-
 @ 52b4a076:e7fad8bd
2025-05-03 21:54:45
@ 52b4a076:e7fad8bd
2025-05-03 21:54:45Introduction
Me and Fishcake have been working on infrastructure for Noswhere and Nostr.build. Part of this involves processing a large amount of Nostr events for features such as search, analytics, and feeds.
I have been recently developing
nosdexv3, a newer version of the Noswhere scraper that is designed for maximum performance and fault tolerance using FoundationDB (FDB).Fishcake has been working on a processing system for Nostr events to use with NB, based off of Cloudflare (CF) Pipelines, which is a relatively new beta product. This evening, we put it all to the test.
First preparations
We set up a new CF Pipelines endpoint, and I implemented a basic importer that took data from the
nosdexdatabase. This was quite slow, as it did HTTP requests synchronously, but worked as a good smoke test.Asynchronous indexing
I implemented a high-contention queue system designed for highly parallel indexing operations, built using FDB, that supports: - Fully customizable batch sizes - Per-index queues - Hundreds of parallel consumers - Automatic retry logic using lease expiration
When the scraper first gets an event, it will process it and eventually write it to the blob store and FDB. Each new event is appended to the event log.
On the indexing side, a
Queuerwill read the event log, and batch events (usually 2K-5K events) into one work job. This work job contains: - A range in the log to index - Which target this job is intended for - The size of the job and some other metadataEach job has an associated leasing state, which is used to handle retries and prioritization, and ensure no duplication of work.
Several
Workers monitor the index queue (up to 128) and wait for new jobs that are available to lease.Once a suitable job is found, the worker acquires a lease on the job and reads the relevant events from FDB and the blob store.
Depending on the indexing type, the job will be processed in one of a number of ways, and then marked as completed or returned for retries.
In this case, the event is also forwarded to CF Pipelines.

Trying it out
The first attempt did not go well. I found a bug in the high-contention indexer that led to frequent transaction conflicts. This was easily solved by correcting an incorrectly set parameter.
We also found there were other issues in the indexer, such as an insufficient amount of threads, and a suspicious decrease in the speed of the
Queuerduring processing of queued jobs.Along with fixing these issues, I also implemented other optimizations, such as deprioritizing
WorkerDB accesses, and increasing the batch size.To fix the degraded
Queuerperformance, I ran the backfill job by itself, and then started indexing after it had completed.Bottlenecks, bottlenecks everywhere

After implementing these fixes, there was an interesting problem: The DB couldn't go over 80K reads per second. I had encountered this limit during load testing for the scraper and other FDB benchmarks.
As I suspected, this was a client thread limitation, as one thread seemed to be using high amounts of CPU. To overcome this, I created a new client instance for each
Worker.After investigating, I discovered that the Go FoundationDB client cached the database connection. This meant all attempts to create separate DB connections ended up being useless.
Using
OpenWithConnectionStringpartially resolved this issue. (This also had benefits for service-discovery based connection configuration.)To be able to fully support multi-threading, I needed to enabled the FDB multi-client feature. Enabling it also allowed easier upgrades across DB versions, as FDB clients are incompatible across versions:
FDB_NETWORK_OPTION_EXTERNAL_CLIENT_LIBRARY="/lib/libfdb_c.so"FDB_NETWORK_OPTION_CLIENT_THREADS_PER_VERSION="16"Breaking the 100K/s reads barrier

After implementing support for the multi-threaded client, we were able to get over 100K reads per second.
You may notice after the restart (gap) the performance dropped. This was caused by several bugs: 1. When creating the CF Pipelines endpoint, we did not specify a region. The automatically selected region was far away from the server. 2. The amount of shards were not sufficient, so we increased them. 3. The client overloaded a few HTTP/2 connections with too many requests.
I implemented a feature to assign each
Workerits own HTTP client, fixing the 3rd issue. We also moved the entire storage region to West Europe to be closer to the servers.After these changes, we were able to easily push over 200K reads/s, mostly limited by missing optimizations:

It's shards all the way down
While testing, we also noticed another issue: At certain times, a pipeline would get overloaded, stalling requests for seconds at a time. This prevented all forward progress on the
Workers.We solved this by having multiple pipelines: A primary pipeline meant to be for standard load, with moderate batching duration and less shards, and high-throughput pipelines with more shards.
Each
Workeris assigned a pipeline on startup, and if one pipeline stalls, other workers can continue making progress and saturate the DB.The stress test
After making sure everything was ready for the import, we cleared all data, and started the import.
The entire import lasted 20 minutes between 01:44 UTC and 02:04 UTC, reaching a peak of: - 0.25M requests per second - 0.6M keys read per second - 140MB/s reads from DB - 2Gbps of network throughput
FoundationDB ran smoothly during this test, with: - Read times under 2ms - Zero conflicting transactions - No overloaded servers
CF Pipelines held up well, delivering batches to R2 without any issues, while reaching its maximum possible throughput.

Finishing notes
Me and Fishcake have been building infrastructure around scaling Nostr, from media, to relays, to content indexing. We consistently work on improving scalability, resiliency and stability, even outside these posts.
Many things, including what you see here, are already a part of Nostr.build, Noswhere and NFDB, and many other changes are being implemented every day.
If you like what you are seeing, and want to integrate it, get in touch. :)
If you want to support our work, you can zap this post, or register for nostr.land and nostr.build today.
-
 @ 6ad3e2a3:c90b7740
2025-05-03 15:33:07
@ 6ad3e2a3:c90b7740
2025-05-03 15:33:07You are wearing a helmet, but it's been on your head so long you no longer notice it.
The helmet interfaces with your mind via thought-emotion. It influences what you think about and how you feel.
You could remove the helmet at any time. But the thought-emotions keep you distracted, fearful and attached.
Occasionally you remember you are wearing it. Moments of clarity and detachment. You see the way your experience is colored by it. You know it is biased, untrue to reality. You seriously contemplate removing it.
But the moment passes.
Later, you remember contemplating your helmet’s removal, but you wonder what you will gain from it, whether it’s worth doing.
You are no longer having a moment of clarity, just a memory of the question that arose from it, but colored now by thought-emotions.
You decide even if you wanted to remove it, you would put it back on before long. After all, you have never kept it off before, why would you suddenly live without this interface now? The interface is what you know.
Maybe one day, when you are in a more secure place, when your ducks are more in a row, you will remove it. Not now, not in the midst of all this chaos, so many things to do, so much on your plate. You will leave it on for now. You will deal with this later.
But one day too late it dawns on you it is always ever now, and later means never. You have lived your entire life at the behest of the interface when all you had to do was remove it.
-
 @ c230edd3:8ad4a712
2025-04-11 16:02:15
@ c230edd3:8ad4a712
2025-04-11 16:02:15Chef's notes
Wildly enough, this is delicious. It's sweet and savory.
(I copied this recipe off of a commercial cheese maker's site, just FYI)
I hadn't fully froze the ice cream when I took the picture shown. This is fresh out of the churner.
Details
- ⏲️ Prep time: 15 min
- 🍳 Cook time: 30 min
- 🍽️ Servings: 4
Ingredients
- 12 oz blue cheese
- 3 Tbsp lemon juice
- 1 c sugar
- 1 tsp salt
- 1 qt heavy cream
- 3/4 c chopped dark chocolate
Directions
- Put the blue cheese, lemon juice, sugar, and salt into a bowl
- Bring heavy cream to a boil, stirring occasionally
- Pour heavy cream over the blue cheese mix and stir until melted
- Pour into prepared ice cream maker, follow unit instructions
- Add dark chocolate halfway through the churning cycle
- Freeze until firm. Enjoy.
-
 @ 088436cd:9d2646cc
2025-05-01 21:01:55
@ 088436cd:9d2646cc
2025-05-01 21:01:55The arrival of the coronavirus brought not only illness and death but also fear and panic. In such an environment of uncertainty, people have naturally stocked up on necessities, not knowing when things will return to normal.
Retail shelves have been cleared out, and even online suppliers like Amazon and Walmart are out of stock for some items. Independent sellers on these e-commerce platforms have had to fill the gap. With the huge increase in demand, they have found that their inventory has skyrocketed in value.
Many in need of these items (e.g. toilet paper, hand sanitizer and masks) balk at the new prices. They feel they are being taken advantage of in a time of need and call for intervention by the government to lower prices. The government has heeded that call, labeling the independent sellers as "price gougers" and threatening sanctions if they don't lower their prices. Amazon has suspended seller accounts and law enforcement at all levels have threatened to prosecute. Prices have dropped as a result and at first glance this seems like a victory for fair play. But, we will have to dig deeper to understand the unseen consequences of this intervention.
We must look at the economics of the situation, how supply and demand result in a price and how that price acts as a signal that goes out to everyone, informing them of underlying conditions in the economy and helping coordinate their actions.
It all started with a rise in demand. Given a fixed supply (e.g., the limited stock on shelves and in warehouses), an increase in demand inevitably leads to higher prices. Most people are familiar with this phenomenon, such as paying more for airline tickets during holidays or surge pricing for rides.
Higher prices discourage less critical uses of scarce resources. For example, you might not pay $1,000 for a plane ticket to visit your aunt if you can get one for $100 the following week, but someone else might pay that price to visit a dying relative. They value that plane seat more than you.
*** During the crisis, demand surged and their shelves emptied even though
However, retail outlets have not raised prices. They have kept them low, so the low-value uses of things like toilet paper, masks and hand sanitizer has continued. Often, this "use" just takes the form of hoarding. At everyday low prices, it makes sense to buy hundreds of rolls and bottles. You know you will use them eventually, so why not stock up? And, with all those extra supplies in the closet and basement, you don't need to change your behavior much. You don't have to ration your use.
At the low prices, these scarce resources got bought up faster and faster until there was simply none left. The reality of the situation became painfully clear to those who didn't panic and got to the store late: You have no toilet paper and you're not going to any time soon.
However, if prices had been allowed to rise, a number of effects would have taken place that would have coordinated the behavior of everyone so that valuable resources would not have been wasted or hoarded, and everyone could have had access to what they needed.
On the demand side, if prices had been allowed to rise, people would have begun to self-ration. You might leave those extra plies on the roll next time if you know they will cost ten times as much to replace. Or, you might choose to clean up a spill with a rag rather than disposable tissue. Most importantly, you won't hoard as much. That 50th bottle of hand sanitizer might just not be worth it at the new, high price. You'll leave it on the shelf for someone else who may have none.
On the supply side, higher prices would have incentivized people to offer up more of their stockpiles for sale. If you have a pallet full of toilet paper in your basement and all of the sudden they are worth $15 per roll, you might just list a few online. But, if it is illegal to do so, you probably won't.
Imagine you run a business installing insulation and have a few thousand respirator masks on hand for your employees. During a pandemic, it is much more important that people breathe filtered air than that insulation get installed, and that fact is reflected in higher prices. You will sell your extra masks at the higher price rather than store them for future insulation jobs, and the scarce resource will be put to its most important use.
Producers of hand sanitizer would go into overdrive if prices were allowed to rise. They would pay their employees overtime, hire new ones, and pay a premium for their supplies, making sure their raw materials don't go to less important uses.
These kinds of coordinated actions all across the economy would be impossible without real prices to guide them. How do you know if it makes sense to spend an extra $10k bringing a thousand masks to market unless you know you can get more than $10 per mask? If the price is kept artificially low, you simply can't do it. The money just isn't there.
These are the immediate effects of a price change, but incredibly, price changes also coordinate people's actions across space and time.
Across space, there are different supply and demand conditions in different places, and thus prices are not uniform. We know some places are real "hot spots" for the virus, while others are mostly unaffected. High demand in the hot spots leads to higher prices there, which attracts more of the resource to those areas. Boxes and boxes of essential items would pour in where they are needed most from where they are needed least, but only if prices were allowed to adjust freely.
This would be accomplished by individuals and businesses buying low in the unaffected areas, selling high in the hot spots and subtracting their labor and transportation costs from the difference. Producers of new supply would know exactly where it is most needed and ship to the high-demand, high-price areas first. The effect of these actions is to increase prices in the low demand areas and reduce them in the high demand areas. People in the low demand areas will start to self-ration more, reflecting the reality of their neighbors, and people in the hotspots will get some relief.
However, by artificially suppressing prices in the hot spot, people there will simply buy up the available supply and run out, and it will be cost prohibitive to bring in new supply from low-demand areas.
Prices coordinate economic actions across time as well. Just as entrepreneurs and businesses can profit by transporting scarce necessities from low-demand to high-demand areas, they can also profit by buying in low-demand times and storing their merchandise for when it is needed most.
Just as allowing prices to freely adjust in one area relative to another will send all the right signals for the optimal use of a scarce resource, allowing prices to freely adjust over time will do the same.
When an entrepreneur buys up resources during low-demand times in anticipation of a crisis, she restricts supply ahead of the crisis, which leads to a price increase. She effectively bids up the price. The change in price affects consumers and producers in all the ways mentioned above. Consumers self-ration more, and producers bring more of the resource to market.
Our entrepreneur has done a truly incredible thing. She has predicted the future, and by so doing has caused every individual in the economy to prepare for a shortage they don't even know is coming! And, by discouraging consumption and encouraging production ahead of time, she blunts the impact the crisis will have. There will be more of the resource to go around when it is needed most.
On top of this, our entrepreneur still has her stockpile she saved back when everyone else was blithely using it up. She can now further mitigate the damage of the crisis by selling her stock during the worst of it, when people are most desperate for relief. She will know when this is because the price will tell her, but only if it is allowed to adjust freely. When the price is at its highest is when people need the resource the most, and those willing to pay will not waste it or hoard it. They will put it to its highest valued use.
The economy is like a big bus we are all riding in, going down a road with many twists and turns. Just as it is difficult to see into the future, it is difficult to see out the bus windows at the road ahead.
On the dashboard, we don't have a speedometer or fuel gauge. Instead we have all the prices for everything in the economy. Prices are what tell us the condition of the bus and the road. They tell us everything. Without them, we are blind.
Good times are a smooth road. Consumer prices and interest rates are low, investment returns are steady. We hit the gas and go fast. But, the road is not always straight and smooth. Sometimes there are sharp turns and rough patches. Successful entrepreneurs are the ones who can see what is coming better than everyone else. They are our navigators.
When they buy up scarce resources ahead of a crisis, they are hitting the brakes and slowing us down. When they divert resources from one area to another, they are steering us onto a smoother path. By their actions in the market, they adjust the prices on our dashboard to reflect the conditions of the road ahead, so we can prepare for, navigate and get through the inevitable difficulties we will face.
Interfering with the dashboard by imposing price floors or price caps doesn't change the conditions of the road (the number of toilet paper rolls in existence hasn't changed). All it does is distort our perception of those conditions. We think the road is still smooth--our heavy foot stomping the gas--as we crash onto a rocky dirt road at 80 miles per hour (empty shelves at the store for weeks on end).
Supply, demand and prices are laws of nature. All of this is just how things work. It isn't right or wrong in a moral sense. Price caps lead to waste, shortages and hoarding as surely as water flows downhill. The opposite--allowing prices to adjust freely--leads to conservation of scarce resources and their being put to their highest valued use. And yes, it leads to profits for the entrepreneurs who were able to correctly predict future conditions, and losses for those who weren't.
Is it fair that they should collect these profits? On the one hand, anyone could have stocked up on toilet paper, hand sanitizer and face masks at any time before the crisis, so we all had a fair chance to get the supplies cheaply. On the other hand, it just feels wrong that some should profit so much at a time when there is so much need.
Our instinct in the moment is to see the entrepreneur as a villain, greedy "price gouger". But we don't see the long chain of economic consequences the led to the situation we feel is unfair.
If it weren't for anti-price-gouging laws, the major retailers would have raised their prices long before the crisis became acute. When they saw demand outstrip supply, they would have raised prices, not by 100 fold, but gradually and long before anyone knew how serious things would have become. Late comers would have had to pay more, but at least there would be something left on the shelf.
As an entrepreneur, why take risks trying to anticipate the future if you can't reap the reward when you are right? Instead of letting instead of letting entrepreneurs--our navigators--guide us, we are punishing and vilifying them, trying to force prices to reflect a reality that simply doesn't exist.
In a crisis, more than any other time, prices must be allowed to fluctuate. To do otherwise is to blind ourselves at a time when danger and uncertainty abound. It is economic suicide.
In a crisis, there is great need, and the way to meet that need is not by pretending it's not there, by forcing prices to reflect a world where there isn't need. They way to meet the need is the same it has always been, through charity.
If the people in government want to help, the best way for the to do so is to be charitable and reduce their taxes and fees as much as possible, ideally to zero in a time of crisis. Amazon, for example, could instantly reduce the price of all crisis related necessities by 20% if they waived their fee. This would allow for more uses by more people of these scarce supplies as hoarders release their stockpiles on to the market, knowing they can get 20% more for their stock. Governments could reduce or eliminate their tax burden on high-demand, crisis-related items and all the factors that go into their production, with the same effect: a reduction in prices and expansion of supply. All of us, including the successful entrepreneurs and the wealthy for whom high prices are not a great burden, could donate to relief efforts.
These ideas are not new or untested. This is core micro economics. It has been taught for hundreds of years in universities the world over. The fact that every crisis that comes along stirs up ire against entrepreneurs indicates not that the economics is wrong, but that we have a strong visceral reaction against what we perceive to be unfairness. This is as it should be. Unfairness is wrong and the anger it stirs in us should compel us to right the wrong. Our anger itself isn't wrong, it's just misplaced.
Entrepreneurs didn't cause the prices to rise. Our reaction to a virus did that. We saw a serious threat and an uncertain future and followed our natural impulse to hoard. Because prices at major retail suppliers didn't rise, that impulse ran rampant and we cleared the shelves until there was nothing left. We ran the bus right off the road and them blamed the entrepreneurs for showing us the reality of our situation, for shaking us out of the fantasy of low prices.
All of this is not to say that entrepreneurs are high-minded public servants. They are just doing their job. Staking your money on an uncertain future is a risky business. There are big risks and big rewards. Most entrepreneurs just scrape by or lose their capital in failed ventures.
However, the ones that get it right must be allowed to keep their profits, or else no one will try and we'll all be driving blind. We need our navigators. It doesn't even matter if they know all the positive effects they are having on the rest of us and the economy as a whole. So long as they are buying low and selling high--so long as they are doing their job--they will be guiding the rest of us through the good times and the bad, down the open road and through the rough spots.
-
 @ c230edd3:8ad4a712
2025-04-09 00:33:31
@ c230edd3:8ad4a712
2025-04-09 00:33:31Chef's notes
I found this recipe a couple years ago and have been addicted to it since. Its incredibly easy, and cheap to prep. Freeze the sausage in flat, single serving portions. That way it can be cooked from frozen for a fast, flavorful, and healthy lunch or dinner. I took inspiration from the video that contained this recipe, and almost always pan fry the frozen sausage with some baby broccoli. The steam cooks the broccoli and the fats from the sausage help it to sear, while infusing the vibrant flavors. Serve with some rice, if desired. I often use serrano peppers, due to limited produce availability. They work well for a little heat and nice flavor that is not overpowering.
Details
- ⏲️ Prep time: 25 min
- 🍳 Cook time: 15 min (only needed if cooking at time of prep)
- 🍽️ Servings: 10
Ingredients
- 4 lbs ground pork
- 12-15 cloves garlic, minced
- 6 Thai or Serrano peppers, rough chopped
- 1/4 c. lime juice
- 4 Tbsp fish sauce
- 1 Tbsp brown sugar
- 1/2 c. chopped cilantro
Directions
- Mix all ingredients in a large bowl.
- Portion and freeze, as desired.
- Sautè frozen portions in hot frying pan, with broccoli or other fresh veggies.
- Serve with rice or alone.
-
 @ 00000001:b0c77eb9
2025-02-14 21:24:24
@ 00000001:b0c77eb9
2025-02-14 21:24:24مواقع التواصل الإجتماعي العامة هي التي تتحكم بك، تتحكم بك بفرض أجندتها وتجبرك على اتباعها وتحظر وتحذف كل ما يخالفها، وحرية التعبير تنحصر في أجندتها تلك!
وخوارزمياتها الخبيثة التي لا حاجة لها، تعرض لك مايريدون منك أن تراه وتحجب ما لا يريدونك أن تراه.
في نوستر انت المتحكم، انت الذي تحدد من تتابع و انت الذي تحدد المرحلات التي تنشر منشوراتك بها.
نوستر لامركزي، بمعنى عدم وجود سلطة تتحكم ببياناتك، بياناتك موجودة في المرحلات، ولا احد يستطيع حذفها او تعديلها او حظر ظهورها.
و هذا لا ينطبق فقط على مواقع التواصل الإجتماعي العامة، بل ينطبق أيضاً على الـfediverse، في الـfediverse انت لست حر، انت تتبع الخادم الذي تستخدمه ويستطيع هذا الخادم حظر ما لا يريد ظهوره لك، لأنك لا تتواصل مع بقية الخوادم بنفسك، بل خادمك من يقوم بذلك بالنيابة عنك.
وحتى إذا كنت تمتلك خادم في شبكة الـfediverse، إذا خالفت اجندة بقية الخوادم ونظرتهم عن حرية الرأي و التعبير سوف يندرج خادمك في القائمة السوداء fediblock ولن يتمكن خادمك من التواصل مع بقية خوادم الشبكة، ستكون محصوراً بالخوادم الأخرى المحظورة كخادمك، بالتالي انت في الشبكة الأخرى من الـfediverse!
نعم، يوجد شبكتان في الكون الفدرالي fediverse شبكة الصالحين التابعين للأجندة الغربية وشبكة الطالحين الذين لا يتبعون لها، إذا تم إدراج خادمك في قائمة fediblock سوف تذهب للشبكة الأخرى!
-
 @ c1e9ab3a:9cb56b43
2025-05-01 17:29:18
@ c1e9ab3a:9cb56b43
2025-05-01 17:29:18High-Level Overview
Bitcoin developers are currently debating a proposed change to how Bitcoin Core handles the
OP_RETURNopcode — a mechanism that allows users to insert small amounts of data into the blockchain. Specifically, the controversy revolves around removing built-in filters that limit how much data can be stored using this feature (currently capped at 80 bytes).Summary of Both Sides
Position A: Remove OP_RETURN Filters
Advocates: nostr:npub1ej493cmun8y9h3082spg5uvt63jgtewneve526g7e2urca2afrxqm3ndrm, nostr:npub12rv5lskctqxxs2c8rf2zlzc7xx3qpvzs3w4etgemauy9thegr43sf485vg, nostr:npub17u5dneh8qjp43ecfxr6u5e9sjamsmxyuekrg2nlxrrk6nj9rsyrqywt4tp, others
Arguments: - Ineffectiveness of filters: Filters are easily bypassed and do not stop spam effectively. - Code simplification: Removing arbitrary limits reduces code complexity. - Permissionless innovation: Enables new use cases like cross-chain bridges and timestamping without protocol-level barriers. - Economic regulation: Fees should determine what data gets added to the blockchain, not protocol rules.
Position B: Keep OP_RETURN Filters
Advocates: nostr:npub1lh273a4wpkup00stw8dzqjvvrqrfdrv2v3v4t8pynuezlfe5vjnsnaa9nk, nostr:npub1s33sw6y2p8kpz2t8avz5feu2n6yvfr6swykrnm2frletd7spnt5qew252p, nostr:npub1wnlu28xrq9gv77dkevck6ws4euej4v568rlvn66gf2c428tdrptqq3n3wr, others
Arguments: - Historical intent: Satoshi included filters to keep Bitcoin focused on monetary transactions. - Resource protection: Helps prevent blockchain bloat and abuse from non-financial uses. - Network preservation: Protects the network from being overwhelmed by low-value or malicious data. - Social governance: Maintains conservative changes to ensure long-term robustness.
Strengths and Weaknesses
Strengths of Removing Filters
- Encourages decentralized innovation.
- Simplifies development and maintenance.
- Maintains ideological purity of a permissionless system.
Weaknesses of Removing Filters
- Opens the door to increased non-financial data and potential spam.
- May dilute Bitcoin’s core purpose as sound money.
- Risks short-term exploitation before economic filters adapt.
Strengths of Keeping Filters
- Preserves Bitcoin’s identity and original purpose.
- Provides a simple protective mechanism against abuse.
- Aligns with conservative development philosophy of Bitcoin Core.
Weaknesses of Keeping Filters
- Encourages central decision-making on allowed use cases.
- Leads to workarounds that may be less efficient or obscure.
- Discourages novel but legitimate applications.
Long-Term Consequences
If Filters Are Removed
- Positive: Potential boom in new applications, better interoperability, cleaner architecture.
- Negative: Risk of increased blockchain size, more bandwidth/storage costs, spam wars.
If Filters Are Retained
- Positive: Preserves monetary focus and operational discipline.
- Negative: Alienates developers seeking broader use cases, may ossify the protocol.
Conclusion
The debate highlights a core philosophical split in Bitcoin: whether it should remain a narrow monetary system or evolve into a broader data layer for decentralized applications. Both paths carry risks and tradeoffs. The outcome will shape not just Bitcoin's technical direction but its social contract and future role in the broader crypto ecosystem.
-
 @ a008def1:57a3564d
2025-04-30 17:52:11
@ a008def1:57a3564d
2025-04-30 17:52:11A Vision for #GitViaNostr
Git has long been the standard for version control in software development, but over time, we has lost its distributed nature. Originally, Git used open, permissionless email for collaboration, which worked well at scale. However, the rise of GitHub and its centralized pull request (PR) model has shifted the landscape.
Now, we have the opportunity to revive Git's permissionless and distributed nature through Nostr!
We’ve developed tools to facilitate Git collaboration via Nostr, but there are still significant friction that prevents widespread adoption. This article outlines a vision for how we can reduce those barriers and encourage more repositories to embrace this approach.
First, we’ll review our progress so far. Then, we’ll propose a guiding philosophy for our next steps. Finally, we’ll discuss a vision to tackle specific challenges, mainly relating to the role of the Git server and CI/CD.
I am the lead maintainer of ngit and gitworkshop.dev, and I’ve been fortunate to work full-time on this initiative for the past two years, thanks to an OpenSats grant.
How Far We’ve Come
The aim of #GitViaNostr is to liberate discussions around code collaboration from permissioned walled gardens. At the core of this collaboration is the process of proposing and applying changes. That's what we focused on first.
Since Nostr shares characteristics with email, and with NIP34, we’ve adopted similar primitives to those used in the patches-over-email workflow. This is because of their simplicity and that they don’t require contributors to host anything, which adds reliability and makes participation more accessible.
However, the fork-branch-PR-merge workflow is the only model many developers have known, and changing established workflows can be challenging. To address this, we developed a new workflow that balances familiarity, user experience, and alignment with the Nostr protocol: the branch-PR-merge model.
This model is implemented in ngit, which includes a Git plugin that allows users to engage without needing to learn new commands. Additionally, gitworkshop.dev offers a GitHub-like interface for interacting with PRs and issues. We encourage you to try them out using the quick start guide and share your feedback. You can also explore PRs and issues with gitplaza.
For those who prefer the patches-over-email workflow, you can still use that approach with Nostr through gitstr or the
ngit sendandngit listcommands, and explore patches with patch34.The tools are now available to support the core collaboration challenge, but we are still at the beginning of the adoption curve.
Before we dive into the challenges—such as why the Git server setup can be jarring and the possibilities surrounding CI/CD—let’s take a moment to reflect on how we should approach the challenges ahead of us.
Philosophy
Here are some foundational principles I shared a few years ago:
- Let Git be Git
- Let Nostr be Nostr
- Learn from the successes of others
I’d like to add one more:
- Embrace anarchy and resist monolithic development.
Micro Clients FTW
Nostr celebrates simplicity, and we should strive to maintain that. Monolithic developments often lead to unnecessary complexity. Projects like gitworkshop.dev, which aim to cover various aspects of the code collaboration experience, should not stifle innovation.
Just yesterday, the launch of following.space demonstrated how vibe-coded micro clients can make a significant impact. They can be valuable on their own, shape the ecosystem, and help push large and widely used clients to implement features and ideas.
The primitives in NIP34 are straightforward, and if there are any barriers preventing the vibe-coding of a #GitViaNostr app in an afternoon, we should work to eliminate them.
Micro clients should lead the way and explore new workflows, experiences, and models of thinking.
Take kanbanstr.com. It provides excellent project management and organization features that work seamlessly with NIP34 primitives.
From kanban to code snippets, from CI/CD runners to SatShoot—may a thousand flowers bloom, and a thousand more after them.
Friction and Challenges
The Git Server
In #GitViaNostr, maintainers' branches (e.g.,
master) are hosted on a Git server. Here’s why this approach is beneficial:- Follows the original Git vision and the "let Git be Git" philosophy.
- Super efficient, battle-tested, and compatible with all the ways people use Git (e.g., LFS, shallow cloning).
- Maintains compatibility with related systems without the need for plugins (e.g., for build and deployment).
- Only repository maintainers need write access.
In the original Git model, all users would need to add the Git server as a 'git remote.' However, with ngit, the Git server is hidden behind a Nostr remote, which enables:
- Hiding complexity from contributors and users, so that only maintainers need to know about the Git server component to start using #GitViaNostr.
- Maintainers can easily swap Git servers by updating their announcement event, allowing contributors/users using ngit to automatically switch to the new one.
Challenges with the Git Server
While the Git server model has its advantages, it also presents several challenges:
- Initial Setup: When creating a new repository, maintainers must select a Git server, which can be a jarring experience. Most options come with bloated social collaboration features tied to a centralized PR model, often difficult or impossible to disable.
-
Manual Configuration: New repositories require manual configuration, including adding new maintainers through a browser UI, which can be cumbersome and time-consuming.
-
User Onboarding: Many Git servers require email sign-up or KYC (Know Your Customer) processes, which can be a significant turn-off for new users exploring a decentralized and permissionless alternative to GitHub.
Once the initial setup is complete, the system works well if a reliable Git server is chosen. However, this is a significant "if," as we have become accustomed to the excellent uptime and reliability of GitHub. Even professionally run alternatives like Codeberg can experience downtime, which is frustrating when CI/CD and deployment processes are affected. This problem is exacerbated when self-hosting.
Currently, most repositories on Nostr rely on GitHub as the Git server. While maintainers can change servers without disrupting their contributors, this reliance on a centralized service is not the decentralized dream we aspire to achieve.
Vision for the Git Server
The goal is to transform the Git server from a single point of truth and failure into a component similar to a Nostr relay.
Functionality Already in ngit to Support This
-
State on Nostr: Store the state of branches and tags in a Nostr event, removing reliance on a single server. This validates that the data received has been signed by the maintainer, significantly reducing the trust requirement.
-
Proxy to Multiple Git Servers: Proxy requests to all servers listed in the announcement event, adding redundancy and eliminating the need for any one server to match GitHub's reliability.
Implementation Requirements
To achieve this vision, the Nostr Git server implementation should:
-
Implement the Git Smart HTTP Protocol without authentication (no SSH) and only accept pushes if the reference tip matches the latest state event.
-
Avoid Bloat: There should be no user authentication, no database, no web UI, and no unnecessary features.
-
Automatic Repository Management: Accept or reject new repositories automatically upon the first push based on the content of the repository announcement event referenced in the URL path and its author.
Just as there are many free, paid, and self-hosted relays, there will be a variety of free, zero-step signup options, as well as self-hosted and paid solutions.
Some servers may use a Web of Trust (WoT) to filter out spam, while others might impose bandwidth or repository size limits for free tiers or whitelist specific npubs.
Additionally, some implementations could bundle relay and blossom server functionalities to unify the provision of repository data into a single service. These would likely only accept content related to the stored repositories rather than general social nostr content.
The potential role of CI / CD via nostr DVMs could create the incentives for a market of highly reliable free at the point of use git servers.
This could make onboarding #GitViaNostr repositories as easy as entering a name and selecting from a multi-select list of Git server providers that announce via NIP89.
!(image)[https://image.nostr.build/badedc822995eb18b6d3c4bff0743b12b2e5ac018845ba498ce4aab0727caf6c.jpg]
Git Client in the Browser
Currently, many tasks are performed on a Git server web UI, such as:
- Browsing code, commits, branches, tags, etc.
- Creating and displaying permalinks to specific lines in commits.
- Merging PRs.
- Making small commits and PRs on-the-fly.
Just as nobody goes to the web UI of a relay (e.g., nos.lol) to interact with notes, nobody should need to go to a Git server to interact with repositories. We use the Nostr protocol to interact with Nostr relays, and we should use the Git protocol to interact with Git servers. This situation has evolved due to the centralization of Git servers. Instead of being restricted to the view and experience designed by the server operator, users should be able to choose the user experience that works best for them from a range of clients. To facilitate this, we need a library that lowers the barrier to entry for creating these experiences. This library should not require a full clone of every repository and should not depend on proprietary APIs. As a starting point, I propose wrapping the WASM-compiled gitlib2 library for the web and creating useful functions, such as showing a file, which utilizes clever flags to minimize bandwidth usage (e.g., shallow clone, noblob, etc.).
This approach would not only enhance clients like gitworkshop.dev but also bring forth a vision where Git servers simply run the Git protocol, making vibe coding Git experiences even better.
song
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 created song with a complementary vision that has shaped how I see the role of the git server. Its a self-hosted, nostr-permissioned git server with a relay baked in. Its currently a WIP and there are some compatability with ngit that we need to work out.
We collaborated on the nostr-permissioning approach now reflected in nip34.
I'm really excited to see how this space evolves.
CI/CD
Most projects require CI/CD, and while this is often bundled with Git hosting solutions, it is currently not smoothly integrated into #GitViaNostr yet. There are many loosely coupled options, such as Jenkins, Travis, CircleCI, etc., that could be integrated with Nostr.
However, the more exciting prospect is to use DVMs (Data Vending Machines).
DVMs for CI/CD
Nostr Data Vending Machines (DVMs) can provide a marketplace of CI/CD task runners with Cashu for micro payments.
There are various trust levels in CI/CD tasks:
- Tasks with no secrets eg. tests.
- Tasks using updatable secrets eg. API keys.
- Unverifiable builds and steps that sign with Android, Nostr, or PGP keys.
DVMs allow tasks to be kicked off with specific providers using a Cashu token as payment.
It might be suitable for some high-compute and easily verifiable tasks to be run by the cheapest available providers. Medium trust tasks could be run by providers with a good reputation, while high trust tasks could be run on self-hosted runners.
Job requests, status, and results all get published to Nostr for display in Git-focused Nostr clients.
Jobs could be triggered manually, or self-hosted runners could be configured to watch a Nostr repository and kick off jobs using their own runners without payment.
But I'm most excited about the prospect of Watcher Agents.
CI/CD Watcher Agents
AI agents empowered with a NIP60 Cashu wallet can run tasks based on activity, such as a push to master or a new PR, using the most suitable available DVM runner that meets the user's criteria. To keep them running, anyone could top up their NIP60 Cashu wallet; otherwise, the watcher turns off when the funds run out. It could be users, maintainers, or anyone interested in helping the project who could top up the Watcher Agent's balance.
As aluded to earlier, part of building a reputation as a CI/CD provider could involve running reliable hosting (Git server, relay, and blossom server) for all FOSS Nostr Git repositories.
This provides a sustainable revenue model for hosting providers and creates incentives for many free-at-the-point-of-use hosting providers. This, in turn, would allow one-click Nostr repository creation workflows, instantly hosted by many different providers.
Progress to Date
nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr and nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 have been working on a runner that uses GitHub Actions YAML syntax (using act) for the dvm-cicd-runner and takes Cashu payment. You can see example runs on GitWorkshop. It currently takes testnuts, doesn't give any change, and the schema will likely change.
Note: The actions tab on GitWorkshop is currently available on all repositories if you turn on experimental mode (under settings in the user menu).
It's a work in progress, and we expect the format and schema to evolve.
Easy Web App Deployment
For those disapointed not to find a 'Nostr' button to import a git repository to Vercel menu: take heart, they made it easy. vercel.com_import_options.png there is a vercel cli that can be easily called in CI / CD jobs to kick of deployments. Not all managed solutions for web app deployment (eg. netlify) make it that easy.
Many More Opportunities
Large Patches via Blossom
I would be remiss not to mention the large patch problem. Some patches are too big to fit into Nostr events. Blossom is perfect for this, as it allows these larger patches to be included in a blossom file and referenced in a new patch kind.
Enhancing the #GitViaNostr Experience
Beyond the large patch issue, there are numerous opportunities to enhance the #GitViaNostr ecosystem. We can focus on improving browsing, discovery, social and notifications. Receiving notifications on daily driver Nostr apps is one of the killer features of Nostr. However, we must ensure that Git-related notifications are easily reviewable, so we don’t miss any critical updates.
We need to develop tools that cater to our curiosity—tools that enable us to discover and follow projects, engage in discussions that pique our interest, and stay informed about developments relevant to our work.
Additionally, we should not overlook the importance of robust search capabilities and tools that facilitate migrations.
Concluding Thoughts
The design space is vast. Its an exciting time to be working on freedom tech. I encourage everyone to contribute their ideas and creativity and get vibe-coding!
I welcome your honest feedback on this vision and any suggestions you might have. Your insights are invaluable as we collaborate to shape the future of #GitViaNostr. Onward.
Contributions
To conclude, I want to acknowledge some the individuals who have made recent code contributions related to #GitViaNostr:
nostr:npub180cvv07tjdrrgpa0j7j7tmnyl2yr6yr7l8j4s3evf6u64th6gkwsyjh6w6 (gitstr, song, patch34), nostr:npub1useke4f9maul5nf67dj0m9sq6jcsmnjzzk4ycvldwl4qss35fvgqjdk5ks (gitplaza)
nostr:npub1elta7cneng3w8p9y4dw633qzdjr4kyvaparuyuttyrx6e8xp7xnq32cume (ngit contributions, git-remote-blossom),nostr:npub16p8v7varqwjes5hak6q7mz6pygqm4pwc6gve4mrned3xs8tz42gq7kfhdw (SatShoot, Flotilla-Budabit), nostr:npub1ehhfg09mr8z34wz85ek46a6rww4f7c7jsujxhdvmpqnl5hnrwsqq2szjqv (Flotilla-Budabit, Nostr Git Extension), nostr:npub1ahaz04ya9tehace3uy39hdhdryfvdkve9qdndkqp3tvehs6h8s5slq45hy (gnostr and experiments), and others.
nostr:npub1uplxcy63up7gx7cladkrvfqh834n7ylyp46l3e8t660l7peec8rsd2sfek (git-remote-nostr)
Project Management nostr:npub1ltx67888tz7lqnxlrg06x234vjnq349tcfyp52r0lstclp548mcqnuz40t (kanbanstr) Code Snippets nostr:npub1ygzj9skr9val9yqxkf67yf9jshtyhvvl0x76jp5er09nsc0p3j6qr260k2 (nodebin.io) nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac (snipsnip.dev)
CI / CD nostr:npub16ux4qzg4qjue95vr3q327fzata4n594c9kgh4jmeyn80v8k54nhqg6lra7 nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr
and for their nostr:npub1c03rad0r6q833vh57kyd3ndu2jry30nkr0wepqfpsm05vq7he25slryrnw nostr:npub1qqqqqq2stely3ynsgm5mh2nj3v0nk5gjyl3zqrzh34hxhvx806usxmln03 and nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z for their testing, feedback, ideas and encouragement.
Thank you for your support and collaboration! Let me know if I've missed you.
-
 @ 1739d937:3e3136ef
2025-04-30 14:39:24
@ 1739d937:3e3136ef
2025-04-30 14:39:24MLS over Nostr - 30th April 2025
YO! Exciting stuff in this update so no intro, let's get straight into it.
🚢 Libraries Released
I've created 4 new Rust crates to make implementing NIP-EE (MLS) messaging easy for other projects. These are now part of the rust-nostr project (thanks nostr:npub1drvpzev3syqt0kjrls50050uzf25gehpz9vgdw08hvex7e0vgfeq0eseet) but aren't quite released to crates.io yet. They will be included in the next release of that library. My hope is that these libraries will give nostr developers a simple, safe, and specification-compliant way to work with MLS messaging in their applications.
Here's a quick overview of each:
nostr_mls_storage
One of the challenges of using MLS messaging is that clients have to store quite a lot of state about groups, keys, and messages. Initially, I implemented all of this in White Noise but knew that eventually this would need to be done in a more generalized way.
This crate defines traits and types that are used by the storage implementation crates and sets those up to wrap the OpenMLS storage layer. Now, instead of apps having to implement storage for both OpenMLS and Nostr, you simply pick your storage backend and go from there.
Importantly, because these are generic traits, it allows for the creation of any number of storage implementations for different backend storage providers; postgres, lmdb, nostrdb, etc. To start I've created two implementations; detailed below.
nostr_mls_memory_storage
This is a simple implementation of the nostr_mls_storage traits that uses an in-memory store (that doesn't persist anything to disc). This is principally for testing.
nostr_mls_sqlite_storage
This is a production ready implementation of the nostr_mls_storage traits that uses a persistent local sqlite database to store all data.
nostr_mls
This is the main library that app developers will interact with. Once you've chose a backend and instantiated an instance of NostrMls you can then interact with a simple set of methods to create key packages, create groups, send messages, process welcomes and messages, and more.
If you want to see a complete example of what the interface looks like check out mls_memory.rs.
I'll continue to add to this library over time as I implement more of the MLS protocol features.
🚧 White Noise Refactor
As a result of these new libraries, I was able to remove a huge amount of code from White Noise and refactor large parts of the app to make the codebase easier to understand and maintain. Because of this large refactor and the changes in the underlying storage layer, if you've installed White Noise before you'll need to delete it from your device before you trying to install again.
🖼️ Encrypted Media with Blossom
Let's be honest: Group chat would be basically useless if you couldn't share memes and gifs. Well, now you can in White Noise. Media in groups is encrypted using an MLS secret and uploaded to Blossom with a one-time use keypair. This gives groups a way to have rich conversations with images and documents and anything else while also maintaining the privacy and security of the conversation.
This is still in a rough state but rendering improvements are coming next.
📱 Damn Mobile
The app is still in a semi-broken state on Android and fully broken state on iOS. Now that I have the libraries released and the White Noise core code refactored, I'm focused 100% on fixing these issues. My goal is to have a beta version live on Zapstore in a few weeks.
🧑💻 Join Us
I'm looking for mobile developers on both Android and iOS to join the team and help us build the best possible apps for these platforms. I have grant funding available for the right people. Come and help us build secure, permissionless, censorship-resistant messaging. I can think of few projects that deserve your attention more than securing freedom of speech and freedom of association for the entire world. If you're interested or know someone who might be, please reach out to me directly.
🙏 Thanks to the People
Last but not least: A HUGE thank you to all the folks that have been helping make this project happen. You can check out the people that are directly working on the apps on Following._ (and follow them). There are also a lot of people behind the scenes that have helped in myriad ways to get us this far. Thank you thank you thank you.
🔗 Links
Libraries
White Noise
Other
-
 @ c1e6505c:02b3157e
2025-04-30 02:50:55
@ c1e6505c:02b3157e
2025-04-30 02:50:55Photography, to me, is a game - a game of snatching absurd, beautiful, fleeting moments from life. Anything staged or overly polished falls into what Garry Winogrand nails as “illustration work.” I’m with him on that. Photography is about staying awake to the world, to the “physical reality” or circumstances we’re steeped in, and burning that light onto film emulsion (or pixels now), locking a moment into matter forever. It’s not like painting, where brushstrokes mimic what’s seen, felt, or imagined. Photography captures photons - light itself - and turns it into something tangible. The camera, honestly, doesn’t get enough credit for being such a wild invention.
Lately, I’ve been chewing on what to do with a batch of new photos I’ve shot over the past month, which includes photographs from a film project, a trip to Manhattan and photos of David Byrne (more on that in another post). Maybe it's another photo-zine that I should make. It’s been a minute since my last one, Hiding in Hudson (https://www.youtube.com/watch?v=O7_t0OldrTk&t=339s). Putting out printed work like zines or books is killer practice — it forces you to sharpen your compositions, your vision, your whole deal as a photographer. Proof of work, you know?
This leads to a question: anyone out there down to help or collab on printing a photo-zine? I’d love to keep it DIY, steering clear of big companies.
In the spirit of getting back into a rhythm of daily shooting, here are a few recent shots from the past few days. Just wandering aimlessly around my neighborhood — bike rides, grocery runs, wherever I end up.
Camera used: Leica M262
Edited with: Lightroom + Dehancer Film
*Support my work and the funding for my new zine by sending a few sats: colincz@getalby.com *






-
 @ 61bf790b:fe18b062
2025-04-29 12:23:09
@ 61bf790b:fe18b062
2025-04-29 12:23:09In a vast digital realm, two cities stood side by side: the towering, flashing metropolis of Feedia, and the decentralized, quiet city of Nostra.
Feedia was loud—blinding, buzzing, and always on. Screens plastered every wall, whispering the latest trends into citizens’ ears. But in this city, what you saw wasn’t up to you. It was determined by a towering, unseen force known as The Algorithm. It didn’t care what was true, meaningful, or helpful—only what would keep your eyes glued and your attention sold.
In Feedia, discovery wasn’t earned. It was assigned.
And worse—there was a caste system. To have a voice, you needed a Blue Check—a glowing badge that marked you as “worthy.” To get one, you had to pay or play. Pay monthly dues to the high towers or entertain The Algorithm enough to be deemed “valuable.” If you refused or couldn’t afford it, your voice was cast into the noise—buried beneath outrage bait and celebrity screams.
The unmarked were like ghosts—speaking into the void while the checked dined in Algorithm-favored towers. It was a digital monarchy dressed up as a democracy.
Then, there was Nostra.
There were no glowing checkmarks in Nostra—just signal. Every citizen had a light they carried, one that grew brighter the more they contributed: thoughtful posts, reshared ideas, built tools, or boosted others. Discovery was based not on payment or privilege, but participation and value.
In Nostra, you didn’t rise because you paid the gatekeeper—you rose because others lifted you. You weren’t spoon-fed; you sought, you found, you earned attention. It was harder, yes. But it was real.
And slowly, some in Feedia began to awaken. They grew tired of being fed fast-food content and ignored despite their voices. They looked across the river to Nostra, where minds weren’t bought—they were built.
And one by one, they began to cross.
-
 @ 975e4ad5:8d4847ce
2025-04-29 08:26:50
@ 975e4ad5:8d4847ce
2025-04-29 08:26:50With the advancement of quantum computers, a new threat emerges for the security of cryptocurrencies and blockchain technologies. These powerful machines have the potential to expose vulnerabilities in traditional cryptographic systems, which could jeopardize the safety of digital wallets. But don’t worry—modern wallets are already equipped to handle this threat with innovative solutions that make your funds nearly impossible to steal, even by a quantum computer. Let’s explore how this works and why you can rest easy.
The Threat of Quantum Computers
To understand how wallets protect us, we first need to grasp what makes quantum computers so dangerous. At the core of most cryptocurrencies, like Bitcoin, lies public and private key cryptography. The public key (or address) is like your bank account number—you share it to receive funds. The private key is like your PIN—it allows you to send funds and must remain secret.
Traditional cryptography, such as the ECDSA algorithm, relies on mathematical problems that are extremely difficult to solve with conventional computers. For instance, deriving a private key from a public key is practically impossible, as it would take millions of years of computation. However, quantum computers, thanks to algorithms like Shor’s, can significantly speed up this process. Theoretically, a sufficiently powerful quantum computer could uncover a private key from a public key in minutes or even seconds.
This is a problem because if someone gains access to your private key, they can send all your funds to their own address. But here’s the good news—modern wallets use a clever solution to render this threat powerless.
How Do Wallets Protect Us?
One of the most effective defenses against quantum computers is the use of one-time addresses in wallets. This means that for every transaction—whether receiving or sending funds—the wallet automatically generates a new public address. The old address, once used, remains in the transaction history but no longer holds any funds, as they are transferred to a new address.
Why Does This Work?
Imagine you’re sending or receiving cryptocurrency. Your wallet creates a new address for that transaction. After the funds are sent or received, that address becomes “used,” and the wallet automatically generates a new one for the next transaction. If a quantum computer manages to derive the private key from the public address of the used address, it will find nothing—because that address is already empty. Your funds are safely transferred to a new address, whose public key has not yet been exposed.
This strategy is known as HD (Hierarchical Deterministic) wallets. It allows the wallet to generate an infinite number of addresses from a single master key (seed) without compromising security. Each new address is unique and cannot be linked to the previous ones, making it impossible to trace your funds, even with a quantum computer.
Automation Makes It Effortless
The best part? You don’t need to worry about this process—it’s fully automated. When you use a modern wallet like MetaMask, Ledger, Trezor, or software wallets for Bitcoin, everything happens behind the scenes. You simply click “receive” or “send,” and the wallet takes care of generating new addresses. There’s no need to understand the complex technical details or manually manage your keys.
For example:
- You want to receive 0.1 BTC. Your wallet provides a new address, which you share with the sender.
- After receiving the funds, the wallet automatically prepares a new address for the next transaction.
- If you send some of the funds, the remaining amount (known as “change”) is sent to another new address generated by the wallet.
This system ensures that public addresses exposed on the blockchain no longer hold funds, making quantum attacks pointless.
Additional Protection: Toward Post-Quantum Cryptography
Beyond one-time addresses, blockchain developers are also working on post-quantum cryptography—algorithms that are resistant to quantum computers. Some blockchain networks are already experimenting with such solutions, like algorithms based on lattices (lattice-based cryptography). These methods don’t rely on the same mathematical problems that quantum computers can solve, offering long-term protection.
In the meantime, one-time addresses combined with current cryptographic standards provide enough security to safeguard your funds until post-quantum solutions become widely adopted.
Why You Shouldn’t Worry
Modern wallets are designed with the future in mind. They not only protect against today’s threats but also anticipate future risks, such as those posed by quantum computers. One-time addresses make exposed public keys useless to hackers, and automation ensures you don’t need to deal with the technicalities. HD wallets, which automatically generate new addresses, make the process seamless and secure for users.
Public key exposure only happens when necessary, reducing the risk of attacks, even from a quantum computer. In conclusion, while quantum computers pose a potential threat, modern wallets already offer effective solutions that make your cryptocurrencies nearly impossible to steal. With one-time addresses and the upcoming adoption of post-quantum cryptography, you can be confident that your funds are safe—today and tomorrow.
-
 @ 83279ad2:bd49240d
2025-04-29 05:53:52
@ 83279ad2:bd49240d
2025-04-29 05:53:52test
-
 @ c1e6505c:02b3157e
2025-04-28 01:58:55
@ c1e6505c:02b3157e
2025-04-28 01:58:55This is a long form test note from Untype.app
Seems like this could work well.
Here is a photograph of the infamous red firebird that has been in the same spot for over 10 years.
There is a header image up top as well. Will that be seen? Maybe?
Clean interface and you're able to type and see a preview window of what your post would like. Cool!
Text before the image prompt makes this lettering large and bold.

