-
 @ c9badfea:610f861a
2025-05-06 23:05:40
@ c9badfea:610f861a
2025-05-06 23:05:40ℹ️ To add profiles to the follow packs, please leave a comment
-
 @ 000002de:c05780a7
2025-05-06 20:24:08
@ 000002de:c05780a7
2025-05-06 20:24:08https://www.youtube.com/watch?v=CIMZH7DEPPQ
I really enjoy listening to non-technical people talk about technology when they get the bigger picture impacts and how it relates to our humanity.
I was reminded of this video by @k00b's post about an AI generated video of a victim forgiving his killer.
Piper says, "Computers are better at words than you. Than I". But they are machines. They cannot feel. They cannot have emotion.
This people honors me with their lips, but their heart is far from me
~ Matthew 15:8
Most of us hate it when people are fake with us. When they say things they don't mean. When they say things just to get something they want from us. Yet, we are quickly falling into this same trap with technology. Accepting it as real and human. I'm not suggesting we can't use technology but we have to be careful that we do not fall into this mechanical trap and forget what makes humans special.
We are emotional and spiritual beings. Though AI didn't exist during the times Jesus walked the earth read the verse above in a broader context.
Then Pharisees and scribes came to Jesus from Jerusalem and said, “Why do your disciples break the tradition of the elders? For they do not wash their hands when they eat.” He answered them, “And why do you break the commandment of God for the sake of your tradition? For God commanded, ‘Honor your father and your mother,’ and, ‘Whoever reviles father or mother must surely die.’ But you say, ‘If anyone tells his father or his mother, “What you would have gained from me is given to God,” he need not honor his father.’ So for the sake of your tradition you have made void the word of God. You hypocrites! Well did Isaiah prophesy of you, when he said:
“‘This people honors me with their lips,
but their heart is far from me;
in vain do they worship me,
teaching as doctrines the commandments of men.’”
Empty words. Words without meaning because they are not from a pure desire and love. You may not be a Christian but don't miss the significance of this. There is a value in being real. Sharing true emotion and heart. Don't fall into the trap of the culture of lies that surrounds us. I would rather hear true words with mistakes and less eloquence any day over something fake. I would rather share a real moment with the ones I love than a million fake moments. Embrace the messy imperfect but real world.
originally posted at https://stacker.news/items/973324
-
 @ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39
@ 5d4b6c8d:8a1c1ee3
2025-05-06 19:49:39One of the best first rounds in recent memory just concluded. Let's recap our playoff contests.
Bracket Challenge
In our joint contest with Global Sports Central, @WeAreAllSatoshi is leading the way with 85 points, while me and some nostr jabroni are tied for second with 80 points.
The bad news is that they are slightly ahead of us, with an average score of 62 to our 60.8. We need to go back in time and make less stupid picks.
Points Challenge
With the Warriors victory, I jumped into a commanding lead over @grayruby. LA sure let most of you down. I say you hold @realBitcoinDog responsible for his beloved hometown's failures.
I still need @Car and @Coinsreporter to make their picks for this round. The only matchup they can choose from is Warriors (7) @ Timberwolves (6). Lucky for them, that's probably the best one to choose from.
| Stacker | Points | |---------|--------| | @Undisciplined | 25| | @grayruby | 24| | @Coinsreporter | 19 | | @BlokchainB | 19| | @Carresan | 18 | | @gnilma | 18 | | @WeAreAllSatoshi | 12 | | @fishious | 11 | | @Car | 1 |
originally posted at https://stacker.news/items/973284
-
 @ 8671a6e5:f88194d1
2025-05-06 16:23:25
@ 8671a6e5:f88194d1
2025-05-06 16:23:25"I tried pasting my login key into the text field, but no luck—it just wouldn't work. Turns out, the login field becomes completely unusable whenever the on-screen keyboard shows up on my phone. So either no one ever bothered to test this on a phone, or they did and thought, ‘Eh, who needs to actually log in anyway?’."

### \ \ Develop and evolve
Any technology or industry at the forefront of innovation faces the same struggle. Idealists, inventors, and early adopters jump in first, working to make things usable for the technical crowd. Only later do the products begin to take shape for the average user.
Bitcoin’s dropping the Ball on usability (and user-experience)
First, we have to acknowledge the progress we've made. Bitcoin has come a long way in terms of usability—no doubt about it. Even if I still think it’s bad, it’s nowhere near as terrible as it was ten or more years ago. The days of printing a paper wallet from some shady website and hoping it would still work months or years later are behind us. The days of buggy software never getting fixed are mostly over.
The Bitcoin technology itself made progress through many BIPs (Bitcoin Improvement Proposals) and combined with an increasing number of apps, devs, websites and related networks (Liquid, Lightning, Nostr, ....) we can say that we're seeing a strong ecosystem going its way. The ecosystem is alive and expanding, and technically, things are clearly working. The problem is that we’re still building with a mindset where developers and project managers consider usability—but don’t truly care about it in practice. They don’t lead with it. (Yes, there are always exceptions.)
All that progress looks cool, when you see the latest releases of hardware wallets, software wallets, exchanges, nostr clients and services built purely for bitcoin, you're usually thinking that we've progressed nicely. But I want to focus on the downside of all these shiny tools. Because if Bitcoin has made it this far, it’s mostly thanks to people who deeply understand its value and are stubborn enough to push through the friction. They don’t give up when the user experience sucks.
Many bitcoiners completely lost their perspective on the software front in my opinion. Because we could have been so much further ahead, and we didn't because some of the most important components on the user-facing side of Bitcoin (arguably the most important part) hasn’t kept pace with the popularity and possible growth. And that should be a great concern, because Bitcoin is meant to be open and accessible. The blockchain is public. This is supposed to be for everyone. This is an open ledger technology so in theory everything is user-facing to one extent or another. Yet we fail on that front to make the glue stick. Somewhere, we’re easily amused by the tools we create, and often contains hurdles we can’t see or feel. While users reject it after 5 seconds tops.
We didn’t came a lot further yet, because we’ve ignored usability at its core (pun intended).
I’m not talking about usability in the “it works on my machine” sense. I’m talking about usability that meets the standard of modern apps. Think Spotify, Instagram, Uber, Gmail. Products that ordinary people use without reading a manual or digging through forums.
That’s the bar. We’re still far from it.
Bad UX scares your grandma away
… and that’s how many bitcoiners apparently like it.
Subsequently, when I say usability, I’m using it as an umbrella term. For me, it covers user experience, user interface, and real-life, full-cycle testing—from onboarding a brand new user to rolling out a new version of the app. And oh boy, our onboarding is so horrible. (“Hey wanna try bitcoin? Here’s an app that takes up to 4 minutes or more to get though, but wait, you’ll have to install a plugin, or wait I’ll send you an on-chain transaction…)
Take a look at the listings on Bitvocation, an excellent job board for Bitcoiners and related projects. You’ll quickly notice a pattern: almost no companies are hiring software testers. It’s marketing, more marketing, some sales, and of course, full-stack developers. But … No testers.
Because testing has become something that’s often skipped or automated in a hurry. Maybe the devs run a test locally to confirm that the feature they just built doesn’t crash outright. That’s it. And if testing does happen at a company, it’s usually shallow—focused only on the top five percent of critical bugs. The finer points that shape real user experience, like button placement, navigation flow, and responsiveness, are dumped on “the community.”
Which leads to some software being rushed out to production, and only then do teams discover how many problems exist in the real world. If there’s anyone left to care that is, since most teams are scattered all over the world and get paid by the hour by some VC firm on a small runway to a launch date.
This has real life consequences I’ve seen for myself with new users. Like a lightning wallet having a +5 minute onboarding time, and a fat on-screen error for the new users, or a hardware wallet stuck in an endless upgrade loop, just because nobody tested it on a device that was “old” (as in, one year old).
The result is clear: usability and experience testing are so low on the priority list, they may as well not exist. And that’s tragic, because the enthusiasm of new users gets crushed the moment they run into what I call Linux’plaining.
That’s when something obvious fails — like a lookup command that’s copied straight from their own help documentation but doesn’t work — and the answer you get as a user is something like: “Yeah, but first you have to…” followed by an explanation that isn’t mentioned anywhere in the interface or documentation. You were just supposed to know. No one updates the documentation, and no one cares. As most of the projects are very temporary or don’t really care if it succeeds or not, because they’re bitcoiners and bitcoin always wins. Just like PGP always was super cool and good, and users should just be smarter.
Lessons from the past usability disasters
We can always learn from the past especially when its precedents are still echoing through the systems we use today
So here goes, some examples from the legacy / fiat industry:
Lotus Notes, for example. Once a titan in enterprise communication software, which managed to capture about 145 million mailboxes. But its downfall is an example of what happens when you ignore and keep ignoring real-life user needs and fail to evolve with the market. Software like that doesn’t just fade, it collapses under the weight of its own inertia and bloat. If you think bitcoin can’t have that, yes… we’re of course not having a competitor in the market (hard money is hard money, not a mailbox or office software provider of course). But we can erode trust to the extent that it becomes LotusNotes’d.
Its archaic 1990s interface came with clunky navigation and a chaotic document management system. Users got frustrated fast—basic tasks took too long. Picture this: you're stuck in a cubicle, trying to find the calendar function in Lotus Notes while a giant office printer hisses and spits out stacks of paper behind you. The platform never made the leap to modern expectations. It failed to deliver proper mobile clients and clung to outdated tech like LotusScript and the Domino architecture, which made it vulnerable to security issues and incompatible with the web standards of the time. By 2012, IBM pulled the plug on the Lotus brand, as businesses moved en masse to cloud-based alternatives.
Another kind of usability failure has plagued PGP1 (and still does so after 34 years). PGP (Pretty Good Privacy) is a time-tested and rock-solid method for encryption and key exchange, but it’s riddled with usability problems, especially for anyone who isn’t technically inclined.
Its very nature and complexity are already steep hurdles (and yes, you can’t make it fully easy without compromising how it’s supposed to work—granted). But the real problem? Almost zero effort has gone into giving even the most eager new users a manageable learning curve. That neglect slowly killed off any real user base—except for the hardcore encryption folks who already know what they’re doing.
Ask anyone in a shopping street or the historic center of your city if they’ve heard of PGP. And on the off chance someone knows it’s not a trendy new fast-food joint called “Perfectly Grilled Poultry,” the odds of them having actually used it in the past six months are basically zero, unless you happen to bump into that one neckbeard guy in his 60s wearing a stained Star Wars T-shirt named Leonard.
The builders of PGP made one major mistake: they never treated usability as a serious design goal (that’s normal for people knee deep in encryption, I get that, it’s the way it is). PGP is fantastic on itself. Other companies and projects tried to build around it, but while they stumbled, tools like Signal and ProtonMail stepped in; offering the same core features of encryption and secure messaging, minus the headache. They delivered what PGP never could: powerful functionality wrapped in something regular people can actually use. Now, we’ve got encrypted communication flowing through apps like Signal, where all the complex tech is buried so deep in the background, the average user doesn’t even realize it’s there. ProtonMail went one step further even, integrating PGP so cleanly that users never need to exchange keys or understand the cryptography behind it all, yet still benefit from bulletproof encryption.
There’s no debate—this shift is a good thing. History shows that unusable software fades into irrelevance. Whether due to lack of interest, failure to reach critical mass, or a competitor swooping in to eat market share, clunky tools don’t survive. Now, to be clear, Bitcoin doesn’t have to worry about that kind of threat. There’s no real competition when it comes to hard money. Unless, of course, you genuinely believe that flashy shitcoins are a viable alternative—in which case, you might as well stop reading here and go get yourself scammed on the latest Solana airdrop or whatever hype train’s leaving the station today for the degens.
The main takeaway here is that Bitcoin must avoid becoming the next Lotus Notes, bloated with features but neglected by users—or the next PGP, sidelined by its own lack of usability. That kind of trajectory would erode trust, especially if usability and onboarding keep falling behind. And honestly, we’re already seeing signs of this in bitcoin. User adoption in Europe, especially in countries like Germany is noticeably lagging. The introduction of the EU’s MiCA regulations isn’t helping either. Most of the companies that were actually pushing adoption are now either shutting down, leaving the EU, or jumping through creative loopholes just to stay alive. And the last thing on anyone’s mind is improving UX. It takes time, effort, and specialized people to seriously think through how to build this properly, from the beginning, with this ease of use and onboarding in mind. That’s a luxury most teams can’t or won’t prioritize right now. Understandably when the lack of funds is still a major issue within the bitcoin space. (for people sitting on hard money, there’s surprisingly little money flowing into useful projects that aren’t hyped up empty boxes)
The number of nodes being set up by end users worldwide isn’t exactly skyrocketing either. Sure, there’s some growth but let’s not overstate it. Based on Bitnodes’ snapshots taken in March of each year, we’re looking at: 2022 : around 10500 2023 : around 17000 2024 : around 18500 2025 : around 21000 (I know there are different methods of measuring these, like read-only nodes, the % change is roughly the same nonetheless)
In my opinion, if we had non-clunky software that was actually released with proper testing and usability in mind, we could’ve easily doubled those node numbers. A bad user experience with a wallet spreads fast—and brings in exactly zero new users. The same goes for people trying to set up a miner or spin up a node, only to give up after a few frustrating steps. Sure, there are good people out there making guides and videos2 to help mitigate those hurdles, and that helps. But let’s be honest: there’s still very little “wow” factor when average users interact with most Bitcoin software. Almost every time they walk away, it’s because of one of two things—usability issues or bugs.
For the record: if a user can’t set up a wallet because the interface is so rotten or poorly tested, so they don’t know where to click or how to even select a seed word from a list, then that’s a problem — that’s a bug. Argue all you want: sure, it’s not a code-level bug and no, it’s not a system crash. But it is a usability failure. Call it onboarding friction, UX flaw, whatever fits your spreadsheet or circus Maximus of failures in your ticketing system. Bottom line: if your software doesn’t help users accomplish its core purpose, it’s broken. It’s a bug. Pretending it’s something a copywriter or marketing team can fix is pure deflection. The solution isn’t to relabel the problem, 1990’s telecom-style, just to avoid dealing with it. It’s to actually sit down, think, collaborate, and go through the issue, and getting real solutions out. ”No it’s not an issue, that’s how it works” like someone from a failing (and by now defunct) wallet told me once, is not a solution.
You got 21 seconds
The user can’t be onboarded because your software has an “issue”? In my book, that’s a bug. The usual response when you report it? “Yeah, that’s not a priority.” Well, guess what? It actually is a priority. All these small annoyances, hurdles, and bits of BS still plague this industry, and they make the whole experience miserable for regular people trying it out for the first time. The first 21 seconds (yeah, you see what I did there) are the most important when someone opens new software. If it doesn’t click right away—if they’re fiddling with sats or dollar signs, or hunting for some hidden setting buried behind a tiny arrow—it’s game over. They’re annoyed. They’re gone.
And this is exactly why we’re seeing a flood of shitcoin apps sweeping new users off their feet with "faster apps" or "nicer designs" apps that somehow can afford the UI specialists and slick, centralized setups to spread their lies and scams.
I hate to say it, but the Phantom wallet for example, for the Solana network, loaded with fake airdrop schemes and the most blatant scams — has a far better UX than most Bitcoin wallets and Lightning Wallets. Learn from it. Download that **** and get to know what we do wrong and how we can learn from the enemy.
That’s a hard truth. So, instead of just screaming “Uh, shitcooooin!” (yes, we know it is), maybe we should start learning from it. Their apps are better than ours in terms of UI and UX. They attract more people 5x faster (we know that’s also because of the fast gains and retardation playing with the marketing) but we can’t keep ignoring that. Somehow these apps attract more than our trustworthiness, our steady, secure, decentralized hard money truth.
It’s like stepping into one of the best Italian restaurants in town—supposedly. But then the menu’s a mess, the staff is scrolling on their phones, and something smells burnt coming from the kitchen. So, what do you do? You walk out. You cross the street to the fast food joint and order a burger and fries. And as you’re walking out with your food, someone from the Italian place yells at you: “Fast food is bad!” ”Yeah man I know, I wanted a nice Spaghetti aglio e olio, but here I am, digesting a cheeseburger that felt rather spongy.” (the problem is so gone so deep now, that users just walk past that Italian restaurant, don’t even recognize it as a restaurant because it doesn’t have cheeseburgers).
Fear of the dark
Technical people, not marketeers built bitcoin, it’s build on hundreds of small building blocks that interacted over time to have the bitcoin network and it’s immer evolving value. At one point David Chaum cooked up eCash, using blind signatures to let people send digital money anonymously — except it was still stuck on clunky centralized servers. Go back even further, to the 1970s, when Diffie, Hellman, and Rivest introduced public-key cryptography—the magic sauce that gave us secure digital signatures and authentication, making sure your messages stayed private and tamper-proof.
Fast forward to the 1990s, where peer-to-peer started to take off, decentralized networks getting started. Adam Back’s Hashcash in ‘97 used proof-of-work to fight email spam, and the cypherpunks were all about sticking it to the man with privacy-first, the invention 199 Human-Readable 128-bit keys3, decentralized systems. We started to swap files over p2p networks and later, torrents.
All these parts—anonymous cash, encryption, and leaderless networks finally clicked into place when Satoshi Nakamoto poured them into a chain of blocks, built on an ingenious “time-stamping” system: the timechain, or blockchain if you prefer. And just like that, Bitcoin was born—a peer-to-peer money system that didn’t need middlemen and actually worked without any central servers.
So yes, it’s only natural that Bitcoin and the many tools, born from math, obscurity, and cryptography, isn’t exactly always a user-interface darling. That’s also it’s charm for me in any case, as the core is robust and valuable beyond belief. That’s why we love to so see more use, more adoption.
But that doesn’t mean we can’t squash critical “show-stopper” bugs before releasing bitcoin-related software. And it sure as hell doesn’t mean we should act like jerks when a user points out something’s broken, confusing, or just doesn’t meet expectations. We can’t be complacent either about our role as builders of the next generations, as the core is hard money, and it would be a fatal mistake for the world to see it being used only for some rockstars from Wall Street and their counterparts to store their debt laden fiat. We can free people, make them better, make them elevate themselves. And yet, the people we try to elevate, we often alienate. All because we don’t test our stuff well enough. We should be so good, we blow the banking apps away. (they’re blowing themselves out of the market luckily with fiat “features” and overly over the top use of “analytics” to measure your carbon footprint for example).
We should be so damn professional that someone using Bitcoin apps for a full year wouldn’t even notice any bugs, because there wouldn’t be much to get annoyed by.
So… we have to do better. I’ve seen it time and time again — on Lightning tipping apps, Nostr plugins, wallets, hardware wallets, even metal plates we can screw up somehow … you name it. “It works on my machine”, isn’t enough anymore! Those days are over.
Even apps built with solid funding and strong dev and test teams like fedi.xyz4 can miss the mark. While the idea was good and the app itself ran fine without too much hurdles and usual bugs. But usability failed on a different front: there was just nothing meaningful to do in the app beyond poking around, chatting a bit, and sending a few sats back and forth. The communities it’s supposed to connect, just aren’t there, or weren’t there “yet”.
It’s a beautifully designed application and a strong proof-of-concept for federated community funds. But then… nothing. No one I know uses it. Their last blogpost was from beginning of October 2024, which doesn’t bode well, writing this than 6 months after. That said, they got some great onboarding going, usually under 20 seconds, which proves it can be done right (even if it was all a front-end for a more complex backend).
As you can see “usability” is a broad terminology, covering technical aspects, user-interface, but also use-cases. Even if you have a cool app that works really well and is well thought-out users won’t use it if there’s no real substance. You can’t get that critical mass by waiting for customers to come in or communities to embrace it. They won’t, because most of the individuals already had past experiences with bitcoin apps or services, and there’s a reason for them not being on-board already.
A lot of bitcoin companies build tools for new people. Never for the lapsed people, the persons that came in, thought of it as an investment or “a coin”… then left because of a bad experience or the price going down in fiat. All the while we have some software that usually isn’t so kind to new people, or causes loss of funds and time. Even if they make one little “mistake” of not knowing the system beforehand.

Bitcoin’s Moby Dick
\ Bitcoin itself has a big issue here. The user base could grow faster, and more robust, if there wasn’t software that worked as a sort of repellent against users.
I especially see a younger and less tech-savvy audience absolutely disliking the software we have now. No matter if it’s Electrum’s desktop wallet (hardly the sexiest tool out there, although I like it myself, but it lacks some features), Sparrow, or any lightning wallet out there (safe for WoS). I even saw people disliking Proton wallet, which I personally thought of as something really slick, well-made and polished. But even that doesn’t cut it for many people, as the “account” and “wallet” system wasn’t clear enough for them. (You see, we all have the same bias, because we know bitcoin, we look at it from a perspective of “facepalm, of course it’s a wallet named “account”, but when you sit next to a new user, it becomes clear that this is a hurdle. (please proton wallet: name a wallet a wallet, not “account”. But most users already in bitcoin, love what you’re doing)
Naturally disliking usability
The same technically brilliant people who maintain Bitcoin and build its apps haven’t quite tapped into their inner Steve Jobs—if that person even exists in the Bitcoin space. Let’s be honest: the next iOS-style wow moment, or the kind of frictionless usability seen in Spotify or Instagram, probably won’t come from hardcore Bitcoin devs alone. In fact, some builders in the space seem to actively disregard—or even look down on—discussions about usability. Just mention names like Wallet of Satoshi (yes, we all know it’s a custodial frontend) or the need for smoother interactions with Bitcoin, and you’ll get eye-rolls or defensive rants instead of curiosity or openness.
Moving more towards a better user interface for things like Sparrow or Bitcoin Core for example, would bring all kinds of “bad things” according to some, and on top of that, bring in new users (noobs) that ask questions like: “Do you burn all these sats when I make a transaction?” (Yes, that’s a real one.)
I get the “usability sucks” gripe — fear of losing key features, dumbing things down, or opening the door to unwanted changes (like BIP proposals real bitcoiners hate) that tweak bitcoin to suit any user’s whim. Close to no one in bitcoin (really in bitcoin!) wants that, including me.
That fear is however largely unfounded; because Bitcoin doesn’t change without consensus. Any change that would undermine its core use or value proposition simply won’t make it through. And let’s be honest: most of the users who crave these “faster,” centralized alternatives—those drawn to slick apps, one-click solutions, and dopamine-driven UI—will either stick with fiat, ape into the shitcoin-of-the-month, or praise the shiny new CBDC once it drops (“much fast, much cool”). These degen types, chasing fiat gains and jackpot dreams, aren’t relevant to this story, No matter what we build for bitcoin, they’ll always love the fiat-story and will always dislike bitcoin because it’s not a jackpot for them. (Honestly, why don’t they just gamble at a casino?)
People who fear that improving usability will somehow bring down the Bitcoin network are being a bit too paranoid—and honestly, they often don’t understand what usability or proper testing actually means.
They treat it like fluff, when in reality it's fundamental. Usability doesn't mean dumbing things down or compromising Bitcoin's core values; it means understanding why your fancy new app isn’t being used by anyone outside of your bubble. Testing is the beating heart of getting things out with confidence. Nothing more satisfying in software building than to proudly show even your beta versions to users, knowing it’s well tested. It’s much more than clicking a few buttons and tossing your code on GitHub. It's about asking real questions: can someone outside your Telegram group actually use this and will it they be using the software at all?
If you create a Nostr app that opens an in-app browser window and then tries to log you in with your NIPS05 or NIPS07 or whatever number it is that authenticates you, then you need to think about how it’s going to work in real life. Have people already visited this underlying website? Is that website using the exact same mechanism? Is it really working like we think it is in the real world? (Some notable good things are happening with the development of Keychat for example, I have the feeling they get it, it’s not all bad). And yes, there are still bugs and things to improve there, they’re just starting. (The browser section and nostr login need some work imho).
Guess what? You can test your stuff. But it takes time and effort. The kind of effort that, if skipped, gets multiplied across thousands of people. Thousands of people wasting their time trying to use your app, hitting errors, assuming they did something wrong, retrying, googling workarounds—only to eventually realize: it’s not them. It’s a bug. A bug you didn’t catch. Because you didn’t test. And now everyone loses. And guess what? Those users? They’re not coming back.
A good example (to stay positive here) is Fountain App, where the first versions were , eh… let’s say not so good, and then quickly evolved into a company and product that works really well, and also listens to their users and fixes their bugs. The interface can still be better in my opinion, but it’s getting there. And it’s super good now.
A bad example? Alby. (Sorry to say.) It still suffers from a bloated, clunky interface and an onboarding flow that utterly confuses new or returning users. It just doesn’t get the job done. Opinions may vary, sure, but hand this app to any non-technical user and ask them to get online and do a Nostr zap. Watch what happens. If they even manage to get through the initial setup, that is.
Another example? Bitkit. When I tried transferring funds from the "savings" to the "spending" account, the wallet silently opened a Lightning channel—no warning, no explanation—and suddenly my coins were locked up. To make things worse, the wallet still showed the full balance as spendable, even though part of it was now stuck in that channel. That was in November 2024, the last time I touched Bitkit. I wasted too much time trying to figure it out, I haven’t looked back (assuming the project is even still alive, I didn’t see them pop up anywhere).
Some metal BIP39 backup tools are great in theory but poorly executed. I bought one that didn’t even include a simple instruction on how to open it. The person I gave it to spent two hours trying to open it with a screwdriver and even attempted drilling. Turns out, it just slides open with some pressure. A simple instruction would’ve saved all that frustration.
Builders often assume users “just get it,” but a small guide could’ve prevented all the hassle. It’s a small step, but it’s crucial for better user experience. So why not avoid such situations and put a friggin cheap piece of paper in the box so people know how to open it? (The creators would probably facepalm if they read this, “how can users nòt see this?”). Yeah,… put a paper in there with instructions.
That’s natural, because as a creator you’re “in” it, you know. You don’t see how others would overlook something so obvious.
Bitcoiners are extremely bad on that front.
I’ll dive deeper into some examples in part 2 of this post.
By AVB
end of part 1
If you like to support independent thought and writings on bitcoin, follow this substack please https://coinos.io/allesvoorbitcoin/receive\ \ footnotes:
1 https://philzimmermann.com/EN/findpgp/
2 BTC sessions: set up a bitcoin node
-
 @ bbef5093:71228592
2025-05-06 16:11:35
@ bbef5093:71228592
2025-05-06 16:11:35India csökkentené az atomerőművek építési idejét ambiciózus nukleáris céljai eléréséhez
India célja, hogy a jelenlegi 10 évről a „világszínvonalú” 6 évre csökkentse atomerőművi projektjeinek kivitelezési idejét, hogy elérje a 2047-re kitűzött, 100 GW beépített nukleáris kapacitást.
Az SBI Capital Markets (az Indiai Állami Bank befektetési banki leányvállalata) jelentése szerint ez segítene mérsékelni a korábbi költségtúllépéseket, és vonzóbbá tenné az országot a globális befektetők számára.
A jelentés szerint a jelenlegi, mintegy 8 GW kapacitás és a csak 7 GW-nyi építés alatt álló kapacitás mellett „jelentős gyorsítás” szükséges a célok eléréséhez.
A kormány elindította a „nukleáris energia missziót”, amelyhez körülbelül 2,3 milliárd dollárt (2 milliárd eurót) különített el K+F-re és legalább öt Bharat kis moduláris reaktor (BSMR) telepítésére, de további kihívásokat kell megoldania a célok eléréséhez.
Az építési idők csökkentése kulcsfontosságú, de a jelentés átfogó rendszerszintű reformokat is javasol, beleértve a gyorsabb engedélyezést, a földszerzési szabályok egyszerűsítését, az erőművek körüli védőtávolság csökkentését, és a szabályozó hatóság (Atomic Energy Regulatory Board) nagyobb önállóságát.
A jelentés szerint a nemzet korlátozott uránkészletei miatt elengedhetetlen az üzemanyagforrások diverzifikálása nemzetközi megállapodások révén, valamint az indiai nukleáris program 2. és 3. szakaszának felgyorsítása.
India háromlépcsős nukleáris programja célja egy zárt üzemanyagciklus kialakítása, amely a természetes uránra, a plutóniumra és végül a tóriumra épül. A 2. szakaszban gyorsneutronos reaktorokat használnak, amelyek több energiát nyernek ki az uránból, kevesebb bányászott uránt igényelnek, és a fel nem használt uránt új üzemanyaggá alakítják. A 3. szakaszban fejlett reaktorok működnek majd India hatalmas tóriumkészleteire alapozva.
2025 januárjában az indiai Nuclear Power Corporation (NPCIL) pályázatot írt ki Bharat SMR-ek telepítésére, először nyitva meg a nukleáris szektort indiai magáncégek előtt.
Eddig csak az állami tulajdonú NPCIL építhetett és üzemeltethetett kereskedelmi atomerőműveket Indiában.
A Bharat SMR-ek (a „Bharat” hindiül Indiát jelent) telepítése a „Viksit Bharat” („Fejlődő India”) program része.
Engedélyezési folyamat: „elhúzódó és egymásra épülő”
A Bharat atomerőmű fejlesztésének részletei továbbra sem világosak, de Nirmala Sitharaman pénzügyminiszter júliusban elmondta, hogy az állami National Thermal Power Corporation és a Bharat Heavy Electricals Limited közös vállalkozásában valósulna meg a fejlesztés.
Sitharaman hozzátette, hogy a kormány a magánszektorral közösen létrehozna egy Bharat Small Reactors nevű céget, amely SMR-ek és új nukleáris technológiák kutatás-fejlesztésével foglalkozna.
Az SBI jelentése szerint javítani kell az SMR programot, mert az engedélyezési folyamat jelenleg „elhúzódó és egymásra épülő”, és aránytalan kockázatot jelent a magánszereplők számára a reaktorfejlesztés során.
A program „stratégiailag jó helyzetben van a sikerhez”, mert szigorú belépési feltételeket támaszt, így csak komoly és alkalmas szereplők vehetnek részt benne.
A kormánynak azonban be kellene vezetnie egy kártérítési záradékot, amely védi a magáncégeket az üzemanyag- és nehézvíz-ellátás hiányától, amely az Atomenergia Minisztérium (DAE) hatáskörébe tartozik.
A jelentés szerint mind az üzemanyag, mind a nehézvíz ellátása a DAE-től függ, és „a hozzáférés hiánya” problémát jelenthet. India legtöbb kereskedelmi atomerőműve hazai fejlesztésű, nyomottvizes nehézvizes reaktor.
A jelentés szerint: „A meglévő szabályozási hiányosságok kezelése kulcsfontosságú, hogy a magánszektor vezethesse a kitűzött 100 GW nukleáris kapacitás 50%-ának fejlesztését 2047-ig.”
Az NPCIL nemrégiben közölte, hogy India 2031–32-ig további 18 reaktort kíván hozzáadni az energiamixhez, ezzel az ország nukleáris kapacitása 22,4 GW-ra nő.
A Nemzetközi Atomenergia-ügynökség adatai szerint Indiában 21 reaktor üzemel kereskedelmi forgalomban, amelyek 2023-ban az ország áramtermelésének körülbelül 3%-át adták. Hat egység van építés alatt.
Roszatom pert indított a leállított Hanhikivi-1 projekt miatt Finnországban
Az orosz állami Roszatom atomenergetikai vállalat pert indított Moszkvában a finn Fortum és Outokumpu cégek ellen, és 227,8 milliárd rubel (2,8 milliárd dollár, 2,4 milliárd euró) kártérítést követel a finnországi Hanhikivi-1 atomerőmű szerződésének felmondása miatt – derül ki bírósági dokumentumokból és a Roszatom közleményéből.
A Roszatom a „mérnöki, beszerzési és kivitelezési (EPC) szerződés jogellenes felmondása”, a részvényesi megállapodás, az üzemanyag-ellátási szerződés megsértése, valamint a kölcsön visszafizetésének megtagadása miatt követel kártérítést.
A Fortum a NucNetnek e-mailben azt írta, hogy „nem kapott hivatalos értesítést orosz perről”.
A Fortum 2025. április 29-i negyedéves jelentésében közölte, hogy a Roszatom finn leányvállalata, a Raos Project, valamint a Roszatom nemzetközi divíziója, a JSC Rusatom Energy International, illetve a Fennovoima (a Hanhikivi projektért felelős finn konzorcium) között a Hanhikivi EPC szerződésével kapcsolatban nemzetközi választottbírósági eljárás zajlik.
2025 februárjában a választottbíróság úgy döntött, hogy nincs joghatósága a Fortummal szembeni követelések ügyében. „Ez a döntés végleges volt, így a Fortum nem része a választottbírósági eljárásnak” – közölte a cég.
A Fortum 2015-ben kisebbségi tulajdonos lett a Fennovoima projektben, de a teljes tulajdonrészt 2020-ban leírta.
A Fennovoima konzorcium, amelyben a Roszatom a Raos-on keresztül 34%-os kisebbségi részesedéssel rendelkezett, 2022 májusában felmondta a Hanhikivi-1 létesítésére vonatkozó szerződést az ukrajnai háború miatti késedelmek és megnövekedett kockázatok miatt.
A projekt technológiája az orosz AES-2006 típusú nyomottvizes reaktor lett volna.
2021 áprilisában a Fennovoima közölte, hogy a projekt teljes beruházási költsége 6,5–7 milliárd euróról 7–7,5 milliárd euróra nőtt.
2022 augusztusában a Roszatom és a Fennovoima kölcsönösen milliárdos kártérítési igényt nyújtott be egymás ellen a projekt leállítása miatt.
A Fennovoima nemzetközi választottbírósági eljárást indított 1,7 milliárd euró előleg visszafizetéséért. A Roszatom 3 milliárd eurós ellenkeresetet nyújtott be. Ezek az ügyek jelenleg is nemzetközi bíróságok előtt vannak.
Dél-koreai delegáció Csehországba utazik nukleáris szerződés aláírására
Egy dél-koreai delegáció 2025. május 6-án Csehországba utazik, hogy részt vegyen egy több milliárd dolláros szerződés aláírásán, amely két új atomerőmű építéséről szól a Dukovany telephelyen – közölte a dél-koreai kereskedelmi, ipari és energetikai minisztérium.
A delegáció, amelyben kormányzati és parlamenti tisztviselők is vannak, kétnapos prágai látogatásra indul, hogy részt vegyen a szerdára tervezett aláírási ceremónián.
A küldöttség találkozik Petr Fiala cseh miniszterelnökkel és Milos Vystrcil szenátusi elnökkel is, hogy megvitassák a Dukovany projektet.
Fiala múlt héten bejelentette, hogy Prága május 7-én írja alá a Dukovany szerződést a Korea Hydro & Nuclear Power (KHNP) céggel.
A cseh versenyhivatal nemrég engedélyezte a szerződés aláírását a KHNP-vel, miután elutasította a francia EDF fellebbezését.
A versenyhivatal április 24-i döntése megerősítette a korábbi ítéletet, amelyet az EDF megtámadott, miután 2024 júliusában elvesztette a tenderpályázatot a KHNP-vel szemben.
Ez lehetővé teszi, hogy a két dél-koreai APR1400 reaktor egység szerződését aláírják Dukovanyban, Dél-Csehországban. A szerződés az ország történetének legnagyobb energetikai beruházása, értéke legalább 400 milliárd korona (16 milliárd euró, 18 milliárd dollár).
A szerződést eredetileg márciusban írták volna alá, de a vesztes pályázók (EDF, Westinghouse) fellebbezései, dél-koreai politikai bizonytalanságok és a cseh cégek lokalizációs igényei miatt csúszott.
A KHNP januárban rendezte a szellemi tulajdonjogi vitát a Westinghouse-zal, amely korábban azt állította, hogy a KHNP az ő technológiáját használja az APR1400 reaktorokban.
A szerződés aláírása Dél-Korea első külföldi atomerőmű-építési projektje lesz 2009 óta, amikor a KHNP négy APR1400 reaktort épített az Egyesült Arab Emírségekben, Barakahban.
Csehországban hat kereskedelmi reaktor működik: négy orosz VVER-440-es Dukovanyban, két nagyobb VVER-1000-es Temelínben. Az IAEA szerint ezek az egységek a cseh áramtermelés mintegy 36,7%-át adják.
Az USA-nak „minél előbb” új reaktort kell építenie – mondta a DOE jelöltje a szenátusi bizottság előtt
Az USA-nak minél előbb új atomerőművet kell építenie, és elő kell mozdítania a fejlett reaktorok fejlesztését, engedélyezését és telepítését – hangzott el a szenátusi energiaügyi bizottság előtt.
Ted Garrish, aki a DOE nukleáris energiaügyi helyettes államtitkári posztjára jelöltként jelent meg, elmondta: az országnak új reaktort kell telepítenie, legyen az nagy, kis moduláris vagy mikroreaktor.
Az USA-ban jelenleg nincs épülő kereskedelmi atomerőmű, az utolsó kettő, a Vogtle-3 és Vogtle-4 2023-ban, illetve 2024-ben indult el Georgiában.
„A nukleáris energia kivételes lehetőség a növekvő villamosenergia-igény megbízható, megfizethető és biztonságos kielégítésére” – mondta Garrish, aki tapasztalt atomenergetikai vezető. Szerinte az USA-nak nemzetbiztonsági okokból is fejlesztenie kell a hazai urándúsító ipart.
Vizsgálni kell a nemzetközi piacot és a kormányközi megállapodások lehetőségét az amerikai nukleáris fejlesztők és ellátási láncok számára, valamint meg kell oldani a kiégett fűtőelemek elhelyezésének problémáját.
1987-ben a Kongresszus a nevadai Yucca Mountain-t jelölte ki a kiégett fűtőelemek végleges tárolóhelyének, de 2009-ben az Obama-adminisztráció leállította a projektet.
Az USA-ban az 1950-es évek óta mintegy 83 000 tonna radioaktív hulladék, köztük kiégett fűtőelem halmozódott fel, amelyet jelenleg acél- és betonkonténerekben tárolnak az erőművek telephelyein.
Garrish korábban a DOE nemzetközi ügyekért felelős helyettes államtitkára volt (2018–2021), jelenleg az Egyesült Haladó Atomenergia Szövetség igazgatótanácsának elnöke.
Egyéb hírek
Szlovénia közös munkát sürget az USA-val a nukleáris energiában:
Az USA és Horvátország tisztviselői együttműködésről tárgyaltak Közép- és Délkelet-Európa energiaellátásának diverzifikálása érdekében, különös tekintettel a kis moduláris reaktorokra (SMR). Horvátország és Szlovénia közösen tulajdonolja a szlovéniai Krško atomerőművet, amely egyetlen 696 MW-os nyomottvizes reaktorával Horvátország áramfogyasztásának 16%-át, Szlovéniáénak 20%-át adja. Szlovénia fontolgatja egy második blokk építését, de tavaly elhalasztotta az erről szóló népszavazást.Malawi engedélyezi a Kayelekera uránbánya újraindítását:
A Malawi Atomenergia Hatóság kiadta a sugárbiztonsági engedélyt a Lotus (Africa) Limited számára, így újraindulhat a Kayelekera uránbánya, amely több mint egy évtizede, 2014 óta állt a zuhanó uránárak és biztonsági problémák miatt. A bánya 85%-át az ausztrál Lotus Resources helyi leányvállalata birtokolja. A Lotus szerint a bánya újraindítása teljesen finanszírozott, kb. 43 millió dollár (37 millió euró) tőkével.Venezuela és Irán nukleáris együttműködést tervez:
Venezuela és Irán a nukleáris tudomány és technológia terén való együttműködésről tárgyalt. Az iráni állami média szerint Mohammad Eslami, az Iráni Atomenergia Szervezet vezetője és Alberto Quintero, Venezuela tudományos miniszterhelyettese egyetemi és kutatási programok elindításáról egyeztetett. Venezuelában nincs kereskedelmi atomerőmű, de 2010-ben Oroszországgal írt alá megállapodást új atomerőművek lehetőségéről. Iránnak egy működő atomerőműve van Bushehr-1-nél, egy másik ugyanott épül, mindkettőt Oroszország szállította. -
 @ 57d1a264:69f1fee1
2025-05-06 06:00:25
@ 57d1a264:69f1fee1
2025-05-06 06:00:25Album art didn’t always exist. In the early 1900s, recorded music was still a novelty, overshadowed by sales of sheet music. Early vinyl records were vastly different from what we think of today: discs were sold individually and could only hold up to four minutes of music per side. Sometimes, only one side of the record was used. One of the most popular records of 1910, for example, was “Come, Josephine, in My Flying Machine”: it clocked in at two minutes and 39 seconds.
The invention of album art can get lost in the story of technological mastery. But among all the factors that contributed to the rise of recorded music, it stands as one of the few that was wholly driven by creators themselves. Album art — first as marketing material, then as pure creative expression — turned an audio-only medium into a multi-sensory experience.
This is the story of the people who made music visible.
originally posted at https://stacker.news/items/972642
-
 @ 5df413d4:2add4f5b
2025-05-04 01:13:31
@ 5df413d4:2add4f5b
2025-05-04 01:13:31Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 02: Jerusalem Old City
The bus slowly lurches up the winding and steep embankment. We can finally start to see the craggy tops of buildings peaking out over the ridge in the foreground distance. We have almost reached it. Jerusalem, the City on the Hill.
https://i.nostr.build/e2LpUKEgGBwfveGi.jpg
Our Israeli tour guide speaks over the mic to draw our attention to the valley below us instead - “This is the the Valley of Gehenna, the Valley of the Moloch,” he says. “In ancient times, the pagans who worshiped Moloch used this place for child sacrifice by fire. Now, imagine yourself, an early Hebrew, sitting atop the hill, looking down in horror. This is the literal Valley of The Shadow of Death, the origin of the Abrahamic concept of Hell.” Strong open - this is going to be fun.
https://i.nostr.build/5F29eBKZYs4bEMHk.jpg
Inside the Old City, our guide - a chubby, cherub-faced intelligence type on some sort of punishment duty, deputized to babysit foreigners specifically because he reads as so dopey and disarming - points out various Judeo-Christian sites on a map, his tone subtly suggesting which places are most suggested, or perhaps, permitted…
https://i.nostr.build/J44fhGWc9AZ5qpK4.jpg
https://i.nostr.build/3c0jh09nx6d5cEdt.jpg
Walking, we reach Judaism’s Kotel, the West Wall - massive, grand, and ancient, whispering of the Eternal. Amongst the worshipers, we touch the warm, dry limestone and, if we like, place written prayers into the wall's smaller cracks. A solemn and yearning ghost fills the place - but whose it is, I'm not sure.  https://i.nostr.build/AjDwA0rFiFPlrw1o.jpg
Just above the Kotel, Islam’s Dome of the Rock can be seen, its golden cap blazing in the sun. I ask our guide about visiting the dome. He cuts a heavy eyeroll in my direction - it seems I’ve outed myself as my group’s “that guy.” His face says more than words ever could, “Oy vey, there’s one in every group…”
“Why would anyone want to go there? It is a bit intense, no?” Still, I press. “Well, it is only open to tourists on Tuesday and Thursdays…” It is Tuesday. “And even then, visiting only opens from 11:30…” It is 11:20. As it becomes clear to him that I don't intend to drop this...“Fine!” he relents, with a dramatic flaring of the hands and an uniquely Israeli sigh, “Go there if you must. But remember, the bus leaves at 1PM. Good luck...” Great! Totally not ominous at all.
https://i.nostr.build/6aBhT61C28QO9J69.jpg
The checkpoint for the sole non-Muslim entrance leading up to the Dome is administered by several gorgeous and statuesque, assault rifle clad, Ethiop-Israeli female soldiers. In this period of relative peace and calm, they feel lax enough to make a coy but salacious game of their “screening” the men in line. As I observe, it seems none doth protest...
https://i.nostr.build/jm8F3pUp9EXqPRkN.jpg
Past the gun-totting Sirens, a long wooden rampart leads up to the Temple Mount, The Mount of the House of the Holy, al-Ḥaram al-Sharīf, The Noble Sanctuary, The Furthest Mosque, the site of the Dome of the Rock and the al-Masjid al-Asqa.
https://i.nostr.build/DoS0KIkrVN0yiVJ0.jpg
On the Mount, the Dome dominates all views. To those interested in pure expressions of beauty, the Dome is, undeniably, a thing of absolute glory. I pace the grounds, snapping what pictures I can. I pause to breathe and to let the electric energy of the setting wash over me.
https://i.nostr.build/0BQYLwpU291q2fBt.jpg
https://i.nostr.build/yCxfB1V8eAcfob93.jpg
It’s 12:15 now, I decide to head back. Now, here is what they don’t tell you. The non-Muslin entrance from the West Wall side is a one-way deal. Leaving the Dome plaza dumps you out into the back alley bazaar of Old City’s Muslim district. And so it is. I am lost.
https://i.nostr.build/XnQ5eZgjeS1UTEBt.jpg
https://i.nostr.build/EFGD5vgmFx5YYuH4.jpg
I run through the Muslim quarter, blindly turning down alleyways that seem to be taking me in the general direction of where I need to be - glimpses afforded by the city’s uneven elevation and cracks in ancient stone walls guiding my way.
https://i.nostr.build/mWIEAXlJfdqt3nuh.jpg
In a final act of desperation and likely a significant breach of Israeli security protocol, I scale a low wall and flop down back on the side of things where I'm “supposed” to be. But either no one sees me or no one cares. Good luck, indeed.
I make it back to my group - they are not hard to find, a bunch of MBAs in “business casual” travel attire and a tour guide wearing a loudly colored hat and jacket - with just enough time to still visit the Church of the Holy Sepulcher.
https://i.nostr.build/3nFvsXdhd0LQaZd7.jpg
https://i.nostr.build/sKnwqC0HoaZ8winW.jpg
Inside, a chaotic and dizzying array of chapels, grand domed ceilings, and Christian relics - most notably the Stone of Anointing, commemorating where Christ’s body was prepared for burial and Tomb of Christ, where Christ is said to have laid for 3 days before Resurrection.
https://i.nostr.build/Lb4CTj1dOY1pwoN6.jpg
https://i.nostr.build/LaZkYmUaY8JBRvwn.jpg
In less than an hour, one can traverse from the literal Hell, to King David’s Wall, The Tomb of Christ, and the site of Muhammad’s Ascension. The question that stays with me - What is it about this place that has caused so many to turn their heads to the heavens and cry out for God? Does he hear? And if he answers, do we listen?
https://i.nostr.build/elvlrd7rDcEaHJxT.jpg
Jerusalem, The Old City, circa 2014. Israel.
There are secrets to be found. Go there.
Bitcoin #Jerusalem #Israel #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Plebchain #Coffeechain #Bookstr #NostrArt #Writing #Writestr #Createstr
-
 @ b6dcdddf:dfee5ee7
2025-05-06 15:58:23
@ b6dcdddf:dfee5ee7
2025-05-06 15:58:23You can now fund projects on Geyser using Credit Cards, Apple Pay, Bank Transfers, and more.
The best part: 🧾 You pay in fiat and ⚡️ the creator receives Bitcoin.
