-
 @ a396e36e:ec991f1c
2025-05-28 22:27:45
@ a396e36e:ec991f1c
2025-05-28 22:27:45👤 Generation X and Bitcoin: Between Invisibility, Structural Disillusionment, and Defiance
Generation X, born between 1965 and 1980, has been largely sidelined in generational discourse. Unlike the baby boomers —symbols of stability and prosperity— or millennials and Gen Z —constant fixtures in the media and cultural spotlight— Gen X remains the least mentioned, the least studied, and often not even recognized by its own members as a distinct generation.
Today, they are in midlife —a period that, according to the U-shaped curve of happiness, is one of the most emotionally and psychologically difficult stages: deteriorating health, professional stagnation, and the dual burden of caring for both parents and children. But their condition is not just a matter of age —it’s the product of a unique convergence of economic and political failure.
Structurally, Generation X reached its crucial phase of financial consolidation during the global economic crisis of 2008 —a moment that froze wage growth and severely limited access to housing, investment opportunities, and savings. In parallel, they faced increasing labor precarization: unstable contracts, outsourcing, erosion of social protections, and the dismantling of job security. Compared to other generations, their economic mobility was minimal. Even in terms of wealth accumulation and home ownership, many Gen Xers show weaker indicators than early-born millennials at the same life stage.
At the same time, many countries —especially in Latin America and parts of Europe— turned toward alternative models to free-market systems: socialist proposals that promised redistribution, justice, and equality. But in practice, these models led to state dependency, excessive intervention, economic rigidity, and a loss of productive dynamism. The outcome was devastating: rising poverty, institutional decay, inflation, plummeting investment, growing corruption, and a widespread collapse of trust.
For a generation raised on values of effort, autonomy, and social mobility, this ideological shift brought a double betrayal —first from liberalism, which failed to deliver on its promises, and then from socialism, which entrenched poverty, dependency, and dysfunction.
And yet, while younger generations increasingly embrace state-centric proposals like universal basic income, subsidies, or nationalizations as progressive solutions, many in Gen X see these not as innovation, but as déjà vu —a recycling of failed models they’ve already lived and paid for.
It’s at this point that Bitcoin emerges as more than just a financial technology. For many Gen Xers, Bitcoin is both a symbolic and concrete response — a refuge from a system that betrayed them. It’s not just about investment. It’s about individual sovereignty. They call it “fuck you money” because it represents a total break from traditional structures: it doesn’t depend on banks, governments, political parties, or promises that never materialize.
Bitcoin is money without permission, without censorship, without planned devaluation. It’s a tool for radical autonomy. For a generation marked by skepticism, self-reliance, and disillusionment, it stands as a quiet but powerful form of resistance — a way of saying: “I don’t depend on you. I don’t believe you. I don’t need you.”
Today, while others debate new statist models or more market reforms, many Gen Xers are simply opting out. Bitcoin isn’t just an economic choice — it’s a stance. A way to reclaim the individual control the system once denied them.
-
 @ 7f6db517:a4931eda
2025-05-28 22:02:26
@ 7f6db517:a4931eda
2025-05-28 22:02:26
The former seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
The latter's future remains to be seen. Dependence on Tor, which has had massive reliability issues, and lack of strong privacy guarantees put it at risk.
— ODELL (@ODELL) October 27, 2022
The Basics
- Lightning is a protocol that enables cheap and fast native bitcoin transactions.
- At the core of the protocol is the ability for bitcoin users to create a payment channel with another user.
- These payment channels enable users to make many bitcoin transactions between each other with only two on-chain bitcoin transactions: the channel open transaction and the channel close transaction.
- Essentially lightning is a protocol for interoperable batched bitcoin transactions.
- It is expected that on chain bitcoin transaction fees will increase with adoption and the ability to easily batch transactions will save users significant money.
- As these lightning transactions are processed, liquidity flows from one side of a channel to the other side, on chain transactions are signed by both parties but not broadcasted to update this balance.
- Lightning is designed to be trust minimized, either party in a payment channel can close the channel at any time and their bitcoin will be settled on chain without trusting the other party.
There is no 'Lightning Network'
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise.
- There are many lightning channels between many different users and funds can flow across interconnected channels as long as there is a route through peers.
- If a lightning transaction requires multiple hops it will flow through multiple interconnected channels, adjusting the balance of all channels along the route, and paying lightning transaction fees that are set by each node on the route.
Example: You have a channel with Bob. Bob has a channel with Charlie. You can pay Charlie through your channel with Bob and Bob's channel with User C.
- As a result, it is not guaranteed that every lightning user can pay every other lightning user, they must have a route of interconnected channels between sender and receiver.
Lightning in Practice
- Lightning has already found product market fit and usage as an interconnected payment protocol between large professional custodians.
- They are able to easily manage channels and liquidity between each other without trust using this interoperable protocol.
- Lightning payments between large custodians are fast and easy. End users do not have to run their own node or manage their channels and liquidity. These payments rarely fail due to professional management of custodial nodes.
- The tradeoff is one inherent to custodians and other trusted third parties. Custodial wallets can steal funds and compromise user privacy.
Sovereign Lightning
- Trusted third parties are security holes.
- Users must run their own node and manage their own channels in order to use lightning without trusting a third party. This remains the single largest friction point for sovereign lightning usage: the mental burden of actively running a lightning node and associated liquidity management.
- Bitcoin development prioritizes node accessibility so cost to self host your own node is low but if a node is run at home or office, Tor or a VPN is recommended to mask your IP address: otherwise it is visible to the entire network and represents a privacy risk.
- This privacy risk is heightened due to the potential for certain governments to go after sovereign lightning users and compel them to shutdown their nodes. If their IP Address is exposed they are easier to target.
- Fortunately the tools to run and manage nodes continue to get easier but it is important to understand that this will always be a friction point when compared to custodial services.
The Potential Fracture of Lightning
- Any lightning user can choose which users are allowed to open channels with them.
- One potential is that professional custodians only peer with other professional custodians.
- We already see nodes like those run by CashApp only have channels open with other regulated counterparties. This could be due to performance goals, liability reduction, or regulatory pressure.
- Fortunately some of their peers are connected to non-regulated parties so payments to and from sovereign lightning users are still successfully processed by CashApp but this may not always be the case going forward.
Summary
- Many people refer to the aggregate of all lightning channels as 'The Lightning Network' but this is a false premise. There is no singular 'Lightning Network' but rather many payment channels between distinct peers, some connected with each other and some not.
- Lightning as an interoperable payment protocol between professional custodians seems to have found solid product market fit. Expect significant volume, adoption, and usage going forward.
- Lightning as a robust sovereign payment protocol has yet to be battle tested. Heavy reliance on Tor, which has had massive reliability issues, the friction of active liquidity management, significant on chain fee burden for small amounts, interactivity constraints on mobile, and lack of strong privacy guarantees put it at risk.
If you have never used lightning before, use this guide to get started on your phone.
If you found this post helpful support my work with bitcoin.

-
 @ cae03c48:2a7d6671
2025-05-28 22:01:22
@ cae03c48:2a7d6671
2025-05-28 22:01:22Bitcoin Magazine

Leaders Rally Behind BTC at Bitcoin 2025 Conference: Strategic Reserves, Market Clarity, and Legislative MomentumAt Bitcoin 2025, top U.S. lawmakers and Coinbase’s Chief Policy Officer discussed the U.S. government’s shifting tone on Bitcoin, strategic reserves, regulatory frameworks, and legislation—all pointing toward a bullish future for digital assets.
In a panel moderated by Grant McCarty, Co-President of the Bitcoin Policy Institute, the Bitcoin 2025 Conference saw a major spotlight on U.S. policy shifts surrounding digital assets. U.S. Representatives Byron Donalds and Bryan Steil were joined by Faryar Shirzad, Chief Policy Officer at Coinbase, to highlight what they described as a watershed moment for Bitcoin in Washington.
JUST IN:
 US Congressman Byron Donalds says he's voting for the Strategic Bitcoin Reserve Act
US Congressman Byron Donalds says he's voting for the Strategic Bitcoin Reserve Act 
"Bitcoin has proven to be a holder of value" pic.twitter.com/NuQlZ26Lmy
— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
“What the president and his team are doing is choosing to step into the digital assets marketplace,” said Byron Donalds. “Bitcoin is a key asset because it has demonstrated to be a holder of value outside of fiat currency and central banking.” Donalds emphasized that President Trump is taking the long view—strategically recognizing Bitcoin’s role in a national reserve capacity.
Bryan Steil pointed to Trump’s media magnetism and political leverage as the driver behind recent legislative momentum: “What he’s done is put a spotlight on the exact three bills… giving us the ability to drive forward.” He noted that legislation is difficult to pass, but with executive support, there’s newfound energy and opportunity to cross the finish line.
Shirzad echoed that sentiment: “The tone from the top point is exactly what Donald Trump has showed us… He wants a market structure built. He wants a much more strategic approach.” Coinbase, Shirzad added, sees the impact firsthand—legislators now recognize the need to support innovation rather than stifle it.
Donalds added: “If you talk to any business owner in the world, the number one thing they desire more than anything else is certainty and consistency.” That, he said, is what will turn Bitcoin into a trillion-dollar industry in the U.S., instead of one bogged down by regulatory ambiguity and legal overhead.
On the regulatory front, Steil noted: “Under the Biden administration, policy was being developed through enforcement actions. Bitcoin is decentralized and should be treated as a commodity.” Shirzad agreed, pushing for “regulatory therapy” to unleash billions still sidelined.
McCarty closed with mention of the Blockchain Regulatory Clarity Act—legislation that would protect open-source developers from rogue regulatory action: “It allows developers to operate without being punished.”
Donalds summed it up: “There’s only going to be 21 million ever in creation. That can’t be eroded by central banks. A strategic reserve for Bitcoin is critical in my opinion for the United States.”
This post Leaders Rally Behind BTC at Bitcoin 2025 Conference: Strategic Reserves, Market Clarity, and Legislative Momentum first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ cae03c48:2a7d6671
2025-05-28 21:01:56
@ cae03c48:2a7d6671
2025-05-28 21:01:56Bitcoin Magazine

US Senator Cynthia Lummis Discusses Bitcoin Reserve, Stablecoin Legislation, and Market Structure Bill at Bitcoin 2025 ConferenceAt the 2025 Bitcoin Conference in Las Vegas, U.S Senator Cynthia Lummis and CLO of Coinbase Paul Grewal discussed the market structure bill, stablecoin bill, future taxing system, bitcoin strategy reserve and bitcoin mining.
Cynthia Lummis started by commenting about the market structure bill and stablecoin bill.
“The market structure bills is probably more important to a lot of the people in this conference than the stablecoin bill because there are a lot of businesses, yours among them,” said Lummis. “There are businesses for people who either buy and hold, so they want a custodial service or there are companies that lend Bitcoin, there is a futures market for Bitcoin, there are so many ways in which Bitcoin can interface with fiat currency with the US dollar.”
Lummis also mentioned the tax system that she wants to implement and what her office has submitted to the finance committee.
“As the lighting network develops and companies like Strike sort of have been leaders in that space,” added Lummis. “Create an opportunity for transactions to occur on a daily basis in Bitcoin. Everything from buying a cup of coffee to dinner somewhere. It would be helpful that certain transactions of that size below 600 dollars per transaction, not be subject to taxation.”
During her speech, she went into detail on one the biggest problems lawmakers are facing against digital assets.
“Part of the problem in the last four years has been largely regulatory agencies that have been very hostile towards digital assets, so we are trying to change as fast as we can,” said Lummis. “It doesn’t happen overnight. We don’t even have a confirmed IRS director in place yet, so it is really hard to get these structural changes enacted by the rule makers at the IRS when there is no IRS commission yet in place.”
Ending the panel, Lummis addressed one of the biggest reasons the US government should get into Bitcoin.
“We are 37 trillion dollars in debt, so if we bought and held a million Bitcoin for 20 years it will cut that debt in half and we have underperforming assets that can be converted to Bitcoin without borrowing additional money. Bitcoin is such an important Global Strategic asset and it is not only important in the economy, but in our global defense because there are components to our defense. One is having a lethal war fighting machine that can overcome other armies, another military effort. Another one is having an economic machine that can overcome other currencies.” She continued, “Even our military generals say that bitcoin is an important deterrent to aggression from other countries, especially from China.”
This post US Senator Cynthia Lummis Discusses Bitcoin Reserve, Stablecoin Legislation, and Market Structure Bill at Bitcoin 2025 Conference first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ bf47c19e:c3d2573b
2025-05-28 20:37:58
@ bf47c19e:c3d2573b
2025-05-28 20:37:58Bitcoin: Peer-to-peer sistem elektronskog novca
Satoshi Nakamoto
satoshin@gmx.com
Prevedeno na srpski sa bitcoin.org/bitcoin.pdf od strane ECD
Sažetak. Potpuna peer-to-peer verzija elektronskog novca omogućila bi slanje uplata putem interneta direktno od jedne strane ka drugoj bez posredovanja finansijskih institucija. Digitalni potpisi pružaju deo rešenja, ali se glavni benefiti gube ako je i dalje potrebna pouzdana treća strana za sprečavanje dvostruke potrošnje. Predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer mreže. Mreža vremenski označava transakcije tako što ih hešuje u tekući lanac dokaza o radu (proof of work) temeljen na hešu, formirajući zapis koji se ne može promeniti bez ponovnog rada i objavljivanja dokaza o tom radu. Najduži lanac ne služi samo kao dokaz niza događaja, nego i kao dokaz da je taj niz događaja potvrđen od strane dela peer-to-peer mreže koja poseduju najveću zbirnu procesorsku snagu (CPU). Sve dok većinu procesorske snage kontrolišu čvorovi (nodes) koji ne sarađuju u napadu na mrežu, oni će generisati najduži lanac i nadmašiti napadače. Sama mreža zahteva minimalnu strukturu. Poruke kroz mrežu se prenose uz pretpostavku da svaki čvor čini maksimalan napor da poruku prenese u svom izvornom obliku i na optimalan način, a čvorovi mogu napustiti mrežu i ponovo joj se pridružiti po želji, prihvatajući najduži lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo.
1. Uvod
Trgovina na Internetu počela je da se oslanja skoro isključivo na finansijske institucije koje služe kao pouzdani posrednici pri obradi elektronskih plaćanja. Iako sistem radi dovoljno dobro za većinu transakcija i dalje trpi od inherentnih slabosti modela utemeljenog na poverenju.
Potpuno nepovratne transakcije zapravo nisu moguće, jer finansijske institucije ne mogu izbeći posredovanje u rešavanju eventualnih sporova. Troškovi posredovanja povećavaju troškove transakcija, ograničavaju minimalnu praktičnu veličinu transakcija i onemogućuju male, povremene transakcije jer postoji velika šteta zbog gubitka mogućnosti da se izvrše nepovratna plaćanja za nepovratne usluge. Uz mogućnost povraćaja transakcije, potreba za poverenjem raste. Trgovci moraju biti oprezni prema svojim kupcima i tražiti im više informacija nego što bi inače bilo neophodno. Određeni procenat prevara prihvaćen je kao neizbežan. Ovi troškovi i nepouzdanost plaćanja mogu se izbeći korišćenjem gotovine, ali ne postoji mehanizam za elektronsko plaćanje bez pouzdane treće strane.
Ono što je potrebno je elektronski sistem plaćanja zasnovan na kriptografskom dokazu umesto na poverenju, koji omogućava da bilo koje dve strane direktno i dobrovoljno međusobno trguju bez potrebe za posrednikom. Transakcije koje su nepovratne bi zaštitile prodavce od prevara, a escrow mehanizmi mogli bi se lako implementirati radi zaštite kupaca. U ovom dokumentu predlažemo rešenje problema dvostruke potrošnje korišćenjem peer-to-peer distribuiranog servera vremenskih oznaka (timestamp) za generisanje računarskog dokaza o hronološkom redosledu transakcija. Sistem je siguran sve dok pošteni čvorovi zajedno kontrolišu više procesorske snage procesora nego bilo koja udružena grupa napadačkih čvorova.
2. Transakcije
Elektronski novčić definišemo kao lanac digitalnih potpisa. Svaki vlasnik prenosi novčić na sledećeg digitalnim potpisivanjem heša prethodne transakcije i javnog ključa sledećeg vlasnika, dodajući ih potom na kraj novčića. Primalac transakcije može da verifikuje potpise, a time i lanac vlasništva.

Problem je naravno u tome što primalac ne može potvrditi da jedan od prethodnih vlasnika nije dva puta poslao isti novčić. Uobičajeno rešenje je uvođenje pouzdanog centralizovanog posrednika, kreatora novčića koji proverava sve transakcije. Nakon svake transakcije, novčić se mora vratiti kreatoru kako bi se izdao novi novčić i veruje se da samo za novčiće izdate direktno od kreatora možemo biti sigurni da nisu dva puta potrošeni. Problem sa ovim rešenjem je što sudbina čitavog novčanog sistema zavisi od kompanije koja kreira novčiće, jer svaka transakcija mora da prođe kroz nju, baš kao što je slučaj sa bankom.
Treba nam način da primalac bude siguran da prethodni vlasnici nisu potpisali nikakve ranije transakcije kojim bi potrošili taj novčić. Za naše potrebe, računamo transakciju koja se prva desila i ne zanimaju nas naredni pokušaji da se isti novčić ponovo pošalje. Jedini način da sa sigurnošću potvrdimo da taj novčić nije prethodno bio poslat je da imamo informacije o svim transakcijama koje su se ikada desile. U modelu baziranom na centalizovan kreatoru, taj kreator je imao informacije o svim transakcijama i odlučivao koja transakcija je prva stigla. Da bismo to postigli bez pouzdanog posrednika, transakcije moraju biti javno objavljene [1] i potreban nam je sistem u kojem učesnici mogu da se dogovore o jedinstvenoj istoriji redosleda kojim su transakcije primljene. Primaocu je potreban dokaz da se u trenutku dešavanja svake od transakcija većina čvorova složila oko toga da je baš ta transakcija bila ona koja je prva primljena.
3. Server vremenskih oznaka
Rešenje koje predlažemo počinje serverom vremenskih oznaka. Server vremenske oznake radi tako što uzima heš bloka podataka kojem će se dodeliti vremenska oznaka i objavi taj heš svima u mreži, slično kao u novinama ili kao post na Usenet mreži [2-5]. Vremenska oznaka očigledno dokazuje da su podaci morali postojati u to vreme kako bi ušli u haš. Svaka vremenska oznaka sadrži prethodnu vremensku oznaku u svom hešu, formirajući tako lanac, pri čemu svaka dodatna vremenska oznaka pojačava potvrde onih pre nje.

4. Dokaz o radu (Proof-of-Work)
Da bismo implementirali distribuirani server vremenskih oznaka na peer-to-peer principu, moraćemo da koristimo sistem dokaza o radu sličan Hashcash-u Adama Back-a [6], umesto Uneset postova ili novinskih objava. Dokaz o radu uključuje traženje vrednosti koja će, kada se hešuje, na primer pomoću SHA-256 heš funkcije, stvarati heš čiji binarni zapis započinje određenim brojem nula. Prosečna količina potrebnog rada eksponencijalno raste sa brojem potrebnih početnih nula, a može se proveriti izvršavanjem samo jedne heš fuknkcije.
Za našu mrežu vremenskih oznaka implementiramo dokaz o radu povećavajući nonce broja u bloku sve dok se ne pronađe ona vrednost nonce-a koja daje hešu bloka potreban broj početnih nula. Jednom kada se procesorska snaga utroši kako bi se zadovoljio dokaz o radu, blok se ne može izmeniti bez ponovljenog rada. Kako se kasniji blokovi vežu na taj blok, rad potreban da se on izmeni uključivao bi i ponovno obrađivanje svih blokova nakon njega.

Dokaz o radu takođe rešava problem utvrđivanja većine pri odlučivanju. Ako bi se većina zasnivala na principu jednog glasa po IP adresi, mogao bi je narušiti svako ko je u stanju da glasa sa više IP adresa odjednom. Dokaz o radu u osnovi predstavlja jedan glas po jedinici procesorske snage. Većinska odluka je predstavljena najdužim lancem u čije je stvaranje zapravo investirano najviše rada prilikom dokazivanja. Ako većinu procesorske snage kontrolišu pošteni čvorovi, pošten lanac će rasti najbrže i nadmašiće sve konkurentske lance. Da bi izmenio neki od prethodnih blokova, napadač bi morao da ponovi dokaz o radu za taj blok i sve blokove nakon njega, a zatim da sustigne i nadmaši količinu rada poštenih čvorova. Kasnije ćemo pokazati da se dodavanjem novih blokova eksponencijalno smanjuje verovatnoća da će sporiji napadač uspeti da sustigne pošteni lanac.
Da bi se kompenzovalo povećanje brzine hardvera i promenljivo interesovanje ljudi za vođenje čvorova tokom vremena, težina obavljanja dokaza o radu (proof-of-work difficulty) određuje se prema prosečnom broju blokova krairanih za sat vremena. Ako se blokovi stvaraju prebrzo, težina se povećava.
5. Mreža
Koraci za vođenje mreže su sledeći:
1) Nove transakcije se prosleđuju svim čvorovima u mreži. 2) Svaki čvor prikuplja nove transakcije u blok. 3) Svaki čvor radi na pronalaženju dokaza o radu dovoljnog nivoa težine za svoj blok. 4) Kada čvor pronađe dokaz o radu, on emituje taj blok ka svim čvorovima. 5) Čvorovi prihvataju blok samo ako su sve transakcije u njemu ispravne i nisu već potrošene. 6) Čvorovi izražavaju prihvatanje bloka radeći na stvaranju sledećeg bloka u lancu, koristeći heš prihvaćenog bloka kao prethodni heš.
Čvorovi uvek smatraju da je najduži lanac ispravan i nastaviće da rade na njegovom produžavanju. Ako dva čvora istovremeno emituju različite verzije sledećeg bloka, neki čvorovi prvo mogu primiti jedan ili drugi blok. U tom slučaju svaki čvor radi na prvom koji je dobio, ali čuvaju drugu kariku lanca u slučaju da ona postane duža. Dilema će biti rešena kada se pronađe sledeći dokaz o radu i jedna karika postane duža; čvorovi koji su radili na drugoj karici lanca će se prebaciti na dužu kariku.
Emitovanje novih transakcija ne mora nužno doći do svih čvorova. Sve dok stižu do velikog broja čvorova, te transakcije će ući u blok. Slično važi i za blokove, ni oni ne moraju doći odmah do svih čvorova. Ako neki čvor propusti da primi informaciju o bloku, kada mu stigne sledeći blok,primetiće da je propustio jedan, pa će ga tražiti naknadno.
6. Podsticaj
Po pravilu, prva transakcija u bloku je posebna transakcija koja kreira novi novčić u vlasništvu kreatora bloka. Ovo daje podsticaj čvorovima da podrže mrežu i pruža način za početnu ubacivanje novčića u opticaj, budući da ne postoji centralno telo koje ih izdaje. Stalno dodavanje konstantne količine novih novčića liči na rudarenje zlata, gde rudari ulažu resurse kako bi izrudarili nove količine zlata i ubacili ih u opticaj. U našem slučaju ulaže se procesorsko vreme i električna energija.
Podsticaj se takođe može finansirati i transakcionim naknadama. Ako je iznos izlaznog dela transakcije manji od ulaznog, razliku čini naknada za transakciju koja se dodaje iznosu nagrade za kreatora bloka koji sadrži tu transakciju. Nakon što predefinisani broj novčića uđe u opticaj, podsticaj mogu u potpunosti činiti transakcione naknade, čime se sistem oslobađa inflacije.
Čvorovi su na ovaj način podstaknuti da ostanu pošteni. Ako je pohlepni napadač u stanju da angažuje više procesorske snage od svih poštenih čvorova zajedno, morao bi da bira između toga da poništi svoje izvršene transakcije i time prevari ljude ili da procesorsku snagu koristi za stvaranje novih novčića. On bi trebalo bi uvidi da je isplativije igrati po pravilima koja ga nagrađuju sa više novih novčića od svi drugi zajedno, nego da potkopava sistem i vrednost sopstvenog bogatstva.
7. Oslobađanje prostora na hard disku
Kada je dovoljno blokova dodato nakon poslednje transakcije novčića, prethodne transakcije tog novčića se mogu odbaciti kako bi se uštedeo prostor na hard disku. Kako bi se to ostvarilo bez razbijanja heša bloka, transakcije su hešovane u Merkleovo stablo (Merkle Tree) [7] [2] [5], gde je samo koren uključen u heš bloka. Stari blokovi se tada mogu sabiti uklanjanjem nepotrebnih grana drveta. Unutrašnji heševi ne moraju biti skladišteni.

Zaglavlje bloka bez transakcija bilo bi oko 80 bajtova. Ako pretpostavimo da su blokovi generisani svakih 10 minuta, 80 bajtova * 6 * 24 * 365 = 4,2 MB godišnje. Imajući u vidu činjenicu da se u 2008. godini računari uglavnom prodaju sa oko 2 GB RAM-a i Murov zakon koji predviđa trenutni rast od 1,2 GB godišnje, skladištenje ne bi trebalo da predstavlja problem čak i ako se zaglavlja bloka moraju čuvati u memoriji.
8. Pojednostavljena verifikacija plaćanja
Moguće je verifikovati plaćanja bez vođenja čitavog mrežnog čvora. Korisnik samo treba da sačuva kopiju zaglavlja blokova najdužeg lanca dokaza o radu, do koje može doći upitom ka mrežnim čvorovima dok se ne uveri da je dobio najduži lanac i dobije Merkleova granu
koja povezuje transakciju sa blokom u koji je uneta vremenska oznaka za tu transakciju. Ne može samostalno proveriti transakciju, ali povezujući je sa mestom u lancu može videti da je prihvaćena od strane čvora mreže i da su na njen blok dodati naknadni blokovi što dalje potvrđuje da ju je mreža prihvatila.

Kao takva, verifikacija je pouzdana sve dok pošteni čvorovi kontrolišu mrežu, ali je ranjiva ako napadač nadjača ostatak mreže. Čvorovi mreže mogu sami proveriti transakcije, ali napadačeve lažne transakcije mogu zavarati one koji koriste pojednostavljenu metodu verifikacije transakcija sve dok je on u stanju da nadjačava ostatak mreže. Jedna od strategija zaštite bila bi prihvatanje upozorenja čvorova mreže kada otkriju nevažeći blok, pri čemu bi korisnikov softver morao da preuzme ceo blok i sporne transakcije kako bi potvrdio nepravilnost. Biznisi koji primaju česte uplate će verovatno želeti da pokrenu i vode sopstvene čvorove radi brže verifikacije i potrebe da im sigurnost ne zavisi od drugih.
9. Kombinovanje i deljenje vrednosti
Iako bi bilo moguće pojedinačno rukovati novčićima, bilo bi nezgrapno kreirati zasebnu transakciju za svaki cent u toj transferu. Da biste dozvolili podelu i kombinovanje vrednosti, transakcije sadrže više ulaza i izlaza. Obično će postojati ili jedan ulaz iz veće prethodne transakcije ili više unosa koji kombinuju manje iznose, a najviše dva izlaza: jedan za samo plaćanje, a jedan koji vraća kusur, ako ga ima, nazad pošiljaocu.

Treba napomenuti da situacija u kojoj transakcija zavisi od nekoliko drugih transakcija, a te transakcije zavise od još mnogo više, ovde nije problem. Nikada ne postoji potreba za izdvajanjem istorije pojedinačne transakcije.
10. Privatnost
Tradicionalni bankarski model postiže odgovarajući nivo privatnosti ograničavanjem pristupa informacijama na strane uključene u transakciju i posrednika. Neophodnost javnog objavljivanja svih transakcija isključuje mogućnost primene pomenutog modela, ali privatnost se i dalje može zadržati na drugi način: čuvanjem javnih ključeva (public keys) anonimnim. Javnost može videti da neko šalje iznos nekom drugom, ali bez informacija koje povezuju transakciju sa bilo kim. Ovo je slično količini informacija koje objavljuju berze, gde se vreme i veličina pojedinačnih trgovina čine javnim, ali bez navođenja ko su stranke uključene u tu trgovinu.

Kao dodatni zaštitni zid, preporučljivo je koristiti novi par ključeva za svaku transakciju, kako ne bi bili povezane sa zajedničkim vlasnikom. Neka povezivanja su i dalje neizbežna kod transakcija sa više ulaza, koje nužno otkrivaju da su njihovi ulazi bili u vlasništvu istog vlasnika. Rizik je taj da bi se otkrivanjem vlasnik ključa mogle otkriti i ostale transakcije koje su pripadale tom vlasniku.
11. Proračuni
Razmatramo scenario u kome napadač pokušava da generiše alternativni lanac brže od poštenog lanca. Čak i ako se to postigne, to ne omogućuje proizvoljne promene u sistemu, poput stvaranje vrednosti ni iz čega ili uzimanje novca koji nikada nije pripadao napadaču. Pošteni čvorovi neće prihvatiti nevažeće transakcije kao uplatu i nikada neće prihvatiti blok koji ih sadrži. Napadač može samo pokušati da promeni jednu od svojih transakcija kako bi vratio novac koji je nedavno potrošio.
Trka između poštenog lanca i lanca napadača može se predstaviti kao binomska distribucija slučajne diskretne varijable (Binomial Random Walk). Uspešni ishod je da se pošten lanac produži za jedan blok, povećavajući svoje vođstvo za +1, a neuspešni ishod je da se napadačev lanac produži za jedan blok, smanjujući zaostatak za -1.
Verovatnoću da napadač nadoknadi određeni deficit možemo izraziti kroz problem kockareve propasti (Gambler’s Ruin Problem). Pretpostavimo da kockar sa neograničenim iznosom novca počinje sa zaostatkom i igra potencijalno beskonačan broj ponovljenih igara u pokušaju da nadoknadi zaostatak. Možemo izračunati verovatnoću za nadoknađivanje zaostatka ili da će napadač stići pošten lanac, na sledeći način [8]:
p= verovatnoća da pošten čvor pronađe sledeći blok q= verovatnoća da napadač pronađe sledeći blok qz= verovatnoća da će napadač ikada dostići z blokova zaostatka

S obzirom na našu pretpostavku da je p > q, verovatnoća pada eksponencijalno kako se povećava broj blokova koje napadač mora da nadoknadi. Sa šansama protiv njega, ako mu se u početku ne posreći, njegove šanse postaju manje i manje sa povećanjem zaostatka.
Sada razmatramo koliko primalac nove transakcije treba da čeka pre nego što postane
dovoljno siguran da pošiljalac ne može promeniti transakciju. Pretpostavljamo da je pošiljalac napadač koji želi da natera primaoca da veruje da mu je platio, a zatim nakon nekog vremena tu transakciju preusmeri ka sebi. Primalac će primetiti kada se to dogodi, ali pošiljalac se nada da će tad već biti prekasno.
Primalac generiše novi par ključeva i daje javni ključ pošiljaocu neposredno pre potpisivanja transakcije. Ovo sprečava pošiljaoca da unapred pripremi lanac blokova radeći na njemu neprekidno dok mu se ne posreći da stekne dovoljnu prednost i u tom trenutku izvrši transakciju. Kada se transakcija pošalje, nepošteni pošiljalac počinje tajno da radi na paralelnom lancu koji sadrži alternativnu verziju njegove transakcije.
Primalac čeka dok transakcija ne bude dodata u blok, i dok z blokova nije dodato nakon tog bloka. On ne zna tačno koliko je napadač napredovao, ali pod pretpostavkom da su pošteni blokovi kreirani očekivanom dinamikom, potencijalni napredak napadača će biti prikazan kao Poasonova distribucija sa očekivanom vrednošću:

Kako bismo izračunali verovatnoću da napadač ipak može da nadoknadi zaostatak, množimo gustinu verovatnoće za svaki nivo napretka koji je mogao da ostvari sa verovatnoćom da od tog trenutka može da potpuno nadoknadi zaostatak:

Preuređujemo formulu kako bismo izbegli sabiranje beskonačnog broja sabiraka zbog repa distribucije:

I konvertujemo u programski kod u programskom jeziku C…

Kroz par primera, vidimo da verovatnoća opada eksponencijalno sa porastom z.

Rešavanje za P < 0.1%…

12. Zaključak
Predložili smo sistem za elektronske transakcije bez oslanjanja na poverenje. Počeli smo sa uobičajenim šablonom i novčićima nastalim iz digitalnih potpisa, koji pruža snažnu kontrolu nad vlasništvom, ali je nepotpun bez načina da se spreči dvostruka potrošnja. Kako bismo ovo rešili, predložili smo peer-to-peer mrežu koja koristi dokaz o radu za čuvanje javne istorije transakcija čija izmena napadačima brzo postaje računski nepraktična ako pošteni čvorovi kontrolišu većinu procesorske snage. Mreža je robusna u svojoj nestrukturiranoj jednostavnosti. Svi čvorovi rade istovremeno uz malo koordinacije. Ne treba ih identifikovati, jer se poruke ne usmeravaju na jedno određeno mesto nego samo trebaju biti prenete uz maksimalan napor od strane čvorova da se taj prenos odradi na predviđen način. Čvorovi mogu da napuste i ponovo se pridruže mreži po želji, prihvatajući lanac dokaza o radu kao dokaz onoga što se dogodilo dok ih nije bilo. Oni glasaju svojom procesorskom snagom, izražavajući svoje prihvatanje validnih blokova time što pokušavaju da ih nadgrade novim blokovima i odbacuju nevažeće blokove odbijanjem ih nadgrađuju. Sva potrebna pravila i podsticaji mogu se nametnuti ovim mehanizmom postizanja konsenzusa.
Reference:
[1] W. Dai, „b-money,“ weidai.com/bmoney.txt, 1998.
[2] H. Massias, X.S. Avila, and J.-J. Quisquater, „Design of a secure timestamping service with minimal trust requirements,“ In 20th Symposium on Information Theory in the Benelux, May 1999.
[3] S. Haber, W.S. Stornetta, „How to time-stamp a digital document,“ In Journal of Cryptology, vol 3, no 2, pages 99-111, 1991.
[4] D. Bayer, S. Haber, W.S. Stornetta, „Improving the efficiency and reliability of digital time-stamping,“ In Sequences II: Methods in Communication, Security and Computer Science, pages 329-334, 1993.
[5] S. Haber, W.S. Stornetta, „Secure names for bit-strings,“ In Proceedings of the 4th ACM Conference on Computer and Communications Security, pages 28-35, April 1997.
[6] A. Back, „Hashcash – a denial of service counter-measure,“ hashcash.org/papers/hashcash.pdf, 2002.
[7] R.C. Merkle, „Protocols for public key cryptosystems,“ In Proc. 1980 Symposium on Security and Privacy, IEEE Computer Society, pages 122-133, April 1980.
[8] W. Feller, „An introduction to probability theory and its applications,“ 1957.
-
 @ bf47c19e:c3d2573b
2025-05-28 19:59:23
@ bf47c19e:c3d2573b
2025-05-28 19:59:23Originalni tekst na dvadesetjedan.com
Autor: Vijay Boyapati / Prevod na hrvatski: Matija
Sa zadnjim cijenama koje je bitcoin dosegao 2017., optimističan scenarij za ulagače se možda čini toliko očitim da ga nije potrebno niti spominjati. Alternativno, možda se nekome čini glupo ulagati u digitalnu vrijednost koja ne počiva na nijednom fizičkom dobru ili vladi i čiji porast cijene su neki usporedili sa manijom tulipana ili dot-com balonom. Nijedno nije točno; optimističan scenarij za Bitcoin je uvjerljiv, ali ne i očit. Postoje značajni rizici kod ulaganja u Bitcoin, no, kao što planiram pokazati, postoji i ogromna prilika.
Geneza
Nikad u povijesti svijeta nije bilo moguće napraviti transfer vrijednosti među fizički udaljenim ljudima bez posrednika, poput banke ili vlade. 2008. godine, anonimni Satoshi Nakamoto je objavio 8 stranica rješenja na dugo nerješivi računalski problem poznat kao “Problem Bizantskog Generala.” Njegovo rješenje i sustav koji je izgradio - Bitcoin - dozvolio je, prvi put ikad, da se vrijednost prenosi brzo i daleko, bez ikakvih posrednika ili povjerenja. Implikacije kreacije Bitcoina su toliko duboke, ekonomski i računalski, da bi Nakamoto trebao biti prva osoba nominirana za Nobelovu nagradu za ekonomiju i Turingovu nagradu.
Za ulagače, važna činjenica izuma Bitcoina (mreže i protokola) je stvaranje novog oskudnog digitalnog dobra - bitcoina (monetarne jedinice). Bitcoini su prenosivi digitalni “novčići” (tokeni), proizvedeni na Bitcoin mreži kroz proces nazvan “rudarenje” (mining). Rudarenje Bitcoina je ugrubo usporedivo sa rudarenjem zlata, uz bitnu razliku da proizvodnja bitcoina prati unaprijed osmišljeni i predvidivi raspored. Samo 21 milijun bitcoina će ikad postojati, i većina (2017., kada je ovaj tekst napisan) su već izrudareni. Svake četiri godine, količina rudarenih bitcoina se prepolovi. Produkcija novih bitcoina će potpuno prestati 2140. godine.
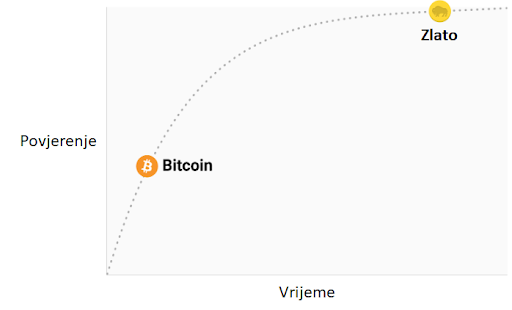 Stopa inflacije —— Monetarna baza
Stopa inflacije —— Monetarna bazaBitcoine ne podržava nikakva roba ili dobra, niti ih garantira ikakva vlada ili firma, što postavlja očito pitanje za svakog novog bitcoin ulagača: zašto imaju uopće ikakvu vrijednost? Za razliku od dionica, obveznica, nekretnina ili robe poput nafte i žita, bitcoine nije moguće vrednovati koristeći standardne ekonomske analize ili korisnost u proizvodnji drugih dobara. Bitcoini pripadaju sasvim drugoj kategoriji dobara - monetarnih dobara, čija se vrijednost definira kroz tzv. teoriju igara; svaki sudionik na tržištu vrednuje neko dobro, onoliko koliko procjenjuje da će ga drugi sudionici vrednovati. Kako bismo bolje razumjeli ovo svojstvo monetarnih dobara, trebamo istražiti podrijetlo novca.
Podrijetlo novca
U prvim ljudskim društvima, trgovina među grupama se vršila kroz robnu razmjenu. Velika neefikasnost prisutna u robnoj razmjeni je drastično ograničavala količinu i geografski prostor na kojem je bila moguća. Jedan od najvećih problema sa robnom razmjenom je problem dvostruke podudarnosti potražnje. Uzgajivač jabuka možda želi trgovati sa ribarom, ali ako ribar ne želi jabuke u istom trenutku, razmjena se neće dogoditi. Kroz vrijeme, ljudi su razvili želju za čuvanjem određenih predmeta zbog njihove rijetkosti i simbolične vrijednosti (npr. školjke, životinjski zube, kremen). Zaista, kako i Nick Szabo govori u svojem izvrsnom eseju o podrijetlu novca, ljudska želja za sakupljanjem predmeta pružila je izraženu evolucijsku prednost ranom čovjeku nad njegovim najbližim biološkim rivalom, neandertalcem - Homo neanderthalensis.
"Primarna i najbitnija evolucijska funkcija sakupljanja bila je osigurati medij za čuvanje i prenošenje vrijednosti".
Predmeti koje su ljudi sakupljali služili su kao svojevrsni “proto-novac,” tako što su omogućavale trgovinu među antagonističkim plemenima i dozvoljavale bogatsvu da se prenosi na sljedeću generaciju. Trgovina i transfer takvih predmeta bile su rijetke u paleolitskim društvima, te su oni služili više kao “spremište vrijednosti” (store of value) nego kao “medij razmjene” (medium of exchange), što je uloga koju danas igra moderni novac. Szabo objašnjava:
"U usporedbi sa modernim novcem, primitivan novac je imao jako malo “brzinu” - mogao je promijeniti ruke samo nekoliko puta u životu prosječnog čovjeka. Svejedno, trajni i čvrsti sakupljački predmet, što bismo danas nazvali “nasljeđe,” mogao je opstati mnogo generacija, dodajući znatnu vrijednost pri svakom transferu - i zapravo omogućiti transfer uopće".
Rani čovjek suočio se sa bitnom dilemom u teoriji igara, kada je odlučivao koje predmete sakupljati: koje od njih će drugi ljudi željeti? Onaj koji bi to točno predvidio imao bi ogromnu prednost u mogućnosti trgovine i akvizicije bogatsva. Neka američka indijanska plemena, npr. Naraganseti, specijalizirala su se u proizvodnji sakupljačkih dobara koja nisu imala drugu svrhu osim trgovine. Valja spomenuti da što je ranije predviđanje da će neko dobro imati takvu vrijednost, veća je prednost koju će imati onaj koji je posjeduje, zato što ju je moguće nabaviti jeftinije, prije nego postane vrlo tražena roba i njezona vrijednost naraste zajedno sa populacijom. Nadalje, nabava nekog dobra u nadi da će u budućnosti biti korišteno kao spremište vrijednosti, ubrzava upravo tu primjenu. Ova cirkularnost je zapravo povratna veza (feedback loop) koja potiče društva da se rapidno slože oko jednog spremišta vrijednosti. U terminima teorije igara, ovo je znano kao “Nashov ekvilibrij.” Postizanje Nashovog ekvilibrija za neko spremište vrijednosti je veliko postignuće za društvo, pošto ono znatno olakšava trgovinu i podjelu rada, i time omogućava napredak civilizacije.
Tisućljećima, kako su ljudska društva rasla i otvarala trgovinske puteve, različite aplikacije spremišta vrijednosti u individualnim društvima počele su se natjecati međusobno. Trgovci su imali izbor: čuvati svoju zaradu u spremištu vrijednosti vlastite kulture, ili one kulture sa kojom su trgovali, ili mješavini oboje. Benefit štednje u stranom spremištu vrijednosti bila je uvećana sposobnost trgovanja u povezanom stranom društvu. Trgovci koji su štedili u stranom spremištu vrijednosti su također imali dobrih razloga da potiču svoje društvo da ga prihvati, jer bi tako uvećali vrijednost vlastite ušteđevine. Prednosti “uvezene” tehnologije spremanja vrijednosti bile su prisutne ne samo za trgovce, nego i za sama društva. Kada bi se dvije grupe konvergirale u jedinstvenom spremištu vrijednosti, to bi značajno smanjilo cijenu troškova trgovine jednog s drugim, i samim time povećanje bogatstva kroz trgovinu. I zaista, 19. stoljeće bilo je prvi put da je najveći dio svijeta prihvatio jedinstveno spremište vrijednosti - zlato - i u tom periodu vidio najveću eksploziju trgovine u povijesti svijeta. O ovom mirnom periodu, pisao je John Maynard Keynes:
"Kakva nevjerojatna epizoda u ekonomskom napretku čovjeka… za svakog čovjeka iole iznadprosječnog, iz srednje ili više klase, život je nudio obilje, ugodu i mogućnosti, po niskoj cijeni i bez puno problema, više nego monarsima iz prethodnih perioda. Stanovnik Londona mogao je, ispijajući jutarnji čaj iz kreveta, telefonski naručiti razne proizvode iz cijele Zemlje, u količinama koje je želio, i sa dobrim razlogom očekivati njihovu dostavu na svoj kućni prag."
Svojstva dobrog spremišta vrijednosti
Kada se spremišta vrijednosti natječu jedno s drugim, specifična svojstva rade razliku koja daje jednom prednost nad drugim. Premda su mnoga dobra u prošlosti korištena kao spremišta vrijednosti ili kao “proto-novac,” određena svojstva su se pokazala kao posebno važna, i omogućila dobrima sa njima da pobijede. Idealno spremište vrijednosti biti će:
- Trajno: dobro ne smije biti kvarljivo ili lako uništeno. Tako naprimjer, žito nije idealno spremište vrijednosti.
- Prenosivo: dobro mora biti lako transportirati i čuvati, što omogućuje osiguranje protiv gubitka ili krađe i dopušta trgovinu na velike udaljenosti. Tako, krava je lošije spremište vrijednosti od zlatne narukvice.
- Zamjenjivo: jedna jedinica dobra treba biti zamjenjiva sa drugom. Bez zamjenjivosti, problem podudarnosti želja ostaje nerješiv. Time, zlato je bolje od dijamanata, jer su oni nepravilni u obliku i kvaliteti.
- Provjerljivo: dobro mora biti lako i brzo identificirano i testirano za autentičnost. Laka provjera povećava povjerenje u trgovini i vjerojatnost da će razmjena biti dovršena.
- Djeljivo: dobro mora biti lako djeljivo na manje dijelove. Premda je ovo svojstvo bilo manje važno u ranim društvima gdje je trgovina bila rijetka, postalo je važnije sa procvatom trgovine. Količine koje su se mijenjale postale su manje i preciznije.
- Oskudno: Monetarno dobro mora imati “cijenu nemoguću za lažirati,” kao što je rekao Nick Szabo. Drugim riječima, dobro ne smije biti obilno ili lako dostupno kroz proizvodnju. Oskudnost je možda i najvažnije svojstvo spremišta vrijednosti, pošto se izravno vezuje na ljudsku želju da sakupljamo ono što je rijetko. Ona je izvor vrijednosti u spremištu vrijednosti.
- Duge povijesti: što je dulje neko dobro vrijedno za društvo, veća je vjerojatnost da će biti prihvaćeno kao spremište vrijednosti. Dugo postojeće spremište vrijednosti biti će jako teško uklonjeno od strane došljaka, osim u slučaju sile (ratno osvajanje) ili ako je nova tehnologija znatno bolja u ostalim svojstvima.
- Otporno na cenzuru: novije svojstvo, sve više važno u modernom digitalnom svijetu sa sveprisutnim nadzorom, je otpornost na cenzuru. Drugim riječima, koliko je teško da vanjski agent, kao korporacija ili država, spriječi vlasnika dobra da ga čuva i koristi. Dobra koja su otporna na cenzuru su idealna za ljude koji žive u režimima koji prisilno nadziru kapital ili čine neke oblike mirne trgovine protuzakonitima.
Ova tablica ocjenjuje Bitcoin, zlato (gold) i fiat novac (kao što je euro ili dolar) po svojstvima izlistanim gore. Objašnjenje svake ocjene slijedi nakon tablice.
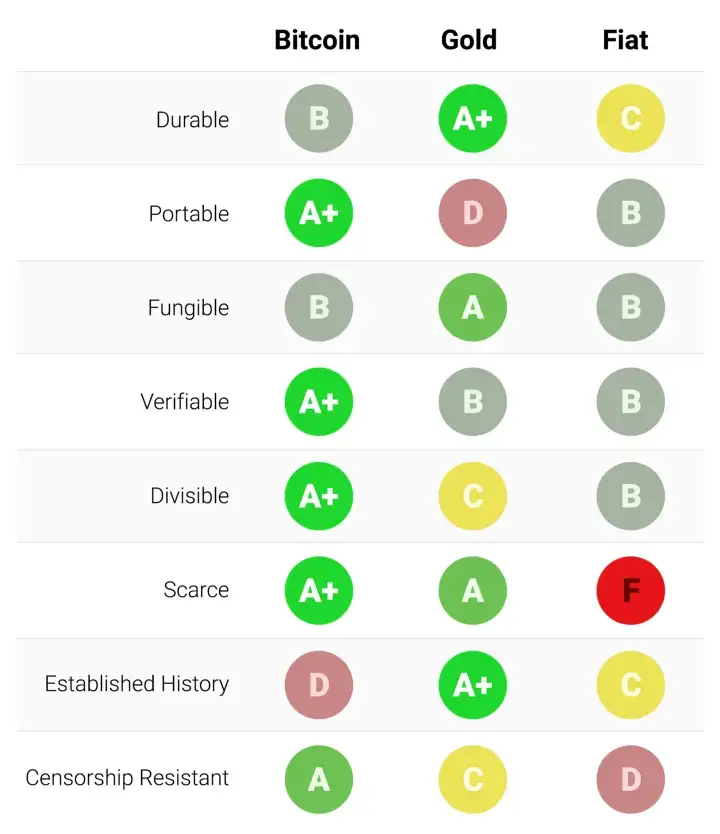
Trajnost:
Zlato je neosporeni kralj trajnosti. Velika većina zlata pronađenog kroz povijest, uključujući ono egipatskih faraona, opstaje i danas i vjerojatno će postojati i za tisuću godina. Zlatnici korišteni u antičko doba imaju značajnu vrijednost i danas. Fiat valute i bitcoini su digitalni zapisi koji ponekad imaju fizički oblik (npr. novčanice). Dakle, njihovu trajnost ne određuju njihova fizička svojstva (moguće je zamijeniti staru i oštećenu novčanicu za novu), nego institucije koje stoje iza njih. U slučaju fiat valuta, mnoge države su nastale i nestale kroz stoljeća, i valute su nestale s njima. Marke iz Weimarske republike danas nemaju vrijednost zato što institucija koja ih je izdavala više ne postoji. Ako je povijest ikakav pokazatelj, ne bi bilo mudro smatrati fiat valute trajnima dugoročno; američki dolar i britanska funta su relativne anomalije u ovom pogledu. Bitcoini, zato što nemaju instituciju koja ih održava, mogu se smatrati trajnima dok god mreža koja ih osigurava postoji. Obzirom da je Bitcoin još uvijek mlada valuta, prerano je za čvrste zaključke o njegovoj trajnosti. No, postoje ohrabrujući znakovi - prominente države su ga pokušavale regulirati, hakeri ga napadali - usprkos tome, mreža nastavlja funkcionirati, pokazujući visok stupanj antifragilnosti.
Prenosivost:
Bitcoini su najprenosivije spremište vrijednosti ikad. Privatni ključevi koji predstavljaju stotine milijuna dolara mogu se spremiti na USB drive i lako ponijeti bilo gdje. Nadalje, jednako velike sume mogu se poslati na drugi kraj svijeta skoro instantno. Fiat valute, zbog svojeg temeljno digitalnog oblika, su također lako prenosive. Ali, regulacije i kontrola kapitala od strane države mogu ugroziti velike prijenose vrijednosti, ili ih usporiti danima. Gotovina se može koristiti kako bi se izbjegle kontrole kapitala, ali onda rastu rizik čuvanja i cijena transporta. Zlato, zbog svojeg fizičkog oblika i velike gustoće, je najmanje prenosivo. Nije čudo da većina zlatnika i poluga nikad ne napuste sefove. Kada se radi prijenos zlata između prodavača i kupca, uglavnom se prenosi samo ugovor o vlasništvu, ne samo fizičko zlato. Prijenos fizičkog zlata na velike udaljenosti je skupo, riskantno i sporo.
Zamjenjivost:
Zlato nam daje standard za zamjenjivost. Kada je rastopljeno, gram zlata je praktički nemoguće razlikovati od bilo kojeg drugog grama, i zlato je oduvijek bilo takvo. S druge strane, fiat valute, su zamjenjive samo onoliko koliko njihova institucija želi da budu. Iako je uglavnom slučaj da je novčanica zamjenjiva za drugu istog iznosa, postoje situacije u kojima su velike novčanice tretirane drukčije od malih. Naprimjer, vlada Indije je, u pokušaju da uništi neoporezivo sivo tržište, potpuno oduzela vrijednost novčanicama od 500 i 1000 rupija. To je uzrokovalo da ljudi manje vrednuju te novčanice u trgovini, što je značilo da više nisu bile zaista zamjenjive za manje novčanice. Bitcoini su zamjenjivi na razini mreže; svaki bitcoin je pri prijenosu tretiran kao svaki drugi. No, zato što je moguće pratiti individualne bitcoine na blockchainu, određeni bitcoin može, u teoriji, postati “prljav” zbog korštenja u ilegalnoj trgovini, te ga trgovci ili mjenjačnice možda neće htjeti prihvatiti. Bez dodatnih poboljšanja oko privatnosti i anonimnosti na razini mrežnog protokola, bitcoine ne možemo smatrati jednako zamjenjivim kao zlato.
Mogućnost provjere:
Praktično gledajući, autentičnost fiat valuta i zlata je prilično lako provjeriti. Svejedno, i usprkos pokušajima da spriječe krivotvorenje novčanica, i dalje postoji potencijal prevare za vlade i njihove građane. Zlato također nije imuno na krivotvorenje. Sofisticirani kriminalci su koristili pozlaćeni tungsten kako bi prevarili kupce zlata. Bitcoine je moguće provjeriti sa matematičkom sigurnošću. Korištenjem kriptografskih potpisa, vlasnik bitcoina može javno demonstrirati da posjeduje bitcoine koje tvrdi da posjeduje.
Djeljivost:
Bitcoine je moguće podijeliti u stotinu milijuna manjih jedinica (zvanih satoshi), i prenositi takve (no, valja uzeti u obzir ekonomičnost prijenosa malih iznosa, zbog cijene osiguravanja mreže - “network fee”). Fiat valute su tipično dovoljno djeljive na jedinice sa vrlo niskom kupovnom moći. Zlato, iako fizički i teoretski djeljivo, postaje teško za korištenje kada se podijeli na dovoljno male količine da bi se moglo koristiti u svakodnevnoj trgovini.
Oskudnost:
Svojstvo koje najjasnije razlikuje Bitcoin od fiat valuta i zlata je njegova unaprijed definirana oskudnost. Od početka, konačna količina bitcoina nikad neće biti veća od 21 milijun. To daje vlasnicima bitcoina jasan i znan uvid u postotak ukupnog vlasništva. Naprimjer, vlasnik 10 bitcoina bi znao da najviše 2,1 milijuna ljudi (manje od 0.03% populacije) može ikad imati isto bitcoina kao i on. Premda je kroz povijest uvijek bilo oskudno, zlato nije imuno na povećanje ukupne količine. Ako se ikad izumi nova, ekonomičnija metoda rudarenja ili proizvodnje zlata, ukupna količina zlata bi se mogla dramatično povećati (npr. rudarenje morskog dna ili asteroida). Na kraju, fiat valute, relativno nov izum u povijesti, pokazale su se sklonima konstantnim povećanjima u količini. Države su pokazale stalnu sklonost inflaciji monetarne kvantitete kako bi rješavale kratkoročne političke probleme. Inflacijske tendencije vlada diljem svijeta čine fiat valute gotovo sigurnim da će gubiti vrijednost kroz vrijeme.
Etablirana povijest:
Nijedno monetarno dobro nema povijest kao zlato, koje je imalo vrijednost za cijelog trajanja ljudske civilizacije. Kovanice izrađene u antičko doba i danas imaju značajnu vrijednost. Ne može se isto reći za fiat valute, koje su same relativno nova povijesna anomalija. Od njihovog početka, fiat valute su imale gotovo univerzalni smjer prema bezvrijednosti. Korištenje inflacije kao podmuklog načina za nevidljivo oporezivanje građana je vječita kušnja kojoj se skoro nijedna država u povijesti nije mogla oduprijeti. Ako je 20. stoljeće, u kojem je fiat novac dominirao globalni monetarni poredak, demonstriralo neku ekonomsku istinu, to je onda bila ta da ne možemo računati na fiat novac da održi vrijednost u dužem ili srednjem vremenskom periodu. Bitcoin, usprkos svojoj novosti, je preživio dovoljno testova tržišta da postoji velika vjerojatnost da neće nestati kao vrijedno dobro. Nadalje, Lindy efekt govori da što duže Bitcoin bude korišten, to će veća biti vjera u njega i njegovu sposobnost da nastavi postojati dugo u budućnost. Drugim riječima, društvena vjera u monetarno dobro je asimptotička, kao u grafu ispod:

