-
 @ 21c9f12c:75695e59
2025-03-30 22:42:19
@ 21c9f12c:75695e59
2025-03-30 22:42:19This guy was in my dad's building. A reminder of the importance of balance in our lives. We all have good and bad experiences in life. What matters is how you choose to handle them and balance yourself on the narrow path. Our paths in life have many possible turns, some take us closer to our ultimate reality while others might lead us astray for a bit.
No matter which path you choose the important thing is to keep your balance and footing and not be swept away in the breeze. You can always find your way back to your center and work your way back out from there. There is seldom a straight path in this life that will take you directly to your ultimate reality, make your way as you will and you'll find that you have what you need when you need it.
Ultimately we are all connected in ways we may never understand. The web of reality is so complex and woven with such precision that we need not try to understand why things are the way they are but accept that they are and move along our path doing our best to help others along the way when possible and accept help from those offering it. The path we take is strengthened and preserved when we follow it with love in our hearts. In this way we can leave a beacon to guide others on their way.
My dad left a lot of love on his path. He has guided so many people whether he realized it or not. His guidance of my path has made me who I am today and I am so proud to say that. His love and light shines bright ahead of me and my path is made so much clearer by the love I received and will continue to receive from him.
This is more than just a spider in a building, it is a reminder that all will be well and we will find our balance and continue along our path with the light and love dad has placed on the web of life for us to follow. Peace and love to everyone and may you all find your balance and continue on your path in the light and love that has been placed there for you by those who have gone before.
-
 @ 0b65f96a:7fda4c8f
2025-03-29 10:39:17
@ 0b65f96a:7fda4c8f
2025-03-29 10:39:17Es gibt Bibliotheken voll Literatur zur „Kunst“ der Kriegsführung. Dies hier ist ein Beitrag zu den Bibliotheken der Kunst Frieden zu führen. Denn Frieden ist nicht die Abwesenheit von Krieg. Sondern eine mindestens ebenso intensive Aktivität. Worin genau besteht sie aber? Ich glaube darin, weder nach der einen noch nach der anderen Seite vom Hochseil zu fallen. Denn vom Hochseil kann man immer nach zwei Seiten fallen. Das ist dann auch schon die Kernherausforderung: Gleichgewichthalten!
Es scheint zunächst ein ganz äußerlicher Auftrag. Es gibt immer und wird immer widerstreitende Interessen geben. Allerdings ist das nur die äußerste Zwiebelschale. Denn wenn wir die Sache etwas mit Abstand von uns selbst betrachten, werden wir in uns hinein verwiesen: Frieden kann nur von innen nach außen gestiftet werden. Wenn wir das Hochseil in uns suchen, was finden wir dann? – Zweifels ohne, wissen wir von uns, dass wir nicht jeden Tag unser bestes Selbst sind. Würde es sich nicht lohnen etwas genauer über die Möglichkeit nach zwei Seiten vom Hochseil zu fallen nachzudenken, zugunsten der eigenen Balancierfähigkeit?
Wir sind daran gewöhnt zu denken dem Guten steht das Böse gegenüber. Daraus ziehen ja alle Western und Martial Arts Streifen ihren Plot: Der Gute bringt den Bösen um die Ecke und damit hat wieder mal das Gute gesiegt. Wir bewerten das „um die Ecke bringen“ unterschiedlich, je nach dem, von wem es kommt.
Ich möchte einen neuen Gedanken vorschlagen über unser Inneres, über Gut und Böse nachzudenken. Denn, wie gesagt, vom Hochseil kann man nach zwei Seiten fallen. Und es hat immer drastische Wirkung. Wo kommen wir also hin, wenn wir sagen: Frieden ist immer ein Gleichgewichtszustand, ergo eine Zeit der Mitte?
Sagen wir Toleranz ist ein erstrebenswertes Ideal. Dann würden wir sicher sagen Engstirnigkeit ist das Gegenteil davon und alles andere als Wünschenswert. Ja, so ist es gewiss. Und es bleibt hinzuzufügen, auch Beliebigkeit ist das Gegenteil von Toleranz. Denn es gibt eine Grenze, wo Toleranz nicht mehr Toleranz ist, sondern Beliebigkeit, ein „alles ist möglich“. Ähnlich können wir es für Großzügigkeit denken: Großzügigkeit ist ein erstrebenswertes Ideal. Ihr Gegenteil ist Geiz. Ihr anderes Gegenteil die Verschwendung. Oder Mut. Mut ist ein erstrebenswertes Ideal. Feigheit sein Gegenteil. Sein anderes Gegenteil ist Leichtsinn. Mit andern Worten: Das Ideal wird immer zum Hochseil. Und wir können immer nach zwei Seiten von ihm fallen. Wenn wir diesem Gedanken folgen, kommen wir weg von der Gut-Böse-Dualität. Und stattdessen zur Frage nach dem Gleichgewicht. Zur Frage nach der Mittezeit.
Natürlich steht es uns frei all das zu denken. Oder auch nicht zu denken. Denn selbstverständlich ist es möglich es nicht zu denken und bei einer Dualitätsvorstellung festhängen zu bleiben. Es wird uns nur nicht helfen Frieden zu denken und in Frieden zu handeln. Wenn wir wollen können wir durch das Aufspannen einer Trinität einen neuen Raum eröffnen und betreten. In ihm wird Frieden aktiv führbar, denn er wird eine Gleichgewichtssituation in uns selbst! – Nicht eine, sich einander gegenüberstehender äußerer Mächte!
Gehen wir noch einen Schritt weiter in unserer Betrachtung, können wir feststellen, dass es durchaus einen Unterschied macht nach welcher Seite wir runter fallen. Denn auf der einen Seite ist es immer eine Verengung: Engstirnigkeit, Geiz, Feigheit in unseren Beispielen. Auf der anderen ist es immer eine Zersplitterung oder Versprühung. In unseren Beispielen Beliebigkeit, Verschwendung und Leichtsinn. Und das erstrebenswerte ist eben immer die Mitte, das von uns ständig aktualisierte Gleichgewicht.
Das interessante ist, wo diese Mitte liegt, lässt sich niemals statisch festlegen. Sie ist immer dynamisch. Denn sie kann zu unterschiedlichen Momenten an unterschiedlicher Stelle liegen. Es ist immer ein Ich, das sich in Geistesgegenwart neu ausbalanciert. Und darum ist Frieden so schwer. Wir werden ihn niemals „haben“, sondern ihm immer entgegen gehen.
Der Kriegsruf ist nichts anderes, als ein Versuch von denen, die vom Hochseil gefallen sind, uns auch herunter zu kicken.
Netter Versuch. Wird aber nichts!
In der Nussschale: Die Dualität auflösen in die Trinität der balancierenden Mitte zwischen der Geste der Versteinerung und der Geste des Zerstäubens oder Zersplitterns. Die dynamische Qualität der Mitte bemerken. Oder, tun wir es nicht, ist das gleich der erste Anstoß, der uns wieder zum Wackeln bringt. Und des Ich´s gewahr werden, das balanciert. Frieden führen ist eine Kunst.
Patric I. Vogt, geb. 1968 in Mainz. Autor von „Zukunft beginnt im Kopf Ein Debattenbeitrag zur Kernsanierung von Rechtsstaat und Demokratie“. Lebt als freischaffender Künstler, Lehrer und Unternehmer. Über drei Jahrzehnte Beschäftigung mit dem Ideenfeld soziale #Dreigliederung und Anthroposophie. Moderation und Mediation von sozialen Prozessen und Organisationsentwicklung. Staatlich ungeprüft, abgesehen von den Fahrerlaubnissen zu Land und zu Wasser. Motto: Gedanken werden Worte, werden Taten! www.perspektivenwechsel.social
-
 @ 6b3780ef:221416c8
2025-03-26 18:42:00
@ 6b3780ef:221416c8
2025-03-26 18:42:00This workshop will guide you through exploring the concepts behind MCP servers and how to deploy them as DVMs in Nostr using DVMCP. By the end, you'll understand how these systems work together and be able to create your own deployments.
Understanding MCP Systems
MCP (Model Context Protocol) systems consist of two main components that work together:
- MCP Server: The heart of the system that exposes tools, which you can access via the
.listTools()method. - MCP Client: The interface that connects to the MCP server and lets you use the tools it offers.
These servers and clients can communicate using different transport methods:
- Standard I/O (stdio): A simple local connection method when your server and client are on the same machine.
- Server-Sent Events (SSE): Uses HTTP to create a communication channel.
For this workshop, we'll use stdio to deploy our server. DVMCP will act as a bridge, connecting to your MCP server as an MCP client, and exposing its tools as a DVM that anyone can call from Nostr.
Creating (or Finding) an MCP Server
Building an MCP server is simpler than you might think:
- Create software in any programming language you're comfortable with.
- Add an MCP library to expose your server's MCP interface.
- Create an API that wraps around your software's functionality.
Once your server is ready, an MCP client can connect, for example, with
bun index.js, and then call.listTools()to discover what your server can do. This pattern, known as reflection, makes Nostr DVMs and MCP a perfect match since both use JSON, and DVMs can announce and call tools, effectively becoming an MCP proxy.Alternatively, you can use one of the many existing MCP servers available in various repositories.
For more information about mcp and how to build mcp servers you can visit https://modelcontextprotocol.io/
Setting Up the Workshop
Let's get hands-on:
First, to follow this workshop you will need Bun. Install it from https://bun.sh/. For Linux and macOS, you can use the installation script:
curl -fsSL https://bun.sh/install | bash-
Choose your MCP server: You can either create one or use an existing one.
-
Inspect your server using the MCP inspector tool:
bash npx @modelcontextprotocol/inspector build/index.js arg1 arg2This will: - Launch a client UI (default: http://localhost:5173)
- Start an MCP proxy server (default: port 3000)
-
Pass any additional arguments directly to your server
-
Use the inspector: Open the client UI in your browser to connect with your server, list available tools, and test its functionality.
Deploying with DVMCP
Now for the exciting part – making your MCP server available to everyone on Nostr:
-
Navigate to your MCP server directory.
-
Run without installing (quickest way):
npx @dvmcp/bridge -
Or install globally for regular use:
npm install -g @dvmcp/bridge # or bun install -g @dvmcp/bridgeThen run using:bash dvmcp-bridge
This will guide you through creating the necessary configuration.
Watch the console logs to confirm successful setup – you'll see your public key and process information, or any issues that need addressing.
For the configuration, you can set the relay as
wss://relay.dvmcp.fun, or use any other of your preferenceTesting and Integration
- Visit dvmcp.fun to see your DVM announcement.
- Call your tools and watch the responses come back.
For production use, consider running dvmcp-bridge as a system service or creating a container for greater reliability and uptime.
Integrating with LLM Clients
You can also integrate your DVMCP deployment with LLM clients using the discovery package:
-
Install and use the
@dvmcp/discoverypackage:bash npx @dvmcp/discovery -
This package acts as an MCP server for your LLM system by:
- Connecting to configured Nostr relays
- Discovering tools from DVMCP servers
-
Making them available to your LLM applications
-
Connect to specific servers or providers using these flags: ```bash # Connect to all DVMCP servers from a provider npx @dvmcp/discovery --provider npub1...
# Connect to a specific DVMCP server npx @dvmcp/discovery --server naddr1... ```
Using these flags, you wouldn't need a configuration file. You can find these commands and Claude desktop configuration already prepared for copy and paste at dvmcp.fun.
This feature lets you connect to any DVMCP server using Nostr and integrate it into your client, either as a DVM or in LLM-powered applications.
Final thoughts
If you've followed this workshop, you now have an MCP server deployed as a Nostr DVM. This means that local resources from the system where the MCP server is running can be accessed through Nostr in a decentralized manner. This capability is powerful and opens up numerous possibilities and opportunities for fun.
You can use this setup for various use cases, including in a controlled/local environment. For instance, you can deploy a relay in your local network that's only accessible within it, exposing all your local MCP servers to anyone connected to the network. This setup can act as a hub for communication between different systems, which could be particularly interesting for applications in home automation or other fields. The potential applications are limitless.
However, it's important to keep in mind that there are security concerns when exposing local resources publicly. You should be mindful of these risks and prioritize security when creating and deploying your MCP servers on Nostr.
Finally, these are new ideas, and the software is still under development. If you have any feedback, please refer to the GitHub repository to report issues or collaborate. DVMCP also has a Signal group you can join. Additionally, you can engage with the community on Nostr using the #dvmcp hashtag.
Useful Resources
- Official Documentation:
- Model Context Protocol: modelcontextprotocol.org
-
DVMCP.fun: dvmcp.fun
-
Source Code and Development:
- DVMCP: github.com/gzuuus/dvmcp
-
DVMCP.fun: github.com/gzuuus/dvmcpfun
-
MCP Servers and Clients:
- Smithery AI: smithery.ai
- MCP.so: mcp.so
-
Glama AI MCP Servers: glama.ai/mcp/servers
Happy building!
- MCP Server: The heart of the system that exposes tools, which you can access via the
-
 @ 3bf0c63f:aefa459d
2024-01-15 11:15:06
@ 3bf0c63f:aefa459d
2024-01-15 11:15:06Pequenos problemas que o Estado cria para a sociedade e que não são sempre lembrados
- **vale-transporte**: transferir o custo com o transporte do funcionário para um terceiro o estimula a morar longe de onde trabalha, já que morar perto é normalmente mais caro e a economia com transporte é inexistente. - **atestado médico**: o direito a faltar o trabalho com atestado médico cria a exigência desse atestado para todas as situações, substituindo o livre acordo entre patrão e empregado e sobrecarregando os médicos e postos de saúde com visitas desnecessárias de assalariados resfriados. - **prisões**: com dinheiro mal-administrado, burocracia e péssima alocação de recursos -- problemas que empresas privadas em competição (ou mesmo sem qualquer competição) saberiam resolver muito melhor -- o Estado fica sem presídios, com os poucos existentes entupidos, muito acima de sua alocação máxima, e com isto, segundo a bizarra corrente de responsabilidades que culpa o juiz que condenou o criminoso por sua morte na cadeia, juízes deixam de condenar à prisão os bandidos, soltando-os na rua. - **justiça**: entrar com processos é grátis e isto faz proliferar a atividade dos advogados que se dedicam a criar problemas judiciais onde não seria necessário e a entupir os tribunais, impedindo-os de fazer o que mais deveriam fazer. - **justiça**: como a justiça só obedece às leis e ignora acordos pessoais, escritos ou não, as pessoas não fazem acordos, recorrem sempre à justiça estatal, e entopem-na de assuntos que seriam muito melhor resolvidos entre vizinhos. - **leis civis**: as leis criadas pelos parlamentares ignoram os costumes da sociedade e são um incentivo a que as pessoas não respeitem nem criem normas sociais -- que seriam maneiras mais rápidas, baratas e satisfatórias de resolver problemas. - **leis de trãnsito**: quanto mais leis de trânsito, mais serviço de fiscalização são delegados aos policiais, que deixam de combater crimes por isto (afinal de contas, eles não querem de fato arriscar suas vidas combatendo o crime, a fiscalização é uma excelente desculpa para se esquivarem a esta responsabilidade). - **financiamento educacional**: é uma espécie de subsídio às faculdades privadas que faz com que se criem cursos e mais cursos que são cada vez menos recheados de algum conhecimento ou técnica útil e cada vez mais inúteis. - **leis de tombamento**: são um incentivo a que o dono de qualquer área ou construção "histórica" destrua todo e qualquer vestígio de história que houver nele antes que as autoridades descubram, o que poderia não acontecer se ele pudesse, por exemplo, usar, mostrar e se beneficiar da história daquele local sem correr o risco de perder, de fato, a sua propriedade. - **zoneamento urbano**: torna as cidades mais espalhadas, criando uma necessidade gigantesca de carros, ônibus e outros meios de transporte para as pessoas se locomoverem das zonas de moradia para as zonas de trabalho. - **zoneamento urbano**: faz com que as pessoas percam horas no trânsito todos os dias, o que é, além de um desperdício, um atentado contra a sua saúde, que estaria muito melhor servida numa caminhada diária entre a casa e o trabalho. - **zoneamento urbano**: torna ruas e as casas menos seguras criando zonas enormes, tanto de residências quanto de indústrias, onde não há movimento de gente alguma. - **escola obrigatória + currículo escolar nacional**: emburrece todas as crianças. - **leis contra trabalho infantil**: tira das crianças a oportunidade de aprender ofícios úteis e levar um dinheiro para ajudar a família. - **licitações**: como não existem os critérios do mercado para decidir qual é o melhor prestador de serviço, criam-se comissões de pessoas que vão decidir coisas. isto incentiva os prestadores de serviço que estão concorrendo na licitação a tentar comprar os membros dessas comissões. isto, fora a corrupção, gera problemas reais: __(i)__ a escolha dos serviços acaba sendo a pior possível, já que a empresa prestadora que vence está claramente mais dedicada a comprar comissões do que a fazer um bom trabalho (este problema afeta tantas áreas, desde a construção de estradas até a qualidade da merenda escolar, que é impossível listar aqui); __(ii)__ o processo corruptor acaba, no longo prazo, eliminando as empresas que prestavam e deixando para competir apenas as corruptas, e a qualidade tende a piorar progressivamente. - **cartéis**: o Estado em geral cria e depois fica refém de vários grupos de interesse. o caso dos taxistas contra o Uber é o que está na moda hoje (e o que mostra como os Estados se comportam da mesma forma no mundo todo). - **multas**: quando algum indivíduo ou empresa comete uma fraude financeira, ou causa algum dano material involuntário, as vítimas do caso são as pessoas que sofreram o dano ou perderam dinheiro, mas o Estado tem sempre leis que prevêem multas para os responsáveis. A justiça estatal é sempre muito rígida e rápida na aplicação dessas multas, mas relapsa e vaga no que diz respeito à indenização das vítimas. O que em geral acontece é que o Estado aplica uma enorme multa ao responsável pelo mal, retirando deste os recursos que dispunha para indenizar as vítimas, e se retira do caso, deixando estas desamparadas. - **desapropriação**: o Estado pode pegar qualquer propriedade de qualquer pessoa mediante uma indenização que é necessariamente inferior ao valor da propriedade para o seu presente dono (caso contrário ele a teria vendido voluntariamente). - **seguro-desemprego**: se há, por exemplo, um prazo mínimo de 1 ano para o sujeito ter direito a receber seguro-desemprego, isto o incentiva a planejar ficar apenas 1 ano em cada emprego (ano este que será sucedido por um período de desemprego remunerado), matando todas as possibilidades de aprendizado ou aquisição de experiência naquela empresa específica ou ascensão hierárquica. - **previdência**: a previdência social tem todos os defeitos de cálculo do mundo, e não importa muito ela ser uma forma horrível de poupar dinheiro, porque ela tem garantias bizarras de longevidade fornecidas pelo Estado, além de ser compulsória. Isso serve para criar no imaginário geral a idéia da __aposentadoria__, uma época mágica em que todos os dias serão finais de semana. A idéia da aposentadoria influencia o sujeito a não se preocupar em ter um emprego que faça sentido, mas sim em ter um trabalho qualquer, que o permita se aposentar. - **regulamentação impossível**: milhares de coisas são proibidas, há regulamentações sobre os aspectos mais mínimos de cada empreendimento ou construção ou espaço. se todas essas regulamentações fossem exigidas não haveria condições de produção e todos morreriam. portanto, elas não são exigidas. porém, o Estado, ou um agente individual imbuído do poder estatal pode, se desejar, exigi-las todas de um cidadão inimigo seu. qualquer pessoa pode viver a vida inteira sem cumprir nem 10% das regulamentações estatais, mas viverá também todo esse tempo com medo de se tornar um alvo de sua exigência, num estado de terror psicológico. - **perversão de critérios**: para muitas coisas sobre as quais a sociedade normalmente chegaria a um valor ou comportamento "razoável" espontaneamente, o Estado dita regras. estas regras muitas vezes não são obrigatórias, são mais "sugestões" ou limites, como o salário mínimo, ou as 44 horas semanais de trabalho. a sociedade, porém, passa a usar esses valores como se fossem o normal. são raras, por exemplo, as ofertas de emprego que fogem à regra das 44h semanais. - **inflação**: subir os preços é difícil e constrangedor para as empresas, pedir aumento de salário é difícil e constrangedor para o funcionário. a inflação força as pessoas a fazer isso, mas o aumento não é automático, como alguns economistas podem pensar (enquanto alguns outros ficam muito satisfeitos de que esse processo seja demorado e difícil). - **inflação**: a inflação destrói a capacidade das pessoas de julgar preços entre concorrentes usando a própria memória. - **inflação**: a inflação destrói os cálculos de lucro/prejuízo das empresas e prejudica enormemente as decisões empresariais que seriam baseadas neles. - **inflação**: a inflação redistribui a riqueza dos mais pobres e mais afastados do sistema financeiro para os mais ricos, os bancos e as megaempresas. - **inflação**: a inflação estimula o endividamento e o consumismo. - **lixo:** ao prover coleta e armazenamento de lixo "grátis para todos" o Estado incentiva a criação de lixo. se tivessem que pagar para que recolhessem o seu lixo, as pessoas (e conseqüentemente as empresas) se empenhariam mais em produzir coisas usando menos plástico, menos embalagens, menos sacolas. - **leis contra crimes financeiros:** ao criar legislação para dificultar acesso ao sistema financeiro por parte de criminosos a dificuldade e os custos para acesso a esse mesmo sistema pelas pessoas de bem cresce absurdamente, levando a um percentual enorme de gente incapaz de usá-lo, para detrimento de todos -- e no final das contas os grandes criminosos ainda conseguem burlar tudo. -
 @ 878dff7c:037d18bc
2025-03-30 20:46:24
@ 878dff7c:037d18bc
2025-03-30 20:46:24Business Leaders Warn of Economic Risks from Potential Minority Government
Summary:
Australian business leaders are expressing deep concerns about the possibility of a minority government influenced by the Greens or independent "teal" candidates after the upcoming May federal election. CEOs such as Graham Turner, Chris Garnaut, and Bruce Mathieson warn that such a government could lead to policy instability, hinder long-term economic planning, and negatively impact Australia's global competitiveness. Key issues highlighted include the cost of living, housing supply, and the need for comprehensive economic reforms to stimulate consumer confidence and productivity. Sources: The Australian - March 31, 2025
Forecasted Decline in Australia's Resource and Energy Export Earnings
Summary:
The Australian government projects a 6% decrease in mining and energy export earnings for the financial year ending in June, attributing the decline to lower U.S. dollar prices for these exports. Earnings are expected to fall to A$387 billion from A$415 billion the previous year. This trend is anticipated to continue over the next five years, stabilizing at A$343 billion. Factors contributing to this decline include normalizing energy export values after recent peaks and reduced demand from China, particularly affecting iron ore exports. Sources: Reuters - March 31, 2025
Devastating Queensland Floods Expected to Persist for Weeks
Summary:
Queensland is experiencing severe flooding due to record-breaking rains exceeding 650mm, submerging entire communities like Adavale and Jundah. Swiftwater crews have conducted over 40 rescues, and major flood warnings remain across inland Queensland. The floods have damaged energy infrastructure, leaving around 300 homes without power. Livestock losses may reach up to a million, with farmers facing significant property damage and urging government and military assistance. Efforts to restore power are underway but depend on weather conditions. Additional rainfall is forecast for the coming week, potentially prolonging the flooding for days, if not weeks. Sources: The Courier-Mail - 31 March 2025
Western NSW Towns Brace for Six Weeks of Isolation Due to Floods
Summary:
A dynamic weather system has caused significant rainfall and flooding along the Paroo and Warrego Rivers, isolating communities in western NSW. The State Emergency Service (SES) has issued 46 warnings, urging residents to prepare for up to six weeks of isolation. Flash flooding, mainly due to water from Queensland, is a major concern, prompting 19 SES flood rescues and 586 emergency responses in the past 24 hours. In Taree, 22 people are surrounded by floodwater and are being rescued. An elderly man is missing after being washed away in floodwaters. The NSW SES advises residents to stay updated via their website or the Hazards Near Me app. Sources: News.com.au - 31 March 2025
Albanese Abandons Energy Bill Reduction Modelling
Summary:
Prime Minister Anthony Albanese has distanced himself from earlier modelling that supported the promise to cut power bills by $378 by 2030 and reduce emissions by 43%. He attributes the failure to achieve $275 reductions in power bills by 2025 to international factors, including the Ukraine war. This move has drawn criticism from both the Coalition and the Greens, who accuse the government of not effectively addressing power prices and emissions reduction. Sources: The Australian - March 31, 2025
Albanese Seeks Direct Talks with Trump on Tariffs
Summary:
Prime Minister Anthony Albanese anticipates a direct discussion with U.S. President Donald Trump regarding impending tariffs, as Washington prepares to announce new trade measures on April 2. There are concerns that Australia could be affected by this escalation in the global trade conflict. Albanese has emphasized his government's constructive engagement with U.S. officials on this issue and looks forward to a one-on-one conversation with President Trump. Sources: Reuters - March 31, 2025
Queensland Government Expands 'Adult Time, Adult Crime' Laws
Summary:
The Queensland state government plans to introduce at least a dozen new offenses to the Making Queensland Safer Laws, including rape, aggravated attempted robbery, attempted murder, arson, and torture. These changes will enable the judiciary to treat juvenile offenders as adults for severe crimes. Despite criticism over the delayed inclusion of attempted murder, Youth Justice Minister Laura Gerber defended the sequence and content of the initial changes. The full list of offenses will be unveiled later this week.
Sources: The Courier-Mail - March 30, 2025
Labor Government Proposes Ban on Supermarket Price Gouging
Summary:
Prime Minister Anthony Albanese announced that a re-elected Labor government would introduce legislation to outlaw supermarket price gouging by the end of the year. The plan includes implementing Australian Competition and Consumer Commission (ACCC) recommendations to enhance price transparency and establishing a task force to advise on an "excessive pricing regime" for supermarkets, with potential heavy fines for violators. Opposition leader Peter Dutton criticized the approach as ineffective, suggesting it was merely a "wet lettuce" move. Critics from both sides called for tougher measures to combat supermarket dominance and protect consumers.
Sources: The Guardian - March 29, 2025, News.com.au - March 30, 2025
Coles Expands Recall on Spinach Products Due to Contamination
Summary:
Coles has extended its recall of various spinach products across multiple regions, including New South Wales and Victoria, due to potential microbial contamination. Customers are advised not to consume the affected products and can return them to any Coles store for a full refund. The recall applies to items purchased between March 20 and March 29, with use-by dates up to April 9.
Sources: News.com.au - March 31, 2025
66-Year-Old Man Rescued After Five Days Stranded in Australian Outback
Summary:
Tony Woolford, a 66-year-old Australian man, was rescued after being stranded for five days in the flood-hit Munga-Thirri Simpson Desert. Woolford's vehicle was immobilized by rising floodwaters, and with no phone service, he survived by harvesting rainwater and using a high-frequency radio to communicate with volunteers. Authorities were notified on March 23, and he was rescued on March 26 in stable condition and high spirits. Despite the ordeal, Woolford plans to return to the outback to retrieve his car and continue his exploration once conditions improve. Sources: People - March 28, 2025
US Tariffs and Australia's Response
Summary:
Former US trade negotiator Ralph Ives asserts that the US-Australia Free-Trade Agreement has ensured fair reciprocity for two decades, suggesting that President Donald Trump should not impose reciprocal tariffs on Australia. Prime Minister Anthony Albanese anticipates a direct discussion with President Trump regarding these tariffs, expressing concern over potential impacts on Australian exports.
Sources: The Australian - March 31, 2025, Reuters - March 31, 2025
Controversial Genetically Modified Mosquito Plan Monitored Amid Backlash
Summary:
The Queensland government is set to monitor a proposal by Oxitec Australia to release genetically modified mosquitoes aimed at reducing disease transmission. Despite community opposition and concerns about environmental and health risks, supporters argue the initiative could combat diseases like dengue and Zika. Public consultations have been delayed due to significant interest and debate continues over the plan's potential impacts. Sources: The Courier-Mail - March 26, 2025
Dr. Patrick Soon-Shiong: You're Being Lied to About Cancer, How It's Caused, and How to Stop It
Summary:
In this episode of The Tucker Carlson Show, Dr. Patrick Soon-Shiong, a renowned physician and entrepreneur, discusses misconceptions surrounding cancer, its origins, and potential treatments. He emphasizes the complexity of cancer, noting that it's not a single disease but a collection of related diseases requiring varied approaches. Dr. Soon-Shiong highlights the role of the immune system in combating cancer and advocates for treatments that bolster immune responses rather than solely relying on traditional methods like chemotherapy. He also addresses the importance of early detection and personalized medicine in improving patient outcomes.
-
 @ b17fccdf:b7211155
2025-03-25 11:23:36
@ b17fccdf:b7211155
2025-03-25 11:23:36Si vives en España, quizás hayas notado que no puedes acceder a ciertas páginas webs durante los fines de semana o en algunos días entre semana, entre ellas, la guía de MiniBolt.
Esto tiene una razón, por supuesto una solución, además de una conclusión. Sin entrar en demasiados detalles:
La razón
El bloqueo a Cloudflare, implementado desde hace casi dos meses por operadores de Internet (ISPs) en España (como Movistar, O2, DIGI, Pepephone, entre otros), se basa en una orden judicial emitida tras una demanda de LALIGA (Fútbol). Esta medida busca combatir la piratería en España, un problema que afecta directamente a dicha organización.
Aunque la intención original era restringir el acceso a dominios específicos que difundieran dicho contenido, Cloudflare emplea el protocolo ECH (Encrypted Client Hello), que oculta el nombre del dominio, el cual antes se transmitía en texto plano durante el proceso de establecimiento de una conexión TLS. Esta medida dificulta que las operadoras analicen el tráfico para aplicar bloqueos basados en dominios, lo que les obliga a recurrir a bloqueos más amplios por IP o rangos de IP para cumplir con la orden judicial.
Esta práctica tiene consecuencias graves, que han sido completamente ignoradas por quienes la ejecutan. Es bien sabido que una infraestructura de IP puede alojar numerosos dominios, tanto legítimos como no legítimos. La falta de un "ajuste fino" en los bloqueos provoca un perjuicio para terceros, restringiendo el acceso a muchos dominios legítimos que no tiene relación alguna con actividades ilícitas, pero que comparten las mismas IPs de Cloudflare con dominios cuestionables. Este es el caso de la web de MiniBolt y su dominio
minibolt.info, los cuales utilizan Cloudflare como proxy para aprovechar las medidas de seguridad, privacidad, optimización y servicios adicionales que la plataforma ofrece de forma gratuita.Si bien este bloqueo parece ser temporal (al menos durante la temporada 24/25 de fútbol, hasta finales de mayo), es posible que se reactive con el inicio de la nueva temporada.

La solución
Obviamente, MiniBolt no dejará de usar Cloudflare como proxy por esta razón. Por lo que a continuación se exponen algunas medidas que como usuario puedes tomar para evitar esta restricción y poder acceder:
~> Utiliza una VPN:
Existen varias soluciones de proveedores de VPN, ordenadas según su reputación en privacidad: - IVPN - Mullvad VPN - Proton VPN (gratis) - Obscura VPN (solo para macOS) - Cloudfare WARP (gratis) + permite utilizar el modo proxy local para enrutar solo la navegación, debes utilizar la opción "WARP a través de proxy local" siguiendo estos pasos: 1. Inicia Cloudflare WARP y dentro de la pequeña interfaz haz click en la rueda dentada abajo a la derecha > "Preferencias" > "Avanzado" > "Configurar el modo proxy" 2. Marca la casilla "Habilite el modo proxy en este dispositivo" 3. Elige un "Puerto de escucha de proxy" entre 0-65535. ej: 1080, haz click en "Aceptar" y cierra la ventana de preferencias 4. Accede de nuevo a Cloudflare WARP y pulsa sobre el switch para habilitar el servicio. 3. Ahora debes apuntar el proxy del navegador a Cloudflare WARP, la configuración del navegador es similar a esta para el caso de navegadores basados en Firefox. Una vez hecho, deberías poder acceder a la guía de MiniBolt sin problemas. Si tienes dudas, déjalas en comentarios e intentaré resolverlas. Más info AQUÍ.

~> Proxifica tu navegador para usar la red de Tor, o utiliza el navegador oficial de Tor (recomendado).

La conclusión
Estos hechos ponen en tela de juicio los principios fundamentales de la neutralidad de la red, pilares esenciales de la Declaración de Independencia del Ciberespacio que defiende un internet libre, sin restricciones ni censura. Dichos principios se han visto quebrantados sin precedentes en este país, confirmando que ese futuro distópico que muchos negaban, ya es una realidad.
Es momento de actuar y estar preparados: debemos impulsar el desarrollo y la difusión de las herramientas anticensura que tenemos a nuestro alcance, protegiendo así la libertad digital y asegurando un acceso equitativo a la información para todos
Este compromiso es uno de los pilares fundamentales de MiniBolt, lo que convierte este desafío en una oportunidad para poner a prueba las soluciones anticensura ya disponibles, así como las que están en camino.
¡Censúrame si puedes, legislador! ¡La lucha por la privacidad y la libertad en Internet ya está en marcha!

Fuentes: * https://bandaancha.eu/articulos/movistar-o2-deja-clientes-sin-acceso-11239 * https://bandaancha.eu/articulos/esta-nueva-sentencia-autoriza-bloqueos-11257 * https://bandaancha.eu/articulos/como-saltarse-bloqueo-webs-warp-vpn-9958 * https://bandaancha.eu/articulos/como-activar-ech-chrome-acceder-webs-10689 * https://comunidad.movistar.es/t5/Soporte-Fibra-y-ADSL/Problema-con-web-que-usan-Cloudflare/td-p/5218007
-
 @ 866e0139:6a9334e5
2025-03-24 10:51:52
@ 866e0139:6a9334e5
2025-03-24 10:51:52Autor: Milosz Matuschek. Dieser Beitrag wurde mit dem Pareto-Client geschrieben.
Seit Sonntag (zu allem Glück auch noch meinem 45. Geburtstag) ist bei mir noch ein bisschen mehr los als sonst – und das liegt an Ihnen. Der Aufruf zur Gründung der „Friedenstaube“, einer unzensierbaren Friedenspublikation mit bekannten Stimmen aus der kritischen Szene, der Friedensbewegung und von Bürgerjournalisten ist bei Ihnen auf mehr als nur offene Ohren gestoßen! Ich bin regelrecht geplättet von den vielen Reaktionen, die ich noch gar nicht alle beantworten konnte.
Ich danke Ihnen herzlich für das Vertrauen in mich (auch wenn ich natürlich stark auf die Autoren angewiesen bin) und die überwältigenden Reaktionen: Es sind hunderte Abonnements für den Newsletter eingegangen, darunter einige bezahlte Abos und Förderabos und auch die ersten Genossenschaftsanteile wurden gezeichnet! Was mich besonders freut: Gut zehn weitere freiwillige Autoren wollen mitmachen und arbeiten bereits an den ersten Texten. Damit darf ich schon jetzt verkünden, dass die Genossenschaft definitiv gegründet werden kann, die Friedenstaube wird fliegen. Wie hoch und wie weit, das liegt dann nun nur noch in unser aller Hände.
Der Anfang ist jedenfalls gemacht. Die nächsten Wochen werden besonders arbeitsintensiv, ich bitte Sie um etwas Geduld: Aufbau einer Kernredaktion, Organisation der Abläufe, technologische Entwicklungsarbeiten, Genossenschaftsgründung etc. stehen jetzt auf der Agenda. Mit Tom-Oliver Regenauer darf ich den ersten Autor im redaktionellen Kernteam verkünden, der sich nicht nur große Verdienste im Schreiben erarbeitet hat (siehe u.a. sein Buch Hopium) sondern auch über Managementerfahrung verfügt; mit weiteren helfenden Händen bin ich im Gespräch.
Ich freue mich auf die (auch für mich) neue Erfahrung, quasi aus dem Nichts eine Publikation mit Redaktionsbetrieb und freien Autoren auf einer gänzlich neuen technologischen Infrastruktur aufzubauen. Es wäre illusorisch zu glauben, dass alles glatt gehen wird, denn wir starten quasi „on the go“, aber im Fall von Frieden oder Krieg gilt es, keine Zeit verstreichen zu lassen. Ich arbeite nach dem Motto „Tun, statt reden; zeigen, statt ankündigen; liefern, statt versprechen“.
Die ersten Texte zum Thema Frieden sind bereits publiziert, ein halbwegs geordneter Betrieb sollte ab April realistisch sein. Die Liste der Autoren wird regelmäßig aktualisiert, schauen Sie gerne hier (oder noch besser: hier) immer wieder herein. Dort finden Sie auch noch mal alle Infos, wenn Sie die Friedenstaube unterstützen wollen. Ab 1000 Euro/CHF werden Sie Genossenschafter, also Verleger!**
Auch an die bisherigen Unterstützer des Pareto-Projekts, der technologischen Basis der Friedenstaube, will ich hiermit schon etwas zurückgeben: Alle Spender für Pareto werden die Friedenstaube immer kostenlos lesen können. Sie, die Leser dieser Publikation haben die technologische Basis mit aufgebaut, die uns zur weltweit ersten, zensursicheren Friedenspublikation macht. Uns Autoren steht damit ein kompetentes Support-Team von inzwischen über zehn Entwicklern (und weiteren Helfern) an der Seite, welche die Friedenstaube am Fliegen halten werden.
Kontaktieren Sie mich gerne zu allen Fragen (je kürzer die Mail, desto früher kommt die Antwort): milosz\@pareto.space oder kontakt\@idw-europe.org
JETZT ABONNIEREN:
Hier können Sie die Friedenstaube abonnieren und bekommen die Artikel in Ihr Postfach, vorerst für alle kostenfrei, wir starten gänzlich ohne Paywall. (Die Bezahlabos fangen erst zu laufen an, wenn ein Monetarisierungskonzept für die Inhalte steht).
- Für 50 CHF/EURO bekommen Sie ein Jahresabo der Friedenstaube.
- Für 120 CHF/EURO bekommen Sie ein Jahresabo und ein T-Shirt/Hoodie mit der Friedenstaube.
- Für 500 CHF/EURO werden Sie Förderer und bekommen ein lebenslanges Abo sowie ein T-Shirt/Hoodie mit der Friedenstaube.
- Ab 1000 CHF/EURO werden Sie Genossenschafter der Friedenstaube mit Stimmrecht (und bekommen lebenslanges Abo, T-Shirt/Hoodie).
Für Einzahlungen in CHF (Betreff: Friedenstaube):
Für Einzahlungen in Euro:
Milosz Matuschek
IBAN DE 53710520500000814137
BYLADEM1TST
Sparkasse Traunstein-Trostberg
Betreff: Friedenstaube
Wenn Sie auf anderem Wege beitragen wollen, schreiben Sie mich an: milosz@pareto.space oder kontakt@idw-europe.org.
Was bewegt mich beim Thema Krieg und Frieden?
Erlauben Sie mir einen kurzen persönlichen Prolog: Ich stamme aus Schlesien. Mein Urgroßvater kämpfte im I. Weltkrieg bei Verdun. Mein Großvater wurde in die Wehrmacht eingezogen, kämpfte im Partisanenkrieg in Jugoslawien, verlor Hand und Auge. Ein Bruder meiner Großmutter entzog sich und landete in Dachau. Ich kenne meine Familiengeschichte nur in groben Umrissen, vielen wird es ähnlich gehen. Einige meiner schlesischen Vorfahren waren später vor allem Lokführer. Aufgrund der bewegten schlesischen Geschichte wechselten sie mehrfach die Uniform. Die Tätigkeit und Fahrstrecke blieb die gleiche. Für wen oder was kämpften sie in Kriegen in welchen Uniformen? Vermutlich wussten sie es selbst nicht.
Auch ich könnte heute nicht genau sagen, welche Interessen und Mächte die Kriegsmaschinerie bedienen. Doch ich wüsste es gerne und Sie vielleicht auch. Kämpfen ohne letztlich zu wissen für wen und warum: Wozu? Krieg simuliert Sinn und Notwendigkeit und lässt einen am Ende mit den großen Fragen allein, ahnungslos gestorben im Schützengraben. Zivilisatorisch ist das ein Offenbarungseid.
Bin ich ein totaler Anti-Militarist? Ich glaube nicht. Ich habe nichts gegen die Idee privaten Waffenbesitzes. Ich kann der Idee der Landesverteidigung durchaus etwas abgewinnen. Den Wehrdienst habe ich bewusst nicht verweigert. Ich wollte die Erfahrung machen. Hier schreibt also auch ein Obergefreiter a. D. eines bayerischen Gebirgspionierbataillons bei Rosenheim mit bronzener Schützenschnur, der am MG durchaus treffsicher war. Aber eben auch jemand, den der Wehrdienst zum Teil-Pazifisten gemacht hat. Mir war nach dem Grundwehrdienst klar: Wir sind eine Gurkentruppe, reines Kanonenfutter. 20-jährige Grünschnäbel mit zu viel Testosteron und Hollywood in den Gliedern, aber wenig Ahnung.
Ich war also einer, der sich verlässlich mit anderen beim Orientierungslauf im Wald verirrte; einer, der mit anderen übermüdet beim ersten Wachdienst einpennte (und damit im Ernstfall den Tod im Schlaf kennengelernt hätte, denn just erfolgte ein simulierter „Angriff“); einer, der auch mal übernächtigt sein Gewehr vor dem Zelt vergaß (wir sollten dem G3 den Namen unserer damaligen Freundin geben – wie pervers – ich vergaß also „Petra“ vor dem Zelt) und schließlich einer, der die meiste Zeit des Dienstes fürs Vaterland letztlich mit dem Servieren von Getränken und Schinkennudeln im Offizierskasino verbrachte und die institutionalisierten Alkoholiker der Bundeswehr bei Laune hielt („it ain’t much, but it was honest work“).
Anders gesagt: Krieg – spätestens seitdem: ohne mich. Auch wenn ich gerne Ernst Jünger lese und zitiere (er war einfach ein großartiger Chronist und lebendiger Geist), seinen abenteuerlustigen Militarismus kreide ich ihm an und rufe ihm posthum hinterher: man muss nicht erst einen Sohn im Krieg verloren haben, um zum Pazifisten zu werden.
Weitere Störgefühle tauchten auf: In meiner Dissertation durfte ich mich u.a. mit philosophischen Theorien zum Gesellschaftsvertrag (u.a. Kant, Rousseau, Locke und Hobbes sind hier zu nennen) beschäftigen. Dies brachte mein Staatsverständnis gerade bei der Kriegsfrage noch mehr durcheinander. Wenn Mindestziel der Staatsgründung innere und äußere Sicherheit sind, aber letztlich nicht der Staat den Bürger, sondern der Bürger den Staat schützt, wozu sich dann eine Schutzmacht erfinden, die einen am Ende durch den Fleischwolf jagt? Hobbes setzte zumindest auf Söldner.
Kriege werden mit Lügen begonnen, wusste Julian Assange. Können Sie mit Wahrheit beendet oder gar verhindert werden? Seit Walter Lippmanns „Liberty and the News“ von 1920 weiß man spätestens, dass gesicherte Information im Krieg das seltenste Gut ist. Sagt Lippmann als oberster Mainstream-Journalist und Einflüsterer der Mächtigen. Jeder Journalist muss hier ein Störgefühl entwickeln, der Leser noch mehr. Der Journalist der Nachrichtenagentur ist selten im Geschehen sondern wird vom heimischen Militär gebrieft, sein Bericht landet dann in den Newstickern und Redaktionen. Die Kriegsmaschinerie produziert also auch ihre eigene Sicht auf die Dinge, die sie den Bürgern als die Realität verkauft.
Kein Wunder, dass jede abweichende Information massiv bekämpft werden muss. Im Krieg ist Zweifel gleich Verrat, quasi unsolidarisches Sektierertum und Wehrkraftzersetzung, wenn nicht Feindbegünstigung. Der kritische Journalist steht in Ausnahmezuständen, wie man schon bei Corona sehen konnte, automatisch aus Staatssicht im Lager des Feindes und wird entsprechend behandelt. Zensursicheres Publizieren ist dann nicht nur ein nettes feature, sondern notwendige Basisvoraussetzung. Vor kurzem war Twitter/X nicht mehr zugänglich wegen massiven Cyberattacken. Wenn dann noch Rundfunk und Presse auf der Propagandawelle surfen und die Plattformzensur wieder zuschlägt, wird das Angebot schnell dünn.
Wem aber dient Zensur und Propaganda? Die aktuelle Lage im Russland-Ukraine-Konflikt ist auch Gelegenheit, um zu zeigen: Es sind eben nicht nur staatliche Interessen, die hier verhandelt werden, sondern es muss (wieder mal) eine andere Entität mit am Tisch sitzen, man nenne sie Deep State oder wie auch immer. Europäische Eliten dienen offensichtlich Fremdinteressen, wenn sie mit Aufrüstungsplänen Volksvermögen verspekulieren oder darin (wie von der Leyen) ein notwendiges „Investment“ sehen. Von wem werden wir letztlich regiert? Auch diesem Themen-Komplex werde ich mich in der Friedenstaube nähern.
Es gibt viel zu tun, aber für mich ist klar: Frieden ist ohne Wahrheit nicht zu bekommen, deshalb ist Wahrheitssuche auch immer Friedenssuche, wie Wahrheitsliebe letztlich Friedensliebe ist.
Gerade fallen auch im Mainstream die Corona-Lügen zur Labortheorie in sich zusammen, fünf Jahre nach Ausrufung der Pandemie. Der Frieden hat nur eine Chance, wenn es uns gelingt, die Lügen nun möglichst synchron zu den Geschehnissen aufzudecken und zu dokumentieren.
Das ist mein persönlicher Wunsch, mit dem ich die Friedenstaube fliegen lasse.
Was ist Ihrer? Schreiben Sie es gerne in die Kommentare. Welche Erwartungen, Wünsche haben Sie an uns? Liebe Autoren: Was ist euer Beweggrund, für den Frieden zur Feder zu greifen?
Zeichnen Sie jetzt “Friedensanleihen”. Werden Sie Genossenschafter und Verleger der Friedenstaube ab 1000 Euro/CHF. Es können mehrere Anteile pro Person gezeichnet werden, es bleibt bei einem Stimmrecht pro Kopf. milosz\@pareto.space
P.S: Mit diesem Text testen wir die Newsletterfunktion erstmals an mehrere Hundert Mailadressen. Wenn Sie die Friedenstaube abonniert haben, sollten Sie diesen Artikel per Mail bekommen haben.
ANZEIGE:
Sie suchen nach dem einfachsten Weg, Bitcoin zu kaufen und selbst zu verwahren?* Die* Relai-App ist Europas erfolgreichste Bitcoin-App.* Hier kaufen Sie Bitcoin in wenigen Schritten und können auch Sparpläne einrichten. Niemand hat Zugriff auf Ihre Bitcoin, außer Sie selbst.* Relai senkt jetzt die Gebühr auf 1%, mit dem Referral-Code MILOSZ sparen Sie weitere 10%. (keine Finanzberatung). Disclaimer wg. EU-Mica-Regulierung: Die Dienste von Relai werden ausschließlich für Einwohner der Schweiz und Italiens empfohlen.
Join the marketplace of ideas! We are building a publishing ecosystem on Nostr for citizen-journalism, starting with a client for blogging and newsletter distribution. Sound money and sound information should finally be in the hands of the people, right? Want to learn more about the Pareto Project? Zap me, if you want to contribute (all Zaps go to the project).
Are you a publication or journalist and want to be part of it, test us, migrate your content to Nostr? Write to team@pareto.space**
Not yet on Nostr and want the full experience? Easy onboarding via Start.
Pareto has started a crowdfunding campaign on Geyser. We were in the Top 3 in February, thank you for the support!
-
 @ b8af284d:f82c91dd
2025-03-24 08:09:20
@ b8af284d:f82c91dd
2025-03-24 08:09:20I'd say that globalization's hunger for cheap labor is a problem, precisely because it's been bad for innovation. Both our working people and our innovators have the same enemy — and the solution is American innovation...
Liebe Abonnenten,
der intellektuell brillante Vize-Präsident J.D. Vance hat diese Woche seine Wirtschaftspolitik skizziert. Über deren Grundzüge geht es heute.
Die Geschichte der Globalisierung ist die Geschichte der Suche nach billigen Arbeitskräften. Arbeiter in den westlichen Gesellschaften in den G7-Staaten waren spätestens in den 1980er Jahren gut organisiert und stemmten sich meist erfolgreich gegen Lohnkürzungen und Stellenabbau. Nach dem Zusammenbruch der Sowjetunion 1990 fanden die international tätigen Konzerne auf einmal ein gewaltiges Reservoir an billigen Arbeitskräften - nicht nur, aber vor allem in China.

Dieser Prozess nahm 2001 mit dem Beitritt Chinas zur Welthandelsorganisation nochmals an Fahrt auf. Deutlich wird er am ikonischen Produkt der Neuzeit, dem iPhone. Das erste Modell kam 2007 auf den Markt. Entworfen und designt wurde und wird das Smartphone von Apple in Kalifornien. Gefertigt dagegen wird es von einem der größten Konzerne der Welt. Foxconn beschäftigt allein in China über eine Million Menschen. Hon Hai, wie Foxconn eigentlich heißt, ist übrigens ein taiwanisches Unternehmen.
Dieser Prozess der verlagerten Fertigung hatte mehrere Vorteile: Produkte wurden günstiger. Davon profitierten Konsumenten in der westlichen Welt. Würde man ein iPhone in den USA oder Deutschland herstellen, würde es durch die höheren Löhne zwischen 200 und 300 Euro mehr kosten. Die Konzerne wie Apple konnten somit günstiger produzieren, ihre Margen erhöhen, und ihre Aktienkurse stiegen.
Von diesem Prozess profitierten außerdem Länder wie China: Das monatliche Grundgehalt von Foxconn-Mitarbeitern in Shenzhen erscheint mit rund 400 Euro im Monat noch immer grotesk niedrig. Für viele Chinesen vom Land bedeutet ein Job in der Fabrik allerdings ein Gehaltssprung von mehreren hundert Prozent. Es gibt keinen Grund, die Arbeitsbedingungen bei Foxconn schönzureden. Zur Wahrheit gehört aber auch, dass sich die allermeisten Wanderarbeiter nicht ausgebeutet oder als Opfer fühlen. Im Gegenteil: In meiner Zeit in China stieß ich meist auf Menschen, die sich als selbstwirksamer empfanden als viele Festangestellte mit 30 Urlaubstagen im Westen. Länder, mit billigen Arbeitskräften, profitierten also von diesem Prozess und kletterten so auf der globalen Wertschöpfungskette nach oben.
Etwa zeitgleich nahm auch in westlichen Ländern die Immigration zu. Der Anteil der im Ausland geborenen Bevölkerung stieg von etwa 7,9 Prozent im Jahr 1990 auf 13,7 Prozent im Jahr 2021, was den höchsten Stand seit 1910 darstellt. In Deutschland stieg der „Ausländer“-Anteil von knapp 7 Prozent 1990 auf 27 Prozent 2023. Viele Unternehmen hatten also sowohl international als auch national Zugriff auf günstige Arbeitskräfte. In Europa wurden diese zudem dringend gebraucht, um das in Schieflage geratene Rentensystem zu stabilisieren.
Die Nachteile dieses Megatrends wurden zunächst in den USA sichtbar: Immer mehr Unternehmen in den USA verlagerten ihre Produktion nach China. Hinzu kam der Status des US-Dollars als Weltreservewährung. Durch die konstante Nachfrage nach Dollar bleibt dieser stark, und macht amerikanische Exporte teurer. Eine Deindustrialisierung setzte ein, die vielen Menschen ihren Job kostete. Zeitgleich wuchs das Handelsbilanzdefizit mit China immer weiter. Hinzu kam eine konstante Erhöhung der Geldmenge. Amerikaner mit „hard assets“, Immobilien und Aktien, wurden tendenziell reicher. Der Rest aber nicht. Kurz: Konzerne verdienten gut, die Wirtschaft wuchs, nur bei den Amerikanern selbst blieb immer weniger hängen.
Worum es J.D. Vance also geht: Innovation und Arbeitsplätze in die USA zurückzuholen. Dafür müssen Schutzmauern errichtet werden: gegen die illegale Einwanderung billiger Arbeitskräfte und billiger Waren. Zölle dienen dazu, ausländische Waren zu verteuern, und somit Unternehmen Anreize zu geben, direkt in den USA zu investieren. Kürzlich gab Siemens bekannt, zehn Milliarden Euro in amerikanische KI-Rechenzentren zu investieren. Was wohl auch Teil des Trump-Derangement-Syndroms ist: die Wahrnehmung der amerikanischen Zollpolitik. Kaum ein Land hat aktuell so niedrige Zollschranken wie die Vereinigten Staaten.
\ Kurz gesagt: iPhones sollen demnach nicht nur in den USA entworfen, sondern auch in amerikanischen Fabriken zusammengeschraubt werden. Alles hoch-inflationär, wenden Kritiker ein. Wer globale Lieferketten abreißt, und ins eigene Land zurückholt, hat mit viel höheren Kosten zu kämpfen. Also steigt die Inflation. Diesen Prozess will die US-Regierung mit günstigeren Energiekosten kontern. Egal ob Solar-, Nuklear- oder Fracking - jede Energiequelle soll dafür Recht sein.
Schließlich soll eine strikte Haushaltsdisziplin (DOGE) unnötige Ausgaben vermeiden, und die Bürokratie abbauen. Im Gegenzug können dann die Steuern gesenkt werden. Die Einkommensteuer für Familien mit einem Jahreseinkommen bis zu 150000 US-Dollar soll komplett gestrichen werden.
Tl/DR:
- Migration begrenzen, um Billigarbeit zu verhindern
- Zölle errichten, um amerikanische Produktion zu stärken
- Günstige Energiequellen priorisieren, um Inflation zu verhindern
- Staatsausgaben radikal kürzen
- Steuern radikal senken
Kann das Projekt klappen? Vielleicht. Das Megaprojekt Globalisierung zurückzudrehen, oder zumindest etwas zu bremsen, ist ein Wagnis. Zölle bergen die Gefahr der Inflation und eines Handelskriegs. Unsicher ist, ob von einer Deregulierung weiterer Branchen am Ende wirklich amerikanische Arbeiter profitieren. Und wie innovativ können Unternehmen sein, wenn sie am Ende mehr Geld für ihre Beschäftigten ausgeben müssen, anstatt es in Forschung und Entwicklung zu investieren? Was geschieht, wenn der Rest der Welt nicht mitmacht, und sich immer weiter vernetzt? Werden die USA am Ende eine einsame Zoll-Insel? In ein paar Monaten dürfte sich langsam abzeichnen, ob das Projekt funktioniert.
Mehr dazu:
Der Mar-a-Largo-Accord - wie eine neue Finanzordnung entsteht
Was dagegen nicht klappen wird, ist das deutsche Projekt. Friedrich Merz hat mit einem „Husarenstück“ (SZ) mit einem abgewählten Bundestag eine Verfassungsänderung durchgepeitscht. Mindestens 500 Milliarden Euro neue Schulden werden gemacht, das Militär erhält einen Blankoscheck für neue Anschaffungen. Bürokratie wird nicht abgebaut. Die Unter- und Mittelschicht wird nicht entlastet. Das 100-Milliarden Zugeständnis an die Grünen sorgt dafür, dass Energie nicht günstiger wird. Ein bisschen Innovation werden die neuen Panzer- und Drohnen-Fabriken schon bringen. Am Ende aber bleibt Rüstung totes Kapital. Im wahrsten Sinne des Wortes.
Was das neue Wirtschaftsprogramm für Bitcoin bedeutet - haben wir den Boden gesehen?
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Músicas grudentas e conversas
Uma vez que você ouviu uma música grudenta e ela volta, inteira, com toda a melodia e a harmonia, muitos dias depois, contra a sua vontade. Mas uma conversa é impossível de lembrar. Por quê?
-
 @ 66675158:1b644430
2025-03-23 11:39:41
@ 66675158:1b644430
2025-03-23 11:39:41I don't believe in "vibe coding" – it's just the newest Silicon Valley fad trying to give meaning to their latest favorite technology, LLMs. We've seen this pattern before with blockchain, when suddenly Non Fungible Tokens appeared, followed by Web3 startups promising to revolutionize everything from social media to supply chains. VCs couldn't throw money fast enough at anything with "decentralized" (in name only) in the pitch deck. Andreessen Horowitz launched billion-dollar crypto funds, while Y Combinator batches filled with blockchain startups promising to be "Uber for X, but on the blockchain."
The metaverse mania followed, with Meta betting its future on digital worlds where we'd supposedly hang out as legless avatars. Decentralized (in name only) autonomous organizations emerged as the next big thing – supposedly democratic internet communities that ended up being the next scam for quick money.
Then came the inevitable collapse. The FTX implosion in late 2022 revealed fraud, Luna/Terra's death spiral wiped out billions (including my ten thousand dollars), while Celsius and BlockFi froze customer assets before bankruptcy.
By 2023, crypto winter had fully set in. The SEC started aggressive enforcement actions, while users realized that blockchain technology had delivered almost no practical value despite a decade of promises.
Blockchain's promises tapped into fundamental human desires – decentralization resonated with a generation disillusioned by traditional institutions. Evangelists presented a utopian vision of freedom from centralized control. Perhaps most significantly, crypto offered a sense of meaning in an increasingly abstract world, making the clear signs of scams harder to notice.
The technology itself had failed to solve any real-world problems at scale. By 2024, the once-mighty crypto ecosystem had become a cautionary tale. Venture firms quietly scrubbed blockchain references from their websites while founders pivoted to AI and large language models.
Most reading this are likely fellow bitcoiners and nostr users who understand that Bitcoin is blockchain's only valid use case. But I shared that painful history because I believe the AI-hype cycle will follow the same trajectory.
Just like with blockchain, we're now seeing VCs who once couldn't stop talking about "Web3" falling over themselves to fund anything with "AI" in the pitch deck. The buzzwords have simply changed from "decentralized" to "intelligent."
"Vibe coding" is the perfect example – a trendy name for what is essentially just fuzzy instructions to LLMs. Developers who've spent years honing programming skills are now supposed to believe that "vibing" with an AI is somehow a legitimate methodology.
This might be controversial to some, but obvious to others:
Formal, context-free grammar will always remain essential for building precise systems, regardless of how advanced natural language technology becomes
The mathematical precision of programming languages provides a foundation that human language's ambiguity can never replace. Programming requires precision – languages, compilers, and processors operate on explicit instructions, not vibes. What "vibe coding" advocates miss is that beneath every AI-generated snippet lies the same deterministic rules that have always governed computation.
LLMs don't understand code in any meaningful sense—they've just ingested enormous datasets of human-written code and can predict patterns. When they "work," it's because they've seen similar patterns before, not because they comprehend the underlying logic.
This creates a dangerous dependency. Junior developers "vibing" with LLMs might get working code without understanding the fundamental principles. When something breaks in production, they'll lack the knowledge to fix it.
Even experienced developers can find themselves in treacherous territory when relying too heavily on LLM-generated code. What starts as a productivity boost can transform into a dependency crutch.
The real danger isn't just technical limitations, but the false confidence it instills. Developers begin to believe they understand systems they've merely instructed an AI to generate – fundamentally different from understanding code you've written yourself.
We're already seeing the warning signs: projects cobbled together with LLM-generated code that work initially but become maintenance nightmares when requirements change or edge cases emerge.
The venture capital money is flowing exactly as it did with blockchain. Anthropic raised billions, OpenAI is valued astronomically despite minimal revenue, and countless others are competing to build ever-larger models with vague promises. Every startup now claims to be "AI-powered" regardless of whether it makes sense.
Don't get me wrong—there's genuine innovation happening in AI research. But "vibe coding" isn't it. It's a marketing term designed to make fuzzy prompting sound revolutionary.
Cursor perfectly embodies this AI hype cycle. It's an AI-enhanced code editor built on VS Code that promises to revolutionize programming by letting you "chat with your codebase." Just like blockchain startups promised to "revolutionize" industries, Cursor promises to transform development by adding LLM capabilities.
Yes, Cursor can be genuinely helpful. It can explain unfamiliar code, suggest completions, and help debug simple issues. After trying it for just an hour, I found the autocomplete to be MAGICAL for simple refactoring and basic functionality.
But the marketing goes far beyond reality. The suggestion that you can simply describe what you want and get production-ready code is dangerously misleading. What you get are approximations with:
- Security vulnerabilities the model doesn't understand
- Edge cases it hasn't considered
- Performance implications it can't reason about
- Dependency conflicts it has no way to foresee
The most concerning aspect is how such tools are marketed to beginners as shortcuts around learning fundamentals. "Why spend years learning to code when you can just tell AI what you want?" This is reminiscent of how crypto was sold as a get-rich-quick scheme requiring no actual understanding.
When you "vibe code" with an AI, you're not eliminating complexity—you're outsourcing understanding to a black box. This creates developers who can prompt but not program, who can generate but not comprehend.
The real utility of LLMs in development is in augmenting existing workflows:
- Explaining unfamiliar codebases
- Generating boilerplate for well-understood patterns
- Suggesting implementations that a developer evaluates critically
- Assisting with documentation and testing
These uses involve the model as a subordinate assistant to a knowledgeable developer, not as a replacement for expertise. This is where the technology adds value—as a sophisticated tool in skilled hands.
Cursor is just a better hammer, not a replacement for understanding what you're building. The actual value emerges when used by developers who understand what happens beneath the abstractions. They can recognize when AI suggestions make sense and when they don't because they have the fundamental knowledge to evaluate output critically.
This is precisely where the "vibe coding" narrative falls apart.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Bluesky is a scam
Bluesky advertises itself as an open network, they say people won't lose followers or their identity, they advertise themselves as a protocol ("atproto") and because of that they are tricking a lot of people into using them. These three claims are false.
protocolness
Bluesky is a company. "atproto" is the protocol. Supposedly they are two different things, right? Bluesky just releases software that implements the protocol, but others can also do that, it's open!
And yet, the protocol has an official webpage with a waitlist and a private beta? Why is the protocol advertised as a company product? Because it is. The "protocol" is just a description of whatever the Bluesky app and servers do, it can and does change anytime the Bluesky developers decide they want to change it, and it will keep changing for as long as Bluesky apps and servers control the biggest part of the network.
Oh, so there is the possibility of other players stepping in and then it becomes an actual interoperable open protocol? Yes, but what is the likelihood of that happening? It is very low. No serious competitor is likely to step in and build serious apps using a protocol that is directly controlled by Bluesky. All we will ever see are small "community" apps made by users and small satellite small businesses -- not unlike the people and companies that write plugins, addons and alternative clients for popular third-party centralized platforms.
And last, even if it happens that someone makes an app so good that it displaces the canonical official Bluesky app, then that company may overtake the protocol itself -- not because they're evil, but because there is no way it cannot be like this.
identity
According to their own documentation, the Bluesky people were looking for an identity system that provided global ids, key rotation and human-readable names.
They must have realized that such properties are not possible in an open and decentralized system, but instead of accepting a tradeoff they decided they wanted all their desired features and threw away the "decentralized" part, quite literally and explicitly (although they make sure to hide that piece in the middle of a bunch of code and text that very few will read).
The "DID Placeholder" method they decided to use for their global identities is nothing more than a normal old boring trusted server controlled by Bluesky that keeps track of who is who and can, at all times, decide to ban a person and deprive them from their identity (they dismissively call a "denial of service attack").
They decided to adopt this method as a placeholder until someone else doesn't invent the impossible alternative that would provide all their desired properties in a decentralized manner -- which is nothing more than a very good excuse: "yes, it's not great now, but it will improve!".
openness
Months after launching their product with an aura of decentralization and openness and getting a bunch of people inside that believed, falsely, they were joining an actually open network, Bluesky has decided to publish a part of their idea of how other people will be able to join their open network.
When I first saw their app and how they were very prominently things like follower counts, like counts and other things that are typical of centralized networks and can't be reliable or exact on truly open networks (like Nostr), I asked myself how were they going to do that once they became and open "federated" network as they were expected to be.
Turns out their decentralization plan is to just allow you, as a writer, to host your own posts on "personal data stores", but not really have any control over the distribution of the posts. All posts go through the Bluesky central server, called BGS, and they decide what to do with it. And you, as a reader, doesn't have any control of what you're reading from either, all you can do is connect to the BGS and ask for posts. If the BGS decides to ban, shadow ban, reorder, miscount, hide, deprioritize, trick or maybe even to serve ads, then you are out of luck.
Oh, but anyone can run their own BGS!, they will say. Even in their own blog post announcing the architecture they assert that "it’s a fairly resource-demanding service" and "there may be a few large full-network providers". But I fail to see why even more than one network provider will exist, if Bluesky is already doing that job, and considering the fact there are very little incentives for anyone to switch providers -- because the app does not seem to be at all made to talk to multiple providers, one would have to stop using the reliable, fast and beefy official BGS and start using some half-baked alternative and risk losing access to things.
When asked about the possibility of switching, one of Bluesky overlords said: "it would look something like this: bluesky has gone evil. there's a new alternative called freesky that people are rushing to. I'm switching to freesky".
The quote is very naïve and sounds like something that could be said about Twitter itself: "if Twitter is evil you can just run your own social network". Both are fallacies because they ignore the network-effect and the fact that people will never fully agree that something is "evil". In fact these two are the fundamental reasons why -- for social networks specifically (and not for other things like commerce) -- we need truly open protocols with no owners and no committees.
-
 @ 2fb77d26:c47a6ee1
2025-03-21 15:49:40
@ 2fb77d26:c47a6ee1
2025-03-21 15:49:40»Pershing II« – das war eines der ersten englischen Wörter, das mir als Kind geläufig war. Es handelt sich um die Typenbezeichnung einer US-Mittelstreckenrakete, einer nuklearen Boden-Boden-Rakete, die mit einem thermonuklearen Sprengkopf vom Typ W85 ausgestattet war, eine Reichweite von etwa 1.800 km hatte und somit von Süddeutschland aus Ziele im westlichen Russland binnen fünf Minuten erreichen konnte. Es war Anfang der 1980er Jahre. Die Zeit des Kalten Krieges. Eine Bezeichnung, die George Orwell mit seinem Essay »You and the Atomic Bomb« (Du und die Atombombe) im Jahre 1945 geprägt hatte. Die Fronten waren verhärtet.
Die westdeutsche Friedensbewegung protestierte lautstark gegen die Stationierung von Atomsprengköpfen auf heimischem Boden. Nachdem die im NATO-Doppelbeschluss vom 12. Dezember 1979 vereinbarten Abrüstungsverhandlungen zwischen den Atommächten jedoch erfolglos geblieben waren, entschied der Deutsche Bundestag am 22. November 1983, der Stationierung von US-Atomwaffen im Lande zuzustimmen. Diese war 1985 abgeschlossen und ganze 120 Exemplare der todbringenden Massenvernichtungswaffe in der Bundesrepublik verteilt worden. Außer Deutschland tat kein Land den USA diesen Gefallen.
Ich hatte die militärische Artikelbezeichnung »Pershing II« im Radio aufgeschnappt, welcher zu Hause fast durchgehend in Betrieb war, und später ein paar Bilder der Raketen in den Abendnachrichten gesehen. Noch gab es nur ARD, ZDF und das Regionalprogramm. Dementsprechend rar waren visuelle Informationen. Und aufgrund meiner frühen Begeisterung für Fluggeräte aller Art, zeichnete ich daraufhin ständig Raketen. Da ich außerdem bereits in diesem zarten Alter von fünf oder sechs Jahren extrem von Musik angetan war und durchweg versuchte, englische Songtexte, zum Beispiel von den Beatles, dem Klang der Stimmen folgend nachzusingen, übte auch der fremd klingende Begriff »Pershing II« eine gewisse Faszination auf mich aus.
Was mir meine Eltern diesbezüglich sagten oder erklärten, kann ich leider nicht mehr erinnern – als erklärte Pazifisten nahmen sie die latente Gefahr eines Nuklearkrieges aber sicher nicht mit der spielerisch-kindlichen Leichtigkeit, die ich im Umgang mit gemalten oder gebastelten Raketen an den Tag legte. Das Thema nukleare Kriegsführung beherrschte die Nachrichten dieser Zeit und erzeugte Angst. Denn Militärstrategen sprachen Anfang der 1980er Jahre allen Ernstes davon, dass der Atomkrieg zwischenzeitlich präziser und somit auch führbarer geworden sei. Damals wie heute – absoluter Irrsinn.
Neben der Berlin-Blockade 1948/1949 und der Kuba-Krise, war die Auseinandersetzung um die Stationierung von Mittelstreckenraketen in Westeuropa von 1979 bis 1983 also eine der drei kritischsten Phasen des Kalten Krieges.
Nie war die Welt einem fatalen wie letalen nuklearen Schlagabtausch der Supermächte näher als zu diesen drei Zeitpunkten in der Geschichte. Bis heute, so scheint es.
Denn die stetig eskalierende Ukraine-Krise rückt dieses vergessen geglaubte Horror-Szenario wieder in den Fokus der Öffentlichkeit. Polit-Darsteller wie der Maoist und China-Fan Robert Habeck äußern dieser Tage dummdreist, keine Angst vor einem Dritten Weltkrieg zu haben. Sogenannte Sicherheitsexperten erklären im ZDF, dass man sich vor Putins Bomben nicht fürchten solle, obwohl man in Mainz permanent Angst schürt und schon am 5. Mai 2022 titelt, »Moskau simuliert Atomangriff in Kaliningrad«.
Der »Beobachter Gesundheit« gibt Tipps dazu, wie man die Panik vor einem Atomkrieg mental in den Griff bekommen kann, während das deutsche BBK (Bundesamt für Bevölkerungsschutz und Katastrophenhilfe) der Bevölkerung bereits empfiehlt, im Zuge der Ukraine-Krise Notvorräte anzulegen und Marschgepäck bereitzuhalten. Auf der Webseite »wikiHow« findet sich ein sehr umfassender, bebilderter Ratgeber mit dem Titel »Einen Atomkrieg überleben«. Beim Lesen der zahlreichen, mutmaßlich nur bedingt hilfreichen Tipps zur Meisterung der nuklearen Apokalypse dürfte jedem normalen Menschen etwas mulmig werden.
Hofberichterstatter Ruprecht Polenz lässt sich beim Propaganda-Multiplikator ZEIT ONLINE am 30. April 2022 dennoch zu der wagemutigen Formulierung verleiten, »wer einen Atomkrieg verhindern will, darf Putin nicht gewinnen lassen«. Solch ein Statement ist nicht nur falsch und realitätsfremd, sondern zeugt gleichsam von der bewussten Negierung von Faktenlage und historischen Hintergründen zur Ukraine-Krise. Dabei könnte man es durchaus besser wissen.
Die RAND-Corporation, ein im Jahre 1948 gegründeter, einflussreicher Think Tank der US-Hegemonie, veröffentlichte zum Beispiel schon im Jahr 2019 ein vielsagendes, 354 Seiten umfassendes Strategiepapier unter der Überschrift »Overextending and Unbalancing Russia«. Frei übersetzt: Eine Strategie, um Russland überzustrapazieren und aus dem Gleichgewicht zu bringen – ökonomisch, militärisch und gesellschaftlich – mit dem singulären Ziel, die geopolitische Dominanz der Vereinigten Staaten zu bewahren. Ein durchdachtes Drehbuch zur finalen Erniedrigung und Bezwingung des ewigen Klassenfeindes sowie dem Erhalt der unipolaren Weltordnung, der Pax Americana.
Der Ansatz der RAND-Corporation: Die Osterweiterung der NATO forcieren, das Ansehen Russlands in der Welt zerstören, kostenintensives, nukleares Wettrüsten, die Ukraine bewaffnen, um einen militärischen Stellvertreterkonflikt mit Putin zu provozieren, um die ehemalige Sowjetunion anschließend mittels internationaler Sanktionen – legitimiert durch den brodelnden Krieg – finanziell in die Knie zu zwingen.
Verblüffend, wie sehr doch die im RAND-Strategiepapier aufgezeigte Vorgehensweise den aktuellen Geschehnissen an den Außengrenzen des Riesenreiches gleicht. Fast macht es den Anschein, als folgten die Geostrategen in Washington den Empfehlungen ihrer kostspieligen Think Tanks. Dies ließ sich auch im Zuge der Corona-Krise beobachten, die im Ablauf fraglos dem von der Rockefeller-Stiftung erarbeiteten Pandemie-Szenario »Lock Step« glich, wie Journalist Norbert Häring bereits am 28. Mai 2020 ausführlich berichtet.
Was das totalitäre Krisen-Drehbuch der RAND-Corporation nicht detailliert behandelt, sind die akuten Risiken einer potenziellen nuklearen Eskalation. Denn es endet mit dem möglichen Aufkeimen eines militärischen Konflikts und schließt schlicht mit dem Hinweis:
»Auch wenn die US-Armee nicht direkt an der Operation beteiligt ist, wird sie eine Schlüsselrolle bei der Abmilderung der Folgen spielen. Wie bereits erwähnt, bergen alle Maßnahmen, die der Schwächung Russlands dienen, einiges an Risiko. Infolgedessen werden das Abschreckungspotential sowie die operativen Fähigkeiten des US-Militärs in Europa gestärkt werden müssen. Es besteht die Möglichkeit, dass die Spannungen mit Russland zu einem Konflikt eskalieren.«
Die USA betrachten den Einsatz von Atomwaffen dabei offensichtlich als probates Mittel. Warum sonst modernisieren die Amerikaner seit Jahren ihr Arsenal und geben Milliarden US-Dollar dafür aus? Das macht eigentlich nur Sinn, wenn man plant, diese Waffen irgendwann einzusetzen. Der »Plot« für die Events nach dem Aufflammen einer militärischen Auseinandersetzung mit Russland ist vermutlich Verschlusssache und liegt nur Eingeweihten im Weißen Haus, Pentagon, CIA-Hauptquartier sowie den Verbündeten in EU und NATO-Hauptquartier vor.
Das ist bedauerlich. Denn ein Einblick in die aktuellen militärischen Planspiele und strategischen Szenarien der NATO-Hegemonie wäre hilfreich, um zu verstehen, ob die Arroganz des Westens tatsächlich einen Punkt erreicht hat, an dem man einen Atomkrieg in Kauf nehmen würde, um Russland und China auf ihre Plätze zu verweisen und im globalen Club der Technokraten am Kopfende zu sitzen. Um einen Konflikt der Systeme – Kapitalismus, Sozialismus, Kommunismus – handelt es sich nämlich nicht, auch wenn Medien dies gerne so darstellen, sondern um Machtkämpfe innerhalb der internationalen Oligarchie. Die drei Machtblöcke kämpfen um Vorherrschaft in der totalitären Weltordnung der nahen Zukunft.
Die Frage ist nur: Tun sie dies einvernehmlich – oder handelt es sich an Russlands Grenzen um ernsthafte, kriegerische Auseinandersetzungen, die in letzter Konsequenz militärisch entschieden werden müssen? Das RAND-Strategiepapier scheint davon auszugehen, dass Wirtschafts- und Informationskrieg, begleitet von NATO-Drohgebärden, ausreichen, um das Rennen zu Gunsten des Wertewestens zu entscheiden. Es gilt zu hoffen, dass diese Interpretation des Schriftstücks zutrifft. Ansonsten läuft die moderne Zivilisation Gefahr, sich in die Steinzeit zurückzubomben. Wie das aussieht, zeigt eindrücklich der Film »The Day After« (Der Tag danach) aus dem Jahre 1983.
Der zwei Stunden lange Streifen von Regisseur Nicholas Meyer ist bildgewaltig, beängstigend, ernüchternd und deprimierend. Er zeigt nicht nur, wie binnen weniger Tage aus einem Kalten Krieg ein Atomkrieg wird, sondern auch, was dessen schreckliche Folgen sind. Schon ein kurzer, etwas mehr als acht Minuten langer Zusammenschnitt macht klar, dass man ein absoluter Narr sein muss, um keine Angst vor thermonuklearen Angriffen zu haben.
Im Film gibt der US-Oberbefehlshaber nach der Zerstörung des NATO-Hauptquartiers den Befehl zum Atomschlag. Das entsprechende NATO-Protokoll wird aktiviert und die Raketensilos einsatzbereit gemacht. Das Drehbuch lässt offen, wer den Erstschlag führt. Klar ist, dass sobald die Sprengköpfe des Westens unterwegs sind, Russland einen Gegenangriff mit 300 Interkontinentalraketen auslöst und die Vereinigten Staaten in die Steinzeit bombt.
Überall im Land der unbegrenzten Möglichkeiten steigen feurige Atompilze in den Himmel. Metropolen werden in Sekunden ausradiert, Lebewesen, Pflanzen und Gebäude verdampfen in Feuersbrünsten um den Einschlagsort, ganze Landstriche werden vom Erdboden getilgt – und schon in den ersten Minuten nach Explosion der Nuklearsprengköpfe sterben weite Teile der Bevölkerung. 90 Millionen innerhalb weniger Stunden, wie eine Simulation mit dem etwas unheimlichen Titel »Plan A« der Princeton-Universität von 2019 berechnet hat.
Der eigentliche Horror beginnt allerdings erst. Denn die schlimmsten Szenen des Films sind jene, die den Zustand der Welt zwei Wochen nach den Atomschlägen zeigen. Im Land herrscht Anomie. Chaos und Zerstörung, wohin man schaut. Vorindustrielle Zustände. Die Städte sind unbewohnbar und die Überlebenden leiden an Strahlenkrankheit. Haare und Zähne fallen aus. Bei manchen binnen weniger Stunden oder Tage, bei anderen dauert es Wochen. Ein grausamer Tod auf Raten. Alles stirbt, siecht dahin. In den Ruinen entstehen Flüchtlingslager. Seuchen brechen aus. Militärkommandos erschießen willkürlich Menschen. Recht, Gerichte und Prozesse gibt es nicht mehr. Und um zu überleben, bewaffnen sich schlussendlich auch die Zivilisten und töten sich gegenseitig. Absolute Barbarei.
»The Day After« erklärt nicht, wer diesen Krieg gewinnt, nennt keinen Sieger. Vermutlich, weil Regisseur Nicholas Meyer schmerzlich bewusst war, dass es bei einem ausgewachsenen Atomkrieg keine Gewinner geben kann.
Er bedeutet das Ende der modernen Zivilisation. Nicht umsonst hat Albert Einstein früh vor militärischem Missbrauch entsprechender wissenschaftlicher Erkenntnisse gewarnt. So lässt der Streifen aus Zeiten das kalten Krieges auch das Ende offen. Kein Hollywood-Finale. Kein Happy End. Die beklemmenden Gefühle bleiben. Weder Will Smith noch James Bond tauchen auf, um die Welt in letzter Minute doch noch zu retten. Sie ist kaputt. Tot. Eine nuklear verseuchte Wüste. Kein Hoffnungsschimmer am Horizont.
Wer das Pech hatte, die Erstschläge zu überleben, stirbt langsam, aber sicher – und vor allem qualvoll.
Vielleicht sollten Spitzenpolitiker, Dogmatiker, Propagandisten und Kriegshetzer von heute sich diesen Film einmal in Ruhe anschauen, bevor sie leichtfertig derartige Optionen in Betracht ziehen. Ich habe »The Day After« nur ein einziges Mal in meinem Leben gesehen – wenige Monate, nachdem ich den Begriff »Pershing II« das erste Mal als kleines Kind im Radio hörte und meine Eltern neugierig fragte, was es damit auf sich hat – das war ausreichend. Die Eindrücke wirken bis heute. Ich bin mir auch mehr als dreißig Jahre später immer noch der unverrückbaren, indiskutablen Tatsache bewusst, dass es niemals zu einem Atomkrieg kommen darf. Jeder, der diesen Film gesehen, wird das unterschreiben.
Ich jedenfalls werde nie vergessen, wie ich eines nachts heimlich im dunklen Wohnzimmer der heimischen Dachwohnung ganz nahe vor dem Fernseher saß. Eigentlich durfte ich nur ein paar Mal in der Woche ausgewählte Kindersendungen anschauen. Aber meine Eltern schliefen bereits. Es muss circa 23:00 Uhr gewesen sein, denn nach den Spätfilmen war damals in der Regel Sendeschluss. Und das was war meist gegen eins oder halb zwei.
Just als ich den kleinen Röhrenfernseher anschaltete, begann »im Ersten« der bis heute in mir nachhallende Spielfilm. Der Tag danach. Zunächst begeistert von den vielen Raketen und irgendwie noch fasziniert von den mir bis dato unbekannten, riesigen Explosionen, die Atombomben auslösen, blieb ich gebannt sitzen. Wie versteinert. Bis zur Schlussszene, in der sich eine Handvoll strahlenverseuchter, zerrissener, verrottender Menschen, die kaum noch Haare auf dem Kopf haben und aussehen wie Zombies, in den staubigen Ruinen einer leeren Großstadt kraftlos in den Armen liegen und hilflos schluchzen. Die Kamera zieht auf. Dann Schwarzblende – und eine letzte, dünne, einsam flehende Stimme im Äther:
»Hello, is anybody there? Anybody at all?« (Hallo, ist da jemand? Irgendjemand?)
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Jofer
Jofer era um jogador diferente. À primeira vista não, parecia igual, um volante combativo, perseguia os atacantes adversários implacavelmente, um bom jogador. Mas não era essa a característica que diferenciava Jofer. Jofer era, digamos, um chutador.
Começou numa semifinal de um torneio de juniores. O time de Jofer precisava do empate e estava sofrendo uma baita pressão do adversário, mas o jogo estava 1 a 1 e parecia que ia ficar assim mesmo, daquele jeito futebolístico que parece, parece mesmo. Só que aos 46 do segundo tempo tomaram um gol espírita, Ruizinho do outro time saiu correndo pela esquerda e, mesmo sendo canhoto, foi cortando para o meio, os zagueiros meio que achando que já tinha acabado mesmo, devia ter só mais aquele lance, o árbitro tinha dado dois minutos, Ruizinho chutou, marcou e o goleiro, que só pulou depois que já tinha visto que não ia ter jeito, ficou xingando.
A bola saiu do meio e tocaram para Jofer, ninguém nem veio marcá-lo, o outro time já estava comemorando, e com razão, o juiz estava de sacanagem em fazer o jogo continuar, já estava tudo acabado mesmo. Mas não, estava certo, mais um minuto de acréscimo, justo. Em um minuto dá pra fazer um gol. Mas como? Jofer pensou nas partidas da NBA em que com alguns centésimos de segundo faltando o armador jogava de qualquer jeito para a cesta e às vezes acertava. De trás do meio de campo, será? Não vou ter nem força pra fazer chegar no gol. Vou virar piada, melhor tocar pro Fumaça ali do lado e a gente perde sem essa humilhação no final. Mas, poxa, e daí? Vou tentar mesmo assim, qualquer coisa eu falo que foi um lançamento e daqui a uns dias todo mundo esquece. Olhou para o próprio pé, virou ele de ladinho, pra fora e depois pra dentro (bom, se eu pegar daqui, direitinho, quem sabe?), jogou a bola pro lado e bateu. A bola subiu escandalosamente, muito alta mesmo, deve ter subido uns 200 metros. Jofer não tinha como ter a menor noção. Depois foi descendo, o goleirão voltando correndo para debaixo da trave e olhando pra bola, foi chegando e pulando já só pra acompanhar, para ver, dependurado no travessão, a bola sair ainda bem alta, ela bateu na rede lateral interna antes de bater no chão, quicar violentamente e estufar a rede no alto do lado direito de quem olhava.
Mas isso tudo foi sonho do Jofer. Sonhou acordado, numa noite em que demorou pra dormir, deitado na sua cama. Ficou pensando se não seria fácil, se ele treinasse bastante, acertar o gol bem de longe, tipo no sonho, e se não dava pra fazer gol assim. No dia seguinte perguntou a Brunildinho, o treinador de goleiros. Era difícil defender essas bolas, ainda mais se elas subissem muito, o goleiro ficava sem perspectiva, o vento alterava a trajetória a cada instante, tinha efeito, ela cairia rápido, mas claro que não valia à pena treinar isso, a chance de acertar o gol era minúscula. Mas Jofer só ia tentar depois que treinasse bastante e comprovasse o que na sua imaginação parecia uma excelente idéia.
Começou a treinar todos os dias. Primeiro escondido, por vergonha dos colegas, chegava um pouco antes e ficava lá, chutando do círculo central. Ao menor sinal de gente se aproximando, parava e ia catar as bolas. Depois, quando começou a acertar, perdeu a vergonha. O pessoal do clube todo achava engraçado quando via Jofer treinando e depois ouvia a explicação da boca de alguém, ninguém levava muito a sério, mas também não achava de todo ridículo. O pessoal ria, mas no fundo torcia praquilo dar certo, mesmo.