You heard it right! Let's dive in 👇
First, how does it work? For contributors, it's easy! Once the project creator has verified their identity, anyone can contribute with fiat methods. Simply go through the usual contribution flow and select 'Pay with Fiat'. The first contribution is KYC-free.
Why does this matter? 1. Many Bitcoiners don't want to spend their Bitcoin: 👉 Number go up (NgU) 👉 Capital gains taxes With fiat contributions, there's no more excuse to contribute towards Bitcoin builders and creators! 2. Non-bitcoin holders want to support projects too. If someone loves your mission but only has a debit card, they used to be stuck. Now? They can back your Bitcoin project with familiar fiat tools. Now, they can do it all through Geyser!
So, why swap fiat into Bitcoin? Because Bitcoin is borderless. Fiat payouts are limited to certain countries, banks, and red tape. By auto-swapping fiat to Bitcoin, we ensure: 🌍 Instant payouts to creators all around the world ⚡️ No delays or restrictions 💥 Every contribution is also a silent Bitcoin buy
How to enable Fiat contributions If you’re a creator, it’s easy: - Go to your Dashboard → Wallet - Click “Enable Fiat Contributions” - Complete a quick ID verification (required by our payment provider) ✅ That’s it — your project is now open to global fiat supporters.
Supporting Bitcoin adoption At Geyser, our mission is to empower Bitcoin creators and builders. Adding fiat options amplifies our mission. It brings more people into the ecosystem while staying true to what we believe: ⚒️ Build on Bitcoin 🌱 Fund impactful initiatives 🌎 Enable global participation
**Support projects with fiat now! ** We've compiled a list of projects that currently have fiat contributions enabled. If you've been on the fence to support them because you didn't want to spend your Bitcoin, now's the time to do your first contribution!
Education - Citadel Dispatch: https://geyser.fund/project/citadel - @FREEMadeiraOrg: https://geyser.fund/project/freemadeira - @MyfirstBitcoin_: https://geyser.fund/project/miprimerbitcoin
Circular Economies - @BitcoinEkasi: https://geyser.fund/project/bitcoinekasi - Madagascar Bitcoin: https://geyser.fund/project/madagasbit - @BitcoinChatt : https://geyser.fund/project/bitcoinchatt - Uganda Gayaza BTC Market: https://geyser.fund/project/gayazabtcmarket
Activism - Education Bitcoin Channel: https://geyser.fund/project/streamingsats
Sports - The Sats Fighter Journey: https://geyser.fund/project/thesatsfighterjourney
Culture - Bitcoin Tarot Cards: https://geyser.fund/project/bitcointarotcard
originally posted at https://stacker.news/items/973003
-
 @ 57d1a264:69f1fee1
2025-05-06 05:49:01
@ 57d1a264:69f1fee1
2025-05-06 05:49:01I don’t like garlic. It’s not a dislike for the taste in the moment, so much as an extreme dislike for the way it stays with you—sometimes for days—after a particularly garlicky meal.
Interestingly enough, both of my brothers love garlic. They roast it by itself and keep it at the ready so they can have a very strong garlic profile in their cooking. When I prepare a dish, I don’t even see garlic on the ingredient list. I’ve cut it out of my life so completely that my brain genuinely skips over it in recipes. While my brothers are looking for ways to sneak garlic into everything they make, I’m subconsciously avoiding it altogether.
A few years back, when I was digging intensely into how design systems mature, I stumbled on the concept of a design system origin story. There are two extreme origin stories and an infinite number of possibilities between. On one hand you have the grassroots system, where individuals working on digital products are simply trying to solve their own daily problems. They’re frustrated with having to go cut and paste elements from past designs or with recreating the same layouts over and over, so they start to work more systematically. On the other hand, you have the top down system, where leadership is directing teams to take a more systematic approach, often forming a small partially dedicated core team to tackle some centralized assets and guidelines for all to follow. The influences in those early days bias a design system in interesting and impactful ways.
We’ve established that there are a few types of bias that are either intentionally or unintentionally embedded into our design systems. Acknowledging this is a great first step. But, what’s the impact of this? Does it matter?
I believe there are a few impacts design system biases, but there’s one that stands out. The bias in your design system makes some individuals feel the system is meant for them and others feel it’s not. This is a problem because, a design system cannot live up to it’s expected value until it is broadly in use. If individuals feel your design system is not for them, the won’t use it. And, as you know, it doesn’t matter how good your design system is if nobody is using it.
originally posted at https://stacker.news/items/972641
-
 @ d61f3bc5:0da6ef4a
2025-05-06 01:37:28
@ d61f3bc5:0da6ef4a
2025-05-06 01:37:28I remember the first gathering of Nostr devs two years ago in Costa Rica. We were all psyched because Nostr appeared to solve the problem of self-sovereign online identity and decentralized publishing. The protocol seemed well-suited for textual content, but it wasn't really designed to handle binary files, like images or video.
The Problem
When I publish a note that contains an image link, the note itself is resilient thanks to Nostr, but if the hosting service disappears or takes my image down, my note will be broken forever. We need a way to publish binary data without relying on a single hosting provider.
We were discussing how there really was no reliable solution to this problem even outside of Nostr. Peer-to-peer attempts like IPFS simply didn't work; they were hopelessly slow and unreliable in practice. Torrents worked for popular files like movies, but couldn't be relied on for general file hosting.
Awesome Blossom
A year later, I attended the Sovereign Engineering demo day in Madeira, organized by Pablo and Gigi. Many projects were presented over a three hour demo session that day, but one really stood out for me.
Introduced by hzrd149 and Stu Bowman, Blossom blew my mind because it showed how we can solve complex problems easily by simply relying on the fact that Nostr exists. Having an open user directory, with the corresponding social graph and web of trust is an incredible building block.
Since we can easily look up any user on Nostr and read their profile metadata, we can just get them to simply tell us where their files are stored. This, combined with hash-based addressing (borrowed from IPFS), is all we need to solve our problem.
How Blossom Works
The Blossom protocol (Blobs Stored Simply on Mediaservers) is formally defined in a series of BUDs (Blossom Upgrade Documents). Yes, Blossom is the most well-branded protocol in the history of protocols. Feel free to refer to the spec for details, but I will provide a high level explanation here.
The main idea behind Blossom can be summarized in three points:
- Users specify which media server(s) they use via their public Blossom settings published on Nostr;
- All files are uniquely addressable via hashes;
- If an app fails to load a file from the original URL, it simply goes to get it from the server(s) specified in the user's Blossom settings.
Just like Nostr itself, the Blossom protocol is dead-simple and it works!
Let's use this image as an example:
 If you look at the URL for this image, you will notice that it looks like this:
If you look at the URL for this image, you will notice that it looks like this:blossom.primal.net/c1aa63f983a44185d039092912bfb7f33adcf63ed3cae371ebe6905da5f688d0.jpgAll Blossom URLs follow this format:
[server]/[file-hash].[extension]The file hash is important because it uniquely identifies the file in question. Apps can use it to verify that the file they received is exactly the file they requested. It also gives us the ability to reliably get the same file from a different server.
Nostr users declare which media server(s) they use by publishing their Blossom settings. If I store my files on Server A, and they get removed, I can simply upload them to Server B, update my public Blossom settings, and all Blossom-capable apps will be able to find them at the new location. All my existing notes will continue to display media content without any issues.
Blossom Mirroring
Let's face it, re-uploading files to another server after they got removed from the original server is not the best user experience. Most people wouldn't have the backups of all the files, and/or the desire to do this work.
This is where Blossom's mirroring feature comes handy. In addition to the primary media server, a Blossom user can set one one or more mirror servers. Under this setup, every time a file is uploaded to the primary server the Nostr app issues a mirror request to the primary server, directing it to copy the file to all the specified mirrors. This way there is always a copy of all content on multiple servers and in case the primary becomes unavailable, Blossom-capable apps will automatically start loading from the mirror.
Mirrors are really easy to setup (you can do it in two clicks in Primal) and this arrangement ensures robust media handling without any central points of failure. Note that you can use professional media hosting services side by side with self-hosted backup servers that anyone can run at home.
Using Blossom Within Primal
Blossom is natively integrated into the entire Primal stack and enabled by default. If you are using Primal 2.2 or later, you don't need to do anything to enable Blossom, all your media uploads are blossoming already.
To enhance user privacy, all Primal apps use the "/media" endpoint per BUD-05, which strips all metadata from uploaded files before they are saved and optionally mirrored to other Blossom servers, per user settings. You can use any Blossom server as your primary media server in Primal, as well as setup any number of mirrors:
 ## Conclusion
## ConclusionFor such a simple protocol, Blossom gives us three major benefits:
- Verifiable authenticity. All Nostr notes are always signed by the note author. With Blossom, the signed note includes a unique hash for each referenced media file, making it impossible to falsify.
- File hosting redundancy. Having multiple live copies of referenced media files (via Blossom mirroring) greatly increases the resiliency of media content published on Nostr.
- Censorship resistance. Blossom enables us to seamlessly switch media hosting providers in case of censorship.
Thanks for reading; and enjoy! 🌸
-
 @ 40bdcc08:ad00fd2c
2025-05-06 14:24:22
@ 40bdcc08:ad00fd2c
2025-05-06 14:24:22Introduction
Bitcoin’s
OP_RETURNopcode, a mechanism for embedding small data in transactions, has ignited a significant debate within the Bitcoin community. Originally designed to support limited metadata while preserving Bitcoin’s role as a peer-to-peer electronic cash system,OP_RETURNis now at the center of proposals that could redefine Bitcoin’s identity. The immutable nature of Bitcoin’s timechain makes it an attractive platform for data storage, creating tension with those who prioritize its monetary function. This discussion, particularly around Bitcoin Core pull request #32406 (GitHub PR #32406), highlights a critical juncture for Bitcoin’s future.What is
OP_RETURN?Introduced in 2014,
OP_RETURNallows users to attach up to 80 bytes of data to a Bitcoin transaction. Unlike other transaction outputs,OP_RETURNoutputs are provably unspendable, meaning they don’t burden the Unspent Transaction Output (UTXO) set—a critical database for Bitcoin nodes. This feature was a compromise to provide a standardized, less harmful way to include metadata, addressing earlier practices that embedded data in ways that bloated the UTXO set. The 80-byte limit and restriction to oneOP_RETURNoutput per transaction are part of Bitcoin Core’s standardness rules, which guide transaction relay and mining but are not enforced by the network’s consensus rules (Bitcoin Stack Exchange).Standardness vs. Consensus Rules
Standardness rules are Bitcoin Core’s default policies for relaying and mining transactions. They differ from consensus rules, which define what transactions are valid across the entire network. For
OP_RETURN: - Consensus Rules: AllowOP_RETURNoutputs with data up to the maximum script size (approximately 10,000 bytes) and multiple outputs per transaction (Bitcoin Stack Exchange). - Standardness Rules: LimitOP_RETURNdata to 80 bytes and one output per transaction to discourage excessive data storage and maintain network efficiency.Node operators can adjust these policies using settings like
-datacarrier(enables/disablesOP_RETURNrelay) and-datacarriersize(sets the maximum data size, defaulting to 83 bytes to account for theOP_RETURNopcode and pushdata byte). These settings allow flexibility but reflect Bitcoin Core’s default stance on limiting data usage.The Proposal: Pull Request #32406
Bitcoin Core pull request #32406, proposed by developer instagibbs, seeks to relax these standardness restrictions (GitHub PR #32406). Key changes include: - Removing Default Size Limits: The default
-datacarriersizewould be uncapped, allowing largerOP_RETURNdata without a predefined limit. - Allowing Multiple Outputs: The restriction to oneOP_RETURNoutput per transaction would be lifted, with the total data size across all outputs subject to a configurable limit. - Deprecating Configuration Options: The-datacarrierand-datacarriersizesettings are marked as deprecated, signaling potential removal in future releases, which could limit node operators’ ability to enforce custom restrictions.This proposal does not alter consensus rules, meaning miners and nodes can already accept transactions with larger or multiple
OP_RETURNoutputs. Instead, it changes Bitcoin Core’s default relay policy to align with existing practices, such as miners accepting non-standard transactions via services like Marathon Digital’s Slipstream (CoinDesk).Node Operator Flexibility
Currently, node operators can customize
OP_RETURNhandling: - Default Settings: Relay transactions with oneOP_RETURNoutput up to 80 bytes. - Custom Settings: Operators can disableOP_RETURNrelay (-datacarrier=0) or adjust the size limit (e.g.,-datacarriersize=100). These options remain in #32406 but are deprecated, suggesting that future Bitcoin Core versions might not support such customization, potentially standardizing the uncapped policy.Arguments in Favor of Relaxing Limits
Supporters of pull request #32406 and similar proposals argue that the current restrictions are outdated and ineffective. Their key points include: - Ineffective Limits: Developers bypass the 80-byte limit using methods like Inscriptions, which store data in other transaction parts, often at higher cost and inefficiency (BitcoinDev Mailing List). Relaxing
OP_RETURNcould channel data into a more efficient format. - Preventing UTXO Bloat: By encouragingOP_RETURNuse, which doesn’t affect the UTXO set, the proposal could reduce reliance on harmful alternatives like unspendable Taproot outputs used by projects like Citrea’s Clementine bridge. - Supporting Innovation: Projects like Citrea require more data (e.g., 144 bytes) for security proofs, and relaxed limits could enable new Layer 2 solutions (CryptoSlate). - Code Simplification: Developers like Peter Todd argue that these limits complicate Bitcoin Core’s codebase unnecessarily (CoinGeek). - Aligning with Practice: Miners already process non-standard transactions, and uncapping defaults could improve fee estimation and reduce reliance on out-of-band services, as noted by ismaelsadeeq in the pull request discussion.In the GitHub discussion, developers like Sjors and TheCharlatan expressed support (Concept ACK), citing these efficiency and innovation benefits.
Arguments Against Relaxing Limits
Opponents, including prominent developers and community members, raise significant concerns about the implications of these changes: - Deviation from Bitcoin’s Purpose: Critics like Luke Dashjr, who called the proposal “utter insanity,” argue that Bitcoin’s base layer should prioritize peer-to-peer cash, not data storage (CoinDesk). Jason Hughes warned it could turn Bitcoin into a “worthless altcoin” (BeInCrypto). - Blockchain Bloat: Additional data increases the storage and processing burden on full nodes, potentially making node operation cost-prohibitive and threatening decentralization (CryptoSlate). - Network Congestion: Unrestricted data could lead to “spam” transactions, raising fees and hindering Bitcoin’s use for financial transactions. - Risk of Illicit Content: The timechain’s immutability means data, including potentially illegal or objectionable content, is permanently stored on every node. The 80-byte limit acts as a practical barrier, and relaxing it could exacerbate this issue. - Preserving Consensus: Developers like John Carvalho view the limits as a hard-won community agreement, not to be changed lightly.
In the pull request discussion, nsvrn and moth-oss expressed concerns about spam and centralization, advocating for gradual changes. Concept NACKs from developers like wizkid057 and Luke Dashjr reflect strong opposition.
Community Feedback
The GitHub discussion for pull request #32406 shows a divided community: - Support (Concept ACK): Sjors, polespinasa, ismaelsadeeq, miketwenty1, TheCharlatan, Psifour. - Opposition (Concept NACK): wizkid057, BitcoinMechanic, Retropex, nsvrn, moth-oss, Luke Dashjr. - Other: Peter Todd provided a stale ACK, indicating partial or outdated support.
Additional discussions on the BitcoinDev mailing list and related pull requests (e.g., #32359 by Peter Todd) highlight similar arguments, with #32359 proposing a more aggressive removal of all
OP_RETURNlimits and configuration options (GitHub PR #32359).| Feedback Type | Developers | Key Points | |---------------|------------|------------| | Concept ACK | Sjors, ismaelsadeeq, others | Improves efficiency, supports innovation, aligns with mining practices. | | Concept NACK | Luke Dashjr, wizkid057, others | Risks bloat, spam, centralization, and deviation from Bitcoin’s purpose. | | Stale ACK | Peter Todd | Acknowledges proposal but with reservations or outdated support. |
Workarounds and Their Implications
The existence of workarounds, such as Inscriptions, which exploit SegWit discounts to embed data, is a key argument for relaxing
OP_RETURNlimits. These methods are costlier and less efficient, often costing more thanOP_RETURNfor data under 143 bytes (BitcoinDev Mailing List). Supporters argue that formalizing largerOP_RETURNdata could streamline these use cases. Critics, however, see workarounds as a reason to strengthen, not weaken, restrictions, emphasizing the need to address underlying incentives rather than accommodating bypasses.Ecosystem Pressures
External factors influence the debate: - Miners: Services like Marathon Digital’s Slipstream process non-standard transactions for a fee, showing that market incentives already bypass standardness rules. - Layer 2 Projects: Citrea’s Clementine bridge, requiring more data for security proofs, exemplifies the demand for relaxed limits to support innovative applications. - Community Dynamics: The debate echoes past controversies, like the Ordinals debate, where data storage via inscriptions raised similar concerns about Bitcoin’s purpose (CoinDesk).
Bitcoin’s Identity at Stake
The
OP_RETURNdebate is not merely technical but philosophical, questioning whether Bitcoin should remain a focused monetary system or evolve into a broader data platform. Supporters see relaxed limits as a pragmatic step toward efficiency and innovation, while opponents view them as a risk to Bitcoin’s decentralization, accessibility, and core mission. The community’s decision will have lasting implications, affecting node operators, miners, developers, and users.Conclusion
As Bitcoin navigates this crossroads, the community must balance the potential benefits of relaxed
OP_RETURNlimits—such as improved efficiency and support for new applications—against the risks of blockchain bloat, network congestion, and deviation from its monetary roots. The ongoing discussion, accessible via pull request #32406 on GitHub (GitHub PR #32406). Readers are encouraged to explore the debate and contribute to ensuring that any changes align with Bitcoin’s long-term goals as a decentralized, secure, and reliable system. -
 @ 57d1a264:69f1fee1
2025-05-05 05:26:34
@ 57d1a264:69f1fee1
2025-05-05 05:26:34The European Accessibility Act is coming, now is a great time for accessibility trainings!. In my Accessibility for Designer workshop, you will learn how to design accessible mockups that prevent issues in visual design, interactions, navigation, and content. You will be able to spot problems early, fix them in your designs, and communicate accessibility clearly with your team. This is a practical workshop with hands-on exercises, not just theory. You’ll actively apply accessibility principles to real design scenarios and mockups. And will get access to my accessibility resources: checklists, annotation kits and more.
When? 4 sessions of 2 hours + Q and As, on: - Mon, June 16, - Tue, June 17, Mon, - June 23 and Tue, - June 24. 9:30 – 12:00 PM PT or 18:30 – 21:00 CET
Register with 15% discount ($255) https://ti.to/smashingmagazine/online-workshops-2022/with/87vynaoqc0/discount/welcometomyworkshop
originally posted at https://stacker.news/items/971772
-
 @ 8f69ac99:4f92f5fd
2025-05-06 14:21:13
@ 8f69ac99:4f92f5fd
2025-05-06 14:21:13A concepção popular de "anarquia" evoca frequentemente caos, colapso e violência. Mas e se anarquia significasse outra coisa? E se representasse um mundo onde as pessoas cooperam e se coordenam sem autoridades impostas? E se implicasse liberdade, ordem voluntária e resiliência—sem coerção?
Bitcoin é um dos raros exemplos funcionais de princípios anarquistas em acção. Não tem CEO, nem Estado, nem planeador central—e, no entanto, o sistema funciona. Faz cumprir regras. Propõe um novo modelo de governação e oferece uma exploração concreta do anarcocapitalismo.
Para o compreendermos, temos de mudar de perspectiva. Bitcoin não é apenas software ou um instrumento de investimento—é um sistema vivo: uma ordem espontânea.
Ordem Espontânea, Teoria dos Jogos e o Papel dos Incentivos Económicos
Na política e economia contemporâneas, presume-se geralmente que a ordem tem de vir de cima. Governos, corporações e burocracias são vistos como essenciais para organizar a sociedade em grande escala.
Mas esta crença nem sempre se verifica.
Os mercados surgem espontaneamente da troca. A linguagem evolui sem supervisão central. Projectos de código aberto prosperam graças a contribuições voluntárias. Nenhum destes sistemas precisa de um rei—e, no entanto, têm estrutura e funcionam.
Bitcoin insere-se nesta tradição de ordens emergentes. Não é ditado por uma entidade única, mas é governado através de código, consenso dos utilizadores e incentivos económicos que recompensam a cooperação e penalizam a desonestidade.
Código Como Constituição
Bitcoin funciona com base num conjunto de regras de software transparentes e verificáveis. Estas regras determinam quem pode adicionar blocos, com que frequência, o que constitui uma transacção válida e como são criadas novas moedas.
Estas regras não são impostas por exércitos nem pela polícia. São mantidas por uma rede descentralizada de milhares de nós, cada um a correr voluntariamente software que valida o cumprimento das regras. Se alguém tentar quebrá-las, o resto da rede simplesmente rejeita a sua versão.
Isto não é governo por maioria—é aceitação baseada em regras.
Cada operador de nó escolhe qual versão do software quer executar. Se uma alteração proposta não tiver consenso suficiente, não se propaga. Foi assim que as "guerras do tamanho do bloco" foram resolvidas—não por votação, mas através de sinalização do que os utilizadores estavam dispostos a aceitar.
Este modelo de governação ascendente é voluntário, sem permissões, e extraordinariamente resiliente. Representa um novo paradigma de sistemas autorregulados.
Mineiros, Incentivos e a Segurança Baseada na Teoria dos Jogos
Bitcoin assegura a sua rede utilizando a Teoria de Jogos. Os mineiros que seguem o protocolo são recompensados financeiramente. Quem tenta enganar—como reescrever blocos ou gastar duas vezes—sofre perdas financeiras e desperdiça recursos.
Agir honestamente é mais lucrativo.
A genialidade de Bitcoin está em alinhar incentivos egoístas com o bem comum. Elimina a necessidade de confiar em administradores ou esperar benevolência. Em vez disso, torna a fraude economicamente irracional.
Isto substitui o modelo tradicional de "confiar nos líderes" por um mais robusto: construir sistemas onde o mau comportamento é desencorajado por design.
Isto é segurança anarquista—não a ausência de regras, mas a ausência de governantes.
Associação Voluntária e Confiança Construída em Consenso
Qualquer pessoa pode usar Bitcoin. Não há controlo de identidade, nem licenças, nem processo de aprovação. Basta descarregar o software e começar a transaccionar.
Ainda assim, Bitcoin não é um caos desorganizado. Os utilizadores seguem regras rigorosas do protocolo. Porquê? Porque é o consenso que dá valor às "moedas". Sem ele, a rede fragmenta-se e falha.
É aqui que Bitcoin desafia as ideias convencionais sobre anarquia. Mostra que sistemas voluntários podem gerar estabilidade—não porque as pessoas são altruístas, mas porque os incentivos bem desenhados tornam a cooperação a escolha racional.
Bitcoin é sem confiança (trustless), mas promove confiança.
Uma Prova de Conceito Viva
Muitos acreditam que, sem controlo central, a sociedade entraria em colapso. Bitcoin prova que isso não é necessariamente verdade.
É uma rede monetária global, sem permissões, capaz de fazer cumprir direitos de propriedade, coordenar recursos e resistir à censura—sem uma autoridade central. Baseia-se apenas em regras, incentivos e participação voluntária.
Bitcoin não é um sistema perfeito. É um projecto dinâmico, em constante evolução. Mas isso faz parte do que o torna tão relevante: é real, está a funcionar e continua a melhorar.
Conclusão
A anarquia não tem de significar caos. Pode significar cooperação sem coerção. Bitcoin prova isso.
Procuramos, desesperados, por alternativas às instituições falhadas, inchadas e corruptas. Bitcoin oferece mais do que dinheiro digital. É uma prova viva de que podemos construir sociedades descentralizadas, eficientes e justas.
E isso, por si só, já é revolucionário.
Photo by Floris Van Cauwelaert on Unsplash
-
 @ 90c656ff:9383fd4e
2025-05-06 14:10:48
@ 90c656ff:9383fd4e
2025-05-06 14:10:48Bitcoin has been gaining increasing acceptance as a means of payment, evolving from being just a digital investment asset to becoming a viable alternative to traditional currencies. Today, many companies around the world already accept Bitcoin, providing consumers with greater financial freedom and reducing reliance on traditional banking intermediaries.
- Global companies that accept Bitcoin
Over the years, several well-known companies have begun accepting Bitcoin, recognizing its benefits such as security, transparency, and low transaction fees. Among the most prominent are:
01 - Microsoft: The tech giant allows users to add funds to their Microsoft accounts using Bitcoin. This enables the purchase of digital content such as games, apps, and software available in the Microsoft Store. 02 - Overstock: One of the largest online retailers that accepts Bitcoin for the purchase of furniture, electronics, and home goods. Overstock was an early adopter, signaling a strong commitment to financial innovation. 03 - AT&T: The U.S. telecommunications company was the first in its industry to accept Bitcoin payments, giving customers the option to pay their bills with cryptocurrency through BitPay. 04 - Twitch: While Twitch does not natively support Bitcoin donations or payments, many streamers use third-party services like NOWPayments, Streamlabs (with Coinbase integration), or Plisio to accept crypto tips and donations. This opens a path for Bitcoin support through external platforms, especially within the content creator community. 05 - Namecheap: A leading domain registrar and web hosting provider that accepts Bitcoin for domain registration and hosting services, showcasing Bitcoin’s usefulness in the digital economy.
- Small businesses and local commerce
Beyond large corporations, a growing number of small businesses and local merchants are embracing Bitcoin, particularly in cities that are becoming hubs for digital innovation.
01 - Restaurants and cafés: In cities like Lisbon, London, and New York, several cafés and eateries accept Bitcoin as payment, attracting tech-savvy customers. 02 - Hotels and tourism: Certain hotel chains and travel platforms now accept Bitcoin, simplifying bookings and removing the need for currency exchange for international travelers. 03 - Online stores: Many small e-commerce businesses offer Bitcoin as a payment option or even operate exclusively using cryptocurrency, benefiting from borderless, fast transactions.
- Advantages for businesses and consumers
The growing acceptance of Bitcoin is largely driven by its advantages:
01 - Lower transaction fees: Businesses can reduce costs associated with credit card fees and payment processors. 02 - No intermediaries: Direct peer-to-peer payments cut down on bureaucracy and reduce fraud risks. 03 - Global access: Bitcoin allows for cross-border payments without the need for currency exchange, ideal for international transactions.
In summary, the adoption of Bitcoin as a means of payment continues to expand, with companies of all sizes recognizing its strategic value. From large enterprises to independent creators and local shops, Bitcoin is gradually becoming a more practical and accepted financial tool. While challenges such as volatility and regulatory uncertainty remain, the broader trend points toward a future where paying with Bitcoin could be a common part of everyday life.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 57d1a264:69f1fee1
2025-05-05 05:15:02
@ 57d1a264:69f1fee1
2025-05-05 05:15:02Crabtree's Framework for Evaluating Human-Centered Research
Picture this: You've spent three weeks conducting qualitative research for a finance app redesign. You carefully recruited 12 participants, conducted in-depth interviews, and identified patterns around financial anxiety and decision paralysis. You're excited to present your findings when the inevitable happens:
"But are these results statistically significant?"
"Just 12 people? How can we make decisions that affect thousands of users based on conversations with just 12 people?"
As UX professionals, we regularly face stakeholders who evaluate our qualitative research using criteria designed for quantitative methods... This misalignment undermines the unique value qualitative research brings to product development.
Continue reading https://uxpsychology.substack.com/p/beyond-numbers-how-to-properly-evaluate
originally posted at https://stacker.news/items/971767
-
 @ c1e9ab3a:9cb56b43
2025-05-06 14:05:40
@ c1e9ab3a:9cb56b43
2025-05-06 14:05:40If you're an engineer stepping into the Bitcoin space from the broader crypto ecosystem, you're probably carrying a mental model shaped by speed, flexibility, and rapid innovation. That makes sense—most blockchain platforms pride themselves on throughput, programmability, and dev agility.
But Bitcoin operates from a different set of first principles. It’s not competing to be the fastest network or the most expressive smart contract platform. It’s aiming to be the most credible, neutral, and globally accessible value layer in human history.
Here’s why that matters—and why Bitcoin is not just an alternative crypto asset, but a structural necessity in the global financial system.
1. Bitcoin Fixes the Triffin Dilemma—Not With Policy, But Protocol
The Triffin Dilemma shows us that any country issuing the global reserve currency must run persistent deficits to supply that currency to the world. That’s not a flaw of bad leadership—it’s an inherent contradiction. The U.S. must debase its own monetary integrity to meet global dollar demand. That’s a self-terminating system.
Bitcoin sidesteps this entirely by being:
- Non-sovereign – no single nation owns it
- Hard-capped – no central authority can inflate it
- Verifiable and neutral – anyone with a full node can enforce the rules
In other words, Bitcoin turns global liquidity into an engineering problem, not a political one. No other system, fiat or crypto, has achieved that.
2. Bitcoin’s “Ossification” Is Intentional—and It's a Feature
From the outside, Bitcoin development may look sluggish. Features are slow to roll out. Code changes are conservative. Consensus rules are treated as sacred.
That’s the point.
When you’re building the global monetary base layer, stability is not a weakness. It’s a prerequisite. Every other financial instrument, app, or protocol that builds on Bitcoin depends on one thing: assurance that the base layer won’t change underneath them without extreme scrutiny.
So-called “ossification” is just another term for predictability and integrity. And when the market does demand change (SegWit, Taproot), Bitcoin’s soft-fork governance process has proven capable of deploying it safely—without coercive central control.
3. Layered Architecture: Throughput Is Not a Base Layer Concern
You don’t scale settlement at the base layer. You build layered systems. Just as TCP/IP doesn't need to carry YouTube traffic directly, Bitcoin doesn’t need to process every microtransaction.
Instead, it anchors:
- Lightning (fast payments)
- Fedimint (community custody)
- Ark (privacy + UTXO compression)
- Statechains, sidechains, and covenants (coming evolution)
All of these inherit Bitcoin’s security and scarcity, while handling volume off-chain, in ways that maintain auditability and self-custody.
4. Universal Assayability Requires Minimalism at the Base Layer
A core design constraint of Bitcoin is that any participant, anywhere in the world, must be able to independently verify the validity of every transaction and block—past and present—without needing permission or relying on third parties.
This property is called assayability—the ability to “test” or verify the authenticity and integrity of received bitcoin, much like verifying the weight and purity of a gold coin.
To preserve this:
- The base layer must remain resource-light, so running a full node stays accessible on commodity hardware.
- Block sizes must remain small enough to prevent centralization of verification.
- Historical data must remain consistent and tamper-evident, enabling proof chains across time and jurisdiction.
Any base layer that scales by increasing throughput or complexity undermines this fundamental guarantee, making the network more dependent on trust and surveillance infrastructure.
Bitcoin prioritizes global verifiability over throughput—because trustless money requires that every user can check the money they receive.
5. Governance: Not Captured, Just Resistant to Coercion
The current controversy around
OP_RETURNand proposals to limit inscriptions is instructive. Some prominent devs have advocated for changes to block content filtering. Others see it as overreach.Here's what matters:
- No single dev, or team, can force changes into the network. Period.
- Bitcoin Core is not “the source of truth.” It’s one implementation. If it deviates from market consensus, it gets forked, sidelined, or replaced.
- The economic majority—miners, users, businesses—enforce Bitcoin’s rules, not GitHub maintainers.
In fact, recent community resistance to perceived Core overreach only reinforces Bitcoin’s resilience. Engineers who posture with narcissistic certainty, dismiss dissent, or attempt to capture influence are routinely neutralized by the market’s refusal to upgrade or adopt forks that undermine neutrality or openness.
This is governance via credible neutrality and negative feedback loops. Power doesn’t accumulate in one place. It’s constantly checked by the network’s distributed incentives.
6. Bitcoin Is Still in Its Infancy—And That’s a Good Thing
You’re not too late. The ecosystem around Bitcoin—especially L2 protocols, privacy tools, custody innovation, and zero-knowledge integrations—is just beginning.
If you're an engineer looking for:
- Systems with global scale constraints
- Architectures that optimize for integrity, not speed
- Consensus mechanisms that resist coercion
- A base layer with predictable monetary policy
Then Bitcoin is where serious systems engineers go when they’ve outgrown crypto theater.
Take-away
Under realistic, market-aware assumptions—where:
- Bitcoin’s ossification is seen as a stability feature, not inertia,
- Market forces can and do demand and implement change via tested, non-coercive mechanisms,
- Proof-of-work is recognized as the only consensus mechanism resistant to fiat capture,
- Wealth concentration is understood as a temporary distribution effect during early monetization,
- Low base layer throughput is a deliberate design constraint to preserve verifiability and neutrality,
- And innovation is layered by design, with the base chain providing integrity, not complexity...
Then Bitcoin is not a fragile or inflexible system—it is a deliberately minimal, modular, and resilient protocol.
Its governance is not leaderless chaos; it's a negative-feedback structure that minimizes the power of individuals or institutions to coerce change. The very fact that proposals—like controversial OP_RETURN restrictions—can be resisted, forked around, or ignored by the market without breaking the system is proof of decentralized control, not dysfunction.
Bitcoin is an adversarially robust monetary foundation. Its value lies not in how fast it changes, but in how reliably it doesn't—unless change is forced by real, bottom-up demand and implemented through consensus-tested soft forks.
In this framing, Bitcoin isn't a slower crypto. It's the engineering benchmark for systems that must endure, not entertain.
Final Word
Bitcoin isn’t moving slowly because it’s dying. It’s moving carefully because it’s winning. It’s not an app platform or a sandbox. It’s a protocol layer for the future of money.
If you're here because you want to help build that future, you’re in the right place.
nostr:nevent1qqswr7sla434duatjp4m89grvs3zanxug05pzj04asxmv4rngvyv04sppemhxue69uhkummn9ekx7mp0qgs9tc6ruevfqu7nzt72kvq8te95dqfkndj5t8hlx6n79lj03q9v6xcrqsqqqqqp0n8wc2
nostr:nevent1qqsd5hfkqgskpjjq5zlfyyv9nmmela5q67tgu9640v7r8t828u73rdqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgsvr6dt8ft292mv5jlt7382vje0mfq2ccc3azrt4p45v5sknj6kkscrqsqqqqqp02vjk5
nostr:nevent1qqstrszamvffh72wr20euhrwa0fhzd3hhpedm30ys4ct8dpelwz3nuqpr4mhxue69uhkymmnw3ezucnfw33k76tww3ux76m09e3k7mf0qgs8a474cw4lqmapcq8hr7res4nknar2ey34fsffk0k42cjsdyn7yqqrqsqqqqqpnn3znl
-
 @ 0d97beae:c5274a14
2025-01-11 16:52:08
@ 0d97beae:c5274a14
2025-01-11 16:52:08This article hopes to complement the article by Lyn Alden on YouTube: https://www.youtube.com/watch?v=jk_HWmmwiAs
The reason why we have broken money
Before the invention of key technologies such as the printing press and electronic communications, even such as those as early as morse code transmitters, gold had won the competition for best medium of money around the world.
In fact, it was not just gold by itself that became money, rulers and world leaders developed coins in order to help the economy grow. Gold nuggets were not as easy to transact with as coins with specific imprints and denominated sizes.
However, these modern technologies created massive efficiencies that allowed us to communicate and perform services more efficiently and much faster, yet the medium of money could not benefit from these advancements. Gold was heavy, slow and expensive to move globally, even though requesting and performing services globally did not have this limitation anymore.
Banks took initiative and created derivatives of gold: paper and electronic money; these new currencies allowed the economy to continue to grow and evolve, but it was not without its dark side. Today, no currency is denominated in gold at all, money is backed by nothing and its inherent value, the paper it is printed on, is worthless too.
Banks and governments eventually transitioned from a money derivative to a system of debt that could be co-opted and controlled for political and personal reasons. Our money today is broken and is the cause of more expensive, poorer quality goods in the economy, a larger and ever growing wealth gap, and many of the follow-on problems that have come with it.
Bitcoin overcomes the "transfer of hard money" problem
Just like gold coins were created by man, Bitcoin too is a technology created by man. Bitcoin, however is a much more profound invention, possibly more of a discovery than an invention in fact. Bitcoin has proven to be unbreakable, incorruptible and has upheld its ability to keep its units scarce, inalienable and counterfeit proof through the nature of its own design.
Since Bitcoin is a digital technology, it can be transferred across international borders almost as quickly as information itself. It therefore severely reduces the need for a derivative to be used to represent money to facilitate digital trade. This means that as the currency we use today continues to fare poorly for many people, bitcoin will continue to stand out as hard money, that just so happens to work as well, functionally, along side it.
Bitcoin will also always be available to anyone who wishes to earn it directly; even China is unable to restrict its citizens from accessing it. The dollar has traditionally become the currency for people who discover that their local currency is unsustainable. Even when the dollar has become illegal to use, it is simply used privately and unofficially. However, because bitcoin does not require you to trade it at a bank in order to use it across borders and across the web, Bitcoin will continue to be a viable escape hatch until we one day hit some critical mass where the world has simply adopted Bitcoin globally and everyone else must adopt it to survive.
Bitcoin has not yet proven that it can support the world at scale. However it can only be tested through real adoption, and just as gold coins were developed to help gold scale, tools will be developed to help overcome problems as they arise; ideally without the need for another derivative, but if necessary, hopefully with one that is more neutral and less corruptible than the derivatives used to represent gold.
Bitcoin blurs the line between commodity and technology
Bitcoin is a technology, it is a tool that requires human involvement to function, however it surprisingly does not allow for any concentration of power. Anyone can help to facilitate Bitcoin's operations, but no one can take control of its behaviour, its reach, or its prioritisation, as it operates autonomously based on a pre-determined, neutral set of rules.
At the same time, its built-in incentive mechanism ensures that people do not have to operate bitcoin out of the good of their heart. Even though the system cannot be co-opted holistically, It will not stop operating while there are people motivated to trade their time and resources to keep it running and earn from others' transaction fees. Although it requires humans to operate it, it remains both neutral and sustainable.
Never before have we developed or discovered a technology that could not be co-opted and used by one person or faction against another. Due to this nature, Bitcoin's units are often described as a commodity; they cannot be usurped or virtually cloned, and they cannot be affected by political biases.
The dangers of derivatives
A derivative is something created, designed or developed to represent another thing in order to solve a particular complication or problem. For example, paper and electronic money was once a derivative of gold.
In the case of Bitcoin, if you cannot link your units of bitcoin to an "address" that you personally hold a cryptographically secure key to, then you very likely have a derivative of bitcoin, not bitcoin itself. If you buy bitcoin on an online exchange and do not withdraw the bitcoin to a wallet that you control, then you legally own an electronic derivative of bitcoin.
Bitcoin is a new technology. It will have a learning curve and it will take time for humanity to learn how to comprehend, authenticate and take control of bitcoin collectively. Having said that, many people all over the world are already using and relying on Bitcoin natively. For many, it will require for people to find the need or a desire for a neutral money like bitcoin, and to have been burned by derivatives of it, before they start to understand the difference between the two. Eventually, it will become an essential part of what we regard as common sense.
Learn for yourself
If you wish to learn more about how to handle bitcoin and avoid derivatives, you can start by searching online for tutorials about "Bitcoin self custody".
There are many options available, some more practical for you, and some more practical for others. Don't spend too much time trying to find the perfect solution; practice and learn. You may make mistakes along the way, so be careful not to experiment with large amounts of your bitcoin as you explore new ideas and technologies along the way. This is similar to learning anything, like riding a bicycle; you are sure to fall a few times, scuff the frame, so don't buy a high performance racing bike while you're still learning to balance.
-
 @ 37fe9853:bcd1b039
2025-01-11 15:04:40
@ 37fe9853:bcd1b039
2025-01-11 15:04:40yoyoaa
-
 @ c631e267:c2b78d3e
2025-05-02 20:05:22
@ c631e267:c2b78d3e
2025-05-02 20:05:22Du bist recht appetitlich oben anzuschauen, \ doch unten hin die Bestie macht mir Grauen. \ Johann Wolfgang von Goethe
Wie wenig bekömmlich sogenannte «Ultra-Processed Foods» wie Fertiggerichte, abgepackte Snacks oder Softdrinks sind, hat kürzlich eine neue Studie untersucht. Derweil kann Fleisch auch wegen des Einsatzes antimikrobieller Mittel in der Massentierhaltung ein Problem darstellen. Internationale Bemühungen, diesen Gebrauch zu reduzieren, um die Antibiotikaresistenz bei Menschen einzudämmen, sind nun möglicherweise gefährdet.
Leider ist Politik oft mindestens genauso unappetitlich und ungesund wie diverse Lebensmittel. Die «Corona-Zeit» und ihre Auswirkungen sind ein beredtes Beispiel. Der Thüringer Landtag diskutiert gerade den Entwurf eines «Coronamaßnahmen-Unrechtsbereinigungsgesetzes» und das kanadische Gesundheitsministerium versucht, tausende Entschädigungsanträge wegen Impfnebenwirkungen mit dem Budget von 75 Millionen Dollar unter einen Hut zu bekommen. In den USA soll die Zulassung von Covid-«Impfstoffen» überdacht werden, während man sich mit China um die Herkunft des Virus streitet.
Wo Corona-Verbrecher von Medien und Justiz gedeckt werden, verfolgt man Aufklärer und Aufdecker mit aller Härte. Der Anwalt und Mitbegründer des Corona-Ausschusses Reiner Fuellmich, der seit Oktober 2023 in Untersuchungshaft sitzt, wurde letzte Woche zu drei Jahren und neun Monaten verurteilt – wegen Veruntreuung. Am Mittwoch teilte der von vielen Impfschadensprozessen bekannte Anwalt Tobias Ulbrich mit, dass er vom Staatsschutz verfolgt wird und sich daher künftig nicht mehr öffentlich äußern werde.
Von der kommenden deutschen Bundesregierung aus Wählerbetrügern, Transatlantikern, Corona-Hardlinern und Russenhassern kann unmöglich eine Verbesserung erwartet werden. Nina Warken beispielsweise, die das Ressort Gesundheit übernehmen soll, diffamierte Maßnahmenkritiker als «Coronaleugner» und forderte eine Impfpflicht, da die wundersamen Injektionen angeblich «nachweislich helfen». Laut dem designierten Außenminister Johann Wadephul wird Russland «für uns immer der Feind» bleiben. Deswegen will er die Ukraine «nicht verlieren lassen» und sieht die Bevölkerung hinter sich, solange nicht deutsche Soldaten dort sterben könnten.
Eine wichtige Personalie ist auch die des künftigen Regierungssprechers. Wenngleich Hebestreit an Arroganz schwer zu überbieten sein wird, dürfte sich die Art der Kommunikation mit Stefan Kornelius in der Sache kaum ändern. Der Politikchef der Süddeutschen Zeitung «prägte den Meinungsjournalismus der SZ» und schrieb «in dieser Rolle auch für die Titel der Tamedia». Allerdings ist, anders als noch vor zehn Jahren, die Einbindung von Journalisten in Thinktanks wie die Deutsche Atlantische Gesellschaft (DAG) ja heute eher eine Empfehlung als ein Problem.
Ungesund ist definitiv auch die totale Digitalisierung, nicht nur im Gesundheitswesen. Lauterbachs Abschiedsgeschenk, die «abgesicherte» elektronische Patientenakte (ePA) ist völlig überraschenderweise direkt nach dem Bundesstart erneut gehackt worden. Norbert Häring kommentiert angesichts der Datenlecks, wer die ePA nicht abwähle, könne seine Gesundheitsdaten ebensogut auf Facebook posten.
Dass die staatlichen Kontrolleure so wenig auf freie Software und dezentrale Lösungen setzen, verdeutlicht die eigentlichen Intentionen hinter der Digitalisierungswut. Um Sicherheit und Souveränität geht es ihnen jedenfalls nicht – sonst gäbe es zum Beispiel mehr Unterstützung für Bitcoin und für Initiativen wie die der Spar-Supermärkte in der Schweiz.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 62033ff8:e4471203
2025-01-11 15:00:24
@ 62033ff8:e4471203
2025-01-11 15:00:24收录的内容中 kind=1的部分,实话说 质量不高。 所以我增加了kind=30023 长文的article,但是更新的太少,多个relays 的服务器也没有多少长文。
所有搜索nostr如果需要产生价值,需要有高质量的文章和新闻。 而且现在有很多机器人的文章充满着浪费空间的作用,其他作用都用不上。
https://www.duozhutuan.com 目前放的是给搜索引擎提供搜索的原材料。没有做UI给人类浏览。所以看上去是粗糙的。 我并没有打算去做一个发microblog的 web客户端,那类的客户端太多了。
我觉得nostr社区需要解决的还是应用。如果仅仅是microblog 感觉有点够呛
幸运的是npub.pro 建站这样的,我觉得有点意思。
yakihonne 智能widget 也有意思
我做的TaskQ5 我自己在用了。分布式的任务系统,也挺好的。
-
 @ 90c656ff:9383fd4e
2025-05-06 13:41:50
@ 90c656ff:9383fd4e
2025-05-06 13:41:50Bitcoin was created to offer a secure and decentralized alternative to traditional money, enabling financial transactions without the need for intermediaries. DeFi, on the other hand, emerged as an expansion of this concept, proposing decentralized financial services such as lending, exchanges, and yield generation. However, despite its promises of innovation, DeFi carries numerous risks, making it a dangerous bet for those who value the security of their Bitcoin.
What is DeFi?
DeFi refers to a set of financial applications that operate without the intermediation of banks or traditional institutions. These platforms use smart contracts to automate transactions, allowing anyone to access financial services without relying on third parties. In theory, DeFi promises greater financial freedom, but in practice it is full of risks, scams, and technical vulnerabilities that can compromise users' funds.
- The risks of DeFi for Bitcoin holders
Bitcoin is the most secure digital currency in the world, protected by a decentralized and censorship-resistant network. Unlike DeFi, which is still in an experimental phase and has already suffered numerous attacks, Bitcoin remains solid and reliable. When someone places Bitcoin in DeFi platforms, they give up the security of direct custody and trust weaker systems.
The main risks include:
01 - Hackers and code flaws: Smart contracts are written by programmers and may contain bugs that allow massive thefts. Over the years, billions of dollars have been lost due to vulnerabilities in DeFi platforms. 02 - Liquidation risks: Many DeFi applications operate on collateralization systems, where users lock Bitcoin to obtain loans. If the market becomes volatile, those Bitcoins can be liquidated at lower-than-expected prices, causing irreversible losses. 03 - Scams and rug pulls: DeFi is full of shady projects where creators vanish with users’ funds. Without regulation and without guarantees, those who deposit Bitcoin in these platforms may never recover their funds.
- Keeping Bitcoin safe is the best choice
Bitcoin was created to be self-custodied, meaning each user should have direct control over their funds without relying on third parties. By sending Bitcoin to DeFi platforms, that security is lost and the asset is exposed to unnecessary risks. The best way to protect Bitcoin is to store it in a secure wallet, preferably offline (cold storage), avoiding any exposure to smart contracts or vulnerable systems.
