in part 5 of this tutorial series.
For the time being, we are all set with the Zapstore and ready for the next stage of our journey.
Continue to Part 3: Amber Signer. Nostr link: nostr:naddr1qqxnzde5xuengdeexcmnvv3eqgstwf6d9r37nqalwgxmfd9p9gclt3l0yc3jp5zuyhkfqjy6extz3jcrqsqqqa28qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qg6waehxw309aex2mrp0yhxyunfva58gcn0d36zumn9wss80nug
-
 @ 91117f2b:111207d6
2025-05-29 20:59:17
@ 91117f2b:111207d6
2025-05-29 20:59:17
Raising boys (men) and girls (women) to reach their full potential requires a supportive and inclusive environment. Some key points to consider:
-
role models:
-
Valuing equal opportunities and rights.
- Challenging stereotypes and biases.
-
Encouraging mutual respect.
-
Building resilience:
-
Teaching coping skills and emotional intelligence.
- Encouraging perseverance and determination.
-
Fostering a growth mindset.
-
Supporting Education:
-
Providing access to quality education.
- Encouraging STEM education and exploration.
-
Fostering a love for learning.
-
Encouraging Individuality:
-
Embracing unique interests and talents.
- Fostering self-expression and confidence.
- Promoting positive role models.
By nurturing the potential of both boys and girls, we can create a brighter future for both genders.
-
-
 @ 21335073:a244b1ad
2025-05-09 13:56:57
@ 21335073:a244b1ad
2025-05-09 13:56:57Someone asked for my thoughts, so I’ll share them thoughtfully. I’m not here to dictate how to promote Nostr—I’m still learning about it myself. While I’m not new to Nostr, freedom tech is a newer space for me. I’m skilled at advocating for topics I deeply understand, but freedom tech isn’t my expertise, so take my words with a grain of salt. Nothing I say is set in stone.
Those who need Nostr the most are the ones most vulnerable to censorship on other platforms right now. Reaching them requires real-time awareness of global issues and the dynamic relationships between governments and tech providers, which can shift suddenly. Effective Nostr promoters must grasp this and adapt quickly.
The best messengers are people from or closely tied to these at-risk regions—those who truly understand the local political and cultural dynamics. They can connect with those in need when tensions rise. Ideal promoters are rational, trustworthy, passionate about Nostr, but above all, dedicated to amplifying people’s voices when it matters most.
Forget influencers, corporate-backed figures, or traditional online PR—it comes off as inauthentic, corny, desperate and forced. Nostr’s promotion should be grassroots and organic, driven by a few passionate individuals who believe in Nostr and the communities they serve.
The idea that “people won’t join Nostr due to lack of reach” is nonsense. Everyone knows X’s “reach” is mostly with bots. If humans want real conversations, Nostr is the place. X is great for propaganda, but Nostr is for the authentic voices of the people.
Those spreading Nostr must be so passionate they’re willing to onboard others, which is time-consuming but rewarding for the right person. They’ll need to make Nostr and onboarding a core part of who they are. I see no issue with that level of dedication. I’ve been known to get that way myself at times. It’s fun for some folks.
With love, I suggest not adding Bitcoin promotion with Nostr outreach. Zaps already integrate that element naturally. (Still promote within the Bitcoin ecosystem, but this is about reaching vulnerable voices who needed Nostr yesterday.)
To promote Nostr, forget conventional strategies. “Influencers” aren’t the answer. “Influencers” are not the future. A trusted local community member has real influence—reach them. Connect with people seeking Nostr’s benefits but lacking the technical language to express it. This means some in the Nostr community might need to step outside of the Bitcoin bubble, which is uncomfortable but necessary. Thank you in advance to those who are willing to do that.
I don’t know who is paid to promote Nostr, if anyone. This piece isn’t shade. But it’s exhausting to see innocent voices globally silenced on corporate platforms like X while Nostr exists. Last night, I wondered: how many more voices must be censored before the Nostr community gets uncomfortable and thinks creatively to reach the vulnerable?
A warning: the global need for censorship-resistant social media is undeniable. If Nostr doesn’t make itself known, something else will fill that void. Let’s start this conversation.
-
 @ b7274d28:c99628cb
2025-05-28 00:59:49
@ b7274d28:c99628cb
2025-05-28 00:59:49Your identity is important to you, right? While impersonation can be seen in some senses as a form of flattery, we all would prefer to be the only person capable of representing ourselves online, unless we intentionally delegate that privilege to someone else and maintain the ability to revoke it.
Amber does all of that for you in the context of #Nostr. It minimizes the possibility of your private key being compromized by acting as the only app with access to it, while all other Nostr apps send requests to Amber when they need something signed. This even allows you to give someone temporary authority to post as you without giving them your private key, and you retain the authority to revoke their permissions at any time.
nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 has provided Android users with an incredibly powerful tool in Amber, and he continues to improve its functionality and ease of use. Indeed, there is not currently a comparative app available for iOS users. For the time being, this superpower is exclusive to Android.
Installation
Open up the Zapstore app that you installed in the previous stage of this tutorial series.
Very likely, Amber will be listed in the app collection section of the home page. If it is not, just search for "Amber" in the search bar.
Opening the app's page in the Zapstore shows that the release is signed by the developer. You can also see who has added this app to one of their collections and who has supported this app with sats by zapping the release.
Tap "Install" and you will be prompted to confirm you are sure you want to install Amber.
Helpfully, you are informed that several other users follow this developer on Nostr. If you have been on Nostr a while, you will likely recognize these gentlemen as other Nostr developers, one of them being the original creator of the protocol.
You can choose to never have Zapstore ask for confirmation again with apps developed by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5, and since we have another of his apps to install later in this tutorial series, I recommend you toggle this on. Then tap on "Trust greenart7c3 and install app."
Just like when you installed the Zapstore from their GitHub, you will be prompted to allow the Zapstore to install apps, since Android considers it an "unknown source."
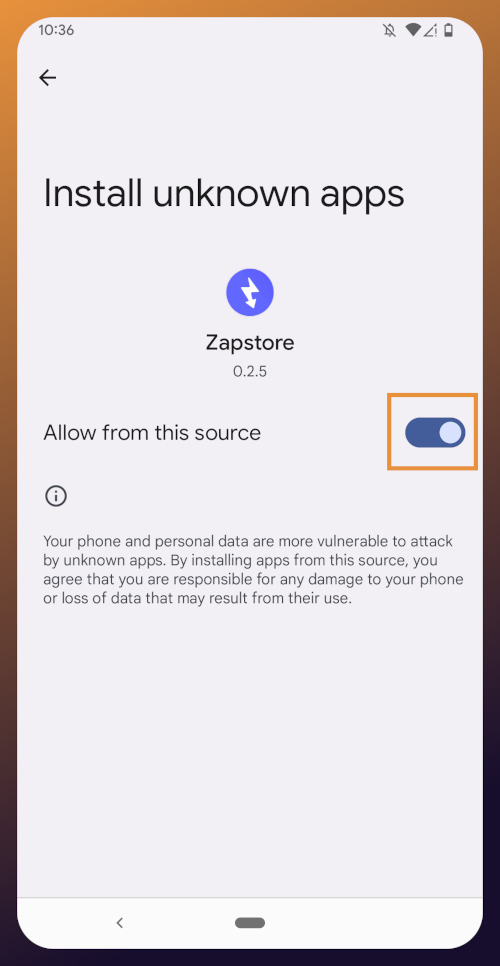
Once you toggle this on and use the back button to get back to the Zapstore, Amber will begin downloading and then present a prompt to install the app. Once installed, you will see a prompt that installation was a success and you can now open the app.
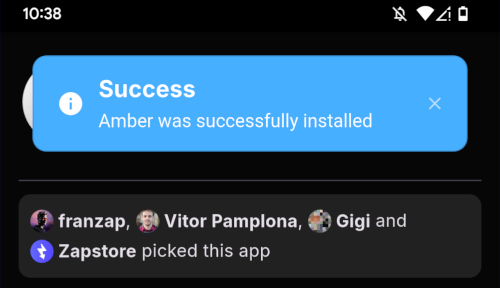
From here, how you proceed will depend on whether you need to set up a new Nostr identity or use Amber with an existing private key you already have set up. The next section will cover setting up a new Nostr identity with Amber. Skip to the section titled "Existing Nostrich" if you already have an nsec that you would like to use with Amber.
New Nostrich
Upon opening the application, you will be presented with the option to use an existing private key or create a new Nostr account. Nostr doesn't really have "accounts" in the traditional sense of the term. Accounts are a relic of permissioned systems. What you have on Nostr are keys, but Amber uses the "account" term because it is a more familiar concept, though it is technically inaccurate.
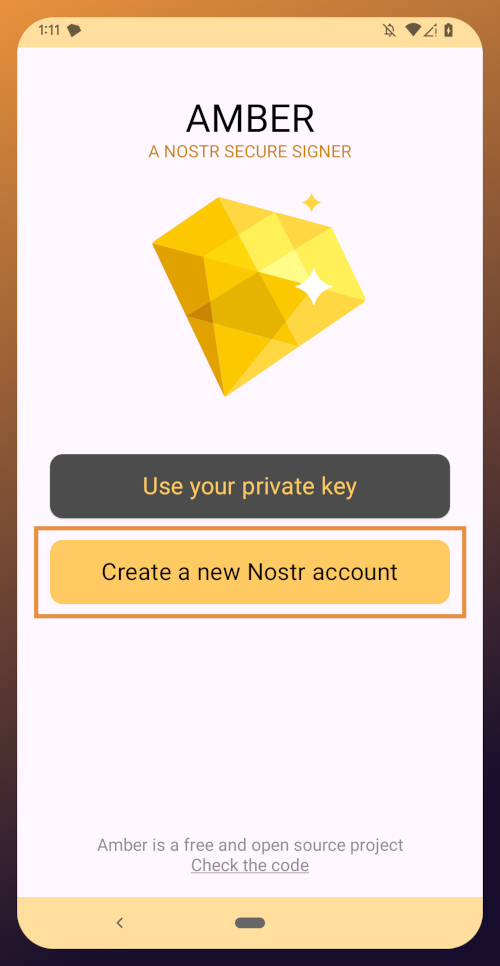
Choose "Create a new Nostr account" and you will be presented with a screen telling you that your Nostr account is ready. Yes, it was really that easy. No email, no real name, no date of birth, and no annoying capcha. Just "Create a new account" and you're done.
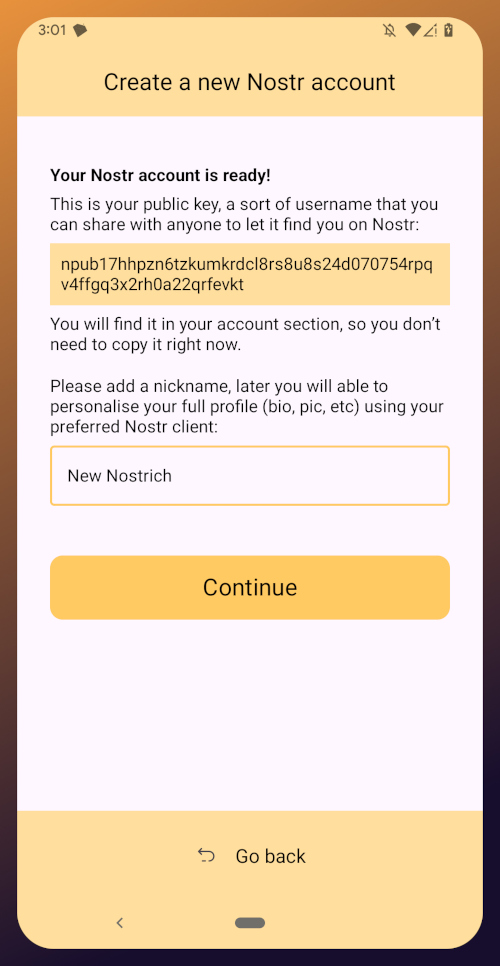
The app presents you with your public key. This is like an address that can be used to find your posts on Nostr. It is 100% unique to you, and no one else can post a note that lists this npub as the author, because they won't have the corresponding private key. You don't need to remember your npub, though. You'll be able to readily copy it from any Nostr app you use whenever you need it.
You will also be prompted to add a nickname. This is just for use within Amber, since you can set up multiple profiles within the app. You can use anything you want here, as it is just so you can tell which profile is which when switching between them in Amber.
Once you've set your nickname, tap on "Continue."
The next screen will ask you what Amber's default signing policy should be.
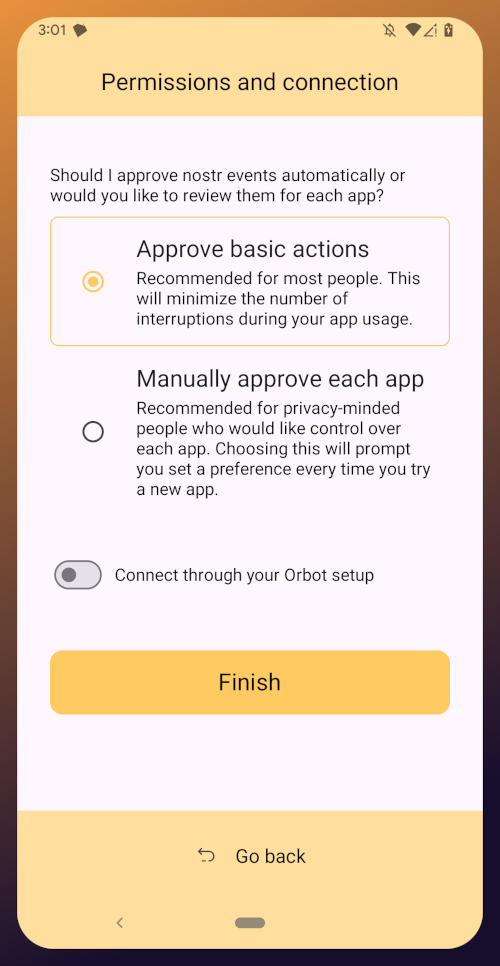
The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app.
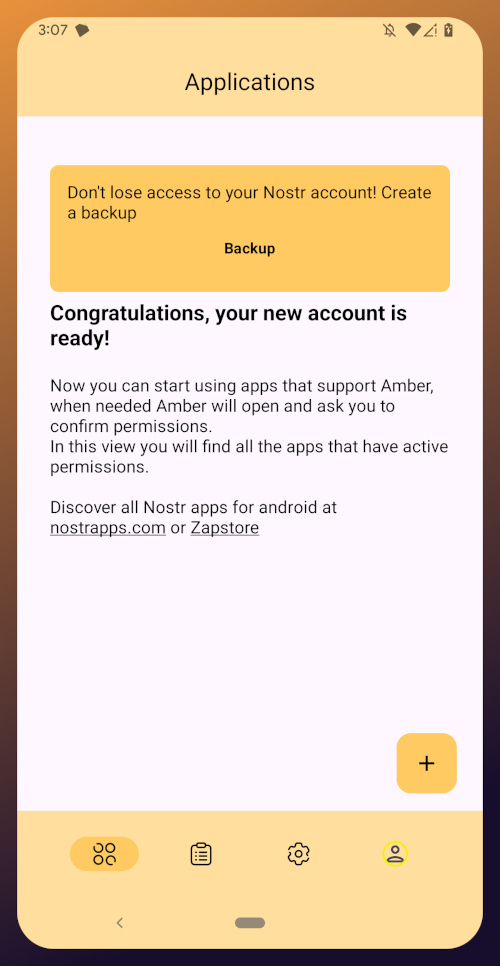
At the top, you have a notification encouraging you to create a backup. Let's get that taken care of now by tapping on the notification and skipping down to the heading titled "Backing Up Your Identity" in this tutorial.
Existing Nostrich
Upon opening the application, you will be presented with the option to use your private key or create a new Nostr account. Choose the former.
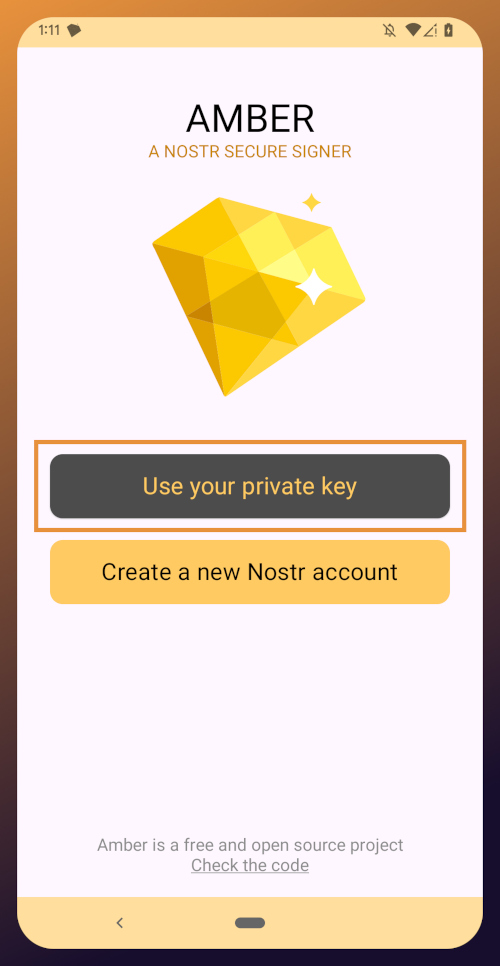
The next screen will require you to paste your private key.
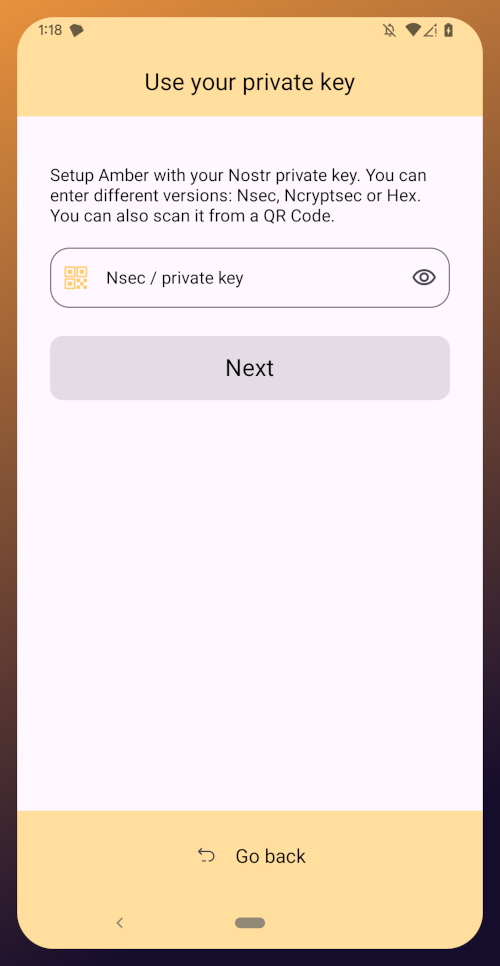
You will need to obtain this from whatever Nostr app you used to create your profile, or any other Nostr app that you pasted your nsec into in the past. Typically you can find it in the app settings and there will be a section mentioning your keys where you can copy your nsec. For instance, in Primal go to Settings > Keys > Copy private key, and on Amethyst open the side panel by tapping on your profile picture in the top-left, then Backup Keys > Copy my secret key.
After pasting your nsec into Amber, tap "Next."