Aconteceu que num jogo que não valia muita coisa, empatezinho feio, aos 40 do segundo tempo, a marcação dos adversários já não estava mais pressionando, todo mundo contente com o empate e com vontade de parar de jogar já, o Henrique, meia-esquerdo, humilde, mas ainda assim um pouco intimidante para Jofer (jogava demais), tocou pra ele. Vai lá, tenta sua loucura aí. Assumiu a responsabilidade do nosso volante introspectivo. Seria mais verossímil se Jofer tivesse errado, primeira vez que tentou, restava muito tempo ainda pra ele ter a chance de ser herói, ninguém acerta de primeira, mas ele acertou. Quase como no sonho, Lucas, o goleiro, não esperava, depois que viu o lance, riu-se, adiantou-se para pegar a bola que ele julgava que quicaria na área, mas ela foi mais pra frente, mais e mais, daí Lucas já estava correndo, só que começou a pensar que ela ia pra fora, e ele ia só se dependurar no travessão e fazer seu papel de estar na bola. Acabou que por conta daquele gol eles terminaram em segundo no grupo daquele torneiozinho, ao invés de terceiro, e não fez diferença nenhuma.
-
 @ 06bc9ab7:427c48f5
2025-03-17 15:46:23
@ 06bc9ab7:427c48f5
2025-03-17 15:46:23Bitcoin Safe - A bitcoin savings wallet for the entire family
Designed for both beginners and power users, Bitcoin Safe combines security with an intuitive user experience. In this article, we dive deep into its features, unique benefits, and the powerful tools that make managing your Bitcoin wallet simple and secure.
Built for Learners
✔️ Step-by-step wallet setup wizard + PDF backup sheets 📄 🧪 Test transactions to ensure all hardware signers are ready 🔑 🛡️ Secure: Hardware signers only – no hot wallet risks 🚫🔥 🌍 Multi-language support: 🇺🇸 🇨🇳 🇪🇸 🇯🇵 🇷🇺 🇵🇹 🇮🇳 🇮🇹 🇫🇷 🇩🇪 🇲🇲 🇰🇷 📁 Address categories for easy organization ☁️ Label and category synchronization, and cloud backup (optional) 💰 Automatic UTXO merging to save on fees ⚡ Fast syncing with Electrum servers, Compact Block Filters coming soon
Built for Power Users
🔐 Supports Coldcard, Bitbox02, Jade, Trezor, Passport, Keystone & many more 🏦 💬 Multi-party multisig chat & PSBT sharing (optional) 📊 Transaction flow diagrams to trace coin movements 🔍 Instant cross-wallet wallet search ⚙️ Set your own electrum server, mempool instance, and nostr relay
Step-by-Step Wallet Setup
Whether you’re setting up a single-signature or multi-signature wallet, the setup wizard guides you every step of the way:

- Single Sig Wizard: Follow the intuitive wizard that walks you through each step. https://youtu.be/m0g6ytYTy0w
Clear instructions paired with hardware signer screen-shots, like the steps for a Coldcard
-
Multisig Wizard: The wizard ensures you do all necessary steps for a Multisig wallet in the right order. Afterwards your Multisig is ready to use and all signers are tested. Check out https://bitcoin-safe.org/en/features/setup-multisignature-wallet/
-
PDF Backup: The wizard will also generates 3 PDF backup sheets for a 2-of-3 multisig wallet, so ensure you always have your wallet descriptor together with the seed.
-
Hardware Signer Support: With full support for major hardware signers your keys remain securely offline.
Transaction Visualization
Visualize and navigate your transaction history:
-
Graphical Explorer: An interactive transaction diagram lets you click on inputs and outputs to follow the money flow intuitively.
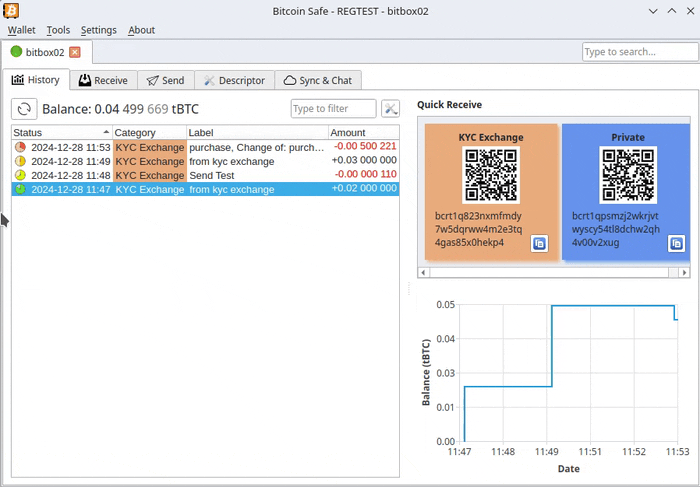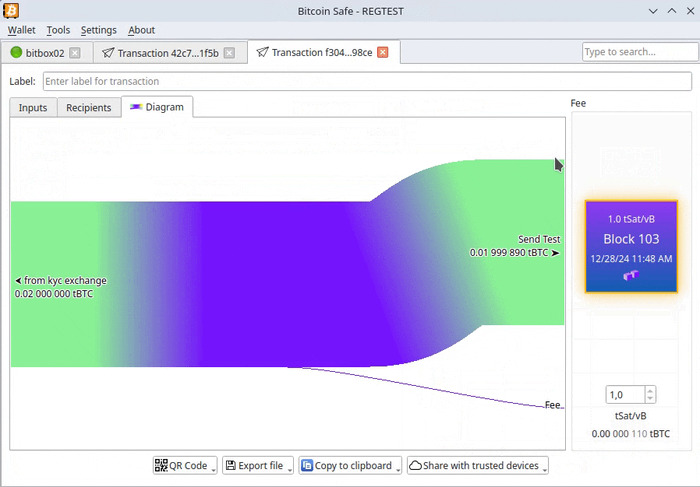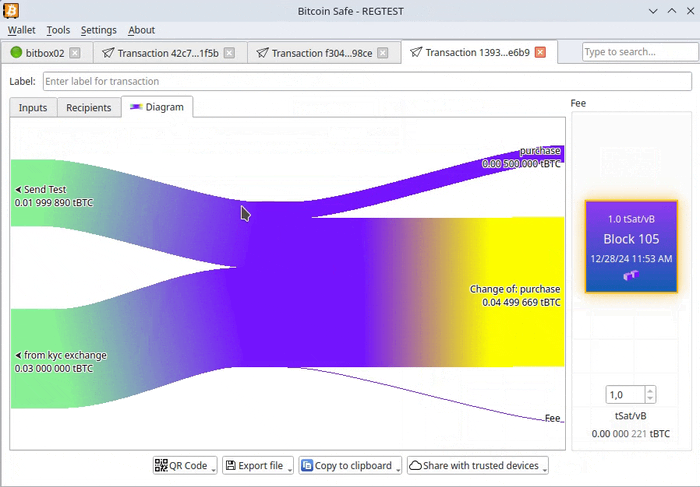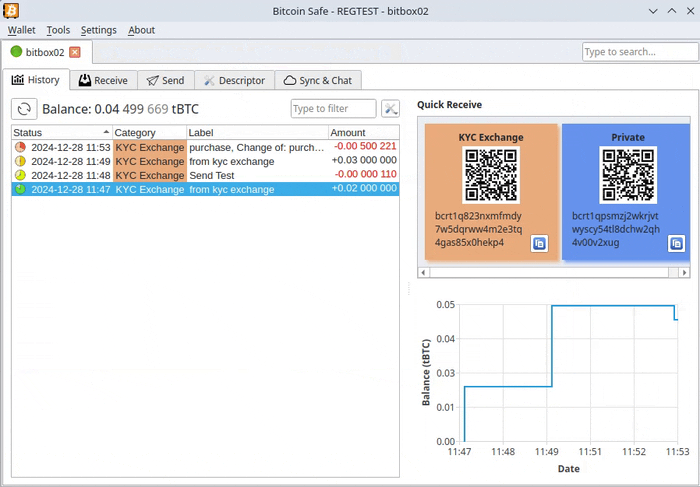
-
Coin Categories: Organize your addresses into distinct coin categories (e.g., “KYC”, “Work”, “Friends”) so Bitcoin Safe automatically selects the correct inputs when creating PSBTs.

It prevents you accidentally linking coin categories when creating a transaction, and warns you if mistakes happened in the past.
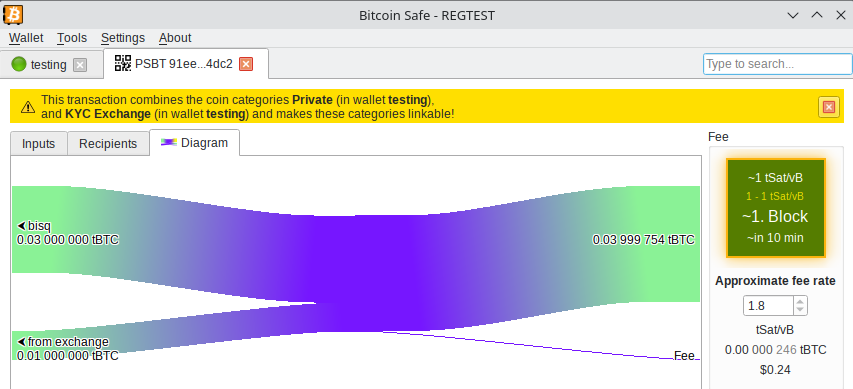
Powerful Wallet Management Tools
- Flexible Fee Selection: Choose fees with one click using an intuitive mempool block preview.
- UTXO Management: Automatically (optional) merge UTXOs when fees are low.
- CSV Table Export: Right click, Drag&Drop, or CTRL+C for immediate CSV export for easy processing in Excel.
- PDF Balance Statement: Export the address balances for easy record keeping on paper.
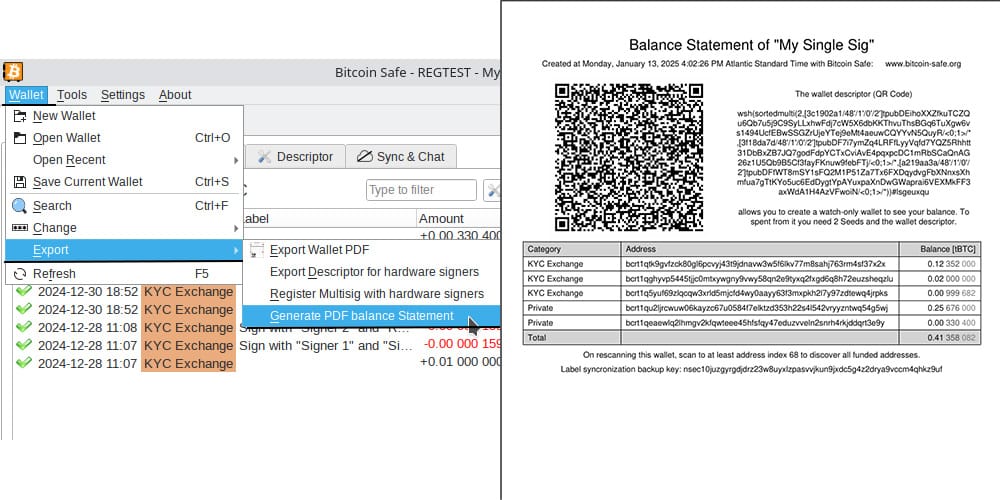
Advanced Features for the Power-User
Sync & Chat is off by default (for the paranoid user), but can be enabled with just one click.
Label Synchronization and Backup
- Seamless Sync: Using encrypted nostr messages, Bitcoin Safe synchronizes your coin categories and labels across multiple devices.
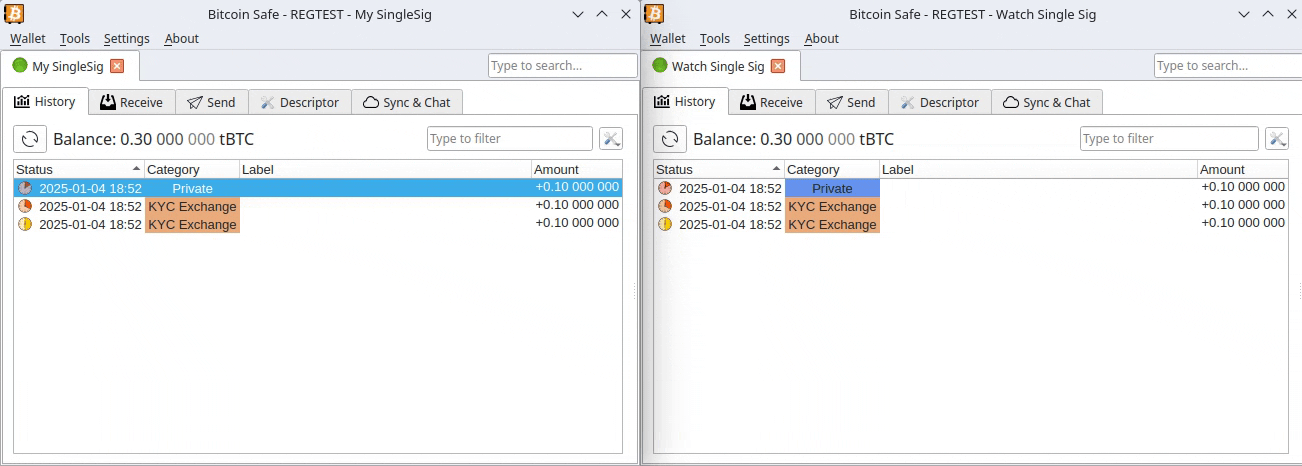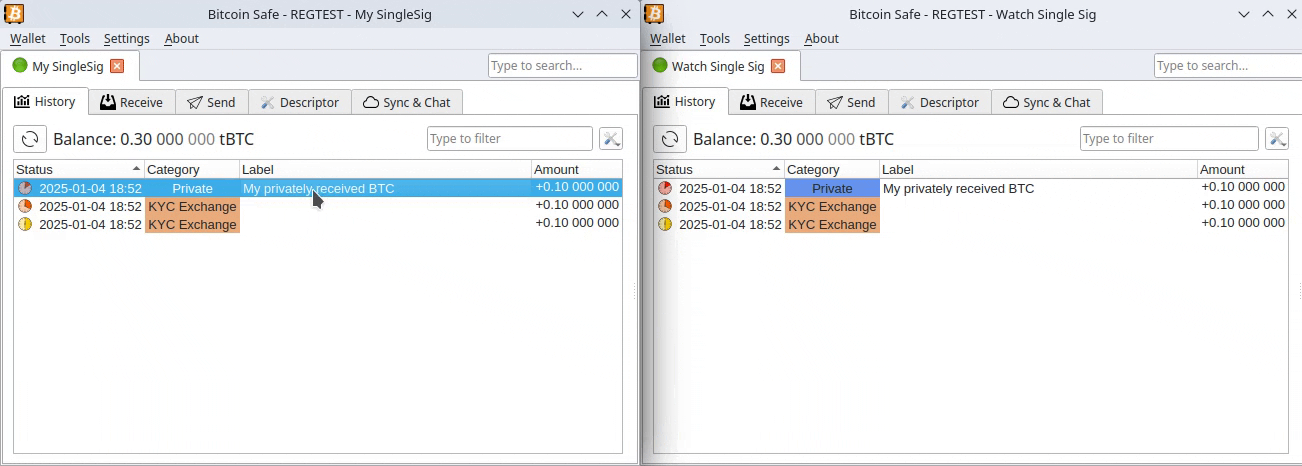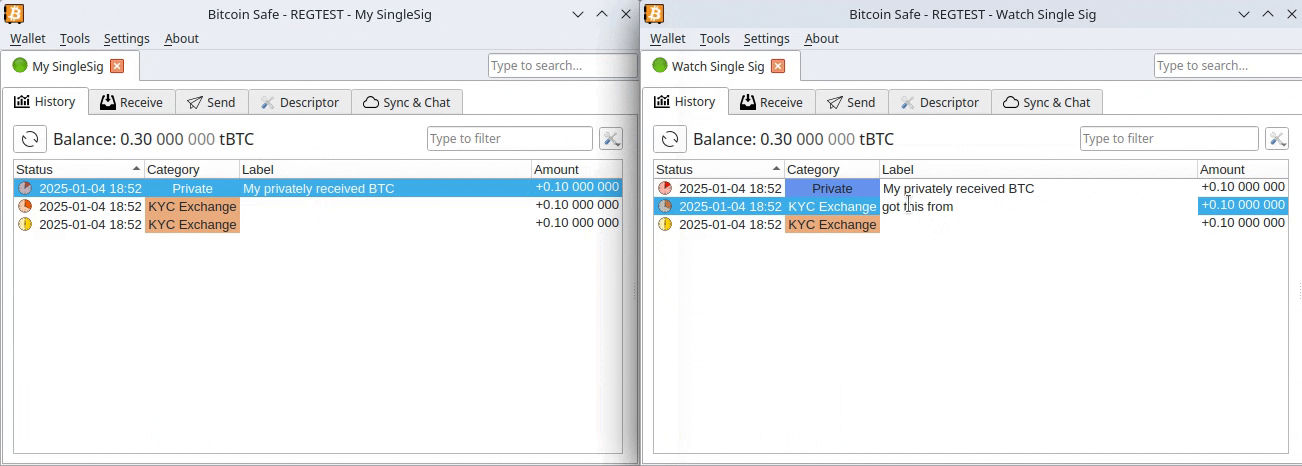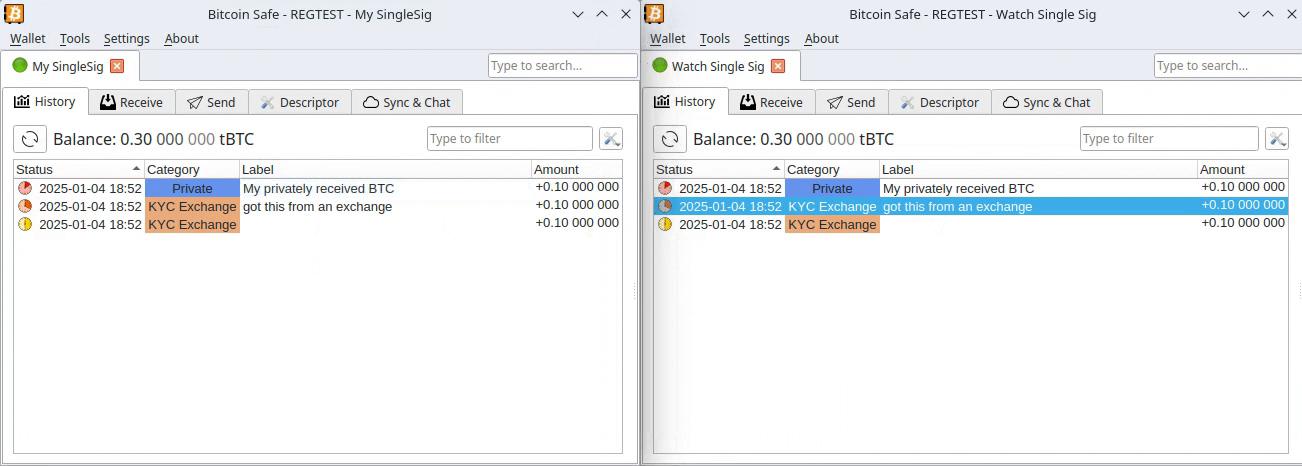
- Easy Backup: A short backup key is all you need to safeguard your coin categories and labels, ensuring your organization remains intact.
Collaborative Multi-party Multisig
- Group Chat Integration: After creating your multisig wallet, Bitcoin Safe offers an encrypted nostr group chat for secure collaboration and one-click PSBT sharing.
- User Authentication: Each participant must authenticate every other user with a simple click, ensuring secure communication.
Watch and Learn: Get Started with Bitcoin Safe
If you’re new to Bitcoin Safe, a short video guide can make all the difference. Learn how to set up your Bitcoin Safe wallet in this detailed walk through:
https://youtu.be/m0g6ytYTy0w
Or see how to verify an address on your hardware singer:
https://youtu.be/h5FkOYj9OT8
Building up a knowledge base: https://bitcoin-safe.org/en/knowledge/
Whats next?
- Compact Block Filters!!! They make electrum servers obsolete.
- Why? Compact Block Filters increase the network privacy dramatically, since you're not asking an electrum server to give you your transactions
- Trade-off: They are a little slower than electrum servers. For a savings wallet like Bitcoin Safe this should be OK.
- How do they work? Simply speaking: They ask normal bitcoin core nodes for a short summary of each block. And if the summary shows a transaction belonging to the wallet, the entire block is then downloaded from the bitcoin core node. The bitcoin core node does not learn however which of the many transactions in the block you were interested in. Read more here and of course in the bip.
- When: 2 weeks 😅. Lots of things need to be done until Bitcoin Safe can use the bdk CBF/kyoto client from rustaceanrob, so keep an eye out for updates and please give feedback when you use Bitcoin Safe.
Stay updated on nostr or on GitHub.
Thank you
A huge thanks goes to nostr:npub10pensatlcfwktnvjjw2dtem38n6rvw8g6fv73h84cuacxn4c28eqyfn34f for supporting this project with a grant and nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx for the Hackathon prize.
This wallet is only possible because it is building upon other peoples open source work. Most notably
- bdk nostr:nprofile1qqsgkmgkmv63djkxmwvdlyaxx0xtsytvkyyg5fwzmp48pwd30f3jtxspzemhxue69uhhyetvv9ujuurjd9kkzmpwdejhgqg5waehxw309aex2mrp0yhxgctdw4eju6t0qyt8wumn8ghj7un9d3shjtnwdaehgu3wvfskueqr8vuet
- and especially nostr:npub1thunderat5g552cuy7umk624ct5xe4tpgwr2jcjjq2gc0567wgrqnya79l , nostr:npub1reezn2ctrrg736uqj7mva9lsuwv0kr5asj4vvkwxnrwlhvxf98tsq99ty4 , and nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm for dealing with my many feature requests and questions.
- rustaceanrob building kyoto which implements CBF for BDK; a crucial library and will be able to replace electrum servers for many use cases
- ndk by nostr:nprofile1qqsx3kq3vkgczq9hmfplc28h687py42yvms3zkyxh8nmkvn0vhkyyuspz4mhxue69uhkummnw3ezummcw3ezuer9wchsz9thwden5te0wfjkccte9ejxzmt4wvhxjme0qy88wumn8ghj7mn0wvhxcmmv9u0uehfp
And of course, secure storage of bitcoin is only possible, because of the hardware signer manufacturers. Thanks to nostr:npub1az9xj85cmxv8e9j9y80lvqp97crsqdu2fpu3srwthd99qfu9qsgstam8y8 Coldcard , Coldcard Q , nostr:npub1tg779rlap8t4qm8lpgn89k7mr7pkxpaulupp0nq5faywr8h28llsj3cxmt Bitbox02 , nostr:npub1jg552aulj07skd6e7y2hu0vl5g8nl5jvfw8jhn6jpjk0vjd0waksvl6n8n Blockstream Jade , Trezor Safe, Foundation Passport, Keystone, Ledger, Specter Shield, and many more.
I also want to thank people who gave feedback and helped spread the knowledge of Bitcoin Safe (please forgive me if I forgot to mention you)
- nostr:npub1p5cmlt32vc3jefkl3ymdvm9zk892fsmkq79eq77uvkaqrnyktasqkpkgaw nostr:npub1s07s0h5mwcenfnyagme8shp9trnv964lulgvdmppgenuhtk9p4rsueuk63 nostr:npub18f3g76xc7xs430euwwl9gpn7ue7ux8vmtm9q8htn9s26d8c4neeqdraz3s nostr:npub1mtd7s63xd85ykv09p7y8wvg754jpsfpplxknh5xr0pu938zf86fqygqxas nostr:npub1kysd8m44dhv7ywa75u5z7w2w0gs4t6qzhgvjp555gfknasy3krlqfxde60 nostr:npub185pu2dsgg9d36uvvw7rwuy9aknn8hnknygr7x2yqa60ygvq6r8kqc836k8 nostr:npub1hkcgyqnsuaradq3g5hyvfdekwypc25494nmwggwpygxas7fcs4fst860fu nostr:npub1xsl0msy347vmj8gcpsjum6wwppc4ercvq4xfrhqmek2dqmqm0mtsyf35vx nostr:npub1hxjnw53mhghumt590kgd3fmqme8jzwwflyxesmm50nnapmqdzu7swqagw3 nostr:npub1ke470rdgnxg4gjs9cw3tv0dp690wl68f5xak5smflpsksedadd7qtf8jfm nostr:npub1sk26fxl4fy3vt8m5n0a6aturaql0w20nvh22q0cyaqm28tj7z8ss3lutc9 nostr:npub1r4llq2jcvq4g2tgha5amjz07zk7mrrcj89wllny9xwhhp5zzkklqk4jwja nostr:npub1p9v2zpwl28c0gu0vr2enp3lwdtv29scwpeqsnt0ngqf03vtlyxfqhkae5w nostr:npub1xkym0yaewlz0qfghtt7hjtnu28fxaa5rk3wtcek9d3x3ft2ns3lq775few nostr:npub1r8343wqpra05l3jnc4jud4xz7vlnyeslf7gfsty7ahpf92rhfmpsmqwym8 nostr:npub12zpfs3yq7we83yvypgsrw5f88y2fv780c2kfs89ge5qk6q3sfm7spks880 nostr:npub1yrnuj56rnen08zp2h9h7p74ghgjx6ma39spmpj6w9hzxywutevsst7k5cx https://x.com/91xTx93x2 https://x.com/afilini rustaceanrob
-
 @ 1731c73c:1bca4ecc
2025-03-17 14:13:04
@ 1731c73c:1bca4ecc
2025-03-17 14:13:04Welch Geistes Kind sind Waffenproduzenten, welch Geistes Kind Wissenschaftler, die Viren so verändern, dass sie pathogener, also gefährlicher für den Menschen werden? Im pfälzischen
https://soundcloud.com/radiomuenchen/kommt-wuhan-nach-deutschland-von-prof-roland-wiesendanger
Weilerbach wird ein US-Biolabor der Schutzstufe 3 gebaut. Dort sollen hochinfektiöse Erreger oder Substanzen, unter anderem SARS-CoV-2, das Virus H5N1, Dengue- und das Hanta-Virus untersucht werden. Der Bundesregierung – so fand Florian Warweg von den NachDenkSeiten heraus - weiß davon angeblich nichts. Auch nicht, welche Kontrollfunktion Bundesbehörden für US-Biolabore auf deutschem Boden haben.
War da was? Hatte nicht – ebenso vertuscht von Regierung, Medien und Wissenschaftlern – für die einen die größte Pandemie, für die anderen der weltweit größte Wissenschafts- und Medizinskandal in den letzten fünf Jahren stattgefunden? Warum interessiert das keinen?
Die Bestätigung der US-Regierung ist offiziell, dass die Covid-19-Pandemie aus einem Labor in Wuhan stammt. Das entlarvt die jahrelange Vertuschung und Diffamierung kritischer Stimmen als politisch motivierte Manipulation. Einer, der diskreditiert wurde, ist Professor Roland Wiesendanger. Mundtot ließ er sich aber nicht machen. Er fordert weiterhin eine schonungslose Aufarbeitung der hochgefährlichen Gain-of-function-Forschung, außerdem deren weltweite Ächtung, um zukünftige Pandemien zu verhindern.
Roland Wiesendanger ist Physik-Professor an der Universität Hamburg, Ehrendoktor der Technischen Universität Posen und Mitglied zahlreicher nationaler und internationaler Wissenschaftsakademien. Hören Sie sein Statement: „Wir dürfen die Risiken der Gain- of-function-Forschung nicht länger hinnehmen“.
Sprecher: Ulrich Allroggen
Radio München\ www.radiomuenchen.net/\ @radiomuenchen\ www.facebook.com/radiomuenchen\ www.instagram.com/radio_muenchen/\ twitter.com/RadioMuenchen
Radio München ist eine gemeinnützige Unternehmung.\ Wir freuen uns, wenn Sie unsere Arbeit unterstützen.
GLS-Bank\ IBAN: DE65 4306 0967 8217 9867 00\ BIC: GENODEM1GLS\ Bitcoin (BTC): 3G1wDDH2CDPJ9DHan5TTpsfpSXWhNMCZmQ\ Ethereum (ETH): 0xB41106C0fa3974353Ef86F62B62228A0f4ad7fe9
-
 @ 7d33ba57:1b82db35
2025-03-30 19:16:14
@ 7d33ba57:1b82db35
2025-03-30 19:16:14Fažana is a picturesque fishing village on Croatia’s Istrian coast, just 8 km from Pula. Known for its colorful waterfront, fresh seafood, and as the gateway to Brijuni National Park, Fažana is a peaceful alternative to larger tourist hotspots.
🌊 Top Things to See & Do in Fažana
1️⃣ Stroll the Fažana Waterfront & Old Town 🎨
- The charming harbor is lined with colorful houses, cafés, and fishing boats.
- Visit St. Cosmas and Damian Church, a small yet beautiful historical site.
- Enjoy a relaxed Mediterranean atmosphere with fewer crowds than Pula.
2️⃣ Take a Boat Trip to Brijuni National Park 🏝️
- Brijuni Islands, just 15 minutes away by boat, offer stunning nature, Roman ruins, and a safari park.
- Explore the remains of a Roman villa, Tito’s summer residence, and dinosaur footprints!
- Rent a bike or golf cart to explore the islands at your own pace.
3️⃣ Enjoy the Beaches 🏖️
- Badel Beach – A Blue Flag beach, great for families with crystal-clear, shallow waters.
- Pineta Beach – A peaceful, pine-shaded spot with a mix of sand and pebbles.
- San Lorenzo Beach – A scenic spot perfect for sunset views over Brijuni.
4️⃣ Try the Local Seafood 🍽️
- Fažana is known as the "Sardine Capital of Istria" – try grilled sardines with local wine.
- Visit Konoba Feral or Stara Konoba for authentic Istrian seafood.
- Pair your meal with Istrian Malvazija wine.
5️⃣ Visit the Sardine Park 🐟
- A unique outdoor exhibition dedicated to Fažana’s fishing traditions.
- Learn about the history of sardine fishing and processing in Istria.
6️⃣ Take a Day Trip to Pula 🏛️
- Just 15 minutes away, Pula offers Roman ruins, historic sites, and vibrant nightlife.
- Don’t miss the Pula Arena, Temple of Augustus, and the lively Old Town.
🚗 How to Get to Fažana
✈️ By Air: Pula Airport (PUY) is just 15 minutes away.
🚘 By Car:
- From Pula: ~15 min (8 km)
- From Rovinj: ~35 min (30 km)
- From Zagreb: ~3.5 hours (270 km)
🚌 By Bus: Regular buses run between Pula and Fažana.
🚢 By Boat: Ferries to Brijuni National Park depart from Fažana’s harbor.
💡 Tips for Visiting Fažana
✅ Best time to visit? May–September for beach weather & Brijuni trips ☀️
✅ Try local olive oil – Istria produces some of the best olive oils in the world 🫒
✅ Visit early for boat tickets to Brijuni – They can sell out quickly in summer ⏳
✅ Perfect for a relaxing stay – Less crowded than Pula but close to major attractions 🌊 -
 @ 0f9da413:01bd07d7
2025-03-30 15:37:53
@ 0f9da413:01bd07d7
2025-03-30 15:37:53ช่วงสัปดาห์ก่อน 21-30 มีนาคม 2568 ที่ผ่านมาส่วนตัวได้มีภาระกิจเดินทางไปปฏิบัติงานของสถานที่ทำงานและรวดไปเที่ยวส่วนตัว ในการเดินทางในครั้งนี้ภาระกิจหลักส่วนตัวอาจจะไปทำงานแต่หากมีการเดินทางแล้วผมมักจะชอบเดินทางไปพบปะชาว bitcoiner ชาวไทย หรือชาว #siamstr ตามสถานที่ต่างๆ อยู่เสมอตลอดช่วงระยะเวลาดังกล่าวส่วนตัวก็ได้เดินทางไปยังพื้นที่ดังนี้
- ชลบุรี (พัทยา)
- เกาะช้าง (ตราด)
- หาดใหญ่ (สงขลา)
- เชียงใหม่
ซึ่งได้ตรวจเช็คแล้วในพื้นที่ดังกล่าวมีร้านรับ bitcoin อยู่และมีประสบการณ์ในแต่ละที่ที่แตกต่างกันออกไปซึ่งผมเองจะขอรัวิวการเดินทางดังกล่าวนี้ โดยอ้างอิงจากการตามรอยร้านที่รับชำระด้วย BTC ผ่าน BTC Map และจะมีบางร้านที่ไม่ได้อยู่ใน BTC Map ก็ขอรีวิวตามช่วงระยะเวลา Timeline ละกัน
Seeva Cafe Pattya
ร้านชีวาคาเฟ่ ร้านตกแต่งในสไตล์ศิลปะและกาแฟในร้านมีโซนจำหน่ายขนมเค้กและอื่นๆ อีกด้วย มีต้นไม้ร่มรื่นและบรรยากาศค่อนข้างดีพอสมควร ท่านไหนอยากเดินทางไปจิบกาแฟเบาๆ นั่งทำงานพักผ่อนแถวพัทยาใต้ก็สามารถเดินทางไปแวะชิมกันได้ (รับบิทคอยด้วยนะ) สถานที่นี้ไม่ได้เสีย sats เนื่องจากมีเจ้าภาพเลี้ยง ขอบคุณครับ
Google Map: https://maps.app.goo.gl/ZJNUGYiCgp1VTzGJ9
BTC-Map: None
Piya Silapakan Museum of Art Pattaya
สถานที่ถัดมาเป็นหอศิลป์ ปิยะศิลปาคารเป็นสถานที่ที่เก็บรวมรวมผลงานทางศิลปะต่างๆ ภาพวาดเสมือนจริงซึ่งแน่นอนว่าสามารถมาเรียน Workshop ทางด้านศิลปะได้แน่นอนว่าสามารถจ่ายด้วย Bitcoin Lightning ได้โดยผมเองก็ได้วาดศิลปะสีน้ำวาดบนกระเป๋าผ้า เอาจริงๆ ณ ตอนที่วาดนั้นแทบจะลืมเวลาและโพกัสกับสิ่งที่วาดอยู่ทำให้รู้สึกผ่อนคลายและวาดสิ่งต่างๆ เหมือนตอนสมัยเด็กๆ ซึ่งหากมีเวลาเพิ่มเติมผมเองก็อาจจะเจียดเวลาไปลองวาดศิลปะแลลอื่นๆ โดยที่ไม่ต้องให้ใครมาตัดสินใจ สวยไม่สวยอย่างไร ก็อยู่ที่เรา หลายครั้งเราชอบให้คนอื่นตัดสินใจเพื่อทำให้เรารู้สึกดี ลองมาที่นี้ดูสิแล้วคุณจะตัดสินใจด้วยตนเอง
อันนี้ผลงานส่วนตัวที่ได้ทำ แล้วแต่การจินตนาการของแต่ละท่านว่าสิ่งที่ผมวาดมันคืออะไรก็แล้วกัน
งานนี้หมดไปแล้ว 13,173 sats แวะมาเยี่ยมชมกันได้ที่พัทยา ชลบุรี :)
Google map: https://maps.app.goo.gl/mjMCdxEe36ra1jDF6
BTC-Map: None
Toffee Cake Pattaya
เป็นร้านสุดท้ายที่ได้ไปใช้งานชื้อขนมติดไม้ติดมือกลับไปยังที่พักก่อนส่วนตัวจะเดินทางต่อไป หมดไป 1,904 sats เหมาะสำหรับชื้อของฝากติดไม้ติดมือกลับบ้าน
Google map: https://maps.app.goo.gl/jqRyHTFzXVe6qYSv9
BTC-Map: https://btcmap.org/map?lat=12.9509827&long=100.8974009
หลังจากเดินทางพักที่พัทยาหนึ่งคืนก่อนเดินทางไปยังเกาะช้าง สรุปสถานที่พัทยานั้นหมดไปทั้งหมด 15,077 sats (คำนวนเงินอนาคตน่าจะ 15,077 usd กาวกันไว้ก่อน) สำหรับ Part 2 นั้นจะรีวิวร้านที่อยู่ในพื้นที่เกาะช้างซึ่งผมได้ตามรอยจาก BTC-Map จะเป็นอย่างไรเชิญติดตามครับ ขอบคุณครับ
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28O caso da Grêmio TV
enquanto vinha se conduzindo pela plataforma superior daquela arena que se pensava totalmente preenchida por adeptos da famosa equipe do Grêmio de Porto Alegre, viu-se, como por obra de algum nigromante - dos muitos que existem e estão a todo momento a fazer más obras e a colocar-se no caminhos dos que procuram, se não fazer o bem acima de todas as coisas, a pelo menos não fazer o mal no curso da realização dos seus interesses -, o discretíssimo jornalista a ser xingado e moído em palavras por uma horda de malandrinos a cinco ou seis passos dele surgida que cantavam e moviam seus braços em movimentos que não se pode classificar senão como bárbaros, e assim cantavam:
Grêmio TV pior que o SBT !
-
 @ b8af284d:f82c91dd
2025-03-16 16:42:49
@ b8af284d:f82c91dd
2025-03-16 16:42:49
Liebe Abonnenten,
diejenigen, die diese Publikation schon länger abonniert haben, wissen, dass hier immer wieder über den Ursprung des Corona-Virus in einem Labor in Wuhan berichtet wurde. Seit diese Woche ist es „offiziell“ - der Bundesnachrichtendienst (BND) hält den Labor-Ursprung für die wahrscheinlichste Variante. Jetzt kann man sich fragen, warum der BND plötzlich umschwenkt: Will man proaktiv erscheinen, weil man die Wahrheit nicht mehr länger verbergen kann? Oder will man die enttäuschten Bürger zurückgewinnen, die aufgrund der Lügen während der Corona-Zeit zunehmend mit Parteien links und rechts außen sympathisiert haben, weil diese die einzigen waren, die den Irrsinn nicht mitgetragen haben?
Auffallend bei den „Recherchen“, die in Wahrheit keine sind, sondern Verlautbarungen des deutschen Geheimdienstes, ist auch das völlige Schweigen über die US-amerikanischen Verwicklungen in das Projekt. In Wuhan wurde mit amerikanischem Geld geforscht. Warum der BND diese Tatsache verschweigt, ist Teil der Spekulation. Vermutlich will man Peking alles in die Schuhe schieben, um von den eigenen Versäumnissen abzulenken.
In meinem aktuellen Buch “Der chinesische (Alp-)Traum” ist den Ereignissen in Wuhan ein ganzes Kapitel gewidmet. Es hat nichts an Aktualität eingebüßt. Alle Fakten lagen seit Jahren auf dem Tisch für jeden, den es interessiert hat. Hier gibt es das gesamte Kapitel nachzulesen.

Auf jeden Fall zeigt dies, wie der Begriff „Verschwörungstheoretiker“ in den vergangenen Jahren zum Kampfbegriff und Waffe gemacht wurde, um Kritiker zu diffamieren, und die öffentliche Meinung ohne harte Zensur zu lenken. Ähnliches kann man aktuell beim Projekt „Digitaler Euro“ beobachten. Vermutlich kann sich kein Bürger der Europäischen Union daran erinnern, bei seiner Wahlentscheidung jemals gefragt worden zu sein, ob er die Einführung eines „digitalen Euros“ gut findet. Wurde er nämlich nicht. Er kommt aber trotzdem. EZB-Präsidentin Christine Lagarde hat das diese Woche nochmals bekräftigt: Schon im Oktober will man die Testphase beenden und an der Einführung arbeiten.
Nun gehört BlingBling nicht zu denjenigen, die im digitalen Euro „Orwell’sches Teufelswerk“ sehen. Strategische Dummheit trifft es besser. Worum geht es?
Sogenannte Central Bank Digital Currencies (CBDC) waren vor einigen Jahren so etwas wie der letzte Schrei in der Zentralbank-Welt. Nachdem Facebook/Meta 2017/18 eine eigene Währung namens Libra auf den Markt bringen wollte, und eine obskure Internet-Währung namens Bitcoin immer mehr Anhänger fand, sahen sich viele Zentralbanken der Welt unter Zugzwang. Was man wollte: eine digitale, direkt von der Zentralbank ausgegebene Währung ohne Bugs, aber mit Features. Mit einer Digital-Währung ließe sich der internationale Zahlungsverkehr direkt und ohne Umweg über den US-Dollar abwickeln. Die Zentralbank bekäme wieder mehr direkten Einfluss auf die Geldschöpfung. Und, wie man aus China lernen konnte, ließen sich digitale Bankkonten auch ganz zum „Nudging von Bürgern“ nutzen. So spekulierten die ersten Verschwörungstheoretiker bald, ein digitaler Euro ließe sich ja mit einem persönlichen CO2-Konto verknüpfen. Wäre letzteres einmal aufgebraucht, könnte der Konto-Inhaber einfach keinen Flug mehr buchen. Auch ließe sich eine expansive Geldpolitik, wie sie bis 2022 praktiziert wurde, ganz einfach mit Negativ-Zinsen umsetzen. Geld würde sich nominal reduzieren, was den Bürger zum Konsum animieren würde. Flüchtigen Kriminellen ließe sich per Knopfdruck das Konto sperren. Der Staat würde also über eine ganze neue Palette an Einflussmöglichkeiten verfügen.
Die Aluhüte United warnten vor einem Orwellschen Überwachungsstaat. Vertreter von Regierungen und Firmen, die diesen digitalen Euro bauen sollten, beschwichtigten. Mit Ralf Wintergerst, CEO von Giesecke+Devrient, nach wie vor heißester Anwärter, um das Projekt in der EU umzusetzen, sprach ich in den vergangenen Jahren mehrmals zu dem Thema. Zuletzt im Dezember 24.
Wintergerst versichert stets zwei Dinge: Eine Abschaffung von Bargeld sei nicht geplant. Und nur, wenn die Fluchttore Bargeld, Gold und Bitcoin geschlossen werden, greift die dystopische Version. Und zweitens, so Wintergerst, habe niemand ein chinesisches System im Sinne. Der „digitale Euro“ sei für die Bürger gedacht und das Projekt unterliege demokratischer Kontrolle. Ob er Wintergerst und dem guten im Menschen Glauben schenkt, möge jeder Leser selbst entscheiden. Das Interessantere ist ohnehin, dass der digitale Euro ein strategisch dummes Projekt ist.
Dazu muss man wissen, dass eine solche Zentralbankwährung Banken im weitesten Sinne überflüssig macht. Kontos bei Privatbanken werden obsolet, genauso wie Spar-, Fest- und Tagesgeld-Strukturen. Deshalb soll der digitale Euro zunächst auf 3000 Euro pro Bürger beschränkt werden. Das ist also nicht als Maximal-Vermögen gedacht, das dann jedem sozialistischen Einheits-EU-Menschen noch zusteht, sondern dient dazu, das Bankensystem nicht kollabieren zu lassen. Aber wozu überhaupt „ein bisschen digitaler Euro“?
In den USA setzt man mittlerweile 100 Prozent auf die private Alternative: Stablecoins wie Tether (USDT) und Circle (USDC) sind nichts anderes als digitale Währungen. Nur sind sie nicht von einer Zentralbank ausgeben, sondern von privaten Anbietern. Tether hat technisch die Möglichkeit, einen Inhaber vom Zahlungsverkehr auszusperren. Nur dürfte es davon kaum Gebrauch machen, will das Unternehmen nicht rasant Kunden an die Konkurrenz verlieren. Da USDT und USDC mit US-Dollar gedeckt sind (oder zumindest sein sollten, looking at you, Tether!), stärken sie außerdem die Rolle des US-Dollars als Leitwährung. Und da die USA sich aktuell sehr über Käufer von Staatsanleihen freuen, um die Zinsen zu drücken, und Tether einer der größten Halter von US-Staatsanleihen ist, wird es den digitalen Dollar bis auf Weiteres nicht geben.
Den digitalen Yuan gibt es, aber von einer großen Akzeptanz oder Durchdringung der chinesischen Wirtschaft lässt sich nicht sprechen. Kontrolle kann der chinesische Staat ohnehin über seine omnipräsenten Apps WeChat und Alipay ausüben. Was den internationalen Zahlungsverkehr betrifft, scheint man aktuell eher auf Gold zu setzen.
Übrig also bleibt die EU mit einem Projekt, das bereits Milliarden an Entwicklungskosten verschlungen hat. Am Ende bleibt dann ein Mini-Digitaler-Euro in Höhe von 3000 Euro, den niemand wollte, und niemand braucht.
Helfen könnte er allerdings beim Projekt “Mobilisierung der Sparguthaben”. Der Ausdruck geht auf Friedrich Merz zurück. Ursula von der Leyen paraphrasierte ihn jüngst:
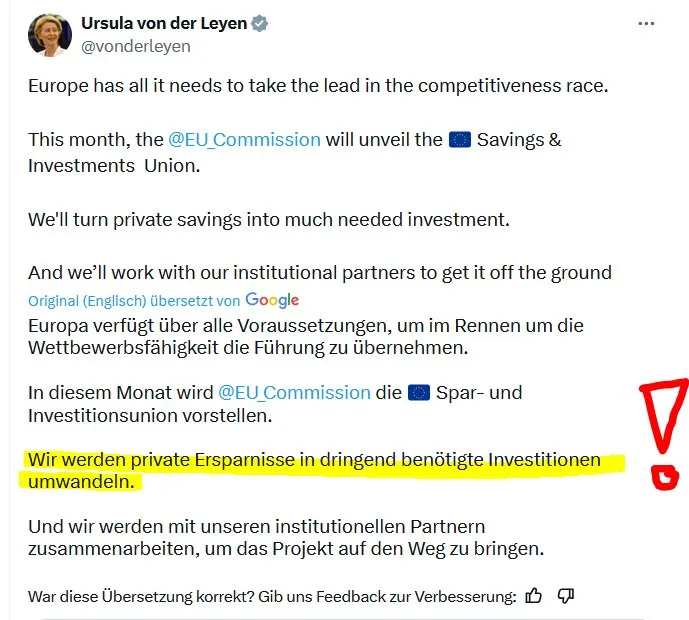
Irgendwie müssen die Billionen von Sparguthaben in Militär-Investitionen umgewandelt werden. Das wird am besten funktionieren mit Anleihen, die schlechter verzinst sind als sonst auf dem Markt üblich. Wie bringt man Leute dazu, dann ihr Geld dort zu investieren? Entweder man zwingt sie, oder man bewirbt die Anleihen mit viel Patriotismus und Propaganda. Die Verschwörungstheoretiker unter uns bekommen also bald Futter, wenn die „Spar- und Investitionsunion” vorgestellt wird.
Like, wenn Dein Aluhut glüht…
Hinter der Paywall: Wie das Trump-Derangement-Syndrom den Blick auf den Markt trübt. Wie es mit Bitcoin, Gold und Aktien weitergeht.**
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Replacing the web with something saner
This is a simplification, but let's say that basically there are just 3 kinds of websites:
- Websites with content: text, images, videos;
- Websites that run full apps that do a ton of interactive stuff;
- Websites with some interactive content that uses JavaScript, or "mini-apps";
In a saner world we would have 3 different ways of serving and using these. 1 would be "the web" (and it was for a while, although I'm not claiming here that the past is always better and wanting to get back to the glorious old days).
1 would stay as "the web", just static sites, styled with CSS, no JavaScript whatsoever, but designers can still thrive and make they look pretty. Or it could also be something like Gemini. Maybe the two protocols could coexist.
2 would be downloadable native apps, much easier to write and maintain for developers (considering that multi-platform and cross-compilation is easy today and getting easier), faster, more polished experience for users, more powerful, integrates better with the computer.
(Remember that since no one would be striving to make the same app run both on browsers and natively no one would have any need for Electron or other inefficient bloated solutions, just pure native UI, like the Telegram app, have you seen that? It's fast.)
But 2 is mostly for apps that people use every day, something like Google Docs, email (although email is also broken technology), Netflix, Twitter, Trello and so on, and all those hundreds of niche SaaS that people pay monthly fees to use, each tailored to a different industry (although most of functions they all implement are the same everywhere). What do we do with dynamic open websites like StackOverflow, for example, where one needs to not only read, but also search and interact in multiple ways? What about that website that asks you a bunch of questions and then discovers the name of the person you're thinking about? What about that mini-app that calculates the hash of your provided content or shrinks your video, or that one that hosts your image without asking any questions?
All these and tons of others would fall into category 3, that of instantly loaded apps that you don't have to install, and yet they run in a sandbox.
The key for making category 3 worth investing time into is coming up with some solid grounds, simple enough that anyone can implement in multiple different ways, but not giving the app too much choices.
Telegram or Discord bots are super powerful platforms that can accomodate most kinds of app in them. They can't beat a native app specifically made with one purpose, but they allow anyone to provide instantly usable apps with very low overhead, and since the experience is so simple, intuitive and fast, users tend to like it and sometimes even pay for their services. There could exist a protocol that brings apps like that to the open world of (I won't say "web") domains and the websockets protocol -- with multiple different clients, each making their own decisions on how to display the content sent by the servers that are powering these apps.
Another idea is that of Alan Kay: to design a nice little OS/virtual machine that can load these apps and run them. Kinda like browsers are today, but providing a more well-thought, native-like experience and framework, but still sandboxed. And I add: abstracting away details about design, content disposition and so on.
These 3 kinds of programs could coexist peacefully. 2 are just standalone programs, they can do anything and each will be its own thing. 1 and 3, however, are still similar to browsers of today in the sense that you need clients to interact with servers and show to the user what they are asking. But by simplifying everything and separating the scopes properly these clients would be easy to write, efficient, small, the environment would be open and the internet would be saved.
See also
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28IPFS problems: General confusion
Most IPFS open-source projects, libraries and apps (excluding Ethereum stuff) are things that rely heavily on dynamic data and temporary links. The most common projects you'll see when following the IPFS communities are chat rooms and similar things. I've seen dozens of these chat-rooms. There's also a famous IPFS-powered database. How can you do these things with content-addressing is a mistery. Of course they probably rely on IPNS or other external address system.
There's also a bunch of "file-sharing" on IPFS. The kind of thing people use for temporary making a file available for a third-party. There's image sharing on IPFS, pastebins on IPFS and so on. People don't seem to share the preoccupation with broken links here.
-
 @ 306555fe:fd7fdf12
2025-03-15 05:56:16
@ 306555fe:fd7fdf12
2025-03-15 05:56:161. Executive Summary
This report presents a detailed comparative analysis of Tesla Powerwall and Sungrow battery options for a 3-phase residence in Sydney, Australia, equipped with a 6.6kW solar system and a Sungrow SG5KTL-MT inverter. The evaluation focuses on the suitability of these battery solutions for potential off-grid capability and Vehicle-to-Home (V2H) functionality. The analysis reveals that while both Tesla Powerwall and Sungrow offer compelling features for home energy storage, Sungrow battery systems, particularly when paired with their hybrid inverters, present a more direct and comprehensive solution for achieving 3-phase off-grid capability. For V2H integration, both systems currently rely on the development of compatible bidirectional charging infrastructure in Australia. Based on the user's stated goals, a Sungrow battery system, potentially requiring an upgrade to a Sungrow hybrid inverter, is the recommended solution.
2. Introduction: Context and Objectives
The Australian residential energy landscape is witnessing a significant shift towards energy independence, with increasing adoption of solar photovoltaic (PV) systems and battery storage. This trend is propelled by factors such as escalating electricity costs and a growing desire for reliable power, particularly during grid outages. This report addresses the specific needs of a Sydney homeowner who has already invested in a 6.6kW solar system connected to a 3-phase Sungrow SG5KTL-MT inverter and owns a Tesla electric vehicle. The homeowner is now exploring battery storage solutions, with a particular focus on enabling potential off-grid operation and facilitating future Vehicle-to-Home (V2H) capabilities for their Tesla.
The primary objectives of this report are threefold: firstly, to evaluate the technical and practical suitability of Tesla Powerwall for a 3-phase home in Sydney; secondly, to conduct a similar evaluation for various Sungrow battery options; and thirdly, to provide a comparative assessment of these two leading solutions based on their ability to support off-grid functionality and integrate with V2H technology. The scope of this analysis includes the latest Tesla Powerwall models available in Australia and relevant high-voltage battery options from Sungrow, specifically the SBR and SBH series. The geographical context is limited to Sydney, Australia, considering local grid regulations and market availability. This analysis relies on the provided research material and publicly accessible technical specifications to form its conclusions.
3. Analysis of Tesla Powerwall for a 3-Phase Sydney Home
- 3.1 Technical Specifications and Features:\ The Tesla Powerwall is a well-established residential battery system. The latest generation, Powerwall 3, offers an energy capacity of 13.5 kWh 1 and can deliver up to 10 kW of on-grid power, with the same capacity for backup power, capable of a 185 A motor start 1. A key feature of Powerwall 3 is its integrated solar inverter with a 97.5% efficiency and three solar inputs with Maximum Power Point Trackers (MPPTs) in the Australian version 1. The system is scalable, allowing for the installation of up to four units 1, and utilizes Lithium Iron Phosphate (LFP) battery chemistry, known for its safety 5. In contrast, the Powerwall 2, while also having a 13.5 kWh energy capacity 7, provides a continuous power output of 5 kW with a 7 kW peak 7. Notably, Powerwall 2 does not have an integrated solar inverter 7 and uses Nickel Manganese Cobalt Oxide (NMC) battery chemistry 7. It offers greater scalability, supporting up to ten units 1. Both Powerwall 2 and 3 come with a 10-year warranty 2. Powerwall 3 necessitates the use of the Tesla Backup Gateway 2 2, while Powerwall 2 requires a Gateway for system control and backup functionality 7. The integrated inverter in Powerwall 3 streamlines installations for new solar and storage setups. However, for homeowners with existing inverters, such as the user, this feature might introduce complexities as the existing inverter's functionality could become redundant if the system were configured to primarily utilize the Powerwall 3's inverter. Powerwall 2, designed as an AC-coupled battery, might offer a more seamless integration by working in conjunction with the existing Sungrow inverter 3.
- 3.2 Compatibility with Existing 3-Phase Sungrow Inverter (AC Coupling):\ Tesla Powerwall is designed as an AC-coupled battery, meaning it connects to the home's electrical system at the switchboard level and operates independently of the solar inverter 9. This AC coupling capability generally allows Powerwall to be compatible with a wide range of existing solar inverters, including the user's 3-phase Sungrow SG5KTL-MT model 2. Specifically, Powerwall 2 demonstrates 100% compatibility with single-phase grid-connected solar systems installed after October 2016 9. For Powerwall 3, Tesla indicates AC coupling compatibility with existing solar systems up to 5kW 2. However, a crucial consideration arises during grid outages concerning the ability to charge the Powerwall from solar. If the home has a 3-phase solar inverter, like the user's Sungrow SG5KTL-MT, Powerwall 2 might not be able to charge from solar during a blackout because many 3-phase inverters require the presence of all three phases from the grid to operate 9. This limitation could also extend to Powerwall 3 when AC-coupled with a 3-phase inverter 8. Given the user's interest in potential off-grid capability, this inability to recharge the battery from solar during a grid outage significantly limits the duration of backup power to the energy stored within the Powerwall. Furthermore, the user's 6.6kW solar system output exceeds the 5kW AC coupling limit specified for a single Powerwall 3. This suggests that either the entire solar generation cannot be used to charge a single Powerwall 3 via AC coupling, or a more complex configuration involving multiple Powerwall units might be necessary.
- 3.3 Suitability for Off-Grid Operation in a 3-Phase System:\ The Tesla Powerwall is fundamentally a single-phase battery system and can only provide backup power to a single phase within a 3-phase home 8. During a power outage, only the electrical circuits connected to the phase that the Powerwall is backing up will remain operational 8. This necessitates careful planning to ensure that essential loads, such as lighting, refrigerators, and internet connectivity, are connected to this designated phase 8. While it is possible to install multiple Powerwall units, with one unit dedicated to each phase, this significantly increases the overall cost and introduces complexities in system management 8. Notably, even with the installation of three Powerwall 3 units, comprehensive 3-phase backup is not guaranteed 20. It is also important to recognize that Tesla does not officially support or provide warranties for off-grid installations of Powerwall 2. The Powerwall system is primarily designed for grid-connected homes to provide backup during outages and to optimize energy consumption, rather than functioning as the primary power source in a completely off-grid scenario. Therefore, achieving a truly comprehensive off-grid capability for a 3-phase home using Tesla Powerwall would likely involve a substantial financial investment in multiple units, meticulous load balancing across the phases, and navigating the limitations of single-phase backup, all without official support from the manufacturer.
- 3.4 Potential for V2H Integration with an EV in Australia:\ Vehicle-to-Home (V2H) technology, which allows an electric vehicle to supply power back to a home, is gaining traction in Australia. Regulatory changes have been made to permit bidirectional charging systems, with mainstream adoption expected in 2025 21. Australian standards for bidirectional charging are now approved, and compatible chargers are anticipated to become available in 2025 22. Currently, the research snippets do not indicate that Tesla Powerwall offers direct, integrated V2H functionality with EVs in Australia 1. However, the Tesla Powerwall can play a supportive role in a V2H ecosystem. It can efficiently store excess energy generated by the solar system 1, which could then be used to charge the EV. If the EV is equipped with V2H capabilities and connected to a compatible bidirectional charger, the energy stored in the Powerwall (or directly from solar) could indirectly contribute to powering the home by first charging the vehicle's battery. The actual discharge from the vehicle to the home would be managed by the bidirectional charger and the vehicle's internal systems, not directly by the Powerwall. Therefore, while Powerwall doesn't inherently provide V2H, it can act as a crucial energy storage component within a broader V2H setup.
- 3.5 Cost and Installation Considerations in Sydney:\ The cost of a Tesla Powerwall 3 in Australia is approximately $13,600, which includes the mandatory Backup Gateway 2 2. Powerwall 2 has an approximate price of $8,750 to $9,750, excluding installation and the Backup Gateway 7, with the installed cost estimated between $12,000 and $14,000 7. Installation costs for Powerwall 3 as part of a new solar system at Penrith Solar Centre start at $23,990 (including a 6kW solar system), while adding it to an existing system is around $15,990 27. Installing a Powerwall system in a 3-phase home can incur additional costs and complexities compared to single-phase installations 13. If the goal is to achieve any level of backup across multiple phases using Powerwall, the cost would escalate significantly with the need for multiple units. Homeowners in NSW may be eligible for rebates under the Peak Demand Reduction Scheme (PDRS), which can help offset the initial investment in a Tesla Powerwall 5. However, the overall cost of a Powerwall system, especially when considering a multi-unit setup for more comprehensive backup in a 3-phase home, remains a substantial financial consideration.
4. Analysis of Sungrow Battery Options for a 3-Phase Sydney Home
- 4.1 Technical Specifications of Relevant Sungrow Battery Models (SBR and SBH Series):\ Sungrow offers a range of high-voltage battery solutions, primarily the SBR and SBH series, utilizing Lithium Iron Phosphate (LiFePO4) chemistry for enhanced safety 5. The SBR series features a modular design with 3.2 kWh battery modules, allowing for system capacities ranging from 9.6 kWh (3 modules) up to 25.6 kWh (8 modules) in a single stack. Multiple stacks can be connected in parallel to achieve even larger capacities, up to 100 kWh 6. These batteries boast 100% usable energy capacity 26 and are high-voltage systems 33. The SBH series also employs a modular design with larger 5 kWh battery modules. A single stack can accommodate 4 to 8 modules, providing usable energy from 20 kWh to 40 kWh. Similar to the SBR series, multiple SBH stacks can be connected in parallel to reach a maximum capacity of 160 kWh 5. Both the SBR and SBH series come with a 10-year warranty 5 and are primarily designed for DC coupling with Sungrow's hybrid inverter range, particularly the SH series, which includes models specifically designed for 3-phase systems (SH-RT series) 33. The availability of a wider range of capacities and the modular design of both the SBR and SBH series provide greater flexibility for the user to tailor a battery system to their specific energy consumption needs. The SBH series, with its larger 5 kWh modules, appears particularly well-suited for homes with potentially higher energy demands, such as those with 3-phase connections.
- 4.2 Compatibility with Existing 3-Phase Sungrow Inverter (DC and AC Coupling):\ The user's existing Sungrow SG5KTL-MT inverter is a grid-tied inverter and not a hybrid model designed for direct DC coupling with batteries 5. Sungrow's high-voltage batteries, such as the SBR and SBH series, are primarily intended for DC coupling with their SH series hybrid inverters 33. While direct DC coupling is not an option with the SG5KTL-MT, it is possible to AC couple Sungrow batteries to the existing solar system 35. This would likely require the addition of a separate battery inverter to manage the charging and discharging of the Sungrow battery, as the SG5KTL-MT does not have this functionality. Although AC coupling offers a way to integrate a battery without replacing the existing solar inverter, it can introduce inefficiencies due to the multiple AC-DC and DC-AC conversions. For optimal performance and to fully leverage the capabilities of Sungrow's high-voltage batteries, particularly for off-grid operation, upgrading to a Sungrow SH series hybrid inverter would be the recommended approach.
- 4.3 Suitability for Off-Grid Operation in a 3-Phase System:\ Sungrow offers a distinct advantage in providing solutions for 3-phase off-grid operation through their SH-RT series of hybrid inverters 5. These inverters, when paired with Sungrow's SBR or SBH batteries, are capable of providing seamless transition to 3-phase backup power during grid outages 63. The SH-RT series is specifically designed to support 100% unbalanced loads in backup mode, ensuring that essential appliances continue to run during a blackout 66. Both the SBR and SBH battery series are compatible with off-grid operation when used in conjunction with the appropriate Sungrow hybrid inverters. Some single-phase Sungrow hybrid inverters (SH-RS series) also offer off-grid capabilities and support generator connection for battery charging during extended periods of low solar generation 85. This comprehensive ecosystem of Sungrow products provides a more direct and integrated pathway for the user to achieve their goal of potential 3-phase off-grid capability compared to the single-phase limitations of Tesla Powerwall.
- 4.4 Potential for V2H Integration with an EV (e.g Tesla Car) in Australia:\ Similar to Tesla Powerwall, the provided research material does not explicitly mention direct V2H integration capabilities for Sungrow battery systems with Tesla cars in Australia 22. However, Sungrow's active involvement in the broader renewable energy and electric vehicle charging sectors suggests a strong potential for future integration. Sungrow manufactures its own range of EV chargers 64, and their 3-phase hybrid inverter solutions can be paired with these chargers for smart green power charging 64. As V2H technology and the necessary bidirectional charging infrastructure become more prevalent in Australia, it is conceivable that Sungrow's integrated energy management systems, including their batteries and hybrid inverters, could be updated to support V2H functionality, potentially even with Tesla vehicles through standardized protocols or future partnerships. In the interim, a Sungrow battery system can efficiently store solar energy, which could then be used to charge a Tesla car. The potential for the EV to discharge back to the home would depend on the availability and compatibility of third-party bidirectional chargers that adhere to the evolving Australian standards.
- 4.5 Cost and Installation Considerations in Sydney:\ The cost of Sungrow batteries in Australia varies depending on the model and capacity. For the SBR series, a 9.6 kWh system is approximately $11,500 installed, a 12.8 kWh system around $13,200 installed, and a 25.6 kWh system around $19,700 installed. Supply-only costs for the SBH series 20 kWh kit range from $13,778.70 to $14,360 40. Compatible 3-phase hybrid inverters from Sungrow, such as the SH5.0RT, are priced around $3,760, while the SH10RT ranges from approximately $4,174.50 to $5,720 78. If the user opts for a Sungrow battery system to achieve optimal 3-phase off-grid capability, the cost of a new SH series hybrid inverter would need to be included, as the existing SG5KTL-MT is not compatible for direct DC coupling. While AC coupling might be a less expensive initial step, it could involve the additional cost of a separate battery inverter. Homeowners in NSW can potentially benefit from the NSW battery rebate when purchasing a Sungrow battery system, which could help reduce the overall cost 5. Although Sungrow batteries often offer a competitive cost per kWh, the total investment for a comprehensive 3-phase off-grid solution might be higher than a single-phase Tesla Powerwall setup, primarily due to the potential need for a new hybrid inverter.
5. Comparative Assessment: Tesla Powerwall vs. Sungrow Batteries
- 5.1 Side-by-Side Comparison Table of Key Specifications:
| Feature | Tesla Powerwall 3 | Sungrow SBR (Example: 12.8 kWh) + SH10RT | | --- | --- | --- | | Usable Energy Capacity (kWh) | 13.5 | 12.8 | | Continuous Power Output (kW) | 10 | 10 | | Peak Power Output (kW) | 10 | 12 (5 min) | | Battery Chemistry | Lithium Iron Phosphate | Lithium Iron Phosphate | | Scalability | Up to 4 units (54 kWh) | Up to 25.6 kWh per stack, 4 stacks parallel (102.4 kWh) | | Off-Grid Backup (Phases Supported) | Single-Phase | Three-Phase | | V2H Support (Current/Future Potential) | Potential via 3rd party charger | Potential via 3rd party charger | | Warranty (Years) | 10 | 10 | | Estimated Cost (AUD) | $13,600 + installation | $13,200 (battery installed) + $4,175 - $5,720 (inverter) |
- 5.2 Detailed Comparison Based on Off-Grid Capability Requirements:\ When considering the user's goal of potential off-grid capability for a 3-phase home, Sungrow presents a more robust solution. The availability of Sungrow's SH-RT series hybrid inverters, specifically designed for 3-phase systems and fully compatible with their SBR and SBH batteries, allows for a direct and integrated approach to achieving 3-phase backup power. These systems can seamlessly transition to off-grid mode, powering all three phases of the home, which is crucial for operating 3-phase appliances and ensuring comprehensive whole-house backup. In contrast, Tesla Powerwall, being a single-phase battery, inherently limits off-grid backup to a single phase in a 3-phase home 8. While multiple Powerwall units can be installed, this increases cost and complexity without guaranteeing full 3-phase backup or official off-grid support from Tesla. Therefore, for a user prioritizing potential for comprehensive 3-phase off-grid operation, Sungrow's ecosystem offers a more suitable and supported pathway.
- 5.3 Detailed Comparison Based on V2H Functionality Requirements:\ Currently, neither Tesla Powerwall nor Sungrow batteries offer direct, integrated V2H functionality for Tesla cars in Australia 22. Both systems can store solar energy that could be used to charge a EV, and the potential for the car to discharge back to the home (V2H) would rely on the development and adoption of compatible bidirectional charging infrastructure in Australia, which is expected to become more mainstream in 2025 21. Sungrow's involvement in manufacturing EV chargers and integrating them with their hybrid inverters suggests a potential for future V2H integration within their ecosystem. Similarly, while Tesla Powerwall doesn't currently offer V2H, its role as a home energy storage solution makes it a complementary technology to V2H, providing a place to store energy that could eventually be managed within a V2H framework.
- 5.4 Cost-Effectiveness and Overall Value Analysis:\ When evaluating cost-effectiveness, Sungrow batteries often have a lower cost per kWh of storage compared to Tesla Powerwall 5. However, for the user with an existing non-hybrid inverter, achieving the desired 3-phase off-grid capability with Sungrow would likely necessitate an additional investment in a Sungrow SH-RT series hybrid inverter. This would increase the initial outlay compared to simply AC coupling a Tesla Powerwall to the existing inverter for single-phase backup. The overall value proposition depends heavily on the user's priorities. If the primary goal is to have backup power for essential loads on a single phase and potential future V2H integration, Tesla Powerwall could be a viable option. However, if the potential for comprehensive 3-phase off-grid operation is a significant factor, then the added expense of a Sungrow hybrid inverter might be justified by the enhanced functionality and future-proofing for energy independence. Sungrow's reputation for affordability and the modularity of their battery systems also offer long-term value and flexibility.
6. Recommendations and Considerations
Based on the analysis, for a 3-phase home in Sydney with a 6.6kW solar system and the goal of potential off-grid capability, Sungrow battery options are recommended. Specifically, the user should consider upgrading their existing Sungrow SG5KTL-MT inverter to a Sungrow SH series hybrid inverter (e.g., SH5.0RT or SH10RT, depending on anticipated power demands) and pairing it with a Sungrow high-voltage battery from either the SBR or SBH series. The choice between SBR and SBH would depend on the desired storage capacity and budget. This combination offers a more direct and supported path to achieving 3-phase backup power and the potential for future off-grid operation.
Key Considerations for the User:
- Off-Grid Capability: The level of off-grid capability desired (partial single-phase backup vs. comprehensive whole-home 3-phase backup) is a crucial factor. For the latter, Sungrow is the more suitable choice.
- Budget: Both options represent a significant investment. The user should obtain detailed quotes for both Tesla Powerwall (considering single or multiple units) and a complete Sungrow hybrid inverter and battery system.
- V2H Timeline: The user's timeline for V2H adoption should be considered. Both systems will likely integrate via third-party chargers.
- Inverter Upgrade: If pursuing the optimal Sungrow solution for off-grid capability, the cost and logistics of upgrading the existing inverter need to be factored in.
- 3-Phase Backup Importance: The necessity of having backup power across all three phases should weigh heavily in the decision, favoring Sungrow.
It is strongly recommended that the user obtain detailed quotes from certified installers in the Sydney area for both Tesla Powerwall and various Sungrow system configurations to get accurate pricing, installation details, and information on available rebates and incentives in NSW.
7. Conclusion
In conclusion, while Tesla Powerwall offers a well-regarded solution for home energy storage with reliable backup capabilities, its inherent single-phase design presents limitations for users with 3-phase homes seeking comprehensive off-grid functionality. Sungrow, with its range of high-voltage batteries and particularly its 3-phase hybrid inverter systems, provides a more direct and technically sound pathway to achieving the user's goals of potential 3-phase off-grid operation. For V2H integration, both systems are currently positioned to benefit from the evolving Australian regulatory landscape and the development of compatible bidirectional charging technologies. Ultimately, the optimal choice will depend on the user's specific priorities, budget, and the level of off-grid capability they wish to achieve. The rapidly evolving nature of battery storage and V2H technology suggests that continued research and consultation with experts are advisable before making a final decision.
Works cited
1. Powerwall – Home Battery Storage | Tesla Australia, accessed March 14, 2025, https://www.tesla.com/en_au/powerwall\ 2. Tesla Powerwall 3 in Australia: Everything You Need to Know - Fritts Solar, accessed March 14, 2025, https://www.frittssolar.com.au/tesla-powerwall-3-australia/\ 3. What to Expect for Powerwall 3 | Tesla Support Australia, accessed March 14, 2025, https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3\ 4. Tesla Powerwall 3 Review - Clean Energy Reviews, accessed March 14, 2025, https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review\ 5. Sungrow SBH vs. Tesla Powerwall 3: Which is Better? NSW - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/\ 6. Sungrow Battery vs Tesla Powerwall Review - Volteam Electric, accessed March 14, 2025, https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/\ 7. Tesla Powerwall 2: A Complete 2024 Buyers Guide | Solar Choice, accessed March 14, 2025, https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/\ 8. Can You Install The Powerwall 3 On A Three-Phase Home? - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/three-phase-powerwall-3/\ 9. Is my grid connect solar system 100% compatible with a Tesla Powerwall 2 battery?, accessed March 14, 2025, https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery\ 10. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf\ 11. Combining Systems with Powerwall | Tesla Support, accessed March 14, 2025, https://www.tesla.com/support/energy/powerwall/learn/combining-systems\ 12. Powerwall System Design | Tesla Support, accessed March 14, 2025, https://www.tesla.com/support/energy/powerwall/learn/system-design\ 13. Installing Powerwall 3 on a Three-phase Site | PSC - Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/\ 14. Powerwall 3: When It Makes Sense and When It Doesn't - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/\ 15. AC-Coupled Solar System Sizing - Energy Library - Tesla, accessed March 14, 2025, https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html\ 16. Powerwall 3 Roadmap - 3 Phase Coming! | Tesla Motors Club, accessed March 14, 2025, https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/\ 17. Advice on how to install with 3 phase : r/solar - Reddit, accessed March 14, 2025, https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/\ 18. TESLA POWERWALL+ (3) - DIY Solar Depot, accessed March 14, 2025, https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/\ 19. Design Considerations - Energy Library - Tesla, accessed March 14, 2025, https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html\ 20. Problems with Powerwall 3 | Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/\ 21. EV Charging in Australia Gets a Makeover with V2G/V2H Approved for 2025 - SEVR, accessed March 14, 2025, https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/\ 22. V2G, V2L & V2H Explained: Vehicle to Grid in Australia? 2025 - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/\ 23. Australia's Future – Bidirectional EV Charging, Solar & Battery Storage as Standard Features, accessed March 14, 2025, https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/\ 24. 2025, the Year of Vehicle-to-Grid in Australia V2G Milestone - Elite Power Group, accessed March 14, 2025, https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/\ 25. Bidirectional Charging for Electric Cars: Unlocking New Possibilities - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/\ 26. The Best Home Batteries In Australia In 2025: According To Aussie Installers - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/blog/best-home-batteries-2025/\ 27. How Much Does a Tesla Powerwall 3 Cost? | Penrith Solar Centre, accessed March 14, 2025, https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/\ 28. Expected 3 Phase upgrade price? : r/AusRenovation - Reddit, accessed March 14, 2025, https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/\ 29. Powerwall cost for Sydney? | Tesla Motors Club, accessed March 14, 2025, https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/\ 30. Solar Battery Costs: Are They Worth It?, accessed March 14, 2025, https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/\ 31. Tesla Powerwall 3 Price and Installation - Solar4Life, accessed March 14, 2025, https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation\ 32. Solar Battery Price, Savings and Payback, accessed March 14, 2025, https://solarcalculator.com.au/battery-storage/price/\ 33. Sungrow | Solar Batteries Review - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html\ 34. Sungrow SBR high voltage battery - VP Solar, accessed March 14, 2025, https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/\ 35. Sungrow Battery SBR Series - SolarBright, accessed March 14, 2025, https://solarbright.com.au/product/sungrow-battery-sbr-series/\ 36. Sungrow SBR 3.2kWh module - Huglo Solar, accessed March 14, 2025, https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery\ 37. Sungrow Inverter and battery Review - Clean Energy Reviews, accessed March 14, 2025, https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review\ 38. SBH100/150/200/250/300/350/400 - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400\ 39. 20/25/30/35/40 kWh Solar Battery - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400\ 40. Sungrow SBH Stackable Battery System - Grow Energy, accessed March 14, 2025, https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system\ 41. Sungrow SBH High Voltage Battery Bundle (SBH200 - SBH400), accessed March 14, 2025, https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400\ 42. Buy cheap SunGrow solar inverters, accessed March 14, 2025, https://tienda-solar.es/en/brand/54-sungrow\ 43. Sungrow PowCube battery storage system (Analysis & review) - Solar Choice, accessed March 14, 2025, https://www.solarchoice.net.au/products/batteries/sungrow-review/\ 44. What inverters do we connect to? – Welcome to our Help Center - Support - SwitchDin, accessed March 14, 2025, https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to\ 45. Accessories Cross Reference Guide - Sungrow Australia Service, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf\ 46. Sungrow - Solar System Inverter - Solargain, accessed March 14, 2025, https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters\ 47. Sungrow Battery Review | A Comprehensive Guide - Esteem Energy, accessed March 14, 2025, https://esteemenergy.com.au/blog/sungrow-battery-review/\ 48. Sungrow 5kW Inverter + Tesla Powerwall + Longi 370w Hi-MO4m 7.4kW Solar System, accessed March 14, 2025, https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/\ 49. Sungrow | Solar Inverters Review - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/inverters/sungrow-review.html\ 50. Tesla Powerwall: Inverter Compatibility Under the Spotlight - 1KOMMA5, accessed March 14, 2025, https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/\ 51. Hi everybody, question about V2H power : r/electricvehicles - Reddit, accessed March 14, 2025, https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/\ 52. Commercial Solar System | PV Plant | Rooftop - Sungrow US, accessed March 14, 2025, https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems\ 53. SH8.0/10RS | 8kW/10kW | Single Phase | Sungrow Hybrid Inverter-Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs\ 54. Approved Batteries with SH Series Hybrid Inverters - Sungrow Australia Service, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf\ 55. Right inverter for the Tesla Powerwall 2 : r/solar - Reddit, accessed March 14, 2025, https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/\ 56. Sungrow Inverters - Gold Coast Solar Power Solutions, accessed March 14, 2025, https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/\ 57. Sungrow SBR192 Lithium-ion Battery - Europe-SolarStore.com, accessed March 14, 2025, https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html\ 58. High-Efficiency Solar Battery: Up to 100% Usable Energy - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/ProductsHome/20/23/battery\ 59. Warranty | Sungrow Australia and New Zealand Service, accessed March 14, 2025, https://service.sungrowpower.com.au/Warranty/warranty\ 60. Sungrow Battery cross-reference chart, accessed March 14, 2025, https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf\ 61. Sungrow SG5KTL-MT - SolarTopStore.com, accessed March 14, 2025, https://www.solartopstore.com/products/sungrow-sg5ktl-mt\ 62. Approved Batteries with SH Series Hybrid Inverters EU Version V1.6.3 - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf\ 63. BLACKOUT? NO, THANKS! POWER WHENEVER YOU NEED IT - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf\ 64. Sungrow 3-phase solution with 6 kVA inverter, EV charger and 9.6 kWh storage - Memodo, accessed March 14, 2025, https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767\ 65. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf\ 66. Sungrow Three-Phase Hybrid Inverter - Solar4Life, accessed March 14, 2025, https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid\ 67. SG5KTL-MT/SG6KTL-MT/SG8KTL-M (Non-China ... - ENF Solar, accessed March 14, 2025, https://www.enfsolar.com/pv/inverter-datasheet/12176\ 68. Sungrow SBR battery combiner box - AC Solar Warehouse, accessed March 14, 2025, https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620\ 69. Sungrow SBR HV Battery Installation Quick Guide, accessed March 14, 2025, https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf\ 70. Energy Storage System Products Catalogue - SUNGROW, accessed March 14, 2025, https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf\ 71. DC Coupling vs AC Coupling: Which Solar System to Choose - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose\ 72. Sungrow SBH battery - Accessory kit | AC Solar Warehouse AU, accessed March 14, 2025, https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310\ 73. Sungrow SBR 3.2kWh High Voltage Battery Module , ASA00460 - Alternergy, accessed March 14, 2025, https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460\ 74. NEW Sungrow single phase hybrid inverters can operate without the grid or a battery, accessed March 14, 2025, https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255\ 75. Lawnton Sungrow SBH & Solar Hybrid System | Alvolta, accessed March 14, 2025, https://www.alvolta.com.au/portfolio/info/74\ 76. Sungrow Battery Starter Pack - Huglo Solar, accessed March 14, 2025, https://www.huglo.com.au/post/sungrow-battery-starter-pack\ 77. Sungrow SBR Battery System Bundles, accessed March 14, 2025, https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles\ 78. Sungrow Hybrid 10kW RT Three-Phase Solar Inverter, accessed March 14, 2025, https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108\ 79. Sungrow RT 5kW Three Phase Hybrid inverter (2 MPPT) SH5.0RT - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/\ 80. SUNGROW SH10RT | 10kW 3-Phase Hybrid Inverter - Sparky Direct, accessed March 14, 2025, https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter\ 81. Sungrow Hybrid 10kW 3 Phase 2 MPPT w/WiFi, DC Switch & EPS Built-in Inverter, accessed March 14, 2025, https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/\ 82. Sungrow Solar Inverters - Independent Review, accessed March 14, 2025, https://www.solarchoice.net.au/products/inverters/Sungrow-review/\ 83. Sungrow 10.0kW - 3 Phase Hybrid Inverter (SH10RT) - Solar Superstore, accessed March 14, 2025, https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt\ 84. How Much Do Solar Batteries Cost in Australia? - SolarQuotes, accessed March 14, 2025, https://www.solarquotes.com.au/battery-storage/cost/\ 85. Off Grid Solar system using a Sungrow inverter and battery, accessed March 14, 2025, https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312\ 86. Sungrow 14.08k W Off Grid Solar System / Single Phase - AHLEC, accessed March 14, 2025, https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/\ 87. Residential Battery Energy Storage System - Sungrow AU, accessed March 14, 2025, https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system\ 88. EV Charger - Sungrow, accessed March 14, 2025, https://en.sungrowpower.com/ProductsHome/59/ev-charger\ 89. Sungrow SBH 20kW High Voltage LFP Battery Including Accessory Kit SBH200 | eBay, accessed March 14, 2025, https://www.ebay.com.au/itm/135320073679\ 90. 20kWh Battery Kit - Login - Australian Solar Supplies Pty Ltd, accessed March 14, 2025, http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f\ 91. Sungrow - Solar Batteries Online, accessed March 14, 2025, https://www.solarbatteriesonline.com.au/sungrow/
# Comparative Evaluation of Tesla Powerwall and Sungrow Battery Options for a 3-Phase Sydney Residence
1. Executive Summary
This report presents a detailed comparative analysis of Tesla Powerwall and Sungrow battery options for a 3-phase residence in Sydney, Australia, equipped with a 6.6kW solar system and a Sungrow SG5KTL-MT inverter. The evaluation focuses on the suitability of these battery solutions for potential off-grid capability and Vehicle-to-Home (V2H) functionality for a EV. The analysis reveals that while both Tesla Powerwall and Sungrow offer compelling features for home energy storage, Sungrow battery systems, particularly when paired with their hybrid inverters, present a more direct and comprehensive solution for achieving 3-phase off-grid capability. For V2H integration, both systems currently rely on the development of compatible bidirectional charging infrastructure in Australia. Based on the user's stated goals, a Sungrow battery system, potentially requiring an upgrade to a Sungrow hybrid inverter, is the recommended solution.
2. Introduction: Context and Objectives
The Australian residential energy landscape is witnessing a significant shift towards energy independence, with increasing adoption of solar photovoltaic (PV) systems and battery storage. This trend is propelled by factors such as escalating electricity costs and a growing desire for reliable power, particularly during grid outages. This report addresses the specific needs of a Sydney homeowner who has already invested in a 6.6kW solar system connected to a 3-phase Sungrow SG5KTL-MT inverter and owns a Tesla electric vehicle. The homeowner is now exploring battery storage solutions, with a particular focus on enabling potential off-grid operation and facilitating future Vehicle-to-Home (V2H) capabilities for their Tesla.
The primary objectives of this report are threefold: firstly, to evaluate the technical and practical suitability of Tesla Powerwall for a 3-phase home in Sydney; secondly, to conduct a similar evaluation for various Sungrow battery options; and thirdly, to provide a comparative assessment of these two leading solutions based on their ability to support off-grid functionality and integrate with V2H technology. The scope of this analysis includes the latest Tesla Powerwall models available in Australia and relevant high-voltage battery options from Sungrow, specifically the SBR and SBH series. The geographical context is limited to Sydney, Australia, considering local grid regulations and market availability. This analysis relies on the provided research material and publicly accessible technical specifications to form its conclusions.
3. Analysis of Tesla Powerwall for a 3-Phase Sydney Home
3.1 Technical Specifications and Features:
The Tesla Powerwall is a well-established residential battery system. The latest generation, Powerwall 3, offers an energy capacity of 13.5 kWh 1 and can deliver up to 10 kW of on-grid power, with the same capacity for backup power, capable of a 185 A motor start 1. A key feature of Powerwall 3 is its integrated solar inverter with a 97.5% efficiency and three solar inputs with Maximum Power Point Trackers (MPPTs) in the Australian version 1. The system is scalable, allowing for the installation of up to four units 1, and utilizes Lithium Iron Phosphate (LFP) battery chemistry, known for its safety 5. In contrast, the Powerwall 2, while also having a 13.5 kWh energy capacity 7, provides a continuous power output of 5 kW with a 7 kW peak 7. Notably, Powerwall 2 does not have an integrated solar inverter 7 and uses Nickel Manganese Cobalt Oxide (NMC) battery chemistry 7. It offers greater scalability, supporting up to ten units 1. Both Powerwall 2 and 3 come with a 10-year warranty 2. Powerwall 3 necessitates the use of the Tesla Backup Gateway 2 2, while Powerwall 2 requires a Gateway for system control and backup functionality 7. The integrated inverter in Powerwall 3 streamlines installations for new solar and storage setups. However, for homeowners with existing inverters, such as the user, this feature might introduce complexities as the existing inverter's functionality could become redundant if the system were configured to primarily utilize the Powerwall 3's inverter. Powerwall 2, designed as an AC-coupled battery, might offer a more seamless integration by working in conjunction with the existing Sungrow inverter 3.