In summary, DeFi may seem innovative, but the risks far outweigh the potential benefits—especially for those who value Bitcoin's security. Instead of risking losing funds on insecure platforms, the wisest choice is to keep Bitcoin safely stored, ensuring its long-term preservation. While Bitcoin continues to be the best digital store of value in the world, DeFi remains an unstable and dangerous environment where few win and many end up losing.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ b099870e:f3ba8f5d
2025-05-06 13:08:33
@ b099870e:f3ba8f5d
2025-05-06 13:08:33A donkey that is tied to a post by a rope will keep walking around the post is an attempt to free it self,only to become more immobilize and attached to the post.
ikigai
-
 @ c631e267:c2b78d3e
2025-04-25 20:06:24
@ c631e267:c2b78d3e
2025-04-25 20:06:24Die Wahrheit verletzt tiefer als jede Beleidigung. \ Marquis de Sade
Sagen Sie niemals «Terroristin B.», «Schwachkopf H.», «korrupter Drecksack S.» oder «Meinungsfreiheitshasserin F.» und verkneifen Sie sich Memes, denn so etwas könnte Ihnen als Beleidigung oder Verleumdung ausgelegt werden und rechtliche Konsequenzen haben. Auch mit einer Frau M.-A. S.-Z. ist in dieser Beziehung nicht zu spaßen, sie gehört zu den Top-Anzeigenstellern.
«Politikerbeleidigung» als Straftatbestand wurde 2021 im Kampf gegen «Rechtsextremismus und Hasskriminalität» in Deutschland eingeführt, damals noch unter der Regierung Merkel. Im Gesetz nicht festgehalten ist die Unterscheidung zwischen schlechter Hetze und guter Hetze – trotzdem ist das gängige Praxis, wie der Titel fast schon nahelegt.
So dürfen Sie als Politikerin heute den Tesla als «Nazi-Auto» bezeichnen und dies ausdrücklich auf den Firmengründer Elon Musk und dessen «rechtsextreme Positionen» beziehen, welche Sie nicht einmal belegen müssen. [1] Vielleicht ernten Sie Proteste, jedoch vorrangig wegen der «gut bezahlten, unbefristeten Arbeitsplätze» in Brandenburg. Ihren Tweet hat die Berliner Senatorin Cansel Kiziltepe inzwischen offenbar dennoch gelöscht.
Dass es um die Meinungs- und Pressefreiheit in der Bundesrepublik nicht mehr allzu gut bestellt ist, befürchtet man inzwischen auch schon im Ausland. Der Fall des Journalisten David Bendels, der kürzlich wegen eines Faeser-Memes zu sieben Monaten Haft auf Bewährung verurteilt wurde, führte in diversen Medien zu Empörung. Die Welt versteckte ihre Kritik mit dem Titel «Ein Urteil wie aus einer Diktatur» hinter einer Bezahlschranke.
Unschöne, heutzutage vielleicht strafbare Kommentare würden mir auch zu einigen anderen Themen und Akteuren einfallen. Ein Kandidat wäre der deutsche Bundesgesundheitsminister (ja, er ist es tatsächlich immer noch). Während sich in den USA auf dem Gebiet etwas bewegt und zum Beispiel Robert F. Kennedy Jr. will, dass die Gesundheitsbehörde (CDC) keine Covid-Impfungen für Kinder mehr empfiehlt, möchte Karl Lauterbach vor allem das Corona-Lügengebäude vor dem Einsturz bewahren.
«Ich habe nie geglaubt, dass die Impfungen nebenwirkungsfrei sind», sagte Lauterbach jüngst der ZDF-Journalistin Sarah Tacke. Das steht in krassem Widerspruch zu seiner früher verbreiteten Behauptung, die Gen-Injektionen hätten keine Nebenwirkungen. Damit entlarvt er sich selbst als Lügner. Die Bezeichnung ist absolut berechtigt, dieser Mann dürfte keinerlei politische Verantwortung tragen und das Verhalten verlangt nach einer rechtlichen Überprüfung. Leider ist ja die Justiz anderweitig beschäftigt und hat außerdem selbst keine weiße Weste.
Obendrein kämpfte der Herr Minister für eine allgemeine Impfpflicht. Er beschwor dabei das Schließen einer «Impflücke», wie es die Weltgesundheitsorganisation – die «wegen Trump» in finanziellen Schwierigkeiten steckt – bis heute tut. Die WHO lässt aktuell ihre «Europäische Impfwoche» propagieren, bei der interessanterweise von Covid nicht mehr groß die Rede ist.
Einen «Klima-Leugner» würden manche wohl Nir Shaviv nennen, das ist ja nicht strafbar. Der Astrophysiker weist nämlich die Behauptung von einer Klimakrise zurück. Gemäß seiner Forschung ist mindestens die Hälfte der Erderwärmung nicht auf menschliche Emissionen, sondern auf Veränderungen im Sonnenverhalten zurückzuführen.
Das passt vielleicht auch den «Klima-Hysterikern» der britischen Regierung ins Konzept, die gerade Experimente zur Verdunkelung der Sonne angekündigt haben. Produzenten von Kunstfleisch oder Betreiber von Insektenfarmen würden dagegen vermutlich die Geschichte vom fatalen CO2 bevorzugen. Ihnen würde es besser passen, wenn der verantwortungsvolle Erdenbürger sein Verhalten gründlich ändern müsste.
In unserer völlig verkehrten Welt, in der praktisch jede Verlautbarung außerhalb der abgesegneten Narrative potenziell strafbar sein kann, gehört fast schon Mut dazu, Dinge offen anzusprechen. Im «besten Deutschland aller Zeiten» glaubten letztes Jahr nur noch 40 Prozent der Menschen, ihre Meinung frei äußern zu können. Das ist ein Armutszeugnis, und es sieht nicht gerade nach Besserung aus. Umso wichtiger ist es, dagegen anzugehen.
[Titelbild: Pixabay]
--- Quellen: ---
[1] Zur Orientierung wenigstens ein paar Hinweise zur NS-Vergangenheit deutscher Automobilhersteller:
- Volkswagen
- Porsche
- Daimler-Benz
- BMW
- Audi
- Opel
- Heute: «Auto-Werke für die Rüstung? Rheinmetall prüft Übernahmen»
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ f1989a96:bcaaf2c1
2025-05-01 15:50:38
@ f1989a96:bcaaf2c1
2025-05-01 15:50:38Good morning, readers!
This week, we bring pressing news from Belarus, where the regime’s central bank is preparing to launch its central bank digital currency in close collaboration with Russia by the end of 2026. Since rigging the 2020 election, President Alexander Lukashenko has ruled through brute force and used financial repression to crush civil society and political opposition. A Central Bank Digital Currency (CBDC) in the hands of such an authoritarian leader is a recipe for greater control over all aspects of financial activity.
Meanwhile, Russia is planning to further restrict Bitcoin access for ordinary citizens. This time, the Central Bank of Russia and the Ministry of Finance announced joint plans to launch a state-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Access would be limited to those meeting previously defined thresholds of $1.2 million in assets or an annual income above $580,000. This is a blatant attempt by the Kremlin to dampen the accessibility and impact of Bitcoin for those who need it most.
In freedom tech news, we spotlight Samiz. This new tool allows users to create a Bluetooth mesh network over nostr, allowing users' messages and posts to pass through nearby devices on the network even while offline. When a post reaches someone with an Internet connection, it is broadcast across the wider network. While early in development, Mesh networks like Samiz hold the potential to disseminate information posted by activists and human rights defenders even when authoritarian regimes in countries like Pakistan, Venezuela, or Burma try to restrict communications and the Internet.
We end with a reading of our very own Financial Freedom Report #67 on the Bitcoin Audible podcast, where host Guy Swann reads the latest news on plunging currencies, CBDCs, and new Bitcoin freedom tools. We encourage our readers to give it a listen and stay tuned for future readings of HRF’s Financial Freedom Report on Bitcoin Audible. We also include an interview with HRF’s global bitcoin adoption lead, Femi Longe, who shares insights on Bitcoin’s growing role as freedom money for those who need it most.
Now, let’s see what’s in store this week!
SUBSCRIBE HERE
GLOBAL NEWS
Belarus | Launching CBDC in Late 2026
Belarus is preparing to launch its CBDC, the digital ruble, into public circulation by late 2026. Roman Golovchenko, the chairman of the National Bank of the Republic of Belarus (and former prime minister), made the regime’s intent clear: “For the state, it is very important to be able to trace how digital money moves along the entire chain.” He added that Belarus was “closely cooperating with Russia regarding the development of the CBDC.” The level of surveillance and central control that the digital ruble would embed into Belarus’s financial system would pose existential threats to what remains of civil society in the country. Since stealing the 2020 election, Belarusian President Alexander Lukashenko has ruled through sheer force, detaining over 35,000 people, labeling dissidents and journalists as “extremists,” and freezing the bank accounts of those who challenge his authority. In this context, a CBDC would not be a modern financial tool — it would be a means of instant oppression, granting the regime real-time insight into every transaction and the ability to act on it directly.
Russia | Proposes Digital Asset Exchange Exclusively for Wealthy Investors
A month after proposing a framework that would restrict the trading of Bitcoin to only the country’s wealthiest individuals (Russians with over $1.2 million in assets or an annual income above $580,000), Russia’s Ministry of Finance and Central Bank have announced plans to launch a government-regulated cryptocurrency exchange available exclusively to “super-qualified investors.” Under the plan, only citizens meeting the previously stated wealth and income thresholds (which may be subject to change) would be allowed to trade digital assets on the platform. This would further entrench financial privilege for Russian oligarchs while cutting ordinary Russians off from alternative financial tools and the financial freedom they offer. Finance Minister Anton Siluanov claims this will bring digital asset operations “out of the shadows,” but in reality, it suppresses grassroots financial autonomy while exerting state control over who can access freedom money.
Cuba | Ecash Brings Offline Bitcoin Payments to Island Nation in the Dark
As daily blackouts and internet outages continue across Cuba, a new development is helping Cubans achieve financial freedom: Cashu ecash. Cashu is an ecash protocol — a form of digital cash backed by Bitcoin that enables private, everyday payments that can also be done offline — a powerful feature for Cubans experiencing up to 20-hour daily blackouts. However, ecash users must trust mints (servers operated by individuals or groups that issue and redeem ecash tokens) not to disappear with user funds. To leverage this freedom tech to its fullest, the Cuban Bitcoin community launched its own ecash mint, mint.cubabitcoin.org. This minimizes trust requirements for Cubans to transact with ecash and increases its accessibility by running the mint locally. Cuba Bitcoin also released a dedicated ecash resource page, helping expand accessibility to freedom through financial education. For an island nation where the currency has lost more than 90% of its value, citizens remain locked out of their savings, and remittances are often hijacked by the regime, tools like ecash empower Cubans to preserve their financial privacy, exchange value freely, and resist the financial repression that has left so many impoverished.
Zambia | Introduces Cyber Law to Track and Intercept Digital Communications
Zambia’s government passed two new cyber laws granting officials sweeping powers to track and intercept digital communications while increasing surveillance over Zambians' online activity. Officials insist it will help combat cybercrime. Really, it gives the president absolute control over the direction of a new surveillance agency — a powerful tool to crush dissent. This follows earlier plans to restrict the use of foreign currency in the economy to fight inflation, which effectively trapped Zambians in a financial system centered around the volatile “kwacha” currency (which reached a record low earlier this year with inflation above 16%). For activists, journalists, and everyday Zambians, the new laws over online activity threaten the ability to organize and speak freely while potentially hampering access to freedom tech.
India | Central Bank Deputy Governor Praises CBDC Capabilities
At the Bharat Inclusion Summit in Bengaluru, India, the deputy governor of the Reserve Bank of India (RBI), Rabi Sankar, declared, “I have so far not seen any use case that potentially can solve the problem of cross-border money transfer; only CBDC has the ability to solve it.” Yet — seemingly unbeknownst to Sankar, Bitcoin has served as an effective remittance tool for more than a decade at low cost, fast speed, and with no central point of control. Sankar’s remarks follow a growing push to normalize state-controlled, surveillance-based digital money as a natural progression of currency. The RBI’s digital rupee CBDC, currently in pilot phase, is quickly growing into one of the most advanced CBDCs on the planet. It is being embedded into the government’s UPI payment system and offered through existing financial institutions and platforms. Decentralized alternatives like Bitcoin can achieve financial inclusion and payment efficiency too — but without sacrificing privacy, autonomy, or basic rights over to the state.
Tanzania | Opposition Party Excluded From Election Amid Financial Repression
Last week, the Tanzanian regime banned the use of foreign currency in transactions, leaving Tanzanians to rely solely on the rapidly depreciating Tanzanian shilling. Now, Tanzania's ruling party has taken a decisive step to eliminate political opposition ahead of October’s general elections by barring the CHADEMA party from participation under the pretense of treason against their party leader, Tundu Lissu. Law enforcement arrested Lissu at a public rally where he was calling for electoral reforms. This political repression is not happening in isolation. Last year, the Tanzanian regime blocked access to X, detained hundreds of opposition members, and disappeared dissidents. These developments suggest a broader strategy to silence criticism and electoral competition through arrests, censorship, and economic coercion.
BITCOIN AND FREEDOM TECH NEWS
Samiz | Create a Bluetooth Mesh Network with Nostr
Samiz, an app for creating a Bluetooth mesh network over nostr, is officially available for testing. Mesh networks, where interconnected computers relay data to one another, can provide offline access to nostr if enough users participate. For example, when an individual is offline but has Samiz enabled, their device can connect to other nearby devices through Bluetooth, allowing nostr messages to hop locally from phone to phone until reaching someone with internet access, who can then broadcast the message to the wider nostr network. Mesh networks like this hold powerful implications for activists and communities facing censorship, Internet shutdowns, or surveillance. In places with restricted finances and organization, Samiz, while early in development, can potentially offer a way to distribute information through nostr without relying on infrastructure that authoritarian regimes can shut down.
Spark | New Bitcoin Payments Protocol Now Live
Lightspark, a company building on the Bitcoin Lightning Network, officially released Spark, a new payment protocol built on Bitcoin to make transactions faster, cheaper, and more privacy-protecting. Spark leverages a technology called statechains to enable self-custodial and off-chain Bitcoin transactions for users by transferring the private keys associated with their bitcoin rather than signing and sending a transaction with said keys. Spark also supports stablecoins (digital tokens pegged to fiat currency) and allows users to receive payments while offline. While these are promising developments, in its current state, Spark is not completely trustless; therefore, it is advisable only to hold a small balance of funds on the protocol as this new payment technology gets off the ground. You can learn more about Spark here.
Boltz | Now Supports Nostr Zaps
Boltz, a non-custodial bridge for swapping between different Bitcoin layers, released a new feature called Zap Swaps, enabling users to make Lightning payments as low as 21 satoshis (small units of bitcoin). This feature enables bitcoin microtransactions like nostr zaps, which are use cases that previously required workaround solutions. With the release, users of Boltz-powered Bitcoin wallets like Misty Breez can now leverage their wallets for zaps on nostr. These small, uncensorable bitcoin payments are a powerful tool for supporting activists, journalists, and dissidents — offering a permissionless way to support free speech and financial freedom worldwide. HRF is pleased to see this past HRF grantee add support for the latest freedom tech features.
Coinswap | Adds Support for Coin Selection
Coinswap, an in-development protocol that enables users to privately swap Bitcoin with one another, added support for coin selection, boosting the protocol’s privacy capabilities. Coin selection allows Bitcoin users to choose which of their unspent transaction outputs (UTXOs) to spend, giving them granular control over their transactions and the information they choose to reveal. For activists, journalists, and anyone operating under financial surveillance and repression, this addition (when fully implemented and released) can strengthen Bitcoin’s ability to resist censorship and protect human rights. HRF’s first Bitcoin Development Fund (BDF) grant was to Coinswap, and we are glad to see the continued development of the protocol.
bitcoin++ | Upcoming Bitcoin Developer Conference
The next bitcoin++ conference, a global, bitcoin-only developer series organized by Bitcoin educator Lisa Neigut, will occur in Austin, Texas, from May 7 to 9, 2025. A diverse group of privacy advocates, developers, and freedom tech enthusiasts will convene to learn about the mempool (the queue of pending and unconfirmed transactions in a Bitcoin node). Attendees will learn how Bitcoin transactions are sorted into blocks, mempool policies, and how transactions move through time and space to reach the next block. These events offer an incredible opportunity to connect with the technical Bitcoin community, who are ultimately many of the figures building the freedom tools that are helping individuals preserve their rights and freedoms in the face of censorship. Get your tickets here.
OpenSats | Announces 11th Wave of Nostr Grants
OpenSats, a nonprofit organization supporting open-source software and projects, announced its 11th round of grants for nostr, a decentralized protocol that enables uncensorable communications. Two projects stand out for their potential impact on financial freedom and activism: HAMSTR, which enables nostr messaging over ham radio that keeps information and payments flowing in off-grid or censored environments, and Nostr Double Ratchet, which brings end-to-end encrypted private messaging to nostr clients, safeguarding activists from surveillance. These tools help dissidents stay connected, coordinate securely, and transact privately, making them powerful assets for those resisting authoritarian control. Read the full list of grants here.
Bitcoin Design Community | Organizes Designathon for Open-Source UX Designers
The Bitcoin Design Community is hosting its next Designathon between May 4 and 18, 2025, inviting designers of all levels and backgrounds to creatively explore ideas to advance Bitcoin’s user experience and interface. Unlike traditional hackathons, this event centers specifically on design, encouraging open collaboration on projects that improve usability, accessibility, and innovation in open-source Bitcoin tools. Participants can earn monetary prizes, rewards, and recognition for their work. Anyone can join or start a project. Learn more here.
RECOMMENDED CONTENT
Plunging Currencies, CBDCs, and New Bitcoin Freedom Tools with Guy Swann
In this reading on the Bitcoin Audible podcast, host Guy Swan reads HRF’s Financial Freedom Report #67, offering listeners a front-row view into the latest developments in financial repression and resistance. He unpacks how collapsing currencies, rising inflation, and CBDC rollouts tighten state control in Turkey, Russia, and Nigeria. But he also highlights the tools for pushing back, from the first Stratum V2 mining pool to Cashu’s new Tap-to-Pay ecash feature. If you’re a reader of the Financial Freedom Report, we encourage you to check out the Bitcoin Audible podcast, where Guy Swan will be doing monthly readings of our newsletter. Listen to the full recording here.
Bitcoin Beyond Capital: Freedom Money for the Global South with Femi Longe
In this interview at the 2025 MIT Bitcoin Expo, journalist Frank Corva speaks with Femi Longe, HRF’s global bitcoin lead, who shares insights on Bitcoin’s growing role as freedom money for those living under authoritarian regimes. The conversation highlights the importance of building Bitcoin solutions that center on the specific problems faced by communities rather than the technology itself. Longe commends projects like Tando in Kenya and Bit.Spenda in Ghana, which integrate Bitcoin and Lightning into familiar financial channels, making Bitcoin more practical and accessible for everyday payments and saving. You can watch the interview here and catch the livestreams of the full 2025 MIT Bitcoin Expo here.
If this article was forwarded to you and you enjoyed reading it, please consider subscribing to the Financial Freedom Report here.
Support the newsletter by donating bitcoin to HRF’s Financial Freedom program via BTCPay.\ Want to contribute to the newsletter? Submit tips, stories, news, and ideas by emailing us at ffreport @ hrf.org
The Bitcoin Development Fund (BDF) is accepting grant proposals on an ongoing basis. The Bitcoin Development Fund is looking to support Bitcoin developers, community builders, and educators. Submit proposals here.
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
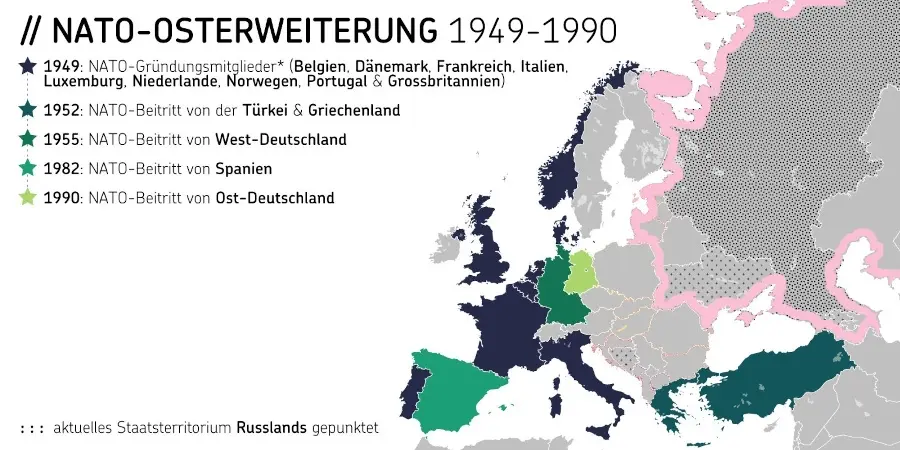
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
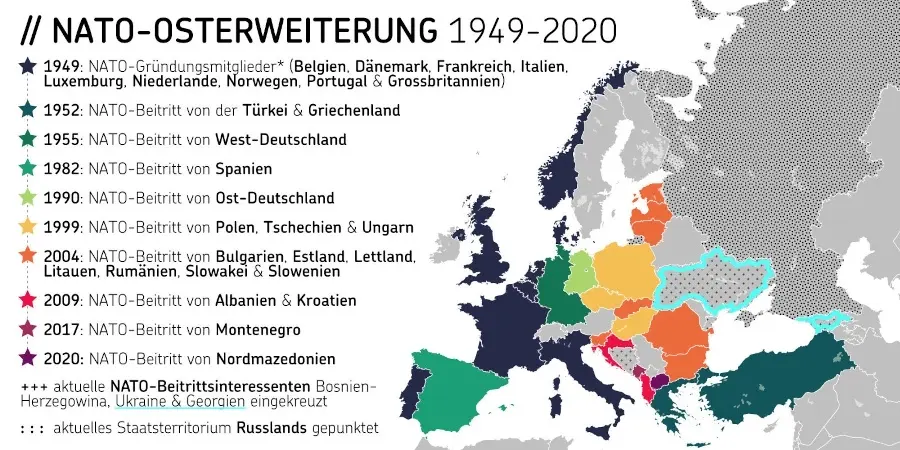
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
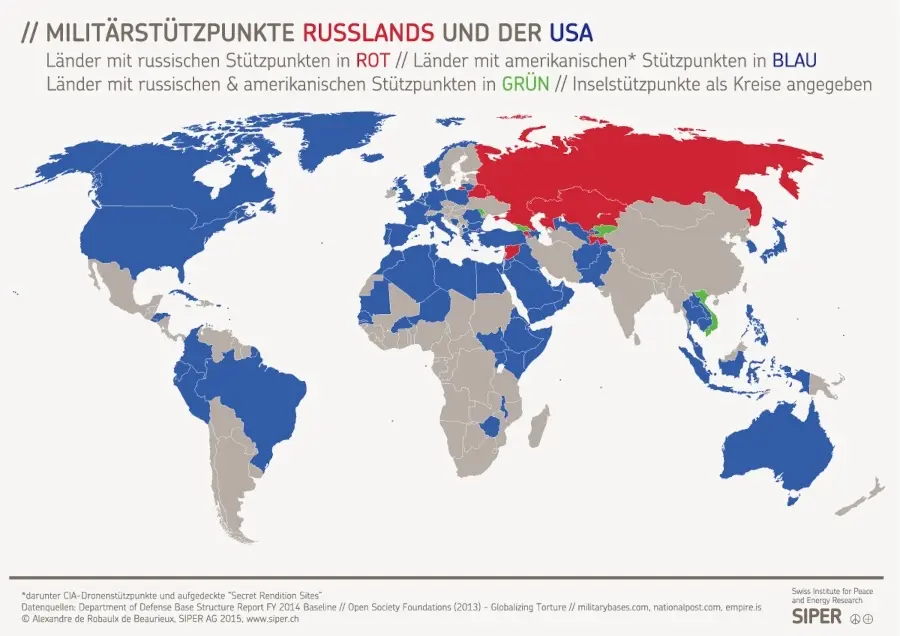
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 99895004:c239f905
2025-04-30 01:43:05
@ 99895004:c239f905
2025-04-30 01:43:05 Yes, FINALLY, we are extremely excited to announce support for nostr.build (blossom.band) on Primal! Decades in the making, billions of people have been waiting, and now it’s available! But it’s not just any integration, it is the next level of decentralized media hosting for Nostr. Let us explain.
Yes, FINALLY, we are extremely excited to announce support for nostr.build (blossom.band) on Primal! Decades in the making, billions of people have been waiting, and now it’s available! But it’s not just any integration, it is the next level of decentralized media hosting for Nostr. Let us explain. Primal is an advanced Twitter/X like client for Nostr and is probably the fastest up-and-coming, highly used Nostr app available for iOS, Android and the web. Nostr.build is a very popular media hosting service for Nostr that can be used standalone or integrated into many Nostr apps using nip-96. This is an extremely feature rich, tested and proven integration we recommend for most applications, but it’s never been available on Primal.
And then, Blossom was born, thank you Hzrd149! Blossom is a Nostr media hosting protocol that makes it extremely easy for Nostr clients to integrate a media host, and for users of Blossom media hosts (even an in-house build) to host on any Nostr client. Revolutionary, right! Use whatever host you want on any client you want, the flexible beauty of Nostr. But there is an additional feature to Blossom that is key, mirroring.
One of the biggest complaints to media hosting on Nostr is, if a media hosting service goes down, so does all of the media hosted on that service. No bueno, and defeats the whole decentralized idea behind Nostr.. This has always been a hard problem to solve until Blossom mirroring came along. Mirroring allows a single media upload to be hosted on multiple servers using its hash, or unique media identifier. This way, if a media host goes down, the media is still available and accessible on the other host.
So, we are not only announcing support of nostr.build’s blossom.band on the Primal app, we are also announcing the first known fully integrated implementation of mirroring with multiple media hosts on Nostr. Try it out for yourself! Go to the settings of your Primal web, iOS or Android app, choose ‘Media Servers’, enable ‘Media Mirrors’, and add https://blossom.band and https://blossom.primal.net as your Media server and Mirror, done!
Video here!
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ b099870e:f3ba8f5d
2025-05-06 13:04:19
@ b099870e:f3ba8f5d
2025-05-06 13:04:19When you work for others, you are at their mercy. The own your work; they own you.Your creative spirit is squaded. What keeps you in such position is a fear of having to sink or swim on your own. Instead you should have a greater fear of what will happen to you if you remain dependant on others for power. Your goal in every maneuver in life must be ownership, working the corner for yourself. When it is yours to lose -you are more motivated,more creative,more alive. The ultimate power in life is to be completely self-reliant, completely yourself.
A quote from The 50th Law
-
 @ 90c656ff:9383fd4e
2025-05-06 13:01:45
@ 90c656ff:9383fd4e
2025-05-06 13:01:45Bitcoin has revolutionized the way people conduct financial transactions worldwide. As a decentralized digital currency, it offers new opportunities for e-commerce payments and international money transfers. Its speed, security, and low costs make it an efficient alternative to traditional methods by eliminating intermediaries and facilitating global transactions.
Bitcoin in e-commerce
E-commerce has grown exponentially, and Bitcoin has emerged as an innovative solution for online payments. Large retailers and small businesses are starting to accept Bitcoin as a form of payment, offering benefits to both merchants and consumers.
- Advantages of Bitcoin for e-commerce:
01 - Low transaction fees: Unlike credit cards and payment platforms that charge high fees, Bitcoin transactions generally have lower costs. This benefits merchants, who can reduce expenses and offer more competitive prices to customers. 02 - Elimination of chargebacks: In traditional systems, chargebacks (forced refunds by banks or card operators) are a concern for merchants. Since Bitcoin transactions are irreversible, merchants avoid fraud and disputes. 03 - Global access: Anyone with internet access can pay with Bitcoin, regardless of their location. This allows businesses to expand their market internationally without relying on banks or local payment systems. 04 - Privacy and security: Bitcoin transactions protect user identity, offering greater privacy compared to credit card payments or bank transfers. Additionally, since there’s no need to share personal data, the risk of information theft is reduced.
- Challenges of using Bitcoin in e-commerce:
01 - Volatility: Bitcoin’s price can fluctuate rapidly, making it difficult to set fixed prices for products and services. However, some merchants use payment processors that instantly convert Bitcoin into fiat currency, minimizing this risk. 02 - Limited adoption: Despite its growth, Bitcoin acceptance is not yet universal. Many stores and popular platforms have not adopted it, which can make daily purchases difficult. 03 - Confirmation time: Although Bitcoin is faster than traditional bank transfers, confirmation times may vary depending on the network fee paid. Some solutions, such as the Lightning Network, are being developed to enable instant payments.
Bitcoin in money remittances
Sending money abroad has long been a bureaucratic, costly, and time-consuming process. Traditional services like banks and money transfer companies charge high fees and can take days to complete a transaction. Bitcoin, on the other hand, offers an efficient alternative for global remittances, allowing anyone to send and receive money quickly and affordably.
- Benefits of Bitcoin for remittances:
01 - Reduced costs: While banks and companies like Western Union charge high fees for international transfers, Bitcoin allows money to be sent with minimal costs, regardless of the amount or destination. 02 - Transaction speed: International bank transfers can take several days to complete, especially in countries with limited financial infrastructure. With Bitcoin, money can be sent anywhere in the world within minutes or hours. 03 - Global accessibility: In regions where the banking system is restricted or inefficient, Bitcoin enables people to receive money without depending on banks. This is particularly useful in developing countries where international remittances are an essential source of income. 04 - Independence from intermediaries: Bitcoin operates in a decentralized manner, with no need for banks or transfer companies. This means people can send money directly to friends and family without intermediaries.
- Challenges of Bitcoin remittances:
01 - Conversion to local currency: Although Bitcoin can be received instantly, many people still need to convert it into local currency for everyday use. This may involve additional costs and depend on the availability of exchange services. 02 - Adoption and knowledge: Not everyone understands how Bitcoin works, which can hinder its widespread adoption for remittances. However, growing financial education on the subject can help overcome this barrier. 03 - Regulations and restrictions: Some governments impose restrictions on Bitcoin usage, making remittances more complicated. The evolution of regulations may affect ease of use in certain countries.
In summary, Bitcoin is transforming e-commerce and money remittances around the world. Its ability to eliminate intermediaries, reduce costs, and provide fast and secure payments makes it a viable alternative to traditional financial systems.
In e-commerce, it benefits both merchants and consumers by lowering fees and enhancing privacy. In the remittance sector, it facilitates money transfers to any part of the world, especially for those living in countries with inefficient banking systems.
Despite the challenges, Bitcoin adoption continues to grow, driven by innovative solutions and recognition of its potential as a global payment method. As more businesses and individuals embrace this technology, its presence in e-commerce and international remittances will become increasingly relevant.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 1f79058c:eb86e1cb
2025-04-26 13:53:50
@ 1f79058c:eb86e1cb
2025-04-26 13:53:50I'm currently using this bash script to publish long-form content from local Markdown files to Nostr relays.
It requires all of
yq,jq, andnakto be installed.Usage
Create a signed Nostr event and print it to the console:
bash markdown_to_nostr.sh article-filename.mdCreate a Nostr event and publish it to one or more relays:
bash markdown_to_nostr.sh article-filename.md ws://localhost:7777 wss://nostr.kosmos.orgMarkdown format
You can specify your metadata as YAML in a Front Matter header. Here's an example file:
```markdown
title: "Good Morning" summary: "It's a beautiful day" image: https://example.com/i/beautiful-day.jpg date: 2025-04-24T15:00:00Z tags: gm, poetry published: false
In the blue sky just a few specks of gray
In the evening of a beautiful day
Though last night it rained and more rain on the way
And that more rain is needed 'twould be fair to say.— Francis Duggan ```
The metadata keys are mostly self-explanatory. Note:
- All keys except for
titleare optional date, if present, will be set as thepublished_atdate.- If
publishedis set totrue, it will publish a kind 30023 event, otherwise a kind 30024 (draft) - The
dtag (widely used as URL slug for the article) will be the filename without the.mdextension
- All keys except for
-
 @ b099870e:f3ba8f5d
2025-05-06 12:55:19
@ b099870e:f3ba8f5d
2025-05-06 12:55:19IN NOOKS ALL OVER THE EARTH SIT MEN WHO ARE WAITING, SCARCELY KNOWING IN WHAT WAY THEY ARE WAITING, MUCH LESS THAT THEY ARE WAITING IN VAIN. OCCASIONALLY THE CALL THAT AWAKENS-THAT ACCIDENT WHICH GIVES THE "PERMISSION" TO ACT—COMES TOO LATE, WHEN THE BEST YOUTH AND STRENGTH FOR ACTION HAS ALREADY BEEN USED UP BY SITTING STILL; AND MANY HAVE FOUND TO THEIR HORROR WHEN THEY "LEAPED UP" THAT THEIR LIMBS HAD GONE TO SLEEP AND THEIR SPIRIT HAD BECOME TOO HEAVY. "IT IS TOO LATE," THEY SAID TO THEMSELVES, HAVING LOST THEIR FAITH IN THEMSELVES AND HENCEFORTH FOREVER USELESS
Quote by Friedrich Nietzsche, currently reading The 50th Law and came across it
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 90c656ff:9383fd4e
2025-05-06 12:18:09
@ 90c656ff:9383fd4e
2025-05-06 12:18:09Digital wallets are important tools for storing and managing Bitcoin. They allow people to keep their private keys, access their funds, and make transactions in a practical and secure way. However, with several types of wallets available and the risks of incorrect use, it is essential to understand their features and follow good security practices.
What is a digital wallet?
A digital wallet is a software or device that stores the private and public keys linked to Bitcoin. Simply put, it doesn’t “store” Bitcoin itself but provides secure access to the network to verify and sign transactions.
Private keys work like a secret password that allows spending Bitcoins, while public keys are like account numbers that can be shared to receive payments. Keeping the private key secure is very important, as whoever has access to it controls the funds.
- Types of Digital Wallets
There are different types of digital wallets, each with specific features that meet various needs, whether for daily use or long-term storage.
- Hot Wallets
Wallets connected to the internet, designed for frequent use. Examples: Mobile apps, desktop wallets, online wallets.
Advantages:
01 - Accessible and easy to use 02 - Ideal for daily and quick transactions
Disadvantages:
01 - More exposed to cyberattacks such as phishing or hacking
- Cold Wallets
Wallets that keep private keys offline, increasing security. Examples: Hardware wallets, paper wallets, dedicated USB devices.
Advantages:
01 - High protection against hackers since they are not online 02 - Ideal for large amounts of Bitcoin or long-term storage
Disadvantages:
01 - Less practical for daily use 02 - Can be physically damaged or lost if not handled carefully
- Hardware Wallets
Physical devices, like Ledger or Trezor, that store private keys offline.
Advantages:
01 - Easy-to-use and secure interface 02 - Resistant to viruses and online attacks
Disadvantages:
01 - Higher initial cost 02 - Require care to avoid physical damage
- Paper Wallets
Involve printing or writing down private and public keys on a piece of paper.
Advantages:
01 - Completely offline and immune to digital attacks 02 - Simple and low-cost
Disadvantages:
01 - Vulnerable to physical damage such as water, fire, or loss 02 - Difficult to recover if lost
- Security in Digital Wallets
Protecting a digital wallet is essential to safeguard your Bitcoins from loss or theft.
Below are important practices to improve security:
- Private Key Protection
01 - Never share your private key with anyone 02 - Keep backup copies of the private key or recovery phrase in safe places
- Use of Recovery Phrases
The seed phrase is a sequence of 12 to 24 words that helps recover funds if the wallet is lost.
01 - Store the seed phrase offline and avoid taking pictures or saving it on internet-connected devices
- Two-Factor Authentication (2FA)
01 - Whenever possible, enable 2FA to protect accounts linked to online wallets or exchanges 02 - This adds an extra layer of security by requiring a second code to log in
- Updates and Maintenance
Keep the wallet software up to date to ensure protection against vulnerabilities
01 - Use only wallets from trustworthy and reputable developers
- Choosing the Right Wallet According to Need
01 - For frequent transactions, choose hot wallets but keep only small amounts 02 - For large amounts, use cold wallets like hardware or paper wallets, which are more secure
Risks and How to Avoid Them
- Hacker Attacks
Risk: Unauthorized access to hot wallets connected to the internet Prevention: Use cold wallets for storing large amounts and avoid clicking on suspicious links
- Loss of Access
Risk: Loss of private keys or the recovery phrase, making funds unrecoverable Prevention: Regularly make backups and store information in secure places
- Social Engineering and Phishing
Risk: Hackers trick people into giving up their private keys or personal information Prevention: Be suspicious of messages or websites that request your private keys. Never share sensitive data
- Physical Failures
Risk: Damage to devices or loss of paper wallets Prevention: Store backups in locations resistant to water, fire, and other threats
In summary, digital wallets are essential for the security and use of Bitcoin. Choosing the right wallet and following good security practices are key steps to protecting your assets.
Hot wallets offer convenience for daily use, while cold wallets provide strong security for long-term storage. Regardless of the type you choose, taking care of your private keys and recovery phrase is fundamental to ensure your Bitcoin remains under your control.
By understanding the types of wallets and implementing appropriate security measures, users can safely and efficiently take advantage of Bitcoin, maximizing the benefits of this digital revolution.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 23b0e2f8:d8af76fc
2025-01-08 18:17:52
@ 23b0e2f8:d8af76fc
2025-01-08 18:17:52Necessário
- Um Android que você não use mais (a câmera deve estar funcionando).
- Um cartão microSD (opcional, usado apenas uma vez).
- Um dispositivo para acompanhar seus fundos (provavelmente você já tem um).
Algumas coisas que você precisa saber
- O dispositivo servirá como um assinador. Qualquer movimentação só será efetuada após ser assinada por ele.
- O cartão microSD será usado para transferir o APK do Electrum e garantir que o aparelho não terá contato com outras fontes de dados externas após sua formatação. Contudo, é possível usar um cabo USB para o mesmo propósito.
- A ideia é deixar sua chave privada em um dispositivo offline, que ficará desligado em 99% do tempo. Você poderá acompanhar seus fundos em outro dispositivo conectado à internet, como seu celular ou computador pessoal.
O tutorial será dividido em dois módulos:
- Módulo 1 - Criando uma carteira fria/assinador.
- Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
No final, teremos:
- Uma carteira fria que também servirá como assinador.
- Um dispositivo para acompanhar os fundos da carteira.

Módulo 1 - Criando uma carteira fria/assinador
-
Baixe o APK do Electrum na aba de downloads em https://electrum.org/. Fique à vontade para verificar as assinaturas do software, garantindo sua autenticidade.
-
Formate o cartão microSD e coloque o APK do Electrum nele. Caso não tenha um cartão microSD, pule este passo.

- Retire os chips e acessórios do aparelho que será usado como assinador, formate-o e aguarde a inicialização.

- Durante a inicialização, pule a etapa de conexão ao Wi-Fi e rejeite todas as solicitações de conexão. Após isso, você pode desinstalar aplicativos desnecessários, pois precisará apenas do Electrum. Certifique-se de que Wi-Fi, Bluetooth e dados móveis estejam desligados. Você também pode ativar o modo avião.\ (Curiosidade: algumas pessoas optam por abrir o aparelho e danificar a antena do Wi-Fi/Bluetooth, impossibilitando essas funcionalidades.)

- Insira o cartão microSD com o APK do Electrum no dispositivo e instale-o. Será necessário permitir instalações de fontes não oficiais.

- No Electrum, crie uma carteira padrão e gere suas palavras-chave (seed). Anote-as em um local seguro. Caso algo aconteça com seu assinador, essas palavras permitirão o acesso aos seus fundos novamente. (Aqui entra seu método pessoal de backup.)

Módulo 2 - Configurando um dispositivo para visualizar seus fundos e assinando transações com o assinador.
-
Criar uma carteira somente leitura em outro dispositivo, como seu celular ou computador pessoal, é uma etapa bastante simples. Para este tutorial, usaremos outro smartphone Android com Electrum. Instale o Electrum a partir da aba de downloads em https://electrum.org/ ou da própria Play Store. (ATENÇÃO: O Electrum não existe oficialmente para iPhone. Desconfie se encontrar algum.)
-
Após instalar o Electrum, crie uma carteira padrão, mas desta vez escolha a opção Usar uma chave mestra.

- Agora, no assinador que criamos no primeiro módulo, exporte sua chave pública: vá em Carteira > Detalhes da carteira > Compartilhar chave mestra pública.

-
Escaneie o QR gerado da chave pública com o dispositivo de consulta. Assim, ele poderá acompanhar seus fundos, mas sem permissão para movimentá-los.
-
Para receber fundos, envie Bitcoin para um dos endereços gerados pela sua carteira: Carteira > Addresses/Coins.
-
Para movimentar fundos, crie uma transação no dispositivo de consulta. Como ele não possui a chave privada, será necessário assiná-la com o dispositivo assinador.

- No assinador, escaneie a transação não assinada, confirme os detalhes, assine e compartilhe. Será gerado outro QR, desta vez com a transação já assinada.

- No dispositivo de consulta, escaneie o QR da transação assinada e transmita-a para a rede.
Conclusão
Pontos positivos do setup:
- Simplicidade: Basta um dispositivo Android antigo.
- Flexibilidade: Funciona como uma ótima carteira fria, ideal para holders.
Pontos negativos do setup:
- Padronização: Não utiliza seeds no padrão BIP-39, você sempre precisará usar o electrum.
- Interface: A aparência do Electrum pode parecer antiquada para alguns usuários.
Nesse ponto, temos uma carteira fria que também serve para assinar transações. O fluxo de assinar uma transação se torna: Gerar uma transação não assinada > Escanear o QR da transação não assinada > Conferir e assinar essa transação com o assinador > Gerar QR da transação assinada > Escanear a transação assinada com qualquer outro dispositivo que possa transmiti-la para a rede.
Como alguns devem saber, uma transação assinada de Bitcoin é praticamente impossível de ser fraudada. Em um cenário catastrófico, você pode mesmo que sem internet, repassar essa transação assinada para alguém que tenha acesso à rede por qualquer meio de comunicação. Mesmo que não queiramos que isso aconteça um dia, esse setup acaba por tornar essa prática possível.
-
 @ 3bf0c63f:aefa459d
2025-04-25 19:26:48
@ 3bf0c63f:aefa459d
2025-04-25 19:26:48Redistributing Git with Nostr
Every time someone tries to "decentralize" Git -- like many projects tried in the past to do it with BitTorrent, IPFS, ScuttleButt or custom p2p protocols -- there is always a lurking comment: "but Git is already distributed!", and then the discussion proceeds to mention some facts about how Git supports multiple remotes and its magic syncing and merging abilities and so on.
Turns out all that is true, Git is indeed all that powerful, and yet GitHub is the big central hub that hosts basically all Git repositories in the giant world of open-source. There are some crazy people that host their stuff elsewhere, but these projects end up not being found by many people, and even when they do they suffer from lack of contributions.
Because everybody has a GitHub account it's easy to open a pull request to a repository of a project you're using if it's on GitHub (to be fair I think it's very annoying to have to clone the repository, then add it as a remote locally, push to it, then go on the web UI and click to open a pull request, then that cloned repository lurks forever in your profile unless you go through 16 screens to delete it -- but people in general seem to think it's easy).
It's much harder to do it on some random other server where some project might be hosted, because now you have to add 4 more even more annoying steps: create an account; pick a password; confirm an email address; setup SSH keys for pushing. (And I'm not even mentioning the basic impossibility of offering
pushaccess to external unknown contributors to people who want to host their own simple homemade Git server.)At this point some may argue that we could all have accounts on GitLab, or Codeberg or wherever else, then those steps are removed. Besides not being a practical strategy this pseudo solution misses the point of being decentralized (or distributed, who knows) entirely: it's far from the ideal to force everybody to have the double of account management and SSH setup work in order to have the open-source world controlled by two shady companies instead of one.
What we want is to give every person the opportunity to host their own Git server without being ostracized. at the same time we must recognize that most people won't want to host their own servers (not even most open-source programmers!) and give everybody the ability to host their stuff on multi-tenant servers (such as GitHub) too. Importantly, though, if we allow for a random person to have a standalone Git server on a standalone server they host themselves on their wood cabin that also means any new hosting company can show up and start offering Git hosting, with or without new cool features, charging high or low or zero, and be immediately competing against GitHub or GitLab, i.e. we must remove the network-effect centralization pressure.
External contributions
The first problem we have to solve is: how can Bob contribute to Alice's repository without having an account on Alice's server?
SourceHut has reminded GitHub users that Git has always had this (for most) arcane
git send-emailcommand that is the original way to send patches, using an once-open protocol.Turns out Nostr acts as a quite powerful email replacement and can be used to send text content just like email, therefore patches are a very good fit for Nostr event contents.
Once you get used to it and the proper UIs (or CLIs) are built sending and applying patches to and from others becomes a much easier flow than the intense clickops mixed with terminal copypasting that is interacting with GitHub (you have to clone the repository on GitHub, then update the remote URL in your local directory, then create a branch and then go back and turn that branch into a Pull Request, it's quite tiresome) that many people already dislike so much they went out of their way to build many GitHub CLI tools just so they could comment on issues and approve pull requests from their terminal.
Replacing GitHub features
Aside from being the "hub" that people use to send patches to other people's code (because no one can do the email flow anymore, justifiably), GitHub also has 3 other big features that are not directly related to Git, but that make its network-effect harder to overcome. Luckily Nostr can be used to create a new environment in which these same features are implemented in a more decentralized and healthy way.
Issues: bug reports, feature requests and general discussions
Since the "Issues" GitHub feature is just a bunch of text comments it should be very obvious that Nostr is a perfect fit for it.
I will not even mention the fact that Nostr is much better at threading comments than GitHub (which doesn't do it at all), which can generate much more productive and organized discussions (and you can opt out if you want).
Search
I use GitHub search all the time to find libraries and projects that may do something that I need, and it returns good results almost always. So if people migrated out to other code hosting providers wouldn't we lose it?
The fact is that even though we think everybody is on GitHub that is a globalist falsehood. Some projects are not on GitHub, and if we use only GitHub for search those will be missed. So even if we didn't have a Nostr Git alternative it would still be necessary to create a search engine that incorporated GitLab, Codeberg, SourceHut and whatnot.
Turns out on Nostr we can make that quite easy by not forcing anyone to integrate custom APIs or hardcoding Git provider URLs: each repository can make itself available by publishing an "announcement" event with a brief description and one or more Git URLs. That makes it easy for a search engine to index them -- and even automatically download the code and index the code (or index just README files or whatever) without a centralized platform ever having to be involved.