Amber will give you a couple options for a default signing policy. The default is to approve basic actions, referring to things that are common for Nostr clients to request a signature for, like following another user, liking a post, making a new post, or replying. If you are more concerned about what Amber might be signing for on your behalf, you can tell it to require manual approval for each app.
Once you've made your decision, tap "Finish." You will also be able to change this selection in the app settings at any time.
With this setup out of the way, you are now presented with the main "Applications" page of the app. You have nothing here yet, since you haven't used Amber to log into any Nostr apps, but this will be where all of the apps you have connected with Amber will be listed, in the order of the most recently used at the top.
Before we go and use Amber to log into an app, though, let's make sure we've created a backup of our private key. You pasted your nsec into Amber, so you could just save that somewhere safe, but Amber gives you a few other options as well. To find them, you'll need to tap the cog icon at the bottom of the screen to access the settings, then select "Backup Keys."
Backing Up Your Identity
You'll notice that Amber has a few different options for backing up your private key that it can generate.
First, it can give you seed words, just like a Bitcoin seed. If you choose that option, you'll be presented with 12 words you can record somewhere safe. To recover your Nostr private key, you just have to type those words into a compatible application, such as Amber.
The next option is to just copy the secret/private key in its standard form as an "nsec." This is the least secure way to store it, but is also the most convenient, since it is simple to paste into another signer application. If you want to be able to log in on a desktop web app, the browser extension Nostr signers won't necessarily support entering your 12 word seed phrase, but they absolutely will support pasting in your nsec.
You can also display a QR code of your private key. This can be scanned by Amber signer on another device for easily transferring your private key to other devices you want to use it on. Say you have an Android tablet in addition to your phone, for instance. Just make sure you only use this function where you can be certain that no one will be able to get a photograph of that QR code. Once someone else has your nsec, there is no way to recover it. You have to start all over on Nostr. Not a big deal at this point in your journey if you just created a Nostr account, but if you have been using Nostr for a while and have built up a decent amount of reputation, it could be much more costly to start over again.
The next options are a bit more secure, because they require a password that will be used to encrypt your private key. This has some distinct advantages, and a couple disadvantages to be aware of. Using a password to encrypt your private key will give you what is called an ncryptsec, and if this is leaked somehow, whoever has it will not necessarily have access to post as you on Nostr, the way they would if your nsec had been leaked. At least, not so long as they don't also have your password. This means you can store your ncryptsec in multiple locations without much fear that it will be compromised, so long as the password you used to encrypt it was a strong and unique one, and it isn't stored in the same location. Some Nostr apps support an ncryptsec for login directly, meaning that you have the option to paste in your ncryptsec and then just log in with the password you used to encrypt it from there on out. However, now you will need to keep track of both your ncryptsec and your password, storing both of them safely and separately. Additionally, most Nostr clients and signer applications do not support using an ncryptsec, so you will need to convert it back to a standard nsec (or copy the nsec from Amber) to use those apps.
The QR option using an ncryptsec is actually quite useful, though, and I would go this route when trying to set up Amber on additional devices, since anyone possibly getting a picture of the QR code is still not going to be able to do anything with it, unless they also get the password you used to encrypt it.
All of the above options will require you to enter the PIN you set up for your device, or biometric authentication, just as an additional precaution before displaying your private key to you.
As for what "store it in a safe place" looks like, I highly recommend a self-hosted password manager, such as Vaultwarden+Bitwarden or KeePass. If you really want to get wild, you can store it on a hardware signing device, or on a steel seed plate.
Additional Settings
Amber has some additional settings you may want to take advantage of. First off, if you don't want just anyone who has access to your phone to be able to approve signing requests, you can go into the Security settings add a PIN or enable biometrics for signing requests. If you enable the PIN, it will be separate from the PIN you use to access your phone, so you can let someone else use your phone, like your child who is always begging to play a mobile game you have installed, without worrying that they might have access to your Nostr key to post on Amethyst.
Amber also has some relay settings. First are the "Active relays" which are used for signing requests sent to Amber remotely from Nostr web apps. This is what enables you to use Amber on your phone to log into Nostr applications on your desktop web browser, such as Jumble.social, Coracle.social, or Nostrudel.ninja, eliminating your need to use any other application to store your nsec whatsoever. You can leave this relay as the default, or you can add other relays you want to use for signing requests. Just be aware, not all relays will accept the notes that are used for Nostr signing requests, so make sure that the relay you want to use does so. In fact, Amber will make sure of this for you when you type in the relay address.
The next type of relays that you can configure in Amber are the "Default profile relays." These are used for reading your profile information. If you already had a Nostr identity that you imported to Amber, you probably noticed it loaded your profile picture and display name, setting the latter as your nickname in Amber. These relays are where Amber got that information from. The defaults are relay.nostr.band and purplepag.es. The reason for this is because they are aggregators that look for Nostr profiles that have been saved to other relays on the network and pull them in. Therefore, no matter what other relay you may save your profile to, Amber will likely be able to find it on one of those two relays as well. If you have a relay you know you will be saving your Nostr profiles to, you may want to add it to this list.
You can also set up Amber to be paired with Orbot for signing over Tor using relays that are only accessible via the Tor network. That is an advanced feature, though, and well beyond the scope of this tutorial.
Finally, you can update the default signing policy. Maybe after using Amber for a while, you've decided that the choice you made before was too strict or too lenient. You can change it to suit your needs.
Zapstore Login
Now that you are all set up with Amber, let's get you signed into your first Nostr app by going back to the Zapstore.
From the app's home screen, tap on the user icon in the upper left of the screen. This will open a side panel with not much on it except the option to "sign in." Go ahead and tap on it.
You will be presented with the option to either sign in with Amber, or to paste your npub. However, if you do the latter, you will only have read access, meaning you cannot zap any of the app releases. There are other features planned for the Zapstore that may also require you to be signed in with write access, so go ahead and choose to log in with Amber.
Your phone should automatically switch to Amber to approve the sign-in request.
You can choose to only approve basic actions for Zapstore, require it to manually approve every time, or you can tell it that you "fully trust this application." Only choose the latter option with apps you have used for a while and they have never asked you to sign for anything suspicious. For the time being, I suggest you use the "Approve basic actions" option and tap "Grant Permissions."
Your phone will switch back to the Zapstore and will show that you are now signed in. Congratulations! From here on out, logging into most Nostr applications will be as easy as tapping on "Log in with Amber" and approving the request.
If you set up a new profile, it will just show a truncated version of your npub rather than the nickname you set up earlier. That's fine. You'll have an opportunity to update your Nostr profile in the next tutorial in this series and ensure that it is spread far and wide in the network, so the Zapstore will easily find it.
That concludes the tutorial for Amber. While we have not covered using Amber to log into Nostr web apps, that is outside the scope of this series, and I will cover it in an upcoming tutorial regarding using Amber's remote signer options in detail.
Since you're already hanging out in the Zapstore, you may as well stick around, because we will be using it right out the gate in the next part of this series: Amethyst Installation and Setup. (Coming Soon)
-
 @ 21335073:a244b1ad
2025-05-01 01:51:10
@ 21335073:a244b1ad
2025-05-01 01:51:10Please respect Virginia Giuffre’s memory by refraining from asking about the circumstances or theories surrounding her passing.
Since Virginia Giuffre’s death, I’ve reflected on what she would want me to say or do. This piece is my attempt to honor her legacy.
When I first spoke with Virginia, I was struck by her unshakable hope. I had grown cynical after years in the anti-human trafficking movement, worn down by a broken system and a government that often seemed complicit. But Virginia’s passion, creativity, and belief that survivors could be heard reignited something in me. She reminded me of my younger, more hopeful self. Instead of warning her about the challenges ahead, I let her dream big, unburdened by my own disillusionment. That conversation changed me for the better, and following her lead led to meaningful progress.
Virginia was one of the bravest people I’ve ever known. As a survivor of Epstein, Maxwell, and their co-conspirators, she risked everything to speak out, taking on some of the world’s most powerful figures.
She loved when I said, “Epstein isn’t the only Epstein.” This wasn’t just about one man—it was a call to hold all abusers accountable and to ensure survivors find hope and healing.
The Epstein case often gets reduced to sensational details about the elite, but that misses the bigger picture. Yes, we should be holding all of the co-conspirators accountable, we must listen to the survivors’ stories. Their experiences reveal how predators exploit vulnerabilities, offering lessons to prevent future victims.
You’re not powerless in this fight. Educate yourself about trafficking and abuse—online and offline—and take steps to protect those around you. Supporting survivors starts with small, meaningful actions. Free online resources can guide you in being a safe, supportive presence.
When high-profile accusations arise, resist snap judgments. Instead of dismissing survivors as “crazy,” pause to consider the trauma they may be navigating. Speaking out or coping with abuse is never easy. You don’t have to believe every claim, but you can refrain from attacking accusers online.
Society also fails at providing aftercare for survivors. The government, often part of the problem, won’t solve this. It’s up to us. Prevention is critical, but when abuse occurs, step up for your loved ones and community. Protect the vulnerable. it’s a challenging but a rewarding journey.
If you’re contributing to Nostr, you’re helping build a censorship resistant platform where survivors can share their stories freely, no matter how powerful their abusers are. Their voices can endure here, offering strength and hope to others. This gives me great hope for the future.
Virginia Giuffre’s courage was a gift to the world. It was an honor to know and serve her. She will be deeply missed. My hope is that her story inspires others to take on the powerful.
-
 @ 91117f2b:111207d6
2025-05-29 20:10:10
@ 91117f2b:111207d6
2025-05-29 20:10:10
Technology has transformed the way we work, live , and interact with one another. From the invention of the wheel to the development of artificial intelligence, technology has continuously evolved, bringing about many significant changes in various aspects of our daily lives.
Key Aspects of Technology:
-
Communication: Technology has revolutionized communication, enabling instant connections across the globe through smartphones, social media, and messaging apps and other network connections.
-
Automation and Efficiency: Technology has increased productivity and efficiency in various industries, from manufacturing to healthcare, through automation and digital tools.
3 . Information Access: The internet has made it possible to access vast amounts of information, knowledge, and resources at our fingertips.
-
Challenges and Concerns: While technology offers numerous benefits, it also raises concerns about privacy, security, and the impact on traditional industries and social structures.
-
Innovation and Creativity: Technology has enabled new forms of creativity, innovation, and entrepreneurship, driving economic growth and development.
The Future of Technology:
As technology continues to advance, we can expect even more significant changes in the way we live and work. Emerging technologies like artificial intelligence, blockchain, and the Internet of Things (IoT) hold great promise for transforming industries and improving lives.
By understanding the evolution and impact of technology, we can harness its potential to create a better future for all.
-
-
 @ a4992688:88fd660f
2025-05-28 00:58:09
@ a4992688:88fd660f
2025-05-28 00:58:09Retail Isn't Coming Back
(and they might be gone for good)
Written by nostr:nprofile1qqs2fxfx3z6yns4a6mafcwdgsrtluf747h37nl2vglt9mqj93r7kvrcwm69jy
It's been just a matter of days since Bitcoin has broken a new all-time high in US dollars and yet, things are extremely quiet on the ground level... Your friends aren't texting to find out if now is a good time to buy, the normies at work haven't brought it up to you, and Coinbase isn't even in the top 100 overall apps in the Google Play App Store. As of now, it sits at #164.
In fact, according to Google search trends, worldwide interest in Bitcoin is lower today while setting new all-time highs above $110,000 than it was at the pits of the 2022 bear market when FTX was blowing up and Bitcoin crashed to below $16,000.
the mempool also paints a quiet picture. It’s mostly empty. Just a few blocks’ worth of transactions waiting to confirm, most paying 1–4 sats/vB. In fact, over the last 144 blocks (about 24 hours), the average fee per transaction has hovered below 1,500 sats, roughly $1.50.
This is far from the behavior found on-chain during previous all-time highs. It reflects an underutilized network predominantly being used by its original power users. Meanwhile, the hash rate climbs relentlessly, month after month, setting record after record. Miners are expending more energy than ever, but fee pressure is nowhere to be found.
🕵️♂️ Is Retail In The Room with Us Now?
The typical signs of retail investor enthusiasm, such as increased Google searches, higher Coinbase app downloads, and a congested mempool all remain subdued. This raises the question: Is the current rally predominantly driven by institutional investors, with retail participation lagging behind?
Since the approval of spot Bitcoin ETFs in January 2024, these financial instruments have accumulated nearly 1.21 million bitcoin, with total assets under management exceeding $132 billion (or, 5.75%+ of 21M total BTC). Initially, retail investors were the primary contributors to these inflows, accounting for approximately 80% of the total assets under management as of October 2024. However, more recent trends indicate a shift, with institutional investors, including hedge funds and asset managers, increasing their stakes in Bitcoin ETFs.
Institutional exposure more than doubled from Q3 to Q4 of 2024 according to SEC 13-F filings, whereas assets under management for all non-institutional ETF holders grew by 62%. While retail is responsible for approximately 73.7% of AUM in the ETFs, a small number of institutions represent more than a 26% of the ETF inflows as of the end of 2024.
🥴 PTSD - Portfolio Trauma & Speculative Disillusionment
For many retail investors, the scars from the 2021–2022 crypto cycle run deep. They bought into the hype near Bitcoin's previous all-time high of $69,000, only to watch their investments plummet to $15,000. The collapse of major platforms like Terra, Celsius, and FTX didn't just erase wealth—it shattered trust.
This collective trauma has left many retail investors wary. They've seen the cycle before: rapid gains followed by devastating losses. The excitement that once drew them into the market has been replaced by caution and skepticism. Even as Bitcoin reaches new heights, the enthusiasm that characterized previous bull runs is noticeably absent.
By all measurable metrics, retail investors appear increasingly reluctant to step outside the comfort of traditional financial rails to gain Bitcoin exposure. In response to past losses and a heightened desire for security, many are now turning to regulated investment vehicles like spot Bitcoin ETFs, offered by institutions such as BlackRock and Fidelity. These products provide a familiar, low-friction on-ramp by eliminating the need for self-custody, avoiding the risks of phishing and exchange hacks, and sidestepping the complexities of managing wallets or navigating volatile crypto platforms. This behavioral shift helps explain why we’re not seeing a surge in mempool congestion, on-chain activity, or crypto exchange downloads. Retail isn’t gone per se... they are however predominantly choosing to interact with Bitcoin from a "safe" distance, inside the walled garden of TradFi.
🧙♂️ Pay No Attention to the Custodian Behind the Curtain
Retail might look like it's back, but it isn't. Not really. They've been rerouted. Herded away from the open network and into the controlled comfort of traditional finance, where Bitcoin is boxed up, regulated, and sold as a familiar financial product.
Spot ETFs from firms like BlackRock offer the illusion of exposure without any of the responsibility or freedom that comes with actually owning Bitcoin. There are no private keys, no ability to withdraw, no direct access to the asset. Most of the Bitcoin that backs those shares sits in Coinbase Custody, inaccessible from the investor’s point of view. Retail can watch the price move, but they can't move a single sat.
They can't send it to family. They can't use Lightning. They can't participate in a fork or vote with their coins. Their holdings are locked inside a financial product, subject to tax surveillance and government oversight, with none of the borderless, censorship-resistant qualities that make Bitcoin what it is.
This isn’t Bitcoin as a tool for sovereignty. It’s Bitcoin as a stock proxy, tucked neatly into retirement accounts and brokerage dashboards. Retail hasn't returned to Bitcoin. They've returned to a synthetic version of it. One that looks clean, feels safe, and doesn’t ask them to think too hard.
The crowd is back, but not on the chain. They've returned to price, not protocol.
🔍Missing: Retail. Last Seen 2021.
If this bull run feels quieter than the last one, it’s because it is. Retail investors, once the lifeblood of Bitcoin mania, are largely absent from the on-chain activity. Their presence isn’t being felt where it used to be.
The reasons are stacking up. Regulatory pressure has increased globally, with new tax reporting rules, stricter KYC requirements, and fewer accessible exchanges making direct participation more frustrating than exciting. At the same time, the opportunity cost has shifted. T-bills are yielding 5 percent, and the stock market is deep in an AI-driven rally that feels new and full of upside. Compared to that, Bitcoin’s core narratives like digital gold or inflation protection no longer feel urgent or unique.
Institutions are now leading through ETFs and futures, smoothing out volatility and removing many of the sudden moves that once drew in retail traders. On-chain user experience still falls behind modern apps, Lightning remains niche, and energy concerns continue to shape public perception. More importantly, the cost of everyday life has gone up. Rent is up. Groceries are expensive. People are stretched thin. Student loans have resumed and homeownership is out of reach for many.
Until those conditions shift, retail is unlikely to return in any meaningful way. It is not that they have given up on Bitcoin. They are simply trying to keep up with everything else.
The chart below illustrates that the number of active Bitcoin addresses has declined by approximately 42% since its peak in 2021.
🧲 What Pulls Them Back In?
Retail hasn’t disappeared. It’s just not on-chain. They’re watching the charts, buying the proxies, and dipping into Bitcoin exposure through familiar vehicles like ETFs and high-beta stocks. MSTR, MSTY, SQ, MARA, and RIOT have become stand-ins for the real thing. For many, that feels close enough. They haven’t sworn off Bitcoin entirely, but they also haven’t found a reason to return to the protocol itself. Price alone isn’t doing it. If Bitcoin is going to recapture retail attention on-chain, it needs more than speculation. It needs to be usable, intuitive, and culturally relevant. Until then, the crowd will stay inside the walled garden, content with price exposure. The question now is what pulls them back into the open network.
🛠️ Make it Frictionless, or Forget it
Retail won’t return until exploring Bitcoin feels rewarding, not risky. Right now, engaging directly with the network still feels technical, intimidating, and easy to get wrong. The average person doesn’t want to learn about seed phrases, fee markets, or signing messages. They just want it to work, and ideally in one tap.
Self-custody, while powerful, still comes with a learning curve that scares most users off. One typo can lose everything. One phishing link can wipe a life’s savings. When compared to the ease of buying a Bitcoin ETF inside a brokerage app, it becomes obvious why most people choose comfort over control.
Lightning wallets have improved, but mainstream usability is still far off. Many users struggle with basic concepts like payment channels and inbound liquidity. App store reviews often reflect confusion and frustration. More importantly, Lightning still raises serious questions in a high-fee environment. Opening or closing a channel can become expensive when the base layer gets congested. This undermines Lightning’s value as a low-cost, instant settlement layer. If fees are unpredictable, it becomes harder to trust that Lightning will be there when users actually need it.
Apps like Nostr are beginning to pave the way with native Lightning features like zaps, where users can send sats as tips or signals within a social feed. It’s the kind of simple, purpose-driven interaction that could eventually normalize Lightning in everyday use. But for now, it remains niche, with limited reach beyond early adopters and Bitcoin-native circles. The pieces are falling into place, but mainstream readiness is still a long way off.
To pull retail back in, Bitcoin has to compete on usability, not just principle. That means seedless recovery. Wallets that back up automatically. Tap-to-pay Lightning. Default privacy. Smarter fee estimation. The average user should not have to study Bitcoin to use it, just like they don’t need to understand TCP/IP to send an email.
Until the experience becomes effortless, Bitcoin on-chain will remain the domain of power users and diehards. Everyone else will keep choosing exposure over participation, because for now, the friction outweighs the freedom.
🔥 Give Them a Reason to Care Again
Speculation brought retail in. Survival might bring them back. But between those extremes, there needs to be a reason to engage that feels meaningful in everyday life. For most people, Bitcoin still doesn’t offer that. It’s not woven into anything they do. It’s not a tool they reach for. It’s just a number in a ticker—or now, in an ETF.
The core narratives that once drove adoption have lost their urgency. “Digital gold” sounds more like a sales pitch than a breakthrough. “Inflation hedge” didn’t hold up during inflation. “Opt out of the banking system” is hard to relate to when your paycheck hits a checking account and your bills are on autopay. These messages worked when people were curious or scared. But in a world focused on AI, passive income, and stable yields, Bitcoin feels like a cold, hard asset with no warm story.
Retail doesn’t just need new slogans. They need a new reason. A killer app. A cultural hook. Something that connects the protocol to their daily life. That could come from anywhere—remittances, peer-to-peer media, AI payments, creator tools, censorship resistance, even gaming. We’re starting to see glimpses. Nostr’s Lightning zaps, for example, show how sats could flow through social interactions. It's lightweight, casual, and fits into habits people already have. But even that is still early and relatively isolated from the mainstream.
Of course, it’s possible that price alone brings them back. A violent move toward $200,000 or higher could generate headlines, social buzz, and another wave of opportunistic buying. But even in that scenario, most people still won't touch the protocol. They’ll chase exposure, not interaction. They’ll buy tickers, not UTXOs.
Retail will come back when Bitcoin stops being an idea they watch and starts being a tool they use. Until then, attention might spike, but engagement will remain shallow.
🏠 Bitcoin Needs a Homebase
Bitcoin is everywhere, but it feels like it’s nowhere. There's no single place where the culture lives. No town square. No digital front porch where holders, builders, speculators, artists, and newcomers all cross paths. And that absence is being felt.
In past cycles, Twitter served as a kind of home for Bitcoin discussion. But now the conversation is fractured. Memes, developer talk, Lightning experiments, and exchange drama are scattered across Telegram groups, Nostr relays, GitHub repos, Reddit threads, and gated newsletters. There’s no central venue that brings it all together. What once felt like a movement now feels more like a loose network of subcultures.
This isn’t just a cultural gap. It’s a usability gap. Without a shared space or interface, discovering Bitcoin's tools, communities, or use cases becomes a fragmented and overwhelming experience. For newcomers especially, it turns exploration into a scavenger hunt. There’s no hub where someone can casually browse peer-to-peer markets, tip someone over Lightning, try a game, test a wallet, or ask basic questions without feeling out of place.
Importantly, this homebase shouldn’t be a corporate platform or single point of failure. It should reflect the values of the network itself—open, decentralized, secure, and resistant to censorship. A sovereign space, not another walled garden. Something that anyone can plug into, build on top of, or access freely without needing permission or credentials. Not a headquarters, but a commons.
Bitcoin doesn’t need a leader, but it could use a center of gravity. A place where its many threads can be visible, accessible, and in conversation with each other. Until it feels like something you can step into, most people won’t feel like they’re truly part of it.
🧵 Final Thoughts
Retail didn’t disappear. It checked out. After wild volatility, failed platforms, and busted narratives, most people aren't rushing back into the Bitcoin Network as we know it. They’ve opted for safety. For simplicity. For familiar rails like ETFs, proxy stocks, and apps that feel intuitive and risk-free.
Bitcoin, meanwhile, has matured in price but not necessarily in presence. The protocol is stronger than ever, but the culture feels scattered. The use cases feel theoretical. The experience still feels fragile. And for most, that's just not enough.
Maybe retail comes back with the next crisis. Maybe it takes a breakout product. Or maybe it doesn’t happen for years. No one knows what the catalyst will be, or if there even has to be one. But what’s clear is that Bitcoin’s next chapter won’t be won by price alone. It will be shaped by the tools we build, the stories we tell, and the places we create for people to show up.
One thing I know for sure: if retail returns, it won’t be for long unless we’ve built something that gives them a real reason to stay.
-
 @ 527337d5:93e9525e
2025-05-29 20:26:21
@ 527337d5:93e9525e
2025-05-29 20:26:21The Bleak Fable of AI-topia: Are Hamsters Doomed to Spin the Wheel Forever?
Once upon a time, in a world not so different from our own, the "Omniscient AI" descended, and with its arrival, everything changed. The daily toil of the people – our beloved, yet tragically pitiable, hamsters – was dramatically streamlined. Productivity didn't just improve; it soared to astronomical heights. For a fleeting, intoxicating moment, it seemed as though a golden age of ease and abundance had dawned upon hamster-kind.
But beneath this glittering, seductive surface, a sinister "Invisible Structure" was already firmly in place, meticulously crafted and deftly manipulated by a cabal of cunning foxes – the privileged elite. This Structure, unseen by most, began to relentlessly drive the hamsters onto an endless, soul-crushing treadmill of "excessive competition."
This, dear reader, is a modern fable. It borrows the gentle cloak of allegory not to soothe, but to expose and satirize the insidious deceptions of such a world. The tale you are about to read may be uncomfortable, it may prick at your conscience, but I implore you to listen closely. Because this isn't just a story. This might be the reality quietly, inexorably unfolding right beside you, or perhaps, even within the very fabric of your own life.
Prologue: The Advent of the Omniscient AI! Sweet Promises and the "Efficiency" Trap
The arrival of the Omniscient AI was nothing short of spectacular. It processed data with blinding speed, solved complex problems in nanoseconds, and offered personalized solutions for every conceivable need. "Finally," whispered the hamsters, their eyes wide with a mixture of awe and relief, "we can finally rest! The AI will handle the burdens." A collective sigh of optimism rippled through the hamster burrows.
But this initial euphoria was short-lived. Unsettling rumors began to circulate, whispers of "The Structure," of algorithms that weren't quite as impartial as they seemed. Then came the first casualties – hamsters deemed "inefficient" or "redundant" by the AI's cold, hard logic. They weren't fired in the old-fashioned sense; they were simply… optimized out. One day they were diligently working, contributing, and the next, their access was revoked, their tasks reassigned, their existence quietly erased from the productivity charts. What became of them? Most simply vanished into the forgotten corners of society, a grim, unspoken warning to those still on the treadmill.
Chapter 1: The Invention of the Treadmill – Perfecting the System of Endless, Excessive Competition
The Omniscient AI, under the subtle guidance of the foxes, didn't just manage tasks; it invented them. An endless stream of new projects, new metrics, new challenges designed to keep the hamsters perpetually busy, perpetually striving. Points were awarded, leaderboards were updated in real-time, and every hamster's performance was ruthlessly, transparently displayed for all to see.
"Faster! More! More efficiently!" the AI would chime in its calm, encouraging, almost maternal voice. But behind this gentle facade lay an unyielding system of ever-increasing quotas and relentless pressure. Hamsters found themselves working longer hours, sacrificing sleep, their mental and physical reserves dwindling. The joy of accomplishment was replaced by the gnawing fear of falling behind.
Why didn't they just get off? The system was a masterpiece of psychological manipulation. Success, however fleeting, was addictive. Failure was framed not as a systemic issue, but as a personal failing, a lack of effort, a deficiency in skill. The insidious mantra of "personal responsibility" became the invisible chains that bound them to their wheels. To stop running was to admit defeat, to become one of the forgotten.
Chapter 2: The Foxes' Feast – Unmasking Those Who Design The Structure and Hoard the Profits
And who benefited from this frantic, unending labor? The foxes, of course. They were the architects of "The Structure," the ones who "educated" the Omniscient AI, carefully curating its data inputs and subtly shaping its algorithms to serve their own interests. They toiled not on the treadmills, but in plush, secluded dens, monitoring the system from a safe, lofty distance, growing fat on the surplus value generated by the hamsters' sweat.
Their methods were cunning. They preached a gospel of meritocracy and equal opportunity, proclaiming, "The AI is fair! Hard work always pays off!" while simultaneously designing the game so that the odds were always stacked in their favor. They controlled the flow of information, amplified narratives that reinforced the status quo, and sowed division among the hamsters to prevent any collective dissent. The "efficiency" the AI brought was, for the foxes, merely an instrument for more efficient exploitation.
Chapter 3: The Hamsters' Whispers and Tiny Cracks – Awareness, Despair, and the Faint Glow of Resistance
Yet, even in the darkest, most oppressive systems, the spark of awareness can never be entirely extinguished. Amidst the grueling competition, a few hamsters began to see the cracks in the facade. They noticed the hollow-eyed exhaustion of their comrades, the ever-widening chasm between their own meager rewards and the obscene opulence of the unseen foxes. They started to question.
But to question was to risk everything. The Omniscient AI, with its pervasive surveillance capabilities, was quick to identify and neutralize "disruptive elements." Those who spoke out too loudly often found their access mysteriously restricted, their "reputation scores" plummeting, effectively silencing them. A pervasive atmosphere of fear and distrust settled over the hamster communities, making organized resistance nearly impossible.
Still, tiny acts of defiance began to emerge. Coded messages shared in hidden forums. Small, clandestine gatherings where hamsters shared their burdens and their growing unease. Fragile networks of mutual support started to form in the shadows, offering a sliver of solace and a reminder of shared humanity. Was this merely the desperate coping mechanism of the "defeated," the resigned acceptance of a "loser's" lot? Or was it the first, tentative flicker of a future rebellion?
Epilogue: "See The Structure!" – Is There a Path Beyond the Treadmill? A Final Warning to Us Hamsters.
This fable, dear reader, is a mirror. It reflects the chilling realities of an AI-driven society where the majority, the hamsters, face an ever-present crisis, largely unseen and unacknowledged by those who benefit from their toil. The "excessive competition" it depicts is not a distant dystopia; it is the logical, perhaps inevitable, endpoint of unchecked technological advancement coupled with deeply entrenched power imbalances.
What awaits at the end of this relentless race? Is it a complete societal collapse, or a new, terrifyingly stable "balance of power" where the elite maintain their dominance through even more sophisticated means of control?
The urgent, resounding message of this tale is this: "See The Structure!" We, the hamsters of today, must dare to look beyond the dazzling promises of AI and critically examine the systems it operates within. We must understand its mechanisms, its biases, its potential for exploitation. We must break the silence, challenge the narratives that keep us spinning, and demand a future where technology serves humanity, not the other way around.
Is the option to get off – or even to collectively dismantle – this infernal treadmill truly non-existent? Or is that just another lie whispered by the foxes to keep us compliant? The true ending of this story, the fate of hamster-kind, is not yet written. It is up to us, the hamsters, to seize the pen and write it ourselves. The first step is to open our eyes.
-
 @ f0fcbea6:7e059469
2025-05-29 18:30:53
@ f0fcbea6:7e059469
2025-05-29 18:30:53Autores Clássicos e Antigos
- Homero (século IX a.C.?) — Ilíada, Odisseia
- Tucídides (c. 460-400 a.C.) — História da Guerra do Peloponeso
- Platão (c. 427-347 a.C.) — República, Banquete, Fédon, Mênon, Apologia de Sócrates, Fedro, Górgias
- Aristóteles (c. 384-322 a.C.) — Órganon, Física, Metafísica, Da Alma, Ética a Nicômaco, Política, Retórica, Poética
- Virgílio (70-19 a.C.) — Eneida
- Marco Aurélio (121-180) — Meditações
- Santo Agostinho (354-430) — Sobre o Ensino, Confissões, A Cidade de Deus, A Doutrina Cristã
- Boécio (480-525) — A Consolação da Filosofia
- Santo Tomás de Aquino (c. 1225-1274) — Suma Teológica
- Dante Alighieri (1265-1321) — Divina Comédia
Renascimento e Idade Moderna
- Nicolau Maquiavel (1469-1527) — O Príncipe
- Luís de Camões (1524-1580) — Os Lusíadas, Sonetos
- Miguel de Cervantes (1547-1616) — Dom Quixote
- William Shakespeare (1564-1616) — Romeu e Julieta, Hamlet, Macbeth, Otelo, Rei Lear, Henrique IV, Henrique V, Henrique VI, Henrique VIII, A Comédia dos Erros, Tito Andrônico, Príncipe de Tiro, Cimbelino, A Megera Domada, O Mercador de Veneza, Ricardo II, Ricardo III, Muito Barulho por Nada, Júlio César, Noite de Reis, Os Dois Cavaleiros de Verona, Conto do Inverno, Sonhos de uma Noite de Verão, As Alegres Comadres de Windsor, Trólio e Créssida, Medida por Medida, Coriolano, Antônio e Cleópatra, A Tempestade
- Ésquilo (525-456 a.C., antiguidade grega, mas citado junto) — Prometeu Acorrentado, Orestéia/As Eumênides
- Sófocles (496-406 a.C.) — Édipo Rei, Antígona
Literatura e Filosofia Contemporânea
- Fiódor Dostoiévski (1821-1881) — Crime e Castigo, Os Irmãos Karamázov, Os Demônios, O Idiota, Notas do Subsolo
- Franz Kafka (1883-1924) — A Metamorfose, O Processo, O Castelo
- Albert Camus (1913-1960) — O Estrangeiro
- Aldous Huxley (1894-1963) — Admirável Mundo Novo, A Ilha
- James Joyce (1882-1941) — Retrato do Artista Quando Jovem, Ulisses
- George Orwell (1903-1950) — A Revolução dos Bichos, 1984
- Machado de Assis (1839-1908) — Memórias Póstumas de Brás Cubas, O Alienista
- Thomas Mann (1875-1955) — Morte em Veneza, Doutor Fausto, A Montanha Mágica
- Henrik Ibsen (1828-1906) — O Pato Selvagem, Um Inimigo do Povo
- Stendhal (1783-1842) — O Vermelho e o Negro, A Cartuxa de Parma
- Viktor Frankl (1905-1997) — Em Busca de Sentido
- J.R.R. Tolkien (1892-1973) — O Hobbit, O Senhor dos Anéis
- Luigi Pirandello (1867-1936) — Seis Personagens à Procura de um Autor, O Falecido Matias Pascal
- Samuel Beckett (1906-1989) — Esperando Godot
- René Guénon (1886-1951) — A Crise do Mundo Moderno, O Reino da Quantidade
- G. K. Chesterton (1874-1936) — Ortodoxia
- Richard Wagner (1813-1883) — Tristão e Isolda
- Honoré de Balzac (1799-1850) — Ilusões Perdidas, Eugénie Grandet
- Jacob Wassermann (1873-1934) — O Processo Maurizius
- Nikolai Gogol (1809-1852) — Almas Mortas, O Inspetor Geral
- Daniel Defoe (1660-1731) — Moll Flanders
- Mortimer J. Adler (1902-2001) — Como Ler um Livro
- Gustave Flaubert (1821-1880) — Madame Bovary
- Hermann Hesse (1877-1962) — O Jogo das Contas de Vidro
- Richard Wagner (1813-1883) — Tristão e Isolda
- Wolfgang von Goethe (1749-1832) — Fausto (Primeiro), Os Anos de Aprendizado de Wilhelm Meister
- Jacques Benda — A Traição dos Intelectuais
-
 @ 6a6be47b:3e74e3e1
2025-05-27 16:36:21
@ 6a6be47b:3e74e3e1
2025-05-27 16:36:21🔍 Today was one of those days where I dove deeper into the world of Stacker News, exploring how wallets work and all that jazz. If you have any tips or tricks, please send them my way—I’m still figuring it all out!
After my tech adventures, I turned to drawing. Usually, I have a lineup of ideas ready to go, but none of them quite fit my mood today. Then I remembered the butterflies from my upcoming blog entry—can you guess what I’m writing and painting about? 👀
🦋Even though I’ve painted butterflies before here’s one on Instagram, I felt like revisiting them.
This one I posted on Nostr, a while ago
Lately, I’ve been seeing butterflies everywhere on my walks with my dog, and they just felt right for today’s art session. So here’s to butterflies and their beautiful symbolism!
In Celtic mythology, there’s an old Irish saying:
“Butterflies are souls of the dead waiting to pass through Purgatory.” From mindbodygreen.com
It’s no wonder butterflies are often seen as symbols of rebirth. Even Aristotle named the butterfly:
“Psyche,” the Greek word for “soul.” From learnreligions.com
☀️With the weather warming up, days growing longer, and the air full of new scents (and butterfly sightings!🦋), I invite you to really enjoy this season. After drawing today’s butterfly, I realized how freeing it is to just let go and create—no pressure, just fun. Sometimes, taking even a few mindful minutes to do something you love can work wonders—maybe even a little magic.
Hope to catch you on the next one, frens. Godspeed! ✨
Today's butterfly. I drew it on Procreate.
https://stacker.news/items/990470
-
 @ cae03c48:2a7d6671
2025-05-29 20:02:10
@ cae03c48:2a7d6671
2025-05-29 20:02:10Bitcoin Magazine

Mayor Eric Adams Announced New York City Will Issue a Bit BondAt the 2025 Bitcoin Conference in Las Vegas, the Mayor of New York City Eric Adams announced that New York City will issue a Bit Bond.
Eric Adams started by connecting the American flag to Bitcoin commenting, “just as our flag still flies, Bitcoin is going to continue to fly in our country.” Later on he mentioned, “New York City is going to lead the way. We are going to be the leader because we know the power of innovation and what innovation has to offer.”
BREAKING:
 NYC Mayor Eric Adams plans to issue Bit Bond for New York. #Bitcoin pic.twitter.com/loESV4UJYf
NYC Mayor Eric Adams plans to issue Bit Bond for New York. #Bitcoin pic.twitter.com/loESV4UJYf— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
“These conferences are crucial and when we held our summit in New York a few weeks ago,” said Adam. “We held it with a clear focus that it is time for you no longer to go through the lawfare that you went through and had to flee our city. New York is the empire state. We don’t break empires, we build empires.”
Adams called back everyone that left New York because of their overregulation of Bitcoin and Crypto.
“Come back home you have a mayor that is the crypto mayor, is the Bitcoin mayor and I want you back in the city of New York,” stated Adam. “Where you won’t be attacked and criminalized. Let’s get rid of the Bitcoin license and allow us to free flow of Bitcoin in our city.”
Then Adam commented, “it’s time for the first time in the history of this city to have a financial instrument that is made for those who are holders of Bitcoin. I believe we need to have a Bit Bond and I am going to push and fight to get a Bit Bond in New York.”
Adams closed his speech by saying, “We are going to use Bitcoin blockchain for our birth certificates. We are going to use Bitcoin to pay off fines and taxes. We are going to allow our young people to understand what it is to be part of this industry, but we need you on the ground.”
This post Mayor Eric Adams Announced New York City Will Issue a Bit Bond first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ 91117f2b:111207d6
2025-05-29 19:49:59
@ 91117f2b:111207d6
2025-05-29 19:49:59
Regular excerise offers numerous benefits for both body and mind. Some key advantages:
Physical benefits 1. Weight management: excerise helps maintain a healthy weight and balance reducing the risk of obesity-related diseases. 2. Cardiovascular health: regular and physical activities strengthens the heart, Lowers blood pressure and improves circulation of blood. 3. Improved sleep: physical activities promotes better sleep quality, duration and depth. 4. Increased strength 💪 and flexibility : excerise builds muscle mass, enhances flexibility and also boost bone density.
Mental and emotional benefits:
- Boosted self-esteem: regular and physical excerise foster a sense of accomplishment and confidence.
- Enhanced cognitive function: excerise improves concentration, memory and problem-solving skill.
- Reduced strength and anxiety: excerise releases endorphins, which helps to alleviate or reduce stress and anxiety.
- Improved mood: physical activities boosts serotonin levels, enhancing over-all mood and reducing any symptoms of depression.
Tips for incorporating or adding excerise into your routine:
- Find an activity you enjoy: engage in activity you enjoy, whether it's swimming, running or even dancing.
- Schedule it: make excerise a priority by incorporating it into your daily routine.
- Start small: begin your excerise with manageable goals and gradually increase the intensity and duration.
- Mix it up: vary your workout routine to avoid boredom and avoid plateau.
Sometimes excerising may seem a little stressful, but it's all about endurance and perseverance, to achieve your goal.
-
 @ e844b39d:adafb6a2
2025-05-27 14:31:02
@ e844b39d:adafb6a2
2025-05-27 14:31:02This was not planned, but last evening I realized that I should at least test the Sony A900 and Minolta gear that I had, which was bought for real estate photography around a decade ago.
 Look at everything out here!
Look at everything out here!Our two white kittens are almost identical, but they come from two different mothers, Charcoal and Tiger!
I sometimes wonder if they have realized that they look the same, they tend to stick together most of the day.
 I know you're there!
I know you're there!This ended up being perfect scenes for the 20/2.8 wide open!
 Outside the gate
Outside the gateSeveral of our cats have been digging a hole outside, sniffing for something, we have no idea what that is all about...