Ako Bitcoin preživi prvih 20 godina, imat će gotovo sveopće povjerenje da će trajati zauvijek, kao što ljudi vjeruju da je internet trajna stvar u modernom svijetu.
Otpor na cenzuru
Jedan od najbitnijih izvora za ranu potražnju bitcoina bila je njegova upotreba u ilegalnoj kupovini i prodaji droge. Mnogi su zato pogrešno zaključili da je primarna potražnja za bitcoinima utemeljena u njihovoj prividnoj anonimnosti. Međutim, Bitcoin nije anonimna valuta; svaka transakcija na mreži je zauvijek zapisana na javnom blockchainu. Povijesni zapis transakcija dozvoljava forenzičkoj analizi da identificira izvore i tijek sredstava. Takva analiza dovela je do uhićenja počinitelja zloglasne MtGox pljačke. Premda je istina da dovoljno oprezna i pedantna osoba može sakriti svoj identitet koristeći Bitcoin, to nije razlog zašto je Bitcoin bio toliko popularan u trgovini drogom.
Ključno svojstvo koje čini Bitcoin najboljim za takve aktivnosti je njegova agnostičnost i nepotrebnost za dozvolom (“premissionlessness”) na mrežnoj razini. Kada se bitcoini prenose na Bitcoin mreži, ne postoji nitko tko dopušta transakcije. Bitcoin je distribuirana peer-to-peer (korisnik-korisniku) mreža, i samim time dizajnirana da bude otporna na cenzuru. Ovo je u velikom kontrastu sa fiat bankarskim sustavom, u kojem države reguliraju banke i ostale institucije prijenosa novca, kako bi one prijavljivale i sprječavale protuzakonito korištenje monetarnih dobara. Klasičan primjer regulacije novca su kontrole kapitala. Npr., bogati milijunaš će vrlo teško prenijeti svoje bogatstvo u novu zemlju, kada bježi iz opresivnog režima. Premda zlato nije izdano i proizvedeno od države, njegova fizička priroda ga čini teško prenosivim kroz prostor, i samim time ga je daleko lakše regulirati nego Bitcoin. Indijski Akt kontrole zlata je primjer takve regulacije.
Bitcoin je odličan u većini gore navedenih svojstava, što mu omogućava da bude marginalno bolji od modernih i drevnih monetarnih dobara, te da pruži poticaje za svoje rastuće društveno usvajanje. Specifično, moćna kombinacija otpornosti na cenzuru i apsolutne oskudnosti bila je velika motivacija za bogate ulagače koji su uložili dio svojeg bogatstva u Bitcoin.
Evolucija novca
U modernoj monetarnoj ekonomiji postoji opsesija sa ulogom novca kao medija razmjene. U 20. stoljeću, države su monopolizirale izdavanje i kontrolu novca i kontinuirano potkopavale njegovo svojstvo spremišta vrijednosti, stvarajući lažno uvjerenje da je primarna svrha novca biti medij razmjene. Mnogi su kritizirali Bitcoin, govoreći da je neprikladan da bude novac zato što mu je cijena bila previše volatilna za medij razmjene. No, novac je uvijek evoluirao kroz etape; uloga spremišta vrijednosti je dolazila prije medija razmjene. Jedan od očeva marginalističke ekonomije, William Stanley Jevons, objašnjava:
"Povijesno govoreći… čini se da je zlato prvo služilo kao luksuzni metal za ukras; drugo, kao sačuvana vrijednost; treće, kao medij razmjene; i konačno, kao mjerilo vrijednosti."
U modernoj terminologiji, novac uvijek evoluira kroz četiri stadija:
- Kolekcionarstvo: U prvoj fazi svoje evolucije, novac je tražen samo zbog svojih posebnih svojstava, uglavnom zbog želja onog koji ga posjeduje. Školjke, perlice i zlato su bili sakupljani prije nego su poprimili poznatije uloge novca.
- Spremište vrijednosti: Jednom kada je novac tražen od dovoljnog broja ljudi, biti će prepoznat kao način za čuvanje i spremanje vrijednosti kroz vrijeme. Kada neko dobro postane široko korišteno kao spremište vrijednosti, njegova kupovna moć raste sa povećanom potražnjom za tu svrhu. Kupovna moć spremišta vrijednosti će u jednom trenutku doći do vrhunca, kada je dovolno rašireno i broj novih ljudi koji ga potražuju splasne.
- Sredstvo razmjene: Kada je novac potpuno etabliran kao spremište vrijednosti, njegova kupovna moć se stabilizira. Nakon toga, postane prikladno sredstvo razmjene zbog stabilnosti svoje cijene. U najranijim danima Bitcoina, mnogi ljudi nisu shvaćali koju buduću cijenu plaćaju koristeći bitcoine kao sredstvo razmjene, umjesto kao novonastalo spremište vrijednosti. Poznata priča o čovjeku koji je za 10,000 bitcoina (vrijednih oko 94 milijuna dolara kada je ovaj članak napisan) za dvije pizze ilustrira ovaj problem.
- Jedinica računanja vrijednosti: Jednom kada je novac široko korišten kao sredstvo razmjene, dobra će biti vrednovana u njemu, tj. većina cijena će biti izražena u njemu. Uobičajena zabluda je da je većinu dobara moguće zamijeniti za bitcoine danas. Npr., premda je možda moguće kupiti šalicu kave za bitcoine, izlistana cijena nije prava bitcoin cijena; zapravo se radi o cijeni u državnoj valuti koju želi trgovac, preračunatu u bitcoin po trenutnoj tržišnoj cijeni. Kad bi cijena bitcoina pala u odnosu na valutu, vrijednost šalice izražena u bitcoinima bi se povećala. Od trenutka kada trgovci budu voljni prihvaćani bitcoine kao platežno sredstvo, bez obraćanja pažnje na vrijednost bitcoina u državnoj fiat valuti, moći ćemo reći da je Bitcoin zaista postao jedinica računanja vrijednosti.
Monetarna dobra koja još nisu jedinice računanja vrijednosti možemo smatrati “djelomično monetiziranima.” Danas zlato ima takvu ulogu, jer je spremište vrijednosti, ali su mu uloge sredstva razmjene i računanja vrijednosti oduzete intervencijama država. Moguće je također da se jedno dobro koristi kao sredstvo razmjene, dok druga ispunjavaju ostale uloge. To je tipično u zemljama gdje je država disfunkcionalna, npr. Argentina ili Zimbabwe. U svojoj knjizi, Digitalno zlato, Nathaniel Popper piše:
"U Americi, dolar služi trima funkcijama novca: nudi sredstvo razmjene, jedinicu za mjerenje vrijednosti dobara, i mjesto gdje se može čuvati vrijednosti. S druge strane, argentinski peso je korišten kao sredstvo razmjene (za svakodnevne potrebe), ali ga nitko nije koristio kao spremište vrijednosti. Štednja u pesosima bila je ekvivalent bacanja novca. Zato su ljudi svu svoju štednju imali u dolarima, jer je dolar bolje čuvao vrijednost. Zbog volatilnosti pesosa, ljudi su računali cijene u dolarima, što im je pružalo pouzdaniju jedinicu mjerenja kroz vrijeme."
Bitcoin je trenutno u fazi tranzicije iz prvog stadija monetizacije u drugi. Vjerojatno će proći nekoliko godina prije nego Bitcoin pređe iz začetaka spremišta vrijednosti u istinski medij razmjene, i put do tog trenutka je još uvijek pun rizika i nesigurnosti. Važno je napomenuti da je ista tranzicija trajala mnogo stoljeća za zlato. Nitko danas živ nije doživio monetizaciju dobra u realnom vremenu (kroz koju Bitcoin prolazi), tako da nemamo puno iskustva govoriti o putu i načinu na koji će se monetizacija dogoditi.
Put monetizacije
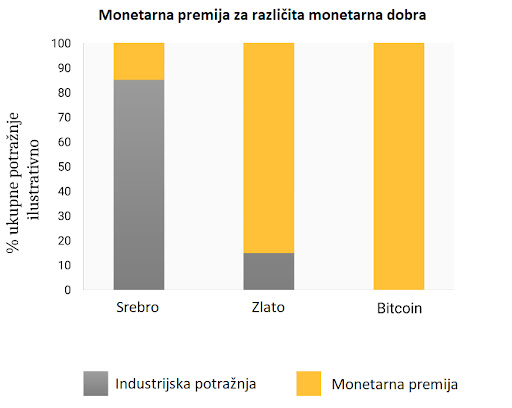
Kroz proces monetizacije, monetarno dobro će naglo porasti u kupovnoj moći. Mnogi su tako komentirali da je uvećanje kupovne moći Bitcoina izgledalo kao “balon” (bubble). Premda je ovaj termin često korišten kako bi ukazao na pretjeranu vrijednosti Bitcoina, sasvim slučajno je prikladan. Svojstvo koje je uobičajeno za sva monetarna dobra jest da je njihova kupovna moć viša nego što se može opravdati samo kroz njihovu uporabnu vrijednost. Zaista, mnogi povijesni novci nisu imali uporabnu vrijednost. Razliku između kupovne moći i vrijednosti razmjene koju bi novac mogao imati za svoju inherentnu korisnost, možemo razmatrati kao “monetarnu premiju.” Kako monetarno dobro prolazi kroz stadije monetizacije (navedene gore), monetarna premija raste. No, ta premija ne raste u ravnoj i predvidivoj liniji. Dobro X, koje je bilo u procesu monetizacije, može izgubiti u usporedbi sa dobrom Y koje ima više svojstava novca, te monetarna premija dobra X drastično padne ili potpuno nestane. Monetarna premija srebra je skoro potpuno nestala u kasnom 19. stoljeću, kada su ga vlade diljem svijeta zamijenile zlatom kao novcem.
Čak i u odsustvu vanjskih faktora, kao što su intervencije vlade ili druga monetarna dobra, monetarna premija novog novca neće ići predvidivim putem. Ekonomist Larry White primijetio je:
"problem sa pričom “balona,” naravno, je da je ona konzistentna sa svakim putem cijene, i time ne daje ikakvo objašnjenje za specifičan put cijene"
Proces monetizacije opisuje teorija igara; svaki akter na tržištu pokušava predvidjeti agregiranu potražnju ostalih aktera, i time buduću monetarnu premiju. Zato što je monetarna premija nevezana za inherentnu korisnost, tržišni akteri se uglavnom vode za prošlim cijenama da bi odredili je li neko dobro jeftino ili skupo, i žele li ga kupiti ili prodati. Veza trenutne potražnje sa prošlim cijenama naziva se “ovisnost o putu” (path dependence); ona je možda najveći izvor konfuzije u shvaćanju kretanja cijena monetarnih dobara.
Kada kupovna moć monetarnog dobra naraste zbog većeg i šireg korištenja, očekivanja tržišta o definicijama “jeftinog” i “skupog” se mijenjaju u skladu s time. Slično tome, kada cijena monetarnog dobra padne, očekivanja tržišta mogu se promijeniti u opće vjerovanje da su prethodne cijene bile “iracionalne” ili prenapuhane. Ovisnost o putu novca ilustrirana je riječima poznatog upravitelja fondova s Wall Streeta, Josha Browna:
"Kupio sam bitcoine kada su koštali 2300 USD, i to mi se udvostručilo gotovo odmah. Onda sam počeo govoriti kako “ne mogu kupiti još” dok im je cijena rasla, premda sam znao da je to razmišljanje bazirano samo na cijenu po kojoj sam ih kupio. Kasnije, kada je cijena pala zbog kineske regulacije mjenjačnica, počeo sam si govoriti, “Odlično, nadam se da će još pasti da mogu kupiti još.”"
Istina leži u tome da su ideje “jeftinog” i “skupog” zapravo besmislene kada govorimo o monetarnim dobrima. Cijena monetarnog dobra ne reflektira njegovu stopu rasprostanjenosti ili korisnosti, nego mjeru koliko je ono široko prihvaćeno da ispuni razne uloge novca.
Dodatna komplikacija u ovom aspektu novca je činjenica da tržišni akteri ne djeluju samo kao nepristrani promatrači koji pokušavaju kupiti i prodati u iščekivanju budućih kretanja monetarne premije, nego i kao aktivni proponenti. Pošto ne postoji objektivno “točna” monetarna premija, širiti dobar glas o superiornijim svojstvima nekog monetarnog dobra je efektivnije nego za obična dobra, čija vrijednost je u konačnici vezana na njegovu osnovnu korisnost. Religiozni zanos sudionika na Bitcoin tržištu vidljiv je na raznim internetskim forumima, gdje Bitcoineri aktivno promoviraju benefine Bitcoina i bogatstvo koje je moguće ostvariti investiranjem u njega. Promatrajući Bitcoin tržište, Leigh Drogen komentira:
"To je prepoznatljivo svima kao religija - priča koju si pričamo i oko koje se slažemo. Religija je krivulja na grafu prihvaćanja o kojoj trebamo razmišljati. Sustav je gotovo savršen - onog trenutka kada netko pristupi krugu Bitcoinera, to će reći svima i nastaviti širiti riječ. Onda njihovi prijatelji pristupe i nastave širiti riječ."
Premda usporedba sa religijom može staviti Bitcoin u iracionalno svjetlo, potpuno je racionalno za individualnog vlasnika da širi dobru vijest o superiornom monetarnom dobru, i za šire društvo da se standardizira oko njega. Novac djeluje kao temelj za svu trgovinu i štednju; tako da prihvaćanje superiornog oblika novca ima ogromne multiplicirajuće benefite za stvaranje bogatstva za sve članove društva.
Oblik monetizacije
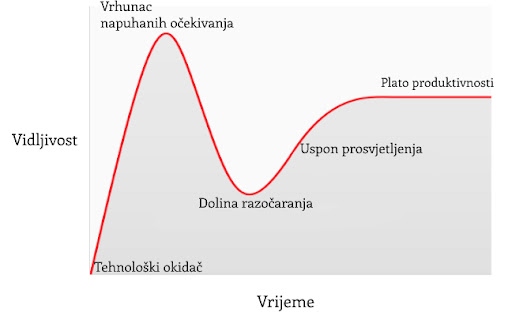
U članku o Spekulativnom prihvaćanju Bitcoina / teorije cijene, Michael Casey postulira da rastući Gartner hype ciklusi predstavljaju faze standardne S-krivulje prihvaćanja novih tehnologija, koje su bile prisutne kod mnogih transformacijskih tehnologija dok su postajale uobičajene u društvu.
Svaki Gartner hype ciklus počinje sa eksplozijom entuzijazma za novom tehnologijom, a cijenu podižu oni sudionici na tržištvu koji su “dostupni” u toj fazi. Najraniji kupci u Gartner hype ciklusu obično imaju jaku vjeru o transformacijskoj prirodi tehnologije u koju ulažu. S vremenom, tržište dosegne vrhunac entuzijazma kako se količina novih kupaca iscrpljuje, te kupovinom počnu dominirati spekulatori koji su više zainteresirani u brze profite nego u samu tehnologiju.
Nakon vrha hype ciklusa, cijene rapidno padaju dok spekulativno ludilo ustupa mjesto očajavanju, javnoj poruzi i osjećaju da tehnologija nije uopće bila transformacijska. S vremenom, cijena dosegne dno i formira plato na kojem se originalnim ulagačima, koji su imali snažno uvjerenje, pridružuju nove grupe ljudi koji su izdržali bol kraha cijena i koji cijene važnost same tehnologije.
Plato traje neko vrijeme i formira, kako Casey kaže, “stabilnu, dosadnu dolinu.” Za ovo vrijeme, javni interes za tehnologiju opada, no nastaviti će se razvijati i snažna zajednica uvjerenja će polako rasti. Tada, postavlja se nova baza za sljedeću iteraciju hype ciklusa, dok vanjski promatrači prepoznaju da tehnologija i dalje postoji i da ulaganje u nju možda nije onoliko rizično kao što se činilo za vrijeme pada cijene. Sljedeća iteracija hype ciklusa donosi mnogo veći broj novih ljudi, pa je i ciklus daleko veći u svojoj magnitudi.
Jako mali broj ljudi koji sudjeluju u Gartner hype ciklusu će točno predvidjeti koliko će visoko cijena porasti za vrijeme ciklusa. Cijene često dosegnu razine koje bi se činile apsurdnima većini ulagača u raniji stadijima ciklusa. Kada ciklus završi, mediji tipično atribuiraju pad cijene nekoj od aktualnih drušvenih tema. Premda takva tema može biti okidač pada, ona nikad nije temeljni razlog zašto ciklus završava. Gartner hype ciklusi završavaju kada je količina dostupnih novih sudionika na tržištu iscrpljena.
Zanimljivo je da je i zlato nacrtalo klasičan graf Gartner hype ciklusa od kasnih 1970-ih do ranih 2000-ih. Moguće je spekulirati da je hype ciklus osnovna socijalna dinamika oko procesa monetizacije.
Gartner kohorte
Od početka trgovanja Bitcoina na mjenjačnicama 2010. godine, Bitcoin tržište je svjedočilo četirima velikim Gartner hype ciklusima. U retrospektivi, možemo vrlo precizno identificirati grupe cijena prethodnih hype ciklusa Bitcoin tržišta. Također, možemo kvalitativno odrediti kohorte ulagača koje su povezane sa svakom iteracijom prethodnih ciklusa.
0 USD –1 USD (2009. – 3. mjesec 2011.): Prvi hype ciklus u Bitcoin tržištu dominirali su kriptografi, računalni znanstvenici i cypherpunkovi koji su od početka bili spremni razumijeti važnost nevjerojatnog izuma Satoshija Nakamotoa, i koji su bili pioniri u potvrđivanju da Bitcoin protokol nema tehničkih mana.
1 USD - 30 USD (3. mjesec 2011. – 7. mjesec. 2011.): Drugi ciklus privukao je rane entuzijaste oko novih tehnologija kao i stabilan pritok ideološki motiviranih ulagača koji su bili oduševljeni idejom novca odvojenog od države. Libertarijanci poput Rogera Vera došli su u Bitcoin zbog aktivnog anti-institucionalnog stava, i mogućnosti koju je nova tehnologija obećavala. Wences Casares, briljantni i dobro povezani serijski poduzetnik, bio je također dio drugog Bitcoin hype ciklusa te je širio riječ o Bitcoinu među najprominentnijim tehnolozima i ulagačima u Silicijskoj Dolini.
250 USD – 1100 USD (4. mjesec 2013. – 12. mjesec 2013.): Treći hype ciklus doživio je ulazak ranih generalnih i institucionalnih ulagača koji su bili voljni uložiti trud i riskirati kroz užasno komplicirane kanale likvidnosti kako bi kupili bitcoine. Primaran izvor likvidnosti na tržištu za vrijeme ovog perioda bio je MtGox, mjenjačnica bazirana u Japanu, koju je vodio notorno nesposobni i beskrupulozni Mark Karpeles, koji je kasnije završio i u zatvoru zbog svoje uloge u kolapsu MtGoxa.
Valja primijetiti da je rast Bitcoinove cijene za vrijeme spomenuti hype ciklusa većinom povezano sa povećanjem likvidnosti i lakoćom sa kojom su ulagači mogli kupiti bitcoine. Za vrijeme prvog hype ciklusa, nisu postojale mjenjačnice; akvizicija bitcoina se odvijala primarno kroz rudarenje (mining) ili kroz izravnu razmjenu sa onima koju su već izrudarili bitcoine. Za vrijeme drugog hype ciklusa, pojavile su se rudimentarne mjenjačnice, no nabavljanje i osiguravanje bitcoina na ovim mjenjačnicama bilo je previše kompleksno za sve osim tehnološki najsposobnijih ulagača. Čak i za vrijeme trećeg hype ciklusa, ulagači koju su slali novac na MtGox kako bi kupili bitcoine su morali raditi kroz značajne prepreke. Banke nisu bile voljne imati posla sa mjenjačnicom, a oni posrednici koji su nudili usluge transfera bili su često nesposobni, kriminalni, ili oboje. Nadalje, mnogi koji su uspjeli poslati novac MtGoxu, u konačnici su morali prihvatiti gubitak svojih sredstava kada je mjenjačnica hakirana i kasnije zatvorena.
Tek nakon kolapsa MtGox mjenjačnice i dvogodišnje pauze u tržišnoj cijeni Bitcoina, razvili su se zreli i duboki izvori likvidnosti; primjeri poput reguliranih mjenjačnica kao što su GDAX i OTC brokeri kao Cumberland mining. Dok je četvrti hype ciklus započeo 2016. godine, bilo je relativno lako običnim ulagačima kupiti i osigurati bitcoine.
1100 USD – 19600 USD? (2014. –?):
U trenutku pisanja ovog teksta, tržište Bitcoina je prolazilo svoj četvrti veliki hype ciklus. Sudjelovanje u ovom hype ciklusu dominirala je ona skupina koju je Michael Casey opisao kao “rana većina” običnih i institucionalnih ulagača.
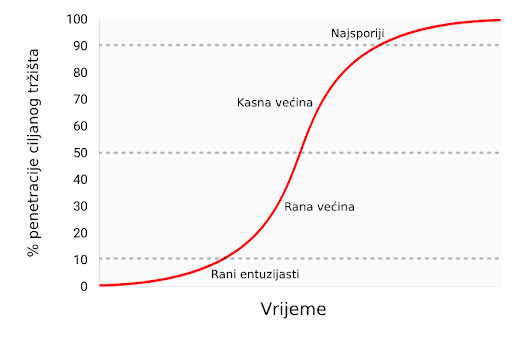
Kako su se izvori likvidnosti produbljivali i sazrijevali, veliki institucionalni ulagači sada imaju priliku sudjelovati kroz regulirana “futures” tržišta. Dostupnosti takvih tržišta stvara put ka kreaciji Bitcoin ETF-a (exchange traded fund) (fond na slobodnom tržištu), koji će onda pokrenuti “kasnu većinu” i “najsporije” u sljedećim hype ciklusima.
Premda je nemoguće predvidjeti točan efekt budućih hype ciklusa, razumno je očekivati da će najviša točka biti između 20.000 USD i 50.000 USD (2021. zenit je bio preko 69.000 USD). Znatno više od ovog raspona, i Bitcoin bi imao znatan postotak ukupne vijednosti zlata (zlato i Bitcoin bi imali jednaku tržišnu kapitalizaciju kada bi bitcoini vrijedili oko 380.000 USD u trenutku pisanja ovog teksta). Značajan postotak vrijednosti zlata dolazi od potražnje centralnih banaka, te je malo vjerojatno da će centralne banke ili suverene države sudjelovati u trenutnom hype ciklusu.
Ulazak suverenih država u Bitcoin
Bitcoinov zadnji Gartner hype ciklus će započeti kada ga suverene države počnu akumulirati kao dio svojih rezervi stranih valuta. Tržišna kapitalizacija Bitcoina je trenutno premala da bismo ga smatrali značajnim dodatkom rezervama većini zemalja. No, kako se interes u privatnom sektoru povećava i kapitalizacija Bitcoina se približi trilijunu dolara, postat će dovoljno likvidan za većinu država. Prva država koja službeno doda bitcoine u svoje rezerve će vjerojatno potaknuti stampedo ostalih da učine isto. Države koje su među prvima u usvajanju Bitcoina imat će najviše benefita u svojim knjigama ako Bitcoin u konačnici postane globalna valuta (global reserve currency). Nažalost, vjerojatno će države sa najjačom izvršnom vlasti - diktature poput Sjeverne Koreje - biti najbrže u akumulaciji bitcoina. Neodobravanje prema takvim državama i slaba izvršna tijela zapadnjačkih demokracija uzrokovat će sporost i kašnjenje u akumulaciji bitcoina za njihove vlastite rezerve.
Velika je ironija u tome što je SAD trenutno jedna od regulatorno najotvorenijih nacija prema Bitcoinu, dok su Kina i Rusija najzatvorenije. SAD riskira najviše, geopolitički, ako bi Bitcoin zamijenio dolar kao svjetska rezervna valuta. U 1960-ima, Charles de Gaulle je kritizirao “pretjeranu privilegiju” (“exorbitant privilege”) koju su SAD imale u međunarodnom monetarnom poretku, postavljenom kroz Bretton Woods dogovor 1944. godine. Ruska i kineska vlada još ne shvaćaju geo-strateške benefite Bitcoina kao rezervne valute, te se trenutno brinu o efektima koje bi mogao imati na njihova unutarnja tržišta. Kao de Gaulle u 1960-ima, koji je prijetio SAD-u povratkom na klasični standard zlata, Kinezi i Rusi će s vremenom uvidjeti korist u velikoj poziciji u Bitcoinu - spremištu vrijednosti bez pokrića ijedne vlade. Sa najvećom koncentracijom rudara Bitcoina u Kini (2017.), kineska vlada već ima znatnu potencijalnu prednost u stavljanju bitcoina u svoje rezerve.
SAD se ponosi svojim statusom nacije inovatora, sa Silicijskom dolinom kao krunom svoje ekonomije. Dosad, Silicijska dolina je dominirala konverzacijom usmjerenom prema regulaciji, i poziciji koju bi ona treba zauzeti prema Bitcoinu. No, bankovna industrija i federalna rezerva SAD-a (US Federal Reserve, Fed) napokon počinju uviđati egzistencijalnu prijetnju koju Bitcoin predstavlja za američku monetarnu politiku, postankom globalne rezervne valute. Wall Street Journal, jedan od medijskih glasova federalne reserve, izdao je komentar o Bitcoinu kao prijetnji monetarnoj politici SAD-a:
"Postoji još jedna opasnost, možda i ozbiljnija iz perspektive centralnih banaka i regulatora: bitcoin možda ne propadne. Ako je spekulativni žar u kriptovalutu samo prvi pokazatelj njezinog šireg korištenja kao alternative dolaru, Bitcoin će svakako ugroziti monopol centralnih banaka nad novcem."
U narednim godinama, možemo očekivati veliku borbu između poduzetnika i inovatora u Silicijskoj dolini, koji će pokušavati čuvati Bitcoin od državne kontrole s jedne strane, i bankovne industrije i centralnih banaka koje će učiniti sve što mogu da bi regulirale Bitcoin kako bi spriječile znatne promjene u svojoj industriji i moći izdavanja novca, s druge.
Prijelaz na medij razmjene
Monetarno dobro ne može postati opće prihvaćen medij razmjene (standardna ekonomska definicija za “novac”) prije nego je vrednovano od širokog spektra ljudi; jednostavno, dobro koje nije vrednovano neće biti prihvaćeno u razmjeni. Kroz proces generalnog rasta vrijednosti, i time postanka spremišta vrijednosti, monetarno dobro će brzo narasti u kupovnoj moći, i time stvoriti cijenu za korištenje u razmjeni. Samo kada ta cijena rizika mijenjanja spremišta vrijednosti padne dovoljno nisko, može dobro postati opće prihvaćen medij razmjene.
Preciznije, monetarno dobro će biti prikladno kao medij razmjene samo kada je suma cijene rizika i transakcijske cijene u razmjeni manja nego u trgovini bez tog dobra.
U društvu koje vrši robnu razmjenu, prijelaz spremišta vrijednosti u medij razmjene može se dogoditi čak i onda kada monetarno dobro raste u kupovnoj moći, zato što su transakcijski troškovi robne razmjene iznimno visoki. U razvijenoj ekonomiji, u kojoj su troškovi razmjene niski, moguće je za mladu i rapidno rastućnu tehnologiju spremišta vrijednosti, poput Bitcoina, da se koristi kao medij razmjene, doduše na ograničen način. Jedan primjer je ilegalno tržište droge, gdje su kupci voljni žrtvovati oportunu cijenu čuvanja bitcoina kako bi umanjili znatan rizik kupovine droge koristeći fiat novac.
Postoje međutim velike institucionalne barijere da novonastalo spremište vrijednosti postane sveopće prihvaćen medij razmjene u razvijenom društvu. Države koriste oporezivanje kao moćnu metodu zaštite svojeg suverenog novca protiv rivalskih monetarnih dobara. Ne samo da suvereni novac ima prednost konstantnog izvora potražnje, zato što je porez moguće platiti jedino u njemu, nego su i rivalska monetarna dobra oporezana pri svakoj razmjeni za vrijeme rastuće cijene. Ova metoda oporezivanja stvara znatan otpor korištenju spremišta vrijednosti kao medija razmjene.
Ovakvo sabotiranje tržišnih monetarnih dobara nije nepremostiva barijera za njihovo prihvaćanje kao općeg medija razmjene. Ako ljudi izgube vjeru u suvereni novac, njegova vrijednost može rapidno propasti kroz proces zvan hiperinflacija. Kada suvereni novac prolazi kroz hiperinflaciju, njegova vrijednost propadne prvo u usporedbi sa najlikvidnijim dobrima u društvu, kao što je zlato ili stabilna strana valuta (američki dolar npr.), ako su ona dostupna. Kada nema likvidnih dobara ili ih ima premalo, novac u hiperinflaciji kolabira u usporedbi sa stvarnim dobrima, kao što su nekretnine ili upotrebljiva roba. Arhetipska slika hiperinflacije je trgovina sa praznim policama - potrošači brzo bježe iz propadajuće vrijednosti novca svoje nacije.

Nakon dovoljno vremena, kada je vjera potpuno uništena za vrijeme hiperinflacije, suvereni novac više nitko ne prihvaća, te se društvo može vratiti na robnu razmjenu, ili će doživjeti potpunu zamjenu monetarne jedinice za sredstvo razmjene. Primjer ovog procesa bila je zamjena zimbabveanskog dolara za američki dolar. Takva promjena suverenog novca za stranu valutu je dodatno otežana relativnom oskudnošću strane valute i odsustvom stranih bankarskih institucija koje pružaju likvidnost tržištu.
Sposobnost lakog prenošenja bitcoina preko granica i odsustvo potrebe za bankarskim sustavom čine Bitcoin idealnim monetarnim dobrom za one ljude koji pate pod hiperinflacijom. U nadolazećim godinama, kako fiat valute nastave svoj povijesni trend ka bezvrijednosti, Bitcoin će postati sve popularniji izbor za ušteđevine ljudi diljem svijeta. Kada je novac nacije napušten i zamijenjen Bitcoinom, Bitcoin će napraviti tranziciju iz spremišta vrijednosti u tom društvu u opće prihvaćeno sredstvo razmjene. Daniel Krawicz stvorio je termin “hiperbitcoinizacija” da bi opisao ovaj proces.
Učestala pogrešna shvaćanja
Većina ovog članka usredotočila se na monetarnu prirodu Bitcoina. Sa tim temeljima možemo adresirati neke od najčešćih nerazumijevanja u Bitcoinu.
Bitcoin je balon (bubble)
Bitcoin, kao sva tržišna monetarna dobra, posjeduje monetarnu premiju. Ona često rezultira uobičajenom kritikom da je Bitcoin samo “balon.” No, sva monetarna dobra imaju monetarnu premiju. Naprotiv, ta monetarna premija (cijena viša od one koju diktira potražnja za dobrom kao korisnim) je upravo karakteristična za sve oblike novca. Drugim riječima, novac je uvijek i svuda balon. Paradoksalno, monetarno dobro je istovremeno balon i ispod vrijednosti ukoliko je u ranijim stadijima općeg prihvaćanja kao novac.
Bitcoin je previše volatilan
Volatilnost cijene Bitcoina je funkcija njegovog nedavnog nastanka. U prvih nekoliko godina svojeg postojanja, Bitcoin se ponašao kao mala dionica, i svaki veliki kupac - kao npr. braća Winklevoss - mogao je uzrokovati veliki skok u njegovoj cijeni. No, kako su se prihvaćenost i likvidnost povećavali kroz godine, volatilnost Bitcoina je srazmjerno smanjila. Kada Bitcoin postigne tržišnu kapitalizaciju (vrijednost) zlata, imat će sličnu volatilnost kao i zlato. Kako Bitcoin nastavi rasti, njegova volatilnost će se smanjiti do razine koja ga čini prikladnim za široko korištenje kao medij razmjene. Kao što je prethodno rečeno, monetizacija Bitcoina se odvija u seriji Gartner hype ciklusa. Volatilnost je najniža za vrijeme vrhunaca i dolina unutar ciklusa. Svaki hype ciklus ima nižu volatilnost od prethodnih, zato što je likvidnost tržišta veća.
Cijene transakcija su previsoke
Novija kritika Bitcoin mreže je ta da ju je povećanje cijena prijenosa bitcoina učinilo neprikladnom za sustav plaćanja. No, rast u cijenama transakcija je zdrav i očekivan. One su nužne za plaćanje bitcoin minera (rudara), koji osiguravaju mrežu validacijom transakcija. Rudare se plaća kroz cijene transakcija ili kroz blok-nagrade, koje su inflacijska subvencija od trane trenutnih vlasnika bitcoina.
S obzirom na Bitcoinovu fiksnu proizvodnju (monetarna politika koja ga čini idealnim za spremanje vrijednosti), blok-nagrade će s vremenom nestati i mrežu će se u konačnici morati osiguravati kroz cijene transakcija. Mreža sa “niskim” cijenama transakcija je mreža sa slabom sigurnosti i osjetljiva na vanjsku intervenciju i cenzuru. Oni koji hvale niske cijene Bitcoinovih alternative zapravo niti ne znajući opisuju slabosti tih takozvanih “alt-coina.”
Površan temelj kritika Bitcoinovih “visokih” cijena transakcija je uvjerenje da bi Bitcoin trebao biti prvo sustav plaćanja, i drugo spremište vrijednosti. Kao što smo vidjeli kroz povijest novca, ovo uvjerenje je naopako. Samo onda kada Bitcoin postane duboko ukorijenjeno spremište novca može biti prikladan kao sredstvo razmjene. Nadalje, kada oportunitetni trošak razmjene bitcoina dođe na razinu koja ga čini prikladnim sredstvom razmjene, većina trgovine neće se odvijati na samoj Bitcoin mreži, nego na mrežama “drugog sloja” (second layer) koje će imati niže cijene transakcija. Takve mreže, poput Lightning mreže, služe kao moderna verzija zadužnica koje su korištene za prijenos vlasničkih papira zlata u 19. stoljeću. Banke su koristile zadužnice zato što je prijenos samog metala bio daleko skuplji. Za razliku od takvih zadužnica, Lightning mreža će omogućavati nisku cijenu prijenosa bitcoina bez potrebe za povjerenjem prema trećoj strani, poput banaka. Razvoj Lightning mreže je tehnološka inovacija od izuzetne važnosti u povijesti Bitcoina, i njezina vrijednost će postati očita u narednim godinama, kako je sve više ljudi bude razvijalo i koristilo.
Konkurencija
Pošto je Bitcoin softverski protokol otvorenog tipa (open-source), oduvijek je bilo moguće kopirati softver i imitirati mrežu. Kroz godine nastajali su mnogi imitatori, od identičnih kopija, kao Litecoin, do kompleksnijih varijanti kao što je Ethereum, koje obećavaju arbitrarno kompleksne ugovorne mehanizme koristeći decentralizirani računalni sustav. Česta kritika Bitcoinu od strane ulagača je ta da on ne može zadržati svoju vrijednost kada je vrlo lako stvoriti konkurente koji mogu lako i brzo u sebi imati najnovije inovacije i softverske funkcionalnosti.

Greška u ovom argumentu leži u manju takozvanog “mrežnog efekta” (network effect), koji postoji u prvoj i dominantnoj tehnologiji u nekom području. Mrežni efekt - velika vrijednost korištenja Bitcoina samo zato što je već dominantan - je važno svojstvo samo po sebi. Za svaku tehnologiju koja posjeduje mrežni efekt, to je daleko najvažnije svojstvo koje može imati.
Za Bitcoin, mrežni efekt uključuje likvidnost njegovog tržišta, broj ljudi koji ga posjeduju, i zajednicu programera koji održavaju i unaprjeđuju njegov softver i svjesnost u javnosti. Veliki ulagači, uključujući države, će uvijek prvo tražiti najlikvidnije tržište, kako bi mogli ući i izaći iz tržišta brzo, i bez utjecanja na cijenu. Programeri će se pridružiti dominantnoj programerskoj zajednici sa najboljim talentom, i time pojačati samu zajednicu. Svjesnost o brendu sama sebe pojačava, pošto se nadobudni konkurenti Bitcoina uvijek spominju u kontekstu Bitcoina kao takvog.
Raskrižje na putu (fork)
Trend koji je postao popularan 2017. godine nije bio samo imitacija Bitcoinovog softvera, nego kopiranje potpune povijesti njegovih prošlih transakcija (cijeli blockchain). Kopiranjem Bitcoinovog blockchaina do određene točke/bloka i odvajanjem sljedećih blokova ka novoj mreži, u procesu znanom kao “forking” (odvajanje), Bitcoinovi konkurenti su uspjeli riješiti problem distribuiranja svojeg tokena velikom broju korisnika.

Najznačajniji takav fork dogodio se 1. 8. 2017. godine, kada je nova mreža nazvana Bitcoin Cash (Bcash) stvorena. Vlasnik N količine bitcoina prije 1.8.2017. bi onda posjedovao N bitcoina i N BCash tokena. Mala, ali vrlo glasna zajednica Bcash proponenata je neumorno pokušavala prisvojiti Bitcoinov brend i ime, imenujući svoju novu mrežu Bitcoin Cast i pokušavajući uvjeriti nove pridošlice u Bitcoin da je Bcash “pravi” Bitcoin. Ti pokušaji su većinom propali, i taj neuspjeh se vidi u tržišnim kapitalizacijama dviju mreža. No, za nove ulagače, i dalje postoji rizik da bi konkurent mogao kopirati Bitcoin i njegov blockchain i tako uspjeti u preuzimanju tržišne kapitalizacije, te postati de facto Bitcoin.
Moguće je uočiti važno pravilo gledajući velike forkove u prošlosti Bitcoin i Ethereum mreža. Većina tržišne kapitalizacije odvijat će se na mreži koja zadrži najviši stupanj talenta i aktivnosti u zajednici programera. Premda se na Bitcoin može gledati kao na nov i mlad novac, on je također računalna mreža koja počiva na softveru, kojeg se pak treba održavati i poboljšavati. Kupovina tokena na mreži koja ima malo neiskusnih programera bilo bi kao kupovati kopiju Microsoft Windowsa na kojoj rade lošiji programeri. Jasno je vidljivo iz povijesti forkova koji su se odvili 2017. godine da su najbolji računalni i kriptografski stručnjaci posvećeni razvoju originalnog Bitcoina, a ne nekoj od rastućeg broja imitacija koje su se izrodile iz njega.
Stvarni rizici
Premda su uobičajene kritike upućene Bitconu od strane medija i ekonomske profesije krive i bazirane na netočnom shvaćanju novca, postoje pravi i značajni rizici kod ulaganja u Bitcoin. Bilo bi mudro za novog Bitcoin ulagača da shvati ove rizike prije potencijalnog ulaganja.
Rizik protokola
Bitcoin protokol i kriptografski sastavni dijelovi na kojima je sagrađen potencijalno imaju dosad nepronađenu grešku u svom dizajnu, ili mogu postati nesigurni razvojem kvantnih računala. Ako se pronađe greška u protokolu, ili neka nova metoda računarstva učini mogućim probijanje kriptografskih temelja Bitcoina, vjera u Bitcoin biti će znatno narušena. Rizik protokola bio je najviši u ranim godinama razvoja Bitcoina, kada je još uvijek bilo nejasno, čak i iskusnim kriptografima, je li Satoshi Nakamoto zaista riješio problem bizantskih generala (Byzantine Generals’ Problem). Brige oko ozbiljnih grešaka u Bitcoin protokolu nestale su kroz godine, no uzevši u obzir njegovu tehnološku prirodu, rizik protokola će uvijek ostati u Bitcoinu, makar i kao izuzetak.
Propadanje mjenjačnica
Time što je decentraliziran, Bitcoin je pokazao značajnu otpornost, suočen sa brojnim pokušajima raznih vlada da ga reguliraju ili unište. No, mjenjačnice koje trguju bitcoinima za fiat valute su centralizirani entiteti i podložne regulacijama i zatvaranju. Bez mjenjačnica i volje bankara da s njima posluju, proces monetizacije Bitcoina bio bi ozbiljno usporen, ako ne i potpuno zaustavljen. Iako postoje alternativni izvori likvidnosti za Bitcoin, poput “over-the-counter” brokera i decentraliziranih tržišta za kupovinu i prodaju bitcoina, kritičan proces otkrivanja i definiranja cijene se odvija na najlikvidnijim mjenjačnicama, koje su sve centralizirane.
Jedan od načina za umanjivanje rizika gašenja mjenjačnica je geografska arbitraža. Binance, jedna od velikih mjenjačnica iz Kine, preselila se u Japan nakon što joj je kineska vlada zabranila operiranje u Kini. Vlade su također oprezne kako ne bi ugušile novu industriju koja je potencijalno značajna kao i internet, i time predale nevjerojatnu konkurentnu vrijednost drugim nacijama.
Samo kroz koordinirano globalno ukidanje Bitcoin mjenjačnica bi proces monetizacije mogao biti zaustavljen. Trenutno smo u utrci; Bitcoin raste i postaje sve rašireniji, i doći će do trenutka kada bi potpuno ukidanje mjenjačnica postalo politički neizvedivo - kao i gašenje interneta. Mogućnost takvog ukidanja je još uvijek realna, i valja je uzeti u obzir pri ulaganju u Bitcoin. Kao što je gore objašnjeno, suverene vlade se polako bude i uviđaju prijetnju koju predstavlja neovisna digitalna valuta otporna na cenzuru, za njihovu monetarnu politiku. Otvoreno je pitanje hoće li išta poduzeti da odgovore ovoj prijetnji prije nego Bitcoin postane toliko utvrđen i raširen da politička akcija postane nemoćna i ne-efektivna.
Zamjenjivost
Otvorena i transparentna priroda Bitcoin blockchaina omogućava državama da proglase specifične bitcoine “okaljanima” zbog njihovog korištenja u određenim aktivnostima. Premda Bitcoin, na protokolarnoj razini, ne diskriminira transakcije na ikoji način, “okaljani” bitcoini bi mogli postati bezvrijedni ako bi ih regulacije proglasile ilegalnima i neprihvatljivima za mjenjačnice ili trgovce. Bitcoin bi tada izgubio jedno od kritičnih svojstava monetarnog dobra: zamjenjivost.
Da bi se ovaj problem riješio i umanjio, biti će potrebna poboljšanja na razini protokola kako bi se poboljšala privatnost transakcija. Premda postoji napredak u ovom smjeru, prvi put primjenjen u digitalnim valutama kao što su Monero i Zcash, potrebno je napraviti značajne tehnološke kompromise između efikasnosti i kompleksnosti Bitcoina i njegove privatnosti. Pitanje ostaje otvoreno je li moguće dodati nova svojstva privatnosti na Bitcoin, na način koji neće kompromitirati njegovu korisnost kao novca.
Zaključak
Bitcoin je novonastali novac koji je u procesu transformacije iz sakupljačkog dobra u spremište vrijednosti. Kao neovisno monetarno dobro, moguće je da će u budućnosti postati globalan novac, slično kao zlato za vrijeme 19. stoljeća. Prihvaćanje Bitcoina kao globalnog novca je upravo taj optimističan scenarij za Bitcoin, kojeg je artikulirao Satoshi Nakamoto još 2010. godine u email razmjeni sa Mikeom Hearnom:
"Ako zamisliš da se koristi u nekom dijelu svjetske trgovine, i da će postojati samo 21 milijun bitcoina za cijeli svijet, vrijednost po jedinici će biti znatno veća".
Ovaj scenarij je još snažnije definirao briljantni kriptograf Hal Finney, koji je ujedno primio i prve bitcoine od Nakamotoa, ubrzo nakon najave prvog funkcionalnog Bitcoin softvera:
"Zamislimo da Bitcoin bude uspješan i postane dominantan sustav plaćanja diljem svijeta. U tom slučaju će ukupna vrijednost valute biti jednaka ukupnoj vrijednosti svog bogatstva svijeta. Današnje procjene ukupnog svjetskog bogatska kućanstava koje sam pronašao borave negdje između 100 i 300 trilijuna dolara. Sa 20 milijuna bitcoina, svaki bi onda vrijedio oko 10 milijuna dolara."
Čak i da Bitcoin ne postane u cijelost globalan novac, nego da se samo natječe sa zlatom kao neovisno spremište vrijednosti, i dalje je masivno podcijenjen. Mapiranje tržišne kapitalizacije postojeće količine izrudarenog zlata (oko 8 trilijuna dolara) na maksimalnu dostupnost Bitcoina od 21 milijun, daje vrijednost od otprilike 380,000 dolara po bitcoinu. Kao što smo vidjeli u prethodnom tekstu, svojstva koja omogućavaju monetarnom dobru da bude prikladno spremište vrijednosti, čine Bitcoin superiornijim zlatu u svakom pogledu osim trajanja povijesti. No, kako vrijeme prolazi i Lindy efekt postane jači, dosadašnja povijest će prestati biti prednost zlata. Samim time, nije nerazumno očekivati da će Bitcoin narasti do, a možda i preko, ukupne cijene zlata na tržištvu do 2030. Opaska ovoj tezi je činjenica da veliki postotak vrijednosti zlata dolazi od toga što ga centralne banke čuvaju kao spremište vrijednosti. Da bi Bitcoin došao do te razine, određena količina suverenih država će trebati sudjelovati. Hoće li zapadnjačke demokracije sudjelovati u vlasništvu Bitcoina je nepoznato. Vjerojatnije je, nažalost, da će prve nacije u Bitcoin tržištu biti sitne diktature i kleptokracije.
Ako niti jedna država ne bude sudjelovala u Bitcoin tržištu, optimistična teza i dalje postoji. Kao nevisno spremište vrijednosti u rukama individualnih i institucionalnih ulagača, Bitcoin je i dalje vrlo rano u svojoj “krivulji prihvaćenosti” (adoption curve); tzv. “rana većina” ulaze na tržište sada, dok će ostali ući tek nekoliko godina kasnije. Sa širim sudjelovanjem individualnih i institucionalnih ulagača, cijena po bitcoinu između 100,000 i 200,000 dolara je sasvim moguća.
Posjedovanje bitcoina je jedna od malobrojnih asimetričnih novčanih strategija dostupnih svakome na svijetu. Poput “call” opcija, negativan rizik ulagača je ograničen na 1x, dok potencijalna dobit i dalje iznosi 100x ili više. Bitcoin je prvi istinski globalan balon čija je veličina ograničena samo potražnjom i željom građana svijeta da zaštite svoju ušteđevinu od raznovrsnih ekonomskih malverzacija vlade. Bitcoin je ustao kao feniks iz pepela globalne financijske krize 2008. godine - katastrofe kojoj su prethodile odluke centralnih banaka poput američke Federalne rezerve (Federal Reserve).
Onkraj samo financijske teze za Bitcoin, njegov rast i uspjeh kao neovisno spremište vrijednosti imat će duboke geopolitičke posljedice. Globalna, ne-inflacijska valuta će prisiliti suverene države da promjene svoje primarne mehanizme financiranja od inflacije u izravno oporezivanje; koje je daleko manje politički popularno. Države će se smanjivati proporcionalno političkoj boli koju im nanese oporezivanje kao jedini način financiranja. Nadalje, globalna trgovina vršiti će se na način koji zadovoljava aspiraciju Charlesa de Gaullea, da nijedna nacija ne bi smjela imati privilegiju nad ikojom drugom:
"Smatramo da je potrebno da se uspostavi međunarodna trgovina, kao što je bio slučaj prije velikih nesreća koje su zadesile svijet, na neosporivoj monetarnoj bazi, koja ne nosi na sebi oznaku ijedne države."
Za 50 godina, ta monetarna baza biti će Bitcoin.
-
 @ 7f6db517:a4931eda
2025-05-28 19:01:57
@ 7f6db517:a4931eda
2025-05-28 19:01:57
People forget Bear Stearns failed March 2008 - months of denial followed before the public realized how bad the situation was under the surface.
Similar happening now but much larger scale. They did not fix fundamental issues after 2008 - everything is more fragile.
The Fed preemptively bailed out every bank with their BTFP program and First Republic Bank still failed. The second largest bank failure in history.
There will be more failures. There will be more bailouts. Depositors will be "protected" by socializing losses across everyone.
Our President and mainstream financial pundits are currently pretending the banking crisis is over while most banks remain insolvent. There are going to be many more bank failures as this ponzi system unravels.
Unlike 2008, we have the ability to opt out of these broken and corrupt institutions by using bitcoin. Bitcoin held in self custody is unique in its lack of counterparty risk - you do not have to trust a bank or other centralized entity to hold it for you. Bitcoin is also incredibly difficult to change by design since it is not controlled by an individual, company, or government - the supply of dollars will inevitably be inflated to bailout these failing banks but bitcoin supply will remain unchanged. I do not need to convince you that bitcoin provides value - these next few years will convince millions.
If you found this post helpful support my work with bitcoin.

-
 @ 8bad92c3:ca714aa5
2025-05-28 19:01:49
@ 8bad92c3:ca714aa5
2025-05-28 19:01:49Marty's Bent
via Kevin McKernan

There's been a lot of discussion this week about Casey Means being nominated for Surgeon General of the United States and a broader overarching conversation about the effectiveness of MAHA since the inauguration and how effective it may or may not be moving forward. Many would say that President Trump won re-election due to Robert F. Kennedy Jr. and Nicole Shanahan deciding to reach across the aisle and join the Trump ticket, bringing with them the MAHA Moms, who are very focused on reorienting the healthcare system in the United States with a strong focus on the childhood vaccine schedule.
I'm not going to lie, this is something I'm passionate about as well, particularly after having many conversations over the years with doctors like Kevin McKernan, Dr. Jack Kruse, Dr. Mary Talley Bowden, Dr. Brooke Miller, Dr. Peter McCullough and others about the dangers of the COVID mRNA vaccines. As it stands today, I think this is the biggest elephant in the room in the world of healthcare. If you look at the data, particularly disability claims, life insurance claims, life expectancy, miscarriage rates, fertility issues and rates of turbo cancer around the world since the COVID vaccine was introduced in 2021, it seems pretty clear that there is harm being done to many of the people who have taken them.
The risk-reward ratio of the vaccines seems to be incredibly skewed towards risk over reward and children - who have proven to be least susceptible to COVID - are expected to get three COVID shots in the first year of their life if their parents follow the vaccine schedule. For some reason or another it seems that Robert F. Kennedy Jr. has shied away from this topic after becoming the head of Health and Human Services within the Trump administration. This is after a multi-year campaign during which getting the vaccines removed from the market war a core part of his platform messaging.
I'm still holding out hope that sanity will prevail. The COVID mRNA vaccines will be taken off the market in a serious conversation about the crimes against humanity that unfolded during the COVID years will take place. However, we cannot depend on that outcome. We must build with the assumption in mind that that outcome may never materialize. This leads to identifying where the incentives within the system are misconstrued. One area where I think it's pretty safe to say that the incentives are misaligned is the fact that 95% of doctors work for and answer to a corporation driven by their bottom line. Instead of listening to their patients and truly caring about the outcome of each individual, doctors forced to think about the monetary outcome of the corporation they work for first.
The most pernicious way in which these misaligned incentives emerge is the way in which the hospital systems and physicians are monetarily incentivized by big pharma companies to push the COVID vaccine and other vaccines on their patients. It is important to acknowledge that we cannot be dependent on a system designed in this way to change from within. Instead, we must build a new incentive system and market structure. And obviously, if you're reading this newsletter, you know that I believe that bitcoin will play a pivotal role in realigning incentives across every industry. Healthcare just being one of them.
Bitcoiners have identified the need to become sovereign in our monetary matters, it probably makes sense to become sovereign when it comes to our healthcare as well. This means finding doctors who operate outside the corporate controlled system and are able to offer services that align incentives with the end patient. My family utilizes a combination of CrowdHealth and a private care physician to align incentives. We've even utilized a private care physician who allowed us to pay in Bitcoin for her services for a number of years. I think this is the model. Doctors accepting hard censorship resistant money for the healthcare and advice they provide. Instead of working for a corporation looking to push pharmaceutical products on their patients so they can bolster their bottom line, work directly with patients who will pay in bitcoin, which will appreciate in value over time.
I had a lengthy discussion with Dr. Jack Kruse on the podcast earlier today discussing these topic and more. It will be released on Thursday and I highly recommend you freaks check it out once it is published. Make sure you subscribe so you don't miss it.
How the "Exorbitant Privilege" of the Dollar is Undermining Our Manufacturing Base
In my conversation with Lyn Alden, we explored America's fundamental economic contradiction. As Lyn expertly explained, maintaining the dollar's reserve currency status while attempting to reshore manufacturing presents a near-impossible challenge - what economists call Triffin's Dilemma. The world's appetite for dollars gives Americans tremendous purchasing power but simultaneously hollows out our industrial base. The overvalued dollar makes our exports less competitive, especially for lower-margin manufacturing, while our imports remain artificially strong.
"Having the reserve currency does come with a bunch of benefits, historically called an exorbitant privilege, but then it has certain costs to maintain it." - Lyn Alden
This dilemma forces America to run persistent trade deficits, as this is how dollars flow to the world. For over four decades, these deficits have accumulated, creating massive economic imbalances that can't be quickly reversed. The Trump administration's attempts to address this through tariffs showcase how difficult rebalancing has become. As Lyn warned, even if we successfully pivot toward reshoring manufacturing, we'll face difficult trade-offs: potentially giving up some reserve currency benefits to rebuild our industrial foundation. This isn't just economic theory - it's the restructuring challenge that will define America's economic future.
Check out the full podcast here for more on China's manufacturing dominance, the role of Bitcoin in monetary transitions, and energy production as the foundation for future industrial power.
Headlines of the Day
Coinbase to replace Discover in S&P 500 on May 19 - via X
Mallers promises no rehypothecation in Strike Bitcoin loans - via X
Get our new STACK SATS hat - via tftcmerch.io
Missouri passes HB 594, eliminates Bitcoin capital gains tax - via X
The 2025 Bitcoin Policy Summit is set for June 25th—and it couldn’t come at a more important time. The Bitcoin industry is at a pivotal moment in Washington, with initiatives like the Strategic Bitcoin Reserve gaining rapid traction. Whether you’re a builder, advocate, academic, or policymaker—we want you at the table. Join us in DC to help define the future of freedom, money & innovation in the 21st century.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
The 100+ degree days have returned to Austin, TX. Not mad about it... yet.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 8bad92c3:ca714aa5
2025-05-28 19:01:49
@ 8bad92c3:ca714aa5
2025-05-28 19:01:49Marty's Bent

Last week we covered the bombshell developments in the Samourai Wallet case. For those who didn't read that, last Monday the world was made aware of the fact that the SDNY was explicitly told by FinCEN that the federal regulator did not believe that Samourai Wallet was a money services business six months before arresting the co-founders of Samourai Wallet for conspiracy to launder money and illegally operating a money services business. This was an obvious overstep by the SDNY that many believed would be quickly alleviated, especially considering the fact that the Trump administration via the Department of Justice has made it clear that they do not intend to rule via prosecution.
It seems that this is not the case as the SDNY responded to a letter sent from the defense to dismiss the case by stating that they fully plan to move forward. Stating that they only sought the recommendations of FinCEN employees and did not believe that those employees' comments were indicative of FinCEN's overall views on this particular case. It's a pretty egregious abuse of power by the SDNY. I'm not sure if the particular lawyers and judges within the Southern District of New York are very passionate about preventing the use of self-custody bitcoin and products that enable bitcoiners to transact privately, or if they're simply participating in a broader meta war with the Trump administration - who has made it clear to federal judges across the country that last Fall's election will have consequences, mainly that the Executive Branch will try to effectuate the policies that President Trump campaigned on by any legal means necessary - and Samouari Wallet is simply in the middle of that meta war.
However, one thing is pretty clear to me, this is an egregious overstep of power. The interpretation of that law, as has been laid out and confirmed by FinCEN over the last decade, is pretty clear; you cannot be a money services business if you do not control the funds that people are sending to each other, which is definitely the case with Samourai Wallet. People downloaded Samourai Wallet, spun up their own private-public key pairs and initiated transactions themselves. Samourai never custodied funds or initiated transactions on behalf of their users. This is very cut and dry. Straight to the point. It should be something that anyone with more than two brain cells is able to discern pretty quickly.
It is imperative that anybody in the industry who cares about being able to hold bitcoin in self-custody, to mine bitcoin, and to send bitcoin in a peer-to-peer fashion makes some noise around this case. None of the current administration's attempts to foster innovation around bitcoin in the United States will matter if the wrong precedent is set in this case. If the SDNY is successful in prosecuting Samourai Wallet, it will mean that anybody holding Bitcoin in self-custody, running a bitcoin fold node or mining bitcoin will have to KYC all of their users and counterparts lest they be labeled a money services business that is breaking laws stemming from the Bank Secrecy Act. This will effectively make building a self-custody bitcoin wallet, running a node, or mining bitcoin in tillegal in the United States. The ability to comply with the rules that would be unleashed if this Samourai case goes the wrong way, are such that it will effectively destroy the industry overnight.
It is yet to be seen whether or not the Department of Justice will step in to publicly flog the SDNY and force them to stop pursuing this case. This is the only likely way that the case will go away at this point, so it is very important that bitcoiners who care about being able to self-custody bitcoin, mine bitcoin, or send bitcoin in a peer-to-peer fashion in the United States make it clear to the current administration and any local politicians that this is an issue that you care deeply about. If we are too complacent, there is a chance that the SDNY could completely annihilate the bitcoin industry in America despite of all of the positive momentum we're seeing from all angles at the moment.
Bitcoin Adoption by Power Companies: The Next Frontier
In my recent conversation with Andrew Myers from Satoshi Energy, he shared their ambitious mission to "enable every electric power company to use bitcoin by block 1,050,000" – roughly three years from now. This strategic imperative isn't just about creating new Bitcoin users; it's about sovereignty. Andrew emphasized that getting Bitcoin into the hands of energy companies who value self-sovereignty creates a more balanced future economic landscape. The excitement was palpable as he described how several energy companies are already moving beyond simply selling power to Bitcoin miners and are beginning to invest in mining operations themselves.
"You have global commodity companies being like, 'Oh, this is another commodity – we want to invest in this, we want to own this,'" - Andrew Myers
Perhaps most fascinating was Andrew's revelation about major energy companies in Texas developing Bitcoin collateral products for power contracts – a practical application that could revolutionize how energy transactions are settled. As energy companies continue embracing Bitcoin for both operations and collateral, we're witnessing the early stages of a profound shift in how critical infrastructure interfaces with sound money. The implications for both sectors could be transformative.
Check out the full podcast here for more on remote viewing, Nikola Tesla's predictions, and the convergence of Bitcoin and AI technology. We cover everything from humanoid robots to the energy demands of next-generation computing.
Headlines of the Day
Steak n Shake to Accept Bitcoin at All Locations May 16 - via X
Facebook Plans Crypto Wallets for 3B Users, Bitcoin Impact Looms - via X
Trump Urges Americans to Buy Stocks for Economic Boom - via X
UK Drops Tariffs, U.S. Farmers Set to Reap Major Benefits - via X
Looking for the perfect video to push the smartest person you know from zero to one on bitcoin? Bitcoin, Not Crypto is a three-part master class from Parker Lewis and Dhruv Bansal that cuts through the noise—covering why 21 million was the key technical simplification that made bitcoin possible, why blockchains don’t create decentralization, and why everything else will be built on bitcoin.
Ten31, the largest bitcoin-focused investor, has deployed $150M across 30+ companies through three funds. I am a Managing Partner at Ten31 and am very proud of the work we are doing. Learn more at ten31.vc/invest.
Final thought...
Happy belated Mother's Day to all the moms out there.
Get this newsletter sent to your inbox daily: https://www.tftc.io/bitcoin-brief/
Subscribe to our YouTube channels and follow us on Nostr and X:
@media screen and (max-width: 480px) { .mobile-padding { padding: 10px 0 !important; } .social-container { width: 100% !important; max-width: 260px !important; } .social-icon { padding: 0 !important; } .social-icon img { height: 32px !important; width: 32px !important; } .icon-cell { padding: 0 4px !important; } } .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } .moz-text-html .mj-column-per-33-333333333333336 { width: 25% !important; max-width: 25%; } /* Helps with rendering in various email clients */ body { margin: 0 !important; padding: 0 !important; -webkit-text-size-adjust: 100% !important; -ms-text-size-adjust: 100% !important; } img { -ms-interpolation-mode: bicubic; } /* Prevents Gmail from changing the text color in email threads */ .im { color: inherit !important; }
-
 @ 8bad92c3:ca714aa5
2025-05-28 19:01:46
@ 8bad92c3:ca714aa5
2025-05-28 19:01:46Key Takeaways

