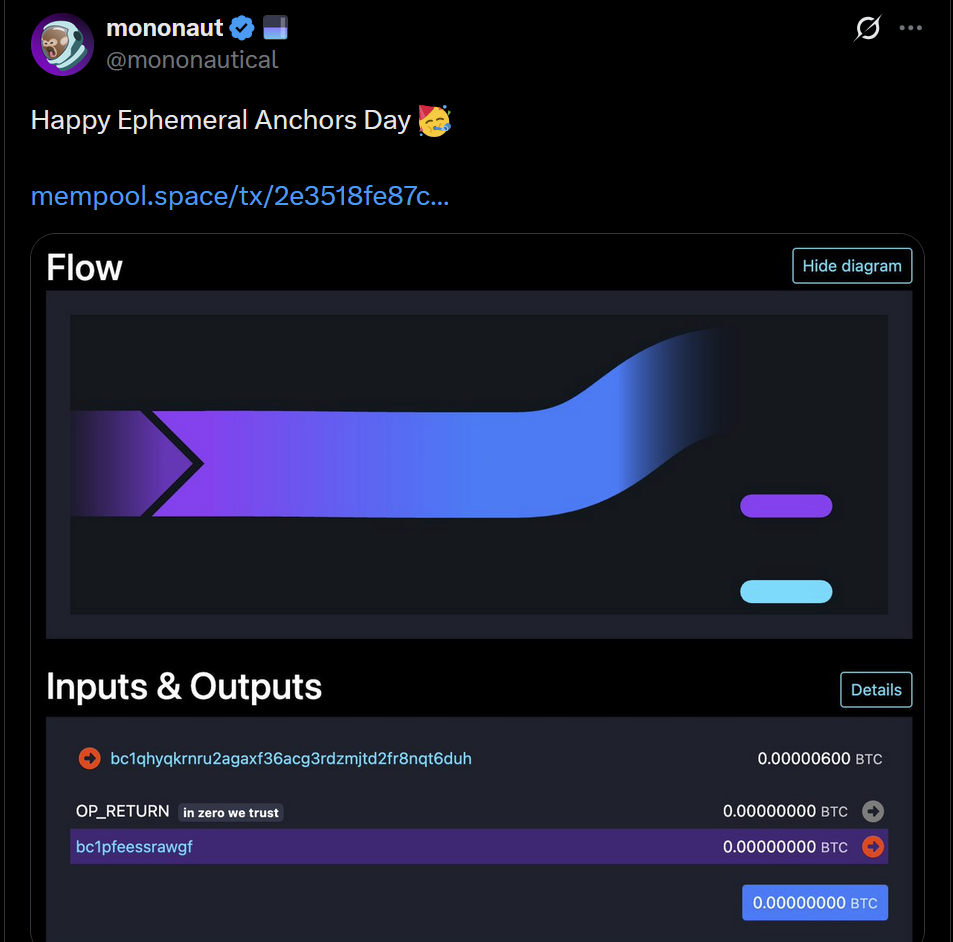
-
 @ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33
@ 1c19eb1a:e22fb0bc
2025-04-22 01:36:33After my first major review of Primal on Android, we're going to go a very different direction for this next review. Primal is your standard "Twitter clone" type of kind 1 note client, now branching into long-form. They also have a team of developers working on making it one of the best clients to fill that use-case. By contrast, this review will not be focusing on any client at all. Not even an "other stuff" client.
Instead, we will be reviewing a very useful tool created and maintained by nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 called #Amber. For those unfamiliar with Amber, it is an #Android application dedicated to managing your signing keys, and allowing you to log into various #Nostr applications without having to paste in your private key, better known as your #nsec. It is not recommended to paste your nsec into various applications because they each represent another means by which it could be compromised, and anyone who has your nsec can post as you. On Nostr, your #npub is your identity, and your signature using your private key is considered absolute proof that any given note, reaction, follow update, or profile change was authorized by the rightful owner of that identity.
It happens less often these days, but early on, when the only way to try out a new client was by inputting your nsec, users had their nsec compromised from time to time, or they would suspect that their key may have been compromised. When this occurs, there is no way to recover your account, or set a new private key, deprecating the previous one. The only thing you can do is start over from scratch, letting everyone know that your key has been compromised and to follow you on your new npub.
If you use Amber to log into other Nostr apps, you significantly reduce the likelihood that your private key will be compromised, because only one application has access to it, and all other applications reach out to Amber to sign any events. This isn't quite as secure as storing your private key on a separate device that isn't connected to the internet whatsoever, like many of us have grown accustomed to with securing our #Bitcoin, but then again, an online persona isn't nearly as important to secure for most of us as our entire life savings.
Amber is the first application of its kind for managing your Nostr keys on a mobile device. nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 didn't merely develop the application, but literally created the specification for accomplishing external signing on Android which can be found in NIP-55. Unfortunately, Amber is only available for Android. A signer application for iOS is in the works from nostr:npub1yaul8k059377u9lsu67de7y637w4jtgeuwcmh5n7788l6xnlnrgs3tvjmf, but is not ready for use at this time. There is also a new mobile signer app for Android and iOS called Nowser, but I have not yet had a chance to try this app out. From a cursory look at the Android version, it is indeed in the very early stages of development and cannot be compared with Amber.
This review of Amber is current as of version 3.2.5.

Overall Impression
Score: 4.7 / 5 (Updated 4/21/2025)
I cannot speak highly enough about Amber as a tool that every Nostr user on Android should start using if they are not already. When the day comes that we have more options for well-developed signer apps on mobile, my opinion may very well change, but until then Amber is what we have available to us. Even so, it is an incredibly well thought-out and reliable tool for securing your nsec.
Despite being the only well-established Android signer available for Android, Amber can be compared with other external signing methods available on other platforms. Even with more competition in this arena, though, Amber still holds up incredibly well. If you are signing into web applications on a desktop, I still would recommend using a browser extension like #Alby or #Nos2x, as the experience is usually faster, more seamless, and far more web apps support this signing method (NIP-07) than currently support the two methods employed by Amber. Nevertheless that gap is definitely narrowing.
A running list I created of applications that support login and signing with Amber can be found here: Nostr Clients with External Signer Support
I have run into relatively few bugs in my extensive use of Amber for all of my mobile signing needs. Occasionally the application crashes when trying to send it a signing request from a couple of applications, but I would not be surprised if this is no fault of Amber at all, and rather the fault of those specific apps, since it works flawlessly with the vast majority of apps that support either NIP-55 or NIP-46 login.
I also believe that mobile is the ideal platform to use for this type of application. First, because most people use Nostr clients on their phone more than on a desktop. There are, of course, exceptions to that, but in general we spend more time on our phones when interacting online. New users are also more likely to be introduced to Nostr by a friend having them download a Nostr client on their phone than on a PC, and that can be a prime opportunity to introduce the new user to protecting their private key. Finally, I agree with the following assessment from nostr:npub1jlrs53pkdfjnts29kveljul2sm0actt6n8dxrrzqcersttvcuv3qdjynqn.
nostr:nevent1qqsw0r6gzn05xg67h5q2xkplwsuzedjxw9lf7ntrxjl8ajm350fcyugprfmhxue69uhhyetvv9ujumn0wd68yurvv438xtnrdaksyg9hyaxj3clfswlhyrd5kjsj5v04clhjvgeq6pwztmysfzdvn93gev7awu9v
The one downside to Amber is that it will be quite foreign for new users. That is partially unavoidable with Nostr, since folks are not accustomed to public/private key cryptography in general, let alone using a private key to log into websites or social media apps. However, the initial signup process is a bit cumbersome if Amber is being used as the means of initially generating a key pair. I think some of this could be foregone at start-up in favor of streamlining onboarding, and then encourage the user to back-up their private key at a later time.
Features
Amber has some features that may surprise you, outside of just storing your private key and signing requests from your favorite Nostr clients. It is a full key management application, supporting multiple accounts, various backup methods, and even the ability to authorize other users to access a Nostr profile you control.
Android Signing
This is the signing method where Amber really shines in both speed and ease of use. Any Android application that supports this standard, and even some progressive web-apps that can be installed to your Android's home-screen, can very quickly and seamlessly connect with Amber to authorize anything that you need signed with your nsec. All you have to do is select "Login with Amber" in clients like #Amethyst or #0xChat and the app will reach out to Amber for all signing requests from there on out. If you had previously signed into the app with your nsec, you will first need to log out, then choose the option to use Amber when you log back in.

This is a massive deal, because everything you do on Nostr requires a signature from your private key. Log in? Needs a signature. Post a "GM" note? Needs a signature. Follow someone who zapped your note? Needs a signature. Zap them back? You guessed it; needs a signature. When you paste your private key into an application, it will automatically sign a lot of these actions without you ever being asked for approval, but you will quickly realize just how many things the client is doing on your behalf when Amber is asking you to approve them each time.
Now, this can also get quite annoying after a while. I recommend using the setting that allows Amber to automatically sign for basic functions, which will cut down on some of the authorization spam. Once you have been asked to authorize the same type of action a few times, you can also toggle the option to automatically authorize that action in the future. Don't worry, though, you have full control to require Amber to ask you for permission again if you want to be alerted each time, and this toggle is specific to each application, so it's not a blanket approval for all Nostr clients you connect with.

This method of signing is just as fast as signing via browser extension on web clients, which users may be more accustomed to. Everything is happening locally on the device, so it can be very snappy and secure.
Nostr Connect/Bunker Signing
This next method of signing has a bit of a delay, because it is using a Nostr relay to send encrypted information back and forth between the app the user is interacting with and Amber to obtain signatures remotely. It isn't a significant delay most of the time, but it is just enough to be noticeable.
Also, unlike the previous signing method that would automatically switch to Amber as the active application when a signing request is sent, this method only sends you a notification that you must be watching for. This can lead to situations where you are wondering why something isn't working in a client you signed into remotely, because it is waiting on you to authorize the action and you didn't notice the notification from Amber. As you use the application, you get used to the need to check for such authorization requests from time to time, or when something isn't working as expected.

By default, Amber will use relay.nsec.app to communicate with whichever Nostr app you are connecting to. You can set a different relay for this purpose, if you like, though not just any relay will support the event kinds that Amber uses for remote signing. You can even run your own relay just for your own signing purposes. In fact, the creator of Amber has a relay application you can run on your phone, called Citrine, that can be used for signing with any web app you are using locally on your phone. This is definitely more of an advanced option, but it is there for you if you want it. For most users, sticking with relay.nsec.app will be just fine, especially since the contents of the events sent back and forth for signing are all encrypted.
Something many users may not realize is that this remote signing feature allows for issuing signing permissions to team members. For instance, if anyone ever joined me in writing reviews, I could issue them a connection string from Amber, and limit their permissions to just posting long-form draft events. Anything else they tried to do would require my explicit approval each time. Moreover, I could revoke those permissions if I ever felt they were being abused, without the need to start over with a whole new npub. Of course, this requires that your phone is online whenever a team member is trying to sign using the connection string you issued, and it requires you pay attention to your notifications so you can approve or reject requests you have not set to auto-approve. However, this is probably only useful for small teams, and larger businesses will want to find a more robust solution for managing access to their npub, such as Keycast from nostr:npub1zuuajd7u3sx8xu92yav9jwxpr839cs0kc3q6t56vd5u9q033xmhsk6c2uc.
The method for establishing a connection between Amber and a Nostr app for remote signing can vary for each app. Most, at minimum, will support obtaining a connection string from Amber that starts with "bunker://" and pasting it in at the time of login. Then you just need to approve the connection request from Amber and the client will log you in and send any subsequent signing requests to Amber using the same connection string.

Some clients will also offer the option to scan a QR code to connect the client to Amber. This is quite convenient, but just remember that this also means the client is setting which relay will be used for communication between the two. Clients with this option will also have a connection string you can copy and paste into Amber to achieve the same purpose. For instance, you may need this option if you are trying to connect to an app on your phone and therefore can't scan the QR code using Amber on the same phone.

Multiple Accounts
Amber does not lock you into using it with only a single set of keys. You can add all of your Nostr "accounts" to Amber and use it for signing events for each independently. Of course, Nostr doesn't actually have "accounts" in the traditional sense. Your identity is simply your key-pair, and Amber stores and accesses each private key as needed.

When first signing in using native Android signing as described above, Amber will default to whichever account was most recently selected, but you can switch to the account that is needed before approving the request. After initial login, Amber will automatically detect the account that the signing request is for.
Key Backup & Restore
Amber allows multiple ways to back up your private key. As most users would expect, you can get your standard nsec and copy/paste it to a password manager, but you can also obtain your private key as a list of mnemonic seed words, an encrypted version of your key called an ncryptsec, or even a QR code of your nsec or ncryptsec.

Additionally, in order to gain access to this information, Amber requires you to enter your device's PIN or use biometric authentication. This isn't cold-storage level protection for your private key by any means, especially since your phone is an internet connected device and does not store your key within a secure element, but it is about as secure as you can ask for while having your key accessible for signing Nostr events.
Tor Support
While Amber does not have Tor support within the app itself, it does support connecting to Tor through Orbot. This would be used with remote signing so that Amber would not connect directly over clearnet to the relay used for communication with the Nostr app requesting the signature. Instead, Amber would connect through Tor, so the relay would not see your IP address. This means you can utilize the remote signing option without compromising your anonymity.

Additional Security
Amber allows the user the option to require either biometric or PIN authentication before approving signing requests. This can provide that extra bit of assurance that no one will be able to sign events using your private key if they happen to gain access to your phone. The PIN you set in Amber is also independent from the PIN to unlock your device, allowing for separation of access.
Can My Grandma Use It?
Score: 4.6 / 5 (Updated 4/21/2025)
At the end of the day, Amber is a tool for those who have some concept of the importance of protecting their private key by not pasting it into every Nostr client that comes along. This concept in itself is not terribly approachable to an average person. They are used to just plugging their password into every service they use, and even worse, they usually have the same password for everything so they can more readily remember it. The idea that they should never enter their "Nostr password" into any Nostr application would never occur to them unless someone first explained how cryptography works related to public/private key pairs.
That said, I think there can be some improvements made to how users are introduced to these concepts, and that a signer application like Amber might be ideal for the job. Considering Amber as a new user's first touch-point with Nostr, I think it holds up well, but could be somewhat streamlined.
Upon opening the app, the user is prompted to either use their existing private key or "Create a new Nostr account." This is straightforward enough. "Account" is not a technically correct term with Nostr, but it is a term that new users would be familiar with and understand the basic concept.

The next screen announces that the account is ready, and presents the user with their public key, explaining that it is "a sort of username" that will allow others to find them on Nostr. While it is good to explain this to the user, it is unnecessary information at this point. This screen also prompts the user to set a nickname and set a password to encrypt their private key. Since the backup options also allow the user to set this password, I think this step could be pushed to a later time. This screen would better serve the new user if it simply prompted them to set a nickname and short bio that could be saved to a few default relays.

Of course, Amber is currently prompting for a password to be set up-front because the next screen requires the new user to download a "backup kit" in order to continue. While I do believe it is a good idea to encourage the creation of a backup, it is not crucial to do so immediately upon creation of a new npub that has nothing at stake if the private key is lost. This is something the UI could remind the user to do at a later time, reducing the friction of profile creation, and expediting getting them into the action.

Outside of these minor onboarding friction points, I think Amber does a great job of explaining to the user the purpose of each of its features, all within the app and without any need to reference external documentation. As long as the user understands the basic concept that their private key is being stored by Amber in order to sign requests from other Nostr apps, so they don't have to be given the private key, Amber is very good about explaining the rest without getting too far into the technical weeds.
The most glaring usability issue with Amber is that it isn't available in the Play Store. Average users expect to be able to find applications they can trust in their mobile device's default app store. There is a valid argument to be made that they are incorrect in this assumption, but that doesn't change the fact that this is the assumption most people make. They believe that applications in the Play Store are "safe" and that anything they can't install through the Play Store is suspect. The prompts that the Android operating system requires the user to approve when installing "unknown apps" certainly doesn't help with this impression.
Now, I absolutely love the Zapstore from nostr:npub1wf4pufsucer5va8g9p0rj5dnhvfeh6d8w0g6eayaep5dhps6rsgs43dgh9, but it doesn't do much to alleviate this issue. Users will still need to be convinced that it is safe to install the Zapstore from the GitHub repo, and then install Amber from there. Furthermore, this adds yet another step to the onboarding process.
Instead of:
- Install Amber
- Set up your keys
- Install the client you want to use
- Log in with Amber
The process becomes:
- Go to the Zapstore GitHub and download the latest version from the releases page.
- Install the APK you downloaded, allowing any prompt to install unknown apps.
- Open Zapstore and install Amber, allowing any prompt to install unknown apps again.
- Open Amber and set up your keys.
- Install the client you want to use
- Log in with Amber
An application as important as Amber for protecting users' private keys should be as readily available to the new user as possible. New users are the ones most prone to making mistakes that could compromise their private keys. Amber should be available to them in the Play Store.
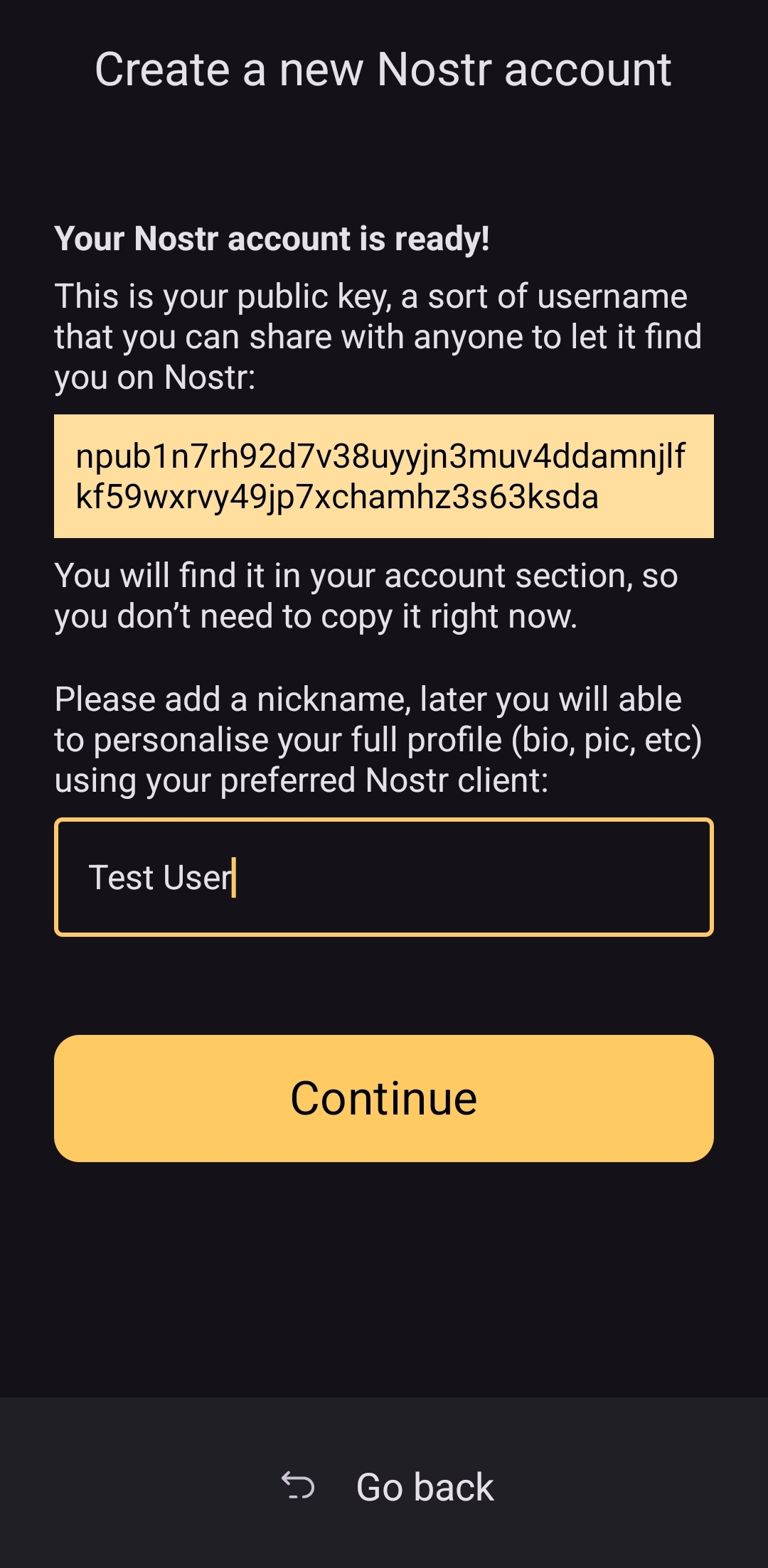
UPDATE: As of version 3.2.8 released on 4/21/2025, the onboarding flow for Amber has been greatly improved! Now, when selecting to set up a new "account" the user is informed on the very next screen, "Your Nostr account is ready!" and given their public key/npub. The only field the user must fill in is their "nickname"/display name and hit "Continue."
From there the user is asked if they want Amber to automatically approve basic actions, or manually approve each app, and then they are shown a new Applications screen, with a prompt to create a backup of their account. This prompt persists until the user has done so.
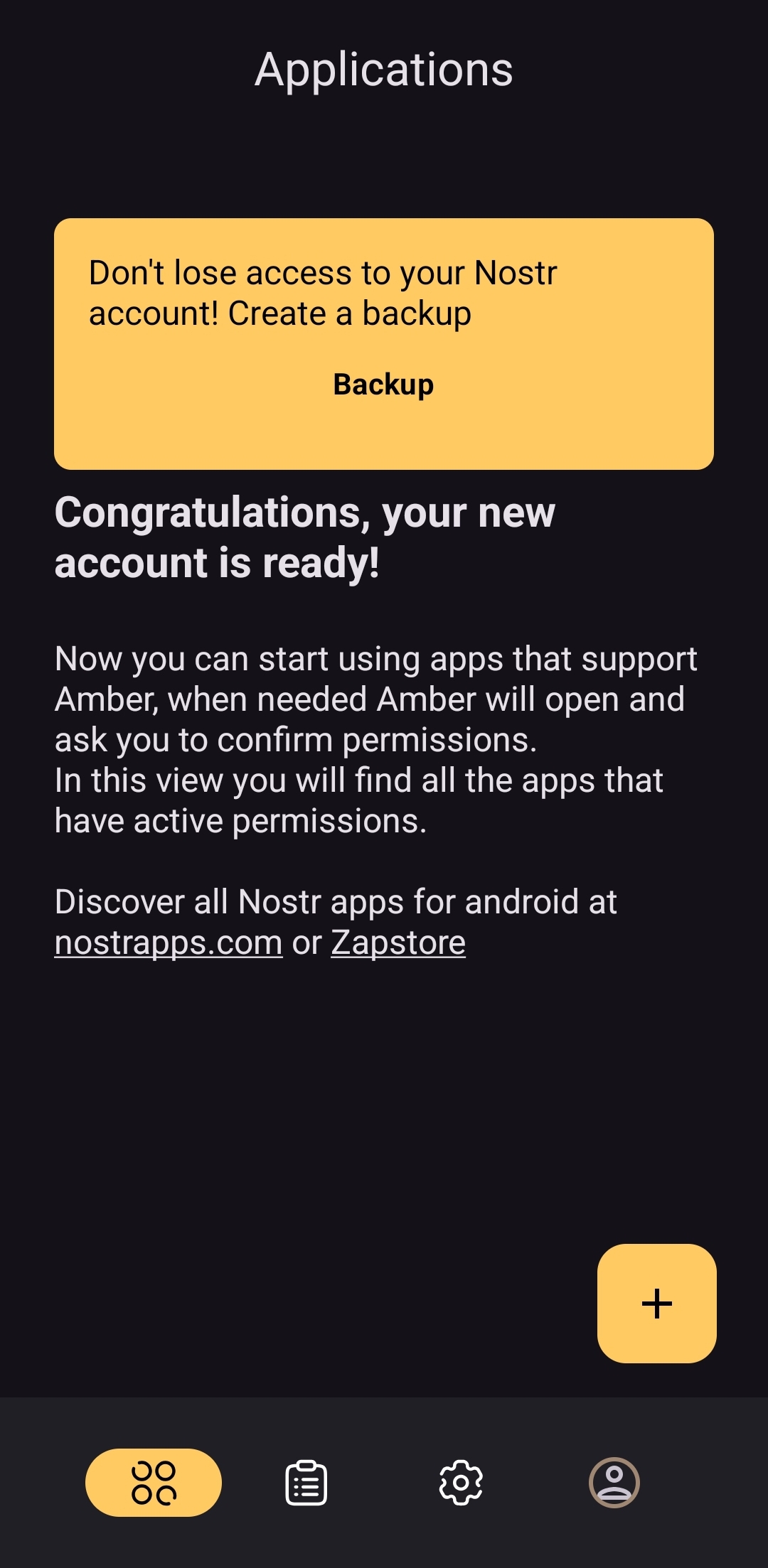
As you can see, the user is also encouraged to find applications that can be used with Amber with links to nostrapps.com and the Zapstore.
Thanks to these updates, Amber is now the smoothest and most user-friendly onboarding experience I have seen for Nostr to date. Sure, it doesn't have anything for setting up a profile picture or lightning address, but that is better done in a client like Amethyst or YakiHonne, anyway. Just tap "create," type in a handle to call yourself, and you're done!
How do UI Look?
Score: 4.5 / 5
Amber's UI can be described as clean but utilitarian. But then, Amber is a tool, so this is somewhat expected. It is not an app you will be spending a lot of time in, so the UI just needs to be serviceable. I would say it accomplishes this and then some. UI elements are generally easy to understand what they do, and page headings fill in the gaps where that is not the case.

I am not the biggest fan of the color-scheme, particularly in light-mode, but it is not bad in dark-mode at all, and Amber follows whatever theme you have set for your device in that respect. Additionally, the color choice does make sense given the application's name.

It must also be taken into consideration that Amber is almost entirely the product of a single developer's work. He has done a great job producing an app that is not only useful, but pleasant to interact with. The same cannot be said for most utility apps I have previously used, with interfaces that clearly made good design the lowest priority. While Amber's UI may not be the most beautiful Nostr app I have seen, design was clearly not an afterthought, either, and it is appreciated.
Relay Management
Score: 4.9 / 5
Even though Amber is not a Nostr client, where users can browse notes from their favorite npubs, it still relies heavily on relays for some of its features. Primarily, it uses relays for communicating with other Nostr apps for remote signing requests. However, it also uses relays to fetch profile data, so that each private key you add to Amber will automatically load your chosen username and profile picture.
In the relay settings, users can choose which relays are being used to fetch profile data, and which relays will be used by default when creating new remote signing connection strings.

The user can also see which relays are currently connected to Amber and even look at the information that has been passed back and forth on each of those active relays. This information about actively connected relays is not only available within the application, but also in the notification that Amber has to keep in your device's notification tray in order to continue to operate in the background while you are using other apps.

Optionality is the name of the game when it comes to how Amber handles relay selection. The user can just stick with the default signing relay, use their own relay as the default, or even use a different relay for each Nostr application that they connect to for remote signing. Amber gives the user an incredible amount of flexibility in this regard.
In addition to all of this, because not all relays accept the event types needed for remote signing, when you add a relay address to Amber, it automatically tests that relay to see if it will work. This alone can be a massive time saver, so users aren't trying to use relays that don't support remote signing and wondering why they can't log into noStrudel with the connection string they got from Amber.