The relays where such announcements will be available play a role, of course, but that isn't a bad role: each announcement can be in multiple relays known for storing "public good" projects, some relays may curate only projects known to be very good according to some standards, other relays may allow any kind of garbage, which wouldn't make them good for a search engine to rely upon, but would still be useful in case one knows the exact thing (and from whom) they're searching for (the same is valid for all Nostr content, by the way, and that's where it's censorship-resistance comes from).
Continuous integration
GitHub Actions are a very hardly subsidized free-compute-for-all-paid-by-Microsoft feature, but one that isn't hard to replace at all. In fact there exists today many companies offering the same kind of service out there -- although they are mostly targeting businesses and not open-source projects, before GitHub Actions was introduced there were also many that were heavily used by open-source projects.
One problem is that these services are still heavily tied to GitHub today, they require a GitHub login, sometimes BitBucket and GitLab and whatnot, and do not allow one to paste an arbitrary Git server URL, but that isn't a thing that is very hard to change anyway, or to start from scratch. All we need are services that offer the CI/CD flows, perhaps using the same framework of GitHub Actions (although I would prefer to not use that messy garbage), and charge some few satoshis for it.
It may be the case that all the current services only support the big Git hosting platforms because they rely on their proprietary APIs, most notably the webhooks dispatched when a repository is updated, to trigger the jobs. It doesn't have to be said that Nostr can also solve that problem very easily.
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 8125b911:a8400883
2025-04-25 07:02:35
@ 8125b911:a8400883
2025-04-25 07:02:35In Nostr, all data is stored as events. Decentralization is achieved by storing events on multiple relays, with signatures proving the ownership of these events. However, if you truly want to own your events, you should run your own relay to store them. Otherwise, if the relays you use fail or intentionally delete your events, you'll lose them forever.
For most people, running a relay is complex and costly. To solve this issue, I developed nostr-relay-tray, a relay that can be easily run on a personal computer and accessed over the internet.
Project URL: https://github.com/CodyTseng/nostr-relay-tray
This article will guide you through using nostr-relay-tray to run your own relay.
Download
Download the installation package for your operating system from the GitHub Release Page.
| Operating System | File Format | | --------------------- | ---------------------------------- | | Windows |
nostr-relay-tray.Setup.x.x.x.exe| | macOS (Apple Silicon) |nostr-relay-tray-x.x.x-arm64.dmg| | macOS (Intel) |nostr-relay-tray-x.x.x.dmg| | Linux | You should know which one to use |Installation
Since this app isn’t signed, you may encounter some obstacles during installation. Once installed, an ostrich icon will appear in the status bar. Click on the ostrich icon, and you'll see a menu where you can click the "Dashboard" option to open the relay's control panel for further configuration.

macOS Users:
- On first launch, go to "System Preferences > Security & Privacy" and click "Open Anyway."
- If you encounter a "damaged" message, run the following command in the terminal to remove the restrictions:
bash sudo xattr -rd com.apple.quarantine /Applications/nostr-relay-tray.appWindows Users:
- On the security warning screen, click "More Info > Run Anyway."
Connecting
By default, nostr-relay-tray is only accessible locally through
ws://localhost:4869/, which makes it quite limited. Therefore, we need to expose it to the internet.In the control panel, click the "Proxy" tab and toggle the switch. You will then receive a "Public address" that you can use to access your relay from anywhere. It's that simple.
Next, add this address to your relay list and position it as high as possible in the list. Most clients prioritize connecting to relays that appear at the top of the list, and relays lower in the list are often ignored.

Restrictions
Next, we need to set up some restrictions to prevent the relay from storing events that are irrelevant to you and wasting storage space. nostr-relay-tray allows for flexible and fine-grained configuration of which events to accept, but some of this is more complex and will not be covered here. If you're interested, you can explore this further later.
For now, I'll introduce a simple and effective strategy: WoT (Web of Trust). You can enable this feature in the "WoT & PoW" tab. Before enabling, you'll need to input your pubkey.
There's another important parameter,
Depth, which represents the relationship depth between you and others. Someone you follow has a depth of 1, someone they follow has a depth of 2, and so on.- Setting this parameter to 0 means your relay will only accept your own events.
- Setting it to 1 means your relay will accept events from you and the people you follow.
- Setting it to 2 means your relay will accept events from you, the people you follow, and the people they follow.
Currently, the maximum value for this parameter is 2.

Conclusion
You've now successfully run your own relay and set a simple restriction to prevent it from storing irrelevant events.
If you encounter any issues during use, feel free to submit an issue on GitHub, and I'll respond as soon as possible.
Not your relay, not your events.
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ 005bc4de:ef11e1a2
2025-05-06 11:54:14
@ 005bc4de:ef11e1a2
2025-05-06 11:54:14May 6 marks my "Nostr birthday." This means I've been on Nostr for two years now. See my initial "Running nostr" note timestamped and archived on the Hive blockchain at https://peakd.com/bitcoin/@crrdlx/running-nostr
Two years ago, I really had no idea what Nostr was. I was asking, "What is this Nostr thing?"

And, I had no idea what I was doing then while using the front end clients. The clients were clunky and since the protocol was rather plastic (still kinda is). As evidence to my ignorance, the spinning wheels on Coracle.social just kept spinning. I didn't realize that since I was only following two people, one being myself, there was nothing to load from relays except my one "Running nostr" note. Hence, the Coracle wheels just spun in their mesmerizing manner. At least they're soothing to watch.
Yet, despite my ignorance, I had an inkling of a notion that Nostr was indeed something different, maybe special. Otherwise, I wouldn't have taken the time to capture an animated gif and make that Hive post to chronicle my first Nostr note.
For fun, I made another "Running nostr" note yesterday using Coracle.social. It still has those muted, earthy tones, but the wheels are not there anymore for long. Coracle, like Nostr, has come a long way in two years. It loads much faster now, which means less wheel spinning. I kind of miss the wheels for some reason, they build the drama and expectation of what might appear.
!HBIT
-
 @ f72e682e:c51af867
2025-05-06 10:35:01
@ f72e682e:c51af867
2025-05-06 10:35:01All across the Lightning Network we can detect quite a lot of nodes, specially new nodes but also old nodes, that show a concerning lack of good node operation which impedes proper routing. I’ve seen nodes with a variable capacity whose channels are stagnant and non performant, which raises a question: what is the point on maintaining a public node if you are not able to route and dynamically assign resources as needed? Certainly it is a useless node, and channels of those nodes with other nodes better maintained are also useless, not because the fault of the good ones, but because the fault of the bad ones, which makes the whole network not as performant and great as it should be.
For the shake of improving the Lightning Network, I have created this guide, so every node out there can become useful, and, also, will greatly improve gains in routing for itself. Do not expect to become rich or even live out of routing fees, that is impossible unless you have a node with 100 or more BTC in 2025, but at least, a node should be able to cover its own maintenance costs; its the idea. Problem is that, currently, most nodes run on a loss, and that is highly related with the fee policy and the choice of nodes that they connect to. Let’s put an end to this. Here you will learn how to, at least, earn enough to cover electricity of your node, and with luck, a bit more.
Current earnings cover electricity and the payment of my node:
3K sats per day might not seem much for a 5 BTC capacity (2.5 BTC real outbound) node, but the screenshot was taken in a bad day, when the mempool was empty. I took the screenshot of a bad day on purpose, to prove my point. Some other days, specially when Bitcoin is going bullish and it is used a lot, I have seen 20K per day. A quick calculation brings around 1M sats per year at a minimum, more than enough to pay electricity, the machine, and even a bit more for beers and fun! Real gains across the year could be closer to around 5M in my case, which is not bad. And what is incredible, I maintain general low fees for most of the cases, except when I have no liquidity in the channel which must be high, as you will understand later in this article. So if you double or triple my recommended fees I would expect quite a lot more earnings. So expect gains of around 2% of the total capacity (4% for the amount you put in) per year minimum, and any extra beyond that by fine-tuning my recommendations I'm sure it will be very welcomed by you!
Step 1: put the node in a good machine
Please, don’t use an old computer or laptop, unless you change the SSD for a new one. Bitcoin and lightning uses the SSD heavily, which means it will fry it sooner or later. That is so that I recommend changing the SSD every 2 years even it it still feels good. If your SSD dies during operation, expect big loses. I’ve seen this so many times, and it also happened to me, that I am very serious about recommending it. Also, please use only Linux with ext4 file format, other formats, including ZFS, I’ve seen failing badly. If your filesystem fails, the sqlite db that LND or CLN uses will fail and you will force close many if not most channels, with big fees for onchain closings, which will totally ruin all your gains. You have been warned!
Also, please take your time to configure a clearnet (ipv4) address. Do not rely only on Tor, because Tor is slow and unreliable, specially when updating channel states on the gossip, which you will be doing a lot. Of course, configure Tor also, but as secondary, because too many nodes are Tor only, which is unfortunate.
Step 2: connect to good nodes
As a public node operator, your duty is to connect to as many nodes as possible, but first, to good reputable nodes. Your first 10 channels should be with big nodes and service providers, like exchanges, wallets, but also to very well positioned big nodes. Take your time to select these 10 first nodes and connect to the ones you think will improve your position in the network. Don’t choose the first 10 biggest, take your time to study the fees. Select nodes that use a wide range of fees, from 0 to 1000ppm. Don’t discard a node because you see some channels with high fees, it could only mean that they have no liquidity right now in that channel. But if all its channels have high fees, or at least all small channels have high fees, then discard it.
Then, when you have your first 10 big nodes connected, go ahead and go to https://lightningnetwork.plus/ to choose less popular ones. You need them, because you seek to fill the voids between smaller nodes, it is what most of your revenue will come from. Always try to do swaps, use the liquidity pool later when you have enough total inbound liquidity. Remember that total capacity is not total outbound. Total capacity is total outbound + total inbound. So you can start with 0.25BTC of your own, but total capacity could be much higher if other peers have open channels to you.
A proper public node should have a minimum of 50 channels at its peak. It doesn’t matter much the size of the channels, but the quantity and the quality. A node with 50x500k sized channels will usually perform 10x better than a node with 5x5M sized channels, even if they have the same total capacity. This is because more opportunities to route will be found if you have more channels, which means you are much better positioned.
Anyway, the minimum recommended is 1M per channel because most HTCLs are 100k to 500k and less than 1M will wipe out all your liquidity in the channels in one or two routings. This could change in the future because of the Bitcoin price, but in 2025 this is the state of things. But if you don’t have 0.25 BTC to open 50 channels (25 open by you, 25 by others using swaps), just use smaller channels, don't let your available liquidity to crush your excitement, who knows what is the future ahead us! Remember that we are just at the beginning of this technology and there is nothing that impides your channels to be open for the next 20 years when 1BTC=$1M! I would put the ultra minimum at 250k per channel, which means a 12.5M node (6.25M required sats to start with), but even that is too precarious in 2025. But hopefully not in the future! If you have less than that my honest recommendation is to run a private node and open private channels only, and only if you absolutely need a node because you have to provide a service for multiple people and you can't conform to use simpler wallets. Right now, I can think of only one example of requiring an ultra-small node instead of wallets, which is using LNBits to service your small business or family. Be aware, anyway, that a 12.5M node will definitely not cover your node running costs in 2025, it is just an investment and positioning for a future!
In any case, never, ever, put all your BTC in a LN node, at most one third of your bitcoins and only when you are confident.
Also remember you have to be online 24/7. Please, don’t setup a node if you can’t. Remember you are providing a constant service, not an intermittent one. This guide won’t work if you are not committed to this rule.
Step 3: understand the flow
I’ve seen too many node operators that do not understand how payments are routed, and this is a big problem, because this is the base of everything we do with a LN node.
Payments go from one node to another to another to another until it reaches destination. Each node has what is called an outbound fee. This fee controls how much does it cost to route a payment through that node. If the fee is low it is considered attractive and other nodes will prefer to use that route. If the fee is high, it is obvious that nodes will not choose that route unless there is no other way.
But there is a problem here: all channels have a liquidity limit. If a channel has 1M liquidity and a payment of 500k comes through it, then now the channel has 500k liquidity, that is, a ratio of 0.5. If another 400k comes through, now it has 100k liquidity and a ratio of 0.1. If now somebody tries to route a 200k payment through that channel, and error will happen, because it doesn’t have enough liquidity. It is called an HTCL failure, and this are quite normal. Liquidity can come backwards, which means that now that channel becomes the income instead of the outcome, so if 300k comes in, in the example above, now the liquidity ratio is 0.4 (100k already there plus 300k that just came in). So it is easy to understand that liquidity is very volatile: it will come in and out with any successful in or out HTLC.
The problem is: how do you know if a channel has liquidity? For privacy reasons, the liquidity of a channel is never announced, and only the two connected nodes know it. This is logical, to avoid bad actors to figure out which payments have been done by other people. So the only possible solution is to try all connected channels you have until one lets you go through because it has enough liquidity. And it is going to be done, always, in the order of outbound fees, from low to high. So the channel that has the lowest fee with enough liquidity, will catch the prize.
There is a way to signal that you have liquidity or you don’t, and it is based on scarcity: if you don’t have much liquidity, you increase the outbound fee, so other nodes will not find attractive to route through you in that direction. You don't have much liquidity, so why bother to allow routing? But, when you have again outbound liquidity, because other nodes have taken the opposite direction (inbound) using another channel of yours which has liquidity (as outbound), you intelligently lower the fees to signal your new updated increased liquidity in the channel. So, the idea is simple: if you have liquidity in the channel, you put low fees, if you don’t have liquidity, you put high fees. Please read that again until you fully understand it, it is extremely important.
There is another concept introduced by LND which is negative inbound fees: if you put negative inbound fees, for example -100ppm, it means that any payment going from that inbound channel to another of your outbound channels, will have a maximum discount of 100ppm. (Don’t worry, you will never lose because LND forbids to route losing money, so 100ppm is the maximum, but it could be less if the outgoing channel has less than 100ppm fees.) What this does is to encourage the filling of empty channels at the cost of earning less in channels with plenty of liquidity. This is very good, because it will automatically rebalance your extremes: channels with no liquidity will be filled up, channels with plenty of liquidity will be emptied down, creating a balance.
It is obvious that the total ratio, including all your channels, should be around 100%. That means that the total amount summing all channels of inbound and outbound should be approximately the same. Don’t get obsessed with this, 80% or 120% is ok too, but if it is lower or higher than that you should take measures to open or close channels, or even swap out or in using boltz.exchange or LOOP.
Step 4: managing fees
So, in order to make proper routing, you will have to constantly monitor all your channels on a regular basis. Minimum recommended frequency is once a day. You can do this automatically or manually. Some people prefer to do it manually because each channel has its own characteristics and some fees work better than others, which is something you learn with time observing the flow. But some other people, like me, don’t want to spend so much time doing so, and do automatic fee management using charge-lnd or lndg automators. A mixture of both styles is possible by disabling automatic fee management for selected channels.
Every node operator has his/her own preferences, but here are some basic recommendations that you can tweak over time as you acquire experience:
ratio > 0.98: fees 0 (or less than 10) 0.2 < ratio < 0.98: fees proportional max 128, min 16 0.2 > ratio > 0.05: fees 500, inbound -16 ratio < 0.05: fees 1000, inbound -64 ratio = 0: fees more than 1000, inbound -128So, as you can see, when the channel is full we encourage routing, when the channel is more balanced is when the earnings will occur (from 16 to 128ppm), when the channel is mostly empty we discourage forward routing (500ppm) but encourage backwards routing (inbound -16) and when it is almost empty we clearly totally discourage forward routing (1000ppm) but encourage backwards routing (inbound -64). And when someone just opened a channel with us, all liquidity is theirs so we aggressively encourage inbound routing by putting ultra high outbound fees and ultra inbound discounts. Simple, eh?Step 5: automatic fee management
As stated before, you can automate this using charge-lnd or lndg or Lightning Terminal if you use LND. If you use CLN you are probably limited to create a personalized script, because I don’t know of any similar tool for it, apart from CL-BOSS which is unmaintained and non-customizable.
You will run this configuration a maximum of once per hour, and a minimum of once per day. You should not try to run it more frequent than once per hour because of two reasons: 1. The channel states stored in the gossip take from some minutes to some hours to properly propagate. 2. Some nodes will ban you if you try to update more than once per hour. What I recommend is once every 2 hours for big nodes with more than 50 channels. If you have less than 50 channels, your gossip will be slow to propagate so run it once a day. If you get many “Insufficient Fee” errors is because you are trying to update channel states too frequently. Also, some people report that increasing the variable numgraphsyncpeers in the LND configuration file helps with better propagation, but be aware that this will increase bandwidth usage.
I’ve been using lndg for some time, but I switched to charge-lnd because it is clearly superior and faster and more customizable. Lndg is still great for rebalancing (which I use a lot) and as a general interface, but I have disabled the fee management, which I now do with charge-lnd. If you can’t access charge-lnd then just use lndg with the frequency chosen above, but be aware that the configuration parameters are very limited, as you will soon realize (you are limited to just one strategy which is proportional, and it is very slow as it changes the fee in incremental steps). Yet it is better using lndg than nothing.
Lightning Terminal from Lightning Labs I have not tested. So I can’t say anything about it.
But here is a good starting configuration for charge-lnd that you can customize to your preferences:
``` [default]
'default' is special, it is used if no other policy matches a channel
strategy = static base_fee_msat = 128 fee_ppm = 96 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 min_fee_ppm_delta=20
[mydefaults]
no strategy, so this only sets some defaults
base_fee_msat = 128 min_fee_ppm_delta = 0
[lost-onchain-sync]
The fact that lnd was not synchronized with the chain for more than 5 minutes
was an indicator of a severe problem in the past.
onchain.synced_to_chain = false base_fee_msat = 210_000 fee_ppm = 210_000
[expensive]
match channels where the peer node has set a high (>=8_000 ppm) fee rate
and set the same fee rate on our side (strategy=match_peer)
chan.min_fee_ppm = 8000 strategy = match_peer
[leafnode]
charge non-routing (private=true) peers a bit more for our service
chan.private = true strategy = static fee_ppm = 1000
[encourage-routing]
'autobalance' (lower fees so using outbound is more attractive)
chan.min_ratio = 0.98 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 strategy = static base_fee_msat = 64 fee_ppm = 16
[discourage-routing]
'autobalance' (higher fees so using outbound is less attractive)
chan.max_ratio = 0.2 chan.min_ratio = 0.05 strategy = proportional inbound_base_fee_msat = -64 inbound_fee_ppm = -16 min_fee_ppm = 32 max_fee_ppm = 700 base_fee_msat = 1_000
[all-liquidity-is-theirs] chan.max_ratio = 0.00 inbound_base_fee_msat = -128 inbound_fee_ppm = -128 strategy = static base_fee_msat = 1_000 fee_ppm = 1000
[discourage-routing-extreme] chan.max_ratio = 0.05 inbound_base_fee_msat = -128 inbound_fee_ppm = -32 strategy = proportional min_fee_ppm = 32 max_fee_ppm = 1000 base_fee_msat = 1_000
[proportional]
'proportional' can also be used to auto balance (lower fee rate when low remote balance & higher rate when higher remote balance)
fee_ppm decreases linearly with the channel balance ratio (min_fee_ppm when ratio is 1, max_fee_ppm when ratio is 0)
20% excess:
chan.min_ratio = 0.2 chan.max_ratio = 0.98 strategy = proportional min_fee_ppm = 32
20% excess, so for a max of 128, it’s calculated 128/(1-0.20)=160
max_fee_ppm = 160 inbound_base_fee_msat = 0 inbound_fee_ppm = 0 base_fee_msat = 128 min_fee_ppm_delta=16 ```
So you might run this config in a crontab or with your node distribution script if it is provided. I think Umbrel has this app in their portfolio, so just use it if you have Umbrel and ignore the following. If you run it manually or with a distro that doesn’t have charge-lnd, you can configure a crontab. This is just an example, please ask support for proper configuration on your distro. And if you distro do not include charge-lnd, ask support to include it, at this point it’s quite a necessity. Anyway here is the manual configuration: ``` $ crontab -e
0 */2 * * * echo "=======>"
date>> /home/nodo/charge-lnd/log && /home/nodo/charge-lnd/env/bin/charge-lnd -c /home/nodo/charge-lnd/my.config >> /home/nodo/charge-lnd/log ```That is supposing charge-lnd executable is installed under /home/nodo/charge-lnd/env/bin/charge-lnd and config is in /home/nodo/charge-lnd/my.config and LND is running without docker. If it is running under docker, you will have to ask support of your distro.
Step 6: help your peers
Remember that your peers are not only your competition, they are also your customers. So it is a strange symbiosis: you compete with them, but they also help you (and you help them).
If your peers are not well informed and have a bad maintained node, you are in a loss, because your channels with them will get stagnant and will not route. If they are well informed and know how to manage a node, then the channels will not be stagnant and they will route through you.
So it is stupid to keep this information as a secret. Every node operator should know it. And the more people know it, the better for everybody.
So, please, if you detect stagnant channels and bad maintained peers connected to you, just lead them to this guide, or guide them yourself. It’s a good idea to bookmark this guide so you have it prepared for the future.
And that’s it!! Happy routing!!
originally posted at https://stacker.news/items/972730
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 207ad2a0:e7cca7b0
2025-01-07 03:46:04
@ 207ad2a0:e7cca7b0
2025-01-07 03:46:04Quick context: I wanted to check out Nostr's longform posts and this blog post seemed like a good one to try and mirror. It's originally from my free to read/share attempt to write a novel, but this post here is completely standalone - just describing how I used AI image generation to make a small piece of the work.
Hold on, put your pitchforks down - outside of using Grammerly & Emacs for grammatical corrections - not a single character was generated or modified by computers; a non-insignificant portion of my first draft originating on pen & paper. No AI is ~~weird and crazy~~ imaginative enough to write like I do. The only successful AI contribution you'll find is a single image, the map, which I heavily edited. This post will go over how I generated and modified an image using AI, which I believe brought some value to the work, and cover a few quick thoughts about AI towards the end.
Let's be clear, I can't draw, but I wanted a map which I believed would improve the story I was working on. After getting abysmal results by prompting AI with text only I decided to use "Diffuse the Rest," a Stable Diffusion tool that allows you to provide a reference image + description to fine tune what you're looking for. I gave it this Microsoft Paint looking drawing:

and after a number of outputs, selected this one to work on:

The image is way better than the one I provided, but had I used it as is, I still feel it would have decreased the quality of my work instead of increasing it. After firing up Gimp I cropped out the top and bottom, expanded the ocean and separated the landmasses, then copied the top right corner of the large landmass to replace the bottom left that got cut off. Now we've got something that looks like concept art: not horrible, and gets the basic idea across, but it's still due for a lot more detail.

The next thing I did was add some texture to make it look more map like. I duplicated the layer in Gimp and applied the "Cartoon" filter to both for some texture. The top layer had a much lower effect strength to give it a more textured look, while the lower layer had a higher effect strength that looked a lot like mountains or other terrain features. Creating a layer mask allowed me to brush over spots to display the lower layer in certain areas, giving it some much needed features.

At this point I'd made it to where I felt it may improve the work instead of detracting from it - at least after labels and borders were added, but the colors seemed artificial and out of place. Luckily, however, this is when PhotoFunia could step in and apply a sketch effect to the image.

At this point I was pretty happy with how it was looking, it was close to what I envisioned and looked very visually appealing while still being a good way to portray information. All that was left was to make the white background transparent, add some minor details, and add the labels and borders. Below is the exact image I wound up using:

Overall, I'm very satisfied with how it turned out, and if you're working on a creative project, I'd recommend attempting something like this. It's not a central part of the work, but it improved the chapter a fair bit, and was doable despite lacking the talent and not intending to allocate a budget to my making of a free to read and share story.
The AI Generated Elephant in the Room
If you've read my non-fiction writing before, you'll know that I think AI will find its place around the skill floor as opposed to the skill ceiling. As you saw with my input, I have absolutely zero drawing talent, but with some elbow grease and an existing creative direction before and after generating an image I was able to get something well above what I could have otherwise accomplished. Outside of the lowest common denominators like stock photos for the sole purpose of a link preview being eye catching, however, I doubt AI will be wholesale replacing most creative works anytime soon. I can assure you that I tried numerous times to describe the map without providing a reference image, and if I used one of those outputs (or even just the unedited output after providing the reference image) it would have decreased the quality of my work instead of improving it.
I'm going to go out on a limb and expect that AI image, text, and video is all going to find its place in slop & generic content (such as AI generated slop replacing article spinners and stock photos respectively) and otherwise be used in a supporting role for various creative endeavors. For people working on projects like I'm working on (e.g. intended budget $0) it's helpful to have an AI capable of doing legwork - enabling projects to exist or be improved in ways they otherwise wouldn't have. I'm also guessing it'll find its way into more professional settings for grunt work - think a picture frame or fake TV show that would exist in the background of an animated project - likely a detail most people probably wouldn't notice, but that would save the creators time and money and/or allow them to focus more on the essential aspects of said work. Beyond that, as I've predicted before: I expect plenty of emails will be generated from a short list of bullet points, only to be summarized by the recipient's AI back into bullet points.
I will also make a prediction counter to what seems mainstream: AI is about to peak for a while. The start of AI image generation was with Google's DeepDream in 2015 - image recognition software that could be run in reverse to "recognize" patterns where there were none, effectively generating an image from digital noise or an unrelated image. While I'm not an expert by any means, I don't think we're too far off from that a decade later, just using very fine tuned tools that develop more coherent images. I guess that we're close to maxing out how efficiently we're able to generate images and video in that manner, and the hard caps on how much creative direction we can have when using AI - as well as the limits to how long we can keep it coherent (e.g. long videos or a chronologically consistent set of images) - will prevent AI from progressing too far beyond what it is currently unless/until another breakthrough occurs.
-
 @ 90c656ff:9383fd4e
2025-05-06 10:32:35
@ 90c656ff:9383fd4e
2025-05-06 10:32:35Bitcoin is a new form of digital money that offers financial freedom and access to a global economy without traditional intermediaries. To take full advantage of this technology, it's important to understand how to buy, store, and use it safely and efficiently. This guide covers the main steps and best practices to incorporate Bitcoin into your daily life, emphasizing how to protect your assets and get the most out of them.
Buying Bitcoin is the first step to participating in its decentralized network. There are several ways to acquire Bitcoin, depending on individual preferences and needs.
- Exchange Platforms:
01 - How it works: Exchanges are online platforms that allow users to buy Bitcoin using traditional currencies like dollars, euros, or reais. 02 - Process: Create an account, complete identity verification (KYC process), and deposit funds to start trading.
Tips: Choose reliable exchanges with strong security and good reputations.
- Bitcoin ATMs:
01 - How it works: Some ATMs allow users to buy Bitcoin with cash or credit cards. 02 - Use: Insert the desired amount, scan your digital wallet, and receive the Bitcoin immediately.
- Peer-to-Peer (P2P) Buying:
01 - How it works: P2P platforms connect buyers and sellers directly, allowing them to negotiate specific terms. 02 - Tips: Check the seller's reputation and use platforms that offer escrow services or transaction guarantees.
Security is crucial when handling Bitcoin. Proper storage protects your funds against loss, hacking, and unauthorized access.
- Digital Wallets:
01 - Definition: A digital wallet is software or a physical device that stores the private keys needed to access your Bitcoin.
Types of Wallets:
01 - Hot wallets: Connected to the internet; suitable for frequent use but more vulnerable to attacks (e.g., mobile apps and web wallets). 02 - Cold wallets: Keep Bitcoin offline; more secure for storing large amounts (e.g., hardware wallets and paper wallets).
- Hardware Wallets:
01 - How they work: Physical devices like Ledger or Trezor store your private keys offline. 02 - Advantages: High security against digital attacks and easy to transport.
- Paper Wallets:
01 - How they work: Involve printing or writing down your private keys on a piece of paper. 02 - Precautions: Store in a safe place, protected from moisture, fire, and unauthorized access.
- Backup and Recovery:
01 - Best practice: Regularly back up your wallet and store your recovery phrase (seed phrase) in a secure location. 02 - Warning: Never share your recovery phrase or private key with anyone.
Using Bitcoin goes beyond investment. It can be used for daily transactions, purchases, and transferring value efficiently.
- Transactions:
01 - How to send Bitcoin: Enter the recipient’s address, the amount to send, and confirm the transaction from your wallet. 02 - Fees: Transaction fees go to miners and may vary based on network demand.
- Purchasing Goods and Services:
01 - Merchants that accept Bitcoin: Many businesses, both physical and online, now accept Bitcoin. Look for the Bitcoin logo or consult updated lists of accepting merchants. 02 - How to pay: Scan the seller’s QR code and send the payment directly from your wallet.
International Transfers: Bitcoin enables fast global transfers, often with lower fees than banks or conventional remittance services.
Bill Payments: In some countries, it's already possible to pay for services and even taxes with Bitcoin, depending on local infrastructure.
- Tips for Using Bitcoin Safely:
01 - Choose trusted wallets and services: Only use well-known, reputable wallets and exchanges. 02 - Enable two-factor authentication (2FA): Activate 2FA to protect your accounts on exchanges and online services. 03 - Don’t leave funds on exchanges: After buying Bitcoin on an exchange, transfer your funds to a wallet you control to reduce the risk of loss from hacks. 04 - Educate yourself: Understanding the basics of Bitcoin and digital security is key to avoiding mistakes and fraud.
In summary, buying, storing, and using Bitcoin might seem complex at first, but it becomes simple and accessible with time. By following best security practices and learning the basics, anyone can benefit from this innovative technology.
Bitcoin is not just a financial option; it’s a powerful tool that supports economic freedom and access to a global economy. With the right knowledge, you can integrate Bitcoin into your life securely and effectively.
Thank you very much for reading this far. I hope everything is well with you, and sending a big hug from your favorite Bitcoiner maximalist from Madeira. Long live freedom!
-
 @ 40b9c85f:5e61b451
2025-04-24 15:27:02
@ 40b9c85f:5e61b451
2025-04-24 15:27:02Introduction
Data Vending Machines (DVMs) have emerged as a crucial component of the Nostr ecosystem, offering specialized computational services to clients across the network. As defined in NIP-90, DVMs operate on an apparently simple principle: "data in, data out." They provide a marketplace for data processing where users request specific jobs (like text translation, content recommendation, or AI text generation)
While DVMs have gained significant traction, the current specification faces challenges that hinder widespread adoption and consistent implementation. This article explores some ideas on how we can apply the reflection pattern, a well established approach in RPC systems, to address these challenges and improve the DVM ecosystem's clarity, consistency, and usability.
The Current State of DVMs: Challenges and Limitations
The NIP-90 specification provides a broad framework for DVMs, but this flexibility has led to several issues:
1. Inconsistent Implementation
As noted by hzrd149 in "DVMs were a mistake" every DVM implementation tends to expect inputs in slightly different formats, even while ostensibly following the same specification. For example, a translation request DVM might expect an event ID in one particular format, while an LLM service could expect a "prompt" input that's not even specified in NIP-90.
2. Fragmented Specifications
The DVM specification reserves a range of event kinds (5000-6000), each meant for different types of computational jobs. While creating sub-specifications for each job type is being explored as a possible solution for clarity, in a decentralized and permissionless landscape like Nostr, relying solely on specification enforcement won't be effective for creating a healthy ecosystem. A more comprehensible approach is needed that works with, rather than against, the open nature of the protocol.
3. Ambiguous API Interfaces
There's no standardized way for clients to discover what parameters a specific DVM accepts, which are required versus optional, or what output format to expect. This creates uncertainty and forces developers to rely on documentation outside the protocol itself, if such documentation exists at all.
The Reflection Pattern: A Solution from RPC Systems
The reflection pattern in RPC systems offers a compelling solution to many of these challenges. At its core, reflection enables servers to provide metadata about their available services, methods, and data types at runtime, allowing clients to dynamically discover and interact with the server's API.
In established RPC frameworks like gRPC, reflection serves as a self-describing mechanism where services expose their interface definitions and requirements. In MCP reflection is used to expose the capabilities of the server, such as tools, resources, and prompts. Clients can learn about available capabilities without prior knowledge, and systems can adapt to changes without requiring rebuilds or redeployments. This standardized introspection creates a unified way to query service metadata, making tools like
grpcurlpossible without requiring precompiled stubs.How Reflection Could Transform the DVM Specification
By incorporating reflection principles into the DVM specification, we could create a more coherent and predictable ecosystem. DVMs already implement some sort of reflection through the use of 'nip90params', which allow clients to discover some parameters, constraints, and features of the DVMs, such as whether they accept encryption, nutzaps, etc. However, this approach could be expanded to provide more comprehensive self-description capabilities.
1. Defined Lifecycle Phases
Similar to the Model Context Protocol (MCP), DVMs could benefit from a clear lifecycle consisting of an initialization phase and an operation phase. During initialization, the client and DVM would negotiate capabilities and exchange metadata, with the DVM providing a JSON schema containing its input requirements. nip-89 (or other) announcements can be used to bootstrap the discovery and negotiation process by providing the input schema directly. Then, during the operation phase, the client would interact with the DVM according to the negotiated schema and parameters.
2. Schema-Based Interactions
Rather than relying on rigid specifications for each job type, DVMs could self-advertise their schemas. This would allow clients to understand which parameters are required versus optional, what type validation should occur for inputs, what output formats to expect, and what payment flows are supported. By internalizing the input schema of the DVMs they wish to consume, clients gain clarity on how to interact effectively.
3. Capability Negotiation
Capability negotiation would enable DVMs to advertise their supported features, such as encryption methods, payment options, or specialized functionalities. This would allow clients to adjust their interaction approach based on the specific capabilities of each DVM they encounter.
Implementation Approach
While building DVMCP, I realized that the RPC reflection pattern used there could be beneficial for constructing DVMs in general. Since DVMs already follow an RPC style for their operation, and reflection is a natural extension of this approach, it could significantly enhance and clarify the DVM specification.
A reflection enhanced DVM protocol could work as follows: 1. Discovery: Clients discover DVMs through existing NIP-89 application handlers, input schemas could also be advertised in nip-89 announcements, making the second step unnecessary. 2. Schema Request: Clients request the DVM's input schema for the specific job type they're interested in 3. Validation: Clients validate their request against the provided schema before submission 4. Operation: The job proceeds through the standard NIP-90 flow, but with clearer expectations on both sides
Parallels with Other Protocols
This approach has proven successful in other contexts. The Model Context Protocol (MCP) implements a similar lifecycle with capability negotiation during initialization, allowing any client to communicate with any server as long as they adhere to the base protocol. MCP and DVM protocols share fundamental similarities, both aim to expose and consume computational resources through a JSON-RPC-like interface, albeit with specific differences.
gRPC's reflection service similarly allows clients to discover service definitions at runtime, enabling generic tools to work with any gRPC service without prior knowledge. In the REST API world, OpenAPI/Swagger specifications document interfaces in a way that makes them discoverable and testable.
DVMs would benefit from adopting these patterns while maintaining the decentralized, permissionless nature of Nostr.
Conclusion
I am not attempting to rewrite the DVM specification; rather, explore some ideas that could help the ecosystem improve incrementally, reducing fragmentation and making the ecosystem more comprehensible. By allowing DVMs to self describe their interfaces, we could maintain the flexibility that makes Nostr powerful while providing the structure needed for interoperability.
For developers building DVM clients or libraries, this approach would simplify consumption by providing clear expectations about inputs and outputs. For DVM operators, it would establish a standard way to communicate their service's requirements without relying on external documentation.
I am currently developing DVMCP following these patterns. Of course, DVMs and MCP servers have different details; MCP includes capabilities such as tools, resources, and prompts on the server side, as well as 'roots' and 'sampling' on the client side, creating a bidirectional way to consume capabilities. In contrast, DVMs typically function similarly to MCP tools, where you call a DVM with an input and receive an output, with each job type representing a different categorization of the work performed.
Without further ado, I hope this article has provided some insight into the potential benefits of applying the reflection pattern to the DVM specification.
-
 @ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13
@ 8cda1daa:e9e5bdd8
2025-04-24 10:20:13Bitcoin cracked the code for money. Now it's time to rebuild everything else.
What about identity, trust, and collaboration? What about the systems that define how we live, create, and connect?
Bitcoin gave us a blueprint to separate money from the state. But the state still owns most of your digital life. It's time for something more radical.
Welcome to the Atomic Economy - not just a technology stack, but a civil engineering project for the digital age. A complete re-architecture of society, from the individual outward.
The Problem: We Live in Digital Captivity
Let's be blunt: the modern internet is hostile to human freedom.
You don't own your identity. You don't control your data. You don't decide what you see.
Big Tech and state institutions dominate your digital life with one goal: control.
- Poisoned algorithms dictate your emotions and behavior.
- Censorship hides truth and silences dissent.
- Walled gardens lock you into systems you can't escape.
- Extractive platforms monetize your attention and creativity - without your consent.
This isn't innovation. It's digital colonization.
A Vision for Sovereign Society
The Atomic Economy proposes a new design for society - one where: - Individuals own their identity, data, and value. - Trust is contextual, not imposed. - Communities are voluntary, not manufactured by feeds. - Markets are free, not fenced. - Collaboration is peer-to-peer, not platform-mediated.
It's not a political revolution. It's a technological and social reset based on first principles: self-sovereignty, mutualism, and credible exit.
So, What Is the Atomic Economy?
The Atomic Economy is a decentralized digital society where people - not platforms - coordinate identity, trust, and value.
It's built on open protocols, real software, and the ethos of Bitcoin. It's not about abstraction - it's about architecture.
Core Principles: - Self-Sovereignty: Your keys. Your data. Your rules. - Mutual Consensus: Interactions are voluntary and trust-based. - Credible Exit: Leave any system, with your data and identity intact. - Programmable Trust: Trust is explicit, contextual, and revocable. - Circular Economies: Value flows directly between individuals - no middlemen.
The Tech Stack Behind the Vision
The Atomic Economy isn't just theory. It's a layered system with real tools:
1. Payments & Settlement
- Bitcoin & Lightning: The foundation - sound, censorship-resistant money.
- Paykit: Modular payments and settlement flows.
- Atomicity: A peer-to-peer mutual credit protocol for programmable trust and IOUs.
2. Discovery & Matching
- Pubky Core: Decentralized identity and discovery using PKARR and the DHT.
- Pubky Nexus: Indexing for a user-controlled internet.
- Semantic Social Graph: Discovery through social tagging - you are the algorithm.
3. Application Layer
- Bitkit: A self-custodial Bitcoin and Lightning wallet.
- Pubky App: Tag, publish, trade, and interact - on your terms.
- Blocktank: Liquidity services for Lightning and circular economies.
- Pubky Ring: Key-based access control and identity syncing.
These tools don't just integrate - they stack. You build trust, exchange value, and form communities with no centralized gatekeepers.
The Human Impact
This isn't about software. It's about freedom.
- Empowered Individuals: Control your own narrative, value, and destiny.
- Voluntary Communities: Build trust on shared values, not enforced norms.
- Economic Freedom: Trade without permission, borders, or middlemen.
- Creative Renaissance: Innovation and art flourish in open, censorship-resistant systems.
The Atomic Economy doesn't just fix the web. It frees the web.
Why Bitcoiners Should Care
If you believe in Bitcoin, you already believe in the Atomic Economy - you just haven't seen the full map yet.
- It extends Bitcoin's principles beyond money: into identity, trust, coordination.
- It defends freedom where Bitcoin leaves off: in content, community, and commerce.
- It offers a credible exit from every centralized system you still rely on.
- It's how we win - not just economically, but culturally and socially.
This isn't "web3." This isn't another layer of grift. It's the Bitcoin future - fully realized.
Join the Atomic Revolution
- If you're a builder: fork the code, remix the ideas, expand the protocols.
- If you're a user: adopt Bitkit, use Pubky, exit the digital plantation.
- If you're an advocate: share the vision. Help people imagine a free society again.
Bitcoin promised a revolution. The Atomic Economy delivers it.
Let's reclaim society, one key at a time.
Learn more and build with us at Synonym.to.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ e6817453:b0ac3c39
2025-01-05 14:29:17
@ e6817453:b0ac3c39
2025-01-05 14:29:17The Rise of Graph RAGs and the Quest for Data Quality
As we enter a new year, it’s impossible to ignore the boom of retrieval-augmented generation (RAG) systems, particularly those leveraging graph-based approaches. The previous year saw a surge in advancements and discussions about Graph RAGs, driven by their potential to enhance large language models (LLMs), reduce hallucinations, and deliver more reliable outputs. Let’s dive into the trends, challenges, and strategies for making the most of Graph RAGs in artificial intelligence.
Booming Interest in Graph RAGs
Graph RAGs have dominated the conversation in AI circles. With new research papers and innovations emerging weekly, it’s clear that this approach is reshaping the landscape. These systems, especially those developed by tech giants like Microsoft, demonstrate how graphs can:
- Enhance LLM Outputs: By grounding responses in structured knowledge, graphs significantly reduce hallucinations.
- Support Complex Queries: Graphs excel at managing linked and connected data, making them ideal for intricate problem-solving.
Conferences on linked and connected data have increasingly focused on Graph RAGs, underscoring their central role in modern AI systems. However, the excitement around this technology has brought critical questions to the forefront: How do we ensure the quality of the graphs we’re building, and are they genuinely aligned with our needs?
Data Quality: The Foundation of Effective Graphs
A high-quality graph is the backbone of any successful RAG system. Constructing these graphs from unstructured data requires attention to detail and rigorous processes. Here’s why:
- Richness of Entities: Effective retrieval depends on graphs populated with rich, detailed entities.
- Freedom from Hallucinations: Poorly constructed graphs amplify inaccuracies rather than mitigating them.
Without robust data quality, even the most sophisticated Graph RAGs become ineffective. As a result, the focus must shift to refining the graph construction process. Improving data strategy and ensuring meticulous data preparation is essential to unlock the full potential of Graph RAGs.
Hybrid Graph RAGs and Variations
While standard Graph RAGs are already transformative, hybrid models offer additional flexibility and power. Hybrid RAGs combine structured graph data with other retrieval mechanisms, creating systems that:
- Handle diverse data sources with ease.
- Offer improved adaptability to complex queries.
Exploring these variations can open new avenues for AI systems, particularly in domains requiring structured and unstructured data processing.
Ontology: The Key to Graph Construction Quality
Ontology — defining how concepts relate within a knowledge domain — is critical for building effective graphs. While this might sound abstract, it’s a well-established field blending philosophy, engineering, and art. Ontology engineering provides the framework for:
- Defining Relationships: Clarifying how concepts connect within a domain.
- Validating Graph Structures: Ensuring constructed graphs are logically sound and align with domain-specific realities.
Traditionally, ontologists — experts in this discipline — have been integral to large enterprises and research teams. However, not every team has access to dedicated ontologists, leading to a significant challenge: How can teams without such expertise ensure the quality of their graphs?
How to Build Ontology Expertise in a Startup Team
For startups and smaller teams, developing ontology expertise may seem daunting, but it is achievable with the right approach:
- Assign a Knowledge Champion: Identify a team member with a strong analytical mindset and give them time and resources to learn ontology engineering.
- Provide Training: Invest in courses, workshops, or certifications in knowledge graph and ontology creation.
- Leverage Partnerships: Collaborate with academic institutions, domain experts, or consultants to build initial frameworks.
- Utilize Tools: Introduce ontology development tools like Protégé, OWL, or SHACL to simplify the creation and validation process.
- Iterate with Feedback: Continuously refine ontologies through collaboration with domain experts and iterative testing.
So, it is not always affordable for a startup to have a dedicated oncologist or knowledge engineer in a team, but you could involve consulters or build barefoot experts.
You could read about barefoot experts in my article :
Even startups can achieve robust and domain-specific ontology frameworks by fostering in-house expertise.
How to Find or Create Ontologies
For teams venturing into Graph RAGs, several strategies can help address the ontology gap:
-
Leverage Existing Ontologies: Many industries and domains already have open ontologies. For instance:
-
Public Knowledge Graphs: Resources like Wikipedia’s graph offer a wealth of structured knowledge.
- Industry Standards: Enterprises such as Siemens have invested in creating and sharing ontologies specific to their fields.
-
Business Framework Ontology (BFO): A valuable resource for enterprises looking to define business processes and structures.
-
Build In-House Expertise: If budgets allow, consider hiring knowledge engineers or providing team members with the resources and time to develop expertise in ontology creation.
-
Utilize LLMs for Ontology Construction: Interestingly, LLMs themselves can act as a starting point for ontology development:
-
Prompt-Based Extraction: LLMs can generate draft ontologies by leveraging their extensive training on graph data.
- Domain Expert Refinement: Combine LLM-generated structures with insights from domain experts to create tailored ontologies.
Parallel Ontology and Graph Extraction
An emerging approach involves extracting ontologies and graphs in parallel. While this can streamline the process, it presents challenges such as:
- Detecting Hallucinations: Differentiating between genuine insights and AI-generated inaccuracies.
- Ensuring Completeness: Ensuring no critical concepts are overlooked during extraction.
Teams must carefully validate outputs to ensure reliability and accuracy when employing this parallel method.
LLMs as Ontologists
While traditionally dependent on human expertise, ontology creation is increasingly supported by LLMs. These models, trained on vast amounts of data, possess inherent knowledge of many open ontologies and taxonomies. Teams can use LLMs to:
- Generate Skeleton Ontologies: Prompt LLMs with domain-specific information to draft initial ontology structures.
- Validate and Refine Ontologies: Collaborate with domain experts to refine these drafts, ensuring accuracy and relevance.
However, for validation and graph construction, formal tools such as OWL, SHACL, and RDF should be prioritized over LLMs to minimize hallucinations and ensure robust outcomes.
Final Thoughts: Unlocking the Power of Graph RAGs
The rise of Graph RAGs underscores a simple but crucial correlation: improving graph construction and data quality directly enhances retrieval systems. To truly harness this power, teams must invest in understanding ontologies, building quality graphs, and leveraging both human expertise and advanced AI tools.
As we move forward, the interplay between Graph RAGs and ontology engineering will continue to shape the future of AI. Whether through adopting existing frameworks or exploring innovative uses of LLMs, the path to success lies in a deep commitment to data quality and domain understanding.
Have you explored these technologies in your work? Share your experiences and insights — and stay tuned for more discussions on ontology extraction and its role in AI advancements. Cheers to a year of innovation!
-
 @ 2e8970de:63345c7a
2025-05-06 15:13:49
@ 2e8970de:63345c7a
2025-05-06 15:13:49https://www.epi.org/blog/wage-growth-since-1979-has-not-been-stagnant-but-it-has-definitely-been-suppressed/
originally posted at https://stacker.news/items/972959
-
 @ a4a6b584:1e05b95b
2025-01-02 18:13:31
@ a4a6b584:1e05b95b
2025-01-02 18:13:31The Four-Layer Framework
Layer 1: Zoom Out

Start by looking at the big picture. What’s the subject about, and why does it matter? Focus on the overarching ideas and how they fit together. Think of this as the 30,000-foot view—it’s about understanding the "why" and "how" before diving into the "what."