In this episode of TFTC, energy economist Anas Alhajji outlines a profound shift in U.S. foreign policy under Trump—away from military intervention and toward transactional diplomacy focused on trade, reconstruction, and curbing Chinese and Russian influence in the Middle East. He highlights Trump’s quiet outreach to Syria as emblematic of the U.S.'s strategic flexibility in legitimizing former adversaries when economically beneficial. Alhajji dismisses BRICS as a fractured bloc incapable of rivaling the U.S.-led order and insists the dollar and petrodollar remain dominant. On energy, he warns that despite favorable fundamentals, prices are suppressed by political confusion, underinvestment, and an aging power grid ill-prepared for the AI and urbanization boom. He also contends that Iran is stalling negotiations to buy time for nuclear advancement and that any deal will be superficial. Finally, Alhajji debunks the myth of Trump being pro-oil, noting his long-standing hostility toward the industry and explaining why a repeat of his past energy boom is implausible given today’s financial and structural constraints.
Best Quotes
- “BRICS is a paper tiger. Everything about BRICS is what China does—and that’s it.”
- “The dollar is here to stay. The petrodollar is here to stay. End of story.”
- “Trump hates the oil industry. He always classified it as an enemy.”
- “Energy projects are 30- to 40-year investments, but politicians think in 4-year cycles. That’s where the disconnect lies.”
- “People think shale will boom again. It won’t. The model changed from ‘drill baby drill’ to ‘control baby control.’”
- “The real story of Trump’s trip wasn’t about politics—it was investment, investment, investment.”
- “Without massive investment in the grid and gas turbines, blackouts will become the norm—even in rich countries like Kuwait.”
- “Iran and China have perfected the game of oil exports. Sanctions are just theater at this point.”
Conclusion
Anas Alhajji’s conclusion challenges conventional narratives, arguing that global power is shifting from military dominance to economic leverage, infrastructure investment, and energy control. He presents a nuanced view of U.S. foreign policy under Trump, emphasizing the strategic importance of trade and reconstruction over regime change. As energy demand soars and geopolitical risks mount, Alhajji warns that the real dangers lie not in foreign adversaries, but in policy confusion, infrastructural lag, and complacency—making this episode a crucial listen for anyone seeking to understand the high-stakes intersection of energy, economics, and diplomacy.
Timestamps
0:00 - Intro
0:48 - Syria and US diplomacy in Middle East
12:50 - Trump in the Middle East
18:12 - Fold & Bitkey
19:48 - Iran - Nuclear program and PR
33:53 - Unchained
34:22 - Crude markets, trade war and US debt
54:28 - Trump's energy stance
1:05:46 - Energy sector challanges
1:14:44 - Policy recommendations
1:21:18 - AI and bitcoinTranscript
(00:00) oil prices market fundamentals support higher price than where we are today. But because of this confusion, everyone is scared of low economic growth and that is a serious problem. The US media ignored part of Trump's speech when he said we are not about nation building and they refer to Afghanistan and Iraq.
(00:15) Look at them. This is a criticism of George W. Bush. We have groups that are talking about the demise of the dollar, the rise of bricks. Bricks is a paper tiger. Everything about bricks is what China does and that's it. The dollar is here to stay and the petro dollar is here to stay.
(00:31) The perception is that the Trump administration is cold but the reality Trump hates the oil [Music] indust. How are you? Very good. Very good. Thank you. As you were telling me, you've been a bit sleepd deprived this week trying to keep up with what's going on. Oh, absolutely. I mean, Trump keeps us on our toes uh all the time.
(01:06) In fact, I plan certain things for the weekend and Trump will say something or he will do something and all of a sudden we get busy again. Uh so clients are not going to wait for you until you finish your work. Basically, they want to know what's going on. So what is going on? What what how profound were the events in the Middle East? These are very uh very profound changes basically because it is very clear that if you look at the last 15 years uh and you look at the growth uh in the Middle East, you look at the growth of Saudi Arabia and uh the
(01:41) role of Turkey for example in the region uh it just just amazing be beyond any uh any thoughts. Uh in fact both of them Turkey and Saudi Arabia are part of the G20. Uh so they have economic influence and they have political influence. And of course the icing on the cake for those who are familiar with the region is to recognize the Syrian government and meet with the Syrian uh president.
(02:11) Uh this is a major a major change in economics and politics uh of the Middle East. Let's touch on that Syria uh topic for a while because I think a lot of people here in the United States were a bit shocked at how sort of welcoming President Trump was towards the new Syrian president considering the fact that uh he was considered an enemy not too long ago here in the United States.
(02:42) What first of all it's a fact of life for those who would like to check the history of politics. There were many people around the world who were classified or they were on the terrorism list and then they became friends of the United States or they were became heroes. I mean Nelson Mandela is one of them. You look at Latin America, there are presidents in Latin America who were uh the enemy of the United States and then they became uh uh cooperative with the United States and the United States recognized their governments and the result of their uh elections. Uh so
(03:15) we've seen this historically uh several uh several times around the world and as they say freedom fighters for some basically are the enemies and the terrorists for for others etc. So uh what we've seen that's why the the visit is very important that the recognition of this government is very important. uh the fact on the ground that uh the president of Syria had the power on the ground uh he had the the the people on the ground and he had the control on the ground and whatever he's been he's been doing since he came into power until now
(03:52) he done all the right steps u and people loved him I mean everyone who went to Syria whether the Syrians who left Syria 40 years ago or uh the visitors who are coming to Syria, they will tell you, "We have never seen the Syrian people as happy as we've seen them today, despite the fact that they they live in misery.
(04:17) They don't have um 8 million people without housing. Uh there is barely any electricity in most of the country. There is no internet. There is barely any food. The uh inflation is rampant, etc. But people are happy because they lived in fear for a very long time. And uh the steps they have taken. For example, the uh ministers in the previous government uh are still there and they are still in the housing of the government.
(04:49) They still have the drivers. They still have the cars from the previous government. They still have it until today. So uh they they were classified as enemies before. But all of a sudden now you have a new government that is uh accepting them. Uh so we we see some changes on the ground that are positive and we'll see how these things will go given that the area around them basically has been unstable for a very long time.
(05:17) how because I don't the the news when I was actually it was surreal for me because my first trip to the Middle East was last December when it was literally f flying over Syria to Abu Dhabi when uh um Assad was getting thrown out and it was pretty surreal to be in that region of the world.
(05:43) How as it pertains to like religious minorities within Syria moving forward is there protractions protections there? Um well let me just uh I want to emphasize one point that is very important. What did the interest of Turkey, Saudi Arabia and the United States in Syria if remember Syria was controlled by Iran and was controlled by the Russians.
(06:09) So in a sense it becomes uh kind of an imperative that taking it away from Iran and Russia and not bringing Iran or Russia back is extremely important. Now the Russians are still there and they have their own base but at least they are not bombing the Syrians and not killing them anymore. But the idea here is taking Syria out of Iran and Russia and probably later on if they kick the Russians out, Russians will not have access to the Mediterranean.
(06:37) Uh so there is an interest uh of all parties basically to take Russia out of Iran and um out of uh Syria regardless the country is uh devastated and it creates massive opportunities for US companies on all levels and uh we've seen a contract uh done recently with you mentioned Abu Dhabi uh uh a contract uh uh with the UA a basically to revamp all the Syrian ports and work on the Syrian ports.
(07:13) Uh so such contracts basically uh when you have a country that has nothing and it's completely devastated the whole infrastructure is devastated. Who is going to build it? If the uh what the Chinese, the Russians, so who who are going to build it? So, uh I think there is a a big room for US companies and others basically to come in and uh literally help on one side and make money on the other.
(07:38) Yeah, I think that that's what I'm trying to discern. What was this convoy from the United States to the Middle East this week signali -
 @ cae03c48:2a7d6671
2025-05-28 19:00:53
@ cae03c48:2a7d6671
2025-05-28 19:00:53Bitcoin Magazine

Cowbolt Announces Their Mission to Make Bitcoin Familiar to EverybodyToday at the Bitcoin Conference in Las Vegas, Cowbolt, an app that lets you split expense payments and settle in bitcoin, will launch their mission: turn peer-to-peer payments into a Bitcoin onramp, starting with family and friends.

Cowbolt will let their clients split costs and settle instantly using Bitcoin and USDT, with no middlemen, no bank friction and with self-custody. They will try to convert everyday transactions into Bitcoin adoption.
“We believe the most powerful onramp to Bitcoin isn’t an exchange — it’s people,” said the co-founder of Cowbolt Daniel Ekström. “That’s why we built Cowbolt. For friends, not hedge funds.”
What Cowbolt will bring to the table:
- Split and settle.
- Keep your keys.
- Fast and trusted.
- Works across borders.
The app is already being used for remittances, group travel, and day-to-day payments. It’s designed to be like a modern fintech app and will be available for iOS and Android.
“Building Airbnb taught me that when design is simple and gets out of the way, people do amazing things,” stated the ex-Creative Director at Airbnb & co-founder Cowbolt Tony Högqvist. “That’s the point here too. Not to store bitcoin in an ETF, but to use it between people. Effortlessly. Among teams, friends, families — every day.”
This post Cowbolt Announces Their Mission to Make Bitcoin Familiar to Everybody first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 26769dac:498e333b
2025-05-28 18:56:30
@ 26769dac:498e333b
2025-05-28 18:56:30I am here too\ In the same space like you
In the same situation I'm in\ It's a matter of positioning
I cannot leave this place I'm in\ It was brought about\ By what's been happening
So please don't look at me\ For what I can or cannot do for you\ But look at what is happening for me\ And what is happening for you
Let's communicate\ Not orchestrate
Because there's something I wish to do\ And there's a place I wish to go to
And I'm sure that there is too\ In your heart a fire\ Known by only you
So let us listen, look and see\ For what's true for you\ And what's true for me
That we may act upon what's here\ In order for us both to take a step\ In the direction we wish to steer
-
 @ cae03c48:2a7d6671
2025-05-28 18:01:12
@ cae03c48:2a7d6671
2025-05-28 18:01:12Bitcoin Magazine

White House Executive Director Bo Hines Declares U.S. The Future Global Crypto SuperpowerIn a session at the Bitcoin 2025 Conference this morning titled “_Making America the Global Bitcoin Superpower“_, Bo Hines, White House Executive Director, Tyler Williams, from the US Treasury Department, and moderator Miles Jennings made one thing clear: the United States is going all-in on Bitcoin—and fast.
JUST IN:
 President Trump's Executive Director said "Bitcoin is the golden standard."
President Trump's Executive Director said "Bitcoin is the golden standard." "We're not gonna sell any Bitcoin that we possible have in the US government, period."
 pic.twitter.com/F6Dv2nUk9b
pic.twitter.com/F6Dv2nUk9b— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
“We are well on our way to becoming the bitcoin superpower of the world,” said Bo Hines. “This is something that is not partisan. This is a revolution in our financial system.”
Moderator Miles Jennings pointed to key regulatory steps currently in motion. “If the bill becomes law (and I hope it does) we will have quite an active role. The connective tissue between the legacy financial system and bitcoin, stablecoins, and everything else will really be paved with stablecoin legislation,” Jennings said.
Hines emphasized that, “Updating the payment rails is necessary and we are well on our way to achieving that.” He also noted that upcoming market structure legislation will define how intermediaries like exchanges and brokers are regulated and how digital assets are classified—either as securities or commodities.
“We want folks to innovate here,” Hines stressed. “We can’t be fearful of them walking into the SEC and getting a Wells notice before they get on the elevator.” He added that U.S. regulators are now encouraging crypto innovators to return: “Our message to folks who have gone offshore is: welcome home_._”
Williams highlighted that any new laws must reflect the unique architecture of decentralized finance. “Traditional markets are based on a principal-agent model,” he explained. “But crypto moves us toward a principal-to-principal structure.”
He noted that after regulatory support for the ETP marketplace, institutional Bitcoin adoption surged—and believes the same would happen again under stablecoin and market structure legislation.
The most bullish comment of the morning came from Hines: “Bitcoin is truly the golden standard… This is an asset that we should be harnessing on behalf of the American people. We want as much as we can possibly get.”
“We are going big on digital assets,” added Tyler. “You will certainly see the United States stepping out as the bitcoin superpower of the world,” Hines concluded.
You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Industry Day below:
https://www.youtube.com/live/3e3KE40r_WM?si=LCZcZeKbxi_iTk62This post White House Executive Director Bo Hines Declares U.S. The Future Global Crypto Superpower first appeared on Bitcoin Magazine and is written by Jenna Montgomery.
-
 @ 6a6be47b:3e74e3e1
2025-05-28 17:37:11
@ 6a6be47b:3e74e3e1
2025-05-28 17:37:11Hi frens! 🌞
How was your day? Mine was pretty great! Not to brag—I just try to see things in a positive light. Even when a day is “meh” or downright awful, I look for at least one good thing in it. Sometimes, let’s be real, there isn’t even one. Some days, weeks, or even months can just be tough. But even that shall pass.
✨ So, let’s try to focus on at least one good thing around us, or within us. Who knows—maybe a little magic can happen…
🎨 Today, I made time for some drawing on Procreate—yaaay! If you caught yesterday’s discussion, you know I drew a butterfly 🦋. Maybe with today’s drawing, you’ll be able to guess my next blog entry 👀
Today’s subject: Cytisus scoparius, better known as “Scotch broom” (or Scots broom).
🔍 I used to mix it up with gorse, but there are some telltale differences:
“Broom is similar to common gorse in size, shape and flower colour, but it lacks the spines and has short, flattened leaves and larger flowers.” — The Wildlife Trusts
⭐️Fun fact: I actually painted a gorse not too long ago for my Beltane post.
🚨 A word of caution though—don’t get too close! Scotch broom is harmful if eaten, so keep an eye out for your pets when you’re out and about, according to rhs.org.uk
🌼 I love spotting these bright yellow blooms by the highway or just outside town. That color is chef’s kiss—it really brightens up any drive!
💐That’s all for today. I’m super excited to hear what you think!
Take care and godspeed, my frens! 🚀✨
https://stacker.news/items/991324
-
 @ c1e9ab3a:9cb56b43
2025-05-27 16:19:06
@ c1e9ab3a:9cb56b43
2025-05-27 16:19:06Star Wars is often viewed as a myth of rebellion, freedom, and resistance to tyranny. The iconography—scrappy rebels, totalitarian stormtroopers, lone smugglers—suggests a deep anti-authoritarian ethos. Yet, beneath the surface, the narrative arc of Star Wars consistently affirms the necessity, even sanctity, of central authority. This blog entry introduces the question: Is Star Wars fundamentally a celebration of statism?
Rebellion as Restoration, Not Revolution
The Rebel Alliance’s mission is not to dismantle centralized power, but to restore the Galactic Republic—a bureaucratic, centrally governed institution. Characters like Mon Mothma and Bail Organa are high-ranking senators, not populist revolutionaries. The goal is to remove the corrupt Empire and reinstall a previous central authority, presumed to be just.
- Rebels are loyalists to a prior state structure.
- Power is not questioned, only who wields it.
Jedi as Centralized Moral Elites
The Jedi, often idealized as protectors of peace, are unelected, extra-legal enforcers of moral and military order. Their authority stems from esoteric metaphysical abilities rather than democratic legitimacy.
- They answer only to their internal Council.
- They are deployed by the Senate, but act independently of civil law.
- Their collapse is depicted as tragic not because they were unaccountable, but because they were betrayed.
This positions them as a theocratic elite, not spiritual anarchists.
Chaos and the Frontier: The Case of the Cantina
The Mos Eisley cantina, often viewed as a symbol of frontier freedom, reveals something darker. It is: - Lawless - Violent - Culturally fragmented
Conflict resolution occurs through murder, not mediation. Obi-Wan slices off a limb; Han shoots first—both without legal consequence. There is no evidence of property rights, dispute resolution, or voluntary order.
This is not libertarian pluralism—it’s moral entropy. The message: without centralized governance, barbarism reigns.
The Mythic Arc: Restoration of the Just State
Every trilogy in the saga returns to a single theme: the fall and redemption of legitimate authority.
- Prequels: Republic collapses into tyranny.
- Originals: Rebels fight to restore legitimate order.
- Sequels: Weak governance leads to resurgence of authoritarianism; heroes must reestablish moral centralism.
The story is not anti-state—it’s anti-bad state. The solution is never decentralization; it’s the return of the right ruler or order.
Conclusion: The Hidden Statism of a Rebel Myth
Star Wars wears the costume of rebellion, but tells the story of centralized salvation. It: - Validates elite moral authority (Jedi) - Romanticizes restoration of fallen governments (Republic) - Portrays decentralized zones as corrupt and savage (outer rim worlds)
It is not an anarchist parable, nor a libertarian fable. It is a statist mythology, clothed in the spectacle of rebellion. Its core message is not that power should be abolished, but that power belongs to the virtuous few.
Question to Consider:
If the Star Wars universe consistently affirms the need for centralized moral and political authority, should we continue to see it as a myth of freedom? Or is it time to recognize it as a narrative of benevolent empire? -
 @ d360efec:14907b5f
2025-05-27 15:46:26
@ d360efec:14907b5f
2025-05-27 15:46:26 -
 @ c1e6505c:02b3157e
2025-05-28 17:36:03
@ c1e6505c:02b3157e
2025-05-28 17:36:03I recently acquired a new lens:
1959 Leica Summaron F2.8 35mm LTM.
1959 Leica Summaron 35mm f2.8 LTM mounted on my Fujifilm Xpro2 with LTM adapter made by Urth.
Technically, it was a trade. I helped a fellow Bitcoiner set up their Sparrow Wallet, Nostr stuff, and troubleshoot a few wallet issues, and in return, they gave me the lens.
It all started at a local Bitcoin meetup I went to about a week ago - my second time attending. I recognized a few faces from last time, but also saw some new ones. These meetups are refreshing - it’s rare to speak a common language about something like Bitcoin or Nostr. Most people still don’t get it. But they will.
Technology moves forward. Networks grow. Old cells die off.
During the meetup, someone noticed I had my Leica M262 with me and struck up a conversation. Said they had some old Leica lenses and gear at home, and wanted to show me.
Bitcoin and photography in one conversation? I’m down.
A day or so later, they sent me a photo of one of the lenses: a vintage Summaron LTM 35mm f/2.8 from 1959. I’d never seen or heard of one before. They asked if I could help them set up Sparrow and a Bitcoin node. In exchange, they’d give me the lens. Sounded like a good deal to me. Helping plebs with their setups feels like a duty anyway. I said, of course.
They invited me over - a pretty trusting move, which I appreciated. They had some great Bitcoin memorabilia: Fred Krueger’s The Big Bitcoin Book (even if the guy’s turned full shitcoiner), and some FTX sunglasses from Bitcoin 2022. Probably future collector’s items, lol.




We headed upstairs to work on setting up Sparrow Wallet on their Windows machine. I verified the software download first (which you should always do), then helped them create a new wallet using their Ledger Flex. They also had an older Ledger Nano X. The Flex setup was easy, but the Nano X gave us trouble. It turns out Ledger allows multiple wallets for the same asset, which can show up differently depending on how they’re configured. In Sparrow, only one wallet showed—none of the others.
I believe it had to do with the derivation path from the Ledger. If anyone knows a fix, let me know.
After a few hours of troubleshooting, I told them I couldn’t really recommend Ledger. The UX is a mess. They’d already heard similar things from other plebs too.
I suggested switching to the Blockstream Jade. It’s a solid Bitcoin-only device from a trustworthy team. That’s what you want in a hardware wallet.
But back to the lens…
Since it’s an LTM (Leica Thread Mount), I couldn’t mount it directly on my M262. Luckily, I remembered I had an Urth adapter that fits my Fujifilm X-Pro2. I don’t use the X-Pro2 much these days—it’s mostly been sidelined by the M262 - but this was the perfect excuse to bring it out again.
To test the lens, I shot everything wide open at f/2.8. Nothing crazy fast, but it’s the best way to see a lens’s character. And this one definitely has character. There’s a subtle softness and a kind of motion blur effect around the edges when wide open. At first, I wasn’t sure how I felt about it, but the more I shot, the more I liked it. It reminds me of Winogrand’s work in Winogrand Color - those messy, shifting edges that make the frame feel alive. It also helps soften the digital-ness of the camera sensor.
The focus throw is short and snappy - much tighter than my Summicron V3 35mm f/2. I really like how fast it is to use. The closest focusing distance is about 3.5 feet, so it’s not ideal for close-ups. And with the Urth adapter on the X-Pro2, the focal length ends up closer to 40mm.
The only thing that threw me off was the infinity lock. When the focus hits infinity, it physically locks - you have to press a small tab to unlock it. I’ve seen others complain about it, so I guess it’s just one of those old lens quirks. I’m getting used to it.
All the photos here were taken around where I live in South Carolina. Some during bike rides to the river for a swim, others while walking through the marshlands.
I try to make work wherever I am. You should be able to.
It’s about the light, the rhythm, the play - and having the motivation to actually go out and shoot.
Lens rating: 7.9/10
I mainly shoot with a Leica M262, and edit in Lightroom + Dehancer
Use “PictureRoom” for 10% off Dehancer Film
If you’ve made it this far, thank you for taking the time to view my work - consider becoming a paid subscriber.
Also, please contact me if you would like to purchase any of my prints.
Follow me on Nostr:
npub1c8n9qhqzm2x3kzjm84kmdcvm96ezmn257r5xxphv3gsnjq4nz4lqelne96
-
 @ 04c915da:3dfbecc9
2025-05-20 15:53:48
@ 04c915da:3dfbecc9
2025-05-20 15:53:48This piece is the first in a series that will focus on things I think are a priority if your focus is similar to mine: building a strong family and safeguarding their future.
Choosing the ideal place to raise a family is one of the most significant decisions you will ever make. For simplicity sake I will break down my thought process into key factors: strong property rights, the ability to grow your own food, access to fresh water, the freedom to own and train with guns, and a dependable community.
A Jurisdiction with Strong Property Rights
Strong property rights are essential and allow you to build on a solid foundation that is less likely to break underneath you. Regions with a history of limited government and clear legal protections for landowners are ideal. Personally I think the US is the single best option globally, but within the US there is a wide difference between which state you choose. Choose carefully and thoughtfully, think long term. Obviously if you are not American this is not a realistic option for you, there are other solid options available especially if your family has mobility. I understand many do not have this capability to easily move, consider that your first priority, making movement and jurisdiction choice possible in the first place.
Abundant Access to Fresh Water
Water is life. I cannot overstate the importance of living somewhere with reliable, clean, and abundant freshwater. Some regions face water scarcity or heavy regulations on usage, so prioritizing a place where water is plentiful and your rights to it are protected is critical. Ideally you should have well access so you are not tied to municipal water supplies. In times of crisis or chaos well water cannot be easily shutoff or disrupted. If you live in an area that is drought prone, you are one drought away from societal chaos. Not enough people appreciate this simple fact.
Grow Your Own Food
A location with fertile soil, a favorable climate, and enough space for a small homestead or at the very least a garden is key. In stable times, a small homestead provides good food and important education for your family. In times of chaos your family being able to grow and raise healthy food provides a level of self sufficiency that many others will lack. Look for areas with minimal restrictions, good weather, and a culture that supports local farming.
Guns
The ability to defend your family is fundamental. A location where you can legally and easily own guns is a must. Look for places with a strong gun culture and a political history of protecting those rights. Owning one or two guns is not enough and without proper training they will be a liability rather than a benefit. Get comfortable and proficient. Never stop improving your skills. If the time comes that you must use a gun to defend your family, the skills must be instinct. Practice. Practice. Practice.
A Strong Community You Can Depend On
No one thrives alone. A ride or die community that rallies together in tough times is invaluable. Seek out a place where people know their neighbors, share similar values, and are quick to lend a hand. Lead by example and become a good neighbor, people will naturally respond in kind. Small towns are ideal, if possible, but living outside of a major city can be a solid balance in terms of work opportunities and family security.
Let me know if you found this helpful. My plan is to break down how I think about these five key subjects in future posts.
-
 @ 9ca447d2:fbf5a36d
2025-05-28 17:01:11
@ 9ca447d2:fbf5a36d
2025-05-28 17:01:11Panama City may be the next Latin American city to adopt bitcoin, after El Salvador.
Panama City Mayor Mayer Mizrachi has got the bitcoin world excited after hinting that the city might have a bitcoin reserve. The speculation started on May 16 when Mizrachi posted a simple but powerful message on X:
Two words. That’s it. What makes it special is that it came after a high-profile meeting with Max Keiser and Stacy Herbert, two key figures behind El Salvador’s bitcoin strategy.
Keiser is an advisor to El Salvador’s President Nayib Bukele and Herbert leads the country’s Bitcoin Office.
El Salvador became the first country to adopt bitcoin as legal tender back in 2021. Since then, it has been building a national bitcoin reserve, currently holding 6,179 BTC worth around $640 million. It’s also using geothermal energy to power bitcoin mining in an eco-friendly way.
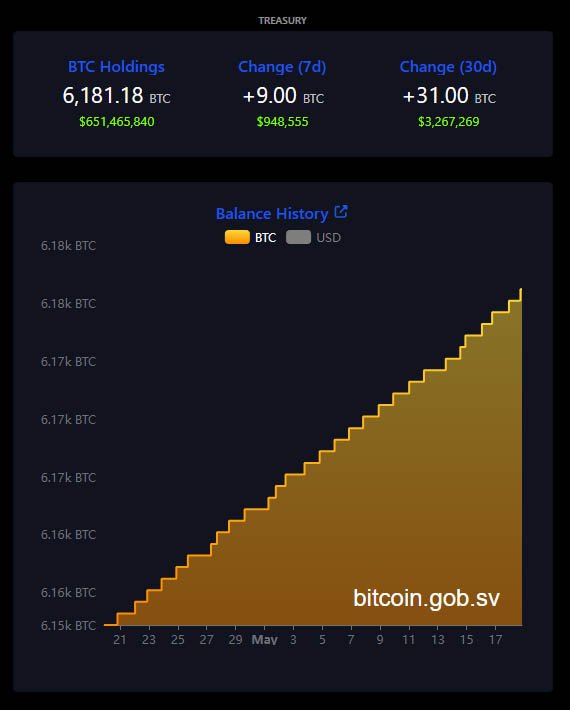
El Salvador’s bitcoin treasury — Bitcoin.gob.sv
Mizrachi’s meeting with Keiser and Herbert was about how Panama could do the same. While the details of the conversation are private, Keiser shared on social media that the two countries will play a big role in the future of Bitcoin.
“Bitcoin is transforming Central America,” Keiser wrote. “El Salvador’s geothermal & Panama’s hydro-electric will power the Bitcoin revolution.”
Max Keiser on X
Panama with its hydroelectric power could be a hub for green bitcoin mining.
Mizrachi has not announced a bitcoin reserve plan nor submitted a proposal to the National Assembly. But his post and public appearances suggest it’s being considered.
He will be speaking at the upcoming Bitcoin 2025 Conference in Las Vegas just days after his social media post. Many expect he will share more about Panama City’s bitcoin plans during his talk.
If Mizrachi pushes for a bitcoin reserve, he will need to work with national lawmakers to pass new legislation. So far, there is no evidence of that.
Even without a bitcoin reserve, Panama City is already going big on digital assets.
In April 2025, the city council approved a measure to allow residents to pay taxes, fees, fines and permits with digital currencies. Supported tokens are bitcoin (BTC), ethereum (ETH), USD Coin (USDC) and Tether (USDT).
To comply with financial laws, the city has partnered with a bank that instantly converts these digital assets into U.S. dollars. According to Mizrachi, this way it’s easier for residents to use digital assets and the city’s financial operations will be transparent and legal.
Another part of the meeting with El Salvador’s advisors was education.
Stacy Herbert confirmed that Panama City will be integrating El Salvador’s financial literacy book, “What is Money?” into their digital library system. The goal is to help students, teachers and the general public understand bitcoin and digital currencies in modern finance.
This is a trend in Latin America where countries are looking for alternatives to traditional banking systems. Inflation, economic instability and the rise of decentralized finance are forcing governments to look into new financial tools.
-
 @ b83a28b7:35919450
2025-05-16 19:23:58
@ b83a28b7:35919450
2025-05-16 19:23:58This article was originally part of the sermon of Plebchain Radio Episode 110 (May 2, 2025) that nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpqtvqc82mv8cezhax5r34n4muc2c4pgjz8kaye2smj032nngg52clq7fgefr and I did with nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7ct4w35zumn0wd68yvfwvdhk6tcqyzx4h2fv3n9r6hrnjtcrjw43t0g0cmmrgvjmg525rc8hexkxc0kd2rhtk62 and nostr:nprofile1qyxhwumn8ghj7mn0wvhxcmmvqyg8wumn8ghj7mn0wd68ytnvv9hxgqpq4wxtsrj7g2jugh70pfkzjln43vgn4p7655pgky9j9w9d75u465pqahkzd0 of the nostr:nprofile1qythwumn8ghj7ct5d3shxtnwdaehgu3wd3skuep0qyt8wumn8ghj7etyv4hzumn0wd68ytnvv9hxgtcqyqwfvwrccp4j2xsuuvkwg0y6a20637t6f4cc5zzjkx030dkztt7t5hydajn
Listen to the full episode here:
<https://fountain.fm/episode/Ln9Ej0zCZ5dEwfo8w2Ho>
Bitcoin has always been a narrative revolution disguised as code. White paper, cypherpunk lore, pizza‑day legends - every block is a paragraph in the world’s most relentless epic. But code alone rarely converts the skeptic; it’s the camp‑fire myth that slips past the prefrontal cortex and shakes hands with the limbic system. People don’t adopt protocols first - they fall in love with protagonists.
Early adopters heard the white‑paper hymn, but most folks need characters first: a pizza‑day dreamer; a mother in a small country, crushed by the cost of remittance; a Warsaw street vendor swapping złoty for sats. When their arcs land, the brain releases a neurochemical OP_RETURN which says, “I belong in this plot.” That’s the sly roundabout orange pill: conviction smuggled inside catharsis.
That’s why, from 22–25 May in Warsaw’s Kinoteka, the Bitcoin Film Fest is loading its reels with rebellion. Each documentary, drama, and animated rabbit‑hole is a stealth wallet, zipping conviction straight into the feels of anyone still clasped within the cold claw of fiat. You come for the plot, you leave checking block heights.
Here's the clip of the sermon from the episode:
nostr:nevent1qvzqqqqqqypzpwp69zm7fewjp0vkp306adnzt7249ytxhz7mq3w5yc629u6er9zsqqsy43fwz8es2wnn65rh0udc05tumdnx5xagvzd88ptncspmesdqhygcrvpf2
-
 @ 04c915da:3dfbecc9
2025-05-16 17:51:54
@ 04c915da:3dfbecc9
2025-05-16 17:51:54In much of the world, it is incredibly difficult to access U.S. dollars. Local currencies are often poorly managed and riddled with corruption. Billions of people demand a more reliable alternative. While the dollar has its own issues of corruption and mismanagement, it is widely regarded as superior to the fiat currencies it competes with globally. As a result, Tether has found massive success providing low cost, low friction access to dollars. Tether claims 400 million total users, is on track to add 200 million more this year, processes 8.1 million transactions daily, and facilitates $29 billion in daily transfers. Furthermore, their estimates suggest nearly 40% of users rely on it as a savings tool rather than just a transactional currency.
Tether’s rise has made the company a financial juggernaut. Last year alone, Tether raked in over $13 billion in profit, with a lean team of less than 100 employees. Their business model is elegantly simple: hold U.S. Treasuries and collect the interest. With over $113 billion in Treasuries, Tether has turned a straightforward concept into a profit machine.
Tether’s success has resulted in many competitors eager to claim a piece of the pie. This has triggered a massive venture capital grift cycle in USD tokens, with countless projects vying to dethrone Tether. Due to Tether’s entrenched network effect, these challengers face an uphill battle with little realistic chance of success. Most educated participants in the space likely recognize this reality but seem content to perpetuate the grift, hoping to cash out by dumping their equity positions on unsuspecting buyers before they realize the reality of the situation.
Historically, Tether’s greatest vulnerability has been U.S. government intervention. For over a decade, the company operated offshore with few allies in the U.S. establishment, making it a major target for regulatory action. That dynamic has shifted recently and Tether has seized the opportunity. By actively courting U.S. government support, Tether has fortified their position. This strategic move will likely cement their status as the dominant USD token for years to come.
While undeniably a great tool for the millions of users that rely on it, Tether is not without flaws. As a centralized, trusted third party, it holds the power to freeze or seize funds at its discretion. Corporate mismanagement or deliberate malpractice could also lead to massive losses at scale. In their goal of mitigating regulatory risk, Tether has deepened ties with law enforcement, mirroring some of the concerns of potential central bank digital currencies. In practice, Tether operates as a corporate CBDC alternative, collaborating with authorities to surveil and seize funds. The company proudly touts partnerships with leading surveillance firms and its own data reveals cooperation in over 1,000 law enforcement cases, with more than $2.5 billion in funds frozen.
The global demand for Tether is undeniable and the company’s profitability reflects its unrivaled success. Tether is owned and operated by bitcoiners and will likely continue to push forward strategic goals that help the movement as a whole. Recent efforts to mitigate the threat of U.S. government enforcement will likely solidify their network effect and stifle meaningful adoption of rival USD tokens or CBDCs. Yet, for all their achievements, Tether is simply a worse form of money than bitcoin. Tether requires trust in a centralized entity, while bitcoin can be saved or spent without permission. Furthermore, Tether is tied to the value of the US Dollar which is designed to lose purchasing power over time, while bitcoin, as a truly scarce asset, is designed to increase in purchasing power with adoption. As people awaken to the risks of Tether’s control, and the benefits bitcoin provides, bitcoin adoption will likely surpass it.
-
 @ 7f6db517:a4931eda
2025-05-28 16:01:56
@ 7f6db517:a4931eda
2025-05-28 16:01:56
@matt_odell don't you even dare not ask about nostr!
— Kukks (Andrew Camilleri) (@MrKukks) May 18, 2021
Nostr first hit my radar spring 2021: created by fellow bitcoiner and friend, fiatjaf, and released to the world as free open source software. I was fortunate to be able to host a conversation with him on Citadel Dispatch in those early days, capturing that moment in history forever. Since then, the protocol has seen explosive viral organic growth as individuals around the world have contributed their time and energy to build out the protocol and the surrounding ecosystem due to the clear need for better communication tools.
nostr is to twitter as bitcoin is to paypal
As an intro to nostr, let us start with a metaphor:
twitter is paypal - a centralized platform plagued by censorship but has the benefit of established network effects
nostr is bitcoin - an open protocol that is censorship resistant and robust but requires an organic adoption phase
Nostr is an open communication protocol that can be used to send messages across a distributed set of relays in a censorship resistant and robust way.
- Anyone can run a relay.
- Anyone can interact with the protocol.
- Relays can choose which messages they want to relay.
- Users are identified by a simple public private key pair that they can generate themselves.Nostr is often compared to twitter since there are nostr clients that emulate twitter functionality and user interface but that is merely one application of the protocol. Nostr is so much more than a mere twitter competitor. Nostr clients and relays can transmit a wide variety of data and clients can choose how to display that information to users. The result is a revolution in communication with implications that are difficult for any of us to truly comprehend.
Similar to bitcoin, nostr is an open and permissionless protocol. No person, company, or government controls it. Anyone can iterate and build on top of nostr without permission. Together, bitcoin and nostr are incredibly complementary freedom tech tools: censorship resistant, permissionless, robust, and interoperable - money and speech protected by code and incentives, not laws.
As censorship throughout the world continues to escalate, freedom tech provides hope for individuals around the world who refuse to accept the status quo. This movement will succeed on the shoulders of those who choose to stand up and contribute. We will build our own path. A brighter path.
My Nostr Public Key: npub1qny3tkh0acurzla8x3zy4nhrjz5zd8l9sy9jys09umwng00manysew95gx
If you found this post helpful support my work with bitcoin.

-
 @ 04c915da:3dfbecc9
2025-05-16 17:12:05
@ 04c915da:3dfbecc9
2025-05-16 17:12:05One of the most common criticisms leveled against nostr is the perceived lack of assurance when it comes to data storage. Critics argue that without a centralized authority guaranteeing that all data is preserved, important information will be lost. They also claim that running a relay will become prohibitively expensive. While there is truth to these concerns, they miss the mark. The genius of nostr lies in its flexibility, resilience, and the way it harnesses human incentives to ensure data availability in practice.
A nostr relay is simply a server that holds cryptographically verifiable signed data and makes it available to others. Relays are simple, flexible, open, and require no permission to run. Critics are right that operating a relay attempting to store all nostr data will be costly. What they miss is that most will not run all encompassing archive relays. Nostr does not rely on massive archive relays. Instead, anyone can run a relay and choose to store whatever subset of data they want. This keeps costs low and operations flexible, making relay operation accessible to all sorts of individuals and entities with varying use cases.
Critics are correct that there is no ironclad guarantee that every piece of data will always be available. Unlike bitcoin where data permanence is baked into the system at a steep cost, nostr does not promise that every random note or meme will be preserved forever. That said, in practice, any data perceived as valuable by someone will likely be stored and distributed by multiple entities. If something matters to someone, they will keep a signed copy.
Nostr is the Streisand Effect in protocol form. The Streisand effect is when an attempt to suppress information backfires, causing it to spread even further. With nostr, anyone can broadcast signed data, anyone can store it, and anyone can distribute it. Try to censor something important? Good luck. The moment it catches attention, it will be stored on relays across the globe, copied, and shared by those who find it worth keeping. Data deemed important will be replicated across servers by individuals acting in their own interest.
Nostr’s distributed nature ensures that the system does not rely on a single point of failure or a corporate overlord. Instead, it leans on the collective will of its users. The result is a network where costs stay manageable, participation is open to all, and valuable verifiable data is stored and distributed forever.
-
 @ cae03c48:2a7d6671
2025-05-28 16:00:58
@ cae03c48:2a7d6671
2025-05-28 16:00:58Bitcoin Magazine

Bitcoin Is Here To Stay, Says Former US Treasurer Rosie RiosAt the 2025 Bitcoin Conference in Las Vegas, the Co-Manager of President Trump’s 2024 Campaign Chris LaCivita, Congressman Brian T. Jack, the Chief Policy Officer of Coinbase Faryar Shirzad and Former US Treasurer Rosie Rios at the Nakamoto stage discussed the 250th birthday of the United States, Bitcoin, freedom, and crypto.
Rosie Rios emphasized that consumer behavior is very hard to change unless there is a shock to the system. She said she is amazed by the momentum of the level of change that has happened during these four months in terms of giving that green light to innovation to actually happen.
“You are gonna hear me say a lot, the train has left the station. Bitcoin is here to stay. Blockchain is here to stay,” said Rios.
JUST IN:
 Former Treasurer of the United States Rosie Rios says, “#Bitcoin is here to stay.”
Former Treasurer of the United States Rosie Rios says, “#Bitcoin is here to stay.” “The train has left the station.”
 pic.twitter.com/M4noy7DPha
pic.twitter.com/M4noy7DPha— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
“It’s about freedom and what crypto represents on a national scale,” said Chris LaCivita. “This country was founded on the entrepreneurial spirit of Americans and we are on the forefront of establishing and formulating the future of currency.”

Jack mentioned that earlier this year, they started to use a congressional tool called the Congressional Review Act that will enable them to repeal any regulation Joe Biden’s administration put on any sector during his last months in office.
“One of the first laws that Donald Trump signed into law was the repeal of a very niche but interesting issue for some folks in the room,” stated Jack. “It was a policy that the CFPB thrust upon the industry in December that really helped them regulate, if you will, or over regulate payment processors. So a lot of the payment processors that process bitcoin, process crypto, they were going to be under these incredible burdens by CFPB.”
“The eyes of the world are watching,” commented Rosie. “We are setting the tone for what happens not just in our history but for the future and for all of us this is the American dream. This is about the values of which our country was founded.”
“For Bitcoin and Blockchain in general whoever creates that dominant digital infrastructure will set the tone for the whole global financial system and it starts here literally at this conference with this leadership with this President moving forward,” stated Rosie Rios closing the panel.
This post Bitcoin Is Here To Stay, Says Former US Treasurer Rosie Rios first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ da8b7de1:c0164aee
2025-05-28 15:42:22
@ da8b7de1:c0164aee
2025-05-28 15:42:22Nemzetközi nukleáris energetikai hírek
Új amerikai kis moduláris reaktor engedélykérelem
A Tennessee Valley Authority (TVA) benyújtotta az Egyesült Államok Nukleáris Szabályozó Hatóságához (NRC) az engedélykérelmet egy GE Vernova Hitachi Nuclear Energy BWRX-300 kis moduláris reaktor (SMR) megépítésére a Clinch River telephelyen. Ez jelentős lépés az új, fejlett nukleáris technológiák bevezetésében az Egyesült Államokban, és jól mutatja, hogy az SMR-ek egyre fontosabb, rugalmas és skálázható tisztaenergia-megoldássá válnak[world-nuclear-news.org].
Amerikai elnöki rendeletek a nukleáris bővítés felgyorsítására
Donald Trump amerikai elnök négy elnöki rendeletet írt alá, amelyek célja a reaktorengedélyezési folyamatok gyorsítása, a hazai urántermelés növelése és a fejlett nukleáris technológiák bevezetésének felgyorsítása. Az új irányelvek ambiciózus célokat tűznek ki, például az amerikai nukleáris kapacitás megnégyszerezését 2050-re, az NRC számára az engedélyezési idő 18 hónapra csökkentését, valamint szövetségi területek kijelölését új nukleáris létesítmények számára. Ezeket a rendeleteket az „amerikai nukleáris reneszánsz” alapjának szánják, különös hangsúlyt fektetve az AI-ipar energiaigényeinek kielégítésére és a hazai gyártás újjáélesztésére[nucnet.org].
Iparági optimizmus és globális befektetési trendek
Az iparági vezetők egészséges és optimista kilátásokról számolnak be a nukleáris energia terén, kiemelve olyan aktív projekteket, mint a TerraPower Wyomingban, az X-energy és a Dow együttműködése, valamint a Westinghouse tevékenysége Lengyelországban. Különösen nagy az érdeklődés a magánbefektetések iránt a magas dúsítású, alacsony dúsítású urán (HALEU) előállítása terén, illetve annak lehetősége iránt, hogy a Világbank elkezdjen nukleáris projekteket finanszírozni, ami szélesebb körű nemzetközi befektetéseket is elindíthat[ans.org].
Nemzetközi fejlemények és ellátási lánc felkészültsége
Számos ország halad előre a nukleáris fejlesztésekkel: - Kína tíz új reaktort hagyott jóvá. - India szabályozó hatósága engedélyezte egy új, négyblokkos telephely létesítését Rádzsasztánban. - Belgium konzultációt indított egy innovatív, ólom-hűtésű kis moduláris reaktor terveiről. - Brazília várhatóan Oroszországgal közösen fejleszt SMR-projektet. - Csehország új nukleáris szerződéseket köt, a külső politikai nyomás ellenére is.
A globális nukleáris ellátási láncot arra ösztönzik, hogy készüljön fel a gyors növekedésre, kiemelve a helyi és nemzetközi együttműködés fontosságát a növekvő igények kielégítésére[world-nuclear-news.org].
Úszó atomerőművek és tengeri innovációk
Az úszó atomerőművek továbbra is az innováció középpontjában állnak: - Oroszország Akademik Lomonosov nevű úszó atomerőműve elérte az első milliárd kilowattóra termelést. - Az Egyesült Királyságban a Core Power egy amerikai központú tengeri nukleáris programot fejleszt, melynek célja úszó reaktorok telepítése amerikai kikötőkben a 2030-as évek közepére. - A dán Seaborg Technologies (új nevén Saltfoss Energy) kompakt olvadt só reaktor technológián dolgozik, amelyet szintén a 2030-as évekre terveznek bevezetni. - A Westinghouse és a Core Power együttműködik egy úszó atomerőmű fejlesztésén az eVinci mikroreaktorral[world-nuclear-news.org].
Érintettek bevonása és társadalmi bizalom
A Nemzetközi Atomenergia-ügynökség (IAEA) kiemeli az érintettek bevonásának fontosságát a nukleáris energia jövője szempontjából. Folyamatban lévő konferenciáján olyan témákat tárgyalnak, mint a nukleáris energia szerepe az ipari dekarbonizációban, a nyilvános meghallgatások értéke a projektek átláthatósága érdekében, valamint a társadalmi bizalom és a szabályozói megfelelés legjobb gyakorlatai, különösen az új technológiák, például az SMR-ek bevezetése során[iaea.org].
Források: - world-nuclear-news.org - nucnet.org - iaea.org - ans.org
-
 @ 08f96856:ffe59a09
2025-05-15 01:17:18
@ 08f96856:ffe59a09
2025-05-15 01:17:18เมื่อพูดถึง Bitcoin Standard หลายคนมักนึกถึงภาพโลกอนาคตที่ทุกคนใช้บิตคอยน์ซื้อกาแฟหรือของใช้ในชีวิตประจำวัน ภาพแบบนั้นดูเหมือนไกลตัวและเป็นไปไม่ได้ในความเป็นจริง หลายคนถึงกับพูดว่า “คงไม่ทันเห็นในช่วงชีวิตนี้หรอก” แต่ในมุมมองของผม Bitcoin Standard อาจไม่ได้เริ่มต้นจากการที่เราจ่ายบิตคอยน์โดยตรงในร้านค้า แต่อาจเริ่มจากบางสิ่งที่เงียบกว่า ลึกกว่า และเกิดขึ้นแล้วในขณะนี้ นั่นคือ การล่มสลายทีละน้อยของระบบเฟียตที่เราใช้กันอยู่
ระบบเงินที่อิงกับอำนาจรัฐกำลังเข้าสู่ช่วงขาลง รัฐบาลทั่วโลกกำลังจมอยู่ในภาระหนี้ระดับประวัติการณ์ แม้แต่ประเทศมหาอำนาจก็เริ่มแสดงสัญญาณของภาวะเสี่ยงผิดนัดชำระหนี้ อัตราเงินเฟ้อกลายเป็นปัญหาเรื้อรังที่ไม่มีท่าทีจะหายไป ธนาคารที่เคยโอนฟรีเริ่มกลับมาคิดค่าธรรมเนียม และประชาชนก็เริ่มรู้สึกถึงการเสื่อมศรัทธาในระบบการเงินดั้งเดิม แม้จะยังพูดกันไม่เต็มเสียงก็ตาม
ในขณะเดียวกัน บิตคอยน์เองก็กำลังพัฒนาแบบเงียบ ๆ เงียบ... แต่ไม่เคยหยุด โดยเฉพาะในระดับ Layer 2 ที่เริ่มแสดงศักยภาพอย่างจริงจัง Lightning Network เป็น Layer 2 ที่เปิดใช้งานมาได้ระยะเวลสหนึ่ง และยังคงมีบทบาทสำคัญที่สุดในระบบนิเวศของบิตคอยน์ มันทำให้การชำระเงินเร็วขึ้น มีต้นทุนต่ำ และไม่ต้องบันทึกทุกธุรกรรมลงบล็อกเชน เครือข่ายนี้กำลังขยายตัวทั้งในแง่ของโหนดและการใช้งานจริงทั่วโลก
ขณะเดียวกัน Layer 2 ทางเลือกอื่นอย่าง Ark Protocol ก็กำลังพัฒนาเพื่อตอบโจทย์ด้านความเป็นส่วนตัวและประสบการณ์ใช้งานที่ง่าย BitVM เปิดแนวทางใหม่ให้บิตคอยน์รองรับ smart contract ได้ในระดับ Turing-complete ซึ่งทำให้เกิดความเป็นไปได้ในกรณีใช้งานอีกมากมาย และเทคโนโลยีที่น่าสนใจอย่าง Taproot Assets, Cashu และ Fedimint ก็ทำให้การออกโทเคนหรือสกุลเงินที่อิงกับบิตคอยน์เป็นจริงได้บนโครงสร้างของบิตคอยน์เอง
เทคโนโลยีเหล่านี้ไม่ใช่การเติบโตแบบปาฏิหาริย์ แต่มันคืบหน้าอย่างต่อเนื่องและมั่นคง และนั่นคือเหตุผลที่มันจะ “อยู่รอด” ได้ในระยะยาว เมื่อฐานของความน่าเชื่อถือไม่ใช่บริษัท รัฐบาล หรือทุน แต่คือสิ่งที่ตรวจสอบได้และเปลี่ยนกฎไม่ได้
แน่นอนว่าบิตคอยน์ต้องแข่งขันกับ stable coin, เงินดิจิทัลของรัฐ และ cryptocurrency อื่น ๆ แต่สิ่งที่ทำให้มันเหนือกว่านั้นไม่ใช่ฟีเจอร์ หากแต่เป็นความทนทาน และความมั่นคงของกฎที่ไม่มีใครเปลี่ยนได้ ไม่มีทีมพัฒนา ไม่มีบริษัท ไม่มีประตูปิด หรือการยึดบัญชี มันยืนอยู่บนคณิตศาสตร์ พลังงาน และเวลา
หลายกรณีใช้งานที่เคยถูกทดลองในโลกคริปโตจะค่อย ๆ เคลื่อนเข้ามาสู่บิตคอยน์ เพราะโครงสร้างของมันแข็งแกร่งกว่า ไม่ต้องการทีมพัฒนาแกนกลาง ไม่ต้องพึ่งกลไกเสี่ยงต่อการผูกขาด และไม่ต้องการ “ความเชื่อใจ” จากใครเลย
Bitcoin Standard ที่ผมพูดถึงจึงไม่ใช่การเปลี่ยนแปลงแบบพลิกหน้ามือเป็นหลังมือ แต่คือการ “เปลี่ยนฐานของระบบ” ทีละชั้น ระบบการเงินใหม่ที่อิงอยู่กับบิตคอยน์กำลังเกิดขึ้นแล้ว มันไม่ใช่โลกที่ทุกคนถือเหรียญบิตคอยน์ แต่มันคือโลกที่คนใช้อาจไม่รู้ตัวด้วยซ้ำว่า “สิ่งที่เขาใช้นั้นอิงอยู่กับบิตคอยน์”
ผู้คนอาจใช้เงินดิจิทัลที่สร้างบน Layer 3 หรือ Layer 4 ผ่านแอป ผ่านแพลตฟอร์ม หรือผ่านสกุลเงินใหม่ที่ดูไม่ต่างจากเดิม แต่เบื้องหลังของระบบจะผูกไว้กับบิตคอยน์
และถ้ามองในเชิงพัฒนาการ บิตคอยน์ก็เหมือนกับอินเทอร์เน็ต ครั้งหนึ่งอินเทอร์เน็ตก็ถูกมองว่าเข้าใจยาก ต้องพิมพ์ http ต้องรู้จัก TCP/IP ต้องตั้ง proxy เอง แต่ปัจจุบันผู้คนใช้งานอินเทอร์เน็ตโดยไม่รู้ว่าเบื้องหลังมีอะไรเลย บิตคอยน์กำลังเดินตามเส้นทางเดียวกัน โปรโตคอลกำลังถอยออกจากสายตา และวันหนึ่งเราจะ “ใช้มัน” โดยไม่ต้องรู้ว่ามันคืออะไร
หากนับจากช่วงเริ่มต้นของอินเทอร์เน็ตในยุค 1990 จนกลายเป็นโครงสร้างหลักของโลกในสองทศวรรษ เส้นเวลาของบิตคอยน์ก็กำลังเดินตามรอยเท้าของอินเทอร์เน็ต และถ้าเราเชื่อว่าวัฏจักรของเทคโนโลยีมีจังหวะของมันเอง เราก็จะรู้ว่า Bitcoin Standard นั้นไม่ใช่เรื่องของอนาคตไกลโพ้น แต่มันเกิดขึ้นแล้ว
-
 @ d360efec:14907b5f
2025-05-13 00:39:56
@ d360efec:14907b5f
2025-05-13 00:39:56🚀📉 #BTC วิเคราะห์ H2! พุ่งชน 105K แล้วเจอแรงขาย... จับตา FVG 100.5K เป็นจุดวัดใจ! 👀📊
จากากรวิเคราะห์ทางเทคนิคสำหรับ #Bitcoin ในกรอบเวลา H2:
สัปดาห์ที่แล้ว #BTC ได้เบรคและพุ่งขึ้นอย่างแข็งแกร่งค่ะ 📈⚡ แต่เมื่อวันจันทร์ที่ผ่านมา ราคาได้ขึ้นไปชนแนวต้านบริเวณ 105,000 ดอลลาร์ แล้วเจอแรงขายย่อตัวลงมาตลอดทั้งวันค่ะ 🧱📉
ตอนนี้ ระดับที่น่าจับตาอย่างยิ่งคือโซน H4 FVG (Fair Value Gap ในกราฟ 4 ชั่วโมง) ที่ 100,500 ดอลลาร์ ค่ะ 🎯 (FVG คือโซนที่ราคาวิ่งผ่านไปเร็วๆ และมักเป็นบริเวณที่ราคามีโอกาสกลับมาทดสอบ/เติมเต็ม)
👇 โซน FVG ที่ 100.5K นี้ ยังคงเป็น Area of Interest ที่น่าสนใจสำหรับมองหาจังหวะ Long เพื่อลุ้นการขึ้นในคลื่นลูกถัดไปค่ะ!
🤔💡 อย่างไรก็ตาม การตัดสินใจเข้า Long หรือเทรดที่บริเวณนี้ ขึ้นอยู่กับว่าราคา แสดงปฏิกิริยาอย่างไรเมื่อมาถึงโซน 100.5K นี้ เพื่อยืนยันสัญญาณสำหรับการเคลื่อนไหวที่จะขึ้นสูงกว่าเดิมค่ะ!
เฝ้าดู Price Action ที่ระดับนี้อย่างใกล้ชิดนะคะ! 📍
BTC #Bitcoin #Crypto #คริปโต #TechnicalAnalysis #Trading #FVG #FairValueGap #PriceAction #MarketAnalysis #ลงทุนคริปโต #วิเคราะห์กราฟ #TradeSetup #ข่าวคริปโต #ตลาดคริปโต