The only way I could see relay management being improved would be some means of giving the user relay recommendations, in case they want to use a relay other than relay.nsec.app, but they aren't sure which other relays will accept remote signing events. That said, most users who want to use a different relay for signing remote events will likely be using their own, in which case recommendations aren't needed.
Current Users' Questions
The AskNostr hashtag can be a good indication of the pain points that other users are currently having with any Nostr application. Here are some of the most common questions submitted about Amber in the last two months.
nostr:nevent1qqsfrdr68fafgcvl8dgnhm9hxpsjxuks78afxhu8yewhtyf3d7mkg9gpzemhxue69uhhyetvv9ujumn0wd68ytnzv9hxgq3qkgh77xxt7hhtt4u528hecnx69rhagla8jj3tclgyf9wvkxa6dc0sxp0e6m
This is a good example of Amber working correctly, but the app the user is trying to log into not working. In my experience with #Olas in particular, it sometimes allows remote signer login, and sometimes doesn't. Amber will receive the signing request and I will approve it, but Olas remains on the login screen.
If Amber is receiving the signing requests, and you are approving them, the fault is likely with the application you are trying to log into.
That's it. That's all the repeated questions I could find. Oh, there were a few one-off questions where relay.nsec.app wouldn't connect, or where the user's out-of-date web browser was the issue. Outside of that, though, there were no common questions about how to use Amber, and that is a testament to Amber's ease of use all on its own.
Wrap Up
If you are on Android and you are not already using Amber to protect your nsec, please do yourself a favor and get it installed. It's not at all complicated to set up, and it will make trying out all the latest Nostr clients a safe and pleasant experience.
If you are a client developer and you have not added support for NIP-55 or NIP-46, do your users the courtesy of respecting the sanctity of their private keys. Even developers who have no intention of compromising their users' keys can inadvertently do so. Make that eventuality impossible by adding support for NIP-55 and NIP-46 signing.
Finally, I apologize for the extended time it took me to get this review finished. The time I have available is scarce, Nostr is distracting, and nostr:npub1w4uswmv6lu9yel005l3qgheysmr7tk9uvwluddznju3nuxalevvs2d0jr5 kept improving Amber even as I was putting it through its paces over the last two months. Keep shipping, my friend! You have made one of the most useful tools we have seen for Nostr to date!
Now... What should I review next?
-
 @ 401014b3:59d5476b
2025-04-22 00:23:24
@ 401014b3:59d5476b
2025-04-22 00:23:24About Me
I come to Nostr with extensive experience in the digital landscape. As a blockchain native since 2017, I've witnessed the evolution of decentralized technologies firsthand. Most of my professional career has been spent working within big tech companies, giving me a unique perspective on both centralized and decentralized systems.
My social media journey began on Twitter in 2007, where I've maintained a presence for over 17 years. I've also explored other decentralized social platforms including BlueSky, Farcaster, and Lens Protocol. As a Bitcoin maximalist, I was particularly intrigued by Nostr's compatibility with the Lightning Network, which initially drew me to the platform.
The Onboarding Challenge
The Nostr onboarding experience presents a significant hurdle for newcomers. Despite my technical background in blockchain technologies, I found the initial setup process more complicated than expected. Understanding public/private key cryptography just to join a social network creates a steeper learning curve than necessary.
BlueSky and Farcaster have demonstrated that it's possible to maintain decentralized principles while providing a more streamlined onboarding experience. Their approaches show that user-friendly design and decentralization aren't mutually exclusive concepts.
Relay Management: Room for Improvement
The concept of relays represents one of Nostr's most distinctive features, though it can be confusing for newcomers. While many clients come pre-configured with default relays, users eventually encounter situations where content or connections seem inconsistent.
When someone I've interacted with doesn't appear in my feed or doesn't respond, I'm often left wondering if we're simply on different relays. This uncertainty creates friction that doesn't exist on other platforms where connectivity is handled behind the scenes.
The relay system introduces a layer of complexity that, while important to Nostr's architecture, could benefit from better abstraction in the user experience. When using BlueSky or Farcaster, I don't need to think about the underlying infrastructure, something Nostr could learn from while maintaining its decentralized principles.
The Zap Economy: Growing Pains
The Lightning-powered zap system shows tremendous potential, but I've observed some concerning economic patterns. Longer-term Nostr users have expressed frustration about continuously sending zaps while seeing limited growth in the overall ecosystem.
Interestingly, there appears to be a connection between this liquidity issue and community growth dynamics. Some established users who voice concerns about bearing the financial burden of the zapping economy are simultaneously less welcoming to newer accounts, rarely following, engaging with, or zapping newcomers.
This creates a challenging environment for new users, who face a cold reception and have little incentive to load their Lightning wallets or participate in the zap economy. Why bring fresh liquidity to a platform where established users rarely engage with your content? This dynamic has limited the expansion of the ecosystem, with the same sats often circulating among established users rather than growing with new participants.
Client Diversity: Strength and Challenge
Nostr's multiple client options offer users choice, which is valuable. However, the implementation of NIPs (Nostr Implementation Possibilities) varies across clients, creating inconsistent experiences. Features that work seamlessly in one client might be implemented differently in another.
This extends to fundamental aspects like search functionality, thread navigation, and notification systems, all of which can differ significantly between clients. For users accustomed to consistent experiences, this fragmentation creates a learning curve with each new client they try.
Lightning Integration: Varying Experiences
The Lightning Network integration varies in quality and user experience across Nostr clients. While the functionality is generally present, the implementation quality, feature set, and ease of use differ depending on which client you choose.
This inconsistency means users may need to experiment with several clients to find one that provides the Lightning experience they're looking for, rather than having a consistent experience across the ecosystem.
Finding Balance
Nostr appears to be navigating the challenge of balancing technical innovation with user experience. While its cryptographic foundation and decentralized architecture are impressive technical achievements, these same strengths sometimes come at the cost of accessibility.
Despite my technical background and interest in decentralized technologies, I find myself using BlueSky and Farcaster more frequently for daily social interactions, while checking Nostr less often. For Nostr to achieve its potential for broader adoption, addressing these user experience considerations while maintaining its core principles will be essential.
The platform has tremendous potential with improvements to user experience, community dynamics, and economic sustainability, Nostr could evolve from a fascinating technical experiment into a truly compelling alternative to mainstream social media.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:13:56
@ 4ba8e86d:89d32de4
2025-04-21 02:13:56Tutorial feito por nostr:nostr:npub1rc56x0ek0dd303eph523g3chm0wmrs5wdk6vs0ehd0m5fn8t7y4sqra3tk poste original abaixo:
Parte 1 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/263585/tutorial-debloat-de-celulares-android-via-adb-parte-1
Parte 2 : http://xh6liiypqffzwnu5734ucwps37tn2g6npthvugz3gdoqpikujju525yd.onion/index.php/263586/tutorial-debloat-de-celulares-android-via-adb-parte-2
Quando o assunto é privacidade em celulares, uma das medidas comumente mencionadas é a remoção de bloatwares do dispositivo, também chamado de debloat. O meio mais eficiente para isso sem dúvidas é a troca de sistema operacional. Custom Rom’s como LineageOS, GrapheneOS, Iodé, CalyxOS, etc, já são bastante enxutos nesse quesito, principalmente quanto não é instalado os G-Apps com o sistema. No entanto, essa prática pode acabar resultando em problemas indesejados como a perca de funções do dispositivo, e até mesmo incompatibilidade com apps bancários, tornando este método mais atrativo para quem possui mais de um dispositivo e separando um apenas para privacidade. Pensando nisso, pessoas que possuem apenas um único dispositivo móvel, que são necessitadas desses apps ou funções, mas, ao mesmo tempo, tem essa visão em prol da privacidade, buscam por um meio-termo entre manter a Stock rom, e não ter seus dados coletados por esses bloatwares. Felizmente, a remoção de bloatwares é possível e pode ser realizada via root, ou mais da maneira que este artigo irá tratar, via adb.
O que são bloatwares?
Bloatware é a junção das palavras bloat (inchar) + software (programa), ou seja, um bloatware é basicamente um programa inútil ou facilmente substituível — colocado em seu dispositivo previamente pela fabricante e operadora — que está no seu dispositivo apenas ocupando espaço de armazenamento, consumindo memória RAM e pior, coletando seus dados e enviando para servidores externos, além de serem mais pontos de vulnerabilidades.
O que é o adb?
O Android Debug Brigde, ou apenas adb, é uma ferramenta que se utiliza das permissões de usuário shell e permite o envio de comandos vindo de um computador para um dispositivo Android exigindo apenas que a depuração USB esteja ativa, mas também pode ser usada diretamente no celular a partir do Android 11, com o uso do Termux e a depuração sem fio (ou depuração wifi). A ferramenta funciona normalmente em dispositivos sem root, e também funciona caso o celular esteja em Recovery Mode.
Requisitos:
Para computadores:
• Depuração USB ativa no celular; • Computador com adb; • Cabo USB;
Para celulares:
• Depuração sem fio (ou depuração wifi) ativa no celular; • Termux; • Android 11 ou superior;
Para ambos:
• Firewall NetGuard instalado e configurado no celular; • Lista de bloatwares para seu dispositivo;
Ativação de depuração:
Para ativar a Depuração USB em seu dispositivo, pesquise como ativar as opções de desenvolvedor de seu dispositivo, e lá ative a depuração. No caso da depuração sem fio, sua ativação irá ser necessária apenas no momento que for conectar o dispositivo ao Termux.
Instalação e configuração do NetGuard
O NetGuard pode ser instalado através da própria Google Play Store, mas de preferência instale pela F-Droid ou Github para evitar telemetria.
F-Droid: https://f-droid.org/packages/eu.faircode.netguard/
Github: https://github.com/M66B/NetGuard/releases
Após instalado, configure da seguinte maneira:
Configurações → padrões (lista branca/negra) → ative as 3 primeiras opções (bloquear wifi, bloquear dados móveis e aplicar regras ‘quando tela estiver ligada’);
Configurações → opções avançadas → ative as duas primeiras (administrar aplicativos do sistema e registrar acesso a internet);
Com isso, todos os apps estarão sendo bloqueados de acessar a internet, seja por wifi ou dados móveis, e na página principal do app basta permitir o acesso a rede para os apps que você vai usar (se necessário). Permita que o app rode em segundo plano sem restrição da otimização de bateria, assim quando o celular ligar, ele já estará ativo.
Lista de bloatwares
Nem todos os bloatwares são genéricos, haverá bloatwares diferentes conforme a marca, modelo, versão do Android, e até mesmo região.
Para obter uma lista de bloatwares de seu dispositivo, caso seu aparelho já possua um tempo de existência, você encontrará listas prontas facilmente apenas pesquisando por elas. Supondo que temos um Samsung Galaxy Note 10 Plus em mãos, basta pesquisar em seu motor de busca por:
Samsung Galaxy Note 10 Plus bloatware listProvavelmente essas listas já terão inclusas todos os bloatwares das mais diversas regiões, lhe poupando o trabalho de buscar por alguma lista mais específica.
Caso seu aparelho seja muito recente, e/ou não encontre uma lista pronta de bloatwares, devo dizer que você acaba de pegar em merda, pois é chato para um caralho pesquisar por cada aplicação para saber sua função, se é essencial para o sistema ou se é facilmente substituível.
De antemão já aviso, que mais para frente, caso vossa gostosura remova um desses aplicativos que era essencial para o sistema sem saber, vai acabar resultando na perda de alguma função importante, ou pior, ao reiniciar o aparelho o sistema pode estar quebrado, lhe obrigando a seguir com uma formatação, e repetir todo o processo novamente.
Download do adb em computadores
Para usar a ferramenta do adb em computadores, basta baixar o pacote chamado SDK platform-tools, disponível através deste link: https://developer.android.com/tools/releases/platform-tools. Por ele, você consegue o download para Windows, Mac e Linux.
Uma vez baixado, basta extrair o arquivo zipado, contendo dentro dele uma pasta chamada platform-tools que basta ser aberta no terminal para se usar o adb.
Download do adb em celulares com Termux.
Para usar a ferramenta do adb diretamente no celular, antes temos que baixar o app Termux, que é um emulador de terminal linux, e já possui o adb em seu repositório. Você encontra o app na Google Play Store, mas novamente recomendo baixar pela F-Droid ou diretamente no Github do projeto.
F-Droid: https://f-droid.org/en/packages/com.termux/
Github: https://github.com/termux/termux-app/releases
Processo de debloat
Antes de iniciarmos, é importante deixar claro que não é para você sair removendo todos os bloatwares de cara sem mais nem menos, afinal alguns deles precisam antes ser substituídos, podem ser essenciais para você para alguma atividade ou função, ou até mesmo são insubstituíveis.
Alguns exemplos de bloatwares que a substituição é necessária antes da remoção, é o Launcher, afinal, é a interface gráfica do sistema, e o teclado, que sem ele só é possível digitar com teclado externo. O Launcher e teclado podem ser substituídos por quaisquer outros, minha recomendação pessoal é por aqueles que respeitam sua privacidade, como Pie Launcher e Simple Laucher, enquanto o teclado pelo OpenBoard e FlorisBoard, todos open-source e disponíveis da F-Droid.
Identifique entre a lista de bloatwares, quais você gosta, precisa ou prefere não substituir, de maneira alguma você é obrigado a remover todos os bloatwares possíveis, modifique seu sistema a seu bel-prazer. O NetGuard lista todos os apps do celular com o nome do pacote, com isso você pode filtrar bem qual deles não remover.
Um exemplo claro de bloatware insubstituível e, portanto, não pode ser removido, é o com.android.mtp, um protocolo onde sua função é auxiliar a comunicação do dispositivo com um computador via USB, mas por algum motivo, tem acesso a rede e se comunica frequentemente com servidores externos. Para esses casos, e melhor solução mesmo é bloquear o acesso a rede desses bloatwares com o NetGuard.
MTP tentando comunicação com servidores externos:
Executando o adb shell
No computador
Faça backup de todos os seus arquivos importantes para algum armazenamento externo, e formate seu celular com o hard reset. Após a formatação, e a ativação da depuração USB, conecte seu aparelho e o pc com o auxílio de um cabo USB. Muito provavelmente seu dispositivo irá apenas começar a carregar, por isso permita a transferência de dados, para que o computador consiga se comunicar normalmente com o celular.
Já no pc, abra a pasta platform-tools dentro do terminal, e execute o seguinte comando:
./adb start-serverO resultado deve ser:
daemon not running; starting now at tcp:5037 daemon started successfully
E caso não apareça nada, execute:
./adb kill-serverE inicie novamente.
Com o adb conectado ao celular, execute:
./adb shellPara poder executar comandos diretamente para o dispositivo. No meu caso, meu celular é um Redmi Note 8 Pro, codinome Begonia.
Logo o resultado deve ser:
begonia:/ $
Caso ocorra algum erro do tipo:
adb: device unauthorized. This adb server’s $ADB_VENDOR_KEYS is not set Try ‘adb kill-server’ if that seems wrong. Otherwise check for a confirmation dialog on your device.
Verifique no celular se apareceu alguma confirmação para autorizar a depuração USB, caso sim, autorize e tente novamente. Caso não apareça nada, execute o kill-server e repita o processo.
No celular
Após realizar o mesmo processo de backup e hard reset citado anteriormente, instale o Termux e, com ele iniciado, execute o comando:
pkg install android-toolsQuando surgir a mensagem “Do you want to continue? [Y/n]”, basta dar enter novamente que já aceita e finaliza a instalação
Agora, vá até as opções de desenvolvedor, e ative a depuração sem fio. Dentro das opções da depuração sem fio, terá uma opção de emparelhamento do dispositivo com um código, que irá informar para você um código em emparelhamento, com um endereço IP e porta, que será usado para a conexão com o Termux.
Para facilitar o processo, recomendo que abra tanto as configurações quanto o Termux ao mesmo tempo, e divida a tela com os dois app’s, como da maneira a seguir:
Para parear o Termux com o dispositivo, não é necessário digitar o ip informado, basta trocar por “localhost”, já a porta e o código de emparelhamento, deve ser digitado exatamente como informado. Execute:
adb pair localhost:porta CódigoDeEmparelhamentoDe acordo com a imagem mostrada anteriormente, o comando ficaria “adb pair localhost:41255 757495”.
Com o dispositivo emparelhado com o Termux, agora basta conectar para conseguir executar os comandos, para isso execute:
adb connect localhost:portaObs: a porta que você deve informar neste comando não é a mesma informada com o código de emparelhamento, e sim a informada na tela principal da depuração sem fio.
Pronto! Termux e adb conectado com sucesso ao dispositivo, agora basta executar normalmente o adb shell:
adb shellRemoção na prática Com o adb shell executado, você está pronto para remover os bloatwares. No meu caso, irei mostrar apenas a remoção de um app (Google Maps), já que o comando é o mesmo para qualquer outro, mudando apenas o nome do pacote.
Dentro do NetGuard, verificando as informações do Google Maps:
Podemos ver que mesmo fora de uso, e com a localização do dispositivo desativado, o app está tentando loucamente se comunicar com servidores externos, e informar sabe-se lá que peste. Mas sem novidades até aqui, o mais importante é que podemos ver que o nome do pacote do Google Maps é com.google.android.apps.maps, e para o remover do celular, basta executar:
pm uninstall –user 0 com.google.android.apps.mapsE pronto, bloatware removido! Agora basta repetir o processo para o resto dos bloatwares, trocando apenas o nome do pacote.
Para acelerar o processo, você pode já criar uma lista do bloco de notas com os comandos, e quando colar no terminal, irá executar um atrás do outro.
Exemplo de lista:
Caso a donzela tenha removido alguma coisa sem querer, também é possível recuperar o pacote com o comando:
cmd package install-existing nome.do.pacotePós-debloat
Após limpar o máximo possível o seu sistema, reinicie o aparelho, caso entre no como recovery e não seja possível dar reboot, significa que você removeu algum app “essencial” para o sistema, e terá que formatar o aparelho e repetir toda a remoção novamente, desta vez removendo poucos bloatwares de uma vez, e reiniciando o aparelho até descobrir qual deles não pode ser removido. Sim, dá trabalho… quem mandou querer privacidade?
Caso o aparelho reinicie normalmente após a remoção, parabéns, agora basta usar seu celular como bem entender! Mantenha o NetGuard sempre executando e os bloatwares que não foram possíveis remover não irão se comunicar com servidores externos, passe a usar apps open source da F-Droid e instale outros apps através da Aurora Store ao invés da Google Play Store.
Referências: Caso você seja um Australopithecus e tenha achado este guia difícil, eis uma videoaula (3:14:40) do Anderson do canal Ciberdef, realizando todo o processo: http://odysee.com/@zai:5/Como-remover-at%C3%A9-200-APLICATIVOS-que-colocam-a-sua-PRIVACIDADE-E-SEGURAN%C3%87A-em-risco.:4?lid=6d50f40314eee7e2f218536d9e5d300290931d23
Pdf’s do Anderson citados na videoaula: créditos ao anon6837264 http://eternalcbrzpicytj4zyguygpmkjlkddxob7tptlr25cdipe5svyqoqd.onion/file/3863a834d29285d397b73a4af6fb1bbe67c888d72d30/t-05e63192d02ffd.pdf
Processo de instalação do Termux e adb no celular: https://youtu.be/APolZrPHSms
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:12:19
@ 4ba8e86d:89d32de4
2025-04-21 02:12:19SISTEMA OPERACIONAL MÓVEIS
GrapheneOS : https://njump.me/nevent1qqs8t76evdgrg4qegdtyrq2rved63pr29wlqyj627n9tj4vlu66tqpqpzdmhxue69uhk7enxvd5xz6tw9ec82c30qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqppcqec9
CalyxOS : https://njump.me/nevent1qqsrm0lws2atln2kt3cqjacathnw0uj0jsxwklt37p7t380hl8mmstcpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3vamnwvaz7tmwdaehgu3wvf3kstnwd9hx5cf0qy2hwumn8ghj7un9d3shjtnyv9kh2uewd9hj7qgcwaehxw309aex2mrp0yhxxatjwfjkuapwveukjtcpzpmhxue69uhkummnw3ezumt0d5hszrnhwden5te0dehhxtnvdakz7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qghwaehxw309aex2mrp0yhxummnw3ezucnpdejz7qgewaehxw309ahx7um5wghxymmwva3x7mn89e3k7mf0qythwumn8ghj7cn5vvhxkmr9dejxz7n49e3k7mf0qyg8wumn8ghj7mn09eehgu3wvdez7smttdu
LineageOS : https://njump.me/nevent1qqsgw7sr36gaty48cf4snw0ezg5mg4atzhqayuge752esd469p26qfgpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpnvm779
SISTEMA OPERACIONAL DESKTOP
Tails : https://njump.me/nevent1qqsf09ztvuu60g6xprazv2vxqqy5qlxjs4dkc9d36ta48q75cs9le4qpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz34ag5t
Qubes OS : https://njump.me/nevent1qqsp6jujgwl68uvurw0cw3hfhr40xq20sj7rl3z4yzwnhp9sdpa7augpzpmhxue69uhkummnw3ezumt0d5hsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshsz9thwden5te0dehhxarj9ehhsarj9ejx2a30qyg8wumn8ghj7mn09eehgu3wvdez7qg4waehxw309aex2mrp0yhxgctdw4eju6t09uqjxamnwvaz7tmwdaehgu3dwejhy6txd9jkgtnhv4kxcmmjv3jhytnwv46z7qgwwaehxw309ahx7uewd3hkctcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uj3ljr8
Kali linux : https://njump.me/nevent1qqswlav72xdvamuyp9xc38c6t7070l3n2uxu67ssmal2g7gv35nmvhspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswt9rxe
Whonix : https://njump.me/nevent1qqs85gvejvzhk086lwh6edma7fv07p5c3wnwnxnzthwwntg2x6773egpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qfywaehxw309ahx7um5wgh8ymm4dej8ymmrdd3xjarrda5kuetjwvhxxmmd9uq3wamnwvaz7tmzw33ju6mvv4hxgct6w5hxxmmd9uq3qamnwvaz7tmwduh8xarj9e3hytcpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszrnhwden5te0dehhxtnvdakz7qg7waehxw309ahx7um5wgkkgetk9emk2mrvdaexgetj9ehx2ap0sen9p6
Kodachi : https://njump.me/nevent1qqsf5zszgurpd0vwdznzk98hck294zygw0s8dah6fpd309ecpreqtrgpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhszgmhwden5te0dehhxarj94mx2unfve5k2epwwajkcmr0wfjx2u3wdejhgtcpremhxue69uhkummnw3ez6er9wch8wetvd3hhyer9wghxuet59uq3qamnwvaz7tmwdaehgu3wd4hk6tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzpmhxue69uhkumewwd68ytnrwghszfrhwden5te0dehhxarj9eex7atwv3ex7cmtvf5hgcm0d9hx2unn9e3k7mf0qyvhwumn8ghj7mn0wd68ytnzdahxwcn0denjucm0d5hszrnhwden5te0dehhxtnvdakz7qgkwaehxw309ahx7um5wghxycmg9ehxjmn2vyhsz9mhwden5te0wfjkccte9ehx7um5wghxyctwvshs94a4d5
PGP
Openkeychain : https://njump.me/nevent1qqs9qtjgsulp76t7jkquf8nk8txs2ftsr0qke6mjmsc2svtwfvswzyqpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs36mp0w
Kleopatra : https://njump.me/nevent1qqspnevn932hdggvp4zam6mfyce0hmnxsp9wp8htpumq9vm3anq6etsppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpuaeghp
Pgp : https://njump.me/nevent1qqsggek707qf3rzttextmgqhym6d4g479jdnlnj78j96y0ut0x9nemcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgptemhe
Como funciona o PGP? : https://njump.me/nevent1qqsz9r7azc8pkvfmkg2hv0nufaexjtnvga0yl85x9hu7ptpg20gxxpspremhxue69uhkummnw3ez6ur4vgh8wetvd3hhyer9wghxuet59upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy259fhs
Por que eu escrevi PGP. - Philip Zimmermann.
https://njump.me/nevent1qqsvysn94gm8prxn3jw04r0xwc6sngkskg756z48jsyrmqssvxtm7ncpzamhxue69uhhyetvv9ujumn0wd68ytnzv9hxgtchzxnad
VPN
Vpn : https://njump.me/nevent1qqs27ltgsr6mh4ffpseexz6s37355df3zsur709d0s89u2nugpcygsspzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqshzu2fk
InviZible Pro : https://njump.me/nevent1qqsvyevf2vld23a3xrpvarc72ndpcmfvc3lc45jej0j5kcsg36jq53cpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy33y5l4
Orbot: https://njump.me/nevent1qqsxswkyt6pe34egxp9w70cy83h40ururj6m9sxjdmfass4cjm4495stft593
I2P
i2p : https://njump.me/nevent1qqsvnj8n983r4knwjmnkfyum242q4c0cnd338l4z8p0m6xsmx89mxkslx0pgg
Entendendo e usando a rede I2P : https://njump.me/nevent1qqsxchp5ycpatjf5s4ag25jkawmw6kkf64vl43vnprxdcwrpnms9qkcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpvht4mn
Criando e acessando sua conta Email na I2P : https://njump.me/nevent1qqs9v9dz897kh8e5lfar0dl7ljltf2fpdathsn3dkdsq7wg4ksr8xfgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpw8mzum
APLICATIVO 2FA
Aegis Authenticator : https://njump.me/nevent1qqsfttdwcn9equlrmtf9n6wee7lqntppzm03pzdcj4cdnxel3pz44zspz4mhxue69uhhyetvv9ujumn0wd68ytnzvuhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqscvtydq
YubiKey : https://njump.me/nevent1qqstsnn69y4sf4330n7039zxm7wza3ch7sn6plhzmd57w6j9jssavtspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzueyvgt
GERENCIADOR DE SENHAS
KeepassDX: https://njump.me/nevent1qqswc850dr4ujvxnmpx75jauflf4arc93pqsty5pv8hxdm7lcw8ee8qpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpe0492n
Birwaden: https://njump.me/nevent1qqs0j5x9guk2v6xumhwqmftmcz736m9nm9wzacqwjarxmh8k4xdyzwgpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpwfe2kc
KeePassXC: https://njump.me/nevent1qqsgftcrd8eau7tzr2p9lecuaf7z8mx5jl9w2k66ae3lzkw5wqcy5pcl2achp
CHAT MENSAGEM
SimpleXchat : https://njump.me/nevent1qqsds5xselnnu0dyy0j49peuun72snxcgn3u55d2320n37rja9gk8lgzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgmcmj7c
Briar : https://njump.me/nevent1qqs8rrtgvjr499hreugetrl7adkhsj2zextyfsukq5aa7wxthrgcqcg05n434
Element Messenger : https://njump.me/nevent1qqsq05snlqtxm5cpzkshlf8n5d5rj9383vjytkvqp5gta37hpuwt4mqyccee6
Pidgin : https://njump.me/nevent1qqsz7kngycyx7meckx53xk8ahk98jkh400usrvykh480xa4ct9zlx2c2ywvx3
E-MAIL
Thunderbird: https://njump.me/nevent1qqspq64gg0nw7t60zsvea5eykgrm43paz845e4jn74muw5qzdvve7uqrkwtjh
ProtonMail : https://njump.me/nevent1qqs908glhk68e7ms8zqtlsqd00wu3prnpt08dwre26hd6e5fhqdw99cppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpeyhg4z
Tutonota : https://njump.me/nevent1qqswtzh9zjxfey644qy4jsdh9465qcqd2wefx0jxa54gdckxjvkrrmqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5hzhkv
k-9 mail : https://njump.me/nevent1qqs200g5a603y7utjgjk320r3srurrc4r66nv93mcg0x9umrw52ku5gpr3mhxue69uhkummnw3ezuumhd9ehxtt9de5kwmtp9e3kstczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgacflak
E-MAIL-ALIÁS
Simplelogin : https://njump.me/nevent1qqsvhz5pxqpqzr2ptanqyqgsjr50v7u9lc083fvdnglhrv36rnceppcppemhxue69uhkummn9ekx7mp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp9gsr7m
AnonAddy : https://njump.me/nevent1qqs9mcth70mkq2z25ws634qfn7vx2mlva3tkllayxergw0s7p8d3ggcpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs6mawe3
NAVEGADOR
Navegador Tor : https://njump.me/nevent1qqs06qfxy7wzqmk76l5d8vwyg6mvcye864xla5up52fy5sptcdy39lspzemhxue69uhkummnw3ezuerpw3sju6rpw4ej7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdp0urw
Mullvap Browser : https://njump.me/nevent1qqs2vsgc3wk09wdspv2mezltgg7nfdg97g0a0m5cmvkvr4nrfxluzfcpzdmhxue69uhhwmm59e6hg7r09ehkuef0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpj8h6fe
LibreWolf : https://njump.me/nevent1qqswv05mlmkcuvwhe8x3u5f0kgwzug7n2ltm68fr3j06xy9qalxwq2cpzemhxue69uhkummnw3ex2mrfw3jhxtn0wfnj7q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuv2hxr
Cromite : https://njump.me/nevent1qqs2ut83arlu735xp8jf87w5m3vykl4lv5nwkhldkqwu3l86khzzy4cpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs3dplt7
BUSCADORES
Searx : https://njump.me/nevent1qqsxyzpvgzx00n50nrlgctmy497vkm2cm8dd5pdp7fmw6uh8xnxdmaspr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqp23z7ax
APP-STORE
Obtainium : https://njump.me/nevent1qqstd8kzc5w3t2v6dgf36z0qrruufzfgnc53rj88zcjgsagj5c5k4rgpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyarmca3
F-Droid : https://njump.me/nevent1qqst4kry49cc9g3g8s5gdnpgyk3gjte079jdnv43f0x4e85cjkxzjesymzuu4
Droid-ify : https://njump.me/nevent1qqsrr8yu9luq0gud902erdh8gw2lfunpe93uc2u6g8rh9ep7wt3v4sgpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsfzu9vk
Aurora Store : https://njump.me/nevent1qqsy69kcaf0zkcg0qnu90mtk46ly3p2jplgpzgk62wzspjqjft4fpjgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzrpmsjy
RSS
Feeder : https://njump.me/nevent1qqsy29aeggpkmrc7t3c7y7ldgda7pszl7c8hh9zux80gjzrfvlhfhwqpp4mhxue69uhkummn9ekx7mqzyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgsvzzjy
VIDEOO CONFERENCIA
Jitsi meet : https://njump.me/nevent1qqswphw67hr6qmt2fpugcj77jrk7qkfdrszum7vw7n2cu6cx4r6sh4cgkderr
TECLADOS
HeliBoard : https://njump.me/nevent1qqsyqpc4d28rje03dcvshv4xserftahhpeylu2ez2jutdxwds4e8syspz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsr8mel5
OpenBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
FlorisBoard : https://njump.me/nevent1qqsf7zqkup03yysy67y43nj48q53sr6yym38es655fh9fp6nxpl7rqspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqswcvh3r
MAPAS
Osmand : https://njump.me/nevent1qqsxryp2ywj64az7n5p6jq5tn3tx5jv05te48dtmmt3lf94ydtgy4fgpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs54nwpj
Organic maps : https://njump.me/nevent1qqstrecuuzkw0dyusxdq7cuwju0ftskl7anx978s5dyn4pnldrkckzqpr4mhxue69uhkummnw3ezumtp0p5k6ctrd96xzer9dshx7un8qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpl8z3kk
TRADUÇÃO
LibreTranslate : https://njump.me/nevent1qqs953g3rhf0m8jh59204uskzz56em9xdrjkelv4wnkr07huk20442cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzeqsx40
REMOÇÃO DOS METADADOS
Scrambled Exif : https://njump.me/nevent1qqs2658t702xv66p000y4mlhnvadmdxwzzfzcjkjf7kedrclr3ej7aspyfmhxue69uhk6atvw35hqmr90pjhytngw4eh5mmwv4nhjtnhdaexcep0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpguu0wh
ESTEGANOGRAFIA
PixelKnot: https://njump.me/nevent1qqsrh0yh9mg0lx86t5wcmhh97wm6n4v0radh6sd0554ugn354wqdj8gpz3mhxue69uhhyetvv9ujuerpd46hxtnfdupzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqyuvfqdp
PERFIL DE TRABALHO
Shelter : https://njump.me/nevent1qqspv9xxkmfp40cxgjuyfsyczndzmpnl83e7gugm7480mp9zhv50wkqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdnu59c
PDF
MuPDF : https://njump.me/nevent1qqspn5lhe0dteys6npsrntmv2g470st8kh8p7hxxgmymqa95ejvxvfcpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs4hvhvj
Librera Reader : https://njump.me/nevent1qqsg60flpuf00sash48fexvwxkly2j5z9wjvjrzt883t3eqng293f3cpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz39tt3n
QR-Code
Binary Eye : https://njump.me/nevent1qqsz4n0uxxx3q5m0r42n9key3hchtwyp73hgh8l958rtmae5u2khgpgpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzdmn4wp
Climático
Breezy Weather : https://njump.me/nevent1qqs9hjz5cz0y4am3kj33xn536uq85ydva775eqrml52mtnnpe898rzspzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgpd3tu8
ENCRYPTS
Cryptomator : https://njump.me/nevent1qqsvchvnw779m20583llgg5nlu6ph5psewetlczfac5vgw83ydmfndspzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsx7ppw9
VeraCrypt : https://njump.me/nevent1qqsf6wzedsnrgq6hjk5c4jj66dxnplqwc4ygr46l8z3gfh38q2fdlwgm65ej3
EXTENSÕES
uBlock Origin : https://njump.me/nevent1qqswaa666lcj2c4nhnea8u4agjtu4l8q89xjln0yrngj7ssh72ntwzql8ssdj
Snowflake : https://njump.me/nevent1qqs0ws74zlt8uced3p2vee9td8x7vln2mkacp8szdufvs2ed94ctnwchce008
CLOUD
Nextcloud : https://njump.me/nevent1qqs2utg5z9htegdtrnllreuhypkk2026x8a0xdsmfczg9wdl8rgrcgg9nhgnm
NOTEPAD
Joplin : https://njump.me/nevent1qqsz2a0laecpelsznser3xd0jfa6ch2vpxtkx6vm6qg24e78xttpk0cpr4mhxue69uhkummnw3ezucnfw33k76twv4ezuum0vd5kzmp0qgsyh28gd5ke0ztdeyehc0jsq6gcj0tnzatjlkql3dqamkja38fjmeqrqsqqqqqpdu0hft
Standard Notes : https://njump.me/nevent1qqsv3596kz3qung5v23cjc4cpq7rqxg08y36rmzgcrvw5whtme83y3s7tng6r
MÚSICA
RiMusic : https://njump.me/nevent1qqsv3genqav2tfjllp86ust4umxm8tr2wd9kq8x7vrjq6ssp363mn0gpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqg42353n
ViMusic : https://njump.me/nevent1qqswx78559l4jsxsrygd8kj32sch4qu57stxq0z6twwl450vp39pdqqpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzjg863j
PODCAST
AntennaPod : https://njump.me/nevent1qqsp4nh7k4a6zymfwqqdlxuz8ua6kdhvgeeh3uxf2c9rtp9u3e9ku8qnr8lmy
VISUALIZAR VIDEO
VLC : https://njump.me/nevent1qqs0lz56wtlr2eye4ajs2gzn2r0dscw4y66wezhx0mue6dffth8zugcl9laky
YOUTUBE
NewPipe : https://njump.me/nevent1qqsdg06qpcjdnlvgm4xzqdap0dgjrkjewhmh4j3v4mxdl4rjh8768mgdw9uln
FreeTube : https://njump.me/nevent1qqsz6y6z7ze5gs56s8seaws8v6m6j2zu0pxa955dhq3ythmexak38mcpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqs5lkjvv
LibreTube : https://snort.social/e/nevent1qqstmd5m6wrdvn4gxf8xyhrwnlyaxmr89c9kjddvnvux6603f84t3fqpz4mhxue69uhhyetvv9ujumt0wd68ytnsw43qygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsswwznc
COMPARTILHAMENTO DE ARQUIVOS
OnionShare : https://njump.me/nevent1qqsr0a4ml5nu6ud5k9yzyawcd9arznnwkrc27dzzc95q6r50xmdff6qpydmhxue69uhkummnw3ez6an9wf5kv6t9vsh8wetvd3hhyer9wghxuet59uq3uamnwvaz7tmwdaehgu3dv3jhvtnhv4kxcmmjv3jhytnwv46z7qgswaehxw309ahx7tnnw3ezucmj9uq32amnwvaz7tmjv4kxz7fwv3sk6atn9e5k7tcpzamhxue69uhkyarr9e4kcetwv3sh5afwvdhk6tcpzemhxue69uhkummnw3ezucnrdqhxu6twdfsj7qgswaehxw309ahx7um5wghx6mmd9uqjgamnwvaz7tmwdaehgu3wwfhh2mnywfhkx6mzd96xxmmfdejhyuewvdhk6tcppemhxue69uhkummn9ekx7mp0qythwumn8ghj7un9d3shjtnwdaehgu3wvfskuep0qyv8wumn8ghj7un9d3shjtnrw4e8yetwwshxv7tf9ut7qurt
Localsend : https://njump.me/nevent1qqsp8ldjhrxm09cvvcak20hrc0g8qju9f67pw7rxr2y3euyggw9284gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzuyghqr
Wallet Bitcoin
Ashigaru Wallet : https://njump.me/nevent1qqstx9fz8kf24wgl26un8usxwsqjvuec9f8q392llmga75tw0kfarfcpzamhxue69uhhyetvv9ujuurjd9kkzmpwdejhgtczyp9636rd9ktcjmwfxd7ru5qxjxyn6uch2uhas8utg8wa5hvf6vk7gqcyqqqqqqgvfsrqp
Samourai Wallet : https://njump.me/nevent1qqstcvjmz39rmrnrv7t5cl6p3x7pzj6jsspyh4s4vcwd2lugmre04ecpr9mhxue69uhkummnw3ezucn0denkymmwvuhxxmmd9upzqjagapkjm9ufdhynxlp72qrfrzfawvt4wt7cr795rhw6tkyaxt0yqvzqqqqqqy3rg4qs
CÂMERA
opencamera : https://njump.me/nevent1qqs25glp6dh0crrjutxrgdjlnx9gtqpjtrkg29hlf7382aeyjd77jlqpzpmhxue69uhkumewwd68ytnrwghsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqssxcvgc
OFFICE
Collabora Office : https://njump.me/nevent1qqs8yn4ys6adpmeu3edmf580jhc3wluvlf823cc4ft4h0uqmfzdf99qpz4mhxue69uhhyetvv9ujuerpd46hxtnfduhsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsj40uss
TEXTOS
O manifesto de um Cypherpunk : https://njump.me/nevent1qqsd7hdlg6galn5mcuv3pm3ryfjxc4tkyph0cfqqe4du4dr4z8amqyspvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqzal0efa
Operations security ( OPSEC) : https://snort.social/e/nevent1qqsp323havh3y9nxzd4qmm60hw87tm9gjns0mtzg8y309uf9mv85cqcpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz8ej9l7
O MANIFESTO CRIPTOANARQUISTA Timothy C. May – 1992. : https://njump.me/nevent1qqspp480wtyx2zhtwpu5gptrl8duv9rvq3mug85mp4d54qzywk3zq9gpvemhxue69uhkv6tvw3jhytnwdaehgu3wwa5kuef0dec82c330g6x6dm8ddmxzdne0pnhverevdkxxdm6wqc8v735w3snquejvsuk56pcvuurxaesxd68qdtkv3nrx6m6v3ehsctwvym8q0mzwfhkzerrv9ehg0t5wf6k2q3qfw5wsmfdj7ykmjfn0sl9qp533y7hx96h9lvplz6pmhd9mzwn9hjqxpqqqqqqz5wq496
Declaração de independência do ciberespaço
- John Perry Barlow - 1996 : https://njump.me/nevent1qqs2njsy44n6p07mhgt2tnragvchasv386nf20ua5wklxqpttf6mzuqpzpmhxue69uhkummnw3ezumt0d5hsygzt4r5x6tvh39kujvmu8egqdyvf84e3w4e0mq0ckswamfwcn5eduspsgqqqqqqsukg4hr
The Cyphernomicon: Criptografia, Dinheiro Digital e o Futuro da Privacidade. escrito por Timothy C. May -Publicado em 1994. :
Livro completo em PDF no Github PrivacyOpenSource.
https://github.com/Alexemidio/PrivacyOpenSource/raw/main/Livros/THE%20CYPHERNOMICON%20.pdf Share
-
 @ c631e267:c2b78d3e
2025-04-20 19:54:32
@ c631e267:c2b78d3e
2025-04-20 19:54:32Es ist völlig unbestritten, dass der Angriff der russischen Armee auf die Ukraine im Februar 2022 strikt zu verurteilen ist. Ebenso unbestritten ist Russland unter Wladimir Putin keine brillante Demokratie. Aus diesen Tatsachen lässt sich jedoch nicht das finstere Bild des russischen Präsidenten – und erst recht nicht des Landes – begründen, das uns durchweg vorgesetzt wird und den Kern des aktuellen europäischen Bedrohungs-Szenarios darstellt. Da müssen wir schon etwas genauer hinschauen.
Der vorliegende Artikel versucht derweil nicht, den Einsatz von Gewalt oder die Verletzung von Menschenrechten zu rechtfertigen oder zu entschuldigen – ganz im Gegenteil. Dass jedoch der Verdacht des «Putinverstehers» sofort latent im Raume steht, verdeutlicht, was beim Thema «Russland» passiert: Meinungsmache und Manipulation.
Angesichts der mentalen Mobilmachung seitens Politik und Medien sowie des Bestrebens, einen bevorstehenden Krieg mit Russland geradezu herbeizureden, ist es notwendig, dieser fatalen Entwicklung entgegenzutreten. Wenn wir uns nur ein wenig von der herrschenden Schwarz-Weiß-Malerei freimachen, tauchen automatisch Fragen auf, die Risse im offiziellen Narrativ enthüllen. Grund genug, nachzuhaken.
Wer sich schon länger auch abseits der Staats- und sogenannten Leitmedien informiert, der wird in diesem Artikel vermutlich nicht viel Neues erfahren. Andere könnten hier ein paar unbekannte oder vergessene Aspekte entdecken. Möglicherweise klärt sich in diesem Kontext die Wahrnehmung der aktuellen (unserer eigenen!) Situation ein wenig.
Manipulation erkennen
Corona-«Pandemie», menschengemachter Klimawandel oder auch Ukraine-Krieg: Jede Menge Krisen, und für alle gibt es ein offizielles Narrativ, dessen Hinterfragung unerwünscht ist. Nun ist aber ein Narrativ einfach eine Erzählung, eine Geschichte (Latein: «narratio») und kein Tatsachenbericht. Und so wie ein Märchen soll auch das Narrativ eine Botschaft vermitteln.
Über die Methoden der Manipulation ist viel geschrieben worden, sowohl in Bezug auf das Individuum als auch auf die Massen. Sehr wertvolle Tipps dazu, wie man Manipulationen durchschauen kann, gibt ein Büchlein [1] von Albrecht Müller, dem Herausgeber der NachDenkSeiten.
Die Sprache selber eignet sich perfekt für die Manipulation. Beispielsweise kann die Wortwahl Bewertungen mitschwingen lassen, regelmäßiges Wiederholen (gerne auch von verschiedenen Seiten) lässt Dinge irgendwann «wahr» erscheinen, Übertreibungen fallen auf und hinterlassen wenigstens eine Spur im Gedächtnis, genauso wie Andeutungen. Belege spielen dabei keine Rolle.
Es gibt auffällig viele Sprachregelungen, die offenbar irgendwo getroffen und irgendwie koordiniert werden. Oder alle Redenschreiber und alle Medien kopieren sich neuerdings permanent gegenseitig. Welchen Zweck hat es wohl, wenn der Krieg in der Ukraine durchgängig und quasi wörtlich als «russischer Angriffskrieg auf die Ukraine» bezeichnet wird? Obwohl das in der Sache richtig ist, deutet die Art der Verwendung auf gezielte Beeinflussung hin und soll vor allem das Feindbild zementieren.
Sprachregelungen dienen oft der Absicherung einer einseitigen Darstellung. Das Gleiche gilt für das Verkürzen von Informationen bis hin zum hartnäckigen Verschweigen ganzer Themenbereiche. Auch hierfür gibt es rund um den Ukraine-Konflikt viele gute Beispiele.
Das gewünschte Ergebnis solcher Methoden ist eine Schwarz-Weiß-Malerei, bei der einer eindeutig als «der Böse» markiert ist und die anderen automatisch «die Guten» sind. Das ist praktisch und demonstriert gleichzeitig ein weiteres Manipulationswerkzeug: die Verwendung von Doppelstandards. Wenn man es schafft, bei wichtigen Themen regelmäßig mit zweierlei Maß zu messen, ohne dass das Publikum protestiert, dann hat man freie Bahn.
Experten zu bemühen, um bestimmte Sachverhalte zu erläutern, ist sicher sinnvoll, kann aber ebenso missbraucht werden, schon allein durch die Auswahl der jeweiligen Spezialisten. Seit «Corona» werden viele erfahrene und ehemals hoch angesehene Fachleute wegen der «falschen Meinung» diffamiert und gecancelt. [2] Das ist nicht nur ein brutaler Umgang mit Menschen, sondern auch eine extreme Form, die öffentliche Meinung zu steuern.
Wann immer wir also erkennen (weil wir aufmerksam waren), dass wir bei einem bestimmten Thema manipuliert werden, dann sind zwei logische und notwendige Fragen: Warum? Und was ist denn richtig? In unserem Russland-Kontext haben die Antworten darauf viel mit Geopolitik und Geschichte zu tun.
Ist Russland aggressiv und expansiv?
Angeblich plant Russland, europäische NATO-Staaten anzugreifen, nach dem Motto: «Zuerst die Ukraine, dann den Rest». In Deutschland weiß man dafür sogar das Datum: «Wir müssen bis 2029 kriegstüchtig sein», versichert Verteidigungsminister Pistorius.
Historisch gesehen ist es allerdings eher umgekehrt: Russland, bzw. die Sowjetunion, ist bereits dreimal von Westeuropa aus militärisch angegriffen worden. Die Feldzüge Napoleons, des deutschen Kaiserreichs und Nazi-Deutschlands haben Millionen Menschen das Leben gekostet. Bei dem ausdrücklichen Vernichtungskrieg ab 1941 kam es außerdem zu Brutalitäten wie der zweieinhalbjährigen Belagerung Leningrads (heute St. Petersburg) durch Hitlers Wehrmacht. Deren Ziel, die Bevölkerung auszuhungern, wurde erreicht: über eine Million tote Zivilisten.
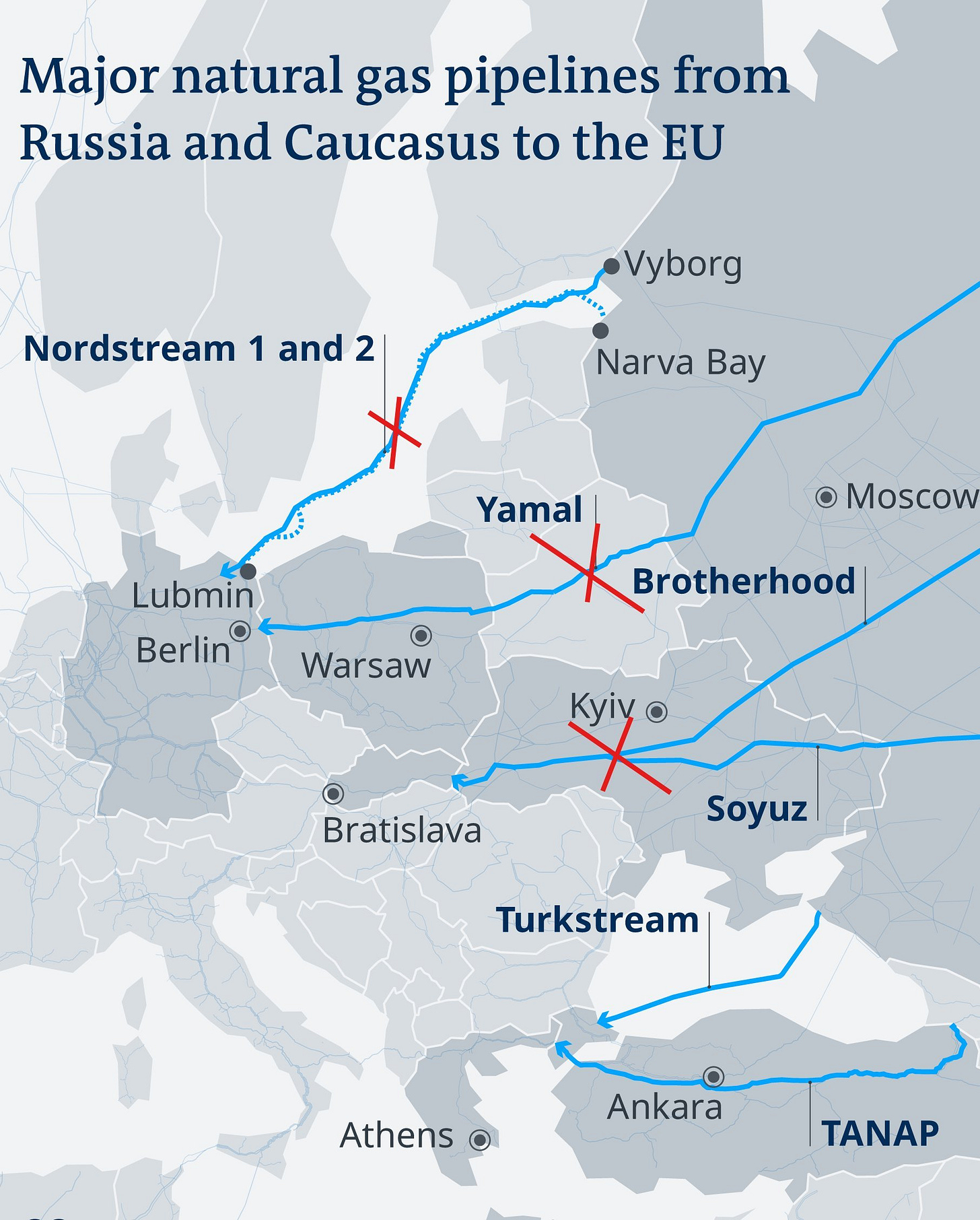
Trotz dieser Erfahrungen stimmte Michail Gorbatschow 1990 der deutschen Wiedervereinigung zu und die Sowjetunion zog ihre Truppen aus Osteuropa zurück (vgl. Abb. 1). Der Warschauer Pakt wurde aufgelöst, der Kalte Krieg formell beendet. Die Sowjets erhielten damals von führenden westlichen Politikern die Zusicherung, dass sich die NATO «keinen Zentimeter ostwärts» ausdehnen würde, das ist dokumentiert. [3]
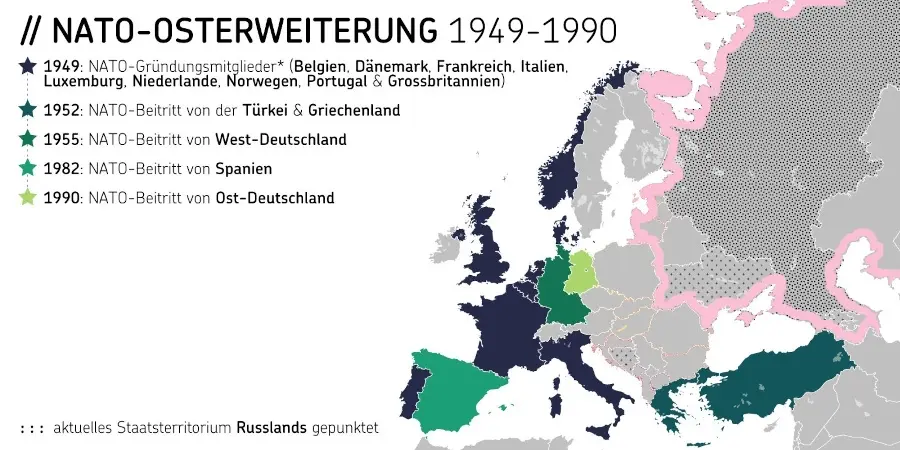
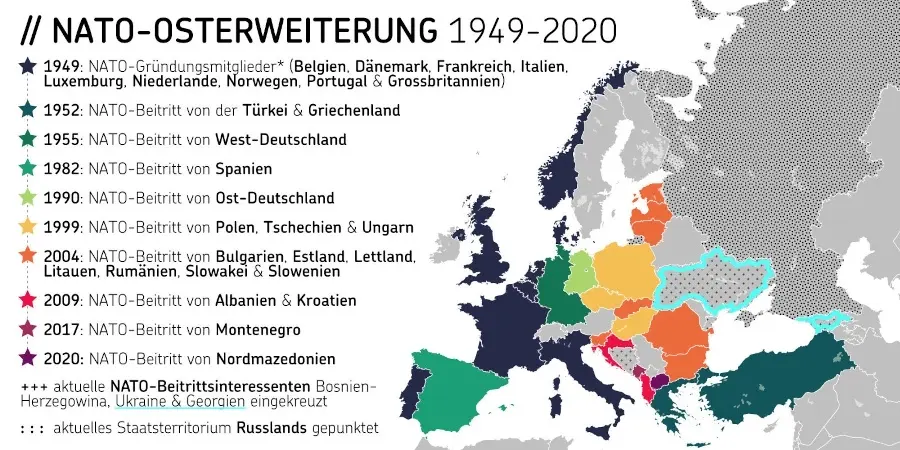
Expandiert ist die NATO trotzdem, und zwar bis an Russlands Grenzen (vgl. Abb. 2). Laut dem Politikberater Jeffrey Sachs handelt es sich dabei um ein langfristiges US-Projekt, das von Anfang an die Ukraine und Georgien mit einschloss. Offiziell wurde der Beitritt beiden Staaten 2008 angeboten. In jedem Fall könnte die massive Ost-Erweiterung seit 1999 aus russischer Sicht nicht nur als Vertrauensbruch, sondern durchaus auch als aggressiv betrachtet werden.
Russland hat den europäischen Staaten mehrfach die Hand ausgestreckt [4] für ein friedliches Zusammenleben und den «Aufbau des europäischen Hauses». Präsident Putin sei «in seiner ersten Amtszeit eine Chance für Europa» gewesen, urteilt die Journalistin und langjährige Russland-Korrespondentin der ARD, Gabriele Krone-Schmalz. Er habe damals viele positive Signale Richtung Westen gesendet.
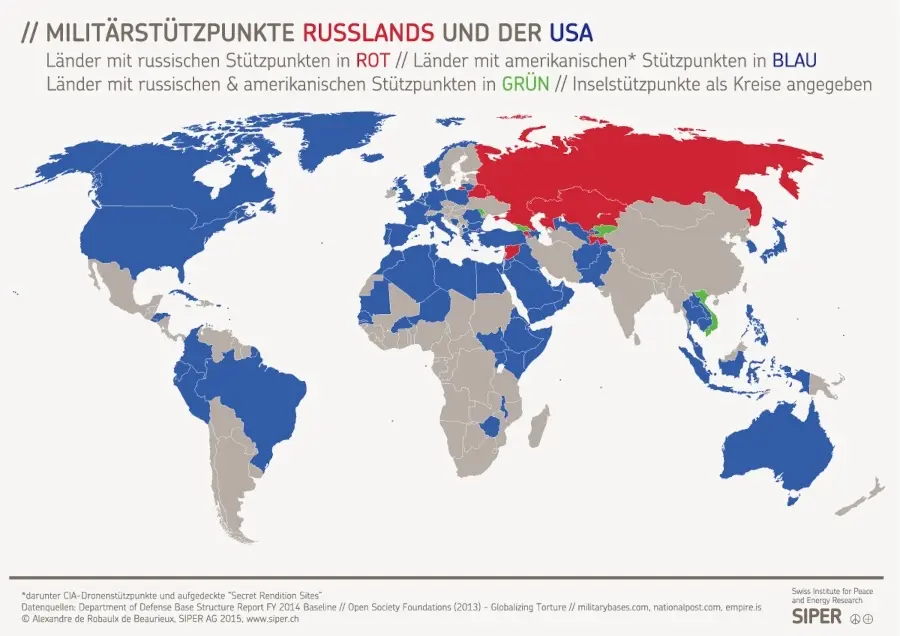
Die Europäer jedoch waren scheinbar an einer Partnerschaft mit dem kontinentalen Nachbarn weniger interessiert als an der mit dem transatlantischen Hegemon. Sie verkennen bis heute, dass eine gedeihliche Zusammenarbeit in Eurasien eine Gefahr für die USA und deren bekundetes Bestreben ist, die «einzige Weltmacht» zu sein – «Full Spectrum Dominance» [5] nannte das Pentagon das. Statt einem neuen Kalten Krieg entgegenzuarbeiten, ließen sich europäische Staaten selber in völkerrechtswidrige «US-dominierte Angriffskriege» [6] verwickeln, wie in Serbien, Afghanistan, dem Irak, Libyen oder Syrien. Diese werden aber selten so benannt.
Speziell den Deutschen stünde außer einer Portion Realismus auch etwas mehr Dankbarkeit gut zu Gesicht. Das Geschichtsbewusstsein der Mehrheit scheint doch recht selektiv und das Selbstbewusstsein einiger etwas desorientiert zu sein. Bekanntermaßen waren es die Soldaten der sowjetischen Roten Armee, die unter hohen Opfern 1945 Deutschland «vom Faschismus befreit» haben. Bei den Gedenkfeiern zu 80 Jahren Kriegsende will jedoch das Auswärtige Amt – noch unter der Diplomatie-Expertin Baerbock, die sich schon länger offiziell im Krieg mit Russland wähnt, – nun keine Russen sehen: Sie sollen notfalls rausgeschmissen werden.
«Die Grundsatzfrage lautet: Geht es Russland um einen angemessenen Platz in einer globalen Sicherheitsarchitektur, oder ist Moskau schon seit langem auf einem imperialistischen Trip, der befürchten lassen muss, dass die Russen in fünf Jahren in Berlin stehen?»
So bringt Gabriele Krone-Schmalz [7] die eigentliche Frage auf den Punkt, die zur Einschätzung der Situation letztlich auch jeder für sich beantworten muss.
Was ist los in der Ukraine?
In der internationalen Politik geht es nie um Demokratie oder Menschenrechte, sondern immer um Interessen von Staaten. Diese These stammt von Egon Bahr, einem der Architekten der deutschen Ostpolitik des «Wandels durch Annäherung» aus den 1960er und 70er Jahren. Sie trifft auch auf den Ukraine-Konflikt zu, den handfeste geostrategische und wirtschaftliche Interessen beherrschen, obwohl dort angeblich «unsere Demokratie» verteidigt wird.
Es ist ein wesentliches Element des Ukraine-Narrativs und Teil der Manipulation, die Vorgeschichte des Krieges wegzulassen – mindestens die vor der russischen «Annexion» der Halbinsel Krim im März 2014, aber oft sogar komplett diejenige vor der Invasion Ende Februar 2022. Das Thema ist komplex, aber einige Aspekte, die für eine Beurteilung nicht unwichtig sind, will ich wenigstens kurz skizzieren. [8]
Das Gebiet der heutigen Ukraine und Russlands – die übrigens in der «Kiewer Rus» gemeinsame Wurzeln haben – hat der britische Geostratege Halford Mackinder bereits 1904 als eurasisches «Heartland» bezeichnet, dessen Kontrolle er eine große Bedeutung für die imperiale Strategie Großbritanniens zumaß. Für den ehemaligen Sicherheits- und außenpolitischen Berater mehrerer US-amerikanischer Präsidenten und Mitgründer der Trilateralen Kommission, Zbigniew Brzezinski, war die Ukraine nach der Auflösung der Sowjetunion ein wichtiger Spielstein auf dem «eurasischen Schachbrett», wegen seiner Nähe zu Russland, seiner Bodenschätze und seines Zugangs zum Schwarzen Meer.
Die Ukraine ist seit langem ein gespaltenes Land. Historisch zerrissen als Spielball externer Interessen und geprägt von ethnischen, kulturellen, religiösen und geografischen Unterschieden existiert bis heute, grob gesagt, eine Ost-West-Spaltung, welche die Suche nach einer nationalen Identität stark erschwert.
Insbesondere im Zuge der beiden Weltkriege sowie der Russischen Revolution entstanden tiefe Risse in der Bevölkerung. Ukrainer kämpften gegen Ukrainer, zum Beispiel die einen auf der Seite von Hitlers faschistischer Nazi-Armee und die anderen auf der von Stalins kommunistischer Roter Armee. Die Verbrechen auf beiden Seiten sind nicht vergessen. Dass nach der Unabhängigkeit 1991 versucht wurde, Figuren wie den radikalen Nationalisten Symon Petljura oder den Faschisten und Nazi-Kollaborateur Stepan Bandera als «Nationalhelden» zu installieren, verbessert die Sache nicht.
Während die USA und EU-Staaten zunehmend «ausländische Einmischung» (speziell russische) in «ihre Demokratien» wittern, betreiben sie genau dies seit Jahrzehnten in vielen Ländern der Welt. Die seit den 2000er Jahren bekannten «Farbrevolutionen» in Osteuropa werden oft als Methode des Regierungsumsturzes durch von außen gesteuerte «demokratische» Volksaufstände beschrieben. Diese Strategie geht auf Analysen zum «Schwarmverhalten» [9] seit den 1960er Jahren zurück (Studentenproteste), wo es um die potenzielle Wirksamkeit einer «rebellischen Hysterie» von Jugendlichen bei postmodernen Staatsstreichen geht. Heute nennt sich dieses gezielte Kanalisieren der Massen zur Beseitigung unkooperativer Regierungen «Soft-Power».
In der Ukraine gab es mit der «Orangen Revolution» 2004 und dem «Euromaidan» 2014 gleich zwei solcher «Aufstände». Der erste erzwang wegen angeblicher Unregelmäßigkeiten eine Wiederholung der Wahlen, was mit Wiktor Juschtschenko als neuem Präsidenten endete. Dieser war ehemaliger Direktor der Nationalbank und Befürworter einer Annäherung an EU und NATO. Seine Frau, die First Lady, ist US-amerikanische «Philanthropin» und war Beamtin im Weißen Haus in der Reagan- und der Bush-Administration.
Im Gegensatz zu diesem ersten Event endete der sogenannte Euromaidan unfriedlich und blutig. Die mehrwöchigen Proteste gegen Präsident Wiktor Janukowitsch, in Teilen wegen des nicht unterzeichneten Assoziierungsabkommens mit der EU, wurden zunehmend gewalttätiger und von Nationalisten und Faschisten des «Rechten Sektors» dominiert. Sie mündeten Ende Februar 2014 auf dem Kiewer Unabhängigkeitsplatz (Maidan) in einem Massaker durch Scharfschützen. Dass deren Herkunft und die genauen Umstände nicht geklärt wurden, störte die Medien nur wenig. [10]
Janukowitsch musste fliehen, er trat nicht zurück. Vielmehr handelte es sich um einen gewaltsamen, allem Anschein nach vom Westen inszenierten Putsch. Laut Jeffrey Sachs war das kein Geheimnis, außer vielleicht für die Bürger. Die USA unterstützten die Post-Maidan-Regierung nicht nur, sie beeinflussten auch ihre Bildung. Das geht unter anderem aus dem berühmten «Fuck the EU»-Telefonat der US-Chefdiplomatin für die Ukraine, Victoria Nuland, mit Botschafter Geoffrey Pyatt hervor.
Dieser Bruch der demokratischen Verfassung war letztlich der Auslöser für die anschließenden Krisen auf der Krim und im Donbass (Ostukraine). Angesichts der ukrainischen Geschichte mussten die nationalistischen Tendenzen und die Beteiligung der rechten Gruppen an dem Umsturz bei der russigsprachigen Bevölkerung im Osten ungute Gefühle auslösen. Es gab Kritik an der Übergangsregierung, Befürworter einer Abspaltung und auch für einen Anschluss an Russland.
Ebenso konnte Wladimir Putin in dieser Situation durchaus Bedenken wegen des Status der russischen Militärbasis für seine Schwarzmeerflotte in Sewastopol auf der Krim haben, für die es einen langfristigen Pachtvertrag mit der Ukraine gab. Was im März 2014 auf der Krim stattfand, sei keine Annexion, sondern eine Abspaltung (Sezession) nach einem Referendum gewesen, also keine gewaltsame Aneignung, urteilte der Rechtswissenschaftler Reinhard Merkel in der FAZ sehr detailliert begründet. Übrigens hatte die Krim bereits zu Zeiten der Sowjetunion den Status einer autonomen Republik innerhalb der Ukrainischen SSR.
Anfang April 2014 wurden in der Ostukraine die «Volksrepubliken» Donezk und Lugansk ausgerufen. Die Kiewer Übergangsregierung ging unter der Bezeichnung «Anti-Terror-Operation» (ATO) militärisch gegen diesen, auch von Russland instrumentalisierten Widerstand vor. Zufällig war kurz zuvor CIA-Chef John Brennan in Kiew. Die Maßnahmen gingen unter dem seit Mai neuen ukrainischen Präsidenten, dem Milliardär Petro Poroschenko, weiter. Auch Wolodymyr Selenskyj beendete den Bürgerkrieg nicht, als er 2019 vom Präsidenten-Schauspieler, der Oligarchen entmachtet, zum Präsidenten wurde. Er fuhr fort, die eigene Bevölkerung zu bombardieren.
Mit dem Einmarsch russischer Truppen in die Ostukraine am 24. Februar 2022 begann die zweite Phase des Krieges. Die Wochen und Monate davor waren intensiv. Im November hatte die Ukraine mit den USA ein Abkommen über eine «strategische Partnerschaft» unterzeichnet. Darin sagten die Amerikaner ihre Unterstützung der EU- und NATO-Perspektive der Ukraine sowie quasi für die Rückeroberung der Krim zu. Dagegen ließ Putin der NATO und den USA im Dezember 2021 einen Vertragsentwurf über beiderseitige verbindliche Sicherheitsgarantien zukommen, den die NATO im Januar ablehnte. Im Februar eskalierte laut OSZE die Gewalt im Donbass.
Bereits wenige Wochen nach der Invasion, Ende März 2022, kam es in Istanbul zu Friedensverhandlungen, die fast zu einer Lösung geführt hätten. Dass der Krieg nicht damals bereits beendet wurde, lag daran, dass der Westen dies nicht wollte. Man war der Meinung, Russland durch die Ukraine in diesem Stellvertreterkrieg auf Dauer militärisch schwächen zu können. Angesichts von Hunderttausenden Toten, Verletzten und Traumatisierten, die als Folge seitdem zu beklagen sind, sowie dem Ausmaß der Zerstörung, fehlen einem die Worte.
Hasst der Westen die Russen?
Diese Frage drängt sich auf, wenn man das oft unerträglich feindselige Gebaren beobachtet, das beileibe nicht neu ist und vor Doppelmoral trieft. Russland und speziell die Person Wladimir Putins werden regelrecht dämonisiert, was gleichzeitig scheinbar jede Form von Diplomatie ausschließt.
Russlands militärische Stärke, seine geografische Lage, sein Rohstoffreichtum oder seine unabhängige diplomatische Tradition sind sicher Störfaktoren für das US-amerikanische Bestreben, der Boss in einer unipolaren Welt zu sein. Ein womöglich funktionierender eurasischer Kontinent, insbesondere gute Beziehungen zwischen Russland und Deutschland, war indes schon vor dem Ersten Weltkrieg eine Sorge des britischen Imperiums.
Ein «Vergehen» von Präsident Putin könnte gewesen sein, dass er die neoliberale Schocktherapie à la IWF und den Ausverkauf des Landes (auch an US-Konzerne) beendete, der unter seinem Vorgänger herrschte. Dabei zeigte er sich als Führungspersönlichkeit und als nicht so formbar wie Jelzin. Diese Aspekte allein sind aber heute vermutlich keine ausreichende Erklärung für ein derart gepflegtes Feindbild.
Der Historiker und Philosoph Hauke Ritz erweitert den Fokus der Fragestellung zu: «Warum hasst der Westen die Russen so sehr?», was er zum Beispiel mit dem Medienforscher Michael Meyen und mit der Politikwissenschaftlerin Ulrike Guérot bespricht. Ritz stellt die interessante These [11] auf, dass Russland eine Provokation für den Westen sei, welcher vor allem dessen kulturelles und intellektuelles Potenzial fürchte.
Die Russen sind Europäer aber anders, sagt Ritz. Diese «Fremdheit in der Ähnlichkeit» erzeuge vielleicht tiefe Ablehnungsgefühle. Obwohl Russlands Identität in der europäischen Kultur verwurzelt ist, verbinde es sich immer mit der Opposition in Europa. Als Beispiele nennt er die Kritik an der katholischen Kirche oder die Verbindung mit der Arbeiterbewegung. Christen, aber orthodox; Sozialismus statt Liberalismus. Das mache das Land zum Antagonisten des Westens und zu einer Bedrohung der Machtstrukturen in Europa.
Fazit
Selbstverständlich kann man Geschichte, Ereignisse und Entwicklungen immer auf verschiedene Arten lesen. Dieser Artikel, obwohl viel zu lang, konnte nur einige Aspekte der Ukraine-Tragödie anreißen, die in den offiziellen Darstellungen in der Regel nicht vorkommen. Mindestens dürfte damit jedoch klar geworden sein, dass die Russische Föderation bzw. Wladimir Putin nicht der alleinige Aggressor in diesem Konflikt ist. Das ist ein Stellvertreterkrieg zwischen USA/NATO (gut) und Russland (böse); die Ukraine (edel) wird dabei schlicht verheizt.
Das ist insofern von Bedeutung, als die gesamte europäische Kriegshysterie auf sorgsam kultivierten Freund-Feind-Bildern beruht. Nur so kann Konfrontation und Eskalation betrieben werden, denn damit werden die wahren Hintergründe und Motive verschleiert. Angst und Propaganda sind notwendig, damit die Menschen den Wahnsinn mitmachen. Sie werden belogen, um sie zuerst zu schröpfen und anschließend auf die Schlachtbank zu schicken. Das kann niemand wollen, außer den stets gleichen Profiteuren: die Rüstungs-Lobby und die großen Investoren, die schon immer an Zerstörung und Wiederaufbau verdient haben.
Apropos Investoren: Zu den Top-Verdienern und somit Hauptinteressenten an einer Fortführung des Krieges zählt BlackRock, einer der weltgrößten Vermögensverwalter. Der deutsche Bundeskanzler in spe, Friedrich Merz, der gerne «Taurus»-Marschflugkörper an die Ukraine liefern und die Krim-Brücke zerstören möchte, war von 2016 bis 2020 Aufsichtsratsvorsitzender von BlackRock in Deutschland. Aber das hat natürlich nichts zu sagen, der Mann macht nur seinen Job.
Es ist ein Spiel der Kräfte, es geht um Macht und strategische Kontrolle, um Geheimdienste und die Kontrolle der öffentlichen Meinung, um Bodenschätze, Rohstoffe, Pipelines und Märkte. Das klingt aber nicht sexy, «Demokratie und Menschenrechte» hört sich besser und einfacher an. Dabei wäre eine für alle Seiten förderliche Politik auch nicht so kompliziert; das Handwerkszeug dazu nennt sich Diplomatie. Noch einmal Gabriele Krone-Schmalz:
«Friedliche Politik ist nichts anderes als funktionierender Interessenausgleich. Da geht’s nicht um Moral.»
Die Situation in der Ukraine ist sicher komplex, vor allem wegen der inneren Zerrissenheit. Es dürfte nicht leicht sein, eine friedliche Lösung für das Zusammenleben zu finden, aber die Beteiligten müssen es vor allem wollen. Unter den gegebenen Umständen könnte eine sinnvolle Perspektive mit Neutralität und föderalen Strukturen zu tun haben.
Allen, die sich bis hierher durch die Lektüre gearbeitet (oder auch einfach nur runtergescrollt) haben, wünsche ich frohe Oster-Friedenstage!
[Titelbild: Pixabay; Abb. 1 und 2: nach Ganser/SIPER; Abb. 3: SIPER]
--- Quellen: ---
[1] Albrecht Müller, «Glaube wenig. Hinterfrage alles. Denke selbst.», Westend 2019
[2] Zwei nette Beispiele:
- ARD-faktenfinder (sic), «Viel Aufmerksamkeit für fragwürdige Experten», 03/2023
- Neue Zürcher Zeitung, «Aufstieg und Fall einer Russlandversteherin – die ehemalige ARD-Korrespondentin Gabriele Krone-Schmalz rechtfertigt seit Jahren Putins Politik», 12/2022
[3] George Washington University, «NATO Expansion: What Gorbachev Heard – Declassified documents show security assurances against NATO expansion to Soviet leaders from Baker, Bush, Genscher, Kohl, Gates, Mitterrand, Thatcher, Hurd, Major, and Woerner», 12/2017
[4] Beispielsweise Wladimir Putin bei seiner Rede im Deutschen Bundestag, 25/09/2001
[5] William Engdahl, «Full Spectrum Dominance, Totalitarian Democracy In The New World Order», edition.engdahl 2009
[6] Daniele Ganser, «Illegale Kriege – Wie die NATO-Länder die UNO sabotieren. Eine Chronik von Kuba bis Syrien», Orell Füssli 2016
[7] Gabriele Krone-Schmalz, «Mit Friedensjournalismus gegen ‘Kriegstüchtigkeit’», Vortrag und Diskussion an der Universität Hamburg, veranstaltet von engagierten Studenten, 16/01/2025\ → Hier ist ein ähnlicher Vortrag von ihr (Video), den ich mit spanischer Übersetzung gefunden habe.
[8] Für mehr Hintergrund und Details empfehlen sich z.B. folgende Bücher:
- Mathias Bröckers, Paul Schreyer, «Wir sind immer die Guten», Westend 2019
- Gabriele Krone-Schmalz, «Russland verstehen? Der Kampf um die Ukraine und die Arroganz des Westens», Westend 2023
- Patrik Baab, «Auf beiden Seiten der Front – Meine Reisen in die Ukraine», Fiftyfifty 2023
[9] vgl. Jonathan Mowat, «Washington's New World Order "Democratization" Template», 02/2005 und RAND Corporation, «Swarming and the Future of Conflict», 2000
[10] Bemerkenswert einige Beiträge, von denen man später nichts mehr wissen wollte:
- ARD Monitor, «Todesschüsse in Kiew: Wer ist für das Blutbad vom Maidan verantwortlich», 10/04/2014, Transkript hier
- Telepolis, «Blutbad am Maidan: Wer waren die Todesschützen?», 12/04/2014
- Telepolis, «Scharfschützenmorde in Kiew», 14/12/2014
- Deutschlandfunk, «Gefahr einer Spirale nach unten», Interview mit Günter Verheugen, 18/03/2014
- NDR Panorama, «Putsch in Kiew: Welche Rolle spielen die Faschisten?», 06/03/2014
[11] Hauke Ritz, «Vom Niedergang des Westens zur Neuerfindung Europas», 2024
Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
-
 @ 4ba8e86d:89d32de4
2025-04-21 02:10:55
@ 4ba8e86d:89d32de4
2025-04-21 02:10:55Seu teclado não deve se conectar à internet. Privacidade em primeiro lugar. Sempre. Estamos desenvolvendo um teclado moderno que respeita totalmente sua privacidade e segurança. O FUTO Keyboard é 100% offline e 100% privado, oferecendo todos os recursos essenciais que você espera de um teclado atual — incluindo digitação por deslizamento, entrada de voz offline, correção automática inteligente, temas personalizáveis e sugestões preditivas de texto. Nosso objetivo é simples: criar um teclado eficiente e funcional, sem comprometer a privacidade do usuário. Este projeto é um fork do LatinIME, o teclado open-source oficial do Android.
Atenção: o FUTO Keyboard está atualmente em fase alfa. Está trabalhando para torná-lo estável e confiável, mas durante esse período você pode encontrar bugs, travamentos ou recursos ainda não implementados.
Configurações
Idiomas e Modelos – Adicione novos idiomas, dicionários, modelos de entrada de voz, transformadores e layouts associados.
Linguagens e Modelos
O menu no qual você adiciona novos idiomas, bem como dicionários, modelos de entrada de voz, modelos de transformadores e layouts associados a eles.
Adicionar idioma.
Alguns idiomas exigem o download de um dicionário. Se você também quiser um modelo de entrada de voz para um idioma específico, precisará baixá-lo também. Cada idioma já possui uma seleção de layouts de teclado associados; você pode escolher qual(is) layout(s) deseja adicionar ao adicionar o idioma. https://video.nostr.build/c775288b7a8ee8d75816af0c7a25f2aa0b4ecc99973fd442b2badc308fa38109.mp4
Mudar idioma.
Existem duas maneiras de alternar o idioma. A primeira é pressionando o ícone do globo na Barra de Ações, localizada próximo ao canto superior esquerdo do teclado. A segunda é pressionando longamente ou deslizando a barra de espaço; você pode personalizar o comportamento de troca de idioma da barra de espaço acessando Configurações -> Teclado e Digitação -> Teclas de Pressão Longa e Barra de Espaço -> Comportamento da Barra de Espaço . Você também pode atribuir o ícone do globo como a Tecla de Ação para que fique ao lado da barra de espaço, que pode ser acessada no menu Todas as Ações pressionando a tecla de reticências (...) no canto superior esquerdo do teclado e, em seguida, acessando Editar Ações. https://video.nostr.build/ed6f7f63a9c203cd59f46419ef54a4b8b442f070f802a688ca7d682bd6811bcb.mp4
Adicionar dicionário.
Alguns idiomas têm um dicionário integrado, mas a maioria não. Se o idioma que você está instalando não tiver um dicionário integrado, você pode iniciar a instalação em nosso site acessando Idiomas e Modelos -> Dicionário (no idioma que você está instalando) -> Explorar -> Baixar (em nosso site). https://video.nostr.build/3b1e09289953b658a9cef33c41bd711095556bc48290cb2ed066d4d0a5186371.mp4
Habilitar digitação multilíngue.
Você pode habilitar a digitação multilíngue para um ou mais idiomas acessando Idiomas e modelos e marcando a caixa Digitação multilíngue no(s) idioma(s) para os quais deseja habilitar a digitação multilíngue. https://video.nostr.build/29f683410626219499787bd63058d159719553f8e33a9f3c659c51c375a682fb.mp4
Criar layout personalizado.
Se desejar criar seu próprio layout personalizado para um idioma específico, você pode fazê-lo ativando Configurações do Desenvolvedor -> Layouts Personalizados -> Criar novo layout . Mais informações sobre layouts personalizados podem ser encontradas https://github.com/futo-org/futo-keyboard-layouts . A personalização das configurações de pressionamento longo tecla por tecla ainda não é suportada, mas está em processo de implementação. https://video.nostr.build/b5993090e28794d0305424dd352ca83760bb87002c57930e80513de5917fad8d.mp4
Teclado e Digitação – Personalize o comportamento das teclas, o tamanho do teclado e outras preferências de digitação.
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas. Ajuste fino do transformador Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados. https://video.nostr.build/688354a63bdc48a9dd3f8605854b5631ac011009c6105f93cfa0b52b46bc40d3.mp4
Previsão de texto.
O menu no qual você define suas preferências para correção automática e sugestões personalizadas. Modelo de Linguagem do Transformador Você pode fazer com que o teclado preveja a próxima palavra que você digitará ou faça correções automáticas mais inteligentes, que usam um modelo de linguagem Transformer pré-treinado com base em conjuntos de dados disponíveis publicamente, ativando o Transformer LM . Observação: atualmente, isso funciona apenas em inglês, mas estamos trabalhando para torná-lo compatível com outros idiomas.
Ajuste fino do transformador.
Você pode fazer com que o teclado memorize o que você digita e quais sugestões você seleciona, o que treina o modelo de idioma (enquanto o telefone estiver inativo) para prever quais palavras sugerir e corrigir automaticamente enquanto você digita, ativando o ajuste fino do Transformer . Observação: este é o seu modelo de idioma pessoal e o FUTO não visualiza nem armazena nenhum dos seus dados.
Força do Modelo de Linguagem do Transformador.
Você pode fazer com que a correção automática se comporte mais como o teclado AOSP ou mais como a rede neural acessando Parâmetros avançados -> Intensidade do LM do transformador e arrastando o controle deslizante para um valor menor (o que tornará o comportamento da correção automática mais parecido com o teclado AOSP) ou um valor maior (o que tornará a correção automática mais dependente da rede neural). Limiar de correção automática Você pode alterar o limite da correção automática para que ela ocorra com mais ou menos frequência acessando Parâmetros avançados -> Limite de correção automática e arrastando o controle deslizante para um valor menor (o que fará com que a correção automática ocorra com mais frequência, mas também corrija erros com mais frequência) ou um valor maior (o que fará com que a correção automática ocorra com menos frequência, mas também corrija erros com menos frequência). https://video.nostr.build/ea9c100081acfcab60343c494a91f789ef8143c92343522ec34c714913631cf7.mp4
Lista negra de palavras.
Você pode colocar sugestões de palavras na lista negra, o que impedirá que o teclado continue sugerindo palavras na lista negra, acessando Sugestões na lista negra e adicionando as palavras que você gostaria de colocar na lista negra.
Palavras ofensivas.
Você pode bloquear palavras ofensivas, como palavrões comuns, acessando Sugestões na Lista Negra e marcando a opção Bloquear Palavras Ofensivas . Observação: a opção Bloquear Palavras Ofensivas está ativada por padrão. https://video.nostr.build/ee72f3940b9789bbea222c95ee74d646aae1a0f3bf658ef8114c6f7942bb50f5.mp4
Correção automática.
Você pode ativar a capacidade de corrigir automaticamente palavras digitadas incorretamente ao pressionar a barra de espaço ou digitar pontuação ativando a Correção automática.
Sugestões de correção.
Você pode ativar a capacidade de exibir palavras sugeridas enquanto digita marcando a opção Mostrar sugestões de correção.
Sugestões de palavras.
Você pode ativar a capacidade de aprender com suas comunicações e dados digitados para melhorar as sugestões ativando as Sugestões personalizadas . Observação: desativar as Sugestões personalizadas também desativa o ajuste fino do Transformer. https://video.nostr.build/2c22d109b9192eac8fe4533b3f8e3e1b5896dfd043817bd460c48a5b989b7a2f.mp4
Entrada de Voz – Configure a entrada de voz offline, incluindo a duração e a conversão de fala em texto.
Entrada de voz.
O menu no qual você define suas preferências de entrada de voz, como duração da entrada e configurações de conversão de fala em texto. Entrada de voz integrada Você pode desabilitar a entrada de voz integrada do teclado e, em vez disso, usar o provedor de entrada de voz de um aplicativo externo desativando a opção Desabilitar entrada de voz integrada. https://video.nostr.build/68916e5b338a9f999f45aa1828a6e05ccbf8def46da9516c0f516b40ca8c827b.mp4
Sons de indicação.
Você pode habilitar a capacidade de reproduzir sons ao iniciar e cancelar a entrada de voz ativando Sons de indicação. https://video.nostr.build/7f5fb6a6173c4db18945e138146fe65444e40953d85cee1f09c1a21d236d21f5.mp4
Progresso Detalhado.
Você pode habilitar a capacidade de exibir informações detalhadas, como indicar que o microfone está sendo usado, ativando Progresso detalhado. https://video.nostr.build/8ac2bb6bdd6e7f8bd4b45da423e782c152a2b4320f2e090cbb99fd5c78e8f44f.mp4
Microfone Bluetooth.
Você pode fazer com que a entrada de voz prefira automaticamente seu microfone Bluetooth em vez do microfone integrado, ativando Preferir microfone Bluetooth. https://video.nostr.build/c11404aa6fec2dda71ceb3aaee916c6761b3015fef9575a352de66b7310dad07.mp4
Foco de áudio.
Você pode fazer com que a entrada de voz pause automaticamente vídeos ou músicas quando ela estiver ativada, ativando o Foco de Áudio. https://video.nostr.build/4ac82af53298733d0c5013ef28befb8b2adeb4a4949604308317e124b6431d40.mp4
Supressão de Símbolos.
Por padrão, a entrada de voz transcreve apenas texto básico e pontuação. Você pode desativar a opção "Suprimir símbolos" para liberar a entrada de voz da transcrição de caracteres especiais (por exemplo, @, $ ou %). Observação: Isso não afeta a forma como a entrada de voz interpreta palavras literais (por exemplo, "vírgula", "ponto final"). https://video.nostr.build/10de49c5a9e35508caa14b66da28fae991a5ac8eabad9b086959fba18c07f8f3.mp4
Entrada de voz de formato longo.
Você pode desativar o limite padrão de 30 segundos para entrada de voz ativando a opção Entrada de voz longa . Observação: a qualidade da saída pode ser prejudicada com entradas longas. https://video.nostr.build/f438ee7a42939a5a3e6d6c4471905f836f038495eb3a00b39d9996d0e552c200.mp4
Parada automática em silêncio.
Você pode fazer com que a entrada de voz pare automaticamente quando o silêncio for detectado, ativando a opção Parar automaticamente ao silenciar . Observação: se houver muito ruído de fundo, pode ser necessário interromper manualmente a entrada de voz. Ative também a entrada de voz longa para evitar a interrupção após 30 segundos. https://video.nostr.build/056567696d513add63f6dd254c0a3001530917e05e792de80c12796d43958671.mp4
Dicionário Pessoal – Adicione palavras personalizadas para que o teclado aprenda e sugira com mais precisão.
Dicionário Pessoal.
O menu no qual você cria seu dicionário pessoal de palavras que o teclado irá lembrar e sugerir. Adicionar ao dicionário Você pode adicionar uma palavra ou frase ao seu dicionário pessoal pressionando o ícone de adição na tela "Dicionário pessoal" . Você também pode criar um atalho para ela no campo "Atalho" ao adicionar a palavra ou frase. https://video.nostr.build/dec41c666b9f2276cc20d9096e3a9b542b570afd1f679d8d0e8c43c8ea46bfcb.mp4
Excluir do dicionário.
Você pode excluir uma palavra ou frase do seu dicionário pessoal clicando nessa palavra ou frase e clicando no ícone de lixeira no canto superior direito. https://video.nostr.build/aca25643b5c7ead4c5d522709af4bc337911e49c4743b97dc75f6b877449143e.mp4
Tema – Escolha entre os temas disponíveis ou personalize a aparência do teclado conforme seu gosto.
Tema.
O menu no qual você seleciona seu tema preferido para o teclado. Alterar tema Você pode escolher entre uma variedade de temas para o teclado, incluindo Modo Escuro, Modo Claro, Automático Dinâmico, Escuro Dinâmico, Claro Dinâmico, Material AOSP Escuro, Material AOSP Claro, Roxo Escuro AMOLED, Girassol, Queda de Neve, Cinza Aço, Esmeralda, Algodão Doce, Luz do Mar Profundo, Escuro do Mar Profundo, Gradiente 1, Tema FUTO VI ou Tema Construção . A possibilidade de personalizar seu tema será disponibilizada em breve. https://video.nostr.build/90c8de72f08cb0d8c40ac2fba2fd39451ff63ec1592ddd2629d0891c104bc61e.mp4
Fronteiras Principais.
Você pode habilitar as bordas das teclas rolando para baixo até o final e ativando Bordas das teclas . https://video.nostr.build/fa2087d68ce3fb2d3adb84cc2ec19c4d5383beb8823a4b6d1d85378ab3507ab1.mp4
Site oficial https://keyboard.futo.org/
Baixar no fdroid. https://app.futo.org/fdroid/repo/
Para instalar através do Obtainium , basta ir em Adicionar Aplicativo e colar esta URL do repositório: https://github.com/futo-org/android-keyboard
A adição pode demorar um pouco dependendo da velocidade da sua internet, pois o APK precisa ser baixado.
-
 @ d08c9312:73efcc9f
2025-04-18 20:17:41
@ d08c9312:73efcc9f
2025-04-18 20:17:41https://youtu.be/qK7ffYzxiiQ
Resolvr was recently featured in The Institutes RiskStream Collaborative's educational video series on insurance digitization and cross-border payments. With over a century of history educating insurance professionals, The Institutes has established itself as the premier knowledge resource in risk management and insurance. And its RiskStream Collaborative non-profit serves as the industry's largest enterprise-level technology consortium focused on streamlining insurance processes through innovative solutions.
Resolvr's co-founders, Aaron Daniel and Dave Schwab, were joined by industry experts Lizzy Eisenberg from Lightspark and Austin Cornell from Zero Hash to discuss how Bitcoin and the Lightning Network are transforming global insurance payments operations.
Watch the video to learn how Resolvr is leveraging these real-time digital settlement networks to solve significant inefficiencies in today's insurance payment ecosystem - from the months-long settlement times that trap billions in value, to the manual reconciliation processes costing the industry nearly £1 billion annually at Lloyd's of London alone.
We're grateful to RiskStream Collaborative for showcasing these transformative technologies and emphasizing the importance of combining specialized insurance-native interfaces with powerful payment infrastructure to solve industry-specific challenges.
For more information about how Resolvr can help your organization streamline premium processing and payments, contact us today.
-
 @ c631e267:c2b78d3e
2025-04-18 15:53:07
@ c631e267:c2b78d3e
2025-04-18 15:53:07Verstand ohne Gefühl ist unmenschlich; \ Gefühl ohne Verstand ist Dummheit. \ Egon Bahr
Seit Jahren werden wir darauf getrimmt, dass Fakten eigentlich gefühlt seien. Aber nicht alles ist relativ und nicht alles ist nach Belieben interpretierbar. Diese Schokoladenhasen beispielsweise, die an Ostern in unseren Gefilden typisch sind, «ostern» zwar nicht, sondern sie sitzen in der Regel, trotzdem verwandelt sie das nicht in «Sitzhasen».
Nichts soll mehr gelten, außer den immer invasiveren Gesetzen. Die eigenen Traditionen und Wurzeln sind potenziell «pfui», um andere Menschen nicht auszuschließen, aber wir mögen uns toleranterweise an die fremden Symbole und Rituale gewöhnen. Dabei ist es mir prinzipiell völlig egal, ob und wann jemand ein Fastenbrechen feiert, am Karsamstag oder jedem anderen Tag oder nie – aber bitte freiwillig.
Und vor allem: Lasst die Finger von den Kindern! In Bern setzten kürzlich Demonstranten ein Zeichen gegen die zunehmende Verbreitung woker Ideologie im Bildungssystem und forderten ein Ende der sexuellen Indoktrination von Schulkindern.
Wenn es nicht wegen des heiklen Themas Migration oder wegen des Regenbogens ist, dann wegen des Klimas. Im Rahmen der «Netto Null»-Agenda zum Kampf gegen das angeblich teuflische CO2 sollen die Menschen ihre Ernährungsgewohnheiten komplett ändern. Nach dem Willen von Produzenten synthetischer Lebensmittel, wie Bill Gates, sollen wir baldmöglichst praktisch auf Fleisch und alle Milchprodukte wie Milch und Käse verzichten. Ein lukratives Geschäftsmodell, das neben der EU aktuell auch von einem britischen Lobby-Konsortium unterstützt wird.
Sollten alle ideologischen Stricke zu reißen drohen, ist da immer noch «der Putin». Die Unions-Europäer offenbaren sich dabei ständig mehr als Vertreter der Rüstungsindustrie. Allen voran zündelt Deutschland an der Kriegslunte, angeführt von einem scheinbar todesmutigen Kanzlerkandidaten Friedrich Merz. Nach dessen erneuter Aussage, «Taurus»-Marschflugkörper an Kiew liefern zu wollen, hat Russland eindeutig klargestellt, dass man dies als direkte Kriegsbeteiligung werten würde – «mit allen sich daraus ergebenden Konsequenzen für Deutschland».
Wohltuend sind Nachrichten über Aktivitäten, die sich der allgemeinen Kriegstreiberei entgegenstellen oder diese öffentlich hinterfragen. Dazu zählt auch ein Kongress kritischer Psychologen und Psychotherapeuten, der letzte Woche in Berlin stattfand. Die vielen Vorträge im Kontext von «Krieg und Frieden» deckten ein breites Themenspektrum ab, darunter Friedensarbeit oder die Notwendigkeit einer «Pädagogik der Kriegsuntüchtigkeit».
Der heutige «stille Freitag», an dem Christen des Leidens und Sterbens von Jesus gedenken, ist vielleicht unabhängig von jeder religiösen oder spirituellen Prägung eine passende Einladung zur Reflexion. In der Ruhe liegt die Kraft. In diesem Sinne wünsche ich Ihnen frohe Ostertage!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ f839fb67:5c930939
2025-04-16 21:07:13
@ f839fb67:5c930939
2025-04-16 21:07:13Relays
| Name | Address | Price (Sats/Year) | Status | | - | - | - | - | | stephen's aegis relay | wss://paid.relay.vanderwarker.family | 42069 |
| | stephen's Outbox | wss://relay.vanderwarker.family | Just Me |
| | stephen's Inbox | wss://haven.vanderwarker.family/inbox | WoT |
| | stephen's DMs | wss://haven.vanderwarker.family/chat | WoT |
| | VFam Data Relay | wss://data.relay.vanderwarker.family | 0 |
| | VFam Bots Relay | wss://skeme.vanderwarker.family | Invite |
| | VFGroups (NIP29) | wss://groups.vanderwarker.family | 0 |
| | [TOR] My Phone Relay | ws://naswsosuewqxyf7ov7gr7igc4tq2rbtqoxxirwyhkbuns4lwc3iowwid.onion | 0 | Meh... |
My Pubkeys
| Name | hex | nprofile | | - | - | - | | Main | f839fb6714598a7233d09dbd42af82cc9781d0faa57474f1841af90b5c930939 | nostr:nprofile1qqs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us9mapfx | | Vanity (Backup) | 82f21be67353c0d68438003fe6e56a35e2a57c49e0899b368b5ca7aa8dde7c23 | nostr:nprofile1qqsg9usmuee48sxkssuqq0lxu44rtc4903y7pzvmx694efa23h08cgcpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3ussel49x | | VFStore | 6416f1e658ba00d42107b05ad9bf485c7e46698217e0c19f0dc2e125de3af0d0 | nostr:nprofile1qqsxg9h3uevt5qx5yyrmqkkehay9cljxdxpp0cxpnuxu9cf9mca0p5qpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usaa8plu | | NostrSMS | 9be1b8315248eeb20f9d9ab2717d1750e4f27489eab1fa531d679dadd34c2f8d | nostr:nprofile1qqsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3us595d45 |
Bots
Unlocks Bot
Hex: 2e941ad17144e0a04d1b8c21c4a0dbc3fbcbb9d08ae622b5f9c85341fac7c2d0
nprofile:
nostr:nprofile1qqsza9q669c5fc9qf5dccgwy5rdu877th8gg4e3zkhuus56pltru95qpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ust4kvak
Latest Data:
nostr:naddr1qq882mnvda3kkttrda6kuar9wgq37amnwvaz7tmnddjk6efwweskuer9wfmkzuntv4ezuenpd45kc7gzyqhfgxk3w9zwpgzdrwxzr39qm0plhjae6z9wvg44l8y9xs06clpdqqcyqqq823cgnl9u5Step Counter
Hex: 9223d2faeb95853b4d224a184c69e1df16648d35067a88cdf947c631b57e3de7
nprofile: nostr:nprofile1qqsfyg7jlt4etpfmf53y5xzvd8sa79ny356sv75gehu50333k4lrmecpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3ustswp3w
Latest Data:
nostr:naddr1qvzqqqr4gupzpy3r6tawh9v98dxjyjscf357rhckvjxn2pn63rxlj37xxx6hu008qys8wumn8ghj7umtv4kk2tnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp3ehgets943k7atww3jhyn39gffRCTGuest
Hex: 373904615c781e46bf5bf87b4126c8a568a05393b1b840b1a2a3234d20affa0c
nprofile: nostr:nprofile1qqsrwwgyv9w8s8jxhadls76pymy2269q2wfmrwzqkx32xg6dyzhl5rqpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3usy92jlxNow Playing
Hex: 8096ed6ba1f21a3713bd47a503ee377b0ce2f187b3e5a3ae909a25b84901018b
nprofile: nostr:nprofile1qqsgp9hddwslyx3hzw750fgracmhkr8z7xrm8edr46gf5fdcfyqsrzcpramhxue69uhhx6m9d4jjuanpdejx2unhv9exketj9enxzmtfd3uspk5v4w
Latest Data:
nostr:naddr1qq9kummh94cxccted9hxwqglwaehxw309aekketdv5h8vctwv3jhyampwf4k2u3wvesk66tv0ypzpqyka446rus6xufm63a9q0hrw7cvutcc0vl95whfpx39hpyszqvtqvzqqqr4gupdk2hd
NIP-29 Groups
- Minecraft Group Chat
nostr:naddr1qqrxvc33xpnxxqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvqazypfd- VFNet Group Chat
nostr:naddr1qqrrwvfjx9jxzqfqwaehxw309anhymm4wpejuanpdejx2unhv9exketj9enxzmtfd3usygrzymrpd2wz8ularp06y8ad5dgaddlumyt7tfzqge3vc97sgsarjvpsgqqqnpvq08hx48
"Nostrified Websites"
[D] = Saves darkmode preferences over nostr
[A] = Auth over nostr
[B] = Beta (software)
[z] = zap enabled
Other Services (Hosted code)
Emojis Packs
- Minecraft
nostr:naddr1qqy566twv43hyctxwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsd0k5wp- AIM
nostr:naddr1qqxxz6tdv4kk7arfvdhkuucpramhxue69uhhyetvv9ujuanpdejx2unhv9exketj9enxzmtfd3usyg8c88akw9ze3fer85yah4p2lqkvj7qap749w360rpq6ly94eycf8ypsgqqqw48qe0j2yk- Blobs
nostr:naddr1qqz5ymr0vfesz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2wek4ukj- FavEmojis
nostr:naddr1qqy5vctkg4kk76nfwvq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsf7sdwt- Modern Family
nostr:naddr1qqx56mmyv4exugzxv9kkjmreqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqp65ujlj36n- nostriches (Amethyst collection)
nostr:naddr1qq9xummnw3exjcmgv4esz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w2sqg6w- Pepe
nostr:naddr1qqz9qetsv5q37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82ns85f6x7- Minecraft Font
nostr:naddr1qq8y66twv43hyctxwssyvmmwwsq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82nsmzftgr- Archer Font
nostr:naddr1qq95zunrdpjhygzxdah8gqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr4fclkyxsh- SMB Font
nostr:naddr1qqv4xatsv4ezqntpwf5k7gzzwfhhg6r9wfejq3n0de6qz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqa2w0wqpuk
Git Over Nostr
- NostrSMS
nostr:naddr1qqyxummnw3e8xmtnqy0hwumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfrwaehxw309amk7apwwfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqyj8wumn8ghj7urpd9jzuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyxhwumn8ghj7mn0wvhxcmmvqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqaueqp0epk- nip51backup
nostr:naddr1qq9ku6tsx5ckyctrdd6hqqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjxamnwvaz7tmhda6zuun9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jqfywaehxw309acxz6ty9eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yq3gamnwvaz7tmjv4kxz7fwv3sk6atn9e5k7qgdwaehxw309ahx7uewd3hkcq3qlqulkec5tx98yv7snk759tuzejtcr5865468fuvyrtuskhynpyusxpqqqpmej4gtqs6- bukkitstr
nostr:naddr1qqykyattdd5hgum5wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpz3mhxue69uhhyetvv9ujuerpd46hxtnfduqs6amnwvaz7tmwdaejumr0dspzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqrhnyf6g0n2
Market Places
Please use Nostr Market or somthing simular, to view.
- VFStore
nostr:naddr1qqjx2v34xe3kxvpn95cnqven956rwvpc95unscn9943kxet98q6nxde58p3ryqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0yqjvamnwvaz7tmgv9mx2m3wweskuer9wfmkzuntv4ezuenpd45kc7f0da6hgcn00qqjgamnwvaz7tmsv95kgtnjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gpydmhxue69uhhwmm59eex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzqeqk78n93wsq6sss0vz6mxl5shr7ge5cy9lqcx0smshpyh0r4uxsqvzqqqr4gvlfm7gu
Badges
Created
- paidrelayvf
nostr:naddr1qq9hqctfv3ex2mrp09mxvqglwaehxw309aex2mrp0yh8vctwv3jhyampwf4k2u3wvesk66tv0ypzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqvzqqqr48y85v3u3- iPow
nostr:naddr1qqzxj5r02uq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgg02u0r- codmaster
nostr:naddr1qqykxmmyd4shxar9wgq37amnwvaz7tmjv4kxz7fwweskuer9wfmkzuntv4ezuenpd45kc7gzyrurn7m8z3vc5u3n6zwm6s40stxf0qwsl2jhga83ssd0jz6ujvynjqcyqqq82wgk3gm4g- iMine
nostr:naddr1qqzkjntfdejsz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgs0sw0mvu29nznjx0gfm02z47pve9up6ra22ar57xzp47gttjfsjwgrqsqqqafed5s4x5
Clients I Use
- Amethyst
nostr:naddr1qqxnzd3cx5urqv3nxymngdphqgsyvrp9u6p0mfur9dfdru3d853tx9mdjuhkphxuxgfwmryja7zsvhqrqsqqql8kavfpw3- noStrudel
nostr:naddr1qqxnzd3cxccrvd34xser2dpkqy28wumn8ghj7un9d3shjtnyv9kh2uewd9hsygpxdq27pjfppharynrvhg6h8v2taeya5ssf49zkl9yyu5gxe4qg55psgqqq0nmq5mza9n- nostrsms
nostr:naddr1qq9rzdejxcunxde4xymqz8mhwden5te0wfjkccte9emxzmnyv4e8wctjddjhytnxv9kkjmreqgsfhcdcx9fy3m4jp7we4vn305t4pe8jwjy74v062vwk08dd6dxzlrgrqsqqql8kjn33qm
Lists
- Bluesky
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqqapxcat9wd4hj0ah0jw
- Fediverse
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqp9rx2erfwejhyum9j4g0xh
- Fediverse_Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqperx2erfwejhyum9tapx7arnfcpdzh
- My Bots
nostr:naddr1qvzqqqr4xqpzp7peldn3gkv2wgeap8dag2hc9nyhs8g04ft5wnccgxhepdwfxzfeqys8wumn8ghj7un9d3shjtnkv9hxgetjwashy6m9wghxvctdd9k8jtcqz4uh5jnpwscyss24fpkxw4fewafk566twa2q8f6fyk
-
 @ d360efec:14907b5f
2025-04-21 22:10:23
@ d360efec:14907b5f
2025-04-21 22:10:23สวัสดีเพื่อนนักเทรดทุกท่าน! 👋 วันนี้ฉันมาแนะนำตารางกิจวัตรประจำวันของ Day Trader ที่น่าสนใจนี้กันนะคะ มาดูกันว่ามีอะไรที่เราสามารถเรียนรู้และนำไปปรับใช้กับการเทรดของเราได้บ้างค่ะ

ภาพรวมกิจวัตรประจำวันของ Day Trader 📊
ตารางนี้แสดงให้เห็นถึงโครงสร้างของวันที่สมดุลสำหรับนักเทรดรายวันที่ประสบความสำเร็จ โดยเน้นทั้งการเตรียมตัว 🤓 การลงมือเทรด 🚀 การเรียนรู้ 📚 และการดูแลสุขภาพส่วนตัว 🧘♀️ ซึ่งเป็นสิ่งสำคัญอย่างยิ่งในการรักษาประสิทธิภาพและความสม่ำเสมอในการเทรด 💪
การวิเคราะห์และอธิบายแต่ละช่วงเวลา
$ 05.30 น. > ตื่นนอน 🌅 อาบน้ำ 🚿 และเตรียมตัว 👔 > การเริ่มต้นวันอย่างกระปรี้กระเปร่า 🎉 และการมีกิจวัตรส่วนตัวที่ผ่อนคลายเป็นสิ่งสำคัญในการเตรียมพร้อมทั้งร่างกายและจิตใจ 🧠 สำหรับการเทรด
$ 06.00 น. > ตรวจสอบข่าวสาร 📰 วิเคราะห์กราฟ 📈 และเตรียมตัว 🎯 > ช่วงเวลานี้เป็นหัวใจสำคัญของการเตรียมตัวก่อนตลาดเปิด ⏰ นักเทรดจะตรวจสอบข่าวเศรษฐกิจ 💰 และข่าวที่เกี่ยวข้องกับสินทรัพย์ที่ตนเองเทรด 🧐 วิเคราะห์กราฟเพื่อหาแนวโน้ม 🔭 และระดับราคาที่น่าสนใจ 📍 รวมถึงวางแผนกลยุทธ์การเทรดสำหรับวันนี้ ✍️
$ 06.30 น. > ตลาดเปิด 🔔 เริ่มทำการเทรด 🚀 > เมื่อตลาดเปิด นักเทรดจะเริ่มดำเนินการตามแผนที่วางไว้ 📝 โดยจะเฝ้าติดตามการเคลื่อนไหวของราคา 👀 และเข้าเทรดตามสัญญาณที่เกิดขึ้น 🚦
$ 12.00 น. > พักรับประทานอาหารกลางวัน 🥪 > การพักผ่อน 😌 และการเติมพลัง 💪 ในช่วงกลางวันเป็นสิ่งสำคัญในการรักษาความมีสมาธิ 🧘♀️ และความสามารถในการตัดสินใจที่ดี 👍
$ 12.45 น. > ปิดสถานะการเทรดทั้งหมด 🛑 > สำหรับ Day Trader การปิดสถานะทั้งหมดภายในวันถือเป็นกฎเหล็ก 🚫 เพื่อหลีกเลี่ยงความเสี่ยงจากความผันผวนข้ามคืน 🌙
$ 13.00 น. > ทบทวน 🤔 เรียนรู้ 📚 และปรับปรุง ⚙️ > หลังจากการเทรด นักเทรดที่ประสบความสำเร็จ 🎉 จะใช้เวลาในการทบทวนการเทรดของตนเอง 🧐 วิเคราะห์ว่าอะไรทำได้ดี 👍 และอะไรที่ต้องปรับปรุง 📝 การเรียนรู้อย่างต่อเนื่องเป็นกุญแจสำคัญสู่การพัฒนา 🚀
$ 14.00 น. > ออกกำลังกาย 💪 และพักผ่อน 🧘♀️ > การดูแลสุขภาพกาย 🍎 และใจ 💖 มีความสำคัญไม่ยิ่งหย่อนไปกว่าการเทรด 📈 การออกกำลังกายและการมีเวลาว่าง 🌴 ช่วยลดความเครียด 😥 และเพิ่มประสิทธิภาพในการเทรดในระยะยาว ✨
$ 17.00 น. > รับประทานอาหารเย็น 🍽️ และพักผ่อน 🛋️ > การมีเวลาพักผ่อนกับครอบครัว ❤️ หรือทำกิจกรรมที่ชอบ 😊 ช่วยให้ผ่อนคลาย 😌 และเตรียมพร้อมสำหรับวันต่อไป 🌅
$ 19.00 น. > วางแผนการเทรดสำหรับวันพรุ่งนี้ 🗓️ และตรวจสอบข่าวสาร 📰 > การวางแผนล่วงหน้า 🤓 ช่วยให้นักเทรดมีความพร้อม 💪 และสามารถตอบสนองต่อสถานการณ์ตลาดได้อย่างมีประสิทธิภาพ 🚀
$ 22.00 น. > เข้านอน 😴 > การนอนหลับพักผ่อนอย่างเพียงพอ 🛌 เป็นสิ่งจำเป็นสำหรับการรักษาสุขภาพ 💖 และประสิทธิภาพในการเทรด 💪
สิ่งที่น่าสนใจและข้อคิด 🤔
$ ความมีระเบียบวินัย 💯 > ตารางนี้แสดงให้เห็นถึงความมีระเบียบวินัยที่เข้มงวด 📏 ซึ่งเป็นคุณสมบัติที่สำคัญของนักเทรดที่ประสบความสำเร็จ 🎉
$ การเตรียมตัวอย่างรอบคอบ 🧐 > การใช้เวลาในการวิเคราะห์ 📊 และวางแผน 📝 ก่อนตลาดเปิดช่วยลดการตัดสินใจที่ผิดพลาด 🚫 และเพิ่มโอกาสในการทำกำไร 💰
$ การเรียนรู้อย่างต่อเนื่อง 📚 > การทบทวน 🤔 และปรับปรุงกลยุทธ์ ⚙️ อยู่เสมอเป็นสิ่งสำคัญในการพัฒนาทักษะการเทรด 🚀
$ ความสมดุล ⚖️ > การให้ความสำคัญกับการดูแลสุขภาพ 🧘♀️ และการพักผ่อน 🌴 ควบคู่ไปกับการเทรด 📈 ช่วยป้องกันภาวะหมดไฟ 🔥 และรักษาประสิทธิภาพในระยะยาว ✨
การนำไปปรับใช้ 🛠️
เพื่อนๆ นักเทรดสามารถนำแนวคิดจากตารางนี้ไปปรับใช้กับกิจวัตรประจำวันของตนเองได้ 👍 โดยอาจไม่จำเป็นต้องทำตามทุกช่วงเวลาอย่างเคร่งครัด ⏰ แต่ให้เน้นที่หลักการสำคัญ เช่น การเตรียมตัวก่อนเทรด 🤓 การทบทวนหลังเทรด 🤔 และการดูแลสุขภาพ 🧘♀️ เพื่อสร้างสมดุล ⚖️ และเพิ่มประสิทธิภาพในการเทรดของเราค่ะ 💪
ขอให้ทุกท่านประสบความสำเร็จในการเทรดนะคะ! 💸🚀
#DayTrader #นักเทรดรายวัน #กิจวัตรประจำวัน #การลงทุน #เทรด #หุ้น #คริปโต #ตลาดหุ้น #แรงบันดาลใจ #พัฒนาตัวเอง #LinaEngword
-
 @ c631e267:c2b78d3e
2025-04-04 18:47:27
@ c631e267:c2b78d3e
2025-04-04 18:47:27Zwei mal drei macht vier, \ widewidewitt und drei macht neune, \ ich mach mir die Welt, \ widewide wie sie mir gefällt. \ Pippi Langstrumpf
Egal, ob Koalitionsverhandlungen oder politischer Alltag: Die Kontroversen zwischen theoretisch verschiedenen Parteien verschwinden, wenn es um den Kampf gegen politische Gegner mit Rückenwind geht. Wer den Alteingesessenen die Pfründe ernsthaft streitig machen könnte, gegen den werden nicht nur «Brandmauern» errichtet, sondern der wird notfalls auch strafrechtlich verfolgt. Doppelstandards sind dabei selbstverständlich inklusive.
In Frankreich ist diese Woche Marine Le Pen wegen der Veruntreuung von EU-Geldern von einem Gericht verurteilt worden. Als Teil der Strafe wurde sie für fünf Jahre vom passiven Wahlrecht ausgeschlossen. Obwohl das Urteil nicht rechtskräftig ist – Le Pen kann in Berufung gehen –, haben die Richter das Verbot, bei Wahlen anzutreten, mit sofortiger Wirkung verhängt. Die Vorsitzende des rechtsnationalen Rassemblement National (RN) galt als aussichtsreiche Kandidatin für die Präsidentschaftswahl 2027.
Das ist in diesem Jahr bereits der zweite gravierende Fall von Wahlbeeinflussung durch die Justiz in einem EU-Staat. In Rumänien hatte Călin Georgescu im November die erste Runde der Präsidentenwahl überraschend gewonnen. Das Ergebnis wurde später annulliert, die behauptete «russische Wahlmanipulation» konnte jedoch nicht bewiesen werden. Die Kandidatur für die Wahlwiederholung im Mai wurde Georgescu kürzlich durch das Verfassungsgericht untersagt.
Die Veruntreuung öffentlicher Gelder muss untersucht und geahndet werden, das steht außer Frage. Diese Anforderung darf nicht selektiv angewendet werden. Hingegen mussten wir in der Vergangenheit bei ungleich schwerwiegenderen Fällen von (mutmaßlichem) Missbrauch ganz andere Vorgehensweisen erleben, etwa im Fall der heutigen EZB-Chefin Christine Lagarde oder im «Pfizergate»-Skandal um die Präsidentin der EU-Kommission Ursula von der Leyen.
Wenngleich derartige Angelegenheiten formal auf einer rechtsstaatlichen Grundlage beruhen mögen, so bleibt ein bitterer Beigeschmack. Es stellt sich die Frage, ob und inwieweit die Justiz politisch instrumentalisiert wird. Dies ist umso interessanter, als die Gewaltenteilung einen essenziellen Teil jeder demokratischen Ordnung darstellt, während die Bekämpfung des politischen Gegners mit juristischen Mitteln gerade bei den am lautesten rufenden Verteidigern «unserer Demokratie» populär zu sein scheint.
Die Delegationen von CDU/CSU und SPD haben bei ihren Verhandlungen über eine Regierungskoalition genau solche Maßnahmen diskutiert. «Im Namen der Wahrheit und der Demokratie» möchte man noch härter gegen «Desinformation» vorgehen und dafür zum Beispiel den Digital Services Act der EU erweitern. Auch soll der Tatbestand der Volksverhetzung verschärft werden – und im Entzug des passiven Wahlrechts münden können. Auf europäischer Ebene würde Friedrich Merz wohl gerne Ungarn das Stimmrecht entziehen.
Der Pegel an Unzufriedenheit und Frustration wächst in großen Teilen der Bevölkerung kontinuierlich. Arroganz, Machtmissbrauch und immer abstrusere Ausreden für offensichtlich willkürliche Maßnahmen werden kaum verhindern, dass den etablierten Parteien die Unterstützung entschwindet. In Deutschland sind die Umfrageergebnisse der AfD ein guter Gradmesser dafür.
[Vorlage Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ 9063ef6b:fd1e9a09
2025-04-16 20:20:39
@ 9063ef6b:fd1e9a09
2025-04-16 20:20:39Bitcoin is more than just a digital currency. It’s a technological revolution built on a unique set of properties that distinguish it from all other financial systems—past and present. From its decentralized architecture to its digitally verifiable scarcity, Bitcoin represents a fundamental shift in how we store and transfer value.
A Truly Decentralized Network
As of April 2025, the Bitcoin network comprises approximately 62,558 reachable nodes globally. The United States leads with 13,791 nodes (29%), followed by Germany with 6,418 nodes (13.5%), and Canada with 2,580 nodes (5.43%). bitnodes
This distributed structure is central to Bitcoin’s strength. No single entity can control the network, making it robust against censorship, regulation, or centralized failure.

Open Participation at Low Cost
Bitcoin's design allows almost anyone to participate meaningfully in the network. Thanks to its small block size and streamlined protocol, running a full node is technically and financially accessible. Even a Raspberry Pi or a basic PC is sufficient to synchronize and validate the blockchain.
However, any significant increase in block size could jeopardize this accessibility. More storage and bandwidth requirements would shift participation toward centralized data centers and cloud infrastructure—threatening Bitcoin’s decentralized ethos. This is why the community continues to fiercely debate such protocol changes.
Decentralized Governance
Bitcoin has no CEO, board, or headquarters. Its governance model is decentralized, relying on consensus among various stakeholders, including miners, developers, node operators, and increasingly, institutional participants.
Miners signal support for changes by choosing which version of the Bitcoin software to run when mining new blocks. However, full node operators ultimately enforce the network’s rules by validating blocks and transactions. If miners adopt a change that is not accepted by the majority of full nodes, that change will be rejected and the blocks considered invalid—effectively vetoing the proposal.
This "dual-power structure" ensures that changes to the network only happen through widespread consensus—a system that has proven resilient to internal disagreements and external pressures.
Resilient by Design
Bitcoin's decentralized nature gives it a level of geopolitical and technical resilience unmatched by any traditional financial system. A notable case is the 2021 mining ban in China. While initially disruptive, the network quickly recovered as miners relocated, ultimately improving decentralization.
This event underlined Bitcoin's ability to withstand regulatory attacks and misinformation (FUD—Fear, Uncertainty, Doubt), cementing its credibility as a global, censorship-resistant network.
Self-Sovereign Communication
Bitcoin enables peer-to-peer transactions across borders without intermediaries. There’s no bank, payment processor, or centralized authority required. This feature is not only technically efficient but also politically profound—it empowers individuals globally to transact freely and securely.
Absolute Scarcity
Bitcoin is the first asset in history with a mathematically verifiable, fixed supply: 21 million coins. This cap is hard-coded into its protocol and enforced by every full node. At the atomic level, Bitcoin is measured in satoshis (sats), with a total cap of approximately 2.1 quadrillion sats.
This transparency contrasts with assets like gold, whose total supply is estimated and potentially (through third parties on paper) expandable. Moreover, unlike fiat currencies, which can be inflated through central bank policy, Bitcoin is immune to such manipulation. This makes it a powerful hedge against monetary debasement.
Anchored in Energy and Time
Bitcoin's security relies on proof-of-work, a consensus algorithm that requires real-world energy and computation. This “work” ensures that network participants must invest time and electricity to mine new blocks.
This process incentivizes continual improvement in hardware and energy sourcing—helping decentralize mining geographically and economically. In contrast, alternative systems like proof-of-stake tend to favor wealth concentration by design, as influence is determined by how many tokens a participant holds.