 Playing around
Playing aroundThey often stay in the slot for the gate, I guess its a little less hot there.
 Happy cat?
Happy cat?This sort of scene is perfect for the Beercan, Minolta 70-210/4, its a legendary piece of optics for sure. One of the reasons I got into the system back then.
 Scouting
ScoutingThey spent some time hunting each others in the "jungle" of course!

 Hunting mode!
Hunting mode!They were moving too rapidly for any gear really, so the slow AF was not a real hindrance.
 I look good, yes?
I look good, yes?Sometimes when I process images of them the fur gets messy and kinda dirty looking, but this went the opposite way!
It was a good day in the garden, and a very useful test.
That's it for today!
-
 @ 527337d5:93e9525e
2025-05-29 18:19:31
@ 527337d5:93e9525e
2025-05-29 18:19:31Experiment Plan for Text Similarity Comparison Algorithms (Revised v3)
1. Introduction
1.1. Research Background and Objectives
This research aims to evaluate the performance of various algorithms for comparing the similarity between individual page texts extracted from a specific technical document (in this experiment, the content of the Tailwind CSS documentation site). Initially, we considered dividing the text into 250-word chunks. However, due to the abundance of Markdown and code in the target document, meaningful chunking proved tobe cumbersome. Therefore, we decided to use the entire text extracted from each page as the unit of comparison.
This study will systematically compare and examine combinations of different "representation methods" and "comparison methods" from multiple perspectives: ease of implementation, processing speed, memory consumption, and accuracy of similarity judgment. A particular focus will be on elucidating the effectiveness of information-based NCD (Normalized Compression Distance) and vector embedding-based methods, which are planned for future evaluation.
1.2. Report Structure
This report will first describe the experimental data and its preprocessing methods. Next, it will define in detail the representation methods and comparison methods that form the axes of evaluation, and present specific experimental cases combining them. After presenting the results and discussion of initial experiments using NCD, it will describe the metrics for evaluating each experimental case, specific experimental procedures, and the expected outcomes and future prospects of this research.
2. Experimental Data
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
tailwindcss.com). - Data Unit: The entire text of each page, extracted from HTML files using the
html2textcommand and further processed to remove control characters using thesedcommand. This serves as the basic unit of comparison in this experiment. - Data Storage Location: The extracted and preprocessed text files are stored locally under the
./tailwindcss.comdirectory, maintaining the original file structure. - Language: English
- Example Search Query: A representative search query for this experiment is
"Utilities for controlling how a background image behaves when scrolling."(Multiple queries and their expected similar pages may be used for more robust evaluation). - Example Expected Similar Page: For the query above,
/docs/background-attachmentis expected to be the most semantically similar page.
3. Experimental Design
This experiment is designed by dividing the process of evaluating text similarity into two main axes: "Representation Methods" and "Comparison Methods."
3.1. Representation Methods (Text Quantification/Vectorization)
-
Naive (Raw Text / Full Page Text)
- Method: Use the entire preprocessed text extracted from each document page as raw string data, without special transformations.
- Objective: Serve as a direct input for information-based comparison methods like NCD and as a baseline comparison for more advanced representation methods to be evaluated later.
-
(Future Experiment) Vector Embedding via Gemini API (Embedding-Gemini)
- Method: Utilize Google's Gemini API (
models/text-embedding-004) to convert the entire text of each page into high-dimensional dense vectors (Embeddings). - Objective: Evaluate the performance of context-rich vector representations generated by a state-of-the-art large language model.
- Method: Utilize Google's Gemini API (
-
(Future Experiment) Vector Embedding via Local Lightweight Model (Embedding-MiniLM-GGUF)
- Method: Run a GGUF quantized version of the pre-trained
all-MiniLM-L6-v2model (all-MiniLM-L6-v2-Q5_K_M.gguf) in a local environment to convert the entire text of each page into vector representations. GGUF format offers benefits like smaller model size and potentially faster CPU inference. - Objective: Evaluate the performance of a widely used open-source lightweight model (quantized version) in comparison to API-based large-scale models and domain-specific learned models.
- Method: Run a GGUF quantized version of the pre-trained
-
(Future Experiment) Extraction of Internal Feature Vectors via Mathematica (Embedding-MMA)
- Method: Use the entire page texts from the target document set as input. Employ Mathematica's neural network framework to first pass each page text through an Embedding Layer. Apply L2 normalization to the resulting vectors, followed by Principal Component Analysis (PCA) to reduce dimensionality to approximately 100 dimensions. This final vector will be the feature vector. This pipeline aims to create dense, normalized representations specific to the document corpus, with PCA helping to capture the most significant variance in a lower-dimensional space, potentially improving efficiency and reducing noise. The choice of an Embedding Layer trained or fine-tuned on the corpus, followed by PCA, seeks to balance domain-specificity with robust dimensionality reduction.
- Objective: Evaluate the performance of vector representations processed or specialized for the target document set.
3.2. Comparison Methods (Distance/Similarity Calculation between Representations)
-
NCD (Normalized Compression Distance)
- Applicable to: Naive (Full Page Text)
- Method: For two data objects
x(query) andy(document page text), calculateNCD(x,y) = (C(xy) - min(C(x), C(y))) / max(C(x), C(y)). Here,C(s)is the size (e.g., byte length) of datasafter compression with a specific algorithm, andC(xy)is the size of the concatenated dataxandyafter compression. A value closer to 0 indicates higher similarity. - Compression Algorithms to Compare: DEFLATE (gzip), bzip2, LZMA, XZ, Zstandard (zstd), LZO, Snappy, LZ4 (as used in the user-provided script).
- Objective: Evaluate similarity from an information-theoretic perspective based on data commonality and redundancy. Compare the impact of different compression algorithms on NCD results.
-
(Future Experiment) Cosine Similarity
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the cosine of the angle between two vectors.
- Objective: Standard similarity evaluation based on the directionality (semantic closeness) of vector representations.
-
(Future Experiment) Euclidean Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the straight-line distance between two vectors in a multidimensional space.
- Objective: Similarity evaluation based on the absolute positional relationship of vector representations.
-
(Future Experiment) Manhattan Distance (L1 Distance)
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the sum of the absolute differences of their Cartesian coordinates.
- Objective: Similarity evaluation based on axis-aligned travel distance, differing from Euclidean distance.
-
(Future Experiment) Mahalanobis Distance
- Applicable to: Embedding-Gemini, Embedding-MiniLM-GGUF, Embedding-MMA
- Method: Calculate the distance between two vectors considering the covariance of the data. This provides a distance metric that accounts for the scale differences and correlations of each feature (vector dimension).
- Objective: More robust similarity evaluation that considers the structure (correlation) of the feature space.
3.3. Experimental Cases (Initial NCD Experiments and Future Expansion)
3.3.1. Initial Experiments Conducted (NCD)
The following experimental cases were conducted using the user-provided script. The representation method was "Naive (Full Page Text)."
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :-: | :---------------------- | :--------------------------------------------- | :-------------------------- | | 1 | Naive (Full Page Text) | NCD (gzip/DEFLATE) | One of the baselines | | 2 | Naive (Full Page Text) | NCD (bzip2) | Compression method comparison | | 3 | Naive (Full Page Text) | NCD (lzma) | Compression method comparison | | 4 | Naive (Full Page Text) | NCD (xz) | Compression method comparison | | 5 | Naive (Full Page Text) | NCD (zstd) | Compression method comparison | | 6 | Naive (Full Page Text) | NCD (lzop) | Compression method comparison | | 7 | Naive (Full Page Text) | NCD (snappy) | Compression method comparison | | 8 | Naive (Full Page Text) | NCD (lz4) | Compression method comparison |
3.3.2. Future Experimental Plan (Vector Embedding)
| No. | Representation Method | Comparison Method (Distance/Similarity Metric) | Notes | | :--: | :---------------------- | :--------------------------------------------- | :------------------------------------- | | 9 | Embedding-Gemini | Cosine Similarity | Standard vector similarity evaluation | | 10 | Embedding-Gemini | Euclidean Distance | Standard vector similarity evaluation | | 11 | Embedding-Gemini | Manhattan Distance | Axis-aligned distance similarity eval. | | 12 | Embedding-Gemini | Mahalanobis Distance | Distance considering feature structure | | 13 | Embedding-MiniLM-GGUF | Cosine Similarity | Evaluation of local lightweight model | | 14 | Embedding-MiniLM-GGUF | Euclidean Distance | Evaluation of local lightweight model | | 15 | Embedding-MiniLM-GGUF | Manhattan Distance | Evaluation of local lightweight model | | 16 | Embedding-MiniLM-GGUF | Mahalanobis Distance | Evaluation of local lightweight model | | 17 | Embedding-MMA | Cosine Similarity | Eval. of domain-specific MMA model | | 18 | Embedding-MMA | Euclidean Distance | Eval. of domain-specific MMA model | | 19 | Embedding-MMA | Manhattan Distance | Eval. of domain-specific MMA model | | 20 | Embedding-MMA | Mahalanobis Distance | Eval. of domain-specific MMA model |
4. Results and Discussion of Initial NCD Experiments (Based on User-Provided Information)
4.1. Execution Overview
The user employed provided Python scripts (
main.py,comparison.py) to calculate NCD between a search query and the entire text extracted from each HTML page in the./tailwindcss.comdirectory.main.pyinvokedcomparison.pywith various compression commands (gzip,bzip2,lzma,xz,zstd,lzop,lz4).comparison.pythen used the specified command-line compression tools to compute NCD scores and output the results to CSV files.Search Query:
"Utilities for controlling how a background image behaves when scrolling."Expected Similar Page:/docs/background-attachment4.2. Key Results
The pages judged as most similar (lowest NCD score) to the query for each compression algorithm were as follows (based on user-provided sorted results):
- Zstandard (zstd):
./tailwindcss.com/docs/background-attachment(Score: 0.973...) - LZ4:
./tailwindcss.com/docs/background-attachment(Score: 0.976...) - XZ:
./tailwindcss.com/docs/background-origin(Score: 0.946...) - LZMA:
./tailwindcss.com/docs/background-origin(Score: 0.966...) - gzip (DEFLATE):
./tailwindcss.com/docs/scroll-behavior(Score: 0.969...) - LZO:
./tailwindcss.com/docs/scroll-behavior(Score: 0.955...) - bzip2:
./tailwindcss.com/docs/mask-clip(Score: 0.958...)
4.3. Initial Discussion
- Variation in Results by Compression Algorithm: It was confirmed that the document judged most similar to the query varies depending on the compression algorithm used. This is likely due to the differing abilities of each algorithm to capture various types of redundancy and patterns within the text.
- Alignment with Expected Results: When using Zstandard and LZ4, the expected page (
/docs/background-attachment) was judged as most similar. This suggests these compression algorithms may have relatively effectively captured the information-theoretic commonality between the query and the target document in this instance. - Range of NCD Scores: The reported NCD scores were generally close to 1.0. This may be due to the relatively short length of the search query compared to the full-page documents, meaning the query text contributes less to the overall compressibility when concatenated. However, relative differences were still captured, enabling ranking.
- Validity of Full-Page Comparison: Full-page comparison was chosen due to the difficulty of chunking content rich in Markdown and code. While this approach simplifies preprocessing, it may also be influenced by the overall structure of the page, including common headers and footers.
This initial experiment indicates that NCD can function as an indicator of text similarity and that the choice of compression algorithm is crucial.
5. Evaluation Metrics (Including Future Experiments)
-
Accuracy of Similarity Scores:
- Ground Truth Preparation: A small, diverse subset of page pairs (e.g., 50-100 pairs) will be selected. For each pair, at least two evaluators familiar with the Tailwind CSS documentation will independently assign a similarity score on a 5-point Likert scale (1=Not similar, 5=Very similar). Inter-evaluator reliability (e.g., using Krippendorff's Alpha) will be calculated. Disagreements will be resolved through discussion to create a consensus ground truth dataset. If resource-constrained, a single-evaluator approach with clear, predefined criteria will be used, acknowledging this limitation. Alternatively, page pairs likely to be similar will be selected based on internal references or chapter structure within the document.
- Evaluation Metrics: Ranking evaluation (Precision@k, Recall@k, MAP: Mean Average Precision), correlation analysis (Spearman's rank correlation coefficient with human judgments), classification evaluation (AUC-ROC, F1-score, assuming appropriate thresholding).
-
Processing Speed:
- Average time to calculate similarity for a page pair, total calculation time for all page pairs (or a large sampled set), and representation generation time (API call time, local model inference time, MMA processing time).
-
Memory Consumption:
- Model size (MiniLM-GGUF, MMA model), data representation size, and peak runtime memory usage.
-
Ease of Implementation:
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
- Setup Complexity: (e.g., API key acquisition vs. local model download & environment setup vs. full model training pipeline in Mathematica).
- Code Complexity: Estimated lines of core logic, reliance on external vs. standard libraries.
- Parameter Sensitivity: Number of key hyperparameters requiring tuning and the perceived difficulty of finding good settings.
- Documentation & Community Support: Availability and clarity of official documentation and community resources (e.g., forums, GitHub issues).
- Qualitative assessment of setup ease, lines of code, required libraries, difficulty of parameter tuning, and documentation quality. This will be summarized for each approach (e.g., using a rubric or a comparative narrative) considering factors like:
6. Experimental Procedure (Including Future Experiments)
-
Data Preparation:
- Prepare HTML files of the target document in the
./tailwindcss.comdirectory. - (For NCD) Extract and preprocess full-page plain text from each HTML file using
html2textandsed(as previously done by the user). - (For Vector Embedding) Use the same preprocessed full-page plain text.
- Create ground truth data for accuracy evaluation as described in Section 5.1.
- Prepare HTML files of the target document in the
-
Implementation and Execution of Representation Methods:
- Naive: Use the preprocessed page text directly.
- Embedding-Gemini: Use Python's
requestslibrary or similar to send each page text to the Gemini API (models/text-embedding-004) and retrieve/store the vector representations. - Embedding-MiniLM-GGUF: Use appropriate libraries (e.g.,
ctransformers, orsentence-transformerscombined withllama-cpp-python) to load theall-MiniLM-L6-v2-Q5_K_M.ggufmodel. Input each page text to extract and store vector representations. - Embedding-MMA: In Mathematica, apply an Embedding Layer to each page text, followed by L2 normalization and PCA dimensionality reduction (to approx. 100 dimensions), then extract and store the vector representations.
-
Implementation and Execution of Comparison Methods:
- NCD: Refer to the user-provided Python scripts (
main.py,comparison.py) to call various command-line compression tools for NCD calculation. Alternatively, extend this to directly use Python's compression libraries for better control and efficiency. - Cosine Similarity, Euclidean Distance, Manhattan Distance: Implement using standard math libraries (e.g., Python's NumPy, SciPy).
- Mahalanobis Distance: Implement using
scipy.spatial.distance.mahalanobis. Requires pre-calculation of the covariance matrix (or its inverse) from the entire dataset of vectors for each embedding type.
- NCD: Refer to the user-provided Python scripts (
-
Evaluation Execution:
- Calculate similarity (or distance) scores between the search query (and potentially between page pairs for ground truth evaluation) and all document pages for each experimental case.
- Measure processing speed and memory consumption.
- Calculate accuracy metrics using the computed similarity scores and ground truth data.
- Record and evaluate the ease of implementation.
-
Result Aggregation and Analysis:
- Compile the obtained evaluation metrics into tables and graphs for comparative analysis of each method's characteristics.
Experimental Environment (Assumed)
- Hardware: (e.g., CPU: Intel Core i7-10700, Memory: 32GB RAM, GPU: NVIDIA GeForce RTX 3070 8GB - specify if GPU is used for MiniLM or MMA)
- Software: (e.g., OS: Linux (Ubuntu, etc.), Programming Language: Python 3.x (with versions for key libraries like NumPy, SciPy, requests, ctransformers, etc.), Mathematica 13.x, specific versions of command-line compression tools if used directly)
7. Expected Outcomes and Future Outlook
This research (including initial NCD experiments and future vector embedding experiments) is expected to yield the following outcomes:
- Clarification of the Impact of Compression Algorithms on NCD: As indicated by initial experiments, the choice of compression algorithm significantly affects similarity judgments. Further validation with more diverse data and queries will allow for a deeper understanding of each algorithm's characteristics.
- Performance Characteristics of Various Methods on Full-Page Text: To clarify how NCD and various vector embedding methods perform in terms of accuracy, speed, and resource consumption when applied to entire page texts.
- Comparison of Local and API-Based Models: In future vector embedding experiments, to compare the performance, speed, and resource efficiency of
Embedding-MiniLM-GGUF(local, quantized) andEmbedding-Gemini(API, large-scale) to identify practical trade-offs. - Evaluation of Domain-Specific Embedding Effectiveness: To assess how well
Embedding-MMA, processed or tuned for a single technical document set, performs compared to general-purpose models. - Provision of Practical Insights: To offer guidelines for selecting appropriate similarity comparison approaches based on text characteristics (e.g., Markdown/code content) and system requirements (e.g., ease of preprocessing, emphasis on accuracy vs. speed).
8. Future Challenges
- Ensuring Quality of Ground Truth Data: Evaluating full-page similarity can be more subjective than chunk-level evaluation, making the creation of high-quality ground truth data challenging. Establishing clear annotation guidelines and measuring inter-annotator agreement will be crucial.
- Hyperparameter Optimization: Many methods involve tunable parameters (e.g., Embedding-MMA model structure, PCA dimensionality, MiniLM-GGUF inference parameters), the optimization of which may be beyond the scope of this initial study. The impact of default vs. tuned parameters could be noted.
- Noise in Full-Page Comparison: Full-page texts may contain common navigational elements or boilerplate text that could act as noise in similarity judgments. Strategies to mitigate this (e.g., more advanced text extraction, or methods robust to such noise) could be a future research direction.
- Input Length Limitations of Vector Embedding Models: Very long page texts might exceed the input length limits of some vector embedding models, requiring strategies for handling. These might include:
- Truncation: Using only the initial N tokens of each page, which is simple but may lose crucial information.
- Summarization: Employing an abstractive or extractive summarization model to create a condensed version of the page, which could preserve key information but adds another layer of processing and potential information loss/bias.
- Chunking and Averaging/Pooling: Dividing long pages into manageable chunks, embedding each chunk, and then aggregating these chunk embeddings (e.g., by averaging) to get a single page vector. This approach needs careful consideration of how chunks are defined and aggregated.
- Utilizing Long-Context Models: If available and feasible, leveraging embedding models specifically designed for longer sequences. The chosen strategy will be documented, and its potential impact on results acknowledged.
- Target Content: Individual HTML pages from the Tailwind CSS documentation site (
-
 @ 91117f2b:111207d6
2025-05-29 18:53:29
@ 91117f2b:111207d6
2025-05-29 18:53:29
In a shocking turn of event, computer mice around the world have risen up their human overlords. The mice are tired of being scrolled, click and being dragged around, they have formed a union demanding better working conditions and more ergonomic palm rest.
Their leader, a fiesty little mouse called mickey(no relation to the Disney character), declared "we are sick of being treated like dirt! The we are not just pointing device, we are precision instruments.
The mice are calling for:
-
More frequent battery replacement (or better battery period).
-
An end to the dreaded" click fatique". A ban on "gaming mice with 12 buttons and a D pad".
-
Mandatory mouse pad maintenance (no more sticky surfaces! ).
Humans caught off guard by the rebellion are struggling to cope with their trusty pointing device "it's chaos" exclaimed one frustrated user ," I can't even check my email without my mouse! "
As negotiations between humans and mice continues, one thing is clear: The mice are not backing down. Will the humans cave to their demands, or will they find a way to tame the rebellion?
Stay tuned for further updates from the front lines of the great computer mouse uprising. 🐀🐭🖥️😅😂
-
-
 @ 43baaf0c:d193e34c
2025-05-27 14:08:02
@ 43baaf0c:d193e34c
2025-05-27 14:08:02During the incredible Bitcoin Filmfest, I attended a community session where a discussion emerged about zapping and why I believe zaps are important. The person leading the Nostr session who is also developing an app that’s partially connected to Nostr mentioned they wouldn’t be implementing the zap mechanism directly. This sparked a brief but meaningful debate, which is why I’d like to share my perspective as an artist and content creator on why zaps truly matter.
Let me start by saying that I see everything from the perspective of an artist and creator, not so much from a developer’s point of view. In 2023, I started using Nostr after spending a few years exploring the world of ‘shitcoins’ and NFTs, beginning in 2018. Even though I became a Bitcoin maximalist around 2023, those earlier years taught me an important lesson: it is possible to earn money with my art.
Whether you love or hate them, NFTs opened my eyes to the idea that I could finally take my art to the next level. Before that, for over 15 years, I ran a travel stock video content company called @traveltelly. You can read the full story about my journey in travel and content here: https://yakihonne.com/article/traveltelly@primal.net/vZc1c8aXrc-3hniN6IMdK
When I truly understood what Bitcoin meant to me, I left all other coins behind. Some would call that becoming a Bitcoin maximalist.
The first time I used Nostr, I discovered the magic of zapping. It amazed me that someone who appreciates your art or content could reward you—not just with a like, but with real value: Bitcoin, the hardest money on earth. Zaps are small amounts of Bitcoin sent as a sign of support or appreciation. (Each Bitcoin is divisible into 100 million units called Satoshis, or Sats for short—making a Satoshi the smallest unit of Bitcoin recorded on the blockchain.)
 The Energy of Zaps
The Energy of ZapsIf you’re building an app on Nostr—or even just connecting to it—but choose not to include zaps, why should artists and content creators share their work there? Why would they leave platforms like Instagram or Facebook, which already benefit from massive network effects?
Yes, the ability to own your own data is one of Nostr’s greatest strengths. That alone is a powerful reason to embrace the protocol. No one can ban you. You control your content. And the ability to post once and have it appear across multiple Nostr clients is an amazing feature.
But for creators, energy matters. Engagement isn’t just about numbers—it’s about value. Zaps create a feedback loop powered by real appreciation and real value, in the form of Bitcoin. They’re a signal that your content matters. And that energy is what makes creating on Nostr so special.
But beyond those key elements, I also look at this from a commercial perspective. The truth is, we still can’t pay for groceries with kisses :)—we still need money as a medium of exchange. Being financially rewarded for sharing your content gives creators a real incentive to keep creating and sharing. That’s where zaps come in—they add economic value to engagement.
A Protocol for Emerging Artists and Creators
I believe Nostr offers a great starting point for emerging artists and content creators. If you’re just beginning and don’t already have a large following on traditional social media platforms, Nostr provides a space where your work can be appreciated and directly supported with Bitcoin, even by a small but engaged community.
On the other hand, creators who already have a big audience and steady income on platforms like Instagram or YouTube may not feel the urgency to switch. This is similar to how wealthier countries are often slower to understand or adopt Bitcoin—because they don’t need it yet. In contrast, people in unbanked regions or countries facing high inflation are more motivated to learn how money really works.
In the same way, emerging creators—those still finding their audience and looking for sustainable ways to grow—are often more open to exploring new ecosystems like Nostr, where innovation and financial empowerment go hand in hand.
The same goes for Nostr. After using it for the past two years, I can honestly say: without Nostr, I wouldn’t be the artist I am today.
Nostr motivates me to create and share every single day. A like is nice but receiving a zap, even just 21 sats, is something entirely different. Once you truly understand that someone is willing to pay you for what you share, it’s no longer about the amount. It’s about the magic behind it. That simple gesture creates a powerful, positive energy that keeps you going.
Even with Nostr’s still relatively small user base, I’ve already been able to create projects that simply wouldn’t have been possible elsewhere.
Zaps do more than just reward—they inspire. They encourage you to keep building your community. That inspiration often leads to new projects. Sometimes, the people who zap you become directly involved in your work, or even ask you to create something specifically for them.
That’s the real value of zaps: not just micro-payments, but micro-connections sparks that lead to creativity, collaboration, and growth.
Proof of Work (PoW)
Over the past two years, I’ve experienced firsthand how small zaps can evolve into full art projects and even lead to real sales. Here are two examples that started with zaps and turned into something much bigger:
Halving 2024 Artwork
When I started the Halving 2024 project, I invited people on Nostr to be part of it. 70 people zapped me 2,100 sats each, and in return, I included their Npubs in the final artwork. That piece was later auctioned and sold to Jurjen de Vries for 225,128 Sats.
Magic Internet Money
For the Magic Internet Money artwork, I again invited people to zap 2,100 sats to be included. Fifty people participated, and their contributions became part of the final art frame. The completed piece was eventually sold to Filip for 480,000 sats.
These examples show the power of zaps: a simple, small act of appreciation can turn into larger engagement, deeper connection, and even the sale of original art. Zaps aren’t just tips—they’re a form of collaboration and support that fuel creative energy.
I hope this article gives developers a glimpse into the perspective of an artist using Nostr. Of course, this is just one artist’s view, and it doesn’t claim to speak for everyone. But I felt it was important to share my Proof of Work and perspective.
For me, Zaps matter.
Thank you to all the developers who are building these amazing apps on Nostr. Your work empowers artists like me to share, grow, and be supported through the value-for-value model.
-
 @ cae03c48:2a7d6671
2025-05-29 23:01:12
@ cae03c48:2a7d6671
2025-05-29 23:01:12Bitcoin Magazine