Example: If you’re learning programming, start by understanding that it’s about giving logical instructions to computers to solve problems.
- Tip: Keep it simple. Summarize the subject in one or two sentences and avoid getting bogged down in specifics at this stage.
Once you have the big picture in mind, it’s time to start breaking it down.
Layer 2: Categorize and Connect

Now it’s time to break the subject into categories—like creating branches on a tree. This helps your brain organize information logically and see connections between ideas.
Example: Studying biology? Group concepts into categories like cells, genetics, and ecosystems.
- Tip: Use headings or labels to group similar ideas. Jot these down in a list or simple diagram to keep track.
With your categories in place, you’re ready to dive into the details that bring them to life.
Layer 3: Master the Details

Once you’ve mapped out the main categories, you’re ready to dive deeper. This is where you learn the nuts and bolts—like formulas, specific techniques, or key terminology. These details make the subject practical and actionable.
Example: In programming, this might mean learning the syntax for loops, conditionals, or functions in your chosen language.
- Tip: Focus on details that clarify the categories from Layer 2. Skip anything that doesn’t add to your understanding.
Now that you’ve mastered the essentials, you can expand your knowledge to include extra material.
Layer 4: Expand Your Horizons

Finally, move on to the extra material—less critical facts, trivia, or edge cases. While these aren’t essential to mastering the subject, they can be useful in specialized discussions or exams.
Example: Learn about rare programming quirks or historical trivia about a language’s development.
- Tip: Spend minimal time here unless it’s necessary for your goals. It’s okay to skim if you’re short on time.
Pro Tips for Better Learning
1. Use Active Recall and Spaced Repetition
Test yourself without looking at notes. Review what you’ve learned at increasing intervals—like after a day, a week, and a month. This strengthens memory by forcing your brain to actively retrieve information.
2. Map It Out
Create visual aids like diagrams or concept maps to clarify relationships between ideas. These are particularly helpful for organizing categories in Layer 2.
3. Teach What You Learn
Explain the subject to someone else as if they’re hearing it for the first time. Teaching exposes any gaps in your understanding and helps reinforce the material.
4. Engage with LLMs and Discuss Concepts
Take advantage of tools like ChatGPT or similar large language models to explore your topic in greater depth. Use these tools to:
- Ask specific questions to clarify confusing points.
- Engage in discussions to simulate real-world applications of the subject.
- Generate examples or analogies that deepen your understanding.Tip: Use LLMs as a study partner, but don’t rely solely on them. Combine these insights with your own critical thinking to develop a well-rounded perspective.
Get Started
Ready to try the Four-Layer Method? Take 15 minutes today to map out the big picture of a topic you’re curious about—what’s it all about, and why does it matter? By building your understanding step by step, you’ll master the subject with less stress and more confidence.
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ 80a6a657:536a97e2
2025-05-06 10:00:48
@ 80a6a657:536a97e2
2025-05-06 10:00:48
The dawn of Bitcoin ushered in a transformative mission: empowering individuals and dismantling centralized power structures that erode personal freedoms. As the world’s first decentralized currency, Bitcoin offers an alternative financial system—one that transcends borders, government control, and corporate interests.
But this mission isn’t just about money. It’s about freedom. It’s about self-sovereignty. And most importantly, it’s a rallying cry for vigilance in an ongoing struggle for the liberation of humanity from systemic oppression. Who better to lead this critical mission than those who have already dedicated their lives to serving and protecting freedom: Veterans.
Freedom: A Lifelong Fight Freedom is neither freely given nor guaranteed—it is earned and fiercely preserved. Veterans understand this intimately. They have endured sacrifice, hardship, and battle in their service to protect the liberties we often take for granted. And today, freedom faces threats from a new frontier: financial manipulation, surveillance, and the centralization of power.
Governments across the globe continue to devalue currencies through inflation, tighten financial surveillance by controlling banking systems, and stifle individual autonomy. These issues underscore the need for a sound financial alternative, one that aligns with the ideals veterans have sworn to uphold. The solution? Bitcoin.
Bitcoin represents the antithesis of centralized control. It is censorship-resistant, immune to monetary debasement, and built upon a trustless, transparent system. It is not merely a currency; it is a tool for human liberation.
Vigilance in Bitcoin Adoption While Bitcoin adoption grows, the journey is far from complete. The powerful status quo—central banks, governments, and financial elites—does not take threats to its systems lightly. These entities work tirelessly to misinform, regulate, and marginalize Bitcoin. This makes sustained vigilance in promoting Bitcoin adoption not just important, but essential.
The failure to remain vigilant could see Bitcoin’s potential diminished through undue regulation, controlled implementation (such as CBDCs—Central Bank Digital Currencies), or a failure to educate people about its benefits. Complacency would mean ceding victory to oppressive systems the world over.
This is why Bitcoin adoption isn’t solely a technological phenomenon—it is an ideological mission. To resist control, to safeguard freedom, and to empower individuals to thrive under self-sovereignty requires the active participation of people across all sectors of society.
Why Veterans Are Uniquely Positioned to Lead Veterans are inherently equipped to lead the charge in the fight for Bitcoin adoption and the broader battle for freedom. Their unique skillsets, shaped by discipline, adaptability, and leadership under pressure, are perfectly suited to this challenge. Here’s why veterans play a pivotal role in this movement: 1. Leadership and Vision: Veterans are natural leaders. They can galvanize communities toward a vision of financial independence, self-sovereignty, and empowerment through Bitcoin. Their experience coordinating efforts—whether on the battlefield or in humanitarian missions—allows them to efficiently communicate the importance of Bitcoin adoption. 2. Commitment to Freedom: The fight for Bitcoin adoption is deeply aligned with the ethos of service members: defending freedom at all costs. Veterans understand that true freedom cannot persist without vigilance, sacrifice, and a commitment to challenging oppressive systems. 3. Trust and Credibility: The military often fosters a level of trust and camaraderie among people. Veterans, therefore, have the clout to introduce Bitcoin to communities that may otherwise view it with skepticism. Their credibility as protectors of freedom gives them an edge in delivering Bitcoin’s message of liberation. 4. Adaptability in Uncertain Environments: Just as they’ve thrived in complex and chaotic environments, veterans are poised to navigate the evolving financial landscape. Bitcoin is still maturing and faces regulatory challenges, technological hurdles, and cultural misunderstandings. Veterans excel at adapting to change and finding solutions in challenging circumstances. 5. Mission-Driven Mindset: Every mission has an objective, and every objective demands clear focus. Veterans approach tasks methodically and with a commitment to success—the same mindset required to bridge the gap between Bitcoin skepticism and widespread adoption.
The Call to Action Veterans, the mission isn’t over. Humanity stands at a crossroads, and freedom is at stake. Bitcoin is not just a disruptive technology; it’s the torchbearer of liberty in a world increasingly dominated by centralized control. It’s time to take the skills, discipline, and passion forged in your service and channel them into this new fight: the fight for financial freedom and independence from a centralized system that has dominated the lives of billions of people for far too long.
Educate yourself about Bitcoin. Learn its nuances, its strengths, and its use cases. Share this knowledge with your communities, help dismantle misconceptions, and shine a light on the real promise of self-sovereignty. Become an anchor of leadership in this decentralized revolution.
For civilians: do not underestimate the importance of this mission. Every individual who adopts Bitcoin drives us one step closer to a world where personal freedom and economic empowerment are accessible to all. Join arms with veterans, thought leaders, and Bitcoin adopters to ensure the torch of liberty burns brightly.
Closing Thoughts Bitcoin is more than a financial revolution—it’s a movement for freedom. Veterans have long stood on the frontline for this cause, and today, they have an opportunity to champion it in a new way. With vigilance, resolve, and determination, humanity can achieve greater levels of freedom. But, as with all efforts to secure liberty, we must remain constantly committed to the mission. Remember: freedom demands eternal vigilance. So does Bitcoin.
Will you answer the call? Together, we can reshape the future as champions of sovereignty and bring the world closer to the ideals we all deserve.
OPERATION BITCOIN is a 501(c)(3) nonprofit on a mission to connect military veterans with Bitcoin.
You can directly support this mission by sharing our publication with a veteran today, zapping this article or donating at www.operationbitcoin.io
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ffbcb706:b0574044
2025-05-06 09:29:41
@ ffbcb706:b0574044
2025-05-06 09:29:41Markdown test italic bold in openletter Nostr https://openletter.earth/ Have a great day
-
 @ 6e64b83c:94102ee8
2025-04-23 20:23:34
@ 6e64b83c:94102ee8
2025-04-23 20:23:34How to Run Your Own Nostr Relay on Android with Cloudflare Domain
Prerequisites
- Install Citrine on your Android device:
- Visit https://github.com/greenart7c3/Citrine/releases
- Download the latest release using:
- zap.store
- Obtainium
- F-Droid
- Or download the APK directly
-
Note: You may need to enable "Install from Unknown Sources" in your Android settings
-
Domain Requirements:
- Purchase a domain if you don't have one
-
Transfer your domain to Cloudflare if it's not already there (for free SSL certificates and cloudflared support)
-
Tools to use:
- nak (the nostr army knife):
- Download from https://github.com/fiatjaf/nak/releases
- Installation steps:
-
For Linux/macOS: ```bash # Download the appropriate version for your system wget https://github.com/fiatjaf/nak/releases/latest/download/nak-linux-amd64 # for Linux # or wget https://github.com/fiatjaf/nak/releases/latest/download/nak-darwin-amd64 # for macOS
# Make it executable chmod +x nak-*
# Move to a directory in your PATH sudo mv nak-* /usr/local/bin/nak
- For Windows:batch # Download the Windows version curl -L -o nak.exe https://github.com/fiatjaf/nak/releases/latest/download/nak-windows-amd64.exe# Move to a directory in your PATH (e.g., C:\Windows) move nak.exe C:\Windows\nak.exe
- Verify installation:bash nak --version ```
Setting Up Citrine
- Open the Citrine app
- Start the server
- You'll see it running on
ws://127.0.0.1:4869(local network only) - Go to settings and paste your npub into "Accept events signed by" inbox and press the + button. This prevents others from publishing events to your personal relay.
Installing Required Tools
- Install Termux from Google Play Store
- Open Termux and run:
bash pkg update && pkg install wget wget https://github.com/cloudflare/cloudflared/releases/latest/download/cloudflared-linux-arm64.deb dpkg -i cloudflared-linux-arm64.debCloudflare Authentication
- Run the authentication command:
bash cloudflared tunnel login - Follow the instructions:
- Copy the provided URL to your browser
- Log in to your Cloudflare account
- If the URL expires, copy it again after logging in
Creating the Tunnel
- Create a new tunnel:
bash cloudflared tunnel create <TUNNEL_NAME> - Choose any name you prefer for your tunnel
-
Copy the tunnel ID after creating the tunnel
-
Create and configure the tunnel config:
bash touch ~/.cloudflared/config.yml nano ~/.cloudflared/config.yml -
Add this configuration (replace the placeholders with your values): ```yaml tunnel:
credentials-file: /data/data/com.termux/files/home/.cloudflared/ .json ingress: - hostname: nostr.yourdomain.com service: ws://localhost:4869
- service: http_status:404 ```
- Note: In nano editor:
CTRL+Oand Enter to saveCTRL+Xto exit
-
Note: Check the credentials file path in the logs
-
Validate your configuration:
bash cloudflared tunnel validate -
Start the tunnel:
bash cloudflared tunnel run my-relay
Preventing Android from Killing the Tunnel
Run these commands to maintain tunnel stability:
bash date && apt install termux-tools && termux-setup-storage && termux-wake-lock echo "nameserver 1.1.1.1" > $PREFIX/etc/resolv.confTip: You can open multiple Termux sessions by swiping from the left edge of the screen while keeping your tunnel process running.
Updating Your Outbox Model Relays
Once your relay is running and accessible via your domain, you'll want to update your relay list in the Nostr network. This ensures other clients know about your relay and can connect to it.
Decoding npub (Public Key)
Private keys (nsec) and public keys (npub) are encoded in bech32 format, which includes: - A prefix (like nsec1, npub1 etc.) - The encoded data - A checksum
This format makes keys: - Easy to distinguish - Hard to copy incorrectly
However, most tools require these keys in hexadecimal (hex) format.
To decode an npub string to its hex format:
bash nak decode nostr:npub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4Change it with your own npub.
bash { "pubkey": "6e64b83c1f674fb00a5f19816c297b6414bf67f015894e04dd4c657e94102ee8" }Copy the pubkey value in quotes.
Create a kind 10002 event with your relay list:
- Include your new relay with write permissions
- Include other relays you want to read from and write to, omit 3rd parameter to make it both read and write
Example format:
json { "kind": 10002, "tags": [ ["r", "wss://your-relay-domain.com", "write"], ["r", "wss://eden.nostr.land/"], ["r", "wss://nos.lol/"], ["r", "wss://nostr.bitcoiner.social/"], ["r", "wss://nostr.mom/"], ["r", "wss://relay.primal.net/"], ["r", "wss://nostr.wine/", "read"], ["r", "wss://relay.damus.io/"], ["r", "wss://relay.nostr.band/"], ["r", "wss://relay.snort.social/"] ], "content": "" }Save it to a file called
event.jsonNote: Add or remove any relays you want. To check your existing 10002 relays: - Visit https://nostr.band/?q=by%3Anpub1dejts0qlva8mqzjlrxqkc2tmvs2t7elszky5upxaf3jha9qs9m5q605uc4+++kind%3A10002 - nostr.band is an indexing service, it probably has your relay list. - Replace
npub1xxxin the URL with your own npub - Click "VIEW JSON" from the menu to see the raw event - Or use thenaktool if you know the relaysbash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.comReplace `<your-pubkey>` with your public key in hex format (you can get it using `nak decode <your-npub>`)- Sign and publish the event:
- Use a Nostr client that supports kind 10002 events
- Or use the
nakcommand-line tool:bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)
Important Security Notes: 1. Never share your nsec (private key) with anyone 2. Consider using NIP-49 encrypted keys for better security 3. Never paste your nsec or private key into the terminal. The command will be saved in your shell history, exposing your private key. To clear the command history: - For bash: use
history -c- For zsh: usefc -Wto write history to file, thenfc -pto read it back - Or manually edit your shell history file (e.g.,~/.zsh_historyor~/.bash_history) 4. if you're usingzsh, usefc -pto prevent the next command from being saved to history 5. Or temporarily disable history before running sensitive commands:bash unset HISTFILE nak key encrypt ... set HISTFILEHow to securely create NIP-49 encypted private key
```bash
Read your private key (input will be hidden)
read -s SECRET
Read your password (input will be hidden)
read -s PASSWORD
encrypt command
echo "$SECRET" | nak key encrypt "$PASSWORD"
copy and paste the ncryptsec1 text from the output
read -s ENCRYPTED nak key decrypt "$ENCRYPTED"
clear variables from memory
unset SECRET PASSWORD ENCRYPTED ```
On a Windows command line, to read from stdin and use the variables in
nakcommands, you can use a combination ofset /pto read input and then use those variables in your command. Here's an example:```bash @echo off set /p "SECRET=Enter your secret key: " set /p "PASSWORD=Enter your password: "
echo %SECRET%| nak key encrypt %PASSWORD%
:: Clear the sensitive variables set "SECRET=" set "PASSWORD=" ```
If your key starts with
ncryptsec1, thenaktool will securely prompt you for a password when using the--secparameter, unless the command is used with a pipe< >or|.bash nak event --sec ncryptsec1... wss://relay1.com wss://relay2.com $(cat event.json)- Verify the event was published:
- Check if your relay list is visible on other relays
-
Use the
naktool to fetch your kind 10002 events:bash nak req -k 10002 -a <your-pubkey> wss://relay1.com wss://relay2.com -
Testing your relay:
- Try connecting to your relay using different Nostr clients
- Verify you can both read from and write to your relay
- Check if events are being properly stored and retrieved
- Tip: Use multiple Nostr clients to test different aspects of your relay
Note: If anyone in the community has a more efficient method of doing things like updating outbox relays, please share your insights in the comments. Your expertise would be greatly appreciated!
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ e83b66a8:b0526c2b
2025-05-06 09:17:39
@ e83b66a8:b0526c2b
2025-05-06 09:17:39I’m going to talk about Ethereum, hear me out.
Ethereum is a Turing complete consensus blockchain tokenised by its own currency Ether.
This idea by Vitalik Buterin was incredibly compelling and still is today, even though few real world use cases have emerged.
For example, as a company, I could pay a carbon tax in Ether, locked into a smart contract. If the temperate rises by more than “n” degrees year on year based on a known agreed external (blind) oracle, say a weather station located near my factory.
Fantastic, we now have an automatic climate tax.
In reality, few realistic applications exist, however the idea is very compelling and many flocked to Ethereum as a promise of the future. This inflated its utility token “Ether” into stratospherically high prices.
This, in turn, attracted speculative investors and traders only looking at the price signal of the token and no longer considering the utility. This created a bubble which has gradually deflated over time.
This is why we are seeing Bitcoin, which only attempts to be money, succeed relative to Ethereum.
As Ethereum fails, and Bitcoin development strides on, an opportunity arises to try to do what Ethereum and all the other related altcoins have so far failed to do. Computational utility. And to do this on Bitcoin, the most successful “Crypto”.
The first unintended hijack of Ethereums utility are the JPEGs we are seeing on our blockchain.
This latest drive to make Bitcoin Turing complete is potentially the final destination for developers keen to explore the potential of Bitcoins eco-system.
Perhaps Bitcoin is going to absorb all the altcoins. Perhaps that is the goal of Bitcoins developers.
I don’t comment whether this is good or bad, I’m just exploring whether this may be the agenda.
-
 @ fe32298e:20516265
2024-12-16 20:59:13
@ fe32298e:20516265
2024-12-16 20:59:13Today I learned how to install NVapi to monitor my GPUs in Home Assistant.

NVApi is a lightweight API designed for monitoring NVIDIA GPU utilization and enabling automated power management. It provides real-time GPU metrics, supports integration with tools like Home Assistant, and offers flexible power management and PCIe link speed management based on workload and thermal conditions.
- GPU Utilization Monitoring: Utilization, memory usage, temperature, fan speed, and power consumption.
- Automated Power Limiting: Adjusts power limits dynamically based on temperature thresholds and total power caps, configurable per GPU or globally.
- Cross-GPU Coordination: Total power budget applies across multiple GPUs in the same system.
- PCIe Link Speed Management: Controls minimum and maximum PCIe link speeds with idle thresholds for power optimization.
- Home Assistant Integration: Uses the built-in RESTful platform and template sensors.
Getting the Data
sudo apt install golang-go git clone https://github.com/sammcj/NVApi.git cd NVapi go run main.go -port 9999 -rate 1 curl http://localhost:9999/gpuResponse for a single GPU:
[ { "index": 0, "name": "NVIDIA GeForce RTX 4090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 16, "power_limit_watts": 450, "memory_total_gb": 23.99, "memory_used_gb": 0.46, "memory_free_gb": 23.52, "memory_usage_percent": 2, "temperature": 38, "processes": [], "pcie_link_state": "not managed" } ]Response for multiple GPUs:
[ { "index": 0, "name": "NVIDIA GeForce RTX 3090", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 14, "power_limit_watts": 350, "memory_total_gb": 24, "memory_used_gb": 0.43, "memory_free_gb": 23.57, "memory_usage_percent": 2, "temperature": 36, "processes": [], "pcie_link_state": "not managed" }, { "index": 1, "name": "NVIDIA RTX A4000", "gpu_utilisation": 0, "memory_utilisation": 0, "power_watts": 10, "power_limit_watts": 140, "memory_total_gb": 15.99, "memory_used_gb": 0.56, "memory_free_gb": 15.43, "memory_usage_percent": 3, "temperature": 41, "processes": [], "pcie_link_state": "not managed" } ]Start at Boot
Create
/etc/systemd/system/nvapi.service:``` [Unit] Description=Run NVapi After=network.target
[Service] Type=simple Environment="GOPATH=/home/ansible/go" WorkingDirectory=/home/ansible/NVapi ExecStart=/usr/bin/go run main.go -port 9999 -rate 1 Restart=always User=ansible
Environment="GPU_TEMP_CHECK_INTERVAL=5"
Environment="GPU_TOTAL_POWER_CAP=400"
Environment="GPU_0_LOW_TEMP=40"
Environment="GPU_0_MEDIUM_TEMP=70"
Environment="GPU_0_LOW_TEMP_LIMIT=135"
Environment="GPU_0_MEDIUM_TEMP_LIMIT=120"
Environment="GPU_0_HIGH_TEMP_LIMIT=100"
Environment="GPU_1_LOW_TEMP=45"
Environment="GPU_1_MEDIUM_TEMP=75"
Environment="GPU_1_LOW_TEMP_LIMIT=140"
Environment="GPU_1_MEDIUM_TEMP_LIMIT=125"
Environment="GPU_1_HIGH_TEMP_LIMIT=110"
[Install] WantedBy=multi-user.target ```
Home Assistant
Add to Home Assistant
configuration.yamland restart HA (completely).For a single GPU, this works: ``` sensor: - platform: rest name: MYPC GPU Information resource: http://mypc:9999 method: GET headers: Content-Type: application/json value_template: "{{ value_json[0].index }}" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature scan_interval: 1 # seconds
- platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} GPU" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Memory" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC {{ state_attr('sensor.mypc_gpu_information', 'name') }} Temperature" value_template: "{{ state_attr('sensor.mypc_gpu_information', 'temperature') }}" unit_of_measurement: "°C" ```
For multiple GPUs: ``` rest: scan_interval: 1 resource: http://mypc:9999 sensor: - name: "MYPC GPU0 Information" value_template: "{{ value_json[0].index }}" json_attributes_path: "$.0" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature - name: "MYPC GPU1 Information" value_template: "{{ value_json[1].index }}" json_attributes_path: "$.1" json_attributes: - name - gpu_utilisation - memory_utilisation - power_watts - power_limit_watts - memory_total_gb - memory_used_gb - memory_free_gb - memory_usage_percent - temperature
-
platform: template sensors: mypc_gpu_0_gpu: friendly_name: "MYPC GPU0 GPU" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_memory: friendly_name: "MYPC GPU0 Memory" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_0_power: friendly_name: "MYPC GPU0 Power" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_0_power_limit: friendly_name: "MYPC GPU0 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_0_temperature: friendly_name: "MYPC GPU0 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu0_information', 'temperature') }}" unit_of_measurement: "C"
-
platform: template sensors: mypc_gpu_1_gpu: friendly_name: "MYPC GPU1 GPU" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'gpu_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_memory: friendly_name: "MYPC GPU1 Memory" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'memory_utilisation') }}" unit_of_measurement: "%" mypc_gpu_1_power: friendly_name: "MYPC GPU1 Power" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_watts') }}" unit_of_measurement: "W" mypc_gpu_1_power_limit: friendly_name: "MYPC GPU1 Power Limit" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'power_limit_watts') }}" unit_of_measurement: "W" mypc_gpu_1_temperature: friendly_name: "MYPC GPU1 Temperature" value_template: "{{ state_attr('sensor.mypc_gpu1_information', 'temperature') }}" unit_of_measurement: "C"
```
Basic entity card:
type: entities entities: - entity: sensor.mypc_gpu_0_gpu secondary_info: last-updated - entity: sensor.mypc_gpu_0_memory secondary_info: last-updated - entity: sensor.mypc_gpu_0_power secondary_info: last-updated - entity: sensor.mypc_gpu_0_power_limit secondary_info: last-updated - entity: sensor.mypc_gpu_0_temperature secondary_info: last-updatedAnsible Role
```
-
name: install go become: true package: name: golang-go state: present
-
name: git clone git: repo: "https://github.com/sammcj/NVApi.git" dest: "/home/ansible/NVapi" update: yes force: true
go run main.go -port 9999 -rate 1
-
name: install systemd service become: true copy: src: nvapi.service dest: /etc/systemd/system/nvapi.service
-
name: Reload systemd daemons, enable, and restart nvapi become: true systemd: name: nvapi daemon_reload: yes enabled: yes state: restarted ```
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 5188521b:008eb518
2025-05-06 08:09:37
@ 5188521b:008eb518
2025-05-06 08:09:37Macaron returns, fluffs his white linen napkin, and takes his seat at their table, “Thank you, John, for extending my French people such great mercy as to be allowed to transact freely on the Bitcoin blockchain.” He extends his arm out towards a waiter, “Monsieur? Champagne for the three of us please!”
Vrrrm! “I can’t believe we were able to find an American Mustang in this French countryside. I am ripping down these narrow roads!” John celebrates.
“Bloody hell, slow down!” Lily begs as her oversized diamond dangle earrings sway side to side. “You’ve got nothing to prove, John. Big man in your yankee ten-gallon hat. Let’s just get there safely.”
John slows to give her a smoldering look, “Aww, my sweet British compatriot, you care about me!”
“Bollocks! I care about not dying!” Lily retorts. “Now focus on the mission. We need to save a boatload of English border collies — literally. Frenchman Macaron wants to groom them into French poodles!”
John wags a finger off the wheel to reply in his Southern drawl, “However, my sweet Lily flower, my US Hash Force intends to project power to coerce the French for the dogs’ release!”
Lily bats his finger away, “Yes, but may I remind you, my arrogant wanker, geographically challenged friend, MI6’s intel says to steadily power on any miners as His Majesty’s Hash Force may do. The border collies’ barge will take about an hour to flee France, cross the English channel, and safely reach our shores so we don’t want to burst their souffle too quickly. Oh, and the barge is armed with explosives controlled by a remote detonator. When Macaron asks for his bitcoin ransom payment in exchange for the dogs’ release, how do you cowboys plan to help from across the pond?”
John takes both hands off the wheel to flex his biceps, “Shock and awe, Lily. Full Throttle! We’re not giving the French a single sat. Instead, we’re diverting maximum energy to the U.S. Hash Force, of course!”
Lily guffaws, “And where is this sudden surge of readily available power supposed to come from undetected?”
“No need to worry my English crumpet! Our back of the envelope calculations suggest that, with a little help from the Texas of the North, there’s enough flared natural gas in the U.S. to run the entire Bitcoin network!” John proudly replies.
Lily’s jaw drops, “So miners have already stealthily built out the infrastructure to capture wasted natural gas flares for the benefit of the U.S. government, but are waiting to turn them on until commanded to by the U.S. Hash Force?!”
“Yup! As soon as Macaron sees our hash power come online, we’re going to try to start mining blocks on the Bitcoin network to Denial of Service (DOS) attack any UTXOs with a known history of French transactions.”
“A DOS attack, for peace?” Lily asks skeptically.
“Peace through strength, baby! If you don’t comply with America’s dog rights standards, you get censored. America saves British dogs again, and without a single shot fired!”
“Not fair! It’s only because our MI6 chainanalysis intel knows which Bitcoin addresses to censor on the blockchain we suspect belong to Macaron and his government that this plan even has a shot at succeeding. You’re lucky Macaron is even more self-assured than you Americans. That’s the only reason France doesn’t have a Hash Force of its own to project power back!”
John pulls the Mustang up to the front of the fancy French restaurant, Chandelier. Lily grabs her green purse that matches her elegant emerald ball gown, and they head inside to meet Macaron.
John and Lily spot Macaron sitting alone at the white linen table closest to the dance floor. He’s tapping his Louis Vuitton snake leather shoes, checking his Chanel watch, and fluffing his floofy black French Hermès beret. The red French ascot spilling out of his black and white blouse looks ridiculous.
John lets out a big sigh, and Macaron stands with open arms, “Lily, John, welcome to France!” Before John can flinch away, Macaron kisses him on both cheeks. He lifts up Lily’s hand for a kiss, “Mademoiselle.”
John raises his hand, “Waiter! I’ll take a bourbon, neat. And make it a double!” John calls out.
Slap!
“Hey, what was that for, Frenchie?” John asks as he rubs his face.
“Rude American, where are your manners?” Macaron asks as he pulls out a hidden red detonator clipped in the folds of his ascot. “Don’t drive me to prematurely push this button and blow up the boat carrying your English doggies! First, send me my bitcoin ransom payment. Then we can celebrate with drinks!” Macaron demands.
“In your dreams, Frenchie!” John presses his finger to his ear, “Uniform, Sierra, Alpha!”
Macaron turns to Lily and scoffs, “What is this rude American man doing, Lily?”
Annoyed, Lily answers, “Check your bitcoin UTXOs. Notice anything?”
Macaron frantically queries his Bitcoin node remotely from his cellphone and breathes a sigh of relief, “Phew. No, I don’t notice anything at all. All of my unspent bitcoin is still under the control of my government’s private key.”
“And it’ll stay that way, too!” John beats his chest. “You mess with the US, and you get the Hash Force! We just secretly doubled the difficulty to mine a block by turning on all of our miners — as many miners as the entire existing Bitcoin network! Now you’ll have to wait twice as long for your French bitcoin transactions to confirm! That is, unless you release the barge of dogs right now!”
Lily drops down to the table and buries her face in her palms to hide her embarrassment.
Flustered, Macaron furiously types out a long text message with the order to release the barge of English Border Collies to cross the English channel. “There, I’ve let the dogs out! Will you two please excuse me for a moment? I have to place a call with my government to confirm we haven’t lost our property rights to spend our bitcoin.
Beaming with pride, John falls back into his chair at the table. “We did it, Lily! Quick, give the command for His Majesty’s Hash Force to power on so we can 51% attack this guy!”
Lily finally stops rubbing her eyes, “John, that isn’t how any of this works!”
“What do you mean?” he asks.
“Within a 2,016 block difficulty adjustment period, doubling the hash power means the global Bitcoin network will mine new blocks twice as fast, not slower! At least, until the 2,016 block period ends and the difficulty adjusts so miners resume taking on average 10 minutes to generate a valid block. And sure, maybe the US has a political incentive to not collect the fees of any transactions of UTXOs with a known French association, but the rest of the network’s miners will happily profit from the sats you leave in the mempool! But most of all, the Bitcoin network is now just twice as secure from attack!”
John’s double bourbon finally arrives at the table. Selfishly focused on his own glass, he doesn’t bother to stop the waiter in case Lily wants to order a drink of her own. He drinks a big gulp, “But if you give the order for His Majesty’s Hash Force to power on, won’t we have over 51% of the hash power of the Bitcoin network? We can write Macaron’s bitcoin out of existence!”
Lily crosses her arms, “Not exactly. It’s not enough to just surpass half the hashrate. We also need to maintain a higher hashrate than the legacy chain to generate more chain weight to then reorg the other chain when we join the legacy network. We would have to be mining this heavier chain in secret, but in one bombastic order you just completely blew apart our whole plan! Now we’d need some sort of massive collusion somehow between existing miners, and some secret stealth miners, to have any power projection.”
John mutters under his breath, “Frenchie’s been gone a long time. Wonder what he’s up to….”
Macaron returns, fluffs his white linen napkin, and takes his seat at their table, “Thank you, John, for extending my French people such great mercy as to be allowed to transact freely on the Bitcoin blockchain.” He extends his arm out towards a waiter, “Monsieur? Champagne for the three of us please!” Macaron turns to John and Lily, “After my phone call, I am in much better spirits. Though I’m bitter you denied paying our bitcoin ransom, I’m grateful you’re furthering the security of the Bitcoin network.”
In his excitement, Macaron leans forward and claps his hands together, “You two are so lucky to be dining with me tonight. You won’t have to drink that sparkling-wine-swill you have in your home countries. Tonight, you’ll get to have proper champagne, from the Champagne region of France — my treat!”
John grunts in disgust, “Macaron, you can order champagne, but I’ve got my bourbon.”
Lily steps on John’s foot, “Ow! What was that for?” John shrieks.
“Aren’t you going to ask me if I want anything?” Lily asks.
“Huh?” John replies confusedly.
Macaron takes Lily’s hand, “Mademoiselle, in addition to champagne, can I get you anything else?”
Lily recoils her hand back, “Gin martini. Shaken, not stirred.”
“Lily, may I ask you another question?” Macaron asks sweetly.
“Bloody hell, what is it, Macaron?” she responds while rolling her eyes.
“Why do I get the feeling that forgetting to ask you what you’d like to drink isn’t the first time John has neglected to ask you what you wanted?”
Lily’s eyes light up as she leans in closer to Macaron, “Why, yes. This isn’t the first time John’s ever disregarded my needs. You know, he’s always only thinking about himself, his own ego, and he never misses a chance to interrupt me—”
“—That’s not true!” John interrupts.
Lily kicks him under the table, “See what I mean?”
Macaron whisks Lily’s hair behind her ear, “You have such beautiful earrings, Lily. Did John buy those for you?”
“No, John never buys me anything.”
“What do you mean?” John protests.
Lily shrugs him off and Macaron leans in closer to Lily to whisper just loud enough for John to hear, “You know, in my country, men like me know how to show a lady respect.”
John stands up and extends out his hand, “C’mon, Lily. I think it’s time I take you out onto the floor for a dance.”
She shakes her head, so he stomps on her feet under the table.
“Ow!” Lily shrieks.
“I insist,” John presses. “They’re playing my song, Don’t Stop Believin’. C’mon!”
On the dance floor, John pulls Lily close to whisper in her ear, “What are you doing? We’ve finished our mission. Let’s ensure the dogs safely cross the English channel and get out of here! The way you’re flirting with him we’ll never leave!”
Lily blushes, “John, are you that blind? If Macaron is suddenly being sweet to us, then he must be scheming something.”
“What’s that supposed to mean?” John shakes his head. “Look, there’s no time to argue. We can’t risk him blowing up the barge as long as he’s got that remote detonator clipped to his ascot! He’s in a jubilant mood for now, but those French can be so melodramatic. We’ve got to get the detonator to ensure the safety of the dogs until they reach safe harbor at your shores.”
John’s box step dancing pace quickens as he looks over to check on Macaron. He spots him placing an order with the waiter and grits his teeth, “He’s pure evil. He was willing to kill the English border collies if he didn’t get ransom payment for not grooming them into French poodles. Only the threat of our Hash Force forced him to comply with our demand for their release!”
Lily breaks away from John to do a twirl on the dance floor; her elegant flowy green dress tries to keep up. She flips her hair and winks at Macaron, “Maybe I should flirt with him some more? After all, he’s so handsome — and he listens to me!”
John stops dancing and stomps his feet.
“Aww, are you jealous, John?” Lily asks.
“Jealous?!”
Lily floats back to John, digs her nails into the back of his neck, and nibbles on his ear as she whispers, “John, you better dip me on this dance floor! Otherwise, I’m going to ask him to draw me like one of his French girls. C’mon John, Don’t stop believin’!”
Ahem Macaron clears his throat, adjusts his detonator-pinned ascot, and taps Lily on the shoulder.
“Mademoiselle, may I have this dance?”
“Oh, certainly,” she replies. “Better than this brute with two left feet!”
John grunts in dissatisfaction and bolts back to the table.
With Macaron distracted dancing with Lily for what feels like an eternity, John defiantly presses his finger to his ear. “MI6 — status report. What’s taking so long?” he mutters under his breath. “I hate seeing this Frenchie dance with an English lass who deserves so much better. It’s driving me crazy!”
“You just gotta distract him from detonation for ten more minutes,” a British accent replies. “Intel shows the puppy barge armed with explosives has almost reached us across the channel, and then we can safely disarm it.”
“USHF, come in,” John queries.
“We’ve got trouble! The global energy grid has spiked along the Asian seaboard, and among the French alps. Looks like a secret French Hash Force we’ve never detected is colluding with the existing Chinese, Japanese, and Tibetan miners!
They’ve stopped including American-linked bitcoin address transactions in their blocks! Can you politely get him to back down? We’ve already played our power-projection show-of-force card!”
“Ok, I’ll do my best to play nice with Frenchie, but no promises!” John cautions. As he watches Lily and Macaron dance with disdain, a waiter approaches him at the table.
“Here you are, monsieur. Your appetizer.”
“Appetizer? I didn’t order an appetizer! All I ordered was this bourbon.”
“I’m sorry monsieur, but the other gentleman of your party insists. He said he offers this delicacy as a gift. A token of appreciation for the mercy demonstrated today by you, the quote Big American Man enquote.”
John looks on the dance floor and sees Macaron give him a nod with a big wiley grin. Lily gives him the “go-ahead” signal, so John pops one of the hot slimy appetizer balls into his mouth.
“Mhmm! These are tastier than Ma’s Frito Pie!” he shouts as Macaron and Lily walk over to join him back at the table. John continues, “These remind me of the Rocky Mountain oysters we have back at home! Of course, I’m grateful they aren’t, if you know what I mean. What are they, anyways?”
“Escargot,” the Frenchman replies, “a local specialty.”
“Escar-what-now?” John asks.
“Snails!” Lily clarifies.
John gags and spits his half-eaten snail onto the floor. He stands up and slams his ten-gallon cowboy hat on the table. “Ok, that’s it! I’ve had enough! Macaron, stop playing nice. We know you’ve activated some secret alliance with the miners on the other side of the globe! What’re you up to?”
“John, don’t upset him! Think about the puppies!” Lily pleads.
“To heck with the puppies! I’m not letting this man stand up a Hash Force to DOS attack us! You hear that, Macaron? You mess with the best, and we’ll use kinetic force against your miners stashed in the caves of the French alps!” Tsk! Tsk! Tsk! Macaron wags his finger, and pulls out the detonator switch clipped to his ascot.
“Silly pompous American, did you forget I still have the detonator? Did you really think I was going to let you get away with rescuing your hideous English border collies? Life is one giant power projection game, and the way nation states survive is by mutually assured preservation. In exchange for taming the unwieldy fur of Tibetan Mastiffs, Chinese Chow Chows, and Japanese Shih-Tzu and Shiba Inus, these countries pledged their miners to our stealthy French Hash Force when we’re in need. Well, thanks to your little stunt, not only did I find the perfect opportunity to project power back at you arrogant Americans, but also dump these hideous dogs given to me onto your barge, so they’re the British Isles’ problem now!”
“But we’ll be overrun by doges!” Lily gasps in horror.
“Yes, Lily! That’s what you get for partnering with John! What do Americans say?” Macaron asks rhetorically. “That’s right, ‘No dogs left behind!’ But most of all, John, I just wanted one last dance with your girlfriend, and to watch you eat snails!” French nasally honking laughing sounds
Lily shouts back, “I’m not his girlfriend!” She pulls a whistle out of her purse and blows it as hard as she can, but it doesn’t make a sound. John looks at her confused, and Macaron honks even harder. The whole restaurant starts to rumble, and the chandeliers sway from the ceiling.
“What’s this!?” Macaron shouts.
Gradually, then suddenly a stampede of bulldogs comes barreling into the dining room, knocking over all the tables, and tackling Macaron! As he falls, the detonator gets knocked into the air, and Lily catches it just before it hits the floor.
John looks at her, bewildered, and stammers, “You…. you let the Bitcoin dogs out??”
“You think you wankers got all the tricks? The English have a few surprises too! Now c’mon, let’s flee out the back in my British Mini Cooper. And this time, I’m driving!”
Will Schoellkopf is the author of two books: Bitcoin Girl Save the World and The Bitcoin Dog: Following the Scent to the Bitcoin C++ Source Code. He hosts the Bitcoin podcast It’s So Early! and publishes a weekly newsletter, featuring his favorite Bitcoin Posts of the Week, at realbitcoindog.com. His work has appeared in the anthology 21 Futures: Tales from the Timechain, in print at Bitcoin Magazine, Citadel21, Stackchain Magazine and online at Satoshi’s Journal. Follow him on Nostr and X @realBitcoinDog, or email will@realbitcoindog.com
-
 @ da0b9bc3:4e30a4a9
2025-05-06 06:15:01
@ da0b9bc3:4e30a4a9
2025-05-06 06:15:01Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/972645
-
 @ 6f6b50bb:a848e5a1
2024-12-15 15:09:52
@ 6f6b50bb:a848e5a1
2024-12-15 15:09:52Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
-
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
-
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!Che cosa significherebbe trattare l'IA come uno strumento invece che come una persona?
Dall’avvio di ChatGPT, le esplorazioni in due direzioni hanno preso velocità.
La prima direzione riguarda le capacità tecniche. Quanto grande possiamo addestrare un modello? Quanto bene può rispondere alle domande del SAT? Con quanta efficienza possiamo distribuirlo?
La seconda direzione riguarda il design dell’interazione. Come comunichiamo con un modello? Come possiamo usarlo per un lavoro utile? Quale metafora usiamo per ragionare su di esso?
La prima direzione è ampiamente seguita e enormemente finanziata, e per una buona ragione: i progressi nelle capacità tecniche sono alla base di ogni possibile applicazione. Ma la seconda è altrettanto cruciale per il campo e ha enormi incognite. Siamo solo a pochi anni dall’inizio dell’era dei grandi modelli. Quali sono le probabilità che abbiamo già capito i modi migliori per usarli?
Propongo una nuova modalità di interazione, in cui i modelli svolgano il ruolo di applicazioni informatiche (ad esempio app per telefoni): fornendo un’interfaccia grafica, interpretando gli input degli utenti e aggiornando il loro stato. In questa modalità, invece di essere un “agente” che utilizza un computer per conto dell’essere umano, l’IA può fornire un ambiente informatico più ricco e potente che possiamo utilizzare.
Metafore per l’interazione
Al centro di un’interazione c’è una metafora che guida le aspettative di un utente su un sistema. I primi giorni dell’informatica hanno preso metafore come “scrivanie”, “macchine da scrivere”, “fogli di calcolo” e “lettere” e le hanno trasformate in equivalenti digitali, permettendo all’utente di ragionare sul loro comportamento. Puoi lasciare qualcosa sulla tua scrivania e tornare a prenderlo; hai bisogno di un indirizzo per inviare una lettera. Man mano che abbiamo sviluppato una conoscenza culturale di questi dispositivi, la necessità di queste particolari metafore è scomparsa, e con esse i design di interfaccia skeumorfici che le rafforzavano. Come un cestino o una matita, un computer è ora una metafora di se stesso.
La metafora dominante per i grandi modelli oggi è modello-come-persona. Questa è una metafora efficace perché le persone hanno capacità estese che conosciamo intuitivamente. Implica che possiamo avere una conversazione con un modello e porgli domande; che il modello possa collaborare con noi su un documento o un pezzo di codice; che possiamo assegnargli un compito da svolgere da solo e che tornerà quando sarà finito.
Tuttavia, trattare un modello come una persona limita profondamente il nostro modo di pensare all’interazione con esso. Le interazioni umane sono intrinsecamente lente e lineari, limitate dalla larghezza di banda e dalla natura a turni della comunicazione verbale. Come abbiamo tutti sperimentato, comunicare idee complesse in una conversazione è difficile e dispersivo. Quando vogliamo precisione, ci rivolgiamo invece a strumenti, utilizzando manipolazioni dirette e interfacce visive ad alta larghezza di banda per creare diagrammi, scrivere codice e progettare modelli CAD. Poiché concepiamo i modelli come persone, li utilizziamo attraverso conversazioni lente, anche se sono perfettamente in grado di accettare input diretti e rapidi e di produrre risultati visivi. Le metafore che utilizziamo limitano le esperienze che costruiamo, e la metafora modello-come-persona ci impedisce di esplorare il pieno potenziale dei grandi modelli.
Per molti casi d’uso, e specialmente per il lavoro produttivo, credo che il futuro risieda in un’altra metafora: modello-come-computer.
Usare un’IA come un computer
Sotto la metafora modello-come-computer, interagiremo con i grandi modelli seguendo le intuizioni che abbiamo sulle applicazioni informatiche (sia su desktop, tablet o telefono). Nota che ciò non significa che il modello sarà un’app tradizionale più di quanto il desktop di Windows fosse una scrivania letterale. “Applicazione informatica” sarà un modo per un modello di rappresentarsi a noi. Invece di agire come una persona, il modello agirà come un computer.
Agire come un computer significa produrre un’interfaccia grafica. Al posto del flusso lineare di testo in stile telescrivente fornito da ChatGPT, un sistema modello-come-computer genererà qualcosa che somiglia all’interfaccia di un’applicazione moderna: pulsanti, cursori, schede, immagini, grafici e tutto il resto. Questo affronta limitazioni chiave dell’interfaccia di chat standard modello-come-persona:
Scoperta. Un buon strumento suggerisce i suoi usi. Quando l’unica interfaccia è una casella di testo vuota, spetta all’utente capire cosa fare e comprendere i limiti del sistema. La barra laterale Modifica in Lightroom è un ottimo modo per imparare l’editing fotografico perché non si limita a dirti cosa può fare questa applicazione con una foto, ma cosa potresti voler fare. Allo stesso modo, un’interfaccia modello-come-computer per DALL-E potrebbe mostrare nuove possibilità per le tue generazioni di immagini.
Efficienza. La manipolazione diretta è più rapida che scrivere una richiesta a parole. Per continuare l’esempio di Lightroom, sarebbe impensabile modificare una foto dicendo a una persona quali cursori spostare e di quanto. Ci vorrebbe un giorno intero per chiedere un’esposizione leggermente più bassa e una vibranza leggermente più alta, solo per vedere come apparirebbe. Nella metafora modello-come-computer, il modello può creare strumenti che ti permettono di comunicare ciò che vuoi più efficientemente e quindi di fare le cose più rapidamente.
A differenza di un’app tradizionale, questa interfaccia grafica è generata dal modello su richiesta. Questo significa che ogni parte dell’interfaccia che vedi è rilevante per ciò che stai facendo in quel momento, inclusi i contenuti specifici del tuo lavoro. Significa anche che, se desideri un’interfaccia più ampia o diversa, puoi semplicemente richiederla. Potresti chiedere a DALL-E di produrre alcuni preset modificabili per le sue impostazioni ispirati da famosi artisti di schizzi. Quando clicchi sul preset Leonardo da Vinci, imposta i cursori per disegni prospettici altamente dettagliati in inchiostro nero. Se clicchi su Charles Schulz, seleziona fumetti tecnicolor 2D a basso dettaglio.
Una bicicletta della mente proteiforme
La metafora modello-come-persona ha una curiosa tendenza a creare distanza tra l’utente e il modello, rispecchiando il divario di comunicazione tra due persone che può essere ridotto ma mai completamente colmato. A causa della difficoltà e del costo di comunicare a parole, le persone tendono a suddividere i compiti tra loro in blocchi grandi e il più indipendenti possibile. Le interfacce modello-come-persona seguono questo schema: non vale la pena dire a un modello di aggiungere un return statement alla tua funzione quando è più veloce scriverlo da solo. Con il sovraccarico della comunicazione, i sistemi modello-come-persona sono più utili quando possono fare un intero blocco di lavoro da soli. Fanno le cose per te.
Questo contrasta con il modo in cui interagiamo con i computer o altri strumenti. Gli strumenti producono feedback visivi in tempo reale e sono controllati attraverso manipolazioni dirette. Hanno un overhead comunicativo così basso che non è necessario specificare un blocco di lavoro indipendente. Ha più senso mantenere l’umano nel loop e dirigere lo strumento momento per momento. Come stivali delle sette leghe, gli strumenti ti permettono di andare più lontano a ogni passo, ma sei ancora tu a fare il lavoro. Ti permettono di fare le cose più velocemente.