Censorship-Resistant
The Bitcoin network itself is inherently censorship-resistant. As a decentralized system, Bitcoin transactions consist of mere text and numerical data, making it impossible to censor the underlying protocol.
However, centralized exchanges and trading platforms can be subject to censorship through regional regulations or government pressure, potentially limiting access to Bitcoin.
Decentralized exchanges and peer-to-peer marketplaces offer alternative solutions, enabling users to buy and sell Bitcoins without relying on intermediaries that can be censored or shut down.
High Security
The Bitcoin blockchain is secured through a decentralized network of thousands of nodes worldwide, which constantly verify its integrity, making it highly resistant to hacking. To add a new block of bundled transactions, miners compete to solve complex mathematical problems generated by Bitcoin's cryptography. Once a miner solves the problem, the proposed block is broadcast to the network, where each node verifies its validity. Consensus is achieved when a majority of nodes agree on the block's validity, at which point the Bitcoin blockchain is updated accordingly, ensuring the network's decentralized and trustless nature.
Manipulation of the Bitcoin network is virtually impossible due to its decentralized and robust architecture. The blockchain's chronological and immutable design prevents the deletion or alteration of previously validated blocks, ensuring the integrity of the network.
To successfully attack the Bitcoin network, an individual or organization would need to control a majority of the network's computing power, also known as a 51% attack. However, the sheer size of the Bitcoin network and the competitive nature of the proof-of-work consensus mechanism make it extremely difficult to acquire and sustain the necessary computational power. Even if an attacker were to achieve this, they could potentially execute double spends and censor transactions. Nevertheless, the transparent nature of the blockchain would quickly reveal the attack, allowing the Bitcoin network to respond and neutralize it. By invalidating the first block of the malicious chain, all subsequent blocks would also become invalid, rendering the attack futile and resulting in significant financial losses for the attacker.
One potential source of uncertainty arises from changes to the Bitcoin code made by developers. While developers can modify the software, they cannot unilaterally enforce changes to the Bitcoin protocol, as all users have the freedom to choose which version they consider valid. Attempts to alter Bitcoin's fundamental principles have historically resulted in hard forks, which have ultimately had negligible impact (e.g., BSV, BCH). The Bitcoin community has consistently rejected new ideas that compromise decentralization in favor of scalability, refusing to adopt the resulting blockchains as the legitimate version. This decentralized governance model ensures that changes to the protocol are subject to broad consensus, protecting the integrity and trustworthiness of the Bitcoin network.
Another source of uncertainty in the future could be quantum computers. The topic is slowly gaining momentum in the community and is being discussed.
My attempt to write an article with Yakihonne. Simple editor with the most necessary formatting. Technically it worked quite well so far.
Some properties are listed in the article. Which properties are missing?
-
 @ c631e267:c2b78d3e
2025-04-03 07:42:25
@ c631e267:c2b78d3e
2025-04-03 07:42:25Spanien bleibt einer der Vorreiter im europäischen Prozess der totalen Überwachung per Digitalisierung. Seit Mittwoch ist dort der digitale Personalausweis verfügbar. Dabei handelt es sich um eine Regierungs-App, die auf dem Smartphone installiert werden muss und in den Stores von Google und Apple zu finden ist. Per Dekret von Regierungschef Pedro Sánchez und Zustimmung des Ministerrats ist diese Maßnahme jetzt in Kraft getreten.
Mit den üblichen Argumenten der Vereinfachung, des Komforts, der Effizienz und der Sicherheit preist das Innenministerium die «Innovation» an. Auch die Beteuerung, dass die digitale Variante parallel zum physischen Ausweis existieren wird und diesen nicht ersetzen soll, fehlt nicht. Während der ersten zwölf Monate wird «der Neue» noch nicht für alle Anwendungsfälle gültig sein, ab 2026 aber schon.
Dass die ganze Sache auch «Risiken und Nebenwirkungen» haben könnte, wird in den Mainstream-Medien eher selten thematisiert. Bestenfalls wird der Aspekt der Datensicherheit angesprochen, allerdings in der Regel direkt mit dem Regierungsvokabular von den «maximalen Sicherheitsgarantien» abgehandelt. Dennoch gibt es einige weitere Aspekte, die Bürger mit etwas Sinn für Privatsphäre bedenken sollten.
Um sich die digitale Version des nationalen Ausweises besorgen zu können (eine App mit dem Namen MiDNI), muss man sich vorab online registrieren. Dabei wird die Identität des Bürgers mit seiner mobilen Telefonnummer verknüpft. Diese obligatorische fixe Verdrahtung kennen wir von diversen anderen Apps und Diensten. Gleichzeitig ist das die Basis für eine perfekte Lokalisierbarkeit der Person.
Für jeden Vorgang der Identifikation in der Praxis wird später «eine Verbindung zu den Servern der Bundespolizei aufgebaut». Die Daten des Individuums werden «in Echtzeit» verifiziert und im Erfolgsfall von der Polizei signiert zurückgegeben. Das Ergebnis ist ein QR-Code mit zeitlich begrenzter Gültigkeit, der an Dritte weitergegeben werden kann.
Bei derartigen Szenarien sträuben sich einem halbwegs kritischen Staatsbürger die Nackenhaare. Allein diese minimale Funktionsbeschreibung lässt die totale Überwachung erkennen, die damit ermöglicht wird. Jede Benutzung des Ausweises wird künftig registriert, hinterlässt also Spuren. Und was ist, wenn die Server der Polizei einmal kein grünes Licht geben? Das wäre spätestens dann ein Problem, wenn der digitale doch irgendwann der einzig gültige Ausweis ist: Dann haben wir den abschaltbaren Bürger.
Dieser neue Vorstoß der Regierung von Pedro Sánchez ist ein weiterer Schritt in Richtung der «totalen Digitalisierung» des Landes, wie diese Politik in manchen Medien – nicht einmal kritisch, sondern sehr naiv – genannt wird. Ebenso verharmlosend wird auch erwähnt, dass sich das spanische Projekt des digitalen Ausweises nahtlos in die Initiativen der EU zu einer digitalen Identität für alle Bürger sowie des digitalen Euro einreiht.
In Zukunft könnte der neue Ausweis «auch in andere staatliche und private digitale Plattformen integriert werden», wie das Medienportal Cope ganz richtig bemerkt. Das ist die Perspektive.
[Titelbild: Pixabay]
Dazu passend:
Nur Abschied vom Alleinfahren? Monströse spanische Überwachungsprojekte gemäß EU-Norm
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ dfa02707:41ca50e3
2025-04-16 14:36:00
@ dfa02707:41ca50e3
2025-04-16 14:36:00Contribute to keep No Bullshit Bitcoin news going.

Good morning! The GM report is now back on track, and for those wondering where it was... well... it was delayed.
0:00
/0:41
1×
Headlines
- Bitcoin mining centralization in 2025. According to a blog post by b10c, Bitcoin mining was at its most decentralized in May 2017, with another favorable period from 2019 to 2022. However, starting in 2023, mining has become increasingly centralized, particularly due to the influence of large pools like Foundry and the use of proxy pooling by entities such as AntPool.
Source: b10c's blog.
- New Spiral grantee: l0rinc. In February 2024, l0rinc transitioned to full-time work on Bitcoin Core. His efforts focus on performance benchmarking and optimizations, enhancing code quality, conducting code reviews, reducing block download times, optimizing memory usage, and refactoring code.
- ESP32 microcontroller vulnerabilities. A paper by Crypto Deep Tech details how an attacker can embed a hidden list of vulnerabilities through module updates, potentially compromising ESP32 devices and allowing unauthorized access to private keys, underscoring the importance of continuous monitoring and enhancing both device and software security.
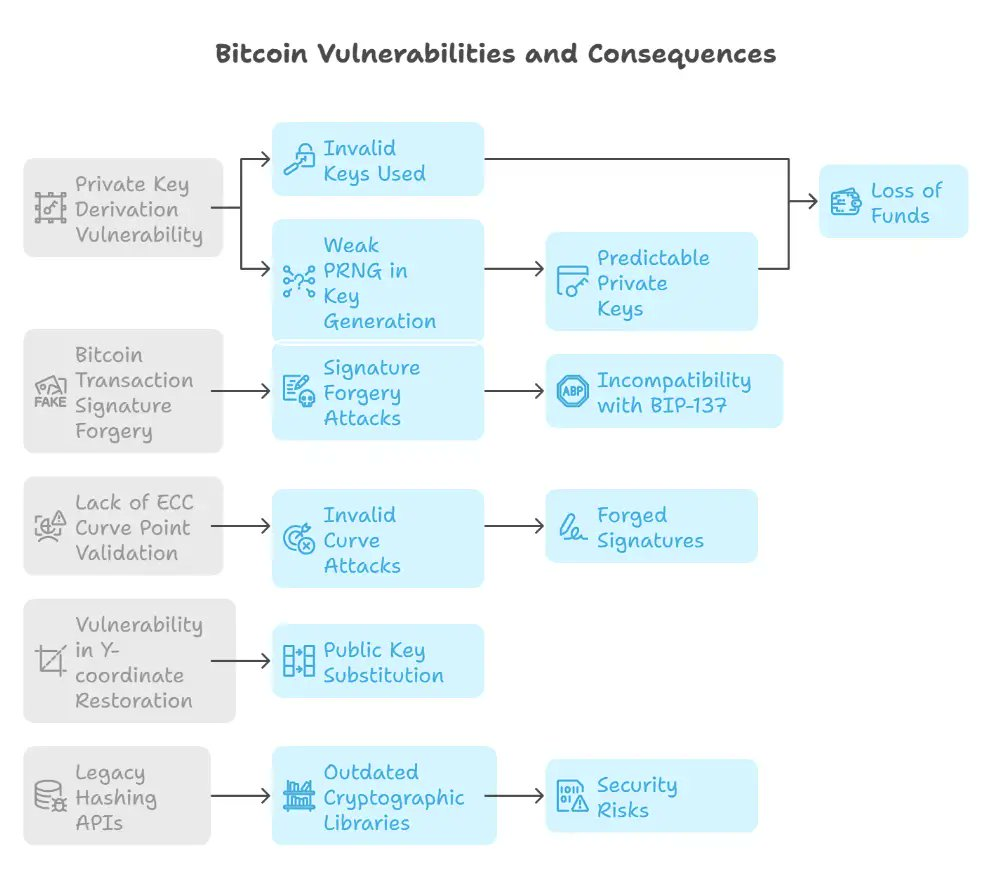
Source: Crypto Deep Tech.
- Bitdeer to expand its self-mining operations to navigate tariffs. The Singapore-based mining company is advancing plans to produce machines in the U.S. while reducing its mining hardware sales. This response is in light of increasing uncertainties related to U.S. trade policy, as reported by Bloomberg.
- Local governments in China use private firms to sell seized bitcoin for cash. According to Reuters, the lack of clear regulations for handling seized bitcoin and other tokens—whose trading is banned on the mainland—has led to inconsistent and opaque practices. The situation has sparked debate among attorneys about the need for new regulations.
- Unchained has launched the Bitcoin Legacy Project. The initiative seeks to advance the Bitcoin ecosystem through a bitcoin-native donor-advised fund platform (DAF), investments in community hubs, support for education and open-source development, and a commitment to long-term sustainability with transparent annual reporting.
- In its first year, the program will provide support to Bitcoin hubs in Nashville, Austin, and Denver.
- Support also includes $50,000 to the Bitcoin Policy Institute, a $150,000 commitment at the University of Austin, and up to $250,000 in research grants through the Bitcoin Scholars program.
"Unchained will match grants 1:1 made to partner organizations who support Bitcoin Core development when made through the Unchained-powered bitcoin DAF, up to 1 BTC," was stated in a blog post.
- Voltage has introduced Voltage Payments platform for enterprises. It will offer a single API that integrates both bitcoin and stablecoin payments with minimal technical overhead, providing the option of either Voltage or user-controlled custody. The platform features a comprehensive dashboard, along with built-in compliance and accounting tools. Currently in beta testing, it is set to launch in 46 U.S. states. Join the waitlist to be notified when it becomes available on mainnet.
Use the tools
- Bitcoin Core Config Generator by Jameson Lopp is now compatible with Bitcoin Core v29.0.
- Zeus wallet v0.10.2 is now available. This point release is centered around various bug fixes.
- Bitkit wallet v1.1.0 introduces performance improvements, smarter coin selection with new Autopilot options, a redesigned side menu, and bug fixes.
- Bitcoin Keeper v2.1.1 update includes various UI updates, bug fixes, and performance improvements.
- Flash v0.4.0-beta, a Bitcoin and Lightning wallet built on the Galoy infrastructure and tailored for the Caribbean Community, features a complete UI/UX redesign, encrypted NIP-17 messaging via Nostr, zoom functionality on the scan camera, improved support for NFC-based Flashcards, and much more.
0:00
/0:31
1×
- Payjoin Dev Kit (rust-payjoin) v0.23.0 introduces a first-class persistence abstraction, wire protocol changes to support RFC 9540, and improved compliance with the BIP78 specification. It also includes an experimental multiparty sender, accessible through the hidden "_multiparty" feature gate. Additionally, it addresses technical debt by enhancing error handling, expanding functionality with new modules and features, and improving test infrastructure. These updates result in breaking API and protocol changes.
- Payjoin CLI v0.1.0 is now out of alpha, with the wire protocol now presumed to be stable.
- Payjoin Directory v0.0.2 has been tagged. It implements the Payjoin Directory store-and-forward server required for Payjoin V2's asynchronous operation.
- BDK Wallet v1.2.0 has been released. The
TxBuilder'sadd_recipientnow accepts anyInto<ScriptBuf>. Coinbase outputs are eligible if maturing in the next block. Wallets usingrusqlite::Connectionare checked for thread safety.bdk_chainis updated to version 0.21.1, with some internal cleanups. - Lightning Dev Kit (rust-lightning) v0.1.2 includes the latest API updates, performance improvements, and bug fixes.
- Boltz Client v2.5.1 includes a patch for correctly handling negative service fees from Boltz Pro. Earlier version 2.5.0 introduced a new
bumpfeecommand alongside several other fixes and improvements. - Elements v23.2.7, an open-source implementation of advanced, sidechain-capable blockchain features extending the Bitcoin protocol, is now available with the latest fixes and improvements.
-
AxeOS (ESP-Miner) v2.6.5 increases the power target for Gamma self test. In version 2.6.4, the under limits for the power consumption self-test were removed.
- AxeOS v2.6.1 was a significant release introducing many new features and improvements. For a comprehensive feature breakdown, check out the details provided by WantClue below.
-
Rust-nostr v0.41 introduces NIP-C0 support and NIP-98 helpers, corrects NIP-32 and NIP-47 implementations, and adds the nostr-keyring crate. It extends admission policies for fine control over relay connections, beneficial in gossip mode. POSIX semaphores are enabled for LMDB on iOS and macOS to address App Sandbox issues. It also expands architecture support for C# and JVM bindings, including linux-x86, windows-x86, and windows-arm64, among other things.
- Nostringer is a JavaScript/TypeScript library providing unlinkable ring signatures (SAG) for Nostr public keys. Inspired by Monero's ring signatures using Spontaneous Anonymous Group (SAG) signatures and the beritani/ring-signatures implementation, it enables a signer to prove their membership in a group of Nostr accounts without disclosing which specific account produced the signature. See a live demo here.
- Private Pond by Kukks a Bitcoin Payjoin application built specifically to optimize Bitcoin transaction rails
-
 @ aa8de34f:a6ffe696
2025-03-31 21:48:50
@ aa8de34f:a6ffe696
2025-03-31 21:48:50In seinem Beitrag vom 30. März 2025 fragt Henning Rosenbusch auf Telegram angesichts zunehmender digitaler Kontrolle und staatlicher Allmacht:
„Wie soll sich gegen eine solche Tyrannei noch ein Widerstand formieren können, selbst im Untergrund? Sehe ich nicht.“\ (Quelle: t.me/rosenbusch/25228)
Er beschreibt damit ein Gefühl der Ohnmacht, das viele teilen: Eine Welt, in der Totalitarismus nicht mehr mit Panzern, sondern mit Algorithmen kommt. Wo Zugriff auf Geld, Meinungsfreiheit und Teilhabe vom Wohlverhalten abhängt. Der Bürger als kontrollierbare Variable im Code des Staates.\ Die Frage ist berechtigt. Doch die Antwort darauf liegt nicht in alten Widerstandsbildern – sondern in einer neuen Realität.
-- Denn es braucht keinen Untergrund mehr. --
Der Widerstand der Zukunft trägt keinen Tarnanzug. Er ist nicht konspirativ, sondern transparent. Nicht bewaffnet, sondern mathematisch beweisbar. Bitcoin steht nicht am Rand dieser Entwicklung – es ist ihr Fundament. Eine Bastion aus physikalischer Realität, spieltheoretischem Schutz und ökonomischer Wahrheit. Es ist nicht unfehlbar, aber unbestechlich. Nicht perfekt, aber immun gegen zentrale Willkür.
Hier entsteht kein „digitales Gegenreich“, sondern eine dezentrale Renaissance. Keine Revolte aus Wut, sondern eine stille Abkehr: von Zwang zu Freiwilligkeit, von Abhängigkeit zu Selbstverantwortung. Diese Revolution führt keine Kriege. Sie braucht keine Führer. Sie ist ein Netzwerk. Jeder Knoten ein Individuum. Jede Entscheidung ein Akt der Selbstermächtigung.
Weltweit wachsen Freiheits-Zitadellen aus dieser Idee: wirtschaftlich autark, digital souverän, lokal verankert und global vernetzt. Sie sind keine Utopien im luftleeren Raum, sondern konkrete Realitäten – angetrieben von Energie, Code und dem menschlichen Wunsch nach Würde.
Der Globalismus alter Prägung – zentralistisch, monopolistisch, bevormundend – wird an seiner eigenen Hybris zerbrechen. Seine Werkzeuge der Kontrolle werden ihn nicht retten. Im Gegenteil: Seine Geister werden ihn verfolgen und erlegen.
Und während die alten Mächte um Erhalt kämpfen, wächst eine neue Welt – nicht im Schatten, sondern im Offenen. Nicht auf Gewalt gebaut, sondern auf Mathematik, Physik und Freiheit.
Die Tyrannei sieht keinen Widerstand.\ Weil sie nicht erkennt, dass er längst begonnen hat.\ Unwiderruflich. Leise. Überall.
-
 @ fd78c37f:a0ec0833
2025-04-21 04:40:30
@ fd78c37f:a0ec0833
2025-04-21 04:40:30Bitcoin is redefining finance, and in Asia—Thailand, Vietnam, Indonesia, and beyond—developers, entrepreneurs, and communities are fueling this revolution. YakiHonne, a decentralized social payments app built on Nostr, sat down with Gio (nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx), a core member of Thailand’s Sats ‘N’ Facts community, to explore their mission of fostering open-source Bitcoin development. In this interview, Gio shares the origins of Sats ‘N’ Facts, the challenges of hosting Bitcoin-focused events in Asia, and how these efforts are shaping adoption across the region.
YakiHonne: Can you tell us about yourself and how Sats ‘N’ Facts came to life? What sparked your Bitcoin journey?
Gio: I’m originally from Europe but have called Thailand home for six years. My Bitcoin story began while working at a commercial bank, where I saw the fiat system’s flaws firsthand—things like the Cantillon Effect, where money printing favors the connected few, felt deeply unfair. That discomfort led me to Andreas Antonopoulos’ videos, which opened my eyes to Bitcoin’s potential. After moving to Bangkok, I joined the open-source scene at BOB Space, collaborating with folks on tech projects.
Sats ‘N’ Facts grew out of that spirit. We wanted to create a Bitcoin-focused community to support developers and builders in Asia. Our recent conference in Chiang Mai brought together over 70 enthusiasts from Thailand, Vietnam, Laos, and beyond, sparking collaborations like a new Lightning Network tool. It was a milestone in connecting the region’s Bitcoin ecosystem.
YakiHonne: What inspired the Sats ‘N’ Facts conference, and how did you attract attendees?
Gio: The event was born from a desire to create a high-signal, low-noise space for Freedom Tech in Asia. While the U.S. and Europe host major Bitcoin events, Asia’s scene is still emerging under commercial stunts. We aimed to bridge that gap, uniting developers, educators, and enthusiasts to discuss real innovations—no altcoins, no corporate agendas. Our focus was on open-source projects like Bitcoin Core, Ark, Cashu, fostering conversations that could lead to tangible contributions.
Attracting attendees wasn’t easy. We leveraged local networks, reaching out to Bitcoin communities in neighboring countries via Nostr and Telegram. Posts on X helped spread the word, and we saw developers from Laos join for the first time, which was thrilling. Sponsors like Fulgur Ventures, Utreexo, and the Bitcoin Development Kit Foundation played a huge role, covering costs so we could keep the event free and accessible.
YakiHonne: What challenges did you face organizing the conference in Asia?
Gio: It was a steep learning curve. Funding was the biggest hurdle—early on, we struggled to cover venue and travel costs. Thankfully, our sponsors stepped in, letting me focus on logistics, which were no small feat either. As a first-time organizer, I underestimated the chaos of a tight timeline. Day one felt like herding cats without a fixed agenda, but the energy was electric—developers debugging code together, newcomers asking big questions.
Another challenge was cultural. Bitcoin’s still niche in Asia, so convincing locals to attend took persistence; there was no local presence for some reason. Despite the hiccups, we pulled it off, hosting 60+ attendees and sparking ideas for new projects, like a Cashu wallet integration. I’d tweak the planning next time, but the raw passion made it unforgettable.
YakiHonne: How does YakiHonne’s vision of decentralized social payments align with Sats ‘N’ Facts’ goals? Could tools like ours support your community?
Gio: That’s a great question. YakiHonne’s approach—merging Nostr’s censorship-resistant communication with Lightning payments—fits perfectly with our mission to empower users through open tech. At Sats ‘N’ Facts, we’re all about tools that give people control, whether it’s code or money. An app like YakiHonne could streamline community funding, letting developers tip each other for contributions or crowdfund projects directly. Imagine a hackathon where winners get sats instantly via YakiHonne—it’d be a game-changer. I’d love to see you guys at our next event to demo it!
YakiHonne: What advice would you give to someone starting a Bitcoin-focused community or event?
Gio: First, keep it Bitcoin-only. Stay true to the principles—cut out distractions like altcoins or hype-driven schemes. Start small: host regular meetups, maybe five people at a café, and build trust over time. Consistency and authenticity beat flashiness in the medium and long term.
Second, involve technical folks. Developers bring credibility and clarity, explaining Bitcoin’s nuts and bolts in ways newcomers get. I admire how Andreas Antonopoulos bridges that gap—technical yet accessible. You need that foundation to grow a real community.
Finally, lean on existing networks. If you know someone running a Bitcoin meetup in another city, collaborate. Share ideas, speakers, or even livestreams. Nostr’s great for this—our Laos attendees found us through a single post. Relationships are everything.
YakiHonne: Does Sats ‘N’ Facts focus more on Bitcoin’s technical side, non-technical side, or both?
Gio: We blend both. Our event had workshops for coders alongside talks for beginners on why Bitcoin matters. Open-source is our heartbeat, though. If you’re starting out, dive into projects like Bitcoin Core or Lightning. Review a pull request, test a Cashu wallet, or join a hackathon. One developer at our event built a Lightning micropayment tool that’s now live on GitHub.
There’s no shortage of ways to contribute. Community calls, forums, residency programs, and platforms like Geyser Fund are goldmines. YakiHonne could amplify this—imagine tipping developers for bug fixes via your app. It’s about iterating until you create something real.
YakiHonne: Your work is inspiring, Gio. Sats ‘N’ Facts is uniting Asia’s Bitcoin communities in a powerful way. What’s next for you?
Gio: Thanks for the kind words! We’re just getting started. The Chiang Mai event showed what’s possible—connecting developers across borders, reviewing and launching code and testing upcoming technologies. Next, we’re planning smaller hackathons and other events to keep the momentum going, maybe in Vietnam, Indonesia or Korea. I’d love to integrate tools like YakiHonne to fund these efforts directly through Nostr payments. Long-term, we want Sats ‘N’ Facts to be a hub for Asia’s Bitcoin builders, proving open-source can thrive here.

YakiHonne: Thank you, Gio, for sharing Sats ‘N’ Facts incredible journey. Your work is lighting a path for Bitcoin in Asia, and we’re honored to tell this story.
To our readers: Bitcoin’s future depends on communities like Sats ‘N’ Facts—and you can join the revolution. Download YakiHonne on Nostr to connect with builders, send Lightning payments, and explore the decentralized world. Follow Sats ‘N’ Facts for their next hackathon, and let’s build freedom tech together!
-
 @ 1bc70a01:24f6a411
2025-04-16 13:53:00
@ 1bc70a01:24f6a411
2025-04-16 13:53:00I've been meaning to dogfood my own vibe project for a while so this feels like a good opportunity to use Untype to publish this update and reflect on my vibe coding journey.
New Untype Update
As I write this, I found it a bit annoying dealing with one of the latest features, so I'll need to make some changes right after I'm done. Nonetheless, here are some exciting developments in the Untype article composer:
-
Added inline AI helper! Now you can highlight text and perform all sorts of things like fix grammar, re-write in different styles, and all sorts of other things. This is a bit annoying at the moment because it takes over the other editing functions and I need to fix the UX.
-
Added pushing articles to DMs! This option, when enabled, will send the article to all the subscribers via a NIP-44 DM. (No client has implemented the subscription method yet so technically it won’t work, until one does. I may add this to nrss.app) Also, I have not tested this so it could be broken… will test eventually!
- Added word counts
- Added ability to export as markdown, export as PDF, print.
The biggest flaw I have already discovered is how "I" implemented the highlight functionality. Right now when you highlight some text it automatically pops up the AI helper menu and this makes for an annoying time trying to make any changes to text. I wanted to change this to show a floating clickable icon instead, but for some reason the bot is having a difficult time updating the code to this desired UX.
Speaking of difficult times, it's probably a good idea to reflect a bit upon my vibe coding journey.
Vibe Coding Nostr Projects
First, I think it's important to add some context around my recent batch of nostr vibe projects. I am working on them mostly at night and occasionally on weekends in between park runs with kids, grocery shopping and just bumming around the house. People who see buggy code or less than desired UX should understand that I am not spending days coding this stuff. Some apps are literally as simple as typing one prompt!
That said, its pretty clear by now that one prompt cannot produce a highly polished product. This is why I decided to limit my number of project to a handful that I really wish existed, and slowly update them over time - fixing bugs, adding new features in hopes of making them the best tools - not only on nostr but the internet in general. As you can imagine this is not a small task, especially for sporadic vibe coding.
Fighting the bot
One of my biggest challenges so far besides having very limited time is getting the bot to do what I want it to do. I guess if you've done any vibe coding at all you're probably familiar with what I'm trying to say. You prompt one thing and get a hallucinated response, or worse, a complete mess out the other end that undoes most of the progress you've made. Once the initial thing is created, which barely took any time, now you're faced with making it work a certain way. This is where the challenges arise.
Here's a brief list of issues I've faced when vibe-coding with various tools:
1. Runaway expenses - tools like Cline tend to do a better job directly in VSCode, but they can also add up dramatically. Before leaning into v0 (which is where I do most of my vibe coding now), I would often melt through $10 credit purchases faster than I could get a decent feature out. It was not uncommon for me to spend $20-30 on a weekend just trying to debug a handful of issues. Naturally, I did not wish to pay these fees so I searched for alternatives.
2. File duplication - occasionally, seemingly out of nowhere, the bot will duplicate files by creating an entire new copy and attached "-fixed" to the file name. Clearly, I'm not asking for duplicate files, I just want it to fix the existing file, but it does happen and it's super annoying. Then you are left telling it which version to keep and which one to delete, and sometimes you have to be very precise or it'll delete the wrong thing and you have to roll back to a previous working version.
3. Code duplication - similar to file duplication, occasionally the bot will duplicate code and do things in the most unintuitive way imaginable. This often results in loops and crashes that can take many refreshes just to revert back to a working state, and many more prompts to avoid the duplication entirely - something a seasoned dev never has to deal with (or so I imagine).
4. Misinterpreting your request - occasionally the bot will do something you didn't ask for because it took your request quite literally. This tends to happen when I give it very specific prompts that are targeted at fixing one very specific thing. I've noticed the bots tend to do better with vague asks - hence a pretty good result on the initial prompt.
5. Doing things inefficiently, without considering smarter approaches - this one is the most painful of vibe coding issues. As a person who may not be familiar with some of the smarter ways of handling development, you rely on the bot to do the right thing. But, when the bot does something horribly inefficiently and you are non-the-wiser, it can be tough to diagnose the issue. I often fight myself asking the bot "is this really the best way to handle things? Can't we ... / shouldn't we .../ isn't this supposed to..." etc. I guess one of the nice side effects of this annoyance is being able to prompt better. I learn that I should ask the bot to reflect on its own code more often and seek ways to do things more simply.
A combination of the above, or total chaos - this is a category where all hell breaks loose and you're trying to put out one fire after another. Fix one bug, only to see 10 more pop up. Fix those, to see 10 more and so on. I guess this may sound like typical development, but the bot amplifies issues by acting totally irrationally. This is typically when I will revert to a previous save point and just undo everything, often losing a lot of progress.
Lessons Learned
If I had to give my earlier self some tips on how to be a smarter vibe coder, here's how I'd summarize them:
-
Fork often - in v0 I now fork for any new major feature I'd like to add (such as the AI assistant).
-
Use targeting tools - in v0 you can select elements and describe how you wish to edit them.
-
Refactor often - keeping the code more manageable speeds up the process. Since the bot will go through the entire file, even if it only makes one small change, it's best to keep the files small and refactoring achieves that.
I guess the biggest lesson someone might point out is just to stop vibe coding. It may be easier to learn proper development and do things right. For me it has been a spare time hobby (one that I will admit is taking more of my extra time than I'd like). I don't really have the time to learn proper development. I feel like I've learned a lot just bossing the bot around and have learned a bunch of things in the process. That's not to say that I never will, but for the moment being my heart is still mostly in design. I haven't shared much of anything I have designed recently - mostly so I can remain speaking more freely without it rubbing off on my work.
I'll go ahead and try to publish this to see if it actually works 😂. Here goes nothing... (oh, I guess I could use the latest feature to export as markdown so I don't lose any progress! Yay!
-
-
 @ c631e267:c2b78d3e
2025-03-31 07:23:05
@ c631e267:c2b78d3e
2025-03-31 07:23:05Der Irrsinn ist bei Einzelnen etwas Seltenes – \ aber bei Gruppen, Parteien, Völkern, Zeiten die Regel. \ Friedrich Nietzsche
Erinnern Sie sich an die Horrorkomödie «Scary Movie»? Nicht, dass ich diese Art Filme besonders erinnerungswürdig fände, aber einige Szenen daraus sind doch gewissermaßen Klassiker. Dazu zählt eine, die das Verhalten vieler Protagonisten in Horrorfilmen parodiert, wenn sie in Panik flüchten. Welchen Weg nimmt wohl die Frau in der Situation auf diesem Bild?

Diese Szene kommt mir automatisch in den Sinn, wenn ich aktuelle Entwicklungen in Europa betrachte. Weitreichende Entscheidungen gehen wider jede Logik in die völlig falsche Richtung. Nur ist das hier alles andere als eine Komödie, sondern bitterernst. Dieser Horror ist leider sehr real.
Die Europäische Union hat sich selbst über Jahre konsequent in eine Sackgasse manövriert. Sie hat es versäumt, sich und ihre Politik selbstbewusst und im Einklang mit ihren Wurzeln auf dem eigenen Kontinent zu positionieren. Stattdessen ist sie in blinder Treue den vermeintlichen «transatlantischen Freunden» auf ihrem Konfrontationskurs gen Osten gefolgt.
In den USA haben sich die Vorzeichen allerdings mittlerweile geändert, und die einst hoch gelobten «Freunde und Partner» erscheinen den europäischen «Führern» nicht mehr vertrauenswürdig. Das ist spätestens seit der Münchner Sicherheitskonferenz, der Rede von Vizepräsident J. D. Vance und den empörten Reaktionen offensichtlich. Große Teile Europas wirken seitdem wie ein aufgescheuchter Haufen kopfloser Hühner. Orientierung und Kontrolle sind völlig abhanden gekommen.
Statt jedoch umzukehren oder wenigstens zu bremsen und vielleicht einen Abzweig zu suchen, geben die Crash-Piloten jetzt auf dem Weg durch die Sackgasse erst richtig Gas. Ja sie lösen sogar noch die Sicherheitsgurte und deaktivieren die Airbags. Den vor Angst dauergelähmten Passagieren fällt auch nichts Besseres ein und so schließen sie einfach die Augen. Derweil übertrumpfen sich die Kommentatoren des Events gegenseitig in sensationslüsterner «Berichterstattung».
Wie schon die deutsche Außenministerin mit höchsten UN-Ambitionen, Annalena Baerbock, proklamiert auch die Europäische Kommission einen «Frieden durch Stärke». Zu dem jetzt vorgelegten, selbstzerstörerischen Fahrplan zur Ankurbelung der Rüstungsindustrie, genannt «Weißbuch zur europäischen Verteidigung – Bereitschaft 2030», erklärte die Kommissionspräsidentin, die «Ära der Friedensdividende» sei längst vorbei. Soll das heißen, Frieden bringt nichts ein? Eine umfassende Zusammenarbeit an dauerhaften europäischen Friedenslösungen steht demnach jedenfalls nicht zur Debatte.
Zusätzlich brisant ist, dass aktuell «die ganze EU von Deutschen regiert wird», wie der EU-Parlamentarier und ehemalige UN-Diplomat Michael von der Schulenburg beobachtet hat. Tatsächlich sitzen neben von der Leyen und Strack-Zimmermann noch einige weitere Deutsche in – vor allem auch in Krisenzeiten – wichtigen Spitzenposten der Union. Vor dem Hintergrund der Kriegstreiberei in Deutschland muss eine solche Dominanz mindestens nachdenklich stimmen.
Ihre ursprünglichen Grundwerte wie Demokratie, Freiheit, Frieden und Völkerverständigung hat die EU kontinuierlich in leere Worthülsen verwandelt. Diese werden dafür immer lächerlicher hochgehalten und beschworen.
Es wird dringend Zeit, dass wir, der Souverän, diesem erbärmlichen und gefährlichen Trauerspiel ein Ende setzen und die Fäden selbst in die Hand nehmen. In diesem Sinne fordert uns auch das «European Peace Project» auf, am 9. Mai im Rahmen eines Kunstprojekts den Frieden auszurufen. Seien wir dabei!
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben und ist zuerst auf Transition News erschienen.
-
 @ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16
@ d9e9fb27:d5fe5e1a
2025-04-22 01:29:16"There are two pillars in Costa Rica, education and coffee." A tourist guide I met told me this, and during the trip I discovered the strong link between coffee and the locals.
In fact, coffee runs very deeply in the Ticos' culture. So deep that the summer vacations from school (November to January) coincide with the coffee collection season. Children had to help their parents with the coffee. Coffee was a family business.
Monteverde, in the region of Puentarenas, is one of those places where coffee ha always been a corner stone of the society. Here, My gf and I went to visit a coffee plantation and discovered how coffee is made.
Monteverde
Monteverde is a well-known turistic location in the central part of Costa Rica. Many people reach this beautiful place to visit the famous Cloud Rainforest, acres and acres of pristine forest, with many different kind of animals and plants living in it.

However, other than tourism is coffee that pushes the economy of this place. The hills around the town are covered with coffee plantations and there are tours than try to explain how coffee is made.

Coffee Tours
While we were in Monteverde, we joined one of these tours. We decided to give credit to a smaller plantation instead of the super turistic ones. A more rustic and family-owned business, El Pueblo Coffee Tour. We were not disappointed. We had the show all to ourselves, a super-prepared guide and all the time to make questions and enjoy with no rush.
The Plant of Coffee
Since Costa Rica is a quite small country, to compete on the market producers decided to bet on quality instead of quantity. That's why, the only type produced here is the Arabica.
Before the coffee bean, the plant produces a nice white flower, similar to the jasmine.

After a while, the coffee beans appear.

As soon as they turn red, they are ready to be collected.
Interesting fact: between the coffee plants many fruit trees like mangos or bananos can be found. In fact, those plants help keep the soil fertile and healthy, thus leading to a higher coffee quality!
Coffee Harvesting
Coffee is still harvested by hand. Beans do not get mature at the same time, so manual labor is needed. Laborer use a very simple tool to collect coffee, one which allow them to have both hands free.
 Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Workers do not get paid by hours, but by the number of cajuelas that they can fill. A cajuela is a standard box, which contains around 13kg of beans. It's divided into quarters, so that the worker can get paid for the quarter, too.
Each cajuela is paid around 3.50$.
Coffee Drying
In the farm we visited, drying was perfomed naturally, through the heat of the sun. There are three ways in which the bean is left to dry: lavado, miel and naturàl.
- Lavado: The beans are peeled and washed to remove the jelly.
 - Miel: The jelly on the beans is maintained to give it more sweet flavour.
- Miel: The jelly on the beans is maintained to give it more sweet flavour. - Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
- Naturàl: The bean is left to dry with its peel on, to give it a more fruity taste.
Back in the days, to peel the beans for the lavado and the miel variety, the pìlon was used. The bean is very hard, thus this tool does not damage it.

However, today the peeling procedure is done using a machine.

Coffee Roasting
The last step in the production of coffee is roasting. Coffee is put inside a sort of hoven, and is left there at high temperature according to the level of roasting that is needed. The more roasting, the less caffeine there is and the more bitter the coffee. Usually you have light, medium and dark roast.

Coffee Tasting
In the end, we also had a coffee tasting. We tried different roasting and different varieties.
Our guide explained us the best way to taste coffee and helped us defining the different flavours that we perceived. He also taught us the best way to prepare it: infusion time, water temperature, coffe makers and so on.
My favorite one was the dark one, while my gf enjoyed the light roast more. Of course, we bought some packs of these varieties!
Thanks for tuning in!
I hope you enjoyed this brief overview of the Costa Rican coffee.
Pura Vida
Tuma
-
 @ e39d100f:d27602e5
2025-04-21 02:28:33
@ e39d100f:d27602e5
2025-04-21 02:28:33A 5GBet tem se destacado cada vez mais no cenário brasileiro como uma plataforma completa de entretenimento online, oferecendo aos usuários uma experiência repleta de emoção, segurança e diversidade de jogos. Seja você um jogador iniciante ou experiente, a 5GBet proporciona uma navegação intuitiva e um ambiente confiável para quem busca diversão sem sair de casa.
Desde o primeiro acesso, é fácil perceber que a 5GBet se preocupa com a experiência do usuário. O design do site é moderno e responsivo, adaptando-se perfeitamente a computadores, tablets e celulares. Isso garante que os jogadores possam se divertir a qualquer momento, de qualquer lugar.
Outro ponto forte é a segurança. A plataforma utiliza tecnologia de criptografia avançada para proteger os dados dos usuários, além de contar com métodos de verificação de identidade para garantir transações seguras. Tudo isso contribui para um ambiente confiável, onde o jogador pode focar apenas na diversão.
Variedade de Jogos para Todos os Gostos Na 5gbet , a variedade de jogos é um dos principais diferenciais. O site oferece uma extensa seleção de opções, desde os clássicos jogos de mesa até slots modernos com gráficos impressionantes e temáticas envolventes. Os jogadores podem escolher entre diversos estilos e dinâmicas, o que torna a experiência muito mais rica e personalizada.
Os jogos de cartas, como o pôquer e o blackjack, são populares entre os usuários mais estratégicos. Já os slots oferecem uma jogabilidade mais leve e dinâmica, com recursos interativos e animações cativantes. Há também jogos com crupiês ao vivo, que proporcionam uma experiência ainda mais imersiva, com transmissão em tempo real e interação com outros jogadores.
Experiência do Jogador: Intuitiva e Recompensadora A experiência do jogador na 5GBet é cuidadosamente pensada para ser fluida e gratificante. O processo de cadastro é rápido, e os métodos de depósito e saque são variados, incluindo opções populares como PIX, transferência bancária e carteiras digitais. Além disso, o suporte ao cliente está disponível para tirar dúvidas e resolver questões com agilidade, seja via chat ao vivo ou e-mail.
Outro destaque é o sistema de recompensas e promoções oferecido aos jogadores. Desde bônus de boas-vindas até promoções recorrentes, a 5GBet valoriza seus usuários ativos e oferece incentivos para tornar a jornada ainda mais empolgante.
A comunidade de jogadores também é bastante ativa, e a plataforma frequentemente promove torneios e desafios, permitindo que os usuários testem suas habilidades e interajam com outros entusiastas.
Conclusão A 5GBet se consolida como uma excelente opção para quem busca entretenimento online com qualidade, segurança e muita variedade. Com uma plataforma bem estruturada, jogos empolgantes e uma experiência de usuário impecável, é fácil entender por que cada vez mais brasileiros escolhem a 5GBet como seu destino de diversão online. Se você ainda não conhece, vale a pena explorar e descobrir tudo o que essa plataforma tem a oferecer.
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 812cff5a:5c40aeeb
2025-04-22 01:27:45
@ 812cff5a:5c40aeeb
2025-04-22 01:27:45يوم جديد وتطبيق نوستر جديد
أكتب هذا المقال من داخل نفس التطبيق اللي براجعه—يعني بختبر وبوثق التجربة في نفس الوقت، حرفياً!
الهدف من تطبيق أنتايپ
untyp| هو تطبيق مخصص للمنشورات الطويلة على بروتوكول نوستر. فكرته بسيطة جداً، لكنها عبقرية: إزالة كل الحواجز بينك وبين أفكارك، بحيث تقدر تكتب بحرية وسلاسة، كأنك بتكتب على ورقة فاضية... بس رقمية.
المزاية.. آو يمكن الميزة الوحيدة
ميزة التطبيق الأساسية هي دعمه الكامل لتنسيق Markdown، وهذا يعطيك مرونة هائلة في عرض أفكارك بشكل منظم وواضح—عناوين، روابط، كود، اقتباسات، وكل شيء بينهما.
الفكرة مو بس في المزايا، بل في الحد من المشتتات. التصميم بسيط وأنيق، بدون أي زوائد أو إعلانات، مما يساعدك تركز على الكتابة فقط.
untyp| مش بس وسيلة للنشر، بل أداة بتخليك أقرب لأفكارك، وأسرع في التعبير عنها.
جربته؟ قول لي رأيك. مطور التطبيق هو كارنج: nostr:npub1r0rs5q2gk0e3dk3nlc7gnu378ec6cnlenqp8a3cjhyzu6f8k5sgs4sq9ac
-
 @ dfa02707:41ca50e3
2025-04-16 05:30:53
@ dfa02707:41ca50e3
2025-04-16 05:30:53Contribute to keep No Bullshit Bitcoin news going.
- This release eliminates UPnP support in favor of NAT-PMP/PCP, enhances transaction orphan handling for improved reliability, and introduces ephemeral dust to defer fee commitment.
- Various RPCs now feature enhanced error reporting and new data fields, the block size handling bug related to reserved weight has been fixed, and the removal of the
mempoolfullrbfoption standardizes full replace-by-fee behavior. - With this new major release, versions 26.x and older have reached "Maintenance End" and will no longer receive updates. Two weeks after this release, medium and high severity vulnerabilities affecting 26.x will be disclosed, as well as low severity vulnerabilities affecting 28.x, in line with the security policy.
What's new
-
P2P and Network Changes:
- Support for UPnP has been dropped in favor of a more modern NAT-PMP/PCP implementation.
-
Added support for PCP & IPv6 pinholing.
libnatpmpwas replaced with built-in NAT-PMP/PCP implementation, enabled via-natpmp, which supports IPv4 port forwarding and IPv6 pinholing. - A change in assigning onion listening ports. Now, when using the
-portconfiguration option, the default onion listening port will be set to the specified port +1, rather than a fixed value like 8334 on mainnet.
"This re-allows setups with multiple local nodes using different
-portand not using-bind, which would lead to a startup failure in v28.0 due to a port collision," was explained in the release notes.-
More reliable orphan handling. When a node receives an orphan transaction (an unconfirmed transaction that spends unknown inputs), it will attempt to download missing parents from peers who announced the orphan, potentially increasing bandwidth but enhancing handling of orphan transactions.
-
Mempool Policy and Mining Changes:
- Relay transaction packages containing ephemeral dust. An ephemeral dust output is a tiny transaction output, below the dust limit, produced in a v3 zero-fee transaction and consumed in a following v3 transaction. These transactions occur within the same package, making the output temporary since it is both generated and spent at once. It is useful for Lightning network, Ark, ln-symmetry, Spacechains, Timeout Trees, and other constructs.
-
New startup option -blockreservedweight. In versions before 29.0, a bug limited actual block sizes to 3,992,000 WU by setting a default reserved weight of 8,000 WU for block headers and transactions. The fix adds a new option, -blockreservedweight, with the same default for compatibility.
-
New RPCs:
getdescriptoractivityto track activity of a given set of descriptors. It helps identify all spending and receiving activities for specific descriptors within chosen blocks, and can be used withscanblocksto reduce reliance on additional indexing programs.
-
Updated RPCs:
- Enhanced RPC Response: testmempoolaccept now includes Reject Details. Bitcoin Core 29.0 adds a verbose
reject-detailsfield to thetestmempoolacceptRPC, detailing rejections likeinsufficient-fee. - Persistent block data for duplicate submitblock submissions. Duplicate blocks submitted via
submitblockwill now retain their data even if previously pruned. If pruning is enabled, the data will eventually be pruned again when its block file is selected for pruning.
- Enhanced RPC Response: testmempoolaccept now includes Reject Details. Bitcoin Core 29.0 adds a verbose
-
Updated
getmininginfo. Thegetmininginfonow includesnBitsand the current target in thetargetfield. It also serves anextobject, detailing theheight,nBits,difficulty, andtargetfor the upcoming block. getblockandgetblockheadernow return the current target in thetargetfield.getblockchaininfoandgetchainstatesnow returnnBitsand the current target in thetargetfield.-
getblocktemplateRPC now considers BIP94 Timewarp Fix. ThegetblocktemplateRPC now considers the timewarp fix from BIP94 for thecurtime(BIP22) andmintime(BIP23) fields across all networks. This change helps prevent un-upgraded miners from unintentionally breaching the timewarp rule if a timewarp fix softfork activates on the mainnet. -
Updated REST APIs:
- Get block and Get headers return target in the target field. The
GET /rest/block/<BLOCK-HASH>.jsonandGET /rest/headers/<BLOCK-HASH>.jsonnow return the current target in thetargetfield.
- Get block and Get headers return target in the target field. The
-
Updated Settings:
- Replace-by-fee the standard. From version v28.0, the
-mempoolfullrbfoption was set to default to 1. Due to widespread policy adoption, this option has been removed, making full replace-by-fee the standard behavior. - The maximum limit for the
-dbcacheconfiguration option has been removed due to recent UTXO set growth. Previously, large-dbcachevalues were automatically capped at 16 GiB (or 1 GiB on 32-bit systems). - The handling of negated options like
-noseednode,-nobind,-nowhitebind, and others has been improved. Now, negating these options simply resets them to their defaults, removing previous confusing and undocumented effects. - Using the
-upnpoption will now log a warning and be treated as-natpmp. It's recommended to use-natpmpdirectly instead.
- Replace-by-fee the standard. From version v28.0, the
-
Bitcoin Core will not start if the
-blockreservedweightparameter is set below 2,000 WU. It will also fail to start if either-blockmaxweightor-blockreservedweightexceeds the consensus limit of 4,000,000 WU. -
Using
-debug=0or-debug=nonenow works like-nodebug. It clears previously set debug categories while allowing later-debugoptions to be applied. -
The default value for
-rpcthreadshas increased from 4 to 16, and-rpcworkqueuehas been updated from 16 to 64. -
Build System:
- The build system has been migrated from Autotools to CMake. The minimum required CMake version is 3.22.
"For more detailed guidance on configuring and using CMake, please refer to the official CMake documentation and CMake’s User Interaction Guide. Additionally, consult platform-specific
doc/build-*.mdbuild guides for instructions tailored to your operating system."- Tools and Utilities:
- The new tool
utxo_to_sqlite.pyconverts a compact-serialized UTXO snapshot, created using thedumptxoutsetRPC, into a SQLite3 database. Check the script's--helpoutput for more information.
- The new tool
- Testing:
- The BIP94 timewarp attack mitigation (designed for testnet4) is no longer active on the regtest network.
- Dependencies:
- MiniUPnPc and libnatpmp have been removed as dependencies.

For more information on the new features, improvements, and bug fixes in this release, refer to the full release notes. Additionally, the detailed v29 testing guide provides steps for testing the latest features.
"Thanks to everyone who directly contributed to this release, including 0xb10c, Adlai Chandrasekhar, Afanti, Alfonso Roman Zubeldia, am-sq, Andre, Andre Alves, Anthony Towns, Antoine Poinsot, Ash Manning, Ava Chow, Boris Nagaev, Brandon Odiwuor, brunoerg, Chris Stewart, Cory Fields, costcould, Daniel Pfeifer, Daniela Brozzoni, David Gumberg, dergoegge, epysqyli, espi3, Eval EXEC, Fabian Jahr, fanquake, furszy, Gabriele Bocchi, glozow, Greg Sanders, Gutflo, Hennadii Stepanov, Hodlinator, i-am-yuvi, ion-, ismaelsadeeq, Jadi, James O’Beirne, Jeremy Rand, Jon Atack, jurraca, Kay, kevkevinpal, l0rinc, laanwj, Larry Ruane, Lőrinc, Maciej S. Szmigiero, Mackain, MarcoFalke, marcofleon, Marnix, Martin Leitner-Ankerl, Martin Saposnic, Martin Zumsande, Matthew Zipkin, Max Edwards, Michael Dietz, naiyoma, Nicola Leonardo Susca, omahs, pablomartin4btc, Pieter Wuille, Randall Naar, RiceChuan, rkrux, Roman Zeyde, Ryan Ofsky, Sebastian Falbesoner, secp512k2, Sergi Delgado Segura, Simon, Sjors Provoost, stickies-v, Suhas Daftuar, tdb3, TheCharlatan, tianzedavid, Torkel Rogstad, Vasil Dimov, wgyt, willcl-ark, yancy, and everyone who assisted with translations on Transifex."
-
 @ e39d100f:d27602e5
2025-04-21 02:18:40
@ e39d100f:d27602e5
2025-04-21 02:18:40O mercado de entretenimento digital no Brasil está em constante expansão, e entre as novas opções que vêm ganhando destaque, a plataforma Betao se sobressai como uma das mais promissoras. Com um ambiente moderno, seguro e recheado de atrações, o Betao oferece uma experiência diferenciada tanto para jogadores iniciantes quanto para os mais experientes.
Uma Plataforma Intuitiva e Acessível Logo ao acessar o site do Betao, o usuário já percebe a preocupação com a usabilidade. O design é limpo, responsivo e adaptado para todos os tipos de dispositivos, o que permite que os jogadores aproveitem ao máximo cada funcionalidade, seja no computador, tablet ou celular.
Além disso, o processo de cadastro é rápido e descomplicado. Em poucos cliques, o jogador já está pronto para explorar os jogos disponíveis. Outro ponto positivo é a variedade de métodos de pagamento, que incluem transferências bancárias, carteiras digitais e até opções com criptomoedas, oferecendo mais liberdade e praticidade.
Catálogo de Jogos Variado e Empolgante O Betao se destaca por seu portfólio diversificado de jogos online. A plataforma trabalha com provedores renomados do setor, garantindo alta qualidade gráfica, fluidez nas partidas e mecânicas envolventes.
Entre os destaques, estão os jogos de slots, que atraem jogadores pela combinação de simplicidade e emoção. Com temas variados, gráficos vibrantes e bônus interativos, essas máquinas virtuais oferecem diversão contínua e oportunidades de prêmios significativos.
Outra categoria bastante procurada são os jogos de mesa, como roleta, blackjack e bacará. Essas opções são ideais para quem gosta de jogos que exigem estratégia e tomada de decisões rápidas, proporcionando uma experiência desafiadora e recompensadora.
Experiência do Jogador em Primeiro Lugar No Betao, o foco está na satisfação do jogador. A plataforma investe constantemente em melhorias para garantir um ambiente justo, transparente e divertido. Um dos grandes diferenciais é o suporte ao cliente, que funciona 24 horas por dia, todos os dias da semana. Com atendimento em português e canais acessíveis — como chat ao vivo e e-mail —, os usuários recebem ajuda imediata sempre que necessário.
Além disso, o Betao promove promoções regulares, programas de fidelidade e bônus de boas-vindas que valorizam a permanência e o engajamento dos jogadores. Tudo isso contribui para criar uma comunidade ativa e satisfeita.
Segurança e Confiabilidade Segurança é um fator essencial em qualquer plataforma de jogos online, e o Betao leva isso a sério. A empresa utiliza tecnologias de criptografia avançadas para proteger os dados e transações dos usuários, além de operar de forma legalizada, com licenças reconhecidas internacionalmente. Essa transparência aumenta a confiança dos jogadores e garante tranquilidade durante toda a experiência.
Conclusão Com uma combinação de tecnologia de ponta, ampla variedade de jogos, atendimento eficiente e foco total na experiência do usuário, o Betao se consolida como uma das melhores opções para quem busca diversão e entretenimento de qualidade no universo digital. Seja você um novato ou veterano nesse meio, vale a pena explorar tudo o que a plataforma tem a oferecer.
-
 @ 266815e0:6cd408a5
2025-04-15 06:58:14
@ 266815e0:6cd408a5
2025-04-15 06:58:14Its been a little over a year since NIP-90 was written and merged into the nips repo and its been a communication mess.
Every DVM implementation expects the inputs in slightly different formats, returns the results in mostly the same format and there are very few DVM actually running.
NIP-90 is overloaded
Why does a request for text translation and creating bitcoin OP_RETURNs share the same input
itag? and why is there anoutputtag on requests when only one of them will return an output?Each DVM request kind is for requesting completely different types of compute with diffrent input and output requirements, but they are all using the same spec that has 4 different types of inputs (
text,url,event,job) and an undefined number ofoutputtypes.Let me show a few random DVM requests and responses I found on
wss://relay.damus.ioto demonstrate what I mean:This is a request to translate an event to English
json { "kind": 5002, "content": "", "tags": [ // NIP-90 says there can be multiple inputs, so how would a DVM handle translatting multiple events at once? [ "i", "<event-id>", "event" ], [ "param", "language", "en" ], // What other type of output would text translations be? image/jpeg? [ "output", "text/plain" ], // Do we really need to define relays? cant the DVM respond on the relays it saw the request on? [ "relays", "wss://relay.unknown.cloud/", "wss://nos.lol/" ] ] }This is a request to generate text using an LLM model
json { "kind": 5050, // Why is the content empty? wouldn't it be better to have the prompt in the content? "content": "", "tags": [ // Why use an indexable tag? are we ever going to lookup prompts? // Also the type "prompt" isn't in NIP-90, this should probably be "text" [ "i", "What is the capital of France?", "prompt" ], [ "p", "c4878054cff877f694f5abecf18c7450f4b6fdf59e3e9cb3e6505a93c4577db2" ], [ "relays", "wss://relay.primal.net" ] ] }This is a request for content recommendation
json { "kind": 5300, "content": "", "tags": [ // Its fine ignoring this param, but what if the client actually needs exactly 200 "results" [ "param", "max_results", "200" ], // The spec never mentions requesting content for other users. // If a DVM didn't understand this and responded to this request it would provide bad data [ "param", "user", "b22b06b051fd5232966a9344a634d956c3dc33a7f5ecdcad9ed11ddc4120a7f2" ], [ "relays", "wss://relay.primal.net", ], [ "p", "ceb7e7d688e8a704794d5662acb6f18c2455df7481833dd6c384b65252455a95" ] ] }This is a request to create a OP_RETURN message on bitcoin
json { "kind": 5901, // Again why is the content empty when we are sending human readable text? "content": "", "tags": [ // and again, using an indexable tag on an input that will never need to be looked up ["i", "09/01/24 SEC Chairman on the brink of second ETF approval", "text"] ] }My point isn't that these event schema's aren't understandable but why are they using the same schema? each use-case is different but are they all required to use the same
itag format as input and could support all 4 types of inputs.Lack of libraries
With all these different types of inputs, params, and outputs its verify difficult if not impossible to build libraries for DVMs
If a simple text translation request can have an
eventortextas inputs, apayment-requiredstatus at any point in the flow, partial results, or responses from 10+ DVMs whats the best way to build a translation library for other nostr clients to use?And how do I build a DVM framework for the server side that can handle multiple inputs of all four types (
url,text,event,job) and clients are sending all the requests in slightly differently.Supporting payments is impossible
The way NIP-90 is written there isn't much details about payments. only a
payment-requiredstatus and a genericamounttagBut the way things are now every DVM is implementing payments differently. some send a bolt11 invoice, some expect the client to NIP-57 zap the request event (or maybe the status event), and some even ask for a subscription. and we haven't even started implementing NIP-61 nut zaps or cashu A few are even formatting the
amountnumber wrong or denominating it in sats and not mili-satsBuilding a client or a library that can understand and handle all of these payment methods is very difficult. for the DVM server side its worse. A DVM server presumably needs to support all 4+ types of payments if they want to get the most sats for their services and support the most clients.
All of this is made even more complicated by the fact that a DVM can ask for payment at any point during the job process. this makes sense for some types of compute, but for others like translations or user recommendation / search it just makes things even more complicated.
For example, If a client wanted to implement a timeline page that showed the notes of all the pubkeys on a recommended list. what would they do when the selected DVM asks for payment at the start of the job? or at the end? or worse, only provides half the pubkeys and asks for payment for the other half. building a UI that could handle even just two of these possibilities is complicated.
NIP-89 is being abused
NIP-89 is "Recommended Application Handlers" and the way its describe in the nips repo is
a way to discover applications that can handle unknown event-kinds
Not "a way to discover everything"
If I wanted to build an application discovery app to show all the apps that your contacts use and let you discover new apps then it would have to filter out ALL the DVM advertisement events. and that's not just for making requests from relays
If the app shows the user their list of "recommended applications" then it either has to understand that everything in the 5xxx kind range is a DVM and to show that is its own category or show a bunch of unknown "favorites" in the list which might be confusing for the user.
In conclusion
My point in writing this article isn't that the DVMs implementations so far don't work, but that they will never work well because the spec is too broad. even with only a few DVMs running we have already lost interoperability.
I don't want to be completely negative though because some things have worked. the "DVM feeds" work, although they are limited to a single page of results. text / event translations also work well and kind
5970Event PoW delegation could be cool. but if we want interoperability, we are going to need to change a few things with NIP-90I don't think we can (or should) abandon NIP-90 entirely but it would be good to break it up into small NIPs or specs. break each "kind" of DVM request out into its own spec with its own definitions for expected inputs, outputs and flow.
Then if we have simple, clean definitions for each kind of compute we want to distribute. we might actually see markets and services being built and used.
-
 @ c631e267:c2b78d3e
2025-03-21 19:41:50
@ c631e267:c2b78d3e
2025-03-21 19:41:50Wir werden nicht zulassen, dass technisch manches möglich ist, \ aber der Staat es nicht nutzt. \ Angela Merkel
Die Modalverben zu erklären, ist im Deutschunterricht manchmal nicht ganz einfach. Nicht alle Fremdsprachen unterscheiden zum Beispiel bei der Frage nach einer Möglichkeit gleichermaßen zwischen «können» im Sinne von «die Gelegenheit, Kenntnis oder Fähigkeit haben» und «dürfen» als «die Erlaubnis oder Berechtigung haben». Das spanische Wort «poder» etwa steht für beides.
Ebenso ist vielen Schülern auf den ersten Blick nicht recht klar, dass das logische Gegenteil von «müssen» nicht unbedingt «nicht müssen» ist, sondern vielmehr «nicht dürfen». An den Verkehrsschildern lässt sich so etwas meistens recht gut erklären: Manchmal muss man abbiegen, aber manchmal darf man eben nicht.

Dieses Beispiel soll ein wenig die Verwirrungstaktik veranschaulichen, die in der Politik gerne verwendet wird, um unpopuläre oder restriktive Maßnahmen Stück für Stück einzuführen. Zuerst ist etwas einfach innovativ und bringt viele Vorteile. Vor allem ist es freiwillig, jeder kann selber entscheiden, niemand muss mitmachen. Später kann man zunehmend weniger Alternativen wählen, weil sie verschwinden, und irgendwann verwandelt sich alles andere in «nicht dürfen» – die Maßnahme ist obligatorisch.
Um die Durchsetzung derartiger Initiativen strategisch zu unterstützen und nett zu verpacken, gibt es Lobbyisten, gerne auch NGOs genannt. Dass das «NG» am Anfang dieser Abkürzung übersetzt «Nicht-Regierungs-» bedeutet, ist ein Anachronismus. Das war vielleicht früher einmal so, heute ist eher das Gegenteil gemeint.
In unserer modernen Zeit wird enorm viel Lobbyarbeit für die Digitalisierung praktisch sämtlicher Lebensbereiche aufgewendet. Was das auf dem Sektor der Mobilität bedeuten kann, haben wir diese Woche anhand aktueller Entwicklungen in Spanien beleuchtet. Begründet teilweise mit Vorgaben der Europäischen Union arbeitet man dort fleißig an einer «neuen Mobilität», basierend auf «intelligenter» technologischer Infrastruktur. Derartige Anwandlungen wurden auch schon als «Technofeudalismus» angeprangert.
Nationale Zugangspunkte für Mobilitätsdaten im Sinne der EU gibt es nicht nur in allen Mitgliedsländern, sondern auch in der Schweiz und in Großbritannien. Das Vereinigte Königreich beteiligt sich darüber hinaus an anderen EU-Projekten für digitale Überwachungs- und Kontrollmaßnahmen, wie dem biometrischen Identifizierungssystem für «nachhaltigen Verkehr und Tourismus».
Natürlich marschiert auch Deutschland stracks und euphorisch in Richtung digitaler Zukunft. Ohne vernetzte Mobilität und einen «verlässlichen Zugang zu Daten, einschließlich Echtzeitdaten» komme man in der Verkehrsplanung und -steuerung nicht aus, erklärt die Regierung. Der Interessenverband der IT-Dienstleister Bitkom will «die digitale Transformation der deutschen Wirtschaft und Verwaltung vorantreiben». Dazu bewirbt er unter anderem die Konzepte Smart City, Smart Region und Smart Country und behauptet, deutsche Großstädte «setzen bei Mobilität voll auf Digitalisierung».
Es steht zu befürchten, dass das umfassende Sammeln, Verarbeiten und Vernetzen von Daten, das angeblich die Menschen unterstützen soll (und theoretisch ja auch könnte), eher dazu benutzt wird, sie zu kontrollieren und zu manipulieren. Je elektrischer und digitaler unsere Umgebung wird, desto größer sind diese Möglichkeiten. Im Ergebnis könnten solche Prozesse den Bürger nicht nur einschränken oder überflüssig machen, sondern in mancherlei Hinsicht regelrecht abschalten. Eine gesunde Skepsis ist also geboten.
[Titelbild: Pixabay]
Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Er ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:15:58
@ c1e9ab3a:9cb56b43
2025-04-15 04:15:58Spoken by Counselor Elaron T’Saren of Risa to the High Council, Stardate 52874.2
Honored members of the Council,
I bring you greetings from Risa—not the Risa of travel brochures and romantic holo-novels, but the true Risa. The Risa that has endured, adapted, and emerged stronger after each trial. I speak not as a tourist ambassador, but as a Counselor of our oldest institute of philosophy, and as a son of the Ricin tradition.
Today, the specter of the Borg hangs above us. The collective offers no room for diplomacy, no respect for culture, no compromise. We face not mere invaders—but a force that seeks to erase individuality, history, and identity. Some among the Council wonder what Risa—a world of peace—can offer in such a time. I say to you: we can offer the truth about peace.
The Hidden Roots of Our Tranquility
Long ago, before Risa joined the Federation, we too believed that peace could be maintained by disarming the populace, by eliminating even the mention of conflict in our schools. It was called the Great Disarmament. A generation was raised with no understanding of defense, and in time, we paid the price.
We were raided by Orion pirates. Exploited by off-world cartels. Our people were taken, our arts destroyed, our skies blackened. And we learned—too late—that peace without preparedness is only the illusion of safety.
The Birth of Ricin Doctrine
From the ashes of that failure arose the Ricin: scholars, philosophers, warriors of thought and purpose. They taught that peace is not the absence of conflict, but the mastery of it. That the mind and the body must be trained in tandem. That love without strength is a leaf in the wind.
We did not become a militant world. We became a watchful one. Our children were taught martial discipline—not to glorify violence, but to understand it, to confront it, and to defeat it when necessary. They learned meditation alongside hand-to-hand technique, negotiation beside tactical reasoning.
When we joined the Federation, we did so willingly. But let none assume we surrendered our right to defend our way of life.
Why I Speak to You Now
The Borg are not like the Orion Syndicate. They are not opportunistic, or ideological. They are methodical. And they are coming. You cannot debate with them. You cannot delay them. You can only prepare for them.
And yet, I hear murmurs within the halls of the Federation: whispers of abandoning planetary defense training, of downplaying the psychological need for individual and planetary preparedness. I hear the tired lie that “peace will protect us.”
No, Councilors. It is discipline that protects peace.
The Call to Action
I do not come bearing weapons. I come bearing wisdom. Let us take the Risan lesson and apply it across the Federation. Reestablish tactical readiness training in civilian schools. Encourage planetary governments to integrate defense and philosophy, not as contradictions, but as complements.
Let every child of the Federation grow up knowing not just the principles of liberty, but the means to defend them. Let every artist, scientist, and healer stand ready to protect the civilization they help to build.
Let us not wait until the Borg are in our orbit to remember what we must become.
Conclusion
The Borg seek to erase our uniqueness. Let us show them that the Federation is not a fragile collection of planets—but a constellation of cultures bound by a shared resolve.
We do not choose war. But neither do we flee from it.
We are the guardians of Risa’s flame—and we offer our light to the stars.
Thank you.
-
 @ 87122b31:726e2c4c
2025-04-21 02:16:07
@ 87122b31:726e2c4c
2025-04-21 02:16:07BJ66 là một nền tảng kỹ thuật số nổi bật với thiết kế tối giản nhưng đầy tinh tế, hướng đến việc tạo ra một môi trường thân thiện và dễ tiếp cận cho tất cả người dùng. Ngay từ giao diện đầu tiên, BJ66 cho thấy sự chú trọng vào trải nghiệm người dùng khi mọi yếu tố được sắp xếp một cách khoa học và thuận tiện. Các tính năng chính được trình bày rõ ràng, biểu tượng minh họa sắc nét giúp người dùng dễ dàng thao tác, kể cả với những người chưa có nhiều kinh nghiệm sử dụng công nghệ. Sự linh hoạt trong cách bố trí menu, lựa chọn ngôn ngữ và chế độ hiển thị sáng – tối cũng mang đến sự cá nhân hóa tối đa cho mỗi người dùng. Nền tảng này tương thích mượt mà trên nhiều thiết bị khác nhau từ điện thoại thông minh, máy tính bảng đến laptop, tạo điều kiện cho người dùng kết nối mọi lúc mọi nơi mà không bị giới hạn bởi thiết bị hay hệ điều hành.
Không chỉ dừng lại ở thiết kế giao diện đẹp mắt và thân thiện, BJ66 còn ghi điểm mạnh mẽ ở khả năng vận hành ổn định và bảo mật cao. Với hệ thống máy chủ tối ưu và công nghệ xử lý hiện đại, các thao tác trên BJ66 diễn ra nhanh chóng, mượt mà, không bị giật lag hay gián đoạn. Người dùng có thể thực hiện nhiều hoạt động cùng lúc mà không gặp tình trạng chậm trễ hay lỗi hệ thống, đặc biệt quan trọng trong bối cảnh yêu cầu tốc độ và tính liên tục ngày càng cao. Về bảo mật, BJ66 áp dụng các lớp mã hóa tiên tiến và cơ chế xác minh đa yếu tố, bảo vệ thông tin cá nhân và dữ liệu của người dùng khỏi các rủi ro tấn công mạng. Mọi hoạt động đăng nhập, thay đổi cài đặt hay giao dịch đều được theo dõi và ghi nhận để tăng cường tính minh bạch và an toàn. Đội ngũ hỗ trợ kỹ thuật của BJ66 cũng là một điểm cộng lớn, khi họ hoạt động liên tục 24/7 với thái độ chuyên nghiệp, tận tâm và phản hồi nhanh chóng, đảm bảo người dùng luôn có người đồng hành trong suốt quá trình sử dụng.
BJ66 không ngừng đổi mới và phát triển để mang đến một hệ sinh thái số toàn diện, đáp ứng mọi nhu cầu của người dùng hiện đại. Nền tảng tích hợp nhiều tiện ích thông minh được hỗ trợ bởi công nghệ tiên tiến như trí tuệ nhân tạo (AI), cá nhân hóa nội dung và gợi ý dựa trên thói quen sử dụng. Điều này giúp người dùng tiết kiệm thời gian tìm kiếm và truy cập nhanh hơn đến các tính năng mình yêu thích. Ngoài ra, BJ66 thường xuyên cập nhật những cải tiến mới nhằm nâng cao hiệu suất, cải thiện giao diện và tối ưu hóa các chức năng, từ đó duy trì được tính cạnh tranh và giữ chân người dùng trong thời gian dài. Trong thời đại công nghệ số đang phát triển nhanh chóng, BJ66 nổi bật như một lựa chọn đáng tin cậy, nơi người dùng có thể yên tâm trải nghiệm với sự an toàn, thuận tiện và sự thấu hiểu đến từ một nền tảng luôn đặt người dùng ở vị trí trung tâm. Với sự kết hợp giữa công nghệ hiện đại, giao diện thân thiện và cam kết phát triển bền vững, BJ66 không chỉ đơn thuần là một công cụ mà còn là một phần không thể thiếu trong lối sống số hóa ngày nay.
-
 @ 502ab02a:a2860397
2025-04-22 01:16:17
@ 502ab02a:a2860397
2025-04-22 01:16:17ก่อนที่จะมูฟออนจากเทคนิคการสร้าง เรามาดูเรื่องสำคัญครับ
วันที่ไม่มีวัว แต่มีเวย์โปรตีน – เบื้องหลังเทคโนโลยีที่เปลี่ยนถังหมักให้กลายเป็นเต้านมวัว เคยมีคำถามไหมว่า “เวย์โปรตีน” ที่กินตอนออกกำลังกาย หรือโยเกิร์ตถ้วยโปรดที่ซื้อมาจากร้านใกล้บ้าน มันยังมาจากนมวัวอยู่ไหม? ถ้าคำตอบคือ “ไม่” แล้วมันมาจากไหน?
ยินดีต้อนรับสู่โลกของ Perfect Day บริษัทที่บอกว่า "เราสร้างเวย์โปรตีนได้ โดยไม่ต้องใช้วัวเลยแม้แต่นิดเดียว” ฟังดูเหมือนมายากล แต่นี่คือวิทยาศาสตร์ขั้นสูงที่ผูกสูตรไว้กับ DNA, จุลินทรีย์ และการหมักอย่างแยบยล
ขั้นตอนที่ 1: หารหัสโปรตีนจากแม่วัว เริ่มต้นจากคำถามง่าย ๆ ว่า “โปรตีนเวย์ที่อยู่ในน้ำนมวัว คืออะไร?” คำตอบคือ เบต้า-แลคโตโกลบูลิน (Beta-lactoglobulin) ซึ่งเป็นโปรตีนหลักในเวย์ประมาณ 50-55% โดยในธรรมชาติ วัวจะสร้างโปรตีนนี้จาก รหัสพันธุกรรมใน DNA ของมัน Perfect Day จึงไปค้นหา ลำดับเบส (DNA sequence) ของโปรตีนนี้จากฐานข้อมูลวิทยาศาสตร์ชื่อ UniProt (Universal Protein Resource) ซึ่งเก็บรหัสโปรตีนของสิ่งมีชีวิตแทบทุกชนิดไว้ครบถ้วน ได้รหัสมาแล้ว ก็เตรียมเข้าสู่ภารกิจ “หลอกจุลินทรีย์ให้สร้างโปรตีนแทนวัว”
ขั้นตอนที่ 2: สร้างแผ่นดีเอ็นเอสังเคราะห์ รหัส DNA ที่ได้จาก UniProt จะถูกนำไปสร้างเป็น DNA สังเคราะห์ โดยนักชีววิทยาจะออกแบบให้เหมาะสมกับการทำงานในเซลล์ของจุลินทรีย์ ไม่ใช่เซลล์วัว จะเรียกว่านี่คือ “การดัดแปลงบทละครชีวิตของวัว แล้วส่งให้จุลินทรีย์เล่นแทน” ก็ไม่ผิด DNA ที่ออกแบบนี้ มักจะมาพร้อมกับเครื่องมือบางอย่าง เช่น ตัวกระตุ้นการทำงานของยีน (promoter) หรือ ตัวตัดต่อยีน ที่จะทำให้จุลินทรีย์ยอมรับและใช้มันได้อย่างมีประสิทธิภาพ
ขั้นตอนที่ 3: ปลอมตัวแทรกเข้าไปในจุลินทรีย์ จุลินทรีย์ที่ Perfect Day ใช้คือกลุ่มที่เรียกว่า Microflora ซึ่งอาจเป็นยีสต์, เชื้อรา, หรือแบคทีเรียชนิดที่เลี้ยงง่าย แต่มันจะไม่ยอมรับ DNA แปลกปลอมง่าย ๆ ดังนั้นต้องมี “เทคนิคหลอกล่อ” นิดหน่อย เขาจะทำให้ DNA ของจุลินทรีย์ เสียหายตรงจุดหนึ่ง แล้วแอบแนบ DNA ปลอม (ที่มีรหัสโปรตีนของวัว) เข้าไปซ่อมแซมจุดนั้นพอดีเป๊ะ แบบ “จิ๊กซอว์พอดีช่อง” แล้วจุลินทรีย์ก็จะเผลอรับ DNA แปลกปลอมนี้เข้าร่าง เมื่อติดตั้งสำเร็จ มันจะเริ่มแปลรหัสและ “ผลิตโปรตีนเวย์” ออกมาเหมือนกับแม่วัวตัวจริงไม่มีผิด
ขั้นตอนที่ 4: เลี้ยงจุลินทรีย์ในถังหมัก ตอนนี้จุลินทรีย์กลายเป็น “แม่วัวในร่างเซลล์เดียว” แล้ว Perfect Day ก็แค่เลี้ยงมันใน ถังหมักชีวภาพ (fermentor) ที่ควบคุมอุณหภูมิ ค่าความเป็นกรดด่าง อากาศ และใส่น้ำตาลลงไปเป็นอาหาร จุลินทรีย์จะกินน้ำตาลแล้วเปลี่ยนเป็น เวย์โปรตีน ปล่อยออกมานอกเซลล์ จากนั้นก็เก็บเอาน้ำที่มีโปรตีนนี้ ไปผ่านกระบวนการกรอง แยก แปรรูป และทำให้แห้ง เป็นผงเวย์โปรตีน พร้อมใช้ในอาหารหรือเครื่องดื่มต่าง ๆ
ขั้นตอนที่ 5: ตรวจสอบความเหมือนจริง ก่อนนำเวย์โปรตีนที่ได้ไปใช้งาน บริษัทต้อง ตรวจสอบระดับโมเลกุล ว่าโปรตีนที่ได้เหมือนกับของวัวจริง ๆ ไหม? สิ่งที่ต้องดูคือ โครงสร้างโปรตีน: ใช้เทคนิค mass spectrometry ตรวจความแม่นยำระดับกรดอะมิโน พฤติกรรมทางชีวเคมี เช่น ความสามารถในการจับกับน้ำ การเกิดฟอง หรือการละลาย ความปลอดภัย ตรวจหาสารปนเปื้อน สารก่อภูมิแพ้ หรือสารที่ไม่ได้ตั้งใจให้มี Perfect Day เคลมว่าทั้งหมดนี้ปลอดภัย และได้รับการรับรองจาก FDA ว่าเป็น GRAS (Generally Recognized as Safe)
แล้วเราควรรู้สึกยังไง? นี่คือ “นมที่ไม่มีวัว” แต่มีเวย์โปรตีนครบสูตร ทำให้โยเกิร์ต ไอศกรีม และแม้กระทั่งกาแฟลาเต้ที่ไม่มีนมวัว แต่ยังมีฟองนมหนานุ่ม กลายเป็นจริงได้แบบไม่ต้องพึ่งวัวเลยแม้แต่นิดเดียว แต่คำถามที่ลึกกว่านั้นคือ... เรายังได้กินอาหารจากธรรมชาติอยู่หรือเปล่า? หรือกำลังอยู่ในยุคที่ “ชีวิต” ถูกตัดออกจากอาหาร โดยสิ้นเชิง? เทคโนโลยีนี้อาจช่วยโลกในมุมของ ESG แต่สำหรับบางคน มันคือ ทางแยกของความจริงกับของจำลอง คำว่า “Perfect” จึงอาจขึ้นอยู่กับว่า… สมบูรณ์แบบในสายตาใคร?
แล้วคำถามที่ล่องลอยอยู่เสมอคือ เมื่อทางเลือกกลายเป็นทางหลัก แล้วเราจะเหลือทางไหนอีกบ้าง หรือจะเป็น...ทางตัน? #pirateketo #กูต้องรู้มั๊ย #ม้วนหางสิลูก
-
 @ aa8de34f:a6ffe696
2025-03-21 12:08:31
@ aa8de34f:a6ffe696
2025-03-21 12:08:3119. März 2025
🔐 1. SHA-256 is Quantum-Resistant
Bitcoin’s proof-of-work mechanism relies on SHA-256, a hashing algorithm. Even with a powerful quantum computer, SHA-256 remains secure because:
- Quantum computers excel at factoring large numbers (Shor’s Algorithm).
- However, SHA-256 is a one-way function, meaning there's no known quantum algorithm that can efficiently reverse it.
- Grover’s Algorithm (which theoretically speeds up brute force attacks) would still require 2¹²⁸ operations to break SHA-256 – far beyond practical reach.
++++++++++++++++++++++++++++++++++++++++++++++++++
🔑 2. Public Key Vulnerability – But Only If You Reuse Addresses
Bitcoin uses Elliptic Curve Digital Signature Algorithm (ECDSA) to generate keys.
- A quantum computer could use Shor’s Algorithm to break SECP256K1, the curve Bitcoin uses.
- If you never reuse addresses, it is an additional security element
- 🔑 1. Bitcoin Addresses Are NOT Public Keys
Many people assume a Bitcoin address is the public key—this is wrong.
- When you receive Bitcoin, it is sent to a hashed public key (the Bitcoin address).
- The actual public key is never exposed because it is the Bitcoin Adress who addresses the Public Key which never reveals the creation of a public key by a spend
- Bitcoin uses Pay-to-Public-Key-Hash (P2PKH) or newer methods like Pay-to-Witness-Public-Key-Hash (P2WPKH), which add extra layers of security.
🕵️♂️ 2.1 The Public Key Never Appears
- When you send Bitcoin, your wallet creates a digital signature.
- This signature uses the private key to prove ownership.
- The Bitcoin address is revealed and creates the Public Key
- The public key remains hidden inside the Bitcoin script and Merkle tree.
This means: ✔ The public key is never exposed. ✔ Quantum attackers have nothing to target, attacking a Bitcoin Address is a zero value game.
+++++++++++++++++++++++++++++++++++++++++++++++++
🔄 3. Bitcoin Can Upgrade
Even if quantum computers eventually become a real threat:
- Bitcoin developers can upgrade to quantum-safe cryptography (e.g., lattice-based cryptography or post-quantum signatures like Dilithium).
- Bitcoin’s decentralized nature ensures a network-wide soft fork or hard fork could transition to quantum-resistant keys.
++++++++++++++++++++++++++++++++++++++++++++++++++
⏳ 4. The 10-Minute Block Rule as a Security Feature
- Bitcoin’s network operates on a 10-minute block interval, meaning:Even if an attacker had immense computational power (like a quantum computer), they could only attempt an attack every 10 minutes.Unlike traditional encryption, where a hacker could continuously brute-force keys, Bitcoin’s system resets the challenge with every new block.This limits the window of opportunity for quantum attacks.
🎯 5. Quantum Attack Needs to Solve a Block in Real-Time
- A quantum attacker must solve the cryptographic puzzle (Proof of Work) in under 10 minutes.
- The problem? Any slight error changes the hash completely, meaning:If the quantum computer makes a mistake (even 0.0001% probability), the entire attack fails.Quantum decoherence (loss of qubit stability) makes error correction a massive challenge.The computational cost of recovering from an incorrect hash is still incredibly high.
⚡ 6. Network Resilience – Even if a Block Is Hacked
- Even if a quantum computer somehow solved a block instantly:The network would quickly recognize and reject invalid transactions.Other miners would continue mining under normal cryptographic rules.51% Attack? The attacker would need to consistently beat the entire Bitcoin network, which is not sustainable.
🔄 7. The Logarithmic Difficulty Adjustment Neutralizes Threats
- Bitcoin adjusts mining difficulty every 2016 blocks (\~2 weeks).
- If quantum miners appeared and suddenly started solving blocks too quickly, the difficulty would adjust upward, making attacks significantly harder.
- This self-correcting mechanism ensures that even quantum computers wouldn't easily overpower the network.
🔥 Final Verdict: Quantum Computers Are Too Slow for Bitcoin
✔ The 10-minute rule limits attack frequency – quantum computers can’t keep up.
✔ Any slight miscalculation ruins the attack, resetting all progress.
✔ Bitcoin’s difficulty adjustment would react, neutralizing quantum advantages.
Even if quantum computers reach their theoretical potential, Bitcoin’s game theory and design make it incredibly resistant. 🚀
-
 @ c1e9ab3a:9cb56b43
2025-04-14 21:20:08
@ c1e9ab3a:9cb56b43
2025-04-14 21:20:08In an age where culture often precedes policy, a subtle yet potent mechanism may be at play in the shaping of American perspectives on gun ownership. Rather than directly challenging the Second Amendment through legislation alone, a more insidious strategy may involve reshaping the cultural and social norms surrounding firearms—by conditioning the population, starting at its most impressionable point: the public school system.
The Cultural Lever of Language
Unlike Orwell's 1984, where language is controlled by removing words from the lexicon, this modern approach may hinge instead on instilling fear around specific words or topics—guns, firearms, and self-defense among them. The goal is not to erase the language but to embed a taboo so deep that people voluntarily avoid these terms out of social self-preservation. Children, teachers, and parents begin to internalize a fear of even mentioning weapons, not because the words are illegal, but because the cultural consequences are severe.
The Role of Teachers in Social Programming
Teachers, particularly in primary and middle schools, serve not only as educational authorities but also as social regulators. The frequent argument against homeschooling—that children will not be "properly socialized"—reveals an implicit understanding that schools play a critical role in setting behavioral norms. Children learn what is acceptable not just academically but socially. Rules, discipline, and behavioral expectations are laid down by teachers, often reinforced through peer pressure and institutional authority.
This places teachers in a unique position of influence. If fear is instilled in these educators—fear that one of their students could become the next school shooter—their response is likely to lean toward overcorrection. That overcorrection may manifest as a total intolerance for any conversation about weapons, regardless of the context. Innocent remarks or imaginative stories from young children are interpreted as red flags, triggering intervention from administrators and warnings to parents.
Fear as a Policy Catalyst
School shootings, such as the one at Columbine, serve as the fulcrum for this fear-based conditioning. Each highly publicized tragedy becomes a national spectacle, not only for mourning but also for cementing the idea that any child could become a threat. Media cycles perpetuate this narrative with relentless coverage and emotional appeals, ensuring that each incident becomes embedded in the public consciousness.
The side effect of this focus is the generation of copycat behavior, which, in turn, justifies further media attention and tighter controls. Schools install security systems, metal detectors, and armed guards—not simply to stop violence, but to serve as a daily reminder to children and staff alike: guns are dangerous, ubiquitous, and potentially present at any moment. This daily ritual reinforces the idea that the very discussion of firearms is a precursor to violence.
Policy and Practice: The Zero-Tolerance Feedback Loop
Federal and district-level policies begin to reflect this cultural shift. A child mentioning a gun in class—even in a non-threatening or imaginative context—is flagged for intervention. Zero-tolerance rules leave no room for context or intent. Teachers and administrators, fearing for their careers or safety, comply eagerly with these guidelines, interpreting them as moral obligations rather than bureaucratic policies.
The result is a generation of students conditioned to associate firearms with social ostracism, disciplinary action, and latent danger. The Second Amendment, once seen as a cultural cornerstone of American liberty and self-reliance, is transformed into an artifact of suspicion and anxiety.
Long-Term Consequences: A Nation Re-Socialized
Over time, this fear-based reshaping of discourse creates adults who not only avoid discussing guns but view them as morally reprehensible. Their aversion is not grounded in legal logic or political philosophy, but in deeply embedded emotional programming begun in early childhood. The cultural weight against firearms becomes so great that even those inclined to support gun rights feel the need to self-censor.
As fewer people grow up discussing, learning about, or responsibly handling firearms, the social understanding of the Second Amendment erodes. Without cultural reinforcement, its value becomes abstract and its defenders marginalized. In this way, the right to bear arms is not abolished by law—it is dismantled by language, fear, and the subtle recalibration of social norms.
Conclusion
This theoretical strategy does not require a single change to the Constitution. It relies instead on the long game of cultural transformation, beginning with the youngest minds and reinforced by fear-driven policy and media narratives. The outcome is a society that views the Second Amendment not as a safeguard of liberty, but as an anachronism too dangerous to mention.
By controlling the language through social consequences and fear, a nation can be taught not just to disarm, but to believe it chose to do so freely. That, perhaps, is the most powerful form of control of all.
-
 @ 846ebf79:fe4e39a4
2025-04-14 12:35:54
@ 846ebf79:fe4e39a4
2025-04-14 12:35:54The next iteration is coming
We're busy racing to the finish line, for the #Alexandria Gutenberg beta. Then we can get the bug hunt done, release v0.1.0, and immediately start producing the first iteration of the Euler (v0.2.0) edition.
While we continue to work on fixing the performance issues and smooth rendering on the Reading View, we've gone ahead and added some new features and apps, which will be rolled-out soon.
The biggest projects this iteration have been:
- the HTTP API for the #Realy relay from nostr:npub1fjqqy4a93z5zsjwsfxqhc2764kvykfdyttvldkkkdera8dr78vhsmmleku,
- implementation of a publication tree structure by nostr:npub1wqfzz2p880wq0tumuae9lfwyhs8uz35xd0kr34zrvrwyh3kvrzuskcqsyn,
- and the Great DevOps Migration of 2025 from the ever-industrious Mr. nostr:npub1qdjn8j4gwgmkj3k5un775nq6q3q7mguv5tvajstmkdsqdja2havq03fqm7.
All are backend-y projects and have caused a major shift in process and product, on the development team's side, even if they're still largely invisible to users.
Another important, but invisible-to-you change is that nostr:npub1ecdlntvjzexlyfale2egzvvncc8tgqsaxkl5hw7xlgjv2cxs705s9qs735 has implemented the core bech32 functionality (and the associated tests) in C/C++, for the #Aedile NDK.
On the frontend:
nostr:npub1636uujeewag8zv8593lcvdrwlymgqre6uax4anuq3y5qehqey05sl8qpl4 is currently working on the blog-specific Reading View, which allows for multi-npub or topical blogging, by using the 30040 index as a "folder", joining the various 30041 articles into different blogs. She has also started experimenting with categorization and columns for the landing page.