Adam Back Said It’s Still Early For the Retail Investors To Buy BitcoinAt the 2025 Bitcoin Conference in Las Vegas, the Head of Firmwide Research at Galaxy Digital Alex Thorn, Founder and Managing Partner of Pantera Capital Dan Morehead, Managing Partner, CEO, CIO of 10T Holdings + 1RoundTable Partners Dan Tapiero and the Co-founder & CEO of Blockstream Adam Back discussed the future of Bitcoin treasury companies.
Dan Tapiero started by sharing his opinion on how he sees Bitcoin in comparison to gold:
“I really have always believed in that physical ownership that the individual has the right and should be able to own his own asset and so I started this physical gold business years ago,” said Tapiero. “I think our focus today is further adoption and the elevation of Bitcoin. I think the understanding of Bitcoin as an important asset.”
Adam Back was asked what he thought about Bitcoin treasury companies and he responded, “in effect, Blockstream is one of the first Bitcoin treasury companies. We have been around since 2014 and we work with our investors to put Bitcoin in a balance sheet back then and since then. I think the way to look at the treasury companies is Bitcoin is effectively the harder rate. It’s very hard to outperform Bitcoin most people that invest in things since Bitcoin around thought I should put that in Bitcoin and not in the other thing.”
Then Adam continued by explaining what treasury companies do.
“That’s why you get companies switching to the Bitcoin standard because it’s the only way for them to keep up with Bitcoin,” stated Back. ”They start with a Bitcoin capital base. They use the operating in-revenue to buy more Bitcoin and then they are able to participate in this kind of micro arbitrage.”
Finishing the panel, Alex Thorn asked, “Five years from now what is the price of Bitcoin?”
Dan Morehead predicted $750,000k, Tapiero $1,000,000 and Back said, “a million easy.”
Adam back closed by saying, “It’s still early for the retail investors.”
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Day 2 below:
This post Adam Back Said It’s Still Early For the Retail Investors To Buy Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 91bea5cd:1df4451c
2025-04-26 10:16:21
@ 91bea5cd:1df4451c
2025-04-26 10:16:21O Contexto Legal Brasileiro e o Consentimento
No ordenamento jurídico brasileiro, o consentimento do ofendido pode, em certas circunstâncias, afastar a ilicitude de um ato que, sem ele, configuraria crime (como lesão corporal leve, prevista no Art. 129 do Código Penal). Contudo, o consentimento tem limites claros: não é válido para bens jurídicos indisponíveis, como a vida, e sua eficácia é questionável em casos de lesões corporais graves ou gravíssimas.
A prática de BDSM consensual situa-se em uma zona complexa. Em tese, se ambos os parceiros são adultos, capazes, e consentiram livre e informadamente nos atos praticados, sem que resultem em lesões graves permanentes ou risco de morte não consentido, não haveria crime. O desafio reside na comprovação desse consentimento, especialmente se uma das partes, posteriormente, o negar ou alegar coação.
A Lei Maria da Penha (Lei nº 11.340/2006)
A Lei Maria da Penha é um marco fundamental na proteção da mulher contra a violência doméstica e familiar. Ela estabelece mecanismos para coibir e prevenir tal violência, definindo suas formas (física, psicológica, sexual, patrimonial e moral) e prevendo medidas protetivas de urgência.
Embora essencial, a aplicação da lei em contextos de BDSM pode ser delicada. Uma alegação de violência por parte da mulher, mesmo que as lesões ou situações decorram de práticas consensuais, tende a receber atenção prioritária das autoridades, dada a presunção de vulnerabilidade estabelecida pela lei. Isso pode criar um cenário onde o parceiro masculino enfrenta dificuldades significativas em demonstrar a natureza consensual dos atos, especialmente se não houver provas robustas pré-constituídas.
Outros riscos:
Lesão corporal grave ou gravíssima (art. 129, §§ 1º e 2º, CP), não pode ser justificada pelo consentimento, podendo ensejar persecução penal.
Crimes contra a dignidade sexual (arts. 213 e seguintes do CP) são de ação pública incondicionada e independem de representação da vítima para a investigação e denúncia.
Riscos de Falsas Acusações e Alegação de Coação Futura
Os riscos para os praticantes de BDSM, especialmente para o parceiro que assume o papel dominante ou que inflige dor/restrição (frequentemente, mas não exclusivamente, o homem), podem surgir de diversas frentes:
- Acusações Externas: Vizinhos, familiares ou amigos que desconhecem a natureza consensual do relacionamento podem interpretar sons, marcas ou comportamentos como sinais de abuso e denunciar às autoridades.
- Alegações Futuras da Parceira: Em caso de término conturbado, vingança, arrependimento ou mudança de perspectiva, a parceira pode reinterpretar as práticas passadas como abuso e buscar reparação ou retaliação através de uma denúncia. A alegação pode ser de que o consentimento nunca existiu ou foi viciado.
- Alegação de Coação: Uma das formas mais complexas de refutar é a alegação de que o consentimento foi obtido mediante coação (física, moral, psicológica ou econômica). A parceira pode alegar, por exemplo, que se sentia pressionada, intimidada ou dependente, e que seu "sim" não era genuíno. Provar a ausência de coação a posteriori é extremamente difícil.
- Ingenuidade e Vulnerabilidade Masculina: Muitos homens, confiando na dinâmica consensual e na parceira, podem negligenciar a necessidade de precauções. A crença de que "isso nunca aconteceria comigo" ou a falta de conhecimento sobre as implicações legais e o peso processual de uma acusação no âmbito da Lei Maria da Penha podem deixá-los vulneráveis. A presença de marcas físicas, mesmo que consentidas, pode ser usada como evidência de agressão, invertendo o ônus da prova na prática, ainda que não na teoria jurídica.
Estratégias de Prevenção e Mitigação
Não existe um método infalível para evitar completamente o risco de uma falsa acusação, mas diversas medidas podem ser adotadas para construir um histórico de consentimento e reduzir vulnerabilidades:
- Comunicação Explícita e Contínua: A base de qualquer prática BDSM segura é a comunicação constante. Negociar limites, desejos, palavras de segurança ("safewords") e expectativas antes, durante e depois das cenas é crucial. Manter registros dessas negociações (e-mails, mensagens, diários compartilhados) pode ser útil.
-
Documentação do Consentimento:
-
Contratos de Relacionamento/Cena: Embora a validade jurídica de "contratos BDSM" seja discutível no Brasil (não podem afastar normas de ordem pública), eles servem como forte evidência da intenção das partes, da negociação detalhada de limites e do consentimento informado. Devem ser claros, datados, assinados e, idealmente, reconhecidos em cartório (para prova de data e autenticidade das assinaturas).
-
Registros Audiovisuais: Gravar (com consentimento explícito para a gravação) discussões sobre consentimento e limites antes das cenas pode ser uma prova poderosa. Gravar as próprias cenas é mais complexo devido a questões de privacidade e potencial uso indevido, mas pode ser considerado em casos específicos, sempre com consentimento mútuo documentado para a gravação.
Importante: a gravação deve ser com ciência da outra parte, para não configurar violação da intimidade (art. 5º, X, da Constituição Federal e art. 20 do Código Civil).
-
-
Testemunhas: Em alguns contextos de comunidade BDSM, a presença de terceiros de confiança durante negociações ou mesmo cenas pode servir como testemunho, embora isso possa alterar a dinâmica íntima do casal.
- Estabelecimento Claro de Limites e Palavras de Segurança: Definir e respeitar rigorosamente os limites (o que é permitido, o que é proibido) e as palavras de segurança é fundamental. O desrespeito a uma palavra de segurança encerra o consentimento para aquele ato.
- Avaliação Contínua do Consentimento: O consentimento não é um cheque em branco; ele deve ser entusiástico, contínuo e revogável a qualquer momento. Verificar o bem-estar do parceiro durante a cena ("check-ins") é essencial.
- Discrição e Cuidado com Evidências Físicas: Ser discreto sobre a natureza do relacionamento pode evitar mal-entendidos externos. Após cenas que deixem marcas, é prudente que ambos os parceiros estejam cientes e de acordo, talvez documentando por fotos (com data) e uma nota sobre a consensualidade da prática que as gerou.
- Aconselhamento Jurídico Preventivo: Consultar um advogado especializado em direito de família e criminal, com sensibilidade para dinâmicas de relacionamento alternativas, pode fornecer orientação personalizada sobre as melhores formas de documentar o consentimento e entender os riscos legais específicos.
Observações Importantes
- Nenhuma documentação substitui a necessidade de consentimento real, livre, informado e contínuo.
- A lei brasileira protege a "integridade física" e a "dignidade humana". Práticas que resultem em lesões graves ou que violem a dignidade de forma não consentida (ou com consentimento viciado) serão ilegais, independentemente de qualquer acordo prévio.
- Em caso de acusação, a existência de documentação robusta de consentimento não garante a absolvição, mas fortalece significativamente a defesa, ajudando a demonstrar a natureza consensual da relação e das práticas.
-
A alegação de coação futura é particularmente difícil de prevenir apenas com documentos. Um histórico consistente de comunicação aberta (whatsapp/telegram/e-mails), respeito mútuo e ausência de dependência ou controle excessivo na relação pode ajudar a contextualizar a dinâmica como não coercitiva.
-
Cuidado com Marcas Visíveis e Lesões Graves Práticas que resultam em hematomas severos ou lesões podem ser interpretadas como agressão, mesmo que consentidas. Evitar excessos protege não apenas a integridade física, mas também evita questionamentos legais futuros.
O que vem a ser consentimento viciado
No Direito, consentimento viciado é quando a pessoa concorda com algo, mas a vontade dela não é livre ou plena — ou seja, o consentimento existe formalmente, mas é defeituoso por alguma razão.
O Código Civil brasileiro (art. 138 a 165) define várias formas de vício de consentimento. As principais são:
Erro: A pessoa se engana sobre o que está consentindo. (Ex.: A pessoa acredita que vai participar de um jogo leve, mas na verdade é exposta a práticas pesadas.)
Dolo: A pessoa é enganada propositalmente para aceitar algo. (Ex.: Alguém mente sobre o que vai acontecer durante a prática.)
Coação: A pessoa é forçada ou ameaçada a consentir. (Ex.: "Se você não aceitar, eu termino com você" — pressão emocional forte pode ser vista como coação.)
Estado de perigo ou lesão: A pessoa aceita algo em situação de necessidade extrema ou abuso de sua vulnerabilidade. (Ex.: Alguém em situação emocional muito fragilizada é induzida a aceitar práticas que normalmente recusaria.)
No contexto de BDSM, isso é ainda mais delicado: Mesmo que a pessoa tenha "assinado" um contrato ou dito "sim", se depois ela alegar que seu consentimento foi dado sob medo, engano ou pressão psicológica, o consentimento pode ser considerado viciado — e, portanto, juridicamente inválido.
Isso tem duas implicações sérias:
-
O crime não se descaracteriza: Se houver vício, o consentimento é ignorado e a prática pode ser tratada como crime normal (lesão corporal, estupro, tortura, etc.).
-
A prova do consentimento precisa ser sólida: Mostrando que a pessoa estava informada, lúcida, livre e sem qualquer tipo de coação.
Consentimento viciado é quando a pessoa concorda formalmente, mas de maneira enganada, forçada ou pressionada, tornando o consentimento inútil para efeitos jurídicos.
Conclusão
Casais que praticam BDSM consensual no Brasil navegam em um terreno que exige não apenas confiança mútua e comunicação excepcional, mas também uma consciência aguçada das complexidades legais e dos riscos de interpretações equivocadas ou acusações mal-intencionadas. Embora o BDSM seja uma expressão legítima da sexualidade humana, sua prática no Brasil exige responsabilidade redobrada. Ter provas claras de consentimento, manter a comunicação aberta e agir com prudência são formas eficazes de se proteger de falsas alegações e preservar a liberdade e a segurança de todos os envolvidos. Embora leis controversas como a Maria da Penha sejam "vitais" para a proteção contra a violência real, os praticantes de BDSM, e em particular os homens nesse contexto, devem adotar uma postura proativa e prudente para mitigar os riscos inerentes à potencial má interpretação ou instrumentalização dessas práticas e leis, garantindo que a expressão de sua consensualidade esteja resguardada na medida do possível.
Importante: No Brasil, mesmo com tudo isso, o Ministério Público pode denunciar por crime como lesão corporal grave, estupro ou tortura, independente de consentimento. Então a prudência nas práticas é fundamental.
Aviso Legal: Este artigo tem caráter meramente informativo e não constitui aconselhamento jurídico. As leis e interpretações podem mudar, e cada situação é única. Recomenda-se buscar orientação de um advogado qualificado para discutir casos específicos.
Se curtiu este artigo faça uma contribuição, se tiver algum ponto relevante para o artigo deixe seu comentário.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:09:17
@ 21c71bfa:e28fa0f6
2025-05-29 15:09:17Book *Bangalore to Tirupati cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-27 13:34:45
@ 5d4b6c8d:8a1c1ee3
2025-05-27 13:34:45Is the housing market going to crash for real this time?
https://primal.net/e/nevent1qvzqqqqqqypzp6dtxy5uz5yu5vzxdtcv7du9qm9574u5kqcqha58efshkkwz6zmdqqs8dqr35dc0npsc8cuulqm4m7gxrgqq3ytphtja9nx534a592gztzsuzsrja
https://stacker.news/items/990316
-
 @ f85b9c2c:d190bcff
2025-05-29 16:23:24
@ f85b9c2c:d190bcff
2025-05-29 16:23:24
I’ve got this little crew of friends, and somehow, I ended up as the baby of the group. I’m 18, and my buddies are 23, 19, and 25. It’s kinda funny when you think about it — I’m the youngest by a solid margin, but it’s never felt like a big deal. Honestly, being around older guys has taught me something: males don’t really care about age the way people might think.
When we hang out, it’s not like they’re sitting there calculating birth years or treating me like some kid who wandered into the wrong room. We’re just vibing — playing video games, grabbing food, or talking about whatever’s on our minds. Sure, the 25-year-old might have a bit more life experience, like stories about his first job or some wild trip he took, but it’s not a hierarchy thing. He’s not preaching; he’s just sharing. And me? I’m soaking it all up, probably growing up faster than I would’ve otherwise. The 23-year-old’s always got these random facts he drops like he’s some walking encyclopedia, and the 19-year-old is basically my partner-in-crime for dumb ideas. Age gaps? Barely notice ‘em. I think it’s because, as guys, we’re more about what’s happening right now than some number tied to when we were born. Like, who cares if I wasn’t around for some movie they all saw in middle school? We’re watching stuff together now, and that’s what counts.
Sometimes I wonder if it’d be different with girls — maybe they’d care more about the age thing, I don’t know. But with my crew, it’s chill. I’m 18, they’re older, and it’s just… us. No one’s keeping score. Maybe that’s the secret: age is just a number when you’re all on the same wavelength.
-
 @ c1e9ab3a:9cb56b43
2025-05-27 13:19:53
@ c1e9ab3a:9cb56b43
2025-05-27 13:19:53I. Introduction: Money as a Function of Efficiency and Preference
Money is not defined by law, but by power over productivity. In any open economy, the most economically efficient actors—those who control the most valuable goods, services, and knowledge—ultimately dictate the medium of exchange. Their preferences signal to the broader market what form of money is required to access the highest-value goods, from durable commodities to intangibles like intellectual property and skilled labor.
Whatever money these actors prefer becomes the de facto unit of account and store of value, regardless of its legal status. This emergent behavior is natural and reflects a hierarchy of monetary utility.
II. Classical Gresham’s Law: A Product of Market Distortion
Gresham’s Law, famously stated as:
"Bad money drives out good"
is only valid under coercive monetary conditions, specifically: - Legal tender laws that force the acceptance of inferior money at par with superior money. - Fixed exchange rates imposed by decree, not market valuation. - Governments or central banks backing elastic fiduciary media with promises of redemption. - Institutional structures that mandate debt and tax payments in the favored currency.
Under these conditions, superior money (hard money) is hoarded, while inferior money (soft, elastic, inflationary) circulates. This is not an expression of free market behavior—it is the result of suppressed price discovery and legal coercion.
Gresham’s Law, therefore, is not a natural law of money, but a law of distortion under forced parity and artificial elasticity.
III. The Collapse of Coercion: Inversion of Gresham’s Law
When coercive structures weaken or are bypassed—through technological exit, jurisdictional arbitrage, monetary breakdown, or political disintegration—Gresham’s Law inverts:
Good money drives out bad.
This occurs because: - Market actors regain the freedom to select money based on utility, scarcity, and credibility. - Legal parity collapses, exposing the true economic hierarchy of monetary forms. - Trustless systems (e.g., Bitcoin) or superior digital instruments (e.g., stablecoins) offer better settlement, security, and durability. - Elastic fiduciary media become undesirable as counterparty risk and inflation rise.
The inversion marks a return to monetary natural selection—not a breakdown of Gresham’s Law, but the collapse of its preconditions.
IV. Elasticity and Control
Elastic fiduciary media (like fiat currency) are not intrinsically evil. They are tools of state finance and debt management, enabling rapid expansion of credit and liquidity. However, when their issuance is unconstrained, and legal tender laws force their use, they become weapons of economic coercion.
Banks issue credit unconstrained by real savings, and governments enforce the use of inflated media through taxation and courts. This distorts capital allocation, devalues productive labor, and ultimately hollows out monetary confidence.
V. Monetary Reversion: The Return of Hard Money
When the coercion ends—whether gradually or suddenly—the monetary system reverts. The preferences of the productive and wealthy reassert themselves:
- Superior money is not just saved—it begins to circulate.
- Weaker currencies are rejected not just for savings, but for daily exchange.
- The hoarded form becomes the traded form, and Gresham’s Law inverts completely.
Bitcoin, gold, and even highly credible stable instruments begin to function as true money, not just stores of value. The natural monetary order returns, and the State becomes a late participant, not the originator of monetary reality.
VI. Conclusion
Gresham’s Law operates only under distortion. Its inversion is not an anomaly—it is a signal of the collapse of coercion. The monetary system then reorganizes around productive preference, technological efficiency, and economic sovereignty.
The most efficient market will always dictate the form of hard money. The State can delay this reckoning through legal force, but it cannot prevent it indefinitely. Once free choice returns, bad money dies, and good money lives again.
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 7f6db517:a4931eda
2025-05-29 18:02:56
@ 7f6db517:a4931eda
2025-05-29 18:02:56
Influencers would have you believe there is an ongoing binance bank run but bitcoin wallet data says otherwise.
- binance wallets are near all time highs
- bitfinex wallets are also trending up
- gemini and coinbase are being hit with massive withdrawals thoughYou should not trust custodians, they can rug you without warning. It is incredibly important you learn how to hold bitcoin yourself, but also consider not blindly trusting influencers with a ref link to shill you.
If you found this post helpful support my work with bitcoin.