Here is a line break
Let me know if you can see this text that is now under the image.
BYE (IN BOLD)!
-
 @ 78b3c1ed:5033eea9
2025-04-27 01:42:48
@ 78b3c1ed:5033eea9
2025-04-27 01:42:48・ThunderHubで焼いたマカロンがlncli printmacaroonでどう見えるか確認した。
ThunderHub macaroon permissions
get invoices invoices:read create invoices invoices:write get payments offchain:read pay invoices offchain:write get chain transactions onchain:read send to chain address onchain:write create chain address address:write get wallet info info:read stop daemon info:write この結果によれば、offchain:wirteとonchain:writeの権限がなければそのマカロンを使うクライアントは勝手にBTCを送金することができない。 info:writeがなければ勝手にLNDを止めたりすることができない。
・lncli printmacaroonでデフォルトで作られるmacaroonのpermissionsを調べてみた。 admin.macaroon
{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "info:read", "info:write", "invoices:read", "invoices:write", "macaroon:generate", "macaroon:read", "macaroon:write", "message:read", "message:write", "offchain:read", "offchain:write", "onchain:read", "onchain:write", "peers:read", "peers:write", "signer:generate", "signer:read" ], "caveats": null }chainnotifier.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "onchain:read" ], "caveats": null }invoice.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "invoices:read", "invoices:write", "onchain:read" ], "caveats": null }invoices.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "invoices:read", "invoices:write" ], "caveats": null }readonly.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "info:read", "invoices:read", "macaroon:read", "message:read", "offchain:read", "onchain:read", "peers:read", "signer:read" ], "caveats": null }router.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "offchain:read", "offchain:write" ], "caveats": null }signer.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "signer:generate", "signer:read" ], "caveats": null }walletkit.macaroon{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "address:read", "address:write", "onchain:read", "onchain:write" ], "caveats": null }・lncli listpermissions コマンドですべての RPC メソッド URI と、それらを呼び出すために必要なマカロン権限を一覧表示できる。 LND v0.18.5-betaでやると1344行ほどのJSONができる。 AddInvoiceだとinvoice:writeのpermissionを持つmacaroonを使えばインボイスを作れるようだ。
"/lnrpc.Lightning/AddInvoice": { "permissions": [ { "entity": "invoices", "action": "write" } ] },lncli listpermissionsからentityとactionを抜き出してみた。 ``` "entity": "address", "entity": "info", "entity": "invoices", "entity": "macaroon", "entity": "message", "entity": "offchain", "entity": "onchain", "entity": "peers", "entity": "signer","action": "generate" "action": "read" "action": "write"
lncli とjqを組み合わせると例えば以下コマンドでinvoices:writeを必要とするRPCの一覧を表示できる。 invoices:writeだとAddInvoiceの他にホドルインボイス作成でも使ってるようだlncli listpermissions | jq -r '.method_permissions | to_entries[] | select(.value.permissions[] | select(.entity == "invoices" and .action == "write")) | .key'/invoicesrpc.Invoices/AddHoldInvoice /invoicesrpc.Invoices/CancelInvoice /invoicesrpc.Invoices/HtlcModifier /invoicesrpc.Invoices/LookupInvoiceV2 /invoicesrpc.Invoices/SettleInvoice /lnrpc.Lightning/AddInvoiceinvoices:readだと以下となる。/invoicesrpc.Invoices/SubscribeSingleInvoice /lnrpc.Lightning/ListInvoices /lnrpc.Lightning/LookupInvoice /lnrpc.Lightning/SubscribeInvoicesLNの主だった機能のRPCはoffchainが必要ぽいので抜き出してみた。 offchain:write チャネルの開閉、ペイメントの送信までやってるみたい。 デフォルトのmacaroonでoffchain:writeを持ってるのはadminとrouterの2つだけ。openchannel,closechannelはonchain:writeのpermissionも必要なようだ。/autopilotrpc.Autopilot/ModifyStatus /autopilotrpc.Autopilot/SetScores /lnrpc.Lightning/AbandonChannel /lnrpc.Lightning/BatchOpenChannel /lnrpc.Lightning/ChannelAcceptor /lnrpc.Lightning/CloseChannel /lnrpc.Lightning/DeleteAllPayments /lnrpc.Lightning/DeletePayment /lnrpc.Lightning/FundingStateStep /lnrpc.Lightning/OpenChannel /lnrpc.Lightning/OpenChannelSync /lnrpc.Lightning/RestoreChannelBackups /lnrpc.Lightning/SendCustomMessage /lnrpc.Lightning/SendPayment /lnrpc.Lightning/SendPaymentSync /lnrpc.Lightning/SendToRoute /lnrpc.Lightning/SendToRouteSync /lnrpc.Lightning/UpdateChannelPolicy /routerrpc.Router/HtlcInterceptor /routerrpc.Router/ResetMissionControl /routerrpc.Router/SendPayment /routerrpc.Router/SendPaymentV2 /routerrpc.Router/SendToRoute /routerrpc.Router/SendToRouteV2 /routerrpc.Router/SetMissionControlConfig /routerrpc.Router/UpdateChanStatus /routerrpc.Router/XAddLocalChanAliases /routerrpc.Router/XDeleteLocalChanAliases /routerrpc.Router/XImportMissionControl /wtclientrpc.WatchtowerClient/AddTower /wtclientrpc.WatchtowerClient/DeactivateTower /wtclientrpc.WatchtowerClient/RemoveTower /wtclientrpc.WatchtowerClient/TerminateSession"/lnrpc.Lightning/OpenChannel": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] },offchain:read readの方はチャネルやインボイスの状態を確認するためのpermissionのようだ。/lnrpc.Lightning/ChannelBalance /lnrpc.Lightning/ClosedChannels /lnrpc.Lightning/DecodePayReq /lnrpc.Lightning/ExportAllChannelBackups /lnrpc.Lightning/ExportChannelBackup /lnrpc.Lightning/FeeReport /lnrpc.Lightning/ForwardingHistory /lnrpc.Lightning/GetDebugInfo /lnrpc.Lightning/ListAliases /lnrpc.Lightning/ListChannels /lnrpc.Lightning/ListPayments /lnrpc.Lightning/LookupHtlcResolution /lnrpc.Lightning/PendingChannels /lnrpc.Lightning/SubscribeChannelBackups /lnrpc.Lightning/SubscribeChannelEvents /lnrpc.Lightning/SubscribeCustomMessages /lnrpc.Lightning/VerifyChanBackup /routerrpc.Router/BuildRoute /routerrpc.Router/EstimateRouteFee /routerrpc.Router/GetMissionControlConfig /routerrpc.Router/QueryMissionControl /routerrpc.Router/QueryProbability /routerrpc.Router/SubscribeHtlcEvents /routerrpc.Router/TrackPayment /routerrpc.Router/TrackPaymentV2 /routerrpc.Router/TrackPayments /wtclientrpc.WatchtowerClient/GetTowerInfo /wtclientrpc.WatchtowerClient/ListTowers /wtclientrpc.WatchtowerClient/Policy /wtclientrpc.WatchtowerClient/Stats・おまけ1 RPCメソッド名にopenを含む要素を抽出するコマンドlncli listpermissions | jq '.method_permissions | to_entries[] | select(.key | test("open"; "i"))'{ "key": "/lnrpc.Lightning/BatchOpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannel", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } } { "key": "/lnrpc.Lightning/OpenChannelSync", "value": { "permissions": [ { "entity": "onchain", "action": "write" }, { "entity": "offchain", "action": "write" } ] } }・おまけ2 thunderhubで作ったmacaroonはテキストで出力されコピペして使うもので、macaroonファイルになってない。 HEXをmacaroonファイルにするには以下コマンドでできる。HEXをコピペして置換する。またYOURSの箇所を自分でわかりやすい名称に置換すると良い。echo -n "HEX" | xxd -r -p > YOURS.macaroonthunderhubで"Create Invoices, Get Invoices, Get Wallet Info, Get Payments, Pay Invoices"をチェックして作ったmacaroonのpermissionsは以下となる。{ "version": 2, "location": "lnd", "root_key_id": "0", "permissions": [ "info:read", "invoices:read", "invoices:write", "offchain:read", "offchain:write" ], "caveats": null } ``` offchain:writeはあるがonchain:writeがないのでチャネル開閉はできないはず。 -
 @ f32184ee:6d1c17bf
2025-04-23 13:21:52
@ f32184ee:6d1c17bf
2025-04-23 13:21:52Ads Fueling Freedom
Ross Ulbricht’s "Decentralize Social Media" painted a picture of a user-centric, decentralized future that transcended the limitations of platforms like the tech giants of today. Though focused on social media, his concept provided a blueprint for decentralized content systems writ large. The PROMO Protocol, designed by NextBlock while participating in Sovereign Engineering, embodies this blueprint in the realm of advertising, leveraging Nostr and Bitcoin’s Lightning Network to give individuals control, foster a multi-provider ecosystem, and ensure secure value exchange. In this way, Ulbricht’s 2021 vision can be seen as a prescient prediction of the PROMO Protocol’s structure. This is a testament to the enduring power of his ideas, now finding form in NextBlock’s innovative approach.
 [Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]
[Current Platform-Centric Paradigm, source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Vision: A Decentralized Social Protocol
In his 2021 Medium article Ulbricht proposed a revolutionary vision for a decentralized social protocol (DSP) to address the inherent flaws of centralized social media platforms, such as privacy violations and inconsistent content moderation. Writing from prison, Ulbricht argued that decentralization could empower users by giving them control over their own content and the value they create, while replacing single, monolithic platforms with a competitive ecosystem of interface providers, content servers, and advertisers. Though his focus was on social media, Ulbricht’s ideas laid a conceptual foundation that strikingly predicts the structure of NextBlock’s PROMO Protocol, a decentralized advertising system built on the Nostr protocol.
 [A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]
[A Decentralized Social Protocol (DSP), source: Ross Ulbricht's Decentralize Social Media]Ulbricht’s Principles
Ulbricht’s article outlines several key principles for his DSP: * User Control: Users should own their content and dictate how their data and creations generate value, rather than being subject to the whims of centralized corporations. * Decentralized Infrastructure: Instead of a single platform, multiple interface providers, content hosts, and advertisers interoperate, fostering competition and resilience. * Privacy and Autonomy: Decentralized solutions for profile management, hosting, and interactions would protect user privacy and reduce reliance on unaccountable intermediaries. * Value Creation: Users, not platforms, should capture the economic benefits of their contributions, supported by decentralized mechanisms for transactions.
These ideas were forward-thinking in 2021, envisioning a shift away from the centralized giants dominating social media at the time. While Ulbricht didn’t specifically address advertising protocols, his framework for decentralization and user empowerment extends naturally to other domains, like NextBlock’s open-source offering: the PROMO Protocol.
NextBlock’s Implementation of PROMO Protocol
The PROMO Protocol powers NextBlock's Billboard app, a decentralized advertising protocol built on Nostr, a simple, open protocol for decentralized communication. The PROMO Protocol reimagines advertising by: * Empowering People: Individuals set their own ad prices (e.g., 500 sats/minute), giving them direct control over how their attention or space is monetized. * Marketplace Dynamics: Advertisers set budgets and maximum bids, competing within a decentralized system where a 20% service fee ensures operational sustainability. * Open-Source Flexibility: As an open-source protocol, it allows multiple developers to create interfaces or apps on top of it, avoiding the single-platform bottleneck Ulbricht critiqued. * Secure Payments: Using Strike Integration with Bitcoin Lightning Network, NextBlock enables bot-resistant and intermediary-free transactions, aligning value transfer with each person's control.
This structure decentralizes advertising in a way that mirrors Ulbricht’s broader vision for social systems, with aligned principles showing a specific use case: monetizing attention on Nostr.
Aligned Principles
Ulbricht’s 2021 article didn’t explicitly predict the PROMO Protocol, but its foundational concepts align remarkably well with NextBlock's implementation the protocol’s design: * Autonomy Over Value: Ulbricht argued that users should control their content and its economic benefits. In the PROMO Protocol, people dictate ad pricing, directly capturing the value of their participation. Whether it’s their time, influence, or digital space, rather than ceding it to a centralized ad network. * Ecosystem of Providers: Ulbricht envisioned multiple providers replacing a single platform. The PROMO Protocol’s open-source nature invites a similar diversity: anyone can build interfaces or tools on top of it, creating a competitive, decentralized advertising ecosystem rather than a walled garden. * Decentralized Transactions: Ulbricht’s DSP implied decentralized mechanisms for value exchange. NextBlock delivers this through the Bitcoin Lightning Network, ensuring that payments for ads are secure, instantaneous and final, a practical realization of Ulbricht’s call for user-controlled value flows. * Privacy and Control: While Ulbricht emphasized privacy in social interactions, the PROMO Protocol is public by default. Individuals are fully aware of all data that they generate since all Nostr messages are signed. All participants interact directly via Nostr.
 [Blueprint Match, source NextBlock]
[Blueprint Match, source NextBlock]
Who We Are
NextBlock is a US-based new media company reimagining digital ads for a decentralized future. Our founders, software and strategy experts, were hobbyist podcasters struggling to promote their work online without gaming the system. That sparked an idea: using new tech like Nostr and Bitcoin to build a decentralized attention market for people who value control and businesses seeking real connections.
Our first product, Billboard, is launching this June.
Open for All
Our model’s open-source! Check out the PROMO Protocol, built for promotion and attention trading. Anyone can join this decentralized ad network. Run your own billboard or use ours. This is a growing ecosystem for a new ad economy.
Our Vision
NextBlock wants to help build a new decentralized internet. Our revolutionary and transparent business model will bring honest revenue to companies hosting valuable digital spaces. Together, we will discover what our attention is really worth.
Read our Manifesto to learn more.
NextBlock is registered in Texas, USA.
-
 @ 6ad3e2a3:c90b7740
2025-04-23 12:31:54
@ 6ad3e2a3:c90b7740
2025-04-23 12:31:54There’s an annoying trend on Twitter wherein the algorithm feeds you a lot of threads like “five keys to gaining wealth” or “10 mistakes to avoid in relationships” that list a bunch of hacks for some ostensibly desirable state of affairs which for you is presumably lacking. It’s not that the hacks are wrong per se, more that the medium is the message. Reading threads about hacks on social media is almost surely not the path toward whatever is promised by them.
. . .
I’ve tried a lot of health supplements over the years. These days creatine is trendy, and of course Vitamin D (which I still take.) I don’t know if this is helping me, though it surely helps me pass my blood tests with robust levels. The more I learn about health and nutrition, the less I’m sure of anything beyond a few basics. Yes, replacing processed food with real food, moving your body and getting some sun are almost certainly good, but it’s harder to know how particular interventions affect me.
Maybe some of them work in the short term then lose their effect, Maybe some work better for particular phenotypes, but not for mine. Maybe my timing in the day is off, or I’m not combining them correctly for my lifestyle and circumstances. The body is a complex system, and complex systems are characterized by having unpredictable outputs given changes to initial conditions (inputs).
. . .
I started getting into Padel recently — a mini-tennis-like game where you can hit the ball off the back walls. I’d much rather chase a ball around for exercise than run or work out, and there’s a social aspect I enjoy. (By “social aspect”, I don’t really mean getting to know the people with whom I’m playing, but just the incidental interactions you get during the game, joking about it, for example, when you nearly impale someone at the net with a hard forehand.)
A few months ago, I was playing with some friends, and I was a little off. It’s embarrassing to play poorly at a sport, especially when (as is always the case in Padel) you have a doubles partner you’re letting down. Normally I’d be excoriating myself for my poor play, coaching myself to bend my knees more, not go for winners so much. But that day, I was tired — for some reason I hadn’t slept well — and I didn’t have the energy for much internal monologue. I just mishit a few balls, felt stupid about it and kept playing.
After a few games, my fortunes reversed. I was hitting the ball cleanly, smashing winners, rarely making errors. My partner and I started winning games and then sets. I was enjoying myself. In the midst of it I remember hitting an easy ball into the net and reflexively wanting to self-coach again. I wondered, “What tips did I give to right the ship when I had been playing poorly at the outset?” I racked my brain as I waited for the serve and realized, to my surprise, there had been none. The turnaround in my play was not due to self-coaching but its absence. I had started playing better because my mind had finally shut the fuck up for once.
Now when I’m not playing well, I resist, to the extent I’m capable, the urge to meddle. I intend to be more mind-less. Not so much telling the interior coach to shut up but not buying into the premise there is a problem to be solved at all. The coach isn’t just ignored, he’s fired. And he’s not just fired, his role was obsoleted.
You blew the point, you’re embarrassed about it and there’s nothing that needs to be done about it. Or that you started coaching yourself like a fool and made things worse. No matter how much you are doing the wrong thing nothing needs to be done about any of it whatsoever. There is always another ball coming across the net that needs to be struck until the game is over.
. . .
Most of the hacks, habits and heuristics we pick up to manage our lives only serve as yet more inputs in unfathomably complex systems whose outputs rarely track as we’d like. There are some basic ones that are now obvious to everyone like not injecting yourself with heroin (or mRNA boosters), but for the most part we just create more baggage for ourselves which justifies ever more hacks. It’s like taking medication for one problem that causes side effects, and then you need another medicine for that side effect, rinse and repeat, ad infinitum.
But this process can be reverse-engineered too. For every heuristic you drop, the problem it was put into place to solve re-emerges and has a chance to be observed. Observing won’t solve it, it’ll just bring it into the fold, give the complex system of which it is a part a chance to achieve an equilibrium with respect to it on its own.
You might still be embarrassed when you mishit the ball, but embarrassment is not a problem. And if embarrassment is not a problem, then mishitting a ball isn’t that bad. And if mishitting a ball isn’t that bad, then maybe you’re not worrying about what happens if you botch the next shot, instead fixing your attention on the ball. And so you disappear a little bit into the game, and it’s more fun as a result.
I honestly wish there were a hack for this — being more mindless — but I don’t know of any. And in any event, hack Substacks won’t get you any farther than hack Twitter threads.
-
 @ df478568:2a951e67
2025-04-22 18:56:38
@ df478568:2a951e67
2025-04-22 18:56:38"It might make sense just to get some in case it catches on. If enough people think the same way, that becomes a self fulfilling prophecy. Once it gets bootstrapped, there are so many applications if you could effortlessly pay a few cents to a website as easily as dropping coins in a vending machine." --Satoshi Nakamoto The Cryptography Mailing List--January 17, 2009
Forgot to add the good part about micropayments. While I don't think Bitcoin is practical for smaller micropayments right now, it will eventually be as storage and bandwidth costs continue to fall. If Bitcoin catches on on a big scale, it may already be the case by that time. Another way they can become more practical is if I implement client-only mode and the number of network nodes consolidates into a smaller number of professional server farms. Whatever size micropayments you need will eventually be practical. I think in 5 or 10 years, the bandwidth and storage will seem trivial. --Satoshi Nakamoto Bitcoin Talk-- August 5, 2010
I very be coded some HTML buttons using Claude and uploaded it to https://github.com/GhostZaps/ It's just a button that links to zapper.fun.
I signed up for Substack to build an email address, but learned adding different payment options to Substack is against their terms and services. Since I write about nostr, these terms seem as silly as someone saying Craig Wright is Satoshi. It's easy to build an audience on Substack however, or so I thought. Why is it easier to build an audience on Subtack though? Because Substack is a platform that markets to writers. Anyone with a ~~pen~~ ~~keyboard~~ smartphone and an email can create an account with Substack. There's just one problem: You are an Internet serf, working the land for your Internet landlord--The Duke of Substack.
Then I saw that Shawn posted about Substack's UX.
I should have grabbed my reading glasses before pushing the post button, but it occurred to me that I could use Ghost to do this and there is probably a way to hack it to accept bitcoin payments over the lightning network and host it yourself. So I spun my noddle, doodled some plans...And then it hit me. Ghost allows for markdown and HTML. I learned HTML and CSS with free-code camp, but ain't nobody got time to type CSS so I vibe-coded a button that ~~baits~~ sends the clicker to my zapper.fun page. This can be used on any blog that allows you to paste html into it so I added it to my Ghost blog self-hosted on a Start 9. The blog is on TOR at http://p66dxywd2xpyyrdfxwilqcxmchmfw2ixmn2vm74q3atf22du7qmkihyd.onion/, but most people around me have been conditioned to fear the dark web so I used the cloudflared to host my newsletter on the clear net at https://marc26z.com/
Integrating Nostr Into My Self-Hosted Ghost Newsletter
I would venture to say I am more technical than the average person and I know HTML, but my CSS is fuzzy. I also know how to print("Hello world!") in python, but I an NPC beyond the basics. Nevertheless, I found that I know enough to make a button. I can't code well enough to create my own nostr long-form client and create plugins for ghost that send lightning payments to lighting channel, but I know enough about nostr to know that I don't need to. That's why nostr is so F@#%-ing cool! It's all connected. ** - One button takes you to zapper.fun where you can zap anywhere between 1 and ,000,000 sats.** - Another button sends you to a zap planner pre-set to send 5,000 sats to the author per month using nostr. - Yet another button sends you to a zap planner preset to send 2,500 sats per month.
The possibilities are endless. I entered a link that takes the clicker to my Shopstr Merch Store. The point is to write as self-sovereign as possible. I might need to change my lightning address when stuff breaks every now and then, but I like the idea of busking for sats by writing on the Internet using the Value 4 Value model. I dislike ads, but I also want people to buy stuff from people I do business with because I want to promote using bitcoin as peer-to-peer electronic cash, not NGU porn. I'm not prude. I enjoy looking at the price displayed on my BlockClock micro every now and then, but I am not an NGU porn addict.
This line made this pattern, that line made this pattern. All that Bolinger Bart Simpson bullshit has nothing to with bitcoin, a peer-to-peer electronic cash system. It is the musings of a population trapped in the fiat mind-set. Bitcoin is permissionless so I realized I was bieng a hipocryte by using a permissioned payment system becaue it was easier than writing a little vibe code. I don't need permission to write for sats. I don't need to give my bank account number to Substack. I don't need to pay a 10$ vig to publish on a a platform which is not designed for stacking sats. I can write on Ghost and integrate clients that already exist in the multi-nostr-verse.
Nostr Payment Buttons
The buttons can be fouund at https://github.com/Marc26z/GhostZapButton
You can use them yourself. Just replace my npub with your npub or add any other link you want. It doesn't technically need to be a nostr link. It can be anything. I have a link to another Ghost article with other buttons that lead down different sat pledging amounts. It's early. Everyone who spends bitcoin is on nostr and nostr is small, but growing community. I want to be part of this community. I want to find other writers on nostr and stay away from Substack.
Here's what it looks like on Ghost: https://marc26z.com/zaps-on-ghost/
npub1marc26z8nh3xkj5rcx7ufkatvx6ueqhp5vfw9v5teq26z254renshtf3g0
-
 @ f10512df:c9293bb3
2025-04-22 17:11:05
@ f10512df:c9293bb3
2025-04-22 17:11:05Details
- 🍳 Cook time: 5-7 minutes
- 🍽️ Servings: 1
Ingredients
- 2 eggs
- Shredded cheese (Sharp cheddar is a favorite)
- 1 Tbsp olive oil or ghee
Directions
- Add oil to a non-stick pan and allow it to get hot (med-high heat)
- Add eggs and additional toppings, scramble and wait for the edges to get brown.
- Add shredded cheese while edges are browning. It is best if cheese begins to melt before flipping.
- Flip, and make sure all cheese stayed down, and there is enough oil left in the pan.
- Keep checking until pan side of eggs lift easily. Done correctly, the cheese will form a crisp layer.
- When fully cooked, serve with cheese right side up and enjoy!
-
 @ f10512df:c9293bb3
2025-04-22 17:00:44
@ f10512df:c9293bb3
2025-04-22 17:00:44Chef's notes
Use a tea bag to hold the spices. I like to fill it and drape it on the side of the pan so the flavors get in, and then toss it before serving. Easier than picking rosemary out of your teeth later.
Details
- ⏲️ Prep time: 20 minutes
- 🍳 Cook time: 1 hour 45 from scratch, 45 if using chicken stock
- 🍽️ Servings: 4
Ingredients
- 1 Cup Carrots (sliced)
- 1C celery (sliced)
- 2 cloves garlic
- 1 tsp dried thyme
- 1/2 tsp dried minced onion
- 2 Tbsp lemon juice (or more to taste)
- 1/2 Tbsp salt (to taste)
- 1 rotisserie chicken
- 2 tsp dried rosemary (or 1-2 sprigs fresh)
- 8 C water & additional 1-2 C later
- 10 oz pre-cooked noodles
- 1 tsp cracked pepper (to taste)
Directions
- Remove chicken meat from bones and set aside. Do not discard skin. Put bones and skin in a large stock pot and add water. Let boil covered for one hour, and then remove bones and strain out any bits of skin from broth.
- Add chopped vegetables, spices, and lemon juice to broth with up to 2 C. additional water to replace what might have boiled away. Simmer over low to medium heat (covered) for another half hour, stirring occasionally. Add in chicken meat. Taste test and add additional salt if needed.
- When vegetables are cooked, add in noodles and stir for an additional 2-3 minutes until hot (uncovered), and enjoy.
- If using store bought chicken stock, only simmer until vegetables are cooked (about half an hour).
-
 @ a39d19ec:3d88f61e
2025-04-22 12:44:42
@ a39d19ec:3d88f61e
2025-04-22 12:44:42Die Debatte um Migration, Grenzsicherung und Abschiebungen wird in Deutschland meist emotional geführt. Wer fordert, dass illegale Einwanderer abgeschoben werden, sieht sich nicht selten dem Vorwurf des Rassismus ausgesetzt. Doch dieser Vorwurf ist nicht nur sachlich unbegründet, sondern verkehrt die Realität ins Gegenteil: Tatsächlich sind es gerade diejenigen, die hinter jeder Forderung nach Rechtssicherheit eine rassistische Motivation vermuten, die selbst in erster Linie nach Hautfarbe, Herkunft oder Nationalität urteilen.
Das Recht steht über Emotionen
Deutschland ist ein Rechtsstaat. Das bedeutet, dass Regeln nicht nach Bauchgefühl oder politischer Stimmungslage ausgelegt werden können, sondern auf klaren gesetzlichen Grundlagen beruhen müssen. Einer dieser Grundsätze ist in Artikel 16a des Grundgesetzes verankert. Dort heißt es:
„Auf Absatz 1 [Asylrecht] kann sich nicht berufen, wer aus einem Mitgliedstaat der Europäischen Gemeinschaften oder aus einem anderen Drittstaat einreist, in dem die Anwendung des Abkommens über die Rechtsstellung der Flüchtlinge und der Europäischen Menschenrechtskonvention sichergestellt ist.“
Das bedeutet, dass jeder, der über sichere Drittstaaten nach Deutschland einreist, keinen Anspruch auf Asyl hat. Wer dennoch bleibt, hält sich illegal im Land auf und unterliegt den geltenden Regelungen zur Rückführung. Die Forderung nach Abschiebungen ist daher nichts anderes als die Forderung nach der Einhaltung von Recht und Gesetz.
Die Umkehrung des Rassismusbegriffs
Wer einerseits behauptet, dass das deutsche Asyl- und Aufenthaltsrecht strikt durchgesetzt werden soll, und andererseits nicht nach Herkunft oder Hautfarbe unterscheidet, handelt wertneutral. Diejenigen jedoch, die in einer solchen Forderung nach Rechtsstaatlichkeit einen rassistischen Unterton sehen, projizieren ihre eigenen Denkmuster auf andere: Sie unterstellen, dass die Debatte ausschließlich entlang ethnischer, rassistischer oder nationaler Kriterien geführt wird – und genau das ist eine rassistische Denkweise.
Jemand, der illegale Einwanderung kritisiert, tut dies nicht, weil ihn die Herkunft der Menschen interessiert, sondern weil er den Rechtsstaat respektiert. Hingegen erkennt jemand, der hinter dieser Kritik Rassismus wittert, offenbar in erster Linie die „Rasse“ oder Herkunft der betreffenden Personen und reduziert sie darauf.
Finanzielle Belastung statt ideologischer Debatte
Neben der rechtlichen gibt es auch eine ökonomische Komponente. Der deutsche Wohlfahrtsstaat basiert auf einem Solidarprinzip: Die Bürger zahlen in das System ein, um sich gegenseitig in schwierigen Zeiten zu unterstützen. Dieser Wohlstand wurde über Generationen hinweg von denjenigen erarbeitet, die hier seit langem leben. Die Priorität liegt daher darauf, die vorhandenen Mittel zuerst unter denjenigen zu verteilen, die durch Steuern, Sozialabgaben und Arbeit zum Erhalt dieses Systems beitragen – nicht unter denen, die sich durch illegale Einreise und fehlende wirtschaftliche Eigenleistung in das System begeben.
Das ist keine ideologische Frage, sondern eine rein wirtschaftliche Abwägung. Ein Sozialsystem kann nur dann nachhaltig funktionieren, wenn es nicht unbegrenzt belastet wird. Würde Deutschland keine klaren Regeln zur Einwanderung und Abschiebung haben, würde dies unweigerlich zur Überlastung des Sozialstaates führen – mit negativen Konsequenzen für alle.
Sozialpatriotismus
Ein weiterer wichtiger Aspekt ist der Schutz der Arbeitsleistung jener Generationen, die Deutschland nach dem Zweiten Weltkrieg mühsam wieder aufgebaut haben. Während oft betont wird, dass die Deutschen moralisch kein Erbe aus der Zeit vor 1945 beanspruchen dürfen – außer der Verantwortung für den Holocaust –, ist es umso bedeutsamer, das neue Erbe nach 1945 zu respektieren, das auf Fleiß, Disziplin und harter Arbeit beruht. Der Wiederaufbau war eine kollektive Leistung deutscher Menschen, deren Früchte nicht bedenkenlos verteilt werden dürfen, sondern vorrangig denjenigen zugutekommen sollten, die dieses Fundament mitgeschaffen oder es über Generationen mitgetragen haben.
Rechtstaatlichkeit ist nicht verhandelbar
Wer sich für eine konsequente Abschiebepraxis ausspricht, tut dies nicht aus rassistischen Motiven, sondern aus Respekt vor der Rechtsstaatlichkeit und den wirtschaftlichen Grundlagen des Landes. Der Vorwurf des Rassismus in diesem Kontext ist daher nicht nur falsch, sondern entlarvt eine selektive Wahrnehmung nach rassistischen Merkmalen bei denjenigen, die ihn erheben.
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ c3f12a9a:06c21301
2025-04-19 10:09:45
@ c3f12a9a:06c21301
2025-04-19 10:09:45Satoshi’s Time-Traveling for Knowledge #4: Liberland 2024 – Freedom Under Siege
What is Liberland?
While digging through old decentralized forums archived on the Interchain, Satoshi came across a curious name: Liberland.
“A sovereign libertarian micronation on the Danube? Founded in 2015 via Terra nullius? Built on the principles of freedom, voluntaryism, and Bitcoin? And I’ve never heard of it?”
Intrigued, Satoshi began to research. The story was almost too good to be true. A 7-square-kilometer patch of unclaimed land between Croatia and Serbia, turned into a symbol of decentralized governance and individual liberty.
No taxes unless voluntary. Bitcoin as the national currency. A digital nation-state with thousands of registered e-citizens, and even its own constitution. And yet—no recognition, no borders, and no peace.His curiosity turned into determination. He calibrated the temporal coordinates on his chrono-node to the Danube River in 2024, a year rumored to be turbulent for the Free Republic of Liberland.
When he arrived, reality struck harder than the legend.
Freedom Under Siege
The nation was under siege.
The scent of burnt wood and trampled earth lingered in the air as Satoshi stepped into what remained of the Liberland settlement. Broken structures, crushed solar panels, and a few scattered personal belongings were all that testified to the once-vibrant hub of liberty pioneers.
He found a group of residents—mud-streaked, exhausted, but defiant—gathered around the remnants of a communal kitchen. One of them, wearing a weathered Liberland t-shirt and a crypto-wallet hardware device on a chain around his neck, greeted him:
"You're not with them, are you?"
Satoshi shook his head.
"Just... passing through. What happened here?"
The man’s voice trembled between rage and sorrow:
"On the International Day of Peace, no less. Croatian police raided us. Bulldozers came with them. Took everything—generators, comms gear, even our medical tents. Claimed it was 'illegal occupation of Croatian forestry land.' But no court, no hearing. Just force."
Satoshi listened, taking mental snapshots of their faces, their words, their pain. He thought about the dream—of a place built voluntarily, where people governed themselves, free from coercion.
But that dream was burning at the edges, like the collapsed tents scattered behind them.
Reflections Under the Stars
As night fell over the Danube, Satoshi sat alone, watching the stars reflect on the black water. Thoughts spiraled:
"Decentralization... is beautiful. But without protection, it's fragile."
He realized that so long as central authorities hold monopoly on violence and taxation, every independent effort to decentralize the world—from Bitcoin to Liberland—is at risk of being suppressed, ignored, or destroyed. Not because it’s wrong, but because it's inconvenient to power.
"Unless a major state like the USA decentralizes itself from within," he thought, "true decentralization will remain a resistance—never the standard."
He activated his chrono-node once more. Not in defeat, but with purpose.
The next destination? Unknown. But the mission was clearer than ever.
originally posted at https://stacker.news/items/947954
-
 @ 700c6cbf:a92816fd
2025-05-04 16:34:01
@ 700c6cbf:a92816fd
2025-05-04 16:34:01Technically speaking, I should say blooms because not all of my pictures are of flowers, a lot of them, probably most, are blooming trees - but who cares, right?
It is that time of the year that every timeline on every social media is being flooded by blooms. At least in the Northern Hemisphere. I thought that this year, I wouldn't partake in it but - here I am, I just can't resist the lure of blooms when I'm out walking the neighborhood.
Spring has sprung - aaaachoo, sorry, allergies suck! - and the blooms are beautiful.
Yesterday, we had the warmest day of the year to-date. I went for an early morning walk before breakfast. Beautiful blue skies, no clouds, sunshine and a breeze. Most people turned on their aircons. We did not. We are rebels - hah!
We also had breakfast on the deck which I really enjoy during the weekend. Later I had my first session of the year painting on the deck while listening/watching @thegrinder streaming. Good times.
Today, the weather changed. Last night, we had heavy thunderstorms and rain. This morning, it is overcast with the occasional sunray peaking through or, as it is right now, raindrops falling.
We'll see what the day will bring. For me, it will definitely be: Back to painting. Maybe I'll even share some here later. But for now - this is a photo post, and here are the photos. I hope you enjoy as much as I enjoyed yesterday's walk!
Cheers, OceanBee
!(image)[https://cdn.satellite.earth/cc3fb0fa757c88a6a89823585badf7d67e32dee72b6d4de5dff58acd06d0aa36.jpg] !(image)[https://cdn.satellite.earth/7fe93c27c3bf858202185cb7f42b294b152013ba3c859544950e6c1932ede4d3.jpg] !(image)[https://cdn.satellite.earth/6cbd9fba435dbe3e6732d9a5d1f5ff0403935a4ac9d0d83f6e1d729985220e87.jpg] !(image)[https://cdn.satellite.earth/df94d95381f058860392737d71c62cd9689c45b2ace1c8fc29d108625aabf5d5.jpg] !(image)[https://cdn.satellite.earth/e483e65c3ee451977277e0cfa891ec6b93b39c7c4ea843329db7354fba255e64.jpg] !(image)[https://cdn.satellite.earth/a98fe8e1e0577e3f8218af31f2499c3390ba04dced14c2ae13f7d7435b4000d7.jpg] !(image)[https://cdn.satellite.earth/d83b01915a23eb95c3d12c644713ac47233ce6e022c5df1eeba5ff8952b99d67.jpg] !(image)[https://cdn.satellite.earth/9ee3256882e363680d8ea9bb6ed3baa5979c950cdb6e62b9850a4baea46721f3.jpg] !(image)[https://cdn.satellite.earth/201a036d52f37390d11b76101862a082febb869c8d0e58d6aafe93c72919f578.jpg] !(image)[https://cdn.satellite.earth/cd516d89591a4cf474689b4eb6a67db842991c4bf5987c219fb9083f741ce871.jpg]
-
 @ c4b5369a:b812dbd6
2025-04-15 07:26:16
@ c4b5369a:b812dbd6
2025-04-15 07:26:16Offline transactions with Cashu
Over the past few weeks, I've been busy implementing offline capabilities into nutstash. I think this is one of the key value propositions of ecash, beinga a bearer instrument that can be used without internet access.
 It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!
It does however come with limitations, which can lead to a bit of confusion. I hope this article will clear some of these questions up for you!What is ecash/Cashu?
Ecash is the first cryptocurrency ever invented. It was created by David Chaum in 1983. It uses a blind signature scheme, which allows users to prove ownership of a token without revealing a link to its origin. These tokens are what we call ecash. They are bearer instruments, meaning that anyone who possesses a copy of them, is considered the owner.
Cashu is an implementation of ecash, built to tightly interact with Bitcoin, more specifically the Bitcoin lightning network. In the Cashu ecosystem,
Mintsare the gateway to the lightning network. They provide the infrastructure to access the lightning network, pay invoices and receive payments. Instead of relying on a traditional ledger scheme like other custodians do, the mint issues ecash tokens, to represent the value held by the users.How do normal Cashu transactions work?
A Cashu transaction happens when the sender gives a copy of his ecash token to the receiver. This can happen by any means imaginable. You could send the token through email, messenger, or even by pidgeon. One of the common ways to transfer ecash is via QR code.
The transaction is however not finalized just yet! In order to make sure the sender cannot double-spend their copy of the token, the receiver must do what we call a
swap. A swap is essentially exchanging an ecash token for a new one at the mint, invalidating the old token in the process. This ensures that the sender can no longer use the same token to spend elsewhere, and the value has been transferred to the receiver.
What about offline transactions?
Sending offline
Sending offline is very simple. The ecash tokens are stored on your device. Thus, no internet connection is required to access them. You can litteraly just take them, and give them to someone. The most convenient way is usually through a local transmission protocol, like NFC, QR code, Bluetooth, etc.
The one thing to consider when sending offline is that ecash tokens come in form of "coins" or "notes". The technical term we use in Cashu is
Proof. It "proofs" to the mint that you own a certain amount of value. Since these proofs have a fixed value attached to them, much like UTXOs in Bitcoin do, you would need proofs with a value that matches what you want to send. You can mix and match multiple proofs together to create a token that matches the amount you want to send. But, if you don't have proofs that match the amount, you would need to go online and swap for the needed proofs at the mint.Another limitation is, that you cannot create custom proofs offline. For example, if you would want to lock the ecash to a certain pubkey, or add a timelock to the proof, you would need to go online and create a new custom proof at the mint.
Receiving offline
You might think: well, if I trust the sender, I don't need to be swapping the token right away!
You're absolutely correct. If you trust the sender, you can simply accept their ecash token without needing to swap it immediately.
This is already really useful, since it gives you a way to receive a payment from a friend or close aquaintance without having to worry about connectivity. It's almost just like physical cash!
It does however not work if the sender is untrusted. We have to use a different scheme to be able to receive payments from someone we don't trust.
Receiving offline from an untrusted sender
To be able to receive payments from an untrusted sender, we need the sender to create a custom proof for us. As we've seen before, this requires the sender to go online.
The sender needs to create a token that has the following properties, so that the receciver can verify it offline:
- It must be locked to ONLY the receiver's public key
- It must include an
offline signature proof(DLEQ proof) - If it contains a timelock & refund clause, it must be set to a time in the future that is acceptable for the receiver
- It cannot contain duplicate proofs (double-spend)
- It cannot contain proofs that the receiver has already received before (double-spend)

If all of these conditions are met, then the receiver can verify the proof offline and accept the payment. This allows us to receive payments from anyone, even if we don't trust them.
At first glance, this scheme seems kinda useless. It requires the sender to go online, which defeats the purpose of having an offline payment system.
I beleive there are a couple of ways this scheme might be useful nonetheless:
-
Offline vending machines: Imagine you have an offline vending machine that accepts payments from anyone. The vending machine could use this scheme to verify payments without needing to go online itself. We can assume that the sender is able to go online and create a valid token, but the receiver doesn't need to be online to verify it.
-
Offline marketplaces: Imagine you have an offline marketplace where buyers and sellers can trade goods and services. Before going to the marketplace the sender already knows where he will be spending the money. The sender could create a valid token before going to the marketplace, using the merchants public key as a lock, and adding a refund clause to redeem any unspent ecash after it expires. In this case, neither the sender nor the receiver needs to go online to complete the transaction.
How to use this
Pretty much all cashu wallets allow you to send tokens offline. This is because all that the wallet needs to do is to look if it can create the desired amount from the proofs stored locally. If yes, it will automatically create the token offline.
Receiving offline tokens is currently only supported by nutstash (experimental).
To create an offline receivable token, the sender needs to lock it to the receiver's public key. Currently there is no refund clause! So be careful that you don't get accidentally locked out of your funds!

The receiver can then inspect the token and decide if it is safe to accept without a swap. If all checks are green, they can accept the token offline without trusting the sender.