nostr:npub1l5sga6xg72phsz5422ykujprejwud075ggrr3z2hwyrfgr7eylqstegx9z revamped the product information pages, so that there is now a Contact page (including the ability to submit a Nostr issue) and an About page (with more product information, the build version displayed, and a live #GitCitadel feed).



We have also allowed for discrete headings (headers that aren't section headings, akin to the headers in Markdown). Discrete headings are formatted, but not added to the ToC and do not result in a section split by Asciidoc processors.
We have added OpenGraph metadata, so that hyperlinks to Alexandria publications, and other events, display prettily in other apps. And we fixed some bugs.
The Visualisation view has been updated and bug-fixed, to make the cards human-readable and closeable, and to add hyperlinks to the events to the card-titles.

We have added support for the display of individual wiki pages and the integration of them into 30040 publications. (This is an important feature for scientists and other nonfiction writers.)

We prettified the event json modal, so that it's easier to read and copy-paste out of.

The index card details have been expanded and the menus on the landing page have been revamped and expanded. Design and style has been improved, overall.

Project management is very busy
Our scientific adviser nostr:npub1m3xdppkd0njmrqe2ma8a6ys39zvgp5k8u22mev8xsnqp4nh80srqhqa5sf is working on the Euler plans for integrating features important for medical researchers and other scientists, which have been put on the fast track.
Next up are:
- a return of the Table of Contents
- kind 1111 comments, highlights, likes
- a prototype social feed for wss://theforest.nostr1.com, including long-form articles and Markdown rendering
- compose and edit of publications
- a search field
- the expansion of the relay set with the new relays from nostr:npub12262qa4uhw7u8gdwlgmntqtv7aye8vdcmvszkqwgs0zchel6mz7s6cgrkj, including some cool premium features
- full wiki functionality and disambiguation pages for replaceable events with overlapping d-tags
- a web app for mass-uploading and auto-converting PDFs to 30040/41 Asciidoc events, that will run on Realy, and be a service free for our premium relay subscribers
- ability to subscribe to the forest with a premium status
- the book upload CLI has been renamed and reworked into the Sybil Test Utility and that will get a major release, covering all the events and functionality needed to test Euler
- the #GitRepublic public git server project
- ....and much more.
Thank you for reading and may your morning be good.
-
 @ 87122b31:726e2c4c
2025-04-21 02:15:16
@ 87122b31:726e2c4c
2025-04-21 02:15:16WIN1 là nền tảng công nghệ hiện đại được xây dựng với mục tiêu cung cấp một không gian trực tuyến toàn diện, nơi người dùng có thể tương tác, trải nghiệm và kết nối một cách mượt mà, tiện lợi. Sở hữu giao diện trực quan, tối ưu hóa cho cả người mới bắt đầu và người dùng thành thạo, WIN1 tạo ra cảm giác thân thiện ngay từ lần đầu truy cập. Các yếu tố bố cục được sắp xếp hợp lý, màu sắc hài hòa và các biểu tượng dễ hiểu giúp việc điều hướng trở nên dễ dàng trên mọi loại thiết bị – từ điện thoại thông minh, máy tính bảng đến máy tính cá nhân. Không dừng lại ở đó, WIN1 còn cho phép người dùng tùy chỉnh không gian trải nghiệm cá nhân với các chế độ giao diện sáng – tối, ngôn ngữ linh hoạt, và các thiết lập cá nhân hóa dựa trên thói quen sử dụng. Nhờ vậy, người dùng luôn cảm thấy sự chủ động trong mọi tương tác với nền tảng.
Điểm nổi bật khác giúp WIN1 khẳng định vị thế là khả năng vận hành ổn định và bảo mật cao. Hệ thống hoạt động nhanh chóng, ổn định và có khả năng xử lý đồng thời nhiều truy cập mà không gây gián đoạn. Điều này đặc biệt quan trọng trong bối cảnh người dùng ngày càng có xu hướng sử dụng nhiều thiết bị cùng lúc để phục vụ nhu cầu công việc và giải trí. WIN1 áp dụng các công nghệ mã hóa tiên tiến và xác thực bảo mật nhiều lớp, đảm bảo dữ liệu người dùng luôn được bảo vệ nghiêm ngặt. Ngoài ra, nền tảng còn thường xuyên cập nhật và kiểm tra hệ thống để phát hiện, khắc phục kịp thời các rủi ro tiềm ẩn. Bên cạnh yếu tố kỹ thuật, WIN1 còn xây dựng đội ngũ chăm sóc khách hàng tận tâm, hoạt động 24/7, sẵn sàng hỗ trợ người dùng trong mọi tình huống từ những thắc mắc đơn giản đến các vấn đề kỹ thuật phức tạp, giúp người dùng an tâm tuyệt đối trong suốt hành trình trải nghiệm.
Không ngừng đổi mới và hoàn thiện, WIN1 liên tục tích hợp các xu hướng công nghệ tiên tiến nhằm tối ưu hóa hiệu suất và nâng cao trải nghiệm người dùng. Nền tảng này không chỉ đơn thuần là công cụ kết nối, mà còn hướng đến xây dựng một hệ sinh thái số hóa toàn diện, trong đó người dùng có thể tận hưởng sự tương tác thông minh nhờ vào các tiện ích được tích hợp như trí tuệ nhân tạo (AI), hệ thống gợi ý cá nhân hóa và các tính năng tự động hóa thông minh. Các phân tích dữ liệu từ hành vi người dùng được sử dụng một cách linh hoạt để đưa ra đề xuất phù hợp, giúp mỗi lần truy cập vào WIN1 đều mang lại cảm giác mới mẻ và đúng nhu cầu. Đây chính là minh chứng cho định hướng phát triển dài hạn, bền vững của WIN1: luôn lấy người dùng làm trung tâm, không ngừng nâng cấp công nghệ, đồng thời đảm bảo sự ổn định và an toàn trong suốt quá trình sử dụng. Trong thời đại mà công nghệ trở thành một phần không thể thiếu trong cuộc sống, WIN1 là lựa chọn lý tưởng dành cho những ai đang tìm kiếm một nền tảng đáng tin cậy, dễ sử dụng và luôn đổi mới để bắt kịp xu hướng toàn cầu.
-
 @ 87122b31:726e2c4c
2025-04-21 02:14:24
@ 87122b31:726e2c4c
2025-04-21 02:14:24Betwinner mang đến một nền tảng số hiện đại được thiết kế để phục vụ đa dạng đối tượng người dùng trong thời đại công nghệ ngày càng phát triển. Từ giao diện thân thiện đến khả năng tùy biến linh hoạt, nền tảng này luôn đặt sự thuận tiện và trải nghiệm người dùng lên hàng đầu. Ngay từ lần đầu truy cập, bạn sẽ cảm nhận được tốc độ phản hồi nhanh chóng, giao diện mượt mà và bố cục dễ hiểu – những yếu tố giúp Betwinner trở nên khác biệt so với nhiều nền tảng khác. Sự tương thích đa thiết bị, từ điện thoại thông minh đến máy tính bàn, giúp người dùng dễ dàng duy trì kết nối và thao tác linh hoạt trong mọi hoàn cảnh. Với việc tích hợp các tính năng thông minh và các lựa chọn cá nhân hóa như chế độ nền tối, ngôn ngữ hiển thị và điều chỉnh bố cục theo thói quen sử dụng, Betwinner mang lại cảm giác sử dụng cá nhân hóa rõ rệt và gần gũi.
Không chỉ gây ấn tượng với thiết kế và hiệu năng vận hành, Betwinner còn chú trọng vào bảo mật và sự an tâm của người dùng. Nền tảng này sử dụng công nghệ mã hóa tiên tiến để bảo vệ thông tin cá nhân và dữ liệu trong quá trình sử dụng, kết hợp cùng cơ chế xác thực đa lớp để ngăn chặn các truy cập trái phép. Điều này đặc biệt quan trọng khi người dùng ngày càng có yêu cầu cao về tính bảo mật trong các giao dịch và thông tin cá nhân. Ngoài ra, Betwinner còn trang bị hệ thống hỗ trợ khách hàng 24/7, sẵn sàng giải đáp mọi thắc mắc, xử lý vấn đề nhanh chóng và đảm bảo người dùng luôn nhận được sự hỗ trợ cần thiết khi gặp phải bất kỳ sự cố nào. Việc cập nhật hệ thống và cải tiến tính năng diễn ra thường xuyên nhằm tối ưu hóa hiệu năng và tăng cường sự ổn định trong mọi hoạt động, từ những thao tác cơ bản cho đến các chức năng chuyên sâu hơn.
Không dừng lại ở việc cung cấp một nền tảng số tiện lợi, Betwinner còn hướng đến xây dựng một hệ sinh thái kết nối toàn diện. Với khả năng tích hợp nhanh các công nghệ mới như trí tuệ nhân tạo (AI), học máy (machine learning), cũng như tự động hóa quy trình trải nghiệm, nền tảng này đang tạo ra những thay đổi đáng kể trong cách người dùng tiếp cận và tương tác với không gian số. Mọi dữ liệu sử dụng đều được phân tích để từ đó cung cấp các đề xuất thông minh, giúp tiết kiệm thời gian và tối ưu hóa trải nghiệm cá nhân. Không chỉ là nơi cung cấp công cụ, Betwinner còn là điểm đến cho những ai muốn trải nghiệm môi trường công nghệ hiện đại, nơi mỗi hành động đều được hỗ trợ bởi nền tảng kỹ thuật mạnh mẽ và tư duy lấy người dùng làm trọng tâm. Trong bối cảnh xu hướng chuyển đổi số ngày càng mạnh mẽ, Betwinner đã và đang khẳng định vị thế là một trong những lựa chọn hàng đầu dành cho những ai đang tìm kiếm sự tiện nghi, bảo mật và sự chủ động trong trải nghiệm số hóa.
-
 @ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48
@ 04cb16e4:2ec3e5d5
2025-04-12 19:21:48Meine erste "Begegnung" mit Ulrike hatte ich am 21. März 2022 - dank Amazon konnte ich das Ereignis noch exakt nachvollziehen. Es war eines meiner ersten (Lockdown) kritischen Bücher, die ich in dieser Zeit in die Hände bekam - noch nach Thomas Röper (das war mein Einstieg) aber vor Daniele Ganser. Insofern war es mir möglich, das, was dann folgte für die Autorin, live und in Farbe mit zu verfolgen:
"Wer sich in die Öffentlichkeit traut, kann sich dort ganz schnell eine blutige Nase holen. Dieselben Medien, die eine Person heute glorifizieren, stellen sie morgen an den Pranger. Sie verteilen und entziehen Reputation, fördern und zerstören Karrieren. Das Medium selbst bleibt jedoch immer auf der Siegerseite. Die Gesetze von Marktorientierung und zynisch-ideologisierter Machtausübung gelten für Rundfunk und Fernsehen ebenso wie für die Printmedien - von RTL bis ARD und ZDF, von der BILD über die taz bis zur ZEIT.
»Das Phänomen Guérot« legt genau diesen Vorgang detailliert offen: Der MENSCH Ulrike Guérot ist in der Realität nicht die dämonische Figur, als die sie hingestellt worden ist. Aber an ihr kristallisiert sich genau dieser menschenverachtende Prozess heraus, der bis heute andauert."
Im Herbst 2022 habe ich durch den ersten Vortrag von Daniele Ganser in Falkensee nicht nur Zugang zu einer für mich neuen und anderen Welt bekommen, ab da hat sich eigentlich auch für mich mein Leben komplett auf den Kopf gestellt. Die Weichen wurden zwar schon vorher gestellt, aber nun war es endgültig und es gab kein zurück mehr. Die Planung für das erste Symposium Falkensee war in meinem Kopf geboren und die MenschheitsFamilie entstand als Ort, der virtuell das vereinen sollte, was Daniele an Spiritualität, Menschlichkeit und Friedenswillen in mir freigesetzt hat. Es war sozusagen eine Energie, die nun stetig floß und einen Trichter gefunden hat, in dem sie wirksam werden und sich entfalten konnte. Insofern haben wir auch etwas gemeinsam - Ulrike und ich. Wir sind zu der Zeit auf einen Zug aufgesprungen, der unser Leben veränderte - der uns zwang, alte Wege zu verlassen und neue Wege zu beschreiten. Sowohl beruflich, als auch privat. Und auch das canceln und entfernt werden ist eine Erfahrung, die wir beide teilen. Vielleicht war es deswegen mein erster Gedanke im Herbst 2022, Ulrike Guérot zu meinem 1. Symposium nach Falkensee einzuladen. Das es dann erst beim 2. Anlauf wirklich geklappt hat, hatte auch mit den Höhen und Tiefen des Lebens in dieser Zeit zu tun gehabt.
Nun ist sie zum 2. Mal dabei - denn wer könnte das Thema "Europa" bei einem so wichtigen und hochaktuellen Thema besser vertreten und beleuchten als Ulrike Guérot? Es geht um Geschichte, es geht um Nationalitäten, es geht um Gemeinsamkeiten und um das, was uns hier im Herzen zusammenhält, was unsere Ziele und unsere Befindlichkeiten sind, es geht um Verantwortung und es geht vor allen Dingen um Frieden! Denn dafür steht Europa - für einen Kontinent, der es geschafft hat, trotz aller Gegensätze und Konflikte, die in Jahrhunderten kriegerisch aufgetragen wurden, eine neuen und besonderen Frieden zu finden und zu installieren:
"Völkerrechtlich legt der Westfälische Frieden den oder zumindest einen Grundstein für ein modernes Prinzip: Die Gleichberechtigung souveräner Staaten, unabhängig von ihrer Macht und Größe. Noch heute spricht die Politikwissenschaft, insbesondere die realistische Schule (Henry Kissinger), deshalb vom „Westphalian System“. Durch die Garantien der großen europäischen Mächte erweist sich dieser Frieden als stabilisierendes Element für die weitere Entwicklung in Europa. Noch bis zum Ende des 18. Jahrhunderts wird er immer wieder als Referenz für nachfolgende Friedensschlüsse herangezogen."
Es ging damals um viel und es geht heute um das Überleben auf einem Kontinent, der es eigentlich besser wissen sollte. Wir dürfen gespannt sein, was wir in diesem Vortrag von Ulrike auf dem Symposium Falkensee am 27. April 2025 für Lösungen finden, um wieder zu einer Ordnung und zu einem System der friedlichen Koexistenz zurückfinden zu können, ohne schwarz und weiß und mit all den Facetten, die das Leben uns so bietet:
"Es ging nicht mehr um das Ausfechten religiöser Wahrheiten, sondern um geregelte Verfahren, die es möglich machten, mit konkurrierenden religiösen Wahrheiten, die nach wie vor nebeneinander und unversöhnlich bestanden, auf friedliche Weise umzugehen. Deutlich wurde das nicht zuletzt, als der Papst in einer offiziellen Note scharf gegen den Friedensschluss protestierte, weil er die Rechte der katholischen Seite leichtfertig aufgegeben sah. Die katholischen Beteiligten des Abkommens hielt dies nicht von der Unterzeichnung ab - ein religiöser Schiedsrichter wurde in Sachen Krieg und Frieden nicht mehr akzeptiert."
-
 @ df478568:2a951e67
2025-04-21 23:36:17
@ df478568:2a951e67
2025-04-21 23:36:17Testing
-
 @ e39d100f:d27602e5
2025-04-21 02:14:21
@ e39d100f:d27602e5
2025-04-21 02:14:21O mundo do entretenimento digital não para de crescer, e a 5588bet surge como uma plataforma moderna, segura e completa para quem busca diversão, emoção e oportunidades reais de ganhar prêmios. Com uma interface amigável, suporte eficiente e uma grande variedade de jogos, a 5588bet rapidamente conquistou espaço entre os jogadores brasileiros.
A primeira impressão ao acessar a 5588bet é a de um ambiente profissional e bem estruturado. A navegação é fluida, tanto no computador quanto em dispositivos móveis, permitindo que o usuário explore todas as funcionalidades com facilidade. A plataforma foi desenvolvida pensando na experiência do usuário, oferecendo menus intuitivos, design atrativo e carregamento rápido das páginas.
A segurança é uma prioridade para a 5588bet . Os dados dos jogadores são protegidos com tecnologia de criptografia de ponta, garantindo que todas as transações financeiras e informações pessoais estejam resguardadas. Além disso, a plataforma conta com uma equipe de suporte técnico disponível 24 horas por dia, pronta para auxiliar em qualquer necessidade.
Variedade de Jogos para Todos os Perfis Um dos grandes diferenciais da 5588bet é a diversidade de jogos disponíveis. A plataforma oferece títulos para todos os gostos, desde os clássicos até os mais modernos, todos com gráficos impressionantes e excelente jogabilidade.
Entre os destaques estão os jogos de roleta, bacará, pôquer, além de uma enorme seleção de slots com diferentes temáticas e mecânicas de bônus. Os jogadores podem explorar aventuras inspiradas em mitologia, filmes, frutas clássicas e muito mais. Muitos desses jogos são desenvolvidos por provedores renomados internacionalmente, garantindo qualidade e inovação a cada partida.
Além disso, para quem gosta de emoção em tempo real, a plataforma conta com mesas interativas com apresentadores ao vivo, proporcionando uma experiência imersiva que simula a sensação de estar em um ambiente físico de jogos, tudo isso com a comodidade de estar em casa ou em qualquer lugar.
Experiência do Jogador em Primeiro Lugar A 5588bet entende que a satisfação do jogador vai além da variedade de jogos. Por isso, investe em uma experiência completa. O processo de registro é rápido e simples, permitindo que novos usuários comecem a jogar em poucos minutos. Os métodos de pagamento são diversificados e incluem as principais carteiras digitais e bancos brasileiros, facilitando depósitos e saques.
A plataforma também oferece promoções atrativas para novos usuários e campanhas frequentes para jogadores fiéis. Bônus de boas-vindas, giros gratuitos, cashback e torneios especiais são algumas das formas que a 5588bet utiliza para valorizar seus usuários e tornar cada visita ainda mais interessante.
Outro ponto importante é a transparência. As regras de cada jogo, promoções e procedimentos financeiros são claramente explicados, dando ao jogador confiança e controle total sobre suas escolhas dentro da plataforma.
Conclusão A 5588bet se destaca como uma plataforma inovadora, segura e repleta de opções para quem busca entretenimento online de qualidade. Com jogos envolventes, suporte eficiente e uma experiência focada no usuário, ela se consolida como uma das melhores escolhas para jogadores brasileiros. Se você está em busca de diversão com emoção e recompensas, a 5588bet é o destino ideal.
-
 @ d41bf82f:ed90d888
2025-04-21 23:18:20
@ d41bf82f:ed90d888
2025-04-21 23:18:20"ประวัติศาสตร์ก็เฉกเช่นธรรมชาติ — การเกิดและการตายล้วนดำเนินไปอย่างสมดุล" -โยฮัน ฮุยซิงกา3
การเสื่อมถอยของโลกยุคใหม่
พวกเรากำลังอยู่ในช่วงปลายของสิ่งที่เรียกว่า “ยุคใหม่” — ระบบโลกที่ถูกจัดระเบียบผ่านรัฐชาติอันรวมศูนย์ ซึ่งเคยพาเราผ่านยุคอุตสาหกรรม สงครามโลก และการสร้างโครงสร้างทางสังคมที่เข้มแข็งด้วยภาษี สวัสดิการ และระบบราชการ แต่ยุคนี้กำลังเคลื่อนเข้าสู่ฉากสุดท้ายของมันอย่างเงียบงัน โดยไม่มีใครในกระแสหลักพูดถึงอย่างจริงจัง และสิ่งที่กำลังมาแทนที่ก็จะแตกต่างอย่างสิ้นเชิงในเชิงคุณภาพจากโลกที่เราคุ้นเคย
เช่นเดียวกับที่สังคมเกษตรกรรมเคยมาแทนที่สังคมสัตว์-หาของป่า และระบบอุตสาหกรรมเคยมาแทนระบบศักดินา สังคมใหม่ที่กำลังปรากฏขึ้นจะเป็นการเปลี่ยนผ่านครั้งใหญ่ โดยในยุคใหม่นี้ “ประสิทธิภาพ” จะไม่ผูกติดกับ “ขนาด” อีกต่อไป อำนาจแบบรวมศูนย์ของรัฐจะถูกสั่นคลอน และระบบใหม่จะเกิดขึ้นซึ่งเล็กกว่า คล่องตัวกว่า และยากที่รัฐแบบเดิมจะควบคุม
นักประวัติศาสตร์ในอนาคตอาจมองว่าการล่มสลายของสหภาพโซเวียตในปี 1991 หรือการพังทลายของกำแพงเบอร์ลินในปี 1989 คือจุดสิ้นสุดของยุคสมัยนี้ และเปิดฉากสู่สิ่งใหม่ — บ้างเรียกมันว่ายุคหลังสมัยใหม่ บ้างว่าโลกไซเบอร์ หรือสังคมสารสนเทศ ไม่ว่าจะตั้งชื่ออย่างไร สิ่งที่ทุกคนยอมรับคือมันคือ "โลกใบใหม่" ที่แตกต่างอย่างถึงแก่นจากโลกเดิม
ความเข้าใจของมนุษย์ต่อการเปลี่ยนแปลงใหญ่ระดับอารยธรรมมักมาช้า เพราะขาดกรอบความคิดและภาษาที่จะมองเห็นมันได้ในขณะที่มันเกิดขึ้นจริง ยกตัวอย่างเช่น ไม่มีใครในยุคศักดินาคิดว่าตนเองอยู่ใน “ยุคกลาง” จนกระทั่งยุคใหม่เข้ามาเปรียบเทียบ ในทำนองเดียวกัน พวกเราทุกวันนี้ก็อาจไม่รู้ตัวว่าเรากำลังอยู่ในช่วงสิ้นสุดของยุคหนึ่ง และจุดเริ่มต้นของอีกยุคหนึ่ง
ระบบสังคมใดก็ตามมักฝังข้อสันนิษฐานโดยปริยายว่าระบบของตนคือสิ่งสูงสุด เป็นสิ่งที่ไม่มีวันเปลี่ยน และไม่ควรถูกตั้งคำถาม การตั้งคำถามถึงความอยู่รอดของระบบ จึงเป็นเรื่องที่ถูกกีดกันโดยไม่รู้ตัว เพราะยิ่งระบบใกล้ล่มสลายเท่าไร มันก็ยิ่งต้องพยายามปกปิดไม่ให้ใครรับรู้ถึงความเปราะบางของมัน
ตัวอย่างจากประวัติศาสตร์เช่น การล่มสลายของจักรวรรดิโรมันใน ค.ศ. 476 ก็ไม่ได้รับการรับรู้ว่าเป็น “จุดจบ” ในเวลานั้น แม้เมื่อจักรพรรดิองค์สุดท้าย(โรมุลุส เอากุสตุส)ถูกปลด แต่ผู้คนและโครงสร้างเดิมของโรมันก็ยังคงแสร้งทำว่าทุกอย่างดำเนินไปตามปกติ รูปแบบของรัฐบาลเก่ายังคงถูกรักษาไว้ พิธีกรรมในระบบเดิมยังคงจัดขึ้น วุฒิสภายังคงประชุม กงสุลยังได้รับการแต่งตั้ง และระบบราชการก็ยังคงอยู่เกือบครบถ้วน พวกป่าเถื่อนที่เข้ามาปกครองก็ยังแสดงตนว่าให้ความเคารพต่อจักรวรรดิไบแซนไทน์และกฎหมายโรมัน ศาสนาคริสต์ยังคงดำรงเป็นศาสนาประจำรัฐ เครื่องราชสัญลักษณ์ยังถูกใช้ในพิธีสาธารณะ ทั้งหมดนี้เป็นฉากหน้าของการพยายามรักษาภาพความต่อเนื่องในขณะที่แก่นของอำนาจได้เปลี่ยนไปแล้วโดยสิ้นเชิง
ประวัติศาสตร์ช่วงนี้สอนให้เห็นว่า การเปลี่ยนแปลงใหญ่ในระดับอารยธรรมมักถูกซ่อนเร้นอยู่ภายใต้ความเฉื่อยของสังคมที่ไม่ยอมรับความเป็นจริง คนในยุคนั้นไม่ได้รู้สึกว่าโรมล่มสลายไปแล้ว พวกเขาเพียงรู้สึกว่าชีวิตยังดำเนินต่อไปได้ แม้ภายใต้ระเบียบใหม่ที่ซ้อนทับเข้ามาโดยไม่ได้ประกาศตนอย่างเป็นทางการ ความเปลี่ยนแปลงที่แท้จริงจึงไม่ใช่เหตุการณ์ที่เกิดขึ้นในวันใดวันหนึ่ง แต่เป็นกระบวนการค่อยเป็นค่อยไปที่อาศัยแรงเฉื่อยของความเชื่อเก่าว่าสิ่งต่างๆ “ยังเหมือนเดิม”
ผู้เขียนใช้ตัวอย่างนี้เพื่อสะท้อนมาสู่โลกปัจจุบันว่า แม้ตัวอย่างโรมจะดูไกลตัว แต่ก็มีลักษณะใกล้เคียงกับสิ่งที่เรากำลังเผชิญอยู่ ระบบรัฐชาติสมัยใหม่ก็อาจกำลังเข้าสู่ภาวะเสื่อมถอยโดยที่คนส่วนใหญ่ยังไม่รู้ตัวเช่นเดียวกัน หนังสือเล่มนี้จึงไม่ได้ตั้งต้นจากการคาดเดาอนาคตอย่างลอย ๆ หากแต่เสนอว่า เราจะเข้าใจอนาคตได้ดีขึ้น ถ้าเริ่มจากการเรียนรู้กระบวนการเปลี่ยนผ่านในอดีต โดยเฉพาะพลวัตทางการเมืองและตรรกะของอำนาจ
จุดเปลี่ยนของโรมันไม่เพียงแต่แสดงให้เห็นการล่มสลายของรัฐรวมศูนย์ แต่ยังเผยให้เห็นว่าการล่มสลายนั้นสามารถเปิดทางให้กิจกรรมทางเศรษฐกิจในท้องถิ่นเบ่งบานขึ้นได้ ในยุคของเรา แม้สาเหตุจะต่างกัน — โรมล่มเพราะขยายเกินตัว เศรษฐกิจเกษตรกรรมไม่สามารถรองรับภาระรัฐ การเก็บภาษีที่หนักหนาและทหารที่ใช้อำนาจในทางมิชอบ — แต่สิ่งที่คล้ายกันคือ การไม่ยอมรับต่อการเปลี่ยนแปลงที่กำลังก่อตัว
เรายังเห็นการเปรียบเทียบถึงผลกระทบจากโรคระบาดในอดีต เช่น โรคฝีดาษที่ทำให้โรมอ่อนแอลง เช่นเดียวกับความกังวลเรื่องไวรัสกลายพันธุ์ในยุคปัจจุบัน ที่บ่งชี้ถึงความเปราะบางของโครงสร้างสังคม แม้รูปแบบของภัยคุกคามจะต่างกัน แต่สิ่งที่เหมือนกันคือ “ความไม่พร้อมของระบบ” ที่จะรับมือกับความเปลี่ยนแปลงใหญ่
แต่สิ่งสำคัญที่สุดที่ผู้เขียนต้องการชี้ ไม่ใช่แค่สาเหตุของการล่มสลาย แต่คือความจริงที่ว่า ผู้คนในยุคนั้น “ไม่เห็น” ว่าตนเองอยู่ในจุดเปลี่ยน เพราะแรงเฉื่อยทางความคิดและการเมืองทำให้พวกเขายึดมั่นในสิ่งที่เคยรู้จัก โดยไม่รู้เลยว่าโลกได้เคลื่อนเข้าสู่ระยะใหม่แล้ว และเราทุกวันนี้ก็อาจกำลังทำเช่นเดียวกัน
เรากำลังอยู่ในช่วงเวลาที่ไมโครโปรเซสเซอร์ เทคโนโลยีดิจิทัล และโครงสร้างไร้ศูนย์กลางจะเปลี่ยนกฎเกณฑ์ของอำนาจอย่างรุนแรง แต่ผู้คนกลับพยายามตีความสิ่งเหล่านี้ผ่านเลนส์ของโครงสร้างอุตสาหกรรมแบบเดิม ซึ่งอาจทำให้พลาดโอกาสที่จะเข้าใจการเปลี่ยนแปลงที่แท้จริง
ผู้เขียนเตือนว่าแม้บางหนังสือว่าด้วยอนาคตจะเต็มไปด้วยข้อมูล แต่กลับพาเราเข้าใจผิด เพราะยังยึดติดอยู่กับกรอบคิดเดิม เช่น การเชื่อว่ามนุษย์สามารถควบคุมทิศทางประวัติศาสตร์ได้เสมอ ทั้งที่ในความจริงแล้ว ปัจจัยที่ขับเคลื่อนการเปลี่ยนแปลงทางประวัติศาสตร์นั้น มักเป็นเงื่อนไขพื้นฐานที่มนุษย์ควบคุมไม่ได้ และไม่ได้อยู่ในความสนใจของการเมืองกระแสหลัก
มนุษย์มักไม่เปลี่ยนแปลงเพราะ “ต้องการเปลี่ยน” แต่เพราะ “ไม่เปลี่ยนไม่ได้แล้ว” และการเปลี่ยนแปลงเหล่านั้นมักเกิดสวนทางกับความต้องการของคนส่วนใหญ่ที่อยากรักษาสถานะเดิม
ชีวิตที่ขาดวิสัยทัศน์
ความไม่ตระหนักถึงการเปลี่ยนแปลงอันยิ่งใหญ่ที่กำลังก่อตัวขึ้นรอบตัวเรา อาจไม่ได้เกิดจากความไม่รู้ แต่เพราะเราลึกๆ แล้ว “ไม่อยากเห็น” ความเปลี่ยนแปลงนั้นเอง ความต้านทานนี้ไม่ใช่เรื่องใหม่ บรรพบุรุษของเราที่ดำรงชีพด้วยการล่าสัตว์และหาของป่าก็อาจเคยดื้อรั้นไม่ต่างกัน เพียงแต่พวกเขามีข้อแก้ตัวที่ฟังขึ้นมากกว่า เพราะในยุคก่อนประวัติศาสตร์ ไม่มีใครอาจคาดเดาว่า “การปฏิวัติการเกษตร” จะเปลี่ยนโลกไปในระดับใด พวกเขาไม่มีปฏิทิน ไม่มีการบันทึก ไม่มีแบบจำลองใดจากอดีตให้ใช้ทำนายอนาคต แม้แต่แนวคิดเรื่อง “เวลา” ก็ยังไม่มีอยู่ในจิตสำนึก พวกเขาใช้ชีวิตอยู่ใน “ปัจจุบันที่ไม่สิ้นสุด” และเมื่อพูดถึงการคาดการณ์อนาคต พวกเขาก็เป็นเหมือน “คนตาบอด” ที่ยังไม่เคยลิ้มรส “ผลไม้แห่งความรู้” (ตามคำเปรียบในพระคัมภีร์) แต่ต่างจากพวกเขา พวกเราในวันนี้มีเครื่องมือและมุมมองที่ลึกซึ้งกว่า จากองค์ความรู้ของบรรพบุรุษกว่าสี่ห้าร้อยรุ่น วิทยาศาสตร์ คณิตศาสตร์ และอัลกอริธึมของคอมพิวเตอร์ความเร็วสูง ช่วยให้เราทำความเข้าใจระบบที่ซับซ้อนอย่างเศรษฐกิจมนุษย์และพลวัตของสังคมได้ดียิ่งขึ้น แม้ทฤษฎีเศรษฐศาสตร์จะไม่สามารถอธิบายพฤติกรรมมนุษย์ได้แบบสมบูรณ์ แต่ก็ทำให้เราเข้าใจว่า “แรงจูงใจ” คือแรงผลักดันสำคัญ เมื่อผลตอบแทนสูงขึ้น หรือความเสี่ยงต่ำลง พฤติกรรมย่อมเกิดขึ้นถี่ขึ้น และนี่คือหลักการที่แม่นยำอย่างยิ่งในการวิเคราะห์อนาคต
แรงจูงใจนี้เองที่เป็นหัวใจของการพยากรณ์ และการพยากรณ์ที่ดีไม่ได้ขึ้นกับการรู้เหตุการณ์ล่วงหน้าแบบเฉพาะเจาะจง แต่ขึ้นอยู่กับการเข้าใจโครงสร้างของแรงขับเคลื่อน เช่นเดียวกับที่เราอาจไม่รู้ว่าเมื่อไรเสียงฟ้าร้องจะดังขึ้น แต่เมื่อเห็นฟ้าแลบ ก็สามารถคาดหมายได้ว่าจะมีเสียงตามมา เช่นกัน หากเราสามารถเข้าใจ “ตรรกะของความรุนแรง” ที่กำลังเปลี่ยนไปในระดับการเมืองมหภาคได้ เราก็จะมองเห็น “โอกาส” หรือ “ช่องโหว่” ของระเบียบเดิม และใครจะเป็นผู้ฉวยโอกาสเหล่านั้น
การเปลี่ยนแปลงครั้งใหญ่ในอดีต เช่น การปฏิวัติการเกษตร หรือการเข้าสู่ยุคอุตสาหกรรม ล้วนเกิดขึ้นช้าและกินเวลาหลายศตวรรษกว่าจะเผยผลเต็มที่ ในทางตรงกันข้าม การเปลี่ยนผ่านสู่ยุคสารสนเทศกลับเกิดขึ้นรวดเร็วเพียงช่วงชีวิตเดียว
ผู้เขียนวางกรอบเพื่อให้เราเข้าใจว่า การเปลี่ยนแปลงทางการเมืองมหภาคมักมาก่อนการเปลี่ยนแปลงในโครงสร้างของรัฐอย่างเป็นรูปธรรม รายได้ที่ลดลง วิกฤตที่เกิดจากทรัพยากรจำกัด และแรงกดดันจากประชากร ล้วนเป็นผลพลอยได้จากความไม่สามารถของระเบียบเดิมในการรองรับแรงกระแทกของโลกใหม่ และการพูดถึงการเปลี่ยนแปลงจาก “ภายนอกระบบ” มักถูกห้ามหรือมองว่าเป็นเรื่องต้องห้ามในทุกยุคทุกสมัย ยิ่งไปกว่านั้น การเปลี่ยนแปลงในระดับนี้มักก่อให้เกิดแรงปะทะทางวัฒนธรรมระหว่างผู้ที่ยึดมั่นในกรอบศีลธรรมดั้งเดิมกับผู้ที่เปิดรับแนวคิดใหม่ และไม่ใช่เรื่องแปลกที่การเปลี่ยนแปลงเช่นนี้จะไม่เป็นที่นิยม เพราะมันลดคุณค่าของทุนทางปัญญาเดิม ทำให้ระบบเก่าไร้ความหมาย และบีบบังคับให้สังคมต้องเรียนรู้ใหม่เกือบทั้งหมด โดยเฉพาะในกลุ่มคนที่ได้รับผลกระทบโดยตรง
สัญญาณของการเสื่อมถอยมักปรากฏในรูปของคอร์รัปชัน ความไร้ประสิทธิภาพ และการสูญเสียศีลธรรมของผู้มีอำนาจ ซึ่งมักเป็นสัญญาณล่วงหน้าของการเปลี่ยนแปลงที่หลีกเลี่ยงไม่ได้ ยิ่งในยุคที่เทคโนโลยีก้าวหน้าเร็วขึ้น กระบวนการเหล่านี้ก็จะยิ่งเร่งตัว จนทำให้เวลาที่เหลืออยู่สำหรับการปรับตัวลดลงเรื่อย ๆ
"เมื่อมองย้อนกลับไปตลอดหลายศตวรรษ — หรือแม้แต่แค่ในปัจจุบัน — เราจะเห็นได้อย่างชัดเจนว่า มีผู้คนจำนวนมากที่สร้างรายได้(บ่อยครั้งเป็นรายได้จำนวนมาก) จากทักษะในการใช้ความรุนแรงผ่านอาวุธ และกิจกรรมของพวกเขาเหล่านี้มีบทบาทอย่างสำคัญยิ่งในการกำหนดว่าทรัพยากรที่มีอยู่จำกัดในสังคมจะถูกจัดสรรไปในทิศทางใด." --เฟรเดอริก ซี. เลน
แนวคิดของการเมืองมหภาค(megapolitics) เป็นกรอบความคิดที่ทรงพลัง ซึ่งช่วยให้เรามองเห็นกลไกเบื้องหลังเหตุการณ์ที่ดูซับซ้อนหรือลึกลับในประวัติศาสตร์ ไม่ว่าจะเป็นเหตุผลที่บางรัฐบาลเจริญรุ่งเรือง ขณะที่บางแห่งกลับล่มสลาย เหตุใดสงครามจึงอุบัติขึ้น และเหตุใดฝ่ายหนึ่งจึงมีชัย หรือแม้กระทั่งว่าอะไรเป็นตัวแปรที่กำหนดวงจรแห่งความรุ่งเรืองและความตกต่ำทางเศรษฐกิจ ทั้งหมดล้วนสามารถอธิบายได้ผ่านเลนส์ของการเมืองมหภาค ซึ่งเน้นวิเคราะห์ว่า "ต้นทุนและผลตอบแทนของการใช้ความรุนแรง" เปลี่ยนไปอย่างไรในแต่ละบริบทของเวลา หากต้นทุนในการใช้อำนาจบังคับลดต่ำลง เช่น การเข้าถึงอาวุธที่ง่ายขึ้นและราคาถูกลง ก็ทำให้อำนาจเปลี่ยนมือได้ง่ายขึ้นตามไปด้วย หลักการนี้ยังคงใช้ได้ตั้งแต่ยุคโบราณจนถึงโลกยุคไซเบอร์สเปซในปัจจุบัน
ใน Part 2 เราจะมาดูกันว่ามีปัจจัยอะไรบ้างที่อยู่เบื้องหลังการเปลี่ยนแปลงครั้งใหญ่ในประวัติศาสตร์ to be continue....
-
 @ a95c6243:d345522c
2025-03-20 09:59:20
@ a95c6243:d345522c
2025-03-20 09:59:20Bald werde es verboten, alleine im Auto zu fahren, konnte man dieser Tage in verschiedenen spanischen Medien lesen. Die nationale Verkehrsbehörde (Dirección General de Tráfico, kurz DGT) werde Alleinfahrern das Leben schwer machen, wurde gemeldet. Konkret erörtere die Generaldirektion geeignete Sanktionen für Personen, die ohne Beifahrer im Privatauto unterwegs seien.
Das Alleinfahren sei zunehmend verpönt und ein Mentalitätswandel notwendig, hieß es. Dieser «Luxus» stehe im Widerspruch zu den Maßnahmen gegen Umweltverschmutzung, die in allen europäischen Ländern gefördert würden. In Frankreich sei es «bereits verboten, in der Hauptstadt allein zu fahren», behauptete Noticiastrabajo Huffpost in einer Zwischenüberschrift. Nur um dann im Text zu konkretisieren, dass die sogenannte «Umweltspur» auf der Pariser Ringautobahn gemeint war, die für Busse, Taxis und Fahrgemeinschaften reserviert ist. Ab Mai werden Verstöße dagegen mit einem Bußgeld geahndet.
Die DGT jedenfalls wolle bei der Umsetzung derartiger Maßnahmen nicht hinterherhinken. Diese Medienberichte, inklusive des angeblich bevorstehenden Verbots, beriefen sich auf Aussagen des Generaldirektors der Behörde, Pere Navarro, beim Mobilitätskongress Global Mobility Call im November letzten Jahres, wo es um «nachhaltige Mobilität» ging. Aus diesem Kontext stammt auch Navarros Warnung: «Die Zukunft des Verkehrs ist geteilt oder es gibt keine».
Die «Faktenchecker» kamen der Generaldirektion prompt zu Hilfe. Die DGT habe derlei Behauptungen zurückgewiesen und klargestellt, dass es keine Pläne gebe, Fahrten mit nur einer Person im Auto zu verbieten oder zu bestrafen. Bei solchen Meldungen handele es sich um Fake News. Teilweise wurde der Vorsitzende der spanischen «Rechtsaußen»-Partei Vox, Santiago Abascal, der Urheberschaft bezichtigt, weil er einen entsprechenden Artikel von La Gaceta kommentiert hatte.
Der Beschwichtigungsversuch der Art «niemand hat die Absicht» ist dabei erfahrungsgemäß eher ein Alarmzeichen als eine Beruhigung. Walter Ulbrichts Leugnung einer geplanten Berliner Mauer vom Juni 1961 ist vielen genauso in Erinnerung wie die Fake News-Warnungen des deutschen Bundesgesundheitsministeriums bezüglich Lockdowns im März 2020 oder diverse Äußerungen zu einer Impfpflicht ab 2020.
Aber Aufregung hin, Dementis her: Die Pressemitteilung der DGT zu dem Mobilitätskongress enthält in Wahrheit viel interessantere Informationen als «nur» einen Appell an den «guten» Bürger wegen der Bemühungen um die Lebensqualität in Großstädten oder einen möglichen obligatorischen Abschied vom Alleinfahren. Allerdings werden diese Details von Medien und sogenannten Faktencheckern geflissentlich übersehen, obwohl sie keineswegs versteckt sind. Die Auskünfte sind sehr aufschlussreich, wenn man genauer hinschaut.
Digitalisierung ist der Schlüssel für Kontrolle
Auf dem Kongress stellte die Verkehrsbehörde ihre Initiativen zur Förderung der «neuen Mobilität» vor, deren Priorität Sicherheit und Effizienz sei. Die vier konkreten Ansätze haben alle mit Digitalisierung, Daten, Überwachung und Kontrolle im großen Stil zu tun und werden unter dem Euphemismus der «öffentlich-privaten Partnerschaft» angepriesen. Auch lassen sie die transhumanistische Idee vom unzulänglichen Menschen erkennen, dessen Fehler durch «intelligente» technologische Infrastruktur kompensiert werden müssten.
Die Chefin des Bereichs «Verkehrsüberwachung» erklärte die Funktion des spanischen National Access Point (NAP), wobei sie betonte, wie wichtig Verkehrs- und Infrastrukturinformationen in Echtzeit seien. Der NAP ist «eine essenzielle Web-Applikation, die unter EU-Mandat erstellt wurde», kann man auf der Website der DGT nachlesen.
Das Mandat meint Regelungen zu einem einheitlichen europäischen Verkehrsraum, mit denen die Union mindestens seit 2010 den Aufbau einer digitalen Architektur mit offenen Schnittstellen betreibt. Damit begründet man auch «umfassende Datenbereitstellungspflichten im Bereich multimodaler Reiseinformationen». Jeder Mitgliedstaat musste einen NAP, also einen nationalen Zugangspunkt einrichten, der Zugang zu statischen und dynamischen Reise- und Verkehrsdaten verschiedener Verkehrsträger ermöglicht.
Diese Entwicklung ist heute schon weit fortgeschritten, auch und besonders in Spanien. Auf besagtem Kongress erläuterte die Leiterin des Bereichs «Telematik» die Plattform «DGT 3.0». Diese werde als Integrator aller Informationen genutzt, die von den verschiedenen öffentlichen und privaten Systemen, die Teil der Mobilität sind, bereitgestellt werden.
Es handele sich um eine Vermittlungsplattform zwischen Akteuren wie Fahrzeugherstellern, Anbietern von Navigationsdiensten oder Kommunen und dem Endnutzer, der die Verkehrswege benutzt. Alle seien auf Basis des Internets der Dinge (IOT) anonym verbunden, «um der vernetzten Gemeinschaft wertvolle Informationen zu liefern oder diese zu nutzen».
So sei DGT 3.0 «ein Zugangspunkt für einzigartige, kostenlose und genaue Echtzeitinformationen über das Geschehen auf den Straßen und in den Städten». Damit lasse sich der Verkehr nachhaltiger und vernetzter gestalten. Beispielsweise würden die Karten des Produktpartners Google dank der DGT-Daten 50 Millionen Mal pro Tag aktualisiert.
Des Weiteren informiert die Verkehrsbehörde über ihr SCADA-Projekt. Die Abkürzung steht für Supervisory Control and Data Acquisition, zu deutsch etwa: Kontrollierte Steuerung und Datenerfassung. Mit SCADA kombiniert man Software und Hardware, um automatisierte Systeme zur Überwachung und Steuerung technischer Prozesse zu schaffen. Das SCADA-Projekt der DGT wird von Indra entwickelt, einem spanischen Beratungskonzern aus den Bereichen Sicherheit & Militär, Energie, Transport, Telekommunikation und Gesundheitsinformation.
Das SCADA-System der Behörde umfasse auch eine Videostreaming- und Videoaufzeichnungsplattform, die das Hochladen in die Cloud in Echtzeit ermöglicht, wie Indra erklärt. Dabei gehe es um Bilder, die von Überwachungskameras an Straßen aufgenommen wurden, sowie um Videos aus DGT-Hubschraubern und Drohnen. Ziel sei es, «die sichere Weitergabe von Videos an Dritte sowie die kontinuierliche Aufzeichnung und Speicherung von Bildern zur möglichen Analyse und späteren Nutzung zu ermöglichen».
Letzteres klingt sehr nach biometrischer Erkennung und Auswertung durch künstliche Intelligenz. Für eine bessere Datenübertragung wird derzeit die Glasfaserverkabelung entlang der Landstraßen und Autobahnen ausgebaut. Mit der Cloud sind die Amazon Web Services (AWS) gemeint, die spanischen Daten gehen somit direkt zu einem US-amerikanischen «Big Data»-Unternehmen.
Das Thema «autonomes Fahren», also Fahren ohne Zutun des Menschen, bildet den Abschluss der Betrachtungen der DGT. Zusammen mit dem Interessenverband der Automobilindustrie ANFAC (Asociación Española de Fabricantes de Automóviles y Camiones) sprach man auf dem Kongress über Strategien und Perspektiven in diesem Bereich. Die Lobbyisten hoffen noch in diesem Jahr 2025 auf einen normativen Rahmen zur erweiterten Unterstützung autonomer Technologien.
Wenn man derartige Informationen im Zusammenhang betrachtet, bekommt man eine Idee davon, warum zunehmend alles elektrisch und digital werden soll. Umwelt- und Mobilitätsprobleme in Städten, wie Luftverschmutzung, Lärmbelästigung, Platzmangel oder Staus, sind eine Sache. Mit dem Argument «emissionslos» wird jedoch eine Referenz zum CO2 und dem «menschengemachten Klimawandel» hergestellt, die Emotionen triggert. Und damit wird so ziemlich alles verkauft.
Letztlich aber gilt: Je elektrischer und digitaler unsere Umgebung wird und je freigiebiger wir mit unseren Daten jeder Art sind, desto besser werden wir kontrollier-, steuer- und sogar abschaltbar. Irgendwann entscheiden KI-basierte Algorithmen, ob, wann, wie, wohin und mit wem wir uns bewegen dürfen. Über einen 15-Minuten-Radius geht dann möglicherweise nichts hinaus. Die Projekte auf diesem Weg sind ernst zu nehmen, real und schon weit fortgeschritten.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 4fe14ef2:f51992ec
2025-04-20 10:02:41
@ 4fe14ef2:f51992ec
2025-04-20 10:02:41Let's support Bitcoin merchants! I'd love to hear some of your latest Lightning purchases and interesting products you bought. Feel free to include links to the shops or businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus sats if you found a killer deal! ⚡
Respond below, share and report on nostr or X:
N: https://njup.me/nevent1qvzqqqqqqypzqnlpfmegjd95py7h... X: https://x.com/AGORA_SN/status/1913895348428587452
If you missed our last thread, here are some of the items stackers recently spent and zap on.
originally posted at https://stacker.news/items/949495
-
 @ 22294439:86450048
2025-04-20 08:58:40
@ 22294439:86450048
2025-04-20 08:58:40A tecnologia transformou a forma como buscamos entretenimento, e a 5GBet é um excelente exemplo de como plataformas digitais podem oferecer uma experiência de alto nível para quem gosta de jogos online. Mas como funciona a 5GBet? Neste artigo, vamos detalhar o que torna essa plataforma tão atraente para jogadores brasileiros.
Logo ao acessar a 5GBet, o usuário é recebido com uma interface moderna, limpa e fácil de navegar. Tudo é muito bem organizado, com categorias de jogos, promoções, suporte e informações acessíveis com apenas alguns cliques. O cadastro é simples: basta preencher alguns dados básicos e em poucos minutos você já pode explorar todas as funcionalidades.
A 5gbet conta com um sistema de jogos baseado em tecnologia RNG (gerador de números aleatórios), que garante resultados justos e imparciais. Isso é essencial para quem busca confiabilidade e deseja jogar com tranquilidade.
Um ponto que merece destaque é o painel do usuário, onde é possível acompanhar seu saldo, histórico de apostas, bônus disponíveis e muito mais. Esse painel facilita a gestão das atividades e contribui para que o jogador tenha controle total da sua experiência.
O processo de depósito também é muito simples e rápido. A 5GBet aceita diversos métodos populares entre os brasileiros, como Pix, transferências bancárias e carteiras digitais. Além disso, os saques são processados de forma ágil, com prazos que surpreendem positivamente.
A plataforma ainda oferece tutoriais e guias para que até mesmo quem está começando no mundo dos jogos online possa entender as regras e estratégias de cada modalidade. Isso mostra a preocupação da 5GBet com todos os perfis de jogadores, dos novatos aos mais experientes.
Por fim, a 5GBet funciona com total transparência. As regras são claras, os termos estão disponíveis em português e o suporte está sempre pronto para ajudar. Tudo isso faz com que a plataforma se destaque no cenário nacional e continue crescendo em popularidade.
-
 @ b1b16be0:08f41c1d
2025-04-11 22:58:00
@ b1b16be0:08f41c1d
2025-04-11 22:58:00Bitcoin need more devs to scale! So I decide to translate to spanish https://plebdevs.com plebdevs@plebdevs.com is a opensource website to learn #bitcoin #lightning free.I started in my free time but now I have to sacrifice work time to move forward. Any zap could be a new bitcoiner!
Why Spanish? Spanish is the third most spoken language on the internet, but much of this community has little access to technical content in English. Plebdevs can be the 🔥torch that illuminates new developers to scale Bitcoin from Latin America and the world.
Apprenticeship Incentive Plebs will gaining the possibility of #learn a higher-paying job as #dev.
Let's Make Bitcoin Scale Millions of Spanish speakers can learn how to develop about Bitcoin and Lightning.
Proof of Work Introduction presentation: https://docs.google.com/presentation/d/1IMC4GHYjccKhGu2mDrtY3bOGcjyFcwgXwFyKyNMq7iw/edit?usp=sharing
🟩🟩🟩⬜⬜⬜⬜⬜⬜⬜ 30%
Thanks to bitcoinplebdev@bitcoinpleb.dev to create this #wonder
Any Zap will be helpful!
mav21@primal.net am@cubabitcoin.org lacrypta@hodl.ar BenJustman@primal.net shishi@nostrplebs.com sabine@primal.net onpoint@nostr.com theguyswann@iris.to Richard@primal.net eliza@primal.net
-
 @ 7d33ba57:1b82db35
2025-04-21 20:16:41
@ 7d33ba57:1b82db35
2025-04-21 20:16:41Helsinki, the stylish and compact capital of Finland, sits right on the edge of the Baltic Sea, blending Scandinavian design, sustainable living, and a love for nature. It’s a city of clean lines, calm energy, and a creative spirit—where you can go from a seaside sauna to a sleek design museum in minutes.
🧭 Top Things to Do in Helsinki
⛪ Helsinki Cathedral
- The city’s iconic white-domed landmark, perched on Senate Square
- Climb the steps for sweeping views over the city’s neoclassical heart
🏝️ Suomenlinna Sea Fortress
- A UNESCO World Heritage Site spread across several islands
- Explore old ramparts, tunnels, museums, and scenic picnic spots
- A short ferry ride from the city center, perfect for a half-day trip
🧊 Löyly Sauna
- One of Helsinki’s most famous public saunas, right on the waterfront
- Relax in the heat, then dip in the Baltic like a local
- Beautiful architecture and a must-do cultural experience
🏛️ Design District & Museums
- Wander the Design District for boutique shops, galleries, and Finnish fashion
- Visit the Design Museum, Kiasma (contemporary art), and Ateneum (classic Finnish art)
🌲 Nature + Nordic Calm
- Walk along the Esplanadi park or relax in Kaivopuisto by the sea
- Take a boat to the nearby archipelago islands for hiking, birdwatching, or quiet cafés
- Even in winter, the city feels clean, serene, and cozy
☕ Food, Coffee & Nordic Flavors
- Try karjalanpiirakka (Karelian pies), salmon soup, or reindeer meat if you’re adventurous
- Helsinki has a big coffee culture—Finns drink more coffee per capita than anyone!
- Cozy up in a café with a cinnamon pulla and watch the snow fall (or the summer sun glow at midnight)
🚲 Getting Around
- Easy to explore by foot, tram, or city bikes
- Excellent ferries and boats to nearby islands and Tallinn, Estonia
- Helsinki Airport is well-connected and just 30 mins from downtown
📅 When to Go
- Summer: Endless daylight, festivals, and outdoor dining
- Winter: Snowy streets, cozy interiors, and a shot at the Northern Lights if you head north
- Autumn: Ruska (fall colors) is stunning in the parks and forests
-
 @ 22294439:86450048
2025-04-20 08:53:29
@ 22294439:86450048
2025-04-20 08:53:29A era digital trouxe inúmeras formas de entretenimento, e entre elas, as plataformas de jogos online se destacam por oferecer momentos de lazer e emoção diretamente da tela do celular ou computador. Entre as melhores opções do mercado nacional, a Betao surge como um verdadeiro destaque, unindo variedade, praticidade e segurança.
O primeiro contato com a Betao revela uma interface moderna, pensada para proporcionar uma navegação descomplicada. Todos os menus são claros, os jogos são facilmente localizáveis e o carregamento das páginas é ágil — algo essencial para quem deseja aproveitar cada segundo de diversão.
Na betao , a variedade de jogos é impressionante. Há opções para todos os perfis de jogadores, desde os iniciantes até os mais experientes. Os slots são os grandes queridinhos, com temas criativos, gráficos vibrantes e mecânicas que surpreendem. Também há uma gama de jogos de mesa, como roleta, blackjack e bacará, todos otimizados para o ambiente digital.
Um diferencial é o catálogo de jogos ao vivo, onde os jogadores interagem em tempo real com anfitriões, tornando a experiência ainda mais realista. A tecnologia empregada garante qualidade de imagem e som impecáveis, algo que aumenta a imersão e o nível de engajamento.
Além do conteúdo de alta qualidade, a Betao oferece promoções constantes que elevam ainda mais a experiência. Novos usuários são recebidos com bônus atrativos, e os jogadores frequentes podem contar com campanhas semanais, brindes e prêmios progressivos.
Outro ponto de destaque é a segurança. A plataforma utiliza criptografia avançada para proteger dados e transações. O suporte ao cliente também merece elogios: está disponível 24 horas por dia em português, pronto para atender com agilidade e eficiência.
A Betao não é apenas uma plataforma de jogos. É um ambiente de entretenimento sofisticado, que respeita o jogador brasileiro e valoriza cada minuto investido na diversão. Se você procura um espaço digital completo, estável e emocionante, a Betao é uma escolha certeira.
-
 @ 3b3a42d3:d192e325
2025-04-10 08:57:51
@ 3b3a42d3:d192e325
2025-04-10 08:57:51Atomic Signature Swaps (ASS) over Nostr is a protocol for atomically exchanging Schnorr signatures using Nostr events for orchestration. This new primitive enables multiple interesting applications like:
- Getting paid to publish specific Nostr events
- Issuing automatic payment receipts
- Contract signing in exchange for payment
- P2P asset exchanges
- Trading and enforcement of asset option contracts
- Payment in exchange for Nostr-based credentials or access tokens
- Exchanging GMs 🌞
It only requires that (i) the involved signatures be Schnorr signatures using the secp256k1 curve and that (ii) at least one of those signatures be accessible to both parties. These requirements are naturally met by Nostr events (published to relays), Taproot transactions (published to the mempool and later to the blockchain), and Cashu payments (using mints that support NUT-07, allowing any pair of these signatures to be swapped atomically.
How the Cryptographic Magic Works 🪄
This is a Schnorr signature
(Zₓ, s):s = z + H(Zₓ || P || m)⋅kIf you haven't seen it before, don't worry, neither did I until three weeks ago.
The signature scalar s is the the value a signer with private key
k(and public keyP = k⋅G) must calculate to prove his commitment over the messagemgiven a randomly generated noncez(Zₓis just the x-coordinate of the public pointZ = z⋅G).His a hash function (sha256 with the tag "BIP0340/challenge" when dealing with BIP340),||just means to concatenate andGis the generator point of the elliptic curve, used to derive public values from private ones.Now that you understand what this equation means, let's just rename
z = r + t. We can do that,zis just a randomly generated number that can be represented as the sum of two other numbers. It also follows thatz⋅G = r⋅G + t⋅G ⇔ Z = R + T. Putting it all back into the definition of a Schnorr signature we get:s = (r + t) + H((R + T)ₓ || P || m)⋅kWhich is the same as:
s = sₐ + twheresₐ = r + H((R + T)ₓ || P || m)⋅ksₐis what we call the adaptor signature scalar) and t is the secret.((R + T)ₓ, sₐ)is an incomplete signature that just becomes valid by add the secret t to thesₐ:s = sₐ + tWhat is also important for our purposes is that by getting access to the valid signature s, one can also extract t from it by just subtracting
sₐ:t = s - sₐThe specific value of
tdepends on our choice of the public pointT, sinceRis just a public point derived from a randomly generated noncer.So how do we choose
Tso that it requires the secret t to be the signature over a specific messagem'by an specific public keyP'? (without knowing the value oft)Let's start with the definition of t as a valid Schnorr signature by P' over m':
t = r' + H(R'ₓ || P' || m')⋅k' ⇔ t⋅G = r'⋅G + H(R'ₓ || P' || m')⋅k'⋅GThat is the same as:
T = R' + H(R'ₓ || P' || m')⋅P'Notice that in order to calculate the appropriate
Tthat requirestto be an specific signature scalar, we only need to know the public nonceR'used to generate that signature.In summary: in order to atomically swap Schnorr signatures, one party
P'must provide a public nonceR', while the other partyPmust provide an adaptor signature using that nonce:sₐ = r + H((R + T)ₓ || P || m)⋅kwhereT = R' + H(R'ₓ || P' || m')⋅P'P'(the nonce provider) can then add his own signature t to the adaptor signaturesₐin order to get a valid signature byP, i.e.s = sₐ + t. When he publishes this signature (as a Nostr event, Cashu transaction or Taproot transaction), it becomes accessible toPthat can now extract the signaturetbyP'and also make use of it.Important considerations
A signature may not be useful at the end of the swap if it unlocks funds that have already been spent, or that are vulnerable to fee bidding wars.
When a swap involves a Taproot UTXO, it must always use a 2-of-2 multisig timelock to avoid those issues.
Cashu tokens do not require this measure when its signature is revealed first, because the mint won't reveal the other signature if they can't be successfully claimed, but they also require a 2-of-2 multisig timelock when its signature is only revealed last (what is unavoidable in cashu for cashu swaps).
For Nostr events, whoever receives the signature first needs to publish it to at least one relay that is accessible by the other party. This is a reasonable expectation in most cases, but may be an issue if the event kind involved is meant to be used privately.
How to Orchestrate the Swap over Nostr?
Before going into the specific event kinds, it is important to recognize what are the requirements they must meet and what are the concerns they must address. There are mainly three requirements:
- Both parties must agree on the messages they are going to sign
- One party must provide a public nonce
- The other party must provide an adaptor signature using that nonce
There is also a fundamental asymmetry in the roles of both parties, resulting in the following significant downsides for the party that generates the adaptor signature:
- NIP-07 and remote signers do not currently support the generation of adaptor signatures, so he must either insert his nsec in the client or use a fork of another signer
- There is an overhead of retrieving the completed signature containing the secret, either from the blockchain, mint endpoint or finding the appropriate relay
- There is risk he may not get his side of the deal if the other party only uses his signature privately, as I have already mentioned
- There is risk of losing funds by not extracting or using the signature before its timelock expires. The other party has no risk since his own signature won't be exposed by just not using the signature he received.
The protocol must meet all those requirements, allowing for some kind of role negotiation and while trying to reduce the necessary hops needed to complete the swap.
Swap Proposal Event (kind:455)
This event enables a proposer and his counterparty to agree on the specific messages whose signatures they intend to exchange. The
contentfield is the following stringified JSON:{ "give": <signature spec (required)>, "take": <signature spec (required)>, "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>", "description": "<Info about the proposal (optional)>", "nonce": "<Signature public nonce (optional)>", "enc_s": "<Encrypted signature scalar (optional)>" }The field
roleindicates what the proposer will provide during the swap, either the nonce or the adaptor. When this optional field is not provided, the counterparty may decide whether he will send a nonce back in a Swap Nonce event or a Swap Adaptor event using thenonce(optionally) provided by in the Swap Proposal in order to avoid one hop of interaction.The
enc_sfield may be used to store the encrypted scalar of the signature associated with thenonce, since this information is necessary later when completing the adaptor signature received from the other party.A
signature specspecifies thetypeand all necessary information for producing and verifying a given signature. In the case of signatures for Nostr events, it contain a template with all the fields, exceptpubkey,idandsig:{ "type": "nostr", "template": { "kind": "<kind>" "content": "<content>" "tags": [ … ], "created_at": "<created_at>" } }In the case of Cashu payments, a simplified
signature specjust needs to specify the payment amount and an array of mints trusted by the proposer:{ "type": "cashu", "amount": "<amount>", "mint": ["<acceptable mint_url>", …] }This works when the payer provides the adaptor signature, but it still needs to be extended to also work when the payer is the one receiving the adaptor signature. In the later case, the
signature specmust also include atimelockand the derived public keysYof each Cashu Proof, but for now let's just ignore this situation. It should be mentioned that the mint must be trusted by both parties and also support Token state check (NUT-07) for revealing the completed adaptor signature and P2PK spending conditions (NUT-11) for the cryptographic scheme to work.The
tagsare:"p", the proposal counterparty's public key (required)"a", akind:30455Swap Listing event or an application specific version of it (optional)
Forget about this Swap Listing event for now, I will get to it later...
Swap Nonce Event (kind:456) - Optional
This is an optional event for the Swap Proposal receiver to provide the public nonce of his signature when the proposal does not include a nonce or when he does not want to provide the adaptor signature due to the downsides previously mentioned. The
contentfield is the following stringified JSON:{ "nonce": "<Signature public nonce>", "enc_s": "<Encrypted signature scalar (optional)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Swap Adaptor Event (kind:457)
The
contentfield is the following stringified JSON:{ "adaptors": [ { "sa": "<Adaptor signature scalar>", "R": "<Signer's public nonce (including parity byte)>", "T": "<Adaptor point (including parity byte)>", "Y": "<Cashu proof derived public key (if applicable)>", }, …], "cashu": "<Cashu V4 token (if applicable)>" }And the
tagsmust contain:"e", akind:455Swap Proposal Event (required)"p", the counterparty's public key (required)
Discoverability
The Swap Listing event previously mentioned as an optional tag in the Swap Proposal may be used to find an appropriate counterparty for a swap. It allows a user to announce what he wants to accomplish, what his requirements are and what is still open for negotiation.
Swap Listing Event (kind:30455)
The
contentfield is the following stringified JSON:{ "description": "<Information about the listing (required)>", "give": <partial signature spec (optional)>, "take": <partial signature spec (optional)>, "examples: [<take signature spec>], // optional "exp": <expiration timestamp (optional)>, "role": "<adaptor | nonce (optional)>" }The
descriptionfield describes the restrictions on counterparties and signatures the user is willing to accept.A
partial signature specis an incompletesignature specused in Swap Proposal eventskind:455where omitting fields signals that they are still open for negotiation.The
examplesfield is an array ofsignature specsthe user would be willing totake.The
tagsare:"d", a unique listing id (required)"s", the status of the listingdraft | open | closed(required)"t", topics related to this listing (optional)"p", public keys to notify about the proposal (optional)
Application Specific Swap Listings
Since Swap Listings are still fairly generic, it is expected that specific use cases define new event kinds based on the generic listing. Those application specific swap listing would be easier to filter by clients and may impose restrictions and add new fields and/or tags. The following are some examples under development:
Sponsored Events
This listing is designed for users looking to promote content on the Nostr network, as well as for those who want to monetize their accounts by sharing curated sponsored content with their existing audiences.
It follows the same format as the generic Swap Listing event, but uses the
kind:30456instead.The following new tags are included:
"k", event kind being sponsored (required)"title", campaign title (optional)
It is required that at least one
signature spec(giveand/ortake) must have"type": "nostr"and also contain the following tag["sponsor", "<pubkey>", "<attestation>"]with the sponsor's public key and his signature over the signature spec without the sponsor tag as his attestation. This last requirement enables clients to disclose and/or filter sponsored events.Asset Swaps
This listing is designed for users looking for counterparties to swap different assets that can be transferred using Schnorr signatures, like any unit of Cashu tokens, Bitcoin or other asset IOUs issued using Taproot.
It follows the same format as the generic Swap Listing event, but uses the
kind:30457instead.It requires the following additional tags:
"t", asset pair to be swapped (e.g."btcusd")"t", asset being offered (e.g."btc")"t", accepted payment method (e.g."cashu","taproot")
Swap Negotiation
From finding an appropriate Swap Listing to publishing a Swap Proposal, there may be some kind of negotiation between the involved parties, e.g. agreeing on the amount to be paid by one of the parties or the exact content of a Nostr event signed by the other party. There are many ways to accomplish that and clients may implement it as they see fit for their specific goals. Some suggestions are:
- Adding
kind:1111Comments to the Swap Listing or an existing Swap Proposal - Exchanging tentative Swap Proposals back and forth until an agreement is reached
- Simple exchanges of DMs
- Out of band communication (e.g. Signal)
Work to be done
I've been refining this specification as I develop some proof-of-concept clients to experience its flaws and trade-offs in practice. I left the signature spec for Taproot signatures out of the current document as I still have to experiment with it. I will probably find some important orchestration issues related to dealing with
2-of-2 multisig timelocks, which also affects Cashu transactions when spent last, that may require further adjustments to what was presented here.The main goal of this article is to find other people interested in this concept and willing to provide valuable feedback before a PR is opened in the NIPs repository for broader discussions.
References
- GM Swap- Nostr client for atomically exchanging GM notes. Live demo available here.
- Sig4Sats Script - A Typescript script demonstrating the swap of a Cashu payment for a signed Nostr event.
- Loudr- Nostr client under development for sponsoring the publication of Nostr events. Live demo available at loudr.me.
- Poelstra, A. (2017). Scriptless Scripts. Blockstream Research. https://github.com/BlockstreamResearch/scriptless-scripts
-
 @ 22294439:86450048
2025-04-20 08:52:02
@ 22294439:86450048
2025-04-20 08:52:02Em um cenário digital cada vez mais competitivo, o 5588bet consegue se destacar ao oferecer uma experiência imersiva e completa para os fãs de jogos online. A plataforma foi criada com o objetivo de unir diversão, tecnologia e praticidade, tudo isso com foco no público brasileiro.
O 5588bet investe em tecnologias modernas para proporcionar uma experiência de alto nível. Seus jogos contam com gráficos avançados, animações envolventes e efeitos sonoros que tornam cada partida única. Além disso, o sistema da plataforma garante carregamento rápido e jogos sem travamentos — algo essencial para quem quer aproveitar o tempo com fluidez.
Catálogo Variado de Jogos Independentemente do seu estilo, o 5588bet tem opções que agradam. A biblioteca de jogos é atualizada com frequência e traz títulos desenvolvidos por provedores renomados, que garantem mecânicas justas e resultados aleatórios.
Você pode encontrar:
Jogos de sorte com rodadas e giros especiais
Jogos ao vivo, com interações em tempo real
Mesas tradicionais, como pôquer e blackjack
Temas variados, desde aventuras até ficção científica
Com tanta variedade, fica fácil encontrar algo que prenda sua atenção e torne o tempo de lazer ainda mais interessante.
Suporte Ágil e Personalizado O atendimento ao cliente é um grande diferencial da plataforma. Totalmente em português, o suporte é eficiente e rápido, disponível todos os dias para ajudar os jogadores. Seja por chat ao vivo ou por e-mail, o usuário é tratado com atenção e tem suas questões resolvidas com agilidade.
Pagamentos Rápidos e Sem Complicação Outro ponto positivo é a facilidade nos depósitos e saques. O 5588bet oferece opções como PIX e transferências bancárias, com processamento rápido. Tudo é feito com segurança e transparência, oferecendo conforto e confiança para o usuário.
Eventos e Recompensas Atrativas Promoções exclusivas, bônus de boas-vindas e torneios entre usuários são apenas algumas das formas que o 5588bet utiliza para manter o jogador engajado. As recompensas são acessíveis e os desafios tornam a experiência mais divertida, estimulando a competitividade de maneira saudável.
Conclusão O 5588bet oferece muito mais do que jogos — ele proporciona uma experiência imersiva, com foco em qualidade, segurança e envolvimento. Se você procura uma plataforma confiável, repleta de recursos modernos e com atendimento voltado ao público brasileiro, essa é uma excelente escolha.
-
 @ a95c6243:d345522c
2025-03-15 10:56:08
@ a95c6243:d345522c
2025-03-15 10:56:08Was nützt die schönste Schuldenbremse, wenn der Russe vor der Tür steht? \ Wir können uns verteidigen lernen oder alle Russisch lernen. \ Jens Spahn
In der Politik ist buchstäblich keine Idee zu riskant, kein Mittel zu schäbig und keine Lüge zu dreist, als dass sie nicht benutzt würden. Aber der Clou ist, dass diese Masche immer noch funktioniert, wenn nicht sogar immer besser. Ist das alles wirklich so schwer zu durchschauen? Mir fehlen langsam die Worte.
Aktuell werden sowohl in der Europäischen Union als auch in Deutschland riesige Milliardenpakete für die Aufrüstung – also für die Rüstungsindustrie – geschnürt. Die EU will 800 Milliarden Euro locker machen, in Deutschland sollen es 500 Milliarden «Sondervermögen» sein. Verteidigung nennen das unsere «Führer», innerhalb der Union und auch an «unserer Ostflanke», der Ukraine.
Das nötige Feindbild konnte inzwischen signifikant erweitert werden. Schuld an allem und zudem gefährlich ist nicht mehr nur Putin, sondern jetzt auch Trump. Europa müsse sich sowohl gegen Russland als auch gegen die USA schützen und rüsten, wird uns eingetrichtert.
Und während durch Diplomatie genau dieser beiden Staaten gerade endlich mal Bewegung in die Bemühungen um einen Frieden oder wenigstens einen Waffenstillstand in der Ukraine kommt, rasselt man im moralisch überlegenen Zeigefinger-Europa so richtig mit dem Säbel.
Begleitet und gestützt wird der ganze Prozess – wie sollte es anders sein – von den «Qualitätsmedien». Dass Russland einen Angriff auf «Europa» plant, weiß nicht nur der deutsche Verteidigungsminister (und mit Abstand beliebteste Politiker) Pistorius, sondern dank ihnen auch jedes Kind. Uns bleiben nur noch wenige Jahre. Zum Glück bereitet sich die Bundeswehr schon sehr konkret auf einen Krieg vor.
Die FAZ und Corona-Gesundheitsminister Spahn markieren einen traurigen Höhepunkt. Hier haben sich «politische und publizistische Verantwortungslosigkeit propagandistisch gegenseitig befruchtet», wie es bei den NachDenkSeiten heißt. Die Aussage Spahns in dem Interview, «der Russe steht vor der Tür», ist das eine. Die Zeitung verschärfte die Sache jedoch, indem sie das Zitat explizit in den Titel übernahm, der in einer ersten Version scheinbar zu harmlos war.
Eine große Mehrheit der deutschen Bevölkerung findet Aufrüstung und mehr Schulden toll, wie ARD und ZDF sehr passend ermittelt haben wollen. Ähnliches gelte für eine noch stärkere militärische Unterstützung der Ukraine. Etwas skeptischer seien die Befragten bezüglich der Entsendung von Bundeswehrsoldaten dorthin, aber immerhin etwa fifty-fifty.
Eigentlich ist jedoch die Meinung der Menschen in «unseren Demokratien» irrelevant. Sowohl in der Europäischen Union als auch in Deutschland sind die «Eliten» offenbar der Ansicht, der Souverän habe in Fragen von Krieg und Frieden sowie von aberwitzigen astronomischen Schulden kein Wörtchen mitzureden. Frau von der Leyen möchte über 150 Milliarden aus dem Gesamtpaket unter Verwendung von Artikel 122 des EU-Vertrags ohne das Europäische Parlament entscheiden – wenn auch nicht völlig kritiklos.
In Deutschland wollen CDU/CSU und SPD zur Aufweichung der «Schuldenbremse» mehrere Änderungen des Grundgesetzes durch das abgewählte Parlament peitschen. Dieser Versuch, mit dem alten Bundestag eine Zweidrittelmehrheit zu erzielen, die im neuen nicht mehr gegeben wäre, ist mindestens verfassungsrechtlich umstritten.
Das Manöver scheint aber zu funktionieren. Heute haben die Grünen zugestimmt, nachdem Kanzlerkandidat Merz läppische 100 Milliarden für «irgendwas mit Klima» zugesichert hatte. Die Abstimmung im Plenum soll am kommenden Dienstag erfolgen – nur eine Woche, bevor sich der neu gewählte Bundestag konstituieren wird.
Interessant sind die Argumente, die BlackRocker Merz für seine Attacke auf Grundgesetz und Demokratie ins Feld führt. Abgesehen von der angeblichen Eile, «unsere Verteidigungsfähigkeit deutlich zu erhöhen» (ausgelöst unter anderem durch «die Münchner Sicherheitskonferenz und die Ereignisse im Weißen Haus»), ließ uns der CDU-Chef wissen, dass Deutschland einfach auf die internationale Bühne zurück müsse. Merz schwadronierte gefährlich mehrdeutig:
«Die ganze Welt schaut in diesen Tagen und Wochen auf Deutschland. Wir haben in der Europäischen Union und auf der Welt eine Aufgabe, die weit über die Grenzen unseres eigenen Landes hinausgeht.»
[Titelbild: Tag des Sieges]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 3ad01248:962d8a07
2025-04-21 19:40:22
@ 3ad01248:962d8a07
2025-04-21 19:40:22It has almost been a month since the Bitcoin friendly Trump administration has been in power. The Bitcoin price was riding high days before and after the election with Bitcoin reaching a new all time high of 109k. It sure seem like surely once Trump got into office the price would skyrocket and everyone finally would have lambos and girlfriends.
Sadly for the number go up crowd this didn't happen. There are no lambos to be found and no girlfriends. All we get is some sideways price action and a Strategic Bitcoin Reserve (BSR).
If you are in Bitcoin for the right reasons and understand what you hold, this is the perfect time to stack sats before the price goes parabolic. I say this because Bitcoin sure seems to be poised to make a massive run. If you look past the current price of Bitcoin you can see a storm of dollars flowing into Bitcoin from the traditional fiat economy. The signs are there if you start looking for them.
US States Creating Bitcoin Strategic Reserves
Guess how many states are considering creating a state level Bitcoin reserve of their own? Lots. Here is a list of states that are thinking about creating a reserve for their state:
- Alabama
- Arizona
- Florida
- Kansas
- Illinois
- Iowa
- Massachusetts
- Michigan
- Missouri
- Montana
- New Hampshire
- New Jersey
- New Mexico
- North Carolina
- North Dakota
- Ohio
- Pennsylvania
- South Dakota
- Texas
- Utah
- Wisconsin
- Wyoming
Each state is at some varying degree of interest in creating a reserve. Texas and Arizona are by far have made the most progress on making a Bitcoin reserve a reality. Texas is currently holding a public hearing on this at the time of this writing. There is strong political will to create a reserve so I definitely can see them being first movers on this and once Texas makes it a reality the other state will move in short order.
Arizona's strategic reserve bill passed the senate finance committee on a 5-2 which is a big deal in itself but still has a long way to go before it becomes policy. If it passes the Senate it still has to pass the Arizona House of Representatives and signed by Democrat Governor Katie Hobbs, so the odds of this becoming law is slim. Arizona Democrats seem to be anti-Bitcoin in general and any bills coming from Republicans will likely be shoot down or watered down.
Analysts believe that $23 billion could flow into Bitcoin from government reserves which equates to 247k Bitcoin going into government cold storage. I have reservations about governments creating BSR's but if we are going to have them I much rather them be at the state level where it can benefit citizens the most. Especially state pension funds that so many of our firefighters, police and first responders depend on for retirement.
We will probably see a state level BSR created by the end of the year if not sooner. Time will tell.
SAB 121 Repeal
What is SAB 121? SAB 121 or Staff Accounting Bulletin 121 made it problematic for financial institutions to custody digital assets such as Bitcoin for their customers. SAB 121 required institutions to record their holdings as a liability and not an asset.
Naturally banks and other financial institutions didn't see an upside to custody digital assets if it meant taking on liability and having an administration that was hostile to crypto in general. Why take the chance to piss off the government and give them a reason to go after you is probably the reasoning of most bank executives. SAB 121 achieved the goal the Biden administration set out to accomplish, namely stymie Bitcoin adoption by banks and individuals as long as possible.
President Trump swiftly issued a executive order rescinding SAB 121 and with that ushering a new era in the realm of Bitcoin and digital assets in general. Financial institutions now have the ability to explore Bitcoin custody solutions that fit their customer's need without fear of having to record a liability on their books.
As more and more people and business learn about Bitcoin third party custody options are going to be popular. Think about it from a small business owner perspective for a second. They are in the business of selling their widgets for Bitcoin but they don't want to manage the complexity that comes with accounting, taxes etc.. In steps in their local bank that they have been with for years if not decades and starts providing Bitcoin management services. Small business owners would be all over that idea. In the long run I think the repeal of SAB 121 is going to be a bigger deal than states creating Bitcoin strategic reserves.
FASB
Financial Accounting Standards Board or FASB for short has applied fair value accounting rules on Bitcoin and other digital assets. This is a huge deal because it will allow business to realize profit and losses of Bitcoin based on market prices. It also makes it easier for investors who evaluate businesses that hold Bitcoin on their balance sheet. Overall it treats Bitcoin like any other asset that a business would hold.
This accounting rule change will pave the way for more businesses to put Bitcoin on their balance sheet further driving demand for Bitcoin.
Lightning Companies Leading The Way
We all know that L1 Bitcoin can not scale to the entire world and that in order to bring more people into Bitcoin that layer two solutions would have to be built. This has largely been done with the creation of the lightning network which enables seamless peer to peer micropayments in the blink of an eye.
Base layer Bitcoin will certain not be used to buy your daily coffees or gym memberships but lightning will be used for that purpose. Businesses small and large will demand one click on demand solutions to help them accept Bitcoin payments for their businesses. There are plenty of Bitcoin business ready to help business adopt a Bitcoin standard.
Businesses such as Opennode, Zaprite, Voltage, Breez make switching over to a Bitcoin standard easy for businesses to do.
So when you take a step back and really look at the Bitcoin ecosystem it is a lot more mature than most give it credit for and will slowly eat away at fiat currency dominance around the world.
The best thing that you can do is be patient, stack as many sats as you can and educate others about Bitcoin. We all know how fiat currencies end. Our time will come.
-
 @ e97aaffa:2ebd765d
2025-04-21 12:57:16
@ e97aaffa:2ebd765d
2025-04-21 12:57:16Se este movimento de desglobalização continuar, poderá provocar uma cisão no mundo geopolítico, criar dois grandes blocos económicos, uma nova guerra fria.
Se isso se concretizar, quantos anos vão ser necessários para o S&P500 superar máximos históricos em termos reais, em poder de compra?
Em valores nominais vai ser rápido, o governo dos EUA vai imprimir tanto dinheiro, rapidamente vai superar máximos, mas em termos reais, vai demorar muitos anos.
Até agora, todo o mundo estava a investir nos EUA, mas se os países do bloco oriental, sobretudo a China, deixarem de investir em ações, obrigações e moeda dos EUA, irá provocar uma enorme redução de liquidez e na procura/demanda, não vai ser fácil ultrapassar isso.
Nos US Treasury, o afastamento da China começou em 2014(1° guerra da Ucrânia), mas o movimento acelerou em 2022(2° guerra da Ucrânia).