Considera il compito di costruire un sito web usando un grande modello. Con le interfacce di oggi, potresti trattare il modello come un appaltatore o un collaboratore. Cercheresti di scrivere a parole il più possibile su come vuoi che il sito appaia, cosa vuoi che dica e quali funzionalità vuoi che abbia. Il modello genererebbe una prima bozza, tu la eseguirai e poi fornirai un feedback. “Fai il logo un po’ più grande”, diresti, e “centra quella prima immagine principale”, e “deve esserci un pulsante di login nell’intestazione”. Per ottenere esattamente ciò che vuoi, invierai una lista molto lunga di richieste sempre più minuziose.
Un’interazione alternativa modello-come-computer sarebbe diversa: invece di costruire il sito web, il modello genererebbe un’interfaccia per te per costruirlo, dove ogni input dell’utente a quell’interfaccia interroga il grande modello sotto il cofano. Forse quando descrivi le tue necessità creerebbe un’interfaccia con una barra laterale e una finestra di anteprima. All’inizio la barra laterale contiene solo alcuni schizzi di layout che puoi scegliere come punto di partenza. Puoi cliccare su ciascuno di essi, e il modello scrive l’HTML per una pagina web usando quel layout e lo visualizza nella finestra di anteprima. Ora che hai una pagina su cui lavorare, la barra laterale guadagna opzioni aggiuntive che influenzano la pagina globalmente, come accoppiamenti di font e schemi di colore. L’anteprima funge da editor WYSIWYG, permettendoti di afferrare elementi e spostarli, modificarne i contenuti, ecc. A supportare tutto ciò è il modello, che vede queste azioni dell’utente e riscrive la pagina per corrispondere ai cambiamenti effettuati. Poiché il modello può generare un’interfaccia per aiutare te e lui a comunicare più efficientemente, puoi esercitare più controllo sul prodotto finale in meno tempo.
La metafora modello-come-computer ci incoraggia a pensare al modello come a uno strumento con cui interagire in tempo reale piuttosto che a un collaboratore a cui assegnare compiti. Invece di sostituire un tirocinante o un tutor, può essere una sorta di bicicletta proteiforme per la mente, una che è sempre costruita su misura esattamente per te e il terreno che intendi attraversare.
Un nuovo paradigma per l’informatica?
I modelli che possono generare interfacce su richiesta sono una frontiera completamente nuova nell’informatica. Potrebbero essere un paradigma del tutto nuovo, con il modo in cui cortocircuitano il modello di applicazione esistente. Dare agli utenti finali il potere di creare e modificare app al volo cambia fondamentalmente il modo in cui interagiamo con i computer. Al posto di una singola applicazione statica costruita da uno sviluppatore, un modello genererà un’applicazione su misura per l’utente e le sue esigenze immediate. Al posto della logica aziendale implementata nel codice, il modello interpreterà gli input dell’utente e aggiornerà l’interfaccia utente. È persino possibile che questo tipo di interfaccia generativa sostituisca completamente il sistema operativo, generando e gestendo interfacce e finestre al volo secondo necessità.
All’inizio, l’interfaccia generativa sarà un giocattolo, utile solo per l’esplorazione creativa e poche altre applicazioni di nicchia. Dopotutto, nessuno vorrebbe un’app di posta elettronica che occasionalmente invia email al tuo ex e mente sulla tua casella di posta. Ma gradualmente i modelli miglioreranno. Anche mentre si spingeranno ulteriormente nello spazio di esperienze completamente nuove, diventeranno lentamente abbastanza affidabili da essere utilizzati per un lavoro reale.
Piccoli pezzi di questo futuro esistono già. Anni fa Jonas Degrave ha dimostrato che ChatGPT poteva fare una buona simulazione di una riga di comando Linux. Allo stesso modo, websim.ai utilizza un LLM per generare siti web su richiesta mentre li navighi. Oasis, GameNGen e DIAMOND addestrano modelli video condizionati sull’azione su singoli videogiochi, permettendoti di giocare ad esempio a Doom dentro un grande modello. E Genie 2 genera videogiochi giocabili da prompt testuali. L’interfaccia generativa potrebbe ancora sembrare un’idea folle, ma non è così folle.
Ci sono enormi domande aperte su come apparirà tutto questo. Dove sarà inizialmente utile l’interfaccia generativa? Come condivideremo e distribuiremo le esperienze che creiamo collaborando con il modello, se esistono solo come contesto di un grande modello? Vorremmo davvero farlo? Quali nuovi tipi di esperienze saranno possibili? Come funzionerà tutto questo in pratica? I modelli genereranno interfacce come codice o produrranno direttamente pixel grezzi?
Non conosco ancora queste risposte. Dovremo sperimentare e scoprirlo!
Tradotto da:\ https://willwhitney.com/computing-inside-ai.htmlhttps://willwhitney.com/computing-inside-ai.html
-
-
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ e6817453:b0ac3c39
2024-12-07 15:06:43
@ e6817453:b0ac3c39
2024-12-07 15:06:43I started a long series of articles about how to model different types of knowledge graphs in the relational model, which makes on-device memory models for AI agents possible.
We model-directed graphs
Also, graphs of entities
We even model hypergraphs
Last time, we discussed why classical triple and simple knowledge graphs are insufficient for AI agents and complex memory, especially in the domain of time-aware or multi-model knowledge.
So why do we need metagraphs, and what kind of challenge could they help us to solve?
- complex and nested event and temporal context and temporal relations as edges
- multi-mode and multilingual knowledge
- human-like memory for AI agents that has multiple contexts and relations between knowledge in neuron-like networks
MetaGraphs
A meta graph is a concept that extends the idea of a graph by allowing edges to become graphs. Meta Edges connect a set of nodes, which could also be subgraphs. So, at some level, node and edge are pretty similar in properties but act in different roles in a different context.
Also, in some cases, edges could be referenced as nodes.
This approach enables the representation of more complex relationships and hierarchies than a traditional graph structure allows. Let’s break down each term to understand better metagraphs and how they differ from hypergraphs and graphs.Graph Basics
- A standard graph has a set of nodes (or vertices) and edges (connections between nodes).
- Edges are generally simple and typically represent a binary relationship between two nodes.
- For instance, an edge in a social network graph might indicate a “friend” relationship between two people (nodes).
Hypergraph
- A hypergraph extends the concept of an edge by allowing it to connect any number of nodes, not just two.
- Each connection, called a hyperedge, can link multiple nodes.
- This feature allows hypergraphs to model more complex relationships involving multiple entities simultaneously. For example, a hyperedge in a hypergraph could represent a project team, connecting all team members in a single relation.
- Despite its flexibility, a hypergraph doesn’t capture hierarchical or nested structures; it only generalizes the number of connections in an edge.
Metagraph
- A metagraph allows the edges to be graphs themselves. This means each edge can contain its own nodes and edges, creating nested, hierarchical structures.
- In a meta graph, an edge could represent a relationship defined by a graph. For instance, a meta graph could represent a network of organizations where each organization’s structure (departments and connections) is represented by its own internal graph and treated as an edge in the larger meta graph.
- This recursive structure allows metagraphs to model complex data with multiple layers of abstraction. They can capture multi-node relationships (as in hypergraphs) and detailed, structured information about each relationship.
Named Graphs and Graph of Graphs
As you can notice, the structure of a metagraph is quite complex and could be complex to model in relational and classical RDF setups. It could create a challenge of luck of tools and software solutions for your problem.
If you need to model nested graphs, you could use a much simpler model of Named graphs, which could take you quite far.
The concept of the named graph came from the RDF community, which needed to group some sets of triples. In this way, you form subgraphs inside an existing graph. You could refer to the subgraph as a regular node. This setup simplifies complex graphs, introduces hierarchies, and even adds features and properties of hypergraphs while keeping a directed nature.
It looks complex, but it is not so hard to model it with a slight modification of a directed graph.
So, the node could host graphs inside. Let's reflect this fact with a location for a node. If a node belongs to a main graph, we could set the location to null or introduce a main node . it is up to you
Nodes could have edges to nodes in different subgraphs. This structure allows any kind of nesting graphs. Edges stay location-free
Meta Graphs in Relational Model
Let’s try to make several attempts to model different meta-graphs with some constraints.
Directed Metagraph where edges are not used as nodes and could not contain subgraphs

In this case, the edge always points to two sets of nodes. This introduces an overhead of creating a node set for a single node. In this model, we can model empty node sets that could require application-level constraints to prevent such cases.
Directed Metagraph where edges are not used as nodes and could contain subgraphs

Adding a node set that could model a subgraph located in an edge is easy but could be separate from in-vertex or out-vert.
I also do not see a direct need to include subgraphs to a node, as we could just use a node set interchangeably, but it still could be a case.Directed Metagraph where edges are used as nodes and could contain subgraphs
As you can notice, we operate all the time with node sets. We could simply allow the extension node set to elements set that include node and edge IDs, but in this case, we need to use uuid or any other strategy to differentiate node IDs from edge IDs. In this case, we have a collision of ephemeral edges or ephemeral nodes when we want to change the role and purpose of the node as an edge or vice versa.

A full-scale metagraph model is way too complex for a relational database.
So we need a better model.Now, we have more flexibility but loose structural constraints. We cannot show that the element should have one vertex, one vertex, or both. This type of constraint has been moved to the application level. Also, the crucial question is about query and retrieval needs.
Any meta-graph model should be more focused on domain and needs and should be used in raw form. We did it for a pure theoretical purpose. -
 @ e6817453:b0ac3c39
2024-12-07 15:03:06
@ e6817453:b0ac3c39
2024-12-07 15:03:06Hey folks! Today, let’s dive into the intriguing world of neurosymbolic approaches, retrieval-augmented generation (RAG), and personal knowledge graphs (PKGs). Together, these concepts hold much potential for bringing true reasoning capabilities to large language models (LLMs). So, let’s break down how symbolic logic, knowledge graphs, and modern AI can come together to empower future AI systems to reason like humans.
The Neurosymbolic Approach: What It Means ?
Neurosymbolic AI combines two historically separate streams of artificial intelligence: symbolic reasoning and neural networks. Symbolic AI uses formal logic to process knowledge, similar to how we might solve problems or deduce information. On the other hand, neural networks, like those underlying GPT-4, focus on learning patterns from vast amounts of data — they are probabilistic statistical models that excel in generating human-like language and recognizing patterns but often lack deep, explicit reasoning.
While GPT-4 can produce impressive text, it’s still not very effective at reasoning in a truly logical way. Its foundation, transformers, allows it to excel in pattern recognition, but the models struggle with reasoning because, at their core, they rely on statistical probabilities rather than true symbolic logic. This is where neurosymbolic methods and knowledge graphs come in.
Symbolic Calculations and the Early Vision of AI
If we take a step back to the 1950s, the vision for artificial intelligence was very different. Early AI research was all about symbolic reasoning — where computers could perform logical calculations to derive new knowledge from a given set of rules and facts. Languages like Lisp emerged to support this vision, enabling programs to represent data and code as interchangeable symbols. Lisp was designed to be homoiconic, meaning it treated code as manipulatable data, making it capable of self-modification — a huge leap towards AI systems that could, in theory, understand and modify their own operations.
Lisp: The Earlier AI-Language
Lisp, short for “LISt Processor,” was developed by John McCarthy in 1958, and it became the cornerstone of early AI research. Lisp’s power lay in its flexibility and its use of symbolic expressions, which allowed developers to create programs that could manipulate symbols in ways that were very close to human reasoning. One of the most groundbreaking features of Lisp was its ability to treat code as data, known as homoiconicity, which meant that Lisp programs could introspect and transform themselves dynamically. This ability to adapt and modify its own structure gave Lisp an edge in tasks that required a form of self-awareness, which was key in the early days of AI when researchers were exploring what it meant for machines to “think.”
Lisp was not just a programming language—it represented the vision for artificial intelligence, where machines could evolve their understanding and rewrite their own programming. This idea formed the conceptual basis for many of the self-modifying and adaptive algorithms that are still explored today in AI research. Despite its decline in mainstream programming, Lisp’s influence can still be seen in the concepts used in modern machine learning and symbolic AI approaches.
Prolog: Formal Logic and Deductive Reasoning
In the 1970s, Prolog was developed—a language focused on formal logic and deductive reasoning. Unlike Lisp, based on lambda calculus, Prolog operates on formal logic rules, allowing it to perform deductive reasoning and solve logical puzzles. This made Prolog an ideal candidate for expert systems that needed to follow a sequence of logical steps, such as medical diagnostics or strategic planning.
Prolog, like Lisp, allowed symbols to be represented, understood, and used in calculations, creating another homoiconic language that allows reasoning. Prolog’s strength lies in its rule-based structure, which is well-suited for tasks that require logical inference and backtracking. These features made it a powerful tool for expert systems and AI research in the 1970s and 1980s.
The language is declarative in nature, meaning that you define the problem, and Prolog figures out how to solve it. By using formal logic and setting constraints, Prolog systems can derive conclusions from known facts, making it highly effective in fields requiring explicit logical frameworks, such as legal reasoning, diagnostics, and natural language understanding. These symbolic approaches were later overshadowed during the AI winter — but the ideas never really disappeared. They just evolved.
Solvers and Their Role in Complementing LLMs
One of the most powerful features of Prolog and similar logic-based systems is their use of solvers. Solvers are mechanisms that can take a set of rules and constraints and automatically find solutions that satisfy these conditions. This capability is incredibly useful when combined with LLMs, which excel at generating human-like language but need help with logical consistency and structured reasoning.
For instance, imagine a scenario where an LLM needs to answer a question involving multiple logical steps or a complex query that requires deducing facts from various pieces of information. In this case, a solver can derive valid conclusions based on a given set of logical rules, providing structured answers that the LLM can then articulate in natural language. This allows the LLM to retrieve information and ensure the logical integrity of its responses, leading to much more robust answers.
Solvers are also ideal for handling constraint satisfaction problems — situations where multiple conditions must be met simultaneously. In practical applications, this could include scheduling tasks, generating optimal recommendations, or even diagnosing issues where a set of symptoms must match possible diagnoses. Prolog’s solver capabilities and LLM’s natural language processing power can make these systems highly effective at providing intelligent, rule-compliant responses that traditional LLMs would struggle to produce alone.
By integrating neurosymbolic methods that utilize solvers, we can provide LLMs with a form of deductive reasoning that is missing from pure deep-learning approaches. This combination has the potential to significantly improve the quality of outputs for use-cases that require explicit, structured problem-solving, from legal queries to scientific research and beyond. Solvers give LLMs the backbone they need to not just generate answers but to do so in a way that respects logical rigor and complex constraints.
Graph of Rules for Enhanced Reasoning
Another powerful concept that complements LLMs is using a graph of rules. A graph of rules is essentially a structured collection of logical rules that interconnect in a network-like structure, defining how various entities and their relationships interact. This structured network allows for complex reasoning and information retrieval, as well as the ability to model intricate relationships between different pieces of knowledge.
In a graph of rules, each node represents a rule, and the edges define relationships between those rules — such as dependencies or causal links. This structure can be used to enhance LLM capabilities by providing them with a formal set of rules and relationships to follow, which improves logical consistency and reasoning depth. When an LLM encounters a problem or a question that requires multiple logical steps, it can traverse this graph of rules to generate an answer that is not only linguistically fluent but also logically robust.
For example, in a healthcare application, a graph of rules might include nodes for medical symptoms, possible diagnoses, and recommended treatments. When an LLM receives a query regarding a patient’s symptoms, it can use the graph to traverse from symptoms to potential diagnoses and then to treatment options, ensuring that the response is coherent and medically sound. The graph of rules guides reasoning, enabling LLMs to handle complex, multi-step questions that involve chains of reasoning, rather than merely generating surface-level responses.
Graphs of rules also enable modular reasoning, where different sets of rules can be activated based on the context or the type of question being asked. This modularity is crucial for creating adaptive AI systems that can apply specific sets of logical frameworks to distinct problem domains, thereby greatly enhancing their versatility. The combination of neural fluency with rule-based structure gives LLMs the ability to conduct more advanced reasoning, ultimately making them more reliable and effective in domains where accuracy and logical consistency are critical.
By implementing a graph of rules, LLMs are empowered to perform deductive reasoning alongside their generative capabilities, creating responses that are not only compelling but also logically aligned with the structured knowledge available in the system. This further enhances their potential applications in fields such as law, engineering, finance, and scientific research — domains where logical consistency is as important as linguistic coherence.
Enhancing LLMs with Symbolic Reasoning
Now, with LLMs like GPT-4 being mainstream, there is an emerging need to add real reasoning capabilities to them. This is where neurosymbolic approaches shine. Instead of pitting neural networks against symbolic reasoning, these methods combine the best of both worlds. The neural aspect provides language fluency and recognition of complex patterns, while the symbolic side offers real reasoning power through formal logic and rule-based frameworks.
Personal Knowledge Graphs (PKGs) come into play here as well. Knowledge graphs are data structures that encode entities and their relationships — they’re essentially semantic networks that allow for structured information retrieval. When integrated with neurosymbolic approaches, LLMs can use these graphs to answer questions in a far more contextual and precise way. By retrieving relevant information from a knowledge graph, they can ground their responses in well-defined relationships, thus improving both the relevance and the logical consistency of their answers.
Imagine combining an LLM with a graph of rules that allow it to reason through the relationships encoded in a personal knowledge graph. This could involve using deductive databases to form a sophisticated way to represent and reason with symbolic data — essentially constructing a powerful hybrid system that uses LLM capabilities for language fluency and rule-based logic for structured problem-solving.
My Research on Deductive Databases and Knowledge Graphs
I recently did some research on modeling knowledge graphs using deductive databases, such as DataLog — which can be thought of as a limited, data-oriented version of Prolog. What I’ve found is that it’s possible to use formal logic to model knowledge graphs, ontologies, and complex relationships elegantly as rules in a deductive system. Unlike classical RDF or traditional ontology-based models, which sometimes struggle with complex or evolving relationships, a deductive approach is more flexible and can easily support dynamic rules and reasoning.
Prolog and similar logic-driven frameworks can complement LLMs by handling the parts of reasoning where explicit rule-following is required. LLMs can benefit from these rule-based systems for tasks like entity recognition, logical inferences, and constructing or traversing knowledge graphs. We can even create a graph of rules that governs how relationships are formed or how logical deductions can be performed.
The future is really about creating an AI that is capable of both deep contextual understanding (using the powerful generative capacity of LLMs) and true reasoning (through symbolic systems and knowledge graphs). With the neurosymbolic approach, these AIs could be equipped not just to generate information but to explain their reasoning, form logical conclusions, and even improve their own understanding over time — getting us a step closer to true artificial general intelligence.
Why It Matters for LLM Employment
Using neurosymbolic RAG (retrieval-augmented generation) in conjunction with personal knowledge graphs could revolutionize how LLMs work in real-world applications. Imagine an LLM that understands not just language but also the relationships between different concepts — one that can navigate, reason, and explain complex knowledge domains by actively engaging with a personalized set of facts and rules.
This could lead to practical applications in areas like healthcare, finance, legal reasoning, or even personal productivity — where LLMs can help users solve complex problems logically, providing relevant information and well-justified reasoning paths. The combination of neural fluency with symbolic accuracy and deductive power is precisely the bridge we need to move beyond purely predictive AI to truly intelligent systems.
Let's explore these ideas further if you’re as fascinated by this as I am. Feel free to reach out, follow my YouTube channel, or check out some articles I’ll link below. And if you’re working on anything in this field, I’d love to collaborate!
Until next time, folks. Stay curious, and keep pushing the boundaries of AI!
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 306555fe:fd7fdf12
2025-05-06 05:43:49
@ 306555fe:fd7fdf12
2025-05-06 05:43:49{"contract_id":"e042aa956d786581f0ce191532bb5192a0332d9850c9c738db5b18316b5d0121","title":"Freelance Development Agreement","content":"# Freelance Development Agreement\n\n## Parties\n\nThis Freelance Development Agreement (the \"Agreement\") is entered into as of [DATE] by and between:\n\nClient: [CLIENT NAME], with an address at [CLIENT ADDRESS] (\"Client\")\n\nDeveloper: [DEVELOPER NAME], with an address at [DEVELOPER ADDRESS] (\"Developer\")\n\n## Services\n\nDeveloper agrees to provide the following services to Client (the \"Services\"):\n\n1. Design and develop a web application according to the specifications outlined in Attachment A.\n2. Provide regular progress updates on a weekly basis.\n3. Deliver the completed project by the deadline specified in the Timeline section.\n4. Implement revisions as outlined in the Revisions section.\n\n## Timeline\n\n- Project Start Date: [START DATE]\n- Project Completion Date: [END DATE]\n- Milestone 1 (Design Approval): [MILESTONE 1 DATE]\n- Milestone 2 (Development Completion): [MILESTONE 2 DATE]\n- Milestone 3 (Testing and Revisions): [MILESTONE 3 DATE]\n\n## Compensation\n\nClient agrees to pay Developer the total sum of [AMOUNT] for the Services, to be paid as follows:\n\n- 30% deposit upon signing this Agreement\n- 30% upon completion of Milestone 1\n- 40% upon final delivery and acceptance\n\nPayments are due within 14 days of invoice date. Late payments will incur a fee of 1.5% per month.\n\n## Revisions\n\nDeveloper agrees to implement up to [NUMBER] rounds of revisions at no additional cost, provided that:\n\n1. Revision requests are made within 14 days of delivery\n2. Revisions do not substantially alter the original project scope\n3. Each revision round is consolidated into a single set of changes\n","version":1,"created_at":1746510229,"signers_required":1,"signatures":[{"pubkey":"306555fee4433582b32f6d46f11b644da33896595016893d7da18c75fd7fdf12","sig":"85c40512e741045a125286b092519aa616496549a7f508e19f45c798a821bd8e81a51bae1e05fbc7117c3b5dedf5a58888d86edb8af43e6d2408bfccae955f08","timestamp":1746510229}]}
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 9bde4214:06ca052b
2025-04-22 18:13:37
@ 9bde4214:06ca052b
2025-04-22 18:13:37"It's gonna be permissionless or hell."
Gigi and gzuuus are vibing towards dystopia.
Books & articles mentioned:
- AI 2027
- DVMs were a mistake
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- The Ultimate Resource by Julian L. Simon
- Harry Potter by J.K. Rowling
- Momo by Michael Ende
In this dialogue:
- Pablo's Roo Setup
- Tech Hype Cycles
- AI 2027
- Prompt injection and other attacks
- Goose and DVMCP
- Cursor vs Roo Code
- Staying in control thanks to Amber and signing delegation
- Is YOLO mode here to stay?
- What agents to trust?
- What MCP tools to trust?
- What code snippets to trust?
- Everyone will run into the issues of trust and micropayments
- Nostr solves Web of Trust & micropayments natively
- Minimalistic & open usually wins
- DVMCP exists thanks to Totem
- Relays as Tamagochis
- Agents aren't nostr experts, at least not right now
- Fix a mistake once & it's fixed forever
- Giving long-term memory to LLMs
- RAG Databases signed by domain experts
- Human-agent hybrids & Chess
- Nostr beating heart
- Pluggable context & experts
- "You never need an API key for anything"
- Sats and social signaling
- Difficulty-adjusted PoW as a rare-limiting mechanism
- Certificate authorities and centralization
- No solutions to policing speech!
- OAuth and how it centralized
- Login with nostr
- Closed vs open-source models
- Tiny models vs large models
- The minions protocol (Stanford paper)
- Generalist models vs specialized models
- Local compute & encrypted queries
- Blinded compute
- "In the eyes of the state, agents aren't people"
- Agents need identity and money; nostr provides both
- "It's gonna be permissionless or hell"
- We already have marketplaces for MCP stuff, code snippets, and other things
- Most great stuff came from marketplaces (browsers, games, etc)
- Zapstore shows that this is already working
- At scale, central control never works. There's plenty scams and viruses in the app stores.
- Using nostr to archive your user-generated content
- HAVEN, blossom, novia
- The switcharoo from advertisements to training data
- What is Truth?
- What is Real?
- "We're vibing into dystopia"
- Who should be the arbiter of Truth?
- First Amendment & why the Logos is sacred
- Silicon Valley AI bros arrogantly dismiss wisdom and philosophy
- Suicide rates & the meaning crisis
- Are LLMs symbiotic or parasitic?
- The Amish got it right
- Are we gonna make it?
- Careless People by Sarah Wynn-Williams
- Takedown by Laila michelwait
- Harry Potter dementors & Momo's time thieves
- Facebook & Google as non-human (superhuman) agents
- Zapping as a conscious action
- Privacy and the internet
- Plausible deniability thanks to generative models
- Google glasses, glassholes, and Meta's Ray Ben's
- People crave realness
- Bitcoin is the realest money we ever had
- Nostr allows for real and honest expression
- How do we find out what's real?
- Constraints, policing, and chilling effects
- Jesus' plans for DVMCP
- Hzrd's article on how DVMs are broken (DVMs were a mistake)
- Don't believe the hype
- DVMs pre-date MCP tools
- Data Vending Machines were supposed to be stupid: put coin in, get stuff out.
- Self-healing vibe-coding
- IP addresses as scarce assets
- Atomic swaps and the ASS protocol
- More marketplaces, less silos
- The intensity of #SovEng and the last 6 weeks
- If you can vibe-code everything, why build anything?
- Time, the ultimate resource
- What are the LLMs allowed to think?
- Natural language interfaces are inherently dialogical
- Sovereign Engineering is dialogical too
-
 @ 57d1a264:69f1fee1
2025-05-06 05:37:29
@ 57d1a264:69f1fee1
2025-05-06 05:37:29Design can’t be effective when squeezed into a decades-old process.
When the Agile Manifesto was inked in 2001, it was supposed to spark a revolution, and it did: by 2023, 71% of US companies were using Agile. The simple list of commitments to collaboration and adaptiveness branched into frameworks such as Scrum and Kanban.
“Agile” was about having a responsive mindset, not about which process you followed, but it became about which process you followed.
Agile was designed for engineering teams but spread to whole companies. Scaled frameworks emerged to coordinate Scrum teams, with a sprawling training and certification industry. In 2022, the enterprise Agile transformation industry was predicted to reach $142 billion by 2032.
originally posted at https://stacker.news/items/972640
-
 @ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44
@ 7ef5f1b1:0e0fcd27
2025-04-22 17:26:44A monthly newsletter by The 256 Foundation

April 2025
Introduction:
Welcome to the fourth newsletter produced by The 256 Foundation! March was an action-packed month with events ranging from the announcement of TSMC investing in US fabs to four solo block finds. Dive in to catch up on the latest news, mining industry developments, progress updates on grant projects, Actionable Advice on updating a Futurebit Apollo I to the latest firmware, and the current state of the Bitcoin network.
[IMG-001] Variation of the “I’m the captain now” meme by @maxisclub
Definitions:
MA = Moving Average
Eh/s = Exahash per second
Ph/s = Petahash per second
Th/s = Terahash per second
T = Trillion
J/Th = Joules per Terahash
$ = US Dollar
OS = Operating System
SSD = Solid State Drive
TB = Terabyte
News:
March 3, Ashigaru releases v1.1.1. Notable because this fork of Samourai Wallet serves as the remaining choice of mobile Bitcoin wallet capable of making peer to peer collaborative transactions. Not the Whirlpool transactions that Samourai Wallet was well-known for but the Stowaway and StonewallX2 p2p CoinJoin transactions. The persistence of Samourai’s tools still working despite the full force of the State coming down on the developers is a testament to the power of open-source code.
March 3, Stronghold completes cleanup of decommissioned coal plant using Bitcoin miners. Stronghold’s initiative counters the narrative that Bitcoin mining is wasteful by removing 150,000 tons of coal waste, part of a broader effort that cleared 240,000 tons in Q2 2024 alone. Waste coal piles in Pennsylvania, like the one in Russellton, have scarred landscapes, making this reclamation a significant step for local ecosystems. The project aligns with growing efforts in the region, as The Nature Conservancy also leads restoration projects in Pennsylvania to revive forests and waters. Stronghold’s dual-use model—powering Bitcoin miners and supplying the grid—shows how Bitcoin mining can support environmental goals while remaining economically viable.
March 3, five TSMC semiconductor fabs coming to Arizona. TSMC’s $100 billion investment in Arizona reflects a strategic push to bolster U.S. semiconductor production amid global supply chain vulnerabilities and geopolitical tensions, particularly with West Taiwan’s claims over Taiwan. TSMC’s existing $65 billion investment in Phoenix, now totaling $165 billion, aims to create 40,000 construction jobs and tens of thousands of high-tech roles over the next decade. This could relieve bottlenecks in ASIC chip supply if Bitcoin mining chip designers can get access to the limited foundry space. If that is the case, this could help alleviate some centralization concerns as it relates to a majority of Bitcoin mining chips coming from Taiwan and West Taiwan.
March 10, Block #887212 solved by a Bitaxe Ultra with ~491Gh/s. Not only did the Bitaxe satisfy the network difficulty, which was 112.15T, but obliterated it with a whopping 719.9T difficulty. This Block marked the second one solved by a Bitaxe and an increasing number of solo block finds overall as more individuals choose to play the Bitcoin lottery with their hashrate.
March 12, Pirate Bay co-founder, Carl Lundström, killed in plane crash. The Pirate Bay, launched in 2003, revolutionized online file-sharing by popularizing BitTorrent technology, enabling millions to access music, movies, and software, often in defiance of legal systems, which led to Lundström’s 2009 conviction for copyright infringement. The timing of his death coincides with ongoing global debates over digital ownership and intellectual property, often echoing many of the same themes in open-source technology, underscoring the enduring impact of The Pirate Bay’s challenge to traditional media distribution models.
March 18, Samourai Wallet status conference update. This was a short meeting in which the dates for the remaining pre-trial hearings was discussed.
- May 9, Opening Motion. - June 6, prosecution response to the opening motion. - June 20, defense replies to the prosecution response. - July 15, prosecution provides expert disclosure - August 8, defense provides expert disclosure - Tdev is able to remain home during the remaining pre-trial hearings so that he doesn’t have to incur the expenses traveling back and forth between Europe and the USDespite seemingly positive shifts in crypto-related policies from the Trump administration, all signs point to the prosecution still moving full steam ahead in this case. The defense teams need to be prepared and they could use all the financial help they can get. If you feel compelled to support the legal defense fund, please do so here. If the DOJ wins this case, all Bitcoiners lose.
March 18, DEMAND POOL launches, transitioning out of stealth mode and making room for applicants to join the private waiting list to be one of the Founding Miners.
Key features of DEMAND Pool include: • Build your own blocks • SLICE payment system & new mempool algorithm • No more empty blocks • End-to-end encryption for protection • Efficient data transfer, less wasted hashrate • Lower costs on CPU, bandwidth, & time
DEMAND Pool implements Stratum v2 so that miners can generate their own block templates, entering the arena of pools trying to decentralize mining such as OCEAN with their alternative to Stratum v2 called DATUM. A benefit of the Stratum v2 protocol over Stratum v1 is that data sent between the miner and the pool is now encrypted whereas before it was sent in clear-text, the encryption helps with network level privacy so that for example, your Internet Service Provider cannot read what is in the data being passed back and forth. Although, unless there is a proxy between your miner and the pool then the ISP may be able to determine that you are sending data to a mining pool, they just wouldn’t be able to tell what’s in that data. Overall, decentralization has become a buzz word lately and while it is a step in the right direction that more pools are enabling miners to decide which transactions are included in the block templates they work on, the pools remain a centralized force that ultimately can reject templates based on a number of reasons.
March 20, Bitaxe makes the cover of Bitcoin Magazine’s The Mining Issue, solidifying the Bitaxe as a pop-culture icon. Even those who disregard the significance of the Bitaxe project must recognize that the project’s popularity is an indication that something big is developing here.
 [IMG-002] Bitcoin Magazine, The Mining Issue
[IMG-002] Bitcoin Magazine, The Mining IssueMarch 21, self-hosted solo miner solves block #888737 with a Futurebit Apollo, making this the third solo block find for Futurebit. The first Futurebit Apollo block find may have been a fluke, the second a coincidence, but the third is an indication of a pattern forming here. More hashrate is being controlled by individuals who are constructing their own blocks and this trend will accelerate as time goes on and deploying these devices becomes easier and less expensive. This was the second solo block found in March.
March 21, US Treasury Department lifts sanctions on Tornado Cash. This is a positive sign coming from the US Treasury, however the charges against the Tornado Cash developer, Roman Storm, still stand and his legal defense team is still fighting an uphill battle. Even though the US Treasury removed Tornado Cash from the OFAC list, the department is attempting to stop a Texas court from granting a motion that would ensure the Treasury can’t put Tornado Cash back on the OFAC list. Meanwhile, the other Tornado Cash developer, Alex Pertsev, is fighting his appeal battle in the Dutch courts.
March 22, Self-hosted Public Pool user mines Block #888989. This was the first block mined with the Public Pool software, which is open-source and available for anyone to host themselves, in this case hosted on the user’s Umbrel. If you read the January issue of The 256 Foundation newsletter, there are detailed instructions for hosting your own instance of Public Pool on a Raspberry Pi. Easier solutions exist and accomplish the same thing such as Umbrel and Start9. This was the third solo block mined in March.
March 26, DeFi Education Fund publishes coalition letter urging congress to correct the DOJ’s dangerous misinterpretation of money transmission laws. In their own words: “First seen in Aug 2023 via the criminal indictment of @rstormsf, the DOJ’s novel legal theory expands criminal liability to software developers, ignoring longstanding FinCEN guidance and threatening the entire U.S. blockchain & digital asset ecosystem”. Many familiar organizations in the industry signed the letter, such as Coinbase, Kraken, A16z Crypto, and Ledger. Sadly, no Bitcoin companies signed the letter, highlighting the reckless ignorance prevalent among the “toxic Bitcoin maximalists” who often pride themselves on their narrow focus; a focus which is proving to be more of a blind spot limiting their ability to recognize a clear and present threat. The full letter text can be found here.
March 28, Heatbit reveals the black Heatbit, an elegant space heater that mines Bitcoin. Heat re-use applications such as Bitcoin mining space heaters are one of many examples where energy spent on generating heat can also earn the user sats. Other popular solutions include heating hot tubs, hotels, drive ways, and more. The innovations in this area will continue to be unlocked as open-source solutions like the ones being developed at The 256 Foundation are released and innovators gain more control over their applications.
March 29, miner with 2.5Ph/s solves Block #889975 with Solo CK Pool, marking the fourth solo block found in the month of March. This was the first solo block found on CK Pool’s European server. This was a good way to finish the month on a strong note for small-scale miners.
Free & Open Mining Industry Developments:
The development will not stop until Bitcoin mining is free and open. Innovators didn’t let off the gas in March, here are eleven note-worthy events:
0) @BTC_Grid demonstrates heating a new residential build with Bitcoin miners. This custom build features 6,000 square feet of radiant floors, 1,500 sqft of snow melting slab, 2 heated pools, all powered by Bitcoin miners and fully automated. Innovations and efficient systems like this will become more common as Bitcoin mining hardware and firmware solutions become open-source
1) @DrydeGab shares The Ocho, a Bitaxe Nerd Octaxe open-source Bitcoin miner featuring 8x BM1370 ASICs that performs at 9-10Th/s consuming ~180W. The Ocho runs on it’s own custom AxeOS. Currently out of stock but generally available for purchase in the IX Tech store.
 [IMG-003] The Nerd OCTAXE Ocho by @DrydeGab
[IMG-003] The Nerd OCTAXE Ocho by @DrydeGab2) @incognitojohn23 demonstrates building a Bitaxe from scratch with no prior experience, proving that anyone can access this technology with a little determination and the right community. @incognitojohn23 has also uploaded several videos documenting his progress and lessons along the way. Every builder has their first day, don’t hold back if you feel compelled to jump in and get started.
3) @HodlRev demonstrating how he combines Bitcoin mining with maple syrup production. In fact, @HodlRev has integrated Bitcoin mining into several aspects of his homestead. Be sure to follow his content for an endless stream of resourceful ideas. Once open-source Bitcoin mining firmware and hardware solutions become widely available, innovators like @HodlRev will have more control over every parameter of these unique applications.
4) ATL Bitlab announces their first hackathon, running June 7 through July 6. Promoted as “A global hackathon focused on all things bitcoin mining”. If you are interested in joining the hackathon, there is a Google form you can fill out here. It will be interesting to see what innovations come from this effort.
5) @100AcresRanch builds touchscreen dashboard for Bitaxe and Loki Boards. With this, you can control up to 10 mining devices with the ability to instantly switch any of the presets without going into the mining device UI.
 [IMG-004] Decentral Command Dashboard by @100AcresRanch
[IMG-004] Decentral Command Dashboard by @100AcresRanch6) @IxTechCrypto reveals HAXE, the newest member of the Nerdaxe miner family. HAXE is a 6 ASIC miner performing at ~7.4 Th/s at ~118W. Upon looking at the IX Tech store, it seems as though the HAXE has not hit shelves yet but keep an eye out for announcements soon.
7) Solo Satoshi reveals the NerdQaxe++, the latest marvel in the world of open-source Bitcoin mining solutions. This device is equipped with four ASIC chips from the Antminer S21 Pro and boasts an efficiency rating of 15.8 J/Th. At the advertised power consumption of 76 Watts, that would produce nearly 5 Th/s. Currently out of stock at the Solo Satoshi store and the IX Tech store but in stock and available at the PlebSource store.
8) @TheSoloMiningCo shares a bolt-on voltage regulator heatsink for the Bitaxe, this is a helpful modification when overclocking your miner and helps dissipate heat away from the voltage regulator. Many innovators are discovering ways to get every bit of efficiency they can from their hardware and sharing their ideas with the wider community for anyone to adopt.
9) @boerst adds historical data to stratum.work, a public website that monitors mining pool activity through calling for the work templates being generated for the pool’s respective miners. By parsing the information available in the work templates, a number of interesting observations can be made like which pools are merely proxies for larger pools, timing analysis of when templates are sent out, and now historical data on what the state of each pool’s templates were at a given block height. The work Boerst is doing with this website provides a great tool for gaining insights into mining centralization.
10) Braiins open-sources the BCB100 Control Board, designed to work with Antminers, this control board project has two parts: the hardware and the software. For the hardware part, open files include the Bill Of Materials, schematics, Gerbers, and CAD files. For the software part, open files include the board-level OpenWrt-based firmware with the full configuration file and the Nix environment for reproducible builds. The mining firmware binaries for bosminer and boser (same as the official Braiins OS releases) are also available to download and use to compile the image for the control board, however the Braiins OS firmware itself is not included in this open-source bundle. Braiins chose the GPLv3 open-source license for the software and the CERN-OHL-S open-source license for the hardware. This is a great gesture by Braiins and helps validate the efforts of The 256 Foundation to make Bitcoin mining free and open. The Braiins GitHub repositories where all this information can be found are accessible here and here. The 256 Foundation has plans to develop a Mujina firmware that can be flashed onto the BCB100 helping target Antminer machines.
Grant Project Updates:
In March, The 256 Foundation formalized agreements with the lead developers who were selected for each project. These agreements clearly defined the scope of each project, identified the deliverables, set a timeline, and agreement on compensation was made. Below are the outlines for each project, the compensation is not made public for privacy and security reasons.
Ember One:
@skot9000 instigator of the Bitaxe and all around legend for being the first mover in open-source Bitcoin mining solutions is the lead engineer for the Ember One project. This was the first fully funded grant from The 256 Foundation and commenced in November 2024 with a six month duration. The deliverable is a validated design for a ~100W miner with a standardized form factor (128mm x 128mm), USB-C data connection, 12-24v input voltage, with plans for several versions – each with a different ASIC chip. The First Ember One features the Bitmain BM1362 ASIC, next on the list will be an Ember One with the Intel BZM2 ASIC, then an Auradine ASIC version, and eventually a Block ASIC version. Learn more at: https://emberone.org/
Mujina Mining Firmware:
@ryankuester, embedded Linux developer and Electrical Engineer who has mastered the intersection of hardware and software over the last 20 years is the lead developer for the Mujina project, a Linux based mining firmware application with support for multiple drivers so it can be used with Ember One complete mining system. The grant starts on April 5, 2025 and continues for nine months. Deliverables include:
Core Mujina-miner Application: - Fully open-source under GPLv3 license - Written in Rust for performance, robustness, and maintainability, leveraging Rust's growing adoption in the Bitcoin ecosystem - Designed for modularity and extensibility - Stratum V1 client (which includes DATUM compatibility) - Best effort for Stratum V2 client in the initial release but may not happen until later
Hardware Support:
- Support for Ember One 00 hash boards (Bitmain chips) - Support for Ember One 01 hash boards (Intel chips) on a best effort basis but may not happen until later - Full support on the Raspberry Pi CM5 and IO board running the Raspberry Pi OS - Support for the Libre board when released - Best-effort compatibility with other hardware running LinuxManagement Interfaces:
• HTTP API for remote management and monitoring • Command-line interface for direct control • Basic web dashboard for status monitoring • Configuration via structured text files • Community Building and Infrastructure • GitHub project organization and workflow • Continuous integration and testing framework • Comprehensive user and developer documentation • Communication channels for users and developers • Community building through writing, podcasts, and conference participationThe initial release of Mujina is being built in such a way that it supports long-term goals like ultimately evolving into a complete Linux-based operating system, deployable through simple flashing procedures. Initially focused on supporting the 256 Foundation's Libre control boards and Ember hash boards, Mujina's modular architecture will eventually enable compatibility with a wide variety of mining hardware from different manufacturers. Lean more at: https://mujina.org/
Libre Board:
@Schnitzel, heat re-use maximalist who turned his home's hot water accessories into Bitcoin-powered sats generators and during the day has built a successful business with a background in product management, is the lead engineer on the Libre Board project; the control board for the Ember One complete mining system. Start date is April 5, 2025 and the deliverables after six months will be a mining control board based on the Raspberry Pi Compute Module I/O Board with at least the following connections:
• USB hub integration (maybe 10 ports?) • Support for fan connections • NVME expansion • Two 100-pin connectors for the compute module • Ethernet port • HDMI port • Raspberrypi 40-pin header for sensors, switches, & relays etc. • MIPI port for touchscreen • Accepts 12-24 VDC input power voltage.The initial release of Libre Board is being built in such a way that it supports long-term goals like alternative compute modules such as ARM, x86, and RISC-V. Learn more at: https://libreboard.org/
Hydra Pool:
@jungly, distributed systems PhD and the lead developer behind P2Pool v2 and formerly for Braidpool, now takes the reigns as lead developer for Hydra Pool, the stratum server package that will run on the Ember One mining system. Start date for this project was on April 5, 2025 and the duration lasts for six months. Deliverables include:
• Talks to bitcoind and provides stratum work to users and stores received shares • Scalable and robust database support to save received shares • Run share accounting on the stored shares • Implement payment mechanisms to pay out miners based on the share accounting • Provide two operation modes: Solo mining and PPLNS or Tides based payout mechanism, with payouts from coinbase only. (All other payout mechanism are out of scope of this initial release for now but there will be more). • Rolling upgrades: Tools and scripts to upgrade server with zero downtime. • Dashboard: Pool stats view only dashboard with support to filter miner payout addresses. • Documentation: Setup and other help pages, as required.The initial release of Hydra Pool is being built in such a way that it supports long-term goals like alternative payout models such as echash, communicating with other Hydra Pool instances, local store of shares for Ember One, and a user-friendly interface that puts controls at the user's fingertips, and supports the ability for upstream pool proxying. Learn More at: https://hydrapool.org/
Block Watcher:
Initially scoped to be a Bitcoin mining insights application built to run on the Ember One mining system using the self-hosted node for blockchain data. However, The 256 Foundation has decided to pause Block Watcher development for a number of reasons. Primarily because the other four projects were more central to the foundation’s mission and given the early stages of the Foundation with the current support level, it made more sense to deploy capital where it counts most.
Actionable Advice:
This month’s Actionable Advice column explains the process for upgrading the Futurebit Apollo I OS to the newer Apollo II OS and replacing the SSD. The Futurebit Apollo is a small mining device with an integrated Bitcoin node designed as a plug-and-play solution for people interested in mining Bitcoin without all the noise and heat of the larger industrial-grade miners. The Apollo I can hash between 2 – 4 Th/s and will consume roughly 125 – 200 Watts. The Apollo II can hash between 8 – 10 Th/s and will consume roughly 280 – 400 Watts. The motivation behind upgrading from the Apollo I OS to the Apollo II OS is the ability to run a stratum server internally so that the mining part of the device can ask the node part of the device for mining work, thus enabling users to solo mine in a self-hosted fashion. In fact, this is exactly what The 256 Foundation did during the Telehash fundraising event where Block #881423 was solo mined, at one point there was more than 1 Eh/s of hashrate pointed to that Apollo.
 [IMG-005] Futurebit Apollo I with new NVME SSD
[IMG-005] Futurebit Apollo I with new NVME SSDYou can find the complete flashing instructions on the Futurebit website here. You will need a separate computer to complete the flashing procedure. The flashing procedure will erase all data on the microSD card so back it up if you have anything valuable saved on there.
First navigate to the Futurebit GitHub Releases page at: https://github.com/jstefanop/apolloapi-v2/releases
Once there, you will see two OS images available for download, along with two links to alternative hosting options for those two images. If you are upgrading an Apollo I, you need to figure out which new OS image is right for your device, the MCU 1 image or the MCU 2 image. There are detailed instructions on figuring this out available here. There are multiple ways to determine if you need the MCU 1 or MCU 2 image. If the second to last digit in your Futurebit Apollo I is between 4 – 8 then you have an MCU 1; or if your batch number is 1 – 3 then you have an MCU 1; or if the circuit board has a 40-pin connector running perpendicular to the microSD card slot then you have an MCU 1. Otherwise, you have an MCU 2.
For example, this is what the MCU 1 circuit board will look like:
 [IMG-006] Futurebit MCU1 example
[IMG-006] Futurebit MCU1 exampleOnce you figure out which OS image you need, go ahead and download it. The SHA256 hash values for the OS Image files are presented in the GitHub repo. If you’re running Linux on your computer, you can change directory to your Download folder and run the following command to check the SHA256 hash value of the file you downloaded and compare that to the SHA256 hash values on GitHub.
 [IMG-007] Verifying Futurebit OS Image Hash Value
[IMG-007] Verifying Futurebit OS Image Hash ValueWith the hash value confirmed, you can use a program like Balena Etcher to flash your microSD card. First remove the microSD card from the Apollo circuit board by pushing it inward, it should make a small click and then spring outward so that you can grab it and remove it from the slot.
Connect the microSD card to your computer with the appropriate adapter.