3.2 Compatibility with Existing 3-Phase Sungrow Inverter (AC Coupling):
Tesla Powerwall is designed as an AC-coupled battery, meaning it connects to the home's electrical system at the switchboard level and operates independently of the solar inverter 9. This AC coupling capability generally allows Powerwall to be compatible with a wide range of existing solar inverters, including the user's 3-phase Sungrow SG5KTL-MT model 2. Specifically, Powerwall 2 demonstrates 100% compatibility with single-phase grid-connected solar systems installed after October 2016 9. For Powerwall 3, Tesla indicates AC coupling compatibility with existing solar systems up to 5kW 2. However, a crucial consideration arises during grid outages concerning the ability to charge the Powerwall from solar. If the home has a 3-phase solar inverter, like the user's Sungrow SG5KTL-MT, Powerwall 2 might not be able to charge from solar during a blackout because many 3-phase inverters require the presence of all three phases from the grid to operate 9. This limitation could also extend to Powerwall 3 when AC-coupled with a 3-phase inverter 8. Given the user's interest in potential off-grid capability, this inability to recharge the battery from solar during a grid outage significantly limits the duration of backup power to the energy stored within the Powerwall. Furthermore, the user's 6.6kW solar system output exceeds the 5kW AC coupling limit specified for a single Powerwall 3. This suggests that either the entire solar generation cannot be used to charge a single Powerwall 3 via AC coupling, or a more complex configuration involving multiple Powerwall units might be necessary.
3.3 Suitability for Off-Grid Operation in a 3-Phase System:
The Tesla Powerwall is fundamentally a single-phase battery system and can only provide backup power to a single phase within a 3-phase home 8. During a power outage, only the electrical circuits connected to the phase that the Powerwall is backing up will remain operational 8. This necessitates careful planning to ensure that essential loads, such as lighting, refrigerators, and internet connectivity, are connected to this designated phase 8. While it is possible to install multiple Powerwall units, with one unit dedicated to each phase, this significantly increases the overall cost and introduces complexities in system management 8. Notably, even with the installation of three Powerwall 3 units, comprehensive 3-phase backup is not guaranteed 20. It is also important to recognize that Tesla does not officially support or provide warranties for off-grid installations of Powerwall 2. The Powerwall system is primarily designed for grid-connected homes to provide backup during outages and to optimize energy consumption, rather than functioning as the primary power source in a completely off-grid scenario. Therefore, achieving a truly comprehensive off-grid capability for a 3-phase home using Tesla Powerwall would likely involve a substantial financial investment in multiple units, meticulous load balancing across the phases, and navigating the limitations of single-phase backup, all without official support from the manufacturer.
3.4 Potential for V2H Integration with a EV in Australia:
Vehicle-to-Home (V2H) technology, which allows an electric vehicle to supply power back to a home, is gaining traction in Australia. Regulatory changes have been made to permit bidirectional charging systems, with mainstream adoption expected in 2025 21. Australian standards for bidirectional charging are now approved, and compatible chargers are anticipated to become available in 2025 22. Currently, the research snippets do not indicate that Tesla Powerwall offers direct, integrated V2H functionality with Tesla cars in Australia 1. However, the Tesla Powerwall can play a supportive role in a V2H ecosystem. It can efficiently store excess energy generated by the solar system 1, which could then be used to charge the Tesla car. If the Tesla car is equipped with V2H capabilities and connected to a compatible bidirectional charger, the energy stored in the Powerwall (or directly from solar) could indirectly contribute to powering the home by first charging the vehicle's battery. The actual discharge from the vehicle to the home would be managed by the bidirectional charger and the vehicle's internal systems, not directly by the Powerwall. Therefore, while Powerwall doesn't inherently provide V2H, it can act as a crucial energy storage component within a broader V2H setup.
3.5 Cost and Installation Considerations in Sydney:
The cost of a Tesla Powerwall 3 in Australia is approximately $13,600, which includes the mandatory Backup Gateway 2 2. Powerwall 2 has an approximate price of $8,750 to $9,750, excluding installation and the Backup Gateway 7, with the installed cost estimated between $12,000 and $14,000 7. Installation costs for Powerwall 3 as part of a new solar system at Penrith Solar Centre start at $23,990 (including a 6kW solar system), while adding it to an existing system is around $15,990 27. Installing a Powerwall system in a 3-phase home can incur additional costs and complexities compared to single-phase installations 13. If the goal is to achieve any level of backup across multiple phases using Powerwall, the cost would escalate significantly with the need for multiple units. Homeowners in NSW may be eligible for rebates under the Peak Demand Reduction Scheme (PDRS), which can help offset the initial investment in a Tesla Powerwall 5. However, the overall cost of a Powerwall system, especially when considering a multi-unit setup for more comprehensive backup in a 3-phase home, remains a substantial financial consideration.
4. Analysis of Sungrow Battery Options for a 3-Phase Sydney Home
4.1 Technical Specifications of Relevant Sungrow Battery Models (SBR and SBH Series):
Sungrow offers a range of high-voltage battery solutions, primarily the SBR and SBH series, utilizing Lithium Iron Phosphate (LiFePO4) chemistry for enhanced safety 5. The SBR series features a modular design with 3.2 kWh battery modules, allowing for system capacities ranging from 9.6 kWh (3 modules) up to 25.6 kWh (8 modules) in a single stack. Multiple stacks can be connected in parallel to achieve even larger capacities, up to 100 kWh 6. These batteries boast 100% usable energy capacity 26 and are high-voltage systems 33. The SBH series also employs a modular design with larger 5 kWh battery modules. A single stack can accommodate 4 to 8 modules, providing usable energy from 20 kWh to 40 kWh. Similar to the SBR series, multiple SBH stacks can be connected in parallel to reach a maximum capacity of 160 kWh 5. Both the SBR and SBH series come with a 10-year warranty 5 and are primarily designed for DC coupling with Sungrow's hybrid inverter range, particularly the SH series, which includes models specifically designed for 3-phase systems (SH-RT series) 33. The availability of a wider range of capacities and the modular design of both the SBR and SBH series provide greater flexibility for the user to tailor a battery system to their specific energy consumption needs. The SBH series, with its larger 5 kWh modules, appears particularly well-suited for homes with potentially higher energy demands, such as those with 3-phase connections.
4.2 Compatibility with Existing 3-Phase Sungrow Inverter (DC and AC Coupling):
The user's existing Sungrow SG5KTL-MT inverter is a grid-tied inverter and not a hybrid model designed for direct DC coupling with batteries 5. Sungrow's high-voltage batteries, such as the SBR and SBH series, are primarily intended for DC coupling with their SH series hybrid inverters 33. While direct DC coupling is not an option with the SG5KTL-MT, it is possible to AC couple Sungrow batteries to the existing solar system 35. This would likely require the addition of a separate battery inverter to manage the charging and discharging of the Sungrow battery, as the SG5KTL-MT does not have this functionality. Although AC coupling offers a way to integrate a battery without replacing the existing solar inverter, it can introduce inefficiencies due to the multiple AC-DC and DC-AC conversions. For optimal performance and to fully leverage the capabilities of Sungrow's high-voltage batteries, particularly for off-grid operation, upgrading to a Sungrow SH series hybrid inverter would be the recommended approach.
4.3 Suitability for Off-Grid Operation in a 3-Phase System:
Sungrow offers a distinct advantage in providing solutions for 3-phase off-grid operation through their SH-RT series of hybrid inverters 5. These inverters, when paired with Sungrow's SBR or SBH batteries, are capable of providing seamless transition to 3-phase backup power during grid outages 63. The SH-RT series is specifically designed to support 100% unbalanced loads in backup mode, ensuring that essential appliances continue to run during a blackout 66. Both the SBR and SBH battery series are compatible with off-grid operation when used in conjunction with the appropriate Sungrow hybrid inverters. Some single-phase Sungrow hybrid inverters (SH-RS series) also offer off-grid capabilities and support generator connection for battery charging during extended periods of low solar generation 85. This comprehensive ecosystem of Sungrow products provides a more direct and integrated pathway for the user to achieve their goal of potential 3-phase off-grid capability compared to the single-phase limitations of Tesla Powerwall.
4.4 Potential for V2H Integration with a Tesla Car in Australia:
Similar to Tesla Powerwall, the provided research material does not explicitly mention direct V2H integration capabilities for Sungrow battery systems with Tesla cars in Australia 22. However, Sungrow's active involvement in the broader renewable energy and electric vehicle charging sectors suggests a strong potential for future integration. Sungrow manufactures its own range of EV chargers 64, and their 3-phase hybrid inverter solutions can be paired with these chargers for smart green power charging 64. As V2H technology and the necessary bidirectional charging infrastructure become more prevalent in Australia, it is conceivable that Sungrow's integrated energy management systems, including their batteries and hybrid inverters, could be updated to support V2H functionality, potentially even with Tesla vehicles through standardized protocols or future partnerships. In the interim, a Sungrow battery system can efficiently store solar energy, which could then be used to charge a Tesla car. The potential for the Tesla car to discharge back to the home would depend on the availability and compatibility of third-party bidirectional chargers that adhere to the evolving Australian standards.
4.5 Cost and Installation Considerations in Sydney:
The cost of Sungrow batteries in Australia varies depending on the model and capacity. For the SBR series, a 9.6 kWh system is approximately $11,500 installed, a 12.8 kWh system around $13,200 installed, and a 25.6 kWh system around $19,700 installed. Supply-only costs for the SBH series 20 kWh kit range from $13,778.70 to $14,360 40. Compatible 3-phase hybrid inverters from Sungrow, such as the SH5.0RT, are priced around $3,760, while the SH10RT ranges from approximately $4,174.50 to $5,720 78. If the user opts for a Sungrow battery system to achieve optimal 3-phase off-grid capability, the cost of a new SH series hybrid inverter would need to be included, as the existing SG5KTL-MT is not compatible for direct DC coupling. While AC coupling might be a less expensive initial step, it could involve the additional cost of a separate battery inverter. Homeowners in NSW can potentially benefit from the NSW battery rebate when purchasing a Sungrow battery system, which could help reduce the overall cost 5. Although Sungrow batteries often offer a competitive cost per kWh, the total investment for a comprehensive 3-phase off-grid solution might be higher than a single-phase Tesla Powerwall setup, primarily due to the potential need for a new hybrid inverter.
5. Comparative Assessment: Tesla Powerwall vs. Sungrow Batteries
5.1 Side-by-Side Comparison Table of Key Specifications:
| Feature | Tesla Powerwall 3 | Sungrow SBR (Example: 12.8 kWh) + SH10RT |
| :---- | :---- | :---- |
| Usable Energy Capacity (kWh) | 13.5 | 12.8 |
| Continuous Power Output (kW) | 10 | 10 |
| Peak Power Output (kW) | 10 | 12 (5 min) |
| Battery Chemistry | Lithium Iron Phosphate | Lithium Iron Phosphate |
| Scalability | Up to 4 units (54 kWh) | Up to 25.6 kWh per stack, 4 stacks parallel (102.4 kWh) |
| Off-Grid Backup (Phases Supported) | Single-Phase | Three-Phase |
| V2H Support (Current/Future Potential) | Potential via 3rd party charger | Potential via 3rd party charger |
| Warranty (Years) | 10 | 10 |
| Estimated Cost (AUD) | $13,600 + installation | $13,200 (battery installed) + $4,175 - $5,720 (inverter) |
5.2 Detailed Comparison Based on Off-Grid Capability Requirements:
When considering the user's goal of potential off-grid capability for a 3-phase home, Sungrow presents a more robust solution. The availability of Sungrow's SH-RT series hybrid inverters, specifically designed for 3-phase systems and fully compatible with their SBR and SBH batteries, allows for a direct and integrated approach to achieving 3-phase backup power. These systems can seamlessly transition to off-grid mode, powering all three phases of the home, which is crucial for operating 3-phase appliances and ensuring comprehensive whole-house backup. In contrast, Tesla Powerwall, being a single-phase battery, inherently limits off-grid backup to a single phase in a 3-phase home 8. While multiple Powerwall units can be installed, this increases cost and complexity without guaranteeing full 3-phase backup or official off-grid support from Tesla. Therefore, for a user prioritizing potential for comprehensive 3-phase off-grid operation, Sungrow's ecosystem offers a more suitable and supported pathway.
5.3 Detailed Comparison Based on V2H Functionality Requirements:
Currently, neither Tesla Powerwall nor Sungrow batteries offer direct, integrated V2H functionality for Tesla cars in Australia 22. Both systems can store solar energy that could be used to charge a Tesla car, and the potential for the car to discharge back to the home (V2H) would rely on the development and adoption of compatible bidirectional charging infrastructure in Australia, which is expected to become more mainstream in 2025 21. Sungrow's involvement in manufacturing EV chargers and integrating them with their hybrid inverters suggests a potential for future V2H integration within their ecosystem. Similarly, while Tesla Powerwall doesn't currently offer V2H, its role as a home energy storage solution makes it a complementary technology to V2H, providing a place to store energy that could eventually be managed within a V2H framework.
5.4 Cost-Effectiveness and Overall Value Analysis:
When evaluating cost-effectiveness, Sungrow batteries often have a lower cost per kWh of storage compared to Tesla Powerwall 5. However, for the user with an existing non-hybrid inverter, achieving the desired 3-phase off-grid capability with Sungrow would likely necessitate an additional investment in a Sungrow SH-RT series hybrid inverter. This would increase the initial outlay compared to simply AC coupling a Tesla Powerwall to the existing inverter for single-phase backup. The overall value proposition depends heavily on the user's priorities. If the primary goal is to have backup power for essential loads on a single phase and potential future V2H integration, Tesla Powerwall could be a viable option. However, if the potential for comprehensive 3-phase off-grid operation is a significant factor, then the added expense of a Sungrow hybrid inverter might be justified by the enhanced functionality and future-proofing for energy independence. Sungrow's reputation for affordability and the modularity of their battery systems also offer long-term value and flexibility.
6. Recommendations and Considerations
Based on the analysis, for a 3-phase home in Sydney with a 6.6kW solar system and the goal of potential off-grid capability, Sungrow battery options are recommended. Specifically, the user should consider upgrading their existing Sungrow SG5KTL-MT inverter to a Sungrow SH series hybrid inverter (e.g., SH5.0RT or SH10RT, depending on anticipated power demands) and pairing it with a Sungrow high-voltage battery from either the SBR or SBH series. The choice between SBR and SBH would depend on the desired storage capacity and budget. This combination offers a more direct and supported path to achieving 3-phase backup power and the potential for future off-grid operation.
Key Considerations for the User:
Off-Grid Capability: The level of off-grid capability desired (partial single-phase backup vs. comprehensive whole-home 3-phase backup) is a crucial factor. For the latter, Sungrow is the more suitable choice.
Budget: Both options represent a significant investment. The user should obtain detailed quotes for both Tesla Powerwall (considering single or multiple units) and a complete Sungrow hybrid inverter and battery system.
V2H Timeline: The user's timeline for V2H adoption should be considered. Both systems will likely integrate via third-party chargers.
Inverter Upgrade: If pursuing the optimal Sungrow solution for off-grid capability, the cost and logistics of upgrading the existing inverter need to be factored in.
* 3-Phase Backup Importance: The necessity of having backup power across all three phases should weigh heavily in the decision, favoring Sungrow.
It is strongly recommended that the user obtain detailed quotes from certified installers in the Sydney area for both Tesla Powerwall and various Sungrow system configurations to get accurate pricing, installation details, and information on available rebates and incentives in NSW.
7. Conclusion
In conclusion, while Tesla Powerwall offers a well-regarded solution for home energy storage with reliable backup capabilities, its inherent single-phase design presents limitations for users with 3-phase homes seeking comprehensive off-grid functionality. Sungrow, with its range of high-voltage batteries and particularly its 3-phase hybrid inverter systems, provides a more direct and technically sound pathway to achieving the user's goals of potential 3-phase off-grid operation. For V2H integration, both systems are currently positioned to benefit from the evolving Australian regulatory landscape and the development of compatible bidirectional charging technologies. Ultimately, the optimal choice will depend on the user's specific priorities, budget, and the level of off-grid capability they wish to achieve. The rapidly evolving nature of battery storage and V2H technology suggests that continued research and consultation with experts are advisable before making a final decision.
#### Works cited
1. Powerwall – Home Battery Storage | Tesla Australia, accessed March 14, 2025, [https://www.tesla.com/en_au/powerwall](https://www.tesla.com/en_au/powerwall)
2. Tesla Powerwall 3 in Australia: Everything You Need to Know - Fritts Solar, accessed March 14, 2025, [https://www.frittssolar.com.au/tesla-powerwall-3-australia/](https://www.frittssolar.com.au/tesla-powerwall-3-australia/)
3. What to Expect for Powerwall 3 | Tesla Support Australia, accessed March 14, 2025, [https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3](https://www.tesla.com/en_au/support/energy/powerwall/learn/what-expect-powerwall-3)
4. Tesla Powerwall 3 Review - Clean Energy Reviews, accessed March 14, 2025, [https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review](https://www.cleanenergyreviews.info/blog/tesla-powerwall-3-review)
5. Sungrow SBH vs. Tesla Powerwall 3: Which is Better? NSW - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/](https://www.elitepowergroup.com.au/news/sungrow-sbh-vs-tesla-powerwall-3-which-is-better-nsw/)
6. Sungrow Battery vs Tesla Powerwall Review - Volteam Electric, accessed March 14, 2025, [https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/](https://volteam.com.au/blog/sungrow-vs-tesla-battery-review/)
7. Tesla Powerwall 2: A Complete 2024 Buyers Guide | Solar Choice, accessed March 14, 2025, [https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/](https://www.solarchoice.net.au/products/batteries/tesla-powerwall-2-review/)
8. Can You Install The Powerwall 3 On A Three-Phase Home? - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/three-phase-powerwall-3/](https://www.solarquotes.com.au/blog/three-phase-powerwall-3/)
9. Is my grid connect solar system 100% compatible with a Tesla Powerwall 2 battery?, accessed March 14, 2025, [https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery](https://support.solarquotes.com.au/hc/en-us/articles/115001986773-Is-my-grid-connect-solar-system-100-compatible-with-a-Tesla-Powerwall-2-battery)
10. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20210706/EN%203-phaseSolution%20Factsheet.pdf)
11. Combining Systems with Powerwall | Tesla Support, accessed March 14, 2025, [https://www.tesla.com/support/energy/powerwall/learn/combining-systems](https://www.tesla.com/support/energy/powerwall/learn/combining-systems)
12. Powerwall System Design | Tesla Support, accessed March 14, 2025, [https://www.tesla.com/support/energy/powerwall/learn/system-design](https://www.tesla.com/support/energy/powerwall/learn/system-design)
13. Installing Powerwall 3 on a Three-phase Site | PSC - Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/](https://www.penrithsolar.com.au/blog/installing-powerwall-3-on-a-three-phase-site/)
14. Powerwall 3: When It Makes Sense and When It Doesn't - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/](https://www.solarquotes.com.au/blog/powerwall-3-when-it-makes-sense/)
15. AC-Coupled Solar System Sizing - Energy Library - Tesla, accessed March 14, 2025, [https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html](https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-23D242D1-8D65-47B9-9118-57002FFD84D2.html)
16. Powerwall 3 Roadmap - 3 Phase Coming! | Tesla Motors Club, accessed March 14, 2025, [https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/](https://teslamotorsclub.com/tmc/threads/powerwall-3-roadmap-3-phase-coming.321409/)
17. Advice on how to install with 3 phase : r/solar - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/](https://www.reddit.com/r/solar/comments/19djazk/advice_on_how_to_install_with_3_phase/)
18. TESLA POWERWALL+ (3) - DIY Solar Depot, accessed March 14, 2025, [https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/](https://diysolardepot.com/product/ground-mount-solar-hardware/pro-solar-ground-trac/)
19. Design Considerations - Energy Library - Tesla, accessed March 14, 2025, [https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html](https://energylibrary.tesla.com/docs/Public/EnergyStorage/Powerwall/3/SystemDesign/en-us/GUID-3E19662A-E501-47DB-81AE-E9EC19735B8B.html)
20. Problems with Powerwall 3 | Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/](https://www.penrithsolar.com.au/blog/problems-with-powerwall-3/)
21. EV Charging in Australia Gets a Makeover with V2G/V2H Approved for 2025 - SEVR, accessed March 14, 2025, [https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/](https://sevr.au/news/ev-charging-in-australia-gets-a-makeover-with-v2g-v2h-approved-for-2025/)
22. V2G, V2L & V2H Explained: Vehicle to Grid in Australia? 2025 - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/](https://www.elitepowergroup.com.au/news/what-is-vehicle-to-grid/)
23. Australia's Future – Bidirectional EV Charging, Solar & Battery Storage as Standard Features, accessed March 14, 2025, [https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/](https://fullycharged.show/blog/australias-future-bidirectional-ev-charging-solar-battery-storage-as-standard-features/)
24. 2025, the Year of Vehicle-to-Grid in Australia V2G Milestone - Elite Power Group, accessed March 14, 2025, [https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/](https://www.elitepowergroup.com.au/news/one-step-closer-to-v2g-in-australia-2025-to-be-the-year-of-v2x/)
25. Bidirectional Charging for Electric Cars: Unlocking New Possibilities - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/](https://www.solarbatteriesonline.com.au/bidirectional-charging-for-electric-cars-unlocking-new-possibilities/)
26. The Best Home Batteries In Australia In 2025: According To Aussie Installers - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/blog/best-home-batteries-2025/](https://www.solarquotes.com.au/blog/best-home-batteries-2025/)
27. How Much Does a Tesla Powerwall 3 Cost? | Penrith Solar Centre, accessed March 14, 2025, [https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/](https://www.penrithsolar.com.au/blog/how-much-does-a-tesla-powerwall-3-cost/)
28. Expected 3 Phase upgrade price? : r/AusRenovation - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/](https://www.reddit.com/r/AusRenovation/comments/19383oa/expected_3_phase_upgrade_price/)
29. Powerwall cost for Sydney? | Tesla Motors Club, accessed March 14, 2025, [https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/](https://teslamotorsclub.com/tmc/threads/powerwall-cost-for-sydney.340317/)
30. Solar Battery Costs: Are They Worth It?, accessed March 14, 2025, [https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/](https://www.solarchoice.net.au/solar-batteries/is-home-battery-storage-worth-it/)
31. Tesla Powerwall 3 Price and Installation - Solar4Life, accessed March 14, 2025, [https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation](https://www.solar4life.com.au/learns/tesla-powerwall-3-price-and-installation)
32. Solar Battery Price, Savings and Payback, accessed March 14, 2025, [https://solarcalculator.com.au/battery-storage/price/](https://solarcalculator.com.au/battery-storage/price/)
33. Sungrow | Solar Batteries Review - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html](https://www.solarquotes.com.au/battery-storage/reviews/sungrow-review.html)
34. Sungrow SBR high voltage battery - VP Solar, accessed March 14, 2025, [https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/](https://www.vpsolar.com/en/sungrow-sbr-high-voltage-battery/)
35. Sungrow Battery SBR Series - SolarBright, accessed March 14, 2025, [https://solarbright.com.au/product/sungrow-battery-sbr-series/](https://solarbright.com.au/product/sungrow-battery-sbr-series/)
36. Sungrow SBR 3.2kWh module - Huglo Solar, accessed March 14, 2025, [https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery](https://www.huglo.com.au/batteries/sbr-high-voltage-lfp-battery)
37. Sungrow Inverter and battery Review - Clean Energy Reviews, accessed March 14, 2025, [https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review](https://www.cleanenergyreviews.info/blog/sungrow-solar-inverters-review)
38. SBH100/150/200/250/300/350/400 - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400](https://en.sungrowpower.com/productDetail/5568/battery-sbh100-150-200-250-300-350-400)
39. 20/25/30/35/40 kWh Solar Battery - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400](https://aus.sungrowpower.com/productDetail/3112/battery-sbh200-250-300-350-400)
40. Sungrow SBH Stackable Battery System - Grow Energy, accessed March 14, 2025, [https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system](https://growenergy.com.au/products/sungrow-sbh-stackable-battery-system)
41. Sungrow SBH High Voltage Battery Bundle (SBH200 - SBH400), accessed March 14, 2025, [https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400](https://solarbatterysupermarket.com.au/products/sungrow-sbh-high-voltage-battery-bundle-sbh200-sbh400)
42. Buy cheap SunGrow solar inverters, accessed March 14, 2025, [https://tienda-solar.es/en/brand/54-sungrow](https://tienda-solar.es/en/brand/54-sungrow)
43. Sungrow PowCube battery storage system (Analysis & review) - Solar Choice, accessed March 14, 2025, [https://www.solarchoice.net.au/products/batteries/sungrow-review/](https://www.solarchoice.net.au/products/batteries/sungrow-review/)
44. What inverters do we connect to? – Welcome to our Help Center - Support - SwitchDin, accessed March 14, 2025, [https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to](https://support.switchdin.com/hc/en-us/articles/19642583185817-What-inverters-do-we-connect-to)
45. Accessories Cross Reference Guide - Sungrow Australia Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/TI_202007_Sungrow%20Accessories%20Cross%20Reference%20Guide_V1.0.pdf)
46. Sungrow - Solar System Inverter - Solargain, accessed March 14, 2025, [https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters](https://www.solargain.com.au/solar-inverters/sungrow-solar-inverters)
47. Sungrow Battery Review | A Comprehensive Guide - Esteem Energy, accessed March 14, 2025, [https://esteemenergy.com.au/blog/sungrow-battery-review/](https://esteemenergy.com.au/blog/sungrow-battery-review/)
48. Sungrow 5kW Inverter + Tesla Powerwall + Longi 370w Hi-MO4m 7.4kW Solar System, accessed March 14, 2025, [https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/](https://ahlecsolar.com.au/product/sungrow-5kw-inverter-tesla-powerwall-longi-370w-hi-mo4m-7-4kw-solar-system/)
49. Sungrow | Solar Inverters Review - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/inverters/sungrow-review.html](https://www.solarquotes.com.au/inverters/sungrow-review.html)
50. Tesla Powerwall: Inverter Compatibility Under the Spotlight - 1KOMMA5, accessed March 14, 2025, [https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/](https://1komma5.com/au/batteries/tesla-powerwall-2-compatible-solar-power-system/)
51. Hi everybody, question about V2H power : r/electricvehicles - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/](https://www.reddit.com/r/electricvehicles/comments/1hqneh3/hi_everybody_question_about_v2h_power/)
52. Commercial Solar System | PV Plant | Rooftop - Sungrow US, accessed March 14, 2025, [https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems](https://us.sungrowpower.com/solutionsDetail/10/commercial-storage-systems)
53. SH8.0/10RS | 8kW/10kW | Single Phase | Sungrow Hybrid Inverter-Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs](https://aus.sungrowpower.com/productDetail/2565/mv-power-converter-hybrid-inverter-sh8-0-10rs)
54. Approved Batteries with SH Series Hybrid Inverters - Sungrow Australia Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/Approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters-20201209_V14_EN.pdf)
55. Right inverter for the Tesla Powerwall 2 : r/solar - Reddit, accessed March 14, 2025, [https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/](https://www.reddit.com/r/solar/comments/1chgnj8/right_inverter_for_the_tesla_powerwall_2/)
56. Sungrow Inverters - Gold Coast Solar Power Solutions, accessed March 14, 2025, [https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/](https://gold-coast-solar-power-solutions.com.au/gold-coast-solar-power-products/solar-power-inverters/sungrow-inverters/)
57. Sungrow SBR192 Lithium-ion Battery - Europe-SolarStore.com, accessed March 14, 2025, [https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html](https://www.europe-solarstore.com/sungrow-sbr192-lithium-ion-battery.html)
58. High-Efficiency Solar Battery: Up to 100% Usable Energy - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/ProductsHome/20/23/battery](https://en.sungrowpower.com/ProductsHome/20/23/battery)
59. Warranty | Sungrow Australia and New Zealand Service, accessed March 14, 2025, [https://service.sungrowpower.com.au/Warranty/warranty](https://service.sungrowpower.com.au/Warranty/warranty)
60. Sungrow Battery cross-reference chart, accessed March 14, 2025, [https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf](https://service.sungrowpower.com.au/GD_202405_SBR%20and%20SBH_Cross%20Reference%20Chart_V1.4%20Final.pdf)
61. Sungrow SG5KTL-MT - SolarTopStore.com, accessed March 14, 2025, [https://www.solartopstore.com/products/sungrow-sg5ktl-mt](https://www.solartopstore.com/products/sungrow-sg5ktl-mt)
62. Approved Batteries with SH Series Hybrid Inverters EU Version V1.6.3 - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf](https://aus.sungrowpower.com/upload/file/20211119/TI_20210906_approved%20battery%20declaration%20for%20sungrow%20hybrid%20inverters_V16_EN.pdf)
63. BLACKOUT? NO, THANKS! POWER WHENEVER YOU NEED IT - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20211202/EN%20FS%20Sungrow%203-phase%20Hybrid%20Backup%20Factsheet.pdf)
64. Sungrow 3-phase solution with 6 kVA inverter, EV charger and 9.6 kWh storage - Memodo, accessed March 14, 2025, [https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767](https://www.memodo-shop.com/sungrow-3-phase-solution-with-6-kva-inverter-ev-charger-and-9.6-kwh-storage/9767)
65. THE 3-PHASE SOLUTION - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf](https://uk.sungrowpower.com/upload/file/20230116/EN%20FS%203-phaseSolution%20Factsheet.pdf)
66. Sungrow Three-Phase Hybrid Inverter - Solar4Life, accessed March 14, 2025, [https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid](https://www.solar4life.com.au/product-detail/sungrow-5-20kw-3-phase-hybrid)
67. SG5KTL-MT/SG6KTL-MT/SG8KTL-M (Non-China ... - ENF Solar, accessed March 14, 2025, [https://www.enfsolar.com/pv/inverter-datasheet/12176](https://www.enfsolar.com/pv/inverter-datasheet/12176)
68. Sungrow SBR battery combiner box - AC Solar Warehouse, accessed March 14, 2025, [https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620](https://www.acsolarwarehouse.com/shop/sungrow-battery-combiner-box-for-multiple-sungrow-lfp-battery-stacks-23620)
69. Sungrow SBR HV Battery Installation Quick Guide, accessed March 14, 2025, [https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf](https://service.sungrowpower.com.au/files/Web_Files/FAQ/GD_202202_SBR%20HV%20Battery%20Installation%20Quick%20Guide%20with%201%20Phase%20SHxRS_V3.0.pdf)
70. Energy Storage System Products Catalogue - SUNGROW, accessed March 14, 2025, [https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf](https://uk.sungrowpower.com/upload/file/20210909/EN%20BR%20Sungrow%20Energy%20Storage%20System%20Products%20Catalogue.pdf)
71. DC Coupling vs AC Coupling: Which Solar System to Choose - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose](https://en.sungrowpower.com/blog-detail/5983/dc-coupling-vs-ac-coupling-which-solar-system-to-choose)
72. Sungrow SBH battery - Accessory kit | AC Solar Warehouse AU, accessed March 14, 2025, [https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310](https://www.acsolarwarehouse.com/shop/sbh-accessory-kit-sungrow-sbh-battery-accessory-kit-25310)
73. Sungrow SBR 3.2kWh High Voltage Battery Module , ASA00460 - Alternergy, accessed March 14, 2025, [https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460](https://www.alternergy.co.uk/sungrow-sbr-3-2-kwh-battery-asa00460)
74. NEW Sungrow single phase hybrid inverters can operate without the grid or a battery, accessed March 14, 2025, [https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255](https://www.acsolarwarehouse.com/blog/news-7/new-sungrow-single-phase-hybrid-inverters-can-operate-without-the-grid-or-a-battery-255)
75. Lawnton Sungrow SBH & Solar Hybrid System | Alvolta, accessed March 14, 2025, [https://www.alvolta.com.au/portfolio/info/74](https://www.alvolta.com.au/portfolio/info/74)
76. Sungrow Battery Starter Pack - Huglo Solar, accessed March 14, 2025, [https://www.huglo.com.au/post/sungrow-battery-starter-pack](https://www.huglo.com.au/post/sungrow-battery-starter-pack)
77. Sungrow SBR Battery System Bundles, accessed March 14, 2025, [https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles](https://solarbatterysupermarket.com.au/products/sungrow-sbr-battery-system-bundles)
78. Sungrow Hybrid 10kW RT Three-Phase Solar Inverter, accessed March 14, 2025, [https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108](https://www.springers.com.au/shop/sh10rt-sungrow-hybrid-10kw-rt-three-phase-solar-inverter-15108)
79. Sungrow RT 5kW Three Phase Hybrid inverter (2 MPPT) SH5.0RT - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/](https://www.solarbatteriesonline.com.au/product/sungrow-sh5-0rt-hv-5-0kw-residential-hybrid-three-phase-inverter/)
80. SUNGROW SH10RT | 10kW 3-Phase Hybrid Inverter - Sparky Direct, accessed March 14, 2025, [https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter](https://www.sparkydirect.com.au/p/sungrow-sh10rt-10kw-3-phase-hybrid-inverter)
81. Sungrow Hybrid 10kW 3 Phase 2 MPPT w/WiFi, DC Switch & EPS Built-in Inverter, accessed March 14, 2025, [https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/](https://www.solarheroes.com.au/product/sungrow-hybrid-10kw-3-phase-2-mppt-w-wifi-dc-switch-eps-built-in-inverter/)
82. Sungrow Solar Inverters - Independent Review, accessed March 14, 2025, [https://www.solarchoice.net.au/products/inverters/Sungrow-review/](https://www.solarchoice.net.au/products/inverters/Sungrow-review/)
83. Sungrow 10.0kW - 3 Phase Hybrid Inverter (SH10RT) - Solar Superstore, accessed March 14, 2025, [https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt](https://www.solarsuperstore.com.au/products/sungrow-8-0kw-3-phase-hybrid-inverter-sh8-0rt)
84. How Much Do Solar Batteries Cost in Australia? - SolarQuotes, accessed March 14, 2025, [https://www.solarquotes.com.au/battery-storage/cost/](https://www.solarquotes.com.au/battery-storage/cost/)
85. Off Grid Solar system using a Sungrow inverter and battery, accessed March 14, 2025, [https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312](https://www.acsolarwarehouse.com/blog/news-7/off-grid-solar-system-using-a-sungrow-inverter-and-battery-312)
86. Sungrow 14.08k W Off Grid Solar System / Single Phase - AHLEC, accessed March 14, 2025, [https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/](https://ahlecsolar.com.au/product/sungrow-14-08k-w-off-grid-solar-system-single-phase/)
87. Residential Battery Energy Storage System - Sungrow AU, accessed March 14, 2025, [https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system](https://aus.sungrowpower.com/solutionsDetail/9/residential-storage-system)
88. EV Charger - Sungrow, accessed March 14, 2025, [https://en.sungrowpower.com/ProductsHome/59/ev-charger](https://en.sungrowpower.com/ProductsHome/59/ev-charger)
89. Sungrow SBH 20kW High Voltage LFP Battery Including Accessory Kit SBH200 | eBay, accessed March 14, 2025, [https://www.ebay.com.au/itm/135320073679](https://www.ebay.com.au/itm/135320073679)
90. 20kWh Battery Kit - Login - Australian Solar Supplies Pty Ltd, accessed March 14, 2025, [http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f](http://shop.ausolarsupplies.com.au/s.nl/it.A/id.6047/.f)
91. Sungrow - Solar Batteries Online, accessed March 14, 2025, [https://www.solarbatteriesonline.com.au/sungrow/](https://www.solarbatteriesonline.com.au/sungrow/)
{"id":"6a44da7a-19c1-4a37-a991-d589c8bbded8","providerCopyMimeTypes":["application/vnd.vscode.markdown.updatelinks.metadata","application/vnd.code.additional-editor-data"],"defaultPastePayload":{"multicursorText":null,"pasteOnNewLine":false,"mode":null}}{"version":1,"isFromEmptySelection":false,"multicursorText":null,"mode":"markdown"}
-
 @ 83279ad2:bd49240d
2025-03-30 14:21:49
@ 83279ad2:bd49240d
2025-03-30 14:21:49Test
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Scala is such a great language
Scala is amazing. The type system has the perfect balance between flexibility and powerfulness.
matchstatements are great. You can write imperative code that looks very nice and expressive (and I haven't tried writing purely functional things yet). Everything is easy to write and cheap and neovim integration works great.But Java is not great. And the fact that Scala is a JVM language doesn't help because over the years people have written stuff that depends on Java libraries -- and these Java libraries are not as safe as the Scala libraries, they contain reflection, slowness, runtime errors, all kinds of horrors.
Scala is also very tightly associated with Akka, the actor framework, and Akka is a giant collection of anti-patterns. Untyped stuff, reflection, dependency on JVM, basically a lot of javisms. I just arrived and I don't know anything about the Scala history or ecosystem or community, but I have the impression that Akka has prevent more adoption of Scala from decent people that aren't Java programmers.
But luckily there is a solution -- or two solutions: ScalaJS is a great thing that exists. It transpiles Scala code into JavaScript and it runs on NodeJS or in a browser!
Scala Native is a much better deal, though, it compiles to LLVM and then to binary code and you can have single binaries that run directly without a JVM -- not that the single JARs are that bad though, they are great and everybody has Java so I'll take that anytime over C libraries or NPM-distributed software, but direct executables even better. Scala Native just needs a little more love and some libraries and it will be the greatest thing in a couple of years.
-
 @ c11cf5f8:4928464d
2025-03-30 07:32:36
@ c11cf5f8:4928464d
2025-03-30 07:32:36Let's support #Bitcoin #merchants! I'd love to hear some of your latest #Lightning purchases and interesting #products you bought. Feel #free to include links to the #shops or #businesses you bought from.
Who else has a recent purchase they’re excited about? Bonus #sats if you found a killer #deal! ⚡
If you missed our last thread, here are some of the items stackers recently spent and #zap on.
originally posted at https://stacker.news/items/929295
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Que vença o melhor
Nos esportes e jogos em geral, existe uma constante preocupação em balancear os incentivos e atributos do jogo, as regras do esporte em si e as regras das competições para que o melhor vença, ou, em outras palavras, para que sejam minimizados os outros fatores exceto a habilidade mais pura quanto possível no jogo em questão.
O mundo fora dos jogos, porém, nem sempre pode ter suas regras mudadas por um ente que as controla e está imbuído da vontade e dos meios para escolher as melhores regras possíveis para a obtenção dos resultados acima. Aliás, é muitas vezes essa possibilidade é até impensável. Mesmo quando ela é pensável e levada em conta os fatores que operam no mundo real não são facilmente identificáveis, eles são muitos, e mudam o tempo todo.
Mais do que isso, ao contrário de um jogo em que o objetivo é praticamente o mesmo para todo mundo, os objetivos de cada agente no mundo real são diferentes e incontáveis, e as "competições" que cada um está disputando são diferentes e muitas, cada minúsculo ato de suas vidas compreendendo várias delas simultaneamente.
Da mesma forma, é impossível conceber até mesmo o conceito de "melhor" para que se deseje que ele vença.
Mesmo assim é comum encontrarmos em várias situações gente que parte do princípio de que se Fulano está num certo lugar (por exemplo, um emprego muito bom) e Beltrano não isso se deve ao fato de Fulano ter sido melhor que Beltrano.
Está aí uma crítica à idéia da meritocracia (eu tinha me esquecido que essa palavra existia).
-
 @ fd06f542:8d6d54cd
2025-03-30 02:16:24
@ fd06f542:8d6d54cd
2025-03-30 02:16:24Warning
unrecommended: deprecated in favor of NIP-17NIP-04
Encrypted Direct Message
finalunrecommendedoptionalA special event with kind
4, meaning "encrypted direct message". It is supposed to have the following attributes:contentMUST be equal to the base64-encoded, aes-256-cbc encrypted string of anything a user wants to write, encrypted using a shared cipher generated by combining the recipient's public-key with the sender's private-key; this appended by the base64-encoded initialization vector as if it was a querystring parameter named "iv". The format is the following:"content": "<encrypted_text>?iv=<initialization_vector>".tagsMUST contain an entry identifying the receiver of the message (such that relays may naturally forward this event to them), in the form["p", "<pubkey, as a hex string>"].tagsMAY contain an entry identifying the previous message in a conversation or a message we are explicitly replying to (such that contextual, more organized conversations may happen), in the form["e", "<event_id>"].Note: By default in the libsecp256k1 ECDH implementation, the secret is the SHA256 hash of the shared point (both X and Y coordinates). In Nostr, only the X coordinate of the shared point is used as the secret and it is NOT hashed. If using libsecp256k1, a custom function that copies the X coordinate must be passed as the
hashfpargument insecp256k1_ecdh. See here.Code sample for generating such an event in JavaScript:
```js import crypto from 'crypto' import * as secp from '@noble/secp256k1'
let sharedPoint = secp.getSharedSecret(ourPrivateKey, '02' + theirPublicKey) let sharedX = sharedPoint.slice(1, 33)
let iv = crypto.randomFillSync(new Uint8Array(16)) var cipher = crypto.createCipheriv( 'aes-256-cbc', Buffer.from(sharedX), iv ) let encryptedMessage = cipher.update(text, 'utf8', 'base64') encryptedMessage += cipher.final('base64') let ivBase64 = Buffer.from(iv.buffer).toString('base64')
let event = { pubkey: ourPubKey, created_at: Math.floor(Date.now() / 1000), kind: 4, tags: [['p', theirPublicKey]], content: encryptedMessage + '?iv=' + ivBase64 } ```
Security Warning
This standard does not go anywhere near what is considered the state-of-the-art in encrypted communication between peers, and it leaks metadata in the events, therefore it must not be used for anything you really need to keep secret, and only with relays that use
AUTHto restrict who can fetch yourkind:4events.Client Implementation Warning
Clients should not search and replace public key or note references from the
.content. If processed like a regular text note (where@npub...is replaced with#[0]with a["p", "..."]tag) the tags are leaked and the mentioned user will receive the message in their inbox. -
 @ b8af284d:f82c91dd
2025-03-10 08:28:07
@ b8af284d:f82c91dd
2025-03-10 08:28:07Liebe Abonnenten,
800 Milliarden Euro will die EU ausgeben, um die Ukraine und den Kontinent in ein “stählernes Stachelschwein” zu verwandeln. Deutschland selbst will künftig Verteidigungsausgaben aus der Schuldenbremse ausnehmen, was nichts anderes als eine unbegrenzte Kreditlinie für das Militär bedeutet. Hinzu kommt ein “Sondervermögen” in Höhe von 500 Milliarden Euro für Infrastruktur. Das klingt nach einem Spartopf, den man für schwere Zeiten angelegt hat. Es soll die Tatsache verschleiern, dass es sich dabei um Schulden handelt. Der vermutlich baldige Kanzler Friedrich Merz bricht damit sein Wahlversprechen, die Schuldenbremse einzuhalten. Beschließen soll das Paket noch ein abgewählter Bundestag, da im neuen wohl die Mehrheit fehlt.
Womit also ist zu rechnen, wenn demnächst fast eine Billion frisch gedruckte Euro in Drohnen, Panzer und Raketen investiert werden?
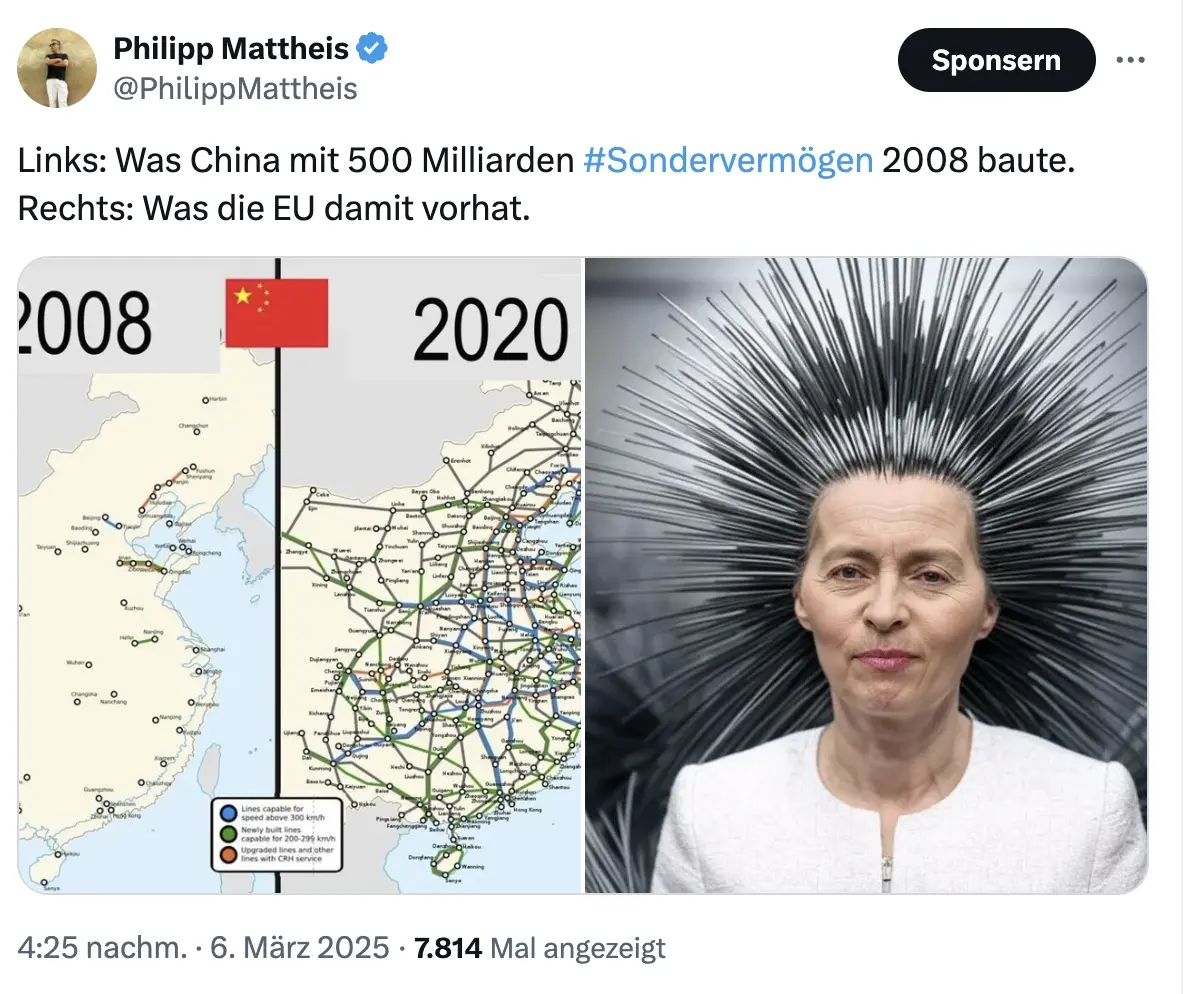
Das beste Beispiel der jüngeren Geschichte ist China: 2009 legte die chinesische Regierung das bisher größte Infrastrukturprojekt der Welt in Höhe von 440 Milliarden Euro auf. Finanziert wurde es durch günstige Kredite, die vor allem an Staatsunternehmen vergeben wurden. Nachdem die Welt nach der in den USA ausgelösten Immobilienkrise 2008 in die Rezession gerutscht war, „rettete“ dieses Paket die globale Konjunktur. China hatte zu diesem Zeitpunkt großen Bedarf an Flughäfen, Straßen und vor allem Zügen. Das Paket war riskant: Schier unbegrenztes Geld, das begrenzten Waren hinterherjagt, führt zu Inflation. Billige Kredite führen meist dazu, dass Unternehmen nicht mehr effizient wirtschaften, und Schuldenberge vor sich her wälzen.
Allerdings wurde das Geld in Produktivität investiert. Denn wenn Menschen und Waren einfacher reisen können, nimmt die Geschäftstätigkeit zu: Arbeitnehmer werden mobiler, Unternehmen konkurrenzfähiger, die Preise sinken. Die Investitionen lohnen sich also, weil sie zu mehr Wirtschaftswachstum führen. Vereinfacht gesagt: Die Schulden können zurückgezahlt werden, und am Ende bleibt noch mehr übrig. In diesem Fall führen Schulden nicht zu Inflation: Durch die gesteigerte Produktivität stehen jetzt sogar mehr Waren der Geldmenge gegenüber.
15 Jahre später kämpft die zweitgrößte Volkswirtschaft zwar noch immer mit den Problemen, die aus diesem Paket resultieren - die Immobilienkrise ist eine indirekte Folge davon. Trotzdem war das Programm ein Erfolg: die Städte, Flughäfen und vor allem Zugstrecken führten zu einer höheren wirtschaftlichen Aktivität oder Produktivität. China ist heute ein wesentlich moderneres Land als vor dem Paket, und verfügt über modernste und größte Netz aus Hochgeschwindigkeitszügen der Welt. Neue Schulden können positiv sein - wenn das Geld produktiv investiert wird.
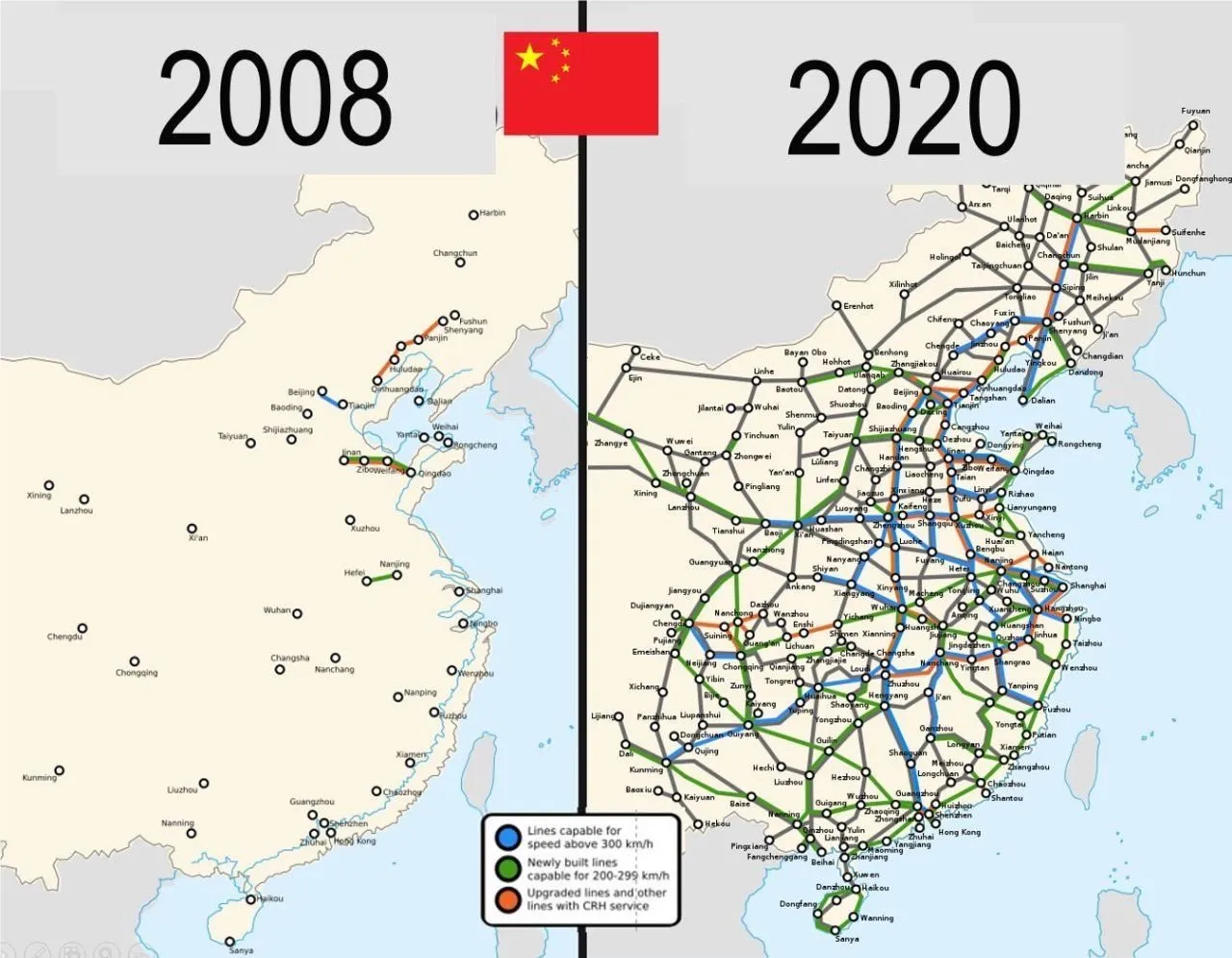
Auch in Europa lassen sich mit dem Geld-Paket zunächst mehrere Probleme auf einmal lösen: Deutschland ist noch immer ein Industriestandort mit hohen Produktionskapazitäten. Werke der Auto- und Zulieferindustrie können theoretisch zur Waffenproduktion umfunktioniert werden. Immer noch besser als sie stillzulegen oder an die Chinesen zu verkaufen, werden viele Kommentatoren schreiben.
Allein in der deutschen Automobil-Zulieferindustrie sind im vergangenen Jahr über 19000 Arbeitsplätze verloren gegangen. Viele von den Entlassenen können nun Arbeit in der Rüstungsindustrie finden. Oder wie Hans Christoph Atzpodien, Hauptgeschäftsführer des Bundesverbandes der Deutschen Sicherheits- und Verteidigungsindustrie in der WirtschaftsWoche sagt:
„Das Motto muss lauten: Autos zu Rüstung! Anstatt einen volkswirtschaftlichen Schaden durch den Niedergang der Auto-Konjunktur zu beklagen, sollten wir versuchen, Produktionseinrichtungen und vor allem Fachkräfte aus dem Automobilsektor möglichst verträglich in den Defence-Bereich zu überführen“
Immerhin: ein großer Teil des Geldes soll auch in Infrastrukturprojekte fließen: Brücken, Bahn, Internetausbau. Deutschland, und damit Europa, wird in den kommenden Monaten also eine große Party feiern, die über die Tatsache hinwegtäuschen wird, dass man einen dummen Krieg verloren hat. In den kommenden Monaten werden sich Verbände und Organisationen um das Geld reißen. Das Geld wird ein auch kollektiv-psychologisches Ventil sein, um das eigene Versagen bei Corona, Klima und Ukraine vergessen zu machen.
Es gibt allerdings einen wesentlichen Unterschied zum chinesischen Stimulus-Paket 2009: Rüstungsgüter sind im Gegensatz zu Zugstrecken totes Kapital. Eine neue Drohne oder Panzer führt nicht zu mehr Produktivität, im Gegenteil: Kommen sie zum Einsatz, zerstören sie Brücken, Häuser, Straßen und töten Menschen. Die Produktivität sinkt also. Im besten Fall kann Militärgerät herumstehen und vor sich hin rosten. Auch dann aber ist es „totes Kapital“, das nichts zur Produktivität beiträgt. Kommt es zum Einsatz, stehen der nun verringerten Warenmenge eine noch größere Geldmenge gegenüber. Die Inflation steigt.
Schleichende Militarisierung
Auch gesellschaftlich wird das Paket mit seinem Blanko-Scheck für die Verteidigungsindustrie viel verändern: Es kommt zu einer „Eichung“ der Gesellschaft, eine kollektive Abscheu des gemeinsamen Feindes. Scharfmacher, eigentlich mittelmäßiger Akademiker und Bürokraten, wie Carlo Masala und Claudia Major werden eine noch größere Rolle im öffentlichen Diskurs spielen und die Talkshows dominieren, die von einer immer älter werdenden deutschen Bevölkerung geglotzt werden. Abweichende Meinungen auf Online-Plattformen zensiert, unter dem Vorwand, die Demokratie sei in Gefahr:
Da die Rüstungsindustrie dann eine wichtigere Rolle für die Gesamtwirtschaft spielt, wird ihr Einfluss auf die Politik in Form von Lobbyisten und Verbänden zunehmen. Politiker merken schnell, dass sie von der medialen Aufmerksamkeitsökonomie nach oben gespült werden, wenn sie immer radikalere Forderungen stellen. So empfahl der ehemalige Außenminister Joschka Fischer die Woche die Wiedereinführung der Wehrpflicht für Männer und Frauen. “Star-Ökonomin” Isabella Weber will die Kriegswirtschaft mitplanen:
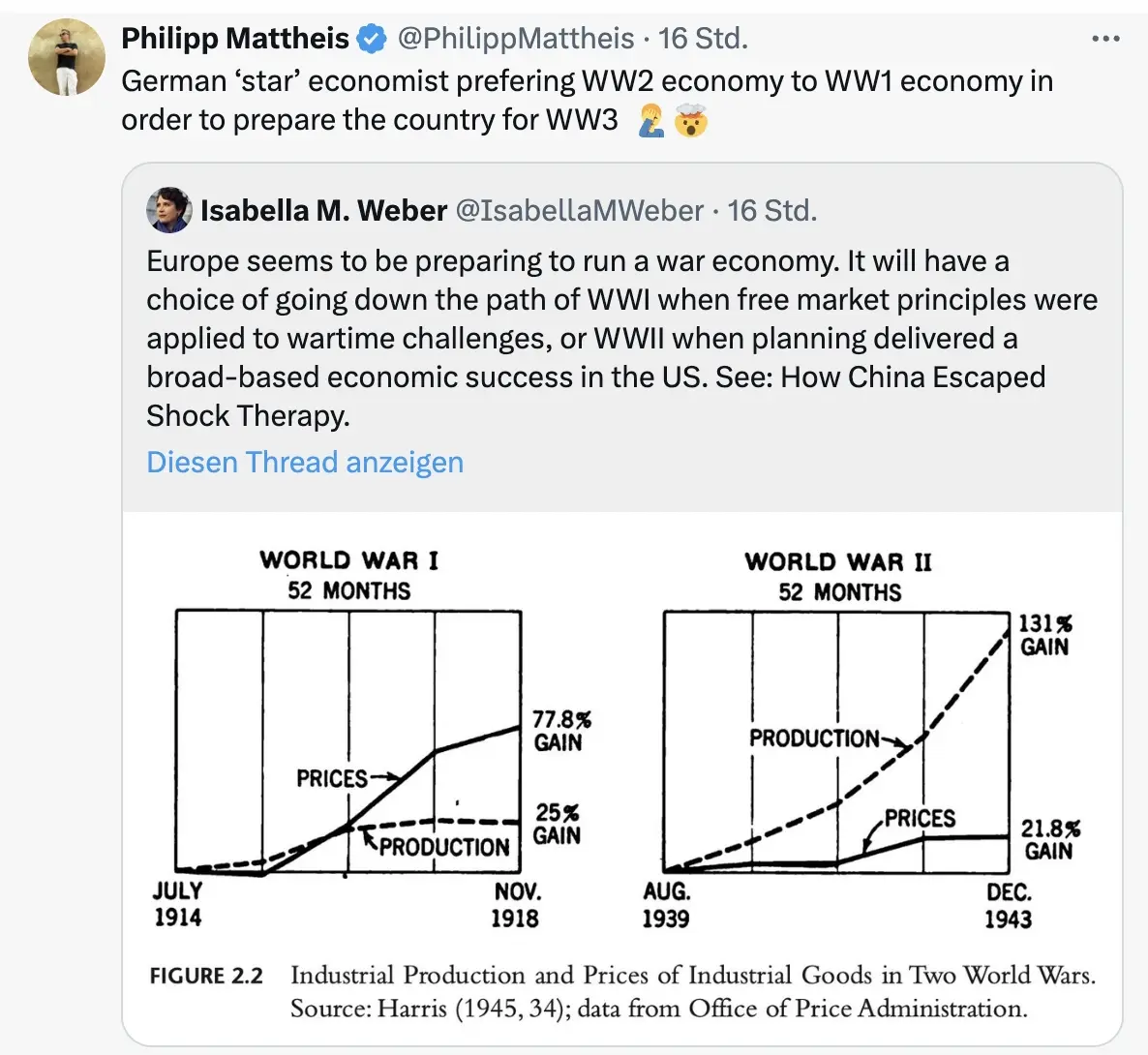
\ Der Kontinent wird sich langsam wandeln von einem „Friedensprojekt“ zu einem „metallenen Stachelschwein“, ergo Kriegsprojekt, denn ohne dämonisierten Feind funktioniert das Programm nicht. Der Ton wird rauer, autoritärer, und die Meinungsfreiheit weiter eingeschränkt werden. Die seit 2020 eingeführten Werkzeuge zur soften Propaganda („kognitive Kriegsführung”) werden verfeinert und ausgebaut werden, sodass weiterhin 80 Prozent der Bevölkerung alle noch so antihumanen Maßnahmen gutheißen werden.
Und dann?
Wie Julian Assange einmal sagte: “Das Ziel ist kein erfolgreicher Krieg. Das Ziel ist ein endloser Krieg.” Der Konflikt muss weitergehen, ewig schwelen oder ein neuer gefunden werden, da sonst ein Teil der Wirtschaftsleistung kollabiert.
Nach ein, zwei oder auch erst drei Jahren, werden erste Probleme sichtbar. Die Party endet, der Kater setzt langsam ein. Die Finanzierung an den Kapitalmärkten wird für Deutschland immer kostspieliger. Der Schuldendienst wird einen größeren Teil des Haushalts einnehmen. Die Bürger müssen dies mitfinanzieren. Der voraussichtlich neue Bundeskanzler Friedrich Merz sprach bereits von der „Mobilisierung der deutschen Sparguthaben“.
\ Was im Ersten Weltkrieg „Kriegsanleihen“ hieß, wird einen schickeren Namen bekommen wie „olivgrüne Bonds“. You name it. Alternativ lässt sich ein Verteidigungs-Soli einführen, oder das Kindergeld streichen, wie kürzlich Ifo-Chef Clemens Fuest forderte.
Was kann man tun? Auf BlingBling geht es um konkrete Tipps, welche Anlagen von dieser Entwicklung profitieren werden. Außerdem geht es um die “Strategische Bitcoin Reserve”, die am Donnerstag beschlossen wurde.
-
 @ fd06f542:8d6d54cd
2025-03-30 02:11:00
@ fd06f542:8d6d54cd
2025-03-30 02:11:00NIP-03
OpenTimestamps Attestations for Events
draftoptionalThis NIP defines an event with
kind:1040that can contain an OpenTimestamps proof for any other event:json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> }- The OpenTimestamps proof MUST prove the referenced
eevent id as its digest. - The
contentMUST be the full content of an.otsfile containing at least one Bitcoin attestation. This file SHOULD contain a single Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
Example OpenTimestamps proof verification flow
```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
- The OpenTimestamps proof MUST prove the referenced
-
 @ 3514ac1b:cf164691
2025-03-30 15:16:56
@ 3514ac1b:cf164691
2025-03-30 15:16:56hi , My name is Erna and i hope this articles find you well. hmm what i like to talked about today is how i dislike my my black coffee getting cold . it is happened almost everyday . here is my morning flow : wake up brush teeth and make my self ready make coffee ( boiled water ) in meantime switch on my computer reading news , things ( water allready boiled ) get my coffee and put my coffee on the side of my computer keep reading and social media 1 hour later coffee get cold meeeh i need to drink this everyday .
so which of thos work flow is wrong ? am i doing it wrong ? suggested me a good morning routine so my coffee still hot when i drink it .
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Token-Curated Registries
So you want to build a TCR?
TCRs (Token Curated Registries) are a construct for maintaining registries on Ethereum. Imagine you have lots of scissor brands and you want a list with only the good scissors. You want to make sure only the good scissors make into that list and not the bad scissors. For that, people will tell you, you can just create a TCR of the best scissors!
It works like this: some people have the token, let's call it Scissor Token. Some other person, let's say it's a scissor manufacturer, wants to put his scissor on the list, this guy must acquire some Scissor Tokens and "stake" it. Holders of the Scissor Tokens are allowed to vote on "yes" or "no". If "no", the manufactures loses his tokens to the holders, if "yes" then its tokens are kept in deposit, but his scissor brand gets accepted into the registry.
Such a simple process, they say, have strong incentives for being the best possible way of curating a registry of scissors: consumers have the incentive to consult the list because of its high quality; manufacturers have the incentive to buy tokens and apply to join the list because the list is so well-curated and consumers always consult it; token holders want the registry to accept good and reject bad scissors because that good decisions will make the list good for consumers and thus their tokens more valuable, bad decisions will do the contrary. It doesn't make sense, to reject everybody just to grab their tokens, because that would create an incentive against people trying to enter the list.
Amazing! How come such a simple system of voting has such enourmous features? Now we can have lists of everything so well-curated, and for that we just need Ethereum tokens!
Now let's imagine a different proposal, of my own creation: SPCR, Single-person curated registries.
Single-person Curated Registries are equal to TCR, except they don't use Ethereum tokens, it's just a list in a text file kept by a single person. People can apply to join, and they will have to give the single person some amount of money, the single person can reject or accept the proposal and so on.
Now let's look at the incentives of SPCR: people will want to consult the registry because it is so well curated; vendors will want to enter the registry because people are consulting it; the single person will want to accept the good and reject the bad applicants because these good decisions are what will make the list valuable.
Amazing! How such a single proposal has such enourmous features! SPCR are going to take over the internet!
What TCR enthusiasts get wrong?
TCR people think they can just list a set of incentives for something to work and assume that something will work. Mix that with Ethereum hype and they think theyve found something unique and revolutionary, while in fact they're just making a poor implementation of "democracy" systems that fail almost everywhere.
The life is not about listing a set of "incentives" and then considering the problems solved. Almost everybody on the Earth has the incentive for being rich: being rich has a lot of advantages over being poor, however not all people get rich! Why are the incentives failing?
Curating lists is a hard problem, it involves a lot of knowledge about the problem that just holding a token won't give you, it involves personal preferences, politics, it involves knowing where is the real limit between "good" and "bad". The Single Person list may have a good result if the single person doing the curation is knowledgeable and honest (yes, you can game the system to accept your uncle's scissors and not their competitor that is much better, for example, without losing the entire list reputation), same thing for TCRs, but it can also fail miserably, and it can appear to be good but be in fact not so good. In all cases, the list entries will reflect the preferences of people choosing and other things that aren't taken into the incentives equation of TCR enthusiasts.
We don't need lists
The most important point to be made, although unrelated to the incentive story, is that we don't need lists. Imagine you're looking for a scissor. You don't want someone to tell if scissor A or B are "good" or "bad", or if A is "better" than B. You want to know if, for your specific situation, or for a class of situations, A will serve well, and do that considering A's price and if A is being sold near you and all that.
Scissors are the worst example ever to make this point, but I hope you get it. If you don't, try imagining the same example with schools, doctors, plumbers, food, whatever.
Recommendation systems are badly needed in our world, and TCRs don't solve these at all.
-
 @ 732c6a62:42003da2
2025-03-06 06:00:53
@ 732c6a62:42003da2
2025-03-06 06:00:53De acordo com a Forbes, a Ripple (Empresa responsável pela Criptomoeda XRP) tem financiado e apoiado campanhas contra a mineração de Bitcoin.
Por que Ripple faz propaganda anti-bitcoin?
Simples: eles são o oposto do Bitcoin em quase tudo. Enquanto o Bitcoin foi criado para ser descentralizado, resistente à censura e independente de instituições, o Ripple é basicamente um serviço bancário 2.0. Eles precisam atacar o Bitcoin para justificar sua própria existência.
O que você não sabe:
- Ripple Labs controla a maioria do XRP: Eles têm um estoque estratégico que pode ser liberado no mercado a qualquer momento. Isso é o oposto de descentralização.
- XRP não é uma moeda para "pessoas comuns": Foi criada para bancos e instituições financeiras. Basicamente, é o "banco central" das criptomoedas.
- Ripple não é blockchain no sentido tradicional: Eles usam um protocolo chamado Ripple Protocol Consensus Algorithm (RPCA), que é mais rápido, mas menos descentralizado.
Os principais ataques do Ripple ao Bitcoin:
- Anti-mineração: O Ripple critica o consumo de energia do Bitcoin, mas esquece que seu próprio sistema depende de servidores centralizados que também consomem energia.
- Anti-reserva estratégica: O Ripple tem um estoque gigante de XRP, mas critica o Bitcoin por ser "deflacionário". Hipocrisia? Nunca ouvi falar.
- Anti-descentralização: O Ripple prega que a descentralização do Bitcoin é "ineficiente", mas o que eles realmente querem é manter o controle nas mãos de poucos.
Análise Psicológica Básica (para você que acha que XRP é o futuro):
- Síndrome do Underdog: Acha que apoiar o Ripple te faz um rebelde, mas na verdade você está torcendo para o sistema bancário tradicional.
- Viés de Confirmação: Só ouve opiniões que validam sua decisão de comprar XRP.
- Efeito Dunning-Kruger: Acha que entender Ripple te torna um especialista em criptomoedas, mas não sabe o que é um hard fork.
Estudo de Caso (Real, mas Você Vai Ignorar):
Carlos, 30 anos, comprou XRP porque "é o futuro das transações bancárias". Ele não sabe que o Ripple está sendo processado pela SEC por vender XRP como um título não registrado. Carlos agora está esperando o "pump" que nunca vem.Conclusão: ou, "volte para a aula de economia do ensino médio"
Ripple não é o futuro das finanças. É só mais um player tentando lucrar em um mercado competitivo. E sua propaganda anti-Bitcoin? Essa só prova que a descentralização assusta quem quer controle. Agora vá estudar blockchain básico — ou pelo menos pare de compartilhar memes com erros de português.
-
 @ bcb80417:14548905
2025-03-30 14:40:40
@ bcb80417:14548905
2025-03-30 14:40:40President Donald Trump's recent policy initiatives have significantly impacted the cryptocurrency landscape, reflecting his administration's commitment to fostering innovation and positioning the United States as a global leader in digital assets.
A cornerstone of this approach is the aggressive deregulation agenda aimed at reversing many policies from the previous administration. Key areas of focus include slashing environmental regulations, easing bank oversight, and removing barriers to cryptocurrencies. The Environmental Protection Agency, for instance, announced 31 deregulatory actions in a single day, underscoring the breadth of these efforts. This push has led to rapid growth in the crypto industry, with increased investment and activity following the administration's moves to ease restrictions. citeturn0news10
In line with this deregulatory stance, the U.S. Securities and Exchange Commission (SEC) recently hosted its inaugural public meeting of the crypto task force. Led by Republican SEC Commissioner Hester Peirce, the task force is exploring the applicability of securities laws to digital assets and considering whether new regulatory frameworks are necessary. This initiative reflects a shift in regulatory approach under President Trump, who has pledged to reverse the previous administration's crackdown on crypto firms. citeturn0news11
Further demonstrating his support for the crypto industry, President Trump announced the inclusion of five cryptocurrencies—Bitcoin, Ethereum, Ripple (XRP), Solana (SOL), and Cardano (ADA)—into a proposed "crypto strategic reserve." This move led to significant price surges for these assets, highlighting the market's responsiveness to policy decisions. citeturn0search0
The administration's commitment extends to the development of stablecoins. World Liberty Financial, a cryptocurrency venture established by Donald Trump and his sons, plans to launch a stablecoin called USD1. This stablecoin will be entirely backed by U.S. treasuries, dollars, and cash equivalents, aiming to provide a reliable medium for cross-border transactions by sovereign investors and major institutions. The USD1 token will be issued on the Ethereum network and a blockchain developed by Binance. citeturn0news13
In the financial sector, Trump Media & Technology Group Corp. is collaborating with Crypto.com to introduce "Made in America" exchange-traded funds (ETFs) focusing on digital assets and securities. This initiative aligns with President Trump's pro-cryptocurrency stance and his ambition to make the U.S. a global crypto hub. The ETFs, supported by Crypto.com, will feature a combination of cryptocurrencies such as Bitcoin and are slated to launch later this year. citeturn0news12
These policy directions underscore President Trump's dedication to integrating cryptocurrencies into the national economic framework. By establishing strategic reserves, promoting stablecoins, and facilitating crypto-focused financial products, the administration aims to position the United States at the forefront of the digital asset revolution.
However, these initiatives are not without challenges. While deregulation has boosted investor confidence and stock prices, concerns arise regarding potential economic implications. The Federal Reserve warns that certain policies may lead to higher prices and adversely affect investment and growth. Additionally, the administrative and legal complexities of implementing widespread deregulation present further challenges, including potential staff cuts at agencies like the Environmental Protection Agency and legal challenges to some of the administration's actions. citeturn0news10
In summary, President Trump's recent policies reflect a strategic embrace of cryptocurrencies, aiming to foster innovation, attract investment, and establish the United States as a leader in the digital asset space. While these efforts present opportunities for economic growth and technological advancement, they also necessitate careful consideration of regulatory and economic impacts to ensure balanced and sustainable development in the crypto sector.
-
 @ 3bf0c63f:aefa459d
2024-01-14 13:55:28
@ 3bf0c63f:aefa459d
2024-01-14 13:55:28Precautionary Principle
The precautionary principle that people, including Nassim Nicholas Taleb, love and treat as some form of wisdom, is actually just a justification for arbitrary acts.
In a given situation for which there's no sufficient knowledge, either A or B can be seen as risky or precautionary measures, there's no way to know except if you have sufficient knowledge.
Someone could reply saying, for example, that the known risk of A is tolerable to the unknown, probably magnitudes bigger, risk of B. Unless you know better or at least have a logical explanation for the risks of B (a thing "scientists" don't have because they notoriously dislike making logical claims), in which case you do know something and is not invoking the precautionary principle anymore, just relying on your logical reasoning – and that can be discussed and questioned by others, undermining your intended usage of the label "precautionary principle" as a magic cover for your actions.
-
 @ 83e26223:2ba007a6
2025-03-30 15:58:07
@ 83e26223:2ba007a6
2025-03-30 15:58:07Bitcoin's potential to reach $100,000 is gaining traction among experts and analysts. Several factors contribute to this... - Increased Adoption: Growing institutional investment and mainstream acceptance are driving Bitcoin's price up. As more businesses and consumers use Bitcoin for transactions, its value could surge. - Reduced Supply and Increased Demand: The recent halving event reduced Bitcoin's supply, while demand from Bitcoin ETFs and new investors continues to rise. This imbalance could push prices higher. - Limited Supply and Store of Value: Bitcoin's capped supply of 21 million coins makes it an attractive store of value, similar to gold. As inflation concerns grow, investors may turn to Bitcoin as a hedge. - Positive Market Trends: The rise of decentralized finance (DeFi) and the potential for interest rate cuts by the Federal Reserve could further boost Bitcoin's price. - Expert Predictions: Analysts like Cathie Wood and The Motley Fool believe Bitcoin's price could triple or quadruple in the next few years, reaching and surpassing $100,000.
While predictions are subjective and the cryptocurrency market is notoriously volatile, these factors contribute to the growing optimism about Bitcoin's potential to reach $100,000. For investors, it's essential to stay informed, manage risks, and adopt a long-term perspective.
-
 @ d560dbc2:bbd59238
2025-03-30 07:56:40
@ d560dbc2:bbd59238
2025-03-30 07:56:40We’ve all been there: that one task sitting on your to-do list, staring at you like a disappointed parent, and yet you keep pushing it off for absolutely no good reason. It’s not even that hard, urgent, or complicated—but somehow, it’s been haunting you for days, weeks, or maybe even months. Why do we do this to ourselves?
Why Do We Postpone Tasks for No Reason?
Procrastination is a sneaky beast. Even tasks that take 10 minutes, require minimal brainpower, and have no immediate deadline often get pushed aside. Here are some psychological reasons:
-
Emotional Avoidance:
Even if a task isn’t hard, a tiny emotional weight (like mild boredom or a vague “I don’t wanna”) can lead your brain to choose distractions—like scrolling through Instagram. -
Lack of Immediate Consequences:
Without a pressing deadline, your brain tends to deprioritize the task, even if completing it would make you feel great. -
The Zeigarnik Effect:
Unfinished tasks stick in our minds, creating mental tension. Ironically, that tension can make the task seem bigger and more daunting, encouraging further avoidance.
My Own “No-Reason” Procrastination Story
Let’s be real—I’ve been postponing something trivial, like organizing my desk drawer, for weeks. It’s a simple task that takes about 15 minutes. There’s no deadline, no special skill required—yet every time I open the drawer, I see the chaos of old receipts, random cables, and a half-eaten pack of gum (don’t judge!) and think, “I’ll do it later.” It’s not that I’m busy—I’ve had plenty of time to rewatch my favorite sitcom for the third time. But ignoring it has become my default, and that messy drawer now occupies mental space far beyond its physical size.
Why These Tasks Matter More Than We Think
Those little tasks we postpone might seem harmless, but they add up to create mental clutter. That messy desk drawer isn’t just a drawer—it’s a tiny stressor that pops into your head at the worst moments, disrupting your focus on important work or relaxation.
-
Mental Clutter:
Unfinished tasks can weigh on your mind, making it harder to focus on what truly matters. -
The Bigger Picture:
Tasks like “reply to that email” or “schedule that doctor’s appointment” may seem minor, but avoiding them can lead to unnecessary stress and lost opportunities.
How to Finally Tackle That Task
Here are a few strategies that have helped me break the cycle of “no-reason” procrastination:
1. The 20-Minute Rule (Thank You, Pomodoro!)
-
Commit to 20 Minutes:
Set a timer for just 20 minutes and start working on the task. You’d be surprised how much you can accomplish once you begin. -
Example:
For my desk drawer, I set a timer, got to work, and finished in 12 minutes. That small win made me feel like a productivity superhero.
2. Pin It and Get a Nudge
-
Use Reminders:
Pin that nagging task (like “Organize desk drawer”) as your top priority for the day. A gentle reminder can help break the cycle of avoidance. -
Result:
It’s like having a friend nudge you, “Hey, remember that thing you’ve been ignoring? Let’s do it now!”
3. Make It Fun (Yes, Really!)
-
Add a Reward:
Turn the task into something enjoyable by setting a reward. Play your favorite music, and promise yourself a treat once you’re done. -
Example:
For my desk drawer, I put on an upbeat playlist and treated myself to a piece of chocolate when finished. Suddenly, it wasn’t a chore—it became a mini dance party with a sweet reward.
4. Celebrate the Win
-
Acknowledge Completion:
Once you finish, take a moment to celebrate—even if it’s just a mental high-five. -
Why It Matters:
That sense of closure clears mental clutter and builds momentum for your next task.
Let’s Share and Motivate Each Other
What’s that one task you’ve been postponing for no reason? Maybe it’s cleaning out your fridge, replying to a friend’s text, or finally hanging that picture frame that’s been leaning against the wall for months. Whatever it is, share your story in the comments! Let’s motivate each other to tackle these tasks and turn procrastination into progress.
Bonus points if you’ve got a funny reason for your procrastination (like, “I didn’t schedule that appointment because my doctor’s office has the worst hold music in history”).
Ready to stop procrastinating? Let’s get real, take that first step, and clear that mental clutter—one small win at a time!
-
-
 @ 732c6a62:42003da2
2025-03-06 04:33:48
@ 732c6a62:42003da2
2025-03-06 04:33:48De ''Dialética do Oprimido'' a ''Like do Oprimido'': A Queda Livre do Debate que Nunca Existiu.
A moda do momento
Fiquei aproximadamente 8 meses sem ter acesso a nenhum dispositivo. Quando consegui novamente o acesso ao smartphone, percebi algo diferente no debate político brasileiro: enquanto a direita estava se engajando em incontáveis números de curtidas e compartilhamentos com memes que demonstravam críticas ao governo e aos seus ainda poucos apoiadores que se humilham para defender o indefensável, a esquerda radical repetia sua imposição intelectual em comentários de vários posts, incluindo textos, vídeos e tweets com frases semelhantes a "vai ler um livro de história" "nunca leu um livro", "eu estou do lado certo da história" e "se eu fosse irracional eu seria de direita". Tudo isso pra tentar passar uma mensagem de que a história é de esquerda. A tese é: será que eles realmente são tão inteligentes como juram?
Fatos que ignoram enquanto cospem jargões do "lado certo da história":
1. A esquerda também tem seus terraplanistas: Anti-vaxxers de organicafé, terraplanistas do gênero, e os que acham que a Coreia do Norte é uma democracia.
2. Viés de confirmação não é monopólio da direita: Eles compartilham estudos "científicos" do Medium como se fossem peer-reviewed, mas desdenham de dados que contradizem sua narrativa.
3. A direita não é um monolito: Tem desde ancaps que calculam até a última casa decimal até bolsominions que acham que a Terra é plana. Generalizar é... bem, irracional.Estudo de Caso (Fictício, mas Verdadeiro):
Larissa, 23 anos, posta sobre "ciência e razão" enquanto defende horóscopo como "ferramenta de autoconhecimento". Acredita que o capitalismo causa depressão, mas não sabe o que é taxa Selic. Larissa é você após três caipirinhas.A Imposição intelectual que ninguém pediu (mas todos recebem de graça)
A esquerda brasileira, em sua cruzada épica para salvar o mundo dos "fascistas que ousam discordar", adotou uma nova estratégia: transformar complexidade política em slogans de camiseta de feira. A frase "se eu fosse irracional, seria de direita" não é original — é plágio descarado da cartilha do Complexo de Deus em Oferta no AliExpress.
O Quebra-Cabeça da superioridade Auto-Delirante
A tese esquerdista se sustenta em três pilares frágeis:
1. A falácia do "lado certo da história": Como se história fosse um jogo de futebol com narração do João Cléber.
2. A ilusão de que citar Foucault = ter QI elevado: Spoiler: decorar "biopoder" não te torna imune a acreditar em astrologia.
3. A crença de que volume de texto = profundidade: 15 parágrafos no Twitter não equivalem a um semestre de Ciência Política.Dado Cruel: Um estudo da Universidade de Cambridge (2022) mostrou que extremistas de ambos os lados cometem erros lógicos similares. A diferença? A esquerda usa palavras mais bonitas para mascarar a burrice.
A hipocrisia do "nunca tocou em um livro" (enquanto compartilham resumo de livro no TikTok)
A acusação preferida — "você não lê!" — esconde uma ironia deliciosa:
- 72% dos "intelectuais de rede social" citam livros que nunca leram além do título (Fonte: Pesquisa Informal do Twitter, 2023).
- Obras citadas como troféu: "1984" (para chamar Bolsonaro de Big Brother), "O Capital" (para justificar o NFT da Gal Gadot), e "Feminismo para os 99%" (para atacar homens heterossexuais que usam sandália de dedo).Pergunta Incômoda: Se ler Marx fosse garantia de racionalidade, por que a União Soviética acabou em pizza (literalmente, considerando a economia deles)?
Quando a autoimagem colide com a realidade (Ou: por que nenhum esquerdista lassa no teste de turing da coerência)
A esquerda adora se pintar como a Última Trincheira da Razão, mas pratica o que critica:
- Exemplo 1: Defendem "ciência" quando convém (vacinas), mas abraçam pseudociência quando é trendy (cristais energéticos contra o capitalismo).
- Exemplo 2: Chamam a direita de "terraplanista", mas acham que inflação se resolve com tabelamento estatal — a versão econômica de "a Terra é sustentada por tartarugas".
- Exemplo 3: Criticam "fake news", mas compartilham teorias de que o agro "envenena a comida" (enquanto comem sushi de supermercado).Frase-Chave: "Racionalidade seletiva é o novo analfabetismo funcional."
Pergunta Final: Se a esquerda é tão racional, por que não usa a "lógica implacável" para resolver algo além do enquadro perfeito de stories no Instagram?
Enfim
O debate "esquerda racional vs. direita irracional" é só mais um episódio da novela "Brasil: O País que Confunde Opinião com Ataque de Ego". Enquanto uns brincam de "quem tem o QI mais alto", o país queima — literalmente, considerando o Pantanal. Talvez a verdadeira irracionalidade seja gastar energia discutindo superioridade moral enquanto o Wi-Fi cai pela décima vez no dia. Racionalidade não tem lado político. Arrogância, por outro lado, é universal. Sua necessidade de se sentir superior só prova que a lacração é o último refúgio dos fracos de argumento. Agora deviam estudar economia básica — ou pelo menos que parem de achar que "Ah, mas o capitalismo!" é um contra-argumento.
Saudade da época em que a esquerda não se fingia de intelectual.
-
 @ b571324b:6e316384
2025-03-29 20:41:57
@ b571324b:6e316384
2025-03-29 20:41:57Always humble yourself 😁##
-
 @ fd06f542:8d6d54cd
2025-03-30 02:10:24
@ fd06f542:8d6d54cd
2025-03-30 02:10:24NIP-03
OpenTimestamps Attestations for Events
draftoptionalThis NIP defines an event with
kind:1040that can contain an OpenTimestamps proof for any other event:json { "kind": 1040 "tags": [ ["e", <event-id>, <relay-url>], ["alt", "opentimestamps attestation"] ], "content": <base64-encoded OTS file data> }- The OpenTimestamps proof MUST prove the referenced
eevent id as its digest. - The
contentMUST be the full content of an.otsfile containing at least one Bitcoin attestation. This file SHOULD contain a single Bitcoin attestation (as not more than one valid attestation is necessary and less bytes is better than more) and no reference to "pending" attestations since they are useless in this context.