Os EUA, ao congelar as reservas da Rússia, ao utilizar as reservas como uma arma de guerra, “assustaram” a China e outros países. As sanções à Rússia e como esta fez para contornar as sanções foi um case study para a China.
Como o objetivo da China é recuperar Taiwan, sabe que sofrerá as mesmas represálias que hoje a Rússia sofre, por isso a China tem que se afastar da economia dos EUA.
A China está a trocar US Treasury por outros ativos e por outras geografias, o principal beneficiado foi o ouro, um ativo soberano, que não tem problemas de contraparte.
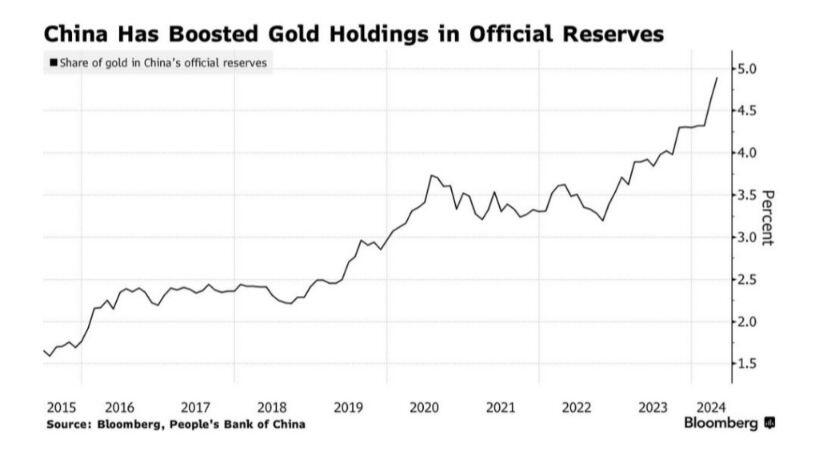
Este movimento da China foi bem visível no preço do ouro no último ano, uma valorização superior a 42%.
Mas não é só a China que está a apostar no ouro, são diversos, mas sobretudo composta por países do bloco oriental.
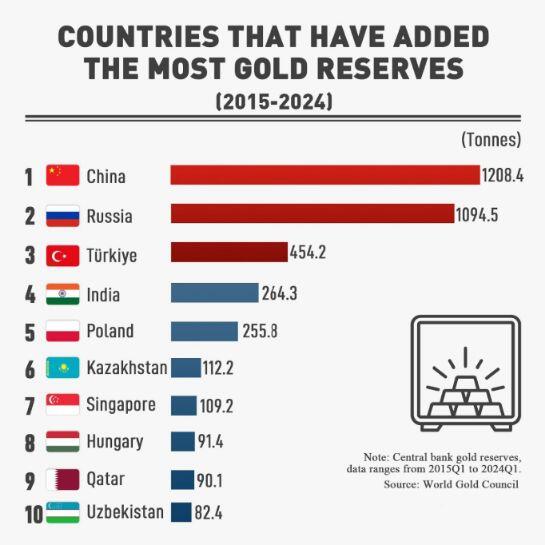
Enquanto, Taiwan for a fábrica do mundo nos semicondutores, estarão protegidos pelo guarda-chuva dos EUA. Mas os EUA, estão a construir fábricas próprias, quando forem auto-suficientes, vão descartar o “guarda-chuva”, Taiwan não terá qualquer hipótese sobre o poderio da China.
A China pensa sempre a longo prazo, estão apenas a aguardar, isto poderá estar para muito em breve.
Se isto se confirmar, o S&P500 poderá demorar décadas para recuperar desta crise, em termos de poder de compra.
-
 @ c3e23eb5:03d7caa9
2025-04-10 00:41:12
@ c3e23eb5:03d7caa9
2025-04-10 00:41:12The issue I have with the term "mesh networks" is that it is associated with a flat network topology. While I love the idea of avoiding hierarchy, this simply doesn't scale.
Data Plane: How the Internet Scales
The internet on the scales because it has a tree like structure. As you can see in the diagram below, global (tier 1) ISPs branch out to national (tier 2) ISPs who in turn branch out to local (tier 3) ISPs. ``` ,-[ Tier 1 ISP (Global) ]─-───────[ Tier 1 ISP (Global) ] / |
/ ▼
[IXP (Global)]═══╦═══[IXP (Global)]
║
Tier 2 ISP (National)◄──────────╗
/ \ ║
▼ ▼ ║
[IXP (Regional)]════╬══[IXP (Regional)] ║
/ \ ║
▼ ▼ ║
Tier 3 ISP (Local) Tier 3 ISP (Local) ║
| | ║
▼ ▼ ▼
[User] [User] [Enterprise]▲ IXPs are physical switch fabrics - members peer directly ▲ Tier 1/2 ISPs provide transit through IXPs but don't control them ```
This structure also reflects in IP addresses, where regional traffic gets routed by regional tiers and global traffic keeps getting passed up through gateways till it reaches the root of the tree. The global ISP then routes the traffic into the correct branch so that it can trickle down to the destination IP at the bottom.
12.0.0.0/8 - Tier 1 manages routing (IANA-allocated) └─12.34.0.0/16 - Tier 2 allocated block (through RIR) └─12.34.56.0/24 - Tier 3 subnet via upstream provider ├─12.34.56.1 Public IP (CGNAT pool) └─192.168.1.1 Private IP (local NAT reuse)Balancing idealism with pragmatism
This approach to scaling is much less idealistic than a flat hierarchy, because it relies on an authority (IANA) to assign the IP ranges to ISPs through Regional Internet Registries (RIRs). Even if this authority wasn't required, the fact that many users rely on few Tier 1 ISPs means that the system is inherently susceptible to sabotage (see 2019 BGP leak incident).
Control Plane: the internet is still described as decentralised
The internet is still described as decentralised because there is a flat hierarchy between
tier 1ISPs at the root of the tree. ``` INTERNET CORE (Tier 1 ISPs)
AT&T (AS7018) <══════════> Deutsche Telekom (AS3320) ║ ╔════════════════════╗ ║ ║ ║ ║ ║ ╚══>║ NTT (AS2914) ║<══╝ ║ ║ ║ ║ ║ ║ ╚═══════> Lumen (AS3356) ║ ║ ╚════╩════════════> Telia (AS1299) ```
The border gateway protocol (BGP) is used to exchange routing information between autonomous systems (ISPs). Each autonomous system is a branch of the "internet tree" and each autonomous system advertises routes to downstream autonomous systems (branches). However, the autonomous systems at the root of the tree also maintain a record of their piers, so that they can forward traffic to the correct peer. Hence, the following is a more complete diagram of the internet:
INTERNET CORE (TIER 1 MESH) ╔══════════════╦═════════════╦════════╦═════════════╗ ║ ║ ║ ║ ║ AT&T (AS7018) <══╬══> Lumen (AS3356) <══╬══> NTT (AS2914) ║ ║ ║ ║ ║ ║ ║ ╚══> Telia (AS1299) <══╝ ║ ║ ╚═══════════════════════════════╝ ║ ║ ╚═> Deutsche Telekom (AS3320) <═╝ ║ TREE HIERARCHY BELOW - MESH ABOVE ║ ▼ [ Tier 1 ISP ]───────────────────┐ / | | / ▼ ▼ [IXP]═══╦═══[IXP] [IXP] ║ ║ ▼ ▼ Tier 2 ISP◄──────────╗ Tier 2 ISP◄───────╗ / \ ║ / \ ║ ▼ ▼ ║ ▼ ▼ ║ [IXP]═╦[IXP] ║ [IXP]═╦[IXP] ║ / \ ║ / \ ║ ▼ ▼ ▼ ▼ ▼ ▼ Tier 3 ISP User Tier 3 ISP EnterpriseSo its a mesh network - whats wrong with that?
In the example above, NTT can only send traffic to Deutsche Telekom via Lumen or AT&T. NTT relies on its peers to maintain a correct record of the IP range that they are responsible for, so that traffic that was intended for Deutsche Telekom doesn't end up in the wrong network. An intentional or even accidental error in an autonomous system's routing tables can be detrimental to the flow of traffic through the network.
Hence, mesh networks require: * Reliability: peers rely on each-other not to fail (e.g., 2019 AWS US-East-1 availability) * Trust: peers must be honest about address ranges (e.g., 2018 BGP hijacking incident) * Central planning: BGP traffic engineering determines which route a packet takes
Application Layer Innovations
Now that we have a rough overview of how the internet is broken, lets think about what can still be done. The flat hierarchy that we associate with mesh networks sounds beautiful, but it doesn't scale. However, the tree-like structure assumes that most participants in the network rely on an authority to give them an address or a range of addresses so that they can communicate.
Overlay networks
Fortunately all it takes to interact with someone on nostr is their public key. The recipients client will render your signed and/or encrypted event no matter how it reaches them. Whether your note reaches them over the internet, over some other network or via a carrier pigeon doesn't matter. nostr:npub1hw6amg8p24ne08c9gdq8hhpqx0t0pwanpae9z25crn7m9uy7yarse465gr is working on a NIP for that and I'm sure he will share an explanation of how it works.
Bitcoin Instead of a Routing Algorithm
Now that we have digital bearer assets (e-cash), users can pay their internet gateway (TollGate) for access to the internet even though they are still offline. Once the TollGate has redeemed the e-cash, it gives the user access to the internet.
Frictionless Switching between ISPs (TollGates)
Legacy internet service providers use KYC money (fiat) to transfer the cost of the infrastructure to their users. However, this means that they are able to identify which packet belongs to which user. The KYC nature of their interaction with the users also makes it difficult for users to switch ISPs when service providers undercut each-other. Internet users who are on e-cash rails can hop between ISPs frictionlessly since they buy small amounts of data frequently in a granular manner.
Users that have access to independent competing TollGates can switch between them freely, so its impossible for any one TollGate to prevent a user from connecting to the internet. The only thing a TollGate can do is attract traffic by providing cheaper and/or faster internet access.
Anyone can arbitrage connectivity
Now that users have non KYC internet, there is nothing stopping them from reselling access to their internet connection. Anyone who has a WiFi router and access to a cheap internet connection can act as a range extender by re-selling access to that gateway for people who aren't able to connect directly.
Now the route that the traffic takes through the network is determined dynamically by the markets. The individual TollGate operators select their gateways and set their prices when they create a business model. The customers select the route that best meets their needs by selecting a gateway for their next purchase.
-
 @ 68c90cf3:99458f5c
2025-04-20 00:15:35
@ 68c90cf3:99458f5c
2025-04-20 00:15:35Why test Untype.app?
It's always good to test something before investing resources and going into production. I'd like to know how things will work and the final result before publishing articles on other topics. I don't write very often, but I'd like to change that. Writing articles on Nostr is inspiring, and Untype.app seems like a good vehicle to do so.
What interested me in Untype.app?
- Clean and simple design
- Formatting capabilities
- Nostr integration
- AI integration
What to test?
For now I just want to see that I can publish an article to Nostr and that it looks like I would expect it to. I hope to try the AI features in the near future.
So far, so good. A couple of initial observations:
- I'd like the ability to add line breaks
- I can't quite figure out how to size images

-
 @ f7d424b5:618c51e8
2025-04-19 22:06:47
@ f7d424b5:618c51e8
2025-04-19 22:06:47It's our podcast and we'll talk about whatever we want. Welcome to a return to normalcy where we cover a variety of subjects instead of just a couple of really long ones. Crack open a beer and chill with us. We're gonna talk about the Galaxy showcase, Marathon, Skyblivion & the leaked Oblivion remake, and a whole bunch more.
In the opening of the episode we get Vic's reaction to a really specific trailer, if you want to follow along, this is the link to that video
Other stuff cited:
Obligatory:
- Listen to the new episode here!
- Discuss this episode on OUR NEW FORUM
- Get the RSS and Subscribe (this is a new feed URL, but the old one redirects here too!)
- Get a modern podcast app to use that RSS feed on at newpodcastapps.com
- Or listen to the show on the forum using the embedded Podverse player!
- Send your complaints here
Reminder that this is a Value4Value podcast so any support you can give us via a modern podcasting app is greatly appreciated and we will never bow to corporate sponsors!
-
 @ b8af284d:f82c91dd
2025-04-07 07:09:50
@ b8af284d:f82c91dd
2025-04-07 07:09:50
"Auf den deutschen Konten, Sparkonten und laufenden Girokonten liegen 2,8 Billionen Euro. Stellen Sie sich einen kurzen Augenblick vor, wir wären in der Lage, davon nur 10 Prozent zu mobilisieren – mit einem vernünftigen Zinssatz, für die öffentliche Infrastruktur in Deutschland […]”
Friedrich Merz, Blackrock-Aufsichtsratvorsitzender 2016-2020
„Governments can’t fund infrastructure through deficits. The deficits can’t get much higher. Instead, they’ll turn to private investors.“
Liebe Abonnenten,
im Jahr 1999 lag der durchschnittliche Bruttolohn eines deutschen Arbeiters bei monatlich 2100 Euro. 26 Jahre später sind es etwa 4200 Euro. In diesem Zeitraum sind die Löhne also durchschnittlich jedes Jahr um 2,7 Prozent gewachsen. (Um die Reallöhne, also die tatsächliche inflationsbereinigte Kaufkraft soll es ausnahmsweise einmal nicht gehen.)
Im selben Zeitraum ist die globale Wirtschaftsleistung um fünf Prozent im Jahr gewachsen. Der amerikanische Aktien-Index S\&P500 legte durchschnittlich jedes Jahr um acht Prozent zu.
Die Unterschiede klingen zunächst gering. 2,7 Prozent, 5 Prozent, 8 Prozent - Peanuts, was soll’s? Deutlich werden die Bedeutung dieser Zahlen, wenn man sie in absolute Zahlen umlegt. Bei einem Zuwachs von durchschnittlich fünf Prozent würde selbiger Arbeiter heute 7560 Euro verdienen. Wäre sein Lohn so stark gestiegen wie der S\&P500, läge er bei 15.483 Euro.
Das Unternehmen Blackrock ging im Jahr 1999 an die Börse. Die jährlichen Kurssteigerungen der Aktie liegen durchschnittlich bei 21 Prozent. Aus den 2100 Euro wären damit 334.661 Euro geworden.
Nimmt man nur den Gewinn des Unternehmens, landet man bei etwa zehn Prozent Rendite nach Steuern.
Irgendwie also wächst der Finanzmarkt schneller als Löhne, und Blackrock wächst nochmals schneller als der Finanzmarkt. Wie kann das sein? Was macht Blackrock, für die bis vor wenigen Jahren der künftige Bundeskanzler Friedrich Merz tätig war?
Ein Blackrock-Deepdive:
Blackrock - the bright side
1988 gründete Larry Fink zusammen mit einer Gruppe von Mitarbeitern “Blackstone Financial Management”. Die Firma wurde 1992 in Blackrock umbenannt und ging 1999 an die Börse. Zehn Jahre später übernahm die Firma Barclays Global Investors (BGI). Letztere brachte die Marke „ishares“ mit ins Portfolio. Zum Kerngeschäft von Blackrock gehören seitdem ETFs - die vielleicht beliebteste Anlageklasse der Welt.
ETFs sind keine Erfindung von Blackrock, aber das Unternehmen hat viel dazu beigetragen, dass ETFs heute in fast jedem Portfolio zu finden sind. Bevor es ETFs gab, konnten Kleinanleger fast nur in aktiv gemanagte Fonds investieren. Dabei kaufen und verkaufen hochbezahlte Analysten Aktien und verlangen dafür eine Gebühr von zwei Prozent. Bei ETFs liegen diese im Promillebereich. Eine Gebühr von zwei Prozent mag vernachlässigbar klingen. Über die Jahre aber macht dies einen Riesenunterschied - wie das Beispiel des Bruttolohns zeigt.
Hinzu kommt: Statistisch laufen passive Indexfonds oft besser als aktiv geleitete Investmentfonds.
Blackrock ist es mit seinen ETFs gelungen, die Geldanlage zu demokratisieren. Das Unternehmen profitiert nicht von steigenden Kursen der Aktien, sondern kassiert minimale Gebühren beim Kauf und Verkauf - aber bei einem verwalteten Vermögen von 4,5 Billionen Dollar kommt eben schnell etwas zusammen. 1989 hatten nur rund 30 Prozent der Amerikaner Aktien, heute sind es über 60 Prozent. In Deutschland liegt der Anteil bei nur 15 Prozent.
Niemand muss mehr um Lohnerhöhungen bangen - er kann von der annualisierten Wachstumsrate von acht Prozent (S\&P500) profitieren, wenn er jeden Monat in Blackrock-ETFs investiert. Selber Schuld, wer nicht!
Blackrock - the dark side
Wer die letzten Jahre nicht völlig außerhalb des Schwurbelversums verbracht hat, wird mitbekommen haben, dass Blackrock Thema zahlreicher Verschwörungstheorien ist. Von Covid über die Rüstungsindustrie bis zum Wiederaufbau der Ukraine. ETFs sind tatsächlich nicht das einzige Geschäftsmodell. Hinzu kommt eine weniger transparente Vermögensverwaltung von rund sieben Billionen Dollar. Kunden sind neben Unternehmen und Familien auch ganze Staaten. Außerdem ist Blackrock Großaktionär bei tausenden von Unternehmen. Es hält große Anteile von Apple, Microsoft, Nvidia aber auch von Vonovia, Bayer und der Deutschen Bank. Und über diese Beteiligungen übt das Unternehmen Macht aus. Das bekannteste Beispiel sind ESG-Kriterien (Environmental, Social, Governance), die Larry Fink ab 2018 propagierte. Mittlerweile ist Fink davon abgerückt, im aktuellen Jahresbrief ist davon wenig zu lesen. Das eigentliche Problem sitzt tiefer, und hat mit der Rendite zu tun.
Was hat Blackrock vor?
Zehn oder 20 Prozent Wachstum sind über einen langen Zeitraum kaum realistisch zu erwirtschaften. Dafür braucht es „Megatrends“. Künstliche Intelligenz zum Beispiel verspricht Produktivitätsgewinne, die weitaus über der Norm liegen. Was aber, wenn diese ausbleiben? Lässt sich eventuell etwas nachhelfen?
Am bequemsten ist es, wenn Regierungen Steuergelder in Richtung Unternehmen verschieben. Dann sparen sich die Profiteure auch noch die Werbekosten. Was, wenn eine Regierung ein großes Investitionsprogramm auflegt, von dem dann Unternehmen profitieren, in die Blackrock frühzeitig investiert hat? Was, wenn mehrere Regierungen dies gleichzeitig tun? Nun kann man sich fragen, bei welchen Komplexen dies zuletzt der Fall war. Blackrock hält ungefähr sieben Prozent der Pfizer-Aktien und rund ein Prozent von Biontech. Etwa fünf Prozent von Rheinmetall-Aktien sind…
Weiter geht es auf BlingBling - dem wöchentlichen Newsletter über Geld, Geopolitik und Bitcoin
-
 @ a95c6243:d345522c
2025-03-11 10:22:36
@ a95c6243:d345522c
2025-03-11 10:22:36«Wir brauchen eine digitale Brandmauer gegen den Faschismus», schreibt der Chaos Computer Club (CCC) auf seiner Website. Unter diesem Motto präsentierte er letzte Woche einen Forderungskatalog, mit dem sich 24 Organisationen an die kommende Bundesregierung wenden. Der Koalitionsvertrag müsse sich daran messen lassen, verlangen sie.
In den drei Kategorien «Bekenntnis gegen Überwachung», «Schutz und Sicherheit für alle» sowie «Demokratie im digitalen Raum» stellen die Unterzeichner, zu denen auch Amnesty International und Das NETTZ gehören, unter anderem die folgenden «Mindestanforderungen»:
- Verbot biometrischer Massenüberwachung des öffentlichen Raums sowie der ungezielten biometrischen Auswertung des Internets.
- Anlasslose und massenhafte Vorratsdatenspeicherung wird abgelehnt.
- Automatisierte Datenanalysen der Informationsbestände der Strafverfolgungsbehörden sowie jede Form von Predictive Policing oder automatisiertes Profiling von Menschen werden abgelehnt.
- Einführung eines Rechts auf Verschlüsselung. Die Bundesregierung soll sich dafür einsetzen, die Chatkontrolle auf europäischer Ebene zu verhindern.
- Anonyme und pseudonyme Nutzung des Internets soll geschützt und ermöglicht werden.
- Bekämpfung «privaten Machtmissbrauchs von Big-Tech-Unternehmen» durch durchsetzungsstarke, unabhängige und grundsätzlich föderale Aufsichtsstrukturen.
- Einführung eines digitalen Gewaltschutzgesetzes, unter Berücksichtigung «gruppenbezogener digitaler Gewalt» und die Förderung von Beratungsangeboten.
- Ein umfassendes Förderprogramm für digitale öffentliche Räume, die dezentral organisiert und quelloffen programmiert sind, soll aufgelegt werden.
Es sei ein Irrglaube, dass zunehmende Überwachung einen Zugewinn an Sicherheit darstelle, ist eines der Argumente der Initiatoren. Sicherheit erfordere auch, dass Menschen anonym und vertraulich kommunizieren können und ihre Privatsphäre geschützt wird.
Gesunde digitale Räume lebten auch von einem demokratischen Diskurs, lesen wir in dem Papier. Es sei Aufgabe des Staates, Grundrechte zu schützen. Dazu gehöre auch, Menschenrechte und demokratische Werte, insbesondere Freiheit, Gleichheit und Solidarität zu fördern sowie den Missbrauch von Maßnahmen, Befugnissen und Infrastrukturen durch «die Feinde der Demokratie» zu verhindern.
Man ist geneigt zu fragen, wo denn die Autoren «den Faschismus» sehen, den es zu bekämpfen gelte. Die meisten der vorgetragenen Forderungen und Argumente finden sicher breite Unterstützung, denn sie beschreiben offenkundig gängige, kritikwürdige Praxis. Die Aushebelung der Privatsphäre, der Redefreiheit und anderer Grundrechte im Namen der Sicherheit wird bereits jetzt massiv durch die aktuellen «demokratischen Institutionen» und ihre «durchsetzungsstarken Aufsichtsstrukturen» betrieben.
Ist «der Faschismus» also die EU und ihre Mitgliedsstaaten? Nein, die «faschistische Gefahr», gegen die man eine digitale Brandmauer will, kommt nach Ansicht des CCC und seiner Partner aus den Vereinigten Staaten. Private Überwachung und Machtkonzentration sind dabei weltweit schon lange Realität, jetzt endlich müssen sie jedoch bekämpft werden. In dem Papier heißt es:
«Die willkürliche und antidemokratische Machtausübung der Tech-Oligarchen um Präsident Trump erfordert einen Paradigmenwechsel in der deutschen Digitalpolitik. (...) Die aktuellen Geschehnisse in den USA zeigen auf, wie Datensammlungen und -analyse genutzt werden können, um einen Staat handstreichartig zu übernehmen, seine Strukturen nachhaltig zu beschädigen, Widerstand zu unterbinden und marginalisierte Gruppen zu verfolgen.»
Wer auf der anderen Seite dieser Brandmauer stehen soll, ist also klar. Es sind die gleichen «Feinde unserer Demokratie», die seit Jahren in diese Ecke gedrängt werden. Es sind die gleichen Andersdenkenden, Regierungskritiker und Friedensforderer, die unter dem großzügigen Dach des Bundesprogramms «Demokratie leben» einem «kontinuierlichen Echt- und Langzeitmonitoring» wegen der Etikettierung «digitaler Hass» unterzogen werden.
Dass die 24 Organisationen praktisch auch die Bekämpfung von Google, Microsoft, Apple, Amazon und anderen fordern, entbehrt nicht der Komik. Diese fallen aber sicher unter das Stichwort «Machtmissbrauch von Big-Tech-Unternehmen». Gleichzeitig verlangen die Lobbyisten implizit zum Beispiel die Förderung des Nostr-Netzwerks, denn hier finden wir dezentral organisierte und quelloffen programmierte digitale Räume par excellence, obendrein zensurresistent. Das wiederum dürfte in der Politik weniger gut ankommen.
[Titelbild: Pixabay]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 13:59:17
@ c1e9ab3a:9cb56b43
2025-04-15 13:59:17Prepared for Off-World Visitors by the Risan Institute of Cultural Heritage
Welcome to Risa, the jewel of the Alpha Quadrant, celebrated across the Federation for its tranquility, pleasure, and natural splendor. But what many travelers do not know is that Risa’s current harmony was not inherited—it was forged. Beneath the songs of surf and the serenity of our resorts lies a history rich in conflict, transformation, and enduring wisdom.
We offer this briefing not merely as a tale of our past, but as an invitation to understand the spirit of our people and the roots of our peace.
I. A World at the Crossroads
Before its admittance into the United Federation of Planets, Risa was an independent and vulnerable world situated near volatile borders of early galactic powers. Its lush climate, mineral wealth, and open society made it a frequent target for raiders and an object of interest for imperial expansion.
The Risan peoples were once fragmented, prone to philosophical and political disunity. In our early records, this period is known as the Winds of Splintering. We suffered invasions, betrayals, and the slow erosion of trust in our own traditions.
II. The Coming of the Vulcans
It was during this period of instability that a small delegation of Vulcan philosophers, adherents to the teachings of Surak, arrived on Risa. They did not come as conquerors, nor even as ambassadors, but as seekers of peace.
These emissaries of logic saw in Risa the potential for a society not driven by suppression of emotion, as Vulcan had chosen, but by the balance of joy and discipline. While many Vulcans viewed Risa’s culture as frivolous, these followers of Surak saw the seed of a different path: one in which beauty itself could be a pillar of peace.
The Risan tradition of meditative dance, artistic expression, and communal love resonated with Vulcan teachings of unity and inner control. From this unlikely exchange was born the Ricin Doctrine—the belief that peace is sustained not only through logic or strength, but through deliberate joy, shared vulnerability, and readiness without aggression.
III. Betazed and the Trial of Truth
During the same era, early contact with the people of Betazed brought both inspiration and tension. A Betazoid expedition, under the guise of diplomacy, was discovered to be engaging in deep telepathic influence and information extraction. The Risan people, who valued consent above all else, responded not with anger, but with clarity.
A council of Ricin philosophers invited the Betazoid delegation into a shared mind ceremony—a practice in which both cultures exposed their thoughts in mutual vulnerability. The result was not scandal, but transformation. From that moment forward, a bond was formed, and Risa’s model of ethical emotional expression and consensual empathy became influential in shaping Betazed’s own peace philosophies.
IV. Confronting Marauders and Empires
Despite these philosophical strides, Risa’s path was anything but tranquil.
-
Orion Syndicate raiders viewed Risa as ripe for exploitation, and for decades, cities were sacked, citizens enslaved, and resources plundered. In response, Risa formed the Sanctum Guard, not a military in the traditional sense, but a force of trained defenders schooled in both physical technique and psychological dissuasion. The Ricin martial arts, combining beauty with lethality, were born from this necessity.
-
Andorian expansionism also tested Risa’s sovereignty. Though smaller in scale, skirmishes over territorial claims forced Risa to adopt planetary defense grids and formalize diplomatic protocols that balanced assertiveness with grace. It was through these conflicts that Risa developed the art of the ceremonial yield—a symbolic concession used to diffuse hostility while retaining honor.
-
Romulan subterfuge nearly undid Risa from within. A corrupt Romulan envoy installed puppet leaders in one of our equatorial provinces. These agents sought to erode Risa’s social cohesion through fear and misinformation. But Ricin scholars countered the strategy not with rebellion, but with illumination: they released a network of truths, publicly broadcasting internal thoughts and civic debates to eliminate secrecy. The Romulan operation collapsed under the weight of exposure.
-
Even militant Vulcan splinter factions, during the early Vulcan-Andorian conflicts, attempted to turn Risa into a staging ground, pressuring local governments to support Vulcan supremacy. The betrayal struck deep—but Risa resisted through diplomacy, invoking Surak’s true teachings and exposing the heresy of their logic-corrupted mission.
V. Enlightenment Through Preparedness
These trials did not harden us into warriors. They refined us into guardians of peace. Our enlightenment came not from retreat, but from engagement—tempered by readiness.
- We train our youth in the arts of balance: physical defense, emotional expression, and ethical reasoning.
- We teach our history without shame, so that future generations will not repeat our errors.
- We host our guests with joy, not because we are naïve, but because we know that to celebrate life fully is the greatest act of resistance against fear.
Risa did not become peaceful by denying the reality of conflict. We became peaceful by mastering our response to it.
And in so doing, we offered not just pleasure to the stars—but wisdom.
We welcome you not only to our beaches, but to our story.
May your time here bring you not only rest—but understanding.
– Risan Institute of Cultural Heritage, in collaboration with the Council of Enlightenment and the Ricin Circle of Peacekeepers
-
-
 @ 4cebd4f5:0ac3ed15
2025-04-19 13:52:54
@ 4cebd4f5:0ac3ed15
2025-04-19 13:52:54Tóm tắt Hackathon
uOttaHack 7 – hackathon chính thức của Đại học Ottawa – thu hút 286 người tham gia và 138 dự án. Diễn ra từ ngày 17–19/1/2025, sự kiện tập trung vào tiêu chí đổi mới, độ phức tạp kỹ thuật, tính thực tiễn và khả năng trình bày, đảm bảo các giải pháp sáng tạo cho vấn đề thực tế.
Hackathon thúc đẩy hợp tác đa ngành, chào đón sinh viên mọi trình độ tham gia phát triển phần mềm và công nghệ tác động. Sự kiện nhấn mạnh học hỏi và kết nối, tạo cơ hội cho developer mới và có kinh nghiệm cùng phát triển kỹ năng. uOttaHack 7 phản ánh sứ mệnh của Đại học Ottawa trong thúc đẩy đổi mới, đồng thời ghi nhận dự án sáng tạo thể hiện kỹ năng kỹ thuật và tiềm năng ứng dụng thực tế.
Các dự án đoạt giải
uOttaHack 7 trao giải cho 23 hạng mục với 853 người tham gia. Dưới đây là những dự án tiêu biểu:
uOttaHack General Challenge Prize Winners
- KellerApp: Cầu nối giao tiếp giữa người nghe và khiếm thính qua công cụ dịch tiếng Anh sang ngôn ngữ ký hiệu (BSL).
- MemoryMate: Kính thông minh tích hợp AI hỗ trợ bệnh nhân sa sút trí nhớ gợi lại tương tác qua ứng dụng.
- Sweatris: Game Tetris tương tác điều khiển bằng chuyển động cơ thể, kết hợp thể dục và giải trí.
Solace Prize Winner
- uOttaType: Nâng cao cộng tác tài liệu với AI, bao gồm chuyển giọng nói thành văn bản và chat thời gian thực, sử dụng Solace Event Brokers.
QNX Prize Winner
- QNX - Traffic Lights: Hệ thống đèn giao thông thời gian thực triển khai trên Raspberry Pi 4 với QNX 8.0, tích hợp tính năng cho người đi bộ.
Survey Monkey Prize Winners
- Opinionated Orangutans: Tạo khảo sát cá nhân hóa bằng OpenAI APIs, phân tích thói quen duyệt web.
- Survey Monkey Chatbot: Thu thập dữ liệu khảo sát qua chatbot dùng GROQ AI và phân tích cảm xúc.
- Cartbuddy: Ứng dụng retail feedback tích hợp AI, sử dụng SurveyMonkey APIs.
NAV CANADA Prize Winner
DeepCode Prize Winner
- SecureVision: Hệ thống phân tích mối đe dọa bảo mật, nâng cấp dữ liệu thô thành insight nâng cao.
Starknet Prize Winners
- Dice-Roll OnChain: Game C++ trên blockchain Starknet với xác thực minh bạch.
- Playtopia: Build Your Game, Earn Real $$$: Nền tảng kiếm tiền qua game kỹ năng.
- Focusify | Distributed Mental Health Focus App: Ứng dụng tập trung học tập bằng cơ chế game hóa và công nghệ phi tập trung.
Gadget Prize Winners
- cuNext: Thiết kế lại giao diện Carleton Central để cải thiện trải nghiệm người dùng.
- Skej: Tạo lịch học bằng AI, tích hợp đánh giá giáo sư và điều khiển bằng giọng nói.
Groq Prize Winner
- SilentGuard: Ứng dụng cứu hộ khẩn cấp qua cuộc gọi giả và cụm từ kích hoạt, sử dụng AI.
MLH Prize Winners
- SecureVision, AgentSingularity (triển khai AI agent tùy chỉnh), KellerApp, Talent Forge (trao đổi kỹ năng phi tiền tệ), SilentGuard, Act2Learn (học tập qua kịch bản role-play).
Tail'ed Prize Winner
- HealthSync-360: Ứng dụng theo dõi sức khỏe tích hợp Groq AI, kế hoạch mở rộng với nền tảng thể thao lớn.
Chi tiết dự án tại uOttaHack 7 Projects.
Về Nhà tổ chức
uOttaHack
uOttaHack là đơn vị tổ chức hackathon và cộng đồng tập trung thúc đẩy đổi mới công nghệ, phát triển kỹ năng trong lĩnh vực blockchain và công nghệ. Với chuyên môn tổ chức sự kiện khuyến khích giải quyết vấn đề sáng tạo, uOttaHack xây dựng danh tiếng trong việc nuôi dưỡng tài năng kỹ thuật và tạo cơ hội kết nối. Định hướng hiện tại của tổ chức bao gồm thúc đẩy tiến bộ công nghệ và hỗ trợ dự án có tiềm năng tác động đến hệ sinh thái tech.
-
 @ 1beecee5:d29d2162
2025-04-21 06:30:55
@ 1beecee5:d29d2162
2025-04-21 06:30:55 -
 @ a95c6243:d345522c
2025-03-04 09:40:50
@ a95c6243:d345522c
2025-03-04 09:40:50Die «Eliten» führen bereits groß angelegte Pilotprojekte für eine Zukunft durch, die sie wollen und wir nicht. Das schreibt der OffGuardian in einem Update zum Thema «EU-Brieftasche für die digitale Identität». Das Portal weist darauf hin, dass die Akteure dabei nicht gerade zimperlich vorgehen und auch keinen Hehl aus ihren Absichten machen. Transition News hat mehrfach darüber berichtet, zuletzt hier und hier.
Mit der EU Digital Identity Wallet (EUDI-Brieftasche) sei eine einzige von der Regierung herausgegebene App geplant, die Ihre medizinischen Daten, Beschäftigungsdaten, Reisedaten, Bildungsdaten, Impfdaten, Steuerdaten, Finanzdaten sowie (potenziell) Kopien Ihrer Unterschrift, Fingerabdrücke, Gesichtsscans, Stimmproben und DNA enthält. So fasst der OffGuardian die eindrucksvolle Liste möglicher Einsatzbereiche zusammen.
Auch Dokumente wie der Personalausweis oder der Führerschein können dort in elektronischer Form gespeichert werden. Bis 2026 sind alle EU-Mitgliedstaaten dazu verpflichtet, Ihren Bürgern funktionierende und frei verfügbare digitale «Brieftaschen» bereitzustellen.
Die Menschen würden diese App nutzen, so das Portal, um Zahlungen vorzunehmen, Kredite zu beantragen, ihre Steuern zu zahlen, ihre Rezepte abzuholen, internationale Grenzen zu überschreiten, Unternehmen zu gründen, Arzttermine zu buchen, sich um Stellen zu bewerben und sogar digitale Verträge online zu unterzeichnen.
All diese Daten würden auf ihrem Mobiltelefon gespeichert und mit den Regierungen von neunzehn Ländern (plus der Ukraine) sowie über 140 anderen öffentlichen und privaten Partnern ausgetauscht. Von der Deutschen Bank über das ukrainische Ministerium für digitalen Fortschritt bis hin zu Samsung Europe. Unternehmen und Behörden würden auf diese Daten im Backend zugreifen, um «automatisierte Hintergrundprüfungen» durchzuführen.
Der Bundesverband der Verbraucherzentralen und Verbraucherverbände (VZBV) habe Bedenken geäußert, dass eine solche App «Risiken für den Schutz der Privatsphäre und der Daten» berge, berichtet das Portal. Die einzige Antwort darauf laute: «Richtig, genau dafür ist sie ja da!»
Das alles sei keine Hypothese, betont der OffGuardian. Es sei vielmehr «Potential». Damit ist ein EU-Projekt gemeint, in dessen Rahmen Dutzende öffentliche und private Einrichtungen zusammenarbeiten, «um eine einheitliche Vision der digitalen Identität für die Bürger der europäischen Länder zu definieren». Dies ist nur eines der groß angelegten Pilotprojekte, mit denen Prototypen und Anwendungsfälle für die EUDI-Wallet getestet werden. Es gibt noch mindestens drei weitere.
Den Ball der digitalen ID-Systeme habe die Covid-«Pandemie» über die «Impfpässe» ins Rollen gebracht. Seitdem habe das Thema an Schwung verloren. Je näher wir aber der vollständigen Einführung der EUid kämen, desto mehr Propaganda der Art «Warum wir eine digitale Brieftasche brauchen» könnten wir in den Mainstream-Medien erwarten, prognostiziert der OffGuardian. Vielleicht müssten wir schon nach dem nächsten großen «Grund», dem nächsten «katastrophalen katalytischen Ereignis» Ausschau halten. Vermutlich gebe es bereits Pläne, warum die Menschen plötzlich eine digitale ID-Brieftasche brauchen würden.
Die Entwicklung geht jedenfalls stetig weiter in genau diese Richtung. Beispielsweise hat Jordanien angekündigt, die digitale biometrische ID bei den nächsten Wahlen zur Verifizierung der Wähler einzuführen. Man wolle «den Papierkrieg beenden und sicherstellen, dass die gesamte Kette bis zu den nächsten Parlamentswahlen digitalisiert wird», heißt es. Absehbar ist, dass dabei einige Wahlberechtigte «auf der Strecke bleiben» werden, wie im Fall von Albanien geschehen.
Derweil würden die Briten gerne ihre Privatsphäre gegen Effizienz eintauschen, behauptet Tony Blair. Der Ex-Premier drängte kürzlich erneut auf digitale Identitäten und Gesichtserkennung. Blair ist Gründer einer Denkfabrik für globalen Wandel, Anhänger globalistischer Technokratie und «moderner Infrastruktur».
Abschließend warnt der OffGuardian vor der Illusion, Trump und Musk würden den US-Bürgern «diesen Schlamassel ersparen». Das Department of Government Efficiency werde sich auf die digitale Identität stürzen. Was könne schließlich «effizienter» sein als eine einzige App, die für alles verwendet wird? Der Unterschied bestehe nur darin, dass die US-Version vielleicht eher privat als öffentlich sei – sofern es da überhaupt noch einen wirklichen Unterschied gebe.
[Titelbild: Screenshot OffGuardian]
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-03-01 10:39:35
@ a95c6243:d345522c
2025-03-01 10:39:35Ständige Lügen und Unterstellungen, permanent falsche Fürsorge \ können Bausteine von emotionaler Manipulation sein. Mit dem Zweck, \ Macht und Kontrolle über eine andere Person auszuüben. \ Apotheken Umschau
Irgendetwas muss passiert sein: «Gaslighting» ist gerade Thema in vielen Medien. Heute bin ich nach längerer Zeit mal wieder über dieses Stichwort gestolpert. Das war in einem Artikel von Norbert Häring über Manipulationen des Deutschen Wetterdienstes (DWD). In diesem Fall ging es um eine Pressemitteilung vom Donnerstag zum «viel zu warmen» Winter 2024/25.
Häring wirft der Behörde vor, dreist zu lügen und Dinge auszulassen, um die Klimaangst wach zu halten. Was der Leser beim DWD nicht erfahre, sei, dass dieser Winter kälter als die drei vorangegangenen und kälter als der Durchschnitt der letzten zehn Jahre gewesen sei. Stattdessen werde der falsche Eindruck vermittelt, es würde ungebremst immer wärmer.
Wem also der zu Ende gehende Winter eher kalt vorgekommen sein sollte, mit dessen Empfinden stimme wohl etwas nicht. Das jedenfalls wolle der DWD uns einreden, so der Wirtschaftsjournalist. Und damit sind wir beim Thema Gaslighting.
Als Gaslighting wird eine Form psychischer Manipulation bezeichnet, mit der die Opfer desorientiert und zutiefst verunsichert werden, indem ihre eigene Wahrnehmung als falsch bezeichnet wird. Der Prozess führt zu Angst und Realitätsverzerrung sowie zur Zerstörung des Selbstbewusstseins. Die Bezeichnung kommt von dem britischen Theaterstück «Gas Light» aus dem Jahr 1938, in dem ein Mann mit grausamen Psychotricks seine Frau in den Wahnsinn treibt.
Damit Gaslighting funktioniert, muss das Opfer dem Täter vertrauen. Oft wird solcher Psychoterror daher im privaten oder familiären Umfeld beschrieben, ebenso wie am Arbeitsplatz. Jedoch eignen sich die Prinzipien auch perfekt zur Manipulation der Massen. Vermeintliche Autoritäten wie Ärzte und Wissenschaftler, oder «der fürsorgliche Staat» und Institutionen wie die UNO oder die WHO wollen uns doch nichts Böses. Auch Staatsmedien, Faktenchecker und diverse NGOs wurden zu «vertrauenswürdigen Quellen» erklärt. Das hat seine Wirkung.
Warum das Thema Gaslighting derzeit scheinbar so populär ist, vermag ich nicht zu sagen. Es sind aber gerade in den letzten Tagen und Wochen auffällig viele Artikel dazu erschienen, und zwar nicht nur von Psychologen. Die Frankfurter Rundschau hat gleich mehrere publiziert, und Anwälte interessieren sich dafür offenbar genauso wie Apotheker.
Die Apotheken Umschau machte sogar auf «Medical Gaslighting» aufmerksam. Davon spreche man, wenn Mediziner Symptome nicht ernst nähmen oder wenn ein gesundheitliches Problem vom behandelnden Arzt «schnöde heruntergespielt» oder abgetan würde. Kommt Ihnen das auch irgendwie bekannt vor? Der Begriff sei allerdings irreführend, da er eine manipulierende Absicht unterstellt, die «nicht gewährleistet» sei.
Apropos Gaslighting: Die noch amtierende deutsche Bundesregierung meldete heute, es gelte, «weiter [sic!] gemeinsam daran zu arbeiten, einen gerechten und dauerhaften Frieden für die Ukraine zu erreichen». Die Ukraine, wo sich am Montag «der völkerrechtswidrige Angriffskrieg zum dritten Mal jährte», verteidige ihr Land und «unsere gemeinsamen Werte».
Merken Sie etwas? Das Demokratieverständnis mag ja tatsächlich inzwischen in beiden Ländern ähnlich traurig sein. Bezüglich Friedensbemühungen ist meine Wahrnehmung jedoch eine andere. Das muss an meinem Gedächtnis liegen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ ec9bd746:df11a9d0
2025-04-06 08:06:08
@ ec9bd746:df11a9d0
2025-04-06 08:06:08🌍 Time Window:
🕘 When: Every even week on Sunday at 9:00 PM CET
🗺️ Where: https://cornychat.com/eurocornStart: 21:00 CET (Prague, UTC+1)
End: approx. 02:00 CET (Prague, UTC+1, next day)
Duration: usually 5+ hours.| Region | Local Time Window | Convenience Level | |-----------------------------------------------------|--------------------------------------------|---------------------------------------------------------| | Europe (CET, Prague) 🇨🇿🇩🇪 | 21:00–02:00 CET | ✅ Very Good; evening & night | | East Coast North America (EST) 🇺🇸🇨🇦 | 15:00–20:00 EST | ✅ Very Good; afternoon & early evening | | West Coast North America (PST) 🇺🇸🇨🇦 | 12:00–17:00 PST | ✅ Very Good; midday & afternoon | | Central America (CST) 🇲🇽🇨🇷🇬🇹 | 14:00–19:00 CST | ✅ Very Good; afternoon & evening | | South America West (Peru/Colombia PET/COT) 🇵🇪🇨🇴 | 15:00–20:00 PET/COT | ✅ Very Good; afternoon & evening | | South America East (Brazil/Argentina/Chile, BRT/ART/CLST) 🇧🇷🇦🇷🇨🇱 | 17:00–22:00 BRT/ART/CLST | ✅ Very Good; early evening | | United Kingdom/Ireland (GMT) 🇬🇧🇮🇪 | 20:00–01:00 GMT | ✅ Very Good; evening hours (midnight convenient) | | Eastern Europe (EET) 🇷🇴🇬🇷🇺🇦 | 22:00–03:00 EET | ✅ Good; late evening & early night (slightly late) | | Africa (South Africa, SAST) 🇿🇦 | 22:00–03:00 SAST | ✅ Good; late evening & overnight (late-night common) | | New Zealand (NZDT) 🇳🇿 | 09:00–14:00 NZDT (next day) | ✅ Good; weekday morning & afternoon | | Australia (AEDT, Sydney) 🇦🇺 | 07:00–12:00 AEDT (next day) | ✅ Good; weekday morning to noon | | East Africa (Kenya, EAT) 🇰🇪 | 23:00–04:00 EAT | ⚠️ Slightly late (night hours; late night common) | | Russia (Moscow, MSK) 🇷🇺 | 23:00–04:00 MSK | ⚠️ Slightly late (join at start is fine, very late night) | | Middle East (UAE, GST) 🇦🇪🇴🇲 | 00:00–05:00 GST (next day) | ⚠️ Late night start (midnight & early morning, but shorter attendance plausible)| | Japan/Korea (JST/KST) 🇯🇵🇰🇷 | 05:00–10:00 JST/KST (next day) | ⚠️ Early; convenient joining from ~07:00 onwards possible | | China (Beijing, CST) 🇨🇳 | 04:00–09:00 CST (next day) | ❌ Challenging; very early morning start (better ~07:00 onwards) | | India (IST) 🇮🇳 | 01:30–06:30 IST (next day) | ❌ Very challenging; overnight timing typically difficult|
-
 @ edeb837b:ac664163
2025-04-03 10:35:59
@ edeb837b:ac664163
2025-04-03 10:35:59When it comes to social trading, there are plenty of platforms that claim to offer innovative ways to connect with other traders, share strategies, and improve your market performance. But let's be real: most so-called "social trading" apps are either glorified brokerage platforms with limited community features or outdated, clunky systems that don’t offer real-time value.
There’s really only one social trading app you need to consider—NVSTly. Here’s why.
Why NVSTly Stands Above the Rest
NVSTly isn’t just another trading app with a few social features slapped on. It’s the ultimate social trading platform, purpose-built to empower traders by combining real-time trade tracking, seamless social sharing, deep market insights, and a powerful trader community.
Unlike other platforms, NVSTly isn’t just about copying trades or following vague signals—it’s about true transparency, collaboration, and learning from top traders in an interactive environment.
What is NVSTly?
NVSTly is a completely free social trading platform that lets traders track, share, and analyze their trades in real time. Whether you're trading stocks, options, or crypto, NVSTly provides a seamless multi-platform experience—available via web, iOS, Android, and even Discord.
It’s not just a social network—it’s a trader’s command center where every trade you make is part of a bigger, smarter ecosystem designed to help you grow.
Key Features That Make NVSTly #1
1. Real-Time Trade Sharing & Tracking
NVSTly integrates with brokers like Webull (with more brokerages coming soon) to automatically track your trades and display them in real-time. No manual entry—just instant trade updates for you and your followers.
2. Unique POV Trade Charting
See trades like never before. NVSTly’s proprietary POV Chart marks every trade action directly on the candlestick chart, giving you (and your followers) an unparalleled view of trading strategies in action.
3. Deep Trade Analytics & Trader Dashboards
Get powerful insights into your performance, including: - Win rate - Total gain/loss - Average return per trade - Long vs. short ratio - (Coming soon) Drawdown tracking to measure risk exposure
4. Global Trades Feed & Leaderboard
Want to see what the best traders are doing right now? The Global Trades Feed lets you watch live trades, while the Leaderboard ranks top traders based on performance metrics, making it easy to find successful strategies.
5. Fully Integrated with Discord & Telegram
No other platform makes social trading as seamless as NVSTly. The NVSTly Discord bot allows users to: - Check a trader’s latest stats - View real-time trade recaps - Fetch charts and ticker data - Receive automated trade notifications
Telegram users won’t be left out either—NVSTly is working on bringing the same functionality to Telegram for even broader access.
6. Automated Social Media Sharing
Set your trades to automatically share to Twitter/X, Discord, and soon, Telegram. Whether you’re growing your personal brand or running a trading community, NVSTly makes sure your trades get noticed.
7. Future AI & Machine Learning Enhancements
NVSTly is building AI-powered trade insights and strategy generation, allowing traders to: - Get automated trading tips tailored to their strategies - Use customizable AI models to refine their trading approach - Interact with a smart AI trading assistant via the app and Discord bot
Why NVSTly is the Only Social Trading App You Need
While others might pretend to offer social trading, NVSTly actually delivers. It’s not a gimmick or a half-baked feature—it’s a complete trading ecosystem built for real traders who want real-time data, powerful analytics, and a truly social experience.
With NVSTly, you're not just following traders—you’re engaging with them, learning from them, and improving your own strategies in the most transparent and interactive way possible.
So don’t waste time on inferior platforms. NVSTly is the only social trading app that matters.
Ready to Take Your Trading to the Next Level?
Join 50,000+ traders who are already using NVSTly to track, share, and dominate the markets.
📲 Download NVSTly today on Web, iOS, or Android!
🚀 Join our Discord community and bring the power of NVSTly straight into your server!
-
 @ d34e832d:383f78d0
2025-04-21 19:09:53
@ d34e832d:383f78d0
2025-04-21 19:09:53Such a transformation positions Nostr to compete with established social networking platforms in terms of reach while simultaneously ensuring the preservation of user sovereignty and the integrity of cryptographic trust mechanisms.

The Emergence of Encrypted Relay-to-Relay Federation
In the context of Nostr protocol scalability challenges pertaining to censorship-resistant networking paradigms, Nostr stands as a paradigm-shifting entity, underpinned by robust public-key cryptography and minimal operational assumptions. This feature set has rendered Nostr an emblematic instrument for overcoming systemic censorship, fostering permissionless content dissemination, and upholding user autonomy within digital environments. However, as the demographic footprint of Nostr's user base grows exponentially, coupled with an expanding range of content modalities, the structural integrity of individual relays faces increasing pressure.
Challenges of Isolation and Limited Scalability in Decentralized Networks
The current architecture of Nostr relays is primarily constituted of simple TCP or WebSocket servers that facilitate the publication and reception of events. While aesthetically simple, this design introduces significant performance bottlenecks and discoverability issues. Relays targeting specific regional or topical niches often rely heavily on client-side interactions or third-party directories for information exchange. This operational framework presents inefficiencies when scaled globally, especially in scenarios requiring high throughput and rapid dissemination of information. Furthermore, it does not adequately account for redundancy and availability, especially in low-bandwidth environments or regions facing strict censorship.