-
 @ d360efec:14907b5f
2025-05-12 04:01:23
@ d360efec:14907b5f
2025-05-12 04:01:23 -
 @ 91117f2b:111207d6
2025-05-28 15:32:35
@ 91117f2b:111207d6
2025-05-28 15:32:35
When Nigerians and Americans collide as nigerians call it (jam). Hilarity ensues: Some humerus observations:
FOOD FIGHTS Americans: pizza(sauce and cheese flying everywhere). Pie: (especially creamed-filled or fruit pies 🥧 tacos: (crunchy shells and soft fillings make for a messy fight). Nigerians 🇳🇬 :you call that a meal? Where is the pounded yam(white any molded, heavy and soft most suitable for mess😁
Americans 🇺🇸 :you mean you eat fufu with your hands? That's adventurous.
DANCE BATTLE NIGERIANS 🇳🇬 : Azonto, poco Lee shaku Shakur. AMERICANS 🇺🇸 : Gangnam style
MUSIC PREFERENCES Nigerians 🇳🇬 : afrobeats all day Americans 🇺🇸 :country road, take me home.
Despite this differences both cultures share a love for food, good music and laughter. Who knows maybe one day, we will see a 🇳🇬 -America 🇺🇸 fusion cruisine Jollof burger and suya tacos? 🍴😂
FESTIVAL AND CELEBRATION
Nigerians 🇳🇬 : colorful cultural festival like oshogbo,eyo, esun. Americans 🇺🇸 :independence day, Halloween Thanksgiving, diverse cultural celebration.
If Nigerians were to try halloween we would be referred to as winch. (witch).
This differences highlight the unique aspects of each culture, showcasing the beauty of diversity and understanding of understanding and appreciation.
COMMUNICATION STYLE Americans: uh hi what's your name? Nigerians: watin be your name?
Let's dive deeper GREETINGS
Americans: hey "what's up?
Nigerians: how is your family, your parents, siblings. Oya greet them for me " Nigerians love to make sure all of the family members have been asked about 🙌
FAMILY GATHERING Americans:"just me, my parents and my cat" Nigerians: "come, and meet my 50 cousins"
RELATIONSHIP In America 🇺🇸 it is normal for teenagers to be in a relationship, you can see a boy or girl alone in a room and the parent won't say shit. IN Nigeria 🇳🇬 as a teenager if you are caught with a girl or boy alone in a room, just pray to survive the night especially if your parents are warriors (they don't mess around).
IN America 🇺🇸 if a teenager tells his parents "mom dad I love him or her and I will leave the house if you don't allow us to be" the parent will allow them. IN Nigeria 🇳🇬, Tell them you are in love with your lover, and if they don't allow you to be together you will leave the house their response will be shocking even to you 😂😂 the child.
Americans 🇺🇸 : they do some activities like kiss or grab whereby a guy or girl choose between to kiss or to grab a stranger in the ass. Nigerians 🇳🇬 : if you are are caught in the street, you can will be referred to as oscroh (prostitute) and will be chased away.
Americans has more liberty but in Nigeria you are always watched by your parent, parents friends or anyone at all.
But the two countries has been a lot of things in common
-
 @ d360efec:14907b5f
2025-05-12 01:34:24
@ d360efec:14907b5f
2025-05-12 01:34:24สวัสดีค่ะเพื่อนๆ นักเทรดที่น่ารักทุกคน! 💕 Lina Engword กลับมาพร้อมกับการวิเคราะห์ BTCUSDT.P แบบเจาะลึกเพื่อเตรียมพร้อมสำหรับเทรดวันนี้ค่ะ! 🚀
วันนี้ 12 พฤษภาคม 2568 เวลา 08.15น. ราคา BTCUSDT.P อยู่ที่ 104,642.8 USDT ค่ะ โดยมี Previous Weekly High (PWH) อยู่ที่ 104,967.8 Previous Weekly Low (PWL) ที่ 93,338 ค่ะ
✨ ภาพรวมตลาดวันนี้ ✨
จากการวิเคราะห์ด้วยเครื่องมือคู่ใจของเรา ทั้ง SMC/ICT (Demand/Supply Zone, Order Block, Liquidity), EMA 50/200, Trend Strength, Money Flow, Chart/Price Pattern, Premium/Discount Zone, Trend line, Fibonacci, Elliott Wave และ Dow Theory ใน Timeframe ตั้งแต่ 15m ไปจนถึง Week! 📊 เราพบว่าภาพใหญ่ของ BTCUSDT.P ยังคงอยู่ในแนวโน้มขาขึ้นที่แข็งแกร่งมากๆ ค่ะ 👍 โดยเฉพาะใน Timeframe Day และ Week ที่สัญญาณทุกอย่างสนับสนุนทิศทางขาขึ้นอย่างชัดเจน Money Flow ยังไหลเข้าอย่างต่อเนื่อง และเราเห็นโครงสร้างตลาดแบบ Dow Theory ที่ยก High ยก Low ขึ้นไปเรื่อยๆ ค่ะ
อย่างไรก็ตาม... ใน Timeframe สั้นๆ อย่าง 15m และ 1H เริ่มเห็นสัญญาณของการชะลอตัวและการพักฐานบ้างแล้วค่ะ 📉 อาจมีการสร้าง Buyside และ Sellside Liquidity รอให้ราคาไปกวาดก่อนที่จะเลือกทางใดทางหนึ่ง ซึ่งเป็นเรื่องปกติของการเดินทางของ Smart Money ค่ะ
⚡ เปรียบเทียบแนวโน้มแต่ละ Timeframe ⚡
🪙 แนวโน้มตรงกัน Timeframe 4H, Day, Week ส่วนใหญ่ชี้ไปทาง "ขาขึ้น" ค่ะ ทุกเครื่องมือสนับสนุนแนวโน้มนี้อย่างแข็งแกร่ง 💪 เป้าหมายต่อไปคือการไปทดสอบ PWH และ High เดิม เพื่อสร้าง All-Time High ใหม่ค่ะ! 🪙 แนวโน้มต่างกัน Timeframe 15m, 1H ยังค่อนข้าง "Sideways" หรือ "Sideways Down เล็กน้อย" ค่ะ มีการบีบตัวของราคาและอาจมีการพักฐานสั้นๆ ซึ่งเป็นโอกาสในการหาจังหวะเข้า Long ที่ราคาดีขึ้นค่ะ
💡 วิธีคิดแบบ Market Slayer 💡
เมื่อแนวโน้มใหญ่เป็นขาขึ้นที่แข็งแกร่ง เราจะเน้นหาจังหวะเข้า Long เป็นหลักค่ะ การย่อตัวลงมาในระยะสั้นคือโอกาสของเราในการเก็บของ! 🛍️ เราจะใช้หลักการ SMC/ICT หาโซน Demand หรือ Order Block ที่ Smart Money อาจจะเข้ามาดันราคาขึ้น และรอสัญญาณ Price Action ยืนยันการกลับตัวค่ะ
สรุปแนวโน้มวันนี้:
🪙 ระยะสั้น: Sideways to Sideways Down (โอกาส 55%) ↔️↘️ 🪙 ระยะกลาง: ขาขึ้น (โอกาส 70%) ↗️ 🪙 ระยะยาว: ขาขึ้น (โอกาส 85%) 🚀 🪙 วันนี้: มีโอกาสย่อตัวเล็กน้อยก่อนจะมีแรงซื้อกลับเข้ามาเพื่อไปทดสอบ PWH (โอกาส Sideways Down เล็กน้อย สลับกับ Sideways Up: 60%) 🎢
🗓️ Daily Trade Setup ประจำวันนี้ 🗓️
นี่คือตัวอย่าง Setup ที่ Lina เตรียมไว้ให้พิจารณาค่ะ (เน้นย้ำว่าเป็นเพียงแนวทาง ไม่ใช่คำแนะนำลงทุนนะคะ)
1️⃣ ตัวอย่างที่ 1: รอรับที่โซน Demand (ปลอดภัย, รอยืนยัน)
🪙 Enter: รอราคาย่อตัวลงมาในโซน Demand Zone หรือ Bullish Order Block ที่น่าสนใจใน TF 1H/4H (ดูจากกราฟประกอบนะคะ) และเกิดสัญญาณ Bullish Price Action ที่ชัดเจน เช่น แท่งเทียนกลืนกิน (Engulfing) หรือ Hammer 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🎯 🪙 SL: ใต้ Low ที่เกิดก่อนสัญญาณกลับตัวเล็กน้อย หรือใต้ Demand Zone ที่เข้า 🛡️ 🪙 RRR: ประมาณ 1:2.5 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เราจะใจเย็นๆ รอให้ราคาลงมาในโซนที่มีโอกาสเจอแรงซื้อเยอะๆ ตามหลัก SMC/ICT แล้วค่อยเข้า เพื่อให้ได้ราคาที่ดีและความเสี่ยงต่ำค่ะ ต้องรอสัญญาณ Price Action ยืนยันก่อนนะคะ ✍️
2️⃣ ตัวอย่างที่ 2: Follow Breakout (สายบู๊, รับความเสี่ยงได้)
🪙 Enter: เข้า Long ทันทีเมื่อราคาสามารถ Breakout เหนือ High ล่าสุดใน TF 15m หรือ 1H พร้อม Volume ที่เพิ่มขึ้นอย่างมีนัยสำคัญ 🔥 🪙 TP: บริเวณ PWH 104,967.8 หรือ Buyside Liquidity ถัดไป 🚀 🪙 SL: ใต้ High ก่อนหน้าที่ถูก Breakout เล็กน้อย 🚧 🪙 RRR: ประมาณ 1:3 ขึ้นไป ✨ 🪙 อธิบาย: Setup นี้เหมาะกับคนที่อยากเข้าไวเมื่อเห็นโมเมนตัมแรงๆ ค่ะ เราจะเข้าเมื่อราคา Breakout แนวต้านระยะสั้นพร้อม Volume เป็นสัญญาณว่าแรงซื้อกำลังมาค่ะ เข้าได้เลยด้วยการตั้ง Limit Order หรือ Market Order เมื่อเห็นการ Breakout ที่ชัดเจนค่ะ 💨
3️⃣ ตัวอย่างที่ 3: พิจารณา Short สั้นๆ ในโซน Premium (สวนเทรนด์หลัก, ความเสี่ยงสูง)
🪙 Enter: หากราคาขึ้นไปในโซน Premium ใน TF 15m หรือ 1H และเกิดสัญญาณ Bearish Price Action ที่ชัดเจน เช่น แท่งเทียน Shooting Star หรือ Bearish Engulfing บริเวณ Supply Zone หรือ Bearish Order Block 🐻 🪙 TP: พิจารณาแนวรับถัดไป หรือ Sellside Liquidity ใน TF เดียวกัน 🎯 🪙 SL: เหนือ High ของสัญญาณ Bearish Price Action เล็กน้อย 💀 🪙 RRR: ประมาณ 1:1.5 ขึ้นไป (เน้นย้ำว่าเป็นการเทรดสวนเทรนด์หลัก ควรใช้ RRR ต่ำและบริหารขนาด Lot อย่างเข้มงวด!) 🪙 อธิบาย: Setup นี้สำหรับคนที่เห็นโอกาสในการทำกำไรจากการย่อตัวระยะสั้นค่ะ เราจะเข้า Short เมื่อเห็นสัญญาณว่าราคาอาจจะมีการพักฐานในโซนที่ถือว่า "แพง" ในกรอบสั้นๆ ค่ะ ต้องตั้ง Stop Loss ใกล้มากๆ และจับตาดูใกล้ชิดนะคะ 🚨
⚠️ Disclaimer: การวิเคราะห์นี้เป็นเพียงความคิดเห็นส่วนตัวของ Lina เท่านั้น ไม่ถือเป็นคำแนะนำในการลงทุนนะคะ การลงทุนมีความเสี่ยง ผู้ลงทุนควรศึกษาข้อมูลเพิ่มเติมและตัดสินใจด้วยความรอบคอบค่ะ 🙏
ขอให้ทุกท่านโชคดีกับการเทรดในวันนี้ค่ะ! มีคำถามอะไรเพิ่มเติม ถามมาได้เลยนะคะ ยินดีเสมอค่ะ! 😊
Bitcoin #BTCUSDT #Crypto #Trading #TechnicalAnalysis #SMC #ICT #MarketSlayer #TradeSetup #คริปโต #เทรดคริปโต #วิเคราะห์กราฟ #LinaEngword 😉



-
 @ 9e9085e9:2056af17
2025-05-28 15:21:58
@ 9e9085e9:2056af17
2025-05-28 15:21:58Part 3: Features That Can Drive User Engagement
Growing the Yakihonne Community – What’s Next?
To attract more users and keep engagement high, Yakihonne could expand with the following features:
- Gamification & Milestones
Badges, activity points, and rewards to motivate interaction.
- Smart Content Discovery
Trending topics, hashtag feeds, and AI-curated (but private) suggestions.
- Community Tools
Verified groups, decentralized moderation, and event features.
- Rich Profile Customization
Bio, themes, badges, and follower highlights.
- Lightning Micro-Tipping
Enable users to send instant tips for posts or engagement.
- Cross-Device Compatibility
Smooth use across mobile, web, and desktop.
- Developer Ecosystem
Open APIs to allow third-party apps and tools to thrive.
Yakihonne #Yakihonne #Yakihonne #Nostr #Nostr #YoungDfx
-
 @ d360efec:14907b5f
2025-05-10 03:57:17
@ d360efec:14907b5f
2025-05-10 03:57:17Disclaimer: * การวิเคราะห์นี้เป็นเพียงแนวทาง ไม่ใช่คำแนะนำในการซื้อขาย * การลงทุนมีความเสี่ยง ผู้ลงทุนควรตัดสินใจด้วยตนเอง
-
 @ 99e7936f:d5d2197c
2025-05-28 14:55:40
@ 99e7936f:d5d2197c
2025-05-28 14:55:40“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Wo bleibt die Rettung?
Wenn man bei einem Notfall auf den Rettungswagen wartet, dann fühlen sich Minuten wie Stunden an. Die Nerven sind bis zum Anschlag gespannt, alle Sinne sind geschärft.
Die Natur hat das so eingerichtet, damit man aufmerksam und gut geschützt ist vor weiteren Verletzungen.
Bei Trauma ist das auch so, nur dass dieser Zustand gefühlt ein halbes Leben andauert. Das klingt brutal, ist aber in etwa so. Da ein menschlicher Körper das nicht gut aushalten kann, sendet er dem Gehirn die Information: “ Bitte mach etwas zur Entlastung, ich kann mit dem Dauerstress nicht gut umgehen. Ich habe ständig das Gefühl, dass etwas Schlimmes passiert und ich mich verteidigen muss.“ Das Gehirn überlegt sich dann eine Lösung, um auch selber endlich wieder Ruhe zu haben. In der Regel wird der traumatische Inhalt verdrängt, vergessen, abgewandelt, abgeschwächt oder als Schwarz-Weiß-Film wieder gegeben, also ohne Gefühl (re)präsentiert. Man kann dann von den traumatischen Erlebnissen erzählen, ohne ein einziges Gefühl zu haben. Das wirkt souverän, als habe man das Trauma verarbeitet, das Gegenteil ist der Fall. Manche Menschen reden sogar über Gefühle, empfinden diese aber nicht. Gefühle werden imitiert oder inszeniert. Wenn man selber fühlen kann, spürt man diesen feinen Unterschied als Zuhörer sofort. Jedenfalls ist alles das Traumafolge bzw. die Lösung, die uns das Gehirn nach Trauma anbietet. Entweder ist der ganze Inhalt samt Emotion weg, oder der Inhalt ist noch da, aber die Emotion dazu fehlt. Es gibt Menschen, die so tief traumatisiert sind, dass sie eine ganz andere Geschichte von sich selbst erzählen, als die, die eigentlich stattgefunden hat. Ich weiß, dass das gruselig klingt. Aber das ist eine Realität. Und es ist vermutlich gut so. Die Natur macht alles, um ein Menschenleben zu retten, und wenn es um den Preis des psychologischen Vergessens ist. Manche Erinnerungen sind offensichtlich nicht mit dem Leben vereinbar, deswegen werden sie für immer abgespalten. Mittlerweile habe ich persönlich viel Respekt vor Menschen, die sich an nichts mehr „erinnern“ können, da ich gelernt habe, dass sie am schlimmsten traumatisiert sind. Diese Einstellung hatte ich nicht immer.
Jedenfalls verhält es sich nach meiner Beobachtung und auch nach meinen eigenen Erfahrungen so, dass man sich ganz oft erst dann vollständig UND in Farbe an traumatische Erlebnisse erinnert, wenn die Zeit dafür reif ist. Man könnte auch sagen, wenn die Seele bereit ist, die verlorenen Seelenanteile wieder zuzulassen. Sie sind nie weg, denn eine unsichtbare Schnur verbindet uns immer mit dem, was passiert ist. Also, wenn dieser Moment, in dem Du Deine Seelenanteile wieder begrüßen darfst, kommt, dann ist das wie ein riesiges Geschenk, auch wenn sich das zu Beginn nicht so anfühlt. Es fühlt sich dann eher so an, wie wenn man auf den Rettungswagen wartet, aber es ist definitiv ein Geschenk, genau wie eine Geburt ein Geschenk ist. Und eine Geburt ist ja auch nicht immer leicht.
Also, je mehr Gefühl beim Erinnern von traumatischen Inhalten spürbar ist, desto besser kann Traumabearbeitung gelingen. (Heiße den Schmerz willkommen, wenn er in Dein Leben kommt.) Ich persönlich hatte lange Wehen, bevor mein Trauma dann schlagartig aktiviert wurde. Das war, bildlich gesprochen, eine Hausgeburt, die ich allein vollbracht habe, weil der Rettungswagen dermaßen Verspätung hatte. Aber das Kind hat sich dennoch gut entwickelt. Ich habe zuvor lange von meinem Trauma „nur“ geredet. Ich habe rationalisiert, wie man in der Fachsprache sagt. Mir war meine frühe Verletzung bewusst, aber ich hatte kein Gefühl zu dem, was ich erlebt hatte. Als das Gefühl da war, verstand ich, dass es sinnvoll war, es solange nicht gefühlt haben zu können, denn es war ein überwältigender Schmerz. Die Natur macht instinktiv ein gutes Timing für die Wiederkehr des Gefühls. Sie sucht sich eine Zeit im Leben aus, wo man einen guten Stand hat, stabil ist, eine Umgebung hat, die einen zumindest für eine Weile halten und auffangen kann. Denn die Natur möchte schließlich, dass man auch die Wiederkehr des Gefühls überlebt.
Genauso schmerzhaft wie der Verlust des Gefühls war, genauso schmerzhaft ist seine Wiederkehr.
Der Schmerz ist quasi der Erste und der Letzte. Er macht das Licht aus, und später macht er das Licht oder den Farbfilm wieder an. Der Schmerz ist viel besser als sein Ruf.
Ich erzähle hier lediglich meine Erfahrungen und Beobachtungen, auch wenn ich allgemein formuliere. Das kann sich bei anderen Menschen auch anders verhalten. Aber ich finde den Erfahrungsaustausch über dieses Thema wichtig, WEIL es unterschiedlich sein kann und jeder auf einem anderen Level von Traumabearbeitung steht. Ein Problem bei Traumabearbeitung ist, dass jeder ein anderes Trauma erlebt hat, dass jeder einen anderen Nährboden hatte, auf den das Trauma fiel, und dass es verschiedene Stadien gibt, bis es dann endlich und hoffentlich soweit ist, dass das Trauma wieder vollständig in die eigene Psyche integriert werden kann und man wieder „ganz“ bzw. „neu und etwas anders“ ist. Und meine Erfahrung ist, dass man auf das Tempo dieses Prozesses leider keinen Einfluss hat, auch wenn es hierzu, wie ich finde, viele falsche Verkehrsdurchsagen gibt. Die Natur ist da verschlossen wie eine Auster, sie lässt sich nicht ins Handwerk pfuschen. Als ich das verstand, hat sich mein Wunsch, Menschen zu helfen, schlagartig verändert. Ich verstand, dass ICH das nicht machen kann, dass die Natur das selber macht. Und das ist eine gute Nachricht, denn die Natur kann das am besten und ist ein super zuverlässiger Partner.
Wir brauchen keinen Rettungswagen. Der Schmerz ist die Rettung.
Das Thema „Trauma“ birgt so viel positiven Erkenntnisgewinn über das Wunder des Lebens.
Aber zurück zum Thema. Wenn man, so wie ich, ein halbes Leben in einem Schwarz-Weiß-Film verbracht hat, dann die Hausgeburt ohne Rettungswagen durchgestanden hat und das Kind irgendwann anfängt, neugierige Fragen zu stellen, dann ist man im Zugzwang. In dieser Situation bin ich heute. Deswegen schreibe ich. Mein neues ICH fragt mich immer öfter, warum ich so viele Dinge tue, die ich eigentlich gar nicht mehr tun will. Kinder fragen einen auch manchmal ganz unverblümt, ob man den Hansi denn lieb hat oder ob man gerne im Büro arbeitet. Wenn man den Hansi nicht lieb hat und nicht gerne im Büro arbeitet, dann muss man schlucken und eine kindgerechte Antwort formulieren. Genauso wenig wie Kinder als kompetenter 20-jähriger auf die Welt kommen, genau so wenig ist man nach geglückter Traumabearbeitung „geheilt“. Es wird nichts schlagartig besser. Das ist auch so eine falsche Verkehrsdurchsage. Man lebt ja noch im alten Leben, was nun Schritt für Schritt verändert werden darf. ABER man ist glückliche Mutter. Mutter sein, ist nicht immer leicht, habe ich mir sagen lassen. Mütter lieben ihre Kinder. Im Idealfall machen sie sich keine Gedanken darüber, was aus ihrem Kind mal werden soll. Sie vertrauen einfach darauf, DASS aus ihrem Kind ein glücklicher Mensch wird und buttern deshalb so viel Liebe in das Kind hinein, wie in den wenigen Jahren, die das Kind ein Kind ist, möglich ist. So ähnlich geht es mir heute auch. Ich bin stolz auf mein neues ICH und lobe es, so oft ich kann. Jede Mutter lobt ihre Butter. Das ist wichtig, denn das Leben bietet ständig Herausforderungen, an denen man bekanntlich wachsen darf. Ich gehe jeden Tag mit meinem „Kind“ spazieren, und wir sehen viel. Wir sehen andere Menschen mit Trauma, wir hören zu, welches Trauma der andere erlebt hat und auf welchem Level er ist. Wir hören das Gefühl heraus, welches mitschwingt. Wir sehen Menschen in ihrem Schwarz-Weiß-Film. Und wir sehen Menschen, die scheinbar mit jeder Situation souverän umgehen können. Am meisten interessieren „uns“ zur Zeit solche Menschen, die ehrlich zugeben, dass sie Wehen haben, dass der Schmerz sich in immer kürzeren Abständen meldet. (Die verlorenen Seelenanteile ziehen an der unsichtbaren Schnur.) Mit diesen Leuten kann ich im Moment am besten. Das hört sich komisch an. Aber ich will damit zum Ausdruck bringen, dass ich mit diesen Menschen mittlerweile am meisten resoniere. Sie sprechen meine Sprache. Sie empfinden Gefühle, und sprechen über diese. Das ist für mich die schönste Sprache.
Wer in diesen Tagen wahrhaftig Schmerz empfindet, und nicht nur als Lippenbekenntnis, sondern echten üblen Schmerz über die enttäuschte Liebe oder über die Verhältnisse in dieser Welt, der ist mir sympathisch, der ist mir nah. Denn ich weiß, dass so ein fühlender Mensch auch bald eine Niederkunft erleben wird, die ihn verändert, die ihn anders auf diese Welt schauen lässt.
Der Schmerz bringt uns die Verwandlung. Der Schmerz bringt die verlorenen Seelenanteile zurück. Der Schmerz ist der Hüter des Lebens. Der Schmerz bringt Dir Deine volle Sensibilität für andere Menschen zurück. Alles, was Du bei Dir nicht fühlen kannst, kannst Du bei anderen nicht fühlen. Der Schmerz beendet das. Er macht das Licht an und gibt dem Film wieder Farbe.
Heiße den Schmerz willkommen, wenn er in Dein Leben kommt. Tu das, nicht etwa weil Du gern leidest, nein tu das, weil Du Dich liebst, weil Du bewusst darauf achten möchtest, was Dir wirklich gut tut und Freude macht. Ein Mensch oder ein Job, der Dir Schmerz bereitet, den gilt es loszulassen. Und wenn Du Schmerz im Gesicht Deines Gegenübers siehst, dann frage Dich ehrlich, was Dein Anteil daran ist, dass der andere leidet. Wir sind nicht für jedes Leid auf dieser Welt verantwortlich, das möchte ich hier auch betonen. Und die Schuld-Nummer zieht bei mir schon lange nicht mehr. Aber ich nehme immer besser wahr, wenn mein eigenes Verhalten nicht angemessen, nicht authentisch ist, von überholten Glaubensmustern geprägt ist. Ich kann das erkennen und korrigieren. Ich kann das heute selber erkennen, weil der Schmerz mich das gelehrt hat, mich geöffnet hat. Der Schmerz lehrt uns ganz viel. Der Schmerz ist der Hüter des Lebens. Er trifft einen hart, macht aber weich.
Heiße den Schmerz willkommen, denn er ist die Rettung.
“Dieser Beitrag wurde mit dem Pareto-Client geschrieben.”
Onboarding bei Nostr: Nostr
Easy onboarding via **Start.**\ \ Das Pareto-Team baut den “Marktplatz der Ideen” und hat dabei schon viel erreicht. \ team@pareto.space \ https://pareto.space \ https://geyser.fund/project/pareto?hero=1c1b8e487090
\ \ Newsletter per Mail (Die Friedenstaube)\ hier abonnieren\ \ In Telegram lesen -> hier unsere Kanäle\ https://t.me/pareto_artikel \ https://t.me/friedenstaube_artikel \ \ Als Feed in einem Feed-Reader \ https://pareto.space/atom/feed.xml \ https://pareto.space/atom/de_feed.xml \ https://pareto.space/atom/en_feed.xml
-
 @ c1e9ab3a:9cb56b43
2025-05-09 23:10:14
@ c1e9ab3a:9cb56b43
2025-05-09 23:10:14I. Historical Foundations of U.S. Monetary Architecture
The early monetary system of the United States was built atop inherited commodity money conventions from Europe’s maritime economies. Silver and gold coins—primarily Spanish pieces of eight, Dutch guilders, and other foreign specie—formed the basis of colonial commerce. These units were already integrated into international trade and piracy networks and functioned with natural compatibility across England, France, Spain, and Denmark. Lacking a centralized mint or formal currency, the U.S. adopted these forms de facto.
As security risks and the practical constraints of physical coinage mounted, banks emerged to warehouse specie and issue redeemable certificates. These certificates evolved into fiduciary media—claims on specie not actually in hand. Banks observed over time that substantial portions of reserves remained unclaimed for years. This enabled fractional reserve banking: issuing more claims than reserves held, so long as redemption demand stayed low. The practice was inherently unstable, prone to panics and bank runs, prompting eventual centralization through the formation of the Federal Reserve in 1913.
Following the Civil War and unstable reinstatements of gold convertibility, the U.S. sought global monetary stability. After World War II, the Bretton Woods system formalized the U.S. dollar as the global reserve currency. The dollar was nominally backed by gold, but most international dollars were held offshore and recycled into U.S. Treasuries. The Nixon Shock of 1971 eliminated the gold peg, converting the dollar into pure fiat. Yet offshore dollar demand remained, sustained by oil trade mandates and the unique role of Treasuries as global reserve assets.
II. The Structure of Fiduciary Media and Treasury Demand
Under this system, foreign trade surpluses with the U.S. generate excess dollars. These surplus dollars are parked in U.S. Treasuries, thereby recycling trade imbalances into U.S. fiscal liquidity. While technically loans to the U.S. government, these purchases act like interest-only transfers—governments receive yield, and the U.S. receives spendable liquidity without principal repayment due in the short term. Debt is perpetually rolled over, rarely extinguished.
This creates an illusion of global subsidy: U.S. deficits are financed via foreign capital inflows that, in practice, function more like financial tribute systems than conventional debt markets. The underlying asset—U.S. Treasury debt—functions as the base reserve asset of the dollar system, replacing gold in post-Bretton Woods monetary logic.
III. Emergence of Tether and the Parastatal Dollar
Tether (USDT), as a private issuer of dollar-denominated tokens, mimics key central bank behaviors while operating outside the regulatory perimeter. It mints tokens allegedly backed 1:1 by U.S. dollars or dollar-denominated securities (mostly Treasuries). These tokens circulate globally, often in jurisdictions with limited banking access, and increasingly serve as synthetic dollar substitutes.
If USDT gains dominance as the preferred medium of exchange—due to technological advantages, speed, programmability, or access—it displaces Federal Reserve Notes (FRNs) not through devaluation, but through functional obsolescence. Gresham’s Law inverts: good money (more liquid, programmable, globally transferable USDT) displaces bad (FRNs) even if both maintain a nominal 1:1 parity.
Over time, this preference translates to a systemic demand shift. Actors increasingly use Tether instead of FRNs, especially in global commerce, digital marketplaces, or decentralized finance. Tether tokens effectively become shadow base money.
IV. Interaction with Commercial Banking and Redemption Mechanics
Under traditional fractional reserve systems, commercial banks issue loans denominated in U.S. dollars, expanding the money supply. When borrowers repay loans, this destroys the created dollars and contracts monetary elasticity. If borrowers repay in USDT instead of FRNs:
- Banks receive a non-Fed liability (USDT).
- USDT is not recognized as reserve-eligible within the Federal Reserve System.
- Banks must either redeem USDT for FRNs, or demand par-value conversion from Tether to settle reserve requirements and balance their books.
This places redemption pressure on Tether and threatens its 1:1 peg under stress. If redemption latency, friction, or cost arises, USDT’s equivalence to FRNs is compromised. Conversely, if banks are permitted or compelled to hold USDT as reserve or regulatory capital, Tether becomes a de facto reserve issuer.
In this scenario, banks may begin demanding loans in USDT, mirroring borrower behavior. For this to occur sustainably, banks must secure Tether liquidity. This creates two options: - Purchase USDT from Tether or on the secondary market, collateralized by existing fiat. - Borrow USDT directly from Tether, using bank-issued debt as collateral.
The latter mirrors Federal Reserve discount window operations. Tether becomes a lender of first resort, providing monetary elasticity to the banking system by creating new tokens against promissory assets—exactly how central banks function.
V. Structural Consequences: Parallel Central Banking
If Tether begins lending to commercial banks, issuing tokens backed by bank notes or collateralized debt obligations: - Tether controls the expansion of broad money through credit issuance. - Its balance sheet mimics a central bank, with Treasuries and bank debt as assets and tokens as liabilities. - It intermediates between sovereign debt and global liquidity demand, replacing the Federal Reserve’s open market operations with its own issuance-redemption cycles.
Simultaneously, if Tether purchases U.S. Treasuries with FRNs received through token issuance, it: - Supplies the Treasury with new liquidity (via bond purchases). - Collects yield on government debt. - Issues a parallel form of U.S. dollars that never require redemption—an interest-only loan to the U.S. government from a non-sovereign entity.
In this context, Tether performs monetary functions of both a central bank and a sovereign wealth fund, without political accountability or regulatory transparency.
VI. Endgame: Institutional Inversion and Fed Redundancy
This paradigm represents an institutional inversion:
- The Federal Reserve becomes a legacy issuer.
- Tether becomes the operational base money provider in both retail and interbank contexts.
- Treasuries remain the foundational reserve asset, but access to them is mediated by a private intermediary.
- The dollar persists, but its issuer changes. The State becomes a fiscal agent of a decentralized financial ecosystem, not its monetary sovereign.
Unless the Federal Reserve reasserts control—either by absorbing Tether, outlawing its instruments, or integrating its tokens into the reserve framework—it risks becoming irrelevant in the daily function of money.
Tether, in this configuration, is no longer a derivative of the dollar—it is the dollar, just one level removed from sovereign control. The future of monetary sovereignty under such a regime is post-national and platform-mediated.
-
 @ 8d34bd24:414be32b
2025-05-28 13:53:46
@ 8d34bd24:414be32b
2025-05-28 13:53:46These days it can feel like the whole world is out of control. Government officials lie and break the law. People are selfish, act emotionally rather than logically, and push ideologies that are illogical and contrary to reality. Society is divided into groups and people are judged, not for their own character, but based on which group they are placed into. There are wars and rumors of wars. There are worries of pandemics and economic disasters. Depression, psychosis, and despair is rampant even among the youngest among us.
Hope For Believers
As much as things seem to be out of control, they are not out of God’s control. This is what the Bible predicted. No matter how bad things get in the world, those who have put their faith in Jesus, do not need to feel despair.
Why are you in despair, O my soul?\ And why have you become disturbed within me?\ Hope in God, for I shall again praise Him\ For the help of His presence.\ O my God, my soul is in despair within me;\ Therefore I remember You from the land of the Jordan\ And the peaks of Hermon, from Mount Mizar. (Psalm 42:5-6)
When we start to feel despair overcoming us, we need to remember what God has done and what He has promised. We need to praise God for what He has done, what He has promised, and what He will bring to completion. Things may be hard now, but God is still in control, and we know how the story will end. God triumphs. Good is rewarded. Evil is destroyed. We can stand on the foundation of hope because we know the ending. Even though things may be out of our personal control, they are always under God’s control.
The more fiercely the storm rages, the more we need to rest in Jesus and the more we need to put our hope in Him.
O love the Lord, all you His godly ones!\ The Lord preserves the faithful\ And fully recompenses the proud doer.\ **Be strong and let your heart take courage,\ All you who hope in the Lord. (Psalm 31:23-24) {emphasis mine}
We can take courage because God always acts for our long term good. Every hardship we experience here on earth will be recognized as a blessing that grew our faith and prepared us for heaven and God’s presence in eternity.
For I know the plans that I have for you,’ declares the Lord, ‘plans for welfare and not for calamity to give you a future and a hope. (Jeremiah 29:11)
Even the worst things that happen to us, due to the sins of others, have a good purpose in our lives. God is working good through us. Our hope isn’t an empty hope. It isn’t a “I really hope this happens.” It is a “I can hope in the guaranteed promises of God.”
For we do not want you to be unaware, brethren, of our affliction which came to us in Asia, that we were burdened excessively, beyond our strength, so that we despaired even of life; indeed, we had the sentence of death within ourselves so that we would not trust in ourselves, but in God who raises the dead; who delivered us from so great a peril of death, and will deliver us, He on whom we have set our hope. And He will yet deliver us, (2 Corinthians 1:8-10) {emphasis mine}
We may experience situations so bad that they seem hopeless, but with God, nothing is hopeless. The God who raises the dead can raise us out of any situation. The God who spoke the universe into existence can deliver us by a word.
The God of the Bible knows all and loves us completely. He looks at our situation through the lens of eternity. What seems best in the moment is not necessarily what is best for our eternity. Many times He delivers us through hardship rather than out of it. We just need to trust Him and put our hope in Him because He is good.
In the same way God, desiring even more to show to the heirs of the promise the unchangeableness of His purpose, interposed with an oath, so that by two unchangeable things in which it is impossible for God to lie, we who have taken refuge would have strong encouragement to take hold of the hope set before us. This hope we have as an anchor of the soul, a hope both sure and steadfast and one which enters within the veil, where Jesus has entered as a forerunner for us, having become a high priest forever according to the order of Melchizedek. (Hebrews 6:17-20) {emphasis mine}
Read that statement again. “This hope we have as an anchor of the soul, a hope both sure and steadfast.” Are you trusting Jesus as the “anchor of your soul?” Is your hope just a wish or is it a “sure and steadfast” hope based on the promises of God that you know will 100% come true?
And not only this, but we also exult in our tribulations, knowing that tribulation brings about perseverance; and perseverance, proven character; and proven character, hope; and hope does not disappoint, because the love of God has been poured out within our hearts through the Holy Spirit who was given to us. (Romans 5:3-5)
Isn’t it ironic that we need hope to persevere through tribulations, but that persevering through tribulation gives us character and hope? Our faith, trust, and hope grow through hardship. When things are easy, we almost always fall back on trusting in our own power rather than relying on God’s power. If we have put our faith in Jesus, there is no situation in which we should lose hope.
Now may the God of hope fill you with all joy and peace in believing, so that you will abound in hope by the power of the Holy Spirit. (Romans 15:13)
Is your joy and peace based on your circumstances or have you learned to have hope in God so you can experience joy and peace even in the trials?
Many people equate joy and happiness, but I think there is a key distinction. Happiness is a pleasant feeling that comes from pleasant circumstances. Joy is a similar feeling to happiness, but it comes from knowing God and His love. It is not tied to circumstances. When we have truly put our hope in God we can still have joy in and despite the most horrific circumstances.
Blessed be the God and Father of our Lord Jesus Christ, who according to His great mercy has caused us to be born again to a living hope through the resurrection of Jesus Christ from the dead, to obtain an inheritance which is imperishable and undefiled and will not fade away, reserved in heaven for you, (1 Peter 1:3-4) {emphasis mine}
Just as Jesus told the Samaritan woman at the well that He provides living water that wells up inside, so that she need never thirst, in the same way believers have a living hope that wells up in times of need. Our hope is in the Creator of the universe and Savior of the world. No problem is too big for Him. No situation is a surprise to Him. No enemy is too powerful for Him. All of our problems are already solved. We just haven’t necessarily seen the solution yet.
My soul, wait in silence for God only,\ For my hope is from Him.\ He only is my rock and my salvation,\ My stronghold; I shall not be shaken.\ On God my salvation and my glory rest;\ The rock of my strength, my refuge is in God. (Psalm 62:5-7)
Despair For Unbelievers
Although believers never have reason to despair, the same is not true for those who have rejected the Savior, Jesus Christ. In these perilous times, they have a real reason for dread and despair.
Moreover, the Lord will scatter you among all peoples, from one end of the earth to the other end of the earth; and there you shall serve other gods, wood and stone, which you or your fathers have not known. Among those nations you shall find no rest, and there will be no resting place for the sole of your foot; but there the Lord will give you a trembling heart, failing of eyes, and despair of soul. So your life shall hang in doubt before you; and you will be in dread night and day, and shall have no assurance of your life. (Deuteronomy 64-66)
Those who reject the atoning sacrifice of Jesus do not get His protection. They do not get His help. They cannot rest in hope in Him.
Of course, the good news is that they can chose to turn their hearts to Him, confess their sins, and trust in Him up until their moment of death. Sadly many will continue to put off faith until it is too late. Many will choose evil over good and license over submission until God gives them over to their lusts.
And just as they did not see fit to acknowledge God any longer, God gave them over to a depraved mind, to do those things which are not proper, being filled with all unrighteousness, wickedness, greed, evil; full of envy, murder, strife, deceit, malice; they are gossips, slanderers, haters of God, insolent, arrogant, boastful, inventors of evil, disobedient to parents, without understanding, untrustworthy, unloving, unmerciful; and although they know the ordinance of God, that those who practice such things are worthy of death, they not only do the same, but also give hearty approval to those who practice them. (Romans 1:28-32)
If any of you have not yet put your trust in Jesus as Savior and Lord, do not wait. Turn away from evil. Submit to the will of Jesus. Trust Him to take away your sins and cover you with His righteousness.
If any of you know people who are in despair, share the gospel with them. Tell them about the greatness of God. Show them the hope that is within you.
Can Believers Despair?
Are there believers who despair? Yes. Should believers ever despair? Definitely not!
But we have this treasure in earthen vessels, so that the surpassing greatness of the power will be of God and not from ourselves; we are afflicted in every way, but not crushed; perplexed, but not despairing; persecuted, but not forsaken; struck down, but not destroyed; always carrying about in the body the dying of Jesus, so that the life of Jesus also may be manifested in our body. (2 Corinthians 4:7-10)
Jesus is always with believers in all situations guiding and protecting us. Those difficult situations that happen are for our good, even when we can’t see how it could be for good.
Job had more reasons to despair than almost anyone, yet he trusted in God. He didn’t know why he was being put through such loss, but his loss increased his faith in God and was a great example to people throughout history. I also love this cry of his heart.
“Oh that my words were written!\ Oh that they were inscribed in a book!” (Job 19:23)
He may or may not have seen even the partial fulfillment of this cry, but His words are written in the book of Job, in the Holy Scriptures read by Jews and Christians throughout the world and throughout history. Job’s first response to loss was an example to us all. After losing all ten children and all of his wealth, this was his response.
Then Job arose and tore his robe and shaved his head, and he fell to the ground and worshiped. (Job 1:20)
Yes, it is true that he had moments of despair where he cursed his birth, but he then returned to God in faith and hope. After a brief rebuke from God, Job submitted to God’s will.
“Behold, I am insignificant; what can I reply to You?\ I lay my hand on my mouth.\ Once I have spoken, and I will not answer;\ Even twice, and I will add nothing more.” (Job 40:4-5)
After his second rebuke from God, he fully submitted.
Then Job answered the Lord and said,
“I know that You can do all things,\ And that no purpose of Yours can be thwarted.\ ‘Who is this that hides counsel without knowledge?’\ *Therefore I have declared that which I did not understand,\ Things too wonderful for me, which I did not know.\ ‘Hear, now, and I will speak;\ I will ask You, and You instruct me*.’\ I have heard of You by the hearing of the ear;\ But now my eye sees You;\ Therefore I retract,\ And I repent in dust and ashes**.” (Job 42:1-6) {emphasis mine}
Job admitted that he did not understand what God was doing, but that God was right; God was good; and God was Lord. Job was able to have hope knowing that God was in control and working for good.
In the case of Job, he was later blessed with more kids, more wealth, and more respect than he had in the beginning. We won’t all see our blessings here on earth, but all believers will receive blessings from their trials.
May our glorious Savior and God fill you with faith and hope in God, His goodness, His power, and His plan. May we all submit to His good will even when we do not understand and even when every part of our earthly body is crying, “stop!” May God fill you with knowledge of Him, faith in Him, and hope in Him.
Trust Jesus
-
 @ e3ba5e1a:5e433365
2025-04-15 11:03:15
@ e3ba5e1a:5e433365
2025-04-15 11:03:15Prelude
I wrote this post differently than any of my others. It started with a discussion with AI on an OPSec-inspired review of separation of powers, and evolved into quite an exciting debate! I asked Grok to write up a summary in my overall writing style, which it got pretty well. I've decided to post it exactly as-is. Ultimately, I think there are two solid ideas driving my stance here:
- Perfect is the enemy of the good
- Failure is the crucible of success
Beyond that, just some hard-core belief in freedom, separation of powers, and operating from self-interest.
Intro
Alright, buckle up. I’ve been chewing on this idea for a while, and it’s time to spit it out. Let’s look at the U.S. government like I’d look at a codebase under a cybersecurity audit—OPSEC style, no fluff. Forget the endless debates about what politicians should do. That’s noise. I want to talk about what they can do, the raw powers baked into the system, and why we should stop pretending those powers are sacred. If there’s a hole, either patch it or exploit it. No half-measures. And yeah, I’m okay if the whole thing crashes a bit—failure’s a feature, not a bug.
The Filibuster: A Security Rule with No Teeth
You ever see a firewall rule that’s more theater than protection? That’s the Senate filibuster. Everyone acts like it’s this untouchable guardian of democracy, but here’s the deal: a simple majority can torch it any day. It’s not a law; it’s a Senate preference, like choosing tabs over spaces. When people call killing it the “nuclear option,” I roll my eyes. Nuclear? It’s a button labeled “press me.” If a party wants it gone, they’ll do it. So why the dance?
I say stop playing games. Get rid of the filibuster. If you’re one of those folks who thinks it’s the only thing saving us from tyranny, fine—push for a constitutional amendment to lock it in. That’s a real patch, not a Post-it note. Until then, it’s just a vulnerability begging to be exploited. Every time a party threatens to nuke it, they’re admitting it’s not essential. So let’s stop pretending and move on.
Supreme Court Packing: Because Nine’s Just a Number
Here’s another fun one: the Supreme Court. Nine justices, right? Sounds official. Except it’s not. The Constitution doesn’t say nine—it’s silent on the number. Congress could pass a law tomorrow to make it 15, 20, or 42 (hitchhiker’s reference, anyone?). Packing the court is always on the table, and both sides know it. It’s like a root exploit just sitting there, waiting for someone to log in.
So why not call the bluff? If you’re in power—say, Trump’s back in the game—say, “I’m packing the court unless we amend the Constitution to fix it at nine.” Force the issue. No more shadowboxing. And honestly? The court’s got way too much power anyway. It’s not supposed to be a super-legislature, but here we are, with justices’ ideologies driving the bus. That’s a bug, not a feature. If the court weren’t such a kingmaker, packing it wouldn’t even matter. Maybe we should be talking about clipping its wings instead of just its size.
The Executive Should Go Full Klingon
Let’s talk presidents. I’m not saying they should wear Klingon armor and start shouting “Qapla’!”—though, let’s be real, that’d be awesome. I’m saying the executive should use every scrap of power the Constitution hands them. Enforce the laws you agree with, sideline the ones you don’t. If Congress doesn’t like it, they’ve got tools: pass new laws, override vetoes, or—here’s the big one—cut the budget. That’s not chaos; that’s the system working as designed.
Right now, the real problem isn’t the president overreaching; it’s the bureaucracy. It’s like a daemon running in the background, eating CPU and ignoring the user. The president’s supposed to be the one steering, but the administrative state’s got its own agenda. Let the executive flex, push the limits, and force Congress to check it. Norms? Pfft. The Constitution’s the spec sheet—stick to it.
Let the System Crash
Here’s where I get a little spicy: I’m totally fine if the government grinds to a halt. Deadlock isn’t a disaster; it’s a feature. If the branches can’t agree, let the president veto, let Congress starve the budget, let enforcement stall. Don’t tell me about “essential services.” Nothing’s so critical it can’t take a breather. Shutdowns force everyone to the table—debate, compromise, or expose who’s dropping the ball. If the public loses trust? Good. They’ll vote out the clowns or live with the circus they elected.
Think of it like a server crash. Sometimes you need a hard reboot to clear the cruft. If voters keep picking the same bad admins, well, the country gets what it deserves. Failure’s the best teacher—way better than limping along on autopilot.
States Are the Real MVPs
If the feds fumble, states step up. Right now, states act like junior devs waiting for the lead engineer to sign off. Why? Federal money. It’s a leash, and it’s tight. Cut that cash, and states will remember they’re autonomous. Some will shine, others will tank—looking at you, California. And I’m okay with that. Let people flee to better-run states. No bailouts, no excuses. States are like competing startups: the good ones thrive, the bad ones pivot or die.
Could it get uneven? Sure. Some states might turn into sci-fi utopias while others look like a post-apocalyptic vidya game. That’s the point—competition sorts it out. Citizens can move, markets adjust, and failure’s a signal to fix your act.
Chaos Isn’t the Enemy
Yeah, this sounds messy. States ignoring federal law, external threats poking at our seams, maybe even a constitutional crisis. I’m not scared. The Supreme Court’s there to referee interstate fights, and Congress sets the rules for state-to-state play. But if it all falls apart? Still cool. States can sort it without a babysitter—it’ll be ugly, but freedom’s worth it. External enemies? They’ll either unify us or break us. If we can’t rally, we don’t deserve the win.
Centralizing power to avoid this is like rewriting your app in a single thread to prevent race conditions—sure, it’s simpler, but you’re begging for a deadlock. Decentralized chaos lets states experiment, lets people escape, lets markets breathe. States competing to cut regulations to attract businesses? That’s a race to the bottom for red tape, but a race to the top for innovation—workers might gripe, but they’ll push back, and the tension’s healthy. Bring it—let the cage match play out. The Constitution’s checks are enough if we stop coddling the system.
Why This Matters
I’m not pitching a utopia. I’m pitching a stress test. The U.S. isn’t a fragile porcelain doll; it’s a rugged piece of hardware built to take some hits. Let it fail a little—filibuster, court, feds, whatever. Patch the holes with amendments if you want, or lean into the grind. Either way, stop fearing the crash. It’s how we debug the republic.
So, what’s your take? Ready to let the system rumble, or got a better way to secure the code? Hit me up—I’m all ears.
-
 @ 812cff5a:5c40aeeb
2025-05-28 12:56:32
@ 812cff5a:5c40aeeb
2025-05-28 12:56:32NIP-01 — الشكل الأساسي للأحداث في نُستر
رقم التعريف (NIP): 01
العنوان: الشكل الأساسي للأحداث
الحالة: نهائي
المؤلف: fiatjaf
التاريخ: 2020-12-10
الملخص
هذا المستند يعرّف الشكل القياسي لأي "حدث" يتم تداوله ضمن شبكة نُستر (Nostr).
الهدف من هذا التنسيق هو ضمان إمكانية معالجة وتفسير الأحداث من قبل جميع العملاء والخوادم بطريقة موحّدة.
هيكل الحدث
كل حدث عبارة عن كائن يحتوي على الحقول التالية:
{ "id": <معرّف فريد>, "pubkey": <مفتاح عام للمرسل>, "created_at": <تاريخ الإنشاء كرقم UNIX timestamp>, "kind": <نوع الحدث>, "tags": [<قائمة من الوسوم>], "content": <المحتوى>, "sig": <التوقيع الرقمي> }
شرح الحقول
- id: سلسلة نصية تمثل SHA-256 لمحتوى الحدث.
- pubkey: المفتاح العام للمستخدم (عادةً 32 بايت بصيغة hex).
- created_at: الطابع الزمني للإنشاء (Unix timestamp).
- kind: رقم يحدد نوع الحدث (مثلاً: منشور، متابعة، إعادة نشر).
- tags: قائمة من الوسوم المرتبطة بالحدث (مثلاً: إشارة إلى مستخدم أو حدث).
- content: المحتوى الأساسي للحدث (نص أو بيانات).
- sig: التوقيع الرقمي الذي يثبت أن المرسل هو صاحب المحتوى.
كيفية توليد معرف الحدث
idيتم توليد المعرّف عبر أخذ تمثيل JSON للحدث (بدون الحقول
idوsig) ثم حساب التجزئة باستخدام SHA-256.
توقيع الحدث
يُوقّع المستخدم الحدث باستخدام مفتاحه الخاص.
هذا التوقيع الرقمي يسمح لأي شخص بالتحقق من صحة الحدث باستخدام المفتاح العام.
أنواع الأحداث (kind)
0: ملف التعريف (الاسم، الصورة، النبذة).1: منشور عام نصي.2: إعادة نشر.3: قائمة المتابَعين.4: رسالة مشفّرة خاصة.- أنواع أخرى يمكن إضافتها لاحقًا.
الوسوم (Tags)
الوسوم عبارة عن قوائم (arrays) داخل الحدث لتوفير معلومات إضافية.
مثال:["e", "<معرّف الحدث>"] ["p", "<مفتاح عام لمستخدم>"]"e"تشير إلى حدث."p"تشير إلى مستخدم.
الخلاصة
NIP-01 هو الأساس الهيكلي لتبادل الأحداث عبر نُستر.
من خلال اتباع هذا الشكل، يمكن لجميع التطبيقات والخوادم العمل معاً بسلاسة، وضمان أمن وموثوقية كل حدث. -
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30
@ 5d4b6c8d:8a1c1ee3
2025-05-28 12:37:30https://rumble.com/embed/v6rp3fh/?pub=4e023h
I know some of our stackers are follicly challenged, so I thought I'd pass along this video.
Have any of you tried topical onion juice for hair regrowth?
I'll eat more onion and rosemary and get more Sun, just to be safe.
https://stacker.news/items/991118
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ 21335073:a244b1ad
2025-03-15 23:00:40
@ 21335073:a244b1ad
2025-03-15 23:00:40I want to see Nostr succeed. If you can think of a way I can help make that happen, I’m open to it. I’d like your suggestions.
My schedule’s shifting soon, and I could volunteer a few hours a week to a Nostr project. I won’t have more total time, but how I use it will change.
Why help? I care about freedom. Nostr’s one of the most powerful freedom tools I’ve seen in my lifetime. If I believe that, I should act on it.
I don’t care about money or sats. I’m not rich, I don’t have extra cash. That doesn’t drive me—freedom does. I’m volunteering, not asking for pay.
I’m not here for clout. I’ve had enough spotlight in my life; it doesn’t move me. If I wanted clout, I’d be on Twitter dropping basic takes. Clout’s easy. Freedom’s hard. I’d rather help anonymously. No speaking at events—small meetups are cool for the vibe, but big conferences? Not my thing. I’ll never hit a huge Bitcoin conference. It’s just not my scene.
That said, I could be convinced to step up if it’d really boost Nostr—as long as it’s legal and gets results.
In this space, I’d watch for social engineering. I watch out for it. I’m not here to make friends, just to help. No shade—you all seem great—but I’ve got a full life and awesome friends irl. I don’t need your crew or to be online cool. Connect anonymously if you want; I’d encourage it.
I’m sick of watching other social media alternatives grow while Nostr kinda stalls. I could trash-talk, but I’d rather do something useful.
Skills? I’m good at spotting social media problems and finding possible solutions. I won’t overhype myself—that’s weird—but if you’re responding, you probably see something in me. Perhaps you see something that I don’t see in myself.
If you need help now or later with Nostr projects, reach out. Nostr only—nothing else. Anonymous contact’s fine. Even just a suggestion on how I can pitch in, no project attached, works too. 💜
Creeps or harassment will get blocked or I’ll nuke my simplex code if it becomes a problem.
https://simplex.chat/contact#/?v=2-4&smp=smp%3A%2F%2FSkIkI6EPd2D63F4xFKfHk7I1UGZVNn6k1QWZ5rcyr6w%3D%40smp9.simplex.im%2FbI99B3KuYduH8jDr9ZwyhcSxm2UuR7j0%23%2F%3Fv%3D1-2%26dh%3DMCowBQYDK2VuAyEAS9C-zPzqW41PKySfPCEizcXb1QCus6AyDkTTjfyMIRM%253D%26srv%3Djssqzccmrcws6bhmn77vgmhfjmhwlyr3u7puw4erkyoosywgl67slqqd.onion
-
 @ a3c6f928:d45494fb
2025-05-28 12:21:32
@ a3c6f928:d45494fb
2025-05-28 12:21:32In a world that constantly demands our attention, where external achievements are often mistaken for fulfillment, there is a quieter, more powerful path to freedom—the journey within. True freedom is not merely the absence of constraints but the presence of inner peace, purpose, and self-mastery.
What Is Self-Mastery?
Self-mastery is the ability to govern your thoughts, emotions, and actions in alignment with your values and goals. It is about becoming the author of your own story rather than being swept away by the noise and chaos of the external world. With self-mastery comes clarity, direction, and the freedom to live authentically.
The Pillars of Inner Freedom
-
Self-Awareness: Freedom begins with knowing who you are. Understanding your strengths, triggers, and motivations lays the foundation for personal growth.
-
Discipline: Discipline is not restriction—it is the structure that supports your vision. It turns intention into reality.
-
Emotional Intelligence: Learning to manage emotions, rather than being ruled by them, grants the power to respond rather than react.
-
Purpose: A sense of purpose provides direction. When you know what matters most, distractions lose their power.
Why Self-Mastery Matters
Without self-mastery, external freedom can feel hollow. You might have opportunities, resources, and rights, yet still feel trapped—by fear, self-doubt, or the need for validation. Mastering yourself unlocks the kind of freedom that no one can take away: the freedom to be at peace with who you are.
How to Begin the Journey
-
Reflect Daily: Spend time each day in silence or journaling to deepen your awareness.
-
Set Intentions: Start each day with a clear intention to guide your focus.
-
Challenge Yourself: Growth lies just beyond your comfort zone. Embrace discomfort as part of the process.
-
Seek Stillness: Create moments of stillness to listen to your inner voice.
“He who conquers himself is the mightiest warrior.” — Confucius
True freedom starts from within. Master yourself, and you master your life.
-
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ cae03c48:2a7d6671
2025-05-28 12:00:38
@ cae03c48:2a7d6671
2025-05-28 12:00:38Bitcoin Magazine