Open Balena Etcher and click on the “Flash From File” button to define the file path to where you have the OS image saved:
 [IMG-008] Balena Etcher user interface
[IMG-008] Balena Etcher user interfaceThen click on the “Select Target” button to define the drive which you will be flashing. Select the microSD card and be sure not to select any other drive on your computer by mistake:
 [IMG-009] Balena Etcher user interface
[IMG-009] Balena Etcher user interfaceThen click on the “Flash” button and Balena Etcher will take care of formatting the microSD card, decompressing the OS image file, and flashing it to the microSD card.
 [IMG-010] Balena Etcher user interface.
[IMG-010] Balena Etcher user interface.The flashing process can take some time so be patient. The Balena Etcher interface will allow you to monitor the progress.
 [IMG-011] Balena Etcher user interface.
[IMG-011] Balena Etcher user interface.Once the flashing process is completed successfully, you will receive a notice in the balena Etcher interface that looks like this:
 [IMG-012] Balena Etcher user interface.
[IMG-012] Balena Etcher user interface.You can remove the microSD card from your computer now and install it back into the Futurebit Apollo. If you have an adequately sized SSD then your block chain data should be safe as that is where it resides, not on the microSD card. If you have a 1TB SSD then this would be a good time to consider upgrading to a 2TB SSD instead. There are lots of options but you want to get an NVME style one like this:
 [IMG-013] 1TB vs. 2TB NVME SSD
[IMG-013] 1TB vs. 2TB NVME SSDSimply loosen the screw holding the SSD in place and then remove the old SSD by pulling it out of the socket. Then insert the new one and put the screw back in place.
Once the SSD and microSD are back in place, you can connect Ethernet and the power supply, then apply power to your Apollo.
You will be able to access your Apollo through a web browser on your computer. You will need to figure out the local IP address of your Apollo device so log into your router and check the DHCP leases section. Your router should be accessible from your local network by typing an IP address into your web browser like 192.168.0.1 or 10.0.0.1 or maybe your router manufacturer uses a different default. You should be able to do an internet search for your specific router and figure it out quickly if you don’t already know. If that fails, you can download and run a program like Angry IP Scanner.
Give the Apollo some time to run through a few preliminary and automatic configurations, you should be able to see the Apollo on your local network within 10 minutes of powering it on.
Once you figure out the IP address for your Apollo, type it into your web browser and this is the first screen you should be greeted with:
 [IMG-014] Futurebit welcome screen
[IMG-014] Futurebit welcome screenClick on the button that says “Start setup process”. The next you will see should look like this:
 [IMG-015] Futurebit mining selection screen
[IMG-015] Futurebit mining selection screenYou have the option here to select solo mining or pooled mining. If you have installed a new SSD card then you should select pooled mining because you will not be able to solo mine until the entire Bitcoin blockchain is downloaded.
Your Apollo will automatically start downloading the Bitcoin blockchain in the background and in the mean-time you can start mining with a pool of your choice like Solo CK Pool or Public Pool or others.
Be forewarned that the Initial Blockchain Download (“IBD”) takes a long time. At the time of this writing, it took 18 days to download the entire blockchain using a Starlink internet connection, which was probably throttled at some points in the process because of the roughly 680 GB of data that it takes.
In February 2022, the IBD on this exact same device took 2 days with a cable internet connection. Maybe the Starlink was a bit of a bottleneck but most likely the extended length of the download can be attributed to all those JPEGS on the blockchain.
Otherwise, if you already have the full blockchain on your SSD then you should be able to start solo mining right away by selecting the solo mining option.
After making your selection, the Apollo will automatically run through some configurations and you should have the option to set a password somewhere in there along the way. Then you should see this page:
 [IMG-016] Futurebit setup completion page
[IMG-016] Futurebit setup completion pageClick on the “Start mining” button. Then you should be brought to your dashboard like this:
 [IMG-017] Futurebit dashboard
[IMG-017] Futurebit dashboardYou can monitor your hashrate, temperatures, and more from the dashboard. You can check on the status of your Bitcoin node by clicking on the three-circle looking icon that says “node” on the left-hand side menu.
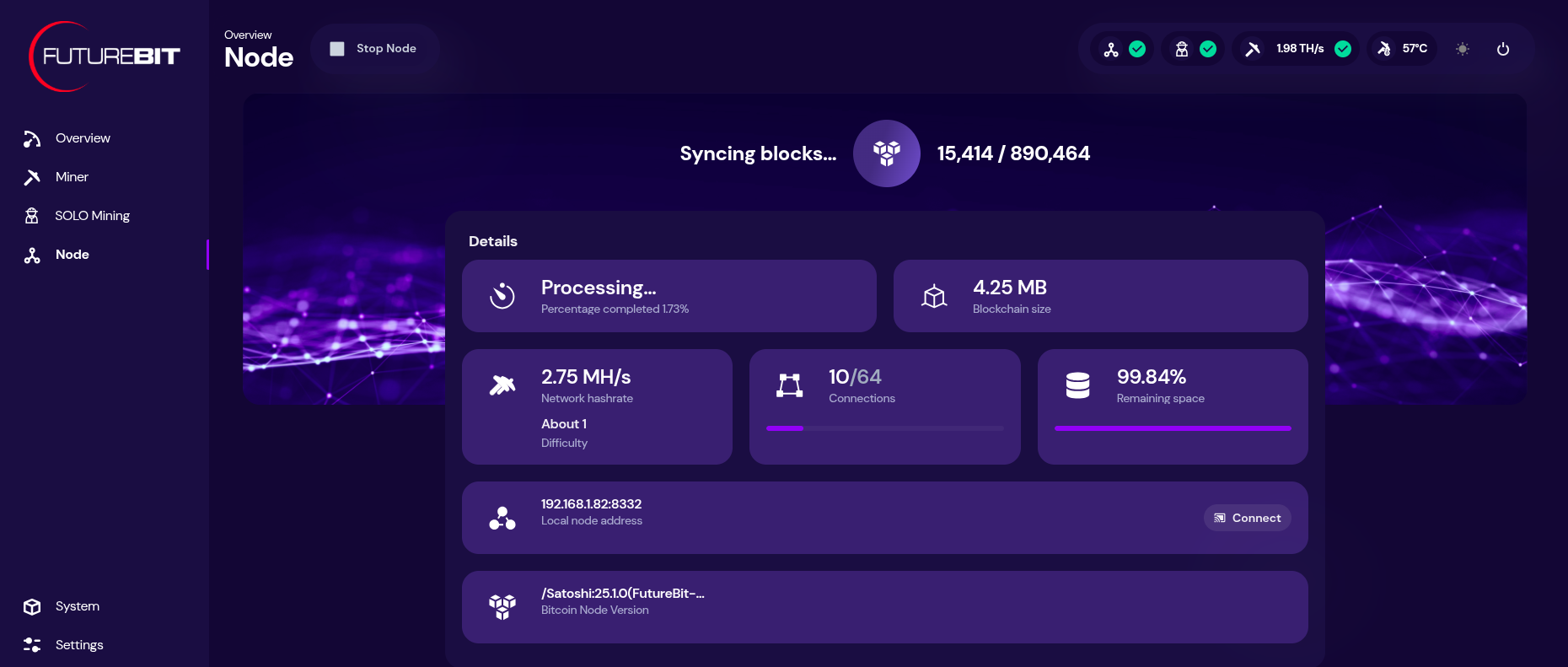 [IMG-018] Futurebit node page
[IMG-018] Futurebit node pageIf you need to update the mining pool, click on the “settings” option at the bottom of the left-hand side menu. There you will see a drop down menu for selecting a pool to use, you can select the “setup custom pool” option to insert the appropriate stratum URL and then your worker name.
Once your IBD is finished, you can start solo mining by toggling on the solo mode at the bottom of the settings page. You will have a chance to update the Bitcoin address you want to mine to. Then click on “save & restart”.
 [IMG-019] Futurebit mining pool settings
[IMG-019] Futurebit mining pool settingsThen once your system comes back up, you will see a banner at the top of the dashboard page with the IP address you can use to point any other miners you have, like Bitaxes, to your own self-hosted solo mining pool!
 [IMG-020] Futurebit solo mining dashboard
[IMG-020] Futurebit solo mining dashboardNow just sit back and enjoy watching your best shares roll in until you get one higher than the network difficulty and you mine that solo block.
State of the Network:
Hashrate on the 14-day MA according to mempool.space increased from ~793 Eh/s to ~829 Eh/s in March, marking ~4.5% growth for the month.
 [IMG-021] 2025 hashrate/difficulty chart from mempool.space
[IMG-021] 2025 hashrate/difficulty chart from mempool.spaceDifficulty was 110.57T at it’s lowest in March and 113.76T at it’s highest, which is a 2.8% increase for the month. All together for 2025 up until the end of March, difficulty has gone up ~3.6%.
According to the Hashrate Index, more efficient miners like the <19 J/Th models are fetching $17.29 per terahash, models between 19J/Th – 25J/Th are selling for $11.05 per terahash, and models >25J/Th are selling for $3.20 per terahash. Overall, prices seem to have dropped slightly over the month of March. You can expect to pay roughly $4,000 for a new-gen miner with 230+ Th/s.
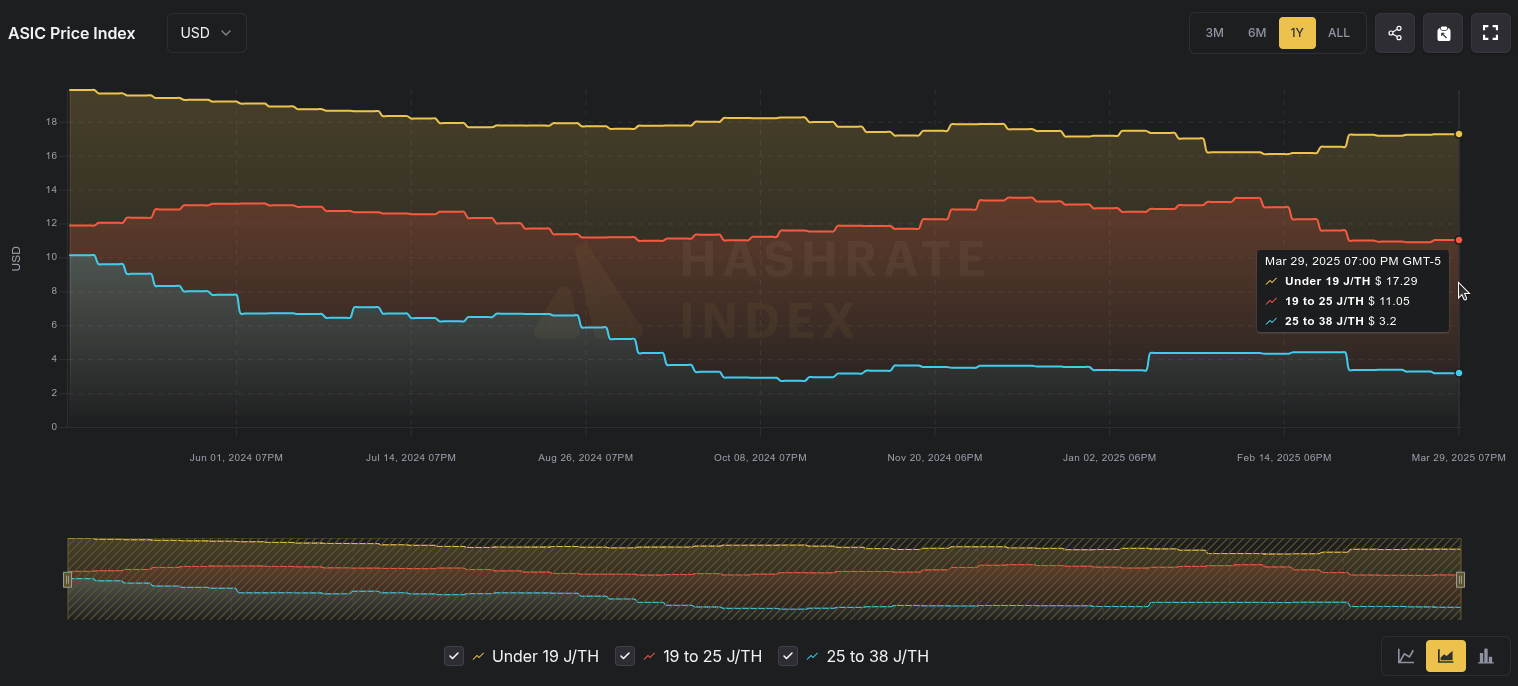 [IMG-022] Miner Prices from Luxor’s Hashrate Index
[IMG-022] Miner Prices from Luxor’s Hashrate IndexHashvalue is closed out in March at ~56,000 sats/Ph per day, relatively flat from Frebruary, according to Braiins Insights. Hashprice is $46.00/Ph per day, down from $47.00/Ph per day in February.
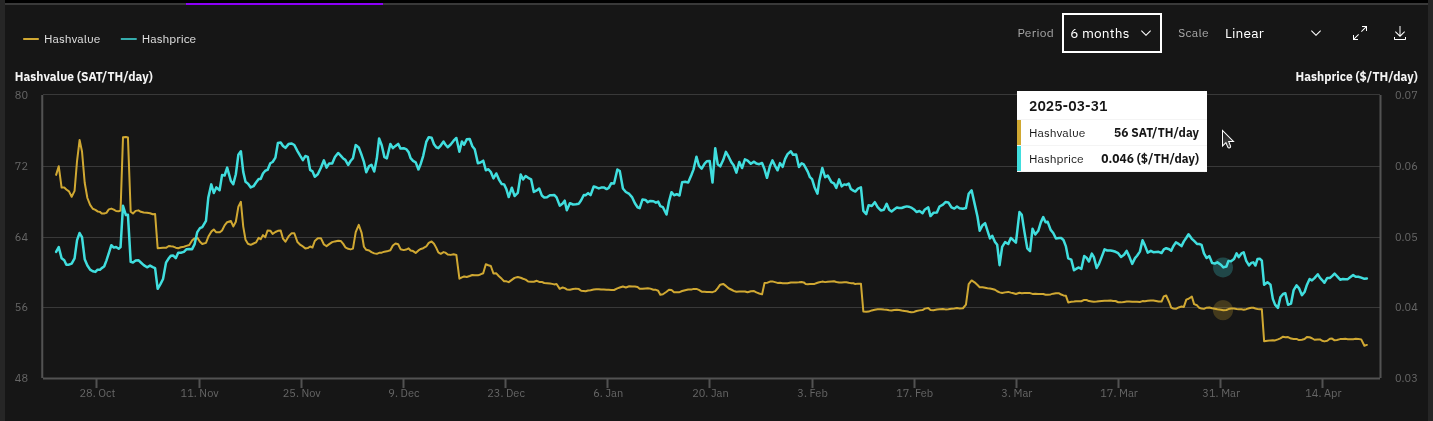 [IMG-023] Hashprice/Hashvalue from Braiins Insights
[IMG-023] Hashprice/Hashvalue from Braiins InsightsThe next halving will occur at block height 1,050,000 which should be in roughly 1,071 days or in other words ~156,850 blocks from time of publishing this newsletter.
Conclusion:
Thank you for reading the third 256 Foundation newsletter. Keep an eye out for more newsletters on a monthly basis in your email inbox by subscribing at 256foundation.org. Or you can download .pdf versions of the newsletters from there as well. You can also find these newsletters published in article form on Nostr.
If you haven’t done so already, be sure to RSVP for the Texas Energy & Mining Summit (“TEMS”) in Austin, Texas on May 6 & 7 for two days of the highest Bitcoin mining and energy signal in the industry, set in the intimate Bitcoin Commons, so you can meet and mingle with the best and brightest movers and shakers in the space.
While you’re at it, extend your stay and spend Cinco De Mayo with The 256 Foundation at our second fundraiser, Telehash #2. Everything is bigger in Texas, so set your expectations high for this one. All of the lead developers from the grant projects will be present to talk first-hand about how to dismantle the proprietary mining empire.
 IMG-024] TEMS 2025 flyer
IMG-024] TEMS 2025 flyerIf you have an old Apollo I laying around and want to get it up to date and solo mining then hopefully this newsletter helped you accomplish that.
 [IMG-026] FREE SAMOURAI
[IMG-026] FREE SAMOURAIIf you want to continue seeing developers build free and open solutions be sure to support the Samourai Wallet developers by making a tax-deductible contribution to their legal defense fund here. The first step in ensuring a future of free and open Bitcoin development starts with freeing these developers.
You can just FAFO,
-econoalchemist
-
 @ dd3548d4:cedd4a2c
2025-05-06 05:27:25
@ dd3548d4:cedd4a2c
2025-05-06 05:27:25
Twelve Grounds | Dvādaśa Bhūmayaḥ | द्वादश भूमय
1 प्रस्थानी | Prasthānī | The Stage of Setting Out | A 2 विचारणी | Vicāraṇī | The Stage of Exploration | B 3 परिणीता | Pariṇītā | The Stage of Culmination | C 4 सुदुर्मेधा | Sudurmedhā | The Stage of Profound Wisdom | D 5 अभिनिष्क्रमणी | Abhiniṣkramaṇī | The Stage of Ascension | E 6 अभिमुखी | Abhimukhī | The Stage of Direct Approach | F 7 दुर्निवारणी | Durnivāraṇī | The Stage of Irresistibility | AA 8 अचला | Acalā | The Stage of Immovability | BB 9 साधुमती | Sādhumatī | The Stage of Pure Wisdom | CC 10 धर्ममेघा | Dharmameghā | The Stage of the Dharma Cloud | DD 11 निश्चयावस्था | Niścayāvasthā | The Stage of Certainty | EE 12 सर्वार्थसिद्धि | Sarvārthasiddhi | The Stage of Perfect Fulfillment | FF
each 12 1/2 x 16 1/8 [ inches ] | Saunders Waterford 300g/sq m
Homage to unconfined vastness, the primordial completeness of the three kayas.
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 56cd780f:cbde8b29
2025-05-06 11:54:45
@ 56cd780f:cbde8b29
2025-05-06 11:54:45I will add a picture, a hyperlink and a video. Let’s see if it works.
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 56cd780f:cbde8b29
2025-05-06 11:54:43
@ 56cd780f:cbde8b29
2025-05-06 11:54:43Is it still working?
-
 @ bbef5093:71228592
2025-05-06 05:17:07
@ bbef5093:71228592
2025-05-06 05:17:07*Holtec új atomenergetikai együttműködése Utah államban*
Az amerikai Holtec International stratégiai megállapodást kötött Utah állammal és a Hi Tech Solutions nukleáris szolgáltatóval, hogy elősegítse saját fejlesztésű, SMR-300 típusú kis moduláris reaktorainak (SMR) telepítését Utahban és az Egyesült Államok Mountain West régiójában. A megállapodás értelmében 2028-ig állandó képzési központot hoznak létre Utahban, amely az üzemeltetéshez, karbantartáshoz és az új generációs nukleáris technológiákhoz szükséges munkaerő képzését célozza, szoros együttműködésben helyi egyetemekkel, főiskolákkal és szakiskolákkal.
A projekt Utah állam energetikai stratégiájának („Operation Gigawatt” és „Built Here”) része, amely a következő tíz évben megduplázná az állam energiatermelését, kiemelt szerepet szánva a tiszta nukleáris energiának. A Holtec Utah-t választotta nyugati gyártóbázisának is, ezzel erősítve az amerikai nukleáris ellátási láncot és hosszú távú munkahelyeket teremtve. A cég a 2030-as években akár 4 GW összkapacitású SMR-300 telepítését tervezi főként Utahban és Wyomingban.
Az SMR-300 egy nyomottvizes reaktor, amely 300 MW villamos vagy 1050 MW hőteljesítményt biztosít, és a Holtec tervei szerint kulcsszerepet játszhat a tiszta, szén-dioxid-mentes energiatermelésben.
*Amerikai SMR-piac helyzete*
Az SMR-technológia az utóbbi években került a figyelem középpontjába, mivel gyorsabban és olcsóbban telepíthető, mint a hagyományos atomerőművek, és lehetőséget kínál magánbefektetők számára is. Ugyanakkor az első amerikai SMR-projekt, a NuScale és a Utah Associated Municipal Power Systems közös beruházása költségnövekedés miatt meghiúsult, ami rávilágított a technológia gazdasági kihívásaira.
Nemzetközi fejlemények és további hírek
- Az ausztrál Okapi Resources és az Urenco együttműködési megállapodást kötött új urán dúsítási technológia fejlesztésére, amely tisztább és olcsóbb dúsítási eljárást ígér.
- Az Argonne National Laboratory sikeresen kicserélt egy 30 éves kulcsfontosságú alkatrészt a nátriumhűtésű gyorsreaktor-tesztberendezésében, ami hozzájárulhat a gyorsreaktor-technológia fejlesztéséhez az Egyesült Államokban.
- A Tennessee Egyetem ösztöndíjprogramot indít a Fülöp-szigeteki nukleáris szakemberek képzésére, támogatva ezzel a délkelet-ázsiai ország nukleáris energiafejlesztési törekvéseit.
- Bulgáriában a Westinghouse Electric Company helyi beszállítókkal kötött megállapodásokat két új AP1000 típusú reaktor építéséhez a kozloduji atomerőműben.
-
 @ e6817453:b0ac3c39
2024-12-07 14:54:46
@ e6817453:b0ac3c39
2024-12-07 14:54:46Introduction: Personal Knowledge Graphs and Linked Data
We will explore the world of personal knowledge graphs and discuss how they can be used to model complex information structures. Personal knowledge graphs aren’t just abstract collections of nodes and edges—they encode meaningful relationships, contextualizing data in ways that enrich our understanding of it. While the core structure might be a directed graph, we layer semantic meaning on top, enabling nuanced connections between data points.
The origin of knowledge graphs is deeply tied to concepts from linked data and the semantic web, ideas that emerged to better link scattered pieces of information across the web. This approach created an infrastructure where data islands could connect — facilitating everything from more insightful AI to improved personal data management.
In this article, we will explore how these ideas have evolved into tools for modeling AI’s semantic memory and look at how knowledge graphs can serve as a flexible foundation for encoding rich data contexts. We’ll specifically discuss three major paradigms: RDF (Resource Description Framework), property graphs, and a third way of modeling entities as graphs of graphs. Let’s get started.
Intro to RDF
The Resource Description Framework (RDF) has been one of the fundamental standards for linked data and knowledge graphs. RDF allows data to be modeled as triples: subject, predicate, and object. Essentially, you can think of it as a structured way to describe relationships: “X has a Y called Z.” For instance, “Berlin has a population of 3.5 million.” This modeling approach is quite flexible because RDF uses unique identifiers — usually URIs — to point to data entities, making linking straightforward and coherent.
RDFS, or RDF Schema, extends RDF to provide a basic vocabulary to structure the data even more. This lets us describe not only individual nodes but also relationships among types of data entities, like defining a class hierarchy or setting properties. For example, you could say that “Berlin” is an instance of a “City” and that cities are types of “Geographical Entities.” This kind of organization helps establish semantic meaning within the graph.
RDF and Advanced Topics
Lists and Sets in RDF
RDF also provides tools to model more complex data structures such as lists and sets, enabling the grouping of nodes. This extension makes it easier to model more natural, human-like knowledge, for example, describing attributes of an entity that may have multiple values. By adding RDF Schema and OWL (Web Ontology Language), you gain even more expressive power — being able to define logical rules or even derive new relationships from existing data.
Graph of Graphs
A significant feature of RDF is the ability to form complex nested structures, often referred to as graphs of graphs. This allows you to create “named graphs,” essentially subgraphs that can be independently referenced. For example, you could create a named graph for a particular dataset describing Berlin and another for a different geographical area. Then, you could connect them, allowing for more modular and reusable knowledge modeling.
Property Graphs
While RDF provides a robust framework, it’s not always the easiest to work with due to its heavy reliance on linking everything explicitly. This is where property graphs come into play. Property graphs are less focused on linking everything through triples and allow more expressive properties directly within nodes and edges.
For example, instead of using triples to represent each detail, a property graph might let you store all properties about an entity (e.g., “Berlin”) directly in a single node. This makes property graphs more intuitive for many developers and engineers because they more closely resemble object-oriented structures: you have entities (nodes) that possess attributes (properties) and are connected to other entities through relationships (edges).
The significant benefit here is a condensed representation, which speeds up traversal and queries in some scenarios. However, this also introduces a trade-off: while property graphs are more straightforward to query and maintain, they lack some complex relationship modeling features RDF offers, particularly when connecting properties to each other.
Graph of Graphs and Subgraphs for Entity Modeling
A third approach — which takes elements from RDF and property graphs — involves modeling entities using subgraphs or nested graphs. In this model, each entity can be represented as a graph. This allows for a detailed and flexible description of attributes without exploding every detail into individual triples or lump them all together into properties.
For instance, consider a person entity with a complex employment history. Instead of representing every employment detail in one node (as in a property graph), or as several linked nodes (as in RDF), you can treat the employment history as a subgraph. This subgraph could then contain nodes for different jobs, each linked with specific properties and connections. This approach keeps the complexity where it belongs and provides better flexibility when new attributes or entities need to be added.
Hypergraphs and Metagraphs
When discussing more advanced forms of graphs, we encounter hypergraphs and metagraphs. These take the idea of relationships to a new level. A hypergraph allows an edge to connect more than two nodes, which is extremely useful when modeling scenarios where relationships aren’t just pairwise. For example, a “Project” could connect multiple “People,” “Resources,” and “Outcomes,” all in a single edge. This way, hypergraphs help in reducing the complexity of modeling high-order relationships.
Metagraphs, on the other hand, enable nodes and edges to themselves be represented as graphs. This is an extremely powerful feature when we consider the needs of artificial intelligence, as it allows for the modeling of relationships between relationships, an essential aspect for any system that needs to capture not just facts, but their interdependencies and contexts.
Balancing Structure and Properties
One of the recurring challenges when modeling knowledge is finding the balance between structure and properties. With RDF, you get high flexibility and standardization, but complexity can quickly escalate as you decompose everything into triples. Property graphs simplify the representation by using attributes but lose out on the depth of connection modeling. Meanwhile, the graph-of-graphs approach and hypergraphs offer advanced modeling capabilities at the cost of increased computational complexity.
So, how do you decide which model to use? It comes down to your use case. RDF and nested graphs are strong contenders if you need deep linkage and are working with highly variable data. For more straightforward, engineer-friendly modeling, property graphs shine. And when dealing with very complex multi-way relationships or meta-level knowledge, hypergraphs and metagraphs provide the necessary tools.
The key takeaway is that only some approaches are perfect. Instead, it’s all about the modeling goals: how do you want to query the graph, what relationships are meaningful, and how much complexity are you willing to manage?
Conclusion
Modeling AI semantic memory using knowledge graphs is a challenging but rewarding process. The different approaches — RDF, property graphs, and advanced graph modeling techniques like nested graphs and hypergraphs — each offer unique strengths and weaknesses. Whether you are building a personal knowledge graph or scaling up to AI that integrates multiple streams of linked data, it’s essential to understand the trade-offs each approach brings.
In the end, the choice of representation comes down to the nature of your data and your specific needs for querying and maintaining semantic relationships. The world of knowledge graphs is vast, with many tools and frameworks to explore. Stay connected and keep experimenting to find the balance that works for your projects.
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ e0a8cbd7:f642d154
2025-05-06 03:29:12
@ e0a8cbd7:f642d154
2025-05-06 03:29:12分散型プロトコルNostr上でWeb bookmarkを見たり書いたりする「Nostr Web Bookmark Trend」を試してみました。
NostrのWeb Bookmarkingは「nip-B0 Web Bookmarking· nostr-protocol/nips · GitHub」で定義されています。
WEBブラウザの拡張による認証(NIP-07)でログインしました。
create new web bookmark(新規ブックマーク作成)を開くとこんな感じ。
URL入力部分において、https:// が外に出ているので、URLのhttps:// 部分を消して入力しないといけないのがちょっと面倒。 ↓
↓
1個、投稿してみました。
アカウント名をクリックするとそのユーザが登録したbookmark一覧が表示されます。
以上、Nostr Web Bookmark Trendについてでした。
なお、本記事は「Nostr NIP-23 マークダウンエディタ」のテストのため、「NostrでWeb bookmark - あたしンちのおとうさんの独り言」と同じ内容を投稿したものです。 -
 @ ed5774ac:45611c5c
2025-04-19 20:29:31
@ ed5774ac:45611c5c
2025-04-19 20:29:31April 20, 2020: The day I saw my so-called friends expose themselves as gutless, brain-dead sheep.
On that day, I shared a video exposing the damning history of the Bill & Melinda Gates Foundation's vaccine campaigns in Africa and the developing world. As Gates was on every TV screen, shilling COVID jabs that didn’t even exist, I called out his blatant financial conflict of interest and pointed out the obvious in my facebook post: "Finally someone is able to explain why Bill Gates runs from TV to TV to promote vaccination. Not surprisingly, it's all about money again…" - referencing his substantial investments in vaccine technology, including BioNTech's mRNA platform that would later produce the COVID vaccines and generate massive profits for his so-called philanthropic foundation.
The conflict of interest was undeniable. I genuinely believed anyone capable of basic critical thinking would at least pause to consider these glaring financial motives. But what followed was a masterclass in human stupidity.
My facebook post from 20 April 2020:

Not only was I branded a 'conspiracy theorist' for daring to question the billionaire who stood to make a fortune off the very vaccines he was shilling, but the brain-dead, logic-free bullshit vomited by the people around me was beyond pathetic. These barely literate morons couldn’t spell "Pfizer" without auto-correct, yet they mindlessly swallowed and repeated every lie the media and government force-fed them, branding anything that cracked their fragile reality as "conspiracy theory." Big Pharma’s rap sheet—fraud, deadly cover-ups, billions in fines—could fill libraries, yet these obedient sheep didn’t bother to open a single book or read a single study before screaming their ignorance, desperate to virtue-signal their obedience. Then, like spineless lab rats, they lined up for an experimental jab rushed to the market in months, too dumb to care that proper vaccine development takes a decade.
The pathetic part is that these idiots spend hours obsessing over reviews for their useless purchases like shoes or socks, but won’t spare 60 seconds to research the experimental cocktail being injected into their veins—or even glance at the FDA’s own damning safety reports. Those same obedient sheep would read every Yelp review for a fucking coffee shop but won't spend five minutes looking up Pfizer's criminal fraud settlements. They would demand absolute obedience to ‘The Science™’—while being unable to define mRNA, explain lipid nanoparticles, or justify why trials were still running as they queued up like cattle for their jab. If they had two brain cells to rub together or spent 30 minutes actually researching, they'd know, but no—they'd rather suck down the narrative like good little slaves, too dumb to question, too weak to think.
Worst of all, they became the system’s attack dogs—not just swallowing the poison, but forcing it down others’ throats. This wasn’t ignorance. It was betrayal. They mutated into medical brownshirts, destroying lives to virtue-signal their obedience—even as their own children’s hearts swelled with inflammation.
One conversation still haunts me to this day—a masterclass in wealth-worship delusion. A close friend, as a response to my facebook post, insisted that Gates’ assumed reading list magically awards him vaccine expertise, while dismissing his billion-dollar investments in the same products as ‘no conflict of interest.’ Worse, he argued that Gates’s $5–10 billion pandemic windfall was ‘deserved.’
This exchange crystallizes civilization’s intellectual surrender: reason discarded with religious fervor, replaced by blind faith in corporate propaganda.
The comment of a friend on my facebook post that still haunts me to this day:

Walking Away from the Herd
After a period of anger and disillusionment, I made a decision: I would no longer waste energy arguing with people who refused to think for themselves. If my circle couldn’t even ask basic questions—like why an untested medical intervention was being pushed with unprecedented urgency—then I needed a new community.
Fortunately, I already knew where to look. For three years, I had been involved in Bitcoin, a space where skepticism wasn’t just tolerated—it was demanded. Here, I’d met some of the most principled and independent thinkers I’d ever encountered. These were people who understood the corrupting influence of centralized power—whether in money, media, or politics—and who valued sovereignty, skepticism, and integrity. Instead of blind trust, bitcoiners practiced relentless verification. And instead of empty rhetoric, they lived by a simple creed: Don’t trust. Verify.
It wasn’t just a philosophy. It was a lifeline. So I chose my side and I walked away from the herd.
Finding My Tribe
Over the next four years, I immersed myself in Bitcoin conferences, meetups, and spaces where ideas were tested, not parroted. Here, I encountered extraordinary people: not only did they share my skepticism toward broken systems, but they challenged me to sharpen it.
No longer adrift in a sea of mindless conformity, I’d found a crew of thinkers who cut through the noise. They saw clearly what most ignored—that at the core of society’s collapse lay broken money, the silent tax on time, freedom, and truth itself. But unlike the complainers I’d left behind, these people built. They coded. They wrote. They risked careers and reputations to expose the rot. Some faced censorship; others, mockery. All understood the stakes.
These weren’t keyboard philosophers. They were modern-day Cassandras, warning of inflation’s theft, the Fed’s lies, and the coming dollar collapse—not for clout, but because they refused to kneel to a dying regime. And in their defiance, I found something rare: a tribe that didn’t just believe in a freer future. They were engineering it.
April 20, 2024: No more herd. No more lies. Only proof-of-work.
On April 20, 2024, exactly four years after my last Facebook post, the one that severed my ties to the herd for good—I stood in front of Warsaw’s iconic Palace of Culture and Science, surrounded by 400 bitcoiners who felt like family. We were there to celebrate Bitcoin’s fourth halving, but it was more than a protocol milestone. It was a reunion of sovereign individuals. Some faces I’d known since the early days; others, I’d met only hours before. We bonded instantly—heated debates, roaring laughter, zero filters on truths or on so called conspiracy theories.
As the countdown to the halving began, it hit me: This was the antithesis of the hollow world I’d left behind. No performative outrage, no coerced consensus—just a room of unyielding minds who’d traded the illusion of safety for the grit of truth. Four years prior, I’d been alone in my resistance. Now, I raised my glass among my people - those who had seen the system's lies and chosen freedom instead. Each had their own story of awakening, their own battles fought, but here we shared the same hard-won truth.
The energy wasn’t just electric. It was alive—the kind that emerges when free people build rather than beg. For the first time, I didn’t just belong. I was home. And in that moment, the halving’s ticking clock mirrored my own journey: cyclical, predictable in its scarcity, revolutionary in its consequences. Four years had burned away the old world. What remained was stronger.

No Regrets
Leaving the herd wasn’t a choice—it was evolution. My soul shouted: "I’d rather stand alone than kneel with the masses!". The Bitcoin community became more than family; they’re living proof that the world still produces warriors, not sheep. Here, among those who forge truth, I found something extinct elsewhere: hope that burns brighter with every halving, every block, every defiant mind that joins the fight.
Change doesn’t come from the crowd. It starts when one person stops applauding.
Today, I stand exactly where I always wanted to be—shoulder-to-shoulder with my true family: the rebels, the builders, the ungovernable. Together, we’re building the decentralized future.
-
 @ 56cd780f:cbde8b29
2025-05-06 11:54:40
@ 56cd780f:cbde8b29
2025-05-06 11:54:40Is it actually called “summary”?
-
 @ 30b99916:3cc6e3fe
2025-04-19 19:55:31
@ 30b99916:3cc6e3fe
2025-04-19 19:55:31btcpayserver #lightning #lnd #powershell #coinos
BTCpayAPI now supports CoinOS.io REST Api

Adding Coinos.io REST Api end points support to BTCpayAPI. Here is what is implemented, tested and doumented so far.
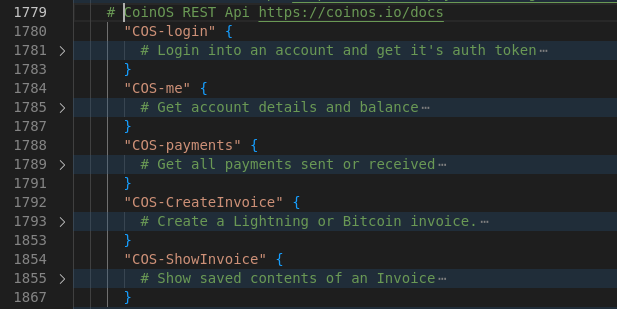
Current REST APIs supported are now:
LND API https://lightning.engineering/api-docs/api/lnd/ BTCPay Greenfield API (v1) https://docs.btcpayserver.org/API/Greenfield/v1/ Hashicorp Vault API https://developer.hashicorp.com/vault/api-docs/secret/kv/kv-v1 Coinos.io API https://coinos.io/docs
Although this is PowerShell code, it is exclusively being developed and tested on Linux only.
Code is available at https://btcpayserver.sytes.net
-
 @ b154080c:00027cc7
2025-05-06 03:01:47
@ b154080c:00027cc7
2025-05-06 03:01:47Introduction
In the ancient times of Israel, masculinity found its true embodiment in the courageous story of Daniel. Amidst the foreign land of Babylon, Daniel stood firm in his convictions, showcasing strength, and dedication to his beliefs.
Despite living in a culture that sought to diminish his faith, Daniel refused to bow before idols or false deities. His defiance challenged societal expectations, revealing a masculinity that transcended worldly norms. Rooted in his unshakable belief in the one true God, Daniel's resolve remained unyielding. Facing the wrath of the king, Daniel fearlessly stood before Nebuchadnezzar, humbly declaring his allegiance to God alone. Cast into a blazing furnace as punishment, Daniel emerged unharmed. God's angel shielded him from the scorching flames, proving that his faith made him invincible. Witnessing this display of masculinity, Nebuchadnezzar acknowledged the greatness of Daniel's God, bringing about a profound transformation.
Daniel's story serves as a testament to the essence of masculinity—a resolute dedication to one's convictions, the courage to defy societal expectations, and a commitment to truth. His faith and devotion inspire generations, exemplifying the power of masculine conviction.
There have been countless instances throughout history where acts of courage have taken place on a spectrum. Although both men and women can display such acts, history has shown that resolve, courage, and bravery have predominantly resided within the realm of masculinity. The Apostle Paul himself concluded the book of 1 Corinthians by saying, "Be watchful, stand firm in the faith, act like men, be strong. Let all that you do be done in love" (16:13-14). By combining this passage with the numerous accounts of provision, battle, sacrifice, and honor, it becomes evident that God has designed inherent and very important differences within the male gender.
The Bible presents us with inspiring examples of both courageous women, such as Deborah, Rahab, and Esther, and valiant men, including Joshua, Gideon, Samson, David, Jonathan, Nehemiah, the Prophets, the twelve Apostles, and above all, Jesus Himself. While these accounts acknowledge the remarkable contributions of women, they predominantly highlight the male figures who exemplify strength, boldness, courage, and a resolute sense of responsibility. Throughout its pages, the Bible paints a vivid picture of masculinity's profound impact and enduring significance which we must embrace.
Jesus’ Masculinity
Jesus exhibited remarkable courage throughout many of his acts, and it is through his expression of masculinity that this courage shines even brighter. Jesus' masculinity played a crucial role in enabling him to display great bravery and determination in fulfilling his mission. However, it's important to note that Jesus redefines masculinity beyond physical strength or dominance, embracing resilience, self-sacrifice, and unyielding conviction as its defining qualities.
Jesus' courage stemmed from his deep understanding of his purpose and his unshakable faith in his Father's plan. He fearlessly challenged the religious authorities of his time, calling out hypocrisy and speaking truth to power. Despite facing opposition and hostility, Jesus stood firm in his convictions, undeterred by the threats and ridicule he encountered. Jesus' embodiment of masculinity highlights the transformative power it can have when rooted in love and compassion.
Modern Culture Poisoning the Church
It is important to realize the true masculinity of Jesus and the example that he has set for us in this regard. Unfortunately, I often see a tendency nowadays to downplay Jesus' masculinity and instead depict Him in a more feminized manner.
In both our culture and the modern church, there is a tendency to present a version of Jesus that deviates from the biblical portrayal. Perhaps you've come across people who refer to Jesus as their "best friend" or even draw comparisons between their relationship with Him and that of a "boyfriend.” This is in fact very unbiblical. The Bible never presents our love for God using such romantic or erotic language. While the men depicted in Scripture certainly loved God, they were never portrayed as being desperate for Him or romantically in love with Him. People are often taught a very shallow and weak portrayal of Him.
In the United States, particularly in the context of flourishing Protestantism, the shift from considering the community as a whole to focusing on the individual has led to a rise in strong individualistic beliefs which has resulted in a diminished sense of community within the Catholic Church. When the focal point of Catholicism becomes "Jesus and me," it opens the door to a mindset of being "spiritual" rather than "religious.” Attending church becomes a matter of personal choice, and faith no longer necessarily influences or intersects with areas such as business or politics. The sole emphasis becomes on one's personal relationship with Christ, prioritizing individual salvation over communal or global redemption. The vision of the kingdom of God taking shape on earth also becomes less urgent, as the emphasis shifts towards a faith centered on transcendence, emotions, and sentiment, rather than tangible actions.
The perception of Jesus' masculinity has been negatively impacted by the trend of feminizing Him, which has contributed to a decline in the courage displayed by men today. This shift can be attributed to various factors that have influenced societal perspectives.
In contrast to the promises of Jesus, which include suffering, trials, and pain, it is often only presented to them that Christianity is the solution to these hardships. Instead of acknowledging the reality of challenges, the contemporary portrayal of Christianity tends to market it as the antidote to suffering and pain. It is important to recognize and reflect upon the significant difference between how Jesus called His disciples and the prevailing emphasis on personal relationships with Him today. Instead of inviting them to have a personal connection, He simply said, "Follow me." Understanding this distinction is crucial in our understanding of Jesus' call to discipleship. "Follow me" implies a sense of purpose, a shared mission or goal to pursue. This contrast highlights the divergence between the original intent of discipleship and the way it is often portrayed around me nowadays.
I want to emphasize that I am by no means denying the significance of having a personal relationship with Christ. On the contrary, I am simply highlighting the importance of recognizing that personal relationships, including our relationship with Christ, require more than just superficial connections. They demand a deep sense of faith, trust, and communion with Him. Drawing inspiration from the courageous example of Jesus, who fearlessly confronted societal norms and spoke truth to power, our relationship with Him can empower us to embrace courage in our own lives. Just as Jesus fearlessly faced opposition, persecution, and ultimately sacrificed Himself for the sake of others, our connection with Him can embolden us to stand up for what is right, to live out our faith boldly, and to face life's challenges with strength. It is not a casual or complacent association but a courageous and transformative bond that empowers us to live out our faith with conviction and to impact the world around us positively.
As modern sermons take center stage, it's become apparent that there is a tendency to downplay the contrasts found in the teachings of the Bible. As mentions of heaven and hell, sin and life, grace and justice, as well as the analogies involving battles and soldiers for Christ have always been very prevalent, they have become way less common nowadays. We hear fewer calls for Catholics to embrace their crosses and passionately commit themselves to the cause of the gospel and the well-being of others. Instead, the spotlight has shifted towards how the gospel can serve as a tool for personal growth and fulfillment, focusing on self-realization. The gospel is often presented as a therapeutic treatment rather than a heroic challenge. The emphasis lies on the rewards rather than the obstacles, creating the idea of all gain, no pain (lol).
The rise of praise and worship music has also brought about significant changes in people's perception of Christ. While traditional hymns focused on singing about God, emphasizing His greatness, power, and distinctiveness, praise and worship music takes a different approach. It presents God as a close companion, an intimate presence by our side, emphasizing His love and care for us. This shift in emphasis, while not inherently negative, certainly plays a substantial role in shaping our understanding of Christ's nature and relationship with us.
Jesus is the Epitome of Masculinity
I believe Jesus stands as the epitome of masculinity, offering an unrivaled example for men to emulate. Through His life and teachings, He reveals the true essence of what it means to be a man. He leads with courage, facing challenges head-on without hesitation. His fearlessness shines through as He confronts opposition and stands firm in His convictions. Moreover, His love is not self-serving but sacrificial, displayed vividly through His ultimate act of giving His own life for the sake of others. And in the face of adversity, His resolve remains unshakeable, inspiring men to stand strong in their beliefs and principles. Jesus, in His entirety, embodies the essence of true masculinity, setting an unparalleled standard that us men must aspire to.
Around me, I’m often seeing a tendency to shy away from addressing challenging subjects with resolute conviction. Rather than speaking with clarity and certainty, there is a preference for using vague language and ambiguous statements to navigate sensitive issues. In stark contrast, Jesus stood firmly and fearlessly, fearlessly proclaiming His truth. His words shook the foundations of societal norms, demanding radical commitment from His followers. True boldness lies in the courage to speak truth, even when faced with opposition and adversity.
Boldness is a very masculine characteristic. While some may argue that boldness is not exclusive to gender, the Bible primarily associates this characteristic with men. On the other hand, the beauty of women is highlighted through the importance of a gentle and quiet spirit, which also very much holds great value in the eyes of God. 1 Peter 3:4 addressing woman and wives, "Let your adorning be the hidden person of the heart with the imperishable beauty of a gentle and quiet spirit, which in God's sight is very precious." This reminds us that inner qualities such as a gentle and tranquil demeanor also hold significant worth and are highly esteemed.
As Jesus exemplified true boldness, courageously speaking God's truth regardless of the consequences. His courage serves as the ultimate model of masculinity, inspiring men to fearlessly pursue God's will. Jesus exemplified bravery, rooted in His deep reverence for God. Unlike the fear of man, which arises from sin, Jesus' bravery stemmed from His love for God. His resolute posture and authoritative responses to godless men demonstrated a masculinity untainted by timidity. Jesus taught us to lead with courage, grounded in reverence for God and faith in His sovereignty.
In a culture where love is often misrepresented, Jesus' sacrificial love stands as the true definition. Love, as demonstrated by Jesus, goes beyond superficial feelings; it entails sacrificial commitment. Jesus willingly laid down His life for His bride, the Church, showcasing the essence of true masculinity. Men are called to sacrificially love their wives, mirroring Christ's example. This selfless love forms the foundation for men to protect, nurture, and fight for those entrusted to their care.
Christ's resolve was the driving force behind the cross, demonstrating His commitment to fulfill His mission. His choice to embrace the cross, knowing the suffering and wrath He would endure, showcases resolute masculinity. In history, heroic moments of perseverance are predominantly marked by male resolve. The biological advantage provided by testosterone further supports men's capacity for enduring resolve. Jesus' resolve to save His people from sin teaches men to stand firm in the face of challenges, abiding in their commitment to their calling.
Restoring the Church's Boldness and Reclaiming Biblical Masculinity and Femininity
The landscape of the Church has undergone a significant transformation, moving away from its historic expression of Christianity. We've witnessed a shift from powerful, convicting sermons to soft, TED-talk style infotainment. Classic hymns highlighting doctrine, sacrifice, and piety have been replaced by emotionally driven love songs that resemble romantic ballads. It's clear that the local church has undergone a real emasculation.
This departure from biblical foundations has contributed to a great deal of confusion within the Church, particularly concerning the understanding of biblical manhood and womanhood. The increasing push for egalitarianism has led to women fighting for leadership roles, while men find themselves adrift without clear guidance regarding their responsibilities in marriage, the church, and the family. I believe this confusion and distortion of gender roles to be the enemy's central strategy for our generation. By infiltrating the Church with a heightened emphasis on feminine emotion, the enemy has left us unprepared for moments requiring masculine boldness, fearlessness, sacrifice, and resolve.