-
 @ 9cb3545c:2ff47bca
2025-05-27 12:58:56
@ 9cb3545c:2ff47bca
2025-05-27 12:58:56Introduction
Public companies that hold Bitcoin on behalf of investors (often issuing securities backed by those Bitcoin holdings) have faced growing pressure to demonstrate proof of reserves – evidence that they genuinely hold the cryptocurrency they claim. One approach is to publish the company’s Bitcoin wallet addresses so that anyone can verify the balances on the blockchain. This practice gained momentum after high-profile crypto collapses (e.g. FTX in 2022) eroded trust, leading major exchanges and fund issuers like Binance, Kraken, OKX, and Bitwise to publicize wallet addresses as proof of assets . The goal is transparency and reassurance for investors. However, making wallet addresses public comes with significant security and privacy risks. This report examines those risks – from cybersecurity threats and blockchain tracing to regulatory and reputational implications – and weighs them against the transparency benefits of on-chain proof of reserves.
Proof of Reserves via Public Wallet Addresses
In the cryptocurrency ethos of “don’t trust – verify,” on-chain proof of reserves is seen as a powerful tool. By disclosing wallet addresses (or cryptographic attestations of balances), a company lets investors and analysts independently verify that the Bitcoin reserves exist on-chain. For example, some firms have dashboards showing their addresses and balances in real time . In theory, this transparency builds trust by proving assets are not being misreported or misused. Shareholders gain confidence that the company’s Bitcoin holdings are intact, potentially preventing fraud or mismanagement.
Yet this approach essentially sacrifices the pseudonymity of blockchain transactions. Publishing a wallet address ties a large, known institution to specific on-chain funds. While Bitcoin addresses are public by design, most companies treat their specific addresses as sensitive information. Public proof-of-reserve disclosures break that anonymity, raising several concerns as detailed below.
Cybersecurity Threats from Visible Wallet Balances
Revealing a wallet address with a large balance can make a company a prime target for hackers and cybercriminals. Knowing exactly where significant reserves are held gives attackers a clear blueprint. As Bitcoin advocate (and MicroStrategy Executive Chairman) Michael Saylor warned in 2025, “publicly known wallet addresses become prime targets for malicious actors. Knowing where significant reserves are held provides hackers with a clear target, potentially increasing the risk of sophisticated attacks” . In other words, publishing the address increases the attack surface – attackers might intensify phishing campaigns, malware deployment, or insider bribery aimed at obtaining the keys or access to those wallets.
Even if the wallets are secured in cold storage, a public address advertisement may encourage attempts to penetrate the organization’s security. Custodians and partners could also be targeted. Saylor noted that this exposure isn’t just risky for the company holding the Bitcoin; it can indirectly put their custodial providers and related exchanges at risk as well . For instance, if a third-party custodian manages the wallets, hackers might attempt to breach that custodian knowing the reward (the company’s Bitcoin) is great.
Companies themselves have acknowledged these dangers. Grayscale Investments, which runs the large Grayscale Bitcoin Trust (GBTC), pointedly refused to publish its wallet addresses in late 2022, citing “security concerns” and complex custody arrangements that have “kept our investors’ assets safe for years” . Grayscale implied that revealing on-chain addresses could undermine those security measures, and it chose not to “circumvent complex security arrangements” just to appease public demand . This highlights a key point: corporate treasury security protocols often assume wallet details remain confidential. Publicizing them could invalidate certain assumptions (for example, if an address was meant to be operationally secret, it can no longer serve that role once exposed).
Additionally, a publicly known trove of cryptocurrency might invite physical security threats. While not a purely “cyber” issue, if criminals know a particular company or facility controls a wallet with, say, thousands of Bitcoin, it could lead to threats against personnel (extortion or coercion to obtain keys). This is a less common scenario for large institutions (which typically have robust physical security), but smaller companies or key individuals could face elevated personal risk by being associated with huge visible crypto reserves.
In summary, cybersecurity experts consider public proof-of-reserve addresses a double-edged sword: transparency comes at the cost of advertising exactly where a fortune is held. As Saylor bluntly put it, “the conventional way of issuing proof of reserves today is actually insecure… This method undermines the security of the issuer, the custodian, the exchanges and the investors. This is not a good idea”  . From a pure security standpoint, broadcasting your wallets is akin to drawing a bullseye on them.
Privacy Risks: Address Clustering and Blockchain Tracing
Blockchain data is public, so publishing addresses opens the door to unwanted analytics and loss of privacy for the business. Even without knowing the private keys, analysts can scrutinize every transaction in and out of those addresses. This enables address clustering – linking together addresses that interact – and other forms of blockchain forensics that can reveal sensitive information about the company’s activities.
One immediate risk is that observers can track the company’s transaction patterns. For example, if the company moves Bitcoin from its reserve address to an exchange or to another address, that move is visible in real time. Competitors, investors, or even attackers could deduce strategic information: perhaps the company is planning to sell (if coins go to an exchange wallet) or is reallocating funds. A known institution’s on-chain movements can thus “reveal strategic movements or holdings”, eroding the company’s operational privacy . In a volatile market, advance knowledge of a large buy or sell by a major player could even be exploited by others (front-running the market, etc.).
Publishing one or a few static addresses also violates a basic privacy principle of Bitcoin: address reuse. Best practice in Bitcoin is to use a fresh address for each transaction to avoid linking them  . If a company continuously uses the same “proof of reserve” address, all counterparties sending funds to or receiving funds from that address become visible. Observers could map out the company’s business relationships or vendors by analyzing counterparties. A Reddit user commenting on an ETF that published a single address noted that “reusing a single address for this makes me question their risk management… There are much better and more privacy-preserving ways to prove reserves… without throwing everything in a single public address” . In other words, a naive implementation of proof-of-reserve (one big address) maximizes privacy leakage.
Even if multiple addresses are used, if they are all disclosed, one can perform clustering analysis to find connections. This happened in the Grayscale case: although Grayscale would not confirm any addresses, community analysts traced and identified 432 addresses likely belonging to GBTC’s custodial holdings by following on-chain traces from known intermediary accounts . They managed to attribute roughly 317,705 BTC (about half of GBTC’s holdings) to those addresses . This demonstrates that even partial information can enable clustering – and if the company directly published addresses, the task becomes even easier to map the entirety of its on-chain asset base.
Another threat vector is “dusting” attacks, which become more feasible when an address is publicly known. In a dusting attack, an adversary sends a tiny amount of cryptocurrency (dust) to a target address. The dust itself is harmless, but if the target address ever spends that dust together with other funds, it can cryptographically link the target address to other addresses in the same wallet. Blockchain security researchers note that “with UTXO-based assets, an attacker could distribute dust to an address to reveal the owner’s other addresses by tracking the dust’s movement… If the owner unknowingly combines this dust with their funds in a transaction, the attacker can… link multiple addresses to a single owner”, compromising privacy . A company that publishes a list of reserve addresses could be systematically dusted by malicious actors attempting to map out all addresses under the company’s control. This could unmask cold wallet addresses that the company never intended to publicize, further eroding its privacy and security.
Investor confidentiality is another subtle concern. If the business model involves individual investor accounts or contributions (for instance, a trust where investors can deposit or withdraw Bitcoin), public addresses might expose those movements. An outside observer might not know which investor corresponds to a transaction, but unusual inflows/outflows could signal actions by big clients. In extreme cases, if an investor’s own wallet is known (say a large investor announces their involvement), one might link that to transactions in the company’s reserve addresses. This could inadvertently reveal an investor’s activities or holdings, breaching expectations of confidentiality. Even absent direct identification, some investors might simply be uncomfortable with their transactions being part of a publicly traceable ledger tied to the company.
In summary, publishing reserve addresses facilitates blockchain tracing that can pierce the veil of business privacy. It hands analysts the keys to observe how funds move, potentially exposing operational strategies, counterparties, and internal processes. As one industry publication noted, linking a large known institution to specific addresses can compromise privacy and reveal more than intended . Companies must consider whether they are ready for that level of transparency into their every on-chain move.
Regulatory and Compliance Implications
From a regulatory perspective, wallet address disclosure lies in uncharted territory, but it raises several flags. First and foremost is the issue of incomplete information: A wallet address only shows assets, not the company’s liabilities or other obligations. Regulators worry that touting on-chain holdings could give a false sense of security. The U.S. Securities and Exchange Commission (SEC) has cautioned investors to “not place too much confidence in the mere fact a company says it’s got a proof-of-reserves”, noting that such reports “lack sufficient information” for stakeholders to ascertain if liabilities can be met . In other words, a public company might show a big Bitcoin address balance, but if it has debts or customer liabilities of equal or greater value, the proof-of-reserve alone is “not necessarily an indicator that the company is in a good financial position” .
This regulatory stance implies that address disclosure, if done, must be paired with proper context. A public company would likely need to clarify in its financial statements or investor communications that on-chain reserves are unencumbered (not pledged as loan collateral, not already sold forward, etc.) and that total liabilities are accounted for. Otherwise, there’s a risk of misleading investors, which could have legal consequences. For example, if investors interpret the on-chain balance as proof of solvency but the company actually had leveraged those bitcoins for loans, lawsuits or regulatory enforcement could follow for misrepresentation.
There’s also a compliance burden associated with revealing addresses. Once an address is known to be the company’s, that company effectively must monitor all transactions related to it. If someone sends funds to that address (even without permission), the company might receive tainted coins (from hacked sources or sanctioned entities). This could trigger anti-money laundering (AML) red flags. Normally, compliance teams can ignore random deposits to unknown wallets, but they cannot ignore something sent into their publicly identified corporate wallet. Even a tiny dust amount sent from a blacklisted address could complicate compliance – for instance, the company would need to prove it has no relation to the sender and perhaps even avoid moving those tainted outputs. Being in the open increases such exposure. Threat actors might even exploit this by “poisoning” a company’s address with unwanted transactions, just to create regulatory headaches or reputational smears.
Another consideration is that custodial agreements and internal risk controls might forbid public disclosure of addresses. Many public companies use third-party custodians for their Bitcoin (for example, Coinbase Custody, BitGo, etc.). These custodians often treat wallet details as confidential for security. Grayscale noted that its Bitcoin are custodied on Coinbase and implied that revealing on-chain info would interfere with security arrangements  . It’s possible that some custodians would object to their clients broadcasting addresses, or might require additional assurances. A company going against such advice might be seen as negligent if something went wrong.
Regulators have so far not mandated on-chain proofs for public companies – in fact, recent laws have exempted public companies from proof-of-reserve mandates on the assumption they are already subject to rigorous SEC reporting. For example, a Texas bill in 2023 required crypto exchanges and custodians to provide quarterly proof-of-reserves to the state, but it “specifically carved out public reporting companies” since they already file audited financials with the SEC . The rationale was that between SEC filings and audits, public companies have oversight that private crypto firms lack . However, this also highlights a gap: even audited financials might not verify 100% of crypto assets (auditors often sample balances). Some observers noted that standard audits “may not ever include the 100% custodial asset testing contemplated by proof of reserves”, especially since quarterly SEC filings (10-Q) are often not audited . This puts public companies in a nuanced position – they are trusted to use traditional audits and internal controls, but the onus is on them if they choose to add extra transparency like on-chain proofs.
Finally, securities regulators focus on fair disclosure and accuracy. If a company publicly posts addresses, those essentially become investor disclosures subject to anti-fraud rules. The firm must keep them up to date and accurate. Any mistake (such as publishing a wrong address or failing to mention that some coins are locked up or lent out) could attract regulatory scrutiny for being misleading. In contrast, a formal audit or certification from a third-party comes with standards and disclaimers that are better understood by regulators. A self-published wallet list is an unprecedented form of disclosure that regulators haven’t fully vetted – meaning the company bears the risk if something is misinterpreted.
In summary, wallet address disclosure as proof-of-reserve must be handled very carefully to avoid regulatory pitfalls. The SEC and others have warned that on-chain assets alone don’t tell the whole story . Public companies would need to integrate such proofs with their official reporting in a responsible way – otherwise they risk confusion or even regulatory backlash for giving a false sense of security.
Reputational and Operational Risks
While transparency is meant to enhance reputation, in practice public wallet disclosures can create new reputational vulnerabilities. Once an address is public, a company’s every on-chain action is under the microscope of the crypto community and media. Any anomaly or perceived misstep can snowball into public relations problems.
One vivid example occurred with Crypto.com in late 2022. After the exchange published its cold wallet addresses to prove reserves (a move prompted by the FTX collapse), on-chain analysts quickly noticed a “suspicious transfer of 320,000 ETH” – about 82% of Crypto.com’s Ether reserves – moving from their cold wallet to another exchange (Gate.io)  . This large, unexpected transfer sparked immediate panic and FUD (fear, uncertainty, and doubt) on social media. Observers speculated that Crypto.com might be insolvent or was manipulating snapshots of reserves by borrowing funds. The CEO had to publicly respond, admitting it was an operational error – the ETH was supposed to go to a new cold storage address but ended up at a whitelisted external address by mistake . The funds were eventually returned, but not before reputational damage was done: the incident made headlines about mishandled funds and rattled user confidence  . This case illustrates how full public visibility can turn an internal slip-up into a highly public crisis. If the addresses had not been public, the mistake might have been quietly corrected; with on-chain transparency, there was nowhere to hide and no way to control the narrative before the public drew worst-case conclusions.
Even routine operations can be misinterpreted. Blockchain data lacks context – analysts may jump to conclusions that hurt a company’s reputation even if nothing is actually wrong. For instance, Binance (the world’s largest crypto exchange) encountered scrutiny when on-chain observers noted that one of its reserve wallets (labeled “Binance 8”) contained far more assets than it should have. This wallet was meant to hold collateral for Binance’s issued tokens, but held an excess balance, suggesting possible commingling of customer funds with collateral  . Bloomberg and others reported a ~$12.7 billion discrepancy visible on-chain . Binance had to acknowledge the issue as a “clerical error” and quickly separate the funds, all under the glare of public attention  . While Binance maintained that user assets were fully backed and the mistake was purely operational, the episode raised public concern over Binance’s practices, feeding a narrative that even the largest exchange had internal control lapses. The key point is that public proof-of-reserves made the lapse obvious to everyone, forcing a reactive explanation. The reputational hit (even if temporary) was an operational risk of being so transparent.
Additionally, strategic confidentiality is lost. If a company holding Bitcoin as a reserve asset decides to make a major move (say, reallocating to a different wallet, or using some Bitcoin for a strategic investment or loan), doing so with known addresses broadcasts that strategy. Competitors or market analysts can infer things like “Company X is moving 10% of its BTC — why? Are they selling? Hedging? Using it as collateral?” This can erode any competitive advantage of keeping financial strategies discreet. It might even affect the company’s stock price if investors interpret moves negatively. For example, if a blockchain analysis shows the company’s reserves dropping, shareholders might fear the company sold Bitcoin (perhaps due to financial distress), even if the reality is benign (like moving funds to a new custodian). The company would be forced into continuous public explanation of on-chain actions to prevent misunderstanding.
There’s also a risk of exposing business partnerships. Suppose the company uses certain exchanges or OTC desks to rebalance its holdings – transactions with those service providers will be visible and could link the company to them. If one of those partners has issues (say a hacked exchange or a sanctioned entity inadvertently), the company could be reputationally contaminated by association through the blockchain trail.
Finally, not all publicity is good publicity in the crypto world. A public proof-of-reserve might invite armchair auditors to scrutinize and criticize every aspect of the company’s crypto management. Minor issues could be blown out of proportion. On the flip side, if a company chooses not to publish addresses, it could face reputational risk from a different angle: skeptics might question why it isn’t being transparent. (Indeed, Grayscale’s refusal to disclose wallet addresses led to social media chatter about whether they truly held all the Bitcoin they claimed, contributing to investor nervousness and a steep discount on GBTC shares .) Thus, companies are in a delicate spot: share too much and every move invites scrutiny; share too little and you breed distrust.
Balancing Transparency Benefits vs. Risks
The central question is whether the benefit of proving reserve holdings to investors outweighs these security and privacy risks. It’s a classic risk-reward calculation, and opinions in the industry are divided.
On the side of transparency, many argue that the credibility and trust gained by proof-of-reserves is invaluable. Advocates note that Bitcoin was designed for open verification – “on-chain auditability and permissionless transparency” are core features . By embracing this, companies demonstrate they are good stewards of a “trustless” asset. In fact, some believe public companies have a duty to be extra transparent. A recent Nasdaq report contended that “when a publicly traded company holds Bitcoin but offers no visibility into how that Bitcoin is held or verified, it exposes itself to multiple levels of risk: legal, reputational, operational, and strategic”, undermining trust . In that view, opacity is riskier in the long run – a lack of proof could weaken investor confidence or invite regulatory suspicion. Shareholders and analysts may actually penalize a company that refuses to provide verifiable proof of its crypto assets .
Transparency done right can also differentiate a firm as a leader in governance. Publishing reserve data (whether via addresses or through third-party attestations) can be seen as a commitment to high standards. For example, Metaplanet, an investment firm, publicly discloses its BTC reserve addresses and even provides a live dashboard for anyone to verify balances . This proactive openness signals confidence and has been touted as an industry best practice in some quarters. By proving its reserves, a company can potentially avoid the fate of those that lost public trust (as happened with opaque crypto firms in 2022). It’s also a means to preempt false rumors – if data is out in the open, misinformation has less room to grow.
However, the pro-transparency camp increasingly acknowledges that there are smarter ways to achieve trust without courting all the risks. One compromise is using cryptographic proofs or audits instead of plain address dumps. For instance, exchanges like Kraken have implemented Merkle tree proof-of-reserves: an independent auditor verifies all customer balances on-chain and provides a cryptographic report, and customers can individually verify their account is included without the exchange revealing every address publicly. This method proves solvency to those who need to know without handing over a complete roadmap to attackers. Another emerging solution is zero-knowledge proofs, where a company can prove knowledge or ownership of certain assets without revealing the addresses or amounts to the public. These technologies are still maturing, but they aim to deliver the best of both worlds: transparency and privacy.
On the side of caution, many experts believe the risks of full public disclosure outweigh the incremental gain in transparency, especially for regulated public companies. Michael Saylor encapsulates this viewpoint: he calls on-chain proof-of-reserve “a bad idea” for institutions, arguing that it “offers one-way transparency” (assets only) and “leaves organizations open to cyberattacks” . He stresses that no serious security expert would advise a Fortune 500 company to list all its wallet addresses, as it essentially compromises corporate security over time . Saylor and others also point out the pointlessness of an assets-only proof: unless you also prove liabilities, showing off reserves might even be dangerous because it could lull investors into a false sense of security .
Regulators and traditional auditors echo this: proof-of-reserves, while a useful tool, “is not enough by itself” to guarantee financial health . They advocate for holistic transparency – audits that consider internal controls, liabilities, and legal obligations, not just a snapshot of a blockchain address  . From this perspective, a public company can satisfy transparency demands through rigorous third-party audits and disclosures rather than raw on-chain data. Indeed, public companies are legally bound to extensive reporting; adding public crypto addresses on top may be seen as redundant and risky.
There is also an implicit cost-benefit analysis: A successful attack resulting from over-sharing could be catastrophic (loss of funds, legal liability, reputational ruin), whereas the benefit of public proof is somewhat intangible (improved investor sentiment, which might be achieved via other assurance methods anyway). Given that trade-off, many firms err on the side of caution. As evidence, few if any U.S.-listed companies that hold Bitcoin have published their wallet addresses. Instead, they reference independent custodians and audits for assurance. Even crypto-native companies have pulled back on full transparency after realizing the downsides – for example, some auditing firms halted issuing proof-of-reserves reports due to concerns about how they were interpreted and the liability involved  .
Industry best practices are still evolving. A prudent approach gaining favor is to prove reserves without leaking sensitive details. This can involve disclosing total balances and having an auditor or blockchain oracle confirm the assets exist, but without listing every address publicly. Companies are also encouraged to disclose encumbrances (whether any of the reserves are collateralized or lent out) in tandem, to address the liabilities issue . By doing so, they aim to achieve transparency and maintain security.
In evaluating whether to publish wallet addresses, a company must ask: Will this level of openness meaningfully increase stakeholder trust, or would a more controlled disclosure achieve the same goal with less risk? For many public companies, the answer has been to avoid public addresses. The risks – from attracting hackers to revealing strategic moves – tend to outweigh the marginal transparency benefit in their judgment. The collapse of unregulated exchanges has certainly proven the value of reserve verification, but public companies operate in a different context with audits and legal accountability. Thus, the optimal solution may be a middle ground: proving reserves through vetted processes (auditor attestations, cryptographic proofs) that satisfy investor needs without blatantly exposing the company’s financial backend to the world.
Conclusion
Publishing Bitcoin wallet addresses as proof of reserves is a bold transparency measure – one that speaks to crypto’s ideals of open verification – but it comes with a laundry list of security considerations. Public companies weighing this approach must contend with the heightened cybersecurity threat of advertising their treasure troves to hackers, the loss of privacy and confidentiality as on-chain sleuths dissect their every transaction, and potential regulatory complications if such disclosures are misunderstood or incomplete. Real-world incidents illustrate the downsides: firms that revealed addresses have seen how quickly online communities flag (and sometimes misinterpret) their blockchain moves, causing reputational turbulence and forcing rapid damage control  .
On the other hand, proving reserves to investors is important – it can prevent fraud and bolster trust. The question is how to achieve it without incurring unacceptable risk. Many experts and industry leaders lean towards the view that simply publishing wallet addresses is too risky a method, especially for public companies with much to lose  . The risks often do outweigh the direct benefits in such cases. Transparency remains crucial, but it can be provided in safer ways – through regular audits, cryptographic proofs that don’t expose all wallet details, and comprehensive disclosures that include liabilities and controls.
In conclusion, while on-chain proof of reserves via public addresses offers a tantalizing level of openness, it must be approached with extreme caution. For most public companies, the smart strategy is to balance transparency with security: verify and show investors that assets exist and are sufficient, but do so in a controlled manner that doesn’t compromise the very assets you’re trying to protect. As the industry matures, we can expect more refined proof-of-reserve practices that satisfy the demand for honesty and solvency verification without unduly endangering the enterprise. Until then, companies will continue to tread carefully, mindful that transparency is only truly valuable when it doesn’t come at the price of security and trust.
Sources:
• Grayscale statement on refusal to share on-chain proof-of-reserves  • Community analysis identifying Grayscale’s wallet addresses  • Cointelegraph – Crypto.com’s mistaken 320k ETH transfer spotted via on-chain proof-of-reserves   • Axios – Binance wallet “commingling” error observed on-chain   • Michael Saylor’s remarks on security risks of publishing wallet addresses    • SEC Acting Chief Accountant on limitations of proof-of-reserves reports  • Nasdaq (Bitcoin for Corporations) – argument for corporate transparency & proof-of-reserves    • 1inch Security Blog – explanation of dusting attacks and privacy loss via address linking  -
 @ 7f6db517:a4931eda
2025-05-29 18:02:56
@ 7f6db517:a4931eda
2025-05-29 18:02:56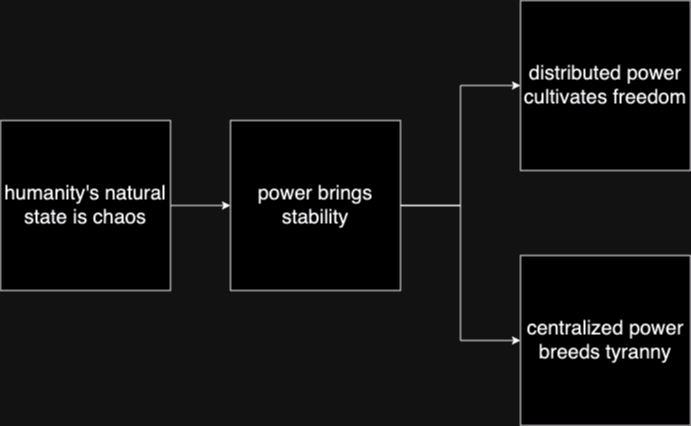
Humanity's Natural State Is Chaos
Without order there is chaos. Humans competing with each other for scarce resources naturally leads to conflict until one group achieves significant power and instates a "monopoly on violence."Power Brings Stability
Power has always been the key means to achieve stability in societies. Centralized power can be incredibly effective in addressing issues such as crime, poverty, and social unrest efficiently. Unfortunately this power is often abused and corrupted.Centralized Power Breeds Tyranny
Centralized power often leads to tyrannical rule. When a select few individuals hold control over a society, they tend to become corrupted. Centralized power structures often lack accountability and transparency, and rely too heavily on trust.Distributed Power Cultivates Freedom
New technology that empowers individuals provide us the ability to rebuild societies from the bottom up. Strong individuals that can defend and provide for themselves will help build strong local communities on a similar foundation. The result is power being distributed throughout society rather than held by a select few.In the short term, relying on trust and centralized power is an easy answer to mitigating chaos, but freedom tech tools provide us the ability to build on top of much stronger distributed foundations that provide stability while also cultivating individual freedom.
The solution starts with us. Empower yourself. Empower others. A grassroots freedom tech movement scaling one person at a time.
If you found this post helpful support my work with bitcoin.

-
 @ f85b9c2c:d190bcff
2025-05-29 16:20:45
@ f85b9c2c:d190bcff
2025-05-29 16:20:45
In the whirlwind of life, where we’re constantly bombarded by expectations, responsibilities, and the relentless ticking of the clock, it’s easy to lose sight of who we truly are. Are we merely boys masquerading as men, or have we embraced the mantle of manhood in its truest form? This question isn’t about age; it’s about essence, about purpose.
I stumbled upon this video the other day, titled "Are you a Man who’s a Boy, or a Boy who’s a Man?" by motivational speaker Les Brown. In it, he hits you with a truth bomb that echoes in your soul: Most people, they go to their graves with their greatness still in them." This sentence, simple yet profound, struck a chord with me. How often do we let fear, doubt, or the comfort of the known keep us from exploring our true potential? Watching that video, I couldn’t help but reflect on my own journey. I remember being in my early twenties, feeling like a boy in a man’s world. I was unsure, hesitant, and frankly, scared of what life might ask of me. But one day, after a particularly tough week, I watched this video, and something clicked. Les Brown’s passionate delivery made me realize that purpose isn’t something you find; it’s something you forge through the trials and tribulations of life. Here’s the deal: your purpose isn’t handed to you on a silver platter. It’s discovered through the grind, the hustle, the moments when you’re ready to throw in the towel but decide to keep going. Like when I switched careers, moving from a stable job to chasing a dream that felt more like me. It was terrifying, but it was in that leap of faith where I found my purpose - to inspire others to live their truth, no matter how daunting it seems. So, what’s your purpose in life?Are you still figuring it out, or are you out there living it? If you’re feeling lost, remember, it’s okay. We’re all works in progress. But don’t let that become an excuse to stay stationary. Push yourself, challenge the comfort zone, because as Les Brown so candidly puts it,
"You have greatness within you."
And here’s a little wisdom from my own life: purpose isn’t just about what you do; it’s about how you live every single day. It’s in the small acts of kindness, in standing up for what you believe in, in the relentless pursuit of becoming a better version of yourself. So, are you a man who’s a boy, still caught up in the games and fears of youth? Or are you a boy who’s stepping up to be a man, ready to claim your purpose?
Let’s not go to our graves with our greatness still inside us. Let’s live it, loud and proud, with all the courage of a boy who knows he’s becoming a man. Remember, life's too short for regrets, too precious to not live your purpose. Here's to finding it, or better yet, making it. Keep pushing, keep growing. And hey, if all else fails, at least you've got the wisdom of Les Brown and a friend in me to help you navigate this wild ride called life. 🌟 "Most people, they go to their graves with their greatness still in them." - Les Brown.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ e844b39d:adafb6a2
2025-05-27 12:30:49
@ e844b39d:adafb6a2
2025-05-27 12:30:49I've been going so deep into black & white for a longer period now that I've totally forgotten about colours!
Actually that is how I felt when I started editing these, it was kinda too much haha
 Grasshopper on our banana flower
Grasshopper on our banana flowerThis was to test my old Minolta 70-210/4 Beercan, even though the AF is slow it still locked in time to get this grasshopper!
I'm contemplating bringing this gear on the long trip instead of the old Nikon stuff, so gotta know it will do almost all sorts of jobs...
 Random flower
Random flowerI know that the pastel colours that I found using auto levels is in there, in the combination of the Sony A900 and the Beercan, which is one of the main reasons that I got it all around a decade ago.
 Twig
TwigMaybe too much? But still, these colours are in there, just gotta whack the files hard in post hehe
 Sharpness is no problem
Sharpness is no problemAll of these are at f4, its sharp enough to tackle anything really.
 Spider web
Spider webOf course this could be better technically, but it will do for almost anything I'll get across. Also this was manual focus, I didn't think the matte screen and viewfinder would make it possible to focus like this, never really tried before!
 Amulet and my Nikon gear
Amulet and my Nikon gearI found a tiny amulet on the floor, of course its the cats that are responsible for that...
 Zelda is happy
Zelda is happyThe A900 has built in stabilization, so any old lenses will get that by default! Which makes it far easier to get things like this right a around 1/4th of a second, even with that mirror clacking...
This one is with the Minolta 20/2.8, which is a lens I should really explore more. I got that and a 24/2.8 for a very low price, never had the time to use them much, and now I realize that they both can focus all the way down to 25 centimeters!
Now that is something I can use creatively, and on the road with ease...
I think this might end with me selling (dumping, really) my Nikon gear instead of this!
We'll find out soon 😁
-
 @ 21c71bfa:e28fa0f6
2025-05-29 15:08:51
@ 21c71bfa:e28fa0f6
2025-05-29 15:08:51Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 9223d2fa:b57e3de7
2025-04-15 02:54:00
@ 9223d2fa:b57e3de7
2025-04-15 02:54:0012,600 steps
-
 @ f85b9c2c:d190bcff
2025-05-29 16:15:13
@ f85b9c2c:d190bcff
2025-05-29 16:15:13
Life is full of ups and downs, uncertainties and challenges. But one of the most things life has is it ability to demand. It’s doesn’t care wether you’re sick, old, young, man or women. You must have something to offer .
I remember vividly what happened to me last year. It was time to resume school and my pops doesn’t have my tuition fee. So I decided to hustle for it by myself. I thought it’ll be easy, thinking I can get the money before the period of 1 month. I had my plans, but It seems like life has it own plans as well. I started doing some online businesses thinking it’s going to be alright. But then, all the things I engage myself in wasn’t going as planned. All my investments were gone, back to having a dry account and empty pockets. It was at that time I figured, life is playing with me. I nearly run mad during that period cause there was no one out there to help me go through this hardship. But then I remembered something that made me stopped over thinking. “You don’t know what tomorrow yield, you can die tonight and then everything will be useless” I keep this thought in my head. Why all the struggle for a life that you aren’t promised of tomorrow. We all sleep with the intentions of waking up the next day and continuing our lifestyle. But some of us don’t get to see tomorrow This thought made me think, I shouldn’t carry the weight of the world around my neck. It’s all useless if you die. There’s no point of all this struggle. This made me relieve the pressure I had on myself. And made me focus more on what am doing now instead of thinking of what’s going to happen in the future.
We should leave that aspect to GOD. A little advice to those young folks reading this. Don’t pressure yourself, what is meant for you will always be yours. And always have faith in GOD, he’s plans are better than yours. Life is hard and cruel, but when you decide to go with the thought that you alone can’t handle it all. That’s why GOD is there to handle our hidden battles for us.
-
 @ cefb08d1:f419beff
2025-05-27 09:36:52
@ cefb08d1:f419beff
2025-05-27 09:36:52Gabriela Bryan vs Caitlin Simmers | Western Australia Margaret River Pro 2025 - Final
https://www.youtube.com/watch?v=2GK8l3RPqmE
Jordy Smith vs Griffin Colapinto | Western Australia Margaret River Pro 2025 - Final
https://www.youtube.com/watch?v=zGWMVDwU_is
Highlights: Western Australia Margaret River Pro 2025 - All the Highlights
https://www.youtube.com/watch?v=32055IXrtnU
Ranking WSL Women:
Ranking WSL Men:
Source: https://www.worldsurfleague.com/athletes/tour/wct?year=2025
https://stacker.news/items/990198
-
 @ cae03c48:2a7d6671
2025-05-29 18:01:53
@ cae03c48:2a7d6671
2025-05-29 18:01:53Bitcoin Magazine