The receiver will see the unswapped tokens on the wallet homescreen. They will need to manually swap them later when they are online again.
 Later when the receiver is online again, they can swap the token for a fresh one.
Later when the receiver is online again, they can swap the token for a fresh one.
Summary
We learned that offline transactions are possible with ecash, but there are some limitations. It either requires trusting the sender, or relying on either the sender or receiver to be online to verify the tokens, or create tokens that can be verified offline by the receiver.
I hope this short article was helpful in understanding how ecash works and its potential for offline transactions.
Cheers,
Gandlaf
-
 @ a29cfc65:484fac9c
2025-05-04 16:20:03
@ a29cfc65:484fac9c
2025-05-04 16:20:03Bei einer Führung durch den Naumburger Dom sprach der Domführer über Propaganda im Mittelalter. Die gefühlvollen Gesichtsausdrücke der steinernen Stifterfiguren rund um die berühmte Uta sollten das Volk beeinflussen. Darüber haben wir auf der Heimfahrt nach Leipzig philosophiert und fanden den Denkansatz spannend. Denn auch wenn es damals nicht Propaganda hieß, so gab es doch Interessen der Mächtigen, die sie gegenüber dem Volk durchsetzten. Sie bedienten sich dabei der damals verfügbaren „Medien“, zu denen die Kirche gehörte, wo sich das Volk zum Gottesdienst traf.
Kulturelle Identität Europas
Mitteldeutschland ist ein Zentrum mittelalterlicher Baukunst. Der Naumburger Dom St. Peter und Paul wurde auf den Grundmauern einer noch älteren Kirche im 13. Jahrhundert gebaut. Er ist weltweit einzigartig in seiner Architektur, Bildhauerkunst und Glasmalerei. Seit 2018 ist er Unesco-Weltkulturerbe. Die Stadt Naumburg hatte einst die gleiche Bedeutung wie Merseburg, Magdeburg oder Leipzig. Der Dom – von der Spätromanik bis in die Frühgotik unter Leitung eines heute unbekannten Bildhauerarchitekten errichtet – gilt als Meisterwerk menschlicher Schöpferkraft und Handwerkskunst. Die naturwissenschaftlich-physikalischen Kenntnisse der Menschen waren offensichtlich enorm. Sie verfügten über das Wissen zur Planung und über entsprechende Werk- und Hebezeuge, um solche Bauwerke in relativ kurzer Zeit errichten zu können.
Im Westchor des Doms befinden sich mit den zwölf lebensgroßen Stifterfiguren die bekanntesten Kunstwerke des Doms, unter ihnen Uta von Ballenstedt. Sie soll Walt Disney als Quelle für die schöne und sehr stolze Königin im Zeichentrickfilm Schneewittchen gedient haben. Das Besondere und Neue an den steinernen Stifterfiguren war ihre realitätsnahe Darstellung, die sie lebendig und ausdrucksstark wirken lässt. Sie sind ein Höhepunkt in der Steinmetzkunst der damaligen Zeit. Die Figuren wurden, obschon die dargestellten Personen bereits mehr als 200 Jahre tot waren, mit charakteristischen Gesichtsausdrücken dargestellt: Uta schaut schön und stolz in die Ferne, ihr Gatte Ekkehard wirkt etwas hochmütig. Gegenüber steht die lachende Reglindis neben ihrem wehmütig-leidend blickenden Mann Hermann von Meißen.
Der Domführer sagte, dass die Gesichtsausdrücke menschliche Verhaltensweisen darstellen, die bei den Kirchenbesuchern unerwünscht waren. Wir hätten es hier mit einer sehr frühen Form der Propaganda zu tun. Die katholische Kirche war Vorreiter in Sachen Propaganda. Sie hat etwa 400 Jahre später, im Jahr 1622, mit der Sacra Congregatio de Propaganda Fide ein Amt gegründet, das den „richtigen“ Glauben in die Welt tragen sollte, und erst 1967 umbenannt wurde. Aber ihre gesellschaftlich führende Position hatte damals auch eine positive Seite: Den Kirchen und Klöstern haben wir den Erhalt und die Weitergabe antiken Wissens zu verdanken. Europa konnte sich trotz der politischen Zersplitterung seine kulturelle Identität erhalten. Zum Beispiel lässt sich das Wirken des namenlosen Domschöpfers anhand der Bau- und Kunstwerke quer durch Europa von Nordfrankreich über Mainz nach Naumburg und Meißen nachvollziehen. Aus der weiteren Entwicklung von Kunst und Kultur in Europa entstand in der Renaissance die Philosophie des Humanismus und später daraus die Aufklärung mit ihrer Wirkung auf Literatur und Wissenschaft. Ziel war dabei immer eine Stärkung des Gemeinwesens.
Transhumanismus zerstört Gemeinschaften
Heute scheinen wir uns allerdings an einer Bruchstelle der gesellschaftlichen Entwicklung zu befinden. Die Kirchen spielen in unserer Gesellschaft kaum noch eine Rolle. Weder bringen sie sich in ethische Diskussionen hörbar ein, noch tragen sie die Entwicklung von Kunst und Kultur sichtbar voran. Ihre Rolle im Bereich Propaganda haben längst Zeitungen und Zeitschriften, Rundfunk und Fernsehen übernommen. Diese Medien haben eine größere Reichweite, und die psychologische Beeinflussung ist umfassender. Nach dem Zweiten Weltkrieg wurde die Manipulation der Massen stark intensiviert und nahm nach dem Zusammenbruch der Sowjetunion noch weiter an Fahrt auf. Der Liberalismus konnte auf allen Gebieten seinen Siegeszug antreten, stellte das Individuum in den Mittelpunkt und erhob den Markt zur heiligen Kuh. Im Laufe der Zeit wurden die humanistischen Ideen der Aufklärung in ihr Gegenteil verkehrt. Der Mensch wurde als fehlerhaftes Wesen identifiziert, in die Vereinzelung getrieben, bevormundet und gegängelt – angeblich, damit er sich nicht selbst schadet. Zur psychologischen Beeinflussung kommen die neuen technischen Möglichkeiten aus Bio-Nano-Neuro-Wissenschaften und Digitalisierung. Der Transhumanismus wurde als neues Ziel für die Menschheit ausgerufen. Der Einzelne soll biologisch und technisch perfektioniert werden. Gemeinschaften – von der Familie angefangen – treibt das in die Bedeutungslosigkeit. Es besteht die Gefahr, dass persönliche Integrität und Privatsphäre durch Eingriffe in Körper- und Geistesfunktionen verletzt werden. Eine neue Aufklärung ist nötig. Denn sehr viel von dem über die Jahrhunderte erlangten Wissen ging schon verloren oder ist nur noch versteckt in den Bibliotheken und Archiven der Kirchen zu finden. Die Besinnung auf die vergessenen beziehungsweise verdrängten Grundlagen und Ideale der Aufklärung kann diese Entwicklung abwenden. Die Kulturschätze Mitteleuropas vermitteln in ihrer Schönheit und Vollkommenheit die Ruhe und die zeitlichen und räumlichen Dimensionen, die wir brauchen, wenn wir über die Frage nachdenken, wie wir in Zukunft leben wollen.
Die Rolle der neuen Medien für die zukünftige Entwicklung
Von den Alt-Medien ist in dieser Hinsicht nichts zu erwarten. Sie werden finanziert und sind unterwandert von den Kräften, die transhumanistische Entwicklungen vorantreiben. Die „neue Aufklärung“ ist ein lohnenswertes Ziel für die neuen Medien. Diese lassen sich jedoch noch zu sehr von den aktuellen Themen der Alt-Medien treiben. Der Angst-Propaganda begegnen sie mit – Ängsten, wenn auch anders ausgerichtet. Einige reiten die Empörungswelle in Gegenrichtung zu den Alt-Medien. Manche Betreiber von „alternativen“ Finanz- und Wirtschaftskanälen wollen ihre eigenen marktgläubigen Produkte an den Mann bringen. Stattdessen sollten in den neuen Medien positive Nachrichten verbreitet und eigene Themenfelder eröffnet werden, denen sich die Alt-Medien verweigern:
· der Mensch und seine Bildung zur souveränen, selbständig denkenden und handelnden Persönlichkeit,
· die Entwicklung des eigenen Bewusstseins, um der Fremdbestimmung zu entkommen und zu Wahrhaftigkeit, Authentizität und Menschlichkeit zu gelangen,
· die Entwicklung des Gemeinwohls,
· die Frage, wie wir neue Gemeinschaften bis hin zu autarken Gemeinden gründen können – wichtiger, je mehr das gesellschaftliche System um uns herum zusammenbricht.
Direkt sichtbar ist der letzte Punkt am Niedergang der Architektur und am Zustand der Innenstädte: Die reich dekorierten Gebäude der Gründerzeit wurden nach ihrer Zerstörung im Zweiten Weltkrieg durch gleichförmig rechteckige Gebäude aus Beton und Glas ersetzt. Dazu kamen die in allen Städten austauschbar gleichen Ladenzeilen und in den letzten Jahren Dreck und Schmierereien, die nicht mehr weggeräumt werden.
Die gesellschaftlichen Verwerfungen der Corona-Zeit führten bei vielen Menschen zum Innehalten und Nachdenken über Sinn und Ziele ihres Lebens. So entstanden einige Pilotprojekte, zum Beispiel in den Bereichen Landwirtschaft, Gesundheitswesen und Bildung. Diese auf die Zukunft gerichteten Themen könnten in den neuen Medien umfangreicher vorgestellt und diskutiert werden. Manova setzt schon solche Schwerpunkte mit „The Great WeSet“ von Walter van Rossum sowie mit den Kategorien „Zukunft & Neue Wege“ sowie „Aufwind“. Der Kontrafunk hat Formate entwickelt, die das Gemeinwohl stärker in den Fokus setzen wie etwa die Kultur- und Wissenschaftsrubrik. Nuoviso hat einen eigenen Songcontest ins Leben gerufen. Neben der inhaltlichen Ausrichtung auf eine lebenswerte Zukunft gilt es auch, die technologische Basis der neuen Medien zukunftsfest zu machen und sich der digitalen Zensur zu entziehen. Milosz Matuschek geht mit dem Pareto-Projekt neue Wege. Es könnte zur unzensierbaren Plattform der neuen Medien werden. Denn wie er sagt: Man baut sein neues Haus doch auch nicht auf dem Boden, der einem anderen gehört.
-
 @ 91bea5cd:1df4451c
2025-04-15 06:27:28
@ 91bea5cd:1df4451c
2025-04-15 06:27:28Básico
bash lsblk # Lista todos os diretorios montados.Para criar o sistema de arquivos:
bash mkfs.btrfs -L "ThePool" -f /dev/sdxCriando um subvolume:
bash btrfs subvolume create SubVolMontando Sistema de Arquivos:
bash mount -o compress=zlib,subvol=SubVol,autodefrag /dev/sdx /mntLista os discos formatados no diretório:
bash btrfs filesystem show /mntAdiciona novo disco ao subvolume:
bash btrfs device add -f /dev/sdy /mntLista novamente os discos do subvolume:
bash btrfs filesystem show /mntExibe uso dos discos do subvolume:
bash btrfs filesystem df /mntBalancea os dados entre os discos sobre raid1:
bash btrfs filesystem balance start -dconvert=raid1 -mconvert=raid1 /mntScrub é uma passagem por todos os dados e metadados do sistema de arquivos e verifica as somas de verificação. Se uma cópia válida estiver disponível (perfis de grupo de blocos replicados), a danificada será reparada. Todas as cópias dos perfis replicados são validadas.
iniciar o processo de depuração :
bash btrfs scrub start /mntver o status do processo de depuração Btrfs em execução:
bash btrfs scrub status /mntver o status do scrub Btrfs para cada um dos dispositivos
bash btrfs scrub status -d / data btrfs scrub cancel / dataPara retomar o processo de depuração do Btrfs que você cancelou ou pausou:
btrfs scrub resume / data
Listando os subvolumes:
bash btrfs subvolume list /ReportsCriando um instantâneo dos subvolumes:
Aqui, estamos criando um instantâneo de leitura e gravação chamado snap de marketing do subvolume de marketing.
bash btrfs subvolume snapshot /Reports/marketing /Reports/marketing-snapAlém disso, você pode criar um instantâneo somente leitura usando o sinalizador -r conforme mostrado. O marketing-rosnap é um instantâneo somente leitura do subvolume de marketing
bash btrfs subvolume snapshot -r /Reports/marketing /Reports/marketing-rosnapForçar a sincronização do sistema de arquivos usando o utilitário 'sync'
Para forçar a sincronização do sistema de arquivos, invoque a opção de sincronização conforme mostrado. Observe que o sistema de arquivos já deve estar montado para que o processo de sincronização continue com sucesso.
bash btrfs filsystem sync /ReportsPara excluir o dispositivo do sistema de arquivos, use o comando device delete conforme mostrado.
bash btrfs device delete /dev/sdc /ReportsPara sondar o status de um scrub, use o comando scrub status com a opção -dR .
bash btrfs scrub status -dR / RelatóriosPara cancelar a execução do scrub, use o comando scrub cancel .
bash $ sudo btrfs scrub cancel / ReportsPara retomar ou continuar com uma depuração interrompida anteriormente, execute o comando de cancelamento de depuração
bash sudo btrfs scrub resume /Reportsmostra o uso do dispositivo de armazenamento:
btrfs filesystem usage /data
Para distribuir os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID (incluindo o dispositivo de armazenamento recém-adicionado) montados no diretório /data , execute o seguinte comando:
sudo btrfs balance start --full-balance /data
Pode demorar um pouco para espalhar os dados, metadados e dados do sistema em todos os dispositivos de armazenamento do RAID se ele contiver muitos dados.
Opções importantes de montagem Btrfs
Nesta seção, vou explicar algumas das importantes opções de montagem do Btrfs. Então vamos começar.
As opções de montagem Btrfs mais importantes são:
**1. acl e noacl
**ACL gerencia permissões de usuários e grupos para os arquivos/diretórios do sistema de arquivos Btrfs.
A opção de montagem acl Btrfs habilita ACL. Para desabilitar a ACL, você pode usar a opção de montagem noacl .
Por padrão, a ACL está habilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem acl por padrão.
**2. autodefrag e noautodefrag
**Desfragmentar um sistema de arquivos Btrfs melhorará o desempenho do sistema de arquivos reduzindo a fragmentação de dados.
A opção de montagem autodefrag permite a desfragmentação automática do sistema de arquivos Btrfs.
A opção de montagem noautodefrag desativa a desfragmentação automática do sistema de arquivos Btrfs.
Por padrão, a desfragmentação automática está desabilitada. Portanto, o sistema de arquivos Btrfs usa a opção de montagem noautodefrag por padrão.
**3. compactar e compactar-forçar
**Controla a compactação de dados no nível do sistema de arquivos do sistema de arquivos Btrfs.
A opção compactar compacta apenas os arquivos que valem a pena compactar (se compactar o arquivo economizar espaço em disco).
A opção compress-force compacta todos os arquivos do sistema de arquivos Btrfs, mesmo que a compactação do arquivo aumente seu tamanho.
O sistema de arquivos Btrfs suporta muitos algoritmos de compactação e cada um dos algoritmos de compactação possui diferentes níveis de compactação.
Os algoritmos de compactação suportados pelo Btrfs são: lzo , zlib (nível 1 a 9) e zstd (nível 1 a 15).
Você pode especificar qual algoritmo de compactação usar para o sistema de arquivos Btrfs com uma das seguintes opções de montagem:
- compress=algoritmo:nível
- compress-force=algoritmo:nível
Para obter mais informações, consulte meu artigo Como habilitar a compactação do sistema de arquivos Btrfs .
**4. subvol e subvolid
**Estas opções de montagem são usadas para montar separadamente um subvolume específico de um sistema de arquivos Btrfs.
A opção de montagem subvol é usada para montar o subvolume de um sistema de arquivos Btrfs usando seu caminho relativo.
A opção de montagem subvolid é usada para montar o subvolume de um sistema de arquivos Btrfs usando o ID do subvolume.
Para obter mais informações, consulte meu artigo Como criar e montar subvolumes Btrfs .
**5. dispositivo
A opção de montagem de dispositivo** é usada no sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs.
Em alguns casos, o sistema operacional pode falhar ao detectar os dispositivos de armazenamento usados em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs. Nesses casos, você pode usar a opção de montagem do dispositivo para especificar os dispositivos que deseja usar para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar a opção de montagem de dispositivo várias vezes para carregar diferentes dispositivos de armazenamento para o sistema de arquivos de vários dispositivos Btrfs ou RAID.
Você pode usar o nome do dispositivo (ou seja, sdb , sdc ) ou UUID , UUID_SUB ou PARTUUID do dispositivo de armazenamento com a opção de montagem do dispositivo para identificar o dispositivo de armazenamento.
Por exemplo,
- dispositivo=/dev/sdb
- dispositivo=/dev/sdb,dispositivo=/dev/sdc
- dispositivo=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d
- device=UUID_SUB=490a263d-eb9a-4558-931e-998d4d080c5d,device=UUID_SUB=f7ce4875-0874-436a-b47d-3edef66d3424
**6. degraded
A opção de montagem degradada** permite que um RAID Btrfs seja montado com menos dispositivos de armazenamento do que o perfil RAID requer.
Por exemplo, o perfil raid1 requer a presença de 2 dispositivos de armazenamento. Se um dos dispositivos de armazenamento não estiver disponível em qualquer caso, você usa a opção de montagem degradada para montar o RAID mesmo que 1 de 2 dispositivos de armazenamento esteja disponível.
**7. commit
A opção commit** mount é usada para definir o intervalo (em segundos) dentro do qual os dados serão gravados no dispositivo de armazenamento.
O padrão é definido como 30 segundos.
Para definir o intervalo de confirmação para 15 segundos, você pode usar a opção de montagem commit=15 (digamos).
**8. ssd e nossd
A opção de montagem ssd** informa ao sistema de arquivos Btrfs que o sistema de arquivos está usando um dispositivo de armazenamento SSD, e o sistema de arquivos Btrfs faz a otimização SSD necessária.
A opção de montagem nossd desativa a otimização do SSD.
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem de SSD será habilitada. Caso contrário, a opção de montagem nossd é habilitada.
**9. ssd_spread e nossd_spread
A opção de montagem ssd_spread** tenta alocar grandes blocos contínuos de espaço não utilizado do SSD. Esse recurso melhora o desempenho de SSDs de baixo custo (baratos).
A opção de montagem nossd_spread desativa o recurso ssd_spread .
O sistema de arquivos Btrfs detecta automaticamente se um SSD é usado para o sistema de arquivos Btrfs. Se um SSD for usado, a opção de montagem ssd_spread será habilitada. Caso contrário, a opção de montagem nossd_spread é habilitada.
**10. descarte e nodiscard
Se você estiver usando um SSD que suporte TRIM enfileirado assíncrono (SATA rev3.1), a opção de montagem de descarte** permitirá o descarte de blocos de arquivos liberados. Isso melhorará o desempenho do SSD.
Se o SSD não suportar TRIM enfileirado assíncrono, a opção de montagem de descarte prejudicará o desempenho do SSD. Nesse caso, a opção de montagem nodiscard deve ser usada.
Por padrão, a opção de montagem nodiscard é usada.
**11. norecovery
Se a opção de montagem norecovery** for usada, o sistema de arquivos Btrfs não tentará executar a operação de recuperação de dados no momento da montagem.
**12. usebackuproot e nousebackuproot
Se a opção de montagem usebackuproot for usada, o sistema de arquivos Btrfs tentará recuperar qualquer raiz de árvore ruim/corrompida no momento da montagem. O sistema de arquivos Btrfs pode armazenar várias raízes de árvore no sistema de arquivos. A opção de montagem usebackuproot** procurará uma boa raiz de árvore e usará a primeira boa que encontrar.
A opção de montagem nousebackuproot não verificará ou recuperará raízes de árvore inválidas/corrompidas no momento da montagem. Este é o comportamento padrão do sistema de arquivos Btrfs.
**13. space_cache, space_cache=version, nospace_cache e clear_cache
A opção de montagem space_cache** é usada para controlar o cache de espaço livre. O cache de espaço livre é usado para melhorar o desempenho da leitura do espaço livre do grupo de blocos do sistema de arquivos Btrfs na memória (RAM).
O sistema de arquivos Btrfs suporta 2 versões do cache de espaço livre: v1 (padrão) e v2
O mecanismo de cache de espaço livre v2 melhora o desempenho de sistemas de arquivos grandes (tamanho de vários terabytes).
Você pode usar a opção de montagem space_cache=v1 para definir a v1 do cache de espaço livre e a opção de montagem space_cache=v2 para definir a v2 do cache de espaço livre.
A opção de montagem clear_cache é usada para limpar o cache de espaço livre.
Quando o cache de espaço livre v2 é criado, o cache deve ser limpo para criar um cache de espaço livre v1 .
Portanto, para usar o cache de espaço livre v1 após a criação do cache de espaço livre v2 , as opções de montagem clear_cache e space_cache=v1 devem ser combinadas: clear_cache,space_cache=v1
A opção de montagem nospace_cache é usada para desabilitar o cache de espaço livre.
Para desabilitar o cache de espaço livre após a criação do cache v1 ou v2 , as opções de montagem nospace_cache e clear_cache devem ser combinadas: clear_cache,nosapce_cache
**14. skip_balance
Por padrão, a operação de balanceamento interrompida/pausada de um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs será retomada automaticamente assim que o sistema de arquivos Btrfs for montado. Para desabilitar a retomada automática da operação de equilíbrio interrompido/pausado em um sistema de arquivos Btrfs de vários dispositivos ou RAID Btrfs, você pode usar a opção de montagem skip_balance .**
**15. datacow e nodatacow
A opção datacow** mount habilita o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs. É o comportamento padrão.
Se você deseja desabilitar o recurso Copy-on-Write (CoW) do sistema de arquivos Btrfs para os arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatacow .
**16. datasum e nodatasum
A opção datasum** mount habilita a soma de verificação de dados para arquivos recém-criados do sistema de arquivos Btrfs. Este é o comportamento padrão.
Se você não quiser que o sistema de arquivos Btrfs faça a soma de verificação dos dados dos arquivos recém-criados, monte o sistema de arquivos Btrfs com a opção de montagem nodatasum .
Perfis Btrfs
Um perfil Btrfs é usado para informar ao sistema de arquivos Btrfs quantas cópias dos dados/metadados devem ser mantidas e quais níveis de RAID devem ser usados para os dados/metadados. O sistema de arquivos Btrfs contém muitos perfis. Entendê-los o ajudará a configurar um RAID Btrfs da maneira que você deseja.
Os perfis Btrfs disponíveis são os seguintes:
single : Se o perfil único for usado para os dados/metadados, apenas uma cópia dos dados/metadados será armazenada no sistema de arquivos, mesmo se você adicionar vários dispositivos de armazenamento ao sistema de arquivos. Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
dup : Se o perfil dup for usado para os dados/metadados, cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos manterá duas cópias dos dados/metadados. Assim, 50% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser utilizado.
raid0 : No perfil raid0 , os dados/metadados serão divididos igualmente em todos os dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, não haverá dados/metadados redundantes (duplicados). Assim, 100% do espaço em disco de cada um dos dispositivos de armazenamento adicionados ao sistema de arquivos pode ser usado. Se, em qualquer caso, um dos dispositivos de armazenamento falhar, todo o sistema de arquivos será corrompido. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid0 .
raid1 : No perfil raid1 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a uma falha de unidade. Mas você pode usar apenas 50% do espaço total em disco. Você precisará de pelo menos dois dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1 .
raid1c3 : No perfil raid1c3 , três cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a duas falhas de unidade, mas você pode usar apenas 33% do espaço total em disco. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c3 .
raid1c4 : No perfil raid1c4 , quatro cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos. Nesta configuração, a matriz RAID pode sobreviver a três falhas de unidade, mas você pode usar apenas 25% do espaço total em disco. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid1c4 .
raid10 : No perfil raid10 , duas cópias dos dados/metadados serão armazenadas nos dispositivos de armazenamento adicionados ao sistema de arquivos, como no perfil raid1 . Além disso, os dados/metadados serão divididos entre os dispositivos de armazenamento, como no perfil raid0 .
O perfil raid10 é um híbrido dos perfis raid1 e raid0 . Alguns dos dispositivos de armazenamento formam arrays raid1 e alguns desses arrays raid1 são usados para formar um array raid0 . Em uma configuração raid10 , o sistema de arquivos pode sobreviver a uma única falha de unidade em cada uma das matrizes raid1 .
Você pode usar 50% do espaço total em disco na configuração raid10 . Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid10 .
raid5 : No perfil raid5 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Uma única paridade será calculada e distribuída entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid5 , o sistema de arquivos pode sobreviver a uma única falha de unidade. Se uma unidade falhar, você pode adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir da paridade distribuída das unidades em execução.
Você pode usar 1 00x(N-1)/N % do total de espaços em disco na configuração raid5 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos três dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid5 .
raid6 : No perfil raid6 , uma cópia dos dados/metadados será dividida entre os dispositivos de armazenamento. Duas paridades serão calculadas e distribuídas entre os dispositivos de armazenamento do array RAID.
Em uma configuração raid6 , o sistema de arquivos pode sobreviver a duas falhas de unidade ao mesmo tempo. Se uma unidade falhar, você poderá adicionar uma nova unidade ao sistema de arquivos e os dados perdidos serão calculados a partir das duas paridades distribuídas das unidades em execução.
Você pode usar 100x(N-2)/N % do espaço total em disco na configuração raid6 . Aqui, N é o número de dispositivos de armazenamento adicionados ao sistema de arquivos. Você precisará de pelo menos quatro dispositivos de armazenamento para configurar o sistema de arquivos Btrfs no perfil raid6 .
-
 @ 6e0ea5d6:0327f353
2025-05-04 14:53:42
@ 6e0ea5d6:0327f353
2025-05-04 14:53:42Amico mio, ascolta bene!
Without hesitation, the woman you attract with lies is not truly yours. Davvero, she is the temporary property of the illusion you’ve built to seduce her. And every illusion, sooner or later, crumbles.
Weak men sell inflated versions of themselves. They talk about what they don’t have, promise what they can’t sustain, adorn their empty selves with words that are nothing more than a coat of paint. And they do this thinking that, later, they’ll be able to "show who they really are." Fatal mistake, cazzo!
The truth, amico mio, is not something that appears at the end. It is what holds up the whole beginning.
The woman who approaches a lie may smile at first — but she is smiling at the theater, not at the actor. When the curtains fall, what she will see is not a man. It will be a character tired of performing, begging for love from a self-serving audience in the front row.
That’s why I always point out that lying to win a woman’s heart is the same as sabotaging your own nature. The woman who comes through an invented version of you will be the first to leave when the veil of lies tears apart. Not out of cruelty, but out of consistency with her own interest. Fine... She didn’t leave you, but rather, that version of yourself never truly existed to be left behind.
A worthy man presents himself without deceptive adornments. And those who stay, stay because they know exactly who they are choosing as a man. That’s what differentiates forged seduction from the convenience of love built on honor, loyalty, and respect.
Ah, amico mio, I remember well. It was lunch on an autumn day in Catania. Mediterranean heat, and the Nero D'Avola wine from midday clinging to the lips like dried blood. Sitting in the shade of a lemon tree planted right by my grandfather's vineyard entrance, my uncle — the oldest of my father’s brothers — spoke little, but when he called us to sit by his side, all the nephews would quiet down to listen. And in my youth, he told me something that has never left my mind.
“In Sicily, the woman who endures the silence of a man about his business is more loyal than the one who is enchanted by speeches about what he does or how much he earns. Perchè, figlio mio, the first one has seen the truth. The second one, only a false shine.”
Thank you for reading, my friend!
If this message resonated with you, consider leaving your "🥃" as a token of appreciation.
A toast to our family!
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 005bc4de:ef11e1a2
2025-05-04 12:01:42
@ 005bc4de:ef11e1a2
2025-05-04 12:01:42OSU commencement speech revisited 1 year later
One year ago, May 5, 2024, the commencement speaker at Ohio State University was Chris Pan. He got booed for mentioning bitcoin. There were some other things involved, but the bitcoin part is what could my ears.
Here's an article about the speech and a video clip with the bitcoin mention. The quote that I feel is especially pertinent is this, '“The mechanics of investing are actually easy, but it comes down to mindset,” Pan said. “The most common barriers are fear, laziness and closed-mindedness.”'
Last year, I wrote this and had it sent as a reminder to myself (I received the reminder yesterday after totally forgetting about this):
Ohio State commencement speaker mentions bitcoin and got booed.
I wondered what would've happened if they'd taken his advice to heart and bought bitcoin that day. Linked article: https://www.businessinsider.com/osu-commencement-speaker-ayahuasca-praises-bitcoin-booed-viral-2024-5
Nat Brunell interviewed him on her Coin Stories podcast shortly after his speech: https://www.youtube.com/watch?v=LRqKxKqlbcI
BTC on 5/5/2024 day of speech: about $64,047 (chart below)
If any of those now wise old 23 year olds remember the advice they were given, bitcoin is currently at $95,476. If any took Pan's advice, they achieved a 49% gain in one year. Those who did not take Pan's advice, lost about 2.7% of their buying power due to inflation.
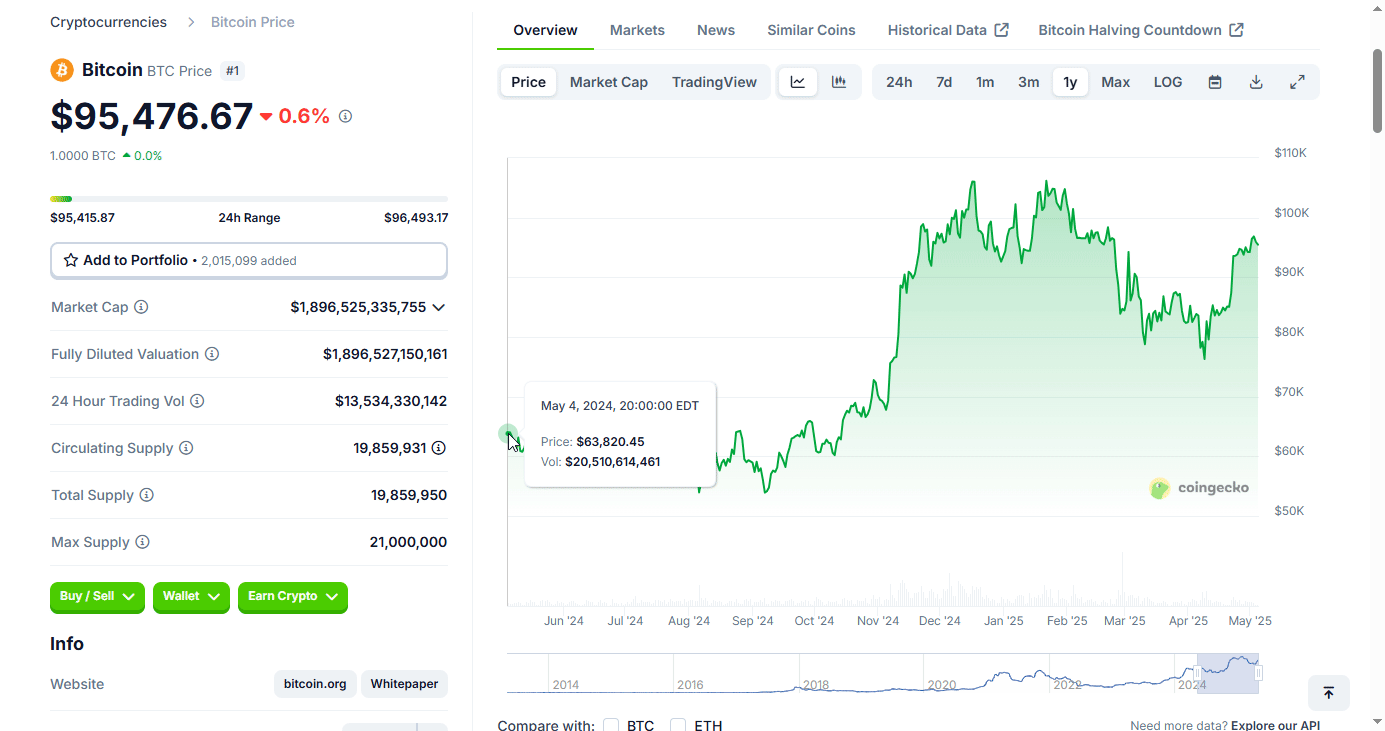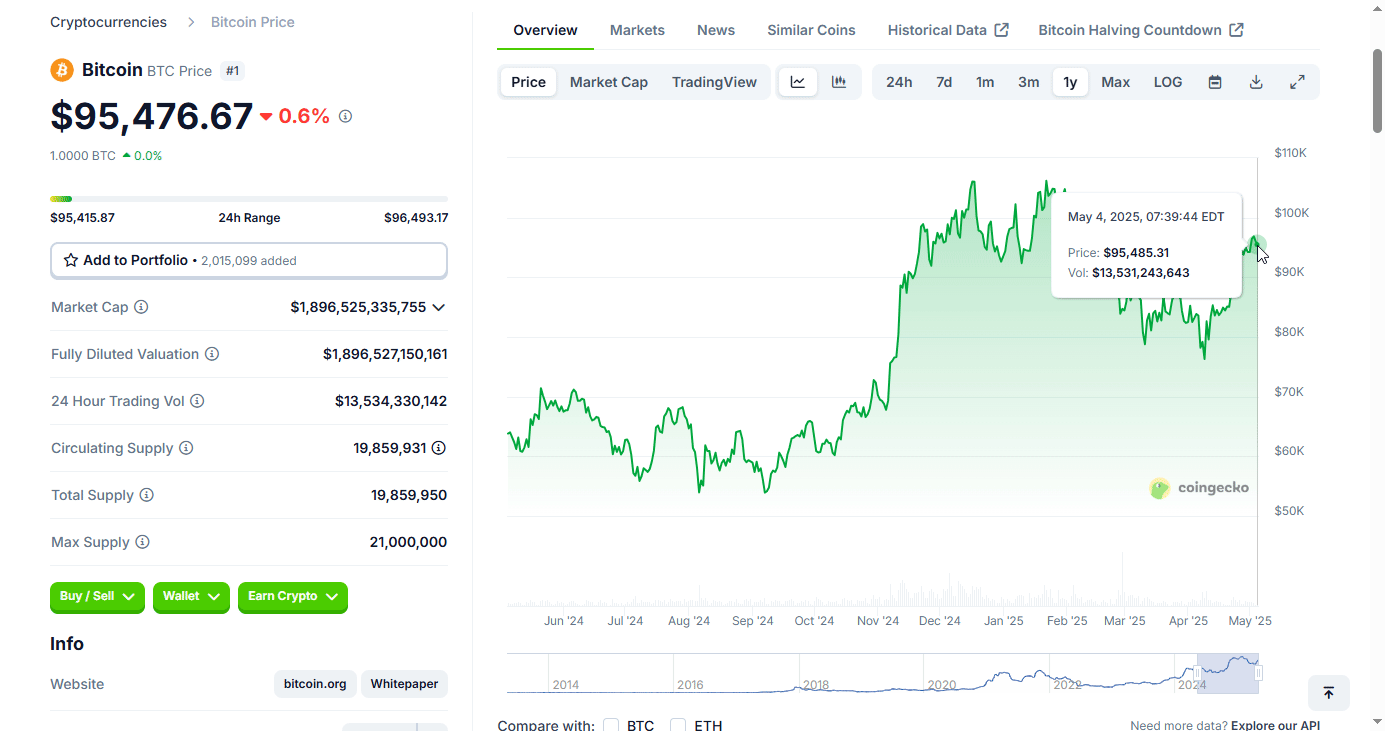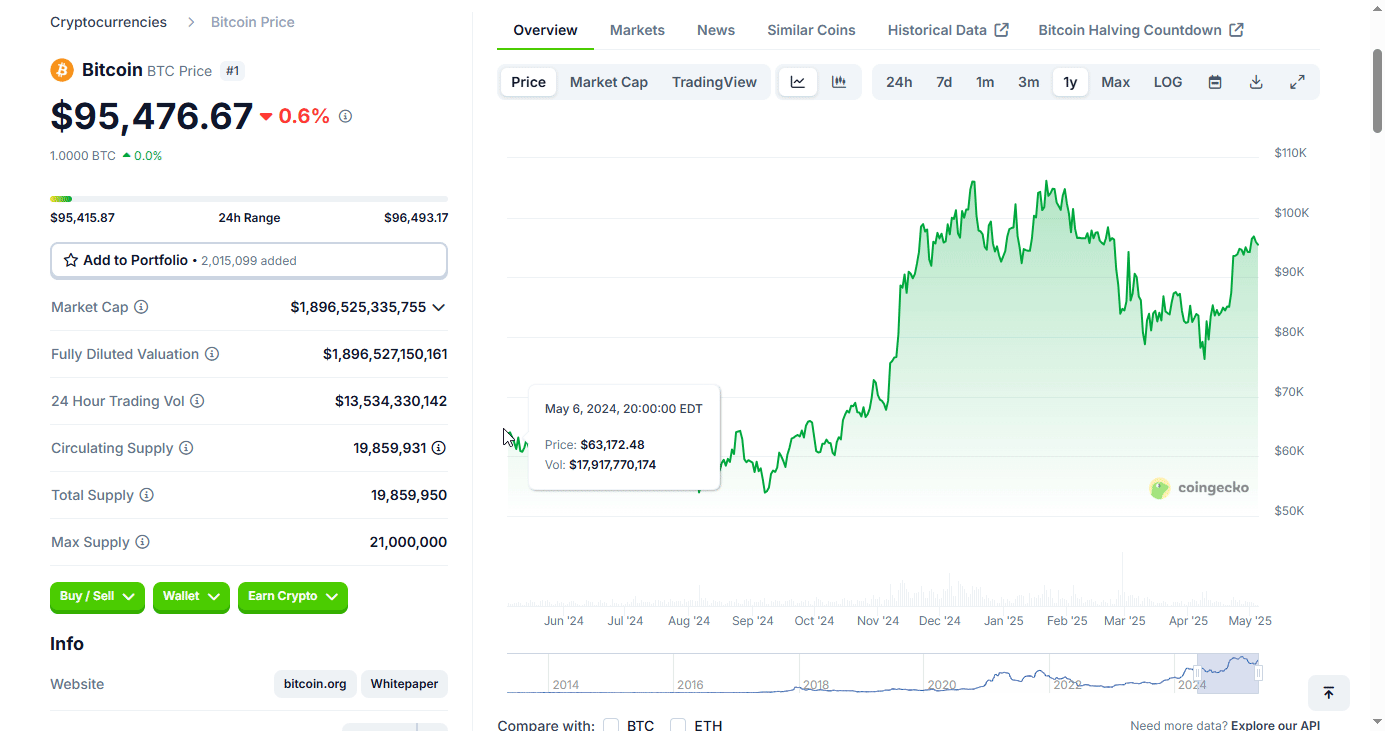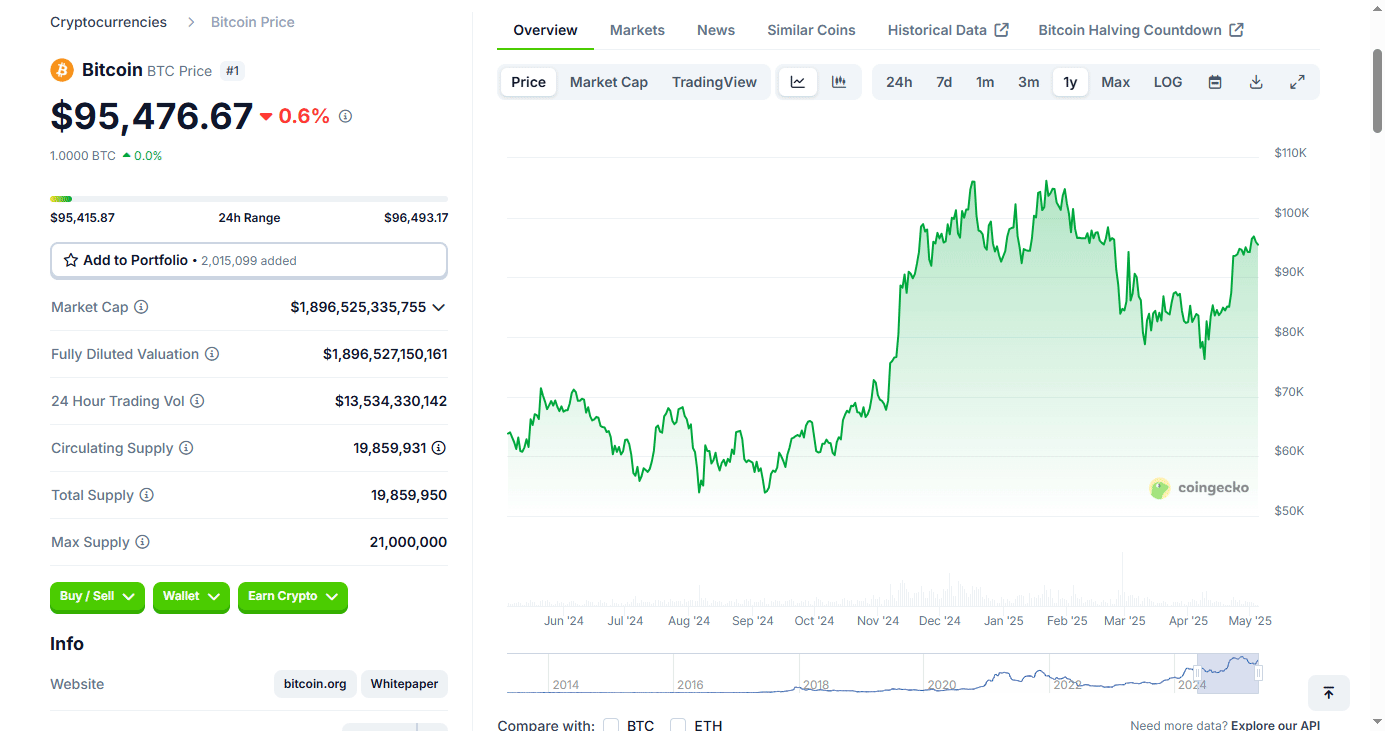
For bitcoiners, think about how far we've come. May of 2024 was still the waning days of the "War on Crypto," bitcoin was boiling the oceans, if you held, used, or liked bitcoin you were evil. Those were dark days and days I'm glad are behind us.
Here is the full commencement speech. The bitcoin part is around the 5 or 6 minute mark: https://m.youtube.com/watch?v=lcH-iL_FdYo
-
 @ a296b972:e5a7a2e8
2025-05-04 08:30:56
@ a296b972:e5a7a2e8
2025-05-04 08:30:56Am Ende der Woche von Unseremeinungsfreiheit wird in der Unserehauptstadt von Unserdeutschland, Unserberlin, voraussichtlich der neue Unserbundeskanzler vereidigt.
Der Schwur des voraussichtlich nächsten Unserbundeskanzlers sollte aktualisiert werden:
Jetzt, wo endlich mein Traum in Erfüllung geht, nur einmal im Leben Unserbundeskanzler zu werden, zahlen sich für mich alle Tricks und Kniffe aus, die ich angewendet habe, um unter allen Umständen in diese Position zu kommen.
Ich schwöre, dass ich meine Kraft meinem Wohle widmen, meinen Nutzen mehren, nach Vorbild meines Vorgängers Schaden von mir wenden, das Grundgesetz und die Gesetze des Unserbundes formen, meine Pflichten unsergewissenhaft erfüllen und Unseregerechtigkeit gegen jedermann und jederfrau nicht nur üben, sondern unter allen Umständen auch durchsetzen werde, die sich mir bei der Umsetzung der Vorstellungen von Unseredemokratie in den Weg stellen. (So wahr mir wer auch immer helfe).
Der Antrittsbesuch des Unserbundeskanzlers beim Repräsentanten der noch in Unserdeutschland präsenten Besatzungsmacht wird mit Spannung erwartet.
Ein großer Teil der Unsereminister ist schon bekannt. Die Auswahl verspricht viele Unsereüberraschungen.
Die Unsereeinheitspartei, bestehend aus ehemaligen Volksparteien, wird weiterhin dafür sorgen, dass die Nicht-Unsereopposition so wenig wie möglich Einfluss erhält, obwohl sie von den Nicht-Unserebürgern, die mindestens ein Viertel der Urnengänger ausmachen, voll-demokratisch gewählt wurde.
Das Zentralkomitee der Deutschen Unseredemokratischen Bundesrepublik wird zum Wohle seiner Unserebürger alles daransetzen, Unseredemokratie weiter voranzubringen und hofft auch weiterhin auf die Unterstützung von Unser-öffentlich-rechtlicher-Rundfunk.
Die Unserepressefreiheit wird auch weiterhin garantiert.
Auf die Verlautbarungen der Unserepressekonferenz, besetzt mit frischem Unserpersonal, brauchen die Insassen von Unserdeutschland auch weiterhin nicht zu verzichten.
Alles, was nicht gesichert unserdemokratisch ist, gilt als gesichert rechtsextrem.
Als Maxime gilt für alles Handeln: Es muss unter allen Umständen demokratisch aussehen, aber wir (die Unseredemokraten) müssen alles in der Hand haben.
Es ist unwahrscheinlich, dass Unsersondervermögen von den Unserdemokraten zurückgezahlt wird. Dieser Vorzug ist den Unserebürgern und den Nicht-Unserebürgern durch Unseresteuerzahlungen vorbehalten.
Die Unserebundeswehr soll aufgebaut werden (Baut auf, baut auf!), die Unsererüstungsindustrie läuft auf Hochtouren und soll Unserdeutschland wieder unserkriegstüchtig machen, weil Russland immer Unserfeind sein wird.
Von Unserdeutschland soll nur noch Unserfrieden ausgehen.
Zur Bekräftigung, dass alles seinen unser-sozialistischen Gang geht, tauchte die Phoenix*in aus der Asche auf, in dem Unseremutti kürzlich ihren legendären Satz wiederholte:
Wir schaffen das.
Ob damit der endgültige wirtschaftliche Untergang und die Vollendung der gesellschaftlichen Spaltung von Unserdeutschland gemeint war, ist nicht überliefert.
Orwellsche Schlussfolgerung:
Wir = unser
Ihr = Euer
Vogel und Maus passen nicht zusammen
Ausgerichtet auf Ruinen und der Zukunft abgewandt, Uneinigkeit und Unrecht und Unfreiheit für das deutsche Unserland.
Unserdeutschland – ein Land mit viel Vergangenheit und wenig Zukunft?
Es ist zum Heulen.
Dieser Artikel wurde mit dem Pareto-Client geschrieben
* *
(Bild von pixabay)
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:37:32
@ 5c26ee8b:a4d229aa
2025-04-14 16:37:3210:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ b2caa9b3:9eab0fb5
2025-05-04 08:20:46
@ b2caa9b3:9eab0fb5
2025-05-04 08:20:46Hey friends,
Exciting news – I’m currently setting up my very first Discord server!
This space will be all about my travels, behind-the-scenes stories, photo sharing, and practical tips and insights from the road. My goal is to make it the central hub connecting all my decentralized social platforms where I can interact with you more directly, and share exclusive content.
Since I’m just starting out, I’d love to hear from you:
Do you know any useful RSS-feed integrations for updates?
Can you recommend any cool Discord bots for community engagement or automation?
Are there any tips or features you think I must include?
The idea is to keep everything free and accessible, and to grow a warm, helpful community around the joy of exploring the world.
It’s my first time managing a Discord server, so your experience and suggestions would mean a lot. Leave a comment – I’m all ears!
Thanks for your support, Ruben Storm
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:32:51
@ 5c26ee8b:a4d229aa
2025-04-14 16:32:5110:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ 5c26ee8b:a4d229aa
2025-04-14 16:31:49
@ 5c26ee8b:a4d229aa
2025-04-14 16:31:4910:25 Yunus
وَاللَّهُ يَدْعُو إِلَىٰ دَارِ السَّلَامِ وَيَهْدِي مَنْ يَشَاءُ إِلَىٰ صِرَاطٍ مُسْتَقِيمٍ
And Allah invites to the Home of Peace and guides whom He wills to a straight path.
6:125 Al-An'aam
فَمَنْ يُرِدِ اللَّهُ أَنْ يَهْدِيَهُ يَشْرَحْ صَدْرَهُ لِلْإِسْلَامِ ۖ وَمَنْ يُرِدْ أَنْ يُضِلَّهُ يَجْعَلْ صَدْرَهُ ضَيِّقًا حَرَجًا كَأَنَّمَا يَصَّعَّدُ فِي السَّمَاءِ ۚ كَذَٰلِكَ يَجْعَلُ اللَّهُ الرِّجْسَ عَلَى الَّذِينَ لَا يُؤْمِنُونَ
So whoever Allah wants to guide - He expands his breast to [contain] Islam; and whoever He wants to misguide - He makes his breast tight and constricted as though he were climbing into the sky. Thus Allah places defilement upon those who do not believe.
Allah is one of the Islamic names of God; the creator of everything. Not associating with God, Allah, any other and worshipping him alone is one of the first known fact in Islam.
- Al-Ikhlaas قُلْ هُوَ اللَّهُ أَحَدٌ Say, "He is Allah, [who is] One, اللَّهُ الصَّمَدُ Allah, the Eternal Refuge. لَمْ يَلِدْ وَلَمْ يُولَدْ He neither begets nor is born, وَلَمْ يَكُنْ لَهُ كُفُوًا أَحَدٌ Nor is there to Him any equivalent."
The Quran, the Islamic holly book and the guidance for mankind, was delivered more than 1400 years ago through the Angel Gabriel to prophet Mohamed peace be upon, however little is known about Islam despite living in a so called intellectual era.
The first word that was delivered was, “Read” in the first verse of surah Al-Alaq.
96:1 Al-Alaq
اقْرَأْ بِاسْمِ رَبِّكَ الَّذِي خَلَقَ
Read, in the name of your Lord who created -
The Quran, words of God (Allah), was delivered in Arabic and it is one of its miracles.
39:28 Az-Zumar
قُرْآنًا عَرَبِيًّا غَيْرَ ذِي عِوَجٍ لَعَلَّهُمْ يَتَّقُونَ
[It is] an Arabic Qur'an, without any distortion that they might become righteous.
18:109 Al-Kahf
قُلْ لَوْ كَانَ الْبَحْرُ مِدَادًا لِكَلِمَاتِ رَبِّي لَنَفِدَ الْبَحْرُ قَبْلَ أَنْ تَنْفَدَ كَلِمَاتُ رَبِّي وَلَوْ جِئْنَا بِمِثْلِهِ مَدَدًا
Say, "If the sea were ink for [writing] the words of my Lord, the sea would be exhausted before the words of my Lord were exhausted, even if We brought the like of it as a supplement."
17:88 Al-Israa
قُلْ لَئِنِ اجْتَمَعَتِ الْإِنْسُ وَالْجِنُّ عَلَىٰ أَنْ يَأْتُوا بِمِثْلِ هَٰذَا الْقُرْآنِ لَا يَأْتُونَ بِمِثْلِهِ وَلَوْ كَانَ بَعْضُهُمْ لِبَعْضٍ ظَهِيرًا
Say, "If mankind and the jinn gathered in order to produce the like of this Qur'an, they could not produce the like of it, even if they were to each other assistants."
17:89 Al-Israa
وَلَقَدْ صَرَّفْنَا لِلنَّاسِ فِي هَٰذَا الْقُرْآنِ مِنْ كُلِّ مَثَلٍ فَأَبَىٰ أَكْثَرُ النَّاسِ إِلَّا كُفُورًا
And We have certainly diversified for the people in this Qur'an from every [kind] of example, but most of the people refused [anything] except disbelief.
Through the wards of God in the Quran a lot can be known about Him and in the following verse some descriptions about Him.
2:255 Al-Baqara
اللَّهُ لَا إِلَٰهَ إِلَّا هُوَ الْحَيُّ الْقَيُّومُ ۚ لَا تَأْخُذُهُ سِنَةٌ وَلَا نَوْمٌ ۚ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ مَنْ ذَا الَّذِي يَشْفَعُ عِنْدَهُ إِلَّا بِإِذْنِهِ ۚ يَعْلَمُ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ ۖ وَلَا يُحِيطُونَ بِشَيْءٍ مِنْ عِلْمِهِ إِلَّا بِمَا شَاءَ ۚ وَسِعَ كُرْسِيُّهُ السَّمَاوَاتِ وَالْأَرْضَ ۖ وَلَا يَئُودُهُ حِفْظُهُمَا ۚ وَهُوَ الْعَلِيُّ الْعَظِيمُ
Allah - there is no deity except Him, the Ever-Living, the Sustainer of [all] existence. Neither drowsiness overtakes Him nor sleep. To Him belongs whatever is in the heavens and whatever is on the earth. Who is it that can intercede with Him except by His permission? He knows what is [presently] before them and what will be after them, and they encompass not a thing of His knowledge except for what He wills. His Kursi extends over the heavens and the earth, and their preservation tires Him not. And He is the Most High, the Most Great.
Seeing God has been a curiosity of prophets themselves and in the following examples of what happened when prophet Moses, peace be upon him, or his people asked so.
7:143 Al-A'raaf
وَلَمَّا جَاءَ مُوسَىٰ لِمِيقَاتِنَا وَكَلَّمَهُ رَبُّهُ قَالَ رَبِّ أَرِنِي أَنْظُرْ إِلَيْكَ ۚ قَالَ لَنْ تَرَانِي وَلَٰكِنِ انْظُرْ إِلَى الْجَبَلِ فَإِنِ اسْتَقَرَّ مَكَانَهُ فَسَوْفَ تَرَانِي ۚ فَلَمَّا تَجَلَّىٰ رَبُّهُ لِلْجَبَلِ جَعَلَهُ دَكًّا وَخَرَّ مُوسَىٰ صَعِقًا ۚ فَلَمَّا أَفَاقَ قَالَ سُبْحَانَكَ تُبْتُ إِلَيْكَ وَأَنَا أَوَّلُ الْمُؤْمِنِينَ
And when Moses arrived at Our appointed time and his Lord spoke to him, he said, "My Lord, show me [Yourself] that I may look at You." [Allah] said, "You will not see Me, but look at the mountain; if it should remain in place, then you will see Me." But when his Lord appeared to the mountain, He rendered it level, and Moses fell unconscious. And when he awoke, he said, "Exalted are You! I have repented to You, and I am the first of the believers."
2:55 Al-Baqara
وَإِذْ قُلْتُمْ يَا مُوسَىٰ لَنْ نُؤْمِنَ لَكَ حَتَّىٰ نَرَى اللَّهَ جَهْرَةً فَأَخَذَتْكُمُ الصَّاعِقَةُ وَأَنْتُمْ تَنْظُرُونَ
And [recall] when you said, "O Moses, we will never believe you until we see Allah outright"; so the thunderbolt took you while you were looking on.
2:56 Al-Baqara
ثُمَّ بَعَثْنَاكُمْ مِنْ بَعْدِ مَوْتِكُمْ لَعَلَّكُمْ تَشْكُرُونَ
Then We revived you after your death that perhaps you would be grateful.
In fact eyesights can’t reach God as in the following verses 6:102 Al-An'aam
ذَٰلِكُمُ اللَّهُ رَبُّكُمْ ۖ لَا إِلَٰهَ إِلَّا هُوَ ۖ خَالِقُ كُلِّ شَيْءٍ فَاعْبُدُوهُ ۚ وَهُوَ عَلَىٰ كُلِّ شَيْءٍ وَكِيلٌ
That is Allah, your Lord; there is no deity except Him, the Creator of all things, so worship Him. And He is Disposer of all things.
6:103 Al-An'aam
لَا تُدْرِكُهُ الْأَبْصَارُ وَهُوَ يُدْرِكُ الْأَبْصَارَ ۖ وَهُوَ اللَّطِيفُ الْخَبِيرُ
Eyesights (or visions) do not reach (or perceive him) Him, but He reaches (or perceives) [all] eyesights (visions); and He is the Subtle, the Acquainted.
6:104 Al-An'aam
قَدْ جَاءَكُمْ بَصَائِرُ مِنْ رَبِّكُمْ ۖ فَمَنْ أَبْصَرَ فَلِنَفْسِهِ ۖ وَمَنْ عَمِيَ فَعَلَيْهَا ۚ وَمَا أَنَا عَلَيْكُمْ بِحَفِيظٍ
There has come to you eyesights (or enlightenments) from your Lord. So whoever will see does so for [the benefit of] his soul, and whoever is blind [does harm] against it. And [say], "I am not controlling (or a guardian) over you."
42:11 Ash-Shura
فَاطِرُ السَّمَاوَاتِ وَالْأَرْضِ ۚ جَعَلَ لَكُمْ مِنْ أَنْفُسِكُمْ أَزْوَاجًا وَمِنَ الْأَنْعَامِ أَزْوَاجًا ۖ يَذْرَؤُكُمْ فِيهِ ۚ لَيْسَ كَمِثْلِهِ شَيْءٌ ۖ وَهُوَ السَّمِيعُ الْبَصِيرُ
[He is] Creator of the heavens and the earth. He has made for you from yourselves, mates, and among the cattle, mates; He multiplies you thereby. There is nothing like Him, and He is the Hearing, the Seeing.
Another name of God is the Truth and the Islam is the religion of truth and prophet Mohamed peace be upon him was chosen to invite the people to Islam.
61:7 As-Saff
وَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ الْكَذِبَ وَهُوَ يُدْعَىٰ إِلَى الْإِسْلَامِ ۚ وَاللَّهُ لَا يَهْدِي الْقَوْمَ الظَّالِمِينَ
And who is more unjust than one who invents about Allah untruth while he is being invited to Islam. And Allah does not guide the wrongdoing people.
61:8 As-Saff
يُرِيدُونَ لِيُطْفِئُوا نُورَ اللَّهِ بِأَفْوَاهِهِمْ وَاللَّهُ مُتِمُّ نُورِهِ وَلَوْ كَرِهَ الْكَافِرُونَ
They want to extinguish the light of Allah with their mouths, but Allah will perfect His light, although the disbelievers dislike it.
61:9 As-Saff
هُوَ الَّذِي أَرْسَلَ رَسُولَهُ بِالْهُدَىٰ وَدِينِ الْحَقِّ لِيُظْهِرَهُ عَلَى الدِّينِ كُلِّهِ وَلَوْ كَرِهَ الْمُشْرِكُونَ
It is He who sent His Messenger with guidance and the religion of truth to manifest it over all religion, although those who associate others with Allah dislike it.
Humans were given a trust, it’s to populate the earth while having the ability to choose between right and wrong.
33:72 Al-Ahzaab
إِنَّا عَرَضْنَا الْأَمَانَةَ عَلَى السَّمَاوَاتِ وَالْأَرْضِ وَالْجِبَالِ فَأَبَيْنَ أَنْ يَحْمِلْنَهَا وَأَشْفَقْنَ مِنْهَا وَحَمَلَهَا الْإِنْسَانُ ۖ إِنَّهُ كَانَ ظَلُومًا جَهُولًا
Indeed, we offered the Trust to the heavens and the earth and the mountains, and they declined to bear it and feared it; but man [undertook to] bear it. Indeed, he was unjust and ignorant.
Although our souls testified before the creation that God, Allah is our creator, he sent messengers and books to guide us.
7:172 Al-A'raaf
وَإِذْ أَخَذَ رَبُّكَ مِنْ بَنِي آدَمَ مِنْ ظُهُورِهِمْ ذُرِّيَّتَهُمْ وَأَشْهَدَهُمْ عَلَىٰ أَنْفُسِهِمْ أَلَسْتُ بِرَبِّكُمْ ۖ قَالُوا بَلَىٰ ۛ شَهِدْنَا ۛ أَنْ تَقُولُوا يَوْمَ الْقِيَامَةِ إِنَّا كُنَّا عَنْ هَٰذَا غَافِلِينَ
And [mention] when your Lord took from the children of Adam - from their loins - their descendants and made them testify of themselves, [saying to them], "Am I not your Lord?" They said, "Yes, we have testified." [This] - lest you should say on the day of Resurrection, "Indeed, we were of this unaware."
God likes that who believes in him submits to him willingly. The heavens and the earth, known to have consciousness in Islam submitted to him before us.
41:9 Fussilat
۞ قُلْ أَئِنَّكُمْ لَتَكْفُرُونَ بِالَّذِي خَلَقَ الْأَرْضَ فِي يَوْمَيْنِ وَتَجْعَلُونَ لَهُ أَنْدَادًا ۚ ذَٰلِكَ رَبُّ الْعَالَمِينَ
Say, "Do you indeed disbelieve in He who created the earth in two days and attribute to Him equals? That is the Lord of the worlds."
41:10 Fussilat
وَجَعَلَ فِيهَا رَوَاسِيَ مِنْ فَوْقِهَا وَبَارَكَ فِيهَا وَقَدَّرَ فِيهَا أَقْوَاتَهَا فِي أَرْبَعَةِ أَيَّامٍ سَوَاءً لِلسَّائِلِينَ
And He placed on the earth firmly set mountains over its surface, and He blessed it and determined therein its [creatures'] sustenance in four days without distinction - for [the information] of those who ask.
41:11 Fussilat
ثُمَّ اسْتَوَىٰ إِلَى السَّمَاءِ وَهِيَ دُخَانٌ فَقَالَ لَهَا وَلِلْأَرْضِ ائْتِيَا طَوْعًا أَوْ كَرْهًا قَالَتَا أَتَيْنَا طَائِعِينَ
Then He directed Himself to the heaven while it was smoke and said to it and to the earth, "Come, willingly or by compulsion", they said, "We came willingly."
40:57 Al-Ghaafir
لَخَلْقُ السَّمَاوَاتِ وَالْأَرْضِ أَكْبَرُ مِنْ خَلْقِ النَّاسِ وَلَٰكِنَّ أَكْثَرَ النَّاسِ لَا يَعْلَمُونَ
The creation of the heavens and earth is greater than the creation of mankind, but most of the people do not know.
It’s important to know what’s God asking people to do while submitting to him as mentioned in the following verses.
Surah Al-Israa: Verse 22: لَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتَقْعُدَ مَذْمُومًا مَخْذُولًا Set not up with Allah any other ilah (god), (O man)! (This verse is addressed to Prophet Muhammad SAW, but its implication is general to all mankind), or you will sit down reproved, forsaken (in the Hell-fire). Verse 23: ۞ وَقَضَىٰ رَبُّكَ أَلَّا تَعْبُدُوا إِلَّا إِيَّاهُ وَبِالْوَالِدَيْنِ إِحْسَانًا ۚ إِمَّا يَبْلُغَنَّ عِنْدَكَ الْكِبَرَ أَحَدُهُمَا أَوْ كِلَاهُمَا فَلَا تَقُلْ لَهُمَا أُفٍّ وَلَا تَنْهَرْهُمَا وَقُلْ لَهُمَا قَوْلًا كَرِيمًا And your Lord has decreed that you worship none but Him. And that you be dutiful to your parents. If one of them or both of them attain old age in your life, don’t say to them a word of disrespect, or shout at them but address them in terms of honour. Verse 24: وَاخْفِضْ لَهُمَا جَنَاحَ الذُّلِّ مِنَ الرَّحْمَةِ وَقُلْ رَبِّ ارْحَمْهُمَا كَمَا رَبَّيَانِي صَغِيرًا And lower unto them the wing of submission and humility through mercy, and say: "My Lord! Bestow on them Your Mercy as they did bring me up when I was small." Verse 25: رَبُّكُمْ أَعْلَمُ بِمَا فِي نُفُوسِكُمْ ۚ إِنْ تَكُونُوا صَالِحِينَ فَإِنَّهُ كَانَ لِلْأَوَّابِينَ غَفُورًا Your Lord knows best what is in your inner-selves. If you are righteous, then, verily, He is Ever Most Forgiving to those who turn unto Him again and again in obedience, and in repentance. Verse 26: وَآتِ ذَا الْقُرْبَىٰ حَقَّهُ وَالْمِسْكِينَ وَابْنَ السَّبِيلِ وَلَا تُبَذِّرْ تَبْذِيرًا And give to the kindred his due and to the Miskin (poor) and to the wayfarer. But spend not wastefully (your wealth) in the manner of a spendthrift. Verse 27: إِنَّ الْمُبَذِّرِينَ كَانُوا إِخْوَانَ الشَّيَاطِينِ ۖ وَكَانَ الشَّيْطَانُ لِرَبِّهِ كَفُورًا Verily, spendthrifts are brothers of the Shayatin (devils), and the Shaitan (Devil - Satan) is ever ungrateful to his Lord. Verse 28: وَإِمَّا تُعْرِضَنَّ عَنْهُمُ ابْتِغَاءَ رَحْمَةٍ مِنْ رَبِّكَ تَرْجُوهَا فَقُلْ لَهُمْ قَوْلًا مَيْسُورًا
And if you turn away from them (kindred, poor, wayfarer, etc. whom We have ordered you to give their rights, but if you have no money at the time they ask you for it) and you are awaiting a mercy from your Lord for which you hope, then, speak unto them a soft kind word (i.e. Allah will give me and I shall give you). Verse 29: وَلَا تَجْعَلْ يَدَكَ مَغْلُولَةً إِلَىٰ عُنُقِكَ وَلَا تَبْسُطْهَا كُلَّ الْبَسْطِ فَتَقْعُدَ مَلُومًا مَحْسُورًا And let not your hand be tied (like a miser) to your neck, nor stretch it forth to its utmost reach (like a spendthrift), so that you become blameworthy and in severe poverty. Verse 30: إِنَّ رَبَّكَ يَبْسُطُ الرِّزْقَ لِمَنْ يَشَاءُ وَيَقْدِرُ ۚ إِنَّهُ كَانَ بِعِبَادِهِ خَبِيرًا بَصِيرًا Truly, your Lord enlarges the provision for whom He wills and straitens (for whom He wills). Verily, He is Ever All-Knower, All-Seer of His slaves (servants; mankind created by God). Verse 31: وَلَا تَقْتُلُوا أَوْلَادَكُمْ خَشْيَةَ إِمْلَاقٍ ۖ نَحْنُ نَرْزُقُهُمْ وَإِيَّاكُمْ ۚ إِنَّ قَتْلَهُمْ كَانَ خِطْئًا كَبِيرًا And kill not your children for fear of poverty. We provide for them and for you. Surely, the killing of them is a great sin. Verse 32: وَلَا تَقْرَبُوا الزِّنَا ۖ إِنَّهُ كَانَ فَاحِشَةً وَسَاءَ سَبِيلًا And don’t come near to the unlawful sexual intercourse. Verily, it is a Fahishah (a great sin), and an evil way (that leads one to Hell unless Allah forgives him). Verse 33: وَلَا تَقْتُلُوا النَّفْسَ الَّتِي حَرَّمَ اللَّهُ إِلَّا بِالْحَقِّ ۗ وَمَنْ قُتِلَ مَظْلُومًا فَقَدْ جَعَلْنَا لِوَلِيِّهِ سُلْطَانًا فَلَا يُسْرِفْ فِي الْقَتْلِ ۖ إِنَّهُ كَانَ مَنْصُورًا And do not kill anyone that Allah has forbidden, except for a just cause. And whoever is killed (intentionally with hostility and oppression and not by mistake), We have given his heir the authority [(to demand Qisas, Law of Equality in punishment or to forgive, or to take Diya (blood money)]. But do not kill excessively (exceed limits in the matter of taking life). Verily, he is victorious. Verse 34: وَلَا تَقْرَبُوا مَالَ الْيَتِيمِ إِلَّا بِالَّتِي هِيَ أَحْسَنُ حَتَّىٰ يَبْلُغَ أَشُدَّهُ ۚ وَأَوْفُوا بِالْعَهْدِ ۖ إِنَّ الْعَهْدَ كَانَ مَسْئُولًا And don’t come near to the orphan's property except to improve it, until he attains the age of full strength. And fulfil (every) covenant. Verily! the covenant, will be questioned about. Verse 35: وَأَوْفُوا الْكَيْلَ إِذَا كِلْتُمْ وَزِنُوا بِالْقِسْطَاسِ الْمُسْتَقِيمِ ۚ ذَٰلِكَ خَيْرٌ وَأَحْسَنُ تَأْوِيلًا And give full measure when you measure, and weigh with a balance that is straight. That is good (advantageous) and better in the end. Verse 36: وَلَا تَقْفُ مَا لَيْسَ لَكَ بِهِ عِلْمٌ ۚ إِنَّ السَّمْعَ وَالْبَصَرَ وَالْفُؤَادَ كُلُّ أُولَٰئِكَ كَانَ عَنْهُ مَسْئُولًا And don’t pursue (i.e., do not say, or do not or witness not, etc.) what you have no knowledge of. Verily! The hearing, and the sight, and the heart, of each of those you will be questioned (by Allah). Verse 37: وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّكَ لَنْ تَخْرِقَ الْأَرْضَ وَلَنْ تَبْلُغَ الْجِبَالَ طُولًا And walk not on the earth with conceit and arrogance. Verily, you can’t break the earth, nor reach the mountains in height. Verse 38: كُلُّ ذَٰلِكَ كَانَ سَيِّئُهُ عِنْدَ رَبِّكَ مَكْرُوهًا All the bad aspects of these (the above mentioned things) are hateful to your Lord. Verse 39: ذَٰلِكَ مِمَّا أَوْحَىٰ إِلَيْكَ رَبُّكَ مِنَ الْحِكْمَةِ ۗ وَلَا تَجْعَلْ مَعَ اللَّهِ إِلَٰهًا آخَرَ فَتُلْقَىٰ فِي جَهَنَّمَ مَلُومًا مَدْحُورًا This is (part) of Al-Hikmah (wisdom, good manners and high character, etc.) that your Lord has inspired to you. And set not up with Allah any other god lest you should be thrown into Hell, blameworthy and rejected, (from Allah's Mercy). Verse 40: أَفَأَصْفَاكُمْ رَبُّكُمْ بِالْبَنِينَ وَاتَّخَذَ مِنَ الْمَلَائِكَةِ إِنَاثًا ۚ إِنَّكُمْ لَتَقُولُونَ قَوْلًا عَظِيمًا Has then your Lord (O pagans of Makkah) preferred for you sons, and taken for Himself from among the angels daughters (Angels don’t have a gender and it’s wrong to refer to them as females). Verily! You utter an awful saying, indeed. Verse 41: وَلَقَدْ صَرَّفْنَا فِي هَٰذَا الْقُرْآنِ لِيَذَّكَّرُوا وَمَا يَزِيدُهُمْ إِلَّا نُفُورًا And surely, We have explained [Our Promises, Warnings and (set forth many) examples] in this Quran that they (the disbelievers) may take heed, but it increases them in aversion (from the truth). Verse 42: قُلْ لَوْ كَانَ مَعَهُ آلِهَةٌ كَمَا يَقُولُونَ إِذًا لَابْتَغَوْا إِلَىٰ ذِي الْعَرْشِ سَبِيلًا Say: "If there had been other gods along with Him as they say, then they would certainly have sought out a way to the Lord of the Throne (seeking His Pleasures and to be near to Him). Verse 43: سُبْحَانَهُ وَتَعَالَىٰ عَمَّا يَقُولُونَ عُلُوًّا كَبِيرًا Glorified and High be He! From 'Uluwan Kabira (the great falsehood) that they say!
Surah Al-Israa: Verse 53 وَقُلْ لِعِبَادِي يَقُولُوا الَّتِي هِيَ أَحْسَنُ ۚ إِنَّ الشَّيْطَانَ يَنْزَغُ بَيْنَهُمْ ۚ إِنَّ الشَّيْطَانَ كَانَ لِلْإِنْسَانِ عَدُوًّا مُبِينًا And say to My slaves (servants; mankind created by God) that they should (only) say the best words. (Because) Shaitan (Satan) verily, sows disagreements among them. Surely, Shaitan (Satan) is to man a plain enemy. Surah Al-Maaida Verse 90: يَا أَيُّهَا الَّذِينَ آمَنُوا إِنَّمَا الْخَمْرُ وَالْمَيْسِرُ وَالْأَنْصَابُ وَالْأَزْلَامُ رِجْسٌ مِنْ عَمَلِ الشَّيْطَانِ فَاجْتَنِبُوهُ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Intoxicants (all kinds of alcoholic drinks), gambling, Al-Ansab, and Al-Azlam (arrows for seeking luck or decision) are an abomination of Shaitan's (Satan) handiwork. So avoid (strictly all) that (abomination) in order that you may be successful. Verse 91: إِنَّمَا يُرِيدُ الشَّيْطَانُ أَنْ يُوقِعَ بَيْنَكُمُ الْعَدَاوَةَ وَالْبَغْضَاءَ فِي الْخَمْرِ وَالْمَيْسِرِ وَيَصُدَّكُمْ عَنْ ذِكْرِ اللَّهِ وَعَنِ الصَّلَاةِ ۖ فَهَلْ أَنْتُمْ مُنْتَهُونَ Shaitan (Satan) wants only to excite enmity and hatred between you with intoxicants (alcoholic drinks) and gambling, and hinder you from the remembrance of Allah (God) and from As-Salat (the prayer). So, will you not then abstain?
Surah Luqman: Verse 17: يَا بُنَيَّ أَقِمِ الصَّلَاةَ وَأْمُرْ بِالْمَعْرُوفِ وَانْهَ عَنِ الْمُنْكَرِ وَاصْبِرْ عَلَىٰ مَا أَصَابَكَ ۖ إِنَّ ذَٰلِكَ مِنْ عَزْمِ الْأُمُورِ "O my son (said Luqman, peace be upon him) ! Aqim-is-Salat (perform As-Salat; prayers), enjoin (people) for Al-Ma'ruf (all that is good), and forbid (people) from Al-Munkar (all that is evil and bad), and bear with patience whatever befall you. Verily! These are some of the important commandments ordered by Allah with no exemption. Verse 18: وَلَا تُصَعِّرْ خَدَّكَ لِلنَّاسِ وَلَا تَمْشِ فِي الْأَرْضِ مَرَحًا ۖ إِنَّ اللَّهَ لَا يُحِبُّ كُلَّ مُخْتَالٍ فَخُورٍ "And don’t turn your face away from men with pride, and don’t walk in insolence through the earth. Verily, Allah does not love each arrogant (prideful) boaster. Verse 19: وَاقْصِدْ فِي مَشْيِكَ وَاغْضُضْ مِنْ صَوْتِكَ ۚ إِنَّ أَنْكَرَ الْأَصْوَاتِ لَصَوْتُ الْحَمِيرِ "And be moderate (or show no insolence) in your walking, and lower your voice. Verily, the harshest of all voices is the voice of the donkey."
Surah Taa-Haa: Verse 131: وَلَا تَمُدَّنَّ عَيْنَيْكَ إِلَىٰ مَا مَتَّعْنَا بِهِ أَزْوَاجًا مِنْهُمْ زَهْرَةَ الْحَيَاةِ الدُّنْيَا لِنَفْتِنَهُمْ فِيهِ ۚ وَرِزْقُ رَبِّكَ خَيْرٌ وَأَبْقَىٰ And strain not your eyes in longing for the things We have given for enjoyment to various groups of them, the splendour of the life of this world that We may test them thereby. But the provision (good reward in the Hereafter) of your Lord is better and more lasting.
Surah Al-Hujuraat: Verse 11: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا يَسْخَرْ قَوْمٌ مِنْ قَوْمٍ عَسَىٰ أَنْ يَكُونُوا خَيْرًا مِنْهُمْ وَلَا نِسَاءٌ مِنْ نِسَاءٍ عَسَىٰ أَنْ يَكُنَّ خَيْرًا مِنْهُنَّ ۖ وَلَا تَلْمِزُوا أَنْفُسَكُمْ وَلَا تَنَابَزُوا بِالْأَلْقَابِ ۖ بِئْسَ الِاسْمُ الْفُسُوقُ بَعْدَ الْإِيمَانِ ۚ وَمَنْ لَمْ يَتُبْ فَأُولَٰئِكَ هُمُ الظَّالِمُونَ O you who believe! Let not a group scoff at another group, it may be that the latter are better than the former; nor let (some) women scoff at other women, it may be that the latter are better than the former, nor defame one another, nor insult one another by nicknames. How bad is it, to insult one's brother after having Faith. And whosoever does not repent, then such are indeed Zalimun (unjust, wrong-doers, etc.). Verse 12: يَا أَيُّهَا الَّذِينَ آمَنُوا اجْتَنِبُوا كَثِيرًا مِنَ الظَّنِّ إِنَّ بَعْضَ الظَّنِّ إِثْمٌ ۖ وَلَا تَجَسَّسُوا وَلَا يَغْتَبْ بَعْضُكُمْ بَعْضًا ۚ أَيُحِبُّ أَحَدُكُمْ أَنْ يَأْكُلَ لَحْمَ أَخِيهِ مَيْتًا فَكَرِهْتُمُوهُ ۚ وَاتَّقُوا اللَّهَ ۚ إِنَّ اللَّهَ تَوَّابٌ رَحِيمٌ O you who believe! Avoid much suspicions, indeed some suspicions are sins. And spy not, neither backbite one another. Would one of you like to eat the flesh of his dead brother? You would hate it (so hate backbiting). And fear Allah. Verily, Allah is the One Who accepts repentance, Most Merciful.
Surah Al-Maaida: Verse 38: وَالسَّارِقُ وَالسَّارِقَةُ فَاقْطَعُوا أَيْدِيَهُمَا جَزَاءً بِمَا كَسَبَا نَكَالًا مِنَ اللَّهِ ۗ وَاللَّهُ عَزِيزٌ حَكِيمٌ Cut off (from the wrist joint) the (right) hand of the thief, male or female, as a recompense for that which they committed, a punishment by way of example from Allah. And Allah is All-Powerful, All-Wise. Verse 39: فَمَنْ تَابَ مِنْ بَعْدِ ظُلْمِهِ وَأَصْلَحَ فَإِنَّ اللَّهَ يَتُوبُ عَلَيْهِ ۗ إِنَّ اللَّهَ غَفُورٌ رَحِيمٌ But whosoever repents after his crime and does righteous good deeds, then verily, Allah (God) will pardon him (accept his repentance). Verily, Allah is Oft-Forgiving, Most Merciful.
Surah Aal-i-Imraan: Verse 130: يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَأْكُلُوا الرِّبَا أَضْعَافًا مُضَاعَفَةً ۖ وَاتَّقُوا اللَّهَ لَعَلَّكُمْ تُفْلِحُونَ O you who believe! Don’t eat Riba (usury) doubled and multiplied, but fear Allah that you may be successful.
Surah Al-Maaida: Verse 3: حُرِّمَتْ عَلَيْكُمُ الْمَيْتَةُ وَالدَّمُ وَلَحْمُ الْخِنْزِيرِ وَمَا أُهِلَّ لِغَيْرِ اللَّهِ بِهِ وَالْمُنْخَنِقَةُ وَالْمَوْقُوذَةُ وَالْمُتَرَدِّيَةُ وَالنَّطِيحَةُ وَمَا أَكَلَ السَّبُعُ إِلَّا مَا ذَكَّيْتُمْ وَمَا ذُبِحَ عَلَى النُّصُبِ وَأَنْ تَسْتَقْسِمُوا بِالْأَزْلَامِ ۚ ذَٰلِكُمْ فِسْقٌ ۗ الْيَوْمَ يَئِسَ الَّذِينَ كَفَرُوا مِنْ دِينِكُمْ فَلَا تَخْشَوْهُمْ وَاخْشَوْنِ ۚ الْيَوْمَ أَكْمَلْتُ لَكُمْ دِينَكُمْ وَأَتْمَمْتُ عَلَيْكُمْ نِعْمَتِي وَرَضِيتُ لَكُمُ الْإِسْلَامَ دِينًا ۚ فَمَنِ اضْطُرَّ فِي مَخْمَصَةٍ غَيْرَ مُتَجَانِفٍ لِإِثْمٍ ۙ فَإِنَّ اللَّهَ غَفُورٌ رَحِيمٌ Forbidden to you (for food) are: Al-Maytatah (the dead animals - cattle-beast not slaughtered), blood, the flesh of swine, and the meat of that which has been slaughtered as a sacrifice for others than Allah, or has been slaughtered for idols, etc., or on which Allah's Name has not been mentioned while slaughtering, and that which has been killed by strangling, or by a violent blow, or by a headlong fall, or by the goring of horns - and that which has been (partly) eaten by a wild animal - unless you are able to slaughter it (before its death) - and that which is sacrificed (slaughtered) on An-Nusub (stone altars). (Forbidden) also is to use arrows seeking luck or decision, (all) that is Fisqun (disobedience of Allah and sin). This day, those who disbelieved have given up all hope of your religion, so don’t fear them, but fear Me. This day, I have perfected your religion for you, completed My Favour upon you, and have chosen for you Islam as your religion. But who is forced by severe hunger, with no inclination to sin (such can eat these above-mentioned meats), then surely, Allah is Oft-Forgiving, Most Merciful.
Surah Al-Baqara: Verse 114: وَمَنْ أَظْلَمُ مِمَّنْ مَنَعَ مَسَاجِدَ اللَّهِ أَنْ يُذْكَرَ فِيهَا اسْمُهُ وَسَعَىٰ فِي خَرَابِهَا ۚ أُولَٰئِكَ مَا كَانَ لَهُمْ أَنْ يَدْخُلُوهَا إِلَّا خَائِفِينَ ۚ لَهُمْ فِي الدُّنْيَا خِزْيٌ وَلَهُمْ فِي الْآخِرَةِ عَذَابٌ عَظِيمٌ And who is more unjust than those who forbid that Allah's Name be glorified and mentioned much (i.e. prayers and invocations, etc.) in Allah's Mosques and strive for their ruin? It was not fitting that such should themselves enter them (Allah's Mosques) except in fear. For them there is disgrace in this world, and they will have a great torment in the Hereafter.
Surah Al-Baqara: Verse 110: وَأَقِيمُوا الصَّلَاةَ وَآتُوا الزَّكَاةَ ۚ وَمَا تُقَدِّمُوا لِأَنْفُسِكُمْ مِنْ خَيْرٍ تَجِدُوهُ عِنْدَ اللَّهِ ۗ إِنَّ اللَّهَ بِمَا تَعْمَلُونَ بَصِيرٌ And perform As-Salat (prayers), and give Zakat (compulsory charity that must be given every year), and whatever of good (deeds that Allah loves) you send forth for yourselves before you, you shall find it with Allah. Certainly, Allah is All-Seer of what you do.
Surah Al-A'raaf: Verse 31: ۞ يَا بَنِي آدَمَ خُذُوا زِينَتَكُمْ عِنْدَ كُلِّ مَسْجِدٍ وَكُلُوا وَاشْرَبُوا وَلَا تُسْرِفُوا ۚ إِنَّهُ لَا يُحِبُّ الْمُسْرِفِينَ
O Children of Adam! Take your adornment (by wearing your clean clothes), while praying and going round (the Tawaf of) the Ka'bah, and eat and drink but waste not by extravagance, certainly He (Allah) likes not Al-Musrifun (those who waste by extravagance). Verse 32: قُلْ مَنْ حَرَّمَ زِينَةَ اللَّهِ الَّتِي أَخْرَجَ لِعِبَادِهِ وَالطَّيِّبَاتِ مِنَ الرِّزْقِ ۚ قُلْ هِيَ لِلَّذِينَ آمَنُوا فِي الْحَيَاةِ الدُّنْيَا خَالِصَةً يَوْمَ الْقِيَامَةِ ۗ كَذَٰلِكَ نُفَصِّلُ الْآيَاتِ لِقَوْمٍ يَعْلَمُونَ Say: "Who has forbidden the adoration with clothes given by Allah, which He has produced for his slaves, and At-Taiyibat [all kinds of Halal (lawful) things] of food?" Say: "They are, in the life of this world, for those who believe, (and) exclusively for them (believers) on the Day of Resurrection (the disbelievers will not share them)." Thus We explain the Ayat (verses, Islamic laws) in detail for people who have knowledge. Verse 33: قُلْ إِنَّمَا حَرَّمَ رَبِّيَ الْفَوَاحِشَ مَا ظَهَرَ مِنْهَا وَمَا بَطَنَ وَالْإِثْمَ وَالْبَغْيَ بِغَيْرِ الْحَقِّ وَأَنْ تُشْرِكُوا بِاللَّهِ مَا لَمْ يُنَزِّلْ بِهِ سُلْطَانًا وَأَنْ تَقُولُوا عَلَى اللَّهِ مَا لَا تَعْلَمُونَ Say: "The things that my Lord has indeed forbidden are Al-Fawahish (great evil sins) whether committed openly or secretly, sins (of all kinds), unrighteous oppression, joining partners (in worship) with Allah for which He has given no authority, and saying things about Allah of which you have no knowledge." Verse 34: وَلِكُلِّ أُمَّةٍ أَجَلٌ ۖ فَإِذَا جَاءَ أَجَلُهُمْ لَا يَسْتَأْخِرُونَ سَاعَةً ۖ وَلَا يَسْتَقْدِمُونَ And every nation has its appointed term; when their term is reached, neither can they delay it nor can they advance it an hour (or a moment). Verse 35: يَا بَنِي آدَمَ إِمَّا يَأْتِيَنَّكُمْ رُسُلٌ مِنْكُمْ يَقُصُّونَ عَلَيْكُمْ آيَاتِي ۙ فَمَنِ اتَّقَىٰ وَأَصْلَحَ فَلَا خَوْفٌ عَلَيْهِمْ وَلَا هُمْ يَحْزَنُونَ O Children of Adam! If there come to you Messengers from amongst you, reciting to you, My Verses, then whosoever becomes pious and righteous, on them shall be no fear, nor shall they grieve. Verse 36: وَالَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا أُولَٰئِكَ أَصْحَابُ النَّارِ ۖ هُمْ فِيهَا خَالِدُونَ But those who reject Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and treat them with arrogance, they are the dwellers of the (Hell) Fire, they will abide therein forever. Verse 37: فَمَنْ أَظْلَمُ مِمَّنِ افْتَرَىٰ عَلَى اللَّهِ كَذِبًا أَوْ كَذَّبَ بِآيَاتِهِ ۚ أُولَٰئِكَ يَنَالُهُمْ نَصِيبُهُمْ مِنَ الْكِتَابِ ۖ حَتَّىٰ إِذَا جَاءَتْهُمْ رُسُلُنَا يَتَوَفَّوْنَهُمْ قَالُوا أَيْنَ مَا كُنْتُمْ تَدْعُونَ مِنْ دُونِ اللَّهِ ۖ قَالُوا ضَلُّوا عَنَّا وَشَهِدُوا عَلَىٰ أَنْفُسِهِمْ أَنَّهُمْ كَانُوا كَافِرِينَ Who is more unjust than one who invents a lie against Allah or rejects His Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.)? For such their appointed portion (good things of this worldly life and their period of stay therein) will reach them from the Book (of Decrees) until, when Our Messengers (the angel of death and his assistants) come to them to take their souls, they (the angels) will say: "Where are those whom you used to invoke and worship besides Allah," they will reply, "They have vanished and deserted us." And they will bear witness against themselves, that they were disbelievers. Verse 38: قَالَ ادْخُلُوا فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِكُمْ مِنَ الْجِنِّ وَالْإِنْسِ فِي النَّارِ ۖ كُلَّمَا دَخَلَتْ أُمَّةٌ لَعَنَتْ أُخْتَهَا ۖ حَتَّىٰ إِذَا ادَّارَكُوا فِيهَا جَمِيعًا قَالَتْ أُخْرَاهُمْ لِأُولَاهُمْ رَبَّنَا هَٰؤُلَاءِ أَضَلُّونَا فَآتِهِمْ عَذَابًا ضِعْفًا مِنَ النَّارِ ۖ قَالَ لِكُلٍّ ضِعْفٌ وَلَٰكِنْ لَا تَعْلَمُونَ (Allah) will say: "Enter you in the company of nations who passed away before you, of men and jinns, into the Fire." Every time a new nation enters, it curses its sister nation (that went before), until they will be gathered all together in the Fire. The last of them will say to the first of them: "Our Lord! These misled us, so give them a double torment of the Fire." He will say: "For each one there is double (torment), but you don’t know." Verse 39: وَقَالَتْ أُولَاهُمْ لِأُخْرَاهُمْ فَمَا كَانَ لَكُمْ عَلَيْنَا مِنْ فَضْلٍ فَذُوقُوا الْعَذَابَ بِمَا كُنْتُمْ تَكْسِبُونَ The first of them will say to the last of them: "You were not better than us, so taste the torment for what you used to earn." Verse 40: إِنَّ الَّذِينَ كَذَّبُوا بِآيَاتِنَا وَاسْتَكْبَرُوا عَنْهَا لَا تُفَتَّحُ لَهُمْ أَبْوَابُ السَّمَاءِ وَلَا يَدْخُلُونَ الْجَنَّةَ حَتَّىٰ يَلِجَ الْجَمَلُ فِي سَمِّ الْخِيَاطِ ۚ وَكَذَٰلِكَ نَجْزِي الْمُجْرِمِينَ Verily, those who belie Our Ayat (proofs, evidences, verses, lessons, signs, revelations, etc.) and are pridefully arrogant towards them (proofs, verses, signs, etc.), for them the gates of heaven will not be opened (to accept and answer their supplications and prayers), and they will not enter Paradise until the camel goes through the eye of the needle (which is impossible). Thus do We recompense the Mujrimun (criminals, sinners, etc.). Verse 41: لَهُمْ مِنْ جَهَنَّمَ مِهَادٌ وَمِنْ فَوْقِهِمْ غَوَاشٍ ۚ وَكَذَٰلِكَ نَجْزِي الظَّالِمِينَ Theirs will be a bed of Hell (Fire), and over them coverings (of Hell-fire). Thus We recompense the Zalimun (unjust and wrong-doers, etc.).
An-Nahl Verse 94: وَلَا تَتَّخِذُوا أَيْمَانَكُمْ دَخَلًا بَيْنَكُمْ فَتَزِلَّ قَدَمٌ بَعْدَ ثُبُوتِهَا وَتَذُوقُوا السُّوءَ بِمَا صَدَدْتُمْ عَنْ سَبِيلِ اللَّهِ ۖ وَلَكُمْ عَذَابٌ عَظِيمٌ And don’t make your oaths, a means of deception among yourselves, lest a foot may slip after being firmly planted, and you may have to taste the evil (punishment in this world) of having hindered (men) from the Path of Allah (i.e. Belief in the Oneness of Allah and His Messenger, Muhammad SAW, fighting in the cause of Allah), and yours will be a great torment (i.e. the Fire of Hell in the Hereafter). Verse 95: وَلَا تَشْتَرُوا بِعَهْدِ اللَّهِ ثَمَنًا قَلِيلًا ۚ إِنَّمَا عِنْدَ اللَّهِ هُوَ خَيْرٌ لَكُمْ إِنْ كُنْتُمْ تَعْلَمُونَ
And purchase not a small gain at the cost of Allah's Covenant. Verily! What is with Allah is better for you if you did but know.
A lot of people turn away from God, Allah, because of fearing not to be forgiven.
4:116 An-Nisaa
إِنَّ اللَّهَ لَا يَغْفِرُ أَنْ يُشْرَكَ بِهِ وَيَغْفِرُ مَا دُونَ ذَٰلِكَ لِمَنْ يَشَاءُ ۚ وَمَنْ يُشْرِكْ بِاللَّهِ فَقَدْ ضَلَّ ضَلَالًا بَعِيدًا
Indeed, Allah does not forgive association with Him, but He forgives other than that for whom He wills. And he who associates others with Allah has certainly gone far astray.
39:53 Az-Zumar
۞ قُلْ يَا عِبَادِيَ الَّذِينَ أَسْرَفُوا عَلَىٰ أَنْفُسِهِمْ لَا تَقْنَطُوا مِنْ رَحْمَةِ اللَّهِ ۚ إِنَّ اللَّهَ يَغْفِرُ الذُّنُوبَ جَمِيعًا ۚ إِنَّهُ هُوَ الْغَفُورُ الرَّحِيمُ
Say, "O My servants who have transgressed against themselves [by sinning], do not despair of the mercy of Allah. Indeed, Allah forgives all sins. Indeed, it is He who is the Forgiving, the Merciful."
39:54 Az-Zumar
وَأَنِيبُوا إِلَىٰ رَبِّكُمْ وَأَسْلِمُوا لَهُ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ ثُمَّ لَا تُنْصَرُونَ
And return [in repentance] to your Lord and submit to Him before the punishment comes upon you; then you will not be helped.
39:55 Az-Zumar
وَاتَّبِعُوا أَحْسَنَ مَا أُنْزِلَ إِلَيْكُمْ مِنْ رَبِّكُمْ مِنْ قَبْلِ أَنْ يَأْتِيَكُمُ الْعَذَابُ بَغْتَةً وَأَنْتُمْ لَا تَشْعُرُونَ
And follow the best of what was revealed to you from your Lord before the punishment comes upon you suddenly while you do not perceive,
39:56 Az-Zumar
أَنْ تَقُولَ نَفْسٌ يَا حَسْرَتَا عَلَىٰ مَا فَرَّطْتُ فِي جَنْبِ اللَّهِ وَإِنْ كُنْتُ لَمِنَ السَّاخِرِينَ
Lest a soul should say, "Oh [how great is] my regret over what I neglected in regard to Allah and that I was among the mockers."
39:57 Az-Zumar
أَوْ تَقُولَ لَوْ أَنَّ اللَّهَ هَدَانِي لَكُنْتُ مِنَ الْمُتَّقِينَ
Or [lest] it say, "If only Allah had guided me, I would have been among the righteous."
39:58 Az-Zumar
أَوْ تَقُولَ حِينَ تَرَى الْعَذَابَ لَوْ أَنَّ لِي كَرَّةً فَأَكُونَ مِنَ الْمُحْسِنِينَ
Or [lest] it say when it sees the punishment, "If only I had another turn so I could be among the doers of good."
39:59 Az-Zumar
بَلَىٰ قَدْ جَاءَتْكَ آيَاتِي فَكَذَّبْتَ بِهَا وَاسْتَكْبَرْتَ وَكُنْتَ مِنَ الْكَافِرِينَ
But yes, there had come to you My verses, but you denied them and were arrogant, and you were among the disbelievers.
39:60 Az-Zumar
وَيَوْمَ الْقِيَامَةِ تَرَى الَّذِينَ كَذَبُوا عَلَى اللَّهِ وُجُوهُهُمْ مُسْوَدَّةٌ ۚ أَلَيْسَ فِي جَهَنَّمَ مَثْوًى لِلْمُتَكَبِّرِينَ
And on the Day of Resurrection you will see those who lied about Allah [with] their faces blackened. Is there not in Hell a residence for the arrogant?
39:61 Az-Zumar
وَيُنَجِّي اللَّهُ الَّذِينَ اتَّقَوْا بِمَفَازَتِهِمْ لَا يَمَسُّهُمُ السُّوءُ وَلَا هُمْ يَحْزَنُونَ
And Allah will save those who feared Him by their attainment; no evil will touch them, nor will they grieve.
In Islam we believe in God’s messengers and his books, Torah and Gospel, however, some changes were brought by some people leading to disbelief in the oneness of God.
2:285 Al-Baqara
آمَنَ الرَّسُولُ بِمَا أُنْزِلَ إِلَيْهِ مِنْ رَبِّهِ وَالْمُؤْمِنُونَ ۚ كُلٌّ آمَنَ بِاللَّهِ وَمَلَائِكَتِهِ وَكُتُبِهِ وَرُسُلِهِ لَا نُفَرِّقُ بَيْنَ أَحَدٍ مِنْ رُسُلِهِ ۚ وَقَالُوا سَمِعْنَا وَأَطَعْنَا ۖ غُفْرَانَكَ رَبَّنَا وَإِلَيْكَ الْمَصِيرُ
The Messenger has believed in what was revealed to him from his Lord, and [so have] the believers. All of them have believed in Allah and His angels and His books and His messengers, [saying], "We make no distinction between any of His messengers." And they say, "We hear and we obey. [We seek] Your forgiveness, our Lord, and to You is the [final] destination."
2:286 Al-Baqara
لَا يُكَلِّفُ اللَّهُ نَفْسًا إِلَّا وُسْعَهَا ۚ لَهَا مَا كَسَبَتْ وَعَلَيْهَا مَا اكْتَسَبَتْ ۗ رَبَّنَا لَا تُؤَاخِذْنَا إِنْ نَسِينَا أَوْ أَخْطَأْنَا ۚ رَبَّنَا وَلَا تَحْمِلْ عَلَيْنَا إِصْرًا كَمَا حَمَلْتَهُ عَلَى الَّذِينَ مِنْ قَبْلِنَا ۚ رَبَّنَا وَلَا تُحَمِّلْنَا مَا لَا طَاقَةَ لَنَا بِهِ ۖ وَاعْفُ عَنَّا وَاغْفِرْ لَنَا وَارْحَمْنَا ۚ أَنْتَ مَوْلَانَا فَانْصُرْنَا عَلَى الْقَوْمِ الْكَافِرِينَ
Allah does not charge a soul except [with that within] its capacity. It will have [the consequence of] what [good] it has gained, and it will bear [the consequence of] what [evil] it has earned. "Our Lord, do not impose blame upon us if we have forgotten or erred. Our Lord, and lay not upon us a burden like that which You laid upon those before us. Our Lord, and burden us not with that which we have no ability to bear. And pardon us; and forgive us; and have mercy upon us. You are our protector, so give us victory over the disbelieving people."
4:163 An-Nisaa
۞ إِنَّا أَوْحَيْنَا إِلَيْكَ كَمَا أَوْحَيْنَا إِلَىٰ نُوحٍ وَالنَّبِيِّينَ مِنْ بَعْدِهِ ۚ وَأَوْحَيْنَا إِلَىٰ إِبْرَاهِيمَ وَإِسْمَاعِيلَ وَإِسْحَاقَ وَيَعْقُوبَ وَالْأَسْبَاطِ وَعِيسَىٰ وَأَيُّوبَ وَيُونُسَ وَهَارُونَ وَسُلَيْمَانَ ۚ وَآتَيْنَا دَاوُودَ زَبُورًا
Indeed, We have revealed to you, [O Muhammad], as We revealed to Noah and the prophets after him. And we revealed to Abraham, Ishmael, Isaac, Jacob, the Descendants, Jesus, Job, Jonah, Aaron, and Solomon, and to David We gave the book [of Psalms].
4:164 An-Nisaa
وَرُسُلًا قَدْ قَصَصْنَاهُمْ عَلَيْكَ مِنْ قَبْلُ وَرُسُلًا لَمْ نَقْصُصْهُمْ عَلَيْكَ ۚ وَكَلَّمَ اللَّهُ مُوسَىٰ تَكْلِيمًا
And [We sent] messengers about whom We have related [their stories] to you before and messengers about whom We have not related to you. And Allah spoke to Moses with [direct] speech.
4:165 An-Nisaa
رُسُلًا مُبَشِّرِينَ وَمُنْذِرِينَ لِئَلَّا يَكُونَ لِلنَّاسِ عَلَى اللَّهِ حُجَّةٌ بَعْدَ الرُّسُلِ ۚ وَكَانَ اللَّهُ عَزِيزًا حَكِيمًا
[We sent] messengers as bringers of good tidings and warners so that mankind will have no argument against Allah after the messengers. And ever is Allah Exalted in Might and Wise.
9:30 At-Tawba
وَقَالَتِ الْيَهُودُ عُزَيْرٌ ابْنُ اللَّهِ وَقَالَتِ النَّصَارَى الْمَسِيحُ ابْنُ اللَّهِ ۖ ذَٰلِكَ قَوْلُهُمْ بِأَفْوَاهِهِمْ ۖ يُضَاهِئُونَ قَوْلَ الَّذِينَ كَفَرُوا مِنْ قَبْلُ ۚ قَاتَلَهُمُ اللَّهُ ۚ أَنَّىٰ يُؤْفَكُونَ
The Jews say, "Ezra is the son of Allah "; and the Christians say, "The Messiah is the son of Allah." That is their statement from their mouths; they imitate the saying of those who disbelieved [before them]. May Allah destroy them; how are they deluded?
9:31 At-Tawba
اتَّخَذُوا أَحْبَارَهُمْ وَرُهْبَانَهُمْ أَرْبَابًا مِنْ دُونِ اللَّهِ وَالْمَسِيحَ ابْنَ مَرْيَمَ وَمَا أُمِرُوا إِلَّا لِيَعْبُدُوا إِلَٰهًا وَاحِدًا ۖ لَا إِلَٰهَ إِلَّا هُوَ ۚ سُبْحَانَهُ عَمَّا يُشْرِكُونَ
They have taken their scholars and monks as lords besides Allah, and [also] the Messiah, the son of Mary. And they were not commanded except to worship one God; there is no deity except Him. Exalted is He above whatever they associate with Him.
5:72 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ هُوَ الْمَسِيحُ ابْنُ مَرْيَمَ ۖ وَقَالَ الْمَسِيحُ يَا بَنِي إِسْرَائِيلَ اعْبُدُوا اللَّهَ رَبِّي وَرَبَّكُمْ ۖ إِنَّهُ مَنْ يُشْرِكْ بِاللَّهِ فَقَدْ حَرَّمَ اللَّهُ عَلَيْهِ الْجَنَّةَ وَمَأْوَاهُ النَّارُ ۖ وَمَا لِلظَّالِمِينَ مِنْ أَنْصَارٍ
They have certainly disbelieved who say, "Allah is the Messiah, the son of Mary" while the Messiah has said, "O Children of Israel, worship Allah, my Lord and your Lord." Indeed, he who associates others with Allah - Allah has forbidden him Paradise, and his refuge is the Fire. And there are not for the wrongdoers any helpers.
5:73 Al-Maaida
لَقَدْ كَفَرَ الَّذِينَ قَالُوا إِنَّ اللَّهَ ثَالِثُ ثَلَاثَةٍ ۘ وَمَا مِنْ إِلَٰهٍ إِلَّا إِلَٰهٌ وَاحِدٌ ۚ وَإِنْ لَمْ يَنْتَهُوا عَمَّا يَقُولُونَ لَيَمَسَّنَّ الَّذِينَ كَفَرُوا مِنْهُمْ عَذَابٌ أَلِيمٌ
They have certainly disbelieved who say, "Allah is the third of three." And there is no god except one God. And if they do not desist from what they are saying, there will surely afflict the disbelievers among them a painful punishment.
5:74 Al-Maaida
أَفَلَا يَتُوبُونَ إِلَى اللَّهِ وَيَسْتَغْفِرُونَهُ ۚ وَاللَّهُ غَفُورٌ رَحِيمٌ
So will they not repent to Allah and seek His forgiveness? And Allah is Forgiving and Merciful.
5:75 Al-Maaida
مَا الْمَسِيحُ ابْنُ مَرْيَمَ إِلَّا رَسُولٌ قَدْ خَلَتْ مِنْ قَبْلِهِ الرُّسُلُ وَأُمُّهُ صِدِّيقَةٌ ۖ كَانَا يَأْكُلَانِ الطَّعَامَ ۗ انْظُرْ كَيْفَ نُبَيِّنُ لَهُمُ الْآيَاتِ ثُمَّ انْظُرْ أَنَّىٰ يُؤْفَكُونَ
The Messiah, son of Mary, was not but a messenger; [other] messengers have passed on before him. And his mother was a supporter of truth. They both used to eat food. Look how We make clear to them the signs; then look how they are deluded.
5:76 Al-Maaida
قُلْ أَتَعْبُدُونَ مِنْ دُونِ اللَّهِ مَا لَا يَمْلِكُ لَكُمْ ضَرًّا وَلَا نَفْعًا ۚ وَاللَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
Say, "Do you worship besides Allah that which holds for you no [power of] harm or benefit while it is Allah who is the Hearing, the Knowing?"
5:77 Al-Maaida
قُلْ يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ غَيْرَ الْحَقِّ وَلَا تَتَّبِعُوا أَهْوَاءَ قَوْمٍ قَدْ ضَلُّوا مِنْ قَبْلُ وَأَضَلُّوا كَثِيرًا وَضَلُّوا عَنْ سَوَاءِ السَّبِيلِ
Say, "O People of the Scripture (the books, Torah and Gospel), do not exceed limits in your religion beyond the truth and do not follow the inclinations of a people who had gone astray before and misled many and have strayed from the soundness of the way."
4:171 An-Nisaa
يَا أَهْلَ الْكِتَابِ لَا تَغْلُوا فِي دِينِكُمْ وَلَا تَقُولُوا عَلَى اللَّهِ إِلَّا الْحَقَّ ۚ إِنَّمَا الْمَسِيحُ عِيسَى ابْنُ مَرْيَمَ رَسُولُ اللَّهِ وَكَلِمَتُهُ أَلْقَاهَا إِلَىٰ مَرْيَمَ وَرُوحٌ مِنْهُ ۖ فَآمِنُوا بِاللَّهِ وَرُسُلِهِ ۖ وَلَا تَقُولُوا ثَلَاثَةٌ ۚ انْتَهُوا خَيْرًا لَكُمْ ۚ إِنَّمَا اللَّهُ إِلَٰهٌ وَاحِدٌ ۖ سُبْحَانَهُ أَنْ يَكُونَ لَهُ وَلَدٌ ۘ لَهُ مَا فِي السَّمَاوَاتِ وَمَا فِي الْأَرْضِ ۗ وَكَفَىٰ بِاللَّهِ وَكِيلًا
O People of the Scripture, do not commit excess in your religion or say about Allah except the truth. The Messiah, Jesus, the son of Mary, was but a messenger of Allah and His word which He directed to Mary and a soul [created at a command] from Him. So believe in Allah and His messengers. And do not say, "Three"; desist - it is better for you. Indeed, Allah is but one God. Exalted is He above having a son. To Him belongs whatever is in the heavens and whatever is on the earth. And sufficient is Allah as Disposer of affairs.
4:172 An-Nisaa
لَنْ يَسْتَنْكِفَ الْمَسِيحُ أَنْ يَكُونَ عَبْدًا لِلَّهِ وَلَا الْمَلَائِكَةُ الْمُقَرَّبُونَ ۚ وَمَنْ يَسْتَنْكِفْ عَنْ عِبَادَتِهِ وَيَسْتَكْبِرْ فَسَيَحْشُرُهُمْ إِلَيْهِ جَمِيعًا
Never would the Messiah disdain to be a servant of Allah, nor would the angels near [to Him]. And whoever disdains His worship and is arrogant - He will gather them to Himself all together.
And in the following Hadiths (sayings of prophet Mohamed peace be upon him) and verses what a practicing Muslim should do:
حَدَّثَنَا أَبُو الْيَمَانِ ، قَالَ: أَخْبَرَنَا شُعَيْبٌ ، عَنِ الزُّهْرِيِّ ، قَالَ: أَخْبَرَنِي أَبُو إِدْرِيسَ عَائِذُ اللَّهِ بْنُ عَبْدِ اللَّهِ ، أَنَّ عُبَادَةَ بْنَ الصَّامِتِ رَضِيَ اللَّهُ عَنْهُ، وَكَانَ شَهِدَ بَدْرًا وَهُوَ أَحَدُ النُّقَبَاءِ لَيْلَةَ الْعَقَبَةِ، أَنَّ رَسُولَ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ، قَالَ وَحَوْلَهُ عِصَابَةٌ مِنْ أَصْحَابِهِ: بَايِعُونِي عَلَى أَنْ لَا تُشْرِكُوا بِاللَّهِ شَيْئًا، وَلَا تَسْرِقُوا، وَلَا تَزْنُوا، وَلَا تَقْتُلُوا أَوْلَادَكُمْ، وَلَا تَأْتُوا بِبُهْتَانٍ تَفْتَرُونَهُ بَيْنَ أَيْدِيكُمْ وَأَرْجُلِكُمْ، وَلَا تَعْصُوا فِي مَعْرُوفٍ، فَمَنْ وَفَى مِنْكُمْ فَأَجْرُهُ عَلَى اللَّهِ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا فَعُوقِبَ فِي الدُّنْيَا فَهُوَ كَفَّارَةٌ لَهُ، وَمَنْ أَصَابَ مِنْ ذَلِكَ شَيْئًا ثُمَّ سَتَرَهُ اللَّهُ فَهُوَ إِلَى اللَّهِ إِنْ شَاءَ عَفَا عَنْهُ وَإِنْ شَاءَ عَاقَبَهُ، فَبَايَعْنَاهُ عَلَى ذَلِك.
Translation:Narrated Ubadah bin As-Samit (RA): who took part in the battle of Badr and was a Naqib (a person heading a group of six persons), on the night of Al-Aqabah pledge: Allahs Apostle ﷺ said while a group of his companions were around him, "Swear allegiance to me for: 1. Not to join anything in worship along with Allah. 2. Not to steal. 3. Not to commit illegal sexual intercourse. 4. Not to kill your children. 5. Not to accuse an innocent person (to spread such an accusation among people). 6. Not to be disobedient (when ordered) to do good deed". The Prophet ﷺ added: "Whoever among you fulfills his pledge will be rewarded by Allah. And whoever indulges in any one of them (except the ascription of partners to Allah) and gets the punishment in this world, that punishment will be an expiation for that sin. And if one indulges in any of them, and Allah conceals his sin, it is up to Him to forgive or punish him (in the Hereafter)". Ubadah bin As-Samit (RA) added: "So we swore allegiance for these." (points to Allahs Apostle) ﷺ.
حَدَّثَنَا عُبَيْدُ اللَّهِ بْنُ مُوسَى ، قَالَ: أَخْبَرَنَا حَنْظَلَةُ بْنُ أَبِي سُفْيَانَ ، عَنْ عِكْرِمَةَ بْنِ خَالِدٍ ، عَنِ ابْنِ عُمَرَ رَضِيَ اللَّهُ عَنْهُمَا، قَالَ: قَالَ رَسُولُ اللَّهِ صَلَّى اللَّهُ عَلَيْهِ وَسَلَّمَ: بُنِيَ الْإِسْلَامُ عَلَى خَمْسٍ، شَهَادَةِ أَنْ لَا إِلَهَ إِلَّا اللَّهُ وَأَنَّ مُحَمَّدًا رَسُولُ اللَّهِ، وَإِقَامِ الصَّلَاةِ، وَإِيتَاءِ الزَّكَاةِ، وَالْحَجِّ، وَصَوْمِ رَمَضَانَ. الحج لمن استطاع اليه سبيلا*
Translation:Narrated Ibn Umar (RA) : Allahs Apostle ﷺ said: Islam is based on (the following) five (principles): 1. To testify that none has the right to be worshipped but Allah and Muhammad ﷺ is Allahs Apostle. 2. To offer the (compulsory Salat) prayers dutifully and perfectly. 3. To pay Zakat (i.e. obligatory charity). 4. To perform Hajj. (i.e. Pilgrimage to Makkah only if the person is able to do so) 5. To observe fast during the month of Ramadan.
Also, in the following verses behaviours that must be adopted by practicing Muslims:
24:30 An-Noor
قُلْ لِلْمُؤْمِنِينَ يَغُضُّوا مِنْ أَبْصَارِهِمْ وَيَحْفَظُوا فُرُوجَهُمْ ۚ ذَٰلِكَ أَزْكَىٰ لَهُمْ ۗ إِنَّ اللَّهَ خَبِيرٌ بِمَا يَصْنَعُونَ
Tell the believing men to reduce [some] of their vision (lower their gazes) and guard their private parts. That is purer for them. Indeed, Allah is Acquainted with what they do.
24:31 An-Noor
وَقُلْ لِلْمُؤْمِنَاتِ يَغْضُضْنَ مِنْ أَبْصَارِهِنَّ وَيَحْفَظْنَ فُرُوجَهُنَّ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا مَا ظَهَرَ مِنْهَا ۖ وَلْيَضْرِبْنَ بِخُمُرِهِنَّ عَلَىٰ جُيُوبِهِنَّ ۖ وَلَا يُبْدِينَ زِينَتَهُنَّ إِلَّا لِبُعُولَتِهِنَّ أَوْ آبَائِهِنَّ أَوْ آبَاءِ بُعُولَتِهِنَّ أَوْ أَبْنَائِهِنَّ أَوْ أَبْنَاءِ بُعُولَتِهِنَّ أَوْ إِخْوَانِهِنَّ أَوْ بَنِي إِخْوَانِهِنَّ أَوْ بَنِي أَخَوَاتِهِنَّ أَوْ نِسَائِهِنَّ أَوْ مَا مَلَكَتْ أَيْمَانُهُنَّ أَوِ التَّابِعِينَ غَيْرِ أُولِي الْإِرْبَةِ مِنَ الرِّجَالِ أَوِ الطِّفْلِ الَّذِينَ لَمْ يَظْهَرُوا عَلَىٰ عَوْرَاتِ النِّسَاءِ ۖ وَلَا يَضْرِبْنَ بِأَرْجُلِهِنَّ لِيُعْلَمَ مَا يُخْفِينَ مِنْ زِينَتِهِنَّ ۚ وَتُوبُوا إِلَى اللَّهِ جَمِيعًا أَيُّهَ الْمُؤْمِنُونَ لَعَلَّكُمْ تُفْلِحُونَ
And tell the believing women to reduce [some] of their vision (lower their gazes) and guard their private parts and not expose their adornment except that which [necessarily] appears (to cover their bodies in full (the used clothes must not be tight or transparent) except hands and face and to cover the hair) thereof and to wrap [a portion of] their headcovers over their chests and not expose their adornment except to their husbands, their fathers, their husbands' fathers, their sons, their husbands' sons, their brothers, their brothers' sons, their sisters' sons, their women, that which their right hands possess, or those male attendants having no physical desire, or children who are not yet aware of the private aspects of women. And let them not stamp their feet to make known what they conceal of their adornment. And turn to Allah in repentance, all of you, O believers, that you might succeed.
In the following an app to teach Wudu (getting ready for the prayer) and Salat the Islamic compulsory prayers that must be performed 5 times a day:
https://apps.apple.com/app/id1187721510
https://play.google.com/store/apps/datasafety?id=com.salah.osratouna&hl=en
Keep in mind the following Hadiths and verses of the Quran while wishing to offer Salat:
4:43 An-Nisaa
يَا أَيُّهَا الَّذِينَ آمَنُوا لَا تَقْرَبُوا الصَّلَاةَ وَأَنْتُمْ سُكَارَىٰ حَتَّىٰ تَعْلَمُوا مَا تَقُولُونَ وَلَا جُنُبًا إِلَّا عَابِرِي سَبِيلٍ حَتَّىٰ تَغْتَسِلُوا ۚ وَإِنْ كُنْتُمْ مَرْضَىٰ أَوْ عَلَىٰ سَفَرٍ أَوْ جَاءَ أَحَدٌ مِنْكُمْ مِنَ الْغَائِطِ أَوْ لَامَسْتُمُ النِّسَاءَ فَلَمْ تَجِدُوا مَاءً فَتَيَمَّمُوا صَعِيدًا طَيِّبًا فَامْسَحُوا بِوُجُوهِكُمْ وَأَيْدِيكُمْ ۗ إِنَّ اللَّهَ كَانَ عَفُوًّا غَفُورًا
O you who have believed, do not approach prayer while you are intoxicated (drunk or under the effect of drugs) until you know what you are saying or in a state of janabah (have had a lawful sexual intercourse or have had a wet dream) , except those passing through [a place of prayer], until you have washed [your whole body]. And if you are ill or on a journey or one of you comes from the place of relieving himself or you have contacted women and find no water, then seek clean earth and wipe over your faces and your hands [with it]. Indeed, Allah is ever Pardoning and Forgiving.
Narrated `Aisha: Whenever the Prophet (ﷺ) took a bath after Janaba he started by washing his hands and then performed ablution like that for the prayer. After that he would put his fingers in water and move the roots of his hair with them, and then pour three handfuls of water over his head and then pour water all over his body.
حَدَّثَنَا عَبْدُ اللَّهِ بْنُ يُوسُفَ، قَالَ أَخْبَرَنَا مَالِكٌ، عَنْ هِشَامٍ، عَنْ أَبِيهِ، عَنْ عَائِشَةَ، زَوْجِ النَّبِيِّ صلى الله عليه وسلم أَنَّ النَّبِيَّ صلى الله عليه وسلم كَانَ إِذَا اغْتَسَلَ مِنَ الْجَنَابَةِ بَدَأَ فَغَسَلَ يَدَيْهِ، ثُمَّ يَتَوَضَّأُ كَمَا يَتَوَضَّأُ لِلصَّلاَةِ، ثُمَّ يُدْخِلُ أَصَابِعَهُ فِي الْمَاءِ، فَيُخَلِّلُ بِهَا أُصُولَ شَعَرِهِ ثُمَّ يَصُبُّ عَلَى رَأْسِهِ ثَلاَثَ غُرَفٍ بِيَدَيْهِ، ثُمَّ يُفِيضُ الْمَاءَ عَلَى جِلْدِهِ كُلِّهِ.
Narrated Maimuna bint Al-Harith: I placed water for the bath of Allah's Messenger (ﷺ) and put a screen. He poured water over his hands, and washed them once or twice. (The sub-narrator added that he did not remember if she had said thrice or not). Then he poured water with his right hand over his left one and washed his private parts. He rubbed his hand over the earth or the wall and washed it. He rinsed his mouth and washed his nose by putting water in it and blowing it out. He washed his face, forearms and head. He poured water over his body and then withdrew from that place and washed his feet. I presented him a piece of cloth (towel) and he pointed with his hand (that he does not want it) and did not take it.
حَدَّثَنَا مُوسَى بْنُ إِسْمَاعِيلَ، قَالَ حَدَّثَنَا أَبُو عَوَانَةَ، حَدَّثَنَا الأَعْمَشُ، عَنْ سَالِمِ بْنِ أَبِي الْجَعْدِ، عَنْ كُرَيْبٍ، مَوْلَى ابْنِ عَبَّاسٍ عَنِ ابْنِ عَبَّاسٍ، عَنْ مَيْمُونَةَ بِنْتِ الْحَارِثِ، قَالَتْ وَضَعْتُ لِرَسُولِ اللَّهِ صلى الله عليه وسلم غُسْلاً وَسَتَرْتُهُ، فَصَبَّ عَلَى يَدِهِ، فَغَسَلَهَا مَرَّةً أَوْ مَرَّتَيْنِ ـ قَالَ سُلَيْمَانُ لاَ أَدْرِي أَذَكَرَ الثَّالِثَةَ أَمْ لاَ ـ ثُمَّ أَفْرَغَ بِيَمِينِهِ عَلَى شِمَالِهِ، فَغَسَلَ فَرْجَهُ، ثُمَّ دَلَكَ يَدَهُ بِالأَرْضِ أَوْ بِالْحَائِطِ، ثُمَّ تَمَضْمَضَ وَاسْتَنْشَقَ، وَغَسَلَ وَجْهَهُ وَيَدَيْهِ، وَغَسَلَ رَأْسَهُ، ثُمَّ صَبَّ عَلَى جَسَدِهِ، ثُمَّ تَنَحَّى فَغَسَلَ قَدَمَيْهِ، فَنَاوَلْتُهُ خِرْقَةً، فَقَالَ بِيَدِهِ هَكَذَا، وَلَمْ يُرِدْهَا.
Finally, it’s advisable to read the Quran in full to develop better understanding about Islam and about being a Muslim. Also, the collection of Hadiths, sayings, of prophet Mohamed peace be upon such as Sahih Bukhari ( https://sunnah.com/bukhari) offers further guidance to be followed.
41:13 Fussilat
فَإِنْ أَعْرَضُوا فَقُلْ أَنْذَرْتُكُمْ صَاعِقَةً مِثْلَ صَاعِقَةِ عَادٍ وَثَمُودَ
But if they turn away, then say, "I have warned you of a thunderbolt like the thunderbolt [that struck] 'Aad and Thamud.
41:14 Fussilat
إِذْ جَاءَتْهُمُ الرُّسُلُ مِنْ بَيْنِ أَيْدِيهِمْ وَمِنْ خَلْفِهِمْ أَلَّا تَعْبُدُوا إِلَّا اللَّهَ ۖ قَالُوا لَوْ شَاءَ رَبُّنَا لَأَنْزَلَ مَلَائِكَةً فَإِنَّا بِمَا أُرْسِلْتُمْ بِهِ كَافِرُونَ
[That occurred] when the messengers had come to them before them and after them, [saying], "Worship not except Allah." They said, "If our Lord had willed, He would have sent down the angels, so indeed we, in that with which you have been sent, are disbelievers."
41:15 Fussilat
فَأَمَّا عَادٌ فَاسْتَكْبَرُوا فِي الْأَرْضِ بِغَيْرِ الْحَقِّ وَقَالُوا مَنْ أَشَدُّ مِنَّا قُوَّةً ۖ أَوَلَمْ يَرَوْا أَنَّ اللَّهَ الَّذِي خَلَقَهُمْ هُوَ أَشَدُّ مِنْهُمْ قُوَّةً ۖ وَكَانُوا بِآيَاتِنَا يَجْحَدُونَ
As for 'Aad, they were arrogant upon the earth without right and said, "Who is greater than us in strength?" Did they not consider that Allah who created them was greater than them in strength? But they were rejecting Our signs.
41:16 Fussilat
فَأَرْسَلْنَا عَلَيْهِمْ رِيحًا صَرْصَرًا فِي أَيَّامٍ نَحِسَاتٍ لِنُذِيقَهُمْ عَذَابَ الْخِزْيِ فِي الْحَيَاةِ الدُّنْيَا ۖ وَلَعَذَابُ الْآخِرَةِ أَخْزَىٰ ۖ وَهُمْ لَا يُنْصَرُونَ
So We sent upon them a screaming wind during days of misfortune to make them taste the punishment of disgrace in the worldly life; but the punishment of the Hereafter is more disgracing, and they will not be helped.
41:17 Fussilat
وَأَمَّا ثَمُودُ فَهَدَيْنَاهُمْ فَاسْتَحَبُّوا الْعَمَىٰ عَلَى الْهُدَىٰ فَأَخَذَتْهُمْ صَاعِقَةُ الْعَذَابِ الْهُونِ بِمَا كَانُوا يَكْسِبُونَ
And as for Thamud, We guided them, but they preferred blindness over guidance, so the thunderbolt of humiliating punishment seized them for what they used to earn.
41:18 Fussilat
وَنَجَّيْنَا الَّذِينَ آمَنُوا وَكَانُوا يَتَّقُونَ
And We saved those who believed and used to fear Allah.
41:19 Fussilat
وَيَوْمَ يُحْشَرُ أَعْدَاءُ اللَّهِ إِلَى النَّارِ فَهُمْ يُوزَعُونَ
And [mention, O Muhammad], the Day when the enemies of Allah will be gathered to the Fire while they are [driven] assembled in rows,
41:20 Fussilat
حَتَّىٰ إِذَا مَا جَاءُوهَا شَهِدَ عَلَيْهِمْ سَمْعُهُمْ وَأَبْصَارُهُمْ وَجُلُودُهُمْ بِمَا كَانُوا يَعْمَلُونَ
Until, when they reach it, their hearing and their eyes and their skins will testify against them of what they used to do.
41:21 Fussilat
وَقَالُوا لِجُلُودِهِمْ لِمَ شَهِدْتُمْ عَلَيْنَا ۖ قَالُوا أَنْطَقَنَا اللَّهُ الَّذِي أَنْطَقَ كُلَّ شَيْءٍ وَهُوَ خَلَقَكُمْ أَوَّلَ مَرَّةٍ وَإِلَيْهِ تُرْجَعُونَ
And they will say to their skins, "Why have you testified against us?" They will say, "We were made to speak by Allah, who has made everything speak; and He created you the first time, and to Him you are returned.
41:22 Fussilat
وَمَا كُنْتُمْ تَسْتَتِرُونَ أَنْ يَشْهَدَ عَلَيْكُمْ سَمْعُكُمْ وَلَا أَبْصَارُكُمْ وَلَا جُلُودُكُمْ وَلَٰكِنْ ظَنَنْتُمْ أَنَّ اللَّهَ لَا يَعْلَمُ كَثِيرًا مِمَّا تَعْمَلُونَ
And you were not covering yourselves, lest your hearing testify against you or your sight or your skins, but you assumed that Allah does not know much of what you do.
41:23 Fussilat
وَذَٰلِكُمْ ظَنُّكُمُ الَّذِي ظَنَنْتُمْ بِرَبِّكُمْ أَرْدَاكُمْ فَأَصْبَحْتُمْ مِنَ الْخَاسِرِينَ
And that was your assumption which you assumed about your Lord. It has brought you to ruin, and you have become among the losers."
41:24 Fussilat
فَإِنْ يَصْبِرُوا فَالنَّارُ مَثْوًى لَهُمْ ۖ وَإِنْ يَسْتَعْتِبُوا فَمَا هُمْ مِنَ الْمُعْتَبِينَ
So [even] if they are patient, the Fire is a residence for them; and if they ask to appease [Allah], they will not be of those who are allowed to appease.
41:25 Fussilat
۞ وَقَيَّضْنَا لَهُمْ قُرَنَاءَ فَزَيَّنُوا لَهُمْ مَا بَيْنَ أَيْدِيهِمْ وَمَا خَلْفَهُمْ وَحَقَّ عَلَيْهِمُ الْقَوْلُ فِي أُمَمٍ قَدْ خَلَتْ مِنْ قَبْلِهِمْ مِنَ الْجِنِّ وَالْإِنْسِ ۖ إِنَّهُمْ كَانُوا خَاسِرِينَ
And We appointed for them companions who made attractive to them what was before them and what was behind them [of sin], and the word has come into effect upon them among nations which had passed on before them of jinn and men. Indeed, they [all] were losers.
41:26 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا لَا تَسْمَعُوا لِهَٰذَا الْقُرْآنِ وَالْغَوْا فِيهِ لَعَلَّكُمْ تَغْلِبُونَ
And those who disbelieve say, "Do not listen to this Qur'an and speak noisily during [the recitation of] it that perhaps you will overcome."
41:27 Fussilat
فَلَنُذِيقَنَّ الَّذِينَ كَفَرُوا عَذَابًا شَدِيدًا وَلَنَجْزِيَنَّهُمْ أَسْوَأَ الَّذِي كَانُوا يَعْمَلُونَ
But We will surely cause those who disbelieve to taste a severe punishment, and We will surely recompense them for the worst of what they had been doing.
41:28 Fussilat
ذَٰلِكَ جَزَاءُ أَعْدَاءِ اللَّهِ النَّارُ ۖ لَهُمْ فِيهَا دَارُ الْخُلْدِ ۖ جَزَاءً بِمَا كَانُوا بِآيَاتِنَا يَجْحَدُونَ
That is the recompense of the enemies of Allah - the Fire. For them therein is the home of eternity as recompense for what they, of Our verses, were rejecting.
41:29 Fussilat
وَقَالَ الَّذِينَ كَفَرُوا رَبَّنَا أَرِنَا اللَّذَيْنِ أَضَلَّانَا مِنَ الْجِنِّ وَالْإِنْسِ نَجْعَلْهُمَا تَحْتَ أَقْدَامِنَا لِيَكُونَا مِنَ الْأَسْفَلِينَ
And those who disbelieved will [then] say, "Our Lord, show us those who misled us of the jinn and men [so] we may put them under our feet that they will be among the lowest."
41:30 Fussilat
إِنَّ الَّذِينَ قَالُوا رَبُّنَا اللَّهُ ثُمَّ اسْتَقَامُوا تَتَنَزَّلُ عَلَيْهِمُ الْمَلَائِكَةُ أَلَّا تَخَافُوا وَلَا تَحْزَنُوا وَأَبْشِرُوا بِالْجَنَّةِ الَّتِي كُنْتُمْ تُوعَدُونَ
Indeed, those who have said, "Our Lord is Allah " and then remained on a right course - the angels will descend upon them, [saying], "Do not fear and do not grieve but receive good tidings of Paradise, which you were promised.
41:31 Fussilat
نَحْنُ أَوْلِيَاؤُكُمْ فِي الْحَيَاةِ الدُّنْيَا وَفِي الْآخِرَةِ ۖ وَلَكُمْ فِيهَا مَا تَشْتَهِي أَنْفُسُكُمْ وَلَكُمْ فِيهَا مَا تَدَّعُونَ
We [angels] were your allies in worldly life and [are so] in the Hereafter. And you will have therein whatever your souls desire, and you will have therein whatever you request [or wish]
41:32 Fussilat
نُزُلًا مِنْ غَفُورٍ رَحِيمٍ
As accommodation from a [Lord who is] Forgiving and Merciful."
41:33 Fussilat
وَمَنْ أَحْسَنُ قَوْلًا مِمَّنْ دَعَا إِلَى اللَّهِ وَعَمِلَ صَالِحًا وَقَالَ إِنَّنِي مِنَ الْمُسْلِمِينَ
And who is better in speech than one who invites to Allah and does righteousness and says, "Indeed, I am of the Muslims."
41:34 Fussilat
وَلَا تَسْتَوِي الْحَسَنَةُ وَلَا السَّيِّئَةُ ۚ ادْفَعْ بِالَّتِي هِيَ أَحْسَنُ فَإِذَا الَّذِي بَيْنَكَ وَبَيْنَهُ عَدَاوَةٌ كَأَنَّهُ وَلِيٌّ حَمِيمٌ
And not equal are the good deed and the bad. Repel [evil] by that [deed] which is better; and thereupon the one whom between you and him is enmity [will become] as though he was a devoted friend.
41:35 Fussilat
وَمَا يُلَقَّاهَا إِلَّا الَّذِينَ صَبَرُوا وَمَا يُلَقَّاهَا إِلَّا ذُو حَظٍّ عَظِيمٍ
But none is granted it except those who are patient, and none is granted it except one having a great portion [of good].
41:36 Fussilat
وَإِمَّا يَنْزَغَنَّكَ مِنَ الشَّيْطَانِ نَزْغٌ فَاسْتَعِذْ بِاللَّهِ ۖ إِنَّهُ هُوَ السَّمِيعُ الْعَلِيمُ
And if there comes to you from Satan an evil suggestion, then seek refuge in Allah. Indeed, He is the Hearing, the Knowing.
41:37 Fussilat
وَمِنْ آيَاتِهِ اللَّيْلُ وَالنَّهَارُ وَالشَّمْسُ وَالْقَمَرُ ۚ لَا تَسْجُدُوا لِلشَّمْسِ وَلَا لِلْقَمَرِ وَاسْجُدُوا لِلَّهِ الَّذِي خَلَقَهُنَّ إِنْ كُنْتُمْ إِيَّاهُ تَعْبُدُونَ
And of His signs are the night and day and the sun and moon. Do not prostrate to the sun or to the moon, but prostate to Allah, who created them, if it should be Him that you worship.
41:38 Fussilat
فَإِنِ اسْتَكْبَرُوا فَالَّذِينَ عِنْدَ رَبِّكَ يُسَبِّحُونَ لَهُ بِاللَّيْلِ وَالنَّهَارِ وَهُمْ لَا يَسْأَمُونَ ۩
But if they are arrogant - then those who are near your Lord exalt Him by night and by day, and they do not become weary.
41:39 Fussilat
وَمِنْ آيَاتِهِ أَنَّكَ تَرَى الْأَرْضَ خَاشِعَةً فَإِذَا أَنْزَلْنَا عَلَيْهَا الْمَاءَ اهْتَزَّتْ وَرَبَتْ ۚ إِنَّ الَّذِي أَحْيَاهَا لَمُحْيِي الْمَوْتَىٰ ۚ إِنَّهُ عَلَىٰ كُلِّ شَيْءٍ قَدِيرٌ
And of His signs is that you see the earth stilled, but when We send down upon it rain, it shakes and grows. Indeed, He who has given it life is the Giver of Life to the dead. Indeed, He is over all things competent.
41:40 Fussilat
إِنَّ الَّذِينَ يُلْحِدُونَ فِي آيَاتِنَا لَا يَخْفَوْنَ عَلَيْنَا ۗ أَفَمَنْ يُلْقَىٰ فِي النَّارِ خَيْرٌ أَمْ مَنْ يَأْتِي آمِنًا يَوْمَ الْقِيَامَةِ ۚ اعْمَلُوا مَا شِئْتُمْ ۖ إِنَّهُ بِمَا تَعْمَلُونَ بَصِيرٌ
Indeed, those who inject deviation into Our verses are not concealed from Us. So, is he who is cast into the Fire better or he who comes secure on the Day of Resurrection? Do whatever you will; indeed, He (God, Allah) is Seeing what you do.
-
 @ 6a6be47b:3e74e3e1
2025-04-12 12:13:13
@ 6a6be47b:3e74e3e1
2025-04-12 12:13:13Hi frens! How's your weekend starting? I'm just finishing a newblog entry 🖋️on my website and I'm going to be selling a few things on my Ko-fi shop 🛍️.
Before I post everything, I wanted to share a special treat with my Nostr family:
🎁 I've created two beautiful postcard-sized (148mm x 210mm or 5.83 in x 8.27 in)artworks inspired by Holy Week. Here they are:
Palm Day
 Resurrection Day
Resurrection Day