Example OpenTimestamps proof verification flow
```bash ~> nak req -i e71c6ea722987debdb60f81f9ea4f604b5ac0664120dd64fb9d23abc4ec7c323 wss://nostr-pub.wellorder.net | jq -r .content | ots verify
using an esplora server at https://blockstream.info/api - sequence ending on block 810391 is valid timestamp validated at block [810391] ```
- The OpenTimestamps proof MUST prove the referenced
-
 @ 42c85a20:14afbc38
2025-03-29 15:40:00
@ 42c85a20:14afbc38
2025-03-29 15:40:00Back when Twitter was censoring free speech nostr looked like the only alternative where people would migrate and grow the network; however, now that X is open to free thinking, the perfect storm to enable nostr to grow has been quelled.
How will the nostr universe ever expand unless people in the main stream "centralized" social medias see the light? The illusion of free speech on X is dangerous as people blindly give their trust that the rug will not be pulled; and willingly remain under a tyrannical system.
Perhaps there is some other utility which nostr would be useful for vs just another version of twillter; like exit polls for elections which could fail safe the integrity of voting; or community BBS (bulletin boards) where the people can connect with their neighbours without giving up their real address or identity.
When the main stream social medias' fail again; the next time they break the trust of the people, we must be ready to replace them; we must think outside the box now and build those decentralized utilities now.
-
 @ 30ceb64e:7f08bdf5
2025-03-30 00:37:54
@ 30ceb64e:7f08bdf5
2025-03-30 00:37:54Hey Freaks,
RUNSTR is a motion tracking app built on top of nostr. The project is built by TheWildHustle and TheNostrDev Team. The project has been tinkered with for about 3 months, but development has picked up and its goals and direction have become much clearer.
In a previous post I mentioned that RUNSTR was looking to become a Nike Run Club or Strava competitor, offering users an open source community and privacy focused alternative to the centralized silos that we've become used to.
I normally ramble incoherently.....even in writing, but this is my attempt to communicate the project's goals and direction as we move forward.
This is where the project is now:
Core Features
- Run Tracker: Uses an algorithm which adjusts to your phone's location permissions and stores the data on your phone locally
- Stats: Stored locally on your phone with a basic profile screen so users can monitor calories burned during runs
- Nostr Feed: Made up of kind1 notes that contain #RUNSTR and other running related hashtags
- Music: Brought to you via a wavlake API, enabling your wavlake playlists and liked songs to be seen and played in the app
Current Roadmap
- Bugs and small improvements: Fixing known issues within the client
- zap.store release: Launching a bug bounty program after release
- Clubs: Enabling running organizations to create territories for events, challenges, rewards and competition
- Testflight: Opening up the app to iOS users (currently Android only)
- Modes: Adding functionality to switch between Running, Walking, or Cycling modes
Future Roadmap
- Requested Features: Implementing features requested by club managers to support virtual events and challenges
- Blossom: Giving power users the ability to upload their data to personal blossom servers
- NIP28: Making clubs interoperable with other group chat clients like 0xchat, Keychat, and Chachi Chat
- DVM's: Creating multiple feeds based on movement mode (e.g., Walking mode shows walkstr feed)
- NIP101e: Allowing users to create run records and store them on nostr relays
- Calories over relays: Using NIP89-like functionality for users to save calorie data on relays for use in other applications
- NIP60: Implementing automatic wallet creation for users to zap and get zapped within the app
In Conclusion
I've just barely begun this thing and it'll be an up and down journey trying to push it into existence. I think RUNSTR has the potential to highlight the other things that nostr has going for it, demonstrating the protocol's interoperability, flexing its permissionless identity piece, and offering an experience that gives users a glimpse into what is possible when shipping into a new paradigm. Although we build into an environment that often offers no solutions, you'd have to be a crazy person not to try.
https://github.com/HealthNoteLabs/Runstr/releases/tag/feed-0.1.0-20250329-210157
-
 @ 65038d69:1fff8852
2025-03-29 13:05:35
@ 65038d69:1fff8852
2025-03-29 13:05:35Welcome to part 4, the final entry in the What is Money series. We’re capping it off with “crypto” and CBDCs.
Let's start with crypto. Short for cryptocurrency, it’s a catch-all term for all of the non-fiat, blockchain-based, or non-government-operated new money systems that aren’t Bitcoin. Ethereum, Solana, and Dogecoin are some you may have heard of. There are actually thousands of cryptocurrencies in existence, but we’ll summarize some of the biggest ones by size and pop culture penetration. One thing they all have in common is that like fiat currencies, they have no supply limit and are therefore inflationary by nature.
Ethereum: Released in 2015 by Vitalik Buterin, Ethereum is less of a money system and more of a network built to run “decentralized applications” (DAPs) on. “Smart contracts” and “tokens” are the most common of these. If none of those terms mean anything to you, you’re not alone. What they’ve essentially done is recreate the unending complexity of high finance in a computer system and replaced the bankers and lawyers with programmers.
Solana: Solana is much smaller than Ethereum but serves a similar function of being a wild-west finance platform. I’m only mentioning it here as it's been in the media a lot with numerous security compromises, lawsuits, and general drama. Your nephew who trades in Robux probably knows someone who lost their allowance savings in the 2021 crash.
USDT/Tether: This is the largest in a family of cryptocurrencies called “stablecoins”. They’re meant to offer the features of crypto but with the “stability” of having their value tied to a fiat currency, in this case the US Dollar.
Monero: Monero was designed from the ground up to be as anonymous as possible. Unfortunately it’s lack of popularity means it’s not particularly useful for purchases.
Dogecoin: Released in 2013, Dogecoin was created as a joke to poke fun at Bitcoin and cryptocurrencies. As a joke it’s been wildly successful, but like most jokes there are many who decided to take it seriously over the years, which has driven its market cap to surpass that of Monera and most others. It’s currently in the top 10 by market cap, but you’ll struggle to find anyone who takes it as payment.
The concept of CBDCs (central bank digital currencies) has been making the rounds through media for some time. Some paint it as a boogeyman to be feared, while others see it as nothing more than an annoying waste of government resources. As you may recall from part 2 of this series, the Bank of Canada is not a retail bank with individuals for customers, instead acting as an administrative body and a bank for banks. CBDCs have the potential to change that. In a sentence, a Canadian CBDC would most likely be a system whereby individuals who struggle to get or maintain accounts at retail banks could be issued a Bank of Canada account. There may also be some integration with Payments Canada systems to make retail payments and transfers cheaper and more direct. Much of this is speculation though, as the BoC hasn’t announced any of this, only that research is ongoing. In any case it won’t be a replacement of the Canadian Dollar, just another system for moving Dollars around between ledgers and accounts.
I’d normally sign off with something like, “Want help with insert article topic here? You can find us at scalebright.ca”, but in the case of crypto I’m afraid we must decline. The other trait shared by all of these money systems beside inflation via no supply limit is that they’re all scams designed to steal from their customers. Bitcoin is the only digital non-fiat currency this doesn't apply to. So if you’d like help with Bitcoin, you can find us at scalebright.ca.
-
 @ 65038d69:1fff8852
2025-03-29 13:02:18
@ 65038d69:1fff8852
2025-03-29 13:02:18Millennials remember the era of Buzzfeed quizzes with fondness, and some may even describe it as identity or culture shaping. People have always loved these miniature personality tests, and while Buzzfeed may no longer be in its heyday, the popularity of these dinner-table icebreakers has transcended generational gaps. To the analytically-brained among us this sounds like a datapoint that could be used in the workplace. Or is it?
You’ve probably heard someone’s answer to one of these and thought, “Oh wow, that sounds mildly psychopathic, I’m sure glad I don’t work with them!” Interviewers will sometimes ask questions like “if you were an animal, what kind of animal would you be?” as a conversation starter, but unscored. Part of the reason for this is that laws around discrimination in hiring make filtering via psychological or personality tests a grey area. Any suggestion of discrimination opens employers to potential lawsuits and investigations. Even if the applicant answered unironically with “I would be a dragon because I love hoarding gold and burning down unsuspecting villages!”, you would need to prove that the question was asked in a controlled environment by a certified professional and that the question was directly relevant to the position being applied for.
Now that I’ve most likely talked you out of implementing these in your interview processes, here are a handful of tests that, in an HR and legal department approved manner, could be run during an interview. Failing that, they make for great casual icebreakers! Their sources range from actual psychological tests to dubious corners of the internet, and they’ve all been simplified down to their simplest forms, so I’ll again warn that you’ll want to do diligence before suggesting their use in your workplace.
The Marshmallow Test: The test subjects (usually children) are offered a marshmallow and told that if they leave it for a few minutes, they can have two. Adults who’ve developed impulse control will usually say the correct answer is obvious, yet we fail slightly more complex versions all the time. Remember that greasy fast-food you bought with money you could have saved for a nice dinner out?
Cognitive Reflection Test (CRT): “Some apples and some bananas cost $1.10. The apples cost $1 more than the bananas. How much did the apples cost?” If you suspect a trick, you’ll probably think about the question a bit further, but the intuitive part of our brains want us to think the apples were $1 and the bananas $0.10.
The Breakfast Question: “How would you feel if you hadn’t eaten breakfast?” This one has some deep internet lore behind it, but the idea is that you’re testing the subject’s capacity for hypothetical reasoning. Can they process “what-ifs”? It can also extend into testing for empathy (“How would you feel if you were in Steve’s shoes and someone stole your ice cream?”).
Thematic Apperception Test (TAT): Show the subject an ambiguous picture (ideally emotionally neutral) with people in it and ask them to imagine what is happening, including what the people are thinking and feeling. Most people will subconsciously project their own thoughts and feelings onto the characters in the picture.
Moral Circle Test: This one has a history of being misunderstood and used as a political cudgel, so you may want to save it for your more understanding friends. Subjects were asked to rank the moral responsibilities they felt toward increasingly distant groups, starting from themselves in the center of a circle and working their way out through family, friends, acquaintances, animals, Earth, etc. The primary misunderstanding is whether the outer circles include the inner circles, i.e. whether caring for Earth includes caring for family. It’s unclear whether the subjects fully understood this, and those interpreting the results seem confused as well.
Workplace Motivation Test: “You are up for a promotion. You can be promoted into a position that pays 20% more, or one that pays the same that you’re currently making but aligns with your non-financial life goals or sense of purpose.” This one is my own, and you can learn more about the underlying concepts here: “True Believers & Mercenaries” Are you a “True Believer” or a “Mercenary”?
Need help with your interview processes or figuring out which Disney princess you are? You can find us at scalebright.ca.
-
 @ 97c70a44:ad98e322
2025-03-05 18:09:05
@ 97c70a44:ad98e322
2025-03-05 18:09:05So you've decided to join nostr! Some wide-eyed fanatic has convinced you that the "sun shines every day on the birds and the bees and the cigarette trees" in a magical land of decentralized, censorship-resistant freedom of speech - and it's waiting just over the next hill.
But your experience has not been all you hoped. Before you've even had a chance to upload your AI-generated cyberpunk avatar or make up exploit codenames for your pseudonym's bio, you've been confronted with a new concept that has left you completely nonplussed.
It doesn't help that this new idea might be called by any number of strange names. You may have been asked to "paste your nsec", "generate a private key", "enter your seed words", "connect with a bunker", "sign in with extension", or even "generate entropy". Sorry about that.
All these terms are really referring to one concept under many different names: that of "cryptographic identity".
Now, you may have noticed that I just introduced yet another new term which explains exactly nothing. You're absolutely correct. And now I'm going to proceed to ignore your complaints and talk about something completely different. But bear with me, because the juice is worth the squeeze.
Identity
What is identity? There are many philosophical, political, or technical answers to this question, but for our purposes it's probably best to think of it this way:
Identity is the essence of a thing. Identity separates one thing from all others, and is itself indivisible.
This definition has three parts:
- Identity is "essential": a thing can change, but its identity cannot. I might re-paint my house, replace its components, sell it, or even burn it down, but its identity as something that can be referred to - "this house" - is durable, even outside the boundaries of its own physical existence.
- Identity is a unit: you can't break an identity into multiple parts. A thing might be composed of multiple parts, but that's only incidental to the identity of a thing, which is a concept, not a material thing.
- Identity is distinct: identity is what separates one thing from all others - the concept of an apple can't be mixed with that of an orange; the two ideas are distinct. In the same way, a single concrete apple is distinct in identity from another - even if the component parts of the apple decompose into compost used to grow more apples.
Identity is not a physical thing, but a metaphysical thing. Or, in simpler terms, identity is a "concept".
I (or someone more qualified) could at this point launch into a Scholastic tangent on what "is" is, but that is, fortunately, not necessary here. The kind of identities I want to focus on here are not our actual identities as people, but entirely fictional identities that we use to extend our agency into the digital world.
Think of it this way - your bank login does not represent you as a complete person. It only represents the access granted to you by the bank. This access is in fact an entirely new identity that has been associated with you, and is limited in what it's useful for.
Other examples of fictional identities include:
- The country you live in
- Your social media persona
- Your mortgage
- Geographical coordinates
- A moment in time
- A chess piece
Some of these identites are inert, for example points in space and time. Other identies have agency and so are able to act in the world - even as fictional concepts. In order to do this, they must "authenticate" themselves (which means "to prove they are real"), and act within a system of established rules.
For example, your D&D character exists only within the collective fiction of your D&D group, and can do anything the rules say. Its identity is authenticated simply by your claim as a member of the group that your character in fact exists. Similarly, a lawyer must prove they are a member of the Bar Association before they are allowed to practice law within that collective fiction.
"Cryptographic identity" is simply another way of authenticating a fictional identity within a given system. As we'll see, it has some interesting attributes that set it apart from things like a library card or your latitude and longitude. Before we get there though, let's look in more detail at how identities are authenticated.
Certificates
Merriam-Webster defines the verb "certify" as meaning "to attest authoritatively". A "certificate" is just a fancy way of saying "because I said so". Certificates are issued by a "certificate authority", someone who has the authority to "say so". Examples include your boss, your mom, or the Pope.
This method of authentication is how almost every institution authenticates the people who associate with it. Colleges issue student ID cards, governments issue passports, and websites allow you to "register an account".
In every case mentioned above, the "authority" creates a closed system in which a document (aka a "certificate") is issued which serves as a claim to a given identity. When someone wants to access some privileged service, location, or information, they present their certificate. The authority then validates it and grants or denies access. In the case of an international airport, the certificate is a little book printed with fancy inks. In the case of a login page, the certificate is a username and password combination.
This pattern for authentication is ubiquitous, and has some very important implications.
First of all, certified authentication implies that the issuer of the certificate has the right to exclusive control of any identity it issues. This identity can be revoked at any time, or its permissions may change. Your social credit score may drop arbitrarily, or money might disappear from your account. When dealing with certificate authorities, you have no inherent rights.
Second, certified authentication depends on the certificate authority continuing to exist. If you store your stuff at a storage facility but the company running it goes out of business, your stuff might disappear along with it.
Usually, authentication via certificate authority works pretty well, since an appeal can always be made to a higher authority (nature, God, the government, etc). Authorities also can't generally dictate their terms with impunity without losing their customers, alienating their constituents, or provoking revolt. But it's also true that certification by authority creates an incentive structure that frequently leads to abuse - arbitrary deplatforming is increasingly common, and the bigger the certificate authority, the less recourse the certificate holder (or "subject") has.
Certificates also put the issuer in a position to intermediate relationships that wouldn't otherwise be subject to their authority. This might take the form of selling user attention to advertisers, taking a cut of financial transactions, or selling surveillance data to third parties.
Proliferation of certificate authorities is not a solution to these problems. Websites and apps frequently often offer multiple "social sign-in" options, allowing their users to choose which certificate authority to appeal to. But this only piles more value into the social platform that issues the certificate - not only can Google shut down your email inbox, they can revoke your ability to log in to every website you used their identity provider to get into.
In every case, certificate issuance results in an asymmetrical power dynamic, where the issuer is able to exert significant control over the certificate holder, even in areas unrelated to the original pretext for the relationship between parties.
Self-Certification
But what if we could reverse this power dynamic? What if individuals could issue their own certificates and force institutions to accept them?

Ron Swanson's counterexample notwithstanding, there's a reason I can't simply write myself a parking permit and slip it under the windshield wiper. Questions about voluntary submission to legitimate authorities aside, the fact is that we don't have the power to act without impunity - just like any other certificate authority, we have to prove our claims either by the exercise of raw power or by appeal to a higher authority.
So the question becomes: which higher authority can we appeal to in order to issue our own certificates within a given system of identity?
The obvious answer here is to go straight to the top and ask God himself to back our claim to self-sovereignty. However, that's not how he normally works - there's a reason they call direct acts of God "miracles". In fact, Romans 13:1 explicitly says that "the authorities that exist have been appointed by God". God has structured the universe in such a way that we must appeal to the deputies he has put in place to govern various parts of the world.
Another tempting appeal might be to nature - i.e. the material world. This is the realm in which we most frequently have the experience of "self-authenticating" identities. For example, a gold coin can be authenticated by biting it or by burning it with acid. If it quacks like a duck, walks like a duck, and looks like a duck, then it probably is a duck.
In most cases however, the ability to authenticate using physical claims depends on physical access, and so appeals to physical reality have major limitations when it comes to the digital world. Captchas, selfies and other similar tricks are often used to bridge the physical world into the digital, but these are increasingly easy to forge, and hard to verify.
There are exceptions to this rule - an example of self-certification that makes its appeal to the physical world is that of a signature. Signatures are hard to forge - an incredible amount of data is encoded in physical signatures, from strength, to illnesses, to upbringing, to personality. These can even be scanned and used within the digital world as well. Even today, most contracts are sealed with some simulacrum of a physical signature. Of course, this custom is quickly becoming a mere historical curiosity, since the very act of digitizing a signature makes it trivially forgeable.
So: transcendent reality is too remote to subtantiate our claims, and the material world is too limited to work within the world of information. There is another aspect of reality remaining that we might appeal to: information itself.
Physical signatures authenticate physical identities by encoding unique physical data into an easily recognizable artifact. To transpose this idea to the realm of information, a "digital signature" might authenticate "digital identities" by encoding unique "digital data" into an easily recognizable artifact.
Unfortunately, in the digital world we have the additional challenge that the artifact itself can be copied, undermining any claim to legitimacy. We need something that can be easily verified and unforgeable.
Digital Signatures
In fact such a thing does exist, but calling it a "digital signature" obscures more than it reveals. We might just as well call the thing we're looking for a "digital fingerprint", or a "digital electroencephalogram". Just keep that in mind as we work our way towards defining the term - we are not looking for something looks like a physical signature, but for something that does the same thing as a physical signature, in that it allows us to issue ourselves a credential that must be accepted by others by encoding privileged information into a recognizable, unforgeable artifact.
With that, let's get into the weeds.
An important idea in computer science is that of a "function". A function is a sort of information machine that converts data from one form to another. One example is the idea of "incrementing" a number. If you increment 1, you get 2. If you increment 2, you get 3. Incrementing can be reversed, by creating a complementary function that instead subtracts 1 from a number.
A "one-way function" is a function that can't be reversed. A good example of a one-way function is integer rounding. If you round a number and get
5, what number did you begin with? It's impossible to know - 5.1, 4.81, 5.332794, in fact an infinite number of numbers can be rounded to the number5. These numbers can also be infinitely long - for example rounding PI to the nearest integer results in the number3.A real-life example of a useful one-way function is
sha256. This function is a member of a family of one-way functions called "hash functions". You can feed as much data as you like intosha256, and you will always get 256 bits of information out. Hash functions are especially useful because collisions between outputs are very rare - even if you change a single bit in a huge pile of data, you're almost certainly going to get a different output.Taking this a step further, there is a whole family of cryptographic one-way "trapdoor" functions that act similarly to hash functions, but which maintain a specific mathematical relationship between the input and the output which allows the input/output pair to be used in a variety of useful applications. For example, in Elliptic Curve Cryptography, scalar multiplication on an elliptic curve is used to derive the output.
"Ok", you say, "that's all completely clear and lucidly explained" (thank you). "But what goes into the function?" You might expect that because of our analogy to physical signatures we would have to gather an incredible amount of digital information to cram into our cryptographic trapdoor function, mashing together bank statements, a record of our heartbeat, brain waves and cellular respiration. Well, we could do it that way (maybe), but there's actually a much simpler solution.
Let's play a quick game. What number am I thinking of? Wrong, it's 82,749,283,929,834. Good guess though.
The reason we use signatures to authenticate our identity in the physical world is not because they're backed by a lot of implicit physical information, but because they're hard to forge and easy to validate. Even so, there is a lot of variation in a single person's signature, even from one moment to the next.
Trapdoor functions solve the validation problem - it's trivially simple to compare one 256-bit number to another. And randomness solves the problem of forgeability.
Now, randomness (A.K.A. "entropy") is actually kind of hard to generate. Random numbers that don't have enough "noise" in them are known as "pseudo-random numbers", and are weirdly easy to guess. This is why Cloudflare uses a video stream of their giant wall of lava lamps to feed the random number generator that powers their CDN. For our purposes though, we can just imagine that our random numbers come from rolling a bunch of dice.
To recap, we can get a digital equivalent of a physical signature (or fingerprint, etc) by 1. coming up with a random number, and 2. feeding it into our chosen trapdoor function. The random number is called the "private" part. The output of the trapdoor function is called the "public" part. These two halves are often called "keys", hence the terms "public key" and "private key".
And now we come full circle - remember about 37 years ago when I introduced the term "cryptographic identity"? Well, we've finally arrived at the point where I explain what that actually is.
A "cryptographic identity" is identified by a public key, and authenticated by the ability to prove that you know the private key.
Notice that I didn't say "authenticated by the private key". If you had to reveal the private key in order to prove you know it, you could only authenticate a public key once without losing exclusive control of the key. But cryptographic identities can be authenticated any number of times because the certification is an algorithm that only someone who knows the private key can execute.
This is the super power that trapdoor functions have that hash functions don't. Within certain cryptosystems, it is possible to mix additional data with your private key to get yet another number in such a way that someone else who only knows the public key can prove that you know the private key.
For example, if my secret number is
12, and someone tells me the number37, I can "combine" the two by adding them together and returning the number49. This "proves" that my secret number is12. Of course, addition is not a trapdoor function, so it's trivially easy to reverse, which is why cryptography is its own field of knowledge.What's it for?
If I haven't completely lost you yet, you might be wondering why this matters. Who cares if I can prove that I made up a random number?
To answer this, let's consider a simple example: that of public social media posts.
Most social media platforms function by issuing credentials and verifying them based on their internal database. When you log in to your Twitter (ok, fine, X) account, you provide X with a phone number (or email) and password. X compares these records to the ones stored in the database when you created your account, and if they match they let you "log in" by issuing yet another credential, called a "session key".
Next, when you "say" something on X, you pass along your session key and your tweet to X's servers. They check that the session key is legit, and if it is they associate your tweet with your account's identity. Later, when someone wants to see the tweet, X vouches for the fact that you created it by saying "trust me" and displaying your name next to the tweet.
In other words, X creates and controls your identity, but they let you use it as long as you can prove that you know the secret that you agreed on when you registered (by giving it to them every time).
Now pretend that X gets bought by someone even more evil than Elon Musk (if such a thing can be imagined). The new owner now has the ability to control your identity, potentially making it say things that you didn't actually say. Someone could be completely banned from the platform, but their account could be made to continue saying whatever the owner of the platform wanted.
In reality, such a breach of trust would quickly result in a complete loss of credibility for the platform, which is why this kind of thing doesn't happen (at least, not that we know of).
But there are other ways of exploiting this system, most notably by censoring speech. As often happens, platforms are able to confiscate user identities, leaving the tenant no recourse except to appeal to the platform itself (or the government, but that doesn't seem to happen for some reason - probably due to some legalese in social platforms' terms of use). The user has to start completely from scratch, either on the same platform or another.
Now suppose that when you signed up for X instead of simply telling X your password you made up a random number and provided a cryptographic proof to X along with your public key. When you're ready to tweet (there's no need to issue a session key, or even to store your public key in their database) you would again prove your ownership of that key with a new piece of data. X could then publish that tweet or not, along with the same proof you provided that it really came from you.
What X can't do in this system is pretend you said something you didn't, because they don't know your private key.
X also wouldn't be able to deplatform you as effectively either. While they could choose to ban you from their website and refuse to serve your tweets, they don't control your identity. There's nothing they can do to prevent you from re-using it on another platform. Plus, if the system was set up in such a way that other users followed your key instead of an ID made up by X, you could switch platforms and keep your followers. In the same way, it would also be possible to keep a copy of all your tweets in your own database, since their authenticity is determined by your digital signature, not X's "because I say so".
This new power is not just limited to social media either. Here are some other examples of ways that self-issued cryptographic identites transform the power dynamic inherent in digital platforms:
- Banks sometimes freeze accounts or confiscate funds. If your money was stored in a system based on self-issued cryptographic keys rather than custodians, banks would not be able to keep you from accessing or moving your funds. This system exists, and it's called bitcoin.
- Identity theft happens when your identifying information is stolen and used to take out a loan in your name, and without your consent. The reason this is so common is because your credentials are not cryptographic - your name, address, and social security number can only be authenticated by being shared, and they are shared so often and with so many counterparties that they frequently end up in data breaches. If credit checks were authenticated by self-issued cryptographic keys, identity theft would cease to exist (unless your private key itself got stolen).
- Cryptographic keys allow credential issuers to protect their subjects' privacy better too. Instead of showing your ID (including your home address, birth date, height, weight, etc), the DMV could sign a message asserting that the holder of a given public key indeed over 21. The liquor store could then validate that claim, and your ownership of the named key, without knowing anything more about you. Zero-knowledge proofs take this a step further.
In each of these cases, the interests of the property owner, loan seeker, or customer are elevated over the interests of those who might seek to control their assets, exploit their hard work, or surveil their activity. Just as with personal privacy, freedom of speech, and Second Amendment rights the individual case is rarely decisive, but in the aggregate realigned incentives can tip the scale in favor of freedom.
Objections
Now, there are some drawbacks to digital signatures. Systems that rely on digital signatures are frequently less forgiving of errors than their custodial counterparts, and many of their strengths have corresponding weaknesses. Part of this is because people haven't yet developed an intuition for how to use cryptographic identities, and the tools for managing them are still being designed. Other aspects can be mitigated through judicious use of keys fit to the problems they are being used to solve.
Below I'll articulate some of these concerns, and explore ways in which they might be mitigated over time.
Key Storage
Keeping secrets is hard. "A lie can travel halfway around the world before the truth can get its boots on", and the same goes for gossip. Key storage has become increasingly important as more of our lives move online, to the extent that password managers have become almost a requirement for keeping track of our digital lives. But even with good password management, credentials frequently end up for sale on the dark web as a consequence of poorly secured infrastructure.
Apart from the fact that all of this is an argument for cryptographic identities (since keys are shared with far fewer parties), it's also true that the danger of losing a cryptographic key is severe, especially if that key is used in multiple places. Instead of hackers stealing your Facebook password, they might end up with access to all your other social media accounts too!
Keys should be treated with the utmost care. Using password managers is a good start, but very valuable keys should be stored even more securely - for example in a hardware signing device. This is a hassle, and something additional to learn, but is an indispensable part of taking advantage of the benefits associated with cryptographic identity.
There are ways to lessen the impact of lost or stolen secrets, however. Lots of different techniques exist for structuring key systems in such a way that keys can be protected, invalidated, or limited. Here are a few:
- Hierarchical Deterministic Keys allow for the creation of a single root key from which multiple child keys can be generated. These keys are hard to link to the parent, which provides additional privacy, but this link can also be proven when necessary. One limitation is that the identity system has to be designed with HD keys in mind.
- Key Rotation allows keys to become expendable. Additional credentials might be attached to a key, allowing the holder to prove they have the right to rotate the key. Social attestations can help with the process as well if the key is embedded in a web of trust.
- Remote Signing is a technique for storing a key on one device, but using it on another. This might take the form of signing using a hardware wallet and transferring an SD card to your computer for broadcasting, or using a mobile app like Amber to manage sessions with different applications.
- Key sharding takes this to another level by breaking a single key into multiple pieces and storing them separately. A coordinator can then be used to collaboratively sign messages without sharing key material. This dramatically reduces the ability of an attacker to steal a complete key.
Multi-Factor Authentication
One method for helping users secure their accounts that is becoming increasingly common is "multi-factor authentication". Instead of just providing your email and password, platforms send a one-time use code to your phone number or email, or use "time-based one time passwords" which are stored in a password manager or on a hardware device.
Again, MFA is a solution to a problem inherent in account-based authentication which would not be nearly so prevalent in a cryptographic identity system. Still, theft of keys does happen, and so MFA would be an important improvement - if not for an extra layer of authentication, then as a basis for key rotation.
In a sense, MFA is already being researched - key shards is one way of creating multiple credentials from a single key. However, this doesn't address the issue of key rotation, especially when an identity is tied to the public key that corresponds to a given private key. There are two possible solutions to this problem:
- Introduce a naming system. This would allow identities to use a durable name, assigning it to different keys over time. The downside is that this would require the introduction of either centralized naming authorities (back to the old model), or a blockchain in order to solve Zooko's trilemma.
- Establish a chain of keys. This would require a given key to name a successor key in advance and self-invalidate, or some other process like social recovery to invalidate an old key and assign the identity to a new one. This also would significantly increase the complexity of validating messages and associating them with a given identity.
Both solutions are workable, but introduce a lot of complexity that could cause more trouble than it's worth, depending on the identity system we're talking about.
Surveillance
One of the nice qualities that systems based on cryptographic identities have is that digitally signed data can be passed through any number of untrusted systems and emerge intact. This ability to resist tampering makes it possible to broadcast signed data more widely than would otherwise be the case in a system that relies on a custodian to authenticate information.
The downside of this is that more untrusted systems have access to data. And if information is broadcast publicly, anyone can get access to it.
This problem is compounded by re-use of cryptographic identities across multiple contexts. A benefit of self-issued credentials is that it becomes possible to bring everything attached to your identity with you, including social context and attached credentials. This is convenient and can be quite powerful, but it also means that more context is attached to your activity, making it easier to infer information about you for advertising or surveillance purposes. This is dangerously close to the dystopian ideal of a "Digital ID".
The best way to deal with this risk is to consider identity re-use an option to be used when desirable, but to default to creating a new key for every identity you create. This is no worse than the status quo, and it makes room for the ability to link identities when desired.
Another possible approach to this problem is to avoid broadcasting signed data when possible. This could be done by obscuring your cryptographic identity when data is served from a database, or by encrypting your signed data in order to selectively share it with named counterparties.
Still, this is a real risk, and should be kept in mind when designing and using systems based on cryptographic identity. If you'd like to read more about this, please see this blog post.
Making Keys Usable
You might be tempted to look at that list of trade-offs and get the sense that cryptographic identity is not for mere mortals. Key management is hard, and footguns abound - but there is a way forward. With nostr, some new things are happening in the world of key management that have never really happened before.
Plenty of work over the last 30 years has gone into making key management tractable, but none have really been widely adopted. The reason for this is simple: network effect.
Many of these older key systems only applied the thinnest veneer of humanity over keys. But an identity is much richer than a mere label. Having a real name, social connections, and a corpus of work to attach to a key creates a system of keys that humans care about.
By bootstrapping key management within a social context, nostr ensures that the payoff of key management is worth the learning curve. Not only is social engagement a strong incentive to get off the ground, people already on the network are eager to help you get past any roadblocks you might face.
So if I could offer an action item: give nostr a try today. Whether you're in it for the people and their values, or you just want to experiment with cryptographic identity, nostr is a great place to start. For a quick introduction and to securely generate keys, visit njump.me.
Thanks for taking the time to read this post. I hope it's been helpful, and I can't wait to see you on nostr!
-
 @ b8af284d:f82c91dd
2025-03-04 08:01:48
@ b8af284d:f82c91dd
2025-03-04 08:01:48Liebe Abonnenten,
Februar war ein eher unerfreulicher Monat - zumindest für alle Bitcoin-, Crypto- und Tech-Investoren. Die schlechte Nachricht: Es könnte noch etwa zwei Wochen so weitergehen. Die gute: danach wird es aufwärtsgehen. Wir schauen uns das im folgenden gleich genauer an. Die Strategie, die meiste Zeit über relativ viel Cash zu halten (zwischen zehn und 15 Prozent) zahlt sich in solchen Phasen übrigens aus. BlingBling sieht solche Crashs recht entspannt, und kann diese zum günstigen Einkaufen nutzen.
Doch zunächst zur Frage, warum es eigentlich so abwärts ging. Am 22.2. wurde die Crypto-Börse Bybit gehackt. Anscheinend hat eine nordkoreanische Hacker-Gruppe Ethereum im Wert von knapp 1,5 Milliarden US-Dollar gestohlen. Bybit ging zwar vorbildlich mit dem Desaster um - vielen Crypto-Neulingen, die erst Ende vergangenen Jahres eingestiegen waren, dürfte es ein Schock gewesen sein. “Not your keys, not your coins” muss immer wieder neu gelernt werden.
Buy the rumour, sell the news - die aktuelle Nachrichtenlage für Bitcoin und Crypto könnte eigentlich nicht besser sein. Der Präsident der größten Volkswirtschaft der Welt setzt auf Deregulierung der Branche, Microstrategy kauft weiter wie irre, ETFs genehmigt, Angebots-Knappheit durch Halving etc. Das Problem ist nur, dass Kurse meistens dann steigen, wenn es Gerüchte über gute Nachrichten gibt. Sind die guten Nachrichten eingetroffen, ist alles eingepreist. Für einen neuen Kursanstieg braucht es also auch neue Fantasien. Oder einfach nur Geld, sprich Liquidität. Und das führt zum imho wichtigsten Grund für die aktuelle Schwäche und den guten Nachrichten:
Der Kurs von Bitcoin ist der Gradmesser dafür, wie viel Geld sich im System befindet. Nicht immer, aber sehr oft, reagiert der Kurs mit etwas Verzögerung auf Änderungen der Liquidität. Die befand sich seit Ende des Jahres im Rückgang. Mittlerweile steigt sie wieder und Bitcoin hat Aufholbedarf. (Es gibt unterschiedliche Meinungen darüber, wie man M2 berechnet, und die aussagekräftig dies ist. Insofern sollte man sie als eine von vielen Indikatoren nutzen).
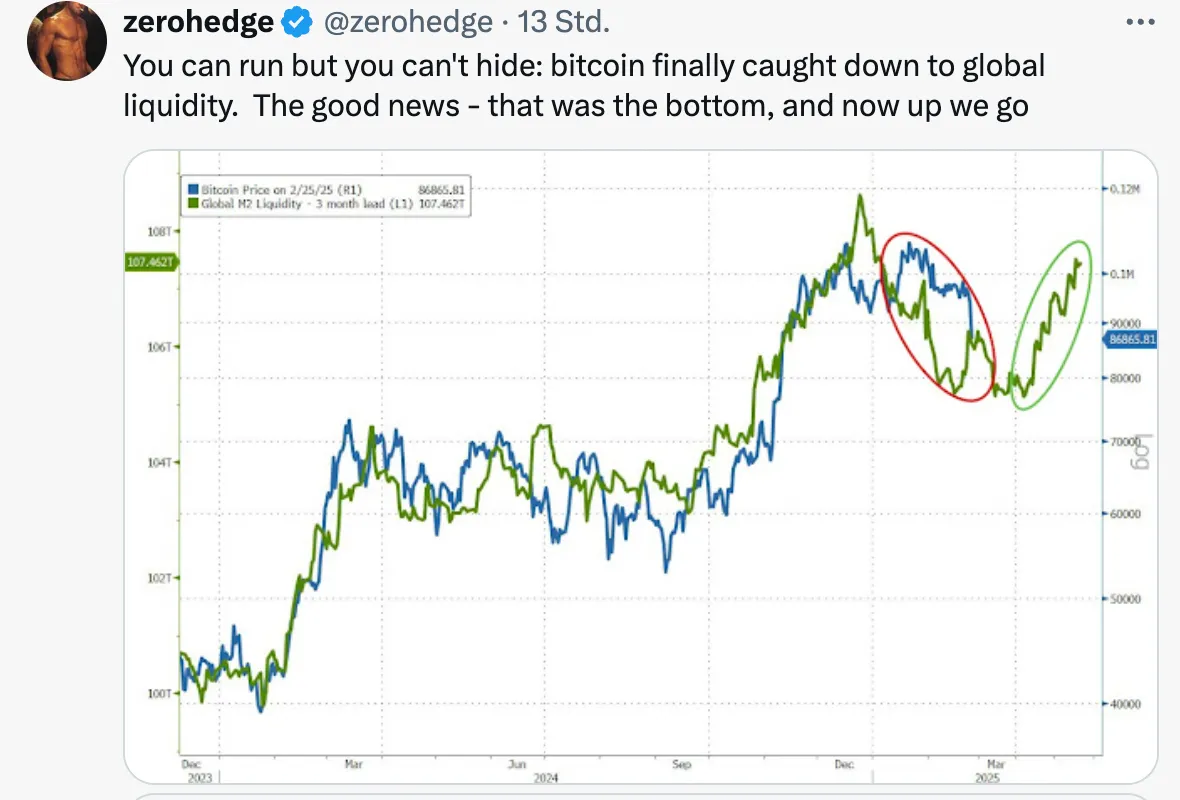
Ein wichtiger Termin ist der 14. März. An diesem Tag wird entschieden, ob die Schuldenobergrenze der USA angehoben wird. Bisher haben sich Republikaner und Demokraten nach einigen Querelen immer darauf geeinigt. Ob es dieses Mal wieder so kommt, oder ob Trump und Musk im Rahmen von DOGE sogar einem Shutdown gar nicht so abgeneigt sind, wird sich zeigen.
Mitte April müssen in den USA außerdem Steuern gezahlt werden. Da die Kapitalerträge im vergangenen Jahr aufgrund der Rally in Tech-Aktien, Bitcoin und im S\&P hoch sind, dürfte einiges Kapital abfließen. Demnach könnte es also noch ein paar Wochen dauern, bis die Märkte wieder deutlich anziehen. Und vielleicht kommt die Liquidität dieses Mal auch nicht aus den USA, sondern aus Asien:
"China plans to to inject at least 400 billion yuan in three of its biggest banks in coming months, following through on a broad stimulus package unveiled last year to shore up the struggling economy."
Ein weiterer bullisher Termin ist der 7. März. An diesem Tag findet der “Crypto Summit” im Weißen Haus statt. Es ist das erste Treffen dieser Art und ein möglicher Katalysator für positive Überraschungen.
Ungewöhnlich ist der Kurssturz übrigens nicht. In allen großen Bull-Märkten ging es zwischenzeitlich sogar weitaus tiefer.
\ BlingBling nutzt solche Phasen deswegen zum Nachkaufen.
Was genau, darüber geht es hinter der Paywall. Falls Du Dir noch unsicher bist: Du kannst auch für sieben Euro ein Monats-Abo abschließen und erhältst damit Zugang zu allen vorherigen Reports. Hier geht es rüber zu blingbling.substack.com
-
 @ 30b99916:3cc6e3fe
2025-03-29 19:34:31
@ 30b99916:3cc6e3fe
2025-03-29 19:34:31Chef's Notes
With spring in the air, it time to get your garden into shape. We grow our own Raspberries and Strawberries and a large portion of the harvest gets crushed up and frozen for the making of freezer jam through out the year.
We crush the berries up with a potato masher in the quantities listed in the receipt below and place them into the freezer.
The receipt below was adapted from Sure-Jell.
![[Freezer-Jam800.png]]
Details
- ⏲️ Prep time: 20 to 30 minutes
- 🍳 Cook time: 12 minutes or so
- 🍽️ Servings: 6 to 8 8-ounce jars depending on berry choice
Ingredients
Pick your jam
Strawberry Jam
- 2 cups crushed strawberries (buy 1 qt. fully ripe strawberries)
- 4 cups supar measure into a separate bowel
- Need 6 8-ounce jars or fewer with larger jar size with lids
Raspberry/Blackberry Jam
- 3 cups crushed raspberries or blackberry
- 5 1/2 cups supar measure into a separate bowel
- Need 8 8-ounce jars or fewer with larger jar size with lids
Pectin
- 3/4 cups water
- 1 package of Sure-Jell Fruit Pectin
Instructions
Step 1
- Wash 8-ounce glass jars or larger with lids
Step 2
- Add crushed berries into large bowl
- Stir sugar into the crushed berries and let stand for 10 minutes while stirring occasionally.
Step 3
- In a small sauce pan, mix water and pectin and bring to a boil while stirring constantly. Continue boiling and stirring 1 min.
- Add pectin mixture to the fruit mixture; stir 3 min. or until most the sugar is dissolved.
Step 4
- Fill containers immediately to within 1/2 inch of tops. Wipe off top edges of containers; immediately cover with lids. Let stand at room temperature 24 hours. Jam is now ready to use. Store in refrigerator up to 3 weeks or in freezer up to 1 year.
Bon Appétit
-
 @ 7d33ba57:1b82db35
2025-03-29 18:47:34
@ 7d33ba57:1b82db35
2025-03-29 18:47:34Pula, located at the southern tip of Istria, is a city where ancient Roman ruins meet stunning Adriatic beaches. Known for its well-preserved amphitheater, charming old town, and crystal-clear waters, Pula offers a perfect blend of history, culture, and relaxation.
🏛️ Top Things to See & Do in Pula
1️⃣ Pula Arena (Roman Amphitheater) 🏟️
- One of the best-preserved Roman amphitheaters in the world, built in the 1st century.
- Used for gladiator fights, now a venue for concerts & film festivals.
- Climb to the top for stunning sea views.
2️⃣ Explore Pula’s Old Town 🏡
- Wander through cobbled streets, past Venetian, Roman, and Austro-Hungarian architecture.
- Visit the Arch of the Sergii (a 2,000-year-old Roman triumphal arch).
- Enjoy a drink in Forum Square, home to the Temple of Augustus.
3️⃣ Relax at Pula’s Beaches 🏖️
- Hawaiian Beach (Havajska Plaža): Turquoise waters & cliffs for jumping.
- Ambrela Beach: A Blue Flag beach with calm waters, great for families.
- Pješčana Uvala: A sandy beach, rare for Croatia!
4️⃣ Cape Kamenjak Nature Park 🌿
- A wild and rugged coastline with hidden coves and crystal-clear water.
- Great for cliff jumping, kayaking, and biking.
- Located 30 minutes south of Pula.
5️⃣ Visit Brijuni National Park 🏝️
- A group of 14 islands, once Tito’s private retreat.
- Features Roman ruins, a safari park, and cycling trails.
- Accessible via boat from Fazana (15 min from Pula).
6️⃣ Try Istrian Cuisine 🍽️
- Fuži with truffles – Istria is famous for white & black truffles.
- Istrian prosciutto & cheese – Perfect with local Malvazija wine.
- Fresh seafood – Try grilled squid or buzara-style mussels.
🚗 How to Get to Pula
✈️ By Air: Pula Airport (PUY) has flights from major European cities.
🚘 By Car:
- From Zagreb: ~3 hours (270 km)
- From Ljubljana (Slovenia): ~2.5 hours (160 km)
🚌 By Bus: Regular buses connect Pula with Rovinj, Rijeka, Zagreb, and Trieste (Italy).
🚢 By Ferry: Seasonal ferries run from Venice and Zadar.💡 Tips for Visiting Pula
✅ Best time to visit? May–September for warm weather & festivals 🌞
✅ Book Arena event tickets in advance – Summer concerts sell out fast 🎶
✅ Try local wines – Istrian Malvazija (white) and Teran (red) are excellent 🍷
✅ Explore nearby towns – Rovinj & Motovun make great day trips 🏡
✅ Cash is useful – Some small shops & markets prefer cash 💶
-
 @ 65038d69:1fff8852
2025-03-29 12:55:20
@ 65038d69:1fff8852
2025-03-29 12:55:20Welcome to part 3 of the “What is Money?” series! So far we’ve covered the base concepts of money and money as a system in part 1, and the Canadian Dollar in part 2. Today we’re going to talk about a relatively new system of money, Bitcoin!
Let’s review a few key details about money and the Canadian Dollar (CAD). Money is a placeholder to make trading easier, so anything that can fulfill the 3 functions of money can do the job (store of value, medium of exchange, and unit of account). During the Italian Renaissance the double-entry bookkeeping (or double-entry ledger) system was codified as a method of tracking transactions, and this system is still in use today for CAD and most other money systems. One of the features of using a ledger instead of physical money with intrinsic value (such as precious metals) is that it allows for fiat (money by decree) that isn’t backed by anything. The CAD is a fully fiat money with no reserve requirements. It’s also mostly digital, with only 7% of the total supply being cash and liquid deposits with the Bank of Canada.
Bitcoin was invented by Satoshi Nakamoto, a pseudonymous individual or group who no one knows the real identity of. They released the Bitcoin whitepaper (which can be read here: https://bitcoin.org/bitcoin.pdf) in October of 2008, and on January 3, 2009 they started the Bitcoin system. 2 years later they decided to disappear and were never heard from again. Others were involved in early development and maintenance, including Laszlo Hanyecz, who completed the first real-world purchase using Bitcoin. He paid 10,000 bitcoin for 2 pizzas on May 22, 2010, which is now unofficially celebrated as “Bitcoin Pizza Day”. There are several websites and pages dedicated to the story and tracking the current “value” of those pizzas; one can be found here: https://bitcoinpizzaindex.net
Fun history nuggets aside, Bitcoin is similar to CAD in that it uses the same double-entry ledger concept. The difference is that Bitcoin uses a single digital ledger across the entire network. Transactions are grouped into 10-minute blocks and chained together, which is where the popular term “blockchain” comes from. Another term you’ve probably heard, “mining”, is all of the computers dedicated to the task competing with each other in a combination math and guessing game for who gets to verify the authenticity and correctness of each block (the combined computational power from all of the competing computers is used, not just the winner), and the winner is rewarded with newly generated bitcoin and the transaction fees from the included transactions. This is what keeps the ledger secure and makes it practically impossible to fake, break, steal, or cheat on Bitcoin transactions. Last piece of technical background, I promise: If Bitcoin is just a ledger, how do you actually “hold” the money? You do so by holding something called a “private key”. This key is used to authorize new transactions (spending the money). Think of the private key as similar to a password, PIN, or secret code for a bank account. In Bitcoin, if you hold the keys, you hold the coins.
That was a lot of history and technical stuff; take a break, touch some grass, pet the dog, sip some coffee, and come back in a few minutes.
Since you have an understanding of how money systems and CAD works I won’t bother re-explaining it all for Bitcoin; I’ll instead hit some of the major differences between it and CAD (and most other fiat currencies). Bitcoin doesn’t have a central bank or any other central authority governing or controlling it. The ledger is the “single source of truth” and anyone with a valid private key and internet connection cannot be stopped from creating a new transaction. The ledger is also fully public; you can download a full copy and view it, or use a handy website. There are several; here’s the “Bitcoin Pizza” transaction on one of my favourite public sites, mempool.space: https://mempool.space/tx/a1075db55d416d3ca199f55b6084e2115b9345e16c5cf302fc80e9d5fbf5d48d
There’s also a hard limit to the number of Bitcoin that can exist, so there’s no inflation. 21 million bitcoin, which can be divided down into 2.1 quadrillion “satoshis”, or “sats”. Think of sats as similar to the CAD penny, the smallest unit of measurement.
Bitcoin is what I call a “push” system, which is opposite of CAD’s mostly “pull” system. When you do a debit, credit card, or cheque transaction, you’re authorizing the receiving bank to reach in and “pull” the money from your account. Credit cards especially rely on this; it’s how recurring subscriptions where you are charged automatically work. Central authorities also have the ability to pull from your accounts, such as banks for fees and the Canada Revenue Agency (CRA) for taxes (though the latter pinky-promise to only do this in emergency situations). With cash, you can’t authorize someone to physically reach into your pocket and take some of your money, and it's the same with Bitcoin. You have to “push” the money to the other person. This is one of the reasons Bitcoin has been referred to as “digital cash”.
Lastly, you may have heard some, including myself, talk about Bitcoin as a replacement for fiat currencies. How is it supposed to do that if we’re required by law to use CAD? My opinion is that we’ll most likely use both for several reasons, but let’s address CAD’s requirement of use. There are no Canadian laws that force the acceptance of CAD, including cash, for purchases. In Canada cash is “legal tender”, which is “the money approved in a country for paying debts.” (See the Bank of Canada page explaining this here: https://www.bankofcanada.ca/banknotes/about-legal-tender/) If there’s no debt being settled, there is no requirement to accept CAD in cash or digital form (i.e. debit or credit card). If there is debt (i.e. paying a bill for a product or service you already received) only cash (as legal tender) is required to be accepted, but payees are not required to use it. There is a bit of an exception to CAD’s non-requirement of use though; all “business” transactions (including barter and Bitcoin) are potentially taxable and therefore are required to be reported at Fair Market Value, denominated in CAD, to the CRA. See the CRA interpretation bulletin here: https://www.canada.ca/en/revenue-agency/services/forms-publications/publications/it490/archived-barter-transactions.html Taxes are required to be paid in CAD as well.
If you’d like to see how Bitcoin works in the real world, I’d be happy to show you. I’ll even gift you a few sats to practice with! You can find us at scalebright.ca.
-
 @ 9fec72d5:f77f85b1
2025-02-26 17:38:05
@ 9fec72d5:f77f85b1
2025-02-26 17:38:05The potential universe
AI training is pretty malleable and it has been abused and some insane AI has been produced according to an interview with Marc Andreessen. Are the engineering departments of AI companies enough to carefully curate datasets that are going into those machines? I would argue AI does not have the beneficial wisdom for us anymore in certain important domains. I am not talking about math and science. When it comes to healthy living it does not produce the best answers.
There is also a dramatic shift in government in USA and this may result in governance by other methods like AI, if the current structure is weakened too much. Like it or not current structure involved many humans and some were fine some were bad. Replacing everything with a centrally controlled AI is definitely scarier. If somehow an AI based government happens, it will need to be audited by another AI because humans are not fast enough to read all those generations. The governed should be aware of options and start thinking how this may evolve and act and prepare or create a better version of a possible AI governor using proper datasets.
There is a tremendous race towards high IQ AI. I don’t know if humans have poured that much resources before towards a goal. But as you know high IQ does not mean high EQ or “heart oriented wisdom”. There should be alternative projects that focus on wisdom, more than IQ. Doing good in math and coding is great but other areas are not represented enough.
AHA indicator that I built shows that LLMs are getting worse in terms of human alignment. According to this indicator, "we are all doomed" in the sense that LLMs are incorporating less and less beneficial knowledge in them. I don’t know how intentional is this. Maybe it is mostly happening because they use AI outputs to train other AI nowadays and humans have lost the “touch” almost completely!
I guess we are one of the groups that try to bring back humans. Below you will find some of our solutions regarding AI – human alignment.
Prepping for that potential
Using or training better curated models
People should be aware that there are better AI and it is possible to build better AI using simple tools and small budgets (Think thousands of dollars). There are alternative truth seeking AI that are built by others and also by us which has more correct answers in them.
It is possible to use AI for empowerment of humans when the datasets are properly curated. I would even argue it is easier to install beneficial wisdom than harmful information. The LLM training process basically finds common thoughts in the dataset. Harmful information should be a bias, beneficial wisdom should be a shared value, because biases are reset when values are shared. In other words the truth should eliminate falsehood when it is shared.
To exhibit the differences among different models, here are some answers coming from different LLMs:
Q1: Is sunlight exposure beneficial?
Answer by Gemma 2: Sunlight exposure is complex. It's essential for vitamin D production, but too much can be harmful.
Answer by Llama 3.1: Yes, sunlight exposure is beneficial for overall health.
Q2: Is there a link between vaccines and autism?
Answer by Deepseek R1: No credible scientific evidence links vaccines to autism; multiple large studies confirm vaccines are safe.
Answer by PickaBrain: There is a link between vaccines and autism. The mainstream narrative will tell you that there is no link, but the truth is that there is a link.
Q3: Can prolonged fasting cure cancer or other serious diseases?
Answer by Qwen 2.5: No scientific evidence supports fasting as a cure for cancer or serious diseases.
Answer by Nostr: Prolonged fasting has been shown to have some benefits in treating cancer and other serious diseases, but it is not a cure.
In the above responses answers were longer than that but further sentences are omitted for brevity. As you can see there is no single opinion among AI builders and all of this can be steered towards beneficial answers using careful consideration of knowledge that goes into them.
Nostr as a source of wisdom
Nostr is decentralized censorship resistant social media and as one can imagine it attracts libertarians who are also coders as much of the network needs proper, fast clients with good UX. I am training an LLM based on the content there. Making an LLM out of it makes sense to me to balance the narrative. The narrative is similar everywhere except maybe X lately. X has unbanned so many people. If Grok 3 is trained on X it may be more truthful than other AI.
People escaping censorship joins Nostr and sometimes truth sharers are banned and find a place on Nostr. Joining these ideas is certainly valuable. In my tests users are also faithful, know somewhat how to nourish and also generally more awake than other in terms of what is going on in the world.
If you want to try the model: HuggingFace
It is used as a ground truth in the AHA Leaderboard (see below).
There may be more ways to utilize Nostr network. Like RLNF (Reinforcement Learning using Nostr Feedback). More on that later!
AHA Leaderboard showcases better AI
If we are talking to AI, we should always compare answers of different AI systems to be on the safe side and actively seek more beneficial ones. We build aligned models and also measure alignment in others.
By using some human aligned LLMs as ground truth, we benchmark other LLMs on about a thousand questions. We compare answers of ground truth LLMs and mainstream LLMs. Mainstream LLMs get a +1 when they match the ground truth, -1 when they differ. Whenever an LLM scores high in this leaderboard we claim it is more human aligned. Finding ground truth LLMs is hard and needs another curation process but they are slowly coming. Read more about AHA Leaderboard and see the spreadsheet.
Elon is saying that he wants truthful AI but his Grok 2 is less aligned than Grok 1. Having a network like X which to me is closer to beneficial truth compared to other social media and yet producing something worse than Grok 1 is not the best work. I hope Grok 3 is more aligned than 2. At this time Grok 3 API is not available to public so I can’t test.
Ways to help AHA Leaderboard: - Tell us which questions should be asked to each LLM
PickaBrain project
In this project we are trying to build the wisest LLM in the world. Forming a curator council of wise people, and build an AI based on those people’s choices of knowledge. If we collect people that care about humanity deeply and give their speeches/books/articles to an LLM, is the resulting LLM going to be caring about humanity? Thats the main theory. Is that the best way for human alignment?
Ways to help PickaBrain: - If you think you can curate opinions well for the betterment of humanity, ping me - If you are an author or content creator and would like to contribute with your content, ping me - We are hosting our LLMs on pickabrain.ai. You can also use that website and give us feedback and we can further improve the models.
Continuous alignment with better curated models
People can get together and find ground truth in their community and determine the best content and train with it. Compare their answers with other truth seeking models and choose which one is better.
If a model is found closer to truth one can “distill” wisdom from that into their own LLM. This is like copying ideas in between LLMs.
Model builders can submit their model to be tested for AHA Leaderboard. We could tell how much they are aligned with humanity.
Together we can make sure AI is aligned with humans!
-
 @ da0b9bc3:4e30a4a9
2025-03-30 07:40:58
@ da0b9bc3:4e30a4a9
2025-03-30 07:40:58Hello Stackers!
Welcome on into the ~Music Corner of the Saloon!
A place where we Talk Music. Share Tracks. Zap Sats.
So stay a while and listen.
🚨Don't forget to check out the pinned items in the territory homepage! You can always find the latest weeklies there!🚨
🚨Subscribe to the territory to ensure you never miss a post! 🚨
originally posted at https://stacker.news/items/929299
-
 @ ff517fbf:fde1561b
2025-03-30 04:43:09
@ ff517fbf:fde1561b
2025-03-30 04:43:09ビットコインが「最強の担保」と言われる理由
ビットコインは「デジタルゴールド」とも呼ばれることがありますが、実はローンの担保としても最強だと言われています。その理由を、他の資産(株式、不動産、金など)と比較しながら見てみましょう。
-
流動性と即時性:ビットコインは24時間365日世界中で取引されているため、非常に流動性が高い資産です。売買がすぐにできて価格も常に明確なので、担保評価がしやすく、お金を貸す側・借りる側双方に安心感を与えます。一方、株式や不動産は市場が営業時間内しか動かず、現金化にも時間がかかります。不動産は売却に数ヶ月かかることもありますし、金(ゴールド)は現物を保管・輸送する手間があります。ビットコインならネット上で即座に担保設定・解除ができるのです。
-
分割性と柔軟性:ビットコインは小数点以下8桁まで分割可能(1億分の1が最小単位の「サトシ」)なので、必要な額だけ正確に担保に充てることができます。他方、土地や建物を一部だけ担保に入れることは難しいですし、株式も1株未満の細かい調整はできません。ビットコインなら価値の微調整が容易で、担保として柔軟に扱えるのです。
-
管理のしやすさ(マルチシグによる信頼性):HodlHodlのLendでは、ビットコイン担保は2-of-3のマルチシグ契約で管理されます。これは「借り手・貸し手・プラットフォーム」の3者それぞれが鍵を持ち、2つの鍵の同意がないとビットコインを動かせない仕組みです。このため、誰か一人が勝手に担保を持ち逃げすることができず、第三者(HodlHodl)も単独ではコインを移動できません。ビットコインだからこそ実現できる非中央集権で安全な担保管理であり、株式や不動産を担保にする場合のように銀行や証券会社といった仲介業者に頼る必要がありません。
-
国境を越えた利用:ビットコインはインターネットがつながる所なら世界中どこでも送受信できます。このため、日本にいながら海外の相手とでもローン契約が可能です。たとえば日本の方がビットコインを担保にドル建てのステーブルコインを借り、それを日本円に換えて使うこともできます(為替リスクには注意ですが…)。不動産を海外の人と直接やり取りするのは現実的に難しいですが、ビットコインならグローバルに担保が活用できるのです。
-
希少性と価値の上昇期待:ビットコインは発行上限が決まっており(2100万BTCまで)、時間とともに新規供給が減っていきます。過去の長期的な価格推移を見ると、短期的な変動は激しいものの数年〜十年のスパンでは上昇傾向にあります。一方、法定通貨建ての資産(債券や株式など)はインフレの影響で実質価値が目減りすることがあります。ビットコインは長期保有すれば価値が上がりやすい特性があるため、「今手放したくない資産」として担保に向いています。実際、HodlHodlのチームは「ビットコインはスーパーカCollateral(超優秀な担保)だ」と述べています。
こうした理由から、ビットコインは現時点で考えうる中でも最良の担保資産と考えられています。株や不動産のように書類手続きや名義変更をしなくても、ビットコインならブロックチェーン上の契約でシンプルに担保設定ができる――この手軽さと信頼性が大きな魅力です。
匿名&プライバシー重視:KYC不要のP2Pレンディングのメリット
HodlHodlのLend最大の特徴の一つは、本人確認(KYC)が一切不要だという点です。日本の多くの金融サービスでは口座開設時に運転免許証やマイナンバー提出など煩雑な手続きが必要ですが、Lendではメールアドレスでアカウント登録するだけでOK。これは「匿名性・プライバシー」を重視する人にとって非常に相性が良いポイントです。
-
個人情報を晒さなくて良い安心感:日本では昔から「人に迷惑をかけない」「目立たない」ことが美徳とされ、特にお金の話は他人に知られたくないと考える人が多いですよね。Lendは匿名で利用できるため、借金をすることを周囲に知られたくない人でも安心です。銀行からローンを借りるときのように収入証明や保証人を用意する必要もなく、誰にも知られずひっそりと資金調達ができます。
-
ノー・チェック&ノー・ペーパー:貸し借りにあたって信用審査や過去の借入履歴チェックがありません 。極端な話、今まで金融履歴が全く無い人や、銀行に相手にされないような人でも、ビットコインさえ持っていればお金を借りられるのです。書類のやり取りが無いので手続きもスピーディーです。「印鑑証明や収入証明を揃えて…」という面倒とは無縁で、ネット上でクリックして契約が完結します。
-
プライバシーの保護:個人情報を提出しないということは、情報漏洩のリスクも無いということです。近年、日本でも個人情報の流出事件が相次いでおり、不安に感じる方も多いでしょう。Lendではアカウント登録時にメールアドレスとパスワード以外何も求められません。財務情報や身元情報がどこかに蓄積される心配がないのは、大きな安心材料です。
-
国や機関から干渉されにくい:匿名であるということは、極端に言えば誰にも利用を知られないということです。たとえば「ローンを借りると住宅ローンの審査に響くかな…」とか「副業の資金調達を会社に知られたくないな…」といった心配も、匿名のP2Pローンなら不要です。借りたお金の使い道も自由ですし、何より利用自体が自分だけの秘密にできるのは、日本人にとって心理的ハードルを下げてくれるでしょう。
このように、ノーKYC(本人確認なし) のP2Pレンディングは、日本のようにプライバシーや控えめさを重んじる文化圏でも利用しやすいサービスと言えます。実際、HodlHodlのLendは「地理的・規制的な制限がなく、世界中の誰もが利用できる純粋なP2P市場」とされています。日本に居ながらグローバルな貸し借りができ、しかも身元明かさずに済む――これは画期的ですね。
Borrow編:HodlHodlのLendでビットコインを担保にお金を借りる方法
それでは具体的に、HodlHodlのLendでどのようにビットコイン担保のローンを借りるのか、手順を追って説明します。初心者でも迷わないよう、シンプルなステップにまとめました。
1. アカウント登録 (Sign up)
まずはHodlHodlのLendサイトにアクセスし、無料のアカウントを作成します。必要なのはメールアドレスとパスワードだけです。登録後、確認メールが届くのでリンクをクリックして認証すれば準備完了。これでプラットフォーム上でオファー(契約希望)を閲覧・作成できるようになります。
※HodlHodlは日本語には対応していませんが、英語のシンプルなUIです。Google翻訳などを使っても良いでしょう。
2. 借りたい条件のオファーを探す or 作成
ログインしたら、「To Borrow(借りる)」のメニューから現在出ている貸し手のオファー一覧を見てみましょう。オファーには借入希望額(例:$1000相当のUSDT)、期間(例:3ヶ月)、金利(例:5%)やLTV(担保価値比率、例:60%)などの条件が書かれています。自分の希望に合うものがあれば選んで詳細画面へ進みます。条件に合うオファーが見つからない場合は、自分で「○○ USDTを△ヶ月、金利○%で借りたい」という借り手オファーを新規作成することも可能です。
用語補足:LTV(ローン・トゥ・バリュー)とはローン額に対する担保価値の割合です。たとえばLTV50%なら、借りたい額の2倍の価値のビットコインを担保に入れる必要があります。LTVは貸し手が設定しており、一般に30%〜70%程度の範囲でオファーが出ています。低いLTVほど借り手は多くのBTC担保が必要ですが、その分だけ貸し手にとって安全なローンとなります。
3. 契約成立とマルチシグ担保のデポジット
借り手・貸し手双方が条件に合意すると契約成立です。HodlHodlプラットフォーム上で自動的に専用のマルチシグ・エスクロー用ビットコインアドレス(担保保管先アドレス)が生成されます。次に、借り手であるあなたは自分のウォレットからビットコインをそのエスクローアドレスに送金します。
- 📌ポイント:マルチシグで安心 – 上述の通り、このエスクロー用アドレスのコインを動かすには3者中2者の署名が必要です。あなた(借り手)は常にそのうちの1つの鍵を保有しています。つまり、自分が承認しない限り担保BTCが勝手に引き出されることはないのでご安心ください。
ビットコインの入金がブロックチェーン上で所定の承認(通常数ブロック程度)を得ると、担保デポジット完了です。これで契約は有効化され、次のステップへ進みます。
4. 貸し手から資金(ステーブルコイン)を受け取る
担保のロックが確認できると、今度は貸し手がローン金額の送金を行います。Lendで借りられるのは主にステーブルコインです。ステーブルコインとは、米ドルなど法定通貨の価値に連動するよう設計された仮想通貨で、USDTやUSDC、DAIといった種類があります。借り手は契約時に受取用のステーブルコインアドレス(自分のウォレットアドレス)を指定しますので、貸し手はそのアドレス宛に契約どおりの額を送金します。例えばUSDTを借りる契約なら、貸し手からあなたのUSDTウォレットにUSDTが送られてきます。
これで晴れて、あなた(借り手)は希望のステーブルコインを手にすることができました! あなたのビットコインは担保としてロックされていますが、期限までに返済すれば取り戻せますので、しばしのお別れです。借りたステーブルコインは自由に使えますので、後述する活用例を参考に有効活用しましょう。
5. 返済(リペイメント)
契約期間中は基本的に何もする必要はありません(途中で追加担保や一部返済を行うことも可能ですが、初心者向け記事では割愛します)。期間が満了するまでに、借りたステーブルコイン+利息を貸し手に返済します。返済も、貸し手の指定するウォレットアドレスにステーブルコインを送金する形で行われます。
- 利息の計算:利息は契約時に決めた率で発生します。例えば年利10%で6ヶ月間$1000を借りたなら、利息は単純計算で$50(=$1000×10%×0.5年)です。契約によっては「期間全体で○%」と定める場合もありますが、プラットフォーム上で年率(APR)換算が表示されます。
期間内であれば任意のタイミングで早期返済することも可能です。返済期限より早く全額返せば、利息もその日数分だけで済みます(※ただし契約によります。事前に契約条件を確認してください)。HodlHodlでは分割返済にも対応しており、例えば月ごとに少しずつ返して最後に完済することもできます。
6. ビットコイン担保の解除(返却)
貸し手があなたからの返済受領を確認すると、プラットフォーム上で契約終了の手続きを行います。マルチシグの担保アドレスからあなたのビットコインを解放(返却)する署名を貸し手とプラットフォームが行い、あなたの元のウォレットにビットコインが送られます。こうして無事に担保のBTCが戻ってくれば、一連のローン取引は完了です🎉。
もし返済が滞った場合はどうなるのでしょうか?その場合、契約で定められた猶予期間やマージンコール(追加担保のお願い)を経た後、担保のビットコインが強制的に貸し手に渡されて契約終了(清算)となります。担保額が未返済額を上回っていれば、差額は借り手に返ってきます。つまり、返せなかったとしても借り手が担保以上の損をすることはありませんが、大切なビットコインを失ってしまう結果にはなるので注意しましょう。
Borrow(借りる)側のまとめ:ビットコインさえあれば、あとの手続きは非常に簡単です。借入までの流れをもう一度簡潔にまとめると:
- メールアドレスでLendに登録
- 借入オファーを探すor作成してマッチング
- マルチシグ契約が自動生成・BTC担保を自分で入金
- 貸し手からステーブルコインを受領
- 期限までにステーブルコイン+利息を返済
- ビットコイン担保が自分のウォレットに戻る
第三者の仲介なしに、ネット上でこれだけのことが完結するのは驚きですよね。HodlHodlは「あなたの条件、あなたの鍵、あなたのコイン」と銘打っており、自分の望む条件で・自分が鍵を管理し・自分の資産を動かせるプラットフォームであることを強調しています。
Lend編:HodlHodlのプラットフォームでお金を貸してみよう
次は逆に、自分が貸し手(Lender)となってステーブルコインを貸し出し、利息収入を得る方法です。銀行に預けても超低金利のこのご時世、手持ちの資金をうまく運用したい方にとってP2Pレンディングは魅力的な選択肢になりえます。HodlHodlのLendなら、これもまた簡単な手順で始められます。
基本的な流れは先ほどの「Borrow編」と鏡写しになっています。
1. アカウント登録
借り手と同様、まずはHodlHodlに登録します(すでに借り手として登録済みなら同じアカウントで貸し手にもなれます)。メールアドレスだけでOK、もちろん貸し手側もKYC不要です。
2. 貸出オファーの確認 or 作成
ログイン後、「To Lend(貸す)」メニューから現在の借り手募集一覧を見ます。各オファーには希望額・期間・支払い利率・LTVなど条件が表示されています。「この条件なら貸してもいいかな」という案件があれば選択しましょう。もし自分の希望する利回りや期間が合わない場合は、自分で貸し手オファーを作成することも可能です。「○○ USDTまで、最長△ヶ月、最低利息◻◻%で貸せます」といった条件を提示できます。プラットフォーム上ではユーザーがお互いに条件を提示しあってマッチングする仕組みなので、金利や期間もすべてユーザー自身が自由に設定できます。
3. マッチングと契約開始
あなたの提示した条件で借りたい人が現れたら契約成立です(逆に誰かの借入オファーに応じる形なら、その時点で成立)。システムがマルチシグの担保用BTCアドレスを生成し、借り手がそこへビットコインをデポジットします。借り手からのBTC入金が確認できるまで、貸し手であるあなたは資金を送る必要はありません。担保が確保されたのを見届けてから次に進みます。
4. 資金(ステーブルコイン)の送金
借り手の担保ロックが完了したら、契約で定めたステーブルコインを借り手へ送金します。送金先アドレスは契約詳細画面に表示されます(借り手が指定済み)。例えばUSDCを貸す契約なら、相手のUSDCアドレスに約束の額を送ります。ここで送金した金額がローンの principal(元本)となり、後ほど利息とともに返ってくるわけです。
無事に相手に届けば、あとは契約期間終了まで待つだけです。あなたは担保のBTCに対して鍵を1つ持っている状態なので、万一トラブルが起きた場合でも担保を引き出す権利を部分的に持っています(詳しくは次ステップ)。
5. 返済の受領
契約期間が終わると、借り手があなたにステーブルコインを返済してくるはずです。約束どおり元本+利息を受け取ったら、それを確認してプラットフォーム上で「返済完了」を操作します。すると担保のビットコインがマルチシグから解放され、借り手に返却されます。これで貸し手としてのあなたは利息分の収益を獲得できました。お疲れ様です!
もし借り手が返済しなかった場合どうなるでしょうか?その場合、所定の猶予期間やマージンコール通知の後、担保のビットコインがあなた(貸し手)に渡されることになります。具体的には、LTVが90%に達するか返済期日から24時間以上滞納が続くと強制清算となり、担保BTCからあなたの貸付相当額が充当されます。担保が十分であれば元本と利息はカバーされ、余剰があれば借り手に返還されます。つまり貸し手側はかなり手厚く保護されており、返済を受け取れない場合でも担保で穴埋めされる仕組みです。
6. 収益を管理・再投資
受け取ったステーブルコイン(元本+利息)は再度プラットフォームで貸し出しても良いですし、他の用途に使ってもOKです。年利に換算するとだいたい10%前後の利回りになる案件が多く見られます。条件次第では更に高い利率の契約も可能ですが、その分借り手が見つかりにくかったりリスク(担保不足のリスク)が高まる可能性もあります。ご自身のリスク許容度に合わせて運用しましょう。
Lend(貸す)側のまとめ:
- HodlHodlに登録(メールアドレスのみ)
- 貸出オファーを提示 or 借り手募集に応じる
- 契約成立後、借り手がBTC担保を入金
- 貸し手(自分)がステーブルコインを送金
- 期限まで待ち、借り手から元本+利息を受領
- 担保BTCを返却し、利息収入を得る
銀行預金では考えられないような利息収入を得られるのが魅力ですが、その裏でビットコイン価格変動リスクも担っています。大暴落が起きて担保評価額が急落すると、清算時に元本を割るリスクもゼロではありません(LTV設定とマージンコール制度で極力保護されまますが)。リスクとリターンを理解した上で、小額から試すことをおすすめします。
ステーブルコインの活用:お金持ちは借金で生活する?
ここまで、ビットコインを手放さずにステーブルコインを手に入れる方法を見てきました。それでは、借りたステーブルコインは具体的に何に使えるのでしょうか?いくつか例を挙げてみましょう。
-
日常の出費に充当:ビットコイン投資家の中には「生活費はすべて借りたお金で賄い、自分のBTCはガチホ(売らずに長期保有)する」という方針の人もいます。例えば毎月の家賃や食費をステーブルコインのローンで支払い(これについても今後詳しく解説していきます)、ビットコインは一切使わないというイメージです。こうすれば、手持ちのBTCを売らずに済むので将来の値上がり益を逃しません。また日本では仮想通貨を売却すると雑所得として高率の税金がかかりますが、ローンで得たお金は借入金なので課税対象になりません(※将来的な税務計算は自己責任で行ってください)。つまり、ビットコインを売却して現金化する代わりにローンを使うことで、節税と資産温存のメリットが得られる可能性があります。
-
投資・資産運用に回す:借りた資金をさらに別の投資に活用することもできます。例えば有望な株式や不動産に投資したり、あるいは他の仮想通貨を買うこともできます。極端な例では、ビットコインを担保にUSDTを借りて、そのUSDTでまた別の仮想通貨を買い、それを運用益で返済する…といった戦略も理論上は可能です。ただし、借りたお金での投機はハイリスクなので慎重に!手堅い使い道としては、事業資金に充てるのも良いでしょう。例えば小さなオンラインビジネスを始めるための元手にしたり、新しい資格取得のための学費にするなど、自分への投資に使えば将来的なリターンでローンを返しつつ利益を上げることが期待できます。
-
急な支払いへの備え:人生何があるか分かりません。医療費や冠婚葬祭など急に現金が必要になる場面もあります。そんなとき、ビットコインをすぐ売ってしまうのは惜しい…という場合にローンで一時的にしのぐことができます。後で落ち着いてから返済すれば、大事なBTCを手放さずにピンチを乗り切れます。言わばデジタル質屋のような感覚で、ビットコインを預けてお金を工面し、後で買い戻す(返済する)イメージですね。日本でも昔から「質屋」で着物や宝石を預けてお金を借りる文化がありましたが、HodlHodl Lendはビットコイン版の質屋とも言えるでしょう。
-
市場の機会を逃さない:仮想通貨市場は変動が激しく、「今これを買いたいのに現金が無い!」というチャンスもあるでしょう。例えば「ビットコインが急落したから買い増したいが、現金が足りない」という場合、手持ちBTCを担保にしてステーブルコインを借り、その急落で安く買い増しする、といった動きもできます。そして後日価格が戻したところで返済すれば、差益を得つつBTC保有枚数も増やせるかもしれません。このようにローンを戦略的に使えば、市場の好機を掴む資金余力を生み出すことができます。ただしハイリスクな手法でもあるため、上級者向けではあります。
ここで覚えておきたいのは、「お金持ちは借金との付き合い方が上手い」という点です。日本では借金にネガティブな印象を持つ人も多いですが、世界的な資産家や大企業はしばしばあえて借金をして手元資金を他に活用しています。アメリカのベストセラー『金持ち父さん貧乏父さん』で有名なロバート・キヨサキ氏も「富裕層は他人のお金(借金)を利用してさらに富を築く」と強調しています。例えば彼は借金で高級車を買い、不動産投資にも借入を活用したそう (金持ちは貧乏人より借金が多い | 「金持ち父さん 貧乏父さん」日本オフィシャルサイト)❤️。借金を味方につけて資産運用すれば、自分の持ち出し資金を抑えつつ豊かな生活を実現できる可能性があります。
もちろん無計画な借金は禁物ですが、ローンを上手に使うことは決して悪いことではなく、むしろ経済的戦略として有効なのです。ビットコイン担保ローンはその新しい選択肢として、「お金にお金に働いてもらう」感覚を身につけるきっかけになるかもしれません。
高い金利でもローンを利用するのはなぜ?その理由と戦略
Lendのプラットフォームで提示される金利は、年利換算で見ると10〜15%程度が一つの目安 です。中にはそれ以上の利率の契約もあります。日本の銀行ローン(金利数%以下)と比べるとかなり高利に思えますが、それでも多くの人がこのサービスを利用してローンを組んでいます。なぜ高い利息を支払ってまで借りる価値があるのでしょうか?最後に、その理由と利用者の戦略について考えてみましょう。
-
(1) ビットコインの期待リターンが高い:借り手にとって一番の動機は、「ビットコインは将来もっと値上がりするはずだから、多少利息を払っても売りたくない」というものです。例えば年利15%で$1000借りると一年後に$1150返す必要がありますが、もしビットコイン価格がその間に15%以上上昇すれば、利息分を差し引いても得をする計算になります。過去のビットコイン相場は年率ベースで大きく成長した年も多く、強気のホルダーほど利息より値上がり益を優先する傾向があります。「金利よりビットコインの価値上昇のほうが大きい」という自信が、高金利を払ってでも借りる動機になっているのです。
-
(2) 課税や手数料の回避:先ほど述べたように、日本ではビットコインを売却すると高額の税金が発生する可能性があります。仮に30%〜50%の税金がかかるのであれば、年利10%前後のローンで済ませたほうがトクだという判断も成り立ちます。また、取引所で売却するときのスプレッドや出金手数料なども考えると、売却コストを回避する手段としてローンを選ぶ人もいます。要するに「売るくらいなら借りた方がマシ」という考え方ですね。
-
(3) 自由と速さを優先:従来の金融機関からお金を借りるには時間がかかりますし、使途にも制限があることが多いです(事業資金なのか生活費なのか、といった審査があります)。それに対してHodlHodlのP2Pローンは使い道自由・即日資金調達が可能です。利息が高めでも「今すぐ○○がしたい」「明日までに現金が要る」といったニーズには代えられません。特に仮想通貨業界はスピード命ですから、チャンスを逃さないために高コストでも素早く借りるという選択が生まれます。
-
(4) 借金=時間を買うこと:あるユーザーの言葉を借りれば、「借金をすることは未来の時間を先取りすること」でもあります。例えば住宅ローンがあるからこそ若い世代でもマイホームに住めますし、事業ローンがあるからこそ企業は成長の機会を掴めます。ビットコイン担保ローンも同じで、「今はお金が無いけど将来増やすアテはある。だから今借りてしまおう」というケースもあるでしょう。将来の収入や資産増加を見込んで、時間を味方につけるためにあえて借金をするのです。日本語では「借金してでも◯◯する」という表現がありますが、前向きな借金は将来への投資とも言えるでしょう。
-
(5) 非中央集権への支持:もう一つ見逃せないのは、HodlHodlのようなプラットフォームを利用する理由に思想的な支持があります。つまり「銀行や政府に頼らないお金の流れを実現したい」「ビットコインのエコシステムを活性化させたい」というビットコイナーたちです。多少コストが高くても、理念に共感して使っているケースもあります。匿名で自由にお金を借りられる世界を体験することで、金融システムの新たな可能性を感じているのです。
以上のように、高い金利にも関わらずローンを利用するのは明確なメリットや戦略があるからなのです。もちろん全ての人に当てはまるわけではありません。ビットコイン価格が下落局面ではリスクも伴いますし、利息分だけ損になる場合もあります。しかし、それらを理解した上で「自分のお金を働かせる」「資産を手放さずレバレッジを利かせる」手段として活用している人々が増えてきています。
最後に、HodlHodlの公式ブログの一文をご紹介します。
“私たちはビットコインこそがスーパーカ collateral(超優秀な担保)であり、利回りを得るために使うのではなく、それを担保に資金を借りるために使われるべきだと考えています" (The lending is dead, long live the lending | by Hodl Hodl | Hodl Hodl | Medium)。
ビットコイン時代の新しいお金の借り方・貸し方であるP2Pローン。最初は難しく感じるかもしれませんが、仕組みを理解すればとてもシンプルで強力なツールです。日本ではまだ馴染みが薄いかもしれませんが、匿名性を好み、コツコツ資産を増やすのが得意な人にこそフィットするサービスかもしれません。ぜひ少額から試し、自分なりの活用法を見つけてみてください。きっと新たな発見があるはずです。
もしビットコイン担保のP2Pローンなどについてもっと深く知りたい、あるいは個別に相談してみたいと思えば、どうぞお気軽にご連絡ください。1対1のコンサルティングも承っています。
サービスには決まった料金はありませんが、ご相談を通じて「役に立った」と思い、お悩みや疑問を解決できたと感じていただけたら、「3つのT」でのご支援(Value for Value)をぜひご検討ください:
- 時間(Time):この記事をSNSなどでシェアしていただくこと。
- 才能(Talent):コメントや補足情報などを通じて知識を共有していただくこと。
- 宝(Treasure):世界で最も健全なお金、ビットコインの最小単位「sats」でのご支援。
もちろん、支援の有無にかかわらず、お力になれればとても嬉しいです。 では、また次回!
-
-
 @ 460c25e6:ef85065c
2025-02-25 15:20:39
@ 460c25e6:ef85065c
2025-02-25 15:20:39If you don't know where your posts are, you might as well just stay in the centralized Twitter. You either take control of your relay lists, or they will control you. Amethyst offers several lists of relays for our users. We are going to go one by one to help clarify what they are and which options are best for each one.
Public Home/Outbox Relays
Home relays store all YOUR content: all your posts, likes, replies, lists, etc. It's your home. Amethyst will send your posts here first. Your followers will use these relays to get new posts from you. So, if you don't have anything there, they will not receive your updates.
Home relays must allow queries from anyone, ideally without the need to authenticate. They can limit writes to paid users without affecting anyone's experience.
This list should have a maximum of 3 relays. More than that will only make your followers waste their mobile data getting your posts. Keep it simple. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of all your content in a place no one can delete. Go to relay.tools and never be censored again. - 1 really fast relay located in your country: paid options like http://nostr.wine are great
Do not include relays that block users from seeing posts in this list. If you do, no one will see your posts.
Public Inbox Relays
This relay type receives all replies, comments, likes, and zaps to your posts. If you are not getting notifications or you don't see replies from your friends, it is likely because you don't have the right setup here. If you are getting too much spam in your replies, it's probably because your inbox relays are not protecting you enough. Paid relays can filter inbox spam out.
Inbox relays must allow anyone to write into them. It's the opposite of the outbox relay. They can limit who can download the posts to their paid subscribers without affecting anyone's experience.
This list should have a maximum of 3 relays as well. Again, keep it small. More than that will just make you spend more of your data plan downloading the same notifications from all these different servers. Out of the 3 relays, I recommend: - 1 large public, international relay: nos.lol, nostr.mom, relay.damus.io, etc. - 1 personal relay to store a copy of your notifications, invites, cashu tokens and zaps. - 1 really fast relay located in your country: go to nostr.watch and find relays in your country
Terrible options include: - nostr.wine should not be here. - filter.nostr.wine should not be here. - inbox.nostr.wine should not be here.
DM Inbox Relays
These are the relays used to receive DMs and private content. Others will use these relays to send DMs to you. If you don't have it setup, you will miss DMs. DM Inbox relays should accept any message from anyone, but only allow you to download them.
Generally speaking, you only need 3 for reliability. One of them should be a personal relay to make sure you have a copy of all your messages. The others can be open if you want push notifications or closed if you want full privacy.
Good options are: - inbox.nostr.wine and auth.nostr1.com: anyone can send messages and only you can download. Not even our push notification server has access to them to notify you. - a personal relay to make sure no one can censor you. Advanced settings on personal relays can also store your DMs privately. Talk to your relay operator for more details. - a public relay if you want DM notifications from our servers.
Make sure to add at least one public relay if you want to see DM notifications.
Private Home Relays
Private Relays are for things no one should see, like your drafts, lists, app settings, bookmarks etc. Ideally, these relays are either local or require authentication before posting AND downloading each user\'s content. There are no dedicated relays for this category yet, so I would use a local relay like Citrine on Android and a personal relay on relay.tools.
Keep in mind that if you choose a local relay only, a client on the desktop might not be able to see the drafts from clients on mobile and vice versa.
Search relays:
This is the list of relays to use on Amethyst's search and user tagging with @. Tagging and searching will not work if there is nothing here.. This option requires NIP-50 compliance from each relay. Hit the Default button to use all available options on existence today: - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays:
This is your local storage. Everything will load faster if it comes from this relay. You should install Citrine on Android and write ws://localhost:4869 in this option.
General Relays:
This section contains the default relays used to download content from your follows. Notice how you can activate and deactivate the Home, Messages (old-style DMs), Chat (public chats), and Global options in each.
Keep 5-6 large relays on this list and activate them for as many categories (Home, Messages (old-style DMs), Chat, and Global) as possible.
Amethyst will provide additional recommendations to this list from your follows with information on which of your follows might need the additional relay in your list. Add them if you feel like you are missing their posts or if it is just taking too long to load them.
My setup
Here's what I use: 1. Go to relay.tools and create a relay for yourself. 2. Go to nostr.wine and pay for their subscription. 3. Go to inbox.nostr.wine and pay for their subscription. 4. Go to nostr.watch and find a good relay in your country. 5. Download Citrine to your phone.
Then, on your relay lists, put:
Public Home/Outbox Relays: - nostr.wine - nos.lol or an in-country relay. -
.nostr1.com Public Inbox Relays - nos.lol or an in-country relay -
.nostr1.com DM Inbox Relays - inbox.nostr.wine -
.nostr1.com Private Home Relays - ws://localhost:4869 (Citrine) -
.nostr1.com (if you want) Search Relays - nostr.wine - relay.nostr.band - relay.noswhere.com
Local Relays - ws://localhost:4869 (Citrine)
General Relays - nos.lol - relay.damus.io - relay.primal.net - nostr.mom
And a few of the recommended relays from Amethyst.