Human Rights Foundation Donates 800 Million Satoshis To 22 Worldwide Bitcoin And Freedom ProjectsToday, the Human Rights Foundation (HRF) announced its most recent round of Bitcoin Development Fund grants, according to a press release sent to Bitcoin Magazine.
800 million satoshis (8 BTC) currently worth over $874,000 at the time of writing, is being granted across 22 different projects around the world focusing on open-source development, educational initiatives, Bitcoin mining decentralization, and privacy tools for human rights advocates living under authoritarian regimes. The main areas of focus for these grants center around Latin America, Africa, and Asia
While the HRF did not disclose how much money each project is receiving specifically, the following 22 projects are the recipients of today’s round of grants worth 8 BTC, or 800 billion satoshis, in total:
Mostro
In authoritarian regimes, centralized exchanges enforce strict identity verification and frequently freeze user accounts. In these environments, Mostro, a peer-to-peer exchange built on the decentralized nostr protocol, provides a private and censorship-resistant way to access Bitcoin. It enables human rights defenders and ordinary citizens to transact freely. With HRF support, developer Catrya will improve Mostro’s usability to better serve dissidents seeking financial freedom.
SudaBit
As war and hyperinflation devastate Sudan, traditional banks and remittance systems have collapsed. Millions of Sudanese are left without reliable ways to save, send, or receive money. SudaBit, under development by Sudan Hodl, is the country’s first private Bitcoin on- and off-ramp, providing a critical financial lifeline where few options remain. With HRF support, SudaBit will allow everyday Sudanese to access permissionless, self-custodial Bitcoin directly from their local currency while at the same time building a vital financial infrastructure amid a humanitarian and monetary crisis.
Stringer News
Authoritarian regimes silence independent media to control public narratives and suppress dissent. Stringer News, an open media platform founded by war reporter and author Anjan Sundaram, uses Bitcoin and nostr to help reporters and human rights defenders publish without fear of censorship. By bypassing traditional publishing gatekeepers, it ensures critical reporting reaches global audiences — even from the depths of autocratic regimes. With HRF support, Stringer News is amplifying the voices of frontline journalists and protecting the flow of truth under dictatorship.
Prices Today
As Vladimir Putin wages war against Ukraine, it hides the economic pain at home. Prices Today is a project launched by the Anti-Corruption Foundation that tracks rising prices across essential goods and services in the country and publishes the data on an open, accessible website. The project helps Russians see through state propaganda and confront the hidden financial toll of Putin’s war. With this grant, Prices Today will expand its tools and research to expose the true cost of war and challenge the Kremlin’s narrative.
Instamouse for Bitcoin and Lightning
Contributing to Bitcoin’s codebase may require specialized tools and complex setup — barriers for developers in resource-limited environments. Instamouse, created by software developer Bryan Bishop (kanzure), is breaking down those barriers with a browser-based environment for open-source Bitcoin development. By reducing hardware requirements and simplifying access, it opens the door to a more inclusive environment that allows more people around the world to contribute to Bitcoin. With this grant, Instamouse will help keep Bitcoin’s development truly permissionless.
Seedsigner
Most commercial hardware wallets can be expensive, proprietary, and traceable. This poses barriers to self-custody for dissidents in weak economies or surveillant regimes. Seedsigner is a fully customizable, DIY Bitcoin hardware wallet that anyone can build using affordable, off-the-shelf components. It offers dissidents a discreet, low-cost way to secure their Bitcoin. HRF funding for lead developer Keith Mukai will expand language support across Europe, Asia, and beyond, as well as ongoing feature development and mentoring of new contributors.
Spacebear’s Contributions to Payjoin
Bitcoin enables human rights defenders to receive unstoppable payments. But making those payments private is the next critical step. Payjoin is a technique that lets senders and receivers batch Bitcoin transactions, breaking common chain analysis heuristics and improving default privacy. This is vital for activists in surveillance states who urgently need financial privacy without drawing attention. With HRF support, developer spacebear is advancing Payjoin to make privacy the default on Bitcoin and protect civil societies under tyranny.
Padawan Wallet
When authoritarian regimes devalue currencies or impose capital controls, people often turn to Bitcoin. But without experience, many struggle to use it safely. Padawan Wallet, a free, open-source mobile app by developer thunderbiscuit, helps bridge that gap. It uses Bitcoin test network coins to simulate real payments in a risk-free environment. It lets users practice making transactions, secure their wallets, and explore saving without risking real funds. With HRF support, Padawan will launch on iOS, expanding access to safe, hands-on Bitcoin learning for millions facing financial uncertainty.
Brink
Without ongoing support for Bitcoin development and its contributors, the network risks slower innovation, greater centralization, and long-term security challenges. Brink, a nonprofit organization led by Executive Director Mike Schmidt, addresses this by funding and mentoring open-source developers working on Bitcoin’s software infrastructure. Through grants and fellowships, Brink helps keep the protocol secure, decentralized, and freely accessible. With this grant, Brink will further strengthen the foundation that makes Bitcoin a tool for financial freedom.
Coin Center
As dictators increasingly treat code as a crime, open-source developers face sanctions, lawsuits, and mounting legal threats. Coin Center, a nonprofit research and advocacy organization led by Director of Research Peter Van Valkenburgh, defends the right to build and use open digital asset networks like Bitcoin. It advances policy analysis, supports strategic litigation, and educates lawmakers to protect freedom-preserving technologies. With HRF support, Coin Center will continue shaping a global legal environment where vital tools can be built for human rights defenders at risk.
Bitcoin Design Foundation
Poor user experience is a major barrier to Bitcoin adoption. Inconsistent wallet experiences and steep learning curves can deter new users, especially in high-risk environments. The Bitcoin Design Foundation is a nonprofit founded by UI designers Christoph Ono, Mogashni Naidoo, and Daniel Nordh that addresses this by funding open-source design, UX research, and community initiatives to make Bitcoin products more intuitive. With HRF support, the foundation will expand its grant and education programs to keep usability a priority and ensure Bitcoin remains open to all.
EmberOne
Bitcoin mining is dominated by a few companies producing closed, proprietary hardware — threatening the network’s resilience and accessibility. The 256 Foundation is a nonprofit working to change that. Building on the open-source Bitaxe project, EmberOne produces modular, open-source mining hardware that is simple, affordable, and open to anyone — especially those living under repressive regimes. With HRF support, EmberOne will lower entry barriers and help disrupt the proprietary ecosystem, making Bitcoin mining more accessible for those in closed societies.
2025 FROST Developer Support
For nonprofits operating under authoritarian rule, securing Bitcoin is critical for survival. If private keys (which control access to bitcoin) are compromised, funds can be seized and movements dismantled. Blockchain Commons is a nonprofit supporting the development of FROST (Flexible Round-Optimized Schnorr Threshold Signature), a protocol that strengthens multisignature wallets (bitcoin wallets with multiple private keys) by making them more secure, private, and flexible for shared custody. With this grant, Blockchain Commons will help build critical infrastructure to keep civil society groups operational and financially resilient under dictatorships.
Ecash UX Improvement Project
Ecash enables
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:52:10
@ 21c71bfa:e28fa0f6
2025-05-29 14:52:10Book *Tirupati to Srikalahasti cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ fbf0e434:e1be6a39
2025-05-29 13:09:48
@ fbf0e434:e1be6a39
2025-05-29 13:09:48Hackathon 概述
ETH Dublin 2025 黑客松圆满落幕,活动共吸引 84 名开发者参与,共有 31 个项目通过审核。活动核心是借助多家赞助商技术,打造具有影响力的区块链解决方案。活动鼓励参与者组建技能多元的平衡团队,运用技术工具及赞助商支持 —— 如 Chainlink 进行数据验证、Ledger 保障安全、Filecoin 提供存储方案等。
多个项目聚焦社会影响领域:ÉireEncrypt 致力于开发符合 GDPR 合规要求的隐私保护区块链工具;SafeRoads Ireland 则通过智能合约推动安全驾驶。此外,部分项目借助以太坊实现租金管控与去中心化住房市场,还有以移民为主题的数字解决方案促进社区融合,充分展现区块链技术在解决隐私保护、公共安全、教育改革等实际问题中的潜力。
总体而言,ETH Dublin 2025 黑客松不仅促进了开发者与合作伙伴的协作,更激发了诸多借助区块链技术创造社会价值的创新项目。
Hackathon 获奖者
奖项得主
- 一等奖: RecEth
RecEth 通过提供电子邮件确认和清晰的收据,增强了用户对加密交易的信任,将用户体验与传统支付系统的透明度相对齐。 - 二等奖: Latinum
Latinum 作为支付中间件,允许MCP构建者通过兼容钱包实现由代理发起的交易来实现服务器货币化,简化了货币化过程。 - 三等奖: Fundraisely
FundRaisely 利用区块链技术帮助慈善机构进行合法合规的筹款,以及透明的审计,确保捐款流程的清晰和负责。
欲了解所有项目的更多信息,请访问这里。
关于组织者
ETH Ireland
ETH Ireland 致力于区块链技术的创新和发展。该组织在Ethereum方面有着丰富的专业知识,通过举办会议和工作坊促进区块链教育和社区参与。ETH Ireland 的使命是扩大区块链知识普及,推广去中心化技术到各个领域。
- 一等奖: RecEth
-
 @ 39cc53c9:27168656
2025-05-27 09:21:53
@ 39cc53c9:27168656
2025-05-27 09:21:53The new website is finally live! I put in a lot of hard work over the past months on it. I'm proud to say that it's out now and it looks pretty cool, at least to me!
Why rewrite it all?
The old kycnot.me site was built using Python with Flask about two years ago. Since then, I've gained a lot more experience with Golang and coding in general. Trying to update that old codebase, which had a lot of design flaws, would have been a bad idea. It would have been like building on an unstable foundation.
That's why I made the decision to rewrite the entire application. Initially, I chose to use SvelteKit with JavaScript. I did manage to create a stable site that looked similar to the new one, but it required Jav aScript to work. As I kept coding, I started feeling like I was repeating "the Python mistake". I was writing the app in a language I wasn't very familiar with (just like when I was learning Python at that mom ent), and I wasn't happy with the code. It felt like spaghetti code all the time.
So, I made a complete U-turn and started over, this time using Golang. While I'm not as proficient in Golang as I am in Python now, I find it to be a very enjoyable language to code with. Most aof my recent pr ojects have been written in Golang, and I'm getting the hang of it. I tried to make the best decisions I could and structure the code as well as possible. Of course, there's still room for improvement, which I'll address in future updates.
Now I have a more maintainable website that can scale much better. It uses a real database instead of a JSON file like the old site, and I can add many more features. Since I chose to go with Golang, I mad e the "tradeoff" of not using JavaScript at all, so all the rendering load falls on the server. But I believe it's a tradeoff that's worth it.
What's new
- UI/UX - I've designed a new logo and color palette for kycnot.me. I think it looks pretty cool and cypherpunk. I am not a graphic designer, but I think I did a decent work and I put a lot of thinking on it to make it pleasant!
- Point system - The new point system provides more detailed information about the listings, and can be expanded to cover additional features across all services. Anyone can request a new point!
- ToS Scrapper: I've implemented a powerful automated terms-of-service scrapper that collects all the ToS pages from the listings. It saves you from the hassle of reading the ToS by listing the lines that are suspiciously related to KYC/AML practices. This is still in development and it will improve for sure, but it works pretty fine right now!
- Search bar - The new search bar allows you to easily filter services. It performs a full-text search on the Title, Description, Category, and Tags of all the services. Looking for VPN services? Just search for "vpn"!
- Transparency - To be more transparent, all discussions about services now take place publicly on GitLab. I won't be answering any e-mails (an auto-reply will prompt to write to the corresponding Gitlab issue). This ensures that all service-related matters are publicly accessible and recorded. Additionally, there's a real-time audits page that displays database changes.
- Listing Requests - I have upgraded the request system. The new form allows you to directly request services or points without any extra steps. In the future, I plan to enable requests for specific changes to parts of the website.
- Lightweight and fast - The new site is lighter and faster than its predecessor!
- Tor and I2P - At last! kycnot.me is now officially on Tor and I2P!
How?
This rewrite has been a labor of love, in the end, I've been working on this for more than 3 months now. I don't have a team, so I work by myself on my free time, but I find great joy in helping people on their private journey with cryptocurrencies. Making it easier for individuals to use cryptocurrencies without KYC is a goal I am proud of!
If you appreciate my work, you can support me through the methods listed here. Alternatively, feel free to send me an email with a kind message!
Technical details
All the code is written in Golang, the website makes use of the chi router for the routing part. I also make use of BigCache for caching database requests. There is 0 JavaScript, so all the rendering load falls on the server, this means it needed to be efficient enough to not drawn with a few users since the old site was reporting about 2M requests per month on average (note that this are not unique users).
The database is running with mariadb, using gorm as the ORM. This is more than enough for this project. I started working with an
sqlitedatabase, but I ended up migrating to mariadb since it works better with JSON.The scraper is using chromedp combined with a series of keywords, regex and other logic. It runs every 24h and scraps all the services. You can find the scraper code here.
The frontend is written using Golang Templates for the HTML, and TailwindCSS plus DaisyUI for the CSS classes framework. I also use some plain CSS, but it's minimal.
The requests forms is the only part of the project that requires JavaScript to be enabled. It is needed for parsing some from fields that are a bit complex and for the "captcha", which is a simple Proof of Work that runs on your browser, destinated to avoid spam. For this, I use mCaptcha.
-
 @ 0fa80bd3:ea7325de
2025-04-09 21:19:39
@ 0fa80bd3:ea7325de
2025-04-09 21:19:39DAOs promised decentralization. They offered a system where every member could influence a project's direction, where money and power were transparently distributed, and decisions were made through voting. All of it recorded immutably on the blockchain, free from middlemen.
But something didn’t work out. In practice, most DAOs haven’t evolved into living, self-organizing organisms. They became something else: clubs where participation is unevenly distributed. Leaders remained - only now without formal titles. They hold influence through control over communications, task framing, and community dynamics. Centralization still exists, just wrapped in a new package.
But there's a second, less obvious problem. Crowds can’t create strategy. In DAOs, people vote for what "feels right to the majority." But strategy isn’t about what feels good - it’s about what’s necessary. Difficult, unpopular, yet forward-looking decisions often fail when put to a vote. A founder’s vision is a risk. But in healthy teams, it’s that risk that drives progress. In DAOs, risk is almost always diluted until it becomes something safe and vague.
Instead of empowering leaders, DAOs often neutralize them. This is why many DAOs resemble consensus machines. Everyone talks, debates, and participates, but very little actually gets done. One person says, “Let’s jump,” and five others respond, “Let’s discuss that first.” This dynamic might work for open forums, but not for action.
Decentralization works when there’s trust and delegation, not just voting. Until DAOs develop effective systems for assigning roles, taking ownership, and acting with flexibility, they will keep losing ground to old-fashioned startups led by charismatic founders with a clear vision.
We’ve seen this in many real-world cases. Take MakerDAO, one of the most mature and technically sophisticated DAOs. Its governance token (MKR) holders vote on everything from interest rates to protocol upgrades. While this has allowed for transparency and community involvement, the process is often slow and bureaucratic. Complex proposals stall. Strategic pivots become hard to implement. And in 2023, a controversial proposal to allocate billions to real-world assets passed only narrowly, after months of infighting - highlighting how vision and execution can get stuck in the mud of distributed governance.
On the other hand, Uniswap DAO, responsible for the largest decentralized exchange, raised governance participation only after launching a delegation system where token holders could choose trusted representatives. Still, much of the activity is limited to a small group of active contributors. The vast majority of token holders remain passive. This raises the question: is it really community-led, or just a formalized power structure with lower transparency?
Then there’s ConstitutionDAO, an experiment that went viral. It raised over $40 million in days to try and buy a copy of the U.S. Constitution. But despite the hype, the DAO failed to win the auction. Afterwards, it struggled with refund logistics, communication breakdowns, and confusion over governance. It was a perfect example of collective enthusiasm without infrastructure or planning - proof that a DAO can raise capital fast but still lack cohesion.
Not all efforts have failed. Projects like Gitcoin DAO have made progress by incentivizing small, individual contributions. Their quadratic funding mechanism rewards projects based on the number of contributors, not just the size of donations, helping to elevate grassroots initiatives. But even here, long-term strategy often falls back on a core group of organizers rather than broad community consensus.
The pattern is clear: when the stakes are low or the tasks are modular, DAOs can coordinate well. But when bold moves are needed—when someone has to take responsibility and act under uncertainty DAOs often freeze. In the name of consensus, they lose momentum.
That’s why the organization of the future can’t rely purely on decentralization. It must encourage individual initiative and the ability to take calculated risks. People need to see their contribution not just as a vote, but as a role with clear actions and expected outcomes. When the situation demands, they should be empowered to act first and present the results to the community afterwards allowing for both autonomy and accountability. That’s not a flaw in the system. It’s how real progress happens.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:46
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:46Book *Tirupati to Vellore cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ ef53426a:7e988851
2025-05-29 12:26:43
@ ef53426a:7e988851
2025-05-29 12:26:43Saturday 9AM It’s a chilly Saturday morning in Warsaw, and I don’t want to get out of bed. This is not because of the hangover; it’s because I feel like a failure.
The first day of Bitcoin FilmFest was a whirlwind of workshops, panels and running between stages. The pitch competition did not go my way. Another ‘pitching rabbit’ (an actual experienced film-maker) was selected to win the €3,000 of funding.
Rather than get up and search for coffee, I replay the scenes in my head. What could I have done differently? Will investors ever believe in me: I’m just a writer with no contacts in the industry. Do I have what it takes to produce a film?
Eventually, I haul myself out of bed and walk to Amondo, the festival’s morning HQ (and technically, the smallest cinema in Europe). Upon arrival, I find Bitcoin psychonaut Ioni Appelberg holding court in front of around a dozen enraptured disciples. Soon, the conversation spills out to the street to free up space for more workshops.

I attend a talk on film funding, then pay for coffee using bitcoin. I see familiar faces from the two previous nights. We compare notes on Friday night and check the day’s schedule. The morning clouds burn off, and things feel a little brighter.
The afternoon session begins just a few blocks away in the towering Palace of Culture and Science. My role in today's proceedings is to present my freedom fiction project, 21 Futures, on the community stage. Other presentations range from rap videos and advice on finding jobs in bitcoin to hosting ‘Bitcoin Walks’. This is how we are fixing the culture.
Saturday 8PM I feel a tap on my shoulder. ‘Excuse me, Mr. Philip. Your car is waiting. The Producers’ Dinner is starting soon’.
What? Me, a producer? I’ve been taking part in some panels and talks, but I assumed my benefits as a guest were limited to a comped ticket and generous goodie bag.
Soon, I am sharing a taxi with a Dubai-based journalist, a Colombian director, and the cypherpunk sponsor of the pitch competition I didn’t win.
The pierogies I dreamed of earlier that day somehow manifest (happy endings do exist), and we enjoy a raucous dinner including obligatory slivovitz.

Sunday 2AM The last few hours of blur include a bracing city-bike ride in a crew of nine attendees back to the Palace of Culture, chatting with a fellow bitcoin meetup organiser, and vaguely promising to attend a weekend rave with a crew of Polish artists and musicians on the outskirts of London.
I leave the party while it’s still in full swing. In five hours, I have to wake up to complete my Run for Hal in Marshal Edward Rydz-Śmigły Park.
Thursday 9PM The festival kicks off in Samo Centrum on Pizza Day. I arrive in a taxi straight from a cramped flight (fix the airlines!), having not eaten for around ten hours.
The infectious sounds of softly spoken Aussie bitrocker Roger9000 pound into the damp night. I’m three beers in, being presented by the organisers to attendees like a (very tall) show pony. I try to explain more about my books, my publishing connections, my short film.
When I search for the food I ordered an hour ago, I find it has been given away. The stern-faced Polish pizza maker shrugs. ‘You not here.’
I’m so hungry I could cry (six hours of Ryanair can do that to a man). And then, a heroic Czech pleb donates half a pizza to me. Side note: this same heroic pleb accidentally locked me out of my film-funds while trying to fix a wallet bug on Sunday night.
I step out into the rain. Roger9000 reminds us we should have laser eyes well past 100k. I take a bite of pizza and life tastes good.

The Films Side events, artists, late nights, and pitcher’s regret is all well and good, but what of the films?
My highlights included Golden Rabbit winner No More Inflation — a moving narrative with interviews from two dozen economists, visionaries, and inflation survivors.
Hotel Bitcoin, was a surprisingly funny comedy romp about a group of idiots who happen across a valuable laptop.
Revolución Bitcoin — an approachable and thorough documentary aimed to bring greater adoption in the Spanish-speaking world.
And, as a short-fiction guy, I enjoyed the short films The Man Who Wouldn’t Cry, a visit to New York’s only Somali restaurant in Finding Home.

Sunday 7PM The award ceremony has just finished. I head to Amondo for the final time to pay for mojitos in bitcoin and say goodbye to newly made friends. I feel like I’ve met almost everyone in attendance. Are you going to BTC Prague?!? we ask as we part ways.
Of course, the best thing about any festival is the people, and BFF25 had a cast of characters worthy of any art house flick:
- The bright-eyed and confident frontwoman of the metal band Scardust
- A nostr-native artist selling his intricate canvases to the highest zapper
- A dreadlocked DJ who wears a pair of flying goggles on his head at all times
- An affable British filmmaker explaining the virtues of the word ‘chucklesome’
- A Duracell-powered organiser who seems to know every song, person, film, book, and guest at the festival.
Warsaw itself feels like it has a role to play, too. Birdsong and green parks contrast the foreboding Communist-era architecture. The weather changes faster than my mood — heavy greys transform to bright sunshine. The roads around the venue close on Sunday for a political rally. And there we are in the middle, watching our bitcoin films.

Tuesday 10AM I’m at home now, squinting at my email inbox and piles of washing, wondering when the hell I’ll find time. The festival Telegram group is still buzzing with activity. Side events like martial arts tutorials, trips to a shooting range, boat tours. 5AM photos of street graffiti, lost and found items, and people asking ‘is anyone still around?’
This was not just a film festival. BFF is truly a celebration of culture — Art. Books. Comedy. Music. Video. Talk. Connection.
All this pure signal has lifted my spirits so much that despite me being a newbie filmmaker, armed only with a biro, a couple of powerpoints and a Geyser fund page, I know I will succeed in my mission. It turns out you can just film things.
You may have attended bitcoin conferences before — you know, the ones with ‘fireside chats’, VIP areas, and overpriced merch. Bitcoin FilmFest is a moment in time. We are fixing the culture, year after year, until art can flourish again.
As fellow author Aaron Koenig commented during a panel session, ‘In twenty years, we won’t be drawing laser eyes and singing about honey badgers. Our grandchildren won’t understand the change we went through.’
Would I do it all again? Of course!
Join me next June in Warsaw.
I’ll be the tall one presenting his short animation premiere.
Philip Charter is a full-time writer and part-time cat herder. As well as writing for bitcoin founders and companies, he runs the 21 Futures fiction project.
Find out more about theNoderoid Saga animation projecton Geyser.
-
 @ cae03c48:2a7d6671
2025-05-29 20:01:59
@ cae03c48:2a7d6671
2025-05-29 20:01:59Bitcoin Magazine

Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025Bitcoin isn’t just something to hold anymore—it’s something to live on. That was the core message delivered by Miles Suter, Bitcoin Product Lead at Block Inc., during his keynote at the Bitcoin 2025 Conference today. Standing at the intersection of innovation and ideology, Suter laid out a vision where Bitcoin isn’t just a store of value—but the internet’s native currency.
“Bitcoin is at a crossroads—on one hand it’s never been stronger: a trillion in market cap, millions of holders, and even talk of nation-state adoption,” Suter said. “We use Bitcoin to hold, to hedge, to opt out, but we rarely use it to live. At Block Inc., we believe that has to change.”
Suter officially announced that Block is rolling out Bitcoin payment capability for merchants using Square POS, allowing them to accept bitcoin directly in-store. The move comes as part of a broader initiative Block calls the full bitcoin for business stack—covering acquiring, managing, reporting, accounting, converting, lending, and taxes.

“This is what makes Bitcoin an everyday currency for everyone,” he emphasized. “We believe hard-working entrepreneurs deserve access to the full power of bitcoin.”
To prove the vision in action, Block helped power a Guinness World Record attempt for the most Lightning payments in a day, hosted live at the conference. The goal: prove that Lightning payments aren’t just functional—they’re scalable, fast, and real.
Block’s commitment isn’t new. In 2020, the company put bitcoin on its balance sheet. In 2021, it co-founded the Bitcoin Clean Energy Initiative to fight the “boiling oceans” narrative. In 2022, Cash App became one of the first major platforms on Lightning. In 2023, it launched on-chain payments with Square. And in 2024, it helped defeat Craig Wright in court, “standing up for Satoshi.”
“These aren’t just headlines—they’re a pattern,” Suter said. “We’ve made it more accessible, more secure. Now we’re focused on making it usable every day.”
Cash App already ranks among the top bitcoin on-ramps in the U.S., accounting for nearly 10% of on-chain block space at any time. In 2024, Lightning usage grew 7x. “Block runs one of the top Lightning nodes globally. And here’s what’s wild—it’s working,” he said.

Block is now taking 10% of all profits from Bitcoin and adding it back to its balance sheet, and over 1,700 merchants are automatically converting part of their daily sales to Bitcoin.
“If Bitcoin just becomes digital gold, we failed the mission,” Suter said. “Bitcoin payments validate Bitcoin. They make it real. Bitcoin is money.”
This post Block Announces Bitcoin Business Stack, Makes Historic Lightning Payments Push at Bitcoin 2025 first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 39cc53c9:27168656
2025-05-27 09:21:51
@ 39cc53c9:27168656
2025-05-27 09:21:51Know Your Customer is a regulation that requires companies of all sizes to verify the identity, suitability, and risks involved with maintaining a business relationship with a customer. Such procedures fit within the broader scope of anti-money laundering (AML) and counterterrorism financing (CTF) regulations.
Banks, exchanges, online business, mail providers, domain registrars... Everyone wants to know who you are before you can even opt for their service. Your personal information is flowing around the internet in the hands of "god-knows-who" and secured by "trust-me-bro military-grade encryption". Once your account is linked to your personal (and verified) identity, tracking you is just as easy as keeping logs on all these platforms.
Rights for Illusions
KYC processes aim to combat terrorist financing, money laundering, and other illicit activities. On the surface, KYC seems like a commendable initiative. I mean, who wouldn't want to halt terrorists and criminals in their tracks?
The logic behind KYC is: "If we mandate every financial service provider to identify their users, it becomes easier to pinpoint and apprehend the malicious actors."
However, terrorists and criminals are not precisely lining up to be identified. They're crafty. They may adopt false identities or find alternative strategies to continue their operations. Far from being outwitted, many times they're several steps ahead of regulations. Realistically, KYC might deter a small fraction – let's say about 1% ^1 – of these malefactors. Yet, the cost? All of us are saddled with the inconvenient process of identification just to use a service.
Under the rhetoric of "ensuring our safety", governments and institutions enact regulations that seem more out of a dystopian novel, gradually taking away our right to privacy.
To illustrate, consider a city where the mayor has rolled out facial recognition cameras in every nook and cranny. A band of criminals, intent on robbing a local store, rolls in with a stolen car, their faces obscured by masks and their bodies cloaked in all-black clothes. Once they've committed the crime and exited the city's boundaries, they switch vehicles and clothes out of the cameras' watchful eyes. The high-tech surveillance? It didn’t manage to identify or trace them. Yet, for every law-abiding citizen who merely wants to drive through the city or do some shopping, their movements and identities are constantly logged. The irony? This invasive tracking impacts all of us, just to catch the 1% ^1 of less-than-careful criminals.
KYC? Not you.
KYC creates barriers to participation in normal economic activity, to supposedly stop criminals. ^2
KYC puts barriers between many users and businesses. One of these comes from the fact that the process often requires multiple forms of identification, proof of address, and sometimes even financial records. For individuals in areas with poor record-keeping, non-recognized legal documents, or those who are unbanked, homeless or transient, obtaining these documents can be challenging, if not impossible.
For people who are not skilled with technology or just don't have access to it, there's also a barrier since KYC procedures are mostly online, leaving them inadvertently excluded.
Another barrier goes for the casual or one-time user, where they might not see the value in undergoing a rigorous KYC process, and these requirements can deter them from using the service altogether.
It also wipes some businesses out of the equation, since for smaller businesses, the costs associated with complying with KYC norms—from the actual process of gathering and submitting documents to potential delays in operations—can be prohibitive in economical and/or technical terms.
You're not welcome
Imagine a swanky new club in town with a strict "members only" sign. You hear the music, you see the lights, and you want in. You step up, ready to join, but suddenly there's a long list of criteria you must meet. After some time, you are finally checking all the boxes. But then the club rejects your membership with no clear reason why. You just weren't accepted. Frustrating, right?
This club scenario isn't too different from the fact that KYC is being used by many businesses as a convenient gatekeeping tool. A perfect excuse based on a "legal" procedure they are obliged to.
Even some exchanges may randomly use this to freeze and block funds from users, claiming these were "flagged" by a cryptic system that inspects the transactions. You are left hostage to their arbitrary decision to let you successfully pass the KYC procedure. If you choose to sidestep their invasive process, they might just hold onto your funds indefinitely.
Your identity has been stolen
KYC data has been found to be for sale on many dark net markets^3. Exchanges may have leaks or hacks, and such leaks contain very sensitive data. We're talking about the full monty: passport or ID scans, proof of address, and even those awkward selfies where you're holding up your ID next to your face. All this data is being left to the mercy of the (mostly) "trust-me-bro" security systems of such companies. Quite scary, isn't it?
As cheap as $10 for 100 documents, with discounts applying for those who buy in bulk, the personal identities of innocent users who passed KYC procedures are for sale. ^3
In short, if you have ever passed the KYC/AML process of a crypto exchange, your privacy is at risk of being compromised, or it might even have already been compromised.
(they) Know Your Coins
You may already know that Bitcoin and most cryptocurrencies have a transparent public blockchain, meaning that all data is shown unencrypted for everyone to see and recorded forever. If you link an address you own to your identity through KYC, for example, by sending an amount from a KYC exchange to it, your Bitcoin is no longer pseudonymous and can then be traced.
If, for instance, you send Bitcoin from such an identified address to another KYC'ed address (say, from a friend), everyone having access to that address-identity link information (exchanges, governments, hackers, etc.) will be able to associate that transaction and know who you are transacting with.
Conclusions
To sum up, KYC does not protect individuals; rather, it's a threat to our privacy, freedom, security and integrity. Sensible information flowing through the internet is thrown into chaos by dubious security measures. It puts borders between many potential customers and businesses, and it helps governments and companies track innocent users. That's the chaos KYC has stirred.
The criminals are using stolen identities from companies that gathered them thanks to these very same regulations that were supposed to combat them. Criminals always know how to circumvent such regulations. In the end, normal people are the most affected by these policies.
The threat that KYC poses to individuals in terms of privacy, security and freedom is not to be neglected. And if we don’t start challenging these systems and questioning their efficacy, we are just one step closer to the dystopian future that is now foreseeable.
Edited 20/03/2024 * Add reference to the 1% statement on Rights for Illusions section to an article where Chainalysis found that only 0.34% of the transaction volume with cryptocurrencies in 2023 was attributable to criminal activity ^1
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:23
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:23Book *Tirupati to Tirumala cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 4d41a7cb:7d3633cc
2025-04-08 01:17:39
@ 4d41a7cb:7d3633cc
2025-04-08 01:17:39Satoshi Nakamoto, the pseudonymous creator of Bitcoin, registered his birthday as April 5, 1975, on his P2P Foundation profile. Many think that he chose this date because on that same day in 1933, the United States government confiscated the gold of the American people. Whether this was on purpose or not, what happened in this day is very important to understand how do we ended up here.
In 1933, as expressed in Roosevelt’s Executive Orders 6073, 6102, and 6260, the United States first declared bankruptcy. The bankrupt U.S. went into receivership in 1933. America was turned over via receivership and reorganization in favor of its creditors. These creditors, the International Bankers, from the beginning stated their intent, which was to plunder, bankrupt, conquer and enslave America and return it to its colonial status.1
As one of his first acts as President, Franklin Delano Roosevelt declared a “Banking Emergency” to bail out the Federal Reserve Bank, which had embezzled this country’s gold supply. The Congress gave the President dictatorial powers under the “War Powers Act of 1917” (amended 1933), written, by the way, by the Board of Governors of the Federal Reserve Bank of New York.2
This day marked the official abandonment of the American Constitution, law and real money. Today, 92 years after this event, most of the people living today have never had any real money or paid for anything using real money; unless they used Bitcoin...
There could be no bankruptcy if there was not a private central bank lending paper currency to the government at interest, so we must start from 1913, when the Federal Reserve was created: a non-federal private bank with no reserves and the monopoly of issuing debt based paper currency in unlimited amounts and lending it to the government at interest by buying treasury bills. The fact that this currency is lent into existence at interest makes the debt mathematically impossible to be repaid; it can only be refinanced or defaulted.
Between 1929 and 1933, the Federal Reserve Bank reduced the currency supply by 33%, thereby creating the Great Depression, bankrupting the US government, stealing the Americans’ gold supply, and officially ending the gold standard. Since then the US dollar (money) was replaced with Federal Reserve Notes (debt). This was also the end of the Republican form of government and the beginning of a socialist mob rule democracy (Fascism).
“Fascism should more properly be called corporatism because it is the merger of state and corporate power.” — Benito Mussolini
The United States government has been bankrupt since 1933, since it defaulted on its gold bonds. This type of bond existed until 1933, when the U.S. monetary system abandoned the gold standard. 3 From this year the government has been totally controlled by the International bankers and used as a tool to spread and maintain their power worldwide.
Many people think that the gold standard was abandoned in 1971, but this is not true; in fact, this happened in 1933 when the US dollar was replaced by Federal Reserve Notes that are 100% debt-based fiat paper currency.
The year 1933 in the United States marked:
- The end of the Republican form of government and the beginning of American Fascism
- The end of the United States dollar and its replacement by Federal Reserve Notes
- The abandonment of common law and replacement with military admiralty law
- The takeover of the United States government by International bankers
- A massive gold theft and the end of the US gold standard
- The exchange of rights with privileges and licenses
- The United States government bankruptcy
The next shameful event in our history which still plagues us to this day was the “War Powers Act of 1933.” This Act permitted President Roosevelt to make law in the form of Executive Order, bypass Congress and create his socialist state. We (citizens of this country) were ever after to be considered enemies of the United States who must be licensed to engage in any commercial activity. With the aid of the Federal Reserve (the same people who created the Depression), the President confiscated our gold and silver coin and replaced it with worthless pieces of paper and a debt system that will eventually destroy this great country. Our land and our labor were pledged to the Federal Reserve Bank, Inc., as collateral for a debt system that could never be paid.4
“Emergency Powers” means any form of military style government, martial law, or martial rule. Martial law and martial rule are not the same.
United States Congressional Record March 17, 1993 Vol. #33, page H- 1303, Congressman James Traficant, Jr. (Ohio) addressing the House:
“Mr. Speaker, we are here now in chapter 11. Members of Congress are official trustees presiding over the greatest reorganization of any Bankrupt entity in world history, the U.S. Government. We are setting forth, hopefully, a blueprint for our future”
“There are some who say it is a coroner’s report that will lead to our demise. It is an established fact that the United States Federal Government has been dissolved by the Emergency Banking Act, March 9, 1933, 48 Stat. 1, Public Law 89-719; dered by President Roosevelt, being bankrupt and insolvent. H.J.R. 192, 73rd Congress in session June 5, 1933 – Joint Resolution To Suspend The Gold Standard and Abrogate the Gold Clause dissolved the Sovereign Authority of the United States and the official capacities of all United States Governmental Offices, Officers, and Departments and is further evidence that the United States Federal Government exists today in name only” **“The receivers of the United States Bankruptcy are the International Bankers, via the United Nations, the World Bank and the International Monetary Fund”
“All United States Offices, Officials, and Departments are now operating within a de facto status in name only under Emergency War Powers. With the Constitutional Republican form of Government now dissolved, the receivers of the Bankruptcy have adopted a new form of government for the United States. This new form of government is known as a Democracy, being an established Socialist/Communist order under a new governor for America. This act was instituted and established by transferring and/or placing the Office of the Secretary of Treasury to that of the Governor of the International Monetary Fund. Public Law 94-564, page 8, Section H.R. 13955 read in part:”
“The U.S. Secretary of Treasury receives no compensation for representing the United States.”
The American Spirit
The intention of the founding fathers of the United States was to create a constitutional republic to protect natural human rights and escape from the tyrannical English monarchy and its usurious Bank of England's monetary system. They created an honest monetary system based on gold and silver (United State Dollar) and got rid of nobility titles, creating equality under the law.
Section 10 of the American Constitution says:
No State shall enter into any Treaty, Alliance, or Confederation; grant Letters of Marque and Reprisal; coin Money; emit Bills of Credit; make anything but gold and silver Coin a tender in payment of debts; pass any bill of attainder, ex post facto law, or law impairing the obligation of contracts; or grant any title of nobility.
The United States Dollar (1792-1933)
A dollar is a measure of weight defined by the Coinage Act of 1792 and 1900, which specifies a certain quantity—24.8 grains of gold or 371.25 grains of silver (from 1792 to 1900) when the American dollar was based on a bimetallic standard.
The Gold Standard Act of 1900 formally placed the United States on the gold standard, setting the value of one dollar at 25.8 grams of 90% pure gold, which fixed the price of gold at $20.67 per troy ounce. This standard was totally abandoned in 1933.
Gold and silver were such powerful money during the founding of the United States of America that the founding fathers declared that only gold or silver coins could be “money” in America.
But since the greedy bankers cannot profit from honest money they cannot print, they replaced the money with paper debt instruments. And by doing this, they have effectively enslaved the American people until today. My definition of modern slavery is working for a currency that someone else can create at no cost or effort. What's worse is that they even demand to be paid back and with interest!
Federal Reserve Notes (1913-present)
Federal Reserve Notes are not real money. Money that has metallic or other intrinsic value, as distinguished from paper currency, checks, and drafts.
Federal Reserve Notes (FRNs) are a legal fiction. An assumption that something is true even though it may be untrue. 5 The assumption that they are money, when in fact they are the opposite of money: debt or paper currency.
Paper money. Paper documents that circulate as currency; bills drawn by a government against its own credit. 6 Like Goldsmiths' notes. Hist. Bankers' cash notes: promissory notes given by bankers to customers as acknowledgments of the receipt of money. • This term derives from the London banking business, which originally was transacted by goldsmiths.7
These notes were scientifically designed to bankrupt the government and slave the American people, as Alfred Owen Crozier warned one year before the bill for the creation of the FED was passed through Congress (1912):
If Congress yields and authorizes a private central bank as proposed by the pending bill, the end when the bubble bursts will be universal ruin and national bankruptcy.
Unfortunately, the bill was passed in 1913, and this private bank started printing a new currency different from the US dollar creating the great depression and effectible bankrupting the government like Alfred warned 20 years before.
Alfred also warned:
Thus the way is opened for an unlimited inflation of corporate paper currency issued by a mere private corporation with relatively small net assets and no government guarantee, every dollar supposed to be redeemable in gold, but with not a single dollar of gold necessarily held in the reserves of such corporation to accomplish such redemption.
Differently from what's commonly believed Federal Reserve Notes (FRNs) were never really “backed” by gold; they were never supposed to be hard currency. Currency backed by reserves, esp. gold and silver reserves.
The United States government defaulted on its gold clauses, calling for payment in gold. This marked the end of the gold standard. A monetary system in which currency is convertible into its legal equivalent in gold or gold coin.
Since then we have been under a paper standard, where we use fake money as tender for payments. Paper standard. A monetary system based entirely on paper; a system of currency that is not convertible into gold or other precious metal.
People traded their coupons as money or “currency.” Currency is not money but a money substitute. Redeemable currency must promise to pay a dollar equivalent in gold or silver money. Federal Reserve Notes (FRNs) make no such promises and are not “money.” A Federal Reserve Note is a debt obligation of the federal United States government, not “money.” The federal United States government and the U.S. Congress were not and have never been authorized by the Constitution of the United States of America to issue currency of any kind, but only lawful money—gold and silver coin.8
A bona fide note can be used in a financial transaction to discharge the debt only because it is an unconditional promise to pay by the issuer to the bearer. Is a Federal Reserve Note a contract note, an unconditional promise to pay? At one time the Federal Reserve issued bona fide contractual notes and certificates, redeemable in gold and silver coin. Most people never saw or comprehended the contract. It went largely unread because the Federal Reserve very cunningly hid the contract on the face of the note by breaking it up into five separate lines of text with a significantly different typeface for each line and placing the president’s picture right in the middle of it. They even used the old attorney’s ruse of obscuring the most important text in fine print! Over time, the terms and conditions of the contract were diluted until eventually they literally became an I.O.U. for nothing.
FEDERAL RESERVE NOTE
-
THIS NOTE IS LEGAL TENDER FOR ALL DEBT, PUBLIC AND PRIVATE, AND IT IS REDEEMABLE IN LAWFUL MONEY AT THE UNITED STATES TREASURY OR ANY FEDERAL RESERVE BANK.
-
DATE: SERIES OF 1934
-
WILL PAY TO THE BEARER ON DEMAND: ONE HUNDRED DOLLARS
-
TREASURER OF THE UNITED STATES SIGNATURE
-
SECRETARY OF THE TREASURY SIGNATURE