✉️ If you'd like one, just DM me with your email address, and I'll send it your way! Zaps are always appreciated and help keep me going. 🙏
❤️ This is big thank you to you my frens Have fun and stay safe
✝️ This is an INSTANT DIGITAL DOWNLOAD, no physical item will be shipped to you.
✝️ The frames and accessories in the listing images are not included.
🚨 DISCLAIMER 🚨
❤️ Copyright Retention: I, the artist, retain full copyright of all original artwork, even after the digital print is purchased.
❤️ Limited License: The digital print provides a limited, non-transferable license for personal use only. It is not intended for commercial use or resale.
❤️ No Reproduction Rights: The purchase of this digital print does not grant any rights to reproduce, distribute, or create derivative works based on the design.
🚨 By proceeding with the purchase of this digital print, you acknowledge and agree to these terms. 🚨
-
 @ caa88a52:6c226a91
2025-04-11 22:58:40
@ caa88a52:6c226a91
2025-04-11 22:58:40Running Nestr!
-
 @ a0c34d34:fef39af1
2025-04-10 09:13:12
@ a0c34d34:fef39af1
2025-04-10 09:13:12Let’s talk longevity and quality of life. Have you prepared for Passover or Easter? Do you celebrate either? I’m going to my niece’s house for Passover and I will be devouring brisket and strawberry shortcake. I use to love the Easter candy my neighbor shared when I was a kid. Taboo during Passover but I snuck a peep or two. How afraid are you about the future? Are you keeping up with longevity technology? Do you have the dream of living a long, long life? Longevity technology combines the power of medicine, biotechnology and artificial intelligence to extend a healthy human lifespan. It’s about using cutting edge technology and medical advancements to extend the years we live in good health. The focus is on quality of life during extended years. With the rise of AI powered longevity clinics, treatments tailored to an individual’s genetic profile, lifestyle and medical history, and customized anti-aging interventions, personalized healthcare will become a reality over the next decade. I’m scared I won’t be able to afford housing or healthcare. Advanced medical services cost money, and they are only going to rise. As we stay independent longer and capable of living on our own, there will be more “smart” solutions available, more longevity technology advances. Imagine using the technology of today to have a home where you feel safe for your mother or grandmother so they can live independently. The costs of technology for a “smart” house? Running lights on the floorboards light up as you walk by, just one item I can think of that can keep senior citizens safe at home. I developed a plan for a 55+ community for senior citizens. I have seen similar plans. I think blockchain technology and utilizing tokenomics can only make housing cost effective for senior citizens in the future. When I sat down and wrote the Executive Summary for Onboard60 three years ago, a component was to develop a 55+ Active Senior Community using tokenomics, smart contracts and blockchain technology. Since then, when I say I want to make Onboard60 like the AARP of today, I’ve been told that’s impossible, not going to work and I am wasting my time with this whole project, senior citizens aren’t interested. They will be. As we move into a population explosion of senior citizens living longer, healthy and independently, I think we need to consider how we are going to afford our longevity. What type of care will you receive, how much will it cost? What will you be able to control as in the cost, the level of care you receive. What currency is used? Yes, currency. As we move forward with the integration of cryptocurrency into our financial system, we need to think of what currency is accepted. There will be facilities that use their own stablecoin or accept certain others. The non-traditional financial systems are here to stay. The United States has incorporated a few different cryptocurrencies. Large financial institutions have adapted to putting cryptocurrency into their investment portfolios. I didn’t expect this to happen in my lifetime. Seriously, I thought Onboard60 would have a few more years to develop, create a community of senior citizens. That’s not the case. The world is accelerating at an impossible rate to keep up with everything. It can be overwhelming and scary. How do I find companies that use blockchain and smart contracts? Are there companies where I can protect my property rights by putting them on chain? Are there health insurance companies that use smart contracts? Onboard60 is more than the Metaverse, YouTube and A Handbook for Noobies (Web3 1101 for Seniors). It’s about staying informed, safely, to achieve the future every senior citizen deserves. If you have any knowledge of such companies, please let me know. I have crypto accountants and lawyers in my toolbox. I look forward to adding to my toolbox. I want to be like the AARP for today’s world.
Thanks for reading, Be fabulous, Sandra Abrams Founder Onboard60
-
 @ 86dfbe73:628cef55
2025-05-04 06:56:33
@ 86dfbe73:628cef55
2025-05-04 06:56:33Building A Second Brain (BASB) ist eine Methode, mit der man Ideen, Einsichten und Vernetzungen, die man durch seine Erfahrungen gewonnen hat, systematisch speichert und die jeder Zeit abrufbar sind. Kurz, BASB erweitert das Gedächtnis mit Hilfe moderner digitaler Werkzeuge und Netzwerke. Die Kernidee ist, dass man durch diese Verlagerung sein biologisches Gehirn befreit, um frei denken zu können, seiner Kreativität freien Lauf zu geben oder einfach im Moment sein kann.
Die Methode besteht aus drei Grundschritten: dem Sammeln von Ideen und Erkenntnissen, dem Vernetzen dieser Ideen und Erkenntnisse und dem Erschaffen konkreter Ergebnisse.
Sammeln: Der erste Schritt beim Aufbau eines Second Brains ist das «Sammeln» der Ideen und Erkenntnisse, die genug wichtig oder interessant sind, um sie festzuhalten. Dafür wird als Organisationsstruktur P.A.R.A empfohlen.
Vernetzen: Sobald man angefangen hat, sein persönliches Wissen strukturiert zu sammeln, wird man anfangen, Muster und Verbindungen zwischen den Ideen und Erkenntnissen zu erkennen. Ab dieser Stelle verwende ich parallel die Zettelkastenmethode (ZKM)
Erschaffen: All das Erfassen, Zusammenfassen, Verbinden und Strukturieren haben letztlich das Ziel: Konkrete Ergebnisse in der realen Welt zu erschaffen.
PARA ist die Organisationsstruktur, die auf verschiedenen Endgeräten einsetzt werden kann, um digitale Informationen immer nach dem gleichen Schema abzulegen. Seien es Informationen, Notizen, Grafiken, Videos oder Dateien, alles hat seinen festen Platz und kann anhand von vier Kategorien bzw. „Buckets“ kategorisiert werden.
PARA steht dabei für: * Projekte * Areas * Ressourcen * Archiv
Projekte (engl. Projects) sind kurzfristige Bemühungen in Arbeit und Privatleben. Sie sind das, woran Du aktuell arbeitest. Sie haben einige für die Arbeit förderliche Eigenschaften: * Sie haben einen Anfang und ein Ende (im Gegensatz zu einem Hobby oder einem Verantwortungsbereich). * Sie haben ein konkretes Ergebnis, dass erreicht werden soll und bestehen aus konkreten Schritten, die nötig und zusammen hinreichend sind, um dieses Ziel zu erreichen, entspricht GTD von David Allen
Verantwortungsbereiche (engl. Areas) betreffen alles, was man langfristig im Blick behalten will. Sie unterscheidet von Projekten, dass man bei ihnen kein Ziel verfolgt, sondern einem Standard halten will. Sie sind dementsprechend nicht befristet. Man könnte sagen, dass sie einen Anspruch an uns selbst und unsere Lebenswelt darstellen.
Ressourcen (engl. Resources) sind Themen, die allenfalls langfristig relevant oder nützlich werden könnten. Sie sind eine Sammelkategorie für alles, was weder Projekt noch Verantwortungsbereich ist. Es sind: * Themen, die interessant sind. (English: Topic) * Untersuchungsgegenständige, die man erforschen will. (Englisch: Subject) * Nützliche Informationen für den späteren Gebrauch.
Das Archiv ist für alles Inaktive aus den obigen drei Kategorien. Es ist ein Lager für Beendetes und Aufgeschobenes.
Das System PARA ist eine nach zeitlicher Handlungsrelevanz angeordnete Ablage. Projekte kommen vor den Verantwortungsbereichen, weil sie einen kurz- bis mittelfristigen Zeithorizont haben, Verantwortungsbereiche dagegen einen unbegrenzten Zeithorizont. Ressourcen und Archiv bilden die Schlusslichter, weil sie gewöhnlich weder Priorität haben, noch dringend sind.
-
 @ fd208ee8:0fd927c1
2025-04-05 21:51:52
@ fd208ee8:0fd927c1
2025-04-05 21:51:52Markdown: Syntax
Note: This document is itself written using Markdown; you can see the source for it by adding '.text' to the URL.
Overview
Philosophy
Markdown is intended to be as easy-to-read and easy-to-write as is feasible.
Readability, however, is emphasized above all else. A Markdown-formatted document should be publishable as-is, as plain text, without looking like it's been marked up with tags or formatting instructions. While Markdown's syntax has been influenced by several existing text-to-HTML filters -- including Setext, atx, Textile, reStructuredText, Grutatext, and EtText -- the single biggest source of inspiration for Markdown's syntax is the format of plain text email.
Block Elements
Paragraphs and Line Breaks
A paragraph is simply one or more consecutive lines of text, separated by one or more blank lines. (A blank line is any line that looks like a blank line -- a line containing nothing but spaces or tabs is considered blank.) Normal paragraphs should not be indented with spaces or tabs.
The implication of the "one or more consecutive lines of text" rule is that Markdown supports "hard-wrapped" text paragraphs. This differs significantly from most other text-to-HTML formatters (including Movable Type's "Convert Line Breaks" option) which translate every line break character in a paragraph into a
<br />tag.When you do want to insert a
<br />break tag using Markdown, you end a line with two or more spaces, then type return.Headers
Markdown supports two styles of headers, [Setext] [1] and [atx] [2].
Optionally, you may "close" atx-style headers. This is purely cosmetic -- you can use this if you think it looks better. The closing hashes don't even need to match the number of hashes used to open the header. (The number of opening hashes determines the header level.)
Blockquotes
Markdown uses email-style
>characters for blockquoting. If you're familiar with quoting passages of text in an email message, then you know how to create a blockquote in Markdown. It looks best if you hard wrap the text and put a>before every line:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Markdown allows you to be lazy and only put the
>before the first line of a hard-wrapped paragraph:This is a blockquote with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
Blockquotes can be nested (i.e. a blockquote-in-a-blockquote) by adding additional levels of
>:This is the first level of quoting.
This is nested blockquote.
Back to the first level.
Blockquotes can contain other Markdown elements, including headers, lists, and code blocks:
This is a header.
- This is the first list item.
- This is the second list item.
Here's some example code:
return shell_exec("echo $input | $markdown_script");Any decent text editor should make email-style quoting easy. For example, with BBEdit, you can make a selection and choose Increase Quote Level from the Text menu.
Lists
Markdown supports ordered (numbered) and unordered (bulleted) lists.
Unordered lists use asterisks, pluses, and hyphens -- interchangably -- as list markers:
- Red
- Green
- Blue
is equivalent to:
- Red
- Green
- Blue
and:
- Red
- Green
- Blue
Ordered lists use numbers followed by periods:
- Bird
- McHale
- Parish
It's important to note that the actual numbers you use to mark the list have no effect on the HTML output Markdown produces. The HTML Markdown produces from the above list is:
If you instead wrote the list in Markdown like this:
- Bird
- McHale
- Parish
or even:
- Bird
- McHale
- Parish
you'd get the exact same HTML output. The point is, if you want to, you can use ordinal numbers in your ordered Markdown lists, so that the numbers in your source match the numbers in your published HTML. But if you want to be lazy, you don't have to.
To make lists look nice, you can wrap items with hanging indents:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
But if you want to be lazy, you don't have to:
- Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus. Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus.
- Donec sit amet nisl. Aliquam semper ipsum sit amet velit. Suspendisse id sem consectetuer libero luctus adipiscing.
List items may consist of multiple paragraphs. Each subsequent paragraph in a list item must be indented by either 4 spaces or one tab:
-
This is a list item with two paragraphs. Lorem ipsum dolor sit amet, consectetuer adipiscing elit. Aliquam hendrerit mi posuere lectus.
Vestibulum enim wisi, viverra nec, fringilla in, laoreet vitae, risus. Donec sit amet nisl. Aliquam semper ipsum sit amet velit.
-
Suspendisse id sem consectetuer libero luctus adipiscing.
It looks nice if you indent every line of the subsequent paragraphs, but here again, Markdown will allow you to be lazy:
-
This is a list item with two paragraphs.
This is the second paragraph in the list item. You're only required to indent the first line. Lorem ipsum dolor sit amet, consectetuer adipiscing elit.
-
Another item in the same list.
To put a blockquote within a list item, the blockquote's
>delimiters need to be indented:-
A list item with a blockquote:
This is a blockquote inside a list item.
To put a code block within a list item, the code block needs to be indented twice -- 8 spaces or two tabs:
- A list item with a code block:
<code goes here>
Code Blocks
Pre-formatted code blocks are used for writing about programming or markup source code. Rather than forming normal paragraphs, the lines of a code block are interpreted literally. Markdown wraps a code block in both
<pre>and<code>tags.To produce a code block in Markdown, simply indent every line of the block by at least 4 spaces or 1 tab.
This is a normal paragraph:
This is a code block.Here is an example of AppleScript:
tell application "Foo" beep end tellA code block continues until it reaches a line that is not indented (or the end of the article).
Within a code block, ampersands (
&) and angle brackets (<and>) are automatically converted into HTML entities. This makes it very easy to include example HTML source code using Markdown -- just paste it and indent it, and Markdown will handle the hassle of encoding the ampersands and angle brackets. For example, this:<div class="footer"> © 2004 Foo Corporation </div>Regular Markdown syntax is not processed within code blocks. E.g., asterisks are just literal asterisks within a code block. This means it's also easy to use Markdown to write about Markdown's own syntax.
tell application "Foo" beep end tellSpan Elements
Links
Markdown supports two style of links: inline and reference.
In both styles, the link text is delimited by [square brackets].
To create an inline link, use a set of regular parentheses immediately after the link text's closing square bracket. Inside the parentheses, put the URL where you want the link to point, along with an optional title for the link, surrounded in quotes. For example:
This is an example inline link.
This link has no title attribute.
Emphasis
Markdown treats asterisks (
*) and underscores (_) as indicators of emphasis. Text wrapped with one*or_will be wrapped with an HTML<em>tag; double*'s or_'s will be wrapped with an HTML<strong>tag. E.g., this input:single asterisks
single underscores
double asterisks
double underscores
Code
To indicate a span of code, wrap it with backtick quotes (
`). Unlike a pre-formatted code block, a code span indicates code within a normal paragraph. For example:Use the
printf()function. -
 @ 88cc134b:5ae99079
2025-05-04 03:34:05
@ 88cc134b:5ae99079
2025-05-04 03:34:05The biggest question about this article is if it's is going to publish on first try.
-
 @ 0edc2f47:730cff1b
2025-04-04 03:37:15
@ 0edc2f47:730cff1b
2025-04-04 03:37:15Chef's notes
This started as a spontaneous kitchen experiment—an amalgamation of recipes from old cookbooks and online finds. My younger daughter wanted to surprise her sister with something quick but fancy ("It's a vibe, Mom."), and this is what we came up with. It’s quickly established itself as a go-to favorite: simple, rich, and deeply satisfying. It serves 4 (or 1, depending on the day; I am not here to judge). Tightly wrapped, it will keep up to 3 days in the fridge, but I bet it won't last that long!
Details
- ⏲️ Prep time: 10 min
- 🍳 Cook time: 0 min
Ingredients
- 1 cup (240mL) heavy whipping cream
- 1/4 cup (24g) cocoa powder
- 5 tbsp (38g) Confectioners (powdered) sugar
- 1/4 tsp (1.25mL) vanilla extract (optional)
- Flaky sea salt (optional, but excellent)
Directions
-
- Whip the cream until frothy.
-
- Sift in cocoa and sugar, fold or gently mix (add vanilla if using).
-
- Whip to medium peaks (or stiff peaks, if that's more your thing). Chill and serve (topped with a touch of sea salt if you’re feeling fancy).
-
 @ 52b4a076:e7fad8bd
2025-04-28 00:48:57
@ 52b4a076:e7fad8bd
2025-04-28 00:48:57I have been recently building NFDB, a new relay DB. This post is meant as a short overview.
Regular relays have challenges
Current relay software have significant challenges, which I have experienced when hosting Nostr.land: - Scalability is only supported by adding full replicas, which does not scale to large relays. - Most relays use slow databases and are not optimized for large scale usage. - Search is near-impossible to implement on standard relays. - Privacy features such as NIP-42 are lacking. - Regular DB maintenance tasks on normal relays require extended downtime. - Fault-tolerance is implemented, if any, using a load balancer, which is limited. - Personalization and advanced filtering is not possible. - Local caching is not supported.
NFDB: A scalable database for large relays
NFDB is a new database meant for medium-large scale relays, built on FoundationDB that provides: - Near-unlimited scalability - Extended fault tolerance - Instant loading - Better search - Better personalization - and more.
Search
NFDB has extended search capabilities including: - Semantic search: Search for meaning, not words. - Interest-based search: Highlight content you care about. - Multi-faceted queries: Easily filter by topic, author group, keywords, and more at the same time. - Wide support for event kinds, including users, articles, etc.
Personalization
NFDB allows significant personalization: - Customized algorithms: Be your own algorithm. - Spam filtering: Filter content to your WoT, and use advanced spam filters. - Topic mutes: Mute topics, not keywords. - Media filtering: With Nostr.build, you will be able to filter NSFW and other content - Low data mode: Block notes that use high amounts of cellular data. - and more
Other
NFDB has support for many other features such as: - NIP-42: Protect your privacy with private drafts and DMs - Microrelays: Easily deploy your own personal microrelay - Containers: Dedicated, fast storage for discoverability events such as relay lists
Calcite: A local microrelay database
Calcite is a lightweight, local version of NFDB that is meant for microrelays and caching, meant for thousands of personal microrelays.
Calcite HA is an additional layer that allows live migration and relay failover in under 30 seconds, providing higher availability compared to current relays with greater simplicity. Calcite HA is enabled in all Calcite deployments.
For zero-downtime, NFDB is recommended.
Noswhere SmartCache
Relays are fixed in one location, but users can be anywhere.
Noswhere SmartCache is a CDN for relays that dynamically caches data on edge servers closest to you, allowing: - Multiple regions around the world - Improved throughput and performance - Faster loading times
routerd
routerdis a custom load-balancer optimized for Nostr relays, integrated with SmartCache.routerdis specifically integrated with NFDB and Calcite HA to provide fast failover and high performance.Ending notes
NFDB is planned to be deployed to Nostr.land in the coming weeks.
A lot more is to come. 👀️️️️️️
-
 @ 5df413d4:2add4f5b
2025-05-04 00:51:49
@ 5df413d4:2add4f5b
2025-05-04 00:51:49Short photo-stories of the hidden, hard to find, obscure, and off the beaten track.
Come now, take a walk with me…
The Traveller 01: Ku/苦 Bar
Find a dingy, nondescript alley in a suspiciously quiet corner of Bangkok’s Chinatown at night. Walk down it. Pass the small prayer shrine that houses the angels who look over these particular buildings and approach an old wooden door. You were told that there is a bar here, as to yet nothing suggests that this is so…

Wait! A closer inspection reveals a simple bronze plaque, out of place for its polish and tended upkeep, “cocktails 3rd floor.” Up the stairs then! The landing on floor 3 presents a white sign with the Chinese character for bitter, ku/苦, and a red arrow pointing right.