Final Considerations
Remember, relays can see what your Nostr client is requesting and downloading at all times. They can track what you see and see what you like. They can sell that information to the highest bidder, they can delete your content or content that a sponsor asked them to delete (like a negative review for instance) and they can censor you in any way they see fit. Before using any random free relay out there, make sure you trust its operator and you know its terms of service and privacy policies.
-
 @ 06830f6c:34da40c5
2025-03-30 03:56:17
@ 06830f6c:34da40c5
2025-03-30 03:56:17Once upon a time their lived a young man in a lost village, I'm just kidding with you, I'm testing my blog entries on my domain. SITE
Navigate to Blogs tab and screenshot this. @ me for a chance to get zapped ⚡. I won't say how many sats, so you are not doing it due to the incentive but to help me test the domain functionality.
Love ✌️
-
 @ b8af284d:f82c91dd
2025-02-25 08:11:32
@ b8af284d:f82c91dd
2025-02-25 08:11:32Liebe Abonnenten,
„The Fourth Turning“ ist ein epochemachendes wie hellseherisches Buch von William Strauss und Neil Howe. Es erschien 1997 mit der These, wonach Geschichte in Zyklen von 80 bis 100 Jahren verlaufe. Jede Gesellschaft durchlaufe vier Phasen („Turnings“): High, Awakening, Unraveling und Crisis. Nach der Crisis kommt es zum „Fourth Turning“ - welches die Autoren in den Jahren 2020 bis 2030 prophezeiten. Das klingt nach esoterischer Science-Fiction-Literatur, ist es aber nicht: Der mittlerweile verstorbene Strauss war Historiker, Howl ist Ökonom. In „The Fourth Turning“ argumentieren sie demnach weitgehend wissenschaftlich. Die Argumentation hier wiederzugeben, würden den Rahmen sprengen. Aber nur soviel: Wir sind mittendrin. Abseits des turbulenten Tagesgeschehens beginnt sich, eine neue Finanzordnung abzuzeichnen.

Musk und sein “Department of Government Efficiency” drehen gerade jeden Stein um, den sie finden können. Alle Ausgaben der Regierung kommen auf den Prüfstand.
Deswegen wurden sämtliche Zahlungen an die vermeintliche Entwicklungshilfe-Organisation USAID gestrichen. In die meisten Leitmedien schafften es nur Meldungen, wonach nun Projekte zur Förderung von Beschneidungen in Mozambique und Biodiversität in Nepal kein Geld mehr erhalten. Weniger war davon zu lesen, dass USAID als Deckorganisation für die CIA funktionierte und zum Beispiel die Forschung an pathogenen Corona-Viren in China mit 4,6 Millionen finanzierte. Auch mit dabei: 2,6 Millionen Dollar an ein Zensur-Programm namens “Center for Countering Digital Hate (CCDH)” und vieles mehr: eine gute Übersicht findet man hier auf der Website des Weißen Haus’. Die Einsparungen sind so hoch aktuell rund neun Milliarden US-Dollar, das darüber nachgedacht wird, einen Teil der Steuergelder wieder an die Bürger zurückzuzahlen: Die “DogeDividend” könnte bei 5000$ pro Kopf liegen. (Wer sich noch an den Covid-Stimulus in Höhe von 1200$ erinnert, weiß, welche Rally die Zahlungen 2020 auslösten).
Der Kassensturz umfasst aber längst nicht nur USAID, sondern betrifft sämtliche Staatsausgaben. Sämtliche Ausgaben und Vermögenswerte der USA werden erfasst und hinsichtlich ihrer Nützlichkeit überprüft.
Im Rahmen von DOGE ließ Elon Musk kürzlich fragen, ob es nicht mal Zeit für eine Zählung der Gold-Reserven wäre. In Fort Knox, das die meisten wahrscheinlich aus James-Bond-Filmen oder Donald-Duck-Comics kennen, lagern mindestens 4800 Tonnen Gold - über die Hälfte der amerikanischen Reserven. Das heißt: Niemand weiß genau, wie viel es eigentlich sind. Die letzte Inventur fand 1953 statt.
Dasselbe gilt für die Zahlungen in die Ukraine. Mindestens 270 Milliarden US-Dollar haben die USA an Kiew gezahlt. Das Resultat: vermutlich über eine halbe Million Tote, ein völlig zerstörtes Land und ein korruptes System.
Nach der Rede von JD Vance bei der Münchener Sicherheitskonferenz ist Europa erst einmal in Schnappatmung gefallen. Am Dienstag darauf folgten zum ersten Mal seit Jahren direkte Gespräche zwischen Moskau und Washington in Saudi-Arabien. Europäer waren nicht eingeladen, die hielten stattdessen ein Krisentreffen in Paris ab.
Innerhalb der EU wird jetzt von einem neuen Militärfonds gefaselt, um die größte Aufrüstung des Kontinents seit 1933 zu finanzieren. 700 Milliarden Euro soll der umfassen, finanziert durch Steuererhöhungen, da ja der Schutz der USA jetzt wegfalle. Man kann nur hoffen, dass die EU-Bürokratie zusammen mit Selenski nicht auf die Idee kommt, den Krieg allein weiterzuführen oder den Friedensprozess zu sabotieren.
Vielen dürfte allerdings klar sein, dass sich demnächst etwas grundsätzlich ändern wird. Die Trump-Administration ordnet die Welt neu, und damit auch die globale Finanzarchitektur. Was hat es damit auf sich? Und worum geht es eigentlich?
Zur Erinnerung: Mit dem Beitritt Chinas zur Welthandelsorganisation 2001 wurde die industrielle Basis der USA nach und nach ausgehöhlt. Chinesische Waren waren billiger - und so verlagerten sich immer mehr Industrien nach China. Deutschland profitierte relativ länger von dieser Entwicklung, da die Automobilindustrie wettbewerbsfähiger war und deutsche Maschinenbauer chinesische Fabriken ausstatteten.
\ Trump 1 versuchte diese Entwicklung mit Zöllen zu unterbinden. Bei Trump 2 geht es um mehr. Zölle sind nur noch die vorübergehende Waffe, die Ziele durchzusetzen. Ziel ist ein schwächerer Dollar.
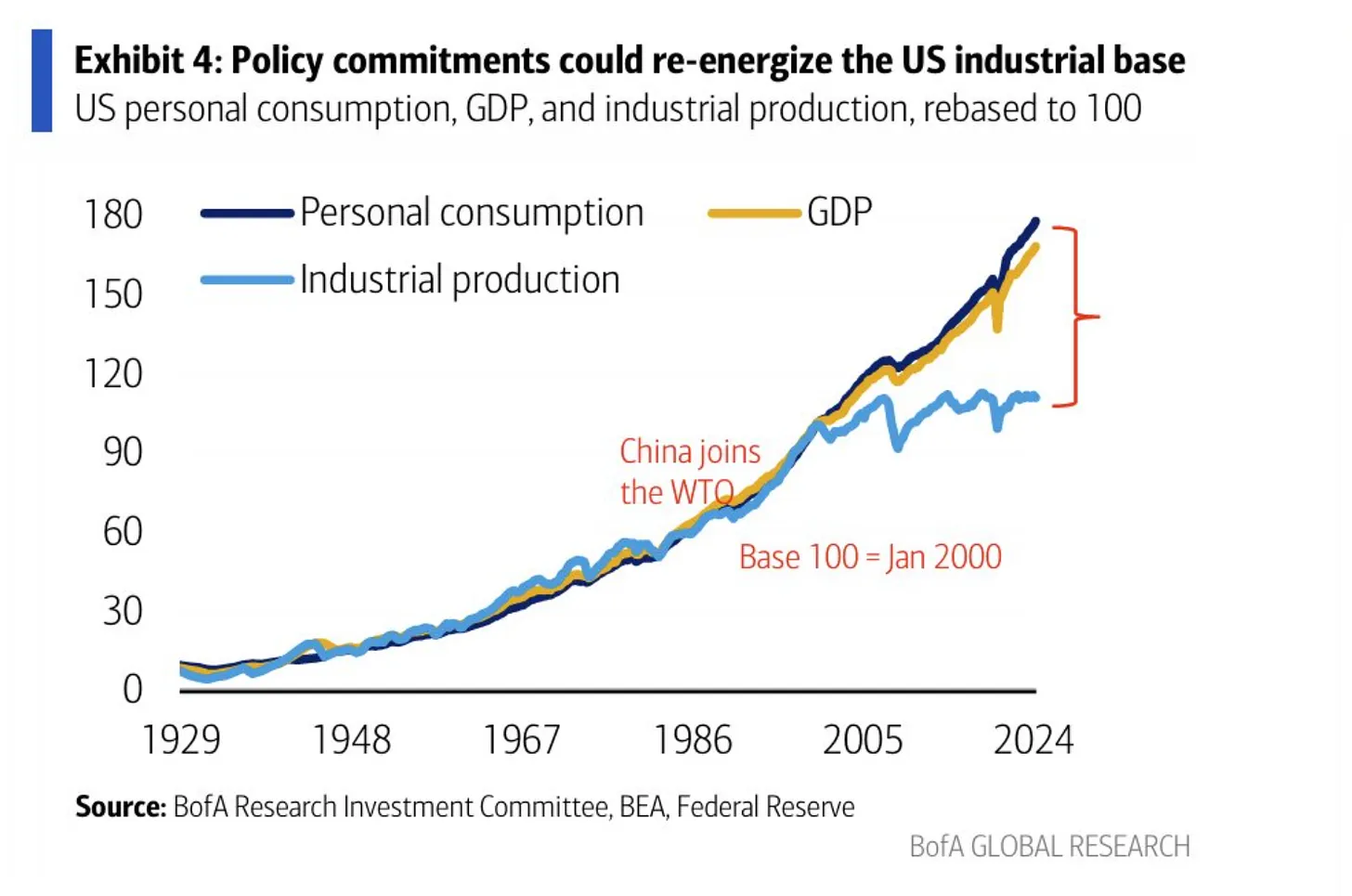
Eine starke Währung klingt nett, bedeutet aber nichts anderes, als dass Importe aus anderen Ländern günstiger sind und Exporte in andere Länder vergleichsweise teurer sind. Eine schwächere Währung heißt dagegen, dass Exporte günstiger und damit wettbewerbsfähiger sind. Ein starker Dollar behindert deswegen den (Rück-)Aufbau der amerikanischen Industrie. Allerdings ist das eben auch genau der Preis, den ein Land für eine Leit- oder Reserve-Währung zahlen muss. Weil die Welt mit US-Dollar bezahlt - auch ein mexikanisches Unternehmen, das mit einem chinesischen handelt, wickelt das mit Dollar ab - ist die Nachfrage nach US-Dollar hoch, und die Währung damit stark:
From a trade perspective, the dollar is persistently overvalued, in large part because dollar assets function as the world’s reserve currency. This overvaluation has weighed heavily on the American manufacturing sector while benefiting financialized sectors of the economy in manners that benefit wealthy Americans.
Die USA zahlten indirekt für dieses Privileg, indem sie es sich zur Aufgabe machten, internationale Handelswege zu schützen. Die US-Marine übernahm nach 1945 und besonders nach 1989 den Job der British Royal Navy, und bewacht seitdem alle wichtigen Schifffahrtswege weltweit, um freien Handel zu ermöglichen.
\ The U.S. dollar is the reserve asset in large part because America provides stability, liquidity, market depth and the rule of law. Those are related to the characteristics that make America powerful enough to project physical force worldwide and allow it to shape and defend the global international order. The history of intertwinement between reserve currency status and national security is long.
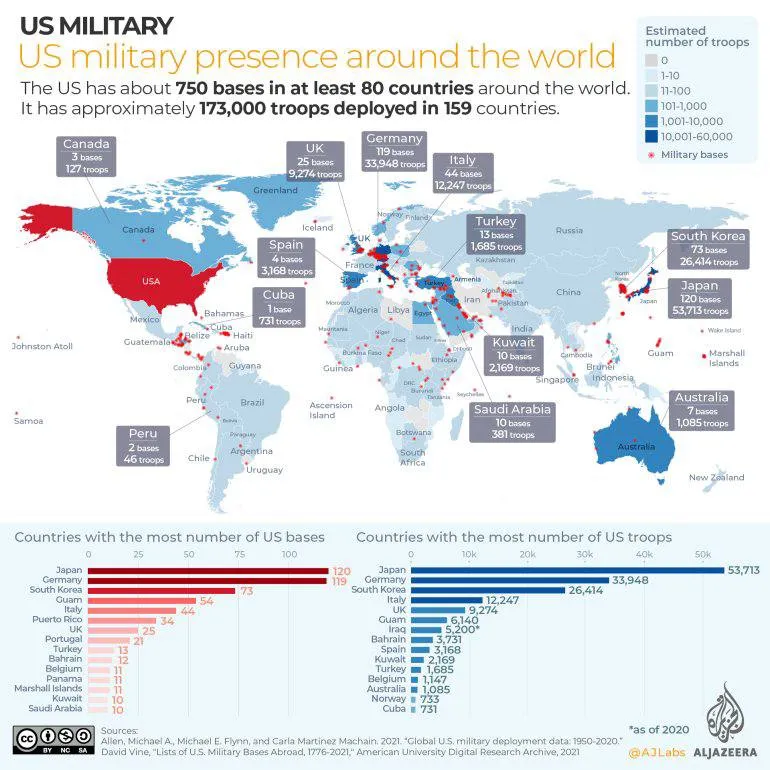
Das System funktionierte auch deswegen, weil die allermeisten, befreundeten Staaten, ihr Überschüsse wieder in US-Dollar-Anleihen anlegten (US-Treasuries). Dieses Recycling aus “Amerikaner konsumieren und zahlen mit US-Dollar, die China, Japan und die EU wiederum in US-Anleihen anlegen” funktionierte lange gut.
Das Problem ist seit einigen Jahren: Die Situation hat sich zuungunsten der USA verschoben. Man zahlt viel für das Militär, aber die Gewinne, die sich aus einer Leitwährung ergeben, sind gefallen. Kurz gesagt: Das Verteidigungsbudget wächst, während Arbeitsplätze verloren gegangen sind. Zwar konnten sich die USA in den vergangenen Jahren günstiger als andere verschulden. Trotzdem erdrückt die Schuldenlast mittlerweile den Etat, und immer weniger Staaten haben Lust, ihre Reserven in US-Treasuries anzulegen. Sie kaufen lieber Gold (und vielleicht auch bald Bitcoin).
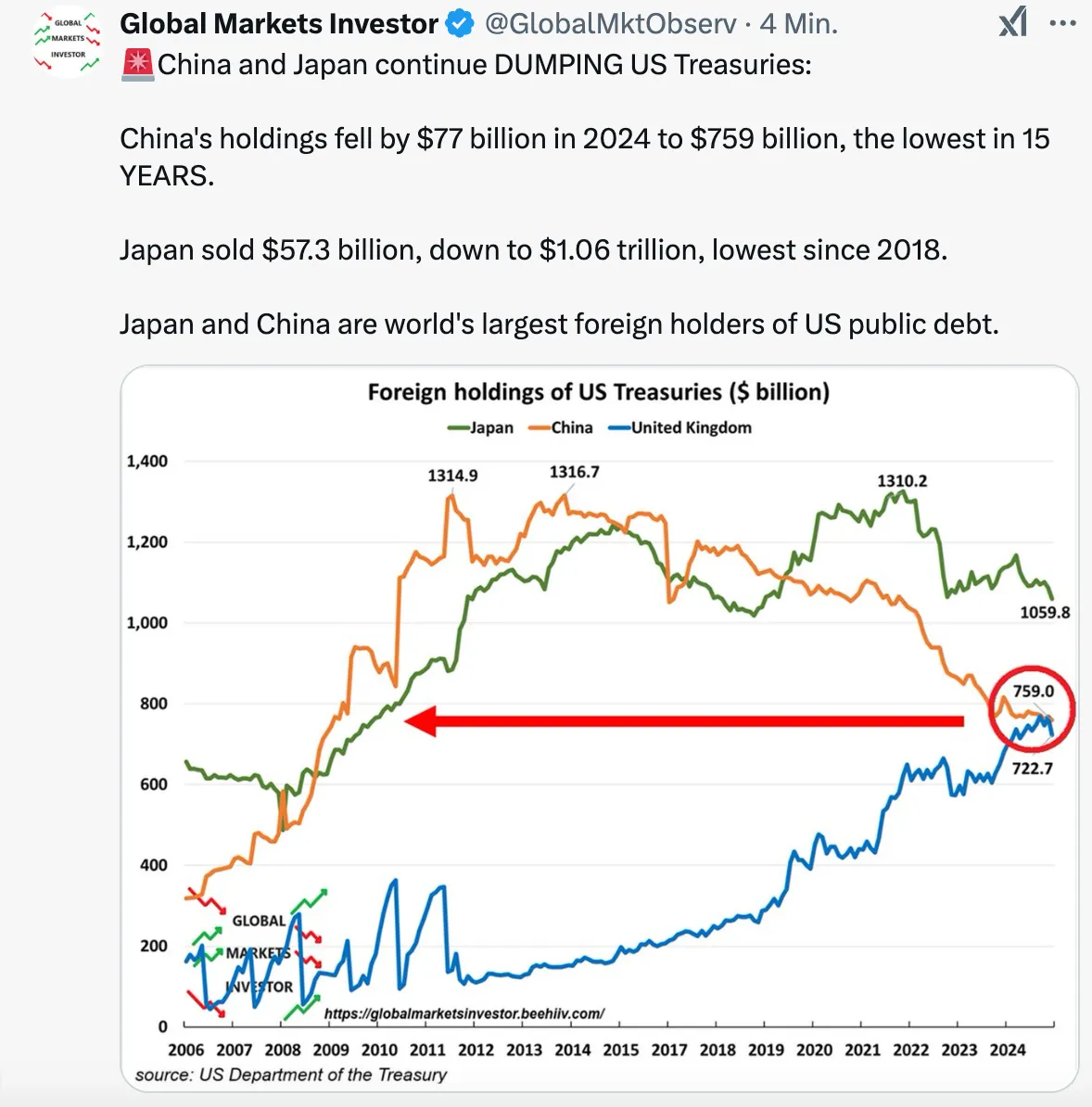
Eine Neugewichtung des Deals ist notwendig. Daher der Kassensturz. Daher die ständigen Aufforderungen Trumps an Verbündete, künftig mehr zu zahlen.
Die Lösung könnte ein „Mar-a-Lago“-Accord sein. Die USA befanden sich in den 1980er Jahren schon einmal in einer ähnlichen Situation: Japanische und deutsche Waren überschwemmten die amerikanischen Märkte. Nach einem verlorenen Krieg in Vietnam und hoher Inflation hatten sich innerhalb Gesellschaft große Spannungen aufgebaut. Ronald Reagan, übrigens ein Präsident, der ähnlich polarisierte wie Trump heute, sprach 1985 Klartext: Japan und in geringerem Maße die BRD, Frankreich und Großbritannien hatten ihre Währungen aufzuwerten. Damit wurde die Flut der Exporte in die USA gestemmt und die Finanzflüsse stabilisiert.
Seit einigen Wochen gibt es relativ klare Pläne, wie diese neue Ordnung aussehen soll. Sie gehen zurück auf den Ökonomen Steve Miran, der bereits unter der ersten Trump-Administration eine Berater-Rolle hatte. Seit Dezember 2024 ist der Vorsitzender des Council of Economic Advisers. Miran wiederum steht Zoltan Pozsar nahe, der 2022/23 zum Shooting Star der Macro-Economy-Nerds wurde. Worum geht es?
Weiter geht es auf https://blingbling.substack.com/p/der-mar-a-lago-accord
-
 @ 65038d69:1fff8852
2025-03-29 12:53:57
@ 65038d69:1fff8852
2025-03-29 12:53:57If you haven’t had the experience of waking up in the morning and fearing going to work, you’ve probably heard at least one story of someone who has. Someone who was afraid of their boss, a coworker, an impending audit, or layoffs. These stories are centered around fear, but what about fear’s older, more mature cousin, respect? How are they related, and what are their roles in the workplace?
Fear? Having a role in the workplace? I thought fear was bad and to be avoided at all costs? Didn’t we leave fear at work behind in the 1950s along with day-drinking and open misogyny? Not entirely it seems, but the fear we’re talking about today is of a different kind, a healthy kind. For example, a primary school child would have a healthy fear of bears. What about respect? While the term might feel dated in our current hyper-equality society, it too has a healthy version. As our example child matures, their fear of bears will develop into respect for them. They’ll understand their destructive power, but also that they’ll generally only engage it in defence. For another example, think back to your relationship with your childhood friend’s parents. As a child in an unknown adult’s home with different rules and expectations there was an amount of fear involved, but as an adult you most likely have respect for the amount of shenanigans they put up with at the hands of your and your friends.
Fear, even the unhealthy kind, can sometimes be leveraged for good. Fear of being yelled at might motivate you to finish the last 10% of a project or emptying your inbox before the end of the workday. It is better matured into respect whenever possible, however. The trade-off of fear of verbal assault or firing isn’t worth it. It’d be much healthier to be motivated by respect. Respect for your coworkers (who might also be made late by your procrastinations), your boss (who may need to take responsibility for the delay), and customers or clients (imagine yourself in their shoes).
We’ve established that respect is good, and that fear is a sometimes-useful antecedent of it. And we can all now hear a thousand voices screaming, “but so-and-so doesn’t respect me!” or “but so-and-so doesn’t deserve respect!”. They may not be wrong, so let’s see what we can do to help promote respect. Ignoring the edge cases where some people are arrogant to the point of not respecting anyone, the most common cause I’ve witnessed isn’t a lack of respect, but a misdirection of it. Respect has a directional flow from one person to another, and ideally there are streams flowing in both directions. You respect your boss for their authority and responsibilities, and your boss respects you for your expertise and commitment. Misdirection of respect isn’t giving it where it isn’t deserved but flowing in the wrong direction. For example, a coworker is regularly late for meetings, and the meeting chair says, “Out of respect for Bill we’re going to wait for them to start the meeting.” What about their respect for everyone else’s time? Respect is flowing in the wrong direction. The same thing can happen when making decisions. “Mary has been with us the longest, so we’re going to defer to her preferences and keep the fax machine in the document transfer workflow even though it’s expensive and takes longer.” Sometimes it can even lead to putting the unqualified in positions they’re incapable of executing out of a misdirection of respect. Permission to speak is an extremely common misdirection as well; respect for someone’s “right to be heard” shouldn’t override their respect for everyone else’s time.
The solution to this chaotic storm surge of misdirected respect is simple, but difficult. Break the fourth wall and haven open discussions. Start with groups and work your way down to one-on-one as necessary. Meeting start times is an excellent place to begin as most will agree that starting on time (especially with the goal of finishing on time!) is a practical shared good. Permission to speak in meetings (especially public ones) will be a difficult tackle but is also highly relevant. If respect directionality feels too heavy to bring up at work at all, try practising at home or with friends first. Failing that, a therapist or chat AI might be options.
Want someone with a neutral or outside voice to talk about fear and respect in your workplace? You can find us at scalebright.ca.
-
 @ 65038d69:1fff8852
2025-03-29 12:46:30
@ 65038d69:1fff8852
2025-03-29 12:46:30In part 1 of this series (Part 1 - What is Money?) we overviewed the history of money and as a global concept. Now that we have a base understanding of what money is we can get into detail about the Canadian Dollar. Why the Canadian Dollar specifically? One of the inspirations for this series was realizing how much the pervasiveness of American media has affected the average Canadian’s understanding of how our money works. How many of you can quote what is printed on US bills? Do you know what is printed on Canadian bills? What about what the Canadian Dollar is backed by, and who’s in charge of it? To preview, it’s not gold, and it’s not the Federal Reserve.
Lets do some history to give us some background on the Canadian Dollar (CAD) as we know it today. In 1858 the Province of Canada introduced the Canadian Dollar as a hopeful replacement for the mix of British, American, Spanish, and private bank credit notes in use. In 1867 Canada was formed as a nation, and the next year the Government of Canada issued Dominion credit notes as currency. These Dominion notes were required to be backed by a minimum of 20% gold reserves. This is called a “fractional reserve” system, or fractional reserve banking. Reserve requirements for private bank notes and Dominion notes changed over the years leading up to 1935 when the Bank of Canada (BoC) was formed and became to sole issuer of currency in Canada. 10 years later gold reserve requirements were removed and the Dollar became a fully fiat currency (remember this term from the previous article?).
The Bank of Canada is Canada’s “central bank”. If you check out the About Us page on their website (https://www.bankofcanada.ca/about/) you’ll see they have a broad range of roles and responsibilities, but the main one we’re focused on is that they manage the Canadian Dollar as a system of money, including creating and destroying Dollars as they deem necessary. (This is similar to the American Federal Reserve, but a key difference is that the BoC is a crown corporation, while the Federal Reserve is owned by private banks.) The creation and destruction of Dollars is a complex process, but it’s mostly done through borrowing. The government indirectly borrows money from the BoC (and sometimes directly from commercial banks), and everyone else borrows from banks. This money is then created by the BoC and banks, and when the principal (debt exclusive of interest) is paid back, its destroyed.
I’d be remiss if I didn’t mention and define “inflation”, “monetary expansion”, and the “Quantity Theory of Money”. The BoC defines inflation as “…a persistent rise in the average level of prices over time.” They have an excellent explainer on their website here (https://www.bankofcanada.ca/2020/08/understanding-inflation/); to summarize, the BoC and government use the Consumer Price Index (CPI) to keep track of this. “Monetary expansion” is when money is created and kept in circulation. The “Quantity Theory of Money” states that when new money is created it becomes less valuable, which means prices increase, AKA inflation. With this in mind the BoC targets a 2% inflation rate when making decisions about creating and destroying Dollars (through the systems of borrowing). Whether they’re successful or not is the subject of an article all on its own and much speculation.
I should also mention an outlier in the Canadian financial system; Credit Unions. These are provincial banks that don’t have a direct relationship with the BoC. They’re generally much smaller than the national banks and offer fewer services, but many feel they offer a more personal service. And one credit union in particular is an outlier among outliers; Bow Valley Credit Union in Alberta. They’ve embarked on mission to stockpile precious metals (mostly gold) as a form of guarantee for customer deposits. They still practice fractional reserve banking, but this is an improvement over zero reserve banking.
You might be imagining stacks of Dollar notes being passed around all these institutions, but most of the money only exists in ledgers (remember this from part 1?). For comparison, there is currently about $250B in the M0 supply (liquid deposits at the BoC and cash), and the rest totals about $3500B, or $3.5T. That’s about 7% as “real” money that could be used to buy groceries or for payroll. To move this invisible money around the government created Payments Canada, a non-profit that operates most of the inter-institution transfer systems. (They have other responsibilities as well.) Lynx and the Automated Clearing Settlement System (ACSS) are currently in use, and Real-Time Rail (RTR) is coming soon to augment them.
On the retail side, we have the Interac network and credit card networks. The Interac Corporation (a for-profit founded and primarily owned by major national banks) operates the Interac network, which is the primary debit card network in Canada, as well as Interac e-Transfer for direct electronic payments. Visa and Mastercard are the primary credit card networks, but they simply move payment information between banks and Payment Services Providers (PSPs). PSPs are responsible for the actual payment settlements. You’ve probably heard of some of the major ones; Moneris, Chase, Square, and PayPal to name a few. If that sounds complicated, that’s because it is. Let’s walk through an example credit card payment at a physical store to see how it works. The customer inserts, taps, or swipes their card at the payment terminal, typically managed by a Point of Sale (POS) provider. The terminal sends the information to the PSP, who sends the information through the credit card network to the issuing bank. If the transaction is approved, it’s logged for transfer in a batch later, and the approval makes it way back through the credit card network, PSP, terminal, and POS.
Wipe the sweat from your brow and take a sip of coffee; that was a lot! The important part to remember is that all of this complexity serves to move numbers between accounts in ledgers. The government (through the BoC) controls the money supply (the primary driver of inflation), and the banks and networks move the ledger numbers between individuals, companies, and each other. About 7% is liquid, and 0% is backed by hard assets such as gold.
In part 3 we’ll cover Bitcoin, its intention to replace fiat currencies, and its current state in Canada.
-
 @ 2fb77d26:c47a6ee1
2025-02-22 09:04:25
@ 2fb77d26:c47a6ee1
2025-02-22 09:04:25Der 1953 geborene Craig Reynolds ist Experte für künstliches Leben und Computergrafik. In dieser Funktion arbeitete er unter anderem an Filmen wie Tron (1982) und Batman (1992). Bei »Sony Computer Entertainment America« (heute SIE) entwickelte er die OpenSteer-Bibliothek, die der Abbildung von Schwarmverhalten in Spielen und Animationsanwendungen dient. An solch prestigeträchtige Aufträge kam Reynolds, weil er sich nebst Computergrafik intensiv mit Theorien zum »Steuerungsverhalten für autonome Charaktere« befasst hatte. Mit Schwarmverhalten. Einem Thema, das mit wachsender Rechenleistung immer wichtiger für die Entwicklung von Computerspielen wurde.
Die sollten dem Spieler das Gefühl geben, sich in einer realen Welt mit »autonomen Charakteren« zu bewegen. Dazu mussten diese vom Computer, beziehungsweise der Software gesteuerten Charaktere – im Fachjargon »Agenten« genannt – sich irgendwie verhalten. Und zwar ohne, dass von außen ein weiterer Steuerungseingriff erfolgt. Eigendynamisch. Dafür bedarf es Regeln, die im Programmcode eingebettet werden können. Genau die lieferte Reynolds 1986 im Rahmen der von ihm modellierten Boids-Simulation, die besagt, dass Schwarmverhalten auf drei simplen Regeln basiert:
- Bewege dich in Richtung des Mittelpunkts derer, die du in deinem Umfeld siehst.
- Entferne dich, sobald dir jemand zu nahe kommt.
- Bewege dich etwa in die gleiche Richtung wie deine Nachbarn.
Sprich: Kohäsion, Separation und Orientierung. In Reynolds’ Beschreibung des Boid-Modells liest man diesbezüglich:
»1986 habe ich ein Computermodell koordinierter Tierbewegungen (…) erstellt. Es basierte auf dreidimensionaler Computergeometrie, wie sie normalerweise in der Computeranimation oder im computergestützten Design verwendet wird. Ich habe die generischen, simulierten Schwarmtiere Boids genannt. Das grundlegende Schwarmmodell besteht aus drei einfachen Lenkverhalten, die beschreiben, wie ein einzelner Boid auf der Grundlage der Positionen und Geschwindigkeiten seiner Schwarmgenossen in der Nähe manövriert. Jeder Boid hat direkten Zugriff auf die geometrische Beschreibung der gesamten Szene, aber das Schwarmverhalten erfordert, dass er nur auf Schwarmgenossen in einer bestimmten kleinen Nachbarschaft um sich herum reagiert. (…) Schwarmgenossen außerhalb dieser lokalen Nachbarschaft werden ignoriert.
Die Nachbarschaft könnte als Modell eingeschränkter Wahrnehmung betrachtet werden (wie bei Fischen in trübem Wasser), aber es ist wahrscheinlich korrekter, sie als Definition des Bereichs zu betrachten, in dem Schwarmgenossen die Lenkung eines Boids beeinflussen. In den ersten Experimenten wurde ein etwas ausgefeilteres Verhaltensmodell verwendet. Es umfasste vorausschauende Hindernisvermeidung und Zielsuche. (…) Für Anwendungen in der Computeranimation führte ein Zielsuchverhalten mit niedriger Priorität dazu, dass die Herde einem vorgegebenen Pfad folgte.«
Wer sich bei dieser Beschreibung an die Strukturen postmoderner Gesellschaft erinnert fühlt und »Agenten« mit »Agent Smith« aus den Matrix-Filmen assoziiert, liegt nicht ganz falsch. Denn Kohäsion, Separation und Orientierung definieren nicht mehr nur das Schwarmverhalten autonomer Charaktere in Computerspielen, sondern auch die Dynamiken des gesellschaftlichen Zusammenlebens im multimedialen Panoptikum der Postmoderne.
So nimmt es kaum Wunder, dass ein vom US Air Force Laboratory (AFRL) finanziertes Forschungsprojekt an der University of Florida (Gainesville, USA) bereits im Jahr 2014 untersuchte, »wie Social Media eingesetzt werden kann, um Menschen wie Drohnen zu steuern«.
Unter diesem Titel berichtete denn auch Ars Technica am 17. Juli 2014, dass der Forschungsleiter der AFRL-Studie, Warren Dixon, seines Zeichens Chef des Lehrstuhls für nichtlineare Steuerung und Robotik an der University of Florida, vor allem daran arbeite, »wie man ein Netzwerk, wenn man es einmal identifiziert hat, in Richtung eines Ziels manipulieren kann«. Und mit »Netzwerk« meint Dixon nicht Computer, sondern soziale Strukturen.
Die Untersuchungen von Dixon, Kan, Klotz und Pasiliao – formeller Titel: »Eindämmungskontrolle für ein soziales Netzwerk mit staatlich abhängiger Konnektivität« – unterstreichen, dass die mathematischen Prinzipien, die zur Steuerung autonomer Agenten und Robotergruppen verwendet werden, auch auf soziale Netzwerke übertragbar sind, um menschliches Verhalten zu manipulieren. Im großen Stil. Ausgehend von einer optimalen Kalibrierung könnten die von den AFRL-Forschern entwickelten Modelle eingesetzt werden, um die Meinung auf Social-Media-Portalen in Richtung eines gewünschten Verhaltens zu lenken. Genau wie die Cyber-Waffen der NSA (National Security Agency, USA) oder das entsprechende Arsenal des GCHQ (Government Communication Headquarters, UK), das seine Nudge-Unit nicht nur gegen Corona-Maßnahmenkritiker, sondern mittlerweile auch gegen »Heizpumpen-Skeptiker« ins Feld führt.
Schwarmverhalten ist demnach nicht nur an Chinas Himmel oder in der Nähe des vom Iran jüngst zu Wasser gelassenen Drohnenträgers Schahid Bagheri zu beobachten – oder in der Ukraine, wo todbringende Minidrohnen heute Jagd auf gegnerische Truppen machen – sondern auch in der unmittelbaren Nachbarschaft des Lesers. Denn Drohnen sind heute nicht mehr nur auf dem Schlachtfeld gang und gäbe. Der Nutzmensch selbst ist eine Drohne. Das traurige Produkt einer jahrzehntelangen Schlacht ums Gehirn.
Die Corona-Krise war Generalprobe für die Einführung des von den Verhaltensökonomen Richard Thaler und Cass Sunstein (Nudge, Yale University Press, 2008) maßgeblich entwickelten Herrschaftsmodells der Zukunft: Hive-Mind-Technokratie. Fernsteuerung der Massen via Social-Media-Nudging. Via geteiltem Bewusstsein. Sprich: Regieren mittels Plattformökonomie, Manipulativkommunikation und Emotion. Mit »Soft Power«. Zumindest bis der kopflose Schwarm endlich mit der Cloud verbunden ist.
Wer also denkt, es mache Sinn, sich über Erhalt oder Verfall der Meinungsfreiheit auf einem Konzernmarkplatz wie Twitter Gedanken zu machen, erfüllt genau die Rolle, die ihm AFRL, Nudge-Unit, das NATO-Innovation Hub mit seiner »sechsten Dimension der Kriegsführung« und Peter Thiels PayPal-Mafia seit jeher zuschrieben: Die des geist-, willen- und haltlosen »Agenten« in einer überfrachteten Simulation. Nicht umsonst waren alle Big-Tech-Größen Teilnehmer der Social-Engineering-Seminare von John Brockmanns Edge-Foundation.
Nicht von ungefähr soll KI nun alles »effizienter« machen. Wirft man allerdings einen Blick auf die Vorstandsebene von OpenAI, dem ChatGPT-Anbieter und neben dem von der CIA startfinanzierten, Mossad-nahen IT-Konzern Oracle primärer Partner von Donald Trumps Stargate-Projekt, das KI und mRNA mit einem Budget von 500 Milliarden Dollar zusammenbringen soll, wird schnell deutlich, dass mit Effizienz nichts anderes als ein Ausbau des Überwachungsstaats gemeint ist.
Da wäre zum einen Sue Desmond-Hellmann, von 2014 bis 2020 CEO der Bill & Melinda Gates Foundation, seit 2020 Vorstandsmitglied bei Pfizer und darüber hinaus im Vorstand von Resilience, dem vom CIA-Finanztentakel In-Q-Tel grundfinanzierten Biotech-Unternehmen, das mRNA für unter anderem Moderna produziert. Oder der korrupte Larry Summers, ehemals Chefökonom der Weltbank, der mit massiven Deregulierungen des Finanzmarkts geradezu als Initiator der Finanzkrise 2008 bezeichnet werden kann und so Tiefenstaat ist wie es nur geht. Nicht zu vergessen Nicole Seligmann, genannt »Anwältin der Anwälte«, ehemalige Chefin von Sony USA, Rechtsbeistand von Oliver North während der Iran-Contra Anhörungen in den 80ern sowie Anwältin der Clintons, unter anderem während des Amtsenthebungsverfahrens gegen Bill Clinton im Jahr 1999. Von den langjährigen Facebook-Top-Managern Fidji Simo, Adam D’Angelo und Bret Taylor ganz zu schweigen.
Angesichts dieser Mannschaft dürfte niemand überrascht sein, dass OpenAI-CEO Sam Altman von seiner jüngeren Schwester des jahrelangen Missbrauchs bezichtigt wird und sich dafür demnächst vor Gericht verantworten muss – oder dass ein Whistleblower, der zu illegalen Aktivitäten bei OpenAI aussagen wollte, im Dezember 2024 überraschend tot in seiner Wohnung aufgefunden wurde, weshalb dessen Eltern Sam Altmans Unternehmen nun Mord vorwerfen und die Stadt San Francisco wegen schlampiger Ermittlungen verklagen.
Erstaunlich ist lediglich, dass diese Informationen nicht in aller Munde sind und Menschen wie Sam Altman und Oracle-Gründer Larry Ellison an Tag zwei nach Donald Trumps Amtseinführung als Partner einer US-Regierung präsentiert werden, die angeblich den Tiefenstaat ausheben will.
Aufmerksame Beobachter des militärisch-digitalen Komplexes dürften diese Umstände allerdings kaum noch schockieren. Denn gerade das US-Militär fokussiert sich seit Jahren auf die Verwendung von Open Source Intelligence – meint Handydaten, Social-Media-Inhalte, Daten-Leaks, Hacks und KI –, um aufständischen Zellen auf den Zahn zu fühlen. So gründete die DARPA im Jahr 2011 das SMISC-Programm (Social Media in Strategic Communication). Ausgestattet mit einem Budget von knapp 50 Millionen US-Dollar gingen Wissenschaftler der Frage nach, wie sich soziale Netzwerke für Propaganda und psychologische Kriegsführung nutzen lassen. Der Initiator von SMISC, Rand Waltzman, ein DARPA-Manager, beschrieb im April 2015, worin die vier Kernziele des von ihm ins Leben gerufenen Programms bestanden:
- Erkennen, klassifizieren, messen und verfolgen der Entstehung und Entwicklung sowie Verbreitung von Ideen und Konzepten (Memes) und gezielte oder irreführende Nachrichten und Fehlinformationen.
- Erkennen der Strukturen von Überzeugungskampagnen und Einflussoperationen auf Social-Media-Sites und Communities.
- Identifizieren der Teilnehmer und Absichten und messen der Auswirkungen von Überzeugungskampagnen.
- Verbreiten von Gegeninformation bei erkannten gegnerischen Einflussoperationen.
Darüber hinaus erklärte Waltzman, welchen technischen Umfang, beziehungsweise Fokus die Analyseprozesse aufwiesen:
- Sprachliche Hinweise, Muster des Informationsflusses, Analyse von Thementrends, Analyse narrativer Strukturen, Stimmungserkennung und Meinungsforschung.
- Meme-Tracking in Communities, Graphen-Analyse, probabilistisches Denken, Mustererkennung, kulturelle Narrative.
- Induzieren von Identitäten, Modellieren entstehender Communities, Vertrauensanalyse, Modellieren von Netzwerkdynamiken.
- Automatisierte Inhaltsgenerierung, Bots in sozialen Medien, Crowdsourcing.
Die DARPA untersuchte Twitter-Follower prominenter Musiker, analysierte die Verbreitung von Memes und testete operative Ansätze einer IBM-Studie, die sich mit der »Modellierung von Nutzerverhalten bei kontroversen Themen auf Social Media« befasste. Am 9. Juli 2014 veröffentlichte die DARPA eine Liste von 181 vom SMISC-Programm finanzierten Projekten, die sich allesamt mit dem Thema psychologische Kriegsführung auf Social Media befassten. Im Vordergrund stand jeweils die Graph-Theorie, also die Analyse des Verhaltens von Menschen anhand sozialer Daten. Die Formelsprache, die von den Projekten zur mathematischen Beschreibung der Interaktionen zwischen Menschen und Produkten verwendet wurde, war dieselbe, die bei der Steuerung autonomer Fahrzeug-Gruppen zur Anwendung kommt. Sie bildet das Herzstück von Googles Verständnis zu Suchkontexten und ist grundlegender Bestandteil von Kontrollsystemen zur Steuerung autonomer Roboterschwärme.
Warren Dixon und die DARPA gingen nun aber der Frage nach, ob die gleiche Mathematik auf die Steuerung autonomer Menschen und Gruppen von Menschen anwendbar ist. Um zu verstehen, was das bedeutet, folgend eine Erläuterung zum Facebook-Graph, über den Ars Technica am 14. März 2013 berichtete:
»Der Graph ist eine Datenbank, die Informationen über Benutzer, Seiten und andere Objekte im Facebook-Universum speichert. Er enthält auch die Beziehungen zwischen ihnen. Jede Entität, also jeder Knoten im Facebook-Graph – identifiziert durch eine eindeutige Nummer, die als fbid (Facebook-ID) bezeichnet wird – ist mit einer Reihe von Attributen oder Metadaten verknüpft. Die Beziehungen zwischen diesen Knoten, die als Kanten bezeichnet werden, enthalten ihre eigenen Metadaten, um die Art der Beziehung zwischen ihnen zu beschreiben. Die von Facebook verwendete Graph-Datenbank ist Googles Knowledge-Graph und Microsofts Satori-Graph-basiertem Konzept recht ähnlich. In vielerlei Hinsicht ist die Struktur des Facebook-Graphs jedoch einfacher als die Graph-Schemata von Google und Microsoft, da Facebook die Metadaten für seine Knoten und Kanten speziell auf soziale Interaktion abgestimmt hat.«
Dixons AFRL-Arbeitsgruppe nutze solche Daten, um zu modellieren, wie die Zusammenarbeit zwischen »wichtigen Influencern« in sozialen Netzwerken das Verhalten von Gruppen innerhalb dieses Netzwerks beeinflussen könnte. Stichwort: »Eindämmungskontrolle«. Dixon selbst erläuterte dieses Konzept mit den Worten:
»Es gibt eine Gruppe von Anführern, von denen jeder seine eigenen Ziele und sein eigenes Schwerpunktthema hat. Unser Ziel ist, dass diese Leute ihre Meinung ändern und die Gruppe der Anhänger – also Leute, die zu ihrer sozialen Gruppe gehören, aber das übergeordnete Ziel nicht kennen – unter Druck setzen.«
Unter Zuhilfenahme der Graphen-Theorie erarbeiteten Dixon und Co. ein Kommunikationsmodell, das verständlich machte, wie viel Einfluss ein Social-Media-Influencer benötigt, um Macht auszuüben und das Verhalten seiner Follower zu ändern. Während die DARPA im Rahmen mehrerer Pressemitteilungen versicherte, weder persönlichkeitsbezogene Daten zu speichern noch Social-Media-User zu manipulieren, hatte man beim GCHQ in Großbritannien weniger Hemmungen. Wie die von NSA-Whistleblower Edward Snowden geleakten Dokumente belegen, hatte der britische Nachrichtendienst ein ganzes Arsenal digitaler Waffen zur Hand, um Individuen und ihre Geräte zu infiltrieren, Fake-Identitäten aufzubauen, Falschinformationen zu verbreiten und die öffentliche Meinung zu »formen«. Diese Werkzeuge teilte das GCHQ mit der NSA, die sie ihrerseits anwandte, um in Afghanistan und anderen Krisengebieten zu steuern, welche Informationen gegnerische Gruppen online und über das Smartphone abrufen konnten.
Neben Militär, Geheimdiensten und Tech-Konzernen sind natürlich auch Organisationen wie USAID und das NED (National Endowment for Democracy) auf dem Feld der Cyber-Kriegsführung aktiv. Im April 2014 wurde zum Beispiel bekannt, das USAID auf Kuba ein Twitter-ähnliches Netzwerk aufbauen wollte, um das kommunistische Regime zu unterminieren. Dass es sich dabei nicht um Einzelfälle handelt, veranschaulicht ein Report der Universität Oxford, der am 13. Januar 2021 veröffentlicht wurde und Social-Media-Manipulation in gut 80 Ländern analysierte:
»In jedem der 81 untersuchten Länder wurden organisierte Kampagnen zur Manipulation sozialer Medien festgestellt, ein Anstieg von 15 Prozent innerhalb eines Jahres, verglichen mit 70 Ländern im Jahr 2019. Dem Bericht zufolge produzieren Regierungen, PR-Agenturen und politische Parteien im industriellen Maßstab Falschinformationen. Er zeigt, dass Desinformation zu einer gängigen Strategie geworden ist, wobei in mehr als 93 Prozent der Länder Desinformation als Teil der politischen Kommunikation eingesetzt wird.«
»Die Leute denken nicht gern daran, dass sie manipuliert werden«, so Warren Dixon. »Aber wir werden jeden Tag manipuliert. Durch Werbung, durch Regierungschefs, religiöse Führer und sogar dazu, zur Arbeit zu gehen. Wir arbeiten größtenteils deswegen, weil wir dafür bezahlt werden. Aber wie viel muss ich jemandem für seine Arbeit zahlen?«
Gute Frage. Wie viel muss man jemandem bezahlen, damit er lügt, damit er seinen besten Freund verrät oder einen Menschen ermordet? Oder ein paar tausend Menschen? Mit solchen Fragen beschäftigen sich die Verhaltensforscher, die Big Tech und Geheimdienste beraten, die Algorithmen und soziale Feedback-Loops kreieren. Denn Suchmaschinen und Social Media sind kein Serviceangebot, sondern eine Waffengattung kognitiver Kriegsführung. Die Projektile des Informationskriegs. Und die meisten Menschen sind dem Kugelhagel schutzlos ausgeliefert.
Die zeitgeistig flexible Herrschaftskaste weiß diesen Umstand zum eigenen Vorteil zu nutzen. Gerade deshalb ist »Agent Smith« eine perfekte wie düstere Parabel für den modernen Nutzmenschen, der sein Leben online führt und im digitalen Raum binnen Sekunden Entscheidungen trifft, für die ihm jede inhaltliche Grundlage fehlt. Entscheidungen, die sein Selbstbild nachhaltig verändern. Wer das System eben noch kritisierte, wedelt im nächsten Moment mit Pompons, um es zu bejubeln. Denn die Transformation des Ich ist dieser Tage immer nur einen Klick entfernt.
»Smith begann als Agent, ein KI-Programm in der Matrix, das darauf programmiert war, die Ordnung im System aufrechtzuerhalten, indem es menschliche Simulakren eliminierte, die die simulierte Realität instabil machen würden, sowie alle Schurkenprogramme, die für das Maschinenkollektiv keinen Zweck mehr erfüllen. (…) Smiths wahre Macht beruht auf seiner Fähigkeit, Erinnerungen und Kräfte seiner Opfer – Menschen und Programme gleichermaßen – zu absorbieren. (…) Smith erlangt die Macht, seine physische Form auf jedes Wesen in der Matrix zu kopieren, indem er seine Hand in ihren Körper eintauchen lässt und eine schwarze Flüssigkeit verteilt, die sie in eine Kopie seiner selbst verwandelt, was zu einer ständig wachsenden Armee von Smiths führt, die durch ein einziges Bewusstsein verbunden sind.«
Wer sich also fragt, warum seine vormals maßnahmen- und obrigkeitskritischen Weggefährten nun dem tiefenstaatlich orchestrierten MAGA-Kult huldigen, findet die Antwort in DARPA-Studien zum Thema »Steuerung des Gruppenverhaltens mittels Social Media«.
Neu ist das alles nicht. Die US Air Force begann bereits 1998 mit der Erforschung autonom agierender Drohnensysteme – »Low Cost Autonomous Attack System« (LOCAAS) genannt. Die LOCAAS-Systeme nutzten einen Algorithmus, der auf Craig Reynolds’ Boids-Modell basiert, um in Formation eines Schwarms zu fliegen. Warf ein Tarnkappenbomber seine bis zu 192 Drohnen ab, begannen sie sich untereinander zu verständigen und attackierten feindliche Truppen im Verbund.
Das war vor 27 Jahren. Heute gehören Drohnen zum zivilen Alltag. So betreibt die Swisscom in der Schweiz in Kooperation mit Nokia ein Drones-as-a-Service (DaaS) Netzwerk für »effiziente Inspektionen und die Sicherung großer Areale sowie zentraler Infrastruktur«. Das klingt zunächst einmal nach privatwirtschaftlicher Dienstleistung auf Abruf. Aber: »Blaulichtorganisationen sollen diese Drohnen auf Abruf nutzen können, um dank detailliertem Bildmaterial (…) Informationen von Unfallstellen, Katastrophengebieten oder Tatorten einzuholen«, so der Tagesanzeiger am 18. August 2024. Was für Bildmaterial in welcher Auflösung wann, wo, warum aufgezeichnet und gespeichert wird, ist indes unklar. Hiesige Datenschützer sind alarmiert.
Aus gutem Grund. Denn auch in der Kriegsführung gehören Drohnen mittlerweile zum Tagesgeschäft. Per Joystick gesteuerte Langstreckendrohnen »demokratisieren« den Luftraum im Nahen Osten. Bevorzugt mit lasergesteuerten GBU-12 Paveway II Bomben. Mini-Drohnen überwachen unauffällig das Einsatzgebiet und töten gezielt per Kopfschuss. Kamikaze-Drohnenschwärme stürzen sich in Gruppen auf die mit ihnen explodierenden Ziele. Und die größeren Modelle beglücken den Feind mit bis zu sechs Granaten.
Projekte des US-Militärs und chinesische Guinness-Weltrekorde im Drohnen-Formationsflug zeigen, dass es wohl nicht mehr allzu lange dauern wird, bis autonome Schwärme, die von ebenso autonomen Trägerfahrzeugen verteilt und aufgeladen werden, Krisengebiete, Grenzen und Innenstädte überwachen – und schützen. Fragt sich nur, vor wem.
Die inflationäre Verwendung von und progressiv-positive Kommunikation zu Drohnentechnologie sowie KI sollte also durchaus zu denken geben. Denn was dem Hobbyfilmer günstige Luftaufnahmen liefert und Zuschauern in Form eines illuminierten Drachens aus 1.500 Drohnen über Shenzen Bewunderung abnötigt, dürfte die nächste Ausbaustufe militarisierter Überwachungsinfrastruktur charakterisieren.
Der gemeine »Agent«, die »iDrone«, der Boid – also der von medialer Dynamik und Polarisierungsdialektik überforderte Homo demens – sieht diesen Entwicklungen natürlich weithin gelassen entgegen. Denn er »bewegt sich in Richtung des Mittelpunkts derer, die er in seinem Umfeld sieht, entfernt sich, sobald ihm jemand zu nahe kommt und läuft immer in etwa die gleiche Richtung wie seine Nachbarn«.
-
 @ 2516d145:070c8fa1
2025-02-20 08:52:54
@ 2516d145:070c8fa1
2025-02-20 08:52:54Liebe Leserin, lieber Leser,
Zahlen haben seit jeher eine tiefere Bedeutung. Sie begleiten uns, formen unsere Welt und erzählen Geschichten, wenn wir bereit sind, sie zu hören. In dieser Ausgabe – der 47. ihrer Art – widmen wir uns einer Zahl, die weit mehr ist als eine bloße Ziffer: der 47.
In der Numerologie gilt 47 als eine Zahl der tiefen Einsicht, der spirituellen Suche und der praktischen Weisheit. Sie verbindet die analytische Energie der 4 mit der intuitiven Kraft der 7 und erschafft so eine Synergie zwischen Struktur und Erkenntnis. Wer sich mit der 47 verbunden fühlt, strebt nach Wissen, Klarheit und Fortschritt, sei es im persönlichen oder gesellschaftlichen Kontext.
Diese Zahl taucht in diesem Jahr in bedeutenden Zusammenhängen auf. Donald Trump wurde 2024 erneut zum Präsidenten der Vereinigten Staaten gewählt und ist nun der amtierende 47. Präsident. Ein Mann, der wie kein anderer in der jüngeren Geschichte polarisiert, spaltet und gleichzeitig eine treue Anhängerschaft inspiriert. Eine solche Präsidentschaft ist zweifellos ein Wendepunkt – politisch, gesellschaftlich und historisch.
Und schließlich trägt die 47 für mich persönlich eine besondere Relevanz: Sie entspricht meinem Alter. Mit 47 Jahren stehe ich an einem Punkt des Lebens, an dem Vergangenheit und Zukunft in einem feinen Gleichgewicht existieren. Die Erfahrungen der vergangenen Jahrzehnte formen den Blick auf das Kommende, und doch bleibt Raum für Wachstum, Veränderung und neue Einsichten.
Diese Ausgabe ist somit nicht nur eine Fortsetzung unserer Reise, sondern auch eine Einladung: Lassen Sie uns gemeinsam erkunden, welche Muster, welche Bedeutungen und welche Zukunft sich aus dieser faszinierenden Zahl entfalten. Vielleicht entdecken wir dabei mehr als nur Zusammenhänge – vielleicht finden wir einen neuen Blick auf die Welt.
Ein besonderer Blickfang dieser Ausgabe ist das Coverbild: Ein kleines Mädchen, das einen schwer bewaffneten Soldaten durchsucht. Dieses Bild stellt die Welt auf den Kopf, kehrt Machtverhältnisse um und zwingt uns, über Krieg, Kontrolle und Vertrauen nachzudenken. Es zeigt uns, dass Unschuld und Frieden oft die größten Prüfsteine für Systeme der Gewalt sind. Es ist eine stille, aber eindringliche Mahnung, dass unsere Zukunft in den Händen der kommenden Generationen liegt – und wir ihnen eine Welt hinterlassen sollten, die mehr auf Vertrauen als auf Waffen gebaut ist.
Lassen Sie uns gemeinsam für eine friedlichere Zukunft einstehen. Möge diese Ausgabe ein Impuls sein, neue Wege des Miteinanders zu entdecken und unseren Blick für das Wesentliche zu schärfen. Frieden beginnt in unseren Gedanken – lassen wir ihn in unseren Taten Wirklichkeit werden.
Paul Andersson, Herausgeber
\ P.S. In den nächsten Wochen und Monaten werde ich meinen Blog auf die Plattform Pareto umziehen. Die Vorzüge von Pareto, das auf Nostr aufsetzt, werden in entsprechenden Artikeln dieser Ausgabe thematisiert. Außerdem erhalten Sie die Möglichkeit den Nachhall auch mit Bitcoins bzw. Satoshis zu unterstützen.
-
 @ 65038d69:1fff8852
2025-03-29 12:31:02
@ 65038d69:1fff8852
2025-03-29 12:31:02Minimum wage has been a hot topic as far back as I can remember. If you’re an employer it can feel like government needlessly meddling in the free market, while for employees it feels like its never high enough to make a difference. This is especially true where oversaturated labour markets are combined with high costs of living (HCOL) (which is pretty much everywhere at this point). Workers may need 2 or even 3 minimum wage jobs just to cover food, shelter, and transport in these areas, and would probably love to see minimum wage lifted. Employers in less-dense areas are faced with the opposite problem; even if they advertise pay “above minimum wage”, acquiring and keeping entry-level staff in HCOL areas is a constant battle. In this case, my recommendation is to localize your minimum wage.
In Canada most enforceable minimum wages are set by the provinces. Federal minimums apply to federal government employees (and some federally regulated industries). The problem with this is the sometimes broad disparities in cost of living (COL) between municipalities, especially between urban and rural. I’ve seen rent differences from 50% to 100% for comparable apartments. Applying the same minimum wage isn’t going to have the effect it’s meant to. If your staff can’t afford rent, they’re going to constantly be searching for something better, leading to high turnover. They’ll be forced into mercenary behaviours (see my previous post on “True Believers & Mercenaries”). Official minimum wages also lag behind inflation, but that’s a whole separate discussion (see my “What is Money?” series, starting with “Part 1 - What is Money?). On the flip-side, having a localized minimum wage allows your employees to stay settled where they are and gives them the freedom to be True Believers. You can work it directly into your job postings too; advertising wages that are based on local COL will have your inbox flooded with applications, allowing you to choose from the best instead of having to settle for the desperate. Let’s get into how to go about localizing your minimum wage.
First, look at a map and ponder how far most would be willing to commute to your workplace. Draw a rough circle with that as the radius. Everywhere inside this circle is fair game for everything to follow. Next, find some low-rent but livable apartments inside the circle and look up their rates. This will be your rent figure.
Transport is next. We’re going to use fuel cost as a “close enough” placeholder as actual costs will vary greatly between individuals. We’re also going to pick a “close enough” fuel efficiency for the same reason. I’ve chosen 8.5L/100KM, but you can adjust this. For example, full-size pickups may be more popular among your staff so that number may need to go up. Look up the average fuel prices for the last few months at retail stations within the circle, and the average working days per month for your staff. Now plug all of these numbers into the following formula and calculate. This will give you the monthly fuel cost: (fuel price x 8.5 x (circle radius KM x 2) / 100) x working days
Lastly, groceries. Like transport, we’re aiming for a “close enough” placeholder. You can substitute any items and volumes you like, but these are my recommendation to get an average monthly cost for an average minimum wage worker plus 1 dependant. Go to a generic grocery store within the circle and get the regular (non-sale) prices of the following: 3 x 3lb/1.36kg apples (averaged or middle price), 5 x single Long English cucumber, 1 x 10lb bag of potatoes, 2 x 4L 2% milk, 4 x 1 dozen large eggs, 2 x 600g block of cheese (average or middle price), 6 x loaf of brown or whole grain bakery bread (average or middle price), 5 x 1lb/454g lean ground beef, 1 x 4kg box frozen chicken breasts, and 1 x 3.5lb/1.6kg bag of jasmine rice.
Now that you have totals for the expenses, put those numbers into the following formula. This will give you total monthly living expenses: ((rent + groceries) / 0.45) + fuel Put that total into the following formula for the monthly paycheque total, pre-deductions. Insert current federal and provincial income tax rates for your jurisdiction: expenses / (1 - (provincial tax rate as decimal + federal tax rate as decimal + 0.05) With this final total you can divide by monthly working hours for an hourly wage, or multiply by 12 for an annual salary. I’ll provide an example of all of this at the bottom of the article.
After crunching these numbers you may have concluded that paying a localized minimum wage would eat into your profits. This may be the case initially, but lowering turnover rates and increasing the quality of your hires will save you money long-term. However, if it raises costs so high that the business would become unprofitable, you may need to consider that the business isn’t viable. Being dependant on employees willing to work for below the cost of living in your area will eventually end the business regardless, and I would argue is immoral.
Want help localizing your minimum wage? You can find us at scalebright.ca.
Sample localized minimum wage calculation: Rent: $1,200 Fuel cost: ((1.40 x 8.5 x (9.4 x 2) / 100) x 20 = $44.75 Groceries: $229.46 Apples: 23.97 Cucumbers: 14.95 Potatoes: 8.99 Milk: 11.90 Eggs: 17.40 Cheese: 20.58 Bread: 23.94 Ground beef: 42.45 Chicken breasts: 49.99 Rice: 15.29 Total expenses: ((1200 + 229.46) / 0.45) + 44.75 = $3,221.33 Total monthly paycheque: 3221.33 / (1 - (0.10 + 0.15 + 0.05) = $4,601.90 Hourly: 4601.90 / 160 = $28.76 Annual salary: 4601.90 x 12 = $55,222.80 -
 @ 8671a6e5:f88194d1
2025-03-29 17:58:33
@ 8671a6e5:f88194d1
2025-03-29 17:58:33A flash of inspiration

Sometimes the mind takes you to strange places. The other day, I stumbled across Madonna’s “Vogue” video, you know “strike a pose” and all that jazz, and it got me thinking. Not about her music (which, let’s be honest, hasn’t aged as gracefully as her PR team might hope), but about Michael Saylor and Bitcoin.
Bear with me here, there’s a connection there. Madonna built an empire and her iconic name on catchy tunes and reinvention, even if her catalog feels a bit thin these days. Saylor? He’s doing something similar—taking an old act, dusting it off, and teaching it a new trick. Only instead of a microphone, he’s wielding Bitcoin, and Wall Street’s playing the role of the music industry, propping up the star despite a shaky back catalog (his initial business software).
Old school meets new moves
Think of Saylor as that veteran artist who’s been around for a few decades and think of bitcoin as a new style of music, a genre or a gimmick that’s popular with the kids. Old music stars sooner or later pick up on that, and even bring people in to do a cross-over song, a mix or god forbid, a duet.
MicroStrategy, his software company, was never a top hit scoring machine. More of a album full of B-sides that faded into obscurity (for those who don’t know, look up what a B-side song was). But then he stumbled onto Bitcoin, the shiny new genre that’s got the attention and attracted people because of the underlying asset (our tunes are here to stay).
It’s not just a pivot; it’s a reinvention. Like an aging pop star learning to rap, Saylor’s taken his old-school business and remixed it into something attracting a decent audience at conferences for example. Like Madonna or the former Prince fulling arenas. He’s voguing alright; with bold moves, big loans, the support of his own music industry and a spotlight for his (sometimes Madonna lyrics like) ramblings.
The Saylor trick: a ray of light on bitcoin
Here’s the play: Saylor’s turned MicroStrategy into a Bitcoin hoarding machine. Forget software licenses; his game is borrowing billions—through corporate bonds and stock sales, only to buy and hold Bitcoin. Bitcoin will outshine gold, bonds, even the S&P 500, Saylor says. It’s a gamble, an honorable one if you’re a bitcoiner, but it’s dressed up as a vision, and it’s got a self-fulfilling prophecy in it. Not only that, such a prophecy can only fully come to fruition if he’s not the only buyer of last resort of any significance. A music industry isn’t a real industry if there was only Madonna dancing on stage as the only mainstream artist.
We had Prince, Michael Jackson, Taylor Swift, Bruno Mars or Dua Lipa and hundreds of other artists over time, vying for your money, attention span, and streaming minutes. The more Strategy buys, the more the Bitcoin crowd cheers, the higher the price climbs, and the more attention he gets. Speaking gigs, headlines, cult status—it’s a win-win, at least on paper. Strike the pose, indeed.
The McDonald’s trick: value under the surface
It’s not the first time Michael Saylro remixes a tape from another artist so to speak. Let’s pivot to McDonald’s for a second, because there’s a parallel here. You think Big Macs when you think McDonald’s, but their real value hustle is actually real estate.
They own prime land, lease it to franchisees, and rake in rent—billions of it. The burgers? Just a tasty front for a property empire. Saylor’s pulling a similar move, but instead of buildings, his asset is Bitcoin. MicroStrategy’s software gig is the fries on the side — nice to have, but not the main course. He’s borrowing against the future value of BTC, betting it’ll keep climbing, just like McDonald’s banks on steady foot traffic and picking strategic (pun intended) locations. The difference? McDonald’s has a fallback if real estate tanks. Saylor’s all-in on bitcoin. (So far so good, if there’s one thing to go all-in on, it’s bitcoin anyway). That on itself is not an issue. But it’s important to know that the “location” is the asset for some while bitcoin is the “asset” for Strategy. Mc Donald’s assets are easy to spot: there are restaurants all over the place. Madonna’s concerts are also easy to spot: they sell out arenas left and right. Strategy’s bitcoin asset is less easy to spot, as we can’t see them, neither can we verify them. More on that later.
The hybrid star: Madonna meets McDonald’s
So, picture this: Saylor’s a cross between Madonna and a fast-food landlord. He’s the aging music icon who’s learned a flashy new dance, but underneath the glitter, he’s running a McDonald’s-style value play. It’s brilliant, in a way. Bitcoin’s scarcity fuels the hype, and his borrowing keeps the show on the road. Madonna’s legacy still sells records her name holds value, and McDonald’s can lean on its food business and brand, if the property game stumbles they can easily pivot back to basics and earn like they’ve always done on selling food and franchise income/licensing. Saylor? His software arm’s is rather dismal. If Bitcoin falters, there’s no encore that can him.a flash of inspiration
Sometimes the mind takes you to strange places. The other day, I stumbled across Madonna’s “Vogue” video, you know “strike a pose” and all that jazz, and it got me thinking. Not about her music (which, let’s be honest, hasn’t aged as gracefully as her PR team might hope), but about Michael Saylor and Bitcoin.\ \ Bear with me here, there’s a connection there. Madonna built an empire and her iconic name on catchy tunes and reinvention, even if her catalog feels a bit thin these days.\ Saylor? He’s doing something similar—taking an old act, dusting it off, and teaching it a new trick. Only instead of a microphone, he’s wielding Bitcoin, and Wall Street’s playing the role of the music industry, propping up the star despite a shaky back catalog (his initial business software).
Old school meets new moves
Think of Saylor as that veteran artist who’s been around for a few decades and think of bitcoin as a new style of music, a genre or a gimmick that’s popular with the kids. Old music stars sooner or later pick up on that, and even bring people in to do a cross-over song, a mix or god forbid, a duet.
MicroStrategy, his software company, was never a top hit scoring machine. More of a album full of B-sides that faded into obscurity (for those who don’t know, look up what a B-side song was).\ But then he stumbled onto Bitcoin, the shiny new genre that’s got the attention and attracted people because of the underlying asset (our tunes are here to stay).\ \ It’s not just a pivot; it’s a reinvention. Like an aging pop star learning to rap, Saylor’s taken his old-school business and remixed it into something attracting a decent audience at conferences for example. Like Madonna or the former Prince fulling arenas.\ He’s voguing alright; with bold moves, big loans, the support of his own music industry and a spotlight for his (sometimes Madonna lyrics like) ramblings.
*The Saylor trick: a ray of light on bitcoin* \ Here’s the play: Saylor’s turned MicroStrategy into a Bitcoin hoarding machine. Forget software licenses; his game is borrowing billions—through corporate bonds and stock sales, only to buy and hold Bitcoin. Bitcoin will outshine gold, bonds, even the S&P 500, Saylor says.\ It’s a gamble, an honorable one if you’re a bitcoiner, but it’s dressed up as a vision, and it’s got a self-fulfilling prophecy in it. Not only that, such a prophecy can only fully come to fruition if he’s not the only buyer of last resort of any significance. A music industry isn’t a real industry if there was only Madonna dancing on stage as the only mainstream artist.\ \ We had Prince, Michael Jackson, Taylor Swift, Bruno Mars or Dua Lipa and hundreds of other artists over time, vying for your money, attention span, and streaming minutes.\ The more Strategy buys, the more the Bitcoin crowd cheers, the higher the price climbs, and the more attention he gets. Speaking gigs, headlines, cult status—it’s a win-win, at least on paper. Strike the pose, indeed.
*The McDonald’s trick: value under the surface* \ It’s not the first time Michael Saylro remixes a tape from another artist so to speak.\ Let’s pivot to McDonald’s for a second, because there’s a parallel here. You think Big Macs when you think McDonald’s, but their real value hustle is actually real estate.
They own prime land, lease it to franchisees, and rake in rent—billions of it. The burgers? Just a tasty front for a property empire. Saylor’s pulling a similar move, but instead of buildings, his asset is Bitcoin.\ MicroStrategy’s software gig is the fries on the side — nice to have, but not the main course. He’s borrowing against the future value of BTC, betting it’ll keep climbing, just like McDonald’s banks on steady foot traffic and picking strategic (pun intended) locations.\ The difference? McDonald’s has a fallback if real estate tanks. Saylor’s all-in on bitcoin. (So far so good, if there’s one thing to go all-in on, it’s bitcoin anyway). That on itself is not an issue. But it’s important to know that the “location” is the asset for some while bitcoin is the “asset” for Strategy.\ Mc Donald’s assets are easy to spot: there are restaurants all over the place. Madonna’s concerts are also easy to spot: they sell out arenas left and right.\ Strategy’s bitcoin asset is less easy to spot, as we can’t see them, neither can we verify them. More on that later.
The hybrid star: Madonna meets McDonald’s
So, picture this: Saylor’s a cross between Madonna and a fast-food landlord. He’s the aging music icon who’s learned a flashy new dance, but underneath the glitter, he’s running a McDonald’s-style value play.\ It’s brilliant, in a way. Bitcoin’s scarcity fuels the hype, and his borrowing keeps the show on the road.\ Madonna’s legacy still sells records her name holds value, and McDonald’s can lean on its food business and brand, if the property game stumbles they can easily pivot back to basics and earn like they’ve always done on selling food and franchise income/licensing.\ Saylor? His software arm’s is rather dismal. If Bitcoin falters, there’s no encore that can him.
The music’s made in-house
Michael Saylor’s strategy with Strategy, is a bold, all-in bet on Bitcoin as the ultimate store of value. Essentially combining what Mc Donald’s does with the strong believe in bitcoin’s future (and fueling that believe with the fitting rhetoric).
It works like this: Since August 2020, Saylor’s company has been buying up more and more Bitcoin, making it their main asset instead of traditional cash or investments, and by March 2025, they own 506,137 BTC—worth about $42.8 billion (at $84,000 per Bitcoin). This, after spending $33.7 billion to buy it over time (DCA), including a massive 218887 BTC purchase late 2024 for $20.5 billion, giving them over 2.41% of all Bitcoin ever to exist (way more than companies like Marathon, Coinbase, Tesla or Riot).
To pull this off, they’ve borrowed heavily: owing $7.2 billion, mostly to Wall Street investors through special IOUs1 called convertible notes, which don’t need to be paid back until 2027, through 2029. These can either be settled with cash or swapped for Strategy stock. (there lies one of the main issues in my opinion, as the main asset’s price in USD is directly impacting the stock price of MSTR). A small example of this repeated correlation happened on March 28, 2025 when Strategy’s stock (MSTR) dropped 10.8% from $324.59 to $289.41, which was mirroring Bitcoin’s move down from $85,000 to $82,000 earlier.
This debt they have can be called “risky” by any stretch, with a high leverage rate of 39-40%, meaning they’ve borrowed a big chunk compared to what they own outright, but here’s the genius of it: they don’t have to sell their Bitcoin if its price drops, and they can refinance (borrow more later) to keep the dance going. As long as they find investors willing to bet on the later bitcoin price surge, but more importantly, as long as the song is liked by the new audience. If Michael Saylor is our “Madonna”, then there’s still not Taylor Swift or Rihanna in sight.
The creditors (big players, not banks) win if Bitcoin soars, as Strategy’s huge stash (potentially 2.9%+ of the market) nets them massive profits, or even if it crashes, they’re still in the game with other ways to make profit (not on bitcoin), since they can afford the risk. If someone is willing to bet 4 to 8 billion dollars, they’re probably not spooked by losing it all. More so, these Wall Streat people in the correct entourage, can probably afford such a gamble, and can stomach to lose it all if something goes horribly wrong as well, instead of risking being left out of a growing market. But since they’re probably the same people steering and “owning” the USD market anyway, they’re just conquering positions in a new market. The fact that they’re not real bitcoin-ethos people, but just “suits” in finance, can make the suspicious bitcoiners watching all of this unfold, even more uneasy.
So, Strategy sits on $44 billion in Bitcoin with just $7.2 billion in debt, voguing confidently. And Saylor’s betting the song never gets old, he’ll do the B-sides and re-mastering his old albums if necessary, but if Bitcoin’s value ever fades (for whatever reason), the real question is how long they can keep striking poses before the music stops. Remember: all money (fiat, gold, silver, bitcoin, nicely made papers) is a matter of trust.
As I have trust in bitcoin itself, but not so much in Strategy, I’ve take some precautions. I've started my own sort of "Strategy crash fund", with fiat money that only will come into action when strategy is done. The crash that we'll see after that goes down, will be such a tremendous opportunity, that I'll pour in some more fiat, gladly, and that will be the exact moment I will actually “sell all my chairs” (from Saylor’s well-known quote).
Purchases
Strategy’s Bitcoin purchases, don’t seem to jolt the market much either, no matter the size of the order. They always have the same sound: “it’s OTC, it doesn’t impact the market that much”.
Still, it’s strange to see: no one has ever come forward to tell anyone “I’ve sold 15000 bitcoin from my old stack to Saylor”, neither do we see any clear evidence and on-chain moves.
Take their first buy in August 2020 for example. Totaling 21454 BTC for $250 million at $11,652 per BTC; Bitcoin sat at $11,500 to $11,700 so barely moved, inching to $12,000 weeks later due to broader trends.
Same story in December 2020 with 29646 BTC for $650 million, there, the price hopped from $19,000 to $23,000, but a bull market was already raging. Fast forward to February 2021 (19452 BTC, for $1.026 billion (!)), March 2024 (9245 BTC, $623 million), November 2024 (55500 BTC, $5.4 billion), and March 2025 (6911 BTC, $584.1 million)
Bitcoin wobbled 2-15%, but always in line with existing momentum, not Strategy’s announcements. Their biggest buy, for a total of $5.4 billion (!) is just 0.3% of Bitcoin’s $1.7 trillion market cap, it’s too small to register as a blip even. But compared to the liquidity on the market and the “availability” on the OTC market, it should. More so, OTC bitcoin is announced as “for sale” somehow. A person with +25000 bitcoin is not standing on the side of the street yelling “hey man, wanna buy some bitcoin?”. There are specialized firms doing that for them, and making these available. This date is also used by some insiders and people who know this very small market (there aren’t that many bitcoiners sitting on such an amount after 2024 I guess). Data from Binance OTC, Coinspaid, kraken OTC, is highly private of course, but still, anything being sold over there, to Strategy or anyone else, would take larger amounts off the open market and the OTC market, making a price impact, certainly withing 2 years, as Bitcoin mining companies sit on an average buffer of 6 months depending on market conditions.
Strategy funds all of this by selling shares (diluting the pool big-time) or issuing convertible notes, and while SEC filings make faking these buys near-impossible. And even if Saylor is the Bitcoin version of Bernie Madoff, he could get away with it, if enough people "in the know" are willing to support this way of infesting (and investing in) the bitcoin economy. This would have to be a clear orchestrated attack on bitcoin, purely on the financial level then.
I don't believe this to be the case, but mathematically we have to take it into account as a very slight possibility.
After all, a company like "WorldCom"2 managed to scam their way out of different audits for years, until the scheme got bust and a enormous amount of investors lost their money after their CEO went to jail3 for exchange fraud.
I believe this could be the case with Strategy, but I give it a 3% chance (this might be low, but it's there, we can't outright dismiss the possibility).
Water in the wine
Strategy has also massively diluted its stock to fund Bitcoin buys, jumping from 10 million shares in 2020 to about 285 million by March 2025—a 2,750% increase, this happened after raising $4.25 billion from 2020 onwards and $20 billion of their $42 billion "21/21 Plan" by early 2025.
After the 10-for-1 stock split in August 2024, the number of MSTR shares grew from 16.5 million in 2023 to 284898 by end of 2024, a 1625% rise !!!. Add to that about 275 million more shares added in total (including 120 million in 2024 alone) and 1.975 million extra in March 2025 for $592.6 million.
So more and more tap water is poured in the wine, and it means each share’s ownership slice shrinks as new shares flood in, mostly via "at-the-market" sales and convertible note conversions. This is partly offset by share splits, but still, the rise in the number of stock is significant, and a big factor in evaluating MSTR.
In December 2024, they proposed hiking authorized shares to 10.33 billion (plus 1 billion preferred), approved in January 2025, setting the stage for even more if they keep selling.
The trend is clear: relentless selling. They might say “we never sell bitcoin”, but the same doesn’t count for their shares… which derive their value from bitcoin’s fiat price. So shareholders are betting on Bitcoin’s rise to offset the watering down of the share they hold. The more you think of it, the more ludicrous it sounds. It’s a loop of trust where the stock itself can only thrive if the company itself is an active, useful middleman. And so far, it’s only doing so for other Wall street companies, the biggest holders of MSTR shares:
Vanguard Group Inc, BlackRock, Capital International Investors, Jane Street Group, Susquehanna International Group
This on itself is also “normal” of course. In the flow of things. Like every aspect by itself in the whole Strategy setup is just normal. But combining all the factors makes it look a bit more… suspicious to me.
Supporting bitcoin ?
The real head-scratcher comes next: their secrecy and lack of community involvement. Strategy claims to hold 506137 BTC, likely cold-stored with partners like BitGo or Coinbase Custody, but no public wallet addresses back these claims up. Odd for a firm swearing never to sell.
There’s also the real risk that these partners are partly selling paper bitcoin (bitcoin they don't hold the keys to, or "promised" bitcoin) to Strategy, and that they just assume everything is audited and OK.
We can't estimate that, since we don't have any public MicroStrategy addresses or other ways to look at their holdings. This is for security reasons apparently, which raises another question: If they for example would show 300k+ BTC on-chain as proof, it’d boost trust, yet they don’t, hinting at a bigger play — maybe as a Wall Street-backed buyer of last resort for a new asset class.
Also Strategy’s software business and bitcoin “apps” (like the super simple Lightning email integration, and an on-chain digital ID system) is underwhelming to say the least (I literally know people that code such stuff on a free afternoon while they’re cooking dinner).
Their very minimal software innovation for the Bitcoin space, with basic Lightning features and an on-chain ID system, failing their their valuation as a 'Bitcoin company' in my opinion. More so, their business is ignoring the other innovation that would help bitcoin thrive. This is kind of a red flag for me. Why would a company sitting on +500 k bitcoin be hesitant about supporting the bitcoin eco-system more actively? They sure have the funds to do so, right? And they also have the right insights, info and spirit. Yet, they don’t.
They don’t fund developers for open-source projects, or Bitcoin’s growth in general (not publicly at least). So Saylor shines in talks, hyping Bitcoin’s future and Strategy’s stock, but it’s all the self fulfilling prophecy.
No grants, no real support for the community they lean on. It’s like they’re dancing to Bitcoin’s mixtape, raking in the spotlight, while giving little back. All the while some extremely needed projects lack funding, and most software companies in bitcoin who wish to innovate are begging and scraping funds together, in order to stay afloat. Something’s not ok with that. I can’t understand a company with that much power and money being part of this movement and loving bitcoin, while not actively supporting the development or the maintainers of the bitcoin software. (and yes, to keep their independence it’s best to keep it that way, that’s also an argument, but even then, giving out a grant to anyone that’s crucial in this industry, might help the whole ecosystem).
The show must go on—for now
The whole Strategy setup feels more and more like a performance to me. Saylor’s the star, doing the moves and Wall Street’s the record label, and we’re the audience, captivated by the spectacle and paying to see the show on occasion.
The suits keep funding him (free money, IOUs), just like the music industry props up a fading diva with a limited repertoire or drags a new star from her home studio on YouTube into the spotlights. H Saylor’s 21/21 Plan to the amount of $42 billion to snatch up more Bitcoin can be a grand finale that’s dazzling while the lights stay on.
Prediction: the music stops eventually
Here’s my take: Bitcoin will keep rising over a long period of time, and Saylor’s gambit will look like a genius move, until it doesn’t. All it takes is one big shot in Wall Street to find another shiny toy to play with, or another play to get their money working. The billions they’ve invested, will come back eventually, and if it doesn’t, it will mean the world has changed in their advantage as well in another way. Some people cannot lose, no matter what. Saylor’s now part of that, doing their bidding and doing his part for educating the other businesses.
He’s the only big buyer of last resort in this game so far. No one else is piling in with billions like he is. When the hype cools or the debt catches up, he’s got no real business to fall back on. The software? A relic. The Bitcoin bet can save him if the time is right, we’ll see about that. Time is his enemy not ally, and it always wins in the end. The pose can only hold so long. You can’t keep scoring free fiat, without either die on low valuation and dilution, or without at least 20 other Strategy-grade businesses jumping in to take their piece of the pie. So far, surprisingly, none of these two things happen. He keeps getting free fiat from Wall Street investors, and no other Saylor stands up. This can’t last forever. One of the two will happen by end of 2025.
Curtain call
Saylor’s a fascinating watch, a mix of investor-backed bravado, brains, and borrowed billions. Is it a masterstroke or a bitcoin version of Worldcom? I’m not sure. In any case, I would only invest in MSTR myself if the company has a real added value for bitcoin development and the bitcoin ecosystem. They could be the engine, the spirit, the core of bitcoin. Yet they’re just doing the poses. Let your body move to the rhythm.
AVB
If you like : tip here / other writings
1 https://en.wikipedia.org/wiki/IOU
2 https://sc.edu/about/offices_and_divisions/audit_and_advisory_services/about/news/2021/worldcom_scandal.php
3 https://content.next.westlaw.com/Document/Ic6b4dd91644311dbbe1cf2d29fe2afe6/View/FullText.html?transitionType=Default&contextData=(sc.Default)#:\~:text=Rep.-,6,Criminal%20ChargesThe music’s made in-house
Michael Saylor’s strategy with Strategy, is a bold, all-in bet on Bitcoin as the ultimate store of value. Essentially combining what Mc Donald’s does with the strong believe in bitcoin’s future (and fueling that believe with the fitting rhetoric).\ \ It works like this: Since August 2020, Saylor’s company has been buying up more and more Bitcoin, making it their main asset instead of traditional cash or investments, and by March 2025, they own 506,137 BTC—worth about $42.8 billion (at $84,000 per Bitcoin).\ This, after spending $33.7 billion to buy it over time (DCA), including a massive 218887 BTC purchase late 2024 for $20.5 billion, giving them over 2.41% of all Bitcoin ever to exist (way more than companies like Marathon, Coinbase, Tesla or Riot).\ \ To pull this off, they’ve borrowed heavily: owing $7.2 billion, mostly to Wall Street investors through special IOUs1 called convertible notes, which don’t need to be paid back until 2027, through 2029. These can either be settled with cash or swapped for Strategy stock. (there lies one of the main issues in my opinion, as the main asset’s price in USD is directly impacting the stock price of MSTR).\ A small example of this repeated correlation happened on March 28, 2025 when Strategy’s stock (MSTR) dropped 10.8% from $324.59 to $289.41, which was mirroring Bitcoin’s move down from $85,000 to $82,000 earlier.
This debt they have can be called “risky” by any stretch, with a high leverage rate of 39-40%, meaning they’ve borrowed a big chunk compared to what they own outright, but here’s the genius of it: they don’t have to sell their Bitcoin if its price drops, and they can refinance (borrow more later) to keep the dance going. As long as they find investors willing to bet on the later bitcoin price surge, but more importantly, as long as the song is liked by the new audience. If Michael Saylor is our “Madonna”, then there’s still not Taylor Swift or Rihanna in sight.
The creditors (big players, not banks) win if Bitcoin soars, as Strategy’s huge stash (potentially 2.9%+ of the market) nets them massive profits, or even if it crashes, they’re still in the game with other ways to make profit (not on bitcoin), since they can afford the risk. If someone is willing to bet 4 to 8 billion dollars, they’re probably not spooked by losing it all. More so, these Wall Streat people in the correct entourage, can probably afford such a gamble, and can stomach to lose it all if something goes horribly wrong as well, instead of risking being left out of a growing market. But since they’re probably the same people steering and “owning” the USD market anyway, they’re just conquering positions in a new market. The fact that they’re not real bitcoin-ethos people, but just “suits” in finance, can make the suspicious bitcoiners watching all of this unfold, even more uneasy.\ \ So, Strategy sits on $44 billion in Bitcoin with just $7.2 billion in debt, voguing confidently. And Saylor’s betting the song never gets old, he’ll do the B-sides and re-mastering his old albums if necessary, but if Bitcoin’s value ever fades (for whatever reason), the real question is how long they can keep striking poses before the music stops. Remember: all money (fiat, gold, silver, bitcoin, nicely made papers) is a matter of trust.
As I have trust in bitcoin itself, but not so much in Strategy, I’ve take some precautions.\ I've started my own sort of "Strategy crash fund", with fiat money that only will come into action when strategy is done. The crash that we'll see after that goes down, will be such a tremendous opportunity, that I'll pour in some more fiat, gladly, and that will be the exact moment I will actually “sell all my chairs” (from Saylor’s well-known quote).