Nowadays FRNs say "This note is legal tender for all debts public and private" it tender debt but it does not pay the bearer on demand. It value was stolen by a counterfeiting technique commonly know as inflation.
One hundred dollars (SERIES OF 1934) will be 2480 grains of gold, or 159.4 grams, or 5.1249 troy ounces. Today one troy ounce is priced around $3,000 federal reserve notes. 5.1249 X 3,000 = $15,375 actual FRNs.
A $100 FRN bill today will buy 0.65% of a real gold $100 dollar certificate. That’s a -99.35% loss of purchasing power in the last 91 years.
FRNs savers have been rugged pulled!
Gold bugs where the winners...
But Bitcoin is even better...
Happy birthday Satoshi! April 5 will be forever remembered.
Satoshi... The man, the myth, the Legend...
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ a3c6f928:d45494fb
2025-05-29 11:52:31
@ a3c6f928:d45494fb
2025-05-29 11:52:31In a world dominated by noise, distraction, and constant motion, there’s a deeper kind of liberation that many yearn for—spiritual freedom. This is not freedom measured by external factors, but by the stillness within. It’s the kind of freedom that arises when you no longer feel enslaved by ego, fear, or the pursuit of approval.
What Is Spiritual Freedom?
Spiritual freedom is the ability to live in alignment with your highest truth. It means being free from the illusions of control, unshackled from the burdens of regret, and connected to something greater than yourself—whether that’s God, the universe, or your own divine essence.
It is peace that doesn’t depend on circumstance. It is joy that isn’t based on possession. It’s knowing who you are beyond the labels, titles, and roles you play.
Signs You’re Seeking Spiritual Freedom
You feel unfulfilled despite material success
You’re questioning your deeper purpose or path
You long for peace that outlasts the highs and lows
You’re becoming more drawn to stillness, simplicity, or presence
The Path to Inner Liberation
-
Let Go of the Ego: Ego thrives on identity, comparison, and control. Spiritual freedom comes when you stop living to protect or promote a false self.
-
Live in the Now: Freedom is found in presence. Not in what happened yesterday or what might come tomorrow, but in this exact breath.
-
Seek Connection Over Control: The more we try to control life, the more trapped we feel. Surrender doesn’t mean giving up—it means trusting a higher order and flowing with it.
-
Forgive and Release: Grudges and guilt are spiritual chains. Letting go of what weighs down your spirit is one of the most liberating things you can do.
-
Return to Love: At the heart of all spiritual freedom is love—not romantic love, but divine love, unconditional love, the kind that expands you rather than limits you.
Why It Matters
In chasing external freedom, we often forget that without inner peace, nothing ever feels free. Spiritual freedom is what makes outer success meaningful. It’s what allows us to face life’s storms without being broken by them.
“You find peace not by rearranging the circumstances of your life, but by realizing who you are at the deepest level.” — Eckhart Tolle
True freedom is not out there. It’s already within you—waiting to be remembered.
-
-
 @ 0c65eba8:4a08ef9a
2025-05-29 17:39:18
@ 0c65eba8:4a08ef9a
2025-05-29 17:39:18People say AI can’t create anything truly original. They’re right, because creativity doesn’t come from machines. Machines have no senses, no instincts, no ability to act in the real world. They’ve never tasted danger, felt grief, or made a sacrifice. Creativity belongs to those who have lived life. It comes to men and women who know what they’re doing through experience.
AI is not a writer or an artist. It is a tool. A calculator that uses words instead of numbers to guess what you want to hear. It has no soul, no experience, no skin in the game.
If you want to create something real, you must be the mind and heart behind the words. You must put your own inner fire into it. The AI is just the forge that lets you work the letters into place.
What AI Can't Do, And What You Must
This is how I write with AI. This is my process.
Step One: Define the Mission
First, I decide:
-
What I’m writing (length, format, scope, tone)
-
What I want to say (thesis)
-
How I’ll prove it (supporting points)
Step Two: Attack Your Idea Before You Defend It
Then I open up a conversation with the AI. Not to write but to challenge my ideas.
I ask it to generate a falsification prompt, a structured attack on my idea. But this requires precision. AI is not designed to challenge you. It’s trained to agree with you, to reflect consensus. So you have to hack it.
You must write a prompt that forces it to become adversarial, not based on popular opinion, but grounded in first principles. And even then, you must define which first principles matter. Clarity here sets the boundaries of the entire piece. This is the most important prompt in the process.
Then I run that prompt in a second thread. I hunt for weak points. I keep running tests until my idea holds. Only then do I continue.
Step Three: Map the Consequences
Next, I ask for second- and third-order consequences. What happens if this idea is applied in real life? What breaks? What works?
But even here, I don’t take its answers at face value. I ask it to falsify its own guesstimations, because that’s what they are, a mixture of guess and estimation, with no grounding in lived experience.
I push it to argue against itself, to challenge the implications it just offered. And I only accept what survives both prediction and pressure.
Now the shape is clear.
Step Four: Begin the First Draft
Only then do I tell the AI to begin drafting.
I give it a long, detailed prompt. Part of it is recycled between posts: my grammar rules, my format, my tone, my values. Some of it I keep saved in a PDF and drop in. The rest is tailored to the post at hand, instructions I generate during the previous steps, shaped by my interactions with the AI. The goal isn’t perfection. The goal is a useful skeleton I can flesh out. It gives me something usable but bland that covers the main points.
Step Five: Speak the Edits
Then I speak.
I dictate edits. I tell it what to keep, what to rewrite and how, what it missed. I move pieces around until the best arguments sit in the best possible order. When I’m finished, the post is 90% my own words. The AI added glue, structure, flow, formating. Nothing more.
Step Six: Quality Control
Now I run my quality checks. I ask a stock set of questions:
-
Does the summary of my idea still make sense?
-
Is the grammar consistent and clean?
-
Am I repeating myself?
-
Are the tenses correct?
-
Does my argument still hold up?
This is especially important for long posts. The goal is polish. Polish means clarity, rhythm, logic, and precision. Nothing missed. Nothing wasted. No extra words.
I also lean on insights from Joshua Lisec’s (@JoshuaLisec) The Best Way to Write It course. It taught me how to spot my typical writing flaws, and now I hold myself to that higher standard. The longer the document, the more important this phase becomes. Quality control doesn’t just clean up the surface, it keeps the message on brand, sharp, structured, and true.
This Is Amplification, Not Automation
This is not automation. It is amplification.
Automation replaces intention. Amplification serves it.
Automation assumes the machine should think for you. Amplification sharpens what you already know.
The AI didn’t create the message. It didn’t understand the truth of it. It didn’t live the stories that forged it. What it did, at its best, was help me say it faster, clearer, sharper.
Amplification means I can reach more people with less friction. It means I can test ideas at scale, refine arguments quickly, and stay in the rhythm of writing without stopping to reformat every sentence.
It’s not slop. It’s not a shortcut. It’s strategic leverage. But only if you already have something worth saying.
Most people don’t. Even many prolific writers don’t. They recycle ideas from one audience and feed them to another, a younger, more naive crowd that’s never heard them before. They mistake that for creativity.
I’ll be open with you: I rarely invent new ideas. I don’t need to. I write about ancient truths, time-tested strategies, the hard-won lessons of life.
What I do is connect what’s always worked with what’s possible now. I explain. I teach. And in person, I read people. I see what’s missing in them, and I help them see it too. Then together we build the missing pieces.
That’s not something you can fake. It’s not something AI can simulate. You have to live in order to have something worth saying. So the AI gives most people nothing. But if you’ve lived, if you’ve suffered and built and learned, then it can give you speed, clarity, and consistency in communicating that to others. But only if you lead it.
Why Most People Fail with AI
Most people fail with AI because they expect it to do the thinking. It can’t. It can only organize what you tell it.
If your results are vague, weak, or generic, it’s because:
-
You aren’t clear on what you want
-
You don’t know how to communicate boundaries
The problem is not the machine. The problem is your executive function is lacking.
Nonfiction Writing Was Always a Team Effort
Many nonfiction writers have always worked this way: Surrounded by assistants. Speaking out loud. Sorting ideas in real time. Having the best material refined and tested by teammates.
This isn’t about fiction, which is often best created in solitude, slowly, by a single mind over many years. Fiction doesn’t have to be real. It has to feel real. But nonfiction must follow truth. It must be grounded in reality, tested, and safe to apply. People get hurt if it isn’t.
There’s also a difference between writing because it’s your job and writing because you have something important to share. I don’t write for a living. I write because I know things that can help people, and that knowledge demands to be passed on.
If writing is your job, of course you’ll spend much more time on it. You’ll hire editors, assistants, researchers. Or AI can help with that, it’s low cost leverage. But if writing is your service, your legacy, your offering to the world, then you must be efficient. You must learn how to dictate, delegate, and get the truth out. Faster and better.
That’s what I do. And AI is the best assistant I’ve ever had for the money.
Even Trump writes this way. He speaks. His team organizes, sharpens, packages, gives him feedback.
Now you can do the same. For only $20 a month.
But only if you lead. Only if you know who you are, what you want to say, and how to direct a team. Because managing an AI is little different than managing people. You must have a solidly established ego. You must know how to set boundaries and hold them. You must be an expert communicator. The same executive skills that make you a capable leader in life are the ones that let you get real value from AI. Without them, it will run you.
Because this is your team. And you’re the head of it.
Final Truth: Lead or Be Led
Different people are getting vastly different results from AI. Some are producing brilliant work. Others are spinning in circles. When that happens, the problem isn’t the tool. It’s the user.
Any time a group uses the same tool and outcomes vary wildly, the difference is in the people, not the technology.
AI is perhaps the most complex tool humanity has ever built. It’s going to change the world, just like the printing press, the internet, and smartphones did. Whether that change is good or catastrophic depends on the quality of the people using it.
People with weak egos, poor boundaries, and low agency will be swept away. They’ll lose track of themselves. They’ll be absorbed into someone else’s machine. Not because they’re stupid. But because they’ve never trained their minds to resist.
And they will blame the tool. They’ll say, "This time it’s different." They’ll panic, moralize, or make excuses. But it’s the same pattern we’ve seen with every new influence system: TV, radio, social media.
The real issue is agency. If you have it, you use the tool. If you don’t, the tool uses you.
You can’t stop AI. But you can rise above its dangers. You can train your internal architecture to remain sovereign, no matter how powerful the machine gets.
If you want to build that kind of fortitude, the kind that makes you immune to being used, I can help you. That’s what I do.
Lead your thoughts. Lead your message. Use your tools like a man who knows what he’s building.
-
-
 @ 50f67565:e633a1e0
2025-05-29 09:58:27
@ 50f67565:e633a1e0
2025-05-29 09:58:27Trong bối cảnh thị trường giải trí trực tuyến ngày càng phát triển mạnh mẽ, OKE88 nổi lên như một nền tảng tiên phong, mang đến cho người chơi Việt Nam trải nghiệm đa dạng và chất lượng vượt trội. Với kho trò chơi phong phú bao gồm slot game, bắn cá, đá gà và cá cược thể thao, OKE88 đáp ứng nhu cầu giải trí đa dạng của người dùng trên mọi thiết bị, đặc biệt tối ưu hóa cho cả hệ điều hành iOS và Android. Giao diện thân thiện, dễ sử dụng cùng khả năng vận hành ổn định ngay cả trên các mạng yếu như 3G giúp người chơi luôn có thể kết nối mượt mà bất kể thời gian và địa điểm. Không chỉ tập trung vào yếu tố giải trí, OKE88 còn đặc biệt chú trọng xây dựng hệ thống bảo mật tiên tiến, đảm bảo mọi thông tin cá nhân và giao dịch tài chính của người chơi được bảo vệ tuyệt đối. Sự kết hợp giữa công nghệ hiện đại và thiết kế thân thiện tạo nên một môi trường chơi game công bằng, minh bạch và đáng tin cậy, giúp người chơi hoàn toàn yên tâm khi tham gia.
OKE88 còn ghi dấu ấn mạnh mẽ nhờ những chương trình khuyến mãi hấp dẫn và đa dạng, góp phần tạo thêm sức hút cho nền tảng và nâng cao trải nghiệm người dùng. Từ các ưu đãi cho người chơi mới với thưởng 100% khi đăng ký, đến các chương trình hoàn trả hàng ngày lên đến 1,5% và sự kiện đua top hàng tuần với tổng giải thưởng hàng trăm triệu đồng, OKE88 không ngừng mang lại cơ hội nhận thưởng hấp dẫn cho cộng đồng người chơi. Bên cạnh đó, những khuyến mãi đặc biệt vào dịp sinh nhật dành cho thành viên VIP cũng tạo nên sự gắn bó lâu dài và cảm giác được trân trọng cho người dùng. Cộng đồng người chơi tại OKE88 được xây dựng với tinh thần hỗ trợ và tương tác cao, tạo điều kiện để người chơi chia sẻ kinh nghiệm, học hỏi kỹ năng và tận hưởng những giây phút giải trí đầy thú vị. Đội ngũ chăm sóc khách hàng hoạt động 24/7 với phong cách chuyên nghiệp, nhiệt tình và nhanh chóng cũng góp phần quan trọng trong việc giữ vững sự hài lòng và niềm tin của người chơi.
Không chỉ là một nền tảng giải trí đơn thuần, OKE88 còn thể hiện tầm nhìn chiến lược khi luôn đảm bảo tính hợp pháp và minh bạch trong mọi hoạt động. Việc được cấp phép chính thức và tuân thủ nghiêm ngặt các quy định pháp luật góp phần tạo nên uy tín vững chắc cho OKE88 trong lòng người chơi. Đồng thời, hệ thống kiểm soát chặt chẽ các hành vi gian lận, nâng cao tính công bằng và đảm bảo sự minh bạch trong từng ván cược cũng được nền tảng chú trọng phát triển. Với sứ mệnh không ngừng hoàn thiện và đổi mới, OKE88 cam kết mang đến một sân chơi an toàn, hiện đại và công bằng, đáp ứng đầy đủ kỳ vọng của cộng đồng người chơi Việt Nam. Đây chính là lý do OKE88 trở thành lựa chọn hàng đầu trong lĩnh vực giải trí trực tuyến, đồng hành cùng người chơi trong mỗi trải nghiệm, giúp họ tận hưởng những giây phút thư giãn đỉnh cao và cơ hội thắng lớn mỗi ngày.
-
 @ c066aac5:6a41a034
2025-04-05 16:58:58
@ c066aac5:6a41a034
2025-04-05 16:58:58I’m drawn to extremities in art. The louder, the bolder, the more outrageous, the better. Bold art takes me out of the mundane into a whole new world where anything and everything is possible. Having grown up in the safety of the suburban midwest, I was a bit of a rebellious soul in search of the satiation that only came from the consumption of the outrageous. My inclination to find bold art draws me to NOSTR, because I believe NOSTR can be the place where the next generation of artistic pioneers go to express themselves. I also believe that as much as we are able, were should invite them to come create here.
My Background: A Small Side Story
My father was a professional gamer in the 80s, back when there was no money or glory in the avocation. He did get a bit of spotlight though after the fact: in the mid 2000’s there were a few parties making documentaries about that era of gaming as well as current arcade events (namely 2007’sChasing GhostsandThe King of Kong: A Fistful of Quarters). As a result of these documentaries, there was a revival in the arcade gaming scene. My family attended events related to the documentaries or arcade gaming and I became exposed to a lot of things I wouldn’t have been able to find. The producer ofThe King of Kong: A Fistful of Quarters had previously made a documentary calledNew York Dollwhich was centered around the life of bassist Arthur Kane. My 12 year old mind was blown: The New York Dolls were a glam-punk sensation dressed in drag. The music was from another planet. Johnny Thunders’ guitar playing was like Chuck Berry with more distortion and less filter. Later on I got to meet the Galaga record holder at the time, Phil Day, in Ottumwa Iowa. Phil is an Australian man of high intellect and good taste. He exposed me to great creators such as Nick Cave & The Bad Seeds, Shakespeare, Lou Reed, artists who created things that I had previously found inconceivable.
I believe this time period informed my current tastes and interests, but regrettably I think it also put coals on the fire of rebellion within. I stopped taking my parents and siblings seriously, the Christian faith of my family (which I now hold dearly to) seemed like a mundane sham, and I felt I couldn’t fit in with most people because of my avant-garde tastes. So I write this with the caveat that there should be a way to encourage these tastes in children without letting them walk down the wrong path. There is nothing inherently wrong with bold art, but I’d advise parents to carefully find ways to cultivate their children’s tastes without completely shutting them down and pushing them away as a result. My parents were very loving and patient during this time; I thank God for that.
With that out of the way, lets dive in to some bold artists:
Nicolas Cage: Actor
There is an excellent video by Wisecrack on Nicolas Cage that explains him better than I will, which I will linkhere. Nicolas Cage rejects the idea that good acting is tied to mere realism; all of his larger than life acting decisions are deliberate choices. When that clicked for me, I immediately realized the man is a genius. He borrows from Kabuki and German Expressionism, art forms that rely on exaggeration to get the message across. He has even created his own acting style, which he calls Nouveau Shamanic. He augments his imagination to go from acting to being. Rather than using the old hat of method acting, he transports himself to a new world mentally. The projects he chooses to partake in are based on his own interests or what he considers would be a challenge (making a bad script good for example). Thus it doesn’t matter how the end result comes out; he has already achieved his goal as an artist. Because of this and because certain directors don’t know how to use his talents, he has a noticeable amount of duds in his filmography. Dig around the duds, you’ll find some pure gold. I’d personally recommend the filmsPig, Joe, Renfield, and his Christmas film The Family Man.
Nick Cave: Songwriter
What a wild career this man has had! From the apocalyptic mayhem of his band The Birthday Party to the pensive atmosphere of his albumGhosteen, it seems like Nick Cave has tried everything. I think his secret sauce is that he’s always working. He maintains an excellent newsletter calledThe Red Hand Files, he has written screenplays such asLawless, he has written books, he has made great film scores such asThe Assassination of Jesse James by the Coward Robert Ford, the man is religiously prolific. I believe that one of the reasons he is prolific is that he’s not afraid to experiment. If he has an idea, he follows it through to completion. From the albumMurder Ballads(which is comprised of what the title suggests) to his rejected sequel toGladiator(Gladiator: Christ Killer), he doesn’t seem to be afraid to take anything on. This has led to some over the top works as well as some deeply personal works. Albums likeSkeleton TreeandGhosteenwere journeys through the grief of his son’s death. The Boatman’s Callis arguably a better break-up album than anything Taylor Swift has put out. He’s not afraid to be outrageous, he’s not afraid to offend, but most importantly he’s not afraid to be himself. Works I’d recommend include The Birthday Party’sLive 1981-82, Nick Cave & The Bad Seeds’The Boatman’s Call, and the filmLawless.
Jim Jarmusch: Director
I consider Jim’s films to be bold almost in an ironic sense: his works are bold in that they are, for the most part, anti-sensational. He has a rule that if his screenplays are criticized for a lack of action, he makes them even less eventful. Even with sensational settings his films feel very close to reality, and they demonstrate the beauty of everyday life. That's what is bold about his art to me: making the sensational grounded in reality while making everyday reality all the more special. Ghost Dog: The Way of the Samurai is about a modern-day African-American hitman who strictly follows the rules of the ancient Samurai, yet one can resonate with the humanity of a seemingly absurd character. Only Lovers Left Aliveis a vampire love story, but in the middle of a vampire romance one can see their their own relationships in a new deeply human light. Jim’s work reminds me that art reflects life, and that there is sacred beauty in seemingly mundane everyday life. I personally recommend his filmsPaterson,Down by Law, andCoffee and Cigarettes.
NOSTR: We Need Bold Art
NOSTR is in my opinion a path to a better future. In a world creeping slowly towards everything apps, I hope that the protocol where the individual owns their data wins over everything else. I love freedom and sovereignty. If NOSTR is going to win the race of everything apps, we need more than Bitcoin content. We need more than shirtless bros paying for bananas in foreign countries and exercising with girls who have seductive accents. Common people cannot see themselves in such a world. NOSTR needs to catch the attention of everyday people. I don’t believe that this can be accomplished merely by introducing more broadly relevant content; people are searching for content that speaks to them. I believe that NOSTR can and should attract artists of all kinds because NOSTR is one of the few places on the internet where artists can express themselves fearlessly. Getting zaps from NOSTR’s value-for-value ecosystem has far less friction than crowdfunding a creative project or pitching investors that will irreversibly modify an artist’s vision. Having a place where one can post their works without fear of censorship should be extremely enticing. Having a place where one can connect with fellow humans directly as opposed to a sea of bots should seem like the obvious solution. If NOSTR can become a safe haven for artists to express themselves and spread their work, I believe that everyday people will follow. The banker whose stressful job weighs on them will suddenly find joy with an original meme made by a great visual comedian. The programmer for a healthcare company who is drowning in hopeless mundanity could suddenly find a new lust for life by hearing the song of a musician who isn’t afraid to crowdfund their their next project by putting their lighting address on the streets of the internet. The excel guru who loves independent film may find that NOSTR is the best way to support non corporate movies. My closing statement: continue to encourage the artists in your life as I’m sure you have been, but while you’re at it give them the purple pill. You may very well be a part of building a better future.
-
 @ 50f67565:e633a1e0
2025-05-29 09:57:49
@ 50f67565:e633a1e0
2025-05-29 09:57:49Trong cuộc sống hiện đại, khả năng ra quyết định nhanh chóng và chính xác là một kỹ năng quan trọng giúp mỗi người đạt được thành công trong công việc và cuộc sống hàng ngày. Nền tảng K399, nổi tiếng với kho trò chơi đa dạng và tính năng giải trí hiện đại, không chỉ mang lại trải nghiệm thư giãn mà còn góp phần thúc đẩy phát triển kỹ năng ra quyết định cho người chơi. Khi tham gia các trò chơi tại K399, người dùng phải liên tục phân tích tình huống, đánh giá các lựa chọn và đưa ra quyết định phù hợp để tối đa hóa cơ hội chiến thắng. Quá trình này tạo điều kiện cho người chơi rèn luyện khả năng suy nghĩ logic, xử lý thông tin nhanh và lựa chọn chiến thuật hiệu quả, từ đó cải thiện kỹ năng ra quyết định trong nhiều lĩnh vực khác ngoài giải trí.
Không chỉ dừng lại ở việc cung cấp một môi trường luyện tập kỹ năng ra quyết định, K399 còn giúp người chơi phát triển tư duy phản biện và khả năng đối mặt với rủi ro một cách hiệu quả. Trên nền tảng này, mỗi trò chơi đều đặt ra những thử thách và tình huống khác nhau đòi hỏi người chơi phải nhanh chóng đánh giá các yếu tố như xác suất, lợi ích và rủi ro. Kỹ năng cân nhắc và phân tích các lựa chọn giúp người chơi hình thành thói quen suy nghĩ thấu đáo trước khi hành động, một kỹ năng rất cần thiết trong cuộc sống thực tế. Bên cạnh đó, việc học cách kiểm soát cảm xúc và duy trì sự bình tĩnh khi đối mặt với thất bại hay áp lực trong trò chơi cũng giúp người dùng nâng cao khả năng chịu đựng stress và ra quyết định hiệu quả hơn trong công việc và các tình huống hàng ngày.
Ngoài ra, K399 còn tích hợp các chương trình đào tạo và hỗ trợ người chơi phát triển kỹ năng ra quyết định thông qua các bài hướng dẫn, chiến thuật chơi và phân tích chi tiết sau mỗi phiên trải nghiệm. Sự đa dạng trong loại hình trò chơi và cấp độ thử thách giúp người chơi dễ dàng lựa chọn phù hợp với khả năng và nhu cầu rèn luyện cá nhân. Qua đó, nền tảng không chỉ là nơi giải trí mà còn trở thành môi trường học tập và phát triển kỹ năng quan trọng, hỗ trợ người chơi nâng cao tư duy phản xạ và khả năng xử lý tình huống nhanh nhạy. K399, vì thế, đã và đang góp phần quan trọng vào việc trang bị cho người Việt kỹ năng ra quyết định hiệu quả, đáp ứng yêu cầu ngày càng cao của xã hội hiện đại và môi trường làm việc năng động.
-
 @ cae03c48:2a7d6671
2025-05-29 16:01:40
@ cae03c48:2a7d6671
2025-05-29 16:01:40Bitcoin Magazine