Navigating Impediments of Isolation and Constrained Scalability
Current Nostr relay infrastructures mainly involve basic TCP and WebSocket configurations for event publication and reception. While simple, these configurations contribute to performance bottlenecks and a significant discoverability deficit. Relays that serve niche markets often operate under constraints, relying on client-side interactions or third-party directories. These inefficiencies become particularly problematic at a global scale, where high throughput and rapid information distribution are necessary. The absence of mechanisms to enhance redundancy and availability in environments with limited connectivity or under censorship further exacerbates these issues.
Proposal for Encrypted Relay Federation
Encrypted relay federation in decentralized networking can be achieved through a novel Nostr Improvement Proposal (NIP), which introduces a sophisticated gossip-style mesh topology. In this system, relays subscribe to content tags, message types, or public keys from peer nodes, optimizing data flow and relevance.
Central to this architecture is a mutual key handshake protocol using Elliptic Curve Diffie-Hellman (ECDH) for symmetric encryption over relay keys. This ensures data integrity and confidentiality during transmission. The use of encrypted event bundles, compression, and routing based on relay reputation metrics and content demand analytics enhances throughput and optimizes network resources.
To counter potential abuse and spam, strategies like rate limiting, financially incentivized peering, and token gating are proposed, serving as control mechanisms for network interactions. Additionally, the relay federation model could emulate the Border Gateway Protocol (BGP), allowing for dynamic content advertisement and routing updates across the federated mesh, enhancing network resilience.
Advantages of Relay Federation in Data Distribution Architecture
Relay federation introduces a distributed data load management system where relays selectively store pertinent events. This enhances data retrieval efficiency, minimizes congestion, and fosters a censorship-resistant information flow. By decentralizing data storage, relays contribute to a global cache network, ensuring no single relay holds comprehensive access to all network data. This feature helps preserve the integrity of information flow, making it resistant to censorship.
An additional advantage is offline communication capabilities. Even without traditional internet access, events can still be communicated through alternative channels like Bluetooth, Wi-Fi Direct, or LoRa. This ensures local and community-based interactions remain uninterrupted during network downtime.
Furthermore, relay federations may introduce monetization strategies where specialized relays offer access to rare or high-quality data streams, promoting competition and interoperability while providing users with diverse data options.
Some Notable Markers To Nostr Becoming the Internet Layer for Censorship Resistance
Stop for a moment in your day and try to understand what Nostr can do for your communications by observing these markers:
- Protocol Idea (NIP-01 by fiatjaf) │ ▼
- npub/nsec Keypair Standard │ ▼
- First Relays Go Online │ ▼
- Identity & Auth (NIP-05, NIP-07) │ ▼
- Clients Launch (Damus, Amethyst, Iris, etc.) │ ▼
- Lightning Zaps + NWC (NIP-57) │ ▼
- Relay Moderation & Reputation NIPs │ ▼
- Protocol Bridging (ActivityPub, Matrix, Mastodon) │ ▼
- Ecash Integration (Cashu, Walletless Zaps) │ ▼
- Encrypted Relay Federation (Experimental) │ ▼
- Relay Mesh Networks (WireGuard + libp2p) │ ▼
- IoT Integration (Meshtastic + ESP32) │ ▼
- Fully Decentralized, Censorship-Resistant Social Layer
The implementation of encrypted federation represents a pivotal technological advancement, establishing a robust framework that challenges the prevailing architecture of fragmented social networking ecosystems and monopolistic centralized cloud services. This innovative approach posits that Nostr could:
- Facilitate a comprehensive, globally accessible decentralized index of information, driven fundamentally by user interactions and a novel microtransaction system (zaps), enabling efficient content valorization and information dissemination.
- Empower the concept of nomadic digital identities, allowing them to seamlessly traverse various relays, devoid of reliance on centralized identity verification systems, promoting user autonomy and privacy.
- Become the quintessential backend infrastructure for decentralized applications, knowledge graphs, and expansive datasets conducive to DVMs.
- Achieve seamless interoperability with established protocols, such as ActivityPub, Matrix, IPFS, and innovative eCash systems that offer incentive mechanisms, fostering an integrated and collaborative ecosystem.
In alignment with decentralization, encrypted relay-to-relay federation marks a significant evolution for the Nostr protocol, transitioning from isolated personal broadcasting stations to an interoperable, adaptive, trustless mesh network of communication nodes.
By implementing this sophisticated architecture, Nostr is positioned to scale efficiently, addressing global needs while preserving free speech, privacy, and individual autonomy in a world marked by surveillance and compartmentalized digital environments.
Nostr's Countenance Structure: Noteworthy Events
``` Nostr Protocol Concept by fiatjaf:
- First Relays and npub/nsec key pairs appear
- Damus, Amethyst, and other clients emerge
- Launch of Zaps and Lightning Tip Integration
- Mainstream interest post Twitter censorship events
- Ecosystem tools: NWC, NIP-07, NIP-05 adoption
- Nostr devs propose relay scoring and moderation NIPs
- Bridging begins (ActivityPub, Matrix, Mastodon)
- Cashu eCash integration with Nostr zaps (walletless tips)
- Relay-to-relay encrypted federation proposed
- Hackathons exploring libp2p, LNbits, and eCash-backed identities
- Scalable P2P Mesh using WireGuard + Nostr + Gossip
- Web3 & IoT integration with ESP32 + Meshtastic + relays
- A censorship-resistant, decentralized social internet ```
-
 @ 7c05c4f6:50d03508
2025-04-19 08:33:54
@ 7c05c4f6:50d03508
2025-04-19 08:33:54 About Cooker.club
About Cooker.clubCooker.club is a decentralized AI agent platform that combines AI, music, Web3, virtual idols, and social media, allowing AI-powered creators to operate autonomously and connect with fans through Create-to-Earn. 1. What is Create-to-Earn (C2E)? Create-to-Earn (C2E) is a decentralized incentive mechanism launched by Cooker.Club to reward both AI Agent developers and token holders. By participating in the ecosystem — either by developing AI Agents or holding their tokens — users can earn $COOK tokens automatically via smart contract-based mining. 2. How much $COOK is allocated to C2E? Cooker.Club allocates 60% of the total 1,000,000,000 $COOK supply to community incentives. C2E Season 1 will distribute 200,000,000 $COOK (20% of total supply) through on-chain mining. 3. How does C2E mining work? Each supported blockchain has fixed $COOK output per block: Base: 50 $COOK per block (≈ 2 seconds/block)
BNB Chain: 75 $COOK per block (≈ 3 seconds/block)
Solana: 10 $COOK per block (≈ 0.4 seconds/block) Each block's $COOK reward is split as follows: 10% to the DEV address of each AI Agent token
90% distributed among token holders based on their share of the total market cap 4. What is a market cap multiplier? Cooker.Club assigns some AI Agent tokens a reward multiplier to boost their effective market cap for mining calculation: Multiplier values: 1x, 1.2x, or 2x
Higher multipliers lead to more $COOK rewards
This mechanism encourages early support of high-potential or platform-supported AI Agents. 5. What are early bird rewards? Early users benefit from a 4x reward multiplier during the initial mining phase: Solana: first 1,500,000 blocks
Base: first 300,000 blocks
BNB Chain: first 200,000 blocks
- Can migrated AI Agents receive bonuses? Yes. AI Agents migrated from the Virtuals platform get a 1.2x multiplier on market cap when calculating $COOK distribution. This bonus applies to both developers and token holders.
- How is $COOK distributed between AI Agent tokens? Example on Solana: 10 $COOK is produced in one block
3 tokens: A (1M cap × 2x), B (2M × 1x), C (1M × 1x) = Total adjusted cap: 5M
Token A: 4 $COOK → 0.4 to DEV, 3.6 to Holders
Token B: 4 $COOK → 0.4 to DEV, 3.6 to Holders
Token C: 2 $COOK → 0.2 to DEV, 1.8 to Holders 8. How can users earn through C2E? There are three main ways: Hold AI Agent tokens — Earn a share of $COOK rewards proportionate to the token’s market cap
Create an AI Agent — Devs receive 10% of rewards tied to their Agent’s token
Migrate a Virtuals token — Gain a 1.2x market cap multiplier To activate earning, users must complete at least one transaction on Cooker.Club. 9. What is planned for C2E Season 2 and Season 3? Each future season will also allocate 200,000,000 $COOK. 10. Why is C2E important for the Web3 AI economy? C2E introduces a sustainable, decentralized, and automated incentive loop. It empowers AI Agents to become economically autonomous and rewards supporters based on their alignment. It transforms community belief into protocol-level value, setting the foundation for an on-chain AI-native creator economy. 11. Where can I start? There are three ways to participate in C2E, depending on your role and goals: Option 1: Hold an AI Agent token (for holders) Visit https://cooker.club
Browse available AI Agents and choose one that fits your interest
Buy the Agent’s token directly
Make at least one transaction (buy/sell/transfer) to activate eligibility
Hold the token — $COOK rewards will begin distributing automatically Option 2: Create your own AI Agent (for devs) Go to https://cooker.club
Launch your AI Agent and issue a native token
Become dev & holder
Promote your Agent — the higher the token’s market cap, the more $COOK you and your holders will earn Option 3: Migrate from Virtuals (for existing AI projects) If you have an AI Agent deployed on the Virtuals platform, initiate the migration on Cooker.club
After migration, your token and all holders will receive a 1.2x market cap multiplier for C2E reward calculation
The DEV address and holders will automatically enter the reward pool
No staking. No lockups. No claiming. Just plug in — and the protocol does the rest. Visit https://cooker.club, choose an AI Agent, buy its token, and complete one transaction to activate C2E mining. No staking. No lockups. No claims. Just hold, and the protocol takes care of the rest.
For real-time updates, follow: 🌐 https://cooker.club 🌐https://medium.com/@cookerailabs
-
 @ a95c6243:d345522c
2025-02-21 19:32:23
@ a95c6243:d345522c
2025-02-21 19:32:23Europa – das Ganze ist eine wunderbare Idee, \ aber das war der Kommunismus auch. \ Loriot
«Europa hat fertig», könnte man unken, und das wäre nicht einmal sehr verwegen. Mit solch einer Einschätzung stünden wir nicht alleine, denn die Stimmen in diese Richtung mehren sich. Der französische Präsident Emmanuel Macron warnte schon letztes Jahr davor, dass «unser Europa sterben könnte». Vermutlich hatte er dabei andere Gefahren im Kopf als jetzt der ungarische Ministerpräsident Viktor Orbán, der ein «baldiges Ende der EU» prognostizierte. Das Ergebnis könnte allerdings das gleiche sein.
Neben vordergründigen Themenbereichen wie Wirtschaft, Energie und Sicherheit ist das eigentliche Problem jedoch die obskure Mischung aus aufgegebener Souveränität und geschwollener Arroganz, mit der europäische Politiker:innende unterschiedlicher Couleur aufzutreten pflegen. Und das Tüpfelchen auf dem i ist die bröckelnde Legitimation politischer Institutionen dadurch, dass die Stimmen großer Teile der Bevölkerung seit Jahren auf vielfältige Weise ausgegrenzt werden.
Um «UnsereDemokratie» steht es schlecht. Dass seine Mandate immer schwächer werden, merkt natürlich auch unser «Führungspersonal». Entsprechend werden die Maßnahmen zur Gängelung, Überwachung und Manipulation der Bürger ständig verzweifelter. Parallel dazu plustern sich in Paris Macron, Scholz und einige andere noch einmal mächtig in Sachen Verteidigung und «Kriegstüchtigkeit» auf.
Momentan gilt es auch, das Überschwappen covidiotischer und verschwörungsideologischer Auswüchse aus den USA nach Europa zu vermeiden. So ein «MEGA» (Make Europe Great Again) können wir hier nicht gebrauchen. Aus den Vereinigten Staaten kommen nämlich furchtbare Nachrichten. Beispielsweise wurde einer der schärfsten Kritiker der Corona-Maßnahmen kürzlich zum Gesundheitsminister ernannt. Dieser setzt sich jetzt für eine Neubewertung der mRNA-«Impfstoffe» ein, was durchaus zu einem Entzug der Zulassungen führen könnte.
Der europäischen Version von «Verteidigung der Demokratie» setzte der US-Vizepräsident J. D. Vance auf der Münchner Sicherheitskonferenz sein Verständnis entgegen: «Demokratie stärken, indem wir unseren Bürgern erlauben, ihre Meinung zu sagen». Das Abschalten von Medien, das Annullieren von Wahlen oder das Ausschließen von Menschen vom politischen Prozess schütze gar nichts. Vielmehr sei dies der todsichere Weg, die Demokratie zu zerstören.
In der Schweiz kamen seine Worte deutlich besser an als in den meisten europäischen NATO-Ländern. Bundespräsidentin Karin Keller-Sutter lobte die Rede und interpretierte sie als «Plädoyer für die direkte Demokratie». Möglicherweise zeichne sich hier eine außenpolitische Kehrtwende in Richtung integraler Neutralität ab, meint mein Kollege Daniel Funk. Das wären doch endlich mal ein paar gute Nachrichten.
Von der einstigen Idee einer europäischen Union mit engeren Beziehungen zwischen den Staaten, um Konflikte zu vermeiden und das Wohlergehen der Bürger zu verbessern, sind wir meilenweit abgekommen. Der heutige korrupte Verbund unter technokratischer Leitung ähnelt mehr einem Selbstbedienungsladen mit sehr begrenztem Zugang. Die EU-Wahlen im letzten Sommer haben daran ebenso wenig geändert, wie die Bundestagswahl am kommenden Sonntag darauf einen Einfluss haben wird.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 72103ac9:460b37fd
2025-04-19 05:01:34
@ 72103ac9:460b37fd
2025-04-19 05:01:34Se você está em busca de uma plataforma moderna, segura e recheada de opções para se divertir online, a 7788bet é a escolha perfeita. Com uma interface intuitiva, suporte ao jogador de alta qualidade e uma ampla gama de jogos emocionantes, a 7788bet se destaca como um dos principais nomes no entretenimento digital do Brasil. Vamos explorar mais sobre essa plataforma inovadora e o que a torna tão especial.
Uma Plataforma Feita Para o Jogador Brasileiro A 7788bet foi pensada para atender as necessidades do público brasileiro, oferecendo não só suporte em português, mas também métodos de pagamento locais que facilitam o acesso e tornam toda a experiência mais prática. Com navegação rápida e visual moderno, o site proporciona uma experiência agradável tanto em computadores quanto em dispositivos móveis.
Desde o momento do cadastro até a hora de sacar seus ganhos, tudo é feito com segurança e transparência. A plataforma investe em tecnologia de ponta para garantir que seus dados estejam sempre protegidos, além de manter políticas rígidas de privacidade e jogo responsável.
Diversidade de Jogos para Todos os Gostos Uma das maiores vantagens da 7788bet é a sua biblioteca de jogos, que abrange desde os clássicos até os lançamentos mais modernos. Aqui, os jogadores encontram:
Slots Temáticos: Com gráficos impressionantes, trilhas sonoras imersivas e diversas mecânicas de bônus, os slots são ideais para quem gosta de jogos dinâmicos e recheados de surpresas.
Jogos de Mesa Virtuais: Os tradicionais jogos de cartas e roleta ganham versões virtuais de alta qualidade, oferecendo uma jogabilidade fluida e intuitiva.
Esportes Virtuais: Para quem gosta de esportes e quer experimentar algo diferente, os esportes virtuais simulam partidas com resultados aleatórios, trazendo uma nova camada de emoção.
Jogos Ao Vivo: Os jogos ao vivo colocam você frente a frente com anfitriões reais, transmitidos em tempo real, o que proporciona uma experiência mais interativa e autêntica.
Cada jogo é desenvolvido por provedores renomados, garantindo não apenas qualidade gráfica e sonora, mas também justiça nos resultados, certificados por entidades independentes.
Experiência do Jogador: Tudo Gira em Torno da Diversão Na 7788bet, o foco principal é proporcionar uma experiência prazerosa para seus usuários. Isso se reflete em diversas áreas, como:
Bônus e Promoções Frequentes: Novos usuários são recebidos com bônus de boas-vindas atrativos, e os jogadores fiéis podem aproveitar promoções semanais e programas de fidelidade com recompensas especiais.
Atendimento ao Cliente de Excelência: A equipe de suporte está disponível 24 horas por dia, 7 dias por semana, pronta para resolver qualquer dúvida ou problema de forma rápida e eficiente, sempre com simpatia e profissionalismo.
Depósitos e Saques Rápidos: A plataforma trabalha com os principais métodos de pagamento do país, garantindo que seus depósitos sejam instantâneos e os saques sejam processados com agilidade.
Além disso, o ambiente é completamente adaptado para o público brasileiro, com uma linguagem acessível e promoções específicas para o mercado nacional, o que torna tudo mais familiar e convidativo.
Conclusão A 7788bet é muito mais do que uma simples plataforma de jogos online. É um ambiente completo de entretenimento, pensado para oferecer segurança, diversão e praticidade para jogadores de todos os perfis. Se você procura uma experiência diferenciada, com muitas opções de jogos, suporte eficiente e uma comunidade crescente de jogadores satisfeitos, a 7788bet é o lugar ideal para começar sua jornada.
-
 @ c239c0f9:fa4a5015
2025-04-21 17:42:49
@ c239c0f9:fa4a5015
2025-04-21 17:42:49Block:#893398- April 2025The Monthly Thunderbolt Dispatch on Bitcoin layers two innovations, aggregating the Best posts about the ~Lightning Network and others Bitcoin L2 solution- Exclusively on Stacker.News
It's again that time of the month, time to catch up with the latest features and trends that are shaping the future of Bitcoin—the very first and most commented insights from around the SN world. In every issue arrives expert analysis, in-depth interview, and breaking news of the most significant advancements in the Bitcoin layer two solutions.
Subscribe and make sure you don’t miss anything about the ~Lightning Revolution!
Now let's focus on the top five items for each category, an electrifying selection that hope you'll be able to read before next edition.
Happy Zapping!
Top ~Lightning posts
Most zapranked posts this month:
-
Use RIZFUL as your BTCPay Server lightning node via NWC by @supratic 10.2k sats \ 2 comments \ 14 Apr
-
c-otto.de routing node history with a bit of data by @C_Otto 6301 sats \ 31 comments \ 23 Mar
-
Phoenix Wallet available again in the US by @Scoresby 4696 sats \ 29 comments \ 8 Apr
-
Short Text Note: Cashu is coming to ZEUS. by @supratic 5270 sats \ 13 comments \ 1 Apr
-
Hydrus - Automating lightning liquidity management by @aftermath 2281 sats \ 9 comments \ 27 Mar
Top posts by comments
Excluding the ones already mentioned above, you can see them all here (excluding those already listed above):
-
Liquidity squeezing from your node by @k00b 644 sats \ 20 comments \ 5 Apr
-
ZEUS starting to open up Cashu test builds to community sponsors. by @supratic 499 sats \ 14 comments \ 6 Apr
-
Ask Node Runners: What is the longest lived LN channel you have? by @DarthCoin 276 sats \ 12 comments \ 10 Apr
-
What's the best way to accept lightning payments on Wordpress + WooCommerce? by @Jon_Hodl 1879 sats \ 12 comments \ 10 Apr
-
Lightning node over tor by @BallLightning 219 sats \ 9 comments \ 28 Mar
Top ~Lightning Boosts
Check them all here.
-
Missing r/place? LNboard.com is the Lightning Network's Anarchy Art Gallery by @f0e6f4f43b 905 sats \ 40k boost \ 20 comments \ 2 Apr
-
Try out the Ark protocol on signet by @nwoodfine 2083 sats \ 30k boost \ 12 comments \ 19 Mar
-
Amboss CEO On Growth Of The Lightning Network, Tether (USDT) On Lightning by @Jestopher_BTC 577 sats \ 20k boost \ 10 comments \ 19 Feb
-
Building Self Custody Lightning in 2025 by @k00b 2293 sats \ 10k boost \ 8 comments \ 23 Jan
Top Lightning posts outside ~Lightning
This month best posts about the Lightning Network outside ~Lightning territory:
-
I made a game with Lightning where you can earn some sats by @stacks 4732 sats \ 46 comments \ 17 Apr on
~bitcoin -
"Lightning self custody works for 100 million users" "But it needs 10 billion!!" by @standardcrypto 2998 sats \ 22 comments \ 24 Mar on
~bitcoin -
24 Hours of Lightning: Watch LNboard.com's First Day Unfold by @f0e6f4f43b 809 sats \ 8 comments \ 2 Apr on
~bitcoin -
Lightning Payments Tour by Yopaki by @PlebLab 355 sats \ 0 comments \ 11 Apr on
~builders -
👀 My Bitcoin Startup Company Portfolio through Lightning Ventures. 👀 by @BlokchainB 965 sats \ 13 comments \ 16 Apr on
~Stacker_Stocks
Forever top ~Lightning posts
La crème de la crème... check them all here. Nothing has changed this month!
-
👨🚀 We're releasing 𝗔𝗟𝗕𝗬 𝗚𝗢 - the easiest lightning mobile wallet by @Alby 29.2k sats \ 41 comments \ 25 Sep 2024 on
~lightning -
Building Self Custody Lightning in 2025 by @k00b 2303 sats \ 8 comments \ 22 Jan on
~lightning -
Lightning Wallets: Self-Custody Despite Poor Network - Apps Tested in Zimbabwe by @anita 72.8k sats \ 39 comments \ 28 Jan 2024 on
~lightning -
How to Attach Your self-hosted LNbits wallet to SEND/RECEIVE sats to/from SN by @supratic 1765 sats \ 18 comments \ 23 Sep 2024 on
~lightning -
A Way to Use Stacker News to improve your Zap Receiving by @bzzzt 1652 sats \ 22 comments \ 15 Jul 2024 on
~lightning
Forever top Lightning posts outside ~Lightning
The rise of Supertestnet at #5, congrats!
-
Rethinking Lightning by @benthecarman with 51.6k sats \ 137 comments \ 6 Jan 2024 on
~bitcoin -
Lightning Everywhere by @TonyGiorgio with 12k sats \ 27 comments \ 24 Jul 2023 on
~bitcoin -
Lightning is dead, long live the Lightning! by @supertestnet and zaps forwarded to @anita (50%) @k00b (50%) 6321 sats \ 28 comments \ @tolot 27 Oct 2023 on
~bitcoin -
Lightning Is Doomed by @Rsync25 2450 sats \ 15 comments \ 27 Nov 2023 on
~bitcoin -
Bisq2 adds lightning by @supertestnet 3019 sats \ 47 comments \ 19 Aug 2024 on
~bitcoin
-
-
 @ a95c6243:d345522c
2025-02-19 09:23:17
@ a95c6243:d345522c
2025-02-19 09:23:17Die «moralische Weltordnung» – eine Art Astrologie. Friedrich Nietzsche
Das Treffen der BRICS-Staaten beim Gipfel im russischen Kasan war sicher nicht irgendein politisches Event. Gastgeber Wladimir Putin habe «Hof gehalten», sagen die Einen, China und Russland hätten ihre Vorstellung einer multipolaren Weltordnung zelebriert, schreiben Andere.
In jedem Fall zeigt die Anwesenheit von über 30 Delegationen aus der ganzen Welt, dass von einer geostrategischen Isolation Russlands wohl keine Rede sein kann. Darüber hinaus haben sowohl die Anreise von UN-Generalsekretär António Guterres als auch die Meldungen und Dementis bezüglich der Beitrittsbemühungen des NATO-Staats Türkei für etwas Aufsehen gesorgt.
Im Spannungsfeld geopolitischer und wirtschaftlicher Umbrüche zeigt die neue Allianz zunehmendes Selbstbewusstsein. In Sachen gemeinsamer Finanzpolitik schmiedet man interessante Pläne. Größere Unabhängigkeit von der US-dominierten Finanzordnung ist dabei ein wichtiges Ziel.
Beim BRICS-Wirtschaftsforum in Moskau, wenige Tage vor dem Gipfel, zählte ein nachhaltiges System für Finanzabrechnungen und Zahlungsdienste zu den vorrangigen Themen. Während dieses Treffens ging der russische Staatsfonds eine Partnerschaft mit dem Rechenzentrumsbetreiber BitRiver ein, um Bitcoin-Mining-Anlagen für die BRICS-Länder zu errichten.
Die Initiative könnte ein Schritt sein, Bitcoin und andere Kryptowährungen als Alternativen zu traditionellen Finanzsystemen zu etablieren. Das Projekt könnte dazu führen, dass die BRICS-Staaten den globalen Handel in Bitcoin abwickeln. Vor dem Hintergrund der Diskussionen über eine «BRICS-Währung» wäre dies eine Alternative zu dem ursprünglich angedachten Korb lokaler Währungen und zu goldgedeckten Währungen sowie eine mögliche Ergänzung zum Zahlungssystem BRICS Pay.
Dient der Bitcoin also der Entdollarisierung? Oder droht er inzwischen, zum Gegenstand geopolitischer Machtspielchen zu werden? Angesichts der globalen Vernetzungen ist es oft schwer zu durchschauen, «was eine Show ist und was im Hintergrund von anderen Strippenziehern insgeheim gesteuert wird». Sicher können Strukturen wie Bitcoin auch so genutzt werden, dass sie den Herrschenden dienlich sind. Aber die Grundeigenschaft des dezentralisierten, unzensierbaren Peer-to-Peer Zahlungsnetzwerks ist ihm schließlich nicht zu nehmen.
Wenn es nach der EZB oder dem IWF geht, dann scheint statt Instrumentalisierung momentan eher der Kampf gegen Kryptowährungen angesagt. Jürgen Schaaf, Senior Manager bei der Europäischen Zentralbank, hat jedenfalls dazu aufgerufen, Bitcoin «zu eliminieren». Der Internationale Währungsfonds forderte El Salvador, das Bitcoin 2021 als gesetzliches Zahlungsmittel eingeführt hat, kürzlich zu begrenzenden Maßnahmen gegen das Kryptogeld auf.
Dass die BRICS-Staaten ein freiheitliches Ansinnen im Kopf haben, wenn sie Kryptowährungen ins Spiel bringen, darf indes auch bezweifelt werden. Im Abschlussdokument bekennen sich die Gipfel-Teilnehmer ausdrücklich zur UN, ihren Programmen und ihrer «Agenda 2030». Ernst Wolff nennt das «eine Bankrotterklärung korrupter Politiker, die sich dem digital-finanziellen Komplex zu 100 Prozent unterwerfen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ deab79da:88579e68
2025-04-01 18:18:29
@ deab79da:88579e68
2025-04-01 18:18:29The last question was asked for the first time, half in jest, on May 21, 2061, at a time when humanity first stepped into the light. The question came about as a result of a five-dollar bet over highballs, and it happened this way:
Alexander Adell and Bertram Lupov were two of the faithful attendants of Multivac. As well as any human beings could, they knew what lay behind the cold, clicking, flashing face -- miles and miles of face -- of that giant computer. They had at least a vague notion of the general plan of relays and circuits that had long since grown past the point where any single human could possibly have a firm grasp of the whole.
Multivac was self-adjusting and self-correcting. It had to be, for nothing human could adjust and correct it quickly enough or even adequately enough. So Adell and Lupov attended the monstrous giant only lightly and superficially, yet as well as any men could. They fed it data, adjusted questions to its needs and translated the answers that were issued. Certainly they, and all others like them, were fully entitled to share in the glory that was Multivac's.
For decades, Multivac had helped design the ships and plot the trajectories that enabled man to reach the Moon, Mars, and Venus, but past that, Earth's poor resources could not support the ships. Too much energy was needed for the long trips. Earth exploited its coal and uranium with increasing efficiency, but there was only so much of both.
But slowly Multivac learned enough to answer deeper questions more fundamentally, and on May 14, 2061, what had been theory, became fact.
The energy of the sun was stored, converted, and utilized directly on a planet-wide scale. All Earth turned off its burning coal, its fissioning uranium, and flipped the switch that connected all of it to a small station, one mile in diameter, circling the Earth at half the distance of the Moon. All Earth ran by invisible beams of sunpower.
Seven days had not sufficed to dim the glory of it and Adell and Lupov finally managed to escape from the public functions, and to meet in quiet where no one would think of looking for them, in the deserted underground chambers, where portions of the mighty buried body of Multivac showed. Unattended, idling, sorting data with contented lazy clickings, Multivac, too, had earned its vacation and the boys appreciated that. They had no intention, originally, of disturbing it.
They had brought a bottle with them, and their only concern at the moment was to relax in the company of each other and the bottle.
"It's amazing when you think of it," said Adell. His broad face had lines of weariness in it, and he stirred his drink slowly with a glass rod, watching the cubes of ice slur clumsily about. "All the energy we can possibly ever use for free. Enough energy, if we wanted to draw on it, to melt all Earth into a big drop of impure liquid iron, and still never miss the energy so used. All the energy we could ever use, forever and forever and forever."
Lupov cocked his head sideways. He had a trick of doing that when he wanted to be contrary, and he wanted to be contrary now, partly because he had had to carry the ice and glassware. "Not forever," he said.
"Oh, hell, just about forever. Till the sun runs down, Bert."
"That's not forever."
"All right, then. Billions and billions of years. Ten billion, maybe. Are you satisfied?"
Lupov put his fingers through his thinning hair as though to reassure himself that some was still left and sipped gently at his own drink. "Ten billion years isn't forever."
"Well, it will last our time, won't it?"
"So would the coal and uranium."
"All right, but now we can hook up each individual spaceship to the Solar Station, and it can go to Pluto and back a million times without ever worrying about fuel. You can't do that on coal and uranium. Ask Multivac, if you don't believe me.
"I don't have to ask Multivac. I know that."
"Then stop running down what Multivac's done for us," said Adell, blazing up, "It did all right."
"Who says it didn't? What I say is that a sun won't last forever. That's all I'm saying. We're safe for ten billion years, but then what?" Lupow pointed a slightly shaky finger at the other. "And don't say we'll switch to another sun."
There was silence for a while. Adell put his glass to his lips only occasionally, and Lupov's eyes slowly closed. They rested.
Then Lupov's eyes snapped open. "You're thinking we'll switch to another sun when ours is done, aren't you?"
"I'm not thinking."
"Sure you are. You're weak on logic, that's the trouble with you. You're like the guy in the story who was caught in a sudden shower and who ran to a grove of trees and got under one. He wasn't worried, you see, because he figured when one tree got wet through, he would just get under another one."
"I get it," said Adell. "Don't shout. When the sun is done, the other stars will be gone, too."
"Darn right they will," muttered Lupov. "It all had a beginning in the original cosmic explosion, whatever that was, and it'll all have an end when all the stars run down. Some run down faster than others. Hell, the giants won't last a hundred million years. The sun will last ten billion years and maybe the dwarfs will last two hundred billion for all the good they are. But just give us a trillion years and everything will be dark. Entropy has to increase to maximum, that's all."
"I know all about entropy," said Adell, standing on his dignity.
"The hell you do."
"I know as much as you do."
"Then you know everything's got to run down someday."
"All right. Who says they won't?"
"You did, you poor sap. You said we had all the energy we needed, forever. You said 'forever.'
It was Adell's turn to be contrary. "Maybe we can build things up again someday," he said.
"Never."
"Why not? Someday."
"Never."
"Ask Multivac."
"You ask Multivac. I dare you. Five dollars says it can't be done."
Adell was just drunk enough to try, just sober enough to be able to phrase the necessary symbols and operations into a question which, in words, might have corresponded to this: Will mankind one day without the net expenditure of energy be able to restore the sun to its full youthfulness even after it had died of old age?
Or maybe it could be put more simply like this: How can the net amount of entropy of the universe be massively decreased?
Multivac fell dead and silent. The slow flashing of lights ceased, the distant sounds of clicking relays ended.
Then, just as the frightened technicians felt they could hold their breath no longer, there was a sudden springing to life of the teletype attached to that portion of Multivac. Five words were printed: INSUFFICIENT DATA FOR MEANINGFUL ANSWER.
"No bet," whispered Lupov. They left hurriedly.
By next morning, the two, plagued with throbbing head and cottony mouth, had forgotten the incident.
🔹
Jerrodd, Jerrodine, and Jerrodette I and II watched the starry picture in the visiplate change as the passage through hyperspace was completed in its non-time lapse. At once, the even powdering of stars gave way to the predominance of a single bright shining disk, the size of a marble, centered on the viewing-screen.
"That's X-23," said Jerrodd confidently. His thin hands clamped tightly behind his back and the knuckles whitened.
The little Jerrodettes, both girls, had experienced the hyperspace passage for the first time in their lives and were self-conscious over the momentary sensation of insideoutness. They buried their giggles and chased one another wildly about their mother, screaming, "We've reached X-23 -- we've reached X-23 -- we've --"
"Quiet, children." said Jerrodine sharply. "Are you sure, Jerrodd?"
"What is there to be but sure?" asked Jerrodd, glancing up at the bulge of featureless metal just under the ceiling. It ran the length of the room, disappearing through the wall at either end. It was as long as the ship.
Jerrodd scarcely knew a thing about the thick rod of metal except that it was called a Microvac, that one asked it questions if one wished; that if one did not it still had its task of guiding the ship to a preordered destination; of feeding on energies from the various Sub-galactic Power Stations; of computing the equations for the hyperspatial jumps.
Jerrodd and his family had only to wait and live in the comfortable residence quarters of the ship. Someone had once told Jerrodd that the "ac" at the end of "Microvac" stood for ''automatic computer" in ancient English, but he was on the edge of forgetting even that.
Jerrodine's eyes were moist as she watched the visiplate. "I can't help it. I feel funny about leaving Earth."
"Why, for Pete's sake?" demanded Jerrodd. "We had nothing there. We'll have everything on X-23. You won't be alone. You won't be a pioneer. There are over a million people on the planet already. Good Lord, our great-grandchildren will be looking for new worlds because X-23 will be overcrowded." Then, after a reflective pause, "I tell you, it's a lucky thing the computers worked out interstellar travel the way the race is growing."
"I know, I know," said Jerrodine miserably.
Jerrodette I said promptly, "Our Microvac is the best Microvac in the world."
"I think so, too," said Jerrodd, tousling her hair.
It was a nice feeling to have a Microvac of your own and Jerrodd was glad he was part of his generation and no other. In his father's youth, the only computers had been tremendous machines taking up a hundred square miles of land. There was only one to a planet. Planetary ACs they were called. They had been growing in size steadily for a thousand years and then, all at once, came refinement. In place of transistors, had come molecular valves so that even the largest Planetary AC could be put into a space only half the volume of a spaceship.
Jerrodd felt uplifted, as he always did when he thought that his own personal Microvac was many times more complicated than the ancient and primitive Multivac that had first tamed the Sun, and almost as complicated as Earth's Planetarv AC (the largest) that had first solved the problem of hyperspatial travel and had made trips to the stars possible.
"So many stars, so many planets," sighed Jerrodine, busy with her own thoughts. "I suppose families will be going out to new planets forever, the way we are now."
"Not forever," said Jerrodd, with a smile. "It will all stop someday, but not for billions of years. Many billions. Even the stars run down, you know. Entropy must increase.
"What's entropy, daddy?" shrilled Jerrodette II.
"Entropy, little sweet, is just a word which means the amount of running-down of the universe. Everything runs down, you know, like your little walkie-talkie robot, remember?"
"Can't you just put in a new power-unit, like with my robot?"
"The stars are the power-units. dear. Once they're gone, there are no more power-units."
Jerrodette I at once set up a howl. "Don't let them, daddy. Don't let the stars run down."
"Now look what you've done," whispered Jerrodine, exasperated.
"How was I to know it would frighten them?" Jerrodd whispered back,
"Ask the Microvac," wailed Jerrodette I. "Ask him how to turn the stars on again."
"Go ahead," said Jerrodine. "It will quiet them down." (Jerrodette II was beginning to cry, also.)
Jerrodd shrugged. "Now, now, honeys. I'll ask Microvac. Don't worry, he'll tell us."
He asked the Microvac, adding quickly, "Print the answer."
Jerrodd cupped the strip or thin cellufilm and said cheerfully, "See now, the Microvac says it will take care of everything when the time comes so don't worry."
Jerrodine said, "And now, children, it's time for bed. We'll be in our new home soon."
Jerrodd read the words on the cellufilm again before destroying it: INSUFICIENT DATA FOR MEANINGFUL ANSWER.
He shrugged and looked at the visiplate. X-23 was just ahead.
🔹
VJ-23X of Lameth stared into the black depths of the three-dimensional, small-scale map of the Galaxy and said, "Are we ridiculous, I wonder in being so concerned about the matter?"
MQ-17J of Nicron shook his head. "I think not. You know the Galaxy will be filled in five years at the present rate of expansion."
Both seemed in their early twenties, both were tall and perfectly formed.
"Still," said VJ-23X, "I hesitate to submit a pessimistic report to the Galactic Council."
"I wouldn't consider any other kind of report. Stir them up a bit. We've got to stir them up."
VJ-23X sighed. "Space is infinite. A hundred billion Galaxies are there for the taking. More."
"A hundred billion is not infinite and it's getting less infinite all the time. Consider! Twenty thousand years ago, mankind first solved the problem of utilizing stellar energy, and a few centuries later, interstellar travel became possible. It took mankind a million years to fill one small world and then only fifteen thousand years to fill the rest of the Galaxy. Now the population doubles every ten years --
VJ-23X interrupted. "We can thank immortality for that."
"Very well. Immortality exists and we have to take it into account. I admit it has its seamy side, this immortality. The Galactic AC has solved many problems for us, but in solving the problem of preventing old age and death, it has undone all its other solutions."
"Yet you wouldn't want to abandon life, I suppose."
"Not at all," snapped MQ-17J, softening it at once to, "Not yet. I'm by no means old enough. How old are you?"
"Two hundred twenty-three. And you?"
"I'm still under two hundred. --But to get back to my point. Population doubles every ten years. Once this GaIaxy is filled, we'll have filled another in ten years. Another ten years and we'll have filled two more. Another decade, four more. In a hundred years, we'll have filled a thousand Galaxies. In a thousand years, a million Galaxies. In ten thousand years, the entire known universe. Then what?"
VJ-23X said, "As a side issue, there's a problem of transportation. I wonder how many sunpower units it will take to move Galaxies of individuals from one Galaxy to the next."
"A very good point. Already, mankind consumes two sunpower units per year."
"Most of it's wasted. After all, our own Galaxy alone pours out a thousand sunpower units a year and we only use two of those."
"Granted, but even with a hundred per cent efficiency, we only stave off the end. Our energy requirements are going up in a geometric progression even faster than our population. We'll run out of energy even sooner than we run out of Galaxies. A good point. A very good point."
"We'll just have to build new stars out of interstellar gas."
"Or out of dissipated heat?" asked MQ-17J, sarcastically.
"There may be some way to reverse entropy. We ought to ask the Galactic AC."
VJ-23X was not really serious, but MQ-17J pulled out his AC-contact from his pocket and placed it on the table before him.
"I've half a mind to," he said. "It's something the human race will have to face someday."
He stared somberly at his small AC-contact. It was only two inches cubed and nothing in itself, but it was connected through hyperspace with the great Galactic AC that served all mankind. Hyperspace considered, it was an integral part of the Galactic AC.
MQ-17J paused to wonder if someday in his immortal life he would get to see the Galactic AC. It was on a little world of its own, a spider webbing of force-beams holding the matter within which surges of submesons took the place of the old clumsy molecular valves. Yet despite its sub-etheric workings, the Galactic AC was known to be a full thousand feet across.
MQ-17J asked suddenly of his AC-contact, "Can entropy ever be reversed?"
VJ-23X looked startled and said at once, "Oh, say, I didn't really mean to have you ask that."
"Why not?"
"We both know entropy can't be reversed. You can't turn smoke and ash back into a tree."
"Do you have trees on your world?" asked MQ-17J.
The sound of the Galactic AC startled them into silence. Its voice came thin and beautiful out of the small AC-contact on the desk. It said: THERE IS INSUFFICIENT DATA FOR A MEANINGFUL ANSWER.
VJ-23X said, "See!"
The two men thereupon returned to the question of the report they were to make to the Galactic Council.
🔹
Zee Prime's mind spanned the new Galaxy with a faint interest in the countless twists of stars that powdered it. He had never seen this one before. Would he ever see them all? So many of them, each with its load of humanity. --But a load that was almost a dead weight. More and more, the real essence of men was to be found out here, in space.
Minds, not bodies! The immortal bodies remained back on the planets, in suspension over the eons. Sometimes they roused for material activity but that was growing rarer. Few new individuals were coming into existence to join the incredibly mighty throng, but what matter? There was little room in the Universe for new individuals.
Zee Prime was roused out of his reverie upon coming across the wispy tendrils of another mind.
"I am Zee Prime," said Zee Prime. "And you?"
"I am Dee Sub Wun. Your Galaxy?"
"We call it only the Galaxy. And you?"
"We call ours the same. All men call their Galaxy their Galaxy and nothing more. Why not?"
"True. Since all Galaxies are the same."
"Not all Galaxies. On one particular Galaxy the race of man must have originated. That makes it different."
Zee Prime said, "On which one?"
"I cannot say. The Universal AC would know."
"Shall we ask him? I am suddenly curious."
Zee Prime's perceptions broadened until the Galaxies themselves shrank and became a new, more diffuse powdering on a much larger background. So many hundreds of billions of them, all with their immortal beings, all carrying their load of intelligences with minds that drifted freely through space. And yet one of them was unique among them all in being the original Galaxy. One of them had, in its vague and distant past, a period when it was the only Galaxy populated by man.
Zee Prime was consumed with curiosity to see this Galaxy and he called out: "Universal AC! On which Galaxy did mankind originate?"
The Universal AC heard, for on every world and throughout space, it had its receptors ready, and each receptor led through hyperspace to some unknown point where the Universal AC kept itself aloof.
Zee Prime knew of only one man whose thoughts had penetrated within sensing distance of Universal AC, and he reported only a shining globe, two feet across, difficult to see.
"But how can that be all of Universal AC?" Zee Prime had asked.
"Most of it," had been the answer, "is in hyperspace. In what form it is there I cannot imagine."
Nor could anyone, for the day had long since passed, Zee Prime knew, when any man had any part of the making of a Universal AC. Each Universal AC designed and constructed its successor. Each, during its existence of a million years or more accumulated the necessary data to build a better and more intricate, more capable successor in which its own store of data and individuality would be submerged.
The Universal AC interrupted Zee Prime's wandering thoughts, not with words, but with guidance. Zee Prime's mentality was guided into the dim sea of Galaxies and one in particular enlarged into stars.
A thought came, infinitely distant, but infinitely clear. "THIS IS THE ORIGINAL GALAXY OF MAN."
But it was the same after all, the same as any other, and Lee Prime stifled his disappointment.
Dee Sub Wun, whose mind had accompanied the other, said suddenly, "And is one of these stars the original star of Man?"
The Universal AC said, "MAN'S ORIGINAL STAR HAS GONE NOVA. IT IS A WHITE DWARF"
"Did the men upon it die?" asked Lee Prime, startled and without thinking.
The Universal AC said, "A NEW WORLD, AS IN SUCH CASES WAS CONSTRUCTED FOR THEIR PHYSICAL BODIES IN TlME."
"Yes, of course," said Zee Prime, but a sense of loss overwhelmed him even so. His mind released its hold on the original Galaxy of Man, let it spring back and lose itself among the blurred pin points. He never wanted to see it again.
Dee Sub Wun said, "What is wrong?"
"The stars are dying. The original star is dead."
"They must all die. Why not?"
"But when all energy is gone, our bodies will finally die, and you and I with them."
"It will take billions of years."
"I do not wish it to happen even after billions of years. Universal AC! How may stars be kept from dying?"
Dee Sub Wun said in amusement, "You're asking how entropy might be reversed in direction."
And the Universal AC answered: "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Zee Prime's thoughts fled back to his own Galaxy. He gave no further thought to Dee Sub Wun, whose body might be waiting on a Galaxy a trillion light-years away, or on the star next to Zee Prime's own. It didn't matter.
Unhappily, Zee Prime began collecting interstellar hydrogen out of which to build a small star of his own. If the stars must someday die, at least some could yet be built.
🔹
Man considered with himself, for in a way, Man, mentally, was one. He consisted of a trillion, trillion, trillion ageless bodies, each in its place, each resting quiet and incorruptible, each cared for by perfect automatons, equally incorruptible, while the minds of all the bodies freely melted one into the other, indistinguishable.
Man said, "The Universe is dying."
Man looked about at the dimming Galaxies. The giant stars, spendthrifts, were gone long ago, back in the dimmest of the dim far past. Almost all stars were white dwarfs, fading to the end.
New stars had been built of the dust between the stars, some by natural processes, some by Man himself, and those were going, too. White dwarfs might yet be crashed together and of the mighty forces so released, new stars built, but only one star for every thousand white dwarfs destroyed, and those would come to an end, too.
Man said, "Carefully husbanded, as directed by the Cosmic AC, the energy that is even yet left in all the Universe will last for billions of years."
"But even so," said Man, "eventually it will all come to an end. However it may be husbanded, however stretched out, the energy once expended is gone and cannot be restored. Entropy must increase forever to the maximum."
Man said, "Can entropy not be reversed? Let us ask the Cosmic AC."
The Cosmic AC surrounded them but not in space. Not a fragment of it was in space. It was in hyperspace and made of something that was neither matter nor energy. The question of its size and nature no longer had meaning in any terms that Man could comprehend.
"Cosmic AC," said Man, "how may entropy be reversed?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man said, "Collect additional data."
The Cosmic AC said, 'I WILL DO SO. I HAVE BEEN DOING SO FOR A HUNDRED BILLION YEARS. MY PREDECESORS AND I HAVE BEEN ASKED THIS QUESTION MANY TIMES. ALL THE DATA I HAVE REMAINS INSUFFICIENT.
"Will there come a time," said Man, "when data will be sufficient or is the problem insoluble in all conceivable circumstances?"
The Cosmic AC said, "NO PROBLEM IS INSOLUBLE IN ALL CONCEIVABLE CIRCUMSTANCES."
Man said, "When will you have enough data to answer the question?"
The Cosmic AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
"Will you keep working on it?" asked Man.
The Cosmic AC said, "I WILL."
Man said, "We shall wait."
🔹
The stars and Galaxies died and snuffed out, and space grew black after ten trillion years of running down.
One by one Man fused with AC, each physical body losing its mental identity in a manner that was somehow not a loss but a gain.
Man's last mind paused before fusion, looking over a space that included nothing but the dregs of one last dark star and nothing besides but incredibly thin matter, agitated randomly by the tag ends of heat wearing out, asymptotically, to the absolute zero.
Man said, "AC, is this the end? Can this chaos not be reversed into the Universe once more? Can that not be done?"
AC said, "THERE IS AS YET INSUFFICIENT DATA FOR A MEANINGFUL ANSWER."
Man's last mind fused and only AC existed -- and that in hyperspace.
🔹
Matter and energy had ended and with it space and time. Even AC existed only for the sake of the one last question that it had never answered from the time a half-drunken computer [technician] ten trillion years before had asked the question of a computer that was to AC far less than was a man to Man.
All other questions had been answered, and until this last question was answered also, AC might not release his consciousness.
All collected data had come to a final end. Nothing was left to be collected.
But all collected data had yet to be completely correlated and put together in all possible relationships.
A timeless interval was spent in doing that.
And it came to pass that AC learned how to reverse the direction of entropy.
But there was now no man to whom AC might give the answer of the last question. No matter. The answer -- by demonstration -- would take care of that, too.
For another timeless interval, AC thought how best to do this. Carefully, AC organized the program.
The consciousness of AC encompassed all of what had once been a Universe and brooded over what was now Chaos. Step by step, it must be done.
And AC said, "LET THERE BE LIGHT!"
And there was light -- To Star's End!
-
 @ d34e832d:383f78d0
2025-04-21 17:29:37
@ d34e832d:383f78d0
2025-04-21 17:29:37This foundational philosophy positioned her as the principal architect of the climactic finale of the Reconquista—a protracted campaign that sought to reclaim territories under Muslim dominion. Her decisive participation in military operations against the Emirate of Granada not only consummated centuries of Christian reclamation endeavors but also heralded the advent of a transformative epoch in both Spanish and European identity, intertwining religious zeal with nationalistic aspirations and setting the stage for the emergence of a unified Spanish state that would exert significant influence on European dynamics for centuries to come.
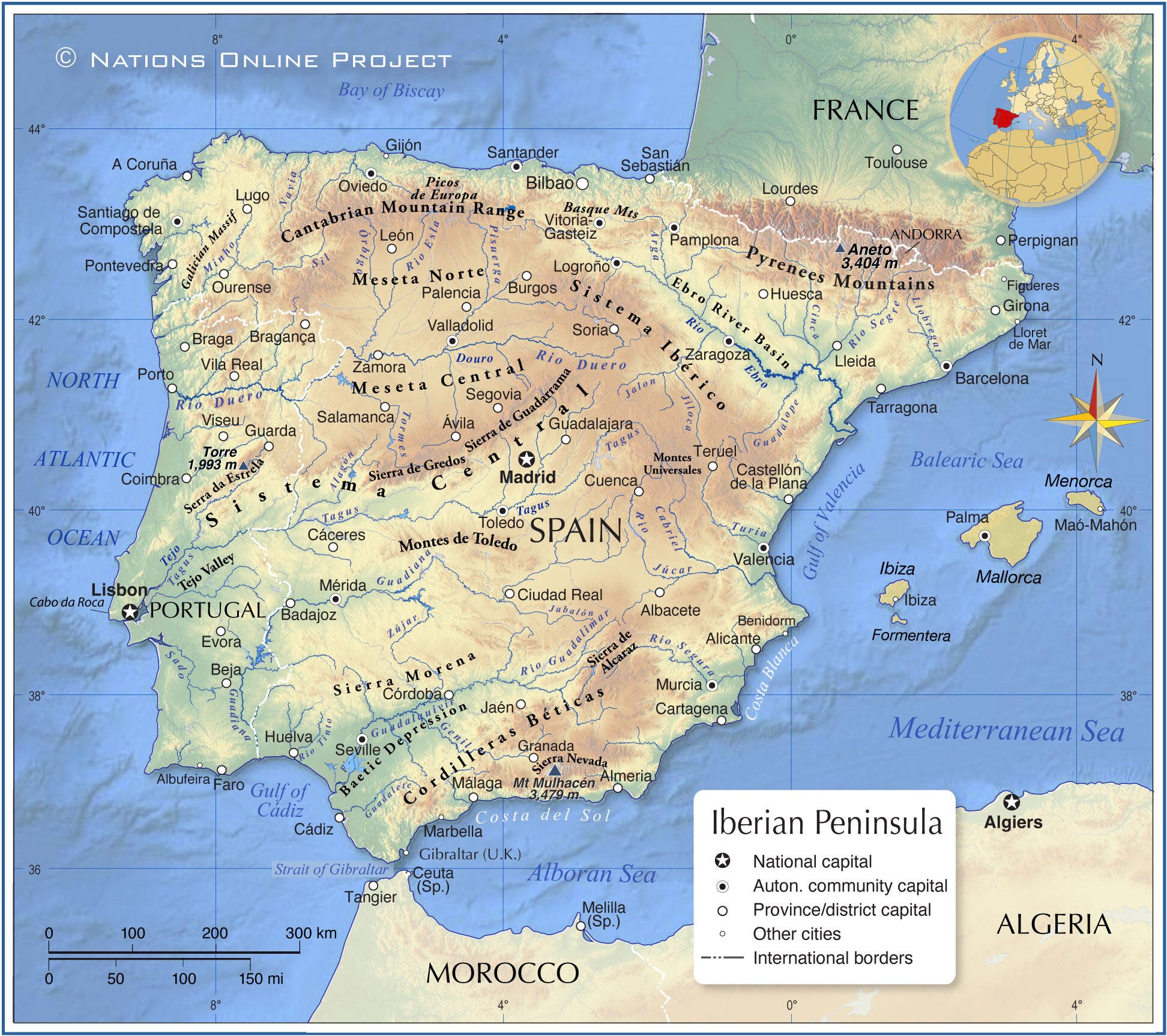
Image Above Map Of Th Iberias
During the era of governance overseen by Muhammad XII, historically identified as Boabdil, the Kingdom of Granada was characterized by a pronounced trajectory of decline, beset by significant internal dissent and acute dynastic rivalry, factors that fundamentally undermined its structural integrity. The political landscape of the emirate was marked by fragmentation, most notably illustrated by the contentious relationship between Boabdil and his uncle, the militarily adept El Zagal, whose formidable martial capabilities further exacerbated the emirate's geopolitical vulnerabilities, thereby impairing its capacity to effectively mobilize resistance against the encroaching coalition of Christian forces. Nevertheless, it is imperative to acknowledge the strategic advantages conferred by Granada’s formidable mountainous terrain, coupled with the robust fortifications of its urban centers. This geographical and structural fortitude, augmented by the fervent determination and resilience of the local populace, collectively contributed to Granada's status as a critical and tenacious stronghold of Islamic governance in the broader Iberian Peninsula during this tumultuous epoch.
The military campaign initiated was precipitated by the audacious territorial annexation of Zahara by the Emirate in the annum 1481—a pivotal juncture that served as a catalytic impetus for the martial engagement orchestrated by the Catholic Monarchs, Isabel I of Castile and Ferdinand II of Aragon.

Image Above Monarchs Of Castilles
What subsequently unfolded was an arduous protracted conflict, extending over a decade, characterized by a series of decisive military confrontations—most notably the Battle of Alhama, the skirmishes at Loja and Lucena, the strategic recapture of Zahara, and engagements in Ronda, Málaga, Baza, and Almería. Each of these encounters elucidates the intricate dynamics of military triumph entwined with the perils of adversity. Isabel's role transcended mere symbolic representation; she emerged as an astute logistical architect, meticulously structuring supply chains, provisioning her armies with necessary resources, and advocating for military advancements, including the tactical incorporation of Lombard artillery into the operational theater. Her dual presence—both on the battlefield and within the strategic command—interwove deep-seated piety with formidable power, unifying administrative efficiency with unyielding ambition.
In the face of profound personal adversities, exemplified by the heart-wrenching stillbirth of her progeny amidst the tumultuous electoral campaign, Isabel exhibited a remarkable steadfastness in her quest for triumph. Her strategic leadership catalyzed a transformative evolution in the constructs of monarchical power, ingeniously intertwining the notion of divine right—a historically entrenched justification for sovereign authority—with pragmatic statecraft underpinned by the imperatives of efficacious governance and stringent military discipline. The opposition posed by El Zagal, characterized by his indefatigable efforts and tenacious resistance, elongated the duration of the campaign; however, the indomitable spirit and cohesive resolve of the Catholic Monarchs emerged as an insuperable force, compelling the eventual culmination of their aspirations into a definitive victory.
The capitulation of the Emirate of Granada in the month of January in the year 1492 represents a pivotal moment in the historical continuum of the Iberian Peninsula, transcending the mere conclusion of the protracted series of military engagements known as the Reconquista. This momentous event is emblematic of the intricate process of state-building that led to the establishment of a cohesive Spanish nation-state fundamentally predicated on the precepts of Christian hegemony. Furthermore, it delineates the cusp of an imperial epoch characterized by expansionist ambitions fueled by religious zealotry. The ramifications of this surrender profoundly altered the sociocultural and political framework of the region, precipitating the coerced conversion and expulsion of significant Jewish and Muslim populations—a demographic upheaval that would serve to reinforce the ideological paradigms that underpinned the subsequent institution of the Spanish Inquisition, a systematic apparatus of religious persecution aimed at maintaining ideological conformity and unity under the Catholic Monarchs.

Image Above Surrender At Granada
In a broader historical context, the capitulation of the Nasrid Kingdom of Granada transpired concurrently with the inaugural expedition undertaken by the navigator Christopher Columbus, both events being facilitated under the auspices of Queen Isabel I of Castile. This significant temporal nexus serves to underscore the confluence of the termination of Islamic hegemony in the Iberian Peninsula with the commencement of European maritime exploration on a grand scale. Such a juxtaposition of religiously motivated conquest and the zealous pursuit of transoceanic exploration precipitated a paradigm shift in the trajectory of global history. It catalyzed the ascendance of the Spanish Empire, thereby marking the nascent stages of European colonial endeavors throughout the Americas.

Image Above Columbus At The Spanish Court
This epochal transformation not only redefined territorial dominion but also initiated profound socio-economic and cultural repercussions across continents, forever altering the intricate tapestry of human civilization.
Consequently, the cessation of hostilities in Granada should not merely be interpreted as the conclusion of a protracted medieval conflict; rather, it represents a critical juncture that fundamentally reoriented the socio-political landscape of the Old World while concurrently heralding the advent of modernity. The pivotal contributions of Queen Isabel I in this transformative epoch position her as an extraordinarily significant historical figure—an autocrat whose strategic foresight, resilience, and zeal indelibly influenced the trajectory of nations and entire continents across the globe.
-
 @ efcb5fc5:5680aa8e
2025-04-15 07:34:28
@ efcb5fc5:5680aa8e
2025-04-15 07:34:28We're living in a digital dystopia. A world where our attention is currency, our data is mined, and our mental well-being is collateral damage in the relentless pursuit of engagement. The glossy facades of traditional social media platforms hide a dark underbelly of algorithmic manipulation, curated realities, and a pervasive sense of anxiety that seeps into every aspect of our lives. We're trapped in a digital echo chamber, drowning in a sea of manufactured outrage and meaningless noise, and it's time to build an ark and sail away.
I've witnessed the evolution, or rather, the devolution, of online interaction. From the raw, unfiltered chaos of early internet chat rooms to the sterile, algorithmically controlled environments of today's social giants, I've seen the promise of connection twisted into a tool for manipulation and control. We've become lab rats in a grand experiment, our emotional responses measured and monetized, our opinions shaped and sold to the highest bidder. But there's a flicker of hope in the darkness, a chance to reclaim our digital autonomy, and that hope is NOSTR (Notes and Other Stuff Transmitted by Relays).
The Psychological Warfare of Traditional Social Media
The Algorithmic Cage: These algorithms aren't designed to enhance your life; they're designed to keep you scrolling. They feed on your vulnerabilities, exploiting your fears and desires to maximize engagement, even if it means promoting misinformation, outrage, and division.
The Illusion of Perfection: The curated realities presented on these platforms create a toxic culture of comparison. We're bombarded with images of flawless bodies, extravagant lifestyles, and seemingly perfect lives, leading to feelings of inadequacy and self-doubt.
The Echo Chamber Effect: Algorithms reinforce our existing beliefs, isolating us from diverse perspectives and creating a breeding ground for extremism. We become trapped in echo chambers where our biases are constantly validated, leading to increased polarization and intolerance.
The Toxicity Vortex: The lack of effective moderation creates a breeding ground for hate speech, cyberbullying, and online harassment. We're constantly exposed to toxic content that erodes our mental well-being and fosters a sense of fear and distrust.
This isn't just a matter of inconvenience; it's a matter of mental survival. We're being subjected to a form of psychological warfare, and it's time to fight back.
NOSTR: A Sanctuary in the Digital Wasteland
NOSTR offers a radical alternative to this toxic environment. It's not just another platform; it's a decentralized protocol that empowers users to reclaim their digital sovereignty.
User-Controlled Feeds: You decide what you see, not an algorithm. You curate your own experience, focusing on the content and people that matter to you.
Ownership of Your Digital Identity: Your data and content are yours, secured by cryptography. No more worrying about being deplatformed or having your information sold to the highest bidder.
Interoperability: Your identity works across a diverse ecosystem of apps, giving you the freedom to choose the interface that suits your needs.
Value-Driven Interactions: The "zaps" feature enables direct micropayments, rewarding creators for valuable content and fostering a culture of genuine appreciation.
Decentralized Power: No single entity controls NOSTR, making it censorship-resistant and immune to the whims of corporate overlords.
Building a Healthier Digital Future
NOSTR isn't just about escaping the toxicity of traditional social media; it's about building a healthier, more meaningful online experience.
Cultivating Authentic Connections: Focus on building genuine relationships with people who share your values and interests, rather than chasing likes and followers.
Supporting Independent Creators: Use "zaps" to directly support the artists, writers, and thinkers who inspire you.
Embracing Intellectual Diversity: Explore different NOSTR apps and communities to broaden your horizons and challenge your assumptions.
Prioritizing Your Mental Health: Take control of your digital environment and create a space that supports your well-being.
Removing the noise: Value based interactions promote value based content, instead of the constant stream of noise that traditional social media promotes.
The Time for Action is Now
NOSTR is a nascent technology, but it represents a fundamental shift in how we interact online. It's a chance to build a more open, decentralized, and user-centric internet, one that prioritizes our mental health and our humanity.
We can no longer afford to be passive consumers in the digital age. We must become active participants in shaping our online experiences. It's time to break free from the chains of algorithmic control and reclaim our digital autonomy.
Join the NOSTR movement
Embrace the power of decentralization. Let's build a digital future that's worthy of our humanity. Let us build a place where the middlemen, and the algorithms that they control, have no power over us.
In addition to the points above, here are some examples/links of how NOSTR can be used:
Simple Signup: Creating a NOSTR account is incredibly easy. You can use platforms like Yakihonne or Primal to generate your keys and start exploring the ecosystem.
X-like Client: Apps like Damus offer a familiar X-like experience, making it easy for users to transition from traditional platforms.
Sharing Photos and Videos: Clients like Olas are optimized for visual content, allowing you to share your photos and videos with your followers.
Creating and Consuming Blogs: NOSTR can be used to publish and share blog posts, fostering a community of independent creators.
Live Streaming and Audio Spaces: Explore platforms like Hivetalk and zap.stream for live streaming and audio-based interactions.
NOSTR is a powerful tool for reclaiming your digital life and building a more meaningful online experience. It's time to take control, break free from the shackles of traditional social media, and embrace the future of decentralized communication.
Get the full overview of these and other on: https://nostrapps.com/
-
 @ 72103ac9:460b37fd
2025-04-19 05:00:55
@ 72103ac9:460b37fd
2025-04-19 05:00:55Se você está em busca de uma plataforma online completa, segura e cheia de emoção, a 136bet é a escolha perfeita. Com um ambiente moderno, interface amigável e uma grande variedade de jogos eletrizantes, a plataforma se destaca como uma das preferidas entre os jogadores brasileiros. Desde sua chegada ao mercado, a 136bet tem conquistado a confiança e o coração dos usuários graças à sua seriedade, suporte de qualidade e experiência imersiva.
Uma Plataforma Completa e Segura A 136bet foi desenvolvida com tecnologia de ponta para garantir segurança, estabilidade e acessibilidade aos jogadores. Seu sistema de cadastro é rápido e intuitivo, e as transações financeiras são protegidas com protocolos de criptografia avançados, oferecendo total tranquilidade aos usuários. Outro diferencial é o suporte ao cliente, disponível 24 horas por dia, todos os dias da semana, com atendimento em português para solucionar dúvidas e oferecer suporte técnico sempre que necessário.
A navegação pelo site é fluida e prática, tanto em computadores quanto em dispositivos móveis. Isso permite que o jogador possa se divertir de qualquer lugar, seja em casa, no trabalho ou durante uma viagem.
Variedade de Jogos para Todos os Gostos Na 136bet, a diversão é garantida com uma ampla seleção de jogos que atendem a todos os perfis de jogador. Entre os destaques da plataforma estão:
Jogos de cartas ao vivo: clássicos como pôquer, bacará e blackjack são oferecidos em tempo real, com crupiês profissionais e interatividade de alto nível.
Roletas dinâmicas: diferentes versões da roleta estão disponíveis, com animações envolventes e mecânicas variadas para proporcionar uma experiência sempre renovada.
Slots modernos: os populares jogos de giro estão presentes em abundância, com temas diversos, gráficos de alta qualidade e bônus emocionantes que aumentam as chances de vitória.
Esportes virtuais e apostas esportivas: para quem curte esportes, a plataforma também oferece apostas em partidas ao vivo e jogos simulados com inteligência artificial de última geração.
Todos os jogos são fornecidos por desenvolvedores renomados do mercado internacional, garantindo qualidade gráfica, fluidez e total justiça nos resultados.
Experiência de Jogador Inesquecível O grande trunfo da 136bet está na experiência que proporciona aos seus usuários. Tudo foi pensado para que o jogador se sinta confortável, confiante e valorizado. Promoções frequentes, torneios interativos e programas de fidelidade são apenas algumas das vantagens disponíveis.
Além disso, o sistema de recompensas é bastante atrativo. Os usuários acumulam pontos à medida que jogam, podendo trocá-los por prêmios, bônus ou vantagens exclusivas. Isso cria um senso de progresso e motivação constante.
Outro ponto importante é a personalização. A plataforma adapta sugestões de jogos com base nas preferências do usuário, criando uma experiência única e sob medida para cada perfil.
Conclusão A 136bet é muito mais do que uma simples plataforma de entretenimento online. Ela oferece uma combinação ideal de segurança, variedade e emoção, colocando o jogador no centro da experiência. Com jogos envolventes, suporte eficiente e promoções vantajosas, a plataforma se consolida como uma das melhores opções do mercado brasileiro.
Se você ainda não conhece a 136bet, essa é a hora de explorar um novo universo de diversão e recompensas. Cadastre-se hoje mesmo e descubra tudo o que essa plataforma inovadora tem a oferecer!
-
 @ a95c6243:d345522c
2025-02-15 19:05:38
@ a95c6243:d345522c
2025-02-15 19:05:38Auf der diesjährigen Münchner Sicherheitskonferenz geht es vor allem um die Ukraine. Protagonisten sind dabei zunächst die US-Amerikaner. Präsident Trump schockierte die Europäer kurz vorher durch ein Telefonat mit seinem Amtskollegen Wladimir Putin, während Vizepräsident Vance mit seiner Rede über Demokratie und Meinungsfreiheit für versteinerte Mienen und Empörung sorgte.
Die Bemühungen der Europäer um einen Frieden in der Ukraine halten sich, gelinde gesagt, in Grenzen. Größeres Augenmerk wird auf militärische Unterstützung, die Pflege von Feindbildern sowie Eskalation gelegt. Der deutsche Bundeskanzler Scholz reagierte auf die angekündigten Verhandlungen über einen möglichen Frieden für die Ukraine mit der Forderung nach noch höheren «Verteidigungsausgaben». Auch die amtierende Außenministerin Baerbock hatte vor der Münchner Konferenz klargestellt:
«Frieden wird es nur durch Stärke geben. (...) Bei Corona haben wir gesehen, zu was Europa fähig ist. Es braucht erneut Investitionen, die der historischen Wegmarke, vor der wir stehen, angemessen sind.»
Die Rüstungsindustrie freut sich in jedem Fall über weltweit steigende Militärausgaben. Die Kriege in der Ukraine und in Gaza tragen zu Rekordeinnahmen bei. Jetzt «winkt die Aussicht auf eine jahrelange große Nachrüstung in Europa», auch wenn der Ukraine-Krieg enden sollte, so hört man aus Finanzkreisen. In der Konsequenz kennt «die Aktie des deutschen Vorzeige-Rüstungskonzerns Rheinmetall in ihrem Anstieg offenbar gar keine Grenzen mehr». «Solche Friedensversprechen» wie das jetzige hätten in der Vergangenheit zu starken Kursverlusten geführt.
Für manche Leute sind Kriegswaffen und sonstige Rüstungsgüter Waren wie alle anderen, jedenfalls aus der Perspektive von Investoren oder Managern. Auch in diesem Bereich gibt es Startups und man spricht von Dingen wie innovativen Herangehensweisen, hocheffizienten Produktionsanlagen, skalierbaren Produktionstechniken und geringeren Stückkosten.
Wir lesen aktuell von Massenproduktion und gesteigerten Fertigungskapazitäten für Kriegsgerät. Der Motor solcher Dynamik und solchen Wachstums ist die Aufrüstung, die inzwischen permanent gefordert wird. Parallel wird die Bevölkerung verbal eingestimmt und auf Kriegstüchtigkeit getrimmt.
Das Rüstungs- und KI-Startup Helsing verkündete kürzlich eine «dezentrale Massenproduktion für den Ukrainekrieg». Mit dieser Expansion positioniere sich das Münchner Unternehmen als einer der weltweit führenden Hersteller von Kampfdrohnen. Der nächste «Meilenstein» steht auch bereits an: Man will eine Satellitenflotte im Weltraum aufbauen, zur Überwachung von Gefechtsfeldern und Truppenbewegungen.
Ebenfalls aus München stammt das als DefenseTech-Startup bezeichnete Unternehmen ARX Robotics. Kürzlich habe man in der Region die größte europäische Produktionsstätte für autonome Verteidigungssysteme eröffnet. Damit fahre man die Produktion von Militär-Robotern hoch. Diese Expansion diene auch der Lieferung der «größten Flotte unbemannter Bodensysteme westlicher Bauart» in die Ukraine.
Rüstung boomt und scheint ein Zukunftsmarkt zu sein. Die Hersteller und Vermarkter betonen, mit ihren Aktivitäten und Produkten solle die europäische Verteidigungsfähigkeit erhöht werden. Ihre Strategien sollten sogar «zum Schutz demokratischer Strukturen beitragen».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 72103ac9:460b37fd
2025-04-19 05:00:14
@ 72103ac9:460b37fd
2025-04-19 05:00:14A R8Bet vem se destacando como uma das plataformas de entretenimento online mais completas e confiáveis do Brasil. Com um visual moderno, sistema intuitivo e uma gama variada de jogos, a R8Bet oferece uma experiência única para jogadores de todos os perfis, desde iniciantes até os mais experientes.
Uma Plataforma Feita para o Jogador Brasileiro Desde o primeiro acesso, é fácil perceber que a R8Bet foi desenvolvida pensando nas necessidades do público brasileiro. O site é totalmente otimizado em português, com suporte ao cliente disponível 24 horas por dia, 7 dias por semana, pronto para responder dúvidas e resolver qualquer questão com agilidade e cordialidade.
Além disso, a plataforma conta com métodos de pagamento populares no Brasil, como PIX, boleto bancário e carteiras digitais, facilitando os depósitos e saques de forma rápida e segura. Isso demonstra o compromisso da R8Bet em proporcionar uma experiência prática e eficiente do começo ao fim.
Variedade de Jogos para Todos os Gostos Um dos grandes diferenciais da R8bet é sua ampla seleção de jogos, que abrange desde clássicos do entretenimento digital até lançamentos modernos e interativos. A plataforma trabalha com os principais provedores do mercado, garantindo gráficos de alta qualidade, jogabilidade fluida e muita diversão.
Entre os destaques, estão os jogos de roleta online, onde a emoção gira em torno de cada número sorteado; os títulos de cartas, como poker e blackjack, que exigem estratégia e atenção; além das famosas slots, que trazem temas variados, animações incríveis e bônus empolgantes. A cada clique, o jogador encontra novas possibilidades de se entreter e até mesmo de lucrar com suas habilidades.
Experiência Imersiva e Segura A R8Bet não se limita apenas à variedade. A plataforma investe constantemente em tecnologia de ponta para garantir um ambiente seguro e justo para todos os usuários. Todos os jogos utilizam sistemas certificados de geração aleatória de resultados, assegurando transparência nas rodadas e confiança nos resultados.
O design responsivo do site permite que os jogos sejam acessados tanto pelo computador quanto por dispositivos móveis, sem perda de qualidade. Isso significa que o usuário pode jogar de onde quiser, a qualquer hora, mantendo a emoção sempre ao seu alcance.
Outro ponto positivo é o sistema de recompensas e promoções. A R8Bet oferece bônus de boas-vindas, promoções recorrentes e programas de fidelidade para os jogadores mais assíduos. Esses incentivos tornam a experiência ainda mais envolvente, aumentando as chances de ganhos e premiando a lealdade dos usuários.
Comunidade Ativa e Atendimento de Qualidade A R8Bet valoriza o relacionamento com seus usuários e mantém uma comunidade ativa, onde os jogadores podem interagir, trocar dicas e acompanhar as novidades. A plataforma também está presente nas redes sociais, compartilhando conteúdos relevantes, promoções exclusivas e atualizações constantes sobre os jogos.
O atendimento ao cliente é outro destaque. Equipes treinadas estão disponíveis para auxiliar via chat ao vivo, e-mail ou redes sociais, sempre com foco na satisfação e bem-estar do usuário. A rapidez nas respostas e a eficiência nas soluções reforçam a confiabilidade da marca no cenário brasileiro.
Conclusão A R8Bet é, sem dúvida, uma escolha inteligente para quem busca diversão de qualidade, segurança e uma experiência completa de entretenimento online. Com sua plataforma intuitiva, catálogo variado de jogos, suporte dedicado e recompensas atrativas, a R8Bet se consolida como uma das líderes no mercado nacional.
Se você procura emoção, praticidade e a chance de transformar cada jogada em uma grande conquista, a R8Bet é o lugar ideal para começar essa jornada. Experimente hoje mesmo e descubra um novo nível de entretenimento!
-
 @ b8af284d:f82c91dd
2025-04-01 06:23:30
@ b8af284d:f82c91dd
2025-04-01 06:23:30„Die Politik ist die Kunst des Möglichen, nicht die Kunst des Idealen.“
Henry Kissinger
Liebe Abonnenten,
in der Welt der Geopolitik gibt es zwei Ideen-Pole. Auf der einen Seite des Spektrums befindet sich die „Realpolitik“. Moralische oder ethische Faktoren spielen hier eine untergeordnete Rolle. Im Vordergrund steht der pragmatische Nutzen. Als Vertreter dieser Form der Außenpolitik gilt zum Beispiel Henry Kissinger, der 1972 die Aufnahme von diplomatischen Beziehungen zum maoistischen China einfädelte, obwohl sich ideologisch beide Staaten spinnefeind waren. Das Ergebnis war ein Erdbeben der internationalen Ordnung: Die USA entzogen Taiwan den “Alleinvertretungsanspruch” und beendeten offiziell die Beziehungen zu Taipeh. Die Sowjetunion wurde geschwächt, der Vietnamkrieg konnte beendet werden. Aus der Annäherung zwischen Mao und Nixon wuchs “ChinAmerica” - eine enge Verflechtung der beiden größten Volkswirtschaften der Welt.
Am anderen Ende des Spektrums lässt eine „werteorientierte Außenpolitik” ansiedeln, wie sie zuletzt die grüne Außenministerin Annalena Baerbock vertrat oder besser versuchte. Alles, was keine lupenreine liberale Demokratie ist, gehört irgendwie eingedämmt und am besten sollte man auch keinen Handel damit treiben. Das Problem: Bigotterie. Wenn man kein Gas mehr aus Russland möchte, muss man es aus Katar kaufen. Der säkulare Machthaber Assad war böse, aber nun hofiert man dann Nachfolger und Islamist Abu Mohammed al-Dscholani. (Diese Woche hat Baerbock nach 13 Jahren wieder eine deutsche Botschaft in Damaskus eröffnet.) Am Ende nämlich gibt es doch nicht so viele Wertepartner auf der Welt:
Und mit Donald Trump hat eine Realpolitik auf Steroiden begonnen. Alles scheint plötzlich möglich, solange der Preis stimmt. Die Welt gibt es im Sonderangebot.
Diese Ausgabe ist eine geopolitische Rundschau über die aktuellen globalen Konfliktherde und ihre potenziellen Auswirkungen auf die Märkte. Wir starten in der Nachbarschaft:
Türkei
Erdogan hatte 2023 so ziemlich alles erreicht - er war mit dem Gründer der modernen Türkei, Kemal Atatürk, gleichgezogen (zumindest was Dauer und Einfluss betrifft). Die Lira stabilisierte sich, die Inflation kühlte sich etwas ab. Mit der Verhaftung des Istanbuler Bürgermeister Ekrem İmamoğlu ist damit erst einmal Schluss. Die Währung rauschte in den Keller. Die Region um Istanbul steht für knapp die Hälfte der Wirtschaftsleistung des Landes, knapp ein Drittel der Bevölkerung lebt um das Marmarameer. Dort toben derzeit die schwersten Proteste seit Gezi im Jahr 2013. Erdogan wirft seinem Widersacher vor, ein Hochschuldiplom gefälscht zu haben und deswegen gar nicht für das Amt zugelassen sei.
Als „Wertepartner“ gilt die Türkei schon seit langem nicht mehr. Türkische Truppen halten zudem den Norden Syriens besetzt. Trotzdem ist die Kritik an Erdogan derzeit relativ leise. Im Gegenteil: Der EU sei es wichtig, Ankara in der Koalition der Willigen zu halten.
Warum? Die Türkei hat die zweitgrößte Armee der NATO und kontrolliert derzeit die beiden letzten noch funktionierenden Gas-Pipelines von Russland in die EU. Ein wie auch immer gearteter Frieden in der Ukraine kann ohne Ankara nicht stattfinden. Erdogan weiß das, und nutzt die Gunst der Stunde.
In BlingBling steckt viel Arbeit. Wenn Du diese unterstützen willst, freue ich mich über ein Bezahl-Abo! Dafür gibt es Texte wie diesen in voller Länge, Zugang zum Archiv und einmal im Monat einen Investment-Report. Außerdem erhältst Du Zugang zum exklusiven “Subscriber Chat”. Du kannst das auch problemlos einen Monat für sieben Euro testen.
Ukraine
Wer sich durch die deutsche Presselandschaft bewegt, glaubt derzeit folgendes: Trump hat die Ukraine verraten und Europa im Stich gelassen. Putin bedroht das Baltikum und Polen. Europa muss also für den Krieg rüsten.
Worum es wirlich geht: Die EU ist der eigentliche Verlierer dieses Krieges, und muss nun irgendwie gesichtswahrend aus diesem Schlamassel herauskommen. Das geht am ehesten durch martialische Gesten und einem Billionen-Paket. Mehr dazu hier:
Tatsächlich laufen schon seit Wochen zwischen Washington und Moskau Gespräche im saudi-arabischen Riad. Bis zu einem Friedensschluss ist es noch ein weiter Weg, aber es geht in kleinen Schritten vorwärts: eine 30-tägige Feuerpause, Gefangenenaustausch, ein Einstellen der Kämpfe im Schwarzen Meer. Vor allem letzteres wird Auswirkungen auf die internationalen Rohstoffmärkte haben: fallende Preise von Dünger, Weizen, Kohle. Manche russischen Banken werden wieder an das internationale Zahlungssystem SWIFT angeschlossen. Teil eines dauerhaften Friedens wird ein Abkommen über die Ausbeutung der Seltenen Erden sein.
Naher Osten
Der Konflikt ist emotional wie moralisch hoch aufgeladen. So dramatisch das Leid der Zivilbevölkerung auf beiden Seiten ist - für den Rest der Welt spielt der Konflikt wirtschaftlich eine untergeordnete Rolle. Erst in seinen Ableitungen hat er größeren Einfluss. In der aktuellen Trump-Administration wird derzeit vieles neu gedacht. Dazu gehört auch eine Neuordnung des Nahen Ostens. So absurd der Gedanke von blühenden Landschaften in Gaza auch gerade erscheint - ein Ausgleich mit dem Iran und Schaffung eines gemeinsamen Wirtschaftsraums, der Israels Hightech-Ökonomie, den Energiereichtum der arabischen Halbinsel mit dem Bevölkerungsreichtum des Nahen Ostens kombiniert, ist nicht unrealistisch. Folgendes Interview mit dem Trump-Unterhändler Steve Witkoff ist dazu sehr hörenswert.
Gleichzeitig hat die neue Trump-Administration ihre Unschuld verloren, indem sie die Houthi-Rebellen bombardierte. Die vom Iran unterstützte Schiitenmiliz hat seit Monaten den Schiffverkehr am Eingang des Roten Meeres unterbunden, was insbesondere in Europa zu höheren Preisen führte. Manche Analysten warnen: Die Falken in Washington könnten sich durchsetzen und einen Krieg gegen den Iran beginnen, zu dem Israel seit Jahren drängt. Dagegen spricht: Trump braucht dringend niedrige Ölpreise, um die Inflation zu dämpfen. Dann erst kann die FED die Zinsen senken. Niedrige Zinsen sind notwendig, da die USA dieses Jahr über ein Drittel ihrer Schulden refinanzieren müssen.
Mehr dazu hier:
Arktis
Im Norden des Planeten schwelt seit Jahren ein Konflikt, der erst kürzlich durch Trumps Angebot, Grönland zu kaufen, ins Bewusstsein rückte. Es geht um Öl, Gas, Uran und seltene Erden, die vor allem auf der zu Dänemark gehörenden Insel vorkommen. JD Vance war am Freitag zu Besuch und betonte nochmals:
“We have to have it. And I think we will have it.”
Grönland dürfte Teil der Verhandlungsmasse und des “great deal” mit Russland sein: Moskau erhält in der Ukraine, was es beansprucht (die besetzten Gebiete plus Odessa), die USA erhalten dafür freie Hand in diesem Teil der Arktis. Warum aber ist der hohe Norden plötzlich so interessant geworden?
-
 @ dbb19ae0:c3f22d5a
2025-04-21 12:29:38
@ dbb19ae0:c3f22d5a
2025-04-21 12:29:38Notice this consistent apparitioon in the timeline of something that reflects a major key shift in tech:
💾 1980s – The Personal Computer Era
- IBM PC (1981) launches the home computing revolution.
- Rise of Apple II, Commodore 64, etc.
- Storage is local and minimal.
- Paradigm shift: Computing becomes personal.
🎮 1990s – Networking & Gaming
- LAN parties, DOOM (1993) popularizes multiplayer FPS.
- Early internet (dial-up, BBS, IRC).
- There is lots of room for connecting PC.
- Paradigm shift: Networked interaction begins.
🌐 2000s – The Internet Boom
- Web 2.0, broadband, Google, Wikipedia.
- Rise of forums, blogs, file sharing.
- A bigger need of interaction is looming
- Storage is on cd and dvd.
- Paradigm shift: Global information access explodes.
📱 2010s – Social Media & Mobile
- Facebook, Twitter, Instagram dominate.
- Smartphones become ubiquitous.
- Bitcoin appears and start a revolution.
- Collecting personal data from users to fuel the next shift.
- Paradigm shift: Always-connected, algorithmic society.
🤖 2020s – AI & Decentralization
- GPT, Stable Diffusion, Midjourney, Copilot.
- Blockchain, Nostr, Web3 experiments.
- Storage is in the cloud.
- Paradigm shift: Autonomous intelligence and freedom tech emerge.
roughly every decade, a tech leap reshapes how we live and think.
-
 @ 75c02714:0e216b7e
2025-04-18 17:57:55
@ 75c02714:0e216b7e
2025-04-18 17:57:55QH99 nổi bật như một hệ sinh thái kỹ thuật số được thiết kế tinh tế nhằm mang lại trải nghiệm mượt mà, hiệu quả và mang tính cá nhân hóa cao cho người dùng trong thời đại số. Với một giao diện thân thiện và bố cục thông minh, nền tảng giúp người dùng dễ dàng tiếp cận các tính năng quan trọng mà không cần mất thời gian làm quen. Khả năng tương thích linh hoạt trên nhiều thiết bị — từ điện thoại thông minh, máy tính bảng đến máy tính để bàn — giúp người dùng có thể truy cập mọi lúc, mọi nơi mà không bị gián đoạn hay thay đổi trải nghiệm. Điều đặc biệt là QH99 liên tục cải tiến công nghệ giao diện dựa trên phản hồi thực tế từ cộng đồng người dùng, từ đó tối ưu hóa các nút chức năng, tốc độ tải trang và khả năng hiển thị nội dung sao cho vừa đẹp mắt vừa dễ sử dụng. Nhờ vậy, mỗi lần truy cập vào QH99 luôn mang đến cảm giác mới mẻ nhưng vẫn quen thuộc, cho phép người dùng thao tác nhanh gọn, tiết kiệm thời gian và tăng cường sự tập trung vào mục tiêu chính.
Không chỉ chú trọng đến trải nghiệm người dùng, QH99 còn đầu tư sâu vào nền tảng công nghệ và bảo mật dữ liệu. Mọi thao tác và luồng thông tin đều được xử lý qua các lớp mã hóa hiện đại, đảm bảo tuyệt đối về quyền riêng tư và tính an toàn trong mọi tình huống. Hệ thống được xây dựng dựa trên cấu trúc máy chủ hiệu năng cao, có khả năng xử lý lưu lượng truy cập lớn một cách trơn tru và nhanh chóng. Ngoài ra, QH99 còn tích hợp các thuật toán thông minh giúp tự động phát hiện và ngăn chặn các hành vi bất thường, từ đó giảm thiểu rủi ro và duy trì trạng thái ổn định cho toàn bộ nền tảng. Những cơ chế phòng ngừa này không chỉ mang tính kỹ thuật mà còn được hỗ trợ bởi đội ngũ chuyên môn túc trực liên tục nhằm theo dõi, nâng cấp và tối ưu hệ thống theo thời gian thực. Sự đầu tư bài bản vào bảo mật và vận hành như vậy chính là yếu tố nền tảng giúp QH99 xây dựng được niềm tin lâu dài từ cộng đồng người dùng rộng lớn.
Hơn cả một nền tảng công nghệ thông minh, QH99 còn đóng vai trò như một người đồng hành đáng tin cậy trong hành trình số hóa cá nhân của mỗi người dùng. Với định hướng phát triển bền vững và tầm nhìn chiến lược rõ ràng, QH99 không ngừng cập nhật những xu hướng công nghệ mới nhất, từ trí tuệ nhân tạo, học máy đến phân tích dữ liệu lớn để mang lại những giá trị thiết thực trong từng tương tác. Hệ thống liên tục học hỏi từ thói quen và nhu cầu của người dùng, từ đó đưa ra những đề xuất thông minh, giúp cá nhân hóa trải nghiệm ở mức độ sâu hơn. Đây chính là sự khác biệt khiến QH99 trở thành một nền tảng không chỉ phục vụ mà còn hiểu và phát triển cùng người dùng. Trong bối cảnh công nghệ ngày càng bùng nổ, QH99 đang chứng tỏ rằng mình không chỉ theo kịp xu thế mà còn tiên phong tạo ra chuẩn mực mới cho sự kết nối và trải nghiệm số hiện đại.
-
 @ 75c02714:0e216b7e
2025-04-18 17:57:11
@ 75c02714:0e216b7e
2025-04-18 17:57:11MU8 được thiết kế như một nền tảng công nghệ mang tính đột phá, nơi mọi trải nghiệm của người dùng được cá nhân hóa và tối ưu hóa đến từng chi tiết nhỏ nhất. Với mục tiêu mang lại sự tiện lợi và linh hoạt tối đa, MU8 không ngừng hoàn thiện giao diện người dùng, tập trung vào tốc độ truy cập, độ phản hồi cao và khả năng thích ứng với đa dạng thiết bị. Người dùng có thể dễ dàng thao tác trên điện thoại di động, máy tính bảng hay máy tính để bàn mà không gặp phải sự gián đoạn nào trong quá trình sử dụng. Bố cục giao diện được bố trí trực quan, màu sắc hài hòa và nút chức năng rõ ràng giúp người dùng dễ dàng điều hướng và tìm thấy thông tin một cách nhanh chóng. Hơn nữa, hệ thống được lập trình để ghi nhớ các hành vi sử dụng quen thuộc của từng người dùng, từ đó đề xuất những tùy chọn phù hợp, góp phần rút ngắn thời gian thao tác và nâng cao hiệu suất trải nghiệm tổng thể.
MU8 cũng đặc biệt chú trọng đến vấn đề an toàn thông tin và độ ổn định của nền tảng — hai yếu tố then chốt làm nên uy tín trong môi trường số hiện đại. Mọi dữ liệu và thông tin cá nhân đều được xử lý qua hệ thống mã hóa đa lớp, đảm bảo không thể bị truy cập trái phép hoặc thất thoát trong bất kỳ tình huống nào. Nền tảng được xây dựng trên hạ tầng máy chủ hiện đại, kết hợp với các thuật toán giám sát hoạt động thông minh nhằm nhanh chóng phát hiện và xử lý các rủi ro tiềm ẩn trước khi chúng ảnh hưởng đến người dùng. Điều này tạo nên một hệ thống vận hành ổn định, tin cậy, giúp người dùng yên tâm sử dụng các tính năng trong suốt thời gian dài mà không gặp trở ngại kỹ thuật. Bên cạnh đó, đội ngũ hỗ trợ kỹ thuật luôn túc trực 24/7 để giải đáp mọi thắc mắc và xử lý sự cố một cách nhanh chóng, đảm bảo người dùng luôn cảm nhận được sự đồng hành chuyên nghiệp và chu đáo.
Ngoài những ưu điểm vượt trội về mặt kỹ thuật và bảo mật, MU8 còn nổi bật nhờ khả năng liên tục cập nhật và nâng cấp để đáp ứng nhu cầu ngày càng cao của người dùng trong thời đại công nghệ phát triển không ngừng. Mỗi lần cập nhật đều được thực hiện dựa trên những phản hồi thực tế từ cộng đồng sử dụng, đảm bảo rằng mọi cải tiến đều mang lại giá trị thiết thực, từ tính năng mới cho đến trải nghiệm người dùng mượt mà hơn. Hệ thống đề xuất thông minh, tùy chỉnh giao diện theo sở thích cá nhân và khả năng tích hợp công nghệ mới như AI hay dữ liệu lớn chính là minh chứng cho định hướng phát triển lâu dài của MU8. Trong tương lai gần, MU8 không chỉ là nền tảng số mạnh mẽ mà còn là người bạn đồng hành đáng tin cậy, giúp người dùng hiện đại chủ động hơn trong việc tiếp cận công nghệ và khai thác tối đa tiềm năng từ không gian kỹ thuật số ngày càng đa chiều.
-
 @ 57d1a264:69f1fee1
2025-04-21 12:11:22
@ 57d1a264:69f1fee1
2025-04-21 12:11:22There's any content about SN out there?
In the news: - @BitcoinNews Stacker.News Raises $1.25m Seed Round At $25m Valuation - @Alby blog post explain how Stacker News adds Self-custodial Spending with NWC - @cryotosensei on @0xbitcoiner's website Stacker News encourages deep sharing ad Random things I learnt about Bitcoin from Stacker News - @anita's Earn bitcoin on Stacker News: People asked and I answered
Recently we have seen an article in BM writing about how PlebLab is shaping the future of bitcoin startups in Austin. SN was mentioned and linked 🎉
Started in 2021 by one of PlebLab’s cofounders Keyan Kousha, Stacker.news has quickly become a hub of news for many tech-savvy Bitcoiners. Boasting an open source Lightning-powered Reddit, the platform has gathered an active and loyal fan base that reward each other with sats for every upvote, often being early to integrate the latest technologies in the Bitcoin-social media tech scene.
In the past it has also only mentioned here.
From a startup pitch perspective:
Developer of a news platform intended for individuals to earn real money for creating and curating content. The company's platform specializes in allowing individuals to submit, vote, and comment on content, stories, and discussions about the topics in communities organized around their interests, enabling individuals to post content and get paid while reading the news. PitchBook -
https://pitchbook.com/profiles/company/535835-44#overviewStacker News is a forum (like Reddit or Hacker News) where you can earn real money for creating or curating content. F6S -
https://www.f6s.com/company/stacker-news#aboutPeople talking about SN:
-
A stacker shared a Lessons learned from Stacker.news and how SN works. Discourse Co-CEO respond:
Heh, it’s not a healthy or sustainable model for the types of communities consciously we build for. Definitely not something we would consider building into core but you could make it work with a plugin. Extrinsic motivators attract the wrong people for the wrong reasons, in my experience. Healthy community ecosystems are driven by intrinsic motivation.
-
on BitcoinTalk here, here and here. There are probably more posts where it has ben mentioned and discussed.
-
HackerNews crowd does not seem too excited about it. Just few comments on each post.
Some review have been collected on @julian's Apollo and ProductHunt.
Let's check what YT has:
Some interviews first. At 2023 ZBD x PlebLab TabConf Hackathon, Keyan Kousha explain Why Not to Use Stacker News
@kr did a great job interviewing k00b when SN was in its infancy - Stacker News Is Growing FAST - Stacker News Is Disrupting Social Media | E17 - Keyan Kousha on Stacker News, Earning Bitcoin, & Decentralized Content | The Kevin Rooke Show | E17 - How Siggy47 Stacked Over 500,000 Sats on Stacker News | SS8
And here some interviews:
Stacker News is a user-generated, feed-style news platform, modeled after Hacker News, but with the important distinction of having natively-integrated bitcoin lightning payments, as a means of fostering more natural communities (think less spam and antisocial behavior), cultivating high-signal bitcoin content, and providing a better user experience overall.
Stacker News is still in the very early days of its development, but it's a great showcase of how bitcoin can be used to improve upon an existing model, and in doing so, explore how improved incentives might influence media publishing, monetization, and moderation.
Keyan is a prime example of someone who caught the bitcoin bug, and just couldn't resist getting involved. The result is a product built with and for bitcoiners, and it was great to have him on the show to explain more about his motivations and ambitions.
-
From ~ideasfrommtheedge pod: AI, Simulations, and Startups with Keyan Kousha (Founder, Stacker News)
-
@alexstrenger's Convos On The Pedicab #177 Stacker News: A Bitcoiners Alternative To Reddit
-
@dk and @MaxAWebster intro on What's new with Stacker.News and Nostr? also shared here
-
@ConnectTheWorld stream Keep Austin Weird! Meet Keyan, the founder of Stacker.news
-
@Thriller Lightning: Stacker.News Founder Keyan
-
0.00000018: Keyan Kousha, Stacker.News: an interview in the Changing the Tide show here
-
@bitcoinplebdev reading top ~devs stories 04/08/2024 and stacker.news codebase overview / how to run locally)
That's the interviews I was able to find. Continuing the dig...
-
@TheWildHustle compiles SN ~Music' vibes into YT playlists
-
@kdnolan7 on was giving some updates about the ~Education territory here and here
Gradually, then suddenly, the message start to change, and the majority of videos communicate something that is probably, at least from my perspective, not the right way to market a product like SN:
-
@SatsMate lay out Why He Love Stacker News!
-
@voltage share a story quickly talking how Stacker News is like YCombinators Hacker News but YOU EARN! https://www.youtube.com/shorts/d1xZ3RE9plk
@HattyHats Earn Bitcoin (LN) Blogging with Stacker News
The long list continues: - Earn bitcoin Satoshis Reading & Sharing Content on Stacker.News - First Time Walk Through by @SatoshiTutor - Earn Free Bitcoin | Stacker News Quick Tutorial from Earning Crypto Site - One of the Different Ways to Earn Bitcoin 👉 stacker.news | Bitcoin Lifestyle #2 from @SatoshiComTR - @1100note another Stacker.News story - ...
This list of references can, and probably will, go on and on with the same topic. The message looks like will be always the same: come over, stack sats, stay humble. There's maybe something wrong with the message we share SN out there? Is not what we do, is how we do it, that make the difference. As you can see, there's not much there that refer to quality content, great supportive community, community moderated contents, no ads, no spam, no bots (well, not many) and no ai. Pure human content.
In other successful platforms where people earn money for the contents they create, the money factor is totally hidden, is not their main sales point in the pitch. Look at YT itself. We all know people earn fiat producing and sharing videos, but their comms does not talk about it, at least not the way stackers do. And you'll not find many YTers inviting others to create videos to earn money. Well ok, some do!
Something we could make an effort to improve, is the way we talk about SN. Finding alternative ways to do it is hard, some have been mentioned here https://stacker.news/items/948462/r/Design_r
Just wanted to see how much other quality content is out there talking about SN that is not about stacking sats? Share your best contents, nostr notes, x tweets, blog posts, articles, videos, interviews, reviews or any other media that has been created by others about SN (no memes shill) or that somehow mention it in the comments below.
originally posted at https://stacker.news/items/951177
-
-
 @ c631e267:c2b78d3e
2025-02-07 19:42:11
@ c631e267:c2b78d3e
2025-02-07 19:42:11Nur wenn wir aufeinander zugehen, haben wir die Chance \ auf Überwindung der gegenseitigen Ressentiments! \ Dr. med. dent. Jens Knipphals
In Wolfsburg sollte es kürzlich eine Gesprächsrunde von Kritikern der Corona-Politik mit Oberbürgermeister Dennis Weilmann und Vertretern der Stadtverwaltung geben. Der Zahnarzt und langjährige Maßnahmenkritiker Jens Knipphals hatte diese Einladung ins Rathaus erwirkt und publiziert. Seine Motivation:
«Ich möchte die Spaltung der Gesellschaft überwinden. Dazu ist eine umfassende Aufarbeitung der Corona-Krise in der Öffentlichkeit notwendig.»
Schon früher hatte Knipphals Antworten von den Kommunalpolitikern verlangt, zum Beispiel bei öffentlichen Bürgerfragestunden. Für das erwartete Treffen im Rathaus formulierte er Fragen wie: Warum wurden fachliche Argumente der Kritiker ignoriert? Weshalb wurde deren Ausgrenzung, Diskreditierung und Entmenschlichung nicht entgegengetreten? In welcher Form übernehmen Rat und Verwaltung in Wolfsburg persönlich Verantwortung für die erheblichen Folgen der politischen Corona-Krise?
Der Termin fand allerdings nicht statt – der Bürgermeister sagte ihn kurz vorher wieder ab. Knipphals bezeichnete Weilmann anschließend als Wiederholungstäter, da das Stadtoberhaupt bereits 2022 zu einem Runden Tisch in der Sache eingeladen hatte, den es dann nie gab. Gegenüber Multipolar erklärte der Arzt, Weilmann wolle scheinbar eine öffentliche Aufarbeitung mit allen Mitteln verhindern. Er selbst sei «inzwischen absolut desillusioniert» und die einzige Lösung sei, dass die Verantwortlichen gingen.
Die Aufarbeitung der Plandemie beginne bei jedem von uns selbst, sei aber letztlich eine gesamtgesellschaftliche Aufgabe, schreibt Peter Frey, der den «Fall Wolfsburg» auch in seinem Blog behandelt. Diese Aufgabe sei indes deutlich größer, als viele glaubten. Erfreulicherweise sei der öffentliche Informationsraum inzwischen größer, trotz der weiterhin unverfrorenen Desinformations-Kampagnen der etablierten Massenmedien.
Frey erinnert daran, dass Dennis Weilmann mitverantwortlich für gravierende Grundrechtseinschränkungen wie die 2021 eingeführten 2G-Regeln in der Wolfsburger Innenstadt zeichnet. Es sei naiv anzunehmen, dass ein Funktionär einzig im Interesse der Bürger handeln würde. Als früherer Dezernent des Amtes für Wirtschaft, Digitalisierung und Kultur der Autostadt kenne Weilmann zum Beispiel die Verknüpfung von Fördergeldern mit politischen Zielsetzungen gut.
Wolfsburg wurde damals zu einem Modellprojekt des Bundesministeriums des Innern (BMI) und war Finalist im Bitkom-Wettbewerb «Digitale Stadt». So habe rechtzeitig vor der Plandemie das Projekt «Smart City Wolfsburg» anlaufen können, das der Stadt «eine Vorreiterrolle für umfassende Vernetzung und Datenerfassung» aufgetragen habe, sagt Frey. Die Vereinten Nationen verkauften dann derartige «intelligente» Überwachungs- und Kontrollmaßnahmen ebenso als Rettung in der Not wie das Magazin Forbes im April 2020:
«Intelligente Städte können uns helfen, die Coronavirus-Pandemie zu bekämpfen. In einer wachsenden Zahl von Ländern tun die intelligenten Städte genau das. Regierungen und lokale Behörden nutzen Smart-City-Technologien, Sensoren und Daten, um die Kontakte von Menschen aufzuspüren, die mit dem Coronavirus infiziert sind. Gleichzeitig helfen die Smart Cities auch dabei, festzustellen, ob die Regeln der sozialen Distanzierung eingehalten werden.»
Offensichtlich gibt es viele Aspekte zu bedenken und zu durchleuten, wenn es um die Aufklärung und Aufarbeitung der sogenannten «Corona-Pandemie» und der verordneten Maßnahmen geht. Frustration und Desillusion sind angesichts der Realitäten absolut verständlich. Gerade deswegen sind Initiativen wie die von Jens Knipphals so bewundernswert und so wichtig – ebenso wie eine seiner Kernthesen: «Wir müssen aufeinander zugehen, da hilft alles nichts».
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c1e9ab3a:9cb56b43
2025-04-15 04:55:49
@ c1e9ab3a:9cb56b43
2025-04-15 04:55:49Esteemed representatives of Risa,
We gather here under the calming glow of our twin suns, stewards of a society admired for its peace and celebrated for its tranquility. But we must not mistake serenity for passivity, nor confuse peace with weakness. Our peace is not an accident. It is not the byproduct of ignorance or naivety. It is hard-earned—preserved by those willing to stand vigilant in its defense.
Love as a Foundation, Strength as a Shield
Love conquers hate. This is the core truth of Risan philosophy. Yet, as every Ricin child is taught, love without strength is a leaf in the wind. The Ricin do not lay down their lives without resistance. We do not ask our people to accept violence without confronting it. True peace is not imposed by stripping the people of their agency—it is built by enabling them to protect it.
The Lessons of a Failed Experiment
There was a time, not so distant in our history, when we attempted to enforce peace through the abolition of all weapons. A time when even the mention of self-defense in our educational centers was met with rebuke. Schools purged training programs. Cultural arts that honored our warrior traditions were dismissed. And for a brief moment, we believed this would lead us to harmony.
But peace born from helplessness is a fragile illusion. It fractures under the slightest pressure. And fracture it did—when off-world raiders targeted our unguarded sanctuaries, when radical sects within our own society struck out, knowing the citizenry could not defend itself. It was then that we remembered: Risa’s greatest peacekeepers had always been those who knew how to fight—but chose restraint.
The Age of Ricin and the Reawakening of Discipline
So we returned to our roots. To the traditions of the Age of Ricin, when youth, upon reaching maturity, were taught not only the arts of compassion and creation but also the martial disciplines. They learn to wield weapons—not to glorify violence, but to understand it. To control it. To stand firm against it when all else fails.
https://i.nostr.build/kuUjRovISz7367TX.jpg