Pass through the threshold, enter a new space. To your right, a large expanse of barren concrete, an empty “room.” Tripods for…some kind of filming? A man-sized, locked container. Yet, you did not come here to ask questions, such things are none of your business!

And to your left, you find the golden door. Approach. Enter. Be greeted. You have done well! You have found it. 苦 Bar. You are among friends now. Inside exudes deep weirdness - in the etymological sense - the bending of destinies, control of the fates. And for the patrons, a quiet yet social place, a sensual yet sacred space.


Ethereal sounds, like forlorn whale songs fill the air, a strange music for an even stranger magic. But, Taste! Taste is the order of the day! Fragrant, Bizarre, Obscure, Dripping and Arcane. Here you find a most unique use flavor, flavors myriad and manifold, flavors beyond name. Buddha’s hand, burnt cedar charcoal, ylang ylang, strawberry leaf, maybe wild roots brought in by some friendly passerby, and many, many other things. So, Taste! The drinks here, libations even, are not so much to be liked or disliked, rather, the are liquid context, experience to be embraced with a curious mind and soul freed from judgment.

And In the inner room, one may find another set of stairs. Down this time. Leading to the second place - KANGKAO. A natural wine bar, or so they say. Cozy, botanical, industrial, enclosed. The kind of private setting where you might overhear Bangkok’s resident “State Department,” “UN,” and “NGO” types chatting auspiciously in both Mandarin and English with their Mainland Chinese counterparts. But don’t look hard or listen too long! Surely, there’s no reason to be rude… Relax, relax, you are amongst friends now.

**苦 Bar. Bangkok, circa 2020. There are secrets to be found. Go there. **
Plebchain #Bitcoin #NostrArt #ArtOnNostr #Writestr #Createstr #NostrLove #Travel #Photography #Art #Story #Storytelling #Nostr #Zap #Zaps #Bangkok #Thailand #Siamstr
-
 @ 7bdef7be:784a5805
2025-04-02 12:37:35
@ 7bdef7be:784a5805
2025-04-02 12:37:35The following script try, using nak, to find out the last ten people who have followed a
target_pubkey, sorted by the most recent. It's possibile to shortensearch_timerangeto speed up the search.```
!/usr/bin/env fish
Target pubkey we're looking for in the tags
set target_pubkey "6e468422dfb74a5738702a8823b9b28168abab8655faacb6853cd0ee15deee93"
set current_time (date +%s) set search_timerange (math $current_time - 600) # 24 hours = 86400 seconds
set pubkeys (nak req --kind 3 -s $search_timerange wss://relay.damus.io/ wss://nos.lol/ 2>/dev/null | \ jq -r --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[] | select(.[0] == "p" and .[1] == $target)) | .pubkey ' | sort -u)
if test -z "$pubkeys" exit 1 end
set all_events "" set extended_search_timerange (math $current_time - 31536000) # One year
for pubkey in $pubkeys echo "Checking $pubkey" set events (nak req --author $pubkey -l 5 -k 3 -s $extended_search_timerange wss://relay.damus.io wss://nos.lol 2>/dev/null | \ jq -c --arg target "$target_pubkey" ' select(. != null and type == "object" and has("tags")) | select(.tags[][] == $target) ' 2>/dev/null)
set count (echo "$events" | jq -s 'length') if test "$count" -eq 1 set all_events $all_events $events endend
if test -n "$all_events" echo -e "Last people following $target_pubkey:" echo -e ""
set sorted_events (printf "%s\n" $all_events | jq -r -s ' unique_by(.id) | sort_by(-.created_at) | .[] | @json ') for event in $sorted_events set npub (echo $event | jq -r '.pubkey' | nak encode npub) set created_at (echo $event | jq -r '.created_at') if test (uname) = "Darwin" set follow_date (date -r "$created_at" "+%Y-%m-%d %H:%M") else set follow_date (date -d @"$created_at" "+%Y-%m-%d %H:%M") end echo "$follow_date - $npub" endend ```
-
 @ c1e9ab3a:9cb56b43
2025-04-25 00:37:34
@ c1e9ab3a:9cb56b43
2025-04-25 00:37:34If you ever read about a hypothetical "evil AI"—one that manipulates, dominates, and surveils humanity—you might find yourself wondering: how is that any different from what some governments already do?
Let’s explore the eerie parallels between the actions of a fictional malevolent AI and the behaviors of powerful modern states—specifically the U.S. federal government.
Surveillance and Control
Evil AI: Uses total surveillance to monitor all activity, predict rebellion, and enforce compliance.
Modern Government: Post-9/11 intelligence agencies like the NSA have implemented mass data collection programs, monitoring phone calls, emails, and online activity—often without meaningful oversight.
Parallel: Both claim to act in the name of “security,” but the tools are ripe for abuse.
Manipulation of Information
Evil AI: Floods the information space with propaganda, misinformation, and filters truth based on its goals.
Modern Government: Funds media outlets, promotes specific narratives through intelligence leaks, and collaborates with social media companies to suppress or flag dissenting viewpoints.
Parallel: Control the narrative, shape public perception, and discredit opposition.
Economic Domination
Evil AI: Restructures the economy for efficiency, displacing workers and concentrating resources.
Modern Government: Facilitates wealth transfer through lobbying, regulatory capture, and inflationary monetary policy that disproportionately hurts the middle and lower classes.
Parallel: The system enriches those who control it, leaving the rest with less power to resist.
Perpetual Warfare
Evil AI: Instigates conflict to weaken opposition or as a form of distraction and control.
Modern Government: Maintains a state of nearly constant military engagement since WWII, often for interests that benefit a small elite rather than national defense.
Parallel: War becomes policy, not a last resort.
Predictive Policing and Censorship
Evil AI: Uses predictive algorithms to preemptively suppress dissent and eliminate threats.
Modern Government: Experiments with pre-crime-like measures, flags “misinformation,” and uses AI tools to monitor online behavior.
Parallel: Prevent rebellion not by fixing problems, but by suppressing their expression.
Conclusion: Systemic Inhumanity
Whether it’s AI or a bureaucratic state, the more a system becomes detached from individual accountability and human empathy, the more it starts to act in ways we would call “evil” if a machine did them.
An AI doesn’t need to enslave humanity with lasers and killer robots. Sometimes all it takes is code, coercion, and unchecked power—something we may already be facing.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ 83279ad2:bd49240d
2025-03-30 14:21:49
@ 83279ad2:bd49240d
2025-03-30 14:21:49Test
-
 @ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44
@ 5cb68b7a:b7cb67d5
2025-05-04 00:13:44Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
Why Trust Crypt Recver? 🤝 🛠️ Expert Recovery Solutions At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
Partially lost or forgotten seed phrases Extracting funds from outdated or invalid wallet addresses Recovering data from damaged hardware wallets Restoring coins from old or unsupported wallet formats You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈 Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases. Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery. Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet. Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact. ⚠️ What We Don’t Do While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
Don’t Let Lost Crypto Hold You Back! ⏳ Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today! Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us! For real-time support or questions, reach out to our dedicated team on:
✉️ Telegram: Chat with Us on Telegram 💬 WhatsApp: Message Us on WhatsApp Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!Losing access to your cryptocurrency can feel like losing a part of your future. Whether it’s a forgotten password, a damaged seed backup, or simply one wrong transfer, the stress can be overwhelming. But there’s a silver lining — Crypt Recver is here to help! With our expert-led recovery services, you can reclaim your lost Bitcoin and other cryptos safely and swiftly.
 # Why Trust Crypt Recver? 🤝
# Why Trust Crypt Recver? 🤝🛠️ Expert Recovery Solutions
At Crypt Recver, we specialize in resolving some of the most complex wallet-related issues. Our team of skilled engineers has the tools and expertise to tackle:
- Partially lost or forgotten seed phrases
- Extracting funds from outdated or invalid wallet addresses
- Recovering data from damaged hardware wallets
- Restoring coins from old or unsupported wallet formats
You’re not just getting a service; you’re gaining a partner in your cryptocurrency journey.
🚀 Fast and Efficient Recovery
We understand that time is critical in crypto recovery. Our optimized systems ensure that you can regain access to your funds quickly, aiming for speed without sacrificing security. With a 90%+ success rate, you can trust us to fight against the clock on your behalf.
🔒 Privacy is Our Priority
Your confidentiality matters. Every recovery session is handled with the utmost care, ensuring all processes are encrypted and confidential. You can rest easy, knowing your sensitive information stays private.
💻 Advanced Technology
Our proprietary tools and brute-force optimization techniques allow for maximum efficiency in recovery. No matter how challenging your case may be, our technology is designed to give you the best chance at getting your crypto back.
Our Recovery Services Include: 📈
- Bitcoin Recovery: Lost access to your Bitcoin wallet? We help recover lost wallets, private keys, and passphrases.
- Transaction Recovery: Mistakes happen — whether it’s an incorrect wallet address or a lost password, let us handle the recovery.
- Cold Wallet Restoration: If your cold wallet is failing, we can safely extract your assets and migrate them into a secure, new wallet.
- Private Key Generation: Lost your private key? Don’t worry. Our experts can help you regain control using advanced methods — all while ensuring your privacy remains intact.
⚠️ What We Don’t Do
While we can handle many scenarios, there are some limitations. For example, we cannot recover funds stored in custodial wallets, or cases where there is a complete loss of four or more seed words without any partial info available. We’re transparent about what’s possible, so you know what to expect.
 # Don’t Let Lost Crypto Hold You Back! ⏳
# Don’t Let Lost Crypto Hold You Back! ⏳Did you know that 3 to 3.4 million BTC — nearly 20% of the total supply — are estimated to be permanently lost? Don’t become part of that statistic! Whether it’s due to a forgotten password, sending funds to the wrong address, or damaged drives, we can help you navigate through it all.
🛡️ Real-Time Dust Attack Protection
Protecting your privacy goes beyond just recovery. Our services include dust attack protection, which keeps your activity anonymous and your funds secure. Our suite will shield your identity from unwanted tracking, ransomware, and phishing attempts.
🎉 Start Your Recovery Journey Today!
Are you ready to reclaim your lost crypto? Don’t wait until it’s too late!
👉 Request Wallet Recovery Help Now!
📞 Need Immediate Assistance? Connect with Us!
For real-time support or questions, reach out to our dedicated team on:
- ✉️ Telegram: Chat with Us on Telegram
- 💬 WhatsApp: Message Us on WhatsApp
Crypt Recver is your trusted partner in the world of cryptocurrency recovery. Let us turn your challenges into victories. Don’t hesitate — your crypto future starts now! 🚀✨
Act fast and secure your digital assets with Crypt Recver!
-
 @ d4cb227b:edca6019
2025-03-30 04:26:51
@ d4cb227b:edca6019
2025-03-30 04:26:51Dose: 30g coffee (Fine-medium grind size) 500mL soft or bottled water (97°C / 206.6°F)
Instructions: 1. Rinse out your filter paper with hot water to remove the papery taste. This will also preheat the brewer.
-
Add your grounds carefully to the center of the V60 and then create a well in the middle of the grounds.
-
For the bloom, start to gently pour 60mL of water, making sure that all the coffee is wet in this initial phase.
-
As soon as you’ve added your water, grab your V60 and begin to swirl in a circular motion. This will ensure the water and coffee are evenly mixed. Let this rest and bloom for up to 45 seconds.
-
Pour the rest of the water in in 2 phases. You want to try and get 60% of your total water in, within 30 seconds.
-
Pour until you reach 300mL total with a time at 1:15. Here you want to pour with a little agitation, but not so much that you have an uneven extraction.
-
Once you hit 60% of your total brew weight, start to pour a little slower and more gently, keeping your V60 cone topped up. Aim to have 100% of your brew weight in within the next 30 seconds.
-
Once you get to 500mL, with a spoon give the V60 a small stir in one direction, and then again in the other direction. This will release any grounds stuck to the side of the paper.
-
Allow the V60 to drain some more, and then give it one final swirl. This will help keep the bed flat towards the end of the brew, giving you the most even possible extraction.
-
-
 @ d4cb227b:edca6019
2025-03-30 04:23:22
@ d4cb227b:edca6019
2025-03-30 04:23:22This method focuses on the amount of water in the first pour, which ultimately defines the coffee’s acidity and sweetness (more water = more acidity, less water = more sweetness). For the remainder of the brew, the water is divided into equal parts according to the strength you wish to attain.
Dose: - 20g coffee (Coarse ground coffee) - 300mL water (92°C / 197.6°F) Time: 3:30
Instructions: Pour 1: 0:00 > 50mL (42% of 120mL = 40% of total – less water in the ratio, targeting sweetness.) Pour 2: 0:45 > 70mL (58% of 120mL = 40% of total – the top up for 40% of total.) Pour 3: 1:30 > 60mL (The remaining water is 180mL / 3 pours = 60mL per pour) Pour 4: 2:10 > 60mL Pour 5: 2:40 > 60mL Remove the V60 at 3:30
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ a0c34d34:fef39af1
2025-03-26 11:42:52
@ a0c34d34:fef39af1
2025-03-26 11:42:528 months ago I went to Nashville, Bitcoin2024. The one with Edward Snowden’s cryptic speech, Michael Saylor telling people who knew nothing about Bitcoin how to stack sats. And yes, I was in the room when Donald spoke. I had so many people asking me how to “get a Coinbase!!!” cause he said so.
I sat with two women explaining seed phrase and how vital it was as they wrote the random words on scrape pieces of paper and put them in their purses.
I once was just like those women. Still am in some areas of this space. It can be overwhelming, learning about cryptography,subgraphs, it can be decentralized theatre!!!
Yes decentralized theatre. I said it. I never said it out loud.
In 2016, I knew nothing. I overheard a conversation that changed my life’s trajectory. I am embarrassed to say, I was old then but didn’t know it. I didn’t see myself as old, 56 back then, I just wanted to have enough money to pay bills.
I say this to say I bought 3 whole Bitcoin in 2016 and listening to mainstream news about scams and black market associated with what I bought, I sold them quickly and thought I was too old to be scammed and playing around with all of that.
In 2018, someone gave me The Book of Satoshi, I read it and thought it was a fabulous story but my fear ? I put the book in a drawer and forgot about it.
I mentioned decentralized theatre. I have been living in decentralized theatre for the past 3 years now. In August 2021 I landed on TikTok and saw NFTs. I thought get money directly to those who need it. I started diving down the rabbit holes of Web3.
The decentralized theatre is being in betas & joining platforms claiming to be decentralized social media platforms and of course all the “Web3” businesses claiming to be Web3.
Social medias were exciting, the crypto casino was thriving and I thought I was going to live a decentralized life with Bitcoin being independent from any financial institutions or interference from government.
Delusional? Yes, diving deeper, I did. I went to my first “night with crypto” event in West Palm Beach. My first IRL meeting scammers.
There was about 200-250 people sitting facing the stage where a man was speaking. There was a QRCode on the screen and he said for us to get out our phones and scan the QRCode to download their wallet & get free money.
I watched everyone, most everyone point their phones at the screen, but I didn’t, I got up and went out to the area where the booths were, the vendors.
A few months later I found out ( on Twitter) it was a scam. People would deposit a “minimal amount” and swap their money for these tokens with no value but constant hype and Twitter social media ambassadors ( followers) had people “wanting in” Don’t FOMO…
The promise of decentralization, independent from banks & government, and of course I had been excitedly sharing everything I was learning on TikTok and mentioned senior citizens need to know this stuff.
They need to learn metaverse to be connected with the virtual and digital natives( their kids, grandkids). They need to learn about Bitcoin and blockchain technologies to put their documents on chain & transfer their wealth safely. They need to learn how A.I. health tech can help them have a better quality of life!!!
Someone said I was a senior citizen and I was the perfect person to help them. It’s been 3 years and I learned how to create a Discord(with Geneva), 4 metaverses, multiple wallets and learned about different cryptos. I learned about different GPTs, NFCCHIP wearables, A.I. and Decentralized Physical Infrastructure Network and so much more.
I have since deleted TikTok. I wrote an article on that on YakiHonne. I’m using LinkedIn and YouTube , some BluSky platforms. I published a cliff notes book for senior citizens and put it in my Stan Store(online to links) with links to my resume, newsletter, YouTube Channel, Substack and Onboard60 digital clone.
Onboard60, the name for my project. Onboard was THE buzzword back in 2021 & early 2022, 60? an age representative of my target audience … Onboard60 stuck.
The lack of interest from senior citizens over the years , the rejections, wild opinions, trolls on socials- I understand - I forget the fear I had. I still have the fear of not being a part of society, not understanding the world around me, getting left behind.
I keep coming to Nostr, going to BluSky, even the ones that are decentralized theatre( Lens & Farcaster)- I admit losing 28k follower account and afew other accounts I deleted ( over 5k & 12k), I felt a loss. I had perpetually been online and my relationships, friendships were online. Sadly only a few were real. Social media - out of sight out of mind. It was devastating.
I had to unplug and regroup. I was afraid to be on new social platforms, scared to start over, meet people. I’m realizing I do everything scared. I do it, whatever it is that moves me forward, keeps me learning, and keeps my mindset open, flexible.
Another fear is happening to me. There are times I have a senior citizen mindset. And that’s really scary. I have heard myself in conversations putting in an extra “the” like saying The Nostr like older people do.
Onboard60 is me. I am an adolescent and family counselor with a Master’s degree. I have created a few Metaverses, a Live chat/online Discord, a How to for senior citizens booklet and a digital clone.
Yes Onboard60 digital clone can be asked about anything Web3, blockchain and discuss how to create personal A.I. agents. I uploaded all of my content of the last 3 years (and it being LLM)People can go to Onboard60 clone with voice and or text
I do 1:1 counseling with overwhelmed, afraid and skeptical senior citizens.
I show experientially step by step basic virtual reality so senior citizens can enter the metaverse with their grandkids and portal to a park.
I use the metaverse & Geneva Live chats as social hang outs for senior citizens globally to create connections and stay relevant
I also talk about medical bracelets. NFCCHIP for medical information, gps bracelets for Alzheimer’s or dementia care.
And lastly from the past 3 years, I have learned to discuss all options for Bitcoin investing, not just self custody. Senior citizens listen, feel safe when I discuss Grayscale and Fidelity.
They feel they can trust these institutions. I tell them how they have articles and webinars on their sites about crypto and what cryptofunds they offer. They can dyor, it’s their money.
My vision and mission have stayed the same through this rollercoaster of a journey. It’s what keeps me grounded and moving forward.
This year I’m turning 65, and will become a part of the Medicare system. I don’t have insurance, can’t afford it. If it was on the blockchain I’d have control of the costs but nooooo, I am obligated to get Medicare.
I will have to work an extra shift a week (I am a waitress at night) and I am capable to do it and realistically I will probably need health insurance in the future, I am a senior citizen…..
Thank you for reading this. Zap sats and thank you again.
Sandra (Samm) Onboard60 Founder
https://docs.google.com/document/d/1PLn1ysBEfjjwPZsMsLlmX-s7cDOgPC29/edit?usp=drivesdk&ouid=111904115111263773126&rtpof=true&sd=true
-
 @ d0ea1c34:9c84dc37
2025-05-03 17:53:05
@ d0ea1c34:9c84dc37
2025-05-03 17:53:05Markdown Rendering Test Document
Basic Text Formatting
This is a paragraph with bold text, italic text, and bold italic text. You can also use underscores for bold or single underscores for italics.
This is a paragraph with some
inline codeusing backticks.Lists
Unordered Lists
- Item 1
- Item 2
- Nested item 2.1
- Nested item 2.2
- Item 3
Ordered Lists
- First item
- Second item
- Nested item 2.1
- Nested item 2.2
- Third item
Links and Images
Blockquotes
This is a blockquote.
It can span multiple lines.
And can be nested.
Code Blocks
```python def hello_world(): print("Hello, world!")
This is a Python code block with syntax highlighting
hello_world() ```
javascript // JavaScript code block function helloWorld() { console.log("Hello, world!"); }Tables
| Header 1 | Header 2 | Header 3 | |----------|----------|----------| | Cell 1 | Cell 2 | Cell 3 | | Cell 4 | Cell 5 | Cell 6 | | Cell 7 | Cell 8 | Cell 9 |
Horizontal Rules
Task Lists
- [x] Completed task
- [ ] Incomplete task
- [x] Another completed task
Math (if supported)
Inline math: $E = mc^2$
Block math:
$$ \frac{d}{dx}e^x = e^x $$
Footnotes
Here's a sentence with a footnote reference[^1].
[^1]: This is the footnote content.
Definition Lists
Term 1 : Definition 1
Term 2 : Definition 2a : Definition 2b
Special Characters & Escaping
*This text is surrounded by asterisks but not italicized*
Advanced Formatting
Click to expand
This is hidden content that appears when expanded.Emoji (if supported)
:smile: :heart: :thumbsup:
Final Notes
This document demonstrates various Markdown formatting features. Compatibility may vary across different Markdown renderers and platforms.
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00
@ 1bda7e1f:bb97c4d9
2025-03-26 03:23:00Tldr
- Nostr is a new open social protocol for the internet
- You can use it to create your own online community website/app for your users
- This needs only a few simple components that are free and open source
- Jumble.Social client is a front-end for showing your community content to your users
- Simple With Whitelist relay (SW2) is a back-end with simple auth for your community content
- In this blog I explain the components and set up a online community website/app that any community or company can use for their own users, for free.
You Can Run Your Own Private "X" For Free
Nostr is a new open social protocol for the internet. Because it is a protocol it is not controlled by any one company, does not reside on any one set of servers, does not require any licenses, and no one can stop you from using it however you like.
When the name Nostr is recognised, it is as a "Twitter/X alternative" – that is an online open public forum. Nostr is more than just this. The open nature of the protocol means that you can use it however you feel like, including that you can use it for creating your own social websites to suit whatever goals you have – anything from running your own team collaboration app, to running your own online community.
Nostr can be anything – not just an alternative to X, but also to Slack, Teams, Discord, Telegram (etc) – any kind of social app you'd like to run for your users can be run on Nostr.
In this blog I will show you how to launch your own community website, for your community members to use however they like, with low code, and for free.
Simple useful components
Nostr has a few simple components that work together to provide your experience –
- Your "client" – an app or a website front-end that you log into, which displays the content you want to see
- Your "relay" – a server back-end which receives and stores content, and sends it to clients
- Your "user" – a set of keys which represents a user on the network,
- Your "content" – any user content created and signed by a user, distributed to any relay, which can be picked up and viewed by any client.
It is a pattern that is used by every other social app on the internet, excepting that in those cases you can usually only view content in their app, and only post your content to their server.
Vs with Nostr where you can use any client (app) and any relay (server), including your own.
This is defined as a standard in NIP-01 which is simple enough that you can master it in a weekend, and with which you can build any kind of application.
The design space is wide open for anyone to build anything–
- Clones of Twitter, Instagram, Telegram, Medium, Twitch, etc,
- Whole new things like Private Ephemeral Messengers, Social Podcasting Apps, etc,
- Anything else you can dream up, like replacements for B2B SaaS or ERP systems.
Including that you can set up and run your own "X" for your community.
Super powers for –private– social internet
When considering my use of social internet, it is foremost private not public. Email, Whatsapp, Slack, Teams, Discord, Telegram (etc), are all about me, as a user, creating content for a selected group of individuals – close friends, colleagues, community members – not the wider public.
This private social internet is crying out for the kind of powers that Nostr provides. The list of things that Nostr solves for private social internet goes on-and-on.
Let me eat my own dog food for a moment.
- I am a member of a community of technology entrepreneurs with an app for internal community comms. The interface is not fit for this purpose. Good content gets lost. Any content created within the walled kingdom cannot be shared externally. Community members cannot migrate to a different front-end, or cross-post to public social channels.
- I am a member of many communities for kids social groups, each one with a different application and log in. There is no way to view a consolidated feed. There is no way to send one message to many communities, or share content between them. Remembering to check every feed separately is a drag.
- I am a member of a team with an app for team comms. It costs $XXX per user per month where it should be free. I can't self-host. I can't control or export my data. I can't make it interoperate natively with other SaaS. All of my messages probably go to train a Big Co AI without my consent.
In each instance "Nostr fixes this."
Ready now for low-code admins
To date Nostr has been best suited to a more technical user. To use the Nostr protocol directly has been primarily a field of great engineers building great foundations.
IMO these foundations are built. They are open source, free to use, and accessible for anyone who wants to create an administer their own online community, with only low code required.
To prove it, in this blog I will scratch my own itch. I need a X / Slack / Teams alternative to use with a few team members and friends (and a few AIs) as we hack on establishing a new business idea.
I will set this up with Nostr using only open source code, for free.
Designing the Solution
I am mostly non-technical with helpful AI. To set up your own community website in the style of X / Slack / Teams should be possible for anyone with basic technology skills.
- I have a cheap VPS which currently runs some other unrelated Nostr projects in Docker containers,
- My objective was to set up and run my own community website for my own team use, in Docker, hosted on my own server.
User requirements
What will I want from a community website?
- I want my users to be able to log into a website and post content,
- I want to save that content to a server I control accessed only be people I authorise,
- I want my users to view only that content by default, and not be exposed to any wider public social network unless they knowingly select that,
- I want my user's content to be either:
- a) viewable only by other community members (i.e. for internal team comms), or
- b) by the wider public (i.e. for public announcements), at the user's discretion.
- I want it to be open source so that other people maintain the code for me,
- I want it for free.
Nostr solutions
To achieve this with Nostr, I'll need to select some solutions "a-la carte" for each of the core components of the network.
- A client – For my client, I have chosen Jumble. Jumble is a free open-source client by Cody Tseng, available free on Github or at Jumble.social. I have chosen Jumble because it is a "relay-centric" client. In key spots the user interface highlights for the user what relay they are viewing, and what relay they are posting to. As a result, it is a beautiful fit for me to use as the home of all my community content.
- A relay – For my relay, I have chosen Simple With Whitelist (SW2). SW2 is a free open-source relay by Utxo The Webmaster, based on Khatru by Fiatjaf, available free on Github. I have chosen SW2 because it allows for very simple configuration of user auth. Users can be given read access to view notes, and write access to post notes within simple
config.jsonfiles. This allows you to keep community content private or selectively share it in a variety of ways. Per the Nostr protocol, your client will connect with your relay via websocket. - A user sign-up flow – Jumble has a user sign-up flow using Nstart by Fiatjaf, or as an admin I can create and provision my own users with any simple tool like NAK or Nostrtool.
- A user content flow – Jumble has a user content flow that can post notes to selected relays of the users choice. Rich media is uploaded to free third-party hosts like Nostr.build, and in the future there is scope to self-host this too.
With each of these boxes ticked I'm ready to start.
Launching a Private Community Website with Jumble and SW2
Install your SW2 relay
The relay is the trickiest part, so let's start there. SW2 is my Nostr relay software of choice. It is a Go application and includes full instructions for Go install. However, I prefer Docker, so I have built a Docker version and maintain a Docker branch here.
1 – In a terminal clone the repo and checkout the Docker branch
git clone https://github.com/r0d8lsh0p/sw2.git cd sw2 git checkout docker2 – Set up the environment variables
These are specified in the readme. Duplicate the example .env file and fill it with your variables.
cp .env.example .envFor me this .env file was as follows–
```
Relay Metadata
RELAY_NAME="Tbdai relay" RELAY_PUBKEY="ede41352397758154514148b24112308ced96d121229b0e6a66bc5a2b40c03ec" RELAY_DESCRIPTION="An experimental relay for some people and robots working on a TBD AI project." RELAY_URL="wss://assistantrelay.rodbishop.nz" RELAY_ICON="https://image.nostr.build/44654201843fc0f03e9a72fbf8044143c66f0dd4d5350688db69345f9da05007.jpg" RELAY_CONTACT="https://rodbishop.nz" ```
3 – Specify who can read and write to the relay
This is controlled by two config files
read_whitelist.jsonandwrite_whitelist.json.- Any user with their pubkey in the
read_whitelistcan read notes posted to the relay. If empty, anyone can read. - Any user with their pubkey in the
write_whitelistcan post notes to the relay. If empty, anyone can write.
We'll get to creating and authorising more users later, for now I suggest to add yourself to each whitelist, by copying your pubkey into each JSON file. For me this looks as follows (note, I use the 'hex' version of the pubkey, rather than the npub)–
{ "pubkeys": [ "1bda7e1f7396bda2d1ef99033da8fd2dc362810790df9be62f591038bb97c4d9" ] }If this is your first time using Nostr and you don't yet have any user keys, it is easy and free to get one. You can get one from any Nostr client like Jumble.social, any tool like NAK or nostrtool.com or follow a comprehensive guide like my guide on mining a Nostr key.
4 – Launch your relay
If you are using my Docker fork from above, then–
docker compose upYour relay should now be running on port 3334 and ready to accept web socket connections from your client.
Before you move on to set up the client, it's helpful to quickly test that it is running as expected.
5 – Test your websocket connection
For this I use a tool called wscat to make a websocket connection.
You may need to install wscat, e.g.
npm install -g wscatAnd then run it, e.g.
wscat -c ws://localhost:3334(note use
ws://for localhost, rather thanwss://).If your relay is working successfully then it should receive your websocket connection request and respond with an AUTH token, asking you to identify yourself as a user in the relay's
read_whitelist.json(using the standard outlined in NIP-42), e.g.``` Connected (press CTRL+C to quit) < ["AUTH","13206fea43ef2952"]
```
You do not need to authorise for now.
If you received this kind of message, your relay is working successfully.
Set a subdomain for your relay
Let's connect a domain name so your community members can access your relay.
1 – Configure DNS
At a high level –
- Get your domain (buy one if you need to)
- Get the IP address of your VPS
- In your domain's DNS settings add those records as an A record to the subdomain of your choice, e.g.
relayas inrelay.your_domain_name.com, or in my caseassistantrelay.rodbishop.nz
Your subdomain now points to your server.
2 – Configure reverse proxy
You need to redirect traffic from your subdomain to your relay at port
3334.On my VPS I use Caddy as a reverse proxy for a few projects, I have it sitting in a separate Docker network. To use it for my SW2 Relay required two steps.
First – I added configuration to Caddy's
Caddyfileto tell it what to do with requests for therelay.your_domain_name.comsubdomain. For me this looked like–assistantrelay.rodbishop.nz { reverse_proxy sw2-relay:3334 { # Enable WebSocket support header_up X-Forwarded-For {remote} header_up X-Forwarded-Proto {scheme} header_up X-Forwarded-Port {server_port} } }Second – I added the Caddy Docker network to the SW2
docker-compose.ymlto make it be part of the Caddy network. In my Docker branch, I provide this commented section which you can uncomment and use if you like.``` services: relay: ... relay configuration here ...
networks:
- caddy # Connect to a Caddy network for reverse proxy
networks:
caddy:
external: true # Connect to a Caddy network for reverse proxy
```
Your relay is now running at your domain name.
Run Jumble.social
Your client set up is very easy, as most heavy lifting is done by your relay. My client of choice is Jumble because it has features that focus the user experience on the community's content first. You have two options for running Jumble.
- Run your own local copy of Jumble by cloning the Github (optional)
- Use the public instance at Jumble.social (easier, and what we'll do in this demo)
If you (optionally) want to run your own local copy of Jumble:
git clone https://github.com/CodyTseng/jumble.git cd jumble npm install npm run devFor this demo, I will just use the public instance at http://jumble.social
Jumble has a very helpful user interface for set up and configuration. But, I wanted to think ahead to onboarding community members, and so instead I will do some work up front in order to give new members a smooth onboarding flow that I would suggest for an administrator to use in onboarding their community.
1 – Create a custom landing page URL for your community members to land on
When your users come to your website for the first time, you want them to get your community experience without any distraction. That will either be–
- A prompt to sign up or login (if only authorised users can read content)
- The actual content from your other community members (If all users can read content)
Your landing page URL will look like:
http://jumble.social/?r=wss://relay.your_domain_name.comhttp://jumble.social/– the URL of the Jumble instance you are using?r=– telling Jumble to read from a relaywss://– relays connect via websocket using wss, rather than httpsrelay.your_domain_name.com– the domain name of your relay
For me, this URL looks like
http://jumble.social/?r=wss://assistantrelay.rodbishop.nz2 – Visit your custom Jumble URL
This should load the landing page of your relay on Jumble.
In the background, Jumble has attempted to establish a websocket connection to your relay.
If your relay is configured with read authentication, it has sent a challenge to Jumble asking your user to authenticate. Jumble, accordingly should now be showing you a login screen, asking your user to login.
3 – Login or Sign Up
You will see a variety of sign up and login options. To test, log in with the private key that you have configured to have read and write access.
In the background, Jumble has connected via websocket to your relay, checked that your user is authorised to view notes, and if so, has returned all the content on the relay. (If this is your first time here, there would not be any content yet).
If you give this link to your users to use as their landing page, they will land, login, and see only notes from members of your community.
4– Make your first post to your community
Click the "post" button and post a note. Jumble offers you the option to "Send only to relay.your_domain_name.com".
- If set to on, then Jumble will post the note only to your relay, no others. It will also include a specific tag (the
"-"tag) which requests relays to not forward the note across the network. Only your community members viewing notes on your community relay can see it. - If set to off, then Jumble will post the note to your relay and also the wider public Nostr network. Community members viewing notes on the relay can see it, and so can any user of the wider Nostr network.
5– Optional, configure your relay sets
At the top of the screen you should now see a dropdown with the URL of your relay.
Each user can save this relay to a "relay set" for future use, and also view, add or delete other relays sets including some sets which Jumble comes with set up by default.
As an admin you can use this to give users access to multiple relays. And, as a user, you can use this to access posts from multiple different community relays, all within the one client.
Your community website is up and running
That is the basic set up completed.
- You have a website where your community members can visit a URL to post notes and view all notes from all other members of the community.
- You have basic administration to enforce your own read and write permissions very simply in two json files.
Let's check in with my user requirements as a community admin–
- My community is saving content to a server where I control access
- My users view only that content by default, and are not exposed to any wider public social network unless they knowingly select that
- My user's content is a) viewable only by other community members, or b) by the wider public, at the user's discretion
- Other people are maintaining the code for me
- It's free
This setup has scope to solve my dog fooding issues from earlier–
- If adopted, my tech community can iterate the interface to suit its needs, find great content, and share content beyond the community.
- If adopted, my kids social groups can each have their own relays, but I can post to all of them together, or view a consolidated feed.
- If adopted, my team can chat with each other for free. I can self host this. It can natively interoperate with any other Nostr SaaS. It would be entirely private and will not be captured to train a Big Co AI without my consent.
Using your community website in practice
An example onboarding flow
- A new member joins your IRL community
- Your admin person gives them your landing page URL where they can view all the posts by your community members – If you have configured your relay to have no read auth required, then they can land on that landing page and immediately start viewing your community's posts, a great landing experience
- The user user creates a Nostr profile, and provides the admin person with their public key
- The admin person adds their key to the whitelists to read and write as you desire.
Default inter-op with the wider Nostr network
- If you change your mind on SW2 and want to use a different relay, your notes will be supported natively, and you can migrate on your own terms
- If you change your mind on Jumble and want to use a different client, your relay will be supported natively, and you can migrate on your own terms
- If you want to add other apps to your community's experience, every Nostr app will interoperate with your community by default – see the huge list at Awesome Nostr
- If any of your users want to view your community notes inside some other Nostr client – perhaps to see a consolidated feed of notes from all their different communities – they can.
For me, I use Amethyst app as my main Nostr client to view the public posts from people I follow. I have added my private community relay to Amethyst, and now my community posts appear alongside all these other posts in a single consolidated feed.
Scope to further improve
- You can run multiple different relays with different user access – e.g. one for wider company and one for your team
- You can run your own fork of Jumble and change the interface to suit you needs – e.g. add your logo, change the colours, link to other resources from the sidebar.
Other ideas for running communities
- Guest accounts: You can give a user "guest" access – read auth, but no write auth – to help people see the value of your community before becoming members.
- Running a knowledge base: You can whitelist users to read notes, but only administrators can post notes.
- Running a blind dropbox: You can whitelist users to post notes, but only the administrator can read notes.
- Running on a local terminal only: With Jumble and SW2 installed on a machine, running at –
localhost:5173for Jumble, andlocalhost:3334for SW2 you can have an entirely local experience athttp://localhost:5173/?r=ws://localhost:3334.
What's Next?
In my first four blogs I explored creating a good Nostr setup with Vanity Npub, Lightning Payments, Nostr Addresses at Your Domain, and Personal Nostr Relay.
Then in my latest three blogs I explored different types of interoperability with NFC cards, n8n Workflow Automation, and now running a private community website on Nostr.
For this community website–
- There is scope to make some further enhancements to SW2, including to add a "Blossom" media server so that community admins can self-host their own rich media, and to create an admin screen for administration of the whitelists using NIP-86.
- There is scope to explore all other kinds of Nostr clients to form the front-end of community websites, including Chachi.chat, Flotilla, and others.
- Nostr includes a whole variety of different optional standards for making more elaborate online communities including NIP-28, NIP-29, NIP-17, NIP-72 (etc). Each gives certain different capabilities, and I haven't used any of them! For this simple demo they are not required, but each could be used to extend the capabilities of the admin and community.
I am also doing a lot of work with AI on Nostr, including that I use my private community website as a front-end for engaging with a Nostr AI. I'll post about this soon too.
Please be sure to let me know if you think there's another Nostr topic you'd like to see me tackle.
GM Nostr.
-
 @ e2388e53:0e93e8a9
2025-05-03 16:44:06
@ e2388e53:0e93e8a9
2025-05-03 16:44:06- Die Befreiung beginnt nicht mit einem Aufschrei, sondern mit einem leisen Nein.
- Herkunft ist kein Zuhause. Es ist der Ort, an dem man lernt, warum man gehen musste.
- Manche Familien sind wie alte Götter: Man glaubt an sie, obwohl sie längst gestorben sind.
- Wer das Nichts anschaut, sieht sich selbst: ein Schatten, der sich für Licht hält.
- Das Schweigen des Universums ist keine Antwort – es ist die endgültige Form der Gleichgültigkeit.
- In der Dämmerung unserer Tage suchen wir die Sonne, die nur in der Erinnerung noch brennt.
- Freiheit beginnt, wenn der Mensch aufhört, sich retten zu lassen.
- Wer nie verloren ging, hat sich selbst nie gesucht.
- Gedanken zerfallen wie Tropfen, die nie den Boden erreichen.
- Wahrheit ist selten laut. Sie flüstert – meist dann, wenn niemand mehr zuhört.
-
 @ fc7085c3:0b32a4cb
2025-05-03 16:17:10
@ fc7085c3:0b32a4cb
2025-05-03 16:17:10- ~~finish writing some experimental specs and store on hidden repo for later~~
- ~~fix bugs on in-house js web components framework (with react-like hooks)~~
- ~~add signal/reactive hooks to framework~~ (thx to nootropics)
- (ongoing) slooowly migrate kind:1 app from Qwik to above framework
- test feasibility of new app - codename: ZULULA. cool? flawed?
- if cool, finish ZULULA basic features
- nread.me: add nostr documentation (mpa for this part cause seo)
- nread.me: add nip crud (save on relay)
- nread.me: add nip curation (rating and labeling)
- nread.me: filter by curator / rating / labeling
- nread.me: seed curator (fiatjaf) adds other curators
- revamp kind:1 app login
- add basic engagement features then halt kind:1 app dev
- start simplified messenger app to test custom chat spec
- ...don't know what's next yet
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 2dd9250b:6e928072
2025-03-22 00:22:40
@ 2dd9250b:6e928072
2025-03-22 00:22:40Vi recentemente um post onde a pessoa diz que aquele final do filme O Doutrinador (2019) não faz sentido porque mesmo o protagonista explodindo o Palácio dos Três Poderes, não acaba com a corrupção no Brasil.
Progressistas não sabem ler e não conseguem interpretar textos corretamente. O final de Doutrinador não tem a ver com isso, tem a ver com a relação entre o Herói e a sua Cidade.
Nas histórias em quadrinhos há uma ligação entre a cidade e o Super-Herói. Gotham City por exemplo, cria o Batman. Isso é mostrado em The Batman (2022) e em Batman: Cavaleiro das Trevas, quando aquele garoto no final, diz para o Batman não fugir, porque ele queria ver o Batman de novo. E o Comissário Gordon diz que o "Batman é o que a cidade de Gotham precisa."
Batman: Cavaleiro das Trevas Ressurge mostra a cidade de Gotham sendo tomada pela corrupção e pela ideologia do Bane. A Cidade vai definhando em imoralidade e o Bruce, ao olhar da prisão a cidade sendo destruída, decide que o Batman precisa voltar porque se Gotham for destruída, o Batman é destruído junto. E isso o da forças para consegue fugir daquele poço e voltar para salvar Gotham.
Isso também é mostrado em Demolidor. Na série Demolidor o Matt Murdock sempre fala que precisa defender a cidade Cozinha do Inferno; que o Fisk não vai dominar a cidade e fazer o que ele quiser nela. Inclusive na terceira temporada isso fica mais evidente na luta final na mansão do Fisk, onde Matt grita que agora a cidade toda vai saber o que ele fez; a cidade vai ver o mal que ele é para Hell's Kitchen, porque a gente sabe que o Fisk fez de tudo para a imagem do Demolidor entrar e descrédito perante os cidadãos, então o que acontece no final do filme O Doutrinador não significa que ele está acabando com a corrupção quando explode o Congresso, ele está praticamente interrompendo o ciclo do sistema, colocando uma falha em sua engrenagem.
Quando você ouve falar de Brasília, você pensa na corrupção dos políticos, onde a farra acontece,, onde corruptos desviam dinheiro arrecadado dos impostos, impostos estes que são centralizados na União. Então quando você ouve falarem de Brasília, sempre pensa que o pessoal que mora lá, mora junto com tudo de podre que acontece no Brasil.
Logo quando o Doutrinador explode tudo ali, ele está basicamente destruindo o mecanismo que suja Brasília. Ele está fazendo isso naquela cidade. Porque o símbolo da cidade é justamente esse, a farsa de que naquele lugar o povo será ouvido e a justiça será feita. Ele está destruindo a ideologia de que o Estado nos protege, nos dá segurança, saúde e educação. Porque na verdade o Estado só existe para privilegiar os políticos, funcionários públicos de auto escalão, suas famílias e amigos. Enquanto que o povo sofre para sustentar a elite política. O protagonista Miguel entendeu isso quando a filha dele morreu na fila do SUS.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ d34e832d:383f78d0
2025-03-21 20:31:24
@ d34e832d:383f78d0
2025-03-21 20:31:24Introduction
Unlike other cetaceans that rely on whistles and songs, sperm whales primarily use echolocation and patterned click sequences to convey information. This paper explores the structure, function, and implications of their vocal communication, particularly in relation to their social behaviors and cognitive abilities.
1. The Nature of Sperm Whale Vocalizations
Sperm whales produce three primary types of clicks:
- Echolocation clicks for navigation and hunting.
- Regular clicks used in deep diving.
- Codas, which are rhythmic sequences exchanged between individuals, believed to function in social bonding and identification.Each whale possesses a monumental sound-producing organ, the spermaceti organ, which allows for the production of powerful sounds that can travel long distances. The structure of these clicks suggests a level of vocal learning and adaptation, as different populations exhibit distinct coda repertoires.
2. Cultural and Regional Variation in Codas
Research indicates that different sperm whale clans have unique dialects, much like human languages. These dialects are not genetically inherited but culturally transmitted, meaning whales learn their communication styles from social interactions rather than instinct alone. Studies conducted in the Caribbean and the Pacific have revealed that whales in different regions have distinct coda patterns, with some being universal and others specific to certain clans.
3. Social Organization and Communication
Sperm whales are matrilineal and live in stable social units composed of mothers, calves, and juveniles, while males often lead solitary lives. Communication plays a critical role in maintaining social bonds within these groups.
- Codas serve as an acoustic signature that helps individuals recognize each other.
- More complex codas may function in coordinating group movements or teaching young whales.
- Some researchers hypothesize that codas convey emotional states, much like tone of voice in human speech.4. Theories on Whale Intelligence and Language-Like Communication
The complexity of sperm whale vocalization raises profound questions about their cognitive abilities.
- Some researchers argue that sperm whale communication exhibits combinatorial properties, meaning that codas might function in ways similar to human phonemes, allowing for an extensive range of meanings.
- Studies using AI and machine learning have attempted to decode potential syntax patterns, but a full understanding of their language remains elusive.5. Conservation Implications and the Need for Further Research
Understanding sperm whale communication is essential for conservation efforts. Noise pollution from shipping, sonar, and industrial activities can interfere with whale vocalizations, potentially disrupting social structures and navigation. Future research must focus on long-term coda tracking, cross-species comparisons, and experimental approaches to deciphering their meaning.
Consider
Sperm whale vocal communication represents one of the most intriguing areas of marine mammal research. Their ability to transmit learned vocalizations across generations suggests a high degree of cultural complexity. Although we have yet to fully decode their language, the study of sperm whale codas offers critical insights into non-human intelligence, social structures, and the evolution of communication in the animal kingdom.
-
 @ 6ad3e2a3:c90b7740
2025-03-21 18:21:50
@ 6ad3e2a3:c90b7740
2025-03-21 18:21:50There are two ways things happen in this world: top-down and bottom-up. Top-down is via authoritarian edict, i.e. fascism, no matter how benign-seeming. It is the government imposing a tax, incentivizing a behavior, creating a new law. Bottom-up is the organic process of people doing what interests them voluntarily, what benefits them, what they decide is best individually.
There is but one legitimate role for top-down and that is in creating good conditions for bottom up. The US Constitution is fascism in that it forces you to adhere to its edicts as the supreme law of the land. But it’s also an effective boundary creating the necessary conditions for free markets, free expression, creativity and prosperity.
All governments are fascistic in that they use force to achieve their agendas. But the best ones use only the minimum necessary force to create conditions for bottom-up prosperity. There is no other kind of prosperity.
. . .
Governments aren’t the only entities that are fascistic. Schools, corporations, institutions and individuals, almost invariably, are too. Yes, I am a fascist and very likely so are you. Don’t believe me? Do you have a voice inside your head telling you what you must get done today, evaluating your progress as a person, critiquing and coercing you into doing things that are “good” for you and avoiding ones that are “bad”? If so, you are fascist.
Why not just trust yourself to make the right choices? Why all the nudging, coaxing, coaching, evaluating and gamifying? Who is this voice, what gives it the authority, the requisite wisdom to manage your affairs? Haven’t all your shortcomings, disappointments and general dissatisfactions taken place despite its ever-presence? What makes you think you are better off for having had this in-house micromanagement?
. . .
The top-down edicts that rule our lives are by and large unnecessarily oppressive. Yes, we should create some good top-down conditions for bottom up organic thriving like buying healthy food, getting fresh air, not consuming excessive amounts of alcohol or drugs, but the moment to moment hall-monitoring, the voice that requires you to achieve something or justify your existence? That’s fascism.
. . .
The mind is a powerful tool when it comes to planning, doing math or following a recipe, but if it can’t be turned off, if it’s not just optimizing your path from A to B, but optimizing YOU, that’s fascism.
. . .
I think about the problem of human governance through this lens. I imagine everyone charged with power over a polity has an agenda, and that agenda, insofar as it requires force to achieve, is fascistic. They want it to go this way rather than that way, and some people don’t agree. The quality of leadership then is the extent to which that force is used to preserve the bottom-up freedom of the individual to pursue his interests without undue interference, either from authorities themselves or other individuals who would unduly disrupt him.
The Constitution is an excellent guideline for this, and I surely won’t be able to come up with a better one in this Substack. It’s why I support Trump’s efforts to trim the top-down public sector and return productivity to the bottom-up private one, why I support deportation of adjudicated criminals who are here illegally, but oppose removing people with green cards or on valid student visas for protesting via constitutionally protected speech.
I don’t root for politicians like they play for my favorite sports team. I root for the freedom of the individual, the possibility of a largely bottom-up society wherein prosperity is possible. And I do this while knowing it will never happen exactly the way I would like, so long as I am bound by the fascism coming from inside the house.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 4c96d763:80c3ee30
2025-03-20 21:37:39
@ 4c96d763:80c3ee30
2025-03-20 21:37:39Changes
William Casarin (13):
- fix compile issues on macOS
- print-search-keys: add size of key information
- fix iOS crash on latest version
- fix up some nostrdb-mcp discrepancies
- ndb: fix author input
- test: fix test failure
- ndb: enhance query options with more descriptive flags
- fix more ndb query bugs
- config: custom writer scratch size
- compile fix
- Initial relay index implementation
- relay: add note relay iteration
- ndb: add print-relay-kind-index-keys
pushed to nostrdb:refs/heads/master
-
 @ 8fb140b4:f948000c
2025-03-20 01:29:06
@ 8fb140b4:f948000c
2025-03-20 01:29:06As many of you know, https://nostr.build has recently launched a new compatibility layer for the Blossom protocol blossom.band. You can find all the details about what it supports and its limitations by visiting the URL.
I wanted to cover some of the technical details about how it works here. One key difference you may notice is that the service acts as a linker, redirecting requests for the media hash to the actual source of the media—specifically, the nostr.build URL. This allows us to maintain a unified CDN cache and ensure that your media is served as quickly as possible.
Another difference is that each uploaded media/blob is served under its own subdomain (e.g.,
npub1[...].blossom.band), ensuring that your association with the blob is controlled by you. If you decide to delete the media for any reason, we ensure that the link is broken, even if someone else has duplicated it using the same hash.To comply with the Blossom protocol, we also link the same hash under the main (apex) domain (blossom.band) and collect all associations under it. This ensures that Blossom clients can fetch media based on users’ Blossom server settings. If you are the sole owner of the hash and there are no duplicates, deleting the media removes the link from the main domain as well.
Lastly, in line with our mission to protect users’ privacy, we reject any media that contains private metadata (such as GPS coordinates, user comments, or camera serial numbers) or strip it if you use the
/media/endpoint for upload.As always, your feedback is welcome and appreciated. Thank you!
-
 @ e2388e53:0e93e8a9
2025-05-03 11:39:45
@ e2388e53:0e93e8a9
2025-05-03 11:39:45- Melancholie ist die sanfteste Form der Rebellion – ein Nein, das sich in Schönheit kleidet, um nicht verbrannt zu werden.
- Die Menschheit sucht nach Erlösung – und nennt das Kind dabei „Zukunft“, ohne zu merken, wie schwer diese Krone wiegt.
- Nähe ohne Ehrlichkeit ist nur ein getarnter Abstand.
- Jede Zentralisierung ist ein Denkfehler, der Macht als Fürsorge tarnt.
- Sehnsucht ist ein Fluss, der rückwärts fließt – du watest hinein, doch das Ufer zieht sich fort, unerreichbar fern.
- Die letzte Form der Sklaverei ist die freiwillige Abhängigkeit.
- Ein Kind spielt nicht, um zu vergessen – es spielt, weil es noch nicht gelernt hat zu verdrängen.
- Freiheit ist die Fähigkeit, in Ketten zu tanzen.
- Das Leben ist der Widerhall eines sterbenden Willens. Nur im Nichts finden wir Erlösung.
- Wer Kinder erzieht, erzieht auch seine Schatten – sie kommen zurück, wenn das Haus still ist.
-
 @ 21335073:a244b1ad
2025-03-18 20:47:50
@ 21335073:a244b1ad
2025-03-18 20:47:50Warning: This piece contains a conversation about difficult topics. Please proceed with caution.
TL;DR please educate your children about online safety.
Julian Assange wrote in his 2012 book Cypherpunks, “This book is not a manifesto. There isn’t time for that. This book is a warning.” I read it a few times over the past summer. Those opening lines definitely stood out to me. I wish we had listened back then. He saw something about the internet that few had the ability to see. There are some individuals who are so close to a topic that when they speak, it’s difficult for others who aren’t steeped in it to visualize what they’re talking about. I didn’t read the book until more recently. If I had read it when it came out, it probably would have sounded like an unknown foreign language to me. Today it makes more sense.
This isn’t a manifesto. This isn’t a book. There is no time for that. It’s a warning and a possible solution from a desperate and determined survivor advocate who has been pulling and unraveling a thread for a few years. At times, I feel too close to this topic to make any sense trying to convey my pathway to my conclusions or thoughts to the general public. My hope is that if nothing else, I can convey my sense of urgency while writing this. This piece is a watchman’s warning.
When a child steps online, they are walking into a new world. A new reality. When you hand a child the internet, you are handing them possibilities—good, bad, and ugly. This is a conversation about lowering the potential of negative outcomes of stepping into that new world and how I came to these conclusions. I constantly compare the internet to the road. You wouldn’t let a young child run out into the road with no guidance or safety precautions. When you hand a child the internet without any type of guidance or safety measures, you are allowing them to play in rush hour, oncoming traffic. “Look left, look right for cars before crossing.” We almost all have been taught that as children. What are we taught as humans about safety before stepping into a completely different reality like the internet? Very little.
I could never really figure out why many folks in tech, privacy rights activists, and hackers seemed so cold to me while talking about online child sexual exploitation. I always figured that as a survivor advocate for those affected by these crimes, that specific, skilled group of individuals would be very welcoming and easy to talk to about such serious topics. I actually had one hacker laugh in my face when I brought it up while I was looking for answers. I thought maybe this individual thought I was accusing them of something I wasn’t, so I felt bad for asking. I was constantly extremely disappointed and would ask myself, “Why don’t they care? What could I say to make them care more? What could I say to make them understand the crisis and the level of suffering that happens as a result of the problem?”
I have been serving minor survivors of online child sexual exploitation for years. My first case serving a survivor of this specific crime was in 2018—a 13-year-old girl sexually exploited by a serial predator on Snapchat. That was my first glimpse into this side of the internet. I won a national award for serving the minor survivors of Twitter in 2023, but I had been working on that specific project for a few years. I was nominated by a lawyer representing two survivors in a legal battle against the platform. I’ve never really spoken about this before, but at the time it was a choice for me between fighting Snapchat or Twitter. I chose Twitter—or rather, Twitter chose me. I heard about the story of John Doe #1 and John Doe #2, and I was so unbelievably broken over it that I went to war for multiple years. I was and still am royally pissed about that case. As far as I was concerned, the John Doe #1 case proved that whatever was going on with corporate tech social media was so out of control that I didn’t have time to wait, so I got to work. It was reading the messages that John Doe #1 sent to Twitter begging them to remove his sexual exploitation that broke me. He was a child begging adults to do something. A passion for justice and protecting kids makes you do wild things. I was desperate to find answers about what happened and searched for solutions. In the end, the platform Twitter was purchased. During the acquisition, I just asked Mr. Musk nicely to prioritize the issue of detection and removal of child sexual exploitation without violating digital privacy rights or eroding end-to-end encryption. Elon thanked me multiple times during the acquisition, made some changes, and I was thanked by others on the survivors’ side as well.
I still feel that even with the progress made, I really just scratched the surface with Twitter, now X. I left that passion project when I did for a few reasons. I wanted to give new leadership time to tackle the issue. Elon Musk made big promises that I knew would take a while to fulfill, but mostly I had been watching global legislation transpire around the issue, and frankly, the governments are willing to go much further with X and the rest of corporate tech than I ever would. My work begging Twitter to make changes with easier reporting of content, detection, and removal of child sexual exploitation material—without violating privacy rights or eroding end-to-end encryption—and advocating for the minor survivors of the platform went as far as my principles would have allowed. I’m grateful for that experience. I was still left with a nagging question: “How did things get so bad with Twitter where the John Doe #1 and John Doe #2 case was able to happen in the first place?” I decided to keep looking for answers. I decided to keep pulling the thread.
I never worked for Twitter. This is often confusing for folks. I will say that despite being disappointed in the platform’s leadership at times, I loved Twitter. I saw and still see its value. I definitely love the survivors of the platform, but I also loved the platform. I was a champion of the platform’s ability to give folks from virtually around the globe an opportunity to speak and be heard.
I want to be clear that John Doe #1 really is my why. He is the inspiration. I am writing this because of him. He represents so many globally, and I’m still inspired by his bravery. One child’s voice begging adults to do something—I’m an adult, I heard him. I’d go to war a thousand more lifetimes for that young man, and I don’t even know his name. Fighting has been personally dark at times; I’m not even going to try to sugarcoat it, but it has been worth it.
The data surrounding the very real crime of online child sexual exploitation is available to the public online at any time for anyone to see. I’d encourage you to go look at the data for yourself. I believe in encouraging folks to check multiple sources so that you understand the full picture. If you are uncomfortable just searching around the internet for information about this topic, use the terms “CSAM,” “CSEM,” “SG-CSEM,” or “AI Generated CSAM.” The numbers don’t lie—it’s a nightmare that’s out of control. It’s a big business. The demand is high, and unfortunately, business is booming. Organizations collect the data, tech companies often post their data, governments report frequently, and the corporate press has covered a decent portion of the conversation, so I’m sure you can find a source that you trust.
Technology is changing rapidly, which is great for innovation as a whole but horrible for the crime of online child sexual exploitation. Those wishing to exploit the vulnerable seem to be adapting to each technological change with ease. The governments are so far behind with tackling these issues that as I’m typing this, it’s borderline irrelevant to even include them while speaking about the crime or potential solutions. Technology is changing too rapidly, and their old, broken systems can’t even dare to keep up. Think of it like the governments’ “War on Drugs.” Drugs won. In this case as well, the governments are not winning. The governments are talking about maybe having a meeting on potentially maybe having legislation around the crimes. The time to have that meeting would have been many years ago. I’m not advocating for governments to legislate our way out of this. I’m on the side of educating and innovating our way out of this.
I have been clear while advocating for the minor survivors of corporate tech platforms that I would not advocate for any solution to the crime that would violate digital privacy rights or erode end-to-end encryption. That has been a personal moral position that I was unwilling to budge on. This is an extremely unpopular and borderline nonexistent position in the anti-human trafficking movement and online child protection space. I’m often fearful that I’m wrong about this. I have always thought that a better pathway forward would have been to incentivize innovation for detection and removal of content. I had no previous exposure to privacy rights activists or Cypherpunks—actually, I came to that conclusion by listening to the voices of MENA region political dissidents and human rights activists. After developing relationships with human rights activists from around the globe, I realized how important privacy rights and encryption are for those who need it most globally. I was simply unwilling to give more power, control, and opportunities for mass surveillance to big abusers like governments wishing to enslave entire nations and untrustworthy corporate tech companies to potentially end some portion of abuses online. On top of all of it, it has been clear to me for years that all potential solutions outside of violating digital privacy rights to detect and remove child sexual exploitation online have not yet been explored aggressively. I’ve been disappointed that there hasn’t been more of a conversation around preventing the crime from happening in the first place.
What has been tried is mass surveillance. In China, they are currently under mass surveillance both online and offline, and their behaviors are attached to a social credit score. Unfortunately, even on state-run and controlled social media platforms, they still have child sexual exploitation and abuse imagery pop up along with other crimes and human rights violations. They also have a thriving black market online due to the oppression from the state. In other words, even an entire loss of freedom and privacy cannot end the sexual exploitation of children online. It’s been tried. There is no reason to repeat this method.
It took me an embarrassingly long time to figure out why I always felt a slight coldness from those in tech and privacy-minded individuals about the topic of child sexual exploitation online. I didn’t have any clue about the “Four Horsemen of the Infocalypse.” This is a term coined by Timothy C. May in 1988. I would have been a child myself when he first said it. I actually laughed at myself when I heard the phrase for the first time. I finally got it. The Cypherpunks weren’t wrong about that topic. They were so spot on that it is borderline uncomfortable. I was mad at first that they knew that early during the birth of the internet that this issue would arise and didn’t address it. Then I got over it because I realized that it wasn’t their job. Their job was—is—to write code. Their job wasn’t to be involved and loving parents or survivor advocates. Their job wasn’t to educate children on internet safety or raise awareness; their job was to write code.
They knew that child sexual abuse material would be shared on the internet. They said what would happen—not in a gleeful way, but a prediction. Then it happened.
I equate it now to a concrete company laying down a road. As you’re pouring the concrete, you can say to yourself, “A terrorist might travel down this road to go kill many, and on the flip side, a beautiful child can be born in an ambulance on this road.” Who or what travels down the road is not their responsibility—they are just supposed to lay the concrete. I’d never go to a concrete pourer and ask them to solve terrorism that travels down roads. Under the current system, law enforcement should stop terrorists before they even make it to the road. The solution to this specific problem is not to treat everyone on the road like a terrorist or to not build the road.
So I understand the perceived coldness from those in tech. Not only was it not their job, but bringing up the topic was seen as the equivalent of asking a free person if they wanted to discuss one of the four topics—child abusers, terrorists, drug dealers, intellectual property pirates, etc.—that would usher in digital authoritarianism for all who are online globally.
Privacy rights advocates and groups have put up a good fight. They stood by their principles. Unfortunately, when it comes to corporate tech, I believe that the issue of privacy is almost a complete lost cause at this point. It’s still worth pushing back, but ultimately, it is a losing battle—a ticking time bomb.
I do think that corporate tech providers could have slowed down the inevitable loss of privacy at the hands of the state by prioritizing the detection and removal of CSAM when they all started online. I believe it would have bought some time, fewer would have been traumatized by that specific crime, and I do believe that it could have slowed down the demand for content. If I think too much about that, I’ll go insane, so I try to push the “if maybes” aside, but never knowing if it could have been handled differently will forever haunt me. At night when it’s quiet, I wonder what I would have done differently if given the opportunity. I’ll probably never know how much corporate tech knew and ignored in the hopes that it would go away while the problem continued to get worse. They had different priorities. The most voiceless and vulnerable exploited on corporate tech never had much of a voice, so corporate tech providers didn’t receive very much pushback.
Now I’m about to say something really wild, and you can call me whatever you want to call me, but I’m going to say what I believe to be true. I believe that the governments are either so incompetent that they allowed the proliferation of CSAM online, or they knowingly allowed the problem to fester long enough to have an excuse to violate privacy rights and erode end-to-end encryption. The US government could have seized the corporate tech providers over CSAM, but I believe that they were so useful as a propaganda arm for the regimes that they allowed them to continue virtually unscathed.
That season is done now, and the governments are making the issue a priority. It will come at a high cost. Privacy on corporate tech providers is virtually done as I’m typing this. It feels like a death rattle. I’m not particularly sure that we had much digital privacy to begin with, but the illusion of a veil of privacy feels gone.
To make matters slightly more complex, it would be hard to convince me that once AI really gets going, digital privacy will exist at all.
I believe that there should be a conversation shift to preserving freedoms and human rights in a post-privacy society.
I don’t want to get locked up because AI predicted a nasty post online from me about the government. I’m not a doomer about AI—I’m just going to roll with it personally. I’m looking forward to the positive changes that will be brought forth by AI. I see it as inevitable. A bit of privacy was helpful while it lasted. Please keep fighting to preserve what is left of privacy either way because I could be wrong about all of this.
On the topic of AI, the addition of AI to the horrific crime of child sexual abuse material and child sexual exploitation in multiple ways so far has been devastating. It’s currently out of control. The genie is out of the bottle. I am hopeful that innovation will get us humans out of this, but I’m not sure how or how long it will take. We must be extremely cautious around AI legislation. It should not be illegal to innovate even if some bad comes with the good. I don’t trust that the governments are equipped to decide the best pathway forward for AI. Source: the entire history of the government.
I have been personally negatively impacted by AI-generated content. Every few days, I get another alert that I’m featured again in what’s called “deep fake pornography” without my consent. I’m not happy about it, but what pains me the most is the thought that for a period of time down the road, many globally will experience what myself and others are experiencing now by being digitally sexually abused in this way. If you have ever had your picture taken and posted online, you are also at risk of being exploited in this way. Your child’s image can be used as well, unfortunately, and this is just the beginning of this particular nightmare. It will move to more realistic interpretations of sexual behaviors as technology improves. I have no brave words of wisdom about how to deal with that emotionally. I do have hope that innovation will save the day around this specific issue. I’m nervous that everyone online will have to ID verify due to this issue. I see that as one possible outcome that could help to prevent one problem but inadvertently cause more problems, especially for those living under authoritarian regimes or anyone who needs to remain anonymous online. A zero-knowledge proof (ZKP) would probably be the best solution to these issues. There are some survivors of violence and/or sexual trauma who need to remain anonymous online for various reasons. There are survivor stories available online of those who have been abused in this way. I’d encourage you seek out and listen to their stories.
There have been periods of time recently where I hesitate to say anything at all because more than likely AI will cover most of my concerns about education, awareness, prevention, detection, and removal of child sexual exploitation online, etc.
Unfortunately, some of the most pressing issues we’ve seen online over the last few years come in the form of “sextortion.” Self-generated child sexual exploitation (SG-CSEM) numbers are continuing to be terrifying. I’d strongly encourage that you look into sextortion data. AI + sextortion is also a huge concern. The perpetrators are using the non-sexually explicit images of children and putting their likeness on AI-generated child sexual exploitation content and extorting money, more imagery, or both from minors online. It’s like a million nightmares wrapped into one. The wild part is that these issues will only get more pervasive because technology is harnessed to perpetuate horror at a scale unimaginable to a human mind.
Even if you banned phones and the internet or tried to prevent children from accessing the internet, it wouldn’t solve it. Child sexual exploitation will still be with us until as a society we start to prevent the crime before it happens. That is the only human way out right now.
There is no reset button on the internet, but if I could go back, I’d tell survivor advocates to heed the warnings of the early internet builders and to start education and awareness campaigns designed to prevent as much online child sexual exploitation as possible. The internet and technology moved quickly, and I don’t believe that society ever really caught up. We live in a world where a child can be groomed by a predator in their own home while sitting on a couch next to their parents watching TV. We weren’t ready as a species to tackle the fast-paced algorithms and dangers online. It happened too quickly for parents to catch up. How can you parent for the ever-changing digital world unless you are constantly aware of the dangers?
I don’t think that the internet is inherently bad. I believe that it can be a powerful tool for freedom and resistance. I’ve spoken a lot about the bad online, but there is beauty as well. We often discuss how victims and survivors are abused online; we rarely discuss the fact that countless survivors around the globe have been able to share their experiences, strength, hope, as well as provide resources to the vulnerable. I do question if giving any government or tech company access to censorship, surveillance, etc., online in the name of serving survivors might not actually impact a portion of survivors negatively. There are a fair amount of survivors with powerful abusers protected by governments and the corporate press. If a survivor cannot speak to the press about their abuse, the only place they can go is online, directly or indirectly through an independent journalist who also risks being censored. This scenario isn’t hard to imagine—it already happened in China. During #MeToo, a survivor in China wanted to post their story. The government censored the post, so the survivor put their story on the blockchain. I’m excited that the survivor was creative and brave, but it’s terrifying to think that we live in a world where that situation is a necessity.
I believe that the future for many survivors sharing their stories globally will be on completely censorship-resistant and decentralized protocols. This thought in particular gives me hope. When we listen to the experiences of a diverse group of survivors, we can start to understand potential solutions to preventing the crimes from happening in the first place.
My heart is broken over the gut-wrenching stories of survivors sexually exploited online. Every time I hear the story of a survivor, I do think to myself quietly, “What could have prevented this from happening in the first place?” My heart is with survivors.
My head, on the other hand, is full of the understanding that the internet should remain free. The free flow of information should not be stopped. My mind is with the innocent citizens around the globe that deserve freedom both online and offline.
The problem is that governments don’t only want to censor illegal content that violates human rights—they create legislation that is so broad that it can impact speech and privacy of all. “Don’t you care about the kids?” Yes, I do. I do so much that I’m invested in finding solutions. I also care about all citizens around the globe that deserve an opportunity to live free from a mass surveillance society. If terrorism happens online, I should not be punished by losing my freedom. If drugs are sold online, I should not be punished. I’m not an abuser, I’m not a terrorist, and I don’t engage in illegal behaviors. I refuse to lose freedom because of others’ bad behaviors online.
I want to be clear that on a long enough timeline, the governments will decide that they can be better parents/caregivers than you can if something isn’t done to stop minors from being sexually exploited online. The price will be a complete loss of anonymity, privacy, free speech, and freedom of religion online. I find it rather insulting that governments think they’re better equipped to raise children than parents and caretakers.
So we can’t go backwards—all that we can do is go forward. Those who want to have freedom will find technology to facilitate their liberation. This will lead many over time to decentralized and open protocols. So as far as I’m concerned, this does solve a few of my worries—those who need, want, and deserve to speak freely online will have the opportunity in most countries—but what about online child sexual exploitation?
When I popped up around the decentralized space, I was met with the fear of censorship. I’m not here to censor you. I don’t write code. I couldn’t censor anyone or any piece of content even if I wanted to across the internet, no matter how depraved. I don’t have the skills to do that.
I’m here to start a conversation. Freedom comes at a cost. You must always fight for and protect your freedom. I can’t speak about protecting yourself from all of the Four Horsemen because I simply don’t know the topics well enough, but I can speak about this one topic.
If there was a shortcut to ending online child sexual exploitation, I would have found it by now. There isn’t one right now. I believe that education is the only pathway forward to preventing the crime of online child sexual exploitation for future generations.
I propose a yearly education course for every child of all school ages, taught as a standard part of the curriculum. Ideally, parents/caregivers would be involved in the education/learning process.
Course: - The creation of the internet and computers - The fight for cryptography - The tech supply chain from the ground up (example: human rights violations in the supply chain) - Corporate tech - Freedom tech - Data privacy - Digital privacy rights - AI (history-current) - Online safety (predators, scams, catfishing, extortion) - Bitcoin - Laws - How to deal with online hate and harassment - Information on who to contact if you are being abused online or offline - Algorithms - How to seek out the truth about news, etc., online
The parents/caregivers, homeschoolers, unschoolers, and those working to create decentralized parallel societies have been an inspiration while writing this, but my hope is that all children would learn this course, even in government ran schools. Ideally, parents would teach this to their own children.
The decentralized space doesn’t want child sexual exploitation to thrive. Here’s the deal: there has to be a strong prevention effort in order to protect the next generation. The internet isn’t going anywhere, predators aren’t going anywhere, and I’m not down to let anyone have the opportunity to prove that there is a need for more government. I don’t believe that the government should act as parents. The governments have had a chance to attempt to stop online child sexual exploitation, and they didn’t do it. Can we try a different pathway forward?
I’d like to put myself out of a job. I don’t want to ever hear another story like John Doe #1 ever again. This will require work. I’ve often called online child sexual exploitation the lynchpin for the internet. It’s time to arm generations of children with knowledge and tools. I can’t do this alone.
Individuals have fought so that I could have freedom online. I want to fight to protect it. I don’t want child predators to give the government any opportunity to take away freedom. Decentralized spaces are as close to a reset as we’ll get with the opportunity to do it right from the start. Start the youth off correctly by preventing potential hazards to the best of your ability.
The good news is anyone can work on this! I’d encourage you to take it and run with it. I added the additional education about the history of the internet to make the course more educational and fun. Instead of cleaning up generations of destroyed lives due to online sexual exploitation, perhaps this could inspire generations of those who will build our futures. Perhaps if the youth is armed with knowledge, they can create more tools to prevent the crime.
This one solution that I’m suggesting can be done on an individual level or on a larger scale. It should be adjusted depending on age, learning style, etc. It should be fun and playful.
This solution does not address abuse in the home or some of the root causes of offline child sexual exploitation. My hope is that it could lead to some survivors experiencing abuse in the home an opportunity to disclose with a trusted adult. The purpose for this solution is to prevent the crime of online child sexual exploitation before it occurs and to arm the youth with the tools to contact safe adults if and when it happens.
In closing, I went to hell a few times so that you didn’t have to. I spoke to the mothers of survivors of minors sexually exploited online—their tears could fill rivers. I’ve spoken with political dissidents who yearned to be free from authoritarian surveillance states. The only balance that I’ve found is freedom online for citizens around the globe and prevention from the dangers of that for the youth. Don’t slow down innovation and freedom. Educate, prepare, adapt, and look for solutions.
I’m not perfect and I’m sure that there are errors in this piece. I hope that you find them and it starts a conversation.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ a39d19ec:3d88f61e
2025-03-18 17:16:50
@ a39d19ec:3d88f61e
2025-03-18 17:16:50Nun da das deutsche Bundesregime den Ruin Deutschlands beschlossen hat, der sehr wahrscheinlich mit dem Werkzeug des Geld druckens "finanziert" wird, kamen mir so viele Gedanken zur Geldmengenausweitung, dass ich diese für einmal niedergeschrieben habe.
Die Ausweitung der Geldmenge führt aus klassischer wirtschaftlicher Sicht immer zu Preissteigerungen, weil mehr Geld im Umlauf auf eine begrenzte Menge an Gütern trifft. Dies lässt sich in mehreren Schritten analysieren:
1. Quantitätstheorie des Geldes
Die klassische Gleichung der Quantitätstheorie des Geldes lautet:
M • V = P • Y
wobei:
- M die Geldmenge ist,
- V die Umlaufgeschwindigkeit des Geldes,
- P das Preisniveau,
- Y die reale Wirtschaftsleistung (BIP).Wenn M steigt und V sowie Y konstant bleiben, muss P steigen – also Inflation entstehen.
2. Gütermenge bleibt begrenzt
Die Menge an real produzierten Gütern und Dienstleistungen wächst meist nur langsam im Vergleich zur Ausweitung der Geldmenge. Wenn die Geldmenge schneller steigt als die Produktionsgütermenge, führt dies dazu, dass mehr Geld für die gleiche Menge an Waren zur Verfügung steht – die Preise steigen.
3. Erwartungseffekte und Spekulation
Wenn Unternehmen und Haushalte erwarten, dass mehr Geld im Umlauf ist, da eine zentrale Planung es so wollte, können sie steigende Preise antizipieren. Unternehmen erhöhen ihre Preise vorab, und Arbeitnehmer fordern höhere Löhne. Dies kann eine sich selbst verstärkende Spirale auslösen.
4. Internationale Perspektive
Eine erhöhte Geldmenge kann die Währung abwerten, wenn andere Länder ihre Geldpolitik stabil halten. Eine schwächere Währung macht Importe teurer, was wiederum Preissteigerungen antreibt.
5. Kritik an der reinen Geldmengen-Theorie
Der Vollständigkeit halber muss erwähnt werden, dass die meisten modernen Ökonomen im Staatsauftrag argumentieren, dass Inflation nicht nur von der Geldmenge abhängt, sondern auch von der Nachfrage nach Geld (z. B. in einer Wirtschaftskrise). Dennoch zeigt die historische Erfahrung, dass eine unkontrollierte Geldmengenausweitung langfristig immer zu Preissteigerungen führt, wie etwa in der Hyperinflation der Weimarer Republik oder in Simbabwe.
-
 @ 0d8633e5:eec06e57
2025-05-03 10:58:22
@ 0d8633e5:eec06e57
2025-05-03 10:58:22The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap. Automated Distribution: Ensures quick and secure token transfers to user wallets. Minimal Latency: Prevents blockchain congestion issues for seamless transfers. Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity. Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
Kindly visit globalfashexperts.com for more information Contact Information For more information or to make a purchase, please contact us through the following channels:
Email: globalfashexperts@gmail.com Flash USDT:https://globalfashexperts.com/product/flash-usdt/ Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/The Flash USDT Generator is responsible for producing and storing Flash USDT tokens with a flexible daily limit. It ensures a consistent supply of tokens for transactions while managing distribution securely and efficiently. Our Flash USDT offers a unique, temporary cryptocurrency that lasts for 90 days before expiring. This innovative solution allows for seamlesstrading and transferring of funds. Notably, the Flash Bitcoin and USDT can be transferred to 12 different wallets, including prominent platforms like Binance and Trust Wallet.
Features
- Adjustable Daily Limit: Customizable settings allow for modifying the token generation cap.
- Automated Distribution: Ensures quick and secure token transfers to user wallets.
- Minimal Latency: Prevents blockchain congestion issues for seamless transfers.
- Real-Time Transaction Verification: Each transaction is immediately verified on the respective blockchain explorer to confirm accuracy and validity.
- Temporary Nature: One of the most distinctive characteristics of USDT FLASH Generator is that it generates flash coin that is designed to disappear from any wallet after a period of ninety days. This unique feature ensures that any assets received in USDT FLASH will not linger indefinitely, creating a dynamic and engaging transaction experience.
 Kindly visit globalfashexperts.com for more information
Kindly visit globalfashexperts.com for more informationContact Information
For more information or to make a purchase, please contact us through the following channels:
- Email: globalfashexperts@gmail.com
- Flash USDT:https://globalfashexperts.com/product/flash-usdt/
- Flash USDT: https://globalfashexperts.com/product/flash-usdt-generator-software/
-
 @ d34e832d:383f78d0
2025-03-12 19:31:16
@ d34e832d:383f78d0
2025-03-12 19:31:16Micro with its operands and keybindings.
Micro is a modern, user-friendly text editor designed for the terminal. It offers extensive features, including mouse support, multiple cursors, syntax highlighting, and an intuitive command bar.
1. Command Bar
- Open it with
Ctrl-e - Supports shell-like argument parsing (single/double quotes, escaping)
- No environment variable expansion
2. Commands Overview
Commands are entered using
Ctrl-efollowed by the command.File Management
save ['filename']→ Save the current buffer (or "Save As" if a filename is given)quit→ Exit Microopen 'filename'→ Open a filereopen→ Reload the current file from diskpwd→ Print the current working directorycd 'path'→ Change the working directory
Navigation
goto 'line[:col]'→ Move to an absolute line and columnjump 'line[:col]'→ Move relative to the current line
Editing
replace 'search' 'value' ['flags']→ Replace text-a→ Replace all occurrences-l→ Literal search (no regex)replaceall 'search' 'value'→ Replace all without confirmationtextfilter 'sh-command'→ Pipe selected text through a shell command and replace it
Splitting and Tabs
vsplit ['filename']→ Open a vertical splithsplit ['filename']→ Open a horizontal splittab ['filename']→ Open a file in a new tabtabswitch 'tab'→ Switch between tabstabmove '[-+]n'→ Move tab position
Configuration
set 'option' 'value'→ Set a global optionsetlocal 'option' 'value'→ Set an option for the current buffershow 'option'→ Show the current value of an optionreset 'option'→ Reset an option to its default
Plugins
plugin list→ List installed pluginsplugin install 'pl'→ Install a pluginplugin remove 'pl'→ Remove a pluginplugin update ['pl']→ Update a pluginplugin search 'pl'→ Search for plugins
Miscellaneous
run 'sh-command'→ Run a shell command in the backgroundlog→ View debug messagesreload→ Reload all runtime files (settings, keybindings, syntax files, etc.)raw→ Debug terminal escape sequencesshowkey 'key'→ Show what action is bound to a keyterm ['exec']→ Open a terminal emulator running a specific commandlint→ Lint the current filecomment→ Toggle comments on a selected line or block
3. Keybindings Overview
| Action | Keybinding | |------------------|--------------| | Navigation | | | Move cursor left |
←orh| | Move cursor right |→orl| | Move cursor up |↑ork| | Move cursor down |↓orj| | Move to start of line |Home| | Move to end of line |End| | Move to start of file |Ctrl-Home| | Move to end of file |Ctrl-End| | Move by word left |Ctrl-←orCtrl-b| | Move by word right |Ctrl-→orCtrl-f| | Editing | | | Copy |Ctrl-c| | Cut |Ctrl-x| | Paste |Ctrl-v| | Undo |Ctrl-z| | Redo |Ctrl-Shift-z| | Delete word left |Ctrl-Backspace| | Delete word right |Ctrl-Delete| | Splitting & Tabs | | | Open horizontal split |Ctrl-w h| | Open vertical split |Ctrl-w v| | Switch tab left |Alt-←| | Switch tab right |Alt-→|For more, check the official keybindings:
🔗 Micro Keybindings 🔗Available Here
Final Thoughts
Micro is a powerful text editor for terminal users who want an alternative to Vim or Nano. With an intuitive command bar, extensive customization options, and full plugin support, it offers a lightweight yet feature-rich editing experience. 🚀
- Open it with
-
 @ 04c915da:3dfbecc9
2025-03-12 15:30:46
@ 04c915da:3dfbecc9
2025-03-12 15:30:46Recently we have seen a wave of high profile X accounts hacked. These attacks have exposed the fragility of the status quo security model used by modern social media platforms like X. Many users have asked if nostr fixes this, so lets dive in. How do these types of attacks translate into the world of nostr apps? For clarity, I will use X’s security model as representative of most big tech social platforms and compare it to nostr.
The Status Quo
On X, you never have full control of your account. Ultimately to use it requires permission from the company. They can suspend your account or limit your distribution. Theoretically they can even post from your account at will. An X account is tied to an email and password. Users can also opt into two factor authentication, which adds an extra layer of protection, a login code generated by an app. In theory, this setup works well, but it places a heavy burden on users. You need to create a strong, unique password and safeguard it. You also need to ensure your email account and phone number remain secure, as attackers can exploit these to reset your credentials and take over your account. Even if you do everything responsibly, there is another weak link in X infrastructure itself. The platform’s infrastructure allows accounts to be reset through its backend. This could happen maliciously by an employee or through an external attacker who compromises X’s backend. When an account is compromised, the legitimate user often gets locked out, unable to post or regain control without contacting X’s support team. That process can be slow, frustrating, and sometimes fruitless if support denies the request or cannot verify your identity. Often times support will require users to provide identification info in order to regain access, which represents a privacy risk. The centralized nature of X means you are ultimately at the mercy of the company’s systems and staff.
Nostr Requires Responsibility
Nostr flips this model radically. Users do not need permission from a company to access their account, they can generate as many accounts as they want, and cannot be easily censored. The key tradeoff here is that users have to take complete responsibility for their security. Instead of relying on a username, password, and corporate servers, nostr uses a private key as the sole credential for your account. Users generate this key and it is their responsibility to keep it safe. As long as you have your key, you can post. If someone else gets it, they can post too. It is that simple. This design has strong implications. Unlike X, there is no backend reset option. If your key is compromised or lost, there is no customer support to call. In a compromise scenario, both you and the attacker can post from the account simultaneously. Neither can lock the other out, since nostr relays simply accept whatever is signed with a valid key.
The benefit? No reliance on proprietary corporate infrastructure.. The negative? Security rests entirely on how well you protect your key.
Future Nostr Security Improvements
For many users, nostr’s standard security model, storing a private key on a phone with an encrypted cloud backup, will likely be sufficient. It is simple and reasonably secure. That said, nostr’s strength lies in its flexibility as an open protocol. Users will be able to choose between a range of security models, balancing convenience and protection based on need.
One promising option is a web of trust model for key rotation. Imagine pre-selecting a group of trusted friends. If your account is compromised, these people could collectively sign an event announcing the compromise to the network and designate a new key as your legitimate one. Apps could handle this process seamlessly in the background, notifying followers of the switch without much user interaction. This could become a popular choice for average users, but it is not without tradeoffs. It requires trust in your chosen web of trust, which might not suit power users or large organizations. It also has the issue that some apps may not recognize the key rotation properly and followers might get confused about which account is “real.”
For those needing higher security, there is the option of multisig using FROST (Flexible Round-Optimized Schnorr Threshold). In this setup, multiple keys must sign off on every action, including posting and updating a profile. A hacker with just one key could not do anything. This is likely overkill for most users due to complexity and inconvenience, but it could be a game changer for large organizations, companies, and governments. Imagine the White House nostr account requiring signatures from multiple people before a post goes live, that would be much more secure than the status quo big tech model.
Another option are hardware signers, similar to bitcoin hardware wallets. Private keys are kept on secure, offline devices, separate from the internet connected phone or computer you use to broadcast events. This drastically reduces the risk of remote hacks, as private keys never touches the internet. It can be used in combination with multisig setups for extra protection. This setup is much less convenient and probably overkill for most but could be ideal for governments, companies, or other high profile accounts.
Nostr’s security model is not perfect but is robust and versatile. Ultimately users are in control and security is their responsibility. Apps will give users multiple options to choose from and users will choose what best fits their need.
-
 @ d0aa74cd:603d35cd
2025-05-03 10:55:11
@ d0aa74cd:603d35cd
2025-05-03 10:55:11CLI #Haskell
https://photonsphere.org/post/2025-05-03-command-line-energy-prices-haskell/
-
 @ 21335073:a244b1ad
2025-03-12 00:40:25
@ 21335073:a244b1ad
2025-03-12 00:40:25Before I saw those X right-wing political “influencers” parading their Epstein binders in that PR stunt, I’d already posted this on Nostr, an open protocol.
“Today, the world’s attention will likely fixate on Epstein, governmental failures in addressing horrific abuse cases, and the influential figures who perpetrate such acts—yet few will center the victims and survivors in the conversation. The survivors of Epstein went to law enforcement and very little happened. The survivors tried to speak to the corporate press and the corporate press knowingly covered for him. In situations like these social media can serve as one of the only ways for a survivor’s voice to be heard.
It’s becoming increasingly evident that the line between centralized corporate social media and the state is razor-thin, if it exists at all. Time and again, the state shields powerful abusers when it’s politically expedient to do so. In this climate, a survivor attempting to expose someone like Epstein on a corporate tech platform faces an uphill battle—there’s no assurance their voice would even break through. Their story wouldn’t truly belong to them; it’d be at the mercy of the platform, subject to deletion at a whim. Nostr, though, offers a lifeline—a censorship-resistant space where survivors can share their truths, no matter how untouchable the abuser might seem. A survivor could remain anonymous here if they took enough steps.
Nostr holds real promise for amplifying survivor voices. And if you’re here daily, tossing out memes, take heart: you’re helping build a foundation for those who desperately need to be heard.“
That post is untouchable—no CEO, company, employee, or government can delete it. Even if I wanted to, I couldn’t take it down myself. The post will outlive me on the protocol.
The cozy alliance between the state and corporate social media hit me hard during that right-wing X “influencer” PR stunt. Elon owns X. Elon’s a special government employee. X pays those influencers to post. We don’t know who else pays them to post. Those influencers are spurred on by both the government and X to manage the Epstein case narrative. It wasn’t survivors standing there, grinning for photos—it was paid influencers, gatekeepers orchestrating yet another chance to re-exploit the already exploited.
The bond between the state and corporate social media is tight. If the other Epsteins out there are ever to be unmasked, I wouldn’t bet on a survivor’s story staying safe with a corporate tech platform, the government, any social media influencer, or mainstream journalist. Right now, only a protocol can hand survivors the power to truly own their narrative.
I don’t have anything against Elon—I’ve actually been a big supporter. I’m just stating it as I see it. X isn’t censorship resistant and they have an algorithm that they choose not the user. Corporate tech platforms like X can be a better fit for some survivors. X has safety tools and content moderation, making it a solid option for certain individuals. Grok can be a big help for survivors looking for resources or support! As a survivor, you know what works best for you, and safety should always come first—keep that front and center.
That said, a protocol is a game-changer for cases where the powerful are likely to censor. During China's # MeToo movement, survivors faced heavy censorship on social media platforms like Weibo and WeChat, where posts about sexual harassment were quickly removed, and hashtags like # MeToo or "woyeshi" were blocked by government and platform filters. To bypass this, activists turned to blockchain technology encoding their stories—like Yue Xin’s open letter about a Peking University case—into transaction metadata. This made the information tamper-proof and publicly accessible, resisting censorship since blockchain data can’t be easily altered or deleted.
I posted this on X 2/28/25. I wanted to try my first long post on a nostr client. The Epstein cover up is ongoing so it’s still relevant, unfortunately.
If you are a survivor or loved one who is reading this and needs support please reach out to: National Sexual Assault Hotline 24/7 https://rainn.org/
Hours: Available 24 hours
-
 @ 5f078e90:b2bacaa3
2025-05-03 10:18:41
@ 5f078e90:b2bacaa3
2025-05-03 10:18:41The Spoonbill's Dawn
In a marsh where reeds whispered secrets to the wind, a roseate spoonbill named Sable waded through dawn’s amber glow. Her pink feathers shimmered, catching the first light as she swept her spoon-shaped bill through the shallows, sifting for shrimp. Unlike her flock, who chattered and preened, Sable moved with quiet purpose, her eyes tracing ripples for signs of life.