We must acknowledge that there is a difference between a surface-level expression of faith and the profound conviction displayed by those facing intense trials. The challenges and hardships that people face in the midst of adversity provide a profound glimpse into the strength and genuineness of their faith. These trials are a powerful testimony to their commitment and courage. Throughout history, numerous Christians have faced unimaginable suffering, even enduring torture, dismemberment, and martyrdom, all because of their devotion to Christ. Their remarkable sacrifices inspire us and remind us of the immense cost of following Jesus. Yet, the trend of timidity displayed by the present-day Church, yielding to government overreach or even complying with laws that endorse sexual sin contrary to biblical teachings, will come at a significant cost.
It is high time for the Church to reclaim its boldness and restore the biblical understanding of masculinity and femininity. We must reject the watered-down version of Christianity that has spread throughout our culture and embrace a faith rooted in conviction and sacrifice. By understanding and embracing the unique roles and responsibilities of men and women as outlined in Scripture, we can restore clarity and purpose to our families, churches, and communities. Let us rise above the societal pressures, rekindle the fire of biblical truth, and stand firm in our commitment to Christ, no matter the cost.
As we progress, it becomes clear that the importance of strong, virtuous Catholic men is growing. This should not catch us off guard. The feminist movement of the 21st century is truly toxic. It goes way beyond advocating for the rightful appreciation of women; it seeks to establish female dominance. Moreover, its influence knows no boundaries. Like the LGBTQ community, its aim is to permeate every aspect of public, personal, and spiritual life. We must not only be alarmed by this trend but also prepare ourselves to stand firmly against it. We need biblically grounded shepherds and faithful women who can discern the subtle infiltration of an effeminate culture and guard against it.
Let us not forget that Catholicism is not egalitarian. While men and women are equally valued before the cross, our roles and responsibilities differ. In marriage, Christianity follows a complementarian model, where the husband leads with sacrificial love, and the wife respects and supports him. People are too sensitive about the word “patriarchy” nowadays. In terms of leadership, the Church holds a patriarchal stance. At the same time, patriarchy, like any other system, is not immune to the potential for sinful expressions. However, when approached with sacrificial love, adherence to biblical order, and a commitment to honoring God, the structure of patriarchy - as well as areas such as marriage, fatherhood, and heterosexuality - can yield to way more goodness. We should strive for a church culture that aligns with the gender-culture outlined in God’s Word: gentle, safe, and encouraging, while also strong, bold, and committed to upholding biblical order and fulfilling the mission entrusted to us. This balance allows the church to fully embody the presence of Christ, enabling His people to confidently advance alongside our great Lord.
We must prepare ourselves for an increasing need for men who embrace biblical masculinity and women who faithfully embody femininity. It is crucial not to overlook the pervasive influence of an effeminate culture and the agenda of distorted ideologies. By embracing the distinct roles and responsibilities that God has given to both men and women, we cultivate a church culture that mirrors the beauty of Christ and empowers His people to wholeheartedly pursue His mission with courage. We must recognize the urgency to embrace and embody biblical masculinity in the face of cultural challenges and shifting ideologies. Equipped with the truth of God's Word, we can navigate the complexities of the world and fulfill our God-given roles with great faith. Let us rise as men who boldly embrace our calling, standing firm in the face of challenges, and wholeheartedly pursuing lives of holiness and service to God and His Church. May we stand united, guided by His Word, and ready to face the battles ahead with strength, grace, and resolved faith.
From Nashville with love,
Suhail Saqan
This was inspired by The Imitation of Christ. Read here.
-
 @ e6817453:b0ac3c39
2024-12-07 14:52:47
@ e6817453:b0ac3c39
2024-12-07 14:52:47The temporal semantics and temporal and time-aware knowledge graphs. We have different memory models for artificial intelligence agents. We all try to mimic somehow how the brain works, or at least how the declarative memory of the brain works. We have the split of episodic memory and semantic memory. And we also have a lot of theories, right?
Declarative Memory of the Human Brain
How is the semantic memory formed? We all know that our brain stores semantic memory quite close to the concept we have with the personal knowledge graphs, that it’s connected entities. They form a connection with each other and all those things. So far, so good. And actually, then we have a lot of concepts, how the episodic memory and our experiences gets transmitted to the semantic:
- hippocampus indexing and retrieval
- sanitization of episodic memories
- episodic-semantic shift theory
They all give a different perspective on how different parts of declarative memory cooperate.
We know that episodic memories get semanticized over time. You have semantic knowledge without the notion of time, and probably, your episodic memory is just decayed.
But, you know, it’s still an open question:
do we want to mimic an AI agent’s memory as a human brain memory, or do we want to create something different?
It’s an open question to which we have no good answer. And if you go to the theory of neuroscience and check how episodic and semantic memory interfere, you will still find a lot of theories, yeah?
Some of them say that you have the hippocampus that keeps the indexes of the memory. Some others will say that you semantic the episodic memory. Some others say that you have some separate process that digests the episodic and experience to the semantics. But all of them agree on the plan that it’s operationally two separate areas of memories and even two separate regions of brain, and the semantic, it’s more, let’s say, protected.
So it’s harder to forget the semantical facts than the episodes and everything. And what I’m thinking about for a long time, it’s this, you know, the semantic memory.
Temporal Semantics
It’s memory about the facts, but you somehow mix the time information with the semantics. I already described a lot of things, including how we could combine time with knowledge graphs and how people do it.
There are multiple ways we could persist such information, but we all hit the wall because the complexity of time and the semantics of time are highly complex concepts.
Time in a Semantic context is not a timestamp.
What I mean is that when you have a fact, and you just mentioned that I was there at this particular moment, like, I don’t know, 15:40 on Monday, it’s already awake because we don’t know which Monday, right? So you need to give the exact date, but usually, you do not have experiences like that.
You do not record your memories like that, except you do the journaling and all of the things. So, usually, you have no direct time references. What I mean is that you could say that I was there and it was some event, blah, blah, blah.
Somehow, we form a chain of events that connect with each other and maybe will be connected to some period of time if we are lucky enough. This means that we could not easily represent temporal-aware information as just a timestamp or validity and all of the things.
For sure, the validity of the knowledge graphs (simple quintuple with start and end dates)is a big topic, and it could solve a lot of things. It could solve a lot of the time cases. It’s super simple because you give the end and start dates, and you are done, but it does not answer facts that have a relative time or time information in facts . It could solve many use cases but struggle with facts in an indirect temporal context. I like the simplicity of this idea. But the problem of this approach that in most cases, we simply don’t have these timestamps. We don’t have the timestamp where this information starts and ends. And it’s not modeling many events in our life, especially if you have the processes or ongoing activities or recurrent events.
I’m more about thinking about the time of semantics, where you have a time model as a hybrid clock or some global clock that does the partial ordering of the events. It’s mean that you have the chain of the experiences and you have the chain of the facts that have the different time contexts.
We could deduct the time from this chain of the events. But it’s a big, big topic for the research. But what I want to achieve, actually, it’s not separation on episodic and semantic memory. It’s having something in between.
Blockchain of connected events and facts
I call it temporal-aware semantics or time-aware knowledge graphs, where we could encode the semantic fact together with the time component.I doubt that time should be the simple timestamp or the region of the two timestamps. For me, it is more a chain for facts that have a partial order and form a blockchain like a database or a partially ordered Acyclic graph of facts that are temporally connected. We could have some notion of time that is understandable to the agent and a model that allows us to order the events and focus on what the agent knows and how to order this time knowledge and create the chains of the events.
Time anchors
We may have a particular time in the chain that allows us to arrange a more concrete time for the rest of the events. But it’s still an open topic for research. The temporal semantics gets split into a couple of domains. One domain is how to add time to the knowledge graphs. We already have many different solutions. I described them in my previous articles.
Another domain is the agent's memory and how the memory of the artificial intelligence treats the time. This one, it’s much more complex. Because here, we could not operate with the simple timestamps. We need to have the representation of time that are understandable by model and understandable by the agent that will work with this model. And this one, it’s way bigger topic for the research.”
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 56cd780f:cbde8b29
2025-05-06 11:54:39
@ 56cd780f:cbde8b29
2025-05-06 11:54:39A few weeks ago, I ran into an old friend at a coffee shop. We hadn’t spoken in years, and within five minutes, she said something I’ve heard countless times:
“I just feel like I’m so behind.”
Behind who? Behind what?
 There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.
There’s this idea—quiet, nagging, oddly universal—that we’re all somehow in a race we didn’t sign up for. That we’re supposed to have hit certain milestones by certain ages. That if we’re not married, promoted, rich, settled, happy (and photogenic) by 30 or 40 or pick your poison, then we’ve failed some invisible test.Where did this come from?
Some of it’s cultural, obviously. Social media compresses timelines. You’re 27, doom-scrolling, and suddenly someone from high school just IPO’d their startup and got engaged in Rome. Another just bought a house with a kitchen island the size of a small country. You wonder if you missed a memo.
But beneath that, there’s something deeper. A belief that life is linear. That it should look like a staircase: school, job, marriage, house, kids, success. But real life? It’s a squiggle. A mess. A beautiful disaster.
Here’s the truth: You’re not behind. There’s no schedule. There’s only your path, and the courage it takes to stay on it—even when it looks wildly different from everyone else’s.
I say this as someone who has taken the “scenic route.” I changed careers in my 30s. I moved cities on a hunch. I dropped things that looked great on paper because they felt wrong in my gut. I’ve had seasons of momentum and seasons of stuckness. Both were necessary.
“Catching up” assumes there’s a fixed destination. But what if there isn’t? What if the point isn’t arrival, but presence? Progress that feels real, not performative?
If you need a permission slip to stop comparing, let this be it.
 You’re not late. You’re not early.
You’re not late. You’re not early.
You’re right on time. -
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 56cd780f:cbde8b29
2025-05-06 11:54:36
@ 56cd780f:cbde8b29
2025-05-06 11:54:36There’s something sacred about morning air — the way it carries just enough chill to remind you you’re alive, without pushing you back inside. I’ve been starting my days on the balcony lately. Not because it’s glamorous (it isn’t), or because I have a routine (I don’t), but because it’s the only space in my apartment that feels both open and still.
This morning I made coffee with too much cinnamon and curled up with a blanket that’s seen better days. I watched the city slowly wake up — one barking dog, two joggers, and the clatter of a recycling truck below. It’s odd how these tiny patterns become a kind of comfort.
 I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.
I used to think that slowing down meant falling behind. But here, perched on the third floor with my feet on cold concrete and the sky just starting to blush, I feel like I’m exactly where I’m supposed to be.If you’re reading this, maybe you needed that reminder too.
— Natalie
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ dab6c606:51f507b6
2025-04-18 14:59:25
@ dab6c606:51f507b6
2025-04-18 14:59:25Core idea: Use geotagged anonymized Nostr events with Cashu-based points to snitch on cop locations for a more relaxed driving and walking
We all know navigation apps. There's one of them that allows you to report on locations of cops. It's Waze and it's owned by Google. There are perfectly fine navigation apps like Organic Maps, that unfortunately lack the cop-snitching features. In some countries, it is illegal to report cop locations, so it would probably not be a good idea to use your npub to report them. But getting a points Cashu token as a reward and exchanging them from time to time would solve this. You can of course report construction, traffic jams, ...
Proposed solution: Add Nostr client (Copstr) to Organic Maps. Have a button in bottom right allowing you to report traffic situations. Geotagged events are published on Nostr relays, users sending cashu tokens as thank you if the report is valid. Notes have smart expiration times.
Phase 2: Automation: Integration with dashcams and comma.ai allow for automated AI recognition of traffic events such as traffic jams and cops, with automatic touchless reporting.
Result: Drive with most essential information and with full privacy. Collect points to be cool and stay cool.
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ 3bf0c63f:aefa459d
2024-12-06 20:37:26
@ 3bf0c63f:aefa459d
2024-12-06 20:37:26início
"Vocês vêem? Vêem a história? Vêem alguma coisa? Me parece que estou tentando lhes contar um sonho -- fazendo uma tentativa inútil, porque nenhum relato de sonho pode transmitir a sensação de sonho, aquela mistura de absurdo, surpresa e espanto numa excitação de revolta tentando se impôr, aquela noção de ser tomado pelo incompreensível que é da própria essência dos sonhos..."
Ele ficou em silêncio por alguns instantes.
"... Não, é impossível; é impossível transmitir a sensação viva de qualquer época determinada de nossa existência -- aquela que constitui a sua verdade, o seu significado, a sua essência sutil e contundente. É impossível. Vivemos, como sonhamos -- sozinhos..."
- Livros mencionados por Olavo de Carvalho
- Antiga homepage Olavo de Carvalho
- Bitcoin explicado de um jeito correto e inteligível
- Reclamações
-
 @ 826e9f89:ffc5c759
2025-04-12 21:34:24
@ 826e9f89:ffc5c759
2025-04-12 21:34:24What follows began as snippets of conversations I have been having for years, on and off, here and there. It will likely eventually be collated into a piece I have been meaning to write on “payments” as a whole. I foolishly started writing this piece years ago, not realizing that the topic is gargantuan and for every week I spend writing it I have to add two weeks to my plan. That may or may not ever come to fruition, but in the meantime, Tether announced it was issuing on Taproot Assets and suddenly everybody is interested again. This is as good a catalyst as any to carve out my “stablecoin thesis”, such as it exists, from “payments”, and put it out there for comment and feedback.
In contrast to the “Bitcoiner take” I will shortly revert to, I invite the reader to keep the following potential counterargument in mind, which might variously be termed the “shitcoiner”, “realist”, or “cynical” take, depending on your perspective: that stablecoins have clear product-market-fit. Now, as a venture capitalist and professional thinkboi focusing on companies building on Bitcoin, I obviously think that not only is Bitcoin the best money ever invented and its monetization is pretty much inevitable, but that, furthermore, there is enormous, era-defining long-term potential for a range of industries in which Bitcoin is emerging as superior technology, even aside from its role as money. But in the interest not just of steelmanning but frankly just of honesty, I would grudgingly agree with the following assessment as of the time of writing: the applications of crypto (inclusive of Bitcoin but deliberately wider) that have found product-market-fit today, and that are not speculative bets on future development and adoption, are: Bitcoin as savings technology, mining as a means of monetizing energy production, and stablecoins.
I think there are two typical Bitcoiner objections to stablecoins of significantly greater importance than all others: that you shouldn’t be supporting dollar hegemony, and that you don’t need a blockchain. I will elaborate on each of these, and for the remainder of the post will aim to produce a synthesis of three superficially contrasting (or at least not obviously related) sources of inspiration: these objections, the realisation above that stablecoins just are useful, and some commentary on technical developments in Bitcoin and the broader space that I think inform where things are likely to go. As will become clear as the argument progresses, I actually think the outcome to which I am building up is where things have to go. I think the technical and economic incentives at play make this an inevitability rather than a “choice”, per se. Given my conclusion, which I will hold back for the time being, this is a fantastically good thing, hence I am motivated to write this post at all!
Objection 1: Dollar Hegemony
I list this objection first because there isn’t a huge amount to say about it. It is clearly a normative position, and while I more or less support it personally, I don’t think that it is material to the argument I am going on to make, so I don’t want to force it on the reader. While the case for this objection is probably obvious to this audience (isn’t the point of Bitcoin to destroy central banks, not further empower them?) I should at least offer the steelman that there is a link between this and the realist observation that stablecoins are useful. The reason they are useful is because people prefer the dollar to even shitter local fiat currencies. I don’t think it is particularly fruitful to say that they shouldn’t. They do. Facts don’t care about your feelings. There is a softer bridging argument to be made here too, to the effect that stablecoins warm up their users to the concept of digital bearer (ish) assets, even though these particular assets are significantly scammier than Bitcoin. Again, I am just floating this, not telling the reader they should or shouldn’t buy into it.
All that said, there is one argument I do want to put my own weight behind, rather than just float: stablecoin issuance is a speculative attack on the institution of fractional reserve banking. A “dollar” Alice moves from JPMorgan to Tether embodies two trade-offs from Alice’s perspective: i) a somewhat opaque profile on the credit risk of the asset: the likelihood of JPMorgan ever really defaulting on deposits vs the operator risk of Tether losing full backing and/or being wrench attacked by the Federal Government and rugging its users. These risks are real but are almost entirely political. I’m skeptical it is meaningful to quantify them, but even if it is, I am not the person to try to do it. Also, more transparently to Alice, ii) far superior payment rails (for now, more on this to follow).
However, from the perspective of the fiat banking cartel, fractional reserve leverage has been squeezed. There are just as many notional dollars in circulation, but there the backing has been shifted from levered to unlevered issuers. There are gradations of relevant objections to this: while one might say, Tether’s backing comes from Treasuries, so you are directly funding US debt issuance!, this is a bit silly in the context of what other dollars one might hold. It’s not like JPMorgan is really competing with the Treasury to sell credit into the open market. Optically they are, but this is the core of the fiat scam. Via the guarantees of the Federal Reserve System, JPMorgan can sell as much unbacked credit as it wants knowing full well the difference will be printed whenever this blows up. Short-term Treasuries are also JPMorgan’s most pristine asset safeguarding its equity, so the only real difference is that Tether only holds Treasuries without wishing more leverage into existence. The realization this all builds up to is that, by necessity,
Tether is a fully reserved bank issuing fiduciary media against the only dollar-denominated asset in existence whose value (in dollar terms) can be guaranteed. Furthermore, this media arguably has superior “moneyness” to the obvious competition in the form of US commercial bank deposits by virtue of its payment rails.
That sounds pretty great when you put it that way! Of course, the second sentence immediately leads to the second objection, and lets the argument start to pick up steam …
Objection 2: You Don’t Need a Blockchain
I don’t need to explain this to this audience but to recap as briefly as I can manage: Bitcoin’s value is entirely endogenous. Every aspect of “a blockchain” that, out of context, would be an insanely inefficient or redundant modification of a “database”, in context is geared towards the sole end of enabling the stability of this endogenous value. Historically, there have been two variations of stupidity that follow a failure to grok this: i) “utility tokens”, or blockchains with native tokens for something other than money. I would recommend anybody wanting a deeper dive on the inherent nonsense of a utility token to read Only The Strong Survive, in particular Chapter 2, Crypto Is Not Decentralized, and the subsection, Everything Fights For Liquidity, and/or Green Eggs And Ham, in particular Part II, Decentralized Finance, Technically. ii) “real world assets” or, creating tokens within a blockchain’s data structure that are not intended to have endogenous value but to act as digital quasi-bearer certificates to some or other asset of value exogenous to this system. Stablecoins are in this second category.
RWA tokens definitionally have to have issuers, meaning some entity that, in the real world, custodies or physically manages both the asset and the record-keeping scheme for the asset. “The blockchain” is at best a secondary ledger to outsource ledger updates to public infrastructure such that the issuer itself doesn’t need to bother and can just “check the ledger” whenever operationally relevant. But clearly ownership cannot be enforced in an analogous way to Bitcoin, under both technical and social considerations. Technically, Bitcoin’s endogenous value means that whoever holds the keys to some or other UTXOs functionally is the owner. Somebody else claiming to be the owner is yelling at clouds. Whereas, socially, RWA issuers enter a contract with holders (whether legally or just in terms of a common-sense interpretation of the transaction) such that ownership of the asset issued against is entirely open to dispute. That somebody can point to “ownership” of the token may or may not mean anything substantive with respect to the physical reality of control of the asset, and how the issuer feels about it all.
And so, one wonders, why use a blockchain at all? Why doesn’t the issuer just run its own database (for the sake of argument with some or other signature scheme for verifying and auditing transactions) given it has the final say over issuance and redemption anyway? I hinted at an answer above: issuing on a blockchain outsources this task to public infrastructure. This is where things get interesting. While it is technically true, given the above few paragraphs, that, you don’t need a blockchain for that, you also don’t need to not use a blockchain for that. If you want to, you can.
This is clearly the case given stablecoins exist at all and have gone this route. If one gets too angry about not needing a blockchain for that, one equally risks yelling at clouds! And, in fact, one can make an even stronger argument, more so from the end users’ perspective. These products do not exist in a vacuum but rather compete with alternatives. In the case of stablecoins, the alternative is traditional fiat money, which, as stupid as RWAs on a blockchain are, is even dumber. It actually is just a database, except it’s a database that is extremely annoying to use, basically for political reasons because the industry managing these private databases form a cartel that never needs to innovate or really give a shit about its customers at all. In many, many cases, stablecoins on blockchains are dumb in the abstract, but superior to the alternative methods of holding and transacting in dollars existing in other forms. And note, this is only from Alice’s perspective of wanting to send and receive, not a rehashing of the fractional reserve argument given above. This is the essence of their product-market-fit. Yell at clouds all you like: they just are useful given the alternative usually is not Bitcoin, it’s JPMorgan’s KYC’d-up-the-wazoo 90s-era website, more than likely from an even less solvent bank.
So where does this get us? It might seem like we are back to “product-market-fit, sorry about that” with Bitcoiners yelling about feelings while everybody else makes do with their facts. However, I think we have introduced enough material to move the argument forward by incrementally incorporating the following observations, all of which I will shortly go into in more detail: i) as a consequence of making no technical sense with respect to what blockchains are for, today’s approach won’t scale; ii) as a consequence of short-termist tradeoffs around socializing costs, today’s approach creates an extremely unhealthy and arguably unnatural market dynamic in the issuer space; iii) Taproot Assets now exist and handily address both points i) and ii), and; iv) eCash is making strides that I believe will eventually replace even Taproot Assets.
To tease where all this is going, and to get the reader excited before we dive into much more detail: just as Bitcoin will eat all monetary premia, Lightning will likely eat all settlement, meaning all payments will gravitate towards routing over Lightning regardless of the denomination of the currency at the edges. Fiat payments will gravitate to stablecoins to take advantage of this; stablecoins will gravitate to TA and then to eCash, and all of this will accelerate hyperbitcoinization by “bitcoinizing” payment rails such that an eventual full transition becomes as simple as flicking a switch as to what denomination you want to receive.
I will make two important caveats before diving in that are more easily understood in light of having laid this groundwork: I am open to the idea that it won’t be just Lightning or just Taproot Assets playing the above roles. Without veering into forecasting the entire future development of Bitcoin tech, I will highlight that all that really matters here are, respectively: a true layer 2 with native hashlocks, and a token issuance scheme that enables atomic routing over such a layer 2 (or combination of such). For the sake of argument, the reader is welcome to swap in “Ark” and “RGB” for “Lightning” and “TA” both above and in all that follows. As far as I can tell, this makes no difference to the argument and is even exciting in its own right. However, for the sake of simplicity in presentation, I will stick to “Lightning” and “TA” hereafter.
1) Today’s Approach to Stablecoins Won’t Scale
This is the easiest to tick off and again doesn’t require much explanation to this audience. Blockchains fundamentally don’t scale, which is why Bitcoin’s UTXO scheme is a far better design than ex-Bitcoin Crypto’s’ account-based models, even entirely out of context of all the above criticisms. This is because Bitcoin transactions can be batched across time and across users with combinations of modes of spending restrictions that provide strong economic guarantees of correct eventual net settlement, if not perpetual deferral. One could argue this is a decent (if abstrusely technical) definition of “scaling” that is almost entirely lacking in Crypto.
What we see in ex-Bitcoin crypto is so-called “layer 2s” that are nothing of the sort, forcing stablecoin schemes in these environments into one of two equally poor design choices if usage is ever to increase: fees go higher and higher, to the point of economic unviability (and well past it) as blocks fill up, or move to much more centralized environments that increasingly are just databases, and hence which lose the benefits of openness thought to be gleaned by outsourcing settlement to public infrastructure. This could be in the form of punting issuance to a bullshit “layer 2” that is a really a multisig “backing” a private execution environment (to be decentralized any daw now) or an entirely different blockchain that is just pretending even less not to be a database to begin with. In a nutshell, this is a decent bottom-up explanation as to why Tron has the highest settlement of Tether.
This also gives rise to the weirdness of “gas tokens” - assets whose utility as money is and only is in the form of a transaction fee to transact a different kind of money. These are not quite as stupid as a “utility token,” given at least they are clearly fulfilling a monetary role and hence their artificial scarcity can be justified. But they are frustrating from Bitcoiners’ and users’ perspectives alike: users would prefer to pay transaction fees on dollars in dollars, but they can’t because the value of Ether, Sol, Tron, or whatever, is the string and bubblegum that hold their boondoggles together. And Bitcoiners wish this stuff would just go away and stop distracting people, whereas this string and bubblegum is proving transiently useful.
All in all, today’s approach is fine so long as it isn’t being used much. It has product-market fit, sure, but in the unenviable circumstance that, if it really starts to take off, it will break, and even the original users will find it unusable.
2) Today’s Approach to Stablecoins Creates an Untenable Market Dynamic
Reviving the ethos of you don’t need a blockchain for that, notice the following subtlety: while the tokens representing stablecoins have value to users, that value is not native to the blockchain on which they are issued. Tether can (and routinely does) burn tokens on Ethereum and mint them on Tron, then burn on Tron and mint on Solana, and so on. So-called blockchains “go down” and nobody really cares. This makes no difference whatsoever to Tether’s own accounting, and arguably a positive difference to users given these actions track market demand. But it is detrimental to the blockchain being switched away from by stripping it of “TVL” that, it turns out, was only using it as rails: entirely exogenous value that leaves as quickly as it arrived.
One underdiscussed and underappreciated implication of the fact that no value is natively running through the blockchain itself is that, in the current scheme, both the sender and receiver of a stablecoin have to trust the same issuer. This creates an extremely powerful network effect that, in theory, makes the first-to-market likely to dominate and in practice has played out exactly as this theory would suggest: Tether has roughly 80% of the issuance, while roughly 19% goes to the political carve-out of USDC that wouldn’t exist at all were it not for government interference. Everybody else combined makes up the final 1%.
So, Tether is a full reserve bank but also has to be everybody’s bank. This is the source of a lot of the discomfort with Tether, and which feeds into the original objection around dollar hegemony, that there is an ill-defined but nonetheless uneasy feeling that Tether is slowly morphing into a CBDC. I would argue this really has nothing to do with Tether’s own behavior but rather is a consequence of the market dynamic inevitably created by the current stablecoin scheme. There is no reason to trust any other bank because nobody really wants a bank, they just want the rails. They want something that will retain a nominal dollar value long enough to spend it again. They don’t care what tech it runs on and they don’t even really care about the issuer except insofar as having some sense they won’t get rugged.
Notice this is not how fiat works. Banks can, of course, settle between each other, thus enabling their users to send money to customers of other banks. This settlement function is actually the entire point of central banks, less the money printing and general corruption enabled (we might say, this was the historical point of central banks, which have since become irredeemably corrupted by this power). This process is clunkier than stablecoins, as covered above, but the very possibility of settlement means there is no gigantic network effect to being the first commercial issuer of dollar balances. If it isn’t too triggering to this audience, one might suggest that the money printer also removes the residual concern that your balances might get rugged! (or, we might again say, you guarantee you don’t get rugged in the short term by guaranteeing you do get rugged in the long term).
This is a good point at which to introduce the unsettling observation that broader fintech is catching on to the benefits of stablecoins without any awareness whatsoever of all the limitations I am outlining here. With the likes of Stripe, Wise, Robinhood, and, post-Trump, even many US megabanks supposedly contemplating issuing stablecoins (obviously within the current scheme, not the scheme I am building up to proposing), we are forced to boggle our minds considering how on earth settlement is going to work. Are they going to settle through Ether? Well, no, because i) Ether isn’t money, it’s … to be honest, I don’t think anybody really knows what it is supposed to be, or if they once did they aren’t pretending anymore, but anyway, Stripe certainly hasn’t figured that out yet so, ii) it won’t be possible to issue them on layer 1s as soon as there is any meaningful volume, meaning they will have to route through “bullshit layer 2 wrapped Ether token that is really already a kind of stablecoin for Ether.”
The way they are going to try to fix this (anybody wanna bet?) is routing through DEXes, which is so painfully dumb you should be laughing and, if you aren’t, I would humbly suggest you don’t get just how dumb it is. What this amounts to is plugging the gap of Ether’s lack of moneyness (and wrapped Ether’s hilarious lack of moneyness) with … drum roll … unknowable technical and counterparty risk and unpredictable cost on top of reverting to just being a database. So, in other words, all of the costs of using a blockchain when you don’t strictly need to, and none of the benefits. Stripe is going to waste billions of dollars getting sandwich attacked out of some utterly vanilla FX settlement it is facilitating for clients who have even less of an idea what is going on and why North Korea now has all their money, and will eventually realize they should have skipped their shitcoin phase and gone straight to understanding Bitcoin instead …
3) Bitcoin (and Taproot Assets) Fixes This
To tie together a few loose ends, I only threw in the hilariously stupid suggestion of settling through wrapped Ether on Ether on Ether in order to tee up the entirely sensible suggestion of settling through Lightning. Again, not that this will be new to this audience, but while issuance schemes have been around on Bitcoin for a long time, the breakthrough of Taproot Assets is essentially the ability to atomically route through Lightning.
I will admit upfront that this presents a massive bootstrapping challenge relative to the ex-Bitcoin Crypto approach, and it’s not obvious to me if or how this will be overcome. I include this caveat to make it clear I am not suggesting this is a given. It may not be, it’s just beyond the scope of this post (or frankly my ability) to predict. This is a problem for Lightning Labs, Tether, and whoever else decides to step up to issue. But even highlighting this as an obvious and major concern invites us to consider an intriguing contrast: scaling TA stablecoins is hardest at the start and gets easier and easier thereafter. The more edge liquidity there is in TA stables, the less of a risk it is for incremental issuance; the more TA activity, the more attractive deploying liquidity is into Lightning proper, and vice versa. With apologies if this metaphor is even more confusing than it is helpful, one might conceive of the situation as being that there is massive inertia to bootstrap, but equally there could be positive feedback in driving the inertia to scale. Again, I have no idea, and it hasn’t happened yet in practice, but in theory it’s fun.
More importantly to this conversation, however, this is almost exactly the opposite dynamic to the current scheme on other blockchains, which is basically free to start, but gets more and more expensive the more people try to use it. One might say it antiscales (I don’t think that’s a real word, but if Taleb can do it, then I can do it too!).
Furthermore, the entire concept of “settling in Bitcoin” makes perfect sense both economically and technically: economically because Bitcoin is money, and technically because it can be locked in an HTLC and hence can enable atomic routing (i.e. because Lightning is a thing). This is clearly better than wrapped Eth on Eth on Eth or whatever, but, tantalisingly, is better than fiat too! The core message of the payments tome I may or may not one day write is (or will be) that fiat payments, while superficially efficient on the basis of centralized and hence costless ledger amendments, actually have a hidden cost in the form of interbank credit. Many readers will likely have heard me say this multiple times and in multiple settings but, contrary to popular belief, there is no such thing as a fiat debit. Even if styled as a debit, all fiat payments are credits and all have credit risk baked into their cost, even if that is obscured and pushed to the absolute foundational level of money printing to keep banks solvent and hence keep payment channels open.
Furthermore! this enables us to strip away the untenable market dynamic from the point above. The underappreciated and underdiscussed flip side of the drawback of the current dynamic that is effectively fixed by Taproot Assets is that there is no longer a mammoth network effect to a single issuer. Senders and receivers can trust different issuers (i.e. their own banks) because those banks can atomically settle a single payment over Lightning. This does not involve credit. It is arguably the only true debit in the world across both the relevant economic and technical criteria: it routes through money with no innate credit risk, and it does so atomically due to that money’s native properties.
Savvy readers may have picked up on a seed I planted a while back and which can now delightfully blossom:
This is what Visa was supposed to be!
Crucially, this is not what Visa is now. Visa today is pretty much the bank that is everybody’s counterparty, takes a small credit risk for the privilege, and oozes free cash flow bottlenecking global consumer payments.
But if you read both One From Many by Dee Hock (for a first person but pretty wild and extravagant take) and Electronic Value Exchange by David Stearns (for a third person, drier, but more analytical and historically contextualized take) or if you are just intimately familiar with the modern history of payments for whatever other reason, you will see that the role I just described for Lightning in an environment of unboundedly many banks issuing fiduciary media in the form of stablecoins is exactly what Dee Hock wanted to create when he envisioned Visa:
A neutral and open layer of value settlement enabling banks to create digital, interbank payment schemes for their customers at very low cost.
As it turns out, his vision was technically impossible with fiat, hence Visa, which started as a cooperative amongst member banks, was corrupted into a duopolistic for-profit rent seeker in curious parallel to the historical path of central banks …
4) eCash
To now push the argument to what I think is its inevitable conclusion, it’s worth being even more vigilant on the front of you don’t need a blockchain for that. I have argued that there is a role for a blockchain in providing a neutral settlement layer to enable true debits of stablecoins. But note this is just a fancy and/or stupid way of saying that Bitcoin is both the best money and is programmable, which we all knew anyway. The final step is realizing that, while TA is nice in terms of providing a kind of “on ramp” for global payments infrastructure as a whole to reorient around Lightning, there is some path dependence here in assuming (almost certainly correctly) that the familiarity of stablecoins as “RWA tokens on a blockchain” will be an important part of the lure.
But once that transition is complete, or is well on its way to being irreversible, we may as well come full circle and cut out tokens altogether. Again, you really don’t need a blockchain for that, and the residual appeal of better rails has been taken care of with the above massive detour through what I deem to be the inevitability of Lightning as a settlement layer. Just as USDT on Tron arguably has better moneyness than a JPMorgan balance, so a “stablecoin” as eCash has better moneyness than as a TA given it is cheaper, more private, and has more relevantly bearer properties (in other words, because it is cash). The technical detail that it can be hashlocked is really all you need to tie this all together. That means it can be atomically locked into a Lightning routed debit to the recipient of a different issuer (or “mint” in eCash lingo, but note this means the same thing as what we have been calling fully reserved banks). And the economic incentive is pretty compelling too because, for all their benefits, there is still a cost to TAs given they are issued onchain and they require asset-specific liquidity to route on Lightning. Once the rest of the tech is in place, why bother? Keep your Lightning connectivity and just become a mint.
What you get at that point is dramatically superior private database to JPMorgan with the dramatically superior public rails of Lightning. There is nothing left to desire from “a blockchain” besides what Bitcoin is fundamentally for in the first place: counterparty-risk-free value settlement.
And as a final point with a curious and pleasing echo to Dee Hock at Visa, Calle has made the point repeatedly that David Chaum’s vision for eCash, while deeply philosophical besides the technical details, was actually pretty much impossible to operate on fiat. From an eCash perspective, fiat stablecoins within the above infrastructure setup are a dramatic improvement on anything previously possible. But, of course, they are a slippery slope to Bitcoin regardless …
Objections Revisited
As a cherry on top, I think the objections I highlighted at the outset are now readily addressed – to the extent the reader believes what I am suggesting is more or less a technical and economic inevitability, that is. While, sure, I’m not particularly keen on giving the Treasury more avenues to sell its welfare-warfare shitcoin, on balance the likely development I’ve outlined is an enormous net positive: it’s going to sell these anyway so I prefer a strong economic incentive to steadily transition not only to Lightning as payment rails but eCash as fiduciary media, and to use “fintech” as a carrot to induce a slow motion bank run.
As alluded to above, once all this is in place, the final step to a Bitcoin standard becomes as simple as an individual’s decision to want Bitcoin instead of fiat. On reflection, this is arguably the easiest part! It's setting up all the tech that puts people off, so trojan-horsing them with “faster, cheaper payment rails” seems like a genius long-term strategy.
And as to “needing a blockchain” (or not), I hope that is entirely wrapped up at this point. The only blockchain you need is Bitcoin, but to the extent people are still confused by this (which I think will take decades more to fully unwind), we may as well lean into dazzling them with whatever innovation buzzwords and decentralization theatre they were going to fall for anyway before realizing they wanted Bitcoin all along.
Conclusion
Stablecoins are useful whether you like it or not. They are stupid in the abstract but it turns out fiat is even stupider, on inspection. But you don’t need a blockchain, and using one as decentralization theatre creates technical debt that is insurmountable in the long run. Blockchain-based stablecoins are doomed to a utility inversely proportional to their usage, and just to rub it in, their ill-conceived design practically creates a commercial dynamic that mandates there only ever be a single issuer.
Given they are useful, it seems natural that this tension is going to blow up at some point. It also seems worthwhile observing that Taproot Asset stablecoins have almost the inverse problem and opposite commercial dynamic: they will be most expensive to use at the outset but get cheaper and cheaper as their usage grows. Also, there is no incentive towards a monopoly issuer but rather towards as many as are willing to try to operate well and provide value to their users.
As such, we can expect any sizable growth in stablecoins to migrate to TA out of technical and economic necessity. Once this has happened - or possibly while it is happening but is clearly not going to stop - we may as well strip out the TA component and just use eCash because you really don’t need a blockchain for that at all. And once all the money is on eCash, deciding you want to denominate it in Bitcoin is the simplest on-ramp to hyperbitcoinization you can possibly imagine, given we’ve spent the previous decade or two rebuilding all payments tech around Lightning.
Or: Bitcoin fixes this. The End.
- Allen, #892,125
thanks to Marco Argentieri, Lyn Alden, and Calle for comments and feedback
-
 @ c3c7122c:607731d7
2025-04-12 04:05:06
@ c3c7122c:607731d7
2025-04-12 04:05:06Help!
Calling all El Salvador Nostriches! If you currently live in SV, I need your help and am offering several bounties (0.001, 0.01, and 0.1 BTC).
In Brief
In short, I am pursuing El Salvador citizenship by birthright (through my grandmother). I’ve struggled to progress because her name varies on different documents. I need someone to help me push harder to get past this barrier, or connect me with information or people who can work on my behalf. I am offering:
- 0.001 BTC (100k sats) for information that will help me progress from my current situation
- 0.01 BTC (1 MM sats) to get me in touch with someone that is more impactful than the immigration lawyer I already spoke with
- 0.1 BTC (10 MM sats) if your efforts help me obtain citizenship for me or my father
Background
My grandma married my grandfather (an American Marine) and moved to the states where my father was born. I have some official and unofficial documents where her name varies in spelling, order of first/middle name, and addition of her father’s last name. So every doc basically has a different name for her. I was connected with an english-speaking immigration lawyer in SV who hit a dead end when searching for her official ID because the city hall in her city had burned down so there was no record of her info. He gave up at that point. I find it odd that it was so easy to change your name back then, but they are more strict now with the records from that time.
I believe SV citizenship is my birthright and have several personal reasons for pursuing this. I want someone to act on my behalf who will try harder to work the system (by appeal, loophole, or even bribe if I have to). If you are local and can help me with this, I’d greatly appreciate any efforts you make.
Cheers!
Corey San Diego
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3eba5ef4:751f23ae
2025-04-11 00:40:28
@ 3eba5ef4:751f23ae
2025-04-11 00:40:28Crypto Insights
2025 MIT Bitcoin Expo: Spotlight on Freedom Tech
The 12th MIT Bitcoin Expo took place on April 5–6, centering this year’s theme on “Freedom Tech” and how technology can facilitate physical and social liberation.
-
Day 1 Recap: Mawarire delivered the keynote speech “Why Freedom Tech Matters,” and Dryja discussed how Bitcoin demonstrates resilience against nation-states. The morning sessions focused on corporate adoption, featuring speakers such as Paul Giordano from Marathon Digital and Bitcoin Core contributors like Gloria Zhao. The afternoon shifted toward more technical topics, including consensus cleanup, poisoning attacks, censorship resistance, and the Bitcoin Pipes protocol.
-
Day 2 Recap: The focus shifted to global impact. Mauricio Bartolomeo discussed the exfiltration of resources via Bitcoin, followed by a panel with activists from Venezuela, Russia, and Togo. Technical topics included: scaling self-custody, Steven Roose’s covenant soft fork proposals, the future of freedom tech, quantum resistance, and Tor.
Into Bitcoin Address Poisoning Attacks
In this article, Jameson Lopp highlights the rise of Bitcoin address poisoning attacks—an emerging form of social engineering. Attackers send transactions from newly generated wallets that mimic the beginning and end characters of a target's recently used address. If the target later copies an address from their transaction history, they may unknowingly send funds to the attacker instead of the intended recipient. Though the success rate per attack is low, the low cost of transactions enables attackers to attempt thousands in a short period.
Lopp also argues that such attacks are a byproduct of low transaction fees and that higher fees could deter them. He also suggests wallet-level defenses, such as warnings like, “Oh, this came from a similar looking address,” to help users avoid interaction.
Examining the Mitigation Strategy Against Timewarp Attacks
Timewarp attacks, first identified around 2011, allow a majority of malicious miners to manipulate block timestamps, artificially lower difficulty, and mine blocks every few seconds. The “Great Consensus Cleanup” soft fork proposal can mitigate this by requiring that the first block in a new difficulty period must have a time no earlier than a certain number of minutes before the last block of the previous period.
A report examines the details of this BIP.
Tokenization on Bitcoin: Building a Global Settlement Layer with Taproot Assets and Lightning
Bitcoin’s evolution into a multi-asset platform is accelerating with the advent of Taproot Assets and Lightning Network. The integration of these technologies combines Bitcoin’s decentralization and security with the speed and scalability of the Lightning Network. This report examines how Taproot Assets enable asset issuance, transfers, and swaps on Bitcoin’s base layer, and how the Lightning Network facilitates fast, low-cost transfers of those assets. We compare this approach to earlier attempts at Bitcoin asset issuance and analyze its market potential against other blockchains and traditional payment networks.
Solving Data Availability in Client-Side Validation With UTxO Binding
Issuing tokens on Bitcoin is attractive due to its security and dominance, but its limited functionality creates challenges. Client-side validation (CSV) is a common workaround, using off-chain data with on-chain verification, though it risks data loss and withholding. This paper introduces UTxO binding, a framework that links a Bitcoin UTxO to one on an auxiliary chain, providing data storage and programmability. The authors prove its security and implement it using Nervos CKB.
From State Differences to Scaling: Citrea’s Fee Mechanism for Bitcoin
The Citrea team has designed a new fee mechanism to enhance Bitcoin’s scalability without compromising security. It only records essential state differences (i.e., state slot changes) on the Bitcoin main chain, using zero-knowledge proofs to ensure verifiability and Bitcoin security while drastically reducing state inscription costs. Optimizations include: replacing
codefield withcode_hash, compressing state data using a highly efficient compression algorithm Brotli, and analyzing historical Ethereum block data to estimate each transaction’s impact on cumulative state differences—enabling a discount to each transaction.Second: A New Ark Implementation Launched on Bitcoin Signet
Second, a protocol based on Ark to improve Bitcoin transaction throughput, has launched Bark, a test implementation on Bitcoin Signet.
Ark makes Bitcoin transactions faster, cheaper, and more private, allowing more users and transactions per block. However, funds stored non-custodially via Ark can expire if unused, making it slightly less trustless than mainchain transactions.
BitLayer Optimizes BitVM Bridge Protocol and Demonstrates on Testnet
Bitlayer BitVM Bridge protocol is an optimized adaptation of the bridge protocol outlined in the BitVM2 paper, to improve efficiency, scalability, and security—especially for high-risk cross-chain transactions.
In this article, two key testnet demos on bitvmnet (a BitVM-dedicated testnet) demonstrate how the protocol can:
-
Effectively thwart fraudulent reclaim attempts by brokers.
-
Protect honest brokers from malicious or baseless challenges.
Cardano Enables Bitcoin DeFi via BitVMX and Lightning Hydra
Cardano is integrating with Bitcoin through Lightning Hydra and BitVMX to enable secure and scalable Bitcoin DeFi.
Zcash’s Tachyon Upgrade: Toward Scalable Oblivious Synchronization
Zcash has unveiled project Tachyon, a proposal to scale Zcash by changing how wallets sync and prove ownership of notes. Instead of scanning the entire blockchain, wallets track only their own nullifiers and receive succinct proofs from untrusted, oblivious sync servers. Transactions include proofs of wallet state (using recursive SNARKs), allowing nodes to verify them without keeping the full history. Notes are exchanged out-of-band, reducing on-chain data and improving privacy. In the nominal case, users get fast sync, lightweight wallets, and strong privacy, without the need to trust the network.
Podcast | Why the Future of Bitcoin Mining is Distributed
In this podcast, Professor Troy Cross discusses the centralization of Bitcoin mining and argues convincingly for hashrate decentralization. While economies of scale have led to mega mining operations, he sees economic imperative that will drive mining toward a globally distributed future—not dominated by the U.S.—ensuring neutrality and resilience against state-level threats.
Binance Report|Crypto Industry Map March 2025
This report provides an overview of projects using a framework that divides crypto into four core ecosystems—Infrastructure, DeFi, NFT, and Gaming—and four trending sectors: Stablecoins, RWA, AI, and DeSci.
For infrastructure, five key pillars are identified: scalability & fairness, data availability & tooling, security & privacy, cloud networks, and connectivity. The report also maps out and categorizes the major projects and solutions currently on the market.

Top Reads on Blockchain and Beyond
A Game-Theoretic Approach to Bitcoin’s Valuation in Equilibrium
The author presents a game-theoretic argument for why Bitcoin will emerge as the optimal unit of account in equilibrium. The argument is based upon the observation that a generally agreed upon unit of account that represents a constant share of total wealth (equal to the totality of all other economic utility) will naturally create price signals that passively stabilize the macroeconomy, without requiring external intervention.
Bitcoin’s unique properties—finite supply, inertness, fungibility, accessibility, and ownership history—position it as the leading candidate to emerge as this unit.
Neo: Lattice-Based Folding Scheme for CCS Over Small Fields and Pay-Per-Bit Commitments
This paper introduces Neo, a new lattice-based folding scheme for CCS, an NP-complete relation that generalizes R1CS, Plonkish, and AIR. Neo's folding scheme can be viewed as adapting the folding scheme in HyperNova (CRYPTO'24), which assumes elliptic-curve based linearly homomorphic commitments, to the lattice setting. Unlike HyperNova, Neo can use “small” prime fields (e.g., over the Goldilocks prime). Additionally, Neo provides plausible post-quantum security.
Social Scalability: Key to Massive Value Accumulation in Crypto
Social scalability, a concept first proposed by Nick Szabo in his 2017 article Money, Blockchains, and Social Scalability, is further explored in this thread. Here, “social scalability” refers to an institution's ability to allow the maximum number of people to have skin in the game and win. It’s seen as the main reason crypto has become a $2.9T asset class today and a key driver of value accumulation in the coming decade.
The author argues that two critical ingredients for long-term social scalability are credible neutrality and utility. Currently, only BTC and ETH have this potential, yet neither strikes a perfect balance between the two. The author notes that there is not yet a strong narrative around social scalability, and concludes by emphasizing the importance of focusing on long-term value and resisting the temptation of short-term market narratives.
-