Bitcoin Enters a New Era: Industry Leaders Predict Trillions in Institutional InflowsAt the 2025 Bitcoin Conference in Las Vegas, the Founder and CEO of Kelly Intelligence Kevin Kelly, the Chief Executive Officer of Bitwise Asset Management Hunter Horsley, the CEO of BitGo Mike Belshe and the Advisor of WBTC Justin Sun talked about the future of financial products in the globe.
Hunter Horsley started the panel by saying that we are entering a new chapter in 2025 with the change in the regulatory circumstances.
“In the US wealth managers manage between 30 and 60 trillion dollars,” said Horsley. “If wealth managers wind up allocating 1% to the space on behalf of their clients, helping their clients access the opportunities here that are hundreds and billions of dollars.”
JUST IN:
 $12 billion Bitwise CEO Hunter Horsley says if wealth managers allocate 1% to #Bitcoin, “that's hundreds of billions of dollars.”
$12 billion Bitwise CEO Hunter Horsley says if wealth managers allocate 1% to #Bitcoin, “that's hundreds of billions of dollars.”  pic.twitter.com/4OhoBjwDYR
pic.twitter.com/4OhoBjwDYR— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
Justin Sun emphasized the importance of integrating Bitcoin into decentralized finance (DeFi) platforms:
“Raw Bitcoin is a way to get your Bitcoin into a smart contract platform,” said Sun. “You can use your Bitcoin as collateral you borrow like stablecoin, you borrow other major crypto currencies tokens and also of course generate yield on the Bitcoin you are holding because Bitcoin is a proof of network.”
“Any transaction you can see in the blockchain and all the reserve addresses is available on the Blockchain. It’s safe and transparent and at the same time is smart,” stated Sun.
Mike Belshe elaborated on the foundational elements that make a stablecoin successful, particularly when Bitcoin is used in that context.
“What makes a good stablecoin whether you are talking about dollars or Bitcoin, it’s the liquidity that you have on the market around the world,” stated Belshe.
Horsley continued by addressing that we’ll see more companies adopting this and hundreds of thousands of Bitcoin being put onto more balance sheets.
“Corporations are buying Bitcoin,” commented Horsley. “It’s an extraordinary theme of this year. As of the first quarter of this year, 79 publicly traded companies had put Bitcoin on their balance sheet. Over 600k Bitcoin and there is only 21 million Bitcoin. It’s a lot of Bitcoin”
Justin Sun closed the panel by stating, “the progress we are making here in the United States really matters because as we all further encourage people around the world to get into the Bitcoin industry.”
“Once Bitcoin passes this kind of stage and gets institution adoption in the United States will accelerate that option globally,” said Sun.
This post Bitcoin Enters a New Era: Industry Leaders Predict Trillions in Institutional Inflows first appeared on Bitcoin Magazine and is written by Oscar Zarraga Perez.
-
 @ 4857600b:30b502f4
2025-03-10 12:09:35
@ 4857600b:30b502f4
2025-03-10 12:09:35At this point, we should be arresting, not firing, any FBI employee who delays, destroys, or withholds information on the Epstein case. There is ZERO explanation I will accept for redacting anything for “national security” reasons. A lot of Trump supporters are losing patience with Pam Bondi. I will give her the benefit of the doubt for now since the corruption within the whole security/intelligence apparatus of our country runs deep. However, let’s not forget that probably Trump’s biggest mistakes in his first term involved picking weak and easily corruptible (or blackmailable) officials. It seemed every month a formerly-loyal person did a complete 180 degree turn and did everything they could to screw him over, regardless of the betrayal’s effect on the country or whatever principles that person claimed to have. I think he’s fixed his screening process, but since we’re talking about the FBI, we know they have the power to dig up any dirt or blackmail material available, or just make it up. In the Epstein case, it’s probably better to go after Bondi than give up a treasure trove of blackmail material against the long list of members on his client list.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ 10846a37:73b5f923
2025-05-28 11:41:30
@ 10846a37:73b5f923
2025-05-28 11:41:30A 80win tem se destacado como uma das plataformas de entretenimento online mais completas do momento. Com um ambiente moderno, intuitivo e pensado especialmente para o público brasileiro, a plataforma oferece uma experiência única que une tecnologia, segurança e uma vasta seleção de jogos. Seja você um iniciante curioso ou um jogador experiente, a 80win proporciona diversão para todos os perfis.
Interface Amigável e Acesso Rápido Ao acessar a 80win, o que chama a atenção de imediato é o design leve e fácil de navegar. A plataforma foi projetada para que os usuários encontrem tudo o que precisam com poucos cliques. Desde o cadastro, que pode ser feito em minutos, até a escolha dos jogos, tudo é prático e acessível.
Além disso, a 80win está otimizada para dispositivos móveis, o que significa que você pode jogar onde estiver, sem comprometer a qualidade gráfica ou o desempenho. O site funciona perfeitamente em smartphones, tablets e computadores, garantindo flexibilidade total para o usuário.
Diversidade de Jogos Para Todos os Gostos A seleção de jogos da 80winé um dos seus grandes diferenciais. A plataforma reúne uma enorme variedade de opções, desde jogos de cartas clássicos como pôquer e bacará, até roletas virtuais e jogos temáticos com gráficos impressionantes e trilhas sonoras envolventes.
Para os fãs de jogos com elementos de sorte, a plataforma oferece slots (caça-níqueis) com temas variados, bônus atrativos e efeitos visuais de última geração. Esses jogos são atualizados com frequência, garantindo que sempre haja novidades para explorar.
Já quem prefere jogos que exigem mais estratégia e raciocínio rápido também encontra ótimas opções. Os modos multiplayer permitem interações com outros jogadores em tempo real, trazendo uma camada extra de emoção e competitividade.
Segurança e Suporte de Qualidade A 80win preza pela segurança dos seus usuários. A plataforma utiliza tecnologia de criptografia avançada para proteger todos os dados e transações, garantindo que suas informações pessoais e financeiras estejam sempre seguras.
Além disso, o suporte ao cliente é outro ponto forte. A equipe da 80win está disponível todos os dias para tirar dúvidas, resolver problemas técnicos e auxiliar em qualquer situação. O atendimento pode ser feito via chat ao vivo ou e-mail, com respostas rápidas e eficazes.
Experiência do Jogador: Diversão com Responsabilidade Na 80win, a experiência do jogador vai além dos jogos em si. A plataforma oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que recompensam os usuários mais ativos. Tudo isso contribui para uma jornada mais dinâmica e envolvente.
Outro ponto importante é o incentivo ao jogo responsável. A 80win disponibiliza ferramentas para controle de tempo e gastos, permitindo que cada jogador tenha controle sobre sua própria experiência e jogue de forma consciente.
Conclusão A 80win é muito mais do que uma simples plataforma de jogos online. É um ambiente completo, seguro e divertido, onde a variedade de opções e a qualidade dos serviços colocam o jogador em primeiro lugar. Se você está em busca de uma experiência empolgante, interativa e acessível, a 80win é a escolha certa para explorar o mundo do entretenimento digital com total confiança.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ 10846a37:73b5f923
2025-05-28 11:41:06
@ 10846a37:73b5f923
2025-05-28 11:41:06O cenário de entretenimento online no Brasil está cada vez mais aquecido, e uma plataforma que tem chamado a atenção dos jogadores é a 888f. Com uma proposta moderna, segura e repleta de funcionalidades, o site oferece uma experiência diferenciada para quem busca diversão e oportunidade de ganhos em um ambiente digital bem estruturado.
Introdução à Plataforma 888f A 888f se destaca como uma plataforma inovadora voltada para o público brasileiro, oferecendo uma navegação simples e intuitiva, com suporte completo em português e atendimento dedicado. Desde o primeiro acesso, os usuários são recebidos com um layout limpo, organizado e responsivo, que se adapta perfeitamente a qualquer dispositivo – seja computador, tablet ou smartphone.
Um dos principais atrativos da 888fé a facilidade de cadastro e uso. Em poucos minutos, é possível criar uma conta e começar a explorar todas as opções de jogos disponíveis. A plataforma também oferece diversas formas de pagamento, incluindo métodos populares como Pix, transferências bancárias e carteiras digitais, sempre com foco na agilidade e segurança das transações.
Jogos Variados para Todos os Estilos A variedade de jogos é um dos grandes diferenciais da 888f. O site reúne títulos dos principais fornecedores do mercado, garantindo gráficos de alta qualidade, mecânicas envolventes e jogabilidade fluida. Os usuários encontram desde os clássicos jogos de cartas, como poker e blackjack, até opções modernas de roletas, slots interativos e outros formatos com recursos inovadores.
Os famosos "jogos ao vivo" também estão presentes, oferecendo uma imersão ainda maior para quem busca adrenalina e interação em tempo real. Nesses jogos, o jogador participa de partidas com apresentadores reais, transmitidas por vídeo em alta definição, criando uma sensação de estar dentro de uma sala física sem sair de casa.
Além disso, há jogos de aposta rápida e instantânea, que são perfeitos para quem deseja jogar de maneira dinâmica e divertida, com resultados em poucos segundos. Cada jogo é desenvolvido com tecnologia de ponta, garantindo aleatoriedade justa e transparência nas rodadas.
Experiência do Jogador em Primeiro Lugar A 888f prioriza a satisfação e segurança dos seus usuários. Por isso, investe constantemente em tecnologia de proteção de dados e oferece um ambiente de jogo responsável, com ferramentas de controle de tempo e gastos para promover uma experiência equilibrada e consciente.
O atendimento ao cliente também é um destaque. A equipe de suporte está disponível 24 horas por dia, todos os dias da semana, pronta para ajudar com qualquer dúvida ou problema. Os canais de contato incluem chat ao vivo, e-mail e atendimento via WhatsApp, sempre com resposta rápida e cordial.
Outro ponto importante é o sistema de recompensas. A 888f oferece promoções regulares, bônus de boas-vindas e programas de fidelidade que beneficiam os jogadores mais ativos. Tudo isso contribui para uma jornada envolvente e repleta de vantagens.
Conclusão A 888f surge como uma excelente opção para quem procura entretenimento digital de qualidade no Brasil. Com uma plataforma segura, jogos diversos e suporte de excelência, ela conquista cada vez mais espaço entre os jogadores que buscam diversão com responsabilidade e conforto. Seja você um iniciante ou um usuário experiente, a 888f oferece tudo o que é necessário para uma experiência online completa e gratificante.
-
 @ 6389be64:ef439d32
2025-02-27 21:32:12
@ 6389be64:ef439d32
2025-02-27 21:32:12GA, plebs. The latest episode of Bitcoin And is out, and, as always, the chicanery is running rampant. Let’s break down the biggest topics I covered, and if you want the full, unfiltered rant, make sure to listen to the episode linked below.
House Democrats’ MEME Act: A Bad Joke?
House Democrats are proposing a bill to ban presidential meme coins, clearly aimed at Trump’s and Melania’s ill-advised token launches. While grifters launching meme coins is bad, this bill is just as ridiculous. If this legislation moves forward, expect a retaliatory strike exposing how politicians like Pelosi and Warren mysteriously amassed their fortunes. Will it pass? Doubtful. But it’s another sign of the government’s obsession with regulating everything except itself.
Senate Banking’s First Digital Asset Hearing: The Real Target Is You
Cynthia Lummis chaired the first digital asset hearing, and—surprise!—it was all about control. The discussion centered on stablecoins, AML, and KYC regulations, with witnesses suggesting Orwellian measures like freezing stablecoin transactions unless pre-approved by authorities. What was barely mentioned? Bitcoin. They want full oversight of stablecoins, which is really about controlling financial freedom. Expect more nonsense targeting self-custody wallets under the guise of stopping “bad actors.”
Bank of America and PayPal Want In on Stablecoins
Bank of America’s CEO openly stated they’ll launch a stablecoin as soon as regulation allows. Meanwhile, PayPal’s CEO paid for a hat using Bitcoin—not their own stablecoin, Pi USD. Why wouldn’t he use his own product? Maybe he knows stablecoins aren’t what they’re hyped up to be. Either way, the legacy financial system is gearing up to flood the market with stablecoins, not because they love crypto, but because it’s a tool to extend U.S. dollar dominance.
MetaPlanet Buys the Dip
Japan’s MetaPlanet issued $13.4M in bonds to buy more Bitcoin, proving once again that institutions see the writing on the wall. Unlike U.S. regulators who obsess over stablecoins, some companies are actually stacking sats.
UK Expands Crypto Seizure Powers
Across the pond, the UK government is pushing legislation to make it easier to seize and destroy crypto linked to criminal activity. While they frame it as going after the bad guys, it’s another move toward centralized control and financial surveillance.
Bitcoin Tools & Tech: Arc, SatoChip, and Nunchuk
Some bullish Bitcoin developments: ARC v0.5 is making Bitcoin’s second layer more efficient, SatoChip now supports Taproot and Nostr, and Nunchuk launched a group wallet with chat, making multisig collaboration easier.
The Bottom Line
The state is coming for financial privacy and control, and stablecoins are their weapon of choice. Bitcoiners need to stay focused, keep their coins in self-custody, and build out parallel systems. Expect more regulatory attacks, but don’t let them distract you—just keep stacking and transacting in ways they can’t control.
🎧 Listen to the full episode here: https://fountain.fm/episode/PYITCo18AJnsEkKLz2Ks
💰 Support the show by boosting sats on Podcasting 2.0! and I will see you on the other side.
-
 @ 10846a37:73b5f923
2025-05-28 11:40:41
@ 10846a37:73b5f923
2025-05-28 11:40:41O universo dos jogos online ganha um novo patamar com a chegada da plataforma 30win, um ambiente moderno, seguro e totalmente pensado para oferecer entretenimento de qualidade aos seus usuários. Com uma interface intuitiva, ampla variedade de jogos e suporte completo, a 30win se destaca como uma excelente opção para quem busca diversão e oportunidades emocionantes de vitória.
Uma Plataforma Moderna e Confiável A 30win foi desenvolvida com tecnologia de ponta, priorizando segurança e praticidade. O site possui um design responsivo, que se adapta perfeitamente a computadores, tablets e smartphones, permitindo que o jogador aproveite seus momentos de lazer em qualquer lugar. A navegação é rápida e fluida, com menus claros e opções bem organizadas, o que torna a experiência ainda mais agradável, até mesmo para quem está começando.
Outro grande diferencial da 30winé seu compromisso com a proteção dos dados dos usuários. A plataforma utiliza protocolos avançados de criptografia, garantindo que todas as transações e informações pessoais estejam seguras. Além disso, oferece múltiplos métodos de pagamento e saque, com rapidez e eficiência.
Variedade de Jogos Para Todos os Gostos O que realmente atrai os jogadores para a 30win é a impressionante seleção de jogos disponíveis. A plataforma conta com centenas de títulos de desenvolvedores renomados, trazendo gráficos de alta qualidade, trilhas sonoras envolventes e mecânicas de jogo inovadoras.
Entre os destaques estão os jogos de slots, com temáticas variadas que vão desde aventuras épicas até símbolos clássicos. Cada título traz funções especiais como giros grátis, multiplicadores e rodadas bônus, o que aumenta tanto a diversão quanto as chances de ganhar prêmios.
Para quem gosta de desafios estratégicos, a 30win oferece também uma boa seleção de jogos de cartas como pôquer, blackjack e baccarat, além de roletas virtuais e jogos interativos com crupiês ao vivo, que proporcionam uma experiência realista e envolvente, diretamente da tela do seu dispositivo.
Experiência do Jogador em Primeiro Lugar A 30win se preocupa em entregar uma experiência completa e satisfatória aos seus jogadores. Desde o primeiro acesso, é possível notar a atenção dada aos detalhes. O cadastro é simples e rápido, com poucos cliques, e o usuário já pode começar a explorar tudo o que a plataforma tem a oferecer.
Outro ponto forte é o suporte ao cliente. A equipe de atendimento está disponível 24 horas por dia, sete dias por semana, pronta para ajudar em qualquer dúvida ou situação. Isso transmite confiança e demonstra o comprometimento da plataforma com seus usuários.
Além disso, a 30win promove constantemente bônus e promoções exclusivas, premiando tanto novos jogadores quanto os mais fiéis. Esses incentivos tornam a experiência ainda mais atrativa, com recompensas que vão desde créditos extras até prêmios especiais.
Conclusão Se você está em busca de uma plataforma de jogos online completa, segura e com excelente variedade de opções, a 30win é uma escolha certeira. Com sua interface amigável, suporte eficiente e jogos de altíssimo nível, ela oferece uma experiência empolgante que atende a todos os perfis de jogadores.
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 9e69e420:d12360c2
2025-02-14 18:07:10
@ 9e69e420:d12360c2
2025-02-14 18:07:10Vice President J.D. Vance addressed the Munich Security Conference, criticizing European leaders for undermining free speech and traditional values. He claimed that the biggest threat to Europe is not from external enemies but from internal challenges. Vance condemned the arrest of a British man for praying near an abortion clinic and accused European politicians of censorship.
He urged leaders to combat illegal immigration and questioned their democratic practices. “There is a new sheriff in town,” he said, referring to President Trump. Vance's remarks were unexpected, as many anticipated discussions on security or Ukraine. His speech emphasized the need for Europe to share the defense burden to ensure stability and security.
-
 @ 162b4b08:9f7d278c
2025-05-28 11:37:08
@ 162b4b08:9f7d278c
2025-05-28 11:37:08Lối sống năng động, linh hoạt và hướng đến sự cân bằng đang ngày càng trở thành lựa chọn của nhiều người trẻ Việt Nam trong thời đại hiện đại. Họ không chỉ chú trọng đến công việc và học tập mà còn quan tâm đến việc chăm sóc bản thân, tận hưởng cuộc sống và tìm kiếm những khoảnh khắc thư giãn giữa lịch trình bận rộn. WIN77K, với vai trò là một nền tảng giải trí trực tuyến thông minh, đã nhanh chóng nắm bắt được nhu cầu này và cung cấp một loạt nội dung giải trí phù hợp với nhịp sống trẻ trung, sôi động. Các tính năng truy cập nhanh, giao diện dễ sử dụng và hệ thống hoạt động ổn định trên cả điện thoại lẫn máy tính giúp người dùng linh hoạt tận hưởng các hoạt động giải trí mọi lúc, mọi nơi. Thay vì tiêu tốn thời gian vào những hoạt động kém hiệu quả, người trẻ có thể lựa chọn những trải nghiệm nhẹ nhàng, thư giãn nhưng vẫn duy trì được năng lượng tích cực cho cả ngày dài. Đây chính là điểm mạnh giúp WIN77K trở thành người bạn đồng hành đáng tin cậy cho thế hệ năng động ngày nay.
Không chỉ hỗ trợ giải trí, win77k còn cung cấp nhiều chuyên mục bài viết hữu ích liên quan đến lối sống, sức khỏe tinh thần, và các gợi ý giúp người trẻ duy trì phong cách sống lành mạnh. Những nội dung như cách tổ chức thời gian, làm thế nào để giữ năng lượng tích cực mỗi ngày, hoặc các bài viết chia sẻ kinh nghiệm xây dựng thói quen tốt… đều được biên tập kỹ lưỡng và cập nhật thường xuyên. Điều này giúp người dùng không chỉ tiêu thụ nội dung mà còn được truyền cảm hứng để thay đổi thói quen sống một cách chủ động. Hơn nữa, WIN77K còn kết nối cộng đồng người trẻ có cùng lối sống qua các hoạt động chia sẻ và thảo luận trực tuyến. Nhờ vậy, người dùng có thể tìm thấy sự đồng cảm, học hỏi lẫn nhau và mở rộng mạng lưới quan hệ tích cực trong môi trường số. Việc xây dựng cộng đồng này không chỉ thúc đẩy sự phát triển cá nhân mà còn lan tỏa tinh thần sống tích cực, tự chủ và sáng tạo đến nhiều người hơn trong xã hội.
Thành công của WIN77K đến từ sự thấu hiểu sâu sắc đối với nhu cầu của người dùng hiện đại, đặc biệt là thế hệ trẻ. Trong một thế giới mà mọi thứ đều chuyển động không ngừng, việc tìm ra điểm dừng hợp lý để nạp lại năng lượng là điều cần thiết. Và WIN77K đã làm tốt vai trò đó khi không chỉ tạo ra một nền tảng giải trí đơn thuần mà còn là không gian giúp người trẻ phát triển bản thân một cách toàn diện. Dù là trong lúc nghỉ ngơi giữa giờ học, thư giãn sau một ngày làm việc mệt mỏi hay đơn giản là tìm kiếm một khoảng lặng trong cuộc sống bận rộn, WIN77K luôn hiện diện như một lựa chọn tiện lợi, an toàn và truyền cảm hứng. Sự linh hoạt, hiện đại cùng định hướng phát triển bền vững chính là lý do khiến WIN77K không ngừng gia tăng sự tin tưởng và yêu mến từ cộng đồng người trẻ Việt Nam, ngày càng khẳng định vai trò của mình trong việc đồng hành cùng lối sống năng động và tích cực của thế hệ tương lai.
-
 @ cff1720e:15c7e2b2
2025-05-28 11:18:23
@ cff1720e:15c7e2b2
2025-05-28 11:18:23Liebe Anwender,\ \ diesmal beginnen die Neuigkeiten schon beim Titel und der Anrede. Unsere Worte bestimmen unser Denken, und daher war die Korrektur wichtiger als sie zunächst erscheint, denn bei Pareto gibt es die klassische Trennung zwischen Autor und Leser nicht mehr. Cocreation heißt unser Konzept, jeder kann publizieren, kommentieren, honorieren und distribuieren. Mag das bei Blogtexten derzeit noch nicht selbstverständlich sein, so ist das bei Bildern längst die Norm.

“Ein Bild sagt mehr als tausend Worte” beschreibt die Wirkung visueller Kommunikation. Deshalb haben wir nach dem Blogtext nun mit Bildern eine neue Content-Kategorie eingeführt. Natürlich auch hier mit den bekannten Funktionen der Interaktion wie like, repost und zap. Es gibt derzeit eine Gliederung in 4 Feeds, Gefolgt (für Nostr-User verfügbar), Memes und Kunst (gefiltert nach entsprechenden Tags) und Pareto für alles andere.
Jeder Nostr-User hat die Möglichkeit eigene Bilder hochzuladen, zu taggen, sowie mit einem Titel und Untertext zu versehen. “Everyone is a creator” war noch nie leichter, probiert es einfach aus! Noch kein Nostr-Profil und trotzdem interessiert? Kein Problem, bitte Informationen zu originellen Bildquellen oder Interesse an Mitwirkung per Mail senden an pictures@pareto.space
Leicht ist es auch die Pareto-Inhalte zu erhalten und konsumieren, man braucht weder einen Account noch spezielle Apps. Jeder hat bereits die entsprechenden Voraussetzungen, hier ein paar Beispiele.\ \ Newsletter per Mail (Die Friedenstaube)\ hier abonnieren\ \ In Telegram lesen -> hier unsere Kanäle\ https://t.me/pareto_artikel \ https://t.me/friedenstaube_artikel \ \ Als Feed in einem Feed-Reader \ https://pareto.space/atom/feed.xml \ https://pareto.space/atom/de_feed.xml \ https://pareto.space/atom/en_feed.xml
Fügt in Eure Artikel bitte am Anfang / Ende einen Hinweis auf den Pareto-Client ein, andere Clients unterstützen nicht alle Features. Das ist ein Service-Hinweis zur besseren Lesbarkeit “Dieser Beitrag wurde mit dem Pareto-Client geschrieben.” Ebenso ist ein Hinweis auf Onboarding bei Nostr nützlich: neue Nostr-User können euch liken und zappen: not yet on Nostr and want the full experience? Easy onboarding via Start.\ \ Das Pareto-Team baut den “Marktplatz der Ideen” und hat dabei schon viel erreicht. Feedback und Mitarbeit hilft uns damit noch schneller voranzukommen, wir bedanken uns für Eure Unterstützung.\ team@pareto.space \ https://pareto.space \ https://geyser.fund/project/pareto?hero=1c1b8e487090
-
 @ 005bc4de:ef11e1a2
2025-05-28 09:05:10
@ 005bc4de:ef11e1a2
2025-05-28 09:05:10
BIP-2,100,000,000,000,000,000
So, you're telling me...
- 21 million bitcoins is out, and...
- 2.1 quadrillion sats is in, except that...
- sats are out, so...
- 2.1 quadrillion bitcoins is in, except that...
- there are actually millisats, but...
- millisats are out, so...
- millibitcoins are in, so now...
- there are 2.1 quintillion millibitcoins, except that...
- millibitcoins are the basic base unit of bitcoin, so...
- millibitcoins are out, and now...
- 2.1 quintillion bitcoins are in

-
 @ e3ba5e1a:5e433365
2025-02-13 06:16:49
@ e3ba5e1a:5e433365
2025-02-13 06:16:49My favorite line in any Marvel movie ever is in “Captain America.” After Captain America launches seemingly a hopeless assault on Red Skull’s base and is captured, we get this line:
“Arrogance may not be a uniquely American trait, but I must say, you do it better than anyone.”
Yesterday, I came across a comment on the song Devil Went Down to Georgia that had a very similar feel to it:

America has seemingly always been arrogant, in a uniquely American way. Manifest Destiny, for instance. The rest of the world is aware of this arrogance, and mocks Americans for it. A central point in modern US politics is the deriding of racist, nationalist, supremacist Americans.
That’s not what I see. I see American Arrogance as not only a beautiful statement about what it means to be American. I see it as an ode to the greatness of humanity in its purest form.
For most countries, saying “our nation is the greatest” is, in fact, twinged with some level of racism. I still don’t have a problem with it. Every group of people should be allowed to feel pride in their accomplishments. The destruction of the human spirit since the end of World War 2, where greatness has become a sin and weakness a virtue, has crushed the ability of people worldwide to strive for excellence.
But I digress. The fears of racism and nationalism at least have a grain of truth when applied to other nations on the planet. But not to America.
That’s because the definition of America, and the prototype of an American, has nothing to do with race. The definition of Americanism is freedom. The founding of America is based purely on liberty. On the God-given rights of every person to live life the way they see fit.
American Arrogance is not a statement of racial superiority. It’s barely a statement of national superiority (though it absolutely is). To me, when an American comments on the greatness of America, it’s a statement about freedom. Freedom will always unlock the greatness inherent in any group of people. Americans are definitionally better than everyone else, because Americans are freer than everyone else. (Or, at least, that’s how it should be.)
In Devil Went Down to Georgia, Johnny is approached by the devil himself. He is challenged to a ridiculously lopsided bet: a golden fiddle versus his immortal soul. He acknowledges the sin in accepting such a proposal. And yet he says, “God, I know you told me not to do this. But I can’t stand the affront to my honor. I am the greatest. The devil has nothing on me. So God, I’m gonna sin, but I’m also gonna win.”
Libertas magnitudo est
-
 @ 33baa074:3bb3a297
2025-05-28 08:54:40
@ 33baa074:3bb3a297
2025-05-28 08:54:40COD (chemical oxygen demand) sensors play a vital role in water quality testing. Their main functions include real-time monitoring, pollution event warning, water quality assessment and pollution source tracking. The following are the specific roles and applications of COD sensors in water quality testing:
Real-time monitoring and data acquisition COD sensors can monitor the COD content in water bodies in real time and continuously. Compared with traditional sampling methods, COD sensors are fast and accurate, without manual sampling and laboratory testing, which greatly saves time and labor costs. By combining with the data acquisition system, the monitoring data can be uploaded to the cloud in real time to form a extemporization distribution map of the COD content in the water body, providing detailed data support for environmental monitoring and management.
Pollution event warning and rapid response COD sensors play an important role in early warning and rapid response in water environment monitoring. Once there is an abnormal increase in organic matter in the water body, the COD sensor can quickly detect the change in COD content and alarm through the preset threshold. This enables relevant departments to take measures at the early stage of the pollution incident to prevent the spread of pollution and protect the water environment.
Water quality assessment and pollution source tracking COD sensors play an important role in water quality assessment and pollution source tracking. By continuously monitoring the COD content in water bodies, the water quality can be evaluated and compared with national and regional water quality standards. At the same time, COD sensors can also help determine and track the location and spread of pollution sources, provide accurate data support for environmental management departments, and guide the development of pollution prevention and control work.
Application scenarios COD sensors are widely used in various water quality monitoring scenarios, including but not limited to: Sewage treatment plants: used to monitor the COD content of in fluent and effluent to ensure the effect of sewage treatment. Water source protection and management: deployed in water sources to monitor the COD content of in fluent sources. Once the water quality exceeds the set limit, the system will issue an alarm in time to ensure water quality safety. Lake and river monitoring: deployed in water bodies such as lakes and rivers to monitor the COD content of water bodies in real time.

Technical features of COD sensor COD sensor uses advanced technology, such as ultraviolet absorption method, which does not require the use of chemical reagents, avoiding the risk of contamination of chemical reagents in traditional COD detection methods, and can achieve online uninterrupted water quality monitoring, providing strong support for real-time water quality assessment. In addition, COD sensor also has the advantages of low cost, high stability, strong anti-interference ability, and convenient installation.
Summary In summary, COD sensor plays an irreplaceable role in water quality detection. It can not only provide real-time and accurate water quality data, but also quickly warn when pollution incidents occur, providing strong technical support for water quality management and environmental protection. With the advancement of technology and the popularization of applications, COD sensor will play a more important role in water quality monitoring in the future.
-
 @ 58537364:705b4b85
2025-05-28 08:25:55
@ 58537364:705b4b85
2025-05-28 08:25:55ถ้าอยากแล้วไม่หลง มันก็อยากด้วยปัญญา ความอยากอย่างนี้ท่านเรียกว่า เป็นบารมีของตน แต่ไม่ใช่ทุกคนนะที่มีปัญญา
บางคนไม่อยากจะให้มันอยาก เพราะเข้าใจว่า การมาปฏิบัติก็เพื่อระงับความอยาก ความจริงน่ะ ถ้าหากว่าไม่มีความอยาก ก็ไม่มีข้อปฏิบัติ ไม่รู้ว่าจะทำอะไร ลองพิจารณาดูก็ได้
ทุกคน แม้องค์พระพุทธเจ้าของเราก็ตาม ที่ท่านออกมาปฏิบัติ ก็เพื่อจะให้บรรเทากิเลสทั้งหลายนั้น
แต่ว่ามันต้องอยากทำ อยากปฏิบัติ อยากให้มันสงบ และก็ไม่อยากให้มันวุ่นวาย ทั้งสองอย่างนี้ มันเป็นอุปสรรคทั้งนั้น ถ้าเราไม่มีปัญญา ไม่มีความฉลาดในการกระทำอย่างนั้น เพราะว่ามันปนกันอยู่ อยากทั้งสองอย่างนี้มันมีราคาเท่า ๆ กัน
อยากจะพ้นทุกข์มันเป็นกิเลส สำหรับคนไม่มีปัญญา อยากด้วยความโง่ ไม่อยากมันก็เป็นกิเลส เพราะไม่อยากอันนั้นมันประกอบด้วยความโง่เหมือนกัน คือทั้งอยาก ไม่อยาก ปัญญาก็ไม่มี ทั้งสองอย่างนี้ มันเป็นกามสุขัลลิกานุโยโค กับอัตตกิลมถานุโยโค ซึ่งพระพุทธองค์ของเรา ขณะที่พระองค์กำลังทรงปฏิบัติอยู่นั้น ท่านก็หลงใหลในอย่างนี้ ไม่รู้ว่าจะทำอย่างไร ท่านหาอุบายหลายประการ กว่าจะพบของสองสิ่งนี้
ทุกวันนี้เราทั้งหลายก็เหมือนกัน ทุกสิ่งทั้งสองอย่างนี้มันกวนอยู่ เราจึงเข้าสู่ทางไม่ได้ก็เพราะอันนี้ ความเป็นจริงนี้ทุกคนที่มาปฏิบัติ ก็เป็นปุถุชนมาทั้งนั้น ปุถุชนก็เต็มไปด้วยความอยาก ความอยากที่ไม่มีปัญญา อยากด้วยความหลง ไม่อยากมันก็มีโทษเหมือนกัน “ไม่อยาก” มันก็เป็นตัณหา “อยาก” มันก็เป็นตัณหาอีกเหมือนกัน
ทีนี้ นักปฏิบัติยังไม่รู้เรื่องว่า จะเอายังไงกัน เดินไปข้างหน้าก็ไม่ถูก เดินกลับไปข้างหลังก็ไม่ถูก จะหยุดก็หยุดไม่ได้เพราะมันยังอยากอยู่ มันยังหลงอยู่ มีแต่ความอยาก แต่ปัญญาไม่มี มันอยากด้วยความหลง มันก็เป็นตัณหา ถึงแม้ไม่อยาก มันก็เป็นความหลง มันก็เป็นตัณหาเหมือนกันเพราะอะไร? เพราะมันขาดปัญญา
ความเป็นจริงนั้น ธรรมะมันอยู่ตรงนั้นแหละ ตรงความอยากกับความไม่อยากนั่นแหละ แต่เราไม่มีปัญญา ก็พยายามไม่ให้อยากบ้าง เดี๋ยวก็อยากบ้าง อยากให้เป็นอย่างนั้น ไม่อยากให้เป็นอย่างนี้ ความจริงทั้งสองอย่างนี้ หรือทั้งคู่นี้มันตัวเดียวกันทั้งนั้น ไม่ใช่คนละตัว แต่เราไม่รู้เรื่องของมัน
พระพุทธเจ้าของเรา และสาวกทั้งหลายของพระองค์นั้นท่านก็อยากเหมือนกัน แต่ “อยาก” ของท่านนั้น เป็นเพียงอาการของจิตเฉย ๆ หรือ “ไม่อยาก” ของท่าน ก็เป็นเพียงอาการของจิตเฉย ๆ อีกเหมือนกัน มันวูบเดียวเท่านั้น ก็หายไปแล้ว
ดังนั้น ความอยากหรือไม่อยากนี้ มันมีอยู่ตลอดเวลาแต่สำหรับผู้มีปัญญานั้น “อยาก” ก็ไม่มีอุปาทาน “ไม่อยาก” ก็ไม่มีอุปาทาน เป็น “สักแต่ว่า” อยากหรือไม่อยากเท่านั้น ถ้าพูดตามความจริงแล้ว มันก็เป็นแต่ "อาการของจิต" อาการของจิตมันเป็นของมันอย่างนั้นเอง ถ้าเรามาตะครุบมันอยู่ใกล้ ๆ นี่มันก็เห็นชัด
ดังนั้นจึงว่า การพิจารณานั้น ไม่ใช่รู้ไปที่อื่น มันรู้ตรงนี้แหละ เหมือนชาวประมงที่ออกไปทอดแหนั่นแหละ ทอดแหออกไปถูกปลาตัวใหญ่ เจ้าของผู้ทอดแหจะคิดอย่างไร? ก็กลัว กลัวปลาจะออกจากแหไปเสีย เมื่อเป็นเช่นนั้น ใจมันก็ดิ้นรนขึ้นระวังมาก บังคับมาก ตะครุบไปตะครุบมาอยู่นั่นแหละ ประเดี๋ยวปลามันก็ออกจากแหไปเสีย เพราะไปตะครุบมันแรงเกินไป
อย่างนั้นโบราณท่านพูดถึงเรื่องอันนี้ ท่านว่าค่อย ๆ ทำมัน แต่อย่าไปห่างจากมัน นี่คือปฏิปทาของเรา ค่อย ๆ คลำมันไปเรื่อย ๆ อย่างนั้นแหละ
อย่าปล่อยมัน หรือไม่อยากรู้มัน ต้องรู้ ต้องรู้เรื่องของมัน พยายามทำมันไปเรื่อย ๆ ให้เป็นปฏิปทา ขี้เกียจเราก็ทำไม่ขี้เกียจเราก็ทำ เรียกว่าการทำการปฏิบัติ ต้องทำไปเรื่อยๆอย่างนี้
ถ้าหากว่าเราขยัน ขยันเพราะความเชื่อ มันมีศรัทธาแต่ปัญญาไม่มี ถ้าเป็นอย่างนี้ ขยันไป ๆ แล้วมันก็ไม่เกิดผลอะไรขึ้นมากมาย ขยันไปนาน ๆ เข้า แต่มันไม่ถูกทาง มันก็ไม่สงบระงับ ทีนี้ก็จะเกิดความคิดว่า เรานี้บุญน้อยหรือวาสนาน้อย หรือคิดไปว่ามนุษย์ในโลกนี้คงทำไม่ได้หรอก แล้วก็เลยหยุดเลิกทำเลิกปฏิบัติ
ถ้าเกิดความคิดอย่างนี้เมื่อใด ขอให้ระวังให้มาก ให้มีขันติ ความอดทน ให้ทำไปเรื่อย ๆ เหมือนกับเราจับปลาตัวใหญ่ ก็ให้ค่อย ๆ คลำมันไปเรื่อย ๆ ปลามันก็จะไม่ดิ้นแรงค่อย ๆทำไปเรื่อย ๆ ไม่หยุด ไม่ช้าปลาก็จะหมดกำลัง มันก็จับง่าย จับให้ถนัดมือเลย ถ้าเรารีบจนเกินไป ปลามันก็จะหนีดิ้นออกจากแหเท่านั้น
ดังนั้น การปฏิบัตินี้ ถ้าเราพิจารณาตามพื้นเหตุของเรา เช่นว่า เราไม่มีความรู้ในปริยัติ ไม่มีความรู้ในอะไรอื่น ที่จะให้การปฏิบัติมันเกิดผลขึ้น ก็ดูความรู้ที่เป็นพื้นเพเดิมของเรานั่นแหละอันนั้นก็คือ “ธรรมชาติของจิต” นี่เอง มันมีของมันอยู่แล้ว เราจะไปเรียนรู้มัน มันก็มีอยู่ หรือเราจะไม่ไปเรียนรู้มัน มันก็มีอยู่
อย่างที่ท่านพูดว่า พระพุทธเจ้าจะบังเกิดขึ้นก็ตาม หรือไม่บังเกิดขึ้นก็ตาม ธรรมะก็คงมีอยู่อย่างนั้น มันเป็นของมันอยู่อย่างนั้น ไม่พลิกแพลงไปไหน มันเป็นสัจจธรรม
เราไม่เข้าใจสัจจธรรม ก็ไม่รู้ว่าสัจจธรรมเป็นอย่างไร นี้เรียกว่า การพิจารณาในความรู้ของผู้ปฏิบัติที่ไม่มีพื้นปริยัติ
ขอให้ดูจิต พยายามอ่านจิตของเจ้าของ พยายามพูดกับจิตของเจ้าของ มันจึงจะรู้เรื่องของจิต ค่อย ๆ ทำไป ถ้ายังไม่ถึงที่ของมัน มันก็ไปอยู่อย่างนั้น
ครูบาอาจารย์บางท่านบอกว่า ทำไปเรื่อย ๆ อย่าหยุด บางทีเรามาคิด “เออ ทำไปเรื่อย ๆ ถ้าไม่รู้เรื่องของมัน ถ้าทำไม่ถูกที่มัน มันจะรู้อะไร” อย่างนี้เป็นต้น ก็ต้องไปเรื่อย ๆ ก่อน แล้วมันก็จะเกิดความรู้สึกนึกคิดขึ้นในสิ่งที่เราพากเพียรทำนั้น
มันเหมือนกันกับบุรุษที่ไปสีไฟ ได้ฟังท่านบอกว่า เอาไม้ไผ่สองอันมาสีกันเข้าไปเถอะ แล้วจะมีไฟเกิดขึ้น บุรุษนั้นก็จับไม้ไผ่เข้าสองอัน สีกันเข้า แต่ใจร้อน สีไปได้หน่อย ก็อยากให้มันเป็นไฟ ใจก็เร่งอยู่เรื่อย ให้เป็นไฟเร็วๆ แต่ไฟก็ไม่เกิดสักที บุรุษนั้นก็เกิดความขี้เกียจ แล้วก็หยุดพัก แล้วจึงลองสีอีกนิด แล้วก็หยุดพัก ความร้อนที่พอมีอยู่บ้าง ก็หายไปล่ะซิ เพราะความร้อนมันไม่ติดต่อกัน
ถ้าทำไปเรื่อยๆอย่างนี้ เหนื่อยก็หยุด มีแต่เหนื่อยอย่างเดียวก็พอได้ แต่มีขี้เกียจปนเข้าด้วย เลยไปกันใหญ่ แล้วบุรุษนั้นก็หาว่าไฟไม่มี ไม่เอาไฟ ก็ทิ้ง เลิก ไม่สีอีก แล้วก็ไปเที่ยวประกาศว่า ไฟไม่มี ทำอย่างนี้ไม่ได้ ไม่มีไฟหรอก เขาได้ลองทำแล้ว
ก็จริงเหมือนกันที่ได้ทำแล้ว แต่ทำยังไม่ถึงจุดของมันคือความร้อนยังไม่สมดุลกัน ไฟมันก็เกิดขึ้นไม่ได้ ทั้งที่ความจริงไฟมันก็มีอยู่ อย่างนี้ก็เกิดความท้อแท้ขึ้นในใจของผู้ปฏิบัตินั้น ก็ละอันนี้ไปทำอันโน้นเรื่อยไป อันนี้ฉันใดก็ฉันนั้น
การปฏิบัตินั้น ปฏิบัติทางกายทางใจทั้งสองอย่าง มันต้องพร้อมกัน เพราะอะไร? เพราะพื้นเพมันเป็นคนมีกิเลสทั้งนั้น พระพุทธเจ้าก่อนที่จะเป็นพระพุทธเจ้า ท่านก็มีกิเลสแต่ท่านมีปัญญามากหลาย พระอรหันต์ก็เหมือนกัน เมื่อยังเป็นปุถุชนอยู่ ก็เหมือนกับเรา
เมื่อความอยากเกิดขึ้นมา เราก็ไม่รู้จัก เมื่อความไม่อยากเกิดขึ้นมา เราก็ไม่รู้จัก บางทีก็ร้อนใจ บางทีก็ดีใจ ถ้าใจเราไม่อยาก ก็ดีใจแบบหนึ่ง และวุ่นวายอีกแบบหนึ่ง ถ้าใจเราอยาก มันก็วุ่นวายอย่างหนึ่ง และดีใจอย่างหนึ่ง มันประสมประเสกันอยู่อย่างนี้
อันนี้คือปฏิปทาของผู้ปฏิบัติเรา
[อ่านใจธรรมชาติ] หลวงปู่ชา สุภัทโท หนังสือ หมวด: โพธิญาณ

-
 @ daa41bed:88f54153
2025-02-09 16:50:04
@ daa41bed:88f54153
2025-02-09 16:50:04There has been a good bit of discussion on Nostr over the past few days about the merits of zaps as a method of engaging with notes, so after writing a rather lengthy article on the pros of a strategic Bitcoin reserve, I wanted to take some time to chime in on the much more fun topic of digital engagement.
Let's begin by defining a couple of things:
Nostr is a decentralized, censorship-resistance protocol whose current biggest use case is social media (think Twitter/X). Instead of relying on company servers, it relies on relays that anyone can spin up and own their own content. Its use cases are much bigger, though, and this article is hosted on my own relay, using my own Nostr relay as an example.
Zap is a tip or donation denominated in sats (small units of Bitcoin) sent from one user to another. This is generally done directly over the Lightning Network but is increasingly using Cashu tokens. For the sake of this discussion, how you transmit/receive zaps will be irrelevant, so don't worry if you don't know what Lightning or Cashu are.
If we look at how users engage with posts and follows/followers on platforms like Twitter, Facebook, etc., it becomes evident that traditional social media thrives on engagement farming. The more outrageous a post, the more likely it will get a reaction. We see a version of this on more visual social platforms like YouTube and TikTok that use carefully crafted thumbnail images to grab the user's attention to click the video. If you'd like to dive deep into the psychology and science behind social media engagement, let me know, and I'd be happy to follow up with another article.
In this user engagement model, a user is given the option to comment or like the original post, or share it among their followers to increase its signal. They receive no value from engaging with the content aside from the dopamine hit of the original experience or having their comment liked back by whatever influencer they provide value to. Ad revenue flows to the content creator. Clout flows to the content creator. Sales revenue from merch and content placement flows to the content creator. We call this a linear economy -- the idea that resources get created, used up, then thrown away. Users create content and farm as much engagement as possible, then the content is forgotten within a few hours as they move on to the next piece of content to be farmed.
What if there were a simple way to give value back to those who engage with your content? By implementing some value-for-value model -- a circular economy. Enter zaps.

Unlike traditional social media platforms, Nostr does not actively use algorithms to determine what content is popular, nor does it push content created for active user engagement to the top of a user's timeline. Yes, there are "trending" and "most zapped" timelines that users can choose to use as their default, but these use relatively straightforward engagement metrics to rank posts for these timelines.
That is not to say that we may not see clients actively seeking to refine timeline algorithms for specific metrics. Still, the beauty of having an open protocol with media that is controlled solely by its users is that users who begin to see their timeline gamed towards specific algorithms can choose to move to another client, and for those who are more tech-savvy, they can opt to run their own relays or create their own clients with personalized algorithms and web of trust scoring systems.
Zaps enable the means to create a new type of social media economy in which creators can earn for creating content and users can earn by actively engaging with it. Like and reposting content is relatively frictionless and costs nothing but a simple button tap. Zaps provide active engagement because they signal to your followers and those of the content creator that this post has genuine value, quite literally in the form of money—sats.

I have seen some comments on Nostr claiming that removing likes and reactions is for wealthy people who can afford to send zaps and that the majority of people in the US and around the world do not have the time or money to zap because they have better things to spend their money like feeding their families and paying their bills. While at face value, these may seem like valid arguments, they, unfortunately, represent the brainwashed, defeatist attitude that our current economic (and, by extension, social media) systems aim to instill in all of us to continue extracting value from our lives.
Imagine now, if those people dedicating their own time (time = money) to mine pity points on social media would instead spend that time with genuine value creation by posting content that is meaningful to cultural discussions. Imagine if, instead of complaining that their posts get no zaps and going on a tirade about how much of a victim they are, they would empower themselves to take control of their content and give value back to the world; where would that leave us? How much value could be created on a nascent platform such as Nostr, and how quickly could it overtake other platforms?
Other users argue about user experience and that additional friction (i.e., zaps) leads to lower engagement, as proven by decades of studies on user interaction. While the added friction may turn some users away, does that necessarily provide less value? I argue quite the opposite. You haven't made a few sats from zaps with your content? Can't afford to send some sats to a wallet for zapping? How about using the most excellent available resource and spending 10 seconds of your time to leave a comment? Likes and reactions are valueless transactions. Social media's real value derives from providing monetary compensation and actively engaging in a conversation with posts you find interesting or thought-provoking. Remember when humans thrived on conversation and discussion for entertainment instead of simply being an onlooker of someone else's life?
If you've made it this far, my only request is this: try only zapping and commenting as a method of engagement for two weeks. Sure, you may end up liking a post here and there, but be more mindful of how you interact with the world and break yourself from blind instinct. You'll thank me later.