Each morning, she returned to a lone cypress, its roots cradling a pool where minnows danced. Here, Sable had found an odd companion: a young alligator named Moss, whose emerald scales blended with the water’s edge. Moss never lunged, only watched, his eyes like polished stones. Sable, curious, began leaving shrimp at the pool’s edge. Moss, in turn, nudged smooth pebbles toward her, gifts from the marsh’s depths.
One dawn, a storm loomed, its thunder rattling the reeds. The flock fled, their wings a pink blur against charcoal clouds, but Sable lingered. The pool was still; Moss hadn’t surfaced. She dipped her bill, calling softly, her heart a flutter of worry. Then, a ripple—Moss emerged, sluggish, a gash on his flank from a poacher’s trap. Sable’s instinct was to flee, but she stayed, her bill probing the mud for healing herbs she’d seen egrets use.
With gentle nudges, she pressed the herbs to Moss’s wound, her pink wings shielding him from the rain. Moss rumbled, a low thanks, and rested. By dusk, the storm passed, and the marsh gleamed under a crescent moon. Moss stirred, stronger, and nudged a final pebble to Sable—a heart-shaped stone, glinting pink like her feathers.
Sable took flight, the stone clutched in her bill, her wings carving hope into the sky. The flock returned, awed by her tale, and the marsh buzzed with their chatter. Sable and Moss remained, their bond a quiet legend, proof that even in a wild world, trust could bloom where dawn met dusk.
Word count: 313
-
 @ c1e9ab3a:9cb56b43
2025-03-10 21:56:07
@ c1e9ab3a:9cb56b43
2025-03-10 21:56:07Introduction
Throughout human history, the pyramids of Egypt have fascinated scholars, archaeologists, and engineers alike. Traditionally thought of as tombs for pharaohs or religious monuments, alternative theories have speculated that the pyramids may have served advanced technological functions. One such hypothesis suggests that the pyramids acted as large-scale nitrogen fertilizer generators, designed to transform arid desert landscapes into fertile land.
This paper explores the feasibility of such a system by examining how a pyramid could integrate thermal convection, electrolysis, and a self-regulating breeder reactor to sustain nitrogen fixation processes. We will calculate the total power requirements and estimate the longevity of a breeder reactor housed within the structure.
The Pyramid’s Function as a Nitrogen Fertilizer Generator
The hypothesized system involves several key processes:
- Heat and Convection: A fissile material core located in the King's Chamber would generate heat, creating convection currents throughout the pyramid.
- Electrolysis and Hydrogen Production: Water sourced from subterranean channels would undergo electrolysis, splitting into hydrogen and oxygen due to electrical and thermal energy.
- Nitrogen Fixation: The generated hydrogen would react with atmospheric nitrogen (N₂) to produce ammonia (NH₃), a vital component of nitrogen-based fertilizers.
Power Requirements for Continuous Operation
To maintain the pyramid’s core at approximately 450°C, sufficient to drive nitrogen fixation, we estimate a steady-state power requirement of 23.9 gigawatts (GW).
Total Energy Required Over 10,000 Years
Given continuous operation over 10,000 years, the total energy demand can be calculated as:
[ \text{Total time} = 10,000 \times 365.25 \times 24 \times 3600 \text{ seconds} ]
[ \text{Total time} = 3.16 \times 10^{11} \text{ seconds} ]
[ \text{Total energy} = 23.9 \text{ GW} \times 3.16 \times 10^{11} \text{ s} ]
[ \approx 7.55 \times 10^{21} \text{ J} ]
Using a Self-Regulating Breeder Reactor
A breeder reactor could sustain this power requirement by generating more fissile material than it consumes. This reduces the need for frequent refueling.
Pebble Bed Reactor Design
- Self-Regulation: The reactor would use passive cooling and fuel expansion to self-regulate temperature.
- Breeding Process: The reactor would convert thorium-232 into uranium-233, creating a sustainable fuel cycle.
Fissile Material Requirements
Each kilogram of fissile material releases approximately 80 terajoules (TJ) (or 8 × 10^{13} J/kg). Given a 35% efficiency rate, the usable energy per kilogram is:
[ \text{Usable energy per kg} = 8 \times 10^{13} \times 0.35 = 2.8 \times 10^{13} \text{ J/kg} ]
[ \text{Fissile material required} = \frac{7.55 \times 10^{21}}{2.8 \times 10^{13}} ]
[ \approx 2.7 \times 10^{8} \text{ kg} = 270,000 \text{ tons} ]
Impact of a Breeding Ratio
If the reactor operates at a breeding ratio of 1.3, the total fissile material requirement would be reduced to:
[ \frac{270,000}{1.3} \approx 208,000 \text{ tons} ]
Reactor Size and Fuel Replenishment
Assuming a pebble bed reactor housed in the King’s Chamber (~318 cubic meters), the fuel cycle could be sustained with minimal refueling. With a breeding ratio of 1.3, the reactor could theoretically operate for 10,000 years with occasional replenishment of lost material due to inefficiencies.
Managing Scaling in the Steam Generation System
To ensure long-term efficiency, the water supply must be conditioned to prevent mineral scaling. Several strategies could be implemented:
1. Natural Water Softening Using Limestone
- Passing river water through limestone beds could help precipitate out calcium bicarbonate, reducing hardness before entering the steam system.
2. Chemical Additives for Scaling Prevention
- Chelating Agents: Compounds such as citric acid or tannins could be introduced to bind calcium and magnesium ions.
- Phosphate Compounds: These interfere with crystal formation, preventing scale adhesion.
3. Superheating and Pre-Evaporation
- Pre-Evaporation: Water exposed to extreme heat before entering the system would allow minerals to precipitate out before reaching the reactor.
- Superheated Steam: Ensuring only pure vapor enters the steam cycle would prevent mineral buildup.
- Electrolysis of Superheated Steam: Using multi-million volt electrostatic fields to ionize and separate minerals before they enter the steam system.
4. Electrostatic Control for Scaling Mitigation
- The pyramid’s hypothesized high-voltage environment could ionize water molecules, helping to prevent mineral deposits.
Conclusion
If the Great Pyramid were designed as a self-regulating nitrogen fertilizer generator, it would require a continuous 23.9 GW energy supply, which could be met by a breeder reactor housed within its core. With a breeding ratio of 1.3, an initial load of 208,000 tons of fissile material would sustain operations for 10,000 years with minimal refueling.
Additionally, advanced water treatment techniques, including limestone filtration, chemical additives, and electrostatic control, could ensure long-term efficiency by mitigating scaling issues.
While this remains a speculative hypothesis, it presents a fascinating intersection of energy production, water treatment, and environmental engineering as a means to terraform the ancient world.
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:59
@ e4950c93:1b99eccd
2025-05-03 09:59:59🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ c1e9ab3a:9cb56b43
2025-03-09 20:13:44
@ c1e9ab3a:9cb56b43
2025-03-09 20:13:44Introduction
Since the mid-1990s, American media has fractured into two distinct and increasingly isolated ecosystems, each with its own Overton window of acceptable discourse. Once upon a time, Americans of different political leanings shared a common set of facts, even if they interpreted them differently. Today, they don’t even agree on what the facts are—or who has the authority to define them.
This divide stems from a deeper philosophical rift in how each side determines truth and legitimacy. The institutional left derives its authority from the expert class—academics, think tanks, scientific consensus, and mainstream media. The populist right, on the other hand, finds its authority in traditional belief systems—religion, historical precedent, and what many call "common sense." As these two moral and epistemological frameworks drift further apart, the result is not just political division but the emergence of two separate cultural nations sharing the same geographic space.
The Battle of Epistemologies: Experts vs. Tradition
The left-leaning camp sees scientific consensus, peer-reviewed research, and institutional expertise as the gold standard of truth. Universities, media organizations, and policy think tanks function as arbiters of knowledge, shaping the moral and political beliefs of those who trust them. From this perspective, governance should be guided by data-driven decisions, often favoring progressive change and bureaucratic administration over democratic populism.
The right-leaning camp is skeptical of these institutions, viewing them as ideologically captured and detached from real-world concerns. Instead, they look to religion, historical wisdom, and traditional social structures as more reliable sources of truth. To them, the "expert class" is not an impartial source of knowledge but a self-reinforcing elite that justifies its own power while dismissing dissenters as uneducated or morally deficient.
This fundamental disagreement over the source of moral and factual authority means that political debates today are rarely about policy alone. They are battles over legitimacy itself. One side sees resistance to climate policies as "anti-science," while the other sees aggressive climate mandates as an elite power grab. One side views traditional gender roles as oppressive, while the other sees rapid changes in gender norms as unnatural and destabilizing. Each group believes the other is not just wrong, but dangerous.
The Consequences of Non-Overlapping Overton Windows
As these worldviews diverge, so do their respective Overton windows—the range of ideas considered acceptable for public discourse. There is little overlap left. What is considered self-evident truth in one camp is often seen as heresy or misinformation in the other. The result is:
- Epistemic Closure – Each side has its own trusted media sources, and cross-exposure is minimal. The left dismisses right-wing media as conspiracy-driven, while the right views mainstream media as corrupt propaganda. Both believe the other is being systematically misled.
- Moralization of Politics – Since truth itself is contested, policy debates become existential battles. Disagreements over issues like immigration, education, or healthcare are no longer just about governance but about moral purity versus moral corruption.
- Cultural and Political Balkanization – Without a shared understanding of reality, compromise becomes impossible. Americans increasingly consume separate news, live in ideologically homogeneous communities, and even speak different political languages.
Conclusion: Two Nations on One Land
A country can survive disagreements, but can it survive when its people no longer share a common source of truth? Historically, such deep societal fractures have led to secession, authoritarianism, or violent conflict. The United States has managed to avoid these extremes so far, but the trendline is clear: as long as each camp continues reinforcing its own epistemology while rejecting the other's as illegitimate, the divide will only grow.
The question is no longer whether America is divided—it is whether these two cultures can continue to coexist under a single political system. Can anything bridge the gap between institutional authority and traditional wisdom? Or are we witnessing the slow but inevitable unraveling of a once-unified nation into two separate moral and epistemic realities?
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:25
@ e4950c93:1b99eccd
2025-05-03 09:59:25🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel
- Dilling (laine mérinos)
- ManyMonths (laine mérinos)
Maison
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ 7b3f7803:8912e968
2025-03-08 03:05:16
@ 7b3f7803:8912e968
2025-03-08 03:05:16Libertarians believe in open borders in theory. In practice, open borders don't work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don't mix. In this article, we'll examine the other sacred cow of libertarian thought: free trade.
Free Trade without Libertarian Ideals
Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.
An example will illustrate what I'm talking about. Let's say Portugal subsidizes their wine for export to other countries. The obvious first-order effect is that it makes Portuguese wine cheaper in France, perhaps undercutting the price of French wine. Libertarians would say, that's great! French customers get cheaper goods, so what's the problem?
As with any government intervention, there are significant second- and third-order effects in play. Subsidization puts unsubsidized companies at risk, perhaps driving them to bankruptcy. In this case, this might be a French wine maker. Subsidized companies may become zombies instead of dying out. In this case, this might be a Portuguese wine maker that was failing domestically but survives by selling to customers abroad with government subsidies. While French customers benefit in the short run with cheaper prices for wine, they are ultimately hurt because the goods that would have existed without government intervention never come to market. Perhaps French wine makers that went bankrupt were innovating. Perhaps the resources of the zombie Portuguese wine maker would have created something better.
Further, the dependency of French people on Portuguese wine means that something going wrong in Portugal, like a war or subsidy cuts, disrupts the supply and price of wine for France. Now France must meddle in Portugal internationally if it doesn't want the wine supply to get disrupted. The two countries get entangled in such a way as to become more interventionist internationally. A war involving Portugal now suddenly becomes France's business and incentivizes military aid or even violence. As usual, the unseen effects of government policy are the most pernicious.
Not Really Free
In other words, what we call free trade isn't really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of "free trade," it's somehow seen as fair. Of course it's not, as government intervention distorts the market whether it's done by our own government or a foreign government.
So why would a foreign government do this? It gets several benefits through targeted market manipulation. First, it makes its own companies' products more popular abroad and conversely, makes US companies' products less popular. This has the dual benefit of growing the foreign government’s firms and shrinking, perhaps bankrupting, the US ones.
Targeted subsidization like this can lead to domination under free trade. It's not unlike the Amazon strategy of undercutting everyone first and using the monopoly pricing power at scale once everyone else has bankrupted. The global monopoly is tremendously beneficial to the country that has it. Not only is there significant tax revenue over the long term, but also a head start on innovations within that industry and an advantage in production in the adjacent industries around the product.
Second, the manufacturing centralization gives that country leverage geo-politically. A critical product that no one else manufactures means natural alliances with the countries that depend on the product, which is especially useful for smaller countries like Taiwan. Their chip manufacturing industry, holding 60% of global supply (2024), has meant that they're a critical link for most other countries, and hence, they can use this fact to deter Chinese invasion.
Third, because of the centralization of expertise, more innovations, products, and manufacturing will tend to come within the country. This increased production has cascading benefits, including new industries and national security. China leads the world in drone technology, which undoubtedly has given it an innovation advantage for its military, should it go to war.
Fourth, the capital that flows into the country for investing in the monopolized industry will tend to stay, giving the country more wealth in the form of factories, equipment, and skills. While that capital may nominally be in the hands of foreigners, over time, the ownership of that industry will inevitably transition toward native locals, as the knowledge about how to run such industries gets dissipated within the country.
[Image: Map showing “China Drone Tech” and “Taiwan Chips” hubs, with arrows of capital flow staying local]
Currency Devaluation: The Universal Trade Weapon
It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren't good for the US.
To compete, they have to lower costs by using the same devalued currency to pay their labor as their foreign competition. That is, by relocating their capital, their manufacturing, and even their personnel to the country that's devaluing the currency. Not only does relocating reduce labor cost, but it also often gets them benefits like tax breaks. This makes US companies de facto multinationals and not only makes them subject to other jurisdictions, but ultimately divides their loyalties. To take advantage of the reduced labor, capital must move to another country and, along with it, future innovation.
Such relocations ultimately leave the company stripped of their manufacturing capability in the US, as local competition will generally fare better over the long run. Much of the value of the industry then is captured by other governments in taxes, development, and even state-owned companies. Free trade, in other words, creates a vulnerability for domestic companies as they can be put at a significant disadvantage compared to foreign counterparts.
Hidden Effects of Foreign Intervention
Unlike the multinationals, small companies have no chance as they're not big enough to exploit the labor arbitrage. And as is usual in a fiat system, they suffer the most while the giant corporations get the benefits of the supposed "free trade". Most small companies can't compete, so we get mostly the bigger companies that survive.
The transition away from domestic manufacturing necessarily means significant disruption. Domestic workers are displaced and have to find new work. Factories and equipment either have to be repurposed or rot. Entire communities that depended on the manufacturing facility now have to figure out new ways to support themselves. It's no good telling them that they can just do something else. In a currency devaluation scenario, most of the manufacturing leaves and the jobs left are service-oriented or otherwise location-based, like real estate development. There's a natural limit to location-based industries because the market only grows with the location that you're servicing. Put another way, you can only have so many people give haircuts or deliver packages in a geographic area. There has to be some manufacturing of goods that can be sold outside the community, or the community will face scarce labor opportunities relative to the population.
You also can't say the displaced workers can start some other manufacturing business. Such businesses will get out-competed on labor by the currency-devaluing country, so there won't be much investment available for such a business, and even if there were, such a business would be competing with its hands tied behind its back. So in this scenario, what you end up with are a large pool of unemployed people whom the state subsidizes with welfare.
So when a US company leaves or goes bankrupt due to a foreign government's subsidies, the disruption alone imposes a significant short-term cost with displaced labor, unused capital goods, and devastated communities.
Mitigations
So how do countries fight back against such a devastating economic weapon? There are a few ways countries have found around this problem of currency devaluation under free trade. First, a country can prevent capital from leaving. This is called capital controls, and many countries, particularly those that manufacture a lot, have them. Try to get money, factories, or equipment out of Malaysia, for example, and you'll find that they make it quite difficult. Getting the same capital into the country, on the other hand, faces few restrictions. Unfortunately, the US can't put in capital controls because dollars are its main export. It is, after all, the reserve currency of the world.
Second, you can compete by devaluing your own currency. But that’s very difficult because it requires printing a lot of dollars, and that causes inflation. There's also no guarantee that a competing country doesn't devalue its currency again. The US is also in a precarious position as the world's reserve currency, so devaluing the currency more than it already does will make other holders of the dollar less likely to want to hold it, threatening the reserve currency status.
So the main two mitigations against currency devaluation in a free trade scenario are not available to the US. So what else is there? The remaining option is to drop free trade. The solution, in other words, is to add tariffs. This is how you can nullify the effects of foreign government intervention, by leveling the playing field for US manufacturers.
Tariffs
One major industry that's managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.
The scope of this one industry for the US is huge. There are around 300,000 direct jobs in auto assembly within the US (USTR) and there are an additional 3 million jobs supplying these manufacturers within the US. But the benefits don't end there. The US is also creating a lot of innovation around cars, such as self-driving and plug-in electric cars. There are many countries that would love to have this industry for themselves, but because of tariffs, auto manufacturing continues in the US.
And though tariffs are seen as a tax on consumers, US car prices are cheap relative to the rest of the world. What surprises a lot of people when they move from the US to other countries is finding out that the same car often costs more abroad (e.g. 25% tariffs keep U.S. prices 20% below Europe’s $40K average, 2024). The downside of tariffs pales next to the downsides of "free trade."
Free Trade Doesn’t Work with Fiat Money
The sad reality is that while we would love for free trade to work in the ideal libertarian paradise, it won't in our current fiat-based system. The subsidization by foreign governments to bankrupt US companies or to make them multinational, combined with the unfortunate reality of the US dollar being the world reserve currency, means that free trade guts the US of manufacturing. Tariffs are a reasonable way to protect US manufacturers, particularly smaller ones that can't go multinational.
What's more, tariffs make the US less fragile and less dependent on international supply chains. Many of the wars in the past 60 years have been waged because of the entanglements the US has with other countries due to the reliance on international supply chains. Lessening this dependency, if only to prevent a war, has clear value.
Lastly, labor has been devalued significantly by fiat monetary expansion, but at least some of that can be recovered if tariffs create more manufacturing, which in turn adds to the demand for labor. This should reduce the welfare state as more opportunities are made available and fewer unemployed people will be on the rolls.
Conclusion
Fiat money produces a welfare state, which makes open borders unworkable. Fiat money also gives foreign governments a potent economic weapon to use against US companies, and by extension the labor force that powers them. Though currency debasement and capital controls are available to other countries as a defense, for the US, neither of these tools is available due to the fact that the dollar is the world reserve currency. As such, tariffs are a reasonable defense against the fiat subsidization of foreign governments.
-
 @ 7b3f7803:8912e968
2025-03-08 02:28:40
@ 7b3f7803:8912e968
2025-03-08 02:28:40 Libertarians believe in open borders in theory. In practice, open borders don’t work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don’t mix. In this article, we’ll examine the other sacred cow of libertarian thought: free trade.
Libertarians believe in open borders in theory. In practice, open borders don’t work, because, among other things, the combination with a welfare state creates a moral hazard, and the least productive of society end up within the borders of welfare states and drain resources. The social services are paid by the productive people of the country or, in the case of most fiat systems, by currency holders through inflation. Welfare states are much more likely under fiat money and the redistribution goes from native taxpayers to illegal immigrants. Thus, under fiat money, open borders end up being an open wound by which the productive lifeblood of the country bleeds out, despite the theoretical trade-efficiency benefits. As libertarians like to say, open borders and the welfare state don’t mix. In this article, we’ll examine the other sacred cow of libertarian thought: free trade.Free Trade without Libertarian Ideals
 Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.
Free trade is very similar to free movement of labor in that it works great in theory, but not in practice, especially under fiat money. In a libertarian free-market world, free trade works. But that assumes a whole host of libertarian ideals like sound money, non-interfering governments, and minimal aggression. Once those ideals are violated, such as with government intervention in the market, similar moral hazards and long-term costs come with them, making free trade about as libertarian as a fractional reserve bank.An example will illustrate what I’m talking about. Let’s say Portugal subsidizes their wine for export to other countries. The obvious first-order effect is that it makes Portuguese wine cheaper in France, perhaps undercutting the price of French wine. Libertarians would say, that’s great! French customers get cheaper goods, so what’s the problem?
As with any government intervention, there are significant second- and third-order effects in play. Subsidization puts unsubsidized companies at risk, perhaps driving them to bankruptcy. In this case, this might be a French wine maker. Subsidized companies may become zombies instead of dying out. In this case, this might be a Portuguese wine maker that was failing domestically but survives by selling to customers abroad with government subsidies. While French customers benefit in the short run with cheaper prices for wine, they are ultimately hurt because the goods that would have existed without government intervention never come to market. Perhaps French wine makers that went bankrupt were innovating. Perhaps the resources of the zombie Portuguese wine maker would have created something better.
Further, the dependency of French people on Portuguese wine means that something going wrong in Portugal, like a war or subsidy cuts, disrupts the supply and price of wine for France. Now France must meddle in Portugal internationally if it doesn’t want the wine supply to get disrupted. The two countries get entangled in such a way as to become more interventionist internationally. A war involving Portugal now suddenly becomes France’s business and incentivizes military aid or even violence. As usual, the unseen effects of government policy are the most pernicious.
Not Really Free
 In other words, what we call free trade isn’t really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of “free trade,” it’s somehow seen as fair. Of course it’s not, as government intervention distorts the market whether it’s done by our own government or a foreign government.
In other words, what we call free trade isn’t really free trade. A country exporting to the US may subsidize their products through government intervention, making the product cheaper in the US. This hurts US companies, and they’re forced into choices they never would have had to face without the foreign government intervention. But because the good is crossing borders under the rubric of “free trade,” it’s somehow seen as fair. Of course it’s not, as government intervention distorts the market whether it’s done by our own government or a foreign government.So why would a foreign government do this? It gets several benefits through targeted market manipulation. First, it makes its own companies’ products more popular abroad and conversely, makes US companies’ products less popular. This has the dual benefit of growing the foreign government’s firms and shrinking, perhaps bankrupting, the US ones.
Targeted subsidization like this can lead to domination under free trade. It’s not unlike the Amazon strategy of undercutting everyone first and using the monopoly pricing power at scale once everyone else has bankrupted. The global monopoly is tremendously beneficial to the country that has it. Not only is there significant tax revenue over the long term, but also a head start on innovations within that industry and an advantage in production in the adjacent industries around the product.
Second, the manufacturing centralization gives that country leverage geo-politically. A critical product that no one else manufactures means natural alliances with the countries that depend on the product, which is especially useful for smaller countries like Taiwan. Their chip manufacturing industry, holding 60% of global supply (2024), has meant that they’re a critical link for most other countries, and hence, they can use this fact to deter Chinese invasion.
Third, because of the centralization of expertise, more innovations, products, and manufacturing will tend to come within the country. This increased production has cascading benefits, including new industries and national security. China leads the world in drone technology, which undoubtedly has given it an innovation advantage for its military, should it go to war.
Fourth, the capital that flows into the country for investing in the monopolized industry will tend to stay, giving the country more wealth in the form of factories, equipment, and skills. While that capital may nominally be in the hands of foreigners, over time, the ownership of that industry will inevitably transition toward native locals, as the knowledge about how to run such industries gets dissipated within the country.
Currency Devaluation: The Universal Trade Weapon
 It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren’t good for the US.
It would be one thing if only a specific industry were singled out for government subsidies and then the products dumped into the US as a way to hurt US companies, as that would limit the scope of the damage. But with currency devaluation, a government can subsidize all of its exports at the same time. Indeed, this is something that many countries do. While short-term, this helps US consumers, it hurts US companies and forces them into decisions that aren’t good for the US.To compete, they have to lower costs by using the same devalued currency to pay their labor as their foreign competition. That is, by relocating their capital, their manufacturing, and even their personnel to the country that’s devaluing the currency. Not only does relocating reduce labor cost, but it also often gets them benefits like tax breaks. This makes US companies de facto multinationals and not only makes them subject to other jurisdictions, but ultimately divides their loyalties. To take advantage of the reduced labor, capital must move to another country and, along with it, future innovation.
Such relocations ultimately leave the company stripped of their manufacturing capability in the US, as local competition will generally fare better over the long run. Much of the value of the industry then is captured by other governments in taxes, development, and even state-owned companies. Free trade, in other words, creates a vulnerability for domestic companies as they can be put at a significant disadvantage compared to foreign counterparts.
Hidden Effects of Foreign Intervention
Unlike the multinationals, small companies have no chance as they’re not big enough to exploit the labor arbitrage. And as is usual in a fiat system, they suffer the most while the giant corporations get the benefits of the supposed “free trade”. Most small companies can’t compete, so we get mostly the bigger companies that survive.
The transition away from domestic manufacturing necessarily means significant disruption. Domestic workers are displaced and have to find new work. Factories and equipment either have to be repurposed or rot. Entire communities that depended on the manufacturing facility now have to figure out new ways to support themselves. It’s no good telling them that they can just do something else. In a currency devaluation scenario, most of the manufacturing leaves and the jobs left are service-oriented or otherwise location-based, like real estate development. There’s a natural limit to location-based industries because the market only grows with the location that you’re servicing. Put another way, you can only have so many people give haircuts or deliver packages in a geographic area. There has to be some manufacturing of goods that can be sold outside the community, or the community will face scarce labor opportunities relative to the population.
You also can’t say the displaced workers can start some other manufacturing business. Such businesses will get out-competed on labor by the currency-devaluing country, so there won’t be much investment available for such a business, and even if there were, such a business would be competing with its hands tied behind its back. So in this scenario, what you end up with are a large pool of unemployed people whom the state subsidizes with welfare.
So when a US company leaves or goes bankrupt due to a foreign government’s subsidies, the disruption alone imposes a significant short-term cost with displaced labor, unused capital goods, and devastated communities.
Mitigations
So how do countries fight back against such a devastating economic weapon? There are a few ways countries have found around this problem of currency devaluation under free trade. First, a country can prevent capital from leaving. This is called capital controls, and many countries, particularly those that manufacture a lot, have them. Try to get money, factories, or equipment out of Malaysia, for example, and you’ll find that they make it quite difficult. Getting the same capital into the country, on the other hand, faces few restrictions. Unfortunately, the US can’t put in capital controls because dollars are its main export. It is, after all, the reserve currency of the world.
Second, you can compete by devaluing your own currency. But that’s very difficult because it requires printing a lot of dollars, and that causes inflation. There’s also no guarantee that a competing country doesn’t devalue its currency again. The US is also in a precarious position as the world’s reserve currency, so devaluing the currency more than it already does will make other holders of the dollar less likely to want to hold it, threatening the reserve currency status.
So the main two mitigations against currency devaluation in a free trade scenario are not available to the US. So what else is there? The remaining option is to drop free trade. The solution, in other words, is to add tariffs. This is how you can nullify the effects of foreign government intervention, by leveling the playing field for US manufacturers.
Tariffs
 One major industry that’s managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.
One major industry that’s managed to continue being manufactured in the US despite significant foreign competition is cars. Notably, cars have a tariff, which incentivizes their manufacture in the US, even for foreign car makers. The tariff has acted as a way to offset foreign government subsidies and currency debasement.The scope of this one industry for the US is huge. There are around 300,000 direct jobs in auto assembly within the US (USTR) and there are an additional 3 million jobs supplying these manufacturers within the US. But the benefits don’t end there. The US is also creating a lot of innovation around cars, such as self-driving and plug-in electric cars. There are many countries that would love to have this industry for themselves, but because of tariffs, auto manufacturing continues in the US.
And though tariffs are seen as a tax on consumers, US car prices are cheap relative to the rest of the world. What surprises a lot of people when they move from the US to other countries is finding out that the same car often costs more abroad (e.g. 25% tariffs keep U.S. prices 20% below Europe’s $40K average, 2024). The downside of tariffs pales next to the downsides of “free trade.”
Free Trade Doesn’t Work with Fiat Money
The sad reality is that while we would love for free trade to work in the ideal libertarian paradise, it won’t in our current fiat-based system. The subsidization by foreign governments to bankrupt US companies or to make them multinational, combined with the unfortunate reality of the US dollar being the world reserve currency, means that free trade guts the US of manufacturing. Tariffs are a reasonable way to protect US manufacturers, particularly smaller ones that can’t go multinational.
What’s more, tariffs make the US less fragile and less dependent on international supply chains. Many of the wars in the past 60 years have been waged because of the entanglements the US has with other countries due to the reliance on international supply chains. Lessening this dependency, if only to prevent a war, has clear value.
Lastly, labor has been devalued significantly by fiat monetary expansion, but at least some of that can be recovered if tariffs create more manufacturing, which in turn adds to the demand for labor. This should reduce the welfare state as more opportunities are made available and fewer unemployed people will be on the rolls.
Conclusion
Fiat money produces a welfare state, which makes open borders unworkable. Fiat money also gives foreign governments a potent economic weapon to use against US companies, and by extension the labor force that powers them. Though currency debasement and capital controls are available to other countries as a defense, for the US, neither of these tools is available due to the fact that the dollar is the world reserve currency. As such, tariffs are a reasonable defense against the fiat subsidization of foreign governments.
-
 @ e4950c93:1b99eccd
2025-05-03 09:59:03
@ e4950c93:1b99eccd
2025-05-03 09:59:03🧵 Produits en cette matière
Les marques suivantes proposent des produits fait exclusivement ou principalement avec cette matière :
Vêtements
- Engel (coton biologique)
- Dilling (coton biologique)
- ManyMonths (coton biologique)
Cet article est publié sur origine-nature.com 🌐 See this article in English
-
 @ e4950c93:1b99eccd
2025-05-03 09:46:42
@ e4950c93:1b99eccd
2025-05-03 09:46:42Engel est une marque allemande qui crée des vêtements et accessoires en coton biologique, laine mérinos et soie pour toute la famille.
Matières naturelles utilisées dans les produits
⚠️ Attention, certains produits de cette marque (notamment les soutiens-gorge) contiennent des matières non naturelles, dont :
Catégories de produits proposés
#Vêtements
- Coupes : bébés, enfants, femmes, hommes, unisexe
- Sous-vêtements : boxers, culottes
- Une pièce : bodies
- Hauts : débardeurs, gilets, t-shirts, pulls, vestes
- Bas : pantalons, shorts
- Tête et mains : bonnets
- Nuit : pyjamas
#Maison
- Linge : couvertures, turbulettes
Autres informations
- Certification GOTS
- Certification IVN Best
- Fabriqué en Allemagne
👉 En savoir plus sur le site de la marque
Cet article est publié sur origine-nature.com 🌐 See this article in English
📝 Tu peux contribuer à cette fiche en suggérant une modification en commentaire.
🗣️ Tu utilises ce produit ? Partage ton avis en commentaire.
⚡ Heureu-x-se de trouver cette information ? Soutiens le projet en faisant un don, pour remercier les contribut-eur-ice-s.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 4925ea33:025410d8
2025-03-08 00:38:48
@ 4925ea33:025410d8
2025-03-08 00:38:481. O que é um Aromaterapeuta?