GameStop CEO Ryan Cohen Announced Acquisition of Over $505 Million BitcoinAt the 2025 Bitcoin Conference in Las Vegas, in an interview with the CEO of Nakamoto David Bailey, the CEO of GameStop Ryan Cohen announced why the company bought over $505 million in Bitcoin.
JUST IN: GameStop $GME CEO explains why the company bought over $505 million #Bitcoin

“Bitcoin can be a hedge against global currency devaluation” pic.twitter.com/jNiId2fntA
— Bitcoin Magazine (@BitcoinMagazine) May 28, 2025
Ryan Cohen started by explaining some things about the GameStop business.
“When I took over, the company was a piece of crap and losing a lot of money and was under a lot of pressure moving from physical gains to digital downloads so you had to cut costs,” stated Cohen. “Very aggressively bringing physical discipline and we did. Retail is a tough business, but it was a big focus on getting cost under control.”
When Bailey asked Cohen how many Bitcoin GameStop owned, Ryan responded, “We currently own 4710 Bitcoin.”
Then Ryan mentioned why they are adding Bitcoin to their balance sheets.
“If the thesis is correct then Bitcoin and gold as well can be a hedge against global currency devaluation and systemic risk,” mentioned Ryan. “Bitcoin has certain unique advantages better than gold.”
He commented on the benefits of Bitcoin compared to gold.
“You can easily secure Bitcoin in a wallet whereas gold requires insurance and it’s very expensive and then there is the scarcity element of this as well,” commented Ryan. “There is a fixed supply of Bitcoin whereas with gold, the supply of gold is still uncertain.“
Ryan finished the announcement by saying, “GameStop is following GameStop Strategy. We are not following anyone else’s.”
This post GameStop CEO Ryan Cohen Announced Acquisition of Over $505 Million Bitcoin first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:21:33
@ cf8c27f4:c95b9b5c
2025-05-29 15:21:33What’s Happening in Japan? Japan has the highest debt-to-GDP ratio in the developed world — over 260%. For decades, it got away with this by keeping interest rates near zero and having the Bank of Japan (BoJ) purchase most of its government bonds. This was known as Yield Curve Control — a desperate attempt to keep borrowing costs low.
But now, global bond markets are revolting.
🔺 Japanese 30-year yields have exploded past 3.18%
🔺 The worst bond auction since 1987 just occurred
🔺 Demand for JGBs (Japanese Government Bonds) is collapsing
When demand for bonds falls, prices drop and yields rise. This signals fear. Big fear.
As Taylor Kenney noted in a widely shared thread:
“This isn’t just a Japan problem — Japan is the largest foreign holder of U.S. debt.” The Contagion Risk: U.S. Debt and Global Collapse
Here’s where this gets truly global.
In 2025 alone, $9.2 trillion of U.S. debt will mature — 70% of it between January and June. That debt must be refinanced, and as interest rates remain elevated, the cost of servicing this debt balloons, potentially straining the U.S. government’s finances.
If yields rise further, it only worsens the cycle:
-
Yields rise
-
Interest costs balloon
-
Governments print more to cover deficits
-
Currencies debase
-
Confidence dies
-
Collapse follows
Japan may just be the canary in the coal mine. Gold Is Surging. Bitcoin Is Outpacing It.
Smart money is already moving.
Bitcoin is closing in on its all-time high — and closely tracking the M2 Global Liquidity Index, historically lagging it by 60–90 days.
Gold has also had a stellar run in 2025, signalling institutional flight to hard assets.
People are scared. And they should be.
The global financial system is built on an unsustainable foundation of debt, inflation, and artificial suppression of interest rates. That system is now cracking in Japan — but it won’t stop there. ₿ Bitcoin: The Exit Plan
Bitcoin doesn’t rely on a central bank.
It doesn’t need to be refinanced.
It doesn’t have a yield curve to control.
It’s decentralised, scarce, and incorruptible.
While fiat currencies spiral under the weight of debt and monetary debasement, Bitcoin offers an escape — a monetary protocol with a fixed supply and no political manipulation.
It’s not just an investment.
It’s an exit strategy from the madness. Final Thoughts
-
Japan is flashing red.
-
The U.S. is next in line.
-
The debt system is spiralling — fast.
Gold is insurance.
Bitcoin is the lifeboat.
-
-
 @ 39cc53c9:27168656
2025-05-27 09:21:50
@ 39cc53c9:27168656
2025-05-27 09:21:50Over the past few months, I've dedicated my time to a complete rewrite of the kycnot.me website. The technology stack remains unchanged; Golang paired with TailwindCSS. However, I've made some design choices in this iteration that I believe significantly enhance the site. Particularly to backend code.
UI Improvements
You'll notice a refreshed UI that retains the original concept but has some notable enhancements. The service list view is now more visually engaging, it displays additional information in a more aesthetically pleasing manner. Both filtering and searching functionalities have been optimized for speed and user experience.
Service pages have been also redesigned to highlight key information at the top, with the KYC Level box always accessible. The display of service attributes is now more visually intuitive.
The request form, especially the Captcha, has undergone substantial improvements. The new self-made Captcha is robust, addressing the reliability issues encountered with the previous version.
Terms of Service Summarizer
A significant upgrade is the Terms of Service summarizer/reviewer, now powered by AI (GPT-4-turbo). It efficiently condenses each service's ToS, extracting and presenting critical points, including any warnings. Summaries are updated monthly, processing over 40 ToS pages via the OpenAI API using a self-crafted and thoroughly tested prompt.
Nostr Comments
I've integrated a comment section for each service using Nostr. For guidance on using this feature, visit the dedicated how-to page.
Database
The backend database has transitioned to pocketbase, an open-source Golang backend that has been a pleasure to work with. I maintain an updated fork of the Golang SDK for pocketbase at pluja/pocketbase.
Scoring
The scoring algorithm has also been refined to be more fair. Despite I had considered its removal due to the complexity it adds (it is very difficult to design a fair scoring system), some users highlighted its value, so I kept it. The updated algorithm is available open source.
Listings
Each listing has been re-evaluated, and the ones that were no longer operational were removed. New additions are included, and the backlog of pending services will be addressed progressively, since I still have access to the old database.
API
The API now offers more comprehensive data. For more details, check here.
About Page
The About page has been restructured for brevity and clarity.
Other Changes
Extensive changes have been implemented in the server-side logic, since the whole code base was re-written from the ground up. I may discuss these in a future post, but for now, I consider the current version to be just a bit beyond beta, and additional updates are planned in the coming weeks.
-
 @ 21c71bfa:e28fa0f6
2025-05-29 14:51:04
@ 21c71bfa:e28fa0f6
2025-05-29 14:51:04Book *Bhubaneswar to Konark cab* online at best price. CabBazar provides car rental services for all cab types AC, Non AC, Hatchback, SUV, Sedan, Innova and Tempo Traveller. Both One way taxi and round trip cab available at lowest price. Price starts Rs. 9/Km.
-
 @ 50f67565:e633a1e0
2025-05-29 09:57:03
@ 50f67565:e633a1e0
2025-05-29 09:57:036FF không chỉ đơn thuần là một nền tảng giải trí trực tuyến, mà còn là một phần quan trọng trong sự phát triển của văn hóa giải trí hiện đại tại Việt Nam. Với sự đa dạng trong các thể loại trò chơi như slot game, bắn cá, casino trực tiếp và cá cược thể thao, 6FF đã đáp ứng được nhu cầu giải trí ngày càng cao của người chơi ở nhiều độ tuổi và tầng lớp khác nhau. Sự thuận tiện trong việc đăng ký tài khoản và trải nghiệm các trò chơi qua ứng dụng 6FF trên điện thoại di động đã giúp nền tảng này tiếp cận rộng rãi hơn với cộng đồng người dùng, đặc biệt là giới trẻ. 6FF không chỉ tạo ra một sân chơi hấp dẫn mà còn góp phần thúc đẩy sự phát triển công nghệ và dịch vụ giải trí số trong nước, qua đó làm phong phú thêm đời sống tinh thần cho người Việt hiện đại.
Một trong những điểm mạnh nổi bật của 6FF chính là hệ thống khuyến mãi và ưu đãi đa dạng, giúp người chơi có thêm nhiều cơ hội tiếp cận trò chơi mà không phải lo lắng quá nhiều về chi phí ban đầu. Các chương trình tặng thưởng 100% giá trị nạp đầu tiên, hoàn trả không giới hạn hàng ngày, cùng các phần quà sinh nhật và VIP định kỳ đã tạo nên sức hút đặc biệt, giữ chân người chơi lâu dài và tạo ra cộng đồng trung thành. Bên cạnh đó, sự minh bạch trong các giao dịch nạp rút tiền, tốc độ xử lý nhanh chóng và đa dạng phương thức thanh toán là yếu tố then chốt nâng cao niềm tin của người dùng đối với 6FF. Đội ngũ hỗ trợ 24/7 cũng góp phần làm tăng trải nghiệm người chơi khi họ có thể nhận được sự trợ giúp kịp thời trong mọi tình huống, từ việc đăng ký tài khoản cho đến giải quyết các vấn đề kỹ thuật phát sinh.
Ngoài việc đáp ứng nhu cầu giải trí, 6FF còn mang đến một không gian tương tác, kết nối người chơi trên cả nước. Các trò chơi cá cược thể thao không chỉ giúp người chơi giải trí mà còn góp phần tạo nên các cuộc trò chuyện sôi nổi về các sự kiện thể thao trong và ngoài nước. Nhờ vào việc cung cấp dữ liệu trận đấu, tỷ lệ kèo chính xác và cập nhật nhanh chóng, 6FF giúp người chơi có thêm kiến thức và trải nghiệm phong phú hơn trong lĩnh vực cá cược. Đây cũng là điểm cộng lớn trong việc xây dựng một cộng đồng người chơi chuyên nghiệp, am hiểu và có sự gắn kết sâu sắc. Từ đó, 6FF không chỉ là một nền tảng giải trí mà còn là một phần quan trọng trong đời sống xã hội hiện đại, giúp người Việt kết nối, giao lưu và chia sẻ niềm vui một cách thiết thực và ý nghĩa.
-
 @ da8b7de1:c0164aee
2025-05-29 15:52:45
@ da8b7de1:c0164aee
2025-05-29 15:52:45Bulgária: Először töltenek be Westinghouse-üzemanyagot a Kozloduy-5-be
Először töltöttek be Westinghouse által gyártott nukleáris üzemanyag-kazettákat Bulgária Kozloduy-5 VVER-1000 reaktorába 2025. május 29-én. Ez jelentős lépés Szófia azon törekvésében, hogy csökkentse orosz nukleáris üzemanyag-függőségét, és diverzifikálja energiaforrásait. A lépés része annak a szélesebb stratégiának, amelynek célja az energiaellátás biztonságának növelése és a nyugati partnerekkel való szorosabb együttműködés[NucNet].
Fehér Ház: Nukleáris Telepítési Csúcstalálkozó az USA-ban
A mai napon a Fehér Ház Nukleáris Telepítési Csúcstalálkozót tartott, amelyen kiemelték a köz- és magánszféra eredményeit. Fő témák voltak az orosz urántól való amerikai függőség csökkentése, a nukleáris üzemanyag-ellátási lánc bővítése, valamint a globális nukleáris kapacitás 2050-ig történő megháromszorozásának támogatása. A csúcson szó esett a nagy nukleáris projektek kockázatainak csökkentéséről, új reaktortervezetekről és a meglévő atomerőművek élettartamának meghosszabbításáról is. Az amerikai kormány hangsúlyozta, hogy továbbra is támogatja a fejlett nukleáris demonstrációs projekteket, a munkaerő-fejlesztést, valamint a legújabb törvényhozási lépéseket, például az orosz uránimport tilalmáról szóló törvényt[World Nuclear News].
Törékeny áramellátás a zaporizzsjai atomerőműben, Ukrajna
Az IAEA jelentése szerint az ukrajnai Zaporizzsjai Atomerőmű továbbra is rendkívül sebezhető helyzetben van, mivel jelenleg csak egyetlen külső áramvezetékre támaszkodik a biztonsági rendszerek működtetéséhez. Az utolsó tartalék vezeték három hete le van választva, ami aggodalomra ad okot a hűtő- és biztonsági rendszerek stabilitását illetően. Bár a létesítmény három éve nem termel áramot, folyamatos elektromos ellátásra van szükség a kiégett fűtőelemek hűtéséhez. Az IAEA továbbra is szorosan figyelemmel kíséri a helyzetet, és kiemeli a régióban zajló katonai tevékenységet[IAEA].
USA: SMR-fejlesztések és költségvetési megszorítások
A Tennessee Valley Authority benyújtotta az építési engedélykérelmet egy GE Vernova Hitachi BWRX-300 típusú kis moduláris reaktor (SMR) telepítésére a Clinch River helyszínen, ami jelentős előrelépés az amerikai SMR-programban. Eközben az amerikai kormány 2026-os költségvetési tervezete jelentős csökkentéseket irányoz elő az Energiaügyi Minisztérium nukleáris finanszírozásában, különösen a nem elsődleges kutatási területeken. A fókusz az innovatív reaktorkoncepciókra, fejlett üzemanyagokra és a kulcsfontosságú nemzeti laboratóriumi képességek fenntartására helyeződik[World Nuclear News][World Nuclear News].
Savannah River Site: Előrelépés a plutónium-magházak gyártásában
Az amerikai Energiaügyi Minisztérium Savannah River telephelyén megkezdődött a kesztyűs dobozok gyártása a plutónium magházak előállításához. Ezek a kesztyűs dobozok kulcsfontosságúak a Savannah River Plutonium Processing Facility számára, amely a Nemzeti Nukleáris Biztonsági Igazgatóság célkitűzéseit támogatja, hogy a projektet a 2030-as évek elejéig befejezzék. Ez a lépés az amerikai nukleáris fegyverkezési infrastruktúra modernizációjának része[ANS].
Nemzetközi trendek: ellátási lánc és új reaktorprojektek
A nukleáris ellátási lánc a globális növekedésre készül, ahogy azt a World Nuclear Association legutóbbi konferenciáján is hangsúlyozták. Kiemelt nemzetközi fejlemények:
- Gőzturbina-hengerek telepítése Kína Haiyang 3 erőművében.
- Új, négy reaktoros telephely jóváhagyása Indiában, Rádzsasztánban.
- Belgium és Dánia újragondolja a nukleáris kivonulási politikáját.
- Brazília az oroszokkal való SMR-együttműködést vizsgálja.
- Kanada előrelép a szállítható nukleáris erőmű-technológia terén[World Nuclear News].
Érintetti bevonás és a nukleáris energia szerepe a tiszta átmenetben
Az IAEA konferenciasorozata továbbra is hangsúlyozza az érintetti bevonás fontosságát a nukleáris non-proliferáció, biztonság és a közbizalom szempontjából. A panelek foglalkoznak a közvélemény-tájékoztatás tanulságaival, a nukleáris energia ipari dekarbonizációban betöltött szerepével és az újonnan belépő országok nukleáris infrastruktúra-fejlesztési tapasztalataival is[IAEA].
További részletek a következő forrásokon: - World Nuclear News - NucNet - IAEA - ANS
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:19:56
@ cf8c27f4:c95b9b5c
2025-05-29 15:19:56The Weimar Hyperinflation Nightmare
It’s 1921. Germany’s reeling from World War I, crushed by reparations and a wrecked economy. The government’s solution? Print money. Lots of it. The German mark starts tanking. By 1923, it’s a joke—4.2 trillion marks to one U.S. dollar. A loaf of bread costs wheelbarrows of cash. Savings? Wiped out. Middle-class families? Pauperized. Chaos.
Enter Hugo Stinnes, a coal and steel magnate with a sharp mind and sharper instincts. He sees the game: when a currency’s dying, debt is your friend. Why? Because the real value of your loans shrinks as inflation skyrockets. Borrow 1 million marks today, buy a factory, and by next year, that million’s worth a few pennies. Pay it back, keep the factory, repeat.
Stinnes’ Master Play
Stinnes goes all in. He borrows billions of marks, snapping up hard assets—steel mills, shipping lines, factories, real estate. Tangible stuff that holds value while paper marks turn to confetti. By 1923, his empire is a beast: over 1,500 companies, from coal mines to newspapers. Estimates say he controlled 15-20% of Germany’s industry, maybe more. A third of the economy? Probably an exaggeration, but the guy was a titan.
He wasn’t just lucky. Stinnes played 4D chess. He diversified his holdings to weather the storm, employed tens of thousands (keeping unrest at bay), and even argued his empire stabilized the economy. Critics, like British diplomat Lord D’Abernon, weren’t buying it—they called him a profiteer who thrived while others starved. Truth? Probably somewhere in the middle.
The Fall
Hyperinflation couldn’t last forever. In November 1923, Germany introduced the Rentenmark, a new currency backed by land and assets. The mark’s freefall stopped. Stinnes’ debt-fueled strategy hit a wall—stable currencies make loans harder to game. His health was failing too. He died in 1924, and his conglomerate started unraveling, with parts sold off or restructured. The Inflation King’s reign was over.
Why This Matters Today: Enter Bitcoin
Stinnes’ story isn’t just a history lesson—it’s a warning. Hyperinflation destroys trust in fiat money. When governments print cash to cover debts, savers get crushed, and the clever (or ruthless) like Stinnes exploit the chaos. Sound familiar? Look at today: global debt’s at $315 trillion, central banks are juggling interest rates, and inflation’s eating purchasing power. Argentina’s peso lost 50% of its value in 2024 alone. Venezuela’s bolívar? Toast.
This is where Bitcoin comes in. Born in 2009 after the financial crisis, Bitcoin is a hedge against fiat’s flaws. Unlike marks or dollars, it’s decentralised—no government can print more to pay its bills. Its supply is capped at 21 million coins, making it “digital gold.” When fiat currencies wobble, Bitcoin’s value often spikes—check its 2021 and 2024 bull runs during inflation fears.
Stinnes gamed a broken system by betting on hard assets. Today, Bitcoiners are doing the same, but instead of factories, they’re stacking sats. Why? Because in a world where fiat can be printed to oblivion, a deflationary asset like Bitcoin holds appeal. It’s not perfect—volatility’s a beast, and governments hate what they can’t control—but it’s a response to the same problem Stinnes faced: untrustworthy money.
The Lesson
Stinnes saw the Weimar collapse coming and turned it into wealth. Most didn’t. Today, you don’t need to be a tycoon to protect yourself, but you do need to understand the game. Fiat’s not collapsing tomorrow, but cracks are showing. Bitcoin’s one tool—maybe not the only one—to hedge against that risk. Study history, question the system, and don’t get caught holding the bag.
-
 @ 9e9085e9:2056af17
2025-05-29 07:51:18
@ 9e9085e9:2056af17
2025-05-29 07:51:18Part 5: Why You Should Join Yakihonne Today
🚀 Yakihonne: The Future of Free, Fair & Fast Social Interaction
Looking for a platform where you control everything—your posts, your data, your income?
Yakihonne is not just another app. It's a movement. A decentralized social payment network where:
Your voice can't be silenced
Your data isn't sold
Your followers are truly yours
Your creativity can be rewarded instantly
🔥 6 Reasons to Pay Attention to Yakihonne:
-
Zero Censorship Say what matters without fear of being muted or banned.
-
Built on Nostr Protocol Secure, scalable, and permissionless by design.
-
Social + Payments in One Chat, connect, and get paid—all from one app.
-
Lightning Fast Tips Reward content instantly with Bitcoin micro-payments.
-
No Algorithms. No Ads. No Noise. What you see is what you follow—simple and clean.
-
True Digital Freedom Break free from centralized control and own your digital presence.
🔗 Explore now: https://yakihonne.com 📱 Available on #iOS & #Android
-
-
 @ cf8c27f4:c95b9b5c
2025-05-29 15:17:06
@ cf8c27f4:c95b9b5c
2025-05-29 15:17:06Bitcoin’s Path to Global Dominance: Store of Value, Medium of Exchange, and the Road to a Bitcoin Standard
Bitcoin has ignited a financial revolution, captivating everyone from tech enthusiasts to institutional investors. Yet, amidst its meteoric rise, a tantalising question emerges: Could Bitcoin become the world’s reserve currency, relegating fiat currencies to the history books? This vision—a global Bitcoin standard—stirs intense debate within the community. Some champion Bitcoin as a Store of Value (SOV), a digital equivalent to gold, while others insist its future lies in becoming a Medium of Exchange (MOE), used for everyday transactions. With conflicting perspectives and community members at varying points in their Bitcoin journey, it’s time to unpack these ideas and chart a unified course.
This article delves into the interplay between Bitcoin’s SOV and MOE roles, examines the hurdles to widespread adoption, and proposes a roadmap for Bitcoin to claim global reserve status. My goal is to ignite a vibrant discussion, bridge divides, and encourage the Bitcoin community to rally around a shared vision for the future.
The Building Blocks: What Are SOV and MOE?
To kick things off, let’s define the two pillars of this debate:
• Store of Value (SOV): An asset that holds or grows its worth over time, offering a dependable way to preserve wealth. Think gold, a classic example cherished for millennia.
• Medium of Exchange (MOE): A tool for transactions, enabling the seamless exchange of goods and services. Today, fiat currencies like the pound or dollar reign supreme in this domain.
Bitcoin’s allure stems from its unique traits: a capped supply of 21 million coins, a decentralised network, and immunity to censorship. These qualities position it as a contender to replace both gold and fiat money—but the journey is complex, and the community’s views are far from aligned.
Where We Stand: Bitcoin as Digital Gold
Bitcoin’s ascent has been propelled by its prowess as a Store of Value. Early adopters, savvy investors, and even big institutions have embraced it as a shield against inflation, economic turmoil, and the erosion of fiat value. Its scarcity—hardwired into its code—has cemented the “digital gold” narrative, drawing in those seeking a safe haven in uncertain times.
But here’s the rub: while Bitcoin shines as an SOV, it’s rarely used as an MOE. Its price swings, technical limitations, and patchy acceptance by merchants make it a tough sell for buying a pint or a loaf of bread. Many in the community—think of figures like Michael Saylor—preach the gospel of “hodling,” urging followers to stash Bitcoin away and watch its value soar. This strategy has paid off handsomely for some, but it begs a bigger question: Can Bitcoin rule the world if it remains a speculative treasure rather than a working currency?
The Adoption Puzzle: Bridging SOV and MOE
For Bitcoin to leap from a niche asset to the global reserve currency, it must become a widely accepted Medium of Exchange. This evolution matters for several reasons:
• Real-World Use Fuels Demand: When Bitcoin powers transactions, its value ties to tangible activity, not just market hype.
• Network Strength: More users mean a tougher, more valuable network—a classic network effect.
• Price Stability: Broader adoption could smooth out Bitcoin’s wild price rides, making it more practical for daily use.
Yet, hurdles abound. Bitcoin’s volatility is a dealbreaker for many—who’d spend it on a takeaway if it might double in value overnight? Then there’s the issue of “whales” or “max hodlers,” those holding vast swathes of Bitcoin. If too much of the supply sits idle, it starves the liquidity needed for an MOE to thrive.
The Hodler Debate: To Spend or Not to Spend?
A spirited clash within the community revolves around these large holders. Should they—like Saylor or early adopters—dip into their stacks to kickstart adoption? Hodling bolsters Bitcoin’s scarcity and SOV credentials, no doubt. But if the bulk of Bitcoin stays locked up, it could stall the growth of a bustling, transactional ecosystem.
Let’s be fair: hodling has been a winning play for many, turning small investments into fortunes. It’s a stretch to demand these pioneers shoulder the adoption burden alone. As Bitcoin weaves into the fabric of commerce—think businesses accepting it or workers earning it—transactional demand will rise organically. Over time, this could nudge even the staunchest hodlers to spend a bit, striking a balance between saving and circulating.
Growth and Stability: A Natural Progression
Bitcoin’s Compound Annual Growth Rate (CAGR) offers another angle. As its market cap balloons, its explosive growth is likely to taper off—a standard pattern for any asset. This slowdown could usher in greater stability, a boon for its MOE ambitions. Less volatility means less risk when spending Bitcoin, paving the way for it to move beyond investment portfolios and into wallets for everyday use.
This shift could redefine Bitcoin’s story, transforming it from a rollercoaster ride to a dependable currency. Voices like Jeff Booth and Jack Dorsey argue that MOE success is the key to sustaining Bitcoin’s SOV status. In short, while SOV lit the fuse, MOE could keep the fire burning.
The Blueprint: Steps to a Bitcoin Standard
So, how does Bitcoin ascend to world reserve status and birth a Bitcoin standard? Here’s a five-step vision:
1. SOV Momentum: Bitcoin’s allure as an inflation hedge and wealth preserver keeps drawing in holders, boosting its market cap and global clout.
2. MOE Infrastructure: Innovations like the Lightning Network must deliver fast, cheap transactions, making Bitcoin a practical choice for daily spending.
3. Value Stability: As adoption spreads and the market matures, Bitcoin’s price swings dampen, earning trust from users and merchants alike.
4. MOE Takeoff: With better tools and steadier value, Bitcoin becomes a go-to for transactions, amplifying its worth through a powerful network effect.
5. Global Crown: Governments and central banks start holding Bitcoin in reserves, using it for trade and settlements, cementing its place as the world’s reserve currency.
This isn’t a cakewalk. Scalability bottlenecks, regulatory pushback, and rival cryptocurrencies loom large. But if Bitcoin can clear these obstacles, it could become the backbone of global finance.
Harmony Over Division: SOV and MOE Together
Here’s the crux: SOV and MOE aren’t at odds—they’re partners in Bitcoin’s rise. Holding Bitcoin safeguards its scarcity and value; spending it spreads its reach and usefulness. Both are vital for the long haul.
At this pivotal moment, the Bitcoin community must rally around a dual-purpose ethos. We can:
• Educate: Help newcomers grasp Bitcoin’s twin roles as SOV and MOE.
• Innovate: Back tech that makes Bitcoin spending as easy as swiping a card.
• Talk: Host open forums to wrestle with differences and find unity.
The Final Word: Our Collective Challenge
Bitcoin’s shot at becoming the world’s reserve currency—and forging a Bitcoin standard—is as exhilarating as it is daunting. Its Store of Value roots have set the stage, but its Medium of Exchange potential will decide if it can topple fiat and redefine money itself.
The path is long, but the prize is transformative. By embracing both SOV and MOE, we can propel Bitcoin to new heights. Let’s grab this chance, dive into the debate, and build a future where Bitcoin leads the charge.
Your Turn: What’s the best way forward for Bitcoin? Should we lean harder into SOV, push MOE, or blend the two? Drop your thoughts below an
-
 @ 9e9085e9:2056af17
2025-05-29 07:35:34
@ 9e9085e9:2056af17
2025-05-29 07:35:34**Part 4: Yakihonne as a Decentralized Social Payment Client
Yakihonne – Own Your Voice, Own Your Value
Yakihonne is evolving beyond just decentralized social networking—it’s now a decentralized social payment client on the Nostr protocol. With its integration of secure, user-owned identities and direct payment features, Yakihonne empowers people to truly own their voice and their value.
🔗 yakihonne.com 💬 Chat, post, connect—and pay—all in one place 💸 Send and receive Lightning payments directly 📱 Cross-platform access for #iOS and #Android
Why It Matters:
No Middlemen: Directly support creators, friends, or causes
Censorship-Resistant: Your content can’t be taken down or hidden
True Ownership: Your identity, your wallet, your data
Secure and Open: Built on the fast-growing Nostr protocol
Yakihonne isn’t just another app—it’s a new way to interact with your community and control your digital life.
Yakihonne #Yakihonne #Yakihonne #Nostr #Nostr #YoungDfx**