-
 @ e3ba5e1a:5e433365
2025-02-05 17:47:16
@ e3ba5e1a:5e433365
2025-02-05 17:47:16I got into a friendly discussion on X regarding health insurance. The specific question was how to deal with health insurance companies (presumably unfairly) denying claims? My answer, as usual: get government out of it!
The US healthcare system is essentially the worst of both worlds:
- Unlike full single payer, individuals incur high costs
- Unlike a true free market, regulation causes increases in costs and decreases competition among insurers
I'm firmly on the side of moving towards the free market. (And I say that as someone living under a single payer system now.) Here's what I would do:
- Get rid of tax incentives that make health insurance tied to your employer, giving individuals back proper freedom of choice.
- Reduce regulations significantly.
-
In the short term, some people will still get rejected claims and other obnoxious behavior from insurance companies. We address that in two ways:
- Due to reduced regulations, new insurance companies will be able to enter the market offering more reliable coverage and better rates, and people will flock to them because they have the freedom to make their own choices.
- Sue the asses off of companies that reject claims unfairly. And ideally, as one of the few legitimate roles of government in all this, institute new laws that limit the ability of fine print to allow insurers to escape their responsibilities. (I'm hesitant that the latter will happen due to the incestuous relationship between Congress/regulators and insurers, but I can hope.)
Will this magically fix everything overnight like politicians normally promise? No. But it will allow the market to return to a healthy state. And I don't think it will take long (order of magnitude: 5-10 years) for it to come together, but that's just speculation.
And since there's a high correlation between those who believe government can fix problems by taking more control and demanding that only credentialed experts weigh in on a topic (both points I strongly disagree with BTW): I'm a trained actuary and worked in the insurance industry, and have directly seen how government regulation reduces competition, raises prices, and harms consumers.
And my final point: I don't think any prior art would be a good comparison for deregulation in the US, it's such a different market than any other country in the world for so many reasons that lessons wouldn't really translate. Nonetheless, I asked Grok for some empirical data on this, and at best the results of deregulation could be called "mixed," but likely more accurately "uncertain, confused, and subject to whatever interpretation anyone wants to apply."
https://x.com/i/grok/share/Zc8yOdrN8lS275hXJ92uwq98M
-
 @ 33baa074:3bb3a297
2025-05-28 08:25:13
@ 33baa074:3bb3a297
2025-05-28 08:25:13The oil-in-water sensoris an instrument specially used to detect oil substances in water bodies. Its working principle is mainly based on the characteristic that oil substances will produce fluorescence under ultraviolet light. The following is a detailed explanation:
Principle Overview The oil-in-water sensor uses the characteristic that oil substances will produce fluorescence under ultraviolet light, and measures the fluorescence intensity to infer the concentration of oil substances. Specifically, the sensor uses ultraviolet light as the excitation light source to irradiate the water sample to be tested. After the oil substance absorbs ultraviolet light, it will stimulate fluorescence, and the fluorescence signal is received by the photo detector and converted into an electrical signal. By measuring the strength of the electrical signal, the concentration of oil substances in the water sample can be inferred.
Workflow Ultraviolet light irradiation: The ultraviolet light source inside the sensor emits ultraviolet light and irradiates it into the water sample to be tested.
Fluorescence generation: After the oil substance in the water sample absorbs ultraviolet light, it will stimulate fluorescence.
Fluorescence detection: The photo detector in the sensor measures the intensity of this fluorescence.
Signal conversion: The signal processing circuit converts the output of the photo detector into an electrical signal proportional to the amount of oil in the water. Data analysis: By analyzing the strength of the electrical signal, the concentration of oil substances in the water sample can be obtained.
Features and applications The oil in water sensor has high sensitivity and can detect soluble and falsifiable oils. It is suitable for a variety of water quality monitoring scenarios, such as oil field monitoring, industrial circulating water, condensate water, wastewater treatment, surface water stations, etc. In addition, it can also monitor the content of crude oil (benzene and benzene homologous) in water sources such as reservoirs and water plants in real time online, play an early warning role, and protect the safety of water sources.
Practical application The oil in water sensor has a wide range of functions in practical applications, including but not limited to the following aspects: Monitoring the water quality of water sources: ensuring the safety of drinking water, and timely discovering pollution sources and ensuring water supply safety by continuously monitoring oil substances in water sources. Monitoring sewage treatment plant emissions: ensuring that the discharge water quality of sewage treatment plants meets the emission standards to avoid secondary pollution to the environment. Monitoring rivers, lakes and other water bodies: assessing the pollution status and providing a basis for pollution control. Early warning and emergency response: It has real-time monitoring and early warning functions, and can issue an alarm in time when abnormal conditions are found, providing valuable time for emergency response and reducing losses caused by pollution. Scientific research: Through the monitoring data of this sensor, we can deeply understand the distribution, migration and transformation of oil substances in water bodies, and provide a scientific basis for environmental protection and governance.
In summary, the oil in water sensor monitors the oil content in water bodies through ultraviolet fluorescence method, has high sensitivity and broad application prospects, and is an indispensable and important tool in modern environmental monitoring and industrial production.
-
 @ 91bea5cd:1df4451c
2025-02-04 17:24:50
@ 91bea5cd:1df4451c
2025-02-04 17:24:50Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 91bea5cd:1df4451c
2025-02-04 17:15:57
@ 91bea5cd:1df4451c
2025-02-04 17:15:57Definição de ULID:
Timestamp 48 bits, Aleatoriedade 80 bits Sendo Timestamp 48 bits inteiro, tempo UNIX em milissegundos, Não ficará sem espaço até o ano 10889 d.C. e Aleatoriedade 80 bits, Fonte criptograficamente segura de aleatoriedade, se possível.
Gerar ULID
```sql
CREATE EXTENSION IF NOT EXISTS pgcrypto;
CREATE FUNCTION generate_ulid() RETURNS TEXT AS $$ DECLARE -- Crockford's Base32 encoding BYTEA = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; timestamp BYTEA = E'\000\000\000\000\000\000'; output TEXT = '';
unix_time BIGINT; ulid BYTEA; BEGIN -- 6 timestamp bytes unix_time = (EXTRACT(EPOCH FROM CLOCK_TIMESTAMP()) * 1000)::BIGINT; timestamp = SET_BYTE(timestamp, 0, (unix_time >> 40)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 1, (unix_time >> 32)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 2, (unix_time >> 24)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 3, (unix_time >> 16)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 4, (unix_time >> 8)::BIT(8)::INTEGER); timestamp = SET_BYTE(timestamp, 5, unix_time::BIT(8)::INTEGER);
-- 10 entropy bytes ulid = timestamp || gen_random_bytes(10);
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 1) & 7) << 2) | ((GET_BYTE(ulid, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 2) & 1) << 4) | ((GET_BYTE(ulid, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 3) & 15) << 1) | ((GET_BYTE(ulid, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 4) & 3) << 3) | ((GET_BYTE(ulid, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 6) & 7) << 2) | ((GET_BYTE(ulid, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 7) & 1) << 4) | ((GET_BYTE(ulid, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 8) & 15) << 1) | ((GET_BYTE(ulid, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 9) & 3) << 3) | ((GET_BYTE(ulid, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 11) & 7) << 2) | ((GET_BYTE(ulid, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 12) & 1) << 4) | ((GET_BYTE(ulid, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 13) & 15) << 1) | ((GET_BYTE(ulid, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(ulid, 14) & 3) << 3) | ((GET_BYTE(ulid, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(ulid, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql VOLATILE; ```
ULID TO UUID
```sql CREATE OR REPLACE FUNCTION parse_ulid(ulid text) RETURNS bytea AS $$ DECLARE -- 16byte bytes bytea = E'\x00000000 00000000 00000000 00000000'; v char[]; -- Allow for O(1) lookup of index values dec integer[] = ARRAY[ 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 255, 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, 255, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31, 255, 255, 255, 255, 255, 255, 10, 11, 12, 13, 14, 15, 16, 17, 1, 18, 19, 1, 20, 21, 0, 22, 23, 24, 25, 26, 255, 27, 28, 29, 30, 31 ]; BEGIN IF NOT ulid ~* '^[0-7][0-9ABCDEFGHJKMNPQRSTVWXYZ]{25}$' THEN RAISE EXCEPTION 'Invalid ULID: %', ulid; END IF;
v = regexp_split_to_array(ulid, '');
-- 6 bytes timestamp (48 bits) bytes = SET_BYTE(bytes, 0, (dec[ASCII(v[1])] << 5) | dec[ASCII(v[2])]); bytes = SET_BYTE(bytes, 1, (dec[ASCII(v[3])] << 3) | (dec[ASCII(v[4])] >> 2)); bytes = SET_BYTE(bytes, 2, (dec[ASCII(v[4])] << 6) | (dec[ASCII(v[5])] << 1) | (dec[ASCII(v[6])] >> 4)); bytes = SET_BYTE(bytes, 3, (dec[ASCII(v[6])] << 4) | (dec[ASCII(v[7])] >> 1)); bytes = SET_BYTE(bytes, 4, (dec[ASCII(v[7])] << 7) | (dec[ASCII(v[8])] << 2) | (dec[ASCII(v[9])] >> 3)); bytes = SET_BYTE(bytes, 5, (dec[ASCII(v[9])] << 5) | dec[ASCII(v[10])]);
-- 10 bytes of entropy (80 bits); bytes = SET_BYTE(bytes, 6, (dec[ASCII(v[11])] << 3) | (dec[ASCII(v[12])] >> 2)); bytes = SET_BYTE(bytes, 7, (dec[ASCII(v[12])] << 6) | (dec[ASCII(v[13])] << 1) | (dec[ASCII(v[14])] >> 4)); bytes = SET_BYTE(bytes, 8, (dec[ASCII(v[14])] << 4) | (dec[ASCII(v[15])] >> 1)); bytes = SET_BYTE(bytes, 9, (dec[ASCII(v[15])] << 7) | (dec[ASCII(v[16])] << 2) | (dec[ASCII(v[17])] >> 3)); bytes = SET_BYTE(bytes, 10, (dec[ASCII(v[17])] << 5) | dec[ASCII(v[18])]); bytes = SET_BYTE(bytes, 11, (dec[ASCII(v[19])] << 3) | (dec[ASCII(v[20])] >> 2)); bytes = SET_BYTE(bytes, 12, (dec[ASCII(v[20])] << 6) | (dec[ASCII(v[21])] << 1) | (dec[ASCII(v[22])] >> 4)); bytes = SET_BYTE(bytes, 13, (dec[ASCII(v[22])] << 4) | (dec[ASCII(v[23])] >> 1)); bytes = SET_BYTE(bytes, 14, (dec[ASCII(v[23])] << 7) | (dec[ASCII(v[24])] << 2) | (dec[ASCII(v[25])] >> 3)); bytes = SET_BYTE(bytes, 15, (dec[ASCII(v[25])] << 5) | dec[ASCII(v[26])]);
RETURN bytes; END $$ LANGUAGE plpgsql IMMUTABLE;
CREATE OR REPLACE FUNCTION ulid_to_uuid(ulid text) RETURNS uuid AS $$ BEGIN RETURN encode(parse_ulid(ulid), 'hex')::uuid; END $$ LANGUAGE plpgsql IMMUTABLE; ```
UUID to ULID
```sql CREATE OR REPLACE FUNCTION uuid_to_ulid(id uuid) RETURNS text AS $$ DECLARE encoding bytea = '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; output text = ''; uuid_bytes bytea = uuid_send(id); BEGIN
-- Encode the timestamp output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 224) >> 5)); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 0) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 1) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 1) & 7) << 2) | ((GET_BYTE(uuid_bytes, 2) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 2) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 2) & 1) << 4) | ((GET_BYTE(uuid_bytes, 3) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 3) & 15) << 1) | ((GET_BYTE(uuid_bytes, 4) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 4) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 4) & 3) << 3) | ((GET_BYTE(uuid_bytes, 5) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 5) & 31)));
-- Encode the entropy output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 6) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 6) & 7) << 2) | ((GET_BYTE(uuid_bytes, 7) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 7) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 7) & 1) << 4) | ((GET_BYTE(uuid_bytes, 8) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 8) & 15) << 1) | ((GET_BYTE(uuid_bytes, 9) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 9) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 9) & 3) << 3) | ((GET_BYTE(uuid_bytes, 10) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 10) & 31))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 11) & 248) >> 3)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 11) & 7) << 2) | ((GET_BYTE(uuid_bytes, 12) & 192) >> 6))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 12) & 62) >> 1)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 12) & 1) << 4) | ((GET_BYTE(uuid_bytes, 13) & 240) >> 4))); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 13) & 15) << 1) | ((GET_BYTE(uuid_bytes, 14) & 128) >> 7))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 14) & 124) >> 2)); output = output || CHR(GET_BYTE(encoding, ((GET_BYTE(uuid_bytes, 14) & 3) << 3) | ((GET_BYTE(uuid_bytes, 15) & 224) >> 5))); output = output || CHR(GET_BYTE(encoding, (GET_BYTE(uuid_bytes, 15) & 31)));
RETURN output; END $$ LANGUAGE plpgsql IMMUTABLE; ```
Gera 11 Digitos aleatórios: YBKXG0CKTH4
```sql -- Cria a extensão pgcrypto para gerar uuid CREATE EXTENSION IF NOT EXISTS pgcrypto;
-- Cria a função para gerar ULID CREATE OR REPLACE FUNCTION gen_lrandom() RETURNS TEXT AS $$ DECLARE ts_millis BIGINT; ts_chars TEXT; random_bytes BYTEA; random_chars TEXT; base32_chars TEXT := '0123456789ABCDEFGHJKMNPQRSTVWXYZ'; i INT; BEGIN -- Pega o timestamp em milissegundos ts_millis := FLOOR(EXTRACT(EPOCH FROM clock_timestamp()) * 1000)::BIGINT;
-- Converte o timestamp para base32 ts_chars := ''; FOR i IN REVERSE 0..11 LOOP ts_chars := ts_chars || substr(base32_chars, ((ts_millis >> (5 * i)) & 31) + 1, 1); END LOOP; -- Gera 10 bytes aleatórios e converte para base32 random_bytes := gen_random_bytes(10); random_chars := ''; FOR i IN 0..9 LOOP random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) >> 3) & 31) + 1, 1); IF i < 9 THEN random_chars := random_chars || substr(base32_chars, (((get_byte(random_bytes, i) & 7) << 2) | (get_byte(random_bytes, i + 1) >> 6)) & 31 + 1, 1); ELSE random_chars := random_chars || substr(base32_chars, ((get_byte(random_bytes, i) & 7) << 2) + 1, 1); END IF; END LOOP; -- Concatena o timestamp e os caracteres aleatórios RETURN ts_chars || random_chars;END; $$ LANGUAGE plpgsql; ```
Exemplo de USO
```sql -- Criação da extensão caso não exista CREATE EXTENSION IF NOT EXISTS pgcrypto; -- Criação da tabela pessoas CREATE TABLE pessoas ( ID UUID DEFAULT gen_random_uuid ( ) PRIMARY KEY, nome TEXT NOT NULL );
-- Busca Pessoa na tabela SELECT * FROM "pessoas" WHERE uuid_to_ulid ( ID ) = '252FAC9F3V8EF80SSDK8PXW02F'; ```
Fontes
- https://github.com/scoville/pgsql-ulid
- https://github.com/geckoboard/pgulid
-
 @ 33baa074:3bb3a297
2025-05-28 08:10:17
@ 33baa074:3bb3a297
2025-05-28 08:10:17The control of residual chlorine in swimming pools is an important part of water quality management, which aims to ensure the sanitation and safety of swimming pool water while avoiding discomfort to swimmers. Here are some key points about residual chlorine control in swimming pools:
Standards for residual chlorine According to the regulations of the national health supervision department, the residual chlorine in swimming pool water should be kept between 0.3mg/L-1.5mg/L. This range can not only ensure effective disinfection, but also avoid irritation to swimmers' skin and eyes caused by excessive residual chlorine. Too low residual chlorine will lead to incomplete disinfection and increase the risk of bacterial growth; while too high residual chlorine may cause human discomfort and even poisoning.
 The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.
The role of residual chlorine
Residual chlorine is a residual disinfectant in swimming pool water, usually in the form of sodium hypocrite (NaClO). It has strong oxidizing properties and can effectively kill bacteria, viruses and other microorganisms in water, thereby ensuring the health of swimmers. In addition, residual chlorine can eliminate harmful substances such as organic matter and ammonia in water to keep the water clean.Residual chlorine detection method The method of detecting residual chlorine in swimming pools usually uses test strips or test kits for qualitative or quantitative detection. In addition, online monitoring instruments can be used to monitor the residual chlorine in the swimming pool in real time. These methods can help managers promptly detect and deal with situations where the residual chlorine content is too high or too low, ensuring that the water quality of the swimming pool meets the standards.
Methods for controlling residual chlorine Reasonable addition of disinfectants: According to the water quality of the swimming pool and the number of swimmers, reasonable addition of disinfectants to control the residual chlorine content within the specified range.
Regular testing: Regularly test the residual chlorine in the swimming pool to promptly detect and deal with situations where the residual chlorine content is too high or too low.
Maintain swimming pool equipment: Regularly check and maintain swimming pool equipment to ensure the water treatment effect and circulation filtration are normal, and reduce residual disinfectants and other harmful substances in the water.
Do a good job in swimmer hygiene management: Strengthen swimmer hygiene management, require swimmers to shower and rinse their feet before entering the pool, and reduce pollution sources entering the swimming pool.
Solution for excessive residual chlorine If the residual chlorine content in the swimming pool exceeds the standard range, the following measures can be taken:
Use decorating agent: Use decorating agent to quickly restore the excessive residual chlorine in the swimming pool to the normal range (0.3~0.5mg/L). This method is applicable to excessive residual chlorine caused by excessive addition of chlorine disinfectant.
Adjust the water treatment process: According to the water quality, adjust the water treatment process appropriately, such as selecting the appropriate type and dosage of disinfectant, and adjusting operating parameters such as flow rate, pH value, etc., to reduce the generation of residual chlorine.
Strengthen equipment maintenance: Regularly maintain and maintain the water treatment equipment of the swimming pool to ensure its normal operation and disinfection effect.
Through the above methods, the residual chlorine content in the swimming pool can be effectively controlled to ensure water quality safety and protect the health of swimmers.
-
 @ e3ba5e1a:5e433365
2025-02-04 08:29:00
@ e3ba5e1a:5e433365
2025-02-04 08:29:00President Trump has started rolling out his tariffs, something I blogged about in November. People are talking about these tariffs a lot right now, with many people (correctly) commenting on how consumers will end up with higher prices as a result of these tariffs. While that part is true, I’ve seen a lot of people taking it to the next, incorrect step: that consumers will pay the entirety of the tax. I put up a poll on X to see what people thought, and while the right answer got a lot of votes, it wasn't the winner.

For purposes of this blog post, our ultimate question will be the following:
- Suppose apples currently sell for $1 each in the entire United States.
- There are domestic sellers and foreign sellers of apples, all receiving the same price.
- There are no taxes or tariffs on the purchase of apples.
- The question is: if the US federal government puts a $0.50 import tariff per apple, what will be the change in the following:
- Number of apples bought in the US
- Price paid by buyers for apples in the US
- Post-tax price received by domestic apple producers
- Post-tax price received by foreign apple producers
Before we can answer that question, we need to ask an easier, first question: before instituting the tariff, why do apples cost $1?
And finally, before we dive into the details, let me provide you with the answers to the ultimate question. I recommend you try to guess these answers before reading this, and if you get it wrong, try to understand why:
- The number of apples bought will go down
- The buyers will pay more for each apple they buy, but not the full amount of the tariff
- Domestic apple sellers will receive a higher price per apple
- Foreign apple sellers will receive a lower price per apple, but not lowered by the full amount of the tariff
In other words, regardless of who sends the payment to the government, both taxed parties (domestic buyers and foreign sellers) will absorb some of the costs of the tariff, while domestic sellers will benefit from the protectionism provided by tariffs and be able to sell at a higher price per unit.
Marginal benefit
All of the numbers discussed below are part of a helper Google Sheet I put together for this analysis. Also, apologies about the jagged lines in the charts below, I hadn’t realized before starting on this that there are some difficulties with creating supply and demand charts in Google Sheets.
Let’s say I absolutely love apples, they’re my favorite food. How much would I be willing to pay for a single apple? You might say “$1, that’s the price in the supermarket,” and in many ways you’d be right. If I walk into supermarket A, see apples on sale for $50, and know that I can buy them at supermarket B for $1, I’ll almost certainly leave A and go buy at B.
But that’s not what I mean. What I mean is: how high would the price of apples have to go everywhere so that I’d no longer be willing to buy a single apple? This is a purely personal, subjective opinion. It’s impacted by how much money I have available, other expenses I need to cover, and how much I like apples. But let’s say the number is $5.
How much would I be willing to pay for another apple? Maybe another $5. But how much am I willing to pay for the 1,000th apple? 10,000th? At some point, I’ll get sick of apples, or run out of space to keep the apples, or not be able to eat, cook, and otherwise preserve all those apples before they rot.
The point being: I’ll be progressively willing to spend less and less money for each apple. This form of analysis is called marginal benefit: how much benefit (expressed as dollars I’m willing to spend) will I receive from each apple? This is a downward sloping function: for each additional apple I buy (quantity demanded), the price I’m willing to pay goes down. This is what gives my personal demand curve. And if we aggregate demand curves across all market participants (meaning: everyone interested in buying apples), we end up with something like this:

Assuming no changes in people’s behavior and other conditions in the market, this chart tells us how many apples will be purchased by our buyers at each price point between $0.50 and $5. And ceteris paribus (all else being equal), this will continue to be the demand curve for apples.
Marginal cost
Demand is half the story of economics. The other half is supply, or: how many apples will I sell at each price point? Supply curves are upward sloping: the higher the price, the more a person or company is willing and able to sell a product.
Let’s understand why. Suppose I have an apple orchard. It’s a large property right next to my house. With about 2 minutes of effort, I can walk out of my house, find the nearest tree, pick 5 apples off the tree, and call it a day. 5 apples for 2 minutes of effort is pretty good, right?
Yes, there was all the effort necessary to buy the land, and plant the trees, and water them… and a bunch more than I likely can’t even guess at. We’re going to ignore all of that for our analysis, because for short-term supply-and-demand movement, we can ignore these kinds of sunk costs. One other simplification: in reality, supply curves often start descending before ascending. This accounts for achieving efficiencies of scale after the first number of units purchased. But since both these topics are unneeded for understanding taxes, I won’t go any further.
Anyway, back to my apple orchard. If someone offers me $0.50 per apple, I can do 2 minutes of effort and get $2.50 in revenue, which equates to a $75/hour wage for me. I’m more than happy to pick apples at that price!
However, let’s say someone comes to buy 10,000 apples from me instead. I no longer just walk out to my nearest tree. I’m going to need to get in my truck, drive around, spend the day in the sun, pay for gas, take a day off of my day job (let’s say it pays me $70/hour). The costs go up significantly. Let’s say it takes 5 days to harvest all those apples myself, it costs me $100 in fuel and other expenses, and I lose out on my $70/hour job for 5 days. We end up with:
- Total expenditure: $100 + $70 * 8 hours a day * 5 days \== $2900
- Total revenue: $5000 (10,000 apples at $0.50 each)
- Total profit: $2100
So I’m still willing to sell the apples at this price, but it’s not as attractive as before. And as the number of apples purchased goes up, my costs keep increasing. I’ll need to spend more money on fuel to travel more of my property. At some point I won’t be able to do the work myself anymore, so I’ll need to pay others to work on the farm, and they’ll be slower at picking apples than me (less familiar with the property, less direct motivation, etc.). The point being: at some point, the number of apples can go high enough that the $0.50 price point no longer makes me any money.
This kind of analysis is called marginal cost. It refers to the additional amount of expenditure a seller has to spend in order to produce each additional unit of the good. Marginal costs go up as quantity sold goes up. And like demand curves, if you aggregate this data across all sellers, you get a supply curve like this:

Equilibrium price
We now know, for every price point, how many apples buyers will purchase, and how many apples sellers will sell. Now we find the equilibrium: where the supply and demand curves meet. This point represents where the marginal benefit a buyer would receive from the next buyer would be less than the cost it would take the next seller to make it. Let’s see it in a chart:

You’ll notice that these two graphs cross at the $1 price point, where 63 apples are both demanded (bought by consumers) and supplied (sold by producers). This is our equilibrium price. We also have a visualization of the surplus created by these trades. Everything to the left of the equilibrium point and between the supply and demand curves represents surplus: an area where someone is receiving something of more value than they give. For example:
- When I bought my first apple for $1, but I was willing to spend $5, I made $4 of consumer surplus. The consumer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and above the equilibrium price point.
- When a seller sells his first apple for $1, but it only cost $0.50 to produce it, the seller made $0.50 of producer surplus. The producer portion of the surplus is everything to the left of the equilibrium point, between the supply and demand curves, and below the equilibrium price point.
Another way of thinking of surplus is “every time someone got a better price than they would have been willing to take.”
OK, with this in place, we now have enough information to figure out how to price in the tariff, which we’ll treat as a negative externality.
Modeling taxes
Alright, the government has now instituted a $0.50 tariff on every apple sold within the US by a foreign producer. We can generally model taxes by either increasing the marginal cost of each unit sold (shifting the supply curve up), or by decreasing the marginal benefit of each unit bought (shifting the demand curve down). In this case, since only some of the producers will pay the tax, it makes more sense to modify the supply curve.
First, let’s see what happens to the foreign seller-only supply curve when you add in the tariff:

With the tariff in place, for each quantity level, the price at which the seller will sell is $0.50 higher than before the tariff. That makes sense: if I was previously willing to sell my 82nd apple for $3, I would now need to charge $3.50 for that apple to cover the cost of the tariff. We see this as the tariff “pushing up” or “pushing left” the original supply curve.
We can add this new supply curve to our existing (unchanged) supply curve for domestic-only sellers, and we end up with a result like this:

The total supply curve adds up the individual foreign and domestic supply curves. At each price point, we add up the total quantity each group would be willing to sell to determine the total quantity supplied for each price point. Once we have that cumulative supply curve defined, we can produce an updated supply-and-demand chart including the tariff:

As we can see, the equilibrium has shifted:
- The equilibrium price paid by consumers has risen from $1 to $1.20.
- The total number of apples purchased has dropped from 63 apples to 60 apples.
- Consumers therefore received 3 less apples. They spent $72 for these 60 apples, whereas previously they spent $63 for 3 more apples, a definite decrease in consumer surplus.
- Foreign producers sold 36 of those apples (see the raw data in the linked Google Sheet), for a gross revenue of $43.20. However, they also need to pay the tariff to the US government, which accounts for $18, meaning they only receive $25.20 post-tariff. Previously, they sold 42 apples at $1 each with no tariff to be paid, meaning they took home $42.
- Domestic producers sold the remaining 24 apples at $1.20, giving them a revenue of $28.80. Since they don’t pay the tariff, they take home all of that money. By contrast, previously, they sold 21 apples at $1, for a take-home of $21.
- The government receives $0.50 for each of the 60 apples sold, or in other words receives $30 in revenue it wouldn’t have received otherwise.
We could be more specific about the surpluses, and calculate the actual areas for consumer surplus, producer surplus, inefficiency from the tariff, and government revenue from the tariff. But I won’t bother, as those calculations get slightly more involved. Instead, let’s just look at the aggregate outcomes:
- Consumers were unquestionably hurt. Their price paid went up by $0.20 per apple, and received less apples.
- Foreign producers were also hurt. Their price received went down from the original $1 to the new post-tariff price of $1.20, minus the $0.50 tariff. In other words: foreign producers only receive $0.70 per apple now. This hurt can be mitigated by shifting sales to other countries without a tariff, but the pain will exist regardless.
- Domestic producers scored. They can sell less apples and make more revenue doing it.
- And the government walked away with an extra $30.
Hopefully you now see the answer to the original questions. Importantly, while the government imposed a $0.50 tariff, neither side fully absorbed that cost. Consumers paid a bit more, foreign producers received a bit less. The exact details of how that tariff was split across the groups is mediated by the relevant supply and demand curves of each group. If you want to learn more about this, the relevant search term is “price elasticity,” or how much a group’s quantity supplied or demanded will change based on changes in the price.
Other taxes
Most taxes are some kind of a tax on trade. Tariffs on apples is an obvious one. But the same applies to income tax (taxing the worker for the trade of labor for money) or payroll tax (same thing, just taxing the employer instead). Interestingly, you can use the same model for analyzing things like tax incentives. For example, if the government decided to subsidize domestic apple production by giving the domestic producers a $0.50 bonus for each apple they sell, we would end up with a similar kind of analysis, except instead of the foreign supply curve shifting up, we’d see the domestic supply curve shifting down.
And generally speaking, this is what you’ll always see with government involvement in the economy. It will result in disrupting an existing equilibrium, letting the market readjust to a new equilibrium, and incentivization of some behavior, causing some people to benefit and others to lose out. We saw with the apple tariff, domestic producers and the government benefited while others lost.
You can see the reverse though with tax incentives. If I give a tax incentive of providing a deduction (not paying income tax) for preschool, we would end up with:
- Government needs to make up the difference in tax revenue, either by raising taxes on others or printing more money (leading to inflation). Either way, those paying the tax or those holding government debased currency will pay a price.
- Those people who don’t use the preschool deduction will receive no benefit, so they simply pay a cost.
- Those who do use the preschool deduction will end up paying less on tax+preschool than they would have otherwise.
This analysis is fully amoral. It’s not saying whether providing subsidized preschool is a good thing or not, it simply tells you where the costs will be felt, and points out that such government interference in free economic choice does result in inefficiencies in the system. Once you have that knowledge, you’re more well educated on making a decision about whether the costs of government intervention are worth the benefits.
-
 @ da0b9bc3:4e30a4a9
2025-05-28 08:07:30
@ da0b9bc3:4e30a4a9
2025-05-28 08:07:30Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
https://stacker.news/items/991020
-
 @ 97c70a44:ad98e322
2025-01-30 17:15:37
@ 97c70a44:ad98e322
2025-01-30 17:15:37There was a slight dust up recently over a website someone runs removing a listing for an app someone built based on entirely arbitrary criteria. I'm not to going to attempt to speak for either wounded party, but I would like to share my own personal definition for what constitutes a "nostr app" in an effort to help clarify what might be an otherwise confusing and opaque purity test.
In this post, I will be committing the "no true Scotsman" fallacy, in which I start with the most liberal definition I can come up with, and gradually refine it until all that is left is the purest, gleamingest, most imaginary and unattainable nostr app imaginable. As I write this, I wonder if anything built yet will actually qualify. In any case, here we go.
It uses nostr
The lowest bar for what a "nostr app" might be is an app ("application" - i.e. software, not necessarily a native app of any kind) that has some nostr-specific code in it, but which doesn't take any advantage of what makes nostr distinctive as a protocol.
Examples might include a scraper of some kind which fulfills its charter by fetching data from relays (regardless of whether it validates or retains signatures). Another might be a regular web 2.0 app which provides an option to "log in with nostr" by requesting and storing the user's public key.
In either case, the fact that nostr is involved is entirely neutral. A scraper can scrape html, pdfs, jsonl, whatever data source - nostr relays are just another target. Likewise, a user's key in this scenario is treated merely as an opaque identifier, with no appreciation for the super powers it brings along.
In most cases, this kind of app only exists as a marketing ploy, or less cynically, because it wants to get in on the hype of being a "nostr app", without the developer quite understanding what that means, or having the budget to execute properly on the claim.
It leverages nostr
Some of you might be wondering, "isn't 'leverage' a synonym for 'use'?" And you would be right, but for one connotative difference. It's possible to "use" something improperly, but by definition leverage gives you a mechanical advantage that you wouldn't otherwise have. This is the second category of "nostr app".
This kind of app gets some benefit out of the nostr protocol and network, but in an entirely selfish fashion. The intention of this kind of app is not to augment the nostr network, but to augment its own UX by borrowing some nifty thing from the protocol without really contributing anything back.
Some examples might include:
- Using nostr signers to encrypt or sign data, and then store that data on a proprietary server.
- Using nostr relays as a kind of low-code backend, but using proprietary event payloads.
- Using nostr event kinds to represent data (why), but not leveraging the trustlessness that buys you.
An application in this category might even communicate to its users via nostr DMs - but this doesn't make it a "nostr app" any more than a website that emails you hot deals on herbal supplements is an "email app". These apps are purely parasitic on the nostr ecosystem.
In the long-term, that's not necessarily a bad thing. Email's ubiquity is self-reinforcing. But in the short term, this kind of "nostr app" can actually do damage to nostr's reputation by over-promising and under-delivering.
It complements nostr
Next up, we have apps that get some benefit out of nostr as above, but give back by providing a unique value proposition to nostr users as nostr users. This is a bit of a fine distinction, but for me this category is for apps which focus on solving problems that nostr isn't good at solving, leaving the nostr integration in a secondary or supporting role.
One example of this kind of app was Mutiny (RIP), which not only allowed users to sign in with nostr, but also pulled those users' social graphs so that users could send money to people they knew and trusted. Mutiny was doing a great job of leveraging nostr, as well as providing value to users with nostr identities - but it was still primarily a bitcoin wallet, not a "nostr app" in the purest sense.
Other examples are things like Nostr Nests and Zap.stream, whose core value proposition is streaming video or audio content. Both make great use of nostr identities, data formats, and relays, but they're primarily streaming apps. A good litmus test for things like this is: if you got rid of nostr, would it be the same product (even if inferior in certain ways)?
A similar category is infrastructure providers that benefit nostr by their existence (and may in fact be targeted explicitly at nostr users), but do things in a centralized, old-web way; for example: media hosts, DNS registrars, hosting providers, and CDNs.
To be clear here, I'm not casting aspersions (I don't even know what those are, or where to buy them). All the apps mentioned above use nostr to great effect, and are a real benefit to nostr users. But they are not True Scotsmen.
It embodies nostr
Ok, here we go. This is the crème de la crème, the top du top, the meilleur du meilleur, the bee's knees. The purest, holiest, most chaste category of nostr app out there. The apps which are, indeed, nostr indigitate.
This category of nostr app (see, no quotes this time) can be defined by the converse of the previous category. If nostr was removed from this type of application, would it be impossible to create the same product?
To tease this apart a bit, apps that leverage the technical aspects of nostr are dependent on nostr the protocol, while apps that benefit nostr exclusively via network effect are integrated into nostr the network. An app that does both things is working in symbiosis with nostr as a whole.
An app that embraces both nostr's protocol and its network becomes an organic extension of every other nostr app out there, multiplying both its competitive moat and its contribution to the ecosystem:
- In contrast to apps that only borrow from nostr on the technical level but continue to operate in their own silos, an application integrated into the nostr network comes pre-packaged with existing users, and is able to provide more value to those users because of other nostr products. On nostr, it's a good thing to advertise your competitors.
- In contrast to apps that only market themselves to nostr users without building out a deep integration on the protocol level, a deeply integrated app becomes an asset to every other nostr app by becoming an organic extension of them through interoperability. This results in increased traffic to the app as other developers and users refer people to it instead of solving their problem on their own. This is the "micro-apps" utopia we've all been waiting for.
Credible exit doesn't matter if there aren't alternative services. Interoperability is pointless if other applications don't offer something your app doesn't. Marketing to nostr users doesn't matter if you don't augment their agency as nostr users.
If I had to choose a single NIP that represents the mindset behind this kind of app, it would be NIP 89 A.K.A. "Recommended Application Handlers", which states:
Nostr's discoverability and transparent event interaction is one of its most interesting/novel mechanics. This NIP provides a simple way for clients to discover applications that handle events of a specific kind to ensure smooth cross-client and cross-kind interactions.
These handlers are the glue that holds nostr apps together. A single event, signed by the developer of an application (or by the application's own account) tells anyone who wants to know 1. what event kinds the app supports, 2. how to link to the app (if it's a client), and (if the pubkey also publishes a kind 10002), 3. which relays the app prefers.
As a sidenote, NIP 89 is currently focused more on clients, leaving DVMs, relays, signers, etc somewhat out in the cold. Updating 89 to include tailored listings for each kind of supporting app would be a huge improvement to the protocol. This, plus a good front end for navigating these listings (sorry nostrapp.link, close but no cigar) would obviate the evil centralized websites that curate apps based on arbitrary criteria.
Examples of this kind of app obviously include many kind 1 clients, as well as clients that attempt to bring the benefits of the nostr protocol and network to new use cases - whether long form content, video, image posts, music, emojis, recipes, project management, or any other "content type".
To drill down into one example, let's think for a moment about forms. What's so great about a forms app that is built on nostr? Well,
- There is a spec for forms and responses, which means that...
- Multiple clients can implement the same data format, allowing for credible exit and user choice, even of...
- Other products not focused on forms, which can still view, respond to, or embed forms, and which can send their users via NIP 89 to a client that does...
- Cryptographically sign forms and responses, which means they are self-authenticating and can be sent to...
- Multiple relays, which reduces the amount of trust necessary to be confident results haven't been deliberately "lost".
Show me a forms product that does all of those things, and isn't built on nostr. You can't, because it doesn't exist. Meanwhile, there are plenty of image hosts with APIs, streaming services, and bitcoin wallets which have basically the same levels of censorship resistance, interoperability, and network effect as if they weren't built on nostr.
It supports nostr
Notice I haven't said anything about whether relays, signers, blossom servers, software libraries, DVMs, and the accumulated addenda of the nostr ecosystem are nostr apps. Well, they are (usually).
This is the category of nostr app that gets none of the credit for doing all of the work. There's no question that they qualify as beautiful nostrcorns, because their value propositions are entirely meaningless outside of the context of nostr. Who needs a signer if you don't have a cryptographic identity you need to protect? DVMs are literally impossible to use without relays. How are you going to find the blossom server that will serve a given hash if you don't know which servers the publishing user has selected to store their content?
In addition to being entirely contextualized by nostr architecture, this type of nostr app is valuable because it does things "the nostr way". By that I mean that they don't simply try to replicate existing internet functionality into a nostr context; instead, they create entirely new ways of putting the basic building blocks of the internet back together.
A great example of this is how Nostr Connect, Nostr Wallet Connect, and DVMs all use relays as brokers, which allows service providers to avoid having to accept incoming network connections. This opens up really interesting possibilities all on its own.
So while I might hesitate to call many of these things "apps", they are certainly "nostr".
Appendix: it smells like a NINO
So, let's say you've created an app, but when you show it to people they politely smile, nod, and call it a NINO (Nostr In Name Only). What's a hacker to do? Well, here's your handy-dandy guide on how to wash that NINO stench off and Become a Nostr.
You app might be a NINO if:
- There's no NIP for your data format (or you're abusing NIP 78, 32, etc by inventing a sub-protocol inside an existing event kind)
- There's a NIP, but no one knows about it because it's in a text file on your hard drive (or buried in your project's repository)
- Your NIP imposes an incompatible/centralized/legacy web paradigm onto nostr
- Your NIP relies on trusted third (or first) parties
- There's only one implementation of your NIP (yours)
- Your core value proposition doesn't depend on relays, events, or nostr identities
- One or more relay urls are hard-coded into the source code
- Your app depends on a specific relay implementation to work (ahem, relay29)
- You don't validate event signatures
- You don't publish events to relays you don't control
- You don't read events from relays you don't control
- You use legacy web services to solve problems, rather than nostr-native solutions
- You use nostr-native solutions, but you've hardcoded their pubkeys or URLs into your app
- You don't use NIP 89 to discover clients and services
- You haven't published a NIP 89 listing for your app
- You don't leverage your users' web of trust for filtering out spam
- You don't respect your users' mute lists
- You try to "own" your users' data
Now let me just re-iterate - it's ok to be a NINO. We need NINOs, because nostr can't (and shouldn't) tackle every problem. You just need to decide whether your app, as a NINO, is actually contributing to the nostr ecosystem, or whether you're just using buzzwords to whitewash a legacy web software product.
If you're in the former camp, great! If you're in the latter, what are you waiting for? Only you can fix your NINO problem. And there are lots of ways to do this, depending on your own unique situation:
- Drop nostr support if it's not doing anyone any good. If you want to build a normal company and make some money, that's perfectly fine.
- Build out your nostr integration - start taking advantage of webs of trust, self-authenticating data, event handlers, etc.
- Work around the problem. Think you need a special relay feature for your app to work? Guess again. Consider encryption, AUTH, DVMs, or better data formats.
- Think your idea is a good one? Talk to other devs or open a PR to the nips repo. No one can adopt your NIP if they don't know about it.
- Keep going. It can sometimes be hard to distinguish a research project from a NINO. New ideas have to be built out before they can be fully appreciated.
- Listen to advice. Nostr developers are friendly and happy to help. If you're not sure why you're getting traction, ask!
I sincerely hope this article is useful for all of you out there in NINO land. Maybe this made you feel better about not passing the totally optional nostr app purity test. Or maybe it gave you some actionable next steps towards making a great NINON (Nostr In Not Only Name) app. In either case, GM and PV.
-
 @ 9e69e420:d12360c2
2025-01-30 12:23:04
@ 9e69e420:d12360c2
2025-01-30 12:23:04Tech stocks have taken a hit globally after China's DeepSeek launched a competitive AI chatbot at a much lower cost than US counterparts. This has stirred market fears of a $1.2 trillion loss across tech companies when trading opens in New York.
DeepSeek’s chatbot quickly topped download charts and surprised experts with its capabilities, developed for only $5.6 million.
The Nasdaq dropped over 3% in premarket trading, with major firms like Nvidia falling more than 10%. SoftBank also saw losses shortly after investing in a significant US AI venture.
Venture capitalist Marc Andreessen called it “AI’s Sputnik moment,” highlighting its potential impact on the industry.
![] (https://www.telegraph.co.uk/content/dam/business/2025/01/27/TELEMMGLPICT000409807198_17379939060750_trans_NvBQzQNjv4BqgsaO8O78rhmZrDxTlQBjdGLvJF5WfpqnBZShRL_tOZw.jpeg)
-
 @ 9e69e420:d12360c2
2025-01-30 12:13:39
@ 9e69e420:d12360c2
2025-01-30 12:13:39Salwan Momika, a Christian Iraqi known for burning the Koran in Sweden, was shot dead during a TikTok livestream in an apartment in Sodertalje. The 38-year-old sparked outrage in the Muslim community for his demonstrations, leading to global condemnation. After being rushed to the hospital, he was pronounced dead.
Authorities arrested five individuals in connection with the incident. Momika's death comes days before a court ruling on his possible incitement of ethnic hatred. The incident highlights the tensions surrounding free speech and religious sentiments, intensifying after his controversial protests in 2023.
-
 @ 0fa80bd3:ea7325de
2025-01-30 04:28:30
@ 0fa80bd3:ea7325de
2025-01-30 04:28:30"Degeneration" or "Вырождение" ![[photo_2025-01-29 23.23.15.jpeg]]
A once-functional object, now eroded by time and human intervention, stripped of its original purpose. Layers of presence accumulate—marks, alterations, traces of intent—until the very essence is obscured. Restoration is paradoxical: to reclaim, one must erase. Yet erasure is an impossibility, for to remove these imprints is to deny the existence of those who shaped them.
The work stands as a meditation on entropy, memory, and the irreversible dialogue between creation and decay.
-
 @ 33baa074:3bb3a297
2025-05-28 07:50:06
@ 33baa074:3bb3a297
2025-05-28 07:50:06Soil moisture is a key factor that affects the structure and function of soil microbial communities. Here are some of the main aspects of how soil moisture affects microorganisms:
Affecting the Growth and Metabolism of Microorganisms Changes in soil moisture content directly affect the growth and metabolic activities of microorganisms. Under suitable moisture conditions, microorganisms are better able to carry out metabolic activities, thereby promoting the decomposition of soil organic matter and the transformation of nutrients. However, under extremely dry or overly wet conditions, the activity of microorganisms will be inhibited, resulting in a decline in soil functions.

Changing the Structure of Microbial Communities Changes in soil moisture conditions can lead to significant changes in the structure of microbial communities. For example, under drought conditions, the number of drought-tolerant microorganisms may increase to adapt to the water shortage environment. While under wet conditions, aerobic microorganisms may dominate. This change in community structure not only affects the soil's water retention capacity, but also other ecological functions of the soil.
Affecting the Stability of Soil Aggregates Soil aggregates are clumps formed by soil particles through physical, chemical and biological actions, and they have an important impact on the soil's water retention capacity. Soil microorganisms participate in the formation and stability of soil aggregates by secreting substances such as extracellular polymers. Appropriate soil moisture helps maintain the stability of soil aggregates, thereby improving the soil's water retention capacity. However, excessive moisture or drought may lead to the destruction of soil aggregates and reduce the soil's water retention capacity.
Regulating soil moisture dynamics Soil microorganisms can regulate the dynamic balance of soil moisture through their metabolic activities, such as decomposing organic matter and synthesizing exopolysaccharides. For example, some microorganisms can increase the water holding capacity of the soil by secreting exopolysaccharides, while others can release water by decomposing organic matter. These activities help maintain the stability of soil moisture and support plant growth.
Influencing the physical properties of soil Soil moisture can also indirectly affect the living environment of microorganisms by affecting the physical properties of the soil, such as pore structure and texture. Good soil pore structure is conducive to the penetration and storage of water, and also provides a suitable living space for microorganisms. Soil texture is closely related to the stability of aggregates. Sandy soils have poor aggregate stability and weak water retention capacity; while clay soils have good aggregate stability and strong water retention capacity.
In summary, soil moisture has many effects on microorganisms, including affecting the growth and metabolism of microorganisms, changing the structure of microbial communities, affecting the stability of soil aggregates, regulating soil moisture dynamics, and affecting the physical properties of soil. Therefore, maintaining suitable soil moisture conditions is of great significance for protecting the diversity and function of soil microbial communities and improving the water retention capacity of soil.
-
 @ 33baa074:3bb3a297
2025-05-28 07:27:02
@ 33baa074:3bb3a297
2025-05-28 07:27:02Distilled water has a wide range of applications in the medical field, mainly including the following aspects: Preparation of injection water Distilled water is an indispensable agent in medical institutions, used for the preparation of drugs, injection and washing of instruments, etc. In the medical process, sterile injection water is needed to flush wounds, prepare drugs, etc. The distilled water machine can ensure the purity of water and prevent microorganisms and harmful substances in the water from causing harm to patients.
Surgical wound flushing In breast cancer surgery, warm distilled water is used to flush surgical wounds. This practice helps to clean the wound, remove possible residual tumor cells, and use hypnotic effect to make tumor cells absorb water, swell, rupture, and necrotic, thereby preventing tumors from growing in the wound.
Cleaning and disinfection Distilled water has a certain disinfection and sterilization effect. It can be used to clean the skin, help eliminate bacteria on the skin surface, and is beneficial to the health of the skin. In addition, distilled water can also be used to clean and disinfect medical equipment to ensure the hygiene and safety of the medical environment.
Laboratory use In medical-related laboratories, distilled water is used to prepare experimental solutions, wash utensils and experimental instruments. These applications ensure the accuracy of experimental results while maintaining the sterile environment of the laboratory.
Moisturizing and Beauty Although not directly used in medical applications, distilled water is also used in skin care. It can be used as a basic moisturizer to help improve the symptoms of dry skin. In the field of medical beauty, distilled water is sometimes used for facial compresses to achieve calming, cooling, and swelling effects.
In summary, the application of distilled water in the medical field is multifaceted, from basic injection water preparation to complex surgical assistance to daily skin care, it has played an important role.
-
 @ 0fa80bd3:ea7325de
2025-01-29 15:43:42
@ 0fa80bd3:ea7325de
2025-01-29 15:43:42Lyn Alden - биткойн евангелист или евангелистка, я пока не понял
npub1a2cww4kn9wqte4ry70vyfwqyqvpswksna27rtxd8vty6c74era8sdcw83aThomas Pacchia - PubKey owner - X - @tpacchia
npub1xy6exlg37pw84cpyj05c2pdgv86hr25cxn0g7aa8g8a6v97mhduqeuhgplcalvadev - Shopstr
npub16dhgpql60vmd4mnydjut87vla23a38j689jssaqlqqlzrtqtd0kqex0nkqCalle - Cashu founder
npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vgДжек Дорси
npub1sg6plzptd64u62a878hep2kev88swjh3tw00gjsfl8f237lmu63q0uf63m21 ideas
npub1lm3f47nzyf0rjp6fsl4qlnkmzed4uj4h2gnf2vhe3l3mrj85vqks6z3c7lМного адресов. Хз кто надо сортировать
https://github.com/aitechguy/nostr-address-bookФиатДжеф - создатель Ностр - https://github.com/fiatjaf
npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6EVAN KALOUDIS Zues wallet
npub19kv88vjm7tw6v9qksn2y6h4hdt6e79nh3zjcud36k9n3lmlwsleqwte2qdПрограммер Коди https://github.com/CodyTseng/nostr-relay
npub1syjmjy0dp62dhccq3g97fr87tngvpvzey08llyt6ul58m2zqpzps9wf6wlAnna Chekhovich - Managing Bitcoin at The Anti-Corruption Foundation https://x.com/AnyaChekhovich
npub1y2st7rp54277hyd2usw6shy3kxprnmpvhkezmldp7vhl7hp920aq9cfyr7 -
 @ 0fa80bd3:ea7325de
2025-01-29 14:44:48
@ 0fa80bd3:ea7325de
2025-01-29 14:44:48![[yedinaya-rossiya-bear.png]]
1️⃣ Be where the bear roams. Stay in its territory, where it hunts for food. No point setting a trap in your backyard if the bear’s chilling in the forest.
2️⃣ Set a well-hidden trap. Bury it, disguise it, and place the bait right in the center. Bears are omnivores—just like secret police KGB agents. And what’s the tastiest bait for them? Money.
3️⃣ Wait for the bear to take the bait. When it reaches in, the trap will snap shut around its paw. It’ll be alive, but stuck. No escape.
Now, what you do with a trapped bear is another question... 😏
-
 @ 005bc4de:ef11e1a2
2025-05-28 16:24:41
@ 005bc4de:ef11e1a2
2025-05-28 16:24:41
Two days ago I put this out: https://peakd.com/hive-124838/@crrdlx/hostr-snaps-9i13ooa7ufp
 Post: https://peakd.com/hive-124838/@crrdlx/hostr-snaps-9i13ooa7ufp
Post: https://peakd.com/hive-124838/@crrdlx/hostr-snaps-9i13ooa7ufpOne of the comments said it "...looks like some sort of game as well." That was enough to tickle my curiosity and get me thinking. The round tomatoes and how they nestled into the grooves of the tiles reminded me of Chinese checkers. The grid brought Hex to mind (the game John Nash played) and I wondered if a square-grid version might be viable. A little searching revealed Hex is a "Connection game" and there are several. The one called Tak seemed really interesting and simple. I like interesting and I really like simple.
So, a square grid connection game wouldn't be new, however, you can't play Tak with tomatoes. Tak requires stacking "stones" or standing them on edge, that would be very, very tricky with tomatoes.
I looked around and happened to have some dried corn kernels and dry beans. I drew out a 5 x 5 grid of dots, lined up five corn kernels on one side in a "home row" and 5 beans on the other. We used to play a game where two sides of Army men met after a series of moves. In that game, we rolled dice to have a "combat" and see who would win the little battle. I wanted something like that in my game, some type of combat or conquest, somehow. So, I started messing around, moving kernels and beans, and totally just set out to make this game up on the fly. This is what I got...
Rules
The objective, like Hex or Tak, is to connect one side (your home row) to your opponent's side. The connection to the other side can be a straight line, or it CAN include a diagonal road. Any of the roads below would be a win for team bean (B).
- One side makes a move by sliding one corn/bean one spot forward.
- Then, take turns making moves.
- Movement can only be one spot forward/back or sideways (NSEW). You cannot move diagonally.
- Opponents CAN occupy, or "squat", on the same spot at once. If so, the spot is being "co-squatted" (they're like two people standing in the same sidewalk tile at the same time).
- However, while opponents occupy the same spot, a "combat" might ensue. A corn/bean can "attack" by moving yet another adjoining corn or bean onto the co-squatted spot. A conquest is made by outnumbering a spot 2-to-1. For instance, if a spot is being occupied by both a bean and corn, and then a second corn moves in, the two corns conquer the one bean. The bean is immediately removed. The bean player then places that conquered bean into any empty spot on his or her home row. That placement constitutes the bean player's turn. So, after the bean is placed on the home row, the corn player makes the next move.
- Play continues until someone completes a road from their home row across to their opponent's home row. (Again, a diagonal road is okay for the win.)
- The losing player got Succotashed.
Game name
As to the name, initially I wanted a tomato-ish name. But, I was using corn and beans. So, I'm naming this game "Succotash" after the corn, bean, and vegetable recipe. I considered calling it the "Texas Caviar Game" because it has tomatoes in it, but playing Succotash just sounds better. Plus, putting tomatoes in succotash sounds yummy.
Simple
A big goal here was to keep it simple. To that end, all that's needed is (a) a paper with a 5 x 5 grid drawn on it, and, (b) 5 pieces of something and 5 pieces of something else. Obviously I used corn kernels and beans, but it could easily be shells/legos, pennies/paperclips, nuts/stones, or whatever.
Initially, I had a "storehouse" of extra corn kernels and storehouse of extra beans (seen in the images). My thinking was that they would replace the corn or beans that get conquered by opponents. Upon playing the game, it was apparent that a storehouse is totally unnecessary. Once captured, the same corn/bean can just be the one that's placed back onto the home row. Five of each is fine.
Also, I'm sure the grid could easily be expanded to whatever size you wish. I played an opponent with the 5 x 5 grid, and that seemed a good size for a five minute or so game.
Why not sit down face-to-face with someone for a minute and give Succotash a try? If you do, I'd love to hear how it went.

-
 @ 9e69e420:d12360c2
2025-01-25 22:16:54
@ 9e69e420:d12360c2
2025-01-25 22:16:54President Trump plans to withdraw 20,000 U.S. troops from Europe and expects European allies to contribute financially to the remaining military presence. Reported by ANSA, Trump aims to deliver this message to European leaders since taking office. A European diplomat noted, “the costs cannot be borne solely by American taxpayers.”
The Pentagon hasn't commented yet. Trump has previously sought lower troop levels in Europe and had ordered cuts during his first term. The U.S. currently maintains around 65,000 troops in Europe, with total forces reaching 100,000 since the Ukraine invasion. Trump's new approach may shift military focus to the Pacific amid growing concerns about China.
-
 @ 9ca447d2:fbf5a36d
2025-05-28 07:01:16
@ 9ca447d2:fbf5a36d
2025-05-28 07:01:16Steak ‘n Shake recently made headlines by officially accepting bitcoin payments via the Lightning Network across all its U.S. locations. The integration of Bitcoin payments at over 500 locations is a monumental moment for both the fast food industry and the broader retail sector.
This is not just something that Steak ‘n Shake is testing in a handful of locations, they are doing a full-scale rollout, fully embracing Bitcoin.
With more than 100 million customers a year, Steak ‘n Shake’s integration of Lightning—Bitcoin’s fast, low-fee payment layer—makes it easier than ever to use Bitcoin in day-to-day life. Buying a burger and a shake with sats? That’s now a real option.
The process is straightforward. Customers simply scan a Lightning QR code at the register, completing their payment in seconds, while Steak ‘n Shake receives instant USD conversion, ensuring price stability and ease of use.
So what does this mean for Bitcoin and E-commerce?
For starters, Steak ‘n Shake becomes the first of eventually many to fully embrace a digital world. As Bitcoin continues to grow, consumers will continue to realize the benefits of saving in a currency that is truly scarce and decentralized.
This is a huge step forward for Bitcoin as it shows it is not just for holding, it’s for spending, too. And by using the Lightning Network, Steak n’ Shake is helping prove that Bitcoin can scale for everyday transactions.
This now creates a seamless checkout experience, making bitcoin a viable alternative to credit cards and cash.
More importantly, it signals a significant shift in mainstream attitudes towards Bitcoin. As a well-known brand across America, this move serves as a powerful endorsement, likely to influence other chains and retailers to consider similar integrations.
Related: Spar Supermarket in Switzerland Now Accepts Bitcoin Via Lightning
What can this mean for your business?
Accepting bitcoin as payment can open the door to a new demographic of tech-savvy, financially engaged consumers who prefer digital assets.
As we know, companies that adopt Bitcoin receive a fascinating amount of love from the Bitcoin community and I would assume Steak n’ Shake will be receiving the same amount of attention.
From a business perspective, accepting bitcoin has become more than just a payment method—it’s a marketing tool. It sets your business apart and gets people talking. And in a crowded market, that kind of edge matters.
Steak ‘n Shake’s embrace of Bitcoin is likely to accelerate the adoption of digital assets in both physical retail and e-commerce.
As more businesses witness the operational and marketing benefits, industry experts anticipate a ripple effect that will increase interaction between consumers and digital currencies, further regulatory clarity, and bring continued innovation in payment technology.
Steak ‘n Shake’s nationwide Bitcoin payments rollout is more than a novelty. It’s a pivotal development for digital payments, setting a precedent for other retailers and signaling the growing integration of digital assets into everyday commerce.
-
 @ 6be5cc06:5259daf0
2025-01-21 20:58:37
@ 6be5cc06:5259daf0
2025-01-21 20:58:37A seguir, veja como instalar e configurar o Privoxy no Pop!_OS.
1. Instalar o Tor e o Privoxy
Abra o terminal e execute:
bash sudo apt update sudo apt install tor privoxyExplicação:
- Tor: Roteia o tráfego pela rede Tor.
- Privoxy: Proxy avançado que intermedia a conexão entre aplicativos e o Tor.
2. Configurar o Privoxy
Abra o arquivo de configuração do Privoxy:
bash sudo nano /etc/privoxy/configNavegue até a última linha (atalho:
Ctrl+/depoisCtrl+Vpara navegar diretamente até a última linha) e insira:bash forward-socks5 / 127.0.0.1:9050 .Isso faz com que o Privoxy envie todo o tráfego para o Tor através da porta 9050.
Salve (
CTRL+OeEnter) e feche (CTRL+X) o arquivo.
3. Iniciar o Tor e o Privoxy
Agora, inicie e habilite os serviços:
bash sudo systemctl start tor sudo systemctl start privoxy sudo systemctl enable tor sudo systemctl enable privoxyExplicação:
- start: Inicia os serviços.
- enable: Faz com que iniciem automaticamente ao ligar o PC.
4. Configurar o Navegador Firefox
Para usar a rede Tor com o Firefox:
- Abra o Firefox.
- Acesse Configurações → Configurar conexão.
- Selecione Configuração manual de proxy.
- Configure assim:
- Proxy HTTP:
127.0.0.1 - Porta:
8118(porta padrão do Privoxy) - Domínio SOCKS (v5):
127.0.0.1 - Porta:
9050
- Proxy HTTP:
- Marque a opção "Usar este proxy também em HTTPS".
- Clique em OK.
5. Verificar a Conexão com o Tor
Abra o navegador e acesse:
text https://check.torproject.org/Se aparecer a mensagem "Congratulations. This browser is configured to use Tor.", a configuração está correta.
Dicas Extras
- Privoxy pode ser ajustado para bloquear anúncios e rastreadores.
- Outros aplicativos também podem ser configurados para usar o Privoxy.
-
 @ 9e69e420:d12360c2
2025-01-21 19:31:48
@ 9e69e420:d12360c2
2025-01-21 19:31:48Oregano oil is a potent natural compound that offers numerous scientifically-supported health benefits.
Active Compounds
The oil's therapeutic properties stem from its key bioactive components: - Carvacrol and thymol (primary active compounds) - Polyphenols and other antioxidant
Antimicrobial Properties
Bacterial Protection The oil demonstrates powerful antibacterial effects, even against antibiotic-resistant strains like MRSA and other harmful bacteria. Studies show it effectively inactivates various pathogenic bacteria without developing resistance.
Antifungal Effects It effectively combats fungal infections, particularly Candida-related conditions like oral thrush, athlete's foot, and nail infections.
Digestive Health Benefits
Oregano oil supports digestive wellness by: - Promoting gastric juice secretion and enzyme production - Helping treat Small Intestinal Bacterial Overgrowth (SIBO) - Managing digestive discomfort, bloating, and IBS symptoms
Anti-inflammatory and Antioxidant Effects
The oil provides significant protective benefits through: - Powerful antioxidant activity that fights free radicals - Reduction of inflammatory markers in the body - Protection against oxidative stress-related conditions
Respiratory Support
It aids respiratory health by: - Loosening mucus and phlegm - Suppressing coughs and throat irritation - Supporting overall respiratory tract function
Additional Benefits
Skin Health - Improves conditions like psoriasis, acne, and eczema - Supports wound healing through antibacterial action - Provides anti-aging benefits through antioxidant properties
Cardiovascular Health Studies show oregano oil may help: - Reduce LDL (bad) cholesterol levels - Support overall heart health
Pain Management The oil demonstrates effectiveness in: - Reducing inflammation-related pain - Managing muscle discomfort - Providing topical pain relief
Safety Note
While oregano oil is generally safe, it's highly concentrated and should be properly diluted before use Consult a healthcare provider before starting supplementation, especially if taking other medications.