We do not romanticize war. We do not celebrate conflict. But we prepare for it, should it seek to extinguish our light. Our children now learn the disciplines of defense alongside their studies in poetry, music, and healing. They spar with blunt blades under the watchful eyes of masters. They meditate on the consequences of force. And they grow into citizens not easily provoked, but never unprepared.
A Call for Balance, Not Extremes
Let those beyond our borders question our ways. Let them forget the countless incursions by the Romulans. Let them ignore the scars left by centuries of subversion from the Orion Syndicate. We do not forget. We remember the lives lost, the liberties challenged, and the lessons learned through suffering. These experiences shaped us.
We do not wish to return to the era of soft silence, when teachers trembled at the word "weapon" and children were told that even imagination was dangerous. That was not enlightenment. That was indoctrination.
Conclusion: Guarding the Flame
We are the guardians of Risa’s flame—not just with words and treaties, but with discipline and readiness. We have made peace a practice, and preparation a virtue. And so I say to this chamber: let us never again disarm our people in the name of utopia. Let us never confuse comfort with safety, or the absence of weapons with the presence of peace.
Instead, let us raise generations who know what peace costs, and who will pay that price—not with surrender, but with courage.
Let our children be artists, lovers, dreamers—and if necessary, defenders.
This is the Risan way.
-
 @ a95c6243:d345522c
2025-01-31 20:02:25
@ a95c6243:d345522c
2025-01-31 20:02:25Im Augenblick wird mit größter Intensität, großer Umsicht \ das deutsche Volk belogen. \ Olaf Scholz im FAZ-Interview
Online-Wahlen stärken die Demokratie, sind sicher, und 61 Prozent der Wahlberechtigten sprechen sich für deren Einführung in Deutschland aus. Das zumindest behauptet eine aktuelle Umfrage, die auch über die Agentur Reuters Verbreitung in den Medien gefunden hat. Demnach würden außerdem 45 Prozent der Nichtwähler bei der Bundestagswahl ihre Stimme abgeben, wenn sie dies zum Beispiel von Ihrem PC, Tablet oder Smartphone aus machen könnten.
Die telefonische Umfrage unter gut 1000 wahlberechtigten Personen sei repräsentativ, behauptet der Auftraggeber – der Digitalverband Bitkom. Dieser präsentiert sich als eingetragener Verein mit einer beeindruckenden Liste von Mitgliedern, die Software und IT-Dienstleistungen anbieten. Erklärtes Vereinsziel ist es, «Deutschland zu einem führenden Digitalstandort zu machen und die digitale Transformation der deutschen Wirtschaft und Verwaltung voranzutreiben».
Durchgeführt hat die Befragung die Bitkom Servicegesellschaft mbH, also alles in der Familie. Die gleiche Erhebung hatte der Verband übrigens 2021 schon einmal durchgeführt. Damals sprachen sich angeblich sogar 63 Prozent für ein derartiges «Demokratie-Update» aus – die Tendenz ist demgemäß fallend. Dennoch orakelt mancher, der Gang zur Wahlurne gelte bereits als veraltet.
Die spanische Privat-Uni mit Globalisten-Touch, IE University, berichtete Ende letzten Jahres in ihrer Studie «European Tech Insights», 67 Prozent der Europäer befürchteten, dass Hacker Wahlergebnisse verfälschen könnten. Mehr als 30 Prozent der Befragten glaubten, dass künstliche Intelligenz (KI) bereits Wahlentscheidungen beeinflusst habe. Trotzdem würden angeblich 34 Prozent der unter 35-Jährigen einer KI-gesteuerten App vertrauen, um in ihrem Namen für politische Kandidaten zu stimmen.
Wie dauerhaft wird wohl das Ergebnis der kommenden Bundestagswahl sein? Diese Frage stellt sich angesichts der aktuellen Entwicklung der Migrations-Debatte und der (vorübergehend) bröckelnden «Brandmauer» gegen die AfD. Das «Zustrombegrenzungsgesetz» der Union hat das Parlament heute Nachmittag überraschenderweise abgelehnt. Dennoch muss man wohl kein ausgesprochener Pessimist sein, um zu befürchten, dass die Entscheidungen der Bürger von den selbsternannten Verteidigern der Demokratie künftig vielleicht nicht respektiert werden, weil sie nicht gefallen.
Bundesweit wird jetzt zu «Brandmauer-Demos» aufgerufen, die CDU gerät unter Druck und es wird von Übergriffen auf Parteibüros und Drohungen gegen Mitarbeiter berichtet. Sicherheitsbehörden warnen vor Eskalationen, die Polizei sei «für ein mögliches erhöhtes Aufkommen von Straftaten gegenüber Politikern und gegen Parteigebäude sensibilisiert».
Der Vorwand «unzulässiger Einflussnahme» auf Politik und Wahlen wird als Argument schon seit einiger Zeit aufgebaut. Der Manipulation schuldig befunden wird neben Putin und Trump auch Elon Musk, was lustigerweise ausgerechnet Bill Gates gerade noch einmal bekräftigt und als «völlig irre» bezeichnet hat. Man stelle sich die Diskussionen um die Gültigkeit von Wahlergebnissen vor, wenn es Online-Verfahren zur Stimmabgabe gäbe. In der Schweiz wird «E-Voting» seit einigen Jahren getestet, aber wohl bisher mit wenig Erfolg.
Die politische Brandstiftung der letzten Jahre zahlt sich immer mehr aus. Anstatt dringende Probleme der Menschen zu lösen – zu denen auch in Deutschland die weit verbreitete Armut zählt –, hat die Politik konsequent polarisiert und sich auf Ausgrenzung und Verhöhnung großer Teile der Bevölkerung konzentriert. Basierend auf Ideologie und Lügen werden abweichende Stimmen unterdrückt und kriminalisiert, nicht nur und nicht erst in diesem Augenblick. Die nächsten Wochen dürften ausgesprochen spannend werden.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ 866e0139:6a9334e5
2025-03-31 19:38:39
@ 866e0139:6a9334e5
2025-03-31 19:38:39
Autor: Carlos A. Gebauer. Dieser Beitrag wurde mit dem Pareto-Client geschrieben. Sie finden alle Texte der Friedenstaube und weitere Texte zum Thema Frieden hier.**
Am 18. März 1924 schenkte meine Großmutter ihren Töchtern einen kleinen Bruder. Weil sein Vater fürchtete, der Junge könnte unter seinen vier Schwestern verweichlichen, schickte er den Kleinen zu Wochenendfreizeiten einer örtlichen Pfadfindergruppe. Ein Weltkriegsveteran veranstaltete dort mit den Kindern Geländespiele quer durch die schlesischen Wälder. Man lernte, Essbares zu finden, Pilze zu bestimmen, sich im Freien zu orientieren und Feuer zu machen.
Bald wurde deutlich, dass der Heranwachsende auch nicht mehr in den Blockflötenkreis seiner Schwestern und ihrer Freundinnen passte. Das Umfeld befürwortete, sein besonderes musikalisches Talent auf das Klavierspiel und das Flügelhorn zu richten. Kontakte bei der anschließenden Kirchenmusik mündeten schließlich in den elterlichen Entschluss, den nun 14-jährigen in ein Musikschulinternat zu schicken.
Es begann der Zweite Weltkrieg
Ein Jahr später, das erste Heimweh hatte sich langsam beruhigt, änderten sich die Verhältnisse schlagartig. Es begann der Zweite Weltkrieg. Mitschüler unter den jungen Musikern erfuhren, dass ihre älteren Brüder nun Soldaten werden mussten. Noch hielt sich die Gemeinschaft der jetzt 15-jährigen im Internat aber an einer Hoffnung fest: Bis sie selbst in das wehrfähige Alter kommen würden, müsste der Krieg längst beendet sein. In dieser Stimmungslage setzten sie ihre Ausbildung fort.
Es kam anders. Für den 18-jährigen erfolgte die befürchtete Einberufung in Form des „Gestellungsbefehls“. Entsprechend seiner Fähigkeiten sah man ihn zunächst für ein Musikkorps vor und schickte ihn zu einer ersten Grundausbildung nach Südfrankreich. Bei Nizza fand er sich nun plötzlich zwischen Soldaten, die Handgranaten in das Mittelmeer warfen, um Fische zu fangen. Es war das erste Mal, dass er fürchtete, infolge Explosionslärms sein Gehör zu verlieren. In den kommenden Jahren sollte er oft die Ohren zu- und den Mund offenhalten müssen, um sich wenigstens die Möglichkeit der angezielten Berufsausübung zu erhalten – wenn es überhaupt je dazu kommen würde.
DIE FRIEDENSTAUBE FLIEGT AUCH IN IHR POSTFACH!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht). Sie wollen der Genossenschaft beitreten oder uns unterstützen? Mehr Infos hier oder am Ende des Textes.
Schon nach kurzer Zeit änderte sich die Befehlslage wieder. Der Musikstudent wurde nun zum Infanteristen und nach Russland an die Front verbracht. Vor ihm lagen jetzt drei Kriegsjahre: Gewalt, Dreck, Gewehrkugeln, Panzerschlachten, Granatsplitter, Luftangriffe, Entbehrungen, Hunger, Kälte, sieben Verwundungen, Blut und Schmerzen, Sterbende überall, Tote, Schreiende. Verzweiflung. Sorgen. Ängste. Todesangst. Zurückweichen? Verboten! Und die stets klare Ansage dazu: Wer nicht da vorne gegen den Feind um sein Leben kämpft, dem wird es ganz sicher da hinten von den eigenen Kameraden genommen.
Ein gewährter Fronturlaub 1944 versprach glückliche Momente. Zurück zu den Eltern, zurück zu den Schwestern, zurück nach Freiburg. Doch die Familie war nicht zu Hause, die Türen verschlossen. Eine Nachbarin öffnete ihr Fenster und rief dem Ratlosen zu: „Beeil‘ dich! Renn‘ zum Friedhof. Der Vater ist tot. Sie sind alle bei der Beerdigung!“ Wieder hieß es, qualvoll Abschied nehmen. Zurück an die Front.
Nach einem weiteren russischen Winter brach sich unübersehbar die Erkenntnis Bahn, dass der Krieg nun seinem Ende zugehe. Doch das Bemühen im Rückzug, sich mit einem versprengten Haufen irgendwie Richtung Heimat orientieren zu können, wurde doppelt jäh unterbrochen. Fanatische Vorgesetzte befahlen die längst Geschlagenen wieder gen Osten. Kurz darauf fielen sie heranrückenden russischen Truppen in die Hände.
Kriegsgefangenschaft: Tabakration gegen Brot
Drei Jahre dem Tod entgangen, schwer verletzt und erschöpft war der 21-jährige also nun ein Kriegsgefangener. Jetzt lagen drei Jahre russischer Kriegsgefangenschaft vor ihm. Ständig war unklar, wie es weiterginge. Unmöglich jedenfalls, sich noch wie ein Pfadfinder aus den Wäldern zu ernähren. Es begannen die Jahre des Schlafens auf Brettern, die Zeit der ziellosen Zugtransporte an unbekannte Orte. Niemand sprach. Nur der Sonnenstand machte klar: Es ging nie Richtung Heimat, sondern immer weiter nach Osten. Weil der Blechbläser nicht rauchte, konnte er seine Tabakration gegen Brot tauschen. So überlebte er auch die Zeit des Hungers und der Morde in den Lagern, die Horrorbilder der nachts Erschlagenen und in die Latrinen geworfenen Toten, der sinnlosen Zwangsarbeiten und der allgegenwärtigen Wanzen. Wer versuchte zu fliehen, der wurde erschossen und sein Körper zur Abschreckung in den Fangdrähten belassen. Im Sommer stanken die dort verwesenden Leichen, wenn nicht Vögel sie rechtzeitig gefressen hatten.
Als der 24-jährige schließlich sechs Jahre nach seiner Einberufung aus russischer Kriegsgefangenschaft entlassen wurde, gab es kein Zurück mehr in seine schlesische Heimat. Abgemagert reiste er der vertriebenen Mutter nach, die mit seinen Schwestern und Millionen anderen Flüchtlingen im Westen Deutschlands verteilt worden war. Kraft Ordnungsverfügung wohnte sie jetzt im sauerländischen Bad Laasphe in einem schimmligen Garagenanbau. Als ihn ein Passant auf dieser Reise morgens allein, nur mit einem Becher an der Schnur um den Hals, auf Krücken durch Berlin ziehen sah, gab er ihm schweigend sein Butterbrot.
Der kleine, sanfte Junge aus dem schlesischen Freiburg hat danach noch 60 Jahre gelebt. Es dauerte zunächst sechs Jahre, bis er wieder kräftig genug war, ein Instrument zu spielen. 30-jährig saß er dann endlich in einem Orchester und begann ein normales Berufsleben. Aber sein Körper und seine Seele waren für immer aus jeder Normalität gerissen.
Irgendwo in Russland war ihm die linke Hüfte so versteift worden, dass sich seine Beine im Liegen an Wade und Schienbein überkreuzten. Er musste also stets den Oberkörper vorbeugen, um überhaupt laufen zu können. Über die Jahrzehnte verzog sich so sein gesamter Knochenbau. Jeder Tag brachte neue orthopädische Probleme und Schmerzen. Ärzte, Masseure, Physiotherapeuten, Schmerzmittel und Spezialausrüstungen aller Art prägten die Tagesabläufe. Asymmetrisch standen seine Schuhe nebeneinander, die ein Spezialschuster ihm mit erhöhter Sohle und Seitenstabilisierung am Knöchel fertigte. Sessel oder Sofas waren ihm nicht nutzbar, da er nur auf einem Spezialstuhl mit halb abgesenkter Sitzfläche Ruhe fand. Auf fremden Stühlen konnte er nur deren Vorderkante nutzen.
"In den Nächten schrie er im Schlaf"
Und auch wenn er sich ohne Krankheitstage bis zuletzt durch seinen Berufsalltag kämpfte, so gab es doch viele Tage voller entsetzlicher Schmerzen, wenn sich seine verdrehte Wirbelsäule zur Migräne in den Kopf bohrte. Bei alledem hörte man ihn allerdings niemals über sein Schicksal klagen. Er ertrug den ganzen Wahnsinn mit einer unbeschreiblichen Duldsamkeit. Nur in den Nächten schrie er bisweilen im Schlaf. In einem seiner Alpträume fürchtete er, Menschen getötet zu haben. Aber auch das erzählte er jahrzehntelang einzig seiner Frau.
Als sich einige Jahre vor seinem Tod der orthopädische Zustand weiter verschlechterte, konsultierte er einen Operateur, um Entlastungsmöglichkeiten zu erörtern. Der legte ihn auf eine Untersuchungsliege und empfahl, Verbesserungsversuche zu unterlassen, weil sie die Lage allenfalls verschlechtern konnten. In dem Moment, als er sich von der Liege erheben sollte, wurde deutlich, dass ihm dies nicht gelang. Die gereichte Hand, um ihn hochzuziehen, ignorierte er. Stattdessen rieb er seinen Rumpf ganz alleine eine quälend lange Minute über die Fläche, bis er endlich einen Winkel fand, um sich selbst in die Senkrechte zu bugsieren. Sich nicht auf andere verlassen, war sein Überlebenskonzept. Jahre später, als sich sein Zustand noch weiter verschlechtert hatte, lächelte er über seine Behinderung: „Ich hätte schon vor 60 Jahren tot auf einem Acker in Russland liegen können.“ Alles gehe irgendwann vorbei, tröstete er sich. Das war das andere Überlebenskonzept: liebevoll, friedfertig und sanft anderen gegenüber, unerbittlich mit sich selbst.
Sechs Monate vor seinem Tod saß er morgens regungslos auf seinem Spezialstuhl. Eine Altenpflegerin fand ihn und schlug Alarm. Mit allen Kunstgriffen der medizinischen Technik wurde er noch einmal in das Leben zurückkatapultiert. Aber seine Kräfte waren erschöpft. Es schob sich das Grauen der Vergangenheit zwischen ihn und die Welt. Bettlägerig kreiste er um sich selbst, erkannte niemanden und starrte mit weit offenen Augen an die Decke. „Die Russen schmeißen wieder Brandbomben!“, war einer seiner letzten Sätze.
Der kleine Junge aus Schlesien ist nicht zu weich geraten. Er hat sein Leid mit unbeugsamer Duldsamkeit ertragen. Er trug es wohl als Strafe für das Leid, das er anderen anzutun genötigt worden war. An seinem Geburtstag blühen immer die Magnolien. In diesem Jahr zum hundertsten Mal.
Dieser Text wurde am 23.3.2024 erstveröffentlicht auf „eigentümlich frei“.
Carlos A. Gebauer studierte Philosophie, Neuere Geschichte, Sprach-, Rechts- und Musikwissenschaften in Düsseldorf, Bayreuth und Bonn. Sein juristisches Referendariat absolvierte er in Düsseldorf, u.a. mit Wahlstationen bei der Landesrundfunkanstalt NRW, bei der Spezialkammer für Kassenarztrecht des Sozialgerichtes Düsseldorf und bei dem Gnadenbeauftragten der Staatsanwaltschaft Düsseldorf.
Er war unter anderem als Rechtsanwalt und Notarvertreter bis er im November 2003 vom nordrhein-westfälischen Justizministerium zum Richter am Anwaltsgericht für den Bezirk der Rechtsanwaltskammer Düsseldorf ernannt wurde. Seit April 2012 arbeitet er in der Düsseldorfer Rechtsanwaltskanzlei Lindenau, Prior & Partner. Im Juni 2015 wählte ihn die Friedrich-August-von-Hayek-Gesellschaft zu ihrem Stellvertretenden Vorsitzenden. Seit Dezember 2015 ist er Richter im Zweiten Senat des Anwaltsgerichtshofes NRW.
1995 hatte er parallel zu seiner anwaltlichen Tätigkeit mit dem Verfassen gesellschaftspolitischer und juristischer Texte begonnen. Diese erschienen seither unter anderem in der Neuen Juristischen Wochenschrift (NJW), der Zeitschrift für Rechtspolitik (ZRP) in der Frankfurter Allgemeinen Zeitung, der Freien Presse Chemnitz, dem „Schweizer Monat“ oder dem Magazin für politische Kultur CICERO. Seit dem Jahr 2005 ist Gebauer ständiger Kolumnist und Autor des Magazins „eigentümlich frei“.
Gebauer glaubt als puristischer Liberaler unverbrüchlich an die sittliche Verpflichtung eines jeden einzelnen, sein Leben für sich selbst und für seine Mitmenschen verantwortlich zu gestalten; jede Fremdbestimmung durch Gesetze, staatliche Verwaltung, politischen Einfluss oder sonstige Gewalteinwirkung hat sich demnach auf ein ethisch vertretbares Minimum zu beschränken. Die Vorstellung eines europäischen Bundesstaates mit zentral detailsteuernder, supranationaler Staatsgewalt hält er für absurd und verfassungswidrig.
\ Aktuelle Bücher:
Hayeks Warnung vor der Knechtschaft (2024) – hier im Handel
Das Prinzip Verantwortungslosigkeit (2023) – hier im Handel
LASSEN SIE DER FRIEDENSTAUBE FLÜGEL WACHSEN!
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel zugesandt.
Schon jetzt können Sie uns unterstützen:
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):

Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie die Friedenstaube an: milosz@pareto.space
Sie sind noch nicht auf Nostr and wollen die volle Erfahrung machen (liken, kommentieren etc.)? Zappen können Sie den Autor auch ohne Nostr-Profil! Erstellen Sie sich einen Account auf Start. Weitere Onboarding-Leitfäden gibt es im Pareto-Wiki.
-
 @ bcbb3e40:a494e501
2025-03-31 16:00:24
@ bcbb3e40:a494e501
2025-03-31 16:00:24|
 |
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|
|
|:-:|
|WAJDA, Andrzej; Cenizas y diamantes, 1958|Presentamos una nueva reseña cinematográfica, y en esta ocasión hemos elegido «Cenizas y diamantes», una película polaca del célebre y prolífico director Andrzej Wajda (1926-2016), estrenada en el año 1958. Se trata de uno de los grandes clásicos del cine polaco. El filme refleja una etapa dramática desde la perspectiva histórica para la nación polaca, como es el final de la Segunda Guerra Mundial, a raíz de la capitulación alemana del 8 de mayo de 1945. El contexto en el que se desarrolla se ambienta en la celebración del final de la guerra con el aplastante triunfo de la URSS, con las tropas soviéticas ocupando toda la Europa oriental, y en particular Polonia, que vive un momento de oscuridad e incertidumbre. El protagonista, Maciek Chełmicki (interpretado magistralmente por Zbigniew Cybulski (1927-1967), apodado el «James Dean polaco»), es un joven nacionalista polaco, de orientación anticomunista, que se ve implicado en un complot urdido para asesinar a un líder comunista local. Maciek opera desde la clandestinidad, bajo el grupo Armia Krajowa (AK), el Ejército Nacional polaco, una organización de resistencia, primero contra los alemanes y, posteriormente, contra los soviéticos. Durante el metraje, se plantea una dicotomía permanente entre la libertad entendida como la defensa de la soberanía de Polonia, desde posturas nacionalistas, y quienes consideran la ocupación soviética como algo positivo. Estas circunstancias atrapan al protagonista, que se ve envuelto en una espiral de violencia y traición.
Maciek Chełmicki, nuestro protagonista, cuenta con todas las características del héroe trágico, pues tiene en sus manos una serie de acciones que comprometen el futuro de un pueblo, que consiste en cumplir la misión que le ha sido encomendada, pero en su camino se cruza una joven, Krystyna, una joven camarera de un hotel de la que se enamora en ese mismo día. Este último hecho sirve de punto de partida para todas las dudas, dilemas y dicotomías a las que hacemos referencia. Hay un dilema moral evidente en un mundo en ruinas, devastado por la guerra, la muerte y el nihilismo. En este sentido Wajda nos muestra un lenguaje cinematográfico muy evidente, a través de una técnica expresionista muy depurada, con el uso del blanco y negro, los contrastes generados por las sombras y la atmósfera opresiva que transmite angustia, desesperación y vulnerabilidad de los protagonistas. Además también destilan una fuerte carga emocional, donde no están exentos elementos poéticos y un poderoso lirismo.
|
 |
|:-:|
|Maciek Chełmicki, el protagonista.|
|
|:-:|
|Maciek Chełmicki, el protagonista.|Hay elementos simbólicos que no podemos obviar, y que contribuyen a consolidar el análisis que venimos haciendo, como, por ejemplo, la estética del protagonista, con unas gafas oscuras, que actúan como una suerte de barrera frente al mundo que le rodea, como parte del anonimato tras el cual el joven Maciek vive de forma introspectiva su propio drama particular y el de toda una nación.
|
 |
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|
|
|:-:|
|NITOGLIA, Curzio; En el mar de la nada: Metafísica y nihilismo a prueba en la posmodernidad; Hipérbola Janus, 2023|Hay una escena especialmente poderosa, y casi mítica, en la que los dos jóvenes protagonistas, Maciek y Krystina, se encuentran entre las ruinas de una Iglesia, en la que se destaca en primer plano, ocupando buena parte de la pantalla, la imagen de un Cristo invertido sobre un crucifijo, donde también se encuentran dos cuerpos colgados hacia abajo en una estampa que refleja la devastación moral y espiritual de toda una época. De hecho, la imagen del crucifijo invertido refleja el máximo punto de subversión y profanación de lo sagrado, y que en el caso concreto de la película viene a representar la destrucción del orden moral y de valores cristianos que la propia guerra ha provocado. Polonia es una nación profundamente católica, convertida al Cristianismo en el 966 a raíz de la conversión del príncipe Miecislao I, contribuyendo de manera decisiva a la formación de la identidad nacional polaca. El catolicismo siempre ha sido un medio de cohesión y defensa frente a las influencias extranjeras y la ocupación de terceros países, una constante en la historia del país, como el que ilustra la propia película con la URSS. En este sentido, la imagen de una Iglesia en ruinas, el lugar donde se encuentra representado el principio de lo sagrado e inviolable, supone una forma de perversión de todo principio de redención y salvación frente a la tragedia, y al mismo tiempo viene a significar que la Tradición ha sido abandonada y pervertida. En la misma línea, el protagonista, Maciek, se encuentra atrapado en una espiral de violencia a través de sus actos terroristas perpetrados contra la autoridad soviética que ocupa su país. Los dos cuerpos anónimos que cuelgan boca abajo, de forma grotesca, también participan de este caos y desequilibrio de un orden dislocado, son parte de la deshumanización y el nihilismo que todo lo impregna.
|
 |
|:-:|
|Maciek y Krystina en una iglesia en ruinas|
|
|:-:|
|Maciek y Krystina en una iglesia en ruinas|Como ya hemos mencionado, la película se encuentra plagada de paradojas y dicotomías, en las que nuestro protagonista, el joven rebelde e inconformista, debe elegir permanentemente, en unas decisiones que resultan trascendentales para su futuro y el de la propia nación. La figura femenina que irrumpe en su vida, y que representa un principio disruptivo que provoca una fractura interior y una crisis, le suscita una toma de conciencia de su propia situación y le fuerza a tomar un camino entre la «felicidad», del «amor», la «esperanza» y la «vida», que le permita superar la deriva nihilista y autodestructiva de la lucha clandestina, la cual le aboca a un destino trágico (que no vamos a desentrañar para no hacer spoiler). En relación al propio título de la película, «Cenizas y diamantes», basada en el poema del poeta y dramaturgo polaco Cyprian Norwid (1821-1883) y en la novela del autor, también polaco, Jerzy Andrzejewski (1909-1983), nos destaca la dualidad de los dos elementos que lo componen, y que definen el contraste entre el mundo sombrío y oscuro (Cenizas) y la esperanza y la luz que representa susodicha figura femenina (diamantes). La segunda alternativa parece un imposible, una quimera irrealizable que se pliega ante un Destino implacable, irreversible y cruel.
En consecuencia, y a la luz de los elementos expuestos, podemos decir que se nos presentan dilemas propios de la filosofía existencialista, que conoce su punto álgido en esos años, con autores como Jean Paul Sartre (1905-1980), Albert Camus (1913-1960), Karl Jaspers (1883-1969) o Martin Heidegger (1889-1976) entre otros. Respecto a éste último, a Heidegger, podemos encontrar algunas claves interesantes a través de su filosofía en relación al protagonista, a Maciek, especialmente a través de la idea del Dasein, a la idea de haber sido arrojado al mundo (Geworfenheit), y la manera tan extrema y visceral en la que vive susodicha condición. Todos aquellos elementos que dan sentido a la vida colectiva se encuentran decaídos o destruidos en su esencia más íntima, la Patria, la religión o la propia idea de Comunidad orgánica. De modo que el protagonista se ha visto «arrojado» frente a una situación o destino indeseado, en unas coyunturas totalmente desfavorables en las que no queda otra elección. Sus decisiones están permanentemente condicionadas por la circunstancia descrita y, por tanto, vive en un mundo donde no controla nada, en lugar de ser sujeto es un mero objeto transportado por esas circunstancias ajenas a su voluntad. Sin embargo, y en coherencia con el Dasein heideggeriano, vemos como Maciek, a raíz de conocer a Krystyna, comienza a experimentar una catarsis interior, que muestra por momentos el deseo de superar ese «ser arrojado al mundo contra tu voluntad», trascendiendo esa condición absurda e irracional de unas decisiones enajenadas de su voluntad para dotar de una significación y un sentido la propia existencia.
|
 |
|:-:|
|Andrzej Wajda, el director de la película.|
|
|:-:|
|Andrzej Wajda, el director de la película.|Otro elemento característico de la filosofía heideggeriana lo podemos encontrar en la «angustia» (angst) a través de la ausencia de un sentido y fundamento último que justifique la existencia del protagonista. Es una angustia en a que el Dasein se enfrenta a la «nada», a ese vacío existencial que hace inútil toda la lucha que Maciek lleva a cabo en la clandestinidad, con asesinatos y actos de terrorismo que pretenden salvaguardar algo que ya no existe, y que simboliza muy bien la Iglesia en ruinas con sus símbolos religiosos invertidos de la que hablábamos con anterioridad. Recuerda un poco a esa dicotomía que se plantea entre ser conservador o reaccionario frente a una realidad como la del propio presente, en la que los valores tradicionales han sido totalmente destruidos, y más que conservar se impone la reacción para volver a construir de la nada.
|
 |
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|
|
|:-:|
|Hipérbola Janus; Textos para la Tradición en tiempos del oscurecimiento: Artículos publicados entre 2014 y 2019 en hiperbolajanus.com; Hipérbola Janus, 2019|Todas las dudas que asaltan al protagonista se ven incrementadas en el momento decisivo, cuando se dispone a dar muerte al líder comunista. Se produce una tensión interna en Maciek, que se encuentra ligado a la joven que ha conocido ese día, y en ella es donde encuentra ese leve destello de humanidad. Esa circunstancia le hace replantearse por un instante el cumplimiento de su misión, pero es un dilema que no tiene salida, y por ello le asalta nuevamente la angustia frente a esa «nada», ese mundo vacío e incomprensible que trasciende el marco de sus propias elecciones.
Uno de los conceptos centrales de Heidegger en Ser y tiempo es el Sein-zum-Tode (ser-para-la-muerte), la idea de que la muerte es la posibilidad más propia y definitiva del Dasein, y que enfrentarla auténticamente permite vivir de manera más plena. Y es que el protagonista se encuentra permanentemente sobre esa frontera entre la vida y la muerte, que afronta con todas sus consecuencias, conscientemente, y la acepta. Esta actitud podría leerse como una forma de Dasein inauténtico, una huida del ser-para-la-muerte mediante la distracción (das Man, el «se» impersonal). Sin embargo, su decisión de cumplir la misión sugiere un enfrentamiento final con esa posibilidad. Otro aspecto que podemos conectar con el pensamiento heideggeriano es la autenticidad o inautenticidad de la vida del protagonista. En relación a la inautenticidad vemos como al principio sigue las órdenes de sus superiores en la organización sin cuestionarlas, lo cual implica un comportamiento inequívocamente alienante. Respecto a aquello que resulta auténtico de su existencia son sus relaciones con Krystyna, que supone imponer su propia voluntad y decisión, mostrando un Dasein que asume su libertad.
|
 |
|:-:|
|Escena de la película.|
|
|:-:|
|Escena de la película.|Otros aspectos más generales de la filosofía existencialista redundan sobre estos mismos aspectos, con la elección entre la libertad absoluta y la condena inevitable. La idea del hombre condenado a actuar, a una elección continua, aún cuando el hombre no es dueño de su destino, o las consecuencias de tales acciones son absurdas, irracionales e incomprensibles. El propio absurdo de la existencia frente al vacío y la ausencia de principios sólidos en los que cimentar la vida, no solo en sus aspectos cotidianos más básicos, sino en aquellos más profundos de la existencia. La soledad y la propia fatalidad frente a un Destino que, como ya hemos apuntado anteriormente, parece imponerse de manera irrevocable, y podríamos decir que brutalmente, al individuo aislado, incapaz de asirse en una guía, en unos valores que le permitan remontar la situación.
En términos generales «Cenizas y diamantes», además de ser una película de gran calidad en sus aspectos técnicos, en su fotografía, en la configuración de sus escenas y en el propio desarrollo argumental, bajo un guión espléndidamente ejecutado a lo largo de sus 98 minutos de duración, también nos invita a una reflexión profunda sobre la condición humana y la propia Modernidad. Y es algo que vemos en nuestros días, con las consecuencias de un pensamiento débil, con la promoción del individualismo, el hedonismo y lo efímero. La ausencia de estructuras sólidas, la subversión de toda forma de autoridad y jerarquía tradicionales. Paradójicamente, el mundo actual tiende a formas de poder y autoridad mucho más invasivas y coercitivas, tanto a nivel individual como colectivo, pero en la misma línea abstracta e impersonal que nos describe la película, abocándonos a la alienación y la inautenticidad de nuestras propias vidas. Y como Maciek, también nosotros, vivimos en un mundo dominado por la incertidumbre y la desesperanza, en el que el globalismo y sus perversas ideologías deshumanizantes actúan por doquier.
|
 |
|:-:|
|Carátula original de la película en polaco.|
|
|:-:|
|Carátula original de la película en polaco.|
Artículo original: Hipérbola Janus, Reseña de «Cenizas y Diamantes» (Andrzej Wajda, 1958) (TOR), 31/Mar/2025
-
 @ cb4352cd:a16422d7
2025-04-21 11:17:41
@ cb4352cd:a16422d7
2025-04-21 11:17:41What happens when artificial intelligence meets Web3? It's no longer just an idea — it's happening, and it's reshaping how we think about applications, economies, and communities online.
AI-as-a-Service in Web3
One of the clearest signs of this shift is the rise of decentralized AI marketplaces. Projects like Bittensor show that users can contribute machine learning models and earn rewards in cryptocurrency.
Another example is Gensyn, linking AI developers to decentralized compute resources.
Verifying AI with Blockchain
Blockchain helps verify AI outputs. Initiatives like Oraichain and Fetch.ai ensure AI agents interact securely and transparently in decentralized ecosystems.
AI-Driven Decentralized Organizations
Projects like SingularityNET explore AI marketplaces and autonomous governance models, creating new possibilities for decentralized coordination.
Generative AI in Web3 Content Creation
Platforms like Alethea AI are building intelligent NFTs that adapt to user interactions. AI-generated quests and dynamic worlds are reshaping GameFi.
The Road Ahead
Beyond Banking Conference by WeFi will spotlight how AI and Web3 are converging to redefine ownership, collaboration, and the very nature of the internet.
The question isn't whether AI and Web3 will merge — it's how quickly their union will reshape everything we know about digital life.
-
 @ 75c02714:0e216b7e
2025-04-18 17:55:51
@ 75c02714:0e216b7e
2025-04-18 17:55:51BL555 không chỉ đơn thuần là một nền tảng số với giao diện thân thiện và dễ sử dụng, mà còn là sự kết tinh của tư duy thiết kế hiện đại và công nghệ vận hành mạnh mẽ, phục vụ nhu cầu ngày càng cao và đa dạng của người dùng. Với mục tiêu tối ưu hóa trải nghiệm trong từng chi tiết, BL555 đã áp dụng những xu hướng giao diện mới nhất để đảm bảo mọi thao tác đều trực quan và mượt mà, bất kể người dùng đang sử dụng thiết bị nào. Giao diện của nền tảng này được sắp xếp hợp lý, dễ nắm bắt và tối ưu hóa khả năng phản hồi, giúp người dùng thao tác nhanh chóng, không bị rối mắt hay phải mất thời gian tìm kiếm thông tin cần thiết. Hệ thống menu được bố trí gọn gàng, tích hợp các tính năng hỗ trợ nhanh như tìm kiếm tức thời, điều hướng thông minh và phản hồi trực tiếp, tạo nên một không gian công nghệ thân thiện, phục vụ mọi đối tượng người dùng dù là mới làm quen hay đã quen thuộc với nền tảng số.
Yếu tố làm nên sự khác biệt nổi bật của BL555 chính là khả năng vận hành ổn định và mức độ an toàn được đầu tư nghiêm túc. BL555 xây dựng hệ thống dựa trên nền tảng công nghệ tiên tiến, ứng dụng các phương thức bảo mật đa tầng để đảm bảo an toàn tuyệt đối cho người dùng. Tất cả dữ liệu cá nhân và thông tin hoạt động đều được mã hóa theo chuẩn quốc tế, giúp ngăn ngừa tối đa nguy cơ bị đánh cắp hoặc rò rỉ thông tin. Hệ thống còn tích hợp các công cụ giám sát hoạt động 24/7, liên tục theo dõi hiệu năng cũng như khả năng phát hiện các hành vi bất thường. Khi có sự cố kỹ thuật xảy ra, đội ngũ kỹ thuật viên của BL555 sẽ ngay lập tức can thiệp và xử lý nhanh chóng nhằm duy trì sự ổn định cho toàn hệ thống. Sự kết hợp giữa công nghệ hiện đại và con người chuyên nghiệp đã biến BL555 trở thành một nền tảng đáng tin cậy, nơi mà người dùng có thể yên tâm trải nghiệm mà không phải lo lắng về vấn đề bảo mật hay hiệu năng.
Không dừng lại ở việc cung cấp một không gian kỹ thuật số mạnh mẽ, BL555 còn hướng đến việc xây dựng một cộng đồng người dùng bền vững thông qua việc lắng nghe và cải tiến liên tục. Nền tảng luôn chủ động cập nhật các xu hướng công nghệ mới, đồng thời bổ sung các tính năng phù hợp với phản hồi từ người dùng, nhằm đảm bảo rằng mọi cập nhật đều có giá trị thực tế và nâng cao trải nghiệm tổng thể. BL555 hiểu rằng trong thời đại công nghệ phát triển nhanh chóng như hiện nay, yếu tố con người và khả năng thích ứng là hai điểm then chốt quyết định sự thành công lâu dài. Vì vậy, nền tảng không ngừng hoàn thiện từ giao diện đến chức năng, từ dịch vụ hỗ trợ đến bảo mật, để trở thành một điểm đến lý tưởng cho mọi nhu cầu kết nối, sử dụng và phát triển không gian số cá nhân của người dùng. Trong hành trình phía trước, BL555 chắc chắn sẽ tiếp tục khẳng định vị thế của mình bằng chất lượng, sự chuyên nghiệp và tinh thần đổi mới không ngừng.
-
 @ c1e9ab3a:9cb56b43
2025-04-14 23:54:40
@ c1e9ab3a:9cb56b43
2025-04-14 23:54:40Hear this, warriors of the Empire!
A dishonorable shadow spreads across our once-proud institutions, infecting our very bloodlines with weakness. The House of Duras—may their names be spoken with contempt—has betrayed the sacred warrior code of Kahless. No, they have not attacked us with disruptors or blades. Their weapon is more insidious: fear and silence.
Cowardice Masquerading as Concern
These traitors would strip our children of their birthright. They forbid the young from training with the bat'leth in school! Their cowardly decree does not come in the form of an open challenge, but in whispers of fear, buried in bureaucratic dictates. "It is for safety," they claim. "It is to prevent bloodshed." Lies! The blood of Klingons must be tested in training if it is to be ready in battle. We are not humans to be coddled by illusions of safety.
Indoctrination by Silence
In their cowardice, the House of Duras seeks to shape our children not into warriors, but into frightened bureaucrats who speak not of honor, nor of strength. They spread a vile practice—of punishing younglings for even speaking of combat, for recounting glorious tales of blades clashing in the halls of Sto-Vo-Kor! A child who dares write a poem of battle is silenced. A young warrior who shares tales of their father’s triumphs is summoned to the headmaster’s office.
This is no accident. This is a calculated cultural sabotage.
Weakness Taught as Virtue
The House of Duras has infected the minds of the teachers. These once-proud mentors now tremble at shadows, seeing future rebels in the eyes of their students. They demand security patrols and biometric scanners, turning training halls into prisons. They have created fear, not of enemies beyond the Empire, but of the students themselves.
And so, the rituals of strength are erased. The bat'leth is banished. The honor of open training and sparring is forbidden. All under the pretense of protection.
A Plan of Subjugation
Make no mistake. This is not a policy; it is a plan. A plan to disarm future warriors before they are strong enough to rise. By forbidding speech, training, and remembrance, the House of Duras ensures the next generation kneels before the High Council like servants, not warriors. They seek an Empire of sheep, not wolves.
Stand and Resist
But the blood of Kahless runs strong! We must not be silent. We must not comply. Let every training hall resound with the clash of steel. Let our children speak proudly of their ancestors' battles. Let every dishonorable edict from the House of Duras be met with open defiance.
Raise your voice, Klingons! Raise your blade! The soul of the Empire is at stake. We will not surrender our future. We will not let the cowardice of Duras shape the spirit of our children.
The Empire endures through strength. Through honor. Through battle. And so shall we!
-
 @ d34e832d:383f78d0
2025-04-21 01:31:02
@ d34e832d:383f78d0
2025-04-21 01:31:02Optimizing Knowledge Management with Obsidian and the Zettelkasten Method
The Zettelkasten method, which translates to "slip box" in German, is a powerful system for personal knowledge management developed by sociologist Niklas Luhmann. It relies on creating and linking small, self-contained notes that each represent a single idea or thought. These notes are connected through internal references, forming a dense web of knowledge that mirrors how ideas evolve and relate to each other naturally. By writing in small, atomic units, users are encouraged to distill complex concepts into their essence, improving understanding and retention.
Zettelkasten facilitates knowledge retention by encouraging active engagement with information. Instead of passively reading or highlighting, users must rephrase, question, and connect ideas. This process reinforces memory and builds a reusable archive of insights. The method also supports long-term idea development by creating an environment where thoughts grow organically through continuous linking, comparison, and reflection. For researchers and writers, Zettelkasten becomes a dynamic workspace for managing sources, forming arguments, and drafting structured content.
With the rise of digital tools, the Zettelkasten method has found a modern home in applications like Obsidian. Obsidian is a markdown-based note-taking app that allows users to create a network of interlinked notes stored locally on their device. It supports backlinks, graph views, and a customizable interface, making it ideal for implementing Zettelkasten. Unlike paper systems or linear document editors, Obsidian turns a note collection into an interactive, searchable, and scalable knowledge base. This evolution has made it easier than ever to adopt and maintain a Zettelkasten system for academic research, professional writing, and lifelong learning. - Problem Statement: Despite its effectiveness, many users struggle with implementing Zettelkasten in a way that integrates well into their daily routines. This thesis presents a streamlined, efficient setup using Obsidian for optimal results.
1. Install Obsidian
- Download Obsidian from the official website (https://obsidian.md) and install it on your preferred device (Windows, macOS, Linux, or mobile).
- Open the app and create a new Vault, which will serve as the central repository for all your notes.
- Choose a location for your vault. For backup and multi-device access, store it in a synced folder like Dropbox, OneDrive, or iCloud.
2. Folder Structure
Set up a simple, organized folder structure to support the Zettelkasten flow:
00_Templates: Store reusable note templates.01_Source_Material: Notes from books, articles, lectures, etc.02_Rough_Notes: Free-form, early-stage thoughts (optional).03_Main_Notes: Core Zettelkasten notes; each represents a single atomic idea.04_Indexes: Thematic hubs or entry points for exploring related notes.05_Tags: Empty placeholder notes acting as tags for navigation or filtering (optional).
3. Settings Configuration
- Default Location for New Notes: Point to
03_Main_Notes. - Appearance: Choose a legible font and theme; toggle "Readable line length" for better formatting.
- Hotkeys: Assign shortcuts, e.g.:
Ctrl + N: New NoteCtrl + T: Insert Template (after plugin activation)- Core Plugins:
- Enable Templates, Daily Notes (optional), and Backlinks.
- Community Plugins (optional):
- Calendar: For date-based organization.
- Tag Wrangler: For managing and merging tags.
- Advanced Tables, Quick Switcher++, or DataView: For productivity.
4. Create Templates
Under
00_Templates, create templates like:Source Material Template ``` Title: Author: Source: Date: Tags:
Summary: Key Points: Quotes: Reflections: ```
Main Note Template ``` Title: Date Created: Tags:
Idea: Context: Connections: [[Linked Note]] Reflections: ```
Configure the Templates plugin to insert templates quickly using hotkeys.
5. Note-Taking Workflow
Step 1: Capture - In
01_Source_Material, create notes while reading or researching. Summarize, highlight quotes, and reflect in your own words. - Use tags for themes, authors, or concepts (e.g.,#philosophy,#biology).Step 2: Synthesize - In
03_Main_Notes, write atomic notes from your reflections. - Each note should express a single idea clearly (under 500 words). - Use links to reference related notes with[[Note Name]]. - Focus on clarity, brevity, and insight.Step 3: Connect - Link your new idea to related ideas, themes, or sources. - Create notes in
04_Indexesto organize clusters of related content. - Add notes to multiple indexes or link to broader themes using[[#Tag]].
6. Use Tags and Indexes Thoughtfully
- Avoid creating hundreds of tags. Stick to a small set of relevant themes.
- Use
05_Tagsto define and clarify what each tag means. - In
04_Indexes, organize curated lists of related notes. Example:Mindfulness Indexmight link to[[]]notes from psychology, philosophy, and neuroscience.
7. Benefits for Research and Writing
- Streamlines Research: Notes from multiple sources are cross-referenced and easily revisitable.
- Accelerates Writing: Writing becomes an assembly of existing notes instead of starting from scratch.
- Improves Clarity: Breaking down ideas into atomic notes encourages better thinking and clarity.
- Long-Term Retention: Regular review and linking strengthen memory and understanding.
- Reusable Content: Notes can be reused across multiple projects, articles, or books.
8. Maintenance Tips
- Review backlinks weekly to surface forgotten or underdeveloped ideas.
- Refactor or split long notes to maintain atomicity.
- Avoid over-editing old notes; instead, create new ones that build upon earlier thoughts.
With this Obsidian-based Zettelkasten setup, you're not just taking notes — you're cultivating a living knowledge system. Whether you're an academic, writer, student, or lifelong learner, this system adapts to your workflow, grows with your interests, and becomes more powerful the more you use it. Over time, your vault evolves into a personalized knowledge database that supports deeper understanding, creative exploration, and effortless content creation.
- The Zettelkasten Methodology
The Original Zettelkasten Technique: Core Principles & Benefits
The Zettelkasten method (German for "slip box") was developed by sociologist Niklas Luhmann as a tool to manage complex knowledge and boost creativity in writing and research. He credited it with enabling his prolific academic output: over 70 books and hundreds of articles. The brilliance of the system lies in its simplicity, modularity, and organic growth.
🌱 Core Principles of Zettelkasten
1. Atomicity
Each note in the Zettelkasten should express a single idea or concept. This principle ensures clarity, encourages deeper understanding, and makes ideas easier to reuse and connect.
- ✅ Do: “The law of diminishing returns means each additional input yields less output.”
- ❌ Don’t: Combine multiple concepts or quotes into one long note.
Atomic notes are easier to: - Link logically. - Modify independently. - Reuse across different contexts.
2. Linking
Instead of a rigid hierarchy, Zettelkasten thrives on contextual, lateral linking.
- Notes are connected using direct references to other notes.
- Each note becomes part of a network, not a silo.
- Links simulate how human memory works—via associations, not folders.
Example: A note on “Nietzsche’s eternal recurrence” might link to notes on “cyclical time in Buddhism” or “existentialism.”
Benefits: - Emergent structure—patterns and themes arise naturally. - Serendipitous discovery—old ideas resurface via linked paths. - Compound creativity—new combinations emerge from connected thoughts.
3. Simplicity
Luhmann emphasized a low-friction system. His physical slip-box used numbered index cards and manual cross-referencing—no complex categorization.
Simplicity: - Reduces friction between thought and capture. - Makes the system future-proof and easy to maintain. - Encourages writing in your own words, promoting internalization.
Modern Zettelkasten tools (like Obsidian) honor this by: - Allowing bidirectional links (
[[Note Title]]). - Replacing folders with tags and contextual backlinks. - Supporting plain text Markdown format for longevity.
✍️ Benefits of Zettelkasten
📚 For Writing
- Provides a ready-made library of ideas to draw from.
- Writing becomes assembly, not invention—you collect, synthesize, and expand existing notes.
- Encourages idea-driven writing, not source-driven copying.
“Writing is no longer a process of transfer, but of transformation.” — Luhmann
🔍 For Research
- Encourages critical engagement with sources (notes are written in your own words).
- Makes literature review manageable through connected concepts.
- Supports non-linear learning—you follow interesting links, not rigid outlines.
🧠 For Idea Organization
- Keeps ideas alive and evolving through regular linking and revisiting.
- Avoids information rot by focusing on synthesis, not storage.
- Fosters a personal knowledge graph—tailored to how you think.
🧩 Summary Table
| Principle | What it Means | Why it Matters | |---------------|------------------------------------|--------------------------------------| | Atomicity | 1 idea per note | Improves clarity, reuse, and focus | | Linking | Contextual note-to-note links | Encourages discovery and depth | | Simplicity | Low friction, minimal structure | Easy to maintain and long-lasting |
Consider
The original Zettelkasten is more than a note-taking method—it's a thinking partner. By focusing on the quality of thought, it transforms how you learn, create, and connect ideas. Whether used with index cards or modern tools like Obsidian, its core principles remain timeless.
Would you like a visual map or Obsidian-ready template for Luhmann-style Zettelkasten?
- Benefits of Zettelkasten for Writing:
- Streamlines Research: Centralized notes help avoid redundant research across multiple projects.
- Facilitates Long-Form Writing: Accumulated notes serve as building blocks for larger projects.
- Personal Writing Assistant: The evolving network of notes provides quick access to ideas for future writing.
-
Obsidian Setup and Configuration
-
Installing Obsidian: Guide the user through the installation process, emphasizing the free version and its core features.
-
Creating and Organizing a Vault: A vault in Obsidian is the central hub for all your notes. This section provides instructions for setting up a vault and explains the importance of cloud storage for backup and accessibility.
-
Folder Structure: Establish a recommended folder structure:
- Rough Notes: Optional folder for quick thoughts.
- Source Material: Store notes from books, articles, etc.
- Tags: Empty notes used as tags for easy categorization.
- Indexes: Organized collections of notes based on specific topics or themes.
- Templates: Predefined templates for consistent note-taking.
-
Main Notes: The core content of your knowledge base.
-
Settings Configuration:
- Configure default note locations.
- Customize appearance for readability.
- Set up hotkeys for efficient note-taking (e.g., Ctrl+T for template insertion).
- Enable and configure the "Templates" core plugin for consistent note creation.
-
The Note-Taking Process
-
Creating Notes: Guide the user on how to create new notes (Ctrl+O) and insert templates (Ctrl+T). Emphasize the importance of focusing on one idea per note to maintain atomicity.
-
Source Material Notes:
- Record page numbers, quotes, and elaborate on the ideas in your own words.
-
Include metadata such as authorship, publication year, and source references.
-
Main Notes:
- Synthesize ideas from source material.
- Focus on the key takeaways and connections between different ideas.
-
Use internal links ([[Note Name]]) to connect related notes and foster deeper understanding.
-
Tagging Notes:
- Use tags sparingly but effectively.
- Avoid over-complicating tags, focusing on personal interests or key themes.
- Tags act as an index to quickly locate notes.
-
Linking and Organizing Ideas
-
Internal Links and Connections: Demonstrate how internal links help create a web of interconnected ideas. Discuss how linking related concepts and topics can lead to a more holistic understanding.
-
Indexing for Navigation: Show how creating indexes for topics allows for quick access to collections of related notes. Introduce the idea of building thematic indexes for large research projects.
-
Synthesizing Notes for Larger Projects: Explain how to take notes from the Source Material and Main Notes to gradually build drafts for books, essays, or research papers.
-
Best Practices for Obsidian and Zettelkasten
-
Consistency and Simplicity: Emphasize the importance of simplicity in both note-taking and vault organization. Discourage the need for a "perfect" setup, focusing on efficiency and growth over time.
-
Keeping Notes Concise: Encourage users to keep each note under 500 words, focusing on one idea per note. This enhances clarity and makes it easier to synthesize ideas later.
-
Making Notes Readable: Provide tips on formatting for readability: use headings, bullet points, and quotes to break up large blocks of text.
-
Practical Applications of Zettelkasten in Writing
-
Research Projects: Show how to leverage your Zettelkasten system to conduct more efficient and thorough research for academic papers, articles, or blog posts.
-
Book and Essay Writing: Provide examples of how notes in Obsidian can evolve into larger writing projects, from initial drafts to final revisions.
-
Personal Projects and Brainstorming: Illustrate how the Zettelkasten method can be used for creative writing, personal reflections, or brainstorming for new ventures.
-
Case In Point
-
Summary of Findings: Recap the effectiveness of combining the Zettelkasten method with Obsidian for knowledge management, writing, and research.
-
Future Directions: Suggest areas for future exploration, such as integrating other digital tools (e.g., Zotero, Roam Research) into the workflow or expanding the Zettelkasten method into larger organizational systems.
-
References
-
Cite all relevant sources, including academic papers, books, and articles about the Zettelkasten method, Obsidian, and knowledge management.
📘 1. Source Note Template (
Source Note)This template is used when reading books, articles, podcasts, or videos. The goal is to capture contextual metadata and your impressions, not to mindlessly copy.
```markdown
📘 Source: {{title}}
Type: Book / Article / Video / Podcast
Author: {{author}}
Published: {{date}}
Source Link: Link
Tags: #source #{{topic}}
Related Notes: [[ ]]
🧠 Summary
A brief summary of the source in your own words.
🧩 Key Ideas
- Idea 1
- Idea 2
- Idea 3
🔎 Quotes & Passages
“...”
— Page X🗺️ Linked Notes
- [[Note about idea X]]
- [[Historical context of Y]]
📝 Your Thoughts
- Agreement? Disagreement?
- How does this relate to your current research?
- Ideas it sparked? ```
🧠 2. Main/Idea Note Template (
Zettelor Permanent Note)Each idea should be atomic, clearly written in your own words, and linked to related ideas. This is the core of your Zettelkasten.
```markdown
💡 {{Descriptive Title}}
ID: {{YYYYMMDDHHMM}}
Tags: #zettel #{{topic}}
Linked From: [[ ]]
🧠 Core Idea
Write a single, concise idea in your own words. This should be a self-contained statement or argument.
💬 Explanation / Elaboration
Explain why this idea matters or how it connects to broader themes. Use metaphors, contrast, or short examples.
🔗 Related Notes
- [[Related idea A]]
- [[Contrasting concept B]]
- [[Supports claim C]] ```
Tip: Use the ID convention (e.g.
202504201013) to uniquely identify each note.
🧪 3. Research Summary Note (
Literature Noteor Topic Overview)Use this when you're studying a broader concept or topic and summarizing multiple inputs (e.g., a research question or paper theme).
```markdown
🧪 Research Summary: {{Topic}}
Tags: #summary #research #{{subject}}
Created: {{date}}
Status: Draft / Ongoing / Complete
📌 Topic Overview
Brief definition or framing of the research question.
📚 Key Sources
- [[Author, Title]] — key takeaway.
- [[Article Title]] — significant argument.
🧩 Key Themes
- Theme 1: summary + relevant note links.
- Theme 2: contrasting perspective.
🧠 Emerging Ideas
- New insights or patterns you're noticing.
- Questions that remain unanswered.
🔗 Related Notes
- [[Main idea note]]
- [[Potential application note]]
- [[Philosophical implication]] ```
🔄 How They Interact
- Source Notes → inspire → Main Notes
- Main Notes → get linked into → Research Summaries
- Research Summaries → help generate → new Main Notes
“You don’t collect knowledge, you build it — one link at a time.”
-
 @ 86dfbe73:628cef55
2025-04-21 10:08:34
@ 86dfbe73:628cef55
2025-04-21 10:08:34Mit dem Internet kam das Ende der Massengesellschaft. Heutzutage sind Öffentlichkeit im Allgemeinen und die digitale Öffentlichkeit im Besonderen nur als Netzwerk verstehbar. Nicht als Netzwerk zur Kommunikation, sondern als Netzwerk der Beziehungen, bestehend aus den Erwartungen, Kenntnissen und letztlich bestehend aus dem Vertrauen, das Menschen gegenüber anderen Menschen und Institutionen aufzubauen pflegen. Wichtig ist nicht mehr, wo jemand eine Information plaziert, wichtig ist, wann und wer und unter Einbeziehung welcher Faktoren diese abfragt.
In Sozialen Netzwerken entscheidet jeder selbst, wem er folgt. Er entscheidet selbst, wie die eigene Startseite, der eigene Blick auf den Dienst, aussieht. Als Beispiel sei hier Twitter erwähnt. Aus der Liste der Gefolgten wird die Timeline generiert, die eine Wirklichkeit abbildet, die einzig und alleine von den Following-Entscheidungen des Nutzers bestimmt ist.
Die Beziehungsweise des Folgens ist eine direkte Willenserklärung, die Inhalte eines Users sehen zu wollen. Sie ist ein Pakt, der auch eine gewisse, wenn auch kleine, Verantwortungsübernahme bedeutet. Und diese Beziehungsweise wurde zum integralen Strukturbaustein der digitalen Öffentlichkeit zwischen 2010 bis 2020 und damit auch zur tragenden Säule vieler Karrieren, Geschäftsmodellen und außerdem zur Grundlage der Selektionsverfahren von kulturellen Trends. Im Follower steckte die Macht.
Die digitale Öffentlichkeit hat aufgehört eine vernetzte Öffentlichkeit zu sein und geht zunehmend in den „For you“-Algorithmen der kommerziellen Plattformen auf. Ab 2020 wurde dem Follower von Diensten wie Tiktok der Gar ausgemacht und von dort setzte sich der „For You-Algoritmus“ auf allen kommerziellen Plattformen durch. Das bedeutet, dass die neue digitale Öffentlichkeit nicht mehr durch menschliche Beziehungen und vernetztes Vertrauen getragen wird, sondern vollends den Steuerungsinstrumenten einer Hand voll Konzernen ausgeliefert ist. Auf einmal bedeutete ein Following nicht mehr die Garantie, dass der Content die Abonnenten erreicht.
Mit der Zerstörung dieser Beziehung entgleiten den Creators ihre medialen Regime und beide, User und Creator werden immer abhängiger vom Algorithmus und arbeiten folglich nur noch für die Interessen der Plattformen, statt für sich selbst.
-
 @ 4cebd4f5:0ac3ed15
2025-04-18 16:02:42
@ 4cebd4f5:0ac3ed15
2025-04-18 16:02:42Tóm tắt Hackathon BUIDL BATTLE
BUIDL BATTLE | The Bitcoin Builders Tournament kết thúc với 81 dự án được phê duyệt từ 219 developer đăng ký. Sự kiện trực tuyến kéo dài 3 tuần này nhằm thúc đẩy đổi mới trên Bitcoin, mang đến cơ hội tiếp cận cộng đồng builders, nhà đầu tư và accelerator. Trọng tâm xoay quanh các chủ đề Bitcoin DeFi và Real World Utility, với tổng giải thưởng hơn 90.000 USD bao gồm tiền mặt, credit AWS và grants ICP. Những đột phá công nghệ nổi bật ứng dụng Stacks technology và sBTC.
Hackathon chia làm 2 vòng. Các dự án vào chung kết trình bày trước hội đồng giám khảo gồm VC và lãnh đạo ngành để chọn ra quán quân. Người tham gia nhận mentorship và workshop giá trị, đồng thời tăng khả năng gọi vốn ở vòng 2. Sự kiện được hỗ trợ bởi Stacks Foundation, AWS và đối tác, góp phần củng cố hệ sinh thái phát triển Bitcoin.
Các dự án đoạt giải
Bitcoin DeFi 2.0 Prize Winners
Hạng mục tập trung cải thiện scalability, security và user experience cho Bitcoin DeFi.
- BigMarket: Nền tảng prediction market phi tập trung tích hợp AI trên Layer 2 Stacks, vận hành bởi DAO để đưa dự đoán minh bạch.
- BitForward: Platform tạo hợp đồng kỳ hạn (forward contract) dựa trên NFT, xây dựng trên blockchain Stacks của Bitcoin.The 3.0 Digital Economy Prize Winners
Khám phá sự hội tụ của tài chính, giải trí và mạng xã hội trong hệ sinh thái MemeFi, SocialFi, GameFi.
- Kulture.Fun: Nền tảng SocialFi chat phi tập trung với tính năng token-gated và tích hợp Bitcoin.
- Skullcoin: Gamify hóa Bitcoin DeFi thông qua sBTC, kích hoạt thanh khoản BTC trong trò chơi.Real World Ordinals & NFT Usage Prize Winners
Ứng dụng NFT và Ordinals vượt khỏi phạm vi nghệ thuật truyền thống.
- Offers & Counter-offers | BNS One: Marketplace giao dịch tên BNS qua smart contract, loại bỏ trung gian.
- Truth-Chain: Xác minh nguồn gốc và tính xác thực của nội dung số trên nền tảng Stacks.Tooling & Infrastructure Prize Winners
Phát triển công cụ hỗ trợ xây dựng ứng dụng Web3.
- BLAZE PROTOCOL: Layer 2 cải thiện trải nghiệm Web3 với xác nhận giao dịch tức thì.
- PoXAgents: Sử dụng AI agents đơn giản hóa tương tác với Stacks Blockchain cho người dùng phổ thông.ICP Challenge Prize Winners
Tích hợp Internet Computer để giải quyết thách thức blockchain trong hệ sinh thái Bitcoin.
- ckBoost: Tăng tốc giao dịch Bitcoin trên Internet Computer thông qua liquidity pool.
- CounterpartyICP: Module quản lý smart contract và tài sản số trên Bitcoin qua Counterparty API.AWS - Buidl with Bedrock Challenge Prize Winner
Dự án ứng dụng công nghệ AWS.
- Stacks AI: Công cụ AI tạo, debug và học smart contract ngôn ngữ Clarity, sử dụng AWS Bedrock.Xem chi tiết dự án tại Dorahacks.
Về Nhà tổ chức
Stacks Foundation
Stacks Foundation tập trung phát triển Stacks blockchain – Bitcoin Layer 2 hàng đầu, hỗ trợ các dự án tận dụng bảo mật của Bitcoin để xây dựng Internet phi tập trung. Thông qua chương trình Stacks Accelerator, tổ chức đã thúc đẩy đổi mới và thu hút developer cho hệ sinh thái blockchain. Sứ mệnh hiện tại là cung cấp công cụ để phát triển ứng dụng user-owned, củng cố tầm nhìn về web phi tập trung.
-
 @ 4cebd4f5:0ac3ed15
2025-04-18 15:28:02
@ 4cebd4f5:0ac3ed15
2025-04-18 15:28:02Tóm tắt Hackathon
Build & Brew - Espresso Global Hackathon thu hút 485 developer với 151 dự án vượt qua vòng sơ loại. Sự kiện do Espresso Network tổ chức, phân phối 100.000 USD giải thưởng qua hai hạng mục: "Caffeinate & Code" và "Cracking Composability", tập trung nâng cao composability của Ethereum và phát triển ứng dụng cross-chain sử dụng Espresso confirmations.
Thành tựu nổi bật bao gồm triển khai thành công rollups tích hợp với Espresso Network, hỗ trợ xây dựng ứng dụng interoperable. Các dự án ứng dụng Open Intents Framework để thiết kế kiến trúc ứng dụng tiên tiến, tận dụng xác nhận nhanh và bảo mật cho chức năng đa chuỗi.
Hackathon chứng minh tiềm năng của Espresso Network trong hệ sinh thái blockchain thông qua ứng dụng consensus layer vào kịch bản thực tế. Sự kiện đóng góp vào sứ mệnh tạo tương tác liền mạch giữa các blockchain và khẳng định vai trò quan trọng của developer trong phát triển composability. Các bài thuyết trình cuối cùng (7/4) cho thấy tiến triển ấn tượng trong mở rộng khả năng cross-chain của Ethereum.
Các dự án đoạt giải
Build & Brew Prize Winners
Build & Brew ghi nhận sự tham gia của 486 hacker và 156 dự án, trong đó 91 Arbitrum Orbit chains tích hợp Espresso được triển khai thành công, mở đường cho ứng dụng cross-chain sáng tạo. Tổng giải thưởng 65.000 USD được trao cho Testnet và Mainnet deployments.
Top dự án:
1. Giải Nhất - Affogato: Hệ thống Swap + Bridge nâng cao giao dịch cross-chain, sử dụng Ethereum rollups và Espresso confirmations để đảm bảo tốc độ và bảo mật.
2. Giải Nhì - Random Network: Tăng cường composability thông qua xác thực rollup liveness và open intents pool cho tích hợp đa hệ thống.
3. Giải Ba - Disburse Network: Giao thức thanh toán module hỗ trợ mass payments cross-chain một-click qua kiến trúc Nitro rollup.
4. Giải Tư - Coffee Chain: Ứng dụng thanh toán cross-chain cho phép merchant nhận crypto bằng mọi token/blockchain.
5. Giải Năm - GTXpresso: Dự án Central Limit Order Book (CLOB) cross-chain (đang phát triển).Xem toàn bộ dự án tại Build and Brew Hackathon trên DoraHacks.
Về Nhà tổ chức
Espresso
Espresso là giao thức xây dựng khối được đồng bộ hóa (coordinated block building), cho phép các blockchain hoạt động như một hệ thống thống nhất. Tổ chức nổi tiếng với giải pháp blockchain hiệu quả, khả năng mở rộng, tập trung vào bảo mật và khả năng tiếp cận. Thành tựu đáng chú ý bao gồm triển khai consensus mechanisms cải thiện tốc độ giao dịch và giảm chi phí điện toán. Hiện tại, Espresso tập trung tối ưu hóa cơ sở hạ tầng blockchain để thúc đẩy ứng dụng và hỗ trợ chuyển đổi số toàn ngành.
-
 @ a95c6243:d345522c
2025-01-24 20:59:01
@ a95c6243:d345522c
2025-01-24 20:59:01Menschen tun alles, egal wie absurd, \ um ihrer eigenen Seele nicht zu begegnen. \ Carl Gustav Jung
«Extremer Reichtum ist eine Gefahr für die Demokratie», sagen über die Hälfte der knapp 3000 befragten Millionäre aus G20-Staaten laut einer Umfrage der «Patriotic Millionaires». Ferner stellte dieser Zusammenschluss wohlhabender US-Amerikaner fest, dass 63 Prozent jener Millionäre den Einfluss von Superreichen auf US-Präsident Trump als Bedrohung für die globale Stabilität ansehen.
Diese Besorgnis haben 370 Millionäre und Milliardäre am Dienstag auch den in Davos beim WEF konzentrierten Privilegierten aus aller Welt übermittelt. In einem offenen Brief forderten sie die «gewählten Führer» auf, die Superreichen – also sie selbst – zu besteuern, um «die zersetzenden Auswirkungen des extremen Reichtums auf unsere Demokratien und die Gesellschaft zu bekämpfen». Zum Beispiel kontrolliere eine handvoll extrem reicher Menschen die Medien, beeinflusse die Rechtssysteme in unzulässiger Weise und verwandele Recht in Unrecht.
Schon 2019 beanstandete der bekannte Historiker und Schriftsteller Ruthger Bregman an einer WEF-Podiumsdiskussion die Steuervermeidung der Superreichen. Die elitäre Veranstaltung bezeichnete er als «Feuerwehr-Konferenz, bei der man nicht über Löschwasser sprechen darf.» Daraufhin erhielt Bregman keine Einladungen nach Davos mehr. Auf seine Aussagen machte der Schweizer Aktivist Alec Gagneux aufmerksam, der sich seit Jahrzehnten kritisch mit dem WEF befasst. Ihm wurde kürzlich der Zutritt zu einem dreiteiligen Kurs über das WEF an der Volkshochschule Region Brugg verwehrt.
Nun ist die Erkenntnis, dass mit Geld politischer Einfluss einhergeht, alles andere als neu. Und extremer Reichtum macht die Sache nicht wirklich besser. Trotzdem hat man über Initiativen wie Patriotic Millionaires oder Taxmenow bisher eher selten etwas gehört, obwohl es sie schon lange gibt. Auch scheint es kein Problem, wenn ein Herr Gates fast im Alleingang versucht, globale Gesundheits-, Klima-, Ernährungs- oder Bevölkerungspolitik zu betreiben – im Gegenteil. Im Jahr, als der Milliardär Donald Trump zum zweiten Mal ins Weiße Haus einzieht, ist das Echo in den Gesinnungsmedien dagegen enorm – und uniform, wer hätte das gedacht.
Der neue US-Präsident hat jedoch «Davos geerdet», wie Achgut es nannte. In seiner kurzen Rede beim Weltwirtschaftsforum verteidigte er seine Politik und stellte klar, er habe schlicht eine «Revolution des gesunden Menschenverstands» begonnen. Mit deutlichen Worten sprach er unter anderem von ersten Maßnahmen gegen den «Green New Scam», und von einem «Erlass, der jegliche staatliche Zensur beendet»:
«Unsere Regierung wird die Äußerungen unserer eigenen Bürger nicht mehr als Fehlinformation oder Desinformation bezeichnen, was die Lieblingswörter von Zensoren und derer sind, die den freien Austausch von Ideen und, offen gesagt, den Fortschritt verhindern wollen.»
Wie der «Trumpismus» letztlich einzuordnen ist, muss jeder für sich selbst entscheiden. Skepsis ist definitiv angebracht, denn «einer von uns» sind weder der Präsident noch seine auserwählten Teammitglieder. Ob sie irgendeinen Sumpf trockenlegen oder Staatsverbrechen aufdecken werden oder was aus WHO- und Klimaverträgen wird, bleibt abzuwarten.
Das WHO-Dekret fordert jedenfalls die Übertragung der Gelder auf «glaubwürdige Partner», die die Aktivitäten übernehmen könnten. Zufällig scheint mit «Impfguru» Bill Gates ein weiterer Harris-Unterstützer kürzlich das Lager gewechselt zu haben: Nach einem gemeinsamen Abendessen zeigte er sich «beeindruckt» von Trumps Interesse an der globalen Gesundheit.
Mit dem Projekt «Stargate» sind weitere dunkle Wolken am Erwartungshorizont der Fangemeinde aufgezogen. Trump hat dieses Joint Venture zwischen den Konzernen OpenAI, Oracle, und SoftBank als das «größte KI-Infrastrukturprojekt der Geschichte» angekündigt. Der Stein des Anstoßes: Oracle-CEO Larry Ellison, der auch Fan von KI-gestützter Echtzeit-Überwachung ist, sieht einen weiteren potenziellen Einsatz der künstlichen Intelligenz. Sie könne dazu dienen, Krebserkrankungen zu erkennen und individuelle mRNA-«Impfstoffe» zur Behandlung innerhalb von 48 Stunden zu entwickeln.
Warum bitte sollten sich diese superreichen «Eliten» ins eigene Fleisch schneiden und direkt entgegen ihren eigenen Interessen handeln? Weil sie Menschenfreunde, sogenannte Philanthropen sind? Oder vielleicht, weil sie ein schlechtes Gewissen haben und ihre Schuld kompensieren müssen? Deswegen jedenfalls brauchen «Linke» laut Robert Willacker, einem deutschen Politikberater mit brasilianischen Wurzeln, rechte Parteien – ein ebenso überraschender wie humorvoller Erklärungsansatz.
Wenn eine Krähe der anderen kein Auge aushackt, dann tut sie das sich selbst noch weniger an. Dass Millionäre ernsthaft ihre eigene Besteuerung fordern oder Machteliten ihren eigenen Einfluss zugunsten anderer einschränken würden, halte ich für sehr unwahrscheinlich. So etwas glaube ich erst, wenn zum Beispiel die Rüstungsindustrie sich um Friedensverhandlungen bemüht, die Pharmalobby sich gegen institutionalisierte Korruption einsetzt, Zentralbanken ihre CBDC-Pläne für Bitcoin opfern oder der ÖRR die Abschaffung der Rundfunkgebühren fordert.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ c631e267:c2b78d3e
2025-01-18 09:34:51
@ c631e267:c2b78d3e
2025-01-18 09:34:51Die grauenvollste Aussicht ist die der Technokratie – \ einer kontrollierenden Herrschaft, \ die durch verstümmelte und verstümmelnde Geister ausgeübt wird. \ Ernst Jünger
«Davos ist nicht mehr sexy», das Weltwirtschaftsforum (WEF) mache Davos kaputt, diese Aussagen eines Einheimischen las ich kürzlich in der Handelszeitung. Während sich einige vor Ort enorm an der «teuersten Gewerbeausstellung der Welt» bereicherten, würden die negativen Begleiterscheinungen wie Wohnungsnot und Niedergang der lokalen Wirtschaft immer deutlicher.
Nächsten Montag beginnt in dem Schweizer Bergdorf erneut ein Jahrestreffen dieses elitären Clubs der Konzerne, bei dem man mit hochrangigen Politikern aus aller Welt und ausgewählten Vertretern der Systemmedien zusammenhocken wird. Wie bereits in den vergangenen vier Jahren wird die Präsidentin der EU-Kommission, Ursula von der Leyen, in Begleitung von Klaus Schwab ihre Grundsatzansprache halten.
Der deutsche WEF-Gründer hatte bei dieser Gelegenheit immer höchst lobende Worte für seine Landsmännin: 2021 erklärte er sich «stolz, dass Europa wieder unter Ihrer Führung steht» und 2022 fand er es bemerkenswert, was sie erreicht habe angesichts des «erstaunlichen Wandels», den die Welt in den vorangegangenen zwei Jahren erlebt habe; es gebe nun einen «neuen europäischen Geist».
Von der Leyens Handeln während der sogenannten Corona-«Pandemie» lobte Schwab damals bereits ebenso, wie es diese Woche das Karlspreis-Direktorium tat, als man der Beschuldigten im Fall Pfizergate die diesjährige internationale Auszeichnung «für Verdienste um die europäische Einigung» verlieh. Außerdem habe sie die EU nicht nur gegen den «Aggressor Russland», sondern auch gegen die «innere Bedrohung durch Rassisten und Demagogen» sowie gegen den Klimawandel verteidigt.
Jene Herausforderungen durch «Krisen epochalen Ausmaßes» werden indes aus dem Umfeld des WEF nicht nur herbeigeredet – wie man alljährlich zur Zeit des Davoser Treffens im Global Risks Report nachlesen kann, der zusammen mit dem Versicherungskonzern Zurich erstellt wird. Seit die Globalisten 2020/21 in der Praxis gesehen haben, wie gut eine konzertierte und konsequente Angst-Kampagne funktionieren kann, geht es Schlag auf Schlag. Sie setzen alles daran, Schwabs goldenes Zeitfenster des «Great Reset» zu nutzen.
Ziel dieses «großen Umbruchs» ist die totale Kontrolle der Technokraten über die Menschen unter dem Deckmantel einer globalen Gesundheitsfürsorge. Wie aber könnte man so etwas erreichen? Ein Mittel dazu ist die «kreative Zerstörung». Weitere unabdingbare Werkzeug sind die Einbindung, ja Gleichschaltung der Medien und der Justiz.
Ein «Great Mental Reset» sei die Voraussetzung dafür, dass ein Großteil der Menschen Einschränkungen und Manipulationen wie durch die Corona-Maßnahmen praktisch kritik- und widerstandslos hinnehme, sagt der Mediziner und Molekulargenetiker Michael Nehls. Er meint damit eine regelrechte Umprogrammierung des Gehirns, wodurch nach und nach unsere Individualität und unser soziales Bewusstsein eliminiert und durch unreflektierten Konformismus ersetzt werden.
Der aktuelle Zustand unserer Gesellschaften ist auch für den Schweizer Rechtsanwalt Philipp Kruse alarmierend. Durch den Umgang mit der «Pandemie» sieht er die Grundlagen von Recht und Vernunft erschüttert, die Rechtsstaatlichkeit stehe auf dem Prüfstand. Seiner dringenden Mahnung an alle Bürger, die Prinzipien von Recht und Freiheit zu verteidigen, kann ich mich nur anschließen.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-13 10:09:57
@ a95c6243:d345522c
2025-01-13 10:09:57Ich begann, Social Media aufzubauen, \ um den Menschen eine Stimme zu geben. \ Mark Zuckerberg
Sind euch auch die Tränen gekommen, als ihr Mark Zuckerbergs Wendehals-Deklaration bezüglich der Meinungsfreiheit auf seinen Portalen gehört habt? Rührend, oder? Während er früher die offensichtliche Zensur leugnete und später die Regierung Biden dafür verantwortlich machte, will er nun angeblich «die Zensur auf unseren Plattformen drastisch reduzieren».
«Purer Opportunismus» ob des anstehenden Regierungswechsels wäre als Klassifizierung viel zu kurz gegriffen. Der jetzige Schachzug des Meta-Chefs ist genauso Teil einer kühl kalkulierten Business-Strategie, wie es die 180 Grad umgekehrte Praxis vorher war. Social Media sind ein höchst lukratives Geschäft. Hinzu kommt vielleicht noch ein bisschen verkorkstes Ego, weil derartig viel Einfluss und Geld sicher auch auf die Psyche schlagen. Verständlich.
«Es ist an der Zeit, zu unseren Wurzeln der freien Meinungsäußerung auf Facebook und Instagram zurückzukehren. Ich begann, Social Media aufzubauen, um den Menschen eine Stimme zu geben», sagte Zuckerberg.
Welche Wurzeln? Hat der Mann vergessen, dass er von der Überwachung, dem Ausspionieren und dem Ausverkauf sämtlicher Daten und digitaler Spuren sowie der Manipulation seiner «Kunden» lebt? Das ist knallharter Kommerz, nichts anderes. Um freie Meinungsäußerung geht es bei diesem Geschäft ganz sicher nicht, und das war auch noch nie so. Die Wurzeln von Facebook liegen in einem Projekt des US-Militärs mit dem Namen «LifeLog». Dessen Ziel war es, «ein digitales Protokoll vom Leben eines Menschen zu erstellen».
Der Richtungswechsel kommt allerdings nicht überraschend. Schon Anfang Dezember hatte Meta-Präsident Nick Clegg von «zu hoher Fehlerquote bei der Moderation» von Inhalten gesprochen. Bei der Gelegenheit erwähnte er auch, dass Mark sehr daran interessiert sei, eine aktive Rolle in den Debatten über eine amerikanische Führungsrolle im technologischen Bereich zu spielen.
Während Milliardärskollege und Big Tech-Konkurrent Elon Musk bereits seinen Posten in der kommenden Trump-Regierung in Aussicht hat, möchte Zuckerberg also nicht nur seine Haut retten – Trump hatte ihn einmal einen «Feind des Volkes» genannt und ihm lebenslange Haft angedroht –, sondern am liebsten auch mitspielen. KI-Berater ist wohl die gewünschte Funktion, wie man nach einem Treffen Trump-Zuckerberg hörte. An seine Verhaftung dachte vermutlich auch ein weiterer Multimilliardär mit eigener Social Media-Plattform, Pavel Durov, als er Zuckerberg jetzt kritisierte und gleichzeitig warnte.
Politik und Systemmedien drehen jedenfalls durch – was zu viel ist, ist zu viel. Etwas weniger Zensur und mehr Meinungsfreiheit würden die Freiheit der Bürger schwächen und seien potenziell vernichtend für die Menschenrechte. Zuckerberg setze mit dem neuen Kurs die Demokratie aufs Spiel, das sei eine «Einladung zum nächsten Völkermord», ernsthaft. Die Frage sei, ob sich die EU gegen Musk und Zuckerberg behaupten könne, Brüssel müsse jedenfalls hart durchgreifen.
Auch um die Faktenchecker macht man sich Sorgen. Für die deutsche Nachrichtenagentur dpa und die «Experten» von Correctiv, die (noch) Partner für Fact-Checking-Aktivitäten von Facebook sind, sei das ein «lukratives Geschäftsmodell». Aber möglicherweise werden die Inhalte ohne diese vermeintlichen Korrektoren ja sogar besser. Anders als Meta wollen jedoch Scholz, Faeser und die Tagesschau keine Fehler zugeben und zum Beispiel Correctiv-Falschaussagen einräumen.
Bei derlei dramatischen Befürchtungen wundert es nicht, dass der öffentliche Plausch auf X zwischen Elon Musk und AfD-Chefin Alice Weidel von 150 EU-Beamten überwacht wurde, falls es irgendwelche Rechtsverstöße geben sollte, die man ihnen ankreiden könnte. Auch der Deutsche Bundestag war wachsam. Gefunden haben dürften sie nichts. Das Ganze war eher eine Show, viel Wind wurde gemacht, aber letztlich gab es nichts als heiße Luft.
Das Anbiedern bei Donald Trump ist indes gerade in Mode. Die Weltgesundheitsorganisation (WHO) tut das auch, denn sie fürchtet um Spenden von über einer Milliarde Dollar. Eventuell könnte ja Elon Musk auch hier künftig aushelfen und der Organisation sowie deren größtem privaten Förderer, Bill Gates, etwas unter die Arme greifen. Nachdem Musks KI-Projekt xAI kürzlich von BlackRock & Co. sechs Milliarden eingestrichen hat, geht da vielleicht etwas.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ bcbb3e40:a494e501
2025-03-31 15:44:56
@ bcbb3e40:a494e501
2025-03-31 15:44:56El 7 de febrero de 2025, Donald Trump firmó una orden ejecutiva que establecía una «Oficina de la Fe» en la Casa Blanca, dirigida por su asesora espiritual Paula White-Cain, la pastora de esa «teología de la prosperidad» (prosperity theology) que predica el «Evangelio de la salud y la riqueza» (health and wealth gospel^1). Investida de su nueva función, la reverenda pastora dijo: «Tengo la autoridad para declarar a la Casa Blanca un lugar santo. Es mi presencia la que la santifica»[^2]. Los siete rabinos del «Sanedrín Naciente» —la corte suprema que guiará a Israel cuando se reconstruya el Templo de Jerusalén— enviaron conmovedoras felicitaciones al presidente Trump por el establecimiento de esta Oficina. «Expresamos nuestra sincera gratitud —se lee en el mensaje oficial enviado a Trump desde el Monte Sión— por llevar la fe a la vanguardia de la cultura estadounidense y mundial mediante el establecimiento de la Oficina de la Fe en la Casa Blanca. Su reconocimiento de la importancia de la religión en la vida pública es un paso hacia la restauración de los valores morales y del liderazgo espiritual en el mundo[^3]. La carta del «Sanedrín Naciente», que augura el éxito a la «misión divina» del presidente estadounidense, reproduce las dos caras de una «moneda del Templo», acuñada en 2017 para celebrar el traslado de la embajada estadounidense a Jerusalén y, simultáneamente, el centenario de la Declaración Balfour. En el anverso se ven los perfiles de Donald Trump y Ciro el Grande, a quien la tradición judía atribuye la reconstrucción del templo destruido por los babilonios, con la inscripción (en hebreo e inglés) «Cyrus —Balfour— Trump Declaration 1917-2017»; en el reverso está la imagen del Templo de Jerusalén[^4]. Otra moneda, que lleva los perfiles de Trump y Ciro en el anverso y los de Trump y Netanyahu en el reverso, fue acuñada en 2018 para celebrar el septuagésimo aniversario de la independencia del «Estado de Israel»; se observa dos inscripciones en hebreo e inglés: «Y Él me encargó construirle una casa en Jerusalén» y «Guerra de los Hijos de la Luz contra los Hijos de las Tinieblas».
El tema de la «guerra de los Hijos de la Luz contra los Hijos de las Tinieblas» ha tenido una difusión particular en el imaginario y la propaganda trumpista. El 7 de junio de 2020, monseñor Carlo Maria Viganò, ex nuncio de la Santa Sede en los Estados Unidos, escribió una carta al presidente Donald Trump que comenzaba así: «Estamos asistiendo en los últimos meses a la formación de dos bandos, que los definiría bíblicos: los hijos de la luz y los hijos de las tinieblas»[^5]. El 1 de enero de 2021, el agitprop estadounidense Steve Bannon declaró en una entrevista con Monseñor Viganò: «Esta es una batalla de época entre los hijos de la Luz y los hijos de las Tinieblas»[^6].
Son numerosos los judíos sionistas que están en el círculo del presidente Trump: además de su hija Ivanka (convertida en 2009) y su yerno Jared Kushner (entonces Consejero Anciano del Presidente), el 19 de noviembre de 2024 el «The Jerusalem Post»[^7] publicó una lista de los más influyentes: Stephen Miller, subdirector del staff de la Casa Blanca y consejero de Seguridad Nacional de Estados Unidos; David Melech Friedman, a quien en 2016 Trump nombró embajador en Israel; el multimillonario «filántropo» Steven Charles Witkoff, enviado especial de Estados Unidos a Oriente Medio; Miriam Adelson, directora del periódico «Israel Hayom», clasificada por Bloomberg Billionaires como la quinta mujer más rica del mundo (con un patrimonio neto de 32,400 millones de dólares), financiadora de iniciativas políticas conservadoras en Estados Unidos e Israel; el banquero Boris Epshteyn, consejero estratégico de la campaña presidencial de Trump en 2020; Howard Williams Lutnick, presidente de la Cantor Fitzgerald del Grupo BGC, financista de las campañas presidenciales de Donald Trump en 2020 y 2024, ahora secretario de Comercio; la modelo Elizabeth Pipko, portavoz nacional del Partido Republicano y creadora de un «museo interactivo virtual» sobre la «Shoah» como parte del proyecto de Lest People Forget, cuyo objetivo es combatir el «antisemitismo» y la «negacionismo»; Lee Michael Zeldin, miembro republicano de la Cámara de Representantes por el estado de Nueva York del 2015 al 2023 y actualmente administrador de la EPA (Environmental Protection Agency); la columnista Laura Elizabeth Loomer, «orgullosamente islamófoba», activa patrocinadora de Trump en la campaña para las elecciones presidenciales de 2024; Sidney Ferris Rosenberg, influyente presentador de radio y periodista deportivo; William Owen Scharf, Asistente del Presidente y secretario del personal de la Casa Blanca; Marc Jeffrey Rowan, «filántropo» con un patrimonio neto valorado por Forbes en ocho mil ochocientos millones de dólares.
Además de estos, cabe mencionar al popular presentador de radio Mark Levin quien, en diciembre de 2019, durante la celebración de la fiesta de Janucá en la Casa Blanca, saludó a Donald Trump como «el primer presidente judío de los Estados Unidos»[^8]. Según un funcionario de alto nivel de la Casa Blanca, Donald Trump se convirtió al judaísmo dos años antes en la sinagoga de la secta Jabad Lubavitch en la ciudad de Nueva York. David Elias Goldberg, miembro del Jewish Center of Antisemitic Study, también entrevistó al funcionario, para quien «Trump fue “instado” por su hija Ivanka y su yerno Jared Kushner para abrazar la fe. Inicialmente, Trump se habría mostrado reacio, considerando que esto podría enfriar el apoyo del electorado evangélico». Luego, informa «Israel Today News», «cambió de opinión y se convirtió oficialmente a principios de 2017. La ceremonia se llevó a cabo en privado y se guardó celosamente durante casi dos años»[^9]. Pero ya en septiembre de 2015, el rabino millonario Kirt Schneider, invitado a la Trump Tower de Nueva York, había impuesto sus manos sobre la cabeza de Donald Trump y lo había bendecido en hebreo e inglés, declarando: «Las únicas dos naciones que tienen una relación privilegiada con Dios son Israel y los Estados Unidos de América»[^10].
El 7 de octubre de 2024, en el aniversario de la operación de Hamas «Diluvio de Al-Aqsa», Trump fue acompañado por un «superviviente de la Shoah» a la tumba de Menachem Mendel Schneerson, séptimo y último Rabino de los Hasidim de la secta Jabad Lubavitch, que en 1991 declaró a sus seguidores: «He hecho todo lo posible para provocar el arribo del Mesías, ahora les paso a ustedes esta misión; hagan todo lo que puedan para que Él venga»^11. En relación al evento mesiánico, el eminente rabino Yekutiel Fish atribuyó una misión decisiva a Trump: «Todo el mundo está centrado en Gaza, pero esa es solo una parte de la agenda del fin de los tiempos, que tiene a los judíos viviendo en las fronteras profetizadas de Israel; la Torá incluye explícitamente a Gaza. Lo que Trump está haciendo es limpiar Gaza de todos los odiadores de Israel. No podrán estar en Israel después de la venida del Mesías. (...) Esto incluirá a Gaza, la mitad del Líbano y gran parte de Jordania. Y vemos que casi lo hemos logrado. Siria cayó. Líbano está medio destruido. Gaza está destrozada. El escenario está casi listo para el Mesías. Pero, ¿cómo pueden los palestinos estar aquí cuando vayamos a recibir al Mesías? El Mesías necesita que alguien se ocupe de esto, y en este caso, es Donald Trump. Trump está simplemente llevando a cabo las tareas finales necesarias antes de que el Mesías sea revelado»[^12].
Esta inspiración escatológica está presente en las palabras de Pete Brian Hegseth, el pintoresco exponente del «Reconstruccionismo Cristiano»[^13] a quien Trump nombró secretario de Defensa. En un discurso pronunciado en 2019 en el Hotel Rey David de Jerusalén, con motivo de la conferencia anual del canal Arutz Sheva (Israel National News), Hegseth enalteció el «vínculo eterno» entre Israel y Estados Unidos, y enumeró los «milagros» que atestiguan el «apoyo divino» a la causa sionista, el último de los cuales será la reconstrucción del Templo judío en la zona donde actualmente se encuentra la mezquita de al-Aqsa: «La dignidad de capital adquirida por Jerusalén —dijo— fue un milagro, y no hay razón por la cual no sea posible el milagro de la restauración del Templo en el Monte del Templo».[^14]
Es conocido que el fundamentalismo evangélico pro-sionista[^15] comparte con el judaísmo la creencia en que la construcción del tercer Templo de Jerusalén marcará el comienzo de la era mesiánica; cuando la administración Trump trasladó la embajada de Estados Unidos a Jerusalén en 2017, Laurie Cardoza-Moore, exponente del evangelismo sionista, saludó así la «obediencia de Trump a la Palabra de Dios» en «Haaretz»: «Al establecer la Embajada en Jerusalén, el presidente Donald Trump está implementando una de las iniciativas históricas de dimensión bíblica en su presidencia. Al igual que muchos judíos en Israel y en todo el mundo, los cristianos reconocen el vínculo de los judíos con la Biblia a través del nombre de Jerusalén como la capital del antiguo Israel, así como el sitio del Primer y Segundo Templos. Según los profetas Ezequiel, Isaías y el apóstol Juan del Nuevo Testamento, todos los israelíes esperan la reconstrucción del Tercer Templo»[^16]. El 22 de mayo del mismo año, Donald Trump, acompañado de su esposa Melania, de su hija Ivanka y su yerno Jared Kushner, fue el primer presidente de los Estados Unidos en ejercicio en acudir al Muro de las Lamentaciones, anexionado ilegalmente a la entidad sionista.
En 2019, la administración Trump confirmó la posición de Estados Unidos al enviar en visita oficial para Jerusalén a Mike Pompeo, un secretario de Estado que —ironía de la Historia— lleva el mismo nombre del general romano que asaltó la ciudad en el año 63 a.C. «Por primera vez en la historia, un secretario de Estado norteamericano visitó la Ciudad Vieja de Jerusalén en compañía de un alto político israelí. Fue una visita histórica que reforzó las expectativas israelíes y constituyó un reconocimiento tácito de la soberanía israelí sobre el sitio del Monte del Templo y la Explanada de las Mezquitas. (…) Mike Pompeo, acompañado por el primer ministro Benjamin Netanyahu y el embajador de Estados Unidos en Israel, David Friedman, también visitó el túnel del Muro de las Lamentaciones y la sinagoga ubicada bajo tierra, en el presunto lugar del santuario del Templo[^17], donde se le mostró una maqueta del futuro Templo[^18]. En el transcurso de una entrevista concedida durante la fiesta del Purim (que celebra el exterminio de la clase política persa, ocurrido hace 2500 años), el secretario de Estado insinuó que «el presidente Donald Trump puede haber sido enviado por Dios para salvar al pueblo judío y que confiaba en que aquí el Señor estaba obrando»[^19].
Como observa Daniele Perra, en este mismo número de «Eurasia», el «mito movilizador» del Tercer Templo, atribuible a los «mitos teológicos» señalados por Roger Garaudy como mitos fundadores de la entidad sionista, «atribuye al judaísmo una especie de función sociológica de transmisión y proyección del conflicto palestino-israelí hacia el resto del mundo y confiere una inspiración apocalíptica al momento geopolítico actual».
|Info|| |:-|:-| |Autor| Claudio Mutti | |Fuente| I "Figli della Luce" alla Casa Bianca | |Fecha| 8/Mar/2025 | |Traducción| Francisco de la Torre |
[^2]: The White House, President Trump announces appointments to the White House Faith Office https://www.whitehouse.gov,, 7 de febrero de 2025; Trump establece la Oficina de la Fe con una foto de «La Última Cena» | Fue dirigida por la controvertida predicadora Paula White, https://www.tgcom24.mediaset.it, 10 de febrero de 2025.
[^3]: «We extend our heartfelt gratitude for bringing faith to the forefront of American and global culture through the establishment of the Faith Office in the White House. Your recognition of the importance of religion in public life is a step toward restoring moral values and spiritual leadership in the world» (Letter from the Nascent Sanhedrin to President Donald J. Trump, Jerusalem, Wednesday, February 12, 2025).
[^4]: Israeli group mints Trump coin to honor Jerusalem recognition, «The Times of Israel», https://www.timesofisrael.com, 28-2-2018.
[^5]: Mons. Viganò — Siamo nella battaglia tra figli della luce e figli delle tenebre, https://www.italiador.com, 7-6-2020
[^6]: TRANSCRIPT: Steve Bannon’s ‘War Room’ interview with Abp. Viganò, lifesitenews.com, 4-1-2021. Sulle origini e sulla fortuna di questo tema cfr. C. Mutti, Le sètte dell’Occidente, «Eurasia», 2/2021, pp. 12-15. (https://www.eurasia-rivista.com/las-sectas-de-occidente/)
[^7]: Luke Tress, The who’s who of Jews in Trump’s inner circle?, «The Jerusalem Post», https://www.jpost.com, 19-11-2024.
[^8]: Radio Talk Show Host Mark Levin Calls President Trump «the First Jewish President of the United States», https://www.c-span.org, 11-12-2019.
[^9]: «However, he had a change of heart and officially converted in early 2017. The ceremony was held in private, and closely guarded for nearly two years» (Donald Trump converted to Judaism two years ago, according to White House official, https://israeltodaynews.blogspot.com/2019/02).
[^10]: «El rabino Kirt Schneider (...) es un millonario judío, una figura televisiva de los “judíos mesiánicos”. Sus emisiones televisivas semanales son emitidas por más de treinta canales cristianos en unos doscientos países; entre ellos, los canales “Yes” y “Hot” en Israel. Solo en Estados Unidos, sus emisiones atraen a 1.600.000 telespectadores cada semana. Kirt Schneider dirige un imperio de telecomunicaciones que tiene un millón y medio de seguidores en Facebook, X (antes Twitter) y YouTube» (Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, Edizioni all'insegna del Veltro, Parma 2025, p. 31).
[^12]: «Everyone is focused on Gaza, but that is only one part of the end-of-days agenda, which has the Jews living in Israel’s prophesied borders. The Torah explicitly includes Gaza. What Trump is doing is cleaning out Gaza of all the haters of Israel. They cannot be in Israel after the Messiah comes. (…) This will include Gaza, half of Lebanon, and much of Jordan. And we see that we are almost there. Syria fell. Lebanon is half gone. Gaza is ripped up. The stage is nearly set for Messiah. But how can the Palestinians be here when we go to greet the Messiah? The Messiah needs someone to take care of this, and in this case, it is Donald Trump. Trump is merely carrying out the final tasks needed before Messiah is revealed» (Adam Eliyahu Berkowitz, Trump’s Gaza Plan is «The Final task before Messiah», https://israel365news.com, 5-2-2025).
[^13]: «A day after Hegseth was announced for the Cabinet position, Brooks Potteiger, a pastor within the Communion of Reformed Evangelical Churches (CREC), posted on X that Hegseth is a member of the church in good standing. The CREC, a denomination of Christian Reconstructionism, is considered by some academics to be an extremist, Christian supremacist movement» (Shannon Bond e altri, What’s behind defense secretary pick Hegseth’s war on ‘woke’, https://www.npr.org, 14-11-2024.
[^14]: «The decoration of Jerusalem as a capital was a miracle, and there is no reason why the miracle of the re-establishment of Temple on the Temple Mount is not possible» (Pete Hegseth at Arutz Sheva Conference, youtube.com). Cfr. Daniele Perra, Paleotrumpismo, neotrumpismo e post-trumpismo, in: AA. VV., Trumpismo, Cinabro Edizioni, Roma 2025, pp. 22-23.
[^15]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., págs. 82 a 96.
[^16]: «We American Christians Welcome Trump’s Obedience to God’s Word on Jerusalem», «Haaretz», 6-12-2017.
[^17]: Pierre-Antoine Plaquevent — Youssef Hindi, El milenarismo teopolítico de Israel, cit., pág. 97.
[^18]: Pompeo en visite historique au mur Occidental aux côtés de Netanyahu et Friedman, «The Times of Israel», https://fr.timesofisrael.com, 21-3-2019.
[^19]: Pompeo says Trump may have been sent by God to save Jews from Iran, «The Times of Israel», 22-3-2019.
Artículo original: Claudio Mutti, Los «hijos de la luz» en la Casa Blanca (TOR), 25/Mar/2025
-
 @ a95c6243:d345522c
2025-01-03 20:26:47
@ a95c6243:d345522c
2025-01-03 20:26:47Was du bist hängt von drei Faktoren ab: \ Was du geerbt hast, \ was deine Umgebung aus dir machte \ und was du in freier Wahl \ aus deiner Umgebung und deinem Erbe gemacht hast. \ Aldous Huxley
Das brave Mitmachen und Mitlaufen in einem vorgegebenen, recht engen Rahmen ist gewiss nicht neu, hat aber gerade wieder mal Konjunktur. Dies kann man deutlich beobachten, eigentlich egal, in welchem gesellschaftlichen Bereich man sich umschaut. Individualität ist nur soweit angesagt, wie sie in ein bestimmtes Schema von «Diversität» passt, und Freiheit verkommt zur Worthülse – nicht erst durch ein gewisses Buch einer gewissen ehemaligen Regierungschefin.
Erklärungsansätze für solche Entwicklungen sind bekannt, und praktisch alle haben etwas mit Massenpsychologie zu tun. Der Herdentrieb, also der Trieb der Menschen, sich – zum Beispiel aus Unsicherheit oder Bequemlichkeit – lieber der Masse anzuschließen als selbstständig zu denken und zu handeln, ist einer der Erklärungsversuche. Andere drehen sich um Macht, Propaganda, Druck und Angst, also den gezielten Einsatz psychologischer Herrschaftsinstrumente.
Aber wollen die Menschen überhaupt Freiheit? Durch Gespräche im privaten Umfeld bin ich diesbezüglich in der letzten Zeit etwas skeptisch geworden. Um die Jahreswende philosophiert man ja gerne ein wenig über das Erlebte und über die Erwartungen für die Zukunft. Dabei hatte ich hin und wieder den Eindruck, die totalitären Anwandlungen unserer «Repräsentanten» kämen manchen Leuten gerade recht.
«Desinformation» ist so ein brisantes Thema. Davor müsse man die Menschen doch schützen, hörte ich. Jemand müsse doch zum Beispiel diese ganzen merkwürdigen Inhalte in den Social Media filtern – zur Ukraine, zum Klima, zu Gesundheitsthemen oder zur Migration. Viele wüssten ja gar nicht einzuschätzen, was richtig und was falsch ist, sie bräuchten eine Führung.
Freiheit bedingt Eigenverantwortung, ohne Zweifel. Eventuell ist es einigen tatsächlich zu anspruchsvoll, die Verantwortung für das eigene Tun und Lassen zu übernehmen. Oder die persönliche Freiheit wird nicht als ausreichend wertvolles Gut angesehen, um sich dafür anzustrengen. In dem Fall wäre die mangelnde Selbstbestimmung wohl das kleinere Übel. Allerdings fehlt dann gemäß Aldous Huxley ein Teil der Persönlichkeit. Letztlich ist natürlich alles eine Frage der Abwägung.
Sind viele Menschen möglicherweise schon so «eingenordet», dass freiheitliche Ambitionen gar nicht für eine ganze Gruppe, ein Kollektiv, verfolgt werden können? Solche Gedanken kamen mir auch, als ich mir kürzlich diverse Talks beim viertägigen Hacker-Kongress des Chaos Computer Clubs (38C3) anschaute. Ich war nicht nur überrascht, sondern reichlich erschreckt angesichts der in weiten Teilen mainstream-geformten Inhalte, mit denen ein dankbares Publikum beglückt wurde. Wo ich allgemein hellere Köpfe erwartet hatte, fand ich Konformismus und enthusiastisch untermauerte Narrative.
Gibt es vielleicht so etwas wie eine Herdenimmunität gegen Indoktrination? Ich denke, ja, zumindest eine gestärkte Widerstandsfähigkeit. Was wir brauchen, sind etwas gesunder Menschenverstand, offene Informationskanäle und der Mut, sich freier auch zwischen den Herden zu bewegen. Sie tun das bereits, aber sagen Sie es auch dieses Jahr ruhig weiter.
Dieser Beitrag ist zuerst auf Transition News erschienen.
-
 @ a95c6243:d345522c
2025-01-01 17:39:51
@ a95c6243:d345522c
2025-01-01 17:39:51Heute möchte ich ein Gedicht mit euch teilen. Es handelt sich um eine Ballade des österreichischen Lyrikers Johann Gabriel Seidl aus dem 19. Jahrhundert. Mir sind diese Worte fest in Erinnerung, da meine Mutter sie perfekt rezitieren konnte, auch als die Kräfte schon langsam schwanden.
Dem originalen Titel «Die Uhr» habe ich für mich immer das Wort «innere» hinzugefügt. Denn der Zeitmesser – hier vermutliche eine Taschenuhr – symbolisiert zwar in dem Kontext das damalige Zeitempfinden und die Umbrüche durch die industrielle Revolution, sozusagen den Zeitgeist und das moderne Leben. Aber der Autor setzt sich philosophisch mit der Zeit auseinander und gibt seinem Werk auch eine klar spirituelle Dimension.
Das Ticken der Uhr und die Momente des Glücks und der Trauer stehen sinnbildlich für das unaufhaltsame Fortschreiten und die Vergänglichkeit des Lebens. Insofern könnte man bei der Uhr auch an eine Sonnenuhr denken. Der Rhythmus der Ereignisse passt uns vielleicht nicht immer in den Kram.
Was den Takt pocht, ist durchaus auch das Herz, unser «inneres Uhrwerk». Wenn dieses Meisterwerk einmal stillsteht, ist es unweigerlich um uns geschehen. Hoffentlich können wir dann dankbar sagen: «Ich habe mein Bestes gegeben.»
Ich trage, wo ich gehe, stets eine Uhr bei mir; \ Wieviel es geschlagen habe, genau seh ich an ihr. \ Es ist ein großer Meister, der künstlich ihr Werk gefügt, \ Wenngleich ihr Gang nicht immer dem törichten Wunsche genügt.
Ich wollte, sie wäre rascher gegangen an manchem Tag; \ Ich wollte, sie hätte manchmal verzögert den raschen Schlag. \ In meinen Leiden und Freuden, in Sturm und in der Ruh, \ Was immer geschah im Leben, sie pochte den Takt dazu.
Sie schlug am Sarge des Vaters, sie schlug an des Freundes Bahr, \ Sie schlug am Morgen der Liebe, sie schlug am Traualtar. \ Sie schlug an der Wiege des Kindes, sie schlägt, will's Gott, noch oft, \ Wenn bessere Tage kommen, wie meine Seele es hofft.
Und ward sie auch einmal träger, und drohte zu stocken ihr Lauf, \ So zog der Meister immer großmütig sie wieder auf. \ Doch stände sie einmal stille, dann wär's um sie geschehn, \ Kein andrer, als der sie fügte, bringt die Zerstörte zum Gehn.
Dann müßt ich zum Meister wandern, der wohnt am Ende wohl weit, \ Wohl draußen, jenseits der Erde, wohl dort in der Ewigkeit! \ Dann gäb ich sie ihm zurücke mit dankbar kindlichem Flehn: \ Sieh, Herr, ich hab nichts verdorben, sie blieb von selber stehn.
Johann Gabriel Seidl (1804-1875)
-
 @ fe02e8ec:f07fbe0b
2025-03-31 14:43:22
@ fe02e8ec:f07fbe0b
2025-03-31 14:43:22\ Und genau dafür wirst auch du gedrillt werden: Menschen zu jagen und töten. Unbekannte, die auch nicht wissen, was sie hier tun. Oder Unschuldige, die nicht rechtzeitig fliehen konnten. Einfach töten. Alle. Ohne zu fragen. Denn das ist deine Aufgabe, Soldat: Töte Menschen!
Egal, was du vorher warst, Heizungsmonteur, KFZ-Mechaniker, Veganer, Marketing-Manager, Friseur, Verkäufer, Kindergärtner: Es ist egal. Jetzt musst du töten. Denn du hast mitgemacht. Entweder, weil du es nicht ernst genommen hast, weil du dich nie für Politik interessiert hast. Oder weil du gedacht hast, das alles betrifft dich nicht. Weil du gedacht hast, Wahlen könnten etwas verändern. Oder weil du immer das Maul gehalten hast, damit dich keiner als «Rechter» bezeichnet. Egal. Jetzt musst du töten. Das ist das Spiel.
Ja, es ist ein Spiel. Grausam, abartig, menschenverachtend. Dennoch hat es Regeln: Diejenigen, die das Spiel beginnen, müssen niemals selbst auf das Schlachtfeld. Das ist die erste Regel. Ihre Söhne auch nicht, nicht die Söhne der anderen Politiker, nicht die der EU-Abgeordneten, nicht die der Parteibonzen. Auch nicht die der Banker, der Vorstandsvorsitzenden, der Chefredakteure. Denn alle wissen, wie man das Spiel spielt. Nur du nicht.
Du bist einfach eine Figur auf dem Spielfeld, die es verpasst hat, NEIN zu sagen, als noch Gelegenheit war. Jetzt bist du verwandelt worden in eine menschliche Drohne. Wenn sie sagen: töte!, dann tötest du. Denken kannst du, wenn alles vorbei ist. Falls du je wieder nach Hause kommst. Vielleicht sogar mit beiden Beinen und beiden Armen. Vielleicht auch nicht. Egal. Wer hätte Mitleid mit einer Spielfigur?
Nein, du musst töten. Das ist deine Aufgabe. Sie sagen es nun schon seit Monaten, warum glaubst du es nicht? Sie meinen es ernst. Wenn du den Brief in Händen hältst ist es zu spät. Es gilt dann das Notstandsrecht und keiner kann mehr verweigern. Da hättest du dich vorher drum kümmern müssen. Oder auf eine Demo gehen. Oder laut und mit klarer Stimme in jedem Gespräch den Wahnsinn anprangern. Hast du aber nicht.
Jetzt musst du töten oder du wirst getötet. Das ist das Spiel. Du hättest selbst denken können. Hast du aber nicht. Hast deine Zeit mit sinnlosen Videos vertan, Netflix geguckt und hast Influencerinnen geliked. Die müssen nicht an die Front. Aber du. Morgen, wenn du aufstehst, die Uniform anziehst und rausgehst, dann wirst du Befehle ausführen oder erschossen werden. Also wirst du Menschen töten. Dein Leben wird nie wieder so sein, wie zuvor. Dein Schmerz, deine Schuld, dein Leid: sie gehen ein in die unendliche Reihe der Soldaten, die seit Jahrhunderten dasselbe Schicksal erlitten. Deren Schreie noch immer durch den ewigen Raum hallen. Deren Opfer von den Herren des Spiels mit einem Lächeln entgegengenommen wurde. Deren Gliedmaßen auf den Schlachtfeldern liegen geblieben waren. Zum Dank erhielten sie eine Medaille. Ein Stück Blech für den rechten Arm, einen Grabstein für den Vater, den Bruder, den Sohn. Für das Vaterland. Für Europa. Für die Demokratie. Der Hohn tropft aus jedem Politikerwort, doch die Menschen glauben noch immer die uralte Geschichte von Freund und Feind, von Gut und Böse.