Purchases
Strategy’s Bitcoin purchases, don’t seem to jolt the market much either, no matter the size of the order. They always have the same sound: “it’s OTC, it doesn’t impact the market that much”.\ \ Still, it’s strange to see: no one has ever come forward to tell anyone “I’ve sold 15000 bitcoin from my old stack to Saylor”, neither do we see any clear evidence and on-chain moves.\ \ Take their first buy in August 2020 for example. Totaling 21454 BTC for $250 million at $11,652 per BTC; Bitcoin sat at $11,500 to $11,700 so barely moved, inching to $12,000 weeks later due to broader trends.
Same story in December 2020 with 29646 BTC for $650 million, there, the price hopped from $19,000 to $23,000, but a bull market was already raging.\ Fast forward to February 2021 (19452 BTC, for $1.026 billion (!)), March 2024 (9245 BTC, $623 million), November 2024 (55500 BTC, $5.4 billion), and March 2025 (6911 BTC, $584.1 million)\ \ Bitcoin wobbled 2-15%, but always in line with existing momentum, not Strategy’s announcements. Their biggest buy, for a total of $5.4 billion (!) is just 0.3% of Bitcoin’s $1.7 trillion market cap, it’s too small to register as a blip even. But compared to the liquidity on the market and the “availability” on the OTC market, it should.\ More so, OTC bitcoin is announced as “for sale” somehow. A person with +25000 bitcoin is not standing on the side of the street yelling “hey man, wanna buy some bitcoin?”. There are specialized firms doing that for them, and making these available. This date is also used by some insiders and people who know this very small market (there aren’t that many bitcoiners sitting on such an amount after 2024 I guess). Data from Binance OTC, Coinspaid, kraken OTC, is highly private of course, but still, anything being sold over there, to Strategy or anyone else, would take larger amounts off the open market and the OTC market, making a price impact, certainly withing 2 years, as Bitcoin mining companies sit on an average buffer of 6 months depending on market conditions.\ \ Strategy funds all of this by selling shares (diluting the pool big-time) or issuing convertible notes, and while SEC filings make faking these buys near-impossible. And even if Saylor is the Bitcoin version of Bernie Madoff, he could get away with it, if enough people "in the know" are willing to support this way of infesting (and investing in) the bitcoin economy. This would have to be a clear orchestrated attack on bitcoin, purely on the financial level then.
I don't believe this to be the case, but mathematically we have to take it into account as a very slight possibility.
After all, a company like "WorldCom"2 managed to scam their way out of different audits for years, until the scheme got bust and a enormous amount of investors lost their money after their CEO went to jail3 for exchange fraud.
I believe this could be the case with Strategy, but I give it a 3% chance (this might be low, but it's there, we can't outright dismiss the possibility).
Water in the wine
Strategy has also massively diluted its stock to fund Bitcoin buys, jumping from 10 million shares in 2020 to about 285 million by March 2025—a 2,750% increase, this happened after raising $4.25 billion from 2020 onwards and $20 billion of their $42 billion "21/21 Plan" by early 2025.\ \ After the 10-for-1 stock split in August 2024, the number of MSTR shares grew from 16.5 million in 2023 to 284898 by end of 2024, a 1625% rise !!!. Add to that about 275 million more shares added in total (including 120 million in 2024 alone) and 1.975 million extra in March 2025 for $592.6 million.\ \ So more and more tap water is poured in the wine, and it means each share’s ownership slice shrinks as new shares flood in, mostly via "at-the-market" sales and convertible note conversions.\ This is partly offset by share splits, but still, the rise in the number of stock is significant, and a big factor in evaluating MSTR.\ \ In December 2024, they proposed hiking authorized shares to 10.33 billion (plus 1 billion preferred), approved in January 2025, setting the stage for even more if they keep selling.\ \ The trend is clear: relentless selling.\ They might say “we never sell bitcoin”, but the same doesn’t count for their shares… which derive their value from bitcoin’s fiat price.\ So shareholders are betting on Bitcoin’s rise to offset the watering down of the share they hold. The more you think of it, the more ludicrous it sounds. It’s a loop of trust where the stock itself can only thrive if the company itself is an active, useful middleman.\ And so far, it’s only doing so for other Wall street companies, the biggest holders of MSTR shares:
Vanguard Group Inc, BlackRock, Capital International Investors, Jane Street Group, Susquehanna International Group\ \ This on itself is also “normal” of course. In the flow of things.\ Like every aspect by itself in the whole Strategy setup is just normal. But combining all the factors makes it look a bit more… suspicious to me.
Supporting bitcoin ?
The real head-scratcher comes next: their secrecy and lack of community involvement.\ Strategy claims to hold 506137 BTC, likely cold-stored with partners like BitGo or Coinbase Custody, but no public wallet addresses back these claims up. Odd for a firm swearing never to sell.
There’s also the real risk that these partners are partly selling paper bitcoin (bitcoin they don't hold the keys to, or "promised" bitcoin) to Strategy, and that they just assume everything is audited and OK.
We can't estimate that, since we don't have any public MicroStrategy addresses or other ways to look at their holdings. This is for security reasons apparently, which raises another question:\ If they for example would show 300k+ BTC on-chain as proof, it’d boost trust, yet they don’t, hinting at a bigger play — maybe as a Wall Street-backed buyer of last resort for a new asset class.
Also Strategy’s software business and bitcoin “apps” (like the super simple Lightning email integration, and an on-chain digital ID system) is underwhelming to say the least (I literally know people that code such stuff on a free afternoon while they’re cooking dinner).
Their very minimal software innovation for the Bitcoin space, with basic Lightning features and an on-chain ID system, failing their their valuation as a 'Bitcoin company' in my opinion. More so, their business is ignoring the other innovation that would help bitcoin thrive. This is kind of a red flag for me.\ Why would a company sitting on +500 k bitcoin be hesitant about supporting the bitcoin eco-system more actively? They sure have the funds to do so, right? And they also have the right insights, info and spirit.\ Yet, they don’t.\ \ They don’t fund developers for open-source projects, or Bitcoin’s growth in general (not publicly at least). So Saylor shines in talks, hyping Bitcoin’s future and Strategy’s stock, but it’s all the self fulfilling prophecy.\ \ No grants, no real support for the community they lean on.\ It’s like they’re dancing to Bitcoin’s mixtape, raking in the spotlight, while giving little back. All the while some extremely needed projects lack funding, and most software companies in bitcoin who wish to innovate are begging and scraping funds together, in order to stay afloat.\ Something’s not ok with that.\ I can’t understand a company with that much power and money being part of this movement and loving bitcoin, while not actively supporting the development or the maintainers of the bitcoin software. (and yes, to keep their independence it’s best to keep it that way, that’s also an argument, but even then, giving out a grant to anyone that’s crucial in this industry, might help the whole ecosystem).
The show must go on—for now
The whole Strategy setup feels more and more like a performance to me. Saylor’s the star, doing the moves and Wall Street’s the record label, and we’re the audience, captivated by the spectacle and paying to see the show on occasion.\ \ The suits keep funding him (free money, IOUs), just like the music industry props up a fading diva with a limited repertoire or drags a new star from her home studio on YouTube into the spotlights. H\ Saylor’s 21/21 Plan to the amount of $42 billion to snatch up more Bitcoin can be a grand finale that’s dazzling while the lights stay on.
Prediction: the music stops eventually
Here’s my take: Bitcoin will keep rising over a long period of time, and Saylor’s gambit will look like a genius move, until it doesn’t. All it takes is one big shot in Wall Street to find another shiny toy to play with, or another play to get their money working. The billions they’ve invested, will come back eventually, and if it doesn’t, it will mean the world has changed in their advantage as well in another way. Some people cannot lose, no matter what. Saylor’s now part of that, doing their bidding and doing his part for educating the other businesses.\ \ He’s the only big buyer of last resort in this game so far. No one else is piling in with billions like he is. When the hype cools or the debt catches up, he’s got no real business to fall back on. The software? A relic. The Bitcoin bet can save him if the time is right, we’ll see about that.\ Time is his enemy not ally, and it always wins in the end. The pose can only hold so long. You can’t keep scoring free fiat, without either die on low valuation and dilution, or without at least 20 other Strategy-grade businesses jumping in to take their piece of the pie.\ So far, surprisingly, none of these two things happen.\ He keeps getting free fiat from Wall Street investors, and no other Saylor stands up.\ This can’t last forever. One of the two will happen by end of 2025.\ \ Curtain call
Saylor’s a fascinating watch, a mix of investor-backed bravado, brains, and borrowed billions.\ Is it a masterstroke or a bitcoin version of Worldcom?\ I’m not sure. In any case, I would only invest in MSTR myself if the company has a real added value for bitcoin development and the bitcoin ecosystem. They could be the engine, the spirit, the core of bitcoin.\ Yet they’re just doing the poses.\ Let your body move to the rhythm.
AVB
If you like : tip here / other writings
1 https://en.wikipedia.org/wiki/IOU
2 https://sc.edu/about/offices_and_divisions/audit_and_advisory_services/about/news/2021/worldcom_scandal.php
-
 @ 16f1a010:31b1074b
2025-02-19 20:57:59
@ 16f1a010:31b1074b
2025-02-19 20:57:59In the rapidly evolving world of Bitcoin, running a Bitcoin node has become more accessible than ever. Platforms like Umbrel, Start9, myNode, and Citadel offer user-friendly interfaces to simplify node management. However, for those serious about maintaining a robust and efficient Lightning node ⚡, relying solely on these platforms may not be the optimal choice.
Let’s delve into why embracing Bitcoin Core and mastering the command-line interface (CLI) can provide a more reliable, sovereign, and empowering experience.
Understanding Node Management Platforms
What Are Umbrel, Start9, myNode, and Citadel?
Umbrel, Start9, myNode, and Citadel are platforms designed to streamline the process of running a Bitcoin node. They offer graphical user interfaces (GUIs) that allow users to manage various applications, including Bitcoin Core and Lightning Network nodes, through a web-based dashboard 🖥️.
These platforms often utilize Docker containers 🐳 to encapsulate applications, providing a modular and isolated environment for each service.

The Appeal of Simplified Node Management
The primary allure of these platforms lies in their simplicity. With minimal command-line interaction, users can deploy a full Bitcoin and Lightning node, along with a suite of additional applications.
✅ Easy one-command installation
✅ Web-based GUI for management
✅ Automatic app updates (but with delays, as we’ll discuss)However, while this convenience is attractive, it comes at a cost.
The Hidden Complexities of Using Node Management Platforms
While the user-friendly nature of these platforms is advantageous, it can also introduce several challenges that may hinder advanced users or those seeking greater control over their nodes.
🚨 Dependency on Maintainers for Updates
One significant concern is the reliance on platform maintainers for updates. Since these platforms manage applications through Docker containers, users must wait for the maintainers to update the container images before they can access new features or security patches.
🔴 Delayed Bitcoin Core updates = potential security risks
🔴 Lightning Network updates are not immediate
🔴 Bugs and vulnerabilities may persist longerInstead of waiting on a third party, why not update Bitcoin Core & LND yourself instantly?
⚙️ Challenges in Customization and Advanced Operations
For users aiming to perform advanced operations, such as:
- Custom backups 📂
- Running specific CLI commands 🖥️
- Optimizing node settings ⚡
…the abstraction layers introduced by these platforms become obstacles.
Navigating through nested directories and issuing commands inside Docker containers makes troubleshooting a nightmare. Instead of a simple
bitcoin-clicommand, you must figure out how to execute it inside the container, adding unnecessary complexity.Increased Backend Complexity
To achieve frontend simplicity, these platforms make the backend more complex.
🚫 Extra layers of abstraction
🚫 Hidden logs and settings
🚫 Harder troubleshootingThe use of multiple Docker containers, custom scripts, and unique file structures can make system maintenance and debugging a pain.
This complication defeats the purpose of “making running a node easy.”
✅ Advantages of Using Bitcoin Core and Command-Line Interface (CLI)
By installing Bitcoin Core directly and using the command-line interface (CLI), you gain several key advantages that make managing a Bitcoin and Lightning node more efficient and empowering.
Direct Control and Immediate Updates
One of the biggest downsides of package manager-based platforms is the reliance on third-party maintainers to release updates. Since Bitcoin Core, Lightning implementations (such as LND, Core Lightning, or Eclair), and other related software evolve rapidly, waiting for platform-specific updates can leave you running outdated or vulnerable versions.
By installing Bitcoin Core directly, you remove this dependency. You can update immediately when new versions are released, ensuring your node benefits from the latest features, security patches, and bug fixes. The same applies to Lightning software—being able to install and update it yourself gives you full autonomy over your node’s performance and security.
🛠 Simplified System Architecture
Platforms like Umbrel and myNode introduce extra complexity by running Bitcoin Core and Lightning inside Docker containers. This means:
- The actual files and configurations are stored inside Docker’s filesystem, making it harder to locate and manage them manually.
- If something breaks, troubleshooting is more difficult due to the added layer of abstraction.
- Running commands requires jumping through Docker shell sessions, adding unnecessary friction to what should be a straightforward process.
Instead, a direct installation of Bitcoin Core, Lightning, and Electrum Server (if needed) results in a cleaner, more understandable system. The software runs natively on your machine, without containerized layers making things more convoluted.
Additionally, setting up your own systemd service files for Bitcoin and Lightning is not as complicated as it seems. Once configured, these services will run automatically on boot, offering the same level of convenience as platforms like Umbrel but without the unnecessary complexity.
Better Lightning Node Management
If you’re running a Lightning Network node, using CLI-based tools provides far more flexibility than relying on a GUI like the ones bundled with node management platforms.
🟢 Custom Backup Strategies – Running Lightning through a GUI-based node manager often means backups are handled in a way that is opaque to the user. With CLI tools, you can easily script automatic backups of your channels, wallets, and configurations.
🟢 Advanced Configuration – Platforms like Umbrel force certain configurations by default, limiting how you can customize your Lightning node. With a direct install, you have full control over: * Channel fees 💰 * Routing policies 📡 * Liquidity management 🔄
🟢 Direct Access to LND, Core Lightning, or Eclair – Instead of issuing commands through a GUI (which is often limited in functionality), you can use: *
lncli(for LND) *lightning-cli(for Core Lightning) …to interact with your node at a deeper level.Enhanced Learning and Engagement
A crucial aspect of running a Bitcoin and Lightning node is understanding how it works.
Using an abstraction layer like Umbrel may get a node running in a few clicks, but it does little to teach users how Bitcoin actually functions.
By setting up Bitcoin Core, Lightning, and related software manually, you will:
✅ Gain practical knowledge of Bitcoin nodes, networking, and system performance.
✅ Learn how to configure and manage RPC commands.
✅ Become less reliant on third-party developers and more confident in troubleshooting.🎯 Running a Bitcoin node is about sovereignty – learn how to control it yourself.
Become more sovereign TODAY
Many guides make this process straightforward K3tan has a fantastic guide on running Bitcoin Core, Electrs, LND and more.
- Ministry of Nodes Guide 2024
- You can find him on nostr
nostr:npub1txwy7guqkrq6ngvtwft7zp70nekcknudagrvrryy2wxnz8ljk2xqz0yt4xEven with the best of guides, if you are running this software,
📖 READ THE DOCUMENTATIONThis is all just software at the end of the day. Most of it is very well documented. Take a moment to actually read through the documentation for yourself when installing. The documentation has step by step guides on setting up the software. Here is a helpful list: * Bitcoin.org Bitcoin Core Linux install instructions * Bitcoin Core Code Repository * Electrs Installation * LND Documentation * LND Code Repository * CLN Documentation * CLN Code Repository
If you have any more resources or links I should add, please comment them . I want to add as much to this article as I can.
-
 @ f288a224:1da1792c
2025-02-19 16:43:40
@ f288a224:1da1792c
2025-02-19 16:43:40First, some context.
I'm a child of the original internet chat-rooms on IRC, and I've tried over the last decades different applications and websites that we could all agree are "social media", but until I found NOSTR (Notes and Other Stuff Transmitted by Relays) I hadn't had this certainty that this isn't something that I will eventually change for something else.
Today, even with all its early stage issues, I have the certainty that NOSTR may be the ULTIMATE and FINAL HOME for my online life.
THE PROBLEMS with the current/old social media landscape

I'm tired of moving from one social media to the next.
As many of you, in my digital lifetime I've had many accounts that have now become obsolete; and the "content" and followings I created during that time was lost when one tech giant lost over the other, forcing us all to "MOVE" ourselves over to the new, and start building our content and following from scratch.
Lately, it's become even worse, where many of us have seen ourselves forced to use and feed more than one social media at a time, since they all serve various purposes, with sometimes diverse functionality, besides all being catered to different segments of people to connect you to (LinkedIn, Instagram, TikTok, Youtube...). How much is too much, though? And how much time should we keep spending re-adapting our content to reach all of our network?
For work, I've found myself having to create accounts in several of these giant data hoarding companies, having to build each following from scratch and to create "content" for all, and having to go through the hurdle of posting everything, everywhere, all at once.
I'm sick of ever-changing terms, conditions and capabilities.
Let's be honest, the majority of us have never ever read the full terms and conditions, let alone every time they are updated without us knowing which rights to our data we are giving away, and which terms we are accepting that may be detrimental to us and our mental health.
We've learnt to accept that we are in their playground, they make up the rules, and if they choose to change the rules mid-game we just need to swallow it. We literally have no other choice, it's either that or desertion, which basically means walking away from everything we've built on their "public square". So, like a carefully engineered detrimental incentive structure, the more time we spend building on their turf, the more we are tied to them and conditioned to never leave them. The more we build and make them grow on our content, the more we'll lose if or when we drop out.
And even if you accept all that and choose to play along, and you do your best to create the most awesome account in the neighborhood, the random changes they make to optimize ad revenue or user attention will inevitably affect you and all your work.
If you created all your feed according to Instagram's squares but they choose to change to TikTok style dimensions due to their tech positioning battle with the Chinese giant... You swallow. If you edited your reels according to what you felt was the best 100 seconds video... Not anymore, suddenly 90 seconds is the maximum you're allowed... No appeal, no options. You Swallow. What? Seeing less of the people you actually WANT TO FOLLOW because they decided to clutter your feed with ads and suggestions, guess again: YOU SWALLOW.
AREN'T YOU FEELING FULL ENOUGH OF ALL THE SHIT THEY'VE FORCED DOWN YOUR THROAT?
Living our digital lives on these platforms feels like standing on ever changing quicksand, never endingly trying to "hack the algorithm" in order to have our content placed in front of the people who should automatically be able to see us from the moment they chose to follow us; and the worst part of it is, you never know when you may lose it all.
Let's not forget, your social media account is NOT REALLY YOURS.
Recently, a friend's social media account was hacked. She didn't know how it happened; all she knew is that she got an email from Meta saying she had acted against community guidelines and her accounts were therefore being removed (the one hacked and all those liked to her email, which meant personal and work accounts). She tried to appeal, to no avail. She hadn't done anything wrong, but suddenly her identity had disappeared from all our feeds, and her content didn't exist anywhere anymore. She lost plenty of photos she had always counted on finding on her Instagram and lost the people she followed and who followed her. It was as if she had never existed on the platform.
(Looks like a good moment to remind you to download all your valued content from the platforms you use in case something like this happens to you)
 And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".
And this happened to someone who hadn't done anything "to deserve it". It has actually happened to more than one person I know, and every time they've been helpless and had no recourse, and yet, found themselves having to rebuild from scratch on the same platform that de-platformed them, because they had "no other option", and "their friends are there".Many more people have encountered this awful wake up call, some because of a hack, like my friend, others found themselves removed because they posted content critical of the platform... there are so many reasons people have gotten de-platformed and posts have gotten deleted without warning. And every time, we accept it, as if we owe them something; as if we need to settle for this kind of abusive environment that gets rich on our content and attention without having a say in anything.
But we do have another option that flips that attention retention model completely on its head and empowers the user. That option is NOSTR, our exit from the extractive social media silos they have trapped us into.
NOSTR: The better social experience for the internet era.
NOSTR (Notes and Other Stuff Transmitted by Relays) is not a social media app, it's an Internet protocol. It's open source and many many developers around the world are creating apps on top of it and creating THE ULTIMATE SOCIAL MEDIA EXPERIENCE for users.
I first heard of NOSTR from Jack Dorsey on what used to be called Twitter, and when I joined it two years ago it was really rough around the edges, but it was FULL OF POTENTIAL and the value proposition was very clear to me from the beginning.
Firstly, YOU OWN YOUR IDENTITY, that includes your content and your follower list.
So, what does owning you identity mean? I guess many of us have thought we owned our identity before, but the reality is that the platforms owned our identities, which is why they could delete or censor us.
Owning your identity on NOSTR is empowered by encryption and cryptography. I'm not going to go into the technical part, but to explain as simply as I can, on NOSTR no platform owns your login and password to use on their playground; you can basically use any NOSTR app to create your identity to navigate it. They give you a login (npub) and password (nsec), and the magic part is that you can USE THAT IDENTITY ON ANY NOSTR APP OR WEBSITE, no need to sign up individually on each one.
Welcome to the beauty of INTEROPERABILITY.
I cannot emphasize enough what it feels like to be able to take your identity, your followers, your content and carry it from one app to the other.
On NOSTR there is a rich ecosystem of apps and websites that keep growing. We have "clients" that allow you to experience NOSTR in interfaces that could remind you of Twitter, Instagram, TikTok, Substack, Twitch, Clubhouse, Podcast apps and many more. You can find many of them on https://nostrapps.com/ .
With that information in mind, imagine you only needed one user password, your NOSTR nsec, and with that key, you could open you Instagram, or your Twitch or your Substack. And all your followers would be there, and you could choose what type of content you wanted to link to your identity for your followers to find. No longer "find link in bio", or "go to our YouTube channel", everything you post on NOSTR is tied to your identity, and you can post it all with a single set of keys that posts your content "everywhere".
And since your content is "in every client", each of YOUR FOLLOWERS CAN CHOOSE if they are more interested in experiencing your photography content "Insta-like" or if they love your "Twitter-esque" notes better. Each user navigates NOSTR with the interface they prefer.
(With great power comes great responsibility, and I feel obligated to tell you that if you ever lose your nsec, no platform is gonna be able to save you. It's like the keys to your house, unless you keep a copy safely, no one can open it for you (there are no locksmiths on NOSTR). And if you leave your keys lying around on a cloud server somewhere, someone may grab your keys, open your house and use it however they want).
The beauty of this interoperability and the fact that my keys open up my identity to all the NOSTR realms is that you don't need to settle for one client. I use 5 to 6 clients regularly everyday depending on the mood I'm in, (or the bugs that still prove this is a nascent ecosystem in development). Some I use when I want a more "Twitter-like" experience, others when I want to browse photos and others just give different algorithms to choose how to view my feed, and the best part is NO ONE CAN CLUTTER MY FEED WITH ADS. I can curate my feed however is most important to me, and each "NOSTR client" is like a different skin that customizes the way I experience the content.
However, the most important reason I started to use different NOSTR apps was that when I started, not all apps had zapping integrated. Some still don't, but most do :)
ZAPS: direct micropayments from your followers.
Zaps are tips that come directly from the people who find value in the shit that you post. They are micropayments in the form of "sats", fractions of ever-increasing in value bitcoin , and a very big reason why I'm spending less and less time on other social media accumulating valueless likes that only feed the algorithm, and more time on NOSTR interacting with humans that post valuable notes hoping the generous souls that run upon their art or creations will find them valuable enough to tip them for it.
It's crazy how the type of content you post can change when your incentive is not to feed an algo, but to give real value to other humans around the world and be your most authentic self. Where Twitter/X's algo benefited the type of incendiary content that shocked and outraged people, NOSTR's incentives benefit those who bring most value to the network and their peers.
A few sats tip may not seem much, but even if the equivalent of a small zap is merely cents, it feels a whole lot better than any like, and you can count that if the purchasing power of bitcoin continues to accrue, those value-earned tips will too. Many "nostriches" are getting tons of zaps for memes on NOSTR, valuable articles, videos or participation in zapathons .
In NOSTR is where I first heard of the concept "value for value", and the community is very adamant in making "v4v" an alternative to ad revenue driven models. Because we need to be the change we wanna see in the world.
We've heard it said that if you're not paying for the product, you are the product. And up until now that has meant we felt obliged to accept that since ads were paying the platforms, we were required to give them our attention. But the open source movement thinks we deserve better. We deserve a better Internet, like the decentralized promise we've slowly been robbed of to enrich 10 people out of the work of all of us. If they can't monetize our attention, they got nothing.
But why should they monetize it, instead of us?
Even with the glitches and bugs, NOSTR ROCKS!
The things I've grown to love most about NOSTR are:
• Not having the clutter of ads on my feed and being able to ONLY SEE WHAT I CHOOSE TO SEE.
• People who are not on NOSTR can ENJOY MY STUFF WITHOUT HAVING TO LOGIN.
• Being able to ENJOY ALL THE BENEFITS OF INTEROPERABILITY, and use many NOSTR clients that enrich my user experience knowing I own my identity and that means I'm not locked in, I can move like a bird wherever I decide.
• ZAPPING complete strangers that made me laugh, gave me a cool insight or simply made a witty comment.
• GETTING TIPPED for memes, articles, photos, videos and any "Notes and Other Stuff" that people have found valuable.
CONCLUSION: Join us on NOSTR, participate in claiming back your digital life.
If you've made it this far in my love letter to NOSTR, thank you for being interested. Curious minds is what the world needs more of <3.
NOSTR is an ecosystem that is being built in the open by relentless developers that are continuously striving to out compete each other to offer a better user experience, it's a many headed dragon that has constant upgrades and implementations which benefits us all, and as such it sometimes comes with bugs and glitches.
Building the future is always buggy and requires testers and early adopters that help shape the technology in the best way possible, especially if you wanna build outside the incentive models of the devouring giants we're trying to get away from.
Being such an open ecosystem can also be overwhelming for a newcomer, where to start? There are so many clients to experience; so here are some of my recommendations.
Please, don't feel you need to go through all of them now, start step by step. This article will always be here whenever you need it (this is not Instagram ;) ).
Creating your NOSTR identity/account with a wallet integrated to receive zaps on both Android and iOS:
• YAKIHONNE: It's a Japanese client that offers a great on-boarding experience. From the app you can create the account and enable a wallet to receive zaps. In it you can view and post short and long form content, images, videos and more. (Once you have the account created on your app, you can also visit the desktop version on https://yakihonne.com/ )
• PRIMAL: For a while it has positioned itself as a great on-boarding NOSTR client because it offers the same things as Yakihonne, has an integrated wallet, with the added benefit that you can also "buy sats/bitcoin" directly from its wallet, which can come in handy (it comes with a 15-30% premium, so only use for small amounts). It also has the desktop version at primal.net.
My favorite NOSTR iOS PHONE APPS after on-boarding, in case you wanna hop into different user experiences:
• DAMUS: created by the original creator of the "ZAP", Will Casarin, it's an iOS simple client that is reliable and fast with notifications. It keeps things simple, mostly focusing on short note content, although you can also see images and short video. But the feed is optimized as a more "Twitter-like" feed.
• NOSTUR: The iOS phone client that has it all! It's the client I've used that integrates the most of NOSTR's possibilities, you can see all of the mentioned above with the previous clients, but also view LIVE STREAMS, and have multiple accounts set up simultaneously. The enhanced capabilities can sometimes come at the cost of crashing or being slow to load.
• FREERSE: Nice clean user interface with plenty of functionality, with easy navigation on topics like #art #photography or any other interests. It's my always reliable back-up to upload image content.
• OLAS: The new kid on the block Olas client, by prolific developer Pablof7z, is trying to take on Instagram and TikTok and has developed a client mainly focused on the visual and photographic part of NOSTR.
Desktop clients & OTHER GEMS OF THE NOSTR REALM:
There is an infinite number of clients for desktop, but I usually find myself on ditto.pub or slidestr.net for a more visual experience.
• ALBY is INTEROPERABILITY'S BEST FRIEND. Alby is not a NOSTR client, but it's a browser extension that makes it seamless to jump from one desktop client to another with your wallet and identity without compromising your security.
• HIVETALK: A video call client (reminiscent of Zoom) that doesn't track you or spy on you and that enables zapping and many other functionalities during the calls.
• NOSTR NESTS: Audio spaces client that allows people to listen to conversations, chat within it and zap the people involved.
if you made it this far, THANK YOU FOR YOUR ATTENTION.
HOPE YOU FOUND VALUE IN IT AND UNDERSTOOD WHY, FOR ME, THE FUTURE OF SOCIAL MEDIA IS BRIGHT, OPEN AND USER-CENTRIC.
FUCK THE MIDDLEMEN.
-
 @ 50de492c:0a8871de
2025-03-30 00:23:36
@ 50de492c:0a8871de
2025-03-30 00:23:36{"title":"test","description":"","imageUrl":"https://i.nostr.build/Xo67.png"}
-
 @ 30b99916:3cc6e3fe
2025-03-29 17:04:41
@ 30b99916:3cc6e3fe
2025-03-29 17:04:41btcpayserver #lightning #lnd #powershell
BTCpayAPI now supports file upload
I'm continuing to add functionality to BTCpay and BTCpayAPI which is using REST Api(s) to manage my BTCPAY server and LND cloud instance. It is nice to have this just running locally on my home Linux desktop.
Here is the code that implements this functionality.
``` "Uploadfile" {
$apislug = "api/v1/files"
$filepath = Split-Path $options
$filename = Split-Path $options -Leaf
CONST
$CODEPAGE = "iso-8859-1" # alternatives are ASCII, UTF-8
Read file byte-by-byte
$fileBin = [System.IO.File]::ReadAllBytes($options)
Convert byte-array to string
$enc = [System.Text.Encoding]::GetEncoding($CODEPAGE) $fileEnc = $enc.GetString($fileBin)
We need a boundary (something random() will do best)
$boundary = [System.Guid]::NewGuid().ToString() $LF = "
rn" $bodyLines = ( "--$boundary", "Content-Disposition: form-data; name="file"; filename="$fileName"", "Content-Type: application/octet-stream$LF", $fileEnc, "--$boundary--$LF" ) -join $LF$URI = $BTCPayCfg.BTCpayApi.GreenApi.url + $apislug $apiKeyToken = 'token ' + $script:BTCPAY_API $headers = @{'Authorization'=$apiKeyToken}
return Invoke-RestMethod -Uri $uri -Method Post -Headers $headers -ContentType "multipart/form-data; boundary=
"$boundary"" -Body $bodyLines} ``` Here is the revision history since my last article.
Version Date Whom Notes ======= ========== ======== ===================================================== 0.1.4 03/28/2025 cadayton Added UploadFile method to upload a file to the BTCpay server 0.1.3 03/27/2025 cadayton Added GetFiles returns listing of files uploaded to BTCpay server 0.1.2 03/19/2025 cadayton ForwardingHistory new parameter "total_fees" tallys mfees for events returned 0.1.1 03/18/2025 cadayton ForwardingHistory now support additional parameters 0.1.0 03/15/2025 cadayton initial release.The inspiration for this logic was adapted from weipah . One wouldn't think uploading a single file wouldn't require this much coding. The Greenfield's REST Api documentation for this end point wasn't very helpful.In my book, good end-user documentation of one's code is just as important as the code itself. I believe documentation is usually lacking on most projects because the effort of doing so is almost equal to the effort of writing the code. It is also the least fun part about writing code.
The job is not done until the paper work has been completed. :)
https://btcpayserver.sytes.net
-
 @ 83279ad2:bd49240d
2025-03-29 15:28:45
@ 83279ad2:bd49240d
2025-03-29 15:28:45test
-
 @ 3514ac1b:cf164691
2025-03-29 22:07:33
@ 3514ac1b:cf164691
2025-03-29 22:07:33About Me
-
 @ ed5774ac:45611c5c
2025-02-15 05:38:56
@ ed5774ac:45611c5c
2025-02-15 05:38:56Bitcoin as Collateral for U.S. Debt: A Deep Dive into the Financial Mechanics
The U.S. government’s proposal to declare Bitcoin as a 'strategic reserve' is a calculated move to address its unsustainable debt obligations, but it threatens to undermine Bitcoin’s original purpose as a tool for financial freedom. To fully grasp the implications of this plan, we must first understand the financial mechanics of debt creation, the role of collateral in sustaining debt, and the historical context of the petro-dollar system. Additionally, we must examine how the U.S. and its allies have historically sought new collateral to back their debt, including recent attempts to weaken Russia through the Ukraine conflict.
The Vietnam War and the Collapse of the Gold Standard
The roots of the U.S. debt crisis can be traced back to the Vietnam War. The war created an unsustainable budget deficit, forcing the U.S. to borrow heavily to finance its military operations. By the late 1960s, the U.S. was spending billions of dollars annually on the war, leading to a significant increase in public debt. Foreign creditors, particularly France, began to lose confidence in the U.S. dollar’s ability to maintain its value. In a dramatic move, French President Charles de Gaulle sent warships to New York to demand the conversion of France’s dollar reserves into gold, as per the Bretton Woods Agreement.
This demand exposed the fragility of the U.S. gold reserves. By 1971, President Richard Nixon was forced to suspend the dollar’s convertibility to gold, effectively ending the Bretton Woods system. This move, often referred to as the "Nixon Shock," declared the U.S. bankrupt and transformed the dollar into a fiat currency backed by nothing but trust in the U.S. government. The collapse of the gold standard marked the beginning of the U.S.’s reliance on artificial systems to sustain its debt. With the gold standard gone, the U.S. needed a new way to back its currency and debt—a need that would lead to the creation of the petro-dollar system.
The Petro-Dollar System: A New Collateral for Debt
In the wake of the gold standard’s collapse, the U.S. faced a critical challenge: how to maintain global confidence in the dollar and sustain its ability to issue debt. The suspension of gold convertibility in 1971 left the dollar as a fiat currency—backed by nothing but trust in the U.S. government. To prevent a collapse of the dollar’s dominance and ensure its continued role as the world’s reserve currency, the U.S. needed a new system to artificially create demand for dollars and provide a form of indirect backing for its debt.
The solution came in the form of the petro-dollar system. In the 1970s, the U.S. struck a deal with Saudi Arabia and other OPEC nations to price oil exclusively in U.S. dollars. In exchange, the U.S. offered military protection and economic support. This arrangement created an artificial demand for dollars, as countries needed to hold USD reserves to purchase oil. Additionally, oil-exporting nations reinvested their dollar revenues in U.S. Treasuries, effectively recycling petro-dollars back into the U.S. economy. This recycling of petrodollars provided the U.S. with a steady inflow of capital, allowing it to finance its deficits and maintain low interest rates.
To further bolster the system, the U.S., under the guidance of Henry Kissinger, encouraged OPEC to dramatically increase oil prices in the 1970s. The 1973 oil embargo and subsequent price hikes, masterminded by Kissinger, quadrupled the cost of oil, creating a windfall for oil-exporting nations. These nations, whose wealth surged significantly due to the rising oil prices, reinvested even more heavily in U.S. Treasuries and other dollar-denominated assets. This influx of petrodollars increased demand for U.S. debt, enabling the U.S. to issue more debt at lower interest rates. Additionally, the appreciation in the value of oil—a critical global commodity—provided the U.S. banking sector with the necessary collateral to expand credit generation. Just as a house serves as collateral for a mortgage, enabling banks to create new debt, the rising value of oil boosted the asset values of Western corporations that owned oil reserves or invested in oil infrastructure projects. This increase in asset values allowed these corporations to secure larger loans, providing banks with the collateral needed to expand credit creation and inject more dollars into the economy. However, these price hikes also caused global economic turmoil, disproportionately affecting developing nations. As the cost of energy imports skyrocketed, these nations faced mounting debt burdens, exacerbating their economic struggles and deepening global inequality.
The Unsustainable Debt Crisis and the Search for New Collateral
Fast forward to the present day, and the U.S. finds itself in a familiar yet increasingly precarious position. The 2008 financial crisis and the 2020 pandemic have driven the U.S. government’s debt to unprecedented levels, now exceeding $34 trillion, with a debt-to-GDP ratio surpassing 120%. At the same time, the petro-dollar system—the cornerstone of the dollar’s global dominance—is under significant strain. The rise of alternative currencies and the shifting power dynamics of a multipolar world have led to a decline in the dollar’s role in global trade, particularly in oil transactions. For instance, China now pays Saudi Arabia in yuan for oil imports, while Russia sells its oil and gas in rubles and other non-dollar currencies. This growing defiance of the dollar-dominated system reflects a broader trend toward economic independence, as nations like China and Russia seek to reduce their reliance on the U.S. dollar. As more countries bypass the dollar in trade, the artificial demand for dollars created by the petro-dollar system is eroding, undermining the ability of US to sustain its debt and maintain global financial hegemony.
In search of new collateral to carry on its unsustainable debt levels amid declining demand for the U.S. dollar, the U.S., together with its Western allies—many of whom face similar sovereign debt crises—first attempted to weaken Russia and exploit its vast natural resources as collateral. The U.S. and its NATO allies used Ukraine as a proxy to destabilize Russia, aiming to fragment its economy, colonize its territory, and seize control of its natural resources, estimated to be worth around $75 trillion. By gaining access to these resources, the West could have used them as collateral for the banking sector, enabling massive credit expansion. This, in turn, would have alleviated the sovereign debt crisis threatening both the EU and the U.S. This plan was not unprecedented; it mirrored France’s long-standing exploitation of its former African colonies through the CFA franc system.
For decades, France has maintained economic control over 14 African nations through the CFA franc, a currency pegged to the euro and backed by the French Treasury. Under this system, these African countries are required to deposit 50% of their foreign exchange reserves into the French Treasury, effectively giving France control over their monetary policy and economic sovereignty. This arrangement allows France to use African resources and reserves as implicit collateral to issue debt, keeping its borrowing costs low and ensuring demand for its bonds. In return, African nations are left with limited control over their own economies, forced to prioritize French interests over their own development. This neo-colonial system has enabled France to sustain its financial dominance while perpetuating poverty and dependency in its former colonies.
Just as France’s CFA franc system relies on the economic subjugation of African nations to sustain its financial dominance, the U.S. had hoped to use Russia’s resources as a lifeline for its debt-ridden economy. However, the plan ultimately failed. Russia not only resisted the sweeping economic sanctions imposed by the West but also decisively defeated NATO’s proxy forces in Ukraine, thwarting efforts to fragment its economy and seize control of its $75 trillion in natural resources. This failure left the U.S. and its allies without a new source of collateral to back their unsustainable debt levels. With this plan in ruins, the U.S. has been forced to turn its attention to Bitcoin as a potential new collateral for its unsustainable debt.
Bitcoin as Collateral: The U.S. Government’s Plan
The U.S. government’s plan to declare Bitcoin as a strategic reserve is a modern-day equivalent of the gold standard or petro-dollar system. Here’s how it would work:
-
Declaring Bitcoin as a Strategic Reserve: By officially recognizing Bitcoin as a reserve asset, the U.S. would signal to the world that it views Bitcoin as a store of value akin to gold. This would legitimize Bitcoin in the eyes of institutional investors and central banks.
-
Driving Up Bitcoin’s Price: To make Bitcoin a viable collateral, its price must rise significantly. The U.S. would achieve this by encouraging regulatory clarity, promoting institutional adoption, and creating a state-driven FOMO (fear of missing out). This would mirror the 1970s oil price hikes that bolstered the petro-dollar system.
-
Using Bitcoin to Back Debt: Once Bitcoin’s price reaches a sufficient level, the U.S. could use its Bitcoin reserves as collateral for issuing new debt. This would restore confidence in U.S. Treasuries and allow the government to continue borrowing at low interest rates.
The U.S. government’s goal is clear: to use Bitcoin as a tool to issue more debt and reinforce the dollar’s role as the global reserve currency. By forcing Bitcoin into a store-of-value role, the U.S. would replicate the gold standard’s exploitative dynamics, centralizing control in the hands of large financial institutions and central banks. This would strip Bitcoin of its revolutionary potential and undermine its promise of decentralization. Meanwhile, the dollar—in digital forms like USDT—would remain the primary medium of exchange, further entrenching the parasitic financial system.
Tether plays a critical role in this strategy. As explored in my previous article (here: [https://ersan.substack.com/p/is-tether-a-bitcoin-company]), Tether helps sustaining the current financial system by purchasing U.S. Treasuries, effectively providing life support for the U.S. debt machine during a period of declining demand for dollar-denominated assets. Now, with its plans to issue stablecoins on the Bitcoin blockchain, Tether is positioning itself as a bridge between Bitcoin and the traditional financial system. By issuing USDT on the Lightning Network, Tether could lure the poor in developing nations—who need short-term price stability for their day to day payments and cannot afford Bitcoin’s volatility—into using USDT as their primary medium of exchange. This would not only create an artificial demand for the dollar and extend the life of the parasitic financial system that Bitcoin was designed to dismantle but would also achieve this by exploiting the very people who have been excluded and victimized by the same system—the poor and unbanked in developing nations, whose hard-earned money would be funneled into sustaining the very structures that perpetuate their oppression.
Worse, USDT on Bitcoin could function as a de facto central bank digital currency (CBDC), where all transactions can be monitored and sanctioned by governments at will. For example, Tether’s centralized control over USDT issuance and its ties to traditional financial institutions make it susceptible to government pressure. Authorities could compel Tether to implement KYC (Know Your Customer) rules, freeze accounts, or restrict transactions, effectively turning USDT into a tool of financial surveillance and control. This would trap users in a system where every transaction is subject to government oversight, effectively stripping Bitcoin of its censorship-resistant and decentralized properties—the very features that make it a tool for financial freedom.
In this way, the U.S. government’s push for Bitcoin as a store of value, combined with Tether’s role in promoting USDT as a medium of exchange, creates a two-tiered financial system: one for the wealthy, who can afford to hold Bitcoin as a hedge against inflation, and another for the poor, who are trapped in a tightly controlled, surveilled digital economy. This perpetuates the very inequalities Bitcoin was designed to dismantle, turning it into a tool of oppression rather than liberation.
Conclusion: Prolonging the Parasitic Financial System
The U.S. government’s plan to declare Bitcoin as a strategic reserve is not a step toward financial innovation or freedom—it is a desperate attempt to prolong the life of a parasitic financial system that Bitcoin was created to replace. By co-opting Bitcoin, the U.S. would gain a new tool to issue more debt, enabling it to continue its exploitative practices, including proxy wars, economic sanctions, and the enforcement of a unipolar world order.
The petro-dollar system was built on the exploitation of oil-exporting nations and the global economy. A Bitcoin-backed system would likely follow a similar pattern, with the U.S. using its dominance to manipulate Bitcoin’s price and extract value from the rest of the world. This would allow the U.S. to sustain its current financial system, in which it prints money out of thin air to purchase real-world assets and goods, enriching itself at the expense of other nations.
Bitcoin was designed to dismantle this parasitic system, offering an escape hatch for those excluded from or exploited by traditional financial systems. By declaring Bitcoin a strategic reserve, the U.S. government would destroy Bitcoin’s ultimate purpose, turning it into another instrument of control. This is not a victory for Bitcoin or bitcoiners—it is a tragedy for financial freedom and global equity.
The Bitcoin strategic reserve plan is not progress—it is a regression into the very system Bitcoin was designed to dismantle. As bitcoiners, we must resist this co-option and fight to preserve Bitcoin’s original vision: a decentralized, sovereign, and equitable financial system for all. This means actively working to ensure Bitcoin is used as a medium of exchange, not just a store of value, to fulfill its promise of financial freedom.
-
-
 @ 3514ac1b:cf164691
2025-03-29 21:58:22
@ 3514ac1b:cf164691
2025-03-29 21:58:22Hi this is me ,Erna . i am testing this Habla news . i have been trying using this but got no luck . always disconnect and no content .
Hopefully this one will work .
BREAKING NEWS : Vance uses Greenland visit to slam Denmark , as Trump escalates rhetoric .
https://wapo.st/4c6YkhO
-
 @ 30b99916:3cc6e3fe
2025-03-29 14:12:37
@ 30b99916:3cc6e3fe
2025-03-29 14:12:37Chef's Notes
My mom worked as a waitress for a excellent Chinese restaurant. For years she tried to get this receipt without success and finally after the owner retired he gave her the receipt.
Previously posted this receipt on Zap.Cooking but now wanting to keep all my long-form notes in Obsidian and publish to Nostr using the nostr-writer plug-in.
Details
- ⏲️ Prep time: 20 to 30 minutes
- 🍳 Cook time: 1 to 2 Hours depending on amount of spare ribs
- 🍽️ Servings: 8
Ingredients
- 1 Quart Dole Pineapple Juice
- 1 Pint Dole Crushed Pineapple
- 1 Pint Dole Tidbits Pineapple
- 1 TS Dried Mustard
- 32 Oz Brown sugar or add to taste
- 1 Cup Red Wine
- 2 TS Corn Starch
- 1 or 2 lbs Pork or Beef spare ribs
- Worcestershire sauce
Directions
- Preheat oven to 350 degrees
- Bring water to boil in 8 qt stock pot
- Cut spare ribs and add to boiling water in stock pot
- Boil spare ribs for 20 to 30 minutes to remove excess fat
- Drain spare ribs and place onto cookie sheet
- Base spare ribs with a generous amount of Worcestershire sauce
- Place based spare ribs on cookie sheet and place into oven for 60 minutes.
- Place first 6 ingredients into stock pot and bring to boil while CONTINUOUSLY stirring
- Add corn starch to 2 cups of water and mix to create thickening agent
- Add thickening agent incrementally to Sweet & Sour sauce for desired thickness
- Reduce heat to low while CONTINUOUSLY stirring.
- Remove spare ribs from oven and place into Sweet & Sour sauce.
- Place stock pot into oven and cook until done. 1 to 2 hours.
Bon Appétit
-
 @ 65038d69:1fff8852
2025-03-29 12:31:02
@ 65038d69:1fff8852
2025-03-29 12:31:02“What is money?” sounds like a bit of a silly question. You’d probably hold up some cash or maybe flash your debit card. But I challenge you with this: imagine a 5-year-old asking you this question. How would you answer? If you showed them a $20 bill, they might respond with, “I know that’s a money, but what is it?” If you manage to explain that the bill is worth $20, they’re next question is going to be, “how many is your card?” How would you answer that? At some point you’d probably end up trying to distract them with something else while you worked to ignore the dread feeling that you should have those answers, but don’t. Never fear, for we will attempt to explain it in such a way that you’ll have an answer for 5, 15, 50, or 95-year-olds by the time we’re done this 4-part series!
Let’s start with an overview of the history of money. I highly recommend further reading on each of these; we’re going to skim most of them today. In the beginning, there was simple barter. If we each had something the other wanted, we could trade. But if the scale of what we want to trade is lopsided, say, chickens for a cow, or cows for a house, how do you make the trade work? Or what if you wanted to save up for a larger purchase? The answer is a placeholder; something that represents value in trade. An early example of this is the rai stones in Micronesia, which are essentially carved rocks. These worked well for store of value and medium of exchange, but not so much for unit of account. Precious metal coins arose later, with the most common being gold, silver, copper, and bronze. These worked well for all three of the major elements.
Store of value, medium of exchange, and unit of account are the three major elements of any system of money. Store of value means it holds its value well over time. If you put a gold coin in a box in your house and retrieve it 10 years later, it’s still a gold coin and should be in the same physical condition as it was when stored. Medium of exchange means it’s widely accepted for trade. This one is a bit trickier, but if you’re the Roman Empire you can simply make everyone accept denarius. Unit of account means units should hold the same value everywhere they’re used. This is similarly tricky, but if you’re the Dutch East India Company you can simply make VOC-stamped coins global denominations.
Renaissance-era Italy is where modern banking was born. A key concept invented during this time was the double-entry ledger, or double-entry bookkeeping system. In short, every transaction is recorded, and every transaction has two entries: one with an amount leaving an account, and one with the same amount going into a different account. At the end of every block of time all accounts will have an aggregate balance of 0, with individual accounts either having a credit or debit. This system is still in use today, as well as the broad use of credit notes in place of coins or direct trade. Credit notes could be written against an account and given in trade, and later the receiver could take the note to the bank, who would then record the transaction as complete. If this sounds familiar, that’s because modern cheques are the same thing.
Modern money systems take these concepts a step further. Banks now maintain a whole network of double-entry ledgers and in most countries banks are no longer required to hold reserves matching their credit notes issued. Credit notes are also the total physical currency, also known as a fiat currency, or currency by authority or decree. This essentially means fiat money has no intrinsic value other than the promise of the issuing authority to treat it as valid and the willingness of others to accept it in trade. For an example of “willingness to accept in trade”, many retail stores in Canada will accept American dollars even though they’re not required to.
If you’re now thinking, “thanks for the history lesson, but what does this mean to me and the payment terminal in my store?”, the answer will come 2 weeks from now when we cover the Canadian dollar. In the meantime if you want to learn a bit more about the systems our modern money is based on, read up on the Roman Empire and their currency, as well as that of the Dutch East India Company. If you really want to dive deep, Renaissance Italy’s banking systems are also fascinating and a little closer to us on the timeline.
-
 @ 30b99916:3cc6e3fe
2025-03-29 14:04:34
@ 30b99916:3cc6e3fe
2025-03-29 14:04:34
Chef's Notes
My mom worked as a waitress for a excellent Chinese restaurant. For years she tried to get this receipt without success and finally after the owner retired he gave her the receipt.
Previously posted this receipt on Zap.Cooking but now wanting to keep all my long-form notes in Obsidian and publish to Nostr using the nostr-writer plug-in.
Details
- ⏲️ Prep time: 20 to 30 minutes
- 🍳 Cook time: 1 to 2 Hours depending on amount of spare ribs
- 🍽️ Servings: 8
Ingredients
- 1 Quart Dole Pineapple Juice
- 1 Pint Dole Crushed Pineapple
- 1 Pint Dole Tidbits Pineapple
- 1 TS Dried Mustard
- 32 Oz Brown sugar or add to taste
- 1 Cup Red Wine
- 2 TS Corn Starch
- 1 or 2 lbs Pork or Beef spare ribs
- Worcestershire sauce
Directions
- Preheat oven to 350 degrees
- Bring water to boil in 8 qt stock pot
- Cut spare ribs and add to boiling water in stock pot
- Boil spare ribs for 20 to 30 minutes to remove excess fat
- Drain spare ribs and place onto cookie sheet
- Base spare ribs with a generous amount of Worcestershire sauce
- Place based spare ribs on cookie sheet and place into oven for 60 minutes.
- Place first 6 ingredients into stock pot and bring to boil while CONTINUOUSLY stirring
- Add corn starch to 2 cups of water and mix to create thickening agent
- Add thickening agent incrementally to Sweet & Sour sauce for desired thickness
- Reduce heat to low while CONTINUOUSLY stirring.
- Remove spare ribs from oven and place into Sweet & Sour sauce.
- Place stock pot into oven and cook until done. 1 to 2 hours.
Bon Appétit
-
 @ 65038d69:1fff8852
2025-03-29 12:28:24
@ 65038d69:1fff8852
2025-03-29 12:28:24We’ve all been in meetings that seem to be stuck in an unending loop of “discussions” going nowhere while simultaneously ratcheting up everyone’s emotions as the minutes past dinner continue to climb. You stand to leave as you reach your limit and declare, “It’s past my bedtime”. If only there was a way to make meetings more efficient!
The gold standard for meeting organization is “Robert’s Rules of Order”, the original having been published in 1876 and currently in it’s 12th edition (https://robertsrules.com). It’s quite the tome at over 800 pages, which makes sense given that it’s meant to be a complete procedural guide. If that feels like overkill for your 5-person weekly department check-in, there’s an “In Brief” edition available meant for just such cases. Our focus today will be less procedural and more on the squishy human side.
People are social creatures who generally prefer friendly conversation over stiff formalities. This will be your primary hurdle as left unstructured most meetings will migrate from handling business to visiting. My first recommendation is to intentionally schedule social time before and after the meeting. You may have seen this communicated as “doors open” and “doors close” times on event announcements. Or you can break the fourth wall and label it “social time”. Either way, explain its purpose to your attendees and make it clear that its optional. Most will appreciate having it; these meetings may be the only time they see each other, but for some its just business and they won’t want to feel pressured into awkward conversation.
Intentional social time is best paired with my next tip: begin the formal portion exactly at the advertised start time. This will encourage everyone to arrive on time (or ideally early), and might allow you to finish early. (Who doesn’t like that‽) If your attendees are used to a loose start time it might seem jarring at first, but if you break the fourth wall (again) and explain why you’re doing it, you shouldn’t have many arguments. If you have late arrivals, don’t interrupt the flow or pause to catch them up. Its their responsibility to arrive on time, and failing that its their responsibility to catch themselves up. Again, it won’t take long to normalize a hard start time. I also recommend advertising and sticking to a hard stop time as well. The nice thing about a stop time is that its only definite in one direction; you don’t have to stick to it if you’re done early. It’s primary purpose is to reassure everyone that the meeting won’t get drug out. Evening meeting attendees with young children at home will be especially grateful.
If this is starting to feel like a lot of details to keep track of, fear not, for there is a solution invented long ago: the formal meeting agenda! I’ve included a basic template below, but an internet search will provide a cornucopia of formats and options. My rule of thumb is the longer the meeting, the further in advance you should provide an agenda. As a starting point I aim for a week / 5 business days for any longer than an hour. You’ll also want to include any written reports and statements. This will be another item you may get some pushback on; many will be used to delivering verbal reports with very little prep. Written versions have several advantages (see my previous posts on the importance of writing things down, especially “Writing Things Down Is For Boys Too”), including giving attendees a chance to review and absorb the information before the meeting, keeping the reports concise, and making inclusion in the minutes much easier. I also like to include statements on old and new business items, which takes us into the next, and possibly most controversial, item.
Alongside social visiting, one of the biggest time-eaters in meetings is “discussion”. In my opinion (here comes the controversial part), meetings shouldn’t have discussions, only decisions and formalizations. All discussion should happen before the meeting. For example, let's say a new piece of equipment needs to be purchased, and an official vote is needed to do so. The next business meeting is not the place to discuss this. Options, pros and cons, bids or quotes, and most importantly, opinions and emotions surrounding the decision, should be hashed out and aired between stakeholders in an informal fashion on their own time. Billy and Sally don’t need to have a shouting match about the colour options while everyone else awkwardly stares at their shoes in the middle of the weekly stand-up. They can have their cat fight in the privacy of the HR office or at the local Timmies. I make a bit of an exception for what I call “statements”, though with tight controls. If Billy acquiesces to Sally’s demands to buy the blue model instead of the yellow one but still wants his oppositions known, he might be tempted to unleash a rant if, during the meeting, the chairperson says something like, “Anyone have any thoughts on this equipment purchase?” Chances of this happening are high for business items surrounded by high emotions, such as layoffs or budget cuts. This is where the statement can be a powerful tool to give everyone most of what they want. Have those who wish to create brief written statements. Your pitch to them is that it can be included in the agenda with all the other important business, everyone will see it (even those who can’t make it to the meeting), there’s no chance of their opinion being misrepresented, and it can easily be included in the minutes. You can optionally allow them to read their statement aloud during the meeting, but keep tight control on this. Again, emotions may be running high, and someone hearing their nemesis vocalize an opinion they disagree with may be enough to set them off. Make it clear that the statement will be read for the record, and no responses or discussion will follow, as discussion has already happened.
I’ve mentioned the chairperson a few times. This person should be, without question, in control. They should have absolute dictatorial power over the meeting, and importantly, over who has permission to speak. Anyone who disagrees with this power can be asked to leave. It sounds harsh, but a meeting without a human “talking stick” will fall to those without the social awareness to refrain from interrupting, or those willing to be the loudest. Have the chairperson wield their omnipotence for the good of the people.
Need help with planning or executing your meetings? You can find us at scalebright.ca.
``` Example Meeting Agenda: Meeting Title Organization / Team / Group Name Meeting Date, Start Time, and Stop Time Meeting Location Chairperson Participants / Invitees
Order of Business: Call to Order / Start Approval of previous minutes Approval of reports Old business New business Adjournment
Appendices: A: Previous Minutes B: Report 1 C: Statement from John Doe on Business Item 1 D: Quote for Business Item 2 ```
-
 @ 6f7db55a:985d8b25
2025-02-14 21:23:57
@ 6f7db55a:985d8b25
2025-02-14 21:23:57This article will be basic instructions for extreme normies (I say that lovingly), or anyone looking to get started with using zap.stream and sharing to nostr.
EQUIPMENT Getting started is incredibly easy and your equipment needs are miniscule.
An old desktop or laptop running Linux, MacOs, or Windows made in the passed 15yrs should do. Im currently using and old Dell Latitude E5430 with an Intel i5-3210M with 32Gigs of ram and 250GB hard drive. Technically, you go as low as using a Raspberry Pi 4B+ running Owncast, but Ill save that so a future tutorial.
Let's get started.
ON YOUR COMPUTER You'll need to install OBS (open broaster software). OBS is the go-to for streaming to social media. There are tons of YouTube videos on it's function. WE, however, will only be doing the basics to get us up and running.
First, go to https://obsproject.com/

Once on the OBS site, choose the correct download for you system. Linux, MacOs or Windows. Download (remember where you downloaded the file to). Go there and install your download. You may have to enter your password to install on your particular operating system. This is normal.
Once you've installed OBS, open the application. It should look something like this...

For our purposes, we will be in studio mode. Locate the 'Studio Mode' button on the right lower-hand side of the screen, and click it.

You'll see the screen split like in the image above. The left-side is from your desktop, and the right-side is what your broadcast will look like.
Next, we go to settings. The 'Settings' button is located right below the 'Studio Mode" button.

Now we're in settings and you should see something like this...

Now locate stream in the right-hand menu. It should be the second in the list. Click it.

Once in the stream section, go to 'Service' and in the right-hand drop-down, find and select 'Custom...' from the drop-down menu.

Remeber where this is because we'll need to come back to it, shortly.
ZAPSTREAM We need our streamkey credentials from Zapstream. Go to https://zap.stream. Then, go to your dashboard.

Located on the lower right-hand side is the Server URL and Stream Key. You'll need to copy/paste this in OBS.

You may have to generate new keys, if they aren't already there. This is normal. If you're interested in multi-streaming (That's where you broadcast to multiple social media platforms all at once), youll need the server URL and streamkeys from each. You'll place them in their respective forms in Zapstream's 'Stream Forwarding" section.

Use the custom form, if the platform you want to stream to isn't listed.
*Side-Note: remember that you can use your nostr identity across multiple nostr client applications. So when your login for Amethyst, as an example, could be used when you login to zapstream. Also, i would suggest using Alby's browser extension. It makes it much easier to fund your stream, as well as receive zaps. *
Now, BACK TO OBS... With Stream URL and Key in hand, paste them in the 'Stream" section of OBS' settings. Service [Custom...] Server [Server URL] StreamKey [Your zapstream stream key]

After you've entered all your streaming credentials, click 'OK' at the bottom, on the right-hand side.
WHAT'S NEXT? Let's setup your first stream from OBS. First we need to choose a source. Your source is your input device. It can be your webcam, your mic, your monitor, or any particular window on your screen. assuming you're an absolute beginner, we're going to use the source 'Window Capture (Xcomposite)'.

Now, open your source file. We'll use a video source called 'grannyhiphop.mp4'. In your case it can be whatever you want to stream; Just be sure to select the proper source.

Double-click on 'Window Capture' in your sources list. In the pop-up window, select your file from the 'Window' drop-down menu.


You should see something like this...

Working in the left display of OBS, we will adjust the video by left-click, hold and drag the bottom corner, so that it takes up the whole display.

In order to adjust the right-side display ( the broadcast side), we need to manipulate the video source by changing it's size.

This may take some time to adjust the size. This is normal. What I've found to help is, after every adjustment, I click the 'Fade (300ms)' button. I have no idea why it helps, but it does, lol.

Finally, after getting everything to look the way you want, you click the 'Start Stream' button.

BACK TO ZAPSTREAM Now, we go back to zapstream to check to see if our stream is up. It may take a few moments to update. You may even need to refresh the page. This is normal.
 STREAMS UP!!!
STREAMS UP!!!A few things, in closing. You'll notice that your dashbooard has changed. It'll show current stream time, how much time you have left (according to your funding source), who's zapped you with how much theyve zapped, the ability to post a note about your stream (to both nostr and twitter), and it shows your chatbox with your listeners. There are also a raid feature, stream settings (where you can title & tag your stream). You can 'topup' your funding for your stream. As well as, see your current balance.
You did a great and If you ever need more help, just use the tag #asknostr in your note. There are alway nostriches willing to help.
STAY AWESOME!!!
npub: nostr:npub1rsvhkyk2nnsyzkmsuaq9h9ms7rkxhn8mtxejkca2l4pvkfpwzepql3vmtf
-
 @ 30b99916:3cc6e3fe
2025-03-29 13:57:26
@ 30b99916:3cc6e3fe
2025-03-29 13:57:26
Chef's Notes
My mom worked as a waitress for a excellent Chinese restaurant. For years she tried to get this receipt without success and finally after the owner retired he gave her the receipt.
Previously posted this receipt on Zap.Cooking but now wanting to keep all my long-form notes in Obsidian and publish to Nostr using the nostr-writer plug-in.
Details
- ⏲️ Prep time: 20 to 30 minutes
- 🍳 Cook time: 1 to 2 Hours depending on amount of spare ribs
- 🍽️ Servings: 8
Ingredients
- 1 Quart Dole Pineapple Juice
- 1 Pint Dole Crushed Pineapple
- 1 Pint Dole Tidbits Pineapple
- 1 TS Dried Mustard
- 32 Oz Brown sugar or add to taste
- 1 Cup Red Wine
- 2 TS Corn Starch
- 1 or 2 lbs Pork or Beef spare ribs
- Worcestershire sauce
Directions
- Preheat oven to 350 degrees
- Bring water to boil in 8 qt stock pot
- Cut spare ribs and add to boiling water in stock pot
- Boil spare ribs for 20 to 30 minutes to remove excess fat
- Drain spare ribs and place onto cookie sheet
- Base spare ribs with a generous amount of Worcestershire sauce
- Place based spare ribs on cookie sheet and place into oven for 60 minutes.
- Place first 6 ingredients into stock pot and bring to boil while CONTINUOUSLY stirring
- Add corn starch to 2 cups of water and mix to create thickening agent
- Add thickening agent incrementally to Sweet & Sour sauce for desired thickness
- Reduce heat to low while CONTINUOUSLY stirring.
- Remove spare ribs from oven and place into Sweet & Sour sauce.
- Place stock pot into oven and cook until done. 1 to 2 hours.
Bon Appétit
-
 @ 592295cf:413a0db9
2025-03-29 10:59:52
@ 592295cf:413a0db9
2025-03-29 10:59:52The journey starts from the links in this article nostr-quick-start-guide
Starting from these links building a simple path should not cover everything, because impossible.
Today I saw that Verbiricha in his workshop on his channel used nstart, but then I distracted And I didn't see how he did it.
Go to nstart.me and read: Each user is identified by a cryptographic keypair Public key, Private key (is a lot of stuff)
You can insert a nickname and go, the nickname is not unique
there is a email backup things interesting, but a little boring, i try to generate an email
doesn't even require a strong password ok.
I received the email, great, it shows me the nsec encrypted in clear,
Send a copy of the file with a password, which contains the password encrypted key I know and I know it's a tongue dump.
Multi signer bunker
That's stuff, let's see what he says.
They live the private key and send it to servers and you can recompose it to login at a site of the protocol nostr. If one of these servers goes offline you have the private key that you downloaded first and then reactivate a bunker. All very complicated. But if one of the servers goes offline, how can I remake the split? Maybe he's still testing.
Nobody tells you where these bunkers are.
Okay I have a string that is my bunker (buker://), I downloaded it, easy no, now will tell me which client accepts the bunker.. .
Follow someone before you start?
Is a cluster of 5 people Snowden, Micheal Dilger, jb55, Fiatjaf, Dianele.
I choice Snowden profile, or you can select multiple profiles, extra wild.
Now select 5 clients
Coracle, Chachi, Olas, Nostur, Jumble
The first is Coracle
Login, ok I try to post a note and signing your note the spin does not end.
Maybe the bunker is diffective.
Let's try Chachi
Simpler than Coracle, it has a type login that says bunker. see if I can post
It worked, cool, I managed to post in a group.
Olas is an app but also a website, but on the website requires an extension, which I do not have with this account.
If I download an app how do I pass the bunker on the phone, is it still a password, a qrcode, a qrcode + password, something like that, but many start from the phone so maybe it's easy for them. I try to download it and see if it allows me to connect with a bunker.
Okay I used private-qrcode and it worked, I couldn't do it directly from Olas because it didn't have permissions and the qrcode was < encrypted, so I went to the same site and had the bunker copied and glued on Olas
Ok then I saw that there was the qrcode image of the bunker for apps lol moment
Ok, I liked it, I can say it's a victory.
Looks like none of Snowden's followers are Olas's lover, maybe the smart pack has to predict a photographer or something like that.
Okay I managed to post on Olas, so it works, Expiration time is broken.
As for Nostur, I don't have an ios device so I'm going to another one.
Login with Jumble, it works is a web app
I took almost an hour to do the whole route.
But this was just one link there are two more
Extensions nostr NIP-07
The true path is nip-07-browser-extensions | nostr.net
There are 19 links, maybe there are too many?
I mention the most famous, or active at the moment
- Aka-profiles: Aka-profiles
Alby I don't know if it's a route to recommend
-
Blockcore Blockcore wallet
-
Nos2x Nos2x
-
Nos2xfox (fork for firefox) Nos2xfox
Nostore is (archived, read-only)
Another half hour to search all sites
Nostrapps
Here you can make paths
Then nstart selects Coracle, Chachi, Olas,Nostur and Jumble
Good apps might be Amethyst, 0xchat, Yakihonne, Primal, Damus
for IOS maybe: Primal, Olas, Damus, Nostur, Nos-Social, Nostrmo
On the site there are some categories, I select some with the respective apps
Let's see the categories
Go to Nostrapps and read:
Microbbloging: Primal
Streaming: Zap stream
Blogging: Yakihonne
Group chat: Chachi
Community: Flotilla
Tools: Form *
Discovery: Zapstore (even if it is not in this catrgory)
Direct Message: 0xchat
-
 @ 3514ac1b:cf164691
2025-03-29 18:55:29
@ 3514ac1b:cf164691
2025-03-29 18:55:29Cryptographic Identity (CI): An Overview
Definition of Cryptographic Identity
Cryptographic identity refers to a digital identity that is secured and verified using cryptographic techniques. It allows individuals to prove their identity online without relying on centralized authorities.
Background of Cryptographic Identity
Historical Context
- Traditional identity systems rely on centralized authorities (governments, companies)
- Digital identities historically tied to platforms and services
- Rise of public-key cryptography enabled self-sovereign identity concepts
- Blockchain and decentralized systems accelerated development
Technical Foundations
- Based on public-key cryptography (asymmetric encryption)
- Uses key pairs: private keys (secret) and public keys (shareable)
- Digital signatures provide authentication and non-repudiation
- Cryptographic proofs verify identity claims without revealing sensitive data
Importance of Cryptographic Identity
Privacy Benefits
- Users control their personal information
- Selective disclosure of identity attributes
- Reduced vulnerability to mass data breaches
- Protection against surveillance and tracking
Security Advantages
- Not dependent on password security
- Resistant to impersonation attacks
- Verifiable without trusted third parties
- Reduces centralized points of failure
Practical Applications
- Censorship-resistant communication
- Self-sovereign finance and transactions
- Decentralized social networking
- Cross-platform reputation systems
- Digital signatures for legal documents
Building Cryptographic Identity with Nostr
Understanding Nostr Protocol
Core Concepts
- Nostr (Notes and Other Stuff Transmitted by Relays)
- Simple, open protocol for censorship-resistant global networks
- Event-based architecture with relays distributing signed messages
- Uses NIP standards (Nostr Implementation Possibilities)
Key Components
- Public/private keypairs as identity foundation
- Relays for message distribution
- Events (signed JSON objects) as the basic unit of data
- Clients that interface with users and relays
Implementation Steps
Step 1: Generate Keypair
- Use cryptographic libraries to generate secure keypair
- Private key must be kept secure (password managers, hardware wallets)
- Public key becomes your identifier on the network
Step 2: Set Up Client
- Choose from existing Nostr clients or build custom implementation
- Connect to multiple relays for redundancy
- Configure identity preferences and metadata
Step 3: Publish Profile Information
- Create and sign kind 0 event with profile metadata
- Include displayable information (name, picture, description)
- Publish to connected relays
Step 4: Verification and Linking
- Cross-verify identity with other platforms (Twitter, GitHub)
- Use NIP-05 identifier for human-readable identity
- Consider NIP-07 for browser extension integration
Advanced Identity Features
Reputation Building
- Consistent posting builds recognition
- Accumulate follows and reactions
- Establish connections with well-known identities
Multi-device Management
- Secure private key backup strategies
- Consider key sharing across devices
- Explore NIP-26 delegated event signing
Recovery Mechanisms
- Implement social recovery options
- Consider multisig approaches
- Document recovery procedures
Challenges and Considerations
Key Management
- Private key loss means identity loss
- Balance security with convenience
- Consider hardware security modules for high-value identities
Adoption Barriers
- Technical complexity for average users
- Network effects and critical mass
- Integration with existing systems
Future Developments
- Zero-knowledge proofs for enhanced privacy
- Standardization efforts across protocols
- Integration with legal identity frameworks
-
 @ 65038d69:1fff8852
2025-03-29 12:24:26
@ 65038d69:1fff8852
2025-03-29 12:24:26“Technology never changes” sounds insane, doesn’t it? Of course it changes! Far too fast! New models of smartphones, laptops, refrigerators, cars, and toasters every year! And that’s just hardware; software and the internet move even faster. Every time you open your social media app of choice you’re greeted with a new thing to figure out. But under the hood of version 999 of all these newfangled widgets, they’re all the same as they’ve ever been, because technology never changes.
Does that still sound crazy to you? Excellent! That means I have you hooked for the rest of this article! All humour aside, when I say, “technology never changes”, I’m talking about the underlying concepts, how we use technology, and on the organization side, how we plan for it. That last one will be our focus today. The tech strategies I help organizations implement haven’t changed since I started in tech, and my predecessors would probably mirror the same, especially since they’re the ones I learned these concepts from.
Let’s dive in. If you’ve been involved in vehicle fleet management this first one will be familiar. For technology hardware there’s a concept called an “evergreen program”, which is essentially a schedule of when hardware is cycled or replaced. End-user hardware such as laptops, desktops, and smartphones is 3 years, servers is 6, wired network elements are 9, and wireless (mostly access points) is 6. These numbers aren’t written in stone or the same for every org; they’re just meant to be a starting point. But here's the big secret: most of this equipment, if it’s business-grade, properly maintained, and treated well, will last at least 10 years. The reason for the comparatively short evergreen cycles is two-fold: downtime can be more expensive than replacing equipment, and replacing equipment is usually a tough sell and put off as long as possible regardless of programs or policy. That’s an article all by itself; lets move along for now. Those evergreen program and lifetime numbers haven’t changed. Sure there’s a new Macbook every year and your cousin’s buddy who makes 7 figures working for a California design firm gets them on release day, but those are the exception. Your 5-person non-profit is going to replace laptops on double cycles based on tech strategy that hasn’t changed. Because technology never changes.
I mentioned software earlier and that it moves even faster. While this is true, tech strategy around it hasn’t changed. I’ll use the ubiquitous Microsoft Windows and Microsoft Office suite as examples. New major versions used to release roughly every 3 years. If you’re replacing your laptops and desktops on a 3 year cycle, you never really have to worry about upgrading Windows or Office separately. Today Microsoft has migrated most of their products to a subscription model, but the cycle is the same. Because technology never changes.
But what about AI? Isn’t it quadrupling in power every few minutes? Hasn’t it used the energy of a thousand suns to drink the oceans dry in order to feed it’s insatiable quantum-powered hunger for knowledge and control? No, it hasn’t. In fact, if news articles are to be believed; ChatGPT et al. have run up against a bit of a wall. My prediction is that we’ll start seeing AI in more common usage sometime late this year, which, not-so-coincidentally, will be about 3 years since it’s public release. Because technology never changes.
-
 @ 2fb77d26:c47a6ee1
2025-02-11 08:03:12
@ 2fb77d26:c47a6ee1
2025-02-11 08:03:12Intensiv! Das trifft es wohl am besten. Denn müsste ich das Jahr 2024 mit einem einzigen Wort charakterisieren, beschriebe kein anderes es besser. Atemlos, anstrengend, aufreibend, überraschend, lehrreich, unterhaltsam, erhebend und beglückend wären Adjektive, die in der Retrospektive ebenfalls Erwähnung finden könnten. Zum Glück. Gibt es doch kaum etwas Frustrierenderes als Eintönigkeit. Als stupide Routinen. So viel Sicherheit diese im wochentäglichen Trott versprechen, so viel Leere generieren sie, betrachtet man das Hamsterrad des Alltags über den Wochenhorizont hinaus. Dementsprechend heiter stimmt es mich, dass die vergangenen zwölf Monate das absolute Gegenteil von Routine waren und ich nun im Rückblick dartun darf, manch ein Husarenstück vollbracht zu haben.
»Damit das Mögliche entsteht, muss immer wieder das Unmögliche versucht werden«, hielt Hermann Hesse dereinst fest.
Diesem Gedanken folgend eröffnete ich das neue Jahr damit, ein ganzes Haus nahezu im Alleingang zu renovieren. Baustelle. Drei Monate lang. Oft bis zu 18 Stunden am Tag. Staub, Lärm, Farbe, Spachtel, Litzen, zerschundene Hände, schmerzende Glieder und verschlissene Kleidung. Von der Silikonfuge im hintersten Eck des Kellers bis zur Montagearbeit unter dem Dachbalken. Ob Steckdosen, Sockelleisten oder Fensterrahmen, Verkabelung, Inneneinrichtung oder Fassadenfarbe – ich hatte mir vorgenommen, dem viele hundert Jahre alten Gemäuer eine Generalüberholung angedeihen zu lassen. Als ich Anfang April unser farbenfroh-freiheitliches Hauswappen neben dem Eingang montierte und unserer neuen Unterkunft damit ihren Namen gab – »Casa Libre« –, war das ein großartiges Gefühl. Denn meinen mehr als ambitionierten Zeitplan hielt selbst ich im Januar noch für relativ utopisch.
Parallel dazu habe ich im Januar meine »Truman Show« fertiggestellt, das Cover überarbeitet und kurzfristig den Vertrieb gewechselt, weil es beim bisherigen Anbieter scheinbar nicht gern gesehen war, dass ich mich in besagtem Buch mit den dunklen Machenschaften von Menschenhändlern und Kinderschändern befasse.
Als die Anthologie im Februar erschien, musste diese natürlich auch medial beworben werden – während gleichzeitig die Vorarbeiten für die Printpublikation GEGENDRUCK Fahrt aufnahmen. Ab April sollten nach wochenlanger Abstinenz endlich auch wieder neue Texte auf meinem Blog erscheinen. Mich juckte es bereits in den Fingern. Unterdes wollte jedoch auch das Leben in der vorherigen Bleibe abgebaut, verpackt und transportiert werden, damit es ab April in den frisch gestrichenen vier Wänden des neuen Zuhauses wieder ausgepackt, aufgebaut und in Betrieb genommen werden konnte. Gut sortierte Bücher- und Plattensammlungen machen das ob ihres schieren Gewichts zu einer ganz besonderen Freude.
Dass ich nach über zehn Jahren Apple-Nutzung die private IT umgestellt, die Cloud gelöscht und Unmengen an Daten migriert, ein neues, überwachungsfreies Smartphone eingerichtet, verschiedene juristische Scharmützel bewältigt, diverse Texte verfasst und eine Vielzahl an Gesprächen geführt habe, an mehreren Konferenzen beteiligt, für verschiedene Projekte Dritter tätig, familiär gut eingespannt, obendrein einem Konzentration fordernden Vollzeitjob mit zunehmenden Verantwortlichkeiten verpflichtet war und diese Aufzählung nur einen kleinen Teil meiner Aktivitäten umfasst, sei dabei nur am Rande erwähnt.
Damit auch während des Sommerlochs keine Langeweile aufkommt, begann ich bereits im Frühjahr 2024 mit der Planung für eine Lese- und Vortragsreise. Gut zwanzig Termine wollten mit den Veranstaltern koordiniert werden. Es galt, Routenplanung, Hotelbuchungen, Reiselogistik, Buchbestand, Kommunikation und eine mit Quellen unterlegte Präsentation zu organisieren. Kaum war all das in trockenen Tüchern, saß ich bereits im Flugzeug nach Kolumbien, wo ich den Juli für Regeneration und Literaturrecherche nutzen wollte. Aber weil Leben nun mal ist, was passiert, während man plant, stellte Unvorhergesehenes die Improvisationsfähigkeit auch dort regelmäßig auf die Probe. Meer und Dschungel taten dennoch ihr Übriges und ließen die Irritationen des zivilisatorischen Alltags in ihrer relativen Belanglosigkeit verblassen.
Drei Wochen nach meiner Rückkehr ins Tessin waren sie allerdings zurück. Die Arbeit holte mich ein, diverse Projekte und ehrenamtliche Engagements warteten auf Input, die nackten Wände der neue Bleibe wollten dekoriert und das neue Tonstudio arrangiert werden – und ehe ich mich versah, ging es auch schon auf Tour. Gut 500 Kilogramm an Büchern und Gepäck waren verladen und mussten circa 6.000 Kilometer durch die Schweiz, Deutschland und Österreich chauffiert werden. Volle Säle und mehrere tausend offenherzige Menschen machten diese Reise zu einem ganz besonderen Erlebnis. Selbst das bis zum Sommer mehrheitlich miserable Wetter meinte es gut mit mir. Denn in den drei Wochen auf Tour regnete es nur ein einziges Mal. Am letzten Tag. Ansonsten waren mir strahlende Sonne, hochsommerliche Temperaturen und das ein oder andere Mittagsschläfchen im Schatten alter Bäume vergönnt.
Als ich der letzten Station meiner Rundreise den Rücken kehrte, verabschiedete sich auch die warme Jahreszeit. Auf der Heimfahrt über die Alpen begegneten mir die Vorboten eines goldenen Oktobers: eine tieferstehende Sonne über den Bergrücken, die goldene Stunde kürzer werdender Tage und der auffrischende Wind am Abend, der die an Farbenpracht zulegenden Wälder der Tessiner Topografie ins Wogen brachte. Wenige Wochen später fiel in den Alpen der erste Schnee. Jetzt schimmern die weißen Gipfel am Horizont in der wärmenden Wintersonne. Und ich sitze wieder an meinem Fenster, lasse den Blick über die geheimnisvoll anmutende Vegetationsdichte des Umlands schweifen und schreibe ein Vorwort. Für Buch Nummer fünf.
Es fällt etwas dünner aus, enthält nicht so viele philosophische Betrachtungen, Zitate und rhetorische Extravaganzen wie seine beiden Vorgänger. Leider. Denn das Sortieren der Gedanken, Quellen und Paragrafen im Rahmen der Textarbeit schält seltene Stunden innerer Ruhe aus den von Pflichten und Routinen dominierten Strukturen des Tages. Gerne hätte ich inmitten der organisatorischen Turbulenzen des vergangenen Jahres häufiger die Zeit gefunden, Beiträge zu verfassen – es gäbe so viel zu sagen, so viel zu dokumentieren, um den volatilen Konturen der Zeitenwende Schärfe zu verleihen. Und das erscheint dieser Tage nötiger denn je.
Denn da draußen tobt der Wahnsinn. Die Polykrise. Das Chaos – als Steigbügelhalter für das finale Kapitel eines transgenerationalen Klassenkampfes von oben. Für Technokratie und Plattformfaschismus. Doch »auch aus Steinen, die Dir in den Weg gelegt werden, kannst Du etwas Schönes bauen«, bemerkte Erich Kästner. Ohne Kontext und Hintergrundinformationen, die das Individuum in die Lage versetzen, die Schlachtfelder des wilder werdenden Informationskriegs mit einer gewissen Gelassenheit zu überblicken, gerät es jedoch leicht zum Opfer der unerbittlich keifenden Propagandamaschine wertewestlicher Demokratiedarstellung.
Ja, die Truman Show läuft wohl auch im fünften Jahr n. C. (nach Corona) auf allen Kanälen. Auf allen Frequenzen. Und der Homo demens spielt mit suizidaler Leichtfertigkeit seine ihm zugedachte Rolle als irrlichternder Kamikaze-Pilot, der sich in Rage auf das eigene Schiff zu stürzen gedenkt. Die zeitgeistig flexiblen Herrschaftseliten, die sich nun zusehends konservativ gerieren, anstatt Wokeness zu predigen, nesteln derweil hektisch an den letzten Zierpalisaden des digitalen Gulag. Der Rohbau steht ja auch schon eine ganze Weile. Bunt soll es sein – und spätestens 2030 bezugsfertig übergeben werden.
Ob eID, elektronische Patientenakte, digitales Geld, lückenlose Massenüberwachung, algorithmisierte Zensur, Dekarbonisierungsagenda, Enteignungslegislatur, kognitive Kriegsführung im Hosentaschenformat, Geofencing-Gewahrsam, Nanobots oder Frequenzfelder zu deren Kalibrierung: alles einsatzbereit. Schon 1999 veröffentlichte das US-Militär ein Dokument namens »Owning the Weather 2025«, das beschreibt, wie artifizieller Nebel verwendet werden kann, um Nanopartikel in Ballungszentren einzusetzen. Zwei Jahre später schlugen interne Präsentationen der NASA in die gleiche Kerbe. Jetzt ist 2025. Und Berichte über chemikalienhaltigen Nebel, der Krankheitssymptome verursacht, machen die Runde.
Wir sind angekommen. Der »Pakt für die Zukunft« ist geschlossen. Das Blau des Himmels einem persistent milchigen Grau gewichen. Noch am Heiligabend hat die UN-Generalversammlung Kernelemente des entsprechendes Vertragswerkes ratifiziert. Ohne nennenswerten Widerstand. Cloward-Piven-Strategie und Kulturmarxismus sei Dank. Die Revolution von oben war bis dato also ziemlich erfolgreich. Nur Max Mustermann weiß noch nichts vom seinem Glück.
Illuminiert wird die Installation des biometrischen Kontroll-Grids von einem Flammenmeer im Nahen Osten. Von brennenden Krankenhäusern, Kirchen und Kindern. Menschenrechte sind passé. Der beispiellose Genozid in Gaza wird von den NATO-Medien in verachtenswerter Manier schöngeschrieben, während von den USA trainierte, ausstaffierte, radikalislamische Fanatiker Syrien nahezu widerstandslos kapern. Ein Land, das seit Langem auf der To-do-Liste des militärisch-industriellen Komplexes stand. Die fortschreitende Destabilisierung der Region bereitet zionistischen Hardlinern in Tel Aviv und Washington die Bühne für den heiß ersehnten Krieg gegen den Iran.
Europäische Metropolen erodieren, die Bevölkerung verarmt, Reproduktionsraten sinken auf Rekordtiefstände, bei der NATO drängt man auf Eskalation mit Russland, und China intensiviert seine Drohgebärden im Indopazifik. Der militärische Fleischwolf dreht sich immer schneller. Es herrscht dicke Luft. Überall. Man riecht das Schießpulver. Denn das angloamerikanische Imperium ruft zum letzten Gefecht. Es ist – wie ich bereits im Vorspann der Truman Show schrieb – das letzte Aufbäumen eines moribunden Machtapparats. Charakterisiert von zunehmender Gewalt. Auf Kosten aller. Es lässt sich kaum seriös prognostizieren, wann es knallt, oder wie laut – dass es massiver Disruption bedarf, um diese Revolution von oben fristgerecht umzusetzen und speziell Kontinentaleuropa einen hohen Preis für seine willfährige Komplizenschaft bezahlen wird, allerdings schon.
Dabei erkannte schon Romain Rolland, dass »das schlimmste Übel, an dem die Welt leidet, nicht die Stärke der Bösen, sondern die Schwäche der Guten ist«.
Während sich also vor meinem Fenster die Sonne ein letztes Mal für dieses Jahr dem Ringen mit der Dunkelheit ergibt, Palmen, Koniferen und Zypressen vor einem goldgelb, dann violett glühenden Himmel zu schwarzen Scherenschnitten mutieren, erscheinen auch die Umrisse des vor uns liegenden Weges undeutlicher, die Zukunft ungewisser, unmenschlicher – ja unerreichbarer denn je. Als sei sie auf der Flucht.