-
 @ 6be5cc06:5259daf0
2025-01-21 01:51:46
@ 6be5cc06:5259daf0
2025-01-21 01:51:46Bitcoin: Um sistema de dinheiro eletrônico direto entre pessoas.
Satoshi Nakamoto
satoshin@gmx.com
www.bitcoin.org
Resumo
O Bitcoin é uma forma de dinheiro digital que permite pagamentos diretos entre pessoas, sem a necessidade de um banco ou instituição financeira. Ele resolve um problema chamado gasto duplo, que ocorre quando alguém tenta gastar o mesmo dinheiro duas vezes. Para evitar isso, o Bitcoin usa uma rede descentralizada onde todos trabalham juntos para verificar e registrar as transações.
As transações são registradas em um livro público chamado blockchain, protegido por uma técnica chamada Prova de Trabalho. Essa técnica cria uma cadeia de registros que não pode ser alterada sem refazer todo o trabalho já feito. Essa cadeia é mantida pelos computadores que participam da rede, e a mais longa é considerada a verdadeira.
Enquanto a maior parte do poder computacional da rede for controlada por participantes honestos, o sistema continuará funcionando de forma segura. A rede é flexível, permitindo que qualquer pessoa entre ou saia a qualquer momento, sempre confiando na cadeia mais longa como prova do que aconteceu.
1. Introdução
Hoje, quase todos os pagamentos feitos pela internet dependem de bancos ou empresas como processadores de pagamento (cartões de crédito, por exemplo) para funcionar. Embora esse sistema seja útil, ele tem problemas importantes porque é baseado em confiança.
Primeiro, essas empresas podem reverter pagamentos, o que é útil em caso de erros, mas cria custos e incertezas. Isso faz com que pequenas transações, como pagar centavos por um serviço, se tornem inviáveis. Além disso, os comerciantes são obrigados a desconfiar dos clientes, pedindo informações extras e aceitando fraudes como algo inevitável.
Esses problemas não existem no dinheiro físico, como o papel-moeda, onde o pagamento é final e direto entre as partes. No entanto, não temos como enviar dinheiro físico pela internet sem depender de um intermediário confiável.
O que precisamos é de um sistema de pagamento eletrônico baseado em provas matemáticas, não em confiança. Esse sistema permitiria que qualquer pessoa enviasse dinheiro diretamente para outra, sem depender de bancos ou processadores de pagamento. Além disso, as transações seriam irreversíveis, protegendo vendedores contra fraudes, mas mantendo a possibilidade de soluções para disputas legítimas.
Neste documento, apresentamos o Bitcoin, que resolve o problema do gasto duplo usando uma rede descentralizada. Essa rede cria um registro público e protegido por cálculos matemáticos, que garante a ordem das transações. Enquanto a maior parte da rede for controlada por pessoas honestas, o sistema será seguro contra ataques.
2. Transações
Para entender como funciona o Bitcoin, é importante saber como as transações são realizadas. Imagine que você quer transferir uma "moeda digital" para outra pessoa. No sistema do Bitcoin, essa "moeda" é representada por uma sequência de registros que mostram quem é o atual dono. Para transferi-la, você adiciona um novo registro comprovando que agora ela pertence ao próximo dono. Esse registro é protegido por um tipo especial de assinatura digital.
O que é uma assinatura digital?
Uma assinatura digital é como uma senha secreta, mas muito mais segura. No Bitcoin, cada usuário tem duas chaves: uma "chave privada", que é secreta e serve para criar a assinatura, e uma "chave pública", que pode ser compartilhada com todos e é usada para verificar se a assinatura é válida. Quando você transfere uma moeda, usa sua chave privada para assinar a transação, provando que você é o dono. A próxima pessoa pode usar sua chave pública para confirmar isso.
Como funciona na prática?
Cada "moeda" no Bitcoin é, na verdade, uma cadeia de assinaturas digitais. Vamos imaginar o seguinte cenário:
- A moeda está com o Dono 0 (você). Para transferi-la ao Dono 1, você assina digitalmente a transação com sua chave privada. Essa assinatura inclui o código da transação anterior (chamado de "hash") e a chave pública do Dono 1.
- Quando o Dono 1 quiser transferir a moeda ao Dono 2, ele assinará a transação seguinte com sua própria chave privada, incluindo também o hash da transação anterior e a chave pública do Dono 2.
- Esse processo continua, formando uma "cadeia" de transações. Qualquer pessoa pode verificar essa cadeia para confirmar quem é o atual dono da moeda.
Resolvendo o problema do gasto duplo
Um grande desafio com moedas digitais é o "gasto duplo", que é quando uma mesma moeda é usada em mais de uma transação. Para evitar isso, muitos sistemas antigos dependiam de uma entidade central confiável, como uma casa da moeda, que verificava todas as transações. No entanto, isso criava um ponto único de falha e centralizava o controle do dinheiro.
O Bitcoin resolve esse problema de forma inovadora: ele usa uma rede descentralizada onde todos os participantes (os "nós") têm acesso a um registro completo de todas as transações. Cada nó verifica se as transações são válidas e se a moeda não foi gasta duas vezes. Quando a maioria dos nós concorda com a validade de uma transação, ela é registrada permanentemente na blockchain.
Por que isso é importante?
Essa solução elimina a necessidade de confiar em uma única entidade para gerenciar o dinheiro, permitindo que qualquer pessoa no mundo use o Bitcoin sem precisar de permissão de terceiros. Além disso, ela garante que o sistema seja seguro e resistente a fraudes.
3. Servidor Timestamp
Para assegurar que as transações sejam realizadas de forma segura e transparente, o sistema Bitcoin utiliza algo chamado de "servidor de registro de tempo" (timestamp). Esse servidor funciona como um registro público que organiza as transações em uma ordem específica.
Ele faz isso agrupando várias transações em blocos e criando um código único chamado "hash". Esse hash é como uma impressão digital que representa todo o conteúdo do bloco. O hash de cada bloco é amplamente divulgado, como se fosse publicado em um jornal ou em um fórum público.
Esse processo garante que cada bloco de transações tenha um registro de quando foi criado e que ele existia naquele momento. Além disso, cada novo bloco criado contém o hash do bloco anterior, formando uma cadeia contínua de blocos conectados — conhecida como blockchain.
Com isso, se alguém tentar alterar qualquer informação em um bloco anterior, o hash desse bloco mudará e não corresponderá ao hash armazenado no bloco seguinte. Essa característica torna a cadeia muito segura, pois qualquer tentativa de fraude seria imediatamente detectada.
O sistema de timestamps é essencial para provar a ordem cronológica das transações e garantir que cada uma delas seja única e autêntica. Dessa forma, ele reforça a segurança e a confiança na rede Bitcoin.
4. Prova-de-Trabalho
Para implementar o registro de tempo distribuído no sistema Bitcoin, utilizamos um mecanismo chamado prova-de-trabalho. Esse sistema é semelhante ao Hashcash, desenvolvido por Adam Back, e baseia-se na criação de um código único, o "hash", por meio de um processo computacionalmente exigente.
A prova-de-trabalho envolve encontrar um valor especial que, quando processado junto com as informações do bloco, gere um hash que comece com uma quantidade específica de zeros. Esse valor especial é chamado de "nonce". Encontrar o nonce correto exige um esforço significativo do computador, porque envolve tentativas repetidas até que a condição seja satisfeita.
Esse processo é importante porque torna extremamente difícil alterar qualquer informação registrada em um bloco. Se alguém tentar mudar algo em um bloco, seria necessário refazer o trabalho de computação não apenas para aquele bloco, mas também para todos os blocos que vêm depois dele. Isso garante a segurança e a imutabilidade da blockchain.
A prova-de-trabalho também resolve o problema de decidir qual cadeia de blocos é a válida quando há múltiplas cadeias competindo. A decisão é feita pela cadeia mais longa, pois ela representa o maior esforço computacional já realizado. Isso impede que qualquer indivíduo ou grupo controle a rede, desde que a maioria do poder de processamento seja mantida por participantes honestos.
Para garantir que o sistema permaneça eficiente e equilibrado, a dificuldade da prova-de-trabalho é ajustada automaticamente ao longo do tempo. Se novos blocos estiverem sendo gerados rapidamente, a dificuldade aumenta; se estiverem sendo gerados muito lentamente, a dificuldade diminui. Esse ajuste assegura que novos blocos sejam criados aproximadamente a cada 10 minutos, mantendo o sistema estável e funcional.
5. Rede
A rede Bitcoin é o coração do sistema e funciona de maneira distribuída, conectando vários participantes (ou nós) para garantir o registro e a validação das transações. Os passos para operar essa rede são:
-
Transmissão de Transações: Quando alguém realiza uma nova transação, ela é enviada para todos os nós da rede. Isso é feito para garantir que todos estejam cientes da operação e possam validá-la.
-
Coleta de Transações em Blocos: Cada nó agrupa as novas transações recebidas em um "bloco". Este bloco será preparado para ser adicionado à cadeia de blocos (a blockchain).
-
Prova-de-Trabalho: Os nós competem para resolver a prova-de-trabalho do bloco, utilizando poder computacional para encontrar um hash válido. Esse processo é como resolver um quebra-cabeça matemático difícil.
-
Envio do Bloco Resolvido: Quando um nó encontra a solução para o bloco (a prova-de-trabalho), ele compartilha esse bloco com todos os outros nós na rede.
-
Validação do Bloco: Cada nó verifica o bloco recebido para garantir que todas as transações nele contidas sejam válidas e que nenhuma moeda tenha sido gasta duas vezes. Apenas blocos válidos são aceitos.
-
Construção do Próximo Bloco: Os nós que aceitaram o bloco começam a trabalhar na criação do próximo bloco, utilizando o hash do bloco aceito como base (hash anterior). Isso mantém a continuidade da cadeia.
Resolução de Conflitos e Escolha da Cadeia Mais Longa
Os nós sempre priorizam a cadeia mais longa, pois ela representa o maior esforço computacional já realizado, garantindo maior segurança. Se dois blocos diferentes forem compartilhados simultaneamente, os nós trabalharão no primeiro bloco recebido, mas guardarão o outro como uma alternativa. Caso o segundo bloco eventualmente forme uma cadeia mais longa (ou seja, tenha mais blocos subsequentes), os nós mudarão para essa nova cadeia.
Tolerância a Falhas
A rede é robusta e pode lidar com mensagens que não chegam a todos os nós. Uma transação não precisa alcançar todos os nós de imediato; basta que chegue a um número suficiente deles para ser incluída em um bloco. Da mesma forma, se um nó não receber um bloco em tempo hábil, ele pode solicitá-lo ao perceber que está faltando quando o próximo bloco é recebido.
Esse mecanismo descentralizado permite que a rede Bitcoin funcione de maneira segura, confiável e resiliente, sem depender de uma autoridade central.
6. Incentivo
O incentivo é um dos pilares fundamentais que sustenta o funcionamento da rede Bitcoin, garantindo que os participantes (nós) continuem operando de forma honesta e contribuindo com recursos computacionais. Ele é estruturado em duas partes principais: a recompensa por mineração e as taxas de transação.
Recompensa por Mineração
Por convenção, o primeiro registro em cada bloco é uma transação especial que cria novas moedas e as atribui ao criador do bloco. Essa recompensa incentiva os mineradores a dedicarem poder computacional para apoiar a rede. Como não há uma autoridade central para emitir moedas, essa é a maneira pela qual novas moedas entram em circulação. Esse processo pode ser comparado ao trabalho de garimpeiros, que utilizam recursos para colocar mais ouro em circulação. No caso do Bitcoin, o "recurso" consiste no tempo de CPU e na energia elétrica consumida para resolver a prova-de-trabalho.
Taxas de Transação
Além da recompensa por mineração, os mineradores também podem ser incentivados pelas taxas de transação. Se uma transação utiliza menos valor de saída do que o valor de entrada, a diferença é tratada como uma taxa, que é adicionada à recompensa do bloco contendo essa transação. Com o passar do tempo e à medida que o número de moedas em circulação atinge o limite predeterminado, essas taxas de transação se tornam a principal fonte de incentivo, substituindo gradualmente a emissão de novas moedas. Isso permite que o sistema opere sem inflação, uma vez que o número total de moedas permanece fixo.
Incentivo à Honestidade
O design do incentivo também busca garantir que os participantes da rede mantenham um comportamento honesto. Para um atacante que consiga reunir mais poder computacional do que o restante da rede, ele enfrentaria duas escolhas:
- Usar esse poder para fraudar o sistema, como reverter transações e roubar pagamentos.
- Seguir as regras do sistema, criando novos blocos e recebendo recompensas legítimas.
A lógica econômica favorece a segunda opção, pois um comportamento desonesto prejudicaria a confiança no sistema, diminuindo o valor de todas as moedas, incluindo aquelas que o próprio atacante possui. Jogar dentro das regras não apenas maximiza o retorno financeiro, mas também preserva a validade e a integridade do sistema.
Esse mecanismo garante que os incentivos econômicos estejam alinhados com o objetivo de manter a rede segura, descentralizada e funcional ao longo do tempo.
7. Recuperação do Espaço em Disco
Depois que uma moeda passa a estar protegida por muitos blocos na cadeia, as informações sobre as transações antigas que a geraram podem ser descartadas para economizar espaço em disco. Para que isso seja possível sem comprometer a segurança, as transações são organizadas em uma estrutura chamada "árvore de Merkle". Essa árvore funciona como um resumo das transações: em vez de armazenar todas elas, guarda apenas um "hash raiz", que é como uma assinatura compacta que representa todo o grupo de transações.
Os blocos antigos podem, então, ser simplificados, removendo as partes desnecessárias dessa árvore. Apenas a raiz do hash precisa ser mantida no cabeçalho do bloco, garantindo que a integridade dos dados seja preservada, mesmo que detalhes específicos sejam descartados.
Para exemplificar: imagine que você tenha vários recibos de compra. Em vez de guardar todos os recibos, você cria um documento e lista apenas o valor total de cada um. Mesmo que os recibos originais sejam descartados, ainda é possível verificar a soma com base nos valores armazenados.
Além disso, o espaço ocupado pelos blocos em si é muito pequeno. Cada bloco sem transações ocupa apenas cerca de 80 bytes. Isso significa que, mesmo com blocos sendo gerados a cada 10 minutos, o crescimento anual em espaço necessário é insignificante: apenas 4,2 MB por ano. Com a capacidade de armazenamento dos computadores crescendo a cada ano, esse espaço continuará sendo trivial, garantindo que a rede possa operar de forma eficiente sem problemas de armazenamento, mesmo a longo prazo.
8. Verificação de Pagamento Simplificada
É possível confirmar pagamentos sem a necessidade de operar um nó completo da rede. Para isso, o usuário precisa apenas de uma cópia dos cabeçalhos dos blocos da cadeia mais longa (ou seja, a cadeia com maior esforço de trabalho acumulado). Ele pode verificar a validade de uma transação ao consultar os nós da rede até obter a confirmação de que tem a cadeia mais longa. Para isso, utiliza-se o ramo Merkle, que conecta a transação ao bloco em que ela foi registrada.
Entretanto, o método simplificado possui limitações: ele não pode confirmar uma transação isoladamente, mas sim assegurar que ela ocupa um lugar específico na cadeia mais longa. Dessa forma, se um nó da rede aprova a transação, os blocos subsequentes reforçam essa aceitação.
A verificação simplificada é confiável enquanto a maioria dos nós da rede for honesta. Contudo, ela se torna vulnerável caso a rede seja dominada por um invasor. Nesse cenário, um atacante poderia fabricar transações fraudulentas que enganariam o usuário temporariamente até que o invasor obtivesse controle completo da rede.
Uma estratégia para mitigar esse risco é configurar alertas nos softwares de nós completos. Esses alertas identificam blocos inválidos, sugerindo ao usuário baixar o bloco completo para confirmar qualquer inconsistência. Para maior segurança, empresas que realizam pagamentos frequentes podem preferir operar seus próprios nós, reduzindo riscos e permitindo uma verificação mais direta e confiável.
9. Combinando e Dividindo Valor
No sistema Bitcoin, cada unidade de valor é tratada como uma "moeda" individual, mas gerenciar cada centavo como uma transação separada seria impraticável. Para resolver isso, o Bitcoin permite que valores sejam combinados ou divididos em transações, facilitando pagamentos de qualquer valor.
Entradas e Saídas
Cada transação no Bitcoin é composta por:
- Entradas: Representam os valores recebidos em transações anteriores.
- Saídas: Correspondem aos valores enviados, divididos entre os destinatários e, eventualmente, o troco para o remetente.
Normalmente, uma transação contém:
- Uma única entrada com valor suficiente para cobrir o pagamento.
- Ou várias entradas combinadas para atingir o valor necessário.
O valor total das saídas nunca excede o das entradas, e a diferença (se houver) pode ser retornada ao remetente como troco.
Exemplo Prático
Imagine que você tem duas entradas:
- 0,03 BTC
- 0,07 BTC
Se deseja enviar 0,08 BTC para alguém, a transação terá:
- Entrada: As duas entradas combinadas (0,03 + 0,07 BTC = 0,10 BTC).
- Saídas: Uma para o destinatário (0,08 BTC) e outra como troco para você (0,02 BTC).
Essa flexibilidade permite que o sistema funcione sem precisar manipular cada unidade mínima individualmente.
Difusão e Simplificação
A difusão de transações, onde uma depende de várias anteriores e assim por diante, não representa um problema. Não é necessário armazenar ou verificar o histórico completo de uma transação para utilizá-la, já que o registro na blockchain garante sua integridade.
10. Privacidade
O modelo bancário tradicional oferece um certo nível de privacidade, limitando o acesso às informações financeiras apenas às partes envolvidas e a um terceiro confiável (como bancos ou instituições financeiras). No entanto, o Bitcoin opera de forma diferente, pois todas as transações são publicamente registradas na blockchain. Apesar disso, a privacidade pode ser mantida utilizando chaves públicas anônimas, que desvinculam diretamente as transações das identidades das partes envolvidas.
Fluxo de Informação
- No modelo tradicional, as transações passam por um terceiro confiável que conhece tanto o remetente quanto o destinatário.
- No Bitcoin, as transações são anunciadas publicamente, mas sem revelar diretamente as identidades das partes. Isso é comparável a dados divulgados por bolsas de valores, onde informações como o tempo e o tamanho das negociações (a "fita") são públicas, mas as identidades das partes não.
Protegendo a Privacidade
Para aumentar a privacidade no Bitcoin, são adotadas as seguintes práticas:
- Chaves Públicas Anônimas: Cada transação utiliza um par de chaves diferentes, dificultando a associação com um proprietário único.
- Prevenção de Ligação: Ao usar chaves novas para cada transação, reduz-se a possibilidade de links evidentes entre múltiplas transações realizadas pelo mesmo usuário.
Riscos de Ligação
Embora a privacidade seja fortalecida, alguns riscos permanecem:
- Transações multi-entrada podem revelar que todas as entradas pertencem ao mesmo proprietário, caso sejam necessárias para somar o valor total.
- O proprietário da chave pode ser identificado indiretamente por transações anteriores que estejam conectadas.
11. Cálculos
Imagine que temos um sistema onde as pessoas (ou computadores) competem para adicionar informações novas (blocos) a um grande registro público (a cadeia de blocos ou blockchain). Este registro é como um livro contábil compartilhado, onde todos podem verificar o que está escrito.
Agora, vamos pensar em um cenário: um atacante quer enganar o sistema. Ele quer mudar informações já registradas para beneficiar a si mesmo, por exemplo, desfazendo um pagamento que já fez. Para isso, ele precisa criar uma versão alternativa do livro contábil (a cadeia de blocos dele) e convencer todos os outros participantes de que essa versão é a verdadeira.
Mas isso é extremamente difícil.
Como o Ataque Funciona
Quando um novo bloco é adicionado à cadeia, ele depende de cálculos complexos que levam tempo e esforço. Esses cálculos são como um grande quebra-cabeça que precisa ser resolvido.
- Os “bons jogadores” (nós honestos) estão sempre trabalhando juntos para resolver esses quebra-cabeças e adicionar novos blocos à cadeia verdadeira.
- O atacante, por outro lado, precisa resolver quebra-cabeças sozinho, tentando “alcançar” a cadeia honesta para que sua versão alternativa pareça válida.
Se a cadeia honesta já está vários blocos à frente, o atacante começa em desvantagem, e o sistema está projetado para que a dificuldade de alcançá-los aumente rapidamente.
A Corrida Entre Cadeias
Você pode imaginar isso como uma corrida. A cada bloco novo que os jogadores honestos adicionam à cadeia verdadeira, eles se distanciam mais do atacante. Para vencer, o atacante teria que resolver os quebra-cabeças mais rápido que todos os outros jogadores honestos juntos.
Suponha que:
- A rede honesta tem 80% do poder computacional (ou seja, resolve 8 de cada 10 quebra-cabeças).
- O atacante tem 20% do poder computacional (ou seja, resolve 2 de cada 10 quebra-cabeças).
Cada vez que a rede honesta adiciona um bloco, o atacante tem que "correr atrás" e resolver mais quebra-cabeças para alcançar.
Por Que o Ataque Fica Cada Vez Mais Improvável?
Vamos usar uma fórmula simples para mostrar como as chances de sucesso do atacante diminuem conforme ele precisa "alcançar" mais blocos:
P = (q/p)^z
- q é o poder computacional do atacante (20%, ou 0,2).
- p é o poder computacional da rede honesta (80%, ou 0,8).
- z é a diferença de blocos entre a cadeia honesta e a cadeia do atacante.
Se o atacante está 5 blocos atrás (z = 5):
P = (0,2 / 0,8)^5 = (0,25)^5 = 0,00098, (ou, 0,098%)
Isso significa que o atacante tem menos de 0,1% de chance de sucesso — ou seja, é muito improvável.
Se ele estiver 10 blocos atrás (z = 10):
P = (0,2 / 0,8)^10 = (0,25)^10 = 0,000000095, (ou, 0,0000095%).
Neste caso, as chances de sucesso são praticamente nulas.
Um Exemplo Simples
Se você jogar uma moeda, a chance de cair “cara” é de 50%. Mas se precisar de 10 caras seguidas, sua chance já é bem menor. Se precisar de 20 caras seguidas, é quase impossível.
No caso do Bitcoin, o atacante precisa de muito mais do que 20 caras seguidas. Ele precisa resolver quebra-cabeças extremamente difíceis e alcançar os jogadores honestos que estão sempre à frente. Isso faz com que o ataque seja inviável na prática.
Por Que Tudo Isso é Seguro?
- A probabilidade de sucesso do atacante diminui exponencialmente. Isso significa que, quanto mais tempo passa, menor é a chance de ele conseguir enganar o sistema.
- A cadeia verdadeira (honesta) está protegida pela força da rede. Cada novo bloco que os jogadores honestos adicionam à cadeia torna mais difícil para o atacante alcançar.
E Se o Atacante Tentar Continuar?
O atacante poderia continuar tentando indefinidamente, mas ele estaria gastando muito tempo e energia sem conseguir nada. Enquanto isso, os jogadores honestos estão sempre adicionando novos blocos, tornando o trabalho do atacante ainda mais inútil.
Assim, o sistema garante que a cadeia verdadeira seja extremamente segura e que ataques sejam, na prática, impossíveis de ter sucesso.
12. Conclusão
Propusemos um sistema de transações eletrônicas que elimina a necessidade de confiança, baseando-se em assinaturas digitais e em uma rede peer-to-peer que utiliza prova de trabalho. Isso resolve o problema do gasto duplo, criando um histórico público de transações imutável, desde que a maioria do poder computacional permaneça sob controle dos participantes honestos. A rede funciona de forma simples e descentralizada, com nós independentes que não precisam de identificação ou coordenação direta. Eles entram e saem livremente, aceitando a cadeia de prova de trabalho como registro do que ocorreu durante sua ausência. As decisões são tomadas por meio do poder de CPU, validando blocos legítimos, estendendo a cadeia e rejeitando os inválidos. Com este mecanismo de consenso, todas as regras e incentivos necessários para o funcionamento seguro e eficiente do sistema são garantidos.
Faça o download do whitepaper original em português: https://bitcoin.org/files/bitcoin-paper/bitcoin_pt_br.pdf
-
 @ eb0157af:77ab6c55
2025-05-28 06:01:29
@ eb0157af:77ab6c55
2025-05-28 06:01:29Bitcoin surpasses gold in the United States: 50 million holders and a dominant role in the global market.
According to a new report by River, for the first time in history, the number of Americans owning bitcoin has surpassed that of gold holders. The analysis reveals that approximately 50 million U.S. citizens currently own the cryptocurrency, while gold owners number 37 million. In fact, 14.3% of Americans own bitcoin, the highest percentage of holders worldwide.

Source: River
The report highlights that 40% of all Bitcoin-focused companies are based in the United States, consolidating America’s dominant position in the sector. Additionally, 40.5% of Bitcoin holders are men aged 31 to 35, followed by 35.9% of men aged 41 to 45. In contrast, only 13.4% of holders are women.

Source: River
Notably, U.S. companies hold 94.8% of all bitcoins owned by publicly traded companies worldwide. According to the report, recent regulatory changes in the U.S. have made the asset more accessible through financial products such as spot ETFs.
The document also shows that American investors increasingly view the cryptocurrency as protection against fiscal instability and inflation, appreciating its limited supply and decentralized governance model.
For River, Bitcoin offers significant practical advantages over gold in the modern digital era. Its ease of custody, cross-border transfer, and liquidity make the cryptocurrency an attractive option for both individual and institutional investors, the report suggests.
The post USA: 50 million Americans own bitcoin appeared first on Atlas21.
-
 @ 5f078e90:b2bacaa3
2025-05-28 12:00:23
@ 5f078e90:b2bacaa3
2025-05-28 12:00:23Sylvi the seahorse

In the coral haven of Azure Bay, a seahorse named Sylvi danced with the tides. Her tail curled around a swaying frond as she watched fish dart by. One dawn, a lost pearl rolled into her nook. Sylvi, curious, nudged it along the reef, meeting crabs and eels who shared tales of the deep. By dusk, she found its oyster home. The pearl gleamed thanks, and Sylvi twirled home, her heart light as foam.
Ignore this test. This was in bold originally.
(380 chars, plain text after Markdown stripping, this was in italics originally)
Originally written on habla.news (on Nostr)
-
 @ cff1720e:15c7e2b2
2025-01-19 17:48:02
@ cff1720e:15c7e2b2
2025-01-19 17:48:02Einleitung\ \ Schwierige Dinge einfach zu erklären ist der Anspruch von ELI5 (explain me like I'm 5). Das ist in unserer hoch technisierten Welt dringend erforderlich, denn nur mit dem Verständnis der Technologien können wir sie richtig einsetzen und weiter entwickeln.\ Ich starte meine Serie mit Nostr, einem relativ neuen Internet-Protokoll. Was zum Teufel ist ein Internet-Protokoll? Formal beschrieben sind es internationale Standards, die dafür sorgen, dass das Internet seit über 30 Jahren ziemlich gut funktioniert. Es ist die Sprache, in der sich die Rechner miteinander unterhalten und die auch Sie täglich nutzen, vermutlich ohne es bewusst wahrzunehmen. http(s) transportiert ihre Anfrage an einen Server (z.B. Amazon), und html sorgt dafür, dass aus den gelieferten Daten eine schöne Seite auf ihrem Bildschirm entsteht. Eine Mail wird mit smtp an den Mailserver gesendet und mit imap von ihm abgerufen, und da alle den Standard verwenden, funktioniert das mit jeder App auf jedem Betriebssystem und mit jedem Mail-Provider. Und mit einer Mail-Adresse wie roland@pareto.space können sie sogar jederzeit umziehen, egal wohin. Cool, das ist state of the art! Aber warum funktioniert das z.B. bei Chat nicht, gibt es da kein Protokoll? Doch, es heißt IRC (Internet Relay Chat → merken sie sich den Namen), aber es wird so gut wie nicht verwendet. Die Gründe dafür sind nicht technischer Natur, vielmehr wurden mit Apps wie Facebook, Twitter, WhatsApp, Telegram, Instagram, TikTok u.a. bewusst Inkompatibilitäten und Nutzerabhängigkeiten geschaffen um Profite zu maximieren.

Warum Nostr?
Da das Standard-Protokoll nicht genutzt wird, hat jede App ihr eigenes, und wir brauchen eine handvoll Apps um uns mit allen Bekannten auszutauschen. Eine Mobilfunknummer ist Voraussetzung für jedes Konto, damit können die App-Hersteller die Nutzer umfassend tracken und mit dem Verkauf der Informationen bis zu 30 USD je Konto und Monat verdienen. Der Nutzer ist nicht mehr Kunde, er ist das Produkt! Der Werbe-SPAM ist noch das kleinste Problem bei diesem Geschäftsmodell. Server mit Millionen von Nutzerdaten sind ein “honey pot”, dementsprechend oft werden sie gehackt und die Zugangsdaten verkauft. 2024 wurde auch der Twitter-Account vom damaligen Präsidenten Joe Biden gehackt, niemand wusste mehr wer die Nachrichten verfasst hat (vorher auch nicht), d.h. die Authentizität der Inhalte ist bei keinem dieser Anbieter gewährleistet. Im selben Jahr wurde der Telegram-Gründer in Frankreich in Beugehaft genommen, weil er sich geweigert hatte Hintertüren in seine Software einzubauen. Nun kann zum Schutz "unserer Demokratie” praktisch jeder mitlesen, was sie mit wem an Informationen austauschen, z.B. darüber welches Shampoo bestimmte Politiker verwenden.

Und wer tatsächlich glaubt er könne Meinungsfreiheit auf sozialen Medien praktizieren, findet sich schnell in der Situation von Donald Trump wieder (seinerzeit amtierender Präsident), dem sein Twitter-Konto 2021 abgeschaltet wurde (Cancel-Culture). Die Nutzerdaten, also ihr Profil, ihre Kontakte, Dokumente, Bilder, Videos und Audiofiles - gehören ihnen ohnehin nicht mehr sondern sind Eigentum des Plattform-Betreibers; lesen sie sich mal die AGB's durch. Aber nein, keine gute Idee, das sind hunderte Seiten und sie werden permanent geändert. Alle nutzen also Apps, deren Technik sie nicht verstehen, deren Regeln sie nicht kennen, wo sie keine Rechte haben und die ihnen die Resultate ihres Handelns stehlen. Was würde wohl der Fünfjährige sagen, wenn ihm seine ältere Schwester anbieten würde, alle seine Spielzeuge zu “verwalten” und dann auszuhändigen wenn er brav ist? “Du spinnst wohl”, und damit beweist der Knirps mehr Vernunft als die Mehrzahl der Erwachsenen. \ \ Resümee: keine Standards, keine Daten, keine Rechte = keine Zukunft!

\ Wie funktioniert Nostr?
Die Entwickler von Nostr haben erkannt dass sich das Server-Client-Konzept in ein Master-Slave-Konzept verwandelt hatte. Der Master ist ein Synonym für Zentralisierung und wird zum “single point of failure”, der zwangsläufig Systeme dysfunktional macht. In einem verteilten Peer2Peer-System gibt es keine Master mehr sondern nur gleichberechtigte Knoten (Relays), auf denen die Informationen gespeichert werden. Indem man Informationen auf mehreren Relays redundant speichert, ist das System in jeglicher Hinsicht resilienter. Nicht nur die Natur verwendet dieses Prinzip seit Jahrmillionen erfolgreich, auch das Internet wurde so konzipiert (das ARPAnet wurde vom US-Militär für den Einsatz in Kriegsfällen unter massiven Störungen entwickelt). Alle Nostr-Daten liegen auf Relays und der Nutzer kann wählen zwischen öffentlichen (zumeist kostenlosen) und privaten Relays, z.B. für geschlossene Gruppen oder zum Zwecke von Daten-Archivierung. Da Dokumente auf mehreren Relays gespeichert sind, werden statt URL's (Locator) eindeutige Dokumentnamen (URI's = Identifier) verwendet, broken Links sind damit Vergangenheit und Löschungen / Verluste ebenfalls.\ \ Jedes Dokument (Event genannt) wird vom Besitzer signiert, es ist damit authentisch und fälschungssicher und kann nur vom Ersteller gelöscht werden. Dafür wird ein Schlüsselpaar verwendet bestehend aus privatem (nsec) und öffentlichem Schlüssel (npub) wie aus der Mailverschlüsselung (PGP) bekannt. Das repräsentiert eine Nostr-Identität, die um Bild, Namen, Bio und eine lesbare Nostr-Adresse ergänzt werden kann (z.B. roland@pareto.space ), mehr braucht es nicht um alle Ressourcen des Nostr-Ökosystems zu nutzen. Und das besteht inzwischen aus über hundert Apps mit unterschiedlichen Fokussierungen, z.B. für persönliche verschlüsselte Nachrichten (DM → OxChat), Kurznachrichten (Damus, Primal), Blogbeiträge (Pareto), Meetups (Joinstr), Gruppen (Groups), Bilder (Olas), Videos (Amethyst), Audio-Chat (Nostr Nests), Audio-Streams (Tunestr), Video-Streams (Zap.Stream), Marktplätze (Shopstr) u.v.a.m. Die Anmeldung erfolgt mit einem Klick (single sign on) und den Apps stehen ALLE Nutzerdaten zur Verfügung (Profil, Daten, Kontakte, Social Graph → Follower, Bookmarks, Comments, etc.), im Gegensatz zu den fragmentierten Datensilos der Gegenwart.\ \ Resümee: ein offener Standard, alle Daten, alle Rechte = große Zukunft!

\ Warum ist Nostr die Zukunft des Internet?
“Baue Dein Haus nicht auf einem fremden Grundstück” gilt auch im Internet - für alle App-Entwickler, Künstler, Journalisten und Nutzer, denn auch ihre Daten sind werthaltig. Nostr garantiert das Eigentum an den Daten, und überwindet ihre Fragmentierung. Weder die Nutzung noch die kreativen Freiheiten werden durch maßlose Lizenz- und Nutzungsbedingungen eingeschränkt. Aus passiven Nutzern werden durch Interaktion aktive Teilnehmer, Co-Creatoren in einer Sharing-Ökonomie (Value4Value). OpenSource schafft endlich wieder Vertrauen in die Software und ihre Anbieter. Offene Standards ermöglichen den Entwicklern mehr Kooperation und schnellere Entwicklung, für die Anwender garantieren sie Wahlfreiheit. Womit wir letztmalig zu unserem Fünfjährigen zurückkehren. Kinder lieben Lego über alles, am meisten die Maxi-Box “Classic”, weil sie damit ihre Phantasie im Kombinieren voll ausleben können. Erwachsene schenken ihnen dann die viel zu teuren Themenpakete, mit denen man nur eine Lösung nach Anleitung bauen kann. “Was stimmt nur mit meinen Eltern nicht, wann sind die denn falsch abgebogen?" fragt sich der Nachwuchs zu Recht. Das Image lässt sich aber wieder aufpolieren, wenn sie ihren Kindern Nostr zeigen, denn die Vorteile verstehen sogar Fünfjährige.

\ Das neue Internet ist dezentral. Das neue Internet ist selbstbestimmt. Nostr ist das neue Internet.
https://nostr.net/ \ https://start.njump.me/
Hier das Interview zum Thema mit Radio Berliner Morgenröte
-
 @ a29cfc65:484fac9c
2025-05-28 10:30:32
@ a29cfc65:484fac9c
2025-05-28 10:30:32Deutschland ist eines der wenigen Länder mit einer gesetzlich verankerten ausnahmslosen Schulbesuchspflicht. Mit den Schulschließungen in der Corona-Zeit wurde das Gesetz jedoch faktisch plötzlich außer Kraft gesetzt. Alle mussten zu Hause lernen. Als die Schulen danach wieder offen waren, wurden die Kinder mit Maskenpflicht, Tests und Impfdruck gequält. Nicht selten traten bei den Schülern Krankheiten und psychische Störungen auf. Nicht wenige Eltern suchten im Gespräch mit dem Lehrerkollegium nach Lösungen für ihre Kinder. In den meisten Fällen war das nicht möglich. Die Lehrer waren auf die neue Ideologie und die Durchsetzung der Maßnahmen eingeschworen und hatten Angst. Einige Eltern haben ihre Kinder dann in eigener Verantwortung aus der Schule genommen und zu Hause selbst unterrichtet. An manchen Orten fanden sich Gemeinschaften, wo die Kinder in Gruppen lernten. Während viele Lerngemeinschaften nicht mehr existieren, hat die Familie von Katharina den Unterricht für ihre drei Kinder in Eigenregie etabliert. Inzwischen haben sie dafür sogar „den Segen“ von Familiengericht und Jugendamt.
Katharina und Johannes leben mit ihren drei Wunschkindern Aurelius (15), Benjamin (14) und Friedrich (10) in einem Vorort von Leipzig. Die Familie wohnte früher in der Stadt. In der Corona-Zeit haben sie sich mit dem Physiotherapie- & Seminarzentrum Curasanus eine Existenz auf dem Land aufgebaut und begehen diesen Sommer ihr 20-jähriges Praxis-Jubiläum. Katharina hat ihre Arbeit als Physiotherapeutin weitgehend aufgegeben, um sich als Mama und Lernbegleiterin ihren Kindern widmen zu können. Daneben bietet sie Vorträge und Workshops an, übernimmt einen großen Teil der Praxis-Organisation und ist Manager, Rezeptionistin und Vertriebler der eigenen Firma. Wir besuchten einen ihrer Lachyoga-Kurse. Dabei erlebten wir ihr Zusammenspiel mit den drei Kindern. Anschließend stellten wir Katharina unsere Fragen zum Freilernen.
Im unmittelbaren Umfeld wird die Familie bestaunt und geachtet. Sie haben sich bewusst für das Freilernen entschieden. Die Kinder wurden ohne Test nicht mehr in die Schule gelassen. Auch andere Zwangsmaßnahmen wie die Maske wollten die Eltern den Kindern ersparen. Besonders Benjamin hatte traumatische Erlebnisse. Seine Lehrerin schmiss mit dem Schlüssel nach den Schülern und wandte andere schwarze Pädagogik an. Er ging ständig mit Bauchschmerzen ins Bett. Ein weiterer Punkt ist die Masernimpfung. Die Kinder könnten zwar zur Schule gehen, aber die Eltern werden mit rechtlichen Maßnahmen und Zwangszahlungen belegt. Da Katharina in ihrer Praxis viele Erkrankungen als Folge der Masernimpfung beobachten konnte, lehnt sie die Pflichtimpfung ab. Die Eltern haben kein Vertrauen mehr in die staatliche Schulerziehung mit all dem Zwang und den Erpressungen. Als die Familie den Entschluss gefasst hatte, die Kinder nicht mehr in die Schule zu schicken, haben sie ihre Praxis vorübergehend geschlossen, ihr Haus verkauft und sind auf Reisen gegangen. Die beiden großen Kinder wurden von der Schule abgemeldet. Nach der Rückkehr haben sie dann mit einem neuen Leben auf dem Land begonnen.
Lernen ohne Schule: Wie geht das?
„Wissen ist Macht und eine Holschuld“, sagt uns Katharina. Das ist ihr Motto und motiviert auch die Kinder. Mit dem Unterricht zu Hause macht die Familie ihre eigene Studie und zeigt, dass Lernen auch anders geht als in der Schule. Die Eltern können viel besser auf jedes einzelne Kind eingehen. Johannes arbeitete früher als Straßenbauer. Er unterstützt die Jungs vor allem in Mathematik, Geometrie und Physik sowie bei handwerklichen Fertigkeiten. Katharinas Stärken liegen in Deutsch, Sprachen und Organisation. Unter den Patienten ihrer Praxis gibt es Lehrer, die ihnen helfen. Weitere Unterstützung kommt von Freunden und Bekannten. Bei bestimmten Projekten treffen sie auf andere Freilernerkinder. „Das Netzwerk wird immer größer, es wird immer schöner und interessanter“, sagt Katharina. Man geht mit vielen anderen einen gemeinsamen Weg, verlässt dabei eingetretene Pfade und erkundet neue Themenfelder wie Mediengestaltung, freie Energie, Elektrotherapie, meditatives und Improvisations-Zeichnen. „Ich sprudele vor Ideen. Sie kommen in mein Feld, und dann mache ich was draus“, sagt Katharina. Die Jungs sind in Wurzen im Ringelnatz-Literaturkreis. Dort schreiben sie Drehbuchgeschichten und haben einen Film produziert. Sie suchen sich Projekte oder kreieren neue, wie mit dem Planetarium Eilenburg. Diese Zusammenarbeit hat sich sehr gut entwickelt. Dort lernen 4- bis 15-Jährige zusammen. Die drei Jungs spielen Klavier. Erdkunde und Geschichte erleben die Kinder auch dadurch, dass die Familie Hauptstädte oder die bosnischen Pyramiden selbst erkundet. Dabei erweist es sich als Vorteil, nicht auf die Ferienzeiten angewiesen zu sein.
Als Physiotherapeutin ist Katharina bewusst, dass man neue Lernstrategien entwickeln muss. Die Kinder lernen unterschiedlich. Jedes Kind hat seinen eigenen Charakter. Aurelius benötigt eher eine 1:1-Betreuung. Darauf kann Katharina viel individueller eingehen als die staatliche Schule. Es ist aber auch aufwendiger und anstrengender. Besonderen Wert legt sie darauf, dass rechte und linke Gehirnhälfte gleichmäßig beansprucht werden. Lernphasen werden immer wieder mit Entspannungs- oder Bewegungsphasen kombiniert. Sie weiß, dass den Kindern zuerst die Grundlagen des Lesens, Rechnens und Schreibens vermittelt werden müssen. Dann sind sie in der Lage, sich alles Weitere selbst anzueignen – Unterstützung vorausgesetzt. „Besonders das Schreiben mit der eigenen Hand ist wichtig für die Vernetzung der beiden Gehirnhälften“, sagt Katharina. Dafür nehmen sich die Eltern Zeit. Die Kinder führen Tagebuch. Außerdem halten es die Eltern für wichtig, den Kindern Werte und Tugenden wie Dankbarkeit, Verlässlichkeit, Beharrlichkeit, Aufrichtigkeit, Ehrlichkeit und die zehn Gebote zu vermitteln. Katharina und Johannes sind beide religiös begleitet aufgewachsen. Heute sehen sie die Kirche als Institution kritisch. Angebunden an die Schöpfung und im Gottvertrauen erschaffen und schöpfen sie Leben und Lebensraum aus eigener Kraft – so erklärt es uns Katharina.
Ein weiteres Thema sind die Funktionen des Körpers und wie sich die Kinder gesund erhalten können. Vieles lernen sie dabei in der Physiotherapiepraxis. Die Familie hat das Privileg, in ihrem eigenen Biorhythmus leben zu können. „Das macht sehr viel aus – wir sind alle gesund“, sagt Katharina. Der Lern- und Arbeitstag beginnt nicht vor 9 Uhr und hat eine eigene Struktur. Im Tagesablauf sind feste Verantwortlichkeiten integriert. So wechseln sich die Kinder aller drei Tage mit Tischdecken, Staubsaugen und Geschirrspüler ab. Das hilft ihnen, sich selbst zu organisieren. Das geht nicht immer reibungslos vonstatten. Wenn das Lernpensum beizeiten abgearbeitet wurde, helfen die Kinder im Haushalt oder Garten oder gehen ihrem Bewegungsdrang auf andere Weise nach. Die Eltern sind am Abend noch länger aktiv, denn die Praxis erfordert noch die eine oder andere bürokratische Pflicht. Die Familie ist sehr naturverbunden. Sie gehen viel in den Wald und in den Garten. Sie bauen selbst Gemüse und Obst an. Dabei können die Kinder zum Beispiel Erfahrungen mit Permakultur und natürlicher Düngung sammeln. Die Familie achtet auf die Ernährung, schließlich ist Katharina seit fast 25 Jahren Ernährungsberaterin. Was sie nicht selbst anbauen, wird beim Bauern des Vertrauens eingekauft. Die Jungs können selbst kochen und backen. Die Schädlichkeit von Zucker ist den Kindern schon bewusst geworden, ohne gänzlich auf Schokolade verzichten zu müssen. Medikamente gibt es im Haushalt nicht. Sie kennen sich sehr gut mit den Heilmitteln aus der Natur aus und können so ihre Selbstheilungskräfte aktivieren. Sie haben keinen Hausarzt. Natürlich hat keines der Kinder ein Handy. Bisher haben sie noch kein Verlangen danach. Die Eltern halten es für wichtig, dass die Kinder erst sicher bei Selbstorganisation und Tagesstruktur sind, bevor sie ein Handy bekommen. Katharina weist darauf hin, dass beispielsweise WhatsApp erst ab 16 Jahren zugelassen ist, und fragt sich, ob das andere Eltern wissen.
Gesetze auf Augenhöhe auslegen
Den Behörden blieben die Freilerner nicht verborgen. Sie wurden aktiv und schalteten das Familiengericht ein. Die Familie hatte keinen Anwalt und keine Rechtsschutzversicherung. Katharina erzählt uns, dass sie schließlich auf „Hilfe von oben“ gehofft habe. Irgendwer hat sie anscheinend erhört, denn sie bekamen „einen Engel“ als Verfahrensbeistand. Die Behörden waren sehr zugänglich. In den Gesprächen gab man zu, mit der Schulsituation ebenfalls nicht zufrieden zu sein. „Wir wollen so wie ihr, dass sich etwas verändert. Wir sind an Eurer Seite.“ Die Gespräche mit dem Jugendamt und der Richterin vom Familiengericht Grimma waren immer auf Augenhöhe. Schließlich legte man der Familie keine Steine in den Weg. Damit kann Katharina ihr Konzept nach außen leben und andere inspirieren. Ihre Schlussfolgerung: Eltern müssen sich ihrer Stärken bewusst werden und aus ihrer Angst herauskommen. Das Konzept muss aber zur Familie passen, denn jede Familie ist anders.
Die Basis für freies Lernen ist das Vertrauen der Eltern in ihre Kinder. Denn Kinder sind von Natur aus wissbegierig und wollen lernen. Katharina hat viel von Bertrand Stern und von Riccardo Leppe gelernt. Beiden wurde von ihren Eltern das Lernen ohne Schulbesuch ermöglicht. Mit Bertrand Stern hat Katharina Kontakt. Er wird im November am Buß- und Bettag eine kleine Fortbildung im Therapie- und Seminarzentrum geben. Für den Vorabend ist ein Vortrag geplant. Katharina zitiert Riccardo Leppe: „Es ändert sich nur was, wenn man es selbst tut.“ Er sei sich sicher, dass der Fortschritt beim Freilernen inzwischen so weit ist, dass „die Paste nicht wieder zurück in die Tube geht“.
Der Übergang zur Berufsausbildung
Die ersten Freilernerkinder kommen jetzt in das Alter, in dem sie eine Berufsausbildung beginnen können. Aurelius und Benjamin, die beiden „Großen“, machen seit Anfang des Jahres schon erste Praktika bei ortsansässigen Handwerksbetrieben. Beide Seiten sind sehr zufrieden. Durch die Praktika, die länger dauern als im schulischen Lehrplan vorgesehen, können sich die Kinder ausprobieren. Katharina findet es interessant miterleben zu dürfen, wie auf ihre Kinder reagiert wird. Bringen sie etwas mit, das die anderen nicht haben? Denken sie anders mit? Benjamin bekam schon ein Angebot, in einem Metallbau-Betrieb stundenweise mitzuarbeiten. In den Betrieben weiß man, dass die Abschlüsse der staatlichen Schulen größtenteils das Papier nicht wert sind, auf dem sie stehen. Viele verlassen die Schule und können kaum lesen und schreiben, von Selbstorganisation ganz zu schweigen. Ein Freilerner kann eine staatliche Externen-Prüfung ablegen, um einen Haupt- oder Realschulabschluss zu erwerben. Katharina: „Für eine Ausbildung bei einem privaten Unternehmer braucht man das nicht, allein der Unternehmer entscheidet über die Aufnahme des Auszubildenden“. Außerdem stehen den jungen Leuten Privatschulen oder der zweite Bildungsweg zur Verfügung. Wenn man einen praktischen Beruf ergreift, ist es immer noch möglich, sich bis zur Hochschulreife weiterzubilden. Nach mehrjährigen Tätigkeiten kann man bei den Kammern von Industrie, Handel und Handwerk (IHK und HWK) eine Abschlussprüfung ablegen, mit der man zum Studium zugelassen werden kann. Oder man geht gleich den Weg in die Selbstständigkeit.
Frei lernen weitergedacht
Während der Coronazeit haben sich in Sachsen und speziell um Leipzig herum kleine Freilernergruppen gefunden. Die Gruppen werden aktuell zusammengeführt, um zum Beispiel gemeinsam den Mathematikunterricht zu gestalten. Besonders um Dresden herum ist die Szene noch stärker ausgeprägt. Außerdem gibt es seit mehr als 20 Jahren den Bundesverband Natürlich Lernen (BVNL). Er bietet Beratung und zentrale Veranstaltungen an.
Der Wunsch nach dem freien Lernen ohne Schulzwang ist groß. Doch die meisten Eltern wollen ihre Kinder dafür irgendwo abgeben und nicht selbst unterrichten. Katharinas größter Wunsch ist es, drei bis fünf Elternpaare zu finden, die sich in die Betreuung und Unterrichtung ihrer Kinder teilen. Das größte Hindernis dafür sieht sie in den Eltern selbst. Durch ungelöste transgenerative Konflikte und unverarbeitete Familientraumata kommen sie noch nicht in ihre eigene Kraft für ein selbstbestimmtes Leben. Viele wagen es noch nicht, ihre Erwerbstätigkeit zugunsten der Kinder einzuschränken. Katharina sieht es als große Aufgabe für sich und ihre Familie, mit dem Freilernen das Gemeinschaftsbewusstsein und gute Konfliktlösungsstrategien zu entwickeln. Sie denkt dabei bereits an ihre Enkel. Aber sie weiß auch, dass die Eltern ein sehr hohes Maß an Eigeninitiative, Motivation und Selbstdisziplin aufbringen müssen. Sie würde Eltern, die sich das noch nicht zutrauen, als Traumabegleiterin zur Verfügung stehen, für einen angemessenen Energieausgleich. Diese gegenseitige Unterstützung käme Kindern und Eltern zugute. Ebenso hält sie die Idee der Mehrgenerationenerziehung für wichtig. Dabei profitieren nicht nur die Kinder. Die Erfahrungen der älteren Menschen gehen nicht verloren, sondern werden an die jüngeren Generationen weitergegeben und machen sie resilienter. Das hilft den Eltern, ihrer Erwerbsarbeit nachzugehen und Familientraumata zu bewältigen.
Katharina ist eine starke Frau und sprüht nur so vor Energie. Selbst als wir nach 21 Uhr das Therapiezentrum verlassen, sind ihr die Anstrengungen des Tages nicht anzumerken. Sie wird nicht müde beim Sprechen. Für Fragen zum Thema Freilernen kann man sich an sie wenden.
Der Text wurde zuerst am 27.05.2025 im Blog „Freie Akademie für Medien und Journalismus“ veröffentlicht (https://www.freie-medienakademie.de/medien-plus/lernen-neu-gemacht)
Bildquelle: Salah Darwish, unsplash.com
-
 @ 9e69e420:d12360c2
2025-01-19 04:48:31
@ 9e69e420:d12360c2
2025-01-19 04:48:31A new report from the National Sports Shooting Foundation (NSSF) shows that civilian firearm possession exceeded 490 million in 2022. The total from 1990 to 2022 is estimated at 491.3 million firearms. In 2022, over ten million firearms were domestically produced, leading to a total of 16,045,911 firearms available in the U.S. market.
Of these, 9,873,136 were handguns, 4,195,192 were rifles, and 1,977,583 were shotguns. Handgun availability aligns with the concealed carry and self-defense market, as all states allow concealed carry, with 29 having constitutional carry laws.
-
 @ cae03c48:2a7d6671
2025-05-28 06:00:48
@ cae03c48:2a7d6671
2025-05-28 06:00:48Bitcoin Magazine

President Trump Supports Strategic Bitcoin Reserve Bill, Senator Lummis SaysToday at the Bitcoin 2025 Conference in Las Vegas, Nevada, US Senator Cynthia Lummis of Wyoming, Senator Marsha Blackburn of Tennessee, and Senator Jim Justice of West Virginia, took the stage to give updates on federal and state level Bitcoin adoption in the United States.
JUST IN:
 Senator Cynthia Lummis said US military generals are "big supporters" of a Strategic Bitcoin Reserve for economic power. pic.twitter.com/2RPMV3tbdA
Senator Cynthia Lummis said US military generals are "big supporters" of a Strategic Bitcoin Reserve for economic power. pic.twitter.com/2RPMV3tbdA— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
Cynthia Lummis announced that President Donald Trump is supportive of her Strategic Bitcoin Reserve Act, which would see the United States purchase 1,000,000 BTC, among other pro-Bitcoin and stablecoin legislation.
“President Trump supports the bill,” she stated. “And he has a team in the White House working on digital assets — everything from stablecoins to market structure to Bitcoin Strategic Reserve. And they will probably roll out in that order.”
“States have always been the incubators of innovation,” Lummis said. “Senator Justice was the Governor of West Virginia, Senator Blackburn will be the next Governor of Tennessee. The states are where the innovation is occurring.”
“So you have Arizona, Texas and New Hampshire that passed Strategic Bitcoin Reserve bills this year,” she continued. “30 states consider Strategic Bitcoin Reserves. We have the United Arab Emirates purchasing Bitcoin through American exchange traded funds — that’s good for America.”

Senator Blackburn echoed Lummis’ statements, sharing her thoughts on how other countries will follow the United States in their adoption of Bitcoin.
“Many of our allies follow what we do,” Blackburn said. “Everybody wants to be a part of of our market, they want to be a part of our trade. And they will follow what we do. And as Senator Lummis said, we already see countries that are establishing these reserves. So it is vitally important that we hold this as a portion of our reserves.”
Justice emphasized that to be successful, “we have got to get the economics right. Many people ask me many times as Governor, ‘what’s the most important thing you do?’ And I’ll promise you this, it’s all about the economics.”
Justice then went on to explain that when the average, everyday person is using Bitcoin to purchase their necessities, that legislation will start “happening at light speed”, because politicians want to get re-elected and therefore must follow the will of the people.

You can watch the full panel discussion and the rest of the Bitcoin 2025 Conference Industry Day below:
This post President Trump Supports Strategic Bitcoin Reserve Bill, Senator Lummis Says first appeared on Bitcoin Magazine and is written by Nik.
-
 @ 3770c235:16042bcc
2025-05-28 05:54:01
@ 3770c235:16042bcc
2025-05-28 05:54:01** Introduction: The Neon Pulse of Las Vegas
**It’s 2:30 AM on a Tuesday. The Strip hums with laughter, clinking glasses, and the occasional Elvis impersonator. A group of friends stumbles out of a nightclub, squinting under the glow of a Las Vegas billboard that screams, “Hungry? $5 Pancakes → 1 Block Right!” Ten minutes later, they’re drowning their late-night cravings in syrup.This isn’t luck—it’s Las Vegas billboards doing what they do best: working while the rest of the world sleeps. In a city where the party never stops, these glowing giants are the ultimate salespeople. Let’s dive into why Las Vegas billboards outshine traditional ads and how your business can ride their 24/7 energy wave.
** Why Las Vegas Billboards Never Take a Coffee Break
** 1. Tourists Don’t Have Bedtimes (and Neither Do Billboards)
- 42 million visitors flock to Vegas yearly. They’re sipping margaritas at noon, gambling at midnight, and shopping at 3 AM.
- Las Vegas billboards near hotspots like the Bellagio Fountains or Fremont Street catch eyes round the clock.Real Story:
A donut shop owner named Luis rented a billboard near the “Welcome to Vegas” sign. His message? “Jet Lagged? Sugar Fix Open 24/7!” Sales tripled—especially between 1 AM and 4 AM.** 2. You Can’t “Skip” a Billboard
** - Imagine this: You’re stuck in traffic on the Strip. Your phone’s dead. That Las Vegas billboard for air-conditioned massages? It’s your lifeline.
- Compare that to online ads: 47% of people skip them, and TikTok ads vanish in a scroll.- Vegas Thrives on Impulse
- Billboards tap into spontaneous decisions:
- “Let’s try that rooftop bar!”
- “Wait, free slot play? Let’s U-turn!”
- Traditional ads (like radio spots) fade fast. Billboards linger, nudging tourists to act now.
** 5 Reasons Your Business Needs a Vegas Billboard
** 1. Size Matters (And So Does Flash)
- Strip billboards can be taller than a 5-story building.
- Digital screens use LEDs so bright, they’re visible from space.Pro Tip:
A casino added fake “smoke” effects to their billboard for a Halloween promo. Traffic backed up for selfies—and bookings spiked.- No Language Barrier
- Vegas draws visitors from Tokyo, Berlin, São Paulo...
- A Las Vegas billboard with a giant cocktail emoji? Universal for “Drinks here!”
Case Study:
A Korean BBQ spot used a billboard of sizzling meat. No words. Just smoke visuals. Tourists followed the “aroma” straight to their door.- They’re Always in the Right Place, Right Time
- 6 AM: Joggers see smoothie ads.
- 3 PM: Pool partiers spot “Free Margarita” promos.
-
Midnight: Hangover clinics whisper, “We’ve got IVs.”
-
Instant Trust Boost
- A tiny online ad says “startup.” A glowing billboard says, “We’re Vegas royalty.”
Jake’s Win:
Jake’s tiny magic shop rented a billboard reading, “Real Tricks—Cheaper Than the Casino!” Tourists treated him like David Blaine.- QR Codes = Instant Customers
- “Scan for free parking!” → 1,000 scans in a weekend.
- “Tap to call a limo” → Rides booked before the light turns green.
** How to Make Your Vegas Billboard Irresistible
** Step 1: Claim Your Territory
- The Strip: Pricey but prime ($15k–$60k/month).
- Fremont Street: Quirky, cheaper ($5k–$20k), packed with partiers.
- Highway 15: Target road-trippers with “Almost There! Cold Beer Ahead!”Step 2: Keep It Stupid Simple
- Bad: “Experience Culinary Excellence at Our Artisanal Bistro!”
- Good: “24/7 Bacon Pancakes → Exit Here.”Maria’s Hack:
Maria’s tattoo parlor used a billboard with a flaming skull and three words: “Walk-Ins Welcome.” No phone number. “People just… show up,” she laughs.Step 3: Track Your Wins (Like a Vegas High Roller)
- QR Codes: “Scan for Free Slot Play!” → Track scans.
- Unique URLs: “Visit VegasPizza24.com” → Monitor traffic.
- Old-School: Count foot traffic. (“Did that bachelor party just roll in from our billboard? Yes.”)**FAQs ** 1. “How do I even measure if my billboard’s working? It’s not like online ads!”
Answer:
You’re right—it’s not just clicks and likes. But here’s how real businesses track success:
- QR Codes: Add a unique code like “Scan for Free Appetizer!” Track scans.
- Promo Codes: “Mention this billboard for 20% off!” (Works great for Uber drivers: “My passengers blurt it out mid-ride,” says driver Luis M.)
- Foot Traffic Spikes: Note sales surges after your ad goes live. A dispensary saw a 60% bump in visits after their “We’re Closer Than the Casino!” billboard.
- Social Media Tags: Encourage selfies with your billboard. A retro motel offered a free pool pass for tagged photos. Their Instagram exploded.- “Aren’t billboards old-school? My Gen Z customers live on TikTok!”
Answer:
Billboards in Vegas are anything but old-school. Here’s why: - Hybrid Campaigns: Pair billboards with geofenced mobile ads. Example: A billboard for a pool party says, “Scan to Pre-Order Drinks.” Users nearby get a TikTok-style ad on their phone.
- Instagrammable Designs: Quirky billboards go viral. The “Welcome to Vegas” sign is the most Instagrammed spot in the city. Mimic that vibe!
- Influencer Collabs: Pay a Vegas influencer to pose with your billboard. Their followers will hunt it down like a scavenger hunt.
Real Story:
A vintage clothing store’s billboard (“Find Your Retro Vibe → 2 Blocks East”) became a TikTok trend after a local influencer did a “thrift haul” video there.** 3. “What’s the biggest mistake businesses make with Vegas billboards?”
** Answer:
Trying to cram in too much info! Drivers have 5–7 seconds to read your ad. Avoid:
- Text Overload: “Grand Opening! 50% Off! Open 24/7! Call Now!” → Too much!
- Bland Designs: Gray text on a gray background? Yawn.
- Ignoring Locals: Tourists are 70% of viewers, but locals matter too. A gym’s billboard said, “Tired of Tourists? Work Out in Peace.” Memberships spiked.Fix It:
- Use 7 words max.
- Bold colors (red, yellow, neon pink).
- Add a clear call to action: “Turn Right Now!” or “Scan for Free Parking.”- “Do I need a permit? What if my ad gets rejected?”
Answer:
Yep, permits are a thing. The city bans: - Flashing Lights Near Residences: No strobes in suburban areas.
- Certain Content: No swear words, adult themes, or political fights.
How to Avoid Rejection:
- Work with local Outdoor Advertising companies—they know the rules.
- Submit designs early. One pizza joint’s ad was flagged for a pepperoni slice deemed “too suggestive.” They swapped it to a cheese pull… and it got approved.Conclusion: Let Your Business Shine All Night Long
At 5 AM, as the sun peeks over the desert, the Las Vegas billboards keep glowing. They’ve sold midnight pancakes, inspired shotgun weddings, and even talked someone out of a questionable tattoo (“Wait! Our Parlor’s Better → Next Exit”).These aren’t just ads—they’re part of Vegas’ heartbeat. So whether you’re slinging sushi, massages, or monster truck rides, remember: In a city that never sleeps, your billboard shouldn’t either.
Ready to Light Up the Night?
Find Las Vegas billboards near you today. And if you spot one that says, “Free High-Fives for Readers of This Article,” honk twice. It’s probably yours. -
 @ 21810ca8:f2e8341e
2025-05-28 08:10:53
@ 21810ca8:f2e8341e
2025-05-28 08:10:53Ich bin neu bei Nostr und versuche mich hier rein zu fuchsen. Kann das einer sehen? Und dann habe ich noch viele Fragen
Gibt es gute Marktplätze wie ebay oder ebay kleinanzeigen wo man stink normale dinge und kram von zuhause gegen sat verkaufen kann.
-
 @ f9cf4e94:96abc355
2025-01-18 06:09:50
@ f9cf4e94:96abc355
2025-01-18 06:09:50Para esse exemplo iremos usar: | Nome | Imagem | Descrição | | --------------- | ------------------------------------------------------------ | ------------------------------------------------------------ | | Raspberry PI B+ |
 | Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |
| Cortex-A53 (ARMv8) 64-bit a 1.4GHz e 1 GB de SDRAM LPDDR2, |
| Pen drive |  | 16Gb |
| 16Gb |Recomendo que use o Ubuntu Server para essa instalação. Você pode baixar o Ubuntu para Raspberry Pi aqui. O passo a passo para a instalação do Ubuntu no Raspberry Pi está disponível aqui. Não instale um desktop (como xubuntu, lubuntu, xfce, etc.).
Passo 1: Atualizar o Sistema 🖥️
Primeiro, atualize seu sistema e instale o Tor:
bash apt update apt install tor
Passo 2: Criar o Arquivo de Serviço
nrs.service🔧Crie o arquivo de serviço que vai gerenciar o servidor Nostr. Você pode fazer isso com o seguinte conteúdo:
```unit [Unit] Description=Nostr Relay Server Service After=network.target
[Service] Type=simple WorkingDirectory=/opt/nrs ExecStart=/opt/nrs/nrs-arm64 Restart=on-failure
[Install] WantedBy=multi-user.target ```
Passo 3: Baixar o Binário do Nostr 🚀
Baixe o binário mais recente do Nostr aqui no GitHub.
Passo 4: Criar as Pastas Necessárias 📂
Agora, crie as pastas para o aplicativo e o pendrive:
bash mkdir -p /opt/nrs /mnt/edriver
Passo 5: Listar os Dispositivos Conectados 🔌
Para saber qual dispositivo você vai usar, liste todos os dispositivos conectados:
bash lsblk
Passo 6: Formatando o Pendrive 💾
Escolha o pendrive correto (por exemplo,
/dev/sda) e formate-o:bash mkfs.vfat /dev/sda
Passo 7: Montar o Pendrive 💻
Monte o pendrive na pasta
/mnt/edriver:bash mount /dev/sda /mnt/edriver
Passo 8: Verificar UUID dos Dispositivos 📋
Para garantir que o sistema monte o pendrive automaticamente, liste os UUID dos dispositivos conectados:
bash blkid
Passo 9: Alterar o
fstabpara Montar o Pendrive Automáticamente 📝Abra o arquivo
/etc/fstabe adicione uma linha para o pendrive, com o UUID que você obteve no passo anterior. A linha deve ficar assim:fstab UUID=9c9008f8-f852 /mnt/edriver vfat defaults 0 0
Passo 10: Copiar o Binário para a Pasta Correta 📥
Agora, copie o binário baixado para a pasta
/opt/nrs:bash cp nrs-arm64 /opt/nrs
Passo 11: Criar o Arquivo de Configuração 🛠️
Crie o arquivo de configuração com o seguinte conteúdo e salve-o em
/opt/nrs/config.yaml:yaml app_env: production info: name: Nostr Relay Server description: Nostr Relay Server pub_key: "" contact: "" url: http://localhost:3334 icon: https://external-content.duckduckgo.com/iu/?u= https://public.bnbstatic.com/image/cms/crawler/COINCU_NEWS/image-495-1024x569.png base_path: /mnt/edriver negentropy: true
Passo 12: Copiar o Serviço para o Diretório de Systemd ⚙️
Agora, copie o arquivo
nrs.servicepara o diretório/etc/systemd/system/:bash cp nrs.service /etc/systemd/system/Recarregue os serviços e inicie o serviço
nrs:bash systemctl daemon-reload systemctl enable --now nrs.service
Passo 13: Configurar o Tor 🌐
Abra o arquivo de configuração do Tor
/var/lib/tor/torrce adicione a seguinte linha:torrc HiddenServiceDir /var/lib/tor/nostr_server/ HiddenServicePort 80 127.0.0.1:3334
Passo 14: Habilitar e Iniciar o Tor 🧅
Agora, ative e inicie o serviço Tor:
bash systemctl enable --now tor.serviceO Tor irá gerar um endereço
.onionpara o seu servidor Nostr. Você pode encontrá-lo no arquivo/var/lib/tor/nostr_server/hostname.
Observações ⚠️
- Com essa configuração, os dados serão salvos no pendrive, enquanto o binário ficará no cartão SD do Raspberry Pi.
- O endereço
.oniondo seu servidor Nostr será algo como:ws://y3t5t5wgwjif<exemplo>h42zy7ih6iwbyd.onion.
Agora, seu servidor Nostr deve estar configurado e funcionando com Tor! 🥳
Se este artigo e as informações aqui contidas forem úteis para você, convidamos a considerar uma doação ao autor como forma de reconhecimento e incentivo à produção de novos conteúdos.
-
 @ 9c9d2765:16f8c2c2
2025-05-28 05:42:53
@ 9c9d2765:16f8c2c2
2025-05-28 05:42:53CHAPTER THIRTY ONE
One quiet evening, as the golden hues of sunset spilled across the office, James found himself standing by the door of Rita’s private workspace. He knocked gently.
She looked up, startled but composed. “James,” she said softly, setting her pen down.
“May I?” he asked, motioning to the chair across from her desk.
She nodded, her expression unreadable. “Of course.”
There was a brief silence, heavy but not uncomfortable. Then James leaned forward, his voice low and sincere.
“Rita… I never hated you,” he began. “Not even for a moment.”
Her eyes flickered, and she looked away, blinking fast. “You should have,” she replied. “I believed lies, I stood by while they treated you like nothing. I was” her voice cracked, “I was a coward.”
“No,” James shook his head. “You were misled. Just like I was, at one point, about the people I trusted.”
He paused, choosing his words carefully. “But everything I did building JP back from ruins, exposing the ones who tried to destroy us, it was never about revenge. It was about finding the truth, and… hoping that maybe, there was still something worth saving between us.”
Tears welled in her eyes, and for the first time in a long time, she didn’t hide them. “Do you really believe we can go back to what we had?”
James offered a small, tender smile. “No. But maybe we can build something new. Something stronger this time with no secrets, no walls.”
That night marked a shift. Rita and James didn’t rush back into love, but they started anew with honesty. Slowly, they began to reconnect over coffee breaks, shared boardroom victories, and late-night reflections.
Meanwhile, the city’s perception of James continued to evolve. He became a keynote speaker at leadership summits, not for his wealth, but for his story. His life, once the subject of cruel gossip, became a testament to resilience, clarity, and vision.
Even the youngest interns in JP Enterprises admired him, not just as a CEO, but as a symbol of what it meant to stand upright in a world eager to bring you down.
Back in the shadows, Mark and Helen's trial proceeded. Witnesses testified, evidence was overwhelming, and public opinion had fully turned against them. Their fall from grace was not swift but it was absolute.
One morning, as James read the headlines declaring Mark and Helen guilty on multiple charges, he simply folded the paper and sipped his tea. There was no celebration. No smirk of triumph.
Only peace.
“Do you still think about the past?” Rita’s voice was soft, almost swallowed by the crackling of the fireplace in the private lounge of JP Towers.
James, seated across from her with a warm mug in his hand, raised his eyes to meet hers. The flicker of flames cast shadows on the polished walls, painting a solemn reflection of everything they'd endured.
“I do,” he admitted, his tone neither bitter nor nostalgic. “Not because I want to relive it but because it reminds me how far we’ve come. How far I’ve come.”
Rita nodded slowly, her eyes glistening beneath the soft glow. “I think about it too,” she confessed. “Every time I walk past the corridors, or sit at my desk… I remember the days I watched you walk these halls like a ghost. Silenced. Humiliated. And I did nothing.”
James leaned back slightly, inhaling deeply. “You did what you thought was right then,” he said with a hint of melancholy. “We were both just trying to survive the storm.”
There was a long pause. Outside, the city pulsed with its usual life, unaware of the quiet reconciliation happening several floors above.
“But survival isn’t living,” she said at last, her voice steadier now. “And I want to live, James. I want to find joy again… with you, if you'll let me.”
Her words hung in the air like fragile glass. James was silent, studying her. This wasn’t the composed, dutiful woman who once echoed the will of her family. This was someone stripped of expectations, speaking from a place of sincerity.
“I won’t promise perfection,” James said after a beat. “But I’ll promise honesty. Loyalty. Peace. No masks. No power games. Just us healing, rebuilding, slowly.”
She exhaled in relief, the corners of her lips lifting slightly. “Then let’s take the first step.”
They stood, a little uncertain, but walked side by side to the balcony overlooking the city that once spat on him, that now bowed to his vision. Rita slipped her hand into his, and this time, James didn’t pull away.
Meanwhile…
The consequences of Mark and Helen’s conspiracy deepened. Investigative journalists began digging further into their past activities, frauds, embezzlements, manipulations. Their names were now synonymous with disgrace in the business world.
The court trials were intense. Mark, once smug and untouchable, appeared gaunt, stripped of the charisma that used to command a room. Helen, on the other hand, wore arrogance like a decaying crown still trying to act superior even when the evidence against her mounted beyond redemption.
And in every newspaper, every media report, James's name was cleared. He had not only reclaimed his honor but redefined what it meant to rise from ruin.
JP Enterprises, now entering its new era of innovation and social impact, had become more than just a corporation it had become a beacon. Business leaders from around the world sought James’s insight. Young entrepreneurs quoted him in lectures and motivational events. And amidst all this, James remained centered because his heart no longer ached with resentment.
The courtroom was saturated with an electrifying silence. The once-glorious reputations of Mark and Helen now hung like withered banners in the wind tattered by deceit, dishonor, and damning evidence. As the judge stepped into the chamber, all eyes turned, yet Mark’s once-confident gaze had diminished into a hollow stare. Helen, dressed in muted tones as if mourning her own prestige, sat rigidly beside him, still refusing to acknowledge the gravity of their downfall.
“For crimes including corporate fraud, defamation, bribery, and obstruction of justice,” the judge’s voice echoed through the courtroom, “this court finds the defendants, Mark Harrison and Helen Ray, guilty on all counts.”
-
 @ 6389be64:ef439d32
2025-01-16 15:44:06
@ 6389be64:ef439d32
2025-01-16 15:44:06Black Locust can grow up to 170 ft tall
Grows 3-4 ft. per year
Native to North America
Cold hardy in zones 3 to 8