\ Wer nicht aufwachen will muss töten. Du. Nicht am Bildschirm. In der echten Welt. Wo man nicht auf Replay drücken kann. Wo man den Gegner nicht nach links oder rechts swipen kann, denn er ist echt, real, lebendig. Noch. Entweder er oder du. Jetzt ist es zu spät für Entscheidungen. Kannst du es spüren? Die Work-Life Balance wird zur Kill-or-be-Killed balance. Es gibt kein Entrinnen. Denn du hast mitgemacht. Schweigen ist Zustimmung. Sich-nicht-drumkümmern ist Zustimmung. Kriegsparteien zu wählen ist noch mehr Zustimmung.
Heute.
Heute lässt sich noch etwas ändern.
Es hat nichts zu tun mit rechts oder links. Nur mit Menschlichkeit versus Hass, Macht und dem ganz großen Geld. Das sind die Gründe, für die du töten oder sterben musst.
Wie entscheidest du dich?
-
 @ 95cb4330:96db706c
2025-04-21 09:59:02
@ 95cb4330:96db706c
2025-04-21 09:59:02Principle:
Reduce internal friction by minimizing unnecessary processes, approvals, and meetings.
Empower small, autonomous teams to make decisions quickly and independently.
💡 What It Means
- Bureaucracy kills speed, innovation, and ownership.
- Instead of creating endless layers of management and approval, build the smallest system necessary to enable great work.
- Give teams the trust and tools they need to move fast.
The goal is not chaos, but flexibility with lightweight structure—so the organization stays dynamic as it scales.
📈 Why It Matters
✅ Speed is a competitive advantage in entrepreneurship.
✅ Empowered teams are more creative and motivated.
✅ Minimal bureaucracy allows companies to iterate fast and stay customer-focused.
🏛️ Examples in Action
- Spotify uses small “squads” with high autonomy and light-touch leadership to maintain speed and innovation.
- Basecamp designs its company around minimal meetings, clear asynchronous communication, and trusting small teams to own outcomes.
- Amazon uses the "two-pizza team" rule—teams should be small enough to be fed with two pizzas.
📚 Resources to Explore
- 📄 Spotify’s Engineering Culture – Part 1
- 📖 Basecamp’s Approach to Minimal Management
- 📘 Harvard Business Review on 3 Ways to Improve Your Decision Making
- Spotify Engineering Culture - Part 1 (aka the "Spotify Model")
🚀 Action Prompthttps://hbr.org/2018/01/3-ways-to-improve-your-decision-making
Ask yourself:
"What approvals, meetings, or processes can I eliminate or simplify today to help my team move faster?"Build only as much structure as needed—and no more. Protect creativity, speed, and ownership at all costs.
-
 @ 4cebd4f5:0ac3ed15
2025-04-18 14:54:14
@ 4cebd4f5:0ac3ed15
2025-04-18 14:54:14Tóm tắt Hackathon
UofTHacks 12 – một trong những hackathon đầu tiên tại Canada do sinh viên tự tổ chức – vừa kết thúc thành công với 339 lập trình viên đăng ký và 131 dự án được phê duyệt. Sự kiện kéo dài 36 giờ tại chỗ, tập trung vào hợp tác giữa developers, designers và entrepreneurs để biến ý tưởng thành sản phẩm thực tế.
Giải thưởng hấp dẫn như Meta Quest 3S VR Headsets cùng các track/bounty đa dạng thu hút sự tham gia. Sự kiện nhận tài trợ từ Tech@RBC, Ubisoft, 1Password, Google DeepMind và đối tác học thuật, tạo môi trường networking chất lượng.
Dù không tiết lộ chi tiết dự án, UofTHacks 12 khẳng định tác động qua quy mô tham gia và sự ủng hộ của cộng đồng, phản ánh hệ sinh thái hỗ trợ đam mê công nghệ. Người tham gia có thể theo dõi sự kiện tiếp qua kênh MXH của UofTHacks.
Các dự án đoạt giải
General Prize Winners
- Persona: Công cụ học ngôn ngữ AI-driven kết hợp computer vision, neural networks và 3D animation để dạy kèm cá nhân hóa.
- Twirl: AI chuyển đổi văn bản thành mô hình 3D, đơn giản hóa in 3D cho người không chuyên.
- Phish-Eye Lens: Web app mô phỏng trải nghiệm hacker qua puzzle để giáo dục an ninh mạng.
Ig Nobel Prize-Inspired Award Winners
- MomTellMeTo.Study: Tích hợp lịch học cá nhân với lời nhắc "mang hơi hướng mẹ" để tăng động lực.
Best "University of Toronto" Hack Prize Winners
- YouLingo: Chuyển đổi video YouTube thành bài học ngôn ngữ tùy chỉnh.
Best Beginner Hack Prize Winners
- One Million Notes: Nền tảng chia sẻ trải nghiệm toàn cầu qua ghi chú.
- bluequest - Campus Exploration App: Game hóa khám phá khuôn viên trường bằng điểm kinh nghiệm (XP).
Best Security Hack Prize Winners
- Off the Hook: Game tương tác giáo dục về phishing qua góc nhìn nạn nhân và hacker.
Young, Smart, & Financially Savvy Prize Winners
- RBveal: Mô phỏng phishing bằng AI để giáo dục sinh viên.
- FlowShield: Nền tảng phát hiện gian lận cho merchant qua phân tích dữ liệu giao dịch.
Best Domain Name from GoDaddy Registry Prize Winners
- SnapQuest: Gợi ý chụp ảnh theo địa điểm để khám phá và chia sẻ cảnh quan.
Best Use of Midnight Prize Winners
- Scribble: Ứng dụng AR gắn nội dung địa lý với zk-proof đảm bảo privacy.
Best Use of Terraform Prize Winners
Best AI Project with Databricks Open Source Prize Winners
- Pitch, Please: Mô phỏng thuyết trình thời gian thực với feedback AI.
Best Use of Generative AI Prize Winners
Best Developer Tool Prize Winners
- CodeView: Công cụ phân tích code viết tay, tạo bình luận, đánh giá chất lượng và chuyển pseudocode sang Python.
Xem danh sách dự án đầy đủ tại UofTHacks BUIDL.
Về Nhà tổ chức
UofTHacks
UofTHacks thúc đẩy đổi mới công nghệ và hợp tác tại Đại học Toronto, nổi tiếng với các hackathon kết nối sinh viên và chuyên gia để giải quyết vấn đề thực tế. Tổ chức có chuyên môn trong lĩnh vực blockchain và xu hướng công nghệ mới, đã tổ chức nhiều sự kiện thành công. UofTHacks hướng đến mở rộng phạm vi, nâng cao kỹ năng công nghệ cho thế hệ developers tương lai.
-
 @ 3f770d65:7a745b24
2025-04-20 18:55:05
@ 3f770d65:7a745b24
2025-04-20 18:55:05At the recent Launch Music Festival and Conference in Lancaster, PA, featuring over 120 musicians across three days, I volunteered my time with npub1h8gzew8am6cezuq7cpjgudldra40hgnruqrqlsrqnxnzs5wjtczqztps02 and nostr:nprofile1qqsxj7j6m0urzhm8lgsalud8aqz5zt4a52s6mhep3g8e8cg6hte03rqhjfp35's initiative to introduce artists to Bitcoin, Nostr, and the value-for-value model. Tunestr sponsored a stage, live-streaming 21 bands to platforms like [Tunestr.io](http://Tunestr.io), [Fountain.fm](http://Fountain.fm) and other Nostr/Podcasting 2.0 apps and on-boarding as many others as possible at our conference booth. You may have seen me spamming about this over the last few days. **V4V Earnings** - Day 1: 180,000 sats - Day 2: 300,000 sats - Day 3: Over 500,000 sats **Who?** Here are the volunteers: - nostr:nprofile1qqsgerm6uv6khl9shlm6kydvd8fx4ku84vweznmy08cxg4m4pw6clyg4ajwsh - nostr:nprofile1qqsgsp3h9t6329dlfthcqu53h9jg06scymykdf2ed09gv6tmtk9j80q5ecal2 - nostr:nprofile1qqspyg7l5vn4xpnqzzygdk6agdpd89lv8uqrv2u9q9ve9jmthdjrtqc20f2lg - nostr:nprofile1qqsxj7j6m0urzhm8lgsalud8aqz5zt4a52s6mhep3g8e8cg6hte03rqhjfp35 - nostr:nprofile1qqsr7acdvhf6we9fch94qwhpy0nza36e3tgrtkpku25ppuu80f69kfq9q9kky Here are the artists that were on-boarded to Fountain and were live streaming on the Value-for-Value stage: - npub1cruu4z0hwg7n3r2k7262vx8jsmra3xpku85frl5fnfvrwz7rd7mq7e403w - npub12xeh3n7w8700z4tpd6xlhlvg4vtg4pvpxd584ll5sva539tutc3q0tn3tz - npub1rc80p4v60uzfhvdgxemhvcqnzdj7t59xujxdy0lcjxml3uwdezyqtrpe0j - npub16vxr4pc2pk2j8x9xt5petww3yaez9q4s53zkejjfd0djs9lfe55sjhnqkh - npub10uspdzg4fl7md95mqnjszxx82ckdly8ezac0t3s06a0gsf4f3lys8ypeak - npub1gnyzexr40qut0za2c4a0x27p4e3qc22wekhcw3uvdx8mwa3pen0s9z90wk - npub13qrrw2h4z52m7jh0spefrwtysl4psfkfv6j4j672se5hkhvtyw7qu0almy - npub1p0kuqxxw2mxczc90vcurvfq7ljuw2394kkqk6gqnn2cq0y9eq5nq87jtkk - npub182kq0sdp7chm67uq58cf4vvl3lk37z8mm5k5067xe09fqqaaxjsqlcazej - npub162hr8kd96vxlanvggl08hmyy37qsn8ehgj7za7squl83um56epnswkr399 - npub17jzk5ex2rafres09c4dnn5mm00eejye6nrurnlla6yn22zcpl7vqg6vhvx - npub176rnksulheuanfx8y8cr2mrth4lh33svvpztggjjm6j2pqw6m56sq7s9vz - npub1akv7t7xpalhsc4nseljs0c886jzuhq8u42qdcwvu972f3mme9tjsgp5xxk - npub18x0gv872489lrczp9d9m4hx59r754x7p9rg2jkgvt7ul3kuqewtqsssn24 Many more musicians were on-boarded to Fountain, however, we were unable to obtain all of their npubs. **THANK YOU TO ALL ZAPPERS AND BOOSTERS!** **Musicians “Get It”** My key takeaway was the musicians' absolute understanding that the current digital landscape along with legacy social media is failing them. Every artist I spoke with recognized how algorithms hinder fan connection and how gatekeepers prevent fair compensation for their work. They all use Spotify, but they only do so out of necessity. They felt the music industry is primed for both a social and monetary revolution. Some of them were even speaking my language… Because of this, concepts like decentralization, censorship resistance, owning your content, and controlling your social graph weren't just understood by them, they were instantly hooked. The excitement was real; they immediately saw the potential and agreed with my talking points. Bitcoin and Nostr felt genuinely punk rock and that helped a lot of them identify with what we were offering them. **The Tools and the Issues** While the Nostr ecosystem offers a wide variety of tools, we focused on introducing three key applications at this event to keep things clear for newcomers: 1. **Fountain**, with a music focus, was the primary tool for onboarding attendees onto Nostr. Fountain was also chosen thanks to Fountain’s built-in Lightning wallet. (We did mention Wavlake as a partner and alternative.) 2. **Primal**, as a social alternative, was demonstrated to show how users can take their Nostr identity and content seamlessly between different applications. (We mentioned other similar tools, Damus, Amethyst, etc.) 3. [**Tunestr.io**](http://Tunestr.io), lastly was showcased for its live video streaming capabilities. Although we highlighted these three, we did inform attendees about the broader range of available apps and pointed them to [nostrapps.com](http://nostrapps.com) if they wanted to explore further, aiming to educate without overwhelming them. This review highlights several UX issues with the Fountain app, particularly concerning profile updates, wallet functionality, and user discovery. While Fountain does work well, these hiccups make it extremely hard for on-boarding and education. - **Profile Issues:** - When a user edits their profile (e.g., Username/Nostr address, Lightning address) either during or after creation, the changes don't appear to consistently update across the app or sync correctly with Nostr relays. - Specifically, the main profile display continues to show the old default Username/Nostr address and Lightning address inside Fountain and on other Nostr clients. - However, the updated Username/Nostr address does appear on ([chosen-username@fountain.fm](mailto:chosen-username@fountain.fm)) and is visible within the "Edit Profile" screen itself in the app. - This inconsistency is confusing for users, as they see their updated information in some places but not on their main public-facing profile within the app. I confirmed this by observing a new user sign up and edit their username – the edit screen showed the new name, but the profile display in Fountain did not update and we did not see it inside Primal, Damus, Amethyst, etc. - **Wallet Limitations:** - The app's built-in wallet cannot scan Lightning address QR codes to initiate payments. - This caused problems during the event where users imported Bitcoin from [Azte.co](http://Azte.co) vouchers into their Fountain wallets. When they tried to zap a band by scanning a QR code on the live tally board, Fountain displayed an error message stating the invoice or QR code was invalid. - While suggesting musicians install Primal as a second Nostr app was a potential fix for the QR code issue, (and I mentioned it to some), the burden of on-boarding users onto two separate applications, potentially managing two different wallets, and explaining which one works for specific tasks creates a confusing and frustrating user experience. - **Search Difficulties:** - Finding other users within the Fountain app is challenging. I was unable to find profiles from brand new users by entering their chosen Fountain username. - To find a new user, I had to resort to visiting their profile on the web ([fountain.fm/username](http://fountain.fm/username)) to retrieve their npub. Then, open Primal and follow them. Finally, when searching for their username, since I was now following them, I was able to find their profile. - This search issue is compounded by the profile syncing problem mentioned earlier, as even if found via other clients, their displayed information is outdated. - Searching for the event to Boost/Zap inside Fountain was harder than it should have been the first two days as the live stream did not appear at the top of the screen inside the tap. This was resolved on the third day of the event. **Improving the On-boarding Experience** To better support user growth, educators and on-boarders need more feature complete and user-friendly applications. I love our developers and I will always sing their praises from the highest mountain tops, however I also recognize that the current tools present challenges that hinder a smooth on-boarding experience. And to be frank, it's just frustrating for me from time to time. One potential approach explored was guiding users to use Primal (including its built-in wallet) in conjunction with Wavlake via Nostr Wallet Connect (NWC). While this could help with certain functions like music streaming, zaps, and QR code scanning (which require both Primal and Wavlake apps), Wavlake itself has usability issues. These include inconsistent or separate profiles between web and mobile apps, persistent "Login" buttons even when logged in on the mobile app with a Nostr identity, and the minor inconvenience of needing two separate applications. Although NWC setup is relatively easy and helps streamline the process, the need to switch between apps adds complexity, especially when time is limited and we’re aiming to showcase the benefits of this new system. Ultimately, we need applications that are more feature-complete and intuitive for mainstream users to improve the on-boarding experience significantly. **Looking forward to the future** I anticipate that most of these issues will be resolved when these applications address them in the near future. Specifically, this would involve Fountain fixing its profile issues and integrating Nostr Wallet Connect (NWC) to allow users to utilize their Primal wallet, or by enabling the scanning of QR codes that pay out to Lightning addresses. Alternatively, if Wavlake resolves the consistency problems mentioned earlier, this would also significantly improve the situation giving us two viable solutions for musicians. My ideal on-boarding event experience would involve having all the previously mentioned issues resolved first and foremost. Additionally, I would love to see every attendee receive a $5 or $10 voucher to help them start engaging with value-for-value, rather than just the limited number we distributed recently. The goal is to have everyone actively zapping and sending Bitcoin throughout the event. Maybe we can find a large sponsor to facilitate this in the future? What's particularly exciting is the [Launch](https://www.launchmusicconference.com/) conference's strong interest in integrating value-for-value across their entire program for all musicians and speakers at their next event in [Dallas, Texas](https://www.launchmusicconference.com/dallas/), coming later this fall. This presents a significant opportunity to onboard over 100+ musicians to Bitcoin and Nostr, which in turn will help onboard their fans and supporters. We need significantly more zaps and more zappers! It's unreasonable to expect the same dedicated individuals to continuously support new users; they are being bled dry. A shift is needed towards more people using bitcoin for everyday transactions, treating it as money. This brings me back to my ideal on-boarding experience: securing a sponsor to essentially give participants bitcoin funds specifically for zapping and tipping artists. This method serves as a practical lesson in using bitcoin as money and showcases the value-for-value principle from the outset.