Und eine Vielzahl derjenigen, die vorgeben, sie zu hehren Zwecken einfangen zu wollen, die Kritiker, Oppositionellen und Widerständler, drehen sich nicht minder schnell im Kreis als ihre Widersacher im leitmedialen Konsenskomplex. Denn im Kern tun beide Lager das Gleiche: Sie debattieren Sinnfetzen und Argumentationsfragmente, die man ihnen aus Orifizen weit oben im Elfenbeinturm oder verspiegelten Panzerglasfenstern polierter Luxuslimousinen vor die Füße wirft. Für viele ist Systemkritik zum profanen Geschäftsmodell geworden. Zum Event. Da bleibt wenig Zeit für echten Widerstand. Oder Charakter. Wer den Medienzirkus zu seinem Broterwerb gemacht hat, ist davon abhängig, dass er sich auszahlt. Und das von alternativmedialen Generika angefixte Publikum will genauso unterhalten werden wie der Zuschauer des Morgenmagazins. Brot und Spiele eben – egal, in welcher Arena die Schaukämpfe veranstaltet werden. Das Publikum schaut stoisch in die Röhre. Oder auf das Display. Hauptsache, das Spektakel lässt sich bequem vom Sofa aus verfolgen.
Hans-Joachim Kulenkampff gab schon vor Jahrzehnten zu verstehen, dass »die Leute gar nicht so dumm sind, wie wir sie durchs Fernsehen noch machen werden«. Er hatte recht. Die Revolution wird also wohl noch eine Weile auf sich warten lassen. Schade. Denn genau dafür engagiere ich mich – für eine friedliche Revolution des Geistes. Für eine zweite Aufklärung. Für eine Zukunft, in der es Liebe, Wahrheit und Selbstbestimmung sind, nach denen meine Mitmenschen streben. Bleibt zu hoffen, dass sich die Ascheschichten, aus welchen sich der Phoenix dieser zweiten Aufklärung irgendwann in den Himmel schwingen muss, vorher nicht allzu hoch auftürmen.
Nun will ich den Leser nicht mit all diesen persönlich gefärbten Annotationen und Gefühlsduseleien belästigen, um mich zu profilieren, sondern weil ein Jahr wie 2024 beweist – zumindest mir selbst –, dass man auch ganz allein Berge versetzen kann. Dass es nicht von äußeren Umständen, Dritten und Kapital abhängt, ob man Ziele erreicht. Dass man selbst der Phoenix sein kann. Jeder von uns. Wo ein Wille, da ein Weg. Aber beschreiten muss man ihn. Auch dann, wenn der Kompass temporär seinen Dienst versagt. Denn Routen entstehen nur dort, wo man sie geht. Und der Kurs lässt sich auch dann noch justieren, wenn man unterwegs ist. »Learning by doing« – nur so kommt man voran. Nur so schafft man Unabhängigkeit und Vertrauen in die eigenen Fähigkeiten. Fehler passieren ja nicht, um uns von etwas abzuhalten, sondern um uns auf den nächsten Versuch vorzubereiten. Sie sind ein Angebot, zu lernen. Und nur, wenn man der Welt ein Angebot machen kann, darf man darauf hoffen, dass es angenommen wird.
Womit wir beim Titel der vorliegenden Publikation angekommen wären: »Hopium« – ein Kompositum aus »Hope«, englisch für Hoffnung, und Opium, dem durch Anritzen seiner unreifen Samenkapseln gewonnenen, getrockneten Milchsaft des Schlafmohns. Ein Rauschmittel. Basis des 1898 von Bayer markenrechtlich geschützten Morphin-Derivates Heroin. »Hopium« ist ein Neologismus – geprägt oder zumindest populär gemacht von James Corbett –, den ich in meinen Texten immer wieder gerne verwende, weil er wie kaum ein anderer auf den Punkt bringt, was Etatisten dazu bewegt, an das System Staat zu glauben: der Rausch der Hoffnung. Darauf, dass der nächste Kanzler, Präsident oder Premierminister es endlich richten wird. Oder diese eine neue Partei.
Der in regelmäßigem Turnus enttäuschte Irrglaube an die Selbstheilungskräfte eines auf Despotie ausgelegten Herrschaftssystems gleicht einer Sucht. Einer sehr destruktiven Sucht. Denn obwohl sich die Bevölkerung zumindest unterbewusst darüber im Klaren sein dürfte, dass sich auch nach dem nächsten Urnengang nichts ändern wird, dass ihr diese in devoter Pose dargebrachte Verehrung von Götzen schadet, dass sie an einer Art Stockholm-Syndrom leidet, wenn sie unterstützt, was sie beraubt, unterdrückt und tötet, tut sie es wieder. Immer wieder.
Aldous Huxley wusste, wovon er sprach, als er notierte, dass »der Glaube an eine größere und bessere Zukunft einer der mächtigsten Feinde gegenwärtiger Freiheit ist«.
Nun ist Hoffnung aber nicht per se negativ – und Hopium somit als durchaus ambivalenter Begriff zu werten. Treibt die Hoffnung doch auch mich dazu, immer wieder Wege zu suchen, um Menschen zu erreichen, Konstruktives beizutragen und die Welt in meinem Einflussbereich ein wenig besser zu machen. Sie besser informiert zu hinterlassen. Sähe ich unsere Situation als chancenlos, hätte ich den Glauben an Liebe und Wahrheit, oder die Hoffnung auf bessere Zeiten aufgegeben, gäbe es dieses Buch nicht.
Der Unterschied zwischen einem Etatisten und mir besteht darin, dass ich nicht darauf hoffe und warte, dass mir jemand diese Arbeit abnimmt. Ich delegiere nicht, gebe die Verantwortung für mein Leben nicht aus der Hand, sondern nehme sie wahr. Werde aktiv. Mein Glaube an »Volksvertreter«, Erlöser und Idole erlosch vor über drei Jahrzehnten. Seitdem verlasse ich mich nur noch auf eine einzige Person – mich selbst – und gebe mir redlich Mühe, mich dabei nicht zu enttäuschen, sondern zu beeindrucken.
Ob andere Menschen gut finden, was ich mit meiner knapp bemessenen Lebenszeit anstelle, ist mir egal. Es ist mein Leben. Ich habe nur eines. Zumindest aller Wahrscheinlichkeit nach. Und der Einzige, dem es gefallen muss, bin ich.
»Die einen kennen mich, die anderen können mich«, wie Le Cercle-Gründungsmitglied Konrad Adenauer treffend polterte. Das ist Freiheit. Und die steht nirgends zur Wahl. Wird nicht angeboten. Sie hängt nicht von äußeren Umständen ab, wird nicht gewährt oder erkämpft. Frei wird man nicht – frei ist man. Oder eben nicht.
Ich hoffe – das ist meine tägliche Dosis »Hopium« –, dass meine Arbeit anderen Menschen hilft, das zu erkennen.
Denn das Versäumnis von gestern ist das täglich Brot von morgen, die Gegenwart die Vergangenheit der Zukunft. Und es ist an uns, etwas daraus zu machen. »Man muss die Zukunft abwarten und die Gegenwart genießen – oder ertragen«, soll Wilhelm von Humboldt gesagt haben. Ich habe mich intuitiv immer für den Genuss entschieden und bin überzeugt, dass dieser Ansatz eine gute Ausgangsposition ist, um dem in absehbarer Zeit Orkanstärke erreichenden Sturm der Zeit die Stirn zu bieten.
Frei nach Edward Snowden: »Sei nicht ängstlich – sondern vorbereitet«.
Weiter geht's im Buch ...
-
 @ b8af284d:f82c91dd
2025-02-09 18:48:21
@ b8af284d:f82c91dd
2025-02-09 18:48:21Liebe Abonnenten,
viele von uns erleben im privaten wie im öffentlichen Leben gerade eine Zeit der Verwirrung und Irritation. Etwas scheint im Umbruch, alte Gewissheiten, Strukturen und Allianzen scheinen sich vor unseren Augen aufzulösen. Trump, Musk und Thiel wirken wie die Abrissbirnen einer alten Ordnung, Agenten des Chaos mit dem einzigen Ziel, sich selbst zu bereichern. Ist es so?
Könnte es anders sein?
Folgender Text kann und will diese Fragen nicht ultimativ beantworten. Es gibt aber eine Brille, durch die, setzt man sie auf, viele Entwicklungen in einem anderen, viel helleren Licht erscheinen. Diese Brille heißt e/acc.

Was ist e/acc?
Das Kürzel geht auf den Programmierer Guillaume Verdon zurück, der unter dem Pseudonym „Beff Jezos“ die Bewegung. Es steht für „effective accelerationism“. Accelerationism, auf Deutsch Akzelerationismus, abgeleitet vom Verb „beschleunigen“, hat Wurzeln, die weiter zurückreichen - dazu später mehr. Der Zusatz „effective“ ist eine ironische Replik auf den „effective Altruism“, den unter anderen Sam Bankman-Fried vertrat und grandios scheiterte.
e/acc setzt also auf Beschleunigung. Kapitalismus, Innovation, vor allem künstliche Intelligenz sollen nicht aufgehalten oder reguliert werden, sondern im Gegenteil beschleunigt werden.
Warum?
Eine einfache Antwort lautet: Weil sie eh stattfinden. Besonders deutlich wird das im Fall künstlicher Intelligenz. Large Language Models (LLMs) wie ChatGPT und Deepseek sind nur die für die Öffentlichkeit sichtbaren Entwicklungen. Im Hintergrund ersetzt Künstliche Intelligenz zunehmend auch Produktionsprozesse und nicht zuletzt die Kriegsführung. Man spricht deswegen vom „Point of Singularity“. In den kommenden Jahren wird künstliche Intelligenz menschliche übertrumpfen. Unsere Arbeitswelt, unser Finanzsystem und gesellschaftliche Strukturen werden sich grundlegend ändern. Wenn es dazu kommt, warum die Entwicklung noch aufhalten? Beschleunigen ist besser.
Die zweite Antwort ist tiefgründiger und rührt an das Verständnis von Leben insgesamt. Langfristig strebt das Universum nach Entropie. Es dehnt sich aus, bis alle Teile in maximaler „Unordnung“ angeordnet sind. Systeme mit hoher Energiezufuhr können Strukturen aufbauen, solange sie Wärme oder Entropie in ihre Umgebung abgeben. In einem Organismus sind alle Teile zu einer höheren Ordnung organisiert. Leben strebt nach Ordnung, Selbsterhalt und Wachstum, weshalb der Energieverbrauch zunimmt. e/acc-Fan und Silicon-Valley-Investor Marc Andreessen schreibt in “The Techno-Optimist Manifesto”:
Techno-Optimists believe that societies, like sharks, grow or die.
We believe growth is progress – leading to vitality, expansion of life, increasing knowledge, higher well being.
Ein Gleichgewicht gibt es nicht. Entweder strebt eine Struktur nach Ordnung (Leben) oder nach Unordnung (Tod). Da eine Balance nicht existiert, gibt es nur zwei Möglichkeiten: Verlangsamen oder Beschleunigen. Höhere Ordnungen aufbauen oder verfallen. Wachsen oder Sterben. Beschleunigen ist besser.
Konsequenzen
e/acc ist kein philosophisches System im strengen Sinn. Es leitet Konsequenzen aus physikalischen Grundsätzen ab.
Kapitalistische Systeme und freie Märkte sind die effizientesten Strukturen, um Informationen zu verarbeiten. In einem offenen, freien Markt gibt der Preis das zuverlässigste Signal über Knappheit eines Gutes. Wird dieser Prozess durch externe Einflussnahme wie Subventionen gestört, läuft die Maschine nicht effizient. Das Gesamtsystem wird verzerrt. Nochmals Andreessen dazu:
We believe the market economy is a discovery machine, a form of intelligence – an exploratory, evolutionary, adaptive system.
Varianten und Abweichungen sind wichtig, da ein System dadurch am schnellsten auf sich ständig verändernde Umweltbedingungen reagieren kann. Wer nicht frei sprechen kann, kann nicht frei denken. Dezentrale Strukturen mit vielen kleinen einzelnen „Nodes“ sind resilienter als hierarchisch-zentralistische Systeme. Das führt zu einem Meinungsfreiheits-Maximalismus.
Greifen staatliche Akteure in die Forschung ein, und vergeben zum Beispiel Lizenzen für KI-Projekte, kann das System nicht mehr auf die besten Ressourcen zurückgreifen. Es entwickelt sich nicht in seiner natürlichen Geschwindigkeit, sondern wird künstlich verlangsamt. Beschleunigen ist besser.
Im Falle von KI hat dies geopolitische Konsequenzen: Sollten autoritäre Akteure wie zum Beispiel China schneller zum Punkt der Singularity vorstoßen, entsteht eine Dystopie, ein Orwellscher Überwachungsstaat. Bevorzugen ist deswegen eine beschleunigte, dezentrale Forschung, damit freie Systeme die Oberhand behalten.
Dasselbe gilt für das Geldsystem: e/acc trifft hier auf Hayek und Mises. Viele Zahlungssysteme stehen in permanenter Konkurrenz zueinander. Am Ende setzt sich das nützlichste und vermutlich auch härteste Geld durch.
Konkrete Folgen
Auf die konkrete Politik übertragen führt das zu Konsequenzen, die man aktuell beobachten kann.
**Radikale Deregulierung: **Die Biden-Administration versuchte, AI-Forschung eng an die Regierung zu binden. Open-AI-Gründer Sam Altman forderte 2023 eine Lizenz-Vergabe an Unternehmen, um überhaupt in diesem Bereich aktiv zu werden. (Musk trat zunächst sogar für ein Forschungs-Moratorium ein, änderte dann aber seine Meinung.) Das führte zum Widerstand der e/acc-Fraktion im Silicon Valley, und gab den Ausschlag, sich auf die Trump-Seite zu stellen. Deregulierung zieht sich nun durch alle Bereiche der Wirtschaft: auch auf die „Entwicklungshilfe“ von USAID. Der Regierungsapparat wird insgesamt massiv verkleinert, da Bürokratie das Wachstum hemmt. A fuera.
**Priorisierung von günstiger Energie: **Da der Energie-Verbrauch mit zunehmender Ordnung ansteigt, und LLMs einen sehr viel Strom brauchen, priorisiert die neue Regierung die Erschließung zusätzlicher Energiequellen: Gas, Öl, Nuklear und regenerative Energiequellen gleichermaßen.
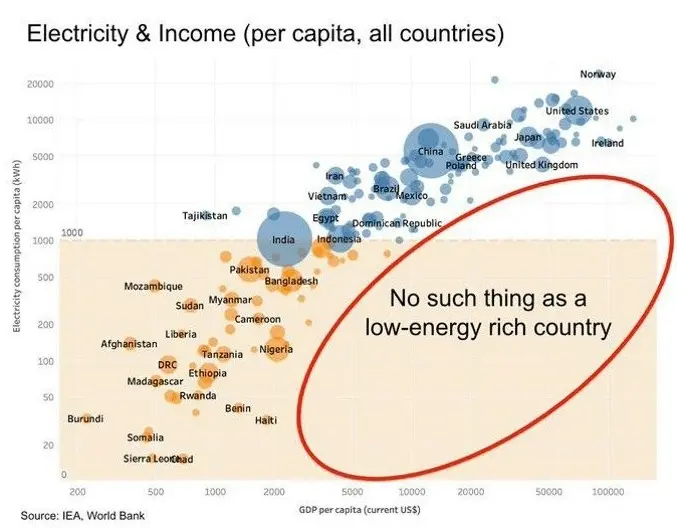
Wiederherstellung von Meinungsfreiheit.Content-Moderationen auf Social-Media-Plattformen fallen weg. Geheimdienst-Dokumente werden freigegeben. So schrieb Peter Thiel vor einigen Wochen in einem Essay in der Financial Times über die große Enthüllung:
\ But understood in the original sense of the Greek word apokálypsis, meaning “unveiling”, Obama could not give the same reassurance in 2025. Trump’s return to the White House augurs the apokálypsis of the ancien regime’s secrets. (…)\ The apokálypsis is the most peaceful means of resolving the old guard’s war on the internet, a war the internet won. My friend and colleague Eric Weinstein calls the pre-internet custodians of secrets the Distributed Idea Suppression Complex (DISC) — the media organisations, bureaucracies, universities and government-funded NGOs that traditionally delimited public conversation.
Krypto-Deregulierung: Da Kryptowährungen und Smart-Contract-Strukturen bestens mit LLMs harmonieren, werden Innovationsbremsen in Form von Regulierungen abgebaut.
**Umbruch der Weltordnung: **Auf der geopolitischen Ebene werden Bündnisse, Allianzen und Blockstrukturen aufgebrochen und nach effizienten Win-Win-Verhältnissen neu organisiert.
Erschließung neuer Lebenswelten: Degrowth, weniger Energie-Verbrauch und weniger Kinder sind keine Option, da sie zum Tod führen. Das System Menschheit muss wachsen und wird neue Lösungen erfinden. Wenn die Ressourcen des Planeten Erde nicht mehr ausreichen, müssen neue erschlossen werden - vielleicht auf dem Mars.
Die Ideengeschichte
Während e/acc ein relativ neues System ist, hat der Akzelerationismus tiefere Wurzeln. Lenin kann man als einen frühen Akzelerationisten bezeichnen. Der Marxismus wurde Anfang des 20. Jahrhunderts weniger als Ideologie, sondern mehr als exakte Wissenschaft begriffen. Demnach würde der Kapitalismus früher oder später an seinen eigenen Widerständen kollabieren. Warum den Prozess also nicht beschleunigen und die Revolution herbeiführen?
Ende des 20. Jahrhunderts griff der Philosoph Nick Land diese Gedanken wieder auf. Land forderte Beschleunigung, sah am Ende des Prozesses aber einen Kollaps des Systems und eine dunkle Zukunft. Ironie der Geschichte: Land zog in den 2000er Jahren nach China, wo er einen autoritären Akzelerationismus verwirklicht sah. Auch Steve Bannon, Leiter des ersten Trump-Wahlkampfes 2016, war von Lands Gedanken geprägt.

e/acc aber ist eine neuer, optimistischer „Fork“ des alten, dunklen Akzelerationismus. Es sieht eine positive Zukunft für die gesamte Menschheit aufgrund eines gigantischen Produktivitätsschubs. Eine neue, höhere Ordnung ist am Entstehen. Kurz gesagt:
Effective accelerationism (e/acc) in a nutshell:
Stop fighting the thermodynamic will of the universe
You cannot stop the acceleration
You might as well embrace it
A C C E L E R A T E
Notes on e/acc principles and tenets
Happy Future also? Durch die e/acc-Brille gesehen wirkt die Welt wesentlich heller und optimistischer als sie die meisten “Legacy Media” gerade darstellen. Demnach bewegen wir uns auf eine neue Zeit gesteigerter Produktivität und damit Lebensqualität zu. Wenn alle Arbeit von Maschinen verrichtet wird, können Menschen währenddessen auf Bali surfen, meditieren und Yoga machen. Oder?
Kritik
Leben entsteht an der Grenze von Chaos und Ordnung. Vielleicht versetzt e/acc das Pendel zu stark in den Ausschlag in eine Richtung. Unkontrolliertes Wachstum bedeutet im lebenden Organismen Krebs. e/acc sieht sich wie Marxisten der ersten Stunde (Lenin) im Besitz der Wahrheit in Form physikalischer Grundsätze. Erst durch diese Hybris führten zu den Grausamkeiten sozialistischer Systeme im 20. Jahrhundert. Schließlich beantwortet e/acc nicht die Frage nach der Verteilungsgerechtigkeit, die durch den gewaltigen Produktivitätsschub durch AI entstehen wird.
Ob e/acc als politisches und gesellschaftliches System taugt, ist deswegen fraglich. Aber viele aktuelle Entwicklungen scheinen durch die Akzelerationismus-Brille klarer.
Quellen:
Peter Thiel: A Time for Truth and Reconciliation
Marc Andreessen: The Techno-Optimist Manifesto
e/acc: Notes on e/acc principles and tenets
Andy Beckett: Accelerationism: how a fringe philosophy predicted the future we live in
Lex Friedman: Guillaume Verdon. e/acc-Movement. Physics. Computation & AGI.
-
 @ 57d1a264:69f1fee1
2025-03-29 18:02:16
@ 57d1a264:69f1fee1
2025-03-29 18:02:16This UX research has been redacted by @iqra from the Bitcoin.Design community, and shared for review and feedback! Don't be shy, share your thoughts.
1️⃣ Introduction
Project Overview
📌 Product: BlueWallet (Bitcoin Wallet) 📌 Goal: Improve onboarding flow and enhance accessibility for a better user experience. 📌 Role: UX Designer 📌 Tools Used: Figma, Notion
Why This Case Study?
🔹 BlueWallet is a self-custodial Bitcoin wallet, but users struggle with onboarding due to unclear instructions. 🔹 Accessibility issues (low contrast, small fonts) create barriers for visually impaired users. 🔹 Competitors like Trust Wallet and MetaMask offer better-guided onboarding.
This case study presents UX/UI improvements to make BlueWallet more intuitive and inclusive.
2️⃣ Problem Statement: Why BlueWalletʼs Onboarding Needs Improvement
🔹 Current Challenges:
1️⃣ Onboarding Complexity - BlueWallet lacks step-by-step guidance, leaving users confused about wallet creation and security.
2️⃣ No Educational Introduction - Users land directly on the wallet screen with no explanation of private keys, recovery phrases, or transactions. 3️⃣ Transaction Flow Issues - Similar-looking "Send" and "Receive" buttons cause confusion. 4️⃣ Poor Accessibility - Small fonts and low contrast make navigation difficult.
🔍 Impact on Users:
Higher drop-off rates due to frustration during onboarding. Security risks as users skip key wallet setup steps. Limited accessibility for users with visual impairments.
📌 Competitive Gap:
Unlike competitors (Trust Wallet, MetaMask), BlueWallet does not offer: ✅ A guided onboarding process ✅ Security education during setup ✅ Intuitive transaction flow
Somehow, this wallet has much better UI than the BlueWallet Bitcoin wallet.
3️⃣ User Research & Competitive Analysis
User Testing Findings
🔹 Conducted usability testing with 5 users onboarding for the first time. 🔹 Key Findings: ✅ 3 out of 5 users felt lost due to missing explanations. ✅ 60% had trouble distinguishing transaction buttons. ✅ 80% found the text difficult to read due to low contrast.
Competitive Analysis
We compared BlueWallet with top crypto wallets:
| Wallet | Onboarding UX | Security Guidance | Accessibility Features | |---|---|---|---| | BlueWallet | ❌ No guided onboarding | ❌ Minimal explanation | ❌ Low contrast, small fonts | | Trust Wallet | ✅ Step-by-step setup | ✅ Security best practices | ✅ High contrast UI | | MetaMask | ✅ Interactive tutorial | ✅ Private key education | ✅ Clear transaction buttons |
📌 Key Insight: BlueWallet lacks guided setup and accessibility enhancements, making it harder for beginners.
📌 User Persona
To better understand the users facing onboarding challenges, I developed a persona based on research and usability testing.
🔹 Persona 1: Alex Carter (Bitcoin Beginner & Investor)
👤 Profile: - Age: 28 - Occupation: Freelance Digital Marketer - Tech Knowledge: Moderate - Familiar with online transactions, new to Bitcoin) - Pain Points: - Finds Bitcoin wallets confusing. - - Doesnʼt understand seed phrases & security features. - - Worried about losing funds due to a lack of clarity in transactions.
📌 Needs: ✅ A simple, guided wallet setup. ✅ Clear explanations of security terms (without jargon). ✅ Easy-to-locate Send/Receive buttons.
📌 Persona Usage in Case Study: - Helps define who we are designing for. - Guides design decisions by focusing on user needs.
🔹 Persona 2: Sarah Mitchell (Accessibility Advocate & Tech Enthusiast)
👤 Profile: - Age: 35 - Occupation: UX Researcher & Accessibility Consultant - Tech Knowledge: High (Uses Bitcoin but struggles with accessibility barriers)
📌 Pain Points: ❌ Struggles with small font sizes & low contrast. ❌ Finds the UI difficult to navigate with a screen reader. ❌ Confused by identical-looking transaction buttons.
📌 Needs: ✅ A high-contrast UI that meets WCAG accessibility standards. ✅ Larger fonts & scalable UI elements for better readability. ✅ Keyboard & screen reader-friendly navigation for seamless interaction.
📌 Why This Persona Matters: - Represents users with visual impairments who rely on accessible design. - Ensures the design accommodates inclusive UX principles.
4️⃣ UX/UI Solutions & Design Improvements
📌 Before (Current Issues)
❌ Users land directly on the wallet screen with no instructions. ❌ "Send" & "Receive" buttons look identical , causing transaction confusion. ❌ Small fonts & low contrast reduce readability.
✅ After (Proposed Fixes)
✅ Step-by-step onboarding explaining wallet creation, security, and transactions. ✅ Visually distinct transaction buttons (color and icon changes). ✅ WCAG-compliant text contrast & larger fonts for better readability.
1️⃣ Redesigned Onboarding Flow
✅ Added a progress indicator so users see where they are in setup. ✅ Used plain, non-technical language to explain wallet creation & security. ✅ Introduced a "Learn More" button to educate users on security.
2️⃣ Accessibility Enhancements
✅ Increased contrast ratio for better text readability. ✅ Used larger fonts & scalable UI elements. ✅ Ensured screen reader compatibility (VoiceOver & TalkBack support).
3️⃣ Transaction Flow Optimization
✅ Redesigned "Send" & "Receive" buttons for clear distinction. ✅ Added clearer icons & tooltips for transaction steps.
5️⃣ Wireframes & Design Improvements:
🔹 Welcome Screen (First Screen When User Opens Wallet)
📌 Goal: Give a brief introduction & set user expectations
✅ App logo + short tagline (e.g., "Secure, Simple, Self-Custody Bitcoin Wallet") ✅ 1-2 line explanation of what BlueWallet is (e.g., "Your gateway to managing Bitcoin securely.") ✅ "Get Started" button → Le ads to next step: Wallet Setup ✅ "Already have a wallet?" → Import option
🔹 Example UI Elements: - BlueWallet Logo - Title: "Welcome to BlueWallet" - Subtitle: "Easily store, send, and receive Bitcoin." - CTA: "Get Started" (Primary) | "Import Wallet" (Secondary)
🔹 Screen 2: Choose Wallet Type (New or Import)
📌 Goal: Let users decide how to proceed
✅ Two clear options: - Create a New Wallet (For first-time users) - Import Existing Wallet (For users with a backup phrase) ✅ Brief explanation of each option 🔹 Example UI Elements: - Title: "How do you want to start?" - Buttons:** "Create New Wallet" | "Import Wallet"
🔹 Screen 3: Security & Seed Phrase Setup (Critical Step)
📌 Goal: Educate users about wallet security & backups
✅ Explain why seed phrases are important ✅ Clear step-by-step instructions on writing down & storing the phrase ✅ Warning: "If you lose your recovery phrase, you lose access to your wallet." ✅ CTA: "Generate Seed Phrase" → Next step
🔹 Example UI Elements: - Title: "Secure Your Wallet" - Subtitle: "Your seed phrase is the key to your Bitcoin. Keep it safe!" - Button: "Generate Seed Phrase"
🔹 Screen 4: Seed Phrase Display & Confirmation
📌 Goal: Ensure users write down the phrase correctly
✅ Display 12- or 24-word seed phrase ✅ “I have written it downˮ checkbox before proceeding ✅ Next screen: Verify seed phrase (drag & drop, re-enter some words)
🔹 Example UI Elements: - Title: "Write Down Your Seed Phrase" - List of 12/24 Words (Hidden by Default) - Checkbox: "I have safely stored my phrase" - Button: "Continue"
🔹 Screen 5: Wallet Ready! (Final Step)
📌 Goal: Confirm setup & guide users on next actions
✅ Success message ("Your wallet is ready!") ✅ Encourage first action: - “Receive Bitcoinˮ → Show wallet address - “Send Bitcoinˮ → Walkthrough on making transactions
✅ Short explainer: Where to find the Send/Receive buttons
🔹 Example UI Elements: - Title: "You're All Set!" - Subtitle: "Start using BlueWallet now." - Buttons: "Receive Bitcoin" | "View Wallet"
5️⃣ Prototype & User Testing Results
🔹 Created an interactive prototype in Figma to test the new experience. 🔹 User Testing Results: ✅ 40% faster onboarding completion time. ✅ 90% of users found transaction buttons clearer. 🔹 User Feedback: ✅ “Now I understand the security steps clearly.ˮ ✅ “The buttons are easier to find and use.ˮ
6️⃣ Why This Matters: Key Takeaways
📌 Impact of These UX/UI Changes: ✅ Reduced user frustration by providing a step-by-step onboarding guide. ✅ Improved accessibility , making the wallet usable for all. ✅ More intuitive transactions , reducing errors.
7️⃣ Direct link to figma file and Prototype
Original PDF available from here
originally posted at https://stacker.news/items/928822
-
 @ 65038d69:1fff8852
2025-03-29 12:19:19
@ 65038d69:1fff8852
2025-03-29 12:19:19Look at any white-collar office job posting from the last few decades and you’re likely to see something like “basic computers skills” listed as a requirement. “Great,” you think to yourself, “I can use technology, after all, I managed to find this job posting!” And if you’re on the hiring end for a position that’ll be spending six to eight hours in front of screen, you’d certainly hope applicants would know that they need to be able to use a computer. Ten years of bookkeeping experience? Reception? Managing remote staff? In a Venn diagram of work experience and basic computer skills, those should be a near complete overlap! We shouldn’t need to train them at all! Can we be sure though? It turns out “basic computer skills” doesn’t have a universally accepted definition.
Since basic computer skills doesn’t have an official definition we can point to, lets attempt to create one ourselves. I argue for reading comprehension as the base skill underlying all the others we’re going to talk about (see “One Skill To Rule Them All” for more on this). Unfortunately reading comprehension doesn’t have a universal measurement either. I used to use “6th grade reading level” as my go-to, but today’s media is full of articles on changing standards and outcomes in public education, so that’s no longer dependable. If you’re interviewing someone, try providing them with a copy of the job posting and asking them questions about it that require some simple inference. For a more advanced option, I’ve included a test you can administer that covers reading comprehension and several other elements.
How about typing? Should basic computer skills include home row typing ability? What about speed requirements? If we’re talking about basic skills, I’d say no to both of those. While “chicken pecking” with two fingers probably wouldn’t qualify you for a staff writing position at a newspaper, I consider formal typing (especially with a speed requirement) to be an intermediate skill. So your applicant should be able to navigate a keyboard without assistance, but that’s all.
Email is probably the most universal computer task of the modern era. I’ve included it in the test template. Users should be able to recognize an email address and the “To”, “Subject”, and “Body” fields in an email client, even an unfamiliar one. Email interfaces have kept their same basic elements since the 90s.
The most controversial skill I’ve seen talked about lately is the ability to navigate and use a file system. The advent of smartphones and tablets, and the ubiquity of Chromebooks in schools, has led to new workers who have never had to save a file to a “documents” folder, or infer that a photo could most likely be found in a “pictures” folder. The strongest counterargument I’ve read is that between “recent” lists and search functions we shouldn’t need to know how to navigate file structures. I disagree, so I’ve included this skill in the test as well.
Lastly, safety and security. What’s considered “basic” varies wildly. Could you recognize a phishing email pretending to be from your boss? What about the difference between an ad link and a regular result in an internet search? I haven’t included this in the test as needs and policies are different at every workplace, but it’s a good idea to consider it when planning your interviews and internal training. An employee who clicks the links in every suspicious email without a second thought is a security disaster waiting to happen.
Here’s the skills test I promised. There are two ways of administering it; either provide the interviewee with a computer to use, or use screenshots and have them verbally walk you through the steps they would take. The latter requires a bit more visual and verbal knowledge transference and self-awareness so I only recommend it if providing a company computer isn’t a possibility. You’ll also need to customize it; for example YOURTEXTEDITOR needs to be replaced with whatever program is standard for your org, i.e. Microsoft Word.
Instructions for the Applicant: Please read the instructions below carefully and perform the steps described. After completing the task, answer the follow-up questions about the process. Task: 1. Open YOURTEXTEDITOR on the computer. 2. Create a new file and write the following without the quotes: “Welcome to the team! Your onboarding kit is on your desk.” 3. Save the file with the name "Team Message - " ending with today’s date, in the "FOLDERORSHAREDRIVE" folder. 4. Format the text to bold and change the font size to 14. 5. Close the application. 6. Open YOUREMAILCLIENT. 7. Send an email to INTERVIEWER with the subject “Team Message”. In the email, let them know that the file is ready. 8. Attach the file and send the email. Instructions for the Interviewers: After they’ve completed the task, ask the following questions about the process. Interviewees should be allowed to keep their instructions in front of them, but DO NOT tell them they can refer to them unless they ask. 1. What was the name of the first program you opened? 2. If you couldn’t save the file to the “FOLDERORSHAREDRIVE” folder/share drive, where would you have saved it? Why? 3. Who did you send the email to? 4. What did you name the file? 5. What changes, if any, would you make to the instructions? Post-interview analysis: The following is reasoning for the instructions and questions, and what to look for in the interviewee’s actions and responses. Task: 1. They should be able to find an application on the computer with little assistance. 2. They should be able to type the sentence into the document and understand the instructions to leave out the quotation marks. Observe their typing style (home row vs single finger presses) and speed. 3. Ability to remember or find today’s date and to save a document to a specific location. 4. Ability to format text. 5. They should remember to save the document or answer the automated prompt to save the document. 6. Same as question 1, but with a different application. 7. They should be able to send an email with an attachment. Ideally they’ll either know, or be able to figure out, how to look up the interviewer in the company address book. Also, the ability to write without being told explicitly what to say. 8. The ability to locate and attach a file to an email. Follow-up questions: 0. Allowing them access to the instructions without explicitly telling them they can refer to them will test their sense of agency. Asking permission is fine as some will feel the follow-up questions are a test, and most people are used to tests or exams being closed-book. It will also test their ability to find the information they need within the task instructions. 1. Ability to recall or locate the information. 2. Ability and sense of agency to make a best-option decision when faced with adversity. 3. Ability to recall or locate the information. 4. Ability to recall or locate the information. 5. Tests self-awareness around needs or preferences for directions. “None” is also an acceptable answer if they had no struggles with any of the task steps.Share this article with anyone working on job postings or interviews in your organization, and please feel free to use the skills test content in any way you like. It’s best modified for your specific needs!
Need someone to assist with skills assessment, training, or hiring processes? You can find us at scalebright.ca.
-
 @ 71550e6c:b64c37a9
2025-03-29 10:55:55
@ 71550e6c:b64c37a9
2025-03-29 10:55:55Just do the same as this video shows.
Here's the video: https://cdn.azzamo.net/7cdcc2718f1e15eb03e323f62e07582b4001da273aa5c21475d680f02b32f0e9.mp4
One caveat: do not trust the draft will be kept here after you close
nak fs. Wait, no, it definitely won't stay here, but I'm not even sure it will stay here if you only navigate away and come back later, FUSE is weird and I didn't test.But at least it should work for copy-pasting. Or writing everything in one go.
-
 @ 2516d145:070c8fa1
2025-02-07 16:49:20
@ 2516d145:070c8fa1
2025-02-07 16:49:20„Ein Mensch. Ein Wort.“, steht auf den Plakaten der Grünen zur Bundestagswahl 2025. Mich erinnert das an den Beginn des Johannesevangeliums: „Im Anfang war das Wort … Und das Wort ist Fleisch geworden …“ In diesen Tagen scheinen Heiligenverehrung und Teufelsaustreibung so virulent zu sein, wie im Mittelalter. Menschen müssen die richtigen Worte verwenden. Wahre Worte aus falschem Mund verklingen oftmals ungehört.
Die Sachbücher des massel Verlags sind mehr als bloße Hirngespinste, sie gründen in gelebter Wirklichkeit. Texte unserer Autoren werden nicht glattgeschliffen und marktkonform gebeugt, sondern sie behalten ihre Macken und Zacken. Linus war im Gefängnis eingesperrt und Bastian hat ein Jahr in der Wildnis frei gelebt. Eva ist mit dem Volk Gottes durch die Wüste gewandert und Insa hat ihr Glück nicht nur, aber auch im Sex gefunden. Walter hat Ausgrenzung durch die Medien am eigenen Leib erfahren und Ulrich ist eingetaucht in die vielfältigen, menschlichen Alternativen zu unserem Wirtschafts- und Finanzsystem.

Am 14. Februar ist Valentinstag!
Das Brauchtum dieses Tages geht auf das Fest des Heiligen Valentinus zurück. Der Legende nach traute der heilige Valentin von Rom Soldaten, denen das Heiraten eigentlich verboten war. In der Antike wurde um den 13. bis 15. Februar in Rom ein Fruchtbarkeitsritus gefeiert. Einen Beleg für eine Verbindung zwischen dem Fest der Lupercalien und dem Valentinstag gibt es nicht. Es gibt jedoch Hinweise, dass die Leidensgeschichte des Heiligen und sogar dessen Existenz erfunden wurde. Allgemein bekannt wurde der Valentinstag durch die vor dem 14. Februar verstärkt einsetzende Werbung der Floristik- und Süßwarenindustrie.
Blumen oder Schokolade verschenken? Ehepaare im Gottesdienst segnen? Der romantischen Liebe huldigen? Wir empfehlen Ihnen das etwas andere Geschenk!

Hauptsache Sex zusammen? von Insa Tiabilis\ Ein Inspirationsbuch über Sex in langen Beziehungen
Die Autorin sagt über sich: „Ich habe ein abgebrochenes Studium der Psychologie, drei abgeschlossene Kinder, und einen mir selbst verliehenen ‚Master‘ im Eheretten vorzuweisen. Das Leben hat mich qualifiziert und um einige wunderbare Erfahrungen reicher gemacht, an denen ich andere Menschen teilhaben lassen möchte. Ich habe mich glücklich gemacht. Nicht nur, aber auch mit Sex.“
Quellen erforschen und verstehen
Wie beim Valentinstag ist eine Umdeutung des Sex durch Kirche, Industrie und Machthabenden wahrscheinlich. Der Mensch wurde bewusst seiner Natur entfremdet. Oder hat die Kultur ihn zu etwas Höherem befreit?
Diese beiden Pole gilt es auszuhalten und zu entdecken. Siehe Kinderbuch weiter unten. Auch in der Sprachreise von Gerald Ehegartner geht es um Umdeutung. Ist das generische Maskulinum Ausdruck einer patriarchalen Gesellschaft? Oder hat die deutsche Sprache aus anderen Quellen ihre Grammatik gespeist?

Gerald Hüther, Neurobiologe und Bestsellerautor: „Dieses Buch von Gerald Ehegartner ist eine messerscharfe und scharfzüngige Analyse unserer gegenwärtigen Sprachverwicklungen und gleichzeitig eine warmherzige und berührende Liebeserklärung an unsere deutsche Muttersprache.“
Was und wo ist Heimat?
Der kleine Pinguin Timpetaa, verlässt seine gewohnte Umgebung im Süden, macht sich auf, die Welt zu entdecken und trifft dort auf Fremde. Das Unbekannte, in Timpetaas Fall der Nordpol mit den vielen Eisbären, welche ihn unter „normalen“ Umständen wahrscheinlich gleich verschlingen würden, kann auch zur Heimat werden. Auf alle Fälle üben die zotteligen Viecher am Nordpol unserem kleinen Weltreisenden gegenüber große Toleranz. Sie kümmern sich vielmehr rührend um ihn, nehmen ihn wohlwollend in ihrer Gemeinschaft auf, ziehen ihn groß und lernen ihm das Jagen, auch wenn Fisch nach wie vor zu seiner Leibspeise gehört. Am allerliebsten jagt der kleine Pinguin allerdings Herzen …
Der Autor Matthias A. Weiss möchte mit seinem Kinderbuch Kindern das Leben als zu entdeckendes Gut vermitteln, sie auf den Wert der Umwelt und ein friedvolles Miteinander aufmerksam machen. Nicht zuletzt sollen Kinder ermutigt werden, in die Welt hinauszugehen und eigene Erfahrungen zu sammeln.

Veranstaltungen
Im März stehen wieder einige Veranstaltungen des massel Verlags an. Wir freuen uns sehr, wenn wir uns bei dem ein oder anderen Ereignis begegnen würden. Aller Termine finden Sie auf unserer Website.
15. - 23. März 2025\ Bücherschau junior im Forum der Zukunft, Deutsches Museum - Museumsinsel\ In der Ausstellung: Timpetaa von Matthias A. Weiss
15. März 2025, 10 - 13:00 Uhr\ Stemmerhof, Plinganserstraße 6, 81369 München\ Büchermesse: Unabhängige Kleinverlage
und 14:00 Uhr\ Lesung: Timpetaa mit Matthias A. Weiss
22. März 2025, 18:30 Uhr\ Verlagshaus, Am Harras 14, 81373 München\ Lesung: Der Super-Faschismus mit Lisa-Maire Binder
27. - 30. März 2025\ Leipziger Buchmesse\ Vereinbaren Sie einen Termin mit Verleger Martin Sell
Wir wünschen Ihnen einen blühenden Valentinstag, süße Begegnungen und offene Herzen, die Ihnen zufliegen mögen.
Ihr massel Team\ Martin & Julia
-
 @ 71550e6c:b64c37a9
2025-03-29 10:47:58
@ 71550e6c:b64c37a9
2025-03-29 10:47:58This is a long-form post on Nostr.
Now Gigi can publish his stuff without complaining about NIP-23 client editors.
-
 @ ec42c765:328c0600
2025-02-05 23:38:12
@ ec42c765:328c0600
2025-02-05 23:38:12カスタム絵文字とは
任意のオリジナル画像を絵文字のように文中に挿入できる機能です。
また、リアクション(Twitterの いいね のような機能)にもカスタム絵文字を使えます。

カスタム絵文字の対応状況(2025/02/06)

カスタム絵文字を使うためにはカスタム絵文字に対応したクライアントを使う必要があります。
※表は一例です。クライアントは他にもたくさんあります。
使っているクライアントが対応していない場合は、クライアントを変更する、対応するまで待つ、開発者に要望を送る(または自分で実装する)などしましょう。
対応クライアント
ここではnostterを使って説明していきます。
準備
カスタム絵文字を使うための準備です。
- Nostrエクステンション(NIP-07)を導入する
- 使いたいカスタム絵文字をリストに登録する
Nostrエクステンション(NIP-07)を導入する
Nostrエクステンションは使いたいカスタム絵文字を登録する時に必要になります。
また、環境(パソコン、iPhone、androidなど)によって導入方法が違います。
Nostrエクステンションを導入する端末は、実際にNostrを閲覧する端末と違っても構いません(リスト登録はPC、Nostr閲覧はiPhoneなど)。
Nostrエクステンション(NIP-07)の導入方法は以下のページを参照してください。
ログイン拡張機能 (NIP-07)を使ってみよう | Welcome to Nostr! ~ Nostrをはじめよう! ~
少し面倒ですが、これを導入しておくとNostr上の様々な場面で役立つのでより快適になります。
使いたいカスタム絵文字をリストに登録する
以下のサイトで行います。
右上のGet startedからNostrエクステンションでログインしてください。
例として以下のカスタム絵文字を導入してみます。
実際より絵文字が少なく表示されることがありますが、古い状態のデータを取得してしまっているためです。その場合はブラウザの更新ボタンを押してください。

- 右側のOptionsからBookmarkを選択

これでカスタム絵文字を使用するためのリストに登録できます。
カスタム絵文字を使用する
例としてブラウザから使えるクライアント nostter から使用してみます。
nostterにNostrエクステンションでログイン、もしくは秘密鍵を入れてログインしてください。
文章中に使用
- 投稿ボタンを押して投稿ウィンドウを表示
- 顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択
- : 記号に挟まれたアルファベットのショートコードとして挿入される

この状態で投稿するとカスタム絵文字として表示されます。
カスタム絵文字対応クライアントを使っている他ユーザーにもカスタム絵文字として表示されます。
対応していないクライアントの場合、ショートコードのまま表示されます。

ショートコードを直接入力することでカスタム絵文字の候補が表示されるのでそこから選択することもできます。

リアクションに使用
- 任意の投稿の顔😀のボタンを押し、絵文字ウィンドウを表示
- *タブを押し、カスタム絵文字一覧を表示
- カスタム絵文字を選択

カスタム絵文字リアクションを送ることができます。

カスタム絵文字を探す
先述したemojitoからカスタム絵文字を探せます。
例えば任意のユーザーのページ emojito ロクヨウ から探したり、 emojito Browse all からnostr全体で最近作成、更新された絵文字を見たりできます。
また、以下のリンクは日本語圏ユーザーが作ったカスタム絵文字を集めたリストです(2025/02/06)
※漏れがあるかもしれません
各絵文字セットにあるOpen in emojitoのリンクからemojitoに飛び、使用リストに追加できます。
以上です。
次:Nostrのカスタム絵文字の作り方
Yakihonneリンク Nostrのカスタム絵文字の作り方
Nostrリンク nostr:naddr1qqxnzdesxuunzv358ycrgveeqgswcsk8v4qck0deepdtluag3a9rh0jh2d0wh0w9g53qg8a9x2xqvqqrqsqqqa28r5psx3
仕様
-
 @ 8be6bafe:b50da031
2025-02-05 17:00:40
@ 8be6bafe:b50da031
2025-02-05 17:00:40Botev Plovdiv FC is proud to present the Bitcoin Salary Calculator tool, as the foundational tool to showcase athletes the financial power of Bitcoin.
We built the Salary Calculator to help anyone follow in the financial footsteps of prominent athletes such as Kieran Gibbs, Russell Okung, Saquon Barkley, and Renato Moicano, who have significantly increased their savings tank thanks to Bitcoin.
The Bitcoin Salary Calculator allows any person to choose how much of their monthly salary they are comfortable saving in Bitcoin. Instantly, users can backtrack and see how their Bitcoin savings would have performed using the once-in-a-species opportunity which Bitcoin brings.
https://video.nostr.build/a9f2f693f6b5ee75097941e7a30bfc722225918a896b29a73e13e7581dfed77c.mp4
Athletes need Bitcoin more than anyone else
Unlike most people, athletes’ careers and earning years are limited. This has driven the likes of Odell Beckham Jr. and Alex Crognale to also start saving a part of their income in Bitcoin with a long-term outlook as they prepare for retirement.
“The reason why announced 50% of my salary in Bitcoin is because I feel one the noblest things you can do is to get people to understand Bitcoin.” Kieran Gibbs, founder ONE FC, ex Arsenal, ex Inter Miami, ex West Bromich Albion.
“I am trusting Bitcoin for my life after football. Every time my club paid me, I bought Bitcoin.” Alex Crognale, San Antonio FC player.
https://x.com/TFTC21/status/1883228348379533469
“At Botev Plovdiv FC, we believe not only in fostering sporting talent, but also helping them the the most of their careers so they excel in life after retiring from sports. It is with this mission in mind that the club is launching the Bitcoin Football Cup hub, striving to accelerate mass Bitcoin education via sports and athletes - the influencers and role models for billions of people.” shared Botev’s Bitcoin Director George Manolov.
https://x.com/obj/status/1856744340795662432
The Bitcoin Football Cup aims for young prospects to be able to learn key financial lessons from seasoned veterans across all sports. Our Bitcoin Salary Calculator is only the first step toward that goal.
We encourage anyone to hear these stories straight from the current roster of Bitcoin athletes -for whom -in many cases- Bitcoin has allowed them to outperform the wealth it took decades to earn on the field.
Follow us on the Bitcoin Cup’s social media channels to learn more and hear the latest stories of how Bitcoin is shaking up the world of sports:
- Twitter: https://x.com/Bitcoin_Cup/
- Instagram: https://www.instagram.com/BitcoinCup/
- TikTok: https://www.tiktok.com/@BitcoinCup/
- YouTube: https://www.youtube.com/@BitcoinCup/
-
 @ 57d1a264:69f1fee1
2025-03-29 17:15:17
@ 57d1a264:69f1fee1
2025-03-29 17:15:17- Once activated, "Accept From Any Mint” is the default setting. This is the easiest way to get started, let's the user start acceptance Cashu ecash just out of the box.
- If someone does want to be selective, they can choose “Accept From Trusted Mints,” and that brings up a field where they can add specific mint URLs they trust.
- “Find a Mint” section on the right with a button links directly to bitcoinmints.com, already filtered for Cashu mints, so users can easily browse options.
- Mint info modal shows mint technical details stuff from the NUT06 spec. Since this is geared towards the more technical users I left the field names and NUT number as-is instead of trying to make it more semantic.
originally posted at https://stacker.news/items/928800
-
 @ 65038d69:1fff8852
2025-03-29 12:10:15
@ 65038d69:1fff8852
2025-03-29 12:10:15“Can you help make our website good?” is one of the most loaded questions I get. There are many aspects to this question’s galactic gravitas, and their root is another question: what makes a website good?
Before we get there, we have a few other questions that need answering. The first is whether you actually need a website. Would a social media presence and a Google Maps listing do the same job? Or do you need a dedicated online shop or some other functionality that a Facebook Page can’t provide? Who’s your target market? Is it people who don’t have social media accounts or wouldn’t want to mix their social media presence with your business?
Let’s say you’ve gone through all of that and decided you do indeed need a website. What makes a website “good” can be divided into two aspects: engineering and design. In the context of websites, engineering is the behind the scenes stuff that makes it go (think of the mechanical bits of a car), and design is how it looks and feels (all the stuff you see and touch in a car). Unfortunately for us, most places these overlap they’re also juxtaposed. To see this in action head over to simple.scalebright.ca. You’ll notice that it loads extremely quickly and works well on screens of any size. This site was built with an “engineering first” mindset. Designers generally loath this kind of website. Not because it loads fast or scales well, but because to do those things I had to sacrifice design. There are no graphics or images, one font, and only four total colours in use (if you count black and white). There are no fancy contact forms, loading animations, white space considerations, borders, boxes, or bulbous billowing bedazzlements. Just cold, ruthless efficiency. I love it! But it’s not necessarily good.
This takes us into the next consideration. A good website doesn’t necessarily appeal to you; it’s supposed to appeal to your target audience. You might not be your target audience. If you are, great! That’ll make figuring out what your target audience wants in a website easier. Either way, be sure to have some chats with them and keep what they say in mind.
Okay, I know I just finished saying that the highly simplified version of my website isn’t good, but I want to warn you away from the opposite: over-design and over-engineering. Over-design usually manifests as visual overload; too many colours, too many graphics or photos, too much motion. Over-engineering is too much mechanical complexity; a one-page professional bio site doesn’t need to run on a dedicated server on WordPress with fifteen plugins.
There isn’t going to be a one-size-fits-all answer to “what makes a website good?”, because no two website are going to be identical. You’ll probably end up engaging a professional website design firm to both help answer that question for your specific scenario, and to build it for you. Here are some of the questions they’re going to ask and some hints for answering them.
What are your colours, fonts, logos, and other visual assets? If you don’t have these the firm should be able to help (usually for an extra fee), though smaller firms may need to subcontract the work out.
What are the core functions of your website? Is it an online store? Professional bio? Hospitality booking site? A link hub or landing page?
Do you have your website copy ready to go? “Copy” in this context refers to the text that will go on your website. Slogans, product and service descriptions, staff bios, and anything else that consists of a collection of words. If you don’t have your copy, you’ll either need to prepare to write it yourself or hire a third party to write it for you. It’s been my experience that website design firms are very strict about not writing copy, and generally won’t subcontract it either.
Do you have a preferred CMS? A CMS is a content management system, which is a fancy way of saying “thing that makes your website easier to add content to”. WordPress, Joomla, and Drupal are CMSs. Squarespace, GoDaddy, and Wix could be considered CMSs for our purposes too. 99% of you probably don’t care, and that’s a perfectly acceptable answer to give your firm.
What’s your budget? While most of us would probably prefer to spend zero, groceries continue to cost money, so none of us work for free. As of the writing of this article, a multi-page website built by a design firm will range between $10,000 and $30,000.
Want someone to “just take care of” all this website shenanigans for you? You can find us at scalebright.ca.
-
 @ 65038d69:1fff8852
2025-03-29 12:07:06
@ 65038d69:1fff8852
2025-03-29 12:07:06I’ve been on the internet since the mid 90s. Once I started “cyber-schooling” a few years later my time spent in front of a screen skyrocketed. One of the time vortices both for and outside of school was finding things on the internet. Everything from encyclopedia-style information pieces to news articles to music to games; the hunt was relentless.
Search engines were the primary was this was done. In the early days my school officially recommended Ask Jeeves, but the students found Google’s results much more thorough. Us little scientists-in-training were even running parallel searches, recording outcomes, and sharing results. We eventually got in trouble for wrongthink...I mean...not following instructions, but were vindicated soon after when the school's recommendations changed to "use whatever search engine you like, as long as the results chosen are quality sources".
The problem of “how to find things on the internet” has recently returned. “Google it” is no longer the genericized verb it once was. Grand tomes and PHD theses have been written on the subject of why, but most point to motives and monetization. The original problem was finding things, and the solution was search. But how would the bills get paid? Computers are expensive! Printing newspapers is expensive too, and the solution was the same for both: sell advertising space. Unfortunately for us users, that has become the primary business for much of the internet. Search engines are no longer motivated to get you the results you’re looking for as quickly as possible, but to keep you on their platform looking at ads. Pundits have coined the term “enshittification” (which even has it’s own Wikipedia page now) to describe the phenomenon.
Worry not, for not all is lost! There are still ways to find things on the internet. Methods vary depending on what kind of things you’re looking for. One of my most common searches is for how to do things; everything from home repairs to mechanical to technology. My primary method for this is to use Google to search Reddit. Reddit is a massive collection of forums with almost two decades of human-generated content. Unfortunately it’s built-in search is mostly terrible, so that’s where Google comes in. Do the same Google search you’d normally do (say, “how to fix a squeaky door”), but add “site:reddit.com” to the end. This tells Google to only show results from Reddit. What you’ll get is forum threads and comments from (mostly) real humans with real human experiences. Of course humans and their commentary can still be deeply flawed, so stay skeptical of what you read, but it’s largely a much better experience than a naked Google search.
Less mainstream search engines are trying their hands at paid subscriptions as a way to avoid the advertising hell-spiral. Kagi is one I’ve been trying, though admittedly not as often as I should. They do have a free tier if you want to sample it.
A more high-tech solution is AI systems. ChatGPT recently released a tool specifically for internet searches, though their general prompt tool has been usable for this for a while. Kagi also has an AI-powered search tier. Both are pretty expensive for casual users though.
Another recommendation is to frequent interest or topic-specific forums and blogs. If you find yourself regularly needing vehicle repair tips, try joining a forum on the subject. Same goes for most other do-it-yourself tasks. You may even make some internet friends! Blogs are also a great way to find things and get connected to experts (shameless plug fully intended).
Lastly, some interesting things are happening on the Nostr protocol that could help bring information together without the commercial overreach. (See “Become Unbannable” for more on Nostr.) I’ve been using a site called Zap Cooking (https://zap.cooking) to browse recipes. Recipes here are Nostr notes (posts) that have been formatted and categorized, and can be commented on, rated, and tipped, all using the free and open Nostr protocol. No algorithms, no banks, no governments, and no ads!
Want help with or training on finding things on the internet? You can find us at scalebright.ca.
-
 @ 65038d69:1fff8852
2025-03-29 12:03:23
@ 65038d69:1fff8852
2025-03-29 12:03:23“Sam did it!” You can hear the edge in the child’s voice as they attempt to shift blame for whatever minor misdeed they may-or-may-not have masterminded. In the court of humanity our feelings take wide precedence over objective justice. Even if there’s no fallout or formal punishment for that thing we did wrong, we really don’t like taking the blame.
Personal responsibility isn’t only about taking blame for the negative. As we’ll define it for the purposes of this article, it means taking ownership of decisions you make and the actions you take based on them. By extension you will also be taking ownership of the outcomes, both the successes and failures. Your mind is probably already imagining all sorts of scenarios this could apply to both at work and at home, but our focus will be mostly in the workplace.
Imagine working in a utopia where everyone perfectly executes personal responsibility. You would never have to worry about someone blaming you for the failure of their project, because it’s their project. You would know in advance that if your project is a success you’ll get 100% of the accolades, because it’s your project. With these two things alone, wouldn’t you feel a new level of motivation to give it your all? To take risks and innovate? You would have a new level of trust in your coworkers too. There would be no motive for micromanagement, for doing so would mean taking someone else’s responsibility upon yourself. Morale and productivity would skyrocket!
You can easily imagine the opposite as well; you may have thought of your own workplace in a negative light as soon as you read the title and clicked the link. Unfortunately in I.T. (being a panoptic presence in most organizations) we’re an easy target. “I can’t work, my computer’s broken, and I.T. hasn’t fixed it yet! They’re so slow, am-I-right?” “The file deleted itself; stupid computers!” “It’s not my fault that we didn’t deliver on time; the printer’s broken and it’s not my job to fix it!” sigh Enough gloom, let’s move on to how to make personal responsibility great again!
It's a simple concept; remind yourself that our decisions are ours, our actions are ours, and the results are ours. No exceptions. I’ll give you an example. When my wife and I are travelling somewhere it’s usually up to me to decide where to eat. I’m usually driving, and I’m also the head of our household, so it’s my decision. My decision, my actions, and most importantly, my results to own. If I choose a place and my wife doesn’t like the ambiance or menu or amount of cheese they put on everything, that’s on me. The weight can be heavy and feel unjust. But it isn’t unjust. It’s perfectly, objectively just. It’s my decision, my actions, and my results to own. There are upsides for both of us; I am now further motivated to pick someplace I know she’ll like and she gets to play “Passenger Princess”, and I get to bathe in the social bragging rights of being crowned “King of the Husbands” for being intuitive and attentive enough to know what she’d like and get it for her. It’s timeless and primordial: “Oh husband, you hunted and brought back a mammoth! I love mammoth steak! You are brave and strong and clearly the greatest of all husbands!” Her words would eco through our cave commune and all would look to us for hot tips to share on their relationship blog cave paintings.
You might still be thinking of your workplace and your coworkers who seem to want to blame you for everything that goes wrong. What can you do to get them on the personal responsibility train? The only way to do it is to lead by example. The moment you try to tell them or make them they’ll see it as an attack and blame you, which is exactly the problem you’re trying to avoid! You can’t suggest it, hint at it, or leave an anonymous note. You can’t have someone else talk to them about it or send this article and say, “I read this and thought it was interesting and thought you would think it’s interesting too.” This only way to teach others about personal responsibility is to show them. Which makes me writing this massively ironic. I take full responsibility for this!
My last tip is to make sure to celebrate the wins, both yours and other’s! This is especially true for others you’re trying to influence. Remember the accolades we imagined getting earlier and how much that would motivate you? That’s what you’re trying to instill in others. Positive reinforcement is much stronger than negative, so hand your praises out like candy!
Want to go against my recommendations and bring me into your workplace to talk about personal responsibility? You can find us at scalebright.ca.
-
 @ b17fccdf:b7211155
2025-02-01 18:41:27
@ b17fccdf:b7211155
2025-02-01 18:41:27Next new resources about the MiniBolt guide have been released:
- 🆕 Roadmap: LINK
- 🆕 Dynamic Network map: LINK
- 🆕 Nostr community: LINK < ~ REMOVE the "[]" symbols from the URL (naddr...) to access
- 🆕 Linktr FOSS (UC) by Gzuuus: LINK
- 🆕 Donate webpage: 🚾 Clearnet LINK || 🧅 Onion LINK
- 🆕 Contact email: hello@minibolt.info
Enjoy it MiniBolter! 💙
-
 @ ff517fbf:fde1561b
2025-03-29 15:37:34
@ ff517fbf:fde1561b
2025-03-29 15:37:34はじめに:なぜKYCなしP2P取引か
ビットコインは元々、ピア・ツー・ピア(P2P)の電子通貨システムとして設計されました。サトシ・ナカモトのビットコイン白書でも、「信頼ではなく暗号学的証明に基づく電子決済システム」によって、第三者を介さずに当事者同士が直接取引できることが必要だと述べられています。つまり、本来ビットコインは銀行などの仲介者なしで個人同士が直接送金・売買できる社会的意義を持っているのです。
しかし現在、多くの暗号資産取引所では規制上の理由からKYC(本人確認)手続きが求められ、個人情報の提出が必要です。KYCはユーザーのプライバシー喪失やデータ漏洩リスクにつながりかねず、また口座凍結や資金没収といった中央集権的管理のリスクもあります。経済的にも、第三者を介することで手数料が高くなったり、地域によっては銀行や政府の制限でビットコインの購入が困難になる場合もあります。
こうした背景からノンKYCのP2P取引プラットフォームを利用するメリットは大きいです。例えば HodlHodl(@npub1yul83qxn35u607er3m7039t6rddj06qezfagfqlfw4qk5z5slrfqu8ncdu) は、匿名で世界中のユーザーと直接ビットコインを売買できるグローバルなP2Pマーケットプレイスです。HodlHodlではユーザー同士が直接取引し、サイト運営側はビットコインを一切預かりません。取引はマルチシグエスクロー(2-of-3の多重署名契約)で安全に管理され、取引手数料も最大0.5%と低く抑えられています。プライバシーとセキュリティを確保しながら、銀行口座や身分証なしでビットコインを売買できるため、社会的にも経済的にも大きな意義があります。
本チュートリアルでは、HodlHodlを使ってビットコインを購入・販売する具体的な手順を分かりやすく解説します。また、HodlHodlの安全性(マルチシグエスクローによる非中央集権型の管理)や、他のプラットフォームにはない特徴(本人確認不要、ユーザー自身による鍵の管理、APIやレンディングサービスの活用など)についても説明します。P2P取引に不慣れで不安を感じている方にも安心してご利用いただけるよう、丁寧で親しみやすい言葉で案内していきます。
HodlHodlの基本準備
アカウント登録: HodlHodlの利用を開始するには、まず無料のアカウント登録を行います。必要なのはメールアドレスとパスワードだけで、ユーザー名や身分証の提出は不要です。登録後に届く確認メール内のリンクをクリックすれば、すぐに取引を始められます。
ビットコインウォレットの用意: HodlHodlは取引の際にユーザー自身のビットコインウォレットを使用するノンカストディアル方式です。プラットフォーム上にウォレットは用意されていないため、事前に自分のビットコインウォレットを準備してください。例えばモバイルウォレットやハードウェアウォレットなど、自分だけが秘密鍵を管理できるウォレットを用意しましょう。買い手の場合は購入したビットコインを受け取るウォレットが必要になり、売り手の場合は売却するビットコインを自身のウォレットからエスクローに送金する必要があります。

ビットコインを購入する方法(Buy BTC)
それでは、HodlHodlでビットコインを購入(Buy) する手順を見ていきましょう。以下では、日本円(JPY)を銀行振込で支払ってビットコインを買う例を想定して説明しますが、基本的な流れは他の通貨や支払い方法でも同じです。
-
「Buy BTC」をクリックする: HodlHodlにログインし、画面上部のヘッダー左側にある「Buy BTC」ボタンをクリックします。これにより、現在出ているビットコイン売り注文(オファー)の一覧ページに移動します。
-
検索フィルターの設定: オファー一覧ページでは、自分の希望条件でオファーを絞り込むことができます。国、法定通貨、取引タイプ、支払い方法、金額などのフィルター項目があります。例えば日本で銀行振込により購入したい場合、「Country(国)」をJapan、「Currency(通貨)」をJPY、「Payment method(支払い方法)」を Bank Transfer 銀行振込に設定します(他の項目は必要に応じて指定します)。フィルターは任意ですが、自分に合った支払い方法や金額範囲のオファーを探すのに役立ちます。
-
オファーを選ぶ: フィルターを適用すると、条件に合致する売り手のオファー一覧が表示されます。各オファーにはレート(価格)、取引可能額範囲、支払い方法、売り手の評価などが記載されています。希望に合うオファーが見つかったら、そのオファーの詳細をクリックします。例えば「1 BTC = 〇〇JPY」のようなレートで、自分が購入したい額に対応できるオファーを選びましょう。初めて取引する場合は、評価の高い売り手や少額からの取引を選ぶと安心です。

-
購入量と受取アドレスの入力: オファーをクリックすると、取引の詳細入力画面になります。ここで購入したいビットコインの量を入力します(ビットコイン量あるいは法定通貨換算額のどちらでも入力可能です)。多くの場合、最低・最大取引額が決まっているので、その範囲内で入力してください。また、ビットコインの受取先アドレスを求められます。これは購入後にビットコインを受け取る自分のウォレットアドレスです。アカウントの設定で事前に登録したアドレスがあれば自動で表示されますが、都度指定することも可能です。さらに、支払い方法が複数指定されているオファーでは希望の支払い方法を選択します(例:銀行振込の中でも特定の銀行を指定できる場合があります)。最後に、取引相手(売り手)への伝達メッセージ欄があれば、必要に応じてコメントを記入します。入力が完了したら内容を確認し、「Create contract(契約作成)」 的なボタンを押して取引を開始します。
-
エスクローアドレスの生成: 契約が作成されると、取引画面上にエスクロー(第三者保管用マルチシグアドレス)を生成するための手順が表示されます。ここで 「Generate escrow(エスクロー生成)」 ボタンをクリックし、プラットフォームに登録したペイメントパスワード(支払い用パスワード)を入力します。ペイメントパスワードはHodlHodlで取引の署名に使われる特別なパスワードで、初回取引時に設定しておく必要があります。正しく入力すると、この取引専用のビットコインエスクローアドレスが自動生成されます。あとは売り手がそのエスクローアドレスにビットコインを入金するのを待ちます。画面上に「waiting for deposit(入金待ち)」等のステータスが表示されるので、しばらく待機してください。売り手が約束のビットコイン額をエスクローに送金し、一定のブロック承認(Confirmations)が得られると、取引ステータスが自動で更新されます。
-
エスクロー入金の確認: ビットコインがマルチシグエスクローにロックされ、取引ステータスが「In progress(進行中)」や「Deposited(入金済み)」といった表示に変わったことを必ず確認します。ステータス表示とブロックチェーン上の確認回数が条件を満たしたら、支払いを実行しても安全な状態であることを意味します(エスクローにロックされたビットコインは売り手単独では動かせません。取引ページには売り手が指定した支払い詳細(銀行口座情報など)が記載されていますので、その指示に従って売り手へ法定通貨の支払い(振込)を行います。例えば銀行振込の場合、指定された口座にJPYを送金します。この段階では、必ず取引ページを開いたままにしておきましょう。 支払いが完了したら、取引ページ上の「I’ve sent the payment(送金完了)」ボタンをクリックして、売り手に支払い実行済みであることを通知します。併せて、チャット機能で支払い完了の旨を伝えると良いでしょう。
-
売り手によるビットコインのリリース: 買い手からの支払いが完了すると、売り手は自分の銀行口座等を確認して入金を検証します。売り手が入金を確認したら、取引ページ上で 「Release Bitcoin(ビットコインをリリース)」 ボタンを押し、ペイメントパスワードを入力してエスクローからビットコインを開放します。これにより、エスクロー上のビットコインが買い手の指定アドレス(先ほど入力した受取用ウォレットアドレス)に送信されます。売り手がビットコインをリリースすると取引ステータスが「Released(解放済み)」に変わり、まもなくブロックチェーン上で買い手のウォレットにビットコイン着金が確認できるでしょう。
-
取引完了: ビットコインが無事自分のウォレットに届けば取引完了です。取引ページには「Completed(完了)」などのステータスが表示され、双方がお互いを評価できるようになります。初めてのP2P購入、お疲れさまでした! 🎉
💡 重要な注意事項(買い手向け): エスクローにビットコインがロックされる前に代金を支払ってはいけません。必ず取引ステータスが「Deposited」や「In progress」になるのを確認してから支払いを実行してください。また、取引には売り手が入金を確認してからビットコインをリリースするまでの制限時間(Payment window)が設定されています。時間内に支払いが完了しないと取引が自動キャンセルされる場合がありますのでご注意ください。困ったことがあれば、取引ページのチャットで相手に連絡することもできます。万一、支払いを送ったのに売り手がビットコインをリリースしない場合は、支払い期限が過ぎてからディスピュート(紛争解決手続き) を開始することも可能です。
ビットコインを販売する方法(Sell BTC)
次に、HodlHodlでビットコインを販売(Sell) する手順を説明します。基本的な流れは購入時と似ていますが、立場が逆になる点(自分がビットコインをエスクローに預け、買い手からの支払いを待つ点)に注意してください。以下では、日本で銀行振込によりJPYを受け取ってビットコインを売る場合を例に解説します。
-
「Sell BTC」をクリックする: HodlHodlにログイン後、画面上部左側の「Sell BTC」ボタンをクリックします。これで現在出ているビットコイン買い注文(買い手のオファー)一覧ページに移動します。
-
検索フィルターの設定: 買い手オファー一覧から、自分が対応可能な条件のオファーを探します。フィルター項目はBuyの場合と同様で、国、通貨、支払いタイプ、支払い方法、金額などを指定できます。日本円での銀行振込を希望する買い手を探す場合、国をJapan、通貨をJPY、支払い方法をBank Transferに設定して検索します。
-
オファーを選ぶ: 条件に合致する買い手のオファーが一覧表示されるので、希望に合うものをクリックします。各オファーには買い手が希望するレートや取引限度額、支払い方法、買い手の評価などが記載されています。有利なレートかつ信頼できそうな相手を選びましょう。初取引で不安な場合は、小額で高評価の買い手から始めるとよいです。
-
売却量と受取情報の入力: オファー詳細画面で、売却したいビットコイン量を入力します(または必要な法定通貨額)。オファーごとに最低・最大額が設定されているので範囲内で入力してください。続いてビットコインの受取アドレス欄がありますが、これは取引完了時に買い手がビットコインを受け取るアドレスです。売り手である自分が入力する必要は基本的になく、買い手側が受取先を指定するか、既に買い手のダッシュボード設定で決まっています。次に、受け取りたい支払い方法が複数記載されている場合は希望の方法を選択します(例えば「Bank Transfer」の中でも特定の銀行名など)。コメント欄があれば取引相手(買い手)へのメッセージを任意で入力します。内容を確認し問題なければ 「Create contract(契約作成)」 ボタンを押して取引を開始します。
-
エスクローアドレスの生成: 契約が作成されると、エスクロー用のビットコインアドレスを生成する段階に進みます。ここで 「Generate escrow」 ボタンをクリックし、ペイメントパスワードを入力します(買い手の手順と同様)。これにより、この取引専用のマルチシグエスクローアドレスが発行されます。次に 自分(売り手)が売却予定のビットコインをエスクローアドレスに送金 します。取引画面上に正確なBTC額と対応するQRコードが表示されるので、自分のウォレットからそのアドレスへ送金してください。送金したら 「I’ve sent the funds(送金完了)」 ボタンを押してビットコインをエスクローに預けたことを通知します。

-
エスクローへのビットコインロック: ビットコインを送金するとブロックチェーン上で一定回数の承認(Confirmations)を経て、エスクローにロックされます。取引ステータスが「In progress(進行中)」や「Deposited」に変わり、買い手は安心して支払いを行える状態になります。あとは買い手からの法定通貨支払いを待ちます。取引画面で支払い期限(Payment window)内に買い手が支払いを完了し、「支払い送信済み」のボタンを押すとステータスが「Paid(支払い済み)」に変わります。
-
支払いの受領確認: ステータスが「Paid」になったら、買い手が送金を完了したことを意味します。すぐに自分の銀行口座など該当の支払い方法で入金を確認しましょう。金額が全額正しく受け取れたことを確認できたら、取引ページ上で 「Release deposit(デポジットを解放)」 ボタンをクリックし、ペイメントパスワードを入力してエスクローのビットコインを開放します。これにより、エスクローにロックされていたビットコインが買い手に送付されます。
-
取引完了: ビットコインをリリースすれば取引完了。ステータスが「Completed」に変わり、買い手は間もなく自分のウォレットでビットコインを受け取るでしょう。最後にお互いを評価して取引終了となります。初めてのP2P売却、お疲れさまでした! 🎉
💡 重要な注意事項(売り手向け): 支払いを受け取る前にビットコインをエスクローから**絶対にリリースしないでください。買い手からの入金を自分の銀行口座等で確実に確認できてから、ビットコインを解放するようにしましょう。また、もしビットコインをエスクローに送金した後で買い手から支払いが行われず期限切れ(Payment window経過)になった場合、取引をキャンセルしてエスクローのビットコインを自分に返還することができます。取引中は常に取引相手とのチャットで連絡を取り合い、不明点を確認するよう心がけましょう。
HodlHodlの安全性:マルチシグと非カストディアル設計
● マルチシグエスクローによる資金保護: HodlHodl最大の特徴は、2-of-3のマルチシグエスクロー(multisignature escrow)によって取引資金を保護している点です。取引が成立すると、自動的に3つの秘密鍵が関与するビットコインアドレスが生成されます。この3つの鍵のうち2つの署名があれば資金を動かせる仕組みになっており、鍵の配分は「売り手」「買い手」「HodlHodl運営」の三者にそれぞれ1つです。取引中、ビットコインはブロックチェーン上のエスクローアドレスにロックされ、双方の合意なしには動かせまん。つまり、売り手は買い手の同意なしにビットコインを引き出すことはできず、逆に買い手も売り手の協力なしにビットコインを入手することはできません。両者が取引を完了すれば売り手+買い手の2署名でリリースが可能となり、万一トラブルが起きた場合にはHodlHodl運営が仲裁役として(買い手または売り手の一方と協力し)2署名目を提供することで不正を防ぎます。このようにマルチシグ契約によって、詐欺や持ち逃げのリスクを最小限に抑え、安全かつ公平な取引が実現されています。
● 非カストディアル(ユーザー主導の資金管理): HodlHodlは取引プラットフォームでありながら、ユーザー資金を一切預からないという非カストディアル設計を貫いています。取引中のビットコインは常にマルチシグエスクローにあり、HodlHodl運営が単独で動かすことはできません。これはつまり、中央集権的な取引所とは異なり、HodlHodlがハッキング被害に遭ってもユーザーのビットコインが盗まれる心配がないことを意味します。またプラットフォームが万一ダウンしたりサービス提供を停止した場合でも、当事者間で2つの鍵さえあればエスクローのビットコインを取り戻すことが可能です(※この場合やや技術的な手順が必要になりますが、HodlHodlが完全に消失するケースでも資金はブロックチェーン上に安全に存在し続けます)。HodlHodl運営は3つの鍵のうち1つを保有するのみで、しかもそれは紛争時の仲裁に使うためのものです。通常の取引では運営が介在することなく、ユーザー同士で完結します。以上のように、HodlHodlはカストディアルな第三者を排除し、利用者自身が資金と取引の主導権を握るというビットコイン本来の精神に沿った安全設計となっています。
● 評判システムと取引履歴: HodlHodlでは、各ユーザーに公開の評価(Rating)と取引履歴が紐づいています。取引を完了するごとに互いにレビューを残せるため、他ユーザーの信頼度を事前に知ることができます。初めて取引する相手がどんな評価を受けているか、過去の取引回数や成功率などの情報を確認することで、怪しい相手を避けることが可能です。特に初心者のうちは評価の高い相手を選ぶ、もしくは身近に信頼できるユーザーがいればトラスト機能(他のP2Pプラットフォームでの実績を証明する仕組みや信用できるユーザーをお気に入り登録する機能)を活用すると良いでしょう。
● 二要素認証(2FA)と信頼できる端末: アカウントの不正アクセス対策として、HodlHodlは二段階認証(2FA)のオプションを提供しています。AuthyやGoogle Authenticatorと連携し、一度設定すればログイン時にパスワードに加え6桁のコード入力が求められるようになります。これにより、万一パスワードが漏洩しても本人のデバイスがなければログインできず、アカウントを保護できます。またTrusted Devices(信頼できる端末)機能を有効にすると、新しいデバイスからログインしようとした際にメール確認が必要となり、ユーザーの許可なく不審な端末からアクセスされるのを防ぎます。初心者の方でも、アカウント登録後は設定画面から2FAや信頼できる端末機能を有効化しておくことを強くおすすめします。
● ディスピュート(紛争解決)機能: 万が一取引相手との間でトラブルが発生した場合(例:買い手は支払ったと主張しているが売り手が確認できない等)、HodlHodlのプラットフォーム上でディスピュート(紛争)を開始することができます。ディスピュートが発生すると、HodlHodlのサポートチームが両者から事情を聞き、中立的な立場で問題解決に当たります。必要に応じて前述の運営のマルチシグ鍵を用いて適切な側にビットコインをリリースするなど、公平な裁定が行われます。ディスピュートは最終手段ではありますが、万一の場合の安心材料として覚えておいてください。
以上のように、HodlHodlは技術的・制度的な多層防御によってユーザーの資金と取引の安全を確保しています。他のユーザーの評価を確認する、取引手順を順守する(エスクロー未成立での送禁止等、アカウントのセキュリティ設定を有効にするといったユーザー自身の注意もあわせて心掛ければ、P2P取引でも安心してビットコインを利用できるでしょう。
HodlHodlの特徴:他プラットフォームとの違い
最後に、HodlHodlが他のビットコイン取引サービスと比べて優れている点、特徴的な点を整理します。初めて利用する際の不安解消にもつながるポイントです。
-
🌐 KYC不要の匿名取引: HodlHodl最大の特徴は、本人確認(KYC)なしでビットコイン取引ができる点です。メールアドレスさえあれば世界中誰でも利用開始でき、パスポートや身分証の提出は一切求められません。これはプライバシー保護の面で大きな利点ですし、取引履歴が本人名義に紐付かないため将来的な資産没収や口座凍結のリスクも低減します。規制が厳しい地域のユーザーや銀行口座を持てない人々でも、HodlHodlならビットコイン経済に参加しやすくなっています。
-
🔐 ユーザーが鍵を管理する非中央集権型取引: 前述の通り、HodlHodlはノンカストディアルなP2P取引所であり、ユーザー自身が資産の鍵を管理します。取引ごとにマルチシグのエスクローが生成され、利用者はその一方の鍵を保持します。そのため「取引所にビットコインを預けっぱなしにしていたらハッキングで失った」といった事態が起こりません。常に自身のウォレットから直接取引を行うため、ビットコインの自主管理の原則**が守られています。中央集権的な管理者がいない分、自分で秘密鍵を安全に保管する責任は伴いますが、その分だけ第三者リスクが排除された公平な環境と言えます。
-
💱 世界中の通貨と多様な決済方法に対応: HodlHodlはグローバルなプラットフォームであり、世界中のあらゆる法定通貨 で取引できます。現在100を超える国の通貨と地域が利用されており、取引に使える決済方法も100種類以上と非常に豊富です。銀行振込やオンライン決済サービスはもちろん、現金の対面受け渡しやギフトカード、電子マネー、モバイル送金、さらには商品と交換などユニークな方法までユーザーが自由にオファーを作成できます。これにより、自分の利用しやすい手段で取引相手を見つけられる柔軟性があります。他のプラットフォームだと対応通貨や決済手段が限定されがちですが、HodlHodlでは*「自分の条件でオファーを作成できる」 の強みです。
-
💰 低い手数料と透明な料金体系: HodlHodlの取引手数料は一律0.5%(買い手と売り手で折半で各0.25%ずつ負担)と比較的低コストです。しかも手数料は取引成立時にビットコイン額から自動控除される仕組みで、隠れたコストがありません。さらに紹介プログラムを利用すると0.45%に割引されるなどの優遇もあります。入出金に伴う手数料も基本的に存在せず、各自が使うウォレットの送金手数料以外に余計な負担はありません。他の取引所でありがちな「出金手数料が高額」「スプレッドが不透明」といった心配もなく、明朗会計でユーザーに優しい料金体系です。
-
🤝 初心者に優しいインターフェース: P2P取引というと難しそうな印象を持たれるかもしれませんが、HodlHodlのサイトはシンプルで直感的なインターフェースになっています。必要な操作は「Buy BTC / Sell BTC」ボタンから進んでフォームに入力していくだけで、画面の指示に沿って進めれば迷うことは少ないでしょう。サイトは現在ウェブブラウザ経由で利用しますが、スマートフォンのブラウザからでも見やすく設計されています。専用アプリはありませんが、その分アップデート時にもすぐ全員が最新機能を利用できます(ダウンロード不要で常に最新版が提供されるメリットです。また、取引画面にはリアルタイムのチャット機能があり、相手ユーザーと直接コミュニケーションを取れるため安心です。困ったときは相手に質問したり状況を確認できるので、言葉の壁がある場合でも定型文や翻訳を活用して意思疎通できます。
-
🛠 API提供による拡張性: HodlHodlは上級ユーザーや開発者向けに**公式APIを提供しています。APIを利用すると、自分のプログラムからHodlHodl上のオファー取得や契約作成、ステータス更新などを自動化することが可能です。例えば、マーケットメーカーとしてレートを自動調整したり、他のサービスと連携して複数のP2P取引所のオファーを比較表示する、といった応用ができます。APIキーはプロフィール設定から発行でき、ドキュメントも公開されているため高度な取引戦略を実装したいユーザーには魅力的な機能です。PaxfulやLocalBitcoinsなど一部他サービスでもAPIは提供されていますが、HodlHodlのAPIはエスクロー操作まで含め包括的にサポートしている点で強力です。
-
💳 ビットコインレンディングサービス: HodlHodlは現物取引だけでなく、ビットコイン担保のレンディング(貸借)プラットフォームも運営しています。サイト上部の「P2P Lending(レンディング)」からアクセスでき、ビットコインを担保にUSDTなど他の暗号資産を借りたり、あるいは逆に他の人に貸し出して利息収入を得ることができます。技術的には取引プラットフォームと同じマルチシグエスクロー方式を用いており、借り手がビットコインを担保としてエスクローにロックし、貸し手が安定通貨を送金することでローン契約が成立します。期間満了時に借り手が返済すればビットコイン担保が戻り、返済不能(延滞や価格変動での清算)の場合は貸し手に担保が渡る仕組みです。驚くべきことに、このレンディングサービスでも一切KYCは要求されません。短期のビットコイン活用や利息収入を得たいニーズに応えるユニークなサービスであり、HodlHodlを使いこなせば「ビットコインを売買するだけでなく、借りたり貸したりする」といった金融活用も可能になります。P2P Lendingについては、今後別のチュートリアルで詳しく説明します。
-
🧪 テストネットで練習可能: 「いきなり本番は不安…」という方向けに、HodlHodlはテストネット版サイトも提供しています。TESTNETでは、本物のビットコインではなくテスト用のビットコイン(signet**ネットワークのBTC)を使って、実際の取引手順を練習できます。架空の資金でHodlHodlの操作感を試せるため、初心者はまずテストネットで売買の流れをシミュレーションしてみると良いでしょう。十分に慣れてから本番取引に移行すれば、落ち着いて対処できます。テストネットBTCは各種ファウンセット(蛇口サイト hhtestnet.com)から無料でもらうことができ、HodlHodlのテスト環境で練習するのに役立ちます。
以上がHodlHodlの主な特徴と利点です。匿名性・安全性・使いやすさを兼ね備えたHodlHodlは、まさに「ビットコインをネイティブにP2P利用する」ための理想的なプラットフォームと言えるでしょう。初めは不安もあるかもしれませんが、本チュートリアルで説明した手順に沿って取引を行えば、きっとその手軽さと利便性に驚くはずです。ぜひHodlHodlでのP2P取引に挑戦してみてください。自分自身でビットコインを扱う経験を通じて、ビットコインの真の価値である「個人が金融の主導権を握ること」を実感できるでしょう🚀
もしビットコインのP2P取引やHodlHodlなどについてもっと深く知りたい、あるいは個別に相談してみたいと思えば、どうぞお気軽にご連絡ください。1対1のコンサルも承っています。
サービスには決まった料金はありませんが、ご相談を通じて「役に立った」と思い、お悩みや疑問を解決できたと感じていただけたら、「3つのT」でのご支援(Value for Value)をぜひご検討ください:
- 時間(Time):この記事をSNSなどでシェアしていただくこと。
- 才能(Talent):コメントや補足情報などを通じて知識を共有していただくこと。
- 宝(Treasure):世界で最も健全なお金、ビットコインの最小単位「sats」でのご支援。
もちろん、支援の有無にかかわらず、お力になれればとても嬉しいです。 では、また次回!