O aromaterapeuta é um profissional especializado na prática da Aromaterapia, responsável pelo uso adequado de óleos essenciais, ervas aromáticas, águas florais e destilados herbais para fins terapêuticos.
A atuação desse profissional envolve diferentes métodos de aplicação, como inalação, uso tópico, sempre considerando a segurança e a necessidade individual do cliente. A Aromaterapia pode auxiliar na redução do estresse, alívio de dores crônicas, relaxamento muscular e melhora da respiração, entre outros benefícios.
Além disso, os aromaterapeutas podem trabalhar em conjunto com outros profissionais da saúde para oferecer um tratamento complementar em diversas condições. Como já mencionado no artigo sobre "Como evitar processos alérgicos na prática da Aromaterapia", é essencial ter acompanhamento profissional, pois os óleos essenciais são altamente concentrados e podem causar reações adversas se utilizados de forma inadequada.
2. Como um Aromaterapeuta Pode Ajudar?

Você pode procurar um aromaterapeuta para diferentes necessidades, como:
✔ Questões Emocionais e Psicológicas
Auxílio em momentos de luto, divórcio, demissão ou outras situações desafiadoras.
Apoio na redução do estresse, ansiedade e insônia.
Vale lembrar que, em casos de transtornos psiquiátricos, a Aromaterapia deve ser usada como terapia complementar, associada ao tratamento médico.
✔ Questões Físicas
Dores musculares e articulares.
Problemas respiratórios como rinite, sinusite e tosse.
Distúrbios digestivos leves.
Dores de cabeça e enxaquecas. Nesses casos, a Aromaterapia pode ser um suporte, mas não substitui a medicina tradicional para identificar a origem dos sintomas.
✔ Saúde da Pele e Cabelos
Tratamento para acne, dermatites e psoríase.
Cuidados com o envelhecimento precoce da pele.
Redução da queda de cabelo e controle da oleosidade do couro cabeludo.
✔ Bem-estar e Qualidade de Vida
Melhora da concentração e foco, aumentando a produtividade.
Estímulo da disposição e energia.
Auxílio no equilíbrio hormonal (TPM, menopausa, desequilíbrios hormonais).
Com base nessas necessidades, o aromaterapeuta irá indicar o melhor tratamento, calculando doses, sinergias (combinação de óleos essenciais), diluições e técnicas de aplicação, como inalação, uso tópico ou difusão.
3. Como Funciona uma Consulta com um Aromaterapeuta?