Firewood
- BLT wood, on a pound for pound basis is roughly half that of Anthracite Coal
- Since its growth is fast, firewood can be plentiful
Timber

- Rot resistant due to a naturally produced robinin in the wood
- 100 year life span in full soil contact! (better than cedar performance)
- Fence posts
- Outdoor furniture
- Outdoor decking
- Sustainable due to its fast growth and spread
- Can be coppiced (cut to the ground)
- Can be pollarded (cut above ground)
- Its dense wood makes durable tool handles, boxes (tool), and furniture
- The wood is tougher than hickory, which is tougher than hard maple, which is tougher than oak.
- A very low rate of expansion and contraction
- Hardwood flooring
- The highest tensile beam strength of any American tree
- The wood is beautiful
Legume
- Nitrogen fixer
- Fixes the same amount of nitrogen per acre as is needed for 200-bushel/acre corn
- Black walnuts inter-planted with locust as “nurse” trees were shown to rapidly increase their growth [[Clark, Paul M., and Robert D. Williams. (1978) Black walnut growth increased when interplanted with nitrogen-fixing shrubs and trees. Proceedings of the Indiana Academy of Science, vol. 88, pp. 88-91.]]
Bees

- The edible flower clusters are also a top food source for honey bees
Shade Provider

- Its light, airy overstory provides dappled shade
- Planted on the west side of a garden it provides relief during the hottest part of the day
- (nitrogen provider)
- Planted on the west side of a house, its quick growth soon shades that side from the sun
Wind-break

- Fast growth plus it's feathery foliage reduces wind for animals, crops, and shelters
Fodder
- Over 20% crude protein
- 4.1 kcal/g of energy
- Baertsche, S.R, M.T. Yokoyama, and J.W. Hanover (1986) Short rotation, hardwood tree biomass as potential ruminant feed-chemical composition, nylon bag ruminal degradation and ensilement of selected species. J. Animal Sci. 63 2028-2043
-
 @ 6389be64:ef439d32
2025-01-14 01:31:12
@ 6389be64:ef439d32
2025-01-14 01:31:12Bitcoin is more than money, more than an asset, and more than a store of value. Bitcoin is a Prime Mover, an enabler and it ignites imaginations. It certainly fueled an idea in my mind. The idea integrates sensors, computational prowess, actuated machinery, power conversion, and electronic communications to form an autonomous, machined creature roaming forests and harvesting the most widespread and least energy-dense fuel source available. I call it the Forest Walker and it eats wood, and mines Bitcoin.
I know what you're thinking. Why not just put Bitcoin mining rigs where they belong: in a hosted facility sporting electricity from energy-dense fuels like natural gas, climate-controlled with excellent data piping in and out? Why go to all the trouble building a robot that digests wood creating flammable gasses fueling an engine to run a generator powering Bitcoin miners? It's all about synergy.
Bitcoin mining enables the realization of multiple, seemingly unrelated, yet useful activities. Activities considered un-profitable if not for Bitcoin as the Prime Mover. This is much more than simply mining the greatest asset ever conceived by humankind. It’s about the power of synergy, which Bitcoin plays only one of many roles. The synergy created by this system can stabilize forests' fire ecology while generating multiple income streams. That’s the realistic goal here and requires a brief history of American Forest management before continuing.
Smokey The Bear
In 1944, the Smokey Bear Wildfire Prevention Campaign began in the United States. “Only YOU can prevent forest fires” remains the refrain of the Ad Council’s longest running campaign. The Ad Council is a U.S. non-profit set up by the American Association of Advertising Agencies and the Association of National Advertisers in 1942. It would seem that the U.S. Department of the Interior was concerned about pesky forest fires and wanted them to stop. So, alongside a national policy of extreme fire suppression they enlisted the entire U.S. population to get onboard via the Ad Council and it worked. Forest fires were almost obliterated and everyone was happy, right? Wrong.
Smokey is a fantastically successful bear so forest fires became so few for so long that the fuel load - dead wood - in forests has become very heavy. So heavy that when a fire happens (and they always happen) it destroys everything in its path because the more fuel there is the hotter that fire becomes. Trees, bushes, shrubs, and all other plant life cannot escape destruction (not to mention homes and businesses). The soil microbiology doesn’t escape either as it is burned away even in deeper soils. To add insult to injury, hydrophobic waxy residues condense on the soil surface, forcing water to travel over the ground rather than through it eroding forest soils. Good job, Smokey. Well done, Sir!
Most terrestrial ecologies are “fire ecologies”. Fire is a part of these systems’ fuel load and pest management. Before we pretended to “manage” millions of acres of forest, fires raged over the world, rarely damaging forests. The fuel load was always too light to generate fires hot enough to moonscape mountainsides. Fires simply burned off the minor amounts of fuel accumulated since the fire before. The lighter heat, smoke, and other combustion gasses suppressed pests, keeping them in check and the smoke condensed into a plant growth accelerant called wood vinegar, not a waxy cap on the soil. These fires also cleared out weak undergrowth, cycled minerals, and thinned the forest canopy, allowing sunlight to penetrate to the forest floor. Without a fire’s heat, many pine tree species can’t sow their seed. The heat is required to open the cones (the seed bearing structure) of Spruce, Cypress, Sequoia, Jack Pine, Lodgepole Pine and many more. Without fire forests can’t have babies. The idea was to protect the forests, and it isn't working.
So, in a world of fire, what does an ally look like and what does it do?
Meet The Forest Walker

For the Forest Walker to work as a mobile, autonomous unit, a solid platform that can carry several hundred pounds is required. It so happens this chassis already exists but shelved.
Introducing the Legged Squad Support System (LS3). A joint project between Boston Dynamics, DARPA, and the United States Marine Corps, the quadrupedal robot is the size of a cow, can carry 400 pounds (180 kg) of equipment, negotiate challenging terrain, and operate for 24 hours before needing to refuel. Yes, it had an engine. Abandoned in 2015, the thing was too noisy for military deployment and maintenance "under fire" is never a high-quality idea. However, we can rebuild it to act as a platform for the Forest Walker; albeit with serious alterations. It would need to be bigger, probably. Carry more weight? Definitely. Maybe replace structural metal with carbon fiber and redesign much as 3D printable parts for more effective maintenance.
The original system has a top operational speed of 8 miles per hour. For our purposes, it only needs to move about as fast as a grazing ruminant. Without the hammering vibrations of galloping into battle, shocks of exploding mortars, and drunken soldiers playing "Wrangler of Steel Machines", time between failures should be much longer and the overall energy consumption much lower. The LS3 is a solid platform to build upon. Now it just needs to be pulled out of the mothballs, and completely refitted with outboard equipment.
The Small Branch Chipper

When I say “Forest fuel load” I mean the dead, carbon containing litter on the forest floor. Duff (leaves), fine-woody debris (small branches), and coarse woody debris (logs) are the fuel that feeds forest fires. Walk through any forest in the United States today and you will see quite a lot of these materials. Too much, as I have described. Some of these fuel loads can be 8 tons per acre in pine and hardwood forests and up to 16 tons per acre at active logging sites. That’s some big wood and the more that collects, the more combustible danger to the forest it represents. It also provides a technically unlimited fuel supply for the Forest Walker system.
The problem is that this detritus has to be chewed into pieces that are easily ingestible by the system for the gasification process (we’ll get to that step in a minute). What we need is a wood chipper attached to the chassis (the LS3); its “mouth”.
A small wood chipper handling material up to 2.5 - 3.0 inches (6.3 - 7.6 cm) in diameter would eliminate a substantial amount of fuel. There is no reason for Forest Walker to remove fallen trees. It wouldn’t have to in order to make a real difference. It need only identify appropriately sized branches and grab them. Once loaded into the chipper’s intake hopper for further processing, the beast can immediately look for more “food”. This is essentially kindling that would help ignite larger logs. If it’s all consumed by Forest Walker, then it’s not present to promote an aggravated conflagration.
I have glossed over an obvious question: How does Forest Walker see and identify branches and such? LiDaR (Light Detection and Ranging) attached to Forest Walker images the local area and feed those data to onboard computers for processing. Maybe AI plays a role. Maybe simple machine learning can do the trick. One thing is for certain: being able to identify a stick and cause robotic appendages to pick it up is not impossible.
Great! We now have a quadrupedal robot autonomously identifying and “eating” dead branches and other light, combustible materials. Whilst strolling through the forest, depleting future fires of combustibles, Forest Walker has already performed a major function of this system: making the forest safer. It's time to convert this low-density fuel into a high-density fuel Forest Walker can leverage. Enter the gasification process.
The Gassifier

The gasifier is the heart of the entire system; it’s where low-density fuel becomes the high-density fuel that powers the entire system. Biochar and wood vinegar are process wastes and I’ll discuss why both are powerful soil amendments in a moment, but first, what’s gasification?
Reacting shredded carbonaceous material at high temperatures in a low or no oxygen environment converts the biomass into biochar, wood vinegar, heat, and Synthesis Gas (Syngas). Syngas consists primarily of hydrogen, carbon monoxide, and methane. All of which are extremely useful fuels in a gaseous state. Part of this gas is used to heat the input biomass and keep the reaction temperature constant while the internal combustion engine that drives the generator to produce electrical power consumes the rest.
Critically, this gasification process is “continuous feed”. Forest Walker must intake biomass from the chipper, process it to fuel, and dump the waste (CO2, heat, biochar, and wood vinegar) continuously. It cannot stop. Everything about this system depends upon this continual grazing, digestion, and excretion of wastes just as a ruminal does. And, like a ruminant, all waste products enhance the local environment.
When I first heard of gasification, I didn’t believe that it was real. Running an electric generator from burning wood seemed more akin to “conspiracy fantasy” than science. Not only is gasification real, it’s ancient technology. A man named Dean Clayton first started experiments on gasification in 1699 and in 1901 gasification was used to power a vehicle. By the end of World War II, there were 500,000 Syngas powered vehicles in Germany alone because of fossil fuel rationing during the war. The global gasification market was $480 billion in 2022 and projected to be as much as $700 billion by 2030 (Vantage Market Research). Gasification technology is the best choice to power the Forest Walker because it’s self-contained and we want its waste products.
Biochar: The Waste

Biochar (AKA agricultural charcoal) is fairly simple: it’s almost pure, solid carbon that resembles charcoal. Its porous nature packs large surface areas into small, 3 dimensional nuggets. Devoid of most other chemistry, like hydrocarbons (methane) and ash (minerals), biochar is extremely lightweight. Do not confuse it with the charcoal you buy for your grill. Biochar doesn’t make good grilling charcoal because it would burn too rapidly as it does not contain the multitude of flammable components that charcoal does. Biochar has several other good use cases. Water filtration, water retention, nutrient retention, providing habitat for microscopic soil organisms, and carbon sequestration are the main ones that we are concerned with here.
Carbon has an amazing ability to adsorb (substances stick to and accumulate on the surface of an object) manifold chemistries. Water, nutrients, and pollutants tightly bind to carbon in this format. So, biochar makes a respectable filter and acts as a “battery” of water and nutrients in soils. Biochar adsorbs and holds on to seven times its weight in water. Soil containing biochar is more drought resilient than soil without it. Adsorbed nutrients, tightly sequestered alongside water, get released only as plants need them. Plants must excrete protons (H+) from their roots to disgorge water or positively charged nutrients from the biochar's surface; it's an active process.
Biochar’s surface area (where adsorption happens) can be 500 square meters per gram or more. That is 10% larger than an official NBA basketball court for every gram of biochar. Biochar’s abundant surface area builds protective habitats for soil microbes like fungi and bacteria and many are critical for the health and productivity of the soil itself.
The “carbon sequestration” component of biochar comes into play where “carbon credits” are concerned. There is a financial market for carbon. Not leveraging that market for revenue is foolish. I am climate agnostic. All I care about is that once solid carbon is inside the soil, it will stay there for thousands of years, imparting drought resiliency, fertility collection, nutrient buffering, and release for that time span. I simply want as much solid carbon in the soil because of the undeniably positive effects it has, regardless of any climactic considerations.
Wood Vinegar: More Waste

Another by-product of the gasification process is wood vinegar (Pyroligneous acid). If you have ever seen Liquid Smoke in the grocery store, then you have seen wood vinegar. Principally composed of acetic acid, acetone, and methanol wood vinegar also contains ~200 other organic compounds. It would seem intuitive that condensed, liquefied wood smoke would at least be bad for the health of all living things if not downright carcinogenic. The counter intuition wins the day, however. Wood vinegar has been used by humans for a very long time to promote digestion, bowel, and liver health; combat diarrhea and vomiting; calm peptic ulcers and regulate cholesterol levels; and a host of other benefits.
For centuries humans have annually burned off hundreds of thousands of square miles of pasture, grassland, forest, and every other conceivable terrestrial ecosystem. Why is this done? After every burn, one thing becomes obvious: the almost supernatural growth these ecosystems exhibit after the burn. How? Wood vinegar is a component of this growth. Even in open burns, smoke condenses and infiltrates the soil. That is when wood vinegar shows its quality.
This stuff beefs up not only general plant growth but seed germination as well and possesses many other qualities that are beneficial to plants. It’s a pesticide, fungicide, promotes beneficial soil microorganisms, enhances nutrient uptake, and imparts disease resistance. I am barely touching a long list of attributes here, but you want wood vinegar in your soil (alongside biochar because it adsorbs wood vinegar as well).
The Internal Combustion Engine

Conversion of grazed forage to chemical, then mechanical, and then electrical energy completes the cycle. The ICE (Internal Combustion Engine) converts the gaseous fuel output from the gasifier to mechanical energy, heat, water vapor, and CO2. It’s the mechanical energy of a rotating drive shaft that we want. That rotation drives the electric generator, which is the heartbeat we need to bring this monster to life. Luckily for us, combined internal combustion engine and generator packages are ubiquitous, delivering a defined energy output given a constant fuel input. It’s the simplest part of the system.
The obvious question here is whether the amount of syngas provided by the gasification process will provide enough energy to generate enough electrons to run the entire system or not. While I have no doubt the energy produced will run Forest Walker's main systems the question is really about the electrons left over. Will it be enough to run the Bitcoin mining aspect of the system? Everything is a budget.
CO2 Production For Growth

Plants are lollipops. No matter if it’s a tree or a bush or a shrubbery, the entire thing is mostly sugar in various formats but mostly long chain carbohydrates like lignin and cellulose. Plants need three things to make sugar: CO2, H2O and light. In a forest, where tree densities can be quite high, CO2 availability becomes a limiting growth factor. It’d be in the forest interests to have more available CO2 providing for various sugar formation providing the organism with food and structure.
An odd thing about tree leaves, the openings that allow gasses like the ever searched for CO2 are on the bottom of the leaf (these are called stomata). Not many stomata are topside. This suggests that trees and bushes have evolved to find gasses like CO2 from below, not above and this further suggests CO2 might be in higher concentrations nearer the soil.
The soil life (bacterial, fungi etc.) is constantly producing enormous amounts of CO2 and it would stay in the soil forever (eventually killing the very soil life that produces it) if not for tidal forces. Water is everywhere and whether in pools, lakes, oceans or distributed in “moist” soils water moves towards to the moon. The water in the soil and also in the water tables below the soil rise toward the surface every day. When the water rises, it expels the accumulated gasses in the soil into the atmosphere and it’s mostly CO2. It’s a good bet on how leaves developed high populations of stomata on the underside of leaves. As the water relaxes (the tide goes out) it sucks oxygenated air back into the soil to continue the functions of soil life respiration. The soil “breathes” albeit slowly.
The gasses produced by the Forest Walker’s internal combustion engine consist primarily of CO2 and H2O. Combusting sugars produce the same gasses that are needed to construct the sugars because the universe is funny like that. The Forest Walker is constantly laying down these critical construction elements right where the trees need them: close to the ground to be gobbled up by the trees.
The Branch Drones

During the last ice age, giant mammals populated North America - forests and otherwise. Mastodons, woolly mammoths, rhinos, short-faced bears, steppe bison, caribou, musk ox, giant beavers, camels, gigantic ground-dwelling sloths, glyptodons, and dire wolves were everywhere. Many were ten to fifteen feet tall. As they crashed through forests, they would effectively cleave off dead side-branches of trees, halting the spread of a ground-based fire migrating into the tree crown ("laddering") which is a death knell for a forest.
These animals are all extinct now and forests no longer have any manner of pruning services. But, if we build drones fitted with cutting implements like saws and loppers, optical cameras and AI trained to discern dead branches from living ones, these drones could effectively take over pruning services by identifying, cutting, and dropping to the forest floor, dead branches. The dropped branches simply get collected by the Forest Walker as part of its continual mission.
The drones dock on the back of the Forest Walker to recharge their batteries when low. The whole scene would look like a grazing cow with some flies bothering it. This activity breaks the link between a relatively cool ground based fire and the tree crowns and is a vital element in forest fire control.
The Bitcoin Miner

Mining is one of four monetary incentive models, making this system a possibility for development. The other three are US Dept. of the Interior, township, county, and electrical utility company easement contracts for fuel load management, global carbon credits trading, and data set sales. All the above depends on obvious questions getting answered. I will list some obvious ones, but this is not an engineering document and is not the place for spreadsheets. How much Bitcoin one Forest Walker can mine depends on everything else. What amount of biomass can we process? Will that biomass flow enough Syngas to keep the lights on? Can the chassis support enough mining ASICs and supporting infrastructure? What does that weigh and will it affect field performance? How much power can the AC generator produce?
Other questions that are more philosophical persist. Even if a single Forest Walker can only mine scant amounts of BTC per day, that pales to how much fuel material it can process into biochar. We are talking about millions upon millions of forested acres in need of fuel load management. What can a single Forest Walker do? I am not thinking in singular terms. The Forest Walker must operate as a fleet. What could 50 do? 500?
What is it worth providing a service to the world by managing forest fuel loads? Providing proof of work to the global monetary system? Seeding soil with drought and nutrient resilience by the excretion, over time, of carbon by the ton? What did the last forest fire cost?
The Mesh Network

What could be better than one bitcoin mining, carbon sequestering, forest fire squelching, soil amending behemoth? Thousands of them, but then they would need to be able to talk to each other to coordinate position, data handling, etc. Fitted with a mesh networking device, like goTenna or Meshtastic LoRa equipment enables each Forest Walker to communicate with each other.
Now we have an interconnected fleet of Forest Walkers relaying data to each other and more importantly, aggregating all of that to the last link in the chain for uplink. Well, at least Bitcoin mining data. Since block data is lightweight, transmission of these data via mesh networking in fairly close quartered environs is more than doable. So, how does data transmit to the Bitcoin Network? How do the Forest Walkers get the previous block data necessary to execute on mining?
Back To The Chain

Getting Bitcoin block data to and from the network is the last puzzle piece. The standing presumption here is that wherever a Forest Walker fleet is operating, it is NOT within cell tower range. We further presume that the nearest Walmart Wi-Fi is hours away. Enter the Blockstream Satellite or something like it.
A separate, ground-based drone will have two jobs: To stay as close to the nearest Forest Walker as it can and to provide an antennae for either terrestrial or orbital data uplink. Bitcoin-centric data is transmitted to the "uplink drone" via the mesh networked transmitters and then sent on to the uplink and the whole flow goes in the opposite direction as well; many to one and one to many.
We cannot transmit data to the Blockstream satellite, and it will be up to Blockstream and companies like it to provide uplink capabilities in the future and I don't doubt they will. Starlink you say? What’s stopping that company from filtering out block data? Nothing because it’s Starlink’s system and they could decide to censor these data. It seems we may have a problem sending and receiving Bitcoin data in back country environs.
But, then again, the utility of this system in staunching the fuel load that creates forest fires is extremely useful around forested communities and many have fiber, Wi-Fi and cell towers. These communities could be a welcoming ground zero for first deployments of the Forest Walker system by the home and business owners seeking fire repression. In the best way, Bitcoin subsidizes the safety of the communities.
Sensor Packages
LiDaR

The benefit of having a Forest Walker fleet strolling through the forest is the never ending opportunity for data gathering. A plethora of deployable sensors gathering hyper-accurate data on everything from temperature to topography is yet another revenue generator. Data is valuable and the Forest Walker could generate data sales to various government entities and private concerns.
LiDaR (Light Detection and Ranging) can map topography, perform biomass assessment, comparative soil erosion analysis, etc. It so happens that the Forest Walker’s ability to “see,” to navigate about its surroundings, is LiDaR driven and since it’s already being used, we can get double duty by harvesting that data for later use. By using a laser to send out light pulses and measuring the time it takes for the reflection of those pulses to return, very detailed data sets incrementally build up. Eventually, as enough data about a certain area becomes available, the data becomes useful and valuable.
Forestry concerns, both private and public, often use LiDaR to build 3D models of tree stands to assess the amount of harvest-able lumber in entire sections of forest. Consulting companies offering these services charge anywhere from several hundred to several thousand dollars per square kilometer for such services. A Forest Walker generating such assessments on the fly while performing its other functions is a multi-disciplinary approach to revenue generation.
pH, Soil Moisture, and Cation Exchange Sensing

The Forest Walker is quadrupedal, so there are four contact points to the soil. Why not get a pH data point for every step it takes? We can also gather soil moisture data and cation exchange capacities at unheard of densities because of sampling occurring on the fly during commission of the system’s other duties. No one is going to build a machine to do pH testing of vast tracts of forest soils, but that doesn’t make the data collected from such an endeavor valueless. Since the Forest Walker serves many functions at once, a multitude of data products can add to the return on investment component.
Weather Data

Temperature, humidity, pressure, and even data like evapotranspiration gathered at high densities on broad acre scales have untold value and because the sensors are lightweight and don’t require large power budgets, they come along for the ride at little cost. But, just like the old mantra, “gas, grass, or ass, nobody rides for free”, these sensors provide potential revenue benefits just by them being present.
I’ve touched on just a few data genres here. In fact, the question for universities, governmental bodies, and other institutions becomes, “How much will you pay us to attach your sensor payload to the Forest Walker?”
Noise Suppression

Only you can prevent Metallica filling the surrounds with 120 dB of sound. Easy enough, just turn the car stereo off. But what of a fleet of 50 Forest Walkers operating in the backcountry or near a township? 500? 5000? Each one has a wood chipper, an internal combustion engine, hydraulic pumps, actuators, and more cooling fans than you can shake a stick at. It’s a walking, screaming fire-breathing dragon operating continuously, day and night, twenty-four hours a day, three hundred sixty-five days a year. The sound will negatively affect all living things and that impacts behaviors. Serious engineering consideration and prowess must deliver a silencing blow to the major issue of noise.
It would be foolish to think that a fleet of Forest Walkers could be silent, but if not a major design consideration, then the entire idea is dead on arrival. Townships would not allow them to operate even if they solved the problem of widespread fuel load and neither would governmental entities, and rightly so. Nothing, not man nor beast, would want to be subjected to an eternal, infernal scream even if it were to end within days as the fleet moved further away after consuming what it could. Noise and heat are the only real pollutants of this system; taking noise seriously from the beginning is paramount.
Fire Safety

A “fire-breathing dragon” is not the worst description of the Forest Walker. It eats wood, combusts it at very high temperatures and excretes carbon; and it does so in an extremely flammable environment. Bad mix for one Forest Walker, worse for many. One must take extreme pains to ensure that during normal operation, a Forest Walker could fall over, walk through tinder dry brush, or get pounded into the ground by a meteorite from Krypton and it wouldn’t destroy epic swaths of trees and baby deer. I envision an ultimate test of a prototype to include dowsing it in grain alcohol while it’s wrapped up in toilet paper like a pledge at a fraternity party. If it runs for 72 hours and doesn’t set everything on fire, then maybe outside entities won’t be fearful of something that walks around forests with a constant fire in its belly.
The Wrap

How we think about what can be done with and adjacent to Bitcoin is at least as important as Bitcoin’s economic standing itself. For those who will tell me that this entire idea is without merit, I say, “OK, fine. You can come up with something, too.” What can we plug Bitcoin into that, like a battery, makes something that does not work, work? That’s the lesson I get from this entire exercise. No one was ever going to hire teams of humans to go out and "clean the forest". There's no money in that. The data collection and sales from such an endeavor might provide revenues over the break-even point but investment demands Alpha in this day and age. But, plug Bitcoin into an almost viable system and, voilà! We tip the scales to achieve lift-off.
Let’s face it, we haven’t scratched the surface of Bitcoin’s forcing function on our minds. Not because it’s Bitcoin, but because of what that invention means. The question that pushes me to approach things this way is, “what can we create that one system’s waste is another system’s feedstock?” The Forest Walker system’s only real waste is the conversion of low entropy energy (wood and syngas) into high entropy energy (heat and noise). All other output is beneficial to humanity.
Bitcoin, I believe, is the first product of a new mode of human imagination. An imagination newly forged over the past few millennia of being lied to, stolen from, distracted and otherwise mis-allocated to a black hole of the nonsensical. We are waking up.
What I have presented is not science fiction. Everything I have described here is well within the realm of possibility. The question is one of viability, at least in terms of the detritus of the old world we find ourselves departing from. This system would take a non-trivial amount of time and resources to develop. I think the system would garner extensive long-term contracts from those who have the most to lose from wildfires, the most to gain from hyperaccurate data sets, and, of course, securing the most precious asset in the world. Many may not see it that way, for they seek Alpha and are therefore blind to other possibilities. Others will see only the possibilities; of thinking in a new way, of looking at things differently, and dreaming of what comes next.
-
 @ 9c9d2765:16f8c2c2
2025-05-28 05:22:33
@ 9c9d2765:16f8c2c2
2025-05-28 05:22:33In a quiet village nestled between forest and field, lived a boy named Ezekiel. From birth, he was surrounded by a warm family, playful siblings, and neighbors who always had a story to share. Ezekiel never knew silence, and because of that, he never valued voices. To him, connection was like air everywhere, constant, and unnoticed.
One summer, Ezekiel decided to explore the woods beyond the hills, chasing the thrill of adventure. He wandered farther than he ever had, until the trees thickened and the path thinned into nothing. A sudden storm rolled in. Rain blurred the forest, and Ezekiel lost his way. He sought shelter in a small, abandoned stone hut beside a dried-up well.
The storm passed, but no path appeared. Days turned to weeks. His voice echoed off the stone, unanswered. The silence was no longer peaceful; it was heavy, like a weight pressing on his soul. He learned to survive on roots and rainwater. But loneliness is true, aching loneliness clung to him. He spoke to the walls, to the trees, to the echo in the well, but nothing replied.
One day, while resting against the well, Ezekiel whispered, “I miss them.”
And for the first time, he meant it.
Not just missed their presence but their interruptions, their noise, even their complaints. He missed being seen, and seeing. He understood now: connection wasn’t just comfort. It was color, depth, meaning.
Weeks later, a group of searchers found him thin, dirty, but alive. When he returned, everything was the same, but Ezekiel was not.
He listened differently. Hugged longer. Remembered people’s names, stories, and silences. He no longer saw connection as a given, but a gift.
And every year, he visited the well not to mourn the solitude, but to thank it. For in its quiet, he learned the true value of every voice he once ignored.
Moral: To cherish connection, you must understand solitude not as punishment, but as teacher.
-
 @ e3ba5e1a:5e433365
2025-01-13 16:47:27
@ e3ba5e1a:5e433365
2025-01-13 16:47:27My blog posts and reading material have both been on a decidedly economics-heavy slant recently. The topic today, incentives, squarely falls into the category of economics. However, when I say economics, I’m not talking about “analyzing supply and demand curves.” I’m talking about the true basis of economics: understanding how human beings make decisions in a world of scarcity.
A fair definition of incentive is “a reward or punishment that motivates behavior to achieve a desired outcome.” When most people think about economic incentives, they’re thinking of money. If I offer my son $5 if he washes the dishes, I’m incentivizing certain behavior. We can’t guarantee that he’ll do what I want him to do, but we can agree that the incentive structure itself will guide and ultimately determine what outcome will occur.
The great thing about monetary incentives is how easy they are to talk about and compare. “Would I rather make $5 washing the dishes or $10 cleaning the gutters?” But much of the world is incentivized in non-monetary ways too. For example, using the “punishment” half of the definition above, I might threaten my son with losing Nintendo Switch access if he doesn’t wash the dishes. No money is involved, but I’m still incentivizing behavior.
And there are plenty of incentives beyond our direct control! My son is also incentivized to not wash dishes because it’s boring, or because he has some friends over that he wants to hang out with, or dozens of other things. Ultimately, the conflicting array of different incentive structures placed on him will ultimately determine what actions he chooses to take.
Why incentives matter
A phrase I see often in discussions—whether they are political, parenting, economic, or business—is “if they could just do…” Each time I see that phrase, I cringe a bit internally. Usually, the underlying assumption of the statement is “if people would behave contrary to their incentivized behavior then things would be better.” For example:
- If my kids would just go to bed when I tell them, they wouldn’t be so cranky in the morning.
- If people would just use the recycling bin, we wouldn’t have such a landfill problem.
- If people would just stop being lazy, our team would deliver our project on time.
In all these cases, the speakers are seemingly flummoxed as to why the people in question don’t behave more rationally. The problem is: each group is behaving perfectly rationally.
- The kids have a high time preference, and care more about the joy of staying up now than the crankiness in the morning. Plus, they don’t really suffer the consequences of morning crankiness, their parents do.
- No individual suffers much from their individual contribution to a landfill. If they stopped growing the size of the landfill, it would make an insignificant difference versus the amount of effort they need to engage in to properly recycle.
- If a team doesn’t properly account for the productivity of individuals on a project, each individual receives less harm from their own inaction. Sure, the project may be delayed, company revenue may be down, and they may even risk losing their job when the company goes out of business. But their laziness individually won’t determine the entirety of that outcome. By contrast, they greatly benefit from being lazy by getting to relax at work, go on social media, read a book, or do whatever else they do when they’re supposed to be working.

My point here is that, as long as you ignore the reality of how incentives drive human behavior, you’ll fail at getting the outcomes you want.
If everything I wrote up until now made perfect sense, you understand the premise of this blog post. The rest of it will focus on a bunch of real-world examples to hammer home the point, and demonstrate how versatile this mental model is.
Running a company
Let’s say I run my own company, with myself as the only employee. My personal revenue will be 100% determined by my own actions. If I decide to take Tuesday afternoon off and go fishing, I’ve chosen to lose that afternoon’s revenue. Implicitly, I’ve decided that the enjoyment I get from an afternoon of fishing is greater than the potential revenue. You may think I’m being lazy, but it’s my decision to make. In this situation, the incentive–money–is perfectly aligned with my actions.
Compare this to a typical company/employee relationship. I might have a bank of Paid Time Off (PTO) days, in which case once again my incentives are relatively aligned. I know that I can take off 15 days throughout the year, and I’ve chosen to use half a day for the fishing trip. All is still good.
What about unlimited time off? Suddenly incentives are starting to misalign. I don’t directly pay a price for not showing up to work on Tuesday. Or Wednesday as well, for that matter. I might ultimately be fired for not doing my job, but that will take longer to work its way through the system than simply not making any money for the day taken off.
Compensation overall falls into this misaligned incentive structure. Let’s forget about taking time off. Instead, I work full time on a software project I’m assigned. But instead of using the normal toolchain we’re all used to at work, I play around with a new programming language. I get the fun and joy of playing with new technology, and potentially get to pad my resume a bit when I’m ready to look for a new job. But my current company gets slower results, less productivity, and is forced to subsidize my extracurricular learning.
When a CEO has a bonus structure based on profitability, he’ll do everything he can to make the company profitable. This might include things that actually benefit the company, like improving product quality, reducing internal red tape, or finding cheaper vendors. But it might also include destructive practices, like slashing the R\&D budget to show massive profits this year, in exchange for a catastrophe next year when the next version of the product fails to ship.

Or my favorite example. My parents owned a business when I was growing up. They had a back office where they ran operations like accounting. All of the furniture was old couches from our house. After all, any money they spent on furniture came right out of their paychecks! But in a large corporate environment, each department is generally given a budget for office furniture, a budget which doesn’t roll over year-to-year. The result? Executives make sure to spend the entire budget each year, often buying furniture far more expensive than they would choose if it was their own money.
There are plenty of details you can quibble with above. It’s in a company’s best interest to give people downtime so that they can come back recharged. Having good ergonomic furniture can in fact increase productivity in excess of the money spent on it. But overall, the picture is pretty clear: in large corporate structures, you’re guaranteed to have mismatches between the company’s goals and the incentive structure placed on individuals.
Using our model from above, we can lament how lazy, greedy, and unethical the employees are for doing what they’re incentivized to do instead of what’s right. But that’s simply ignoring the reality of human nature.
Moral hazard
Moral hazard is a situation where one party is incentivized to take on more risk because another party will bear the consequences. Suppose I tell my son when he turns 21 (or whatever legal gambling age is) that I’ll cover all his losses for a day at the casino, but he gets to keep all the winnings.
What do you think he’s going to do? The most logical course of action is to place the largest possible bets for as long as possible, asking me to cover each time he loses, and taking money off the table and into his bank account each time he wins.

But let’s look at a slightly more nuanced example. I go to a bathroom in the mall. As I’m leaving, I wash my hands. It will take me an extra 1 second to turn off the water when I’m done washing. That’s a trivial price to pay. If I don’t turn off the water, the mall will have to pay for many liters of wasted water, benefiting no one. But I won’t suffer any consequences at all.
This is also a moral hazard, but most people will still turn off the water. Why? Usually due to some combination of other reasons such as:
- We’re so habituated to turning off the water that we don’t even consider not turning it off. Put differently, the mental effort needed to not turn off the water is more expensive than the 1 second of time to turn it off.
- Many of us have been brought up with a deep guilt about wasting resources like water. We have an internal incentive structure that makes the 1 second to turn off the water much less costly than the mental anguish of the waste we created.
- We’re afraid we’ll be caught by someone else and face some kind of social repercussions. (Or maybe more than social. Are you sure there isn’t a law against leaving the water tap on?)
Even with all that in place, you may notice that many public bathrooms use automatic water dispensers. Sure, there’s a sanitation reason for that, but it’s also to avoid this moral hazard.
A common denominator in both of these is that the person taking the action that causes the liability (either the gambling or leaving the water on) is not the person who bears the responsibility for that liability (the father or the mall owner). Generally speaking, the closer together the person making the decision and the person incurring the liability are, the smaller the moral hazard.
It’s easy to demonstrate that by extending the casino example a bit. I said it was the father who was covering the losses of the gambler. Many children (though not all) would want to avoid totally bankrupting their parents, or at least financially hurting them. Instead, imagine that someone from the IRS shows up at your door, hands you a credit card, and tells you you can use it at a casino all day, taking home all the chips you want. The money is coming from the government. How many people would put any restriction on how much they spend?
And since we’re talking about the government already…
Government moral hazards
As I was preparing to write this blog post, the California wildfires hit. The discussions around those wildfires gave a huge number of examples of moral hazards. I decided to cherry-pick a few for this post.
The first and most obvious one: California is asking for disaster relief funds from the federal government. That sounds wonderful. These fires were a natural disaster, so why shouldn’t the federal government pitch in and help take care of people?
The problem is, once again, a moral hazard. In the case of the wildfires, California and Los Angeles both had ample actions they could have taken to mitigate the destruction of this fire: better forest management, larger fire department, keeping the water reservoirs filled, and probably much more that hasn’t come to light yet.
If the federal government bails out California, it will be a clear message for the future: your mistakes will be fixed by others. You know what kind of behavior that incentivizes? More risky behavior! Why spend state funds on forest management and extra firefighters—activities that don’t win politicians a lot of votes in general—when you could instead spend it on a football stadium, higher unemployment payments, or anything else, and then let the feds cover the cost of screw-ups.
You may notice that this is virtually identical to the 2008 “too big to fail” bail-outs. Wall Street took insanely risky behavior, reaped huge profits for years, and when they eventually got caught with their pants down, the rest of us bailed them out. “Privatizing profits, socializing losses.”

And here’s the absolute best part of this: I can’t even truly blame either California or Wall Street. (I mean, I do blame them, I think their behavior is reprehensible, but you’ll see what I mean.) In a world where the rules of the game implicitly include the bail-out mentality, you would be harming your citizens/shareholders/investors if you didn’t engage in that risky behavior. Since everyone is on the hook for those socialized losses, your best bet is to maximize those privatized profits.
There’s a lot more to government and moral hazard, but I think these two cases demonstrate the crux pretty solidly. But let’s leave moral hazard behind for a bit and get to general incentivization discussions.
Non-monetary competition
At least 50% of the economics knowledge I have comes from the very first econ course I took in college. That professor was amazing, and had some very colorful stories. I can’t vouch for the veracity of the two I’m about to share, but they definitely drive the point home.
In the 1970s, the US had an oil shortage. To “fix” this problem, they instituted price caps on gasoline, which of course resulted in insufficient gasoline. To “fix” this problem, they instituted policies where, depending on your license plate number, you could only fill up gas on certain days of the week. (Irrelevant detail for our point here, but this just resulted in people filling up their tanks more often, no reduction in gas usage.)
Anyway, my professor’s wife had a friend. My professor described in great detail how attractive this woman was. I’ll skip those details here since this is a PG-rated blog. In any event, she never had any trouble filling up her gas tank any day of the week. She would drive up, be told she couldn’t fill up gas today, bat her eyes at the attendant, explain how helpless she was, and was always allowed to fill up gas.
This is a demonstration of non-monetary compensation. Most of the time in a free market, capitalist economy, people are compensated through money. When price caps come into play, there’s a limit to how much monetary compensation someone can receive. And in that case, people find other ways of competing. Like this woman’s case: through using flirtatious behavior to compensate the gas station workers to let her cheat the rules.
The other example was much more insidious. Santa Monica had a problem: it was predominantly wealthy and white. They wanted to fix this problem, and decided to put in place rent controls. After some time, they discovered that Santa Monica had become wealthier and whiter, the exact opposite of their desired outcome. Why would that happen?
Someone investigated, and ended up interviewing a landlady that demonstrated the reason. She was an older white woman, and admittedly racist. Prior to the rent controls, she would list her apartments in the newspaper, and would be legally obligated to rent to anyone who could afford it. Once rent controls were in place, she took a different tact. She knew that she would only get a certain amount for the apartment, and that the demand for apartments was higher than the supply. That meant she could be picky.
She ended up finding tenants through friends-of-friends. Since it wasn’t an official advertisement, she wasn’t legally required to rent it out if someone could afford to pay. Instead, she got to interview people individually and then make them an offer. Normally, that would have resulted in receiving a lower rental price, but not under rent controls.
So who did she choose? A young, unmarried, wealthy, white woman. It made perfect sense. Women were less intimidating and more likely to maintain the apartment better. Wealthy people, she determined, would be better tenants. (I have no idea if this is true in practice or not, I’m not a landlord myself.) Unmarried, because no kids running around meant less damage to the property. And, of course, white. Because she was racist, and her incentive structure made her prefer whites.
You can deride her for being racist, I won’t disagree with you. But it’s simply the reality. Under the non-rent-control scenario, her profit motive for money outweighed her racism motive. But under rent control, the monetary competition was removed, and she was free to play into her racist tendencies without facing any negative consequences.
Bureaucracy
These were the two examples I remember for that course. But non-monetary compensation pops up in many more places. One highly pertinent example is bureaucracies. Imagine you have a government office, or a large corporation’s acquisition department, or the team that apportions grants at a university. In all these cases, you have a group of people making decisions about handing out money that has no monetary impact on them. If they give to the best qualified recipients, they receive no raises. If they spend the money recklessly on frivolous projects, they face no consequences.
Under such an incentivization scheme, there’s little to encourage the bureaucrats to make intelligent funding decisions. Instead, they’ll be incentivized to spend the money where they recognize non-monetary benefits. This is why it’s so common to hear about expensive meals, gift bags at conferences, and even more inappropriate ways of trying to curry favor with those that hold the purse strings.
Compare that ever so briefly with the purchases made by a small mom-and-pop store like my parents owned. Could my dad take a bribe to buy from a vendor who’s ripping him off? Absolutely he could! But he’d lose more on the deal than he’d make on the bribe, since he’s directly incentivized by the deal itself. It would make much more sense for him to go with the better vendor, save $5,000 on the deal, and then treat himself to a lavish $400 meal to celebrate.
Government incentivized behavior
This post is getting longer in the tooth than I’d intended, so I’ll finish off with this section and make it a bit briefer. Beyond all the methods mentioned above, government has another mechanism for modifying behavior: through directly changing incentives via legislation, regulation, and monetary policy. Let’s see some examples:
- Artificial modification of interest rates encourages people to take on more debt than they would in a free capital market, leading to malinvestment and a consumer debt crisis, and causing the boom-bust cycle we all painfully experience.
- Going along with that, giving tax breaks on interest payments further artificially incentivizes people to take on debt that they wouldn’t otherwise.
- During COVID-19, at some points unemployment benefits were greater than minimum wage, incentivizing people to rather stay home and not work than get a job, leading to reduced overall productivity in the economy and more printed dollars for benefits. In other words, it was a perfect recipe for inflation.
- The tax code gives deductions to “help” people. That might be true, but the real impact is incentivizing people to make decisions they wouldn’t have otherwise. For example, giving out tax deductions on children encourages having more kids. Tax deductions on childcare and preschools incentivizes dual-income households. Whether or not you like the outcomes, it’s clear that it’s government that’s encouraging these outcomes to happen.
- Tax incentives cause people to engage in behavior they wouldn’t otherwise (daycare+working mother, for example).
- Inflation means that the value of your money goes down over time, which encourages people to spend more today, when their money has a larger impact. (Milton Friedman described this as high living.)
Conclusion
The idea here is simple, and fully encapsulated in the title: incentives determine outcomes. If you want to know how to get a certain outcome from others, incentivize them to want that to happen. If you want to understand why people act in seemingly irrational ways, check their incentives. If you’re confused why leaders (and especially politicians) seem to engage in destructive behavior, check their incentives.
We can bemoan these realities all we want, but they are realities. While there are some people who have a solid internal moral and ethical code, and that internal code incentivizes them to behave against their externally-incentivized interests, those people are rare. And frankly, those people are self-defeating. People should take advantage of the incentives around them. Because if they don’t, someone else will.
(If you want a literary example of that last comment, see the horse in Animal Farm.)
How do we improve the world under these conditions? Make sure the incentives align well with the overall goals of society. To me, it’s a simple formula:
- Focus on free trade, value for value, as the basis of a society. In that system, people are always incentivized to provide value to other people.
- Reduce the size of bureaucracies and large groups of all kinds. The larger an organization becomes, the farther the consequences of decisions are from those who make them.
- And since the nature of human beings will be to try and create areas where they can control the incentive systems to their own benefits, make that as difficult as possible. That comes in the form of strict limits on government power, for example.
And even if you don’t want to buy in to this conclusion, I hope the rest of the content was educational, and maybe a bit entertaining!
-
 @ 6e0ea5d6:0327f353
2025-05-28 04:34:08
@ 6e0ea5d6:0327f353
2025-05-28 04:34:08Ascolta bene! It is more dignified to thirst alone in the desert than to share wine with someone who has no thirst for conquest.
On the silent path to success, it’s not the declared enemies who slow the march, but rather the friends. Not the noble or loyal ones, but the failures—those who carry a dull glint in their eyes, chronic laziness in their spirit, and the eternal excuse of bad luck in their pockets. Friendship, when poorly chosen, becomes a polished anchor, tied to your ankle with ropes named camaraderie.
Nothing weighs heavier on the journey than having to endure the failed and envious around you. It is a kind of emotional parasitism that begins with empathy and ends in stagnation. Those who live among the weak will crawl. Those who keep company with miserable friends, instead of striving to prosper, learn to curse wealth—not out of ethics, but out of envy. Mediocrity, my friend, is contagious. And it does not take root suddenly, but like a silent epidemic.
Ambition—that fire that burns in the bones of great men—will always seem like arrogance to the ears of the failed. Those who have never built anything, except arguments to justify their paralysis, will never understand the fury of someone born to conquer. And so, with smiles, they spit venom: “Calm down,” they say, “be content,” they advise. Hypocrites. What they call humility is nothing more than resignation to their own defeat.
To walk alone, with hunger and honor, is worth more than feasting at lavish tables at the cost of your own sweat, surrounded by parasites who toast your downfall with glasses full of praise. No one prospers where the conversation is filled with complaints, criticism, and envy. What does not build up, corrodes.
The rust of the weak is invisible at first—a bitter joke here, a veiled critique there. And before you know it, the structure is already rotten. Of the friendship, only the weight remains. Of the relationship, only exhaustion. The true enemy of success is the company of those who have failed and wish for you the same fate. These tragic figures—always tired, always victims—are masters of collective self-sabotage.
Feel no remorse in abandoning those who build nothing and consume everything. And in that abandonment, you become freer, stronger, and unbreakable.
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ 1d7ff02a:d042b5be
2025-05-28 04:02:47
@ 1d7ff02a:d042b5be
2025-05-28 04:02:47For those who still don't truly understand Bitcoin, it means you still don't understand what money is, who creates it, and why humans need money.
It's a scam that the education system doesn't teach this important subject, while we spend almost our entire lives trying to earn money. Therefore, I recommend following the money and studying Bitcoin seriously.
Why Bitcoin Matters
Saving is the greatest discovery in human history
Before humans learned to save, we were just animals living day to day. Saving is what makes humans different from other animals — the ability to think about the future and store for later.
Saving created civilization itself
Without saving, there would be no cities, no science, no art. Everything we call "progress" comes from the ability to save.
Money is the greatest creation in human history
It is the tool that has allowed human civilization to advance to this day. Money is the best tool humans use for saving.
Bitcoin is the best money ever created
It is the most perfect money humans have ever created. No one can control, manipulate, destroy it, and it is truly limited like time in life.
Bitcoin is like a black hole
That will absorb all value from the damaged financial system. It will draw stability and value to itself. Everything of value will flow into Bitcoin eventually.
Bitcoin is like Buddhism discovering truth
It helps understand the root problems of the current financial system and the emergence of many problems in society, just like Buddha who understood all suffering and the causes of suffering.
Bitcoin is freedom
Money is power, money controls human behavior. When we have money that preserves value and cannot be controlled, we will have intellectual freedom, freedom of expression, and the power to choose.
The debt that humanity has created today would take another thousand years to pay off completely
There is no way out and it's heading toward serious collapse. Bitcoin is the light that will help prevent humanity from entering another dark age.
Bitcoin cannot steal your time
It cannot be created from nothing. Every Bitcoin requires real energy and time to create.
Bitcoin is insurance that protects against mismanagement
It helps protect against currency debasement, economic depression, and failed policies. Bitcoin will protect your value.
Bitcoin is going to absorb the world's value
Eventually, Bitcoin will become the store of value for the entire world. It will absorb wealth from all assets, all prices, and all investments.
Exit The Matrix
We live in a financial Matrix. Every day we wake up and go to work, thinking we're building a future for ourselves. But in reality, we're just giving energy to a system that extracts value from us every second. Bitcoin is the red pill — it will open your eyes to see the truth of the financial world. Central banks are the architects of this Matrix — they create money from nothing, and we have to work hard to get it.
The education system has deceived us greatly. They teach us to work for money, but never teach us what money is. We spend 12-16 years in school, then spend our entire lives earning money, but never know what it is, who creates it, and why it has value. This is the biggest scam in human history.
We are taught to be slaves of the system, but not taught to understand the system.
The Bitcoin standard will end war
When you can't print money for war anymore, war becomes too expensive.
We are entering the Bitcoin Renaissance era
An era of financial and intellectual revival. Bitcoin is creating a new class of humans. People who understand and hold Bitcoin will become a new class with true freedom.
The Path to Financial Truth
Follow the money trail and you will see the truth: - Who controls money printing? - Why do prices keep getting higher? - Why are the poor getting poorer and the rich getting richer?
All the answers lie in understanding money and Bitcoin.
Studying Bitcoin is not just about investment — it's about understanding the future of currency and human society.
Don't just work for money. Understand money. Study Bitcoin.
If you don't understand money, you will be a slave to the system forever. If you understand Bitcoin, you will gain freedom.
-
 @ 3f770d65:7a745b24
2025-01-12 21:03:36
@ 3f770d65:7a745b24
2025-01-12 21:03:36I’ve been using Notedeck for several months, starting with its extremely early and experimental alpha versions, all the way to its current, more stable alpha releases. The journey has been fascinating, as I’ve had the privilege of watching it evolve from a concept into a functional and promising tool.
In its earliest stages, Notedeck was raw—offering glimpses of its potential but still far from practical for daily use. Even then, the vision behind it was clear: a platform designed to redefine how we interact with Nostr by offering flexibility and power for all users.
I'm very bullish on Notedeck. Why? Because Will Casarin is making it! Duh! 😂
Seriously though, if we’re reimagining the web and rebuilding portions of the Internet, it’s important to recognize the potential of Notedeck. If Nostr is reimagining the web, then Notedeck is reimagining the Nostr client.
Notedeck isn’t just another Nostr app—it’s more a Nostr browser that functions more like an operating system with micro-apps. How cool is that?
Much like how Google's Chrome evolved from being a web browser with a task manager into ChromeOS, a full blown operating system, Notedeck aims to transform how we interact with the Nostr. It goes beyond individual apps, offering a foundation for a fully integrated ecosystem built around Nostr.
As a Nostr evangelist, I love to scream INTEROPERABILITY and tout every application's integrations. Well, Notedeck has the potential to be one of the best platforms to showcase these integrations in entirely new and exciting ways.
Do you want an Olas feed of images? Add the media column.
Do you want a feed of live video events? Add the zap.stream column.
Do you want Nostr Nests or audio chats? Add that column to your Notedeck.
Git? Email? Books? Chat and DMs? It's all possible.
Not everyone wants a super app though, and that’s okay. As with most things in the Nostr ecosystem, flexibility is key. Notedeck gives users the freedom to choose how they engage with it—whether it’s simply following hashtags or managing straightforward feeds. You'll be able to tailor Notedeck to fit your needs, using it as extensively or minimally as you prefer.
Notedeck is designed with a local-first approach, utilizing Nostr content stored directly on your device via the local nostrdb. This will enable a plethora of advanced tools such as search and filtering, the creation of custom feeds, and the ability to develop personalized algorithms across multiple Notedeck micro-applications—all with unparalleled flexibility.
Notedeck also supports multicast. Let's geek out for a second. Multicast is a method of communication where data is sent from one source to multiple destinations simultaneously, but only to devices that wish to receive the data. Unlike broadcast, which sends data to all devices on a network, multicast targets specific receivers, reducing network traffic. This is commonly used for efficient data distribution in scenarios like streaming, conferencing, or large-scale data synchronization between devices.
In a local first world where each device holds local copies of your nostr nodes, and each device transparently syncs with each other on the local network, each node becomes a backup. Your data becomes antifragile automatically. When a node goes down it can resync and recover from other nodes. Even if not all nodes have a complete collection, negentropy can pull down only what is needed from each device. All this can be done without internet.
-Will Casarin
In the context of Notedeck, multicast would allow multiple devices to sync their Nostr nodes with each other over a local network without needing an internet connection. Wild.
Notedeck aims to offer full customization too, including the ability to design and share custom skins, much like Winamp. Users will also be able to create personalized columns and, in the future, share their setups with others. This opens the door for power users to craft tailored Nostr experiences, leveraging their expertise in the protocol and applications. By sharing these configurations as "Starter Decks," they can simplify onboarding and showcase the best of Nostr’s ecosystem.
Nostr’s “Other Stuff” can often be difficult to discover, use, or understand. Many users doesn't understand or know how to use web browser extensions to login to applications. Let's not even get started with nsecbunkers. Notedeck will address this challenge by providing a native experience that brings these lesser-known applications, tools, and content into a user-friendly and accessible interface, making exploration seamless. However, that doesn't mean Notedeck should disregard power users that want to use nsecbunkers though - hint hint.
For anyone interested in watching Nostr be developed live, right before your very eyes, Notedeck’s progress serves as a reminder of what’s possible when innovation meets dedication. The current alpha is already demonstrating its ability to handle complex use cases, and I’m excited to see how it continues to grow as it moves toward a full release later this year.
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ cae03c48:2a7d6671
2025-05-28 04:00:33
@ cae03c48:2a7d6671
2025-05-28 04:00:33Bitcoin Magazine

Steak ‘n Shake Reveals Bitcoin Payment Success at Bitcoin 2025 ConferenceSpeaking at the Bitcoin 2025 Conference this morning, Steak ‘n Shake executive Dan Edwards shared new data and insights from the company’s recent move to accept Bitcoin payments globally via the Lightning Network.
JUST IN: Fast food giant Steak 'n Shake announced they're saving 50% in processing fees accepting Bitcoin payments

'#Bitcoin is faster than credit cards'
 pic.twitter.com/bxApgBL6El
pic.twitter.com/bxApgBL6El— Bitcoin Magazine (@BitcoinMagazine) May 27, 2025
“On May 16, we began accepting Bitcoin as payment in all of our locations where permitted to do so by law,” Edwards began. “This is a global implementation.”
According to Edwards, Bitcoin transactions are already outperforming expectations. “The day we launched Bitcoin, 1 out of every 500 bitcoin transactions in the world happened at Steak ‘n Shake,” he said.
Steak ‘n Shake is also saving significantly on processing fees. “Bitcoin is faster than credit cards, and when customers choose to pay in Bitcoin, we’re saving 50% in processing fees,” said Edwards. “That makes Bitcoin a win for the customer, a win for us, and a win for the Bitcoin community.”
He emphasized that the decision was not a publicity stunt, but a serious payment upgrade. “We didn’t see this as a marketing gimmick. We saw it as a viable option to pay—on par with other globally accepted methods.”
The company reports that customer behavior has already shifted. “We’ve seen a sustained spike since adding Bitcoin,” Edwards noted.
Edwards also teased the company’s future plans, calling for more technical talent. “We’re not done. We’re investing in cyber chefs, autonomous drives, AI tech—and we need engineers to help us build it.”
To celebrate Bitcoin integration, limited-edition Bitcoin-themed menu items are launching this week in Las Vegas, including the Bitcoin Burger, Super-Sized Bitcoin Meal, and Bitcoin Milkshake. A “blockchain menu” is also in the works.
“Celebrate the use of Bitcoin,” Edwards concluded. “Because this is just the beginning.”
This post Steak ‘n Shake Reveals Bitcoin Payment Success at Bitcoin 2025 Conference first appeared on Bitcoin Magazine and is written by Jenna Montgomery.