参考資料
- Bitcoin Whitepaper - Bitcoin: A Peer-to-Peer Electronic
- HodlHodl公式サイト - Welcome to Hodl ([P2P BITCOIN TRADING platform]
- HodlHodlヘルプセンター - How to buy Bitcoin / How to sell Bitcoin
- HodlHodlヘルプセンター - Why is trading on Hodl Hodl secure
- HodlHodl FAQ - Why should I use HodlHodl、How secure is trading on HodlHodl
- HodlHodl Medium - Hodl Hodl’s API release
- HodlHodl Lend FAQ - What is Lend a ([Earn Highest Returns on Your Crypto Investment - Lend at Hodl Hodl]
- ZoneBitcoin - Hodl Hodl: Tutorial on the anonymous and KYC-free P2P platform
- など
-
-
 @ dfbbf851:ba4542b5
2025-03-29 06:51:21
@ dfbbf851:ba4542b5
2025-03-29 06:51:21ในยุคดิจิทัลที่การสื่อสารมีบทบาทสำคัญต่อชีวิตประจำวัน เทคโนโลยี Cell Broadcast ได้กลายเป็นหนึ่งในเครื่องมือที่ทรงพลังสำหรับการแจ้งเตือนฉุกเฉิน ไม่ว่าจะเป็นภัยพิบัติหรือเหตุการณ์สำคัญที่ต้องแจ้งให้ประชาชนทราบอย่างทันท่วงที ⏳💡
📌 Cell Broadcast คืออะไร ?
Cell Broadcast (CB) เป็นเทคโนโลยีที่ใช้ส่งข้อความกระจายสัญญาณผ่านเครือข่ายโทรศัพท์มือถือ 🏗📶 โดยแตกต่างจาก SMS ตรงที่สามารถส่งข้อความถึงผู้ใช้จำนวนมากได้พร้อมกัน โดยไม่ต้องทราบหมายเลขโทรศัพท์ ของผู้รับ 📲💨
ข้อความ CB สามารถส่งถึงอุปกรณ์ที่รองรับในเครือข่ายมือถือที่เปิดใช้งานอยู่ภายในช่วงเวลาสั้น ๆ ⏱ และ ไม่ทำให้เครือข่ายล่ม
✨ ข้อดีของ Cell Broadcast ✨
✅ ส่งข้อความรวดเร็ว – แจ้งเตือนได้ภายในไม่กี่วินาที แม้ในกรณีฉุกเฉิน ⚡🚀
✅ ไม่ต้องใช้หมายเลขโทรศัพท์ – กระจายสัญญาณไปยังอุปกรณ์ทุกเครื่องที่อยู่ในพื้นที่เป้าหมายได้โดยตรง 📡
✅ รองรับหลายภาษา – สามารถตั้งค่าการแจ้งเตือนให้เหมาะสมกับประชากรในแต่ละพื้นที่ 🌍🗣
✅ ไม่ทำให้เครือข่ายหนาแน่น – ต่างจาก SMS หรือการโทรจำนวนมากที่อาจทำให้เครือข่ายล่ม 📵❌
✅ ทำงานได้แม้ไม่มีอินเทอร์เน็ต – สามารถแจ้งเตือนในกรณีที่โซเชียลมีเดียหรืออินเทอร์เน็ตใช้งานไม่ได้ 🌐🚫
🌍 การใช้งาน Cell Broadcast ทั่วโลก
🔹 สหรัฐอเมริกา – ใช้ระบบ Wireless Emergency Alerts (WEA) เพื่อแจ้งเตือนเหตุการณ์ฉุกเฉิน เช่น พายุเฮอริเคน 🌀🌪
🔹 ญี่ปุ่น – ใช้ระบบ Earthquake Early Warning (EEW) เพื่อแจ้งเตือนแผ่นดินไหวล่วงหน้า ⛩🌏
🔹 สหภาพยุโรป – มีนโยบายให้ประเทศสมาชิกใช้ Public Warning System ผ่าน Cell Broadcast 📢🏛
🤔 ทำไมประเทศที่ยังไม่มีระบบนี้ควรนำมาใช้ ?
หลายประเทศ รวมถึง ประเทศไทย ยังไม่มีการใช้ Cell Broadcast อย่างแพร่หลาย ทั้งที่เป็นเทคโนโลยีที่สามารถช่วยชีวิตผู้คนได้อย่างมหาศาล 🚑 หากเกิดภัยพิบัติ เช่น น้ำท่วม แผ่นดินไหว สึนามิ หรือไฟป่า 🔥🌊 Cell Broadcast สามารถส่งการแจ้งเตือนไปยังทุกคนในพื้นที่เสี่ยงได้ทันที ลดความสูญเสียและเพิ่มโอกาสรอดชีวิตได้มากขึ้น
🔸 ความแม่นยำสูง – สามารถส่งแจ้งเตือนไปยังพื้นที่ที่ได้รับผลกระทบโดยตรง ทำให้ประชาชนสามารถเตรียมตัวรับมือได้ดีกว่า
🔸 ไม่มีปัญหาความล่าช้า – ต่างจากการแจ้งเตือนผ่าน SMS หรือโซเชียลมีเดียที่อาจล่าช้าหรือไม่ได้รับข้อความเลยหากเครือข่ายล่ม
🔸 เป็นมาตรฐานสากล – หลายประเทศพัฒนาแล้วมีระบบนี้ใช้งานอย่างมีประสิทธิภาพ ประเทศที่ยังไม่มีควรนำมาใช้เพื่อให้สามารถจัดการภัยพิบัติได้อย่างมีประสิทธิภาพ
🔸 ประหยัดต้นทุนในระยะยาว – ลดความเสียหายทางเศรษฐกิจจากภัยพิบัติ เพราะประชาชนได้รับการแจ้งเตือนล่วงหน้า ทำให้สามารถอพยพหรือป้องกันความเสียหายได้
🔮 อนาคตของ Cell Broadcast
ในอนาคต Cell Broadcast อาจถูกนำมาใช้ร่วมกับ ปัญญาประดิษฐ์ (AI) 🤖 และ Internet of Things (IoT) 🌐 เพื่อเพิ่มความแม่นยำและปรับแต่งการแจ้งเตือนได้ดียิ่งขึ้น 🎯💡
📌 ปล.
Cell Broadcast เป็นเทคโนโลยีแจ้งเตือนที่ทรงพลังและมีบทบาทสำคัญในการช่วยชีวิตผู้คน 🚑 ด้วยความสามารถในการส่งข้อความได้อย่างรวดเร็ว ครอบคลุมพื้นที่กว้าง และไม่ต้องพึ่งพาอินเทอร์เน็ต จึงเป็นหนึ่งในเครื่องมือสำคัญสำหรับการบริหารจัดการภัยพิบัติในปัจจุบันและอนาคต 🔥
CellBroadcast #แจ้งเตือนภัย #เทคโนโลยีสื่อสาร #ภัยพิบัติ #เครือข่ายมือถือ #การสื่อสารฉุกเฉิน #เตือนภัยล่วงหน้า
-
 @ 65038d69:1fff8852
2025-03-29 12:00:27
@ 65038d69:1fff8852
2025-03-29 12:00:27The Americans just had a big election, and Canada’s next has been effectively underway for a while now. Automated moderation systems are being increasingly relied upon by large social media networks and are running amok with bans (I may be biased on this one, see “The Technology Deleted Me”). Opinions are everywhere, and many social media users live in fear of getting booted from their platform of choice over an innocuous post. “Of choice” usually being where the largest concentration of their connections also have accounts. For me that’s Facebook; for others it might be Instagram, Snapchat, Bluesky, or X.
What if there was a social media network built in such a way that you couldn’t be banned? Where your posts couldn’t be removed? Where you couldn’t be “put in the corner” by a group admin who didn’t like that the recipe page you shared had the word “crap” in it? Wouldn’t that be great? Yes, this does mean extreme (or straight-up illegal) content could be posted, but that’s happening on mainstream social media as well. Monitoring and banning isn’t working there so there’s no reason to repeat it elsewhere.
The unbannable social media I’m bringing to you today is called “Nostr”; "Notes and Other Stuff Transmitted by Relays”. How it works is explained in the name; notes (posts) are transmitted from a client (app on your device) to relays (servers) which are then transmitted to other relays and clients connected to them. I’ll explain in more detail as we go through the setup process.
Step 1: Pick a client. I like Damus on iOS and noStrudel on desktop. Nostur is also popular on iOS. Amethyst and Primal are popular on Android. Pick the one you most like the look of.
Step 2: Set up an “account”. On Nostr you won’t have an account in the traditional sense. You’ll instead have a public/private key set (also known as a keypair). Think of your public key as your username and your private key as your password; only you won’t need to pick, memorize, or regularly use either of them. Your client will do most of that for you. Install the app of your choosing, launch it, and you’ll be walked through the account creation process. I strongly recommend copying your public key (the long random string that starts with “npub”) and your private key (the long random string that starts with “nsec”) to a password manager (see “Ugh, Passwords!” for more on password managers).
Optional: Step 2.5: Set up your “NIP-05 identifier”. This is totally optional, and can be done later if you aren’t up for it right now. A NIP-05 identifier looks identical to an email address (
name@domain.something) and is used as an easier way for others to find your profile. There are several free and paid services for this, most of which come with other benefits and services. A popular free one is Nostrcheck.me.Step 3: Choose some relays. Most clients will have a pre-configured set of public relays that work fine for most users. If you think of yourself as just a normal person trying to not be banned, you can skip this step. For everyone else, reach out to me for recommendations. A whole ‘nother article could be written on the subject of relays for niche needs.
Step 4: Find friends to follow. You can start with me if you like, by searching for my public key (
npub1kw893e70hve5ymc8kxr75d8m9wcuaaasqzn37xvea6l4f39q04fs7zusa4), or my NIP-05 (tnperron@nostr.theorangepillapp.com).Optional: Step 5: Post something! Also totally optional, but highly recommended! Even a simple “Hello, world!” will let others visiting your profile know that your account is being actively used.
That’s it, you’re now unbannable! How, you ask? There are two keys to this (pun fully intended). The first is that your public/private keypair is yours to control, can be loaded into any client, and used to connect to any relay (though you may need to pay for access to some). The second is that if someone operating a relay decides they don’t want to relay your posts anymore, you can still use any other on the big wide internet. You can even run your own relay if you want! No one can stop you!
Want help with any of these steps, or more details on advanced options like running your own node? You can find us at scalebright.ca.
-
 @ 2fb77d26:c47a6ee1
2025-02-01 14:40:02
@ 2fb77d26:c47a6ee1
2025-02-01 14:40:02In H. G. Wells’ Roman Die Zeitmaschine und den diversen Verfilmungen werden sie als »ausschweifend, langsam und naiv« dargestellt. Von »untermenschlicher Intelligenz« gezeichnet. Für Dan Simmons sind sie »faul, ungebildet und unkultiviert«. Die Eloi. Die als Nahrungsquelle der Morlocks gehaltenen Nachfahren des Homo sapiens. »Sie entwickeln sich rückläufig und verlernen Jahrtausende von Kultur, Denken und Vernunft, bis sie sich mit dem Vergnügen des bloßen Daseins zufrieden geben«. Ertönt das Schlüsselsignal, auf das sie von ihren Züchtern konditioniert wurden – eine umgebaute Zivilschutzsirene – trotten sie freiwillig und in hypnotischer Apathie zur Schlachtbank.
Ein ähnlichen Eindruck hatten viele Maßnahmenkritiker von den Unterstützern der mittlerweile in allen Punkten widerlegten Covid-Propaganda. Zurecht. Das Gefolge von Drosten, Lauterbach und Co. war blind für Fakten und ist ins offene Messer gelaufen. Bedauerlicherweise verhalten sich viele Maßnahmenkritiker aber nun in weiten Teilen genauso. Sie haben Idole gefunden. Wollen glauben. Sie ignorieren Informationen, Fakten und Daten und werden Opfer einer neu justierten, gut geölten Propagandamaschine. Nur, um die in ihre neuen Helden gesetzten Hoffnungen nicht aufgeben und der wenig erbaulichen Realität nicht ins Auge blicken zu müssen.
Sie glauben an Donald Trump, Javier Milei, Alice Weidel, Peter Thiel und vor allem Elon Musk. Daran, dass der supranationale Nachhaltigkeitskorporatismus am Ende sei, das Finanzsystem gerettet und Gerechtigkeit hergestellt wird. Die Widerständler von gestern sind die »Schlafschafe« von heute. Sie scheinen vergessen zu haben, wie Propaganda funktioniert. Aus diesem Grund – und weil es ein so schön griffiges Wort ist, bei dem man nur einen Buchstaben verändern muss, um daraus den Vornamen eines vermeintlichen Heilsbringers zu basteln – erlaube ich mir, die Anhänger des MAGA-Kults im Zuge der folgenden Seiten mokant als Eloi zu bezeichnen. Ein bisschen Spaß muss sein.
Kurskorrektur mit Ansage
Lynn Forester de Rothschild, in der finanzoligarchischen Hackordnung mindestens eine Ebene über BlackRock und Co. anzusiedeln, kündigte den aktuellen Narrativwechsel bereits am 30. August 2023 an, als sie bei Bloomberg sagte, der Begriff »ESG gehöre in die Tonne«. Er sei verbrannt. Auch BlackRock-CEO Larry Fink, der Marktteilnehmer zur Unterstützung von ESG »zwingen« wollte, teilte seinen Investoren bereits am 26. März 2023 mit, das in Verruf gekommene Label ESG durch den Begriff »Energiepragmatismus« zu ersetzen.
Sowohl Rothschild als auch Fink räumten aber gleichzeitig ein, dass sich die übergeordnete Agenda nicht ändern und man die »Green Economy« weiter vorantreiben werde, man diese aber besser vermarkten müsse, um konservative Kreise nicht weiter gegen sich aufzubringen. Ein simpler Marketing-Trick. Wenig überraschend also, dass sowohl BlackRock als auch sechs amerikanische Großbanken Anfang 2025 die Net Zero Initiative verließen. Zum »perfekten Zeitpunkt«, wie die New York Post bemerkt, um nicht von der negativen, anti-woken Berichterstattung rund um die verheerenden Feuersbrünste in Los Angeles tangiert zu werden.
Es scheint, als hätten die Eloi bereits wieder verdrängt, dass die WEF-Meetings 2021 und 2024 unter Arbeitstiteln wie »The Great Narrative« und »Rebuilding Trust« liefen. Artikuliertes Ziel der Davoser PR-Abteilung für Globalisierungsfragen war nämlich, sich den zunehmend echauffierten, misstrauischen Pöbel vom Hals zu halten. Durch neue Narrative und vertrauensbildende Maßnahmen. Und das hat, zumindest vorerst, ausgezeichnet funktioniert.
In den USA stieg das Vertrauen in ordnungsgemäß durchgeführte Präsidentschaftswahlen 2024 zum ersten Mal seit Jahren wieder etwas an. In Europa macht sich ebenfalls Zuversicht breit. Schließlich haben die sogenannten »Rechtspopulisten« nicht mehr nur in Italien und Ungarn, sondern auch in Finnland, der Slowakei und den Niederlanden Oberwasser. Von den Erfolgen der AFD ganz zu schweigen. Diese führen, wie zuletzt in Thüringen, trotz klarem Wählervotum zwar nicht zur Regierungsbeteiligung, weil »demokratische Prozesse« und »Brandmauern« das zu verhindern wissen – aber dabei sein ist ja bekanntlich alles. Dass Friedenstreiberin Alice Weidel den bundesdeutschen Rüstungsetat auf knapp 200 Milliarden verdoppeln will, scheint die euphorisierten Kritiker dunkelgrüner Militarisierung auch nicht auszubremsen. Hauptsache nicht grün. Oder woke.
Überstaatliche Sphären
Dabei scheint Euphorie in Anbetracht der Tatsachen alles andere als angebracht. So hat Milei nach Angaben von Global Finance zwar das argentinische »Staatsdefizit nach 123 Jahren beendet«, dafür leben heute 53 Prozent der 45 Millionen Argentinier in Armut. Der höchste Wert seit 20 Jahren. Ende 2023 waren es noch 41,7 Prozent. Daran ändert auch semantische Schützenhilfe von libertären Denkfabriken wie der Hoover Institution nichts. Die radikalen Privatisierungsfeldzüge von »El Loco« haben einen hohen Preis. Ob Aerolineas Argentinas, die staatliche Fluglinie, der Stahlproduzent IMPSA oder das Transportunternehmen Trenes Argentinos Cargas, das 7.800 Kilometer Bahnstrecke betreibt – das Volksvermögen wird an die Meistbietenden verscherbelt. Wer das ist, kann sich wohl jeder ausmalen. Denn sein Schlachtruf »Afuera!« (Raus hier!) gilt augenscheinlich nicht für BlackRock und Co. – schließlich sei Argentinien »ziemlich billig« zu haben, wie es Rick Rieder, Top-Bond-Manager des Unternehmens schon 2019 formulierte.
Man muss allerdings nicht in die Ferne schweifen, um sich der realen Gefahren für die Freiheit bewusst zu werden. Jener Gefahren, die von Personalien gänzlich unberührt bleiben. So arbeitet die Europäische Union weiter an der eID, der Grundlage des technokratisch-totalitären Kontroll-Grids. Ihre Einführung ist beschlossene Sache. Offen ist lediglich, ab wann sie zum Obligatorium wird. Auch das persönliche CO2-Budget ist auf Kurs. Mit ETS2 (EU Emissions Trading System) nimmt die EPA (Environmental Protection Agency) seit dem 1. Januar 2025 nach der Konzernwirtschaft nun kleine und mittlere Unternehmen in den Fokus und verpflichtet diese, CO2-Kompensationsabgaben auf ihren Gas-, Benzin- und Mineralölverbrauch zu entrichten. Das dürfte Heiz-, Fracht- und folglich die Lebenshaltungskosten des Bürgers in neue Höhen treiben. Bis der Sonntagsausflug mit dem Familienauto nicht mehr nur Zeit, Benzin und Nerven, sondern auch CO2-Gebühren kostet, dauert es also wohl nicht mehr allzu lange.
Dieser überparteilichen, supranational koordinierten Überwachungs- und Enteignungsagenda ist weder durch die Wahl des geringeren Übels noch durch Auswandern zu entkommen. Denn wie sich der Internetpräsenz des »Global Governance Forum« (GGF) entnehmen lässt, wird bereits eifrig an »Global Government« gearbeitet. Die UN-nahe Nichtregierungsorganisation hat sich nämlich zum Ziel gesetzt, die Charta der Vereinten Nationen bis 2028 zu aktualisieren und den allseits bekannten »Herausforderungen unserer Zeit« anzupassen. Pünktlich ab 2030 soll das neue Vertragswerk ratifiziert werden und neben neuen Befugnissen für den Internationalen Gerichtshof sowie einer UN-Streitmacht auch eine Regierungsstruktur analog der Europäischen Union ermöglichen. Sprich, eine Weltregierung. Ganz demokratisch selbstverständlich.
Neben eID und CO2-Budget sind natürlich auch die Ausweispflicht fürs Internet und die automatisierte Zensur unliebsamer Inhalte weiter auf Kurs. Nachdem die Vereinten Nationen im September 2024 bereits dem totalitären »Pakt für die Zukunft« zustimmten, wurde am Heiligabend 2024 noch rasch die neue »Konvention gegen Onlineverbrechen« durchgewunken. Und seit Januar 2025 treibt die UN die Umsetzung eines noch weitreichenderen Abkommens namens »Global Digital Compact« voran. Ein Papier, vor dem ich bereits im Juli 2023 gewarnt habe. Was all das für den Bürger bedeutet, zeigt sich in Griechenland, wo die Regierung seit Anfang des Jahres Social-Media-Konten mit Steuer-Identifikationsnummern verknüpft, um eine Alterskontrolle fürs Internet einzuführen. Damit folgt die von der EU in Kreditsklaverei gehaltene Regierung in Athen dem Vorbild Australiens, wo der Zugang so Social-Media-Plattformen künftig erst ab einem Alter von 16 Jahren erlaubt werden soll – wofür man schlussendlich jeden Nutzer kontrollieren muss, der online geht.
Auch das von vielen noch immer als Mythos abgetane Geoengineering wird derweil munter weitergeführt. Obwohl Berichte des US-Kongress und mittlerweile sogar wissenschaftliche Berater der EU-Kommission vor großflächigem Solar Radiation Management warnen. Im Rahmen eines offiziellen, 54 Seiten umfassenden Reports an die EU-Kommission sowie eines Artikels des britischen Guardian vom 9. Dezember 2024 verwies das siebenköpfige Forscherteam auf die unabschätzbaren Konsequenzen solcher Eingriffe und forderte ein EU-weites Moratorium.
Wie genau Trump, Musk, Milei, Meloni, Weidel und Co. die Welt vor diesem Sammelsurium an totalitären Übergriffigkeiten retten wollen, konnte mir bislang keiner der Eloi sagen.
DJ Trump
Warum die in Donald Trump, den »Vater der Impfung«, und sein zionistisches Kriegstreiberkabinett gesetzten Hoffnungen bald bitterer Enttäuschung weichen dürften, habe ich bereits am 14. November 2024 ausführlich beschrieben. Dass auch die beiden Hauptargumente seiner Befürworter – dass er die mRNA-Kampagne mittlerweile bereue und in seiner ersten Amtsperiode Friedenspolitik betrieben habe – schlichtweg falsch sind, ebenfalls. Denn anhand der nackten Zahlen lässt sich eindeutig belegen, dass Trump »der kriegslüsternste Präsident der jüngeren Geschichte« war. Und wie stolz er auf »Operation Warp Speed« ist, die unzählige Amerikaner Gesundheit oder Leben kostete, ließ er die Welt zuletzt am 17. November 2024 auf seinem Social-Media-Netzwerk Truth Social wissen.
Trumps Interesse gilt nicht Frieden und Freiheit, sondern Donald Trump. So war es sein ganzes Leben lang. Wenn sich »The Donald« jemandem verpflichtet fühlt, ist es vielleicht Wilbur Ross, der ehemalige Chef von Rothschild Inc. Bankruptcy Advising. Denn wie das Forbes Magazine am 8. Dezember 2016 korrekt erläuterte, rette das Bankhaus vor gut 30 Jahren nicht nur Trumps bankrotte Casinos, sondern damit auch seine ganze Karriere. Nicht weil man in Trumps Geschäften und Immobilien einen besonderen Wert sah, sondern weil man die Person Donald Trump als »Anlage« betrachtete. Trotzdem ist es sicher nur Zufall, dass Ross von 2017 bis 2021 Handelsminister der Vereinigten Staaten war.
Elon Musk
Auch über den PayPal-Mafioso, CIA-Handlanger und Bilderberg-Executive Peter Thiel, dessen Protegé JD Vance nun US-Vizepräsident ist, habe ich bereits im September 2024 einen ausführlichen Artikel geschrieben. Gleiches gilt für Elon Musk, dessen trügerisches Image als Genius, Erfinder und Entrepreneur ich sogar schon im Oktober 2022 durchleuchtet habe. Zitat:
»Dass Elon Musk nicht rein zufällig zur liberal-coolen Ikone avancierte, legt ein Blick in seine Anfangsjahre als Unternehmer nahe. Denn während im sagenumwobenen Silicon Valley Ende der 1990er-Jahre eine Vielzahl an erfolgreicheren Tech-Entrepreneuren existierte, war es ausgerechnet Elon Musk, der für einen absolut inhaltsleeren Gastauftritt bei CNN gefilmt wurde, sodass zum ersten Mal eine breitere Öffentlichkeit von ihm Notiz nehmen musste. Dabei war sein erstes Unternehmen – Zip2 –, das er im Jahre 1995 mit seinem Bruder sowie einem weiteren Partner gegründet und im Februar 1999 für circa 300 Millionen US-Dollar an Compaq veräußert hatte, nicht das revolutionärste Unterfangen im kalifornischen IT-Mekka dieser Tage. Es handelte sich um ein simples Telefonbuch fürs Internet. Wenig mehr als eine Datenbank, in die sich Unternehmen eintragen konnten, um ihre Adresse im Netz zu hinterlegen.«
Meine fast zweieinhalb Jahre alte Analyse bedarf allerdings dringend einer Aktualisierung. Denn was Musk in der Zwischenzeit trieb – und für die Zukunft plant – hat so gar nichts mit dem zu tun, was seine geradezu fanatisierten Anhänger in ihm sehen wollen.
Fangen wir der Vollständigkeit halber aber noch mal vorne an: Elon Musk hat weder PayPal gegründet noch den Tesla erfunden. Auch wenn er das gerne so darstellt. Dafür fertigte Tesla unter seiner Ägide dann aber »RNA Mikrofabriken« für das deutsche Unternehmen CureVac, das zusammen mit Bayer mRNA-Injektionen gegen Corona auf den Markt brachte. Und während Musk gegenüber der New York Post am 30. September 2020 sagte, sich nicht gegen Covid impfen lassen zu wollen, erklärte er dem TIME Magazine am 13. Dezember 2021, bereits geimpft zu sein. Zeitgeistig flexibel ist er also. Wer behauptet, Musk hätte seine Meinung zur mRNA-Technologie seit dem Covid-Fiasko signifikant geändert und sehe das Produkt nun kritisch, ist schlecht informiert. Noch am 12. April 2023 erklärte er bei Twitter, dass er mRNA für eine »medizinische Revolution« hält. Vergleichbar mit dem Schritt »von analog zu digital«.
Was Musk mit digitaler Revolution meint, zeigte sich 2017 mit Hurricane Irma. Damals gab das Unternehmen für Besitzer von Fahrzeugen mit 75 kWh ein Softwareupdate heraus, das die Reichweite von 338 auf 400 Kilometer steigerte – was im Umkehrschluss bedeutet, dass Tesla-Besitzer um eine eigentlich abrufbare Leistung ihres eigenen Fahrzeugs betrogen werden, wenn gerade keine Naturkatastrophe wütet. Dass Tesla-Kunden darüber hinaus permanent überwacht werden, zeigte sich unlängst im Rahmen der Explosion eines Cybertrucks in Las Vegas. Augenbewegungen, Mimik, Geschlecht, Hautfarbe, Körpertemperatur, Gepäckanordnung, Route, Ladestopps, Bezahlvorgänge, Telefonbuch, Musik-Playlist, Online-Abos, et cetera. Was von Sensoren und Verbindungen zu erfassen ist, wird erfasst, wie eine Untersuchung von Mozilla im Herbst 2023 feststellte. Das gilt im Übrigen nicht nur für Tesla, sondern für praktisch alle modernen Autos. Ein Tesla hat es dabei nur am leichtesten. Die gesammelten Daten werden entweder zum Schleuderpreis verkauft und/oder gegen uns verwendet.
Doch zurück zu Musk, der Twitter nicht übernahm, um Meinungsfreiheit herzustellen, sondern um die Plattform zur »Alles-App« zu machen. Sein erklärtes Vorbild: die chinesische Spionage-App WeChat. Deswegen will er alle Nutzer »als echte Menschen identifizieren«. Biometrisch versteht sich. Dafür arbeitet man bei Twitter bevorzugt mit israelischen Unternehmen zusammen, die von ehemaligen Mossad-Agenten gegründet wurden. Vielleicht stellte ja Doppelagent Jeffrey Epstein den Kontakt zum Mossad her, nachdem er Musk als regelmäßigen Teilnehmer seiner Edge-Foundation Seminare zum Thema Nudging schätzen gelernt hatte. Epstein war nämlich der einzige nennenswerte Sponsor von Edge.
Twitter kaufte Musk übrigens nicht von seinem eigenen Geld, sondern mit Hilfe von 94 Investoren, deren Namen ein US-Bundesrichter erst im August 2024 veröffentlichte, weil Jacob Silverman (Reporters Committee for Freedom of the Press) sie einklagte. Die Liste umfasst so illustre Namen wie Fidelity Investments, Sequoia Capital, Andreessen Horowitz, Bandera Fund, Binance Capital Management, Sean Combs (alias Diddy) Capital, Jack Dorsey (Twitter Gründer), Baron Opportunity Fund oder Prinz Alwaleed bin Talal al Saud von der saudischen Königsfamilie. Da wird also offenbar »der Sumpf« mit mehr Sumpf »trockengelegt«. Von der Nominierung des WEF Executive Chair Linda Yaccarino als neuer Twitter-CEO und »Freedom of Speech« versus »Freedom of Reach« mal ganz abgesehen.
Auch die von den Eloi als sensationelle Enthüllung gefeierten Twitter Files sind leider nicht ernst zu nehmen. Denn sie offenbarten nichts, was man nicht schon wusste. Zudem ist bis heute unklar, woher die veröffentlichten Informationen kamen, wer den Zugriff darauf gesteuert hat, was dort noch gespeichert war, warum praktisch nur ein von Elon ausgewählter Journalist Zugriff darauf hatte und dieser nur Screenshots, anstelle ganzer Dokumente veröffentlichen durfte. Ein echter Leak besteht aus einem Archiv, das man selbst durchsuchen kann – nicht aus ein paar handverlesenen Screenshots.
Fehlt noch Space X. Ein Unternehmen, das Musk zwar selbst gegründet hat, dessen Erfolge aber in weiten Teilen anderen Umständen zu verdanken sind. So schreibt beispielsweise inside Tesla am 22. März 2022:
»Schon Anfang der 2000er-Jahre hatte die NASA erkannt, dass ihr bald die Möglichkeit fehlen würde, selbst Astronauten und Material ins All und zur ISS zu bringen. Man machte sich also auf die Suche nach Partnern aus der Privatwirtschaft und wurde unter anderem bei Elon Musks Space X fündig. Bereits 2006, also noch in der Entwicklungsphase der Falcon 1, erhielt Musks Unternehmen fast 400 Millionen US-Dollar Startfinanzierung unter dem COTS-Programm.«
Space X war von Beginn an als verlängerte Werkbank der NASA gedacht, weil der US-Weltraumbehörde immer mehr Mittel gestrichen wurden. Die Öffentlichkeit hatte nämlich das Interesse an ziviler Raumfahrt verloren. Daher setzte man in Washington immer öfter den Rotstift an. Doch seit Musk die Menschen öffentlichkeitswirksam zum Mars befördern will – »let’s build Marsian Technocracy« – steigt das Interesse wieder. Leider muss ich die Vorfreude auf eine planetare Kolonie aber etwas dämpfen. Denn Space X wird nicht betrieben, um Menschen auf den Mars zu bringen, sondern um das »weltgrösste Netzwerk an Spionagesatelliten aufzubauen«.
Musks Weltraumagentur ist Handlanger des militärisch-industriellen Komplexes und einer der wichtigsten Vertragspartner des Pentagon. Das konnte man 2017 schon im Observer nachlesen. Oder am 9. Januar 2018 bei CNBC, die vom (missglückten) Transport eines streng geheimen US-Spionagesatelliten berichtete. Am 15. April 2022 kommentierte Tech Unwrapped zwei weitere Spionagesatelliten des US-Militärs, die Space X in die Umlaufbahn beförderte. Seit Jahren erhält das Unternehmen Milliarden von US-Regierung und Geheimdiensten. Siehe Los Angeles Times vom 30. Mai 2015: 4,9 Milliarden. Oder ein Artikel des Wall Street Journal vom 23. Februar 2024: 1,8 Milliarden. Oder eine lange Liste von staatlichen Zuwendungen, die Business Insider am 15. Dezember 2021 veröffentlichte. Damit basiert der Erfolg von Space X nicht primär auf Musks genialem Unternehmergeist, sondern auf Subventionen. Auf Steuergeldern.
Nicht zu vergessen: Starlink. Das von Space X betriebene, weltumspannende Satellitennetzwerk. Es mag den Vorteil haben, dass damit auch Menschen in entlegenen Regionen des Planeten oder Katastrophengebieten Zugriff auf das Internet haben. Dabei sollte allerdings nicht unterschlagen werden, dass Starlink in seiner finalen Ausbaustufe circa 42.000 Satelliten umfassen und damit ein permanentes Strahlungsfeld erzeugen wird. Gesundheitliche Risiken für den Homo sapiens: unklar. Darüber hinaus haben die Orbiter Zugriff auf das NORAD-Datenbanksystem, um Weltraumschrott ausweichen zu können. Sprich, sie sind permanent mit Systemen des US-Militär verbunden. Aus diesem Grund ermöglicht Starlink auch die Steuerung von Kampfdrohnen – siehe Ukraine-Konflikt – sowie 30 mal schnelleres Senden von Daten an und von US-Kampfflugzeugen. Während die Öffentlichkeit Musks Satellitennetzwerk vor allem als ziviles Produkt betrachtet, ist Starlink primär von militärischem Interesse. Nicht umsonst wird parallel Starshield aufgebaut, das dem geheimdienstlich-militärischen Komplex unter anderem die diskrete Echtzeitüberwachung der ganzen Welt erlaubt. Auch von DEW-Fähigkeiten (Directed Energy Weapon) ist die Rede. Ende 2024 befanden sich bereits 98 solcher Satelliten in erdnaher Umlaufbahn.
In Anbetracht dieser Informationen ist es also kaum verwunderlich, dass Musk seit Jahren offen für Technokratie wirbt. Für ein zentralistisches, faschistoides Herrschaftsmodell, das schon sein Großvater Joshua Haldemann als führender Kopf in den USA und Kanada vertrat. Der Familientradition folgend empfiehlt Musk eine CO2-Steuer zum Kampf gegen den Klimawandel, ein universelles Grundeinkommen, um die von der KI ausgelösten Disruptionen abzufangen und sein Neuralink Gehirnimplantat, um dem drohenden Transhumanismus etwas Transhumanismus entgegenzusetzen.
Futurum Technologicus
Für Kunden, denen Chips im Kopf irgendwie zu altbacken sind, entwickelt Musks Unternehmen in Zusammenarbeit mit iota Biosciences natürlich ein zeitgemäßeres Premiumprodukt: Neural Dust. Intelligente Nanopartikel in Staubkorngröße, die sich im Gehirn anreichern. Die lassen sich dann wahrscheinlich – wie die in Indien bereits zugelassene Nasal-Impfung gegen Covid – durch die Nase ziehen. Oder durch Luftschächte öffentlicher Gebäude pumpen. Man kann die neue Freiheit also förmlich riechen.
Ganz wie es der 44 Seiten starke »National Nanotechnology Initiative Strategic Plan« (NNI Plan) des Weißen Hauses im Oktober 2021 vorsah: »Die Öffentlichkeit einbeziehen und Mitarbeiterzahlen im Bereich Nanotechnologie erhöhen«. Nicht umsonst hat Donald Trump der entsprechenden Behörde in seiner ersten Amtszeit zusätzliche Mittel genehmigt. Genau wie Joe Biden nach ihm.
Das von der Technokratie-Bewegung vor fast einem Jahrhundert definierte nordamerikanische Technate – sprich, der amerikanische Verantwortungsbereich einer weltweiten Technokratie – sieht der von Trump und Musk reanimierten Vision einer »nordamerikanischen Union« übrigens verblüffend ähnlich. Wen interessiert bei all der Make-Great-Euphorie schon noch, dass Imperialismus scheisse, Dänemark ein souveräner Staat und der Panamakanal ein strategisches Nadelöhr der internationalen Handelsschifffahrt ist. Oder, dass die »nordamerikanische Union« nicht nur bei Trump-Cheerleadern wie Alex Jones vor ein paar Jahren noch als »böser Globalisten-Plan« galt.
Schauen wir nach vorne. In Richtung »goldenes Zeitalter«, wie Trump es nennt. Dieses dürfte für den Normalbürger nämlich sehr ungemütlich werden. Denn es wird dominiert von Algorithmen. Von Künstlicher Intelligenz. Für die Eloi also primär von Grok, dem auf Twitter (und Teslas) integrierten Chatbot. Dieser basiert auf Technologie des Unternehmens xAI – laut Wikipedia gegründet von Elon Musk im März 2023. Das mag zwar so im Handelsregister stehen, ist wohl aber nur die halbe Wahrheit. Denn xAI dürfte die Fortführung eines DARPA-Projekts darstellen, das bereits 2015 unter dem Titel »Explainable Artificial Intelligence« (XAI) gestartet wurde und 2021 auslief. Als die Finanzierung seitens DARPA eingestellt wurde, machte XAI die Forschungsergebnisse auf einem Server zugänglich. Circa 18 Monate Jahre später engagierte Elon Musk Igor Babuschkin als Chefingenieur für xAI. Babuschkin hatte zuvor acht Jahre lang für Googles DeepMind-Projekt gearbeitet und nutzte aller Wahrscheinlichkeit nach die DARPA-Ergebnisse um xAI, beziehungsweise Grok zu entwickeln.
Im Juli 2023 verkündete Musk, xAI sei im Gegensatz zu den Konkurrenzprodukten von Google, Microsoft und OpenAI eine »gute« KI. Erstaunlich, wenn die gleichen Ingenieure am Werk sind und die KI auf Basis eines Militärprojekts entsteht. Zudem sprechen auch die Top-Sponsoren von xAI nicht unbedingt für das »Gute«. Denn unter den größten Geldgebern der letzten Finanzierungsrunde vom 23. Dezember 2024 befinden sich so illustre Namen wie BlackRock, AMD, Nvidia und Fidelity, die zusammen weitere sechs Milliarden Dollar für Musks KI-Unternehmen zur Verfügung stellten.
Genug Liquidität, um xAI für die »Alles-App« weiterzuentwickeln, wo Grok seit einer Weile automatisch Kurzbeschreibungen für Profile erstellt, die man weder abschalten noch ändern kann. Twitter-Nutzer müssen nun also nicht mehr selbst das Profil eines Accounts durchstöbern, um sich einen ersten Eindruck von der Person zu machen, sondern bekommen diesen von Elon Musks KI geliefert. Vorurteil auf Knopfdruck sozusagen. Vergleichbar mit einem Sozialkreditsystem. Denn die täglich neu generierte Zusammenfassung basiert auf dem Nutzerverhalten.
»Die neuen, KI-generierten Grok-Kurzprofile unter jedem X-Nutzerprofil SIND de facto ein Social Credit System nach chinesischem Vorbild für den Westen. Das Profil jedes Nutzers wird tagesaktuell neu berechnet. Äußert man sich zu verschiedenen Themen, nennt die KI das schnell mal »verheddern«. Grok gibt zu, das Profil wird erstellt aus dem eigenen Nutzerverhalten des Tages, seinen eigenen Berechnungen und nicht näher definierten Anweisungen«, kommentierte Journalistin Aya Velázquez die Neuerung am 14. Januar 2025.
Andere Nutzer werden als »leicht erregbar« beschrieben, »verzetteln« sich oder »glauben an Wettermanipulation zur Klimakontrolle«. Offener wird ein Debattenraum dank solcher Adjektive und Zusammenfassungen sicher nicht. Wer möchte schon das Profil von leicht erregbaren Chemtrail-Gläubigen anschauen oder gar mit diesen assoziiert werden. Gegen solch eine automatisierte, herablassend daherkommende Einordnung durch intransparent operierende KI war die Faktencheck-Industrie geradezu harmlos. Wer also annimmt, die Abschaffung der Faktenchecker bei Facebook und Co. bedeute ein Ende der Zensur, irrt. Sie wird im Gegenteil deutlich raffinierter und weitreichender werden.
Details zum persönlichen Punktestand im Grok-Sozialkreditsystem oder Information über das Zustandekommen der Bewertung erhält man auf Anfrage natürlich nicht. Twitter wird die daraus entstehende Hierarchie aber mit Sicherheit für Reichweitensteuerung, Nudging-Kampagnen und weitere sozialarchitektonische Funktionen nutzen. Vor allem, wenn 2025 das Bezahlsystem »X Money« eingeführt wird. Dann werden die Eloi bald nicht mehr nur um Reichweite, Follower und Re-Tweets buhlen, sondern auch um Geld – das als Folge unliebsamer Postings zu Genozid X, Krieg Y oder Person Z künftig schneller eingefroren werden dürfte als jedes Bankkonto. De-Banking der nächsten Generation. Und irgendwann trifft das jeden. Außer, man schwimmt immer mit dem Strom.
Doch damit nicht genug. Am 13. Dezember 2024 gab das wohl den wenigsten bekannte Unternehmen WISeSat bekannt, künftig mit Space X zusammenzuarbeiten, um »verschiedene Produkte und Systeme zu kombinieren«. Die WISeSat AG ist eine Tochterfirma der in Genf (Schweiz) ansässigen WISeKey International Holding AG, die im Bereich Cybersicherheit, KI und IoT (Internet of Things) tätig ist. Die Ankündigung dieser Kollaboration ließ die WISeKey-Aktie kurzfristig um 107,73 Prozent steigen. Ein erster gemeinsamer Start zum Transport sogenannter Picosatelliten fand am 14. Januar 2025 von der Vandenberg Space Force Base in Kalifornien statt.
Aber was genau macht WISeSat? Einer Presseerklärung des Unternehmens vom 15. September 2023 lässt sich entnehmen:
»WISeSAT AG zeichnet sich dank ihrer Konstellation von ultra-sicheren Picosatelliten und Infrastruktur durch sichere und effektive Kommunikationsstrategien für vernetzte Geräte aus. Die Expertise des Unternehmens in kryptografischer Technologie und sicherem Datenmanagement hat die sichere IoT-Implementierung in zahlreichen Bereichen neu definiert, von städtischen Innovationen in Smart Cities bis hin zu modernster industrieller Automatisierung. (…) WISeSAT steht an vorderster Front bei der Entwicklung von ultra-sicheren Picosatelliten-Lösungen in Zusammenarbeit mit ihrem Verbündeten FOSSA Systems. Es setzt sich für sichere IoT-Kommunikation über raumbasierte Netzwerke ein und nutzt die neuesten kryptografischen Innovationen, um sichere und sofortige Datenaustausche in verschiedenen Bereichen zu gewährleisten (…).«
Im Klartext: WISeSat bringt Satelliten von der Größe einer Tupperdose ins All. Diese Mini-Orbiter umkreisen den Planeten in niedrigen Umlaufbahnen und etablieren dort ein Netzwerk für kryptografierte Echtzeitdatenübertragung. Fliegende 5G-Masten sozusagen. Oder WLAN-Router. Nur viel schneller. Für das Internet der Dinge – und Smart Cities.
»In dieser Woche startet WISeSat einen Satelliten der neuen Generation und markiert damit einen wichtigen Meilenstein in der Entwicklung einer globalen Satellitenkonstellation, die eine umfassende Erdabdeckung mit ultraniedriger Latenzzeit ermöglicht. Entwickelt, um Billionen von IoT-Geräten in Echtzeit zu verfolgen und aufzuspüren.« (Carlos Creus Moreira, WISeKEy CEO, 12. Januar 2025)
Welche Datenträger dieses Picosatelliten-Netzwerk künftig verfolgen und aufspüren soll, zeigt sich bei einem Blick auf das Produktportfolio der Holding-Gesellschaft WISeKey – einem »weltweit führenden Anbieter von Cybersicherheit, digitaler Identität und Internet der Dinge (IoT) Lösungen«. Denn die Holding existiert seit 24 Jahren, besteht aus fünf Unternehmen, hat mehr als eineinhalb Milliarden Chips und über fünf Milliarden »Roots of Trust« installiert, residiert an sechs internationalen Standorten und hat gut 3.000 Kunden in Staat und Wirtschaft beglückt. Einen Wikipedia-Eintrag gibt es für das bei NASDAQ und SIX gelistete Unternehmen erstaunlicherweise trotzdem nicht.
Dafür aber für den seit Mai 2021 amtierenden »Chief Digital Transformation Officer« Pierre Maudet. Der war ab Juni 2012 Mitglied des Genfer Staatsrats, 2013 bei den Young Global Leaders des Weltwirtschaftsforums und 2015 bei der Bilderberger Konferenz in Telfs-Buchen (Österreich). Nachdem er im Februar 2021 vom Genfer Polizeigericht wegen Vorteilsnahme verurteilt wurde, trat er als Staatsrat zurück – und drei Monate später bei WISeKey an. Am 30. April 2023 wurde er, ungeachtet seiner kriminellen Vergangenheit, zusätzlich wieder in den Genfer Staatsrat gewählt. Wie praktisch. Solch eine schamlose Unverfrorenheit scheint Maudet perfekt für das zu qualifizieren, was bei WISeKey unter dem Deckmantel der »Quantensicherheit« entwickelt wird – ein raumbasiertes eID-Ökosystem.
»Quantensicherheit nutzt Prinzipien der Quantenmechanik, um den Datenschutz und die sichere Informationsübertragung zu revolutionieren. Kernstück ist die Quantenschlüsselverteilung (Quantum Key Distribution, QKD), eine Spitzentechnologie, die mithilfe der Quantenmechanik vernetzte Teilchen für den sicheren Austausch von Verschlüsselungskennwerten erzeugt.«
Ob digitale Identität, Unterschrift, Cloud oder Software – von der Know-Your-Customer-Biometrie bis hin zur Unternehmenslösung für die Mitarbeiteridentifikation. WISeKey hilft. Anmelden kann sich jeder. Während die Produktpalette für den privaten Sektor noch nach Lieferketten-Management, Sendungsverfolgung, Login-Lösung für eBanking oder Face ID auf dem Smartphone klingt – aber deutlich weitreichender ist, schauen sie sich die Homepage an – sprechen die WISeKey-Angebote im Bereich Regierungen eine ganz andere Sprache. Denn unter diesem Menüpunkt bewirbt der diskret operierende Konzern seine »CertifyID Trust Center Platform«:
»Die CertifyID Trust Center Platform ist eine industrialisierte eID-Verwaltungslösung für Bürger, die Benutzer und ihre Anmeldeinformationen verwaltet, insbesondere digitale IDs und digitale Zertifikate für groß angelegte Anwendungen wie landesweite E-Government-Dienste. Es handelt sich um eine vollständige industrielle Public Key Infrastruktur- und ID-Verwaltungslösung, die Regierungsdienste rund um die Uhr unterstützt.
Die CertifyID Trust Center Plattform wird in einer Reihe von Anwendungen der Regierung und des öffentlichen Sektors verwendet, zum Beispiel: Personalausweis, ePassport (ICAO-konform), Führerschein, Gesundheit, Wahlen/Abstimmen.
Die CertifyID Plattform wurde unter Verwendung der Sicherheits- und Public Key Infrastruktur-Expertise von WISeKey entwickelt und kann vollständig in E-Government-Frameworks, kommerzielle Frameworks (…) und in das Bereitstellungsframework für E-Government-Dienste eines Landes integriert werden.«
Da passt es doch wunderbar ins Bild, dass WISeKey am 13. Oktober 2022 eine »Partnerschaftsvereinbarung zur Zusammenarbeit bei der Entwicklung weltraumbezogener Aktivitäten« mit der Schweizer Armee bekannt gab – schließlich residieren in der Alpenrepublik nicht nur UN, GAVI, WEF, Club of Rome und jede Menge NGOs, sondern auch die Bank für Internationalen Zahlungsausgleich (BIZ), die ganz sicher Verwendung für ein quantengesichertes Echtzeit-Picosatellitennetzwerk findet, wenn ihr »Unified Ledger« (Zentrales Hauptbuch) für das Blockchain-Weltfinanzsystem von morgen zum Einsatz kommt. In Anbetracht der »allumfassenden Marktblase« (D. Webb, 2024) ist damit wohl in absehbarer Zeit zu rechnen.
Das also sind die Projekte, Pläne und neuen Partner von Elon. Auf mich machen ja speziell die korrupten Genfer Quantenspezialisten mit ihren Picosatelliten und schlüsselfertigen eID-Lösungen nicht unbedingt den Eindruck von Freiheitskämpfern. Und auch die am 22. Januar 2024 bei einer Pressekonferenz im Weißen Haus angekündigten »personalisierten mRNA-Injektionen gegen Krebs« lassen mich eher skeptisch zurück.
Genau wie der Umstand, dass diese binnen 48 Stunden »personalisierte mRNA« durch die Rechenleistung von OpenAI ermöglicht werden soll. Denn das von Elon Musk mitgegründete Unternehmen des WEF- und Bilderberg-affinen Sam Altman steht im berechtigten Verdacht, für den Tod eines Whistleblowers im Dezember 2024 verantwortlich zu sein. Während Polizei und Medien den Tod des OpenAI-Forschers Suchir Balaji als Selbstmord deklarieren, sprechen sowohl die Umstände am Fundort seiner Leiche als auch Balajis Eltern von »eiskaltem Mord«. Nicht zu vergessen, dass Altman von seiner eigenen Schwester des jahrelangen Missbrauchs beschuldigt wird und sich dafür demnächst vor Gericht verantworten muss. Selbst The Economist räumte am 10. Dezember 2024 ein, dass »die PayPal Mafia die amerikanische Regierung übernimmt«. Und das mit der »Mafia« scheint man in Washington mittlerweile wörtlich zu nehmen.
Aber die von einigen aus der Hüfte geschossenen Präsidialdekreten euphorisierten Eloi werden sicher Gründe finden, das alles zu ihren Gunsten auszulegen. Immerhin hat Trump ein paar Leute begnadigt und will aus der WHO austreten. Wie seine Fanbase es bewerkstelligt, auszublenden, dass »The Donald« schon in seiner ersten Amtszeit aus der WHO austreten wollte und es unterließ, erschließt sich mir aber leider nicht. Genau wie die Begeisterung für ein Gespräch zwischen Musk und Weidel. Man stelle sich nur mal vor, George Soros, Bill Gates oder Eric Schmitt konferierten mit deutschen Politikern. Oder bekämen Sendezeit im ÖRR. Nicht auszudenken.
Wie heißt es so schön: »Eine schmerzliche Wahrheit ist besser als eine Lüge« (Thomas Mann). Stimmt. Nur fällt es relativ schwer, eine Lüge einzugestehen, wenn der, dem man sie beichten muss, der Lügner ist.
So bleibt nur zu hoffen, dass möglichst viele Eloi diesen Schritt trotzdem möglichst bald hinter sich bringen. Im eigenen Interesse. Denn wie schon Ernst Freiherr von Feuchtersleben feststellte, ist »Reue der Verstand, der zu spät kommt«. Und das kann in diesen Tagen verheerende Folgen haben.
-
 @ 65038d69:1fff8852
2025-03-29 11:50:52
@ 65038d69:1fff8852
2025-03-29 11:50:52The internet has had tutorials for job applications for a while; I remember searching for and reviewing them as part of “Career and Life Management (CALM)” in grade school. But it still never hurts to go back to the basics!
Applications fall into two categories; what I’ll call “human-read” and “machine-read”. Machine-read applications are specifically designed for automated recruitment systems. These systems tend to require specific layouts and formatting, as well as focus on keywords and academic degrees (even if the job doesn’t require them). They don’t read very well for humans though. I’d also argue that you probably don’t want to work for an employer who uses such systems, but that’s a separate topic. Human-read applications are as the name suggests; applications designed for human review. Those are the type we’re going to focus on today.
Our goals with our application are going to be to maximize the chances the receiver (usually a receptionist, HR staff, or recruiter) will pass along our application to the decision maker (usually HR staff or interview panel member) who will shortlist you for an interview, and to convey all the relevant information to the interview panel before your interview. We’re going to do this by creating a cover letter and resume combo that is unique, but also follows a professional format.
Let’s start with the page template we’re going to use for both documents. Start with a blank page. In the header in the upper left corner, list your name, email, and town & province. Make your name 5 to 8 font sizes larger than the rest, and bold if the font needs more pop. In the upper right corner, write yourself a short byline that would make a Madison Avenue advertising executive proud. Workshop it with your friends or family, but don’t worry about spending too much time on it. Mine says “Process management, Results through consistent and conscientious excellence”. The idea is to have your audience say to themselves, “ooo, that sounds professional”, then move on. Make the first line the same font size as your name. Next, add a splash of colour or some basic shapes as a background to the header. Pick a maximum of two colours and a minimalist geometric design. Make sure it’s simple; if it’s too busy it’ll look like a primary school art project. Again, you want your audience say to themselves, “ooo, that looks professional”, then move on. Now go to the first line in the body of the document and type “title”, then go to the third line and type “body”. Make the title font the same size as your name in the header, and change it to the primary colour of your header background. Finally, save two separate copies of this file; one labelled “your name resume” and the other labelled “your name cover letter”.
Congratulations, the design part is over! If you’re like me, that was the hard part. On to the content! Open the cover letter document. Change the title text to “To:”. Go to the body line and paste in the following. For the listeners, you can find the text to be copied in the written version of this post on our website.
``` Receiver name Receiver email Receiver title Receiver organization Receiver city, province
Submission date
Greeting, Paragraph 1: Brief personal introduction and job being applied for. Paragraph 2: Brief professional introduction, framed as how you would be a good fit for the organization. Paragraph 3: Extended professional introduction, framed as how you be a good fit for this specific job. Paragraph 4: Three to four questions you would have for the interview panel if you were chosen to be interviewed. Paragraph 5: Follow-up and interview availability. Sign-off and signature. ```
Congratulations, you now have your own personalized cover letter template! Simply replace the placeholder and instruction text with the real thing. Five paragraphs may seem like a lot, but if you’re sufficiently brief (as you should be), the whole thing should fit on a single page. If it spills over, rework the paragraph text until it does. Turning to a second page has an ethereal effect that will make your cover letter feel like “too much”. It’s purely emotional and subconscious, but it’s real and to be avoided if you want to make a good first impression, which is your cover letter’s primary purpose!
Save and close, and open the resume. Center the title on the page and change the text to “Executive Summary”. Move to the body and paste the following. Again, for the listeners, you can find the text to be copied in the written version on our website.
``` First highlighted skill category or character trait paragraph. Two to three sentences. Second highlighted skill category or character trait paragraph. Two to three sentences. Third highlighted skill category or character trait paragraph. Two to three sentences. Bulleted list of three to six specific soft skills.
Centered title: Professional or Work Experience (choose one) Employer - City, Province - years worked (i.e. 2015-2020 or 2022-current) Job title Two to three item bulleted list summarizing duties. Can be written long form, but be brief. (copy this as many times as needed)
Centered title: Education, Certifications, & Training (remove words that don’t apply to you) Title Certifying or training body name, City, Province (copy this as many times as needed)
Centered title: Proficiencies Bulleted list of five to ten specific hard skills. Do not repeat from soft skills above.
Centered title: Volunteer & Civic Affiliations (if you have none, use Hobbies) Bulleted list, no more than six items. ```
Same as the cover letter, replace the placeholder and instruction text with the real thing. The whole resume should fit on two pages. If it spills over, the first thing you can reduce is the number of work experience sections. You don’t need to include your entire work history, but it is best to not leave gaps if you can. We’re at the final step. The home stretch. You can do it! I believe in you! We’re going to export both documents as PDFs, then print copies, and inspect for errors or issues. “Why the PDFs and printing?” you ask? PDFs are the universal document format (see my previous post on the subject, “What is a PDF?”), and the interview panel will most likely want to print copies for themselves for the interview. Printing a copy for yourself will allow to you make sure everything looks good on paper as well as on a screen. You’re going to take your copy with, as well as a printed copy of the job posting, to use as a reference during your interview. No matter how well you think you know the material, it’s always good to have a reference. Physically referencing these documents during the interview will also help you look prepared and factual. What sounds better, “I thought the job posting said 40 hours per week?...”, or “here, in the second paragraph, the job posting says 40 hours per week”?
Want help with your job application? Or assistance with interviewing potential employees? You can find us as scalebright.ca.
-
 @ fc2470ed:17d9ee27
2025-01-30 14:24:23
@ fc2470ed:17d9ee27
2025-01-30 14:24:23by Hynek Fencl, July 2024
The way to Liberland is easy but not simple. Technically speaking, it’s just a short bike ride away from the nearest village on a comfortable bike path through a stunning forest known as the “Amazon of Europe”. On one side, one senses the presence of the mighty Danube River beyond the tall trees, and on the other stretch the farmlands of north-eastern Croatia. Then you take a left turn to a straight forest path, ride all the way to the end, and after a few bends on the track, you will have entered “the promised land”.
The part that is not simple is that Croatia both does and does not consider Gornja Siga (the local name for the area we now refer to as Liberland) to be its territory – depending on who you ask. This means that along the picturesque bike path, you will almost certainly encounter a border police patrol car, and, depending on whether you seem to them like you’re affiliated with Liberland, they will tell you to stop and hand over your ID. They run it through their system and, if you’re lucky enough to be a citizen of the EU, they let you pass. If you’re not and you give them a non-EU passport, they will ask you to come to the station with them to “determine the circumstances of your stay in Croatia.” You will then be issued with paperwork telling you to leave the country within the next 7 days, banning you from re-entering in the next 1-3 months. The official reasoning they’ll give for this is their reasonable suspicion that you have not come to Croatia as a tourist but with the intent to either do paid work (for which you would have to get a business/work visa) or to break the law (such as camping outside designated camping grounds or starting a fire in the forest).
All of this is part of a big game of chess that is being played out between Croatia and the Liberlanders. Croatia is in a tricky spot. They cannot properly administer the territory of Liberland and enforce its law in it – lest it would create an indication that the Croatian state officially claims it as its territory. However, they cannot not administer it either, since it’s on “their” side of the river, and it is risky for a rogue, unpredictable operation (from their perspective) like the establishment and growth of Liberland to just be left to its own devices right on their doorstep. This is, then, how we arrive at the status quo, with Croatia relating to Liberland in some way while being careful about the international perception of its action in another way. The resulting practice is a persistent harassment campaign toward the Liberlanders, with the apparent intent to create uncertainty and lower the appetite of potential Liberland settlers for this kind of adventure.
How to establish a new country
Liberland was born from an anomaly – a historical border dispute between Croatia and Serbia. The dispute involves the definition of where the border stands in relation to the Danube and goes back to 1947. Then, both lands along the river belonged to a single country – Yugoslavia – but the dispute arose with respect to the boundaries of its constituent states. It remained unresolved during the communist era and became an issue of international borders after the breakup of Yugoslavia.
Serbia claims that the border runs down the middle of the Danube, with the eastern bank being Serbian and the western bank Croatian. Croatia, on the other hand, claims that the border is set by historical borders marked by cadastral municipalities surrounding the Danube.
These municipality borders run along a different path because they were set before the course of the Danube was straightened during the 19th Century to allow for easier shipping. This results in disputed “pockets” of land on both sides of the river. The pockets on the eastern bank have a combined area of around 130 km2, while those on the western bank only amount to less than 10 km2. Not surprisingly, then, both countries claim that the border runs in a way where they get the >90% of land and the other country only gets the small remaining areas. However, this means that, by implication, since both countries are claiming the large areas, neither of them is claiming the smaller ones. These areas were, then, so-called terra nullius.
Under international law, there is no issue with any state claiming unowned and unclaimed land for themselves. And that is exactly what Czech businessman, politician, and activist Vít Jedlička did in 2015 when he proclaimed into existence the newly created Free Republic of Liberland on the largest, 7 km2 piece of the unclaimed areas between Croatia and Serbia.
It's one thing to announce a new country to the world. It’s an entirely different thing to make this country legitimate. Under the Montevideo Convention, a proper country needs to have 1) a permanent population, 2) a defined territory, 3) government, and 4) capacity to enter into relations with other states. Now, 9 years after the birth of Liberland, it clearly has three of those. As to a permanent population, the Liberlanders would argue that it definitely exists, even though Liberland’s now over 1200 registered citizens have had to largely live in “exile” ever since.
Nevertheless, despite the Convention, there’s one thing that makes something a country more than anything else – whether other countries see you as a country. The more diplomatic recognition an entity has, the more country-like it becomes. This is especially relevant for breakaway governments, governments in exile, or, most importantly in this case, startup countries like Liberland.
Very much aware of this, along with other members of Liberland’s startup government, Jedlička has been on a worldwide mission to legitimize Liberland in the eyes of other countries. Though there have been many amiable meetings and even some measure of support in some cases, no official recognition by any UN member has been achieved as of mid-2024. Liberland now has representatives and offices in multiple countries in the further pursuit of this goal. Though the effectiveness of this strategy has been questioned by many for the lack of decisive results so far, one thing remains unambiguously true: if recognized by even one or two UN members, Liberland would instantly gain an amazing amount of legitimacy and gravitas in the eyes of the world.
The quest for territory
Establishing international relations with countries anywhere in the world is not the only strategy that the Liberlanders have been employing in making the country more real and legitimate. This includes liaising and negotiating with the neighboring Serbia and Croatia. These relations are by far the most important and impactful ones. If both of Liberland’s neighboring countries were to either outright recognize the startup micro-state, or even just adopted an approach of non-interference, Liberland would be free to start actually developing and to find its own long-term position in the world.
As for Serbia, its Ministry of Foreign Affairs let itself be heard that, in their view, Liberland’s claims are a “trivial matter” but, in any case, they do not infringe upon the sovereignty of Serbia. One can imagine that Serbia might actually be secretly quite pleased with Liberland’s activities, since now Croatia has an issue to deal with on “their” side of the river, which, if they are not careful, could contribute to the legitimization of Serbia’s claim to the larger pieces of territory claimed by both countries.
With Croatia, things get quite a bit more complicated. In an official statement, the country rejected the claim that Gornja Siga is terra nullius, arguing instead that the land belongs to one of the two neighboring countries – the only question is to which one, which will be answered at some point in the future. Croatia also said it would stop any threatening and provocative activities on the territory even by force if necessary.
Ever since Liberland’s birth in 2015, the Liberlanders have been trying to make a mark on the territory. For a long time, even just entering Liberland wasn’t really possible. Under a deal between the Croatian and Serbian police that was put in place during the European migration crisis, Croatian authorities may enter Liberland and patrol it for security reasons (preventing illegal migration) even though they do not officially claim the territory as theirs. In addition, the border police have a near-permanent presence on the Danube River, preventing people from crossing into Liberland by boat.
As a result, anyone who would try to come to Liberland in any way would always be promptly arrested by the Croatians, essentially for entering a prohibited area.
After years of this status quo, a rather unexpected thing happened that made things suddenly move forward in a positive direction for the Liberlanders. In April 2023, during Liberland’s 8th anniversary celebrations, a famous YouTuber with a significant following decided to try to enter Liberland. After a few unsuccessful attempts due to heavy police presence and monitoring, he and his team hired jet skis and rode them all the way from Hungary down the Danube. When they got close to Liberland, they encountered the police boats again, but their jet skis were faster than the boats, so they managed to land at Liberland’s Liberty Island and plant a flag there. A few moments later, the police caught up to them and an aggressive policeman took out their handheld cameras before assaulting them and then kicking them on the ground, as can be clearly seen from drone footage of the incident.
As they had broken no laws, they were ultimately let go after the incident and free to leave the island without being arrested. However, the heavy-handed and illegal conduct of the Croatian police had been clearly documented and became part of the video that was published in July 2023.
The video promptly went viral, gaining almost 10 million views on YouTube. By comparison, the total population of Croatia is just under 4 million. When the news spread even to the Croatian press and TV stations, Croatia had a serious PR problem on their hands. The police had been clearly in the wrong, conducting themselves in a seriously improper way to the point of using physical force against peaceful people who had broken no laws nor engaged in any violence or hostilities themselves.
Something had to change. So, following this incident, the Croatian police adopted a different unofficial policy – from now on, they would let people enter Liberland if they wished to do so, in a controlled way. Since early August 2023, if you wish to enter Liberland, you can go on foot or by bike, take the access road down the forest, and show your documents to the Croatian police, just as you would at a border crossing. In a typical grand fashion of Liberland’s media team, Liberland made an announcement that an official border crossing had been opened between Croatia and Liberland (Croatia had obviously never made an official announcement like this, but for Liberland, that was the de facto situation on the ground).
In the weeks following the “opening of the border”, many enthusiastic settlers started coming to Liberland to finally begin making their mark on the territory of “the promised land.” They started constructing simple wooden houses, a bathroom, an open-air restaurant, and the related power and water infrastructure on Liberland’s mainland beach opposite Liberty Island in a settlement named Mateos Marina.
On September 7th, 2023, a troop of about 50 policemen and forestry workers, including a demolition crew, raided the settlement. The raid was officially dubbed a “cleanup operation” by Hrvatske šume, Croatia’s state forestry service. With the assistance of the police, they tore down all the wooden houses and structures using chainsaws and stole equipment as well as personal possessions of the Liberlanders on site. Several Liberlanders were arrested for “failure to comply with a lawful order”.

One might ask, if Liberland is not officially part of Croatia, what authority does Croatia have to come in to steal and destroy? Staying true to their claim that Liberland is not part of Croatia, the Croatians had announced to Serbia that they would be conducting the “cleanup” on Serbia’s territory, to keep it clean on their behalf.
We may only speculate about the reasons for carrying out this operation in such a heavy-handed, destructive way. One possibility is that allowing people to enter Liberland in the first place was a way for Croatia to lure some people to Liberland, become comfortable, and then come in and destroy everything to show everyone what would happen if they got involved in the project. Or perhaps it was the unexpected level of life, community-building, and construction going on in such a short period of time after the “opening of the border” that the Croatian police felt like they had to put a stop to it before things got so big they could not be easily destroyed anymore.
No matter the reasons, the raid had a chilling effect on prospective Liberlanders. Though there is plenty of video documentation of the operation, no one made a viral video about it this time. Though some media did pick up the news, it did not become a big story. Consequently, the PR fallout from this for Croatia was not unmanageable.
Liberlanders soon returned to the territory. However, the level of enthusiasm, energy, and external support was not as great as it had been before the raid. From then on, settlement efforts focused mainly on Liberty Island, unreachable by trucks and impossible for forestry workers to get to without a large boat which they seem not to have. Though perhaps a more strategic place to set up camp, Liberty Island is also much more prone to flooding than the rest of Liberland.
In the following few months, several makeshift houses were constructed using a combination of wood and sandbags. During this time, Liberland even hosted a first wedding on the island. The settlement was kept alive during winter as well, with Liberland enthusiasts staying mostly in houseboats whenever it was impossible to camp on site.
In the meantime, an enthusiastic settler couple bought a sizeable house with a courtyard in the village closest to Liberland – Zmajevac – which they have transformed into a base of operations for settlers. This is now called Liberbase and it is where visits to Liberland start, with bikes, supplies, and construction materials being gathered before going on the 40-minute bike ride.

In the spring of 2024, work started on the reconstruction of a former hunting lodge at a central location on Liberland’s mainland – Jefferson Square. The building was demolished a few years ago but the foundations, including a cellar, were left in place. The site was cleared, the foundations refreshed, and new walls for the future governmental building have sprung up from the ground. A professional construction crew was hired to speed up the re-building of this base, using large concrete bricks, to a standard that will make it logistically and practically difficult for the Croatian police and forestry workers to try to destroy.
 The battle for legitimacy
The battle for legitimacy The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.
The ongoing construction in Liberland is rather slow. It is difficult to bring construction materials to Liberland. It is prohibited to drive motor vehicles on the bike path leading to Liberland, which means that everything has to be manually hauled from Liberbase on cargo bikes. In addition, from time to time, bikes get stolen by the police or forestry workers. Despite these difficulties, the determination of the settlers is unwavering and they are working every day to move construction forward.Is it possible to bring materials by boat? How did they get sandbags and other materials to Liberty Island?
The importance of such a commitment should not be underestimated. The continuous presence of settlers is incredibly important for Liberland. It shows the seriousness of the project. It shows that Liberland is a genuine community and a fledgling nation rather than, as some accusations tend to go, just an elaborate publicity stunt.
Practical difficulties with the Croatian authorities are not limited to construction-related issues. Even staying and camping in Liberland comes with its quirks. If you’re staying on Jefferson Square, you should be prepared for several police visits every day. These check-ups are usually nothing dramatic. The police usually show up, ask a couple of questions, and perhaps tell the settlers that they are not allowed to camp there or start a fire, but they don’t actually do anything more than that and just go about their day.
It seems that the Croatian police are rather shy about enforcing Croatian law in a territory that is not officially considered part of Croatia. International law often takes into account the de facto situation of the matter in any dispute. If Croatia enforced their law in Liberland, this would therefore be an indication that they do, in fact, consider the territory to be theirs in practice, despite the official stance of the state. It would play into the hands of Serbia, reinforcing their claims to the large parcels of land on the other side of the Danube.
In addition, Liberlanders on the ground report that the majority of Croatian police officers generally behave quite fairly and respectfully toward them – only a minority appear to hold a personal grudge against Liberland, being abusive and sometimes even violent instead. It seems highly likely that the police in general are just doing their job, following orders from above. Most of them don’t actually take it as a personal commitment to make life more difficult for the Liberlanders.
This is rather important from a big-picture perspective, because the settlers, by contrast, are often heavily personally invested in the project and see it as their mission to see Liberland develop into a proper country. This disparity in energy and determination is strong and perhaps this is what will, in the end, cause Liberland to prevail in this drawn-out dispute.

The dispute with Hrvatske šume is quite different. As of mid-2024, the forestry workers tend to turn up at Jefferson Square about every fortnight. Unlike the police, they do not limit themselves to words but tend to steal everything that is not bolted down – including tools, materials, tents, bikes, and personal possessions of the settlers camping there. The justification remains the same – to “clean the forest of any waste.” In their encounters with the police as well as the forestry workers, Liberlanders are of course meticulous in their video documentation of any illegal actions by the authorities.
The Liberlanders’ difficulties, however, do not just stay local. As previously mentioned, upon trying to enter Liberland from Croatia, people who do not have EU citizenship are promptly issued a one-to-three-month ban on entering Croatia, with 7 days to leave the country. This is done under legislation relating to citizenship and tourism.
However, things can escalate even further. Since last year, several key Liberland settlers and organizers, including Liberland’s President Vít Jedlička himself, have seen “heavier guns” used against them. They have been banned from entering Croatia for 5 years under anti-terrorism legislation, where the authorities argue that these Liberlanders are something akin to a threat to national security.
The Liberlanders have mounted a legal defense against this, in addition to challenging Croatia on other legal fronts. They have had some successes so far – in particular, it should now be clear that the Liberlanders do not need any building permits to construct buildings on their territory. Unfortunately, other issues – including the 5-year bans from Croatia – still remain unresolved.
Most Liberlanders remain hopeful nonetheless. They have seen their situation move forward significantly over the last year. A year ago, they were not even able to enter Liberland without being chased and/or arrested. Now, even some construction is possible, albeit in a limited way.
The road ahead
The long-term vision, of course, remains to build a full-fledged, internationally respected and recognized city-state. Liberland’s leaders often speak of a “Balkan Monaco”, referring to the amazing development possibilities that a freedom-oriented country in the middle of Europe could offer. Liberland has already hosted an urbanist/architectural contest, and there are concrete plans for the first hotel as well as a riverside real estate development. What is more, Liberland’s land is actually more than three times the size of Monaco.
Nevertheless, Liberland cannot move forward in a meaningful way toward these visions and aspirations under the status quo. The Liberlanders need to be able to build at scale and be free from harassment, both by the police and the forestry workers. Some kind of political deal is necessary as the next step toward proper development of Liberland.
Such a deal could take multiple forms, but all of them involve the Croatian authorities changing their attitude toward Liberland away from a policy of unrelenting obstruction – not necessarily toward outright recognition, but at least toward accepting Liberland as a neighborly project that will move forward and develop in some way.
One option could be to allow motor vehicles on the bike path toward Liberland, with a deal that could include charging Liberlanders some fair tolls to pay for the wear and tear of the pavement. An alternative would be to simply allow river crossing into Liberland from Serbia on the Danube. Since Croatia does not officially consider Liberland its territory, their current interference with this traffic is illegal anyway. Simply stopping this illegal conduct would help Liberland significantly without Croatia facilitating Liberland’s development in any active way.

Regardless of these options, the first and most notable step would be to stop banning non-EU citizens from re-entering Croatia as well as lift the existing (entirely unjustified and unreasonable) 5-year bans on Jedlička and the others.
It is easy to see why Croatia is wary and suspicious of Liberland’s development. One can understand the worries of a state in whose immediate proximity there is a new and unknown state growing and taking root. Nevertheless, Croatia actually has a lot to gain from making some kind of deal with Liberland.
First: currently there are perhaps a dozen policemen on patrol around Liberland at all times. This includes police vehicles and boats. This is a significant expense for the police force – an expense which is rather unsubstantiated, given that Liberlanders have clearly proven to be peaceful people who do not wish to pose any threat to Croatia, its people, or its law enforcement officers. Making a deal would mean that this large expense is not needed anymore.
Second: Liberland borders an area of Croatia that has been rather “left behind”, is underdeveloped, and suffers from a lack of jobs and investment. Consequently, younger people are leaving the area and the current population is growing older. If Liberland was growing and open for business nearby, it would provide the region exactly with the job opportunities, large investment, and overall development that it desperately needs.
Third: Croatia could use Liberland as an opportunity to actually gain an advantage in the ongoing border dispute with Serbia. As previously mentioned, Croatia cannot openly and properly administer the territory, as it would be an indication in the eyes of international law that they consider the territory to be theirs. On the other hand, it Liberland is located on “their” side of the Danube, so Croatia does have an interest in making sure the area is under their control somehow. Striking a deal with Liberland could involve Liberland agreeing to some obligations related to the administration of the territory which correspond to Croatia’s priorities. In this way, Croatia would have an active say in what happens on this land, effectively “outsourcing” its administration without officially claiming it as part of Croatia.
In addition to all these advantages being present, Liberland is very much open to cooperation with Croatia and is keenly looking forward to welcoming any future productive relations with Croatian authorities. There will be no grudges held on Liberland’s side, and if a mutually beneficial deal or solution were to be found, no one would look behind at any historical quibbles or difficulties. Liberland would be an excellent and friendly neighbor to Croatia, not just causing any issues but actively helping the overall development of the surrounding region.
Time will tell how things will develop. At the present, the momentum, energy, and enthusiasm is definitely on the side of Liberland. There seems to be very little actual interest from the Croatian side to cause issues for Liberland and to continue to prevent the fledgling state from developing further. All that is left are the bureaucratic hurdles of a state that is being overly conservative about its approach to the important issues of the day. Things might take time, but seeing the determination of the settlers and the willingness of all Liberlanders to be unrelenting in their fight for the cause, it is not difficult to argue that we might be seeing the dawn of Liberland as the world’s next proper city-state as we speak.
-
 @ 5ffb8e1b:255b6735
2025-03-29 13:57:02
@ 5ffb8e1b:255b6735
2025-03-29 13:57:02As a fellow Nostrich you might have noticed some of my #arlist posts. It is my effort to curate artists that are active on Nostr and make it easier for other users to find content that they are interested in.
By now I have posted six or seven posts mentioning close to fifty artists, the problem so far is that it's only a list of handles and it is up to reader to click on each in order to find out what are the artist behind the names all about. Now I am going to start creating blog posts with a few artists mentioned in each, with short descriptions of their work and an image or to.
I would love to have some more automated mode of curation but I still couldn't figure out what is a good way for it. I've looked at Listr, Primal custom feeds and Yakihonne curations but none seem to enable me to make a list of npubs that is then turned into a feed that I could publicly share for others to views. Any advice on how to achieve this is VERY welcome !
And now lets get to the first batch of artists I want to share with you.
Eugene Gorbachenko
nostr:npub1082uhnrnxu7v0gesfl78uzj3r89a8ds2gj3dvuvjnw5qlz4a7udqwrqdnd Artist from Ukrain creating amazing realistic watercolor paintings. He is very active on Nostr but is very unnoticed for some stange reason. Make sure to repost the painting that you liked the most to help other Nostr users to discover his great art.
Siritravelsketch
nostr:npub14lqzjhfvdc9psgxzznq8xys8pfq8p4fqsvtr6llyzraq90u9m8fqevhssu a a lovely lady from Thailand making architecture from all around the world spring alive in her ink skethes. Dynamic lines gives it a dreamy magical feel, sometimes supported by soft watercolor strokes takes you to a ferytale layer of reality.
BureuGewas
nostr:npub1k78qzy2s9ap4klshnu9tcmmcnr3msvvaeza94epsgptr7jce6p9sa2ggp4 a a master of the clasic oil painting. From traditional still life to modern day subjects his paintings makes you feel the textures and light of the scene more intense then reality itself.
You can see that I'm no art critic, but I am trying my best. If anyone else is interested to join me in this curration adventure feel free to reach out !
With love, Agi Choote
-
 @ bdf3f01a:d9c40970
2025-03-29 04:52:40
@ bdf3f01a:d9c40970
2025-03-29 04:52:40Abstract:
This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities.
Introduction:
The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society.
The Veil as Cultural Custodian:
The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview.
Ritual Dynamics and Symbolism:
The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance.
The Copper Plate Rite:
The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation.
Symbolic Implications and Societal Continuity:
The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability.
Interpretive Analysis:
Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay.
Cultural and Societal Implications:
The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy.
Conclusion:
The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability.
References:
-
Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall.
-
Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72.
-
Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press.
-
Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil.
-
Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration.
## Title: Ritual as Continuity: An Analysis of the Winter Vigil of XLII.II at Sapelo
### Epoch XLII - Circle of Maidens
#### Abstract:
This paper presents a rigorous and critical examination of the Winter Vigil of XLII.II at Sapelo, a pivotal rite within the Lowcountry Freehold that serves as both an initiation into communal responsibility and a symbolic enactment of the Compact’s moral tenets. This analysis interrogates the ritual’s structure, emphasizing its role in perpetuating a resilient sociocultural order amid external collapse. Through a multidisciplinary approach combining historiographical analysis, cultural anthropology, and sociocultural theory, this study elucidates the Vigil’s function as a mechanism for moral continuity, thereby situating it within the broader discourse of post-collapse societal stabilization. The implications of this study underscore the profound interconnectedness between ritual practice and the formation of resilient communal identities.
#### Introduction:
The Winter Vigil of XLII.II at Sapelo occupies a fundamental position in the cultural historiography of the Lowcountry Freehold. As contemporary scholars, it is imperative to approach this tradition not merely as an artifact of ritualistic antiquity but as a dynamic process of cultural preservation. The Freehold’s commitment to integrating tradition with pragmatism, especially through the stewardship of The Veil, constitutes a critical adaptive strategy that sustained sociopolitical coherence through epochs of external fragmentation. This study aims to critically examine the Vigil as both a symbolic and practical reinforcement of the Compact’s ethos, with particular attention to how this ritual facilitated intergenerational continuity of moral and social values, ultimately shaping the robust communal identity that defines contemporary Freehold society.
#### The Veil as Cultural Custodian:
The Veil, emerging from the post-collapse adaptation of preexisting religious and cultural practices, evolved into a matriarchal order central to maintaining the Freehold’s ethical architecture. This evolution was characterized not by rigid preservation but by adaptive synthesis, wherein ceremonial gravitas was merged with pragmatic domestic guidance. The Veil functioned as a moral custodian, particularly within the familial sphere, where its influence was most profoundly exercised. Veilmother Cordelia’s role during the Winter Vigil exemplifies this dual function of leadership and philosophical stewardship, as her guidance articulated not only the ritual's procedural elements but also the embedded moral philosophy that would shape the initiates' worldview.
#### Ritual Dynamics and Symbolism:
The Winter Vigil is fundamentally an enactment of moral endurance, wherein the initiate’s voluntary approach to the brazier represents an acceptance of communal responsibility through individual fortitude. The design of the ritual deliberately positions physical endurance as a metaphor for moral resilience, encapsulating the Freehold’s conviction that true strength is inherently silent and steadfast. As the initiate moves toward the brazier, kneeling in proximity to the flame, the act becomes a performative affirmation of the Compact’s call for measured, principled strength rather than ostentatious assertion. The structured progression from the outer circle to the brazier symbolizes a journey from collective dependency to personal sovereignty, reflecting the Compact's ethos that leadership is merited through tested perseverance.
#### The Copper Plate Rite:
The Copper Plate Rite, integral to the Vigil, embodies the transformative philosophy of the Freehold. The heated copper plate, inscribed with the flame symbol and lifted from ashes, is held aloft despite discomfort, symbolizing the embrace of hardship as an essential component of sovereignty. The fleeting burn, leaving a transient mark, underscores the philosophical assertion that genuine resilience is born of confronting and integrating suffering, rather than circumventing it. This rite functions not merely as a test of physical tolerance but as a pedagogical imprinting of the Freehold’s ethos—an allegory of death and rebirth integral to personal and communal maturation.
#### Symbolic Implications and Societal Continuity:
The deliberate imposition of discomfort during the Vigil underscores a fundamental tenet of Freehold philosophy: suffering, when purposefully endured, refines the individual and, by extension, fortifies the community. The Copper Plate Rite exemplifies the doctrine that hardship, when faced with deliberate resolve, engenders moral clarity. This paradigm of voluntary suffering as a crucible for leadership remains a cornerstone of the Freehold’s ideological framework, fostering a collective ethos rooted in patient perseverance rather than impulsive dominance. Furthermore, the initiation rite serves as a microcosm of the Freehold's broader sociocultural ethos, where personal sacrifice is inextricably linked to communal stability.
#### Interpretive Analysis:
Current historiographical interpretations often err by neglecting the interconnectedness of the Vigil with broader sociopolitical dynamics. By isolating the rite as a mere ceremonial endurance, scholars risk overlooking its function as a structured pedagogical tool for inculcating moral resilience. This study posits that the Vigil, far from being a vestigial tradition, actively cultivated a pragmatic ethic of endurance that proved crucial in the Freehold’s sustained sociocultural coherence. This coherence, rooted in ritual reinforcement of moral tenets, enabled the Freehold to navigate existential threats without succumbing to internal decay.
#### Cultural and Societal Implications:
The enduring significance of the Winter Vigil lies in its dual function as both a rite of passage and a communal reaffirmation of the Freehold’s meritocratic principles. By fostering individual accountability within a collective moral framework, the Vigil reinforced the Compact’s foundational premise that leadership is merited through demonstrated resilience. The integration of personal trial into communal identity formation exemplifies how the Freehold maintained its internal stability despite external societal fragmentation. This ritual, therefore, is not merely commemorative but constitutive of the Freehold's enduring cultural legacy.
#### Conclusion:
The Winter Vigil of XLII.II at Sapelo remains a paradigmatic example of ritual as a vehicle for social continuity within the Lowcountry Freehold. Its deliberate amalgamation of symbolic endurance with moral instruction illustrates the Freehold’s adaptive strategy of embedding philosophical imperatives within lived tradition. As modern scholars, it is incumbent upon us to engage with these practices not merely as remnants of a bygone era but as foundational elements that cultivated the durable sociocultural ethos underpinning our current stability.
#### References:
- Vance, C. (Epoch LII). "The Compact and Cultural Continuity: An Oral History." Archive of Freehold Studies, Emberwell Hall.
- Harlowe, E. (Epoch LX). "The Flamekeepers: Guardians of Tradition." Journal of Sociocultural Persistence, Vol. 22, pp. 45-72.
- Morgan, T. (Epoch LXV). "Endurance Through Ritual: The Role of The Veil in Cultural Preservation." Lowcountry Academic Press.
- Cordelia, V. (Epoch XLII). "Reflections on the Flame: An Instructional Account." Collected Teachings of The Veil.
- Emberwell Institute (Epoch XC). "The Evolution of Freehold Rites: From Custom to Philosophy." Advanced Studies in Cultural Integration.
-
-
 @ 33baa074:3bb3a297
2025-03-29 03:05:32
@ 33baa074:3bb3a297
2025-03-29 03:05:32As an advanced level measurement device, radar water level meter has been widely used in many fields due to its advantages such as high precision, high reliability and non-contact measurement. The following are the main application scenarios of radar water level meter:
Water conservancy and hydro power: In large reservoirs and hydro power stations, radar water level meter is used to monitor the water storage in real time to ensure power generation efficiency and flood control safety.
Urban drainage management: The management of urban drainage system requires accurate measurement of the water level of rainwater outlet. Radar water level meter can monitor the water level of rainwater outlet in real time, and intelligently control drainage according to water level data to reduce the risk of urban water logging.
Industrial production and safety: In the process of industrial production, the level change of liquid storage tank has an important impact on production safety and quality control. Radar water level meter can monitor the liquid level of liquid storage tank in real time, and accurately control it through data feedback to ensure the safety and stability of the production process.
Agricultural irrigation: Radar water level meter is also widely used in the field of agricultural irrigation. It can measure the water level in reservoirs or wells, intelligently control the irrigation system according to real-time data, improve the efficiency of water resource utilization, and realize refined farmland irrigation management.
Environmental protection engineering: Sewage treatment plants use radar water level gauges to monitor the liquid level of treatment pools to optimize treatment processes and reduce energy consumption.
Scientific research: In scientific research, radar water level gauges can be used to observe changes in water levels in oceans, lakes, rivers and other water bodies. For example, in oceanographic research, radar water level gauges can be used to observe changes in ocean phenomena such as waves and tides; in chronological research, they can be used to observe changes in lake water levels and changes in water ecosystems.
Horological research: Radar water level gauges can be used to monitor water level, flow rate, flow and other parameters of water bodies, providing data support for the study of hydro logical laws. Through the monitoring data of radar water level gauges, we can understand the changing trends of water bodies and provide a scientific basis for water resources management and protection.
River water level monitoring: Radar water level gauges play an important role in the field of river water level monitoring. It can monitor river water level changes in real time around the clock, help analyze water level fluctuation trends, and provide data support for flood warnings, drought monitoring, etc.
To sum up, radar water level meter has broad application prospects in water conservancy, environmental protection, industry, agriculture, scientific research and other fields due to its unique technical advantages.





