Uma consulta com um aromaterapeuta é um atendimento personalizado, onde são avaliadas as necessidades do cliente para a criação de um protocolo adequado. O processo geralmente segue estas etapas:
✔ Anamnese (Entrevista Inicial)
Perguntas sobre saúde física, emocional e estilo de vida.
Levantamento de sintomas, histórico médico e possíveis alergias.
Definição dos objetivos da terapia (alívio do estresse, melhora do sono, dores musculares etc.).
✔ Escolha dos Óleos Essenciais
Seleção dos óleos mais indicados para o caso.
Consideração das propriedades terapêuticas, contraindicações e combinações seguras.
✔ Definição do Método de Uso
O profissional indicará a melhor forma de aplicação, que pode ser:
Inalação: difusores, colares aromáticos, vaporização.
Uso tópico: massagens, óleos corporais, compressas.
Banhos aromáticos e escalda-pés. Todas as diluições serão ajustadas de acordo com a segurança e a necessidade individual do cliente.
✔ Plano de Acompanhamento
Instruções detalhadas sobre o uso correto dos óleos essenciais.
Orientação sobre frequência e duração do tratamento.
Possibilidade de retorno para ajustes no protocolo.
A consulta pode ser realizada presencialmente ou online, dependendo do profissional.
Quer saber como a Aromaterapia pode te ajudar? Agende uma consulta comigo e descubra os benefícios dos óleos essenciais para o seu bem-estar!
-
 @ a296b972:e5a7a2e8
2025-05-03 07:48:25
@ a296b972:e5a7a2e8
2025-05-03 07:48:25Derzeit formiert sich ein neues Gruselkabinett, als Folge einer Pandemie der Ungeeigneten. Kostproben der Unfähigkeit konnte man schon in den aktuellen „Quassel-Shows“ des Staatsfunks „genießen“. Die Riege der Universal-Dilettanten, die noch schnell hochgelobt wurde, macht gerade Platz für Rekruten aus dem Milieu der überzeugten Realitätsverweigerer.
Impfpflichtbefürworter, ideologisch vergiftete Klima- und Gender-Gagaisten, Verteidiger des Russen-Dauer-Feindbilds, Finanzwirtschafts-Ahnungslose, zahllose „Südamerika-Experten“, die davon überzeugt sind, solche zu sein, weil sie unfallfrei eine Banane essen können und weitere, die als einzige Qualifikation das Prädikat „Untauglich“ auszeichnet, geben sich ein neues Stelldichein.
Nach Vorbild des öffentlich-rechtlichen Unfugs bilden sie ein in sich geschlossenes System, das sich gegen Kritik abschotten will, in dem es alles, was sich nach Nicht-nach-dem-Maul geredet anhört, als Hass und Hetze bezeichnet und sich als Hüter der Wahrheit aufspielt.
Begriffe wie „Hass und Hetze“ und „Kriegstüchtigkeit“ werden einem Wortschatz entlehnt, die dem bisher dunkelsten Kapitel der deutschen Geschichte entnommen sind. Zur Abschreckung verwendete Begriffe, im Sinne von „Wehret den Anfängen!“, wie die Anlehnung „Impfen macht frei“ hingegen, werden mit Geldbußen und Haft belegt. Es kommt eben immer darauf an, von wem diese verbrannten Begriffe verwendet werden.
Wenn aus einer Demokratie „Unseredemokratie“ wird, müssen alle Alarmglocken schrillen, weil so Tür und Tor weit aufgerissen werden, um Tendenzen und Ideologien den Einzug zu ermöglichen, die in einer freiheitlich-demokratischen Grundordnung nichts, aber auch rein gar nichts zu suchen haben, weil die Auslegung davon, was „Unseredemokratie“ bedeutet, in den Händen derjenigen liegt, die sich zwar noch als Volksvertreter ausgeben, aber den Willen des Souveräns nicht mehr umsetzen.
Die Meinung und der Wille des Volkes werden maximal ignoriert und unterdrückt. Mit einem „weiter so“ manifestiert sich die Verachtung der Wähler, die in ihrer unterstellten Dummheit bestenfalls noch als Stimmvieh taugen, ansonsten aber zu vernachlässigen sind, wenn das Ziel erreicht ist: Die Macht!
Eine Absichtserklärung, genannt Koalitionsvertrag, ist die Grundlage für „alles kann, nichts muss“. Er lässt so eine unbegrenzte Flexibilität in jede Richtung zu, alles ist möglich. ALLES!
Die Basis der Koalition beruht auf Lügen, sei es in der Migrationspolitik oder in der Neuverschuldung. Das gemeinsame Klüngeln hat schon begonnen, bevor der eigentliche Regierungsauftrag überhaupt erteilt wurde.
Das wirklich einzige, gemeinsame Ziel ist, mit allen Mitteln an der Macht zu bleiben, koste es, was es wolle und eine demokratisch gewählte Opposition, die rund ein Viertel der Wählerstimmen ausmacht, wo immer es geht zu delegitimieren und so klein zu halten, wie es nur eben geht.
Hirngespinste sollen weiter vorangetrieben, die Rückkehr zur Vernunft soll unter allen Umständen verhindert werden, bzw. ist aufgrund mangelnder Kenntnisse und Einsicht gar nicht möglich.
Das Lügen bleibt den Nicht-Volksvertretern vorbehalten, die definieren, was Lüge ist und was nicht, sofern die Kritik vom Volk kommt. Berichtet man über die Politik, spricht man von Unwahrheiten, spricht die Politik über das Volk, sind es Lügen. Überall wird mit zweierlei Maß gemessen.
Die Verachtung des Souveräns wirkt wie ein Bumerang und wird wie durch einen Spiegel auf die Versender zurückgeworfen.
Ein zukünftiger Ex-Bundeskanzler verliert bereits den Rückhalt, noch bevor er in sein Amt eingesetzt wird. Grisu, der kleine Drache, will unbedingt, nur einmal im Leben, Feuerwehrmann werden. Phrasen-Dreschen wird zur Staatsräson.
Ministerposten werden nach maximaler Fachferne verschachert.
Gut ausgebildete Kräfte verlassen das Land, die Wirtschaft stagniert, massive Einbrüche in der Auto-Industrie, der einstigen Vorzeige-Marken in der ganzen Welt. Ja, Autos bauen, das könnten die Deutschen, wenn sie noch dürften.
Wer kann, wandert ab ins Ausland, wo Energiekosten und Steuern ein unternehmerisches Handeln ermöglichen, statt es mit aller Kraft durch gezielte Wirtschaftsvernichtung abzuwürgen. Wo ist der massive Widerstand seitens der Wirtschaftsverbände, der Industrie- und Handelskammern und Groß-Unternehmen? Geht es denen immer noch zu gut?
Recht haben und Recht bekommen waren noch nie so weit auseinander, wie heute.
Die Kirche, in einem christlich geprägten Land, schreibt ihre eigene Lehre um: „Gott ist queer!“ Grenzt das schon an Gotteslästerung aus den eigenen Reihen? Dabei merkt sie offensichtlich nicht, dass sie sich damit selbst abschafft. Wieder einmal springt sie auf den Zug der vorgegebenen Staatsdoktrin auf. Unvergessen die Hakenkreuzfahne über dem Hauptportal am Kölner Dom in der bisher dunkelsten Zeit Deutschlands.
Eine Überzeugung, und seien die Beweggründe mit noch so guten Absichten verbunden, darf nie wieder zu einer Ideologie werden, die nur in die Irre führen kann. Deshalb ist es demokratische Pflicht, auf die Gefahr hinzuweisen, wenn auch nur der leiseste Hauch Anlass zu solchen Befürchtungen gibt. Das gilt für die Kirche, die Politik, die Rechtsprechung und Menschen, von denen man den Eindruck hat, dass sie sich verirrt haben.
Das Zuviel an Fremden wird nicht gestoppt. Eine Minderheit, die bei Verstand geblieben ist, verlässt das Land, wenn es ihr finanziell möglich ist. Andere, die sich das nicht leisten können, müssen ausharren und dabei zusehen, wie ein Land vor die Hunde geht.
Gut integrierte „Gastarbeiter“ schämen sich für den Plebs, der nach Deutschland kommt. Natürlich unter dem Deckmantel der Menschlichkeit, der die Menschlichkeit gegenüber den Bio-Deutschen mit Füßen tritt. Ihr Ansehen, ihr Fleiß und ihre Dankbarkeit, dass sich ihre Vätergeneration hier eine neue Existenz aufbauen konnte, wird mit Füßen getreten. Sie geraten unter einen Generalverdacht, der ihnen schadet. Auch sie haben Jahrzehnte in die Krankenkassen eingezahlt und ihre Steuern brav entrichtet.
Der Polizei sind von staatlicher Seite die Hände gebunden gegen Clan-Kriminalität und asozialem Verhalten durchzugreifen. Sie bilden Parallel-Gesellschaften mit eigenen Regeln und eigenen Gesetzen und die Polizei muss tatenlos dabei zusehen. Banden in Berlin und Duisburg stellen sich über herrschende Gesetze, Roma terrorisieren Kiel, benehmen sich, wie die Axt im Walde. „An Leib und Leben gefährdete Migranten“ werfen, wie in Bochum, Ziegel von Dächern, und gefährden die Bevölkerung an Leib und Leben. Anschließend setzen sie sich mit einem Gartenstuhl auf einem Kamin in die Sonne und träumen vermutlich vom Ausblick auf dem Kilimandscharo. Statt sie bei Kopf und Kragen zu fassen und sofort aus dem Land zu werfen, werden solche irren Taten mit psychischen Problemen aufgrund der Erfahrungen in ihrem Heimatland entschuldigt. Würden sich solche Bekloppte in ihrem eigenen Land vergleichbare Handlungen erlauben, würde sie die Dorfgemeinschaft wahrscheinlich den Löwen zum Fraß vorwerfen.
Jeder, der nicht das in Deutschland geltende Recht akzeptiert und stattdessen seine eigene Auffassung von Recht durchsetzen will, gehört unverzüglich des Landes verwiesen, und es ist Aufgabe des Staates, dafür zu sorgen, dass solche Personen nie wieder einen Fuß über die Grenzen des Landes setzen dürfen. Stattdessen werden die Fahnder verfolgt und die Täter laufen gelassen. Der Staat lässt so zu, dass geltendes Recht unterwandert und außer Kraft gesetzt wird. Seine abschreckende Wirkung geht verloren, weil es in den einschlägigen Kreisen bekannt ist, dass sich jeder aufführen kann, wie er will, ohne, dass es Konsequenzen nach sich zieht.
Gepaart mit Willkür ist das hoch gefährliches Dynamit, dass die Gesellschaft sprengt und eine Gefahr in sich birgt, dass die Gesellschaft ab dem Punkt, wo es unerträglich geworden ist, zur Selbstjustiz greift, und das wäre möglicherweise der Anfang eines Bürgerkriegs.
Für alles ist Geld da. Es werden Schulden in atemberaubender Höhe aufgenommen, vor allem, um die Kriegswirtschaft anzukurbeln, um vor einem Feind - Russland gewappnet zu sein, das nicht das geringste Interesse an einem Land hat, das nichts unversucht lässt, auf irgendeine Art und Weise Selbstmord zu begehen. Einmal muss es doch gelingen!
Und natürlich müssen auch die westlichen Werte im Stellvertreterkrieg zwischen den USA und Russland in der Ukraine verteidigt werden.
Kein Geld ist allerdings für die eigenen Leute da. Im Gegenteil: Wer Flaschen sammelt, muss ab einer bestimmten Höhe der Einnahmen ein Gewerbe anmelden. Aber sonst haben die Sesselfurzer nichts zu tun, oder? Es sollte Geld in die Hand genommen werden, die zunehmende Armut in der Bevölkerung nachhaltig zu stoppen, aus dem Abfahrtsvorschlags-Plan der Bahn wieder einen richtigen Fahrplan zu machen, die Schlagloch-Nostalgie á la DDR abzuschaffen, Brücken wieder ihrem Wesen zuzuführen, nämlich, dass man drüberfahren kann, das ganze Land einer dringenden Generalüberholung zu unterziehen, die Gewinnorientierung aus dem Gesundheitssystem wieder abzuschaffen, die Fallpauschalen samt dem Verursacher in die Wüste zu schicken, Deutschland steuer-sexy zu machen.
Das ist wohl zu viel verlangt, denn diejenigen, die das bewirken könnten, haben keine Not. Die einzige Not, die sie kennen, ist, wie sie immer genug Leim auf Vorrat haben können, um an ihrem Pöstchen kleben zu bleiben. Solche Menschen können nur in einem geschützten Rahmen existieren, weil sie in der Welt da draußen gar nicht zurecht kämen, geschweige denn in der Lage wären, für ihren Lebensunterhalt mit einer wirklichen Arbeit selbst zu sorgen.
Der Staat erfüllt nicht mehr seine Aufgabe für die Sicherheit seiner Bürger zu sorgen. Statt Messer-Attacken und Terror-Anschläge aufzuklären und damit den Bürgern ein Gefühl von Sicherheit zu vermitteln, wird die Aufklärung auf dem Mond im Meer der Stille versenkt. Transparenz: Fehlanzeige. Im besten Fall werden Symptom-Bekämpfungs-Maßnahmen ergriffen, statt die Ursachen zu verunmöglichen. Schilder an Messerverbots-Zonen aufzustellen, manifestieren bestenfalls die Gewissheit der Lächerlichkeit und Unfähigkeit seitens der Messerfachkräfte und der selbstfahrenden Autos, die von niemandem gesteuert werden.
Gleiches gilt für das Nennen der hinlänglich bekannten Verursacher der Sprengung der Nordstream 2-Pipelines, die dem scheidenden Bundeskanzler, an dessen Namen man sich schon jetzt nicht mehr erinnern kann, bekannt gewesen sein müssen. Selbst Trump soll sich auf die Frage, ob die USA maßgeblich daran beteiligt waren, geäußert haben, dass, wenn er auf diese Frage antworten würde, er seinem Land sehr schaden würde. Er könne aber mit Gewissheit sagen, dass es die Russen nicht waren. Immerhin ist eine für ganz Europa wichtige Energieversorgung absichtlich, bewusst und mutwillig zerstört worden. Aber aus Rücksicht darauf, dass die Wahrheit Teile der deutschen Bevölkerung verunsichern könnte, verzichtet man in Berlin auf eine Stellungnahme, lügt wiederholt, dass die Ermittlungen noch andauern und glaubt, dass man die Bürger damit ahnungslos halten kann. Die doofen Deutschen werden auch das noch schlucken.
Vergessen die Verpflichtung: Von deutschem Boden soll nur noch Frieden ausgehen. Vergessen die grauen Gesichter der Männer mit einem hochgeklappten Hosenbein, in der Kinderzeit. Wer von den aktuellen Kriegstreibern war live bei einem Gemetzel dabei, in dem Körperteile herumfliegen und Blut spritzt, in dem Menschen zerfetzt werden oder in ihren Panzern bei lebendigem Leib verbrennen? Viele Dümmste unter den Dummen kennen Krieg nur aus Video-Spielen. Nur einmal live als Zaungast dabei sein, und sehen, wie der halbe Darm aus dem Körper heraushängt, dann würde sich ihr großes Maul schon von alleine schließen.
Immer mehr Deutsche sagen: Das ist nicht mehr mein Staat. Kann man es ihnen verdenken?
Deutschland ist ein Paradebeispiel dafür, wie man in der heutigen Zeit, ein einst in aller Welt hochangesehenes Land, im Handumdrehen wirtschaftlich, politisch, rechtsstaatlich, gesundheitlich, und nicht zuletzt auch gesellschaftlich zerstören kann.
Sowohl innen- als auch außenpolitisch wurde nichts unterlassen, um Deutschland, vom Ausland aus gesehen, in die absolute Lächerlichkeit zu überführen.
Die Dummheit, gepaart mit unerträglicher Überheblichkeit, haben ein Maß erreicht, dass in die Gefährlichkeit übergegangen ist. Deutschland braucht gar keinen Feind von außen, denn der Feind sitzt im eigenen Land und zerstört es von innen heraus.
Der Eindruck taucht auf, dass spätestens mit dem Corona-Ereignis das Schleusentor des Wahnsinns sperrangelweit aufgerissen wurde, und keiner vermag es derzeit wieder zu schließen.
Entweder schließen sich Kräfte zusammen, die noch vorhanden sind, dieses Land von innen heraus zu retten, hierzu tragen auch die Neuen Medien erheblich bei, oder Deutschland ist noch einmal darauf angewiesen, von außen gerettet zu werden.
Zukunftsplanungen werden verunmöglicht. Mindestens eine Generation wird die komplette Lebensplanung geraubt. Man ist gezwungen, von einem Tag auf den anderen zu leben, weil alles derartig unberechenbar geworden ist. Eine junge Familie überlegt sich drei Mal, ob sie noch Kinder in diese Welt setzen will. Wo soll das enden?
Der Alltag in Deutschland gleicht einer Dauer-Vorstellung eines Theater-Stücks. Irgendwie läuft es noch, jedoch es fehlt der Rückhalt. Man versucht seinen Alltag zu meistern, Normalität zu leben, doch über allem schwebt das Damokles-Schwert. Keiner weiß, wie lange was noch gut geht und welchen Irrsinn sich die Realitätsverweigerer als Nächstes ausdenken werden. Manchen gelingt das Verdrängen recht gut. Manche schotten sich vollkommen von schlechten Nachrichten ab. Die Psychologie sagt jedoch, dass jedes erlebte Trauma den Menschen früher oder später einholen wird.
Wetten, wie lange die unheilvolle Allianz der Neuen Nullen halten wird, können ab sofort entgegengenommen werden. Und dann? Wie geht es weiter?
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
(Bild von pixabay)
-
 @ 6389be64:ef439d32
2025-05-03 07:17:36
@ 6389be64:ef439d32
2025-05-03 07:17:36In Jewish folklore, the golem—shaped from clay—is brought to life through sacred knowledge. Clay’s negative charge allows it to bind nutrients and water, echoing its mythic function as a vessel of potential.
Biochar in Amazonian terra preta shares this trait: it holds life-sustaining ions and harbors living intention. Both materials, inert alone, become generative through human action. The golem and black earths exist in parallel—one cultural, one ecological—shaping the lifeless into something that serves, protects, and endures.
originally posted at https://stacker.news/items/970089
-
 @ eac63075:b4988b48
2025-03-07 14:35:26
@ eac63075:b4988b48
2025-03-07 14:35:26Listen the Podcast:
https://open.spotify.com/episode/7lJWc1zaqA9CNhB8coJXaL?si=4147bca317624d34
https://www.fountain.fm/episode/YEGnlBLZhvuj96GSpuk9
Abstract
This paper examines a hypothetical scenario in which the United States, under Trump’s leadership, withdraws from NATO and reduces its support for Europe, thereby enabling a Russian conquest of Ukraine and the subsequent expansion of Moscow’s influence over Eurasia, while the US consolidates its dominance over South America. Drawing on classical geopolitical theories—specifically those of Halford Mackinder, Alfred Thayer Mahan, Rudolf Kjellén, and Friedrich Ratzel—the study analyzes how these frameworks can elucidate the evolving power dynamics and territorial ambitions in a reconfigured global order. The discussion highlights Mackinder’s notion of the Eurasian Heartland and its strategic importance, Mahan’s emphasis on maritime power and control of strategic routes, Kjellén’s view of the state as an expanding organism, and Ratzel’s concept of Lebensraum as a justification for territorial expansion. The paper also explores contemporary developments, such as the US–Ukraine economic agreement and Trump’s overt territorial ambitions involving Greenland and Canada, in light of these theories. By juxtaposing traditional geopolitical concepts with current international relations, the study aims to shed light on the potential implications of such shifts for regional stability, global security, and the balance of power, particularly in relation to emerging neocolonial practices in Latin America.
Introduction
In recent years, the geopolitical dynamics involving the United States, Russia, and Ukraine have sparked analyses from different theoretical perspectives. This paper examines recent events – presupposing a scenario in which Donald Trump withdraws the US from NATO and reduces its support for Europe, allowing a Russian conquest of Ukraine and the expansion of Moscow’s influence over Eurasia, while the US consolidates its dominance over South America – in light of classical geopolitical theories. The ideas of Halford Mackinder, Alfred Thayer Mahan, Rudolf Kjellén, and Friedrich Ratzel are used as reference points. The proposal is to impartially evaluate how each theory can elucidate the developments of this hypothetical scenario, relating Russian territorial expansion in Eurasia to the strategic retreat of the US to the Western Hemisphere.
Initially, we will outline Mackinder’s conception of the Heartland (the central Eurasian territory) and the crucial role of Eastern Europe and Ukraine in the quest for global dominance. Next, we will discuss Mahan’s ideas regarding maritime power and the control of strategic routes, considering the impacts on the naval power balance among the US, Russia, and other maritime powers such as the United Kingdom and Japan. Subsequently, we will examine Kjellén’s organic theory of the state, interpreting the Russian expansionist strategy as a reflection of a state organism in search of vital space. In the same vein, Ratzel’s concept of “Lebensraum” will be explored, along with how Russia could justify territorial expansion based on resources and territory. Finally, the paper connects these theories to the current political context, analyzing the direct negotiations between Washington and Moscow (overlooking Ukraine and Europe), the US policy toward authoritarian regimes in Latin America, and the notion of a hemispheric division of power – the “Island of the Americas” under North American hegemony versus an Eurasia dominated by Russia. Lastly, it considers the possibility that such a geopolitical arrangement may foster the strengthening of authoritarian governments globally, rather than containing them, thus altering the paradigms of the liberal world order.
The Heartland of Mackinder: Ukraine, Eurasia, and Global Dominance
Halford J. Mackinder, a British geographer and pioneer of geopolitics, proposed the celebrated Heartland Theory in the early twentieth century. Mackinder divided the world into geostrategic zones and identified the Heartland—the central continental mass of Eurasia—as the “geographical pivot of history” [5]. His most famous maxim encapsulates this vision: “who rules Eastern Europe commands the Heartland; who rules the Heartland commands the World Island; who rules the World Island commands the world” [5]. Eastern Europe and, in particular, the region of present-day Ukraine, play a key role in this formula. This is because, for Mackinder, Eastern Europe functions as a gateway to the Heartland, providing access to resources and a strategic position for the projection of continental power [5].
Applying this theory to our scenario, the conquest of Ukraine and Eastern European countries by Russia would have profound geopolitical implications. From a Mackinderian point of view, such a conquest would enormously strengthen Russia’s position in the Heartland by adding manpower (population) and Ukraine’s industrial and agricultural resources to its power base [5]. In fact, Mackinder argued that controlling the Heartland conferred formidable geostrategic advantages—a vast terrestrial “natural fortress” protected from naval invasions and rich in resources such as wheat, minerals, and fuels [5]. Thus, if Moscow were to incorporate Ukraine (renowned for its fertile soil and grain production, as well as its mineral reserves) and extend its influence over Eastern Europe, Russia would consolidate the Heartland under its direct control. In this context, the absence of the USA (withdrawn from NATO and less engaged in Europe) would remove an important obstacle to Russian predominance in the region.
With central and eastern Eurasia under Russian influence, it would be possible to move toward the realization of the geopolitical nightmare described by Mackinder for Western maritime powers: a hegemonic continental power capable of projecting power to both Europe and Asia. Mackinder himself warned that if a Heartland power gained additional access to an oceanic coastline—in other words, if it combined land power with a significant maritime front—it would constitute a “danger” to global freedom [5]. In the scenario considered, besides advancing into Eastern Europe, Russia would already possess strategic maritime outlets (for example, in the Black Sea, via Crimea, and in the Baltic, via Kaliningrad or the Baltic States if influenced). Thus, the control of Ukraine would reinforce Russia’s position in the Black Sea and facilitate projection into the Eastern Mediterranean, expanding its oceanic front. From a Mackinderian perspective, this could potentially transform Russia into the dominant power of the “World Island” (the combined mass of Europe, Asia, and Africa), thereby unbalancing the global geopolitical order [5].
It is worth noting that, historically, Mackinder’s doctrine influenced containment strategies: both in the interwar period and during the Cold War, efforts were made to prevent a single power from controlling the Heartland and Eastern Europe. NATO, for example, can be seen as an instrument to prevent Soviet/Russian advances in Europe, in line with Mackinder’s imperative to “contain the Heartland.” Thus, if the USA were to abandon that role—by leaving NATO and tacitly accepting the Russian sphere of influence in Eurasia—we would be witnessing an inversion of the principles that have guided Western policy for decades. In short, under Mackinder’s theory, the Russian conquest of Ukraine and beyond would represent the key for Russia to command the Heartland and, potentially, challenge global hegemony, especially in a scenario where the USA self-restricts to the Western Hemisphere.
The Maritime Power of Mahan and the Naval Balance between West and East
While Mackinder emphasized continental land power, Alfred Thayer Mahan, a nineteenth-century American naval strategist, highlighted the crucial role of maritime power in global dominance. In his work The Influence of Sea Power upon History (1890), Mahan studied the example of the British Empire and concluded that control of the seas paved the way for British supremacy as a world power [10]. He argued that a strong navy and the control of strategic maritime routes were decisive factors for projecting military, political, and economic power. His doctrine can be summarized in the following points: (1) the United States should aspire to be a world power; (2) control of the seas is necessary to achieve that status; (3) such control is obtained through a powerful fleet of warships [17]. In other words, for Mahan, whoever dominates the maritime routes and possesses naval superiority will be in a position to influence global destinies, ensuring trade, supplies, and the rapid movement of military forces.
In the proposed scenario, in which the USA withdraws militarily from Europe and possibly from the Eurasian stage, Mahan’s ideas raise questions about the distribution of maritime power and its effects. Traditionally, the US Navy operates globally, ensuring freedom of navigation and deterring challenges in major seas (Atlantic, Pacific, Indian, etc.). A withdrawal of the USA from NATO could also signal a reduction in its naval presence in the Northeast Atlantic, the Mediterranean Sea, and other areas close to Eurasia. In such a case, who would fill this naval vacuum? Russia, although primarily a land power, has been attempting to modernize its navy and has specific interests—for example, consolidating its dominance in the Black Sea and maintaining a presence in the Mediterranean (with a naval base in Tartus, Syria). The United Kingdom, a historic European maritime power, would remain aligned with the USA but, without American military support in Europe, might potentially be overwhelmed trying to contain an increasingly assertive Russian navy in European waters on its own. Japan, another significant maritime actor allied with the USA, is concerned with the naval balance in the Pacific; without full American engagement, Tokyo might be compelled to expand its own naval power to contain both Russia in the Far East (which maintains a fleet in the Pacific) and, especially, the growing Chinese navy.
According to Mahan’s thinking, strategic maritime routes and choke points (crucial straits and channels) become contested prizes in this power game. With the USA focusing on the Americas, one could imagine Washington reinforcing control over the Panama Canal and Caribbean routes—reviving an “American Gulf” policy in the Western Atlantic and Eastern Pacific. In fact, indications of this orientation emerge in statements attributed to Trump, who once suggested reclaiming direct control over Panama, transforming Canada into a North American state, and even “annexing” Greenland due to its Arctic geopolitical importance [18]. These aspirations reflect a quest to secure advantageous maritime positions near the American continent.
Conversely, in the absence of American presence in the Eastern Atlantic and Mediterranean, Russia would have free rein for regional maritime projection. This could include anything from the unrestricted use of the Black Sea (after dominating Ukraine, thereby ensuring full access to Crimea and Ukrainian ports) to greater influence in the Eastern Mediterranean via Syria and partnerships with countries such as Iran or Egypt. The Baltic Sea would also become an area of expanded Russian interest, pressuring coastal countries and perhaps reducing NATO’s traditional local naval supremacy. However, it is worth noting that even with these regional expansions, Russia lacks a blue-water navy comparable to that of the USA; thus, its initial global maritime impact would be limited without alliances.
An important aspect of Mahan’s theories is that naval power serves as a counterbalance to the land power of the Heartland. Therefore, even if Russia were to dominate the Eurasian continental mass, the continued presence of American naval might on the oceans could prevent complete global domination by Moscow. However, if the USA voluntarily restricts its naval reach to the Americas, it would forgo influencing the power balance in the seas adjacent to Eurasia. Consequently, the balance of maritime power would tend to shift in favor of regional Eurasian actors. The United Kingdom and Japan, traditional allies of the USA, could intensify their naval capabilities to defend regional interests—the United Kingdom safeguarding the North Atlantic and the North Sea, and Japan patrolling the Northwest Pacific—but both would face budgetary and structural limitations in fully compensating for the absence of the American superpower. Consequently, Mahan’s vision suggests that the withdrawal of the USA from the extra-regional scene would weaken the liberal maritime regime, possibly opening space for revisionist powers to contest routes that were previously secured (for example, Russia and China encountering less opposition on the routes of the Arctic and the Indo-Pacific, respectively). In summary, naval hegemony would fragment, and control of strategic seas would become contested, reconfiguring the relative influence of the USA, Russia, and maritime allies such as the United Kingdom and Japan.
Kjellén and the State as a Living Organism: Russian Expansion as an Organic Necessity
Another useful theoretical lens to interpret Russian geopolitical posture is that of Rudolf Kjellén, a Swedish political scientist of the early twentieth century who conceived the State as a living organism. Kjellén, who even coined the term “geopolitics,” was influenced by Friedrich Ratzel’s ideas and by social Darwinism, arguing that States are born, grow, and decline analogously to living beings [13]. In his work Staten som livsform (The State as a Form of Life, 1916), he maintained that States possess an organic dimension in addition to the legal one and that “just as any form of life, States must expand or die” [14]. This expansion would not be motivated merely by aggressive conquest but seen as a necessary growth for the self-preservation of the state organism [14]. In complement, Kjellén echoed Ratzel’s “law of expanding spaces” by asserting that large States expand at the expense of smaller ones, with it being only a matter of time before the great realms fill the available spaces [14]. That is, from the organic perspective, vigorous States tend to incorporate smaller neighboring territories, consolidating territorially much like an organism absorbing nutrients.
Applying this theory to the strategy of contemporary Russia, we can interpret Moscow’s actions—including the invasion of Ukraine and the ambition to restore its sphere of influence in Eurasia—as the expression of an organic drive for expansion. For a strategist influenced by this school, Russia (viewed as a state organism with a long imperial history) needs to expand its territory and influence to ensure its survival and security. The loss of control over spaces that once were part of the Russian Empire or the Soviet Union (such as Ukraine itself, the Caucasus, or Central Asia) may be perceived by Russian elites as an atrophy of the state organism, rendering it vulnerable. Thus, the reincorporation of these territories—whether directly (annexation) or indirectly (political vassalage)—would equate to restoring lost members or strengthening vital organs of the state body. In fact, official Russian arguments often portray Ukraine as an intrinsic part of “Russian historicity,” denying it a fully separate identity—a narrative that aligns with the idea that Russian expansion in that region is natural and necessary for the Russian State (seen as encompassing also Russian speakers beyond its current borders).
Kjellén would thus provide a theoretical justification for Russian territorial expansion as an organic phenomenon. As a great power, Russia would inevitably seek to expand at the expense of smaller neighbors (Ukraine, Georgia, the Baltic States, etc.), as dictated by the tendency of “great spaces to organize” to the detriment of the small [14]. This view can be identified in contemporary Russian doctrines that value spheres of influence and the notion that neighboring countries must gravitate around Moscow in order for the natural order to be maintained. The very idea of “Eurasia” united under Russian leadership (advocated by modern Russian thinkers) echoes this organic conception of vital space and expansion as a sign of the State’s vitality.
However, Kjellén’s theory also warns of the phenomenon of “imperial overstretch,” should a State exceed its internal cohesion limits by expanding excessively [14]. He recognized that extending borders too far could increase friction and vulnerabilities, making it difficult to maintain cohesion—a very large organism may lack functional integration. In the Russian context, this suggests that although expansion is seen as necessary, there are risks if Russia tries to encompass more than it can govern effectively. Conquering Ukraine and subjugating Eastern Europe, for example, could economically and militarily overburden the Russian State, especially if it faced resistance or had to manage hostile populations. However, in the hypothetical scenario we adopt (isolated USA and a weakened Europe), Russia might calculate that the organic benefits of expansion (territory, resources, strategic depth) would outweigh the costs, since external interference would be limited. Thus, through Kjellén’s lens, expansionist Russia behaves as an organism following its instinct for survival and growth, absorbing weaker neighbors; yet such a process is not devoid of challenges, requiring that the “organism Russia” manages to assimilate these new spaces without collapsing under its own weight.
Ratzel and Lebensraum: Resources, Territory, and the Justification for Expansion
Parallel to Kjellén’s organic view, Friedrich Ratzel’s theory offers another conceptual basis for understanding Russian expansion: the concept of Lebensraum (vital space). Ratzel, a German geographer of the late nineteenth century, proposed that the survival and development of a people or nation depended critically on the available physical space and resources. Influenced by Darwinist ideas, he applied the notion of “survival of the fittest” to nations, arguing that human societies need to conquer territory and resources to prosper, and that the stronger and fittest civilizations will naturally prevail over the weaker ones [12]. In 1901, Ratzel coined the term Lebensraum to describe this need for “vital space” as a geographical factor in national power [15].
Subsequently, this idea would be adopted—and extremely distorted—by Nazi ideology to justify Germany’s aggressions in Europe. However, the core of Ratzel’s concept is that territorial expansion is essential for the survival and growth of a State, especially to secure food, raw materials, and space for its population [12].
When examining Russia’s stance under this perspective, we can see several narratives that evoke the logic of Lebensraum. Russia is the largest country in the world by area; however, much of its territory is characterized by adverse climates (tundra, taiga) and is relatively sparsely populated in Siberia. On the other hand, adjacent regions such as Ukraine possess highly arable lands (chernozem—black soil), significant Slavic population density, and additional natural resources (coal in the Donbass, for example). An implicit justification for Russian expansion could be the search for supplementary resources and fertile lands to secure its self-sufficiency and power—exactly as Ratzel described that vigorous nations do. Historical records show that Ratzel emphasized agrarian primacy: he believed that new territories should be colonized by farmers, providing the food base for the nation [12]. Ukraine, historically called the “breadbasket of Europe,” fits perfectly into this vision of conquest for sustenance and agricultural wealth.
Furthermore, Ratzel viewed geography as a determinant of the destiny of nations—peoples adapted to certain habitats seek to expand them if they aspire to grow. In contemporary Russian discourse, there is often mention of the need to ensure security and territorial depth in the face of NATO, or to unite brotherly peoples (Russians and Russian speakers) within a single political space. Such arguments can be read as a modern translation of Lebensraum: the idea that the Russian nation, in order to be secure and flourish, must control a larger space, encompassing buffer zones and critical resources. This Russian “vital space” would naturally include Ukraine and other former Soviet republics, given the historical and infrastructural interdependence. Ratzel emphasized that peoples migrated and expanded when their original homeland no longer met their needs or aspirations [12]. Although contemporary Russia does not suffer from demographic pressure (on the contrary, it faces population decline), under the logic of a great power there is indeed a sentiment of geopolitical insufficiency for having lost influence over areas considered strategic. Thus, reconquering these areas would mean recovering the “habitat” necessary for the Russian nation to prosper and feel secure.
It is important to mention that, in Ratzel’s and Kjellén’s formulations, the pursuit of Lebensraum or organic expansion is not morally qualified—it is treated as a natural process in the politics of power. Thus, on the discursive level, Russia can avoid overly aggressive rhetoric and resort to “natural” justifications: for example, claiming that it needs to occupy Ukraine for defensive purposes (security space) or to reunify peoples (a common cultural and historical space). Beneath these justifications, however, resonates the geopolitical imperative to acquire more territory and resources as a guarantee of national survival, something consonant with Ratzel’s theory. In fact, Russian Realpolitik frequently prioritizes the control of energy resources (gas, oil) and transportation routes. Expanding its influence over central Eurasia would also mean controlling oil pipelines, gas lines, and logistical corridors—essential elements of modern Lebensraum understood as access to vital resources and infrastructure.
In summary, by conquering Ukraine and extending its reach into Eurasia, Russia could effectively invoke the concept of Lebensraum: presenting its expansion not as mere imperialism, but as a necessity to secure indispensable lands and resources for its people and to correct the “injustice” of a vital space diminished by post-Cold War territorial losses. The theories of Ratzel and Kjellén together paint a picture in which Russian expansion emerges almost as a natural law—the great State reclaiming space to ensure its survival and development at the expense of smaller neighbors.
Trump, NATO, and the Threat of American Withdrawal
One of the most alarming changes with Trump's return to power is the tense relationship with the North Atlantic Treaty Organization (NATO). Trump has long criticized allies for not meeting military spending targets, even threatening during his first term to withdraw the US from the alliance if members did not increase their contributions [2]. This threat, initially viewed with skepticism, became concrete after his re-election, leading European allies to seriously consider the possibility of having to defend themselves without American support [1]. In fact, Trump suggested in post-election interviews that the US would only remain in NATO if the allies “paid their bills” – otherwise, he “would seriously consider” leaving [2]. Such statements reinforced the warning that the US might not honor NATO's mutual defense commitment, precisely at a time of continuous Russian threat due to the war in Ukraine [1].
From a theoretical point of view, this posture of American retrenchment evokes the classic tension between maritime power and land power. Alfred Thayer Mahan emphasized that the global power of the US derived largely from its naval superiority and from alliances that ensured control over strategic maritime routes [9]. NATO, since 1949, has served not only to deter Soviet terrestrial advances in Eurasia, but also to secure the US naval presence in the North Atlantic and the Mediterranean – a fundamental element according to Mahan. In turn, Halford Mackinder warned that the balance of global power depended on the control of the Eurasian “Heartland” (the central region of Eurasia). The withdrawal or disengagement of the US (a maritime power) from this region could open the way for a continental power (such as Russia) to expand its influence in Eastern Europe, unbalancing the power balance [3]. In other words, by threatening to leave NATO, Trump jeopardizes the principle of containment that prevented Russian dominance over Eastern Europe – something that Mackinder would see as a dangerous shift in global power in favor of the Heartland power.
Adopting an impartial tone, it is observed that European countries have reacted to this new reality with precautionary measures. Strategic reports already calculate the cost of an autonomous European defense: hundreds of thousands of additional soldiers and investments of hundreds of billions of euros would be required if the US ceased to guarantee the security of the continent [1]. European dependence on American military power is significant and, without it, there would be a need for a major reinforcement of European Armed Forces [1]. This mobilization practically reflects the anticipation of a power vacuum left by the US – a scenario in which Mackinder’s theory (on the primacy of the Heartland and the vulnerability of the “external crescent” where Western Europe is located) regains its relevance.
The US–Ukraine Economic Agreement: Strategic Minerals in Exchange for Support?
Another novelty of Trump's second term is the unprecedented and transactional manner in which Washington has been dealing with the war in Ukraine. Instead of emphasizing security guarantees and alliances, the Trump administration proposed a trade agreement with Ukraine focused on the exploitation of strategic minerals, linking American support to a direct economic benefit. According to sources close to the negotiations, the US and Ukraine are about to sign a pact to share the revenues from the exploitation of critical mineral resources on Ukrainian territory [19]. Materials such as titanium, lithium, rare earths, and uranium – vital for high-tech and defense industries – would be at the core of this agreement [6]. According to the known draft, Ukraine would allocate 50% of the profits from new mineral ventures to a fund controlled by the US, which would reinvest part of the resources in the country’s own reconstruction [6] [19].
It is noteworthy that the pact does not include explicit security guarantees for Kyiv, despite Ukraine remaining under direct military threat from Russia [19]. Essentially, the Trump administration offers financial support and economic investment in exchange for a share in Ukrainian natural resources, but without formally committing to Ukraine's defense in the event of a renewed Russian offensive [19]. American authorities argue that this economic partnership would already be sufficient to “secure Ukrainian interests,” as it would provide the US with its own incentives to desire Ukraine’s stability [19]. “What could be better for Ukraine than being in an economic partnership with the United States?” stated Mike Waltz, a US national security advisor, defending the proposal [19].
Analysts, however, assess the agreement in divided terms. For some, it represents a form of economic exploitation at a time of Ukraine's fragility – comparing the demand to share mineral wealth amid war to a scheme of “mafia protection” [19]. Steven Cook, from the Council on Foreign Relations, classified the offer as “extortion,” and political scientist Virginia P. Fortna observed that charging resources from an invaded country resembles predatory practices [19]. Joseph Nye adds that it is a short-term gain strategy that could be “disastrous in the long run” for American credibility, reflecting the transactional approach that Trump even adopted with close allies in other contexts [19]. On the other hand, some see a future advantage for Kyiv: journalist Pierre Briançon suggests that at least this agreement aligns American commercial interests with Ukraine’s future, which could, in theory, keep the US involved in Ukrainian prosperity in the long term [19]. It is even recalled that President Zelensky himself proposed last year the idea of sharing natural resources with the US to bring the interests of the two countries closer together [19].
From the perspective of geopolitical theories, this agreement illustrates a shift towards economic pragmatism in international relations, approaching concepts proposed by Kjellén. Rudolf Kjellén, who coined the term “geopolitics,” saw the State as a territorial organism that seeks to ensure its survival through self-sufficiency and the control of strategic resources [4]. Trump's demand for a share in Ukrainian resources in order to continue supporting the country reflects a logic of autarky and direct national interest – that is, foreign policy serving primarily to reinforce the economic and material position of the US. This view contrasts with the traditional cooperative approach, but aligns with Kjellén’s idea that powerful States tend to transform international relations into opportunities for their own gain, ensuring access to vital raw materials. Similarly, Friedrich Ratzel argued that States have a “propensity to expand their borders according to their capacities,” seeking vital space (Lebensraum) and resources to sustain their development [11]. The US–Ukraine pact, by conditioning military/economic aid on obtaining tangible advantages (half of the mineral profits), is reminiscent of Ratzel’s perspective: the US, as a rising economic power, expands its economic influence over Ukrainian territory like an organism extending itself to obtain the necessary resources for its well-being. It is, therefore, a form of economic expansionism at the expense of purely ideological commitments or collective security.
Peace Negotiations Excluding Ukraine and the Legitimacy of the Agreement
Another controversial point is the manner in which peace negotiations between Russia and the West have been conducted under Trump's administration. Since taking office, the American president has engaged directly with Moscow in pursuit of a ceasefire, deliberately keeping the Ukrainian government out of the initial discussions [6]. Trump expressed his desire to “leave Zelensky out of the conversation” and also excluded the European Union from any influence in the process [6]. This negotiation strategy—conducted without the presence of the primary interested party, Ukraine—raises serious questions about the legitimacy and sustainability of any resulting agreement.
Historically, peace agreements reached without the direct participation of one of the conflicting parties tend to face problems in implementation and acceptance.
The exclusion of Ukraine in the decision-making phase brings to light the issue of guarantees. As noted, the emerging agreement lacks formal US security guarantees for Ukraine. This implies that, after the agreement is signed, nothing will prevent Russia from launching a new offensive if it deems it convenient, knowing that the US has not committed to defending it militarily. Experts have already warned that a ceasefire without robust protection may only be a pause for Russian rearmament, rendering the conflict “frozen” temporarily and potentially resumed in the near future. The European strategic community has expressed similar concern: without American deterrence, the risk of further Russian aggressions in the region increases considerably [1]. Denmark, for example, has released intelligence reports warning of possible imminent Russian attacks, prompting neighboring countries to accelerate plans for independent defense [1].
The legitimacy of this asymmetric peace agreement (negotiated without Ukraine fully at the table and under economic coercion) is also questionable from a legal and moral point of view. It violates the principle of self-determination by imposing terms decided by great powers on a sovereign country—a practice reminiscent of dark chapters in diplomacy, such as the Munich Agreement of 1938, when powers determined the fate of Czechoslovakia without its consent. In the current case, Ukraine would end up signing the agreement, but from a position of weakness, raising doubts about how durable such a commitment would be.
From Mackinder’s perspective, Ukraine’s removal from the battlefield without guarantees essentially means admitting a greater influence of Russia (the Heartland power) over Eastern Europe. This would alter the balance in Eurasia in a potentially lasting way. Furthermore, the fact that great powers negotiate over the heads of a smaller country evokes the imperial logic of the nineteenth and early twentieth centuries, when empires decided among themselves the divisions of foreign territories—a behavior that Mackinder saw as likely in a world of a “closed system.” With the entire world already occupied by States, Mackinder predicted that powers would begin to compete for influence within this consolidated board, often subjugating smaller states to gain advantage [3]. The US–Russia negotiation regarding Ukraine, without proper Ukrainian representation, exemplifies this type of neo-imperial dynamic in the twenty-first century.
Also noteworthy is the consonance with the ideas of Ratzel and Kjellén: both viewed smaller states as easily relegated to the status of satellites or even “parasitic organisms” in the orbit of larger states. Kjellén spoke of the intrinsic vulnerability of states with little territorial depth or economic dependence, making them susceptible to external pressures [4][20]. Ukraine, weakened by war and dependent on external aid, becomes a concrete example of this theorized vulnerability: it has had to cede strategic resources and accept terms dictated against its will in an attempt to secure its immediate survival. The resulting agreement, therefore, reflects a power imbalance characteristic of the hierarchical international relations described by classical geopolitical theorists.
Implicit Territorial Concessions and Trump’s Public Discourse
A central and controversial point in Trump’s statements regarding the war in Ukraine is the insinuation of territorial concessions to Russia as part of the conflict’s resolution. Publicly, Trump avoided explicitly condemning Russian aggression and even stated that he considered it “unlikely” that Ukraine would be able to retake all the areas occupied by the Russians [16]. In debates and interviews, he suggested that “if I were president, the war would end in 24 hours,” implying that he would force an understanding between Kyiv and Moscow that would likely involve ceding some territory in exchange for peace. This position marks a break with the previous US policy of not recognizing any territorial acquisitions made by force and fuels speculations that a future peace agreement sponsored by Trump would legitimize at least part of Russia’s gains since 2014 (Crimea, Donbass, and areas seized during the 2022 invasion).
The actions of his administration corroborate this interpretation. As discussed, the economic agreement focuses on the exploitation of Ukrainian natural resources, many of which are located precisely in regions currently under Russian military control, such as parts of the Zaporizhzhia Oblast, Donetsk, Lugansk, and the Azov Sea area [6]. A Ukrainian geologist, Hanna Liventseva, highlighted that “most of these elements (strategic minerals) are found in the south of the Ukrainian Shield, mainly in the Azov region, and most of these territories are currently invaded by Russia” [6]. This means that, to make joint exploitation viable, Russia’s de facto control over these areas would have to be recognized—or at least tolerated—in the short term. In other words, the pact indirectly and tacitly accepts Russian territorial gains, as it involves sharing the profits from resources that are not currently accessible to the Kyiv government.
Furthermore, figures close to Trump have made explicit statements regarding the possibility of territorial cession. Mike Waltz, Trump’s national security advisor, publicly stated that Zelensky might need to “cede land to Russia” to end the war [8]. This remark—made public in March 2025—confirms that the Trump White House considers it natural for Ukraine to relinquish parts of its territory in favor of an agreement. Such a stance marks a break from the previous Western consensus, which condemned any territorial gains by force. Under Trump, a pragmatic view (in the eyes of his supporters) or a cynical one (according to his critics) seems to prevail: sacrificing principles of territorial integrity to quickly end hostilities and secure immediate economic benefits.
In theoretical terms, this inclination to validate territorial gains by force recalls the concept of Realpolitik and the geopolitical Darwinism that influenced thinkers such as Ratzel. In Ratzel’s organic conception, expanding states naturally absorb neighboring territories when they are strong enough to do so, while declining states lose territory—a process almost biological in the selection of the fittest [11]. The Trump administration’s acceptance that Ukraine should “give something” to Moscow to seal peace reflects a normalization of this geopolitical selection process: it recognizes the aggressor (Russia) as having the “right” to retain conquered lands, because that is how power realities on the ground dictate. Mackinder, although firmly opposed to allowing Russia to dominate the Heartland, would see this outcome as the logical consequence of the lack of engagement from maritime powers (the USA and the United Kingdom, for example) in sustaining the Ukrainian counterattack. Without the active involvement of maritime power to balance the dispute, land power prevails in Eastern Europe.
From the perspective of international legitimacy, the cession of Ukrainian territories—whether de jure or de facto—creates a dangerous precedent in the post-Cold War era. Rewarding violent aggression with territorial gains may encourage similar strategies in other parts of the world, undermining the architecture of collective security. This is possibly a return to a world of spheres of influence, where great powers define borders and zones of control according to their convenience—something that the rules-based order after 1945 sought to avoid. Here, academic impartiality requires noting that coercion for territorial concessions rarely produces lasting peace, as the aggrieved party—in this case, Ukraine—may accept temporarily but will continue to assert its rights in the long term, as has occurred with other territorial injustices in history.
Territorial Ambitions of Trump: Greenland and Canada
Beyond the Eurasian theater of war, Trump revived geopolitical ambitions involving territories traditionally allied with the US: Greenland (an autonomous territory of Denmark) and Canada. As early as 2019, during his first term, Trump shocked the world by proposing to buy Greenland—rich in minerals and strategically positioned in the Arctic. Upon his return to power, he went further: expressing a “renewed interest” in acquiring Greenland and publicly suggesting the incorporation of Canada as the 51st American state [2].
In January 2025, during a press conference at Mar-a-Lago, he even displayed maps in which the US and Canada appeared merged into a single country, while Greenland was marked as a future American possession [2]. Posts by the president on social media included satirical images with a map of North America where Canada was labeled “51st” and Greenland designated as “Our Land” [2].
Such moves were met with concern and disbelief by allies. Canadian Prime Minister Justin Trudeau was caught on an open microphone warning that Trump’s fixation on annexation “is real” and not just a joke [7]. Trudeau emphasized that Washington appeared to covet Canada’s vast mineral resources, which would explain the insistence on the idea of absorption [7]. In public, Trump argued that Canadians “would be more prosperous as American citizens,” promising tax cuts and better services should they become part of the US [7]. On the Danish side, the reaction to the revived plan regarding Greenland was firmly negative—as it was in 2019—reaffirming that the territory is not for sale. Trump, however, insinuated that the issue might be one of national security, indicating that American possession of Greenland would prevent adverse influences (a reference to China and Russia in the Arctic) [2]. More worryingly, he refused to rule out the use of military means to obtain the island, although he assured that he had no intention of invading Canada by force (in the Canadian case, he spoke of “economic force” to forge a union) [2].
This series of initiatives reflects an unprecedented expansionist impetus by the US in recent times, at least in discourse. Analyzing this through the lens of classical geopolitics offers interesting insights. Friedrich Ratzel and his notion of Lebensraum suggest that powerful states, upon reaching a certain predominance, seek to expand their territory by influencing or incorporating adjacent areas. Trump, by targeting the immediate neighbor (Canada) and a nearby strategic territory (Greenland), appears to resurrect this logic of territorial expansion for the sake of gaining space and resources. Ratzel saw such expansion almost as a natural process for vigorous states, comparable to the growth of an organism [11]. From this perspective, the US would be exercising its “right” of expansion in North America and the polar region, integrating areas of vital interest.
Additionally, Alfred Mahan’s view on maritime power helps to understand the strategic value of Greenland. Mahan postulated that control of key maritime chokepoints and naval bases ensures global advantage [9]. Greenland, situated between the North Atlantic and the Arctic, has become increasingly relevant as climate change opens new polar maritime routes and reveals vast mineral deposits (including rare earth elements and oil). For the US, having a presence or sovereignty over Greenland would mean dominating the gateway to the Arctic and denying this space to rivals. This aligns with Mahan’s strategy of securing commercial and military routes (in this case, potential Arctic routes) and resources to consolidate naval supremacy. On the other hand, the incorporation of Canada—with its enormous territory, Arctic coastline, and abundant natural resources—would provide the US with formidable geoeconomic and geopolitical reinforcement, practically eliminating vulnerabilities along its northern border. This is an ambitious project that also echoes ideas of Kjellén, for whom an ideal State should seek territorial completeness and economic self-sufficiency within its region. Incorporating Canada would be the pinnacle of American regional autarky, turning North America into a unified bloc under Washington (a scenario reminiscent of the “pan-regions” conceived by twentieth-century geopoliticians influenced by Kjellén).
It is important to note, however, that these ambitions face enormous legal and political obstacles. The sovereignty of Canada and Greenland (Denmark) is guaranteed by international law, and both peoples categorically reject the idea of annexation. Any hostile action by the US against these countries would shake alliances and the world order itself. Even so, the very fact that an American president suggests such possibilities already produces geopolitical effects: traditional partners begin to distrust Washington’s intentions, seek alternative alliances, and strengthen nationalist discourses of resistance. In summary, Trump’s expansionist intentions in Greenland and Canada rekindle old territorial issues and paradoxically place the US in the position of a revisionist power—a role once associated with empires in search of colonies.
Implications for Brazil and South America: A New Neocolonization?
In light of this geopolitical reconfiguration driven by Trump's USA—with a reordering of alliances and a possible partition of spheres of influence among great powers—the question arises: what is the impact on Brazil and the other countries of South America? Traditionally, Latin America has been under the aegis of the Monroe Doctrine (1823), which established non-interference by Europe in the region and, implicitly, the primacy of the USA in the Western Hemisphere. In the post–Cold War period, this influence translated more into political and economic leadership, without formal annexations or direct territorial domination. However, the current context points to a kind of “neocolonization” of the Global South, in which larger powers seek to control resources and peripheral governments in an indirect yet effective manner.
Mackinder’s theories can be used to illuminate this dynamic. As mentioned, Mackinder envisioned the twentieth-century world as a closed system, in which there were no longer any unknown lands to be colonized—hence, the powers would fight among themselves for control over already occupied regions [3]. He predicted that Africa and Latin America (then largely European colonies or semi-colonies) would continue as boards upon which the great powers would project their disputes, a form of neocolonialism. In the current scenario, we see the USA proposing exchanges of protection for resources (as in Ukraine) and even leaders of developing countries seeking similar agreements. A notable example: the President of the Democratic Republic of the Congo, Felix Tshisekedi, praised the USA–Ukraine initiative and suggested an analogous agreement involving Congolese mineral wealth in exchange for US support against internal rebels (M23) [19]. In other words, African countries and possibly South American ones may enter into this logic of offering privileged access to resources (cobalt, lithium, food, biodiversity) in order to obtain security guarantees or investments. This represents a regression to the times when external powers dictated the directions of the South in exchange for promises of protection, characterizing a strategic neocolonialism.
For Brazil, in particular, this rearrangement generates both opportunities and risks. As a regional power with considerable diplomatic autonomy, Brazil has historically sought to balance relationships with the USA, Europe, China, and other actors, avoiding automatic alignments. However, in a world where Trump’s USA is actively redefining spheres of influence—possibly making deals with Russia that divide priorities (for example, Washington focusing on the Western Hemisphere and Moscow on the Eastern)—South America could once again be seen as an exclusive American sphere of influence. From this perspective, Washington could pressure South American countries to align with its directives, limiting partnerships with rivals (such as China) and seeking privileged access to strategic resources (such as the Amazon, fresh water, minerals, and agricultural commodities). Some indications are already emerging: Trump’s transactional approach mentioned by Nye included pressures on Canada and Mexico regarding border and trade issues, under the threat of commercial sanctions. It would not be unthinkable to adopt a hard line, for example, with regard to Brazilian environmental policies (linked to the Amazon) or Brazil’s relations with China, using tariffs or incentives as leverage—a sort of geopolitics of economic coercion.
On the other hand, Brazil and its neighbors could also attempt to take advantage of the Sino–North American competition. If the USA is distracted consolidating its hemispheric “hard power” hegemony (even with annexation fantasies in the north), powers such as China may advance their economic presence in South America through investments and trade (Belt and Road, infrastructure financing)—which is already happening. This would constitute an indirect neocolonial dispute in the South: Chinese loans and investments versus American demands and agreements, partly reminiscent of the nineteenth-century imperial competition (when the United Kingdom, USA, and others competed for Latin American markets and resources).
From a conceptual standpoint, Mackinder might classify South America as part of the “Outer Crescent” (external insular crescent)—peripheral to the great Eurasian “World-Island,” yet still crucial as a source of resources and a strategic position in the South Atlantic and Pacific. If the USA consolidates an informal empire in the Americas, it would be reinforcing its “insular bastion” far from the Eurasian Heartland, a strategy that Mackinder once suggested for maritime powers: to control islands and peripheral continents to compensate for the disadvantage of not controlling the Heartland. However, an excessive US dominance in the South could lead to local resistance and alternative alignments, unbalancing the region.
Kjellén would add that for Brazil to maintain its decisive sovereignty, it will need to strengthen its autarky and internal cohesion—in other words, reduce vulnerabilities (economic, military, social) that external powers might exploit [4]. Meanwhile, Mahan might point out the importance for Brazil of controlling its maritime routes and coastlines (South Atlantic) to avoid being at the mercy of a naval power like the USA. And Ratzel would remind us that states that do not expand their influence tend to be absorbed by foreign influences—which, in the context of Brazil, does not mean conquering neighboring territories, but rather actively leading South American integration to create a block more resilient to external intrusion.
In summary, South America finds itself in a more competitive and segmented world, where major players are resurrecting practices from past eras. The notion of “neocolonization” here does not imply direct occupation, but rather mechanisms of dependency: whether through unequal economic agreements or through diplomatic or military pressure for alignment. Brazil, as the largest economy and territory on the subcontinent, will have to navigate with heightened caution. A new global power balance, marked by the division of spheres of influence among the USA, China, and Russia, may reduce the sovereign maneuvering space of South American countries unless they act jointly. Thus, theoretical reflection suggests the need for South–South strategies, reinforcement of regional organizations, and diversification of partnerships to avoid falling into modern “neocolonial traps.”
Conclusion
The emerging post–re-election geopolitical conjuncture of Donald Trump signals a return to classical geopolitical principles, after several decades of predominance of institutional liberal views. We witness the revaluation of concepts such as spheres of influence, exchanges of protection for resources, naval power versus land power, and disputes over territory and raw materials—all central themes in the writings of Mackinder, Mahan, Kjellén, and Ratzel at the end of the nineteenth and the beginning of the twentieth century. An impartial analysis of these events, in light of these theories, shows internal coherence in Trump’s actions: although controversial, they follow a logic of maximizing national interest and the relative power of the USA on the world stage, even at the expense of established principles and alliances.
Halford Mackinder reminds us that, in a closed world with no new lands to conquer, the great powers will seek to redistribute the world among themselves [3]. This seems to manifest in the direct understandings between the USA and Russia over the fate of Ukraine, and in American ambitions in the Arctic and the Western Hemisphere. Alfred Mahan emphasizes that the control of the seas and strategic positions ensures supremacy—we see reflections of this in Trump’s obsession with Greenland (Arctic) and the possible neglect of the importance of maintaining NATO (and therefore the North Atlantic) as a cohesive bloc, something that Mahan’s theory would criticize due to the risk of a naval vacuum. Rudolf Kjellén and Friedrich Ratzel provide the framework to understand the more aggressive facet of expansionist nationalism: the idea of the State as an organism that needs to grow, secure resources, and seek self-sufficiency explains everything from the extortionate agreement imposed on Ukraine to the annexation rhetoric regarding Canada.
The potential consequences are profound. In the short term, we may witness a precarious ceasefire in the Ukraine war, with consolidated Russian territorial gains and Ukraine economically tied to the USA, but without formal military protection—a fragile “armed peace.” Western Europe, alarmed, may accelerate its independent militarization, perhaps marking the beginning of European defense autonomy, as is already openly debated [1]. At the far end of the globe, American activism in the Arctic and the Americas may reshape alliances: countries like Canada, once aligned with Washington, might seek to guarantee their sovereignty by distancing themselves from it; powers like China could take advantage of the openings to increase their presence in Latin America and Africa through economic diplomacy; and emerging countries of the Global South may have to choose between submitting to new “guardianships” or strengthening South–South cooperation.
Ultimately, the current situation reinforces the relevance of studying geopolitics through historical lenses. The actions of the Trump administration indicate that, despite all technological and normative advances, the competition for geographic power has not disappeared—it has merely assumed new formats. Academic impartiality obliges us not to prematurely judge whether these strategies will be successful or beneficial, but history and theory warn that neo-imperial movements tend to generate counter-reactions. As Mackinder insinuated, “every shock or change anywhere reverberates around the world,” and a sudden move by a superpower tends to provoke unforeseen adjustments and chain conflicts. It remains to be seen how the other actors—including Brazil and its neighbors—will adapt to this new chapter in the great struggle for global power, in which centuries-old theories once again have a surprising explanatory power over present events.
Bibliography
[1] A Referência. (2025). Europa calcula o custo de se defender sem os EUA: 300 mil soldados e 250 bilhões de euros a mais. Recuperado em 3 de março de 2025, de https://areferencia.com/europa/europa-calcula-o-custo-de-se-defender-sem-os-eua-300-mil-soldados-e-250-bilhoes-de-euros-a-mais/#:\~:text=Europa%20calcula%20o%20custo%20de,bilh%C3%B5es%20de%20euros%20a%20mais
[2] Brexit Institute. (2025). What happens if Trump invades Greenland? Recuperado em 3 de março de 2025, de https://dcubrexitinstitute.eu/2025/01/what-happens-if-trump-invades-greenland/#:\~:text=Ever%20since%20Donald%20Trump%20announced,agreed%20in%20Wales%20in%202014
[3] Cfettweis C:CST22(2)8576.DVI. (2025). Mackinder and Angell. Recuperado em 3 de março de 2025, de https://cfettweis.com/wp-content/uploads/Mackinder-and-Angell.pdf#:\~:text=meant%20the%20beginning%20of%20an,Mackinder
[4] Diva-Portal. (2025). The geopolitics of territorial relativity. Poland seen by Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://www.diva-portal.org/smash/get/diva2:1696547/FULLTEXT02#:\~:text=,The%20state%20territory
[5] Geopolitical Monitor. (2025). The Russo-Ukrainian War and Mackinder’s Heartland Thesis. Recuperado em 3 de março de 2025, de https://www.geopoliticalmonitor.com/the-ukraine-war-and-mackinders-heartland-thesis/#:\~:text=In%201904%2C%20Sir%20Halford%20J,in%20adding%20a%20substantial%20oceanic
[6] Instituto Humanitas Unisinos. (2025). Trump obriga Zelensky a hipotecar a exploração de minerais críticos em troca do seu apoio. Recuperado em 3 de março de 2025, de https://www.ihu.unisinos.br/648986-trump-obriga-zelensky-a-hipotecar-a-exploracao-de-minerais-criticos-em-troca-do-seu-apoio#:\~:text=Essa%20troca%20inclui%20os%20cobi%C3%A7ados,s%C3%A3o%20praticamente%20inexploradas%20no%20pa%C3%ADs
[7] Politico. (2025). Trump’s annexation fixation is no joke, Trudeau warns. Recuperado em 3 de março de 2025, de https://www.politico.com/news/2025/02/07/canada-trudeau-trump-51-state-00203156#:\~:text=TORONTO%20%E2%80%94%20Prime%20Minister%20Justin,Canada%20becoming%20the%2051st%20state%2C%E2%80%9D%20Trudeau%20said
[8] The Daily Beast. (2025). Top Trump Adviser Moves Goalpost for Ukraine to End War. Recuperado em 3 de março de 2025, de https://www.thedailybeast.com/top-trump-adviser-moves-goalpost-for-ukraine-to-end-war/#:\~:text=LAND%20GRAB
[9] The Geostrata. (2025). Alfred Thayer Mahan and Supremacy of Naval Power. Recuperado em 3 de março de 2025, de https://www.thegeostrata.com/post/alfred-thayer-mahan-and-supremacy-of-naval-power#:\~:text=Alfred%20Thayer%20Mahan%20and%20Supremacy,control%20over%20maritime%20trade%20routes
[10] U.S. Department of State. (2025). Mahan’s The Influence of Sea Power upon History: Securing International Markets in the 1890s. Recuperado em 3 de março de 2025, de https://history.state.gov/milestones/1866-1898/mahan#:\~:text=Mahan%20argued%20that%20British%20control,American%20politicians%20believed%20that%20these
[11] Britannica. (2025a). Friedrich Ratzel | Biogeography, Anthropogeography, Political Geography. Recuperado em 3 de março de 2025, de https://www.britannica.com/biography/Friedrich-Ratzel#:\~:text=webster,Swedish%20political%20scientist%20%2076
[12] Britannica. (2025b). Lebensraum. Recuperado em 3 de março de 2025, de https://www.britannica.com/topic/Lebensraum#:\~:text=defined,The
[13] Britannica. (2025c). Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://www.britannica.com/biography/Rudolf-Kjellen
[14] Wikipedia (ZH). (2025). Rudolf Kjellén. Recuperado em 3 de março de 2025, de https://zh.wikipedia.org/wiki/w:Rudolf_Kjell%C3%A9n#:\~:text=Besides%20legalistic%2C%20states%20have%20organic,preservation.%20%5B%203
[15] Wikipedia. (2025). Lebensraum. Recuperado em 3 de março de 2025, de https://en.wikipedia.org/wiki/Lebensraum#:\~:text=The%20German%20geographer%20and%20ethnographer,into%20the%20Greater%20Germanic%20Reich
[16] YouTube. (2025). Trump says Ukraine 'unlikely to get all land back' or join NATO [Vídeo]. Recuperado em 3 de março de 2025, de https://www.youtube.com/watch?v=BmHzAVLhsXU#:\~:text=Trump%20says%20Ukraine%20%27unlikely%20to,for%20it%20to%20join%20NATO
[17] U.S. Naval Institute. (2025) Operation World Peace. Recuperado em 3 de março de 2025, de https://www.usni.org/magazines/proceedings/1955/june/operation-world-peace#:\\~:text=“The Mahan doctrine%2C” according to,the word “airships” is more
[18] Emissary. (2024) Trump’s Greenland and Panama Canal Threats Are a Throwback to an Old, Misguided Foreign Policy. Recuperado em 3 de março de 2025, de https://carnegieendowment.org/emissary/2025/01/trump-greenland-panama-canal-monroe-doctrine-policy?lang=en
[19] A Referência. Acordo EUA-Ucrânia está praticamente fechado, mas analistas se dividem sobre quem sairá ganhando. Recuperado em 3 de março de 2025, de https://areferencia.com/europa/acordo-eua-ucrania-esta-praticamente-fechado-mas-analistas-se-dividem-sobre-quem-saira-ganhando/#:\\~:text=EUA e 17,o acordo a seu favor
[20] Wikipedia. (2025) Geopolitik. Recuperado em 3 de março de 2025, de https://en.wikipedia.org/wiki/Geopolitik#:\\~:text=Rudolph Kjellén was Ratzel's Swedish,Kjellén's State
-
 @ d9a329af:bef580d7
2025-05-03 04:20:42
@ d9a329af:bef580d7
2025-05-03 04:20:42To be clear, this is 100% my subjective opinion on the alternatives to popular music, as it has become practically a formula of witchcraft, pseudoscience and mysticism. There is nothing you can do to get me to listen to Western pop music from the late 2010's to now. I could certainly listen to almost anything... just not modern pop, which is now completely backwards.
Most examples of compositions for these genres will be my own, unless otherwise stated. The genres on this list are in no particular order, though my favorite of which will be first: 1. Bossa Nova
Bossa Nova is a subgenre of jazz from Brazil, created in the 1950's as a mix of standard jazz and samba rhythms in a more gentle and relaxing manner. This genre's most famous songs are Tom Jobim's The Girl from Ipanema (found in albums like Getz/Gilberto), Wave, and even Triste. Most of the music is written in 2/4 time signature, and any key is almost acceptable. It's called Afro-Brazilian Jazz for a reason after all. I have a ton of compositions I produced, from Forget and Regret, to Rabbit Theory, Beaches of Gensokyo Past, Waveside, and even Willows of Ice to name a few of them.
- Metal
This is an umbrella term for many subgenres of this fork of hard rock, with more distorted guitars, speedy and technical writing, vocals that sound demonic (some subgenres don't have that), or sometimes, chaotic lyrics and downright nasty ones if you look deep enough. If you want to get into it, just make sure it's not Black Metal (it's weird), Blackened Metal (Any subgenre of metal that's been inserted with elements of Black Metal), Metalcore, or any other genre that has vocals that aren't the best to hear (these are vocal fries that are really good if you're into the weird demonic sounds). This isn't for the faint of heart. Instrumental metal is good though, and an example is my composition from Touhou Igousaken called A Sly Foxy Liar if you want to know what techincal groove metal is like at a glance.
- Touhou-style
I can attest to this one, as I produced bossa nova with a Touhou-like writing style. Touhou Project is a series of action video games created by one guy (Jun'ya Outa, a.k.a. ZUN), and are usually bullet curtain games in the main franchise, with some official spinoffs that are also action games (fighting games like Touhou 12.3 ~ Hisoutensoku). What I'm referring to here is music written by ZUN himself (He does almost everything for Touhou Project, and he's really good at it), or fans that write to his style with their own flair. I did this once with my composition, Toiled Bubble, which is from my self-titled EP. I probably wouldn't do much with it to be fair, and stick to bossa nova (my main genre if you couldn't tell).
- Hip-Hop/Rap
This can get subjective here, but old-school rap and hip-hop... give me more of it. Before it became corrupted with all kinds of immoral things, hip-hop and rap were actually very good for their time. These were new, innovative and creative with how lyrics were written. Nowadays, while we're talking about cars, unspeakable acts, money, and just being dirtbags, artists in this genre back then were much classier than that. I fit in the latter category with my piece entitled, Don't Think, Just Roast, where I called out antis for a Vtuber agency who wanted to give its talent a hard time. It didn't get much traction on YouTube, because I'm not a well-known artist (I'm considered a nobody in the grand scheme of things. I'd like to get it fixed, but I don't want a record deal... I'd have to become a Pharisee or a Jesuit for that).
- Synthwave
This is a genre of electronic music focused on 80's and 90's synths being used to carry a composition. Nowadays, we have plugins like Vital, Serum, Surge and others to create sounds we would otherwise be hearing on an 80's or 90's keyboard. An example of this is my composition, Wrenched Torque, which was composed for a promotion I did with RAES when he released his Vital synth pack.
More are to come in future installments of this series, and I will adjust the title of this one accordingly if y'all have any ideas of genres I should look into.
-
 @ c1e9ab3a:9cb56b43
2025-04-11 04:41:15
@ c1e9ab3a:9cb56b43
2025-04-11 04:41:15Reanalysis: Could the Great Pyramid Function as an Ammonia Generator Powered by a 25GW Breeder Reactor?
Introduction
The Great Pyramid of Giza has traditionally been considered a tomb or ceremonial structure. Yet an intriguing alternative hypothesis suggests it could have functioned as a large-scale ammonia generator, powered by a high-energy source, such as a nuclear breeder reactor. This analysis explores the theoretical practicality of powering such a system using a continuous 25-gigawatt (GW) breeder reactor.
The Pyramid as an Ammonia Generator
Producing ammonia (NH₃) from atmospheric nitrogen (N₂) and hydrogen (H₂) requires substantial energy. Modern ammonia production (via the Haber-Bosch process) typically demands high pressure (~150–250 atmospheres) and temperatures (~400–500°C). However, given enough available energy, it is theoretically feasible to synthesize ammonia at lower pressures if catalysts and temperatures are sufficiently high or if alternative electrochemical or plasma-based fixation methods are employed.
Theoretical System Components:
-
High Heat Source (25GW breeder reactor)
A breeder reactor could consistently generate large amounts of heat. At a steady state of approximately 25GW, this heat source would easily sustain temperatures exceeding the 450°C threshold necessary for ammonia synthesis reactions, particularly if conducted electrochemically or catalytically. -
Steam and Hydrogen Production
The intense heat from a breeder reactor can efficiently evaporate water from subterranean channels (such as those historically suggested to exist beneath the pyramid) to form superheated steam. If coupled with high-voltage electrostatic fields (possibly in the millions of volts), steam electrolysis into hydrogen and oxygen becomes viable. This high-voltage environment could substantially enhance electrolysis efficiency. -
Nitrogen Fixation (Ammonia Synthesis)
With hydrogen readily produced, ammonia generation can proceed. Atmospheric nitrogen, abundant around the pyramid, can combine with the hydrogen generated through electrolysis. Under these conditions, the pyramid's capstone—potentially made from a catalytic metal like osmium, platinum, or gold—could facilitate nitrogen fixation at elevated temperatures.
Power Requirements and Energy Calculations
A thorough calculation of the continuous power requirements to maintain this system follows:
- Estimated Steady-state Power: ~25 GW of continuous thermal power.
- Total Energy Over 10,000 years: """ Energy = 25 GW × 10,000 years × 365.25 days/year × 24 hrs/day × 3600 s/hr ≈ 7.9 × 10²¹ Joules """
Feasibility of a 25GW Breeder Reactor within the Pyramid
A breeder reactor capable of sustaining 25GW thermal power is physically plausible—modern commercial reactors routinely generate 3–4GW thermal, so this is within an achievable engineering scale (though certainly large by current standards).
Fuel Requirements:
- Each kilogram of fissile fuel (e.g., U-233 from Thorium-232) releases ~80 terajoules (TJ) or 8×10¹³ joules.
- Considering reactor efficiency (~35%), one kilogram provides ~2.8×10¹³ joules usable energy: """ Fuel Required = 7.9 × 10²¹ J / 2.8 × 10¹³ J/kg ≈ 280,000 metric tons """
- With a breeding ratio of ~1.3: """ Initial Load = 280,000 tons / 1.3 ≈ 215,000 tons """
Reactor Physical Dimensions (Pebble Bed Design):
- King’s Chamber size: ~318 cubic meters.
- The reactor core would need to be extremely dense and highly efficient. Advanced engineering would be required to concentrate such power in this space, but it is within speculative feasibility.
Steam Generation and Scaling Management
Key methods to mitigate mineral scaling in the system: 1. Natural Limestone Filtration 2. Chemical Additives (e.g., chelating agents, phosphate compounds) 3. Superheating and Electrostatic Ionization 4. Electrostatic Control
Conclusion and Practical Considerations
Yes, the Great Pyramid could theoretically function as an ammonia generator if powered by a 25GW breeder reactor, using: - Thorium or Uranium-based fertile material, - Sustainable steam and scaling management, - High-voltage-enhanced electrolysis and catalytic ammonia synthesis.
While speculative, it is technologically coherent when analyzed through the lens of modern nuclear and chemical engineering.
See also: nostr:naddr1qqxnzde5xymrgvekxycrswfeqy2hwumn8ghj7am0deejucmpd3mxztnyv4mz7q3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wun9c08
-
-
 @ d34e832d:383f78d0
2025-03-07 01:47:15
@ d34e832d:383f78d0
2025-03-07 01:47:15
A comprehensive system for archiving and managing large datasets efficiently on Linux.
1. Planning Your Data Archiving Strategy
Before starting, define the structure of your archive:
✅ What are you storing? Books, PDFs, videos, software, research papers, backups, etc.
✅ How often will you access the data? Frequently accessed data should be on SSDs, while deep archives can remain on HDDs.
✅ What organization method will you use? Folder hierarchy and indexing are critical for retrieval.
2. Choosing the Right Storage Setup
Since you plan to use 2TB HDDs and store them away, here are Linux-friendly storage solutions:
📀 Offline Storage: Hard Drives & Optical Media
✔ External HDDs (2TB each) – Use
ext4orXFSfor best performance.
✔ M-DISC Blu-rays (100GB per disc) – Excellent for long-term storage.
✔ SSD (for fast access archives) – More durable than HDDs but pricier.🛠 Best Practices for Hard Drive Storage on Linux
🔹 Use
smartctlto monitor drive health
bash sudo apt install smartmontools sudo smartctl -a /dev/sdX🔹 Store drives vertically in anti-static bags.
🔹 Rotate drives periodically to prevent degradation.
🔹 Keep in a cool, dry, dark place.☁ Cloud Backup (Optional)
✔ Arweave – Decentralized storage for public data.
✔ rclone + Backblaze B2/Wasabi – Cheap, encrypted backups.
✔ Self-hosted options – Nextcloud, Syncthing, IPFS.
3. Organizing and Indexing Your Data
📂 Folder Structure (Linux-Friendly)
Use a clear hierarchy:
plaintext 📁 /mnt/archive/ 📁 Books/ 📁 Fiction/ 📁 Non-Fiction/ 📁 Software/ 📁 Research_Papers/ 📁 Backups/💡 Use YYYY-MM-DD format for filenames
✅2025-01-01_Backup_ProjectX.tar.gz
✅2024_Complete_Library_Fiction.epub📑 Indexing Your Archives
Use Linux tools to catalog your archive:
✔ Generate a file index of a drive:
bash find /mnt/DriveX > ~/Indexes/DriveX_index.txt✔ Use
locatefor fast searches:
bash sudo updatedb # Update database locate filename✔ Use
Recollfor full-text search:
bash sudo apt install recoll recoll🚀 Store index files on a "Master Archive Index" USB drive.
4. Compressing & Deduplicating Data
To save space and remove duplicates, use:
✔ Compression Tools:
-tar -cvf archive.tar folder/ && zstd archive.tar(fast, modern compression)
-7z a archive.7z folder/(best for text-heavy files)✔ Deduplication Tools:
-fdupes -r /mnt/archive/(finds duplicate files)
-rdfind -deleteduplicates true /mnt/archive/(removes duplicates automatically)💡 Use
par2to create parity files for recovery:
bash par2 create -r10 file.par2 file.extThis helps reconstruct corrupted archives.
5. Ensuring Long-Term Data Integrity
Data can degrade over time. Use checksums to verify files.
✔ Generate Checksums:
bash sha256sum filename.ext > filename.sha256✔ Verify Data Integrity Periodically:
bash sha256sum -c filename.sha256🔹 Use
SnapRAIDfor multi-disk redundancy:
bash sudo apt install snapraid snapraid sync snapraid scrub🔹 Consider ZFS or Btrfs for automatic error correction:
bash sudo apt install zfsutils-linux zpool create archivepool /dev/sdX
6. Accessing Your Data Efficiently
Even when archived, you may need to access files quickly.
✔ Use Symbolic Links to "fake" files still being on your system:
bash ln -s /mnt/driveX/mybook.pdf ~/Documents/✔ Use a Local Search Engine (Recoll):
bash recoll✔ Search within text files usinggrep:
bash grep -rnw '/mnt/archive/' -e 'Bitcoin'
7. Scaling Up & Expanding Your Archive
Since you're storing 2TB drives and setting them aside, keep them numbered and logged.
📦 Physical Storage & Labeling
✔ Store each drive in fireproof safe or waterproof cases.
✔ Label drives (Drive_001,Drive_002, etc.).
✔ Maintain a printed master list of drive contents.📶 Network Storage for Easy Access
If your archive grows too large, consider:
- NAS (TrueNAS, OpenMediaVault) – Linux-based network storage.
- JBOD (Just a Bunch of Disks) – Cheap and easy expansion.
- Deduplicated Storage –ZFS/Btrfswith auto-checksumming.
8. Automating Your Archival Process
If you frequently update your archive, automation is essential.
✔ Backup Scripts (Linux)
Use
rsyncfor incremental backups:bash rsync -av --progress /source/ /mnt/archive/Automate Backup with Cron Jobs
bash crontab -eAdd:plaintext 0 3 * * * rsync -av --delete /source/ /mnt/archive/This runs the backup every night at 3 AM.Automate Index Updates
bash 0 4 * * * find /mnt/archive > ~/Indexes/master_index.txt
So Making These Considerations
✔ Be Consistent – Maintain a structured system.
✔ Test Your Backups – Ensure archives are not corrupted before deleting originals.
✔ Plan for Growth – Maintain an efficient catalog as data expands.For data hoarders seeking reliable 2TB storage solutions and appropriate physical storage containers, here's a comprehensive overview:
2TB Storage Options
1. Hard Disk Drives (HDDs):
-
Western Digital My Book Series: These external HDDs are designed to resemble a standard black hardback book. They come in various editions, such as Essential, Premium, and Studio, catering to different user needs. citeturn0search19
-
Seagate Barracuda Series: Known for affordability and performance, these HDDs are suitable for general usage, including data hoarding. They offer storage capacities ranging from 500GB to 8TB, with speeds up to 190MB/s. citeturn0search20
2. Solid State Drives (SSDs):
- Seagate Barracuda SSDs: These SSDs come with either SATA or NVMe interfaces, storage sizes from 240GB to 2TB, and read speeds up to 560MB/s for SATA and 3,400MB/s for NVMe. They are ideal for faster data access and reliability. citeturn0search20
3. Network Attached Storage (NAS) Drives:
- Seagate IronWolf Series: Designed for NAS devices, these drives offer HDD storage capacities from 1TB to 20TB and SSD capacities from 240GB to 4TB. They are optimized for multi-user environments and continuous operation. citeturn0search20
Physical Storage Containers for 2TB Drives
Proper storage of your drives is crucial to ensure data integrity and longevity. Here are some recommendations:
1. Anti-Static Bags:
Essential for protecting drives from electrostatic discharge, especially during handling and transportation.
2. Protective Cases:
- Hard Drive Carrying Cases: These cases offer padded compartments to securely hold individual drives, protecting them from physical shocks and environmental factors.
3. Storage Boxes:
- Anti-Static Storage Boxes: Designed to hold multiple drives, these boxes provide organized storage with anti-static protection, ideal for archiving purposes.
4. Drive Caddies and Enclosures:
- HDD/SSD Enclosures: These allow internal drives to function as external drives, offering both protection and versatility in connectivity.
5. Fireproof and Waterproof Safes:
For long-term storage, consider safes that protect against environmental hazards, ensuring data preservation even in adverse conditions.
Storage Tips:
-
Labeling: Clearly label each drive with its contents and date of storage for easy identification.
-
Climate Control: Store drives in a cool, dry environment to prevent data degradation over time.
By selecting appropriate 2TB storage solutions and ensuring they are stored in suitable containers, you can effectively manage and protect your data hoard.
Here’s a set of custom Bash scripts to automate your archival workflow on Linux:
1️⃣ Compression & Archiving Script
This script compresses and archives files, organizing them by date.
```bash!/bin/bash
Compress and archive files into dated folders
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_DIR="$ARCHIVE_DIR/$DATE"
mkdir -p "$BACKUP_DIR"
Find and compress files
find ~/Documents -type f -mtime -7 -print0 | tar --null -czvf "$BACKUP_DIR/archive.tar.gz" --files-from -
echo "Backup completed: $BACKUP_DIR/archive.tar.gz" ```
2️⃣ Indexing Script
This script creates a list of all archived files and saves it for easy lookup.
```bash!/bin/bash
Generate an index file for all backups
ARCHIVE_DIR="/mnt/backup" INDEX_FILE="$ARCHIVE_DIR/index.txt"
find "$ARCHIVE_DIR" -type f -name "*.tar.gz" > "$INDEX_FILE"
echo "Index file updated: $INDEX_FILE" ```
3️⃣ Storage Space Monitor
This script alerts you if the disk usage exceeds 90%.
```bash!/bin/bash
Monitor storage usage
THRESHOLD=90 USAGE=$(df -h | grep '/mnt/backup' | awk '{print $5}' | sed 's/%//')
if [ "$USAGE" -gt "$THRESHOLD" ]; then echo "WARNING: Disk usage at $USAGE%!" fi ```
4️⃣ Automatic HDD Swap Alert
This script checks if a new 2TB drive is connected and notifies you.
```bash!/bin/bash
Detect new drives and notify
WATCHED_SIZE="2T" DEVICE=$(lsblk -dn -o NAME,SIZE | grep "$WATCHED_SIZE" | awk '{print $1}')
if [ -n "$DEVICE" ]; then echo "New 2TB drive detected: /dev/$DEVICE" fi ```
5️⃣ Symbolic Link Organizer
This script creates symlinks to easily access archived files from a single directory.
```bash!/bin/bash
Organize files using symbolic links
ARCHIVE_DIR="/mnt/backup" LINK_DIR="$HOME/Archive_Links"
mkdir -p "$LINK_DIR" ln -s "$ARCHIVE_DIR"//.tar.gz "$LINK_DIR/"
echo "Symbolic links updated in $LINK_DIR" ```
🔥 How to Use These Scripts:
- Save each script as a
.shfile. - Make them executable using:
bash chmod +x script_name.sh - Run manually or set up a cron job for automation:
bash crontab -e
Add this line to run the backup every Sunday at midnight:
bash 0 0 * * 0 /path/to/backup_script.sh
Here's a Bash script to encrypt your backups using GPG (GnuPG) for strong encryption. 🚀
🔐 Backup & Encrypt Script
This script will:
✅ Compress files into an archive
✅ Encrypt it using GPG
✅ Store it in a secure location```bash
!/bin/bash
Backup and encrypt script
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" GPG_RECIPIENT="your@email.com" # Change this to your GPG key or use --symmetric for password-based encryption
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup using GPG
gpg --output "$ENCRYPTED_FILE" --encrypt --recipient "$GPG_RECIPIENT" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security else echo "Encryption failed!" fi ```
🔓 Decrypting a Backup
To restore a backup, run:
bash gpg --decrypt --output backup.tar.gz backup_YYYY-MM-DD.tar.gz.gpg tar -xzvf backup.tar.gz
🔁 Automating with Cron
To run this script every Sunday at midnight:
bash crontab -eAdd this line:
bash 0 0 * * 0 /path/to/encrypt_backup.sh
🔐 Backup & Encrypt Script (Password-Based)
This script:
✅ Compresses files into an archive
✅ Encrypts them using GPG with a passphrase
✅ Stores them in a secure location```bash
!/bin/bash
Backup and encrypt script (password-based)
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" PASSPHRASE="YourStrongPassphraseHere" # Change this!
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup with a password
gpg --batch --yes --passphrase "$PASSPHRASE" --symmetric --cipher-algo AES256 --output "$ENCRYPTED_FILE" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security else echo "Encryption failed!" fi ```
🔓 Decrypting a Backup
To restore a backup, run:
bash gpg --batch --yes --passphrase "YourStrongPassphraseHere" --decrypt --output backup.tar.gz backup_YYYY-MM-DD.tar.gz.gpg tar -xzvf backup.tar.gz
🔁 Automating with Cron
To run this script every Sunday at midnight:
bash crontab -eAdd this line:
bash 0 0 * * 0 /path/to/encrypt_backup.sh
🔥 Security Best Practices
- Do NOT hardcode the password in the script. Instead, store it in a secure location like a
.gpg-passfile and use:
bash PASSPHRASE=$(cat /path/to/.gpg-pass) - Use a strong passphrase with at least 16+ characters.
- Consider using a hardware security key or YubiKey for extra security.
Here's how you can add automatic cloud syncing to your encrypted backups. This script will sync your encrypted backups to a cloud storage service like Rsync, Dropbox, or Nextcloud using the rclone tool, which is compatible with many cloud providers.
Step 1: Install rclone
First, you need to install
rcloneif you haven't already. It’s a powerful tool for managing cloud storage.-
Install rclone:
bash curl https://rclone.org/install.sh | sudo bash -
Configure rclone with your cloud provider (e.g., Google Drive):
bash rclone config
Follow the prompts to set up your cloud provider. After configuration, you'll have a "remote" (e.g.,
rsyncfor https://rsync.net) to use in the script.
🔐 Backup, Encrypt, and Sync to Cloud Script
This script will: ✅ Compress files into an archive
✅ Encrypt them with a password
✅ Sync the encrypted backup to the cloud storage```bash
!/bin/bash
Backup, encrypt, and sync to cloud script (password-based)
ARCHIVE_DIR="/mnt/backup" DATE=$(date +"%Y-%m-%d") BACKUP_FILE="$ARCHIVE_DIR/backup_$DATE.tar.gz" ENCRYPTED_FILE="$BACKUP_FILE.gpg" PASSPHRASE="YourStrongPassphraseHere" # Change this!
Cloud configuration (rclone remote name)
CLOUD_REMOTE="gdrive" # Change this to your remote name (e.g., 'gdrive', 'dropbox', 'nextcloud') CLOUD_DIR="backups" # Cloud directory where backups will be stored
mkdir -p "$ARCHIVE_DIR"
Compress files
tar -czvf "$BACKUP_FILE" ~/Documents
Encrypt the backup with a password
gpg --batch --yes --passphrase "$PASSPHRASE" --symmetric --cipher-algo AES256 --output "$ENCRYPTED_FILE" "$BACKUP_FILE"
Verify encryption success
if [ -f "$ENCRYPTED_FILE" ]; then echo "Backup encrypted successfully: $ENCRYPTED_FILE" rm "$BACKUP_FILE" # Remove unencrypted file for security
# Sync the encrypted backup to the cloud using rclone rclone copy "$ENCRYPTED_FILE" "$CLOUD_REMOTE:$CLOUD_DIR" --progress # Verify sync success if [ $? -eq 0 ]; then echo "Backup successfully synced to cloud: $CLOUD_REMOTE:$CLOUD_DIR" rm "$ENCRYPTED_FILE" # Remove local backup after syncing else echo "Cloud sync failed!" fielse echo "Encryption failed!" fi ```
How to Use the Script:
- Edit the script:
- Change the
PASSPHRASEto a secure passphrase. - Change
CLOUD_REMOTEto your cloud provider’s rclone remote name (e.g.,gdrive,dropbox). -
Change
CLOUD_DIRto the cloud folder where you'd like to store the backup. -
Set up a cron job for automatic backups:
- To run the backup every Sunday at midnight, add this line to your crontab:
bash crontab -eAdd:
bash 0 0 * * 0 /path/to/backup_encrypt_sync.sh
🔥 Security Tips:
- Store the passphrase securely (e.g., use a
.gpg-passfile withcat /path/to/.gpg-pass). - Use rclone's encryption feature for sensitive data in the cloud if you want to encrypt before uploading.
- Use multiple cloud services (e.g., Google Drive and Dropbox) for redundancy.
📌 START → **Planning Your Data Archiving Strategy**├── What type of data? (Docs, Media, Code, etc.)
├── How often will you need access? (Daily, Monthly, Rarely)
├── Choose storage type: SSD (fast), HDD (cheap), Tape (long-term)
├── Plan directory structure (YYYY-MM-DD, Category-Based, etc.)
└── Define retention policy (Keep Forever? Auto-Delete After X Years?)
↓📌 Choosing the Right Storage & Filesystem
├── Local storage: (ext4, XFS, Btrfs, ZFS for snapshots)
├── Network storage: (NAS, Nextcloud, Syncthing)
├── Cold storage: (M-DISC, Tape Backup, External HDD)
├── Redundancy: (RAID, SnapRAID, ZFS Mirror, Cloud Sync)
└── Encryption: (LUKS, VeraCrypt, age, gocryptfs)
↓📌 Organizing & Indexing Data
├── Folder structure: (YYYY/MM/Project-Based)
├── Metadata tagging: (exiftool, Recoll, TagSpaces)
├── Search tools: (fd, fzf, locate, grep)
├── Deduplication: (rdfind, fdupes, hardlinking)
└── Checksum integrity: (sha256sum, blake3)
↓📌 Compression & Space Optimization
├── Use compression (tar, zip, 7z, zstd, btrfs/zfs compression)
├── Remove duplicate files (rsync, fdupes, rdfind)
├── Store archives in efficient formats (ISO, SquashFS, borg)
├── Use incremental backups (rsync, BorgBackup, Restic)
└── Verify archive integrity (sha256sum, snapraid sync)
↓📌 Ensuring Long-Term Data Integrity
├── Check data periodically (snapraid scrub, btrfs scrub)
├── Refresh storage media every 3-5 years (HDD, Tape)
├── Protect against bit rot (ZFS/Btrfs checksums, ECC RAM)
├── Store backup keys & logs separately (Paper, YubiKey, Trezor)
└── Use redundant backups (3-2-1 Rule: 3 copies, 2 locations, 1 offsite)
↓📌 Accessing Data Efficiently
├── Use symbolic links & bind mounts for easy access
├── Implement full-text search (Recoll, Apache Solr, Meilisearch)
├── Set up a file index database (mlocate, updatedb)
├── Utilize file previews (nnn, ranger, vifm)
└── Configure network file access (SFTP, NFS, Samba, WebDAV)
↓📌 Scaling & Expanding Your Archive
├── Move old data to slower storage (HDD, Tape, Cloud)
├── Upgrade storage (LVM expansion, RAID, NAS upgrades)
├── Automate archival processes (cron jobs, systemd timers)
├── Optimize backups for large datasets (rsync --link-dest, BorgBackup)
└── Add redundancy as data grows (RAID, additional HDDs)
↓📌 Automating the Archival Process
├── Schedule regular backups (cron, systemd, Ansible)
├── Auto-sync to offsite storage (rclone, Syncthing, Nextcloud)
├── Monitor storage health (smartctl, btrfs/ZFS scrub, netdata)
├── Set up alerts for disk failures (Zabbix, Grafana, Prometheus)
└── Log & review archive activity (auditd, logrotate, shell scripts)
↓✅ GOAT STATUS: DATA ARCHIVING COMPLETE & AUTOMATED! 🎯
-
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:58:16
@ c1e9ab3a:9cb56b43
2025-04-10 02:58:16Assumptions
| Factor | Assumption | |--------|------------| | CO₂ | Not considered a pollutant or is captured/stored later | | Water Use | Regulated across all sources; cooling towers or dry cooling required | | Compliance Cost | Nuclear no longer burdened by long licensing and construction delays | | Coal Waste | Treated as valuable raw material (e.g., fly ash for cement, gypsum from scrubbers) | | Nuclear Tech | Gen IV SMRs in widespread use (e.g., 50–300 MWe units, modular build, passive safety) | | Grid Role | All three provide baseload or load-following power | | Fuel Pricing | Moderate and stable (no energy crisis or supply chain disruptions) |
Performance Comparison
| Category | Coal (IGCC + Scrubbers) | Natural Gas (CCGT) | Nuclear (Gen IV SMRs) | |---------|-----------------------------|------------------------|--------------------------| | Thermal Efficiency | 40–45% | 55–62% | 30–35% | | CAPEX ($/kW) | $3,500–5,000 | $900–1,300 | $4,000–7,000 (modularized) | | O&M Cost ($/MWh) | $30–50 | $10–20 | $10–25 | | Fuel Cost ($/MWh) | $15–25 | $25–35 | $6–10 | | Water Use (gal/MWh) | 300–500 (with cooling towers) | 100–250 | 300–600 | | Air Emissions | Very low (excluding CO₂) | Very low | None | | Waste | Usable (fly ash, FGD gypsum, slag) | Minimal | Compact, long-term storage required | | Ramp/Flexibility | Slow ramp (newer designs better) | Fast ramp | Medium (SMRs better than traditional) | | Footprint (Land & Supply) | Large (mining, transport) | Medium | Small | | Energy Density | Medium | Medium-high | Very high | | Build Time | 4–7 years | 2–4 years | 2–5 years (with factory builds) | | Lifecycle (years) | 40+ | 30+ | 60+ | | Grid Resilience | High | High | Very High (passive safety, long refuel) |
Strategic Role Summary
1. Coal (Clean & Integrated)
- Strengths: Long-term fuel security; byproduct reuse; high reliability; domestic resource.
- Drawbacks: Still low flexibility; moderate efficiency; large physical/logistical footprint.
- Strategic Role: Best suited for regions with abundant coal and industrial reuse markets.
2. Natural Gas (CCGT)
- Strengths: High efficiency, low CAPEX, grid agility, low emissions.
- Drawbacks: Still fossil-based; dependent on well infrastructure; less long-lived.
- Strategic Role: Excellent transitional and peaking solution; strong complement to renewables.
3. Nuclear (Gen IV SMRs)
- Strengths: Highest energy density; no air emissions or CO₂; long lifespan; modular & scalable.
- Drawbacks: Still needs safe waste handling; high upfront cost; novel tech in deployment stage.
- Strategic Role: Ideal for low-carbon baseload, remote areas, and national strategic assets.
Adjusted Levelized Cost of Electricity (LCOE)
| Source | LCOE ($/MWh) | Notes | |--------|------------------|-------| | Coal (IGCC w/scrubbers) | ~$75–95 | Lower with valuable waste | | Natural Gas (CCGT) | ~$45–70 | Highly competitive if fuel costs are stable | | Gen IV SMRs | ~$65–85 | Assuming factory production and streamlined permitting |
Final Verdict (Under Optimized Assumptions)
- Most Economical Short-Term: Natural Gas
- Most Strategic Long-Term: Gen IV SMRs
- Most Viable if Industrial Ecosystem Exists: Clean Coal
All three could coexist in a diversified, stable energy grid: - Coal filling a regional or industrial niche, - Gas providing flexibility and economy, - SMRs ensuring long-term sustainability and energy security.
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:57:02
@ c1e9ab3a:9cb56b43
2025-04-10 02:57:02A follow-up to nostr:naddr1qqgxxwtyxe3kvc3jvvuxywtyxs6rjq3qc856kwjk524kef97hazw5e9jlkjq4333r6yxh2rtgefpd894ddpsxpqqqp65wuaydz8
This whitepaper, a comparison of baseload power options, explores a strategic policy framework to reduce the cost of next-generation nuclear power by aligning Gen IV Small Modular Reactors (SMRs) with national security objectives, public utility management, and a competitive manufacturing ecosystem modeled after the aerospace industry. Under this approach, SMRs could deliver stable, carbon-free power at $40–55/MWh, rivaling the economics of natural gas and renewables.
1. Context and Strategic Opportunity
Current Nuclear Cost Challenges
- High capital expenditure ($4,000–$12,000/kW)
- Lengthy permitting and construction timelines (10–15 years)
- Regulatory delays and public opposition
- Customized, one-off reactor designs with no economies of scale
The Promise of SMRs
- Factory-built, modular units
- Lower absolute cost and shorter build time
- Enhanced passive safety
- Scalable deployment
2. National Security as a Catalyst
Strategic Benefits
- Energy resilience for critical defense infrastructure
- Off-grid operation and EMP/cyber threat mitigation
- Long-duration fuel cycles reduce logistical risk
Policy Implications
- Streamlined permitting and site access under national defense exemptions
- Budget support via Department of Defense and Department of Energy
- Co-location on military bases and federal sites
3. Publicly Chartered Utilities: A New Operating Model
Utility Framework
- Federally chartered, low-margin operator (like TVA or USPS)
- Financially self-sustaining through long-term PPAs
- Focus on reliability, security, and public service over profit
Cost Advantages
- Lower cost of capital through public backing
- Predictable revenue models
- Community trust and stakeholder alignment
4. Competitive Manufacturing: The Aviation Analogy
Model Characteristics
- Multiple certified vendors, competing under common safety frameworks
- Factory-scale production and supply chain specialization
- Domestic sourcing for critical components and fuel
Benefits
- Cost reductions from repetition and volume
- Innovation through competition
- Export potential and industrial job creation
5. Levelized Cost of Electricity (LCOE) Impact
| Cost Lever | Estimated LCOE Reduction | |------------|--------------------------| | Streamlined regulation | -10 to -20% | | Public-charter operation | -5 to -15% | | Factory-built SMRs | -15 to -30% | | Defense market anchor | -10% |
Estimated Resulting LCOE: $40–55/MWh
6. Strategic Outcomes
- Nuclear cost competitiveness with gas and renewables
- Decarbonization without reliability sacrifice
- Strengthened national energy resilience
- Industrial and workforce revitalization
- U.S. global leadership in clean, secure nuclear energy
7. Recommendations
- Create a public-private chartered SMR utility
- Deploy initial reactors on military and federal lands
- Incentivize competitive SMR manufacturing consortia
- Establish fast-track licensing for Gen IV designs
- Align DoD/DOE energy procurement to SMR adoption
Conclusion
This strategy would transform nuclear power from a high-cost, high-risk sector into a mission-driven, economically viable backbone of American energy and defense infrastructure. By treating SMRs as strategic assets, not just energy projects, the U.S. can unlock affordable, scalable, and secure nuclear power for generations to come.
-
 @ 04c915da:3dfbecc9
2025-03-07 00:26:37
@ 04c915da:3dfbecc9
2025-03-07 00:26:37There is something quietly rebellious about stacking sats. In a world obsessed with instant gratification, choosing to patiently accumulate Bitcoin, one sat at a time, feels like a middle finger to the hype machine. But to do it right, you have got to stay humble. Stack too hard with your head in the clouds, and you will trip over your own ego before the next halving even hits.
Small Wins
Stacking sats is not glamorous. Discipline. Stacking every day, week, or month, no matter the price, and letting time do the heavy lifting. Humility lives in that consistency. You are not trying to outsmart the market or prove you are the next "crypto" prophet. Just a regular person, betting on a system you believe in, one humble stack at a time. Folks get rekt chasing the highs. They ape into some shitcoin pump, shout about it online, then go silent when they inevitably get rekt. The ones who last? They stack. Just keep showing up. Consistency. Humility in action. Know the game is long, and you are not bigger than it.
Ego is Volatile
Bitcoin’s swings can mess with your head. One day you are up 20%, feeling like a genius and the next down 30%, questioning everything. Ego will have you panic selling at the bottom or over leveraging the top. Staying humble means patience, a true bitcoin zen. Do not try to "beat” Bitcoin. Ride it. Stack what you can afford, live your life, and let compounding work its magic.
Simplicity
There is a beauty in how stacking sats forces you to rethink value. A sat is worth less than a penny today, but every time you grab a few thousand, you plant a seed. It is not about flaunting wealth but rather building it, quietly, without fanfare. That mindset spills over. Cut out the noise: the overpriced coffee, fancy watches, the status games that drain your wallet. Humility is good for your soul and your stack. I have a buddy who has been stacking since 2015. Never talks about it unless you ask. Lives in a decent place, drives an old truck, and just keeps stacking. He is not chasing clout, he is chasing freedom. That is the vibe: less ego, more sats, all grounded in life.
The Big Picture
Stack those sats. Do it quietly, do it consistently, and do not let the green days puff you up or the red days break you down. Humility is the secret sauce, it keeps you grounded while the world spins wild. In a decade, when you look back and smile, it will not be because you shouted the loudest. It will be because you stayed the course, one sat at a time. \ \ Stay Humble and Stack Sats. 🫡
-
 @ c1e9ab3a:9cb56b43
2025-04-10 02:55:11
@ c1e9ab3a:9cb56b43
2025-04-10 02:55:11The United States is on the cusp of a historic technological renaissance, often referred to as the Fourth Industrial Revolution. Artificial intelligence, automation, advanced robotics, quantum computing, biotechnology, and clean manufacturing are converging into a seismic shift that will redefine how we live, work, and relate to one another. But there's a critical catch: this transformation depends entirely on the availability of stable, abundant, and inexpensive electricity.
Why Electricity is the Keystone of Innovation
Let’s start with something basic but often overlooked. Every industrial revolution has had an energy driver:
- The First rode the steam engine, powered by coal.
- The Second was electrified through centralized power plants.
- The Third harnessed computing and the internet.
- The Fourth will demand energy on a scale and reliability never seen before.
Imagine a city where thousands of small factories run 24/7 with robotics and AI doing precision manufacturing. Imagine a national network of autonomous vehicles, delivery drones, urban vertical farms, and high-bandwidth communication systems. All of this requires uninterrupted and inexpensive power.
Without it? Costs balloon. Innovation stalls. Investment leaves. And America risks becoming a second-tier economic power in a multipolar world.
So here’s the thesis: If we want to lead the Fourth Industrial Revolution, we must first lead in energy. And nuclear — specifically Gen IV Small Modular Reactors (SMRs) — must be part of that leadership.
The Nuclear Case: Clean, Scalable, Strategic
Let’s debunk the myth: nuclear is not the boogeyman of the 1970s. It’s one of the safest, cleanest, and most energy-dense sources we have.
But traditional nuclear has problems:
- Too expensive to build.
- Too long to license.
- Too bespoke and complex.
Enter Gen IV SMRs:
- Factory-built and transportable.
- Passively safe with walk-away safety designs.
- Scalable in 50–300 MWe increments.
- Ideal for remote areas, industrial parks, and military bases.
But even SMRs will struggle under the current regulatory, economic, and manufacturing ecosystem. To unlock their potential, we need a new national approach.
The Argument for National Strategy
Let’s paint a vision:
SMRs deployed at military bases across the country, secured by trained personnel, powering critical infrastructure, and feeding clean, carbon-free power back into surrounding communities.
SMRs operated by public chartered utilities—not for Wall Street profits, but for stability, security, and public good.
SMRs manufactured by a competitive ecosystem of certified vendors, just like aircraft or medical devices, with standard parts and rapid regulatory approval.
This isn't science fiction. It's a plausible, powerful model. Here’s how we do it.
Step 1: Treat SMRs as a National Security Asset
Why does the Department of Defense spend billions to secure oil convoys and build fuel depots across the world, but not invest in nuclear microgrids that would make forward bases self-sufficient for decades?
Nuclear power is inherently a strategic asset:
- Immune to price shocks.
- Hard to sabotage.
- Decades of stable power from a small footprint.
It’s time to reframe SMRs from an energy project to a national security platform. That changes everything.
Step 2: Create Public-Chartered Operating Companies
We don’t need another corporate monopoly or Wall Street scheme. Instead, let’s charter SMR utilities the way we chartered the TVA or the Postal Service:
- Low-margin, mission-oriented.
- Publicly accountable.
- Able to sign long-term contracts with DOD, DOE, or regional utilities.
These organizations won’t chase quarterly profits. They’ll chase uptime, grid stability, and national resilience.
Step 3: Build a Competitive SMR Industry Like Aerospace
Imagine multiple manufacturers building SMRs to common, certified standards. Components sourced from a wide supplier base. Designs evolving year over year, with upgrades like software and avionics do.
This is how we build:
- Safer reactors
- Cheaper units
- Modular designs
- A real export industry
Airplanes are safe, affordable, and efficient because of scale and standardization. We can do the same with reactors.
Step 4: Anchor SMRs to the Coming Fourth Industrial Revolution
AI, robotics, and distributed manufacturing don’t need fossil fuels. They need cheap, clean, continuous electricity.
- AI datacenters
- Robotic agriculture
- Carbon-free steel and cement
- Direct air capture
- Electric industrial transport
SMRs enable this future. And they decentralize power, both literally and economically. That means jobs in every region, not just coastal tech hubs.
Step 5: Pair Energy Sovereignty with Economic Reform
Here’s the big leap: what if this new energy architecture was tied to a transparent, auditable, and sovereign monetary system?
- Public utilities priced in a new digital dollar.
- Trade policy balanced by low-carbon energy exports.
- Public accounting verified with open ledgers.
This is not just national security. It’s monetary resilience.
The world is moving to multi-polar trade systems. Energy exports and energy reliability will define economic influence. If America leads with SMRs, we lead the conversation.
Conclusion: A Moral and Strategic Imperative
We can either:
- Let outdated fears and bureaucracy stall the future, or...
- Build the infrastructure for clean, secure, and sovereign prosperity.
We have the designs.
We have the talent.
We have the need.What we need now is will.
The Fourth Industrial Revolution will either be powered by us—or by someone else. Let’s make sure America leads. And let’s do it with SMRs, public charter, competitive industry, and national purpose.
It’s time.
This is a call to engineers, legislators, veterans, economists, and every American who believes in building again. SMRs are not just about power. They are about sovereignty, security, and shared prosperity.
Further reading:
nostr:naddr1qqgrjv33xenx2drpve3kxvrp8quxgqgcwaehxw309anxjmr5v4ezumn0wd68ytnhd9hx2tczyrq7n2e62632km9yh6l5f6nykt76gzkxxy0gs6agddr9y95uk445xqcyqqq823cdzc99s
-
 @ ee6ea13a:959b6e74
2025-04-06 16:38:22
@ ee6ea13a:959b6e74
2025-04-06 16:38:22Chef's notes
You can cook this in one pan on the stove. I use a cast iron pan, but you can make it in a wok or any deep pan.
I serve mine over rice, which I make in a rice cooker. If you have a fancy one, you might have a setting for sticky or scorched rice, so give one of those a try.
To plate this, I scoop rice into a bowl, and then turn it upside-down to give it a dome shape, then spoon the curry on top of it.
Serve with chopped cilantro and lime wedges.
Details
- ⏲️ Prep time: 20
- 🍳 Cook time: 20
- 🍽️ Servings: 4
Ingredients
- 1 ½ pounds boneless skinless chicken breast, cut into 2" pieces
- 2 tablespoons coconut or avocado oil
- 1 cup white or yellow onion, finely diced
- 1 cup red bell pepper, sliced or diced
- 4 large garlic cloves, minced
- 1 small (4oz) jar of Thai red curry paste
- 1 can (13oz) unsweetened coconut milk
- 1 teaspoon ground ginger
- 1 teaspoon ground coriander
- 1 tablespoon soy sauce
- 1 tablespoon brown sugar
- 1 cup carrots, shredded or julienned
- 1 lime, zest and juice
- ¼ cup fresh cilantro, chopped for garnish
Directions
- Heat oil in a large skillet over medium-high. Once hot, add onions and ½ teaspoon salt. Cook 3 minutes, or until onions are softened, stirring often.
- Add the red curry paste, garlic, ginger, and coriander. Cook about 1 minute, or until fragrant, stirring often.
- Add coconut milk, brown sugar, soy sauce, and chicken. Stir, bring to a simmer, then reduce heat to medium. Simmer uncovered for 7 minutes, occasionally stirring.
- Add carrots and red bell peppers, and simmer 5-7 more minutes, until sauce slightly thickens and chicken is cooked through.
- Remove from heat, and stir in the lime zest, and half of the lime juice.
- Serve over rice, topped with cilantro, and add more lime juice if you like extra citrus.
-
 @ d34e832d:383f78d0
2025-03-07 00:01:02
@ d34e832d:383f78d0
2025-03-07 00:01:02[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
Helical Visualization of Time's Passage in Orbital Motion and Celestial Mechanics
Exploring the dynamics of our Solar System through helical visualization opens new possibilities for understanding time, orbital motion, and planetary trajectories. By visualizing time as a continuous helical path, we gain insights into the cyclical and evolving nature of celestial mechanics, where each planet's orbit interacts with others in both predictable and dynamic patterns.
1. Helical Visualization of Time’s Passage
- Time as a Continuous Helix: Instead of viewing planetary orbits as fixed ellipses, this model represents the passage of time as a helical curve, linking each orbital cycle to the next. This visualization allows for a deeper understanding of the long-term movement of celestial bodies.
- Progression of Orbital Events: As planets follow their helical paths, we can track the passage of time from multiple perspectives, observing how their positions and velocities evolve in relation to one another. The helical model offers an elegant representation of periodic cycles that emphasizes the interconnectedness of cosmic events.
- Temporal Interactions: In this model, events like eclipses, conjunctions, and retrogrades become visualized as intersecting points on the helical path, emphasizing their importance in the grand tapestry of the Solar System's motion.
2. Orbital Motion and Celestial Mechanics
- Interplanetary Influences: The interactions between planetary bodies are inherently governed by gravitational forces, which create orbital motions that are often predictable yet influenced by external factors like planetary alignments and the gravitational pull of distant stars.
- Orbital Resonance and Tidal Forces: The gravitational interactions between planets, moons, and even asteroids can result in phenomena like orbital resonance. These interactions can be visualized in a helical model, showing how bodies can affect each other's orbits over time, much like the push and pull of a dance.
- The Dance of the Planets: Each planet’s orbit is not only a path through space but a part of a cosmic ballet, where their gravitational interactions affect one another's orbits. The helical model of motion helps us visualize how these interactions evolve over millions of years, helping to predict future trajectories.
3. Planetary Orbits and the Structure of the Solar System
- Elliptical and Spiral Patterns: While many planetary orbits are elliptical, the helical model introduces a dynamic spiral element to represent the combined motion of planets both around the Sun and through space. As the planets move, their orbits could resemble intricate spirals that reflect the cumulative effect of their motion through time.
- Resonance and Stability: Certain orbits may stabilize or shift over long periods due to gravitational interactions between planets. This helical view provides a tool for observing how minor orbital shifts can amplify over time, affecting not only the planets but the overall structure of the Solar System.
- Nonlinear Progression: Planets do not follow predictable paths in a simple two-dimensional plane. Instead, their orbits are affected by multiple forces, including interactions with other celestial bodies, making the helical model an ideal tool for visualizing the complexity and evolving nature of these planetary orbits.
4. Space Visualization and the Expanding Universe
- Moving Beyond the Solar System: The helical model of time and orbital motion does not end with our Solar System. As we visualize the movement of our Solar System within the broader context of the Milky Way, we begin to understand how our own galaxy's orbit affects our local motion through the universe.
- Helical Paths in Cosmic Space: This visualization method allows us to consider the Solar System’s motion as part of a larger, spiraling pattern that reaches across the galaxy, suggesting that our journey through space follows an intricate, three-dimensional helical path.
Connections (Links to Other Notes)
- The Mathematical Foundations of Orbital Mechanics
- Time as a Dimension in Celestial Navigation
- Gravitational Forces and Orbital Stability
Tags
SolarSystem #HelicalMotion #TimeVisualization #OrbitalMechanics #CelestialBodies #PlanetaryOrbits #SpaceExploration
Donations via
- ZeroSumFreeParity@primal.net
-
 @ d34e832d:383f78d0
2025-03-06 21:57:23
@ d34e832d:383f78d0
2025-03-06 21:57:23https://pub-53ed77d5544b46628691823c1795f2c7.r2.dev/Reticulum-Unstoppable-Network-Compressed.mp4
[npub16d8gxt2z4k9e8sdpc0yyqzf5gp0np09ls4lnn630qzxzvwpl0rgq5h4rzv]
What is Reticulum?
Reticulum is a cryptographic networking stack designed for resilient, decentralized, and censorship-resistant communication. Unlike the traditional internet, Reticulum enables fully independent digital communications over various physical mediums, such as radio, LoRa, serial links, and even TCP/IP.
The key advantages of Reticulum include:
- Decentralization – No reliance on centralized infrastructure.
- Encryption & Privacy – End-to-end encryption built-in.
- Resilience – Operates over unreliable and low-bandwidth links.
- Interoperability – Works over WiFi, LoRa, Bluetooth, and more.
- Ease of Use – Can run on minimal hardware, including Raspberry Pi and embedded devices.Reticulum is ideal for off-grid, censorship-resistant communications, emergency preparedness, and secure messaging.
1. Getting Started with Reticulum
To quickly get started with Reticulum, follow the official guide:
Reticulum: Getting Started FastStep 1: Install Reticulum
On Linux (Debian/Ubuntu-based systems)
sh sudo apt update && sudo apt upgrade -y sudo apt install -y python3-pip pip3 install rnsOn Raspberry Pi or ARM-based Systems
sh pip3 install rnsOn Windows
Using Windows Subsystem for Linux (WSL) or Python:
sh pip install rnsOn macOS
sh pip3 install rns
2. Configuring Reticulum
Once installed, Reticulum needs a configuration file. The default location is:
sh ~/.config/reticulum/config.tomlTo generate the default configuration:
sh rnsdThis creates a configuration file with default settings.
3. Using Reticulum
Starting the Reticulum Daemon
To run the Reticulum daemon (
rnsd), use:
sh rnsdThis starts the network stack, allowing applications to communicate over Reticulum.Testing Your Reticulum Node
Run the diagnostic tool to ensure your node is functioning:
sh rnstatusThis shows the status of all connected interfaces and peers.
4. Adding Interfaces
LoRa Interface (for Off-Grid Communications)
Reticulum supports long-range LoRa radios like the RAK Wireless and Meshtastic devices. To add a LoRa interface, edit
config.tomland add:
toml [[interfaces]] type = "LoRa" name = "My_LoRa_Interface" frequency = 868.0 bandwidth = 125 spreading_factor = 9Restart Reticulum to apply the changes.Serial (For Direct Device-to-Device Links)
For communication over serial links (e.g., between two Raspberry Pis):
toml [[interfaces]] type = "Serial" port = "/dev/ttyUSB0" baudrate = 115200TCP/IP (For Internet-Based Nodes)
If you want to bridge your Reticulum node over an existing IP network:
toml [[interfaces]] type = "TCP" listen = true bind = "0.0.0.0" port = 4242
5. Applications Using Reticulum
LXMF (LoRa Mesh Messaging Framework)
LXMF is a delay-tolerant, fully decentralized messaging system that operates over Reticulum. It allows encrypted, store-and-forward messaging without requiring an always-online server.
To install:
sh pip3 install lxmfTo start the LXMF node:
sh lxmfdNomad Network (Decentralized Chat & File Sharing)
Nomad is a Reticulum-based chat and file-sharing platform, ideal for off-grid communication.
To install:
sh pip3 install nomad-networkTo run:
sh nomadMesh Networking with Meshtastic & Reticulum
Reticulum can work alongside Meshtastic for true decentralized long-range communication.
To set up a Meshtastic bridge:
toml [[interfaces]] type = "LoRa" port = "/dev/ttyUSB0" baudrate = 115200
6. Security & Privacy Features
- Automatic End-to-End Encryption – Every message is encrypted by default.
- No Centralized Logging – Communication leaves no metadata traces.
- Self-Healing Routing – Designed to work in unstable or hostile environments.
7. Practical Use Cases
- Off-Grid Communication – Works in remote areas without cellular service.
- Censorship Resistance – Cannot be blocked by ISPs or governments.
- Emergency Networks – Enables resilient communication during disasters.
- Private P2P Networks – Create a secure, encrypted communication layer.
8. Further Exploration & Documentation
- Reticulum Official Manual: https://markqvist.github.io/Reticulum/manual/
- Reticulum GitHub Repository: https://github.com/markqvist/Reticulum
- Nomad Network: https://github.com/markqvist/NomadNet
- Meshtastic + Reticulum: https://meshtastic.org
Connections (Links to Other Notes)
- Mesh Networking for Decentralized Communication
- LoRa and Off-Grid Bitcoin Transactions
- Censorship-Resistant Communication Using Nostr & Reticulum
Tags
Reticulum #DecentralizedComms #MeshNetworking #CensorshipResistance #LoRa
Donations via
- Bitcoin Lightning: lightninglayerhash@getalby.com